mirror of
https://github.com/LCTT/TranslateProject.git
synced 2024-12-26 21:30:55 +08:00
Merge branch 'master' of https://github.com/LCTT/TranslateProject
This commit is contained in:
commit
eb34e4dd9f
@ -1,10 +1,10 @@
|
||||
Exaile 3.4.1 概述 — 一个全功能的GNOME音乐播放器
|
||||
Exaile 3.4.1 概览:一个全功能的GNOME音乐播放器
|
||||
================================================================================
|
||||
**Exaile** 在过去两年显得有些平静,也许只有一个或者两个稳定版发布,但尽管如此,在功能方面,它是一个和[Rhythmbox][1]或者[Banshee][2]相匹敌的全功能GNOME音乐播放器。然而,在过去的两个月,在"We’re not dead yet"的口号下,推出了一个新的稳定版3.4,同时在11月1日还推出了3.4.1增量版本。事实上,Exaile有很多的功能,我可以继续写很多的文章而不是在一篇文章里全部介绍到,就让我们来看一下一些最显著的特点吧。
|
||||
**Exaile** 在过去两年显得有些平静,也许只有一个或者两个稳定版发布,但尽管如此,在功能方面,它是一个和[Rhythmbox][1]或者[Banshee][2]相匹敌的全功能GNOME音乐播放器。不过,在过去的两个月,在"We’re not dead yet"的口号下,他们推出了一个新的稳定版3.4,同时在11月1日还推出了3.4.1增量版本。事实上,Exaile有很多的功能,我可以继续写很多的文章而不是在一篇文章里全部介绍到,就让我们来看一下一些最显著的特点吧。
|
||||
|
||||
|
||||
|
||||
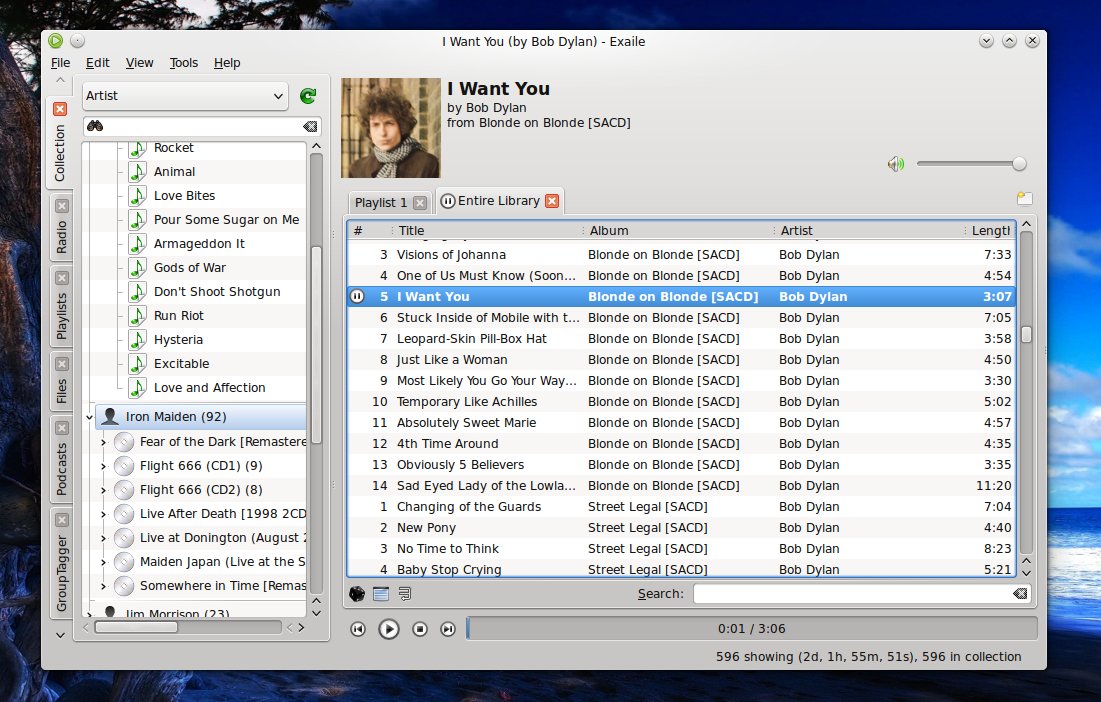
[Exaile][3]是基于GTK-2,用Python写的音乐播放器,它能很好地兼容GNOME,有和旧的Amarok1.4或者Clementine非常类似的界面,以及一些很好的功能。界面主要由两个面板组成,两个都支持标签。左边的面板提供对音乐集,网络音频,只能和自定义播放列表,文件浏览,播客,组标签以及歌词的访问,窗口的主要部分是播放列表(支持多种,带标签的播放列表)和控制按钮。
|
||||
[Exaile][3]是基于GTK-2,用Python写的音乐播放器,它能很好地兼容GNOME,有和旧的Amarok1.4或者Clementine非常类似的界面,以及一些很好的功能。界面主要由两个面板组成,两个都支持标签。左边的面板提供对音乐集,网络音频,智能和自定义播放列表,文件浏览,播客,组标签以及歌词的访问,窗口的主要部分是播放列表(支持多个列表,以标签方式组织的播放列表)和控制按钮。
|
||||
|
||||
Exaile的界面和Clementine或者Amarok1.4非常相似,可以显示或者隐藏左边的标签。
|
||||
|
||||
@ -26,7 +26,7 @@ Exaile的功能几乎不尽其数。你可以在音乐集中组织音乐,听
|
||||
|
||||
|
||||
|
||||
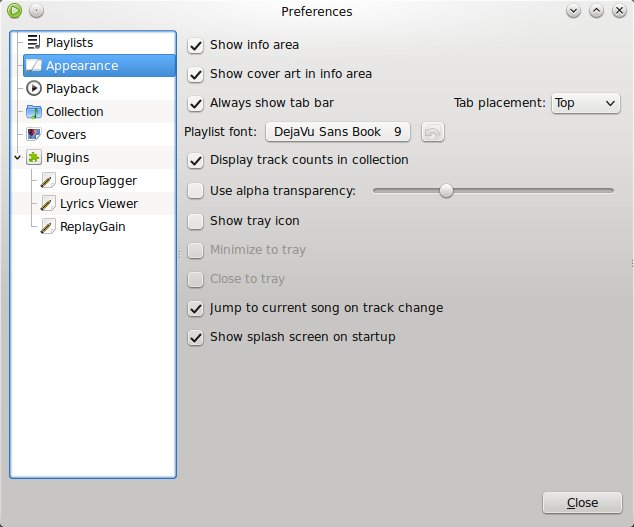
首选项窗口允许多个方面配置Exaile,包括启用或者禁用插件,外观,系统托盘集成或者播放模式。外观设置允许你更改标签的布局,显示或者隐藏便签栏,启用或者禁用透明性或者禁用启动画面。
|
||||
首选项窗口允许配置Exaile的各个方面,包括启用或者禁用插件,外观,系统托盘集成或者播放模式。外观设置允许你更改标签的布局,显示或者隐藏便签栏,启用或者禁用透明性或者禁用启动画面。
|
||||
|
||||
|
||||
|
||||
@ -64,7 +64,7 @@ via: http://www.tuxarena.com/2014/11/exaile-3-4-1-overview-a-feature-complete-gn
|
||||
|
||||
作者:Craciun Dan
|
||||
译者:[ictlyh](https://github.com/ictlyh)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,24 +1,25 @@
|
||||
VirturalBox 5.0 beta版终于发布了
|
||||
VirturalBox 终于进入到 5.0 世代
|
||||
=======================================
|
||||
**甲骨文公司的桌面虚拟化软件获得了近五年来的第一次重大改版,但是更像是改进而不是革命性的的变化。**
|
||||
|
||||
**本月初,甲骨文公司的桌面虚拟化软件获得了近五年来的第一次重大改版,但是更像是改进而不是革命性的的变化。**
|
||||
|
||||
VirtualBox,由Sun公司创建,现在由甲骨文管理的开源虚拟化系统,获得了近5年来第一次的主版本更新发布。
|
||||
|
||||
从发行说明和测试版本身的表现来看,别期望任何真正革命性的改变。在此版本中,VirtualBox在视觉上和技术上都做了一些改进,但和VMware相比,它的主要优势仍然是相同核心功能的自由化。
|
||||
从发行说明和测试版本身的表现来看,别期望任何真正革命性的改变。在此版本中,VirtualBox在视觉上和技术上都做了一些改进,但和VMware相比,它的主要优势仍然是相同核心功能的开源实现。
|
||||
|
||||
VirtualBox 4.0的最后一个主要版本在2010年12月发布,它采用了新的图形化用户界面,新的虚拟化硬件和重组的项目设计,带来了重大的改版。但项目主要版本的发布步伐缓慢,上一次重要版本(版本4.3)在2013年底才发布。从那时起,一切都被正式称为“维修”发布。
|
||||
VirtualBox 4.0的最后一个主要版本在2010年12月发布,它采用了新的图形化用户界面,新的虚拟化硬件和重组的项目设计,进行了重大的改版。但项目主要版本的发布步伐缓慢,上一次重要版本(版本4.3)在2013年底才发布。从那时起,一切都被正式称为“维护”发布。
|
||||
|
||||
**VirtualBox 5.0**
|
||||

|
||||
|
||||
*VirtualBox 5.0的第一个测试版增加了编辑菜单,VM窗口的快捷方式图标等功能,如下面所示。*
|
||||
|
||||
VirtualBox 5.0最大的变化是增加了对硬件辅助虚拟化指令集扩展的支持。AES-NI指令集通常用于加密时的硬件加速,SSE 4.1和SSE 4.2指令集都包括在其中。另外一点是支持Windows和Linux客户机的半虚拟化,一个抽象主机音响的新的架构以及支持客户机中的USB 3(xHCI)控制器。
|
||||
VirtualBox 5.0最大的变化是增加了对硬件辅助虚拟化指令集扩展的支持。AES-NI指令集通常用于加密时的硬件加速,SSE 4.1和SSE 4.2指令集都包括在其中。另外一点是支持Windows和Linux客户机的半虚拟化,一个抽象主机音响设备的新的架构以及支持客户机中的USB 3(xHCI)控制器。
|
||||
|
||||
大部分可用更新都是对VirtualBox 图形化用户界面的改进。一个大的变化就是支持给单个虚拟主机自定义菜单和工具栏,这样很少或者从不使用的选项就可以彻底删除。另外重要的一点是可以在VirtualBox接口内部对虚拟磁盘进行加密,而不依赖于客户机操作系统自身的磁盘加密功能(假设有的话)。
|
||||
大部分可用性更新都是对 VirtualBox 图形化用户界面的改进。一个大的变化就是支持给单个虚拟主机自定义菜单和工具栏,这样很少或者从不使用的选项就可以彻底删除。另外重要的一点是可以在VirtualBox接口内部对虚拟磁盘进行加密,而不依赖于客户机操作系统自身的磁盘加密功能(假设有的话)。
|
||||
|
||||
甲骨文公司提醒由于这是个测试版软件,需要谨慎对待。当然,主界面和客户机系统界面在某方面都可能引起红黑测试版警告。但之前VirtualBox发行版(4.3.26)上创建的Windows 10虚拟机启动和运行都没问题,5.0版本中添加的VirtualBox客户机功能--更好的视频支持,双向复制和粘贴,以及其它功能--安装的时候也没有问题。(更好地支持Windows 10的修复从4.3.18版本后就开始出现)。
|
||||
甲骨文公司提醒由于这是个测试版软件,需要谨慎对待。当然,主界面和客户机系统界面的某个角落打着红黑相间的测试警告标志。但之前VirtualBox发行版(4.3.26)上创建的Windows 10虚拟机启动和运行都没问题,5.0版本中添加的VirtualBox客户机功能--更好的视频支持,双向复制和粘贴,以及其它功能--在安装的时候也没有问题。(从4.3.18版本就改进了对 Windows 10的支持)。
|
||||
|
||||
虽然没有明确指出5.0的最终版什么时候会发布,但是甲骨文公司[鼓励用户][1]在非生产环境中下载和使用测试版,并在[测试版反馈论坛][2]中报告bug文件。
|
||||
虽然没有明确指出5.0的最终版什么时候会发布,但是甲骨文公司[建议用户][1]在非生产环境中下载和使用测试版,并在[测试版反馈论坛][2]中提交bug报告。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
@ -26,7 +27,7 @@ via: http://www.infoworld.com/article/2905098/virtualization/oracle-virtualbox-5
|
||||
|
||||
作者:[Serdar Yegulalp][a]
|
||||
译者:[ictlyh](https://github.com/ictlyh)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
@ -0,0 +1,74 @@
|
||||
Linux Kernel 4.0 Features Live Kernel Patching, PS3 Support
|
||||
================================================================================
|
||||

|
||||
|
||||
**A new stable release of the Linux Kernel [has been announced][1] by Linus Torvalds on the Linux kernel mailing list. **
|
||||
|
||||
Linux 4.0, codenamed ‘Hurr durr I’m a sheep’ — no, really — brings with it a small set of new hardware support, driver improvements, performance tweaks, bug fixes and the like.
|
||||
|
||||
But remarking on the minor-ness of the update, Torvalds’ writes;
|
||||
|
||||
> “Feature-wise, 4.0 doesn’t have all that much special. Much have been made of the new kernel patching infrastructure, but realistically […] we’ve had much bigger changes in other versions. So this is very much a “solid code progress” release.”
|
||||
|
||||
Linus adds that Linux 4.1 is likely to be a ‘bigger release’.
|
||||
|
||||
### New Linux Kernel 4.0 Features ###
|
||||
|
||||
Install Kernel Updates Without Rebooting
|
||||
|
||||
If you’ve ever been put out by the need to reboot your Linux box to finish installing a kernel update you won’t be alone. It’s a minor inconvenience on the desktop, and a major one for servers.
|
||||
|
||||
|
||||
Reboot-free Kernel Updates
|
||||
|
||||
The ability to install/apply security patches to the Linux kernel “live”, without the need to reboot, has been a long-held want of many Linux enthusiasts for years.
|
||||
|
||||
A slew of third-party projects, like [Oracle’s KSplice][2] and Red Hat’s Kpatch, have sought to offer live patching functionality for certain distributions.
|
||||
|
||||
For servers, enterprise and mission-critical use cases where uptime is priority live kernel patching is a pretty big deal.
|
||||
|
||||
The good news is that Linux 4.0 makes having to reboot to complete a kernel update a thing of the past.
|
||||
|
||||
Well, almost.
|
||||
|
||||
The initial groundwork to support reboot-free patching arrives in this latest release, ready for experienced sysadmins to take advantage of in Linux 4.0.
|
||||
|
||||
Desktop Linux distributions should also be able to take advantage of the feature too (though given the complexity involved in configuring the reboot-less functionality on the end-user side it may be a little way off).
|
||||
|
||||
This infrastructure will continue to be refined and improved on over the course of the 4.x series. As it does so I expect we’ll all start to hear more about it.
|
||||
|
||||
#### Other Changes ####
|
||||
|
||||
Although it is considered a small release the latest Linux kernel manages to squeeze in a welcome set of hardware improvements, new drivers and performance tweaks. These include:
|
||||
|
||||
|
||||
- Improvements to Intel ‘Skylake’ platform
|
||||
- Intel Quark SoC support
|
||||
- Various patches to improve Linux running on a Playstation 3
|
||||
- TOpen-source AMD Radeon driver supports DisplayPort Audio
|
||||
- Various misc HID driver tweaks, including Lenovo compact keyboards, Wacom Cintiq 27QHD
|
||||
- Toshiba power settings driver adds USB sleep/charge functionality, rapid charge, sleep w/ music, etc
|
||||
- File System tweaks, including F2FS, BtrfFS, etc
|
||||
|
||||
### Install Linux Kernel 4.0 on Ubuntu ###
|
||||
|
||||
Although classed as stable there is, at present, **no need for desktop users or new-comers to go upgrade**.
|
||||
|
||||
The impatient and adept can take a crack at installing Linux 4.0 in Ubuntu 15.04 Beta by grabbing the appropriate set of packages from [Canonical’s mainline kernel archive][3] or by risking a third-party PPA hosted on Launchpad.
|
||||
|
||||
Ubuntu 15.04 Vivid Vervet is due later this month and will ship with Ubuntu Kernel 3.19 (the Ubuntu kernel is the Linux Kernel plus Ubuntu-specific patches that have not been accepted upstream).
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.omgubuntu.co.uk/2015/04/linux-kernel-4-0-new-features
|
||||
|
||||
作者:[Joey-Elijah Sneddon][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://plus.google.com/117485690627814051450/?rel=author
|
||||
[1]:https://lkml.org/lkml/2015/4/12/178
|
||||
[2]:http://www.omgubuntu.co.uk/2009/10/how-to-install-kernel-updates-without-rebooting
|
||||
[3]:http://kernel.ubuntu.com/~kernel-ppa/mainline/?C=N;O=D
|
||||
@ -1,3 +1,4 @@
|
||||
Translating by weychen
|
||||
10 Top Distributions in Demand to Get Your Dream Job
|
||||
================================================================================
|
||||
We are coming up with a series of five articles which aims at making you aware of the top skills which will help you in getting yours dream job. In this competitive world you can not rely on one skill. You need to have balanced set of skills. There is no measure of a balanced skill set except a few conventions and statistics which changes from time-to-time.
|
||||
@ -140,7 +141,7 @@ That’s all for now. I’ll be coming up with the next article of this series v
|
||||
via: http://www.tecmint.com/top-distributions-in-demand-to-get-your-dream-job/
|
||||
|
||||
作者:[Avishek Kumar][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
译者:[weychen](https://github.com/weychen)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,99 +0,0 @@
|
||||
FSSlc translating
|
||||
|
||||
How to Remember and Restore Running Applications on Next Logon
|
||||
================================================================================
|
||||
You have made some apps running in your Ubuntu and don't want to stop the process, just managed your windows and opened your stuffs needed to work. Then, something else demands your attention or you have battery low in your machine and you have to shut down. No worries. You can have Ubuntu remember all your running applications and restore them the next time you log in.
|
||||
|
||||
Now, to make our Ubuntu remember the applications you have running in our current session and restore them the next time our log in, We will use the dconf-editor. This tool replaces the gconf-editor available in previous versions of Ubuntu but is not available by default. To install the dconf-editor, you need to run sudo apt-get install dconf-editor.
|
||||
|
||||
$ sudo apt-get install dconf-tools
|
||||
|
||||
Once the dconf-editor is installed, you can open dconf-editor from Application Menu. Or you can run it from terminal or run command (alt+f2):
|
||||
|
||||
$ dconf-editor
|
||||
|
||||
In the “dconf Editor” window, click the right arrow next to “org” in the left pane to expand that branch of the tree.
|
||||
|
||||

