mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-03-12 01:40:10 +08:00
Merge branch 'master' of https://github.com/LCTT/TranslateProject
This commit is contained in:
commit
e560f8e79b
@ -1,14 +1,13 @@
|
||||
|
||||
如何在 CentOS 7 上安装和安全配置 MariaDB 10
|
||||
===========================================
|
||||
|
||||
**MariaDB** 是 MySQL 数据库的自由开源分支,与 MySQL 在思想上同出一源,在未来仍将是自由且开源的。
|
||||
**MariaDB** 是 MySQL 数据库的自由开源分支,与 MySQL 在设计思想上同出一源,在未来仍将是自由且开源的。
|
||||
|
||||
在这篇博文中,我将会介绍如何在当前使用最广的 RHEL/CentOS 和 Fedora 发行版上安装 **MariaDB 10.1** 稳定版。
|
||||
|
||||
目前了解到的情况是:Red Hat Enterprise Linux/CentOS 7.0 发行版已将默认的数据库从 MySQL 切换到 MariaDB。
|
||||
|
||||
在本文中需要注意的是,我们假定您能够在服务器中使用 root 帐号工作,或者可以使用 [sudo command][7] 运行任何命令。
|
||||
在本文中需要注意的是,我们假定您能够在服务器中使用 root 帐号工作,或者可以使用 [sudo][7] 命令运行任何命令。
|
||||
|
||||
### 第一步:添加 MariaDB yum 仓库
|
||||
|
||||
@ -39,6 +38,7 @@ baseurl = http://yum.mariadb.org/10.1/rhel7-amd64
|
||||
gpgkey=https://yum.mariadb.org/RPM-GPG-KEY-MariaDB
|
||||
gpgcheck=1
|
||||
```
|
||||
|
||||
[
|
||||

|
||||
][8]
|
||||
@ -52,19 +52,21 @@ gpgcheck=1
|
||||
```
|
||||
# yum install MariaDB-server MariaDB-client -y
|
||||
```
|
||||
|
||||
[
|
||||

|
||||
][9]
|
||||
|
||||
*在 CentOS 7 中安装 MariaDB*
|
||||
|
||||
3. MariaDB 包安装完毕后,立即启动数据库服务守护进程,并可以通过下面的操作设置,在操作系统重启后自动启动服务。
|
||||
3、 MariaDB 包安装完毕后,立即启动数据库服务守护进程,并可以通过下面的操作设置,在操作系统重启后自动启动服务。
|
||||
|
||||
```
|
||||
# systemctl start mariadb
|
||||
# systemctl enable mariadb
|
||||
# systemctl status mariadb
|
||||
```
|
||||
|
||||
[
|
||||

|
||||
][10]
|
||||
@ -73,7 +75,7 @@ gpgcheck=1
|
||||
|
||||
### 第三步:在 CentOS 7 中对 MariaDB 进行安全配置
|
||||
|
||||
4. 现在可以通过以下操作进行安全配置:设置 MariaDB 的 root 账户密码,禁用 root 远程登录,删除测试数据库以及测试帐号,最后需要使用下面的命令重新加载权限。
|
||||
4、 现在可以通过以下操作进行安全配置:设置 MariaDB 的 root 账户密码,禁用 root 远程登录,删除测试数据库以及测试帐号,最后需要使用下面的命令重新加载权限。
|
||||
|
||||
```
|
||||
# mysql_secure_installation
|
||||
@ -84,13 +86,14 @@ gpgcheck=1
|
||||
|
||||
*CentOS 7 中的 MySQL 安全配置*
|
||||
|
||||
5. 在配置完数据库的安全配置后,你可能想检查下 MariaDB 的特性,比如:版本号,默认参数列表,以及通过 MariaDB 命令行登录。如下所示:
|
||||
5、 在配置完数据库的安全配置后,你可能想检查下 MariaDB 的特性,比如:版本号、默认参数列表、以及通过 MariaDB 命令行登录。如下所示:
|
||||
|
||||
```
|
||||
# mysql -V
|
||||
# mysqld --print-defaults
|
||||
# mysql -u root -p
|
||||
```
|
||||
|
||||
[
|
||||

|
||||
][12]
|
||||
@ -101,15 +104,15 @@ gpgcheck=1
|
||||
|
||||
如果你刚开始学习使用 MySQL/MariaDB,可以通过以下指南学习:
|
||||
|
||||
1. [Learn MySQL / MariaDB for Beginners – Part 1][1]
|
||||
2. [Learn MySQL / MariaDB for Beginners – Part 2][2]
|
||||
3. [MySQL Basic Database Administration Commands – Part III][3]
|
||||
4. [20 MySQL (Mysqladmin) Commands for Database Administration – Part IV][4]
|
||||
1. [新手学习 MySQL / MariaDB(一)][1]
|
||||
2. [新手学习 MySQL / MariaDB(二)][2]
|
||||
3. [MySQL 数据库基础管理命令(三)][3]
|
||||
4. [20 MySQL 管理命令 Mysqladmin(四)][4]
|
||||
|
||||
同样查看下面的文档学习如何优化你的 MySQL/MariaDB 服务,并使用工具监控数据库的活动情况。
|
||||
|
||||
1. [15 Tips to Tune and Optimize Your MySQL/MariaDB Performance][5]
|
||||
2. [4 Useful Tools to Monitor MySQL/MariaDB Database Activities][6]
|
||||
1. [15 个 MySQL/MariaDB 调优技巧][5]
|
||||
2. [4 监控 MySQL/MariaDB 数据库的工具][6]
|
||||
|
||||
文章到此就结束了,本文内容比较浅显,文中主要展示了如何在 RHEL/CentOS 和 Fefora 操作系统中安装 **MariaDB 10.1** 稳定版。您可以通过下面的联系方式将您遇到的任何问题或者想法发给我们。
|
||||
|
||||
@ -0,0 +1,111 @@
|
||||
如何在 Linux 中安装最新的 Python 3.6 版本
|
||||
============================================================
|
||||
|
||||
在这篇文章中,我将展示如何在 CentOS/RHEL 7、Debian 以及它的衍生版本比如 Ubuntu(最新的 Ubuntu 16.04 LTS 版本已经安装了最新的 Python 版本)或 Linux Mint 上安装和使用 Python 3.x 。我们的重点是安装可用于命令行的核心语言工具。
|
||||
|
||||
然后,我们也会阐述如何安装 Python IDLE - 一个基于 GUI 的工具,它允许我们运行 Python 代码和创建独立函数。
|
||||
|
||||
### 在 Linux 中安装 Python 3.6
|
||||
|
||||
在我写这篇文章的时候(2017 年三月中旬),在 CentOS 和 Debian 8 中可用的最新 Python 版本分别是 Python 3.4 和 Python 3.5 。
|
||||
|
||||
虽然我们可以使用 [yum][1] 和 [aptitude][2](或 [apt-get][3])安装核心安装包以及它们的依赖,但在这儿,我将阐述如何使用源代码进行安装。
|
||||
|
||||
为什么?理由很简单:这样我们能够获取语言的最新的稳定发行版(3.6),并且提供了一种和 Linux 版本无关的安装方法。
|
||||
|
||||
在 CentOS 7 中安装 Python 之前,请确保系统中已经有了所有必要的开发依赖:
|
||||
|
||||
```
|
||||
# yum -y groupinstall development
|
||||
# yum -y install zlib-devel
|
||||
```
|
||||
|
||||
在 Debian 中,我们需要安装 gcc、make 和 zlib 压缩/解压缩库:
|
||||
|
||||
```
|
||||
# aptitude -y install gcc make zlib1g-dev
|
||||
```
|
||||
|
||||
运行下面的命令来安装 Python 3.6:
|
||||
|
||||
```
|
||||
# wget https://www.python.org/ftp/python/3.6.0/Python-3.6.0.tar.xz
|
||||
# tar xJf Python-3.6.0.tar.xz
|
||||
# cd Python-3.6.0
|
||||
# ./configure
|
||||
# make && make install
|
||||
```
|
||||
|
||||
现在,放松一下,或者饿的话去吃个三明治,因为这可能需要花费一些时间。安装完成以后,使用 `which` 命令来查看主要二进制代码的位置:
|
||||
|
||||
```
|
||||
# which python3
|
||||
# python3 -V
|
||||
```
|
||||
|
||||
上面的命令的输出应该和这相似:
|
||||
|
||||
[
|
||||

|
||||
][4]
|
||||
|
||||
*查看 Linux 系统中的 Python 版本*
|
||||
|
||||
要退出 Python 提示符,只需输入:
|
||||
|
||||
```
|
||||
quit()
|
||||
或
|
||||
exit()
|
||||
```
|
||||
|
||||
然后按回车键。
|
||||
|
||||
恭喜!Python 3.6 已经安装在你的系统上了。
|
||||
|
||||
### 在 Linux 中安装 Python IDLE
|
||||
|
||||
Python IDLE 是一个基于 GUI 的 Python 工具。如果你想安装 Python IDLE,请安装叫做 idle(Debian)或 python-tools(CentOS)的包:
|
||||
|
||||
```
|
||||
# apt-get install idle [On Debian]
|
||||
# yum install python-tools [On CentOS]
|
||||
```
|
||||
|
||||
输入下面的命令启动 Python IDLE:
|
||||
|
||||
```
|
||||
# idle
|
||||
```
|
||||
|
||||
### 总结
|
||||
|
||||
在这篇文章中,我们阐述了如何从源代码安装最新的 Python 稳定版本。
|
||||
|
||||
最后但不是不重要,如果你之前使用 Python 2,那么你可能需要看一下 [从 Python 2 迁移到 Python 3 的官方文档][5]。这是一个可以读入 Python 2 代码,然后转化为有效的 Python 3 代码的程序。
|
||||
|
||||
你有任何关于这篇文章的问题或想法吗?请使用下面的评论栏与我们联系
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
作者简介:
|
||||
|
||||
Gabriel Cánepa - 一位来自阿根廷圣路易斯梅塞德斯镇 (Villa Mercedes, San Luis, Argentina) 的 GNU/Linux 系统管理员,Web 开发者。就职于一家世界领先级的消费品公司,乐于在每天的工作中能使用 FOSS 工具来提高生产力。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.tecmint.com/install-python-in-linux/
|
||||
|
||||
作者:[Gabriel Cánepa][a]
|
||||
译者:[ucasFL](https://github.com/ucasFL)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.tecmint.com/author/gacanepa/
|
||||
|
||||
[1]:http://www.tecmint.com/20-linux-yum-yellowdog-updater-modified-commands-for-package-mangement/
|
||||
[2]:http://www.tecmint.com/linux-package-management/
|
||||
[3]:http://www.tecmint.com/useful-basic-commands-of-apt-get-and-apt-cache-for-package-management/
|
||||
[4]:http://www.tecmint.com/wp-content/uploads/2017/03/Check-Python-Version-in-Linux.png
|
||||
[5]:https://docs.python.org/3.6/library/2to3.html
|
||||
@ -1,3 +1,4 @@
|
||||
# rusking translating
|
||||
What a Linux Desktop Does Better
|
||||
============================================================
|
||||
|
||||
|
||||
@ -0,0 +1,76 @@
|
||||
Hire a DDoS service to take down your enemies
|
||||
========================
|
||||
|
||||
>With the rampant availability of IoT devices, cybercriminals offer denial of service attacks to take advantage of password problems.
|
||||
|
||||

|
||||
|
||||
With the onrush of connected internet of things (IoT) devices, distributed denial-of-service attacks are becoming a dangerous trend. Similar to what happened to [DNS service provider Dyn last fall][3], anyone and everyone is in the crosshairs. The idea of using unprotected IoT devices as a way to bombard networks is gaining momentum.
|
||||
|
||||
The advent of DDoS-for-hire services means that even the least tech-savvy individual can exact revenge on some website. Step on up to the counter and purchase a stresser that can systemically take down a company.
|
||||
|
||||
According to [Neustar][4], almost three quarters of all global brands, organizations and companies have been victims of a DDoS attack. And more than 3,700 [DDoS attacks occur each day][5].
|
||||
|
||||
|
||||
#### [■ RELATED: How can you detect a fake ransom letter?][1]
|
||||
|
||||
|
||||
Chase Cunningham, director of cyber operations at A10 Networks, said to find IoT-enabled devices, all you have to do is go on an underground site and ask around for the Mirai scanner code. Once you have that you can scan for anything talking to the internet that can be used for that type of attack.
|
||||
|
||||
“Or you can go to a site like Shodan and craft a couple of simple queries to look for device specific requests. Once you get that information you just go to your DDoS for hire tool and change the configuration to point at the right target and use the right type of traffic emulator and bingo, nuke whatever you like,” he said.
|
||||
|
||||
“Basically everything is for sale," he added. "You can buy a 'stresser', which is just a simple botnet type offering that will allow anyone who knows how to click the start button access to a functional DDoS botnet.”
|
||||
|
||||
>Once you get that information you just go to your DDoS for hire tool and change the configuration to point at the right target and use the right type of traffic emulator and bingo, nuke whatever you like.
|
||||
|
||||
>Chase Cunningham, A10 director of cyber operations
|
||||
|
||||
Cybersecurity vendor Imperva says for just a few dozen dollars, users can quickly get an attack up and running. The company writes on its website that these kits contain the bot payload and the CnC (command and control) files. Using these, aspiring bot masters (a.k.a. herders) can start distributing malware, infecting devices through a use of spam email, vulnerability scanners, brute force attacks and more.
|
||||
|
||||
|
||||
Most [stressers and booters][6] have embraced a commonplace SaaS (software as a service) business model, based on subscriptions. As the Incapsula [Q2 2015 DDoS report][7] has shown, the average one hour/month DDoS package will cost $38 (with $19.99 at the lower end of the scale).
|
||||
|
||||

|
||||
|
||||
“Stresser and booter services are just a byproduct of a new reality, where services that can bring down businesses and organizations are allowed to operate in a dubious grey area,” Imperva wrote.
|
||||
|
||||
While cost varies, [attacks can run businesses anywhere from $14,000 to $2.35 million per incident][8]. And once a business is attacked, there’s an [82 percent chance they’ll be attacked again][9].
|
||||
|
||||
DDoS of Things (DoT) use IoT devices to build botnets that create large DDoS attacks. The DoT attacks have leveraged hundreds of thousands of IoT devices to attack anything from large service providers to enterprises.
|
||||
|
||||
“Most of the reputable DDoS sellers have changeable configurations for their tool sets so you can easily set the type of attack you want to take place. I haven’t seen many yet that specifically include the option to ‘purchase’ an IoT-specific traffic emulator but I’m sure it’s coming. If it were me running the service I would definitely have that as an option,” Cunningham said.
|
||||
|
||||
According to an IDG News Service story, building a DDoS-for-service can also be easy. Often the hackers will rent six to 12 servers, and use them to push out internet traffic to whatever target. In late October, HackForums.net [shut down][10] its "Server Stress Testing" section, amid concerns that hackers were peddling DDoS-for-hire services through the site for as little as $10 a month.
|
||||
|
||||
Also in December, law enforcement agencies in the U.S. and Europe [arrested][11] 34 suspects involved in DDoS-for-hire services.
|
||||
|
||||
If it is so easy to do so, why don’t these attacks happen more often?
|
||||
|
||||
Cunningham said that these attacks do happen all the time, in fact they happen every second of the day. “You just don’t hear about it because a lot of these are more nuisance attacks than big time bring down the house DDoS type events,” he said.
|
||||
|
||||
Also a lot of the attack platforms being sold only take systems down for an hour or a bit longer. Usually an hour-long attack on a site will cost anywhere from $15 to $50\. It depends, though, sometimes for better attack platforms it can hundreds of dollars an hour, he said.
|
||||
|
||||
The solution to cutting down on these attacks involves users resetting factory preset passwords on anything connected to the internet. Change the default password settings and disable things that you really don’t need.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.csoonline.com/article/3180246/data-protection/hire-a-ddos-service-to-take-down-your-enemies.html
|
||||
|
||||
作者:[Ryan Francis][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.csoonline.com/author/Ryan-Francis/
|
||||
[1]:http://csoonline.com/article/3103122/security/how-can-you-detect-a-fake-ransom-letter.html#tk.cso-infsb
|
||||
[2]:https://www.incapsula.com/ddos/ddos-attacks/denial-of-service.html
|
||||
[3]:http://csoonline.com/article/3135986/security/ddos-attack-against-overwhelmed-despite-mitigation-efforts.html
|
||||
[4]:https://ns-cdn.neustar.biz/creative_services/biz/neustar/www/resources/whitepapers/it-security/ddos/2016-apr-ddos-report.pdf
|
||||
[5]:https://www.a10networks.com/resources/ddos-trends-report
|
||||
[6]:https://www.incapsula.com/ddos/booters-stressers-ddosers.html
|
||||
[7]:https://www.incapsula.com/blog/ddos-global-threat-landscape-report-q2-2015.html
|
||||
[8]:http://www.datacenterknowledge.com/archives/2016/05/13/number-of-costly-dos-related-data-center-outages-rising/
|
||||
[9]:http://www.networkworld.com/article/3064677/security/hit-by-ddos-you-will-likely-be-struck-again.html
|
||||
[10]:http://www.pcworld.com/article/3136730/hacking/hacking-forum-cuts-section-allegedly-linked-to-ddos-attacks.html
|
||||
[11]:http://www.pcworld.com/article/3149543/security/dozens-arrested-in-international-ddos-for-hire-crackdown.html
|
||||
80
sources/talk/20170317 Why AlphaGo Is Not AI.md
Normal file
80
sources/talk/20170317 Why AlphaGo Is Not AI.md
Normal file
@ -0,0 +1,80 @@
|
||||
Why AlphaGo Is Not AI
|
||||
============================================================
|
||||
|
||||
|
||||
>Photo: RobotCub
|
||||
>“There is no AI without robotics,” the author argues.
|
||||
|
||||
_This is a guest post. The views expressed here are solely those of the author and do not represent positions of _ IEEE Spectrum _ or the IEEE._
|
||||
|
||||
What is AI and what is not AI is, to some extent, a matter of definition. There is no denying that AlphaGo, the Go-playing artificial intelligence designed by Google DeepMind that [recently beat world champion Lee Sedol][1], and similar [deep learning approaches][2] have managed to solve quite hard computational problems in recent years. But is it going to get us to _full AI_ , in the sense of an artificial general intelligence, or [AGI][3], machine? Not quite, and here is why.
|
||||
|
||||
One of the key issues when building an AGI is that it will have to make sense of the world for itself, to develop its own, internal meaning for everything it will encounter, hear, say, and do. Failing to do this, you end up with today’s AI programs where all the meaning is actually provided by the designer of the application: the AI basically doesn’t understand what is going on and has a narrow domain of expertise.
|
||||
|
||||
The problem of meaning is perhaps the most fundamental problem of AI and has still not been solved today. One of the first to express it was cognitive scientist Stevan Harnad, in his 1990 paper about “The Symbol Grounding Problem.” Even if you don’t believe we are explicitly manipulating symbols, which is indeed questionable, the problem remains: _the grounding of whatever representation exists inside the system into the real world outside_ .
|
||||
|
||||
To be more specific, the problem of meaning leads us to four sub-problems:
|
||||
|
||||
1. How do you structure the information the agent (human or AI) is receiving from the world?
|
||||
2. How do you link this structured information to the world, or, taking the above definition, how do you build “meaning” for the agent?
|
||||
3. How do you synchronize this meaning with other agents? (Otherwise, there is no communication possible and you get an incomprehensible, isolated form of intelligence.)
|
||||
4. Why does the agent do something at all rather than nothing? How to set all this into motion?
|
||||
|
||||
The first problem, about structuring information, is very well addressed by deep learning and similar unsupervised learning algorithms, used for example in the [AlphaGo program][4]. We have made tremendous progress in this area, in part because of the recent gain in computing power and the use of GPUs that are especially good at parallelizing information processing. What these algorithms do is take a signal that is extremely redundant and expressed in a high dimensional space, and reduce it to a low dimensionality signal, minimizing the loss of information in the process. In other words, it “captures” what is important in the signal, from an information processing point of view.
|
||||
|
||||
“There is no AI without robotics . . . This realization is often called the ‘embodiment problem’ and most researchers in AI now agree that intelligence and embodiment are tightly coupled issues. Every different body has a different form of intelligence, and you see that pretty clearly in the animal kingdom.”</aside>
|
||||
|
||||
The second problem, about linking information to the real world, or creating “meaning,” is fundamentally tied to robotics. Because you need a body to interact with the world, and you need to interact with the world to build this link. That’s why I often say that there is no AI without robotics (although there can be pretty good robotics without AI, but that’s another story). This realization is often called the “embodiment problem” and most researchers in AI now agree that intelligence and embodiment are tightly coupled issues. Every different body has a different form of intelligence, and you see that pretty clearly in the animal kingdom.
|
||||
|
||||
It starts with simple things like making sense of your own body parts, and how you can control them to produce desired effects in the observed world around you, how you build your own notion of space, distance, color, etc. This has been studied extensively by researchers like [J. Kevin O’Regan][5] and his “sensorimotor theory.” It is just a first step however, because then you have to build up more and more abstract concepts, on top of those grounded sensorimotor structures. We are not quite there yet, but that’s the current state of research on that matter.
|
||||
|
||||
The third problem is fundamentally the question of the origin of culture. Some animals show some simple form of culture, even transgenerational acquired competencies, but it is very limited and only humans have reached the threshold of exponentially growing acquisition of knowledge that we call culture. Culture is the essential catalyst of intelligence and an AI without the capability to interact culturally would be nothing more than an academic curiosity.
|
||||
|
||||
However, culture can not be hand coded into a machine; it must be the result of a learning process. The best way to start looking to try to understand this process is in developmental psychology, with the work of Jean Piaget and Michael Tomasello, studying how children acquire cultural competencies. This approach gave birth to a new discipline in robotics called “developmental robotics,” which is taking the child as a model (as illustrated by the [iCub robot][6], pictured above).
|
||||
|
||||
“Culture is the essential catalyst of intelligence and an AI without the capability to interact culturally would be nothing more than an academic curiosity. However, culture can not be hand coded into a machine; it must be the result of a learning process.”</aside>
|
||||
|
||||
It is also closely linked to the study of language learning, which is one of the topics that I mostly focused on as a researcher myself. The work of people like [Luc Steels][7] and many others have shown that we can see language acquisition as an evolutionary process: the agent creates new meanings by interacting with the world, use them to communicate with other agents, and select the most successful structures that help to communicate (that is, to achieve joint intentions, mostly). After hundreds of trial and error steps, just like with biological evolution, the system evolves the best meaning and their syntactic/grammatical translation.
|
||||
|
||||
This process has been tested experimentally and shows striking resemblance with how natural languages evolve and grow. Interestingly, it accounts for instantaneous learning, when a concept is acquired in one shot, something that heavily statistical models like deep learning are _not_ capable to explain. Several research labs are now trying to go further into acquiring grammar, gestures, and more complex cultural conventions using this approach, in particular the [AI Lab][8] that I founded at [Aldebaran][9], the French robotics company—now part of the SoftBank Group—that created the robots [Nao][10], [Romeo][11], and [Pepper][12] (pictured below).
|
||||
|
||||

