mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-01-25 23:11:02 +08:00
Merge branch 'master' of https://github.com/LCTT/TranslateProject
merge from LCTT
This commit is contained in:
commit
e572bbb3d4
@ -0,0 +1,70 @@
|
||||
Ansible 入门秘诀
|
||||
======
|
||||
|
||||
> 用 Ansible 自动化你的数据中心的关键点。
|
||||
|
||||

|
||||
|
||||
Ansible 是一个开源自动化工具,可以从中央控制节点统一配置服务器、安装软件或执行各种 IT 任务。它采用一对多、<ruby>无客户端<rt>agentless</rt></ruby>的机制,从控制节点上通过 SSH 发送指令给远端的客户机来完成任务(当然除了 SSH 外也可以用别的协议)。
|
||||
|
||||
Ansible 的主要使用群体是系统管理员,他们经常会周期性地执行一些安装、配置应用的工作。尽管如此,一些非特权用户也可以使用 Ansible,例如数据库管理员就可以通过 Ansible 用 `mysql` 这个用户来创建数据库、添加数据库用户、定义访问权限等。
|
||||
|
||||
让我们来看一个简单的使用场景,一位系统管理员每天要配置 100 台服务器,并且必须在每台机器上执行一系列 Bash 命令,然后交付给用户。
|
||||
|
||||
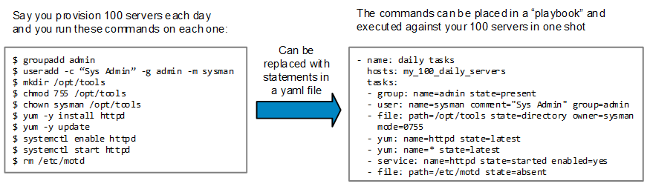
|
||||
|
||||
这是个简单的例子,但应该能够证明:在 yaml 文件里写好命令然后在远程服务器上运行,是一件非常轻松的事。而且如果运行环境不同,就可以加入判断条件,指明某些命令只能在特定的服务器上运行(如:只在那些不是 Ubuntu 或 Debian 的系统上运行 `yum` 命令)。
|
||||
|
||||
Ansible 的一个重要特性是用<ruby>剧本<rt>playbook</rt></ruby>来描述一个计算机系统的最终状态,所以一个剧本可以在服务器上反复执行而不影响其最终状态(LCTT 译注:即是幂等的)。如果某个任务已经被实施过了(如,“用户 `sysman` 已经存在”),那么 Ansible 就会忽略它继续执行后续的任务。
|
||||
|
||||
### 定义
|
||||
|
||||
* <ruby>任务<rt>task</rt></ruby>:是工作的最小单位,它可以是个动作,比如“安装一个数据库服务”、“安装一个 web 服务器”、“创建一条防火墙规则”或者“把这个配置文件拷贝到那个服务器上去”。
|
||||
* <ruby>动作<rt>play</rt></ruby>: 由任务组成,例如,一个动作的内容是要“设置一个数据库,给 web 服务用”,这就包含了如下任务:1)安装数据库包;2)设置数据库管理员密码;3)创建数据库实例;4)为该实例分配权限。
|
||||
* <ruby>剧本<rt>playbook</rt></ruby>:(LCTT 译注:playbook 原指美式橄榄球队的[战术手册][5],也常指“剧本”,此处惯例采用“剧本”译名)由动作组成,一个剧本可能像这样:“设置我的网站,包含后端数据库”,其中的动作包括:1)设置数据库服务器;2)设置 web 服务器。
|
||||
* <ruby>角色<rt>role</rt></ruby>:用来保存和组织剧本,以便分享和再次使用它们。还拿上个例子来说,如果你需要一个全新的 web 服务器,就可以用别人已经写好并分享出来的角色来设置。因为角色是高度可配置的(如果编写正确的话),可以根据部署需求轻松地复用它们。
|
||||
* <ruby>[Ansible 星系][1]<rt>Ansible Galaxy</rt></ruby>:是一个在线仓库,里面保存的是由社区成员上传的角色,方便彼此分享。它与 GitHub 紧密集成,因此这些角色可以先在 Git 仓库里组织好,然后通过 Ansible 星系分享出来。
|
||||
|
||||
这些定义以及它们之间的关系可以用下图来描述:
|
||||
|
||||
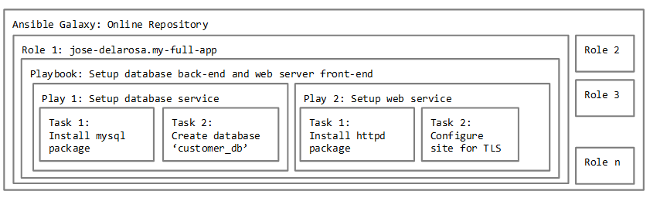
|
||||
|
||||
请注意上面的例子只是组织任务的方式之一,我们当然也可以把安装数据库和安装 web 服务器的剧本拆开,放到不同的角色里。Ansible 星系上最常见的角色是独立安装、配置每个应用服务,你可以参考这些安装 [mysql][2] 和 [httpd][3] 的例子。
|
||||
|
||||
### 编写剧本的小技巧
|
||||
|
||||
学习 Ansible 最好的资源是其[官方文档][4]。另外,像学习其他东西一样,搜索引擎是你的好朋友。我推荐你从一些简单的任务开始,比如安装应用或创建用户。下面是一些有用的指南:
|
||||
|
||||
* 在测试的时候少选几台服务器,这样你的动作可以执行的更快一些。如果它们在一台机器上执行成功,在其他机器上也没问题。
|
||||
* 总是在真正运行前做一次<ruby>测试<rt>dry run</rt></ruby>,以确保所有的命令都能正确执行(要运行测试,加上 `--check-mode` 参数 )。
|
||||
* 尽可能多做测试,别担心搞砸。任务里描述的是所需的状态,如果系统已经达到预期状态,任务会被简单地忽略掉。
|
||||
* 确保在 `/etc/ansible/hosts` 里定义的主机名都可以被正确解析。
|
||||
* 因为是用 SSH 与远程主机通信,主控节点必须要能接受密钥,所以你面临如下选择:1)要么在正式使用之前就做好与远程主机的密钥交换工作;2)要么在开始管理某台新的远程主机时做好准备输入 “Yes”,因为你要接受对方的 SSH 密钥交换请求(LCTT 译注:还有另一个不那么安全的选择,修改主控节点的 ssh 配置文件,将 `StrictHostKeyChecking` 设置成 “no”)。
|
||||
* 尽管你可以在同一个剧本内把不同 Linux 发行版的任务整合到一起,但为每个发行版单独编写剧本会更明晰一些。
|
||||
|
||||
### 总结一下
|
||||
|
||||
Ansible 是你在数据中心里实施运维自动化的好选择,因为它:
|
||||
|
||||
* 无需客户端,所以比其他自动化工具更易安装。
|
||||
* 将指令保存在 YAML 文件中(虽然也支持 JSON),比写 shell 脚本更简单。
|
||||
* 开源,因此你也可以做出自己的贡献,让它更加强大!
|
||||
|
||||
你是怎样使用 Ansible 让数据中心更加自动化的呢?请在评论中分享您的经验。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/2/tips-success-when-getting-started-ansible
|
||||
|
||||
作者:[Jose Delarosa][a]
|
||||
译者:[jdh8383](https://github.com/jdh8383)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://opensource.com/users/jdelaros1
|
||||
[1]:https://galaxy.ansible.com/
|
||||
[2]:https://galaxy.ansible.com/bennojoy/mysql/
|
||||
[3]:https://galaxy.ansible.com/xcezx/httpd/
|
||||
[4]:http://docs.ansible.com/
|
||||
[5]:https://usafootball.com/football-playbook/
|
||||
@ -0,0 +1,80 @@
|
||||
3 款用于学术出版的开源工具
|
||||
======
|
||||
> 学术出版业每年的价值超过 260 亿美元。
|
||||
|
||||
|
||||
|
||||
有一个行业在采用数字化或开源工具方面已落后其它行业,那就是竞争与利润并存的学术出版业。根据 Stephen Buranyi 去年在 [卫报][1] 上发表的一份图表,这个估值超过 190 亿英镑(260 亿美元)的行业,即使是最重要的科学研究方面,至今其系统在选题、出版甚至分享方面仍受限于印刷媒介的诸多限制。全新的数字时代科技展现了一个巨大机遇,可以加速探索、推动科学协作而非竞争,以及将投入从基础建设导向有益于社会的研究。
|
||||
|
||||
非盈利性的 [eLife 倡议][2] 是由研究资金赞助方建立,旨在通过使用数字或者开源技术来走出上述僵局。除了为生命科学和生物医疗方面的重大成就出版开放式获取的期刊,eLife 已将自己变成了一个在研究交流方面的实验和展示创新的平台 —— 而大部分的实验都是基于开源精神的。
|
||||
|
||||
致力于开放出版基础设施项目给予我们加速接触、采用科学技术、提升用户体验的机会。我们认为这种机会对于推动学术出版行业是重要的。大而化之地说,开源产品的用户体验经常是有待开发的,而有时候这种情况会阻止其他人去使用它。作为我们在 OSS(开源软件)开发中投入的一部分,为了鼓励更多用户使用这些产品,我们十分注重用户体验。
|
||||
|
||||
我们所有的代码都是开源的,并且我们也积极鼓励社区参与进我们的项目中。这对我们来说意味着更快的迭代、更多的实验、更大的透明度,同时也拓宽了我们工作的外延。
|
||||
|
||||
我们现在参与的项目,例如 Libero (之前称作 [eLife Continuum][3])和 <ruby>[可重现文档栈][4]<rt>Reproducible Document Stack</rt></ruby> 的开发,以及我们最近和 [Hypothesis][5] 的合作,展示了 OSS 是如何在评估、出版以及新发现的沟通方面带来正面影响的。
|
||||
|
||||
### Libero
|
||||
|
||||
Libero 是面向出版商的服务及应用套餐,它包括一个后期制作出版系统、整套前端用户界面样式套件、Libero 的镜头阅读器、一个 Open API 以及一个搜索及推荐引擎。
|
||||
|
||||
去年我们采取了用户驱动的方式重新设计了 Libero 的前端,可以使用户较少地分心于网站的“陈设”,而是更多地集中关注于研究文章上。我们和 eLife 社区成员测试并迭代了该站点所有的核心功能,以确保给所有人最好的阅读体验。该网站的新 API 也为机器阅读能力提供了更简单的访问途径,其中包括文本挖掘、机器学习以及在线应用开发。
|
||||
|
||||
我们网站上的内容以及引领新设计的样式都是开源的,以鼓励 eLife 和其它想要使用它的出版商后续的产品开发。
|
||||
|
||||
### 可重现文档栈
|
||||
|
||||
在与 [Substance][6] 和 [Stencila][7] 的合作下,eLife 也参与了一个项目来创建可重现文档栈(RDS)—— 一个开放式的创作、编纂以及在线出版可重现的计算型手稿的工具栈。
|
||||
|
||||
今天越来越多的研究人员能够通过 [R Markdown][8] 和 [Python][9] 等语言记录他们的计算实验。这些可以作为实验记录的重要部分,但是尽管它们可以独立于最终的研究文章或与之一同分享,但传统出版流程经常将它们视为次级内容。为了发表论文,使用这些语言的研究人员除了将他们的计算结果用图片的形式“扁平化”提交外别无他法。但是这导致了许多实验价值和代码和计算数据可重复利用性的流失。诸如 [Jupyter][10] 这样的电子笔记本解决方案确实可以使研究员以一种可重复利用、可执行的简单形式发布,但是这种方案仍然是出版的手稿的补充,而不是不可或缺的一部分。
|
||||
|
||||
[可重现文档栈][11] 项目旨在通过开发、发布一个可重现原稿的产品原型来解决这些挑战,该原型将代码和数据视为文档的组成部分,并展示了从创作到出版的完整端对端技术栈。它将最终允许用户以一种包含嵌入代码块和计算结果(统计结果、图表或图形)的形式提交他们的手稿,并在出版过程中保留这些可视、可执行的部分。那时出版商就可以将这些做为出版的在线文章的组成部分而保存。
|
||||
|
||||
### 用 Hypothesis 进行开放式注解
|
||||
|
||||
最近,我们与 [Hypothesis][12] 合作引进了开放式注解,使得我们网站的用户们可以写评语、高亮文章重要部分以及与在线阅读的群体互动。
|
||||
|
||||
通过这样的合作,开源的 Hypothesis 软件被定制得更具有现代化的特性,如单次登录验证、用户界面定制,给予了出版商在他们自己网站上实现更多的控制。这些提升正引导着关于出版学术内容的高质量讨论。
|
||||
|
||||
这个工具可以无缝集成到出版商的网站,学术出版平台 [PubFactory][13] 和内容解决方案供应商 [Ingenta][14] 已经利用了它优化后的特性集。[HighWire][15] 和 [Silverchair][16] 也为他们的出版商提供了实施这套方案的机会。
|
||||
|
||||
### 其它产业和开源软件
|
||||
|
||||
随着时间的推移,我们希望看到更多的出版商采用 Hypothesis、Libero 以及其它开源项目去帮助他们促进重要科学研究的发现以及循环利用。但是 eLife 的创新机遇也能被其它行业所利用,因为这些软件和其它 OSS 技术在其他行业也很普遍。
|
||||
|
||||
数据科学的世界离不开高质量、良好支持的开源软件和围绕它们形成的社区;[TensorFlow][17] 就是这样一个好例子。感谢 OSS 以及其社区,AI 和机器学习的所有领域相比于计算机的其它领域的提升和发展更加迅猛。与之类似的是以 Linux 作为云端 Web 主机的爆炸性增长、接着是 Docker 容器、以及现在 GitHub 上最流行的开源项目之一的 Kubernetes 的增长。
|
||||
|
||||
所有的这些技术使得机构们能够用更少的资源做更多的事情,并专注于创新而不是重新发明轮子上。最后,这就是 OSS 真正的好处:它使得我们从互相的失败中学习,在互相的成功中成长。
|
||||
|
||||
我们总是在寻找与研究和科技界面方面最好的人才和想法交流的机会。你可以在 [eLife Labs][18] 上或者联系 [innovation@elifesciences.org][19] 找到更多这种交流的信息。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/3/scientific-publishing-software
|
||||
|
||||
作者:[Paul Shanno][a]
|
||||
译者:[tomjlw](https://github.com/tomjlw)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://opensource.com/users/pshannon
|
||||
[1]:https://www.theguardian.com/science/2017/jun/27/profitable-business-scientific-publishing-bad-for-science
|
||||
[2]:https://elifesciences.org/about
|
||||
[3]:https://elifesciences.org/inside-elife/33e4127f/elife-introduces-continuum-a-new-open-source-tool-for-publishing
|
||||
[4]:https://elifesciences.org/for-the-press/e6038800/elife-supports-development-of-open-technology-stack-for-publishing-reproducible-manuscripts-online
|
||||
[5]:https://elifesciences.org/for-the-press/81d42f7d/elife-enhances-open-annotation-with-hypothesis-to-promote-scientific-discussion-online
|
||||
[6]:https://github.com/substance
|
||||
[7]:https://github.com/stencila/stencila
|
||||
[8]:https://rmarkdown.rstudio.com/
|
||||
[9]:https://www.python.org/
|
||||
[10]:http://jupyter.org/
|
||||
[11]:https://elifesciences.org/labs/7dbeb390/reproducible-document-stack-supporting-the-next-generation-research-article
|
||||
[12]:https://github.com/hypothesis
|
||||
[13]:http://www.pubfactory.com/
|
||||
[14]:http://www.ingenta.com/
|
||||
[15]:https://github.com/highwire
|
||||
[16]:https://www.silverchair.com/community/silverchair-universe/hypothesis/
|
||||
[17]:https://www.tensorflow.org/
|
||||
[18]:https://elifesciences.org/labs
|
||||
[19]:mailto:innovation@elifesciences.org
|
||||
@ -1,16 +1,18 @@
|
||||
[#]:collector:(lujun9972)
|
||||
[#]:translator:(lujun9972)
|
||||
[#]:reviewer:( )
|
||||
[#]:publisher:( )
|
||||
[#]:url:( )
|
||||
[#]:subject:(Schedule a visit with the Emacs psychiatrist)
|
||||
[#]:via:(https://opensource.com/article/18/12/linux-toy-eliza)
|
||||
[#]:author:(Jason Baker https://opensource.com/users/jason-baker)
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (lujun9972)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-10601-1.html)
|
||||
[#]: subject: (Schedule a visit with the Emacs psychiatrist)
|
||||
[#]: via: (https://opensource.com/article/18/12/linux-toy-eliza)
|
||||
[#]: author: (Jason Baker https://opensource.com/users/jason-baker)
|
||||
|
||||
预约 Emacs 心理医生
|
||||
======
|
||||
Eliza 是一个隐藏于某个 Linux 最流行文本编辑器中的自然语言处理聊天机器人。
|
||||
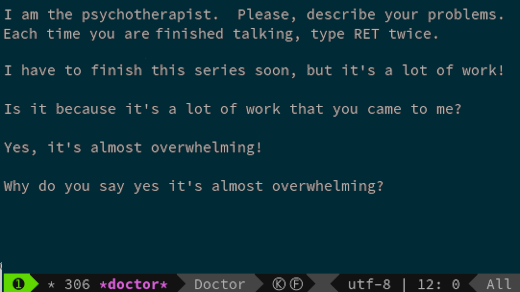
|
||||
|
||||
> Eliza 是一个隐藏于某个 Linux 最流行文本编辑器中的自然语言处理聊天机器人。
|
||||
|
||||

|
||||
|
||||
欢迎你,今天时期 24 天的 Linux 命令行玩具的又一天。如果你是第一次访问本系列,你可能会问什么是命令行玩具呢。我们将会逐步确定这个概念,但一般来说,它可能是一个游戏,或任何能让你在终端玩的开心的其他东西。
|
||||
|
||||
@ -22,24 +24,23 @@ Eliza 是一个隐藏于某个 Linux 最流行文本编辑器中的自然语言
|
||||
|
||||
要启动 [Eliza][1],首先,你需要启动 Emacs。很有可能 Emacs 已经安装在你的系统中了,但若没有,它基本上也肯定在你默认的软件仓库中。
|
||||
|
||||
由于我要求本系列的工具一定要时运行在终端内,因此使用 **-nw** 标志来启动 Emacs 让它在你的终端模拟器中运行。
|
||||
由于我要求本系列的工具一定要时运行在终端内,因此使用 `-nw` 标志来启动 Emacs 让它在你的终端模拟器中运行。
|
||||
|
||||
```
|
||||
$ emacs -nw
|
||||
```
|
||||
|
||||
在 Emacs 中,输入 M-x doctor 来启动 Eliza。对于像我这样有 Vim 背景的人可能不知道这是什么意思,只需要按下 escape,输入 x 然后输入 doctor。然后,向它倾述所有假日的烦恼吧。
|
||||
在 Emacs 中,输入 `M-x doctor` 来启动 Eliza。对于像我这样有 Vim 背景的人可能不知道这是什么意思,只需要按下 `escape`,输入 `x` 然后输入 `doctor`。然后,向它倾述所有假日的烦恼吧。
|
||||
|
||||
Eliza 历史悠久,最早可以追溯到 1960 年代中期的 MIT 人工智能实验室。[维基百科 ][2] 上有它历史的详细说明。
|
||||
|
||||
Eliza 并不是 Emacs 中唯一的娱乐工具。查看 [手册 ][3] 可以看到一整列好玩的玩具。
|
||||
Eliza 历史悠久,最早可以追溯到 1960 年代中期的 MIT 人工智能实验室。[维基百科][2] 上有它历史的详细说明。
|
||||
|
||||
Eliza 并不是 Emacs 中唯一的娱乐工具。查看 [手册][3] 可以看到一整列好玩的玩具。
|
||||
|
||||
![Linux toy:eliza animated][5]
|
||||
|
||||
你有什么喜欢的命令行玩具值得推荐吗?我们时间不多了,但我还是想听听你的建议。请在下面评论中告诉我,我会查看的。另外也欢迎告诉我你们对本次玩具的想法。
|
||||
|
||||
请一定要看看昨天的玩具,[带着这个复刻版吃豆人来到 Linux 终端游乐中心 ][6],然后明天再来看另一个玩具!
|
||||
请一定要看看昨天的玩具,[带着这个复刻版吃豆人来到 Linux 终端游乐中心][6],然后明天再来看另一个玩具!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
@ -48,7 +49,7 @@ via: https://opensource.com/article/18/12/linux-toy-eliza
|
||||
作者:[Jason Baker][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[lujun9972](https://github.com/lujun9972)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,8 +1,8 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-10602-1.html)
|
||||
[#]: subject: (Midori: A Lightweight Open Source Web Browser)
|
||||
[#]: via: (https://itsfoss.com/midori-browser)
|
||||
[#]: author: (Abhishek Prakash https://itsfoss.com/author/abhishek/)
|
||||
@ -10,13 +10,13 @@
|
||||
Midori:轻量级开源 Web 浏览器
|
||||
======
|
||||
|
||||
**这是一个对再次回归的轻量级、快速、开源的 Web 浏览器 Midori 的快速回顾**
|
||||
> 这是一个对再次回归的轻量级、快速、开源的 Web 浏览器 Midori 的快速回顾。
|
||||
|
||||
如果你正在寻找一款轻量级[网络浏览器替代品][1],请试试 Midori。
|
||||
|
||||
[Midori][2]是一款开源的网络浏览器,它更注重轻量级而不是提供大量功能。
|
||||
|
||||
如果你从未听说过 Midori,你可能会认为它是一个新的应用程序,但实际上 Midori 于 2007 年首次发布。
|
||||
如果你从未听说过 Midori,你可能会认为它是一个新的应用程序,但实际上 Midori 首次发布于 2007 年。
|
||||
|
||||
因为它专注于速度,所以 Midori 很快就聚集了一群爱好者,并成为了 Bodhi Linux、SilTaz 等轻量级 Linux 发行版的默认浏览器。
|
||||
|
||||
@ -28,25 +28,23 @@ Midori:轻量级开源 Web 浏览器
|
||||
|
||||
![Midori web browser][4]
|
||||
|
||||
以下是Midori浏览器的一些主要功能
|
||||
以下是 Midori 浏览器的一些主要功能
|
||||
|
||||
* 使用 Vala 编写,带有 GTK+3 和 WebKit 渲染引擎。
|
||||
* 标签、窗口和会话管理
|
||||
* 快速拨号
|
||||
* 默认保存下一个会话的选项卡
|
||||
* 使用 Vala 编写,使用 GTK+3 和 WebKit 渲染引擎。
|
||||
* 标签、窗口和会话管理。
|
||||
* 快速拨号。
|
||||
* 默认保存下一个会话的选项卡。
|
||||
* 使用 DuckDuckGo 作为默认搜索引擎。可以更改为 Google 或 Yahoo。
|
||||
* 书签管理
|
||||
* 可定制和可扩展的界面
|
||||
* 扩展模块可以用 C 和 Vala 编写
|
||||
* 支持 HTML5
|
||||
* 书签管理。
|
||||
* 可定制和可扩展的界面。
|
||||
* 扩展模块可以用 C 和 Vala 编写。
|
||||
* 支持 HTML5。
|
||||
* 少量的扩展程序包括广告拦截器、彩色标签等。没有第三方扩展程序。
|
||||
* 表格历史
|
||||
* 隐私浏览
|
||||
* 可用于 Linux 和 Windows
|
||||
* 表单历史。
|
||||
* 隐私浏览。
|
||||
* 可用于 Linux 和 Windows。
|
||||
|
||||
|
||||
|
||||
小知识:Midori 是日语单词,意思是绿色。如果你因此在猜想一些东西,Midori 的开发者实际不是日本人。
|
||||
小知识:Midori 是日语单词,意思是绿色。如果你因此而猜想的话,但 Midori 的开发者实际不是日本人。
|
||||
|
||||
### 体验 Midori
|
||||
|
||||
@ -54,7 +52,7 @@ Midori:轻量级开源 Web 浏览器
|
||||
|
||||
这几天我一直在使用 Midori。体验基本很好。它支持 HTML5 并能快速渲染网站。广告拦截器也没问题。正如你对任何标准 Web 浏览器所期望的那样,浏览体验挺顺滑。
|
||||
|
||||
缺少扩展一直是 Midori 的弱点所以我不打算谈论这个。
|
||||
缺少扩展一直是 Midori 的弱点,所以我不打算谈论这个。
|
||||
|
||||
我注意到的是它不支持国际语言。我找不到添加新语言支持的方法。它根本无法渲染印地语字体,我猜对其他非[罗曼语言][6]也是一样。
|
||||
|
||||
@ -70,7 +68,7 @@ Midori 没有像 Chrome 那样吃我的内存,所以这是一个很大的优
|
||||
|
||||
如果你使用的是 Ubuntu,你可以在软件中心找到 Midori(Snap 版)并从那里安装。
|
||||
|
||||
![Midori browser is available in Ubuntu Software Center][8]Midori browser is available in Ubuntu Software Center
|
||||
![Midori browser is available in Ubuntu Software Center][8]
|
||||
|
||||
对于其他 Linux 发行版,请确保你[已启用 Snap 支持][9],然后你可以使用以下命令安装 Midori:
|
||||
|
||||
@ -80,6 +78,8 @@ sudo snap install midori
|
||||
|
||||
你可以选择从源代码编译。你可以从 Midori 的网站下载它的代码。
|
||||
|
||||
- [下载 Midori](https://www.midori-browser.org/download/)
|
||||
|
||||
如果你喜欢 Midori 并希望帮助这个开源项目,请向他们捐赠或[从他们的商店购买 Midori 商品][10]。
|
||||
|
||||
你在使用 Midori 还是曾经用过么?你的体验如何?你更喜欢使用哪种其他网络浏览器?请在下面的评论栏分享你的观点。
|
||||
@ -91,7 +91,7 @@ via: https://itsfoss.com/midori-browser
|
||||
作者:[Abhishek Prakash][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
@ -0,0 +1,127 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (leommxj)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-10592-1.html)
|
||||
[#]: subject: (How ASLR protects Linux systems from buffer overflow attacks)
|
||||
[#]: via: (https://www.networkworld.com/article/3331199/linux/what-does-aslr-do-for-linux.html)
|
||||
[#]: author: (Sandra Henry-Stocker https://www.networkworld.com/author/Sandra-Henry_Stocker/)
|
||||
|
||||
ASLR 是如何保护 Linux 系统免受缓冲区溢出攻击的
|
||||
======
|
||||
|
||||
> 地址空间随机化(ASLR)是一种内存攻击缓解技术,可以用于 Linux 和 Windows 系统。了解一下如何运行它、启用/禁用它,以及它是如何工作的。
|
||||
|
||||

|
||||
|
||||
<ruby>地址空间随机化<rt>Address Space Layout Randomization</rt></ruby>(ASLR)是一种操作系统用来抵御缓冲区溢出攻击的内存保护机制。这种技术使得系统上运行的进程的内存地址无法被预测,使得与这些进程有关的漏洞变得更加难以利用。
|
||||
|
||||
ASLR 目前在 Linux、Windows 以及 MacOS 系统上都有使用。其最早出现在 2005 的 Linux 系统上。2007 年,这项技术被 Windows 和 MacOS 部署使用。尽管 ASLR 在各个系统上都提供相同的功能,却有着不同的实现。
|
||||
|
||||
ASLR 的有效性依赖于整个地址空间布局是否对于攻击者保持未知。此外,只有编译时作为<ruby>位置无关可执行文件<rt>Position Independent Executable</rt></ruby>(PIE)的可执行程序才能得到 ASLR 技术的最大保护,因为只有这样,可执行文件的所有代码节区才会被加载在随机地址。PIE 机器码不管绝对地址是多少都可以正确执行。
|
||||
|
||||
### ASLR 的局限性
|
||||
|
||||
尽管 ASLR 使得对系统漏洞的利用更加困难了,但其保护系统的能力是有限的。理解关于 ASLR 的以下几点是很重要的:
|
||||
|
||||
* 它不能*解决*漏洞,而是增加利用漏洞的难度
|
||||
* 并不追踪或报告漏洞
|
||||
* 不能对编译时没有开启 ASLR 支持的二进制文件提供保护
|
||||
* 不能避免被绕过
|
||||
|
||||
### ASLR 是如何工作的
|
||||
|
||||
通过对攻击者在进行缓冲区溢出攻击时所要用到的内存布局中的偏移做了随机化,ASLR 加大了攻击成功的难度,从而增强了系统的控制流完整性。
|
||||
|
||||
通常认为 ASLR 在 64 位系统上效果更好,因为 64 位系统提供了更大的熵(可随机的地址范围)。
|
||||
|
||||
### ASLR 是否正在你的 Linux 系统上运行?
|
||||
|
||||
下面展示的两条命令都可以告诉你的系统是否启用了 ASLR 功能:
|
||||
|
||||
```
|
||||
$ cat /proc/sys/kernel/randomize_va_space
|
||||
2
|
||||
$ sysctl -a --pattern randomize
|
||||
kernel.randomize_va_space = 2
|
||||
```
|
||||
|
||||
上方指令结果中的数值(`2`)表示 ASLR 工作在全随机化模式。其可能为下面的几个数值之一:
|
||||
|
||||
```
|
||||
0 = Disabled
|
||||
1 = Conservative Randomization
|
||||
2 = Full Randomization
|
||||
```
|
||||
|
||||
如果你关闭了 ASLR 并且执行下面的指令,你将会注意到前后两条 `ldd` 的输出是完全一样的。`ldd` 命令会加载共享对象并显示它们在内存中的地址。
|
||||
|
||||
```
|
||||
$ sudo sysctl -w kernel.randomize_va_space=0 <== disable
|
||||
[sudo] password for shs:
|
||||
kernel.randomize_va_space = 0
|
||||
$ ldd /bin/bash
|
||||
linux-vdso.so.1 (0x00007ffff7fd1000) <== same addresses
|
||||
libtinfo.so.6 => /lib/x86_64-linux-gnu/libtinfo.so.6 (0x00007ffff7c69000)
|
||||
libdl.so.2 => /lib/x86_64-linux-gnu/libdl.so.2 (0x00007ffff7c63000)
|
||||
libc.so.6 => /lib/x86_64-linux-gnu/libc.so.6 (0x00007ffff7a79000)
|
||||
/lib64/ld-linux-x86-64.so.2 (0x00007ffff7fd3000)
|
||||
$ ldd /bin/bash
|
||||
linux-vdso.so.1 (0x00007ffff7fd1000) <== same addresses
|
||||
libtinfo.so.6 => /lib/x86_64-linux-gnu/libtinfo.so.6 (0x00007ffff7c69000)
|
||||
libdl.so.2 => /lib/x86_64-linux-gnu/libdl.so.2 (0x00007ffff7c63000)
|
||||
libc.so.6 => /lib/x86_64-linux-gnu/libc.so.6 (0x00007ffff7a79000)
|
||||
/lib64/ld-linux-x86-64.so.2 (0x00007ffff7fd3000)
|
||||
```
|
||||
|
||||
如果将其重新设置为 `2` 来启用 ASLR,你将会看到每次运行 `ldd`,得到的内存地址都不相同。
|
||||
|
||||
```
|
||||
$ sudo sysctl -w kernel.randomize_va_space=2 <== enable
|
||||
[sudo] password for shs:
|
||||
kernel.randomize_va_space = 2
|
||||
$ ldd /bin/bash
|
||||
linux-vdso.so.1 (0x00007fff47d0e000) <== first set of addresses
|
||||
libtinfo.so.6 => /lib/x86_64-linux-gnu/libtinfo.so.6 (0x00007f1cb7ce0000)
|
||||
libdl.so.2 => /lib/x86_64-linux-gnu/libdl.so.2 (0x00007f1cb7cda000)
|
||||
libc.so.6 => /lib/x86_64-linux-gnu/libc.so.6 (0x00007f1cb7af0000)
|
||||
/lib64/ld-linux-x86-64.so.2 (0x00007f1cb8045000)
|
||||
$ ldd /bin/bash
|
||||
linux-vdso.so.1 (0x00007ffe1cbd7000) <== second set of addresses
|
||||
libtinfo.so.6 => /lib/x86_64-linux-gnu/libtinfo.so.6 (0x00007fed59742000)
|
||||
libdl.so.2 => /lib/x86_64-linux-gnu/libdl.so.2 (0x00007fed5973c000)
|
||||
libc.so.6 => /lib/x86_64-linux-gnu/libc.so.6 (0x00007fed59552000)
|
||||
/lib64/ld-linux-x86-64.so.2 (0x00007fed59aa7000)
|
||||
```
|
||||
|
||||
### 尝试绕过 ASLR
|
||||
|
||||
尽管这项技术有很多优点,但绕过 ASLR 的攻击并不罕见,主要有以下几类:
|
||||
|
||||
* 利用地址泄露
|
||||
* 访问与特定地址关联的数据
|
||||
* 针对 ASLR 实现的缺陷来猜测地址,常见于系统熵过低或 ASLR 实现不完善。
|
||||
* 利用侧信道攻击
|
||||
|
||||
### 总结
|
||||
|
||||
ASLR 有很大的价值,尤其是在 64 位系统上运行并被正确实现时。虽然不能避免被绕过,但这项技术的确使得利用系统漏洞变得更加困难了。这份参考资料可以提供 [在 64 位 Linux 系统上的完全 ASLR 的有效性][2] 的更多有关细节,这篇论文介绍了一种利用分支预测 [绕过 ASLR][3] 的技术。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.networkworld.com/article/3331199/linux/what-does-aslr-do-for-linux.html
|
||||
|
||||
作者:[Sandra Henry-Stocker][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[leommxj](https://github.com/leommxj)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.networkworld.com/author/Sandra-Henry_Stocker/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.networkworld.com/article/3242170/linux/invaluable-tips-and-tricks-for-troubleshooting-linux.html
|
||||
[2]: https://cybersecurity.upv.es/attacks/offset2lib/offset2lib-paper.pdf
|
||||
[3]: http://www.cs.ucr.edu/~nael/pubs/micro16.pdf
|
||||
[4]: https://www.facebook.com/NetworkWorld/
|
||||
[5]: https://www.linkedin.com/company/network-world
|
||||
164
published/20190212 Ampersands and File Descriptors in Bash.md
Normal file
164
published/20190212 Ampersands and File Descriptors in Bash.md
Normal file
@ -0,0 +1,164 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (zero-mk)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-10591-1.html)
|
||||
[#]: subject: (Ampersands and File Descriptors in Bash)
|
||||
[#]: via: (https://www.linux.com/blog/learn/2019/2/ampersands-and-file-descriptors-bash)
|
||||
[#]: author: (Paul Brown https://www.linux.com/users/bro66)
|
||||
|
||||
Bash 中的 & 符号和文件描述符
|
||||
======
|
||||
|
||||
> 了解如何将 “&” 与尖括号结合使用,并从命令行中获得更多信息。
|
||||
|
||||

|
||||
|
||||
在我们探究大多数链式 Bash 命令中出现的所有的杂项符号(`&`、`|`、`;`、`>`、`<`、`{`、`[`、`(`、`)`、`]`、`}` 等等)的任务中,[我们一直在仔细研究 & 符号][1]。
|
||||
|
||||
[上次,我们看到了如何使用 & 把可能需要很长时间运行的进程放到后台运行][1]。但是,`&` 与尖括号 `<` 结合使用,也可用于将输出或输出通过管道导向其他地方。
|
||||
|
||||
在 [前面的][2] [尖括号教程中][3],你看到了如何使用 `>`,如下:
|
||||
|
||||
```
|
||||
ls > list.txt
|
||||
```
|
||||
|
||||
将 `ls` 输出传递给 `list.txt` 文件。
|
||||
|
||||
现在我们看到的是简写:
|
||||
|
||||
```
|
||||
ls 1> list.txt
|
||||
```
|
||||
|
||||
在这种情况下,`1` 是一个文件描述符,指向标准输出(`stdout`)。
|
||||
|
||||
以类似的方式,`2` 指向标准错误输出(`stderr`):
|
||||
|
||||
```
|
||||
ls 2> error.log
|
||||
```
|
||||
|
||||
所有错误消息都通过管道传递给 `error.log` 文件。
|
||||
|
||||
回顾一下:`1>` 是标准输出(`stdout`),`2>` 是标准错误输出(`stderr`)。
|
||||
|
||||
第三个标准文件描述符,`0<` 是标准输入(`stdin`)。你可以看到它是一个输入,因为箭头(`<`)指向`0`,而对于 `1` 和 `2`,箭头(`>`)是指向外部的。
|
||||
|
||||
### 标准文件描述符有什么用?
|
||||
|
||||
如果你在阅读本系列以后,你已经多次使用标准输出(`1>`)的简写形式:`>`。
|
||||
|
||||
例如,当(假如)你知道你的命令会抛出一个错误时,像 `stderr`(`2`)这样的东西也很方便,但是 Bash 告诉你的东西是没有用的,你不需要看到它。如果要在 `home/` 目录中创建目录,例如:
|
||||
|
||||
```
|
||||
mkdir newdir
|
||||
```
|
||||
|
||||
如果 `newdir/` 已经存在,`mkdir` 将显示错误。但你为什么要关心这些呢?(好吧,在某些情况下你可能会关心,但并非总是如此。)在一天结束时,`newdir` 会以某种方式让你填入一些东西。你可以通过将错误消息推入虚空(即 ``/dev/null`)来抑制错误消息:
|
||||
|
||||
```
|
||||
mkdir newdir 2> /dev/null
|
||||
```
|
||||
|
||||
这不仅仅是 “让我们不要看到丑陋和无关的错误消息,因为它们很烦人”,因为在某些情况下,错误消息可能会在其他地方引起一连串错误。比如说,你想找到 `/etc` 下所有的 `.service` 文件。你可以这样做:
|
||||
|
||||
```
|
||||
find /etc -iname "*.service"
|
||||
```
|
||||
|
||||
但事实证明,在大多数系统中,`find` 显示的错误会有许多行,因为普通用户对 `/etc` 下的某些文件夹没有读取访问权限。它使读取正确的输出变得很麻烦,如果 `find` 是更大的脚本的一部分,它可能会导致行中的下一个命令排队。
|
||||
|
||||
相反,你可以这样做:
|
||||
|
||||
```
|
||||
find /etc -iname "*.service" 2> /dev/null
|
||||
```
|
||||
|
||||
而且你只得到你想要的结果。
|
||||
|
||||
### 文件描述符入门
|
||||
|
||||
单独的文件描述符 `stdout` 和 `stderr` 还有一些注意事项。如果要将输出存储在文件中,请执行以下操作:
|
||||
|
||||
```
|
||||
find /etc -iname "*.service" 1> services.txt
|
||||
```
|
||||
|
||||
工作正常,因为 `1>` 意味着 “发送标准输出且自身标准输出(非标准错误)到某个地方”。
|
||||
|
||||
但这里存在一个问题:如果你想把命令抛出的错误信息记录到文件,而结果中没有错误信息你该怎么**做**?上面的命令并不会这样做,因为它只写入 `find` 正确的结果,而:
|
||||
|
||||
```
|
||||
find /etc -iname "*.service" 2> services.txt
|
||||
```
|
||||
|
||||
只会写入命令抛出的错误信息。
|
||||
|
||||
我们如何得到两者?请尝试以下命令:
|
||||
|
||||
```
|
||||
find /etc -iname "*.service" &> services.txt
|
||||
```
|
||||
|
||||
…… 再次和 `&` 打个招呼!
|
||||
|
||||
我们一直在说 `stdin`(`0`)、`stdout`(`1`)和 `stderr`(`2`)是“文件描述符”。文件描述符是一种特殊构造,是指向文件的通道,用于读取或写入,或两者兼而有之。这来自于将所有内容都视为文件的旧 UNIX 理念。想写一个设备?将其视为文件。想写入套接字并通过网络发送数据?将其视为文件。想要读取和写入文件?嗯,显然,将其视为文件。
|
||||
|
||||
因此,在管理命令的输出和错误的位置时,将目标视为文件。因此,当你打开它们来读取和写入它们时,它们都会获得文件描述符。
|
||||
|
||||
这是一个有趣的效果。例如,你可以将内容从一个文件描述符传递到另一个文件描述符:
|
||||
|
||||
```
|
||||
find /etc -iname "*.service" 1> services.txt 2>&1
|
||||
```
|
||||
|
||||
这会将 `stderr` 导向到 `stdout`,而 `stdout` 通过管道被导向到一个文件中 `services.txt` 中。
|
||||
|
||||
它再次出现:`&` 发信号通知 Bash `1` 是目标文件描述符。
|
||||
|
||||
标准文件描述符的另一个问题是,当你从一个管道传输到另一个时,你执行此操作的顺序有点违反直觉。例如,按照上面的命令。它看起来像是错误的方式。你应该像这样阅读它:“将输出导向到文件,然后将错误导向到标准输出。” 看起来错误输出会在后面,并且在输出到标准输出(`1`)已经完成时才发送。
|
||||
|
||||
但这不是文件描述符的工作方式。文件描述符不是文件的占位符,而是文件的输入和(或)输出通道。在这种情况下,当你做 `1> services.txt` 时,你的意思是 “打开一个写管道到 `services.txt` 并保持打开状态”。`1` 是你要使用的管道的名称,它将保持打开状态直到该行的结尾。
|
||||
|
||||
如果你仍然认为这是错误的方法,试试这个:
|
||||
|
||||
```
|
||||
find /etc -iname "*.service" 2>&1 1>services.txt
|
||||
```
|
||||
|
||||
并注意它是如何不工作的;注意错误是如何被导向到终端的,而只有非错误的输出(即 `stdout`)被推送到 `services.txt`。
|
||||
|
||||
这是因为 Bash 从左到右处理 `find` 的每个结果。这样想:当 Bash 到达 `2>&1` 时,`stdout` (`1`)仍然是指向终端的通道。如果 `find` 给 Bash 的结果包含一个错误,它将被弹出到 `2`,转移到 `1`,然后留在终端!
|
||||
|
||||
然后在命令结束时,Bash 看到你要打开 `stdout`(`1`) 作为到 `services.txt` 文件的通道。如果没有发生错误,结果将通过通道 `1` 进入文件。
|
||||
|
||||
相比之下,在:
|
||||
|
||||
```
|
||||
find /etc -iname "*.service" 1>services.txt 2>&1
|
||||
```
|
||||
|
||||
`1` 从一开始就指向 `services.txt`,因此任何弹出到 `2` 的内容都会导向到 `1` ,而 `1` 已经指向最终去的位置 `services.txt`,这就是它工作的原因。
|
||||
|
||||
在任何情况下,如上所述 `&>` 都是“标准输出和标准错误”的缩写,即 `2>&1`。
|
||||
|
||||
这可能有点多,但不用担心。重新导向文件描述符在 Bash 命令行和脚本中是司空见惯的事。随着本系列的深入,你将了解更多关于文件描述符的知识。下周见!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.linux.com/blog/learn/2019/2/ampersands-and-file-descriptors-bash
|
||||
|
||||
作者:[Paul Brown][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[zero-mk](https://github.com/zero-mk)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.linux.com/users/bro66
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://linux.cn/article-10587-1.html
|
||||
[2]: https://linux.cn/article-10502-1.html
|
||||
[3]: https://linux.cn/article-10529-1.html
|
||||
@ -0,0 +1,218 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (An-DJ)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-10595-1.html)
|
||||
[#]: subject: (How To Check CPU, Memory And Swap Utilization Percentage In Linux?)
|
||||
[#]: via: (https://www.2daygeek.com/linux-check-cpu-memory-swap-utilization-percentage/)
|
||||
[#]: author: (Vinoth Kumar https://www.2daygeek.com/author/vinoth/)
|
||||
|
||||
如何查看 Linux 下 CPU、内存和交换分区的占用率?
|
||||
======
|
||||
|
||||
在 Linux 下有很多可以用来查看内存占用情况的命令和选项,但是我并没有看见关于内存占用率的更多的信息。
|
||||
|
||||
在大多数情况下我们只想查看内存使用情况,并没有考虑占用的百分比究竟是多少。如果你想要了解这些信息,那你看这篇文章就对了。我们将会详细地在这里帮助你解决这个问题。
|
||||
|
||||
这篇教程将会帮助你在面对 Linux 服务器下频繁的内存高占用情况时,确定内存使用情况。
|
||||
|
||||
而在同时,如果你使用的是 `free -m` 或者 `free -g`,占用情况描述地也并不是十分清楚。
|
||||
|
||||
这些格式化命令属于 Linux 高级命令。它将会对 Linux 专家和中等水平 Linux 使用者非常有用。
|
||||
|
||||
### 方法-1:如何查看 Linux 下内存占用率?
|
||||
|
||||
我们可以使用下面命令的组合来达到此目的。在该方法中,我们使用的是 `free` 和 `awk` 命令的组合来获取内存占用率。
|
||||
|
||||
如果你正在寻找其他有关于内存的文章,你可以导航到如下链接。这些文章有 [free 命令][1]、[smem 命令][2]、[ps_mem 命令][3]、[vmstat 命令][4] 及 [查看物理内存大小的多种方式][5]。
|
||||
|
||||
要获取不包含百分比符号的内存占用率:
|
||||
|
||||
```
|
||||
$ free -t | awk 'NR == 2 {print "Current Memory Utilization is : " $3/$2*100}'
|
||||
或
|
||||
$ free -t | awk 'FNR == 2 {print "Current Memory Utilization is : " $3/$2*100}'
|
||||
|
||||
Current Memory Utilization is : 20.4194
|
||||
```
|
||||
|
||||
要获取不包含百分比符号的交换分区占用率:
|
||||
|
||||
```
|
||||
$ free -t | awk 'NR == 3 {print "Current Swap Utilization is : " $3/$2*100}'
|
||||
或
|
||||
$ free -t | awk 'FNR == 3 {print "Current Swap Utilization is : " $3/$2*100}'
|
||||
|
||||
Current Swap Utilization is : 0
|
||||
```
|
||||
|
||||
要获取包含百分比符号及保留两位小数的内存占用率:
|
||||
|
||||
```
|
||||
$ free -t | awk 'NR == 2 {printf("Current Memory Utilization is : %.2f%"), $3/$2*100}'
|
||||
或
|
||||
$ free -t | awk 'FNR == 2 {printf("Current Memory Utilization is : %.2f%"), $3/$2*100}'
|
||||
|
||||
Current Memory Utilization is : 20.42%
|
||||
```
|
||||
|
||||
要获取包含百分比符号及保留两位小数的交换分区占用率:
|
||||
|
||||
```
|
||||
$ free -t | awk 'NR == 3 {printf("Current Swap Utilization is : %.2f%"), $3/$2*100}'
|
||||
或
|
||||
$ free -t | awk 'FNR == 3 {printf("Current Swap Utilization is : %.2f%"), $3/$2*100}'
|
||||
|
||||
Current Swap Utilization is : 0.00%
|
||||
```
|
||||
|
||||
如果你正在寻找有关于交换分区的其他文章,你可以导航至如下链接。这些链接有 [使用 LVM(逻辑盘卷管理)创建和扩展交换分区][6],[创建或扩展交换分区的多种方式][7] 和 [创建/删除和挂载交换分区文件的多种方式][8]。
|
||||
|
||||
键入 `free` 命令会更好地作出阐释:
|
||||
|
||||
```
|
||||
$ free
|
||||
total used free shared buff/cache available
|
||||
Mem: 15867 3730 9868 1189 2269 10640
|
||||
Swap: 17454 0 17454
|
||||
Total: 33322 3730 27322
|
||||
```
|
||||
|
||||
细节如下:
|
||||
|
||||
* `free`:是一个标准命令,用于在 Linux 下查看内存使用情况。
|
||||
* `awk`:是一个专门用来做文本数据处理的强大命令。
|
||||
* `FNR == 2`:该命令给出了每一个输入文件的行数。其基本上用于挑选出给定的行(针对于这里,它选择的是行号为 2 的行)
|
||||
* `NR == 2`:该命令给出了处理的行总数。其基本上用于过滤给出的行(针对于这里,它选择的是行号为 2 的行)
|
||||
* `$3/$2*100`:该命令将列 3 除以列 2 并将结果乘以 100。
|
||||
* `printf`:该命令用于格式化和打印数据。
|
||||
* `%.2f%`:默认情况下,其打印小数点后保留 6 位的浮点数。使用后跟的格式来约束小数位。
|
||||
|
||||
### 方法-2:如何查看 Linux 下内存占用率?
|
||||
|
||||
我们可以使用下面命令的组合来达到此目的。在这种方法中,我们使用 `free`、`grep` 和 `awk` 命令的组合来获取内存占用率。
|
||||
|
||||
要获取不包含百分比符号的内存占用率:
|
||||
|
||||
```
|
||||
$ free -t | grep Mem | awk '{print "Current Memory Utilization is : " $3/$2*100}'
|
||||
Current Memory Utilization is : 20.4228
|
||||
```
|
||||
|
||||
要获取不包含百分比符号的交换分区占用率:
|
||||
|
||||
```
|
||||
$ free -t | grep Swap | awk '{print "Current Swap Utilization is : " $3/$2*100}'
|
||||
Current Swap Utilization is : 0
|
||||
```
|
||||
|
||||
要获取包含百分比符号及保留两位小数的内存占用率:
|
||||
|
||||
```
|
||||
$ free -t | grep Mem | awk '{printf("Current Memory Utilization is : %.2f%"), $3/$2*100}'
|
||||
Current Memory Utilization is : 20.43%
|
||||
```
|
||||
|
||||
要获取包含百分比符号及保留两位小数的交换空间占用率:
|
||||
|
||||
```
|
||||
$ free -t | grep Swap | awk '{printf("Current Swap Utilization is : %.2f%"), $3/$2*100}'
|
||||
Current Swap Utilization is : 0.00%
|
||||
```
|
||||
|
||||
### 方法-1:如何查看 Linux 下 CPU 的占用率?
|
||||
|
||||
我们可以使用如下命令的组合来达到此目的。在这种方法中,我们使用 `top`、`print` 和 `awk` 命令的组合来获取 CPU 的占用率。
|
||||
|
||||
如果你正在寻找其他有关于 CPU(LCTT 译注:原文误为 memory)的文章,你可以导航至如下链接。这些文章有 [top 命令][9]、[htop 命令][10]、[atop 命令][11] 及 [Glances 命令][12]。
|
||||
|
||||
如果在输出中展示的是多个 CPU 的情况,那么你需要使用下面的方法。
|
||||
|
||||
```
|
||||
$ top -b -n1 | grep ^%Cpu
|
||||
%Cpu0 : 5.3 us, 0.0 sy, 0.0 ni, 94.7 id, 0.0 wa, 0.0 hi, 0.0 si, 0.0 st
|
||||
%Cpu1 : 0.0 us, 0.0 sy, 0.0 ni,100.0 id, 0.0 wa, 0.0 hi, 0.0 si, 0.0 st
|
||||
%Cpu2 : 0.0 us, 0.0 sy, 0.0 ni, 94.7 id, 0.0 wa, 0.0 hi, 5.3 si, 0.0 st
|
||||
%Cpu3 : 5.3 us, 0.0 sy, 0.0 ni, 94.7 id, 0.0 wa, 0.0 hi, 0.0 si, 0.0 st
|
||||
%Cpu4 : 10.5 us, 15.8 sy, 0.0 ni, 73.7 id, 0.0 wa, 0.0 hi, 0.0 si, 0.0 st
|
||||
%Cpu5 : 0.0 us, 5.0 sy, 0.0 ni, 95.0 id, 0.0 wa, 0.0 hi, 0.0 si, 0.0 st
|
||||
%Cpu6 : 5.3 us, 0.0 sy, 0.0 ni, 94.7 id, 0.0 wa, 0.0 hi, 0.0 si, 0.0 st
|
||||
%Cpu7 : 5.3 us, 0.0 sy, 0.0 ni, 94.7 id, 0.0 wa, 0.0 hi, 0.0 si, 0.0 st
|
||||
```
|
||||
|
||||
要获取不包含百分比符号的 CPU 占用率:
|
||||
|
||||
```
|
||||
$ top -b -n1 | grep ^%Cpu | awk '{cpu+=$9}END{print "Current CPU Utilization is : " 100-cpu/NR}'
|
||||
Current CPU Utilization is : 21.05
|
||||
```
|
||||
|
||||
要获取包含百分比符号及保留两位小数的 CPU 占用率:
|
||||
|
||||
```
|
||||
$ top -b -n1 | grep ^%Cpu | awk '{cpu+=$9}END{printf("Current CPU Utilization is : %.2f%"), 100-cpu/NR}'
|
||||
Current CPU Utilization is : 14.81%
|
||||
```
|
||||
|
||||
### 方法-2:如何查看 Linux 下 CPU 的占用率?
|
||||
|
||||
我们可以使用如下命令的组合来达到此目的。在这种方法中,我们使用的是 `top`、`print`/`printf` 和 `awk` 命令的组合来获取 CPU 的占用率。
|
||||
|
||||
如果在单个输出中一起展示了所有的 CPU 的情况,那么你需要使用下面的方法。
|
||||
|
||||
```
|
||||
$ top -b -n1 | grep ^%Cpu
|
||||
%Cpu(s): 15.3 us, 7.2 sy, 0.8 ni, 69.0 id, 6.7 wa, 0.0 hi, 1.0 si, 0.0 st
|
||||
```
|
||||
|
||||
要获取不包含百分比符号的 CPU 占用率:
|
||||
|
||||
```
|
||||
$ top -b -n1 | grep ^%Cpu | awk '{print "Current CPU Utilization is : " 100-$8}'
|
||||
Current CPU Utilization is : 5.6
|
||||
```
|
||||
|
||||
要获取包含百分比符号及保留两位小数的 CPU 占用率:
|
||||
|
||||
```
|
||||
$ top -b -n1 | grep ^%Cpu | awk '{printf("Current CPU Utilization is : %.2f%"), 100-$8}'
|
||||
Current CPU Utilization is : 5.40%
|
||||
```
|
||||
|
||||
如下是一些细节:
|
||||
|
||||
* `top`:是一种用于查看当前 Linux 系统下正在运行的进程的非常好的命令。
|
||||
* `-b`:选项允许 `top` 命令切换至批处理的模式。当你从本地系统运行 `top` 命令至远程系统时,它将会非常有用。
|
||||
* `-n1`:迭代次数。
|
||||
* `^%Cpu`:过滤以 `%CPU` 开头的行。
|
||||
* `awk`:是一种专门用来做文本数据处理的强大命令。
|
||||
* `cpu+=$9`:对于每一行,将第 9 列添加至变量 `cpu`。
|
||||
* `printf`:该命令用于格式化和打印数据。
|
||||
* `%.2f%`:默认情况下,它打印小数点后保留 6 位的浮点数。使用后跟的格式来限制小数位数。
|
||||
* `100-cpu/NR`:最终打印出 CPU 平均占用率,即用 100 减去其并除以行数。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.2daygeek.com/linux-check-cpu-memory-swap-utilization-percentage/
|
||||
|
||||
作者:[Vinoth Kumar][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[An-DJ](https://github.com/An-DJ)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.2daygeek.com/author/vinoth/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.2daygeek.com/free-command-to-check-memory-usage-statistics-in-linux/
|
||||
[2]: https://www.2daygeek.com/smem-linux-memory-usage-statistics-reporting-tool/
|
||||
[3]: https://www.2daygeek.com/ps_mem-report-core-memory-usage-accurately-in-linux/
|
||||
[4]: https://www.2daygeek.com/linux-vmstat-command-examples-tool-report-virtual-memory-statistics/
|
||||
[5]: https://www.2daygeek.com/easy-ways-to-check-size-of-physical-memory-ram-in-linux/
|
||||
[6]: https://www.2daygeek.com/how-to-create-extend-swap-partition-in-linux-using-lvm/
|
||||
[7]: https://www.2daygeek.com/add-extend-increase-swap-space-memory-file-partition-linux/
|
||||
[8]: https://www.2daygeek.com/shell-script-create-add-extend-swap-space-linux/
|
||||
[9]: https://www.2daygeek.com/linux-top-command-linux-system-performance-monitoring-tool/
|
||||
[10]: https://www.2daygeek.com/linux-htop-command-linux-system-performance-resource-monitoring-tool/
|
||||
[11]: https://www.2daygeek.com/atop-system-process-performance-monitoring-tool/
|
||||
[12]: https://www.2daygeek.com/install-glances-advanced-real-time-linux-system-performance-monitoring-tool-on-centos-fedora-ubuntu-debian-opensuse-arch-linux/
|
||||
194
published/20190219 Logical - in Bash.md
Normal file
194
published/20190219 Logical - in Bash.md
Normal file
@ -0,0 +1,194 @@
|
||||
[#]: collector: "lujun9972"
|
||||
[#]: translator: "zero-mk"
|
||||
[#]: reviewer: "wxy"
|
||||
[#]: publisher: "wxy"
|
||||
[#]: url: "https://linux.cn/article-10596-1.html"
|
||||
[#]: subject: "Logical & in Bash"
|
||||
[#]: via: "https://www.linux.com/blog/learn/2019/2/logical-ampersand-bash"
|
||||
[#]: author: "Paul Brown https://www.linux.com/users/bro66"
|
||||
|
||||
Bash 中的逻辑和(&)
|
||||
======
|
||||
> 在 Bash 中,你可以使用 & 作为 AND(逻辑和)操作符。
|
||||
|
||||

|
||||
|
||||
有人可能会认为两篇文章中的 `&` 意思差不多,但实际上并不是。虽然 [第一篇文章讨论了如何在命令末尾使用 & 来将命令转到后台运行][1],在之后剖析了流程管理,第二篇文章将 [ & 看作引用文件描述符的方法][2],这些文章让我们知道了,与 `<` 和 `>` 结合使用后,你可以将输入或输出引导到别的地方。
|
||||
|
||||
但我们还没接触过作为 AND 操作符使用的 `&`。所以,让我们来看看。
|
||||
|
||||
### & 是一个按位运算符
|
||||
|
||||
如果你十分熟悉二进制数操作,你肯定听说过 AND 和 OR 。这些是按位操作,对二进制数的各个位进行操作。在 Bash 中,使用 `&` 作为 AND 运算符,使用 `|` 作为 OR 运算符:
|
||||
|
||||
**AND**:
|
||||
|
||||
```
|
||||
0 & 0 = 0
|
||||
0 & 1 = 0
|
||||
1 & 0 = 0
|
||||
1 & 1 = 1
|
||||
```
|
||||
|
||||
**OR**:
|
||||
|
||||
```
|
||||
0 | 0 = 0
|
||||
0 | 1 = 1
|
||||
1 | 0 = 1
|
||||
1 | 1 = 1
|
||||
```
|
||||
|
||||
你可以通过对任何两个数字进行 AND 运算并使用 `echo` 输出结果:
|
||||
|
||||
```
|
||||
$ echo $(( 2 & 3 )) # 00000010 AND 00000011 = 00000010
|
||||
2
|
||||
$ echo $(( 120 & 97 )) # 01111000 AND 01100001 = 01100000
|
||||
96
|
||||
```
|
||||
|
||||
OR(`|`)也是如此:
|
||||
|
||||
```
|
||||
$ echo $(( 2 | 3 )) # 00000010 OR 00000011 = 00000011
|
||||
3
|
||||
$ echo $(( 120 | 97 )) # 01111000 OR 01100001 = 01111001
|
||||
121
|
||||
```
|
||||
|
||||
说明:
|
||||
|
||||
1. 使用 `(( ... ))` 告诉 Bash 双括号之间的内容是某种算术或逻辑运算。`(( 2 + 2 ))`、 `(( 5 % 2 ))` (`%` 是[求模][3]运算符)和 `((( 5 % 2 ) + 1))`(等于 3)都可以工作。
|
||||
2. [像变量一样][4],使用 `$` 提取值,以便你可以使用它。
|
||||
3. 空格并没有影响:`((2+3))` 等价于 `(( 2+3 ))` 和 `(( 2 + 3 ))`。
|
||||
4. Bash 只能对整数进行操作。试试这样做: `(( 5 / 2 ))` ,你会得到 `2`;或者这样 `(( 2.5 & 7 ))` ,但会得到一个错误。然后,在按位操作中使用除了整数之外的任何东西(这就是我们现在所讨论的)通常是你不应该做的事情。
|
||||
|
||||
**提示:** 如果你想看看十进制数字在二进制下会是什么样子,你可以使用 `bc` ,这是一个大多数 Linux 发行版都预装了的命令行计算器。比如:
|
||||
|
||||
```
|
||||
bc <<< "obase=2; 97"
|
||||
```
|
||||
|
||||
这个操作将会把 `97` 转换成十二进制(`obase` 中的 `o` 代表 “output” ,也即,“输出”)。
|
||||
|
||||
```
|
||||
bc <<< "ibase=2; 11001011"
|
||||
```
|
||||
|
||||
这个操作将会把 `11001011` 转换成十进制(`ibase` 中的 `i` 代表 “input”,也即,“输入”)。
|
||||
|
||||
### && 是一个逻辑运算符
|
||||
|
||||
虽然它使用与其按位表达相同的逻辑原理,但 Bash 的 `&&` 运算符只能呈现两个结果:`1`(“真值”)和`0`(“假值”)。对于 Bash 来说,任何不是 `0` 的数字都是 “真值”,任何等于 `0` 的数字都是 “假值”。什么也是 “假值”同时也不是数字呢:
|
||||
|
||||
```
|
||||
$ echo $(( 4 && 5 )) # 两个非零数字,两个为 true = true
|
||||
1
|
||||
$ echo $(( 0 && 5 )) # 有一个为零,一个为 false = false
|
||||
0
|
||||
$ echo $(( b && 5 )) # 其中一个不是数字,一个为 false = false
|
||||
0
|
||||
```
|
||||
|
||||
与 `&&` 类似, OR 对应着 `||` ,用法正如你想的那样。
|
||||
|
||||
以上这些都很简单……直到它用在命令的退出状态时。
|
||||
|
||||
### && 是命令退出状态的逻辑运算符
|
||||
|
||||
[正如我们在之前的文章中看到的][2],当命令运行时,它会输出错误消息。更重要的是,对于今天的讨论,它在结束时也会输出一个数字。此数字称为“返回码”,如果为 0,则表示该命令在执行期间未遇到任何问题。如果是任何其他数字,即使命令完成,也意味着某些地方出错了。
|
||||
|
||||
所以 0 意味着是好的,任何其他数字都说明有问题发生,并且,在返回码的上下文中,0 意味着“真”,其他任何数字都意味着“假”。对!这 **与你所熟知的逻辑操作完全相反** ,但是你能用这个做什么? 不同的背景,不同的规则。这种用处很快就会显现出来。
|
||||
|
||||
让我们继续!
|
||||
|
||||
返回码 *临时* 储存在 [特殊变量][5] `?` 中 —— 是的,我知道:这又是一个令人迷惑的选择。但不管怎样,[别忘了我们在讨论变量的文章中说过][4],那时我们说你要用 `$` 符号来读取变量中的值,在这里也一样。所以,如果你想知道一个命令是否顺利运行,你需要在命令结束后,在运行别的命令之前马上用 `$?` 来读取 `?` 变量的值。
|
||||
|
||||
试试下面的命令:
|
||||
|
||||
```
|
||||
$ find /etc -iname "*.service"
|
||||
find: '/etc/audisp/plugins.d': Permission denied
|
||||
/etc/systemd/system/dbus-org.freedesktop.nm-dispatcher.service
|
||||
/etc/systemd/system/dbus-org.freedesktop.ModemManager1.service
|
||||
[......]
|
||||
```
|
||||
|
||||
[正如你在上一篇文章中看到的一样][2],普通用户权限在 `/etc` 下运行 `find` 通常将抛出错误,因为它试图读取你没有权限访问的子目录。
|
||||
|
||||
所以,如果你在执行 `find` 后立马执行……
|
||||
|
||||
```
|
||||
echo $?
|
||||
```
|
||||
|
||||
……,它将打印 `1`,表明存在错误。
|
||||
|
||||
(注意:当你在一行中运行两遍 `echo $?` ,你将得到一个 `0` 。这是因为 `$?` 将包含第一个 `echo $?` 的返回码,而这条命令按理说一定会执行成功。所以学习如何使用 `$?` 的第一课就是: **单独执行 `$?`** 或者将它保存在别的安全的地方 —— 比如保存在一个变量里,不然你会很快丢失它。)
|
||||
|
||||
一个直接使用 `?` 变量的用法是将它并入一串链式命令列表,这样 Bash 运行这串命令时若有任何操作失败,后面命令将终止。例如,你可能熟悉构建和编译应用程序源代码的过程。你可以像这样手动一个接一个地运行它们:
|
||||
|
||||
```
|
||||
$ configure
|
||||
.
|
||||
.
|
||||
.
|
||||
$ make
|
||||
.
|
||||
.
|
||||
.
|
||||
$ make install
|
||||
.
|
||||
.
|
||||
.