|
||||
|
||||
Under “org”, click the right arrow next to “gnome.”
|
||||
|
||||

|
||||
|
||||
Under “gnome,” click “gnome-session”. In the right pane, select the “auto-save-session” check box to turn on the option.
|
||||
|
||||

|
||||
|
||||
After you check or tick it, close the “Dconf Editor” by clicking the close button (X) in the upper-left corner of the window which is by default.
|
||||
|
||||

|
||||
|
||||
The next time you log out and log back in, all of your running applications will be restored.
|
||||
|
||||
Hurray, we have successfully configured our Ubuntu 14.04 LTS "Trusty" to remember automatically running applications from our last session.
|
||||
|
||||
Now, on this same tutorial, we'll gonna also learn **how to enable hibernation in our Ubuntu 14.04 LTS**:
|
||||
|
||||
Before getting started, press Ctrl+ALt+T on your keyboard to open the terminal. When it opens, run:
|
||||
|
||||
sudo pm-hibernate
|
||||
|
||||
After your computer turns off, switch it back on. Did your open applications re-open? If hibernate doesn’t work, check if your swap partition is at least as large as your available RAM.
|
||||
|
||||
You can check your Swap Area Partition Size from System Monitor, you can get it from the App Menu or run command in terminal.
|
||||
|
||||
$ gnome-system-monitor
|
||||
|
||||
### Enable Hibernate in System Tray Menu: ###
|
||||
|
||||
The indicator-session was updated to use logind instead of upower. Hibernate is disabled by default in both upower and logind.
|
||||
|
||||
To re-enable hibernate, run the commands below one by one to edit the config file:
|
||||
|
||||
sudo -i
|
||||
|
||||
cd /var/lib/polkit-1/localauthority/50-local.d/
|
||||
|
||||
gedit com.ubuntu.enable-hibernate.pkla
|
||||
|
||||
**Tips: if the config file does not work for you, try another one by changing /var/lib to /etc in the code.**
|
||||
|
||||
Copy and paste below lines into the file and save it.
|
||||
|
||||
[Re-enable hibernate by default in upower]
|
||||
Identity=unix-user:*
|
||||
Action=org.freedesktop.upower.hibernate
|
||||
ResultActive=yes
|
||||
|
||||
[Re-enable hibernate by default in logind]
|
||||
Identity=unix-user:*
|
||||
Action=org.freedesktop.login1.hibernate
|
||||
ResultActive=yes
|
||||
|
||||
Restart your computer and done.
|
||||
|
||||
### Hibernate your laptop when lid is closed: ###
|
||||
|
||||
1.Edit “/etc/systemd/logind.conf” via command:
|
||||
|
||||
$ sudo nano /etc/systemd/logind.conf
|
||||
|
||||
2. Change the line **#HandleLidSwitch=suspend to HandleLidSwitch=hibernate** and save the file.
|
||||
|
||||
3. Run command below or just restart your computer to apply changes:
|
||||
|
||||
$ sudo restart systemd-logind
|
||||
|
||||
That’s it. Enjoy! Now, we have both dconf and hibernation on :) Now, your Ubuntu will completely remember your opened apps and stuffs.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/ubuntu-how-to/remember-running-applications-ubuntu/
|
||||
|
||||
作者:[Arun Pyasi][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://linoxide.com/author/arunp/
|
||||
@ -1,3 +1,4 @@
|
||||
wangjiezhe translating...
|
||||
7 Command Line Tools for Browsing Websites and Downloading Files in Linux
|
||||
================================================================================
|
||||
In the last article, we have covered few useful tools like ‘rTorrent‘, ‘wget‘, ‘cURL‘, ‘w3m‘, and ‘Elinks‘. We got lots of response to cover few other tools of same genre, if you’ve missed the first part you can go through it..
|
||||
@ -137,7 +138,7 @@ That’s all for now. I’ll be here again with another interesting topic you pe
|
||||
via: http://www.tecmint.com/command-line-web-browser-download-file-in-linux/
|
||||
|
||||
作者:[Avishek Kumar][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
译者:[wangjiezhe](https://github.com/wangjiezhe)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,145 +0,0 @@
|
||||
wangjiezhe translating...
|
||||
What is a good alternative to wget or curl on Linux
|
||||
================================================================================
|
||||
If you often need to access a web server non-interactively in a terminal environment (e.g., download a file from the web, or test REST-ful web service APIs), chances are that wget or curl is your go-to tool. With extensive command-line options, both of these tools can handle a variety of non-interactive web access use cases (examples [here][1], [here][2] and [here][3]). However, even powerful tools like these are only as good as your knowledge of how to use them. Unless you are well versed in the nitty and gritty details of their syntax, these tools are nothing more than simple web downloaders for you.
|
||||
|
||||
Billed as a "curl-like tool for humans," [HTTPie][4] is designed to improve on wget and curl in terms of usability. Its main goal is to make command-line interaction of a web server as human-friendly as possible. For that, HTTPie comes with expressive, yet very simple and intuitive syntax. It also displays responses in colorized formats for readability, and offers nice goodies like excellent JSON support and persistent sessions to streamline your workflows.
|
||||
|
||||
I know some of you will be skeptical about replacing a ubiquitously available, perfectly good tool such as wget or curl with totally unheard of software. This view has merit especially if you are a system admin who works with many different hardware boxes. For developers or end-users, however, I would say it's all about productivity. If I've found a user-friendly alternative of a tool, I don't see any problem adopting the easy to use version in my work environment to save my precious time. No need to be loyal and religious about what's being replaced. After all, choice is the best thing about Linux.
|
||||
|
||||
In this post, let me review HTTPie, and show you what I mean by HTTPie being a user-friendly alternative of wget and curl.
|
||||
|
||||
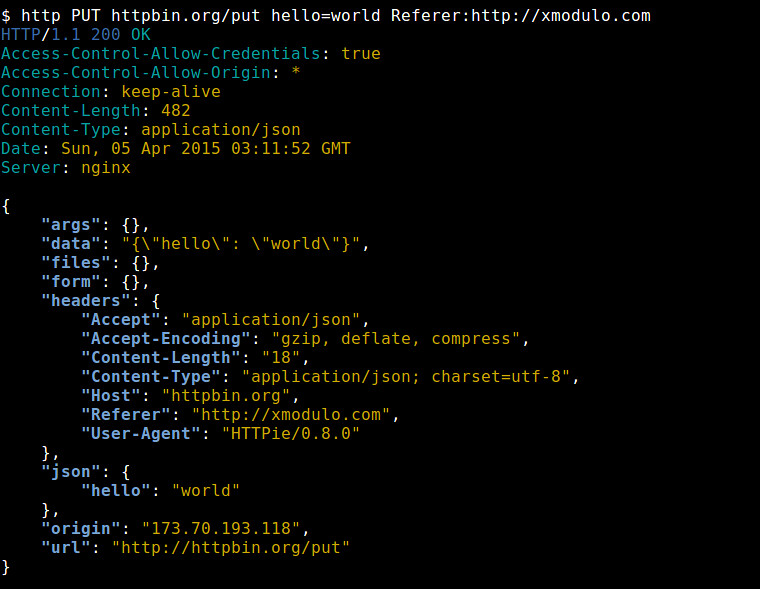
|
||||
|
||||
### Install HTTPie on Linux ###
|
||||
|
||||
HTTPie is written in Python, so you can install it pretty much everywhere (Linux, MacOSX, Windows). Even better, it comes as a prebuilt package on most Linux distributions.
|
||||
|
||||
#### Debian, Ubuntu or Linux Mint: ####
|
||||
|
||||
$ sudo apt-get install httpie
|
||||
|
||||
#### Fedora: ####
|
||||
|
||||
$ sudo yum install httpie
|
||||
|
||||
#### CentOS/RHEL: ####
|
||||
|
||||
First, enable [EPEL repository][5] and then run:
|
||||
|
||||
$ sudo yum install httpie
|
||||
|
||||
For any Linux distribution, an alternative installation method is to use [pip][6].
|
||||
|
||||
$ sudo pip install --upgrade httpie
|
||||
|
||||
### HTTPie Examples ###
|
||||
|
||||
Once you install HTTPie, you can invoke it by typing http command. In the rest of this article, let me show several useful examples of http command.
|
||||
|
||||
#### Example 1: Custom Headers ####
|
||||
|
||||
You can set custom headers in the format of <header:value>. For example, let's send an HTTP GET request to www.test.com, with custom user-agent and referer, as well as a custom header (e.g., MyParam).
|
||||
|
||||
$ http www.test.com User-Agent:Xmodulo/1.0 Referer:http://xmodulo.com MyParam:Foo
|
||||
|
||||
Note that when HTTP GET method is used, you don't need to specify any HTTP method.
|
||||
|
||||
The HTTP request will look like:
|
||||
|
||||
GET / HTTP/1.1
|
||||
Host: www.test.com
|
||||
Accept: */*
|
||||
Referer: http://xmodulo.com
|
||||
Accept-Encoding: gzip, deflate, compress
|
||||
MyParam: Foo
|
||||
User-Agent: Xmodulo/1.0
|
||||
|
||||
#### Example 2: Download a File ####
|
||||
|
||||
You can use http as a file downloader tool. You will need to redirect output to a file as follows.
|
||||
|
||||
$ http www.test.com/my_file.zip > my_file.zip
|
||||
|
||||
Alternatively:
|
||||
|
||||
$ http --download www.test.com/my_file.zip
|
||||
|
||||
#### Example 3: Custom HTTP Method ####
|
||||
|
||||
Besides the default GET method, you can use other methods (e.g., PUT, POST, HEAD). For example, to sent an HTTP PUT request:
|
||||
|
||||
$ http PUT www.test.com name='Dan Nanni' email=dan@email.com
|
||||
|
||||
#### Example 4: Submit a Form ####
|
||||
|
||||
Submitting a form with http command is as easy as:
|
||||
|
||||
$ http -f POST www.test.com name='Dan Nanni' comment='Hi there'
|
||||
|
||||
The '-f' option lets http command serialize data fields, and set 'Content-Type' to "application/x-www-form-urlencoded; charset=utf-8".
|
||||
|
||||
The HTTP POST request will look like:
|
||||
|
||||
POST / HTTP/1.1
|
||||
Host: www.test.com
|
||||
Content-Length: 31
|
||||
Content-Type: application/x-www-form-urlencoded; charset=utf-8
|
||||
Accept-Encoding: gzip, deflate, compress
|
||||
Accept: */*
|
||||
User-Agent: HTTPie/0.8.0
|
||||
|
||||
name=Dan+Nanni&comment=Hi+there
|
||||
|
||||
#### Example 5: JSON Support ####
|
||||
|
||||
HTTPie comes with built-in JSON support, which is nice considering its growing popularity as a data exchange format. In fact, the default content-type used by HTTPie is JSON. So if you send data fields without specifying any content-type, they will automatically be serialized as a JSON object.
|
||||
|
||||
$ http POST www.test.com name='Dan Nanni' comment='Hi there'
|
||||
|
||||
The HTTP POST request will look like:
|
||||
|
||||
POST / HTTP/1.1
|
||||
Host: www.test.com
|
||||
Content-Length: 44
|
||||
Content-Type: application/json; charset=utf-8
|
||||
Accept-Encoding: gzip, deflate, compress
|
||||
Accept: application/json
|
||||
User-Agent: HTTPie/0.8.0
|
||||
|
||||
{"name": "Dan Nanni", "comment": "Hi there"}
|
||||
|
||||
#### Example 6: Input Redirect ####
|
||||
|
||||
Another nice user-friendly feature of HTTPie is input redirection, where you can feed an HTTP request body with buffered data. For example, you can do things like:
|
||||
|
||||
$ http POST api.test.com/db/lookup < my_info.json
|
||||
|
||||
or:
|
||||
|
||||
$ echo '{"name": "Dan Nanni"}' | http POST api.test.com/db/lookup
|
||||
|
||||
### Conclusion ###
|
||||
|
||||
In this article, I introduce to you HTTPie, a possible alternative to wget or curl. Besides these simple examples presented here, you can find a lot of interesting use cases of HTTPie at the [official site][7]. Again, a powerful tool is only as good as your knowledge about the tool. Personally I am sold on HTTPie, as I was looking for a way to test complicated web APIs more easily.
|
||||
|
||||
What's your thought?
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/wget-curl-alternative-linux.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[wangjiezhe](https://github.com/wangjiezhe)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/nanni
|
||||
[1]:http://xmodulo.com/how-to-download-multiple-files-with-wget.html
|
||||
[2]:http://xmodulo.com/how-to-use-custom-http-headers-with-wget.html
|
||||
[3]:http://ask.xmodulo.com/custom-http-header-curl.html
|
||||
[4]:https://github.com/jakubroztocil/httpie
|
||||
[5]:http://xmodulo.com/how-to-set-up-epel-repository-on-centos.html
|
||||
[6]:http://ask.xmodulo.com/install-pip-linux.html
|
||||
[7]:https://github.com/jakubroztocil/httpie
|
||||
@ -0,0 +1,105 @@
|
||||
A Walk Through Some Important Docker Commands
|
||||
================================================================================
|
||||
Hi everyone today we'll learn some important Docker Commands that you'll need to learn before you go with Docker. Docker is an Open Source project that provides an open platform to pack, ship and run any application as a lightweight container. It has no boundaries of Language support, Frameworks or packaging system and can be run anywhere, anytime from a small home computers to high-end servers. It makes them great building blocks for deploying and scaling web apps, databases, and back-end services without depending on a particular stack or provider.
|
||||
|
||||
Docker commands are easy to learn and easy to implement or take into practice. Here are some easy Docker commands you'll need to know to run Docker and fully utilize it.
|
||||
|
||||
### 1. Pulling a Docker Image ###
|
||||
|
||||
First of all, we'll need to pull a docker image to get started cause containers are built using Docker Images. We can get the required docker image from the Docker Registry Hub. Before we pull any image using pull command, we'll need to protect our system as there is identified a malicious issue with pull command. To protect our system from this issue, we'll need to add **127.0.0.1 index.docker.io** into /etc/hosts entry. We can do using our favorite text editor.
|
||||
|
||||
# nano /etc/hosts
|
||||
|
||||
Now, add the following lines into it and then save and exit.
|
||||
|
||||
127.0.0.1 index.docker.io
|
||||
|
||||

|
||||
|
||||
To pull a docker image, we'll need to run the following command.
|
||||
|
||||
# docker pull registry.hub.docker.com/busybox
|
||||
|
||||

|
||||
|
||||
We can check whether any Docker image is available in our local host for the use or not.
|
||||
|
||||
# docker images
|
||||
|
||||