|
||||
>Aldebaran’s humanoid robots: Nao, Romeo, and Pepper.</figcaption>
|
||||
|
||||
Finally, the fourth problem deals with what is called “intrinsic motivation.” Why does the agent do anything at all, rather than nothing. Survival requirements are not enough to explain human behavior. Even perfectly fed and secure, humans don’t just sit idle until hunger comes back. There is more: they explore, they try, and all of that seems to be driven by some kind of intrinsic curiosity. Researchers like [Pierre-Yves Oudeyer][13] have shown that simple mathematical formulations of curiosity, as an expression of the tendency of the agent to maximize its rate of learning, are enough to account for incredibly complex and surprising behaviors (see, for example, [the Playground experiment][14] done at Sony CSL).
|
||||
|
||||
It seems that something similar is needed inside the system to drive its desire to go through the previous three steps: structure the information of the world, connect it to its body and create meaning, and then select the most “communicationally efficient” one to create a joint culture that enables cooperation. This is, in my view, the program of AGI.
|
||||
|
||||
Again, the rapid advances of deep learning and the recent success of this kind of AI at games like Go are very good news because they could lead to lots of really useful applications in medical research, industry, environmental preservation, and many other areas. But this is only one part of the problem, as I’ve tried to show here. I don’t believe deep learning is the silver bullet that will get us to true AI, in the sense of a machine that is able to learn to live in the world, interact naturally with us, understand deeply the complexity of our emotions and cultural biases, and ultimately help us to make a better world.
|
||||
|
||||
**[Jean-Christophe Baillie][15] is founder and president of [Novaquark][16], a Paris-based virtual reality startup developing [Dual Universe][17], a next-generation online world where participants will be able to create entire civilizations through fully emergent gameplay. A graduate from the École Polytechnique in Paris, Baillie received a PhD in AI from Paris IV University and founded the Cognitive Robotics Lab at ENSTA ParisTech and, later, Gostai, a robotics company acquired by the Aldebaran/SoftBank Group in 2012\. This article originally [appeared][18] in LinkedIn.**
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://spectrum.ieee.org/automaton/robotics/artificial-intelligence/why-alphago-is-not-ai
|
||||
|
||||
作者:[Jean-Christophe Baillie][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://www.linkedin.com/in/jcbaillie
|
||||
[1]:http://spectrum.ieee.org/tech-talk/computing/networks/alphago-wins-match-against-top-go-player
|
||||
[2]:http://spectrum.ieee.org/automaton/robotics/artificial-intelligence/facebook-ai-director-yann-lecun-on-deep-learning
|
||||
[3]:https://en.wikipedia.org/wiki/Artificial_general_intelligence
|
||||
[4]:http://spectrum.ieee.org/tech-talk/computing/software/monster-machine-defeats-prominent-pro-player
|
||||
[5]:http://nivea.psycho.univ-paris5.fr/
|
||||
[6]:http://www.icub.org/
|
||||
[7]:https://ai.vub.ac.be/members/steels
|
||||
[8]:http://a-labs.aldebaran.com/labs/ai-lab
|
||||
[9]:https://www.aldebaran.com/en
|
||||
[10]:http://spectrum.ieee.org/automaton/robotics/humanoids/aldebaran-new-nao-robot-demo
|
||||
[11]:http://spectrum.ieee.org/automaton/robotics/humanoids/france-developing-advanced-humanoid-robot-romeo
|
||||
[12]:http://spectrum.ieee.org/robotics/home-robots/how-aldebaran-robotics-built-its-friendly-humanoid-robot-pepper
|
||||
[13]:http://www.pyoudeyer.com/
|
||||
[14]:http://www.pyoudeyer.com/SS305OudeyerP-Y.pdf
|
||||
[15]:https://www.linkedin.com/in/jcbaillie
|
||||
[16]:http://www.dualthegame.com/novaquark
|
||||
[17]:http://www.dualthegame.com/
|
||||
[18]:https://www.linkedin.com/pulse/why-alphago-ai-jean-christophe-baillie
|
||||
@ -1,3 +1,5 @@
|
||||
translating by flankershen
|
||||
|
||||
# Network management with LXD (2.3+)
|
||||
|
||||

|
||||
|
||||
@ -1,95 +0,0 @@
|
||||
wcnnbdk1 translating
|
||||
NMAP Common Scans – Part One
|
||||
========================
|
||||
|
||||
In a previous article, ‘[NMAP Installation][1]’, a listing of ten different ZeNMAP Profiles were listed. Most of the Profiles used various parameters. Most of the parameters represented different scans which can be performed. This article will cover the common four scan types.
|
||||
|
||||
**The Common Four Scan Types**
|
||||
|
||||
The four main scan types which are used most often are the following:
|
||||
|
||||
1. PING Scan (-sP)
|
||||
2. TCP SYN Scan (-sS)
|
||||
3. TCP Connect() Scan (-sT)
|
||||
4. UDP Scan (-sU)
|
||||
|
||||
When using NMAP to perform scans these four scans are the four to keep in mind. The main thing to keep in mind about them is what they do and how they do it. This article covers the PING and UDP scans. The next article will cover the TCP scans.
|
||||
|
||||
**PING Scan (-sP)**
|
||||
|
||||
Some scans can flood the network with packets, but the Ping Scan only puts, at most, two packets on the network. The two packets do not count DNS Lookup or ARP Requests if needed. A minimum of one packet is required per IP Address being scanned.
|
||||
|
||||
A typical PING operation is used to determine if a network host is on-line with the IP Address specified. For example, if I were on the Internet and found that I could not reach a specific Web Server I could PING the Server to determine if it were on-line. The PING would also verify that the route between my system and the Web Server was also functioning.
|
||||
|
||||
**NOTE:** When discussing TCP/IP the information is both useful for the Internet and a Local Area Network (LAN) using TCP/IP. The procedures work for both. The procedures would also work for a Wide Area Network (WAN) just as well.
|
||||
|
||||
If the Domain Name Service (DNS) Server is needed to find the IP Address (if a Domain Name is given) then extra packets are generated. For example, to ‘ping linuxforum.com’ would first require that the IP Address (98.124.199.63) be found for the Domain Name (linuxforum.com). If the command ‘ping 98.124.199.63’ was executed then the DNS Lookup is not needed. If the MAC Address is unknown, then an ARP Request is sent to find the MAC Address of the system with the specified IP Address.
|
||||
|
||||
The PING command sends an Internet Control Message Protocol (ICMP) packet to the given IP Address. The packet is an ICMP Echo Request which needs a response. A response will be sent back if the system is on-line. If a Firewall exists between the two systems a PING can be dropped by the Firewall. Some servers can be configured to ignore PING requests as well to prevent the possibility of a PING of Death.
|
||||
|
||||
**NOTE:** The PING of Death is a malformed PING packet which is sent to a system and causes it to leave a connection open to wait for the rest of the packet. Once a bunch of these are sent to the same system it will refuse any connections since it has all available connection opened. The system is then technically unavailable.
|
||||
|
||||
Once a system receives the ICMP Echo Request it will respond with an ICMP Echo Reply. Once the source system receives the ICMP Echo Reply then it knows the system is on-line.
|
||||
|
||||
Using NMAP you specify a single IP Address or a range of IP Addresses. A PING is then performed on each IP Address when a PING Scan (-sP) is specified.
|
||||
|
||||
In Figure 1 you can see I performed the command ‘nmap -sP 10.0.0.1-10’. The program will try to contact every system with an IP Address of 10.0.0.1 to 10.0.0.10\. An ARP is sent out, three for each IP Address given to the command. In this case thirty requests went out – two for each of the ten IP Addresses.
|
||||
|
||||

|
||||
|
||||
**FIGURE 1**
|
||||
|
||||
Figure 2 shows the Wireshark capture from another machine on the network – yes it is a Windows system. Line 1 shows the first request sent out to IP Address 10.0.0.2\. The IP Address 10.0.0.1 was skipped due to it being the local system on which NMAP was being run. Now we can say that there were only 27 ARP Requests since the local one was skipped. Line 2 shows the ARP Response from the system with the IP Address of 10.0.0.2\. Lines 3 through 10 are ARP Requests for the remaining IP Addresses. Line 11 is another response from the system at IP Address 10.0.0.2 since it has not heard back from the requesting system (10.0.0.1). Line 12 is a response from the source system to 10.0.0.2 responding with ‘SYN’ at Sequence 0\. Line 13 and 14 are the system at 10.0.0.2 responding twice with the Restart (RST) and Synchronize (SYN) response to close the two connections it had opened on Lines 2 and 11\. Notice the Sequence ID is ‘1’ - the source Sequence ID + 1\. Lines 15 on are a continuation of the same.
|
||||
|
||||

|
||||
|
||||
**FIGURE 2**
|
||||
|
||||
Looking back at Figure 1 we can see that there were two hosts found up and running. Of course the local system was found (10.0.0.1) and one other (10.0.0.2). The whole scan took a total time of 14.40 seconds.
|
||||
|
||||
The PING Scan is a fast scan used to find systems which are up and running. No other information is really found about the network or the systems from the scan. The scan is a good start to see what is available on a network so you can perform more complex scans on the on-line systems only. You may also be able to find systems on the network which should not exist. Rogue systems on a network can be dangerous because they can be gathering internal network and system information easily.
|
||||
|
||||
Once you have a list of on-line systems you can then detect what Ports may be open on each system with a UDP Scan.
|
||||
|
||||
**UDP Scan (-sU)**
|
||||
|
||||
Now that you know what systems are available to scan you can concentrate on these IP Addresses only. It is not a good idea to flood a network with a lot of scan activity. Administrators can have programs monitor network traffic and alert them when large amounts of suspicious activities occur.
|
||||
|
||||
The User Datagram Protocol (UDP) is useful to determine open Ports on an on-line system. Since UDP is a connectionless protocol, a response is not needed. This scan can send a UDP packet to a system with a specified Port number. If the target system does not respond then the Port is either closed or filtered. If the Port is open then a response should be made. In most cases a target system will send an ICMP message back that the Port is unreachable. The ICMP information lets NMAP know that the Port is closed. If a Port is open then the target system should respond with an ICMP message to let NMAP know it is an available Port.
|
||||
|
||||
**NOTE: **Only the top 1,000 most used Ports are scanned. A deeper scan will be covered in later articles.
|
||||
|
||||
In my scan I will only perform the scan on the system with the IP Address 10.0.0.2 since I know it is on-line. The scan sends and receives a total of 3,278 packets. The result of the NMAP command ‘sudo nmap -sU 10.0.0.2’ is shown in Figure 3.
|
||||
|
||||

|
||||
|
||||
**FIGURE 3**
|
||||
|
||||
Here you can see that one Port was found open – 137 (netbios-ns). The results from Wireshark are shown in Figure 4\. Not much to see but a bunch of UDP packets.
|
||||
|
||||

|
||||
|
||||
**FIGURE 4**
|
||||
|
||||
What would happen if I turned off the Firewall on the target system? My results are quite a bit different. The NMAP command and results are shown in Figure 5.
|
||||
|
||||

|
||||
|
||||
**FIGURE 5**
|
||||
|
||||
**NOTE:** When performing a UDP Scan you are required to have root permissions.
|
||||
|
||||
The high quantity of the number of packets is due to the fact that UDP is being used. Once the NMAP system sends a request it is not guaranteed that the packet was received. Because of the possible loss of packets the packets are sent multiple times.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.linuxforum.com/threads/nmap-common-scans-part-one.3637/
|
||||
|
||||
作者:[Jarret][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://www.linuxforum.com/members/jarret.268/
|
||||
[1]:https://www.linuxforum.com/threads/nmap-installation.3431/
|
||||
@ -1,4 +1,4 @@
|
||||
|
||||
ucasFL translating
|
||||
# [10 Best Linux Terminal Emulators For Ubuntu And Fedora][12]
|
||||
|
||||
[
|
||||
@ -35,7 +35,7 @@ sudo apt-get install terminator
|
||||
The specialities of **Tilda** are that it does not behave like a normal window instead it can be pulled up and down from the top of the screen with a special hotkey. Additionally, Tilda is highly configurable. It is possible to configure the hotkeys for keybindings, change the appearance and many options that affect the behaviour of Tilda.
|
||||
|
||||
Tilda is available for Ubuntu and Fedora through the package manager, also you can check its GitHub repository: [https://github.com/lanoxx/tilda][14][
|
||||
|
||||
|
||||

