mirror of
https://github.com/LCTT/TranslateProject.git
synced 2024-12-26 21:30:55 +08:00
commit
ebf0b34cfb
@ -1,8 +1,10 @@
|
||||
在linux系统中处理故障和收集系统信息的7种‘dmesg’的用法
|
||||
Linux系统中‘dmesg’命令处理故障和收集系统信息的7种用法
|
||||
==========================================================
|
||||
‘dmesg’命令显示linux内核的环形缓冲区信息,我们可以从中获得诸如系统架构,cpu,挂载的硬件,RAM等多个运行级别的大量的系统信息。当计算机启动时,系统内核(操作系统的核心部分)将会被加载到内存中。在加载的过程中会显示很多的信息,在这些信息中我们可以看到内核检测硬件设备。
|
||||
|
||||
‘dmesg’命令显示linux内核的环形缓冲区信息,我们可以从中获得诸如系统架构、cpu、挂载的硬件,RAM等多个运行级别的大量的系统信息。当计算机启动时,系统内核(操作系统的核心部分)将会被加载到内存中。在加载的过程中会显示很多的信息,在这些信息中我们可以看到内核检测硬件设备。
|
||||
|
||||

|
||||
|
||||
dmesg 命令的使用范例
|
||||
|
||||
‘dmesg’命令设备故障的诊断是非常重要的。在‘dmesg’命令的帮助下进行硬件的连接或断开连接操作时,我们可以看到硬件的检测或者断开连接的信息。‘dmesg’命令在多数基于**Linux**和**Unix**的操作系统中都可以使用。
|
||||
@ -13,7 +15,7 @@ dmesg 命令的使用范例
|
||||
|
||||
### 1. 列出加载到内核中的所有驱动 ###
|
||||
|
||||
我们可以使用如‘**more**’。 ‘**tail**’, ‘**less** ’或者‘**grep**’的文字处理工具来处理‘dmesg’命令的输出。由于dmesg日志的输出不适合在一页中完全显示,因此我们使用管道(pipe)将其输出送到more或者less命令中进行分页显示。
|
||||
我们可以使用如‘**more**’。 ‘**tail**’, ‘**less** ’或者‘**grep**’文字处理工具来处理‘dmesg’命令的输出。由于dmesg日志的输出不适合在一页中完全显示,因此我们使用管道(pipe)将其输出送到more或者less命令单页显示。
|
||||
|
||||
[root@tecmint.com ~]# dmesg | more
|
||||
[root@tecmint.com ~]# dmesg | less
|
||||
@ -49,7 +51,7 @@ dmesg 命令的使用范例
|
||||
[ 0.000000] NX (Execute Disable) protection: active
|
||||
.....
|
||||
|
||||
### 列出所有被检测到的硬件 ###
|
||||
###2. 列出所有被检测到的硬件 ###
|
||||
|
||||
要显示所有被内核检测到的硬盘设备,你可以使用‘**grep**’命令搜索‘**sda**’关键词,如下:
|
||||
|
||||
@ -72,6 +74,8 @@ dmesg 命令的使用范例
|
||||
|
||||
### 3. 只输出dmesg命令的前20行日志 ###
|
||||
|
||||
在‘dmesg’命令后跟随‘head’命令来显示开始几行,‘dmesg | head -20′命令将显示开始的前20行。
|
||||
|
||||
[root@tecmint.com ~]# dmesg | head -20
|
||||
|
||||
[ 0.000000] Initializing cgroup subsys cpuset
|
||||
@ -95,9 +99,9 @@ dmesg 命令的使用范例
|
||||
[ 0.000000] BIOS-e820: [mem 0x000000007dc5cc00-0x000000007dc5ebff] ACPI data
|
||||
[ 0.000000] BIOS-e820: [mem 0x000000007dc5ec00-0x000000007fffffff] reserved
|
||||
|
||||
### 只输出dmesg命令最后20行日志 ###
|
||||
###4. 只输出dmesg命令最后20行日志 ###
|
||||
|
||||
当我们插入可以出的硬件是在‘dmesg’命令后跟随‘tail’命令来输出‘dmesg’命令的最后20行日志是非常有用的。
|
||||
在‘dmesg’命令后跟随‘tail’命令(‘ dmesg | tail -20’)来输出‘dmesg’命令的最后20行日志,当你插入可移动设备时它是非常有用的。
|
||||
|
||||
[root@tecmint.com ~]# dmesg | tail -20
|
||||
|
||||
@ -123,6 +127,7 @@ dmesg 命令的使用范例
|
||||
readahead-collector: finished
|
||||
|
||||
### 5. 搜索包含特定字符串的被检测到的硬件 ###
|
||||
|
||||
由于‘dmesg’命令的输出实在太长了,在其中搜索某个特定的字符串是非常困难的。因此,有必要过滤出一些包含‘**usb**’ ‘**dma**’ ‘**tty**’ ‘**memory**’等字符串的日志行。[grep 命令][1] 的‘**-i**’选项表示忽略大小写。
|
||||
|
||||
[root@tecmint.com log]# dmesg | grep -i usb
|
||||
@ -166,7 +171,7 @@ dmesg 命令的使用范例
|
||||
|
||||
[root@tecmint.com log]# watch "dmesg | tail -20"
|
||||
|
||||
**结论**:dmesg命令在系统dmesg记录实时更改或产生的情况下是非常有用的。你可以使用man dmesg来获取关于dmesg更多的信息。
|
||||
**结论**:dmesg命令在系统dmesg记录实时更改或产生的情况下是非常有用的。你可以使用man dmesg来获取更多关于dmesg的信息。
|
||||
|
||||
----------
|
||||
|
||||
@ -178,13 +183,13 @@ Narad Shrestha
|
||||
- [Facebook profile][f]
|
||||
- [Google+ profile][g]
|
||||
|
||||
他在IT领域拥有超过10年的丰富经验,其中包括各种Linux发行版,开源软件和网络。 Narad始终坚持与人分享知识和自如的运用新技术。
|
||||
他在IT领域拥有超过10年的丰富经验,其中包括各种Linux发行版,开源软件和网络工作。 Narad始终坚持与他人分享IT知识和自如地运用新技术。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.tecmint.com/dmesg-commands/
|
||||
|
||||
译者:[cvsher](https://github.com/cvsher) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
译者:[cvsher](https://github.com/cvsher) 校对:[Caroline](https://github.com/carolinewuyan)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
@ -0,0 +1,40 @@
|
||||
StuntRally 2.4 Is the Most Advanced Free Racing Game on Linux
|
||||
================================================================================
|
||||

|
||||
StuntRally
|
||||
|
||||
**StuntRally, a free racing game that features over 150 tracks and lots of cars, has just reached version 2.4 and and it bring numerous updates and new features.**
|
||||
|
||||
The game is built with the help of several technologies, such as Vdrift, bullet, OGRE, PagedGeometry, and MyGUI, just to name a few, but the developers have manged to put together a very complex and interesting racing title.
|
||||
|
||||
The players can play on 147 track and in 26 different scenarios, which totals four hours of drive time. This is quite a lot, if we keep in mind that StuntRally is completely free.
|
||||
|
||||
Other features included in the are ghost drive (chase your best time car on track), track's ghost (best drive for track, a green ghost car ES, on all tracks), replays (save your drive and watch it from other cameras later), numerous tutorial, a few championships, a few challenges, split-screen racing, and multiplayer.
|
||||
|
||||
To top it all off, the developers also implemented a Track Editor that should allow users to edit road points and their parameters in real time, to change all of the track parameters, to tweak the terrain generator, and even to modify elements of the cars while driving.
|
||||
|
||||
According to the changelog, 6 new maps have been added, 12 old levels have been deleted, a number of tracks have been renewed, a couple of new sceneries named Crystals and GreeceWhite have been added, spaceship hovercrafts have been implemented, new sky textures have been added on half of tracks, new static objects on few tracks are now available, and car tab with bars for stats, speed graph, and a short list view has been added.
|
||||
|
||||
Also, fonts are now bigger and they have been resized, sounds for win, loose, lap, best time, and wrong checkpoint resolution have been added, the multiplayer has been repaired and the nick can no longer appear twice, damage from terrain, height fog, fluids has been implemented on a few tracks, the level editor has received a number of improvements, the steering has been improved, and the surfaces in the game's car tweak window have been fixed.
|
||||
|
||||
Users need to remember that the developers only provide the source package for the game and that means that it needs compiling. This might take a little bit longer, but StuntRally is totally worth it.
|
||||
|
||||
More details about this new release of StuntRally can be found in the [announcement][1].
|
||||
|
||||
Download StuntRally 2.4:
|
||||
|
||||
- [Stunt Rally 2.4 tar.xz][1][binary] [735 MB]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://news.softpedia.com/news/StuntRally-2-4-Is-the-Most-Advance-Free-Racing-Game-on-Linux-454345.shtml
|
||||
|
||||
作者:[Silviu Stahie][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://news.softpedia.com/editors/browse/silviu-stahie
|
||||
[1]:https://code.google.com/p/vdrift-ogre/wiki/VersionHistory
|
||||
[2]:http://sourceforge.net/projects/stuntrally/files/2.4/StuntRally-2.4-linux64.tar.xz/download
|
||||
67
sources/talk/20140808 When Linux Was Perfect Enough.md
Normal file
67
sources/talk/20140808 When Linux Was Perfect Enough.md
Normal file
@ -0,0 +1,67 @@
|
||||
When Linux Was Perfect Enough
|
||||
================================================================================
|
||||
The other day my colleague, friend and sometimes partner-in-crime, Ken Starks, published [an article][1] here on FOSS Force on one of his favorite gripes: things that don’t work right in Linux. This time he was complaining about a font issue in Mint when using KDE. This is nothing new from Ken. In the past he’s written other articles about broken aspects of various Linux distros that never seem to get fixed. It’s his contention that these “small” bugs, which remain unfixed release after release after release, are largely responsible for desktop Linux’s failure to take hold with the general public.
|
||||
|
||||
### He might be right. ###
|
||||
|
||||
For Christmas I bought my roommate a new second generation Nexus 7 tablet running Android, an OS built around the Linux kernel. It “just worked,” out of the box, with no tweaking necessary. During the last seven months she’s used it for hours daily. As far as I know, she’s found no glitches that require fixing. I’m reasonably certain I’d know if she did, since the main reason I gave her the Nexus to begin with was because I had tired of trying to keep her Windows laptop running to her satisfaction. She has no trouble telling me when her computer goes kaput, and she always wants it fixed right now. Facebook waits for no one, you know.
|
||||
|
||||
I point this out because Linux has all but taken over the tablet and phone end of the computing spectrum. Apple makes plenty of money with the iPhone and iPad, but that’s due to their high prices. In market share, they lag far behind Android devices. And Microsoft has proven that Windows isn’t the unbeatable giant it was once thought to be. Even with massive money spent on television ads and conspicuous product placement in nearly every scripted drama on CBS, mobile devices running Windows remain a mere asterisk when looking at market share.
|
||||
|
||||
In other words, Linux is winning the mobile war because Google makes certain that Android “just works” out of the box.
|
||||
|
||||
Today’s average computer users (I loath the word “consumers”) want to get things done on their computers without having to delve under the hood to fix things. This is understandable and isn’t unlike the average automobile owners, who just want to drive their cars without knowing or caring how it works. Just as most drivers take their car to the shop for repair to solve mechanical and computer related issues, most computer users take their devices to the shop with no concern about whether the problem is hardware or software related. They just want the damn thing to work.
|
||||
|
||||
### It wasn’t always this way. ###
|
||||
|
||||
Back in 2002 I installed GNU/Linux for the first time. At that time, like most Americans, I was tethered to a dial-up connection, with broadband not yet being available in my part of the boondocks. I spent seventy bucks or so for a shrink wrapped Powerpack edition of Mandrake 9.0 at a local Best Buy store, which in those days sold both Mandrake and Red Hat, which was still in the desktop business.
|
||||
|
||||
During that age of the dinosaur, Mandrake was considered to be the cat’s meow of easy-to-use Linux distributions. It installed easily, some said easier than Windows, and its partitioning tool made cutting up a disk easier than slicing a piece of mincemeat pie. Indeed, Linux old-timers sometimes openly laughed at Mandrake, insinuating that ease-of-use somehow made Linux less Linux.
|
||||
|
||||
But I loved it and found it to be a whole new world. Gone was the blue screen of death and the nearly daily crashes that were business as usual with Windows. Unfortunately, also gone were a lot of peripherals that had “just worked” in Windows.
|
||||
|
||||
The first thing I had to do after installing Mandrake was to take my white box to Michelle at [Dragonware Computers][2] and have the cheap winmodem swapped out for a hardware modem. Granted, a hardware modem means a more responsive computer, but with the computer store forty miles away, this was a bit of an inconvenience and an expense I could little afford.
|
||||
|
||||
But I didn’t mind. I was free of Microsoft –- and using a “different” operating system made me feel as if I was some sort of computing genus.
|
||||
|
||||
Printers were also a problem, but not as much a problem with Mandrake as with most other distros which required command line work to install. Mandrake offered up a snazzy graphical interface for configuring printers – if you were lucky enough to have a printer that would work in Linux at all. Many, if not most, wouldn’t.
|
||||
|
||||
My still under warranty Lexmark, which in Windows had more whistles and bells than any printer needs, wasn’t supported by the manufacturer, but I was able to find an open source, backwards engineered driver that kinda, sorta worked. It worked fine for printing web pages from the Mozilla browser, but printed Star Office pages in tiny fonts that were crammed up into the upper right corner of the page. The printer also made some very loud mechanical clunking noises which reminded me of the noise a car transmission makes just before it dies.
|
||||
|
||||
The workaround for the Star Office problem was to save everything as a text file and print from a text editor. For the noise that indicated the printer was in self-destruct mode? Try to avoid printing as much as possible was my solution.
|
||||
|
||||
### Other problems abounded – too many for me to remember. ###
|
||||
|
||||
One problem I do remember is that I couldn’t get the sound card to work out of the box, although Mandrake’s interface showed the sound card detected and installed. After days of digging through the forums with no luck, someone finally suggested I might have a problem with permissions. I looked and, lo and behold!, he was right. Mandrake had installed the sound card with permissions which wouldn’t let it work in a user account, yet another one of those things that should have been fixed before the distro was released, as Ken would point-out. Especially in a distro being sold in a shrink wrapped box for seventy dollars a pop – which was considerably more money in 2002 than it is now.
|
||||
|
||||
Oh yes, and I still have a parallel port scanner that I bought new about two weeks before my move to Linux which has been nothing but a brick since, as there’s still no Linux driver for it.
|
||||
|
||||
My point is that back in those days none of this mattered. Most of us were already used to having to fiddle with configuration files and such, even when using “IBM compatible” computers running Microsoft products. Like most users in those days, I’d cut my teeth on command line DOS machines, where printers had to be configured separately for each and every program and where the ability to write a succinct autoexec.bat file was a necessity.
|
||||
|
||||

