mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-03-12 01:40:10 +08:00
commit
eece3ced76
53
sources/talk/20151202 KDE vs GNOME vs XFCE Desktop.md
Normal file
53
sources/talk/20151202 KDE vs GNOME vs XFCE Desktop.md
Normal file
@ -0,0 +1,53 @@
|
||||
KDE vs GNOME vs XFCE Desktop
|
||||
================================================================================
|
||||

|
||||
|
||||
Over many years, many people spent a long time with Linux desktop using either KDE or GNOME. These two environments have grown through the previous years and each of these desktops continued to expand their current user-base. For example, sleeper desktop environment has been XFCE as XFCE offers more robustness than LXDE that lacks much of XFCE’s polish in the default configuration. The XFCE provides all benefits which users enjoyed in the GNOME 2, but with some lightweight experiences which made it a hit on the older computers.
|
||||
|
||||
### The Desktop Theming ###
|
||||
|
||||
After the user has fresh installation, the XFCE will be a bit boring, which lacks some certain visual attractiveness to it. So, don’t misunderstand my words here, the XFCE is still having nice looking desktop, but it may be like vanilla in users’ eyes as well as most people who are new to the XFCE desktop environment. The good news here is that while installing new theme to the XFCE, it is a reasonably easy process as you can easily find the right XFCE theme which appeals to you, after that, you can extract that theme to the proper directory. From this point, the XFCE comes with an important tool located under the Appearance for helping the user to select the chosen theme easily throughout the Graphical User Interface (GUID). There’re no other tools that might be required here, and if the user follows the above directions, it will be a bit simple for everyone who is caring to have a try.
|
||||
|
||||
On the GNOME desktop, the user should follow the similar above approach. The main key difference for this point is that users have to download and then install GNOME Tweak Tool before proceeding with anything. It does not have any huge barriers under any means, but it is simple valid oversight when the user consider that the XFCE does not require any tweak tool in order for installing and activating the new desktop themes. By being under the GNOME, and especially after installing that Tweak tool which is mentioned above, you will need to go ahead and also to make sure that you have the extension of User Themes installed.
|
||||
|
||||
The same as with the XFCE, the user will want to search for, and then download the theme which most appeals personally to him. Then, user can revisit to the GNOME Tweak tool, and click on the Appearance option on left side of that Tweak tool. Then, the user can simply look at the bottom of the page and click on file browse button to right of the Shell Theme. User then can browse to the zipped folder, and click open. In case if this process was successfully done, the user will see an alert that tell him that it was installed without any problems. From this point, user can simply use the pull down menu in order for selecting the theme he wants to use. The same as with the XFCE, process of theme activation is very easy, however, a need to download the non-included application for using a new theme will leave much to be desired.
|
||||
|
||||
Finally, there is the process of the KDE desktop theming. The same as with XFCE, there is no need at all to install any extra tools for making it work. This is one area where there is a feeling that the XFCE has to make the KDE the winner. Not only the installing themes in the KDE is accomplished entirely within the Graphical User Interface, but it’s also even possible to click on (Get New Themes) button and user will be able to locate, view, and also install the new themes automatically.
|
||||
|
||||
However, it should be noted that the KDE is a bit more robust desktop environment comparing to the XFCE. Therefore, it is a bit reasonable now to see why such extra functionalities could be missing from the desktops which are mainly designed to be minimalist. So, we all have to give the KDE props for such outstanding functionality.
|
||||
|
||||
### MATE is not Lightweight Desktop ###
|
||||
|
||||
Before continuing with the comparison between the XFCE, the GNOME 3 and the KDE, it should be clear for experts that we can’t touch the MATE desktop as an option in the comparison. MATE can be considered as the GNOME 2 desktop’s next incarnation, but it’s not mainly marketed to be a lightweight or fast desktop. But instead of that, its primary goal is to be more traditional and comfortable desktop environment where the users can feel right at their home to use it.
|
||||
|
||||
On the other hand, the XFCE comes with a completely other goal set. The XFCE offers its users a more lightweight and yet still visually appealing desktop experience. Then, for everyone who points out that MATE is a lightweight desktop too, it isn’t really targeting that lightweight desktop crowd. Both options may be dressed up for looking quite attractive with the proper theme installed.
|
||||
|
||||
### The Navigation of Desktop ###
|
||||
|
||||
The XFCE honestly offers an obvious navigation which is out of the box. Anyone who is used to the traditional Windows or the GNOME 2/MATE desktop experience will be going to have the ability to navigate around the new XFCE installation without any kind of help. Straight away, adding the applets to panel is still very obvious. The same as with locating installed applications, just use the launcher and simply click on any desired application. With an exception of LXDE and MATE, there is no other desktop that can make the navigation that simple. What can be even better is that fact which the control panel is very easy to use, that is a really big benefit to everyone who is new to the desktop environment. If the user prefer older methods to use his desktop, then GNOME is not an option. With the hot corners as well as the no minimize button, plus the other application layout method, it’ll take the most newcomers getting easily used to it.
|
||||
|
||||
If the user is coming from, as an example, Windows environment, then he is going to be put off by the inability to add applets to the top of his workspace simply with just a mere right-click. Just instead of this, it can be handled by using extensions. Installing extensions in the GNOME is granted and is a brain-dead easy, based on the easy to use (on/off) toggle switches located on the extensions page of the GNOME. Users have to know, sadly, to actually visit that page to enjoy this functionality.
|
||||
|
||||
On the other side, the GNOME is sharing its desire for providing a straight forward and an easy to use control panel, which many of you may think that it is not be a big deal, but it is really something that I by myself find commendable and worth to be mentioned. The KDE offers its users a bit more traditional desktop experience, throughout familiar launchers as well as the ability for getting to the software in more familiar way if they are coming from Windows desktop. The process of adding widgets or applets to the KDE desktop is an easy matter of just right-clicking on the bottom of the desktop. Only the problem with the KDE’s approach is to be that, as many things KDE, the feature which users are actually looking for are hidden. The KDE users might berate my opinion for this, but I still stand by my statement.
|
||||
|
||||
In order for adding a Widget, just right-click on “my panel”, just to see the panel options, but not as an immediate method to install Widgets. You will not actually see the Add Widgets until you select the Panel Options, then the Add Widgets. This not a big deal to me, but later for some users, it becomes unnecessary tidbit of confusion. To make things here more convoluted, after the users manage to locate Widgets area they discover later a brand new term called “Activities”. It is in the same area as the Widgets, yet it is somehow in its own area as to what it does.
|
||||
|
||||
Now don’t misunderstand me, the Activities feature in the KDE is totally great and actually valued. But to look at it from the usability standpoint, I think that it would be better suited in another menu option in order to not confuse the newbies. User is welcome to differ, but to test this with newbies for some extended periods of time can prove the correct over and over again. The rant against the Activities placement aside, the KDE approach to add new widgets is really great. The same as with the KDE themes, user can’t browse through and install the Widgets automatically via using the provided Graphical User Interface. It is a bit fantastic of functionality, and also it could be celebrated such way. The control panel of the KDE is not as easy as the user might like it to be, yet it is a bit clear that this’s something that they are still working on.
|
||||
|
||||
### So, the XFCE is the best desktop, right? ###
|
||||
|
||||
I, by myself, actually run GNOME, KDE, and XFCE on my computers in my office and home. I also have some older machines with OpenBox and LXDE too. Each desktop experience can offer something that is a bit useful to me and may help me to use each machine as I see that it is fit. For me, I have a soft spot in my heart for the XFCE as it is one of the desktop environments which I stuck with for years. But in this article, I’m just writing it on my daily use computer which is in fact, GNOME.
|
||||
|
||||
The main idea here is that I still feel that the XFCE provides a bit better user experience for users who are looking for stable, traditional, and easy to understand desktop environment. You are also welcome to share with us your opinion in the comments section.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.unixmen.com/kde-vs-gnome-vs-xfce-desktop/
|
||||
|
||||
作者:[M.el Khamlichi][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.unixmen.com/author/pirat9/
|
||||
@ -0,0 +1,40 @@
|
||||
Backup (System Restore Point) your Ubuntu/Linux Mint with SystemBack
|
||||
================================================================================
|
||||
System Restore is must have feature for any OS that allows the user to revert their computer's state (including system files, installed applications, and system settings) to that of a previous point in time, which can be used to recover from system malfunctions or other problems.
|
||||
Sometimes installing a program or driver can make your OS go to blank screen. System Restore can return your PC's system files and programs to a time when everything was working fine, potentially preventing hours of troubleshooting headaches. It won't affect your documents, pictures, or other data.