|
||||
][5]Also read - [Terminator Emulator With Multiple Terminals In One Window][1]
|
||||
|
||||
@ -155,5 +155,5 @@ via: http://www.linuxandubuntu.com/home/10-best-linux-terminals-for-ubuntu-and-f
|
||||
[13]:http://www.linuxandubuntu.com/home/10-best-linux-terminals-for-ubuntu-and-fedora#comments
|
||||
[14]:https://github.com/lanoxx/tilda
|
||||
[15]:http://guake-project.org/
|
||||
[16]:http://roxterm.sourceforge.net/index.php?page=index&lang=en
|
||||
[16]:http://roxterm.sourceforge.net/index.php?page=index&lang=en
|
||||
[17]:http://www.eterm.org/
|
||||
|
||||
@ -1,159 +0,0 @@
|
||||
申请翻译
|
||||
Understanding the difference between sudo and su
|
||||
============================================================
|
||||
|
||||
### On this page
|
||||
|
||||
1. [The su command in Linux][7]
|
||||
1. [su -][1]
|
||||
2. [su -c][2]
|
||||
2. [Sudo vs Su][8]
|
||||
1. [Password][3]
|
||||
2. [Default behavior][4]
|
||||
3. [Logging][5]
|
||||
4. [Flexibility][6]
|
||||
3. [Sudo su][9]
|
||||
|
||||
In one of our[ earlier articles][11], we discussed the 'sudo' command in detail. Towards the ends of that tutorial, there was a mention of another similar command 'su' in a small note. Well, in this article, we will discuss in detail the 'su' command as well as how it differs from the 'sudo' command.
|
||||
|
||||
But before we do that, please note that all the instructions and examples mentioned in this tutorial have been tested on Ubuntu 14.04LTS.
|
||||
|
||||
### The su command in Linux
|
||||
|
||||
The main work of the su command is to let you switch to some other user during a login session. In other words, the tool lets you assume the identity of some other user without having to logout and then login (as that user).
|
||||
|
||||
The su command is mostly used to switch to the superuser/root account (as root privileges are frequently required while working on the command line), but - as already mentioned - you can use it to switch to any other, non-root user as well.
|
||||
|
||||
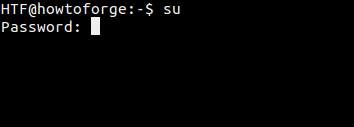
Here's how you can use this command to switch to the root user:
|
||||
|
||||
[
|
||||
|
||||
][12]
|
||||
|
||||
The password that this command requires is also of the root user. So in general, the su command requires you to enter the password of the target user. After the correct password is entered, the tool starts a sub-session inside the existing session on the terminal.
|
||||
|
||||
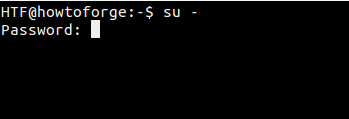
### su -
|
||||
|
||||
There's another way to switch to the root user: run the 'su -' command:
|
||||
|
||||
[
|
||||
|
||||
][13]
|
||||
|
||||
Now, what's the difference between 'su' and 'su -' ? Well, the former keeps the environment of the old/original user even after the switch to root has been made, while the latter creates a new environment (as dictated by the ~/.bashrc of the root user), similar to the case when you explicitly log in as root user from the log-in screen.
|
||||
|
||||
The man page of 'su' also makes it clear:
|
||||
|
||||
```
|
||||
The optional argument - may be used to provide an environment similar to what the user would expect had the user logged in directly.
|
||||
```
|
||||
|
||||
So, you'll agree that logging in with 'su -' makes more sense. But as the 'su' command also exists, one might wonder when that's useful. The following excerpt - taken from the [ArchLinux wiki website][14] - gives a good idea about the benefits and pitfalls of the 'su' command:
|
||||
|
||||
* It sometimes can be advantageous for a system administrator to use the shell account of an ordinary user rather than its own. In particular, occasionally the most efficient way to solve a user's problem is to log into that user's account in order to reproduce or debug the problem.
|
||||
|
||||
* However, in many situations it is not desirable, or it can even be dangerous, for the root user to be operating from an ordinary user's shell account and with that account's environmental variables rather than from its own. While inadvertently using an ordinary user's shell account, root could install a program or make other changes to the system that would not have the same result as if they were made while using the root account. For instance, a program could be installed that could give the ordinary user power to accidentally damage the system or gain unauthorized access to certain data.
|
||||
|
||||
Note: In case you want to pass more arguments after - in 'su -', then you should use the -l command line option that the command offers (instead of -). Here's the definition of - and the -l command line option:
|
||||
|
||||
```
|
||||
-, -l, --login
|
||||
Provide an environment similar to what the user would expect had the user logged in directly.
|
||||
|
||||
When - is used, it must be specified as the last su option. The other forms (-l and --login) do not have this restriction.
|
||||
```
|
||||
|
||||
### su -c
|
||||
|
||||
There's another option of the 'su' command that's worth mentioning: -c. It lets you provide a command that you want to run after switching to the target user.
|
||||
|
||||
The man page of 'su' explains it as:
|
||||
|
||||
```
|
||||
-c, --command COMMAND
|
||||
Specify a command that will be invoked by the shell using its -c.
|
||||
|
||||
The executed command will have no controlling terminal. This option cannot be used to execute interactive programs which need a controlling TTY.
|
||||
```
|
||||
|
||||
Consider the following example template:
|
||||
|
||||
su [target-user] -c [command-to-run]
|
||||
|
||||
So in this case, the 'command-to-run' will be executed as:
|
||||
|
||||
[shell] -c [command-to-run]
|
||||
|
||||
Where 'shell' would be replaced by 'target-user' shell defined in the /etc/passwd file.
|
||||
|
||||
### Sudo vs Su
|
||||
|
||||
Now since we have discussed the basics of the 'su' command as well, it's time we discuss the differences between the 'sudo' and the 'su' commands.
|
||||
|
||||
### Password
|
||||
|
||||
The primary difference between the two is the password they require: while 'sudo' requires current user's password, 'su' requires you to enter the root user password.
|
||||
|
||||
Quite clearly, 'sudo' is a better alternative between the two as far as security is concerned. For example, consider the case of computer being used by multiple users who also require root access. Using 'su' in such a scenario means sharing the root password with all of them, which is not a good practice in general.
|
||||
|
||||
Moreover, in case you want to revoke the superuser/root access of a particular user, the only way is to change the root password and then redistribute the new root password among all the other users.
|
||||
|
||||
With Sudo, on the other hand, you can handle both these scenarios effortlessly. Given that 'sudo' requires users to enter their own password, you don't need to share the root password will all the users in the first place. And to stop a particular user from accessing root privileges, all you have to do is to tweak the corresponding entry in the 'sudoers' file.
|
||||
|
||||
### Default behavior
|
||||
|
||||
The other difference between the two commands is in their default behavior. While 'sudo' only allows you to run a single command with elevated privileges, the 'su' command launches a new shell, allowing you to run as many commands as you want with root privileges until you explicitly exit that sell.
|
||||
|
||||
So the default behavior of the 'su' command is potentially dangerous given the possibility that the user can forget the fact that they are working as root, and might inadvertently make some irrecoverable changes (such as run the 'rm -rf' command in wrong directory). For a detailed discussion on why it's not encouraged to always work as root, head [here][10].
|
||||
|
||||
### Logging
|
||||
|
||||
Although commands run through 'sudo' are executed as the target user (which is 'root' by default), they are tagged with the sudoer's user-name. But in case of 'su', it's not possible to directly trace what a user did after they su'd to the root account.
|
||||
|
||||
### Flexibility
|
||||
|
||||
The 'sudo' command is far more flexible in that you can even limit the commands that you want the sudo-ers to have access to. In other words, users with access to 'sudo' can only be given access to commands that are required for their job. However, with 'su' that's not possible - either you have the privilege to do everything or nothing.
|
||||
|
||||
### Sudo su
|
||||
|
||||
Presumably due to the potential risks involved with using 'su' or logging directly as root, some Linux distributions - like Ubuntu - disable the root user account by default. Users are encouraged to use 'sudo' whenever they need root privileges.
|
||||
|
||||
However, you can still do 'su' successfully, i.e, without entering the root password. All you need to do is to run the following command:
|
||||
|
||||
sudo su
|
||||
|
||||
Since you're running the command with 'sudo', you'll only be required to enter your password. So once that is done, the 'su' command will be run as root, meaning it won't ask for any passwords.
|
||||
|
||||
**PS**: In case you want to enable the root account on your system (although that's strongly discouraged because you can always use 'sudo' or 'sudo su'), you'll have to set the root password manually, which you can do that using the following command:
|
||||
|
||||
sudo passwd root
|
||||
|
||||
### Conclusion
|
||||
|
||||
Both this as well as our previous tutorial (which focuses on 'sudo') should give you a good idea about the available tools that let you do tasks that require escalated (or a completely different set of) privileges. In case you have something to share about 'su' or 'sudo', or want to share your own experience, you are welcome to do that in comments below.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.howtoforge.com/tutorial/sudo-vs-su/
|
||||
|
||||
作者:[Himanshu Arora][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://www.howtoforge.com/tutorial/sudo-vs-su/
|
||||
[1]:https://www.howtoforge.com/tutorial/sudo-vs-su/#su-
|
||||
[2]:https://www.howtoforge.com/tutorial/sudo-vs-su/#su-c
|
||||
[3]:https://www.howtoforge.com/tutorial/sudo-vs-su/#password
|
||||
[4]:https://www.howtoforge.com/tutorial/sudo-vs-su/#default-behavior
|
||||
[5]:https://www.howtoforge.com/tutorial/sudo-vs-su/#logging
|
||||
[6]:https://www.howtoforge.com/tutorial/sudo-vs-su/#flexibility
|
||||
[7]:https://www.howtoforge.com/tutorial/sudo-vs-su/#the-su-command-in-linux
|
||||
[8]:https://www.howtoforge.com/tutorial/sudo-vs-su/#sudo-vs-su
|
||||
[9]:https://www.howtoforge.com/tutorial/sudo-vs-su/#sudo-su
|
||||
[10]:http://askubuntu.com/questions/16178/why-is-it-bad-to-login-as-root
|
||||
[11]:https://www.howtoforge.com/tutorial/sudo-beginners-guide/
|
||||
[12]:https://www.howtoforge.com/images/sudo-vs-su/big/su-command.png
|
||||
[13]:https://www.howtoforge.com/images/sudo-vs-su/big/su-hyphen-command.png
|
||||
[14]:https://wiki.archlinux.org/index.php/Su
|
||||
@ -1,3 +1,5 @@
|
||||
申请翻译
|
||||
|
||||
Many SQL Performance Problems Stem from “Unnecessary, Mandatory Work”
|
||||
============================================================
|
||||
|
||||
|
||||
@ -1,98 +0,0 @@
|
||||
How to Change Root Password of MySQL or MariaDB in Linux
|
||||
============================================================
|
||||
|
||||
|
||||
If you’re [installing MySQL or MariaDB in Linux][1] for the first time, chances are you will be executing mysql_secure_installation script to secure your MySQL installation with basic settings.
|
||||
|
||||
One of these settings is, database root password – which you must keep secret and use only when it is required. If you need to change it (for example, when a database administrator changes roles – or is laid off!).
|
||||
|
||||
**Suggested Read:** [Recover MySQL or MariaDB Root Password in Linux][2]
|
||||
|
||||
This article will come in handy. We will explain how to change a root password of MySQL or MariaDB database server in Linux.
|
||||
|
||||
Although we will use a MariaDB server in this article, the instructions should work for MySQL as well.
|
||||
|
||||
### Change MySQL or MariaDB Root Password
|
||||
|
||||
You know the root password and want to reset it, in this case, let’s make sure MariaDB is running:
|
||||
|
||||
```
|
||||
------------- CentOS/RHEL 7 and Fedora 22+ -------------
|
||||
# systemctl is-active mariadb
|
||||
------------- CentOS/RHEL 6 and Fedora -------------
|
||||
# /etc/init.d/mysqld status
|
||||
```
|
||||
[
|
||||

|
||||
][3]
|
||||
|
||||
Check MySQL Status
|
||||
|
||||
If the above command does not return the word `active` as output or its stopped, you will need to start the database service before proceeding:
|
||||
|
||||
```
|
||||
------------- CentOS/RHEL 7 and Fedora 22+ -------------
|
||||
# systemctl start mariadb
|
||||
------------- CentOS/RHEL 6 and Fedora -------------
|
||||
# /etc/init.d/mysqld start
|
||||
```
|
||||
|
||||
Next, we will login to the database server as root:
|
||||
|
||||
```
|
||||
# mysql -u root -p
|
||||
```
|
||||
|
||||
For compatibility across versions, we will use the following statement to update the user table in the mysql database. Note that you need to replace `YourPasswordHere` with the new password you have chosen for root.
|
||||
|
||||
```
|
||||
MariaDB [(none)]> USE mysql;
|
||||
MariaDB [(none)]> UPDATE user SET password=PASSWORD('YourPasswordHere') WHERE User='root' AND Host = 'localhost';
|
||||
MariaDB [(none)]> FLUSH PRIVILEGES;
|
||||
```
|
||||
|
||||
To validate, exit your current MariaDB session by typing.
|
||||
|
||||
```
|
||||
MariaDB [(none)]> exit;
|
||||
```
|
||||
|
||||
and then press Enter. You should now be able to connect to the server using the new password.
|
||||
|
||||
[
|
||||

|
||||
][4]
|
||||
|
||||
Change MySQL/MariaDB Root Password
|
||||
|
||||
##### Summary
|
||||
|
||||
In this article we have explained how to change the MariaDB / MySQL root password – whether you know the current one or not.
|
||||
|
||||
As always, feel free to drop us a note if you have any questions or feedback using our comment form below. We look forward to hearing from you!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
作者简介:
|
||||
|
||||
Gabriel Cánepa is a GNU/Linux sysadmin and web developer from Villa Mercedes, San Luis, Argentina. He works for a worldwide leading consumer product company and takes great pleasure in using FOSS tools to increase productivity in all areas of his daily work.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.tecmint.com/change-mysql-mariadb-root-password/
|
||||
|
||||
作者:[Gabriel Cánepa][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.tecmint.com/author/gacanepa/
|
||||
|
||||
[1]:http://www.tecmint.com/install-mariadb-in-centos-7/
|
||||
[2]:http://www.tecmint.com/reset-mysql-or-mariadb-root-password/
|
||||
[3]:http://www.tecmint.com/wp-content/uploads/2017/03/Check-MySQL-Status.png
|
||||
[4]:http://www.tecmint.com/wp-content/uploads/2017/03/Change-MySQL-Root-Password.png
|
||||
[5]:http://www.tecmint.com/author/gacanepa/
|
||||
[6]:http://www.tecmint.com/10-useful-free-linux-ebooks-for-newbies-and-administrators/
|
||||
[7]:http://www.tecmint.com/free-linux-shell-scripting-books/
|
||||
@ -1,83 +0,0 @@
|
||||
How to open port on AWS EC2 Linux server
|
||||
============================================================
|
||||
|
||||
|
||||

|
||||
|
||||
_Small tutorial with screenshots which shows how to open port on AWS EC2 Linux server. This will help you to manage port specific services on EC2 server._
|
||||
|
||||
* * *
|
||||
|
||||
AWS i.e. Amazon Web Services is no new term for IT world. Its a cloud services platform offered by Amazon. Under its Free tier account it offers you limited services free of cost for one year. This is one of best place to try out new technologies without spending much on financial front.
|
||||
|
||||
AWS offers server computing as one of their services and they call them as EC (Elastic Computing). Under this we can build our Linux servers. We have already seen [how to setup Linux server on AWS free of cost][11].
|
||||
|
||||
By default, all Linux servers build under EC2 has post 22 i.e. SSH service port (inbound from all IP) is open only. So, if you are hosting any port specific service then relative port needs to be open on AWS firewall for your server.
|
||||
|
||||
Also it has port 1 to 65535 are open too (outbound for all traffic). If you want to change this you can use same below process for editing outbound rules too.
|
||||
|
||||
Setting up firewall rule on AWS for your server is easy job. You will be able to open ports in seconds for your server. I will walk you through procedure with screenshots to open port for EC2 server.
|
||||
|
||||
_Step 1 :_
|
||||
|
||||
Login to AWS account and navigate to EC2 management console. Goto Security Groups under Network & Security menu as highlighted below :
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
* * *
|
||||
|
||||
_Step 2 :_
|
||||
|
||||
On Security Groups screen select you r EC2 server and under Actions menu select Edit inbound rules
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
_Step 3:_
|
||||
|
||||
Now you will be presented with inbound rule window. You can add/edit/delete inbound rules here. There are several protocols like http, nfs etc listed in dropdown menu which auto-populate ports for you. If you have custom service and port you can define it too.
|
||||
|
||||

|
||||
|
||||
|
||||
For example if you want to open port 80 then you have to select :
|
||||
|
||||
* Type : http
|
||||
* Protocol : TCP
|
||||
* Port range : 80
|
||||
* Source : Anywhere (Open port 80 for all incoming req from any IP (0.0.0.0/0), My IP : then it will auto populate your current public internet IP
|
||||
|
||||
* * *
|
||||
|
||||
_Step 4:_
|
||||
|
||||
Thats it. Once you save these settings your server inbound port 80 is open! you can check by telneting to port 80 ofor your EC2 server public DNS (can be found it EC2 server details)
|
||||
|
||||
You can also check it on websites like [ping.eu][12].
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://kerneltalks.com/virtualization/how-to-open-port-on-aws-ec2-linux-server/
|
||||
|
||||
作者:[Shrikant Lavhate ][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://kerneltalks.com/virtualization/how-to-open-port-on-aws-ec2-linux-server/
|
||||
[1]:http://kerneltalks.com/virtualization/how-to-open-port-on-aws-ec2-linux-server/#
|
||||
[2]:http://kerneltalks.com/virtualization/how-to-open-port-on-aws-ec2-linux-server/#
|
||||
[3]:http://kerneltalks.com/virtualization/how-to-open-port-on-aws-ec2-linux-server/#
|
||||
[4]:http://kerneltalks.com/virtualization/how-to-open-port-on-aws-ec2-linux-server/#
|
||||
[5]:http://kerneltalks.com/virtualization/how-to-open-port-on-aws-ec2-linux-server/#
|
||||
[6]:http://kerneltalks.com/virtualization/how-to-open-port-on-aws-ec2-linux-server/#
|
||||
[7]:http://kerneltalks.com/virtualization/how-to-open-port-on-aws-ec2-linux-server/#
|
||||
[8]:http://kerneltalks.com/virtualization/how-to-open-port-on-aws-ec2-linux-server/#
|
||||
[9]:http://kerneltalks.com/virtualization/how-to-open-port-on-aws-ec2-linux-server/#
|
||||
[10]:http://kerneltalks.com/author/shrikant/
|
||||
[11]:http://kerneltalks.com/howto/install-ec2-linux-server-aws-with-screenshots/
|
||||
[12]:http://ping.eu/port-chk/
|
||||
@ -1,3 +1,5 @@
|
||||
#rusking translating
|
||||
|
||||
An introduction to GRUB2 configuration for your Linux machine
|
||||
============================================================
|
||||
|
||||
|
||||
@ -1,113 +0,0 @@
|
||||
ucasFL translating
|
||||
How to Install Latest Python 3.6 Version in Linux
|
||||
============================================================
|
||||
|
||||
In this article we will show how to install and use Python 3.x in CentOS/RHEL 7, Debian and its derivatives such as Ubuntu (latest LTS version already has latest Python installed) or Linux Mint. Our focus will be installing the core language tools that can be used in the command line.
|
||||
|
||||
However, we will also explain how to install the Python IDLE – a GUI-based tool that allows us to run Python code and create standalone functions.
|
||||
|
||||
### Install Python 3.6 in Linux
|
||||
|
||||
At the time of this writing (mid-March 2017), the latest Python 3.x versions available in CentOS 7 and Debian 8are 3.4 and 3.5 respectively.
|
||||
|
||||
Although we can install the core packages and their dependencies using [yum][1] and [aptitude][2] (or [apt-get][3]), we will explain how to perform the installation from source instead.
|
||||
|
||||
Why? The reason is simple: this allows us to have the latest stable release of the language (3.6) and to provide a distribution-agnostic installation method.
|
||||
|
||||
Prior to installing Python in CentOS 7, let’s make sure our system has all the necessary development dependencies:
|
||||
|
||||
```
|
||||
# yum -y groupinstall development
|
||||
# yum -y install zlib-devel
|
||||
```
|
||||
|
||||
In Debian we will need to install gcc, make, and the zlib compression / decompression library:
|
||||
|
||||
```
|
||||
# aptitude -y install gcc make zlib1g-dev
|
||||
```
|
||||
|
||||
To install Python 3.6, run the following commands:
|
||||
|
||||
```
|
||||
# wget https://www.python.org/ftp/python/3.6.0/Python-3.6.0.tar.xz
|
||||
# tar xJf Python-3.6.0.tar.xz
|
||||
# cd Python-3.6.0
|
||||
# ./configure
|
||||
# make
|
||||
# make install
|
||||
```
|
||||
|
||||
Now relax and go grab a sandwich because this may take a while. When the installation is complete, use which to verify the location of the main binary:
|
||||
|
||||
```
|
||||
# which python3
|
||||
# python3 -V
|
||||
```
|
||||
|
||||
The output of the above command should be similar to:
|
||||
|
||||
[
|
||||

