mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-03-27 02:30:10 +08:00
Merge branch 'master' of github.com:LCTT/TranslateProject
This commit is contained in:
commit
db19d328d2
published
13 Linux Cat Command Examples To Manage (Display,Sort,Create etc) Files.mdHow To Display And Set Hostname in Linux.mdHow to Crack a Wi-Fi Network's WPA Password with Reaver.mdPlay A Crossword Game With Adobe’s Leaked Passwords.mdSBackup--A Simple Backup Solution For Your Linux Desktop.md
sources
10 basic examples of linux netstat command.mdBuilt in Audit Trail Tool – Last Command in Linux.mdCentOS 6.5 desktop installation guide with screenshots.mdConfigure Your Browser To Use Tor On Ubuntu or Debian or Linux Mint.mdDaily Ubuntu Tips–Change The Language You Use In Ubuntu.mdHow to Crack a Wi-Fi Network's WPA Password with Reaver.mdHow to Install Linux Kernel 3.12 in Ubuntu 13.10.mdHow to Install and Configure UFW – An Un-complicated FireWall in Debian or Ubuntu.mdInterview with Ding Zhou of Ubuntu Tweak.mdKDE vs GNOME- Settings, Apps, Widgets.mdLinuxCon/CloudOpen Goose Chase Ends in Tie for Grand Prize.mdNew Ubuntu 14.04 LTS Icon Theme Uses Origami Concept.mdOracle Linux 6.5 Arrives with Unbreakable Enterprise Linux Kernel 3.8.mdPersonality Traits of the Best Software Developers.mdSetup Apache 2.4 and Php FPM with mod proxy fcgi on Ubuntu 13.10.mdSetup FTP Server On openSUSE 13.1.mdSetup a jailed shell with jailkit on ubuntu.mdUnvanquished Will Probably Be the Best Free Multiplayer Game on Linux.md
translated
@ -1,14 +1,14 @@
|
||||
13个 Linux Cat命令管理(显示,排序,建立)文件实例
|
||||
13个Cat命令管理(显示,排序,建立)文件实例
|
||||
================================================================================
|
||||

|
||||
|
||||
在Linux系统中,大多数配置文件、Logs文件,甚至shell脚本都使用文本文件格式,因此,Linux系统存在着多种文本编辑器,但当你仅仅想要查看一下这些文件的内容时,可使用一个简单的命令-cat.
|
||||
在Linux系统中,大多数配置文件、日志文件,甚至shell脚本都使用文本文件格式,因此,Linux系统存在着多种文本编辑器,但当你仅仅想要查看一下这些文件的内容时,可使用一个简单的命令-cat。
|
||||
|
||||
cat手册里这样描述:
|
||||
|
||||
> cat命令读取文件内容,并输出到标准设备上面
|
||||
|
||||
cat是一条linux内置命令. 几乎所有linux发行版都内置.接下来,让我们开始学习如何使用.
|
||||
cat是一条linux内置命令. 几乎所有linux发行版都内置(译注:或者说我从未听说过不内置cat命令的发行版)。接下来,让我们开始学习如何使用.
|
||||
|
||||
### 1. 显示文件内容 ###
|
||||
|
||||
@ -19,10 +19,9 @@ cat是一条linux内置命令. 几乎所有linux发行版都内置.接下来,
|
||||
CentOS release 5.10 (Final)
|
||||
Kernel \r on an \m
|
||||
|
||||
### 2. 在运行中显示行号 ###
|
||||
|
||||
当在读取内容很多的配置文件时,在运行中显示行号将会使操作变简单,加上-n参数可以实现.
|
||||
### 2. 同时显示行号 ###
|
||||
|
||||
当在读取内容很多的配置文件时,如果同时显示行号将会使操作变简单,加上-n参数可以实现.
|
||||
|
||||
# cat -n /etc/ntp.conf
|
||||
|
||||
@ -37,9 +36,9 @@ cat是一条linux内置命令. 几乎所有linux发行版都内置.接下来,
|
||||
9 restrict 127.0.0.1
|
||||
10 restrict -6 ::1
|
||||
|
||||
### 3. 在行首显示非空行号 ###
|
||||
### 3. 在非空格行首显示行号 ###
|
||||
|
||||
类似于-n参数,-b也在运行中显示行号.区别在于-b只显示非空行行号.
