mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-03-09 01:30:10 +08:00
commit
e594e30f50
3
.gitmodules
vendored
Normal file
3
.gitmodules
vendored
Normal file
@ -0,0 +1,3 @@
|
||||
[submodule "comic"]
|
||||
path = comic
|
||||
url = https://wxy@github.com/LCTT/comic.git
|
||||
1
comic
Submodule
1
comic
Submodule
@ -0,0 +1 @@
|
||||
Subproject commit 1889dde5a1cb5c96b9b5710916e16759cb29be71
|
||||
@ -1,3 +1,4 @@
|
||||
svtter翻译中..
|
||||
The Many, the Humble, the Ubuntu Users
|
||||
============================================================
|
||||
|
||||
@ -44,7 +45,7 @@ Robin "Roblimo" Miller is a freelance writer and former editor-in-chief at Open
|
||||
via: http://fossforce.com/2017/01/many-humble-ubuntu-users/
|
||||
|
||||
作者:[Robin "Roblimo" Miller][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
译者:[svtter](https://github.com/svtter)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,292 +0,0 @@
|
||||
A comprehensive guide to taking screenshots in Linux using gnome-screenshot
|
||||
============================================================
|
||||
|
||||
### On this page
|
||||
|
||||
1. [About Gnome-screenshot][13]
|
||||
2. [Gnome-screenshot Installation][14]
|
||||
3. [Gnome-screenshot Usage/Features][15]
|
||||
1. [Capturing current active window][1]
|
||||
2. [Window border][2]
|
||||
3. [Adding effects to window borders][3]
|
||||
4. [Screenshot of a particular area][4]
|
||||
5. [Include mouse pointer in snapshot][5]
|
||||
6. [Delay in taking screenshots][6]
|
||||
7. [Run the tool in interactive mode][7]
|
||||
8. [Directly save your screenshot][8]
|
||||
9. [Copy to clipboard][9]
|
||||
10. [Screenshot in case of multiple displays][10]
|
||||
11. [Automate the screen grabbing process][11]
|
||||
12. [Getting help][12]
|
||||
4. [Conclusion][16]
|
||||
|
||||
There are several screenshot taking tools available in the market but most of them are GUI based. If you spend time working on the Linux command line, and are looking for a good, feature-rich command line-based screen grabbing tool, you may want to try out [gnome-screenshot][17]. In this tutorial, I will explain this utility using easy to understand examples.
|
||||
|
||||
Please note that all the examples mentioned in this tutorial have been tested on Ubuntu 16.04 LTS, and the gnome-screenshot version we have used is 3.18.0.
|
||||
|
||||
### About Gnome-screenshot
|
||||
|
||||
Gnome-screenshot is a GNOME tool which - as the name suggests - is used for capturing the entire screen, a particular application window, or any other user defined area. The tool provides several other features, including the ability to apply beautifying effects to borders of captured screenshots.
|
||||
|
||||
### Gnome-screenshot Installation
|
||||
|
||||
The gnome-screenshot tool is pre-installed on Ubuntu systems, but if for some reason you need to install the utility, you can do that using the following command:
|
||||
|
||||
sudo apt-get install gnome-screenshot
|
||||
|
||||
Once the tool is installed, you can launch it by using following command:
|
||||
|
||||
gnome-screenshot
|
||||
|
||||
### Gnome-screenshot Usage/Features
|
||||
|
||||
In this section, we will discuss how the gnome-screenshot tool can be used and what all features it provides.
|
||||
|
||||
By default, when the tool is run without any command line options, it captures the complete screen.
|
||||
|
||||
[
|
||||
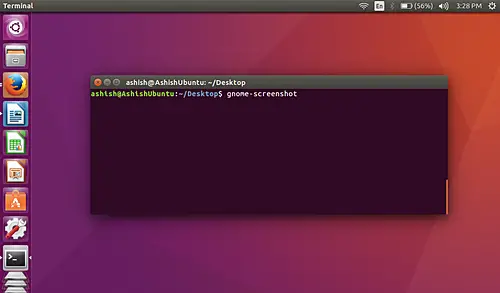
|
||||
][18]
|
||||
|
||||
### Capturing current active window
|
||||
|
||||
If you want, you can limit the screenshot to the current active window by using the -w option.
|
||||
|
||||
gnome-screenshot -w
|
||||
|
||||
[
|
||||
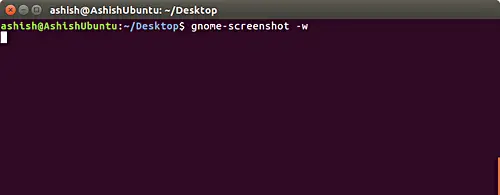
|
||||
][19]
|
||||
|
||||
###
|
||||
Window border
|
||||
|
||||
By default, the utility includes the border of the window it captures, although there's also a specific command line option -b that enables this feature (in case you want to use it somewhere). Here's how it can be used:
|
||||
|
||||
gnome-screenshot -wb
|
||||
|
||||
Of course, you need to use the -w option with -b so that the captured area is the current active window (otherwise, -b will have no effect).
|
||||
|
||||
Moving on and more importantly, you can also remove the border of the window if you want. This can be done using the -B command line option. Following is an example of how you can use this option:
|
||||
|
||||
gnome-screenshot -wB
|
||||
|
||||
Here is an example snapshot:
|
||||
|
||||
[
|
||||
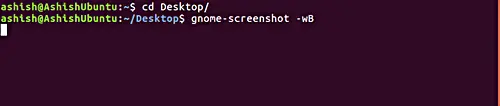
|
||||
][20]
|
||||
|
||||
### Adding effects to window borders
|
||||
|
||||
With the help of the gnome-screenshot tool, you can also add various effects to window borders. This can be done using the --border-effect option.
|
||||
|
||||
You can add any of the effects provided by the utility such as 'shadow' effect (which adds drop shadow to the window), 'border' effect (adds rectangular space around the screenshot), and 'vintage' effect (desaturating the screenshot slightly, tinting it and adding rectangular space around it).
|
||||
|
||||
gnome-screenshot --border-effect=[EFFECT]
|
||||
|
||||
For example, to add the shadow effect, run the following command
|
||||
|
||||
gnome-screenshot –border-effect=shadow
|
||||
|
||||
Here is an example snapshot of the shadow effect:
|
||||
|
||||
[
|
||||

