mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-03-27 02:30:10 +08:00
20150205-3 选题
This commit is contained in:
parent
e3fb947386
commit
f1ace6f2b1
@ -0,0 +1,34 @@
|
||||
GHOST: Another Security Bug Hits Linux, But is it That Bad?
|
||||
================================================================================
|
||||
> GHOST, a newly announced security vulnerability that affects Linux servers and other systems that use the open source glibc library, is not as dangerous to data privacy as the Shellshock or Heartbleed bugs.
|
||||
|
||||

|
||||
|
||||
Heartbleed is not even a year behind us, and the open source world has been hit with another major security vulnerability in the form of [GHOST][1], which involves holes in the Linux glibc library. This time, though, the actual danger may not live up to the hype.
|
||||
|
||||
The GHOST vulnerability, which was announced last week by security researchers at [Qualys][2], resides in the gethostbyname*() functions of the glibc library. glibc is one of the core building blocks of most Linux systems, and gethostbyname*(), which resolves domain names into IP addresses, is widely used in open source applications.
|
||||
|
||||
Attackers can exploit the GHOST security hole to create a buffer overflow, making it possible to execute any kind of code they want and do all sorts of nasty things.
|
||||
|
||||
All of the above suggests that GHOST is bad news indeed. Fortunately for the open source community, however, the actual risk appears small. As TrendMicro [points out][3], the bug that makes the exploit possible has been fixed in glibc since May 2013, meaning that any Linux servers or PCs running more recent versions of the software are safe from attack.
|
||||
|
||||
In addition, gethostbyname*() has been superseded by newer glibc functions that can better handle modern networking environments. Those include ones that use the IPv6 protocol, which gethostbyname*() doesn't support. As a result, newer applications often don't use the gethostbyname*() functions, and are not at risk.
|
||||
|
||||
And perhaps most importantly, there's currently no known way of executing GHOST attacks through the Web. That greatly reduces opportunities for using this vulnerability to steal the data of unsuspecting users or otherwise wreak havoc.
|
||||
|
||||
All in all, then, GHOST doesn't seem like a vulnerability that will prove as serious as Heartbleed or Shellshock, two other recent security problems that affected widely used open source software.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://thevarguy.com/open-source-application-software-companies/020415/ghost-another-security-bug-hits-linux-it-bad
|
||||
|
||||
作者:[Christopher Tozzi][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://thevarguy.com/author/christopher-tozzi
|
||||
[1]:https://community.qualys.com/blogs/laws-of-vulnerabilities/2015/01/27/the-ghost-vulnerability
|
||||
[2]:http://qualys.com/
|
||||
[3]:http://blog.trendmicro.com/trendlabs-security-intelligence/not-so-spooky-linux-ghost-vulnerability/
|
||||
@ -0,0 +1,161 @@
|
||||
How To Install / Configure VNC Server On CentOS 7.0
|
||||
================================================================================
|
||||
Hi there, this tutorial is all about how to install or setup [VNC][1] Server on your very CentOS 7. This tutorial also works fine in RHEL 7. In this tutorial, we'll learn what is VNC and how to install or setup [VNC Server][1] on CentOS 7
|
||||
|
||||
As we know, most of the time as a system administrator we are managing our servers over the network. It is very rare that we will need to have a physical access to any of our managed servers. In most cases all we need is to SSH remotely to do our administration tasks. In this article we will configure a GUI alternative to a remote access to our CentOS 7 server, which is VNC. VNC allows us to open a remote GUI session to our server and thus providing us with a full graphical interface accessible from any remote location.
|
||||
|
||||
VNC server is a Free and Open Source Software which is designed for allowing remote access to the Desktop Environment of the server to the VNC Client whereas VNC viewer is used on remote computer to connect to the server .
|
||||
|
||||
**Some Benefits of VNC server are listed below:**
|
||||
|
||||
Remote GUI administration makes work easy & convenient.
|
||||
Clipboard sharing between host CentOS server & VNC-client machine.
|
||||
GUI tools can be installed on the host CentOS server to make the administration more powerful
|
||||
Host CentOS server can be administered through any OS having the VNC-client installed.
|
||||
More reliable over ssh graphics and RDP connections.
|
||||
|
||||
So, now lets start our journey towards the installation of VNC Server. We need to follow the steps below to setup and to get a working VNC.
|
||||
|
||||
First of all we'll need a working Desktop Environment (X-Windows), if we don't have a working GUI Desktop Environment (X Windows) running, we'll need to install it first.
|
||||
|
||||
**Note: The commands below must be running under root privilege. To switch to root please execute "sudo -s" under a shell or terminal without quotes("")**
|
||||
|
||||
### 1. Installing X-Windows ###
|
||||
|
||||
First of all to install [X-Windows][2] we'll need to execute the below commands in a shell or terminal. It will take few minutes to install its packages.
|
||||
|
||||
# yum check-update
|
||||
# yum groupinstall "X Window System"
|
||||
|
||||

|
||||
|
||||
#yum install gnome-classic-session gnome-terminal nautilus-open-terminal control-center liberation-mono-fonts
|
||||
|
||||

|
||||
|
||||
# unlink /etc/systemd/system/default.target
|
||||
# ln -sf /lib/systemd/system/graphical.target /etc/systemd/system/default.target
|
||||
|
||||

|
||||
|
||||
# reboot
|
||||
|
||||
After our machine restarts, we'll get a working CentOS 7 Desktop.
|
||||
|
||||
Now, we'll install VNC Server on our machine.
|
||||
|
||||
### 2. Installing VNC Server Package ###
|
||||
|
||||
Now, we'll install VNC Server package in our CentOS 7 machine. To install VNC Server, we'll need to execute the following command.
|
||||
|
||||
# yum install tigervnc-server -y
|
||||
|
||||

|
||||
|
||||
### 3. Configuring VNC ###
|
||||
|
||||
Then, we'll need to create a configuration file under **/etc/systemd/system/** directory. We can copy the **vncserver@:1.service** file from example file from **/lib/systemd/system/vncserver@.service**
|
||||
|
||||
# cp /lib/systemd/system/vncserver@.service /etc/systemd/system/vncserver@:1.service
|
||||
|
||||

|
||||
|
||||
Now we'll open **/etc/systemd/system/vncserver@:1.service** in our favorite text editor (here, we're gonna use **nano**). Then find the below lines of text in that file and replace <USER> with your username. Here, in my case its linoxide so I am replacing <USER> with linoxide and finally looks like below.
|
||||
|
||||
ExecStart=/sbin/runuser -l <USER> -c "/usr/bin/vncserver %i"
|
||||
PIDFile=/home/<USER>/.vnc/%H%i.pid
|
||||
|
||||
TO
|
||||
|
||||
ExecStart=/sbin/runuser -l linoxide -c "/usr/bin/vncserver %i"
|
||||
PIDFile=/home/linoxide/.vnc/%H%i.pid
|
||||
|
||||
If you are creating for root user then
|
||||
|
||||
ExecStart=/sbin/runuser -l root -c "/usr/bin/vncserver %i"
|
||||
PIDFile=/root/.vnc/%H%i.pid
|
||||
|
||||

|
||||
|
||||
Now, we'll need to reload our systemd.