|
||||
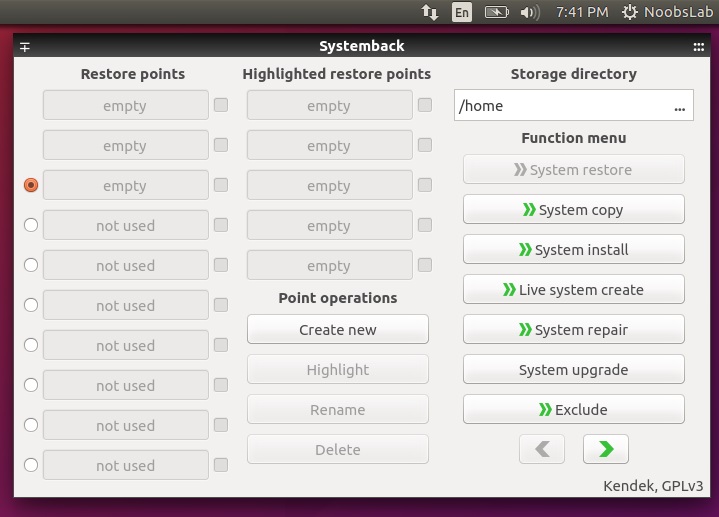
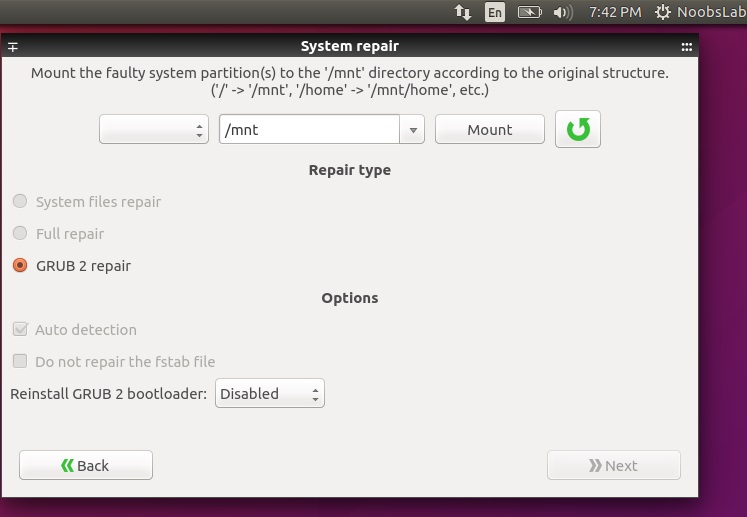
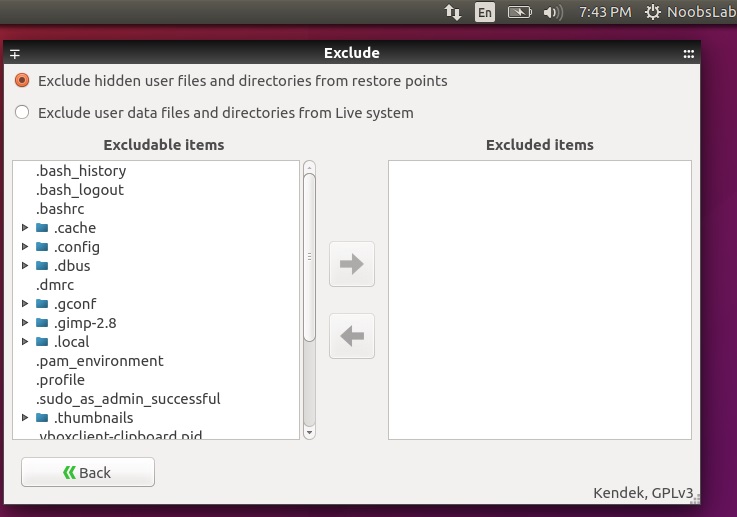
Simple system backup and restore application with extra features. [Systemback][1] makes it easy to create backups of system and users configuration files. In case of problems you can easily restore the previous state of the system. There are extra features like system copying, system installation and Live system creation.
|
||||
|
||||
Screenshots
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||

|
||||
|
||||
**Note**: Using System Restore will not restore documents, music, emails, or personal files of any kind. Depending on your perspective, this is both a positive and negative feature. The bad news is that it won't restore that accidentally deleted file you wish you could get back, though a file recovery program might solve that problem.
|
||||
If no restore point exists on your computer, System Restore has nothing to revert to so the tool won't work for you. If you're trying to recover from a major problem, you'll need to move on to another troubleshooting step.
|
||||
|
||||
>>> Available for Ubuntu 15.10 Wily/16.04/15.04 Vivid/14.04 Trusty/Linux Mint 17.x/other Ubuntu derivatives
|
||||
To install SystemBack Application in Ubuntu/Linux Mint open Terminal (Press Ctrl+Alt+T) and copy the following commands in the Terminal:
|
||||
|
||||
Terminal Commands:
|
||||
|
||||
sudo add-apt-repository ppa:nemh/systemback
|
||||
sudo apt-get update
|
||||
sudo apt-get install systemback
|
||||
|
||||
That's it
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.noobslab.com/2015/11/backup-system-restore-point-your.html
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:https://launchpad.net/systemback
|
||||
@ -1,3 +1,4 @@
|
||||
wyangsun translating
|
||||
How to use Mutt email client with encrypted passwords
|
||||
================================================================================
|
||||
Mutt is an open-source email client written for Linux/UNIX terminal environment. Together with [Alpine][1], Mutt has the most devoted followers among Linux command-line enthusiasts, and for good reasons. Think of anything you expect from an email client, and Mutt has it: multi-protocol support (e.g., POP3, IMAP and SMTP), S/MIME and PGP/GPG integration, threaded conversation, color coding, customizable macros/keybindings, and so on. Besides, terminal-based Mutt is a lightweight alternative for accessing emails compared to bulky web browser-based (e.g., Gmail, Ymail) or GUI-based email clients (e.g., Thunderbird, MS Outlook).
|
||||
@ -135,4 +136,4 @@ via: http://xmodulo.com/mutt-email-client-encrypted-passwords.html
|
||||
|
||||
[a]:http://xmodulo.com/author/nanni
|
||||
[1]:http://xmodulo.com/gmail-command-line-linux-alpine.html
|
||||
[2]:http://dev.mutt.org/trac/wiki/MuttGuide/UseGPG
|
||||
[2]:http://dev.mutt.org/trac/wiki/MuttGuide/UseGPG
|
||||
|
||||
@ -0,0 +1,96 @@
|
||||
Linux and Unix Port Scanning With netcat [nc] Command
|
||||
================================================================================
|
||||
How do I find out which ports are opened on my own server? How do I run port scanning using the nc command instead of [the nmap command on a Linux or Unix-like][1] systems?
|
||||
|
||||
The nmap (“Network Mapper”) is an open source tool for network exploration and security auditing. If nmap is not installed and you do not wish to use all of nmap options you can use netcat/nc command for scanning ports. This may useful to know which ports are open and running services on a target machine. You can use [nmap command for port scanning][2] too.
|
||||
|
||||
### How do I use nc to scan Linux, UNIX and Windows server port scanning? ###
|
||||
|
||||
If nmap is not installed try nc / netcat command as follow. The -z flag can be used to tell nc to report open ports, rather than initiate a connection. Run nc command with -z flag. You need to specify host name / ip along with the port range to limit and speedup operation:
|
||||
|
||||
## syntax ##
|
||||
nc -z -v {host-name-here} {port-range-here}
|
||||
nc -z -v host-name-here ssh
|
||||
nc -z -v host-name-here 22
|
||||
nc -w 1 -z -v server-name-here port-Number-her
|
||||
|
||||
## scan 1 to 1023 ports ##
|
||||
nc -zv vip-1.vsnl.nixcraft.in 1-1023
|
||||
|
||||
Sample outputs:
|
||||
|
||||
Connection to localhost 25 port [tcp/smtp] succeeded!
|
||||
Connection to vip-1.vsnl.nixcraft.in 25 port [tcp/smtp] succeeded!
|
||||
Connection to vip-1.vsnl.nixcraft.in 80 port [tcp/http] succeeded!
|
||||
Connection to vip-1.vsnl.nixcraft.in 143 port [tcp/imap] succeeded!
|
||||
Connection to vip-1.vsnl.nixcraft.in 199 port [tcp/smux] succeeded!
|
||||
Connection to vip-1.vsnl.nixcraft.in 783 port [tcp/*] succeeded!
|
||||
Connection to vip-1.vsnl.nixcraft.in 904 port [tcp/vmware-authd] succeeded!
|
||||
Connection to vip-1.vsnl.nixcraft.in 993 port [tcp/imaps] succeeded!
|
||||
|
||||
You can scan individual port too:
|
||||
|
||||
nc -zv v.txvip1 443
|
||||
nc -zv v.txvip1 80
|
||||
nc -zv v.txvip1 22
|
||||
nc -zv v.txvip1 21
|
||||
nc -zv v.txvip1 smtp
|
||||
nc -zvn v.txvip1 ftp
|
||||
|
||||
## really fast scanner with 1 timeout value ##
|
||||
netcat -v -z -n -w 1 v.txvip1 1-1023
|
||||
|
||||
Sample outputs:
|
||||
|
||||
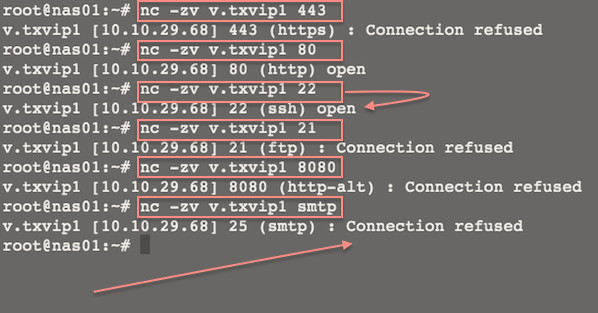
|
||||
|
||||
Fig.01: Linux/Unix: Use Netcat to Establish and Test TCP and UDP Connections on a Server
|
||||
|
||||
Where,
|
||||
|
||||
1. -z : Port scanning mode i.e. zero I/O mode.
|
||||
1. -v : Be verbose [use twice -vv to be more verbose].
|
||||
1. -n : Use numeric-only IP addresses i.e. do not use DNS to resolve ip addresses.
|
||||
1. -w 1 : Set time out value to 1.
|
||||
|
||||
More examples:
|
||||
|
||||
$ netcat -z -vv www.cyberciti.biz http
|
||||
www.cyberciti.biz [75.126.153.206] 80 (http) open
|
||||
sent 0, rcvd 0
|
||||
$ netcat -z -vv google.com https
|
||||
DNS fwd/rev mismatch: google.com != maa03s16-in-f2.1e100.net
|
||||
DNS fwd/rev mismatch: google.com != maa03s16-in-f6.1e100.net
|
||||
DNS fwd/rev mismatch: google.com != maa03s16-in-f5.1e100.net
|
||||
DNS fwd/rev mismatch: google.com != maa03s16-in-f3.1e100.net
|
||||
DNS fwd/rev mismatch: google.com != maa03s16-in-f8.1e100.net
|
||||
DNS fwd/rev mismatch: google.com != maa03s16-in-f0.1e100.net
|
||||
DNS fwd/rev mismatch: google.com != maa03s16-in-f7.1e100.net
|
||||
DNS fwd/rev mismatch: google.com != maa03s16-in-f4.1e100.net
|
||||
google.com [74.125.236.162] 443 (https) open
|
||||
sent 0, rcvd 0
|
||||
$ netcat -v -z -n -w 1 192.168.1.254 1-1023
|
||||
(UNKNOWN) [192.168.1.254] 989 (ftps-data) open
|
||||
(UNKNOWN) [192.168.1.254] 443 (https) open
|
||||
(UNKNOWN) [192.168.1.254] 53 (domain) open
|
||||
|
||||
See also
|
||||
|
||||
- [Scanning network for open ports with the nmap command][3] for more info.
