mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-03-12 01:40:10 +08:00
commit
fa601079d0
@ -1,6 +1,6 @@
|
||||
25个给git熟手的技巧
|
||||
25个 Git 进阶技巧
|
||||
================================================================================
|
||||
我已经使用git差不多18个月了,觉得自己对它应该已经非常了解。然后来自GitHub的[Scott Chacon][1]过来给LVS做培训,[LVS是一个赌博软件供应商和开发商][2](从2013年开始的合同),而我在第一天里就学到了很多。
|
||||
我已经使用git差不多18个月了,觉得自己对它应该已经非常了解。然后来自GitHub的[Scott Chacon][1]过来给LVS做培训([LVS是一个赌博软件供应商和开发商][2],从2013年开始的合同),而我在第一天里就学到了很多。
|
||||
|
||||
作为一个对git感觉良好的人,我觉得分享从社区里掌握的一些有价值的信息,也许能帮某人解决问题而不用做太深入研究。
|
||||
|
||||
@ -15,21 +15,21 @@
|
||||
|
||||
#### 2. Git是基于指针的 ####
|
||||
|
||||
保存在git里的一切都是文件。当你创建一个提交的时候,会建立一个包含你的提交信息和相关数据(名字,邮件地址,日期/时间,前一个提交,等等)的文件,并把它链接到一个文件树中。文件树中包含了对象或其他树的列表。对象或容器是和本次提交相关的实际内容(也是一个文件,你想了解的话,尽管文件名并没有包含在对象里,而是在树中)。所有这些文件都使用对象的SHA-1哈希值作为文件名。
|
||||
保存在git里的一切都是文件。当你创建一个提交的时候,会建立一个包含你的提交信息和相关数据(名字,邮件地址,日期/时间,前一个提交,等等)的文件,并把它链接到一个树文件中。这个树文件中包含了对象或其他树的列表。这里的提到的对象(或二进制大对象)是和本次提交相关的实际内容(它也是一个文件,另外,尽管文件名并没有包含在对象里,但是存储在树中)。所有这些文件都使用对象的SHA-1哈希值作为文件名。
|
||||
|
||||
用这种方式,分支和标签就是简单的文件(基本上是这样),包含指向实际提交的SHA-1哈希值。使用这些索引会带来优秀的灵活性和速度,比如创建一个新分支就只要简单地创建一个包含分支名字和所分出的那个提交的SHA-1索引的文件。当然,你不需要自己做这些,而只要使用Git命令行工具(或者GUI),但是实际上就是这么简单。
|
||||
用这种方式,分支和标签就是简单的文件(基本上是这样),包含指向该提交的SHA-1哈希值。使用这些索引会带来优秀的灵活性和速度,比如创建一个新分支就是简单地用分支名字和所分出的那个提交的SHA-1索引来创建一个文件。当然,你不需要自己做这些,而只要使用Git命令行工具(或者GUI),但是实际上就是这么简单。
|
||||
|
||||
你也许听说过叫HEAD的索引。这只是简单的一个文件,包含了你当前指向的那个提交的SHA-1索引值。如果你正在解决一次合并冲突然后看到了HEAD,这并不是一个特别的分支或分值上一个必须的特殊点,只是标明你当前所在位置。
|
||||
你也许听说过叫HEAD的索引。这只是简单的一个文件,包含了你当前指向的那个提交的SHA-1索引值。如果你正在解决一次合并冲突然后看到了HEAD,这并不是一个特别的分支或分支上的一个必需的特殊位置,只是标明你当前所在位置。
|
||||
|
||||
所有的分支指针都保存在.git/refs/heads里,HEAD在.git/HEAD里,而标签保存在.git/refs/tags里 - 自己可以放心地进去看看。
|
||||
所有的分支指针都保存在.git/refs/heads里,HEAD在.git/HEAD里,而标签保存在.git/refs/tags里 - 自己可以随便进去看看。
|
||||
|
||||
#### 3. 两个父节点 - 当然! ####
|
||||
#### 3. 两个爸爸(父节点) - 你没看错! ####
|
||||
|
||||
在历史中查看一个合并提交的信息时,你将看到有两个父节点(相对于一般工作上的常规提交的情况)。第一个父节点是你所在的分支,第二个是你合并过来的分支。
|
||||
在历史中查看一个合并提交的信息时,你将看到有两个父节点(不同于工作副本上的常规提交的情况)。第一个父节点是你所在的分支,第二个是你合并过来的分支。
|
||||
|
||||
#### 4. 合并冲突 ####
|
||||
|
||||
目前我相信你碰到过合并冲突并且解决过。通常是编辑一下文件,去掉<<<<,====,>>>>标志,保留需要留下的代码。有时能够看到这两个修改之前的代码会很不错,比如,在这两个分支上有冲突的改动之前。下面是一种方式:
|
||||
目前我相信你碰到过合并冲突并且解决过。通常是编辑一下文件,去掉<<<<,====,>>>>标志,保留需要留下的代码。有时能够看到这两个修改之前的代码会很不错,比如,在这两个现在冲突的分支之前的改动。下面是一种方式:
|
||||
|
||||
$ git diff --merge
|
||||
diff --cc dummy.rb
|
||||
@ -45,14 +45,14 @@
|
||||
end
|
||||
end
|
||||
|
||||
如果是二进制文件,比较差异就没那么简单了...通常你要做的就是测试这个二进制文件的两个版本来决定保留哪个(或者在二进制文件编辑器里手工复制冲突部分)。从一个特定分支获取文件拷贝(比如说你在合并master和feature123):
|
||||
如果是二进制文件,比较差异就没那么简单了...通常你要做的就是测试这个二进制文件的两个版本来决定保留哪个(或者在二进制文件编辑器里手工复制冲突部分)。从一个特定分支获取文件拷贝(比如说你在合并master和feature123两个分支):
|
||||
|
||||
$ git checkout master flash/foo.fla # 或者...
|
||||
$ git checkout feature132 flash/foo.fla
|
||||
$ # 然后...
|
||||
$ git add flash/foo.fla
|
||||
|
||||
另一种方式是通过git输出文件 - 你可以输出到另外的文件名,然后再重命名正确的文件(当你决定了要用哪个)为正常的文件名:
|
||||
另一种方式是通过git输出文件 - 你可以输出到另外的文件名,然后当你决定了要用哪个后,再将选定的正确文件复制为正常的文件名:
|
||||
|
||||
$ git show master:flash/foo.fla > master-foo.fla
|
||||
$ git show feature132:flash/foo.fla > feature132-foo.fla
|
||||
@ -71,7 +71,7 @@
|
||||
|
||||
#### 5. 远端服务器 ####
|
||||
|
||||
git的一个超强大的功能就是可以有不止一个远端服务器(实际上你一直都在一个本地仓库上工作)。你并不是一定都要有写权限,你可以有多个可以读取的服务器(用来合并他们的工作)然后写入其他仓库。添加一个新的远端服务器很简单:
|
||||
git的一个超强大的功能就是可以有不止一个远端服务器(实际上你一直都在一个本地仓库上工作)。你并不是一定都要有这些服务器的写权限,你可以有多个可以读取的服务器(用来合并他们的工作)然后写入到另外一个仓库。添加一个新的远端服务器很简单:
|
||||
|
||||
$ git remote add john git@github.com:johnsomeone/someproject.git
|
||||
|
||||
@ -87,10 +87,10 @@ git的一个超强大的功能就是可以有不止一个远端服务器(实
|
||||
|
||||
$ git diff master..john/master
|
||||
|
||||
你也可以查看不在远端分支的HEAD的改动:
|
||||
你也可以查看没有在远端分支上的HEAD的改动:
|
||||
|
||||
$ git log remote/branch..
|
||||
# 注意:..后面没有结束的refspec
|
||||
# 注意:..后面没有结束的特定引用
|
||||
|
||||
#### 6. 标签 ####
|
||||
|
||||
@ -99,7 +99,7 @@ git的一个超强大的功能就是可以有不止一个远端服务器(实
|
||||
建立这两种类型的标签都很简单(只有一个命令行开关的差异)
|
||||
|
||||
$ git tag to-be-tested
|
||||
$ git tag -a v1.1.0 # 会提示输入标签信息
|
||||
$ git tag -a v1.1.0 # 会提示输入标签的信息
|
||||
|
||||
#### 7. 建立分支 ####
|
||||
|
||||
@ -108,7 +108,7 @@ git的一个超强大的功能就是可以有不止一个远端服务器(实
|
||||
$ git branch feature132
|
||||
$ git checkout feature132
|
||||
|
||||
当然,如果你确定自己要新建分支并直接切换过去,可以用一个命令实现:
|
||||
当然,如果你确定自己直接切换到新建的分支,可以用一个命令实现:
|
||||
|
||||
$ git checkout -b feature132
|
||||
|
||||
@ -117,20 +117,20 @@ git的一个超强大的功能就是可以有不止一个远端服务器(实
|
||||
$ git checkout -b twitter-experiment feature132
|
||||
$ git branch -d feature132
|
||||
|
||||
更新:你也可以(像Brian Palmer在原博客文章的评论里提出的)只用“git branch”的-m开关在一个命令里实现(像Mike提出的,如果你只有一个分支参数,就会重命名当前分支):
|
||||
更新:你也可以(像Brian Palmer在原博客文章的评论里提出的)只用“git branch”的-m开关在一个命令里实现(像Mike提出的,如果你只指定了一个分支参数,就会重命名当前分支):
|
||||
|
||||
$ git branch -m twitter-experiment
|
||||
$ git branch -m feature132 twitter-experiment
|
||||
|
||||
#### 8. 合并分支 ####
|
||||
|
||||
在将来什么时候,你希望合并改动。有两种方式:
|
||||
也许在将来的某个时候,你希望将改动合并。有两种方式:
|
||||
|
||||
$ git checkout master
|
||||
$ git merge feature83 # 或者...
|
||||
$ git rebase feature83
|
||||
|
||||
merge和rebase之间的差别是merge会尝试处理改动并建立一个新的混合了两者的提交。rebase会尝试把你从一个分支最后一次分离后的所有改动,一个个加到该分支的HEAD上。不过,在已经将分支推到远端服务器后不要再rebase了 - 这回引起冲突/问题。
|
||||
merge和rebase之间的差别是merge会尝试处理改动并建立一个新的混合了两者的提交。rebase会尝试把你从一个分支最后一次分离后的所有改动,一个个加到该分支的HEAD上。不过,在已经将分支推到远端服务器后不要再rebase了 - 这会引起冲突/问题。
|
||||
|
||||
如果你不确定在哪些分支上还有独有的工作 - 所以你也不知道哪些分支需要合并而哪些可以删除,git branch有两个开关可以帮你:
|
||||
|
||||
@ -147,7 +147,7 @@ merge和rebase之间的差别是merge会尝试处理改动并建立一个新的
|
||||
$ git push origin twitter-experiment:refs/heads/twitter-experiment
|
||||
# origin是我们服务器的名字,而twitter-experiment是分支名字
|
||||
|
||||
更新:感谢Erlend在原博客文章上的评论 - 这个实际上和`git push origin twitter-experiment`效果一样,不过使用完整的语法,你可以在两者之间使用不同的分知名(这样本地分支可以是`add-ssl-support`而远端是`issue-1723`)。
|
||||
更新:感谢Erlend在原博客文章上的评论 - 这个实际上和`git push origin twitter-experiment`效果一样,不过使用完整的语法,你可以在两者之间使用不同的分支名(这样本地分支可以是`add-ssl-support`而远端是`issue-1723`)。
|
||||
|
||||
如果你想在远端服务器上删除一个分支(注意分支名前面的冒号):
|
||||
|
||||
@ -210,7 +210,7 @@ git会基于当前的提交信息自动创建评论。如果你更希望有自
|
||||
|
||||
这会让你进入一个基于菜单的交互式提示。你可以使用命令中的数字或高亮的字母(如果你在终端里打开了高亮的话)来进入相应的模式。然后就只是输入你希望操作的文件的数字了(你可以使用这样的格式,1或者1-4或2,4,7)。
|
||||
|
||||
如果你想进入补丁模式(交互式模式下的‘p’或‘5’),你也可以直接进入:
|
||||
如果你想进入补丁模式(交互式模式下按‘p’或‘5’),你也可以直接进入:
|
||||
|
||||
$ git add -p
|
||||
diff --git a/dummy.rb b/dummy.rb
|
||||
@ -226,11 +226,11 @@ git会基于当前的提交信息自动创建评论。如果你更希望有自
|
||||
end
|
||||
Stage this hunk [y,n,q,a,d,/,e,?]?
|
||||
|
||||
你可以看到下方会有一些选项供选择用来添加该文件的这个改动,该文件的所有改动,等等。使用‘?’命令可以详细解释这些选项。
|
||||
你可以看到下方会有一些选项供选择用来添加该文件的这个改动、该文件的所有改动,等等。使用‘?’命令可以详细解释这些选项。
|
||||
|
||||
#### 12. 从文件系统里保存/取回改动 ####
|
||||
|
||||
有些项目(比如git项目本身)在git文件系统中直接保存额外文件而并没有将它们加入到版本控制中。
|
||||
有些项目(比如Git项目本身)在git文件系统中直接保存额外文件而并没有将它们加入到版本控制中。
|
||||
|
||||
让我们从在git中存储一个随机文件开始:
|
||||
|
||||
@ -251,7 +251,7 @@ git会基于当前的提交信息自动创建评论。如果你更希望有自
|
||||
|
||||
#### 13. 查看日志 ####
|
||||
|
||||
如果不用‘git log’来查看最近的提交你git用不了多久。不过,有一些技巧来更好地应用。比如,你可以使用下面的命令来查看每次提交的具体改动:
|
||||
长时间使用 Git 的话,不会没用过‘git log’来查看最近的提交。不过,有一些技巧来更好地应用。比如,你可以使用下面的命令来查看每次提交的具体改动:
|
||||
|
||||
$ git log -p
|
||||
|
||||
@ -268,7 +268,7 @@ git会基于当前的提交信息自动创建评论。如果你更希望有自
|
||||
|
||||
#### 14. 搜索日志 ####
|
||||
|
||||
如果你想找特定作者可以这样做:
|
||||
如果你想找特定提交者可以这样做:
|
||||
|
||||
$ git log --author=Andy
|
||||
|
||||
@ -278,7 +278,7 @@ git会基于当前的提交信息自动创建评论。如果你更希望有自
|
||||
|
||||
$ git log --grep="Something in the message"
|
||||
|
||||
也有一个更强大的叫做pickaxe的命令用来查找删除或添加某个特定内容的提交(比如,该文件第一次出现或被删除)。这可以告诉你什么时候增加了一行(但这一行里的某个字符后面被改动过就不行了):
|
||||
也有一个更强大的叫做pickaxe的命令用来查找包含了删除或添加的某个特定内容的提交(比如,该内容第一次出现或被删除)。这可以告诉你什么时候增加了一行(但这一行里的某个字符后面被改动过就不行了):
|
||||
|
||||
$ git log -S "TODO: Check for admin status"
|
||||
|
||||
@ -294,7 +294,7 @@ git会基于当前的提交信息自动创建评论。如果你更希望有自
|
||||
|
||||
$ git log --since=2.months.ago --until=1.day.ago
|
||||
|
||||
默认情况下会用OR来组合查询,但你可以轻易地改为AND(如果你有超过一条的标准)
|
||||
默认情况下会用OR来组合查询,但你可以轻易地改为AND(如果你有超过一条的查询标准)
|
||||
|
||||
$ git log --since=2.months.ago --until=1.day.ago --author=andy -S "something" --all-match
|
||||
|
||||
@ -310,7 +310,7 @@ git会基于当前的提交信息自动创建评论。如果你更希望有自
|
||||
$ git show feature132@{yesterday} # 时间相关
|
||||
$ git show feature132@{2.hours.ago} # 时间相关
|
||||
|
||||
注意和之前部分有些不同,末尾的插入符号意思是该提交的父节点 - 开始位置的插入符号意思是不在这个分支。
|
||||
注意和之前部分有些不同,末尾的^的意思是该提交的父节点 - 开始位置的^的意思是不在这个分支。
|
||||
|
||||
#### 16. 选择范围 ####
|
||||
|
||||
@ -321,7 +321,7 @@ git会基于当前的提交信息自动创建评论。如果你更希望有自
|
||||
|
||||
你也可以省略[new],将使用当前的HEAD。
|
||||
|
||||
### Rewinding Time & Fixing Mistakes ###
|
||||
### 时光回溯和后悔药 ###
|
||||
|
||||
#### 17. 重置改动 ####
|
||||
|
||||
@ -329,7 +329,7 @@ git会基于当前的提交信息自动创建评论。如果你更希望有自
|
||||
|
||||
$ git reset HEAD lib/foo.rb
|
||||
|
||||
通常会使用‘unstage’的别名,因为看上去有些不直观。
|
||||
通常会使用‘unstage’的别名,因为上面的看上去有些不直观。
|
||||
|
||||
$ git config --global alias.unstage "reset HEAD"
|
||||
$ git unstage lib/foo.rb
|
||||
@ -369,11 +369,11 @@ git会基于当前的提交信息自动创建评论。如果你更希望有自
|
||||
|
||||
#### 19. 交互式切换基础 ####
|
||||
|
||||
这是一个我之前看过展示却没真正理解过的很赞的功能,现在很简单。假如说你提交了3次但是你希望更改顺序或编辑(或者合并):
|
||||
这是一个我之前看过展示却没真正理解过的很赞的功能,现在觉得它就很简单了。假如说你提交了3次但是你希望更改顺序或编辑(或者合并):
|
||||
|
||||
$ git rebase -i master~3
|
||||
|
||||
然后会启动你的编辑器并带有一些指令。你所要做的就是修改这些指令来选择/插入/编辑(或者删除)提交和保存/退出。然后在编辑完后你可以用`git rebase --continue`命令来让每一条指令生效。
|
||||
然后这会启动你的编辑器并带有一些指令。你所要做的就是修改这些指令来选择/插入/编辑(或者删除)提交和保存/退出。然后在编辑完后你可以用`git rebase --continue`命令来让每一条指令生效。
|
||||
|
||||
如果你有修改,将会切换到你提交时所处的状态,之后你需要使用命令git commit --amend来编辑。
|
||||
|
||||
@ -446,7 +446,7 @@ git会基于当前的提交信息自动创建评论。如果你更希望有自
|
||||
|
||||
$ git branch experimental SHA1_OF_HASH
|
||||
|
||||
如果你访问过的话,你通常可以用git reflog来找到SHA1哈希值。
|
||||
如果你最近访问过的话,你通常可以用git reflog来找到SHA1哈希值。
|
||||
|
||||
另一种方式是使用`git fsck —lost-found`。其中一个dangling的提交就是丢失的HEAD(它只是已删除分支的HEAD,而HEAD^被引用为当前的HEAD所以它并不处于dangling状态)
|
||||
|
||||
@ -460,7 +460,7 @@ via: https://www.andyjeffries.co.uk/25-tips-for-intermediate-git-users/
|
||||
|
||||
作者:[Andy Jeffries][a]
|
||||
译者:[zpl1025](https://github.com/zpl1025)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,14 +1,14 @@
|
||||
Linux有问必答时间--如何在Linux下禁用IPv6
|
||||
Linux有问必答:如何在Linux下禁用IPv6
|
||||
================================================================================
|
||||
> **问题**:我发现我的一个应用程序在尝试通过IPv6建立连接,但是由于我们本地网络不允许分配IPv6的流量,IPv6连接会超时,应用程序的连接会退回到IPv4,这样就会造成不必要的延迟。由于我目前对IPv6没有任何需求,所以我想在我的Linux主机上禁用IPv6。有什么比较合适的方法呢?
|
||||
> **问题**:我发现我的一个应用程序在尝试通过IPv6建立连接,但是由于我们本地网络不允许分配IPv6的流量,IPv6连接会超时,应用程序的连接会回退到IPv4,这样就会造成不必要的延迟。由于我目前对IPv6没有任何需求,所以我想在我的Linux主机上禁用IPv6。有什么比较合适的方法呢?
|
||||
|
||||
IPv6被认为是IPv4——互联网上的传统32位地址空间的替代产品,它为了解决现有IPv4地址空间即将耗尽的问题。然而,由于IPv4已经被每台主机或设备连接到了互联网上,所以想在一夜之间将它们全部切换到IPv6几乎是不可能的。许多IPv4到IPv6的转换机制(例如:双协议栈、网络隧道、代理) 已经被提出来用来促进IPv6能被采用,并且很多应用也正在进行重写,就像我们所说的,来增加对IPv6的支持。有一件事情能确定,就是在可预见的未来里IPv4和IPv6势必将共存。
|
||||
IPv6被认为是IPv4——互联网上的传统32位地址空间——的替代产品,它用来解决现有IPv4地址空间即将耗尽的问题。然而,由于已经有大量主机、设备用IPv4连接到了互联网上,所以想在一夜之间将它们全部切换到IPv6几乎是不可能的。许多IPv4到IPv6的转换机制(例如:双协议栈、网络隧道、代理) 已经被提出来用来促进IPv6能被采用,并且很多应用也正在进行重写,如我们所提倡的,来增加对IPv6的支持。有一件事情可以确定,就是在可预见的未来里IPv4和IPv6势必将共存。
|
||||
|
||||
理想情况下,[向IPv6过渡的进程][1]不应该被最终的用户所看见,但是IPv4/IPv6混合环境有时会让你碰到各种源于IPv4和IPv6之间不经意间的相互作用的问题。举个例子,你会碰到应用程序超时的问题比如apt-get或ssh尝试通过IPv6连接失败、DNS服务器意外清空了IPv6的AAAA记录、或者你支持IPv6的设备不兼容你的互联网服务提供商遗留下的IPv4网络等等等等。
|
||||
理想情况下,[向IPv6过渡的进程][1]不应该被最终的用户所看见,但是IPv4/IPv6混合环境有时会让你碰到各种源于IPv4和IPv6之间不经意间的相互碰撞的问题。举个例子,你会碰到应用程序超时的问题,比如apt-get或ssh尝试通过IPv6连接失败、DNS服务器意外清空了IPv6的AAAA记录、或者你支持IPv6的设备不兼容你的互联网服务提供商遗留下的IPv4网络,等等等等。
|
||||
|
||||
当然这不意味着你应该盲目地在你的Linux机器上禁用IPv6。鉴于IPv6许诺的种种好处,作为社会的一份子我们最终还是要充分拥抱它的,但是作为给最终用户进行故障排除过程的一部分,如果IPv6确实是罪魁祸首那你可以尝试去关闭它。
|
||||
当然这不意味着你应该盲目地在你的Linux机器上禁用IPv6。鉴于IPv6许诺的种种好处,作为社会的一份子我们最终还是要充分拥抱它的,但是作为给最终用户进行故障排除过程的一部分,如果IPv6确实是罪魁祸首,那你可以尝试去关闭它。
|
||||
|
||||
这里有一些让你在Linux中部分或全部禁用IPv6的小技巧(例如:为一个已经确定的网络接口)。这些小贴士应该适用于所有主流的Linux发行版包括Ubuntu、Debian、Linux Mint、CentOS、Fedora、RHEL以及Arch Linux。
|
||||
这里有一些让你在Linux中部分(例如:对于某个特定的网络接口)或全部禁用IPv6的小技巧。这些小贴士应该适用于所有主流的Linux发行版包括Ubuntu、Debian、Linux Mint、CentOS、Fedora、RHEL以及Arch Linux。
|
||||
|
||||
### 查看IPv6在Linux中是否被启用 ###
|
||||
|
||||
@ -24,7 +24,7 @@ IPv6被认为是IPv4——互联网上的传统32位地址空间的替代产品
|
||||
|
||||
### 临时禁用IPv6 ###
|
||||
|
||||
如果你想要在你的Linux系统上临时关闭IPv6,你可以用 /proc 文件系统。"临时",意思是我们所做的禁用IPv6的更改在系统重启后将不被保存。IPv6会在你的Linux机器重启后再次被启用。
|
||||
如果你想要在你的Linux系统上临时关闭IPv6,你可以用 /proc 文件系统。"临时"的意思是我们所做的禁用IPv6的更改在系统重启后将不被保存。IPv6会在你的Linux机器重启后再次被启用。
|
||||
|
||||
要将一个特定的网络接口禁用IPv6,使用以下命令:
|
||||
|
||||
@ -50,7 +50,7 @@ IPv6被认为是IPv4——互联网上的传统32位地址空间的替代产品
|
||||
|
||||
#### 方法一 ####
|
||||
|
||||
第一种方法是请求以上提到的 /proc 对 /etc/sysctl.conf 文件进行修改。
|
||||
第一种方法是通过 /etc/sysctl.conf 文件对 /proc 进行永久修改。
|
||||
|
||||
换句话说,就是用文本编辑器打开 /etc/sysctl.conf 然后添加以下内容:
|
||||
|
||||
@ -69,7 +69,7 @@ IPv6被认为是IPv4——互联网上的传统32位地址空间的替代产品
|
||||
|
||||
#### 方法二 ####
|
||||
|
||||
另一个永久禁用IPv6的方法是在开机的时候执行一个必要的内核参数。
|
||||
另一个永久禁用IPv6的方法是在开机的时候传递一个必要的内核参数。
|
||||
|
||||
用文本编辑器打开 /etc/default/grub 并给GRUB_CMDLINE_LINUX变量添加"ipv6.disable=1"。
|
||||
|
||||
@ -79,7 +79,7 @@ IPv6被认为是IPv4——互联网上的传统32位地址空间的替代产品
|
||||
|
||||
GRUB_CMDLINE_LINUX="xxxxx ipv6.disable=1"
|
||||
|
||||
上面的"xxxxx"代表任意存在着的内核参数,在它后面添加"ipv6.disable=1"。
|
||||
上面的"xxxxx"代表任何已有的内核参数,在它后面添加"ipv6.disable=1"。
|
||||
|
||||