|
||||
|
||||
# systemctl daemon-reload
|
||||
|
||||
Finally, we'll create VNC password for the user . To do so, first you'll need to be sure that you have sudo access to the user, here I will login to user "linoxide" then, execute the following. To login to linoxide we'll run "**su linoxide" without quotes** .
|
||||
|
||||
# su linoxide
|
||||
$ sudo vncpasswd
|
||||
|
||||

|
||||
|
||||
**Make sure that you enter passwords more than 6 characters.**
|
||||
|
||||
### 4. Enabling and Starting the service ###
|
||||
|
||||
To enable service at startup ( Permanent ) execute the commands shown below.
|
||||
|
||||
$ sudo systemctl enable vncserver@:1.service
|
||||
|
||||
Then, start the service.
|
||||
|
||||
$ sudo systemctl start vncserver@:1.service
|
||||
|
||||
### 5. Allowing Firewalls ###
|
||||
|
||||
We'll need to allow VNC services in Firewall now.
|
||||
|
||||
$ sudo firewall-cmd --permanent --add-service vnc-server
|
||||
$ sudo systemctl restart firewalld.service
|
||||
|
||||

|
||||
|
||||
Now you can able to connect VNC server using IP and Port ( Eg : ip-address:1 )
|
||||
|
||||
### 6. Connecting the machine with VNC Client ###
|
||||
|
||||
Finally, we are done installing VNC Server. No, we'll wanna connect the server machine and remotely access it. For that we'll need a VNC Client installed in our computer which will only enable us to remote access the server machine.
|
||||
|
||||

|
||||
|
||||
You can use VNC client like [Tightvnc viewer][3] and [Realvnc viewer][4] to connect Server.
|
||||
To connect with additional users create files with different ports, please go to step 3 to configure and add a new user and port, You'll need to create **vncserver@:2.service** and replace the username in config file and continue the steps by replacing service name for different ports. **Please make sure you logged in as that particular user for creating vnc password**.
|
||||
|
||||
VNC by itself runs on port 5900. Since each user will run their own VNC server, each user will have to connect via a separate port. The addition of a number in the file name tells VNC to run that service as a sub-port of 5900. So in our case, arun's VNC service will run on port 5901 (5900 + 1) and further will run on 5900 + x. Where, x denotes the port specified when creating config file **vncserver@:x.service for the further users**.
|
||||
|
||||
We'll need to know the IP Address and Port of the server to connect with the client. IP addresses are the unique identity number of the machine. Here, my IP address is 96.126.120.92 and port for this user is 1. We can get the public IP address by executing the below command in a shell or terminal of the machine where VNC Server is installed.
|
||||
|
||||
# curl -s checkip.dyndns.org|sed -e 's/.*Current IP Address: //' -e 's/<.*$//'
|
||||
|
||||
### Conclusion ###
|
||||
|
||||
Finally, we installed and configured VNC Server in the machine running CentOS 7 / RHEL 7 (Red Hat Enterprises Linux) . VNC is the most easy FOSS tool for the remote access and also a good alternative to Teamviewer Remote Access. VNC allows a user with VNC client installed to control the machine with VNC Server installed. Here are some commands listed below that are highly useful in VNC . Enjoy !!
|
||||
|
||||
#### Additional Commands : ####
|
||||
|
||||
- To stop VNC service .
|
||||
|
||||
# systemctl stop vncserver@:1.service
|
||||
|
||||
- To disable VNC service from startup.
|
||||
|
||||
# systemctl disable vncserver@:1.service
|
||||
|
||||
- To stop firewall.
|
||||
|
||||
# systemctl stop firewalld.service
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/linux-how-to/install-configure-vnc-server-centos-7-0/
|
||||
|
||||
作者:[Arun Pyasi][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://linoxide.com/author/arunp/
|
||||
[1]:http://en.wikipedia.org/wiki/Virtual_Network_Computing
|
||||
[2]:http://en.wikipedia.org/wiki/X_Window_System
|
||||
[3]:http://www.tightvnc.com/
|
||||
[4]:https://www.realvnc.com/
|
||||
@ -0,0 +1,424 @@
|
||||
How To Scan And Check A WordPress Website Security Using WPScan, Nmap, And Nikto
|
||||
================================================================================
|
||||
### Introduction ###
|
||||
|
||||
Millions of websites are powered by WordPress software and there’s a reason for that. WordPress is the most developer-friendly content management system out there, so you can essentially do anything you want with it. Unfortunately, every day some scary report about a major site being hacked or a sensitive database being compromised hits the web … and freaks everyone out.
|
||||
|
||||
If you haven’t installed WordPress yet, check the following article.
|
||||
On Debian based systems:
|
||||
|
||||
- [How to install WordPress On Ubuntu][1]
|
||||
|
||||
On RPM based systems:
|
||||
|
||||
- [How to install wordpress On CentOS][2]
|
||||
|
||||
Following on from my previous article [How To Secure WordPress Website][3] show you **checklist** allows you to secure your WordPress site with as little effort as possible.
|
||||
|
||||
In this article, will describe to you through the installation of **wpscan** and serve as a guide on how to use wpscan to locate any known vulnerable plugins and themes that may make your site vulnerable to attack. Also, how to install and use **nmap** the free Security Scanner For Network Exploration & Hacking . And at the end we will show you the steps to use **nikto**.
|
||||
|
||||
### WPScan to Test for Vulnerable Plugins and Themes in WordPress ###
|
||||
|
||||
**WPScan** is a black box WordPress Security Scanner written in Ruby which attempts to find known security weaknesses within WordPress installations. Its intended use it to be for security professionals or WordPress administrators to asses the security posture of their WordPress installations. The code base is Open Source and licensed under the GPLv3.
|
||||
|
||||
### Download and Install WPScan ###
|
||||
|
||||
Before we get started with the installation, it is important to note that wpscan will not work on Windows systems, so you will need access to a Linux or OSX installation to proceed. If you only have access to a Windows system you can download Virtualbox and install any Linux distro you like as a Virtual Machine.
|
||||
|
||||
WPScan is hosted on Github, so if it is not already installed we will need to install the git packages before we can continue.
|
||||
|
||||
sudo apt-get install git
|
||||
|
||||
Once git is installed, we need to install the dependencies for wpscan.
|
||||
|
||||
sudo apt-get install libcurl4-gnutls-dev libopenssl-ruby libxml2 libxml2-dev libxslt1-dev ruby-dev ruby1.9.3
|
||||
|
||||
Now we need to clone the wpscan package from github.
|
||||
|
||||
git clone https://github.com/wpscanteam/wpscan.git
|
||||
|
||||
Now we can move to the newly created wpscan directory and install the necessary ruby gems through bundler.
