mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-02-28 01:01:09 +08:00
Merge remote-tracking branch 'LCTT/master'
This commit is contained in:
commit
f16ceea6e3
@ -0,0 +1,165 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (lxbwolf)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-12181-1.html)
|
||||
[#]: subject: (Three Methods Boot CentOS/RHEL 7/8 Systems in Single User Mode)
|
||||
[#]: via: (https://www.2daygeek.com/boot-centos-7-8-rhel-7-8-single-user-mode/)
|
||||
[#]: author: (Magesh Maruthamuthu https://www.2daygeek.com/author/magesh/)
|
||||
|
||||
以单用户模式启动 CentOS/RHEL 7/8 的三种方法
|
||||
======
|
||||
|
||||

|
||||
|
||||
单用户模式,也被称为维护模式,超级用户可以在此模式下恢复/修复系统问题。
|
||||
|
||||
通常情况下,这类问题在多用户环境中修复不了。系统可以启动但功能不能正常运行或者你登录不了系统。
|
||||
|
||||
在基于 [Red Hat][1](RHEL)7/8 的系统中,使用 `runlevel1.target` 或 `rescue.target` 来实现。
|
||||
|
||||
在此模式下,系统会挂载所有的本地文件系统,但不开启网络接口。
|
||||
|
||||
系统仅启动特定的几个服务和修复系统必要的尽可能少的功能。
|
||||
|
||||
当你想运行文件系统一致性检查来修复损坏的文件系统,或忘记 root 密码后重置密码,或要修复系统上的一个挂载点问题时,这个方法会很有用。
|
||||
|
||||
你可以用下面三种方法以单用户模式启动 [CentOS][2]/[RHEL][3] 7/8 系统。
|
||||
|
||||
* 方法 1:通过向内核添加 `rd.break` 参数来以单用户模式启动 CentOS/RHEL 7/8 系统
|
||||
* 方法 2:通过用 `init=/bin/bash` 或 `init=/bin/sh` 替换内核中的 `rhgb quiet` 语句来以单用户模式启动 CentOS/RHEL 7/8 系统
|
||||
* 方法 3:通过用 `rw init=/sysroot/bin/sh` 参数替换内核中的 `ro` 语句以单用户模式启动 CentOS/RHEL 7/8 系统
|
||||
|
||||
### 方法 1
|
||||
|
||||
通过向内核添加 `rd.break` 参数来以单用户模式启动 CentOS/RHEL 7/8 系统。
|
||||
|
||||
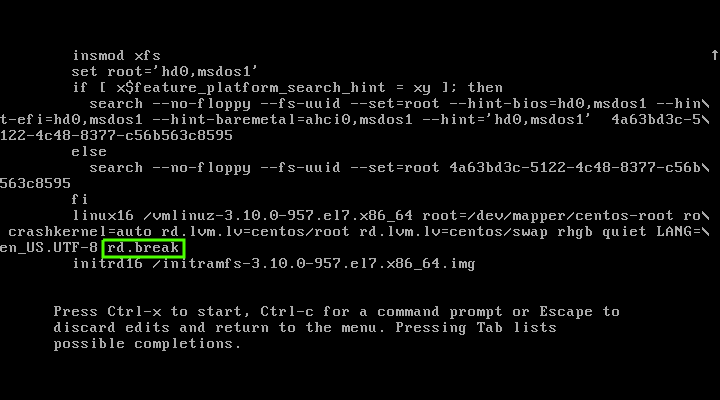
重启你的系统,在 GRUB2 启动界面,按下 `e` 键来编辑选中的内核。你需要选中第一行,第一个是最新的内核,然而如果你想用旧的内核启动系统你也可以选择其他的行。
|
||||
|
||||
|
||||
|
||||
根据你的 RHEL/CentOS 版本,找到 `linux16` 或 `linux` 语句,按下键盘上的 `End` 键,跳到行末,像下面截图中展示的那样添加关键词 `rd.break`,按下 `Ctrl+x` 或 `F10` 来进入单用户模式。
|
||||
|
||||
如果你的系统是 RHEL/CentOS 7,你需要找 `linux16`,如果你的系统是 RHEL/CentOS 8,那么你需要找 `linux`。
|
||||
|
||||
|
||||
|
||||
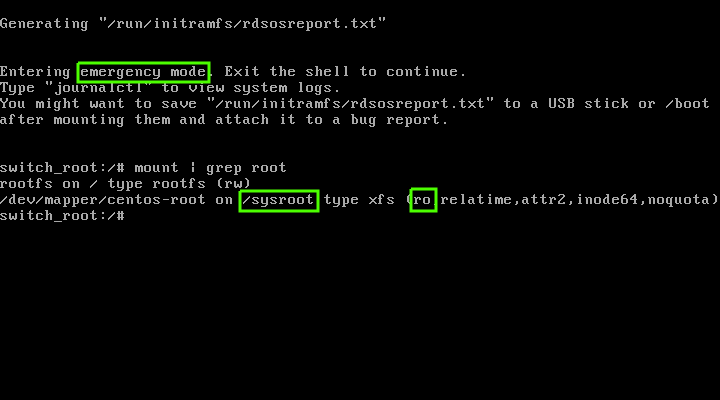
这个修改会让你的 root 文件系统以 “只读(`ro`)” 模式挂载。你可以用下面的命令来验证下。下面的输出也明确地告诉你当前是在 “<ruby>紧急模式<rt>Emergency Mode</rt></ruby>”。
|
||||
|
||||
```
|
||||
# mount | grep root
|
||||
```
|
||||
|
||||
|
||||
|
||||
为了修改 `sysroot` 文件系统,你需要用读写模式(`rw`)重新挂载它。
|
||||
|
||||
```
|
||||
# mount -o remount,rw /sysroot
|
||||
```
|
||||
|
||||
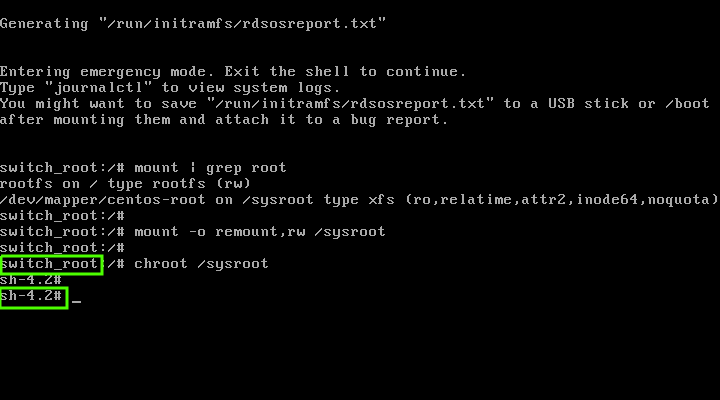
运行下面的命令修改环境,这就是大家熟知的 “监禁目录” 或 “chroot 监狱”。
|
||||
|
||||
```
|
||||
# chroot /sysroot
|
||||
```
|
||||
|
||||
|
||||
|
||||
现在,单用户模式已经完全准备好了。当你修复了你的问题要退出单用户模式时,执行下面的步骤。
|
||||
|
||||
CentOS/RHEL 7/8 默认使用 SELinux,因此创建下面的隐藏文件,这个文件会在下一次启动时重新标记所有文件。
|
||||
|
||||
```
|
||||
# touch /.autorelabel
|
||||
```
|
||||
|
||||
最后,用下面的命令重启系统。你也可以输入两次 `exit` 命令来重启你的系统。
|
||||
|
||||
```
|
||||
# reboot -f
|
||||
```
|
||||
|
||||
### 方法 2
|
||||
|
||||
通过用 `init=/bin/bash` 或 `init=/bin/sh` 替换内核中的 `rhgb quiet` 语句来以单用户模式启动 CentOS/RHEL 7/8 系统。
|
||||
|
||||
重启你的系统,在 GRUB2 启动界面,按下 `e` 键来编辑选中的内核。
|
||||
|
||||

|
||||
|
||||
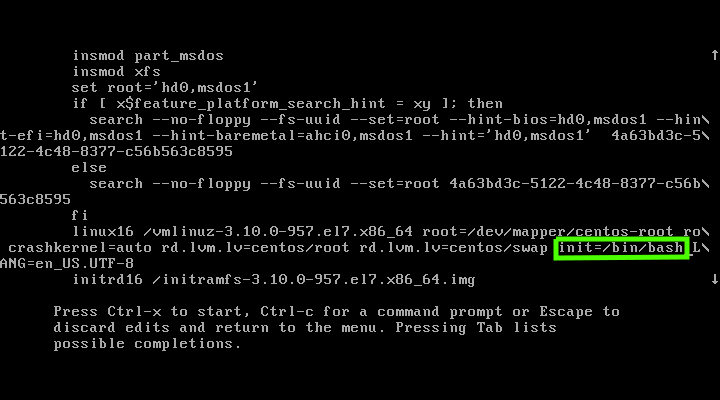
找到语句 `rhgb quiet`,用 `init=/bin/bash` 或 `init=/bin/sh` 替换它,然后按下 `Ctrl+x` 或 `F10` 来进入单用户模式。
|
||||
|
||||
`init=/bin/bash` 的截图。
|
||||
|
||||
|
||||
|
||||
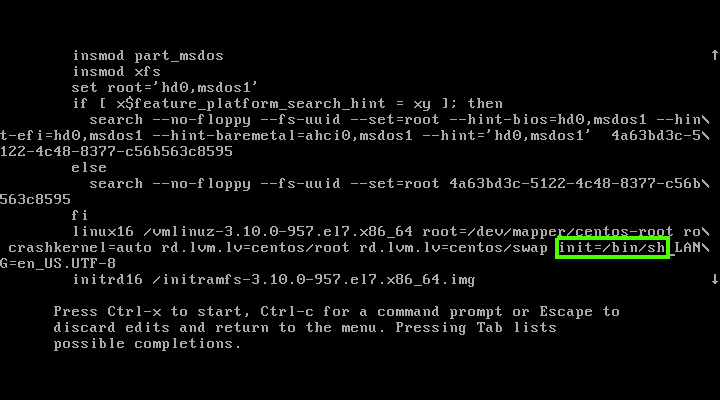
`init=/bin/sh` 的截图。
|
||||
|
||||
|
||||
|
||||
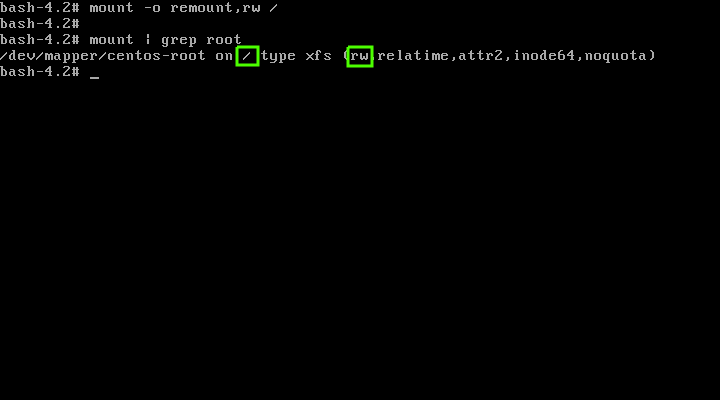
默认情况下,上面的操作会以只读(`ro`)模式挂载你的 `/` 分区,因此你需要以读写(`rw`)模式重新挂载 `/` 文件系统,这样才能修改它。
|
||||
|
||||
```
|
||||
# mount -o remount,rw /
|
||||
```
|
||||
|
||||
|
||||
|
||||
现在你可以执行你的任务了。当结束时,执行下面的命令来开启重启时的 SELinux 重新标记。
|
||||
|
||||
```
|
||||
# touch /.autorelabel
|
||||
```
|
||||
|
||||
最后,重启系统。
|
||||
|
||||
```
|
||||
# exec /sbin/init 6
|
||||
```
|
||||
|
||||
### 方法 3
|
||||
|
||||
通过用 `rw init=/sysroot/bin/sh` 参数替换内核中的 `ro` 单词,以单用户模式启动 CentOS/RHEL 7/8 系统。
|
||||
|
||||
为了中断自动启动的过程,重启你的系统并在 GRUB2 启动界面按下任意键。
|
||||
|
||||
现在会展示你系统上所有可用的内核,选择最新的内核,按下 `e` 键来编辑选中的内核参数。
|
||||
|
||||
找到以 `linux` 或 `linux16` 开头的语句,用 `rw init=/sysroot/bin/sh` 替换 `ro`。替换完后按下 `Ctrl+x` 或 `F10` 来进入单用户模式。
|
||||
|
||||
运行下面的命令把环境切换为 “chroot 监狱”。
|
||||
|
||||
```
|
||||
# chroot /sysroot
|
||||
```
|
||||
|
||||
如果需要,做出必要的修改。修改完后,执行下面的命令来开启重启时的 SELinux 重新标记。
|
||||
|
||||
```
|
||||
# touch /.autorelabel
|
||||
```
|
||||
|
||||
最后,重启系统。
|
||||
|
||||
```
|
||||
# reboot -f
|
||||
```
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.2daygeek.com/boot-centos-7-8-rhel-7-8-single-user-mode/
|
||||
|
||||
作者:[Magesh Maruthamuthu][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[lxbwolf](https://github.com/lxbwolf)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.2daygeek.com/author/magesh/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.2daygeek.com/category/red-hat/
|
||||
[2]: https://www.2daygeek.com/category/centos/
|
||||
[3]: https://www.2daygeek.com/category/rhel/
|
||||
[4]: data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7
|
||||
@ -1,94 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (tinyeyeser )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (How to avoid man-in-the-middle cyber attacks)
|
||||
[#]: via: (https://opensource.com/article/20/4/mitm-attacks)
|
||||
[#]: author: (Jackie Lam https://opensource.com/users/beenverified)
|
||||
|
||||
How to avoid man-in-the-middle cyber attacks
|
||||
======
|
||||
Understanding MITM attacks is the first step in not being a victim of
|
||||
this high-tech style of eavesdropping.