|
||||
Linux as a 1966 “goat.”
|
||||
|
||||
Tinkering with the inner workings of the operating system was simply part of owning a computer. Most of us using computers back then were either geeks or wanna be geeks. We were proud of our ability to tinker and get our machines working just like we wanted. We were the high tech version of the good ol’ boys from an earlier age, who spent their Saturday afternoons under a shade tree modifying their muscle cars with headers, breathers, trick carburetors and the like.
|
||||
|
||||
### And that’s mostly not who’s using computers today. ###
|
||||
|
||||
Today’s computer user just wants the computer to work, without problems, out of the box. They don’t want to have to figure out why Hulu or Netflix doesn’t work or why their fonts display properly in some applications and not in others. They don’t want to hear, “oh, that’s just an easily fixed small bug” after a Linux install any more than they want to hear that an ignition switch that stalls their new Chevy in heavy traffic is “only a glitch which we’ll fix one day.”
|
||||
|
||||
These days, that includes me. While I’m happy I have enough skills to usually fix a bug that made it past the developers at Mint or Fedora, I’d just as soon not have to deal with it. I have work to get done. And when I’m not working, I want to be wasting time with my friends on Facebook, not getting aggravated with my computer.
|
||||
|
||||
To be sure, Linux has changed with the times. In recent years you can pretty much be sure that when you install a major Linux distro on a laptop, Wi-Fi will work out of the box. Also, most of the time all you have to do is plug a new printer into a USB port and, presto!, it’s already up and running. But there are still way too many little niggling problems that need to get fixed – stuff that should have been fixed long ago.
|
||||
|
||||
Maybe if Ken keeps complaining enough…
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://fossforce.com/2014/08/when-linux-was-perfect-enough/
|
||||
|
||||
作者:Christine Hall
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://fossforce.com/2014/07/ripe-linux-nits-to-pick/
|
||||
[2]:http://www.dragonware.com/
|
||||
@ -0,0 +1,126 @@
|
||||
10 More Tweaks To Make Ubuntu Feel Like Home
|
||||
================================================================================
|
||||

|
||||
|
||||
Not too long ago [we gave you 12 tips on how to tweak your Ubuntu installation][1]. However, it’s been a little while since then, and we’ve come up with another 10 things you can do to make Ubuntu feel even more like home.
|
||||
|
||||
These 10 tips are quick and simple to do, so let’s get started!
|
||||
|
||||
### Install TLP ###
|
||||
|
||||

|
||||
|
||||
[We covered TLP a while back][2], which is a piece of software that can optimize your power settings so that you can enjoy a longer battery life. We talked about TLP in depth before, and it’s a good item to mention in this list as well. To install it, run the following command in a terminal:
|
||||
|
||||
sudo add-apt-repository -y ppa:linrunner/tlp && sudo apt-get update && sudo apt-get install -y tlp tlp-rdw tp-smapi-dkms acpi-call-tools && sudo tlp start
|
||||
|
||||
This will add the necessary repository, update the package lists so that it includes the new packages provided by the new repository, installs TLP, and starts the service.
|
||||
|
||||
### System Load Indicator ###
|
||||
|
||||

|
||||
|
||||
Adding a system load indicator to your Ubuntu desktop can give you an idea of how much of your system’s resources are being used at a quick glance. You don’t have to add this if you’d rather not have technical graphs on your desktop, but it’s a good addition for those who are interested in something like this. You can install it by running the terminal command:
|
||||
|
||||
sudo apt-get install indicator-multiload
|
||||
|
||||
Then, find it in the Dash and launch it.
|
||||
|
||||
### Weather Indicator ###
|
||||
|
||||

|
||||
|
||||
Ubuntu used to offer a built-in weather indicator, but since it switched to Gnome 3 as the backbone, this hasn’t been included by default. Instead, you’ll need to install a separate indicator. You can install it by running the command:
|
||||
|
||||
sudo add-apt-repository -y ppa:atareao/atareao && sudo apt-get update && sudo apt-get install -y my-weather-indicator
|
||||
|
||||
This will add another repository, update the package lists, and install the indicator. Then, find it in the Dash and launch it.
|
||||
|
||||
### Install Dropbox or Other Cloud Storage Solution ###
|
||||
|
||||

|
||||
|
||||
One of the things that I have to install on all my Linux systems is Dropbox. Without it, it just really doesn’t feel like home, mainly because all of my most-used files are stored on Dropbox. Installing Dropbox is pretty straightforward, but it takes a bit more than just a simple command. Before you even start, you need to run this command to be able to see the Dropbox icon in the icon tray:
|
||||
|
||||
sudo apt-get install libappindicator1
|
||||
|
||||
Then you need to head to Dropbox’s download page and install the .deb file that you download. You should now have Dropbox going.
|
||||
|
||||
If you’re a bit tired of Dropbox, you can also try using Copy [or even OneDrive][3]. Both services offer more storage for free, which is a big reason to consider using them. I recommend Copy more than OneDrive because Copy can work on all Linux distros.
|
||||
|
||||
### Install Pidgin and Skype ###
|
||||
|
||||

|
||||
|
||||
It’s great to stay connected with friends, and if you use instant messaging, you’re in luck. Pidgin and Skype are both pretty good on Linux, and they are able to connect to all the major networks. Installing Pidgin is as easy as running the command
|
||||
|
||||
sudo apt-get install pidgin
|
||||
|
||||
Installing Skype is also easy — you just need to head to Skype’s download page and get the .deb file under Ubuntu 12.04 multiarch.
|
||||
|
||||
### Remove Keyboard Indicator ###
|
||||
|
||||

|
||||
|
||||
Having the keyboard indicator appear on the desktop can be annoying for some. For English speakers, it just shows “EN”, and it’s potentially annoying because a lot of people don’t have a need to change keyboard layouts or be reminded that they are speaking English. To remove the indicator, choose System Settings, then Text Entry, and then uncheck “Show current input source in the menu bar”.
|
||||
|
||||
### Bring Back Classic Menu ###
|
||||
|
||||

|
||||
|
||||
Before Ubuntu made the switch to Unity, it had used Gnome 2 as the default desktop environment. This included a simple menu for accessing your installed applications, which had categories such as Games, Office, Internet, and more. You can get this “classic menu” back with another simple package. To install, run the command:
|
||||
|
||||
sudo add-apt-repository -y ppa:diesch/testing && sudo apt-get update && sudo apt-get install -y classicmenu-indicator
|
||||
|
||||
### Install Flash and Java ###
|
||||
|
||||
While in the previous tips article I mentioned installing codecs and Silverlight, I should have probably included Flash and Java as they are also major plugins that people need, although sometimes they can be forgotten about. To install both of them, run the command:
|
||||
|
||||
sudo add-apt-repository -y ppa:webupd8team/java && sudo apt-get update && sudo apt-get install oracle-java7-installer flashplugin-installer
|
||||
|
||||
The additional repository is needed for installing Java because Ubuntu no longer includes the proprietary version (which most people recommend for best functionality), but rather just the open source OpenJDK implementation.
|
||||
|
||||
### Install VLC ###
|
||||
|
||||

|
||||
|
||||
The default media player, Totem, is pretty good but it relies on separately-installed codecs to work properly. I’d personally recommend you install the VLC media player, as it includes all codecs and supports virtually every media format under the sun. To install it, just run the command
|
||||
|
||||
sudo apt-get install vlc
|
||||
|
||||
### Install PuTTY (Or Not) ###
|
||||
|
||||

|
||||
|
||||
Lastly, if you’ve used PuTTY for all of your SSH needs, you have two options: install PuTTY for Linux, or just use the terminal directly. Installing PuTTY can be done with the command
|
||||
|
||||
sudo apt-get install putty
|
||||
|
||||
if you want to install it using the terminal. However, there’s no direct need to install it, because you can connect to any remote host with the command
|
||||
|
||||
ssh username@this.domain.here
|
||||
|
||||
where you replace “username” with the username you’d like to connect as, and replace “this.domain.here” with the host’s actual domain name or IP address — both work.
|
||||
|
||||
### What Are Your Recommended Tweaks? ###
|
||||
|
||||
With these additional 10 tweaks, you should feel right at home in your Ubuntu installation, which can easily make or break your Linux experience. There are so many different ways to customize your experience to make it suit your needs; you just have to look around for yourself to see what you want.
|
||||
|
||||
**What other tweaks and recommendations can you share with readers?** Let us know in the comments!
|
||||
|
||||
*Image Credits: Home doormat Via Shutterstock*
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.makeuseof.com/tag/10-tweaks-make-ubuntu-feel-like-home/
|
||||
|
||||
作者:[Danny Stieben][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.makeuseof.com/tag/author/danny/
|
||||
[1]:http://www.makeuseof.com/tag/11-tweaks-perform-ubuntu-installation/
|
||||
[2]:http://www.makeuseof.com/tag/easily-increase-battery-life-tlp-linux/
|
||||
[3]:http://www.makeuseof.com/tag/synchronize-files-ubuntu-onedrive/
|
||||
@ -0,0 +1,66 @@
|
||||
How to Achieve Better Security With Proper Management of Open Source
|
||||
================================================================================
|
||||