|
||||
][21]
|
||||
|
||||
Please note that the above screenshot focuses on a corner of the terminal to give you a clear view of the shadow effect.
|
||||
|
||||
### Screenshot of a particular area
|
||||
|
||||
If you want, you can also capture a particular area of your computer screen using the gnome-screenshot utility. This can be done by using the -a command line option.
|
||||
|
||||
gnome-screenshot -a
|
||||
|
||||
When the above command is run, your mouse pointer will change into a ‘+’ sign. In this mode, you can grab a particular area of your screen by moving the mouse with left-click pressed.
|
||||
|
||||
Here is an example screenshot wherein I cropped a small area of my terminal window.
|
||||
|
||||
[
|
||||
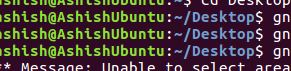
|
||||
][22]
|
||||
|
||||
###
|
||||
Include mouse pointer in snapshot
|
||||
|
||||
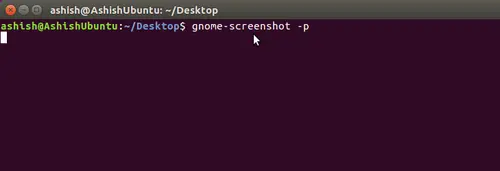
By default, whenever you take screenshot using this tool, it doesn’t include mouse pointer. However, the utility allows you to include the pointer, something which you can do using the -p command line option.
|
||||
|
||||
gnome-screenshot -p
|
||||
|
||||
Here is an example snapshot
|
||||
|
||||
[
|
||||
|
||||
][23]
|
||||
|
||||
### Delay in taking screenshots
|
||||
|
||||
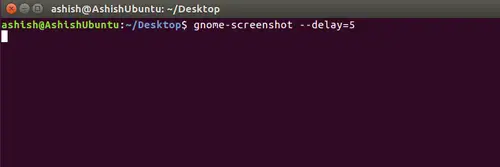
You can also introduce time delay while taking screenshots. For this, you have to assign a value to the --delay option in seconds.
|
||||
|
||||
gnome-screenshot –delay=[SECONDS]
|
||||
|
||||
For example:
|
||||
|
||||
gnome-screenshot --delay=5
|
||||
|
||||
Here is an example screenshot
|
||||
|
||||
[
|
||||
|
||||
][24]
|
||||
|
||||
### Run the tool in interactive mode
|
||||
|
||||
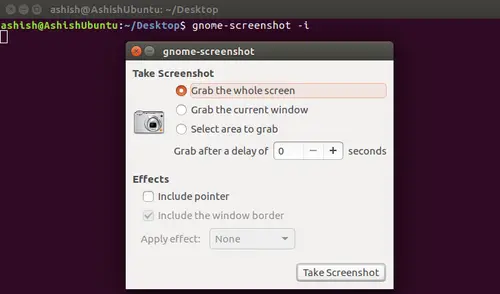
The tool also allows you to access all its features using a single option, which is -i. Using this command line option, user can select one or more of the tool’s features at run time.
|
||||
|
||||
$ gnome-screenshot -i
|
||||
|
||||
Here is an example screenshot
|
||||
|
||||
[
|
||||
|
||||
][25]
|
||||
|
||||
As you can see in the snapshot above, the -i option provides access to many features - such as grabbing the whole screen, grabbing the current window, selecting an area to grab, delay option, effects options - all in an interactive mode.
|
||||
|
||||
### Directly save your screenshot
|
||||
|
||||
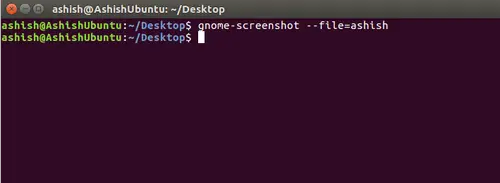
If you want, you can directly save your screenshot from the terminal to your present working directory, meaning you won't be asked to enter a file name for the captured screenshot after the tool is run. This feature can be accessed using the --file command line option which, obviously, requires a filename to be passed to it.
|
||||
|
||||
gnome-screenshot –file=[FILENAME]
|
||||
|
||||
For example:
|
||||
|
||||
gnome-screenshot --file=ashish
|
||||
|
||||
Here is an example snapshot:
|
||||
|
||||
[
|
||||
|
||||
][26]
|
||||
|
||||
### Copy to clipboard
|
||||
|
||||
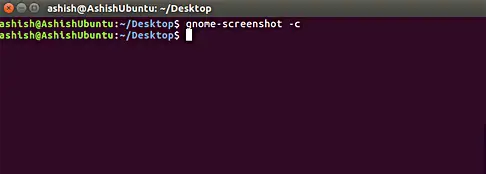
The gnome-screenshot tool also allows you to copy your screenshot to clipboard. This can be done using the -c command line option.
|
||||
|
||||
gnome-screenshot -c
|
||||
|
||||
[
|
||||
|
||||
][27]
|
||||
|
||||
In this mode, you can, for example, directly paste the copied screenshot in any of your image editors (such as GIMP).
|
||||
|
||||
### Screenshot in case of multiple displays
|
||||
|
||||
If there are multiple displays attached to your system and you want to take snapshot of a particular one, then you can use the --display command line option. This option requires a value which should be the display device ID (ID of the screen being grabbed).
|
||||
|
||||
gnome-screenshot --display=[DISPLAY]
|
||||
|
||||
For example:
|
||||
|
||||
gnome-screenshot --display=VGA-0
|
||||
|
||||
In the above example, VGA-0 is the id of the display that I am trying to capture. To find the ID of the display that you want to screenshot, you can use the following command:
|
||||
|
||||
xrandr --query
|
||||
|
||||
To give you an idea, this command produced the following output in my case:
|
||||
|
||||
**$ xrandr --query**
|
||||
Screen 0: minimum 320 x 200, current 1366 x 768, maximum 8192 x 8192
|
||||
**VGA-0** connected primary 1366x768+0+0 (normal left inverted right x axis y axis) 344mm x 194mm
|
||||
1366x768 59.8*+
|
||||
1024x768 75.1 75.0 60.0
|
||||
832x624 74.6
|
||||
800x600 75.0 60.3 56.2
|
||||
640x480 75.0 60.0
|
||||
720x400 70.1
|
||||
**HDMI-0** disconnected (normal left inverted right x axis y axis)
|
||||
|
||||
### Automate the screen grabbing process
|
||||
|
||||
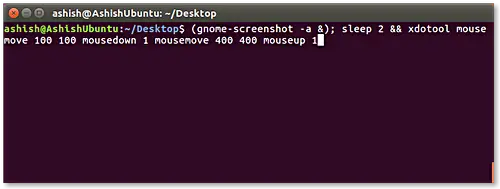
As we have discussed earlier, the -a command line option helps us to grab a particular area of the screen. However, we have to select the area manually using the mouse. If you want, you can automate this process using gnome-screenshot, but in that case, you will have to use an external tool known as xdotool, which is capable of simulating key presses and even mouse events.
|
||||
|
||||
For example:
|
||||
|
||||
(gnome-screenshot -a &); sleep 0.1 && xdotool mousemove 100 100 mousedown 1 mousemove 400 400 mouseup 1
|
||||
|
||||
The mousemove sub-command automatically positions the mouse pointer at specified coordinates X and Y on screen (100 and 100 in the example above). The mousedown subcommand fires an event which performs the same operation as a click (since we wanted left-click, so we used the argument 1) , whereas the mouseup subcommand fires an event which performs the task of a user releasing the mouse-button.
|
||||
|
||||
So all in all, the xdotool command shown above does the same area-grabbing work that you otherwise have to manually do with mouse - specifically, it positions the mouse pointer to 100, 100 coordinates on the screen, selects the area enclosed until the pointer reaches 400,400 coordinates on then screen. The selected area is then captured by gnome-screenshot.
|
||||
|
||||
Here, is the screenshot of the above command:
|
||||
|
||||
[
|
||||
|
||||
][28]
|
||||
|
||||
And this is the output:
|
||||
|
||||
[
|
||||
|
||||
][29]
|
||||
|
||||
For more information on xdotool, head [here][30].
|
||||
|
||||
### Getting help
|
||||
|
||||
If you have a query or in case you are facing a problem related to any of the command line options, then you can use the --help, -? or -h options to get related information.
|
||||
|
||||
gnome-screenshot -h
|
||||
|
||||
For more information on gnome-screenshot, you can go through the command’s manual page or man page.
|
||||
|
||||
man gnome-screenshot
|
||||
|
||||
### Conclusion
|
||||
|
||||
I will recommend that you to use this utlity atleast once as it's not only easy to use for beginners, but also offers a feature-rich experience for advanced usage. Go ahead and give it a try.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.howtoforge.com/tutorial/taking-screenshots-in-linux-using-gnome-screenshot/
|
||||
|
||||
作者:[Himanshu Arora][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://www.howtoforge.com/tutorial/taking-screenshots-in-linux-using-gnome-screenshot/
|
||||
[1]:https://www.howtoforge.com/tutorial/taking-screenshots-in-linux-using-gnome-screenshot/#capturing-current-active-window
|
||||
[2]:https://www.howtoforge.com/tutorial/taking-screenshots-in-linux-using-gnome-screenshot/#window-border
|
||||
[3]:https://www.howtoforge.com/tutorial/taking-screenshots-in-linux-using-gnome-screenshot/#adding-effects-to-window-borders
|
||||
[4]:https://www.howtoforge.com/tutorial/taking-screenshots-in-linux-using-gnome-screenshot/#screenshot-of-a-particular-area
|
||||
[5]:https://www.howtoforge.com/tutorial/taking-screenshots-in-linux-using-gnome-screenshot/#include-mouse-pointer-in-snapshot
|
||||
[6]:https://www.howtoforge.com/tutorial/taking-screenshots-in-linux-using-gnome-screenshot/#delay-in-taking-screenshots
|
||||
[7]:https://www.howtoforge.com/tutorial/taking-screenshots-in-linux-using-gnome-screenshot/#run-the-tool-in-interactive-mode
|
||||
[8]:https://www.howtoforge.com/tutorial/taking-screenshots-in-linux-using-gnome-screenshot/#directly-save-your-screenshot
|
||||
[9]:https://www.howtoforge.com/tutorial/taking-screenshots-in-linux-using-gnome-screenshot/#copy-to-clipboard
|
||||
[10]:https://www.howtoforge.com/tutorial/taking-screenshots-in-linux-using-gnome-screenshot/#screenshot-in-case-of-multiple-displays
|
||||
[11]:https://www.howtoforge.com/tutorial/taking-screenshots-in-linux-using-gnome-screenshot/#automate-the-screen-grabbing-process
|
||||
[12]:https://www.howtoforge.com/tutorial/taking-screenshots-in-linux-using-gnome-screenshot/#getting-help
|
||||
[13]:https://www.howtoforge.com/tutorial/taking-screenshots-in-linux-using-gnome-screenshot/#about-gnomescreenshot
|
||||
[14]:https://www.howtoforge.com/tutorial/taking-screenshots-in-linux-using-gnome-screenshot/#gnomescreenshot-installation
|
||||
[15]:https://www.howtoforge.com/tutorial/taking-screenshots-in-linux-using-gnome-screenshot/#gnomescreenshot-usagefeatures
|
||||
[16]:https://www.howtoforge.com/tutorial/taking-screenshots-in-linux-using-gnome-screenshot/#conclusion
|
||||
[17]:https://linux.die.net/man/1/gnome-screenshot
|
||||
[18]:https://www.howtoforge.com/images/taking-screenshots-in-linux-using-gnome-screenshot/big/gnome-default.png
|
||||
[19]:https://www.howtoforge.com/images/taking-screenshots-in-linux-using-gnome-screenshot/big/activewindow.png
|
||||
[20]:https://www.howtoforge.com/images/taking-screenshots-in-linux-using-gnome-screenshot/big/removeborder.png
|
||||
[21]:https://www.howtoforge.com/images/taking-screenshots-in-linux-using-gnome-screenshot/big/shadoweffect-new.png
|
||||
[22]:https://www.howtoforge.com/images/taking-screenshots-in-linux-using-gnome-screenshot/big/area.png
|
||||
[23]:https://www.howtoforge.com/images/taking-screenshots-in-linux-using-gnome-screenshot/big/includecursor.png
|
||||
[24]:https://www.howtoforge.com/images/taking-screenshots-in-linux-using-gnome-screenshot/big/delay.png
|
||||
[25]:https://www.howtoforge.com/images/taking-screenshots-in-linux-using-gnome-screenshot/big/interactive.png
|
||||
[26]:https://www.howtoforge.com/images/taking-screenshots-in-linux-using-gnome-screenshot/big/ashish.png
|
||||
[27]:https://www.howtoforge.com/images/taking-screenshots-in-linux-using-gnome-screenshot/big/copy.png
|
||||
[28]:https://www.howtoforge.com/images/taking-screenshots-in-linux-using-gnome-screenshot/big/automatedcommand.png
|
||||
[29]:https://www.howtoforge.com/images/taking-screenshots-in-linux-using-gnome-screenshot/big/outputxdo.png
|
||||
[30]:http://manpages.ubuntu.com/manpages/trusty/man1/xdotool.1.html
|
||||
@ -1,339 +0,0 @@
|
||||
Integrate Ubuntu 16.04 to AD as a Domain Member with Samba and Winbind – Part 8
|
||||
============================================================
|
||||
|
||||
|
||||
|
||||
This tutorial describes how to join an Ubuntu machine into a Samba4 Active Directory domain in order to authenticate AD accounts with local ACL for files and directories or to create and map volume shares for domain controller users (act a as file server).
|
||||
|
||||
#### Requirements:
|
||||
|
||||
1. [Create an Active Directory Infrastructure with Samba4 on Ubuntu][1]
|
||||
|
||||
### Step 1: Initial Configurations to Join Ubuntu to Samba4 AD
|
||||
|
||||
1. Before starting to join an Ubuntu host into an Active Directory DC you need to assure that some services are configured properly on local machine.
|
||||
|
||||
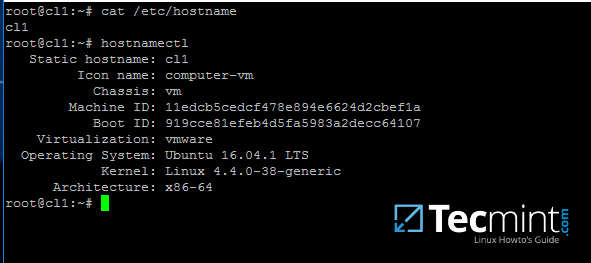
An important aspect of your machine represents the hostname. Setup a proper machine name before joining the domain with the help of hostnamectl command or by manually editing /etc/hostname file.
|
||||
|
||||
```
|
||||
# hostnamectl set-hostname your_machine_short_name
|
||||
# cat /etc/hostname
|
||||
# hostnamectl
|
||||
```
|
||||
[
|
||||
|
||||
][2]
|
||||
|
||||
Set System Hostname
|
||||
|
||||
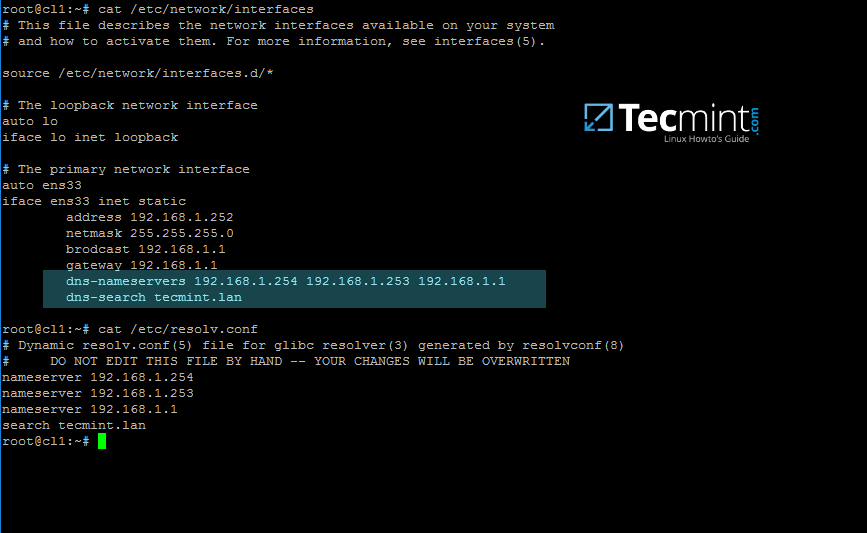
2. On the next step, open and manually edit your machine network settings with the proper IP configurations. The most important settings here are the DNS IP addresses which points back to your domain controller.
|
||||
|
||||
Edit /etc/network/interfaces file and add dns-nameservers statement with your proper AD IP addresses and domain name as illustrated on the below screenshot.
|
||||
|
||||
Also, make sure that the same DNS IP addresses and the domain name are added to /etc/resolv.conf file.
|
||||
|
||||
[
|
||||
|
||||
][3]
|
||||
|
||||
Configure Network Settings for AD
|
||||
|
||||
On the above screenshot, 192.168.1.254 and 192.168.1.253 are the IP addresses of the Samba4 AD DC and Tecmint.lan represents the name of the AD domain which will be queried by all machines integrated into realm.
|
||||
|
||||
3. Restart the network services or reboot the machine in order to apply the new network configurations. Issue a ping command against your domain name in order to test if DNS resolution is working as expected.
|
||||
|
||||
The AD DC should replay with its FQDN. In case you have configured a DHCP server in your network to automatically assign IP settings for your LAN hosts, make sure you add AD DC IP addresses to the DHCP server DNS configurations.
|
||||
|
||||
```
|
||||
# systemctl restart networking.service
|
||||
# ping -c2 your_domain_name
|
||||
```
|
||||
|
||||
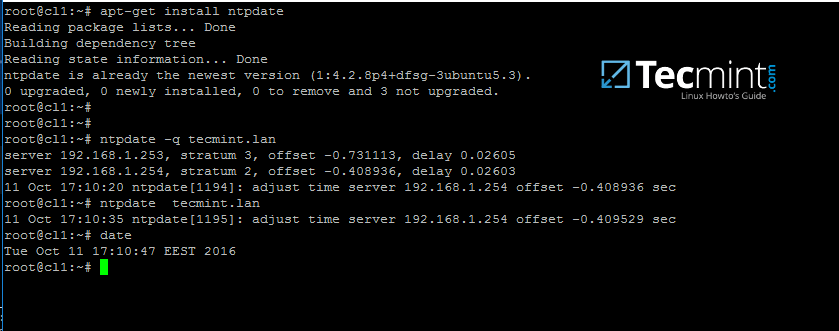
4. The last important configuration required is represented by time synchronization. Install ntpdate package, query and sync time with the AD DC by issuing the below commands.
|
||||
|
||||
```
|
||||
$ sudo apt-get install ntpdate
|
||||
$ sudo ntpdate -q your_domain_name
|
||||
$ sudo ntpdate your_domain_name
|
||||
```
|
||||
[
|
||||
|
||||
][4]
|
||||
|
||||
Time Synchronization with AD
|
||||
|
||||
5. On the next step install the software required by Ubuntu machine to be fully integrated into the domain by running the below command.
|
||||
|
||||
```
|
||||
$ sudo apt-get install samba krb5-config krb5-user winbind libpam-winbind libnss-winbind
|
||||
```
|
||||
[
|
||||

|
||||
][5]
|
||||
|
||||
Install Samba4 in Ubuntu Client
|
||||
|
||||
While the Kerberos packages are installing you should be asked to enter the name of your default realm. Use the name of your domain with uppercases and press Enter key to continue the installation.
|
||||
|
||||
[
|
||||

|
||||
][6]
|
||||
|
||||
Add AD Domain Name
|
||||
|
||||
6. After all packages finish installing, test Kerberos authentication against an AD administrative account and list the ticket by issuing the below commands.
|
||||
|
||||
```
|
||||
# kinit ad_admin_user
|
||||
# klist
|
||||
```
|
||||
[
|
||||