|
||||
][4]
|
||||
|
||||
Check Python Version in Linux
|
||||
|
||||
To exit the Python prompt, simply type.
|
||||
|
||||
```
|
||||
quit()
|
||||
or
|
||||
exit()
|
||||
```
|
||||
|
||||
and press Enter.
|
||||
|
||||
Congratulations! Python 3.6 is now installed on your system.
|
||||
|
||||
### Install Python IDLE in Linux
|
||||
|
||||
Python IDLE is a GUI-based tool for Python. If you wish to install the Python IDLE, grab the package named idle (Debian) or python-tools (CentOS).
|
||||
|
||||
```
|
||||
# apt-get install idle [On Debian]
|
||||
# yum install python-tools [On CentOS]
|
||||
```
|
||||
|
||||
Type the following command to start the Python IDLE.
|
||||
|
||||
```
|
||||
# idle
|
||||
```
|
||||
|
||||
##### Summary
|
||||
|
||||
In this article we have explained how to install the latest Python stable version from source.
|
||||
|
||||
Last, but not least, if you’re coming from Python 2, you may want to take a look at the [2to3 official documentation][5]. This is a program that reads Python 2 code and transforms it into valid Python 3 code.
|
||||
|
||||
Do you have any questions or comments about this article? Feel free to get in touch with us using the form below.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
作者简介:
|
||||
|
||||
Gabriel Cánepa is a GNU/Linux sysadmin and web developer from Villa Mercedes, San Luis, Argentina. He works for a worldwide leading consumer product company and takes great pleasure in using FOSS tools to increase productivity in all areas of his daily work.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.tecmint.com/install-python-in-linux/
|
||||
|
||||
作者:[Gabriel Cánepa][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.tecmint.com/author/gacanepa/
|
||||
|
||||
[1]:http://www.tecmint.com/20-linux-yum-yellowdog-updater-modified-commands-for-package-mangement/
|
||||
[2]:http://www.tecmint.com/linux-package-management/
|
||||
[3]:http://www.tecmint.com/useful-basic-commands-of-apt-get-and-apt-cache-for-package-management/
|
||||
[4]:http://www.tecmint.com/wp-content/uploads/2017/03/Check-Python-Version-in-Linux.png
|
||||
[5]:https://docs.python.org/3.6/library/2to3.html
|
||||
@ -1,3 +1,5 @@
|
||||
vim-kakali translating
|
||||
|
||||
What is Linux VPS Hosting?
|
||||
============================================================
|
||||
|
||||
|
||||
@ -0,0 +1,125 @@
|
||||
How to Build Your Own Media Center with OpenELEC
|
||||
============================================================
|
||||
|
||||

|
||||
|
||||
|
||||
Have you ever wanted to make your own home theater system? If so, this is the guide for you! In this article we’ll go over how to set up a home entertainment system powered by OpenELEC and Kodi. We’ll go over how to make the installation medium, what devices can run the software, how to install it and everything else there is to know!
|
||||
|
||||
|
||||
### Choosing a device
|
||||
|
||||
Before setting up the software in the media center, you’ll need to choose a device. OpenELEC supports a multitude of devices. From regular desktops and laptops to the Raspberry Pi 2/3, etc. With a device chosen, think about how you’ll access the media on the OpenELEC system and get it ready to use.
|
||||
|
||||
**Note:** as OpenELEC is based on Kodi, there are many ways to load playable media (Samba network shares, external devices, etc.).
|
||||
|
||||
### Making the installation disk
|
||||
|
||||
The OpenELEC installation disk requires a USB flash drive of at least 1 GB. This is the only way to install the software, as the developers do not currently distribute an ISO file. A raw IMG file needs to be created instead. Choose the link that corresponds with your device and [download][10] the raw disk image. With the image downloaded, open a terminal and use the command to extract the data from the archive.
|
||||
|
||||
**On Linux/macOS**
|
||||
|
||||
```
|
||||
cd ~/Downloads
|
||||
gunzip -d OpenELEC*.img.gz
|
||||
```
|
||||
|
||||
**On Windows**
|
||||
|
||||
Download [7zip][11], install it, and then extract the archive.
|
||||
|
||||
With the raw .IMG file extracted, download the [Etcher USB creation tool][12] and follow the instructions on the page to install it and create the USB disk.
|
||||
|
||||
**Note:** for Raspberry Pi users, Etcher supports burning to SD cards as well.
|
||||
|
||||
### Installing OpenELEC
|
||||
|
||||
The OpenELEC installation process is probably one of the easiest operating systems to install. To start, plug in the USB device and configure your device to boot from the USB drive. For some, this can be accomplished by pressing the DEL key or F2\. However, as all BIOS are different, it is best to look into the manual and find out.
|
||||
|
||||

|
||||
|
||||
Once in the BIOS, configure it to load the USB stick directly. This will allow the computer to boot the drive, which will bring you to the Syslinux boot screen. Enter “installer” in the prompt, then press the Enter key.
|
||||
|
||||

|
||||
|
||||
By default, the quick installation option is selected. Press Enter to start the install. This will move the installer onto the drive selection page. Select the hard drive where OpenELEC should be installed, then press the Enter key to start the installation process.
|
||||
|
||||

|
||||
|
||||
Once done, reboot the system and load OpenELEC.
|
||||
|
||||
### Configuring OpenELEC
|
||||
|
||||

|
||||
|
||||
On first boot, the user must configure a few things. If your media center device has a wireless network card, OpenELEC will prompt the user to connect it to a wireless access point. Select a network from the list and enter the access code.
|
||||
|
||||

|
||||
|
||||
On the next “Welcome to OpenELEC” screen, the user must configure various sharing settings (SSH and Samba). It is advised that you turn these settings on, as this will make it easier to remotely transfer media files as well as gain command-line access.
|
||||
|
||||
### Adding Media
|
||||
|
||||
To add media to OpenElec (Kodi), first select the section that you want to add media to. Adding media for Photos, Music, etc., is the same process. In this guide we’ll focus on adding videos.
|
||||
|
||||

|
||||
|
||||
Click the “Video” option on the home screen to go to the videos area. Select the “Files” option. On the next page click “Add videos…” This will take the user to the Kodi add-media screen. From here it is possible to add new media sources (both internal and external).
|
||||
|
||||

|
||||
|
||||
OpenELEC automatically mounts external devices (like USB, DVD data discs, etc.), and it can be added by browsing for the folder’s mount point. Usually these devices are placed in “/run.” Alternatively, go back to the page where you clicked on “Add videos…” and click on the device there. Any external device, including DVDs/CDs, will show up there and can be accessed directly. This is a good option for those who don’t understand how to find mount points.
|
||||
|
||||

|
||||
|
||||
Now that the device is selected within Kodi, the interface will ask the user to browse for the individual directory on the device with the media files using the media center’s file browser tool. Once the directory that holds the files is found, add it, give the directory a name and press the OK button to save it.
|
||||
|
||||

|
||||
|
||||
When a user browses “Videos,” they’ll see a clickable folder which brings up the media added from an external device. These folders can easily be played on the system.
|
||||
|
||||
### Using OpenElec
|
||||
|
||||
When the user logs in they’ll see a “home screen.” This home screen has several sections the user is able to click on and go to: Pictures, Videos, Music, Programs, etc. When hovering over any of these sections, subsections appear. For example, when hovering over “Pictures,” the subsections “files” and “Add-ons” appear.
|
||||
|
||||

|
||||
|
||||
If a user clicks on one of the subsections under a section, like “add-ons,” the Kodi add-on chooser appears. This installer will allow users to either browse for new add-ons to install in relation to this subsection (like Picture-related add-ons, etc.) or to launch existing picture-related ones that are already on the system.
|
||||
|
||||
Additionally, clicking the files subsection of any section (e.g. Videos) takes the user directly to any available files in that section.
|
||||
|
||||
### System Settings
|
||||
|
||||

|
||||
|
||||
Kodi has an extensive settings area. To get to the Settings, hover the mouse to the right, and the menu selector will scroll right and reveal “System.” Click on it to open the global system settings area.
|
||||
|
||||
Any setting can be modified and changed by the user, from installing add-ons from the Kodi-repository, to activating various services, to changing the theme, and even the weather. To exit the settings area and return to the home screen, press the “home” icon in the bottom-right corner.
|
||||
|
||||
### Conclusion
|
||||
|
||||
With the OpenELEC installed and configured, you are now free to go and use your very own Linux-powered home-theater system. Out of all of the home-theater-based Linux distributions, this one is the most user-friendly. Do keep in mind that although this operating system is known as “OpenELEC,” it runs Kodi and is compatible with all of the different Kodi add-ons, tools, and programs.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.maketecheasier.com/build-media-center-with-openelec/
|
||||
|
||||
作者:[Derrik Diener][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://www.maketecheasier.com/author/derrikdiener/
|
||||
[1]:https://www.maketecheasier.com/author/derrikdiener/
|
||||
[2]:https://www.maketecheasier.com/build-media-center-with-openelec/#comments
|
||||
[3]:https://www.maketecheasier.com/category/linux-tips/
|
||||
[4]:http://www.facebook.com/sharer.php?u=https%3A%2F%2Fwww.maketecheasier.com%2Fbuild-media-center-with-openelec%2F
|
||||
[5]:http://twitter.com/share?url=https%3A%2F%2Fwww.maketecheasier.com%2Fbuild-media-center-with-openelec%2F&text=How+to+Build+Your+Own+Media+Center+with+OpenELEC
|
||||
[6]:mailto:?subject=How%20to%20Build%20Your%20Own%20Media%20Center%20with%20OpenELEC&body=https%3A%2F%2Fwww.maketecheasier.com%2Fbuild-media-center-with-openelec%2F
|
||||
[7]:https://www.maketecheasier.com/permanently-disable-windows-defender-windows-10/
|
||||
[8]:https://www.maketecheasier.com/repair-mac-hard-disk-with-fsck/
|
||||
[9]:https://support.google.com/adsense/troubleshooter/1631343
|
||||
[10]:http://openelec.tv/get-openelec/category/1-openelec-stable-releases
|
||||
[11]:http://www.7-zip.org/
|
||||
[12]:https://etcher.io/
|
||||
@ -1,3 +1,4 @@
|
||||
#rusking translating
|
||||
Join CentOS 7 Desktop to Samba4 AD as a Domain Member – Part 9
|
||||
============================================================
|
||||
|
||||
|
||||
@ -0,0 +1,174 @@
|
||||
Make Container Management Easy With Cockpit
|
||||
============================================================
|
||||
|
||||

|
||||
|
||||
If you’re looking for an easy way to manage a Linux server that includes containers, you should check out Cockpit.[Creative Commons Zero][6]
|
||||
|
||||
If you administer a Linux server, you’ve probably been in search of a solid administration tool. That quest has probably taken you to such software as [Webmin][14] and [cPanel][15]. But if you’re looking for an easy way to manage a Linux server that also includes Docker, one tool stands above the rest for that particular purpose: [Cockpit][16].
|
||||
|
||||
Why Cockpit? Because it includes the ability to handle administrative tasks such as:
|
||||
|
||||
* Connect and Manage multiple machines
|
||||
|
||||
* Manage containers via Docker
|
||||
|
||||
* Interact with a Kubernetes or Openshift clusters
|
||||
|
||||
* Modify network settings
|
||||
|
||||
* Manage user accounts
|
||||
|
||||
* Access a web-based shell
|
||||
|
||||
* View system performance information by way of helpful graphs
|
||||
|
||||
* View system services and log files
|
||||
|
||||
Cockpit can be installed on [Debian][17], [Red Hat][18], [CentOS][19], [Arch Linux][20], and [Ubuntu][21]. Here, I will focus on installing the system on a Ubuntu 16.04 server that already includes Docker.
|
||||
|
||||
Out of the list of features, the one that stands out is the container management. Why? Because it make installing and managing containers incredibly simple. In fact, you might be hard-pressed to find a better container management solution.
|
||||
With that said, let’s install this solution and see just how easy it is to use.
|
||||
|
||||
### Installation
|
||||
|
||||
As I mentioned earlier, I will be installing Cockpit on an instance of Ubuntu 16.04, with Docker already running. The steps for installation are quite simple. The first thing you must do is log into your Ubuntu server. Next you must add the necessary repository with the command:
|
||||
|
||||
```
|
||||
sudo add-apt-repository ppa:cockpit-project/cockpit
|
||||
```
|
||||
|
||||
When prompted, hit the Enter key on your keyboard and wait for the prompt to return. Once you are back at your bash prompt, update apt with the command:
|
||||
|
||||
```
|
||||
sudo apt-get get update
|
||||
```
|
||||
|
||||
Install Cockpit by issuing the command:
|
||||
|
||||
```
|
||||
sudo apt-get -y install cockpit cockpit-docker
|
||||
```
|
||||
|
||||
After the installation completes, it is necessary to start the Cockpit service and then enable it so it auto-starts at boot. To do this, issue the following two commands:
|
||||
|
||||
```
|
||||
sudo systemctl start cockpit
|
||||
sudo systemctl enable cockpit
|
||||
```
|
||||
|
||||
That’s all there is to the installation.
|
||||
|
||||
### Logging into Cockpit
|
||||
|
||||
To gain access to the Cockpit web interface, point a browser (that happens to be on the same network as the Cockpit server) to http://IP_OF_SERVER:9090, and you will be presented with a login screen (Figure 1).
|
||||
|
||||

|
||||
|
||||
Figure 1: The Cockpit login screen.[Used with permission][1]
|
||||
|
||||
A word of warning with using Cockpit and Ubuntu. Many of the tasks that can be undertaken with Cockpit require administrative access. If you log in with a standard user, you won’t be able to work with some of the tools like Docker. To get around that, you can enable the root user on Ubuntu. This isn’t always a good idea. By enabling the root account, you are bypassing the security system that has been in place for years. However, for the purpose of this article, I will enable the root user with the following two commands:
|
||||
|
||||
```
|
||||
sudo passwd root
|
||||
|
||||
sudo passwd -u root
|
||||
```
|
||||
|
||||
NOTE: Make sure you give the root account a very challenging password.
|
||||
|
||||
Should you want to revert this change, you only need issue the command:
|
||||
|
||||
```
|
||||
sudo passwd -l root
|
||||
```
|
||||
|
||||
With other distributions, such as CentOS and Red Hat, you will be able to log into Cockpit with the username _root_ and the root password, without having to go through the extra hopes as described above.
|
||||
If you’re hesitant to enable the root user, you can always pull down the images, from the server terminal (using the command _docker pull IMAGE_NAME w_ here _IMAGE_NAME_ is the image you want to pull). That would add the image to your docker server, which can then be managed via a regular user. The only caveat to this is that the regular user must be added to the Docker group with the command:
|
||||
|
||||
```
|
||||
sudo usermod -aG docker USER
|
||||
```
|
||||
|
||||
Where USER is the actual username to be added to the group. Once you’ve done that, log out, log back in, and then restart Docker with the command:
|
||||
|
||||
```
|
||||
sudo service docker restart
|
||||
```
|
||||
|
||||
Now the regular user can start and stop the added Docker images/containers without having to enable the root user. The only caveat is that user will not be able to add new images via the Cockpit interface.
|
||||
|
||||
Using Cockpit
|
||||
|
||||
Once you’ve logged in, you will be treated to the Cockpit main window (Figure 2).
|
||||
|
||||
|
||||

|
||||
|
||||
Figure 2: The Cockpit main window.[Used with permission][2]
|
||||
|
||||
You can go through each of the sections to check on the status of the server, work with users, etc., but we want to go right to the containers. Click on the Containers section to display the current running contains as well as the available images (Figure 3).
|
||||
|
||||
|
||||

|
||||
|
||||
Figure 3: Managing containers is incredibly simple with Cockpit.[Used with permission][3]
|
||||
|
||||
To start an image, simply locate the image and click the associated start button. From the resulting popup window (Figure 4), you can check all the information about the image (and adjust as needed), before clicking the Run button.
|
||||
|
||||
|
||||

|
||||
|
||||
Figure 4: Running a Docker image with the help of Cockpit.[Used with permission][4]
|
||||
|
||||
Once the image is running, you can check its status by clicking on the entry under the Containers section and then Stop, Restart, or Delete the instance. You can also click Change resource limits and then adjust either the Memory limit and/or CPU priority.
|
||||
|
||||
### Adding new images
|
||||
|
||||
Say you have logged on as the root user. If so, you can add new images with the help of the Cockpit GUI. From the Containers section, click the Get new image button and then, in the resulting window, search for the image you want to add. Say you want to add the latest official build of Centos. Type centos in the search field and then, once the search results populate, select the official listing and click Download (Figure 5).
|
||||
|
||||
|
||||

|
||||
|
||||
Figure 5: Adding the latest build of the official Centos images to Docker, via Cockpit.[Used with permission][5]
|
||||
|
||||
Once the image has downloaded, it will be available to Docker and can be run via Cockpit.
|
||||
|
||||
### As simple as it gets
|
||||
|
||||
Managing Docker doesn’t get any easier. Yes, there is a caveat when working with Cockpit on Ubuntu, but if it’s your only option, there are ways to make it work. With the help of Cockpit, you can not only easily manage Docker images, you can do so from any web browser that has access to your Linux server. Enjoy your newfound Docker ease.
|
||||
|
||||
_Learn more about Linux through the free ["Introduction to Linux" ][13]course from The Linux Foundation and edX._
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.linux.com/learn/intro-to-linux/2017/3/make-container-management-easy-cockpit
|
||||
|
||||
作者:[JACK WALLEN][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://www.linux.com/users/jlwallen
|
||||
[1]:https://www.linux.com/licenses/category/used-permission
|
||||
[2]:https://www.linux.com/licenses/category/used-permission
|
||||
[3]:https://www.linux.com/licenses/category/used-permission
|
||||
[4]:https://www.linux.com/licenses/category/used-permission
|
||||
[5]:https://www.linux.com/licenses/category/used-permission
|
||||
[6]:https://www.linux.com/licenses/category/creative-commons-zero
|
||||
[7]:https://www.linux.com/files/images/cockpitajpg
|
||||
[8]:https://www.linux.com/files/images/cockpitbjpg
|
||||
[9]:https://www.linux.com/files/images/cockpitcjpg
|
||||
[10]:https://www.linux.com/files/images/cockpitdjpg
|
||||
[11]:https://www.linux.com/files/images/cockpitfjpg
|
||||
[12]:https://www.linux.com/files/images/cockpit-containersjpg
|
||||
[13]:https://training.linuxfoundation.org/linux-courses/system-administration-training/introduction-to-linux
|
||||
[14]:http://www.webmin.com/
|
||||
[15]:http://cpanel.com/
|
||||
[16]:http://cockpit-project.org/
|
||||
[17]:https://www.debian.org/
|
||||
[18]:https://www.redhat.com/en
|
||||
[19]:https://www.centos.org/
|
||||
[20]:https://www.archlinux.org/
|
||||
[21]:https://www.ubuntu.com/
|
||||
@ -1,113 +1,111 @@
|
||||
正在校对 By GitFuture
|
||||
|
||||
使用 Min 浏览器消除 web 噪音
|
||||
============================================================
|
||||