|
||||
|
||||
cd wpscan
|
||||
sudo gem install bundler && bundle install --without test development
|
||||
|
||||
Now that we have wpscan installed, we will walk through using the tool to search for potentially vulnerable files on our WordPress installation. Some of the most important aspects of wpscan are its ability to enumerate not only plugins and themes, but users and timthumb installations as well. WPScan can also perform bruteforce attacks against WordPress– but that is outside of the scope of this article.
|
||||
|
||||
#### Update wpscan ####
|
||||
|
||||
ruby wpscan.rb --update
|
||||
|
||||
#### Enumerate Plugins ####
|
||||
|
||||
To enumerate plugins, all we need to do is launch wpscan with the `--enumerate p` arguments like so.
|
||||
|
||||
ruby wpscan.rb --url http(s)://www.yoursiteurl.com --enumerate p
|
||||
|
||||
or to only display vulnerable plugins:
|
||||
|
||||
ruby wpscan.rb --url http(s)://www.yoursiteurl.com --enumerate vp
|
||||
|
||||
Some example output is posted below:
|
||||
|
||||
| Name: akismet
|
||||
| Location: http://********.com/wp-content/plugins/akismet/
|
||||
|
||||
| Name: audio-player
|
||||
| Location: http://********.com/wp-content/plugins/audio-player/
|
||||
|
|
||||
| * Title: Audio Player - player.swf playerID Parameter XSS
|
||||
| * Reference: http://seclists.org/bugtraq/2013/Feb/35
|
||||
| * Reference: http://secunia.com/advisories/52083
|
||||
| * Reference: http://osvdb.org/89963
|
||||
| * Fixed in: 2.0.4.6
|
||||
|
||||
| Name: bbpress - v2.3.2
|
||||
| Location: http://********.com/wp-content/plugins/bbpress/
|
||||
| Readme: http://********.com/wp-content/plugins/bbpress/readme.txt
|
||||
|
|
||||
| * Title: BBPress - Multiple Script Malformed Input Path Disclosure
|
||||
| * Reference: http://xforce.iss.net/xforce/xfdb/78244
|
||||
| * Reference: http://packetstormsecurity.com/files/116123/
|
||||
| * Reference: http://osvdb.org/86399
|
||||
| * Reference: http://www.exploit-db.com/exploits/22396/
|
||||
|
|
||||
| * Title: BBPress - forum.php page Parameter SQL Injection
|
||||
| * Reference: http://xforce.iss.net/xforce/xfdb/78244
|
||||
| * Reference: http://packetstormsecurity.com/files/116123/
|
||||
| * Reference: http://osvdb.org/86400
|
||||
| * Reference: http://www.exploit-db.com/exploits/22396/
|
||||
|
||||
| Name: contact
|
||||
| Location: http://********.com/wp-content/plugins/contact/
|
||||
|
||||
#### Enumerate Themes ####
|
||||
|
||||
Enumeration of themes works the same as enumeration of plugins, just with the `--enumerate t` argument.
|
||||
|
||||
ruby wpscan.rb --url http(s)://www.host-name.com --enumerate t
|
||||
|
||||
Or to only display vulnerable themes:
|
||||
|
||||
ruby wpscan.rb --url http(s)://www.host-name.com --enumerate vt
|
||||
|
||||
Sample output:
|
||||
|
||||
| Name: path
|
||||
| Location: http://********.com/wp-content/themes/path/
|
||||
| Style URL: http://********.com/wp-content/themes/path/style.css
|
||||
| Description:
|
||||
|
||||
| Name: pub
|
||||
| Location: http://********.com/wp-content/themes/pub/
|
||||
| Style URL: http://********.com/wp-content/themes/pub/style.css
|
||||
| Description:
|
||||
|
||||
| Name: rockstar
|
||||
| Location: http://********.com/wp-content/themes/rockstar/
|
||||
| Style URL: http://********.com/wp-content/themes/rockstar/style.css
|
||||
| Description:
|
||||
|
|
||||
| * Title: WooThemes WooFramework Remote Unauthenticated Shortcode Execution
|
||||
| * Reference: https://gist.github.com/2523147
|
||||
|
||||
| Name: twentyten
|
||||
| Location: http://********.com/wp-content/themes/twentyten/
|
||||
| Style URL: http://********.com/wp-content/themes/twentyten/style.css
|
||||
| Description:
|
||||
|
||||
#### Enumerate Users ####
|
||||
|
||||
WPScan can also be used to enumerate users with valid logins to the WordPress installation. This is usually performed by attackers in order to get a list of users in preparation for a bruteforce attack.
|
||||
|
||||
ruby wpscan.rb --url http(s)://www.host-name.com --enumerate u
|
||||
|
||||
#### Enumerate Timthumb Files ####
|
||||
|
||||
The last function of wpscan we’ll discuss in this article is the ability to enumerate timthumb installations. In recent years, timthumb has become a very common target of attackers due to the numerous vulnerabilities found and posted to online forums, message lists, and advisory boards. Using wpscan to find vulnerable timthumb files is done with the following command.
|
||||
|
||||
ruby wpscan.rb --url http(s)://www.host-name.com --enumerate tt
|
||||
|
||||
### Nmap to Scan for Open Ports on your VPS ###
|
||||
|
||||
**Nmap** is an open source tool for network exploration and security auditing. It was designed to rapidly scan large networks, although it works fine against single hosts. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics
|
||||
|
||||
### Download and install nmap on Debian and Ubuntu ###
|
||||
|
||||
To install nmap for Debian and Ubuntu Linux based server systems type the following apt-get command:
|
||||
|
||||
sudo apt-get install nmap
|
||||
|
||||
**Sample outputs:**
|
||||
|
||||
Reading package lists... Done
|
||||
Building dependency tree
|
||||
Reading state information... Done
|
||||
The following NEW packages will be installed:
|
||||
nmap
|
||||
0 upgraded, 1 newly installed, 0 to remove and 2 not upgraded.
|
||||
Need to get 1,643 kB of archives.
|
||||
After this operation, 6,913 kB of additional disk space will be used.
|
||||
Get:1 http://mirrors.service.networklayer.com/ubuntu/ precise/main nmap amd64 5.21-1.1ubuntu1 [1,643 kB]
|
||||
Fetched 1,643 kB in 0s (16.4 MB/s)
|
||||
Selecting previously unselected package nmap.
|
||||
(Reading database ... 56834 files and directories currently installed.)
|
||||
Unpacking nmap (from .../nmap_5.21-1.1ubuntu1_amd64.deb) ...
|
||||
Processing triggers for man-db ...
|
||||
Setting up nmap (5.21-1.1ubuntu1) ...