|
||||
- Man pages - [nc(1)][4], [nmap(1)][5]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.cyberciti.biz/faq/linux-port-scanning/
|
||||
|
||||
作者:Vivek Gite
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.cyberciti.biz/networking/nmap-command-examples-tutorials/
|
||||
[2]:http://www.cyberciti.biz/tips/linux-scanning-network-for-open-ports.html
|
||||
[3]:http://www.cyberciti.biz/networking/nmap-command-examples-tutorials/
|
||||
[4]:http://www.manpager.com/linux/man1/nc.1.html
|
||||
[5]:http://www.manpager.com/linux/man1/nmap.1.html
|
||||
@ -0,0 +1,108 @@
|
||||
8 things to do after installing openSUSE Leap 42.1
|
||||
================================================================================
|
||||

|
||||
Credit: [Metropolitan Transportation/Flicrk][1]
|
||||
|
||||
> You've installed openSUSE on your PC. Here's what to do next.
|
||||
|
||||
[openSUSE Leap is indeed a huge leap][2], allowing users to run a distro that has the same DNA of SUSE Linux Enterprise. Like any other operating system, some work is needed to get it set up for optimal use.
|
||||
|
||||
Following are some of the things that I did after installing openSUSE Leap on my PC (these are not applicable for server installations). None of them are mandatory, and you may be fine with the basic install. But if you need more out of your openSUSE Leap, follow me.
|
||||
|
||||
### 1. Adding Packman repository ###
|
||||
|
||||
Due to software patents and licences, openSUSE, like many Linux distributions, doesn't offer many applications, codecs, and drivers through official repositories (repos). Instead, these are made available through 3rd party or community repos. The first and most important repository is 'Packman'. Since these repos are not enabled by default, we have to add them. You can do so either using YaST (one of the gems of openSUSE) or by command line (instructions below).
|
||||
|
||||
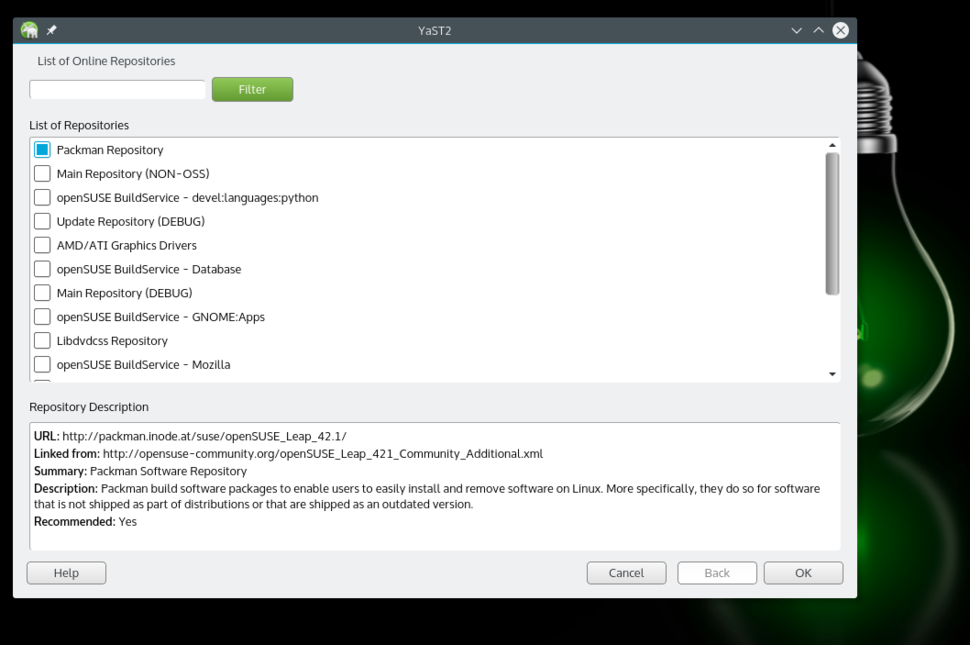
|
||||
Adding Packman repositories.
|
||||
|
||||
Using YaST, go to the Software Repositories section. Click on the 'Add’ button and select 'Community Repositories.' Click 'next.' And once the repos are loaded, select the Packman Repository. Click 'OK,' then import the trusted GnuPG key by clicking on the 'Trust' button.
|
||||
|
||||
Or, using the terminal you can add and enable the Packman repo using the following command:
|
||||
|
||||
zypper ar -f -n packmanhttp://ftp.gwdg.de/pub/linux/misc/packman/suse/openSUSE_Leap_42.1/ packman
|
||||
|
||||
Once the repo is added, you have access to many more packages. To install any application or package, open YaST Software Manager, search for the package and install it.
|
||||
|
||||
### 2. Install VLC ###
|
||||
|
||||
VLC is the Swiss Army knife of media players and can play virtually any media file. You can install VLC from YaST Software Manager or from software.opensuse.org. You will need to install two packages: vlc and vlc-codecs.
|
||||
|
||||
If using terminal, run the following command:
|
||||
|
||||
sudo zypper install vlc vlc-codecs
|
||||
|
||||
### 3. Install Handbrake ###
|
||||
|
||||
If you need to transcode or convert your video files from one format to another, [Handbrake is the tools for you][3]. Handbrake is available through repositories we enabled, so just search for it in YaST and install.
|
||||
|
||||
If you are using the terminal, run the following command:
|
||||
|
||||
sudo zypper install handbrake-cli handbrake-gtk
|
||||
|
||||
(Pro tip: VLC can also transcode audio and video files.)
|
||||
|
||||
### 4. Install Chrome ###
|
||||
|
||||
OpenSUSE comes with Firefox as the default browser. But since Firefox isn't capable of playing restricted media such as Netflix, I recommend installing Chrome. This takes some extra work. First you need to import the trusted key from Google. Open the terminal app and run the 'wget' command to download the key:
|
||||
|
||||
wget https://dl.google.com/linux/linux_signing_key.pub
|
||||
|
||||
Then import the key:
|
||||
|
||||
sudo rpm --import linux_signing_key.pub
|
||||
|
||||
Now head over to the [Google Chrome website][4] and download the 64 bit .rpm file. Once downloaded run the following command to install the browser:
|
||||
|
||||
sudo zypper install /PATH_OF_GOOGLE_CHROME.rpm
|
||||
|
||||
### 5. Install Nvidia drivers ###
|
||||
|
||||
OpenSUSE Leap will work out of the box even if you have Nvidia or ATI graphics cards. However, if you do need the proprietary drivers for gaming or any other purpose, you can install such drivers, but some extra work is needed.
|
||||
|
||||
First you need to add the Nvidia repositories; it's the same procedure we used to add Packman repositories using YaST. The only difference is that you will choose Nvidia from the Community Repositories section. Once it's added, go to **Software Management > Extras** and select 'Extras/Install All Matching Recommended Packages'.
|
||||
|
||||
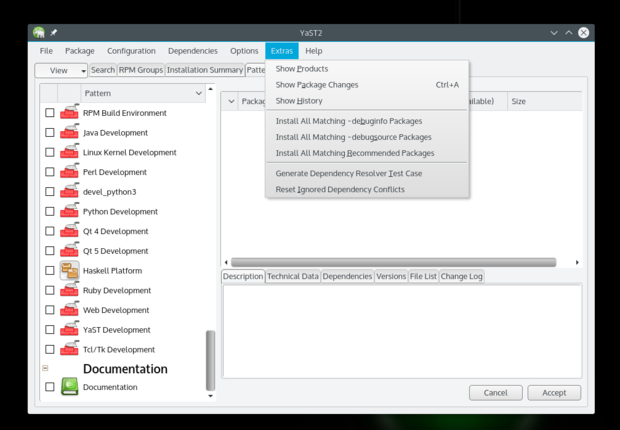
|
||||
|
||||
It will open a dialogue box showing all the packages it's going to install, click OK and follow the instructions. You can also run the following command after adding the Nvidia repository to install the needed Nvidia drivers:
|
||||
|
||||
sudo zypper inr
|
||||
|
||||
(Note: I have never used AMD/ATI cards so I have no experience with them.)
|
||||
|
||||
### 6. Install media codecs ###
|
||||
|
||||
Once you have VLC installed you won't need to install media codecs, but if you are using other apps for media playback you will need to install such codecs. Some developers have written scripts/tools which makes it a much easier process. Just go to [this page][5] and install the entire pack by clicking on the appropriate button. It will open YaST and install the packages automatically (of source you will have to give the root password and trust the GnuPG key, as usual).
|
||||
|
||||
### 7. Install your preferred email client ###
|
||||
|
||||
OpenSUSE comes with Kmail or Evolution, depending on the Desktop Environment you installed on the system. I run Plasma, which comes with Kmail, and this email client leaves a lot to be desired. I suggest trying Thunderbird or Evolution mail. All major email clients are available through official repositories. You can also check my [handpicked list of the best email clients for Linux][7].
|
||||
|
||||
### 8. Enable Samba services from Firewall ###
|
||||
|
||||
OpenSUSE offers a much more secure system out of the box, compared to other distributions. But it also requires a little bit more work for a new user. If you are using Samba protocol to share files within your local network then you will have to allow that service from the Firewall.