|
||||
```
|
||||
|
||||
你也可以把这三行合并成一行……
|
||||
|
||||
```
|
||||
$ configure; make; make install
|
||||
```
|
||||
|
||||
…… 但你要希望上天保佑。
|
||||
|
||||
为什么这样说呢?因为你这样做是有缺点的,比方说 `configure` 执行失败了, Bash 将仍会尝试执行 `make` 和 `sudo make install`——就算没东西可 `make` ,实际上,是没东西会安装。
|
||||
|
||||
聪明一点的做法是:
|
||||
|
||||
```
|
||||
$ configure && make && make install
|
||||
```
|
||||
|
||||
这将从每个命令中获取退出码,并将其用作链式 `&&` 操作的操作数。
|
||||
|
||||
但是,没什么好抱怨的,Bash 知道如果 `configure` 返回非零结果,整个过程都会失败。如果发生这种情况,不必运行 `make` 来检查它的退出代码,因为无论如何都会失败的。因此,它放弃运行 `make`,只是将非零结果传递给下一步操作。并且,由于 `configure && make` 传递了错误,Bash 也不必运行`make install`。这意味着,在一长串命令中,你可以使用 `&&` 连接它们,并且一旦失败,你可以节省时间,因为其他命令会立即被取消运行。
|
||||
|
||||
你可以类似地使用 `||`,OR 逻辑操作符,这样就算只有一部分命令成功执行,Bash 也能运行接下来链接在一起的命令。
|
||||
|
||||
鉴于所有这些(以及我们之前介绍过的内容),你现在应该更清楚地了解我们在 [这篇文章开头][1] 出现的命令行:
|
||||
|
||||
```
|
||||
mkdir test_dir 2>/dev/null || touch backup/dir/images.txt && find . -iname "*jpg" > backup/dir/images.txt &
|
||||
```
|
||||
|
||||
因此,假设你从具有读写权限的目录运行上述内容,它做了什么以及如何做到这一点?它如何避免不合时宜且可能导致执行中断的错误?下周,除了给你这些答案的结果,我们将讨论圆括号,不要错过了哟!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.linux.com/blog/learn/2019/2/logical-ampersand-bash
|
||||
|
||||
作者:[Paul Brown][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[zero-MK](https://github.com/zero-mk)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.linux.com/users/bro66
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://linux.cn/article-10587-1.html
|
||||
[2]: https://linux.cn/article-10591-1.html
|
||||
[3]: https://en.wikipedia.org/wiki/Modulo_operation
|
||||
[4]: https://www.linux.com/blog/learn/2018/12/bash-variables-environmental-and-otherwise
|
||||
[5]: https://www.gnu.org/software/bash/manual/html_node/Special-Parameters.html
|
||||
@ -0,0 +1,135 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-10600-1.html)
|
||||
[#]: subject: (An Automated Way To Install Essential Applications On Ubuntu)
|
||||
[#]: via: (https://www.ostechnix.com/an-automated-way-to-install-essential-applications-on-ubuntu/)
|
||||
[#]: author: (SK https://www.ostechnix.com/author/sk/)
|
||||
|
||||
在 Ubuntu 上自动化安装基本应用的方法
|
||||
======
|
||||
|
||||

|
||||
|
||||
默认安装的 Ubuntu 并未预先安装所有必需的应用。你可能需要在网上花几个小时或者向其他 Linux 用户寻求帮助才能找到并安装 Ubuntu 所需的应用。如果你是新手,那么你肯定需要花更多的时间来学习如何从命令行(使用 `apt-get` 或 `dpkg`)或从 Ubuntu 软件中心搜索和安装应用。一些用户,特别是新手,可能希望轻松快速地安装他们喜欢的每个应用。如果你是其中之一,不用担心。在本指南中,我们将了解如何使用名为 “Alfred” 的简单命令行程序在 Ubuntu 上安装基本应用。
|
||||
|
||||
Alfred 是用 Python 语言编写的自由、开源脚本。它使用 Zenity 创建了一个简单的图形界面,用户只需点击几下鼠标即可轻松选择和安装他们选择的应用。你不必花费数小时来搜索所有必要的应用程序、PPA、deb、AppImage、snap 或 flatpak。Alfred 将所有常见的应用、工具和小程序集中在一起,并自动安装所选的应用。如果你是最近从 Windows 迁移到 Ubuntu Linux 的新手,Alfred 会帮助你在新安装的 Ubuntu 系统上进行无人值守的软件安装,而无需太多用户干预。请注意,还有一个名称相似的 Mac OS 应用,但两者有不同的用途。
|
||||
|
||||
### 在 Ubuntu 上安装 Alfred
|
||||
|
||||
Alfred 安装很简单!只需下载脚本并启动它。就这么简单。
|
||||
|
||||
```
|
||||
$ wget https://raw.githubusercontent.com/derkomai/alfred/master/alfred.py
|
||||
$ python3 alfred.py
|
||||
```
|
||||
|
||||
或者,使用 `wget` 下载脚本,如上所示,只需将 `alfred.py` 移动到 `$PATH` 中:
|
||||
|
||||
```
|
||||
$ sudo cp alfred.py /usr/local/bin/alfred
|
||||
```
|
||||
|
||||
使其可执行:
|
||||
|
||||
```
|
||||
$ sudo chmod +x /usr/local/bin/alfred
|
||||
```
|
||||
|
||||
并使用命令启动它:
|
||||
|
||||
```
|
||||
$ alfred
|
||||
```
|
||||
|
||||
### 使用 Alfred 脚本轻松快速地在 Ubuntu 上安装基本应用程序
|
||||
|
||||
按照上面所说启动 Alfred 脚本。这就是 Alfred 默认界面的样子。
|
||||
|
||||
![][2]
|
||||
|
||||
如你所见,Alfred 列出了许多最常用的应用类型,例如:
|
||||
|
||||
* 网络浏览器,
|
||||
* 邮件客户端,
|
||||
* 消息,
|
||||
* 云存储客户端,
|
||||
* 硬件驱动程序,
|
||||
* 编解码器,
|
||||
* 开发者工具,
|
||||
* Android,
|
||||
* 文本编辑器,
|
||||
* Git,
|
||||
* 内核更新工具,
|
||||
* 音频/视频播放器,
|
||||
* 截图工具,
|
||||
* 录屏工具,
|
||||
* 视频编码器,
|
||||
* 流媒体应用,
|
||||
* 3D 建模和动画工具,
|
||||
* 图像查看器和编辑器,
|
||||
* CAD 软件,
|
||||
* PDF 工具,
|
||||
* 游戏模拟器,
|
||||
* 磁盘管理工具,
|
||||
* 加密工具,
|
||||
* 密码管理器,
|
||||
* 存档工具,
|
||||
* FTP 软件,
|
||||
* 系统资源监视器,
|
||||
* 应用启动器等。
|
||||
|
||||
你可以选择任何一个或多个应用并立即安装它们。在这里,我将安装 “Developer bundle”,因此我选择它并单击 OK 按钮。
|
||||
|
||||
![][3]
|
||||
|
||||
现在,Alfred 脚本将自动你的 Ubuntu 系统上添加必要仓库、PPA 并开始安装所选的应用。
|
||||
|
||||
![][4]
|
||||
|
||||
安装完成后,你将看到以下消息。
|
||||
|
||||
![][5]
|
||||
|
||||
恭喜你!已安装选定的软件包。
|
||||
|
||||
你可以使用以下命令[在 Ubuntu 上查看最近安装的应用][6]:
|
||||
|
||||
```
|
||||
$ grep " install " /var/log/dpkg.log
|
||||
```
|
||||
|
||||
你可能需要重启系统才能使用某些已安装的应用。类似地,你可以方便地安装列表中的任何程序。
|
||||
|
||||
提示一下,还有一个由不同的开发人员编写的类似脚本,名为 `post_install.sh`。它与 Alfred 完全相同,但提供了一些不同的应用。请查看以下链接获取更多详细信息。
|
||||
|
||||
- [Ubuntu Post Installation Script](https://www.ostechnix.com/ubuntu-post-installation-script/)
|
||||
|
||||
这两个脚本能让懒惰的用户,特别是新手,只需点击几下鼠标就能够轻松快速地安装他们想要在 Ubuntu Linux 中使用的大多数常见应用、工具、更新、小程序,而无需依赖官方或者非官方文档的帮助。
|
||||
|
||||
就是这些了。希望这篇文章有用。还有更多好东西。敬请期待!
|
||||
|
||||
干杯!
|
||||
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.ostechnix.com/an-automated-way-to-install-essential-applications-on-ubuntu/
|
||||
|
||||
作者:[SK][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.ostechnix.com/author/sk/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7
|
||||
[2]: http://www.ostechnix.com/wp-content/uploads/2019/02/alfred-1.png
|
||||
[3]: http://www.ostechnix.com/wp-content/uploads/2019/02/alfred-2.png
|
||||
[4]: http://www.ostechnix.com/wp-content/uploads/2019/02/alfred-4.png
|
||||
[5]: http://www.ostechnix.com/wp-content/uploads/2019/02/alfred-5-1.png
|
||||
[6]: https://www.ostechnix.com/list-installed-packages-sorted-installation-date-linux/
|
||||
@ -1,60 +1,56 @@
|
||||
[#]: collector: "lujun9972"
|
||||
[#]: translator: "zero-mk"
|
||||
[#]: reviewer: " "
|
||||
[#]: publisher: " "
|
||||
[#]: url: " "
|
||||
[#]: reviewer: "wxy"
|
||||
[#]: publisher: "wxy"
|
||||
[#]: url: "https://linux.cn/article-10593-1.html"
|
||||
[#]: subject: "Bash-Insulter : A Script That Insults An User When Typing A Wrong Command"
|
||||
[#]: via: "https://www.2daygeek.com/bash-insulter-insults-the-user-when-typing-wrong-command/"
|
||||
[#]: author: "Magesh Maruthamuthu https://www.2daygeek.com/author/magesh/"
|
||||
|
||||
Bash-Insulter : 一个在输入错误命令时侮辱用户的脚本
|
||||
Bash-Insulter:一个在输入错误命令时嘲讽用户的脚本
|
||||
======
|
||||
|
||||
这是一个非常有趣的脚本,每当用户在终端输入错误的命令时,它都会侮辱用户。
|
||||
这是一个非常有趣的脚本,每当用户在终端输入错误的命令时,它都会嘲讽用户。
|
||||
|
||||
它让你在处理一些问题时感到快乐。
|
||||
它让你在解决一些问题时会感到快乐。有的人在受到终端嘲讽的时候感到不愉快。但是,当我受到终端的批评时,我真的很开心。
|
||||
|
||||
有的人在受到终端侮辱的时候感到不愉快。但是,当我受到终端的侮辱时,我真的很开心。
|
||||
|
||||
这是一个有趣的CLI(译者注:command-line interface) 工具,在你弄错的时候,会用随机短语侮辱你。
|
||||
|
||||
此外,它允许您添加自己的短语。
|
||||
这是一个有趣的 CLI 工具,在你弄错的时候,会用随机短语嘲讽你。此外,它允许你添加自己的短语。
|
||||
|
||||
### 如何在 Linux 上安装 Bash-Insulter?
|
||||
|
||||
在安装 Bash-Insulter 之前,请确保您的系统上安装了 git。如果没有,请使用以下命令安装它。
|
||||
在安装 Bash-Insulter 之前,请确保你的系统上安装了 git。如果没有,请使用以下命令安装它。
|
||||
|
||||
对于 **`Fedora`** 系统, 请使用 **[DNF 命令][1]** 安装 git
|
||||
对于 Fedora 系统, 请使用 [DNF 命令][1] 安装 git。
|
||||
|
||||
```
|
||||
$ sudo dnf install git
|
||||
```
|
||||
|
||||
对于 **`Debian/Ubuntu`** 系统,,请使用 **[APT-GET 命令][2]** 或者 **[APT 命令][3]** 安装 git。
|
||||
对于 Debian/Ubuntu 系统,请使用 [APT-GET 命令][2] 或者 [APT 命令][3] 安装 git。
|
||||
|
||||
```
|
||||
$ sudo apt install git
|
||||
```
|
||||
|
||||
对于基于 **`Arch Linux`** 的系统, 请使用 **[Pacman 命令][4]** 安装 git。
|
||||
对于基于 Arch Linux 的系统,请使用 [Pacman 命令][4] 安装 git。
|
||||
|
||||
```
|
||||
$ sudo pacman -S git
|
||||
```
|
||||
|
||||
对于 **`RHEL/CentOS`** systems, 请使用 **[YUM 命令][5]** 安装 git。
|
||||
对于 RHEL/CentOS 系统,请使用 [YUM 命令][5] 安装 git。
|
||||
|
||||
```
|
||||
$ sudo yum install git
|
||||
```
|
||||
|
||||
对于 **`openSUSE Leap`** system, 请使用 **[Zypper 命令][6]** 安装 git。
|
||||
对于 openSUSE Leap 系统,请使用 [Zypper 命令][6] 安装 git。
|
||||
|
||||
```
|
||||
$ sudo zypper install git
|
||||
```
|
||||
|
||||
我们可以通过克隆(clone)开发人员的github存储库轻松地安装它。
|
||||
我们可以通过<ruby>克隆<rt>clone</rt></ruby>开发人员的 GitHub 存储库轻松地安装它。
|
||||
|
||||
首先克隆 Bash-insulter 存储库。
|
||||
|
||||
@ -85,7 +81,7 @@ fi
|
||||
$ sudo source /etc/bash.bashrc
|
||||
```
|
||||
|
||||
你想测试一下安装是否生效吗?你可以试试在终端上输入一些错误的命令,看看它如何侮辱你。
|
||||
你想测试一下安装是否生效吗?你可以试试在终端上输入一些错误的命令,看看它如何嘲讽你。
|
||||
|
||||
```
|
||||
$ unam -a
|
||||
@ -95,9 +91,7 @@ $ pin 2daygeek.com
|
||||
|
||||
![][8]
|
||||
|
||||
如果您想附加您自己的短语,则导航到以下文件并更新它
|
||||
|
||||
您可以在 `messages` 部分中添加短语。
|
||||
如果你想附加你自己的短语,则导航到以下文件并更新它。你可以在 `messages` 部分中添加短语。
|
||||
|
||||
```
|
||||
# vi /etc/bash.command-not-found
|
||||
@ -178,7 +172,7 @@ via: https://www.2daygeek.com/bash-insulter-insults-the-user-when-typing-wrong-c
|
||||
作者:[Magesh Maruthamuthu][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[zero-mk](https://github.com/zero-mk)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,13 +1,13 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-10594-1.html)
|
||||
[#]: subject: (Regex groups and numerals)
|
||||
[#]: via: (https://leancrew.com/all-this/2019/02/regex-groups-and-numerals/)
|
||||
[#]: author: (Dr.Drang https://leancrew.com)
|
||||
|
||||
正则组和数字
|
||||
正则表达式的分组和数字
|
||||
======
|
||||
|
||||
大约一周前,我在编辑一个程序时想要更改一些变量名。我之前认为这将是一个简单的正则表达式查找/替换。只是这没有我想象的那么简单。
|
||||
@ -16,9 +16,9 @@
|
||||
|
||||
![Mistaken BBEdit replacement pattern][2]
|
||||
|
||||
我不能简单地 `30` 替换为 `10`,因为代码中有一些与变量无关的数字 `10`。我认为我很聪明,所以我不想写三个非正则表达式替换,`a10`、`v10` 和 `x10` 每个一个。但是我却没有注意到替换模式中的蓝色。如果我这样做了,我会看到 BBEdit 将我的替换模式解释为“匹配组 13,后面跟着 `0`,而不是”匹配组 1,后面跟着 `30`,后者是我想要的。由于匹配组 13 是空白的,因此所有变量名都会被替换为 `0`。
|
||||
我不能简单地 `30` 替换为 `10`,因为代码中有一些与变量无关的数字 `10`。我认为我很聪明,所以我不想写三个非正则表达式替换,`a10`、`v10` 和 `x10`,每个一个。但是我却没有注意到替换模式中的蓝色。如果我这样做了,我会看到 BBEdit 将我的替换模式解释为“匹配组 13,后面跟着 `0`,而不是”匹配组 1,后面跟着 `30`,后者是我想要的。由于匹配组 13 是空白的,因此所有变量名都会被替换为 `0`。
|
||||
|
||||
你看,BBEdit 可以在搜索模式中匹配多达 99 个组,严格来说,我们应该在替换模式中引用它们时使用两位数字。但在大多数情况下,我们可以使用 `\1` 到 `\9` 而不是 `\01` 到 `\09`,因为这没有歧义。换句话说,如果我尝试将 `a10`、`v10` 和 `x10` 更改为 `az`、`vz` 和 `xz`,那么使用 `\1z`的替换模式就可以了。因为后面的 `z` 意味着不会误解释该模式中 `\1`。
|
||||
你看,BBEdit 可以在搜索模式中匹配多达 99 个分组,严格来说,我们应该在替换模式中引用它们时使用两位数字。但在大多数情况下,我们可以使用 `\1` 到 `\9` 而不是 `\01` 到 `\09`,因为这没有歧义。换句话说,如果我尝试将 `a10`、`v10` 和 `x10` 更改为 `az`、`vz` 和 `xz`,那么使用 `\1z`的替换模式就可以了。因为后面的 `z` 意味着不会误解释该模式中 `\1`。
|
||||
|
||||
因此,在撤消替换后,我将模式更改为这样:
|
||||
|
||||
@ -30,10 +30,9 @@
|
||||
|
||||
![Named BBEdit replacement pattern][4]
|
||||
|
||||
在任何情况下,我从来都没有使用过命名组,无论正则表达式是在文本编辑器还是在脚本中。我的总体感觉是,如果模式复杂到我必须使用变量来跟踪所有组,那么我应该停下来并将问题分解为更小的部分。
|
||||
我从来都没有使用过命名组,无论正则表达式是在文本编辑器还是在脚本中。我的总体感觉是,如果模式复杂到我必须使用变量来跟踪所有组,那么我应该停下来并将问题分解为更小的部分。
|
||||
|
||||
By the way, you may have heard that BBEdit is celebrating its [25th anniversary][5] of not sucking. When a well-documented app has such a long history, the manual starts to accumulate delightful callbacks to the olden days. As I was looking up the notation for named groups in the BBEdit manual, I ran across this note:
|
||||
顺便说一下,你可能已经听说 BBEdit 正在庆祝它诞生[25周年][5]。当一个有良好文档的应用有如此历史时,手册的积累能让人愉快地回到过去的日子。当我在 BBEdit 手册中查找命名组的表示法时,我遇到了这个说明:
|
||||
顺便说一下,你可能已经听说 BBEdit 正在庆祝它诞生[25周年][5]。当一个有良好文档的应用有如此长的历史时,手册的积累能让人愉快地回到过去的日子。当我在 BBEdit 手册中查找命名组的表示法时,我遇到了这个说明:
|
||||
|
||||
![BBEdit regex manual excerpt][6]
|
||||
|
||||
@ -45,8 +44,8 @@ via: https://leancrew.com/all-this/2019/02/regex-groups-and-numerals/
|
||||
|
||||
作者:[Dr.Drang][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
译者:[s](https://github.com/geekpi)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,5 +1,5 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: translator: (mokshal)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: subject: (5 reasons to give Linux for the holidays)
|
||||
|
||||
@ -1,54 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (alim0x)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Booting Linux faster)
|
||||
[#]: via: (https://opensource.com/article/19/1/booting-linux-faster)
|
||||
[#]: author: (Stewart Smith https://opensource.com/users/stewart-ibm)
|
||||
|
||||
Booting Linux faster
|
||||
======
|
||||
Doing Linux kernel and firmware development leads to lots of reboots and lots of wasted time.
|
||||
|
||||
Of all the computers I've ever owned or used, the one that booted the quickest was from the 1980s; by the time your hand moved from the power switch to the keyboard, the BASIC interpreter was ready for your commands. Modern computers take anywhere from 15 seconds for a laptop to minutes for a small home server to boot. Why is there such a difference in boot times?
|
||||
|
||||
A microcomputer from the 1980s that booted straight to a BASIC prompt had a very simple CPU that started fetching and executing instructions from a memory address immediately upon getting power. Since these systems had BASIC in ROM, there was no loading time—you got to the BASIC prompt really quickly. More complex systems of that same era, such as the IBM PC or Macintosh, took a significant time to boot (~30 seconds), although this was mostly due to having to read the operating system (OS) off a floppy disk. Only a handful of seconds were spent in firmware before being able to load an OS.
|
||||
|
||||
Modern servers typically spend minutes, rather than seconds, in firmware before getting to the point of booting an OS from disk. This is largely due to modern systems' increased complexity. No longer can a CPU just come up and start executing instructions at full speed; we've become accustomed to CPU frequency scaling, idle states that save a lot of power, and multiple CPU cores. In fact, inside modern CPUs are a surprising number of simpler CPUs that help start the main CPU cores and provide runtime services such as throttling the frequency when it gets too hot. On most CPU architectures, the code running on these cores inside your CPU is provided as opaque binary blobs.
|
||||
|
||||
On OpenPOWER systems, every instruction executed on every core inside the CPU is open source software. On machines with [OpenBMC][1] (such as IBM's AC922 system and Raptor's TALOS II and Blackbird systems), this extends to the code running on the Baseboard Management Controller as well. This means we can get a tremendous amount of insight into what takes so long from the time you plug in a power cable to the time a familiar login prompt is displayed.
|
||||
|
||||
If you're part of a team that works on the Linux kernel, you probably boot a lot of kernels. If you're part of a team that works on firmware, you're probably going to boot a lot of different firmware images, followed by an OS to ensure your firmware still works. If we can reduce the hardware's boot time, these teams can become more productive, and end users may be grateful when they're setting up systems or rebooting to install firmware or OS updates.
|
||||
|
||||
Over the years, many improvements have been made to Linux distributions' boot time. Modern init systems deal well with doing things concurrently and on-demand. On a modern system, once the kernel starts executing, it can take very few seconds to get to a login prompt. This handful of seconds are not the place to optimize boot time; we have to go earlier: before we get to the OS.
|
||||
|
||||
On OpenPOWER systems, the firmware loads an OS by booting a Linux kernel stored in the firmware flash chip that runs a userspace program called [Petitboot][2] to find the disk that holds the OS the user wants to boot and [kexec][3][()][3] to it. This code reuse leverages the efforts that have gone into making Linux boot quicker. Even so, we found places in our kernel config and userspace where we could improve and easily shave seconds off boot time. With these optimizations, booting the Petitboot environment is a single-digit percentage of boot time, so we had to find more improvements elsewhere.
|
||||
|
||||
Before the Petitboot environment starts, there's a prior bit of firmware called [Skiboot][4], and before that there's [Hostboot][5]. Prior to Hostboot is the [Self-Boot Engine][6], a separate core on the die that gets a single CPU core up and executing instructions out of Level 3 cache. These components are where we can make the most headway in reducing boot time, as they take up the overwhelming majority of it. Perhaps some of these components aren't optimized enough or doing as much in parallel as they could be?
|
||||
|
||||
Another avenue of attack is reboot time rather than boot time. On a reboot, do we really need to reinitialize all the hardware?
|
||||
|
||||
Like any modern system, the solutions to improving boot (and reboot) time have been a mixture of doing more in parallel, dealing with legacy, and (arguably) cheating.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/1/booting-linux-faster
|
||||
|
||||
作者:[Stewart Smith][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/stewart-ibm
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://en.wikipedia.org/wiki/OpenBMC
|
||||
[2]: https://github.com/open-power/petitboot
|
||||
[3]: https://en.wikipedia.org/wiki/Kexec
|
||||
[4]: https://github.com/open-power/skiboot
|
||||
[5]: https://github.com/open-power/hostboot
|
||||
[6]: https://github.com/open-power/sbe
|
||||
[7]: https://linux.conf.au/schedule/presentation/105/
|
||||
[8]: https://linux.conf.au/
|
||||
@ -0,0 +1,79 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Developer happiness: What you need to know)
|
||||
[#]: via: (https://opensource.com/article/19/2/developer-happiness)
|
||||
[#]: author: (Bart Copeland https://opensource.com/users/bartcopeland)
|
||||
|
||||
Developer happiness: What you need to know
|
||||
======
|
||||
Developers need the tools and the freedom to code quickly, without getting bogged down by compliance and security.
|
||||

|
||||
|
||||
A person needs the right tools for the job. There's nothing as frustrating as getting halfway through a car repair, for instance, only to discover you don't have the specialized tool you need to complete the job. The same concept applies to developers: you need the tools to do what you are best at, without disrupting your workflow with compliance and security needs, so you can produce code faster.
|
||||
|
||||
Over half—51%, to be specific—of developers spend only one to four hours each day programming, according to ActiveState's recent [Developer Survey 2018: Open Source Runtime Pains][1]. In other words, the majority of developers spend less than half of their time coding. According to the survey, 50% of developers say security is one of their biggest concerns, but 67% of developers choose not to add a new language when coding because of the difficulties related to corporate policies.
|
||||
|
||||
The result is developers have to devote time to non-coding activities like retrofitting software for security and compliance criteria checked after software and languages have been built. And they won't choose the best tool or language for the job because of corporate policies. Their satisfaction goes down and risk goes up.
|
||||
|
||||
So, developers aren't able to devote time to high-value work. This creates additional business risk because their time-to-market is slowed, and the organization increases tech debt by not empowering developers to decide on "the best" tech, unencumbered by corporate policy drag.
|
||||
|
||||
### Baking in security and compliance workflows
|
||||
|
||||
How can we solve this issue? One way is to integrate security and compliance workflows into the software development process in four easy steps:
|
||||
|
||||
#### 1\. Gather your forces
|
||||
|
||||
Get support from everyone involved. This is an often-forgotten but critical first step. Make sure to consider a wide range of stakeholders, including:
|
||||
|
||||
* DevOps
|
||||
* Developers
|
||||
* InfoSec
|
||||
* Legal/compliance
|
||||
* IT security
|
||||
|
||||
|
||||
|
||||
Stakeholders want to understand the business benefits, so make a solid case for eliminating the security and compliance checkpoints after software builds. You can consider any (or all) of the following in building your business case: time savings, opportunity cost, and developer productivity. By integrating security and compliance workflows into the development process, you also avoid retrofitting of languages.
|
||||
|
||||
#### 2\. Find trustworthy sources
|
||||
|
||||
Next, choose the trusted sources that can be used, along with their license and security requirements. Consider including information such as:
|
||||
|
||||
* Restrictions on usage based on environment or application type and version controls per language
|
||||
* Which open source components are allowable, e.g., specific packages
|
||||
* Which licenses can be used in which types of environments (e.g., research vs. production)
|
||||
* The definition of security levels, acceptable vulnerability risk levels, what risk levels trigger an action, what that action would be, and who would be responsible for its implementation
|
||||
|
||||
|
||||
|
||||
#### 3\. Incorporate security and compliance from day one
|
||||
|
||||
The upshot of incorporating security and compliance workflows is that it ultimately bakes security and compliance into the first line of code. It eliminates the drag of corporate policy because you're coding to spec versus having to fix things after the fact. But to do this, consider mechanisms for automatically scanning code as it's being built, along with using agentless monitoring of your runtime code. You're freeing up your time, and you'll also be able to programmatically enforce policies to ensure compliance across your entire organization.
|
||||
|
||||
New vulnerabilities arise, and new patches and versions become available. Consequently, security and compliance need to be considered when deploying code into production and also when running code. You need to know what, if any, code is at risk and where that code is running. So, the process for deploying and running code should include monitoring, reporting, and updating code in production.
|
||||
|
||||
By integrating security and compliance into your software development process from the start, you can also benefit by tracking where your code is running once deployed and be alerted of new threats as they arise. You will be able to track when your applications were vulnerable and respond with automatic enforcement of your software policies.
|
||||
|
||||
If your software development process has security and compliance workflows baked in, you will improve your productivity. And you'll be able to measure value through increased time spent coding; gains in security and stability; and cost- and time-savings in maintenance and discovery of security and compliance threats.
|
||||
|
||||
### Happiness through integration
|
||||
|
||||
If you don't develop and update software, your organization can't go forward. Developers are a linchpin in the success of your company, which means they need the tools and the freedom to code quickly. You can't let compliance and security needs—though they are critical—bog you down. Developers clearly worry about security, so the happy medium is to "shift left" and integrate security and compliance workflows from the start. You'll get more done, get it right the first time, and spend far less time retrofitting code.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/2/developer-happiness
|
||||
|
||||
作者:[Bart Copeland][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/bartcopeland
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.activestate.com/company/press/press-releases/activestate-developer-survey-examines-open-source-challenges/
|
||||
@ -0,0 +1,76 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (No! Ubuntu is NOT Replacing Apt with Snap)
|
||||
[#]: via: (https://itsfoss.com/ubuntu-snap-replaces-apt-blueprint/)
|
||||
[#]: author: (Abhishek Prakash https://itsfoss.com/author/abhishek/)
|
||||
|
||||
No! Ubuntu is NOT Replacing Apt with Snap
|
||||
======
|
||||
|
||||
Stop believing the rumors that Ubuntu is planning to replace Apt with Snap in the [Ubuntu 19.04 release][1]. These are only rumors.
|
||||
|
||||
![Snap replacing apt rumors][2]
|
||||
|
||||
Don’t get what I am talking about? Let me give you some context.
|
||||
|
||||
There is a ‘blueprint’ on Ubuntu’s launchpad website, titled ‘Replace APT with snap as default package manager’. It talks about replacing Apt (package manager at the heart of Debian) with Snap ( a new packaging system by Ubuntu).
|
||||
|
||||
> Thanks to Snap, the need for APT is disappearing, fast… why don’t we use snap at the system level?
|
||||
|
||||
The post further says “Imagine, for example, being able to run “sudo snap install cosmic” to upgrade to the current release, “sudo snap install –beta disco” (in March) to upgrade to a beta release, or, for that matter, “sudo snap install –edge disco” to upgrade to a pre-beta release. It would make the whole process much easier, and updates could simply be delivered as updates to the corresponding snap, which could then just be pushed to the repositories and there it is. This way, instead of having a separate release updater, it would be possible to A, run all system updates completely and silently in the background to avoid nagging the user (a la Chrome OS), and B, offer release upgrades in the GNOME software store, Mac-style, as banners, so the user can install them easily. It would make the user experience both more consistent and even more user-friendly than it currently is.”
|
||||
|
||||
It might sound good and promising and if you take a look at [this link][3], even you might start believing the rumor. Why? Because at the bottom of the blueprint information, it lists Ubuntu-founder Mark Shuttleworth as the approver.
|
||||
|
||||
![Apt being replaced with Snap blueprint rumor][4]Mark Shuttleworth’s name adds to the confusion
|
||||
|
||||
The rumor got fanned when the Switch to Linux YouTube channel covered it. You can watch the video from around 11:30.
|
||||
|
||||
<https://youtu.be/Xy7v5tdfSZM>
|
||||
|
||||
When this ‘news’ was brought to my attention, I reached out to Alan Pope of Canonical and asked him if he or his colleagues at Canonical (Ubuntu’s parent company) could confirm it.
|
||||
|
||||
Alan clarified that the so called blueprint was not associated with official Ubuntu team. It was created as a proposal by some community member not affiliated with Ubuntu.
|
||||
|
||||
> That’s not anything official. Some random community person made it. Anyone can write a blueprint.
|
||||
>
|
||||
> Alan Pope, Canonical
|
||||
|
||||
Alan further elaborated that anyone can create such blueprints and tag Mark Shuttleworth or other Ubuntu members in it. Just because Mark’s name was listed as the approver, it doesn’t mean he already approved the idea.
|
||||
|
||||
Canonical has no such plans to replace Apt with Snap. It’s not as simple as the blueprint in question suggests.
|
||||
|
||||
After talking with Alan, I decided to not write about this topic because I don’t want to fan baseless rumors and confuse people.
|
||||
|
||||
Unfortunately, the ‘replace Apt with Snap’ blueprint is still being shared on various Ubuntu and Linux related groups and forums. Alan had to publicly dismiss these rumors in a series of tweets:
|
||||
|
||||
> Seen this [#Ubuntu][5] blueprint being shared around the internet. It's not official, not a thing we're doing. Just because someone made a blueprint, doesn't make it fact. <https://t.co/5aUYlT2no5>
|
||||
>
|
||||
> — Alan Pope 🇪🇺🇬🇧 (@popey) [February 23, 2019][6]
|
||||
|
||||
I don’t want you, the It’s FOSS reader, to fell for such silly rumors so I quickly penned this article.
|
||||
|
||||
If you come across ‘apt being replaced with snap’ discussion, you may tell people that it’s not true and provide them this link as a reference.
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://itsfoss.com/ubuntu-snap-replaces-apt-blueprint/
|
||||
|
||||
作者:[Abhishek Prakash][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://itsfoss.com/author/abhishek/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://itsfoss.com/ubuntu-19-04-release-features/
|
||||
[2]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2019/02/snap-replacing-apt.png?resize=800%2C450&ssl=1
|
||||
[3]: https://blueprints.launchpad.net/ubuntu/+spec/package-management-default-snap
|
||||
[4]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2019/02/apt-snap-blueprint.jpg?ssl=1
|
||||
[5]: https://twitter.com/hashtag/Ubuntu?src=hash&ref_src=twsrc%5Etfw
|
||||
[6]: https://twitter.com/popey/status/1099238146393468931?ref_src=twsrc%5Etfw
|
||||
@ -0,0 +1,72 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Teaching scientists how to share code)
|
||||
[#]: via: (https://opensource.com/article/19/2/open-science-git)
|
||||
[#]: author: (Jon Tennant https://opensource.com/users/jon-tennant)
|
||||
|
||||
Teaching scientists how to share code
|
||||
======
|
||||
This course teaches them how to set up a GitHub project, index their project in Zenodo, and integrate Git into an RStudio workflow.
|
||||
|
||||
|
||||
Would it surprise you to learn that most of the world's scholarly research is not owned by the people who funded it or who created it? Rather it's owned by private corporations and locked up in proprietary systems, leading to [problems][1] around sharing, reuse, and reproducibility.
|
||||
|
||||
The open science movement is challenging this system, aiming to give researchers control, ownership, and freedom over their work. The [Open Science MOOC][2] (massively open online community) is a mission-driven project launched in 2018 to kick-start an open scientific revolution and foster more partnerships between open source software and open science.
|
||||
|
||||
The Open Science MOOC is a peer-to-peer community of practice, based around sharing knowledge and ideas, learning new skills, and using these things to develop as individuals so research communities can grow as part of a wider cultural shift towards openness.
|
||||
|
||||
### The curriculum
|
||||
|
||||
The Open Science MOOC is divided into 10 core modules, from the principles of open science to becoming an open science advocate.
|
||||
|
||||
The first module, [Open Research Software and Open Source][3], was released in late 2018. It includes three main tasks, all designed to help make research workflows more efficient and more open for collaboration:
|
||||
|
||||
#### 1\. Setting up your first GitHub project
|
||||
|
||||
GitHub is a powerful project management tool, both for coders and non-coders. This task teaches how to create a community around the platform, select an appropriate license, and write good documentation (including README files, contributing guidelines, and codes of conduct) to foster open collaboration and a welcoming community.
|
||||
|
||||
#### 2\. Indexing your project in Zenodo
|
||||
|
||||
[Zenodo][4] is an open science platform that seamlessly integrates with GitHub to help make projects more permanent, reusable, and citable. This task explains how webhooks between Zenodo and GitHub allow new versions of projects to become permanently archived as they progress. This is critical for helping researchers get a [DOI][5] for their work so they can receive full credit for all aspects of a project. As citations are still a primary form of "academic capital," this is essential for researchers.
|
||||
|
||||
#### 3\. Integrating Git into an RStudio workflow
|
||||
|
||||
This task is about giving research a mega-boost through greater collaborative efficiency and reproducibility. Git enables version control in all forms of text-based content, including data analysis and writing papers. Each time you save your work during the development process, Git saves time-stamped copies. This saves the hassle of trying to "roll back" projects if you delete a file or text by mistake, and eliminates horrific file-naming conventions. (For example, does FINAL_Revised_2.2_supervisor_edits_ver1.7_scream.txt look familiar?) Getting Git to interface with RStudio is the painful part, but this task goes through it, step by step, to ease the stress.
|
||||
|
||||
The third task also gives students the ability to interact directly with the MOOC by submitting pull requests to demonstrate their skills. This also adds their name to an online list of open source champions (aka "open sourcerers").
|
||||
|
||||
The MOOC's inherently interactive style is much more valuable than listening to someone talk at you, either on or off screen, like with many traditional online courses or educational programs. Each task is backed up by expert-gathered knowledge, so students get a rigorous, dual-learning experience.
|
||||
|
||||
### Empowering researchers
|
||||
|
||||
The Open Science MOOC strives to be as open as possible—this means we walk the walk and talk the talk. We are built upon a solid values-based foundation of freedom and equitable access to research. We see this route towards widespread adoption of best scientific practices as an essential part of the research process.
|
||||
|
||||
Everything we produce is openly developed and openly licensed for maximum engagement, sharing, and reuse. An open source workflow underpins our development. All of this happens openly around channels such as [Slack][6] and [GitHub][7] and helps to make the community much more coherent.
|
||||
|
||||
If we can instill the value of open source into modern research, this would empower current and future generations of researchers to think more about fundamental freedoms around knowledge production. We think that is something worth working towards as a community.
|
||||
|
||||
The Open Science MOOC combines the best elements of the open education, open science, and open source worlds. If you're ready to join, [sign up for the full course][3], which is, of course, free.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/2/open-science-git
|
||||
|
||||
作者:[Jon Tennant][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/jon-tennant
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.theguardian.com/science/political-science/2018/jun/29/elsevier-are-corrupting-open-science-in-europe
|
||||
[2]: https://opensciencemooc.eu/
|
||||
[3]: https://eliademy.com/catalog/oer/module-5-open-research-software-and-open-source.html
|
||||
[4]: https://zenodo.org/
|
||||
[5]: https://en.wikipedia.org/wiki/Digital_object_identifier
|
||||
[6]: https://osmooc.herokuapp.com/
|
||||
[7]: https://open-science-mooc-invite.herokuapp.com/
|
||||
@ -0,0 +1,82 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Reducing security risks with centralized logging)
|
||||
[#]: via: (https://opensource.com/article/19/2/reducing-security-risks-centralized-logging)
|
||||
[#]: author: (Hannah Suarez https://opensource.com/users/hcs)
|
||||
|
||||
Reducing security risks with centralized logging
|
||||
======
|
||||
Centralizing logs and structuring log data for processing can mitigate risks related to insufficient logging.
|
||||
|
||||

|
||||
|
||||
Logging and log analysis are essential to securing infrastructure, particularly when we consider common vulnerabilities. This article, based on my lightning talk [Let's use centralized log collection to make incident response teams happy][1] at FOSDEM'19, aims to raise awareness about the security concerns around insufficient logging, offer a way to avoid the risk, and advocate for more secure practices _(disclaimer: I work for NXLog)._
|
||||
|
||||
### Why log collection and why centralized logging?
|
||||
|
||||
Logging is, to be specific, an append-only sequence of records written to disk. In practice, logs help you investigate an infrastructure issue as you try to find a cause for misbehavior. A challenge comes up when you have heterogeneous systems with their own standards and formats, and you want to be able to handle and process these in a dependable way. This often comes at the cost of metadata. Centralized logging solutions require commonality, and that commonality often removes the rich metadata many open source logging tools provide.
|
||||
|
||||
### The security risk of insufficient logging and monitoring
|
||||
|
||||
The Open Web Application Security Project ([OWASP][2]) is a nonprofit organization that contributes to the industry with incredible projects (including many [tools][3] focusing on software security). The organization regularly reports on the riskiest security challenges for application developers and maintainers. In its most recent report on the [top 10 most critical web application security risks][4], OWASP added Insufficient Logging and Monitoring to its list. OWASP warns of risks due to insufficient logging, detection, monitoring, and active response in the following types of scenarios.
|
||||
|
||||
* Important auditable events, such as logins, failed logins, and high-value transactions are not logged.
|
||||
* Warnings and errors generate none, inadequate, or unclear log messages.
|
||||
* Logs are only being stored locally.
|
||||
* The application is unable to detect, escalate, or alert for active attacks in real time or near real time.
|
||||
|
||||
|
||||
|
||||
These instances can be mitigated by centralizing logs (i.e., not storing logs locally) and structuring log data for processing (i.e., in alerting dashboards and security suites).
|
||||
|
||||
For example, imagine a DNS query leads to a malicious site named **hacked.badsite.net**. With DNS monitoring, administrators monitor and proactively analyze DNS queries and responses. The efficiency of DNS monitoring relies on both sufficient logging and log collection in order to catch potential issues as well as structuring the resulting DNS log for further processing:
|
||||
|
||||
```
|
||||
2019-01-29
|
||||
Time (GMT) Source Destination Protocol-Info
|
||||
12:42:42.112898 SOURCE_IP xxx.xx.xx.x DNS Standard query 0x1de7 A hacked.badsite.net
|
||||
```
|
||||
|
||||
You can try this yourself and run through other examples and snippets with the [NXLog Community Edition][5] _(disclaimer again: I work for NXLog)._
|
||||
|
||||
### Important aside: unstructured vs. structured data
|
||||
|
||||
It's important to take a moment and consider the log data format. For example, let's consider this log message:
|
||||
|
||||
```
|
||||
debug1: Failed password for invalid user amy from SOURCE_IP port SOURCE_PORT ssh2
|
||||
```
|
||||
|
||||
This log contains a predefined structure, such as a metadata keyword before the colon ( **debug1** ). However, the rest of the log field is an unstructured string ( **Failed password for invalid user amy from SOURCE_IP port SOURCE_PORT ssh2** ). So, while the message is easily available in a human-readable format, it is not a format a computer can easily parse.
|
||||
|
||||
Unstructured event data poses limitations including difficulty of parsing, searching, and analyzing the logs. The important metadata is too often set in an unstructured data field in the form of a freeform string like the example above. Logging administrators will come across this problem at some point as they attempt to standardize/normalize log data and centralize their log sources.
|
||||
|
||||
### Where to go next
|
||||
|
||||
Alongside centralizing and structuring your logs, make sure you're collecting the right log data—Sysmon, PowerShell, Windows EventLog, DNS debug, NetFlow, ETW, kernel monitoring, file integrity monitoring, database logs, external cloud logs, and so on. Also have the right tools and processes in place to collect, aggregate, and help make sense of the data.
|
||||
|
||||
Hopefully, this gives you a starting point to centralize log collection across diverse sources; send them to outside sources like dashboards, monitoring software, analytics software, specialized software like security information and event management (SEIM) suites; and more.
|
||||
|
||||
What does your centralized logging strategy look like? Share your thoughts in the comments.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/2/reducing-security-risks-centralized-logging
|
||||
|
||||
作者:[Hannah Suarez][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/hcs
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://fosdem.org/2019/schedule/event/lets_use_centralized_log_collection_to_make_incident_response_teams_happy/
|
||||
[2]: https://www.owasp.org/index.php/Main_Page
|
||||
[3]: https://github.com/OWASP
|
||||
[4]: https://www.owasp.org/index.php/Top_10-2017_Top_10
|
||||
[5]: https://nxlog.co/products/nxlog-community-edition/download
|
||||
@ -0,0 +1,62 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Let your engineers choose the license: A guide)
|
||||
[#]: via: (https://opensource.com/article/19/2/choose-open-source-license-engineers)
|
||||
[#]: author: (Jeffrey Robert Kaufman https://opensource.com/users/jkaufman)
|
||||
|
||||
Let your engineers choose the license: A guide
|
||||
======
|
||||
Enabling engineers to make licensing decisions is wise and efficient.
|
||||

|
||||
|
||||
Imagine you are working for a company that will be starting a new open source community project. Great! You have taken a positive first step to give back and enable a virtuous cycle of innovation that the open source community-based development model provides.
|
||||
|
||||
But what about choosing an open source license for your project? You ask your manager for guidance, and she provides some perspective but quickly realizes that there is no formal company policy or guidelines. As any wise manager would do, she asks you to develop formal corporate guidelines for choosing an open source license for such projects.
|
||||
|
||||
Simple, right? You may be surprised to learn some unexpected challenges. This article will describe some of the complexities you may encounter and some perspective based on my recent experience with a similar project at Red Hat.
|
||||
|
||||
It may be useful to quickly review some of the more common forms of open source licensing. Open source licenses may be generally placed into two main buckets, copyleft and permissive.
|
||||
|
||||
> Copyleft licenses, such as the GPL, allow access to source code, modifications to the source, and distribution of the source or binary versions in their original or modified forms. Copyleft additionally provides that essential software freedoms (run, study, change, and distribution) will be allowed and ensured for any recipients of that code. A copyleft license prohibits restrictions or limitations on these essential software freedoms.
|
||||
>
|
||||
> Permissive licenses, similar to copyleft, also generally allow access to source code, modifications to the source, and distribution of the source or binary versions in their original or modified forms. However, unlike copyleft licenses, additional restrictions may be included with these forms of licenses, including proprietary limitations such as prohibiting the creation of modified works or further distribution.
|
||||
|
||||
Red Hat is one of the leading open source development companies, with thousands of open source developers continuously working upstream and contributing to an assortment of open source projects. When I joined Red Hat, I was very familiar with its flagship Red Hat Enterprise Linux offering, often referred to as RHEL. Although I fully expected that the company contributes under a wide assortment of licenses based on project requirements, I thought our preference and top recommendation for our engineers would be GPLv2 due to our significant involvement with Linux. In addition, GPL is a copyleft license, and copyleft ensures that the essential software freedoms (run, study, change, distribute) will be extended to any recipients of that code. What could be better for sustaining the open source ecosystem than a copyleft license?
|
||||
|
||||
Fast forwarding on my journey to craft internal license choice guidelines for Red Hat, the end result was to not have any license preference at all. Instead, we delegate that responsibility, to the maximum extent possible, to our engineers. Why? Because each open source project and community is unique and there are social aspects to these communities that may have preferences towards various licensing philosophies (e.g., copyleft or permissive). Engineers working in those communities understand all these issues and are best equipped to choose the proper license on this knowledge. Mandating certain licenses for code contributions often will conflict with these community norms and result in reduction or prohibition in contributed content.
|
||||
|
||||
For example, perhaps your organization believes that the latest GPL license (GPLv3) is the best for your company due to its updated provisions. If you mandated GPLv3 for all future contributions vs. GPLv2, you would be prohibited from contributing code to the Linux kernel, since that is a GPLv2 project and will likely remain that way for a very long time. Your engineers, being part of that open source community project, would know that and would automatically choose GPLv2 in the absence of such a mandate.
|
||||
|
||||
Bottom line: Enabling engineers to make these decisions is wise and efficient.
|
||||
|
||||
To the extent your organization may have to restrict the use of certain licenses (e.g., due to certain intellectual property concerns), this should naturally be part of your guidelines or policy. I believe it is much better to delegate to the maximum extent possible to those that understand all the nuances, politics, and licensing philosophies of these varied communities and restrict license choice only when absolutely necessary. Even having a preference for a certain license over another can be problematic. Open source engineers may have deeply rooted feelings about copyleft (either for or against), and forcing one license over the other (unless absolutely necessary for business reasons) may result in creating ill-will and ostracizing an engineer or engineering department within your organization
|
||||
|
||||
In summary, Red Hat's guidelines are very simple and are summarized below:
|
||||
|
||||
1. We suggest choosing an open source license from a set of 10 different licenses that are very common and meet the needs of most new open source projects.
|
||||
|
||||
2. We allow the use of other licenses but we ask that a reason is provided to the open source legal team so we can collect and better understand some of the new and perhaps evolving needs of the open source communities that we serve. (As stated above, our engineers are on the front lines and are best equipped to deliver this type of information.)
|
||||
|
||||
3. The open source legal team always has the right to override a decision, but this would be very rare and only would occur if we were aware of some community or legal concern regarding a specific license or project.
|
||||
|
||||
4. Publishing source code without a license is never permitted.
|
||||
|
||||
In summary, the advantages of these guidelines are enormous. They are very efficient and lead to a very low-friction development and approval system within our organization.
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/2/choose-open-source-license-engineers
|
||||
|
||||
作者:[Jeffrey Robert Kaufman][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/jkaufman
|
||||
[b]: https://github.com/lujun9972
|
||||
113
sources/talk/20190228 A Brief History of FOSS Practices.md
Normal file
113
sources/talk/20190228 A Brief History of FOSS Practices.md
Normal file
@ -0,0 +1,113 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (A Brief History of FOSS Practices)
|
||||
[#]: via: (https://itsfoss.com/history-of-foss)
|
||||
[#]: author: (Avimanyu Bandyopadhyay https://itsfoss.com/author/avimanyu/)
|
||||
|
||||
A Brief History of FOSS Practices
|
||||
======
|
||||
|
||||
We focus a great deal about Linux and Free & Open Source Software at It’s FOSS. Ever wondered how old such FOSS Practices are? How did this Practice come by? What is the History behind this revolutionary concept?
|
||||
|
||||
In this history and trivia article, let’s take a look back in time through this brief write-up and note some interesting initiatives in the past that have grown so huge today.
|
||||
|
||||
### Origins of FOSS
|
||||
|
||||
![History of FOSS][1]
|
||||
|
||||
The origins of FOSS goes back to the 1950s. When hardware was purchased, there used to be no additional charges for bundled software and the source code would also be available in order to fix possible bugs in the software.
|
||||
|
||||
It was actually a common Practice back then for users with the freedom to customize the code.
|
||||
|
||||
At that time, mostly academicians and researchers in the industry were the collaborators to develop such software.
|
||||
|
||||
The term Open Source was not there yet. Instead, the term that was popular at that time was “Public Domain Software”. As of today, ideologically, both are very much [different][2] in nature even though they may sound similar.
|
||||
|
||||
<https://youtu.be/0Dt3MCcXay8?list=PLybyE6hxfb7cIzYK1HegM3-ccU-JhovpH>
|
||||
|
||||
Back in 1955, some users of the [IBM 701][3] computer system from Los Angeles, voluntarily founded a group called SHARE. The “SHARE Program Library Agency” (SPLA) distributed information and software through magnetic tapes.
|
||||
|
||||
Technical information shared, was about programming languages, operating systems, database systems, and user experiences for enterprise users of small, medium, and large-scale IBM computers.
|
||||
|
||||
The initiative that is now more than 60 years old, continues to follow its goals quite actively. SHARE has its upcoming event coming up as [SHARE Phoenix 2019][4]. You can download and check out their complete timeline [here][5].
|
||||
|
||||
### The GNU Project
|
||||
|
||||
Announced at MIT on September 27, 1983, by Richard Stallman, the GNU Project is what immensely empowers and supports the Free Software Community today.
|
||||
|
||||
### Free Software Foundation
|
||||
|
||||
The “Free Software Movement” by Richard Stallman established a new norm for developing Free Software.
|
||||
|
||||
He founded The Free Software Foundation (FSF) on 4th October 1985 to support the free software movement. Software that ensures that the end users have freedom in using, studying, sharing and modifying that software came to be called as Free Software.
|
||||
|
||||
**Free as in Free Speech, Not Free Beer**
|
||||
|
||||
<https://youtu.be/MtNcxMuphLc>
|
||||
|
||||
The Free Software Movement laid the following rules to establish the distinctiveness of the idea:
|
||||
|
||||
* The freedom to run the program as you wish, for any purpose (freedom 0).
|
||||
* The freedom to study how the program works, and change it so it does your computing as you wish (freedom 1). Access to the source code is a precondition for this.
|
||||
* The freedom to redistribute copies so you can help your neighbor (freedom 2).
|
||||
* The freedom to distribute copies of your modified versions to others (freedom 3). By doing this you can give the whole community a chance to benefit from your changes. Access to the source code is a precondition for this.
|
||||
|
||||
### The Linux Kernel
|
||||
|
||||
<https://youtu.be/RkUrOSQF1JQ>
|
||||
|
||||
How can we miss this section at It’s FOSS! The Linux kernel was released as freely modifiable source code in 1991 by Linus Torvalds. At first, it was neither Free Software nor used an Open-source software license. In February 1992, Linux was relicensed under the GPL.
|
||||
|
||||
### The Linux Foundation
|
||||
|
||||
The Linux Foundation has a goal to empower open source projects to accelerate technology development and commercial adoption. It is an initiative that was taken in 2000 via the [Open Source Development Labs][6] (OSDL) which later merged with the [Free Standards Group][7].
|
||||
|
||||
Linus Torvalds works at The Linux Foundation who provide complete support to him so that he can work full-time on improving Linux.
|
||||
|
||||
### Open Source
|
||||
|
||||
When the source code of [Netscape][8] Communicator was released in 1998, the label “Open Source” was adopted by a group of individuals at a strategy session held on February 3rd, 1998 in Palo Alto, California. The idea grew from a visionary realization that the [Netscape announcement][9] had changed the way people looked at commercial software.
|
||||
|
||||
This opened up a whole new world, creating a new perspective that revealed the superiority and advantage of an open development process that could be powered by collaboration.
|
||||
|
||||
[Christine Peterson][10] was the one among that group of individuals who originally suggested the term “Open Source” as we perceive today (mentioned [earlier][11]).
|
||||
|
||||
### Evolution of Business Models
|
||||
|
||||
The concept of Open Source is a huge phenomenon right now and there are several companies that continue to adopt the Open Source Approach to this day. [As of April 2015, 78% of companies used Open Source Software][12] with different [Open Source Licenses][13].
|
||||
|
||||
Several organisations have adopted [different business models][14] for Open Source. Red Hat and Mozilla are two good examples.
|
||||
|
||||
So this was a brief recap of some interesting facts from FOSS History. Do let us know your thoughts if you want to share in the comments below.
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://itsfoss.com/history-of-foss
|
||||
|
||||
作者:[Avimanyu Bandyopadhyay][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://itsfoss.com/author/avimanyu/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2019/02/history-of-foss.png?resize=800%2C450&ssl=1
|
||||
[2]: https://opensource.org/node/878
|
||||
[3]: https://en.wikipedia.org/wiki/IBM_701
|
||||
[4]: https://event.share.org/home
|
||||
[5]: https://www.share.org/d/do/11532
|
||||
[6]: https://en.wikipedia.org/wiki/Open_Source_Development_Labs
|
||||
[7]: https://en.wikipedia.org/wiki/Free_Standards_Group
|
||||
[8]: https://en.wikipedia.org/wiki/Netscape
|
||||
[9]: https://web.archive.org/web/20021001071727/http://wp.netscape.com:80/newsref/pr/newsrelease558.html
|
||||
[10]: https://en.wikipedia.org/wiki/Christine_Peterson
|
||||
[11]: https://itsfoss.com/nanotechnology-open-science-ai/
|
||||
[12]: https://www.zdnet.com/article/its-an-open-source-world-78-percent-of-companies-run-open-source-software/
|
||||
[13]: https://itsfoss.com/open-source-licenses-explained/
|
||||
[14]: https://opensource.com/article/17/12/open-source-business-models
|
||||
@ -0,0 +1,56 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (lujun9972)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (IRC vs IRL: How to run a good IRC meeting)
|
||||
[#]: via: (https://opensource.com/article/19/2/irc-vs-irl-meetings)
|
||||
[#]: author: (Ben Cotton https://opensource.com/users/bcotton)
|
||||
|
||||
IRC vs IRL: How to run a good IRC meeting
|
||||
======
|
||||
Internet Relay Chat meetings can be a great way to move a project forward if you follow these best practices.
|
||||

|
||||
|
||||
There's an art to running a meeting in any format. Many people have learned to run in-person or telephone meetings, but [Internet Relay Chat][1] (IRC) meetings have unique characteristics that differ from "in real life" (IRL) meetings. This article will share the advantages and disadvantages of the IRC format as well as tips that will help you lead IRC meetings more effectively.
|
||||
|
||||
Why IRC? Despite the wealth of real-time chat options available today, [IRC remains a cornerstone of open source projects][2]. If your project uses another communication method, don't worry. Most of this advice works for any synchronous text chat mechanism, perhaps with a few tweaks here and there.
|
||||
|
||||
### Challenges of IRC meetings
|
||||
|
||||
IRC meetings pose certain challenges compared to in-person meetings. You know that lag between when one person finishes talking and the next one begins? It's worse in IRC because people have to type what they're thinking. This is slower than talking and—unlike with talking—you can't tell when someone else is trying to compose a message. Moderators must remember to insert long pauses when asking for responses or moving to the next topic. And someone who wants to speak up should insert a brief message (e.g., a period) to let the moderator know.
|
||||
|
||||
IRC meetings also lack the metadata you get from other methods. You can't read facial expressions or tone of voice in text. This means you have to be careful with your word choice and phrasing.
|
||||
|
||||
And IRC meetings make it really easy to get distracted. At least when someone is looking at funny cat GIFs during an in-person meeting, you'll see them smile and hear them laugh at inopportune times. In IRC, unless they accidentally paste the wrong text, there's no peer pressure even to pretend to pay attention. With IRC, you can even be in multiple meetings at once. I've done this, but it's dangerous if you need to be an active participant.
|
||||
|
||||
### Benefits of IRC meetings
|
||||
|
||||
IRC meetings have some unique advantages, too. IRC is a very resource-light medium. It doesn't tax bandwidth or CPU. This lowers the barrier for participation, which is advantageous for both the underprivileged and people who are on the road. For volunteer contributors, it means they may be able to participate during their workday. And it means participants don't need to find a quiet space where they can talk without bothering those around them.
|
||||
|
||||
With a meeting bot, IRC can produce meeting minutes instantly. In Fedora, we use Zodbot, an instance of Debian's [Meetbot][3], to log meetings and provide interaction. When a meeting ends, the minutes and full logs are immediately available to the community. This can reduce the administrative overhead of running the meeting.
|
||||
|
||||
### It's like a normal meeting, but different
|
||||
|
||||
Conducting a meeting via IRC or other text-based medium means thinking about the meeting in a slightly different way. Although it lacks some of the benefits of higher-bandwidth modes of communication, it has advantages, too. Running an IRC meeting provides the opportunity to develop discipline that can help you run any type of meeting.
|
||||
|
||||
Like any meeting, IRC meetings are best when there's a defined agenda and purpose. A good meeting moderator knows when to let the conversation follow twists and turns and when it's time to reel it back in. There's no hard and fast rule here—it's very much an art. But IRC offers an advantage in this regard. By setting the channel topic to the meeting's current topic, people have a visible reminder of what they should be talking about.
|
||||
|
||||
If your project doesn't already conduct synchronous meetings, you should give it some thought. For projects with a diverse set of time zones, finding a mutually agreeable time to hold a meeting is hard. You can't rely on meetings as your only source of coordination. But they can be a valuable part of how your project works.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/2/irc-vs-irl-meetings
|
||||
|
||||
作者:[Ben Cotton][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[lujun9972](https://github.com/lujun9972)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/bcotton
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://en.wikipedia.org/wiki/Internet_Relay_Chat
|
||||
[2]: https://opensource.com/article/16/6/getting-started-irc
|
||||
[3]: https://wiki.debian.org/MeetBot
|
||||
@ -0,0 +1,76 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Why CLAs aren't good for open source)
|
||||
[#]: via: (https://opensource.com/article/19/2/cla-problems)
|
||||
[#]: author: (Richard Fontana https://opensource.com/users/fontana)
|
||||
|
||||
Why CLAs aren't good for open source
|
||||
======
|
||||
Few legal topics in open source are as controversial as contributor license agreements.
|
||||

|
||||
|
||||
Few legal topics in open source are as controversial as [contributor license agreements][1] (CLAs). Unless you count the special historical case of the [Fedora Project Contributor Agreement][2] (which I've always seen as an un-CLA), or, like [Karl Fogel][3], you classify the [DCO][4] as a [type of CLA][5], today Red Hat makes no use of CLAs for the projects it maintains.
|
||||
|
||||
It wasn't always so. Red Hat's earliest projects followed the traditional practice I've called "inbound=outbound," in which contributions to a project are simply provided under the project's open source license with no execution of an external, non-FOSS contract required. But in the early 2000s, Red Hat began experimenting with the use of contributor agreements. Fedora started requiring contributors to sign a CLA based on the widely adapted [Apache ICLA][6], while a Free Software Foundation-derived copyright assignment agreement and a pair of bespoke CLAs were inherited from the Cygnus and JBoss acquisitions, respectively. We even took [a few steps][7] towards adopting an Apache-style CLA across the rapidly growing set of Red Hat-led projects.
|
||||
|
||||
This came to an end, in large part because those of us on the Red Hat legal team heard and understood the concerns and objections raised by Red Hat engineers and the wider technical community. We went on to become de facto leaders of what some have called the anti-CLA movement, marked notably by our [opposition to Project Harmony][8] and our [efforts][9] to get OpenStack to replace its CLA with the DCO. (We [reluctantly][10] sign tolerable upstream project CLAs out of practical necessity.)
|
||||
|
||||
### Why CLAs are problematic
|
||||
|
||||
Our choice not to use CLAs is a reflection of our values as an authentic open source company with deep roots in the free software movement. Over the years, many in the open source community have explained why CLAs, and the very similar mechanism of copyright assignment, are a bad policy for open source.
|
||||
|
||||
One reason is the red tape problem. Normally, open source development is characterized by frictionless contribution, which is enabled by inbound=outbound without imposition of further legal ceremony or process. This makes it relatively easy for new contributors to get involved in a project, allowing more effective growth of contributor communities and driving technical innovation upstream. Frictionless contribution is a key part of the advantage open source development holds over proprietary alternatives. But frictionless contribution is negated by CLAs. Having to sign an unusual legal agreement before a contribution can be accepted creates a bureaucratic hurdle that slows down development and discourages participation. This cost persists despite the growing use of automation by CLA-using projects.
|
||||
|
||||
CLAs also give rise to an asymmetry of legal power among a project's participants, which also discourages the growth of strong contributor and user communities around a project. With Apache-style CLAs, the company or organization leading the project gets special rights that other contributors do not receive, while those other contributors must shoulder certain legal obligations (in addition to the red tape burden) from which the project leader is exempt. The problem of asymmetry is most severe in copyleft projects, but it is present even when the outbound license is permissive.
|
||||
|
||||
When assessing the arguments for and against CLAs, bear in mind that today, as in the past, the vast majority of the open source code in any product originates in projects that follow the inbound=outbound practice. The use of CLAs by a relatively small number of projects causes collateral harm to all the others by signaling that, for some reason, open source licensing is insufficient to handle contributions flowing into a project.
|
||||
|
||||
### The case for CLAs
|
||||
|
||||
Since CLAs continue to be a minority practice and originate from outside open source community culture, I believe that CLA proponents should bear the burden of explaining why they are necessary or beneficial relative to their costs. I suspect that most companies using CLAs are merely emulating peer company behavior without critical examination. CLAs have an understandable, if superficial, appeal to risk-averse lawyers who are predisposed to favor greater formality, paper, and process regardless of the business costs. Still, some arguments in favor of CLAs are often advanced and deserve consideration.
|
||||
|
||||
**Easy relicensing:** If administered appropriately, Apache-style CLAs give the project steward effectively unlimited power to sublicense contributions under terms of the steward's choice. This is sometimes seen as desirable because of the potential need to relicense a project under some other open source license. But the value of easy relicensing has been greatly exaggerated by pointing to a few historical cases involving major relicensing campaigns undertaken by projects with an unusually large number of past contributors (all of which were successful without the use of a CLA). There are benefits in relicensing being hard because it results in stable legal expectations around a project and encourages projects to consult their contributor communities before undertaking significant legal policy changes. In any case, most inbound=outbound open source projects never attempt to relicense during their lifetime, and for the small number that do, relicensing will be relatively painless because typically the number of past contributors to contact will not be large.
|
||||
|
||||
**Provenance tracking:** It is sometimes claimed that CLAs enable a project to rigorously track the provenance of contributions, which purportedly has some legal benefit. It is unclear what is achieved by the use of CLAs in this regard that is not better handled through such non-CLA means as preserving Git commit history. And the DCO would seem to be much better suited to tracking contributions, given that it is normally used on a per-commit basis, while CLAs are signed once per contributor and are administratively separate from code contributions. Moreover, provenance tracking is often described as though it were a benefit for the public, yet I know of no case where a project provides transparent, ready public access to CLA acceptance records.
|
||||
|
||||
**License revocation:** Some CLA advocates warn of the prospect that a contributor may someday attempt to revoke a past license grant. To the extent that the concern is about largely judgment-proof individual contributors with no corporate affiliation, it is not clear why an Apache-style CLA provides more meaningful protection against this outcome compared to the use of an open source license. And, as with so many of the legal risks raised in discussions of open source legal policy, this appears to be a phantom risk. I have heard of only a few purported attempts at license revocation over the years, all of which were resolved quickly when the contributor backed down in the face of community pressure.
|
||||
|
||||
**Unauthorized employee contribution:** This is a special case of the license revocation issue and has recently become a point commonly raised by CLA advocates. When an employee contributes to an upstream project, normally the employer owns the copyrights and patents for which the project needs licenses, and only certain executives are authorized to grant such licenses. Suppose an employee contributed proprietary code to a project without approval from the employer, and the employer later discovers this and demands removal of the contribution or sues the project's users. This risk of unauthorized contributions is thought to be minimized by use of something like the [Apache CCLA][11] with its representations and signature requirement, coupled with some adequate review process to ascertain that the CCLA signer likely was authorized to sign (a step which I suspect is not meaningfully undertaken by most CLA-using companies).
|
||||
|
||||
Based on common sense and common experience, I contend that in nearly all cases today, employee contributions are done with the actual or constructive knowledge and consent of the employer. If there were an atmosphere of high litigation risk surrounding open source software, perhaps this risk should be taken more seriously, but litigation arising out of open source projects remains remarkably uncommon.