|
||||
|
||||
[Min][1] 是一款具有最小设计的 web 浏览器,可以通过简单的功能提供快速操作。
|
||||
[Min][1] 是一款精简设计的 web 浏览器,功能简便,响应迅速。
|
||||
|
||||
当涉及到软件设计时,“最小”并不意味着潜在的低级功能或未开发。如果你喜欢文本编辑器和笔记程序中的最小防干扰工具,那么你会在 Min 浏览器中有同样舒适的感觉。
|
||||
在软件设计中,“简单”并不意味着功能低级、有待改进。你如果喜欢花哨工具比较少的文本编辑器和笔记程序,那么在 Min 浏览器中会有同样舒适的感觉。
|
||||
|
||||
我大多在我的台式机和笔记本电脑上使用 Google Chrome、Chromium和 Firefox。我研究了很多它们的附加功能,所以我可以在我的长期研究和工作中可以访问所有的专业服务。
|
||||
我经常在台式机和笔记本电脑上使用 Google Chrome、Chromium和 Firefox。我研究了它们的很多附加功能,所以我在长期的研究和工作中可以享用它们的特色服务。
|
||||
|
||||
然而,我有时喜欢一个快速、整洁的替代品来上网。随着多个项目的进行,我可以很快打开一大批选项卡甚至是独立窗口的强大浏览器。
|
||||
然而,有时我希望有个快速、整洁的替代品来上网。随着多个项目的进行,我需要很快打开一大批选项卡甚至是独立窗口的强大浏览器。
|
||||
|
||||
我试过其他浏览器选项但很少成功。替代品通常有自己的一套分散注意力的附件和功能,它们会让我开小差。
|
||||
我试过其他浏览器但很少能令我满意。替代品通常有一套独特的花哨的附件和功能,它们会让我开小差。
|
||||
|
||||
Min 浏览器不这样做。它是一个易于使用并在 GitHub 开源的 web浏览器,它不会使我分心。
|
||||
Min 浏览器就不这样。它是一个易于使用,并在 GitHub 开源的 web 浏览器,不会使我分心。
|
||||
|
||||
|
||||
Min 浏览器是最小化浏览器,提供了简单的功能以及迅速的操作。只是不要指望马上上手
|
||||
Min 浏览器是精简的浏览器,提供了简单的功能以及快速的响应。只是不要指望马上上手。
|
||||
|
||||
### 它做些什么
|
||||
|
||||
Min 浏览器提供了 Debian Linux 版本、Windows 和 Mac 机器的版本。它不能与主流跨平台 web 浏览器中的可用功能竞争。
|
||||
Min 浏览器提供了 Debian Linux、Windows 和 Mac 机器的版本。它不能与功能众多的主流跨平台 web 浏览器竞争。
|
||||
|
||||
它不必竞争,但是它的声誉非常好,它可能是补充而不是取代它们。
|
||||
但它不必竞争,它很有名的原因应该是补充而不是取代那些主流浏览器。
|
||||
|
||||
其中一个主要原因是其内置的广告拦截功能。开箱即用的 Min 浏览器不需要配置或寻找兼容的第三方应用程序来拦截广告。
|
||||
|
||||
在 Edit/Preferences 中,关于内容阻止你有三个选项可以点击/取消点击。它很容易修改屏蔽策略来适应你的喜好。阻止跟踪器和广告选项使用 EasyList 和 EasyPrivacy。 如果没有其他原因,请保持此选项选中。
|
||||
在 Edit/Preferences 中,你可以通过三个选项来设置阻止的内容。它很容易修改屏蔽策略来满足你的喜好。阻止跟踪器和广告选项使用 EasyList 和 EasyPrivacy。 如果没有其他原因,请保持此选项选中。
|
||||
|
||||
你还可以阻止脚本和图像。这样做可以最大限度地提高网站加载速度,并真正提高你对恶意代码的防御。
|
||||
你还可以阻止脚本和图像。这样做可以最大限度地提高网站加载速度,并能有效防御恶意代码。
|
||||
|
||||
### 按你的方式搜索
|
||||
|
||||
如果你花费大量时间在搜索上,你会喜欢 Min 处理搜索的方式。这是一个顶级的功能。
|
||||
如果你在搜索上花费大量时间,你会喜欢 Min 处理搜索的方式。这是一个顶级的功能。
|
||||
|
||||
可以直接在浏览器的网址栏中访问搜索功能。Min 使用搜索引擎有 DuckDuckGo 和维基百科。你可以直接在 web 地址栏中输入搜索查询。
|
||||
可以直接在浏览器的网址栏中使用搜索功能。Min 使用搜索引擎 DuckDuckGo 和维基百科的内容进行搜索。你可以直接在 web 地址栏中输入要搜索的东西。
|
||||
|
||||
这种方法很节省时间,因为你不必先进入搜索引擎窗口。 一个额外的好处是可以搜索你的书签。
|
||||
这种方法很节省时间,因为你不必先进入搜索引擎窗口。 还有一个好处是可以搜索你的书签。
|
||||
|
||||
在 Edit/Preferences 菜单中,选择默认的搜索引擎。该列表包括 DuckDuckGo、Google、Bing、Yahoo、Baidu、Wikipedia 和 Yandex。
|
||||
|
||||
尝试将 DuckDuckGo 作为默认搜索引擎。 Min 默认使用这个选项,但它不会强加给你。
|
||||
尝试将 DuckDuckGo 作为默认搜索引擎。 Min 默认使用这个引擎,但你也能更换。
|
||||
|
||||
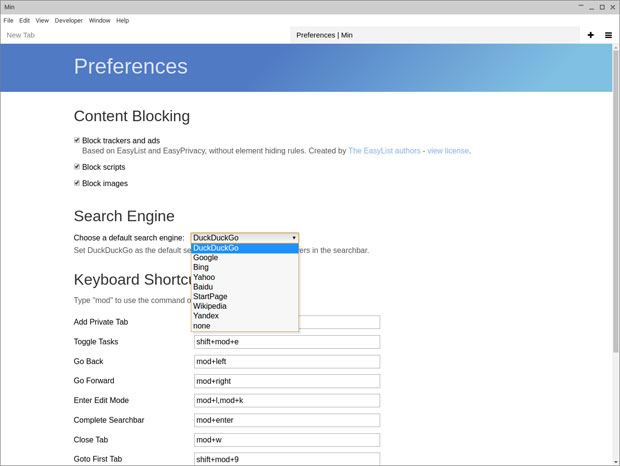
|
||||
Min 浏览器的搜索功能是 URL 栏的一部分。Min 使用 DuckDuckGo 和维基百科作为搜索引擎。你可以直接在 web 地址栏中输入搜索查询。
|
||||
Min 浏览器的搜索功能是 URL 栏的一部分。Min 利用搜索引擎 DuckDuckGo 和维基百科的内容。你可以直接在 web 地址栏中输入要搜索的东西。
|
||||
|
||||
搜索栏会非常快速地显示你问题的答案。它会使用 DuckDuckGo 的信息,包括维基百科条目、计算器以及更多。
|
||||
搜索栏会非常快速地显示问题的答案。它会使用 DuckDuckGo 的信息,包括维基百科条目、计算器和其它的内容。
|
||||
|
||||
它能提供快速片段、答案和网络建议。它是在基于 Google 环境的一个替代。
|
||||
它能快速提供片段、答案和网络建议。它有点像不是基于 Goolge 环境的替代品。
|
||||
|
||||
### 导航辅助
|
||||
|
||||
Min 允许你使用模糊搜索快速跳转到任何网站。它几乎能立即向你抛出建议。
|
||||
Min 允许你使用模糊搜索快速跳转到任何网站。它能立即向你提出建议。
|
||||
|
||||
我喜欢在当前标签旁边打开标签的方式。你不必设置此选项。它在默认情况下没有其他选择,但它是有道理的。
|
||||
我喜欢在当前标签旁边打开标签的方式。你不必设置此选项。它在默认情况下没有其他选择,但这也有道理。
|
||||
|
||||
[
|
||||
|
||||
][2]
|
||||
Min 的一个很酷的操作是将标签整理到任务中,这样你可以随时搜索。(点击图片放大)
|
||||
Min 的一个很酷的功能是将标签整理到任务栏中,这样你随时都可以搜索。(点击图片放大)
|
||||
|
||||
你不用一直点击标签。这使你可以专注于当前的任务,而不会分心。
|
||||
不点击标签,过一会儿它就会消失。这使你可以专注于当前的任务,而不会分心。
|
||||
|
||||
Min 不需要附加工具来控制多个标签。浏览器会显示标签列表,并允许你将它们分组。
|
||||
|
||||
### 保持专注
|
||||
|
||||
Min 在“视图”菜单中隐藏了一个可选的“聚焦模式”。启用后,除了你打开的选项卡外,它会隐藏所有选项卡。 你必须返回到菜单以关闭“聚焦模式”,然后才能打开新选项卡。
|
||||
Min 在“视图”菜单中有一个可选的“聚焦模式”。启用后,除了你打开的选项卡外,它会隐藏其它所有选项卡。 你必须返回到菜单,关闭“聚焦模式”,才能打开新选项卡。
|
||||
|
||||
任务功能还可以帮助你保持专注。你可以从“文件”菜单或使用 Ctrl+Shift+N 创建任务。如果要打开新选项卡,可以在“文件”菜单中选择该选项,或使用 Control+T。
|
||||
任务功能还可以帮助你保持专注。你可以在“文件(File)”菜单或使用 Ctrl+Shift+N 创建任务。如果要打开新选项卡,可以在“文件”菜单中选择该选项,或使用 Control+T。
|
||||
|
||||
调用符合你的风格的新任务。我喜欢能够组织与显示与工作项目或与我的研究的特定部分相关联的所有标签。我可以在任何时间召回整个列表,以轻松快速的方式找到我的浏览记录。
|
||||
按照你的风格打开新任务。我喜欢按组来管理和显示标签,这组标签与工作项目或研究的某些部分相关。我可以在任何时间重新打开整个列表,从而轻松快速的方式找到我的浏览记录。
|
||||
|
||||
另一个整洁的功能是在 tab 区域可以找到段落对齐按钮。单击它启用阅读模式。此模式会保存文章以供将来参考,并删除页面上的一切,以便你可以专注于阅读任务。
|
||||
另一个好用的功能是可以在 tab 区域找到段落对齐按钮。单击它启用阅读模式。此模式会保存文章以供将来参考,并删除页面上的一切,以便你可以专注于阅读任务。
|
||||
|
||||
### 并不完美
|
||||
|
||||
Min 浏览器并不是强大的,功能丰富的完美替代品。它有一些明显的弱点,开发人员花了太长时间而不能改正。
|
||||
Min 浏览器并不是强大的,功能丰富的完美替代品。它有一些明显的缺点,开发人员花了很多时间也没有修正。
|
||||
|
||||
例如,它缺乏一个支持论坛和详细用户指南的开发人员网站。可能部分原因是它的官网在 GitHub,而不是一个独立的开发人员网站。尽管如此,对新用户而言这是一个弱点。
|
||||
例如,它缺乏一个支持论坛和详细用户指南的开发人员网站。可能部分原因是它的官网在 GitHub,而不是一个独立的开发人员网站。尽管如此,对新用户而言这是一个缺点。
|
||||
|
||||
没有网站支持,用户被迫在 GitHub 上寻找自述文件和各种目录列表。你也可以在 Min 浏览器的帮助菜单中访问它们 - 但这没有太多帮助。
|
||||
|
||||
一个例子是当你启动浏览器时,屏幕会显示欢迎界面。它会显示两个按钮,一个人是 “Start Browsing”,另一个是 “Take a Tour.”。但是没有一个按钮可以使用
|
||||
一个例子是当你启动浏览器时,屏幕会显示欢迎界面。它会显示两个按钮,一个人是 “Start Browsing”,另一个是 “Take a Tour.”。但是没有一个按钮可以使用。
|
||||
|
||||
但是,你可以通过单击 Min 窗口顶部的菜单栏开始浏览。但是,缺少导览还没有解决办法。
|
||||
但是,你可以通过单击 Min 窗口顶部的菜单栏开始浏览。但是,还没有解决缺少概览办法。
|
||||
|
||||
### 底线
|
||||
|
||||
Min 并不是一个有完整功能的 web 浏览器。它不是为通常在成熟的 web 浏览器中有的插件和其他许多功能而设计的。然而,Min 通过提供速度和免打扰来达到它重要的目的。
|
||||
Min 并不是一个功能完善、丰富的 web 浏览器。你在功能完善的主流浏览器中所用的插件和其它许多功能都不是 Min 的设计目标。然而,Min 在快速响应和免打扰方面很有用。
|
||||
|
||||
我越使用 Min 浏览器,它对我来说越有效率 - 但是当你第一次使用它时要小心。
|
||||
我越使用 Min 浏览器,我越觉得它高效 - 但是当你第一次使用它时要小心。
|
||||
|
||||
Min 并不复杂或让人困惑 - 它只是有点古怪。你必须要玩弄一下才能明白它如何使用。
|
||||
Min 并不复杂,也不难操作 - 它只是有点古怪。你必须要玩弄一下才能明白它如何使用。
|
||||
|
||||
### 想要提建议么?
|
||||
|
||||
有没有一个你想提议 Linux 程序或发行版?有没有你爱的或者想要了解的?
|
||||
有没有你建议回顾的 Linux 程序或发行版?有没有你爱的或者想要了解的?
|
||||
|
||||
请[在电子邮件中给我发送你的想法][3],我会考虑将来在 Linux Picks and Pans 专栏上登出。
|
||||
请[在电子邮件中给我发送你的想法][3],我会考虑将来在 “Linux Picks and Pans” 专栏上登出。
|
||||
|
||||
并使用下面的读者评论功能提出你的想法!
|
||||
可以使用下方的读者评论功能说出你的想法!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
作者简介:
|
||||
|
||||
Jack M. Germain 从苹果 II 和 PC 的早期起就一直在写关于计算机技术。他仍然有他原来的 IBM PC-Jr 和一些其他遗留的 DOS 和 Windows 盒子。他为 Linux 桌面的开源世界留下过共享软件。他运行几个版本的 Windows 和 Linux 操作系统,还通常不能决定是否用他的平板电脑、上网本或 Android 智能手机,而不是用他的台式机或笔记本电脑。你可以在 Google+ 上与他联系。
|
||||
Jack M. Germain 从苹果 II 和 PC 的早期起就一直在写关于计算机技术。他仍然有他原来的 IBM PC-Jr 和一些其他遗留的 DOS 和 Windows 盒子。他为 Linux 桌面的开源世界留下过共享软件。他运行几个版本的 Windows 和 Linux 操作系统,还通常不能决定是否用他的平板电脑、上网本或 Android 智能手机,还是用他的台式机或笔记本电脑。你可以在 Google+ 上与他联系。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
@ -115,7 +113,7 @@ via: http://www.linuxinsider.com/story/84212.html?rss=1
|
||||
|
||||
作者:[Jack M. Germain][a]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[GitFuture](https://github.com/GitFuture)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
|
||||
94
translated/tech/20170111 NMAP Common Scans – Part One.md
Normal file
94
translated/tech/20170111 NMAP Common Scans – Part One.md
Normal file
@ -0,0 +1,94 @@
|
||||
NMAP 常用扫描简介 - 第一部分
|
||||
========================
|
||||
|
||||
我们之前在‘[NMAP 的安装][1]’一文中,列出了 10 种不同的 ZeNMAP 扫描模式(这里将 Profiles 翻译成了模式,不知是否合适)。大多数的模式使用了各种参数。大多数的参数代表了执行不同的扫描模式。这篇文章将介绍其中的四种通用的扫描类型。
|
||||
|
||||
**四种通用扫描类型**
|
||||
|
||||
下面列出了最常使用的四种扫描类型:
|
||||
|
||||
1. PING 扫描 (-sP)
|
||||
2. TCP SYN 扫描 (-sS)
|
||||
3. TCP Connect() 扫描 (-sT)
|
||||
4. UDP 扫描 (-sU)
|
||||
|
||||
当我们利用 NMAP 来执行扫描的时候,这四种扫描类型是我们需要熟练掌握的。更重要的是需要知道这些命令做了什么并且需要知道这些命令是怎么做的。本文将介绍 PING 扫描和 UDP 扫描。在之后的文中会介绍 TCP 扫描。
|
||||
|
||||
**PING 扫描 (-sP)**
|
||||
|
||||
某些扫描会造成网络拥塞,然而 Ping 扫描在网络中最多只会产生两个包。当然这两个包不包括可能需要的 DNS 搜索和 ARP 请求。每个被扫描的 IP 最少只需要一个包来完成 Ping 扫描。
|
||||
|
||||
通常 Ping 扫描是用来查看在指定的 IP 地址上是否有在线的主机存在。例如,当我拥有网络连接却联不上一台指定的网络服务器的时候,我就可以使用 PING 来判断这台服务器是否在线。PING 同样也可以用来验证我的当前设备与网络服务器之间的路由是否正常。
|
||||
|
||||
**注意:** 当我们讨论 TCP/IP 的时候,相关信息在使用 TCP/IP 协议的英特网与局域网(LAN)中都是相当有用的。这些程序都能工作。同样在广域网(WAN)也能工作得相当好。
|
||||
|
||||
当参数给出的是一个域名的时候,我们就需要域名解析服务来找到相对应的 IP 地址,这个时候将会生成一些额外的包。例如,当我们执行 ‘ping linuxforum.com’ 的时候,需要首先请求域名(linuxforum.com)的 IP 地址(98.124.199.63)。当我们执行 ‘ping 98.124.199.63’ 的时候 DNS 查询就不需要了。当 MAC 地址未知的时候,就需要发送 ARP 请求来获取指定 IP 地址的 MAC 地址了(这里的指定 IP 地址,未必是目的 IP)。
|
||||
|
||||
Ping 命令会向指定的 IP 地址发送一个英特网信息控制协议(ICMP)包。这个包是需要响应的 ICMP Echo 请求。当服务器系统在线的状态下我们会得到一个响应包。当两个系统之间存在防火墙的时候,PING 请求包可能会被防火墙丢弃。一些服务器也会被配置成不响应 PING 请求来避免可能发生的死亡之 PING。(现在的操作系统似乎不太可能)
|
||||
|
||||
**注意:** 死亡之 PING 是一种恶意构造的 PING 包当它被发送到系统的时候,会造成被打开的连接等待一个 rest 包。一旦有一堆这样的恶意请求被系统响应,由于所有的可用连接都已经被打开所以系统将会拒绝所有其它的连接。技术上来说这种状态下的系统就是不可达的。
|
||||
|
||||
当系统收到 ICMP Echo 请求后它将会返回一个 ICMP Echo 响应。当源系统收到 ICMP Echo 响应后我们就能知道目的系统是在线可达的。
|
||||
|
||||
使用 NMAP 的时候你可以指定单个 IP 地址也可以指定 某个 IP 地址段。当被指定为 PING 扫描(-sP)的时候,PING 命令将会对每一个 IP 地址执行。
|
||||
|
||||
在图 1 中你可以看到我执行‘nmap -sP 10.0.0.1-10’命令后的结果。An ARP is sent out, three for each IP Address given to the command. In this case thirty requests went out – two for each of the ten IP Addresses.(这两句话就没有读懂,不清楚具体指的是什么意思,从图2看的话第一句里的三指的是两个 ARP 包和一个 ICMP 包,按照下面一段话的描述的话就是每个 IP 地址会有三个 ARP 请求,但是自己试的时候 Centos6 它发了两个 ARP 请求没获取到 MAC 地址也就就结束了,这里不清楚究竟怎么理解)
|
||||
|
||||