|
||||
|
||||
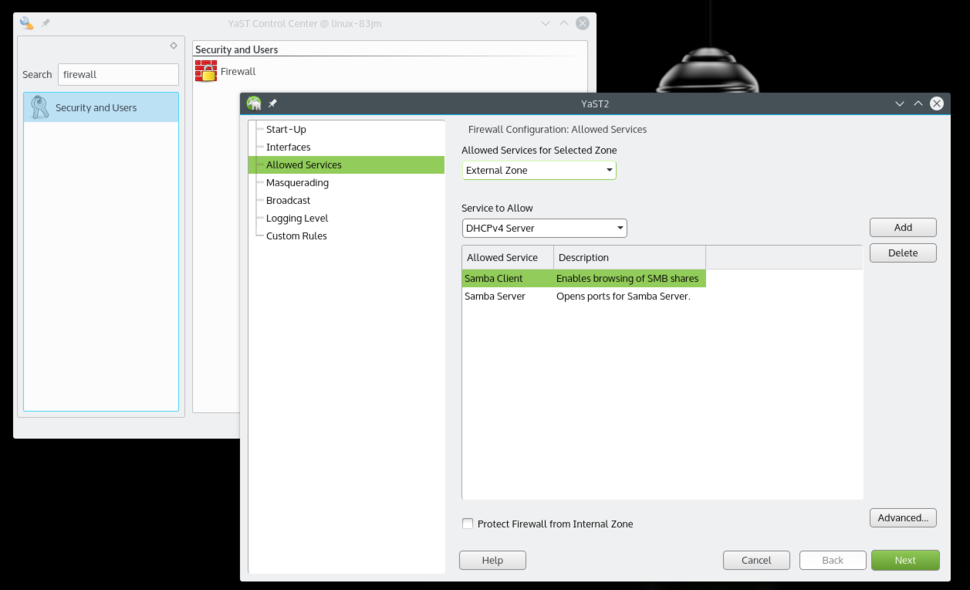
|
||||
Allow Samba Client and Server from Firewall settings.
|
||||
|
||||
Open YaST and search for Firewall. Once in Firewall settings, go to 'Allowed Services' where you will see a drop down list under 'Service to allow.' Select 'Samba Client,' then click 'Add.' Do the same with the 'Samba Server' option. Once both are added, click 'Next,' then click 'Finish,' and now you will be able to share folders from your openSUSE system and also access other machines over the local network.
|
||||
|
||||
That's pretty much all that I did on my new openSUSE system to set it up just the way I like it. If you have any questions, please feel free to ask in the comments below.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.itworld.com/article/3003865/open-source-tools/8-things-to-do-after-installing-opensuse-leap-421.html
|
||||
|
||||
作者:[Swapnil Bhartiya][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.itworld.com/author/Swapnil-Bhartiya/
|
||||
[1]:https://www.flickr.com/photos/mtaphotos/11200079265/
|
||||
[2]:https://www.linux.com/news/software/applications/865760-opensuse-leap-421-review-the-most-mature-linux-distribution
|
||||
[3]:https://www.linux.com/learn/tutorials/857788-how-to-convert-videos-in-linux-using-the-command-line
|
||||
[4]:https://www.google.com/intl/en/chrome/browser/desktop/index.html#brand=CHMB&utm_campaign=en&utm_source=en-ha-na-us-sk&utm_medium=ha
|
||||
[5]:http://opensuse-community.org/
|
||||
[6]:http://www.itworld.com/article/2875981/the-5-best-open-source-email-clients-for-linux.html
|
||||
43
sources/tech/20151202 A new Mindcraft moment.md
Normal file
43
sources/tech/20151202 A new Mindcraft moment.md
Normal file
@ -0,0 +1,43 @@
|
||||
A new Mindcraft moment?
|
||||
=======================
|
||||
|
||||
Credit:Jonathan Corbet
|
||||
|
||||
It is not often that Linux kernel development attracts the attention of a mainstream newspaper like The Washington Post; lengthy features on the kernel community's approach to security are even more uncommon. So when just such a feature hit the net, it attracted a lot of attention. This article has gotten mixed reactions, with many seeing it as a direct attack on Linux. The motivations behind the article are hard to know, but history suggests that we may look back on it as having given us a much-needed push in a direction we should have been going for some time.
|
||||
|
||||
Think back, a moment, to the dim and distant past — April 1999, to be specific. An analyst company named Mindcraft issued a report showing that Windows NT greatly outperformed Red Hat Linux 5.2 and Apache for web-server workloads. The outcry from the Linux community, including from a very young LWN, was swift and strong. The report was a piece of Microsoft-funded FUD trying to cut off an emerging threat to its world-domination plans. The Linux system had been deliberately configured for poor performance. The hardware chosen was not well supported by Linux at the time. And so on.
|
||||
|
||||
Once people calmed down a bit, though, one other fact came clear: the Mindcraft folks, whatever their motivations, had a point. Linux did, indeed, have performance problems that were reasonably well understood even at the time. The community then did what it does best: we sat down and fixed the problems. The scheduler got exclusive wakeups, for example, to put an end to thethundering-herd problem in the acceptance of connection requests. Numerous other little problems were fixed. Within a year or so, the kernel's performance on this kind of workload had improved considerably.
|
||||
|
||||
The Mindcraft report, in other words, was a much-needed kick in the rear that got the community to deal with issues that had been neglected until then.
|
||||
|
||||
The Washington Post article seems clearly slanted toward a negative view of the Linux kernel and its contributors. It freely mixes kernel problems with other issues (the AshleyMadison.com breakin, for example) that were not kernel vulnerabilities at all. The fact that vendors seem to have little interest in getting security fixes to their customers is danced around like a huge elephant in the room. There are rumors of dark forces that drove the article in the hopes of taking Linux down a notch. All of this could well be true, but it should not be allowed to overshadow the simple fact that the article has a valid point.
|
||||
|
||||
We do a reasonable job of finding and fixing bugs. Problems, whether they are security-related or not, are patched quickly, and the stable-update mechanism makes those patches available to kernel users. Compared to a lot of programs out there (free and proprietary alike), the kernel is quite well supported. But pointing at our ability to fix bugs is missing a crucial point: fixing security bugs is, in the end, a game of whack-a-mole. There will always be more moles, some of which we will not know about (and will thus be unable to whack) for a long time after they are discovered and exploited by attackers. These bugs leave our users vulnerable, even if the commercial side of Linux did a perfect job of getting fixes to users — which it decidedly does not.
|
||||
|
||||
The point that developers concerned about security have been trying to make for a while is that fixing bugs is not enough. We must instead realize that we will never fix them all and focus on making bugs harder to exploit. That means restricting access to information about the kernel, making it impossible for the kernel to execute code in user-space memory, instrumenting the kernel to detect integer overflows, and all the other things laid out in Kees Cook's Kernel Summit talk at the end of October. Many of these techniques are well understood and have been adopted by other operating systems; others will require innovation on our part. But, if we want to adequately defend our users from attackers, these changes need to be made.
|
||||
|
||||
Why hasn't the kernel adopted these technologies already? The Washington Post article puts the blame firmly on the development community, and on Linus Torvalds in particular. The culture of the kernel community prioritizes performance and functionality over security and is unwilling to make compromises if they are needed to improve the security of the kernel. There is some truth to this claim; the good news is that attitudes appear to be shifting as the scope of the problem becomes clear. Kees's talk was well received, and it clearly got developers thinking and talking about the issues.
|
||||
|
||||
The point that has been missed is that we do not just have a case of Linus fending off useful security patches. There simply are not many such patches circulating in the kernel community. In particular, the few developers who are working in this area have never made a serious attempt to get that work integrated upstream. Getting any large, intrusive patch set merged requires working with the kernel community, making the case for the changes, splitting the changes into reviewable pieces, dealing with review comments, and so on. It can be tiresome and frustrating, but it's how the kernel works, and it clearly results in a more generally useful, more maintainable kernel in the long run.
|
||||
|
||||
Almost nobody is doing that work to get new security technologies into the kernel. One might cite a "chilling effect" from the hostile reaction such patches can receive, but that is an inadequate answer: developers have managed to merge many changes over the years despite a difficult initial reaction. Few security developers are even trying.
|
||||
|
||||
Why aren't they trying? One fairly obvious answer is that almost nobody is being paid to try. Almost all of the work going into the kernel is done by paid developers and has been for many years. The areas that companies see fit to support get a lot of work and are well advanced in the kernel. The areas that companies think are not their problem are rather less so. The difficulties in getting support for realtime development are a clear case in point. Other areas, such as documentation, tend to languish as well. Security is clearly one of those areas. There are a lot of reasons why Linux lags behind in defensive security technologies, but one of the key ones is that the companies making money on Linux have not prioritized the development and integration of those technologies.
|
||||
|
||||
There are signs that things might be changing a bit. More developers are showing interest in security-related issues, though commercial support for their work is still less than it should be. The reaction against security-related changes might be less knee-jerk negative than it used to be. Efforts like the Kernel Self Protection Project are starting to work on integrating existing security technologies into the kernel.
|
||||
|
||||
We have a long way to go, but, with some support and the right mindset, a lot of progress can be made in a short time. The kernel community can do amazing things when it sets its mind to it. With luck, the Washington Post article will help to provide the needed impetus for that sort of setting of mind. History suggests that we will eventually see this moment as a turning point, when we were finally embarrassed into doing work that has clearly needed doing for a while. Linux should not have a substandard security story for much longer.
|
||||
|
||||
---------------------------
|
||||
|
||||
via: https://lwn.net/Articles/663474/
|
||||
|
||||
作者:Jonathan Corbet
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
@ -0,0 +1,146 @@
|
||||
How to use the Linux ftp command to up- and download files on the shell
|
||||
================================================================================
|
||||
In this tutorial, I will explain how to use the Linux ftp command on the shell. I will show you how to connect to an FTP server, up- and download files and create directories. While there are many nice desktops FTP clients available, the FTP command is still useful when you work remotely on a server over an SSH session and e.g. want to fetch a backup file from your FTP storage.