|
||||
Bill Ledingham is the Chief Technology Officer (CTO) and Executive Vice President of Engineering at Black Duck Software.
|
||||
|
||||
Companies increasingly understand that the key to developing innovative software faster and better than the competition is through the use of open source software (OSS). It’s nearly impossible to use only commercially sourced code and get your software to market with the speed and cost constraints required by today’s product life cycles. Without the ability to choose and integrate best-of-breed OSS, some of the greatest product ideas might never see the light of day.
|
||||
|
||||
With the use of open source, however, comes a different set of challenges. While your teams can gain speed and agility, it’s often more difficult to ascertain the code’s true origin and assure that it is secure.
|
||||
|
||||
As the OpenSSL Heartbleed vulnerability proved, not knowing what code is in your application or finished product can potentially create critical security threats that require time-consuming remediation efforts. Conversely, having an accurate inventory of what OSS components and versions are used and where can prove invaluable for quickly responding to and remediating vulnerabilities.
|
||||
|
||||
### It’s What’s Inside That Counts ###
|
||||
|
||||
The Heartbleed bug reminded developers and companies just how important security is. While there has been widespread debate over whether proprietary or open source software is more secure, the issue is largely moot. The reality is that code defects exist in most pieces of software, regardless of origin, and some affect security.
|
||||
|
||||
Security challenges can become even more complex when open source is integrated with internal, proprietary code. In addition to the obvious risk of not properly managing license compliance, tracking code origins and use throughout an organization can become very difficult, very quickly.
|
||||
|
||||
To have a truly accurate understanding of your potential vulnerabilities, you need to understand three things:
|
||||
|
||||
1. What code is in your current products and applications?
|
||||
1. What code is being used in the front end of the development process and where are developers acquiring these components?
|
||||
1. What components are being used at the back end of the process and where does code need to be validated before it is deployed?
|
||||
|
||||
### Assessing the Situation ###
|
||||
|
||||
All companies should check their code against common vulnerability databases, such as the United States National Institute of Standards and Technology’s [National Vulnerability Database][1] (NVD). Resources like the NVD track security vulnerabilities and provide severity rankings to help companies keep their code secure and up to date.
|
||||
|
||||
If you’ve never reviewed your code against a vulnerability database, it may seem like a daunting task. Fortunately, there are [tools][2] that leverage these databases to regularly and automatically identify all open source security vulnerabilities, alerting and tracking where affected components are in use and in need of remediation.
|
||||
|
||||
Continuously monitoring your codebase helps guarantee that unknown code is identified, code origin is understood, license information is up to date and future security vulnerabilities are quickly flagged for resolution. If your company has an accurate code inventory in place, you can easily find vulnerable code and remediate it to ensure your business – and your customers – remain secure.
|
||||
|
||||
### Preventing Future Problems ###
|
||||
|
||||
Most developers are attracted to OSS because it’s easy to access and free to acquire, usually allowing them to forgo a formal procurement process. Yet, while many development organizations have policies or guidelines for open source use, they are not always enforced and often not properly tracked. It’s important to track what code is coming into your organization, whether it’s been approved for use and where it’s used throughout your organization.
|
||||
|
||||
Once you know what you have, you need to establish governance. By implementing a management framework throughout the development process, you can ensure accurate descriptions of the code are captured and eliminate questions as to what code is where and whether it’s up to date. Manually managing this process is nearly impossible, which is why best-in-class companies actively manage their use of open source through automated code management and audit solutions.
|
||||
|
||||
Although every company and development team is different, the following processes have been proven to help organizations of all sizes manage and secure their use of OSS:
|
||||
|
||||
- **Automate Approvals and Cataloging** – Capture and track all relevant attributes of OSS components, assess license compliance and review possible security vulnerabilities through automated scanning, approval and inventory processes.
|
||||
-
|
||||
- **Maintain Updated Code Versions** – Assess code quality and make sure your product is built using the most updated versions of the code.
|
||||
-
|
||||
- **Verify Code** – Evaluate all OSS in use; audit code for security, license, or export risk and remediate any issues.
|
||||
-
|
||||
- **Ensure Compliance** – Create and implement an open source policy, establish an automated compliance process to ensure open source policies, regulations, legal obligations, etc., are followed across the organization.
|
||||
|
||||
### Active Management is Key ###
|
||||
|
||||
As the use of software across industries proliferates, open source will continue to play a crucial role in developing the newest innovations. To prevent security vulnerabilities in this increasingly complex environment, companies must actively manage the flow of open source throughout their organization and establish processes to regularly check their code against vulnerability databases for fast and easy remediation.
|
||||
|
||||
*Bill Ledingham is the Chief Technology Officer (CTO) and Executive Vice President of Engineering at Black Duck Software. Previously, Bill was CTO of Verdasys, a leader in information and cyber security, where he worked closely with leading Global 2000 companies and government organizations to safeguard their most sensitive information. Bill has been on the founding team of four companies, is active in the Boston start-up community, and has been a partner/investor with CommonAngels for the past 6 years.*
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linux.com/news/software/applications/782953-how-to-achieve-better-security-by-proper-management-of-open-source
|
||||
|
||||
作者:[Bill Ledingham][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.linux.com/community/forums/person/59656
|
||||
[1]:http://nvd.nist.gov/
|
||||
[2]:http://www.blackducksoftware.com/oss-logistics/secure
|
||||
@ -1,117 +0,0 @@
|
||||
disylee来占坑~~
|
||||
Top 10! Fun On The Command Line
|
||||
================================================================================
|
||||
**If you just love making 'top 10'-type lists but are a little embarrassed to say so, tell people you're passionate about data exploration. To impress them even more, explain that you do your data exploration on the command line. But don't ruin the impression by telling them how easy that is!**
|
||||
|
||||
In this article I'll do some data exploration with basic GNU/Linux tools and 'one-column tables', by which I mean simple lists. For more information on the commands used here, see their Linux 'man' pages, or ask for an explanation in the 'Comments' section.
|
||||
|
||||
### Passwords ###
|
||||
|
||||
The first list to explore is Mark Burnett's 2011 compilation of the [10000 most commonly used passwords][1]. The list is ordered most-frequent-first, and is one source of the widely known factoid that 'password' is the most commonly used password, with '123456' in second place. Here I've put the list in a file called passwords, and used the head command to show the first 10 lines:
|
||||
|
||||

|
||||
|
||||
(Burnett explains how he collects his passwords [here][2]. Note that he converted all uppercase letters to lowercase in his list.)
|
||||
|
||||
OK, so 'password' is top of the Burnett list. What about individual digits?
|
||||
|
||||

|
||||
|
||||
Interesting. The digit '1' appears in the password list more than twice as often as the next most-used digit, '2', and the 10 digits are in numerical as well as popularity order, except for 0 and 9. And the top 10 letters?
|
||||
|
||||

|
||||
|
||||
The most frequent letters in the passwords file are EARONISTLC. That's not too far off EAIRTONSLC, which is the frequency pattern in at least [one published table][3] of letter usage in common English words. Does this mean that most passwords are actually common English words, maybe with a few digits thrown in?
|
||||
|
||||
To find out, I'll first convert passwords to a list of letters-only strings, then see how many of those strings are in an English dictionary.
|
||||
|
||||
First I'll delete all the digits in passwords with a **sed** command, then delete all the punctuation marks, then all the blank lines. This creates a list of letters-only passwords. Then I'll prune that list with **sort** and **uniq** to get rid of any duplicates. (For example, 'abc1234def' and 'abc1!2!3!def!' both reduce to 'abcdef'.) According to the wc command, my pruning reduces the 10000 passwords to 8583 letters-only strings:
|
||||
|
||||

|
||||
|
||||
For a handy English dictionary I'll use the file `usr/share/dict/american-english`, which came with my Debian Linux distribution. It contains 99171 words. I'll first convert this wordlist to lowercase-only with the **tr** command, then delete any duplicate entries with **sort** and **uniq** (like 'A' and 'a' both becoming 'a'). That reduces the wordlist to 97723 entries:
|
||||
|
||||

|
||||
|
||||
I can now ask the comm command with the '-23' option to compare the two lists and report just the words in the letters-only file that are not found in the dictionary:
|
||||
|
||||

|
||||
|
||||
The total is 3137, so at least 8583 - 3137 = 5446 'core' passwords in Burnett's lowercase-only list (about 63%) are either plain English words, or plain English words with some digits or punctuation marks added. I wrote at least because a big proportion of the 3137 strings are only slight modifications of plain English words or names, or words or names missing from the /usr/share dictionary. Among the LA's, for example, are 'labtec', 'ladyboy', 'lakeside', 'lalakers', 'lalala', 'laserjet', 'lasvegas', 'lavalamp' and 'lawman'.
|
||||
|
||||
### Placenames ###
|
||||
|
||||
In a previous [Linux Rain article][4], I described how I built a table of Australian placenames with more than 370 000 entries. Using it, I can now answer vital questions like 'Is Round Hill the most popular name for hills in Australia?' and 'Is Sandy Beach tops for beaches, and Rocky Creek for creeks?'
|
||||
|
||||
The placename field in the gazetteer table is number 2, so here goes:
|
||||
|
||||

|
||||
|
||||
Wow. I wasn't even close. (But note how I saved typing by using the **^string1^string2** command. It repeats the last command, but substitutes string2 for string1. Wonderful BASH trick!)
|
||||
|
||||
Another burning question is how many placenames there are with 'Mile' in them, like 'Six Mile Creek', and how they rank:
|
||||
|
||||

|
||||
|
||||
I've noticed a lot of Dead Horse Creeks in my Australian travels, and so has the gazetteer:
|
||||
|
||||

|
||||
|
||||
### Species ###
|
||||
|
||||
The third list to explore comes from a table I published this year of new Australian insect species named in the period 1961-2010. From the table I've pulled out all the 'species epithets', which are the second parts of genus-species combinations like Homo sapiens (you and me) and Apis mellifera (European honeybee).
|
||||
|
||||
(Tech note: The insects table, which is available from the open data Zenodo repository at [https://zenodo.org/record/10481][5], includes subspecies. For my 'top 10' exercise I first isolated all the unique genus-species combinations, to avoid duplication from subspecies like Apis mellifera iberica, Apis mellifera intermissa, etc. The final species file has 18155 species epithets.)
|
||||
|
||||
Most people who make jokes about scientific names use the '-us' ending, as in 'Biggus buggus'. What about entomologists? There are a couple of good, command-line ways to get the last 2 letters of a string, and here I've used both:
|
||||
|
||||

|
||||
|
||||
Yep, entomologists prefer '-us', too. Next, I wonder how many species are named for my home State of Tasmania? (Below I ask head for the first 100 lines to make sure I get all the 'tasman' combinations.)
|
||||
|
||||

|
||||
|
||||
How about Queensland?
|
||||
|
||||

|
||||
|
||||
And generally speaking, what are the top 10 names in that insect species list?
|
||||
|
||||

|
||||
|
||||
Hmm. Apart from the obvious 'australis' and 'australiensis', and the geographical 'occidentalis' (of the west), the other 7 epithets in the 10-most-popular list have been created by entomologists to honour other entomologists. (The epithet 'commoni' honors the Australian butterfly and moth specialist Ian F.B. Common, 1917-2006.)
|
||||
|
||||
### Speechifying ###
|
||||
|
||||
The commands used above work on simple lists. To make a simple list out a block of text, the command line is again your friend. For example, I've saved a rather filibustery [speech][6] in the Australian Senate on 16 July 2014 as the text file hansard. To split hansard into a list of words:
|
||||
|
||||

