mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-02-28 01:01:09 +08:00
20150601-1 选题
This commit is contained in:
parent
2330e21f04
commit
f251d0ee4f
@ -0,0 +1,181 @@
|
||||
How to monitor Linux servers with SNMP and Cacti
|
||||
================================================================================
|
||||
SNMP (or Simple Network Management Protocol) is used to gather data on what is going on within a device, such as load, hard disk states, bandwidth. These data are used by network monitoring tools such as Cacti to generate graphs for monitoring purposes.
|
||||
|
||||
In a typical deployment of Cacti and SNMP, there will be one or more SNMP-enabled devices, and a separate monitoring server where Cacti collects SNMP feeds from those devices. Please keep in mind that all the devices that need to be monitored must be SNMP enabled. In this tutorial, we will be configuring Cacti and SNMP on the same Linux server for demonstration purpose.
|
||||
|
||||
### Configure SNMP on Debian or Ubuntu ###
|
||||
|
||||
To install SNMP agent (snmpd) on a Debian-based system, run the following command.
|
||||
|
||||
root@server:~# apt-get install snmpd
|
||||
|
||||
Then edit its configuration like the following.
|
||||
|
||||
root@server:~# vim /etc/snmp/snmpd.conf
|
||||
|
||||
----------
|
||||
|
||||
# this will make snmpd listen on all interfaces
|
||||
agentAddress udp:161
|
||||
|
||||
# a read only community 'myCommunity' and the source network is defined
|
||||
rocommunity myCommunity 172.17.1.0/24
|
||||
|
||||
sysLocation Earth
|
||||
sysContact email@domain.tld
|
||||
|
||||
After editing the config file, restart snmpd.
|
||||
|
||||
root@server:~# service snmpd restart
|
||||
|
||||
### Configure SNMP on CentOS or RHEL ###
|
||||
|
||||
To install SNMP tools and libraries, run the following command.
|
||||
|
||||
root@server:~# sudo yum install net-snmp
|
||||
|
||||
Then edit an SNMP config file like the following.
|
||||
|
||||
root@server:~# vim /etc/snmp/snmpd.conf
|
||||
|
||||
----------
|
||||
|
||||
# A user 'myUser' is being defined with the community string 'myCommunity' and source network 172.17.1.0/24
|
||||
com2sec myUser 172.17.1.0/24 myCommunity
|
||||
|
||||
# myUser is added into the group 'myGroup' and the permission of the group is defined
|
||||
group myGroup v1 myUser
|
||||
group myGroup v2c myUser
|
||||
view all included .1
|
||||
access myGroup "" any noauth exact all all none
|
||||
|
||||
----------
|
||||
|
||||
root@server:~# service snmpd restart
|
||||
root@server:~# chkconfig snmpd on
|
||||
|
||||
Restart snmpd service, and add it to startup service list.
|
||||
|
||||
### Testing SNMP ###
|
||||
|
||||
SNMP can be tested by running the snmpwalk command. If SNMP has been successfully configured, this command will generate a ton of output.
|
||||
|
||||
root@server:~# snmpwalk -c myCommunity 172.17.1.44 -v1
|
||||
|
||||
----------
|
||||
|
||||
iso.3.6.1.2.1.1.1.0 = STRING: "Linux mrtg 3.5.0-17-generic #28-Ubuntu SMP Tue Oct 9 19:31:23 UTC 2012 x86_64"
|
||||
iso.3.6.1.2.1.1.2.0 = OID: iso.3.6.1.4.1.8072.3.2.10
|
||||
iso.3.6.1.2.1.1.3.0 = Timeticks: (2097) 0:00:20.97
|
||||
|
||||
~~ OUTPUT TRUNCATED ~~
|
||||
|
||||
iso.3.6.1.2.1.92.1.1.2.0 = Gauge32: 1440
|
||||
iso.3.6.1.2.1.92.1.2.1.0 = Counter32: 1
|
||||
iso.3.6.1.2.1.92.1.2.2.0 = Counter32: 0
|
||||
iso.3.6.1.2.1.92.1.3.1.1.2.7.100.101.102.97.117.108.116.1 = Timeticks: (1) 0:00:00.01
|
||||
iso.3.6.1.2.1.92.1.3.1.1.3.7.100.101.102.97.117.108.116.1 = Hex-STRING: 07 DD 0B 12 00 39 27 00 2B 06 00
|
||||
|
||||
### Configure Cacti with SNMP ###
|
||||
|
||||
In this tutorial, we are setting up both Cacti and SNMP on the same Linux server. So go ahead and [install Cacti][2] on your Linux server on which SNMP was just configured.
|
||||
|
||||
After installation, Cacti web interface can be accessed using the link "http://172.17.1.44/cacti", of course, in your case, the IP address of your server.