|
||||
|
||||
### Step 1: Establishing an FTP connection ###
|
||||
|
||||
To connect to the FTP server, we have to type in the terminal window '**ftp**' and then the domain name 'domain.com' or IP address of the FTP server.
|
||||
|
||||
#### Examples: ####
|
||||
|
||||
ftp domain.com
|
||||
|
||||
ftp 192.168.0.1
|
||||
|
||||
ftp user@ftpdomain.com
|
||||
|
||||
**Note: for this example we used an anonymous server.**
|
||||
|
||||
Replace the IP and domain in the above examples with the IP address or domain of your FTP server.
|
||||
|
||||
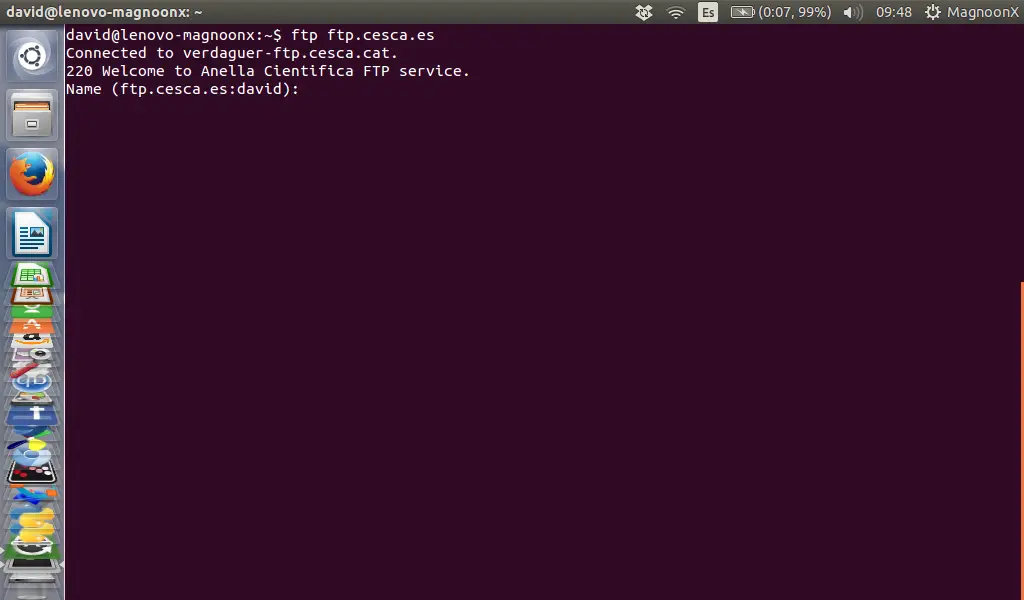
|
||||
|
||||
### Step 2: Login with User and Password ###
|
||||
|
||||
Most FTP servers logins are password protected, so the server will ask us for a '**username**' and a '**password**'.
|
||||
|
||||
If you connect to a so-called anonymous FTP server, then try to use "anonymous" as user name and a nempty password:
|
||||
|
||||
Name: anonymous
|
||||
|
||||
Password:
|
||||
|
||||
The terminal will return a message like this:
|
||||
|
||||
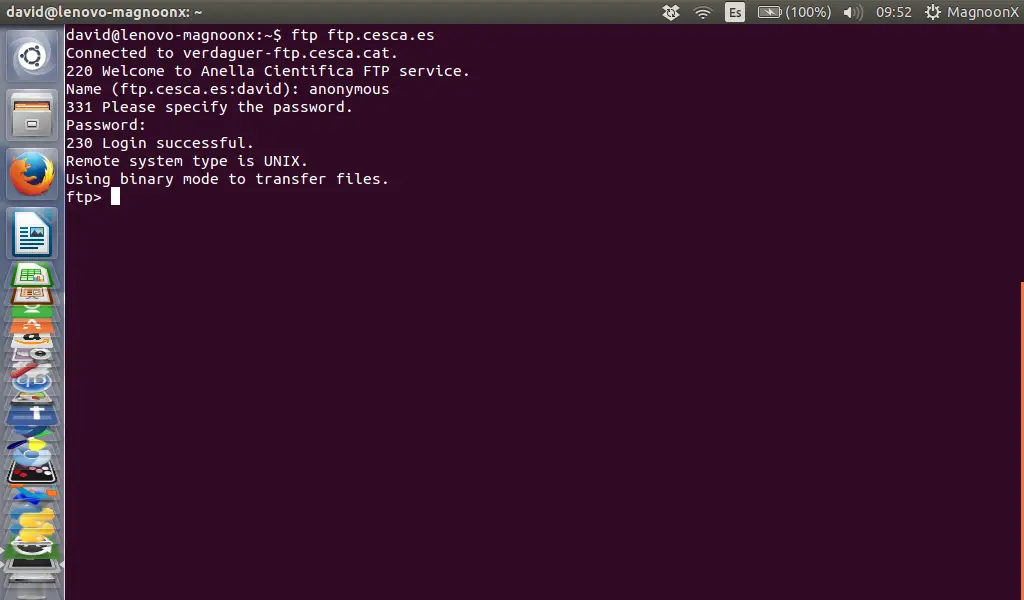
230 Login successful.
|
||||
Remote system type is UNIX.
|
||||
Using binary mode to transfer files.
|
||||
ftp>
|
||||
|
||||
When you are logged in successfully.
|
||||
|
||||
|
||||
|
||||
### Step 3: Working with Directories ###
|
||||
|
||||
The commands to list, move and create folders on an FTP server are almost the same as we would use locally on our computer, ls for list, cd to change directories, mkdir to create directories...
|
||||
|
||||
#### Listing directories with security settings: ####
|
||||
|
||||
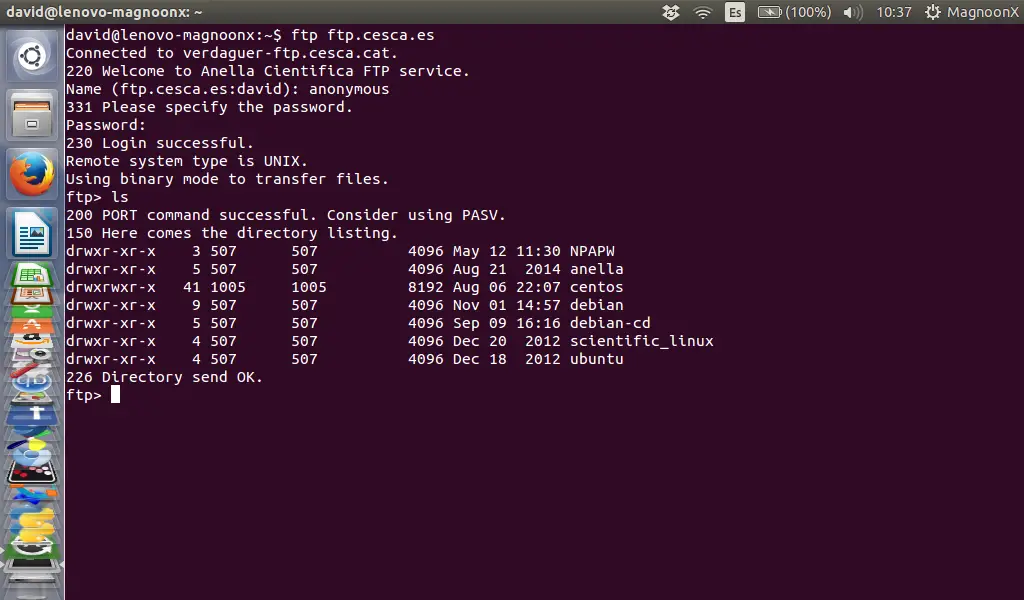
ftp> ls
|
||||
|
||||
The server will return:
|
||||
|
||||
200 PORT command successful. Consider using PASV.
|
||||
150 Here comes the directory listing.
|
||||
directory list
|
||||
....
|
||||
....
|
||||
226 Directory send OK.
|
||||
|
||||
|
||||
|
||||
#### Changing Directories: ####
|
||||
|
||||
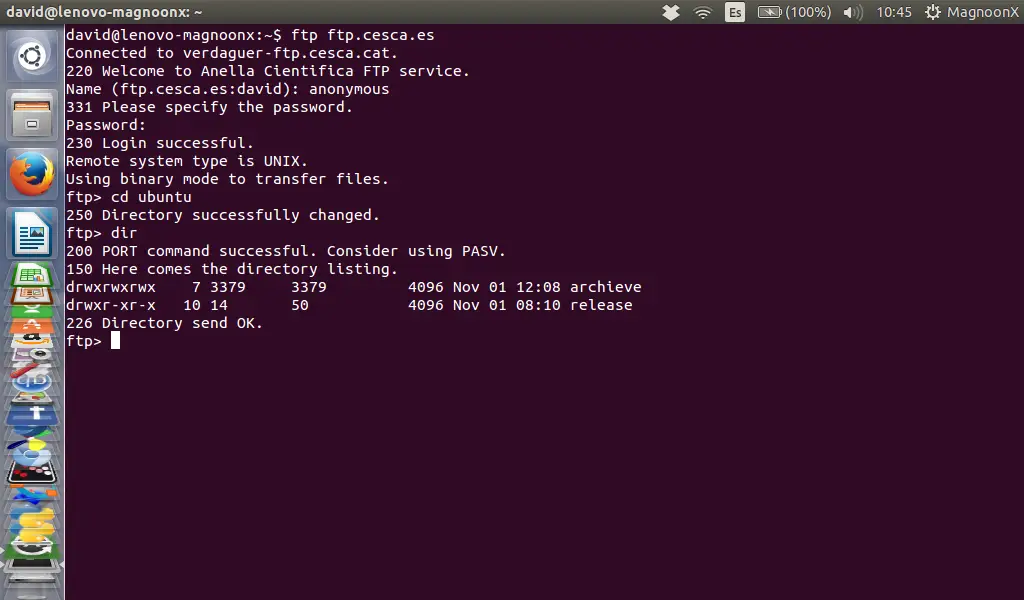
To change the directory we can type:
|
||||
|
||||
ftp> cd directory
|
||||
|
||||
The server will return:
|
||||
|
||||
250 Directory succesfully changed.
|
||||
|
||||
|
||||
|
||||
### Step 4: Downloading files with FTP ###
|
||||
|
||||
Before downloading a file, we should set the local ftp file download directory by using 'lcd' command:
|
||||
|
||||
lcd /home/user/yourdirectoryname
|
||||
|
||||
If you dont specify the download directory, the file will be downloaded to the current directory where you were at the time you started the FTP session.