|
||||
![Security monster][1]
|
||||
|
||||
Whether you're sending data on your computer or talking to someone online, you want to assume some level of security and privacy.
|
||||
|
||||
But what if a third party is eavesdropping online, unbeknownst to you? And worse, what if they're impersonating someone from a business you trust in order to gain damaging information? This could put your personal data into the hands of dangerous, would-be thieves.
|
||||
|
||||
Welcome to what's called a man-in-the-middle (MITM) attack.
|
||||
|
||||
### What are man-in-the-middle attacks?
|
||||
|
||||
A man-in-the-middle attack occurs when a cybercriminal inserts themselves into communications between you, the targeted victim, and a device in order to steal sensitive information that can be used for a variety of criminal purposes—most notably identity theft, says Steve J. J. Weisman, founder of Scamicide.
|
||||
|
||||
"A man-in-the-middle-attack can also occur when the victim believes he or she is communicating with a legitimate app or website," says Weisman, "when the truth is that the victim is communicating with a phony website or app and thereby providing sensitive information to the criminal."
|
||||
|
||||
One of the oldest forms of cyberattacks, MITM attacks have been around since the 1980s. What's more, they're quite common. As Weisman explains, there are a handful of ways a MITM attack can happen:
|
||||
|
||||
* **Attacking a WiFi router that is not properly secured:** This typically occurs when someone is using public WiFi. "While home routers might be vulnerable, it's more common for criminals to attack public WiFi networks," says Weisman. The goal is to spy on unsuspecting people who are handling sensitive information, such as their online bank accounts, he adds.
|
||||
* **Hacking email accounts of banks, financial advisers, and other companies:** "Once [the criminals] have hacked these email systems, they send out emails that appear to come from the legitimate bank or other company," Weisman says. "[They ask] for personal information, such as usernames and passwords, under the guise of an emergency. The targeted victim is lured into providing that information."
|
||||
* **Sending phishing emails:** Thieves might also send emails pretending to be legitimate companies that the targeted victim does business with, asking the recipient for their personal information. "In many instances, the spear-phishing emails will direct the victim to a counterfeit website that appears to be that of a legitimate company with which the victim does business," says Weisman.
|
||||
* **Using malicious code in legitimate websites:** Attackers can also place malicious code—usually JavaScript—into a legitimate website by way of a web application. "When the victim loads the legitimate page, the malicious code just sits in the background until the user enters sensitive information, such as account login or credit card details, which the malicious code then copies and sends to the attackers' servers," says Nicholas McBride, a cybersecurity consultant.
|
||||
|
||||
|
||||
|
||||
### What is an example of an MITM attack?
|
||||
|
||||
The Lenovo case is a well-known example of an MITM attack. In 2014 and 2015, the major computer manufacturer sold consumer laptops with preinstalled software that meddled with how a user's browser communicated with websites. Whenever the user's cursor hovered over a product, this software, called VisualDiscovery, sent pop-up ads from retail partners that sold similar products.
|
||||
|
||||
Here's the kicker: This MITM attack allowed VisualDiscovery to access all of the user's personal data, including social security numbers, info about financial transactions, medical info, and logins and passwords. All without the user knowing or granting permission beforehand. The FTC deemed this a deceptive and unfair online scam. Lenovo agreed to pay $8.3 million in a class-action settlement in 2019.
|
||||
|
||||
### How can I protect myself from an online attack?
|
||||
|
||||
* **Avoid using public WiFi:** Weisman recommends never using public WiFi for financial transactions unless you've installed a reliable virtual private network (VPN) client on your device and have a VPN host you can use and trust. Over a VPN connection, your communications are encrypted, so your information can't be stolen.
|
||||
|
||||
* **Be on the lookout:** Be wary of emails or text messages that ask you to update your password or provide your username or personal information. These methods can be used to steal your identity.
|
||||
|
||||
If you are unsure of the actual identity of the party sending you the email, you can use tools such as a reverse phone or email search. With a reverse phone number lookup, you may be able to find out more about the identity of an unknown texter. And with a reverse email lookup, you can try to determine who might have sent you a message.
|
||||
|
||||
Generally, if something's actually a problem, you'll hear from someone you know and trust within your company, or from someone you can also go and meet, in person, at your bank or school or other organization. Important account information is never the purview of an unknown technician.
|
||||
|
||||
* **Don't click on links contained in emails:** If someone sends you an email telling you that you need to sign into an account, don't click on the link provided in the email. Instead, navigate to the site yourself, log in as you normally would, and look for an alert there. If you don't see an alert message in your account settings, contact a representative by phone using contact information on the site and _not_ from the email.
|
||||
|
||||
* **Install reliable security software:** If you're on Windows, install good open source antivirus like [ClamAV][2]. On all platforms, keep your software up to date with the latest security patches.
|
||||
|
||||
* **Take alerts seriously:** If you're visiting a site that starts with HTTPS, your browser might alert you to an issue, says McBride. For instance, if the domain name on the site's certificate doesn't match the one you're trying to visit. Don't ignore the alert. Heed it and navigate away from the site for now. Verify that you haven't [mistyped it][3], and if the problem persists, contact the site owner if you can.
|
||||
|
||||
* **Use an ad blocker:** Pop-up ads (also known as _adware attacks_) can be used to intercept your personal information, so use an ad blocker. "The truth is, as an individual user, it's hard to protect against a MITM attack," says McBride, "as it is designed to leave the victim in the dark and to prevent them from noticing that there is anything wrong."
|
||||
|
||||
A good open source ad blocker (or "wide-spectrum blocker," in the developer's words) is [uBlock origin][4]. It's available for both Firefox and Chromium (and all Chromium-based browsers, such as Chrome, Brave, Vivaldi, Edge, and so on), and even Safari.
|
||||
|
||||
|
||||
|
||||
|
||||
### Stay alert
|
||||
|
||||
Remember, you don't have to click anything online right away, and you don't have to follow random people's instructions, no matter how urgent they may seem. The internet will still be there after you step away from the computer and verify the identity of a person or site demanding your attention.
|
||||
|
||||
While MITM attacks can happen to anyone, understanding what they are, knowing how they happen, and actively taking steps to prevent them can safeguard you from being a victim.
|
||||
|
||||
* * *
|
||||
|
||||
_This article was originally published on [BeenVerified.com][5] under a [CC BY-SA 2.0][6] license._
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/20/4/mitm-attacks
|
||||
|
||||
作者:[Jackie Lam][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/beenverified
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/security_password_chaos_engineer_monster.png?itok=J31aRccu (Security monster)
|
||||
[2]: https://www.clamav.net
|
||||
[3]: https://opensource.com/article/20/1/stop-typosquatting-attacks
|
||||
[4]: https://github.com/gorhill/uBlock
|
||||
[5]: https://www.beenverified.com/crime/what-is-a-man-in-the-middle-attack/
|
||||
[6]: https://creativecommons.org/licenses/by-sa/2.0/
|
||||
@ -1,328 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (messon007)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Learning to love systemd)
|
||||
[#]: via: (https://opensource.com/article/20/4/systemd)
|
||||
[#]: author: (David Both https://opensource.com/users/dboth)
|
||||
|
||||
Learning to love systemd
|
||||
======
|
||||
systemd is the mother of all processes, responsible for bringing the
|
||||
Linux host up to a state where productive work can be done.
|
||||
![Penguin driving a car with a yellow background][1]
|
||||
|
||||
systemd—yes, all lower-case, even at the beginning of a sentence—is the modern replacement for init and SystemV init scripts. It is also much more.
|
||||
|
||||
Like most sysadmins, when I think of the init program and SystemV, I think of Linux startup and shutdown and not really much else, like managing services once they are up and running. Like init, systemd is the mother of all processes, and it is responsible for bringing the Linux host up to a state in which productive work can be done. Some of the functions assumed by systemd, which is far more extensive than the old init program, are to manage many aspects of a running Linux host, including mounting filesystems, managing hardware, handling timers, and starting and managing the system services that are required to have a productive Linux host.
|
||||
|
||||
This series of articles, which is based in part on excerpts from my three-volume Linux training course, [_Using and administering Linux: zero to sysadmin_][2], explores systemd's functions both at startup and beginning after startup finishes.
|
||||
|
||||
### Linux boot
|
||||
|
||||
The complete process that takes a Linux host from an off state to a running state is complex, but it is open and knowable. Before getting into the details, I'll give a quick overview from when the host hardware is turned on until the system is ready for a user to log in. Most of the time, "the boot process" is discussed as a single entity, but that is not accurate. There are, in fact, three major parts to the full boot and startup process:
|
||||
|
||||
* **Hardware boot:** Initializes the system hardware
|
||||
* **Linux boot:** Loads the Linux kernel and then systemd
|
||||
* **Linux startup:** Where systemd prepares the host for productive work
|
||||
|
||||
|
||||
|
||||
The Linux startup sequence begins after the kernel has loaded either init or systemd, depending upon whether the distribution uses the old or new startup, respectively. The init and systemd programs start and manage all the other processes and are both known as the "mother of all processes" on their respective systems.
|
||||
|
||||
It is important to separate the hardware boot from the Linux boot from the Linux startup and to explicitly define the demarcation points between them. Understanding these differences and what part each plays in getting a Linux system to a state where it can be productive makes it possible to manage these processes and better determine where a problem is occurring during what most people refer to as "boot."
|
||||
|
||||
The startup process follows the three-step boot process and brings the Linux computer up to an operational state in which it is usable for productive work. The startup process begins when the kernel transfers control of the host to systemd.
|
||||
|
||||
### systemd controversy
|
||||
|
||||
systemd can evoke a wide range of reactions from sysadmins and others responsible for keeping Linux systems up and running. The fact that systemd is taking over so many tasks in many Linux systems has engendered pushback and discord among certain groups of developers and sysadmins.
|
||||
|
||||
SystemV and systemd are two different methods of performing the Linux startup sequence. SystemV start scripts and the init program are the old methods, and systemd using targets is the new method. Although most modern Linux distributions use the newer systemd for startup, shutdown, and process management, there are still some that do not. One reason is that some distribution maintainers and some sysadmins prefer the older SystemV method over the newer systemd.
|
||||
|
||||
I think both have advantages.
|
||||
|
||||
#### Why I prefer SystemV
|
||||
|
||||
I prefer SystemV because it is more open. Startup is accomplished using Bash scripts. After the kernel starts the init program, which is a compiled binary, init launches the **rc.sysinit** script, which performs many system initialization tasks. After **rc.sysinit** completes, init launches the **/etc/rc.d/rc** script, which in turn starts the various services defined by the SystemV start scripts in the **/etc/rc.d/rcX.d**, where "X" is the number of the runlevel being started.