|
||||
|
||||
More to the point, I know of no case where an allegation of copyright or patent infringement against an inbound=outbound project, not stemming from an alleged open source license violation, would have been prevented by use of a CLA. Patent risk, in particular, is often cited by CLA proponents when pointing to the risk of unauthorized contributions, but the patent license grants in Apache-style CLAs are, by design, quite narrow in scope. Moreover, corporate contributions to an open source project will typically be few in number, small in size (and thus easily replaceable), and likely to be discarded as time goes on.
|
||||
|
||||
### Alternatives
|
||||
|
||||
If your company does not buy into the anti-CLA case and cannot get comfortable with the simple use of inbound=outbound, there are alternatives to resorting to an asymmetric and administratively burdensome Apache-style CLA requirement. The use of the DCO as a complement to inbound=outbound addresses at least some of the concerns of risk-averse CLA advocates. If you must use a true CLA, there is no need to use the Apache model (let alone a [monstrous derivative][10] of it). Consider the non-specification core of the [Eclipse Contributor Agreement][12]—essentially the DCO wrapped inside a CLA—or the Software Freedom Conservancy's [Selenium CLA][13], which merely ceremonializes an inbound=outbound contribution policy.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/2/cla-problems
|
||||
|
||||
作者:[Richard Fontana][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/fontana
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/article/18/3/cla-vs-dco-whats-difference
|
||||
[2]: https://opensource.com/law/10/6/new-contributor-agreement-fedora
|
||||
[3]: https://www.red-bean.com/kfogel/
|
||||
[4]: https://developercertificate.org
|
||||
[5]: https://producingoss.com/en/contributor-agreements.html#developer-certificate-of-origin
|
||||
[6]: https://www.apache.org/licenses/icla.pdf
|
||||
[7]: https://www.freeipa.org/page/Why_CLA%3F
|
||||
[8]: https://opensource.com/law/11/7/trouble-harmony-part-1
|
||||
[9]: https://wiki.openstack.org/wiki/OpenStackAndItsCLA
|
||||
[10]: https://opensource.com/article/19/1/cla-proliferation
|
||||
[11]: https://www.apache.org/licenses/cla-corporate.txt
|
||||
[12]: https://www.eclipse.org/legal/ECA.php
|
||||
[13]: https://docs.google.com/forms/d/e/1FAIpQLSd2FsN12NzjCs450ZmJzkJNulmRC8r8l8NYwVW5KWNX7XDiUw/viewform?hl=en_US&formkey=dFFjXzBzM1VwekFlOWFWMjFFRjJMRFE6MQ#gid=0
|
||||
@ -0,0 +1,73 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (What's happening in the OpenStack community?)
|
||||
[#]: via: (https://opensource.com/article/19/3/whats-happening-openstack)
|
||||
[#]: author: (Jonathan Bryce https://opensource.com/users/jonathan-bryce)
|
||||
|
||||
What's happening in the OpenStack community?
|
||||
======
|
||||
|
||||
In many ways, 2018 was a transformative year for the OpenStack Foundation.
|
||||
|
||||

|
||||
|
||||
Since 2010, the OpenStack community has been building open source software to run cloud computing infrastructure. Initially, the focus was public and private clouds, but open infrastructure has been pulled into many new important use cases like telecoms, 5G, and manufacturing IoT.
|
||||
|
||||
As OpenStack software matured and grew in scope to support new technologies like bare metal provisioning and container infrastructure, the community widened its thinking to embrace users who deploy and run the software in addition to the developers who build the software. Questions like, "What problems are users trying to solve?" "Which technologies are users trying to integrate?" and "What are the gaps?" began to drive the community's thinking and decision making.
|
||||
|
||||
In response to those questions, the OSF reorganized its approach and created a new "open infrastructure" framework focused on use cases, including edge, container infrastructure, CI/CD, and private and hybrid cloud. And, for the first time, the OSF is hosting open source projects outside of the OpenStack project.
|
||||
|
||||
Following are three highlights from the [OSF 2018 Annual Report][1]; I encourage you to read the entire report for more detailed information about what's new.
|
||||
|
||||
### Pilot projects
|
||||
|
||||
On the heels of launching [Kata Containers][2] in December 2017, the OSF launched three pilot projects in 2018—[Zuul][3], [StarlingX][4], and [Airship][5]—that help further our goals of taking our technology into additional relevant markets. Each project follows the tenets we consider key to the success of true open source, [the Four Opens][6]: open design, open collaboration, open development, and open source. While these efforts are still new, they have been extremely valuable in helping us learn how we should expand the scope of the OSF, as well as showing others the kind of approach we will take.
|
||||
|
||||
While the OpenStack project remained at the core of the team's focus, pilot projects are helping expand usage of open infrastructure across markets and already benefiting the OpenStack community. This has attracted dozens of new developers to the open infrastructure community, which will ultimately benefit the OpenStack community and users.
|
||||
|
||||
There is direct benefit from these contributors working upstream in OpenStack, such as through StarlingX, as well as indirect benefit from the relationships we've built with the Kubernetes community through the Kata Containers project. Airship is similarly bridging the gaps between the Kubernetes and OpenStack ecosystems. This shows users how the technologies work together. A rise in contributions to Zuul has provided the engine for OpenStack CI and keeps our development running smoothly.
|
||||
|
||||
### Containers collaboration
|
||||
|
||||
In addition to investing in new pilot projects, we continued efforts to work with key adjacent projects in 2018, and we made particularly good progress with Kubernetes. OSF staffer Chris Hoge helps lead the cloud provider special interest group, where he has helped standardize how Kubernetes deployments expect to run on top of various infrastructure. This has clarified OpenStack's place in the Kubernetes ecosystem and led to valuable integration points, like having OpenStack as part of the Kubernetes release testing process.
|
||||
|
||||
Additionally, OpenStack Magnum was certified as a Kubernetes installer by the CNCF. Through the Kata Containers community, we have deepened these relationships into additional areas within the container ecosystem resulting in a number of companies getting involved for the first time.
|
||||
|
||||
### Evolving events
|
||||
|
||||
We knew heading into 2018 that the environment around our events was changing and we needed to respond. During the year, we held two successful project team gatherings (PTGs) in Dublin and Denver, reaching capacity for both events while also including new projects and OpenStack operators. We held OpenStack Summits in Vancouver and Berlin, both experiencing increases in attendance and project diversity since Sydney in 2017, with each Summit including more than 30 open source projects. Recognizing this broader audience and the OSF's evolving strategy, the OpenStack Summit was renamed the [Open Infrastructure Summit][7], beginning with the Denver event coming up in April.
|
||||
|
||||
In 2018, we boosted investment in China, onboarding a China Community Manager based in Shanghai and hosting a strategy day in Beijing with 30+ attendees from Gold and Platinum Members in China. This effort will continue in 2019 as we host our first Summit in China: the [Open Infrastructure Summit Shanghai][8] in November.
|
||||
|
||||
We also worked with the community in 2018 to define a new model for events to maximize participation while saving on travel and expenses for the individuals and companies who are increasingly stretched across multiple open source communities. We arrived at a plan that we will implement and iterate on in 2019 where we will collocate PTGs as standalone events adjacent to our Open Infrastructure Summits.
|
||||
|
||||
### Looking ahead
|
||||
|
||||
We've seen impressive progress, but the biggest accomplishment might be in establishing a framework for the future of the foundation itself. In 2018, we advanced the open infrastructure mission by establishing OSF as an effective place to collaborate for CI/CD, container infrastructure, and edge computing, in addition to the traditional public and private cloud use cases. The open infrastructure approach opened a lot of doors in 2018, from the initial release of software from each pilot project, to live 5G demos, to engagement with hyperscale public cloud providers.
|
||||
|
||||
Ultimately, our value comes from the effectiveness of our communities and the software they produce. As 2019 unfolds, our community is excited to apply learnings from 2018 to the benefit of developers, users, and the commercial ecosystem across all our projects.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/3/whats-happening-openstack
|
||||
|
||||
作者:[Jonathan Bryce][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/jonathan-bryce
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.openstack.org/foundation/2018-openstack-foundation-annual-report
|
||||
[2]: https://katacontainers.io/
|
||||
[3]: https://zuul-ci.org/
|
||||
[4]: https://www.starlingx.io/
|
||||
[5]: https://www.airshipit.org/
|
||||
[6]: https://www.openstack.org/four-opens/
|
||||
[7]: https://www.openstack.org/summit/denver-2019/
|
||||
[8]: https://www.openstack.org/summit/shanghai-2019
|
||||
@ -1,496 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (ezio )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Computer Laboratory – Raspberry Pi: Lesson 10 Input01)
|
||||
[#]: via: (https://www.cl.cam.ac.uk/projects/raspberrypi/tutorials/os/input01.html)
|
||||
[#]: author: (Alex Chadwick https://www.cl.cam.ac.uk)
|
||||
|
||||
ezio is translating
|
||||
|
||||
Computer Laboratory – Raspberry Pi: Lesson 10 Input01
|
||||
======
|
||||
|
||||
Welcome to the Input lesson series. In this series, you will learn how to receive inputs to the Raspberry Pi using the keyboard. We will start with just revealing the input, and then move to a more traditional text prompt.
|
||||
|
||||
This first input lesson teaches some theory about drivers and linking, as well as about keyboards and ends up displaying text on the screen.
|
||||
|
||||
### 1 Getting Started
|
||||
|
||||
It is expected that you have completed the OK series, and it would be helpful to have completed the Screen series. Many of the files from that series will be called, without comment. If you do not have these files, or prefer to use a correct implementation, download the template for this lesson from the [Downloads][1] page. If you're using your own implementation, please remove everything after your call to SetGraphicsAddress.
|
||||
|
||||
### 2 USB
|
||||
|
||||
```
|
||||
The USB standard was designed to make simple hardware in exchange for complex software.
|
||||
```
|
||||
|
||||
As you are no doubt aware, the Raspberry Pi model B has two USB ports, commonly used for connecting a mouse and keyboard. This was a very good design decision, USB is a very generic connector, and many different kinds of device use it. It's simple to build new devices for, simple to write device drivers for, and is highly extensible thanks to USB hubs. Could it get any better? Well, no, in fact for an Operating Systems developer this is our worst nightmare. The USB standard is huge. I really mean it this time, it is over 700 pages, before you've even thought about connecting a device.
|
||||
|
||||
I spoke to a number of other hobbyist Operating Systems developers about this and they all say one thing: don't bother. "It will take too long to implement", "You won't be able to write a tutorial on it" and "It will be of little benefit". In many ways they are right, I'm not able to write a tutorial on the USB standard, as it would take weeks. I also can't teach how to write device drivers for all the different devices, so it is useless on its own. However, I can do the next best thing: Get a working USB driver, get a keyboard driver, and then teach how to use these in an Operating System. I set out searching for a free driver that would run in an operating system that doesn't even know what a file is yet, but I couldn't find one. They were all too high level. So, I attempted to write one. Everybody was right, this took weeks to do. However, I'm pleased to say I did get one that works with no external help from the Operating System, and can talk to a mouse and keyboard. It is by no means complete, efficient, or correct, but it does work. It has been written in C and the full source code can be found on the downloads page for those interested.
|
||||
|
||||
So, this tutorial won't be a lesson on the USB standard (at all). Instead we'll look at how to work with other people's code.
|
||||
|
||||
### 3 Linking
|
||||
|
||||
```
|
||||
Linking allows us to make reusable code 'libraries' that anyone can use in their program.
|
||||
```
|
||||
|
||||
Since we're about to incorporate external code into the Operating System, we need to talk about linking. Linking is a process which is applied to programs or Operating System to link in functions. What this means is that when a program is made, we don't necessarily code every function (almost certainly not in fact). Linking is what we do to make our program link to functions in other people's code. This has actually been going on all along in our Operating Systems, as the linker links together all of the different files, each of which is compiled separately.
|
||||
|
||||
```
|
||||
Programs often just call libraries, which call other libraries and so on until eventually they call an Operating System library which we would write.
|
||||
```
|
||||
|
||||
There are two types of linking: static and dynamic. Static linking is like what goes on when we make our Operating Systems. The linker finds all the addresses of the functions, and writes them into the code, before the program is finished. Dynamic linking is linking that occurs after the program is 'complete'. When it is loaded, the dynamic linker goes through the program and links any functions which are not in the program to libraries in the Operating System. This is one of the jobs our Operating System should eventually be capable of, but for now everything will be statically linked.
|
||||
|
||||
The USB driver I have written is suitable for static linking. This means I give you the compiled code for each of my files, and then the linker finds functions in your code which are not defined in your code, and links them to functions in my code. On the [Downloads][1] page for this lesson is a makefile and my USB driver, which you will need to continue. Download them and replace the makefile in your code with this one, and also put the driver in the same folder as that makefile.
|
||||
|
||||
### 4 Keyboards
|
||||
|
||||
In order to get input into our Operating System, we need to understand at some level how keyboards actually work. Keyboards have two types of keys: Normal and Modifier keys. The normal keys are the letters, numbers, function keys, etc. They constitute almost every key on the keyboard. The modifiers are up to 8 special keys. These are left shift, right shift, left control, right control, left alt, right alt, left GUI and right GUI. The keyboard can detect any combination of the modifier keys being held, as well as up to 6 normal keys. Every time a key changes (i.e. is pushed or released), it reports this to the computer. Typically, keyboards also have three LEDs for Caps Lock, Num Lock and Scroll Lock, which are controlled by the computer, not the keyboard itself. Keyboards may have many more lights such as power, mute, etc.
|
||||
|
||||
In order to help standardise USB keyboards, a table of values was produced, such that every keyboard key ever is given a unique number, as well as every conceivable LED. The table below lists the first 126 of values.
|
||||
|
||||
Table 4.1 USB Keyboard Keys
|
||||
| Number | Description | Number | Description | Number | Description | Number | Description | |
|
||||
| ------ | ---------------- | ------- | ---------------------- | -------- | -------------- | --------------- | -------------------- | |
|
||||
| 4 | a and A | 5 | b and B | 6 | c and C | 7 | d and D | |
|
||||
| 8 | e and E | 9 | f and F | 10 | g and G | 11 | h and H | |
|
||||
| 12 | i and I | 13 | j and J | 14 | k and K | 15 | l and L | |
|
||||
| 16 | m and M | 17 | n and N | 18 | o and O | 19 | p and P | |
|
||||
| 20 | q and Q | 21 | r and R | 22 | s and S | 23 | t and T | |
|
||||
| 24 | u and U | 25 | v and V | 26 | w and W | 27 | x and X | |
|
||||
| 28 | y and Y | 29 | z and Z | 30 | 1 and ! | 31 | 2 and @ | |
|
||||
| 32 | 3 and # | 33 | 4 and $ | 34 | 5 and % | 35 | 6 and ^ | |
|
||||
| 36 | 7 and & | 37 | 8 and * | 38 | 9 and ( | 39 | 0 and ) | |
|
||||
| 40 | Return (Enter) | 41 | Escape | 42 | Delete (Backspace) | 43 | Tab | |
|
||||
| 44 | Spacebar | 45 | - and _ | 46 | = and + | 47 | [ and { | |
|
||||
| 48 | ] and } | 49 | \ and | | 50 | # and ~ | 51 | ; and : |
|
||||
| 52 | ' and " | 53 | ` and ~ | 54 | , and < | 55 | . and > | |
|
||||
| 56 | / and ? | 57 | Caps Lock | 58 | F1 | 59 | F2 | |
|
||||
| 60 | F3 | 61 | F4 | 62 | F5 | 63 | F6 | |
|
||||
| 64 | F7 | 65 | F8 | 66 | F9 | 67 | F10 | |
|
||||
| 68 | F11 | 69 | F12 | 70 | Print Screen | 71 | Scroll Lock | |
|
||||
| 72 | Pause | 73 | Insert | 74 | Home | 75 | Page Up | |
|
||||
| 76 | Delete forward | 77 | End | 78 | Page Down | 79 | Right Arrow | |
|
||||
| 80 | Left Arrow | 81 | Down Arrow | 82 | Up Arrow | 83 | Num Lock | |
|
||||
| 84 | Keypad / | 85 | Keypad * | 86 | Keypad - | 87 | Keypad + | |
|
||||
| 88 | Keypad Enter | 89 | Keypad 1 and End | 90 | Keypad 2 and Down Arrow | 91 | Keypad 3 and Page Down | |
|
||||
| 92 | Keypad 4 and Left Arrow | 93 | Keypad 5 | 94 | Keypad 6 and Right Arrow | 95 | Keypad 7 and Home | |
|
||||
| 96 | Keypad 8 and Up Arrow | 97 | Keypad 9 and Page Up | 98 | Keypad 0 and Insert | 99 | Keypad . and Delete | |
|
||||
| 100 | \ and | | 101 | Application | 102 | Power | 103 | Keypad = |
|
||||
| 104 | F13 | 105 | F14 | 106 | F15 | 107 | F16 | |
|
||||
| 108 | F17 | 109 | F18 | 110 | F19 | 111 | F20 | |
|
||||
| 112 | F21 | 113 | F22 | 114 | F23 | 115 | F24 | |
|
||||
| 116 | Execute | 117 | Help | 118 | Menu | 119 | Select | |
|
||||
| 120 | Stop | 121 | Again | 122 | Undo | 123 | Cut | |
|
||||
| 124 | Copy | 125 | Paste | 126 | Find | 127 | Mute | |
|
||||
| 128 | Volume Up | 129 | Volume Down | | | | | |
|
||||
|
||||
The full list can be found in section 10, page 53 of [HID Usage Tables 1.12][2].
|
||||
|
||||
### 5 The Nut Behind the Wheel
|
||||
|
||||
```
|
||||
These summaries and the code they describe form an API - Application Product Interface.
|
||||
```
|
||||
|
||||
Normally, when you work with someone else's code, they provide a summary of their methods, what they do and roughly how they work, as well as how they can go wrong. Here is a table of the relevant instructions required to use my USB driver.
|
||||
|
||||
Table 5.1 Keyboard related functions in CSUD
|
||||
| Function | Arguments | Returns | Description |
|
||||
| ----------------------- | ----------------------- | ----------------------- | ----------------------- |
|
||||
| UsbInitialise | None | r0 is result code | This method is the all-in-one method that loads the USB driver, enumerates all devices and attempts to communicate with them. This method generally takes about a second to execute, though with a few USB hubs plugged in this can be significantly longer. After this method is completed methods in the keyboard driver become available, regardless of whether or not a keyboard is indeed inserted. Result code explained below. |
|
||||
| UsbCheckForChange | None | None | Essentially provides the same effect as UsbInitialise, but does not provide the same one time initialisation. This method checks every port on every connected hub recursively, and adds new devices if they have been added. This should be very quick if there are no changes, but can take up to a few seconds if a hub with many devices is attached. |
|
||||
| KeyboardCount | None | r0 is count | Returns the number of keyboards currently connected and detected. UsbCheckForChange may update this. Up to 4 keyboards are supported by default. Up to this many keyboards may be accessed through this driver. |
|
||||
| KeyboardGetAddress | r0 is index | r0 is address | Retrieves the address of a given keyboard. All other functions take a keyboard address in order to know which keyboard to access. Thus, to communicate with a keyboard, first check the count, then retrieve the address, then use other methods. Note, the order of keyboards that this method returns may change after calls to UsbCheckForChange. |
|
||||
| KeyboardPoll | r0 is address | r0 is result code | Reads in the current key state from the keyboard. This operates via polling the device directly, contrary to the best practice. This means that if this method is not called frequently enough, a key press could be missed. All reading methods simply return the value as of the last poll. |
|
||||
| KeyboardGetModifiers | r0 is address | r0 is modifier state | Retrieves the status of the modifier keys as of the last poll. These are the shift, alt control and GUI keys on both sides. This is returned as a bit field, such that a 1 in the bit 0 means left control is held, bit 1 means left shift, bit 2 means left alt, bit 3 means left GUI and bits 4 to 7 mean the right versions of those previous. If there is a problem r0 contains 0. |
|
||||
| KeyboardGetKeyDownCount | r0 is address | r0 is count | Retrieves the number of keys currently held down on the keyboard. This excludes modifier keys. Normally, this cannot go above 6. If there is an error this method returns 0. |
|
||||
| KeyboardGetKeyDown | r0 is address, r1 is key number | r0 is scan code | Retrieves the scan code (see Table 4.1) of a particular held down key. Normally, to work out which keys are down, call KeyboardGetKeyDownCount and then call KeyboardGetKeyDown up to that many times with increasing values of r1 to determine which keys are down. Returns 0 if there is a problem. It is safe (but not recommended) to call this method without calling KeyboardGetKeyDownCount and interpret 0s as keys not held. Note, the order or scan codes can change randomly (some keyboards sort numerically, some sort temporally, no guarantees are made). |
|
||||
| KeyboardGetKeyIsDown | r0 is address, r1 is scan code | r0 is status | Alternative to KeyboardGetKeyDown, checks if a particular scan code is among the held down keys. Returns 0 if not, or a non-zero value if so. Faster when detecting particular scan codes (e.g. looking for ctrl+c). On error, returns 0. |
|
||||
| KeyboardGetLedSupport | r0 is address | r0 is LEDs | Checks which LEDs a particular keyboard supports. Bit 0 being 1 represents Number Lock, bit 1 represents Caps Lock, bit 2 represents Scroll Lock, bit 3 represents Compose, bit 4 represents Kana, bit 5 represents Power, bit 6 represents Mute and bit 7 represents Compose. As per the USB standard, none of these LEDs update automatically (e.g. Caps Lock must be set manually when the Caps Lock scan code is detected). |
|
||||
| KeyboardSetLeds | r0 is address, r1 is LEDs | r0 is result code | Attempts to turn on/off the specified LEDs on the keyboard. See below for result code values. See KeyboardGetLedSupport for LEDs' values. |
|
||||
|
||||
```
|
||||
Result codes are an easy way to handle errors, but often more elegant solutions exist in higher level code.
|
||||
```
|
||||
|
||||
Several methods return 'result codes'. These are commonplace in C code, and are just numbers which represent what happened in a method call. By convention, 0 always indicates success. The following result codes are used by this driver.
|
||||
|
||||
Table 5.2 - CSUD Result Codes
|
||||
| Code | Description |
|
||||
| ---- | ----------------------------------------------------------------------- |
|
||||
| 0 | Method completed successfully. |
|
||||
| -2 | Argument: A method was called with an invalid argument. |
|
||||
| -4 | Device: The device did not respond correctly to the request. |
|
||||
| -5 | Incompatible: The driver is not compatible with this request or device. |
|
||||
| -6 | Compiler: The driver was compiled incorrectly, and is broken. |
|
||||
| -7 | Memory: The driver ran out of memory. |
|
||||
| -8 | Timeout: The device did not respond in the expected time. |
|
||||
| -9 | Disconnect: The device requested has disconnected, and cannot be used. |
|
||||
|
||||
The general usage of the driver is as follows:
|
||||
|
||||
1. Call UsbInitialise
|
||||
2. Call UsbCheckForChange
|
||||
3. Call KeyboardCount
|
||||
4. If this is 0, go to 2.
|
||||
5. For each keyboard you support:
|
||||
1. Call KeyboardGetAddress
|
||||
2. Call KeybordGetKeyDownCount
|
||||
3. For each key down:
|
||||
1. Check whether or not it has just been pushed
|
||||
2. Store that the key is down
|
||||
4. For each key stored:
|
||||
1. Check whether or not key is released
|
||||
2. Remove key if released
|
||||
6. Perform actions based on keys pushed/released
|
||||
7. Go to 2.
|
||||
|
||||
|
||||
|
||||
Ultimately, you may do whatever you wish to with the keyboard, and these methods should allow you to access all of its functionality. Over the next 2 lessons, we shall look at completing the input side of a text terminal, similarly to most command line computers, and interpreting the commands. In order to do this, we're going to need to have keyboard inputs in a more useful form. You may notice that my driver is (deliberately) unhelpful, because it doesn't have methods to deduce whether or not a key has just been pushed down or released, it only has methods about what is currently held down. This means we'll need to write such methods ourselves.
|
||||
|
||||
### 6 Updates Available
|
||||
|
||||
Repeatedly checking for updates is called 'polling'. This is in contrast to interrupt driven IO, where the device sends a signal when data is ready.
|
||||
|
||||
First of all, let's implement a method KeyboardUpdate which detects the first keyboard and uses its poll method to get the current input, as well as saving the last inputs for comparison. We can then use this data with other methods to translate scan codes to keys. The method should do precisely the following:
|
||||
|
||||
1. Retrieve a stored keyboard address (initially 0).
|
||||
2. If this is not 0, go to 9.
|
||||
3. Call UsbCheckForChange to detect new keyboards.
|
||||
4. Call KeyboardCount to detect how many keyboards are present.
|
||||
5. If this is 0 store the address as 0 and return; we can't do anything with no keyboard.
|
||||
6. Call KeyboardGetAddress with parameter 0 to get the first keyboard's address.
|
||||
7. Store this address.
|
||||
8. If this is 0, return; there is some problem.
|
||||
9. Call KeyboardGetKeyDown 6 times to get each key currently down and store them
|
||||
10. Call KeyboardPoll
|
||||
11. If the result is non-zero go to 3. There is some problem (such as disconnected keyboard).
|
||||
|
||||
|
||||
|
||||
To store the values mentioned above, we will need the following values in the .data section.
|
||||
|
||||
```
|
||||
.section .data
|
||||
.align 2
|
||||
KeyboardAddress:
|
||||
.int 0
|
||||
KeyboardOldDown:
|
||||
.rept 6
|
||||
.hword 0
|
||||
.endr
|
||||
```
|
||||
|
||||
```
|
||||
.hword num inserts the half word constant num into the file directly.
|
||||
```
|
||||
|
||||
```
|
||||
.rept num [commands] .endr copies the commands commands to the output num times.
|
||||
```
|
||||
|
||||
Try to implement the method yourself. My implementation for this is as follows:
|
||||
|
||||
1.
|
||||
```
|
||||
.section .text
|
||||
.globl KeyboardUpdate
|
||||
KeyboardUpdate:
|
||||
push {r4,r5,lr}
|
||||
|
||||
kbd .req r4
|
||||
ldr r0,=KeyboardAddress
|
||||
ldr kbd,[r0]
|
||||
```
|
||||
We load in the keyboard address.
|
||||
2.
|
||||
```
|
||||
teq kbd,#0
|
||||
bne haveKeyboard$
|
||||
```
|
||||
If the address is non-zero, we have a keyboard. Calling UsbCheckForChanges is slow, and so if everything works we avoid it.
|
||||
3.
|
||||
```
|
||||
getKeyboard$:
|
||||
bl UsbCheckForChange
|
||||
```
|
||||
If we don't have a keyboard, we have to check for new devices.
|
||||
4.
|
||||
```
|
||||
bl KeyboardCount
|
||||
```
|
||||
Now we see if a new keyboard has been added.
|
||||
5.
|
||||
```
|
||||
teq r0,#0
|
||||
ldreq r1,=KeyboardAddress
|
||||
streq r0,[r1]
|
||||
beq return$
|
||||
```
|
||||
There are no keyboards, so we have no keyboard address.
|
||||
6.
|
||||
```
|
||||
mov r0,#0
|
||||
bl KeyboardGetAddress
|
||||
```
|
||||
Let's just get the address of the first keyboard. You may want to allow more.
|
||||
7.
|
||||
```
|
||||
ldr r1,=KeyboardAddress
|
||||
str r0,[r1]
|
||||
```
|
||||
Store the keyboard's address.
|
||||
8.
|
||||
```
|
||||
teq r0,#0
|
||||
beq return$
|
||||
mov kbd,r0
|
||||
```
|
||||
If we have no address, there is nothing more to do.
|
||||
9.
|
||||
```
|
||||
saveKeys$:
|
||||
mov r0,kbd
|
||||
mov r1,r5
|
||||
bl KeyboardGetKeyDown
|
||||
|
||||
ldr r1,=KeyboardOldDown
|
||||
add r1,r5,lsl #1
|
||||
strh r0,[r1]
|
||||
add r5,#1
|
||||
cmp r5,#6
|
||||
blt saveKeys$
|
||||
```
|
||||
Loop through all the keys, storing them in KeyboardOldDown. If we ask for too many, this returns 0 which is fine.
|
||||
|
||||
10.
|
||||
```
|
||||
mov r0,kbd
|
||||
bl KeyboardPoll
|
||||
```
|
||||
Now we get the new keys.
|
||||
|
||||
11.
|
||||
```
|
||||
teq r0,#0
|
||||
bne getKeyboard$
|
||||
|
||||
return$:
|
||||
pop {r4,r5,pc}
|
||||
.unreq kbd
|
||||
```
|
||||
Finally we check if KeyboardPoll worked. If not, we probably disconnected.
|
||||
|
||||
|
||||
With our new KeyboardUpdate method, checking for inputs becomes as simple as calling this method at regular intervals, and it will even check for disconnections etc. This is a useful method to have, as our actual key processing may differ based on the situation, and so being able to get the current input in its raw form with one method call is generally applicable. The next method we ideally want is KeyboardGetChar, a method that simply returns the next key pressed as an ASCII character, or returns 0 if no key has just been pressed. This could be extended to support typing a key multiple times if it is held for a certain duration, and to support the 'lock' keys as well as modifiers.
|
||||
|
||||
To make this method it is useful if we have a method KeyWasDown, which simply returns 0 if a given scan code is not in the KeyboardOldDown values, and returns a non-zero value otherwise. Have a go at implementing this yourself. As always, a solution can be found on the downloads page.
|
||||
|
||||
### 7 Look Up Tables
|
||||
|
||||
```
|
||||
In many areas of programming, the larger the program, the faster it is. Look up tables are large, but are very fast. Some problems can be solved by a mixture of look up tables and normal functions.
|
||||
```
|
||||
|
||||
The KeyboardGetChar method could be quite complex if we write it poorly. There are 100s of scan codes, each with different effects depending on the presence or absence of the shift key or other modifiers. Not all of the keys can be translated to a character. For some characters, multiple keys can produce the same character. A useful trick in situations with such vast arrays of possibilities is look up tables. A look up table, much like in the physical sense, is a table of values and their results. For some limited functions, the simplest way to deduce the answer is just to precompute every answer, and just return the correct one by retrieving it. In this case, we could build up a sequence of values in memory such that the nth value into the sequence is the ASCII character code for the scan code n. This means our method would simply have to detect if a key was pressed, and then retrieve its value from the table. Further, we could have a separate table for the values when shift is held, so that the shift key simply changes which table we're working with.
|
||||
|
||||
After the .section .data command, copy the following tables:
|
||||
|
||||
```
|
||||
.align 3
|
||||
KeysNormal:
|
||||
.byte 0x0, 0x0, 0x0, 0x0, 'a', 'b', 'c', 'd'
|
||||
.byte 'e', 'f', 'g', 'h', 'i', 'j', 'k', 'l'
|
||||
.byte 'm', 'n', 'o', 'p', 'q', 'r', 's', 't'
|
||||
.byte 'u', 'v', 'w', 'x', 'y', 'z', '1', '2'
|
||||
.byte '3', '4', '5', '6', '7', '8', '9', '0'
|
||||
.byte '\n', 0x0, '\b', '\t', ' ', '-', '=', '['
|
||||
.byte ']', '\\\', '#', ';', '\'', '`', ',', '.'
|
||||
.byte '/', 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0
|
||||
.byte 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0
|
||||
.byte 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0
|
||||
.byte 0x0, 0x0, 0x0, 0x0, '/', '*', '-', '+'
|
||||
.byte '\n', '1', '2', '3', '4', '5', '6', '7'
|
||||
.byte '8', '9', '0', '.', '\\\', 0x0, 0x0, '='
|
||||
|
||||
.align 3
|
||||
KeysShift:
|
||||
.byte 0x0, 0x0, 0x0, 0x0, 'A', 'B', 'C', 'D'
|
||||
.byte 'E', 'F', 'G', 'H', 'I', 'J', 'K', 'L'
|
||||
.byte 'M', 'N', 'O', 'P', 'Q', 'R', 'S', 'T'
|
||||
.byte 'U', 'V', 'W', 'X', 'Y', 'Z', '!', '"'
|
||||
.byte '£', '$', '%', '^', '&', '*', '(', ')'
|
||||
.byte '\n', 0x0, '\b', '\t', ' ', '_', '+', '{'
|
||||
.byte '}', '|', '~', ':', '@', '¬', '<', '>'
|
||||
.byte '?', 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0
|
||||
.byte 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0
|
||||
.byte 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0
|
||||
.byte 0x0, 0x0, 0x0, 0x0, '/', '*', '-', '+'
|
||||
.byte '\n', '1', '2', '3', '4', '5', '6', '7'
|
||||
.byte '8', '9', '0', '.', '|', 0x0, 0x0, '='
|
||||
```
|
||||
|
||||
```
|
||||
.byte num inserts the byte constant num into the file directly.
|
||||
```
|
||||
|
||||
```
|
||||
Most assemblers and compilers recognise escape sequences; character sequences such as \t which insert special characters instead.
|
||||
```
|
||||
|
||||
These tables map directly the first 104 scan codes onto the ASCII characters as a table of bytes. We also have a separate table describing the effects of the shift key on those scan codes. I've used the ASCII null character (0) for all keys without direct mappings in ASCII (such as the function keys). Backspace is mapped to the ASCII backspace character (8 denoted \b), enter is mapped to the ASCII new line character (10 denoted \n) and tab is mapped to the ASCII horizontal tab character (9 denoted \t).
|
||||
|
||||
The KeyboardGetChar method will need to do the following:
|
||||
|
||||
1. Check if KeyboardAddress is 0. If so, return 0.
|
||||
2. Call KeyboardGetKeyDown up to 6 times. Each time:
|
||||
1. If key is 0, exit loop.
|
||||
2. Call KeyWasDown. If it was, go to the next key.
|
||||
3. If the scan code is more than 103, go to the next key.
|
||||
4. Call KeyboardGetModifiers
|
||||
5. If shift is held, load the address of KeysShift. Otherwise load KeysNormal.
|
||||
6. Read the ASCII value from the table.
|
||||
7. If it is 0, go to the next key otherwise return this ASCII code and exit.
|
||||
3. Return 0.
|
||||
|
||||
|
||||
|
||||
Try to implement this yourself. My implementation is presented below:
|
||||
|
||||
1.
|
||||
```
|
||||
.globl KeyboardGetChar
|
||||
KeyboardGetChar:
|
||||
ldr r0,=KeyboardAddress
|
||||
ldr r1,[r0]
|
||||
teq r1,#0
|
||||
moveq r0,#0
|
||||
moveq pc,lr
|
||||
```
|
||||
Simple check to see if we have a keyboard.
|
||||
|
||||
2.
|
||||
```
|
||||
push {r4,r5,r6,lr}
|
||||
kbd .req r4
|
||||
key .req r6
|
||||
mov r4,r1
|
||||
mov r5,#0
|
||||
keyLoop$:
|
||||
mov r0,kbd
|
||||
mov r1,r5
|
||||
bl KeyboardGetKeyDown
|
||||
```
|
||||
r5 will hold the index of the key, r4 holds the keyboard address.
|
||||
|
||||
1.
|
||||
```
|
||||
teq r0,#0
|
||||
beq keyLoopBreak$
|
||||
```
|
||||
If a scan code is 0, it either means there is an error, or there are no more keys.
|
||||
|
||||
2.
|
||||
```
|
||||
mov key,r0
|
||||
bl KeyWasDown
|
||||
teq r0,#0
|
||||
bne keyLoopContinue$
|
||||
```
|
||||
If a key was already down it is uninteresting, we only want ot know about key presses.
|
||||
|
||||
3.
|
||||
```
|
||||
cmp key,#104
|
||||
bge keyLoopContinue$
|
||||
```
|
||||
If a key has a scan code higher than 104, it will be outside our table, and so is not relevant.
|
||||
|
||||
4.
|
||||
```
|
||||
mov r0,kbd
|
||||
bl KeyboardGetModifiers
|
||||
```
|
||||
We need to know about the modifier keys in order to deduce the character.
|
||||
|
||||
5.
|
||||
```
|
||||
tst r0,#0b00100010
|
||||
ldreq r0,=KeysNormal
|
||||
ldrne r0,=KeysShift
|
||||
```
|
||||
We detect both a left and right shift key as changing the characters to their shift variants. Remember, a tst instruction computes the logical AND and then compares it to zero, so it will be equal to 0 if and only if both of the shift bits are zero.
|
||||
|
||||
6.
|
||||
```
|
||||
ldrb r0,[r0,key]
|
||||
```
|
||||
Now we can load in the key from the look up table.
|
||||
|
||||
7.
|
||||
```
|
||||
teq r0,#0
|
||||
bne keyboardGetCharReturn$
|
||||
keyLoopContinue$:
|
||||
add r5,#1
|
||||
cmp r5,#6
|
||||
blt keyLoop$
|
||||
```
|
||||
If the look up code contains a zero, we must continue. To continue, we increment the index, and check if we've reached 6.
|
||||
|
||||
3.
|
||||
```
|
||||
keyLoopBreak$:
|
||||
mov r0,#0
|
||||
keyboardGetCharReturn$:
|
||||
pop {r4,r5,r6,pc}
|
||||
.unreq kbd
|
||||
.unreq key
|
||||
```
|
||||
We return our key here, if we reach keyLoopBreak$, then we know there is no key held, so return 0.
|
||||
|
||||
|
||||
|
||||
|
||||
### 8 Notepad OS
|
||||
|
||||
Now we have our KeyboardGetChar method, we can make an operating system that just types what the user writes to the screen. For simplicity we'll ignore all the unusual keys. In 'main.s' delete all code after bl SetGraphicsAddress. Call UsbInitialise, set r4 and r5 to 0, then loop forever over the following commands:
|
||||
|
||||
1. Call KeyboardUpdate
|
||||
2. Call KeyboardGetChar
|
||||
3. If it is 0, got to 1
|
||||
4. Copy r4 and r5 to r1 and r2 then call DrawCharacter
|
||||
5. Add r0 to r4
|
||||
6. If r4 is 1024, add r1 to r5 and set r4 to 0
|
||||
7. If r5 is 768 set r5 to 0
|
||||
8. Go to 1
|
||||
|
||||
|
||||
|
||||
Now compile this and test it on the Pi. You should almost immediately be able to start typing text to the screen when the Pi starts. If not, please see our troubleshooting page.
|
||||
|
||||
When it works, congratulations, you've achieved an interface with the computer. You should now begin to realise that you've almost got a primitive operating system together. You can now interface with the computer, issuing it commands, and receive feedback on screen. In the next tutorial, [Input02][3] we will look at producing a full text terminal, in which the user types commands, and the computer executes them.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.cl.cam.ac.uk/projects/raspberrypi/tutorials/os/input01.html
|
||||
|
||||
作者:[Alex Chadwick][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[ezio](https://github.com/oska874)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.cl.cam.ac.uk
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.cl.cam.ac.uk/projects/raspberrypi/tutorials/os/downloads.html
|
||||
[2]: https://www.cl.cam.ac.uk/projects/raspberrypi/tutorials/os/downloads/hut1_12v2.pdf
|
||||
[3]: https://www.cl.cam.ac.uk/projects/raspberrypi/tutorials/os/input02.html
|
||||
@ -1,3 +1,6 @@
|
||||
ezio is translating
|
||||
|
||||
|
||||
In Device We Trust: Measure Twice, Compute Once with Xen, Linux, TPM 2.0 and TXT
|
||||
============================================================
|
||||
|
||||
|
||||
@ -1,73 +0,0 @@
|
||||
Tips for success when getting started with Ansible
|
||||
======
|
||||
|
||||

|
||||
|
||||
Ansible is an open source automation tool used to configure servers, install software, and perform a wide variety of IT tasks from one central location. It is a one-to-many agentless mechanism where all instructions are run from a control machine that communicates with remote clients over SSH, although other protocols are also supported.
|
||||
|
||||
While targeted for system administrators with privileged access who routinely perform tasks such as installing and configuring applications, Ansible can also be used by non-privileged users. For example, a database administrator using the `mysql` login ID could use Ansible to create databases, add users, and define access-level controls.
|
||||
|
||||
Let's go over a very simple example where a system administrator provisions 100 servers each day and must run a series of Bash commands on each one before handing it off to users.
|
||||
|
||||

|
||||
|
||||
This is a simple example, but should illustrate how easily commands can be specified in yaml files and executed on remote servers. In a heterogeneous environment, conditional statements can be added so that certain commands are only executed in certain servers (e.g., "only execute `yum` commands in systems that are not Ubuntu or Debian").
|
||||
|
||||
One important feature in Ansible is that a playbook describes a desired state in a computer system, so a playbook can be run multiple times against a server without impacting its state. If a certain task has already been implemented (e.g., "user `sysman` already exists"), then Ansible simply ignores it and moves on.
|
||||
|
||||
### Definitions
|
||||
|
||||
* **Tasks:**``A task is the smallest unit of work. It can be an action like "Install a database," "Install a web server," "Create a firewall rule," or "Copy this configuration file to that server."
|
||||
* **Plays:**``A play is made up of tasks. For example, the play: "Prepare a database to be used by a web server" is made up of tasks: 1) Install the database package; 2) Set a password for the database administrator; 3) Create a database; and 4) Set access to the database.
|
||||
* **Playbook:**``A playbook is made up of plays. A playbook could be: "Prepare my website with a database backend," and the plays would be 1) Set up the database server; and 2) Set up the web server.
|
||||
* **Roles:**``Roles are used to save and organize playbooks and allow sharing and reuse of playbooks. Following the previous examples, if you need to fully configure a web server, you can use a role that others have written and shared to do just that. Since roles are highly configurable (if written correctly), they can be easily reused to suit any given deployment requirements.
|
||||
* **Ansible Galaxy:**``Ansible [Galaxy][1] is an online repository where roles are uploaded so they can be shared with others. It is integrated with GitHub, so roles can be organized into Git repositories and then shared via Ansible Galaxy.
|
||||
|
||||
|
||||
|
||||
These definitions and their relationships are depicted here:
|
||||
|
||||

|
||||
|
||||
Please note this is just one way to organize the tasks that need to be executed. We could have split up the installation of the database and the web server into separate playbooks and into different roles. Most roles in Ansible Galaxy install and configure individual applications. You can see examples for installing [mysql][2] and installing [httpd][3].
|
||||
|
||||
### Tips for writing playbooks
|
||||
|
||||
The best source for learning Ansible is the official [documentation][4] site. And, as usual, online search is your friend. I recommend starting with simple tasks, like installing applications or creating users. Once you are ready, follow these guidelines:
|
||||
|
||||
* When testing, use a small subset of servers so that your plays execute faster. If they are successful in one server, they will be successful in others.
|
||||
* Always do a dry run to make sure all commands are working (run with `--check-mode` flag).
|
||||
* Test as often as you need to without fear of breaking things. Tasks describe a desired state, so if a desired state is already achieved, it will simply be ignored.
|
||||
* Be sure all host names defined in `/etc/ansible/hosts` are resolvable.
|
||||
* Because communication to remote hosts is done using SSH, keys have to be accepted by the control machine, so either 1) exchange keys with remote hosts prior to starting; or 2) be ready to type in "Yes" to accept SSH key exchange requests for each remote host you want to manage.
|
||||
* Although you can combine tasks for different Linux distributions in one playbook, it's cleaner to write a separate playbook for each distro.
|
||||
|
||||
|
||||
|
||||
### In the final analysis
|
||||
|
||||
Ansible is a great choice for implementing automation in your data center:
|
||||
|
||||
* It's agentless, so it is simpler to install than other automation tools.
|
||||
* Instructions are in YAML (though JSON is also supported) so it's easier than writing shell scripts.
|
||||
* It's open source software, so contribute back to it and make it even better!
|
||||
|
||||
|
||||
|
||||
How have you used Ansible to automate your data center? Share your experience in the comments.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/2/tips-success-when-getting-started-ansible
|
||||
|
||||
作者:[Jose Delarosa][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://opensource.com/users/jdelaros1
|
||||
[1]:https://galaxy.ansible.com/
|
||||
[2]:https://galaxy.ansible.com/bennojoy/mysql/
|
||||
[3]:https://galaxy.ansible.com/xcezx/httpd/
|
||||
[4]:http://docs.ansible.com/
|
||||
@ -1,122 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (How To Get Flatpak Apps And Games Built With OpenGL To Work With Proprietary Nvidia Graphics Drivers)
|
||||
[#]: via: (https://www.linuxuprising.com/2018/06/how-to-get-flatpak-apps-and-games-built.html)
|
||||
[#]: author: (Logix https://plus.google.com/118280394805678839070)
|
||||
|
||||
How To Get Flatpak Apps And Games Built With OpenGL To Work With Proprietary Nvidia Graphics Drivers
|
||||
======
|
||||
**Some applications and games built with OpenGL support and packaged as Flatpak fail to start with proprietary Nvidia drivers. This article explains how to get such Flatpak applications or games them to start, without installing the open source drivers (Nouveau).**
|
||||
|
||||
Here's an example. I'm using the proprietary Nvidia drivers on my Ubuntu 18.04 desktop (`nvidia-driver-390`) and when I try to launch the latest
|
||||
```
|
||||
$ /usr/bin/flatpak run --branch=stable --arch=x86_64 --command=krita --file-forwarding org.kde.krita
|
||||
Gtk-Message: Failed to load module "canberra-gtk-module"
|
||||
Gtk-Message: Failed to load module "canberra-gtk-module"
|
||||
libGL error: No matching fbConfigs or visuals found
|
||||
libGL error: failed to load driver: swrast
|
||||
Could not initialize GLX
|
||||
|
||||
```
|
||||
|
||||
To fix Flatpak games and applications not starting when using OpenGL with proprietary Nvidia graphics drivers, you'll need to install a runtime for your currently installed proprietary Nvidia drivers. Here's how to do this.
|
||||
|
||||
**1\. Add the FlatHub repository if you haven't already. You can find exact instructions for your Linux distribution[here][1].**
|
||||
|
||||
**2. Now you'll need to figure out the exact version of the proprietary Nvidia drivers installed on your system. **
|
||||
|
||||
_This step is dependant of the Linux distribution you're using and I can't cover all cases. The instructions below are Ubuntu-oriented (and Ubuntu flavors) but hopefully you can figure out for yourself the Nvidia drivers version installed on your system._
|
||||
|
||||
To do this in Ubuntu, open `Software & Updates` , switch to the `Additional Drivers` tab and note the name of the Nvidia driver package.
|
||||
|
||||
As an example, this is `nvidia-driver-390` in my case, as you can see here:
|
||||
|
||||
|
||||
|
||||
That's not all. We've only found out the Nvidia drivers major version but we'll also need to know the minor version. To get the exact Nvidia driver version, which we'll need for the next step, run this command (should work in any Debian-based Linux distribution, like Ubuntu, Linux Mint and so on):
|
||||
```
|
||||
apt-cache policy NVIDIA-PACKAGE-NAME
|
||||
|
||||
```
|
||||
|
||||
Where NVIDIA-PACKAGE-NAME is the Nvidia drivers package name listed in `Software & Updates` . For example, to see the exact installed version of the `nvidia-driver-390` package, run this command:
|
||||
```
|
||||
$ apt-cache policy nvidia-driver-390
|
||||
nvidia-driver-390:
|
||||
Installed: 390.48-0ubuntu3
|
||||
Candidate: 390.48-0ubuntu3
|
||||
Version table:
|
||||
* 390.48-0ubuntu3 500
|
||||
500 http://ro.archive.ubuntu.com/ubuntu bionic/restricted amd64 Packages
|
||||
100 /var/lib/dpkg/status
|
||||
|
||||
```
|
||||
|
||||
In this command's output, look for the `Installed` section and note the version numbers (excluding `-0ubuntu3` and anything similar). Now we know the exact version of the installed Nvidia drivers (`390.48` in my example). Remember this because we'll need it for the next step.
|
||||
|
||||
**3\. And finally, you can install the Nvidia runtime for your installed proprietary Nvidia graphics drivers, from FlatHub**
|
||||
|
||||
To list all the available Nvidia runtime packages available on FlatHub, you can use this command:
|
||||
```
|
||||
flatpak remote-ls flathub | grep nvidia
|
||||
|
||||
```
|
||||
|
||||
Hopefully the runtime for your installed Nvidia drivers is available on FlatHub. You can now proceed to install the runtime by using this command:
|
||||
|
||||
* For 64bit systems:
|
||||
|
||||
|
||||
```
|
||||
flatpak install flathub org.freedesktop.Platform.GL.nvidia-MAJORVERSION-MINORVERSION
|
||||
|
||||
```
|
||||
|
||||
Replace MAJORVERSION with the Nvidia driver major version installed on your computer (390 in my example above) and
|
||||
MINORVERSION with the minor version (48 in my example from step 2).
|
||||
|
||||
For example, to install the runtime for Nvidia graphics driver version 390.48, you'd have to use this command:
|
||||
```
|
||||
flatpak install flathub org.freedesktop.Platform.GL.nvidia-390-48
|
||||
|
||||
```
|
||||
|
||||
* For 32bit systems (or to be able to run 32bit applications or games on 64bit), install the 32bit runtime using:
|
||||
|
||||
|
||||
```
|
||||
flatpak install flathub org.freedesktop.Platform.GL32.nvidia-MAJORVERSION-MINORVERSION
|
||||
|
||||
```
|
||||
|
||||
Once again, replace MAJORVERSION with the Nvidia driver major version installed on your computer (390 in my example above) and MINORVERSION with the minor version (48 in my example from step 2).
|
||||
|
||||
For example, to install the 32bit runtime for Nvidia graphics driver version 390.48, you'd have to use this command:
|
||||
```
|
||||
flatpak install flathub org.freedesktop.Platform.GL32.nvidia-390-48
|
||||
|
||||
```
|
||||
|
||||
That is all you need to do to get applications or games packaged as Flatpak that are built with OpenGL to run.
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.linuxuprising.com/2018/06/how-to-get-flatpak-apps-and-games-built.html
|
||||
|
||||
作者:[Logix][a]
|
||||
选题:[lujun9972](https://github.com/lujun9972)
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://plus.google.com/118280394805678839070
|
||||
[1]:https://flatpak.org/setup/
|
||||
[2]:https://www.linuxuprising.com/2018/06/free-painting-software-krita-410.html
|
||||
[3]:https://www.linuxuprising.com/2018/06/winepak-is-flatpak-repository-for.html
|
||||
[4]:https://github.com/winepak/applications/issues/23
|
||||
[5]:https://github.com/flatpak/flatpak/issues/138
|
||||
@ -1,92 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Akira: The Linux Design Tool We’ve Always Wanted?)
|
||||
[#]: via: (https://itsfoss.com/akira-design-tool)
|
||||
[#]: author: (Ankush Das https://itsfoss.com/author/ankush/)
|
||||
|
||||
Akira: The Linux Design Tool We’ve Always Wanted?
|
||||
======
|
||||
|
||||
Let’s make it clear, I am not a professional designer – but I’ve used certain tools on Windows (like Photoshop, Illustrator, etc.) and [Figma][1] (which is a browser-based interface design tool). I’m sure there are a lot more design tools available for Mac and Windows.
|
||||
|
||||
Even on Linux, there is a limited number of dedicated [graphic design tools][2]. A few of these tools like [GIMP][3] and [Inkscape][4] are used by professionals as well. But most of them are not considered professional grade, unfortunately.
|
||||
|
||||
Even if there are a couple more solutions – I’ve never come across a native Linux application that could replace [Sketch][5], Figma, or Adobe **** XD. Any professional designer would agree to that, isn’t it?
|
||||
|
||||
### Is Akira going to replace Sketch, Figma, and Adobe XD on Linux?
|
||||
|
||||
Well, in order to develop something that would replace those awesome proprietary tools – [Alessandro Castellani][6] – came up with a [Kickstarter campaign][7] by teaming up with a couple of experienced developers –
|
||||
[Alberto Fanjul][8], [Bilal Elmoussaoui][9], and [Felipe Escoto][10].
|
||||
|
||||
So, yes, Akira is still pretty much just an idea- with a working prototype of its interface (as I observed in their [live stream session][11] via Kickstarter recently).
|
||||
|
||||
### If it does not exist, why the Kickstarter campaign?
|
||||
|
||||
![][12]
|
||||
|
||||
The aim of the Kickstarter campaign is to gather funds in order to hire the developers and take a few months off to dedicate their time in order to make Akira possible.
|
||||
|
||||
Nonetheless, if you want to support the project, you should know some details, right?
|
||||
|
||||
Fret not, we asked a couple of questions in their livestream session – let’s get into it…
|
||||
|
||||
### Akira: A few more details
|
||||
|
||||
![Akira prototype interface][13]
|
||||
Image Credits: Kickstarter
|
||||
|
||||
As the Kickstarter campaign describes:
|
||||
|
||||
> The main purpose of Akira is to offer a fast and intuitive tool to **create Web and Mobile interfaces** , more like **Sketch** , **Figma** , or **Adobe XD** , with a completely native experience for Linux.
|
||||
|
||||
They’ve also written a detailed description as to how the tool will be different from Inkscape, Glade, or QML Editor. Of course, if you want all the technical details, [Kickstarter][7] is the way to go. But, before that, let’s take a look at what they had to say when I asked some questions about Akira.
|
||||
|
||||
Q: If you consider your project – similar to what Figma offers – why should one consider installing Akira instead of using the web-based tool? Is it just going to be a clone of those tools – offering a native Linux experience or is there something really interesting to encourage users to switch (except being an open source solution)?
|
||||
|
||||
**Akira:** A native experience on Linux is always better and fast in comparison to a web-based electron app. Also, the hardware configuration matters if you choose to utilize Figma – but Akira will be light on system resource and you will still be able to do similar stuff without needing to go online.
|
||||
|
||||
Q: Let’s assume that it becomes the open source solution that Linux users have been waiting for (with similar features offered by proprietary tools). What are your plans to sustain it? Do you plan to introduce any pricing plans – or rely on donations?
|
||||
|
||||
**Akira** : The project will mostly rely on Donations (something like [Krita Foundation][14] could be an idea). But, there will be no “pro” pricing plans – it will be available for free and it will be an open source project.
|
||||
|
||||
So, with the response I got, it definitely seems to be something promising that we should probably support.
|
||||
|
||||
### Wrapping Up
|
||||
|
||||
What do you think about Akira? Is it just going to remain a concept? Or do you hope to see it in action?
|
||||
|
||||
Let us know your thoughts in the comments below.
|
||||
|
||||
![][15]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://itsfoss.com/akira-design-tool
|
||||
|
||||
作者:[Ankush Das][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://itsfoss.com/author/ankush/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.figma.com/
|
||||
[2]: https://itsfoss.com/best-linux-graphic-design-software/
|
||||
[3]: https://itsfoss.com/gimp-2-10-release/
|
||||
[4]: https://inkscape.org/
|
||||
[5]: https://www.sketchapp.com/
|
||||
[6]: https://github.com/Alecaddd
|
||||
[7]: https://www.kickstarter.com/projects/alecaddd/akira-the-linux-design-tool/description
|
||||
[8]: https://github.com/albfan
|
||||
[9]: https://github.com/bilelmoussaoui
|
||||
[10]: https://github.com/Philip-Scott
|
||||
[11]: https://live.kickstarter.com/alessandro-castellani/live-stream/the-current-state-of-akira
|
||||
[12]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2019/01/akira-design-tool-kickstarter.jpg?resize=800%2C451&ssl=1
|
||||
[13]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2019/01/akira-mockup.png?ssl=1
|
||||
[14]: https://krita.org/en/about/krita-foundation/
|
||||
[15]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2019/01/akira-design-tool-kickstarter.jpg?fit=812%2C458&ssl=1
|
||||
@ -1,146 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Top Hex Editors for Linux)
|
||||
[#]: via: (https://itsfoss.com/hex-editors-linux)
|
||||
[#]: author: (Ankush Das https://itsfoss.com/author/ankush/)
|
||||
|
||||
Top Hex Editors for Linux
|
||||
======
|
||||
|
||||
Hex editor lets you view/edit the binary data of a file – which is in the form of “hexadecimal” values and hence the name “Hex” editor. Let’s be frank, not everyone needs it. Only a specific group of users who have to deal with the binary data use it.
|
||||
|
||||
If you have no idea, what it is, let me give you an example. Suppose, you have the configuration files of a game, you can open them using a hex editor and change certain values to have more ammo/score and so on. To know more about Hex editors, you should start with the [Wikipedia page][1].
|
||||
|
||||
In case you already know what’s it used for – let us take a look at the best Hex editors available for Linux.
|
||||
|
||||
### 5 Best Hex Editors Available
|
||||
|
||||
![Best Hex Editors for Linux][2]
|
||||
|
||||
**Note:** The hex editors mentioned are in no particular order of ranking.
|
||||
|
||||
#### 1\. Bless Hex Editor
|
||||
|
||||
![bless hex editor][3]
|
||||
|
||||
**Key Features** :
|
||||
|
||||
* Raw disk editing
|
||||
* Multilevel undo/redo operations.
|
||||
* Multiple tabs
|
||||
* Conversion table
|
||||
* Plugin support to extend the functionality
|
||||
|
||||
|
||||
|
||||
Bless is one of the most popular Hex editor available for Linux. You can find it listed in your AppCenter or Software Center. If that is not the case, you can check out their [GitHub page][4] for the build and the instructions associated.
|
||||
|
||||
It can easily handle editing big files without slowing down – so it’s a fast hex editor.
|
||||
|
||||
#### 2\. GNOME Hex Editor
|
||||
|
||||
![gnome hex editor][5]
|
||||
|
||||
**Key Features:**
|
||||
|
||||
* View/Edit in either Hex/Ascii
|
||||
|
||||
* Edit large files
|
||||
|
||||
*
|
||||
|
||||
|
||||
Yet another amazing Hex editor – specifically tailored for GNOME. Well, I personally use Elementary OS, so I find it listed in the App Center. You should find it in the Software Center as well. If not, refer to the [GitHub page][6] for the source.
|
||||
|
||||
You can use this editor to view/edit in either hex or ASCII. The user interface is quite simple – as you can see in the image above.
|
||||
|
||||
#### 3\. Okteta
|
||||
|
||||
![okteta][7]
|
||||
|
||||
**Key Features:**
|
||||
|
||||
* Customizable data views
|
||||
* Multiple tabs
|
||||
* Character encodings: All 8-bit encodings as supplied by Qt, EBCDIC
|
||||
* Decoding table listing common simple data types.
|
||||
|
||||
|
||||
|
||||
Okteta is a simple hex editor with not so fancy features. Although it can handle most of the tasks. There’s a separate module of it which you can use to embed this in other programs to view/edit files.
|
||||
|
||||
Similar to all the above-mentioned editors, you can find this listed on your AppCenter and Software center as well.
|
||||
|
||||
#### 4\. wxHexEditor
|
||||
|
||||
![wxhexeditor][8]
|
||||
|
||||
**Key Features:**
|
||||
|
||||
* Easily handle big files
|
||||
* Has x86 disassembly support
|
||||
* **** Sector Indication **** on Disk devices
|
||||
* Supports customizable hex panel formatting and colors.
|
||||
|
||||
|
||||
|
||||
This is something interesting. It is primarily a Hex editor but you can also use it as a low level disk editor. For example, if you have a problem with your HDD, you can use this editor to edit the the sectors in raw hex and fix it.
|
||||
|
||||
You can find it listed on your App Center and Software Center. If not, [Sourceforge][9] is the way to go.
|
||||
|
||||
#### 5\. Hexedit (Command Line)
|
||||
|
||||
![hexedit][10]
|
||||
|
||||
**Key Features** :
|
||||
|
||||
* Works via terminal
|
||||
* It’s fast and simple
|
||||
|
||||
|
||||
|
||||
If you want something to work on your terminal, you can go ahead and install Hexedit via the console. It’s my favorite Linux hex editor in command line.
|
||||
|
||||
When you launch it, you will have to specify the location of the file, and it’ll then open it for you.
|
||||
|
||||
To install it, just type in:
|
||||
|
||||
```
|
||||
sudo apt install hexedit
|
||||
```
|
||||
|
||||
### Wrapping Up
|
||||
|
||||
Hex editors could come in handy to experiment and learn. If you are someone experienced, you should opt for the one with more feature – with a GUI. Although, it all comes down to personal preferences.
|
||||
|
||||
What do you think about the usefulness of Hex editors? Which one do you use? Did we miss listing your favorite? Let us know in the comments!
|
||||
|
||||
![][11]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://itsfoss.com/hex-editors-linux
|
||||
|
||||
作者:[Ankush Das][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://itsfoss.com/author/ankush/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://en.wikipedia.org/wiki/Hex_editor
|
||||
[2]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2019/01/Linux-hex-editors-800x450.jpeg?resize=800%2C450&ssl=1
|
||||
[3]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2019/01/bless-hex-editor.jpg?ssl=1
|
||||
[4]: https://github.com/bwrsandman/Bless
|
||||
[5]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2019/01/ghex-hex-editor.jpg?ssl=1
|
||||
[6]: https://github.com/GNOME/ghex
|
||||
[7]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2019/01/okteta-hex-editor-800x466.jpg?resize=800%2C466&ssl=1
|
||||
[8]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2019/01/wxhexeditor.jpg?ssl=1
|
||||
[9]: https://sourceforge.net/projects/wxhexeditor/
|
||||
[10]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2019/01/hexedit-console.jpg?resize=800%2C566&ssl=1
|
||||
[11]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2019/01/Linux-hex-editors.jpeg?fit=800%2C450&ssl=1
|
||||
@ -1,5 +1,5 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
|
||||
251
sources/tech/20190205 5 Linux GUI Cloud Backup Tools.md
Normal file
251
sources/tech/20190205 5 Linux GUI Cloud Backup Tools.md
Normal file
@ -0,0 +1,251 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (5 Linux GUI Cloud Backup Tools)
|
||||
[#]: via: (https://www.linux.com/blog/learn/2019/2/5-linux-gui-cloud-backup-tools)
|
||||
[#]: author: (Jack Wallen https://www.linux.com/users/jlwallen)
|
||||
|
||||
5 Linux GUI Cloud Backup Tools
|
||||
======
|
||||

|
||||
|
||||
We have reached a point in time where most every computer user depends upon the cloud … even if only as a storage solution. What makes the cloud really important to users, is when it’s employed as a backup. Why is that such a game changer? By backing up to the cloud, you have access to those files, from any computer you have associated with your cloud account. And because Linux powers the cloud, many services offer Linux tools.
|
||||
|
||||
Let’s take a look at five such tools. I will focus on GUI tools, because they offer a much lower barrier to entry to many of the CLI tools. I’ll also be focusing on various, consumer-grade cloud services (e.g., [Google Drive][1], [Dropbox][2], [Wasabi][3], and [pCloud][4]). And, I will be demonstrating on the Elementary OS platform, but all of the tools listed will function on most Linux desktop distributions.
|
||||
|
||||
Note: Of the following backup solutions, only Duplicati is licensed as open source. With that said, let’s see what’s available.
|
||||
|
||||
### Insync
|
||||
|
||||
I must confess, [Insync][5] has been my cloud backup of choice for a very long time. Since Google refuses to release a Linux desktop client for Google Drive (and I depend upon Google Drive daily), I had to turn to a third-party solution. Said solution is Insync. This particular take on syncing the desktop to Drive has not only been seamless, but faultless since I began using the tool.
|
||||
|
||||
The cost of Insync is a one-time $29.99 fee (per Google account). Trust me when I say this tool is worth the price of entry. With Insync you not only get an easy-to-use GUI for managing your Google Drive backup and sync, you get a tool (Figure 1) that gives you complete control over what is backed up and how it is backed up. Not only that, but you can also install Nautilus integration (which also allows you to easy add folders outside of the configured Drive sync destination).
|
||||
|
||||
![Insync app][7]
|
||||
|
||||
Figure 1: The Insync app window on Elementary OS.
|
||||
|
||||
[Used with permission][8]
|
||||
|
||||
You can download Insync for Ubuntu (or its derivatives), Linux Mint, Debian, and Fedora from the [Insync download page][9]. Once you’ve installed Insync (and associated it with your account), you can then install Nautilus integration with these steps (demonstrating on Elementary OS):
|
||||
|
||||
1. Open a terminal window and issue the command sudo nano /etc/apt/sources.list.d/insync.list.
|
||||
|
||||
2. Paste the following into the new file: deb <http://apt.insynchq.com/ubuntu> precise non-free contrib.
|
||||
|
||||
3. Save and close the file.
|
||||
|
||||
4. Update apt with the command sudo apt-get update.
|
||||
|
||||
5. Install the necessary package with the command sudo apt-get install insync-nautilus.
|
||||
|
||||
|
||||
|
||||
|
||||
Allow the installation to complete. Once finished, restart Nautilus with the command nautilus -q (or log out and back into the desktop). You should now see an Insync entry in the Nautilus right-click context menu (Figure 2).
|
||||
|
||||

|
||||
|
||||
Figure 2: Insync/Nautilus integration in action.
|
||||
|
||||
[Used with permission][8]
|
||||
|
||||
### Dropbox
|
||||
|
||||
Although [Dropbox][2] drew the ire of many in the Linux community (by dropping support for all filesystems but unencrypted ext4), it still supports a great deal of Linux desktop deployments. In other words, if your distribution still uses the ext4 file system (and you do not opt to encrypt your full drive), you’re good to go.
|
||||
|
||||
The good news is the Dropbox Linux desktop client is quite good. The tool offers a system tray icon that allows you to easily interact with your cloud syncing. Dropbox also includes CLI tools and a Nautilus integration (by way of an additional addon found [here][10]).