|
||||
|
||||
Now, we can use the command 'get' command to download a file, the usage is:
|
||||
|
||||
get file
|
||||
|
||||
The file will be downloaded to the directory previously set with the 'lcd' command.
|
||||
|
||||
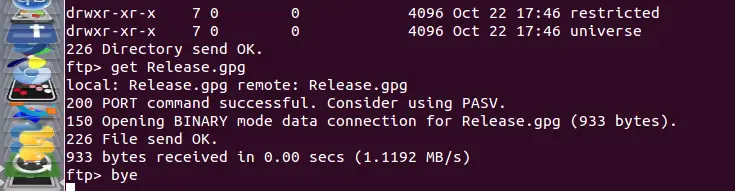
The server will return the next message:
|
||||
|
||||
local: file remote: file
|
||||
200 PORT command successful. Consider using PASV.
|
||||
150 Opening BINARY mode data connection for file (xxx bytes).
|
||||
226 File send OK.
|
||||
XXX bytes received in x.xx secs (x.xxx MB/s).
|
||||
|
||||
|
||||
|
||||
To download several files we can use wildcards. In this example I will download all files with the .xls file extension.
|
||||
|
||||
mget *.xls
|
||||
|
||||
### Step 5: Uploading Files with FTP ###
|
||||
|
||||
We can upload files that are in the local directory where we made the FTP connection.
|
||||
|
||||
To upload a file, we can use 'put' command.
|
||||
|
||||
put file
|
||||
|
||||
When the file that you want to upload is not in the local directory, you can use the absolute path starting with "/" as well:
|
||||
|
||||
put /path/file
|
||||
|
||||
To upload several files we can use the mput command similar to the mget example from above:
|
||||
|
||||
mput *.xls
|
||||
|
||||
### Step 6: Closing the FTP connection ###
|
||||
|
||||
Once we have done the FTP work, we should close the connection for security reasons. There are three commands that we can use to close the connection:
|
||||
|
||||
bye
|
||||
|
||||
exit
|
||||
|
||||
quit
|
||||
|
||||
Any of them will disconnect our PC from the FTP server and will return:
|
||||
|
||||
221 Goodbye
|
||||
|
||||

|
||||
|
||||
If you need some additional help, once you are connected to the FTP server, type 'help' and this will show you all the available FTP commands.
|
||||
|
||||
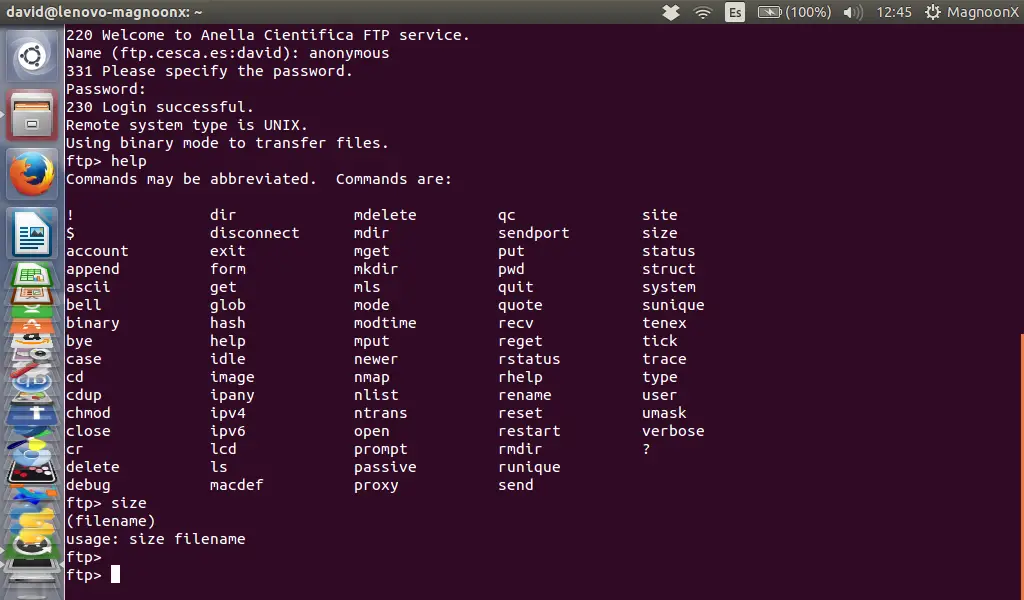
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.howtoforge.com/tutorial/how-to-use-ftp-on-the-linux-shell/
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
@ -1,159 +1,238 @@
|
||||
How to Install and Configure Multihomed ISC DHCP Server on Debian Linux
|
||||
debian linux上安装配置 ISC DHCP Server
|
||||
================================================================================
|
||||
Dynamic Host Control Protocol (DHCP) offers an expedited method for network administrators to provide network layer addressing to hosts on a constantly changing, or dynamic, network. One of the most common server utilities to offer DHCP functionality is ISC DHCP Server. The goal of this service is to provide hosts with the necessary network information to be able to communicate on the networks in which the host is connected. Information that is typically served by this service can include: DNS server information, network address (IP), subnet mask, default gateway information, hostname, and much more.
|
||||
动态主机控制协议(DHCP)给网络管理员提供一种便捷的方式,为不断变化的网络主机或是动态网络提供网络层地址。其中最常用的DHCP服务工具是 ISC DHCP Server。DHCP服务的目的是给给主机提供必要的网络信息以便能够和其他连接在网络中的主机互相通信。DHCP服务一般包括以下信息:DNS服务器信息,网络地址(IP),子网掩码,默认网关信息,主机名等等。
|
||||
|
||||
This tutorial will cover ISC-DHCP-Server version 4.2.4 on a Debian 7.7 server that will manage multiple virtual local area networks (VLAN) but can very easily be applied to a single network setup as well.
|
||||
本节教程介绍4.2.4版的ISC-DHCP-Server如何在Debian7.7上管理多个虚拟局域网(VLAN),但是它也可以非常简单的用于单一网络。
|
||||
|
||||
The test network that this server was setup on has traditionally relied on a Cisco router to manage the DHCP address leases. The network currently has 12 VLANs needing to be managed by one centralized server. By moving this responsibility to a dedicated server, the router can regain resources for more important tasks such as routing, access control lists, traffic inspection, and network address translation.
|
||||
测试用的网络是通过思科路由器依赖传统的方式来管DHCP租约地址,目前有12个VLANs需要通过路由器的集中式服务器来管理。把DHCP这个责任转移到一个专用的服务器上面,路由器可以回收资源去用到更重要的任务上,比如路由寻址,访问控制列表,流量监测以及网络地址转换等。
|
||||
|
||||
The other benefit to moving DHCP to a dedicated server will, in a later guide, involve setting up Dynamic Domain Name Service (DDNS) so that new host’s host-names will be added to the DNS system when the host requests a DHCP address from the server.
|
||||
|
||||
另一个将DHCP服务移动到专用服务器的好处,后续会讲到,建立动态域名服务器(DDNS)这样当主机从服务器请求DHCP地址的时候,新主机的主机名将被添加到DNS系统里面。
|
||||
### Step 1: Installing and Configuring ISC DHCP Server ###
|
||||
### 安装和配置ISC DHCP Server###
|
||||
|
||||
1. To start the process of creating this multi-homed server, the ISC software needs to be installed via the Debian repositories using the ‘apt‘ utility. As with all tutorials, root or sudo access is assumed. Please make the appropriate modifications to the following commands.