|
||||
|
||||
And to look at word frequency in the speech:
|
||||
|
||||

|
||||
|
||||
### Coming soon... ###
|
||||
|
||||
Doing 'top 10' and other rankings from multi-column tables requires a few more command-line tools. I'll demonstrate their use in a future article.
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://thelinuxrain.com/articles/top-10-fun-on-the-command-line
|
||||
|
||||
原文作者:Bob Mesibov(Bob Mesibov is Tasmanian, retired and a keen Linux tinkerer.)
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:https://xato.net/passwords/more-top-worst-passwords/#.U8eD13AvDy0
|
||||
[2]:https://xato.net/passwords/how-i-collect-passwords/#.U8eEdnAvDy0
|
||||
[3]:http://www.rinkworks.com/words/letterfreq.shtml
|
||||
[4]:http://www.thelinuxrain.com/articles/building-a-gazetteer-table-from-kml-files
|
||||
[5]:https://zenodo.org/record/10481
|
||||
[6]:http://parlinfo.aph.gov.au/parlInfo/search/display/display.w3p;db=CHAMBER;id=chamber%2Fhansards%2F232fa1a8-d7e8-4b22-9018-1a99b5a96812%2F0025;query=Id%3A%22chamber%2Fhansards%2F232fa1a8-d7e8-4b22-9018-1a99b5a96812%2F0000%22
|
||||
@ -1,45 +0,0 @@
|
||||
[translating by KayGuoWhu]
|
||||
Linux FAQs with Answers--How to check what libraries are used by a program or process on Linux
|
||||
================================================================================
|
||||
> **Question**: I would like to know which shared libraries are loaded at run-time when I invoke a particular executable. Is there any way to identify shared library dependencies of a program executable or a running process on Linux?
|
||||
|
||||
### Check shared library dependencies of a program executable ###
|
||||
|
||||
To find out what libraries a particular executable depends on, you can use ldd command. This command invokes dynamic linker to find out library dependencies of an executable.
|
||||
|
||||
$ ldd /path/to/program
|
||||
|
||||

|
||||
|
||||
Note that it is NOT recommended to run ldd with any untrusted third-party executable because some versions of ldd may directly invoke the executable to identify its library dependencies, which can be security risk.
|
||||
|
||||
Instead, a safer way to show library dependencies of an unknown application binary is to use the following command.
|
||||
|
||||
$ objdump -p /path/to/program | grep NEEDED
|
||||
|
||||

|
||||
|
||||
Check shared library dependencies of a running process
|
||||
|
||||
If you want to find out what shared libraries are loaded by a running process, you can use pldd command, which shows all shared objects loaded into a process at run-time.
|
||||
|
||||
$ sudo pldd <PID>
|
||||
|
||||
Note that you need root privilege to run pldd command.
|
||||
|
||||
|
||||
|
||||
Alternatively, a command line utility called pmap, which reports memory map of a process, can also show shared library dependencies of a running process.
|
||||
|
||||
$ sudo pmap <PID>
|
||||
|
||||

|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://ask.xmodulo.com/check-library-dependency-program-process-linux.html
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
@ -1,46 +0,0 @@
|
||||
Vic020
|
||||
|
||||
Check Hard drive for bad sectors or bad blocks in linux
|
||||
================================================================================
|
||||
**badblocks** is the command or utility in linux like operating system which can **scan** or test our **hard disk** and **external drive** for **bad sectors**. Bad sectors or **bad blocks** is the space of the disk which can't be used due to the **permanent damage** or OS is unable to access it.
|
||||
|
||||
Badblocks command will detect all **bad blocks(bad sectors)** on our hard disk and save them in a text file so that we can use it with **e2fsck** to configure Operating System(OS) to not store our data on these damaged sectors.
|
||||
|
||||
### Step:1 Use fdisk command to identify your hard drive info ###
|
||||
|
||||
# sudo fdisk -l
|
||||
|
||||
### Step:2 Scan your hard drive for Bad Sectors or Bad Blocks ###
|
||||
|
||||
# sudo badblocks -v /dev/sdb > /tmp/bad-blocks.txt
|
||||
|
||||
Just replace “/dev/sdb” with your own hard disk / partition. When we execute above command a text file “bad-blocks” will be created under /tmp , which will contains all bad blocks.
|
||||
|
||||
Example :
|
||||
|
||||
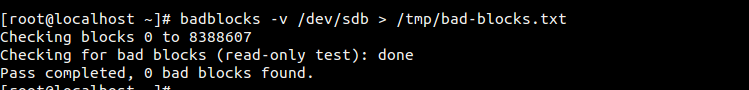
|
||||
|
||||
### Step:3 Inform OS not to use bad blocks for storing data ###
|
||||
|
||||
Once the scanning is completed , if the bad sectors are reported , then use file “bad-blocks.txt” with e2fsck command and force OS not to use these bad blocks for storing data.
|
||||
|
||||
# sudo e2fsck -l /tmp/bad-blocks.txt /dev/sdb
|
||||
|
||||
Note : Before running e2fsck command , you just make sure the drive is not mounted.
|
||||
|
||||
For any futher help on badblocks & e2fsck command , read their man pages
|
||||
|
||||
# man badblocks
|
||||
# man e2fsck
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linuxtechi.com/check-hard-drive-for-bad-sector-linux/
|
||||
|
||||
作者:[Pradeep Kumar][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.linuxtechi.com/author/pradeep/
|
||||
@ -0,0 +1,77 @@
|
||||
Check how much do you type with WhatPulse on Linux
|
||||
================================================================================
|
||||

|
||||
|
||||
If, like me, you are a statistics freak you must install this small application on all your computers: [WhatPulse][1]
|
||||
|
||||
The software tracks a user’s pressed keys, mouse clicks and used [bandwidth][2] and the uptime of the system. Periodically, or by hand, the user can upload to the server the number of keystrokes made; this is called “pulsing”.
|
||||
|
||||
Users can see where they are in a leaderboard of people who have joined the program and compare themselves against people from their own countries. Users can also join teams, which enables them to compare themselves against people with similar interests (Go Linux Users !!).
|
||||
|
||||
There is a basic, and free, version where you can easily see and check all the basic statistics and a premium account where you can see some more stats.
|
||||
|
||||
The software is available for Linux, Windows and Mac.
|
||||
|
||||
### Registration on the website ###
|
||||
|
||||
As first step you have to register your account on the [WhatPulse Website][1] or as alternative when you first start the WhatPulse client there is a practical wizard through which each user has the option to create an account to upload their own statistics (you can also log in with Facebook).
|
||||
|
||||
You will be prompted to login, once you login, you have to search for your computers name, this is because you can login to several computers with this and they’ll all collectively go to the same statistic count. Once you’ve logged in, a small W will appear in your system tray, that’s it, your set up!
|
||||
|
||||
### Installation of WhatPulse on Linux ###
|
||||
|
||||
The official website offer on the [download page][3] a generic version distributed via a .tar.gz archive (available for 32 and 64 bit) and a debian package.
|
||||
|
||||
Personally I’ve installed the debian package on my Mint Qiana and the [Aur Package][4] on My Arch Linux, no problems at all.
|
||||
|
||||
If you want to go with the generic installation please keep in mind that WhatPulse requires several libraries to function. Mainly Qt, because WhatPulse is built on Qt. Here’s a list of requirements:
|
||||
|
||||
- libQtCore
|
||||
- libQtWebKit
|
||||
- libqt4-sql
|
||||
- libqt4-sql-sqlite
|
||||
- openssl-devel (libssl-dev)
|
||||
- libQtScript
|
||||
|
||||
#### Input Statistics ####
|
||||
|
||||
The client needs permissions to be allowed to read your keyboard/mouse input. Run the included interactive .sh script to set up these permissions.
|
||||
|
||||
#### [Network][5] Statistics ####
|
||||
|
||||
To enable the network measurements, you also need the package **libpcap** to allow WhatPulse to hook into the network traffic. If WhatPulse does not find libpcap, it will run but it will not display any network statistics.
|
||||
|
||||

|
||||
|
||||
### Using the Application ###
|
||||
|
||||
By default WhatPulse will start automatically at the login of your graphical session and clicking on the W on your systray you’ll go to the Overview tab that gives a birds-eye view of all the different information gathered about your machine, for instance, the Linux version installed on your PC, processor model, RAM, GPU, total click counts, keystrokes and bandwidth usage. Clicking ‘Pulse’ under these information will upload the gathered data to the main server.
|
||||
|
||||
It’s also possible to select when automatically ‘Pulse’ the data to the server, such as every 50.000 clicks or 1 GB downloaded.
|
||||
|
||||
For further details, you can switch to each category’s pertaining tab. For example, the Input tab shows you the amount of key strokes and clicks your PC has registered during a certain time period. The time period can be sorted on a daily, weekly, monthly, yearly and all-time basis. The ‘all’ setting will show stats since the program was installed.
|
||||
|
||||
Below the keystrokes, you’ll find the keyboard heat map, which basically uses light and warm colors to shows what keys were used more than others during the selected time period, as shown in the screenshot above. Below that, the app displays the total amount of clicks registered in the selected period.
|
||||
|
||||
Under the Network tab, it’s possible to view the daily Internet usage. The application can monitor bandwidth usage of all the network devices, and even shows you bandwidth usage by country. Once again, you can navigate between available data using the arrow buttons at the top-right.
|
||||
|
||||
On the website you’ll see the sum of all your computer statistics with the same information available on the client.
|
||||
|
||||
Disclaimer: The link above to the WhatPulse website contains my referral link, using it when you register will give me a premium account for some time.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linuxaria.com/recensioni/check-how-much-do-you-type-with-whatpulse-on-linux
|
||||
|
||||
作者:[linuxari][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://plus.google.com/100563597940685405833?rel=author
|
||||
[1]:http://whatpulse.org/ref/833872/
|
||||
[2]:http://linuxaria.com/article/tool-command-line-bandwidth-linux
|
||||
[3]:http://www.whatpulse.org/downloads/
|
||||
[4]:https://aur.archlinux.org/packages/whatpulse/
|
||||
[5]:http://linuxaria.com/tag/network
|
||||
@ -0,0 +1,68 @@
|
||||
Disable / Password Protect Single User Mode / RHEL / CentOS / 5.x / 6.x
|
||||
================================================================================
|
||||
Hello All,
|
||||
|
||||
If you have not protected Single User Mode with Password then it is big risk for your Linux Server, So protecting Single User Mode with Password is very important when it comes to security,
|
||||
|
||||
Today in this article i will show you how you can protect Single User Mode with Password on RHEL / CentOS 5.x and RHEL / CentOS 6.x.
|
||||
|
||||
Please execute given commands carefully else your system will not boot properly. First i would request you to read full procedure and then try to follow. Do it at your own risk :-)
|
||||
|
||||