|
||||
|
||||
@ -97,7 +97,7 @@ Fedora、CentOS/RHEL系统:
|
||||
|
||||
### 禁用IPv6之后的其它可选步骤 ###
|
||||
|
||||
这里有一些可选步骤在你禁用IPv6后需要考虑,这是因为当你在内核里禁用IPv6后,其它程序仍然会尝试使用IPv6。在大多数情况下,例如应用程序的运转状态不太会遭到破坏,但是出于效率或安全方面的原因,你要为他们禁用IPv6。
|
||||
这里有一些在你禁用IPv6后需要考虑的可选步骤,这是因为当你在内核里禁用IPv6后,其它程序也许仍然会尝试使用IPv6。在大多数情况下,应用程序的这种行为不太会影响到什么,但是出于效率或安全方面的原因,你可以为他们禁用IPv6。
|
||||
|
||||
#### /etc/hosts ####
|
||||
|
||||
@ -124,7 +124,7 @@ Fedora、CentOS/RHEL系统:
|
||||
|
||||
默认情况下,OpenSSH服务(sshd)会去尝试捆绑IPv4和IPv6的地址。
|
||||
|
||||
要强制sshd只捆绑IPv4地址,用文本编辑器打开 /etc/ssh/sshd_config 并添加以下脚本行。inet只适用于IPv4,而inet6是适用于IPv6的。
|
||||
要强制sshd只捆绑IPv4地址,用文本编辑器打开 /etc/ssh/sshd_config 并添加以下行。inet只适用于IPv4,而inet6是适用于IPv6的。
|
||||
|
||||
$ sudo vi /etc/ssh/sshd_config
|
||||
|
||||
@ -140,7 +140,7 @@ via: http://ask.xmodulo.com/disable-ipv6-linux.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[ZTinoZ](https://github.com/ZTinoZ)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,4 +1,4 @@
|
||||
如何修复:apt-get update无法添加新的CD-ROM
|
||||
如何修复 apt-get update 无法添加新的 CD-ROM 的错误
|
||||
================================================================================
|
||||

|
||||
|
||||
@ -63,8 +63,8 @@
|
||||
via: http://itsfoss.com/fix-failed-fetch-cdrom-aptget-update-add-cdroms/
|
||||
|
||||
作者:[Abhishek][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,4 +1,4 @@
|
||||
Linux 基础:如何修复Ubuntu上“E: /var/cache/apt/archives/ subprocess new pre-removal script returned error exit status 1 ”的错误
|
||||
如何修复 Ubuntu 上“...script returned error exit status 1”的错误
|
||||
================================================================================
|
||||

|
||||
|
||||
@ -6,11 +6,11 @@ Linux 基础:如何修复Ubuntu上“E: /var/cache/apt/archives/ subprocess ne
|
||||
|
||||
> E: /var/cache/apt/archives/ subprocess new pre-removal script returned error exit status 1
|
||||
|
||||

|
||||

|
||||
|
||||
### 解决: ###
|
||||
|
||||
我google了以下并找到了方法。下面是我解决的方法。
|
||||
我google了一下并找到了方法。下面是我解决的方法。
|
||||
|
||||
sudo apt-get clean
|
||||
sudo apt-get update && sudo apt-get upgrade
|
||||
@ -33,11 +33,11 @@ Linux 基础:如何修复Ubuntu上“E: /var/cache/apt/archives/ subprocess ne
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.unixmen.com/linux-basics-how-to-fix-e-varcacheaptarchives-subprocess-new-pre-removal-script-returned-error-exit-status-1-in-ubuntu/
|
||||
via: http://www.unixmen.com/linux-basics-how-to-fix-e-varcacheaptarchives-subprocess-new-pre-removal-script-returned-error-exit-status-1-in-ubuntu/
|
||||
|
||||
作者:[SK][a]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,14 +1,14 @@
|
||||
Ubuntu中,使用Prey定位被盗的笔记本与手机
|
||||
使用Prey定位被盗的Ubuntu笔记本与智能电话
|
||||
===============================================================================
|
||||
Prey是一款跨平台的开源工具,可以帮助你找回被盗的笔记本,台式机,平板和智能手机。它已经获得了广泛的流行,声称帮助召回了成百上千台丢失的笔记本和智能手机。Prey的使用特别简单,首先安装在你的笔记本或者手机上,当你的设备不见了,用你的账号登入Prey网站,并且标记你的设备为“丢失”。只要小偷将设备接入网络,Prey就会马上发送设备的地理位置给你。如果你的笔记本有摄像头,它还会拍下小偷。
|
||||
Prey是一款跨平台的开源工具,可以帮助你找回被盗的笔记本,台式机,平板和智能手机。它已经获得了广泛的流行,声称帮助找回了成百上千台丢失的笔记本和智能手机。Prey的使用特别简单,首先安装在你的笔记本或者手机上,当你的设备不见了,用你的账号登入Prey网站,并且标记你的设备为“丢失”。只要小偷将设备接入网络,Prey就会马上发送设备的地理位置给你。如果你的笔记本有摄像头,它还会拍下该死的贼。
|
||||
|
||||
Prey占用很小的系统资源;你不会对你的设备运行有任何影响。你也可以配合其他你已经在设备上安装的防盗软件使用。Prey采用安全加密的通道,在你的设备与Prey服务器之间进行数据传输。
|
||||
Prey占用很小的系统资源;你不会对你的设备运行有任何影响。你也可以配合其他你已经在设备上安装的防盗软件使用。Prey在你的设备与Prey服务器之间采用安全加密的通道进行数据传输。
|
||||
|
||||
### 在Ubuntu上安装并配置Prey ###
|
||||
|
||||
让我们来看看如何在Ubuntu上安装和配置Prey,需要提醒的是,在配置过程中,我们必须到Prey官网进行账号注册。一旦完成上述工作,Prey将会开始监视的设备了。免费的账号最多可以监视三个设备,如果你需要添加更多的设备,你就需要购买合适的的套餐了。
|
||||
让我们来看看如何在Ubuntu上安装和配置Prey,需要提醒的是,在配置过程中,我们必须到Prey官网进行账号注册。一旦完成上述工作,Prey将会开始监视你的设备了。免费的账号最多可以监视三个设备,如果你需要添加更多的设备,你就需要购买合适的的套餐了。
|
||||
|
||||
想象一下Prey多么流行与被广泛使用,它现在已经被添加到了官方的软件库中了。这意味着你不要往软件包管理器添加任何PPA。很简单地,登录你的终端,运行以下的命令来安装它:
|
||||
可以想象Prey多么流行与被广泛使用,它现在已经被添加到了官方的软件库中了。这意味着你不要往软件包管理器添加任何PPA。很简单,登录你的终端,运行以下的命令来安装它:
|
||||
|
||||
sudo apt-get install prey
|
||||
|
||||
@ -54,7 +54,7 @@ Prey有一个明显的不足。它需要你的设备接入互联网才会发送
|
||||
|
||||
### 结论 ###
|
||||
|
||||
这是一款小巧,非常有用的安全保护应用,可以让你在一个地方追踪你所有的设备,尽管不完美,但是仍然提供了找回被盗设备的机会。它在Linux,Windows和Mac平台上无缝运行。以上就是Prey完整使用的所有细节。
|
||||
这是一款小巧,非常有用的安全保护应用,可以让你在一个地方追踪你所有的设备,尽管不完美,但是仍然提供了找回被盗设备的机会。它在Linux,Windows和Mac平台上无缝运行。以上就是[Prey][2]完整使用的所有细节。
|
||||
|
||||
-------------------------------------------------------------------------------
|
||||
|
||||
@ -62,9 +62,10 @@ via: http://linoxide.com/ubuntu-how-to/anti-theft-application-prey-ubuntu/
|
||||
|
||||
作者:[Aun Raza][a]
|
||||
译者:[wi-cuckoo](https://github.com/wi-cuckoo)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://linoxide.com/author/arunrz/
|
||||
[1]:https://preyproject.com/
|
||||
[2]:https://preyproject.com/plans
|
||||
@ -0,0 +1,63 @@
|
||||
在Ubuntu中安装Visual Studio Code
|
||||
================================================================================
|
||||

|
||||
|
||||
微软令人意外地[发布了Visual Studio Code][1],并支持主要的桌面平台,当然包括linux。如果你是一名需要在ubuntu工作的web开发人员,你可以**非常轻松的安装Visual Studio Code**。
|
||||
|
||||
我将要使用[Ubuntu Make][2]来安装Visual Studio Code。Ubuntu Make,就是以前的Ubuntu开发者工具中心,是一个命令行工具,帮助用户快速安装各种开发工具、语言和IDE。也可以使用Ubuntu Make轻松[安装Android Studio][3] 和其他IDE,如Eclipse。本文将展示**如何在Ubuntu中使用Ubuntu Make安装Visual Studio Code**。(译注:也可以直接去微软官网下载安装包)
|
||||
|
||||
### 安装微软Visual Studio Code ###
|
||||
|
||||
开始之前,首先需要安装Ubuntu Make。虽然Ubuntu Make存在Ubuntu15.04官方库中,**但是需要Ubuntu Make 0.7以上版本才能安装Visual Studio**。所以,需要通过官方PPA更新到最新的Ubuntu Make。此PPA支持Ubuntu 14.04, 14.10 和 15.04。
|
||||
|
||||
注意,**仅支持64位版本**。
|
||||
|
||||
打开终端,使用下列命令,通过官方PPA来安装Ubuntu Make:
|
||||
|
||||
sudo add-apt-repository ppa:ubuntu-desktop/ubuntu-make
|
||||
sudo apt-get update
|
||||
sudo apt-get install ubuntu-make
|
||||
|
||||
安装Ubuntu Make完后,接着使用下列命令安装Visual Studio Code:
|
||||
|
||||
umake web visual-studio-code
|
||||
|
||||
安装过程中,将会询问安装路径,如下图:
|
||||
|
||||

|
||||
|
||||
在抛出一堆要求和条件后,它会询问你是否确认安装Visual Studio Code。输入‘a’来确定:
|
||||
|
||||

|
||||
|
||||
确定之后,安装程序会开始下载并安装。安装完成后,你可以发现Visual Studio Code 图标已经出现在了Unity启动器上。点击图标开始运行!下图是Ubuntu 15.04 Unity的截图:
|
||||
|
||||