|
||||
][7]
|
||||
|
||||
Check Kerberos Authentication with AD
|
||||
|
||||
### Step 2: Join Ubuntu to Samba4 AD DC
|
||||
|
||||
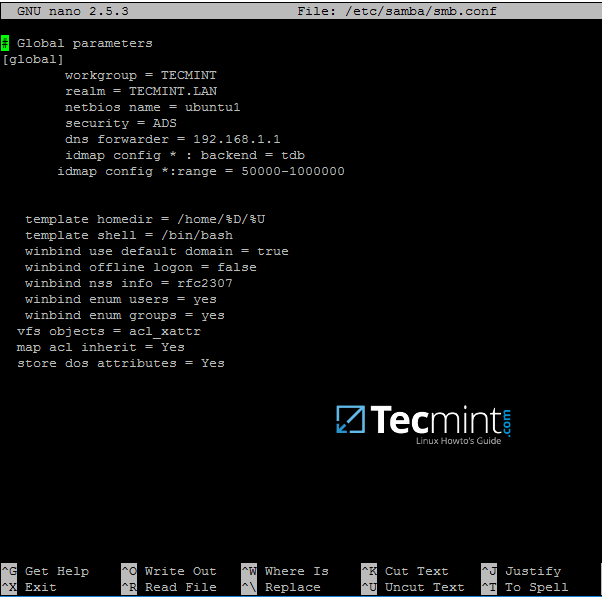
7. The first step in integrating the Ubuntu machine into the Samba4 Active Directory domain is to edit Samba configuration file.
|
||||
|
||||
Backup the default configuration file of Samba, provided by the package manager, in order to start with a clean configuration by running the following commands.
|
||||
|
||||
```
|
||||
# mv /etc/samba/smb.conf /etc/samba/smb.conf.initial
|
||||
# nano /etc/samba/smb.conf
|
||||
```
|
||||
|
||||
On the new Samba configuration file add the below lines:
|
||||
|
||||
```
|
||||
[global]
|
||||
workgroup = TECMINT
|
||||
realm = TECMINT.LAN
|
||||
netbios name = ubuntu
|
||||
security = ADS
|
||||
dns forwarder = 192.168.1.1
|
||||
idmap config * : backend = tdb
|
||||
idmap config *:range = 50000-1000000
|
||||
template homedir = /home/%D/%U
|
||||
template shell = /bin/bash
|
||||
winbind use default domain = true
|
||||
winbind offline logon = false
|
||||
winbind nss info = rfc2307
|
||||
winbind enum users = yes
|
||||
winbind enum groups = yes
|
||||
vfs objects = acl_xattr
|
||||
map acl inherit = Yes
|
||||
store dos attributes = Yes
|
||||
```
|
||||
[
|
||||
|
||||
][8]
|
||||
|
||||
Configure Samba for AD
|
||||
|
||||
Replace workgroup, realm, netbios name and dns forwarder variables with your own custom settings.
|
||||
|
||||
The winbind use default domain parameter causes winbind service to treat any unqualified AD usernames as users of the AD. You should omit this parameter if you have local system accounts names which overlap AD accounts.
|
||||
|
||||
8. Now you should restart all samba daemons and stop and remove unnecessary services and enable samba services system-wide by issuing the below commands.
|
||||
|
||||
```
|
||||
$ sudo systemctl restart smbd nmbd winbind
|
||||
$ sudo systemctl stop samba-ad-dc
|
||||
$ sudo systemctl enable smbd nmbd winbind
|
||||
```
|
||||
|
||||
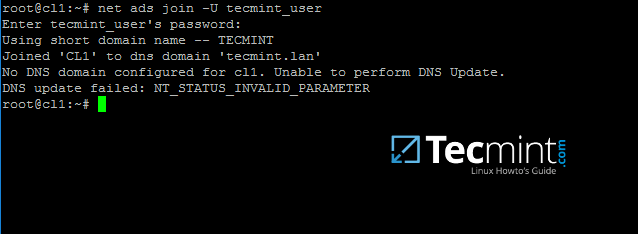
9. Join Ubuntu machine to Samba4 AD DC by issuing the following command. Use the name of an AD DC account with administrator privileges in order for the binding to realm to work as expected.
|
||||
|
||||
```
|
||||
$ sudo net ads join -U ad_admin_user
|
||||
```
|
||||
[
|
||||
|
||||
][9]
|
||||
|
||||
Join Ubuntu to Samba4 AD DC
|
||||
|
||||
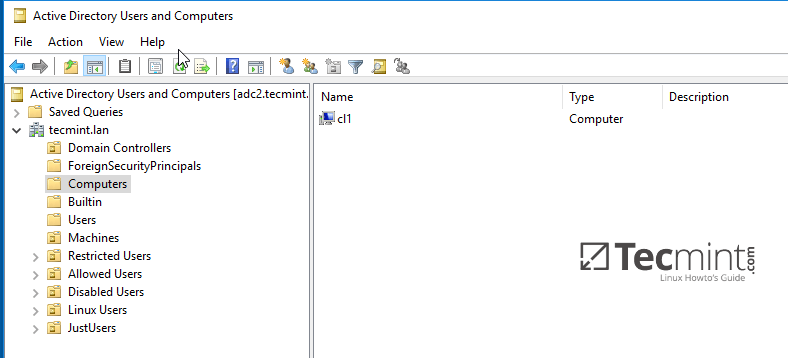
10. From a [Windows machine with RSAT tools installed][10] you can open AD UC and navigate to Computers container. Here, your Ubuntu joined machine should be listed.
|
||||
|
||||
[
|
||||
|
||||
][11]
|
||||
|
||||
Confirm Ubuntu Client in Windows AD DC
|
||||
|
||||
### Step 3: Configure AD Accounts Authentication
|
||||
|
||||
11. In order to perform authentication for AD accounts on the local machine, you need to modify some services and files on the local machine.
|
||||
|
||||
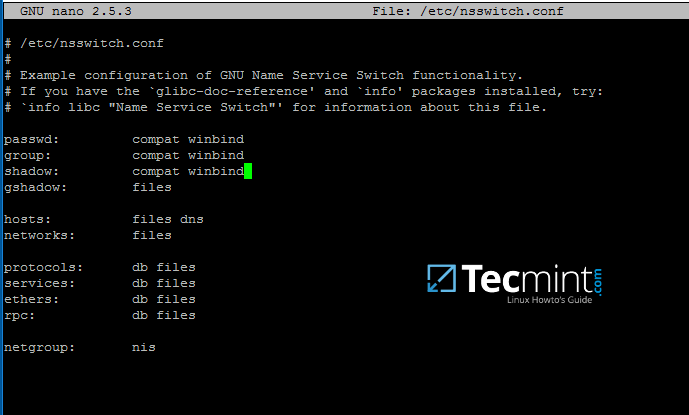
First, open and edit The Name Service Switch (NSS) configuration file.
|
||||
|
||||
```
|
||||
$ sudo nano /etc/nsswitch.conf
|
||||
```
|
||||
|
||||
Next append winbind value for passwd and group lines as illustrated on the below excerpt.
|
||||
|
||||
```
|
||||
passwd: compat winbind
|
||||
group: compat winbind
|
||||
```
|
||||
[
|
||||
|
||||
][12]
|
||||
|
||||
Configure AD Accounts Authentication
|
||||
|
||||
12. In order to test if the Ubuntu machine was successfully integrated to realm run wbinfo command to list domain accounts and groups.
|
||||
|
||||
```
|
||||
$ wbinfo -u
|
||||
$ wbinfo -g
|
||||
```
|
||||
[
|
||||

|
||||
][13]
|
||||
|
||||
List AD Domain Accounts and Groups
|
||||
|
||||
13. Also, check Winbind nsswitch module by issuing the getent command and pipe the results through a filter such as grep to narrow the output only for specific domain users or groups.
|
||||
|
||||
```
|
||||
$ sudo getent passwd| grep your_domain_user
|
||||
$ sudo getent group|grep 'domain admins'
|
||||
```
|
||||
[
|
||||

|
||||
][14]
|
||||
|
||||
Check AD Domain Users and Groups
|
||||
|
||||
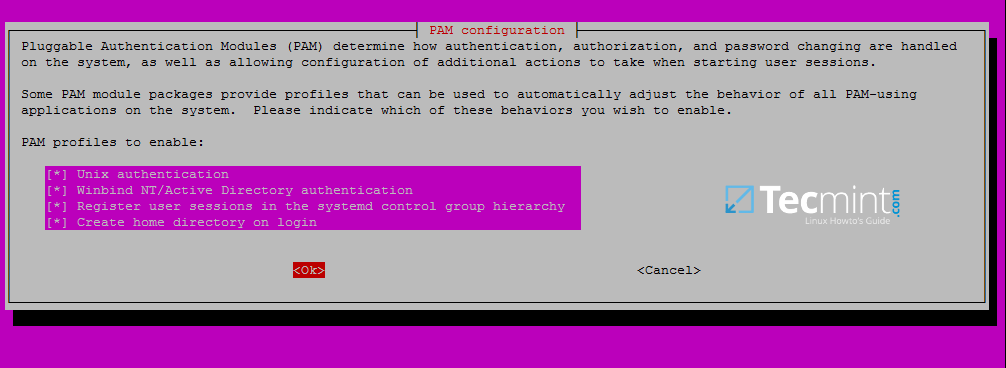
14. In order to authenticate on Ubuntu machine with domain accounts you need to run pam-auth-update command with root privileges and add all the entries required for winbind service and to automatically create home directories for each domain account at the first login.
|
||||
|
||||
Check all entries by pressing `[space]` key and hit ok to apply configuration.
|
||||
|
||||
```
|
||||
$ sudo pam-auth-update
|
||||
```
|
||||
[
|
||||
|
||||
][15]
|
||||
|
||||
Authenticate Ubuntu with Domain Accounts
|
||||
|
||||
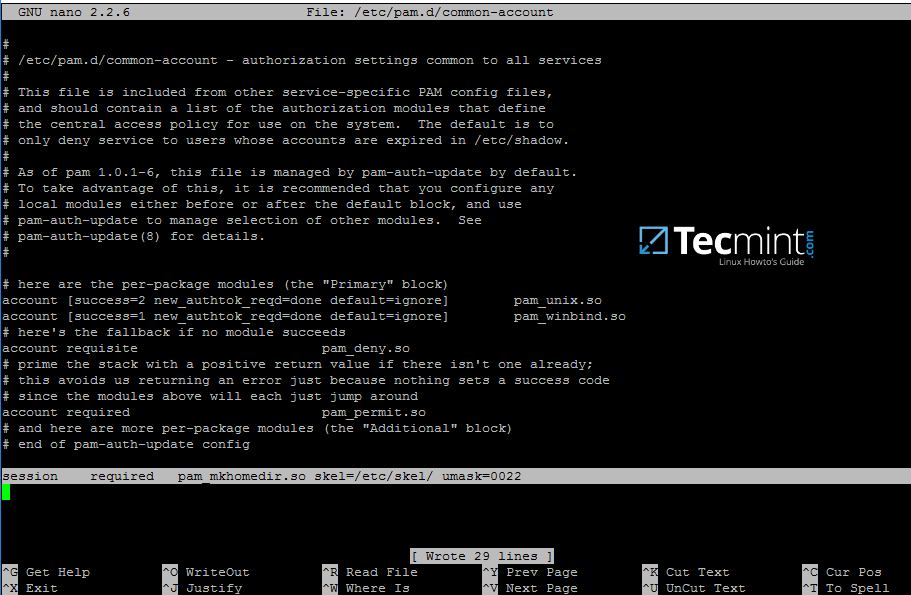
15. On Debian systems you need to manually edit /etc/pam.d/common-account file and the following line in order to automatically create homes for authenticated domain users.
|
||||
|
||||
```
|
||||
session required pam_mkhomedir.so skel=/etc/skel/ umask=0022
|
||||
```
|
||||
[
|
||||
|
||||
][16]
|
||||
|
||||
Authenticate Debian with Domain Accounts
|
||||
|
||||
16. In order for Active Directory users to be able to change password from command line in Linux open /etc/pam.d/common-password file and remove the use_authtok statement from password line to finally look as on the below excerpt.
|
||||
|
||||
```
|
||||
password [success=1 default=ignore] pam_winbind.so try_first_pass
|
||||
```
|
||||
[
|
||||

|
||||
][17]
|
||||
|
||||
Users Allowed to Change Password
|
||||
|
||||
17. To authenticate on Ubuntu host with a Samba4 AD account use the domain username parameter after su – command. Run id command to get extra info about the AD account.
|
||||
|
||||
```
|
||||
$ su - your_ad_user
|
||||
```
|
||||
[
|
||||

|
||||
][18]
|
||||
|
||||
Find AD User Information
|
||||
|
||||
Use [pwd command][19] to see your domain user current directory and passwd command if you want to change password.
|
||||
|
||||
18. To use a domain account with root privileges on your Ubuntu machine, you need to add the AD username to the sudo system group by issuing the below command:
|
||||
|
||||
```
|
||||
$ sudo usermod -aG sudo your_domain_user
|
||||
```
|
||||
|
||||
Login to Ubuntu with the domain account and update your system by running apt-get update command to check if the domain user has root privileges.
|
||||
|
||||
[
|
||||

|
||||
][20]
|
||||
|
||||
Add Sudo User Root Group
|
||||
|
||||
19. To add root privileges for a domain group, open end edit /etc/sudoers file using visudo command and add the following line as illustrated on the below screenshot.
|
||||
|
||||
```
|
||||
%YOUR_DOMAIN\\your_domain\ group ALL=(ALL:ALL) ALL
|
||||
```
|
||||
[
|
||||