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
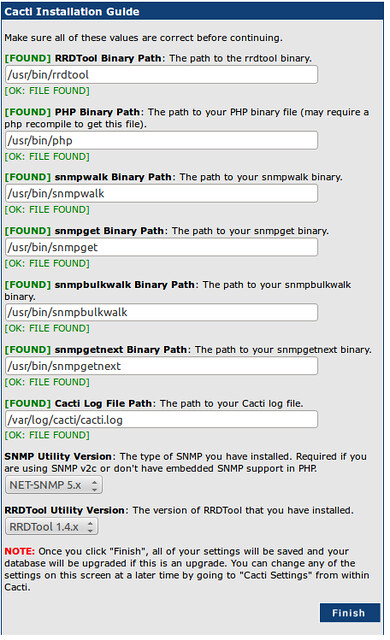
The paths during Cacti installation are usually correct. But they can be double checked if necessary.
|
||||
|
||||
|
||||
|
||||
During the first-time installation, the default username and password for Cacti are "admin" and "admin". You will be forced to change the password after first login.
|
||||
|
||||
|
||||
|
||||
### Add and Manage Devices to Cacti ###
|
||||
|
||||
Cacti will poll devices based on SNMP string that was configured earlier. In this tutorial, we will add only the local server where SNMP is already enabled.
|
||||
|
||||
To add devices, we login as admin and go to console in the Cacti admin panel. We click Console > Devices.
|
||||
|
||||

|
||||
|
||||
There may already be a device named 'localhost'. We do not need it as we will create fresh graphs. We can delete this device from the list. We add a new device by using the 'add' button.
|
||||
|
||||

|
||||
|
||||
Next, we set the device parameters.
|
||||
|
||||

|
||||
|
||||
Now that the device has been added, we specify the graph templates that we want to create. This section can be found in the bottom section of the page.
|
||||
|
||||
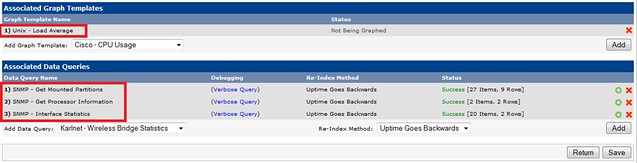
|
||||
|
||||
And then we proceed to creating the graphs.
|
||||
|
||||
|
||||
|
||||
Here, we create graphs for load average, RAM and hard disk, processor.
|
||||
|
||||
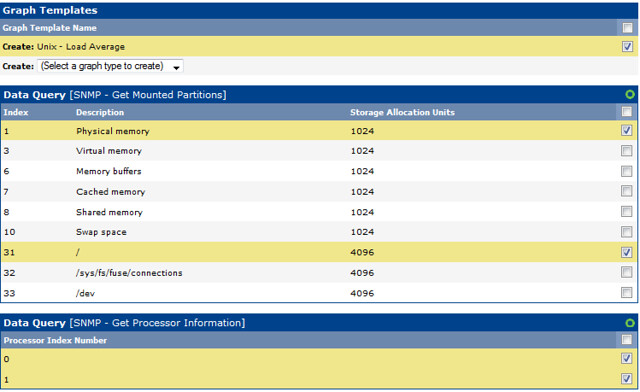
|
||||
|
||||
### Interface Graphs and 64-bit Counters ###
|
||||
|
||||
By default, Cacti uses 32-bit counters in SNMP queries. 32-bit counters are sufficient for most bandwidth graphs, but they do not work correctly for graphs greater than 100 Mbps. If it is known that the bandwidth will exceed more than 100 Mbps, it is always advisable to use 64-bit counters. Using 64-bit counters is not hard at all.
|
||||
|
||||
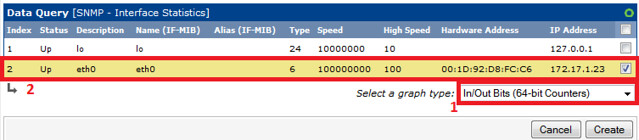
|
||||
|
||||
**Note**: It takes around 15 minutes for Cacti to populate new graphs. There are not alternatives to being patient.
|
||||
|
||||
### Creating Graph Trees ###
|
||||
|
||||
These snapshots illustrate how to create graph trees and how to add graph to those trees.