|
||||
|
||||
### 卸载Visual Studio Code###
|
||||
|
||||
卸载Visual Studio Code,同样使用Ubuntu Make命令。如下:
|
||||
|
||||
umake web visual-studio-code --remove
|
||||
|
||||
如果你不打算使用Ubuntu Make,也可以通过微软官方下载安装文件。
|
||||
|
||||
- [下载Visual Studio Code Linux版][4]
|
||||
|
||||
怎样!是不是超级简单就可以安装Visual Studio Code,这都归功于Ubuntu Make。我希望这篇文章能帮助到你。如果您有任何问题或建议,欢迎给我留言。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://itsfoss.com/install-visual-studio-code-ubuntu/
|
||||
|
||||
作者:[Abhishek][a]
|
||||
译者:[Vic020/VicYu](http://vicyu.net)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://itsfoss.com/author/abhishek/
|
||||
[1]:https://linux.cn/article-5376-1.html
|
||||
[2]:https://wiki.ubuntu.com/ubuntu-make
|
||||
[3]:http://itsfoss.com/install-android-studio-ubuntu-linux/
|
||||
[4]:https://code.visualstudio.com/Download
|
||||
@ -0,0 +1,164 @@
|
||||
如何使用Vault安全的存储密码和API密钥
|
||||
=======================================================================
|
||||
Vault是用来安全的获取秘密信息的工具,它可以保存密码、API密钥、证书等信息。Vault提供了一个统一的接口来访问秘密信息,其具有健壮的访问控制机制和丰富的事件日志。
|
||||
|
||||
对关键信息的授权访问是一个困难的问题,尤其是当有许多用户角色,并且用户请求不同的关键信息时,例如用不同权限登录数据库的登录配置,用于外部服务的API密钥,SOA通信的证书等。当保密信息由不同的平台进行管理,并使用一些自定义的配置时,情况变得更糟,因此,安全的存储、管理审计日志几乎是不可能的。但Vault为这种复杂情况提供了一个解决方案。
|
||||
|
||||
### 突出特点 ###
|
||||
|
||||
**数据加密**:Vault能够在不存储数据的情况下对数据进行加密、解密。开发者们便可以存储加密后的数据而无需开发自己的加密技术,Vault还允许安全团队自定义安全参数。
|
||||
|
||||
**安全密码存储**:Vault在将秘密信息(API密钥、密码、证书)存储到持久化存储之前对数据进行加密。因此,如果有人偶尔拿到了存储的数据,这也没有任何意义,除非加密后的信息能被解密。
|
||||
|
||||
**动态密码**:Vault可以随时为AWS、SQL数据库等类似的系统产生密码。比如,如果应用需要访问AWS S3 桶,它向Vault请求AWS密钥对,Vault将给出带有租期的所需秘密信息。一旦租用期过期,这个秘密信息就不再存储。
|
||||
|
||||
**租赁和更新**:Vault给出的秘密信息带有租期,一旦租用期过期,它便立刻收回秘密信息,如果应用仍需要该秘密信息,则可以通过API更新租用期。
|
||||
|
||||
**撤销**:在租用期到期之前,Vault可以撤销一个秘密信息或者一个秘密信息树。
|
||||
|
||||
### 安装Vault ###
|
||||
|
||||
有两种方式来安装使用Vault。
|
||||
|
||||
**1. 预编译的Vault二进制** 能用于所有的Linux发行版,下载地址如下,下载之后,解压并将它放在系统PATH路径下,以方便调用。
|
||||
|
||||
- [下载预编译的二进制 Vault (32-bit)][1]
|
||||
- [下载预编译的二进制 Vault (64-bit)][2]
|
||||
- [下载预编译的二进制 Vault (ARM)][3]
|
||||
|
||||

|
||||
|
||||
*下载相应的预编译的Vault二进制版本。*
|
||||
|
||||

|
||||
|
||||
*解压下载到本地的二进制版本。*
|
||||
|
||||
祝贺你!您现在可以使用Vault了。
|
||||
|
||||

|
||||
|
||||
**2. 从源代码编译**是另一种在系统中安装Vault的方式。在安装Vault之前需要安装GO和GIT。
|
||||
|
||||
在 **Redhat系统中安装GO** 使用下面的指令:
|
||||
|
||||
sudo yum install go
|
||||
|
||||
在 **Debin系统中安装GO** 使用下面的指令:
|
||||
|
||||
sudo apt-get install golang
|
||||
|
||||
或者
|
||||
|
||||
sudo add-apt-repository ppa:gophers/go
|
||||
|
||||
sudo apt-get update
|
||||
|
||||
sudo apt-get install golang-stable
|
||||
|
||||
在 **Redhat系统中安装GIT** 使用下面的命令:
|
||||
|
||||
sudo yum install git
|
||||
|
||||
在 **Debian系统中安装GIT** 使用下面的命令:
|
||||
|
||||
sudo apt-get install git
|
||||
|
||||
一旦GO和GIT都已被安装好,我们便可以开始从源码编译安装Vault。
|
||||
|
||||
> 将下列的Vault仓库拷贝至GOPATH
|
||||
|
||||
https://github.com/hashicorp/vault
|
||||
|
||||
> 测试下面的文件是否存在,如果它不存在,那么Vault没有被克隆到合适的路径。
|
||||
|
||||
$GOPATH/src/github.com/hashicorp/vault/main.go
|
||||
|
||||
> 执行下面的指令来编译Vault,并将二进制文件放到系统bin目录下。
|
||||
|
||||
make dev
|
||||
|
||||

|
||||
|
||||
### 一份Vault入门教程 ###
|
||||
|
||||
我们已经编制了一份Vault的官方交互式教程,并带有它在SSH上的输出信息。
|
||||
|
||||
**概述**
|
||||
|
||||
这份教程包括下列步骤:
|
||||
|
||||
- 初始化并启封您的Vault
|
||||
- 在Vault中对您的请求授权
|
||||
- 读写秘密信息
|
||||
- 密封您的Vault
|
||||
|
||||
#### **初始化您的Vault**
|
||||
|
||||
首先,我们需要为您初始化一个Vault的工作实例。在初始化过程中,您可以配置Vault的密封行为。简单起见,现在使用一个启封密钥来初始化Vault,命令如下:
|
||||
|
||||
vault init -key-shares=1 -key-threshold=1
|
||||
|
||||
您会注意到Vault在这里输出了几个密钥。不要清除您的终端,这些密钥在后面的步骤中会使用到。
|
||||
|
||||

|
||||
|
||||
#### **启封您的Vault**
|
||||
|
||||
当一个Vault服务器启动时,它是密封的状态。在这种状态下,Vault被配置为知道物理存储在哪里及如何存取它,但不知道如何对其进行解密。Vault使用加密密钥来加密数据。这个密钥由"主密钥"加密,主密钥不保存。解密主密钥需要入口密钥。在这个例子中,我们使用了一个入口密钥来解密这个主密钥。
|
||||
|
||||
vault unseal <key 1>
|
||||
|
||||

|
||||
|
||||
####**为您的请求授权**
|
||||
|
||||
在执行任何操作之前,连接的客户端必须是被授权的。授权的过程是检验一个人或者机器是否如其所申明的那样具有正确的身份。这个身份用在向Vault发送请求时。为简单起见,我们将使用在步骤2中生成的root令牌,这个信息可以回滚终端屏幕看到。使用一个客户端令牌进行授权:
|
||||
|
||||
vault auth <root token>
|
||||
|
||||

|
||||
|
||||
####**读写保密信息**
|
||||
|
||||
现在Vault已经被设置妥当,我们可以开始读写默认挂载的秘密后端里面的秘密信息了。写在Vault中的秘密信息首先被加密,然后被写入后端存储中。后端存储机制绝不会看到未加密的信息,并且也没有在Vault之外解密的需要。
|
||||
|
||||
vault write secret/hello value=world
|
||||
|
||||
当然,您接下来便可以读这个保密信息了:
|
||||
|
||||
vault read secret/hello
|
||||
|
||||

|
||||
|
||||
####**密封您的Vault**
|
||||
|
||||
还有一个用I来密封Vault的API。它将丢掉现在的加密密钥并需要另一个启封过程来恢复它。密封仅需要一个拥有root权限的操作者。这是一种罕见的"打破玻璃过程"的典型部分。
|
||||
|
||||
这种方式中,如果检测到一个入侵,Vault数据将会立刻被锁住,以便最小化损失。如果不能访问到主密钥碎片的话,就不能再次获取数据。
|
||||
|
||||
vault seal
|
||||
|
||||

|
||||
|
||||
这便是入门教程的结尾。
|
||||
|
||||
### 总结 ###
|
||||
|
||||
Vault是一个非常有用的应用,它提供了一个可靠且安全的存储关键信息的方式。另外,它在存储前加密关键信息、审计日志维护、以租期的方式获取秘密信息,且一旦租用期过期它将立刻收回秘密信息。Vault是平台无关的,并且可以免费下载和安装。要发掘Vault的更多信息,请访问其[官方网站][4]。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/how-tos/secure-secret-store-vault/
|
||||
|
||||
作者:[Aun Raza][a]
|
||||
译者:[wwy-hust](https://github.com/wwy-hust)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://linoxide.com/author/arunrz/
|
||||
[1]:https://dl.bintray.com/mitchellh/vault/vault_0.1.0_linux_386.zip
|
||||
[2]:https://dl.bintray.com/mitchellh/vault/vault_0.1.0_linux_amd64.zip
|
||||
[3]:https://dl.bintray.com/mitchellh/vault/vault_0.1.0_linux_arm.zip
|
||||
[4]:https://vaultproject.io/
|
||||
@ -1,8 +1,8 @@
|
||||
在 RedHat/CentOS 7.x 中使用 cmcli 命令管理网络
|
||||
在 RedHat/CentOS 7.x 中使用 nmcli 命令管理网络
|
||||
===============
|
||||
[**Red Hat Enterprise Linux 7** 与 **CentOS 7**][1] 中默认的网络服务由 **NetworkManager** 提供,这是动态控制及配置网络的守护进程,它用于保持当前网络设备及连接处于工作状态,同时也支持传统的 ifcfg 类型的配置文件。
|
||||
NetworkManager 可以用于以下类型的连接:
|
||||
Ethernet,VLANS,Bridges,Bonds,Teams,Wi-Fi,mobile boradband(如移动3G)以及 IP-over-InfiniBand。针对与这些网络类型,NetworkManager 可以配置他们的网络别名,IP 地址,静态路由,DNS,VPN连接以及很多其它的特殊参数。
|
||||
|
||||
NetworkManager 可以用于以下类型的连接:Ethernet,VLANS,Bridges,Bonds,Teams,Wi-Fi,mobile boradband(如移动3G)以及 IP-over-InfiniBand。针对与这些网络类型,NetworkManager 可以配置他们的网络别名,IP 地址,静态路由,DNS,VPN连接以及很多其它的特殊参数。
|
||||
|
||||
可以用命令行工具 nmcli 来控制 NetworkManager。
|
||||
|
||||
@ -24,19 +24,21 @@ Ethernet,VLANS,Bridges,Bonds,Teams,Wi-Fi,mobile boradband(如移
|
||||
|
||||
显示所有连接。
|
||||
|
||||
# nmcli connection show -a
|
||||
# nmcli connection show -a
|
||||
|
||||
仅显示当前活动的连接。
|
||||
|
||||
# nmcli device status
|
||||
|
||||
列出通过 NetworkManager 验证的设备列表及他们的状态。
|
||||
列出 NetworkManager 识别出的设备列表及他们的状态。
|
||||
|
||||

|
||||
|
||||
### 启动/停止 网络接口###
|
||||
|
||||
使用 nmcli 工具启动或停止网络接口,与 ifconfig 的 up/down 是一样的。使用下列命令停止某个接口:
|
||||
使用 nmcli 工具启动或停止网络接口,与 ifconfig 的 up/down 是一样的。
|
||||
|
||||
使用下列命令停止某个接口:
|
||||
|
||||
# nmcli device disconnect eno16777736
|
||||
|
||||
@ -50,7 +52,7 @@ Ethernet,VLANS,Bridges,Bonds,Teams,Wi-Fi,mobile boradband(如移
|
||||
|
||||
# nmcli connection add type ethernet con-name NAME_OF_CONNECTION ifname interface-name ip4 IP_ADDRESS gw4 GW_ADDRESS
|
||||
|
||||
根据你需要的配置更改 NAME_OF_CONNECTION,IP_ADDRESS, GW_ADDRESS参数(如果不需要网关的话可以省略最后一部分)。
|
||||
根据你需要的配置更改 NAME\_OF\_CONNECTION,IP\_ADDRESS, GW\_ADDRESS参数(如果不需要网关的话可以省略最后一部分)。
|
||||
|
||||
# nmcli connection add type ethernet con-name NEW ifname eno16777736 ip4 192.168.1.141 gw4 192.168.1.1
|
||||
|
||||
@ -68,9 +70,11 @@ Ethernet,VLANS,Bridges,Bonds,Teams,Wi-Fi,mobile boradband(如移
|
||||
|
||||