|
||||
|
||||
#### Examples ####
|
||||
|
||||
To find the nmap version, enter:
|
||||
|
||||
nmap -V
|
||||
|
||||
OR
|
||||
|
||||
nmap --version
|
||||
|
||||
**Sample outputs:**
|
||||
|
||||
Nmap version 5.21 ( http://nmap.org )
|
||||
|
||||
### Dowonlad and install nmap on Centos ###
|
||||
|
||||
To install nmap on RHEL based Linux distributions, type the following yum command:
|
||||
|
||||
yum install nmap
|
||||
|
||||
**Sample outputs:**
|
||||
|
||||
Loaded plugins: protectbase, rhnplugin, security
|
||||
0 packages excluded due to repository protections
|
||||
Setting up Install Process
|
||||
Resolving Dependencies
|
||||
--> Running transaction check
|
||||
---> Package nmap.x86_64 2:5.51-2.el6 will be installed
|
||||
--> Finished Dependency Resolution
|
||||
|
||||
Dependencies Resolved
|
||||
|
||||
================================================================================
|
||||
Package Arch Version Repository Size
|
||||
================================================================================
|
||||
Installing:
|
||||
nmap x86_64 2:5.51-2.el6 rhel-x86_64-server-6 2.8 M
|
||||
|
||||
Transaction Summary
|
||||
================================================================================
|
||||
Install 1 Package(s)
|
||||
|
||||
Total download size: 2.8 M
|
||||
Installed size: 0
|
||||
Is this ok [y/N]: y
|
||||
Downloading Packages:
|
||||
nmap-5.51-2.el6.x86_64.rpm | 2.8 MB 00:00
|
||||
Running rpm_check_debug
|
||||
Running Transaction Test
|
||||
Transaction Test Succeeded
|
||||
Running Transaction
|
||||
Installing : 2:nmap-5.51-2.el6.x86_64 1/1
|
||||
Verifying : 2:nmap-5.51-2.el6.x86_64 1/1
|
||||
|
||||
Installed:
|
||||
nmap.x86_64 2:5.51-2.el6
|
||||
|
||||
Complete!
|
||||
|
||||
#### Examples ####
|
||||
|
||||
To find the nmap version, enter:
|
||||
|
||||
nmap --version
|
||||
|
||||
**Sample outputs:**
|
||||
|
||||
Nmap version 5.51 ( http://nmap.org )
|
||||
|
||||
#### Scan Ports with Nmap ####
|
||||
|
||||
You can got a lot of information about your server or host using nmap and it let you to think like someone has malicious intent.
|
||||
|
||||
For this reason, only test it on servers that you own or in situations where you’ve notified the owners.
|
||||
|
||||
The nmap creators actually provide a test server located at:
|
||||
|
||||
scanme.nmap.org
|
||||
|
||||
Some commands may take a long while to complete:
|
||||
|
||||
To scan an IP address or a host name (FQDN), run:
|
||||
|
||||
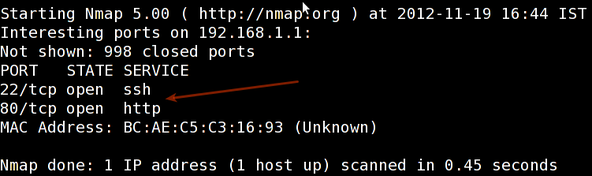
nmap 192.168.1.1
|
||||
|
||||
Sample outputs:
|
||||
|
||||
|
||||
|
||||
Scan for the host operating system:
|
||||
|
||||
sudo nmap -O 192.168.1.1
|
||||
|
||||
pecify a range with “-” or “/24″ to scan a number of hosts at once:
|
||||
|
||||
sudo nmap -PN xxx.xxx.xxx.xxx-yyy
|
||||
|
||||
Scan a network range for available services:
|
||||
|
||||
sudo nmap -sP network_address_range
|
||||
|
||||
Scan without preforming a reverse DNS lookup on the IP address specified. This should speed up your results in most cases:
|
||||
|
||||
sudo nmap -n remote_host
|
||||
|
||||
Scan a specific port instead of all common ports:
|
||||
|
||||
sudo nmap -p port_number remote_host
|
||||
|
||||
Scan a network and find out which servers and devices are up and running
|
||||
|
||||
This is known as host discovery or ping scan:
|
||||
|
||||
nmap -sP 192.168.1.0/24
|
||||
|
||||
Sample outputs:
|
||||
|
||||
Host 192.168.1.1 is up (0.00035s latency).
|
||||
MAC Address: BC:AE:C5:C3:16:93 (Unknown)
|
||||
Host 192.168.1.2 is up (0.0038s latency).
|
||||
MAC Address: 74:44:01:40:57:FB (Unknown)
|
||||
Host 192.168.1.5 is up.
|
||||
Host nas03 (192.168.1.12) is up (0.0091s latency).
|
||||
MAC Address: 00:11:32:11:15:FC (Synology Incorporated)
|
||||
Nmap done: 256 IP addresses (4 hosts up) scanned in 2.80 second
|
||||
|
||||
Understanding port configuration and how to discover what the attack vectors are on your server is only one step to securing your information and your VPS.
|
||||
|
||||
### Nikto to Scan for vulnerabilities in your website ###
|
||||
|
||||
[Nikto][4] Web-scanner is a open source web-server scanner which can be used to scan the web-servers for malicious programs and files. Nikto can be used to scan the outdated versions of programs too. Nikto will provide us a quick and easy scan to find out the dangerous files and programs in server, At the end of scan result with a log file.
|
||||
|
||||
### Download and install Nikto on Linux server ###
|
||||
|
||||
Perl is pre-installed in linux so all you need to do is download nikto from the [project page][5], unpack it into a directory and start your testing.
|
||||
|
||||
wget https://cirt.net/nikto/nikto-2.1.4.tar.gz
|
||||
|
||||
You can unpack it with an archive manager tool or use tar and gzip together with this command.
|
||||
|
||||
tar zxvf nikto-2.1.4.tar.gz
|
||||
cd nikto-2.1.4
|
||||
perl nikto.pl
|
||||
|
||||
This should be your results from a working installation:
|
||||
|
||||
- ***** SSL support not available (see docs for SSL install) *****
|
||||
- Nikto v2.1.4
|
||||
---------------------------------------------------------------------------
|
||||
+ ERROR: No host specified
|
||||
|
||||
-config+ Use this config file
|
||||
-Cgidirs+ scan these CGI dirs: 'none', 'all', or values like "/cgi/ /cgi-a/"
|
||||
-dbcheck check database and other key files for syntax errors
|
||||
-Display+ Turn on/off display outputs
|
||||
-evasion+ ids evasion technique
|
||||
-Format+ save file (-o) format
|
||||
-host+ target host
|
||||
-Help Extended help information
|
||||
-id+ Host authentication to use, format is id:pass or id:pass:realm
|
||||
-list-plugins List all available plugins
|
||||
-mutate+ Guess additional file names
|
||||
-mutate-options+ Provide extra information for mutations
|
||||
-output+ Write output to this file
|
||||
-nocache Disables the URI cache
|
||||
-nossl Disables using SSL
|
||||
-no404 Disables 404 checks
|
||||
-port+ Port to use (default 80)
|
||||
-Plugins+ List of plugins to run (default: ALL)
|
||||
-root+ Prepend root value to all requests, format is /directory
|
||||
-ssl Force ssl mode on port
|
||||
-Single Single request mode
|
||||
-timeout+ Timeout (default 2 seconds)
|
||||
-Tuning+ Scan tuning
|
||||
-update Update databases and plugins from CIRT.net
|
||||
-vhost+ Virtual host (for Host header)
|
||||
-Version Print plugin and database versions
|
||||
+ requires a value
|
||||
|
||||
Note: This is the short help output. Use -H for full help.