|
||||
1. 创建这个多宿主服务器的过程中,需要用apt工具来安装Debian软件仓库中的ISC软件。与其他教程一样需要使用root或者sudo访问权限。请适当的修改以使用下面的命令。(译者注:下面中括号里面是注释,使用的时候请删除,#表示使用的root权限)
|
||||
|
||||
# apt-get install isc-dhcp-server [Installs the ISC DHCP Server software]
|
||||
# dpkg --get-selections isc-dhcp-server [Confirms successful installation]
|
||||
# dpkg -s isc-dhcp-server [Alternative confirmation of installation]
|
||||
|
||||
# apt-get install isc-dhcp-server [安装 the ISC DHCP Server 软件]
|
||||
# dpkg --get-selections isc-dhcp-server [确认软件已经成功安装]
|
||||
# dpkg -s isc-dhcp-server [用另一种方式确认成功安装]
|
||||
|
||||
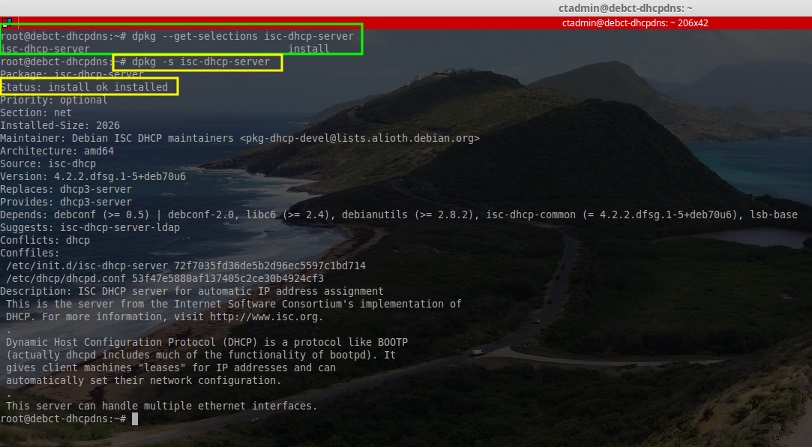
|
||||
|
||||
2. Now that the server software is confirmed installed, it is now necessary to configure the server with the network information that it will need to hand out. At the bare minimum, the administrator needs to know the following information for a basic DHCP scope:
|
||||
|
||||
2. 现在已经确认服务软件安装完毕,现在需要配置服务器,它将分发网络信息。作为管理员你最起码应该了解DHCP的信息如下:
|
||||
- The network addresses
|
||||
- 网络地址
|
||||
- The subnet masks
|
||||
- 子网掩码
|
||||
- The range of addresses to be dynamically assigned
|
||||
- 动态分配的地址范围
|
||||
|
||||
Other useful information to have the server dynamically assign includes:
|
||||
|
||||
其他一些使服务器动态分配的有用信息包括:
|
||||
- Default gateway
|
||||
- 默认网关
|
||||
- DNS server IP addresses
|
||||
- DNS服务器IP地址
|
||||
- The Domain Name
|
||||
- 域名
|
||||
- Host name
|
||||
- 主机名
|
||||
- Network Broadcast addresses
|
||||
- 网络广播地址
|
||||
|
||||
These are merely a few of the many options that the ISC DHCP server can handle. To get a complete list as well as a description of each option, enter the following command after installing the package:
|
||||
|
||||
这只是很少一部分能让ISC DHCP server处理的选项。完整的查看所有选项及其描述需要在安装好软件后输入以下命令:
|
||||
# man dhcpd.conf
|
||||
|
||||
3. Once the administrator has concluded all the necessary information for this server to hand out it is time to configure the DHCP server as well as the necessary pools. Before creating any pools or server configurations though, the DHCP service must be configured to listen on one of the server’s interfaces.
|
||||
|
||||
3. 一旦管理员已经确定了这台服务器需要分发出去的必要信息,那么是时候配置它和分配必要的地址池了。在配置任何地址池或服务器配置之前,DHCP服务必须配置好,来监听这台服务器上面的一个接口。
|
||||
|
||||
On this particular server, a NIC team has been setup and DHCP will listen on the teamed interfaces which were given the name `'bond0'`. Be sure to make the appropriate changes given the server and environment in which everything is being configured. The defaults in this file are okay for this tutorial.
|
||||
|
||||
在这台特定的服务器上,一个网卡设置好后,DHCP会监听命名为`'bond0'`的接口。请适确保适当的更改服务器以及网络环境。下面默认的配置都是针对于本次教程的。
|
||||

|
||||
|
||||
This line will instruct the DHCP service to listen for DHCP traffic on the specified interface(s). At this point, it is time to modify the main configuration file to enable the DHCP pools on the necessary networks. The main configuration file is located at /etc/dhcp/dhcpd.conf. Open the file with a text editor to begin:
|
||||
|
||||
这行指定的是DHCP服务监听接口(一个或多个)上的DHCP流量。修改主要的配置文件分派DHCP池配置在所需要的网络上。主要的配置文件的位置在/etc/dhcp/dhcpd.conf。用文本编辑器打开这个文件
|
||||
# nano /etc/dhcp/dhcpd.conf
|
||||
|
||||
This file is the configuration for the DHCP server specific options as well as all of the pools/hosts one wishes to configure. The top of the file starts of with a ‘ddns-update-style‘ clause and for this tutorial it will remain set to ‘none‘ however in a future article, Dynamic DNS will be covered and ISC-DHCP-Server will be integrated with BIND9 to enable host name to IP address updates.
|
||||
|
||||
这个配置文件可以配置我们想的地址池/主机。文件顶部有‘ddns-update-style‘这样一句,在本教程中它设置为‘none‘。在以后的教程中动态DNS, ISC-DHCP-Server 将被整合到 BIND9为了能够使主机名更新到IP地址。
|
||||
|
||||
4. The next section is typically the area where and administrator can configure global network settings such as the DNS domain name, default lease time for IP addresses, subnet-masks, and much more. Again to know more about all the options be sure to read the man page for the dhcpd.conf file.
|
||||
|
||||
4. 接下来的部分 是管理员配置全局网络设置,如DNS域名,默认的租约时间,IP地址,子网的掩码,以及更多的区域。想更多地了解所有的选项,阅读man手册dhcpd.conf文件,命令如下:
|
||||
|
||||
# man dhcpd.conf
|
||||
|
||||
For this server install, there were a couple of global network options that were configured at the top of the configuration file so that they wouldn’t have to be implemented in every single pool created.
|
||||
|
||||
对于这台服务器,我们需要在顶部配置一些全局网络设置,这腰就不用到每个地址池中单独去设置了。
|
||||
|
||||
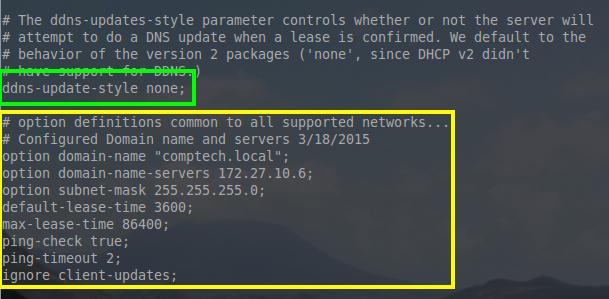
|
||||
|
||||
Lets take a moment to explain some of these options. While they are configured globally in this example, all of them can be configured on a per pool basis as well.
|
||||
下面我们花一点时间来解释一下这些选项,在本例中虽然它们是一些全局,但是也可以为每一个地址池配置。
|
||||
|
||||
- option domain-name “comptech.local”; – All hosts that this DHCP server hosts, will be a member of the DNS domain name “comptech.local”
|
||||
- option domain-name “comptech.local”; – 所有使用这台DHCP服务器的主机,将成为DNS域名“comptech.local”的一员
|
||||
- option domain-name-servers 172.27.10.6; DHCP will hand out DNS server IP of 172.27.10.6 to all of the hosts on all of the networks it is configured to host.
|
||||
- option domain-name-servers 172.27.10.6; DHCP 将向所有配置好的网络主机分发DNS服务器地址172.27.10.6
|
||||
- option subnet-mask 255.255.255.0; – The subnet mask handed out to every network will be a 255.255.255.0 or a /24
|
||||
- option subnet-mask 255.255.255.0; – 分派子网掩码到每一个网络设备 255.255.255.0 或a /24
|
||||
- default-lease-time 3600; – This is the time in seconds that a lease will automatically be valid. The host can re-request the same lease if time runs out or if the host is done with the lease, they can hand the address back early.
|
||||
- default-lease-time 3600; – 有效的地址租约时间,单位是秒。如果租约时间耗尽主机可以重新申请租约。如果租约完成那么相应的地址也将被尽快回收。
|
||||
- max-lease-time 86400; – This is the maximum amount of time in seconds a lease can be held by a host.
|
||||
- max-lease-time 86400; – 这是一个主机最大的租约时间,单位为秒。
|
||||
- ping-check true; – This is an extra test to ensure that the address the server wants to assign out isn’t in use by another host on the network already.
|
||||
- ping-check true; – 这是一个额外的测试,以确保服务器分配出的地址不是一个网络内另一台主机已使用的网络地址。
|
||||
- ping-timeout; – This is how long in second the server will wait for a response to a ping before assuming the address isn’t in use.
|
||||
- ping-timeout; – 假设地址以前没有使用,用这个来检测2个ping值回应之间的时间长度。
|
||||
- ignore client-updates; For now this option is irrelevant since DDNS has been disabled earlier in the configuration file but when DDNS is operating, this option will ignore a hosts to request to update its host-name in DNS.
|
||||
- ignore client-updates; 现在这个选项是可以忽略的,因为DDNS在前面已在配置文件中被禁用,但是当DDNS运行,此选项会忽略一个主机请求的DNS更新其主机名。
|
||||
|
||||
5. The next line in this file is the authoritative DHCP server line. This line means that if this server is to be the server that hands out addresses for the networks configured in this file, then uncomment the authoritative stanza.
|
||||
5. 文件中的下面一行是权威DHCP所在行。这行的意义是如果服务器是为文件中所配置的网络分发地址的服务器,那么就取消注释权威节(uncomment the authoritative stanza.)。
|
||||
|
||||
This server will be the only authority on all the networks it manages so the global authoritative stanza was un-commented by removing the ‘#’ in front of the keyword authoritative.
|
||||
|
||||
通过去掉关键字authoritative 前面的‘#’,取消注释全局权威节。那么该服务器将是它管理网络里面的唯一权威。
|
||||
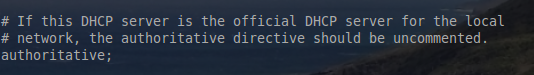
|
||||
Enable ISC Authoritative
|
||||
开启 ISC Authoritative
|
||||
|
||||
By default the server is assumed to NOT be an authority on the network. The rationale behind this is security. If someone unknowingly configures the DHCP server improperly or on a network they shouldn’t, it could cause serious connectivity issues. This line can also be used on a per network basis. This means that if the server is not the entire network’s DHCP server, the authoritative line can instead be used on a per network basis rather than in the global configuration as seen in the above screen-shot.
|
||||
默认情况下服务器被假定为不是网络上的权威。这样做的理由是为了安全。如果有人因为不了解DHCP服务的配置导致配置不当或在一个不该出现的网络里面,这都将会造成非常严重的重连接问题。这行还可用在每个网络中单独使用。这意味着如果该服务器不是整个网络的DHCP服务器,authoritative行可以用在每个单独的网络中,而不是像上面截图显示中的全局配置那样。
|
||||
|
||||
6. The next step is to configure all of the DHCP pools/networks that this server will manage. For brevities sake, this guide will only walk through one of the pools configured. The administrator will need to have gathered all of the necessary network information (ie domain name, network addresses, how many addresses can be handed out, etc).