|
||||
|
||||
Except for the init program itself, all these programs are open and easily knowable scripts. It is possible to read through these scripts and learn exactly what is taking place during the entire startup process, but I don't think many sysadmins actually do that. Each start script is numbered so that it starts its intended service in a specific sequence. Services are started serially, and only one service starts at a time.
|
||||
|
||||
systemd, developed by Red Hat's Lennart Poettering and Kay Sievers, is a complex system of large, compiled binary executables that are not understandable without access to the source code. It is open source, so "access to the source code" isn't hard, just less convenient. systemd appears to represent a significant refutation of multiple tenets of the Linux philosophy. As a binary, systemd is not directly open for the sysadmin to view or make easy changes. systemd tries to do everything, such as managing running services, while providing significantly more status information than SystemV. It also manages hardware, processes, and groups of processes, filesystem mounts, and much more. systemd is present in almost every aspect of the modern Linux host, making it the one-stop tool for system management. All of this is a clear violation of the tenets that programs should be small and that each program should do one thing and do it well.
|
||||
|
||||
#### Why I prefer systemd
|
||||
|
||||
I prefer systemd as my startup mechanism because it starts as many services as possible in parallel, depending upon the current stage in the startup process. This speeds the overall startup and gets the host system to a login screen faster than SystemV.
|
||||
|
||||
systemd manages almost every aspect of a running Linux system. It can manage running services while providing significantly more status information than SystemV. It also manages hardware, processes and groups of processes, filesystem mounts, and much more. systemd is present in almost every aspect of the modern Linux operating system, making it the one-stop tool for system management. (Does this sound familiar?)
|
||||
|
||||
The systemd tools are compiled binaries, but the tool suite is open because all the configuration files are ASCII text files. Startup configuration can be modified through various GUI and command-line tools, as well as adding or modifying various configuration files to suit the needs of the specific local computing environment.
|
||||
|
||||
#### The real issue
|
||||
|
||||
Did you think I could not like both startup systems? I do, and I can work with either one.
|
||||
|
||||
In my opinion, the real issue and the root cause of most of the controversy between SystemV and systemd is that there is [no choice][3] on the sysadmin level. The choice of whether to use SystemV or systemd has already been made by the developers, maintainers, and packagers of the various distributions—but with good reason. Scooping out and replacing an init system, by its extreme, invasive nature, has a lot of consequences that would be hard to tackle outside the distribution design process.
|
||||
|
||||
Despite the fact that this choice is made for me, my Linux hosts boot up and work, which is what I usually care the most about. As an end user and even as a sysadmin, my primary concern is whether I can get my work done, work such as writing my books and this article, installing updates, and writing scripts to automate everything. So long as I can do my work, I don't really care about the start sequence used on my distro.
|
||||
|
||||
I do care when there is a problem during startup or service management. Regardless of which startup system is used on a host, I know enough to follow the sequence of events to find the failure and fix it.
|
||||
|
||||
#### Replacing SystemV
|
||||
|
||||
There have been previous attempts at replacing SystemV with something a bit more modern. For about two releases, Fedora used a thing called Upstart to replace the aging SystemV, but it did not replace init and provided no changes that I noticed. Because Upstart provided no significant changes to the issues surrounding SystemV, efforts in this direction were quickly dropped in favor of systemd.
|
||||
|
||||
Despite the fact that most Linux developers agree that replacing the old SystemV startup is a good idea, many developers and sysadmins dislike systemd for that. Rather than rehash all the so-called issues that people have—or had—with systemd, I will refer you to two good, if somewhat old, articles that should cover most everything. Linus Torvalds, the creator of the Linux kernel, seems disinterested. In a 2014 ZDNet article, _[Linus Torvalds and others on Linux's systemd][4]_, Linus is clear about his feelings.
|
||||
|
||||
> "I don't actually have any particularly strong opinions on systemd itself. I've had issues with some of the core developers that I think are much too cavalier about bugs and compatibility, and I think some of the design details are insane (I dislike the binary logs, for example), but those are details, not big issues."
|
||||
|
||||
In case you don't know much about Linus, I can tell you that if he does not like something, he is very outspoken, explicit, and quite clear about that dislike. He has become more socially acceptable in his manner of addressing his dislike about things.
|
||||
|
||||
In 2013, Poettering wrote a long blog post in which he debunks the [myths about systemd][5] while providing insight into some of the reasons for creating it. This is a very good read, and I highly recommend it.
|
||||
|
||||
### systemd tasks
|
||||
|
||||
Depending upon the options used during the compile process (which are not considered in this series), systemd can have as many as 69 binary executables that perform the following tasks, among others:
|
||||
|
||||
* The systemd program runs as PID 1 and provides system startup of as many services in parallel as possible, which, as a side effect, speeds overall startup times. It also manages the shutdown sequence.
|
||||
* The systemctl program provides a user interface for service management.
|
||||
* Support for SystemV and LSB start scripts is offered for backward compatibility.
|
||||
* Service management and reporting provide more service status data than SystemV.
|
||||
* It includes tools for basic system configuration, such as hostname, date, locale, lists of logged-in users, running containers and virtual machines, system accounts, runtime directories and settings, daemons to manage simple network configuration, network time synchronization, log forwarding, and name resolution.
|
||||
* It offers socket management.
|
||||
* systemd timers provide advanced cron-like capabilities to include running a script at times relative to system boot, systemd startup, the last time the timer was started, and more.
|
||||
* It provides a tool to analyze dates and times used in timer specifications.
|
||||
* Mounting and unmounting of filesystems with hierarchical awareness allows safer cascading of mounted filesystems.
|
||||
* It enables the positive creation and management of temporary files, including deletion.
|
||||
* An interface to D-Bus provides the ability to run scripts when devices are plugged in or removed. This allows all devices, whether pluggable or not, to be treated as plug-and-play, which considerably simplifies device handling.
|
||||
* Its tool to analyze the startup sequence can be used to locate the services that take the most time.
|
||||
* It includes journals for storing system log messages and tools for managing the journals.
|
||||
|
||||
|
||||
|
||||
### Architecture
|
||||
|
||||
Those tasks and more are supported by a number of daemons, control programs, and configuration files. Figure 1 shows many of the components that belong to systemd. This is a simplified diagram designed to provide a high-level overview, so it does not include all of the individual programs or files. Nor does it provide any insight into data flow, which is so complex that it would be a useless exercise in the context of this series of articles.
|
||||
|
||||
![systemd architecture][6]
|
||||
|
||||
A full exposition of systemd would take a book on its own. You do not need to understand the details of how the systemd components in Figure 1 fit together; it's enough to know about the programs and components that enable managing various Linux services and deal with log files and journals. But it's clear that systemd is not the monolithic monstrosity it is purported to be by some of its critics.
|
||||
|
||||
### systemd as PID 1
|
||||
|
||||
systemd is PID 1. Some of its functions, which are far more extensive than the old SystemV3 init program, are to manage many aspects of a running Linux host, including mounting filesystems and starting and managing system services required to have a productive Linux host. Any of systemd's tasks that are not related to the startup sequence are outside the scope of this article (but some will be explored later in this series).
|
||||
|
||||
First, systemd mounts the filesystems defined by **/etc/fstab**, including any swap files or partitions. At this point, it can access the configuration files located in **/etc**, including its own. It uses its configuration link, **/etc/systemd/system/default.target**, to determine which state or target it should boot the host into. The **default.target** file is a symbolic link to the true target file. For a desktop workstation, this is typically going to be the **graphical.target**, which is equivalent to runlevel 5 in SystemV. For a server, the default is more likely to be the **multi-user.target**, which is like runlevel 3 in SystemV. The **emergency.target** is similar to single-user mode. Targets and services are systemd units.
|
||||
|
||||
The table below (Figure 2) compares the systemd targets with the old SystemV startup runlevels. systemd provides the systemd target aliases for backward compatibility. The target aliases allow scripts—and many sysadmins—to use SystemV commands like **init 3** to change runlevels. Of course, the SystemV commands are forwarded to systemd for interpretation and execution.
|
||||
|
||||
**systemd targets** | **SystemV runlevel** | **target aliases** | **Description**
|
||||
---|---|---|---
|
||||
default.target | | | This target is always aliased with a symbolic link to either **multi-user.target** or **graphical.target**. systemd always uses the **default.target** to start the system. The **default.target** should never be aliased to **halt.target**, **poweroff.target**, or **reboot.target**.
|
||||
graphical.target | 5 | runlevel5.target | **Multi-user.target** with a GUI
|
||||
| 4 | runlevel4.target | Unused. Runlevel 4 was identical to runlevel 3 in the SystemV world. This target could be created and customized to start local services without changing the default **multi-user.target**.
|
||||
multi-user.target | 3 | runlevel3.target | All services running, but command-line interface (CLI) only
|
||||
| 2 | runlevel2.target | Multi-user, without NFS, but all other non-GUI services running
|
||||
rescue.target | 1 | runlevel1.target | A basic system, including mounting the filesystems with only the most basic services running and a rescue shell on the main console
|
||||
emergency.target | S | | Single-user mode—no services are running; filesystems are not mounted. This is the most basic level of operation with only an emergency shell running on the main console for the user to interact with the system.
|
||||
halt.target | | | Halts the system without powering it down
|
||||
reboot.target | 6 | runlevel6.target | Reboot
|
||||
poweroff.target | 0 | runlevel0.target | Halts the system and turns the power off
|
||||
|
||||
Each target has a set of dependencies described in its configuration file. systemd starts the required dependencies, which are the services required to run the Linux host at a specific level of functionality. When all the dependencies listed in the target configuration files are loaded and running, the system is running at that target level. In Figure 2, the targets with the most functionality are at the top of the table, with functionality declining towards the bottom of the table.
|
||||
|
||||
systemd also looks at the legacy SystemV init directories to see if any startup files exist there. If so, systemd uses them as configuration files to start the services described by the files. The deprecated network service is a good example of one that still uses SystemV startup files in Fedora.
|
||||
|
||||
Figure 3 (below) is copied directly from the bootup man page. It shows a map of the general sequence of events during systemd startup and the basic ordering requirements to ensure a successful startup.
|
||||
|
||||
|
||||
```
|
||||
cryptsetup-pre.target
|
||||
|
|
||||
(various low-level v
|
||||
API VFS mounts: (various cryptsetup devices...)
|
||||
mqueue, configfs, | |
|
||||
debugfs, ...) v |
|
||||
| cryptsetup.target |
|
||||
| (various swap | | remote-fs-pre.target
|
||||
| devices...) | | | |
|
||||
| | | | | v
|
||||
| v local-fs-pre.target | | | (network file systems)
|
||||
| swap.target | | v v |
|
||||
| | v | remote-cryptsetup.target |
|
||||
| | (various low-level (various mounts and | | |
|
||||
| | services: udevd, fsck services...) | | remote-fs.target
|
||||
| | tmpfiles, random | | | /
|
||||
| | seed, sysctl, ...) v | | /
|
||||
| | | local-fs.target | | /
|
||||
| | | | | | /
|
||||
\\____|______|_______________ ______|___________/ | /
|
||||
\ / | /
|
||||
v | /
|
||||
sysinit.target | /
|
||||
| | /
|
||||
______________________/|\\_____________________ | /
|
||||
/ | | | \ | /
|
||||
| | | | | | /
|
||||
v v | v | | /
|
||||
(various (various | (various | |/
|
||||
timers...) paths...) | sockets...) | |
|
||||
| | | | | |
|
||||
v v | v | |
|
||||
timers.target paths.target | sockets.target | |
|
||||
| | | | v |
|
||||
v \\_______ | _____/ rescue.service |
|
||||
\|/ | |
|
||||
v v |
|
||||
basic.target rescue.target |
|
||||
| |
|
||||
________v____________________ |
|
||||
/ | \ |
|
||||
| | | |
|
||||
v v v |
|
||||
display- (various system (various system |
|
||||
manager.service services services) |
|
||||
| required for | |
|
||||
| graphical UIs) v v
|
||||
| | multi-user.target
|
||||
emergency.service | | |
|
||||
| \\_____________ | _____________/
|
||||
v \|/
|
||||
emergency.target v
|
||||
graphical.target
|
||||
```
|
||||
|
||||
The **sysinit.target** and **basic.target** targets can be considered checkpoints in the startup process. Although one of systemd's design goals is to start system services in parallel, certain services and functional targets must be started before other services and targets can start. These checkpoints cannot be passed until all of the services and targets required by that checkpoint are fulfilled.