|
||||
|
||||
The error is merely telling us we did not fill in the necessary parameters for a test to run. The SSL support can be enabled by installing the necessary perl ssl module (sudo apt-get install libnet-ssleay-perl).
|
||||
|
||||
#### Update the nikto Database ####
|
||||
|
||||
Before performing any scan we need to update the nikto database packages using.
|
||||
|
||||
/usr/local/bin/nikto.pl -update
|
||||
|
||||
To list the available Plugins for nikto we can use the below command.
|
||||
|
||||
nikto.pl -list-plugins // To list the installed plugins //
|
||||
|
||||
#### Scan for vulnerabilities ####
|
||||
|
||||
For a simple test for we will use test a single url.
|
||||
|
||||
perl nikto.pl -h http://www.host-name.com
|
||||
|
||||
**Sample outputs:**
|
||||
|
||||
This will produce fairly verbose output that may be somewhat confusing at first. Take the time to read through the output to understand what each advisory means. Many of the alerts in Nikto will refer to OSVDB numbers. These are Open Source Vulnerability Database ([http://osvdb.org/][6]) designations. You can search on OSVDB for further information about any vulnerabilities identified.
|
||||
|
||||
$ nikto -h http://www.host-name.com
|
||||
- Nikto v2.1.4
|
||||
---------------------------------------------------------------------------
|
||||
+ Target IP: 1.2.3.4
|
||||
+ Target Hostname: host-name.com
|
||||
+ Target Port: 80
|
||||
+ Start Time: 2012-08-11 14:27:31
|
||||
---------------------------------------------------------------------------
|
||||
+ Server: Apache/2.2.22 (FreeBSD) mod_ssl/2.2.22 OpenSSL/1.0.1c DAV/2
|
||||
+ robots.txt contains 4 entries which should be manually viewed.
|
||||
+ mod_ssl/2.2.22 appears to be outdated (current is at least 2.8.31) (may depend on server version)
|
||||
+ ETag header found on server, inode: 5918348, size: 121, mtime: 0x48fc943691040
|
||||
+ mod_ssl/2.2.22 OpenSSL/1.0.1c DAV/2 - mod_ssl 2.8.7 and lower are vulnerable to a remote buffer overflow which may allow a remote shell (difficult to exploit). CVE-2002-0082, OSVDB-756.
|
||||
+ Allowed HTTP Methods: GET, HEAD, POST, OPTIONS, TRACE
|
||||
+ OSVDB-877: HTTP TRACE method is active, suggesting the host is vulnerable to XST
|
||||
+ /lists/admin/: PHPList pre 2.6.4 contains a number of vulnerabilities including remote administrative access, harvesting user info and more. Default login to admin interface is admin/phplist
|
||||
+ OSVDB-2322: /gallery/search.php?searchstring=<script>alert(document.cookie)</script>: Gallery 1.3.4 and below is vulnerable to Cross Site Scripting (XSS). Upgrade to the latest version. http://www.securityfocus.com/bid/8288.
|
||||
+ OSVDB-7022: /calendar.php?year=<script>alert(document.cookie);</script>&month=03&day=05: DCP-Portal v5.3.1 is vulnerable to Cross Site Scripting (XSS). http://www.cert.org/advisories/CA-2000-02.html.
|
||||
+ OSVDB-3233: /phpinfo.php: Contains PHP configuration information
|
||||
+ OSVDB-3092: /system/: This might be interesting...
|
||||
+ OSVDB-3092: /template/: This may be interesting as the directory may hold sensitive files or reveal system information.
|
||||
+ OSVDB-3092: /updates/: This might be interesting...
|
||||
+ OSVDB-3092: /README: README file found.
|
||||
+ 6448 items checked: 1 error(s) and 14 item(s) reported on remote host
|
||||
+ End Time: 2012-08-11 15:52:57 (5126 seconds)
|
||||
---------------------------------------------------------------------------
|
||||
+ 1 host(s) tested
|
||||
$
|
||||
|
||||
**Nikto** is an extremely lightweight, and versatile tool. Because of the fact that Nikto is written in Perl it can be run on almost any host operating system.
|
||||
|
||||
Hope this will will bring you a good idea to scan vulnerbalites for your wordpress website. Following on from my previous article [How To Secure WordPress Website][7] show you **checklist** allows you to secure your WordPress site with as little effort as possible.
|
||||
|
||||
If you have any feedback or comments, feel free to post them in the comment section below.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.unixmen.com/scan-check-wordpress-website-security-using-wpscan-nmap-nikto/
|
||||
|
||||
作者:[anismaj][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.unixmen.com/author/anis/
|
||||
[1]:http://www.unixmen.com/install-wordpress-ubuntu-14-10/
|
||||
[2]:http://www.unixmen.com/install-configure-wordpress-4-0-benny-centos-7/
|
||||
[3]:http://www.unixmen.com/secure-wordpress-website/
|
||||
[4]:http://www.unixmen.com/install-nikto-web-scanner-check-vulnerabilities
|
||||
[5]:https://cirt.net/nikto/
|
||||
[6]:http://osvdb.org/
|
||||
[7]:http://www.unixmen.com/secure-wordpress-website/
|
||||
@ -0,0 +1,171 @@
|
||||
Inxi: Find System And Hardware Information On Linux
|
||||
================================================================================
|
||||
We already have shown different [applications][1] and ways to find the system and hardware information on Linux. In that series, today we will see how to find such details using **inxi**. It can be used for forum technical support, as a debugging tool, to quickly ascertain user system configuration and hardware.
|
||||
|
||||
**Inxi** is a command line tool that can be used to find the complete system and hardware details such as;
|
||||
|
||||
- Hardware,
|
||||
- CPU,
|
||||
- Drivers,
|
||||
- Xorg,
|
||||
- Desktop,
|
||||
- Kernel,
|
||||
- GCC version,
|
||||
- Processes,
|
||||
- RAM usage,
|
||||
- and other useful information.
|
||||
|
||||
### Installation ###
|
||||
|
||||
Inxi is available in the default repositories of most modern GNU/Linux operating systems. So, we can simply install it by running the following commands.
|
||||
|
||||
**On Debian based system:**
|
||||
|
||||
sudo apt-get install inxi
|
||||
|
||||
**On Fedora:**
|
||||
|
||||
sudo yum install inxi
|
||||
|
||||
**On RHEL based systems:**
|
||||
|
||||
Install EPEL repository:
|
||||
|
||||
sudo yum install epel-release
|
||||
|
||||
Then, install inxi using command:
|
||||
|
||||
sudo yum install inxi
|
||||
|
||||
### Usage ###
|
||||
|
||||
To find the quick view of the system information, run the following command from Terminal.