|
||||
][21]
|
||||
|
||||
Add Root Privileges to Domain Group
|
||||
|
||||
Use backslashes to escape spaces contained into your domain group name or to escape the first backslash. In the above example the domain group for TECMINT realm is named “domain admins”.
|
||||
|
||||
The preceding percent sign `(%)` symbol indicates that we are referring to a group, not a username.
|
||||
|
||||
20. In case you are running the graphical version of Ubuntu and you want to login on the system with a domain user, you need to modify LightDM display manager by editing /usr/share/lightdm/lightdm.conf.d/50-ubuntu.conf file, add the following lines and reboot the machine to reflect changes.
|
||||
|
||||
```
|
||||
greeter-show-manual-login=true
|
||||
greeter-hide-users=true
|
||||
```
|
||||
|
||||
It should now be able to perform logins on Ubuntu Desktop with a domain account using either your_domain_username or your_domain_username@your_domain.tld or your_domain\your_domain_username format.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
作者简介:
|
||||
|
||||
I'am a computer addicted guy, a fan of open source and linux based system software, have about 4 years experience with Linux distributions desktop, servers and bash scripting.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.tecmint.com/join-ubuntu-to-active-directory-domain-member-samba-winbind/
|
||||
|
||||
作者:[Matei Cezar][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.tecmint.com/author/cezarmatei/
|
||||
|
||||
[1]:http://www.tecmint.com/install-samba4-active-directory-ubuntu/
|
||||
[2]:http://www.tecmint.com/wp-content/uploads/2017/03/Set-Ubuntu-System-Hostname.png
|
||||
[3]:http://www.tecmint.com/wp-content/uploads/2017/03/Configure-Network-Settings-for-AD.png
|
||||
[4]:http://www.tecmint.com/wp-content/uploads/2017/03/Time-Synchronization-with-AD.png
|
||||
[5]:http://www.tecmint.com/wp-content/uploads/2017/03/Install-Samba4-in-Ubuntu-Client.png
|
||||
[6]:http://www.tecmint.com/wp-content/uploads/2017/03/Add-AD-Domain-Name.png
|
||||
[7]:http://www.tecmint.com/wp-content/uploads/2017/03/Check-Kerberos-Authentication-with-AD.png
|
||||
[8]:http://www.tecmint.com/wp-content/uploads/2017/03/Configure-Samba.png
|
||||
[9]:http://www.tecmint.com/wp-content/uploads/2017/03/Join-Ubuntu-to-Samba4-AD-DC.png
|
||||
[10]:http://www.tecmint.com/manage-samba4-ad-from-windows-via-rsat/
|
||||
[11]:http://www.tecmint.com/wp-content/uploads/2017/03/Confirm-Ubuntu-Client-in-RSAT-.png
|
||||
[12]:http://www.tecmint.com/wp-content/uploads/2017/03/Configure-AD-Accounts-Authentication.png
|
||||
[13]:http://www.tecmint.com/wp-content/uploads/2017/03/List-AD-Domain-Accounts-and-Groups.png
|
||||
[14]:http://www.tecmint.com/wp-content/uploads/2017/03/Check-AD-Domain-Users-and-Groups.png
|
||||
[15]:http://www.tecmint.com/wp-content/uploads/2017/03/Authenticate-Ubuntu-with-Domain-Accounts.png
|
||||
[16]:http://www.tecmint.com/wp-content/uploads/2017/03/Authenticate-Debian-with-Domain-Accounts.png
|
||||
[17]:http://www.tecmint.com/wp-content/uploads/2017/03/AD-Domain-Users-Change-Password.png
|
||||
[18]:http://www.tecmint.com/wp-content/uploads/2017/03/Find-AD-User-Information.png
|
||||
[19]:http://www.tecmint.com/pwd-command-examples/
|
||||
[20]:http://www.tecmint.com/wp-content/uploads/2017/03/Add-Sudo-User-Root-Group.png
|
||||
[21]:http://www.tecmint.com/wp-content/uploads/2017/03/Add-Root-Privileges-to-Domain-Group.jpg
|
||||
[22]:http://www.tecmint.com/author/cezarmatei/
|
||||
[23]:http://www.tecmint.com/10-useful-free-linux-ebooks-for-newbies-and-administrators/
|
||||
[24]:http://www.tecmint.com/free-linux-shell-scripting-books/
|
||||
@ -0,0 +1,239 @@
|
||||
GoTTY – Share Your Linux Terminal (TTY) as a Web Application
|
||||
============================================================
|
||||
|
||||
|
||||
GoTTY is a simple GoLang based command line tool that enables you to share your terminal(TTY) as a web application. It turns command line tools into web applications.
|
||||
|
||||
It employs Chrome OS’ terminal emulator (hterm) to execute a JavaScript based terminal on a web browsers. And importantly, GoTTY runs a web socket server that basically transfers output from the TTYto clients and receives input from clients (that is if input from clients is permitted) and forwards it to the TTY.
|
||||
|
||||
Its architecture (hterm + web socket idea) was inspired by [Wetty program][1] which enables terminal over HTTP and HTTPS.
|
||||
|
||||
#### Prerequisites:
|
||||
|
||||
You should have [GoLang (Go Programming Language)][2] environment installed in Linux to run GoTTY.
|
||||
|
||||
### How To Install GoTTY in Linux Systems
|
||||
|
||||
If you already have a [working GoLang environment][3], run the go get command below to install it:
|
||||
|
||||
```
|
||||
# go get github.com/yudai/gotty
|
||||
```
|
||||
|
||||
The command above will install the GoTTY binary in your GOBIN environment variable, try to check if that is the case:
|
||||
|
||||
```
|
||||
# $GOPATH/bin/
|
||||
```
|
||||
[
|
||||
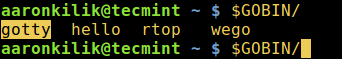
|
||||
][4]
|
||||
|
||||
Check GOBIN Environment
|
||||
|
||||
### How To Use GoTTY in Linux
|
||||
|
||||
To run it, you can use the GOBIN env variable and command auto-completion feature as follows:
|
||||
|
||||
```
|
||||
# $GOBIN/gotty
|
||||
```
|
||||
|
||||
Else, run GoTTY or any other Go program without typing the full path to the binary, add your GOBIN variable to PATH in the `~/.profile` file using the export command below:
|
||||
|
||||
```
|
||||
export PATH="$PATH:$GOBIN"
|
||||
```
|
||||
|
||||
Save the file and close it. Then source the file to effect the changes above:
|
||||
|
||||
```
|
||||
# source ~/.profile
|
||||
```
|
||||
|
||||
The general syntax for running GoTTY commands is:
|
||||
|
||||
```
|
||||
Usage: gotty [options] <Linux command here> [<arguments...>]
|
||||
```
|
||||
|
||||
Now run GoTTY with any command such as the [df command][5] to view system disk partitions space and usage from the web browser:
|
||||
|
||||
```
|
||||
# gotty df -h
|
||||
```
|
||||
|
||||
GoTTY will start a web server at port 8080 by default. Then open the URL: `http://127.0.0.1:8080/`on your web browser and you will see the running command as if it were running on your terminal:
|
||||
|
||||
[
|
||||
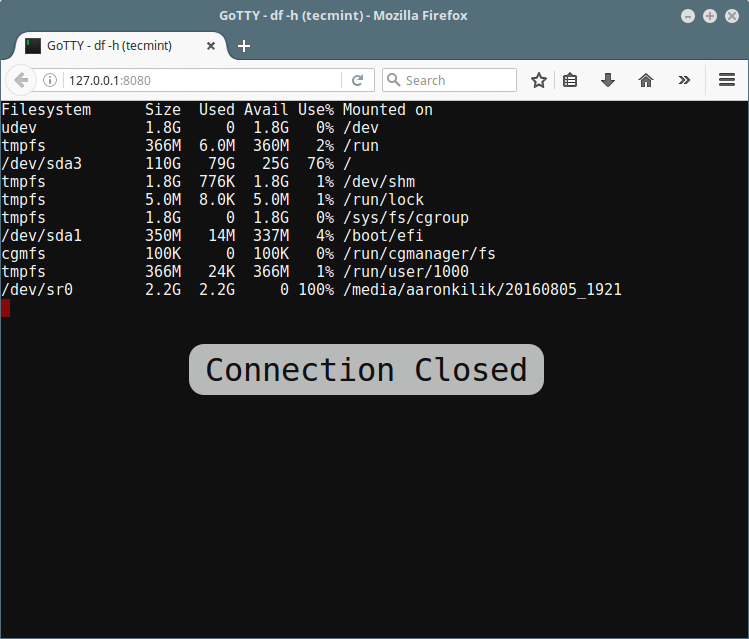
|
||||
][6]
|
||||
|
||||
Gotty Linux Disk Usage
|
||||
|
||||
### How To Customize GoTTY in Linux
|
||||
|
||||
You can alter default options and your terminal (hterm) in the profile file `~/.gotty`, it will load this file by default in case it exists.
|
||||
|
||||
This is the main customization file read by gotty commands, so, create it as follows:
|
||||
|
||||
```
|
||||
# touch ~/.gotty
|
||||
```
|
||||
|
||||
And set your own valid values for the config options (find all config options here) to customize GoTTY for example:
|
||||
|
||||
```
|
||||
// Listen at port 9000 by default
|
||||
port = "9000"
|
||||
// Enable TSL/SSL by default
|
||||
enable_tls = true
|
||||
// hterm preferences
|
||||
// Smaller font and a little bit bluer background color
|
||||
preferences {
|
||||
font_size = 5,
|
||||
background_color = "rgb(16, 16, 32)"
|
||||
}
|
||||
```
|
||||
|
||||
You can set your own index.html file using the `--html` option from the command line:
|
||||
|
||||
```
|
||||
# gotty --index /path/to/index.html uptime
|
||||
```
|
||||
|
||||
### How to Use Security Features in GoTTY
|
||||
|
||||
Because GoTTY doesn’t offer reliable security by default, you need to manually use certain security features explained below.
|
||||
|
||||
#### Permit Clients to Run Commands/Type Input in Terminal
|
||||
|
||||
Note that, by default, GoTTY doesn’t permit clients to type input into the TTY, it only enables window resizing.
|
||||
|
||||
However, you can use the `-w` or `--permit-write` option to allow clients to write to the TTY, which is not recommended due to security threats to the server.
|
||||
|
||||
The following command will use [vi command line editor][7] to open the file fossmint.txt for editing in the web browser:
|
||||
|
||||
```
|
||||
# gotty -w vi fossmint.txt
|
||||
```
|
||||
|
||||
Below is the vi interface as seen from the web browser (use vi commands here as usual):
|
||||
|
||||
[
|
||||
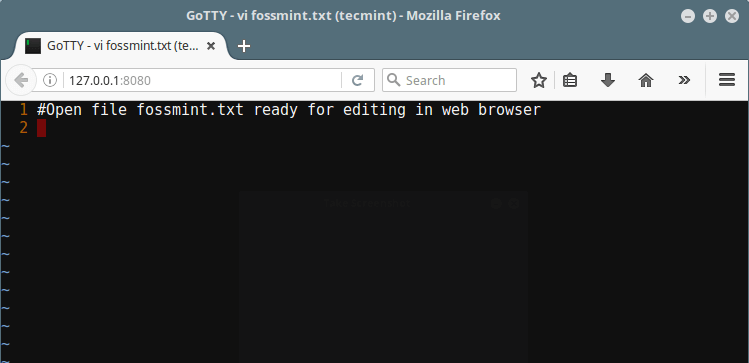
|
||||
][8]
|
||||
|
||||
Gotty Web Vi Editor
|
||||
|
||||
#### Use GoTTY with Basic (Username and Password) Authentication
|
||||
|
||||
Try to activate a basic authentication mechanism, where clients will be required to input the specified username and password to connect to the GoTTY server.
|
||||
|
||||
The command below will restrict client access using the `-c` option to ask users for specified credentials (username: test and password: @67890):
|
||||
|
||||
```
|
||||
# gotty -w -p "9000" -c "test@67890" glances
|
||||
```
|
||||
[
|
||||
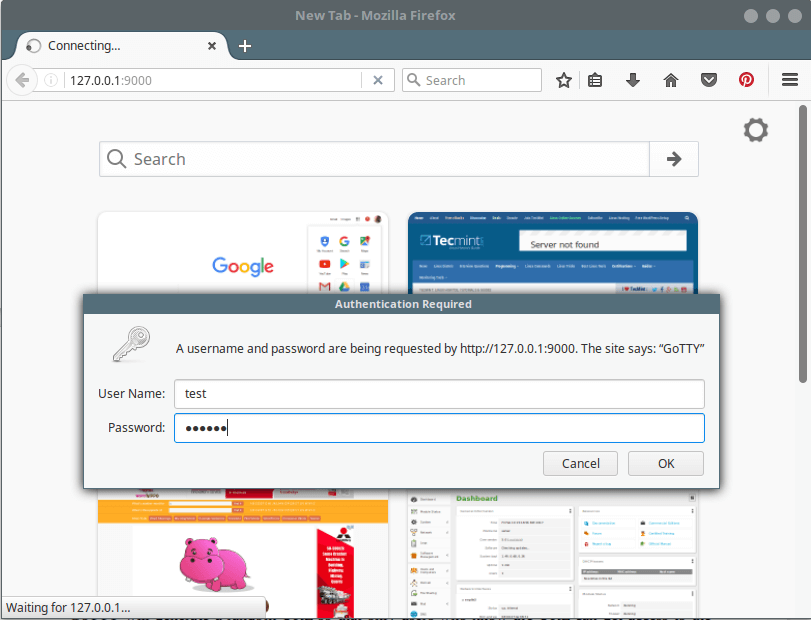
|
||||
][9]
|
||||
|
||||
Gotty with Basic Authentication
|
||||
|
||||
#### Gotty Generate Random URL
|
||||
|
||||
Another way of restricting access to the server is by using the `-r` option. Here, GoTTY will generate a random URL so that only users who know the URL can get access to the server.
|
||||
|
||||
Also use the –title-format “GoTTY – {{ .Command }} ({{ .Hostname }})” option to define the web browsers interface title and [glances command][10] is used to show system monitoring stats:
|
||||
|
||||
```
|
||||
# gotty -r --title-format "GoTTY - {{ .Command }} ({{ .Hostname }})" glances
|
||||
```
|
||||
|
||||
The following is result of the command above as seen from the web browser interface:
|
||||
|
||||
[
|
||||