|
||||
|
||||
The **sysinit.target** is reached when all of the units it depends on are completed. All of those units, mounting filesystems, setting up swap files, starting udev, setting the random generator seed, initiating low-level services, and setting up cryptographic services (if one or more filesystems are encrypted), must be completed but, within the **sysinit.target**, those tasks can be performed in parallel.
|
||||
|
||||
The **sysinit.target** starts up all of the low-level services and units required for the system to be marginally functional and that are required to enable moving onto the **basic.target**.
|
||||
|
||||
After the **sysinit.target** is fulfilled, systemd then starts all the units required to fulfill the next target. The basic target provides some additional functionality by starting units that are required for all of the next targets. These include setting up things like paths to various executable directories, communication sockets, and timers.
|
||||
|
||||
Finally, the user-level targets, **multi-user.target** or **graphical.target**, can be initialized. The **multi-user.target** must be reached before the graphical target dependencies can be met. The underlined targets in Figure 3 are the usual startup targets. When one of these targets is reached, startup has completed. If the **multi-user.target** is the default, then you should see a text-mode login on the console. If **graphical.target** is the default, then you should see a graphical login; the specific GUI login screen you see depends on your default display manager.
|
||||
|
||||
The bootup man page also describes and provides maps of the boot into the initial RAM disk and the systemd shutdown process.
|
||||
|
||||
systemd also provides a tool that lists dependencies of a complete startup or for a specified unit. A unit is a controllable systemd resource entity that can range from a specific service, such as httpd or sshd, to timers, mounts, sockets, and more. Try the following command and scroll through the results.
|
||||
|
||||
|
||||
```
|
||||
`systemctl list-dependencies graphical.target`
|
||||
```
|
||||
|
||||
Notice that this fully expands the top-level target units list required to bring the system up to the graphical target run mode. Use the **\--all** option to expand all of the other units as well.
|
||||
|
||||
|
||||
```
|
||||
`systemctl list-dependencies --all graphical.target`
|
||||
```
|
||||
|
||||
You can search for strings such as "target," "slice," and "socket" using the search tools of the **less** command.
|
||||
|
||||
So now, try the following.
|
||||
|
||||
|
||||
```
|
||||
`systemctl list-dependencies multi-user.target`
|
||||
```
|
||||
|
||||
and
|
||||
|
||||
|
||||
```
|
||||
`systemctl list-dependencies rescue.target`
|
||||
```
|
||||
|
||||
and
|
||||
|
||||
|
||||
```
|
||||
`systemctl list-dependencies local-fs.target`
|
||||
```
|
||||
|
||||
and
|
||||
|
||||
|
||||
```
|
||||
`systemctl list-dependencies dbus.service`
|
||||
```
|
||||
|
||||
This tool helps me visualize the specifics of the startup dependencies for the host I am working on. Go ahead and spend some time exploring the startup tree for one or more of your Linux hosts. But be careful because the systemctl man page contains this note:
|
||||
|
||||
> _"Note that this command only lists units currently loaded into memory by the service manager. In particular, this command is not suitable to get a comprehensive list at all reverse dependencies on a specific unit, as it won't list the dependencies declared by units currently not loaded."_
|
||||
|
||||
### Final thoughts
|
||||
|
||||
Even before getting very deep into systemd, it's obvious that it is both powerful and complex. It is also apparent that systemd is not a single, huge, monolithic, and unknowable binary file. Rather, it is composed of a number of smaller components and subcommands that are designed to perform specific tasks.
|
||||
|
||||
The next article in this series will explore systemd startup in more detail, as well as systemd configuration files, changing the default target, and how to create a simple service unit.
|
||||
|
||||
### Resources
|
||||
|
||||
There is a great deal of information about systemd available on the internet, but much is terse, obtuse, or even misleading. In addition to the resources mentioned in this article, the following webpages offer more detailed and reliable information about systemd startup.
|
||||
|
||||
* The Fedora Project has a good, practical [guide][7] [to systemd][7]. It has pretty much everything you need to know in order to configure, manage, and maintain a Fedora computer using systemd.
|
||||
* The Fedora Project also has a good [cheat sheet][8] that cross-references the old SystemV commands to comparable systemd ones.
|
||||
* For detailed technical information about systemd and the reasons for creating it, check out [Freedesktop.org][9]'s [description of systemd][10].
|
||||
* [Linux.com][11]'s "More systemd fun" offers more advanced systemd [information and tips][12].
|
||||
|
||||
|
||||
|
||||
There is also a series of deeply technical articles for Linux sysadmins by Lennart Poettering, the designer and primary developer of systemd. These articles were written between April 2010 and September 2011, but they are just as relevant now as they were then. Much of everything else good that has been written about systemd and its ecosystem is based on these papers.
|
||||
|
||||
* [Rethinking PID 1][13]
|
||||
* [systemd for Administrators, Part I][14]
|
||||
* [systemd for Administrators, Part II][15]
|
||||
* [systemd for Administrators, Part III][16]
|
||||
* [systemd for Administrators, Part IV][17]
|
||||
* [systemd for Administrators, Part V][18]
|
||||
* [systemd for Administrators, Part VI][19]
|
||||
* [systemd for Administrators, Part VII][20]
|
||||
* [systemd for Administrators, Part VIII][21]
|
||||
* [systemd for Administrators, Part IX][22]
|
||||
* [systemd for Administrators, Part X][23]
|
||||
* [systemd for Administrators, Part XI][24]
|
||||
|
||||
|
||||
|
||||
Alison Chiaken, a Linux kernel and systems programmer at Mentor Graphics, offers a preview of her...
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/20/4/systemd
|
||||
|
||||
作者:[David Both][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/dboth
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/car-penguin-drive-linux-yellow.png?itok=twWGlYAc (Penguin driving a car with a yellow background)
|
||||
[2]: http://www.both.org/?page_id=1183
|
||||
[3]: http://www.osnews.com/story/28026/Editorial_Thoughts_on_Systemd_and_the_Freedom_to_Choose
|
||||
[4]: https://www.zdnet.com/article/linus-torvalds-and-others-on-linuxs-systemd/
|
||||
[5]: http://0pointer.de/blog/projects/the-biggest-myths.html
|
||||
[6]: https://opensource.com/sites/default/files/uploads/systemd-architecture.png (systemd architecture)
|
||||
[7]: https://docs.fedoraproject.org/en-US/quick-docs/understanding-and-administering-systemd/index.html
|
||||
[8]: https://fedoraproject.org/wiki/SysVinit_to_Systemd_Cheatsheet
|
||||
[9]: http://Freedesktop.org
|
||||
[10]: http://www.freedesktop.org/wiki/Software/systemd
|
||||
[11]: http://Linux.com
|
||||
[12]: https://www.linux.com/training-tutorials/more-systemd-fun-blame-game-and-stopping-services-prejudice/
|
||||
[13]: http://0pointer.de/blog/projects/systemd.html
|
||||
[14]: http://0pointer.de/blog/projects/systemd-for-admins-1.html
|
||||
[15]: http://0pointer.de/blog/projects/systemd-for-admins-2.html
|
||||
[16]: http://0pointer.de/blog/projects/systemd-for-admins-3.html
|
||||
[17]: http://0pointer.de/blog/projects/systemd-for-admins-4.html
|
||||
[18]: http://0pointer.de/blog/projects/three-levels-of-off.html
|
||||
[19]: http://0pointer.de/blog/projects/changing-roots
|
||||
[20]: http://0pointer.de/blog/projects/blame-game.html
|
||||
[21]: http://0pointer.de/blog/projects/the-new-configuration-files.html
|
||||
[22]: http://0pointer.de/blog/projects/on-etc-sysinit.html
|
||||
[23]: http://0pointer.de/blog/projects/instances.html
|
||||
[24]: http://0pointer.de/blog/projects/inetd.html
|
||||
@ -1,5 +1,5 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: translator: (Acceleratorrrr)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
@ -7,6 +7,7 @@
|
||||
[#]: via: (https://opensource.com/article/20/4/securing-linux-email)
|
||||
[#]: author: (Marc Skinner https://opensource.com/users/marc-skinner)
|
||||
|
||||
|
||||
How to secure your Linux email services with SSL/TLS
|
||||
======
|
||||
Protect your Linux email services by understanding security
|
||||
|
||||
@ -0,0 +1,127 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (13 tips for getting your talk accepted at a tech conference)
|
||||
[#]: via: (https://opensource.com/article/20/5/tips-conference-proposals)
|
||||
[#]: author: (Todd Lewis https://opensource.com/users/toddlewis)
|
||||
|
||||
13 tips for getting your talk accepted at a tech conference
|
||||
======
|
||||
Before you respond to an event's call for papers, make sure your talk's
|
||||
proposal aligns with these best practices.
|
||||
![All Things Open check-in at registration booth][1]
|
||||
|
||||
As tech conference organizers ramp up for the fall season, you may be seeing calls for papers (CFP) landing in your email box or social media feeds. We at [All Things Open][2] (ATO) have seen a lot of presentation proposals over the years, and we've learned a few things about what makes them successful.
|
||||
|
||||
As we prepare for the eighth annual ATO in October 2020, we thought we'd offer a few best practices for writing successful CFP responses. If you're considering submitting a talk to ATO or another tech event, we hope these tips will help improve the chances that your proposal will be accepted.
|
||||
|
||||
### 1\. Know the event you're submitting a talk to
|
||||
|
||||
This seems like the proverbial _no-brainer_, but some people don't take the time to research an event before they submit a talk. Peruse the conference's website and review the talks, speakers, topics, etc. featured in the last couple of years. You can also find a lot of information simply by googling. The time you invest here will help you avoid a submission that is completely out of context for the event.
|
||||
|
||||
### 2\. Understand what the event is looking for
|
||||
|
||||
Look for information about what the event is looking for and what types of topics or talks it expects will be a good fit. We try to provide as much information as possible about the [ATO conference][3], [why someone would want to speak][4], and [what we're looking for][5] (both general and special interest topics). We also try to make the submission process as easy as possible (no doubt, there is room for improvement), in part because we believe this improves the quality of submissions and makes our review process go more smoothly.
|
||||
|
||||
### 3\. Reach out to the organizer and ask questions
|
||||
|
||||
If you're considering submitting a talk, don't hesitate to reach out and ask the event organizers any questions you have and for guidance specific to the event. If there is no or little response, that should be a red flag. If you have any questions about All Things Open, please reach out directly at [info@allthingsopen.org][6].
|
||||
|
||||
### 4\. Be clear about what attendees will learn from your talk
|
||||
|
||||
This is one of the most common mistakes we see. Only about 25% of the proposals we receive clearly explain the proposed talk's takeaways. One reason you should include this is that nearly every event attendee makes their schedule based on what they will learn if they go to a session. But for organizers and proposal reviewers, having this information clearly stated upfront is pure gold. It simplifies and speeds up the assessment process, which gets you one step closer to being accepted as a speaker. A paragraph titled "Attendee Takeaways" with bullet points is the holy grail for everyone involved.
|
||||
|
||||
### 5\. Keep recommended word counts in mind
|
||||
|
||||
This is another mistake we see a lot. Many talks are submitted with either a single sentence description in the abstract or an extraordinary long volume of text. Neither is a good idea. The only exception we can think of is when a topic is very popular or topical, and that alone is enough to win the day even if the abstract is extremely short (but this is rare). Most abstracts should be between 75 and 250 words, and perhaps more for an extended workshop with prerequisites (e.g., preexisting knowledge or required downloads). Even then, try to keep your proposal as sharp, concise, and on-point as possible.
|
||||
|
||||
Disregard this advice at your own risk; otherwise, there's a high likelihood that your proposal will be met with one of these reactions from reviewers: "They didn't take the time to write any more than this?" or "Sheesh, there's no way I have the time to read all that. I'm going to give it the lowest score and move on."
|
||||
|
||||
### 6\. Choose a good title
|
||||
|
||||
This is a debate we see all the time: Should a talk's title describe what the talk is about, or should it be written to stand out and get attention (e.g., evoking emotion, anchoring to a popular pop culture topic, or asking a compelling question)? There isn't a single correct answer to this question, but we definitely know when a title "works" and when it doesn't. We've seen some very creative titles work well and generate interest, and we've seen very straightforward titles work well, also.
|
||||
|
||||
Here is our rule of thumb: If the talk covers a topic that has been around a while and is not particularly _hot_ right now, try getting creative and spicing it up a bit. If the topic is newer, a more straightforward title describing the talk in plain terms should be good.