|
||||
|
||||
inxi
|
||||
|
||||
**Sample output:**
|
||||
|
||||
CPU~Dual core Intel Core i3-2350M CPU (-HT-MCP-) clocked at Min:800.000Mhz Max:1200.000Mhz Kernel~3.13.0-45-generic x86_64 Up~6:41 Mem~1537.7/3861.3MB HDD~500.1GB(52.5% used) Procs~183 Client~Shell inxi~1.9.17
|
||||
|
||||
Ofcourse, we can retrieve a particular hardware details. For example to retrieve the **Audio/Sound hardware details**, run the following command:
|
||||
|
||||
inxi -A
|
||||
|
||||
**Sample output:**
|
||||
|
||||
Audio: Card: Intel 6 Series/C200 Series Family High Definition Audio Controller driver: snd_hda_intel
|
||||
Sound: Advanced Linux Sound Architecture ver: k3.13.0-45-generic
|
||||
|
||||
Cool, isn’t it?
|
||||
|
||||
Likewise, you can retrieve the details of **Graphic card** information.
|
||||
|
||||
inxi -G
|
||||
|
||||
**Sample output:**
|
||||
|
||||
Graphics: Card: Intel 2nd Generation Core Processor Family Integrated Graphics Controller
|
||||
X.Org: 1.15.1 drivers: intel (unloaded: fbdev,vesa) Resolution: 1366x768@60.0hz
|
||||
GLX Renderer: Mesa DRI Intel Sandybridge Mobile GLX Version: 3.0 Mesa 10.3.0
|
||||
|
||||
What about harddisk information? That’s also possible. To view the full **harddisk** information, run the following command.
|
||||
|
||||
inxi -D
|
||||
|
||||
**Sample Output:**
|
||||
|
||||
Drives: HDD Total Size: 500.1GB (52.5% used) 1: id: /dev/sda model: ST9601325BD size: 500.1GB
|
||||
|
||||
To display the Bios and Motherboard details:
|
||||
|
||||
inxi -M
|
||||
|
||||
**Sample output:**
|
||||
|
||||
Machine: System: Dell (portable) product: Inspiron N5050
|
||||
Mobo: Dell model: 01HXXJ version: A05 Bios: Dell version: A05 date: 08/03/2012
|
||||
|
||||
Not only hardware details, it can also displays the **list of available repositories** in our system.
|
||||
|
||||
inxi -r
|
||||
|
||||
**Sample output:**
|
||||
|
||||
Repos: Active apt sources in file: /etc/apt/sources.list
|
||||
deb http://ubuntu.excellmedia.net/archive/ trusty main restricted
|
||||
deb-src http://ubuntu.excellmedia.net/archive/ trusty main restricted
|
||||
deb http://ubuntu.excellmedia.net/archive/ trusty-updates main restricted
|
||||
deb-src http://ubuntu.excellmedia.net/archive/ trusty-updates main restricted
|
||||
deb http://ubuntu.excellmedia.net/archive/ trusty universe
|
||||
.
|
||||
.
|
||||
Active apt sources in file: /etc/apt/sources.list.d/intellinuxgraphics.list
|
||||
deb https://download.01.org/gfx/ubuntu/14.04/main trusty main #Intel Graphics drivers
|
||||
Active apt sources in file: /etc/apt/sources.list.d/linrunner-tlp-trusty.list
|
||||
Active apt sources in file: /etc/apt/sources.list.d/wseverin-ppa-trusty.list
|
||||
deb http://ppa.launchpad.net/wseverin/ppa/ubuntu trusty main
|
||||
|
||||
Inxi will also display the Weather details of your location. Surprised? Yes, It should.
|
||||
|
||||
inxi -W Erode,Tamilnadu
|
||||
|
||||
Here **Erode** is the District and **Tamilnadu** is a state in India.
|
||||
|
||||
Sample output:
|
||||
|
||||
Weather: Conditions: 79 F (26 C) - Clear Time: February 4, 6:00 PM IST
|
||||
|
||||
### Viewing Complete Hardware details ###
|
||||
|
||||
Tired of finding each hardware details? Well, you can list all details at once using command:
|
||||
|
||||
inxi -F
|
||||
|
||||
**Sample output:**
|
||||
|
||||
System: Host: sk Kernel: 3.13.0-45-generic x86_64 (64 bit) Desktop: LXDE (Openbox 3.5.2) Distro: Ubuntu 14.04 trusty
|
||||
Machine: System: Dell (portable) product: Inspiron N5050
|
||||
Mobo: Dell model: 01HXXJ version: A05 Bios: Dell version: A05 date: 08/03/2012
|
||||
CPU: Dual core Intel Core i3-2350M CPU (-HT-MCP-) cache: 3072 KB flags: (lm nx sse sse2 sse3 sse4_1 sse4_2 ssse3 vmx)
|
||||
Clock Speeds: 1: 800.00 MHz 2: 1000.00 MHz 3: 800.00 MHz 4: 800.00 MHz
|
||||
Graphics: Card: Intel 2nd Generation Core Processor Family Integrated Graphics Controller
|
||||
X.Org: 1.15.1 drivers: intel (unloaded: fbdev,vesa) Resolution: 1366x768@60.0hz
|
||||
GLX Renderer: Mesa DRI Intel Sandybridge Mobile GLX Version: 3.0 Mesa 10.3.0
|
||||
Audio: Card: Intel 6 Series/C200 Series Family High Definition Audio Controller driver: snd_hda_intel
|
||||
Sound: Advanced Linux Sound Architecture ver: k3.13.0-45-generic
|
||||
Network: Card-1: Qualcomm Atheros AR9285 Wireless Network Adapter (PCI-Express) driver: ath9k
|
||||
IF: wlan0 state: up mac:
|
||||
Card-2: Realtek RTL8101E/RTL8102E PCI Express Fast Ethernet controller driver: r8169
|
||||
IF: eth0 state: down mac:
|
||||
Drives: HDD Total Size: 500.1GB (52.5% used) 1: id: /dev/sda model: ST9500325AS size: 500.1GB
|
||||
Partition: ID: / size: 455G used: 245G (57%) fs: ext4 ID: /boot size: 236M used: 159M (72%) fs: ext2
|
||||
ID: swap-1 size: 4.19GB used: 0.00GB (0%) fs: swap
|
||||
RAID: No RAID devices detected - /proc/mdstat and md_mod kernel raid module present
|
||||
Sensors: System Temperatures: cpu: 64.5C mobo: N/A
|
||||
Fan Speeds (in rpm): cpu: N/A
|
||||
Info: Processes: 186 Uptime: 6:52 Memory: 1547.2/3861.3MB Client: Shell (bash) inxi: 1.9.17
|
||||
|
||||
As you see in the above, inxi displays the complete hardware details.
|
||||
|
||||
For more details, refer the man pages.
|
||||
|
||||
man inxi
|
||||
|
||||
### Conclusion ###
|
||||
|
||||
Are you searching for a simple tool which displays your complete system and hardware details? Then, don’t look anywhere, inxi will give you what actually want. And, it is light weight tool available in your default repositories. What else you want more? Give it a try, you won’t be disappointed.