|
||||
|
||||
### 2. Running a Docker Container ###
|
||||
|
||||
Now, after we have successfully pulled a required or desired Docker image. We'll surely want to run that Docker image. We can run a docker container out of the image using docker run command. We have several options and flags to run a docker container on the top of the Docker image. To run a docker image and to get into the container we'll use -t and -i flag as shown below.
|
||||
|
||||
# docker run -it busybox
|
||||
|
||||

|
||||
|
||||
From the above command, we'll get entered into the container and can access its content via the interactive shell. We can press **Ctrl-D** in order to exit from the shell access.
|
||||
|
||||
Now, to run the container in background, we'll detach the shell using -d flag as shown below.
|
||||
|
||||
# docker run -itd busybox
|
||||
|
||||

|
||||
|
||||
If we want to attach into a running container, we can use attach command with the container id. The container id can be fetched using the command **docker ps** .
|
||||
|
||||
# docker attach <container id>
|
||||
|
||||

|
||||
|
||||
### 3. Checking Containers ###
|
||||
|
||||
It is very easy to check the log whether the container is running or not. We can use the following command to check whether there is any docker container running in the real time or not using the following command.
|
||||
|
||||
# docker ps
|
||||
|
||||
Now, to check logs about the running or past running containers we'll need to run the following command.
|
||||
|
||||
# docker ps -a
|
||||
|
||||

|
||||
|
||||
### 4. Inspecting a Docker Container ###
|
||||
|
||||
We can check every information about a Docker Container using the inspect command.
|
||||
|
||||
# docker inspect <container id>
|
||||
|
||||

|
||||
|
||||
### 5. Killing and Deleting Command ###
|
||||
|
||||
We can kill or stop process or docker containers using its docker id as shown below.
|
||||
|
||||
# docker stop <container id>
|
||||
|
||||
To stop every containers running, we'll need to run the following command.
|
||||
|
||||
# docker kill $(docker ps -q)
|
||||
|
||||
Now, if we wanna remove a docker image, run the below command.
|
||||
|
||||
# docker rm <container id>
|
||||
|
||||
If we wanna remove all the docker images at once, we can run the below.
|
||||
|
||||
# docker rm $(docker ps -aq)
|
||||
|
||||
### Conclusion ###
|
||||
|
||||
These docker commands are highly essential to learn to fully utilize and use Docker. Docker gets too simple with these commands providing end users an easy platform for computing. It is extremely easy for anyone to learn about Docker commands with this above tutorial. If you have any questions, suggestions, feedback please write them in the comment box below so that we can improve and update our contents. Thank you ! Enjoy :-)
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/linux-how-to/important-docker-commands/
|
||||
|
||||
作者:[Arun Pyasi][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://linoxide.com/author/arunp/
|
||||
@ -0,0 +1,144 @@
|
||||
Elementary OS 0.3 Freya Screenshots - Download and Install Guide
|
||||
================================================================================
|
||||
Elementary OS is a light weight Ubuntu based operating system which is getting wide spread popularity. It has three versions released to date whereas fourth version is decided to be developed based on upcoming Ubuntu 16.04.
|
||||
|
||||
- **Jupiter (0.1)**: It was the first stable version of Elementary OS based on Ubuntu 10.10 and released on March 2011.
|
||||
- **Luna (0.2)**: Second stable version of Elementary OS based on Ubuntu 12.04 and released on November 2012.
|
||||
- **Freya (0.3)**: Third stable version of Elementary OS based on Ubuntu 14.04 and released on 8th February 2015.
|
||||
- **Loki (0.4)**: Fourth upcoming version of Elementary OS is planned to be based on Ubuntu 16.04 it will get updates till 2021.
|
||||
|
||||
Freya is the latest version (0.3) of Elementary OS available now, initially it was given the name ISIS but it was later changed to avoid any sort of association with a terrorist group named alike. Freya has some very nice preloaded applications.
|
||||
|
||||
### Salient Features ###
|
||||
|
||||
Here are some but not all of the features of Elementary OS 0.3.
|
||||
|
||||
- Better interactive notifications along with notification setting pane including a system-wide “Do Not Disturb” mode
|
||||
- Latest version of Elementary OS provides a better emoji support & drop-in replacements for Microsoft Core fonts for the web applications
|
||||
- Privacy Mode is a new firewall tool which is easy to use and helps protect the computer from harmful scripts and applications
|
||||
- Unified login and lock screens
|
||||
- Applications menu with and improved look and functionality including quicklist actions, drag-and-drop from search, and support for quick math calculations
|
||||
- Multitasking view is redesigned to provide more app-focused utility
|
||||
- Updated software stack (Linux 3.16, Gtk 3.14, and Vala 0.26) for better support and enhanced functionality of latest developed applications
|
||||
- Unified extensible firmware interface (UEFI) support
|
||||
- WiFi connectivity made easier through new captive portal assistant
|
||||
|
||||
### Download 64 bit & 32 bit Version ###
|
||||
|
||||
- [Elementary OS Freya 64 bit][1]
|
||||
- [Elementary OS Freya 32 bit][2]
|
||||
|
||||
### Installing Elementary OS 0.3 (Freya) ###
|
||||
|
||||
Download the ISO file of Elementary OS 0.3 and flash it on a bootable USB drive or to a DVD/CD. Source is available for both 32-bit and 64-bit architectures. Once the computer is booted with the Elementary OS ISO file, there are two options available, either to try without installing or install Elementary OS on the computer, choose the second option. Elementary OS can also be installed along with an already installed operating system, turning it into a dual boot machine.
|
||||
|
||||

|
||||
|
||||
System requirements and available resources are checked before proceeding further. Click continue if your system has enough resources.
|
||||
|
||||

|
||||
|
||||
Installation wizard then provides various installation types. Opt for the option best suits you, normally, first option is chosen by most i.e. “Erase disk and install Elementary”. With this option make sure that your data is backed up properly because the disk (partition) will be erased and all data will be lost.
|
||||
|
||||

|
||||
|
||||
A dialog box shows the list of disk partitions being formatted and used by the Elementary OS, after ensuring data integrity click continue.
|
||||
|
||||

|
||||
|
||||
Choose your location for time zone selection and click continue.
|
||||
|
||||

|
||||
|
||||
Choose your language and click continue.
|
||||
|
||||

|
||||
|
||||
Fill in your information and choose a strong root/administrator password and click continue.
|
||||
|
||||

|
||||
|
||||
Core installation process starts once the personal information is provided, details of components being installed will be flashing on a little dialogue box along with the progress bar.
|
||||
|
||||

|
||||
|
||||
Congratulation! Installation is complete for your latest Elementary OS 0.3 (Freya). A restart is required to update and finalize registries and configurations.
|
||||
|
||||

|
||||
|
||||
At start up the Elementary OS logo shows its elegance and then password protected administrator login and guest session options will appear. Guest section has pretty limited features and has no installation privileges.
|
||||
|
||||

|
||||
|
||||
Here is the first look of the newly installed Elementary OS 0.3.
|
||||
|
||||

|
||||
|
||||
### Customizing Desktop ###
|
||||
|
||||
While Elementary OS 0.3 is best known for their light weight and better looks, everybody has a unique esthetic sense and computer usage habits. Desktop reflects a personalized view of any computer user. Like other operating systems Elementary OS 0.3 also provides various options to customize our desktop through wallpapers, font sizes, themes etc.
|
||||
|
||||
For basic customization, click on Applications > System Settings > Desktop
|
||||
|
||||
We can change wallpapers, dock and make use of hot corners of the desktop.
|
||||
|
||||
Very few wallpapers are provided by default, more can be downloaded from the internet or transferred to your own camera.
|
||||
|
||||

|
||||
|
||||
The real beauty of Elementary OS lies in its elegant Dock panel. With no icons allowed at desktop, a set of application icons at the dock panel enhance the look and provide a quick way to lunch frequently used applications.
|
||||
|
||||

|
||||
|
||||
Users can use the corners of the desktop for customary purposes.
|
||||
|
||||

|
||||
|
||||
Advanced customization can be achieved through the installation of elementary tweaks.
|
||||
|
||||
Add stable Personal Package Archive (PPA) to Advanced Package Tool (APT) repository using the following command.
|
||||
|
||||
sudo add-apt-repository ppa:mpstark/elementary-tweaks-daily
|
||||
|
||||

|
||||
|
||||
Once the package has been added to the repository we need to update the repository using following command
|
||||
|
||||
sudo apt-get update
|
||||
|
||||

|
||||
|
||||
After updating the repository we are ready to install inkscape which is accomplished using the following command
|
||||
|
||||
sudo apt-get install elementary-tweaks
|
||||
|
||||

|
||||
|
||||
We can see an addition of Tweaks option under Applications > System Settings under the Personal section. It now provides us more options to customize our desktop view.
|
||||
|
||||

|
||||
|
||||
For further customizations we also install gnome tweak tool for example unlocking the desktop.
|
||||
|
||||
sudo apt-get install gnome-tweak-tool
|
||||
|
||||

|
||||
|
||||
### Summary ###
|
||||
|
||||
Elementary OS is closely related to Ubuntu distro of Linux and its pros and cons are pretty much similar too. Elementary OS is lightweight, elegant in look and feel, rapidly maturing. It is potentially an alternative for both Windows and OS X operating systems. The latest available Elementary OS 0.3 (Freya) is getting very popular with a better feature base. For further reading, latest updates and downloads please visit the official [website][1].
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/ubuntu-how-to/elementary-os-0-3-freya-install-guide/
|
||||
|
||||
作者:[Aun Raza][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://linoxide.com/author/arunrz/
|
||||
[1]:http://sourceforge.net/projects/elementaryos/files/stable/elementaryos-freya-amd64.20150411.iso/download
|
||||
[2]:http://sourceforge.net/projects/elementaryos/files/stable/elementaryos-freya-i386.20150411.iso/download
|
||||
[3]:http://elementary.io/
|
||||
@ -0,0 +1,174 @@
|
||||
How to Show Dialog Box from Bash Shell Script with Examples
|
||||
================================================================================
|
||||
This tutorial will give couple of examples on how to use utilities like zenity and whiptail in your Bash shell script to provide message / dialog box . With these utilities your script will be able to inform user about the current state of execution, or give an ability to interact. Difference between these two utilities is the way they are displaying message box or dialog. Zenity uses GTK toolkit for creating graphical user interfaces, while whiptail creates message boxes inside terminal window.
|
||||
|
||||
### Zenity Tool ###
|
||||
|
||||
To install zenity on Ubuntu run:
|
||||
|
||||
sudo apt-get install zenity
|
||||
|
||||
Since commands for creating message boxes or dialogs with zenity are pretty self explanatory, we will provide you with couple of examples.
|
||||
|
||||
### Creating information box ###
|
||||
|
||||
zenity --info --title "Information Box" --text "This should be information" --width=300 --height=200
|
||||
|
||||

|
||||
|
||||
Creating Yes/No dialog
|
||||
|
||||
zenity --question --text "Do you want this?" --ok-label "Yeah" --cancel-label="Nope"
|
||||
|
||||

|
||||
|
||||
Creating entry box and storing value in variable
|
||||
|
||||
a=$(zenity --entry --title "Entry box" --text "Please enter the value" --width=300 --height=200)
|
||||
echo $a
|
||||
|
||||

|
||||
|
||||
After entering it, value will be stored in $a variable.
|
||||
|
||||
Here is the working example which takes user's first name, last name and age and displays it.
|
||||
|
||||
#!/bin/bash
|
||||
#
|
||||
# This script will ask for couple of parameters
|
||||
# and then continue to work depending on entered values
|
||||
#
|
||||
|
||||
# Giving the option to user
|
||||
zenity --question --text "Do you want to continue?"
|
||||
|
||||
# Checking if user wants to proceed
|
||||
[ $? -eq 0 ] || exit 1
|
||||
|
||||
# Letting user input some values
|
||||
FIRSTNAME=$(zenity --entry --title "Entry box" --text "Please, enter your first name." --width=300 --height=150)
|
||||
LASTNAME=$(zenity --entry --title "Entry box" --text "Please, enter your last name." --width=300 --height=150)
|
||||
AGE=$(zenity --entry --title "Entry box" --text "Please, enter your age." --width=300 --height=150)
|
||||
|
||||
# Displaying entered values in information box
|
||||
zenity --info --title "Information" --text "You are ${FIRSTNAME} ${LASTNAME} and you are ${AGE}(s) old." --width=300 --height=100
|
||||
|
||||
Here are the screenshots of previous script.
|
||||
|
||||

|
||||
|
||||
First box
|
||||
|
||||

|
||||
|
||||
Entry box
|
||||
|
||||

|
||||
|
||||
Entry box
|
||||
|
||||

|
||||
|
||||
Entry box
|
||||
|
||||

|
||||
|
||||
Information box
|
||||
|
||||
Don't forget refer some of the useful [zenity options][1] that might help you.
|
||||
|
||||
### Whiptail Tool ###
|
||||
|
||||
To install whiptail on Ubuntu run
|
||||
|
||||
sudo apt-get install whiptail
|
||||
|
||||
Commands for creating message box/dialog with whiptail are also self explanatory, so we will provide you with just couple of basic examples.
|
||||
|
||||
### Creating message box ###
|
||||
|
||||
whiptail --msgbox "This is a message" 10 40
|
||||
|
||||

|
||||
|
||||
### Creating Yes/No dialog ###
|
||||
|
||||
whiptail --yes-button "Yeah" --no-button "Nope" --title "Choose the answer" --yesno "Will you choose yes?" 10 30
|
||||
|
||||

|
||||
|
||||
### Creating entry box with default value ###
|
||||
|
||||
whiptail --inputbox "Enter your number please." 10 30 "10"
|
||||
|
||||

|
||||
|
||||
One thing to be aware of when trying to use entered value is that whiptail uses stdout for displaying dialog, and stderr for value output. That way, if you use var=$(...) you wont see dialog box at all, and wont get the entered value. Solution is to switch stdout and stderr. To do that just add **3>&1 1>&2 2>&3** at the end of the whiptail command. Same would be with any whiptail command which you want to use to get some entered value.
|
||||
|
||||
### Creating menu dialog ###
|
||||
|
||||
whiptail --menu "This is a menu. Choose an option:" 20 50 10 1 "first" 2 "second" 3 "third"
|
||||
|
||||

|
||||
|
||||
Here is a **shell script** that asks user to enter a path to a folder and then outputs it's size.
|
||||
|
||||
#!/bin/bash
|
||||
#
|
||||
#
|
||||
|
||||
# Since whiptail has to use stdout to display dialog, entered value will
|
||||
# be stored in stderr. To switch them and get the value to stdout you must
|
||||
# use 3>&1 1>&2 2>&3
|
||||
FOLDER_PATH=$(whiptail --title "Get the size of folder" \
|
||||
--inputbox "Enter folder path:" \
|
||||
10 30 \
|
||||
"/home" \
|
||||
3>&1 1>&2 2>&3)
|
||||
|
||||
if [ -d $FOLDER_PATH ]
|
||||
then
|
||||
size=$(du -hs "$FOLDER_PATH" | awk '{print $1}')
|
||||
whiptail --title "Information" \
|
||||
--msgbox "Size of ${FOLDER_PATH} is ${size}" \
|
||||
10 40
|
||||
elif [ -f $FOLDER_PATH ]
|
||||
then
|
||||
whiptail --title "Warning!!!" \
|
||||
--msgbox "The path you entered is a path to a file not a folder!" \
|
||||
10 40
|
||||
else
|
||||
whiptail --title "Error!!!"
|
||||
--msgbox "Path you entered is not recognized. Please try again" \
|
||||
10 40
|
||||
fi
|
||||
|
||||
Here are the screenshots from previous example:
|
||||
|
||||