|
||||
|
||||
**图 1**
|
||||
|
||||
图 2 中展示了利用 Wireshark 抓取的从网络上另一台计算机发出的请求-的确是在 Windows 系统下完成这次抓取的。第一行展示了发出的第一条请求,广播请求的是 10.0.0.2 IP 地址对应 MAC 地址。由于 NMAP 是在 10.0.0.1 这台机器上执行的,因此 10.0.0.1 被略过了。由于本机 IP 地址被略过,我们现在可以说总共只发出了 27 个 ARP 请求。第二行展示了 10.0.0.2 这台机器的 ARP 响应。第三行到第十行是其它八个 IP 地址的 ARP 请求。第十一行是由于没有收到请求系统(10.0.0.1)的反馈所以发送的另一个 ARP 响应。(自己试的话它发送一个请求收到一个响应就结束了,也没有搜到相关的重发响应是否存在的具体说明,不是十分清楚)第十二行是源系统向 10.0.0.2 响应的 ‘SYN’ 和 Sequence 0。(这行感觉更像是三次握手里的首包)第十三行和第十四行的两次 Restart(RST)和 Synchronize(SYN)响应是用来关闭第二行和第十一行所打开的连接的。(这个描述似乎有问题 ARP 请求怎么会需要 TCP 来关闭连接呢,感觉像是第十二行的响应)注意 Sequence ID 是 ‘1’ - 是源 Sequence ID + 1。(这个不理解,不是应该 ACK = seq + 1 的么)第十五行开始就是类似相同的内容。
|
||||
|
||||

|
||||
|
||||
**图 2**
|
||||
|
||||
回到图 1 中我们可以看到有两台主机在线。其中一台是本机(10.0.0.1)另一台是(10.0.0.2)。整个扫描花费了 14.40 秒。
|
||||
|
||||
PING 扫描是一种用来发现在线主机的快速扫描方式。扫描结果中没有关于网络、系统的其它信息。这是一种较好的初步发现网络上在线主机的方式,接着你就可以针对在线系统执行更加复杂的扫描了。你可能还会发现一些不应该出现在网络上的系统。出现在网络上的流氓软件是很危险的,他们可以很轻易的收集内网信息和相关的系统信息。
|
||||
|
||||
一旦你获得了在线系统的列表,你就可以使用 UDP 扫描来查看哪些端口是可能开启了的。
|
||||
|
||||
**UDP 扫描 (-sU)**
|
||||
|
||||
现在你已经知道了有那些系统是在线的,你的扫描就可以聚焦在这些 IP 地址之上。在整个网络上执行大量的没有针对性的扫描活动可不是一个好主意。系统管理员可以使用程序来监控网络流量当有大量可以活动发生的时候就会触发警报。
|
||||
|
||||
用户数据报协议(UDP)在发现在线系统的开放端口方面十分有用。由于 UDP 不是一个面向连接的协议,因此是不需要响应的。这种扫描方式可以向指定的端口发送一个 UDP 包。如果目标系统没有回应那么这个端口可能是关闭的也可能是被过滤了的。如果端口是开放状态的那么应该会有一个响应。在大多数的情况下目标系统会返回一个 ICMP 信息说端口不可达。ICMP 信息让 NMAP 知道端口是被关闭了。如果端口是开启的状态那么目标系统应该响应 ICMP 信息来告知 NMAP 端口可达。
|
||||
|
||||
**注意: **只有最前面的1024个常用端口会被扫描。(这里将 1000 改成了1024,因为手册中写的是默认扫描 1 到 1024 端口)在后面的文章中我们会介绍如何进行深度扫描。
|
||||
|
||||
由于我知道 10.0.0.2 这个主机是在线的,因此我只会针对这个 IP 地址来执行扫描。扫描过程中总共收发了 3278 个包。‘sudo nmap -sU 10.0.0.2’这个命令的输出结果在图 3 中展现。
|
||||
|
||||

|
||||
|
||||
**图 3**
|
||||
|
||||
在这副图中你可以看见端口 137(netbios-ns)被发现是开放的。在图 4 中展示了 Wireshark 抓包的结果。不能看到所有抓取的包,但是可以看到一长串的 UDP 包。
|
||||
|
||||

|
||||
|
||||
**图 4**
|
||||
|
||||
如果我把目标系统上的防火墙关闭之后会发生什么呢?我的结果有那么一点的不同。NMAP 命令的执行结果在图 5 中展示。
|
||||
|
||||

|
||||
|
||||
**图 5**
|
||||
|
||||
**注意:** 当你执行 UDP 扫描的时候是需要 root 权限的。
|
||||
|
||||
会产生大量的包是由于我们使用了 UDP。当 NMAP 发送 UDP 请求时它是不保证数据包会被收到的。因为数据包可能会在中途丢失因此它会多次发送请求。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.linuxforum.com/threads/nmap-common-scans-part-one.3637/
|
||||
|
||||
作者:[Jarret][a]
|
||||
译者:[wcnnbdk1](https://github.com/wcnnbdk1)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://www.linuxforum.com/members/jarret.268/
|
||||
[1]:https://www.linuxforum.com/threads/nmap-installation.3431/
|
||||
@ -1,155 +1,119 @@
|
||||
### 在 Linux 上用火狐保护你的隐私
|
||||
在 Linux 上用火狐保护你的隐私
|
||||
=============================
|
||||
|
||||
内容
|
||||
[1. 介绍][12]
|
||||
[2. 火狐设置][13]
|
||||
[2.1. 健康报告][1]
|
||||
[2.2. 搜索][2]
|
||||
[2.3. 请勿跟踪][3]
|
||||
[2.4. 禁用 Pocket][4]
|
||||
[3. 附加组件][14]
|
||||
[3.1. HTTPS Everywhere][5]
|
||||
[3.2. Privacy Badger][6]
|
||||
[3.3. Ublock Origin][7]
|
||||
[3.4. NoScript][8]
|
||||
[3.5. Disconnect][9]
|
||||
[3.6. Random Agent Spoofer][10]
|
||||
[4. 系统设置][15]
|
||||
[4.1. 私人 DNS][11]
|
||||
[5. 关闭联想][16]
|
||||
## 介绍
|
||||
|
||||
### 介绍
|
||||
|
||||
隐私和安全正在逐渐成为一个重要的话题。虽然不可能做到 100% 安全,但是,特别是在 Linux 上,还是有几个你能做措施,在你浏览网页的时候保卫你的在线隐私安全。
|
||||
隐私和安全正在逐渐成为一个重要的话题。虽然不可能做到 100% 安全,但是,还是能采取一些措施,特别是在 Linux 上,在你浏览网页的时候保护你的在线隐私安全。
|
||||
|
||||
基于这些目的选择浏览器的时候,火狐或许是你的最佳选择。谷歌 Chrome 不能信任。它是属于谷歌的,一个众所周知的数据收集公司,而且它是闭源的。 Chromium 或许还可以,但并不能保证。只有火狐保持了一定程度的用户权利承诺。
|
||||
|
||||
### 火狐设置
|
||||
|
||||

|
||||
## 火狐设置
|
||||
|
||||
火狐里有几个你能设定的设置,能更好地保护你的隐私。这些设置唾手可得,能帮你控制那些在你浏览的时候分享的数据。
|
||||
|
||||
|
||||
### 健康报告
|
||||
|
||||
你能设置以限制数据发送总量的第一件事就是火狐的健康报告。当然,这些数据只是被发送到 Mozilla ,但是它仍然在传输数据。
|
||||
你首先可以设置的是对火狐健康报告发送的限制,以限制数据发送总量。当然,这些数据只是被发送到 Mozilla,但这也是传输数据。
|
||||
|
||||
|
||||
打开火狐的菜单,点击选项。来到侧边栏里的高级选项卡,点击数据反馈。这里你能禁用任意数据的报告。
|
||||
打开火狐的菜单,点击<ruby>“选项”<rt>Preferences</rt></ruby>。来到侧边栏里的<ruby>“高级”<rt>Advanced</rt></ruby>选项卡,点击<ruby>“数据选项”<rt>Data Choices</rt></ruby>。这里你能禁用任意数据的报告。
|
||||
|
||||
### 搜索
|
||||
|
||||
新版的火狐浏览器默认使用雅虎搜索引擎。一些发行版更改设置,替代使用的是谷歌。两个方法都不理想。火狐有默认使用 DuckDuckGo 的选项。
|
||||
|
||||

|
||||
|
||||

|
||||
center
|
||||
为了启用 DuckDuckGo,你得打开火狐菜单点击<ruby>“选项”<rt>Preferences</rt></ruby>。直接来到侧边栏的<ruby>“搜索”<rt>Search</rt></ruby>选项卡。然后,用<ruby>“默认搜索引擎”<rt>Default Search Engine</rt></ruby>的下拉菜单来选择 DuckDuckGo 。
|
||||
|
||||
为了启用 DuckDuckGo,你得打开火狐菜单点击选项。直接来到侧边栏的搜索选项卡。然后,用默认搜索引擎的下拉菜单来选择 DuckDuckGo 。
|
||||
### <ruby>请勿跟踪<rt>Do Not Track</rt></ruby>
|
||||
|
||||
### 请勿跟踪
|
||||
这个功能并不完美,但它确实向站点发送了一个信号,告诉它们不要使用分析工具来记录你的活动。这些网页或许会遵从,会许不会。但是,最好启用请勿跟踪,也许它们会遵从呢。
|
||||
|
||||
请勿跟踪并不完美,但它确实向网页发送了一个信号,告诉他们不要使用分析工具来记录你的活动。这些网页或许会遵从,会许不会。但是,万一他们会遵从,最好启用请勿跟踪。
|
||||
|
||||

|
||||
|
||||
再次打开火狐的菜单,点击选项,然后是隐私。页面的最上面有一个跟踪部分。点击那一行写着 “ 您还可以管理您的 ‘请勿跟踪’ 设置 ” 的链接。会出现一个有单选框的弹出窗口,那里允许你启用请勿跟踪设置。
|
||||

|
||||
|
||||
再次打开火狐的菜单,点击<ruby>“选项”<rt>Preferences</rt></ruby>,然后是<ruby>“隐私”<rt>Privacy</rt></ruby>。页面的最上面有一个<ruby>“跟踪”<rt>Tracking</rt></ruby>部分。点击那一行写着<ruby>“您还可以管理您的‘请勿跟踪’设置”<rt>You can also manage your Do Not Track settings</rt></ruby>的链接。会出现一个有复选框的弹出窗口,那里允许你启用“请勿跟踪”设置。
|
||||
|
||||
### 禁用 Pocket
|
||||
|
||||
没有任何证据显示 Pocket 正在做一些不好的事情,但是禁用它或许更好,因为它确实连接了一个专有的应用。
|
||||
|
||||
禁用 Pocket 不是太难,但是你得注意只改变 Pocket 相关设置。为了来到你所需的配置页面,在火狐的地址栏里输入`about:config`。
|
||||
|
||||
禁用 Pocket 不是太难,但是你得注意 Pocket 是唯一扰乱你的东西。为了来到你所需的配置页面,在火狐的地址栏里输入`about:config`。
|
||||
页面会加载一个设置表格,在表格的最上面是搜索栏,在那儿搜索 Pocket 。
|
||||
|
||||
你将会看到一个包含结果的新表格。找一下名为 extensions.pocket.enabled 的设置。当你找到它的时候,双击使其转变为“否”。你也能在这儿编辑 Pocket 的其他相关设置。不过没什么必要。注意不要编辑那些跟 Pocket 扩展不直接相关的任何东西。
|
||||
|
||||

|
||||
|
||||
|
||||
这些页面会加载一个设置表格,在表格的最上面是搜索栏,在那儿搜索 Pocket 。
|
||||
## <ruby>附加组件<rt>Add-ons</rt></ruby>
|
||||
|
||||
你将会看到一个包含结果的新表格。找一下名为 extensions.pocket.enabled 的设置。当你找到它的时候,双击使其转变为否。你也能在这儿编辑 Pocket 的其他相关设置。虽说这不是必要的。只是得保证不要编辑那些不是直接跟 Pocket 应用相关设置的任何东西。
|
||||
|
||||
|
||||

|
||||
|
||||
|
||||
### 附加组件
|
||||
|
||||
|
||||

|
||||
|
||||
火狐最有效地保护你隐私和安全的方式来自附加组件。火狐有大量的附加组件库,有许多附加组件是免费、开源的。在这篇指导中着重提到的附加组件,对于安全化你的浏览器方面是名列前茅的。
|
||||

|
||||
|
||||
火狐最有效地保护你隐私和安全的方式来自附加组件。火狐有大量的附加组件库,其中很多是免费、开源的。在这篇指导中着重提到的附加组件,在使浏览器更安全方面是名列前茅的。
|
||||
|
||||
### HTTPS Everywhere
|
||||
|
||||
电子前线基金会开发了HTTPS Everywhere,这是对大量没有使用 SSL 证书的网页、许多不使用`https`前缀的链接、指引用户前往不安全版本的网页等做出的反应。HTTPS Everywhere 确保了如果存在有一个加密版本的网页,用户将会使用它。
|
||||
针对大量没有使用 SSL 证书的网页、许多不使用 `https` 前缀的链接、指引用户前往不安全版本的网页等现状,<ruby>电子前线基金会<rt>Electronic Frontier Foundation</rt></ruby>开发了 HTTPS Everywhere。HTTPS Everywhere 确保了如果存在有一个加密版本的网页,用户将会使用它。
|
||||
|
||||
给火狐设计的 HTTPS Everywhere 已经可以使用,在火狐的附加组件搜索网页上。`https://addons.mozilla.org/en-us/firefox/addon/https-everywhere/`(译者注:对应的中文页面是`https://addons.mozilla.org/zh-CN/firefox/addon/https-everywhere/`)
|
||||
给火狐设计的 HTTPS Everywhere 已经可以使用,在火狐的附加组件搜索网页上。`https://addons.mozilla.org/en-us/firefox/addon/https-everywhere/`(LCTT 译注:对应的中文页面是 `https://addons.mozilla.org/zh-CN/firefox/addon/https-everywhere/`)
|
||||
|
||||
|
||||
### Privacy Badger
|
||||
|
||||
电子前线基金会同样开发了 Privacy Badger。 Privacy Badger 旨在通过阻止不想要的网页跟踪,弥补请勿跟踪功能的不足之处。它同样能通过火狐附加组件仓库安装。`https://addons.mozilla.org/en-us/firefox/addon/privacy-badger17`. (译者注:对应的中文页面是`https://addons.mozilla.org/zh-CN/firefox/addon/privacy-badger17/`)
|
||||
|
||||
电子前线基金会同样开发了 Privacy Badger。 Privacy Badger 旨在通过阻止不想要的网页跟踪,弥补“请勿跟踪”功能的不足之处。它同样能通过火狐附加组件仓库安装。`https://addons.mozilla.org/en-us/firefox/addon/privacy-badger17`。(LCTT 译注:对应的中文页面是`https://addons.mozilla.org/zh-CN/firefox/addon/privacy-badger17/`)
|
||||
|
||||
|
||||
### Ublock Origin
|
||||
|
||||
现在有一类更通用的的隐私附加组件,屏蔽广告。这里的选择是 uBlock Origin ,uBlock Origin 是个更轻量级的广告屏蔽插件,几乎不遗漏所有它会屏蔽的广告。 uBlock Origin 将主要屏蔽所有广告,特别是侵略性的广告。你能在这儿找到它。`https://addons.mozilla.org/en-us/firefox/addon/ublock-origin/`.(译者注:对应的中文页面是`https://addons.mozilla.org/zh-CN/firefox/addon/ublock-origin/`)
|
||||
现在有一类更通用的的隐私附加组件,屏蔽广告。这里的选择是 uBlock Origin,uBlock Origin 是个更轻量级的广告屏蔽插件,几乎不遗漏所有它会屏蔽的广告。 uBlock Origin 将主要屏蔽所有广告,特别是侵略性的广告。你能在这儿找到它。`https://addons.mozilla.org/en-us/firefox/addon/ublock-origin/`。(LCTT 译注:对应的中文页面是 `https://addons.mozilla.org/zh-CN/firefox/addon/ublock-origin/`)
|
||||
|
||||
|
||||
### NoScript
|
||||
|
||||
阻止 JavaScript 是有点争议, JavaScript 虽说驱动了那么多的网站,但还是臭名昭著,因为 JavaScript 成为侵略隐私和攻击的媒介。NoScript 是应对 JavaScript 的绝佳方案。
|
||||
|
||||

|
||||
|
||||

|
||||
NoScript 是一个 JavaScript 的白名单,它通常会屏蔽 JavaScript,除非该站点被添加进白名单中。可以通过插件的“选项”菜单,事先将一个站点加入白名单,或者通过在页面上点击 NoScript 图标的方式添加。
|
||||
|
||||
NoScript 是一个 JavaScript 的白名单,它通常会屏蔽 JavaScript 直到一个网页被添加进白名单中。添加一个网页进白名单能提前完成,通过插件的选项菜单,或者能通过点击页面上的 NoScript 图标完成。
|
||||
|
||||
|
||||