|
||||
|
||||
Titles on an event schedule may be the only thing attendees use to decide what talks to attend. So, run your potential talk titles by colleagues and friends, and seek their opinions. Ask: "If you were attending an event and saw this title on the schedule, would it pique your interest?"
|
||||
|
||||
### 7\. Know the basic criteria that reviewers and organizers use to make decisions
|
||||
|
||||
While this isn't a comprehensive list of review criteria, most reviewers and organizers consider one or more of the following when evaluating talk proposals. Therefore, at minimum, consider this list when you're creating a talk and the components that go with it.
|
||||
|
||||
1. **Timeliness of and estimated interest in the topic:** Is the topic applicable to the session's target audience? Will it deliver value? Is it timely?
|
||||
2. **Educational value:** Based on the abstract and speaker, is it clear that attendees will learn something from the talk? As mentioned in item 4 above, including an "Attendee Takeaways" section is really helpful to establish educational value.
|
||||
3. **Technical value:** Is the technology you intend to showcase applicable, unique, or being used in a new and creative way? Is there a live demo or a hands-on component? While some topics don't lend themselves to a demo, most people are visual learners and are better off if a presentation includes one (if it's relevant). For this reason, we place a lot of value on demos and hands-on content.
|
||||
4. **Diversity:** Yes, there are exceptions, but the majority of events, reviewers, and organizers agree that having a diverse speaker lineup is optimal and results in a better overall event in multiple ways. A topic delivered from a different perspective can often lead to creative breakthroughs for attendees, which is a huge value-add. See item 10 below for more on this.
|
||||
5. **Talk difficulty level:** We identify All Things Open talks as introductory, intermediate, or advanced. Having a good mix of talk levels ensures everyone in attendance can access applicable content. See item 9 below for more on this, but in general, it's smart to indicate your talk's level, whether or not the CFP requests it.
|
||||
|
||||
|
||||
|
||||
### 8\. Stay current on the event's industry or sector
|
||||
|
||||
Submitting a proposal on a relevant topic increases the probability your talk will be accepted. But how do you know what topics are of interest, especially if the CFP doesn't spell it out in simple terms? The best way to know what's timely and interesting is to deeply understand the sector the event focuses on.
|
||||
|
||||
Yes, this requires time and effort, and it implies you enjoy the sector enough to stay current on it, but it will pay off. This knowledge will result in a higher _sector IQ_, which will be reflected in your topic, title, and abstract. It will be recognized by reviewers and immediately set you apart from others. At All Things Open, we spend the majority of our time reading about and staying current on the "open" space so that we can feature relevant, substantive, and informed content. Submitting a talk that is relevant, substantive, and informed greatly enhances the chance it will be accepted.
|
||||
|
||||
### 9\. Describe whether the talk is introductory, intermediate, or advanced
|
||||
|
||||
Some CFPs don't ask for this information, but you should offer it anyway. It will make the reviewers and organizer very happy for multiple reasons, including these:
|
||||
|
||||
1. Unless the event targets attendees with a certain skill or experience level (and most do not), organizers must include content that is appealing to a wide audience, including people of all skill, experience, and expertise levels. Even if an event focuses on a specific type of attendee (perhaps people with higher levels of experience or skills), most want to offer something a little different. Listing the talk level makes this much easier for organizers.
|
||||
2. News flash: Reviewers and organizers don't know everything and are not experts in every possible topic area. As a result, reviewers will sometimes look for a few keywords or other criteria, and adding the talk level can "seal the deal" and get your talk confirmed.
|
||||
|
||||
|
||||
|
||||
### 10\. Tell organizers if you're a member of a historically underrepresented group
|
||||
|
||||
A growing number of events are getting better at recognizing the value of diversity and ensuring their speaker lineup reflects it. If you're part of a group that hasn't typically been included in tech events and leadership, look to see if there is a place to indicate that on the submission form. If not, mention it in a conspicuous place somewhere in the abstract. This does not guarantee approval in any way—your proposal must still be well-written and relevant—but it does give reviewers and organizers pertinent information they may value and take into consideration.
|
||||
|
||||
### 11\. Don't be ashamed of your credentials or speaking experience if it is light
|
||||
|
||||
We talk to a lot of people who would like to deliver a presentation and have a lot to offer, but they never submit a talk because they don't feel they're qualified to speak. _Not true._ Some of the best talks we've seen are from first-time speakers or those very early in their speaking careers. Go ahead and submit the talk, and be honest when discussing your background. Most reviewers and organizers will focus on the substance of the submission over your experience and recognize that new ways of approaching and using technology often come from newbies rather than industry veterans.
|
||||
|
||||
One caveat here: It still pays to know yourself. By this, we mean if you absolutely hate public speaking, have no desire to do it, and are only considering submitting a talk due to, for example, pressure from an employer, the talk is not likely to go well. It's better, to be honest, on the frontend than force something you have no desire to do.
|
||||
|
||||
### 12\. Consider panel sessions carefully
|
||||
|
||||
If you've got an idea for a panel session, please consider it carefully. In more than 10 years of hosting events we've seen some really good panel sessions, but we've seen far more that didn't go so well. Perhaps too many people were on the panel and not everyone had a chance to speak, perhaps a single panel member dominated the entire conversation, or perhaps the moderator didn't keep the dialogue and engagement flowing smoothly. Regardless of the issue, panels have the potential to go very wrong.
|
||||
|
||||
That said, panels can still work and deliver a lot of value to attendees. If you do submit a panel session be sure to keep in mind the amount of time allotted for the session and confirm the number of panel members accordingly. Remember, less is always more when it comes to the panel format. Also, be sure the moderator understands the subject matter being discussed and doesn't mind enforcing format parameters and speaking time limits. Finally, let organizers know panel members and the moderator will engage in a pre-conference walk-through/preparation call before the event to ensure a smooth process in front of a live audience. Remember, organizers are well aware panels can be terrific but can also go in the opposite direction and very easily lead to a lot of negative feedback.
|
||||
|
||||
### 13\. This is not an opportunity to sell
|
||||
|
||||
This is a sensitive topic, but one that absolutely must be mentioned. Over the years we've seen literally hundreds of talks "disqualified" by reviewers because they viewed the talk as a sales pitch. Few things evoke such a visceral response. Yes, there are events, tracks, and session slots where a sales pitch is appropriate (and maybe even required by the company paying your costs). However, make it a priority to know when and where this is appropriate and acceptable. And always, and we mean always, err on the side of making substance the focus of the talk rather than a sales angle.
|
||||
|
||||
It might sound like a cliche, but when a talk is delivered effectively with a focus on substance, people will **want** to buy what you're selling. And if you're not selling anything, they'll want to follow you on social media and generally engage with you—because you delivered value to them. Meaning: You gave them something they can apply themselves (education) or because your delivery style was entertaining and engaging. With rare exceptions, always focus any abstract on substance, and the rest will take care of itself.
|
||||
|
||||
### Go for it!
|
||||
|
||||
We greatly admire and respect anyone who submits a talk for consideration—it takes a lot of time, thought, and courage. Therefore, we go to great lengths to thank everyone who goes through the process; we give free event passes to everyone who applies (regardless of approval or rejection), and we make every effort to host Q&A sessions to provide as much guidance as possible on the front end. Again, the more time and consideration speakers put into the submission process, the easier the lives of reviewers and organizers. We need to make all of this as easy as possible.
|
||||
|
||||
While this is not a comprehensive list of best practices, it includes some of the things we think people can benefit from knowing before submitting a talk. There are a lot of people out there with more knowledge and experience, so please share your best tips for submitting conference proposals in the comments, so we can all learn from you.
|
||||
|
||||
* * *
|
||||
|
||||
_[All Things Open][2] is a universe of platforms and events focusing on open source, open tech, and the open web. It hosts the [All Things Open conference][3], the largest open source/tech/web event on the US East Coast. The conference regularly hosts thousands of attendees and many of the world's most influential companies from a wide variety of industries and sectors. In 2019, nearly 5,000 people attended from 41 US states and 24 countries. Please direct inquiries about ATO to the team at [info@allthingsopen.org][6]._
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/20/5/tips-conference-proposals
|
||||
|
||||
作者:[Todd Lewis][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/toddlewis
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/ato2016_checkin_conference.jpg?itok=DJtoSS6t (All Things Open check-in at registration booth)
|
||||
[2]: https://www.allthingsopen.org/
|
||||
[3]: https://2020.allthingsopen.org/
|
||||
[4]: https://2020.allthingsopen.org/call-for-speakers
|
||||
[5]: https://www.allthingsopen.org/what-were-looking-for/
|
||||
[6]: mailto:info@allthingsopen.org
|
||||
@ -0,0 +1,84 @@
|
||||
[#]: collector: "lujun9972"
|
||||
[#]: translator: " "
|
||||
[#]: reviewer: " "
|
||||
[#]: publisher: " "
|
||||
[#]: url: " "
|
||||
[#]: subject: "How to avoid man-in-the-middle cyber attacks"
|
||||
[#]: via: "https://opensource.com/article/20/4/mitm-attacks"
|
||||
[#]: author: "Jackie Lam https://opensource.com/users/beenverified"
|
||||
|
||||
如何避免中间人攻击
|
||||
======
|
||||
|
||||
首先搞明白到底什么是中间人攻击,才能避免成为此类高科技窃听的受害者。
|
||||
|
||||
![Security monster][1]
|
||||
|
||||
当你使用电脑发送数据或与某人在线通话的时候,你一定采取了某种程度的安全隐私手段。
|
||||
|
||||
但如果有第三方在你不知情的情况下窃听,甚至冒充某个你信任的商业伙伴窃取破坏性的信息呢?你的私人数据就这样被放在了危险分子的手中。
|
||||
|
||||
这就是臭名昭著的中间人攻击。
|
||||
|
||||
### 到底什么是中间人攻击?
|
||||
|
||||
黑客潜入到你与受害者或是某个设备间的通信过程中,窃取敏感信息——多数是身份信息——进而从事各种违法行为的过程,就是一次中间人攻击。Scamicide公司创始人Steve J. J. Weisman介绍说:
|
||||
|
||||
“中间人攻击也可以发生在受害者与某个合法app或网页中间。当受害者以为自己面对的是正常app或网页时,其实Ta 正在与一个仿冒的app或网页互动,将自己的敏感信息透露给不法分子。”
|
||||
|
||||
中间人攻击诞生于1980年代,是最古老的网络攻击形式之一。但它却更为常见。Weisman解释道,发生中间人攻击的场景有很多种:
|
||||
|
||||
* **攻陷一个未有效加密的WiFi路由器**:该场景多见于人们使用公共WiFi的时候。“虽然家用路由器也很脆弱,但黑客攻击公共WiFi网络的情况更为常见。”Weisman说,“黑客的目标就是从毫无戒心的人们那里窃取在线银行账户这样的敏感信息。”
|
||||
* **攻陷银行、金融顾问等机构的电子邮件账户**:“一旦黑客攻陷了这些电子邮件系统,他们就会冒充银行或此类公司给受害者发邮件”,Weisman说,”他们以紧急情况的名义索要个人信息,诸如用户名和密码。受害者很容易被诱骗交出这些信息。“
|
||||
* **发送钓鱼邮件**:窃贼们还可能冒充成与受害者有合作关系的公司,向其索要个人信息。”在多个案例中,钓鱼邮件会引导受害者访问一个伪造的网页,这个伪造的网页看起来就和受害者常常访问的合法公司网页一模一样。“Weisman说道。
|
||||
* **在合法网页中嵌入恶意代码**:攻击者还会把恶意代码——通常是JavaScript——嵌入到一个合法的网页中。”当受害者加载这个合法网页时,恶意代码首先按兵不动,直到用户输入账户登录或是信用卡信息时,恶意代码就会复制这些信息并将其发送至攻击者的服务器。“网络安全专家Nicholas McBride介绍说。
|
||||
|
||||
### 有哪些中间人攻击的著名案例?
|
||||
|
||||
联想作为主流的计算机制造厂商,在2014到2015年售卖的消费级笔记本电脑中预装了一款叫做 VisualDiscovery 的软件,拦截用户的网页浏览行为。当用户的鼠标在某个产品页面经过时,这款软件就会弹出一个来自合作伙伴的类似产品的广告。
|
||||
|
||||
这起中间人攻击事件的关键在于:VisualDiscovery 拥有访问用户所有私人数据的权限,包括身份证号、金融交易信息、医疗信息、登录名和密码等等。所有这些访问行为都是在用户不知情和未获得授权的情况下进行的。联邦交易委员会(FTC)认定此次事件为欺诈与不公平竞争。2019年,联想同意为此支付8300万美元的集体诉讼罚款。