|
||||
|
||||
Entry box
|
||||
|
||||

|
||||
|
||||
Information box
|
||||
|
||||
If you are working in terminal , [manual pages][2] are always available.
|
||||
|
||||
### Conclusion ###
|
||||
|
||||
Choosing the right tool for displaying dialogs will depend on whether you expect your script to be run on desktop machine or server machine. Desktop machine users mostly use window environment and will possibly be able to run the script and interact with appearing windows. However, if you are expecting that the user is someone on server machine, you might want to play it safe and use whiptail or any other utility that will display dialogs in plain terminal window.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/linux-shell-script/bash-shell-script-show-dialog-box/
|
||||
|
||||
作者:[Ilija Lazarevic][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://linoxide.com/author/ilijala/
|
||||
[1]:https://help.gnome.org/users/zenity/stable/
|
||||
[2]:http://linux.die.net/man/1/whiptail
|
||||
@ -0,0 +1,178 @@
|
||||
How to manage remote MySQL databases on Linux VPS using a GUI tool
|
||||
================================================================================
|
||||
If you need to run a MySQL server on a remote [VPS instance][1], how will you manage databases hosted by the server remotely? Perhaps web-based database administration tools such as [phpMyAdmin][2] or [Adminer][3] will first come to mind. These web-based management tools require a backend web server and PHP engine up and running. However, if your VPS instance is used as a standalone database server (e.g., for a multi-tier app), provisioning a whole LAMP stack for occasional database management is a waste of VPS resource. Worse, the LAMP stack with an additional HTTP port can be a source of security vulnerabilities of your VPS.
|
||||
|
||||
Alternatively, you can turn to a native MySQL client running on a client host. Of course a pure command-line MySQL client (mysql-client) can be your default choice if nothing else. But the capabilities of the command-line client are limited, so it is not suitable for production-level database administration such as visual SQL development, performance tuning, schema validation, etc. If you are looking for full-blown MySQL administration features, a MySQL GUI tool will meet your requirements better.
|
||||
|
||||
### What is MySQL Workbench? ###
|
||||
|
||||
Developed as an integrated database tool environment by Oracle, [MySQL Workbench][4] is more than a simple MySQL client. In a nutshell, Workbench is a cross-platform (e.g., Linux, MacOS X, Windows) GUI tool for database design, development and administration. The Community Edition of MySQL Workbench is available for free under the GPL. As a database administrator, you can use Workbench to configure MySQL server, manage MySQL users, perform database backup and recovery, and monitor database health, all in GUI-based user-frienly environment.
|
||||
|
||||
In this tutorial, let's review how to install and use MySQL Workbench on Linux.
|
||||
|
||||
### Install MySQL Workbench on Linux ###
|
||||
|
||||
To set up remote database administration environment, grab any desktop Linux machine where you will be running MySQL Workbench. While some Linux distributions (e.g., Debian/Ubuntu) carry MySQL Workbench in their repositories, it is a good idea to install it from the official repositories, as they offer the latest version. Here is how to set up the official Workbench repository and install Workbench from it.
|
||||
|
||||
#### Debian-based Desktop (Debia, Ubuntu, Mint): ####
|
||||
|
||||
Go to the [official website][5]. Download and install the DEB file for the repository. Choose one that matches with your environment.
|
||||
|
||||
For example, on Ubuntu 14.10:
|
||||
|
||||
$ wget http://dev.mysql.com/get/mysql-apt-config_0.3.4-2ubuntu14.10_all.deb
|
||||
$ sudo dpkg -i mysql-apt-config_0.3.4-2ubuntu14.10_all.deb
|
||||
|
||||
on Debian 7:
|
||||
|
||||
$ wget http://dev.mysql.com/get/mysql-apt-config_0.3.3-1debian7_all.deb
|
||||
$ sudo dpkg -i mysql-apt-config_0.3.3-1debian7_all.deb
|
||||
|
||||
When installing the DEB file, you will see the following package configuration menu, and be asked to choose MySQL product to configure.
|
||||
|
||||
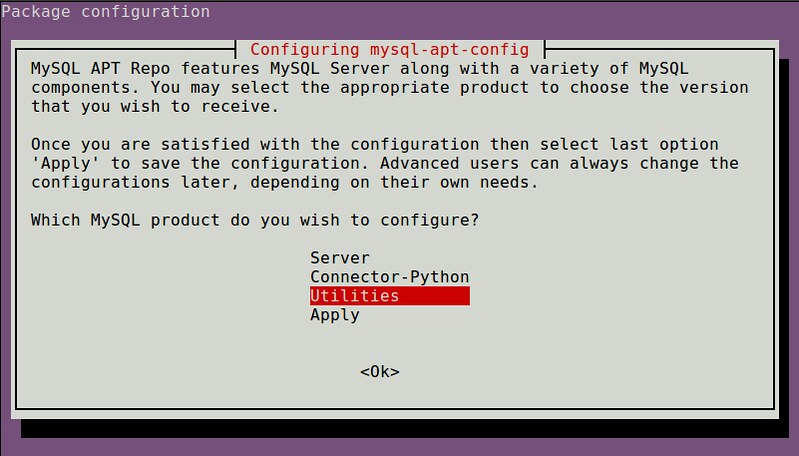
|
||||
|
||||
Choose "Utilities". Once you are done with configuration, choose "Apply" to save it.
|
||||
|
||||
Finally, update package index, and install Workbench.
|
||||
|
||||
$ sudo apt-get update
|
||||
$ sudo apt-get install mysql-workbench
|
||||
|
||||
#### Red Hat-based Desktop (CentOS, Fedora, RHEL): ####
|
||||
|
||||
Go to the [official website][6]. Download and install the RPM repository package for your Linux evironment.
|
||||
|
||||
For example, on CentOS 7:
|
||||
|
||||
$ wget http://dev.mysql.com/get/mysql-community-release-el7-5.noarch.rpm
|
||||
$ sudo yum localinstall mysql-community-release-el7-5.noarch.rpm
|
||||
|
||||
on Fedora 21:
|
||||
|
||||
$ wget http://dev.mysql.com/get/mysql-community-release-fc21-6.noarch.rpm
|
||||
$ sudo yum localinstall mysql-community-release-fc21-6.noarch.rpm
|
||||
|
||||
Verify that "MySQL Tools Community" repository has been set up.
|
||||
|
||||
$ yum repolis enabled
|
||||
|
||||

|
||||
|
||||
Go ahead and install Workbench.
|
||||
|
||||
$ sudo yum install mysql-workbench-community
|
||||
|
||||
### Set up a Secure Remote Database Connection ###
|
||||
|
||||
The next step is to set up a remote connection to your MySQL server running on a VPS. Of course you can connect directly to the remote MySQL server from Workbench GUI (after [enabling remote access][7] in the database server). However, it is a huge security risk to do so, as someone can easily eavesdrop on database access traffic, and a publicly-open MySQL port can be another attack vector.
|
||||
|
||||
A better approach is to disable remote access of MySQL server (i.e., only allow access from 127.0.0.1 of a VPS). Then set up an SSH tunnel between a local client machine and a remote VPS, so that MySQL traffic can be securely relayed via their loopback interfaces. Compared to setting up SSL-based encrypted connections, configuring SSH tunneling requires little effort as it only requires SSH server, which is already deployed on most VPS instances.
|
||||
|
||||
Let's see how we can set up an SSH tunnel for MySQL Workbench.
|
||||
|
||||
In this setup, you don't need to enable remote access of a MySQL server.
|
||||
|
||||
On a local client host where MySQL Workbench will be running, type the following command. Replace 'user' and 'remote_vps' with your own info.
|
||||
|
||||
$ ssh user@remote_vps -L 3306:127.0.0.1:3306 -N
|
||||
|
||||
You will be asked to type an SSH password for your VPS. Once you successfully log in to the VPS, an SSH tunnel will be established between port 3306 of local host and port 3306 of a remote VPS. Note that you won't see any message in the foreground.
|
||||
|
||||
Optionally, you can set the SSH tunnel running in the background. For that, press Ctrl+Z to stop the command, type bg and press ENTER.
|
||||
|
||||

|
||||
|
||||
The SSH tunnel will now be running in the background.
|
||||
|
||||
### Manage a Remote MySQL Server with MySQL Workbench ###
|
||||
|
||||
With an SSH tunnel established, you are ready to connect to a remote MySQL server from MySQL Workbench.
|
||||
|
||||
Launch Workbench by typing:
|
||||
|
||||
$ mysql-workbench
|
||||
|
||||

|
||||
|
||||
Click on the plus icon at the top of the Workbench screen to create a new database connection. Fill in connection information as follows.
|
||||
|
||||
- **Connection Name**: any description (e.g., My remote VPS database)
|
||||
- **Hostname**: 127.0.0.1
|
||||
- **Port**: 3306
|
||||
- **Username**: MySQL username (e.g., root)
|
||||
|
||||
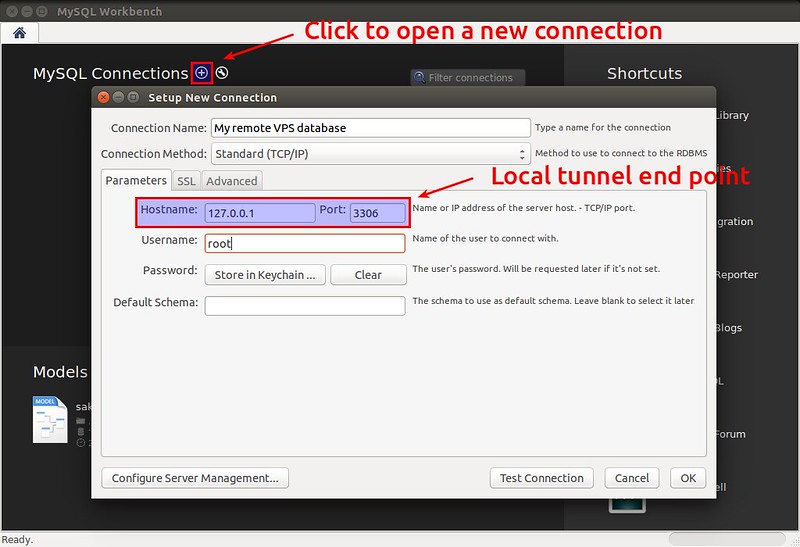
|
||||
|
||||
Note that since the tunnel's local endpoint is 127.0.0.1:3306, the hostname field must be 127.0.0.1, not the IP address/hostname of a remote VPS.
|
||||
|
||||
Once you set up a new database connection, you will see a new box for the connection appear on Workbench window. Click on the box to actually establish a connection to a remote MySQL server.
|
||||
|
||||

|
||||
|
||||
Once you are logged in to the MySQL server, you will see various administrative tasks in the left-side panel. Let's review some of common administrative tasks.
|
||||
|
||||
#### MySQL Server Status ####
|
||||
|
||||
This menus shows real-time dashboard of database server resource usage (e.g., traffic, connections, read/write).
|
||||
|
||||

|
||||
|
||||
#### Client Connections ####
|
||||
|
||||
The total number of client connections is a critical resource to monitor. This menu shows detailed information of individual client connections.
|
||||
|
||||

|
||||
|
||||
#### Users and Privileges ####
|
||||
|
||||
This menu allows you to manage MySQL users, including their resource limits and privileges.
|
||||
|
||||

|
||||
|
||||
#### MySQL Server Administration ####
|
||||
|
||||
You can start or stop a MySQL server, and examine its server logs.
|
||||
|
||||

|
||||
|
||||
#### Database Schema Management ####
|
||||
|
||||
You can view, change or inspect database schema visually. For that, choose and right-click on any database or table under "Schemas" heading.
|
||||
|
||||
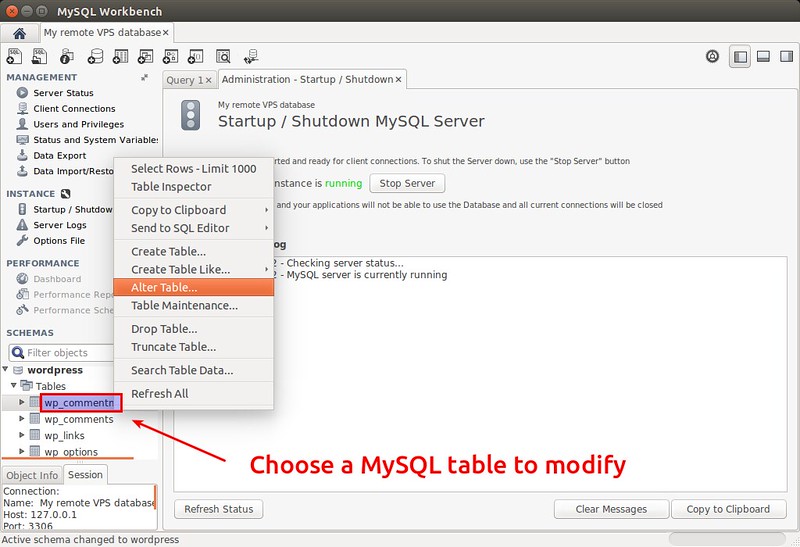
|
||||
|
||||