|
||||
][11]
|
||||
|
||||
Gotty Random URL for Glances Linux Monitoring
|
||||
|
||||
#### Use GoTTY with SSL/TLS
|
||||
|
||||
Because by default, all connections between the server and clients are not encrypted, when you send secret information through GoTTY such as user credentials or any other info, you have to use the `-t` or `--tls` option which enables TLS/SSL on the session:
|
||||
|
||||
GoTTY will by default read the certificate file `~/.gotty.crt` and key file `~/.gotty.key`, therefore, start by creating a self-signed certification as well as the key file using the openssl command below (answer the question asked in order to generate the cert and key files):
|
||||
|
||||
```
|
||||
# openssl req -x509 -nodes -days 365 -newkey rsa:2048 -keyout ~/.gotty.key -out ~/.gotty.crt
|
||||
```
|
||||
|
||||
Then use GoTTY in a secure way with SSL/TLS enabled as follows:
|
||||
|
||||
```
|
||||
# gotty -tr --title-format "GoTTY - {{ .Command }} ({{ .Hostname }})" glances
|
||||
```
|
||||
|
||||
#### Share Your Terminal With Multiple Clients
|
||||
|
||||
You can make use of [terminal multiplexers][12] for sharing a single process with multiple clients, the following command will start a new [tmux session][13] named gotty with [glances command][14] (make sure you have tmux installed):
|
||||
|
||||
```
|
||||
# gotty tmux new -A -s gotty glances
|
||||
```
|
||||
|
||||
To read a different config file, use the –config “/path/to/file” option like so:
|
||||
|
||||
```
|
||||
# gotty -tr --config "~/gotty_new_config" --title-format "GoTTY - {{ .Command }} ({{ .Hostname }})" glances
|
||||
```
|
||||
|
||||
To display the GoTTY version, run the command:
|
||||
|
||||
```
|
||||
# gotty -v
|
||||
```
|
||||
|
||||
Visit the GoTTY GitHub repository to find more usage examples: [https://github.com/yudai/gotty][15]
|
||||
|
||||
That’s all! Have you tried it out? How do you find GoTTY? Share your thoughts with us via the feedback form below.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
作者简介:
|
||||
|
||||
Aaron Kili is a Linux and F.O.S.S enthusiast, an upcoming Linux SysAdmin, web developer, and currently a content creator for TecMint who loves working with computers and strongly believes in sharing knowledge.
|
||||
|
||||
|
||||
|
||||
----------
|
||||
|
||||
|
||||
via: http://www.tecmint.com/gotty-share-linux-terminal-in-web-browser/
|
||||
|
||||
作者:[ Aaron Kili][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.tecmint.com/author/aaronkili/
|
||||
[1]:http://www.tecmint.com/access-linux-server-terminal-in-web-browser-using-wetty/
|
||||
[2]:http://www.tecmint.com/install-go-in-linux/
|
||||
[3]:http://www.tecmint.com/install-go-in-linux/
|
||||
[4]:http://www.tecmint.com/wp-content/uploads/2017/03/Check-Go-Environment.png
|
||||
[5]:http://www.tecmint.com/how-to-check-disk-space-in-linux/
|
||||
[6]:http://www.tecmint.com/wp-content/uploads/2017/03/Gotty-Linux-Disk-Usage.png
|
||||
[7]:http://www.tecmint.com/vi-editor-usage/
|
||||
[8]:http://www.tecmint.com/wp-content/uploads/2017/03/Gotty-Web-Vi-Editor.png
|
||||
[9]:http://www.tecmint.com/wp-content/uploads/2017/03/Gotty-use-basic-authentication.png
|
||||
[10]:http://www.tecmint.com/glances-an-advanced-real-time-system-monitoring-tool-for-linux/
|
||||
[11]:http://www.tecmint.com/wp-content/uploads/2017/03/Gotty-Random-URL-for-Glances-Linux-Monitoring.png
|
||||
[12]:http://www.tecmint.com/tmux-to-access-multiple-linux-terminals-inside-a-single-console/
|
||||
[13]:http://www.tecmint.com/tmux-to-access-multiple-linux-terminals-inside-a-single-console/
|
||||
[14]:http://www.tecmint.com/glances-an-advanced-real-time-system-monitoring-tool-for-linux/
|
||||
[15]:https://github.com/yudai/gotty
|
||||
[16]:http://www.tecmint.com/author/aaronkili/
|
||||
[17]:http://www.tecmint.com/10-useful-free-linux-ebooks-for-newbies-and-administrators/
|
||||
[18]:http://www.tecmint.com/free-linux-shell-scripting-books/
|
||||
@ -1,346 +0,0 @@
|
||||
[调试器的工作原理:第一篇-基础][21]
|
||||
============================================================
|
||||
|
||||
这是调试器工作原理系列文章的第一篇,我不确定这个系列会有多少篇文章,会涉及多少话题,但我仍会从这篇基础开始。
|
||||
|
||||
### 这一篇会讲什么
|
||||
|
||||
我将为大家展示 Linux 中调试器的主要构成模块 - ptrace 系统调用。这篇文章所有代码都是基于 32 位 Ubuntu 操作系统.值得注意的是,尽管这些代码是平台相关的,将他们移植到其他平台应该并不困难。
|
||||
|
||||
### 缘由
|
||||
|
||||
为了理解我们要做什么,让我们先考虑下调试器为了完成调试都需要什么资源。调试器可以开始一个进程并调试这个进程,又或者将自己同某个已经存在的进程关联起来。调试器能够单步执行代码,设定断点并且将程序执行到断点,检查变量的值并追踪堆栈。许多调试器有着更高级的特性,例如在调试器的地址空间内执行表达式或者调用函数,甚至可以在进程执行过程中改变代码并观察效果。
|
||||
|
||||
尽管现代的调试器都十分的复杂 [[1]][13],但他们的工作的原理却是十分的简单。调试器的基础是操作系统与编译器 / 链接器提供的一些基础服务,其余的部分只是[简单的编程][14]。
|
||||
|
||||
### Linux 的调试 - ptrace
|
||||
|
||||
Linux 调试器中的瑞士军刀便是 ptrace 系统调用 [[2]][15]。这是一种复杂却强大的工具,可以允许一个进程控制另外一个进程并从内部替换被控制进程的内核镜像的值[[3]][16].。
|
||||
|
||||
接下来会深入分析。
|
||||
|
||||
### 执行进程的代码
|
||||
|
||||
我将编写一个示例,实现一个在“跟踪”模式下运行的进程。在这个模式下,我们将单步执行进程的代码,就像机器码(汇编代码)被 CPU 执行时一样。我将分段展示、讲解示例代码,在文章的末尾也有完整 c 文件的下载链接,你可以编译、执行或者随心所欲的更改。
|
||||
|
||||
更进一步的计划是实现一段代码,这段代码可以创建可执行用户自定义命令的子进程,同时父进程可以跟踪子进程。首先是主函数:
|
||||
|
||||
```
|
||||
int main(int argc, char** argv)
|
||||
{
|
||||
pid_t child_pid;
|
||||
|
||||
if (argc < 2) {
|
||||
fprintf(stderr, "Expected a program name as argument\n");
|
||||
return -1;
|
||||
}
|
||||
|
||||
child_pid = fork();
|
||||
if (child_pid == 0)
|
||||
run_target(argv[1]);
|
||||
else if (child_pid > 0)
|
||||
run_debugger(child_pid);
|
||||
else {
|
||||
perror("fork");
|
||||
return -1;
|
||||
}
|
||||
|
||||
return 0;
|
||||
}
|
||||
```
|
||||
|
||||
看起来相当的简单:我们用 fork 命令创建了一个新的子进程。if 语句的分支执行子进程(这里称之为“target”),else if 的分支执行父进程(这里称之为“debugger”)。
|
||||
|
||||
下面是 target 进程的代码:
|
||||
|
||||
```
|
||||
void run_target(const char* programname)
|
||||
{
|
||||
procmsg("target started. will run '%s'\n", programname);
|
||||
|
||||
/* Allow tracing of this process */
|
||||
if (ptrace(PTRACE_TRACEME, 0, 0, 0) < 0) {
|
||||
perror("ptrace");
|
||||
return;
|
||||
}
|
||||
|
||||
/* Replace this process's image with the given program */
|
||||
execl(programname, programname, 0);
|
||||
}
|
||||
```
|
||||
|
||||
这段代码中最值得注意的是 ptrace 调用。在 "sys/ptrace.h" 中,ptrace 是如下定义的:
|
||||
|
||||
```
|
||||
long ptrace(enum __ptrace_request request, pid_t pid,
|
||||
void *addr, void *data);
|
||||
```
|
||||
|
||||
第一个参数是 _request_,这是许多预定义的 PTRACE_* 常量中的一个。第二个参数为请求分配进程 ID。第三个与第四个参数是地址与数据指针,用于操作内存。上面代码段中的ptrace调用发起了 PTRACE_TRACEME 请求,这意味着该子进程请求系统内核让其父进程跟踪自己。帮助页面上对于 request 的描述很清楚:
|
||||
|
||||
> 意味着该进程被其父进程跟踪。任何传递给该进程的信号(除了 SIGKILL)都将通过 wait() 方法阻塞该进程并通知其父进程。**此外,该进程的之后所有调用 exec() 动作都将导致 SIGTRAP 信号发送到此进程上,使得父进程在新的程序执行前得到取得控制权的机会**。如果一个进程并不需要它的的父进程跟踪它,那么这个进程不应该发送这个请求。(pid,addr 与 data 暂且不提)
|
||||
|
||||
我高亮了这个例子中我们需要注意的部分。在 ptrace 调用后,run_target 接下来要做的就是通过 execl 传参并调用。如同高亮部分所说明,这将导致系统内核在 execl 创建进程前暂时停止,并向父进程发送信号。
|
||||
|
||||
是时候看看父进程做什么了。
|
||||
|
||||
```
|
||||
void run_debugger(pid_t child_pid)
|
||||
{
|
||||
int wait_status;
|
||||
unsigned icounter = 0;
|
||||
procmsg("debugger started\n");
|
||||
|
||||
/* Wait for child to stop on its first instruction */
|
||||
wait(&wait_status);
|
||||
|
||||
while (WIFSTOPPED(wait_status)) {
|
||||
icounter++;
|
||||
/* Make the child execute another instruction */
|
||||
if (ptrace(PTRACE_SINGLESTEP, child_pid, 0, 0) < 0) {
|
||||
perror("ptrace");
|
||||
return;
|
||||
}
|
||||
|
||||
/* Wait for child to stop on its next instruction */
|
||||
wait(&wait_status);
|
||||
}
|
||||
|
||||
procmsg("the child executed %u instructions\n", icounter);
|
||||
}
|
||||
```
|
||||
|
||||
如前文所述,一旦子进程调用了 exec,子进程会停止并被发送 SIGTRAP 信号。父进程会等待该过程的发生并在第一个 wait() 处等待。一旦上述事件发生了,wait() 便会返回,由于子进程停止了父进程便会收到信号(如果子进程由于信号的发送停止了,WIFSTOPPED 就会返回 true)。
|
||||
|
||||
父进程接下来的动作就是整篇文章最需要关注的部分了。父进程会将 PTRACE_SINGLESTEP 与子进程ID作为参数调用 ptrace 方法。这就会告诉操作系统,“请恢复子进程,但在它执行下一条指令前阻塞”。周而复始地,父进程等待子进程阻塞,循环继续。当 wait() 中传出的信号不再是子进程的停止信号时,循环终止。在跟踪器(父进程)运行期间,这将会是被跟踪进程(子进程)传递给跟踪器的终止信号(如果子进程终止 WIFEXITED 将返回 true)。
|
||||
|
||||
icounter 存储了子进程执行指令的次数。这么看来我们小小的例子也完成了些有用的事情 - 在命令行中指定程序,它将执行该程序并记录它从开始到结束所需要的 cpu 指令数量。接下来就让我们这么做吧。
|
||||
|
||||
### 测试
|
||||
|
||||
我编译了下面这个简单的程序并利用跟踪器运行它:
|
||||
|
||||
```
|
||||
#include <stdio.h>
|
||||
|
||||
int main()
|
||||
{
|
||||
printf("Hello, world!\n");
|
||||
return 0;
|
||||
}
|
||||
|
||||
```
|
||||
|
||||
令我惊讶的是,跟踪器花了相当长的时间,并报告整个执行过程共有超过 100,000 条指令执行。仅仅是一条输出语句?什么造成了这种情况?答案很有趣[[5]][18]。Linux 的 gcc 默认会动态的将程序与 c 的运行时库动态地链接。这就意味着任何程序运行前的第一件事是需要动态库加载器去查找程序运行所需要的共享库。这些代码的数量很大 - 别忘了我们的跟踪器要跟踪每一条指令,不仅仅是主函数的,而是“整个过程中的指令”。
|
||||
|
||||
所以当我将测试程序使用静态编译时(通过比较,可执行文件会多出 500 KB 左右的大小,这部分是 C 运行时库的静态链接),跟踪器提示只有大概 7000 条指令被执行。这个数目仍然不小,但是考虑到在主函数执行前 libc 的初始化以及主函数执行后的清除代码,这个数目已经是相当不错了。此外,printf 也是一个复杂的函数。
|
||||
|
||||
仍然不满意的话,我需要的是“可以测试”的东西 - 例如可以完整记录每一个指令运行的程序执行过程。这当然可以通过汇编代码完成。所以我找到了这个版本的“Hello, world!”并编译了它。
|
||||
|
||||
|
||||
```
|
||||
section .text
|
||||
; The _start symbol must be declared for the linker (ld)
|
||||
global _start
|
||||
|
||||
_start:
|
||||
|
||||
; Prepare arguments for the sys_write system call:
|
||||
; - eax: system call number (sys_write)
|
||||
; - ebx: file descriptor (stdout)
|
||||
; - ecx: pointer to string
|
||||
; - edx: string length
|
||||
mov edx, len
|
||||
mov ecx, msg
|
||||
mov ebx, 1
|
||||
mov eax, 4
|
||||
|
||||
; Execute the sys_write system call
|
||||
int 0x80
|
||||
|
||||
; Execute sys_exit
|
||||
mov eax, 1
|
||||
int 0x80
|
||||
|
||||
section .data
|
||||
msg db 'Hello, world!', 0xa
|
||||
len equ $ - msg
|
||||
```
|
||||
|
||||
|
||||
当然,现在跟踪器提示 7 条指令被执行了,这样一来很容易区分他们。
|
||||
|
||||
|
||||
### 深入指令流
|
||||
|
||||
|
||||
上面那个汇编语言编写的程序使得我可以向你介绍 ptrace 的另外一个强大的用途 - 详细显示被跟踪进程的状态。下面是 run_debugger 函数的另一个版本:
|
||||
|
||||
```
|
||||
void run_debugger(pid_t child_pid)
|
||||
{
|
||||
int wait_status;
|
||||
unsigned icounter = 0;
|
||||
procmsg("debugger started\n");
|
||||
|
||||
/* Wait for child to stop on its first instruction */
|
||||
wait(&wait_status);
|
||||
|
||||
while (WIFSTOPPED(wait_status)) {
|
||||
icounter++;
|
||||
struct user_regs_struct regs;
|
||||
ptrace(PTRACE_GETREGS, child_pid, 0, ®s);
|
||||
unsigned instr = ptrace(PTRACE_PEEKTEXT, child_pid, regs.eip, 0);
|
||||
|
||||
procmsg("icounter = %u. EIP = 0x%08x. instr = 0x%08x\n",
|
||||
icounter, regs.eip, instr);
|
||||
|
||||
/* Make the child execute another instruction */
|
||||
if (ptrace(PTRACE_SINGLESTEP, child_pid, 0, 0) < 0) {
|
||||
perror("ptrace");
|
||||
return;
|
||||
}
|
||||
|
||||
/* Wait for child to stop on its next instruction */
|
||||
wait(&wait_status);
|
||||
}
|
||||
|
||||
procmsg("the child executed %u instructions\n", icounter);
|
||||
}
|
||||
```
|
||||
|
||||
|
||||
不同仅仅存在于 while 循环的开始几行。这个版本里增加了两个新的 ptrace 调用。第一条将进程的寄存器值读取进了一个结构体中。 sys/user.h 定义有 user_regs_struct。如果你查看头文件,头部的注释这么写到:
|
||||
|
||||
```
|
||||
/* The whole purpose of this file is for GDB and GDB only.
|
||||
Don't read too much into it. Don't use it for
|
||||
anything other than GDB unless know what you are
|
||||
doing. */
|
||||
```
|
||||
|
||||
```
|
||||
/* 这个文件只为了GDB而创建
|
||||
不用详细的阅读.如果你不知道你在干嘛,
|
||||
不要在除了 GDB 以外的任何地方使用此文件 */
|
||||
```
|
||||
|
||||
|
||||
不知道你做何感想,但这让我觉得我们找对地方了。回到例子中,一旦我们在 regs 变量中取得了寄存器的值,我们就可以通过将 PTRACE_PEEKTEXT 作为参数、 regs.eip(x86 上的扩展指令指针)作为地址,调用 ptrace ,读取当前进程的当前指令。下面是新跟踪器所展示出的调试效果:
|
||||
|
||||
```
|
||||
$ simple_tracer traced_helloworld
|
||||
[5700] debugger started
|
||||
[5701] target started. will run 'traced_helloworld'
|
||||
[5700] icounter = 1\. EIP = 0x08048080\. instr = 0x00000eba
|
||||
[5700] icounter = 2\. EIP = 0x08048085\. instr = 0x0490a0b9
|
||||
[5700] icounter = 3\. EIP = 0x0804808a. instr = 0x000001bb
|
||||
[5700] icounter = 4\. EIP = 0x0804808f. instr = 0x000004b8
|
||||
[5700] icounter = 5\. EIP = 0x08048094\. instr = 0x01b880cd
|
||||
Hello, world!
|
||||
[5700] icounter = 6\. EIP = 0x08048096\. instr = 0x000001b8
|
||||
[5700] icounter = 7\. EIP = 0x0804809b. instr = 0x000080cd
|
||||
[5700] the child executed 7 instructions
|
||||
```
|
||||
|
||||
|
||||
现在,除了 icounter,我们也可以观察到指令指针与它每一步所指向的指令。怎么来判断这个结果对不对呢?使用 objdump -d 处理可执行文件:
|
||||
|
||||
```
|
||||
$ objdump -d traced_helloworld
|
||||
|
||||
traced_helloworld: file format elf32-i386
|
||||
|
||||
Disassembly of section .text:
|
||||
|
||||
08048080 <.text>:
|
||||
8048080: ba 0e 00 00 00 mov $0xe,%edx
|
||||
8048085: b9 a0 90 04 08 mov $0x80490a0,%ecx
|
||||
804808a: bb 01 00 00 00 mov $0x1,%ebx
|
||||
804808f: b8 04 00 00 00 mov $0x4,%eax
|
||||
8048094: cd 80 int $0x80
|
||||
8048096: b8 01 00 00 00 mov $0x1,%eax
|
||||
804809b: cd 80 int $0x80
|
||||
```
|
||||
|
||||
|
||||
这个结果和我们跟踪器的结果就很容易比较了。
|
||||
|
||||
|
||||
### 将跟踪器关联到正在运行的进程
|
||||
|
||||
|
||||
如你所知,调试器也能关联到已经运行的进程。现在你应该不会惊讶,ptrace 通过 以PTRACE_ATTACH 为参数调用也可以完成这个过程。这里我不会展示示例代码,通过上文的示例代码应该很容易实现这个过程。出于学习目的,这里使用的方法更简便(因为我们在子进程刚开始就可以让它停止)。
|
||||
|
||||
|
||||
### 代码
|
||||
|
||||
|
||||
上文中的简单的跟踪器(更高级的,可以打印指令的版本)的完整c源代码可以在[这里][20]找到。它是通过 4.4 版本的 gcc 以 -Wall -pedantic --std=c99 编译的。
|
||||
|
||||
|
||||
### 结论与计划
|
||||
|
||||
|
||||
诚然,这篇文章并没有涉及很多内容 - 我们距离亲手完成一个实际的调试器还有很长的路要走。但我希望这篇文章至少可以使得调试这件事少一些神秘感。ptrace 是功能多样的系统调用,我们目前只展示了其中的一小部分。
|
||||
|
||||
|
||||
单步调试代码很有用,但也只是在一定程度上有用。上面我通过c的“Hello World!”做了示例。为了执行主函数,可能需要上万行代码来初始化c的运行环境。这并不是很方便。最理想的是在main函数入口处放置断点并从断点处开始分步执行。为此,在这个系列的下一篇,我打算展示怎么实现断点。
|
||||
|
||||
|
||||
|
||||
### 参考
|
||||
|
||||
|
||||
撰写此文时参考了如下文章
|
||||
|
||||
* [Playing with ptrace, Part I][11]
|
||||
* [How debugger works][12]
|
||||
|
||||
|
||||
|
||||
[1] 我没有检查,但我确信 gdb 的代码行数至少有六位数。
|
||||
|
||||
[2] 使用 man 2 ptrace 命令可以了解更多。
|
||||
|
||||
[3] Peek and poke 在系统编程中是很知名的叫法,指的是直接读写内存内容。
|
||||
|
||||
[4] 这篇文章假定读者有一定的 Unix/Linux 编程经验。我假定你知道(至少了解概念)fork,exec 族函数与 Unix 信号。
|
||||
|
||||
[5] 至少你同我一样痴迷与机器/汇编语言。
|
||||
|
||||
[6] 警告:如同我上面所说,文章很大程度上是平台相关的。我简化了一些设定 - 例如,x86指令集不需要调整到 4 字节(我的32位 Ubuntu unsigned int 是 4 字节)。事实上,许多平台都不需要。从内存中读取指令需要预先安装完整的反汇编器。我们这里没有,但实际的调试器是有的。
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://eli.thegreenplace.net/2011/01/23/how-debuggers-work-part-1
|
||||
|
||||
作者:[Eli Bendersky ][a]
|
||||
译者:[译者ID](https://github.com/YYforymj)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://eli.thegreenplace.net/
|
||||
[1]:http://eli.thegreenplace.net/2011/01/23/how-debuggers-work-part-1#id1
|
||||
[2]:http://eli.thegreenplace.net/2011/01/23/how-debuggers-work-part-1#id2
|
||||
[3]:http://eli.thegreenplace.net/2011/01/23/how-debuggers-work-part-1#id3
|
||||
[4]:http://www.jargon.net/jargonfile/p/peek.html
|
||||
[5]:http://eli.thegreenplace.net/2011/01/23/how-debuggers-work-part-1#id4
|
||||
[6]:http://eli.thegreenplace.net/2011/01/23/how-debuggers-work-part-1#id5
|
||||
[7]:http://eli.thegreenplace.net/2011/01/23/how-debuggers-work-part-1#id6
|
||||
[8]:http://eli.thegreenplace.net/tag/articles
|
||||
[9]:http://eli.thegreenplace.net/tag/debuggers
|
||||
[10]:http://eli.thegreenplace.net/tag/programming
|
||||
[11]:http://www.linuxjournal.com/article/6100?page=0,1
|
||||
[12]:http://www.alexonlinux.com/how-debugger-works
|
||||
[13]:http://eli.thegreenplace.net/2011/01/23/how-debuggers-work-part-1#id7
|
||||
[14]:http://en.wikipedia.org/wiki/Small_matter_of_programming
|
||||
[15]:http://eli.thegreenplace.net/2011/01/23/how-debuggers-work-part-1#id8
|
||||
[16]:http://eli.thegreenplace.net/2011/01/23/how-debuggers-work-part-1#id9
|
||||
[17]:http://eli.thegreenplace.net/2011/01/23/how-debuggers-work-part-1#id10
|
||||
[18]:http://eli.thegreenplace.net/2011/01/23/how-debuggers-work-part-1#id11
|
||||
[19]:http://eli.thegreenplace.net/2011/01/23/how-debuggers-work-part-1#id12
|
||||
[20]:https://github.com/eliben/code-for-blog/blob/master/2011/simple_tracer.c
|
||||
[21]:http://eli.thegreenplace.net/2011/01/23/how-debuggers-work-part-1
|
||||
@ -0,0 +1,285 @@
|
||||
|
||||
在linux中使用gnome-screenshot进行截图的综合指南
|
||||
============================================================
|
||||
|
||||
### 在本文中
|
||||
|
||||
1. [关于Gnome-screenshot][13]
|
||||
2. [Gnome-screenshot安装][14]
|
||||
3. [Gnome-screenshot用法/特点][15]
|
||||
1. [捕获当前活动窗口][1]
|
||||
2. [窗体边框][2]
|
||||
3. [添加效果到窗口边框][3]
|
||||
4. [对特定区域的截图][4]
|
||||
5. [在截图中包含鼠标指针][5]
|
||||
6. [延时截图][6]
|
||||
7. [以交互模式运行这个工具][7]
|
||||
8. [直接保存你的截图][8]
|
||||
9. [复制到剪切板][9]
|
||||
10. [多显示器情形下的屏幕截图][10]
|
||||
11. [自动化屏幕截图过程][11]
|
||||
12. [获取帮助][12]
|
||||
4. [总结][16]
|
||||
|
||||
|
||||
在应用市场中有好几种屏幕截图工具可以获得,但其中大多数都是基于GUI的。如果你花时间在linux命令行上工作,而且正在寻找一款优秀的功能丰富的基于命令行的屏幕截图工具,你可能会想尝试[gnome-screenshot][17]。在本教程中,我将使用易于理解的例子来解释这个实用程序。
|
||||
|
||||
请注意,本教程中提到的所有例子已经在Ubuntu 16.04 LTS上测试过,测试所使用的gonme-screenshot版本是3.18.0。
|
||||
|
||||
### 关于Gnome-screenshot
|
||||
|
||||
Gnome-screenshot是一款GNOME工具,顾名思义,它是一款用来对整个屏幕、一个特定的窗口或者用户所定义一些其他区域进行捕获的工具。该工具提供了几个其他的功能,包括对所捕获的截图的边界进行美化的功能。
|
||||
|
||||
### Gnome-screenshot安装
|
||||
|
||||
Ubuntu系统上已经预安装了gnome-screeshot工具,但是如果你出于某些原因需要重新安装这款软件程序,你可以使用下面的命令来进行安装:
|
||||
|
||||
> sudo apt-get install gnome-screeshot
|
||||
|
||||
一旦软件安装完成后,你可以使用下面的命令来启动它:
|
||||
|
||||
> gnome-screenshot
|
||||
|
||||
### Gnome-screenshot用法/特点
|
||||
|
||||
在这部分,我们将讨论gnome-screenshot是如何使用的和它提供的所有功能。
|
||||
[
|
||||