|
||||
|
||||
###增加一个使用 DHCP 的新连接
|
||||
|
||||
增加新的连接,使用DHCP自动分配IP地址,网关,DNS等,你要做的就是将命令行后 ip/gw 地址部分去掉就行了,DHCP会自动分配这些参数。
|
||||
|
||||
例,在 eno 16777736 设备上配置一个 名为 NEW_DHCP 的 DHCP 连接
|
||||
例,在 eno 16777736 设备上配置一个 名为 NEW\_DHCP 的 DHCP 连接
|
||||
|
||||
# nmcli connection add type ethernet con-name NEW_DHCP ifname eno16777736
|
||||
|
||||
@ -79,8 +83,8 @@ Ethernet,VLANS,Bridges,Bonds,Teams,Wi-Fi,mobile boradband(如移
|
||||
via: http://linoxide.com/linux-command/nmcli-tool-red-hat-centos-7/
|
||||
|
||||
作者:[Adrian Dinu][a]
|
||||
译者:[SPccman](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
译者:[SPccman](https://github.com/SPccman)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,111 +0,0 @@
|
||||
translating wi-cuckoo
|
||||
What are good command line HTTP clients?
|
||||
================================================================================
|
||||
The whole is greater than the sum of its parts is a very famous quote from Aristotle, a Greek philosopher and scientist. This quote is particularly pertinent to Linux. In my view, one of Linux's biggest strengths is its synergy. The usefulness of Linux doesn't derive only from the huge raft of open source (command line) utilities. Instead, it's the synergy generated by using them together, sometimes in conjunction with larger applications.
|
||||
|
||||
The Unix philosophy spawned a "software tools" movement which focused on developing concise, basic, clear, modular and extensible code that can be used for other projects. This philosophy remains an important element for many Linux projects.
|
||||
|
||||
Good open source developers writing utilities seek to make sure the utility does its job as well as possible, and work well with other utilities. The goal is that users have a handful of tools, each of which seeks to excel at one thing. Some utilities work well independently.
|
||||
|
||||
This article looks at 3 open source command line HTTP clients. These clients let you download files off the internet from a command line. But they can also be used for many more interesting purposes such as testing, debugging and interacting with HTTP servers and web applications. Working with HTTP from the command-line is a worthwhile skill for HTTP architects and API designers. If you need to play around with an API, HTTPie and cURL will be invaluable.
|
||||
|
||||
----------
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
HTTPie (pronounced aych-tee-tee-pie) is an open source command line HTTP client. It is a a command line interface, cURL-like tool for humans.
|
||||
|
||||
The goal of this software is to make CLI interaction with web services as human-friendly as possible. It provides a simple http command that allows for sending arbitrary HTTP requests using a simple and natural syntax, and displays colorized output. HTTPie can be used for testing, debugging, and generally interacting with HTTP servers.
|
||||
|
||||
#### Features include: ####
|
||||
|
||||
- Expressive and intuitive syntax
|
||||
- Formatted and colorized terminal output
|
||||
- Built-in JSON support
|
||||
- Forms and file uploads
|
||||
- HTTPS, proxies, and authentication
|
||||
- Arbitrary request data
|
||||
- Custom headers
|
||||
- Persistent sessions
|
||||
- Wget-like downloads
|
||||
- Python 2.6, 2.7 and 3.x support
|
||||
- Linux, Mac OS X and Windows support
|
||||
- Plugins
|
||||
- Documentation
|
||||
- Test coverage
|
||||
|
||||
- Website: [httpie.org][1]
|
||||
- Developer: Jakub Roztočil
|
||||
- License: Open Source
|
||||
- Version Number: 0.9.2
|
||||
|
||||
----------
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
cURL is an open source command line tool for transferring data with URL syntax, supporting DICT, FILE, FTP, FTPS, GOPHER, HTTP, HTTPS, IMAP, IMAPS, LDAP, LDAPS, POP3, POP3S, RTMP, RTSP, SCP, SFTP, SMTP, SMTPS, TELNET and TFTP.
|
||||
|
||||
curl supports SSL certificates, HTTP POST, HTTP PUT, FTP uploading, HTTP form based upload, proxies, cookies, user+password authentication (Basic, Digest, NTLM, Negotiate, kerberos...), file transfer resume, proxy tunneling and a busload of other useful tricks.
|
||||
|
||||
#### Features include: ####
|
||||
|
||||
- Config file support
|
||||
- Multiple URLs in a single command line
|
||||
- Range "globbing" support: [0-13], {one,two,three}
|
||||
- Multiple file upload on a single command line
|
||||
- Custom maximum transfer rate
|
||||
- Redirectable stderr
|
||||
- Metalink support
|
||||
|
||||
- Website: [curl.haxx.se][2]
|
||||
- Developer: Daniel Stenberg
|
||||
- License: MIT/X derivate license
|
||||
- Version Number: 7.42.0
|
||||
|
||||
----------
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
Wget is open source software that retrieves content from web servers. Its name is derived from World Wide Web and get. It supports HTTP, HTTPS, and FTP protocols, as well as retrieval through HTTP proxies.
|
||||
|
||||
Wget can follow links in HTML pages and create local versions of remote web sites, fully recreating the directory structure of the original site. This is known as "recursive downloading."
|
||||
|
||||
Wget has been designed for robustness over slow or unstable network connections.
|
||||
|
||||
Features include:
|
||||
|
||||
- Resume aborted downloads, using REST and RANGE
|
||||
- Use filename wild cards and recursively mirror directories
|
||||
- NLS-based message files for many different languages
|
||||
- Optionally converts absolute links in downloaded documents to relative, so that downloaded documents may link to each other locally
|
||||
- Runs on most UNIX-like operating systems as well as Microsoft Windows
|
||||
- Supports HTTP proxies
|
||||
- Supports HTTP cookies
|
||||
- Supports persistent HTTP connections
|
||||
- Unattended / background operation
|
||||
- Uses local file timestamps to determine whether documents need to be re-downloaded when mirroring
|
||||
|
||||
- Website: [www.gnu.org/software/wget/][3]
|
||||
- Developer: Hrvoje Niksic, Gordon Matzigkeit, Junio Hamano, Dan Harkless, and many others
|
||||
- License: GNU GPL v3
|
||||
- Version Number: 1.16.3
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linuxlinks.com/article/20150425174537249/HTTPclients.html
|
||||
|
||||
作者:Frazer Kline
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://httpie.org/
|
||||
[2]:http://curl.haxx.se/
|
||||
[3]:https://www.gnu.org/software/wget/
|
||||
@ -1,135 +0,0 @@
|
||||
What are useful command-line network monitors on Linux
|
||||
================================================================================
|
||||
Network monitoring is a critical IT function for businesses of all sizes. The goal of network monitoring can vary. For example, the monitoring activity can be part of long-term network provisioning, security protection, performance troubleshooting, network usage accounting, and so on. Depending on its goal, network monitoring is done in many different ways, such as performing packet-level sniffing, collecting flow-level statistics, actively injecting probes into the network, parsing server logs, etc.
|
||||
|
||||
While there are many dedicated network monitoring systems capable of 24/7/365 monitoring, you can also leverage command-line network monitors in certain situations, where a dedicated monitor is an overkill. If you are a system admin, you are expected to have hands-on experience with some of well known CLI network monitors. Here is a list of **popular and useful command-line network monitors on Linux**.
|
||||
|
||||
### Packet-Level Sniffing ###
|
||||
|
||||
In this category, monitoring tools capture individual packets on the wire, dissect their content, and display decoded packet content or packet-level statistics. These tools conduct network monitoring from the lowest level, and as such, can possibly do the most fine-grained monitoring at the cost of network I/O and analysis efforts.
|
||||
|
||||
1. **dhcpdump**: a comman-line DHCP traffic sniffer capturing DHCP request/response traffic, and displays dissected DHCP protocol messages in a human-friendly format. It is useful when you are troubleshooting DHCP related issues.
|
||||
|
||||
2. **[dsniff][1]**: a collection of command-line based sniffing, spoofing and hijacking tools designed for network auditing and penetration testing. They can sniff various information such as passwords, NSF traffic, email messages, website URLs, and so on.
|
||||
|
||||
3. **[httpry][2]**: an HTTP packet sniffer which captures and decode HTTP requests and response packets, and display them in a human-readable format.
|
||||
|
||||
4. **IPTraf**: a console-based network statistics viewer. It displays packet-level, connection-level, interface-level, protocol-level packet/byte counters in real-time. Packet capturing can be controlled by protocol filters, and its operation is full menu-driven.
|
||||
|
||||
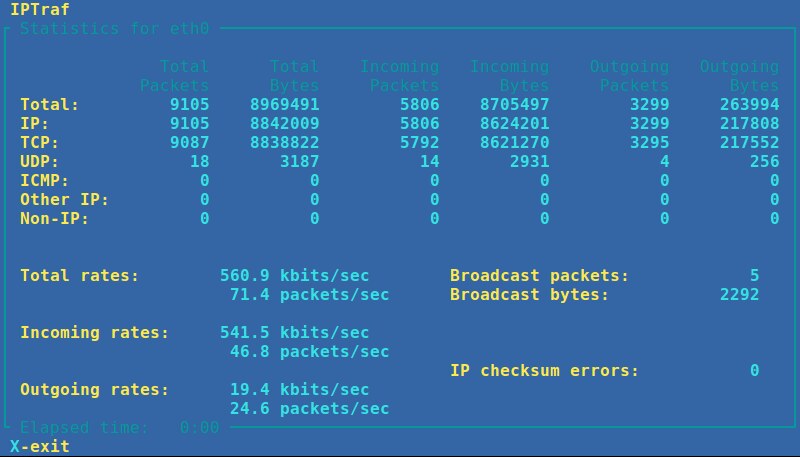
|
||||
|
||||
5. **[mysql-sniffer][3]**: a packet sniffer which captures and decodes packets associated with MySQL queries. It displays the most frequent or all queries in a human-readable format.
|
||||
|
||||
6. **[ngrep][4]**: grep over network packets. It can capture live packets, and match (filtered) packets against regular expressions or hexadecimal expressions. It is useful for detecting and storing any anomalous traffic, or for sniffing particular patterns of information from live traffic.
|
||||
|
||||
7. **[p0f][5]**: a passive fingerprinting tool which, based on packet sniffing, reliably identifies operating systems, NAT or proxy settings, network link types and various other properites associated with an active TCP connection.
|
||||
|
||||
8. **pktstat**: a command-line tool which analyzes live packets to display connection-level bandwidth usages as well as descriptive information of protocols involved (e.g., HTTP GET/POST, FTP, X11).
|
||||
|
||||
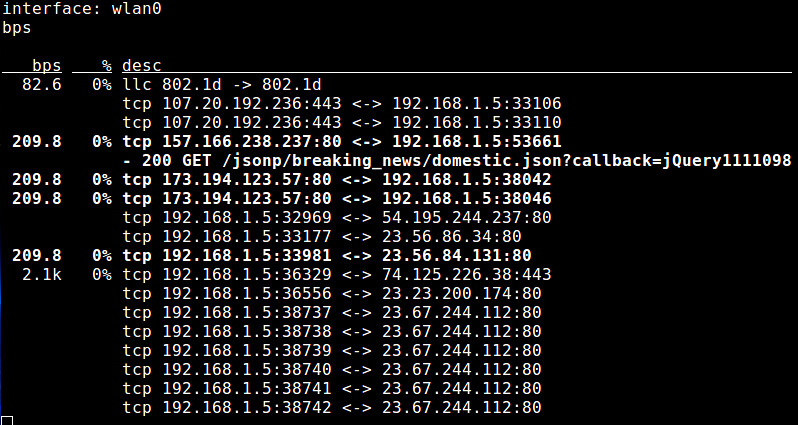
|
||||
|
||||
9. **Snort**: an intrusion detection and prevention tool which can detect/prevent a variety of backdoor, botnets, phishing, spyware attacks from live traffic based on rule-driven protocol analysis and content matching.
|
||||
|
||||
10. **tcpdump**: a command-line packet sniffer which is capable of capturing nework packets on the wire based on filter expressions, dissect the packets, and dump the packet content for packet-level analysis. It is widely used for any kinds of networking related troubleshooting, network application debugging, or [security][6] monitoring.
|
||||
|
||||
11. **tshark**: a command-line packet sniffing tool that comes with Wireshark GUI program. It can capture and decode live packets on the wire, and show decoded packet content in a human-friendly fashion.
|
||||
|
||||
### Flow-/Process-/Interface-Level Monitoring ###
|
||||
|
||||
In this category, network monitoring is done by classifying network traffic into flows, associated processes or interfaces, and collecting per-flow, per-process or per-interface statistics. Source of information can be libpcap packet capture library or sysfs kernel virtual filesystem. Monitoring overhead of these tools is low, but packet-level inspection capabilities are missing.
|
||||
|
||||
12. **bmon**: a console-based bandwidth monitoring tool which shows various per-interface information, including not-only aggregate/average RX/TX statistics, but also a historical view of bandwidth usage.
|
||||
|
||||
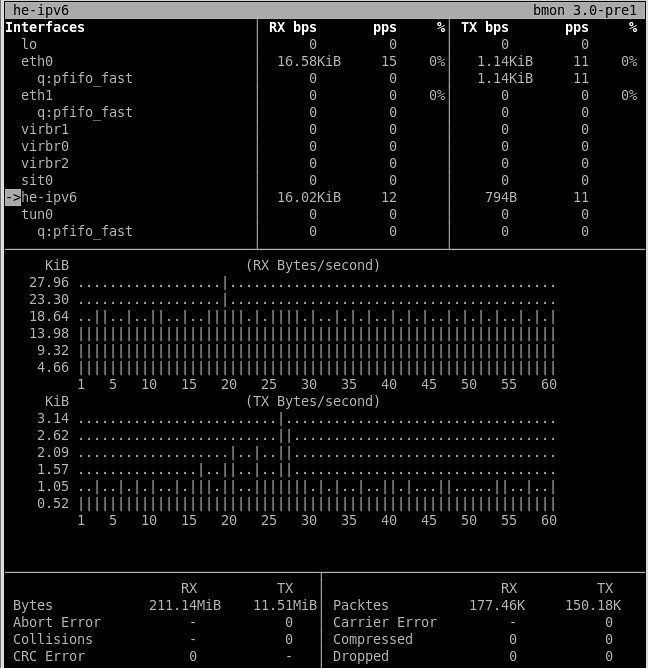
|
||||
|
||||
13. **[iftop][7]**: a bandwidth usage monitoring tool that can shows bandwidth usage for individual network connections in real time. It comes with ncurses-based interface to visualize bandwidth usage of all connections in a sorted order. It is useful for monitoring which connections are consuming the most bandwidth.
|
||||
|
||||
14. **nethogs**: a process monitoring tool which offers a real-time view of upload/download bandwidth usage of individual processes or programs in an ncurses-based interface. This is useful for detecting bandwidth hogging processes.
|
||||
|
||||
15. **netstat**: a command-line tool that shows various statistics and properties of the networking stack, such as open TCP/UDP connections, network interface RX/TX statistics, routing tables, protocol/socket statistics. It is useful when you diagnose performance and resource usage related problems of the networking stack.
|
||||
|
||||
16. **[speedometer][8]**: a console-based traffic monitor which visualizes the historical trend of an interface's RX/TX bandwidth usage with ncurses-drawn bar charts.
|
||||
|
||||
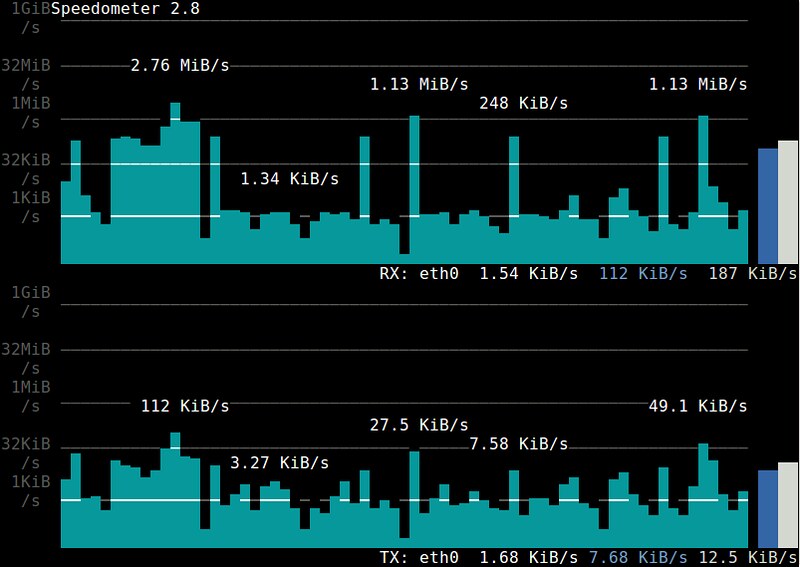
|
||||
|
||||
17. **[sysdig][9]**: a comprehensive system-level debugging tool with a unified interface for investigating different Linux subsystems. Its network monitoring module is capable of monitoring, either online or offline, various per-process/per-host networking statistics such as bandwidth usage, number of connections/requests, etc.
|
||||
|
||||
18. **tcptrack**: a TCP connection monitoring tool which displays information of active TCP connections, including source/destination IP addresses/ports, TCP state, and bandwidth usage.
|
||||
|
||||
|
||||
|
||||
19. **vnStat**: a command-line traffic monitor which maintains a historical view of RX/TX bandwidh usage (e.g., current, daily, monthly) on a per-interface basis. Running as a background daemon, it collects and stores interface statistics on bandwidth rate and total bytes transferred.
|
||||
|
||||
### Active Network Monitoring ###
|
||||
|
||||
Unlike passive monitoring tools presented so far, tools in this category perform network monitoring by actively "injecting" probes into the network and collecting corresponding responses. Monitoring targets include routing path, available bandwidth, loss rates, delay, jitter, system settings or vulnerabilities, and so on.
|
||||
|
||||
20. **[dnsyo][10]**: a DNS monitoring tool which can conduct DNS lookup from open resolvers scattered across more than 1,500 different networks. It is useful when you check DNS propagation or troubleshoot DNS configuration.
|
||||
|
||||
21. **[iperf][11]**: a TCP/UDP bandwidth measurement utility which can measure maximum available bandwidth between two end points. It measures available bandwidth by having two hosts pump out TCP/UDP probe traffic between them either unidirectionally or bi-directionally. It is useful when you test the network capacity, or tune the parameters of network stack. A variant called [netperf][12] exists with more features and better statistics.
|
||||
|
||||
22. **[netcat][13]/socat**: versatile network debugging tools capable of reading from, writing to, or listen on TCP/UDP sockets. They are often used alongside with other programs or scripts for backend network transfer or port listening.
|
||||
|
||||
23. **nmap**: a command-line port scanning and network discovery utility. It relies on a number of TCP/UDP based scanning techniques to detect open ports, live hosts, or existing operating systems on the local network. It is useful when you audit local hosts for vulnerabilities or build a host map for maintenance purpose. [zmap][14] is an alernative scanning tool with Internet-wide scanning capability.
|
||||
|
||||
24. ping: a network testing tool which works by exchaning ICMP echo and reply packets with a remote host. It is useful when you measure round-trip-time (RTT) delay and loss rate of a routing path, as well as test the status or firewall rules of a remote system. Variations of ping exist with fancier interface (e.g., [noping][15]), multi-protocol support (e.g., [hping][16]) or parallel probing capability (e.g., [fping][17]).
|
||||
|
||||
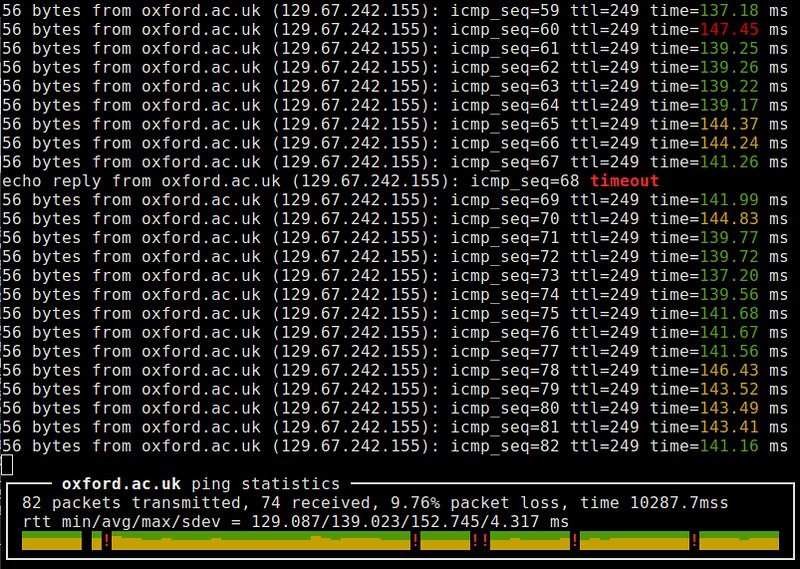
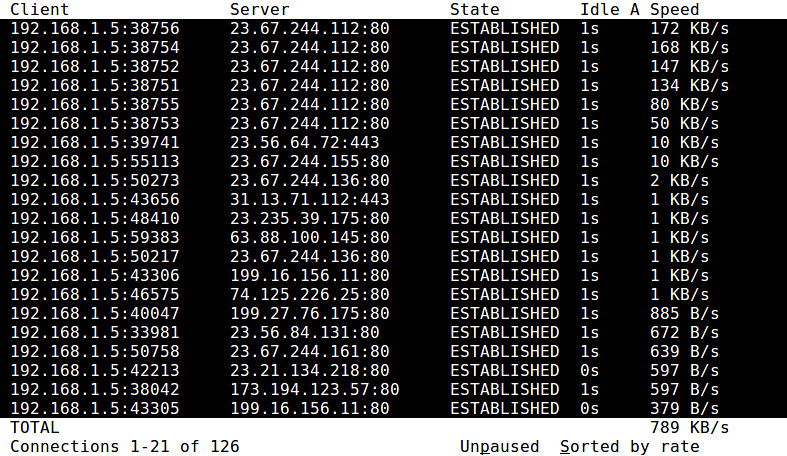
|
||||
|
||||
25. **[sprobe][18]**: a command-line tool that heuristically infers the bottleneck bandwidth between a local host and any arbitrary remote IP address. It uses TCP three-way handshake tricks to estimate the bottleneck bandwidth. It is useful when troubleshooting wide-area network performance and routing related problems.
|
||||
|
||||
26. **traceroute**: a network discovery tool which reveals a layer-3 routing/forwarding path from a local host to a remote host. It works by sending TTL-limited probe packets and collecting ICMP responses from intermediate routers. It is useful when troubleshooting slow network connections or routing related problems. Variations of traceroute exist with better RTT statistics (e.g., [mtr][19]).
|
||||
|
||||
### Application Log Parsing ###
|
||||
|
||||
In this category, network monitoring is targeted at a specific server application (e.g., web server or database server). Network traffic generated or consumed by a server application is monitored by analyzing its log file. Unlike network-level monitors presented in earlier categories, tools in this category can analyze and monitor network traffic from application-level.
|
||||
|
||||
27. **[GoAccess][20]**: a console-based interactive viewer for Apache and Nginx web server traffic. Based on access log analysis, it presents a real-time statistics of a number of metrics including daily visits, top requests, client operating systems, client locations, client browsers, in a scrollable view.
|
||||
|
||||
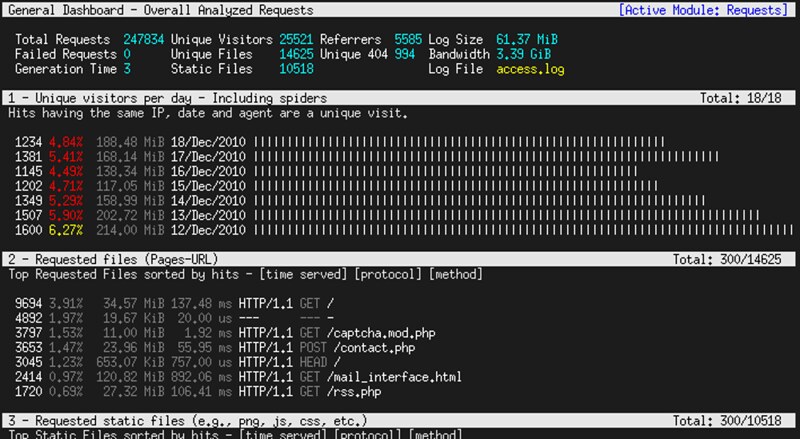
|
||||
|
||||
28. **[mtop][21]**: a command-line MySQL/MariaDB server moniter which visualizes the most expensive queries and current database server load. It is useful when you optimize MySQL server performance and tune server configurations.
|
||||
|
||||
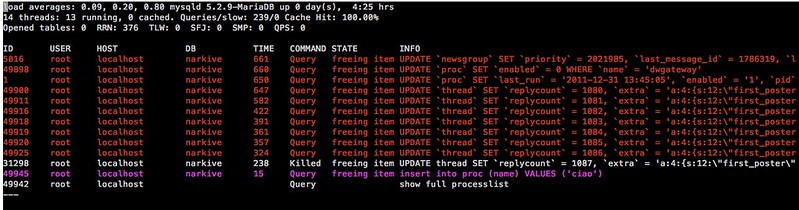
|
||||
|
||||
29. **[ngxtop][22]**: a traffic monitoring tool for Nginx and Apache web server, which visualizes web server traffic in a top-like interface. It works by parsing a web server's access log file and collecting traffic statistics for individual destinations or requests.
|
||||
|
||||
### Conclusion ###
|
||||
|
||||
In this article, I presented a wide variety of command-line network monitoring tools, ranging from the lowest packet-level monitors to the highest application-level network monitors. Knowing which tool does what is one thing, and choosing which tool to use is another, as any single tool cannot be a universal solution for your every need. A good system admin should be able to decide which tool is right for the circumstance at hand. Hopefully the list helps with that.
|
||||
|
||||
You are always welcome to improve the list with your comment!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/useful-command-line-network-monitors-linux.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/nanni
|
||||
[1]:http://www.monkey.org/~dugsong/dsniff/
|
||||
[2]:http://xmodulo.com/monitor-http-traffic-command-line-linux.html
|
||||
[3]:https://github.com/zorkian/mysql-sniffer
|
||||
[4]:http://ngrep.sourceforge.net/
|
||||
[5]:http://lcamtuf.coredump.cx/p0f3/
|
||||
[6]:http://xmodulo.com/recommend/firewallbook
|
||||
[7]:http://xmodulo.com/how-to-install-iftop-on-linux.html
|
||||
[8]:https://excess.org/speedometer/
|
||||
[9]:http://xmodulo.com/monitor-troubleshoot-linux-server-sysdig.html
|
||||
[10]:http://xmodulo.com/check-dns-propagation-linux.html
|
||||
[11]:https://iperf.fr/
|
||||
[12]:http://www.netperf.org/netperf/
|
||||
[13]:http://xmodulo.com/useful-netcat-examples-linux.html
|
||||
[14]:https://zmap.io/
|
||||
[15]:http://noping.cc/
|
||||
[16]:http://www.hping.org/
|
||||
[17]:http://fping.org/
|
||||
[18]:http://sprobe.cs.washington.edu/
|
||||
[19]:http://xmodulo.com/better-alternatives-basic-command-line-utilities.html#mtr_link
|
||||
[20]:http://goaccess.io/
|
||||
[21]:http://mtop.sourceforge.net/
|
||||
[22]:http://xmodulo.com/monitor-nginx-web-server-command-line-real-time.html
|
||||
@ -1,3 +1,5 @@
|
||||
[Trnslating by DongShuaike]
|
||||
|
||||
iptraf: A TCP/UDP Network Monitoring Utility
|
||||
================================================================================
|
||||
[iptraf][1] is an ncurses-based IP LAN monitor that generates various network statistics including TCP info, UDP counts, ICMP and OSPF information, Ethernet load info, node stats, IP checksum errors, and others.
|
||||
|
||||
@ -1,3 +1,5 @@
|
||||
translating by createyuan
|
||||
|
||||
How to Test Your Internet Speed Bidirectionally from Command Line Using ‘Speedtest-CLI’ Tool
|
||||
================================================================================
|
||||
We always need to check the speed of the Internet connection at home and office. What we do for this? Go to websites like Speedtest.net and begin test. It loads JavaScript in the web browser and then select best server based upon ping and output the result. It also uses a Flash player to produce graphical results.
|
||||
@ -129,4 +131,4 @@ via: http://www.tecmint.com/check-internet-speed-from-command-line-in-linux/
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.tecmint.com/author/avishek/
|
||||
[1]:http://www.tecmint.com/speedtest-mini-server-to-test-bandwidth-speed/
|
||||
[1]:http://www.tecmint.com/speedtest-mini-server-to-test-bandwidth-speed/
|
||||
|
||||
@ -1,3 +1,5 @@
|
||||
FSSlc translating
|
||||
|
||||
Conky – The Ultimate X Based System Monitor Application
|
||||
================================================================================
|
||||
Conky is a system monitor application written in ‘C’ Programming Language and released under GNU General Public License and BSD License. It is available for Linux and BSD Operating System. The application is X (GUI) based that was originally forked from [Torsmo][1].
|
||||
@ -144,4 +146,4 @@ via: http://www.tecmint.com/install-conky-in-ubuntu-debian-fedora/
|
||||
[3]:http://ubuntuforums.org/showthread.php?t=281865
|
||||
[4]:http://conky.sourceforge.net/screenshots.html
|
||||
[5]:http://ubuntuforums.org/showthread.php?t=281865/
|
||||
[6]:http://conky.sourceforge.net/
|
||||
[6]:http://conky.sourceforge.net/
|
||||
|
||||
@ -1,96 +0,0 @@
|
||||
Translating by ZTinoZ
|
||||
Install Inkscape - Open Source Vector Graphic Editor
|
||||
================================================================================
|
||||
Inkscape is an open source vector graphic editing tool which uses Scalable Vector Graphics (SVG) and that makes it different from its competitors like Xara X, Corel Draw and Adobe Illustrator etc. SVG is a widely-deployed royalty-free graphics format developed and maintained by the W3C SVG Working Group. It is a cross platform tool which runs fine on Linux, Windows and Mac OS.
|
||||
|
||||
Inkscape development was started in 2003, Inkscape's bug tracking system was hosted on Sourceforge initially but it was migrated to Launchpad afterwards. Its current latest stable version is 0.91. It is under continuous development and bug fixes and we will be reviewing its prominent features and installing process in the article.
|
||||
|
||||
### Salient Features ###
|
||||
|
||||
Lets review the outstanding features of this application categorically.
|
||||
|
||||
#### Creating Objects ####
|
||||
|
||||
- Drawing different colored sized and shaped freehand lines through pencil tool, straight lines and curves through Bezier (pen) tool, applying freehand calligraphic strokes through calligraphic tool etc
|
||||
- Creating, selecting, editing and formatting text through text tool. Manipulating text in plain text boxes, on paths or in shapes
|
||||
- Helps draw various shapes like rectangles, ellipses, circles, arcs, polygons, stars, spirals etc and then resize, rotate and modify (turn sharp edges round) them
|
||||
- Create and embed bitmaps with simple commands
|
||||
|
||||
#### Object manipulation ####
|
||||
|
||||
- Skewing, moving, scaling, rotating objects through interactive manipulations and pacifying the numeric values
|
||||
- Performing raising and lowering Z-order operations
|
||||
- Grouping and ungrouping objects to create a virtual scope for editing or manipulation
|
||||
- Layers form a hierarchal tree and can be locked or rearranged for various manipulations
|
||||
- Distribution and alignment commands
|
||||
|
||||
#### Fill and Stroke ####
|
||||
|
||||
- Copy/paste styles
|
||||
- Pick Color tool
|
||||
- Selecting colors on a continuous plot based on vectors of RGB, HSL, CMS, CMYK and color wheel
|
||||
- Gradient editor helps creating and managing multi-stop gradients
|
||||
- Define an image or selection and use it to pattern fill
|
||||
- Dashed Strokes can be used with few predefined dashed patterns
|
||||
- Beginning, middle and ending marks through path markers
|
||||
|
||||
#### Operation on Paths ####
|
||||
|
||||
- Node Editing: Moving nodes and Bezier handles, node alignment and distribution etc
|
||||
- Boolean operations like yes or no conditions
|
||||
- Simplifying paths with variable levels or thresholds
|
||||
- Path insetting and outsetting along with link and offset objects
|
||||
- Converting bitmap images into paths (color and monochrome paths) through path tracing
|
||||
|
||||
#### Text manipulation ####
|
||||
|
||||
- All installed outlined fonts can be used even for right to left align objects
|
||||
- Formatting text, letter spacing, line spacing or kerning
|
||||
- Text on path and on shapes where both text and path or shapes can be edited or modified
|
||||
|
||||
#### Rendering ####
|
||||
|
||||
- Inkscape fully support anti-aliased display which is a technique that reduces or eliminates aliasing by shading the pixels along the border.
|
||||
- Support for alpha transparency display and PNG export
|
||||
|
||||
### Install Inkscape on Ubuntu 14.04 and 14.10 ###
|
||||
|
||||
In order to install Inkscape on Ubuntu, we will need to first [add its stable Personal Package Archive][1] (PPA) to Advanced Package Tool (APT) repository. Launch the terminal and run following command to add its PPA.
|
||||
|
||||
sudo add-apt-repository ppa:inkscape.dev/stable
|
||||
|
||||