|
||||
|
||||
Cheers!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.unixmen.com/inxi-find-system-hardware-information-linux/
|
||||
|
||||
作者:[SK][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.unixmen.com/author/sk/
|
||||
[1]:http://www.unixmen.com/screenfetch-bash-screenshot-information-tool/
|
||||
@ -0,0 +1,208 @@
|
||||
Linux Basics: Assign Multiple IP Addresses To Single Network Interface Card On CentOS 7
|
||||
================================================================================
|
||||
Some times you might want to use more than one IP address for your network interface card. What are you going to do? Buy an extra network card and assign new IP? No, It’s not necessary(atleast in the small networks). We can now assign multiple ip addresses to single network interface card in CentOS / RHEL 7 systems. Curious to know how? Well, Follow me, It is not that difficult.
|
||||
|
||||
First, let us find the IP address of the network card. In my CentOS 7 server, I use only one network card.
|
||||
|
||||
Run the following command with root user privileges:
|
||||
|
||||
ip addr
|
||||
|
||||
Sample output:
|
||||
|
||||
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN
|
||||
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
|
||||
inet 127.0.0.1/8 scope host lo
|
||||
valid_lft forever preferred_lft forever
|
||||
inet6 ::1/128 scope host
|
||||
valid_lft forever preferred_lft forever
|
||||
2: enp0s3: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
|
||||
link/ether 08:00:27:80:63:19 brd ff:ff:ff:ff:ff:ff
|
||||
inet 192.168.1.150/24 brd 192.168.1.255 scope global enp0s3
|
||||
valid_lft forever preferred_lft forever
|
||||
|
||||
As you see in the above output, my network card name is enp0s3, and its IP address is 192.168.1.150.
|
||||
|
||||
Well, as you may know, the the network card configuration files of your system is stored under **/etc/sysconfig/network-scripts/** directory. Each cards details will be stored in different names, for example **ifcfg-enp0s3**.
|
||||
|
||||
Let us see the details of **ifcfg-enp0s3**.
|
||||
|
||||
cat /etc/sysconfig/network-scripts/ifcfg-enp0s3
|
||||
|
||||
Sample output:
|
||||
|
||||
TYPE="Ethernet"
|
||||
BOOTPROTO="none"
|
||||
DEFROUTE="yes"
|
||||
IPV4_FAILURE_FATAL="no"
|
||||
IPV6INIT="yes"
|
||||
IPV6_AUTOCONF="yes"
|
||||
IPV6_DEFROUTE="yes"
|
||||
IPV6_FAILURE_FATAL="no"
|
||||
NAME="enp0s3"
|
||||
UUID="e9f9caef-cb9e-4a19-aace-767c6ee6f849"
|
||||
ONBOOT="yes"
|
||||
HWADDR="08:00:27:80:63:19"
|
||||
IPADDR0="192.168.1.150"
|
||||
PREFIX0="24"
|
||||
GATEWAY0="192.168.1.1"
|
||||
DNS1="192.168.1.1"
|
||||
IPV6_PEERDNS="yes"
|
||||
IPV6_PEERROUTES="yes"
|
||||
|
||||
Okay, now we will assign multiple addresses in the same subnet.
|
||||
|
||||
Edit file **/etc/sysconfig/network-scripts/ifcfg-enp0s3**:
|
||||
|
||||
vi /etc/sysconfig/network-scripts/ifcfg-enp0s3
|
||||
|
||||
Add extra IP addresses one by one as shown below.
|
||||
|
||||
TYPE="Ethernet"
|
||||
BOOTPROTO="none"
|
||||
DEFROUTE="yes"
|
||||
IPV4_FAILURE_FATAL="no"
|
||||
IPV6INIT="yes"
|
||||
IPV6_AUTOCONF="yes"
|
||||
IPV6_DEFROUTE="yes"
|
||||
IPV6_FAILURE_FATAL="no"
|
||||
NAME="enp0s3"
|
||||
UUID="933cdc9b-b383-4ddd-b219-5a72c69c9cf0"
|
||||
ONBOOT="yes"
|
||||
HWADDR="08:00:27:3F:AB:68"
|
||||
IPADDR0="192.168.1.150"
|
||||
IPADDR1="192.168.1.151"
|
||||
IPADDR2="192.168.1.152"
|
||||
PREFIX0="24"
|
||||
GATEWAY0="192.168.1.1"
|
||||
DNS1="192.168.1.1"
|
||||
IPV6_PEERDNS="yes"
|
||||
IPV6_PEERROUTES="yes"
|
||||
|
||||
As you see above, I have added two more IP addresses: **IPADDR1=”192.168.1.151″ & IPADDR2=”192.168.1.152″**
|
||||
|
||||
Like wise, you can add as many a IP addresses you want.
|
||||
|
||||
Finally, save and close the file. Restart network service to take effect the changes.
|
||||
|
||||
systemctl restart network
|
||||
|
||||
Now, let us check the IP addresses have been added or not.
|
||||
|
||||
ip addr
|
||||
|
||||
Sample output:
|
||||
|
||||
: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN
|
||||
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
|
||||
inet 127.0.0.1/8 scope host lo
|
||||
valid_lft forever preferred_lft forever
|
||||
inet6 ::1/128 scope host
|
||||
valid_lft forever preferred_lft forever
|
||||
2: enp0s3: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
|
||||
link/ether 08:00:27:3f:ab:68 brd ff:ff:ff:ff:ff:ff
|
||||
inet 192.168.1.150/24 brd 192.168.1.255 scope global enp0s3
|
||||
valid_lft forever preferred_lft forever
|
||||
inet 192.168.1.151/24 brd 192.168.1.255 scope global secondary enp0s3
|
||||
valid_lft forever preferred_lft forever
|
||||
inet 192.168.1.152/24 brd 192.168.1.255 scope global secondary enp0s3
|
||||
valid_lft forever preferred_lft forever
|
||||
inet6 fe80::a00:27ff:fe3f:ab68/64 scope link
|
||||
valid_lft forever preferred_lft forever
|
||||
|
||||
As you see above, the single network interface card has three IP addresses.
|
||||
|
||||
Let us ping the newly added IP addresses:
|
||||
|
||||
ping -c 4 192.168.1.151
|
||||
|
||||
Sample output:
|
||||
|
||||
PING 192.168.1.151 (192.168.1.151) 56(84) bytes of data.
|
||||
64 bytes from 192.168.1.151: icmp_seq=1 ttl=64 time=0.048 ms
|
||||
64 bytes from 192.168.1.151: icmp_seq=2 ttl=64 time=0.075 ms
|
||||
64 bytes from 192.168.1.151: icmp_seq=3 ttl=64 time=0.077 ms
|
||||
64 bytes from 192.168.1.151: icmp_seq=4 ttl=64 time=0.077 ms
|
||||
|
||||
--- 192.168.1.151 ping statistics ---
|
||||
4 packets transmitted, 4 received, 0% packet loss, time 2999ms
|
||||
rtt min/avg/max/mdev = 0.048/0.069/0.077/0.013 ms
|
||||
|
||||
----------
|
||||
|
||||
ping -c 4 192.168.1.152
|
||||
|
||||
Sample output:
|
||||
|
||||
PING 192.168.1.152 (192.168.1.152) 56(84) bytes of data.