|
||||
Password Protect
|
||||
|
||||
### 1. For RHEL / CentOS 5.x ###
|
||||
|
||||
#### 1.1 Before doing anything please take backup of your /etc/inittab ####
|
||||
|
||||
cp /etc/inittab /etc/inittab.backup
|
||||
|
||||
**To Disable and Make Single User Mode Password Protected, Execute below command as root :-**
|
||||
|
||||
[root@tejas-barot-linux ~]$ sed -i '1i su:S:wait:/sbin/sulogin'
|
||||
|
||||
**So It will look like below**
|
||||
|
||||
su:S:wait:/sbin/sulogin
|
||||
# Default runlevel. The runlevels used by RHS are:
|
||||
# 0 - halt (Do NOT set initdefault to this)
|
||||
# 1 - Single user mode
|
||||
# 2 - Multiuser, without NFS (The same as 3, if you do not have networking)
|
||||
# 3 - Full multiuser mode
|
||||
# 4 - unused
|
||||
# 5 - X11
|
||||
# 6 - reboot (Do NOT set initdefault to this)
|
||||
#
|
||||
id:3:initdefault:
|
||||
|
||||
*NOTE: If you do not want to use sed command then You can always add “su:S:wait:/sbin/sulogin” at top in /etc/inittab*
|
||||
|
||||
### 2. For RHEL / CentOS 6.x ###
|
||||
|
||||
#### 2.1 Before doing anything please take backup of your /etc/inittab ####
|
||||
|
||||
cp /etc/sysconfig/init /etc/sysconfig/init.backup
|
||||
|
||||
#### 2.2 To Disable and Make Single User Mode Password Protected, Execute below command as root :- ####
|
||||
|
||||
[root@tejas-barot-linux ~]$#sed -i 's/SINGLE=\/sbin\/sushell/SINGLE=\/sbin\/sulogin/' /etc/sysconfig/init
|
||||
|
||||
**So It will look like below**
|
||||
|
||||
SINGLE=/sbin/sulogin
|
||||
|
||||
*NOTE :- If you do not want to use sed command then You can always change to “SINGLE=/sbin/sulogin” in /etc/sysconfig/init*
|
||||
|
||||
Enjoy Linux :) Enjoy Open Source
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.tejasbarot.com/2014/05/05/disable-password-protect-single-user-mode-rhel-centos-5-x-6-x/#axzz39oGCBRuX
|
||||
|
||||
作者:[Tejas Barot][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://plus.google.com/+TejasBarot
|
||||
128
sources/tech/20140811 Echo Command with Practical Examples.md
Normal file
128
sources/tech/20140811 Echo Command with Practical Examples.md
Normal file
@ -0,0 +1,128 @@
|
||||
Echo Command with Practical Examples
|
||||
================================================================================
|
||||
echo command is built in **shell command** , which is used to display the value of a **variable** or **print a line of text**.
|
||||
|
||||
Echo command plays a important role in building a shell script.
|
||||
|
||||
### Synatx : ###
|
||||
|
||||
# echo [Options] [String]
|
||||
|
||||
The items in square brackets are optional. A string can be defined as finite sequence of characters (like letters, numerals, symbols punctuation marks).
|
||||
|
||||
When echo command is used without any options or strings, echo returns a blank line on the display screen followed by the command prompt on the subsequent line. This is because pressing the ENTER key is a signal to the system to start a new line, and thus echo repeats this signal.
|
||||
|
||||
### Options : ###
|
||||
|
||||
|
||||
- -n do not output the trailing newline
|
||||
- -e enable interpretation of backslash escapes
|
||||
- -E disable interpretation of backslash escapes (default)
|
||||
|
||||
If -e is in effect, the following sequences are recognized:
|
||||
|
||||
- \\ backslash
|
||||
- \a alert (BEL)
|
||||
- \b backspace
|
||||
- \c produce no further output
|
||||
- \e escape
|
||||
- \f form feed
|
||||
- \n new line
|
||||
- \r carriage return
|
||||
- \t horizontal tab
|
||||
- \v vertical tab
|
||||
- \0NNN byte with octal value NNN (1 to 3 digits)
|
||||
- \xHH byte with hexadecimal value HH (1 to 2 digits)
|
||||
|
||||
### Example :1 Display the value of System Defined Variables ###
|
||||
|
||||
Using the set command , we can list the system define variables and to print the vaule of these variables we can use echo command :
|
||||
|
||||
jack@localhost:~$ echo $USER
|
||||
jack
|
||||
jack@localhost:~$ echo $HOME
|
||||
/home/jack
|
||||
|
||||
### Example:2 Display the value of User defined Variables : ###
|
||||
|
||||
jack@nextstep4it:~$ var1=`date`
|
||||
jack@nextstep4it:~$ echo "Today's date time is : $var1"
|
||||
Today's date time is : Mon Jul 28 13:11:37 IST 2014
|
||||
|
||||
### Example:3 Display the text String ###
|
||||
|
||||
jack@nextstep4it:~$ echo " Hi this echo command testing"
|
||||
Hi this echo command testing
|
||||
|
||||
### Example:4 Use of backspace in echo command ###
|
||||
|
||||
jack@nextstep4it:~$ echo -e "Ubuntu \bis \bthe \bbest \bDesktop \bOS"
|
||||
|
||||
Above Command will Print :
|
||||
UbuntuisthebestDesktopOS
|
||||
|
||||
### Example:5 Use of tab space in echo command ###
|
||||
|
||||
nextstep4it@nextstep4it:~$ echo -e "Ubuntu \tis \tthe \tbest \tDesktop \tOS"
|
||||
|
||||
Above command will show below output :
|
||||
|
||||
Ubuntu is the best Desktop OS
|
||||
|
||||
### Example:6 Use of Vertical tab in echo Command ###
|
||||
|
||||
jack@nextstep4it:~$ echo -e "Ubuntu \vis \vthe \vbest \vDesktop \vOS"
|
||||
Ubuntu
|
||||
is
|
||||
the
|
||||
best
|
||||
Desktop
|
||||
OS
|
||||
|
||||
### Example:7 Colored output of echo command ###
|
||||
|
||||
echo command can change the font style, background color of fonts and font colors. Escape sequence \033 can be used to alter font properties. -e option has to be used in order to the escape sequence be in effect. Some of escape codes are listed below :
|
||||
|
||||
- [0m: Normal
|
||||
- [1m: Bold fonts
|
||||
- [2m: Font color changes to Purple
|
||||
- [4m: Underlined fonts
|
||||
- [7m: Invert foreground and background colors
|
||||
- [8m: Invisible fonts
|
||||
- [9m: Cross lined fonts
|
||||
- [30m: Font color changes to Grey
|
||||
- [31m: Font color changes to Red
|
||||
- [32m: Font color changes to Green
|
||||
- [33m: Font color changes to Brown
|
||||
- [34m: Font color changes to Blue
|
||||
- [35m: Font color changes to Violet
|
||||
- [36m: Font color changes to Sky Blue
|
||||
- [37m: Font color changes to Light Grey
|
||||
- [38m: Font color changes to Black
|
||||
- [40m: Background color changes to Black
|
||||
- [41m: Background color changes to Red
|
||||
- [42m: Background color changes to Green
|
||||
- [43m: Background color changes to Brown
|
||||
- [44m: Background color changes to Blue
|
||||
- [45m: Background color changes to Violet
|
||||
- [46m: Background color changes to Sky Blue
|
||||
- [47m: Background color changes to Light Grey
|
||||
|
||||
Below command will print the output in red color.
|
||||
|
||||
jack@nextstep4it:~$ echo -e "\033[31mMagic of Linux\033[0m"
|
||||
Magic of Linux
|
||||
|
||||
Below Command will print “Magic of Linux” in bold style and red background color.
|
||||
|
||||
nextstep4it@nextstep4it:~$ echo -e "\033[1m\033[41mMagic of Linux\033[0m"
|
||||
Magic of Linux
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.nextstep4it.com/categories/unix-command/echo-command/
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
@ -0,0 +1,92 @@
|
||||
How to Image and Clone Hard Drives with Clonezilla
|
||||
================================================================================
|
||||
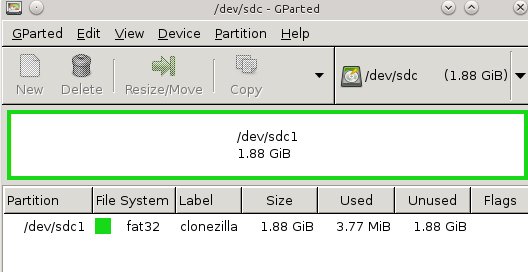
|
||||
Figure 1: Creating a partition on the USB stick for Clonezilla.
|
||||
|
||||
Clonezilla is a partition and disk cloning application for Linux, Free-, Net-, and OpenBSD, Mac OS X, Windows, and Minix. It supports all the major filesystems including EXT, NTFS, FAT, XFS, JFS, and Btrfs, LVM2, and VMWare's enterprise clustering filesystems VMFS3 and VMFS5. Clonezilla supports 32- and 64-bit systems, both legacy and UEFI BIOS, and both MBR and GPT partition tables. It's a good tool for backing up a complete Windows system with all of your installed applications, and I like it for making copies of Linux test systems so that I can trash them with mad experiments and then quickly restore them.
|
||||
|
||||
Clonezilla can also copy unsupported filesystems with the dd command, which copies blocks rather than files, so it doesn't need to understand filesystems. So, the short story is Clonezilla can copy anything. (A quick note on blocks: disk sectors are the smallest addressable storage units on hard disks, and blocks are logical data structures made up of single or multiple sectors.)
|
||||
|
||||
Clonezilla comes in two versions: Clonezilla Live and Clonezilla Server Edition (SE). Clonezilla live is ace for cloning single computers to a local storage device or network share. Clonezilla SE is for larger deployments, and fast multicast cloning an entire network of PCs at once. Clonezilla SE is a wonderful bit of software that we shall cover in the future. Today we shall create a Clonezilla Live USB stick, clone something, and restore it.
|
||||
|
||||
### Clonezilla and Tuxboot ###
|
||||
|
||||
When you visit the download page you'll see [Stable and Alternative Stable releases][1]. There are also Testing releases, which I recommend if you're interested in helping to improve Clonezilla. Stable is based on Debian and includes no non-Free software. Alternative Stable is based on Ubuntu, includes some non-Free firmwares, and it supports UEFI Secure Boot.
|
||||
|
||||
After you [download Clonezilla][2], install [Tuxboot][3] to copy Clonezilla to a USB stick. Tuxboot is a modification of Unetbootin that supports Clonezilla; you can't use Unetbootin because it won't work. Installing Tuxboot is a bit of pain, though Ubuntu users can install Tuxboot the easy way from a personal packages archive (PPA):
|
||||
|
||||
$ sudo apt-add-repository ppa:thomas.tsai/ubuntu-tuxboot
|
||||
$ sudo apt-get update
|
||||
$ sudo apt-get install tuxboot
|
||||
|
||||
If you're not running Ubuntu and your Linux distribution doesn't include a packaged version of Tuxboot, [download the source tarball][4] and follow the instructions in the README.txt file to compile and install it.
|
||||
|
||||
Once you get Tuxboot installed, use it to create your nice live bootable Clonezilla USB stick. First create a FAT32 partition of at least 200 megabytes; figure 1 (above) shows how it's done in GParted. I like to use labels, like "clonezilla", so I know what it is. This example shows a 2GB stick formatted as a single partition.
|
||||
|
||||
Then fire up Tuxboot (figure 2). Check "Pre-downloaded" and click the button with the ellipsis to select your Clonezilla file. It should find your USB stick automatically, and you should check the partition number to make sure it found the right one. In my example that is /dev/sdd1. Click OK, and when it's finished click Exit. It asks you if you want to reboot now, but don't worry because it won't. Now you have a nice portable Clonezilla USB stick you can use almost anywhere.
|
||||
|
||||
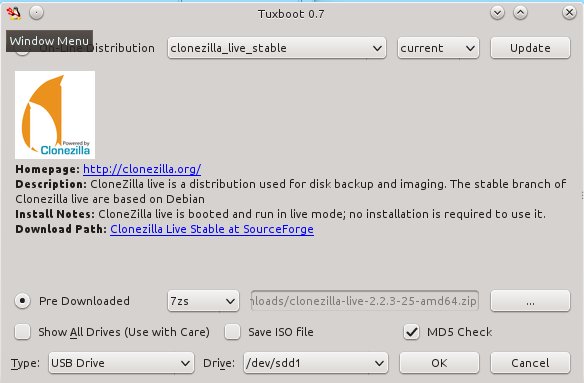
|
||||
Figure 2: Fire up Tuxboot.
|
||||
|
||||
### Creating a Drive Image ###
|
||||
|
||||
Boot up your Clonezilla USB stick on the computer that you want to backup, and the first thing you'll see is a normal-looking boot menu. Boot to the default entry. You'll be asked language and keyboard questions, and when you arrive at the Start Clonezilla menu select Start Clonezilla. In the next menu select device_image, then go to the next screen.
|
||||
|
||||
This screen is a little confusing, with options for local_dev, ssh_server, samba_server, and nfs_server. This is where you select the location for your backup image to be copied to. The size of your destination partition or drive must be the same size or larger than the volume you're copying. If you choose local_dev, then you'll need a local partition with enough room to store your image. An attached USB hard drive is a nice fast and easy option. If you choose any of the server options you'll need a wired Ethernet connection, the IP address of your server, and your login. I'll use a local partition, which means selecting local_dev.