|
||||
|
||||
6. 下一步是配置所有的服务器将要管理的DHCP地址池/网络。简短起见,这个教程将只配置地址池。作为管理员需要收集所有必要的网络信息(比如域名,网络地址,有多少地址能够被分发等等)
|
||||
For this pool the following information was obtained from the network administrator: network id of 172.27.60.0, subnet mask of 255.255.255.0 or a /24, the default gateway for the subnet is 172.27.60.1, and a broadcast address of 172.27.60.255.
|
||||
This information is important to building the appropriate network stanza in the dhcpd.conf file. Without further ado, let’s open the configuration file again using a text editor and then add the new network to the server. This must be done with root/sudo!
|
||||
|
||||
以下这个地址池所用到的信息都是管理员收集整理的:网络id 172.27.60.0, 子网掩码 255.255.255.0 or a /24, 默认网关172.27.60.1,广播地址 172.27.60.255.
|
||||
# nano /etc/dhcp/dhcpd.conf
|
||||
|
||||

|
||||
Configure DHCP Pools and Networks
|
||||
配置DHCP的地址池和网络
|
||||
|
||||
This is the sample created to hand out IP addresses to a network that is used for the creation of VMWare virtual practice servers. The first line indicates the network as well as the subnet mask for that network. Then inside the brackets are all the options that the DHCP server should provide to hosts on this network.
|
||||
|
||||
这例子是分配IP地址给用VMWare创建的虚拟服务器。第一行标明是该网络的子网掩码。括号里面是DHCP服务器应该提供给当前网络上主机的所有选项。
|
||||
|
||||
The first stanza, range 172.27.60.50 172.27.60.254;, is the range of dynamically assignable addresses that the DHCP server can hand out to hosts on this network. Notice that the first 49 addresses aren’t in the pool and can be assigned statically to hosts if needed.
|
||||
|
||||
第一节, range 172.27.60.50 172.27.60.254;是DHCP服务在这个网络上能够给主机动态分发的地址范围。
|
||||
|
||||
The second stanza, option routers 172.27.60.1; , hands out the default gateway address for all hosts on this network.
|
||||
|
||||
第二节,option routers 172.27.60.1;给网络里面所有的主机分发默认网关地址。
|
||||
|
||||
The last stanza, option broadcast-address 172.27.60.255;, indicates what the network’s broadcast address. This address SHOULD NOT be a part of the range stanza as the broadcast address can’t be assigned to a host.
|
||||
|
||||
最后一节, option broadcast-address 172.27.60.255;,说明当前网络的广播地址。这个地址不能被包含在要分发放的地址范围内,因为广播地址不能分配到一个主机上面。
|
||||
Some pointers, be sure to always end the option lines with a semi-colon (;) and always make sure each network created is enclosed in curly braces { }.
|
||||
|
||||
必须要强调的是每行的结尾必须要用(;)来结束,所有创建的网络必须要在{}里面。
|
||||
|
||||
7. If there are more networks to create, continue creating them with their appropriate options and then save the text file. Once all configurations have been completed, the ISC-DHCP-Server process will need to be restarted in order to apply the new changes. This can be accomplished with the following command:
|
||||
|
||||
7. 如果是创建多个网络,持续的创建它们的相应选项最终保存文本文件。一旦配置完成, ISC-DHCP-Server进程需要重启来使新的更改生效。可以通过下面的命令来完成:
|
||||
# service isc-dhcp-server restart
|
||||
|
||||
This will restart the DHCP service and then the administrator can check to see if the server is ready for DHCP requests several different ways. The easiest is to simply see if the server is listening on port 67 via the [lsof command][1]:
|
||||
|
||||
这条命令将重启DHCP服务,管理员能够使用几种不同的方式来检查服务器是否已经可以处理dhcp请求。最简单的方法是通过lsof命令[1]来查看服务器是否在监听67端口,命令如下:
|
||||
|
||||
# lsof -i :67
|
||||
|
||||

|
||||
Check DHCP Listening Port
|
||||
检查DHCP监听端口
|
||||
|
||||
This output indicates that the DHCPD (DHCP Server daemon) is running and listening on port 67. Port 67 in this output was actually converted to ‘bootps‘ due to a port number mapping for port 67 in /etc/services file.
|
||||
|
||||
这里的输出表明DHCPD(DHCP服务守护进程)正在运行并且监听67端口。由于/etc/services文件中67端口的端口映射,输出中的67端口实际上被转换成了“bootps”。
|
||||
|
||||
This is very common on most systems. At this point, the server should be ready for network connectivity and can be confirmed by connecting a machine to the network and having it request a DHCP address from the server.
|
||||
|
||||
在大多数的系统中这是非常普遍的,此时,服务器应该已经为网络连接做好准备,可以通过将一台主机接入网络请求DHCP地址来验证服务是否正常。
|
||||
|
||||
### Step 2: Testing Client Connectivity ###
|
||||
|
||||
### 测试客户端连接 ###
|
||||
8. Most systems now-a-days are using Network Manager to maintain network connections and as such the device should be pre-configured to pull DHCP when the interface is active.
|
||||
|
||||
8. 现在许多系统使用网络管理器来维护网络连接状态,因此这个装置应该预先配置,当接口是活跃的时候来获取DHCP。
|
||||
|
||||
However on machines that aren’t using Network Manager, it may be necessary to manually attempt to pull a DHCP address. The next few steps will show how to do this as well as how to see whether the server is handing out addresses.
|
||||
|
||||
然而当一台设备无法使用网络管理器时,它可能需要手动获取DHCP地址。下面的几步将展示如何做到这一点以及如何查看服务器是否分发地址。
|
||||
|
||||
The ‘[ifconfig][2]‘ utility can be used to check an interface’s configuration. The machine used to test the DHCP server only has one network adapter and it is called ‘eth0‘.
|
||||
|
||||
‘[ifconfig][2]‘工具能够用来检查接口配置。这台设备被用来监测DHCP服务它只有一个网络适配器(网卡),这块网卡被命名为‘eth0‘。
|
||||
|
||||
# ifconfig eth0
|
||||
|
||||

|
||||
Check Network Interface IP Address
|
||||
检查网络接口IP地址
|
||||
|
||||
From this output, this machine currently doesn’t have an IPv4 address, great! Let’s instruct this machine to reach out to the DHCP server and request an address. This machine has the DHCP client utility known as ‘dhclient‘ installed. The DHCP client utility may very from system to system.
|
||||
|
||||
从输出结果上看,这台设备目前没有一个IPv4地址,很好这样便于测试。让这台设备连接到DHCP服务器并发出一个请求。这台设备上安装了一个名为‘dhclient‘ 的DHCP客户端工具。这个客户端工具会因为系统不同而不同。
|
||||
# dhclient eth0
|
||||
|
||||

|
||||
Request IP Address from DHCP
|
||||
从DHCP请求IP地址
|
||||
|
||||
Now the `'inet addr:'` field shows an IPv4 address that falls within the scope of what was configured for the 172.27.60.0 network. Also notice that the proper broadcast address was handed out as well as subnet mask for this network.
|
||||
|
||||
现在 `'inet addr:'` 字段显示了属于172.27.60.0网络地址范围内的IPv4地址。另外要注意:目前该网络配置了正确的子网掩码并且分发了广播地址。
|
||||
|
||||
Things are looking promising but let’s check the server to see if it was actually the place where this machine received this new IP address. To accomplish this task, the server’s system log file will be consulted. While the entire log file may contain hundreds of thousands of entries, only a few are necessary for confirming that the server is working properly. Rather than using a full text editor, this time a utility known as ‘tail‘ will be used to only show the last few lines of the log file.
|
||||
|
||||
看起来还不错,让我们来测试一下,看看它是不是这台设备收到新IP地址的地方。我们参照服务器的日志文件来完成这个任务。虽然这个日志的内容有几十万条,但是里面只有几条是用来确定服务器是否正常工作的。这里我们使用一个工具‘tail’,它只显示日志文件的最后几行,而不是使用一个完整的文本编辑器去查看日志文件。命令如下:
|
||||
|
||||
# tail /var/log/syslog
|
||||
|
||||

|
||||
Check DHCP Logs
|
||||
检查DHCP日志文件
|
||||
|
||||
Voila! The server recorded handing out an address to this host (HRTDEBXENSRV). It is a safe assumption at this point that the server is working as intended and handing out the appropriate addresses for the networks that it is an authority. At this point the DHCP server is up and running. Configure the other networks, troubleshoot, and secure as necessary.
|
||||
|
||||
OK!服务器记录表明它分发了一个地址给这台主机(HRTDEBXENSRV)。服务器按预期运行,给它充当权威的网络分发适合的网络地址。到这里DHCP服务器搭建成功并且运行起来了。配置其他的网络,排查故障,确保安全。
|
||||
|
||||
Enjoy the newly functioning ISC-DHCP-Server and tune in later for more Debian tutorials. In the not too distant future there will be an article on Bind9 and DDNS that will tie into this article.
|
||||
|
||||
更多新的 ISC-DHCP-Server 的功能在以后的Debian教程中会被提及。不久以后将写一篇关于Bind9和DDNS的教程,插入到这篇文章里面。
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.tecmint.com/install-and-configure-multihomed-isc-dhcp-server-on-debian-linux/
|
||||
|
||||
作者:[Rob Turner][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
译者:[ivo-wang](https://github.com/ivo-wang)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.tecmint.com/author/robturner/
|
||||
[1]:http://www.tecmint.com/10-lsof-command-examples-in-linux/
|
||||
[2]:http://www.tecmint.com/ifconfig-command-examples/
|
||||
[2]:http://www.tecmint.com/ifconfig-command-examples/
|
||||
Loading…
Reference in New Issue
Block a user