|
||||
|
||||
Once the PPA has been added to the APT repository we need to update it using following command.
|
||||
|
||||
sudo apt-get update
|
||||
|
||||

|
||||
|
||||
After updating the repository we are ready to install inkscape which is accomplished using the following command.
|
||||
|
||||
sudo apt-get install inkscape
|
||||
|
||||

|
||||
|
||||
Congratulation, Inkscape has been installed now and all set for image editing and making full use of feature rich application.
|
||||
|
||||

|
||||
|
||||
### Conclusion ###
|
||||
|
||||
Inkscape is a feature rich graphic editing tool which empowers its user with state of the art capabilities. It is an open source application which is freely available for installation and customizations and supports wide range of file formats including but not limited to JPEG, PNG, GIF and PDF. Visit its [official website][2] for more news and updates regarding this application.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/tools/install-inkscape-open-source-vector-graphic-editor/
|
||||
|
||||
作者:[Aun Raza][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://linoxide.com/author/arunrz/
|
||||
[1]:https://launchpad.net/~inkscape.dev/+archive/ubuntu/stable
|
||||
[2]:https://inkscape.org/en/
|
||||
@ -1,61 +0,0 @@
|
||||
How To Install Visual Studio Code On Ubuntu
|
||||
================================================================================
|
||||

|
||||
|
||||
Microsoft has done the unexpected by [releasing Visual Studio Code][1] for all major desktop platforms that includes Linux as well. If you are a web developer who happens to be using Ubuntu, you can **easily install Visual Studio Code in Ubuntu**.
|
||||
|
||||
We will be using [Ubuntu Make][2] for installing Visual Studio Code in Ubuntu. Ubuntu Make, previously known as Ubuntu Developer Tools Center, is a command line utility that allows you to easily install various development tools, languages and IDEs. You can easily [install Android Studio][3] and other popular IDEs such as Eclipse with Ubuntu Make. In this tutorial we shall see **how to install Visual Studio Code in Ubuntu with Ubuntu Make**.
|
||||
|
||||
### Install Microsoft Visual Studio Code in Ubuntu ###
|
||||
|
||||
Before installing Visual Studio Code, we need to install Ubuntu Make first. Though Ubuntu Make is available in Ubuntu 15.04 repository, **you’ll need Ubuntu Make 0.7 for Visual Studio**. You can get the latest Ubuntu Make by using the official PPA. The PPA is available for Ubuntu 14.04, 14.10 and 15.04. Also, it **is only available for 64 bit platform**.
|
||||
|
||||
Open a terminal and use the following commands to install Ubuntu Make via official PPA:
|
||||
|
||||
sudo add-apt-repository ppa:ubuntu-desktop/ubuntu-make
|
||||
sudo apt-get update
|
||||
sudo apt-get install ubuntu-make
|
||||
|
||||
Once you have installed Ubuntu Make, use the command below to install Visual Studio Code:
|
||||
|
||||
umake web visual-studio-code
|
||||
|
||||
You’ll be asked to provide a path where it will be installed:
|
||||
|
||||

|
||||
|
||||
After throwing a whole lot of terms and conditions, it will ask for your permission to install Visual Studio Code. Press ‘a’ at this screen:
|
||||
|
||||

|
||||
|
||||
Once you do that it will start downloading and installing it. Once it is installed, you can see that Visual Studio Code icon has already been locked to the Unity Launcher. Just click on it to run it. This is how Visual Studio Code looks like in Ubuntu 15.04 Unity:
|
||||
|
||||

|
||||
|
||||
### Uninstall Visual Studio Code from Ubuntu ###
|
||||
|
||||
To uninstall Visual Studio Code, we’ll use the same command line tool umake. Just use the following command in terminal:
|
||||
|
||||
umake web visual-studio-code --remove
|
||||
|
||||
If you do not want to use Ubuntu Make, you can install Visual Studio Code by downloading the files from Microsoft:
|
||||
|
||||
- [Download Visual Studio Code for Linux][4]
|
||||
|
||||
See, how easy it is to install Visual Studio Code in Ubuntu, all thanks to Ubuntu Make. I hope this tutorial helped you. Feel free to drop a comment if you have any questions or suggestions.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://itsfoss.com/install-visual-studio-code-ubuntu/
|
||||
|
||||
作者:[Abhishek][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://itsfoss.com/author/abhishek/
|
||||
[1]:http://www.geekwire.com/2015/microsofts-visual-studio-expands-to-mac-and-linux-with-new-code-development-tool/
|
||||
[2]:https://wiki.ubuntu.com/ubuntu-make
|
||||
[3]:http://itsfoss.com/install-android-studio-ubuntu-linux/
|
||||
[4]:https://code.visualstudio.com/Download
|
||||
@ -1,170 +0,0 @@
|
||||
Translating by wwy-hust
|
||||
|
||||
|
||||
How to Securely Store Passwords and Api Keys Using Vault
|
||||
================================================================================
|
||||
Vault is a tool that is used to access secret information securely, it may be password, API key, certificate or anything else. Vault provides a unified interface to secret information through strong access control mechanism and extensive logging of events.
|
||||
|
||||
Granting access to critical information is quite a difficult problem when we have multiple roles and individuals across different roles requiring various critical information like, login details to databases with different privileges, API keys for external services, credentials for service oriented architecture communication etc. Situation gets even worse when access to secret information is managed across different platforms with custom settings, so rolling, secure storage and managing the audit logs is almost impossible. But Vault provides a solution to such a complex situation.
|
||||
|
||||
### Salient Features ###
|
||||
|
||||
Data Encryption: Vault can encrypt and decrypt data with no requirement to store it. Developers can now store encrypted data without developing their own encryption techniques and it allows security teams to define security parameters.
|
||||
|
||||
**Secure Secret Storage**: Vault encrypts the secret information (API keys, passwords or certificates) before storing it on to the persistent (secondary) storage. So even if somebody gets access to the stored information by chance, it will be of no use until it is decrypted.
|
||||
|
||||
**Dynamic Secrets**: On demand secrets are generated for systems like AWS and SQL databases. If an application needs to access S3 bucket, for instance, it requests AWS keypair from Vault, which grants the required secret information along with a lease time. The secret information won’t work once the lease time is expired.
|
||||
|
||||
**Leasing and Renewal**: Vault grants secrets with a lease limit, it revokes the secrets as soon as lease expires which can further be renewed through APIs if required.
|
||||
|
||||
**Revocation**: Upon expiring the lease period Vault can revoke a single secret or a tree of secrets.
|
||||
|
||||
### Installing Vault ###
|
||||
|
||||
There are two ways to use Vault.
|
||||
|
||||
**1. Pre-compiled Vault Binary** can be downloaded for all Linux flavors from the following source, once done, unzip it and place it on a system PATH where other binaries are kept so that it can be accessed/invoked easily.
|
||||
|
||||
- [Download Precompiled Vault Binary (32-bit)][1]
|
||||
- [Download Precompiled Vault Binary (64-bit)][2]
|
||||
- [Download Precompiled Vault Binary (ARM)][3]
|
||||
|
||||
Download the desired precompiled Vault binary.
|
||||
|
||||

|
||||
|
||||
Unzip the downloaded binary.
|
||||
|
||||

|
||||
|
||||
unzipCongratulations! Vault is ready to be used.
|
||||
|
||||

|
||||
|
||||
**2. Compiling from source** is another way of installing Vault on the system. GO and GIT are required to be installed and configured properly on the system before we start the installation process.
|
||||
|
||||
To **install GO on Redhat systems** use the following command.
|
||||
|
||||
sudo yum install go
|
||||
|
||||
To **install GO on Debian systems** use the following commands.
|
||||
|
||||
sudo apt-get install golang
|
||||
|
||||
OR
|
||||
|
||||
sudo add-apt-repository ppa:gophers/go
|
||||
|
||||
sudo apt-get update
|
||||
|
||||
sudo apt-get install golang-stable
|
||||
|
||||
To **install GIT on Redhat systems** use the following command.
|
||||
|
||||
sudo yum install git
|
||||
|
||||
To **install GIT on Debian systems** use the following commands.
|
||||
|
||||
sudo apt-get install git
|
||||
|
||||
Once both GO and GIT are installed we start the Vault installation process by compiling from the source.
|
||||
|
||||
> Clone following Vault repository into the GOPATH
|
||||
|
||||
https://github.com/hashicorp/vault
|
||||
|
||||
> Verify if the following clone file exist, if it doesn’t then Vault wasn’t cloned to the proper path.
|
||||
|
||||
$GOPATH/src/github.com/hashicorp/vault/main.go
|
||||
|
||||
> Run following command to build Vault in the current system and put binary in the bin directory.
|
||||
|
||||
make dev
|
||||
|
||||

|
||||
|
||||
### An introductory tutorial of Vault ###
|
||||
|
||||
We have compiled Vault’s official interactive tutorial along with its output on SSH.
|
||||
|
||||
**Overview**
|
||||
|
||||
This tutorial will cover the following steps:
|
||||
|
||||
- Initializing and unsealing your Vault
|
||||
- Authorizing your requests to Vault
|
||||
- Reading and writing secrets
|
||||
- Sealing your Vault
|
||||
|
||||
**Initialize your Vault**
|
||||
|
||||
To get started, we need to initialize an instance of Vault for you to work with.
|
||||
While initializing, you can configure the seal behavior of Vault.
|
||||
Initialize Vault now, with 1 unseal key for simplicity, using the command:
|
||||
|
||||
vault init -key-shares=1 -key-threshold=1
|
||||
|
||||
You'll notice Vault prints out several keys here. Don't clear your terminal, as these are needed in the next few steps.
|
||||
|
||||

|
||||
|
||||
**Unsealing your Vault**
|
||||
|
||||
When a Vault server is started, it starts in a sealed state. In this state, Vault is configured to know where and how to access the physical storage, but doesn't know how to decrypt any of it.
|
||||
Vault encrypts data with an encryption key. This key is encrypted with the "master key", which isn't stored. Decrypting the master key requires a threshold of shards. In this example, we use one shard to decrypt this master key.
|
||||
|
||||
vault unseal <key 1>
|
||||
|
||||

|
||||
|
||||
**Authorize your requests**
|
||||
|
||||
Before performing any operation with Vault, the connecting client must be authenticated. Authentication is the process of verifying a person or machine is who they say they are and assigning an identity to them. This identity is then used when making requests with Vault.
|
||||
For simplicity, we'll use the root token we generated on init in Step 2. This output should be available in the scrollback.
|
||||
Authorize with a client token:
|
||||
|
||||
vault auth <root token>
|
||||
|
||||

|
||||
|
||||
**Read and write secrets**
|
||||
|
||||
Now that Vault has been set-up, we can start reading and writing secrets with the default mounted secret backend. Secrets written to Vault are encrypted and then written to the backend storage. The backend storage mechanism never sees the unencrypted value and doesn't have the means necessary to decrypt it without Vault.
|
||||
|
||||
vault write secret/hello value=world
|
||||
|
||||
Of course, you can then read this data too:
|
||||
|
||||
vault read secret/hello
|
||||
|
||||

|
||||
|
||||
**Seal your Vault**
|
||||
|
||||
There is also an API to seal the Vault. This will throw away the encryption key and require another unseal process to restore it. Sealing only requires a single operator with root privileges. This is typically part of a rare "break glass procedure".
|
||||
This way, if there is a detected intrusion, the Vault data can be locked quickly to try to minimize damages. It can't be accessed again without access to the master key shards.
|
||||
|
||||
vault seal
|
||||
|
||||