|
||||
|
||||
When you select local_dev Clonezilla scans all of your locally-attached storage, including hard disks and USB storage devices, and makes a list of your partitions. Select the one you want to store your new image in, and then it asks which directory to use and shows you a list. Select your desired directory, and the next screen shows all of your mounts and used/available space. Press Enter, and the next screen gives you the option of Beginner or Expert mode. I choose Beginner.
|
||||
|
||||
In the next screen you can choose savedisk, which creates an image of an entire hard disk, or save_parts, which allows you to select individual partitions. I want to select partitions.
|
||||
|
||||
The next screen asks for a name for your new image. After accepting the default or entering your own name, go to the next screen. Clonezilla scans your partitions and creates a checklist so you can pick the ones you want to copy. After making your selections, the next screen gives you the option to do a filesystem check and repair. I'm impatient, so I skip this part.
|
||||
|
||||
The next screen asks if you want Clonezilla to check your newly-created image to make sure it is restorable. I always say yes. Next, it gives you a command-line hint in case you ever want to use the command-line instead of the GUI, and you must press Enter again. You get one more confirmation, and then type y for Yes to make the copy.
|
||||
|
||||
You get to watch a nice red, white, and blue progress screen while Clonezilla creates your new image (figure 3).
|
||||
|
||||
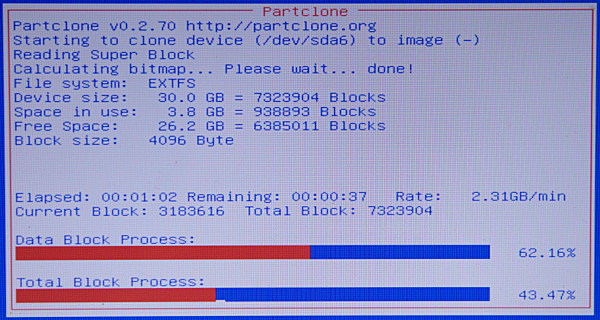
|
||||
Figure 3: Watch the creation of your new image.
|
||||
|
||||
When it's all finished press Enter and then select reboot, and remember to remove your Clonezilla USB stick. Boot up your computer normally, and go look at your nice new Clonezilla image. You should see something like this:
|
||||
|
||||
$ ls -l /2014-08-07-11-img/
|
||||
total 1241448
|
||||
-rw-r--r-- 1 root root 1223 Aug 7 04:22 blkdev.list
|
||||
-rw-r--r-- 1 root root 636 Aug 7 04:22 blkid.list
|
||||
-rw-r--r-- 1 root root 3658 Aug 7 04:24 clonezilla-img
|
||||
-rw-r--r-- 1 root root 12379 Aug 7 04:24 Info-dmi.txt
|
||||
-rw-r--r-- 1 root root 22685 Aug 7 04:24 Info-lshw.txt
|
||||
-rw-r--r-- 1 root root 3652 Aug 7 04:24 Info-lspci.txt
|
||||
-rw-r--r-- 1 root root 171 Aug 7 04:24 Info-packages.txt
|
||||
-rw-r--r-- 1 root root 86 Aug 7 04:24 Info-saved-by-cmd.txt
|
||||
-rw-r--r-- 1 root root 5 Aug 7 04:24 parts
|
||||
-rw------- 1 root root 1270096769 Aug 7 04:24 sda6.ext4-ptcl-img.gz.aa
|
||||
-rw-r--r-- 1 root root 37 Aug 7 04:22 sda-chs.sf
|
||||
-rw-r--r-- 1 root root 1048064 Aug 7 04:22 sda-hidden-data-after-mbr
|
||||
-rw-r--r-- 1 root root 512 Aug 7 04:22 sda-mbr
|
||||
-rw-r--r-- 1 root root 750 Aug 7 04:22 sda-pt.parted
|
||||
-rw-r--r-- 1 root root 625 Aug 7 04:22 sda-pt.parted.compact
|
||||
-rw-r--r-- 1 root root 514 Aug 7 04:22 sda-pt.sf
|
||||
|
||||
### Restoring a Clonezilla Image ###
|
||||
|
||||
Restoring your image is similar to creating it. Again, boot up Clonezilla, go through the same initial steps, select dev_image, and then on the local_dev screen select the location of your image that you want to restore, whether it's on a local device or network share. Then continue through the rest of the screens, making sure that you have the correct restore image and target locations selected.
|
||||
|
||||
You can learn more of Clonezilla's amazing powers at the [Clonezilla Live Documentation page][5].
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linux.com/learn/tutorials/783416-how-to-image-and-clone-hard-drives-with-clonezilla
|
||||
|
||||
作者:[Carla Schroder][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.linux.com/community/forums/person/3734
|
||||
[1]:http://www.linux.com/learn/tutorials/783416-how-to-image-and-clone-hard-drives-with-clonezilla#57_why_ubuntu_based_clonezilla_live.faq
|
||||
[2]:http://clonezilla.org/downloads.php
|
||||
[3]:http://tuxboot.sourceforge.net/
|
||||
[4]:http://sourceforge.net/projects/tuxboot/files/
|
||||
[5]:http://clonezilla.org/clonezilla-live-doc.php
|
||||
@ -0,0 +1,146 @@
|
||||
How to improve your productivity in terminal environment with Tmux
|
||||
================================================================================
|
||||
The introduction of the mouse was a wonderful innovation in making computers more accessible to average people. But for programmers and sysadmins, moving our hands off the keyboard while working on a computer can be distracting.
|
||||
|
||||
As a sysadmin, I spend most of the time working in the terminal environment. Opening tabs and moving around windows through multiple terminals slows me down, and I just can't waste any second when something is going really wrong with my server.
|
||||
|
||||
|
||||
|
||||
[Tmux][1] is one of those tools that are essential for my daily work. With Tmux, I can create complex development environments, and have SSH connections side by side. I can create multiple windows, split panes, attach and detach sessions, etc. After mastering Tmux, you will throw out your mouse away ( just kidding don't do it :D ).
|
||||
|
||||
Tmux (short for "Terminal Multiplexer") lets us launch multiple terminals in a flexible layout on a single screen, so that we can work with them side by side. For example, on one pane we can edit some config files with Vim, while on the other we are using irssi to chat and on other pane, tailing some logs. Then open another window to update your system, and another to SSH to some servers. Navigating through them is just as easy as creating all these windows and panes. It is perfectly configurable and customizable so it can become an extension of your mind.
|
||||
|
||||
### Install Tmux on Linux/OSX ###
|
||||
|
||||
You can install Tmux by compiling it from sources or via your operating system package manager. I recommend you to use a package manager. It's faster and easier than compiling.
|
||||
|
||||
#### OSX: ####
|
||||
|
||||
# sudo brew install tmux
|
||||
# sudo port install tmux
|
||||
|
||||
#### Debian/Ubuntu: ####
|
||||
|
||||
$ sudo apt-get install tmux
|
||||
|
||||
RHEL/CentOS/Fedora (RHEL/CentOS require [EPEL repo][2]):
|
||||
|
||||
$ sudo yum install tmux
|
||||
|
||||
Archlinux:
|
||||
|
||||
$ sudo pacman -S tmux
|
||||
|
||||
### Working with Different Sessions ###
|
||||
|
||||
The best way to use Tmux is working with sessions, so that you can organize your tasks and applications into different sessions the way you want. If you need to change a session, whatever runs inside the session won't stop or get killed. Let's see how it works.
|
||||
|
||||
Let's start a new session named "session", and run top command in it.
|
||||
|
||||
$ tmux new -s new session
|
||||
$ top
|
||||
|
||||
then type **CTRL-b d** to detach from this session. To re-attach to it:
|
||||
|
||||
$ tmux attach-session -t session
|
||||
|
||||
And you will see top still running in the re-attached session.
|
||||
|
||||
Some commands to manage sessions:
|
||||
|
||||
$ tmux list-session
|
||||
$ tmux new-session <session-name>
|
||||
$ tmux attach-session -t <session-name>
|
||||
$ tmux rename-session -t <session-name>
|
||||
$ tmux choose-session -t <session-name>
|
||||
$ tmux kill-session -t <session-name>
|
||||
|
||||
### Working with Different Windows ###
|
||||
|
||||
Often you will need to run multiple commands and perform different tasks in a session. We can organize all of them on multiple windows in one session. A window can be seen as a tab on modern GUI terminal (such iTerm, or Konsole). After configuring our default environment in a session, we will be able to create as many windows as we would need within the same session. Windows, like our apps running in sessions, persist when we detach from the current session. Let's check out an example:
|
||||
|
||||
$ tmux new -s my_session
|
||||
|
||||
|
||||
|
||||
Press **CTRL-b c**
|
||||
|
||||
This will create a new window and move focus into it. Now you can start up another application in the new window. You can write down the name of your current window. In this case I was running top so that's the window's name.
|
||||
|
||||
To rename it just type:
|
||||
**CTRL-b** ,
|
||||
|
||||
The status bar changes to let you rename the current window.
|
||||
|
||||
|
||||
|
||||
Once we create multiple windows in a session, we need a way to move through them. Windows are organized as an array, so every window has a number starting at 0. To jump quickly to other windows:
|
||||
|
||||
**CTRL-b <window number>**
|
||||
|
||||
If we have named our windows, we can look for them with:
|
||||
|
||||
**CTRL-b f**
|
||||
|
||||
and to list all windows:
|
||||
|
||||
**CTRL-b w**
|
||||
|
||||
and to move to a different window one by one:
|
||||
|
||||
**CTRL-b n** (go to the next window)
|
||||
**CTRL-b p** (go to the previous window)
|
||||
|
||||
To leave a window, just type exit or:
|
||||
|
||||
**CTRL-b &**
|
||||
|
||||
You have to confirm if you want to kill off the window.
|
||||
|
||||
### Splitting a Window into Panes ###
|
||||
|
||||
Sometimes you need to type in your editor and check a log at the same time, and having your editor and tail side by side is really useful. With Tmux, we can divide a window into multiple panes. So for example, we can create a dashboard to monitor our servers and a complex development environment with the editor, the compiler and debugger running together side by side.
|
||||
|
||||
Let's create another Tmux session to work with panes. First let's detach from any Tmux session in case we are in a running session.
|
||||
|
||||
**CTRL-b d**
|
||||
|
||||
Start a new session named "panes".
|
||||
|
||||
$ tmux new -s panes
|
||||
|
||||
You can split a window horizontally or vertically. Let's start horizontally by pressing:
|
||||
|
||||
**CTRL-b** "
|
||||
|
||||
Now you have two new panes. Now vertically by pressing:
|
||||
|
||||
**CTRL-b** %
|
||||
|
||||
and now two more:
|
||||
|
||||
|
||||
|
||||
To move through them:
|
||||
|
||||
**CTRL-b <Arrow keys>**
|
||||
|
||||
### Conclusion ###
|
||||
|
||||
I hope this tutorial has been helpful to you. As a bonus, tools such as [Tmuxinator][3] or [Tmuxifier][4] can streamline the process of creating and loading Tmux sessions, windows and panes, so that you can configure Tmux easily. Check them out if you haven't.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/2014/08/improve-productivity-terminal-environment-tmux.html
|
||||
|
||||
作者:[Christopher Valerio][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/valerio
|
||||
[1]:http://tmux.sourceforge.net/
|
||||
[2]:http://xmodulo.com/2013/03/how-to-set-up-epel-repository-on-centos.html
|
||||
[3]:https://github.com/tmuxinator/tmuxinator
|
||||
[4]:https://github.com/jimeh/tmuxifier
|
||||
@ -0,0 +1,39 @@
|
||||
[translating by KayGuoWhu]
|
||||
Linux FAQs with Answers--How to check the last time system was rebooted on Linux
|
||||
================================================================================
|
||||
> **Question**: Is there a way to quickly check how long a Linux system has been running? That is, how can I find out the last time a Linux system was rebooted?
|
||||
|
||||
There are several ways to find out the last system reboot time,
|
||||
|
||||
### Method One ###
|
||||
|
||||
The first method is to use last command.
|
||||
|
||||
$ last reboot
|
||||
|
||||