|
||||
|
||||
### 我如何才能避免遭受中间人攻击?
|
||||
|
||||
* **避免使用公共WiFi:**Weisman建议,从来都不要使用公开的WiFi进行金融交易,除非你安装了可靠的VPN客户端并连接至可信任的VPN服务器。通过VPN连接,你的通信是加密的,信息也就不会失窃。
|
||||
* **时刻注意:**对要求你更新密码或是提供用户名等私人信息的邮件或文本消息要时刻保持警惕。这些手段很可能被用来窃取你的身份信息。
|
||||
|
||||
如果不确定收到的邮件来自于确切哪一方,你可以使用诸如电话反查或是邮件反查等工具。通过电话反查,你可以找出未知发件人的更多身份信息。通过邮件反查,你可以尝试确定谁给你发来了这条消息。
|
||||
|
||||
通常来讲,如果发现某些方面确实有问题,你可以听从公司中某个你认识或是信任的人的意见。或者,你也可以去你的银行、学校或其他某个组织,当面寻求他们的帮助。总之,重要的账户信息绝对不要透露给不认识的“技术人员”。
|
||||
|
||||
* **不要点击邮件中的链接:**如果有人给你发了一封邮件,说你需要登录某个账户,不要点击邮件中的链接。相反,要通过平常习惯的方式自行去访问,并留意是否有告警信息。如果在账户设置中没有看到告警信息,给客服打电话的时候也_不要_联系邮件中留的电话,而是站点页面中的联系人信息。
|
||||
* **安装可靠的安全软件:**如果你使用的是Windows操作系统,安装开源的杀毒软件,如[ClamAV][2]。如果使用的是其他平台,要保持你的软件安装有最新的安全补丁。
|
||||
* **认真对待告警信息:**如果你正在访问的页面以HTTPS开头,浏览器可能会出现一则告警信息。例如,站点证书的域名与你尝试访问的站点域名不相匹配。千万不要忽视此类告警信息。听从告警建议,迅速关掉页面。确认域名没有输入错误的情况下,如果情况依旧,要立刻联系站点所有者。
|
||||
* **使用广告屏蔽软件:**弹窗广告(也叫广告软件攻击)可被用于窃取个人信息,因此你还可以使用广告屏蔽类软件。对个人用户来说,中间人攻击其实是很难防范的,因为它被设计出来的时候,就是为了让受害者始终蒙在鼓里,意识不到任何异常。有一款不错的开源广告屏蔽软件叫 [uBlock origin][4]。可以同时支持Firefox和Chromium(以及所有基于Chromium的浏览器,例如Chrome、Brave、Vivaldi、Edge等),甚至还支持Safari。
|
||||
|
||||
### 保持警惕
|
||||
|
||||
要时刻记住,你并不需要立刻就点击某些链接,你也并不需要跟随某个陌生人的建议,无论这些信息看起来有多么紧急。互联网始终都在。你大可以先离开电脑,去证实一下这些人的真实身份,看看这些”无比紧急“的页面到底是真是假。
|
||||
|
||||
尽管任何人都可能遭遇中间人攻击,只要弄明白何为中间人攻击,理解中间人攻击如何发生,并采取有效的防范措施,就可以保护自己避免成为其受害者。
|
||||
|
||||
* * *
|
||||
|
||||
_This article was originally published on [BeenVerified.com][5] under a [CC BY-SA 2.0][6] license._
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/20/4/mitm-attacks
|
||||
|
||||
作者:[Jackie Lam][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[tinyeyeser](https://github.com/tinyeyeser)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/beenverified
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/security_password_chaos_engineer_monster.png?itok=J31aRccu "Security monster"
|
||||
[2]: https://www.clamav.net
|
||||
[3]: https://opensource.com/article/20/1/stop-typosquatting-attacks
|
||||
[4]: https://github.com/gorhill/uBlock
|
||||
[5]: https://www.beenverified.com/crime/what-is-a-man-in-the-middle-attack/
|
||||
[6]: https://creativecommons.org/licenses/by-sa/2.0/
|
||||
325
translated/tech/20200416 Learning to love systemd.md
Normal file
325
translated/tech/20200416 Learning to love systemd.md
Normal file
@ -0,0 +1,325 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (messon007)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Learning to love systemd)
|
||||
[#]: via: (https://opensource.com/article/20/4/systemd)
|
||||
[#]: author: (David Both https://opensource.com/users/dboth)
|
||||
|
||||
学会爱上systemd
|
||||
======
|
||||
|
||||
systemd是所有进程的源头,负责将Linux主机启动到可以做生产性任务的状态。
|
||||
![Penguin driving a car with a yellow background][1]
|
||||
|
||||
systemd(是的,全小写,即使在句子开头也是小写),是init和SystemV init脚本的现代替代者。它还有更多功能。
|
||||
|
||||
当我想到init和SystemV时,像大多数系统管理员一样,我想到的是Linux的启动和关闭,而没有太多其他的,例如在服务启动和运行后对其进行管理。像init一样,systemd是所有进程的源头,它负责使Linux主机启动到可以做生产性任务的状态。 systemd设定的一些功能比老的init要广泛得多,它要管理正在运行的Linux主机的许多方面,包括挂载文件系统,管理硬件,处理定时器以及启动和管理生产性主机所需的系统服务。
|
||||
|
||||
本系列文章是基于我的部分三期Linux培训课程[_使用和管理Linux:从零开始进行学习系统管理_][2]的摘录,探讨了systemd在启动和启动完成后的功能。
|
||||
|
||||
### Linux启动
|
||||
|
||||
Linux主机从关机状态到运行状态的完整启动过程很复杂,但它是开放的并且是可知的。在详细介绍之前,我将简要介绍一下从主机硬件被上电到系统准备好用户登录(的过程)。大多数时候,“启动过程”被作为单个概念来讨论,但这是不准确的。实际上,完整的引导和启动过程包含三个主要部分:
|
||||
|
||||
* **硬件引导:** 初始化系统硬件
|
||||
* **Linux引导:** 加载Linux内核和systemd
|
||||
* **Linux启动:** systemd启动, 为生产工作做准备
|
||||
|
||||
|
||||
Linux启动阶段在内核加载了init或systemd(取决于具体发行版使用的是旧的方式还是还是新的方式)之后开始。init和systemd程序启动并管理所有其他进程,他们在各自的系统上都被称为“所有进程之母”。
|
||||
|
||||
将硬件引导与Linux引导及Linux启动区分开,并明确定义它们之间的分界点是很重要的。理解他们的差异以及他们每一个在使Linux系统进入生产准备状态所起的作用,才能够管理这些进程并更好地确定大部分人所谓的“启动”问题出在哪里。
|
||||
|
||||
启动过程按照三步引导流程使Linux计算机进入可进行生产工作的状态。当内核将主机的控制权转移到systemd时,启动环节开始。
|
||||
|
||||
### systemd之争
|
||||
|
||||
systemd引起了系统管理员和其他负责维护Linux系统正常运行人员的广泛回应。systemd正在许多Linux系统中接管大量任务的事实造成了某些开发人群和系统管理员群组之间的阻挠和争议。
|
||||
|
||||
SystemV和systemd是执行Linux启动环节的两种不同的方法。 SystemV启动脚本和init程序是老的方法,而使用目标(targets)的systemd是新方法。尽管大多数现代Linux发行版都使用较新的systemd进行启动,关机和进程管理,但仍有一些发行版未采用。原因之一是某些发行版维护者和系统管理员喜欢老的SystemV方法,而不是新的systemd。
|
||||
|
||||
我认为两者都有其优势。
|
||||
|
||||
#### 为何我更喜欢SystemV
|
||||
|
||||
我更喜欢SystemV,因为它更开放。使用Bash脚本来完成启动。内核启动init程序(编译后的二进制)后,init启动 **rc.sysinit** 脚本,该脚本执行许多系统初始化任务。 **rc.sysinit** 执行完后,init启动 **/etc/rc.d/rc** 脚本,该脚本依次启动 **/etc/rc.d/rcX.d** 中由SystemV启动脚本定义的各种服务。 其中“ X”是待启动的运行级别号。
|
||||
|
||||
除了init程序本身之外,所有这些程序都是开放且易于理解的脚本。可以通读这些脚本并确切了解整个启动过程中发生的事情,但是我不认为有太多系统管理员会实际这样做。每个启动脚本都被编了号,以便按特定顺序启动预期的服务。服务是串行启动的,一次只能启动一个服务。
|
||||
|
||||
由Red Hat的Lennart Poettering和Kay Sievers开发的systemd是一个由大的已编译的二进制可执行文件构成的复杂系统,不访问其源码就无法理解。它是开源的,因此“访问其源代码”并不难,只是不太方便。systemd似乎表现出对Linux哲学多个原则的重大驳斥。作为二进制文件,systemd无法被直接打开供系统管理员查看或进行简单更改。systemd试图做所有事情,例如管理正在运行的服务,同时提供比SystemV更多的状态信息。它还管理硬件,进程,进程组,文件系统挂载等。 systemd几乎涉足于现代Linux主机的每方面,使它成为系统管理的一站式工具。所有这些都明显违反了"程序应该小且每个程序都应该只做一件事并且做好"的原则。
|
||||
|
||||
#### 为何我更喜欢systemd
|
||||
|
||||
我更喜欢用systemd作为启动机制,因为它会根据启动阶段并行地启动尽可能多的服务。这样可以加快整个的启动速度,使得主机系统比SystemV更快地到达登录屏幕。
|
||||
|
||||
systemd几乎可以管理正在运行的Linux系统的各个方面。它可以管理正在运行的服务,同时提供比SystemV多得多的状态信息。它还管理硬件,进程和进程组,文件系统挂载等。 systemd几乎涉足于现代Linux操作系统的每方面,使其成为系统管理的一站式工具。(听起来熟悉吧?)