|
||||
|
||||
#### Database Query ####
|
||||
|
||||
You can execute any arbitrary query (as long as your login privilege allows), and inspect its result.
|
||||
|
||||
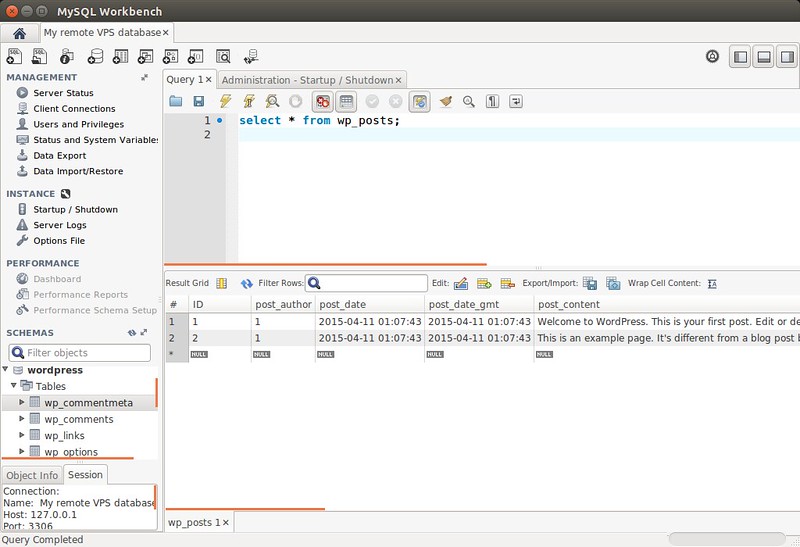
|
||||
|
||||
Note that performance statistics and reports are available for MySQL server 5.6 and higher. For 5.5 and lower, the performance section will be grayed out.
|
||||
|
||||
### Conclusion ###
|
||||
|
||||
The clean and intuitive tabbed interface, comprehensive feature sets, and open-source licensing make MySQL Workbench one of the best visual database design and administration tools out there. One known downside of Workbench is its performance. I notice that Workbench sometimes gets sluggish while running queries on a busy server. Despite its less than stellar performance, I still consider MySQL Workbench an essential tool for any professional MySQL database administrator and designer.
|
||||
|
||||
Have you ever used Workbench in your work environment? Or do you recommend any other GUI tool? Feel free to share your experience.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/remote-mysql-databases-gui-tool.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/nanni
|
||||
[1]:http://xmodulo.com/go/digitalocean
|
||||
[2]:http://ask.xmodulo.com/install-phpmyadmin-centos.html
|
||||
[3]:http://xmodulo.com/set-web-based-database-management-system-adminer.html
|
||||
[4]:http://mysqlworkbench.org/
|
||||
[5]:http://dev.mysql.com/downloads/repo/apt/
|
||||
[6]:http://dev.mysql.com/downloads/repo/yum/
|
||||
[7]:http://xmodulo.com/how-to-allow-remote-access-to-mysql.html
|
||||
@ -0,0 +1,196 @@
|
||||
Linux FAQs with Answers--How to compile ixgbe driver on CentOS, RHEL or Fedora
|
||||
================================================================================
|
||||
> **Question**: I want to build and install the latest ixgbe 10G NIC driver. How can I compile ixgbe driver on CentOS, Fedora or RHEL?
|
||||
|
||||
To use Intel's PCI Express 10G NICs (e.g., 82598, 82599, x540) on your Linux system, you need to install ixgbe driver. While modern Linux distributions come with ixgbe driver pre-installed as a loadable module, the pre-built ixgbe driver is not fully customizable with limited parameters. If you want to enable and customize all available features of the 10G NICs (e.g., RSS, multi-queue, virtual functions, hardware offload), you will need to build the driver from the source.
|
||||
|
||||
Here is how to compile ixgbe driver from the source on Red Hat based platforms (e.g., CentOS, RHEL or Fedora). For Debian based systems, refer to [this guideline][1] instead.
|
||||
|
||||
### Step One: Install Prerequisites ###
|
||||
|
||||
First, set up necessary developmen environment and install matching kernel headers.
|
||||
|
||||
$ sudo yum install gcc make
|
||||
$ sudo yum install kernel-devel
|
||||
|
||||
### Step Two: Compile Ixgbe Driver ###
|
||||
|
||||
Download the latest ixgbe source code from the [official site][2].
|
||||
|
||||
$ wget http://downloads.sourceforge.net/project/e1000/ixgbe%20stable/3.23.2/ixgbe-3.23.2.tar.gz
|
||||
|
||||
Be sure to check supported kernel versions. For example, the ixgbe driver 3.23.2 supports Linux kernel versions 2.6.18 up to 3.18.1.
|
||||
|
||||
Extract the tarball and compile it.
|
||||
|
||||
$ tar -xvf ixgbe-3.23.2.tar.gz
|
||||
$ cd ixgbe-3.23.2/src
|
||||
$ make
|
||||
|
||||
If successful, the compiled driver (ixgbe.ko) will be found in the current directory.
|
||||
|
||||
You can check the information of the compiled driver by running:
|
||||
|
||||
$ modinfo ./ixgbe.ko
|
||||
|
||||
The output will show a list of available parameters of the ixgbe driver.
|
||||
|
||||
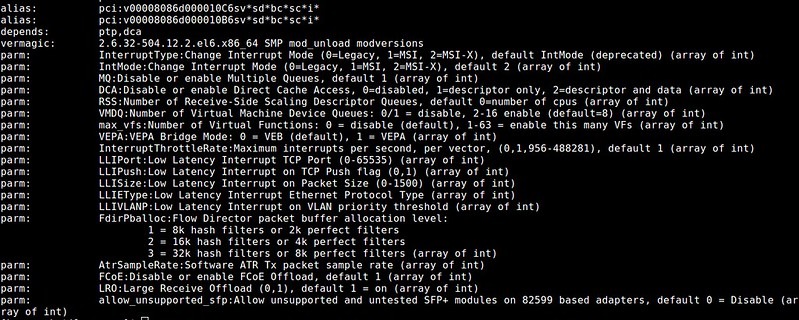
|
||||
|
||||
### Step Three: Load Ixgbe Driver ###
|
||||
|
||||
Now you are ready to load the compiled ixgbe driver.
|
||||
|
||||
If the stock ixgbe driver is already loaded on your system, you need to unload it first. Otherwise, you won't be able to load the new ixgbe driver.
|
||||
|
||||
$ sudo rmmod ixgbe.ko
|
||||
|
||||
Then insert the compiled driver in the kernel by running:
|
||||
|
||||
$ sudo insmod ./ixgbe.ko
|
||||
|
||||
Optionally, you can supply any parameters while loading the driver.
|
||||
|
||||
$ sudo insmod ./ixgbe.ko FdirPballoc=3 RSS=16
|
||||
|
||||
To verify that the driver is loaded successfully, check the output of dmesg command.
|
||||
|
||||
$ dmesg
|
||||
|
||||
----------
|
||||
|
||||
Intel(R) 10 Gigabit PCI Express Network Driver - version 3.23.2
|
||||
Copyright (c) 1999-2014 Intel Corporation.
|
||||
ixgbe 0000:21:00.0: PCI INT A -> GSI 64 (level, low) -> IRQ 64
|
||||
ixgbe 0000:21:00.0: setting latency timer to 64
|
||||
ixgbe: Receive-Side Scaling (RSS) set to 16
|
||||
ixgbe: Flow Director packet buffer allocation set to 3
|
||||
ixgbe: 0000:21:00.0: ixgbe_check_options: Flow Director will be allocated 256kB of packet buffer
|
||||
ixgbe: 0000:21:00.0: ixgbe_check_options: FCoE Offload feature enabled
|
||||
ixgbe 0000:21:00.0: irq 87 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.0: irq 88 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.0: irq 89 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.0: irq 90 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.0: irq 91 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.0: irq 92 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.0: irq 93 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.0: irq 94 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.0: irq 95 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.0: irq 96 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.0: irq 97 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.0: irq 98 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.0: irq 99 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.0: irq 100 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.0: irq 101 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.0: irq 102 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.0: irq 103 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.0: eth3: DCA registration failed: -1
|
||||
ixgbe 0000:21:00.0: PCI Express bandwidth of 32GT/s available
|
||||
ixgbe 0000:21:00.0: (Speed:5.0GT/s, Width: x8, Encoding Loss:20%)
|
||||
ixgbe 0000:21:00.0: eth3: MAC: 2, PHY: 9, SFP+: 3, PBA No: E68793-006
|
||||
ixgbe 0000:21:00.0: 90:e2:ba:5b:e9:1c
|
||||
ixgbe 0000:21:00.0: eth3: Enabled Features: RxQ: 16 TxQ: 16 FdirHash RSC
|
||||
ixgbe 0000:21:00.0: eth3: Intel(R) 10 Gigabit Network Connection
|
||||
ixgbe 0000:21:00.1: PCI INT B -> GSI 68 (level, low) -> IRQ 68
|
||||
ixgbe 0000:21:00.1: setting latency timer to 64
|
||||
ixgbe: 0000:21:00.1: ixgbe_check_options: FCoE Offload feature enabled
|
||||
ixgbe 0000:21:00.0: registered PHC device on eth3
|
||||
ixgbe 0000:21:00.1: irq 104 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.1: irq 105 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.1: irq 106 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.1: irq 107 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.1: irq 108 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.1: irq 109 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.1: irq 110 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.1: irq 111 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.1: irq 112 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.1: irq 113 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.1: irq 114 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.1: irq 115 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.1: irq 116 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.1: irq 117 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.1: irq 118 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.1: irq 119 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.1: irq 120 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.1: irq 121 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.1: irq 122 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.1: irq 123 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.1: irq 124 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.1: irq 125 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.1: irq 126 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.1: irq 127 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.1: irq 128 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.1: irq 129 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.1: irq 130 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.1: irq 131 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.1: irq 132 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.1: irq 133 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.1: irq 134 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.1: irq 135 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.1: irq 136 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.1: irq 137 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.1: irq 138 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.1: irq 139 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.1: irq 140 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.1: irq 141 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.1: irq 142 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.1: irq 143 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.1: irq 144 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.1: irq 145 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.1: irq 146 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.1: irq 147 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.1: irq 148 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.1: irq 149 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.1: irq 150 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.1: irq 151 for MSI/MSI-X
|
||||
ixgbe 0000:21:00.1: irq 152 for MSI/MSI-X
|
||||
ADDRCONF(NETDEV_UP): eth3: link is not ready
|
||||
8021q: adding VLAN 0 to HW filter on device eth3
|
||||
ixgbe 0000:21:00.1: eth4: DCA registration failed: -1
|
||||
ixgbe 0000:21:00.1: PCI Express bandwidth of 32GT/s available
|
||||
ixgbe 0000:21:00.1: (Speed:5.0GT/s, Width: x8, Encoding Loss:20%)
|
||||
ixgbe 0000:21:00.1: eth4: MAC: 2, PHY: 9, SFP+: 4, PBA No: E68793-006
|
||||
ixgbe 0000:21:00.1: 90:e2:ba:5b:e9:1e
|
||||
ixgbe 0000:21:00.1: eth4: Enabled Features: RxQ: 48 TxQ: 48 FdirHash RSC
|
||||
ixgbe 0000:21:00.1: eth4: Intel(R) 10 Gigabit Network Connection
|
||||
ixgbe 0000:21:00.0: eth3: detected SFP+: 3
|
||||
ixgbe 0000:21:00.1: registered PHC device on eth4
|
||||
ADDRCONF(NETDEV_UP): eth4: link is not ready
|
||||
8021q: adding VLAN 0 to HW filter on device eth4
|
||||
ixgbe 0000:21:00.1: eth4: detected SFP+: 4
|
||||
ixgbe 0000:21:00.0: eth3: NIC Link is Up 10 Gbps, Flow Control: RX/TX
|
||||
ADDRCONF(NETDEV_CHANGE): eth3: link becomes ready
|
||||
ixgbe 0000:21:00.1: eth4: NIC Link is Up 10 Gbps, Flow Control: RX/TX
|
||||
ADDRCONF(NETDEV_CHANGE): eth4: link becomes ready
|
||||
eth3: no IPv6 routers present
|
||||
eth4: no IPv6 routers present
|
||||
|
||||
### Step Four: Install Ixgbe Driver ###
|
||||
|
||||
Once you have checked that the driver is loaded successfully, go ahead and install the driver on your system.
|
||||
|
||||
$ sudo make install
|
||||
|
||||
ixgbe.ko will be installed in the following location.
|
||||
|
||||
/lib/modules/<kernel-version>/kernel/drivers/net/ixgbe
|
||||
|
||||
At this point, the compiled driver will be loaded automatically upon boot, or you can load it by running:
|
||||
|
||||
$ sudo modprobe ixgbe
|
||||
|
||||
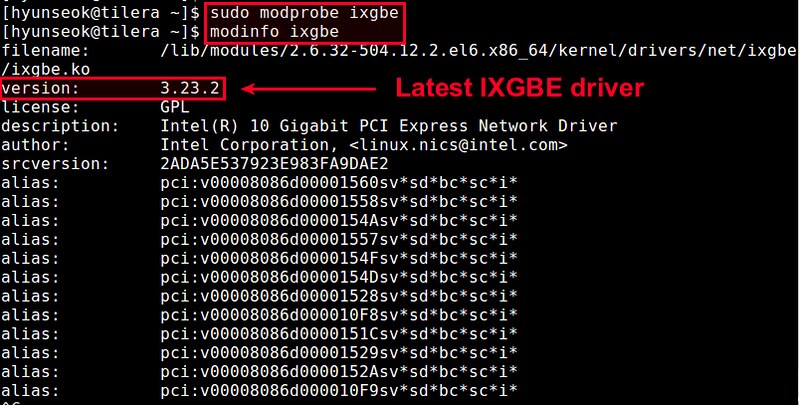
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://ask.xmodulo.com/compile-ixgbe-driver-centos-rhel-fedora.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://ask.xmodulo.com/author/nanni
|
||||
[1]:http://ask.xmodulo.com/download-install-ixgbe-driver-ubuntu-debian.html
|
||||
[2]:http://sourceforge.net/projects/e1000/files/ixgbe%20stable/
|
||||
@ -0,0 +1,55 @@
|
||||
Linux FAQs with Answers--How to configure PCI-passthrough on virt-manager
|
||||
================================================================================
|
||||
> **Question**: I would like to dedicate a physical network interface card to one of my guest VMs created by KVM. For that, I am trying to enable PCI passthrough of the NIC for the VM. How can I add a PCI device to a guest VM with PCI passthrough on virt-manager?
|
||||
|
||||
Modern hypervisors enable efficient resource sharing among multiple guest operating systems by virtualizing and emulating hardware resources. However, such virtualized resource sharing may not always be desirable, or even should be avoided when VM performance is a great concern, or when a VM requires full DMA control of a hardware device. One technique used in this case is so-called "PCI passthrough," where a guest VM is granted an exclusive access to a PCI device (e.g., network/sound/video card). Essentially, PCI passthrough bypasses the virtualization layer, and directly exposes a PCI device to a VM. No other VM can access the PCI device.
|
||||
|
||||
### Requirement for Enabling PCI Passthrough ###
|
||||
|
||||
If you want to enable PCI passthrough for an HVM guest (e.g., a fully-virtualized VM created by KVM), your system (both CPU and motherboard) must meet the following requirement. If your VM is paravirtualized (created by Xen), you can skip this step.
|
||||
|
||||
In order to enable PCI passthrough for an HVM guest VM, your system must support **VT-d** (for Intel processors) or **AMD-Vi** (for AMD processors). Intel's VT-d ("Intel Virtualization Technology for Directed I/O") is available on most high-end Nehalem processors and its successors (e.g., Westmere, Sandy Bridge, Ivy Bridge). Note that VT-d and VT-x are two independent features. A list of Intel/AMD processors with VT-d/AMD-Vi capability can be found [here][1].
|
||||
|
||||
After you verify that your host hardware supports VT-d/AMD-Vi, you then need to do two things on your system. First, make sure that VT-d/AMD-Vi is enabled in system BIOS. Second, enable IOMMU on your kernel during booting. The IOMMU service, which is provided by VT-d,/AMD-Vi, protects host memory access by a guest VM, and is a requirement for PCI passthrough for fully-virtualized guest VMs.
|
||||
|
||||
To enable IOMMU on the kernel for Intel processors, pass "**intel_iommu=on**" boot parameter on your Linux. Follow [this tutorial][2] to find out how to add a kernel boot parameter via GRUB.
|
||||
|
||||
After configuring the boot parameter, reboot your host.
|
||||
|
||||
### Add a PCI Device to a VM on Virt-Manager ###
|
||||
|
||||
Now we are ready to enable PCI passthrough. In fact, assigning a PCI device to a guest VM is straightforward on virt-manager.
|
||||
|
||||
Open the VM's settings on virt-manager, and click on "Add Hardware" button on the left sidebar.
|
||||
|
||||
Choose a PCI device to assign from a PCI device list, and click on "Finish" button.
|
||||
|
||||
|
||||
|
||||
Finally, power on the guest. At this point, the host PCI device should be directly visible inside the guest VM.
|
||||
|
||||
### Troubleshooting ###
|
||||
|
||||
If you see either of the following errors while powering on a guest VM, the error may be because VT-d (or IOMMU) is not enabled on your host.
|
||||
|
||||
Error starting domain: unsupported configuration: host doesn't support passthrough of host PCI devices
|
||||
|
||||
----------
|
||||
|
||||
Error starting domain: Unable to read from monitor: Connection reset by peer
|
||||
|
||||
Make sure that "**intel_iommu=on**" boot parameter is passed to the kernel during boot as described above.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://ask.xmodulo.com/pci-passthrough-virt-manager.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://ask.xmodulo.com/author/nanni
|
||||
[1]:http://wiki.xenproject.org/wiki/VTdHowTo
|
||||
[2]:http://xmodulo.com/add-kernel-boot-parameters-via-grub-linux.html
|
||||
@ -0,0 +1,158 @@
|
||||
HTTP Public Key Pinning Extension HPKP for Apache, NGINX and Lighttpd
|
||||
================================================================================
|
||||
Public Key Pinning means that a certificate chain must include a whitelisted public key. It ensures only whitelisted Certificate Authorities (CA) can sign certificates for `*.example.com`, and not any CA in your browser store. This article has background theory and configuration examples for Apache, Lighttpd and NGINX.