|
||||
|
||||
This command actually shows system uptime for the last few days. Originally the last command is designed to show login history of a particular user. In Linux, a special "pseudo user" named reboot automatically logs in to the system right after the system has rebooted. Thus by checking the login history of reboot user, you can check the last reboot time.
|
||||
|
||||
### Method Two ###
|
||||
|
||||
Another command to check the time of last system boot is to use who command with '-b' option.
|
||||
|
||||
$ who -b
|
||||
|
||||
### Method Three ###
|
||||
|
||||
You can also use uptime command to deduce last reboot time. The uptime command shows you the current time, as well as how long the system has been running. From this information, you can calculate the time when the system was last booted.
|
||||
|
||||
$ uptime
|
||||
|
||||

|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://ask.xmodulo.com/check-last-time-system-rebooted-linux.html
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
@ -1,23 +1,23 @@
|
||||
Latest Intel Linux Graphics Drivers Now Available on Ubuntu 14.04 LTS
|
||||
最新的英特尔Linux图形驱动程序现在可在Ubuntu 14.04 LTS上使用
|
||||
================================================================================
|
||||

|
||||
Intel Makes it Easy to Install Drivers
|
||||
英特尔使驱动安装变得简单
|
||||
|
||||
**A new version of the Intel [Linux Graphics Installer][1] is available to download.**
|
||||
**新版本的英特尔[Linux图形安装程序][1]可下载。**
|
||||
|
||||
The open-source utility offers an easy way to get the latest graphics and video drivers for supported Intel hardware in Ubuntu.
|
||||
这个开源的工具为获取最新的(在Ubuntu上已支持的因特尔设备的)图形和视频驱动提供了简易的途径。
|
||||
|
||||
In **version 1.0.6** the 2014Q2 graphics stack released [at the end of June][2] is made available to Ubuntu 14.04 LTS for the first time.
|
||||
在**版本1.0.6**中首次使其[六月底][2]发布的2014Q2图形堆栈可在Ubuntu 14.04中使用。
|
||||
|
||||
It brings better Bay Trail performance, power saving optimisations, and improves support for Intel Broadwell chips.
|
||||
它也带来了更好的Bay Trail性能,节能优化,并且改善了对英特尔Broadwell芯片的支持。
|
||||
|
||||
Running the latest available stack is the best way for Linux users to “*…stay current with the latest enhancements, optimisations, and fixes,*” say Intel.
|
||||
对Linux用户来说,想要向Intel所说的那样“保持当前最新的改进,优化,和修复”,最好的方法就是运行最新可用的堆栈。
|
||||
|
||||
### Download ###
|
||||
### 下载 ###
|
||||
|
||||
The latest version of the Graphics Installer supports Ubuntu 14.04 LTS and Fedora 20. Ubuntu 13.10 users can continue to use the tool, but won’t be able to grab the most recent set of drivers.
|
||||
最新版本的图形安装程序支持Ubuntu 14.04 LTS和Fedora 20。Ubuntu 13.10的用户可以继续使用这个工具,但不能获取最新的驱动程序。
|
||||
|
||||
Debian installers for Ubuntu 14.04 LTS [32 bit][3] or [64 bit][4] are available from the 01.org website, link below.
|
||||
Ubuntu 14.04 LTS [32位][3]或[64位][4]可用的的Deb安装包可在 01.org 网站下载,链接如下。
|
||||
|
||||
- [Download Intel Graphics Installer 1.0.6 for Ubuntu][5]
|
||||
|
||||
@ -26,7 +26,7 @@ Debian installers for Ubuntu 14.04 LTS [32 bit][3] or [64 bit][4] are available
|
||||
via: http://www.omgubuntu.co.uk/2014/08/intel-graphics-installer-linux-updated-1-0-6
|
||||
|
||||
作者:[Joey-Elijah Sneddon][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
译者:[linuhap](https://github.com/linuhap)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
@ -1,6 +1,7 @@
|
||||
如何用CentOS上的SARG log分析其来分析Squid的log
|
||||
如何用CentOS上的SARG日志分析器来分析Squid日志
|
||||
================================================================================
|
||||
[上一节教程][1]中,我们战士了如何在CentOS上使用Squid配置透明代理。Squid提供了很多有用的特性,但是分析一个原始Squid日志文件并不直接。比如,你如何分析下面Squid log中的时间戳和数字?
|
||||
|
||||
[上一节教程][1]中,我们展示了如何在CentOS上使用Squid配置透明代理。Squid提供了很多有用的特性,但是分析一个原始Squid日志文件并不直接。比如,你如何分析下面Squid日志中的时间戳和数字?
|
||||
|
||||
1404788984.429 1162 172.17.1.23 TCP_MISS/302 436 GET http://facebook.com/ - DIRECT/173.252.110.27 text/html
|
||||
1404788985.046 12416 172.17.1.23 TCP_MISS/200 4169 CONNECT stats.pusher.com:443 - DIRECT/173.255.223.127 -
|
||||
@ -12,7 +13,7 @@
|
||||
1404788990.849 2151 172.17.1.23 TCP_MISS/200 76809 CONNECT fbstatic-a.akamaihd.net:443 - DIRECT/184.26.162.35 -
|
||||
1404788991.140 611 172.17.1.23 TCP_MISS/200 110073 CONNECT fbstatic-a.akamaihd.net:443 - DIRECT/184.26.162.35 –
|
||||
|
||||
SARG(或者说是Squid分析报告生成器)是一款基于web的工具,用于从Squid日志中生成报告。SARG提供了一个易于理解的由Squid处理的网络流量视图,并且它很容易设置与维护。在下面的教程中,我们会展示**如何在CentOS平台上设置SARG**。
|
||||
SARG(或者说是Squid分析报告生成器)是一款基于web的工具,用于从Squid日志中生成报告。SARG提供了一个由Squid处理的网络流量视图,易于理解,并且它可以很容易地设置和维护。在下面的教程中,我们会展示**如何在CentOS平台上设置SARG**。
|
||||
|
||||
我们使用yum来安装安装必要的依赖。
|
||||
|
||||
@ -63,17 +64,17 @@ SARG安装之后,配置文件可以按你的要求修改。下面是一个SARG
|
||||
## we don’t want multiple reports for single day/week/month ##
|
||||
overwrite_report yes
|
||||
|
||||
现在是时候测试运行了,我们用调试模式运行sarg来找出是否存在错误。
|
||||
现在是时候测试运行了,我们用调试模式运行sarg来查看是否存在错误。
|
||||
|
||||
# sarg -x
|
||||
|
||||
如果i一切正常,sarg会根系Squid日志,并在/var/www/html/squid-reports下创建报告。报告也可以在浏览器中通过地址http://<服务器IP>/squid-reports/访问
|
||||
如果i一切正常,sarg会根系Squid日志,并在/var/www/html/squid-reports下创建报告。报告也可以在浏览器中通过地址http://<服务器IP>/squid-reports/访问。
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
、SARG可以用于创建每日、每周、每月的报告。时间范围用“-d”参数来指定,可能的值的形式可能为day-n、 week-n 或者 month-n,n的值向后天/周/月的数量。比如,使用week-1,SARG会生成前面一星期的报告。使用day-2,SARG会准备前面两天的报告。
|
||||
、SARG可以用于创建日、周、月度报告。时间范围用“-d”参数来指定,值的形式很可能为day-n、 week-n 或者 month-n,n的值为向前推移的天/周/月的数量。比如,使用week-1,SARG会生成之前一星期的报告。使用day-2,SARG会生成之前两天的报告。
|
||||
|
||||
作为演示,我们会准备一个计划任务来每天运行SARG。
|
||||
|
||||
@ -90,10 +91,9 @@ SARG安装之后,配置文件可以按你的要求修改。下面是一个SARG
|
||||
|
||||
现在SARG应该会每天准备关于Squid管理的流量报告。这些报告可以很容易地通过SARG网络接口访问。
|
||||
|
||||
To sum up, SARG is a web based tool that analyzes Squid logs and presents the analysis in an informative way. System admins can leverage SARG to monitor what sites are being accessed, and to keep track of top visited sites and top users. This tutorial covers a working configuration for SARG. You can customize the configuration even further to match your requirements.
|
||||
总结一下,SARG一款基于网络的工具,它可以分析Squid日志,并以更详细的方式展示分析。系统管理员可以利用SARG来监视哪些网站被访问了,并跟踪访问量最大的网站和用户。本教程涵盖了SARG配置工作。你甚至可以进一步自定义配置来满足您的要求。
|
||||
总结一下,SARG一款基于网络的工具,它可以分析Squid日志,并以更详细的方式展示分析。系统管理员可以利用SARG来监视哪些网站被访问了,并跟踪访问量最大的网站和用户。本教程包含了SARG配置工作。你可以进一步自定义配置来满足自己的要求。
|
||||
|
||||
希望这篇教程有用
|
||||
希望这篇教程对您有帮助。
|
||||
|
||||
----------
|
||||
|
||||
@ -102,13 +102,13 @@ To sum up, SARG is a web based tool that analyzes Squid logs and presents the an
|
||||
- [Twitter 地址][t]
|
||||
- [LinkedIn 地址][l]
|
||||
|
||||
Sarmed Rahman是一名在孟加拉国的IT专业人士。他坚持写作科学文章,并坚信技术可以通过分享提高。在他的空闲时间里,他爱好游戏与他的朋友在一起
|
||||
Sarmed Rahman是一名孟加拉国的IT专业人士。他坚持时不时地写作技术文章,并坚信技术可以通过分享而提高。在空闲时间里,他喜欢打游戏,喜欢和朋友一起度过。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/2014/07/analyze-squid-logs-sarg-log-analyzer-centos.html
|
||||
|
||||
译者:[geekpi](https://github.com/geekpi) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
译者:[geekpi](https://github.com/geekpi) 校对:[Caroline](https://github.com/carolinewuyan)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
|
||||
126
translated/tech/20140723 Top 10 Fun On The Command Line.md
Normal file
126
translated/tech/20140723 Top 10 Fun On The Command Line.md
Normal file
@ -0,0 +1,126 @@
|
||||
Top 10! Fun On The Command Line
|
||||
================================================================================
|
||||
|
||||
排名前10!在命令行中寻找乐趣
|
||||
================================================================================
|
||||
|
||||
|
||||
**如果你喜欢做‘排名前10'类型的列表但又有点不好意思这样说,那么告诉人们你热爱数据的探索。为了进一步打动他们们,向他们解释你在命令行间的数据探索。但是不要告诉他们这其实很容易,以免你的好形象就这样被毁灭了哦!**
|
||||
|
||||
在这篇文章中,我将基于GNU/Linux工具和'一列的表格'来做一些数据探索,也就是我所说的简单列表。如若想在这里通过命令行查看更多的信息,请查看'man'页,或者在“注释”部分求解。
|
||||
|
||||
### 密码 ###
|
||||
|
||||
在第一个列表里探讨的是马克.伯内特2011著的关于[10000 个最常用的密码][1]汇编。这个列表是有序的、使用最频繁的,也是广为人知的阶乘“密码”的最常用来源之一,与“123456”并列排名第二。在这里,我已经把一个所谓密码的文件列出来了,并且使用head命令把排名前10的列出来了:
|
||||
|
||||