|
||||
|
||||
The Linux Dropbox desktop sync tool works exactly as you’d expect. From the Dropbox system tray drop-down (Figure 3) you can open the Dropbox folder, launch the Dropbox website, view recently changed files, get more space, pause syncing, open the preferences window, find help, and quite Dropbox.
|
||||
|
||||
![Dropbox][12]
|
||||
|
||||
Figure 3: The Dropbox system tray drop-down on Elementary OS.
|
||||
|
||||
[Used with permission][8]
|
||||
|
||||
The Dropbox/Nautilus integration is an important component, as it makes quickly adding to your cloud backup seamless and fast. From the Nautilus file manager, locate and right-click the folder to bad added, and select Dropbox > Move to Dropbox (Figure 4).
|
||||
|
||||
The only caveat to the Dropbox/Nautilus integration is that the only option is to move a folder to Dropbox. To some this might not be an option. The developers of this package would be wise to instead have the action create a link (instead of actually moving the folder).
|
||||
|
||||
Outside of that one issue, the Dropbox cloud sync/backup solution for Linux is a great route to go.
|
||||
|
||||
### pCloud
|
||||
|
||||
pCloud might well be one of the finest cloud backup solutions you’ve never heard of. This take on cloud storage/backup includes features like:
|
||||
|
||||
* Encryption (subscription service required for this feature);
|
||||
|
||||
* Mobile apps for Android and iOS;
|
||||
|
||||
* Linux, Mac, and Windows desktop clients;
|
||||
|
||||
* Easy file/folder sharing;
|
||||
|
||||
* Built-in audio/video players;
|
||||
|
||||
* No file size limitation;
|
||||
|
||||
* Sync any folder from the desktop;
|
||||
|
||||
* Panel integration for most desktops; and
|
||||
|
||||
* Automatic file manager integration.
|
||||
|
||||
|
||||
|
||||
|
||||
pCloud offers both Linux desktop and CLI tools that function quite well. pCloud offers both a free plan (with 10GB of storage), a Premium Plan (with 500GB of storage for a one-time fee of $175.00), and a Premium Plus Plan (with 2TB of storage for a one-time fee of $350.00). Both non-free plans can also be paid on a yearly basis (instead of the one-time fee).
|
||||
|
||||
The pCloud desktop client is quite user-friendly. Once installed, you have access to your account information (Figure 5), the ability to create sync pairs, create shares, enable crypto (which requires an added subscription), and general settings.
|
||||
|
||||
![pCloud][14]
|
||||
|
||||
Figure 5: The pCloud desktop client is incredibly easy to use.
|
||||
|
||||
[Used with permission][8]
|
||||
|
||||
The one caveat to pCloud is there’s no file manager integration for Linux. That’s overcome by the Sync folder in the pCloud client.
|
||||
|
||||
### CloudBerry
|
||||
|
||||
The primary focus for [CloudBerry][15] is for Managed Service Providers. The business side of CloudBerry does have an associated cost (one that is probably well out of the price range for the average user looking for a simple cloud backup solution). However, for home usage, CloudBerry is free.
|
||||
|
||||
What makes CloudBerry different than the other tools is that it’s not a backup/storage solution in and of itself. Instead, CloudBerry serves as a link between your desktop and the likes of:
|
||||
|
||||
* AWS
|
||||
|
||||
* Microsoft Azure
|
||||
|
||||
* Google Cloud
|
||||
|
||||
* BackBlaze
|
||||
|
||||
* OpenStack
|
||||
|
||||
* Wasabi
|
||||
|
||||
* Local storage
|
||||
|
||||
* External drives
|
||||
|
||||
* Network Attached Storage
|
||||
|
||||
* Network Shares
|
||||
|
||||
* And more
|
||||
|
||||
|
||||
|
||||
|
||||
In other words, you use CloudBerry as the interface between the files/folders you want to share and the destination with which you want send them. This also means you must have an account with one of the many supported solutions.
|
||||
Once you’ve installed CloudBerry, you create a new Backup plan for the target storage solution. For that configuration, you’ll need such information as:
|
||||
|
||||
* Access Key
|
||||
|
||||
* Secret Key
|
||||
|
||||
* Bucket
|
||||
|
||||
|
||||
|
||||
|
||||
What you’ll need for the configuration will depend on the account you’re connecting to (Figure 6).
|
||||
|
||||
![CloudBerry][17]
|
||||
|
||||
Figure 6: Setting up a CloudBerry backup for Wasabi.
|
||||
|
||||
[Used with permission][8]
|
||||
|
||||
The one caveat to CloudBerry is that it does not integrate with any file manager, nor does it include a system tray icon for interaction with the service.
|
||||
|
||||
### Duplicati
|
||||
|
||||
[Duplicati][18] is another option that allows you to sync your local directories with either locally attached drives, network attached storage, or a number of cloud services. The options supported include:
|
||||
|
||||
* Local folders
|
||||
|
||||
* Attached drives
|
||||
|
||||
* FTP/SFTP
|
||||
|
||||
* OpenStack
|
||||
|
||||
* WebDAV
|
||||
|
||||
* Amazon Cloud Drive
|
||||
|
||||
* Amazon S3
|
||||
|
||||
* Azure Blob
|
||||
|
||||
* Box.com
|
||||
|
||||
* Dropbox
|
||||
|
||||
* Google Cloud Storage
|
||||
|
||||
* Google Drive
|
||||
|
||||
* Microsoft OneDrive
|
||||
|
||||
* And many more
|
||||
|
||||
|
||||
|
||||
|
||||
Once you install Duplicati (download the installer for Debian, Ubuntu, Fedora, or RedHat from the [Duplicati downloads page][19]), click on the entry in your desktop menu, which will open a web page to the tool (Figure 7), where you can configure the app settings, create a new backup, restore from a backup, and more.
|
||||
|
||||

|
||||
|
||||
To create a backup, click Add backup and walk through the easy-to-use wizard (Figure 8). The backup service you choose will dictate what you need for a successful configuration.
|
||||
|
||||
![Duplicati backup][21]
|
||||
|
||||
Figure 8: Creating a new Duplicati backup for Google Drive.
|
||||
|
||||
[Used with permission][8]
|
||||
|
||||
For example, in order to create a backup to Google Drive, you’ll need an AuthID. For that, click the AuthID link in the Destination section of the setup, where you’ll be directed to select the Google Account to associate with the backup. Once you’ve allowed Duplicati access to the account, the AuthID will fill in and you’re ready to continue. Click Test connection and you’ll be asked to okay the creation of a new folder (if necessary). Click Next to complete the setup of the backup.
|
||||
|
||||
### More Where That Came From
|
||||
|
||||
These five cloud backup tools aren’t the end of this particular rainbow. There are plenty more options where these came from (including CLI-only tools). But any of these backup clients will do a great job of serving your Linux desktop-to-cloud backup needs.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.linux.com/blog/learn/2019/2/5-linux-gui-cloud-backup-tools
|
||||
|
||||
作者:[Jack Wallen][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.linux.com/users/jlwallen
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.google.com/drive/
|
||||
[2]: https://www.dropbox.com/
|
||||
[3]: https://wasabi.com/
|
||||
[4]: https://www.pcloud.com/
|
||||
[5]: https://www.insynchq.com/
|
||||
[6]: /files/images/insync1jpg
|
||||
[7]: https://www.linux.com/sites/lcom/files/styles/rendered_file/public/insync_1.jpg?itok=_SDP77uE (Insync app)
|
||||
[8]: /licenses/category/used-permission
|
||||
[9]: https://www.insynchq.com/downloads
|
||||
[10]: https://www.dropbox.com/install-linux
|
||||
[11]: /files/images/dropbox1jpg
|
||||
[12]: https://www.linux.com/sites/lcom/files/styles/rendered_file/public/dropbox_1.jpg?itok=BYbg-sKB (Dropbox)
|
||||
[13]: /files/images/pcloud1jpg
|
||||
[14]: https://www.linux.com/sites/lcom/files/styles/rendered_file/public/pcloud_1.jpg?itok=cAUz8pya (pCloud)
|
||||
[15]: https://www.cloudberrylab.com
|
||||
[16]: /files/images/cloudberry1jpg
|
||||
[17]: https://www.linux.com/sites/lcom/files/styles/rendered_file/public/cloudberry_1.jpg?itok=s0aP5xuN (CloudBerry)
|
||||
[18]: https://www.duplicati.com/
|
||||
[19]: https://www.duplicati.com/download
|
||||
[20]: /files/images/duplicati2jpg
|
||||
[21]: https://www.linux.com/sites/lcom/files/styles/rendered_file/public/duplicati_2.jpg?itok=Xkn8s3jg (Duplicati backup)
|
||||
@ -1,114 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (LazyWolfLin)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (7 steps for hunting down Python code bugs)
|
||||
[#]: via: (https://opensource.com/article/19/2/steps-hunting-code-python-bugs)
|
||||
[#]: author: (Maria Mckinley https://opensource.com/users/parody)
|
||||
|
||||
7 steps for hunting down Python code bugs
|
||||
======
|
||||
Learn some tricks to minimize the time you spend tracking down the reasons your code fails.
|
||||

|
||||
|
||||
It is 3 pm on a Friday afternoon. Why? Because it is always 3 pm on a Friday when things go down. You get a notification that a customer has found a bug in your software. After you get over your initial disbelief, you contact DevOps to find out what is happening with the logs for your app, because you remember receiving a notification that they were being moved.
|
||||
|
||||
Turns out they are somewhere you can't get to, but they are in the process of being moved to a web application—so you will have this nifty application for searching and reading them, but of course, it is not finished yet. It should be up in a couple of days. I know, totally unrealistic situation, right? Unfortunately not; it seems logs or log messages often come up missing at just the wrong time. Before we track down the bug, a public service announcement: Check your logs to make sure they are where you think they are and logging what you think they should log, regularly. Amazing how these things just change when you aren't looking.
|
||||
|
||||
OK, so you found the logs or tried the call, and indeed, the customer has found a bug. Maybe you even think you know where the bug is.
|
||||
|
||||
You immediately open the file you think might be the problem and start poking around.
|
||||
|
||||
### 1. Don't touch your code yet
|
||||
|
||||
Go ahead and look at it, maybe even come up with a hypothesis. But before you start mucking about in the code, take that call that creates the bug and turn it into a test. This will be an integration test because although you may have suspicions, you do not yet know exactly where the problem is.
|
||||
|
||||
Make sure this test fails. This is important because sometimes the test you make doesn't mimic the broken call; this is especially true if you are using a web or other framework that can obfuscate the tests. Many things may be stored in variables, and it is unfortunately not always obvious, just by looking at the test, what call you are making in the test. I'm not going to say that I have created a test that passed when I was trying to imitate a broken call, but, well, I have, and I don't think that is particularly unusual. Learn from my mistakes.
|
||||
|
||||
### 2. Write a failing test
|
||||
|
||||
Now that you have a failing test or maybe a test with an error, it is time to troubleshoot. But before you do that, let's do a review of the stack, as this makes troubleshooting easier.
|
||||
|
||||
The stack consists of all of the tasks you have started but not finished. So, if you are baking a cake and adding the flour to the batter, then your stack would be:
|
||||
|
||||
* Make cake
|
||||
* Make batter
|
||||
* Add flour
|
||||
|
||||
|
||||
|
||||
You have started making your cake, you have started making the batter, and you are adding the flour. Greasing the pan is not on the list since you already finished that, and making the frosting is not on the list because you have not started that.
|
||||
|
||||
If you are fuzzy on the stack, I highly recommend playing around on [Python Tutor][1], where you can watch the stack as you execute lines of code.
|
||||
|
||||
Now, if something goes wrong with your Python program, the interpreter helpfully prints out the stack for you. This means that whatever the program was doing at the moment it became apparent that something went wrong is on the bottom.
|
||||
|
||||
### 3. Always check the bottom of the stack first
|
||||
|
||||
Not only is the bottom of the stack where you can see which error occurred, but often the last line of the stack is where you can find the issue. If the bottom doesn't help, and your code has not been linted in a while, it is amazing how helpful it can be to run. I recommend pylint or flake8. More often than not, it points right to where there is an error that I have been overlooking.
|
||||
|
||||
If the error is something that seems obscure, your next move might just be to Google it. You will have better luck if you don't include information that is relevant only to your code, like the name of variables, files, etc. If you are using Python 3 (which you should be), it's helpful to include the 3 in the search; otherwise, Python 2 solutions tend to dominate the top.
|
||||
|
||||
Once upon a time, developers had to troubleshoot without the benefit of a search engine. This was a dark time. Take advantage of all the tools available to you.
|
||||
|
||||
Unfortunately, sometimes the problem occurred earlier and only became apparent during the line executed on the bottom of the stack. Think about how forgetting to add the baking powder becomes obvious when the cake doesn't rise.
|
||||
|
||||
It is time to look up the stack. Chances are quite good that the problem is in your code, and not Python core or even third-party packages, so scan the stack looking for lines in your code first. Plus it is usually much easier to put a breakpoint in your own code. Stick the breakpoint in your code a little further up the stack and look around to see if things look like they should.
|
||||
|
||||
"But Maria," I hear you say, "this is all helpful if I have a stack trace, but I just have a failing test. Where do I start?"
|
||||
|
||||
Pdb, the Python Debugger.
|
||||
|
||||
Find a place in your code where you know this call should hit. You should be able to find at least one place. Stick a pdb break in there.
|
||||
|
||||
#### A digression
|
||||
|
||||
Why not a print statement? I used to depend on print statements. They still come in handy sometimes. But once I started working with complicated code bases, and especially ones making network calls, print just became too slow. I ended up with print statements all over the place, I lost track of where they were and why, and it just got complicated. But there is a more important reason to mostly use pdb. Let's say you put a print statement in and discover that something is wrong—and must have gone wrong earlier. But looking at the function where you put the print statement, you have no idea how you got there. Looking at code is a great way to see where you are going, but it is terrible for learning where you've been. And yes, I have done a grep of my code base looking for where a function is called, but this can get tedious and doesn't narrow it down much with a popular function. Pdb can be very helpful.
|
||||
|
||||
You follow my advice, and put in a pdb break and run your test. And it whooshes on by and fails again, with no break at all. Leave your breakpoint in, and run a test already in your test suite that does something very similar to the broken test. If you have a decent test suite, you should be able to find a test that is hitting the same code you think your failed test should hit. Run that test, and when it gets to your breakpoint, do a `w` and look at the stack. If you have no idea by looking at the stack how/where the other call may have gone haywire, then go about halfway up the stack, find some code that belongs to you, and put a breakpoint in that file, one line above the one in the stack trace. Try again with the new test. Keep going back and forth, moving up the stack to figure out where your call went off the rails. If you get all the way up to the top of the trace without hitting a breakpoint, then congratulations, you have found the issue: Your app was spelled wrong. No experience here, nope, none at all.
|
||||
|
||||
### 4. Change things
|
||||
|
||||
If you still feel lost, try making a new test where you vary something slightly. Can you get the new test to work? What is different? What is the same? Try changing something else. Once you have your test, and maybe additional tests in place, it is safe to start changing things in the code to see if you can narrow down the problem. Remember to start troubleshooting with a fresh commit so you can easily back out changes that do not help. (This is a reference to version control, if you aren't using version control, it will change your life. Well, maybe it will just make coding easier. See "[A Visual Guide to Version Control][2]" for a nice introduction.)
|
||||
|
||||
### 5. Take a break
|
||||
|
||||
In all seriousness, when it stops feeling like a fun challenge or game and starts becoming really frustrating, your best course of action is to walk away from the problem. Take a break. I highly recommend going for a walk and trying to think about something else.
|
||||
|
||||
### 6. Write everything down
|
||||
|
||||
When you come back, if you aren't suddenly inspired to try something, write down any information you have about the problem. This should include:
|
||||
|
||||
* Exactly the call that is causing the problem
|
||||
* Exactly what happened, including any error messages or related log messages
|
||||
* Exactly what you were expecting to happen
|
||||
* What you have done so far to find the problem and any clues that you have discovered while troubleshooting
|
||||
|
||||
|
||||
|
||||
Sometimes this is a lot of information, but trust me, it is really annoying trying to pry information out of someone piecemeal. Try to be concise, but complete.
|
||||
|
||||
### 7. Ask for help
|
||||
|
||||
I often find that just writing down all the information triggers a thought about something I have not tried yet. Sometimes, of course, I realize what the problem is immediately after hitting the submit button. At any rate, if you still have not thought of anything after writing everything down, try sending an email to someone. First, try colleagues or other people involved in your project, then move on to project email lists. Don't be afraid to ask for help. Most people are kind and helpful, and I have found that to be especially true in the Python community.
|
||||
|
||||
Maria McKinley will present [Hunting the Bugs][3] at [PyCascades 2019][4], February 23-24 in Seattle.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/2/steps-hunting-code-python-bugs
|
||||
|
||||
作者:[Maria Mckinley][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/parody
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: http://www.pythontutor.com/
|
||||
[2]: https://betterexplained.com/articles/a-visual-guide-to-version-control/
|
||||
[3]: https://2019.pycascades.com/talks/hunting-the-bugs
|
||||
[4]: https://2019.pycascades.com/
|
||||
@ -1,226 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (An-DJ)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (How To Check CPU, Memory And Swap Utilization Percentage In Linux?)
|
||||
[#]: via: (https://www.2daygeek.com/linux-check-cpu-memory-swap-utilization-percentage/)
|
||||
[#]: author: (Vinoth Kumar https://www.2daygeek.com/author/vinoth/)
|
||||
|
||||
How To Check CPU, Memory And Swap Utilization Percentage In Linux?
|
||||
======
|
||||
|
||||
There is a lot of commands and options are available in Linux to check memory utilization but i don’t see much information to check about memory utilization percentage.
|
||||
|
||||
Most of the times we are checking memory utilization alone and we won’t think about how much percentage is used.
|
||||
|
||||
If you want to know those information then you are in the right page.
|
||||
|
||||
We are here to help you out on this in details.
|
||||
|
||||
This tutorial will help you to identify the memory utilization when you are facing high memory utilization frequently in Linux server.
|
||||
|
||||
But the same time, you won’t be getting the clear utilization if you are using `free -m` or `free -g`.
|
||||
|
||||
These format commands fall under Linux advanced commands. It will be very useful for Linux Experts and Middle Level Linux Users.
|
||||
|
||||
### Method-1: How To Check Memory Utilization Percentage In Linux?
|
||||
|
||||
We can use the following combination of commands to get this done. In this method, we are using combination of free and awk command to get the memory utilization percentage.
|
||||
|
||||
If you are looking for other articles which is related to memory then navigate to the following link. Those are **[free Command][1]** , **[smem Command][2]** , **[ps_mem Command][3]** , **[vmstat Command][4]** and **[Multiple ways to check size of physical memory][5]**.
|
||||
|
||||
For `Memory` Utilization Percentage without Percent Symbol:
|
||||
|
||||
```
|
||||
$ free -t | awk 'NR == 2 {print "Current Memory Utilization is : " $3/$2*100}'
|
||||
or
|
||||
$ free -t | awk 'FNR == 2 {print "Current Memory Utilization is : " $3/$2*100}'
|
||||
|
||||
Current Memory Utilization is : 20.4194
|
||||
```
|
||||
|
||||
For `Swap` Utilization Percentage without Percent Symbol:
|
||||
|
||||
```
|
||||
$ free -t | awk 'NR == 3 {print "Current Swap Utilization is : " $3/$2*100}'
|
||||
or
|
||||
$ free -t | awk 'FNR == 3 {print "Current Swap Utilization is : " $3/$2*100}'
|
||||
|
||||
Current Swap Utilization is : 0
|
||||
```
|
||||
|
||||
For `Memory` Utilization Percentage with Percent Symbol and two decimal places:
|
||||
|
||||
```
|
||||
$ free -t | awk 'NR == 2 {printf("Current Memory Utilization is : %.2f%"), $3/$2*100}'
|
||||
or
|
||||
$ free -t | awk 'FNR == 2 {printf("Current Memory Utilization is : %.2f%"), $3/$2*100}'
|
||||
|
||||
Current Memory Utilization is : 20.42%
|
||||
```
|
||||
|
||||
For `Swap` Utilization Percentage with Percent Symbol and two decimal places:
|
||||
|
||||
```
|
||||
$ free -t | awk 'NR == 3 {printf("Current Swap Utilization is : %.2f%"), $3/$2*100}'
|
||||
or
|
||||
$ free -t | awk 'FNR == 3 {printf("Current Swap Utilization is : %.2f%"), $3/$2*100}'
|
||||
|
||||
Current Swap Utilization is : 0.00%
|
||||
```
|
||||
|
||||
If you are looking for other articles which is related to memory then navigate to the following link. Those are **[Create/Extend Swap Partition using LVM][6]** , **[Multiple Ways To Create Or Extend Swap Space][7]** and **[Shell Script to automatically Create/Remove and Mount Swap File][8]**.
|
||||
|
||||
free command output for better clarification:
|
||||
|
||||
```
|
||||
$ free
|
||||
total used free shared buff/cache available
|
||||
Mem: 15867 3730 9868 1189 2269 10640
|
||||
Swap: 17454 0 17454
|
||||
Total: 33322 3730 27322
|
||||
```
|
||||
|
||||
Details are follow:
|
||||
|
||||
* **`free:`** free is a standard command to check memory utilization in Linux.
|
||||
* **`awk:`** awk is a powerful command which is specialized for textual data manipulation.
|
||||
* **`FNR == 2:`** It gives the total number of records for each input file. Basically it’s used to select the given line (Here, it chooses the line number 2).
|
||||
* **`NR == 2:`** It gives the total number of records processed. Basically it’s used to filter the given line (Here, it chooses the line number 2)..
|
||||
* **`$3/$2*100:`** It divides column 2 with column 3 and it’s multiply the results with 100.
|
||||
* **`printf:`** It used to format and print data.
|
||||
* **`%.2f%:`** By default it prints floating point numbers with 6 decimal places. Use the following format to limit a decimal places.
|
||||
|
||||
|
||||
|
||||
### Method-2: How To Check Memory Utilization Percentage In Linux?
|
||||
|
||||
We can use the following combination of commands to get this done. In this method, we are using combination of free, grep and awk command to get the memory utilization percentage.
|
||||
|
||||
For `Memory` Utilization Percentage without Percent Symbol:
|
||||
|
||||
```
|
||||
$ free -t | grep Mem | awk '{print "Current Memory Utilization is : " $3/$2*100}'
|
||||
Current Memory Utilization is : 20.4228
|
||||
```
|
||||
|
||||
For `Swap` Utilization Percentage without Percent Symbol:
|
||||
|
||||
```
|
||||
$ free -t | grep Swap | awk '{print "Current Swap Utilization is : " $3/$2*100}'
|
||||
Current Swap Utilization is : 0
|
||||
```
|
||||
|
||||
For `Memory` Utilization Percentage with Percent Symbol and two decimal places:
|
||||
|
||||
```
|
||||
$ free -t | grep Mem | awk '{printf("Current Memory Utilization is : %.2f%"), $3/$2*100}'
|
||||
Current Memory Utilization is : 20.43%
|
||||
```
|
||||
|
||||
For `Swap` Utilization Percentage with Percent Symbol and two decimal places:
|
||||
|
||||
```
|
||||
$ free -t | grep Swap | awk '{printf("Current Swap Utilization is : %.2f%"), $3/$2*100}'
|
||||
Current Swap Utilization is : 0.00%
|
||||
```
|
||||
|
||||
### Method-1: How To Check CPU Utilization Percentage In Linux?
|
||||
|
||||
We can use the following combination of commands to get this done. In this method, we are using combination of top, print and awk command to get the CPU utilization percentage.
|
||||
|
||||
If you are looking for other articles which is related to memory then navigate to the following link. Those are **[top Command][9]** , **[htop Command][10]** , **[atop Command][11]** and **[Glances Command][12]**.
|
||||
|
||||
If it shows multiple CPU in the output then you need to use the following method.
|
||||
|
||||
```
|
||||
$ top -b -n1 | grep ^%Cpu
|
||||
%Cpu0 : 5.3 us, 0.0 sy, 0.0 ni, 94.7 id, 0.0 wa, 0.0 hi, 0.0 si, 0.0 st
|
||||
%Cpu1 : 0.0 us, 0.0 sy, 0.0 ni,100.0 id, 0.0 wa, 0.0 hi, 0.0 si, 0.0 st
|
||||
%Cpu2 : 0.0 us, 0.0 sy, 0.0 ni, 94.7 id, 0.0 wa, 0.0 hi, 5.3 si, 0.0 st
|
||||
%Cpu3 : 5.3 us, 0.0 sy, 0.0 ni, 94.7 id, 0.0 wa, 0.0 hi, 0.0 si, 0.0 st
|
||||
%Cpu4 : 10.5 us, 15.8 sy, 0.0 ni, 73.7 id, 0.0 wa, 0.0 hi, 0.0 si, 0.0 st
|
||||
%Cpu5 : 0.0 us, 5.0 sy, 0.0 ni, 95.0 id, 0.0 wa, 0.0 hi, 0.0 si, 0.0 st
|
||||
%Cpu6 : 5.3 us, 0.0 sy, 0.0 ni, 94.7 id, 0.0 wa, 0.0 hi, 0.0 si, 0.0 st
|
||||
%Cpu7 : 5.3 us, 0.0 sy, 0.0 ni, 94.7 id, 0.0 wa, 0.0 hi, 0.0 si, 0.0 st
|
||||
```
|
||||
|
||||
For `CPU` Utilization Percentage without Percent Symbol:
|
||||
|
||||
```
|
||||
$ top -b -n1 | grep ^%Cpu | awk '{cpu+=$9}END{print "Current CPU Utilization is : " 100-cpu/NR}'
|
||||
Current CPU Utilization is : 21.05
|
||||
```
|
||||
|
||||
For `CPU` Utilization Percentage with Percent Symbol and two decimal places:
|
||||
|
||||
```
|
||||
$ top -b -n1 | grep ^%Cpu | awk '{cpu+=$9}END{printf("Current CPU Utilization is : %.2f%"), 100-cpu/NR}'
|
||||
Current CPU Utilization is : 14.81%
|
||||
```
|
||||
|
||||
### Method-2: How To Check CPU Utilization Percentage In Linux?
|
||||
|
||||
We can use the following combination of commands to get this done. In this method, we are using combination of top, print/printf and awk command to get the CPU utilization percentage.
|
||||
|
||||
If it shows all together CPU(s) in the single output then you need to use the following method.
|
||||
|
||||
```
|
||||
$ top -b -n1 | grep ^%Cpu
|
||||
%Cpu(s): 15.3 us, 7.2 sy, 0.8 ni, 69.0 id, 6.7 wa, 0.0 hi, 1.0 si, 0.0 st
|
||||
```
|
||||
|
||||
For `CPU` Utilization Percentage without Percent Symbol:
|
||||
|
||||
```
|
||||
$ top -b -n1 | grep ^%Cpu | awk '{print "Current CPU Utilization is : " 100-$8}'
|
||||
Current CPU Utilization is : 5.6
|
||||
```
|
||||
|
||||
For `CPU` Utilization Percentage with Percent Symbol and two decimal places:
|
||||
|
||||
```
|
||||
$ top -b -n1 | grep ^%Cpu | awk '{printf("Current CPU Utilization is : %.2f%"), 100-$8}'
|
||||
Current CPU Utilization is : 5.40%
|
||||
```
|
||||
|
||||
Details are follow:
|
||||
|
||||
* **`top:`** top is one of the best command to check currently running process on Linux system.
|
||||
* **`-b:`** -b option, allow the top command to switch in batch mode. It is useful when you run the top command from local system to remote system.
|
||||
* **`-n1:`** Number-of-iterations
|
||||
* **`^%Cpu:`** Filter the lines which starts with %Cpu
|
||||
* **`awk:`** awk is a powerful command which is specialized for textual data manipulation.
|
||||
* **`cpu+=$9:`** For each line, add column 9 to a variable ‘cpu’.
|
||||
* **`printf:`** It used to format and print data.
|
||||
* **`%.2f%:`** By default it prints floating point numbers with 6 decimal places. Use the following format to limit a decimal places.
|
||||
* **`100-cpu/NR:`** Finally print the ‘CPU Average’ by subtracting 100, divided by the number of records.
|
||||
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.2daygeek.com/linux-check-cpu-memory-swap-utilization-percentage/
|
||||
|
||||
作者:[Vinoth Kumar][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.2daygeek.com/author/vinoth/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.2daygeek.com/free-command-to-check-memory-usage-statistics-in-linux/
|
||||
[2]: https://www.2daygeek.com/smem-linux-memory-usage-statistics-reporting-tool/
|
||||
[3]: https://www.2daygeek.com/ps_mem-report-core-memory-usage-accurately-in-linux/
|
||||
[4]: https://www.2daygeek.com/linux-vmstat-command-examples-tool-report-virtual-memory-statistics/
|
||||
[5]: https://www.2daygeek.com/easy-ways-to-check-size-of-physical-memory-ram-in-linux/
|
||||
[6]: https://www.2daygeek.com/how-to-create-extend-swap-partition-in-linux-using-lvm/
|
||||
[7]: https://www.2daygeek.com/add-extend-increase-swap-space-memory-file-partition-linux/
|
||||
[8]: https://www.2daygeek.com/shell-script-create-add-extend-swap-space-linux/
|
||||
[9]: https://www.2daygeek.com/linux-top-command-linux-system-performance-monitoring-tool/
|
||||
[10]: https://www.2daygeek.com/linux-htop-command-linux-system-performance-resource-monitoring-tool/
|
||||
[11]: https://www.2daygeek.com/atop-system-process-performance-monitoring-tool/
|
||||
[12]: https://www.2daygeek.com/install-glances-advanced-real-time-linux-system-performance-monitoring-tool-on-centos-fedora-ubuntu-debian-opensuse-arch-linux/
|
||||
@ -1,135 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (An Automated Way To Install Essential Applications On Ubuntu)
|
||||
[#]: via: (https://www.ostechnix.com/an-automated-way-to-install-essential-applications-on-ubuntu/)
|
||||
[#]: author: (SK https://www.ostechnix.com/author/sk/)
|
||||
|
||||
An Automated Way To Install Essential Applications On Ubuntu
|
||||
======
|
||||

|
||||
|
||||
The default Ubuntu installation doesn’t come with all essential applications pre-installed . You may need to spend few hours on Internet or ask any Linux user’s help to find and install the necessary applications for your Ubuntu box. If you’re newbie, then you certainly need to spend more time to learn how to search and install applications either from command line (using apt-get or dpkg) or from the Ubuntu software center. Some users, especially newbies, might want to easily and quickly install every applications they like. If you’re one of them, no worries. In this guide, we will see how to install essential applications on Ubuntu using a simple command line utility called **“Alfred”**.
|
||||
|
||||
Alfred is a free, open source script written in **Python** programming language. It uses **Zenity** to create a simple graphical interface that allows the users to easily select and install the applications of their choice with a few mouse clicks. You need not to spend hours to search for all essential applications, PPAs, debs, AppImage, snaps or flatpaks. Alfred brings all common applications, tools and utilities under one-roof and automatically installs the selected applications. If you’re a newbie who is recently migrated from Windows to Ubuntu Linux, Alfred helps you to do an unattended software installation on a freshly installed Ubuntu system, without much user intervention. Please be mindful that there is also a Mac OS app with similar name, but both serves different purposes.
|
||||
|
||||
### Installing Alfred On Ubuntu
|
||||
|
||||
Alfred installation is easy! Just download the script and launch it. It is that simple.
|
||||
|
||||
```
|
||||
$ wget https://raw.githubusercontent.com/derkomai/alfred/master/alfred.py
|
||||
|
||||
$ python3 alfred.py
|
||||
```
|
||||
|
||||
Alternatively, download the script using wget as shown above and just move the **alfred.py** file to your $PATH:
|
||||
|
||||
```
|
||||
$ sudo cp alfred.py /usr/local/bin/alfred
|
||||
```
|
||||
|
||||
Make it executable:
|
||||
|
||||
```
|
||||
$ sudo chmod +x /usr/local/bin/alfred
|
||||
```
|
||||
|
||||
And, launch it using command:
|
||||
|
||||
```
|
||||
$ alfred
|
||||
```
|
||||
|
||||
### Easily And Quickly Install Essential Applications On Ubuntu Using Alfred Script
|
||||
|
||||
Launch Alfred script as described in the installation section above. This is how Alfred default interface looks like.
|
||||
|
||||
![][2]
|
||||
|
||||
As you can see, Alfred lists a lot of most commonly used application types such as,
|
||||
|
||||
* Web browsers,
|
||||
* Mail clients,
|
||||
* Messengers,
|
||||
* Cloud storage clients,
|
||||
* Hardware drivers,
|
||||
* Codecs,
|
||||
* Developer tools,
|
||||
* Android,
|
||||
* Text editors,
|
||||
* Git,
|
||||
* Kernel update tool,
|
||||
* Audio/video players,
|
||||
* Screenshot tools,
|
||||
* Screen recorders,
|
||||
* Video encoders,
|
||||
* Streaming apps,
|
||||
* 3D modelling and animation tools,
|
||||
* Image viewers and editors,
|
||||
* CAD software,
|
||||
* Pdf tools,
|
||||
* Gaming emulators,
|
||||
* Disk management tools,
|
||||
* Encryption tools,
|
||||
* Password managers,
|
||||
* Archive tools,
|
||||
* Ftp software,
|
||||
* System resource monitors,
|
||||
* Application launchers and many.
|
||||
|
||||
|
||||
|
||||
You can pick any one or multiple applications of your choice and install them at once. Here, I am going to install the ‘Developer bundle’, hence I chose it and click OK button.
|
||||
|
||||
![][3]
|
||||
|
||||
Now, Alfred script will automatically add the necessary repositories, ppas on your Ubuntu system and start installing the selected applications.
|
||||
|
||||
![][4]
|
||||
|
||||
Once the installation is completed, you will see the following message.
|
||||
|
||||
![][5]
|
||||
|
||||
Congratulations! The selected packages have been installed.
|
||||
|
||||
You can [**check recently installed applications**][6] on Ubuntu using the following command:
|
||||
|
||||
```
|
||||
$ grep " install " /var/log/dpkg.log
|
||||
```
|
||||
|
||||
You may need to reboot your system in-order to use some of the installed applications. Similarly, you can install any applications from the list without much hazzle.
|
||||
|
||||
For your information, there is also a similar script named **post_install.sh** written by different developer. It is exactly same as Alfred, but provides a few different set of applications. Please check the following link for more details.
|
||||
|
||||
These two scripts allows the lazy users, especially newbies, to be able to easily and fastly install most common apps, tools, updates, utilities they want to use in their Ubuntu Linux with few mouse clicks away, and stop depending on the help of official or non-official documentations.
|
||||
|
||||
And, that’s all for now. Hope this was useful. More good stuffs to come. Stay tuned!
|
||||
|
||||
Cheers!
|
||||
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.ostechnix.com/an-automated-way-to-install-essential-applications-on-ubuntu/
|
||||
|
||||
作者:[SK][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.ostechnix.com/author/sk/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7
|
||||
[2]: http://www.ostechnix.com/wp-content/uploads/2019/02/alfred-1.png
|
||||
[3]: http://www.ostechnix.com/wp-content/uploads/2019/02/alfred-2.png
|
||||
[4]: http://www.ostechnix.com/wp-content/uploads/2019/02/alfred-4.png
|
||||
[5]: http://www.ostechnix.com/wp-content/uploads/2019/02/alfred-5-1.png
|
||||
[6]: https://www.ostechnix.com/list-installed-packages-sorted-installation-date-linux/
|
||||
@ -0,0 +1,177 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (How To Identify That The Linux Server Is Integrated With Active Directory (AD)?)
|
||||
[#]: via: (https://www.2daygeek.com/how-to-identify-that-the-linux-server-is-integrated-with-active-directory-ad/)
|
||||
[#]: author: (Vinoth Kumar https://www.2daygeek.com/author/vinoth/)
|
||||
|
||||
How To Identify That The Linux Server Is Integrated With Active Directory (AD)?
|
||||
======
|
||||
|
||||
Single Sign On (SSO) Authentication is an implemented in most of the organizations due to multiple applications access.
|
||||
|
||||
It allows a user to logs in with a single ID and password to all the applications which is available in the organization.
|
||||
|
||||
It uses a centralized authentication system for all the applications.
|
||||
|
||||
A while ago we had written an article, **[how to integrate Linux system with AD][1]**.
|
||||
|
||||
Today we are going to show you, how to check that the Linux system is integrated with AD using multiple ways.
|
||||
|
||||
It can be done in four ways and we will explain one by one.
|
||||
|
||||
* **`ps Command:`** It report a snapshot of the current processes.
|
||||
* **`id Command:`** It prints user identity.
|
||||
* **`/etc/nsswitch.conf file:`** It is Name Service Switch configuration file.
|
||||
* **`/etc/pam.d/system-auth file:`** It is Common configuration file for PAMified services.
|
||||
|
||||
|
||||
|
||||
### How To Identify That The Linux Server Is Integrated With AD Using PS Command?
|
||||
|
||||
ps command displays information about a selection of the active processes.
|
||||
|
||||
To integrate the Linux server with AD, we need to use either `winbind` or `sssd` or `ldap` service.
|
||||
|
||||
So, use the ps command to filter these services.
|
||||
|
||||
If you found any of these services is running on system then we can decide that the system is currently integrate with AD using “winbind” or “sssd” or “ldap” service.
|
||||
|
||||
You might get the output similar to below if the system is integrated with AD using `SSSD` service.
|
||||
|
||||
```
|
||||
# ps -ef | grep -i "winbind\|sssd"
|
||||
|
||||
root 29912 1 0 2017 ? 00:19:09 /usr/sbin/sssd -f -D
|
||||
root 29913 29912 0 2017 ? 04:36:59 /usr/libexec/sssd/sssd_be --domain 2daygeek.com --uid 0 --gid 0 --debug-to-files
|
||||
root 29914 29912 0 2017 ? 00:29:28 /usr/libexec/sssd/sssd_nss --uid 0 --gid 0 --debug-to-files
|
||||
root 29915 29912 0 2017 ? 00:09:19 /usr/libexec/sssd/sssd_pam --uid 0 --gid 0 --debug-to-files
|
||||
root 31584 26666 0 13:41 pts/3 00:00:00 grep sssd
|
||||
```
|
||||
|
||||
You might get the output similer to below if the system is integrated with AD using `winbind` service.
|
||||
|
||||
```
|
||||
# ps -ef | grep -i "winbind\|sssd"
|
||||
|
||||
root 676 21055 0 2017 ? 00:00:22 winbindd
|
||||
root 958 21055 0 2017 ? 00:00:35 winbindd
|
||||
root 21055 1 0 2017 ? 00:59:07 winbindd
|
||||
root 21061 21055 0 2017 ? 11:48:49 winbindd
|
||||
root 21062 21055 0 2017 ? 00:01:28 winbindd
|
||||
root 21959 4570 0 13:50 pts/2 00:00:00 grep -i winbind\|sssd
|
||||
root 27780 21055 0 2017 ? 00:00:21 winbindd
|
||||
```
|
||||
|
||||
### How To Identify That The Linux Server Is Integrated With AD Using id Command?
|
||||
|
||||
It Prints information for given user name, or the current user. It displays the UID, GUID, User Name, Primary Group Name and Secondary Group Name, etc.,
|
||||
|
||||
If the Linux system is integrated with AD then you might get the output like below. The GID clearly shows that the user is coming from AD “domain users”.
|
||||
|
||||
```
|
||||
# id daygeek
|
||||
|
||||
uid=1918901106(daygeek) gid=1918900513(domain users) groups=1918900513(domain users)
|
||||
```
|
||||
|
||||
### How To Identify That The Linux Server Is Integrated With AD Using nsswitch.conf file?
|
||||
|
||||
The Name Service Switch (NSS) configuration file, `/etc/nsswitch.conf`, is used by the GNU C Library and certain other applications to determine the sources from which to obtain name-service information in a range of categories, and in what order. Each category of information is identified by a database name.
|
||||
|
||||
You might get the output similar to below if the system is integrated with AD using `SSSD` service.
|
||||
|
||||
```
|
||||
# cat /etc/nsswitch.conf | grep -i "sss\|winbind\|ldap"
|
||||
|
||||
passwd: files sss
|
||||
shadow: files sss
|
||||
group: files sss
|
||||
services: files sss
|
||||
netgroup: files sss
|
||||
automount: files sss
|
||||
```
|
||||
|
||||
You might get the output similar to below if the system is integrated with AD using `winbind` service.
|
||||
|
||||
```
|
||||
# cat /etc/nsswitch.conf | grep -i "sss\|winbind\|ldap"
|
||||
|
||||
passwd: files [SUCCESS=return] winbind
|
||||
shadow: files [SUCCESS=return] winbind
|
||||
group: files [SUCCESS=return] winbind
|
||||
```
|
||||
|
||||
You might get the output similer to below if the system is integrated with AD using `ldap` service.
|
||||
|
||||
```
|
||||
# cat /etc/nsswitch.conf | grep -i "sss\|winbind\|ldap"
|
||||
|
||||
passwd: files ldap
|
||||
shadow: files ldap
|
||||
group: files ldap
|
||||
```
|
||||
|
||||
### How To Identify That The Linux Server Is Integrated With AD Using system-auth file?
|
||||
|
||||
It is Common configuration file for PAMified services.
|
||||
|
||||
PAM stands for Pluggable Authentication Module that provides dynamic authentication support for applications and services in Linux.
|
||||
|
||||
system-auth configuration file is provide a common interface for all applications and service daemons calling into the PAM library.
|
||||
|
||||
The system-auth configuration file is included from nearly all individual service configuration files with the help of the include directive.
|
||||
|
||||
You might get the output similar to below if the system is integrated with AD using `SSSD` service.
|
||||
|
||||
```
|
||||
# cat /etc/pam.d/system-auth | grep -i "pam_sss.so\|pam_winbind.so\|pam_ldap.so"
|
||||
or
|
||||
# cat /etc/pam.d/system-auth-ac | grep -i "pam_sss.so\|pam_winbind.so\|pam_ldap.so"
|
||||
|
||||
auth sufficient pam_sss.so use_first_pass
|
||||
account [default=bad success=ok user_unknown=ignore] pam_sss.so
|
||||
password sufficient pam_sss.so use_authtok
|
||||
session optional pam_sss.so
|
||||
```
|
||||
|
||||
You might get the output similar to below if the system is integrated with AD using `winbind` service.
|
||||
|
||||
```
|
||||
# cat /etc/pam.d/system-auth | grep -i "pam_sss.so\|pam_winbind.so\|pam_ldap.so"
|
||||
or
|
||||
# cat /etc/pam.d/system-auth-ac | grep -i "pam_sss.so\|pam_winbind.so\|pam_ldap.so"
|
||||
|
||||
auth sufficient pam_winbind.so cached_login use_first_pass
|
||||
account [default=bad success=ok user_unknown=ignore] pam_winbind.so cached_login
|
||||
password sufficient pam_winbind.so cached_login use_authtok
|
||||
```
|
||||
|
||||
You might get the output similar to below if the system is integrated with AD using `ldap` service.
|
||||
|
||||
```
|
||||
# cat /etc/pam.d/system-auth | grep -i "pam_sss.so\|pam_winbind.so\|pam_ldap.so"
|
||||
or
|
||||
# cat /etc/pam.d/system-auth-ac | grep -i "pam_sss.so\|pam_winbind.so\|pam_ldap.so"
|
||||
|
||||
auth sufficient pam_ldap.so cached_login use_first_pass
|
||||
account [default=bad success=ok user_unknown=ignore] pam_ldap.so cached_login
|
||||
password sufficient pam_ldap.so cached_login use_authtok
|
||||
```
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.2daygeek.com/how-to-identify-that-the-linux-server-is-integrated-with-active-directory-ad/
|
||||
|
||||
作者:[Vinoth Kumar][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.2daygeek.com/author/vinoth/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.2daygeek.com/join-integrate-rhel-centos-linux-system-to-windows-active-directory-ad-domain/
|
||||
@ -0,0 +1,156 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (How to Install VirtualBox on Ubuntu [Beginner’s Tutorial])
|
||||
[#]: via: (https://itsfoss.com/install-virtualbox-ubuntu)
|
||||
[#]: author: (Abhishek Prakash https://itsfoss.com/author/abhishek/)
|
||||
|
||||
How to Install VirtualBox on Ubuntu [Beginner’s Tutorial]
|
||||
======
|
||||
|
||||
**This beginner’s tutorial explains various ways to install VirtualBox on Ubuntu and other Debian-based Linux distributions.**
|
||||
|
||||
Oracle’s free and open source offering [VirtualBox][1] is an excellent virtualization tool, specially for desktop operating systems. I prefer using it over [VMWare Workstation in Linux][2], another virtualization tool.
|
||||
|
||||
You can use virtualization software like VirtualBox for installing and using another operating system within a virtual machine.
|
||||
|
||||
For example, you can [install Linux on VirtualBox inside Windows][3]. Similarly, you can also [install Windows inside Linux using VirtualBox][4].
|
||||
|
||||
You can also use VirtualBox for installing another Linux distribution in your current Linux system. Actually, this is what I use it for. If I hear about a nice Linux distribution, instead of installing it on a real system, I test it on a virtual machine. It’s more convenient when you just want to try out a distribution before making a decision about installing it on your actual machine.
|
||||
|
||||
![Linux installed inside Linux using VirtualBox][5]Ubuntu 18.10 installed inside Ubuntu 18.04
|
||||
|
||||
In this beginner’s tutorial, I’ll show you various ways of installing Oracle VirtualBox on Ubuntu and other Debian-based distributions.
|
||||
|
||||
### Installing VirtualBox on Ubuntu and Debian based Linux distributions
|
||||
|
||||
The installation methods mentioned here should also work for other Debian and Ubuntu-based Linux distributions such as Linux Mint, elementary OS etc.
|
||||
|
||||
#### Method 1: Install VirtualBox from Ubuntu Repository
|
||||
|
||||
**Pros** : Easy installation
|
||||
|
||||
**Cons** : Installs older version
|
||||
|
||||
The easiest way to install VirtualBox on Ubuntu would be to search for it in the Software Center and install it from there.
|
||||
|
||||
![VirtualBox in Ubuntu Software Center][6]VirtualBox is available in Ubuntu Software Center
|
||||
|
||||
You can also install it from the command line using the command:
|
||||
|
||||
```
|
||||
sudo apt install virtualbox
|
||||
```
|
||||
|
||||
However, if you [check the package version before installing it][7], you’ll see that the VirtualBox provided by Ubuntu’s repository is quite old.
|
||||
|
||||
For example, the current VirtualBox version at the time of writing this tutorial is 6.0 but the one in Software Center is 5.2. This means you won’t get the newer features introduced in the [latest version of VirtualBox][8].
|
||||
|
||||
#### Method 2: Install VirtualBox using Deb file from Oracle’s website
|
||||
|
||||
**Pros** : Easily install the latest version
|
||||
|
||||
**Cons** : Can’t upgrade to newer version
|
||||
|
||||
If you want to use the latest version of VirtualBox on Ubuntu, the easiest way would be to [use the deb file][9].
|
||||
|
||||
Oracle provides read to use binary files for VirtualBox releases. If you look at its download page, you’ll see the option to download the deb installer files for Ubuntu and other distributions.
|
||||
|
||||
![VirtualBox Linux Download][10]
|
||||
|
||||
You just have to download this deb file and double click on it to install it. It’s as simple as that.
|
||||
|
||||
However, the problem with this method is that you won’t get automatically updated to the newer VirtualBox releases. The only way is to remove the existing version, download the newer version and install it again. That’s not very convenient, is it?
|
||||
|
||||
#### Method 3: Install VirualBox using Oracle’s repository
|
||||
|
||||
**Pros** : Automatically updates with system updates
|
||||
|
||||
**Cons** : Slightly complicated installation
|
||||
|
||||
Now this is the command line method and it may seem complicated to you but it has advantages over the previous two methods. You’ll get the latest version of VirtualBox and it will be automatically updated to the future releases. That’s what you would want, I presume.
|
||||
|
||||
To install VirtualBox using command line, you add the Oracle VirtualBox’s repository in your list of repositories. You add its GPG key so that your system trusts this repository. Now when you install VirtualBox, it will be installed from Oracle’s repository instead of Ubuntu’s repository. If there is a new version released, VirtualBox install will be updated along with the system updates. Let’s see how to do that.
|
||||
|
||||
First, add the key for the repository. You can download and add the key using this single command.
|
||||
|
||||
```
|
||||
wget -q https://www.virtualbox.org/download/oracle_vbox_2016.asc -O- | sudo apt-key add -
|
||||
```
|
||||
|
||||
```
|
||||
Important for Mint users
|
||||
|
||||
The next step will work for Ubuntu only. If you are using Linux Mint or some other distribution based on Ubuntu, replace $(lsb_release -cs) in the command with the Ubuntu version your current version is based on. For example, Linux Mint 19 series users should use bionic and Mint 18 series users should use xenial. Something like this
|
||||
|
||||
sudo add-apt-repository “deb [arch=amd64] <http://download.virtualbox.org/virtualbox/debian> **bionic** contrib“
|
||||
```
|
||||
|
||||
Now add the Oracle VirtualBox repository in the list of repositories using this command:
|
||||
|
||||
```
|
||||
sudo add-apt-repository "deb [arch=amd64] http://download.virtualbox.org/virtualbox/debian $(lsb_release -cs) contrib"
|
||||
```
|
||||
|
||||
If you have read my article on [checking Ubuntu version][11], you probably know that ‘lsb_release -cs’ will print the codename of your Ubuntu system.
|
||||
|
||||
**Note** : If you see [add-apt-repository command not found][12] error, you’ll have to install software-properties-common package.
|
||||
|
||||
Now that you have the correct repository added, refresh the list of available packages through these repositories and install VirtualBox.
|
||||
|
||||
```
|
||||
sudo apt update && sudo apt install virtualbox-6.0
|
||||
```
|
||||
|
||||
**Tip** : A good idea would be to type sudo apt install **virtualbox–** and hit tab to see the various VirtualBox versions available for installation and then select one of them by typing it completely.
|
||||
|
||||
![Install VirtualBox via terminal][13]
|
||||
|
||||
### How to remove VirtualBox from Ubuntu
|
||||
|
||||
Now that you have learned to install VirtualBox, I would also mention the steps to remove it.
|
||||
|
||||
If you installed it from the Software Center, the easiest way to remove the application is from the Software Center itself. You just have to find it in the [list of installed applications][14] and click the Remove button.
|
||||
|
||||
Another ways is to use the command line.
|
||||
|
||||
```
|
||||
sudo apt remove virtualbox virtualbox-*
|
||||
```
|
||||
|
||||
Note that this will not remove the virtual machines and the files associated with the operating systems you installed using VirtualBox. That’s not entirely a bad thing because you may want to keep them safe to use it later or in some other system.
|
||||
|
||||
**In the end…**
|
||||
|
||||
I hope you were able to pick one of the methods to install VirtualBox. I’ll also write about using it effectively in another article. For the moment, if you have and tips or suggestions or any questions, feel free to leave a comment below.
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://itsfoss.com/install-virtualbox-ubuntu
|
||||
|
||||
作者:[Abhishek Prakash][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://itsfoss.com/author/abhishek/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.virtualbox.org
|
||||
[2]: https://itsfoss.com/install-vmware-player-ubuntu-1310/
|
||||
[3]: https://itsfoss.com/install-linux-in-virtualbox/
|
||||
[4]: https://itsfoss.com/install-windows-10-virtualbox-linux/
|
||||
[5]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2019/02/linux-inside-linux-virtualbox.png?resize=800%2C450&ssl=1
|
||||
[6]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2019/02/virtualbox-ubuntu-software-center.jpg?ssl=1
|
||||
[7]: https://itsfoss.com/know-program-version-before-install-ubuntu/
|
||||
[8]: https://itsfoss.com/oracle-virtualbox-release/
|
||||
[9]: https://itsfoss.com/install-deb-files-ubuntu/
|
||||
[10]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2019/02/virtualbox-download.jpg?resize=800%2C433&ssl=1
|
||||
[11]: https://itsfoss.com/how-to-know-ubuntu-unity-version/
|
||||
[12]: https://itsfoss.com/add-apt-repository-command-not-found/
|
||||
[13]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2019/02/install-virtualbox-ubuntu-terminal.png?resize=800%2C165&ssl=1
|
||||
[14]: https://itsfoss.com/list-installed-packages-ubuntu/
|
||||
187
sources/tech/20190225 Netboot a Fedora Live CD.md
Normal file
187
sources/tech/20190225 Netboot a Fedora Live CD.md
Normal file
@ -0,0 +1,187 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Netboot a Fedora Live CD)
|
||||
[#]: via: (https://fedoramagazine.org/netboot-a-fedora-live-cd/)
|
||||
[#]: author: (Gregory Bartholomew https://fedoramagazine.org/author/glb/)
|
||||
|
||||
Netboot a Fedora Live CD
|
||||
======
|
||||
|
||||

|
||||
|
||||
[Live CDs][1] are useful for many tasks such as:
|
||||
|
||||
* installing the operating system to a hard drive
|
||||
* repairing a boot loader or performing other rescue-mode operations
|
||||
* providing a consistent and minimal environment for web browsing
|
||||
* …and [much more][2].
|
||||
|
||||
|
||||
|
||||
As an alternative to using DVDs and USB drives to store your Live CD images, you can upload them to an [iSCSI][3] server where they will be less likely to get lost or damaged. This guide shows you how to load your Live CD images onto an iSCSI server and access them with the [iPXE][4] boot loader.
|
||||
|
||||
### Download a Live CD Image
|
||||
|
||||
```
|
||||
$ MY_RLSE=27
|
||||
$ MY_LIVE=$(wget -q -O - https://dl.fedoraproject.org/pub/archive/fedora/linux/releases/$MY_RLSE/Workstation/x86_64/iso | perl -ne '/(Fedora[^ ]*?-Live-[^ ]*?\.iso)(?{print $^N})/;')
|
||||
$ MY_NAME=fc$MY_RLSE
|
||||
$ wget -O $MY_NAME.iso https://dl.fedoraproject.org/pub/archive/fedora/linux/releases/$MY_RLSE/Workstation/x86_64/iso/$MY_LIVE
|
||||
```
|
||||
|
||||
The above commands download the Fedora-Workstation-Live-x86_64-27-1.6.iso Fedora Live image and save it as fc27.iso. Change the value of MY_RLSE to download other archived versions. Or you can browse to <https://getfedora.org/> to download the latest Fedora live image. Versions prior to 21 used different naming conventions, and must be [downloaded manually here][5]. If you download a Live CD image manually, set the MY_NAME variable to the basename of the file without the extension. That way the commands in the following sections will reference the correct file.
|
||||
|
||||
### Convert the Live CD Image
|
||||
|
||||
Use the livecd-iso-to-disk tool to convert the ISO file to a disk image and add the netroot parameter to the embedded kernel command line:
|
||||
|
||||
```
|
||||
$ sudo dnf install -y livecd-tools
|
||||
$ MY_SIZE=$(du -ms $MY_NAME.iso | cut -f 1)
|
||||
$ dd if=/dev/zero of=$MY_NAME.img bs=1MiB count=0 seek=$(($MY_SIZE+512))
|
||||
$ MY_SRVR=server-01.example.edu
|
||||
$ MY_RVRS=$(echo $MY_SRVR | tr '.' "\n" | tac | tr "\n" '.' | cut -b -${#MY_SRVR})
|
||||
$ MY_LOOP=$(sudo losetup --show --nooverlap --find $MY_NAME.img)
|
||||
$ sudo livecd-iso-to-disk --format --extra-kernel-args netroot=iscsi:$MY_SRVR:::1:iqn.$MY_RVRS:$MY_NAME $MY_NAME.iso $MY_LOOP
|
||||
$ sudo losetup -d $MY_LOOP
|
||||
```
|
||||
|
||||
### Upload the Live Image to your Server
|
||||
|
||||
Create a directory on your iSCSI server to store your live images and then upload your modified image to it.
|
||||
|
||||
**For releases 21 and greater:**
|
||||
|
||||
```
|
||||
$ MY_FLDR=/images
|
||||
$ scp $MY_NAME.img $MY_SRVR:$MY_FLDR/
|
||||
```
|
||||
|
||||
**For releases prior to 21:**
|
||||
|
||||
```
|
||||
$ MY_FLDR=/images
|
||||
$ MY_LOOP=$(sudo losetup --show --nooverlap --find --partscan $MY_NAME.img)
|
||||
$ sudo tune2fs -O ^has_journal ${MY_LOOP}p1
|
||||
$ sudo e2fsck ${MY_LOOP}p1
|
||||
$ sudo dd status=none if=${MY_LOOP}p1 | ssh $MY_SRVR "dd of=$MY_FLDR/$MY_NAME.img"
|
||||
$ sudo losetup -d $MY_LOOP
|
||||
```
|
||||
|
||||
### Define the iSCSI Target
|
||||
|
||||
Run the following commands on your iSCSI server:
|
||||
|
||||
```
|
||||
$ sudo -i
|
||||
# MY_NAME=fc27
|
||||
# MY_FLDR=/images
|
||||
# MY_SRVR=`hostname`
|
||||
# MY_RVRS=$(echo $MY_SRVR | tr '.' "\n" | tac | tr "\n" '.' | cut -b -${#MY_SRVR})
|
||||
# cat << END > /etc/tgt/conf.d/$MY_NAME.conf
|
||||
<target iqn.$MY_RVRS:$MY_NAME>
|
||||
backing-store $MY_FLDR/$MY_NAME.img
|
||||
readonly 1
|
||||
allow-in-use yes
|
||||
</target>
|
||||
END
|
||||
# tgt-admin --update ALL
|
||||
```
|
||||
|
||||
### Create a Bootable USB Drive
|
||||
|
||||
The [iPXE][4] boot loader has a [sanboot][6] command you can use to connect to and start the live images hosted on your iSCSI server. It can be compiled in many different [formats][7]. The format that works best depends on the type of hardware you’re running. As an example, the following instructions show how to [chain load][8] iPXE from [syslinux][9] on a USB drive.
|
||||
|
||||
First, download iPXE and build it in its lkrn format. This should be done as a normal user on a workstation:
|
||||
|
||||
```
|
||||
$ sudo dnf install -y git
|
||||
$ git clone http://git.ipxe.org/ipxe.git $HOME/ipxe
|
||||
$ sudo dnf groupinstall -y "C Development Tools and Libraries"
|
||||
$ cd $HOME/ipxe/src
|
||||
$ make clean
|
||||
$ make bin/ipxe.lkrn
|
||||
$ cp bin/ipxe.lkrn /tmp
|
||||
```
|
||||
|
||||
Next, prepare a USB drive with a MSDOS partition table and a FAT32 file system. The below commands assume that you have already connected the USB drive to be formatted. **Be careful that you do not format the wrong drive!**
|
||||
|
||||
```
|
||||
$ sudo -i
|
||||
# dnf install -y parted util-linux dosfstools
|
||||
# echo; find /dev/disk/by-id ! -regex '.*-part.*' -name 'usb-*' -exec readlink -f {} \; | xargs -i bash -c "parted -s {} unit MiB print | perl -0 -ne '/^Model: ([^(]*).*\n.*?([0-9]*MiB)/i && print \"Found: {} = \$2 \$1\n\"'"; echo; read -e -i "$(find /dev/disk/by-id ! -regex '.*-part.*' -name 'usb-*' -exec readlink -f {} \; -quit)" -p "Drive to format: " MY_USB
|
||||
# umount $MY_USB?
|
||||
# wipefs -a $MY_USB
|
||||
# parted -s $MY_USB mklabel msdos mkpart primary fat32 1MiB 100% set 1 boot on
|
||||
# mkfs -t vfat -F 32 ${MY_USB}1
|
||||
```
|
||||
|
||||
Finally, install syslinux on the USB drive and configure it to chain load iPXE:
|
||||
|
||||
```
|
||||
# dnf install -y syslinux-nonlinux
|
||||
# syslinux -i ${MY_USB}1
|
||||
# dd if=/usr/share/syslinux/mbr.bin of=${MY_USB}
|
||||
# MY_MNT=$(mktemp -d)
|
||||
# mount ${MY_USB}1 $MY_MNT
|
||||
# MY_NAME=fc27
|
||||
# MY_SRVR=server-01.example.edu
|
||||
# MY_RVRS=$(echo $MY_SRVR | tr '.' "\n" | tac | tr "\n" '.' | cut -b -${#MY_SRVR})
|
||||
# cat << END > $MY_MNT/syslinux.cfg
|
||||
ui menu.c32
|
||||
default $MY_NAME
|
||||
timeout 100
|
||||
menu title SYSLINUX
|
||||
label $MY_NAME
|
||||
menu label ${MY_NAME^^}
|
||||
kernel ipxe.lkrn
|
||||
append dhcp && sanboot iscsi:$MY_SRVR:::1:iqn.$MY_RVRS:$MY_NAME
|
||||
END
|
||||
# cp /usr/share/syslinux/menu.c32 $MY_MNT
|
||||
# cp /usr/share/syslinux/libutil.c32 $MY_MNT
|
||||
# cp /tmp/ipxe.lkrn $MY_MNT
|
||||
# umount ${MY_USB}1
|
||||
```
|
||||
|
||||
You should be able to use this same USB drive to netboot additional iSCSI targets simply by editing the syslinux.cfg file and adding additional menu entries.
|
||||
|
||||
This is just one method of loading iPXE. You could install syslinux directly on your workstation. Another option is to compile iPXE as an EFI executable and place it directly in your [ESP][10]. Yet another is to compile iPXE as a PXE loader and place it on your TFTP server to be referenced by DHCP. The best option depends on your environment.
|
||||
|
||||
### Final Notes
|
||||
|
||||
* You may want to add the –filename \EFI\BOOT\grubx64.efi parameter to the sanboot command if you compile iPXE in its EFI format.
|
||||
* It is possible to create custom live images. Refer to [Creating and using live CD][11] for more information.
|
||||
* It is possible to add the –overlay-size-mb and –home-size-mb parameters to the livecd-iso-to-disk command to create live images with persistent storage. However, if you have multiple concurrent users, you’ll need to set up your iSCSI server to manage separate per-user writeable overlays. This is similar to what was shown in the “[How to Build a Netboot Server, Part 4][12]” article.
|
||||
* The live images support a persistenthome option on their kernel command line (e.g. persistenthome=LABEL=HOME). Used together with CHAP-authenticated iSCSI targets, the persistenthome option provides an interesting alternative to NFS for centralized home directories.
|
||||
|
||||
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://fedoramagazine.org/netboot-a-fedora-live-cd/
|
||||
|
||||
作者:[Gregory Bartholomew][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://fedoramagazine.org/author/glb/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://en.wikipedia.org/wiki/Live_CD
|
||||
[2]: https://en.wikipedia.org/wiki/Live_CD#Uses
|
||||
[3]: https://en.wikipedia.org/wiki/ISCSI
|
||||
[4]: https://ipxe.org/
|
||||
[5]: https://dl.fedoraproject.org/pub/archive/fedora/linux/releases/https://dl.fedoraproject.org/pub/archive/fedora/linux/releases/
|
||||
[6]: http://ipxe.org/cmd/sanboot/
|
||||
[7]: https://ipxe.org/appnote/buildtargets#boot_type
|
||||
[8]: https://en.wikipedia.org/wiki/Chain_loading
|
||||
[9]: https://www.syslinux.org/wiki/index.php?title=SYSLINUX
|
||||
[10]: https://en.wikipedia.org/wiki/EFI_system_partition
|
||||
[11]: https://docs.fedoraproject.org/en-US/quick-docs/creating-and-using-a-live-installation-image/#proc_creating-and-using-live-cd
|
||||
[12]: https://fedoramagazine.org/how-to-build-a-netboot-server-part-4/
|
||||
239
sources/tech/20190226 All about -Curly Braces- in Bash.md
Normal file
239
sources/tech/20190226 All about -Curly Braces- in Bash.md
Normal file
@ -0,0 +1,239 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (All about {Curly Braces} in Bash)
|
||||
[#]: via: (https://www.linux.com/blog/learn/2019/2/all-about-curly-braces-bash)
|
||||
[#]: author: (Paul Brown https://www.linux.com/users/bro66)
|
||||
|
||||
All about {Curly Braces} in Bash
|
||||
======
|
||||
|
||||

|
||||
|
||||
At this stage of our Bash basics series, it would be hard not to see some crossover between topics. For example, you have already seen a lot of brackets in the examples we have shown over the past several weeks, but the focus has been elsewhere.
|
||||
|
||||
For the next phase of the series, we’ll take a closer look at brackets, curly, curvy, or straight, how to use them, and what they do depending on where you use them. We will also tackle other ways of enclosing things, like when to use quotes, double-quotes, and backquotes.
|
||||
|
||||
This week, we're looking at curly brackets or _braces_ : `{}`.
|
||||
|
||||
### Array Builder
|
||||
|
||||
You have already encountered curly brackets before in [The Meaning of Dot][1]. There, the focus was on the use of the dot/period (`.`), but using braces to build a sequence was equally important.
|
||||
|
||||
As we saw then:
|
||||
|
||||
```
|
||||
echo {0..10}
|
||||
```
|
||||
|
||||
prints out the numbers from 0 to 10. Using:
|
||||
|
||||
```
|
||||
echo {10..0}
|
||||
```
|
||||
|
||||
prints out the same numbers, but in reverse order. And,
|
||||
|
||||
```
|
||||
echo {10..0..2}
|
||||
```
|
||||
|
||||
prints every second number, starting with 10 and making its way backwards to 0.