|
||||
|
||||
That is the end of introductory tutorial.
|
||||
|
||||
### Summary ###
|
||||
|
||||
Vault is a very useful application mainly because of providing a reliable and secure way of storing critical information. Furthermore it encrypts the critical information before storing, maintains audit logs, grants secret information for limited lease time and revokes it once lease is expired. It is platform independent and freely available to download and install. To discover more about Vault, readers are encouraged to visit the official website.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/how-tos/secure-secret-store-vault/
|
||||
|
||||
作者:[Aun Raza][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://linoxide.com/author/arunrz/
|
||||
[1]:https://dl.bintray.com/mitchellh/vault/vault_0.1.0_linux_386.zip
|
||||
[2]:https://dl.bintray.com/mitchellh/vault/vault_0.1.0_linux_amd64.zip
|
||||
[3]:https://dl.bintray.com/mitchellh/vault/vault_0.1.0_linux_arm.zip
|
||||
@ -1,112 +0,0 @@
|
||||
How to Setup OpenERP (Odoo) on CentOS 7.x
|
||||
================================================================================
|
||||
Hi everyone, this tutorial is all about how we can setup Odoo (formerly known as OpenERP) on our CentOS 7 Server. Are you thinking to get an awesome ERP (Enterprise Resource Planning) app for your business ?. Then, OpenERP is the best app you are searching as it is a Free and Open Source Software which provides an outstanding features for your business or company.
|
||||
|
||||
[OpenERP][1] is a free and open source traditional OpenERP (Enterprise Resource Planning) app which includes Open Source CRM, Website Builder, eCommerce, Project Management, Billing & Accounting, Point of Sale, Human Resources, Marketing, Manufacturing, Purchase Management and many more modules included for a better way to boost the productivity and sales. Odoo Apps can be used as stand-alone applications, but they also integrate seamlessly so you get a full-featured Open Source ERP when you install several Apps.
|
||||
|
||||
So, here are some quick and easy steps to get your copy of OpenERP installed on your CentOS machine.
|
||||
|
||||
### 1. Installing PostgreSQL ###
|
||||
|
||||
First of all, we'll want to update the packages installed in our CentOS 7 machine to ensure that the latest packages, patches and security are up to date. To update our sytem, we should run the following command in a shell or terminal.
|
||||
|
||||
# yum clean all
|
||||
# yum update
|
||||
|
||||
Now, we'll want to install PostgreSQL Database System as OpenERP uses PostgreSQL for its database system. To install it, we'll need to run the following command.
|
||||
|
||||
# yum install postgresql postgresql-server postgresql-libs
|
||||
|
||||

|
||||
|
||||
After it is installed, we'll need to initialize the database with the following command
|
||||
|
||||
# postgresql-setup initdb
|
||||
|
||||

|
||||
|
||||
We'll then set PostgreSQL to start on every boot and start the PostgreSQL Database server.
|
||||
|
||||
# systemctl enable postgresql
|
||||
# systemctl start postgresql
|
||||
|
||||
As we haven't set a password for the user "postgresql", we'll want to set it now.
|
||||
|
||||
# su - postgres
|
||||
$ psql
|
||||
postgres=# \password postgres
|
||||
postgres=# \q
|
||||
# exit
|
||||
|
||||

|
||||
|
||||
### 2. Configuring Odoo Repository ###
|
||||
|
||||
After our Database Server has been installed correctly, we'll want add EPEL (Extra Packages for Enterprise Linux) to our CentOS server. Odoo (or OpenERP) depends on Python run-time and many other packages that are not included in default standard repository. As such, we'll want to add the Extra Packages for Enterprise Linux (or EPEL) repository support so that Odoo can get the required dependencies. To install, we'll need to run the following command.
|
||||
|
||||
# yum install epel-release
|
||||
|
||||

|
||||
|
||||
Now, after we install EPEL, we'll now add repository of Odoo (OpenERP) using yum-config-manager.
|
||||
|
||||
# yum install yum-utils
|
||||
|
||||
# yum-config-manager --add-repo=https://nightly.odoo.com/8.0/nightly/rpm/odoo.repo
|
||||
|
||||

|
||||
|
||||
### 3. Installing Odoo 8 (OpenERP) ###
|
||||
|
||||
Finally after adding repository of Odoo 8 (OpenERP) in our CentOS 7 machine. We'll can install Odoo 8 (OpenERP) using the following command.
|
||||
|
||||
# yum install -y odoo
|
||||
|
||||
The above command will install odoo along with the necessary dependency packages.
|
||||
|
||||

|
||||
|
||||
Now, we'll enable automatic startup of Odoo in every boot and will start our Odoo service using the command below.
|
||||
|
||||
# systemctl enable odoo
|
||||
# systemctl start odoo
|
||||
|
||||

|
||||
|
||||
### 4. Allowing Firewall ###
|
||||
|
||||
As Odoo uses port 8069, we'll need to allow firewall for remote access. We can allow firewall to port 8069 by running the following command.
|
||||
|
||||
# firewall-cmd --zone=public --add-port=8069/tcp --permanent
|
||||
# firewall-cmd --reload
|
||||
|
||||

|
||||
|
||||
**Note: By default, only connections from localhost are allowed. If we want to allow remote access to PostgreSQL databases, we'll need to add the line shown in the below image to pg_hba.conf configuration file:**
|
||||
|
||||
# nano /var/lib/pgsql/data/pg_hba.conf
|
||||
|
||||

|
||||
|
||||
### 5. Web Interface ###
|
||||
|
||||
Finally, as we have successfully installed our latest Odoo 8 (OpenERP) on our CentOS 7 Server, we can now access our Odoo by browsing to http://ip-address:8069 http://my-site.com:8069 using our favorite web browser. Then, first thing we'll gonna do is we'll create a new database and create a new password for it. Note, the master password is admin by default. Then, we can login to our panel with that username and password.
|
||||
|
||||

|
||||
|
||||
### Conclusion ###
|
||||
|
||||
Odoo 8 (formerly OpenERP) is the best ERP app available in the world of Open Source. We did an excellent work on installing it because OpenERP is a set of many modules which are essential for a complete ERP app for business and company. So, if you have any questions, suggestions, feedback please write them in the comment box below. Thank you ! Enjoy OpenERP (Odoo 8) :-)
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/linux-how-to/setup-openerp-odoo-centos-7/
|
||||
|
||||
作者:[Arun Pyasi][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://linoxide.com/author/arunp/
|
||||
[1]:https://www.odoo.com/
|
||||
@ -1,96 +0,0 @@
|
||||
Linux FAQs with Answers--How to configure a Linux bridge with Network Manager on Ubuntu
|
||||
================================================================================
|
||||
> **Question**: I need to set up a Linux bridge on my Ubuntu box to share a NIC with several other virtual machines or containers created on the box. I am currently using Network Manager on my Ubuntu, so preferrably I would like to configure a bridge using Network Manager. How can I do that?
|
||||
|
||||
Network bridge is a hardware equipment used to interconnect two or more Layer-2 network segments, so that network devices on different segments can talk to each other. A similar bridging concept is needed within a Linux host, when you want to interconnect multiple VMs or Ethernet interfaces within a host. That is one use case of a software Linux bridge.
|
||||
|
||||
There are several different ways to configure a Linux bridge. For example, in a headless server environment, you can use [brctl][1] to manually configure a bridge. In desktop environment, bridge support is available in Network Manager. Let's examine how to configure a bridge with Network Manager.
|
||||
|
||||
### Requirement ###
|
||||
|
||||
To avoid [any issue][2], it is recommended that you have Network Manager 0.9.9 and higher, which is the case for Ubuntu 15.04 and later.
|
||||
|
||||
$ apt-cache show network-manager | grep Version
|
||||
|
||||
----------
|
||||
|
||||
Version: 0.9.10.0-4ubuntu15.1
|
||||
Version: 0.9.10.0-4ubuntu15
|
||||
|
||||
### Create a Bridge ###
|
||||
|
||||
The easiest way to create a bridge with Network Manager is via nm-connection-editor. This GUI tool allows you to configure a bridge in easy-to-follow steps.
|
||||
|
||||
To start, invoke nm-connection-editor.
|
||||
|
||||
$ nm-connection-editor
|
||||
|
||||
The editor window will show you a list of currently configured network connections. Click on "Add" button in the top right to create a bridge.
|
||||
|
||||
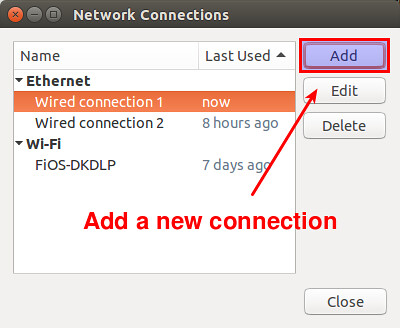
|
||||
|
||||
Next, choose "Bridge" as a connection type.
|
||||
|
||||
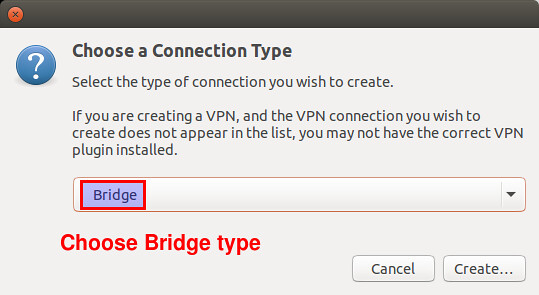
|
||||
|
||||
Now it's time to configure a bridge, including its name and bridged connection(s). With no other bridges created, the default bridge interface will be named bridge0.
|
||||
|
||||
Recall that the goal of creating a bridge is to share your Ethernet interface via the bridge. So you need to add the Ethernet interface to the bridge. This is achieved by adding a new "bridged connection" in the GUI. Click on "Add" button.
|
||||
|
||||
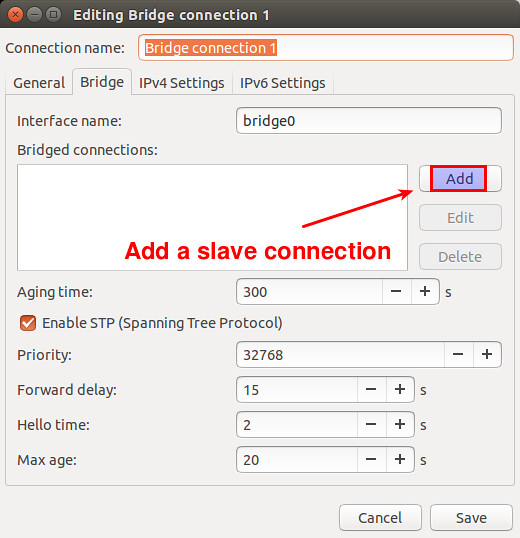
|
||||
|
||||
Choose "Ethernet" as a connection type.
|
||||
|
||||
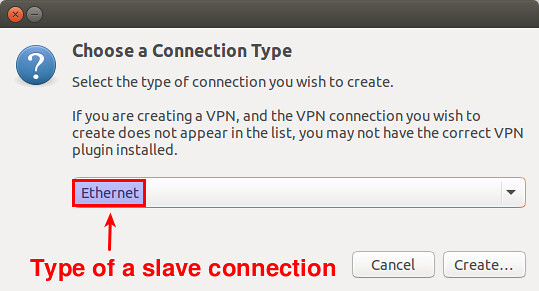
|
||||
|
||||
In "Device MAC address" field, choose the interface that you want to enslave into the bridge. In this example, assume that this interface is eth0.
|
||||
|
||||