|
||||
|
||||
(伯内特解释他是如何手收集这些密码的[这里][2]。你会注意到在列表中他把所有大写字母都转换成小写的。)
|
||||
|
||||
OK,所以'密码'是伯内特列表的顶部。那么个位数字呢?
|
||||
|
||||

|
||||
|
||||
非常有趣的是!数字'1'出现在密码列表中多于是第二个最常用数字'2'的两倍,以及10位数字在数值以及人气排序,除了0和9。而排名前10的字母呢?
|
||||

|
||||
|
||||
在密码文件中出现最频繁的字母依次是EARONISTLC.这个和EAIRTONSLC差不多,也是一个频率模式图至少在 [one published table][3] 中最常适用的英语单词。这是否意味着,大部分密码其实是一些常见的英语单词呢,也许会参杂一些数字呢?
|
||||
|
||||
为了找到答案,我先把密码转换成一个纯字母字符串列表,然后看看有多少字符串是可以在英语词典中找到的。
|
||||
|
||||
|
||||
首先我将通过 **sed**命令删除所有密码中的数字,然后删除所有的标点符号,再删除所有的空行。这将创建出一个纯字母的密码列表。然后我通过**sort** 和 **uniq**来修剪列表的排序,将重复项取出。(例如,'abc1234def'和'abc1!2!3!def!'都剔除剩下'abcdef'.) 。根据wc命令,我把1000个密码减至成8583个纯字母的字符串:
|
||||

|
||||
|
||||
我经常使用一本便携式的英语字典,我通常会使用`usr/share/dict/american-english`,这个文件是来自Debian Linux的一个发行版本。它包含了99171个单词。我会先通过**tr**命令将这个词表转换为纯小写的,然后使用**sort** 和 **uniq**删除掉人和重复的条目排序(例如'A' 和 'a' 都将成为 'a')。这样就将词表的数量减至97723项了:
|
||||
|
||||

|
||||
|
||||
我现在可以用通信命令带'-23'的参数来比较两个列表和报告中纯字母文件而没有出现在字典中的单词:
|
||||

|
||||
|
||||
总数是3137,所以至少有8583 -3137 = 5446个'核心'密码在伯纳特的纯小写字母列表中(大约63%)是简单的英语单词,或者是简单的单词附加一些数字或者标点符号。我之所以写至少是因为在3137个字符串中有很大比例是只有经过轻微修改的纯英语单词、名称、或者在/usr/share字典中未能找到的名称修改而成的。在LA项中,例如,'labtec', 'ladyboy', 'lakeside', 'lalakers', 'lalala', 'laserjet', 'lasvegas', 'lavalamp' and 'lawman'.
|
||||
|
||||
### Placenames ###
|
||||
### 地名 ###
|
||||
|
||||
在之前的一篇[Linux Rain article][4],我描述了如何建立一张37万项澳大利亚的地名表。有了它,我现在可以回答一些类似这样的关键问题“Round Hill是澳大利亚山脉中最流行的名字吗?”和“桑迪是沙滩之最,而岩溪峡谷呢?”
|
||||
|
||||
在地名表中地名字段的排名第2,所以这里有:
|
||||
|
||||

|
||||
|
||||
|
||||
哇。我当时甚至没有关闭。(但是请注意到我是如何通过**^string1^string2**命令保存打印的内容。它重复着最后一个命令,但是用第2个字符串代替了第1个字符串。这是多门经常的BASH绝招!)
|
||||
|
||||
|
||||
另一个亟待解决的问题是有多少地名有'Mile'在其中,例如'Six Mile Creek',而他们的排名又是如何:
|
||||

|
||||
|
||||
我在我的澳洲之旅发现有很多Dead Horse Creeks,因此有这些地名:
|
||||
|
||||

|
||||
|
||||
|
||||
### 种类 ###
|
||||
|
||||
第三个列表是探索我今年出版的1961-2010年期间澳大利亚新种类昆虫名。从这个列表中,我去掉所有“物种的绰号”,这也是种群组合的第二部分像智人(你和我)和西方蜜蜂(欧洲蜜蜂)。
|
||||
|
||||
|
||||
(科技小贴士:这个昆虫表,可以从开发数据Zenodo库中[https://zenodo.org/record/10481][5],包括亚种。在我的‘top 10’练习中,我首先分离出所有独特的种群组合,这样避免了重复的,例如蜜蜂iberica的亚种,以避免蜜蜂的绰号intermissa,等等。最后一个物种文件有18155个绰号。)
|
||||
|
||||
大多数人讲科学名称带玩笑式地用'-us'结局,如'Biggus buggus'.那么昆虫学家呢?有几个不错的,用命令行的方式获取字符串的最后2个字母,在这里我都会用到这2个:
|
||||

|
||||
|
||||
|
||||
|
||||
耶!昆虫学家喜欢也‘-us’结尾。接下来,我不知道有多少物种是以我的家乡State of Tasmania来命名的?(下面我想看看前100行,来确保我得到的所有'tasman'组合.)
|
||||
|
||||

|
||||
|
||||
那么昆士兰呢?
|
||||
|
||||

|
||||
|
||||
一般来说,昆虫物种名单中的前10名分别是什么呢?
|
||||
|
||||

|
||||
|
||||
嗯,除了明显的'australis'和'australiensis',而地理方面的'occidentalis'(西部),另外昆虫学家创建7个在10个最流行列表中的绰号已经旅行了其它昆虫学家的意愿。(加词'commoni'是给澳大利亚蝴蝶和蛾专家Ian F.B. Common,从1917-2006.)
|
||||
|
||||
### Speechifying ###
|
||||
### 演变 ###
|
||||
|
||||
上面使用的命令在一个简单的列表中。从一个文本块做一个简单的列表,这个命令行又再次成为你的朋友。例如,我保存了一个相当filibustery[演讲][6]在澳大利亚参议院于2014年7月16日的文本文件议事录。将议事录分割成一个单词列表:
|
||||

|
||||
|
||||
And to look at word frequency in the speech:
|
||||
|
||||
现在看看讲话中的单词使用频率:
|
||||
|
||||

|
||||
|
||||
### Coming soon... ###
|
||||
### 即将推出... ###
|
||||
|
||||
从多列的表中做'top 10'等排名,需要更多些的命令行工具。我将会在未来的文章中证明他们的用处。
|
||||
|
||||
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://thelinuxrain.com/articles/top-10-fun-on-the-command-line
|
||||
|
||||
原文作者:Bob Mesibov(Bob Mesibov is Tasmanian, retired and a keen Linux tinkerer.)
|
||||
|
||||
译者:[disylee](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:https://xato.net/passwords/more-top-worst-passwords/#.U8eD13AvDy0
|
||||
[2]:https://xato.net/passwords/how-i-collect-passwords/#.U8eEdnAvDy0
|
||||
[3]:http://www.rinkworks.com/words/letterfreq.shtml
|
||||
[4]:http://www.thelinuxrain.com/articles/building-a-gazetteer-table-from-kml-files
|
||||
[5]:https://zenodo.org/record/10481
|
||||
[6]:http://parlinfo.aph.gov.au/parlInfo/search/display/display.w3p;db=CHAMBER;id=chamber%2Fhansards%2F232fa1a8-d7e8-4b22-9018-1a99b5a96812%2F0025;query=Id%3A%22chamber%2Fhansards%2F232fa1a8-d7e8-4b22-9018-1a99b5a96812%2F0000%22
|
||||
@ -0,0 +1,45 @@
|
||||
Linux有问必答--如何查看Linux上程序或进程用到的库
|
||||
================================================================================
|
||||
> **问题**:我想知道当我调用一个特定的可执行文件在运行时载入了哪些共享库。是否有方法可以明确Linux上可执行程序或运行进程的共享库依赖关系?
|
||||
|
||||
|
||||
### 查看可执行程序的共享库依赖关系 ###
|
||||
|
||||
要找出某个特定可执行依赖的库,可以使用ldd命令。这个命令调用动态链接器去找到程序的库文件依赖关系。
|
||||
|
||||
$ ldd /path/to/program
|
||||
|
||||

|
||||
|
||||
注意并不推荐为任何不可信的第三方可执行程序运行ldd,因为某些版本的ldd可能会直接调用可执行程序来明确其库文件依赖关系,这样可能不安全。
|
||||
|
||||
取而代之的是用一个更安全的方式来显示一个未知应用程序二进制文件的库文件依赖,使用如下命令:
|
||||
|
||||
$ objdump -p /path/to/program | grep NEEDED
|
||||
|
||||

|
||||
|
||||
查看运行进程的共享库依赖关系(注:这里缺少###的标题格式?)
|
||||
|
||||
如果你想要找出被一个运行中的进程载入的共享库,你可以使用pldd命令,它会显示出在运行时被载入一个进程里的所有共享对象。
|
||||
|
||||
$ sudo pldd <PID>
|
||||
|
||||
注意你需要root权限去执行pldd命令。
|
||||
|
||||

|
||||
|
||||
或者,也可以选择一个叫做pmap的命令行工具。它报告一个进程的内存映射,也能显示出运行进程的库文件依赖。
|
||||
|
||||
$ sudo pmap <PID>
|
||||
|
||||

|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://ask.xmodulo.com/check-library-dependency-program-process-linux.html
|
||||
|
||||
译者:[KayGuoWhu](https://github.com/KayGuoWhu)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
@ -0,0 +1,44 @@
|
||||
检查linux中的损坏的扇区和区块
|
||||
================================================================================
|
||||
**badblocks**是linux及其类似的操作系统中,扫描检查硬盘和外部设备损坏扇区的命令工具。损坏的扇区或者损坏的区块是硬盘中因为永久损坏或者是操作系统不能读取的空间。
|
||||
|
||||
Badblocks命令可以探测硬盘中所有损坏的扇区或者区块并将结果保存在一个文本文档中,这样,我们就可以使用**e2fsck**命令来配置操作系统不在这些损坏的扇区中存储。
|
||||
|
||||
### 步骤:1 使用fdisk识别硬盘信息 ###
|
||||
|
||||
# sudo fdisk -l
|
||||
|
||||
### 步骤:2 扫描硬盘的损坏扇区或区块 ###
|
||||
|
||||
# sudo badblocks -v /dev/sdb > /tmp/bad-blocks.txt
|
||||
|
||||
只需将“/dev/sdb”替换为自己机器的/分区。执行完成上述命令后,一个名为“bad-blocks”文本文档将会在/tmp下创建,它将包含所有的损坏区块。
|
||||
|
||||
例如:
|
||||
|
||||

|
||||
|
||||
### 步骤:3 告诉操作系统不要使用损坏区块存储 ###
|
||||
|
||||
扫描完成后,如果损坏区块被发现了,然后通过e2fsck命令使用“bad-blocks.txt”,强迫操作系统不使用这些损坏的区块存储数据。
|
||||
|
||||
# sudo e2fsck -l /tmp/bad-blocks.txt /dev/sdb
|
||||
|
||||
注意:在运行e2fsck命令前,请保证设备没有被挂载。
|
||||
|
||||
关于badblocks和e2fsck命令的更多帮助,请参考下列man页面
|
||||
|
||||
# man badblocks
|
||||
# man e2fsck
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linuxtechi.com/check-hard-drive-for-bad-sector-linux/
|
||||
|
||||
作者:[Pradeep Kumar][a]
|
||||
译者:[Vic___](http://www.vicyu.net)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.linuxtechi.com/author/pradeep/
|
||||
Loading…
Reference in New Issue
Block a user