|
||||
][18]
|
||||
#### 捕获当前活动窗口
|
||||
|
||||
如何你需要的话,你可以使用-w选项限制到只对当前活动窗口截图。
|
||||
|
||||
> gnome-screenshot -w
|
||||
|
||||
[
|
||||

|
||||
][19]
|
||||
|
||||
#### 窗口边框
|
||||
|
||||
默认情况下,这个程序会将它捕获的窗口的边框包含在内,尽管还有一个明确的命令行选项-b可以启用此功能(以防你在某处想使用它)。以下是如何使用这个程序的:
|
||||
|
||||
> gnome-screenshot -wb
|
||||
|
||||
当然,你需要同时使用-w选项和-b选项,以便捕获的是当前活动的窗口(否则,-b将没有作用)。
|
||||
|
||||
继续向前且更重要的是,如果你需要的话,你也可以移除窗口的边框。可以使用-B选项来完成。下面是你可以如何使用这个选项的一个例子:
|
||||
|
||||
> gnome-screenshot -wB
|
||||
|
||||
下面是例子的截图:
|
||||
|
||||
[
|
||||

|
||||
][20]
|
||||
|
||||
#### 添加效果到窗口边框
|
||||
|
||||
在gnome-screenshot工具的帮助下,您还可以向窗口边框添加各种效果。这可以使用--border-effect选项来做到。
|
||||
|
||||
你可以添加这款程序所提供的任何效果,比如'shdow'效果(在窗口添加阴影)、'bordor'效果(在屏幕截图周围添加矩形区域)和'vintage'效果(使截图略微淡化,着色并在其周围添加矩形区域)。
|
||||
|
||||
> gnome-screenshot --border-effect=[EFFECT]
|
||||
|
||||
例如,运行下面的命令添加shadow效果:
|
||||
|
||||
> gnome-screenshot –border-effect=shadow
|
||||
|
||||
以下是shadow效果的示例快照:
|
||||
|
||||
[
|
||||