|
||||

|
||||
|
||||
通过火狐附加组件仓库可以安装 NoScript `https://addons.mozilla.org/en-US/firefox/addon/noscript/`
|
||||
如果网页提示不支持你使用的火狐版本,点“无论如何下载”。它已经测试过能在Firefox 51 上使用。
|
||||
如果网页提示不支持你使用的火狐版本,点<ruby>“无论如何下载”<rt>Download Anyway</rt></ruby>。这已经在 Firefox 51 上测试有效。
|
||||
|
||||
### Disconnect
|
||||
|
||||
Disconnect 做很多跟 Privacy Badger 一样的事情,它只是提供了另一个保护的方法。你能在附加组件仓库中找到它 `https://addons.mozilla.org/en-US/firefox/addon/disconnect/` (译者注:对应的中文页面是`https://addons.mozilla.org/zh-CN/firefox/addon/disconnect/`)如果网页提示不支持你使用的火狐版本,点“无论如何下载”。它已经测试过能在Firefox 51 上使用。
|
||||
|
||||
|
||||
Disconnect 做很多跟 Privacy Badger 一样的事情,它只是提供了另一个保护的方法。你能在附加组件仓库中找到它 `https://addons.mozilla.org/en-US/firefox/addon/disconnect/` (LCTT 译注:对应的中文页面是`https://addons.mozilla.org/zh-CN/firefox/addon/disconnect/`)。如果网页提示不支持你使用的火狐版本,点<ruby>“无论如何下载”<rt>Download Anyway</rt></ruby>。这已经在 Firefox 51 上测试有效。
|
||||
|
||||
### Random Agent Spoofer
|
||||
|
||||
Random Agent Spoofer 能改变火狐浏览器的签名,让浏览器看起来像是在其他任意平台上的其他任意浏览器。虽然有许多其他的应用,但是它也能预防浏览器指纹侦查。
|
||||
|
||||
|
||||
浏览器指纹侦查是网站基于所使用的浏览器和操作系统来跟踪用户的另一个方式。相比于 Windows 用户,浏览器指纹侦查更多影响到 Linux 和其他替代性操作系统用户,因为他们的浏览器特征更独特。
|
||||
<ruby>浏览器指纹侦查<rt>Browser Fingerprinting</rt></ruby>是网站基于所使用的浏览器和操作系统来跟踪用户的另一个方式。相比于 Windows 用户,浏览器指纹侦查更多影响到 Linux 和其他替代性操作系统用户,因为他们的浏览器特征更独特。
|
||||
|
||||
|
||||
你能通过火狐附加插件仓库添加 Random Agent Spoofer。`https://addons.mozilla.org/en-us/firefox/addon/random-agent-spoofer/`(译者注:对应的中文页面是`https://addons.mozilla.org/zh-CN/firefox/addon/random-agent-spoofer/`)像其他附加组件那样,页面或许会提示在最新版的火狐兼容性不好。再说一次,那并不是真的。
|
||||
你能通过火狐附加插件仓库添加 Random Agent Spoofer。`https://addons.mozilla.org/en-us/firefox/addon/random-agent-spoofer/`(LCTT 译注:对应的中文页面是`https://addons.mozilla.org/zh-CN/firefox/addon/random-agent-spoofer/`)。像其他附加组件那样,页面或许会提示它不兼容最新版的火狐。再说一次,那并不是真的。
|
||||
|
||||
|
||||

|
||||

|
||||
|
||||
你能通过点击火狐菜单栏上的图标来使用 Random Agent Spoofer。点开后将会出现一个下拉菜单,有不同模拟的浏览器选项。最好的选项之一是选择"Random Desktop" 和任意的改变时间。这样,就不会有绝对的模式来跟踪,也保证了你只能获得网页的桌面版本。
|
||||
你可以通过点击火狐菜单栏上的图标来使用 Random Agent Spoofer。点开后将会出现一个下拉菜单,有不同模拟的浏览器选项。最好的选项之一是选择"Random Desktop" 和任意的改变时间。这样,就不会有绝对的模式来跟踪,也保证了你只能获得网页的桌面版本。
|
||||
|
||||
|
||||
|
||||
### 系统设置
|
||||
## 系统设置
|
||||
|
||||
### 私人 DNS
|
||||
|
||||
避免使用公共或者 ISP 的 DNS 服务器。即使你配置了你的浏览器满足绝对的隐私标准,你向公共 DNS 服务器发出的 DNS 请求暴露了所有你访问过的网页。服务,例如谷歌公共 DNS(IP:8.8.8.8 、8.8.4.4)将会记录你的 IP 地址、关于你的 ISP 和地理位置信息。这些信息或许会被任何合法程序或者强制性的政府请求所分享。
|
||||
请避免使用公共或者 ISP 的 DNS 服务器!即使你配置你的浏览器满足绝对的隐私标准,你向公共 DNS 服务器发出的 DNS 请求却暴露了所有你访问过的网页。诸如谷歌公共 DNS(IP:8.8.8.8 、8.8.4.4)这类的服务将会记录你的 IP 地址、你的 ISP 和地理位置信息。这些信息或许会被任何合法程序或者强制性的政府请求所分享。
|
||||
|
||||
|
||||
> **当我在使用谷歌公共 DNS 服务时,谷歌会记录什么信息?**
|
||||
>
|
||||
> 谷歌公共 DNS 隐私页面有一个完整的收集信息列表。谷歌公共 DNS 遵循谷歌主隐私政策,在我们的隐私中心可以看到。 你客户端 IP 地址是唯一会被临时记录的(一到两天后删除),但是为了让我们的服务更快、更好、更安全,关于 ISP 和城市/都市级别的信息将会被保存更长的时间。
|
||||
> 谷歌公共 DNS 隐私页面有一个完整的收集信息列表。谷歌公共 DNS 遵循谷歌的主隐私政策,在<ruby>“隐私中心”<rt>Privacy Center</rt></ruby>可以看到。 用户的客户端 IP 地址是唯一会被临时记录的(一到两天后删除),但是为了让我们的服务更快、更好、更安全,关于 ISP 和城市/都市级别的信息将会被保存更长的时间。
|
||||
> 参考资料: `https://developers.google.com/speed/public-dns/faq#privacy`
|
||||
|
||||
以上原因,如果可能的话,配置并使用你私人的非转发 DNS 服务器。现在,这项任务或许跟在本地部署一些预先配置好的 DNS 服务器 Docker 容器一样琐碎。例如,假设 docker 服务已经在你的系统安装完成,下列命令将会部署你的私人本地 DNS 服务器:
|
||||
由于以上原因,如果可能的话,配置并使用你私人的非转发 DNS 服务器。现在,这项任务或许跟在本地部署一些预先配置好的 DNS 服务器 Docker 容器一样简单。例如,假设 docker 服务已经在你的系统安装完成,下列命令将会部署你的私人本地 DNS 服务器:
|
||||
|
||||
```
|
||||
# docker run -d --name bind9 -p 53:53/udp -p 53:53 fike/bind9
|
||||
@ -175,7 +139,7 @@ DNS 服务器现在已经启动并正在运行:
|
||||
google.com. 242 IN A 216.58.199.46
|
||||
```
|
||||
|
||||
现在,在`/etc/resolv.conf `里设置你的域名服务器:
|
||||
现在,在 `/etc/resolv.conf` 里设置你的域名服务器:
|
||||
|
||||
|
||||
```
|
||||
@ -183,9 +147,9 @@ google.com. 242 IN A 216.58.199.46
|
||||
nameserver 127.0.0.1
|
||||
```
|
||||
|
||||
### 关闭联想
|
||||
## 结束语
|
||||
|
||||
没有完美的安全隐私解决方案。虽然这篇指导里的步骤明显是个改进。如果你真的很在乎隐私,Tor 浏览器`https://www.torproject.org/projects/torbrowser.html.en`,是最佳选择。Tor 对于日常使用有点过犹不及,但是它的确使用了同样在这篇指导里列出的一些措施。
|
||||
没有完美的安全隐私解决方案。虽然本篇指导里的步骤可以明显改进它们。如果你真的很在乎隐私,Tor 浏览器 `https://www.torproject.org/projects/torbrowser.html.en` 是最佳选择。Tor 对于日常使用有点过犹不及,但是它的确使用了这篇指导里列出的一些措施。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
@ -193,24 +157,8 @@ via: https://linuxconfig.org/protecting-your-privacy-with-firefox-on-linux
|
||||
|
||||
作者:[Nick Congleton][a]
|
||||
译者:[ypingcn](https://ypingcn.github.io/wiki/lctt)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[jasminepeng](https://github.com/jasminepeng)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://linuxconfig.org/protecting-your-privacy-with-firefox-on-linux
|
||||
[1]: https://linuxconfig.org/protecting-your-privacy-with-firefox-on-linux#h2-1-health-report
|
||||
[2]: https://linuxconfig.org/protecting-your-privacy-with-firefox-on-linux#h2-2-search
|
||||
[3]: https://linuxconfig.org/protecting-your-privacy-with-firefox-on-linux#h2-3-do-not-track
|
||||
[4]: https://linuxconfig.org/protecting-your-privacy-with-firefox-on-linux#h2-4-disable-pocket
|
||||
[5]: https://linuxconfig.org/protecting-your-privacy-with-firefox-on-linux#h3-1-https-everywhere
|
||||
[6]: https://linuxconfig.org/protecting-your-privacy-with-firefox-on-linux#h3-2-privacy-badger
|
||||
[7]: https://linuxconfig.org/protecting-your-privacy-with-firefox-on-linux#h3-3-ublock-origin
|
||||
[8]: https://linuxconfig.org/protecting-your-privacy-with-firefox-on-linux#h3-4-noscript
|
||||
[9]: https://linuxconfig.org/protecting-your-privacy-with-firefox-on-linux#h3-5-disconnect
|
||||
[10]: https://linuxconfig.org/protecting-your-privacy-with-firefox-on-linux#h3-6-random-agent-spoofer
|
||||
[11]: https://linuxconfig.org/protecting-your-privacy-with-firefox-on-linux#h4-1-private-dns
|
||||
[12]: https://linuxconfig.org/protecting-your-privacy-with-firefox-on-linux#h1-introduction
|
||||
[13]: https://linuxconfig.org/protecting-your-privacy-with-firefox-on-linux#h2-firefox-settings
|
||||
[14]: https://linuxconfig.org/protecting-your-privacy-with-firefox-on-linux#h3-add-ons
|
||||
[15]: https://linuxconfig.org/protecting-your-privacy-with-firefox-on-linux#h4-system-settings
|
||||
[16]: https://linuxconfig.org/protecting-your-privacy-with-firefox-on-linux#h5-closing-thoughts
|
||||
|
||||
@ -4,7 +4,7 @@
|
||||
|
||||