|
||||
|
||||
systemd工具是编译后的二进制文件,但该工具包是开放的,因为所有配置文件都是ASCII文本文件。可以通过各种GUI和命令行工具来修改启动配置,也可以添加或修改各种配置文件来满足特定的本地计算环境的需求。
|
||||
|
||||
#### 真正的问题
|
||||
|
||||
您认为我不能喜欢两种启动系统吗?我能,我会用它们中的任何一个。
|
||||
|
||||
我认为,SystemV和systemd之间大多数争议的真正问题和根本原因在于,系统管理阶段[没有选择权][3]。使用SystemV还是systemd已经由各种发行版的开发人员,维护人员和打包人员选择了(但有充分的理由)。由于init极端的侵入性, 挖出(scooping out)并替换init系统会带来很多影响,发行版设计过程之外(的环节)很难处理这些影响。
|
||||
|
||||
尽管该选择实际上是为我而选的,我通常最关心的是我的Linux主机仍然可以启动并正常工作。作为最终用户,甚至是系统管理员,我主要关心的是我是否可以完成我的工作,例如写我的书和这篇文章,安装更新以及编写脚本来自动化所有事情。只要我能做我的工作,我就不会真正在意发行版中使用的启动系统。
|
||||
|
||||
在启动或服务管理出现问题时,我会在意。无论主机上使用哪种启动系统,我都足够了解如何沿着事件顺序来查找故障并进行修复。
|
||||
|
||||
#### 替换SystemV
|
||||
|
||||
以前曾有过用更现代的东西替代SystemV的尝试。在大约两个版本中,Fedora使用了一个叫作Upstart的东西来替换老化的SystemV,但是它没有替换init并且没有我能感知到的变化。由于Upstart并未对SystemV的问题进行任何重大更改,因此这个方向的努力很快就被systemd放弃了。
|
||||
|
||||
尽管大部分Linux开发人员都认可替换旧的SystemV启动系统是个好主意,但许多开发人员和系统管理员并不喜欢systemd。与其重新讨论人们在systemd中遇到的或曾经遇到过的所有所谓的问题,不如带您去看两篇好文章,尽管有些陈旧,但它们涵盖了大多数内容。Linux内核的创建者Linus Torvalds对systemd似乎不感兴趣。在2014年ZDNet的文章_[Linus Torvalds和其他人对Linux上的systemd的看法][4]_中,Linus清楚地表达了他的感受。
|
||||
|
||||
>“实际上我对systemd本身没有任何特别强烈的意见。我对一些核心开发人员有一些意见,我认为它们在对待bugs和兼容性方面过于轻率,而且我认为某些设计细节是疯狂的(例如,我不喜欢二进制日志),但这只是细节,不是大问题。”
|
||||
|
||||
如果您对Linus不太了解,我可以告诉您,如果他不喜欢某事,那么他非常直率,坦率,并且非常清楚这种不喜欢。他解决自己对事物不满的方式已经被社会更好地接受了。
|
||||
|
||||
2013年,Poettering写了一篇很长的博客,其中他在揭穿[systemd的神话][5]的同时透露了创建它的一些原因。这是一本很好的读物,我强烈建议您阅读。
|
||||
|
||||
### systemd任务
|
||||
|
||||
根据编译过程中使用的选项(不在本系列中介绍),systemd可以有多达69个二进制可执行文件用于执行任务,其中包括:
|
||||
|
||||
* systemd程序以1号进程(PID 1)运行,并提供使尽可能多服务并行启动的系统启动能力,它额外加快了总体启动时间。它还管理关机顺序。
|
||||
* systemctl程序提供了服务管理的用户接口。
|
||||
* 支持SystemV和LSB启动脚本,以便向后兼容。
|
||||
* 服务管理和报告提供了比SystemV更多的服务状态数据。
|
||||
* 提供基本的系统配置工具,例如主机名,日期,语言环境,已登录用户的列表,正在运行的容器和虚拟机,系统帐户,运行时目录和设置;用于简易网络配置,网络时间同步,日志转发和名称解析的守护程序。
|
||||
* 提供套接字管理。
|
||||
* systemd定时器提供类似cron的高级功能,包括在相对于系统启动,systemd启动,定时器上次启动时刻的某个时间点运行脚本。
|
||||
* 提供了一个工具来分析定时器规格中使用的日期和时间。
|
||||
* 能感知层次的文件系统挂载和卸载可以更安全地级联挂载的文件系统。
|
||||
* 允许主动的创建和管理临时文件,包括删除文件。
|
||||
* D-Bus的接口提供在插入或移除设备时运行脚本的能力。这允许将所有设备(无论是否可插拔)都被视为即插即用,从而大大简化了设备的处理。
|
||||
* 分析启动顺序的工具可用于查找耗时最多的服务。
|
||||
* 包括用于存储系统消息的日志以及管理日志的工具。
|
||||
|
||||
|
||||
### 架构
|
||||
|
||||
这些和更多的任务通过许多守护程序,控制程序和配置文件来支持。图1显示了许多属于systemd的组件。这是一个简化的图,旨在提供概要描述,因此它并不包括所有独立的程序或文件。它也不提供数据流的视角,数据流是如此复杂,因此在本系列文章的背景下没用。
|
||||
|
||||
![系统架构][6]
|
||||
|
||||
完整的systemd讲解就需要一本书。您不需要了解图1中的systemd组件是如何组合在一起的细节。了解支持各种Linux服务管理以及日志文件和日志处理的程序和组件就够了。 但是很明显,systemd并不是某些批评者所说的那样的庞然大物。
|
||||
|
||||
### 作为1号进程的systemd
|
||||
|
||||
systemd是1号进程(PID 1)。它的一些功能(比老的SystemV3 init要广泛得多)用于管理正在运行的Linux主机的许多方面,包括挂载文件系统以及启动和管理Linux生产主机所需的系统服务。与启动顺序无关的任何systemd任务都不在本文讨论范围之内(但本系列后面的一些文章将探讨其中的一些任务)。
|
||||
|
||||
首先,systemd挂载 **/etc/fstab** 所定义的文件系统,包括所有交换文件或分区。此时,它可以访问位于 **/etc** 中的配置文件,包括它自己的配置文件。它使用其配置链接 **/etc/systemd/system/default.target** 来确定将主机引导至哪个状态或目标。 **default.target** 文件是指向真实目标文件的符号链接。对于桌面工作站,通常是 **graphical.target**,它相当于SystemV中的运行级别5。对于服务器,默认值更可能是 **multi-user.target**,相当于SystemV中的运行级别3。 **emergency.target** 类似于单用户模式。目标(targets)和服务(services)是systemd的单位。
|
||||
|
||||
下表(图2)将systemd目标与老的SystemV启动运行级别进行了比较。systemd提供systemd目标别名以便向后兼容。目标别名允许脚本(以及许多系统管理员)使用SystemV命令(如**init 3**)更改运行级别。当然,SystemV命令被转发给systemd进行解释和执行。
|
||||
|
||||
**systemd目标** | **SystemV运行级别** | **目标别名** | **描述**
|
||||
--- | --- | ---- |-
|
||||
default.target | | |此目标总是通过符号连接的方式成为“多用户目标”或“图形化目标”的别名。systemd始终使用 **default.target** 来启动系统。 ** default.target** 绝不应该设为 **halt.target**,**poweroff.target** 或 **reboot.target** 的别名
|
||||
graphic.target | 5 | runlevel5.target |带有GUI的 **Multi-user.target**
|
||||
| 4 | runlevel4.target |未用。在SystemV中运行级别4与运行级别3相同。可以创建并自定义此目标以启动本地服务,而无需更改默认的 **multi-user.target**
|
||||
multi-user.target | 3 | runlevel3.target |所有服务在运行,但仅有命令行界面(CLI)
|
||||
| 2 | runlevel2.target |多用户,没有NFS,其他所有非GUI服务在运行
|
||||
rescue.target | 1 | runlevel1.target |基本系统,包括挂载文件系统,运行最基本的服务和主控制台的恢复shell
|
||||
Emergency.target | S | |单用户模式-没有服务运行;不挂载文件系统。这是最基本的工作级别,只有主控制台上运行的一个紧急Shell供用户与系统交互
|
||||
halt.target | | |在不关电源的情况下停止系统
|
||||
reboot.target | 6 | runlevel6.target |重启
|
||||
poweroff.target | 0 | runlevel0.target |停止系统并关闭电源
|
||||
|
||||
每个目标在其配置文件中都描述了一个依赖集。systemd启动必须的依赖,这些依赖是运行Linux主机到特定功能级别所需的服务。当目标配置文件中列出的所有依赖项被加载并运行后,系统就在该目标级别运行了。 在图2中,功能最多的目标位于表的顶部,从顶向下,功能逐步递减。
|
||||
|
||||
systemd还会检查老的SystemV init目录,以确认是否存在任何启动文件。如果有,systemd会将它们作为配置文件以启动它们描述的服务。网络服务是一个很好的例子,在Fedora中它仍然使用SystemV启动文件。
|
||||
|
||||
图3(如下)是直接从启动手册页复制来的。它显示了systemd启动期间普遍的事件顺序以及确保成功启动的基本顺序要求。
|
||||
|
||||
```
|
||||
cryptsetup-pre.target
|
||||
|
|
||||
(various low-level v
|
||||
API VFS mounts: (various cryptsetup devices...)
|
||||
mqueue, configfs, | |
|
||||
debugfs, ...) v |
|
||||
| cryptsetup.target |
|
||||
| (various swap | | remote-fs-pre.target
|
||||
| devices...) | | | |
|
||||
| | | | | v
|
||||
| v local-fs-pre.target | | | (network file systems)
|
||||
| swap.target | | v v |
|
||||
| | v | remote-cryptsetup.target |
|
||||
| | (various low-level (various mounts and | | |
|
||||
| | services: udevd, fsck services...) | | remote-fs.target
|
||||
| | tmpfiles, random | | | /
|
||||
| | seed, sysctl, ...) v | | /
|
||||
| | | local-fs.target | | /
|
||||
| | | | | | /
|
||||
\\____|______|_______________ ______|___________/ | /
|
||||
\ / | /
|
||||
v | /
|
||||
sysinit.target | /
|
||||
| | /
|
||||
______________________/|\\_____________________ | /
|
||||
/ | | | \ | /
|
||||
| | | | | | /
|
||||
v v | v | | /
|
||||
(various (various | (various | |/
|
||||
timers...) paths...) | sockets...) | |
|
||||
| | | | | |
|
||||
v v | v | |
|
||||
timers.target paths.target | sockets.target | |
|
||||
| | | | v |
|
||||
v \\_______ | _____/ rescue.service |
|
||||
\|/ | |
|
||||
v v |
|
||||
basic.target rescue.target |
|
||||
| |
|
||||
________v____________________ |
|
||||
/ | \ |
|
||||
| | | |
|
||||
v v v |
|
||||
display- (various system (various system |
|
||||
manager.service services services) |
|
||||
| required for | |
|
||||
| graphical UIs) v v
|
||||
| | multi-user.target
|
||||
emergency.service | | |
|
||||
| \\_____________ | _____________/
|
||||
v \|/
|
||||
emergency.target v
|
||||
graphical.target
|
||||
```
|
||||
|
||||
**sysinit.target** 和 **basic.target** 目标可以看作启动过程中的检查点。尽管systemd的设计目标之一是并行启动系统服务,但是某些服务和功能目标必须先启动,然后才能启动其他服务和目标。直到该检查点所需的所有服务和目标被满足后才能通过这些检查点。
|
||||
|
||||
当它依赖的所有单元都完成时,将到达 **sysinit.target**。所有这些单元,挂载文件系统,设置交换文件,启动udev,设置随机数生成器种子,启动低层服务以及配置安全服务(如果一个或多个文件系统是加密的)都必须被完成,但 **sysinit.target** 的这些任务可以并行执行。
|
||||
|
||||
**sysinit.target** 将启动系统接近正常运行所需的所有低层服务和单元,以及转移到 **basic.target** 所需的服务和单元。
|
||||
|
||||
在完成 **sysinit.target** 目标之后,systemd会启动实现下一个目标所需的所有单元。基本目标通过启动所有下一目标所需的单元来提供一些其他功能。包括设置如PATHs为各种可执行程序的路径,设置通信套接字和计时器之类。
|
||||
|
||||
最后,用户级目标 **multi-user.target** 或 **graphical.target** 被初始化。要满足图形目标的依赖必须先达到**multi-user.target**。图3中带下划线的目标是通常的启动目标。当达到这些目标之一时,启动就完成了。如果 **multi-user.target** 是默认设置,那么您应该在控制台上看到文本模式的登录界面。如果 **graphical.target** 是默认设置,那么您应该看到图形的登录界面。您看到的特定的GUI登录界面取决于您默认的显示管理器。
|
||||
|
||||
引导手册页还描述并提供了引导到初始RAM磁盘和systemd关机过程的地图。
|
||||
|
||||
systemd还提供了一个工具,该工具列出了完整启动或指定单元的依赖。单元是可控制的systemd资源实体,其范围从特定服务(例如httpd或sshd)到计时器,挂载,套接字等。尝试以下命令并滚动查看结果。
|
||||
|
||||
```
|
||||
`systemctl list-dependencies graphical.target`
|
||||
```
|
||||
|
||||
注意,这完全展开了使系统进入图形目标运行模式所需的顶层目标单元列表。 也可以使用 **\-all** 选项来展开所有其他单元。
|
||||
|
||||
```
|
||||
`systemctl list-dependencies --all graphical.target`
|
||||
```
|
||||
|
||||
您可以使用 **less** 命令来搜索诸如“target”,“slice”和“ socket”之类的字符串。
|
||||
|
||||
现在尝试下面的方法。
|
||||
|
||||
```
|
||||
`systemctl list-dependencies multi-user.target`
|
||||
```
|
||||
|
||||
和
|
||||
|
||||
|
||||
```
|
||||
`systemctl list-dependencies rescue.target`
|
||||
```
|
||||
|
||||
和
|
||||
|
||||
|
||||
```
|
||||
`systemctl list-dependencies local-fs.target`
|
||||
```
|
||||
|
||||
和
|
||||
|
||||
|
||||
```
|
||||
`systemctl list-dependencies dbus.service`
|
||||
```
|
||||
```
|
||||
`systemctl list-dependencies graphic.target`
|
||||
```
|
||||
|
||||
|
||||
|
||||
这个工具帮助我可视化我正用的主机的启动依赖细节。继续花一些时间探索一个或多个Linux主机的启动树。但是要小心,因为systemctl手册页包含以下注释:
|
||||
|
||||
> _“请注意,此命令仅列出当前被服务管理器加载到内存的单元。尤其是,此命令根本不适合用于获取特定单元的全部反向依赖列表,因为它不会列出被单元声明了但是未加载的依赖项。” _
|
||||
|
||||
### 结尾语
|
||||
|
||||
即使在深入研究systemd之前,很明显能看出它既强大又复杂。显然,systemd不是单一,庞大,整体且不可知的二进制文件。相反,它是由许多较小的组件和旨在执行特定任务的子命令组成。
|
||||
|
||||
本系列的下一篇文章将更详细地探讨systemd的启动,以及systemd的配置文件,更改默认的目标以及如何创建简单服务单元。
|
||||
|
||||
### 资源
|
||||
|
||||
互联网上有大量关于systemd的信息,但是很多都简短,晦涩甚至是误导。除了本文提到的资源外,以下网页还提供了有关systemd启动的更详细和可靠的信息。
|
||||
|
||||
* Fedora项目有一个很好的,实用的[guide to systemd][7]。它有你需要知道的通过systemd来配置,管理和维护Fedora主机所需的几乎所有知识。
|
||||
* Fedora项目还有一个不错的[cheat sheet][8],将老的SystemV命令与对比的systemd命令相互关联。
|
||||
* 有关systemd及其创建原因的详细技术信息,请查看[Freedesktop.org][9]的[systemd描述][10]。
|
||||
* [Linux.com][11]的“systemd的更多乐趣”提供了更高级的systemd [信息和技巧][12]。
|
||||
|
||||
|
||||
还有systemd的设计师和主要开发者Lennart Poettering撰写的针对Linux系统管理员的一系列技术文章。这些文章是在2010年4月至2011年9月之间撰写的,但它们现在和那时一样有用。关于systemd及其生态的其他许多好文都基于这些论文。
|
||||
|
||||
* [重新思考1号进程][13]
|
||||
* [systemd之系统管理员, I][14]
|
||||
* [systemd之系统管理员, II][15]
|
||||
* [systemd之系统管理员, III][16]
|
||||
* [systemd之系统管理员, IV][17]
|
||||
* [systemd之系统管理员, V][18]
|
||||
* [systemd之系统管理员, VI][19]
|
||||
* [systemd之系统管理员, VII][20]
|
||||
* [systemd之系统管理员, VIII][21]
|
||||
* [systemd之系统管理员, IX][22]
|
||||
* [systemd之系统管理员, X][23]
|
||||
* [systemd之系统管理员, XI][24]
|
||||
|
||||
|
||||
|
||||
Mentor Graphics的Linux内核和系统程序员Alison Chiaken预览了此文...