|
||||
|
||||
Then,
|
||||
|
||||
```
|
||||
echo {z..a..2}
|
||||
```
|
||||
|
||||
prints every second letter, starting with _z_ and working its way backwards until _a_.
|
||||
|
||||
And so on and so forth.
|
||||
|
||||
Another thing you can do is combine two or more sequences:
|
||||
|
||||
```
|
||||
echo {a..z}{a..z}
|
||||
```
|
||||
|
||||
This prints out all the two letter combinations of the alphabet, from _aa_ to _zz_.
|
||||
|
||||
Is this useful? Well, actually it is. You see, arrays in Bash are defined by putting elements between parenthesis `()` and separating each element using a space, like this:
|
||||
|
||||
```
|
||||
month=("Jan" "Feb" "Mar" "Apr" "May" "Jun" "Jul" "Aug" "Sep" "Oct" "Nov" "Dec")
|
||||
```
|
||||
|
||||
To access an element within the array, you use its index within brackets `[]`:
|
||||
|
||||
```
|
||||
$ echo ${month[3]} # Array indexes start at [0], so [3] points to the fourth item
|
||||
|
||||
Apr
|
||||
```
|
||||
|
||||
You can accept all those brackets, parentheses, and braces on faith for a moment. We'll talk about them presently.
|
||||
|
||||
Notice that, all things being equal, you can create an array with something like this:
|
||||
|
||||
```
|
||||
letter_combos=({a..z}{a..z})
|
||||
```
|
||||
|
||||
and `letter_combos` points to an array that contains all the 2-letter combinations of the entire alphabet.
|
||||
|
||||
You can also do this:
|
||||
|
||||
```
|
||||
dec2bin=({0..1}{0..1}{0..1}{0..1}{0..1}{0..1}{0..1}{0..1})
|
||||
```
|
||||
|
||||
This last one is particularly interesting because `dec2bin` now contains all the binary numbers for an 8-bit register, in ascending order, starting with 00000000, 00000001, 00000010, etc., until reaching 11111111. You can use this to build yourself an 8-bit decimal-to-binary converter. Say you want to know what 25 is in binary. You can do this:
|
||||
|
||||
```
|
||||
$ echo ${dec2bin[25]}
|
||||
|
||||
00011001
|
||||
```
|
||||
|
||||
Yes, there are better ways of converting decimal to binary as we saw in [the article where we discussed & as a logical operator][2], but it is still interesting, right?
|
||||
|
||||
### Parameter expansion
|
||||
|
||||
Getting back to
|
||||
|
||||
```
|
||||
echo ${month[3]}
|
||||
```
|
||||
|
||||
Here the braces `{}` are not being used as apart of a sequence builder, but as a way of generating _parameter expansion_. Parameter expansion involves what it says on the box: it takes the variable or expression within the braces and expands it to whatever it represents.
|
||||
|
||||
In this case, `month` is the array we defined earlier, that is:
|
||||
|
||||
```
|
||||
month=("Jan" "Feb" "Mar" "Apr" "May" "Jun" "Jul" "Aug" "Sep" "Oct" "Nov" "Dec")
|
||||
```
|
||||
|
||||
And, item 3 within the array points to `"Apr"` (remember: the first index in an array in Bash is `[0]`). That means that `echo ${month[3]}`, after the expansion, translates to `echo "Apr"`.
|
||||
|
||||
Interpreting a variable as its value is one way of expanding it, but there are a few more you can leverage. You can use parameter expansion to manipulate what you read from variable, say, by cutting a chunk off the end.
|
||||
|
||||
Suppose you have a variable like:
|
||||
|
||||
```
|
||||
a="Too longgg"
|
||||
```
|
||||
|
||||
The command:
|
||||
|
||||
```
|
||||
echo ${a%gg}
|
||||
```
|
||||
|
||||
chops off the last two gs and prints " _Too long_ ".
|
||||
|
||||
Breaking this down,
|
||||
|
||||
* `${...}` tells the shell to expand whatever is inside it
|
||||
* `a` is the variable you are working with
|
||||
* `%` tells the shell you want to chop something off the end of the expanded variable ("Too longgg")
|
||||
* and `gg` is what you want to chop off.
|
||||
|
||||
|
||||
|
||||
This can be useful for converting files from one format to another. Allow me to explain with a slight digression:
|
||||
|
||||
[ImageMagick][3] is a set of command line tools that lets you manipulate and modify images. One of its most useful tools ImageMagick comes with is `convert`. In its simplest form `convert` allows you to, given an image in a certain format, make a copy of it in another format.
|
||||
|
||||
The following command takes a JPEG image called _image.jpg_ and creates a PNG copy called _image.png_ :
|
||||
|
||||
```
|
||||
convert image.jpg image.png
|
||||
```
|
||||
|
||||
ImageMagick is often pre-installed on most Linux distros. If you can't find it, look for it in your distro's software manager.
|
||||
|
||||
Okay, end of digression. On to the example:
|
||||
|
||||
With variable expansion, you can do the same as shown above like this:
|
||||
|
||||
```
|
||||
i=image.jpg
|
||||
|
||||
convert $i ${i%jpg}png
|
||||
```
|
||||
|
||||
What you are doing here is chopping off the extension `jpg` from `i` and then adding `png`, making the command `convert image.jpg image.png`.
|
||||
|
||||
You may be wondering how this is more useful than just writing in the name of the file. Well, when you have a directory containing hundreds of JPEG images, you need to convert to PNG, run the following in it:
|
||||
|
||||
```
|
||||
for i in *.jpg; do convert $i ${i%jpg}png; done
|
||||
```
|
||||
|
||||
... and, hey presto! All the pictures get converted automatically.
|
||||
|
||||
If you need to chop off a chunk from the beginning of a variable, instead of `%`, use `#`:
|
||||
|
||||
```
|
||||
$ a="Hello World!"
|
||||
|
||||
$ echo Goodbye${a#Hello}
|
||||
|
||||
Goodbye World!
|
||||
```
|
||||
|
||||
There's quite a bit more to parameter expansion, but a lot of it makes sense only when you are writing scripts. We'll explore more on that topic later in this series.
|
||||
|
||||
### Output Grouping
|
||||
|
||||
Meanwhile, let's finish up with something simple: you can also use `{ ... }` to group the output from several commands into one big blob. The command:
|
||||
|
||||
```
|
||||
echo "I found all these PNGs:"; find . -iname "*.png"; echo "Within this bunch of files:"; ls > PNGs.txt
|
||||
```
|
||||
|
||||
will execute all the commands but will only copy into the _PNGs.txt_ file the output from the last `ls` command in the list. However, doing
|
||||
|
||||
```
|
||||
{ echo "I found all these PNGs:"; find . -iname "*.png"; echo "Within this bunch of files:"; ls; } > PNGs.txt
|
||||
```
|
||||
|
||||
creates the file _PNGs.txt_ with everything, starting with the line " _I found all these PNGs:_ ", then the list of PNG files returned by `find`, then the line "Within this bunch of files:" and finishing up with the complete list of files and directories within the current directory.
|
||||
|
||||
Notice that there is space between the braces and the commands enclosed within them. That’s because `{` and `}` are _reserved words_ here, commands built into the shell. They would roughly translate to " _group the outputs of all these commands together_ " in plain English.
|
||||
|
||||
Also notice that the list of commands has to end with a semicolon (`;`) or the whole thing will bork.
|
||||
|
||||
### Next Time
|
||||
|
||||
In our next installment, we'll be looking at more things that enclose other things, but of different shapes. Until then, have fun!
|
||||
|
||||
Read more:
|
||||
|
||||
[And, Ampersand, and & in Linux][4]
|
||||
|
||||
[Ampersands and File Descriptors in Bash][5]
|
||||
|
||||
[Logical & in Bash][2]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.linux.com/blog/learn/2019/2/all-about-curly-braces-bash
|
||||
|
||||
作者:[Paul Brown][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.linux.com/users/bro66
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.linux.com/blog/learn/2019/1/linux-tools-meaning-dot
|
||||
[2]: https://www.linux.com/blog/learn/2019/2/logical-ampersand-bash
|
||||
[3]: http://www.imagemagick.org/
|
||||
[4]: https://www.linux.com/blog/learn/2019/2/and-ampersand-and-linux
|
||||
[5]: https://www.linux.com/blog/learn/2019/2/ampersands-and-file-descriptors-bash
|
||||
@ -0,0 +1,114 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (How To SSH Into A Particular Directory On Linux)
|
||||
[#]: via: (https://www.ostechnix.com/how-to-ssh-into-a-particular-directory-on-linux/)
|
||||
[#]: author: (SK https://www.ostechnix.com/author/sk/)
|
||||
|
||||
How To SSH Into A Particular Directory On Linux
|
||||
======
|
||||
|
||||

|
||||
|
||||
Have you ever been in a situation where you want to SSH to a remote server and immediately cd into a directory and continue work interactively? You’re on the right track! This brief tutorial describes how to directly SSH into a particular directory of a remote Linux system. Not just SSH into a specific directory, you can run any command immediately right after connecting to an SSH server as described in this guide. It is not that difficult as you might think. Read on.
|
||||
|
||||
### SSH Into A Particular Directory Of A Remote System
|
||||
|
||||
Before I knew this method, I would usually first SSH to the remote remote system using command:
|
||||
|
||||
```
|
||||
$ ssh user@remote-system
|
||||
```
|
||||
|
||||
And then cd into a directory like below:
|
||||
|
||||
```
|
||||
$ cd <some-directory>
|
||||
```
|
||||
|
||||
However, you need not to use two separate commands. You can combine these commands and simplify the task with one command.
|
||||
|
||||
Have a look at the following example.
|
||||
|
||||
```
|
||||
$ ssh -t sk@192.168.225.22 'cd /home/sk/ostechnix ; bash'
|
||||
```
|
||||
|
||||
The above command will SSH into a remote system (192.168.225.22) and immediately cd into a directory named **‘/home/sk/ostechnix/’** directory and leave yourself at the prompt.
|
||||
|
||||
Here, the **-t** flag is used to force pseudo-terminal allocation, which is necessary or an interactive shell.
|
||||
|
||||
Here is the sample output of the above command:
|
||||
|
||||

|
||||
|
||||
You can also use this command as well.
|
||||
|
||||
```
|
||||
$ ssh -t sk@192.168.225.22 'cd /home/sk/ostechnix ; exec bash'
|
||||
```
|
||||
|
||||
Or,
|
||||
|
||||
```
|
||||
$ ssh -t sk@192.168.225.22 'cd /home/sk/ostechnix && exec bash -l'
|
||||
```
|
||||
|
||||
Here, the **-l** flag sets the bash as login shell.
|
||||
|
||||
In the above example, I have used **bash** in the last argument. It is the default shell in my remote system. If you don’t know the shell type on the remote system, use the following command:
|
||||
|
||||
```
|
||||
$ ssh -t sk@192.168.225.22 'cd /home/sk/ostechnix && exec $SHELL'
|
||||
```
|
||||
|
||||
Like I already said, this is not just for cd into directory after connecting to an remote system. You can use this trick to run other commands as well. For example, the following command will land you inside ‘/home/sk/ostechnix/’ directory and then execute ‘uname -a’ command.
|
||||
|
||||
```
|
||||
$ ssh -t sk@192.168.225.22 'cd /home/sk/ostechnix && uname -a && exec $SHELL'
|
||||
```
|
||||
|
||||
Alternatively, you can add the command(s) you wanted to run after connecting to an SSH server on the remote system’s **.bash_profile** file.
|
||||
|
||||
Edit **.bash_profile** file:
|
||||
|
||||
```
|
||||
$ nano ~/.bash_profile
|
||||
```
|
||||
|
||||
Add the command(s) one by one. In my case, I am adding the following line:
|
||||
|
||||
```
|
||||
cd /home/sk/ostechnix >& /dev/null
|
||||
```
|
||||
|
||||
Save and close the file. Finally, run the following command to update the changes.
|
||||
|
||||
```
|
||||
$ source ~/.bash_profile
|
||||
```
|
||||
|
||||
Please note that you should add this line on the remote system’s **.bash_profile** or **.bashrc** file, not in your local system’s. From now on, whenever you login (whether by SSH or direct), the cd command will execute and you will be automatically landed inside “/home/sk/ostechnix/” directory.
|
||||
|
||||
|
||||
And, that’s all for now. Hope this was useful. More good stuffs to come. Stay tuned!
|
||||
|
||||
Cheers!
|
||||
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.ostechnix.com/how-to-ssh-into-a-particular-directory-on-linux/
|
||||
|
||||
作者:[SK][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.ostechnix.com/author/sk/
|
||||
[b]: https://github.com/lujun9972
|
||||
@ -0,0 +1,86 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Linux security: Cmd provides visibility, control over user activity)
|
||||
[#]: via: (https://www.networkworld.com/article/3342454/linux-security-cmd-provides-visibility-control-over-user-activity.html)
|
||||
[#]: author: (Sandra Henry-Stocker https://www.networkworld.com/author/Sandra-Henry_Stocker/)
|
||||
|
||||
Linux security: Cmd provides visibility, control over user activity
|
||||
======
|
||||
|
||||

|
||||
|
||||
There's a new Linux security tool you should be aware of — Cmd (pronounced "see em dee") dramatically modifies the kind of control that can be exercised over Linux users. It reaches way beyond the traditional configuration of user privileges and takes an active role in monitoring and controlling the commands that users are able to run on Linux systems.
|
||||
|
||||
Provided by a company of the same name, Cmd focuses on cloud usage. Given the increasing number of applications being migrated into cloud environments that rely on Linux, gaps in the available tools make it difficult to adequately enforce required security. However, Cmd can also be used to manage and protect on-premises systems.
|
||||
|
||||
### How Cmd differs from traditional Linux security controls
|
||||
|
||||
The leaders at Cmd — Milun Tesovic and Jake King — say organizations cannot confidently predict or control user behavior until they understand how users work routinely and what is considered “normal.” They seek to provide a tool that will granularly control, monitor, and authenticate user activity.
|
||||
|
||||
Cmd monitors user activity by forming user activity profiles (characterizing the activities these users generally perform), noticing abnormalities in their online behavior (login times, commands used, user locations, etc.), and preventing and reporting certain activities (e.g., downloading or modifying files and running privileged commands) that suggest some kind of system compromise might be underway. The product's behaviors are configurable and changes can be made rapidly.
|
||||
|
||||
The kind of tools most of us are using today to detect threats, identify vulnerabilities, and control user privileges have taken us a long way, but we are still fighting the battle to keep our systems and data safe. Cmd brings us a lot closer to identifying the intentions of hostile users whether those users are people who have managed to break into accounts or represent insider threats.
|
||||
|
||||
![1 sources live sessions][1]
|
||||
|
||||
View live Linux sessions
|
||||
|
||||
### How does Cmd work?
|
||||
|
||||
In monitoring and managing user activity, Cmd:
|
||||
|
||||
* Collects information that profiles user activity
|
||||
* Uses the baseline to determine what is considered normal
|
||||
* Detects and proactively prevents threats using specific indicators
|
||||
* Sends alerts to responsible people
|
||||
|
||||
|
||||
|
||||
![2 triggers][3]
|
||||
|
||||
Building custom policies in Cmd
|
||||
|
||||
Cmd goes beyond defining what sysadmins can control through traditional methods, such as configuring sudo privileges, providing much more granular and situation-specific controls.
|
||||
|
||||
Administrators can select escalation policies that can be managed separately from the user privilege controls managed by Linux sysadmins.
|
||||
|
||||
The Cmd agent provides real-time visibility (not after-the-fact log analysis) and can block actions, require additional authentication, or negotiate authorization as needed.
|
||||
|
||||
Also, Cmd supports custom rules based on geolocation if user locations are available. And new policies can be pushed to agents deployed on hosts within minutes.
|
||||
|
||||
![3 command blocked][4]
|
||||
|
||||
Building a trigger query in Cmd
|
||||
|
||||
### Funding news for Cmd
|
||||
|
||||
[Cmd][2] recently got a financial boost, having [completed of a $15 million round of funding][5] led by [GV][6] (formerly Google Ventures) with participation from Expa, Amplify Partners, and additional strategic investors. This brings the company's raised funding to $21.6 million and will help it continue to add new defensive capabilities to the product and grow its engineering teams.
|
||||
|
||||
In addition, the company appointed Karim Faris, general partner at GV, to its board of directors.
|
||||
|
||||
Join the Network World communities on [Facebook][7] and [LinkedIn][8] to comment on topics that are top of mind.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.networkworld.com/article/3342454/linux-security-cmd-provides-visibility-control-over-user-activity.html
|
||||
|
||||
作者:[Sandra Henry-Stocker][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.networkworld.com/author/Sandra-Henry_Stocker/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://images.idgesg.net/images/article/2019/02/1-sources-live-sessions-100789431-large.jpg
|
||||
[2]: https://cmd.com
|
||||
[3]: https://images.idgesg.net/images/article/2019/02/2-triggers-100789432-large.jpg
|
||||
[4]: https://images.idgesg.net/images/article/2019/02/3-command-blocked-100789433-large.jpg
|
||||
[5]: https://www.linkedin.com/pulse/changing-cybersecurity-announcing-cmds-15-million-funding-jake-king/
|
||||
[6]: https://www.gv.com/
|
||||
[7]: https://www.facebook.com/NetworkWorld/
|
||||
[8]: https://www.linkedin.com/company/network-world
|
||||
@ -0,0 +1,165 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (How To Check Password Complexity/Strength And Score In Linux?)
|
||||
[#]: via: (https://www.2daygeek.com/how-to-check-password-complexity-strength-and-score-in-linux/)
|
||||
[#]: author: (Magesh Maruthamuthu https://www.2daygeek.com/author/magesh/)
|
||||
|
||||
How To Check Password Complexity/Strength And Score In Linux?
|
||||
======
|
||||
|
||||
We all know the password importance. It’s a best practices to use hard and guess password.
|
||||
|
||||
Also, i advise you to use the different password for each services such as email, ftp, ssh, etc.,
|
||||
|
||||
In top of that i suggest you guys to change the password frequently to avoid an unnecessary hacking attempt.
|
||||
|
||||
By default RHEL and it’s clone uses `cracklib` module to check password strength.
|
||||
|
||||
We are going to teach you, how to check the password strength using cracklib module.
|
||||
|
||||
If you would like to check the password score which you have created then use the `pwscore` package.
|
||||
|
||||
If you would like to create a good password, basically it should have minimum 12-15 characters length.
|
||||
|
||||
It should be created in the following combinations like, Alphabets (Lower case & Upper case), Numbers and Special Characters.
|
||||
|
||||
There are many utilities are available in Linux to check a password complexity and we are going to discuss about `cracklib` module today.
|
||||
|
||||
### How To Install cracklib module In Linux?
|
||||
|
||||
The cracklib module is available in most of the distribution repository so, use the distribution official package manager to install it.
|
||||
|
||||
For **`Fedora`** system, use **[DNF Command][1]** to install cracklib.
|
||||
|
||||
```
|
||||
$ sudo dnf install cracklib
|
||||
```
|
||||
|
||||
For **`Debian/Ubuntu`** systems, use **[APT-GET Command][2]** or **[APT Command][3]** to install libcrack2.
|
||||
|
||||
```
|
||||
$ sudo apt install libcrack2
|
||||
```
|
||||
|
||||
For **`Arch Linux`** based systems, use **[Pacman Command][4]** to install cracklib.
|
||||
|
||||
```
|
||||
$ sudo pacman -S cracklib
|
||||
```
|
||||
|
||||
For **`RHEL/CentOS`** systems, use **[YUM Command][5]** to install cracklib.
|
||||
|
||||
```
|
||||
$ sudo yum install cracklib
|
||||
```
|
||||
|
||||
For **`openSUSE Leap`** system, use **[Zypper Command][6]** to install cracklib.
|
||||
|
||||
```
|
||||
$ sudo zypper install cracklib
|
||||
```
|
||||
|
||||
### How To Use The cracklib module In Linux To Check Password Complexity?
|
||||
|
||||
I have added few example in this article to make you understand better about this module.
|
||||
|
||||
If you are given any words like, person name or place name or common word then you will be getting an message “it is based on a dictionary word”.
|
||||
|
||||
```
|
||||
$ echo "password" | cracklib-check
|
||||
password: it is based on a dictionary word
|
||||
```
|
||||
|
||||
The default password length in Linux is `Seven` characters. If you give any password less than seven characters then you will be getting an message “it is WAY too short”.
|
||||
|
||||
```
|
||||
$ echo "123" | cracklib-check
|
||||
123: it is WAY too short
|
||||
```
|
||||
|
||||
You will be getting `OK` When you give good password like us.
|
||||
|
||||
```
|
||||
$ echo "ME$2w!@fgty6723" | cracklib-check
|
||||
ME!@fgty6723: OK
|
||||
```
|
||||
|
||||
### How To Install pwscore In Linux?
|
||||
|
||||
The pwscore package is available in most of the distribution official repository so, use the distribution package manager to install it.
|
||||
|
||||
For **`Fedora`** system, use **[DNF Command][1]** to install libpwquality.
|
||||
|
||||
```
|
||||
$ sudo dnf install libpwquality
|
||||
```
|
||||
|
||||
For **`Debian/Ubuntu`** systems, use **[APT-GET Command][2]** or **[APT Command][3]** to install libpwquality.
|
||||
|
||||
```
|
||||
$ sudo apt install libpwquality
|
||||
```
|
||||
|
||||
For **`Arch Linux`** based systems, use **[Pacman Command][4]** to install libpwquality.
|
||||
|
||||
```
|
||||
$ sudo pacman -S libpwquality
|
||||
```
|
||||
|
||||
For **`RHEL/CentOS`** systems, use **[YUM Command][5]** to install libpwquality.
|
||||
|
||||
```
|
||||
$ sudo yum install libpwquality
|
||||
```
|
||||
|
||||
For **`openSUSE Leap`** system, use **[Zypper Command][6]** to install libpwquality.
|
||||
|
||||
```
|
||||
$ sudo zypper install libpwquality
|
||||
```
|
||||
|
||||
If you are given any words like, person name or place name or common word then you will be getting a message “it is based on a dictionary word”.
|
||||
|
||||
```
|
||||
$ echo "password" | pwscore
|
||||
Password quality check failed:
|
||||
The password fails the dictionary check - it is based on a dictionary word
|
||||
```
|
||||
|
||||
The default password length in Linux is `Seven` characters. If you give any password less than seven characters then you will be getting an message “it is WAY too short”.
|
||||
|
||||
```
|
||||
$ echo "123" | pwscore
|
||||
Password quality check failed:
|
||||
The password is shorter than 8 characters
|
||||
```
|
||||
|
||||
You will be getting `password score` When you give good password like us.
|
||||
|
||||
```
|
||||
$ echo "ME!@fgty6723" | pwscore
|
||||
90
|
||||
```
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.2daygeek.com/how-to-check-password-complexity-strength-and-score-in-linux/
|
||||
|
||||
作者:[Magesh Maruthamuthu][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.2daygeek.com/author/magesh/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.2daygeek.com/dnf-command-examples-manage-packages-fedora-system/
|
||||
[2]: https://www.2daygeek.com/apt-get-apt-cache-command-examples-manage-packages-debian-ubuntu-systems/
|
||||
[3]: https://www.2daygeek.com/apt-command-examples-manage-packages-debian-ubuntu-systems/
|
||||
[4]: https://www.2daygeek.com/pacman-command-examples-manage-packages-arch-linux-system/
|
||||
[5]: https://www.2daygeek.com/yum-command-examples-manage-packages-rhel-centos-systems/
|
||||
[6]: https://www.2daygeek.com/zypper-command-examples-manage-packages-opensuse-system/
|
||||
@ -0,0 +1,202 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (How To Find Available Network Interfaces On Linux)
|
||||
[#]: via: (https://www.ostechnix.com/how-to-find-available-network-interfaces-on-linux/)
|
||||
[#]: author: (SK https://www.ostechnix.com/author/sk/)
|
||||
|
||||
How To Find Available Network Interfaces On Linux
|
||||
======
|
||||
|
||||

|
||||
|
||||
One of the common task we do after installing a Linux system is network configuration. Of course, you can configure network interfaces during the installation time. But, some of you might prefer to do it after installation or change the existing settings. As you know already, you must first know how many interfaces are available on the system in-order to configure network settings from command line. This brief tutorial addresses all the possible ways to find available network interfaces on Linux and Unix operating systems.
|
||||
|
||||
### Find Available Network Interfaces On Linux
|
||||
|
||||
We can find the available network cards in couple ways.
|
||||
|
||||
**Method 1 – Using ‘ifconfig’ Command:**
|
||||
|
||||
The most commonly used method to find the network interface details is using **‘ifconfig’** command. I believe some of Linux users might still use this.
|
||||
|
||||
```
|
||||
$ ifconfig -a
|
||||
```
|
||||
|
||||
Sample output:
|
||||
|
||||
```
|
||||
enp5s0: flags=4098<BROADCAST,MULTICAST> mtu 1500
|
||||
ether 24:b6:fd:37:8b:29 txqueuelen 1000 (Ethernet)
|
||||
RX packets 0 bytes 0 (0.0 B)
|
||||
RX errors 0 dropped 0 overruns 0 frame 0
|
||||
TX packets 0 bytes 0 (0.0 B)
|
||||
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
|
||||
|
||||
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
|
||||
inet 127.0.0.1 netmask 255.0.0.0
|
||||
inet6 ::1 prefixlen 128 scopeid 0x10<host>
|
||||
loop txqueuelen 1000 (Local Loopback)
|
||||
RX packets 171420 bytes 303980988 (289.8 MiB)
|
||||
RX errors 0 dropped 0 overruns 0 frame 0
|
||||
TX packets 171420 bytes 303980988 (289.8 MiB)
|
||||
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
|
||||
|
||||
wlp9s0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
|
||||
inet 192.168.225.37 netmask 255.255.255.0 broadcast 192.168.225.255
|
||||
inet6 2409:4072:6183:c604:c218:85ff:fe50:474f prefixlen 64 scopeid 0x0<global>
|
||||
inet6 fe80::c218:85ff:fe50:474f prefixlen 64 scopeid 0x20<link>
|
||||
ether c0:18:85:50:47:4f txqueuelen 1000 (Ethernet)
|
||||
RX packets 564574 bytes 628671925 (599.5 MiB)
|
||||
RX errors 0 dropped 0 overruns 0 frame 0
|
||||
TX packets 299706 bytes 60535732 (57.7 MiB)
|
||||
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
|
||||
```
|
||||
|
||||
As you see in the above output, I have two network interfaces namely **enp5s0** (on board wired ethernet adapter) and **wlp9s0** (wireless network adapter) on my Linux box. Here, **lo** is loopback interface, which is used to access all network services locally. It has an ip address of 127.0.0.1.
|
||||
|
||||
We can also use the same ‘ifconfig’ command in many UNIX variants, for example **FreeBSD** , to list available network cards.
|
||||
|
||||
**Method 2 – Using ‘ip’ Command:**
|
||||
|
||||
The ‘ifconfig’ command is deprecated in the latest Linux versions. So you can use **‘ip’** command to display the network interfaces as shown below.
|
||||
|
||||
```
|
||||
$ ip link show
|
||||
```
|
||||
|
||||
Sample output:
|
||||
|
||||
```
|
||||
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN mode DEFAULT group default qlen 1000
|
||||
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
|
||||
2: enp5s0: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN mode DEFAULT group default qlen 1000
|
||||
link/ether 24:b6:fd:37:8b:29 brd ff:ff:ff:ff:ff:ff
|
||||
3: wlp9s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP mode DORMANT group default qlen 1000
|
||||
link/ether c0:18:85:50:47:4f brd ff:ff:ff:ff:ff:ff
|
||||
```
|
||||
|
||||

|
||||
|
||||
You can also use the following commands as well.
|
||||
|
||||
```
|
||||
$ ip addr
|
||||
|
||||
$ ip -s link
|
||||
```
|
||||
|
||||
Did you notice that these command also shows the connected state of the network interfaces? If you closely look at the above output, you will notice that my Ethernet card is not connected with network cable (see the word **“DOWN”** in the above output). And wireless network card is connected (See the word **“UP”** ). For more details, check our previous guide to [**find the connected state of network interfaces on Linux**][1].
|
||||
|
||||
These two commands (ifconfig and ip) are just enough to find the available network cards on your Linux systems.
|
||||
|
||||
However, there are few other methods available to list network interfaces on Linux. Here you go.
|
||||
|
||||
**Method 3:**
|
||||
|
||||
The Linux Kernel saves the network interface details inside **/sys/class/net** directory. You can verify the list of available interfaces by looking into this directory.
|
||||
|
||||
```
|
||||
$ ls /sys/class/net
|
||||
```
|
||||
|
||||
Output:
|
||||
|
||||
```
|
||||
enp5s0 lo wlp9s0
|
||||
```
|
||||
|
||||
**Method 4:**
|
||||
|
||||
In Linux operating systems, **/proc/net/dev** file contains statistics about network interfaces.
|
||||
|
||||
To view the available network cards, just view its contents using command:
|
||||
|
||||
```
|
||||
$ cat /proc/net/dev
|
||||
```
|
||||
|
||||
Output:
|
||||
|
||||
```
|
||||
Inter-| Receive | Transmit
|
||||
face |bytes packets errs drop fifo frame compressed multicast|bytes packets errs drop fifo colls carrier compressed
|
||||
wlp9s0: 629189631 566078 0 0 0 0 0 0 60822472 300922 0 0 0 0 0 0
|
||||
enp5s0: 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0
|
||||
lo: 303980988 171420 0 0 0 0 0 0 303980988 171420 0 0 0 0 0 0
|
||||
```
|
||||
|
||||
**Method 5: Using ‘netstat’ command**
|
||||
|
||||
The **netstat** command displays various details such as network connections, routing tables, interface statistics, masquerade connections, and multicast memberships.
|
||||
|
||||
```
|
||||
$ netstat -i
|
||||
```
|
||||
|
||||
**Sample output:**
|
||||
|
||||
```
|
||||
Kernel Interface table
|
||||
Iface MTU RX-OK RX-ERR RX-DRP RX-OVR TX-OK TX-ERR TX-DRP TX-OVR Flg
|
||||
lo 65536 171420 0 0 0 171420 0 0 0 LRU
|
||||
wlp9s0 1500 565625 0 0 0 300543 0 0 0 BMRU
|
||||
```
|
||||
|
||||
Please be mindful that netstat is obsolete. The Replacement for “netstat -i” is “ip -s link”. Also note that this method will list only the active interfaces, not all available interfaces.
|
||||
|
||||
**Method 6: Using ‘nmcli’ command**
|
||||
|
||||
The nmcli is nmcli is a command-line tool for controlling NetworkManager and reporting network status. It is used to create, display, edit, delete, activate, and deactivate network connections and display network status.
|
||||
|
||||
If you have Linux system with Network Manager installed, you can list the available network interfaces using nmcli tool using the following commands:
|
||||
|
||||
```
|
||||
$ nmcli device status
|
||||
```
|
||||
|
||||
Or,
|
||||
|
||||
```
|
||||
$ nmcli connection show
|
||||
```
|
||||
|
||||
You know now how to find the available network interfaces on Linux. Next, check the following guides to know how to configure IP address on Linux.
|
||||
|
||||
[How To Configure Static IP Address In Linux And Unix][2]
|
||||
|
||||
[How To Configure IP Address In Ubuntu 18.04 LTS][3]
|
||||
|
||||
[How To Configure Static And Dynamic IP Address In Arch Linux][4]
|
||||
|
||||
[How To Assign Multiple IP Addresses To Single Network Card In Linux][5]
|
||||
|
||||
If you know any other quick ways to do it, please share them in the comment section below. I will check and update the guide with your inputs.
|
||||
|
||||
And, that’s all. More good stuffs to come. Stay tuned!
|
||||
|
||||
Cheers!
|
||||
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.ostechnix.com/how-to-find-available-network-interfaces-on-linux/
|
||||
|
||||
作者:[SK][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.ostechnix.com/author/sk/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.ostechnix.com/how-to-find-out-the-connected-state-of-a-network-cable-in-linux/
|
||||
[2]: https://www.ostechnix.com/configure-static-ip-address-linux-unix/
|
||||
[3]: https://www.ostechnix.com/how-to-configure-ip-address-in-ubuntu-18-04-lts/
|
||||
[4]: https://www.ostechnix.com/configure-static-dynamic-ip-address-arch-linux/
|
||||
[5]: https://www.ostechnix.com/how-to-assign-multiple-ip-addresses-to-single-network-card-in-linux/
|
||||
@ -0,0 +1,290 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (How to Display Weather Information in Ubuntu 18.04)
|
||||
[#]: via: (https://itsfoss.com/display-weather-ubuntu)
|
||||
[#]: author: (Sergiu https://itsfoss.com/author/sergiu/)
|
||||
|
||||
How to Display Weather Information in Ubuntu 18.04
|
||||
======
|
||||
|
||||
You’ve got a fresh Ubuntu install and you’re [customizing Ubuntu][1] to your liking. You want the best experience and the best apps for your needs.
|
||||
|
||||
The only thing missing is a weather app. Luckily for you, we got you covered. Just make sure you have the Universe repository enabled.
|
||||
|
||||
![Tools to Display Weather Information in Ubuntu Linux][2]
|
||||
|
||||
### 8 Ways to Display Weather Information in Ubuntu 18.04
|
||||
|
||||
Back in the Unity days, there were a few popular options like My Weather Indicator to display weather on your system. Those options are either discontinued or not available in Ubuntu 18.04 and higher versions anymore.
|
||||
|
||||
Fortunately, there are many other options to choose from. Some are minimalist and plain simple to use, some offer detailed information (or even present you with news headlines) and some are made for terminal gurus. Whatever your needs may be, the right app is waiting for you.
|
||||
|
||||
**Note:** The presented apps are in no particular order of ranking.
|
||||
|
||||
**Top Panel Apps**
|
||||
|
||||
These applications usually sit on the top panel of your screen. Good for quick look at the temperature.
|
||||
|
||||
#### 1\. OpenWeather Shell Extension
|
||||
|
||||
![Open Weather Gnome Shell Extesnsion][3]
|
||||
|
||||
**Key features:**
|
||||
|
||||
* Simple to install and customize
|
||||
* Uses OpenWeatherMap (by default)
|
||||
* Many Units and Layout options
|
||||
* Can save multiple locations (that can easily be changed)
|
||||
|
||||
|
||||
|
||||
This is a great extension presenting you information in a simple manner. There are multiple ways to install this. It is the weather app that I find myself using the most, because it’s just a simple, no-hassle integrated weather display for the top panel.
|
||||
|
||||
**How to Install:**
|
||||
|
||||
I recommend reading this [detailed tutorial about using GNOME extensions][4]. The easiest way to install this extension is to open up a terminal and run:
|
||||
|
||||
```
|
||||
sudo apt install gnome-shell-extension-weather
|
||||
```
|
||||
|
||||
Then all you have to restart the gnome shell by executing:
|
||||
|
||||
```
|
||||
Alt+F2
|
||||
```
|
||||
|
||||
Enter **r** and press **Enter**.
|
||||
|
||||
Now open up **Tweaks** (gnome tweak tool) and enable **Openweather** in the **Extensions** tab.
|
||||
|
||||
#### 2\. gnome-weather
|
||||
|
||||
![Gnome Weather App UI][5]
|
||||
![Gnome Weather App Top Panel][6]
|
||||
|
||||
**Key features:**
|
||||
|
||||
* Pleasant Design
|
||||
* Integrated into Calendar (Top Panel)
|
||||
* Simple Install
|
||||
* Flatpak install available
|
||||
|
||||
|
||||
|
||||
This app is great for new users. The installation is only one command and the app is easy to use. Although it doesn’t have as many features as other apps, it is still great if you don’t want to bother with multiple settings and a complex install procedure.
|
||||
|
||||
**How to Install:**
|
||||
|
||||
All you have to do is run:
|
||||
|
||||
```
|
||||
sudo apt install gnome-weather
|
||||
```
|
||||
|
||||
Now search for **Weather** and the app should pop up. After logging out (and logging back in), the Calendar extension will be displayed.
|
||||
|
||||
If you prefer, you can get a [flatpak][7] version.
|
||||
|
||||
#### 3\. Meteo
|
||||
|
||||
![Meteo Weather App UI][8]
|
||||
![Meteo Weather System Tray][9]
|
||||
|
||||
**Key features:**
|
||||
|
||||
* Great UI
|
||||
* Integrated into System Tray (Top Panel)
|
||||
* Simple Install
|
||||
* Great features (Maps)
|
||||
|
||||
|
||||
|
||||
Meteo is a snap app on the heavier side. Most of that weight comes from the great Maps features, with maps presenting temperatures, clouds, precipitations, pressure and wind speed. It’s a distinct feature that I haven’t encountered in any other weather app.
|
||||
|
||||
**Note** : After changing location, you might have to quit and restart the app for the changes to be applied in the system tray.
|
||||
|
||||
**How to Install:**
|
||||
|
||||
Open up the **Ubuntu Software Center** and search for **Meteo**. Install and launch.
|
||||
|
||||
**Desktop Apps**
|
||||
|
||||
These are basically desktop widgets. They look good and provide more information at a glance.
|
||||
|
||||
#### 4\. Temps
|
||||
|
||||
![Temps Weather App UI][10]
|
||||
|
||||
**Key features:**
|
||||
|
||||
* Beautiful Design
|
||||
* Useful Hotkeys
|
||||
* Hourly Temperature Graph
|
||||
|
||||
|
||||
|
||||
Temps is an electron app with a beautiful UI (though not exactly “light”). The most unique features are the temperature graphs. The hotkeys might feel unintuitive at first, but they prove to be useful in the long run. The app will minimize when you click somewhere else. Just press Ctrl+Shift+W to bring it back.
|
||||
|
||||
This app is **Open-Source** , and the developer can’t afford the cost of a faster API key, so you might want to create your own API at [OpenWeatherMap][11].
|
||||
|
||||
**How to Install:**
|
||||
|
||||
Go to the website and download the version you need (probably 64-bit). Extract the archive. Open the extracted directory and double-click on **Temps**. Press Ctrl+Shift+W if the window minimizes.
|
||||
|
||||
#### 5\. Cumulus
|
||||
|
||||
![Cumulus Weather App UI][12]
|
||||
|
||||
**Key features:**
|
||||
|
||||
* Color Selector for background and text
|
||||
|
||||
* Re-sizable window
|
||||
|
||||
* Tray Icon (temperature only)
|
||||
|
||||
* Allows multiple instances with different locations etc.
|
||||
|
||||
|
||||
|
||||
|
||||
Cumulus is a greatly customizable weather app, with a backend supporting Yahoo! Weather and OpenWeatherMap. The UI is great and the installer is simple to use. This app has amazing features. It’s one of the few weather apps that allow for multiple instances. You should definitely try it you are looking for an experience tailored to your preferences.
|
||||
|
||||
**How to Install:**
|
||||
|
||||
Go to the website and download the (online) installer. Open up a terminal and **cd** (change directory) to the directory where you downloaded the file.
|
||||
|
||||
Then run
|
||||
|
||||
```
|
||||
chmod +x Cumulus-online-installer-x64
|
||||
./Cumulus-online-installer-x64
|
||||
```
|
||||
|
||||
Search for **Cumulus** and enjoy the app!
|
||||
|
||||
**Terminal Apps**
|
||||
|
||||
You are a terminal dweller? You can check the weather right in your terminal.
|
||||
|
||||
#### 7\. WeGo
|
||||
|
||||
![WeGo Weather App Terminal][13]
|
||||
|
||||
**Key features:**
|
||||
|
||||
* Supports different APIs
|
||||
* Pretty detailed
|
||||
* Customizable config
|
||||
* Multi-language support
|
||||
* 1 to 7 day forecast
|
||||
|
||||
|
||||
|
||||
WeGo is a Go app for displaying weather info in the terminal. It’s install can be a little tricky, but it’s easy to set up. You’ll need to register an API Key [here][14] (if using **forecast.io** , which is default). Once you set it up, it’s fairly practical for someone who mostly works in the terminal.
|
||||
|
||||
**How to Install:**
|
||||
|
||||
I recommend you to check out the GitHub page for complete information on installation, setup and features.
|
||||
|
||||
#### 8\. Wttr.in
|
||||
|
||||
![Wttr.in Weather App Terminal][15]
|
||||
|
||||
**Key features:**
|
||||
|
||||
* Simple install
|
||||
* Easy to use
|
||||
* Lightweight
|
||||
* 3 day forecast
|
||||
* Moon phase
|
||||
|
||||
|
||||
|
||||
If you really live in the terminal, this is the weather app for you. This is as lightweight as it gets. You can specify location (by default the app tries to detect your current location) and a few other parameters (eg. units).
|
||||
|
||||
**How to Install:**
|
||||
|
||||
Open up a terminal and install Curl:
|
||||
|
||||
```
|
||||
sudo apt install curl
|
||||
```
|
||||
|
||||
Then:
|
||||
|
||||
```
|
||||
curl wttr.in
|
||||
```
|
||||
|
||||
That’s it. You can specify location and parameters like so:
|
||||
|
||||
```
|
||||
curl wttr.in/london?m
|
||||
```
|
||||
|
||||
To check out other options type:
|
||||
|
||||
```
|
||||
curl wttr.in/:help
|
||||
```
|
||||
|
||||
If you found some settings you enjoy and you find yourself using them frequently, you might want to add an **alias**. To do so, open **~/.bashrc** with your favorite editor (that’s **vim** , terminal wizard). Go to the end and paste in
|
||||
|
||||
```
|
||||
alias wttr='curl wttr.in/CITY_NAME?YOUR_PARAMS'
|
||||
```
|
||||
|
||||
For example:
|
||||
|
||||
```
|
||||
alias wttr='curl wttr.in/london?m'
|
||||
```
|
||||
|
||||
Save and close **~/.bashrc** and run the command below to source the new file.
|
||||
|
||||
```
|
||||
source ~/.bashrc
|
||||
```
|
||||
|
||||
Now, typing **wttr** in the terminal and pressing Enter should execute your custom command.
|
||||
|
||||
**Wrapping Up**
|
||||
|
||||
These are a handful of the weather apps available for Ubuntu. We hope our list helped you discover an app fitting your needs, be that something with pleasant aesthetics or just a quick tool.
|
||||
|
||||
What is your favorite weather app? Tell us about what you enjoy and why in the comments section.
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://itsfoss.com/display-weather-ubuntu
|
||||
|
||||
作者:[Sergiu][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://itsfoss.com/author/sergiu/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://itsfoss.com/gnome-tricks-ubuntu/
|
||||
[2]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2019/02/display-weather-ubuntu.png?resize=800%2C450&ssl=1
|
||||
[3]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2019/02/open_weather_gnome_shell-1-1.jpg?fit=800%2C383&ssl=1
|
||||
[4]: https://itsfoss.com/gnome-shell-extensions/
|
||||
[5]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2019/02/gnome_weather_ui.jpg?fit=800%2C599&ssl=1
|
||||
[6]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2019/02/gnome_weather_top_panel.png?fit=800%2C587&ssl=1
|
||||
[7]: https://flatpak.org/
|
||||
[8]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2019/02/meteo_ui.jpg?fit=800%2C547&ssl=1
|
||||
[9]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2019/02/meteo_system_tray.png?fit=800%2C653&ssl=1
|
||||
[10]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2019/02/temps_ui.png?fit=800%2C623&ssl=1
|
||||
[11]: https://openweathermap.org/
|
||||
[12]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2019/02/cumulus_ui.png?fit=800%2C651&ssl=1
|
||||
[13]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2019/02/wego_terminal.jpg?fit=800%2C531&ssl=1
|
||||
[14]: https://developer.forecast.io/register
|
||||
[15]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2019/02/wttr_in_terminal.jpg?fit=800%2C526&ssl=1
|
||||
@ -0,0 +1,83 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (3 open source behavior-driven development tools)
|
||||
[#]: via: (https://opensource.com/article/19/2/behavior-driven-development-tools)
|
||||
[#]: author: (Christine Ketterlin Fisher https://opensource.com/users/cketterlin)
|
||||
|
||||
3 open source behavior-driven development tools
|
||||
======
|
||||
Having the right motivation is as important as choosing the right tool when implementing BDD.
|
||||

|
||||
|
||||
[Behavior-driven development][1] (BDD) seems very easy. Tests are written in an easily readable format that allows for feedback from product owners, business sponsors, and developers. Those tests are living documentation for your team, so you don't need requirements. The tools are easy to use and allow you to automate your test suite. Reports are generated with each test run to document every step and show you where tests are failing.
|
||||
|
||||
Quick recap: Easily readable! Living documentation! Automation! Reports! What could go wrong, and why isn't everybody doing this?
|
||||
|
||||
### Getting started with BDD
|
||||
|
||||
So, you're ready to jump in and can't wait to pick the right open source tool for your team. You want it to be easy to use, automate all your tests, and provide easily understandable reports for each test run. Great, let's get started!
|
||||
|
||||
Except, not so fast … First, what is your motivation for trying to implement BDD on your team? If the answer is simply to automate tests, go ahead and choose any of the tools listed below because chances are you're going to see minimal success in the long run.
|
||||
|
||||
### My first effort
|
||||
|
||||
I manage a team of business analysts (BA) and quality assurance (QA) engineers, but my background is on the business analysis side. About a year ago, I attended a talk where a developer talked about the benefits of BDD. He said that he and his team had given it a try during their last project. That should have been the first red flag, but I didn't realize it at the time. You cannot simply choose to "give BDD a try." It takes planning, preparation, and forethought into what you want your team to accomplish.
|
||||
|
||||
However, you can try various parts of BDD without a large investment, and I eventually realized he and his team had written feature files and automated those tests using Cucumber. I also learned it was an experiment done solely by the team's developers, not the BA or QA staff, which defeats the purpose of understanding the end user's behavior.
|
||||
|
||||
During the talk we were encouraged to try BDD, so my test analyst and I went to our boss and said we were willing to give it a shot. And then, we didn't know what to do. We had no guidance, no plan in place, and a leadership team who just wanted to automate testing. I don't think I need to tell you how this story ended. Actually, there wasn't even an end, just a slow fizzle after a few initial attempts at writing behavioral scenarios.
|
||||
|
||||
### A fresh start
|
||||
|
||||
Fast-forward a year, and I'm at a different company with a team of my own and BDD on the brain. I knew there was value there, but I also knew it went deeper than what I had initially been sold. I spent a lot of time thinking about how BDD could make a positive impact, not only on my team, but on our entire development team. Then I read [Discovery: Explore Behaviour Using Examples][2] by Gaspar Nagy and Seb Rose, and one of the first things I learned was that automation of tests is a benefit of BDD, but it should not be the main goal. No wonder we failed!
|
||||
|
||||
This book changed how I viewed BDD and helped me start to fill in the pieces I had been missing. We are now on the (hopefully correct!) path to implementing BDD on our team. It involves active involvement from our product owners, business analysts, and manual and automated testers and buy-in and support from our executive leadership. We have a plan in place for our approach and our measures of success.
|
||||
|
||||
We are still writing requirements (don't ever let anyone tell you that these scenarios can completely replace requirements!), but we are doing so with a more critical eye and evaluating where requirements and test scenarios overlap and how we can streamline the two.
|
||||
|
||||
I have told the team we cannot even try to automate these tests for at least two quarters, at which point we'll evaluate and determine whether we're ready to move forward or not. Our current priorities are defining our team's standard language, practicing writing given/when/then scenarios, learning the Gherkin syntax, determining where to store these tests, and investigating how to integrate these tests into our pipeline.
|
||||
|
||||
### 3 BDD tools to choose
|
||||
|
||||
At its core, BDD is a way to help the entire team understand the end user's actions and behaviors, which will lead to more clear requirements, tests, and ultimately higher-quality applications. Before you pick your tool, do your pre-work. Think about your motivation, and understand that while the different parts and pieces of BDD are fairly simple, integrating them into your team is more challenging and needs careful thought and planning. Also, think about where your people fit in.
|
||||
|
||||
Every organization has different roles, and BDD should not belong solely to developers nor test automation engineers. If you don't involve the business side, you're never going to gain the full benefit of this methodology. Once you have a strategy defined and are ready to move forward with automating your BDD scenarios, there are several open source tools for you to choose from.
|
||||
|
||||
#### Cucumber
|
||||
|
||||
[Cucumber][3] is probably the most recognized tool available that supports BDD. It is widely seen as a straightforward tool to learn and is easy to get started with. Cucumber relies on test scenarios that are written in plain text and follow the given/when/then format. Each scenario is an individual test. Scenarios are grouped into features, which is comparable to a test suite. Scenarios must be written in the Gherkin syntax for Cucumber to understand and execute the scenario's steps. The human-readable steps in the scenarios are tied to the step definitions in your code through the Cucumber framework. To successfully write and automate the scenarios, you need the right mix of business knowledge and technical ability. Identify the skill sets on your team to determine who will write and maintain the scenarios and who will automate them; most likely these should be managed by different roles. Because these tests are executed from the step definitions, reporting is very robust and can show you at which exact step your test failed. Cucumber works well with a variety of browser and API automation tools.
|
||||
|
||||
#### JBehave
|
||||
|
||||
[JBehave][4] is very similar to Cucumber. Scenarios are still written in the given/when/then format and are easily understandable by the entire team. JBehave supports Gherkin but also has its own JBehave syntax that can be used. Gherkin is more universal, but either option will work as long as you are consistent in your choice. JBehave has more configuration options than Cucumber, and its reports, although very detailed, need more configuration to get feedback from each step. JBehave is a powerful tool, but because it can be more customized, it is not quite as easy to get started with. Teams need to ask themselves exactly what features they need and whether or not learning the tool's various configurations is worth the time investment.
|
||||
|
||||
#### Gauge
|
||||
|
||||
Where Cucumber and JBehave are specifically designed to work with BDD, [Gauge][5] is not. If automation is your main goal (and not the entire BDD process), it is worth a look. Gauge tests are written in Markdown, which makes them easily readable. However, without a more standard format, such as the given/when/then BDD scenarios, tests can vary widely and, depending on the author, some tests will be much more digestible for business owners than others. Gauge works with multiple languages, so the automation team can leverage what they already use. Gauge also offers reporting with screenshots to show where the tests failed.
|
||||
|
||||
### What are your needs?
|
||||
|
||||
Implementing BDD allows the team to test the users' behaviors. This can be done without automating any tests at all, but when done correctly, can result in a powerful, reusable test suite. As a team, you will need to identify exactly what your automation needs are and whether or not you are truly going to use BDD or if you would rather focus on automating tests that are written in plain text. Either way, open source tools are available for you to use and to help support your testing evolution.
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/2/behavior-driven-development-tools
|
||||
|
||||
作者:[Christine Ketterlin Fisher][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/cketterlin
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://en.wikipedia.org/wiki/Behavior-driven_development
|
||||
[2]: https://www.amazon.com/gp/product/1983591254/ref=dbs_a_def_rwt_bibl_vppi_i0
|
||||
[3]: https://cucumber.io/
|
||||
[4]: https://jbehave.org/
|
||||
[5]: https://www.gauge.org/
|
||||
@ -0,0 +1,75 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Connecting a VoIP phone directly to an Asterisk server)
|
||||
[#]: via: (https://feeding.cloud.geek.nz/posts/connecting-voip-phone-directly-to-asterisk-server/)
|
||||
[#]: author: (François Marier https://fmarier.org/)
|
||||
|
||||
Connecting a VoIP phone directly to an Asterisk server
|
||||
======
|
||||
|
||||
On my [Asterisk][1] server, I happen to have two on-board ethernet boards. Since I only used one of these, I decided to move my VoIP phone from the local network switch to being connected directly to the Asterisk server.
|
||||
|
||||
The main advantage is that this phone, running proprietary software of unknown quality, is no longer available on my general home network. Most importantly though, it no longer has access to the Internet, without my having to firewall it manually.
|
||||
|
||||
Here's how I configured everything.
|
||||
|
||||
### Private network configuration
|
||||
|
||||
On the server, I started by giving the second network interface a static IP address in `/etc/network/interfaces`:
|
||||
|
||||
```
|
||||
auto eth1
|
||||
iface eth1 inet static
|
||||
address 192.168.2.2
|
||||
netmask 255.255.255.0
|
||||
```
|
||||
|
||||
On the VoIP phone itself, I set the static IP address to `192.168.2.3` and the DNS server to `192.168.2.2`. I then updated the SIP registrar IP address to `192.168.2.2`.
|
||||
|
||||
The DNS server actually refers to an [unbound daemon][2] running on the Asterisk server. The only configuration change I had to make was to listen on the second interface and allow the VoIP phone in:
|
||||
|
||||
```
|
||||
server:
|
||||
interface: 127.0.0.1
|
||||
interface: 192.168.2.2
|
||||
access-control: 0.0.0.0/0 refuse
|
||||
access-control: 127.0.0.1/32 allow
|
||||
access-control: 192.168.2.3/32 allow
|
||||
```
|
||||
|
||||
Finally, I opened the right ports on the server's firewall in `/etc/network/iptables.up.rules`:
|
||||
|
||||
```
|
||||
-A INPUT -s 192.168.2.3/32 -p udp --dport 5060 -j ACCEPT
|
||||
-A INPUT -s 192.168.2.3/32 -p udp --dport 10000:20000 -j ACCEPT
|
||||
```
|
||||
|
||||
### Accessing the admin page
|
||||
|
||||
Now that the VoIP phone is no longer available on the local network, it's not possible to access its admin page. That's a good thing from a security point of view, but it's somewhat inconvenient.
|
||||
|
||||
Therefore I put the following in my `~/.ssh/config` to make the admin page available on `http://localhost:8081` after I connect to the Asterisk server via ssh:
|
||||
|
||||
```
|
||||
Host asterisk
|
||||
LocalForward 8081 192.168.2.3:80
|
||||
```
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://feeding.cloud.geek.nz/posts/connecting-voip-phone-directly-to-asterisk-server/
|
||||
|
||||
作者:[François Marier][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://fmarier.org/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.asterisk.org/
|
||||
[2]: https://feeding.cloud.geek.nz/posts/setting-up-your-own-dnssec-aware/
|
||||
@ -0,0 +1,161 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (MiyoLinux: A Lightweight Distro with an Old-School Approach)
|
||||
[#]: via: (https://www.linux.com/blog/learn/2019/2/miyolinux-lightweight-distro-old-school-approach)
|
||||
[#]: author: (Jack Wallen https://www.linux.com/users/jlwallen)
|
||||
|
||||
MiyoLinux: A Lightweight Distro with an Old-School Approach
|
||||
======
|
||||

|
||||
|
||||
I must confess, although I often wax poetic about the old ways of the Linux desktop, I much prefer my distributions to help make my daily workflow as efficient as possible. Because of that, my taste in Linux desktop distributions veers very far toward the modern side of things. I want a distribution that integrates apps seamlessly, gives me notifications, looks great, and makes it easy to work with certain services that I use.
|
||||
|
||||
However, every so often it’s nice to dip my toes back into those old-school waters and remind myself why I fell in love with Linux in the first place. That’s precisely what [MiyoLinux][1] did for me recently. This lightweight distribution is based on [Devuan][2] and makes use of the [i3 Tiling Window Manager][3].
|
||||
|
||||
Why is it important that MiyoLinux is based on Devuan? Because that means it doesn’t use systemd. There are many within the Linux community who’d be happy to make the switch to an old-school Linux distribution that opts out of systemd. If that’s you, MiyoLinux might just charm you into submission.
|
||||
|
||||
But don’t think MiyoLinux is going to be as easy to get up and running as, say, Ubuntu Linux, Elementary OS, or Linux Mint. Although it’s not nearly as challenging as Arch or Gentoo, MiyoLinux does approach installation and basic usage a bit differently. Let’s take a look at how this particular distro handles things.
|
||||
|
||||
### Installation
|
||||
|
||||
The installation GUI of MiyoLinux is pretty basic. The first thing you’ll notice is that you are presented with a good amount of notes, regarding the usage of the MiyoLinux desktop. If you happen to be testing MiyoLinux via VirtualBox, you’ll wind up having to deal with the frustration of not being able to resize the window (Figure 1), as the Guest Additions cannot be installed. This also means mouse integration cannot be enabled during the installation, so you’ll have to tab through the windows and use your keyboard cursor keys and Enter key to make selections.
|
||||
|
||||
![MiyoLinux][5]
|
||||
|
||||
Figure 1: The first step in the MiyoLinux installation.
|
||||
|
||||
[Used with permission][6]
|
||||
|
||||
Once you click the Install MiyoLinux button, you’ll be prompted to continue using either ‘su” or sudo. Click the use sudo button to continue with the installation.
|
||||
|
||||
The next screen of importance is the Installation Options window (Figure 2), where you can select various options for MiyoLinux (such as encryption, file system labels, disable automatic login, etc.).
|
||||
|
||||
![Configuration][8]
|
||||
|
||||
Figure 2: Configuration Installation options for MiyoLinux.
|
||||
|
||||
[Used with permission][6]
|
||||
|
||||
The MiyoLinux installation does not include an automatic partition tool. Instead, you’ll be prompted to run either cfdisk or GParted (Figure 3). If you don’t know your way around cfdisk, select GParted and make use of the GUI tool.
|
||||
|
||||
![partitioning ][10]
|
||||
|
||||
Figure 3: Select your partitioning tool for MiyoLinux.
|
||||
|
||||
[Used with permission][6]
|
||||
|
||||
With your disk partitioned (Figure 4), you’ll be required to take care of the following steps:
|
||||
|
||||
* Configure the GRUB bootloader.
|
||||
|
||||
* Select the filesystem for the bootloader.
|
||||
|
||||
* Configure time zone and locales.
|
||||
|
||||
* Configure keyboard, keyboard language, and keyboard layout.
|
||||
|
||||
* Okay the installation.
|
||||
|
||||
|
||||
|
||||
|
||||
Once, you’ve okay’d the installation, all packages will be installed and you will then be prompted to install the bootloader. Following that, you’ll be prompted to configure the following:
|
||||
|
||||
* Hostname.
|
||||
|
||||
* User (Figure 5).
|
||||
|
||||
* Root password.
|
||||
|
||||
|
||||
|
||||
|
||||
With the above completed, reboot and log into your new MiyoLinux installation.
|
||||
|
||||
![hostname][12]
|
||||
|
||||
Figure 5: Configuring hostname and username.
|
||||
|
||||
[Creative Commons Zero][13]
|
||||
|
||||
### Usage
|
||||
|
||||
Once you’ve logged into the MiyoLinux desktop, you’ll find things get a bit less-than-user-friendly. This is by design. You won’t find any sort of mouse menu available anywhere on the desktop. Instead you use keyboard shortcuts to open the different types of menus. The Alt+m key combination will open the PMenu, which is what one would consider a fairly standard desktop mouse menu (Figure 6).
|
||||
|
||||
The Alt+d key combination will open the dmenu, a search tool at the top of the desktop, where you can scroll through (using the cursor keys) or search for an app you want to launch (Figure 7).
|
||||
|
||||
![dmenu][15]
|
||||
|
||||
Figure 7: The dmenu in action.
|
||||
|
||||
[Used with permission][6]
|
||||
|
||||
### Installing Apps
|
||||
|
||||
If you open the PMenu, click System > Synaptic Package Manager. From within that tool you can search for any app you want to install. However, if you find Synaptic doesn’t want to start from the PMenu, open the dmenu, search for terminal, and (once the terminal opens), issue the command sudo synaptic. That will get the package manager open, where you can start installing any applications you want (Figure 8).
|
||||
|
||||
![Synaptic][17]
|
||||
|
||||
Figure 8: The Synaptic Package Manager on MiyoLinux.
|
||||
|
||||
[Used with permission][6]
|
||||
|
||||
Of course, you can always install applications from the command line. MiyoLinux depends upon the Apt package manager, so installing applications is as easy as:
|
||||
|
||||
```
|
||||
sudo apt-get install libreoffice -y
|
||||
```
|
||||
|
||||
Once installed, you can start the new package from either the PMenu or dmenu tools.
|
||||
|
||||
### MiyoLinux Accessories
|
||||
|
||||
If you find you need a bit more from the MiyoLinux desktop, type the keyboard combination Alt+Ctrl+a to open the MiyoLinux Accessories tool (Figure 9). From this tool you can configure a number of options for the desktop.
|
||||
|
||||
![Accessories][19]
|
||||
|
||||
Figure 9: Configure i3, Conky, Compton, your touchpad, and more with the Accessories tool.
|
||||
|
||||
[Used with permission][6]
|
||||
|
||||
All other necessary keyboard shortcuts are listed on the default desktop wallpaper. Make sure to put those shortcuts to memory, as you won’t get very far in the i3 desktop without them.
|
||||
|
||||
### A Nice Nod to Old-School Linux
|
||||
|
||||
If you’re itching to throw it back to a time when Linux offered you a bit of challenge to your daily grind, MiyoLinux might be just the operating system for you. It’s a lightweight operating system that makes good use of a minimal set of tools. Anyone who likes their distributions to be less modern and more streamlined will love this take on the Linux desktop. However, if you prefer your desktop with the standard bells and whistles, found on modern distributions, you’ll probably find MiyoLinux nothing more than a fun distraction from the standard fare.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.linux.com/blog/learn/2019/2/miyolinux-lightweight-distro-old-school-approach
|
||||
|
||||
作者:[Jack Wallen][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.linux.com/users/jlwallen
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://sourceforge.net/p/miyolinux/wiki/Home/
|
||||
[2]: https://devuan.org/
|
||||
[3]: https://i3wm.org/
|
||||
[4]: /files/images/miyo1jpg
|
||||
[5]: https://www.linux.com/sites/lcom/files/styles/rendered_file/public/miyo_1.jpg?itok=5PxRDYRE (MiyoLinux)
|
||||
[6]: /licenses/category/used-permission
|
||||
[7]: /files/images/miyo2jpg
|
||||
[8]: https://www.linux.com/sites/lcom/files/styles/rendered_file/public/miyo_2.jpg?itok=svlVr7VI (Configuration)
|
||||
[9]: /files/images/miyo3jpg
|
||||
[10]: https://www.linux.com/sites/lcom/files/styles/rendered_file/public/miyo_3.jpg?itok=lpNzZBPz (partitioning)
|
||||
[11]: /files/images/miyo5jpg
|
||||
[12]: https://www.linux.com/sites/lcom/files/styles/rendered_file/public/miyo_5.jpg?itok=lijIsgZ2 (hostname)
|
||||
[13]: /licenses/category/creative-commons-zero
|
||||
[14]: /files/images/miyo7jpg
|
||||
[15]: https://www.linux.com/sites/lcom/files/styles/rendered_file/public/miyo_7.jpg?itok=I8Ow3PX6 (dmenu)
|
||||
[16]: /files/images/miyo8jpg
|
||||
[17]: https://www.linux.com/sites/lcom/files/styles/rendered_file/public/miyo_8.jpg?itok=oa502KfM (Synaptic)
|
||||
[18]: /files/images/miyo9jpg
|
||||
[19]: https://www.linux.com/sites/lcom/files/styles/rendered_file/public/miyo_9.jpg?itok=gUM4mxEv (Accessories)
|
||||
143
sources/tech/20190301 Guide to Install VMware Tools on Linux.md
Normal file
143
sources/tech/20190301 Guide to Install VMware Tools on Linux.md
Normal file
@ -0,0 +1,143 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Guide to Install VMware Tools on Linux)
|
||||
[#]: via: (https://itsfoss.com/install-vmware-tools-linux)
|
||||
[#]: author: (Ankush Das https://itsfoss.com/author/ankush/)
|
||||
|
||||
Guide to Install VMware Tools on Linux
|
||||
======
|
||||
|
||||
**VMware Tools enhances your VM experience by allowing you to share clipboard and folder among other things. Learn how to install VMware tools on Ubuntu and other Linux distributions.**
|
||||
|
||||
In an earlier tutorial, you learned to [install VMware Workstation on Ubuntu][1]. You can further enhance the functionality of your virtual machines by installing VMware Tools.
|
||||
|
||||
If you have already installed a guest OS on VMware, you must have noticed the requirement for [VMware tools][2] – even though not completely aware of what it is needed for.
|
||||
|
||||
In this article, we will highlight the importance of VMware tools, the features it offers, and the method to install VMware tools on Ubuntu or any other Linux distribution.
|
||||
|
||||
### VMware Tools: Overview & Features
|
||||
|
||||
![Installing VMware Tools on Ubuntu][3]Installing VMware Tools on Ubuntu
|
||||
|
||||
For obvious reasons, the virtual machine (your Guest OS) will not behave exactly like the host. There will be certain limitations in terms of its performance and operationg. And, that is why a set of utilities (VMware Tools) was introduced.
|
||||
|
||||
VMware tools help in managing the guest OS in an efficient manner while also improving its performance.
|
||||
|
||||
#### What exactly is VMware tool responsible for?
|
||||
|
||||
![How to Install VMware tools on Linux][4]
|
||||
|
||||
You have got a vague idea of what it does – but let us talk about the details:
|
||||
|
||||
* Synchronize the time between the guest OS and the host to make things easier.
|
||||
* Unlocks the ability to pass messages from host OS to guest OS. For example, you copy a text on the host to your clipboard and you can easily paste it to your guest OS.
|
||||
* Enables sound in guest OS.
|
||||
* Improves video resolution.
|
||||
* Improves the cursor movement.
|
||||
* Fixes incorrect network speed data.
|
||||
* Eliminates inadequate color depth.
|
||||
|
||||
|
||||
|
||||
These are the major changes that happen when you install VMware tools on Guest OS. But, what exactly does it contain / feature in order to unlock/enhance these functionalities? Let’s see..
|
||||
|
||||
#### VMware tools: Core Feature Details
|
||||
|
||||
![Sharing clipboard between guest and host OS with VMware Tools][5]Sharing clipboard between guest and host OS with VMware Tools
|
||||
|
||||
If you do not want to know what it includes to enable the functionalities, you can skip this part. But, for the curious readers, let us briefly discuss about it:
|
||||
|
||||
**VMware device drivers:** It really depends on the OS. Most of the major operating systems do include device drivers by default. So, you do not have to install it separately. This generally involves – memory control driver, mouse driver, audio driver, NIC driver, VGA driver and so on.
|
||||
|
||||
**VMware user process:** This is where things get really interesting. With this, you get the ability to copy-paste and drag-drop between the host and the guest OS. You can basically copy and paste the text from the host to the virtual machine or vice versa.
|
||||
|
||||
You get to drag and drop files as well. In addition, it enables the pointer release/lock when you do not have an SVGA driver installed.
|
||||
|
||||
**VMware tools lifecycle management** : Well, we will take a look at how to install VMware tools below – but this feature helps you easily install/upgrade VMware tools in the virtual machine.
|
||||
|
||||
**Shared Folders** : In addition to these, VMware tools also allow you to have shared folders between the guest OS and the host.
|
||||
|
||||
![Sharing folder between guest and host OS using VMware Tools in Linux][6]Sharing folder between guest and host OS using VMware Tools in Linux
|
||||
|
||||
Of course, what it does and facilitates also depends on the host OS. For example, on Windows, you get a Unity mode on VMware to run programs on virtual machine and operate it from the host OS.
|
||||
|
||||
### How to install VMware Tools on Ubuntu & other Linux distributions
|
||||
|
||||
**Note:** For Linux guest operating systems, you should already have “Open VM Tools” suite installed, eliminating the need of installing VMware tools separately, most of the time.
|
||||
|
||||
Most of the time, when you install a guest OS, you will get a prompt as a software update or a popup telling you to install VMware tools if the operating system supports [Easy Install][7].
|
||||
|
||||
Windows and Ubuntu does support Easy Install. So, even if you are using Windows as your host OS or trying to install VMware tools on Ubuntu, you should first get an option to install the VMware tools easily as popup message. Here’s how it should look like:
|
||||
|
||||
![Pop-up to install VMware Tools][8]Pop-up to install VMware Tools
|
||||
|
||||
This is the easiest way to get it done. So, make sure you have an active network connection when you setup the virtual machine.
|
||||
|
||||
If you do not get any of these pop ups – or options to easily install VMware tools. You have to manually install it. Here’s how to do that:
|
||||
|
||||
1\. Launch VMware Workstation Player.
|
||||
|
||||
2\. From the menu, navigate through **Virtual Machine - > Install VMware tools**. If you already have it installed, and want to repair the installation, you will observe the same option to appear as “ **Re-install VMware tools** “.
|
||||
|
||||
3\. Once you click on that, you will observe a virtual CD/DVD mounted in the guest OS.
|
||||
|
||||
4\. Open that and copy/paste the **tar.gz** file to any location of your choice and extract it, here we choose the **Desktop**.
|
||||
|
||||
![][9]
|
||||
|
||||
5\. After extraction, launch the terminal and navigate to the folder inside by typing in the following command:
|
||||
|
||||
```
|
||||
cd Desktop/VMwareTools-10.3.2-9925305/vmware-tools-distrib
|
||||
```
|
||||
|
||||
You need to check the name of the folder and path in your case – depending on the version and where you extracted – it might vary.
|
||||
|
||||
![][10]
|
||||
|
||||
Replace **Desktop** with your storage location (such as cd Downloads) and the rest should remain the same if you are installing **10.3.2 version**.
|
||||
|
||||
6\. Now, simply type in the following command to start the installation:
|
||||
|
||||
```
|
||||
sudo ./vmware-install.pl -d
|
||||
```
|
||||
|
||||
![][11]
|
||||
|
||||
You will be asked the password for permission to install, type it in and you should be good to go.
|
||||
|
||||
That’s it. You are done. These set of steps should be applicable to almost any Ubuntu-based guest operating system. If you want to install VMware tools on Ubuntu Server, or any other OS.
|
||||
|
||||
**Wrapping Up**
|
||||
|
||||
Installing VMware tools on Ubuntu Linux is pretty easy. In addition to the easy method, we have also explained the manual method to do it. If you still need help, or have a suggestion regarding the installation, let us know in the comments down below.