|
||||
|
||||
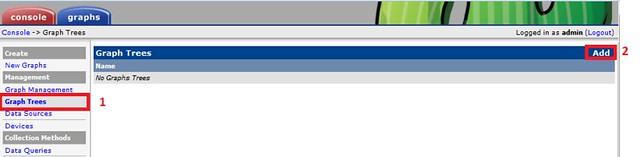
|
||||
|
||||
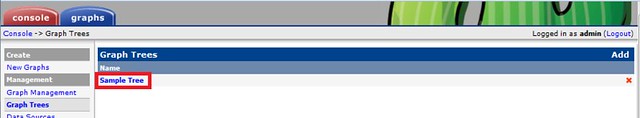
|
||||
|
||||
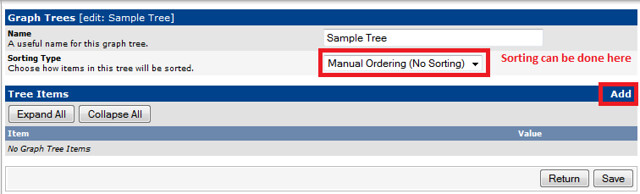
|
||||
|
||||
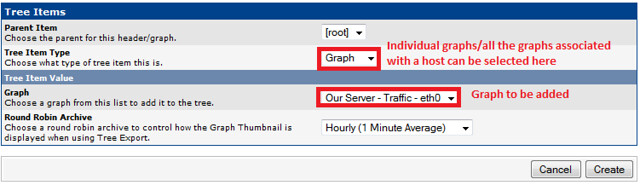
|
||||
|
||||
We can verify the graph in the graph tree.
|
||||
|
||||

|
||||
|
||||
### User Management ###
|
||||
|
||||
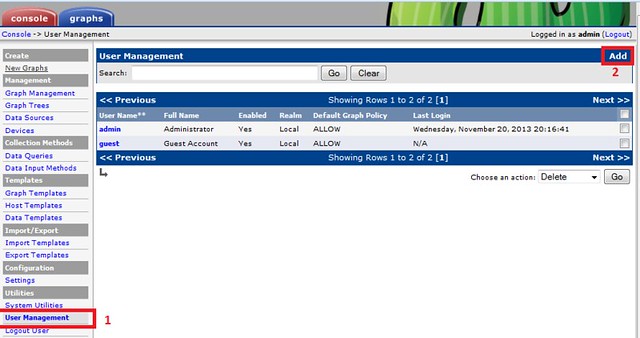
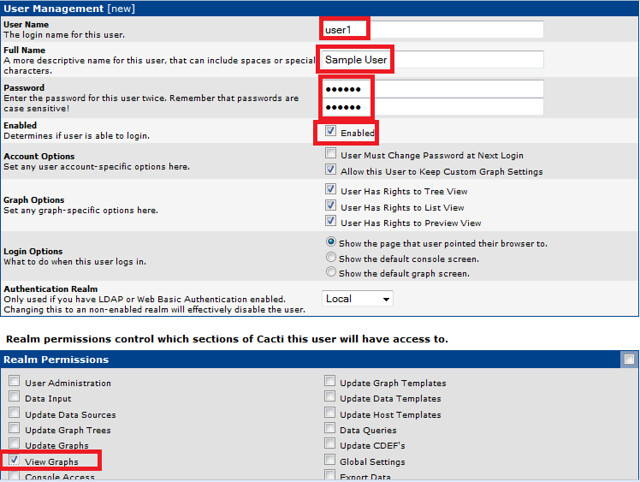
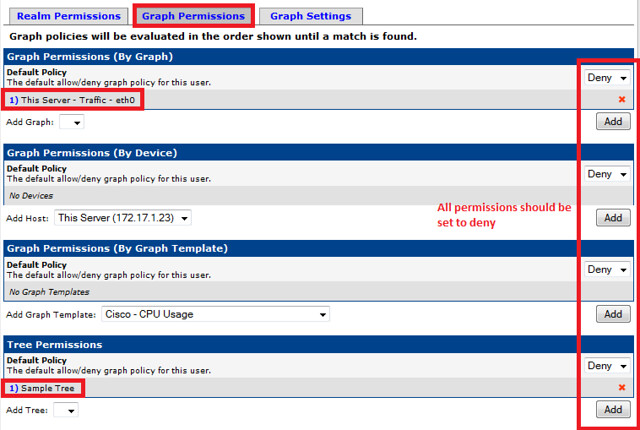
Finally, we create a user with view permission to only the graph that we have created. Cacti has built in user management system, and it is highly customizable.