|
||||
][21]
|
||||
|
||||
请注意,上述屏幕截图主要集中在终端的一个角落,以便您清楚地看到阴影效果。
|
||||
|
||||
#### 对特定区域的截图
|
||||
|
||||
如何你需要,你还可以使用gnome-screenshot程序对你电脑屏幕的某一特定区域进行截图。这可以通过使用-a选项来完成。
|
||||
|
||||
> gnome-screenshot -a
|
||||
|
||||
当上面的命令被运行后,你的鼠标指针将会变成'+'这个符号。在这种模式下,你可以按住鼠标左键移动鼠标来对某个特定区域截图。
|
||||
|
||||
这是一个示例截图,其中我裁剪了我的终端窗口的一小部分。
|
||||
|
||||
[
|
||||

|
||||
][22]
|
||||
|
||||
#### 在截图中包含鼠标指针
|
||||
|
||||
默认情况下,每当你使用这个工具截图的时候,截的图中并不会包含鼠标指针。然而,这个程序是可以让你把指针包括进去的,你可以使用-p命令行选项做到。
|
||||
|
||||
> gnome-screenshot -p
|
||||
|
||||
这是一个示例截图:
|
||||
|
||||
[
|
||||

|
||||
][23]
|
||||
|
||||
#### 延时截图
|
||||
|
||||
截图时你还可以引入时间延迟。要做到这,你不得不给--delay选项赋予一个以秒为单位的值。
|
||||
|
||||
> gnome-screenshot –delay=[SECONDS]
|
||||
|
||||
例如:
|
||||
|
||||
> gnome-screenshot --delay=5
|
||||
|
||||
示例截图如下:
|
||||
|
||||
[
|
||||

|
||||
][24]
|
||||
|
||||
#### 以交互模式运行这个工具
|
||||
|
||||
这个工具还允许你使用一个单独的-i选项来访问其所有功能。使用这个命令行选项,用户可以在运行这个命令时使用这个工具的一个或多个功能。
|
||||
|
||||
> gnome-screenshot -i
|
||||
|
||||
示例截图如下:
|
||||
|
||||
[
|
||||

|
||||
][25]
|
||||
|
||||
你可以从上面的截图中看到,-i选项提供了对很多功能的访问,比如截取整个屏幕、截取当前窗口、选择一个区域进行截图、延时选项和特效选项等都在交互模式里。
|
||||
|
||||
#### 直接保存你的截图
|
||||
|
||||
如果你需要的话,你可以直接将你截的图片从终端中保存到你当前的工作目录,这意味着,在这个程序运行后,它并不要求你为截取的图片输入一个文件名。这个功能可以使用--file命令行选项来获取,很明显,需要给它传递一个文件名。
|
||||
|
||||
> gnome-screenshot –file=[FILENAME]
|
||||
|
||||
例如:
|
||||
|
||||
> gnome-screenshot --file=ashish
|
||||
|
||||
示例截图如下:
|
||||
|
||||
[
|
||||

|
||||
][26]
|
||||
|
||||
#### 复制到剪切板
|
||||
|
||||
gnome-screenshot也允许你把你截的图复制到剪切板。这可以通过使用-c命令行选项做到。
|
||||
|
||||
> gnome-screenshot -c
|
||||
|
||||
[
|
||||

|
||||
][27]
|
||||
|
||||
在这个模式下,例如,你可以把复制的图直接粘贴到你的任何一个图片编辑器中(比如GIMP)。
|
||||
|
||||
#### 多显示器情形下的截图
|
||||
|
||||
如果有多个显示器连接到你的系统,你想对某一个进行截图,那么你可以使用--then命令行选项。需要给这个选项一个显示器设备ID的值(需要被截图的显示器的ID)。
|
||||
|
||||
> gnome-screenshot --display=[DISPLAY]
|
||||
|
||||
例如:
|
||||
|
||||
> gnome-screenshot --display=VGA-0
|
||||
|
||||
在上面的例子中,VAG-0是我正试图对其进行截图的显示器的ID。为了找到你想对其进行截图的显示器的ID,你可以使用下面的命令:
|
||||
|
||||
> xrandr --query
|
||||
|
||||
为了让你明白一些,在我的例子中这个命令产生了下面的输出:
|
||||
|
||||
>**$ xrandr --query**
|
||||
Screen 0: minimum 320 x 200, current 1366 x 768, maximum 8192 x 8192
|
||||
**VGA-0** connected primary 1366x768+0+0 (normal left inverted right x axis y axis) 344mm x 194mm
|
||||
1366x768 59.8*+
|
||||
1024x768 75.1 75.0 60.0
|
||||
832x624 74.6
|
||||
800x600 75.0 60.3 56.2
|
||||
640x480 75.0 60.0
|
||||
720x400 70.1
|
||||
**HDMI-0** disconnected (normal left inverted right x axis y axis)
|
||||
|
||||
|
||||
#### 自动化屏幕截图过程
|
||||
|
||||
正如我们之前讨论的,-a命令行选项可以帮助我们对屏幕的某一个特定区域进行截图。然而,我们不得不用鼠标手动选取这个区域。如果你想的话,你可以使用gnome-screenshot来自动化完成这个过程,但是在那种情形下,你将不得不使用一个名为xdotol的工具,它可以模仿敲打键盘甚至是点击鼠标这些事件。
|
||||
|
||||
例如:
|
||||
|
||||
> (gnome-screenshot -a &); sleep 0.1 && xdotool mousemove 100 100 mousedown 1 mousemove 400 400 mouseup 1
|
||||
|
||||
mousemove子命令自动把鼠标指针定位到明确的X坐标和Y坐标的位置(上面例子中是100和100)。mousedown子命令触发一个与点击执行相同操作的事件(因为我们想左击,所以我们使用了参数1),然而mouseup子命令触发一个执行用户释放鼠标按钮的任务的事件。
|
||||
|
||||
所以总而言之,上面所示的xdotool命令做了一项本来不得不使用鼠标手动执行对同一区域进行截图的工作。特别说明,该命令把鼠标指针定位到屏幕上坐标为100,100的位置并选择封闭区域,直到指针到达屏幕上坐标为400,400的位置。所选择的区域随之被gnome-screenshot捕获。
|
||||
|
||||
这是上述命令的截图:
|
||||
|
||||
[
|
||||

|
||||
][28]
|
||||
|
||||
这是输出的结果:
|
||||
|
||||
[
|
||||

|
||||
][29]
|
||||
|
||||
想获取更多关于xdotool的信息,[请到这来][30]
|
||||
|
||||
#### 获取帮助
|
||||
|
||||
如果你有疑问或者你正面临一个与该命令行的其中某个选项有关的问题,那么你可以使用--help、-?或者-h选项来获取相关信息。
|
||||
|
||||
> gnome-screenshot -h
|
||||
|
||||
### 总结
|
||||
|
||||
我推荐你至少使用一次这个程序,因为它不仅对初学者来说比较简单,而且还提供功能丰富的高级用法体验。动起手来,尝试一下吧。
|
||||
|
||||
|
||||
|
||||
via: https://www.howtoforge.com/tutorial/taking-screenshots-in-linux-using-gnome-screenshot/
|
||||
|
||||
作者:[Himanshu Arora][a]
|
||||
译者:[zhousiyu325](https://github.com/zhousiyu325)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://www.howtoforge.com/tutorial/taking-screenshots-in-linux-using-gnome-screenshot/
|
||||
[1]:https://www.howtoforge.com/tutorial/taking-screenshots-in-linux-using-gnome-screenshot/#capturing-current-active-window
|
||||
[2]:https://www.howtoforge.com/tutorial/taking-screenshots-in-linux-using-gnome-screenshot/#window-border
|
||||
[3]:https://www.howtoforge.com/tutorial/taking-screenshots-in-linux-using-gnome-screenshot/#adding-effects-to-window-borders
|
||||
[4]:https://www.howtoforge.com/tutorial/taking-screenshots-in-linux-using-gnome-screenshot/#screenshot-of-a-particular-area
|
||||
[5]:https://www.howtoforge.com/tutorial/taking-screenshots-in-linux-using-gnome-screenshot/#include-mouse-pointer-in-snapshot
|
||||
[6]:https://www.howtoforge.com/tutorial/taking-screenshots-in-linux-using-gnome-screenshot/#delay-in-taking-screenshots
|
||||
[7]:https://www.howtoforge.com/tutorial/taking-screenshots-in-linux-using-gnome-screenshot/#run-the-tool-in-interactive-mode
|
||||
[8]:https://www.howtoforge.com/tutorial/taking-screenshots-in-linux-using-gnome-screenshot/#directly-save-your-screenshot
|
||||
[9]:https://www.howtoforge.com/tutorial/taking-screenshots-in-linux-using-gnome-screenshot/#copy-to-clipboard
|
||||
[10]:https://www.howtoforge.com/tutorial/taking-screenshots-in-linux-using-gnome-screenshot/#screenshot-in-case-of-multiple-displays
|
||||
[11]:https://www.howtoforge.com/tutorial/taking-screenshots-in-linux-using-gnome-screenshot/#automate-the-screen-grabbing-process
|
||||
[12]:https://www.howtoforge.com/tutorial/taking-screenshots-in-linux-using-gnome-screenshot/#getting-help
|
||||
[13]:https://www.howtoforge.com/tutorial/taking-screenshots-in-linux-using-gnome-screenshot/#about-gnomescreenshot
|
||||
[14]:https://www.howtoforge.com/tutorial/taking-screenshots-in-linux-using-gnome-screenshot/#gnomescreenshot-installation
|
||||
[15]:https://www.howtoforge.com/tutorial/taking-screenshots-in-linux-using-gnome-screenshot/#gnomescreenshot-usagefeatures
|
||||
[16]:https://www.howtoforge.com/tutorial/taking-screenshots-in-linux-using-gnome-screenshot/#conclusion
|
||||
[17]:https://linux.die.net/man/1/gnome-screenshot
|
||||
[18]:https://www.howtoforge.com/images/taking-screenshots-in-linux-using-gnome-screenshot/big/gnome-default.png
|
||||
[19]:https://www.howtoforge.com/images/taking-screenshots-in-linux-using-gnome-screenshot/big/activewindow.png
|
||||
[20]:https://www.howtoforge.com/images/taking-screenshots-in-linux-using-gnome-screenshot/big/removeborder.png
|
||||
[21]:https://www.howtoforge.com/images/taking-screenshots-in-linux-using-gnome-screenshot/big/shadoweffect-new.png
|
||||
[22]:https://www.howtoforge.com/images/taking-screenshots-in-linux-using-gnome-screenshot/big/area.png
|
||||
[23]:https://www.howtoforge.com/images/taking-screenshots-in-linux-using-gnome-screenshot/big/includecursor.png
|
||||
[24]:https://www.howtoforge.com/images/taking-screenshots-in-linux-using-gnome-screenshot/big/delay.png
|
||||
[25]:https://www.howtoforge.com/images/taking-screenshots-in-linux-using-gnome-screenshot/big/interactive.png
|
||||
[26]:https://www.howtoforge.com/images/taking-screenshots-in-linux-using-gnome-screenshot/big/ashish.png
|
||||
[27]:https://www.howtoforge.com/images/taking-screenshots-in-linux-using-gnome-screenshot/big/copy.png
|
||||
[28]:https://www.howtoforge.com/images/taking-screenshots-in-linux-using-gnome-screenshot/big/automatedcommand.png
|
||||
[29]:https://www.howtoforge.com/images/taking-screenshots-in-linux-using-gnome-screenshot/big/outputxdo.png
|
||||
[30]:http://manpages.ubuntu.com/manpages/trusty/man1/xdotool.1.html
|
||||
@ -0,0 +1,339 @@
|
||||
Integrate Ubuntu 16.04 to AD as a Domain Member with Samba and Winbind – Part 8
|
||||
============================================================
|
||||
使用 Samba 和 Winbind 将 Ubuntu 16.04 添加到 AD 域 ——(八)
|
||||
|
||||
这篇文章讲述了如何将 Ubuntu 主机加入到 Samba4 AD 域,并实现使用域帐号登录 Ubuntu 系统。
|
||||
|
||||
#### 要求:
|
||||
|
||||
1. [在 Ubuntu 系统上使用 Samba4 软件来创建活动目录架构][1]
|
||||
|
||||
### 第一步: Ubuntu 系统加入到 Samba4 AD 之前的基本配置
|
||||
|
||||
1、在将 Ubuntu 主机加入到 AD DC 之前,你得先确保 Ubuntu 系统中的一些服务配置正常。
|
||||
|
||||
主机名是你的机器的一个重要标识。因此,在加入域前,使用 hostnamectl 命令或者通过手动编辑 /etc/hostname 文件来为 Ubuntu 主机设置一个合适的主机名。
|
||||
|
||||
```
|
||||
# hostnamectl set-hostname your_machine_short_name
|
||||
# cat /etc/hostname
|
||||
# hostnamectl
|
||||
```
|
||||
[
|
||||

|
||||
][2]
|
||||
|
||||
设置系统主机名
|
||||
|
||||
2、在这一步中,打开并编辑网卡配置文件,为你的主机设置一个合适的 IP 地址。注意把 DNS 地址设置为你的域控制器的地址。
|
||||
|
||||
编辑 /etc/network/interfaces 文件,添加 dns-nameservers 参数,并设置为 AD 服务器的 IP 地址,添加 dns-search 参数,其值为域控制器的主机名,如下图所示。
|
||||
|
||||
并且,把上面设置的 DNS IP 地址和域名添加到 /etc/resolv.conf 配置文件中,如下图所示:
|
||||
|
||||
[
|
||||