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://itsfoss.com/install-vmware-tools-linux
|
||||
|
||||
作者:[Ankush Das][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://itsfoss.com/author/ankush/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://itsfoss.com/install-vmware-player-ubuntu-1310/
|
||||
[2]: https://kb.vmware.com/s/article/340
|
||||
[3]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2019/02/vmware-tools-downloading.jpg?fit=800%2C531&ssl=1
|
||||
[4]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2019/03/install-vmware-tools-linux.png?resize=800%2C450&ssl=1
|
||||
[5]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2019/02/vmware-tools-features.gif?resize=800%2C500&ssl=1
|
||||
[6]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2019/02/vmware-tools-shared-folder.jpg?fit=800%2C660&ssl=1
|
||||
[7]: https://docs.vmware.com/en/VMware-Workstation-Player-for-Linux/15.0/com.vmware.player.linux.using.doc/GUID-3F6B9D0E-6CFC-4627-B80B-9A68A5960F60.html
|
||||
[8]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2019/02/vmware-tools.jpg?fit=800%2C481&ssl=1
|
||||
[9]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2019/02/vmware-tools-extraction.jpg?fit=800%2C564&ssl=1
|
||||
[10]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2019/02/vmware-tools-folder.jpg?fit=800%2C487&ssl=1
|
||||
[11]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2019/02/vmware-tools-installation-ubuntu.jpg?fit=800%2C492&ssl=1
|
||||
61
sources/tech/20190301 How to use sudo access in winSCP.md
Normal file
61
sources/tech/20190301 How to use sudo access in winSCP.md
Normal file
@ -0,0 +1,61 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (How to use sudo access in winSCP)
|
||||
[#]: via: (https://kerneltalks.com/tools/how-to-use-sudo-access-in-winscp/)
|
||||
[#]: author: (kerneltalks https://kerneltalks.com)
|
||||
|
||||
How to use sudo access in winSCP
|
||||
======
|
||||
|
||||
Learn how to use sudo access in winSCP with screenshots.
|
||||
|
||||
![How to use sudo access in winSCP][1]sudo access in winSCP
|
||||
|
||||
First of all you need to check where is your SFTP server binary located on server you are trying to connect with winSCP.
|
||||
|
||||
You can check SFTP server binary location with below command –
|
||||
|
||||
```
|
||||
[root@kerneltalks ~]# cat /etc/ssh/sshd_config |grep -i sftp-server
|
||||
Subsystem sftp /usr/libexec/openssh/sftp-server
|
||||
```
|
||||
|
||||
Here you can see sftp server binary is located at `/usr/libexec/openssh/sftp-server`
|
||||
|
||||
Now open winSCP and click `Advanced` button to open up advanced settings.
|
||||
|
||||
![winSCP advance settings][2]
|
||||
winSCP advance settings
|
||||
|
||||
It will open up advanced setting window like one below. Here select `SFTP `under `Environment` on left hand side panel. You will be presented with option on right hand side.
|
||||
|
||||
Now, add SFTP server value here with command `sudo su -c` here as displayed in screenshot below –
|
||||
|
||||
![SFTP server setting in winSCP][3]
|
||||
SFTP server setting in winSCP
|
||||
|
||||
So we added `sudo su -c /usr/libexec/openssh/sftp-server` in settings here. Now click Ok and connect to server as you normally do.
|
||||
|
||||
After connection you will be able to transfer files from directory where you normally need sudo permission to access.
|
||||
|
||||
That’s it! You logged to server using winSCP and sudo access.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://kerneltalks.com/tools/how-to-use-sudo-access-in-winscp/
|
||||
|
||||
作者:[kerneltalks][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://kerneltalks.com
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://i2.wp.com/kerneltalks.com/wp-content/uploads/2019/03/How-to-use-sudo-access-in-winSCP.png?ssl=1
|
||||
[2]: https://i0.wp.com/kerneltalks.com/wp-content/uploads/2019/03/winscp-advanced-settings.jpg?ssl=1
|
||||
[3]: https://i1.wp.com/kerneltalks.com/wp-content/uploads/2019/03/SFTP-server-setting-in-winSCP.jpg?ssl=1
|
||||
@ -0,0 +1,48 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (qhwdw)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Which Raspberry Pi should you choose?)
|
||||
[#]: via: (https://opensource.com/article/19/3/which-raspberry-pi-choose)
|
||||
[#]: author: (Anderson Silva https://opensource.com/users/ansilva)
|
||||
|
||||
Which Raspberry Pi should you choose?
|
||||
======
|
||||
In the first article in our series on getting started with Raspberry Pi, learn the three criteria for choosing the right model for you.
|
||||
|
||||
|
||||
This is the first article in a 14-day series on getting started with the [Raspberry Pi][1]. Although the series is geared towards people who have never used a Raspberry Pi or Linux or programming, there will definitely be things for more experienced readers—and I encourage those readers to leave comments and tips that build on what I write. If everyone contributes, we can make this series even more useful for beginners, other experienced readers, and even me!
|
||||
|
||||
So, you want to give the Raspberry Pi a shot, but you don't know which model to buy. Maybe you want one for your classroom or your kid, but there are so many options, and you aren't sure which one is right for you.
|
||||
|
||||

|
||||
|
||||
My three main criteria for choosing a new Raspberry Pi are:
|
||||
|
||||
* **Cost:** Don't just consider the cost of the Raspberry Pi board, but also factor the peripherals you will need in order to use it. In the US, the Raspberry Pi's cost varies from $5 (for the Raspberry Pi Zero) to $35 (for the Raspberry Pi 3 B and 3 B+). However, if you pick the Zero you will probably also need a USB hub for your mouse and keyboard, possibly a wireless adapter, and some sort of display adapter. Unless you have most (if not all) of the peripherals needed for whatever you want to do with your Raspberry Pi, make sure to add those to your Pi budget. Also, in some countries, a Raspberry Pi on its own (even without any peripherals) may be a cost burden for many students and teachers.
|
||||
|
||||
* **Availability:** Finding the Raspberry Pi you want can vary depending on your location, as it may be easier (or harder) to get certain versions in some countries. Availability is an even bigger issue after new models are released, and it can take a few days or even weeks for new versions to become available in your market.
|
||||
|
||||
* **Purpose:** Location and cost may not affect everyone, but every buyer must consider why they want a Raspberry Pi. The eight different models vary in RAM, CPU core, CPU speed, physical size, network connectivity, peripheral expansion, etc. For example, if you want the most robust solution with more "horsepower," you probably will want the Raspberry Pi 3 B+, which has the most RAM, fastest CPU, and largest number of cores. If you want something that won't require network connectivity, won't be used for CPU-intensive work, and can be hidden in a small space, you could go with a Raspberry Pi Zero.
|
||||
|
||||
|
||||
[Wikipedia's Raspberry Pi specs chart][2] is an easy way to compare the eight Raspberry Pis models.
|
||||
|
||||
Now that you know what to look for in a Raspberry Pi, in the next article, I will explain how to buy one.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/3/which-raspberry-pi-choose
|
||||
|
||||
作者:[Anderson Silva][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/ansilva
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.raspberrypi.org/
|
||||
[2]: https://en.wikipedia.org/wiki/Raspberry_Pi#Specifications
|
||||
@ -0,0 +1,187 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (lujun9972)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Create a Custom System Tray Indicator For Your Tasks on Linux)
|
||||
[#]: via: (https://fosspost.org/tutorials/custom-system-tray-icon-indicator-linux)
|
||||
[#]: author: (M.Hanny Sabbagh https://fosspost.org/author/mhsabbagh)
|
||||
|
||||
Create a Custom System Tray Indicator For Your Tasks on Linux
|
||||
======
|
||||
|
||||
System Tray icons are still considered to be an amazing functionality today. By just right-clicking on the icon, and then selecting which actions you would like to take, you may ease your life a lot and save many unnecessary clicks on daily basis.
|
||||
|
||||
When talking about useful system tray icons, examples like Skype, Dropbox and VLC do come to mind:
|
||||
|
||||
![Create a Custom System Tray Indicator For Your Tasks on Linux 11][1]
|
||||
|
||||
However, system tray icons can actually be quite a lot more useful; By simply building one yourself for your own needs. In this tutorial, we’ll explain how to do that for you in very simple steps.
|
||||
|
||||
### Prerequisites
|
||||
|
||||
We are going to build a custom system tray indicator using Python. Python is probably installed by default on all the major Linux distributions, so just check it’s there (version 2.7). Additionally, we’ll need the gir1.2-appindicator3 package installed. It’s the library allowing us to easily create system tray indicators.
|
||||
|
||||
To install it on Ubuntu/Mint/Debian:
|
||||
|
||||
```
|
||||
sudo apt-get install gir1.2-appindicator3
|
||||
```
|
||||
|
||||
On Fedora:
|
||||
|
||||
```
|
||||
sudo dnf install libappindicator-gtk3
|
||||
```
|
||||
|
||||
For other distributions, just search for any packages containing appindicator.
|
||||
|
||||
On GNOME Shell, system tray icons are removed starting from 3.26. You’ll need to install the [following extension][2] (Or possibly other extensions) to re-enable the feature on your desktop. Otherwise, you won’t be able to see the indicator we are going to create here.
|
||||
|
||||
### Basic Code
|
||||
|
||||
Here’s the basic code of the indicator:
|
||||
|
||||
```
|
||||
#!/usr/bin/python
|
||||
import os
|
||||
from gi.repository import Gtk as gtk, AppIndicator3 as appindicator
|
||||
|
||||
def main():
|
||||
indicator = appindicator.Indicator.new("customtray", "semi-starred-symbolic", appindicator.IndicatorCategory.APPLICATION_STATUS)
|
||||
indicator.set_status(appindicator.IndicatorStatus.ACTIVE)
|
||||
indicator.set_menu(menu())
|
||||
gtk.main()
|
||||
|
||||
def menu():
|
||||
menu = gtk.Menu()
|
||||
|
||||
command_one = gtk.MenuItem('My Notes')
|
||||
command_one.connect('activate', note)
|
||||
menu.append(command_one)
|
||||
|
||||
exittray = gtk.MenuItem('Exit Tray')
|
||||
exittray.connect('activate', quit)
|
||||
menu.append(exittray)
|
||||
|
||||
menu.show_all()
|
||||
return menu
|
||||
|
||||
def note(_):
|
||||
os.system("gedit $HOME/Documents/notes.txt")
|
||||
|
||||
def quit(_):
|
||||
gtk.main_quit()
|
||||
|
||||
if __name__ == "__main__":
|
||||
main()
|
||||
```
|
||||
|
||||
We’ll explain how the code works later. But for know, just save it in a text file under the name tray.py, and run it using Python:
|
||||
|
||||
```
|
||||
python tray.py
|
||||
```
|
||||
|
||||
You’ll see the indicator working as follows:
|
||||
|
||||
![Create a Custom System Tray Indicator For Your Tasks on Linux 13][3]
|
||||
|
||||
Now, to explain how we did the magic:
|
||||
|
||||
* The first 3 lines of the code are nothing more than just specifying the Python path and importing the libraries we are going to use in our indicator.
|
||||
|
||||
* def main() : This is the main function of the indicator. Under it we write the code to initialize and build the indicator.
|
||||
|
||||
* indicator = appindicator.Indicator.new(“customtray”, “semi-starred-symbolic”, appindicator.IndicatorCategory.APPLICATION_STATUS) : Here we are specially creating a new indicator and calling it `customtray` . This is the special name of the indicator so that the system doesn’t mix it with other indicators that may be running. Also, we used the `semi-starred-symbolic` icon name as the default icon for our indicator. You could possibly change thing to any other things; Say `firefox` (if you want to see Firefox icon being used for the indicator), or any other icon name you would like. The last part regarding the `APPLICATION_STATUS` is just ordinary code for the categorization/scope of that indicator.
|
||||
|
||||
* `indicator.set_status(appindicator.IndicatorStatus.ACTIVE)` : This line just turns the indicator on.
|
||||
|
||||
* `indicator.set_menu(menu())` : Here, we are saying that we want to use the `menu()` function (which we’ll define later) for creating the menu items of our indicator. This is important so that when you click on the indicator, you can see a list of possible actions to take.
|
||||
|
||||
* `gtk.main()` : Just run the main GTK loop.
|
||||
|
||||
* Under `menu()` you’ll see that we are creating the actions/items we want to provide using our indicator. `command_one = gtk.MenuItem(‘My Notes’)` simply initializes the first menu item with the text “My notes”, and then `command_one.connect(‘activate’, note)` connects the `activate` signal of that menu item to the `note()` function defined later; In other words, we are telling our system here: “When this menu item is clicked, run the note() function”. Finally, `menu.append(command_one)` adds that menu item to the list.
|
||||
|
||||
* The lines regarding `exittray` are just for creating an exit menu item to close the indicator any time you want.
|
||||
|
||||
* `menu.show_all()` and `return menu` are just ordinary codes for returning the menu list to the indicator.
|
||||
|
||||
* Under `note(_)` you’ll see the code that must be executed when the “My Notes” menu item is clicked. Here, we just wrote `os.system(“gedit $HOME/Documents/notes.txt”)` ; The `os.system` function is a function that allows us to run shell commands from inside Python, so here we wrote a command to open a file called `notes.txt` under the `Documents` folder in our home directory using the `gedit` editor. This for example can be your daily notes taking program from now on!
|
||||
|
||||
### Adding your Needed Tasks
|
||||
|
||||
There are only 2 things you need to touch in the code:
|
||||
|
||||
1. Define a new menu item under `menu()` for your desired task.
|
||||
|
||||
2. Create a new function to run a specific action when that menu item is clicked.
|
||||
|
||||
|
||||
So, let’s say that you want to create a new menu item, which when clicked, plays a specific video/audio file on your hard disk using VLC? To do it, simply add the following 3 lines in line 17:
|
||||
|
||||
```
|
||||
command_two = gtk.MenuItem('Play video/audio')
|
||||
command_two.connect('activate', play)
|
||||
menu.append(command_two)
|
||||
```
|
||||
|
||||
And the following lines in line 30:
|
||||
|
||||
```
|
||||
def play(_):
|
||||
os.system("vlc /home/<username>/Videos/somevideo.mp4")
|
||||
```
|
||||
|
||||
Replace /home/<username>/Videos/somevideo.mp4 with the path to the video/audio file you want. Now save the file and run the indicator again:
|
||||
|
||||
```
|
||||
python tray.py
|
||||
```
|
||||
|
||||
This is how you’ll see it now:
|
||||
|
||||
![Create a Custom System Tray Indicator For Your Tasks on Linux 15][4]
|
||||
|
||||
And when you click on the newly-created menu item, VLC will start playing!
|
||||
|
||||
To create other items/tasks, simply redo the steps again. Just be careful to replace command_two with another name, like command_three, so that no clash between variables happen. And then define new separate functions like what we did with the play(_) function.
|
||||
|
||||
The possibilities are endless from here; I am using this way for example to fetch some data from the web (using the urllib2 library) and display them for me any time. I am also using it for playing an mp3 file in the background using the mpg123 command, and I am defining another menu item to killall mpg123 to stop playing that audio whenever I want. CS:GO on Steam for example takes a huge time to exit (the window doesn’t close automatically), so as a workaround for this, I simply minimize the window and click on a menu item that I created which will execute killall -9 csgo_linux64.
|
||||
|
||||
You can use this indicator for anything: Updating your system packages, possibly running some other scripts any time you want.. Literally anything.
|
||||
|
||||
### Autostart on Boot
|
||||
|
||||
We want our system tray indicator to start automatically on boot, we don’t want to run it manually each time. To do that, simply add the following command to your startup applications (after you replace the path to the tray.py file with yours):
|
||||
|
||||
```
|
||||
nohup python /home/<username>/tray.py &
|
||||
```
|
||||
|
||||
The very next time you reboot your system, the indicator will start working automatically after boot!
|
||||
|
||||
### Conclusion
|
||||
|
||||
You now know how to create your own system tray indicator for any task that you may want. This method should save you a lot of time depending on the nature and number of tasks you need to run on daily basis. Some users may prefer creating aliases from the command line, but this will require you to always open the terminal window or have a drop-down terminal emulator available, while here, the system tray indicator is always working and available for you.
|
||||
|
||||
Have you used this method to run your tasks before? Would love to hear your thoughts.
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://fosspost.org/tutorials/custom-system-tray-icon-indicator-linux
|
||||
|
||||
作者:[M.Hanny Sabbagh][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[lujun9972](https://github.com/lujun9972)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://fosspost.org/author/mhsabbagh
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://i2.wp.com/fosspost.org/wp-content/uploads/2019/02/Screenshot-at-2019-02-28-0808.png?resize=407%2C345&ssl=1 (Create a Custom System Tray Indicator For Your Tasks on Linux 12)
|
||||
[2]: https://extensions.gnome.org/extension/1031/topicons/
|
||||
[3]: https://i2.wp.com/fosspost.org/wp-content/uploads/2019/03/Screenshot-at-2019-03-02-1041.png?resize=434%2C140&ssl=1 (Create a Custom System Tray Indicator For Your Tasks on Linux 14)
|
||||
[4]: https://i2.wp.com/fosspost.org/wp-content/uploads/2019/03/Screenshot-at-2019-03-02-1141.png?resize=440%2C149&ssl=1 (Create a Custom System Tray Indicator For Your Tasks on Linux 16)
|
||||
51
sources/tech/20190302 How to buy a Raspberry Pi.md
Normal file
51
sources/tech/20190302 How to buy a Raspberry Pi.md
Normal file
@ -0,0 +1,51 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (qhwdw)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (How to buy a Raspberry Pi)
|
||||
[#]: via: (https://opensource.com/article/19/3/how-buy-raspberry-pi)
|
||||
[#]: author: (Anderson Silva https://opensource.com/users/ansilva)
|
||||
|
||||
How to buy a Raspberry Pi
|
||||
======
|
||||
Find out the best ways to get a Raspberry Pi in the second article in our getting started guide
|
||||
|
||||

|
||||
|
||||
The first article in this series on getting started with Raspberry Pi offered some advice on [which model you should buy][1]. Now that you have an idea of which version you want, let's find out how to get one.
|
||||
|
||||
The most obvious—and probably the safest and simplest—way is through the [official Raspberry Pi website][2]. If you click on "Buy a Raspberry Pi" from the homepage, you'll be taken to the organization's [online store][3], where you can find authorized Raspberry Pi sellers in your country where you can place an order. If your country isn't listed, there is a "Rest of the World" option, which should let you put in an international order.
|
||||
|
||||
Second, check Amazon.com or another major online technology retailer in your country that allows smaller shops to sell new and used items. Given the relatively low cost and size of the Raspberry Pi, it should be fairly easy for smaller shop owners to import and export the boards for reselling purposes. Before you place an order, keep an eye on the sellers' reviews though.
|
||||
|
||||
Third, ask your geek friends! You never know if someone has an unused Raspberry Pi gathering dust. I have given at least three Raspberry Pis away to family, not as planned gifts, but because they were just so curious about this mini-computer. I had so many lying around that I just told them to keep one!
|
||||
|
||||
### Don't forget the extras
|
||||
|
||||
One final thought: don't forget that you'll need some peripherals to set up and operate your Raspberry Pi. At a minimum, you'll need a keyboard, an HDMI cable to connect to a display (and a display), a Micro SD card to install the operating system, a power cord, and a mouse will be handy, too.
|
||||
|
||||

|
||||
|
||||
If you don't already have these items, try borrowing them from friends or order them at the same time you buy your Raspberry Pi. You may want to consider one of the starter kits available from the authorized Raspberry Pi vendors—that will avoid the hassle of searching for parts one at a time.
|
||||
|
||||

|
||||
|
||||
Now that you have a Raspberry Pi, in the next article in this series, we'll install the operating system and start using it.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/3/how-buy-raspberry-pi
|
||||
|
||||
作者:[Anderson Silva][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/ansilva
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/article/19/2/which-raspberry-pi-should-you-get
|
||||
[2]: https://www.raspberrypi.org/
|
||||
[3]: https://www.raspberrypi.org/products/
|
||||
@ -0,0 +1,94 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (lujun9972)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Manage Your Mirrors with ArchLinux Mirrorlist Manager)
|
||||
[#]: via: (https://itsfoss.com/archlinux-mirrorlist-manager)
|
||||
[#]: author: (John Paul https://itsfoss.com/author/john/)
|
||||
|
||||
Manage Your Mirrors with ArchLinux Mirrorlist Manager
|
||||
======
|
||||
|
||||
**ArchLinux Mirrorlist Manager is a simple GUI program that allows you to easily manage mirrors in your Arch Linux system.**
|
||||
|
||||
For Linux users, it is important to make sure that you keep your mirror list in good shape. Today we will take a quick look at an application designed to help manage your Arch mirror list.
|
||||
|
||||
![ArchLinux Mirrorlist Manager][1]ArchLinux Mirrorlist Manager
|
||||
|
||||
### What is a Mirror?
|
||||
|
||||
For those new to the world of Linux, Linux operating systems depend on a series of servers placed around the world. These servers contain identical copies of all of the packages and software available for a particular distro. This is why they are called “mirrors”.
|
||||
|
||||
The ultimate goal is to have multiple mirrors in each country. This allows local users to quickly update their systems. However, this is not always true. Sometimes mirrors from another country can be faster.
|
||||
|
||||
### ArchLinux Mirrorlist Manager makes managing mirrors simpler in Arch Linux
|
||||
|
||||
![ArchLinux Mirrorlist Manager][2]Main Screen
|
||||
|
||||
[Managing and sorting][3] the available mirrors in Arch is not easy. It involves fairly lengthy commands. Thankfully, someone came up with a solution.
|
||||
|
||||
Last year, [Rizwan Hasan][4] created a little Python and Qt application entitled [ArchLinux Mirrorlist Manager][5]. You might recognize Rizwan’s name because it is not the first time that we featured something he created on this site. Over a year ago, I wrote about a new Arch-based distro that Rizwan created named [MagpieOS][6]. I imagine that Rizwan’s experience with MagpieOS inspired him to create this application.
|
||||
|
||||
There really isn’t much to ArchLinux Mirrorlist Manager. It allows you to rank mirrors by response speed and limit the results by number and country of origin.
|
||||
|
||||
In other words, if you are located in Germany, you can restrict your mirrors to the 3 fastest in Germany.
|
||||
|
||||
### Install ArchLinux Mirrorlist Manager
|
||||
|
||||
```
|
||||
It is only for Arch Linux users
|
||||
|
||||
Pay attention! ArchLinux Mirrorlist Manager is for Arch Linux distribution only. Don’t try to use it on other Arch-based distributions unless you make sure that the distro uses Arch mirrors. Otherwise, you might face issues that I encountered with Manjaro (explained in the section below).
|
||||
```
|
||||
|
||||
```
|
||||
Mirrorlist Manager alternative for Manjaro
|
||||
|
||||
When it comes to using something Archy, my go-to system is Manjaro. In preparation for this article, I decided to install ArchLinux Mirrorlist Manager on my Manjaro machine. It quickly sorted the available mirror and saved them to my mirror list.
|
||||
|
||||
I then proceeded to try to update my system and immediately ran into problems. When ArchLinux Mirrorlist Manager sorted the mirrors my system was using, it replaced all of my Manjaro mirrors with vanilla Arch mirrors. (Manjaro is based on Arch, but has its own mirrors because the dev team tests all package updates before pushing them to the users to ensure there are no system-breaking bugs.) Thankfully, the Manjaro forum helped me fix my mistake.
|
||||
|
||||
If you are a Manjaro user, please do not make the same mistake that I did. ArchLinux Mirrorlist Manager is only for Arch and Arch-based distros that use Arch’s mirrors.
|
||||
|
||||
Luckily, there is an easy to use terminal application that Manjaro users can use to manage their mirror lists. It is called [Pacman-mirrors][7]. Just like ArchLinux Mirrorlist Manager, you can sort by response speed. Just type `sudo pacman-mirrors --fasttrack`. If you want to limit the results to the five fastest mirrors, you can type `sudo pacman-mirrors --fasttrack 5`. To restrict the results to one or more countries, type `sudo pacman-mirrors --country Germany,Spain,Austria`. You can limit the results to your country by typing `sudo pacman-mirrors --geoip`. You can visit the [Manjaro wiki][7] for more information about Pacman-mirrors.
|
||||
|
||||
After you run Pacman-mirrors, you have to synchronize your package database and update your system by typing `sudo pacman -Syyu`.
|
||||
|
||||
Note: Pacman-mirrors is for **Manjaro only**.
|
||||
```
|
||||
|
||||
ArchLinux Mirrorlist Manager is available in the [Arch User Repository][8]. More advanced Arch users can download the PKGBUILD directly from [the GitHub page][9].
|
||||
|
||||
### Final Thoughts on ArchLinux Mirrorlist Manager
|
||||
|
||||
Even though [ArchLinux Mirrorlist Manager][5] isn’t very useful for me, I’m glad it exists. It shows that Linux users are actively trying to make Linux easier to use. As I said earlier, managing a mirror list on Arch is not easy. Rizwan’s little tool will help make Arch more usable by the beginning user.
|
||||
|
||||
Have you ever used ArchLinux Mirrorlist Manager? What is your method to manage your Arch mirrors? Please let us know in the comments below.
|
||||
|
||||
If you found this article interesting, please take a minute to share it on social media, Hacker News or [Reddit][10].
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://itsfoss.com/archlinux-mirrorlist-manager
|
||||
|
||||
作者:[John Paul][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[lujun9972](https://github.com/lujun9972)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://itsfoss.com/author/john/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2019/02/mirrorlist-manager2.png?ssl=1
|
||||
[2]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2019/02/mirrorlist-manager4.jpg?ssl=1
|
||||
[3]: https://wiki.archlinux.org/index.php/Mirrors
|
||||
[4]: https://github.com/Rizwan-Hasan
|
||||
[5]: https://github.com/Rizwan-Hasan/ArchLinux-Mirrorlist-Manager
|
||||
[6]: https://itsfoss.com/magpieos/
|
||||
[7]: https://wiki.manjaro.org/index.php?title=Pacman-mirrors
|
||||
[8]: https://aur.archlinux.org/packages/mirrorlist-manager
|
||||
[9]: https://github.com/Rizwan-Hasan/MagpieOS-Packages/tree/master/ArchLinux-Mirrorlist-Manager
|
||||
[10]: http://reddit.com/r/linuxusersgroup
|
||||
238
sources/tech/20190304 How to Install MongoDB on Ubuntu.md
Normal file
238
sources/tech/20190304 How to Install MongoDB on Ubuntu.md
Normal file
@ -0,0 +1,238 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (An-DJ)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (How to Install MongoDB on Ubuntu)
|
||||
[#]: via: (https://itsfoss.com/install-mongodb-ubuntu)
|
||||
[#]: author: (Sergiu https://itsfoss.com/author/sergiu/)
|
||||
|
||||
How to Install MongoDB on Ubuntu
|
||||
======
|
||||
|
||||
**This tutorial presents two ways to install MongoDB on Ubuntu and Ubuntu-based Linux distributions.**
|
||||
|
||||
[MongoDB][1] is an increasingly popular free and open-source NoSQL database that stores data in collections of JSON-like, flexible documents, in contrast to the usual table approach you’ll find in SQL databases.
|
||||
|
||||
You are most likely to find MongoDB used in modern web applications. Its document model makes it very intuitive to access and handle with various programming languages.
|
||||
|
||||
![mongodb Ubuntu][2]
|
||||
|
||||
In this article, I’ll cover two ways you can install MongoDB on your Ubuntu system.
|
||||
|
||||
### Installing MongoDB on Ubuntu based Distributions
|
||||
|
||||
1. Install MongoDB using Ubuntu’s repository. Easy but not the latest version of MongoDB
|
||||
2. Install MongoDB using its official repository. Slightly complicated but you get the latest version of MongoDB.
|
||||
|
||||
|
||||
|
||||
The first installation method is easier, but I recommend the second method if you plan on using the latest release with official support.
|
||||
|
||||
Some people might prefer using snap packages. There are snaps available in the Ubuntu Software Center, but I wouldn’t recommend using them; they’re outdated at the moment and I won’t be covering that.
|
||||
|
||||
#### Method 1. Install MongoDB from Ubuntu Repository
|
||||
|
||||
This is the easy way to install MongoDB on your system, you only need to type in a simple command.
|
||||
|
||||
##### Installing MongoDB
|
||||
|
||||
First, make sure your packages are up-to-date. Open up a terminal and type:
|
||||
|
||||
```
|
||||
sudo apt update && sudo apt upgrade -y
|
||||
```
|
||||
|
||||
Go ahead and install MongoDB with:
|
||||
|
||||
```
|
||||
sudo apt install mongodb
|
||||
```
|
||||
|
||||
That’s it! MongoDB is now installed on your machine.
|
||||
|
||||
The MongoDB service should automatically be started on install, but to check the status type
|
||||
|
||||
```
|
||||
sudo systemctl status mongodb
|
||||
```
|
||||
|
||||
![Check if the MongoDB service is running.][3]
|
||||
|
||||
You can see that the service is **active**.
|
||||
|
||||
##### Running MongoDB
|
||||
|
||||
MongoDB is currently a systemd service, so we’ll use **systemctl** to check and modify it’s state, using the following commands:
|
||||
|
||||
```
|
||||
sudo systemctl status mongodb
|
||||
sudo systemctl stop mongodb
|
||||
sudo systemctl start mongodb
|
||||
sudo systemctl restart mongodb
|
||||
```
|
||||
|
||||
You can also change if MongoDB automatically starts when the system starts up ( **default** : enabled):
|
||||
|
||||
```
|
||||
sudo systemctl disable mongodb
|
||||
sudo systemctl enable mongodb
|
||||
```
|
||||
|
||||
To start working with (creating and editing) databases, type:
|
||||
|
||||
```
|
||||
mongo
|
||||
```
|
||||
|
||||
This will start up the **mongo shell**. Please check out the [manual][4] for detailed information on the available queries and options.
|
||||
|
||||
**Note:** Depending on how you plan to use MongoDB, you might need to adjust your Firewall. That’s unfortunately more involved than what I can cover here and depends on your configuration.
|
||||
|
||||
##### Uninstall MongoDB
|
||||
|
||||
If you installed MongoDB from the Ubuntu Repository and want to uninstall it (maybe to install using the officially supported way), type:
|
||||
|
||||
```
|
||||
sudo systemctl stop mongodb
|
||||
sudo apt purge mongodb
|
||||
sudo apt autoremove
|
||||
```
|
||||
|
||||
This should completely get rid of your MongoDB install. Make sure to **backup** any collections or documents you might want to keep since they will be wiped out!
|
||||
|
||||
#### Method 2. Install MongoDB Community Edition on Ubuntu
|
||||
|
||||
This is the way the recommended way to install MongoDB, using the package manager. You’ll have to type a few more commands and it might be intimidating if you are newer to the Linux world.
|
||||
|
||||
But there’s nothing to be afraid of! We’ll go through the installation process step by step.
|
||||
|
||||
##### Installing MongoDB
|
||||
|
||||
The package maintained by MongoDB Inc. is called **mongodb-org** , not **mongodb** (this is the name of the package in the Ubuntu Repository). Make sure **mongodb** is not installed on your system before applying this steps. The packages will conflict. Let’s get to it!
|
||||
|
||||
First, we’ll have to import the public key:
|
||||
|
||||
```
|
||||
sudo apt-key adv --keyserver hkp://keyserver.ubuntu.com:80 --recv 9DA31620334BD75D9DCB49F368818C72E52529D4
|
||||
```
|
||||
|
||||
Now, you need to add a new repository in your sources list so that you can install MongoDB Community Edition and also get automatic updates:
|
||||
|
||||
```
|
||||
echo "deb [ arch=amd64 ] https://repo.mongodb.org/apt/ubuntu $(lsb_release -cs)/mongodb-org/4.0 multiverse" | sudo tee /etc/apt/sources.list.d/mongodb-org-4.0.list
|
||||
```
|
||||
|
||||
To be able to install **mongodb-org** , we’ll have to update our package database so that your system is aware of the new packages available:
|
||||
|
||||
```
|
||||
sudo apt update
|
||||
```
|
||||
|
||||
Now you can ether install the **latest stable version** of MongoDB:
|
||||
|
||||
```
|
||||
sudo apt install -y mongodb-org
|
||||
```
|
||||
|
||||
or a **specific version** (change the version number after **equal** sign)
|
||||
|
||||
```
|
||||
sudo apt install -y mongodb-org=4.0.6 mongodb-org-server=4.0.6 mongodb-org-shell=4.0.6 mongodb-org-mongos=4.0.6 mongodb-org-tools=4.0.6
|
||||
```
|
||||
|
||||
If you choose to install a specific version, make sure you change the version number everywhere. If you only change it in the **mongodb-org=4.0.6** part, the latest version will be installed.
|
||||
|
||||
By default, when updating using the package manager ( **apt-get** ), MongoDB will be updated to the newest updated version. To stop that from happening (and freezing to the installed version), use:
|
||||
|
||||
```
|
||||
echo "mongodb-org hold" | sudo dpkg --set-selections
|
||||
echo "mongodb-org-server hold" | sudo dpkg --set-selections
|
||||
echo "mongodb-org-shell hold" | sudo dpkg --set-selections
|
||||
echo "mongodb-org-mongos hold" | sudo dpkg --set-selections
|
||||
echo "mongodb-org-tools hold" | sudo dpkg --set-selections
|
||||
```
|
||||
|
||||
You have now successfully installed MongoDB!
|
||||
|
||||
##### Configuring MongoDB
|
||||
|
||||
By default, the package manager will create **/var/lib/mongodb** and **/var/log/mongodb** and MongoDB will run using the **mongodb** user account.
|
||||
|
||||
I won’t go into changing these default settings since that is beyond the scope of this guide. You can check out the [manual][5] for detailed information.
|
||||
|
||||
The settings in **/etc/mongod.conf** are applied when starting/restarting the **mongodb** service instance.
|
||||
|
||||
##### Running MongoDB
|
||||
|
||||
To start the mongodb daemon **mongod** , type:
|
||||
|
||||
```
|
||||
sudo service mongod start
|
||||
```
|
||||
|
||||
Now you should verify that the **mongod** process started successfully. This information is stored (by default) at **/var/log/mongodb/mongod.log**. Let’s check the contents of that file:
|
||||
|
||||
```
|
||||
sudo cat /var/log/mongodb/mongod.log
|
||||
```
|
||||
|
||||
![Check MongoDB logs to see if the process is running properly.][6]
|
||||
|
||||
As long as you get this: **[initandlisten] waiting for connections on port 27017** somewhere in there, the process is running properly.
|
||||
|
||||
**Note: 27017** is the default port of **mongod.**
|
||||
|
||||
To stop/restart **mongod** enter:
|
||||
|
||||
```
|
||||
sudo service mongod stop
|
||||
sudo service mongod restart
|
||||
```
|
||||
|
||||
Now, you can use MongoDB by opening the **mongo shell** :
|
||||
|
||||
```
|
||||
mongo
|
||||
```
|
||||
|
||||
##### Uninstall MongoDB
|
||||
|
||||
Run the following commands
|
||||
|
||||
```
|
||||
sudo service mongod stop
|
||||
sudo apt purge mongodb-org*
|
||||
```
|
||||
|
||||
To remove the **databases** and **log files** (make sure to **backup** what you want to keep!):
|
||||
|
||||
```
|
||||
sudo rm -r /var/log/mongodb
|
||||
sudo rm -r /var/lib/mongodb
|
||||
```
|
||||
|
||||
**Wrapping Up**
|
||||
|
||||
MongoDB is a great NoSQL database, easy to integrate into modern projects. I hope this tutorial helped you to set it up on your Ubuntu machine! Let us know how you plan on using MongoDB in the comments below.
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://itsfoss.com/install-mongodb-ubuntu
|
||||
|
||||
作者:[Sergiu][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://itsfoss.com/author/sergiu/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.mongodb.com/
|
||||
[2]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2019/03/mongodb-ubuntu.jpeg?resize=800%2C450&ssl=1
|
||||
[3]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2019/02/mongodb_check_status.jpg?fit=800%2C574&ssl=1
|
||||
[4]: https://docs.mongodb.com/manual/tutorial/getting-started/
|
||||
[5]: https://docs.mongodb.com/manual/
|
||||
[6]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2019/02/mongodb_org_check_logs.jpg?fit=800%2C467&ssl=1
|
||||
53
sources/tech/20190304 Learn Linux with the Raspberry Pi.md
Normal file
53
sources/tech/20190304 Learn Linux with the Raspberry Pi.md
Normal file
@ -0,0 +1,53 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Learn Linux with the Raspberry Pi)
|
||||
[#]: via: (https://opensource.com/article/19/3/learn-linux-raspberry-pi)
|
||||
[#]: author: (Andersn Silva https://opensource.com/users/ansilva)
|
||||
|
||||
Learn Linux with the Raspberry Pi
|
||||
======
|
||||
The fourth article in our guide to getting started with the Raspberry Pi dives into the Linux command line.
|
||||

|
||||
|
||||
In the [third article][1] in this series on getting started with Raspberry Pi, I shared info on installing Raspbian, the official version of Linux for Raspberry Pi. Now that you've installed Raspbian and booted up your new Pi, you're ready to start learning about Linux.
|
||||
|
||||
It's impossible to tackle a topic as big as "how to use Linux" in a short article like this, so instead I'll give you some ideas about how you can use the Raspberry Pi to learn more about Linux in general.
|
||||
|
||||
Start by spending time on the command line (aka the "terminal"). Linux [window managers][2] and graphical interfaces have come a long way since the mid-'90s. Nowadays you can use Linux by pointing-and-clicking on things, just as easily as you can in other operating systems. In my opinion, there is a difference between just "using Linux" and being "a Linux user," and the latter means at a minimum being able to navigate in the terminal.
|
||||
|
||||
|
||||
|
||||
If you want to become a Linux user, start by trying out the following on the command line:
|
||||
|
||||
* Navigate your home directory with commands like **ls** , **cd** , and **pwd**.
|
||||
* Create, delete, and rename directories using the **mkdir** , **rm** , **mv** , and **cp** commands.
|
||||
* Create a text file with a command line editor such as Vi, Vim, Emacs, or Nano.
|
||||
* Try out some other useful commands, such as **chmod** , **chown** , **w** , **cat** , **more** , **less** , **tail** , **free** , **df** , **ps** , **uname** , and **kill**
|
||||
* Look around **/bin** and **/usr/bin** for other commands.
|
||||
|
||||
|
||||
|
||||
The best way to get help with a command is by reading its "man page" (short for manual); type **man <command>** on the command line to pull it up. And make sure to search the internet for Linux command cheat sheets—you should find a lot of options that will help you learn.
|
||||
|
||||
Raspbian, like most Linux distributions, has many commands and over time you will end up using some commands a lot more than others. I've been using Linux on the command line for over two decades, and there are still some commands that I've never used, even ones that have been around as long as I've been using Linux.
|
||||
|
||||
At the end of the day, you can use your graphical interface environment to get work done faster, but make sure to dive into the Linux command line, for that's where you will get the true power and knowledge of the operating system.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/3/learn-linux-raspberry-pi
|
||||
|
||||
作者:[Andersn Silva][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/ansilva
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/article/19/2/how-boot-new-raspberry-pi
|
||||
[2]: https://opensource.com/article/18/8/window-manager
|
||||
@ -0,0 +1,311 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (What you need to know about Ansible modules)
|
||||
[#]: via: (https://opensource.com/article/19/3/developing-ansible-modules)
|
||||
[#]: author: (Jairo da Silva Junior https://opensource.com/users/jairojunior)
|
||||
|
||||
What you need to know about Ansible modules
|
||||
======
|
||||
Learn how and when to develop custom modules for Ansible.
|
||||
|
||||
|
||||
Ansible works by connecting to nodes and sending small programs called modules to be executed remotely. This makes it a push architecture, where configuration is pushed from Ansible to servers without agents, as opposed to the pull model, common in agent-based configuration management systems, where configuration is pulled.
|
||||
|
||||
These modules are mapped to resources and their respective states, which are represented in YAML files. They enable you to manage virtually everything that has an API, CLI, or configuration file you can interact with, including network devices like load balancers, switches, firewalls, container orchestrators, containers themselves, and even virtual machine instances in a hypervisor or in a public (e.g., AWS, GCE, Azure) and/or private (e.g., OpenStack, CloudStack) cloud, as well as storage and security appliances and system configuration.
|
||||
|
||||
With Ansible's batteries-included model, hundreds of modules are included and any task in a playbook has a module behind it.
|
||||
|
||||
The contract for building modules is simple: JSON in the stdout. The configurations declared in YAML files are delivered over the network via SSH/WinRM—or any other connection plugin—as small scripts to be executed in the target server(s). Modules can be written in any language capable of returning JSON, although most Ansible modules (except for Windows PowerShell) are written in Python using the Ansible API (this eases the development of new modules).
|
||||
|
||||
Modules are one way of expanding Ansible capabilities. Other alternatives, like dynamic inventories and plugins, can also increase Ansible's power. It's important to know about them so you know when to use one instead of the other.
|
||||
|
||||
Plugins are divided into several categories with distinct goals, like Action, Cache, Callback, Connection, Filters, Lookup, and Vars. The most popular plugins are:
|
||||
|
||||
* **Connection plugins:** These implement a way to communicate with servers in your inventory (e.g., SSH, WinRM, Telnet); in other words, how automation code is transported over the network to be executed.
|
||||
* **Filters plugins:** These allow you to manipulate data inside your playbook. This is a Jinja2 feature that is harnessed by Ansible to solve infrastructure-as-code problems.
|
||||
* **Lookup plugins:** These fetch data from an external source (e.g., env, file, Hiera, database, HashiCorp Vault).
|
||||
|
||||
|
||||
|
||||
Ansible's official docs are a good resource on [developing plugins][1].
|
||||
|
||||
### When should you develop a module?
|
||||
|
||||
Although many modules are delivered with Ansible, there is a chance that your problem is not yet covered or it's something too specific—for example, a solution that might make sense only in your organization. Fortunately, the official docs provide excellent guidelines on [developing modules][2].
|
||||
|
||||
**IMPORTANT:** Before you start working on something new, always check for open pull requests, ask developers at #ansible-devel (IRC/Freenode), or search the [development list][3] and/or existing [working groups][4] to see if a module exists or is in development.
|
||||
|
||||
Signs that you need a new module instead of using an existing one include:
|
||||
|
||||
* Conventional configuration management methods (e.g., templates, file, get_url, lineinfile) do not solve your problem properly.
|
||||
* You have to use a complex combination of commands, shells, filters, text processing with magic regexes, and API calls using curl to achieve your goals.
|
||||
* Your playbooks are complex, imperative, non-idempotent, and even non-deterministic.
|
||||
|
||||
|
||||
|
||||
In the ideal scenario, the tool or service already has an API or CLI for management, and it returns some sort of structured data (JSON, XML, YAML).
|
||||
|
||||
### Identifying good and bad playbooks
|
||||
|
||||
> "Make love, but don't make a shell script in YAML."
|
||||
|
||||
So, what makes a bad playbook?
|
||||
|
||||
```
|
||||
- name: Read a remote resource
|
||||
command: "curl -v http://xpto/resource/abc"
|
||||
register: resource
|
||||
changed_when: False
|
||||
|
||||
- name: Create a resource in case it does not exist
|
||||
command: "curl -X POST http://xpto/resource/abc -d '{ config:{ client: xyz, url: http://beta, pattern: core.md Dict.md lctt2014.md lctt2016.md lctt2018.md README.md } }'"
|
||||
when: "resource.stdout | 404"
|
||||
|
||||
# Leave it here in case I need to remove it hehehe
|
||||
#- name: Remove resource
|
||||
# command: "curl -X DELETE http://xpto/resource/abc"
|
||||
# when: resource.stdout == 1
|
||||
```
|
||||
|
||||
Aside from being very fragile—what if the resource state includes a 404 somewhere?—and demanding extra code to be idempotent, this playbook can't update the resource when its state changes.
|
||||
|
||||
Playbooks written this way disrespect many infrastructure-as-code principles. They're not readable by human beings, are hard to reuse and parameterize, and don't follow the declarative model encouraged by most configuration management tools. They also fail to be idempotent and to converge to the declared state.
|
||||
|
||||
Bad playbooks can jeopardize your automation adoption. Instead of harnessing configuration management tools to increase your speed, they have the same problems as an imperative automation approach based on scripts and command execution. This creates a scenario where you're using Ansible just as a means to deliver your old scripts, copying what you already have into YAML files.
|
||||
|
||||
Here's how to rewrite this example to follow infrastructure-as-code principles.
|
||||
|
||||
```
|
||||
- name: XPTO
|
||||
xpto:
|
||||
name: abc
|
||||
state: present
|
||||
config:
|
||||
client: xyz
|
||||
url: http://beta
|
||||
pattern: "*.*"
|
||||
```
|
||||
|
||||
The benefits of this approach, based on custom modules, include:
|
||||
|
||||
* It's declarative—resources are properly represented in YAML.
|
||||
* It's idempotent.
|
||||
* It converges from the declared state to the current state.
|
||||
* It's readable by human beings.
|
||||
* It's easily parameterized or reused.
|
||||
|
||||
|
||||
|
||||
### Implementing a custom module
|
||||
|
||||
Let's use [WildFly][5], an open source Java application server, as an example to introduce a custom module for our not-so-good playbook:
|
||||
|
||||
```
|
||||
- name: Read datasource
|
||||
command: "jboss-cli.sh -c '/subsystem=datasources/data-source=DemoDS:read-resource()'"
|
||||
register: datasource
|
||||
|
||||
- name: Create datasource
|
||||
command: "jboss-cli.sh -c '/subsystem=datasources/data-source=DemoDS:add(driver-name=h2, user-name=sa, password=sa, min-pool-size=20, max-pool-size=40, connection-url=.jdbc:h2:mem:demo;DB_CLOSE_DELAY=-1;DB_CLOSE_ON_EXIT=FALSE..)'"
|
||||
when: 'datasource.stdout | outcome => failed'
|
||||
```
|
||||
|
||||
Problems:
|
||||
|
||||
* It's not declarative.
|
||||
* JBoss-CLI returns plaintext in a JSON-like syntax; therefore, this approach is very fragile, since we need a type of parser for this notation. Even a seemingly simple parser can be too complex to treat many [exceptions][6].
|
||||
* JBoss-CLI is just an interface to send requests to the management API (port 9990).
|
||||
* Sending an HTTP request is more efficient than opening a new JBoss-CLI session, connecting, and sending a command.
|
||||
* It does not converge to the desired state; it only creates the resource when it doesn't exist.
|
||||
|
||||
|
||||
|
||||
A custom module for this would look like:
|
||||
|
||||
```
|
||||
- name: Configure datasource
|
||||
jboss_resource:
|
||||
name: "/subsystem=datasources/data-source=DemoDS"
|
||||
state: present
|
||||
attributes:
|
||||
driver-name: h2
|
||||
connection-url: "jdbc:h2:mem:demo;DB_CLOSE_DELAY=-1;DB_CLOSE_ON_EXIT=FALSE"
|
||||
jndi-name: "java:jboss/datasources/DemoDS"
|
||||
user-name: sa
|
||||
password: sa
|
||||
min-pool-size: 20
|
||||
max-pool-size: 40
|
||||
```
|
||||
|
||||
This playbook is declarative, idempotent, more readable, and converges to the desired state regardless of the current state.
|
||||
|
||||
### Why learn to build custom modules?
|
||||
|
||||
Good reasons to learn how to build custom modules include:
|
||||
|
||||
* Improving existing modules
|
||||
* You have bad playbooks and want to improve them, or …
|
||||
* You don't, but want to avoid having bad playbooks.
|
||||
* Knowing how to build a module considerably improves your ability to debug problems in playbooks, thereby increasing your productivity.
|
||||
|
||||
|
||||
|
||||
> "…abstractions save us time working, but they don't save us time learning." —Joel Spolsky, [The Law of Leaky Abstractions][7]
|
||||
|
||||
#### Custom Ansible modules 101
|
||||
|
||||
* JSON (JavaScript Object Notation) in stdout: that's the contract!
|
||||
* They can be written in any language, but …
|
||||
* Python is usually the best option (or the second best)
|
||||
* Most modules delivered with Ansible ( **lib/ansible/modules** ) are written in Python and should support compatible versions.
|
||||
|
||||
|
||||
|
||||
#### The Ansible way
|
||||
|
||||
* First step:
|
||||
|
||||
```
|
||||
git clone https://github.com/ansible/ansible.git
|
||||
```
|
||||
|
||||
* Navigate in **lib/ansible/modules/** and read the existing modules code.
|
||||
|
||||
* Your tools are: Git, Python, virtualenv, pdb (Python debugger)
|
||||
|
||||
* For comprehensive instructions, consult the [official docs][8].
|
||||
|
||||
|
||||
|
||||
|
||||
#### An alternative: drop it in the library directory
|
||||
|
||||
```
|
||||
library/ # if any custom modules, put them here (optional)
|
||||
module_utils/ # if any custom module_utils to support modules, put them here (optional)
|
||||
filter_plugins/ # if any custom filter plugins, put them here (optional)
|
||||
|
||||
site.yml # master playbook
|
||||
webservers.yml # playbook for webserver tier
|
||||
dbservers.yml # playbook for dbserver tier
|
||||
|
||||
roles/
|
||||
common/ # this hierarchy represents a "role"
|
||||
library/ # roles can also include custom modules
|
||||
module_utils/ # roles can also include custom module_utils
|
||||
lookup_plugins/ # or other types of plugins, like lookup in this case
|
||||
```
|
||||
|
||||
* It's easier to start.
|
||||
* Doesn't require anything besides Ansible and your favorite IDE/text editor.
|
||||
* This is your best option if it's something that will be used internally.
|
||||
|
||||
|
||||
|
||||
**TIP:** You can use this directory layout to overwrite existing modules if, for example, you need to patch a module.
|
||||
|
||||
#### First steps
|
||||
|
||||
You could do it in your own—including using another language—or you could use the AnsibleModule class, as it is easier to put JSON in the stdout ( **exit_json()** , **fail_json()** ) in the way Ansible expects ( **msg** , **meta** , **has_changed** , **result** ), and it's also easier to process the input ( **params[]** ) and log its execution ( **log()** , **debug()** ).
|
||||
|
||||
```
|
||||
def main():
|
||||
|
||||
arguments = dict(name=dict(required=True, type='str'),
|
||||
state=dict(choices=['present', 'absent'], default='present'),
|
||||
config=dict(required=False, type='dict'))
|
||||
|
||||
module = AnsibleModule(argument_spec=arguments, supports_check_mode=True)
|
||||
try:
|
||||
if module.check_mode:
|
||||
# Do not do anything, only verifies current state and report it
|
||||
module.exit_json(changed=has_changed, meta=result, msg='Fez alguma coisa ou não...')
|
||||
|
||||
if module.params['state'] == 'present':
|
||||
# Verify the presence of a resource
|
||||
# Desired state `module.params['param_name'] is equal to the current state?
|
||||
module.exit_json(changed=has_changed, meta=result)
|
||||
|
||||
if module.params['state'] == 'absent':
|
||||
# Remove the resource in case it exists
|
||||
module.exit_json(changed=has_changed, meta=result)
|
||||
|
||||
except Error as err:
|
||||
module.fail_json(msg=str(err))
|
||||
```
|
||||
|
||||
**NOTES:** The **check_mode** ("dry run") allows a playbook to be executed or just verifies if changes are required, but doesn't perform them. **** Also, the **module_utils** directory can be used for shared code among different modules.
|
||||
|
||||
For the full Wildfly example, check [this pull request][9].
|
||||
|
||||
### Running tests
|
||||
|
||||
#### The Ansible way
|
||||
|
||||
The Ansible codebase is heavily tested, and every commit triggers a build in its continuous integration (CI) server, [Shippable][10], which includes linting, unit tests, and integration tests.
|
||||
|
||||
For integration tests, it uses containers and Ansible itself to perform the setup and verify phase. Here is a test case (written in Ansible) for our custom module's sample code:
|
||||
|
||||
```
|
||||
- name: Configure datasource
|
||||
jboss_resource:
|
||||
name: "/subsystem=datasources/data-source=DemoDS"
|
||||
state: present
|
||||
attributes:
|
||||
connection-url: "jdbc:h2:mem:demo;DB_CLOSE_DELAY=-1;DB_CLOSE_ON_EXIT=FALSE"
|
||||
...
|
||||
register: result
|
||||
|
||||
- name: assert output message that datasource was created
|
||||
assert:
|
||||
that:
|
||||
- "result.changed == true"
|
||||
- "'Added /subsystem=datasources/data-source=DemoDS' in result.msg"
|
||||
```
|
||||
|
||||
#### An alternative: bundling a module with your role
|
||||
|
||||
Here is a [full example][11] inside a simple role:
|
||||
|
||||
```
|
||||
[*Molecule*]() + [*Vagrant*]() + [*pytest*](): `molecule init` (inside roles/<name>)
|
||||
```
|
||||
|
||||
It offers greater flexibility to choose:
|
||||
|
||||
* Simplified setup
|
||||
* How to spin up your infrastructure: e.g., Vagrant, Docker, OpenStack, EC2
|
||||
* How to verify your infrastructure tests: Testinfra and Goss
|
||||
|
||||
|
||||
|
||||
But your tests would have to be written using pytest with Testinfra or Goss, instead of plain Ansible. If you'd like to learn more about testing Ansible roles, see my article about [using Molecule][12].