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
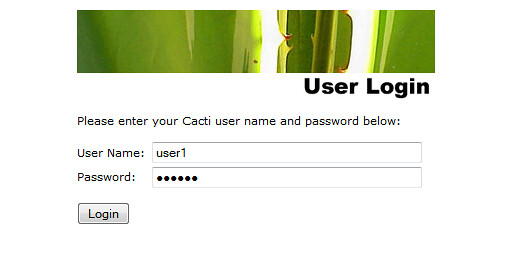
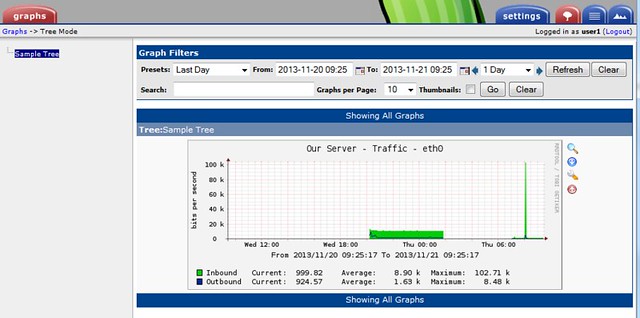
After completing these steps, we can log in with the user 'user1' and verify that only this user is able to view the graph.
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
And thus we have deployed a Cacti server in the network monitoring system. Cacti servers are stable, and can deal with tons of graphs without any problems.
|
||||
|
||||
Hope this helps.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/monitor-linux-servers-snmp-cacti.html
|
||||
|
||||
作者:[Sarmed Rahman][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/sarmed
|
||||
[1]:http://xmodulo.com/install-configure-cacti-linux.html
|
||||
@ -0,0 +1,267 @@
|
||||
How to monitor common services with Nagios
|
||||
================================================================================
|
||||
Nagios comes with a wide range of built-in scripts for monitoring services. This tutorial will cover the process of using some of these scripts for checking common services, such as MySQL, Apache web server, DNS, etc.
|
||||
|
||||
To keep the article focused on service monitoring, we will not be configuring hostgroups or templates, as they have been covered in a [previous tutorial][1]. Nonetheless, they can be tuned to match the requirements.
|
||||
|
||||
### Running Nagios Check in CLI ###
|
||||
|
||||
It is generally recommended to run the Nagios service check scripts in CLI before adding them to Nagios. This will give an idea on whether the execution will be successful and what the output of the script will look like.
|
||||
|
||||
All of the scripts are located at /etc/nagios-plugins/config/ with the executable files stored at /usr/lib/nagios/plugins/
|
||||
|
||||
Here is how it is done.
|
||||
|
||||
root@nagios:~# cd /etc/nagios-plugins/config/
|
||||
|
||||
The provided scripts contain help on the syntax. The example contains partial output.
|
||||
|
||||
root@nagios:~# cat /etc/nagios-plugins/config/tcp_udp.cfg
|
||||
|
||||
----------
|
||||
|
||||
# 'check_tcp' command definition
|
||||
define command{
|
||||
command_name check_tcp
|
||||
command_line /usr/lib/nagios/plugins/check_tcp -H '$HOSTADDRESS$' -p '$ARG1$'
|
||||
|
||||
Now that the syntax is available, TCP port 80 can be checked as follows.
|
||||
|
||||
root@nagios:~# /usr/lib/nagios/plugins/check_tcp -H 10.10.10.1 -p 80
|
||||
|
||||
----------
|
||||
|
||||
TCP OK - 0.000 second response time on port 80|time=0.000222s;;;0.000000;10.000000
|
||||
|
||||
### Example Topology ###
|
||||
|
||||
In this tutorial, the following three servers are being used. Each server runs one or more common services. The Nagios server is running on Ubuntu.
|
||||
|
||||
- Server 1 (10.10.10.1) : MySQL, Apache2
|
||||
- Server 2 (10.10.10.2) : Postfix, Apache2
|
||||
- Server 3 (10.10.10.3): DNS
|
||||
|
||||
First, the servers are defined in Nagios.