|
||||
|
||||
FirewallD 是 CentOS 7 服务器上的一个默认可用的防火墙管理工具。基本上,它是 iptables 的封装,有图形配置工具 firewall-config 和命令行工具 firewall-cmd。使用 iptables 服务,每次改动都要求刷新旧规则,并且从 `/etc/sysconfig/iptables` 读取新规则,然而 firewalld 仅仅会应用改动了的不同部分。
|
||||
FirewallD 是 CentOS 7 服务器上的一个默认可用的防火墙管理工具。基本上,它是 iptables 的封装,有图形配置工具 firewall-config 和命令行工具 firewall-cmd。使用 iptables 服务,每次改动都要求刷新旧规则,并且从 `/etc/sysconfig/iptables` 读取新规则,然而 firewalld 只应用改动了的不同部分。
|
||||
|
||||
### FirewallD zones
|
||||
|
||||
@ -17,72 +17,73 @@ FirewallD 使用 services 和 zones 代替 iptables 的 rules 和 chains 。
|
||||
* **public** — 只接受被选择的传入网络连接,用于公共区域。
|
||||
* **external** — 用于启用伪装的外部网络,只接受被选择的传入网络连接。
|
||||
* **dmz** — DMZ 隔离区,外部受限地访问内部网络,只接受被选择的传入网络连接。
|
||||
* **work** — 对于处在你家庭区域内的计算机,只接受被选择的传入网络连接。
|
||||
* **work** — 对于处在你工作区域内的计算机,只接受被选择的传入网络连接。
|
||||
* **home** — 对于处在你家庭区域内的计算机,只接受被选择的传入网络连接。
|
||||
* **internal** — 对于处在你内部网络的计算机,只接受被选择的传入网络连接。
|
||||
* **trusted** — 所有网络连接都接受。
|
||||
|
||||
列出所有可用的 zones :
|
||||
要列出所有可用的 zones,运行:
|
||||
|
||||
```
|
||||
# firewall-cmd --get-zones
|
||||
work drop internal external trusted home dmz public block
|
||||
```
|
||||
|
||||
列出默认的 zone :
|
||||
|
||||
```
|
||||
# firewall-cmd --get-default-zone
|
||||
public
|
||||
```
|
||||
|
||||
改变默认的 zone :
|
||||
|
||||
```
|
||||
# firewall-cmd --set-default-zone=dmz
|
||||
# firewall-cmd --get-default-zone
|
||||
dmz
|
||||
```
|
||||
|
||||
### FirewallD services
|
||||
### FirewallD 服务
|
||||
|
||||
FirewallD services 使用 XML 配置文件为 firewalld 录入服务信息。
|
||||
FirewallD 服务使用 XML 配置文件,为 firewalld 服务入口信息。
|
||||
|
||||
列出所有可用的服务:
|
||||
|
||||
列出所有可用的 services :
|
||||
```
|
||||
# firewall-cmd --get-services
|
||||
amanda-client amanda-k5-client bacula bacula-client ceph ceph-mon dhcp dhcpv6 dhcpv6-client dns docker-registry dropbox-lansync freeipa-ldap freeipa-ldaps freeipa-replication ftp high-availability http https imap imaps ipp ipp-client ipsec iscsi-target kadmin kerberos kpasswd ldap ldaps libvirt libvirt-tls mdns mosh mountd ms-wbt mysql nfs ntp openvpn pmcd pmproxy pmwebapi pmwebapis pop3 pop3s postgresql privoxy proxy-dhcp ptp pulseaudio puppetmaster radius rpc-bind rsyncd samba samba-client sane smtp smtps snmp snmptrap squid ssh synergy syslog syslog-tls telnet tftp tftp-client tinc tor-socks transmission-client vdsm vnc-server wbem-https xmpp-bosh xmpp-client xmpp-local xmpp-server
|
||||
```
|
||||
|
||||
|
||||
|
||||
XML 配置文件存储在 `/usr/lib/firewalld/services/` 和 `/etc/firewalld/services/` 目录。
|
||||
XML 配置文件存储在 `/usr/lib/firewalld/services/` 和 `/etc/firewalld/services/` 目录下。
|
||||
|
||||
### 用 FirewallD 配置你的防火墙
|
||||
|
||||
|
||||
作为一个例子,假设你正在运行一个 web 服务,端口为 7022 的 SSH 服务和邮件服务,你可以利用 FirewallD 这样配置你的 [RoseHosting VPS][6]:
|
||||
|
||||
首先设置默认区为 dmz。
|
||||
|
||||
首先设置默认 zone 为 dmz。
|
||||
```
|
||||
# firewall-cmd --set-default-zone=dmz
|
||||
# firewall-cmd --get-default-zone
|
||||
dmz
|
||||
```
|
||||
|
||||
添加持久性的 HTTP 和 HTTPS service 规则到 dmz zone :
|
||||
为 dmz 区添加持久性的 HTTP 和 HTTPS 规则:
|
||||
```
|
||||
# firewall-cmd --zone=dmz --add-service=http --permanent
|
||||
# firewall-cmd --zone=dmz --add-service=https --permanent
|
||||
```
|
||||
|
||||
|
||||
开启端口 25 (SMTP) 和端口 465 (SMTPS) :
|
||||
|
||||
```
|
||||
firewall-cmd --zone=dmz --add-service=smtp --permanent
|
||||
firewall-cmd --zone=dmz --add-service=smtps --permanent
|
||||
```
|
||||
|
||||
|
||||
开启 IMAP, IMAPS, POP3 和 POP3S 端口:
|
||||
|
||||
```
|
||||
firewall-cmd --zone=dmz --add-service=imap --permanent
|
||||
firewall-cmd --zone=dmz --add-service=imaps --permanent
|
||||
@ -90,20 +91,21 @@ firewall-cmd --zone=dmz --add-service=pop3 --permanent
|
||||
firewall-cmd --zone=dmz --add-service=pop3s --permanent
|
||||
```
|
||||
|
||||
因为将 SSH 端口改到 7022,所以要移除 ssh 服务(端口 22),开启端口 7022
|
||||
|
||||
将 SSH 端口改到 7022 后,我们移除 ssh service (端口 22),并且开启端口 7022
|
||||
```
|
||||
firewall-cmd --remove-service=ssh --permanent
|
||||
firewall-cmd --add-port=7022/tcp --permanent
|
||||
```
|
||||
|
||||
要实现这些更改,我们需要重新加载防火墙:
|
||||
|
||||
```
|
||||
firewall-cmd --reload
|
||||
```
|
||||
|
||||
|
||||
最后可以列出这些规则:
|
||||
|
||||
### firewall-cmd –list-all
|
||||
|
||||
```
|
||||
@ -125,11 +127,7 @@ rich rules:
|
||||
* * *
|
||||
|
||||
|
||||
|
||||
当然,如果你使用任何一个我们的 [CentOS VPS hosting][7] 服务,你完全不用做这些。在这种情况下,你可以直接叫我们的专家 Linux 管理员为你设置。他们提供 24x7 h 的帮助并且会马上回应你的请求。
|
||||
|
||||
|
||||
PS. 如果你喜欢这篇文章,请按分享按钮分享给你社交网络上的朋友或者直接在下面留下一个回复。谢谢。
|
||||
PS. 如果你喜欢这篇文章,请在下面留下一个回复。谢谢。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
|
||||
@ -0,0 +1,168 @@
|
||||
理解 sudo 与 su 之间的区别
|
||||
============================================================
|
||||
|
||||
### 本文导航
|
||||
|
||||
1. [Linux su 命令][7]
|
||||
1. [su -][1]
|
||||
2. [su -c][2]
|
||||
2. [Sudo vs Su][8]
|
||||
2. [Sudo vs Su][8]
|
||||
1. [关于密码][3]
|
||||
2. [默认行为][4]
|
||||
3. [日志记录][5]
|
||||
4. [灵活性][6]
|
||||
3. [Sudo su][9]
|
||||
|
||||
在[早前的一篇文章][11]中,我们深入讨论了 `sudo` 命令的相关内容。同时,在该文章的末尾有提到相关的命令 `su` 的部分内容。本文,我们将详细讨论关于 su 命令与 sudo 命令之间的区别。
|
||||
|
||||
在开始之前有必要说明一下,文中所涉及到的示例教程都已经在 Ubuntu 14.04 LTS 上测试通过。
|
||||
|
||||
### Linux su 命令
|
||||
|
||||
su 命令的主要作用是让你可以在已登录的会话中切换到另外一个用户。换句话说,这个工具可以让你在不登出当前用户的情况下登录另外一个用户(以该用户的身份)。
|
||||
|
||||
su 命令经常被用于切换到超级用户或 root 用户(因为在命令行下工作,经常需要 root 权限),但是 - 正如前面所提到的 - su 命令也可以用于切换到任意非 root 用户。
|
||||
|
||||
如何使用 su 命令切换到 root 用户,如下:
|
||||
|
||||
[
|
||||

|
||||
][12]
|
||||
|
||||
如上,su 命令要求输入的密码是 root 用户密码。所以,一般 su 命令需要输入目标用户的密码。在输入正确的密码之后,su 命令会在终端的当前会话中打开一个子会话。
|
||||
|
||||
### su -
|
||||
|
||||
还有一种方法可以切换到 root 用户:运行 `su -` 命令,如下:
|
||||
|
||||
[
|
||||

|
||||
][13]
|
||||
|
||||
那么,`su` 命令与 `su -` 命令之间有什么区别呢?前者在切换到 root 用户之后仍然保持旧的或原始用户的环境,而后者则是创建一个新的环境(由 root 用户 ~/.bashrc 文件所设置的环境),相当于使用 root 用户正常登录(从登录屏幕显示登录)。
|
||||
|
||||
`su` 命令手册页很清楚地说明了这一点:
|
||||
|
||||
```
|
||||
可选参数 `-` 可提供的环境为用户在直接登录时的环境。
|
||||
```
|
||||
|
||||
因此,你会觉得使用 `su -` 登录更有意义。但是,同时存在 `su` 命令,那么大家可能会想知道它在什么时候用到。以下内容摘自[ArchLinux wiki website][14] - 关于 `su` 命令的好处和坏处:
|
||||
|
||||
* 有的时候,对于系统管理员来讲,使用其他普通用户的 Shell 账户而不是自己的 Shell 账户更会好一些。尤其是在处理用户问题时,最有效的方法就是是:登录目标用户以便重现以及调试问题。
|
||||
|
||||
* 然而,在多数情况下,当从普通用户切换到 root 用户进行操作时,如果还使用普通用户的环境变量的话,那是不可取甚至是危险的操作。因为是在无意间切换使用普通用户的环境,所以当使用 root 用户进行程序安装或系统更改时,会产生与正常使用 root 用户进行操作时不相符的结果。例如,可以给普通用户安装电源意外损坏系统的程序或获取对某些数据的未授权访问的程序。
|
||||
|
||||
注意:如果你想在 `su -` 命令后面传递更多的参数,那么你必须使用 `su -l` 来实现。以下是 `-` 和 `-l` 命令行选项的说明:
|
||||
|
||||
```
|
||||
-, -l, --login
|
||||
提供相当于用户在直接登录时所期望的环境。
|
||||
|
||||
当使用 - 时,必须放在 su 命令的最后一个选项。其他选项(-l 和 --login)无此限制。
|
||||
```
|
||||
|
||||
### su -c
|
||||
|
||||
还有一个值得一提的 `su` 命令行选项为:`-c`。该选项允许你提供在切换到目标用户之后要运行的命令。
|
||||
|
||||
`su` 命令手册页是这样说明:
|
||||
|
||||
```
|
||||
-c, --command COMMAND
|
||||
使用 -c 选项指定由 Shell 调用的命令。
|
||||
|
||||
被执行的命令无法控制终端。所以,此选项不能用于执行需要控制 TTY 的交互式程序。
|
||||
```
|
||||
|
||||
参考示例:
|
||||
|
||||
```
|
||||
su [target-user] -c [command-to-run]
|
||||
```
|
||||
|
||||
示例中,`command-to-run` 将会被这样执行:
|
||||
|
||||
```
|
||||
[shell] -c [command-to-run]
|
||||
```
|
||||
|
||||
示例中的 `shell` 类型将会被目标用户在 `/etc/passwd` 文件中定义的登录 shell 类型所替代。
|
||||
|
||||
### Sudo vs Su
|
||||
|
||||
现在,我们已经讨论了关于 `su` 命令的基础知识,是时候来探讨一下 `sudo` 和 `su` 命令之间的区别了。
|
||||
|
||||
### 关于密码
|
||||
|
||||
两个命令的最大区别是:`sudo` 命令需要输入当前用户的密码,`su` 命令需要输入 root 用户的密码。
|
||||
|
||||
很明显,就安全而言,`sudo` 命令更好。例如,考虑到需要 root 访问权限的多用户使用的计算机。在这种情况下,使用 `su` 意味着需要与其他用户共享 root 用户密码,这显然不是一种好习惯。
|
||||
|
||||
此外,如果要撤销特定用户的超级用户/root 用户的访问权限,唯一的办法就是更改 root 密码,然后再告知所有其他用户新的 root 密码。
|
||||
|
||||
而使用 `sudo` 命令就不一样了,你可以很好的处理以上的两种情况。鉴于 `sudo` 命令要求输入的是其他用户的密码,所以,不需要共享 root 密码。同时,想要阻止特定用户访问 root 权限,只需要调整 `sudoers` 文件中的相应配置即可。
|
||||
|
||||
### 默认行为
|
||||
|
||||
两个命令之间的另外一个区别是默认行为。`sudo` 命令只允许使用提升的权限运行单个命令,而 `su` 命令会启动一个新的 shell,同时允许使用 root 权限运行尽可能多的命令,直到显示退出登录。
|
||||
|
||||
因此,`su` 命令的默认行为是有风险的,因为用户很有可能会忘记他们正在以 root 用户身份进行工作,于是,无意中做出了一些不可恢复的更改(例如:对错误的目录运行 `rm -rf` 命令)。关于为什么不鼓励以 root 用户身份进行工作的详细内容,请参考[这里][10]
|
||||
|
||||
### 日志记录
|
||||
|
||||
尽管 `sudo` 命令是以目标用户(默认情况下是 root 用户)的身份执行命令,但是他们会使用 sudoer 所配置的用户名来记录是谁执行命令。而 `su` 命令是无法直接跟踪记录用户切换到 root 用户之后执行了什么操作。
|
||||
|
||||
### 灵活性
|
||||
|
||||
`sudo` 命令会比 `su` 命令灵活很多,因为你甚至可以限制 sudo 用户可以访问哪些命令。换句话说,用户通过 `sudo` 命令只能访问他们工作需要的命令。而 `su` 命令让用户有权限做任何事情。
|
||||
|
||||
### Sudo su
|
||||
|
||||
大概是因为使用 `su` 命令或直接以 root 用户身份登录有风险,所以,一些 Linux 发行版(如 Ubuntu)默认禁用 root 用户帐户。鼓励用户在需要 root 权限时使用 `sudo` 命令。
|
||||
|
||||
However, you can still do 'su' successfully, i.e, without entering the root password. All you need to do is to run the following command:
|
||||
然而,您还是可以成功执行 `su` 命令,即不用输入 root 用户的密码。运行以下命令:
|
||||
|
||||
```
|
||||
sudo su
|
||||
```
|
||||
|
||||
由于你使用 `sudo` 运行命令,你只需要输入当前用户的密码。所以,一旦完成操作,`su` 命令将会以 root 用户身份运行,这意味着它不会再要求输入任何密码。
|
||||
|
||||
** PS **:如果你想在系统中启用 root 用户帐户(虽然强烈反对,但你还是可以使用 `sudo` 命令或 `sudo su` 命令),你必须手动设置 root 用户密码 可以使用以下命令:
|
||||
|
||||
```
|
||||
sudo passwd root
|
||||
```
|
||||
|
||||
### 结论
|
||||
|
||||
这篇文章以及之前的教程(其中侧重于 `sudo` 命令)应该能给你一个比较好的建议,当你需要可用的工具来提升(或一组完全不同的)权限来执行任务时。 如果您也想分享关于 `su` 或 `sudo` 的相关内容或者经验,欢迎您在下方进行评论。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.howtoforge.com/tutorial/sudo-vs-su/
|
||||
|
||||
作者:[Himanshu Arora][a]
|
||||
译者:[zhb127](https://github.com/zhb127)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://www.howtoforge.com/tutorial/sudo-vs-su/
|
||||
[1]:https://www.howtoforge.com/tutorial/sudo-vs-su/#su-
|
||||
[2]:https://www.howtoforge.com/tutorial/sudo-vs-su/#su-c
|
||||
[3]:https://www.howtoforge.com/tutorial/sudo-vs-su/#password
|
||||
[4]:https://www.howtoforge.com/tutorial/sudo-vs-su/#default-behavior
|
||||
[5]:https://www.howtoforge.com/tutorial/sudo-vs-su/#logging
|
||||
[6]:https://www.howtoforge.com/tutorial/sudo-vs-su/#flexibility
|
||||
[7]:https://www.howtoforge.com/tutorial/sudo-vs-su/#the-su-command-in-linux
|
||||
[8]:https://www.howtoforge.com/tutorial/sudo-vs-su/#sudo-vs-su
|
||||
[9]:https://www.howtoforge.com/tutorial/sudo-vs-su/#sudo-su
|
||||
[10]:http://askubuntu.com/questions/16178/why-is-it-bad-to-login-as-root
|
||||
[11]:https://www.howtoforge.com/tutorial/sudo-beginners-guide/
|
||||
[12]:https://www.howtoforge.com/images/sudo-vs-su/big/su-command.png
|
||||
[13]:https://www.howtoforge.com/images/sudo-vs-su/big/su-hyphen-command.png
|
||||
[14]:https://wiki.archlinux.org/index.php/Su
|
||||
@ -0,0 +1,99 @@
|
||||
在 Linux 中修改 MySQL 或 MariaDB 的 Root 密码
|
||||
============================================================
|
||||
|
||||
如果你是第一次[安装 MySQL 或 MariaDB][1],你可以执行 `mysql_secure_installation` 脚本来实现基本的安全设置。
|
||||
|
||||
其中的一个设置是数据库的 root 密码 —— 该密码必须保密,并且只在必要的时候使用。如果你需要修改它(例如,当数据库管理员换了人 —— 或者被解雇了!)。
|
||||
|
||||
**建议阅读:**[在 Linux 中恢复 MySQL 或 MariaDB 的 Root 密码][2]
|
||||
|
||||
这篇文章迟早会派上用场的。我们讲说明怎样来在 Linux 中修改 MySQL 或 MariaDB 数据库服务器的 root 密码。
|
||||
|
||||
尽管我们会在本文中使用 MariaDB 服务器,但本文中的用法说明对 MySQL 也有效。
|
||||
|
||||
### 修改 MySQL 或 MariaDB 的 root 密码
|
||||
|
||||
你知道 root 密码,但是想要重置它,对于这样的情况,让我们首先确定 MariaDB 正在运行:
|
||||
|
||||
```
|
||||
------------- CentOS/RHEL 7 and Fedora 22+ -------------
|
||||
# systemctl is-active mariadb
|
||||
------------- CentOS/RHEL 6 and Fedora -------------
|
||||
# /etc/init.d/mysqld status
|
||||
```
|
||||
|
||||
[
|
||||

|
||||
][3]
|
||||
|
||||
*检查 MysQL 状态*
|
||||
|
||||
如果上面的命令返回中没有 `active` 这个关键词,那么该服务就是停止状态,你需要在进行下一步之前先启动数据库服务:
|
||||
|
||||
```
|
||||
------------- CentOS/RHEL 7 and Fedora 22+ -------------
|
||||
# systemctl start mariadb
|
||||
------------- CentOS/RHEL 6 and Fedora -------------
|
||||
# /etc/init.d/mysqld start
|
||||
```
|
||||
|
||||
接下来,我们将以 root 登录进数据库服务器:
|
||||
|
||||
```
|
||||
# mysql -u root -p
|
||||
```
|
||||
|
||||
为了兼容不同版本,我们将使用下面的声明来更新 mysql 数据库的用户表。注意,你需要将 `YourPasswordHere` 替换为你为 root 选择的新密码。
|
||||
|
||||
```
|
||||
MariaDB [(none)]> USE mysql;
|
||||
MariaDB [(none)]> UPDATE user SET password=PASSWORD('YourPasswordHere') WHERE User='root' AND Host = 'localhost';
|
||||
MariaDB [(none)]> FLUSH PRIVILEGES;
|
||||
```
|
||||
|
||||
要验证是否操作成功,请输入以下命令退出当前 MariaDB 会话。
|
||||
|
||||
```
|
||||
MariaDB [(none)]> exit;
|
||||
```
|
||||
|
||||
然后,敲回车。你现在应该可以使用新密码连接到服务器了。
|
||||
|
||||
[
|
||||

|
||||
][4]
|
||||
|
||||
*修改 MysQL/MariaDB Root 密码*
|
||||
|
||||
|
||||
##### 小结
|
||||
|
||||
在本文中,我们说明了如何修改 MariaDB / MySQL 的 root 密码 —— 或许你知道当前所讲的这个方法,也可能不知道。
|
||||
|
||||
像往常一样,如果你有任何问题或者反馈,请尽管使用下面的评论框来留下你宝贵的意见或建议,我们期待着您的留言。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
作者简介:
|
||||
|
||||
Gabriel Cánepa是一位来自阿根廷圣路易斯的 Villa Mercedes 的 GNU/Linux 系统管理员和 web 开发者。他为世界范围内的主要的消费产品公司工作,也很钟情于在他日常工作的方方面面中使用 FOSS 工具来提高生产效率。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.tecmint.com/change-mysql-mariadb-root-password/
|
||||
|
||||
作者:[Gabriel Cánepa][a]
|
||||
译者:[GOLinux](https://github.com/GOLinux)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.tecmint.com/author/gacanepa/
|
||||
|
||||
[1]:http://www.tecmint.com/install-mariadb-in-centos-7/
|
||||
[2]:http://www.tecmint.com/reset-mysql-or-mariadb-root-password/
|
||||
[3]:http://www.tecmint.com/wp-content/uploads/2017/03/Check-MySQL-Status.png
|
||||
[4]:http://www.tecmint.com/wp-content/uploads/2017/03/Change-MySQL-Root-Password.png
|
||||
[5]:http://www.tecmint.com/author/gacanepa/
|
||||
[6]:http://www.tecmint.com/10-useful-free-linux-ebooks-for-newbies-and-administrators/
|
||||
[7]:http://www.tecmint.com/free-linux-shell-scripting-books/
|
||||
@ -0,0 +1,86 @@
|
||||
如何在 AWS EC2 的 Linux 服务器上打开端口
|
||||
============================================================
|
||||
|
||||
_这是一篇用屏幕截图解释如何在 AWS EC2 Linux 服务器上打开端口的教程。它能帮助你管理 EC2 服务器上特定端口的服务。_
|
||||
|
||||
* * *
|
||||
|
||||
AWS(即 Amazon Web Services)不是 IT 世界中的新术语了。它是亚马逊提供的云服务平台。它的免费帐户能为你提供一年的有限免费服务。这是尝试新技术而不用花费金钱的最好的方式之一。
|
||||
|
||||
AWS 提供服务器计算作为他们的服务之一,他们称之为 EC(弹性计算)。使用它可以构建我们的 Linux 服务器。我们已经看到了[如何在 AWS 上设置免费的 Linux 服务器][11]了。
|
||||
|
||||
默认情况下,所有基于 EC2 的 Linux 服务器都只打开 22 端口,即 SSH 服务端口(所有 IP 的入站)。因此,如果你托管了任何特定端口的服务,则要为你的服务器在 AWS 防火墙上打开相应端口。
|
||||
|
||||
同样它的 1 到 65535 的端口是打开的(所有出站流量)。如果你想改变这个,你可以使用下面的方法编辑出站规则。
|
||||
|
||||
在 AWS 上为你的服务器设置防火墙规则很容易。你能够在几秒钟内为你的服务器打开端口。我将用截图指导你如何打开 EC2 服务器的端口。
|
||||
|
||||
_步骤 1 :_
|
||||
|
||||
登录 AWS 帐户并进入 **EC2 管理控制台**。进入<ruby>“网络及安全”<rt>Network & Security </rt></ruby>菜单下的<ruby>**安全组**<rt>Security Groups</rt></ruby>,如下高亮显示:
|
||||
|
||||

|
||||
|
||||
*AWS EC2 管理控制台*
|
||||
|
||||
* * *
|
||||
|
||||
_步骤 2 :_
|
||||
|
||||
在<ruby>安全组<rt>Security Groups</rt></ruby>中选择你的 EC2 服务器,并在 <ruby>**行动**<rt>Actions</rt></ruby> 菜单下选择 <ruby>**编辑入站规则**<rt>Edit inbound rules</rt></ruby>。
|
||||
|
||||

|
||||
|
||||
*AWS 入站规则菜单*
|
||||
|
||||
_步骤 3:_
|
||||
|
||||
现在你会看到入站规则窗口。你可以在此处添加/编辑/删除入站规则。这有几个如 http、nfs 等列在下拉菜单中,它们可以为你自动填充端口。如果你有自定义服务和端口,你也可以定义它。
|
||||
|
||||

|
||||
|
||||
*AWS 添加入站规则*
|
||||
|
||||
比如,如果你想要打开 80 端口,你需要选择:
|
||||
|
||||
* 类型:http
|
||||
* 协议:TCP
|
||||
* 端口范围:80
|
||||
* 源:任何来源(打开 80 端口接受来自任何IP(0.0.0.0/0)的请求),我的 IP:那么它会自动填充你当前的公共互联网 IP
|
||||
|
||||
* * *
|
||||
|
||||
_步骤 4:_
|
||||
|
||||
就是这样了。保存完毕后,你的服务器入站 80 端口将会打开!你可以通过 telnet 到 EC2 服务器公共域名的 80 端口来检验(可以在 EC2 服务器详细信息中找到)。
|
||||
|
||||
|
||||
你也可以在 [ping.eu][12] 等网站上检验。
|
||||
|
||||
* * *
|
||||
|
||||
同样的方式可以编辑出站规则,这些更改都是即时生效的。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://kerneltalks.com/virtualization/how-to-open-port-on-aws-ec2-linux-server/
|
||||
|
||||
作者:[Shrikant Lavhate ][a]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[jasminepeng](https://github.com/jasminepeng)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://kerneltalks.com/virtualization/how-to-open-port-on-aws-ec2-linux-server/
|
||||
[1]:http://kerneltalks.com/virtualization/how-to-open-port-on-aws-ec2-linux-server/#
|
||||
[2]:http://kerneltalks.com/virtualization/how-to-open-port-on-aws-ec2-linux-server/#
|
||||
[3]:http://kerneltalks.com/virtualization/how-to-open-port-on-aws-ec2-linux-server/#
|
||||
[4]:http://kerneltalks.com/virtualization/how-to-open-port-on-aws-ec2-linux-server/#
|
||||
[5]:http://kerneltalks.com/virtualization/how-to-open-port-on-aws-ec2-linux-server/#
|
||||
[6]:http://kerneltalks.com/virtualization/how-to-open-port-on-aws-ec2-linux-server/#
|
||||
[7]:http://kerneltalks.com/virtualization/how-to-open-port-on-aws-ec2-linux-server/#
|
||||
[8]:http://kerneltalks.com/virtualization/how-to-open-port-on-aws-ec2-linux-server/#
|
||||
[9]:http://kerneltalks.com/virtualization/how-to-open-port-on-aws-ec2-linux-server/#
|
||||
[10]:http://kerneltalks.com/author/shrikant/
|
||||
[11]:http://kerneltalks.com/howto/install-ec2-linux-server-aws-with-screenshots/
|
||||
[12]:http://ping.eu/port-chk/
|
||||
Loading…
Reference in New Issue
Block a user