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/3/developing-ansible-modules
|
||||
|
||||
作者:[Jairo da Silva Junior][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/jairojunior
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://docs.ansible.com/ansible/latest/dev_guide/developing_plugins.html#developing-plugins
|
||||
[2]: https://docs.ansible.com/ansible/latest/dev_guide/developing_modules.html
|
||||
[3]: https://groups.google.com/forum/#!forum/ansible-devel
|
||||
[4]: https://github.com/ansible/community/
|
||||
[5]: http://www.wildfly.org/
|
||||
[6]: https://tools.ietf.org/html/rfc7159
|
||||
[7]: https://en.wikipedia.org/wiki/Leaky_abstraction#The_Law_of_Leaky_Abstractions
|
||||
[8]: https://docs.ansible.com/ansible/latest/dev_guide/developing_modules_general.html#developing-modules-general
|
||||
[9]: https://github.com/ansible/ansible/pull/43682/files
|
||||
[10]: https://app.shippable.com/github/ansible/ansible/dashboard
|
||||
[11]: https://github.com/jairojunior/ansible-role-jboss/tree/with_modules
|
||||
[12]: https://opensource.com/article/18/12/testing-ansible-roles-molecule
|
||||
@ -0,0 +1,366 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (5 Ways To Generate A Random/Strong Password In Linux Terminal)
|
||||
[#]: via: (https://www.2daygeek.com/5-ways-to-generate-a-random-strong-password-in-linux-terminal/)
|
||||
[#]: author: (Magesh Maruthamuthu https://www.2daygeek.com/author/magesh/)
|
||||
|
||||
5 Ways To Generate A Random/Strong Password In Linux Terminal
|
||||
======
|
||||
|
||||
Recently we had written an article about **[password strength and password score check][1]** in our website.
|
||||
|
||||
It will help you to validate your password strength and score.
|
||||
|
||||
We can manually create few passwords which we required but if you would like to generate a password for multiple users or servers, what will be the solution.
|
||||
|
||||
Yes, there are many utilities are available in Linux to fulfill this requirements. However, I’m going to include the best five password generators in this article.
|
||||
|
||||
These tools are generates a strong random passwords for you. Navigate to the following article if you would like to update the password on multiple users and servers.
|
||||
|
||||
These tools are easy to use, that’s why i preferred to go with it. By default it will generate a strong password and if you would like to generate a super strong password then use the available options.
|
||||
|
||||
It will help you to generate a super strong password in the following combination. It should have minimum 12-15 characters length, that includes Alphabets (Lower case & Upper case), Numbers and Special Characters.
|
||||
|
||||
These tools are below.
|
||||
|
||||
* `pwgen:` The pwgen program generates passwords which are designed to be easily memorized by humans, while being as secure as possible.
|
||||
* `openssl:` The openssl program is a command line tool for using the various cryptography functions of OpenSSL’s crypto library from the shell.
|
||||
* `gpg:` OpenPGP encryption and signing tool
|
||||
* `mkpasswd:` generate new password, optionally apply it to a user
|
||||
* `makepasswd:` makepasswd generates true random passwords using /dev/urandom, with the emphasis on security over pronounceability.
|
||||
* `/dev/urandom file:` The character special files /dev/random and /dev/urandom (present since Linux 1.3.30) provide an interface to the kernel’s random number generator.
|
||||
* `md5sum:` md5sum is a computer program that calculates and verifies 128-bit MD5 hashes.
|
||||
* `sha256sum:` The program sha256sum is designed to verify data integrity using the SHA-256 (SHA-2 family with a digest length of 256 bits).
|
||||
* `sha1pass:` sha1pass creates a SHA1 password hash. In the absence of a salt value on the command line, a random salt vector will be generated.
|
||||
|
||||
|
||||
|
||||
### How To Generate A Random Strong Password In Linux Using pwgen Command?
|
||||
|
||||
The pwgen program generates passwords which are designed to be easily memorized by humans, while being as secure as possible.
|
||||
|
||||
Human-memorable passwords are never going to be as secure as completely completely random passwords.
|
||||
|
||||
Use `-s` option to generate completely random, hard-to-memorize passwords. These should only be used for machine passwords as we can’t memorize.
|
||||
|
||||
For **`Fedora`** system, use **[DNF Command][2]** to install pwgen.
|
||||
|
||||
```
|
||||
$ sudo dnf install pwgen
|
||||
```
|
||||
|
||||
For **`Debian/Ubuntu`** systems, use **[APT-GET Command][3]** or **[APT Command][4]** to install pwgen.
|
||||
|
||||
```
|
||||
$ sudo apt install pwgen
|
||||
```
|
||||
|
||||
For **`Arch Linux`** based systems, use **[Pacman Command][5]** to install pwgen.
|
||||
|
||||
```
|
||||
$ sudo pacman -S pwgen
|
||||
```
|
||||
|
||||
For **`RHEL/CentOS`** systems, use **[YUM Command][6]** to install pwgen.
|
||||
|
||||
```
|
||||
$ sudo yum install pwgen
|
||||
```
|
||||
|
||||
For **`openSUSE Leap`** system, use **[Zypper Command][7]** to install pwgen.
|
||||
|
||||
```
|
||||
$ sudo zypper install pwgen
|
||||
```
|
||||
|
||||
### How To Use pwgen Command In Linux?
|
||||
|
||||
It’s a simple and straight forward method. Use one of the below preferred examples for you. By default, it generates a human memorable password.
|
||||
|
||||
To do so, simple run the `pwgen` command on your terminal. It generates 160 passwords in a single shot. These 160 passwords are printer with 20 rows and 8 columns.
|
||||
|
||||
```
|
||||
$ pwgen
|
||||
ameiK2oo aibi3Cha EPium0Ie aisoh1Ee Nidee9ae uNga0Bee uPh9ieM1 ahn1ooNg
|
||||
oc5ooTea tai7eKid tae2yieS hiecaiR8 wohY2Ohk Uab2maed heC4aXoh Ob6Nieso
|
||||
Shaeriu3 uy9Juk5u hoht7Doo Fah6yah3 faz9Jeew eKiek4ju as0Xuosh Eiwo4epo
|
||||
oot8teeZ Ui1yoohi Aechae7A Ohdi2ael cae5Thoh Au1aeTei ais0aiC2 Cai2quin
|
||||
Oox9ohz4 neev0Che ahza8AQu Ahz7eica meiBeeW0 Av3bo7ah quoiTu3f taeNg3ae
|
||||
Aiko7Aiz SheiGh8E aesaeSh7 haet6Loo AeTel3oN Ath7zeer IeYah4ie UG3ootha
|
||||
Ohch9Och Phuap6su iel5Xu7s diqui7Bu ieF2dier eeluHa1u Thagei0i Ceeth3oh
|
||||
OCei1ahj zei2aiYo Jahgh1ia ooqu1Cej eez2aiPo Wahd5soo noo7Mei9 Hie5ashe
|
||||
Uith4Or2 Xie3uh2b fuF9Eilu eiN2sha9 zae2YaSh oGh5ephi ohvao4Ae aixu6aeM
|
||||
fo4Ierah iephei6A hae9eeGa eiBeiY3g Aic8Kee9 he8AheCh ohM4bid9 eemae3Zu
|
||||
eesh2EiM cheiGa4j PooV2vii ahpeeg5E aezauX2c Xe7aethu Ahvaph7a Joh2heec
|
||||
Ii5EeShi aij7Uo8e ooy2Ahth mieKe2ni eiQuu8fe giedaQu0 eiPhob3E oox1uo2U
|
||||
eehia4Hu ga9Ahw0a ohxuZei7 eV4OoXio Kid2wu1n ku4Ahf5s uigh8uQu AhWoh0po
|
||||
vo1Eeb2u Ahth7ve5 ieje4eiL ieci1Ach Meephie9 iephieY8 Eesoom7u eakai2Bo
|
||||
uo8Ieche Zai3aev5 aGhahf0E Wowoo5th Oraeb0ah Gah3nah0 ieGhah0p aeCh0OhJ
|
||||
ahQu2feZ ahQu0gah foik7Ush cei1Wai1 Aivi3ooY eephei5U MooZae3O quooRoh7
|
||||
aequae5U pae6Ceiv eizahF1k ohmi7ETa ahyaeK1N Mohw2no8 ooc8Oone coo7Ieve
|
||||
eePhei9h Weequ8eV Vie4iezu neeMiim4 ie6aiZoh Queegh2E shahwi3N Inichie8
|
||||
Sid1aeji mohj4Ko7 lieDi0pe Zeemah6a thuevu2E phi4Ohsh paiKeix1 ooz1Ceph
|
||||
ahV4yore ue2laePh fu1eThui qui7aePh Fahth1nu ohk9puLo aiBeez0b Neengai5
|
||||
```
|
||||
|
||||
To generate a secure random password, use `-s` option with pwgen command.
|
||||
|
||||
```
|
||||
$ pwgen -s
|
||||
CU75lgZd 7HzzKgtA 2ktBJDpR F6XJVhBs UjAm3bNL zO7Dw7JJ pxn8fUvp Ka3lLilG
|
||||
ywJX7iJl D9ajxb6N 78c1HOg2 g8vtWCra Jp6pBGBw oYuev9Vl gbA6gHV8 G6XQoVO5
|
||||
uQN98IU4 50GgQfrX FrTsou2t YQorO4x6 UGer8Yi2 O7DB5nw1 1ax370UR 1xVRPkA1
|
||||
RVaGDr2i Nt11ekUd 9Vm3D244 ck8Lnpd0 SjDt8uWn 5ERT4tf8 4EONFzyY Jc6T83jg
|
||||
WZa6bKPW H4HMo1YU bsDDRik3 gBwV7LOW 9H1QRQ4x 3Ak7RcSe IJu2RBF9 e508xrLC
|
||||
SzTrW191 AslxDa6E IkWWov2b iOb6EmTy qHt82OwG 5ZFO7B53 97zmjOPu A4KZuhYV
|
||||
uQpoJR4D 0eKyOiUr Rz96smeO 3HTABu3N 6W0VmEls uPsp5zpw 8UD3VkMG YTct6Rd4
|
||||
VKo0cVmq E07ZX7j9 kQSlvA69 Nm3fpv3i xWvF2xMu yEfcw8uA oQGVX3l9 grTzx7Xj
|
||||
s4GVEYtM uJl5sYMe n3icRPiY ED3Mup4B k3M9KHI7 IkxqoSM0 dt2cxmMU yb2tUkut
|
||||
2Q9wGZQx 8Rpo11s9 I13siOHu 7GV64Fjv 3VONzD8i SCDfVD3F oiPTx239 6BQakoiJ
|
||||
XUEokiC4 ybL7VGmL el2RfvWk zKc7CLcE 3FqNBSyA NjDWrvZ5 KI3NSX4h VFyo6VPr
|
||||
h4q3XeqZ FDYMoX6f uTU5ZzU3 6u4ob4Ep wiYPt05n CZga66qh upzH6Z9y RuVcqbe8
|
||||
taQv11hq 1xsY67a8 EVo9GLXA FCaDLGb1 bZyh0YN8 0nTKo0Qy RRVUwn9t DuU8mwwv
|
||||
x96LWpCb tFLz3fBG dNb4gCKf n6VYcOiH 1ep6QYFZ x8kaJtrY 56PDWuW6 1R0If4kV
|
||||
2XK0NLQK 4XQqhycl Ip08cn6c Bnx9z2Bz 7gjGlON7 CJxLR1U4 mqMwir3j ovGXWu0z
|
||||
MfDjk5m8 4KwM9SAN oz0fZ5eo 5m8iRtco oP5BpLh0 Z5kvwr1W f34O2O43 hXao1Sp8
|
||||
tKoG5VNI f13fuYvm BQQn8MD3 bmFSf6Mf Z4Y0o17U jT4wO1DG cz2clBES Lr4B3qIY
|
||||
ArKQRND6 8xnh4oIs nayiK2zG yWvQCV3v AFPlHSB8 zfx5bnaL t5lFbenk F2dIeBr4
|
||||
C6RqDQMy gKt28c9O ZCi0tQKE 0Ekdjh3P ox2vWOMI 14XF4gwc nYA0L6tV rRN3lekn
|
||||
lmwZNjz1 4ovmJAr7 shPl9o5f FFsuNwj0 F2eVkqGi 7gw277RZ nYE7gCLl JDn05S5N
|
||||
```
|
||||
|
||||
If you would like to generate a strong five passwords with 14 characters length, use the following format.
|
||||
|
||||
```
|
||||
$ pwgen -s 14 5
|
||||
7YxUwDyfxGVTYD em2NT6FceXjPfT u8jlrljbrclcTi IruIX3Xu0TFXRr X8M9cB6wKNot1e
|
||||
```
|
||||
|
||||
If you really want to generate a super strong random twenty passwords, use the following format.
|
||||
|
||||
```
|
||||
$ pwgen -cnys 14 20
|
||||
mQ3E=vfGfZ,5[B #zmj{i5|ZS){jg Ht_8i7OqJ%N`~2 443fa5iJ\W-L?] ?Qs$o=vz2vgQBR
|
||||
^'Ry0Az|J9p2+0 t2oA/n7U_'|QRx EsX*%_(4./QCRJ ACr-,8yF9&eM[* !Xz1C'bw?tv50o
|
||||
8hfv-fK(VxwQGS q!qj?sD7Xmkb7^ N#Zp\_Y2kr%!)~ 4*pwYs{bq]Hh&Y |4u=-Q1!jS~8=;
|
||||
]{$N#FPX1L2B{h I|01fcK.z?QTz" l~]JD_,W%5bp.E +i2=D3;BQ}p+$I n.a3,.D3VQ3~&i
|
||||
```
|
||||
|
||||
### How To Generate A Random Strong Password In Linux Using openssl Command?
|
||||
|
||||
The openssl program is a command line tool for using the various cryptography functions of OpenSSL’s crypto library from the shell.
|
||||
|
||||
Run the openssl command with the following format to generate a random strong password with 14 characters.
|
||||
|
||||
```
|
||||
$ openssl rand -base64 14
|
||||
WjzyDqdkWf3e53tJw/c=
|
||||
```
|
||||
|
||||
If you would like to generate ten random strong password with 14 characters using openssl command then use the following for loop.
|
||||
|
||||
```
|
||||
$ for pw in {1..10}; do openssl rand -base64 14; done
|
||||
6i0hgHDBi3ohZ9Mil8I=
|
||||
gtn+y1bVFJFanpJqWaA=
|
||||
rYu+wy+0nwLf5lk7TBA=
|
||||
xrdNGykIzxaKDiLF2Bw=
|
||||
cltejRkDPdFPC/zI0Pg=
|
||||
G6aroK6d4xVVYFTrZGs=
|
||||
jJEnFoOk1+UTSx/wJrY=
|
||||
TFxVjBmLx9aivXB3yxE=
|
||||
oQtOLPwTuO8df7dIv9I=
|
||||
ktpBpCSQFOD+5kIIe7Y=
|
||||
```
|
||||
|
||||
### How To Generate A Random Strong Password In Linux Using gpg Command?
|
||||
|
||||
gpg is the OpenPGP part of the GNU Privacy Guard (GnuPG). It is a tool to provide digital encryption and signing services using the OpenPGP standard. gpg features complete key management and all the bells and whistles you would expect from a full OpenPGP implementation.
|
||||
|
||||
Run the gpg command with the following format to generate a random strong password with 14 characters.
|
||||
|
||||
```
|
||||
$ gpg --gen-random --armor 1 14
|
||||
or
|
||||
$ gpg2 --gen-random --armor 1 14
|
||||
jq1mtY4gBa6gIuJrggM=
|
||||
```
|
||||
|
||||
If you would like to generate ten random strong password with 14 characters using gpg command then use the following for loop.
|
||||
|
||||
```
|
||||
$ for pw in {1..10}; do gpg --gen-random --armor 1 14; done
|
||||
or
|
||||
$ for pw in {1..10}; do gpg2 --gen-random --armor 1 14; done
|
||||
F5ZzLSUMet2kefG6Ssc=
|
||||
8hh7BFNs8Qu0cnrvHrY=
|
||||
B+PEt28CosR5xO05/sQ=
|
||||
m21bfx6UG1cBDzVGKcE=
|
||||
wALosRXnBgmOC6+++xU=
|
||||
TGpjT5xRxo/zFq/lNeg=
|
||||
ggsKxVgpB/3aSOY15W4=
|
||||
iUlezWxL626CPc9omTI=
|
||||
pYb7xQwI1NTlM2rxaCg=
|
||||
eJjhtA6oHhBrUpLY4fM=
|
||||
```
|
||||
|
||||
### How To Generate A Random Strong Password In Linux Using mkpasswd Command?
|
||||
|
||||
mkpasswd generates passwords and can apply them automatically to users. With no arguments, mkpasswd returns a new password. It’s part of an expect package so, you have to install expect package to use mkpasswd command.
|
||||
|
||||
For **`Fedora`** system, use **[DNF Command][2]** to install mkpasswd.
|
||||
|
||||
```
|
||||
$ sudo dnf install expect
|
||||
```
|
||||
|
||||
For **`Debian/Ubuntu`** systems, use **[APT-GET Command][3]** or **[APT Command][4]** to install mkpasswd.
|
||||
|
||||
```
|
||||
$ sudo apt install expect
|
||||
```
|
||||
|
||||
For **`Arch Linux`** based systems, use **[Pacman Command][5]** to install mkpasswd.
|
||||
|
||||
```
|
||||
$ sudo pacman -S expect
|
||||
```
|
||||
|
||||
For **`RHEL/CentOS`** systems, use **[YUM Command][6]** to install mkpasswd.
|
||||
|
||||
```
|
||||
$ sudo yum install expect
|
||||
```
|
||||
|
||||
For **`openSUSE Leap`** system, use **[Zypper Command][7]** to install mkpasswd.
|
||||
|
||||
```
|
||||
$ sudo zypper install expect
|
||||
```
|
||||
|
||||
Run the `mkpasswd` command in terminal to generate a random password.
|
||||
|
||||
```
|
||||
$ mkpasswd
|
||||
37_slQepD
|
||||
```
|
||||
|
||||
Run the mkpasswd command with the following format to generate a random strong password with 14 characters.
|
||||
|
||||
```
|
||||
$ mkpasswd -l 14
|
||||
W1qP1uv=lhghgh
|
||||
```
|
||||
|
||||
Run the mkpasswd command with the following format to generate a random strong password with 14 characters. It combinations of alphabetic (Lower & Upper case), Numeric number and special characters.
|
||||
|
||||
```
|
||||
$ mkpasswd -l 14 -d 3 -C 3 -s 3
|
||||
3aad!bMWG49"t,
|
||||
```
|
||||
|
||||
If you would like to generate ten random strong password with 14 characters (It combination of alphabetic (Lower & Upper case), Numeric number and special characters) using mkpasswd command then use the following for loop.
|
||||
|
||||
```
|
||||
$ for pw in {1..10}; do mkpasswd -l 14 -d 3 -C 3 -s 3; done
|
||||
zmSwP[q9;P1r6[
|
||||
E42zcvzM"i3%B\
|
||||
8}1#[email protected]
|
||||
0X:zB(mmU22?nj
|
||||
0sqqL44M}ko(O^
|
||||
43tQ(.6jG;ceRq
|
||||
-jB6cp3x1GZ$e=
|
||||
$of?Rj9kb2N(1J
|
||||
9HCf,nn#gjO79^
|
||||
Tu9m56+Ev_Yso(
|
||||
```
|
||||
|
||||
### How To Generate A Random Strong Password In Linux Using makepasswd Command?
|
||||
|
||||
makepasswd generates true random passwords using /dev/urandom, with the emphasis on security over pronounceability. It can also encrypt plaintext passwords given on the command line.
|
||||
|
||||
Run the `makepasswd` command in terminal to generate a random password.
|
||||
|
||||
```
|
||||
$ makepasswd
|
||||
HdCJafVaN
|
||||
```
|
||||
|
||||
Run the makepasswd command with the following format to generate a random strong password with 14 characters.
|
||||
|
||||
```
|
||||
$ makepasswd --chars 14
|
||||
HxJDv5quavrqmU
|
||||
```
|
||||
|
||||
Run the makepasswd command with the following format to generate ten random strong password with 14 characters.
|
||||
|
||||
```
|
||||
$ makepasswd --chars 14 --count 10
|
||||
TqmKVWnRGeoVNr
|
||||
mPV2P98hLRUsai
|
||||
MhMXPwyzYi2RLo
|
||||
dxMGgLmoFpYivi
|
||||
8p0G7JvJjd6qUP
|
||||
7SmX95MiJcQauV
|
||||
KWzrh5npAjvNmL
|
||||
oHPKdq1uA9tU85
|
||||
V1su9GjU2oIGiQ
|
||||
M2TMCEoahzLNYC
|
||||
```
|
||||
|
||||
### How To Generate A Random Strong Password In Linux Using Multiple Commands?
|
||||
|
||||
Still if you are looking other options then you can use the following utilities to generate a random password in Linux.
|
||||
|
||||
**Using md5sum:** md5sum is a computer program that calculates and verifies 128-bit MD5 hashes.
|
||||
|
||||
```
|
||||
$ date | md5sum
|
||||
9baf96fb6e8cbd99601d97a5c3acc2c4 -
|
||||
```
|
||||
|
||||
**Using /dev/urandom:** The character special files /dev/random and /dev/urandom (present since Linux 1.3.30) provide an interface to the kernel’s random number generator. File /dev/random has major device number 1 and minor device number 8. File /dev/urandom has major device number 1 and minor device number 9.
|
||||
|
||||
```
|
||||
$ cat /dev/urandom | tr -dc 'a-zA-Z0-9' | head -c 14
|
||||
15LQB9J84Btnzz
|
||||
```
|
||||
|
||||
**Using sha256sum:** The program sha256sum is designed to verify data integrity using the SHA-256 (SHA-2 family with a digest length of 256 bits).
|
||||
|
||||
```
|
||||
$ date | sha256sum
|
||||
a114ae5c458ae0d366e1b673d558d921bb937e568d9329b525cf32290478826a -
|
||||
```
|
||||
|
||||
**Using sha1pass:** sha1pass creates a SHA1 password hash. In the absence of a salt value on the command line, a random salt vector will be generated.
|
||||
|
||||
```
|
||||
$ sha1pass
|
||||
$4$9+JvykOv$e7U0jMJL2yBOL+RVa2Eke8SETEo$
|
||||
```
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.2daygeek.com/5-ways-to-generate-a-random-strong-password-in-linux-terminal/
|
||||
|
||||
作者:[Magesh Maruthamuthu][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.2daygeek.com/author/magesh/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.2daygeek.com/how-to-check-password-complexity-strength-and-score-in-linux/
|
||||
[2]: https://www.2daygeek.com/dnf-command-examples-manage-packages-fedora-system/
|
||||
[3]: https://www.2daygeek.com/apt-get-apt-cache-command-examples-manage-packages-debian-ubuntu-systems/
|
||||
[4]: https://www.2daygeek.com/apt-command-examples-manage-packages-debian-ubuntu-systems/
|
||||
[5]: https://www.2daygeek.com/pacman-command-examples-manage-packages-arch-linux-system/
|
||||
[6]: https://www.2daygeek.com/yum-command-examples-manage-packages-rhel-centos-systems/
|
||||
[7]: https://www.2daygeek.com/zypper-command-examples-manage-packages-opensuse-system/
|
||||
@ -0,0 +1,65 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (qhwdw)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (5 ways to teach kids to program with Raspberry Pi)
|
||||
[#]: via: (https://opensource.com/article/19/3/teach-kids-program-raspberry-pi)
|
||||
[#]: author: (Anderson Silva https://opensource.com/users/ansilva)
|
||||
|
||||
5 ways to teach kids to program with Raspberry Pi
|
||||
======
|
||||
The fifth article in our guide to getting started with the Raspberry Pi explores resources for helping kids learn to program.
|
||||

|
||||
|
||||
As countless schools, libraries, and families have proven, the Raspberry Pi is a great way to expose kids to programming. In the first four articles in this series, you've learned about [purchasing][1], [installing][2], and [configuring][3] a Raspberry Pi. In this fifth article, I'll share some helpful resources to get kids started programming with the Raspberry Pi.
|
||||
|
||||
### Scratch
|
||||
|
||||
[Scratch][4] is a great way to introduce kids to basic programming concepts like variables, boolean logic, loops, and more. It's included in Raspbian, and you can find numerous articles and tutorials about Scratch on the internet, including [Is Scratch today like the Logo of the '80s for teaching kids to code?][5] on Opensource.com.
|
||||
|
||||
|
||||
|
||||
### Code.org
|
||||
|
||||
[Code.org][6] is another great online resource for kids learning to program. The organization's mission is to expose more people to coding through courses, tutorials, and the popular Hour of Code event. Many schools—including my fifth-grade son's—use it to expose more kids to programming and computer science concepts.
|
||||
|
||||
### Reading
|
||||
|
||||
Reading books is another great way to learn how to program. You don't necessarily need to speak English to learn how to program, but the more you know, the easier it will be, as most programming languages use English keywords to describe the commands. If your English is good enough to follow this Raspberry Pi series, you are most likely well-equipped to read books, forums, and other publications about programming. One book I recommend is [Python for Kids: A Playful Introduction to Programming][7] by Jason Biggs.
|
||||
|
||||
### Raspberry Jam
|
||||
|
||||
Another way to get your kids into programming is by helping them interact with others at meetups. The Raspberry Pi Foundation sponsors events called [Raspberry Jams][8] around the world where kids and adults can join forces and learn together on the Raspberry Pi. If there isn't a Raspberry Jam in your area, the foundation has a [guidebook][9] and other resources to help you start one.
|
||||
|
||||
### Gaming
|
||||
|
||||
Last, but not least, there's a version of [Minecraft][10] for the Raspberry Pi. Minecraft has grown from a multi-player "digital Lego"-like game into a programming platform where anyone can use Python and other languages to build on Minecraft's virtual world. Check out [Getting Started with Minecraft Pi][11] and [Minecraft Hour of Code Tutorials][12].
|
||||
|
||||
What are your favorite resources for teaching kids to program with Raspberry Pi? Please share them in the comments.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/3/teach-kids-program-raspberry-pi
|
||||
|
||||
作者:[Anderson Silva][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/ansilva
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/article/19/2/how-buy-raspberry-pi
|
||||
[2]: https://opensource.com/article/19/2/how-boot-new-raspberry-pi
|
||||
[3]: https://opensource.com/article/19/3/learn-linux-raspberry-pi
|
||||
[4]: https://scratch.mit.edu/
|
||||
[5]: https://opensource.com/article/17/3/logo-scratch-teach-programming-kids
|
||||
[6]: https://code.org/
|
||||
[7]: https://www.amazon.com/Python-Kids-Playful-Introduction-Programming/dp/1593274076
|
||||
[8]: https://www.raspberrypi.org/jam/#map-section
|
||||
[9]: https://static.raspberrypi.org/files/jam/Raspberry-Jam-Guidebook-2017-04-26.pdf
|
||||
[10]: https://minecraft.net/en-us/edition/pi/
|
||||
[11]: https://projects.raspberrypi.org/en/projects/getting-started-with-minecraft-pi
|
||||
[12]: https://code.org/minecraft
|
||||
@ -0,0 +1,134 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Running the ‘Real Debian’ on Raspberry Pi 3+ [For DIY Enthusiasts])
|
||||
[#]: via: (https://itsfoss.com/debian-raspberry-pi)
|
||||
[#]: author: (Shirish https://itsfoss.com/author/shirish/)
|
||||
|
||||
Running the ‘Real Debian’ on Raspberry Pi 3+ [For DIY Enthusiasts]
|
||||
======
|
||||
|
||||
If you have ever used a Raspberry Pi device, you probably already know that it recommends a Linux distribution called [Raspbian][1].
|
||||
|
||||
Raspbian is a heavily customized form of Debian to run on low-powered ARM processors. It’s not bad. In fact, it’s an excellent OS for Raspberry Pi devices but it’s not the real Debian.
|
||||
|
||||
[Debian purists like me][2] would prefer to run the actual Debian over the Raspberry Pi’s customized Debian version. I trust Debian more than any other distribution to provide me a vast amount of properly vetted free software packages. Moreover, a project like this would help other ARM devices as well.
|
||||
|
||||
Above all, running the official Debian on Raspberry Pi is sort of challenge and I like such challenges.
|
||||
|
||||
![Real Debian on Raspberry Pi][3]
|
||||
|
||||
I am not the only one who thinks like this. There are many other Debian users who share the same feeling and this is why there exists an ongoing project to create a [Debian image for Raspberry Pi][4].
|
||||
|
||||
About two and a half months back, a Debian Developer (DD) named [Gunnar Wolf][5] took over that unofficial Raspberry Pi image generation project.
|
||||
|
||||
I’ll be quickly showing you how can you install this Raspberry Pi Debian Buster preview image on your Raspberry Pi 3 (or higher) devices.
|
||||
|
||||
### Getting Debian on Raspberry Pi [For Experts]
|
||||
|
||||
```
|
||||
Warning
|
||||
|
||||
Be aware this Debian image is very raw and unsupported at the moment. Though it’s very new, I believe experienced Raspberry Pi and Debian users should be able to use it.
|
||||
```
|
||||
|
||||
Now as far as [Debian][6] is concerned, here is the Debian image and instructions that you could use to put the Debian stock image on your Raspberry pi 3 Model B+.
|
||||
|
||||
#### Step 1: Download the Debian Raspberry Pi Buster image
|
||||
|
||||
You can download the preview images using wget command:
|
||||
|
||||
```
|
||||
wget https://people.debian.org/~gwolf/raspberrypi3/20190206/20190206-raspberry-pi-3-buster-PREVIEW.img.xz
|
||||
```
|
||||
|
||||
#### Step 2: Verify checksum (optional)
|
||||
|
||||
It’s optional but you should [verify the checksum][7]. You can do that by downloading the SHA256 hashfile and then comparing it with that of the downloaded Raspberry Pi Debian image.
|
||||
|
||||
At my end I had moved both the .sha256 file as img.xz to a directory to make it easier to check although it’s not necessary.
|
||||
|
||||
```
|
||||
wget https://people.debian.org/~gwolf/raspberrypi3/20190206/20190206-raspberry-pi-3-buster-PREVIEW.img.xz.sha256
|
||||
|
||||
sha256sum -c 20190206-raspberry-pi-3-buster-PREVIEW.img.xz.sha256
|
||||
```
|
||||
|
||||
#### Step 3: Write the image to your SD card
|
||||
|
||||
Once you have verified the image, take a look at it. It is around 400MB in the compressed xzip format. You can extract it to get an image of around 1.5GB in size.
|
||||
|
||||
Insert your SD card. **Before you carry on to the next command please change the sdX to a suitable name that corresponds to your SD card.**
|
||||
|
||||
The command basically extracts the img.xz archive to the SD card. The progress switch/flag enables you to see a progress line with a number as to know how much the archive has extracted.
|
||||
|
||||
```
|
||||
xzcat 20190206-raspberry-pi-3-buster-PREVIEW.img.xz | dd of=/dev/sdX bs=64k oflag=dsync status=progress$ xzcat 20190206-raspberry-pi-3-buster-PREVIEW.img.xz | dd of=/dev/sdX bs=64k oflag=dsync status=progress
|
||||
```
|
||||
|
||||
Once you have successfully flashed your SD card, you should be able test if the installation went ok by sshing into your Raspberry Pi. The default root password is raspberry.
|
||||
|
||||
```
|
||||
ssh root@rpi3
|
||||
```
|
||||
|
||||
If you are curious to know how the Raspberry Pi image was built, you can look at the [build scripts][8].
|
||||
|
||||
You can find more info on the project homepage.
|
||||
|
||||
[DEBIAN RASPBERRY PI IMAGE][15]
|
||||
|
||||
### How to contribute to the Raspberry Pi Buster effort
|
||||
|
||||
There is a mailing list called [debian-arm][9] where people could contribute their efforts and ask questions. As you can see in the list, there is already a new firmware which was released [few days back][10] which might make booting directly a reality instead of the workaround shared above.
|
||||
|
||||
If you want you could make a new image using the raspi3-image-spec shared above or wait for Gunnar to make a new image which might take time.
|
||||
|
||||
Most of the maintainers also hang out at #vmdb2 at #OFTC. You can either use your IRC client or [Riot client][11], register your name at Nickserv and connect with either Gunnar Wolf, Roman Perier or/and Lars Wirzenius, author of [vmdb2][12]. I might do a follow-up on vmdb2 as it’s a nice little tool by itself.
|
||||
|
||||
### The Road Ahead
|
||||
|
||||
If there are enough interest and contributors, for instance, the lowest-hanging fruit would be to make sure that the ARM64 port [wiki page][13] is as current as possible. The benefits are and can be enormous.
|
||||
|
||||
There are a huge number of projects which could benefit from either having a [Pi farm][14] to making your media server or a SiP phone or whatever you want to play/work with.
|
||||
|
||||
Another low-hanging fruit might be synchronization between devices, say an ARM cluster sharing reports to either a Debian desktop by way of notification or on mobile or both ways.
|
||||
|
||||
While I have shared about Raspberry Pi, there are loads of single-board computers on the market already and lot more coming, both from MIPS as well as OpenRISC-V so there is going to plenty of competition in the days ahead.
|
||||
|
||||
Also, OpenRISC-V is and would be open-sourcing lot of its IP so non-free firmware or binary blobs would not be needed. Even MIPS is rumored to be more open which may challenge ARM if MIPS and OpenRISC-V are able to get their logistics and pricing right, but that is a story for another day.
|
||||
|
||||
There are many more vendors, I am just sharing the ones whom I am most interested to see what they come up with.
|
||||
|
||||
I hope the above sheds some light why it makes sense to have Debian on the Raspberry Pi.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://itsfoss.com/debian-raspberry-pi
|
||||
|
||||
作者:[Shirish][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://itsfoss.com/author/shirish/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.raspberrypi.org/downloads/raspbian/
|
||||
[2]: https://itsfoss.com/reasons-why-i-love-debian/
|
||||
[3]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2019/03/debian-raspberry-pi.png?resize=800%2C450&ssl=1
|
||||
[4]: https://wiki.debian.org/RaspberryPi3
|
||||
[5]: https://gwolf.org/node/4139
|
||||
[6]: https://www.debian.org/
|
||||
[7]: https://itsfoss.com/checksum-tools-guide-linux/
|
||||
[8]: https://github.com/Debian/raspi3-image-spec
|
||||
[9]: https://lists.debian.org/debian-arm/2019/02/threads.html
|
||||
[10]: https://alioth-lists.debian.net/pipermail/pkg-raspi-maintainers/Week-of-Mon-20190225/000310.html
|
||||
[11]: https://itsfoss.com/riot-desktop/
|
||||
[12]: https://liw.fi/vmdb2/
|
||||
[13]: https://wiki.debian.org/Arm64Port
|
||||
[14]: https://raspi.farm/
|
||||
[15]: https://wiki.debian.org/RaspberryPi3
|
||||
54
translated/talk/20190121 Booting Linux faster.md
Normal file
54
translated/talk/20190121 Booting Linux faster.md
Normal file
@ -0,0 +1,54 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (alim0x)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Booting Linux faster)
|
||||
[#]: via: (https://opensource.com/article/19/1/booting-linux-faster)
|
||||
[#]: author: (Stewart Smith https://opensource.com/users/stewart-ibm)
|
||||
|
||||
更快启动 Linux
|
||||
======
|
||||
进行 Linux 内核与固件开发的时候,往往需要多次的重启,会浪费大把的时间。
|
||||

|
||||
在所有我拥有或使用过的电脑中,启动最快的那台是 20 世纪 80 年代的电脑。在你把手从电源键移到键盘上的时候,BASIC 解释器已经在等待你输入命令了。对于现代的电脑,启动时间从笔记本电脑的 15 秒到小型家庭服务器的数分钟不等。为什么它们的启动时间有差别?
|
||||
|
||||
那台直接启动到 BASIC 命令行提示符的 20 世纪 80 年代微电脑,有着一颗非常简单的 CPU,它在通电的时候就立即开始从一个存储地址中获取和执行指令。因为这些系统在 ROM 里面有 BASIC,基本不需要载入的时间——你很快就进到 BASIC 命令提示符中了。同时代更加复杂的系统,比如 IBM PC 或 Macintosh,需要一段可观的时间来启动(大约 30 秒),尽管这主要是因为需要从软盘上读取操作系统的缘故。在可以加载操作系统之前,只有很小一部分时间是花在固件上的。
|
||||
|
||||
现代服务器往往在从磁盘上读取操作系统之前,在固件上花费了数分钟而不是数秒。这主要是因为现代系统日益增加的复杂性。CPU 不再能够只是起来就开始全速执行指令,我们已经习惯于 CPU 频率变化,节省能源的待机状态以及 CPU 多核。实际上,在现代 CPU 内部有惊人数量的更简单的处理器,它们协助主 CPU 核心启动并提供运行时服务,比如在过热的时候压制频率。在绝大多数 CPU 架构中,在你的 CPU 内的这些核心上运行的代码都以不透明的二进制 blob 形式提供。
|
||||
|
||||
在 OpenPOWER 系统上,所有运行在 CPU 内部每个核心的指令都是开源的。在有 [OpenBMC][1](比如 IBM 的 AC922 系统和 Raptor 的 TALOS II 以及 Blackbird 系统)的机器上,这还延伸到了运行在基板管理控制器上的代码。这就意味着我们可以一探究竟,到底为什么从接入电源线到显示出熟悉的登陆界面花了这么长时间。
|
||||
|
||||
如果你是内核相关团队的一员,你可能启动过许多内核。如果你是固件相关团队的一员,你可能要启动许多不同的固件映像,接着是一个操作系统,来确保你的固件仍能工作。如果我们可以减少硬件的启动时间,这些团队可以更有生产力,并且终端用户在搭建系统或重启安装固件或系统更新的时候会对此表示感激。
|
||||
|
||||
过去的几年,Linux 发行版的启动时间已经做了很多改善。现代 init 系统在处理并行和按需任务上做得很好。在一个现代系统上,一旦内核开始执行,它可以在短短数秒内进入登陆提示符界面。这里短短的数秒不是优化启动时间的下手之处,我们得到更早的地方:在我们到达操作系统之前。
|
||||
|
||||
在 OpenPOWER 系统上,固件通过启动一个存储在固件闪存芯片上的 Linux 内核来加载操作系统,它运行一个叫做 [Petitboot][2] 的用户态程序去寻找用户想要启动的系统所在磁盘,并通过 [kexec][3] 启动它。有了这些优化,启动 Petitboot 环境只占了启动时间的个位数百分比,所以我们还得从其他地方寻找优化项。
|
||||
|
||||
在 Petitboot 环境启动前,有一个先导固件,叫做 [Skiboot][4],在它之前有个 [Hostboot][5]。在 Hostboot 之前是 [Self-Boot Engine][6],一个 die 上的单独核心,它启动单个 CPU 核心并执行来自 Level 3 缓存的指令。这些组件是我们可以在减少启动时间上取得进展的主要部分,因为它们花费了启动的绝大部分时间。或许这些组件中的一部分没有进行足够的优化或尽可能做到并行?
|
||||
|
||||
另一个研究路径是重启时间而不是启动时间。在重启的时候,我们真的需要对所有硬件重新初始化吗?
|
||||
|
||||
正如任何现代系统那样,改善启动(或重启)时间的方案已经变成了更多并行、解决遗留问题、(可以认为)作弊的结合体。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/1/booting-linux-faster
|
||||
|
||||
作者:[Stewart Smith][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[alim0x](https://github.com/alim0x)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/stewart-ibm
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://en.wikipedia.org/wiki/OpenBMC
|
||||
[2]: https://github.com/open-power/petitboot
|
||||
[3]: https://en.wikipedia.org/wiki/Kexec
|
||||
[4]: https://github.com/open-power/skiboot
|
||||
[5]: https://github.com/open-power/hostboot
|
||||
[6]: https://github.com/open-power/sbe
|
||||
[7]: https://linux.conf.au/schedule/presentation/105/
|
||||
[8]: https://linux.conf.au/
|
||||
@ -0,0 +1,506 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (ezio )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Computer Laboratory – Raspberry Pi: Lesson 10 Input01)
|
||||
[#]: via: (https://www.cl.cam.ac.uk/projects/raspberrypi/tutorials/os/input01.html)
|
||||
[#]: author: (Alex Chadwick https://www.cl.cam.ac.uk)
|
||||
|
||||
|
||||
计算机实验课 – 树莓派: 课程 10 输入01
|
||||
======
|
||||
|
||||
欢迎进入输入课程系列。在本系列,你将会学会如何使用键盘接收输入给树莓派。我们将会从揭示输入开始本课,然后开始传统的文本命令。
|
||||
|
||||
这是第一堂输入课,会教授一些关于驱动和链接的理论,同样也包含键盘的知识,最后以在屏幕上显示文本结束。
|
||||
|
||||
### 1 开始
|
||||
|
||||
希望你已经完成了 OK 系列课程, 这会对你完成屏幕系列课程很有帮助。很多 OK 课程上的文件会被使用而不会做解释。如果你没有这些文件,或者希望使用一个正确的实现, 可以从该堂课的[下载页][1]下载模板。如果你使用你自己的实现,请删除调用了 `SetGraphicsAddress` 之后全部的代码。
|
||||
|
||||
### 2 USB
|
||||
|
||||
```
|
||||
USB 标准的设计目的是通过复杂的硬件来简化硬件。
|
||||
```
|
||||
|
||||
如你所知,树莓派 B 型有两个 USB 接口,通常用来连接一个鼠标和一个键盘。这是一个非常好的设计决策,USB 是一个非常通用的接口, 很多种设备都可以使用它。这就很容易为它设计新外设,很容易为它编写设备驱动, 而且通过 USB 集线器可以非常容易扩展。还能更好吗?当然是不能,实际上对一个操作系统开发者来说,这就是我们的噩梦。USB 标准太大了。 我是真的,在你思考如何连接设备之前,它的文档将近 700 页。
|
||||
|
||||
我和很多爱好操作系统的开发者谈过这些,而他们全部都说几句话:不要抱怨。“实现这个需要花费很久时间”,“你不可能写出关于 USB 的教程”,“收益太小了”。在很多方面,他们是对的,我不可能写出一个关于 USB 标准的教程, 那得花费几周时间。我同样不能教授如何为全部所有的设备编写外设驱动,所以使用自己写的驱动是没什么用的。然而,我可以做仅次于最好的事情是获取一个正常工作的 USB 驱动,拿一个键盘驱动,然后教授如何在操作系统中使用它们。我开始寻找可以运行在一个甚至不知道文件是什么的操作系统的自由驱动,但是我一个都找不到。他们都太高层了。所以我尝试写一个。每个人都是对的,这耗费了我几周时间。然而我高兴的说我我做这些工作没有获取操作系统以外的帮助,并且可以和鼠标和键盘通信。这句不是完整的,高效的,或者正确的,但是它能工作。驱动是以 C 编写的,而且有兴趣的可以在下载页找到全部源代码。
|
||||
|
||||
所以,这一个教程不会是 USB 标准的课程(一点也没有)。实际上我们将会看到如何使用其他人的代码。
|
||||
|
||||
### 3 链接
|
||||
|
||||
```
|
||||
链接允许我们制作可重用的代码库,所有人都可以在他们的程序中使用。
|
||||
```
|
||||
|
||||
既然我们要引进外部代码到操作系统,我们就需要谈一谈链接。链接是一种过程,可以在程序或者操作系统中链接函数。这意味着当一个程序生成之后,我们不必要编写每一个函数(几乎可以肯定,实际上并非如此)。链接就是我们做的用来把我们程序和别人代码中的函数连结在一起。这个实际上已经在我们的操作系统进行了,因为链接器吧所有不同的文件链接在一起,每个都是分开编译的。
|
||||
|
||||
|
||||
```
|
||||
程序经常知识调用库,这些库会调用其它的库,知道最终调用了我们写的操作系统。
|
||||
```
|
||||
|
||||
有两种链接:静态和动态。静态链接就像我们在制作自己的操作系统时进行的。链接器找到全部函数的地址,然后在链接结束前,将这些地址都写入代码中。动态链接是在程序“完成”之后。当程序加载后,动态链接器检查程序,然后在操作系统的库找到所有不在程序里的函数。这就是我们的操作系统最终应该能够完成的一项工作,但是现在所有东西都将是静态链接的。
|
||||
|
||||
我编写的 USB 驱动程序适合静态编译。这意味着我给你我的每个文件的编译后的代码,然后链接器找到你的代码中的那些没有实现的函数,就将这些函数链接到我的代码。在本课的 [下载页][1] 是一个 makefile 和我的 USB 驱动,这是接下来需要的。下载并使用这 makefile 替换你的代码中的 makefile, 同事将驱动放在和这个 makefile 相同的文件夹。
|
||||
|
||||
### 4 键盘
|
||||
|
||||
为了将输入传给我们的操作系统,我们需要在某种程度上理解键盘是如何实际工作的。键盘有两种按键:普通键和修饰键。普通按键是字母、数字、功能键,等等。他们构成了键盘上几乎每一个按键。修饰键是最多 8 个特殊键。他们是左 shift , 右 shift, 左 ctrl,右 ctrl,左 alt, 右 alt,左 GUI 和右 GUI。键盘可以检测出所有的组合中那个修饰键被按下了,以及最多 6 个普通键。每次一个按钮变化了(i.e. 是按下了还是释放了),键盘就会报告给电脑。通常,键盘也会有 3 个 LED 灯,分别指示 Caps 锁定,Num 锁定,和 Scroll 锁定,这些都是由电脑控制的,而不是键盘自己。键盘也可能由更多的灯,比如电源、静音,等等。
|
||||
|
||||
为了帮助标准 USB 键盘,产生了一个按键值的表,每个键盘按键都一个唯一的数字,每个可能的 LED 也类似。下面的表格列出了前 126 个值。
|
||||
|
||||
Table 4.1 USB 键盘值
|
||||
|
||||
| 序号 | 描述 | 序号 | 描述 | 序号 | 描述 | 序号 | 描述 | |
|
||||
| ------ | ---------------- | ------- | ---------------------- | -------- | -------------- | --------------- | -------------------- |----|
|
||||
| 4 | a and A | 5 | b and B | 6 | c and C | 7 | d and D | |
|
||||
| 8 | e and E | 9 | f and F | 10 | g and G | 11 | h and H | |
|
||||
| 12 | i and I | 13 | j and J | 14 | k and K | 15 | l and L | |
|
||||
| 16 | m and M | 17 | n and N | 18 | o and O | 19 | p and P | |
|
||||
| 20 | q and Q | 21 | r and R | 22 | s and S | 23 | t and T | |
|
||||
| 24 | u and U | 25 | v and V | 26 | w and W | 27 | x and X | |
|
||||
| 28 | y and Y | 29 | z and Z | 30 | 1 and ! | 31 | 2 and @ | |
|
||||
| 32 | 3 and # | 33 | 4 and $ | 34 | 5 and % | 35 | 6 and ^ | |
|
||||
| 36 | 7 and & | 37 | 8 and * | 38 | 9 and ( | 39 | 0 and ) | |
|
||||
| 40 | Return (Enter) | 41 | Escape | 42 | Delete (Backspace) | 43 | Tab | |
|
||||
| 44 | Spacebar | 45 | - and _ | 46 | = and + | 47 | [ and { | |
|
||||
| 48 | ] and } | 49 | \ and | 50 | # and ~ | 51 | ; and : |
|
||||
| 52 | ' and " | 53 | ` and ~ | 54 | , and < | 55 | . and > | |
|
||||
| 56 | / and ? | 57 | Caps Lock | 58 | F1 | 59 | F2 | |
|
||||
| 60 | F3 | 61 | F4 | 62 | F5 | 63 | F6 | |
|
||||
| 64 | F7 | 65 | F8 | 66 | F9 | 67 | F10 | |
|
||||
| 68 | F11 | 69 | F12 | 70 | Print Screen | 71 | Scroll Lock | |
|
||||
| 72 | Pause | 73 | Insert | 74 | Home | 75 | Page Up | |
|
||||
| 76 | Delete forward | 77 | End | 78 | Page Down | 79 | Right Arrow | |
|
||||
| 80 | Left Arrow | 81 | Down Arrow | 82 | Up Arrow | 83 | Num Lock | |
|
||||
| 84 | Keypad / | 85 | Keypad * | 86 | Keypad - | 87 | Keypad + | |
|
||||
| 88 | Keypad Enter | 89 | Keypad 1 and End | 90 | Keypad 2 and Down Arrow | 91 | Keypad 3 and Page Down | |
|
||||
| 92 | Keypad 4 and Left Arrow | 93 | Keypad 5 | 94 | Keypad 6 and Right Arrow | 95 | Keypad 7 and Home | |
|
||||
| 96 | Keypad 8 and Up Arrow | 97 | Keypad 9 and Page Up | 98 | Keypad 0 and Insert | 99 | Keypad . and Delete | |
|
||||
| 100 | \ and | 101 | Application | 102 | Power | 103 | Keypad = |
|
||||
| 104 | F13 | 105 | F14 | 106 | F15 | 107 | F16 | |
|
||||
| 108 | F17 | 109 | F18 | 110 | F19 | 111 | F20 | |
|
||||
| 112 | F21 | 113 | F22 | 114 | F23 | 115 | F24 | |
|
||||
| 116 | Execute | 117 | Help | 118 | Menu | 119 | Select | |
|
||||
| 120 | Stop | 121 | Again | 122 | Undo | 123 | Cut | |
|
||||
| 124 | Copy | 125 | Paste | 126 | Find | 127 | Mute | |
|
||||
| 128 | Volume Up | 129 | Volume Down | | | | | |
|
||||
|
||||
完全列表可以在[HID 页表 1.12][2]的 53 页,第 10 节找到
|
||||
|
||||
### 5 车轮后的螺母
|
||||
|
||||
```
|
||||
这些总结和代码的描述组成了一个 API - 应用程序产品接口。
|
||||
|
||||
```
|
||||
|
||||
通常,当你使用其他人的代码,他们会提供一份自己代码的总结,描述代码都做了什么,粗略介绍了是如何工作的,以及什么情况下会出错。下面是一个使用我的 USB 驱动的相关步骤要求。
|
||||
|
||||
Table 5.1 CSUD 中和键盘相关的函数
|
||||
| 函数 | 参数 | 返回值 | 描述 |
|
||||
| ----------------------- | ----------------------- | ----------------------- | -----------------------|
|
||||
| UsbInitialise | None | r0 is result code | 这个方法是一个集多种功能于一身的方法,它加载USB驱动程序,枚举所有设备并尝试与它们通信。这种方法通常需要大约一秒钟的时间来执行,但是如果插入几个USB集线器,执行时间会明显更长。在此方法完成之后,键盘驱动程序中的方法就可用了,不管是否确实插入了键盘。返回代码如下解释。|
|
||||
| UsbCheckForChange | None | None | 本质上提供与 `usbinitialization` 相同的效果,但不提供相同的一次初始化。该方法递归地检查每个连接的集线器上的每个端口,如果已经添加了新设备,则添加它们。如果没有更改,这应该是非常快的,但是如果连接了多个设备的集线器,则可能需要几秒钟的时间。|
|
||||
| KeyboardCount | None | r0 is count | 返回当前连接并检测到的键盘数量。`UsbCheckForChange` 可能会对此进行更新。默认情况下最多支持4个键盘。多达这么多的键盘可以通过这个驱动程序访问。|
|
||||
| KeyboardGetAddress | r0 is index | r0 is address | 检索给定键盘的地址。所有其他函数都需要一个键盘地址,以便知道要访问哪个键盘。因此,要与键盘通信,首先要检查计数,然后检索地址,然后使用其他方法。注意,在调用 `UsbCheckForChange` 之后,此方法返回的键盘顺序可能会改变。
|
||||
|
|
||||
| KeyboardPoll | r0 is address | r0 is result code | 从键盘读取当前键状态。这是通过直接轮询设备来操作的,与最佳实践相反。这意味着,如果没有频繁地调用此方法,可能会错过一个按键。所有读取方法只返回上次轮询时的值。
|
||||
|
|
||||
| KeyboardGetModifiers | r0 is address | r0 is modifier state | 检索上次轮询时修饰符键的状态。这是两边的 `shift` 键、`alt` 键和 `GUI` 键。这回作为一个位字段返回,这样,位0中的1表示左控件被保留,位1表示左 `shift`,位2表示左 `alt` ,位3表示左 `GUI`,位4到7表示前几位的右版本。如果有问题,`r0` 包含0。|
|
||||
| KeyboardGetKeyDownCount | r0 is address | r0 is count | 检索当前按下键盘的键数。这排除了修饰键。这通常不能超过6次。如果有错误,这个方法返回0。|
|
||||
| KeyboardGetKeyDown | r0 is address, r1 is key number | r0 is scan code | 检索特定下拉键的扫描代码(见表4.1)。通常,要计算出哪些键是关闭的,可以调用 `KeyboardGetKeyDownCount`,然后多次调用 `KeyboardGetKeyDown` ,将 `r1` 的值递增,以确定哪些键是关闭的。如果有问题,返回0。在不调用 `KeyboardGetKeyDownCount` 并将0解释为未持有的键的情况下调用此方法是安全的(但不建议这样做)。注意,顺序或扫描代码可以随机更改(有些键盘按数字排序,有些键盘按时间排序,没有任何保证)。|
|
||||
| KeyboardGetKeyIsDown | r0 is address, r1 is scan code | r0 is status | 除了 `KeyboardGetKeyDown` 之外,还可以检查下拉键中是否有特定的扫描代码。如果不是,返回0;如果是,返回一个非零值。当检测特定的扫描代码(例如寻找ctrl+c)更快。出错时,返回0。
|
||||
|
|
||||
| KeyboardGetLedSupport | r0 is address | r0 is LEDs | 检查特定键盘支持哪些led。第0位代表数字锁定,第1位代表大写锁定,第2位代表滚动锁定,第3位代表合成,第4位代表假名,第5位代表能量,第6位代表静音,第7位代表合成。根据USB标准,这些led都不是自动更新的(例如,当检测到大写锁定扫描代码时,必须手动设置大写锁定)。|
|
||||
| KeyboardSetLeds | r0 is address, r1 is LEDs | r0 is result code | 试图打开/关闭键盘上指定的 LED 灯。查看下面的结果代码值。参见 `KeyboardGetLedSupport` 获取 LED 的值。
|
||||
|
|
||||
|
||||
```
|
||||
返回值是一种处理错误的简单方法,但是通常更优雅的解决途径存在于更高层次的代码。
|
||||
```
|
||||
|
||||
有几种方法返回 ‘返回值’。这些都是 C 代码的老生常谈了,就是用数字代表函数调用发生了什么。通常情况, 0 总是代表操作成功。下面的是驱动用到的返回值。
|
||||
|
||||
Table 5.2 - CSUD 返回值
|
||||
|
||||
| 代码 | 描述 |
|
||||
| ---- | ----------------------------------------------------------------------- |
|
||||
| 0 | 方法成功完成。 |
|
||||
| -2 | 参数: 函数调用了无效参数。 |
|
||||
| -4 | 设备: 设备没有正确响应请求。 |
|
||||
| -5 | 不匹配: 驱动不适用于这个请求或者设备。 |
|
||||
| -6 | 编译器: 驱动没有正确编译,或者被破坏了。 |
|
||||
| -7 | 内存: 驱动用尽了内存。 |
|
||||
| -8 | 超时: 设备没有在预期的时间内响应请求。 |
|
||||
| -9 | 断开连接: 被请求的设备断开连接,或者不能使用。 |
|
||||
|
||||
驱动的通常用法如下:
|
||||
|
||||
1. 调用 `UsbInitialise`
|
||||
2. 调用 `UsbCheckForChange`
|
||||
3. 调用 `KeyboardCount`
|
||||
4. 如果返回 0,重复步骤 2。
|
||||
5. 针对你支持的每种键盘:
|
||||
1. 调用 ·KeyboardGetAddress·
|
||||
2. 调用 ·KeybordGetKeyDownCount·
|
||||
3. 针对每个按下的按键:
|
||||
1. 检查它是否已经被按下了
|
||||
2. 保存按下的按键
|
||||
4. 针对每个保存的按键:
|
||||
3. 检查按键是否被释放了
|
||||
4. 如果释放了就删除
|
||||
6. 根据按下/释放的案件执行操作
|
||||
7. 重复步骤 2.
|
||||
|
||||
|
||||
最后,你可能做所有你想对键盘做的事,而这些方法应该允许你访问键盘的全部功能。在接下来的两节课,我们将会着眼于完成文本终端的输入部分,类似于大部分的命令行电脑,以及命令的解释。为了做这些,我们将需要在更有用的形式下得到一个键盘输入。你可能注意到我的驱动是(故意)没有太大帮助,因为它并没有方法来判断是否一个案件刚刚按下或释放了,它只有芳芳来判断当前那个按键是按下的。这就意味着我们需要自己编写这些方法。
|
||||
|
||||
### 6 可用更新
|
||||
|
||||
重复检查更新被称为 ‘轮询’。这是针对驱动 IO 中断而言的,这种情况下设备在准备好后会发一个信号。
|
||||
|
||||
首先,让我们实现一个 `KeyboardUpdate` 方法,检查第一个键盘,并使用轮询方法来获取当前的输入,以及保存最后一个输入来对比。然后我们可以使用这个数据和其它方法来将扫描码转换成按键。这个方法应该按照下面的说明准确操作:
|
||||
|
||||
1. 提取一个保存好的键盘地址(初始值为 0)。
|
||||
2. 如果不是0 ,进入步骤9.
|
||||
3. 调用 `UsbCheckForChange` 检测新键盘。
|
||||
4. 调用 `KeyboardCount` 检测有几个键盘在线。
|
||||
5. 如果返回0,意味着没有键盘可以让我们操作,只能退出了。
|
||||
6. 调用 `KeyboardGetAddress` 参数是 0,获取第一个键盘的地址。
|
||||
7. 保存这个地址。
|
||||
8. 如果这个值是0,那么退出,这里应该有些问题。
|
||||
9. 调用 `KeyboardGetKeyDown` 6 次,获取每次按键按下的值并保存。
|
||||
10. 调用 `KeyboardPoll`
|
||||
11. 如果返回值非 0,进入步骤 3。这里应该有些问题(比如键盘断开连接)。
|
||||
|
||||
要保存上面提到的值,我们将需要下面 `.data` 段的值。
|
||||
|
||||
```
|
||||
.section .data
|
||||
.align 2
|
||||
KeyboardAddress:
|
||||
.int 0
|
||||
KeyboardOldDown:
|
||||
.rept 6
|
||||
.hword 0
|
||||
.endr
|
||||
```
|
||||
|
||||
```
|
||||
.hword num 直接将半字的常数插入文件。
|
||||
```
|
||||
|
||||
```
|
||||
.rept num [commands] .endr 复制 `commands` 命令到输出 num 次。
|
||||
```
|
||||
|
||||
试着自己实现这个方法。对此,我的实现如下:
|
||||
|
||||
1.
|
||||
```
|
||||
.section .text
|
||||
.globl KeyboardUpdate
|
||||
KeyboardUpdate:
|
||||
push {r4,r5,lr}
|
||||
|
||||
kbd .req r4
|
||||
ldr r0,=KeyboardAddress
|
||||
ldr kbd,[r0]
|
||||
```
|
||||
我们加载键盘的地址。
|
||||
|
||||
2.
|
||||
```
|
||||
teq kbd,#0
|
||||
bne haveKeyboard$
|
||||
```
|
||||
如果地址非0,就说明我们有一个键盘。调用 `UsbCheckForChanges` 慢,所以如果全部事情都起作用,我们要避免调用这个函数。
|
||||
|
||||
3.
|
||||
```
|
||||
getKeyboard$:
|
||||
bl UsbCheckForChange
|
||||
```
|
||||
如果我们一个键盘都没有,我们就必须检查新设备。
|
||||
|
||||
4.
|
||||
```
|
||||
bl KeyboardCount
|
||||
```
|
||||
如果有心键盘添加,我们就会看到这个。
|
||||
|
||||
5.
|
||||
```
|
||||
teq r0,#0
|
||||
ldreq r1,=KeyboardAddress
|
||||
streq r0,[r1]
|
||||
beq return$
|
||||
```
|
||||
如果没有键盘,我们就没有键盘地址。
|
||||
|
||||
6.
|
||||
```
|
||||
mov r0,#0
|
||||
bl KeyboardGetAddress
|
||||
```
|
||||
让我们获取第一个键盘的地址。你可能想要更多。
|
||||
|
||||
7.
|
||||
```
|
||||
ldr r1,=KeyboardAddress
|
||||
str r0,[r1]
|
||||
```
|
||||
保存键盘地址。
|
||||
|
||||
8.
|
||||
```
|
||||
teq r0,#0
|
||||
beq return$
|
||||
mov kbd,r0
|
||||
```
|
||||
如果我们没有地址,这里就没有其它活要做了。
|
||||
|
||||
9.
|
||||
```
|
||||
saveKeys$:
|
||||
mov r0,kbd
|
||||
mov r1,r5
|
||||
bl KeyboardGetKeyDown
|
||||
|
||||
ldr r1,=KeyboardOldDown
|
||||
add r1,r5,lsl #1
|
||||
strh r0,[r1]
|
||||
add r5,#1
|
||||
cmp r5,#6
|
||||
blt saveKeys$
|
||||
```
|
||||
Loop through all the keys, storing them in KeyboardOldDown. If we ask for too many, this returns 0 which is fine.
|
||||
查询遍全部按键,在 `KeyboardOldDown` 保存下来。如果我们询问的太多了,返回 0 也是正确的。
|
||||
|
||||
10.
|
||||
```
|
||||
mov r0,kbd
|
||||
bl KeyboardPoll
|
||||
```
|
||||
现在哦我们得到了新的按键。
|
||||
|
||||
11.
|
||||
```
|
||||
teq r0,#0
|
||||
bne getKeyboard$
|
||||
|
||||
return$:
|
||||
pop {r4,r5,pc}
|
||||
.unreq kbd
|
||||
```
|
||||
最后我们要检查 `KeyboardOldDown` 是否工作了。如果没工作,那么我们可能是断开连接了。
|
||||
|
||||
有了我们新的 `KeyboardUpdate` 方法,检查输入变得简单到固定周期调用这个方法,而它甚至可以检查断开连接,等等。这是一个有用的方法,因为我们实际的按键处理会根据条件不同而有所差别,所以能够用一个函数调以它的原始方式获取当前的输入是可行的。下一个方法我们理想希望的是 `KeyboardGetChar`,简单的返回下一个按下的按钮的 ASCII 字符,或者如果没有按键按下就返回 0。这可以扩展到支持将一个按键多次按下,如果它保持了一个特定时间,也支持‘锁定’键和修饰键。
|
||||
|
||||
要使这个方法有用,如果我们有一个 `KeyWasDown` 方法,如果给定的扫描代码不在keyboard dolddown值中,它只返回0,否则返回一个非零值。你可以自己尝试一下。与往常一样,可以在下载页面找到解决方案。
|
||||
|
||||
### 7 查找表
|
||||
|
||||
```
|
||||
在编程的许多领域,程序越大,速度越快。查找表很大,但是速度很快。有些问题可以通过查找表和普通函数的组合来解决。
|
||||
```
|
||||
|
||||
`KeyboardGetChar`方法如果写得不好,可能会非常复杂。有 100 多种扫描代码,每种代码都有不同的效果,这取决于 shift 键或其他修饰符的存在与否。并不是所有的键都可以转换成一个字符。对于一些字符,多个键可以生成相同的字符。在有如此多可能性的情况下,一个有用的技巧是查找表。查找表与物理意义上的查找表非常相似,它是一个值及其结果的表。对于一些有限的函数,推导出答案的最简单方法就是预先计算每个答案,然后通过检索返回正确的答案。在这种情况下,我们可以建立一个序列的值在内存中,n值序列的ASCII字符代码扫描代码n。这意味着我们的方法只会发现如果一个键被按下,然后从表中检索它的值。此外,当按住shift键时,我们可以为值创建一个单独的表,这样shift键就可以简单地更改正在处理的表。
|
||||
|
||||
在 `.section` `.data` 命令之后,复制下面的表:
|
||||
|
||||
```
|
||||
.align 3
|
||||
KeysNormal:
|
||||
.byte 0x0, 0x0, 0x0, 0x0, 'a', 'b', 'c', 'd'
|
||||
.byte 'e', 'f', 'g', 'h', 'i', 'j', 'k', 'l'
|
||||
.byte 'm', 'n', 'o', 'p', 'q', 'r', 's', 't'
|
||||
.byte 'u', 'v', 'w', 'x', 'y', 'z', '1', '2'
|
||||
.byte '3', '4', '5', '6', '7', '8', '9', '0'
|
||||
.byte '\n', 0x0, '\b', '\t', ' ', '-', '=', '['
|
||||
.byte ']', '\\\', '#', ';', '\'', '`', ',', '.'
|
||||
.byte '/', 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0
|
||||
.byte 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0
|
||||
.byte 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0
|
||||
.byte 0x0, 0x0, 0x0, 0x0, '/', '*', '-', '+'
|
||||
.byte '\n', '1', '2', '3', '4', '5', '6', '7'
|
||||
.byte '8', '9', '0', '.', '\\\', 0x0, 0x0, '='
|
||||
|
||||
.align 3
|
||||
KeysShift:
|
||||
.byte 0x0, 0x0, 0x0, 0x0, 'A', 'B', 'C', 'D'
|
||||
.byte 'E', 'F', 'G', 'H', 'I', 'J', 'K', 'L'
|
||||
.byte 'M', 'N', 'O', 'P', 'Q', 'R', 'S', 'T'
|
||||
.byte 'U', 'V', 'W', 'X', 'Y', 'Z', '!', '"'
|
||||
.byte '£', '$', '%', '^', '&', '*', '(', ')'
|
||||
.byte '\n', 0x0, '\b', '\t', ' ', '_', '+', '{'
|
||||
.byte '}', '|', '~', ':', '@', '¬', '<', '>'
|
||||
.byte '?', 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0
|
||||
.byte 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0
|
||||
.byte 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0, 0x0
|
||||
.byte 0x0, 0x0, 0x0, 0x0, '/', '*', '-', '+'
|
||||
.byte '\n', '1', '2', '3', '4', '5', '6', '7'
|
||||
.byte '8', '9', '0', '.', '|', 0x0, 0x0, '='
|
||||
```
|
||||
|
||||
```
|
||||
.byte num 直接插入字节常量 num 到文件。
|
||||
```
|
||||
|
||||
```
|
||||
大部分的汇编器和编译器识别转义序列;插入特殊字符的字符序列,如\t。
|
||||
```
|
||||
|
||||
这些表直接将前 104 个扫描代码映射到 ASCII 字符,作为一个字节表。我们还有一个单独的表来描述 `shift` 键对这些扫描代码的影响。我使用 ASCII `null`字符(0)表示所有没有直接映射的 ASCII 键(例如函数键)。退格映射到ASCII退格字符(8表示 `\b` ), `enter` 映射到ASCII新行字符(10表示 `\n`), `tab` 映射到ASCII水平制表符(9表示 `\t` )。
|
||||
|
||||
|
||||
`KeyboardGetChar` 方法需要做以下工作:
|
||||
1. 检查 `KeyboardAddress` 是否返回 0。如果是,则返回0。
|
||||
2. 调用 `KeyboardGetKeyDown` 最多 6 次。每次:
|
||||
1. 如果按键时0,跳出循环。
|
||||
2. 调用 `KeyWasDown`。 如果返回是,处理下一个按键。
|
||||
3. 如果扫描码超过 103,进入下一个按键。
|
||||
4. 调用 `KeyboardGetModifiers`
|
||||
5. 如果 `shift` 是被按着的,就加载 `KeysShift` 的地址。否则加载 `KeysNormal` 的地址。
|
||||
6. 从表中读出 ASCII 码值。
|
||||
7. 如果是 0,进行下一个按键,否则返回 ASCII 码值并退出。
|
||||
3. 返回0。
|
||||
|
||||
|
||||
试着自己实现。我的实现展示在下面:
|
||||
|
||||
1.
|
||||
```
|
||||
.globl KeyboardGetChar
|
||||
KeyboardGetChar:
|
||||
ldr r0,=KeyboardAddress
|
||||
ldr r1,[r0]
|
||||
teq r1,#0
|
||||
moveq r0,#0
|
||||
moveq pc,lr
|
||||
```
|
||||
简单的检查我们是否有键盘。
|
||||
|
||||
2.
|
||||
```
|
||||
push {r4,r5,r6,lr}
|
||||
kbd .req r4
|
||||
key .req r6
|
||||
mov r4,r1
|
||||
mov r5,#0
|
||||
keyLoop$:
|
||||
mov r0,kbd
|
||||
mov r1,r5
|
||||
bl KeyboardGetKeyDown
|
||||
```
|
||||
r5 will hold the index of the key, r4 holds the keyboard address.
|
||||
`r5` 将会保存按键的索引, `r4` 保存键盘的地址。
|
||||
|
||||
1.
|
||||
```
|
||||
teq r0,#0
|
||||
beq keyLoopBreak$
|
||||
```
|
||||
如果扫描码是0,它要么意味着有错,要么说明没有更多按键了。
|
||||
|
||||
2.
|
||||
```
|
||||
mov key,r0
|
||||
bl KeyWasDown
|
||||
teq r0,#0
|
||||
bne keyLoopContinue$
|
||||
```
|
||||
如果按键已经按下了,那么他就没意思了,我们只想知道按下的按键。
|
||||
|
||||
3.
|
||||
```
|
||||
cmp key,#104
|
||||
bge keyLoopContinue$
|
||||
```
|
||||
如果一个按键有个超过 104 的扫描码,他将会超出我们的表,所以它是无关的按键。
|
||||
|
||||
4.
|
||||
```
|
||||
mov r0,kbd
|
||||
bl KeyboardGetModifiers
|
||||
```
|
||||
我们需要知道修饰键来推断字符。
|
||||
|
||||
5.
|
||||
```
|
||||
tst r0,#0b00100010
|
||||
ldreq r0,=KeysNormal
|
||||
ldrne r0,=KeysShift
|
||||
```
|
||||
当将字符更改为其移位变体时,我们要同时检测左 `shift` 键和右 `shift` 键。记住,`tst` 指令计算的是逻辑和,然后将其与 0 进行比较,所以当且仅当移位位都为 0 时,它才等于0。
|
||||
|
||||
|
||||
1.
|
||||
```
|
||||
ldrb r0,[r0,key]
|
||||
```
|
||||
现在我们可以从查找表加载按键了。
|
||||
|
||||
1.
|
||||
```
|
||||
teq r0,#0
|
||||
bne keyboardGetCharReturn$
|
||||
keyLoopContinue$:
|
||||
add r5,#1
|
||||
cmp r5,#6
|
||||
blt keyLoop$
|
||||
```
|
||||
如果查找码包含一个 0,我们必须继续。为了继续,我们要增加索引,并检查是否到 6 次了。
|
||||
|
||||
1.