|
||||
|
||||
root@nagios:~# vim /etc/nagios3/conf.d/example.cfg
|
||||
|
||||
----------
|
||||
|
||||
define host{
|
||||
use generic-host
|
||||
host_name test-server-1
|
||||
alias test-server-1
|
||||
address 10.10.10.1
|
||||
}
|
||||
|
||||
define host{
|
||||
use generic-host
|
||||
host_name test-server-2
|
||||
alias test-server-2
|
||||
address 10.10.10.2
|
||||
}
|
||||
|
||||
define host{
|
||||
use generic-host
|
||||
host_name test-server-3
|
||||
alias test-server-3
|
||||
address 10.10.10.3
|
||||
}
|
||||
|
||||
### Monitor MySQL Service ###
|
||||
|
||||
#### MySQL Monitoring Requirements ####
|
||||
|
||||
- Monitor whether MySQL is running by checking port 3306.
|
||||
- Monitor the availability of certain database 'testDB'.
|
||||
|
||||
#### MySQL Server Setting ####
|
||||
|
||||
When it comes to checking MySQL, it should be kept in mind that MySQL, by default, listens on only the loopback interface 127.0.0.1. This increases the security of the database. Manual tuning is needed to tell MySQL to listen on other interfaces as well. Here is how it can be done.
|
||||
|
||||
This setting is done on all MySQL servers.
|
||||
|
||||
root@nagios:~# vim /etc/mysql/my.cnf
|
||||
|
||||
The following line is commented out to make MySQL listens on all interfaces.
|
||||
|
||||
#bind-address = 127.0.0.1
|
||||
|
||||
Also, MySQL would not let just any host to connect to it. A user 'nagios' is created for both localhost and for 'any' host. This user is then granted all permission to all databases and will be used for monitoring.
|
||||
|
||||
The following settings are done for all MySQL servers.
|
||||
|
||||
root@nagios:~# mysql -u root –p
|
||||
## MySQL root password here ##
|
||||
|
||||
A user 'nagios@localhost' is created in MySQL server.
|
||||
|
||||
mysql> CREATE USER 'nagios'@'localhost' IDENTIFIED BY 'nagios-pass';
|
||||
mysql> GRANT ALL PRIVILEGES ON *.* TO 'nagios'@'localhost';
|
||||
|
||||
A user 'nagios@any-host' is created.
|
||||
|
||||
mysql> CREATE USER 'nagios'@'%' IDENTIFIED BY 'nagios-pass';
|
||||
mysql> GRANT ALL PRIVILEGES ON *.* TO 'nagios'@'%';
|
||||
|
||||
mysql> FLUSH PRIVILEGES;
|
||||
|
||||
This should enable MySQL to listen on all interfaces, as well as accept incoming connections from user 'nagios' at any host.
|
||||
|
||||
Note that there are possible security implications of this change, so it's worth mentioning a few words:
|
||||
|
||||
- This setting will expose MySQL to all available interfaces, including WAN. It is vital to make sure only legitimate networks have access to the database. Filters such as firewall and TCP wrappers should be used.
|
||||
- The MySQL 'nagios' user password should be very strong. If there are few Nagios servers, then MySQL user 'nagios@servername' should be created instead of 'nagios@%' i.e., any host.
|
||||
|
||||
#### Nagios Configuration for MySQL ####
|
||||
|
||||
The following tuning should do the trick.
|
||||
|
||||
root@nagios:~# vim /etc/nagios3/conf.d/services_nagios2.cfg
|
||||
|
||||
----------
|
||||
|
||||
define service{
|
||||
use generic-service
|
||||
host_name test-server-1
|
||||
;hostgroup can be used instead as well
|
||||
|
||||
service_description Check MYSQL via TCP port
|
||||
check_command check_tcp!3306
|
||||
}
|
||||
|
||||
define service{
|
||||
use generic-service
|
||||
host_name test-server-1
|
||||
;hostgroup can be used instead as well
|
||||
|
||||
service_description Check availability of database 'testDB'
|
||||
check_command check_mysql_database!nagios!nagios-pass!testDB
|
||||
;check_mysql!userName!userPassword!databaseName
|
||||
}
|
||||
|
||||
This way, Nagios can help monitor the accessibility of both MySQL servers and the database stored within the servers.
|
||||
|
||||
### Monitor Apache Web Server ###
|
||||
|
||||
Nagios can be used to monitor Apache web server as well.
|
||||
|
||||
#### Apache Monitoring Requirements ####
|
||||
|
||||
- Monitor whether the apache server is available.
|
||||
|
||||
This task is really easy as Nagios has a built-in command for this.
|
||||
|
||||
root@nagios:~# vim /etc/nagios3/conf.d/services_nagios2.cfg
|
||||
|
||||
----------
|
||||
|
||||
define service{
|
||||
use generic-service
|
||||
host_name test-server-1, test-server-2
|
||||
service_description Check Apache Web Server
|
||||
check_command check_http
|
||||
}
|
||||
|
||||
Now that was really simple.