|
||||
][3]
|
||||
|
||||
为 AD 配置网络设置
|
||||
|
||||
在上面的截图中, 192.168.1.254 和 192.168.1.253 是 Samba4 AD DC 服务器的 IP 地址, Tecmint.lan 是 AD 域名,已加入到这个域中的所有机器都可以查询到该域名。
|
||||
|
||||
3、重启网卡服务或者重启计算机以使网卡配置生效。使用 ping 命令加上域名来检测 DNS 解析是否正常。
|
||||
|
||||
AD DC 应该返回的 FQDN 。如果你的网络中配置了 DHCP 服务器来为局域网中的计算机自动分配 IP 地址,请确保你已经把 AD DC 服务器的 IP 地址添加到 DHCP 服务器的 DNS 配置中。
|
||||
|
||||
```
|
||||
# systemctl restart networking.service
|
||||
# ping -c2 your_domain_name
|
||||
```
|
||||
|
||||
4、最后一步是配置服务器时间同步。安装 ntpdate 包,使用下面的命令来查询并同步 AD DC 服务器的时间。
|
||||
|
||||
```
|
||||
$ sudo apt-get install ntpdate
|
||||
$ sudo ntpdate -q your_domain_name
|
||||
$ sudo ntpdate your_domain_name
|
||||
```
|
||||
[
|
||||

|
||||
][4]
|
||||
|
||||
AD 服务器时间同步
|
||||
|
||||
5、下一步,在 Ubuntu 机器上执行下面的命令来安装加入域环境所必需软件。
|
||||
|
||||
```
|
||||
$ sudo apt-get install samba krb5-config krb5-user winbind libpam-winbind libnss-winbind
|
||||
```
|
||||
[
|
||||

|
||||
][5]
|
||||
|
||||
在 Ubuntu 机器上安装 Samba4 软件
|
||||
|
||||
在 Kerberos 软件包安装的过程中,你会被询问输入默认的域名。输入大写的域名,并按 Enter 键继续安装。
|
||||
|
||||
[
|
||||

|
||||
][6]
|
||||
|
||||
添加 AD 域名
|
||||
|
||||
6、当所有的软件包安装完成之后,使用域管理员帐号来测试 Kerberos 认证,然后执行下面的命令来列出票据信息。
|
||||
|
||||
```
|
||||
# kinit ad_admin_user
|
||||
# klist
|
||||
```
|
||||
[
|
||||

|
||||
][7]
|
||||
|
||||
使用 AD 来检查 Kerberos 认证是否正常
|
||||
|
||||
### 第二步:将 Ubuntu 主机添加到 Samba4 AD DC
|
||||
|
||||
7、将 Ubuntu 主机添加到 Samba4 活动目录域环境中的第一步是编辑 Samba 配置文件。
|
||||
|
||||
备份 Samba 的默认配置文件,这个配置文件是安装 Samba 软件的过程中自动生成的,使用下面的命令来重新初始化配置文件。
|
||||
|
||||
```
|
||||
# mv /etc/samba/smb.conf /etc/samba/smb.conf.initial
|
||||
# nano /etc/samba/smb.conf
|
||||
```
|
||||
|
||||
在新的 Samba 配置文件中添加以下内容:
|
||||
|
||||
```
|
||||
[global]
|
||||
workgroup = TECMINT
|
||||
realm = TECMINT.LAN
|
||||
netbios name = ubuntu
|
||||
security = ADS
|
||||
dns forwarder = 192.168.1.1
|
||||
idmap config * : backend = tdb
|
||||
idmap config *:range = 50000-1000000
|
||||
template homedir = /home/%D/%U
|
||||
template shell = /bin/bash
|
||||
winbind use default domain = true
|
||||
winbind offline logon = false
|
||||
winbind nss info = rfc2307
|
||||
winbind enum users = yes
|
||||
winbind enum groups = yes
|
||||
vfs objects = acl_xattr
|
||||
map acl inherit = Yes
|
||||
store dos attributes = Yes
|
||||
```
|
||||
[
|
||||

|
||||
][8]
|
||||
|
||||
Samba 服务的 AD 环境配置
|
||||
|
||||
根据你本地的实际情况来替换 workgroup , realm , netbios name 和 dns forwarder 的参数值。
|
||||
|
||||
由于 winbind use default domain 这个参数会让 winbind 服务把任何登录系统的帐号都当作 AD 帐号。因此,如果存在本地帐号名跟域帐号同名的情况下,请不要设置该参数。
|
||||
|
||||
8、现在,你应该重启 Samba 后台服务,停止并卸载一些不必要的服务,然后启用 samba 服务的 system-wide 功能,使用下面的命令来完成。
|
||||
|
||||
|
||||
```
|
||||
$ sudo systemctl restart smbd nmbd winbind
|
||||
$ sudo systemctl stop samba-ad-dc
|
||||
$ sudo systemctl enable smbd nmbd winbind
|
||||
```
|
||||
|
||||
9、通过下面的命令,使用域管理员帐号来把 Ubuntu 主机加入到 Samba4 AD DC 中。
|
||||
|
||||
```
|
||||
$ sudo net ads join -U ad_admin_user
|
||||
```
|
||||
[
|
||||

|
||||
][9]
|
||||
|
||||
把 Ubuntu 主机加入到 Samba4 AD DC
|
||||
|
||||
10、在 [安装了 RSAT 工具的 Windows 机器上][10] 打开 AD UC ,展开到包含的计算机。你可以看到已加入域的 Ubuntu 计算机。
|
||||
|
||||
[
|
||||

|
||||
][11]
|
||||
|
||||
确认 Ubuntu 计算机已加入到 Windows AD DC
|
||||
|
||||
### 第三步:配置 AD 帐号认证
|
||||
|
||||
11、为了在本地完成 AD 帐号认证,你需要修改本地机器上的一些服务和配置文件。
|
||||
|
||||
首先,打开并编辑名字服务切换 (NSS) 配置文件。
|
||||
|
||||
```
|
||||
$ sudo nano /etc/nsswitch.conf
|
||||
```
|
||||
|
||||
然后在 passwd 和 group 行添加 winbind 值,如下图所示:
|
||||
|
||||
```
|
||||
passwd: compat winbind
|
||||
group: compat winbind
|
||||
```
|
||||
[
|
||||

|
||||
][12]
|
||||
|
||||
配置 AD 帐号认证
|
||||
|
||||
12、为了测试 Ubuntu 机器是否已加入到域中,你可以使用 wbinfo 命令来列出域帐号和组。
|
||||
|
||||
```
|
||||
$ wbinfo -u
|
||||
$ wbinfo -g
|
||||
```
|
||||
[
|
||||

|
||||
][13]
|
||||
|
||||
列出域帐号和组
|
||||
|
||||
13、同时,使用 getent 命令加上管道符及 grep 参数来过滤指定域用户或组,以测试 Winbind nsswitch 模块是否运行正常。
|
||||
|
||||
```
|
||||
$ sudo getent passwd| grep your_domain_user
|
||||
$ sudo getent group|grep 'domain admins'
|
||||
```
|
||||
[
|
||||

|
||||
][14]
|
||||
|
||||
检查 AD 域用户和组
|
||||
|
||||
14、为了让域帐号在 Ubuntu 机器上完成认证登录,你需要使用 root 帐号运行 pam-auth-update 命令,然后勾选 winbind 服务所需的选项,以让每个域帐号首次登录时自动创建 home 目录。
|
||||
|
||||
查看所有的选项,按 ‘[空格]’键选中,单击 OK 以应用更改。
|
||||
|
||||
```
|
||||
$ sudo pam-auth-update
|
||||
```
|
||||
[
|
||||

|
||||
][15]
|
||||
|
||||
使用域帐号登录 Ubuntu 主机
|
||||
|
||||
15、在 Debian 系统中,如果想让系统自动为登录的域帐号创建家目录,你需要手动编辑 /etc/pam.d/common-account 配置文件,并添加下面的内容。
|
||||
|
||||
```
|
||||
session required pam_mkhomedir.so skel=/etc/skel/ umask=0022
|
||||
```
|
||||
[
|
||||

|
||||
][16]
|
||||
|
||||
使用域帐号登录 Debian 系统
|
||||
|
||||
16、为了让 AD 用户能够在 Linux 的命令行下修改密码,你需要打开 /etc/pam.d/common-password 配置文件,在 password 那一行删除 use_authtok 参数,如下图所示:
|
||||
|
||||
```
|
||||
password [success=1 default=ignore] pam_winbind.so try_first_pass
|
||||
```
|
||||
[
|
||||

|
||||
][17]
|
||||
|
||||
允许域帐号在 Linux 命令行下修改密码
|
||||
|
||||
17、要使用 Samba4 AD 帐号来登录 Ubuntu 主机,在 su - 后面加上域用户名即可。你还可以通过运行 id 命令来查看 AD 帐号的其它信息。
|
||||
|
||||
```
|
||||
$ su - your_ad_user
|
||||
```
|
||||
[
|
||||

|
||||
][18]
|
||||
|
||||
查看 AD 用户信息
|
||||
|
||||
使用 [pwd 命令][19]来查看域帐号的当前目录,如果你想修改域帐号的密码,你可以使用 passwd 命令来完成。
|
||||
|
||||
18、如果想让域帐号在 ubuntu 机器上拥有 root 权限,你可以使用下面的命令来把 AD 帐号添加到 sudo 系统组中:
|
||||
|
||||
```
|
||||
$ sudo usermod -aG sudo your_domain_user
|
||||
```
|
||||
|
||||
登录域帐号登录到 Ubuntu 主机,然后运行 apt-get-update 命令来更新系统,以验证域账号是否拥有 root 权限。
|
||||
|
||||
[
|
||||

|
||||
][20]
|
||||
|
||||
给域帐号添加 root 权限
|
||||
|
||||
19、要为整个域用户组添加 root 权限,使用 vi 命令打开并编辑 /etc/sudoers 配置文件,如下图所示,添加如下内容:
|
||||
|
||||
```
|
||||
%YOUR_DOMAIN\\your_domain\ group ALL=(ALL:ALL) ALL
|
||||
```
|
||||
[
|
||||

|
||||
][21]
|
||||
|
||||
为域帐号组添加 root 权限
|
||||
|
||||
使用反斜杠来转义域用户组的名称中包含的空格,或者用来转义第一个反斜杠。在上面的例子中, TECMINT 域的域用户组的名字是 “domain admins" 。
|
||||
|
||||
前边的 `(%)` 表明我们指定是的用户组而不是用户名。
|
||||
|
||||
20、如果你使用的是图形界面的 Ubuntu 系统,并且你想使用域帐号来登录系统,你需要修改 LightDM 显示管理器,编辑 /usr/share/lightdm/lightdm.conf.d/50-ubuntu.conf 配置文件,添加下面的内容,然后重启系统才能生效。
|
||||
|
||||
```
|
||||
greeter-show-manual-login=true
|
||||
greeter-hide-users=true
|
||||
```
|
||||
|
||||
现在你就可以域帐号来登录 Ubuntu 桌面系统了。使用域用户名或者域用户名@域名.tld 或者域名\域用户名的方式来登录系统。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
作者简介:
|
||||
|
||||
我是一个电脑迷,开源 Linux 系统和软件爱好者,有 4 年多的 Linux 桌面、服务器系统使用和 Base 编程经验。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.tecmint.com/join-ubuntu-to-active-directory-domain-member-samba-winbind/
|
||||
|
||||
作者:[Matei Cezar][a]
|
||||
译者:[rusking](https://github.com/rusking)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.tecmint.com/author/cezarmatei/
|
||||
|
||||
[1]:http://www.tecmint.com/install-samba4-active-directory-ubuntu/
|
||||
[2]:http://www.tecmint.com/wp-content/uploads/2017/03/Set-Ubuntu-System-Hostname.png
|
||||
[3]:http://www.tecmint.com/wp-content/uploads/2017/03/Configure-Network-Settings-for-AD.png
|
||||
[4]:http://www.tecmint.com/wp-content/uploads/2017/03/Time-Synchronization-with-AD.png
|
||||
[5]:http://www.tecmint.com/wp-content/uploads/2017/03/Install-Samba4-in-Ubuntu-Client.png
|
||||
[6]:http://www.tecmint.com/wp-content/uploads/2017/03/Add-AD-Domain-Name.png
|
||||
[7]:http://www.tecmint.com/wp-content/uploads/2017/03/Check-Kerberos-Authentication-with-AD.png
|
||||
[8]:http://www.tecmint.com/wp-content/uploads/2017/03/Configure-Samba.png
|
||||
[9]:http://www.tecmint.com/wp-content/uploads/2017/03/Join-Ubuntu-to-Samba4-AD-DC.png
|
||||
[10]:http://www.tecmint.com/manage-samba4-ad-from-windows-via-rsat/
|
||||
[11]:http://www.tecmint.com/wp-content/uploads/2017/03/Confirm-Ubuntu-Client-in-RSAT-.png
|
||||
[12]:http://www.tecmint.com/wp-content/uploads/2017/03/Configure-AD-Accounts-Authentication.png
|
||||
[13]:http://www.tecmint.com/wp-content/uploads/2017/03/List-AD-Domain-Accounts-and-Groups.png
|
||||
[14]:http://www.tecmint.com/wp-content/uploads/2017/03/Check-AD-Domain-Users-and-Groups.png
|
||||
[15]:http://www.tecmint.com/wp-content/uploads/2017/03/Authenticate-Ubuntu-with-Domain-Accounts.png
|
||||
[16]:http://www.tecmint.com/wp-content/uploads/2017/03/Authenticate-Debian-with-Domain-Accounts.png
|
||||
[17]:http://www.tecmint.com/wp-content/uploads/2017/03/AD-Domain-Users-Change-Password.png
|
||||
[18]:http://www.tecmint.com/wp-content/uploads/2017/03/Find-AD-User-Information.png
|
||||
[19]:http://www.tecmint.com/pwd-command-examples/
|
||||
[20]:http://www.tecmint.com/wp-content/uploads/2017/03/Add-Sudo-User-Root-Group.png
|
||||
[21]:http://www.tecmint.com/wp-content/uploads/2017/03/Add-Root-Privileges-to-Domain-Group.jpg
|
||||
[22]:http://www.tecmint.com/author/cezarmatei/
|
||||
[23]:http://www.tecmint.com/10-useful-free-linux-ebooks-for-newbies-and-administrators/
|
||||
[24]:http://www.tecmint.com/free-linux-shell-scripting-books/
|
||||
Loading…
Reference in New Issue
Block a user