|
||||
```
|
||||
keyLoopBreak$:
|
||||
mov r0,#0
|
||||
keyboardGetCharReturn$:
|
||||
pop {r4,r5,r6,pc}
|
||||
.unreq kbd
|
||||
.unreq key
|
||||
```
|
||||
在这里我们返回我们的按键,如果我们到达 `keyLoopBreak$` ,然后我们就知道这里没有按键被握住,所以返回0。
|
||||
|
||||
### 8 记事本操作系统
|
||||
|
||||
现在我们有了 `KeyboardGetChar` 方法,可以创建一个操作系统,只输入用户对着屏幕所写的内容。为了简单起见,我们将忽略所有不寻常的键。在 `main.s` ,删除`bl SetGraphicsAddress` 之后的所有代码。调用 `UsbInitialise`,将 `r4` 和 `r5` 设置为 0,然后循环执行以下命令:
|
||||
|
||||
1. 调用 `KeyboardUpdate`
|
||||
2. 调用 `KeyboardGetChar`
|
||||
3. 如果返回 0,跳转到步骤1
|
||||
4. 复制 `r4` 和 `r5` 到 `r1` 和 `r2` ,然后调用 `DrawCharacter`
|
||||
5. 把 `r0` 加到 `r4`
|
||||
6. 如果 `r4` 是 1024,将 `r1` 加到 `r5`,然后设置 `r4` 为 0。
|
||||
7. 如果 `r5` 是 768,设置 `r5` 为0
|
||||
8. 跳转到步骤1
|
||||
|
||||
|
||||
|
||||
现在编译这个,然后在 PI 上测试。您几乎可以立即开始在屏幕上输入文本。如果没有,请参阅我们的故障排除页面。
|
||||
|
||||
当它工作时,祝贺您,您已经实现了与计算机的接口。现在您应该开始意识到,您几乎已经拥有了一个原始的操作系统。现在,您可以与计算机交互,发出命令,并在屏幕上接收反馈。在下一篇教程[输入02][3]中,我们将研究如何生成一个全文本终端,用户在其中输入命令,然后计算机执行这些命令。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.cl.cam.ac.uk/projects/raspberrypi/tutorials/os/input01.html
|
||||
|
||||
作者:[Alex Chadwick][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[ezio](https://github.com/oska874)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.cl.cam.ac.uk
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.cl.cam.ac.uk/projects/raspberrypi/tutorials/os/downloads.html
|
||||
[2]: https://www.cl.cam.ac.uk/projects/raspberrypi/tutorials/os/downloads/hut1_12v2.pdf
|
||||
[3]: https://www.cl.cam.ac.uk/projects/raspberrypi/tutorials/os/input02.html
|
||||
@ -1,76 +0,0 @@
|
||||
3款用于学术发表的开源工具
|
||||
======
|
||||
|
||||

|
||||
有一个行业在采用数字或者开源工具方面已落后其它行业,那就是竞争与利润并存的学术出版业。根据 Stephen Buranyi 去年在 [The Guardian][1] 发表的一份图表,这个估值超过190亿英镑(260亿美元)的行业至今在其选择、发表甚至分享最重要的科学研究的系统方面,仍受限于印刷媒介的诸多限制。全新的数字时代科技展现了一个能够加速探索、推动科学合作性而不是竞争性以及将投入重新从基础建设导向有益社会的研究的巨大的机遇。
|
||||
|
||||
非盈利性的 [eLife 倡议][2] 是由研究的资金赞助方建立,旨在通过使用数字或者开源技术来走出上述僵局。除了为生活中科学和生物医疗方面的重大成就出版开放式获取的杂志,eLife 已将自己变成了一个在研究交流方面的创新实验窗口——而大部分的实验都是基于开源精神的。
|
||||
|
||||
参与开源出版项目给予我们加速接触、采用科学技术,提升用户体验的机会。我们认为这种机会对于推动学术出版行业是重要的。大而化之地说,开源产品的用户体验经常是有待开发的,而有时候这种情况会阻止其他人去使用它。作为我们在 OSS 开发中投入的一部分,为了鼓励更多用户使用这些产品,我们十分注重用户体验。
|
||||
|
||||
我们所有的代码都是开源的并且我们也积极鼓励开源社区参与进我们的项目中。这对我们来说意味着更快的迭代、更多的实验、更大的透明度,同时也拓宽了我们工作的外延。
|
||||
|
||||
我们现在参与的项目,例如 Libero (之前称作 [eLife Continuum][3])和 [可复制文档栈][4] 的开发以及我们最近和 [Hypothesis][5] 的合作,展示了 OSS 是如何在校队、发表以及新发现的沟通方面带来正面影响的。
|
||||
|
||||
### Libero
|
||||
|
||||
Libero 是面向发布者的服务及应用套餐,它包括一个后生产出版系统、整套前端用户界面、Libero 的棱镜阅读器、一个开放式的API以及一个搜索推荐引擎。
|
||||
|
||||
去年我们采取了用户导向的途径重新设计了 Libero 的前端,做出了一个使用户较少地分心并更多地集中注意在研究文章上的站点。我们和 eLife 社区成员测试并迭代了站点所有的核心功能以确保给所有人最好的阅读体验。网站的新 API 也给可供机器阅读的内容提供了更简单的访问途径,其中包括文字挖掘、机器学习以及在线应用开发。我们网站上的内容以及引领新设计的样式都是开源的,以鼓励 eLife 和其它想要使用它的发布者后续的开发。
|
||||
|
||||
### 可复制文档栈
|
||||
|
||||
在与 [Substance][6] 和 [Stencila][7] 的合作下,eLife 也参与了一个项目来创建可复制的文档栈(RDS)——一个开放式的创作、编纂以及在线出版可复制的计算型手稿的工具栈。
|
||||
|
||||
今天越来越多的研究员能够通过 [R、Markdown][8] 和 [Python][9] 等语言记录他们的计算型实验。这些可以作为实验记录的重要部分,但是尽管它们可以通过最终的研究文章独立地分享,传统出版流程经常将它们视为次级内容。为了发表论文,使用这些语言的研究员除了将他们的计算结果用图片的形式“扁平化”提交外别无他法。但是这导致了许多实验价值和代码和计算数据可重复利用性的流失。诸如 [Jupyter][10] 的电子笔记本解决方案确实可以使研究员以一种可重复利用、可执行的简单形式发布,但是这种方案仍然独立于整个手稿发布过程之外,而不是集成在其中。
|
||||
|
||||
[可复制文档栈][11] 项目着眼于通过开发、发布一个能够把代码和数据集成在文档自身的产品雏形来突出这些挑战并阐述一个端对端的从创作到出版的完整科技。它将最终允许用户以一种包含嵌入代码块和计算结果(统计结果、图表或图片)的形式提交他们的手稿并在出版过程中保留这些可视、可执行的部分。那时发布者就可以将这些作为发布的在线文章的整体所保存。
|
||||
|
||||
### 用 Hypothesis 进行开放式注解
|
||||
|
||||
最近,我们与 [Hypothesis][12] 合作引进了开放式注解,使得我们网站的用户们可以写评语、高亮文章重要部分以及与在线阅读的群体互动。
|
||||
|
||||
通过这样的合作,开源的 Hypothesis 软件被定制得更具有现代化的特性如单次登录验证、用户界面定制选项,给予了发布者在他们自己网站上更多的控制。这些提升正引导着关于发表的学术内容高质量的讨论。
|
||||
|
||||
这个工具可以无缝集成进发布者的网站,学术发表平台 [PubFactory][13] 和内容解决方案供应商 [Ingenta][14] 已经利用了它优化后的特性集。[HighWire][15] 和 [Silverchair][16] 也为他们的发布者提供了实施这套方案的机会。
|
||||
|
||||
### 其它产业和开源软件
|
||||
|
||||
过段时间,我们希望看到更多的发布者采用 Hypothesis、Libero 以及其它开源软件去帮助他们促进重要科学研究的发现以及循环利用。但是 eLife 所能利用的因这些软件和其它 OSS 科技带来的创新机会在其他产业也很普遍。
|
||||
|
||||
数据科学的世界离不开高质量、强支持的开源软件和围绕它们形成的社区;[TensorFlow][17] 就是这样一个好例子。感谢 OSS 以及其社区,AI 的所有领域和机器学习相比于计算机的其它领域有了迅速的提升和发展。与之类似的是 Linux 云端网页主机、Docker 容器、Github上最流行的开源项目之一的 Kubernetes 使用的爆炸性增长。
|
||||
|
||||
所有的这些科技使得不同团体能够四两拨千斤并集中在创新而不是造轮子上。最后,那才是 OSS 真正的好处:它使得我们从互相的失败中学习,在互相的成功中成长。
|
||||
|
||||
我们总是在寻找与研究和科技界面方面最好的人才和想法交流的机会。你可以在 [eLife Labs][18] 上或者联系 [innovation@elifesciences.org][19] 找到更多这种交流的信息。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/3/scientific-publishing-software
|
||||
|
||||
作者:[Paul Shanno][a]
|
||||
译者:[tomjlw](https://github.com/tomjlw)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://opensource.com/users/pshannon
|
||||
[1]:https://www.theguardian.com/science/2017/jun/27/profitable-business-scientific-publishing-bad-for-science
|
||||
[2]:https://elifesciences.org/about
|
||||
[3]:https://elifesciences.org/inside-elife/33e4127f/elife-introduces-continuum-a-new-open-source-tool-for-publishing
|
||||
[4]:https://elifesciences.org/for-the-press/e6038800/elife-supports-development-of-open-technology-stack-for-publishing-reproducible-manuscripts-online
|
||||
[5]:https://elifesciences.org/for-the-press/81d42f7d/elife-enhances-open-annotation-with-hypothesis-to-promote-scientific-discussion-online
|
||||
[6]:https://github.com/substance
|
||||
[7]:https://github.com/stencila/stencila
|
||||
[8]:https://rmarkdown.rstudio.com/
|
||||
[9]:https://www.python.org/
|
||||
[10]:http://jupyter.org/
|
||||
[11]:https://elifesciences.org/labs/7dbeb390/reproducible-document-stack-supporting-the-next-generation-research-article
|
||||
[12]:https://github.com/hypothesis
|
||||
[13]:http://www.pubfactory.com/
|
||||
[14]:http://www.ingenta.com/
|
||||
[15]:https://github.com/highwire
|
||||
[16]:https://www.silverchair.com/community/silverchair-universe/hypothesis/
|
||||
[17]:https://www.tensorflow.org/
|
||||
[18]:https://elifesciences.org/labs
|
||||
[19]:mailto:innovation@elifesciences.org
|
||||
@ -0,0 +1,121 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (How To Get Flatpak Apps And Games Built With OpenGL To Work With Proprietary Nvidia Graphics Drivers)
|
||||
[#]: via: (https://www.linuxuprising.com/2018/06/how-to-get-flatpak-apps-and-games-built.html)
|
||||
[#]: author: (Logix https://plus.google.com/118280394805678839070)
|
||||
|
||||
如何使得支持 OpenGL 的 Flatpak 应用和游戏在专有 Nvidia 图形驱动下工作
|
||||
======
|
||||
**一些支持 OpenGL 并打包为 Flatpak 的应用和游戏无法使用专有 Nvidia 驱动启动。本文将介绍如何在不安装开源驱动(Nouveau)的情况下启动这些 Flatpak 应用或游戏。**
|
||||
|
||||
这有个例子。我在我的 Ubuntu 18.04 桌面上使用专有的 Nvidia 驱动程序 (`nvidia-driver-390`),当我尝试启动最新版本时:
|
||||
```
|
||||
$ /usr/bin/flatpak run --branch=stable --arch=x86_64 --command=krita --file-forwarding org.kde.krita
|
||||
Gtk-Message: Failed to load module "canberra-gtk-module"
|
||||
Gtk-Message: Failed to load module "canberra-gtk-module"
|
||||
libGL error: No matching fbConfigs or visuals found
|
||||
libGL error: failed to load driver: swrast
|
||||
Could not initialize GLX
|
||||
|
||||
```
|
||||
|
||||
要修复使用 OpenGL 和专有 Nvidia 图形驱动时无法启动的 Flatpak 游戏和应用,你需要为已安装的专有驱动安装运行时。以下是步骤。
|
||||
|
||||
**1\. 如果尚未添加 FlatHub 仓库,请添加它。你可以在[此处][1]找到针对 Linux 发行版的说明。**
|
||||
|
||||
**2. 现在,你需要确定系统上安装的专有 Nvidia 驱动的确切版本。**
|
||||
|
||||
_这一步取决于你使用的 Linux 发行版,我无法涵盖所有情况。下面的说明是面向 Ubuntu(以及 Ubuntu 风格的版本),但希望你可以自己弄清楚系统上安装的 Nvidia 驱动版本._
|
||||
|
||||
要在 Ubuntu 中执行此操作,请打开 `Software&Updates`,切换到 `Additional Drivers` 选项卡并记下 Nvidia 驱动包的名称。
|
||||
|
||||
比如,你可以看到我的是 `nvidia-driver-390`:
|
||||
|
||||

|
||||
|
||||
这里还没完成。我们只是找到了 Nvidia 驱动的主要版本,但我们还需要知道次要版本。要获得我们下一步所需的确切 Nvidia 驱动版本,请运行此命令(应该适用于任何基于 Debian 的 Linux 发行版,如 Ubuntu、Linux Mint 等):
|
||||
```
|
||||
apt-cache policy NVIDIA-PACKAGE-NAME
|
||||
|
||||
```
|
||||
|
||||
NVIDIA-PACKAGE-NAME 是 `Software & Updates` 中列出的 Nvidia 驱动包名称。例如,要查看 `nvidia-driver-390` 包的确切安装版本,请运行以下命令:
|
||||
```
|
||||
$ apt-cache policy nvidia-driver-390
|
||||
nvidia-driver-390:
|
||||
Installed: 390.48-0ubuntu3
|
||||
Candidate: 390.48-0ubuntu3
|
||||
Version table:
|
||||
* 390.48-0ubuntu3 500
|
||||
500 http://ro.archive.ubuntu.com/ubuntu bionic/restricted amd64 Packages
|
||||
100 /var/lib/dpkg/status
|
||||
|
||||
```
|
||||
|
||||
在这个命令的输出中,查找 `Installed` 部分并记下版本号(不包括 `-0ubuntu3` 之类)。现在我们知道了已安装的 Nvidia 驱动的确切版本(我例子中的是 `390.48`)。记住它,因为下一步我们需要。
|
||||
|
||||
**3\. 最后,你可以从 FlatHub 为你已安装的专有 Nvidia 图形驱动安装运行时。**
|
||||
|
||||
要列出 FlatHub 上所有可用的 Nvidia 运行时包,你可以使用以下命令:
|
||||
```
|
||||
flatpak remote-ls flathub | grep nvidia
|
||||
|
||||
```
|
||||
|
||||
幸运地是 FlatHub 上提供这个 Nvidia 驱动的运行时。你现在可以使用以下命令继续安装运行时:
|
||||
|
||||
* 针对 64 位系统:
|
||||
|
||||
|
||||
```
|
||||
flatpak install flathub org.freedesktop.Platform.GL.nvidia-MAJORVERSION-MINORVERSION
|
||||
|
||||
```
|
||||
|
||||
将 MAJORVERSION 替换为 Nvidia 驱动的主要版本(在上面的示例中为 390),将 MINORVERSION 替换为次要版本(步骤2,我例子中的为 48)。
|
||||
|
||||
例如,要为 Nvidia 图形驱动版本 390.48 安装运行时,你必须使用以下命令:
|
||||
```
|
||||
flatpak install flathub org.freedesktop.Platform.GL.nvidia-390-48
|
||||
|
||||
```
|
||||
|
||||
* 对于 32 位系统(或能够在 64 位上运行 32 位的应用或游戏),使用以下命令安装 32 位运行时:
|
||||
|
||||
|
||||
```
|
||||
flatpak install flathub org.freedesktop.Platform.GL32.nvidia-MAJORVERSION-MINORVERSION
|
||||
|
||||
```
|
||||
|
||||
再说一次,将 MAJORVERSION 替换为 Nvidia 驱动的主要版本(在上面的示例中为 390),将 MINORVERSION 替换为次要版本(步骤2,我例子中的为 48)。
|
||||
|
||||
比如,要为 Nvidia 图形驱动版本 390.48 安装 32 位运行时,你需要使用以下命令:
|
||||
```
|
||||
flatpak install flathub org.freedesktop.Platform.GL32.nvidia-390-48
|
||||
|
||||
```
|
||||
|
||||
以上就是你要运行支持 OpenGL 的 Flatpak 的应用或游戏的方法。
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.linuxuprising.com/2018/06/how-to-get-flatpak-apps-and-games-built.html
|
||||
|
||||
作者:[Logix][a]
|
||||
选题:[lujun9972](https://github.com/lujun9972)
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://plus.google.com/118280394805678839070
|
||||
[1]:https://flatpak.org/setup/
|
||||
[2]:https://www.linuxuprising.com/2018/06/free-painting-software-krita-410.html
|
||||
[3]:https://www.linuxuprising.com/2018/06/winepak-is-flatpak-repository-for.html
|
||||
[4]:https://github.com/winepak/applications/issues/23
|
||||
[5]:https://github.com/flatpak/flatpak/issues/138
|
||||
@ -1,132 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (leommxj)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (How ASLR protects Linux systems from buffer overflow attacks)
|
||||
[#]: via: (https://www.networkworld.com/article/3331199/linux/what-does-aslr-do-for-linux.html)
|
||||
[#]: author: (Sandra Henry-Stocker https://www.networkworld.com/author/Sandra-Henry_Stocker/)
|
||||
|
||||
ASLR是如何保护Linux系统免受缓冲区溢出攻击的
|
||||
======
|
||||
|
||||

|
||||
|
||||
地址空间随机化( ASLR )是一种操作系统用来抵御缓冲区溢出攻击的内存保护机制。这种技术使得系统上运行的进程的内存地址无法预测,使得与这些进程有关的漏洞变得更加难以利用。
|
||||
|
||||
ASLR目前在 Linux , Windows 以及 MacOS 系统上都有使用。其最早出现在 2005 的Linux系统上。2007 年,这项技术被 Windows 和 MacOS 部署使用。尽管 ASLR 在各个系统上都提供相同的功能,却有着不同的实现。
|
||||
|
||||
ASLR的有效性依赖于整个地址空间布局对于攻击者保持未知。此外,只有编译时作为位置无关可执行文件(PIE)的程序才能得到ASLR最大的保护,因为只有这样,可执行文件的所有代码节区才会被加载在随机地址。PIE 代码不管绝对地址是多少都可以正确执行。
|
||||
|
||||
**[ 参见:[用于排除Linux故障的宝贵提示和技巧][1] ]**
|
||||
|
||||
### ASLR 的局限性
|
||||
|
||||
尽管 ASLR 使得对系统漏洞的利用更加困难了,但其保护系统的能力是有限的。理解关于 ASLR 的以下几点是很重要的:
|
||||
|
||||
* 不能解决漏洞,而是增加利用漏洞的难度
|
||||
* 并不追踪或报告漏洞
|
||||
* 不能对编译时没有开启 ASLR 支持的二进制文件提供保护
|
||||
* 不能避免被绕过
|
||||
|
||||
|
||||
|
||||
### ASLR 是如何工作的
|
||||
|
||||
|
||||
|
||||
ASLR通过对攻击者在进行缓冲区溢出攻击时所要用到的内存布局中的偏移做随机化来加大攻击成功的难度,从而增强了系统的控制流完整性。
|
||||
|
||||
|
||||
通常认为 ASLR 在64位系统上效果更好,因为64位系统提供了更大的熵(可随机的地址范围)。
|
||||
|
||||
### ASLR 是否正在你的 Linux 系统上运行?
|
||||
|
||||
下面展示的两条命令都可以告诉你你的系统是否启用了 ASLR 功能
|
||||
|
||||
```
|
||||
$ cat /proc/sys/kernel/randomize_va_space
|
||||
2
|
||||
$ sysctl -a --pattern randomize
|
||||
kernel.randomize_va_space = 2
|
||||
```
|
||||
|
||||
上方指令结果中的数值 (2) 表示 ASLR 工作在全随机化模式。其可能为下面的几个数值之一:
|
||||
|
||||
```
|
||||
0 = Disabled
|
||||
1 = Conservative Randomization
|
||||
2 = Full Randomization
|
||||
```
|
||||
|
||||
如果你关闭了 ASLR 并且执行下面的指令,你将会注意到前后两条**ldd**的输出是完全一样的。**ldd**命令会加载共享对象并显示他们在内存中的地址。
|
||||
|
||||
```
|
||||
$ sudo sysctl -w kernel.randomize_va_space=0 <== disable
|
||||
[sudo] password for shs:
|
||||
kernel.randomize_va_space = 0
|
||||
$ ldd /bin/bash
|
||||
linux-vdso.so.1 (0x00007ffff7fd1000) <== same addresses
|
||||
libtinfo.so.6 => /lib/x86_64-linux-gnu/libtinfo.so.6 (0x00007ffff7c69000)
|
||||
libdl.so.2 => /lib/x86_64-linux-gnu/libdl.so.2 (0x00007ffff7c63000)
|
||||
libc.so.6 => /lib/x86_64-linux-gnu/libc.so.6 (0x00007ffff7a79000)
|
||||
/lib64/ld-linux-x86-64.so.2 (0x00007ffff7fd3000)
|
||||
$ ldd /bin/bash
|
||||
linux-vdso.so.1 (0x00007ffff7fd1000) <== same addresses
|
||||
libtinfo.so.6 => /lib/x86_64-linux-gnu/libtinfo.so.6 (0x00007ffff7c69000)
|
||||
libdl.so.2 => /lib/x86_64-linux-gnu/libdl.so.2 (0x00007ffff7c63000)
|
||||
libc.so.6 => /lib/x86_64-linux-gnu/libc.so.6 (0x00007ffff7a79000)
|
||||
/lib64/ld-linux-x86-64.so.2 (0x00007ffff7fd3000)
|
||||
```
|
||||
|
||||
如果将其重新设置为**2**来启用 ASLR,你将会看到每次运行**ldd**,得到的内存地址都不相同。
|
||||
|
||||
```
|
||||
$ sudo sysctl -w kernel.randomize_va_space=2 <== enable
|
||||
[sudo] password for shs:
|
||||
kernel.randomize_va_space = 2
|
||||
$ ldd /bin/bash
|
||||
linux-vdso.so.1 (0x00007fff47d0e000) <== first set of addresses
|
||||
libtinfo.so.6 => /lib/x86_64-linux-gnu/libtinfo.so.6 (0x00007f1cb7ce0000)
|
||||
libdl.so.2 => /lib/x86_64-linux-gnu/libdl.so.2 (0x00007f1cb7cda000)
|
||||
libc.so.6 => /lib/x86_64-linux-gnu/libc.so.6 (0x00007f1cb7af0000)
|
||||
/lib64/ld-linux-x86-64.so.2 (0x00007f1cb8045000)
|
||||
$ ldd /bin/bash
|
||||
linux-vdso.so.1 (0x00007ffe1cbd7000) <== second set of addresses
|
||||
libtinfo.so.6 => /lib/x86_64-linux-gnu/libtinfo.so.6 (0x00007fed59742000)
|
||||
libdl.so.2 => /lib/x86_64-linux-gnu/libdl.so.2 (0x00007fed5973c000)
|
||||
libc.so.6 => /lib/x86_64-linux-gnu/libc.so.6 (0x00007fed59552000)
|
||||
/lib64/ld-linux-x86-64.so.2 (0x00007fed59aa7000)
|
||||
```
|
||||
|
||||
### 尝试绕过 ASLR
|
||||
|
||||
尽管这项技术有很多优点,绕过ASLR的攻击并不罕见,主要有以下几类:
|
||||
|
||||
* 利用地址泄露
|
||||
* 访问与特定地址关联的数据
|
||||
* 针对ASLR 实现的缺陷来猜测地址,常见于系统熵过低或 ASLR 实现不完善。
|
||||
* 利用侧信道攻击
|
||||
|
||||
### 总结
|
||||
|
||||
ASLR 有很大的价值,尤其是在64位系统上运行并被正确实现时。虽然不能避免被绕过,但这项技术的确使得利用系统漏洞变得更加困难了。这份参考资料可以提供更多有关细节 [on the Effectiveness of Full-ASLR on 64-bit Linux][2] ,这篇论文介绍了一种利用分支预测绕过ASLR的技术 [bypass ASLR][3]。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.networkworld.com/article/3331199/linux/what-does-aslr-do-for-linux.html
|
||||
|
||||
作者:[Sandra Henry-Stocker][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[leommxj](https://github.com/leommxj)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.networkworld.com/author/Sandra-Henry_Stocker/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.networkworld.com/article/3242170/linux/invaluable-tips-and-tricks-for-troubleshooting-linux.html
|
||||
[2]: https://cybersecurity.upv.es/attacks/offset2lib/offset2lib-paper.pdf
|
||||
[3]: http://www.cs.ucr.edu/~nael/pubs/micro16.pdf
|
||||
[4]: https://www.facebook.com/NetworkWorld/
|
||||
[5]: https://www.linkedin.com/company/network-world
|
||||
@ -0,0 +1,91 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Akira: The Linux Design Tool We’ve Always Wanted?)
|
||||
[#]: via: (https://itsfoss.com/akira-design-tool)
|
||||
[#]: author: (Ankush Das https://itsfoss.com/author/ankush/)
|
||||
|
||||
Akira:我们一直想要的 Linux 设计工具?
|
||||
======
|
||||
|
||||
先说一下,我不是一个专业的设计师 - 但我在 Windows 上使用了某些工具(如 Photoshop、Illustrator 等)和 [Figma] [1](这是一个基于浏览器的界面设计工具)。我相信 Mac 和 Windows 上还有更多的设计工具。
|
||||
|
||||
即使在 Linux 上,也只有有限的专用[图形设计工具][2]。其中一些工具如 [GIMP][3] 和 [Inkscape][4] 也被专业人士使用。但不幸的是,它们中的大多数都不被视为专业级。
|
||||
|
||||
即使有更多解决方案 - 我也从未遇到过可以取代 [Sketch][5]、Figma 或 Adobe XD 的原生 Linux 应用。任何专业设计师都同意这点,不是吗?
|
||||
|
||||
### Akira 是否会在 Linux 上取代 Sketch、Figma 和 Adobe XD?
|
||||
|
||||
所以,为了开发一些能够取代那些专有工具的应用 - [Alessandro Castellani][6] 发起了一个 [Kickstarter 活动][7],并与几位经验丰富的开发人员 [Alberto Fanjul][8]、[Bilal Elmoussaoui][9] 和 [Felipe Escoto][10] 组队合作。
|
||||
|
||||
是的,Akira 仍然只是一个想法,只有一个界面原型(正如我最近在 Kickstarter 的[直播流][11]中看到的那样)。
|
||||
|
||||
### 如果它还没有,为什么会发起 Kickstarter 活动?
|
||||
|
||||
![][12]
|
||||
|
||||
Kickstarter 活动的目的是收集资金,以便雇用开发人员,并花几个月的时间开发,以使 Akira 成为可能。
|
||||
|
||||
尽管如此,如果你想支持这个项目,你应该知道一些细节,对吧?
|
||||
|
||||
不用担心,我们在他们的直播中问了几个问题 - 让我们看下
|
||||
|
||||
### Akira:更多细节
|
||||
|
||||
![Akira prototype interface][13]
|
||||
图片来源:Kickstarter
|
||||
|
||||
如 Kickstarter 活动描述的那样:
|
||||
|
||||
> Akira 的主要目的是提供一个快速而直观的工具来**创建 Web 和移动界面**,更像是 **Sketch**、**Figma** 或 **Adobe XD**,并且是 Linux 原生体验。
|
||||
|
||||
他们还详细描述了该工具与 Inkscape、Glade 或 QML Editor 的不同之处。当然,如果你想要所有的技术细节,请查看 [Kickstarter][7]。但是,在此之前,让我们看一看当我询问有关 Akira 的一些问题时他们说了些什么。
|
||||
|
||||
问:如果你认为你的项目类似于 Figma - 人们为什么要考虑安装 Akira 而不是使用基于网络的工具?它是否只是这些工具的克隆 - 提供原生 Linux 体验,还是有一些非常有趣的东西可以鼓励用户切换(除了是开源解决方案之外)?
|
||||
|
||||
** Akira:** 与基于网络的 electron 应用相比,Linux 原生体验总是更好、更快。此外,如果你选择使用 Figma,硬件配置也很重要 - 但 Akira 将会占用很少的系统资源,并且你可以在不需要上网的情况下完成类似工作。
|
||||
|
||||
问:假设它成为了 Linux用户一直在等待的开源方案(拥有专有工具的类似功能)。你有什么维护计划?你是否计划引入定价 - 或依赖捐赠?
|
||||
|
||||
**Akira:**该项目主要依靠捐赠(类似于 [Krita 基金会][14] 这样的想法)。但是,不会有“专业版”计划 - 它将免费提供,它将是一个开源项目。
|
||||
|
||||
根据我得到的回答,它看起来似乎很有希望,我们应该支持。
|
||||
|
||||
### 总结
|
||||
|
||||
你怎么认为 Akira?它只是一个概念吗?或者你希望看到进展?
|
||||
|
||||
请在下面的评论中告诉我们你的想法。
|
||||
|
||||
![][15]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://itsfoss.com/akira-design-tool
|
||||
|
||||
作者:[Ankush Das][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://itsfoss.com/author/ankush/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.figma.com/
|
||||
[2]: https://itsfoss.com/best-linux-graphic-design-software/
|
||||
[3]: https://itsfoss.com/gimp-2-10-release/
|
||||
[4]: https://inkscape.org/
|
||||
[5]: https://www.sketchapp.com/
|
||||
[6]: https://github.com/Alecaddd
|
||||
[7]: https://www.kickstarter.com/projects/alecaddd/akira-the-linux-design-tool/description
|
||||
[8]: https://github.com/albfan
|
||||
[9]: https://github.com/bilelmoussaoui
|
||||
[10]: https://github.com/Philip-Scott
|
||||
[11]: https://live.kickstarter.com/alessandro-castellani/live-stream/the-current-state-of-akira
|
||||
[12]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2019/01/akira-design-tool-kickstarter.jpg?resize=800%2C451&ssl=1
|
||||
[13]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2019/01/akira-mockup.png?ssl=1
|
||||
[14]: https://krita.org/en/about/krita-foundation/
|
||||
[15]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2019/01/akira-design-tool-kickstarter.jpg?fit=812%2C458&ssl=1
|
||||
147
translated/tech/20190128 Top Hex Editors for Linux.md
Normal file
147
translated/tech/20190128 Top Hex Editors for Linux.md
Normal file
@ -0,0 +1,147 @@
|
||||
[#]: collector: "lujun9972"
|
||||
[#]: translator: "zero-mk "
|
||||
[#]: reviewer: " "
|
||||
[#]: publisher: " "
|
||||
[#]: url: " "
|
||||
[#]: subject: "Top Hex Editors for Linux"
|
||||
[#]: via: "https://itsfoss.com/hex-editors-linux"
|
||||
[#]: author: "Ankush Das https://itsfoss.com/author/ankush/"
|
||||
|
||||
Top Hex Editors for Linux
|
||||
======
|
||||
|
||||
十六进制编辑器可以让你以十六进制的形式查看/编辑文件的二进制数据,因此其被命名为“十六进制”编辑器。说实话,并不是每个人都需要它。只有必须处理二进制数据的特定用户组才会使用到它。
|
||||
|
||||
如果您不知道,它是什么,让我举个例子。假设您拥有游戏的配置文件,您可以使用十六进制编辑器打开它们并更改某些值以获得更多的弹药/分数等等。 想要了解有关Hex编辑器的更多信息,你可以参阅 [Wikipedia page][1]。
|
||||
|
||||
如果你已经知道它用来干什么了 —— 让我们来看看Linux最好的Hex编辑器。
|
||||
|
||||
### 5个最好的十六进制编辑器
|
||||
|
||||
![Best Hex Editors for Linux][2]
|
||||
|
||||
**注意:**提到的十六进制编辑器没有特定的排名顺序。
|
||||
|
||||
#### 1\. Bless Hex Editor
|
||||
|
||||
![bless hex editor][3]
|
||||
|
||||
**主要特点:**
|
||||
|
||||
* 编辑裸设备(Raw disk )
|
||||
* 多级撤消/重做操作
|
||||
* 多个标签
|
||||
* 转换表
|
||||
* 支持插件扩展功能
|
||||
|
||||
|
||||
|
||||
Bless是Linux上最流行的Hex编辑器之一。您可以在AppCenter或软件中心中找到它。 如果不是这种情况,您可以查看他们的 [GitHub page][4] 获取构建和相关的说明。
|
||||
|
||||
它可以轻松处理编辑大文件而不会降低速度——因此它是一个快速的十六进制编辑器。
|
||||
|
||||
#### 2\. GNOME Hex Editor
|
||||
|
||||
![gnome hex editor][5]
|
||||
|
||||
**主要特点:**
|
||||
|
||||
* 以 十六进制/Ascii格式 查看/编辑
|
||||
|
||||
* 编辑大文件
|
||||
|
||||
*
|
||||
|
||||
|
||||
另一个神奇的十六进制编辑器-专门为GNOME量身定做的。 我个人用的是 Elementary OS, 所以我可以在 软件中心(AppCenter)找到它.。您也可以在软件中心找到它。如果没有,请参考 [GitHub page][6] 获取源代码。
|
||||
|
||||
您可以使用此编辑器以十六进制或ASCII格式 查看/编辑 文件。用户界面非常简单——正如您在上面的图像中看到的那样。
|
||||
|
||||
#### 3\. Okteta
|
||||
|
||||
![okteta][7]
|
||||
|
||||
**主要特点:**
|
||||
|
||||
* 可自定义的数据视图
|
||||
* 多个选项卡
|
||||
* 字符编码:支持Qt、EBCDIC的所有8位编码
|
||||
* 解码表列出常见的简单数据类型
|
||||
|
||||
|
||||
|
||||
Okteta是一个简单的十六进制编辑器,没有那么奇特的功能。虽然它可以处理大部分任务。它有一个单独的模块,你可以使用它嵌入其他程序来查看/编辑文件。
|
||||
|
||||
|
||||
与上述所有编辑器类似,您也可以在应用中心(App Center)和软件中心(Software Center)上找到列出的编辑器。
|
||||
|
||||
#### 4\. wxHexEditor
|
||||
|
||||
![wxhexeditor][8]
|
||||
|
||||
**主要特点:**
|
||||
|
||||
* 轻松处理大文件
|
||||
* 支持x86反汇编
|
||||
* **** Sector Indication **** on Disk devices
|
||||
* 支持自定义十六进制面板格式和颜色
|
||||
|
||||
|
||||
|
||||
这很有趣。它主要是一个十六进制编辑器,但您也可以将其用作低级磁盘编辑器。例如,如果您的硬盘有问题,可以使用此编辑器编辑RAW格式原始数据镜像文件,在十六进制中的扇区并修复它。
|
||||
|
||||
你可以在你的应用中心(App Center)和软件中心(Software Center)找到它。 如果不是, [Sourceforge][9] 是个正确的选择。
|
||||
|
||||
#### 5\. Hexedit (命令行工具)
|
||||
|
||||
![hexedit][10]
|
||||
|
||||
**主要特点:**
|
||||
|
||||
* 运行在命令行终端上
|
||||
* 它又快又简单
|
||||
|
||||
|
||||
|
||||
如果您想在终端上工作,可以继续通过控制台安装hexedit。它是我最喜欢的命令行Linux十六进制编辑器。
|
||||
|
||||
当你启动它时,你必须指定要打开的文件的位置,然后它会为你打开它。
|
||||
|
||||
要安装它,只需输入:
|
||||
|
||||
```
|
||||
sudo apt install hexedit
|
||||
```
|
||||
|
||||
### 结束
|
||||
|
||||
十六进制编辑器可以方便地进行实验和学习。如果你是一个有经验的人,你应该选择一个有更多功能的——GUI。 尽管这一切都取决于个人喜好。
|
||||
|
||||
你认为十六进制编辑器的有用性如何?你用哪一个?我们没有列出你最喜欢的吗?请在评论中告诉我们!
|
||||
|
||||
![][11]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://itsfoss.com/hex-editors-linux
|
||||
|
||||
作者:[Ankush Das][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[zero-mk](https://github.com/zero-mk)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://itsfoss.com/author/ankush/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://en.wikipedia.org/wiki/Hex_editor
|
||||
[2]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2019/01/Linux-hex-editors-800x450.jpeg?resize=800%2C450&ssl=1
|
||||
[3]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2019/01/bless-hex-editor.jpg?ssl=1
|
||||
[4]: https://github.com/bwrsandman/Bless
|
||||
[5]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2019/01/ghex-hex-editor.jpg?ssl=1
|
||||
[6]: https://github.com/GNOME/ghex
|
||||
[7]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2019/01/okteta-hex-editor-800x466.jpg?resize=800%2C466&ssl=1
|
||||
[8]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2019/01/wxhexeditor.jpg?ssl=1
|
||||
[9]: https://sourceforge.net/projects/wxhexeditor/
|
||||
[10]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2019/01/hexedit-console.jpg?resize=800%2C566&ssl=1
|
||||
[11]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2019/01/Linux-hex-editors.jpeg?fit=800%2C450&ssl=1
|
||||
@ -0,0 +1,110 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (LazyWolfLin)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (7 steps for hunting down Python code bugs)
|
||||
[#]: via: (https://opensource.com/article/19/2/steps-hunting-code-python-bugs)
|
||||
[#]: author: (Maria Mckinley https://opensource.com/users/parody)
|
||||
|
||||
7 步检查 Python 代码错误
|
||||
======
|
||||
了解一些技巧助你减少代码查错时间。
|
||||

|
||||
|
||||
在周五的下午三点钟。为什么是这个时间?因为事情总会在周五下午三点钟发生。你收到一条通知,客户发现你的软件出现一个错误。在有了初步的怀疑后,你联系运维,查看你的软件日志以了解发生了什么,因为你记得收到过日志已经移动了的通知。
|
||||
|
||||
结果这些日志被转移到了你获取不到的地方,但他们正在导到一个网页应用中——所以你将可以用这个漂亮的应用来检索日志,但是,这个应用现在还没完成。这个应用预计会在几天内完成。我知道,这完全不符合实际情况,对吧?然而并不是,日志或者日志消息似乎经常在错误的时间出现缺失。在我们开始查错前,一个忠告:经常检查你的日志以确保他们在你认为它们应该在的地方并记录你认为它们应该记的东西。当你不检查的时候,这些东西往往会发生令人惊讶的变化。
|
||||
|
||||
好的,你找到了日志或者尝试了呼叫运维人员,而客户确实发现了一个错误。甚至你可能认为你已经知道错误在哪儿。
|
||||
|
||||
你立即打开你认为可能有问题的文件并开始查错。
|
||||
|
||||
### 1. 不要碰你的代码
|
||||
|
||||
阅读代码,你甚至可能会想到一个假设。但是在开始修改你的代码前,请重现导致错误的调用并把它变成一个测试。这将是一个集成测试,因为你可能还有其他疑问,目前你还没能准确地知道问题在哪儿。
|
||||
|
||||
确保这个测试是失败的。这很重要,因为有时你的测试不能重现失败的调用,尤其是你使用了可以混淆测试的 web 或者其他框架。很多东西可能被存储在变量中,但遗憾的是,只通过观察测试,你在测试里调用的东西并不总是明显可见的。当我尝试着重现这个失败的调用时,我不准备说我创建了一个新测试,但是,对的,我确实已经创建了新的一个测试,但我不认为这是特别不寻常的。从自己的错误中吸取教训。
|
||||
|
||||
### 2. 编写错误的测试
|
||||
|
||||
现在,你有了一个失败的测试或者可能是一个带有错误的测试,那么是时候解决问题了。但是在你开干之前,让我们先检查下调用栈,因为这样可以更轻松地解决问题。
|
||||
|
||||
调用栈包括你已经启动但尚未完成地所有任务。因此,比如你正在烤蛋糕并准备往面糊里加面粉,那你的调用栈将是:
|
||||
|
||||
* 做蛋糕
|
||||
* 打面糊
|
||||
* 加面粉
|
||||
|
||||
你已经开始做蛋糕,开始打面糊,而你现在正在加面粉。往锅底抹油不在这个列表中因为你已经完成了,而做糖霜不在这个列表上因为你还没开始做。
|
||||
|
||||
如果你对调用栈不清楚,我强烈建议你使用 [Python Tutor][1],它能帮你在执行代码时观察调用栈。
|
||||
|
||||
现在,如果你的 Python 程序出现了错误,接收器会帮你打印出当前调用栈。这意味着无论那一时刻程序在做什么,很明显错误发生在调用栈的底部。
|
||||
|
||||
### 3. 始终先检查 stack 的底部
|
||||
|
||||
你不仅能在栈底看到发生了哪个错误,而且通常可以在调用栈的最后一行发现问题。如果栈底对你没有帮助,而你的代码还没有经过代码分析,那么使用代码分析非常有用。我推荐 pylint 或者 flake8。通常情况下,它会指出我一直忽略的错误的地方。
|
||||
|
||||
如果对错误看起来很迷惑,你下一步行动可能是用 Google 搜索它。如果你搜索的内容不包含你的代码的相关信息,如变量名、文件等,那你将获得更好的搜索结果。如果你使用的是 Python 3(你应该使用它),那么搜索内容包含 Python 3 是有帮助的,否则 Python 2 的解决方案往往会占据大多数。
|
||||
|
||||
很久以前,开发者需要在没有搜索引擎的帮助下解决问题。那是一段黑暗的时光。充分利用你可以使用的所有工具。
|
||||
|
||||
不幸的是,有时候问题发生得比较早但只有在调用栈底部执行的地方才变得明显。就像当蛋糕没有膨胀时,忘记加发酵粉的事才被发现。
|
||||
|
||||
那就该检查整个调用栈。问题更可能在你的代码而不是 Python 标准库或者第三方包,所以先检查调用栈内你的代码。另外,在你的代码中放置断点通常会更容易检查代码。在调用栈的代码中放置断点然后看看周围是否如你预期。
|
||||
|
||||
“但是,玛丽,”我听到你说,“如果我有一个调用栈,那这些都是有帮助的,但我只有一个失败的测试。我该从哪里开始?”
|
||||
|
||||
Pdb, 一个 Python 调试器。
|
||||
|
||||
找到你代码里会被这个调用命中的地方。你应该能够找到至少一个这样的地方。在那里打上一个 pdb 的断点。
|
||||
|
||||
#### 一句题外话
|
||||
|
||||
为什么不使用 print 语句呢?我曾经依赖于 print 语句。有时候,他们仍然派得上用场。但当我开始处理复杂的代码库,尤其是有网络调用的代码库,print 语句就变得太慢了。我最终得到所有打印出来的数据,但我没法追踪他们的位置和原因,而且他们变得复杂了。但是主要使用 pdb 还有一个更重要的原因。假设你添加一条 print 语句去发现错误问题,而且 print 语句必须早于错误出现的地方。但是,看看你放 print 语句的函数,你不知道你的代码是怎么执行到那个位置的。查看代码是寻找调用路径的好方法,但看你以前写的代码是恐怖的。是的,我会用 grep 处理我的代码库以寻找调用函数的地方,但这会变得乏味,而且搜索一个通用函数时并不能缩小搜索范围。Pdb 就变得非常有用。
|
||||
|
||||
你遵循我的建议,打上 pdb 断点并运行你的测试。然而测试再次失败,但是没有任何一个断点被打到。保留你的断点,并运行测试套件中一个同这个失败的测试非常相似的测试。如果你有个不错的测试,你应该能够找到一个测试。它会击中了你认为你的失败测试应该击中的代码。运行这个测试,然后当它打到你的断点,按下 `w` 并检查调用栈。如果你不知道如何查看因为其他调用而变得混乱的调用栈,那么在调用栈的中间找到属于你的代码,并在其中堆栈中代码的上一行放置一个断点。再试一次新的测试。如果仍然没打到断点,那么继续,向上追踪调用栈并找出你的调用在哪里脱轨了。如果你一直没有打到断点,最后到了追踪的顶部,那么恭喜你,你发现了问题:你的应用程序拼写错了。没有经验,没有经验,一点都没有经验。
|
||||
|
||||
### 4. 修改代码
|
||||
|
||||
如果你仍觉得迷惑,在你稍微改变了一些的地方尝试新的测试。你能让新的测试跑起来么?有什么不同的呢?有什么相同的呢?尝试改变别的东西。当你有了你的测试,可能也还有其他测试,那就可以开始安全地修改代码,确定是否可以缩小问题范围。记得从一个新提交开始解决问题,以便于可以轻松地撤销无效地更改。(这就是版本控制,如果你没有使用版本控制,这将会改变你的生活。好吧,可能它只是让编码更容易。查阅“版本控制可视指南”,以了解更多。)
|
||||
|
||||
### 5. 休息一下
|
||||
|
||||
尽管如此,当它不再感觉起来像一个有趣的挑战或者游戏而开始变得令人沮丧时,你最好的举措是脱离这个问题。休息一下。我强烈建议你去散步并尝试考虑别的事情。
|
||||
|
||||
### 6. 把一切写下来
|
||||
|
||||
当你回来了,如果你没有突然受到启发,那就把你关于这个问题所知的每一个点信息写下来。这应该包括:
|
||||
|
||||
* 真正造成问题的调用
|
||||
* 真正发生了什么,包括任何错误信息或者相关的日志信息
|
||||
* 你真正期望发生什么
|
||||
* 到目前为止,为了找出问题,你做了什么工作;以及解决问题中你发现的任何线索。
|
||||
|
||||
有时这里有很多信息,但相信我,从零碎中挖掘信息是很烦人。所以尽量简洁,但是要完整。
|
||||
|
||||
### 7. 寻求帮助
|
||||
|
||||
我经常发现写下所有信息能够启迪我想到还没尝试过的东西。当然,有时候我在点击提交按钮后立刻意识到问题是是什么。无论如何,当你在写下所有东西仍一无所获,那就试试向他人发邮件求助。首先是你的同事或者其他参与你的项目的人,然后是项目的邮件列表。不要害怕向人求助。大多数人都是友善和乐于助人的,我发现在 Python 社区里尤其如此。
|
||||
|
||||
Maria McKinley 将在 [PyCascades 2019][4] 发表[代码查错][3],二月 23-24,于西雅图。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/2/steps-hunting-code-python-bugs
|
||||
|
||||
作者:[Maria Mckinley][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[LazyWolfLin](https://github.com/LazyWolfLin)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/parody
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: http://www.pythontutor.com/
|
||||
[2]: https://betterexplained.com/articles/a-visual-guide-to-version-control/
|
||||
[3]: https://2019.pycascades.com/talks/hunting-the-bugs
|
||||
[4]: https://2019.pycascades.com/
|
||||
@ -1,162 +0,0 @@
|
||||
[#]: collector: "lujun9972"
|
||||
[#]: translator: "zero-mk "
|
||||
[#]: reviewer: " "
|
||||
[#]: publisher: " "
|
||||
[#]: url: " "
|
||||
[#]: subject: "Ampersands and File Descriptors in Bash"
|
||||
[#]: via: "https://www.linux.com/blog/learn/2019/2/ampersands-and-file-descriptors-bash"
|
||||
[#]: author: "Paul Brown https://www.linux.com/users/bro66"
|
||||
|
||||
Bash中的&符号和文件描述符
|
||||
======
|
||||
|
||||

|
||||
|
||||
在我们寻求检查所有的clutter(`&`,`|`,`;`,`>`,`<`,`{`,`[`,`(`,) `]`,`}` 等等)是在大多数链式Bash命令中都会出现,[我们一直在仔细研究(`&`)符号][1]。
|
||||
|
||||
[上次,我们看到了如何使用`&`把可能需要很长时间运行的进程放到后台运行][1]。但是,`&`与尖括号`<`结合使用,也可用于管道输出或向其他地方的输入。
|
||||
|
||||
在[前面的][2] [尖括号教程中][3],您看到了如何使用`>`,如下:
|
||||
|
||||
```
|
||||
ls > list.txt
|
||||
```
|
||||
|
||||
将`ls`输出传递给_list.txt_文件。
|
||||
|
||||
现在我们看到的是简写
|
||||
|
||||
```
|
||||
ls 1> list.txt
|
||||
```
|
||||
|
||||
在这种情况下,`1`是一个文件描述符,指向标准输出(`stdout`)。
|
||||
|
||||
以类似的方式,`2`指向标准error(`stderr`):
|
||||
|
||||
```
|
||||
ls 2> error.log
|
||||
```
|
||||
|
||||
所有错误消息都通过管道传递给_error.log_文件。
|
||||
|
||||
回顾一下:`1>`是标准输出(`stdout`),`2>`标准错误输出(`stderr`)。
|
||||
|
||||
第三个标准文件描述符,`0<`标准输入(`stdin`)。您可以看到它是一个输入,因为箭头(`<`)指向`0`,而对于 `1`和`2`,箭头(`>`)是指向外部的。
|
||||
|
||||
### 标准文件描述符有什么用?
|
||||
|
||||
如果您在阅读本系列以后,您已经多次使用标准输出(`1>`)的简写形式:`>`。
|
||||
|
||||
例如,当(假如)你知道你的命令会抛出一个错误时,像`stderr`(`2`)这样的东西也很方便,但是Bash告诉你的东西是没有用的,你不需要看到它。如果要在_home/_目录中创建目录,例如:
|
||||
|
||||
```
|
||||
mkdir newdir
|
||||
```
|
||||
|
||||
如果_newdir/_已经存在,`mkdir`将显示错误。但你为什么要关心?(好吧,在某些情况下你可能会关心,但并非总是如此。)在一天结束时,_newdir_会以某种方式让你填写一些东西。您可以通过将错误消息推入void(即_/dev/null_)来抑制错误消息:
|
||||
|
||||
```
|
||||
mkdir newdir 2> /dev/null
|
||||
```
|
||||
|
||||
这不仅仅是“ _让我们不要看到丑陋和无关的错误消息,因为它们很烦人_ ”,因为在某些情况下,错误消息可能会在其他地方引起一连串错误。比如说,你想找到_/etc_下所有的*.service_文件。你可以这样做:
|
||||
|
||||
```
|
||||
find /etc -iname "*.service"
|
||||
```
|
||||
|
||||
但事实证明,在大多数系统中,`find`显示错误会导致许多行出现问题,因为普通用户对_/etc_下的某些文件夹没有读取访问权限。它使读取正确的输出变得很麻烦,如果`find`是更大的脚本的一部分,它可能会导致行中的下一个命令排队。
|
||||
|
||||
相反,你可以这样做:
|
||||
|
||||
```
|
||||
find /etc -iname "*.service" 2> /dev/null
|
||||
```
|
||||
|
||||
而且你只得到你想要的结果。
|
||||
|
||||
### 文件描述符入门
|
||||
|
||||
单独的文件描述符`stdout`和`stderr`还有一些注意事项。如果要将输出存储在文件中,请执行以下操作:
|
||||
|
||||
```
|
||||
find /etc -iname "*.service" 1> services.txt
|
||||
```
|
||||
|
||||
工作正常,因为`1>`意味着“ _发送标准输出,只有标准输出(非标准错误)_ ”。
|
||||
|
||||
但这里存在一个问题:如果你想保留命令抛出的错误信息的和非错误信息你该怎么*做*?上面的说明并不会这样做,因为它只写入`find`正确的结果
|
||||
|
||||
```
|
||||
find /etc -iname "*.service" 2> services.txt
|
||||
```
|
||||
|
||||
只会写入命令抛出的错误信息。
|
||||
|
||||
我们如何得到两者?请尝试以下命令:
|
||||
|
||||
```
|
||||
find /etc -iname "*.service" &> services.txt
|
||||
```
|
||||
|
||||
…… 再次和`&`打招呼!
|
||||
|
||||
我们一直在说`stdin`(`0`),`stdout`(`1`)和`stderr`(`2`)是_文件描述符_。文件描述符是一种特殊构造,指向文件的通道,用于读取或写入,或两者兼而有之。这来自于将所有内容都视为文件的旧UNIX理念。想写一个设备?将其视为文件。想写入套接字并通过网络发送数据?将其视为文件。想要读取和写入文件?嗯,显然,将其视为文件。
|
||||
|
||||
因此,在管理命令的输出和错误的位置时,将目标视为文件。因此,当您打开它们来读取和写入它们时,它们都会获得文件描述符。
|
||||
|
||||
这是一个有趣的效果。例如,您可以将内容从一个文件描述符传递到另一个文件描述符:
|
||||
|
||||
```
|
||||
find /etc -iname "*.service" 1> services.txt 2>&1
|
||||
```
|
||||
|
||||
该管道`stderr`以`stdout`与`stdout`通过管道被输送到一个文件中,_services.txt的_。
|
||||
|
||||
它再次出现:`&`发信号通知Bash `1`是目标文件描述符。
|
||||
|
||||
标准文件描述符的另一个问题是,当你从一个管道传输到另一个时,你执行此操作的顺序有点违反直觉。例如,按照上面的命令。它看起来像是错误的方式。您可能正在阅读它:“ _将输出传输到文件,然后将错误传递给标准输出。_ ”看起来错误输出会很晚,并且在`1`已经完成时发送。
|
||||
|
||||
但这不是文件描述符的工作方式。文件描述符不是文件的占位符,而是文件的_输入and/or输出通道_。在这种情况下,当你`1> services.txt`这样做时,你会说“ _打开一个写管道到services.txt并保持打开状态_ ”。`1`是您要使用的管道的名称,它将保持打开状态直到该行的结尾。
|
||||
|
||||
如果你仍然认为这是错误的方法,试试这个:
|
||||
|
||||
```
|
||||
find /etc -iname "*.service" 2>&1 1>services.txt
|
||||
```
|
||||
|
||||
并注意它是如何工作的; 注意错误是如何通过管道输送到终端的,所以只有非错误的输出(即`stdout`)被推送到`services.txt`。
|
||||
|
||||
这是因为Bash从左到右处理`find`的每个结果。这样想:当Bash到达`2>&1`时,`stdout` (`1`) 仍然是指向终端的通道。如果`find` Bash的结果包含一个错误,它将被弹出到`2`,转移到`1`,然后离开终端!
|
||||
|
||||
然后在命令结束时,Bash看到您要打开`stdout`作为_services.txt_文件的通道。如果没有发生错误,结果将`1`进入文件。
|
||||
|
||||
相比之下,在
|
||||
|
||||
```
|
||||
find /etc -iname "*.service" 1>services.txt 2>&1
|
||||
```
|
||||
|
||||
`1`从一开始就指向services.txt,因此任何弹出到`2`的内容都会通过`1`进行管道传输,而`1`已经指向services.txt中的最后一个休息位置,这就是它工作的原因。在任何情况下,如上所述`&>`都是“标准输出和标准错误”的缩写,即`2>&1`。
|
||||
|
||||
在任何情况下,如上所述`&>`是“_标准输出和标准误差_”的简写,即`2>&1`。
|
||||
|
||||
这可能有点多,但不用担心。调整文件描述符在Bash命令行和脚本中是司空见惯的事。随着本系列的深入,您将了解更多关于文件描述符的知识。下周见!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.linux.com/blog/learn/2019/2/ampersands-and-file-descriptors-bash
|
||||
|
||||
作者:[Paul Brown][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[zero-mk](https://github.com/zero-mk)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.linux.com/users/bro66
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.linux.com/blog/learn/2019/2/and-ampersand-and-linux
|
||||
[2]: https://www.linux.com/blog/learn/2019/1/understanding-angle-brackets-bash
|
||||
[3]: https://www.linux.com/blog/learn/2019/1/more-about-angle-brackets-bash
|
||||
@ -1,229 +0,0 @@
|
||||
[#]: collector: "lujun9972"
|
||||
[#]: translator: "zero-mk"
|
||||
[#]: reviewer: " "
|
||||
[#]: publisher: " "
|
||||
[#]: url: " "
|
||||
[#]: subject: "Logical & in Bash"
|
||||
[#]: via: "https://www.linux.com/blog/learn/2019/2/logical-ampersand-bash"
|
||||
[#]: author: "Paul Brown https://www.linux.com/users/bro66"
|
||||
|
||||
Bash中的逻辑和(`&`)
|
||||
======
|
||||
|
||||

|
||||
|
||||
有人可能会认为两篇文章中的`&`意思差不多,但实际上并不是。虽然 [第一篇文章讨论了如何在命令末尾使用`&`来将命令转到后台运行][1] 之后分解为解释流程管理, 第二篇文章将 [`&` 看作引用文件描述符的方法][2], 这些文章让我们知道了,与 `<` 和 `>` 结合使用后,你可以将输入或输出引导到别的地方。
|
||||
|
||||
但我们还没接触过作为 AND 操作符使用的`&`。所以,让我们来看看。
|
||||
|
||||
### & 是一个按位运算符
|
||||
|
||||
如果您完全熟悉二进制数操作,您肯定听说过 AND 和 OR 。这些是按位操作,对二进制数的各个位进行操作。在 Bash 中,使用`&`作为AND运算符,使用`|`作为 OR 运算符:
|
||||
|
||||
**AND**
|
||||
|
||||
```
|
||||
0 & 0 = 0
|
||||
|
||||
0 & 1 = 0
|
||||
|
||||
1 & 0 = 0
|
||||
|
||||
1 & 1 = 1
|
||||
```
|
||||
|
||||
**OR**
|
||||
|
||||
```
|
||||
0 | 0 = 0
|
||||
|
||||
0 | 1 = 1
|
||||
|
||||
1 | 0 = 1
|
||||
|
||||
1 | 1 = 1
|
||||
|
||||
```
|
||||
|
||||
|
||||
您可以通过对任何两个数字进行 AND 运算并使用`echo`输出结果:
|
||||
|
||||
```
|
||||
$ echo $(( 2 & 3 )) # 00000010 AND 00000011 = 00000010
|
||||
|
||||
2
|
||||
|
||||
$ echo $(( 120 & 97 )) # 01111000 AND 01100001 = 01100000
|
||||
|
||||
96
|
||||
```
|
||||
|
||||
OR(`|`)也是如此:
|
||||
|
||||
```
|
||||
$ echo $(( 2 | 3 )) # 00000010 OR 00000011 = 00000011
|
||||
|
||||
3
|
||||
|
||||
$ echo $(( 120 | 97 )) # 01111000 OR 01100001 = 01111001
|
||||
|
||||
121
|
||||
```
|
||||
|
||||
|
||||
关于这个不得不说的三件事:
|
||||
|
||||
1. 使用`(( ... ))`告诉 Bash 双括号之间的内容是某种算术或逻辑运算。`(( 2 + 2 ))`, `(( 5 % 2 ))` (`%`是[求模][3]运算符)和`((( 5 % 2 ) + 1))`(等于3)一切都会奏效。
|
||||
|
||||
2. [像变量一样][4], 使用`$`提取值,以便你可以使用它。
|
||||
3. 空格并没有影响: `((2+3))` 将等价于 `(( 2+3 ))` 和 `(( 2 + 3 ))`。
|
||||
4. Bash只能对整数进行操作. 试试这样做: `(( 5 / 2 ))` ,你会得到"2";或者这样 `(( 2.5 & 7 ))` ,但会得到一个错误。然后,在按位操作中使用除整数之外的任何东西(这就是我们现在所讨论的)通常是你不应该做的事情。
|
||||
|
||||
|
||||
|
||||
**提示:** 如果您想看看十进制数字在二进制下会是什么样子,你可以使用 _bc_ ,这是一个大多数 Linux 发行版都预装了的命令行计算器。比如:
|
||||
|
||||
```
|
||||
bc <<< "obase=2; 97"
|
||||
```
|
||||
|
||||
这个操作将会把 `97`转换成十二进制(`obase` 中的 _o_ 代表 _output_ ,也即,_输出_)。
|
||||
|
||||
```
|
||||
bc <<< "ibase=2; 11001011"
|
||||
```
|
||||
这个操作将会把 `11001011`转换成十进制(`ibase` 中的 _i_ 代表 _input_ ,也即,_输入_)。
|
||||
|
||||
### &&是一个逻辑运算符
|
||||
|
||||
虽然它使用与其按位表达相同的逻辑原理,但Bash的`&&`运算符只能呈现两个结果:1(“true”)和0(“false”)。对于Bash来说,任何不是0的数字都是“true”,任何等于0的数字都是“false”。什么也是false也不是数字:
|
||||
|
||||
```
|
||||
$ echo $(( 4 && 5 )) # 两个非零数字, 两个为true = true
|
||||
|
||||
1
|
||||
|
||||
$ echo $(( 0 && 5 )) # 有一个为零, 一个为false = false
|
||||
|
||||
0
|
||||
|
||||
$ echo $(( b && 5 )) # 其中一个不是数字, 一个为false = false
|
||||
|
||||
0
|
||||
```
|
||||
|
||||
与 `&&` 类似, OR 对应着 `||` ,用法正如你想的那样。
|
||||
|
||||
以上这些都很简单... 直到进入命令的退出状态。
|
||||
|
||||
### &&是命令退出状态的逻辑运算符
|
||||
|
||||
[正如我们在之前的文章中看到的][2],当命令运行时,它会输出错误消息。更重要的是,对于今天的讨论,它在结束时也会输出一个数字。此数字称为_exit code_(即_返回码_),如果为0,则表示该命令在执行期间未遇到任何问题。如果是任何其他数字,即使命令完成,也意味着某些地方出错了。
|
||||
所以 0 意味着非常棒,任何其他数字都说明有问题发生,并且,在返回码的上下文中,0 意味着“真”,其他任何数字都意味着“假”。对!这 **与您所熟知的逻辑操作完全相反** ,但是你能用这个做什么? 不同的背景,不同的规则。这种用处很快就会显现出来。
|
||||
|
||||
让我们继续!
|
||||
|
||||
返回码 _临时_ 储存在 [特殊变量][5] `?` 中— 是的,我知道:这又是一个令人迷惑的选择。但不管怎样, [别忘了我们在讨论变量的文章中说过][4], 那时我们说你要用 `$` 符号来读取变量中的值,在这里也一样。所以,如果你想知道一个命令是否顺利运行,你需要在命令结束后,在运行别的命令之前马上用 `$?` 来读取 `?` 的值。
|
||||
|
||||
试试下面的命令:
|
||||
|
||||
```
|
||||
$ find /etc -iname "*.service"
|
||||
|
||||
find: '/etc/audisp/plugins.d': Permission denied
|
||||
|
||||
/etc/systemd/system/dbus-org.freedesktop.nm-dispatcher.service
|
||||
|
||||
/etc/systemd/system/dbus-org.freedesktop.ModemManager1.service
|
||||
|
||||
[等等内容]
|
||||
```
|
||||
|
||||
[正如你在上一篇文章中看到的一样][2],普通用户权限在 _/etc_ 下运行 `find` 通常将抛出错误,因为它试图读取你没有权限访问的子目录。
|
||||
|
||||
所以,如果你在执行 `find` 后立马执行...
|
||||
|
||||
```
|
||||
echo $?
|
||||
```
|
||||
|
||||
...,,它将打印 `1`,表明存在错误。
|
||||
|
||||
注意:当你在一行中运行两遍 `echo $?` ,你将得到一个 `0` 。这是因为 `$?` 将包含 `echo $?` 的返回码,而这条命令按理说一定会执行成功。所以学习如何使用 `$?` 的第一课就是: **单独执行 `$?`** 或者将它保存在别的安全的地方 —— 比如保存在一个变量里,不然你会很快丢失它。)
|
||||
|
||||
一个直接使用 `?` 的用法是将它并入一串链式命令列表,这样 Bash 运行这串命令时若有任何操作失败,后面命令将终止。例如,您可能熟悉构建和编译应用程序源代码的过程。你可以像这样手动一个接一个地运行它们:
|
||||
|
||||
```
|
||||
$ configure
|
||||
|
||||
.
|
||||
|
||||
.
|
||||
|
||||
.
|
||||
|
||||
$ make
|
||||
|
||||
.
|
||||
|
||||
.
|
||||
|
||||
.
|
||||
|
||||
$ make install
|
||||
|
||||
.
|
||||
|
||||
.
|
||||
|
||||
.
|
||||
```
|
||||
|
||||
你也可以把这三行合并成一行...
|
||||
|
||||
```
|
||||
$ configure; make; make install
|
||||
```
|
||||
|
||||
... 但你要希望上天保佑。
|
||||
|
||||
为什么这样说呢?因为你这样做是有缺点的,比方说 `configure` 执行失败了, Bash 将仍会尝试执行 `make` 和 `sudo make install`——就算没东西可 make ,实际上,是没东西会安装。
|
||||
|
||||
聪明一点的做法是:
|
||||
|
||||
```
|
||||
$ configure && make && make install
|
||||
```
|
||||
|
||||
这将从每个命令中获取退出代码,并将其用作链式 `&&` 操作的操作数。
|
||||
但是,没什么好抱怨的,Bash 知道如果 `configure` 返回非零结果,整个过程都会失败。如果发生这种情况,不必运行 `make` 来检查它的退出代码,因为无论如何都会失败的。因此,它放弃运行 `make` ,只是将非零结果传递给下一步操作。并且,由于 `configure && make` 传递了错误,Bash 也不必运行`make install`。这意味着,在一长串命令中,您可以使用 `&&` 连接它们,并且一旦失败,您可以节省时间,因为其他命令会立即被取消运行。
|
||||
|
||||
你可以类似地使用 `||`,OR 逻辑操作符,这样就算只有一部分命令成功执行,Bash 也能运行接下来链接在一起的命令。
|
||||
鉴于所有这些(以及我们之前介绍过的内容),您现在应该更清楚地了解我们在 [本文开头][1] 开头设置的命令行:
|
||||
|
||||
```
|
||||
mkdir test_dir 2>/dev/null || touch backup/dir/images.txt && find . -iname "*jpg" > backup/dir/images.txt &
|
||||
```
|
||||
|
||||
因此,假设您从具有读写权限的目录运行上述内容,它做了什么以及如何做到这一点?它如何避免不合时宜且可能导致执行错误的错误?下周,除了给你这些答案的结果,我们将讨论 brackets: curly, curvy and straight. 不要错过了哟!
|
||||
|
||||
因此,假设您在具有读写权限的目录运行上述内容,它会执行的操作以及如何执行此操作?它如何避免不合时宜且可能导致执行错误的错误?下周,除了给你解决方案,我们将处理包括:卷曲,曲线和直线。不要错过!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.linux.com/blog/learn/2019/2/logical-ampersand-bash
|
||||
|
||||
作者:[Paul Brown][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[zero-MK](https://github.com/zero-mk)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.linux.com/users/bro66
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.linux.com/blog/learn/2019/2/and-ampersand-and-linux
|
||||
[2]: https://www.linux.com/blog/learn/2019/2/ampersands-and-file-descriptors-bash
|
||||
[3]: https://en.wikipedia.org/wiki/Modulo_operation
|
||||
[4]: https://www.linux.com/blog/learn/2018/12/bash-variables-environmental-and-otherwise
|
||||
[5]: https://www.gnu.org/software/bash/manual/html_node/Special-Parameters.html
|
||||
Loading…
Reference in New Issue
Block a user