|
||||
|
||||
### Monitor DNS Service ###
|
||||
|
||||
Nagios can monitor DNS service by asking the DNS server to either resolve a specific fully qualified domain name (FQDN), or by asking the server to use the dig tool. The default FQDN used for testing is www.google.com, but it can be changed as needed. The following file can be modified to do the job.
|
||||
|
||||
root@nagios:~# vim /etc/nagios-plugins/config/dns.cfg
|
||||
|
||||
----------
|
||||
|
||||
## The -H portion can be modified to replace Google ##
|
||||
define command{
|
||||
command_name check_dns
|
||||
command_line /usr/lib/nagios/plugins/check_dns -H www.google.com -s '$HOSTADDRESS$'
|
||||
}
|
||||
|
||||
Then edit the following file.
|
||||
|
||||
root@nagios:~# vim /etc/nagios3/conf.d/services_nagios2.cfg
|
||||
|
||||
----------
|
||||
|
||||
## Nagios asks server-3 to resolve the IP for google.com ##
|
||||
define service{
|
||||
use generic-service
|
||||
host_name test-server-3
|
||||
service_description Check DNS
|
||||
check_command check_dns
|
||||
}
|
||||
|
||||
## Nagios asks server-3 to dig google.com ##
|
||||
define service{
|
||||
use generic-service
|
||||
host_name test-server-3
|
||||
service_description Check DNS via dig
|
||||
check_command check_dig!www.google.com
|
||||
}
|
||||
|
||||
### Monitor Mail Server ###
|
||||
|
||||
Nagios can monitor different mail server components like SMTP, POP, IMAP and mailq. As mentioned earlier, server-2 has postfix mail server set up on it. Nagios will be configured to monitor SMTP and mail queue of the server.
|
||||
|
||||
root@nagios:~# vim /etc/nagios3/conf.d/services_nagios2.cfg
|
||||
|
||||
----------
|
||||
|
||||
define service{
|
||||
use generic-service
|
||||
host_name test-server-2
|
||||
service_description Check SMTP
|
||||
check_command check_smtp
|
||||
}
|
||||
|
||||
define service{
|
||||
use generic-service
|
||||
host_name test-server-2
|
||||
service_description Check Mail Queue
|
||||
check_command check_mailq_postfix!50!100
|
||||
;warning at 50, critical at 100
|
||||
}
|
||||
|
||||
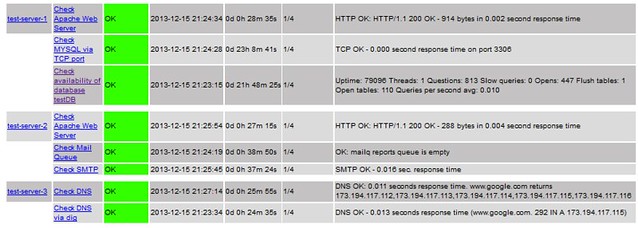
The following screenshot shows a complete overview of all the service checks that have been configured so far.
|
||||
|
||||
|
||||
|
||||
### Port Based Monitoring for Custom Applications ###
|
||||
|
||||
Let us assume that the following custom application is also running in the network, listening on a particular port.
|
||||
|
||||
- Test Server 1: custom application (TCP Port 12345)
|
||||
|
||||
With a little tweaking, Nagios can help monitor this application port as well.
|
||||
|
||||
root@nagios:~# vim /etc/nagios3/conf.d/services_nagios2.cfg
|
||||
|
||||
----------
|
||||
|
||||
define service{
|
||||
use generic-service
|
||||
host_name test-server-1
|
||||
service_description Check server 1 custom application
|
||||
check_command check_tcp!12345
|
||||
}
|
||||
|
||||
On a finishing note, Nagios can monitor many other sectors of a network. The scripts stored in /etc/nagios-plugins/config/ can shed some light on the awesome capabilities of Nagios.
|
||||
|
||||
Some of the scripts provided with Nagios are restricted to the local server only. Examples include server load, number of concurrent processes, number of logged in users. These checks can provide useful insight on what is going on within the Nagios server.
|
||||
|
||||
Hope this helps.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/monitor-common-services-nagios.html
|
||||
|
||||
作者:[Sarmed Rahman][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/sarmed
|
||||
[1]:http://xmodulo.com/install-configure-nagios-linux.html
|
||||
Loading…
Reference in New Issue
Block a user