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/20/4/systemd
|
||||
|
||||
作者:[David Both][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[messon007](https://github.com/messon007)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/dboth
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/car-penguin-drive-linux-yellow.png?itok=twWGlYAc (Penguin driving a car with a yellow background)
|
||||
[2]: http://www.both.org/?page_id=1183
|
||||
[3]: http://www.osnews.com/story/28026/Editorial_Thoughts_on_Systemd_and_the_Freedom_to_Choose
|
||||
[4]: https://www.zdnet.com/article/linus-torvalds-and-others-on-linuxs-systemd/
|
||||
[5]: http://0pointer.de/blog/projects/the-biggest-myths.html
|
||||
[6]: https://opensource.com/sites/default/files/uploads/systemd-architecture.png (systemd architecture)
|
||||
[7]: https://docs.fedoraproject.org/en-US/quick-docs/understanding-and-administering-systemd/index.html
|
||||
[8]: https://fedoraproject.org/wiki/SysVinit_to_Systemd_Cheatsheet
|
||||
[9]: http://Freedesktop.org
|
||||
[10]: http://www.freedesktop.org/wiki/Software/systemd
|
||||
[11]: http://Linux.com
|
||||
[12]: https://www.linux.com/training-tutorials/more-systemd-fun-blame-game-and-stopping-services-prejudice/
|
||||
[13]: http://0pointer.de/blog/projects/systemd.html
|
||||
[14]: http://0pointer.de/blog/projects/systemd-for-admins-1.html
|
||||
[15]: http://0pointer.de/blog/projects/systemd-for-admins-2.html
|
||||
[16]: http://0pointer.de/blog/projects/systemd-for-admins-3.html
|
||||
[17]: http://0pointer.de/blog/projects/systemd-for-admins-4.html
|
||||
[18]: http://0pointer.de/blog/projects/three-levels-of-off.html
|
||||
[19]: http://0pointer.de/blog/projects/changing-roots
|
||||
[20]: http://0pointer.de/blog/projects/blame-game.html
|
||||
[21]: http://0pointer.de/blog/projects/the-new-configuration-files.html
|
||||
[22]: http://0pointer.de/blog/projects/on-etc-sysinit.html
|
||||
[23]: http://0pointer.de/blog/projects/instances.html
|
||||
[24]: http://0pointer.de/blog/projects/inetd.html
|
||||
@ -1,159 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (lxbwolf)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Three Methods Boot CentOS/RHEL 7/8 Systems in Single User Mode)
|
||||
[#]: via: (https://www.2daygeek.com/boot-centos-7-8-rhel-7-8-single-user-mode/)
|
||||
[#]: author: (Magesh Maruthamuthu https://www.2daygeek.com/author/magesh/)
|
||||
|
||||
在单用户模式下启动 CentOS/RHEL 7/8 的三种方法
|
||||
======
|
||||
|
||||
单用户模式,也被称为维护模式,超级用户可以在此模式下恢复/修复系统问题。
|
||||
|
||||
通常情况下,这些问题在多用户环境中修复不了。系统可以启动但功能不能正常运行或者你登录不了系统。
|
||||
|
||||
在基于 **[Red Hat][1]** (RHEL) 7/8 的系统中,使用 `runlevel1.target` 或 `rescue.target` 来实现。
|
||||
|
||||
在此模式下,系统会挂载所有的本地文件系统,但不开启网络接口。
|
||||
|
||||
系统仅启动特定的几个服务和修复系统必要的尽可能少的功能。
|
||||
|
||||
当你想运行文件系统一致性检查来修复损坏的文件系统,或忘记 root 密码后重置密码,或修复系统上的一个挂载点问题时,这个方法会很有用。
|
||||
|
||||
你可以用下面三种方法以单用户模式启动 **[CentOS][2]**/**[RHEL][3]** 7/8 系统。
|
||||
|
||||
* **方法 1:** 通过向内核添加 “rd.break” 参数来以单用户模式启动 CentOS/RHEL 7/8 系统
|
||||
* **方法 2:** 通过用 “init=/bin/bash“ 或 ”init=/bin/sh” 替换内核中的 “rhgb quiet” 语句来以单用户模式启动 CentOS/RHEL 7/8 系统
|
||||
* **方法 3:** 通过用 “rw init=/sysroot/bin/sh” 参数替换内核中的 “ro” 语句以单用户模式启动 CentOS/RHEL 7/8 系统
|
||||
|
||||
|
||||
|
||||
### 方法 1: 通过向内核添加 “rd.break” 参数来以单用户模式启动 CentOS/RHEL 7/8 系统
|
||||
|
||||
重启你的系统,在 GRUB2 启动界面,按下 `e` 键来编辑选中的内核。你需要选中第一行,第一个是最新的内核,然而如果你想用旧的内核启动系统你也可以选择其他的行。
|
||||
|
||||
![][4]
|
||||
|
||||
根据你的 RHEL/CentOS 版本,找到 **“linux16”** 或 **“linux”** 语句,按下键盘上的 ”End“ 按钮,跳到行末,像下面截图中展示的那样添加关键词 **“rd.break”**,按下 **“Ctrl+x”** 或 **“F10”** 来进入单用户模式。
|
||||
|
||||
如果你的系统是 RHEL/CentOS 7,你需要找 **`linux16`**,如果你的系统是 RHEL/CentOS 8,那么你需要找 **`linux`**。
|
||||
|
||||
![][4]
|
||||
|
||||
这个修改会让你的 root 文件系统以 **“只读 (RO)”** 模式挂载。你可以用下面的命令来验证下。下面的输出也明确地告诉你当前是在 **“紧急模式”**。
|
||||
|
||||
```
|
||||
# mount | grep root
|
||||
```
|
||||
|
||||
![][4]
|
||||
|
||||
为了修改 **“sysroot”** 文件系统,你需要用 RW 模式重新挂载它。
|
||||
|
||||
```
|
||||
# mount -o remount,rw /sysroot
|
||||
```
|
||||
|
||||
运行下面的命令修改环境,这就是大家熟知的 “jailed directory” 或 “chroot jail”。
|
||||
|
||||
```
|
||||
# chroot /sysroot
|
||||
```
|
||||
|
||||
![][4]
|
||||
|
||||
现在,单用户模式的前期准备已经完成了。当你修复了你的问题要退出单用户模式时,执行下面的步骤。
|
||||
|
||||
CentOS/RHEL 7/8 默认使用 SELinux,因此创建下面的隐藏文件,这个文件会在下一次启动时重新确认所有文件。
|
||||
|
||||
```
|
||||
# touch /.autorelabel
|
||||
```
|
||||
|
||||
最后,用下面的命令重启系统。你也可以输入两次 “exit” 命令来重启你的系统。
|
||||
|
||||
```
|
||||
# reboot -f
|
||||
```
|
||||
|
||||
### 方法 2: 通过用 “init=/bin/bash“ 或 ”init=/bin/sh” 替换内核中的 “rhgb quiet” 语句来以单用户模式启动 CentOS/RHEL 7/8 系统
|
||||
|
||||
重启你的系统,在 GRUB2 启动界面,按下 `e` 键来编辑选中的内核。
|
||||
|
||||
![][4]
|
||||
|
||||
找到语句 **“rhgb quiet”**,用 **“init=/bin/bash”** 或 **“init=/bin/sh”** 替换它,然后按下 **“Ctrl+x”** 或 **“F10”** 来进入单用户模式。
|
||||
|
||||
**`init=/bin/bash`** 的截图。
|
||||
|
||||
![][4]
|
||||
|
||||
**`init=/bin/sh`** 的截图。
|
||||
|
||||
![][4]
|
||||
|
||||
默认情况下,上面的操作会以只读(RO)模式挂载你的 “/” 分区,因此你需要以读写(RW)模式重新挂载 “/” 文件系统,这样才能修改它。
|
||||
|
||||
```
|
||||
# mount -o remount,rw /
|
||||
```
|
||||
|
||||
![][4]
|
||||
|
||||
现在你可以执行你的任务了。当结束时,执行下面的命令来开启重启时的 SELinux 重新确认。
|
||||
|
||||
```
|
||||
# touch /.autorelabel
|
||||
```
|
||||
|
||||
最后,重启系统。
|
||||
|
||||
```
|
||||
# exec /sbin/init 6
|
||||
```
|
||||
|
||||
### 方法 3: 通过用 “rw init=/sysroot/bin/sh” 参数替换内核中的 “ro” 语句以单用户模式启动 CentOS/RHEL 7/8 系统
|
||||
|
||||
为了中断自动启动的过程,重启你的系统并在 GRUB2 启动界面按下任意键。
|
||||
|
||||
现在会展示你系统上所有可用的内核,选择最新的内核,按下 `e` 键来编辑选中的内核参数。
|
||||
|
||||
找到以 **“linux”** 或 **“linux16”** 开头的语句,用 **“rw init=/sysroot/bin/sh”** 替换 **“ro”**。替换完后按下 **“Ctrl+x”** 或 **“F10”** 来进入单用户模式。
|
||||
|
||||
运行下面的命令把环境切换为 “chroot jail”。
|
||||
|
||||
```
|
||||
# chroot /sysroot
|
||||
```
|
||||
|
||||
如果需要,做出必要的修改。修改完后,执行下面的命令来开启重启时的 SELinux 重新确认。
|
||||
|
||||
```
|
||||
# touch /.autorelabel
|
||||
```
|
||||
|
||||
最后,重启系统。
|
||||
|
||||
```
|
||||
# reboot -f
|
||||
```
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.2daygeek.com/boot-centos-7-8-rhel-7-8-single-user-mode/
|
||||
|
||||
作者:[Magesh Maruthamuthu][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[lxbwolf](https://github.com/lxbwolf)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.2daygeek.com/author/magesh/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.2daygeek.com/category/red-hat/
|
||||
[2]: https://www.2daygeek.com/category/centos/
|
||||
[3]: https://www.2daygeek.com/category/rhel/
|
||||
[4]: data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7
|
||||
Loading…
Reference in New Issue
Block a user