|
||||
|
||||
Click on "General" tab, and enable both checkboxes that say "Automatically connect to this network when it is available" and "All users may connect to this network".
|
||||
|
||||
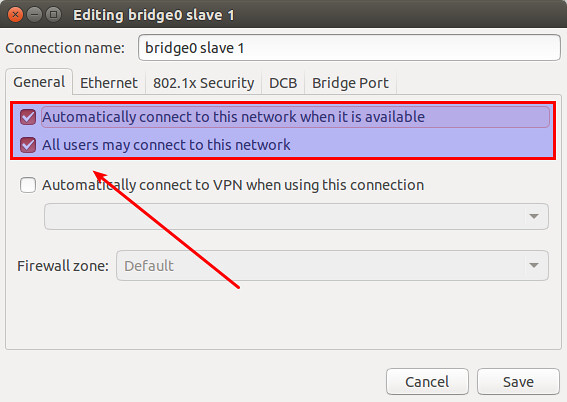
|
||||
|
||||
Save the change.
|
||||
|
||||
Now you will see a new slave connection created in the bridge.
|
||||
|
||||
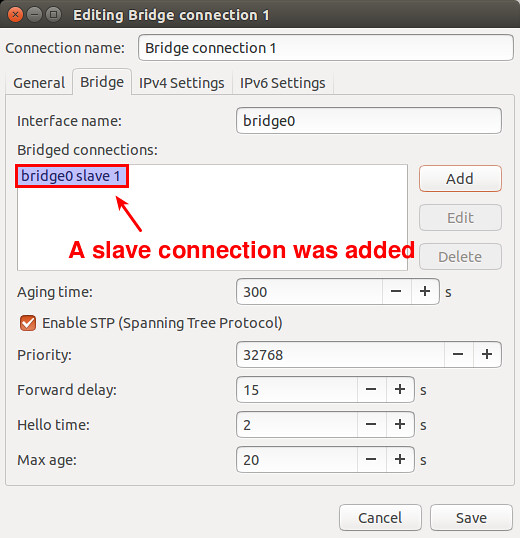
|
||||
|
||||
Click on "General" tab of the bridge, and make sure that top-most two checkboxes are enabled.
|
||||
|
||||
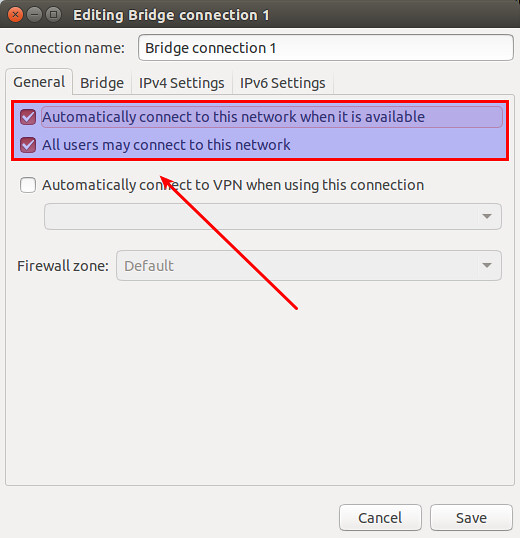
|
||||
|
||||
Go to "IPv4 Settings" tab, and configure either DHCP or static IP address for the bridge. Note that you should use the same IPv4 settings as the enslaved Ethernet interface eth0. In this example, we assume that eth0 is configured via DHCP. Thus choose "Automatic (DHCP)" here. If eth0 is assigned a static IP address, you should assign the same IP address to the bridge.
|
||||
|
||||
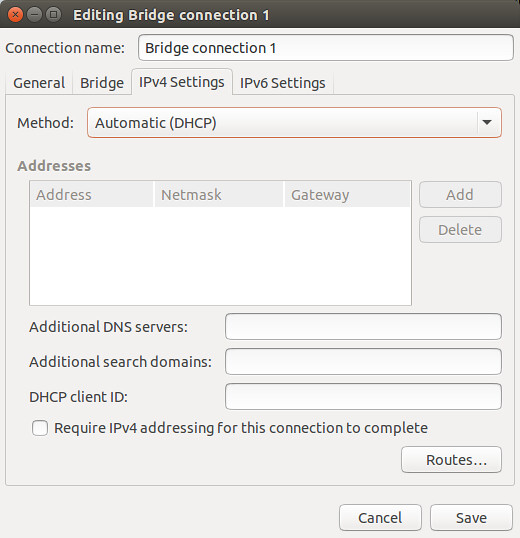
|
||||
|
||||
Finally, save the bridge settings.
|
||||
|
||||
Now you will see an additional bridge connection created in "Network Connections" window. You no longer need a previously-configured wired connection for the enslaved interface eth0. So go ahead and delete the original wired connection.
|
||||
|
||||
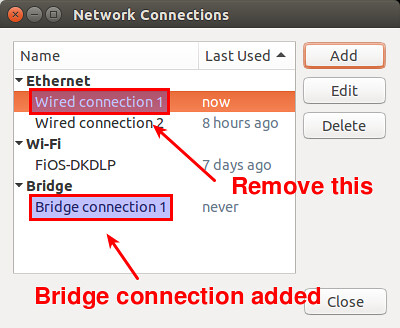
|
||||
|
||||
At this point, the bridge connection will automatically be activated. You will momentarily lose a connection, since the IP address assigned to eth0 is taken over by the bridge. Once an IP address is assigned to the bridge, you will be connected back to your Ethernet interface via the bridge. You can confirm that by checking "Network" settings.
|
||||
|
||||
|
||||
|
||||
Also, check the list of available interfaces. As mentioned, the bridge interface must have taken over whatever IP address was possessed by your Ethernet interface.
|
||||
|
||||
|
||||
|
||||
That's it, and now the bridge is ready to use!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://ask.xmodulo.com/configure-linux-bridge-network-manager-ubuntu.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://ask.xmodulo.com/author/nanni
|
||||
[1]:http://xmodulo.com/how-to-configure-linux-bridge-interface.html
|
||||
[2]:https://bugs.launchpad.net/ubuntu/+source/network-manager/+bug/1273201
|
||||
@ -1,78 +0,0 @@
|
||||
Vic020
|
||||
|
||||
Linux FAQs with Answers--How to install autossh on Linux
|
||||
================================================================================
|
||||
> **Question**: I would like to install autossh on [insert your Linux distro]. How can I do that?
|
||||
|
||||
[autossh][1] is an open-source tool that allows you to monitor an SSH session and restart it automatically should it gets disconnected or stops forwarding traffic. autossh assumes that [passwordless SSH login][2] for a destination host is already setup, so that it can restart a broken SSH session without user's involvement.
|
||||
|
||||
autossh comes in handy when you want to set up [reverse SSH tunnels][3] or [mount remote folders over SSH][4]. Essentially in any situation where persistent SSH sessions are required, autossh can be useful.
|
||||
|
||||
|
||||
|
||||
Here is how to install autossh on various Linux distributions.
|
||||
|
||||
### Install Autossh on Debian or Ubuntu ###
|
||||
|
||||
autossh is available in base repositories of Debian based systems, so installation is easy.
|
||||
|
||||
$ sudo apt-get install autossh
|
||||
|
||||
### Install Autossh on Fedora ###
|
||||
|
||||
Fedora repositories also carry autossh package. So simply use yum command.
|
||||
|
||||
$ sudo yum install autossh
|
||||
|
||||
### Install Autossh on CentOS or RHEL ###
|
||||
|
||||
For CentOS/RHEL 6 or earlier, enable [Repoforge repository][5] first, and then use yum command.
|
||||
|
||||
$ sudo yum install autossh
|
||||
|
||||
For CentOS/RHEL 7, autossh is no longer available in Repoforge repository. You will need to build it from the source (explained below).
|
||||
|
||||
### Install Autossh on Arch Linux ###
|
||||
|
||||
$ sudo pacman -S autossh
|
||||
|
||||
### Compile Autossh from the Source on Debian or Ubuntu ###
|
||||
|
||||
If you would like to try the latest version of autossh, you can build it from the source as follows.
|
||||
|
||||
$ sudo apt-get install gcc make
|
||||
$ wget http://www.harding.motd.ca/autossh/autossh-1.4e.tgz
|
||||
$ tar -xf autossh-1.4e.tgz
|
||||
$ cd autossh-1.4e
|
||||
$ ./configure
|
||||
$ make
|
||||
$ sudo make install
|
||||
|
||||
### Compile Autossh from the Source on CentOS, Fedora or RHEL ###
|
||||
|
||||
On CentOS/RHEL 7, autossh is not available as a pre-built package. So you'll need to compile it from the source as follows.
|
||||
|
||||
$ sudo yum install wget gcc make
|
||||
$ wget http://www.harding.motd.ca/autossh/autossh-1.4e.tgz
|
||||
$ tar -xf autossh-1.4e.tgz
|
||||
$ cd autossh-1.4e
|
||||
$ ./configure
|
||||
$ make
|
||||
$ sudo make install
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://ask.xmodulo.com/install-autossh-linux.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://ask.xmodulo.com/author/nanni
|
||||
[1]:http://www.harding.motd.ca/autossh/
|
||||
[2]:http://xmodulo.com/how-to-enable-ssh-login-without.html
|
||||
[3]:http://xmodulo.com/access-linux-server-behind-nat-reverse-ssh-tunnel.html
|
||||
[4]:http://xmodulo.com/how-to-mount-remote-directory-over-ssh-on-linux.html
|
||||
[5]:http://xmodulo.com/how-to-set-up-rpmforge-repoforge-repository-on-centos.html
|
||||
@ -0,0 +1,110 @@
|
||||
什么是好的命令行HTTP客户端?
|
||||
==============================================================================
|
||||
整体大于各部分之和,这是引自希腊哲学家和科学家的亚里士多德的名言。这句话特别切中Linux。在我看来,Linux最强大的地方之一就是它的协作性。Linux的实用性并不仅仅源自大量的开源程序(命令行)。相反,其协作性来自于这些程序的综合利用,有时是结合更大型的应用。
|
||||
|
||||
Unix哲学引发了一场“软件工具”的运动,关注开发简洁,基础,干净,模块化和扩展性好的代码,并可以运用于其他的项目。这种哲学为许多的Linux项目留下了一个重要的元素。
|
||||
|
||||
好的开源开发者写程序为了确保该程序尽可能运行正确,同时能与其他程序很好地协作。目标就是使用者拥有一堆方便的工具,每一个力求干不止一件事。许多程序能独立工作得很好。
|
||||
|
||||
这篇文章讨论3个开源命令行HTTP客户端。这些客户端可以让你使用命令行从互联网上下载文件。但同时,他们也可以用于许多有意思的地方,如测试,调式和与HTTP服务器或网络应用互动。对于HTTP架构师和API设计人员来说,使用命令行操作HTTP是一个值得花时间学习的技能。如果你需要来回使用API,HTTPie和cURL,这没什么价值。
|
||||
|
||||
-------------
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
HTTPie(发音 aych-tee-tee-pie)是一款开源命令行HTTP客户端。它是一个命令行界面,类cURL的工具。
|
||||
|
||||
该软件的目标是使得与网络服务器的交互尽可能的人性化。其提供了一个简单的http命令,允许使用简单且自然的语句发送任意的HTTP请求,并显示不同颜色的输出。HTTPie可以用于测试,调式和与HTTP服务器的一般交互。
|
||||
|
||||
#### 功能包括:####
|
||||
|
||||
- 可表达,直观的语句
|
||||
- 格式化,颜色区分的终端输出
|
||||
- 内建JSON支持
|
||||
- 表单和文件上传
|
||||
- HTTPS,代理和认证
|
||||
- 任意数据请求
|
||||
- 自定义标题 (此处header不确定是否特别意义)
|
||||
- 持久会话
|
||||
- 类Wget下载
|
||||
- Python 2.6,2.7和3.x支持
|
||||
- Linux,Mac OS X 和 Windows支持
|
||||
- 支持插件
|
||||
- 帮助文档
|
||||
- 测试覆盖 (直译有点别扭)
|
||||
|
||||
- 网站:[httpie.org][1]
|
||||
- 开发者: Jakub Roztočil
|
||||
- 证书: 开源
|
||||
- 版本号: 0.9.2
|
||||
|
||||
----------
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
cURL是一个开源命令行工具,用于使用URL语句传输数据,支持DICT, FILE, FTP, FTPS, GOPHER, HTTP, HTTPS,IMAP, IMAPS, LDAP, LDAPS, POP3, POP3S, RTMP, RTSP, SCP, SFTP, SMTP, SMTPS, TELNET和TFTP。
|
||||
|
||||
cURL支持SSL证书,HTTP POST,HTTP PUT,FTP上传,HTTP基于表单上传,代理,缓存,用户名+密码认证(Basic, Digest, NTLM, Negotiate, kerberos...),文件传输恢复, 代理通道和一些其他实用窍门的总线负载。(这里的名词我不明白其专业意思)
|
||||
|
||||
#### 功能包括:####
|
||||
|
||||
- 配置文件支持
|
||||
- 一个单独命令行多个URL
|
||||
- “globbing”漫游支持: [0-13],{one, two, three}
|
||||
- 一个命令上传多个文件
|
||||
- 自定义最大传输速度
|
||||
- 重定向标准错误输出
|
||||
- Metalink支持
|
||||
|
||||
- 网站: [curl.haxx.se][2]
|
||||
- 开发者: Daniel Stenberg
|
||||
- 证书: MIT/X derivate license
|
||||
- 版本号: 7.42.0
|
||||
|
||||
----------
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
Wget是一个从网络服务器获取信息的开源软件。其名字源于World Wide Web 和 get。Wget支持HTTP,HTTPS和FTP协议,同时也通过HTTP代理获取信息。
|
||||
|
||||
Wget可以根据HTML页面的链接,创建远程网络站点的本地版本,是完全重造源站点的目录结构。这种方式被冠名“recursive downloading。”
|
||||
|
||||
Wget已经设计可以加快低速或者不稳定的网络连接。
|
||||
|
||||
功能包括:
|
||||
|
||||
- 使用REST和RANGE恢复中断的下载
|
||||
- 使用文件名
|
||||
- 多语言的基于NLS的消息文件
|
||||
- 选择性地转换下载文档里地绝对链接为相对链接,使得下载文档可以本地相互链接
|
||||
- 在大多数类UNIX操作系统和微软Windows上运行
|
||||
- 支持HTTP代理
|
||||
- 支持HTTP数据缓存
|
||||
- 支持持续地HTTP连接
|
||||
- 无人照管/后台操作
|
||||
- 当远程对比时,使用本地文件时间戳来决定是否需要重新下载文档 (mirroring没想出合适的表达)
|
||||
|
||||
- 站点: [www.gnu.org/software/wget/][3]
|
||||
- 开发者: Hrvoje Niksic, Gordon Matzigkeit, Junio Hamano, Dan Harkless, and many others
|
||||
- 证书: GNU GPL v3
|
||||
- 版本号: 1.16.3
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linuxlinks.com/article/20150425174537249/HTTPclients.html
|
||||
|
||||
作者:Frazer Kline
|
||||
译者:[wi-cuckoo](https://github.com/wi-cuckoo)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://httpie.org/
|
||||
[2]:http://curl.haxx.se/
|
||||
[3]:https://www.gnu.org/software/wget/
|
||||
@ -0,0 +1,135 @@
|
||||
什么是Linux上实用的命令行式网络监视工具
|
||||
===============================================================================
|
||||
对任何规模的业务来说,网络监视器都是一个重要的功能。网络监视的目标可能千差万别。比如,监视活动的目标可以是保证长期的网络供应、安全保护、对性能进行排查、网络使用统计等。由于它的目标不同,网络监视器使用很多不同的方式来完成任务。比如使用包层面的嗅探,使用流层面的统计数据,向网络中注入探测的流量,分析服务器日志等。
|
||||
|
||||
尽管有许多专用的网络监视系统可以365天24小时监视,但您依旧可以在特定的情况下使用命令行式的网络监视器,某些命令行式的网络监视器在某方面很有用。如果您是系统管理员,那您就应该有亲身使用一些知名的命令行式网络监视器的经历。这里有一份**Linux上流行且实用的网络监视器**列表。
|
||||
|
||||
### 包层面的嗅探器 ###
|
||||
|
||||
在这个类别下,监视工具在链路上捕捉独立的包,分析它们的内容,展示解码后的内容或者包层面的统计数据。这些工具在最底层对网络进行监视、管理,同样的也能进行最细粒度的监视,其代价是部分网络I/O和分析的过程。
|
||||
|
||||
1. **dhcpdump**:一个命令行式的DHCP流量嗅探工具,捕捉DHCP的请求/回复流量,并以用户友好的方式显示解码的DHCP协议消息。这是一款排查DHCP相关故障的实用工具。
|
||||
|
||||
2. **[dsniff][1]**:一个基于命令行的嗅探工具集合,拥有欺骗和劫持功能,被设计用于网络审查和渗透测试。它可以嗅探多种信息,比如密码、NSF流量、email消息、网络地址等。
|
||||
|
||||
3. **[httpry][2]**:一个HTTP报文嗅探器,用于捕获、解码HTTP请求和回复报文,并以用户友好的方式显示这些信息。
|
||||
|
||||
4. **IPTraf**:基于命令行的网络统计数据查看器。它实时显示包层面、连接层面、接口层面、协议层面的报文/字节数。抓包过程由协议过滤器控制,且操作过程全部是菜单驱动的。
|
||||
|
||||

|
||||
|
||||
5. **[mysql-sniffer][3]**:一个用于抓取、解码MySQL请求相关的数据包的工具。它以可读的方式显示最频繁或全部的请求。
|
||||
|
||||
6. **[ngrep][4]**:在网络报文中执行grep。它能实时抓取报文,并用正则表达式或十六进制表达式的方式匹配报文。它是一个可以对异常流量进行检测、存储或者对实时流中特定模式报文进行抓取的实用工具。
|
||||
|
||||
7. **[p0f][5]**:一个被动的基于包嗅探的指纹采集工具,可以可靠地识别操作系统、NAT或者代理设置、网络链路类型以及许多其他与活动的TCP连接相关的属性。
|
||||
|
||||
8. **pktstat**:一个命令行式的工具,通过实时分析报文,显示连接带宽使用情况以及相关的协议(例如,HTTP GET/POST、FTP、X11)等描述信息。
|
||||
|
||||

|
||||
|
||||
13. **[iftop][7]**:一个带宽使用监测工具,可以实时显示某个网络连接的带宽使用情况。它对所有带宽使用情况排序并通过ncurses的接口来进行可视化。他可以方便的监视哪个连接消耗了最多的带宽。
|
||||
|
||||
14. **nethogs**:一个进程监视工具,提供进程相关的实时的上行/下行带宽使用信息,并基于ncurses显示。它对检测占用大量带宽的进程很有用。
|
||||
|
||||
15. **netstat**:一个显示许多TCP/UDP的网络堆栈统计信息的工具。诸如网络接口发送/接收、路由表、协议/套接字的统计信息和属性。当您诊断与网络堆栈相关的性能、资源使用时它很有用。
|
||||
|
||||
16. **[speedometer][8]**:一个可视化某个接口发送/接收的带宽使用的历史趋势,并且基于ncurses的条状图进行显示的工具。
|
||||
|
||||

|
||||
|
||||
17. **[sysdig][9]**:一个对Linux子系统拥有统一调试接口的系统级综合性debug工具。它的网络监视模块可以监视在线或离线、许多进程/主机相关的网络统计数据,例如带宽、连接/请求数等。
|
||||
|
||||
18. **tcptrack**:一个TCP连接监视工具,可以显示活动的TCP连接,包括源/目的IP地址/端口、TCP状态、带宽使用等。
|
||||
|
||||

|
||||
|
||||
19. **vnStat**:一个维护了基于接口的历史接收/发送带宽视图(例如,当前、每日、每月)的流量监视器。作为一个后台守护进程,它收集并存储统计数据,包括接口带宽使用率和传输字节总数。
|
||||
|
||||
### 主动网络监视器 ###
|
||||
|
||||
不同于前面提到的被动的监听工具,这个类别的工具们在监听时会主动的“注入”探测内容到网络中,并且会收集相应的反应。监听目标包括路由路径、可供使用的带宽、丢包率、延时、抖动、系统设置或者缺陷等。
|
||||
|
||||
20. **[dnsyo][10]**:一个DNS检测工具,能够管理多达1500个不同网络的开放解析器集群的DNS查询。它在您检查DNS传播或排查DNS设置的时候很有用。
|
||||
|
||||
21. **[iperf][11]**:一个TCP/UDP带宽测量工具,能够测量两个结点间最大可用带宽。它通过在两个主机间单向或双向的输出TCP/UDP探测流量来测量可用的带宽。它在监测网络容量、调谐网络协议栈参数时很有用。一个叫做[netperf][12]的变种拥有更多的功能及更好的统计数据。
|
||||
|
||||
22. **[netcat][13]/socat**:通用的网络debug工具,可以对TCP/UDP套接字进行读、写或监听。它通常和其他的程序或脚本结合起来在后端对网络传输或端口进行监听。
|
||||
|
||||
23. **nmap**:一个命令行端口扫描和网络发现工具。它依赖于若干基于TCP/UDP的扫描技术来查找开放的端口、活动的主机或者在本地网络存在的操作系统。它在你审查本地主机漏洞或者建立主机映射时很有用。[zmap][14]是一个类似的替代品,是一个用于互联网范围的扫描工具。
|
||||
|
||||
24. ping:一个常用的网络测试工具。通过对ICMP的echo和reply报文进行增强来实现其功能。它在测量路由的RTT、丢包率以及检测远端系统防火墙规则时很有用。ping的变种有更漂亮的界面(例如,[noping][15])、多协议支持(例如,[hping][16])或者并行探测能力(例如,[fping][17])。
|
||||
|
||||

|
||||
|
||||
25. **[sprobe][18]**:一个启发式推断本地主机和任意远端IP地址的网络带宽瓶颈的命令行工具。它使用TCP三次握手机制来评估带宽的瓶颈。它在检测大范围网络性能和路由相关的问题时很有用。
|
||||
|
||||
26. **traceroute**:一个能发现从本地到远端主机的第三层路由/转发路径的网络发现工具。它发送有限TTL的探测报文,收集中间路由的ICMP反馈信息。它在排查低速网络连接或者路由相关的问题时很有用。traceroute的变种有更好的RTT统计功能(例如,[mtr][19])。
|
||||
|
||||
### 应用日志解析器 ###
|
||||
|
||||
在这个类别下,网络监测器把特定的服务器应用程序作为目标(例如,web服务器或者数据库服务器)。由服务器程序产生或消耗的网络流量通过它的日志被分析和监测。不像前面提到的网络层的监视器,这个类别的工具能够在应用层面分析和监控网络流量。
|
||||
|
||||
27. **[GoAccess][20]**:一个针对Apache和Nginx服务器流量的交互式查看器。基于对获取到的日志的分析,它能展示包括日访问量、最多请求、客户端操作系统、客户端位置、客户端浏览器等在内的多个实时的统计信息,并以滚动方式显示。
|
||||
|
||||

|
||||
|
||||
28. **[mtop][21]**:一个面向MySQL/MariaDB服务器的命令行监视器,它可以将当前数据库服务器负载中代价最大的查询以可视化的方式进行显示。它在您优化MySQL服务器性能、调谐服务器参数时很有用。
|
||||
|
||||