|
||||
|
||||
### HTTP Public Key Pinning Extension ###
|
||||
|
||||
An example might be your bank, which always have their certificate from CA Company A. With the current certificate system, CA Company B, CA Company C and the NSA CA can all create a certificate for your bank, which your browser will hapily accept because those companies are also trusted root CA's.
|
||||
|
||||
If the bank implements HPKP and pin's their first intermidiate certificate (from CA Company A), browsers will not accept certificates from CA Company B and CA Company C, even if they have a valid trust path. HPKP also allows your browser to report back the failure to the bank, so that they know they are under attack.
|
||||
|
||||
Public Key Pinning Extension for HTTP (HPKP) is a standard for public key pinning for HTTP user agents that's been in development since 2011. It was started by Google, which, even though it had implemented pinning in Chrome, understood that manually maintaining a list of pinned sites can't scale.
|
||||
|
||||
Here is a quick feature overview of HPKP:
|
||||
|
||||
- HPKP is set at the HTTP level, using the `Public-Key-Pins` response header.
|
||||
- The policy retention period is set with the max-age parameter, it specifies duration in seconds.
|
||||
- The PKP header can only be used over an error-free secure encryption.
|
||||
- If multiple headers are seen, only the first one is processed.
|
||||
- Pinning can be extended to subdomains with the `includeSubDomains` parameter.
|
||||
- When a new PKP header is received, it overwrites previously stored pins and metadata.
|
||||
- A pin consists out of the hashing algorithm and an "Subject Public Key Info" fingerprint.
|
||||
|
||||
This article first has some theory about the workings of HPKP, down below you'll find the part which shows you how to get the required fingerprints and has web server configuration.
|
||||
|
||||
### SPKI Fingerprint - Theory ###
|
||||
|
||||
As explained by Adam Langley in [his post][1], we hash a public key, not a certificate:
|
||||
|
||||
> In general, hashing certificates is the obvious solution, but the wrong one. The problem is that CA certificates are often reissued: there are multiple certificates with the same public key, subject name etc but different extensions or expiry dates. Browsers build certificates chains from a pool of certificates, bottom up, and an alternative version of a certificate might be substituted for the one that you expect.
|
||||
>
|
||||
> For example, StartSSL has two root certificates: one signed with SHA1 and the other with SHA256. If you wished to pin to StartSSL as your CA, which certificate hash would you use? You would have to use both, but how would you know about the other root if I hadn't just told you?
|
||||
>
|
||||
> Conversely, public key hashes must be correct:
|
||||
>
|
||||
> Browsers assume that the leaf certificate is fixed: it's always the starting point of the chain. The leaf certificate contains a signature which must be a valid signature, from its parent, for that certificate. That implies that the public key of the parent is fixed by the leaf certificate. So, inductively, the chain of public keys is fixed, modulo truncation.
|
||||
>
|
||||
> The only sharp edge is that you mustn't pin to a cross-certifying root. For example, GoDaddy's root is signed by Valicert so that older clients, which don't recognise GoDaddy as a root, still trust those certificates. However, you wouldn't want to pin to Valicert because newer clients will stop their chain at GoDaddy.
|
||||
>
|
||||
> Also, we're hashing the SubjectPublicKeyInfo not the public key bit string. The SPKI includes the type of the public key and some parameters along with the public key itself. This is important because just hashing the public key leaves one open to misinterpretation attacks. Consider a Diffie-Hellman public key: if one only hashes the public key, not the full SPKI, then an attacker can use the same public key but make the client interpret it in a different group. Likewise one could force an RSA key to be interpreted as a DSA key etc.
|
||||
|
||||
### Where to Pin ###
|
||||
|
||||
Where should you pin? Pinning your own public key is not the best idea. The key might change or get compromised. You might have multiple certificates in use. The key might change because you rotate your certificates every so often. It might key compromised because the web server was hacked.
|
||||
|
||||
The easiest, but not most secure place to pin is the first intermediate CA certificate. The signature of that certificate is on your websites certificate so the issuing CA's public key must always be in the chain.
|
||||
|
||||
This way you can renew your end certificate from the same CA and have no pinning issues. If the CA issues a different root, then you have a problem, there is no clear solution for this yet. There is one thing you can do to mitigate this:
|
||||
|
||||
- Always have a backup pin and a spare certificate from a different CA.
|
||||
|
||||
The RFC states that you need to provide at least two pins. One of the pins must be present in the chain used in the connection over which the pins were received, the other pin must not be present.
|
||||
|
||||
This other pin is your backup public key. It can also be the SPKI fingerprint of a different CA where you have a certificate issued.
|
||||
|
||||
An alternative and **more secure** take on this issue is to create at least three seperate public keys beforehand (using OpenSSL, see [this page][2] for a Javascript OpenSSL command generator) and to keep two of those keys as a backup in a safe place, offline and off-site.
|
||||
|
||||
You create the SPKI hashes for the three certificates and pin those. You only use the first key as the active certificate. When it is needed, you can then use one of the alternative keys. You do however need to let that certificate sign by a CA to create a certificate pair and that process can take a few days depending on the certificate.
|
||||
|
||||
This is not a problem for the HPKP because we take the SPKI hash of the public key, and not of the certificate. Expiration or a different chain of CA signer do not matter in this case.
|
||||
|
||||
If you have the means and procedures to create and securely save at least three seperate keys as described above and pin those, it would also protect you from your CA provider getting compromised and giving out a fake certificate for your specific website.
|
||||
|
||||
### SPKI Fingerprint ###
|
||||
|
||||
To get the SPKI fingerprint from a certificate we can use the following OpenSSL command, as shown in [the RFC draft][3]:
|
||||
|
||||
openssl x509 -noout -in certificate.pem -pubkey | \
|
||||
openssl asn1parse -noout -inform pem -out public.key;
|
||||
openssl dgst -sha256 -binary public.key | openssl enc -base64
|
||||
|
||||
Result:
|
||||
|
||||
klO23nT2ehFDXCfx3eHTDRESMz3asj1muO+4aIdjiuY=
|
||||
|
||||
The input `certificate.pem` file is the first certificate in the chain for this website. (At the time of writing, `COMODO RSA Domain Validation Secure Server CA, Serial 2B:2E:6E:EA:D9:75:36:6C:14:8A:6E:DB:A3:7C:8C:07.`)
|
||||
|
||||
You need to also do this with your backup public key, ending up with two fingerprints.
|
||||
|
||||
### Bugs ###
|
||||
|
||||
At the time of writing this article (2015-Jan) the only browser supporting HPKP (Chrome) has a serious issue where Chrome doesn't treat the max-age and includeSubdomains directives from HSTS and HPKP headers as mutually exclusive. This means that if you have HSTS and HPKP with different policiesfor max-age or includeSubdomains they will be interchanged. See this bug for more info: [https://code.google.com/p/chromium/issues/detail?id=444511][4]. Thanks to Scott Helme from [https://scotthelme.co.uk][5] for finding and notifying me and the Chromium project about it.
|
||||
|
||||
### Webserver configuration ###
|
||||
|
||||
Below you'll find configuration instructions for the three most populair web servers. Since this is just a HTTP header, almost all web servers will allow you to set this. It needs to be set for the HTTPS website.
|
||||
|
||||
The example below pins the `COMODO RSA Domain Validation Secure Server CA` and the `Comodo PositiveSSL` CA 2 as a backup, with a 30 day expire time including all subdomains.
|
||||
|
||||
#### Apache ####
|
||||
|
||||
Edit your apache configuration file (`/etc/apache2/sites-enabled/website.conf or /etc/apache2/httpd.conf` for example) and add the following to your VirtualHost:
|
||||
|
||||
# Optionally load the headers module:
|
||||
LoadModule headers_module modules/mod_headers.so
|
||||
|
||||
Header set Public-Key-Pins "pin-sha256=\"klO23nT2ehFDXCfx3eHTDRESMz3asj1muO+4aIdjiuY=\"; pin-sha256=\"633lt352PKRXbOwf4xSEa1M517scpD3l5f79xMD9r9Q=\"; max-age=2592000; includeSubDomains"
|
||||
|
||||
#### Lighttpd ####
|
||||
|
||||
The lighttpd variant is just as simple. Add it to your Lighttpd configuration file (`/etc/lighttpd/lighttpd.conf` for example):
|
||||
|
||||
server.modules += ( "mod_setenv" )
|
||||
$HTTP["scheme"] == "https" {
|
||||
setenv.add-response-header = ( "Public-Key-Pins" => "pin-sha256=\"klO23nT2ehFDXCfx3eHTDRESMz3asj1muO+4aIdjiuY=\"; pin-sha256=\"633lt352PKRXbOwf4xSEa1M517scpD3l5f79xMD9r9Q=\"; max-age=2592000; includeSubDomains")
|
||||
}
|
||||
|
||||
#### NGINX ####
|
||||
|
||||
NGINX is even shorter with its config. Add this in the server block for your HTTPS configuration:
|
||||
|
||||
add_header Public-Key-Pins 'pin-sha256="klO23nT2ehFDXCfx3eHTDRESMz3asj1muO+4aIdjiuY="; pin-sha256="633lt352PKRXbOwf4xSEa1M517scpD3l5f79xMD9r9Q="; max-age=2592000; includeSubDomains';
|
||||
|
||||
### Reporting ###
|
||||
|
||||
HPKP reporting allows the user-agent to report any failures back to you.
|
||||
|
||||
If you add an aditional `report-uri="http://example.org/hpkp-report`" parameter to the header and set up a listener there, clients will send reports if they encounter a failure. A report is sent as a POST request to the report-uri with a JSON body like this:
|
||||
|
||||
{
|
||||
"date-time": "2014-12-26T11:52:10Z",
|
||||
"hostname": "www.example.org",
|
||||
"port": 443,
|
||||
"effective-expiration-date": "2014-12-31T12:59:59",
|
||||
"include-subdomains": true,
|
||||
"served-certificate-chain": [
|
||||
"-----BEGINCERTIFICATE-----\nMIIAuyg[...]tqU0CkVDNx\n-----ENDCERTIFICATE-----"
|
||||
],
|
||||
"validated-certificate-chain": [
|
||||
"-----BEGINCERTIFICATE-----\nEBDCCygAwIBA[...]PX4WecNx\n-----ENDCERTIFICATE-----"
|
||||
],
|
||||
"known-pins": [
|
||||
"pin-sha256=\"dUezRu9zOECb901Md727xWltNsj0e6qzGk\"",
|
||||
"pin-sha256=\"E9CqVKB9+xZ9INDbd+2eRQozqbQ2yXLYc\""
|
||||
]
|
||||
}
|
||||
|
||||
### No Enforcment, report only ###
|
||||
|
||||
HPKP can be set up without enforcement, in reporting mode by using the `Public-Key-Pins-Report-Only` response header.
|
||||
|
||||
This approach allows you to set up pinning without your site being unreachable or HPKP being configured incorrectly. You can later move to enforcement by changing the header back to `Public-Key-Pins`.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://raymii.org/s/articles/HTTP_Public_Key_Pinning_Extension_HPKP.html
|
||||
|
||||
作者:[Remy van Elst][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://raymii.org/
|
||||
[1]:http://www.imperialviolet.org/2011/05/04/pinning.html
|
||||
[2]:https://raymii.org/s/software/OpenSSL_Command_Generator.html
|
||||
[3]:https://tools.ietf.org/html/draft-ietf-websec-key-pinning-21#appendix-A
|
||||
[4]:https://code.google.com/p/chromium/issues/detail?id=444511
|
||||
[5]:https://scotthelme.co.uk/
|
||||
290
sources/tech/20150415 Strong SSL Security on nginx.md
Normal file
290
sources/tech/20150415 Strong SSL Security on nginx.md
Normal file
@ -0,0 +1,290 @@
|
||||
Strong SSL Security on nginx
|
||||
================================================================================
|
||||
[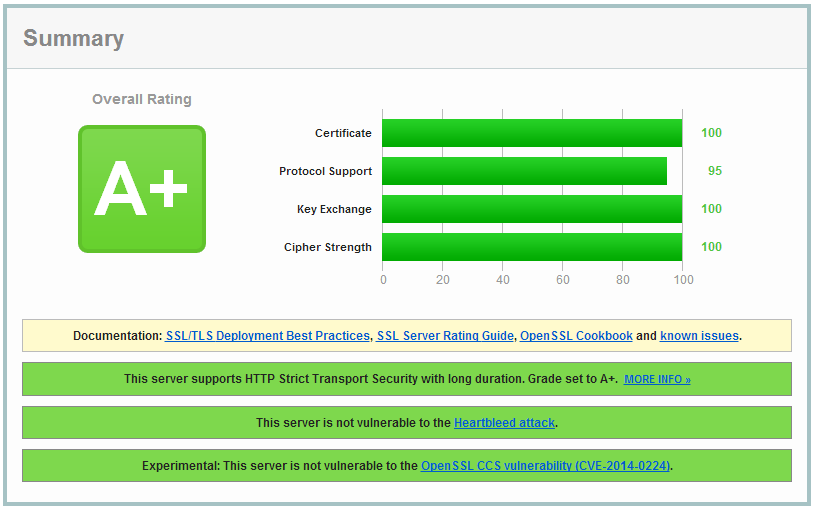][1]
|
||||
|
||||
This tutorial shows you how to set up strong SSL security on the nginx webserver. We do this by disabling SSL Compression to mitigate the CRIME attack, disable SSLv3 and below because of vulnerabilities in the protocol and we will set up a strong ciphersuite that enables Forward Secrecy when possible. We also enable HSTS and HPKP. This way we have a strong and future proof ssl configuration and we get an A on the Qually Labs SSL Test.
|
||||
|
||||
TL;DR: [Copy-pastable strong cipherssuites for NGINX, Apache and Lighttpd: https://cipherli.st][2]
|
||||
|
||||
This tutorial is tested on a Digital Ocean VPS. If you like this tutorial and want to support my website, use this link to order a Digital Ocean VPS: [https://www.digitalocean.com/?refcode=7435ae6b8212][2]
|
||||
|
||||
This tutorial works with the stricter requirements of the SSL Labs test [announced on the 21st of January 2014][4] (It already did before that, if you follow(ed) it you get an A+)
|
||||
|
||||
- [This tutorial is also available for Apache][5]
|
||||
- [This tutorial is also available for Lighttpd][6]
|
||||
- [This tutorial is also available for FreeBSD, NetBSD and OpenBSD over at the BSD Now podcast][7]: [http://www.bsdnow.tv/tutorials/nginx][8]
|
||||
|
||||
You can find more info on the topics by following the links below:
|
||||
|
||||
- [BEAST Attack][9]
|
||||
- [CRIME Attack][10]
|
||||
- [FREAK Attack][11]
|
||||
- [Heartbleed][12]
|
||||
- [Perfect Forward Secrecy][13]
|
||||
- [Dealing with RC4 and BEAST][14]
|
||||
|
||||
We are going to edit the nginx settings in the file `/etc/nginx/sited-enabled/yoursite.com` (On Ubuntu/Debian) or in `/etc/nginx/conf.d/nginx.conf` (On RHEL/CentOS).
|
||||
|
||||
For the entire tutorial, you need to edit the parts between the `server` block for the server config for port 443 (ssl config). At the end of the tutorial you can find the complete config example.
|
||||
|
||||
*Make sure you back up the files before editing them!*
|
||||
|
||||
### The BEAST attack and RC4 ###
|
||||
|
||||
In short, by tampering with an encryption algorithm's CBC - cipher block chaining - mode's, portions of the encrypted traffic can be secretly decrypted. More info on the above link.
|
||||
|
||||
Recent browser versions have enabled client side mitigation for the beast attack. The recommendation was to disable all TLS 1.0 ciphers and only offer RC4. However, [RC4 has a growing list of attacks against it],(http://www.isg.rhul.ac.uk/tls/) many of which have crossed the line from theoretical to practical. Moreover, there is reason to believe that the NSA has broken RC4, their so-called "big breakthrough."
|
||||
|
||||
Disabling RC4 has several ramifications. One, users with shitty browsers such as Internet Explorer on Windows XP will use 3DES in lieu. Triple-DES is more secure than RC4, but it is significantly more expensive. Your server will pay the cost for these users. Two, RC4 mitigates BEAST. Thus, disabling RC4 makes TLS 1.0 users susceptible to that attack, by moving them to AES-CBC (the usual server-side BEAST "fix" is to prioritize RC4 above all else). I am confident that the flaws in RC4 significantly outweigh the risks from BEAST. Indeed, with client-side mitigation (which Chrome and Firefox both provide), BEAST is a nonissue. But the risk from RC4 only grows: More cryptanalysis will surface over time.
|
||||
|
||||
### Factoring RSA-EXPORT Keys (FREAK) ###
|
||||
|
||||
FREAK is a man-in-the-middle (MITM) vulnerability discovered by a group of cryptographers at [INRIA, Microsoft Research and IMDEA][15]. FREAK stands for "Factoring RSA-EXPORT Keys."
|
||||
|
||||
The vulnerability dates back to the 1990s, when the US government banned selling crypto software overseas, unless it used export cipher suites which involved encryption keys no longer than 512-bits.
|
||||
|
||||
It turns out that some modern TLS clients - including Apple's SecureTransport and OpenSSL - have a bug in them. This bug causes them to accept RSA export-grade keys even when the client didn't ask for export-grade RSA. The impact of this bug can be quite nasty: it admits a 'man in the middle' attack whereby an active attacker can force down the quality of a connection, provided that the client is vulnerable and the server supports export RSA.
|
||||
|
||||