|
||||
64 bytes from 192.168.1.152: icmp_seq=1 ttl=64 time=0.034 ms
|
||||
64 bytes from 192.168.1.152: icmp_seq=2 ttl=64 time=0.075 ms
|
||||
64 bytes from 192.168.1.152: icmp_seq=3 ttl=64 time=0.073 ms
|
||||
64 bytes from 192.168.1.152: icmp_seq=4 ttl=64 time=0.075 ms
|
||||
|
||||
--- 192.168.1.152 ping statistics ---
|
||||
4 packets transmitted, 4 received, 0% packet loss, time 2999ms
|
||||
rtt min/avg/max/mdev = 0.034/0.064/0.075/0.018 ms
|
||||
|
||||
If you want to use **different subnet**, then you can change the **PREFIX0=24** line to different subnet, such as **PREFIX1=16**.
|
||||
|
||||
For example, I am going to add Class A IP address(**ex.10.0.0.1**) to my network card.
|
||||
|
||||
TYPE="Ethernet"
|
||||
BOOTPROTO="none"
|
||||
DEFROUTE="yes"
|
||||
IPV4_FAILURE_FATAL="no"
|
||||
IPV6INIT="yes"
|
||||
IPV6_AUTOCONF="yes"
|
||||
IPV6_DEFROUTE="yes"
|
||||
IPV6_FAILURE_FATAL="no"
|
||||
NAME="enp0s3"
|
||||
UUID="933cdc9b-b383-4ddd-b219-5a72c69c9cf0"
|
||||
ONBOOT="yes"
|
||||
HWADDR="08:00:27:3F:AB:68"
|
||||
IPADDR0="192.168.1.150"
|
||||
IPADDR1="192.168.1.151"
|
||||
IPADDR2="192.168.1.152"
|
||||
IPADDR3="10.0.0.1"
|
||||
PREFIX0="24"
|
||||
PREFIX1=16
|
||||
GATEWAY0="192.168.1.1"
|
||||
DNS1="192.168.1.1"
|
||||
IPV6_PEERDNS="yes"
|
||||
IPV6_PEERROUTES="yes"
|
||||
|
||||
Do you notice that I have added a Class A type address(10.0.0.1) and prefix=16.
|
||||
|
||||
Save and close the file. Restart network service,
|
||||
|
||||
Then, ping the new added IP:
|
||||
|
||||
ping -c 4 10.0.0.1
|
||||
|
||||
Sample output:
|
||||
|
||||
PING 10.0.0.1 (10.0.0.1) 56(84) bytes of data.
|
||||
64 bytes from 10.0.0.1: icmp_seq=1 ttl=64 time=0.097 ms
|
||||
64 bytes from 10.0.0.1: icmp_seq=2 ttl=64 time=0.073 ms
|
||||
64 bytes from 10.0.0.1: icmp_seq=3 ttl=64 time=0.074 ms
|
||||
64 bytes from 10.0.0.1: icmp_seq=4 ttl=64 time=0.075 ms
|
||||
|
||||
--- 10.0.0.1 ping statistics ---
|
||||
4 packets transmitted, 4 received, 0% packet loss, time 3000ms
|
||||
rtt min/avg/max/mdev = 0.073/0.079/0.097/0.014 ms
|
||||
|
||||
Similarly, you can add different Gateways too.
|
||||
|
||||
That’s it.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.unixmen.com/linux-basics-assign-multiple-ip-addresses-single-network-interface-card-centos-7/
|
||||
|
||||
作者:[SK][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.unixmen.com/author/sk/
|
||||
@ -0,0 +1,63 @@
|
||||
zBackup – A versatile deduplicating backup tool
|
||||
================================================================================
|
||||
zbackup is a globally-deduplicating backup tool, based on the ideas found in rsync. Feed a large .tar into it, and it will store duplicate regions of it only once, then compress and optionally encrypt the result. Feed another .tar file, and it will also re-use any data found in any previous backups. This way only new changes are stored, and as long as the files are not very different, the amount of storage required is very low. Any of the backup files stored previously can be read back in full at any time.
|
||||
|
||||
### zBackup Features ###
|
||||
|
||||
Parallel LZMA or LZO compression of the stored data
|
||||
Built-in AES encryption of the stored data
|
||||
Possibility to delete old backup data
|
||||
Use of a 64-bit rolling hash, keeping the amount of soft collisions to zero
|
||||
Repository consists of immutable files. No existing files are ever modified
|
||||
Written in C++ only with only modest library dependencies
|
||||
Safe to use in production
|
||||
Possibility to exchange data between repos without recompression
|
||||
|
||||
### Install zBackup in ubuntu ###
|
||||
|
||||
Open the terminal and run the following command
|
||||
|
||||
sudo apt-get install zbackup
|
||||
|
||||
### Using zBackup ###
|
||||
|
||||
zbackup init initializes a backup repository for the backup files to be stored.
|
||||
|
||||
zbackup init [--non-encrypted] [--password-file ~/.my_backup_password ] /my/backup/repo
|
||||
|
||||
zbackup backup backups a tar file generated by tar c to the repository initialized using zbackup init
|
||||
|
||||
zbackup [--password-file ~/.my_backup_password ] [--threads number_of_threads ] backup /my/backup/repo/backups/backup-`date ‘+%Y-%m-%d'`
|
||||
|
||||
zbackup restore restores the backup file to a tar file.
|
||||
|
||||
zbackup [--password-file ~/.my_backup_password [--cache-size cache_size_in_mb restore /my/backup/repo/backups/backup-`date ‘+%Y-%m-%d'` > /my/precious/backup-restored.tar
|
||||
|
||||
### Available Options ###
|
||||
|
||||
- -non-encrypted -- Do not encrypt the backup repository.
|
||||
- --password-file ~/.my_backup_password -- Use the password file specified at ~/.my_backup_password to encrypt the repository and backup file, or to decrypt the backup file.
|
||||
- --threads number_of_threads -- Limit the partial LZMA compression to number_of_threads needed. Recommended for 32-bit architectures.
|
||||
- --cache-size cache_size_in_mb -- Use the cache size provided by cache_size_in_mb to speed up the restoration process.
|
||||
|
||||
### zBackup files ###
|
||||
|
||||
~/.my_backup_password Used to encrypt the repository and backup file, or to decrypt the backup file. See zbackup for further details.
|
||||
|
||||
/my/backup/repo The directory used to hold the backup repository.
|
||||
|
||||
/my/precious/restored-tar The tar used for restoring the backup.
|
||||
|
||||
/my/backup/repo/backups/backup-`date ‘+%Y-%m-%d'` Specifies the backup file.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.ubuntugeek.com/zbackup-a-versatile-deduplicating-backup-tool.html
|
||||
|
||||
作者:[ruchi][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.ubuntugeek.com/author/ubuntufix
|
||||
Loading…
Reference in New Issue
Block a user