|
||||
|
||||
29. **[ngxtop][22]**:一个面向Nginx和Apache服务器的流量监测工具,能够以类似top指令的方式可视化的显示Web服务器的流量。它解析web服务器的查询日志文件并收集某个目的地或请求的流量统计信息。
|
||||
|
||||
### Conclusion ###
|
||||
|
||||
在这篇文章中,我展示了许多的命令行式监测工具,从最底层的包层面的监视器到最高层应用程序层面的网络监视器。知道那个工具的作用是一回事,选择哪个工具使用又是另外一回事。单一的一个工具不能作为您每天使用的通用的解决方案。一个好的系统管理员应该能决定哪个工具更适合当前的环境。希望这个列表对此有所帮助。
|
||||
|
||||
欢迎您通过回复来改进这个列表的内容!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/useful-command-line-network-monitors-linux.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[wwy-hust](https://github.com/wwy-hust)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/nanni
|
||||
[1]:http://www.monkey.org/~dugsong/dsniff/
|
||||
[2]:http://xmodulo.com/monitor-http-traffic-command-line-linux.html
|
||||
[3]:https://github.com/zorkian/mysql-sniffer
|
||||
[4]:http://ngrep.sourceforge.net/
|
||||
[5]:http://lcamtuf.coredump.cx/p0f3/
|
||||
[6]:http://xmodulo.com/recommend/firewallbook
|
||||
[7]:http://xmodulo.com/how-to-install-iftop-on-linux.html
|
||||
[8]:https://excess.org/speedometer/
|
||||
[9]:http://xmodulo.com/monitor-troubleshoot-linux-server-sysdig.html
|
||||
[10]:http://xmodulo.com/check-dns-propagation-linux.html
|
||||
[11]:https://iperf.fr/
|
||||
[12]:http://www.netperf.org/netperf/
|
||||
[13]:http://xmodulo.com/useful-netcat-examples-linux.html
|
||||
[14]:https://zmap.io/
|
||||
[15]:http://noping.cc/
|
||||
[16]:http://www.hping.org/
|
||||
[17]:http://fping.org/
|
||||
[18]:http://sprobe.cs.washington.edu/
|
||||
[19]:http://xmodulo.com/better-alternatives-basic-command-line-utilities.html#mtr_link
|
||||
[20]:http://goaccess.io/
|
||||
[21]:http://mtop.sourceforge.net/
|
||||
[22]:http://xmodulo.com/monitor-nginx-web-server-command-line-real-time.html
|
||||
@ -0,0 +1,95 @@
|
||||
安装Inkscape - 开源适量图形编辑器
|
||||
================================================================================
|
||||
Inkscape是一款开源矢量图形编辑工具,它使用可缩放矢量图形(SVG)图形格式并不同于它的竞争对手如Xara X、Corel Draw和Adobe Illustrator等等。SVG是一个广泛部署、免版税使用的图形格式,由W3C SVG工作组开发和维护。这是一个跨平台工具,完美运行于Linux、Windows和Mac OS上。
|
||||
|
||||
Inkscape始于2003年,起初它的bug跟踪系统托管于Sourceforge上但是 后来迁移到了Launchpad上。当前它最新的一个稳定版本是0.91,它不断地在发展和修改中。我们将在本文里了解一下它的突出特点和安装过程。
|
||||
|
||||
### 显著特性 ###
|
||||
|
||||
让我们直接来了解这款应用程序的显著特性。
|
||||
|
||||
#### 创建对象 ####
|
||||
|
||||
- 用铅笔工具来画出不同颜色、大小和形状的手绘线,用贝塞尔曲线(笔式)工具来画出直线和曲线,通过书法工具来应用到手写的书法笔画上等等
|
||||
- 用文本工具来创建、选择、编辑和格式化文本。在纯文本框、在路径上或在形状里操作文本
|
||||
- 有效绘制各种形状,像矩形、椭圆形、圆形、弧线、多边形、星形和螺旋形等等并调整其大小、旋转并修改(圆角化)它们
|
||||
- 用简单地命令创建并嵌入位图
|
||||
|
||||
#### 对象处理 ####
|
||||
|
||||
- 通过交互式操作和调整数值来扭曲、移动、测量、旋转目标
|
||||
- 执行力提升并减少了Z-order操作。
|
||||
- 对象群组化或取消群组化可以去创建一个虚拟层阶用来编辑或处理
|
||||
- 图层采用层次结构树的结构并且能锁定或以各式各样的处理方式来重新布置
|
||||
- 分布与对齐指令
|
||||
|
||||
#### 填充与边框 ####
|
||||
|
||||
- 复制/粘贴风格
|
||||
- 取色工具
|
||||
- 用RGB, HSL, CMS, CMYK和色盘这四种不同的方式选色
|
||||
- 渐层编辑器能创建和管理多停点渐层
|
||||
- 定义一个图像或其它选择用来进行花纹填充
|
||||
- 用一些预定义泼洒花纹可对边框进行花纹泼洒
|
||||
- 通过路径标示器来开始、对折和结束标示
|
||||
|
||||
#### 路径上的操作 ####
|
||||
|
||||
- 节点编辑:移动节点和贝塞尔曲线掌控,节点的对齐和分布等等
|
||||
- 布尔运算(是或否)
|
||||
- 运用可变的路径起迄点可简化路径
|
||||
- 路径插入和增设连同动态和链接偏移对象
|
||||
- 通过路径追踪把位图图像转换成路径(彩色或单色路径)
|
||||
|
||||
#### 文本处理 ####
|
||||
|
||||
- 所有安装好的外框字体都能用甚至可以从右至左对齐对象
|
||||
- 格式化文本、调整字母间距、行间距或列间距
|
||||
- 路径上的文本和形状上的文本和路径或形状都可以被编辑和修改
|
||||
|
||||
#### 渲染 ####
|
||||
|
||||
- Inkscape完全支持抗锯齿显示,这是一种通过柔化边界上的像素从而减少或消除凹凸锯齿的技术。
|
||||
- 支持alpha透明显示和PNG格式图片的导出
|
||||
|
||||
### 在Ubuntu 14.04和14.10上安装Inkscape ###
|
||||
|
||||
为了在Ubuntu上安装Inkscape,我们首先需要 [添加它的稳定版Personal Package Archive][1] (PPA) 至Advanced Package Tool (APT) 库中。打开终端并运行一下命令来添加它的PPA:
|
||||
|
||||
sudo add-apt-repository ppa:inkscape.dev/stable
|
||||
|
||||

|
||||
|
||||
PPA添加到APT库中后,我们要用以下命令进行更新:
|
||||
|
||||
sudo apt-get update
|
||||
|
||||

|
||||
|
||||
更新好库之后,我们准备用以下命令来完成安装:
|
||||
|
||||
sudo apt-get install inkscape
|
||||
|
||||

|
||||
|
||||
恭喜,现在Inkscape已经被安装好了,我们可以充分利用它的丰富功能特点来编辑制作图像了。
|
||||
|
||||

|
||||
|
||||
### 结论 ###
|
||||
|
||||
Inkscape是一款特点鲜明的图形编辑工具,它给予用户充分发挥自己艺术力的权利。它还是一款自由安装和自定义开源应用并且支持大范围文件类型包括JPEG, PNG, GIF和PDF且不仅这些。访问它的 [官方网站][2] 来获取更多新闻和应用更新。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/tools/install-inkscape-open-source-vector-graphic-editor/
|
||||
|
||||
作者:[Aun Raza][a]
|
||||
译者:[ZTinoZ](https://github.com/ZTinoZ)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://linoxide.com/author/arunrz/
|
||||
[1]:https://launchpad.net/~inkscape.dev/+archive/ubuntu/stable
|
||||
[2]:https://inkscape.org/en/
|
||||
@ -0,0 +1,112 @@
|
||||
如何在CentOS 7.x中安装OpenERP(Odoo)
|
||||
================================================================================
|
||||
各位好,这篇教程关于的是如何在CentOS 7中安装Odoo(就是我们所知的OpenERP)。你是不是在考虑为你的业务安装一个不错的ERP(企业资源规划)软件?那么OpenERP就是你寻找的最好的程序,因为它是一款为你的商务提供杰出特性的自由开源软件。
|
||||
|
||||
[OpenERP][1]是一款自由开源的传统的OpenERP(企业资源规划),它包含了开源CRM、网站构建、电子商务、项目管理、计费账务、销售点、人力资源、市场、生产、采购管理以及其他模块用于提高效率及销售。Odoo可以作为独立程序,但是它可以无缝集成因此你可以在安装数个程序后得到一个全功能的开源ERP。
|
||||
|
||||
因此,下面是在你的CentOS上安装OpenERP的步骤。
|
||||
|
||||
### 1. 安装 PostgreSQL ###
|
||||
|
||||
首先,首先我们需要更新CentOS 7的软件包来确保是最新的包,补丁和安全更新。要更新我们的系统,我们要在shell下运行下面的命令。
|
||||
|
||||
# yum clean all
|
||||
# yum update
|
||||
|
||||
现在我们要安装PostgreSQL,因为OpenERP使用PostgreSQL作为他的数据库。要安装它,我们需要运行下面的命令。
|
||||
|
||||
# yum install postgresql postgresql-server postgresql-libs
|
||||
|
||||

|
||||
|
||||
、安装完成后,我们需要用下面的命令初始化数据库。
|
||||
|
||||
# postgresql-setup initdb
|
||||
|
||||

|
||||
|
||||
我们接着设置PostgreSQL来使它每次开机启动。
|
||||
|
||||
# systemctl enable postgresql
|
||||
# systemctl start postgresql
|
||||
|
||||
因为我们还没有为用户“postgresql”设置密码,我们现在设置。
|
||||
|
||||
# su - postgres
|
||||
$ psql
|
||||
postgres=# \password postgres
|
||||
postgres=# \q
|
||||
# exit
|
||||
|
||||

|
||||
|
||||
### 2. 设置Odoo仓库 ###
|
||||
|
||||
在初始化数据库初始化完成后,我们要添加EPEL(企业版Linux的额外包)到我们的CentOS中。Odoo(或者OpenERP)依赖于Python运行时以及其他包没有包含在标准仓库中。这样我们要位企业版Linux添加额外的包仓库支持来解决Odoo所需要的依赖。要安装完成,我们需要运行下面的命令。
|
||||
|
||||
# yum install epel-release
|
||||
|
||||

|
||||
|
||||
现在,安装EPEL后,我们现在使用yum-config-manager添加Odoo(OpenERp)的仓库。
|
||||
|
||||
# yum install yum-utils
|
||||
|
||||
# yum-config-manager --add-repo=https://nightly.odoo.com/8.0/nightly/rpm/odoo.repo
|
||||
|
||||

|
||||
|
||||
### 3. 安装Odoo 8 (OpenERP) ###
|
||||
|
||||
在CentOS 7中添加Odoo 8(OpenERP)的仓库后。我们使用下面的命令来安装Odoo 8(OpenERP)。
|
||||
|
||||
# yum install -y odoo
|
||||
|
||||
上面的命令会安装odoo以及必须的依赖的包。
|
||||
|
||||

|
||||
|
||||
现在我们使用下面的命令在每次启动后启动Odoo服务。
|
||||
|
||||
# systemctl enable odoo
|
||||
# systemctl start odoo
|
||||
|
||||

|
||||
|
||||
### 4. 防火墙允许 ###
|
||||
|
||||
因为Odoo使用8069端口,我们需要在防火墙中允许远程访问。我们使用下面的命令来在防火墙中允许8069防火墙。
|
||||
|
||||
# firewall-cmd --zone=public --add-port=8069/tcp --permanent
|
||||
# firewall-cmd --reload
|
||||
|
||||

|
||||
|
||||
**注意:默认上,只有本地的连接才允许。如果我们要允许PostgreSQL的远程访问,我们需要在pg_hba.conf添加下面图片中一行**
|
||||
|
||||
# nano /var/lib/pgsql/data/pg_hba.conf
|
||||
|
||||

|
||||
|
||||
### 5. Web接口 ###
|
||||
|
||||
我们已经在CentOS 7中安装了最新的Odoo 8(OpenERP),我们可以在浏览器中输入http://ip-address:8069来访问Odoo。 接着,我们要做的第一件事就是创建一个新的数据库和新的密码。注意,主密码默认是管理员密码。接着,我们可以在面板中输入用户名和密码。
|
||||
|
||||

|
||||
|
||||
### 总结 ###
|
||||
|
||||
Odoo 8(OpenERP)是世界上最好的开源ERP程序。我们做了一件出色的工作来安装它因为OpenERP是由许多模块组成的针对商务和公司的完整ERP程序。因此,如果你有任何问题、建议、反馈请在下面的评论栏写下。谢谢你!享受OpenERP(Odoo 8)吧 :-)
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/linux-how-to/setup-openerp-odoo-centos-7/
|
||||
|
||||
作者:[Arun Pyasi][a]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://linoxide.com/author/arunp/
|
||||
[1]:https://www.odoo.com/
|
||||
@ -0,0 +1,98 @@
|
||||
nux常见问题解答--如何在Ubuntu上使用网络管理配置一个Linux网桥
|
||||
===============================================================================
|
||||
> **Question**: 我需要在我的Ubuntu主机上建立一个Linux网桥,共享一个NIC给其他一些虚拟主机或者主机上创建的容器。我目前正在Ubunut上使用网络管理,所以最好>能使用网络管理来配置一个网桥。我该怎么做?
|
||||
|
||||
|
||||
网桥是一个硬件装备,用来内部连接两个或多个数据链路层(OSI七层模型中第二层),所以使得不同段上的网络设备可以互相访问。当你想要内连多个虚拟机器或者一个>主机里的以太接口时,就需要在Linux主机里有一个类似桥接的概念。
|
||||
|
||||
有很多的方法来配置一个Linux网桥。举个例子,在一个无中心的服务器环境里,你可以使用[brct][1]手动地配置一个网桥。在桌面环境下,在网络管理里有建立网桥支持
|
||||
。那就让我们测试一下如何用网络管理配置一个网桥吧。
|
||||
|
||||
### 要求 ###
|
||||
|
||||
为了避免[任何问题][2],建议你的网络管理版本为0.9.9或者更高,这主要为了配合Ubuntu15.05或者更新的版本。
|
||||
|
||||
$ apt-cache show network-manager | grep Version
|
||||
|
||||
----------
|
||||
|
||||
Version: 0.9.10.0-4ubuntu15.1
|
||||
Version: 0.9.10.0-4ubuntu15
|
||||
|
||||
### 创建一个网桥 ###
|
||||
|
||||
使用网络管理创建网桥最简单的方式就是通过nm-connection-editor。这款GUI(图形用户界面)的工具允许你傻瓜式地配置一个网桥。
|
||||
|
||||
首先,启动nm-connection-editor。
|
||||
|
||||
$ nm-connection-editor
|
||||
|
||||
该编辑器的窗口会显示给你一个列表,关于目前配置好的网络连接。点击右上角的“Click”按钮,创建一个网桥。
|
||||
|
||||

|
||||
|
||||
接下来,选择“Bridge”作为连接类型。
|
||||
|
||||

|
||||
|
||||
现在,开始配置网桥,包括它的名字和桥接。如果没有其他网桥被创建,那么默认的网桥接口会被命名为bridge0。
|
||||
|
||||
回顾一下,创建网桥的目的是为了通过网桥共享你的以太网卡接口。所以你需要添加以太网卡接口到网桥。在图形界面添加一个新的“bridged connection”可以实现上述目的。点击“Add”按钮。
|
||||
|
||||

|
||||
|
||||
选择“Ethernet”作为连接类型。
|
||||
|
||||

|
||||
|
||||
在“Device MAC address”区域,选择你想要控制的接口到bridge里。本例中,假设接口是eth0。
|
||||
|
||||

|
||||
|
||||
点击“General”标签,并且选中两个复选框,分别是“Automatically connect to this network when it is available”和“All users may connect to this network”。
|
||||
|
||||

|
||||
|
||||
保存更改。
|
||||
|
||||
现在,你会在网桥里看见一个新的从属连接被建立。
|
||||
|
||||

|
||||
|
||||
点击网桥的“General”标签,并且确保最上面的两个复选框被选中了。
|
||||
|
||||

|
||||
|
||||
切换到“IPv4 Setting”标签,为网桥配置DHCP或者是静态IP地址。注意,你应该使用相同的IPv4设定作为从属的以太网卡接口eth0。本例中,我们假设eth0是用过DHCP配置的。因此,此处选择“Automatic(DHCP)”。如果eth0被指定了一个静态IP地址,那么你应该指定相同的IP地址给网桥。
|
||||
|
||||

|
||||
|
||||
最后,保存网桥的设置。
|
||||
|
||||
现在,你会看见一个额外的网桥连接被创建在“Network Connection”窗口里。你不再需要一个预先配置的有线连接,为着从属的eth0接口。所以去删除原来的有线连接吧。
|
||||
|
||||

|
||||
|
||||
这时候,网桥连接会被自动激活。你将会暂时失去一个连接,从指定给eth0的IP地址被网桥接管。一旦IP地址指定给了网桥,你将会连接回你的以太网卡接口,通过网桥。你可以通过“Network”设置确认一下。
|
||||
|
||||

|
||||
|
||||
同时,检查可用的接口。提醒一下,网桥接口必须已经取代了任何通过你的以太网卡接口的IP地址。
|
||||
|
||||

|
||||
|
||||
就这么多了,现在,网桥已经可以用了。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://ask.xmodulo.com/configure-linux-bridge-network-manager-ubuntu.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[wi-cuckoo](https://github.com/wi-cuckoo)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://ask.xmodulo.com/author/nanni
|
||||
[1]:http://xmodulo.com/how-to-configure-linux-bridge-interface.html
|
||||
[2]:https://bugs.launchpad.net/ubuntu/+source/network-manager/+bug/1273201
|
||||
@ -0,0 +1,78 @@
|
||||
Linux有问必答--如何安装autossh
|
||||
================================================================================
|
||||
> **提问**: 我打算在linux上安装autossh,我应该怎么做呢?
|
||||
|
||||
[autossh][1] 是一款开源工具,可以帮助管理SSH会话,自动重连和停止转发流量。autossh会假定目标主机已经设定[无密码SSH登陆][2],以便autossh可以重连断开的SSH会话而不用用户操作。
|
||||
|
||||
只要你建立[反向SSH隧道][3]或者[挂载基于SSH的远程文件夹][4],autossh迟早会派上用场。基本上只要需要维持SSH会话,autossh肯定是有用的。
|
||||
|
||||
|
||||

|
||||
|
||||
下面有许多linux发行版autossh的安装方法。
|
||||
|
||||
### Debian 或 Ubuntu 系统 ###
|
||||
|
||||
autossh已经加入基于Debian系统的基础库,所以可以很方便的安装。
|
||||
|
||||
$ sudo apt-get install autossh
|
||||
|
||||
### Fedora 系统 ###
|
||||
|
||||
Fedora库同样包含autossh包,使用yum安装。
|
||||
|
||||
$ sudo yum install autossh
|
||||
|
||||
### CentOS 或 RHEL 系统 ###
|
||||
|
||||
CentOS/RHEL 6 或早期版本, 需要开启第三库[Repoforge库][5], 然后才能使用yum安装.
|
||||
|
||||
$ sudo yum install autossh
|
||||
|
||||
CentOS/RHEL 7以后,autossh 已经不在Repoforge库中. 你需要从源码编译安装(例子在下面).
|
||||
|
||||
|
||||
### Arch Linux 系统 ###
|
||||
|
||||
$ sudo pacman -S autossh
|
||||
|
||||
### Debian 或 Ubuntu 系统中从源码编译安装###
|
||||
|
||||
如果你想要使用最新版本的autossh,你可以自己编译源码安装
|
||||
|
||||
$ sudo apt-get install gcc make
|
||||
$ wget http://www.harding.motd.ca/autossh/autossh-1.4e.tgz
|
||||
$ tar -xf autossh-1.4e.tgz
|
||||
$ cd autossh-1.4e
|
||||
$ ./configure
|
||||
$ make
|
||||
$ sudo make install
|
||||
|
||||
### CentOS, Fedora 或 RHEL 系统中从源码编译安装###
|
||||
|
||||
在CentOS/RHEL 7以后,autossh不在是预编译包。所以你不得不从源码编译安装。
|
||||
|
||||
$ sudo yum install wget gcc make
|
||||
$ wget http://www.harding.motd.ca/autossh/autossh-1.4e.tgz
|
||||
$ tar -xf autossh-1.4e.tgz
|
||||
$ cd autossh-1.4e
|
||||
$ ./configure
|
||||
$ make
|
||||
$ sudo make install
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://ask.xmodulo.com/install-autossh-linux.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[Vic020/VicYu](http://vicyu.net)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://ask.xmodulo.com/author/nanni
|
||||
[1]:http://www.harding.motd.ca/autossh/
|
||||
[2]:http://xmodulo.com/how-to-enable-ssh-login-without.html
|
||||
[3]:http://xmodulo.com/access-linux-server-behind-nat-reverse-ssh-tunnel.html
|
||||
[4]:http://xmodulo.com/how-to-mount-remote-directory-over-ssh-on-linux.html
|
||||
[5]:http://xmodulo.com/how-to-set-up-rpmforge-repoforge-repository-on-centos.html
|
||||
Loading…
Reference in New Issue
Block a user