There are two parts of the attack as the server must also accept "export grade RSA."
|
||||
|
||||
The MITM attack works as follows:
|
||||
|
||||
- In the client's Hello message, it asks for a standard 'RSA' ciphersuite.
|
||||
- The MITM attacker changes this message to ask for 'export RSA'.
|
||||
- The server responds with a 512-bit export RSA key, signed with its long-term key.
|
||||
- The client accepts this weak key due to the OpenSSL/SecureTransport bug.
|
||||
- The attacker factors the RSA modulus to recover the corresponding RSA decryption key.
|
||||
- When the client encrypts the 'pre-master secret' to the server, the attacker can now decrypt it to recover the TLS 'master secret'.
|
||||
- From here on out, the attacker sees plaintext and can inject anything it wants.
|
||||
|
||||
The ciphersuite offered here on this page does not enable EXPORT grade ciphers. Make sure your OpenSSL is updated to the latest available version and urge your clients to also use upgraded software.
|
||||
|
||||
### Heartbleed ###
|
||||
|
||||
Heartbleed is a security bug disclosed in April 2014 in the OpenSSL cryptography library, which is a widely used implementation of the Transport Layer Security (TLS) protocol. Heartbleed may be exploited regardless of whether the party using a vulnerable OpenSSL instance for TLS is a server or a client. It results from improper input validation (due to a missing bounds check) in the implementation of the DTLS heartbeat extension (RFC6520), thus the bug's name derives from "heartbeat". The vulnerability is classified as a buffer over-read, a situation where more data can be read than should be allowed.
|
||||
|
||||
What versions of the OpenSSL are affected by Heartbleed?
|
||||
|
||||
Status of different versions:
|
||||
|
||||
- OpenSSL 1.0.1 through 1.0.1f (inclusive) are vulnerable
|
||||
- OpenSSL 1.0.1g is NOT vulnerable
|
||||
- OpenSSL 1.0.0 branch is NOT vulnerable
|
||||
- OpenSSL 0.9.8 branch is NOT vulnerable
|
||||
|
||||
The bug was introduced to OpenSSL in December 2011 and has been out in the wild since OpenSSL release 1.0.1 on 14th of March 2012. OpenSSL 1.0.1g released on 7th of April 2014 fixes the bug.
|
||||
|
||||
By updating OpenSSL you are not vulnerable to this bug.
|
||||
|
||||
### SSL Compression (CRIME attack) ###
|
||||
|
||||
The CRIME attack uses SSL Compression to do its magic. SSL compression is turned off by default in nginx 1.1.6+/1.0.9+ (if OpenSSL 1.0.0+ used) and nginx 1.3.2+/1.2.2+ (if older versions of OpenSSL are used).
|
||||
|
||||
If you are using al earlier version of nginx or OpenSSL and your distro has not backported this option then you need to recompile OpenSSL without ZLIB support. This will disable the use of OpenSSL using the DEFLATE compression method. If you do this then you can still use regular HTML DEFLATE compression.
|
||||
|
||||
### SSLv2 and SSLv3 ###
|
||||
|
||||
SSL v2 is insecure, so we need to disable it. We also disable SSLv3, as TLS 1.0 suffers a downgrade attack, allowing an attacker to force a connection to use SSLv3 and therefore disable forward secrecy.
|
||||
|
||||
Again edit the config file:
|
||||
|
||||
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
|
||||
|
||||
### Poodle and TLS-FALLBACK-SCSV ###
|
||||
|
||||
SSLv3 allows exploiting of the [POODLE][16] bug. This is one more major reason to disable this.
|
||||
|
||||
Google have proposed an extension to SSL/TLS named [TLSFALLBACKSCSV][17] that seeks to prevent forced SSL downgrades. This is automatically enabled if you upgrade OpenSSL to the following versions:
|
||||
|
||||
- OpenSSL 1.0.1 has TLSFALLBACKSCSV in 1.0.1j and higher.
|
||||
- OpenSSL 1.0.0 has TLSFALLBACKSCSV in 1.0.0o and higher.
|
||||
- OpenSSL 0.9.8 has TLSFALLBACKSCSV in 0.9.8zc and higher.
|
||||
|
||||
[More info on the NGINX documentation][18]
|
||||
|
||||
### The Cipher Suite ###
|
||||
|
||||
Forward Secrecy ensures the integrity of a session key in the event that a long-term key is compromised. PFS accomplishes this by enforcing the derivation of a new key for each and every session.
|
||||
|
||||
This means that when the private key gets compromised it cannot be used to decrypt recorded SSL traffic.
|
||||
|
||||
The cipher suites that provide Perfect Forward Secrecy are those that use an ephemeral form of the Diffie-Hellman key exchange. Their disadvantage is their overhead, which can be improved by using the elliptic curve variants.
|
||||
|
||||
The following two ciphersuites are recommended by me, and the latter by [the Mozilla Foundation][19].
|
||||
|
||||
The recommended cipher suite:
|
||||
|
||||
ssl_ciphers 'AES128+EECDH:AES128+EDH';
|
||||
|
||||
The recommended cipher suite for backwards compatibility (IE6/WinXP):
|
||||
|
||||
ssl_ciphers "ECDHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES128-SHA256:ECDHE-RSA-AES256-SHA:ECDHE-RSA-AES128-SHA:DHE-RSA-AES256-SHA256:DHE-RSA-AES128-SHA256:DHE-RSA-AES256-SHA:DHE-RSA-AES128-SHA:ECDHE-RSA-DES-CBC3-SHA:EDH-RSA-DES-CBC3-SHA:AES256-GCM-SHA384:AES128-GCM-SHA256:AES256-SHA256:AES128-SHA256:AES256-SHA:AES128-SHA:DES-CBC3-SHA:HIGH:!aNULL:!eNULL:!EXPORT:!DES:!MD5:!PSK:!RC4";
|
||||
|
||||
If your version of OpenSSL is old, unavailable ciphers will be discarded automatically. Always use the full ciphersuite above and let OpenSSL pick the ones it supports.
|
||||
|
||||
The ordering of a ciphersuite is very important because it decides which algorithms are going to be selected in priority. The recommendation above prioritizes algorithms that provide perfect forward secrecy.
|
||||
|
||||
Older versions of OpenSSL may not return the full list of algorithms. AES-GCM and some ECDHE are fairly recent, and not present on most versions of OpenSSL shipped with Ubuntu or RHEL.
|
||||
|
||||
#### Prioritization logic ####
|
||||
|
||||
- ECDHE+AESGCM ciphers are selected first. These are TLS 1.2 ciphers and not widely supported at the moment. No known attack currently target these ciphers.
|
||||
- PFS ciphersuites are preferred, with ECDHE first, then DHE.
|
||||
- AES 128 is preferred to AES 256. There has been [discussions][20] on whether AES256 extra security was worth the cost, and the result is far from obvious. At the moment, AES128 is preferred, because it provides good security, is really fast, and seems to be more resistant to timing attacks.
|
||||
- In the backward compatible ciphersuite, AES is preferred to 3DES. BEAST attacks on AES are mitigated in TLS 1.1 and above, and difficult to achieve in TLS 1.0. In the non-backward compatible ciphersuite, 3DES is not present.
|
||||
- RC4 is removed entirely. 3DES is used for backward compatibility. See discussion in [#RC4_weaknesses][21]
|
||||
|
||||
#### Mandatory discards ####
|
||||
|
||||
- aNULL contains non-authenticated Diffie-Hellman key exchanges, that are subject to Man-In-The-Middle (MITM) attacks
|
||||
- eNULL contains null-encryption ciphers (cleartext)
|
||||
- EXPORT are legacy weak ciphers that were marked as exportable by US law
|
||||
- RC4 contains ciphers that use the deprecated ARCFOUR algorithm
|
||||
- DES contains ciphers that use the deprecated Data Encryption Standard
|
||||
- SSLv2 contains all ciphers that were defined in the old version of the SSL standard, now deprecated
|
||||
- MD5 contains all the ciphers that use the deprecated message digest 5 as the hashing algorithm
|
||||
|
||||
### Extra settings ###
|
||||
|
||||
Make sure you also add these lines:
|
||||
|
||||
ssl_prefer_server_ciphers on;
|
||||
ssl_session_cache shared:SSL:10m;
|
||||
|
||||
When choosing a cipher during an SSLv3 or TLSv1 handshake, normally the client's preference is used. If this directive is enabled, the server's preference will be used instead.
|
||||
|
||||
- [More info on sslpreferserver_ciphers][22]
|
||||
- [More info on ssl_ciphers][23]
|
||||
|
||||
### Forward Secrecy & Diffie Hellman Ephemeral Parameters ###
|
||||
|
||||
The concept of forward secrecy is simple: client and server negotiate a key that never hits the wire, and is destroyed at the end of the session. The RSA private from the server is used to sign a Diffie-Hellman key exchange between the client and the server. The pre-master key obtained from the Diffie-Hellman handshake is then used for encryption. Since the pre-master key is specific to a connection between a client and a server, and used only for a limited amount of time, it is called Ephemeral.
|
||||
|
||||
With Forward Secrecy, if an attacker gets a hold of the server's private key, it will not be able to decrypt past communications. The private key is only used to sign the DH handshake, which does not reveal the pre-master key. Diffie-Hellman ensures that the pre-master keys never leave the client and the server, and cannot be intercepted by a MITM.
|
||||
|
||||
All versions of nginx as of 1.4.4 rely on OpenSSL for input parameters to Diffie-Hellman (DH). Unfortunately, this means that Ephemeral Diffie-Hellman (DHE) will use OpenSSL's defaults, which include a 1024-bit key for the key-exchange. Since we're using a 2048-bit certificate, DHE clients will use a weaker key-exchange than non-ephemeral DH clients.
|
||||
|
||||
We need generate a stronger DHE parameter:
|
||||
|
||||
cd /etc/ssl/certs
|
||||
openssl dhparam -out dhparam.pem 4096
|
||||
|
||||
And then tell nginx to use it for DHE key-exchange:
|
||||
|
||||
ssl_dhparam /etc/ssl/certs/dhparam.pem;
|
||||
|
||||
### OCSP Stapling ###
|
||||
|
||||
When connecting to a server, clients should verify the validity of the server certificate using either a Certificate Revocation List (CRL), or an Online Certificate Status Protocol (OCSP) record. The problem with CRL is that the lists have grown huge and takes forever to download.
|
||||
|
||||
OCSP is much more lightweight, as only one record is retrieved at a time. But the side effect is that OCSP requests must be made to a 3rd party OCSP responder when connecting to a server, which adds latency and potential failures. In fact, the OCSP responders operated by CAs are often so unreliable that browser will fail silently if no response is received in a timely manner. This reduces security, by allowing an attacker to DoS an OCSP responder to disable the validation.
|
||||
|
||||
The solution is to allow the server to send its cached OCSP record during the TLS handshake, therefore bypassing the OCSP responder. This mechanism saves a roundtrip between the client and the OCSP responder, and is called OCSP Stapling.
|
||||
|
||||
The server will send a cached OCSP response only if the client requests it, by announcing support for the status_request TLS extension in its CLIENT HELLO.
|
||||
|
||||
Most servers will cache OCSP response for up to 48 hours. At regular intervals, the server will connect to the OCSP responder of the CA to retrieve a fresh OCSP record. The location of the OCSP responder is taken from the Authority Information Access field of the signed certificate.
|
||||
|
||||
- [View my tutorial on enabling OCSP stapling on NGINX][24]
|
||||
|
||||
### HTTP Strict Transport Security ###
|
||||
|
||||
When possible, you should enable [HTTP Strict Transport Security (HSTS)][25], which instructs browsers to communicate with your site only over HTTPS.
|
||||
|
||||
- [View my article on HTST to see how to configure it.][26]
|
||||
|
||||
### HTTP Public Key Pinning Extension ###
|
||||
|
||||
You should also enable the [HTTP Public Key Pinning Extension][27].
|
||||
|
||||
Public Key Pinning means that a certificate chain must include a whitelisted public key. It ensures only whitelisted Certificate Authorities (CA) can sign certificates for `*.example.com`, and not any CA in your browser store.
|
||||
|
||||
I've written an article about it that has background theory and configuration examples for Apache, Lighttpd and NGINX: [https://raymii.org/s/articles/HTTPPublicKeyPinningExtension_HPKP.html][28]
|
||||
|
||||
### Config Example ###
|
||||
|
||||
server {
|
||||
|
||||
listen [::]:443 default_server;
|
||||
|
||||
ssl on;
|
||||
ssl_certificate_key /etc/ssl/cert/raymii_org.pem;
|
||||
ssl_certificate /etc/ssl/cert/ca-bundle.pem;
|
||||
|
||||
ssl_ciphers 'AES128+EECDH:AES128+EDH:!aNULL';
|
||||
|
||||
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
|
||||
ssl_session_cache shared:SSL:10m;
|
||||
|
||||
ssl_stapling on;
|
||||
ssl_stapling_verify on;
|
||||
resolver 8.8.4.4 8.8.8.8 valid=300s;
|
||||
resolver_timeout 10s;
|
||||
|
||||
ssl_prefer_server_ciphers on;
|
||||
ssl_dhparam /etc/ssl/certs/dhparam.pem;
|
||||
|
||||
add_header Strict-Transport-Security max-age=63072000;
|
||||
add_header X-Frame-Options DENY;
|
||||
add_header X-Content-Type-Options nosniff;
|
||||
|
||||
root /var/www/;
|
||||
index index.html index.htm;
|
||||
server_name raymii.org;
|
||||
|
||||
}
|
||||
|
||||
### Conclusion ###
|
||||
|
||||
If you have applied the above config lines you need to restart nginx:
|
||||
|
||||
# Check the config first:
|
||||
/etc/init.d/nginx configtest
|
||||
# Then restart:
|
||||
/etc/init.d/nginx restart
|
||||
|
||||
Now use the [SSL Labs test][29] to see if you get a nice A. And, of course, have a safe, strong and future proof SSL configuration!
|
||||
|
||||
- [Also read the Mozilla page on the subject][30]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://raymii.org/s/tutorials/Strong_SSL_Security_On_nginx.html
|
||||
|
||||
作者:[Remy van Elst][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://raymii.org/
|
||||
[1]:https://www.ssllabs.com/ssltest/analyze.html?d=raymii.org
|
||||
[2]:https://cipherli.st/
|
||||
[3]:https://www.digitalocean.com/?refcode=7435ae6b8212
|
||||
[4]:http://blog.ivanristic.com/2014/01/ssl-labs-stricter-security-requirements-for-2014.html
|
||||
[5]:https://raymii.org/s/tutorials/Strong_SSL_Security_On_Apache2.html
|
||||
[6]:https://raymii.org/s/tutorials/Pass_the_SSL_Labs_Test_on_Lighttpd_%28Mitigate_the_CRIME_and_BEAST_attack_-_Disable_SSLv2_-_Enable_PFS%29.html
|
||||
[7]:http://www.bsdnow.tv/episodes/2014_08_20-engineering_nginx
|
||||
[8]:http://www.bsdnow.tv/tutorials/nginx
|
||||
[9]:https://en.wikipedia.org/wiki/Transport_Layer_Security#BEAST_attack
|
||||
[10]:https://en.wikipedia.org/wiki/CRIME_%28security_exploit%29
|
||||
[11]:http://blog.cryptographyengineering.com/2015/03/attack-of-week-freak-or-factoring-nsa.html
|
||||
[12]:http://heartbleed.com/
|
||||
[13]:https://en.wikipedia.org/wiki/Perfect_forward_secrecy
|
||||
[14]:https://en.wikipedia.org/wiki/Transport_Layer_Security#Dealing_with_RC4_and_BEAST
|
||||
[15]:https://www.smacktls.com/
|
||||
[16]:https://raymii.org/s/articles/Check_servers_for_the_Poodle_bug.html
|
||||
[17]:https://tools.ietf.org/html/draft-ietf-tls-downgrade-scsv-00
|
||||
[18]:http://wiki.nginx.org/HttpSslModule#ssl_protocols
|
||||
[19]:https://wiki.mozilla.org/Security/Server_Side_TLS
|
||||
[20]:http://www.mail-archive.com/dev-tech-crypto@lists.mozilla.org/msg11247.html
|
||||
[21]:https://wiki.mozilla.org/Security/Server_Side_TLS#RC4_weaknesses
|
||||
[22]:http://wiki.nginx.org/HttpSslModule#ssl_prefer_server_ciphers
|
||||
[23]:http://wiki.nginx.org/HttpSslModule#ssl_ciphers
|
||||
[24]:https://raymii.org/s/tutorials/OCSP_Stapling_on_nginx.html
|
||||
[25]:https://en.wikipedia.org/wiki/HTTP_Strict_Transport_Security
|
||||
[26]:https://raymii.org/s/tutorials/HTTP_Strict_Transport_Security_for_Apache_NGINX_and_Lighttpd.html
|
||||
[27]:https://wiki.mozilla.org/SecurityEngineering/Public_Key_Pinning
|
||||
[28]:https://raymii.org/s/articles/HTTP_Public_Key_Pinning_Extension_HPKP.html
|
||||
[29]:https://www.ssllabs.com/ssltest/
|
||||
[30]:https://wiki.mozilla.org/Security/Server_Side_TLS
|
||||
@ -0,0 +1,96 @@
|
||||
如何记住并在下一次登录时还原正在运行的应用
|
||||
================================================================================
|
||||
在你的 Ubuntu 里,你正运行着某些应用,但并不想停掉它们的进程,只想管理一下窗口,并打开那些工作需要的应用。接着,某些其他的事需要你转移注意力或你的机器电量低使得你必须马上关闭电脑。(幸运的是,)你可以让 Ubuntu 记住所有你正运行的应用并在你下一次登录时还原它们。
|
||||
|
||||
现在,为了让我们的 Ubuntu 记住当前会话中正运行的应用并在我们下一次登录时还原它们,我们将会使用到 `dconf-editor`。这个工具代替了前一个 Ubuntu 版本里安装的 `gconf-editor`,但默认情况下并没有在现在这个 Ubuntu 版本(注:这里指的是 Ubuntu 14.04 LTS) 里安装。为了安装 `dconf-editor`, 你需要运行 `sudo apt-get install dconf-editor`命令:
|
||||
|
||||
$ sudo apt-get install dconf-tools
|
||||
|
||||
一旦 `dconf-editor` 安装完毕,你就可以从应用菜单(注:这里指的是 Unity Dash)里打开它或者你可以通过直接在终端里或使用 `alt+f2` 运行下面的命令来启动它:
|
||||
|
||||
$ dconf-editor
|
||||
|
||||
在 “dconf Editor” 窗口中,在左边窗格里点击临近 "org" 的右箭头来展开这个选项的分支。
|
||||
|
||||

|
||||
|
||||
然后在 “org” 下,点击临近 “gnome” 的右箭头。
|
||||
|
||||

|
||||
|
||||
接着在 “gnome” 下点击 “gnome-session”。在右边窗格里,选择 “auto-save-session” 选项框并将它开启。
|
||||
|
||||

|
||||
|
||||
在你检查或对刚才的选项打钩之后,点击默认情况下位于窗口左上角的关闭按钮(X)来关闭 “Dconf Editor”。
|
||||
|
||||

|
||||
|
||||
在你登出并再登录回来时,所有你正运行的应用就可以被还原了。
|
||||
|
||||
欢呼吧,我们已经成功地配置了我们的 Ubuntu 14.04 LTS "Trusty" 来自动记住我们上一次会话中正在运行的应用。
|
||||
|
||||
现在,在这个教程里,我们也将学会 **如何在 Ubuntu 14.04 LTS 里开启休眠功能** :
|
||||
|
||||
在开始之前,在键盘上按 `Ctrl+Alt+T` 来开启终端。在它开启以后,运行:
|
||||
|
||||
sudo pm-hibernate
|
||||
|
||||
在你的电脑关闭后,再重新开启它。这时,你开启的应用被重新打开了吗?如果休眠功能没有发挥作用,请检查你的交换分区大小,它至少要和你可用 RAM 大小相当。
|
||||
|
||||
你可以在系统监视器里查看你的交换分区大小,而系统监视器可以通过在应用菜单或在终端里运行下面的命令来开启:
|
||||
|
||||
$ gnome-system-monitor
|
||||
|
||||
### 在系统托盘里启用休眠功能: ###
|
||||
|
||||
提示模块是通过使用 logind 而不是使用 upower 来更新的。默认情况下,在 upower 和 logind 中,休眠都被禁用了。
|
||||
|
||||
为了开启休眠功能,依次运行下面的命令来编辑配置文件:
|
||||
|
||||
sudo -i
|
||||
|
||||
cd /var/lib/polkit-1/localauthority/50-local.d/
|
||||
|
||||
gedit com.ubuntu.enable-hibernate.pkla
|
||||
|
||||
**提示:假如对你来说,这个配置文件并没有起到作用,请替换上面代码中的 /var/lib 为 /etc 来试试另一个配置文件**
|
||||
|
||||
复制并粘贴下面的代码到文件中并保存:
|
||||
|
||||
[Re-enable hibernate by default in upower]
|
||||
Identity=unix-user:*
|
||||
Action=org.freedesktop.upower.hibernate
|
||||
ResultActive=yes
|
||||
|
||||
[Re-enable hibernate by default in logind]
|
||||
Identity=unix-user:*
|
||||
Action=org.freedesktop.login1.hibernate
|
||||
ResultActive=yes
|
||||
|
||||
重启你的电脑就可以了。
|
||||
|
||||
### 当你盖上笔记本的后盖时,让它休眠: ###
|
||||
|
||||
1.通过下面的命令编辑文件 “/etc/systemd/logind.conf” :
|
||||
|
||||
$ sudo nano /etc/systemd/logind.conf
|
||||
|
||||
2. 将 **#HandleLidSwitch=suspend** 这一行改为 **HandleLidSwitch=hibernate** 并保存文件;
|
||||
|
||||
3. 运行下面的命令或重启你的电脑来应用更改:
|
||||
|
||||
$ sudo restart systemd-logind
|
||||
|
||||
就是这样。享受吧!现在我们有了 dconf 并开启了休眠功能 :) 你的 Ubuntu 将能够完全记住你开启的应用和窗口了。
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/ubuntu-how-to/remember-running-applications-ubuntu/
|
||||
|
||||
作者:[Arun Pyasi][a]
|
||||
译者:[FSSlc](https://github.com/FSSlc)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://linoxide.com/author/arunp/
|
||||
@ -0,0 +1,145 @@
|
||||
Linux 上 wget 或 curl 的更佳替代品
|
||||
================================================================================
|
||||
如果你经常需要通过终端以非交互模式访问网络服务器(例如,从网络上下载文件,或者是测试 RESTful 网络服务接口),可能你会选择的工具是 wget 或 curl。通过大量的命令行选项,这两种工具都可以处理很多非交互网络访问的情况(比如[这里][1],[这里][2],还有[这里][3])。然而,即使像这些一样的强大的工具,也只是与你对如何使用它们的了解程度等同。除非你很精通那些又多又笨(原文是 nitty and gritty)的语法细节,这些工具对于你来说只不过是简单的网络下载器。
|
||||
|
||||
就像宣传的那样,“为人类着想的类 curl 工具”,[HTTPie][4] 设计用来增强 wget 和 curl 的可用性。它的主要目标是使通过命令行与网络服务器进行交互的过程变得尽可能的人性化。为此,HTTPie 支持具有表现力,但又很简单很直观的语法。它以彩色模式显示响应,并且还有一些不错的优点,比如对 JSON 的良好支持,和持久性会话用以作业流程化。
|
||||
|
||||
我知道很多人对把像 wget 和 curl 这样的无处不在的可用的完美工具换成完全没听说过的软件心存怀疑。这种观点是好的,特别是如果你是一个系统管理员、要处理很多不同的硬件的话。然而,对于开发者和终端用户来说,重要的是效率。如果我发现了一个工具的用户友好替代,我没有看到任何问题如果你采用易于使用的版本来节省你宝贵的时间。没有必要对替换掉的工具保持信仰忠诚。毕竟,对于 Linux 来说,最好的事情是可以选择。
|
||||
|
||||
在这篇文章中,让我们来回顾并展示一下我所说的 HTTPie,一个用户友好的 wget 和 curl 的替代。
|
||||
|
||||

|
||||
|
||||
### 在 Linux 上安装 HTTPie ###
|
||||
|
||||
HTTPie 是用 Python 写的,所以你可以在几乎所有地方(Linux,MacOSX,Windows)安装它。而且,在大多数的 Linux 发行版中都有编译好的安装包。
|
||||
|
||||
#### Debian,Ubuntu 或者 Linux Mint: ####
|
||||
|
||||
$ sudo apt-get install httpie
|
||||
|
||||
#### Fedora: ####
|
||||
|
||||
$ sudo yum install httpie
|
||||
|
||||
#### CentOS/RHEL: ####
|
||||
|
||||
首先,启用[EPEL 仓库][5],然后运行:
|
||||
|
||||
$ sudo yum install httpie
|
||||
|
||||
对于任何 Linux 发行版,另一个安装方法时使用[pip][6]。
|
||||
|
||||
$ sudo pip install --upgrade httpie
|
||||
|
||||
### HTTPie 的例子 ###
|
||||
|
||||
当你安装完 HTTPie 后,你可以通过输入 http 命令来调用它。在这篇文章的剩余部分,我会展示几个有用的 http 命令的例子。
|
||||
|
||||
#### 例1:定制头部 ####
|
||||
|
||||
你可以使用 <header:value> 的格式来定制头部。例如,我们发送一个 HTTP GET 请求到 www.test.com ,使用定制用户代理(user-agent)和来源(referer),还有定制头部(比如 MyParam)。
|
||||
|
||||
|
||||
$ http www.test.com User-Agent:Xmodulo/1.0 Referer:http://xmodulo.com MyParam:Foo
|
||||
|
||||
注意到当使用 HTTP GET 方法时,你无需指定任何 HTTP 方法。
|
||||
|
||||
这个 HTTP 请求看起来如下:
|
||||
|
||||
GET / HTTP/1.1
|
||||
Host: www.test.com
|
||||
Accept: */*
|
||||
Referer: http://xmodulo.com
|
||||
Accept-Encoding: gzip, deflate, compress
|
||||
MyParam: Foo
|
||||
User-Agent: Xmodulo/1.0
|
||||
|
||||
#### 例2:下载文件 ####
|
||||
|
||||
你可以把 http 作为文件下载器来使用。你需要像下面一样把输出重定向到文件。
|
||||
|
||||
$ http www.test.com/my_file.zip > my_file.zip
|
||||
|
||||
或者:
|
||||
|
||||
$ http --download www.test.com/my_file.zip
|
||||
|
||||
#### 例3:定制 HTTP 方法 ####
|
||||
|
||||
除了默认的 GET 方法,你还可以使用其他方法(比如 PUT,POST,HEAD)。例如,发送一个 HTTP PUT 请求:
|
||||
|
||||
$ http PUT www.test.com name='Dan Nanni' email=dan@email.com
|
||||
|
||||
#### 例4:提交表单 ####
|
||||
|
||||
使用 http 命令提交表单很容易,如下:
|
||||
|
||||
$ http -f POST www.test.com name='Dan Nanni' comment='Hi there'
|
||||
|
||||
'-f' 选项使 http 命令序列化数据字段,并将 'Content-Type' 设置为 "application/x-www-form-urlencoded; charset=utf-8"。
|
||||
|
||||
这个 HTTP POST 请求看起来如下:
|
||||
|
||||
POST / HTTP/1.1
|
||||
Host: www.test.com
|
||||
Content-Length: 31
|
||||
Content-Type: application/x-www-form-urlencoded; charset=utf-8
|
||||
Accept-Encoding: gzip, deflate, compress
|
||||
Accept: */*
|
||||
User-Agent: HTTPie/0.8.0
|
||||
|
||||
name=Dan+Nanni&comment=Hi+there
|
||||
|
||||
####例5:JSON 支持
|
||||
|
||||
HTTPie 内置 JSON(一种日渐普及的数据交换格式)支持。事实上,HTTPie 默认使用的内容类型(content-type)就是 JSON。因此,当你不指定内容类型发送数据字段时,它们会自动序列化为 JSON 对象。
|
||||
|
||||
$ http POST www.test.com name='Dan Nanni' comment='Hi there'
|
||||
|
||||
这个 HTTP POST 请求看起来如下:
|
||||
|
||||
POST / HTTP/1.1
|
||||
Host: www.test.com
|
||||
Content-Length: 44
|
||||
Content-Type: application/json; charset=utf-8
|
||||
Accept-Encoding: gzip, deflate, compress
|
||||
Accept: application/json
|
||||
User-Agent: HTTPie/0.8.0
|
||||
|
||||
{"name": "Dan Nanni", "comment": "Hi there"}
|
||||
|
||||
#### 例6:输出重定向 ####
|
||||
|
||||
HTTPie 的另外一个用户友好特性是输入重定向,你可以使用缓冲数据提供 HTTP 请求内容。例如:
|
||||
|
||||
$ http POST api.test.com/db/lookup < my_info.json
|
||||
|
||||
或者:
|
||||
|
||||
$ echo '{"name": "Dan Nanni"}' | http POST api.test.com/db/lookup
|
||||
|
||||
### 结束语 ###
|
||||
|
||||
在这篇文章中,我介绍了 HTTPie,一个 wget 和 curl 的可能替代工具。除了这里展示的几个简单的例子,你可以在[官方网站][7]上找到 HTTPie 的很多有趣的应用。再次重复一遍,一款强大的工具也只相当于你对它的了解程度。从个人而言,我更热衷于 HTTPie,因为我在寻找一种更简洁的测试复杂网络接口的方法。
|
||||
|
||||
你怎么看?
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/wget-curl-alternative-linux.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[wangjiezhe](https://github.com/wangjiezhe)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/nanni
|
||||
[1]:http://xmodulo.com/how-to-download-multiple-files-with-wget.html
|
||||
[2]:http://xmodulo.com/how-to-use-custom-http-headers-with-wget.html
|
||||
[3]:http://ask.xmodulo.com/custom-http-header-curl.html
|
||||
[4]:https://github.com/jakubroztocil/httpie
|
||||
[5]:http://xmodulo.com/how-to-set-up-epel-repository-on-centos.html
|
||||
[6]:http://ask.xmodulo.com/install-pip-linux.html
|
||||
[7]:https://github.com/jakubroztocil/httpie
|
||||
@ -0,0 +1,73 @@
|
||||
Linux有问必答--如何在Linux中修改环境变量PATH
|
||||
================================================================================
|
||||
> **提问**: 当我试着运行一个程序时,它提示“command not found”。 但这个程序就在/usr/local/bin下。我该如何添加/usr/local/bin到我的PATH变量下,这样我就可以不用指定路径来运行这个命令了。
|
||||
|
||||
在Linux中,PATH环境变量保存了一系列的目录用于用户在输入的时候搜索命令。PATH变量的值由一系列的由分号分隔的绝对路径组成。每个用户都有特定的PATH环境变量(由系统级的PATH变量初始化)。
|
||||
|
||||
要检查用户的环境变量,用户模式下运行下面的命令:
|
||||
|
||||
$ echo $PATH
|
||||
|
||||
----------
|
||||
|
||||
/usr/lib64/qt-3.3/bin:/bin:/usr/bin:/usr/sbin:/sbin:/home/xmodulo/bin
|
||||
|
||||
或者运行:
|
||||
|
||||
$ env | grep PATH
|
||||
|
||||
----------
|
||||
|
||||
PATH=/usr/lib64/qt-3.3/bin:/bin:/usr/bin:/usr/sbin:/sbin:/home/xmodulo/bin
|
||||
|
||||
如果你的命令不存在于上面任何一个目录内,shell就会抛出一个错误信息:“command not found”。
|
||||
|
||||
如果你想要添加一个另外的目录(比如:/usr/local/bin)到你的PATH变量中,你可以用下面这些命令。
|
||||
|
||||
### 为特定用户修改PATH环境变量 ###
|
||||
|
||||
如果你只想在当前的登录会话中临时地添加一个新的目录(比如:/usr/local/bin)给用户的默认搜索路径,你只需要输入下面的命令。
|
||||
|
||||
$ PATH=$PATH:/usr/local/bin
|
||||
|
||||
检查PATH是否已经更新:
|
||||
|
||||
$ echo $PATH
|
||||
|
||||
----------
|
||||
|
||||
/usr/lib64/qt-3.3/bin:/bin:/usr/bin:/usr/sbin:/sbin:/home/xmodulo/bin:/usr/local/bin
|
||||
|
||||
更新的PATH会在当前的PATH一直有效。然而,更改将在新的会话中失效。
|
||||
|
||||
如果你想要永久更改PATH变量,用编辑器打开~/.bashrc (或者 ~/.bash_profile),接着在最后添加下面这行。
|
||||
|
||||
export PATH=$PATH:/usr/local/bin
|
||||
|
||||
接着运行下面这行永久激活更改:
|
||||
|
||||
$ source ~/.bashrc (or source ~/.bash_profile)
|
||||
|
||||
### 改变系统级的环境变量 ###
|
||||
|
||||
如果你想要永久添加/usr/local/bin到系统级的PATH变量中,像下面这样编辑/etc/profile。
|
||||
|
||||
$ sudo vi /etc/profile
|
||||
|
||||
----------
|
||||
|
||||
export PATH=$PATH:/usr/local/bin
|
||||
|
||||
你重新登录后,更新的环境变量就会生效了。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://ask.xmodulo.com/change-path-environment-variable-linux.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://ask.xmodulo.com/author/nanni
|
||||
@ -0,0 +1,32 @@
|
||||
[已解决] Ubuntu下不能记住亮度设置问题
|
||||
================================================================================
|
||||

|
||||
|
||||
在[解决亮度控制在Ubuntu和Linux Mint下不工作的问题][1]这篇教程里,一些用户提到虽然问题已经得到解决,但是**Ubuntu无法记住亮度设置**,同样的情况在Linux Mint下也会发生。每次开机或从睡眠状态下唤醒,亮度会恢复至最大值或最小值。我知道这种情况很烦。不过幸好我们有很简单的方法来解决**Ubuntu和Linux Mint下的亮度问题**。
|
||||
|
||||
### 解决Ubuntu和Linux下不能记住亮度设置 ###
|
||||
|
||||
[Norbert][2]写了一个脚本,能让Ubuntu和Linux Mint记住亮度设置,不论是开机还是唤醒之后。为了能让你使用这个脚本更简单方便,他把这个适用于Ubuntu 12.04、14.04和14.10的PPA挂在了网上。你需要做的就是输入以下命令:
|
||||
|
||||
sudo add-apt-repository ppa:nrbrtx/sysvinit-backlight
|
||||
sudo apt-get update
|
||||
sudo apt-get install sysvinit-backlight
|
||||
|
||||
安装好之后,重启你的系统。现在就来看看亮度设置有没有被保存下来吧。
|
||||
|
||||
希望这篇小贴士能帮助到你。如果你有任何问题,就[来这儿][3]提bug吧。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://itsfoss.com/ubuntu-mint-brightness-settings/
|
||||
|
||||
作者:[Abhishek][a]
|
||||
译者:[ZTinoZ](https://github.com/ZTinoZ)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://itsfoss.com/author/abhishek/
|
||||
[1]:http://itsfoss.com/fix-brightness-ubuntu-1310/
|
||||
[2]:https://launchpad.net/~nrbrtx/+archive/ubuntu/sysvinit-backlight/+packages
|
||||
[3]:https://launchpad.net/~nrbrtx/+archive/ubuntu/sysvinit-backlight/+packages
|
||||
Loading…
Reference in New Issue
Block a user