|
||||
类似于-n参数,-b也可以显示行号。区别在于-b只在非空行前显示行号。
|
||||
|
||||
#cat -b /etc/ntp.conf
|
||||
|
||||
@ -56,7 +55,7 @@ cat是一条linux内置命令. 几乎所有linux发行版都内置.接下来,
|
||||
|
||||
### 4. 显示tab制表符 ###
|
||||
|
||||
当你想要显示文本中的tab制表位时. 可使用-T参数. 它会在输入结果中标识为 **^I** .
|
||||
当你想要显示文本中的tab制表位时. 可使用-T参数. 它会在输入结果中标识为 **\^I** .
|
||||
|
||||
# cat -T /etc/hosts
|
||||
|
||||
@ -67,7 +66,7 @@ cat是一条linux内置命令. 几乎所有linux发行版都内置.接下来,
|
||||
|
||||
### 5. 显示换行符 ###
|
||||
|
||||
-E参数在每行结尾标识 **$** .如下所示 :
|
||||
-E参数在每行结尾使用 **$** 表示换行符。如下所示 :
|
||||
|
||||
# cat -E /etc/hosts
|
||||
|
||||
@ -87,19 +86,19 @@ cat是一条linux内置命令. 几乎所有linux发行版都内置.接下来,
|
||||
127.0.0.1^I^Ilocalhost.localdomain localhost$
|
||||
::1^I^Ilocalhost6.localdomain6 localhost6$
|
||||
|
||||
### 7. 每页满屏显示 ###
|
||||
### 7. 分屏显示 ###
|
||||
|
||||
当文件内容显示不适合你的屏幕, 可结合cat命令与其它命令满屏显示.使用管道符 ( | ).
|
||||
当文件内容显示超过了你的屏幕大小, 可结合cat命令与其它命令分屏显示。使用管道符 ( | )来连接。
|
||||
|
||||
# cat /proc/meminfo | less
|
||||
|
||||
# cat /proc/meminfo | more
|
||||
|
||||
在less与more显示结果的区别在于less参数可pageup及pagedown上下翻滚.而more仅能使用空格向下翻屏.
|
||||
在less与more显示结果的区别在于less参数可pageup及pagedown上下翻滚。而more仅能使用空格向下翻屏。
|
||||
|
||||
### 8. 同时查看2个文件中的内容 ###
|
||||
|
||||
位于/root文件夹里有两人文件取名linux及desktop,每个文件含有以下内容 :
|
||||
位于/root文件夹里有两个文件取名linux及desktop,每个文件含有以下内容 :
|
||||
|
||||
**Linux** : ubuntu, centos, redhat, mint and slackware
|
||||
|
||||
@ -122,7 +121,7 @@ cat是一条linux内置命令. 几乎所有linux发行版都内置.接下来,
|
||||
|
||||
### 9. 排序显示 ###
|
||||
|
||||
类似. 你也可以结合cat命令与其它命令来进行自定义输出. 如结合 **sort**管道符对内容进行排序显示. 举例 :
|
||||
类似. 你也可以结合cat命令与其它命令来进行自定义输出. 如结合 **sort** ,通过管道符对内容进行排序显示。举例 :
|
||||
|
||||
# cat /root/linux | sort
|
||||
|
||||
@ -134,7 +133,7 @@ cat是一条linux内置命令. 几乎所有linux发行版都内置.接下来,
|
||||
|
||||
### 10. 输入重定向 ###
|
||||
|
||||
你也可将显示结果输出重定向到屏幕或另一个文件. 只需要使用 > 符号(大于号)即可输出生成到另一个文件.
|
||||
你也可将显示结果输出重定向到屏幕或另一个文件。 只需要使用 > 符号(大于号)即可输出生成到另一个文件。
|
||||
|
||||
# cat /root/linux > /root/linuxdistro
|
||||
|
||||
@ -142,7 +141,7 @@ cat是一条linux内置命令. 几乎所有linux发行版都内置.接下来,
|
||||
|
||||
### 11. 新建文件 ###
|
||||
|
||||
Linux下有多种方法新建文件. 其中使用cat就是方法之一.
|
||||
Linux下有多种方法新建文件。其中使用cat就是方法之一.
|
||||
|
||||
# cat > operating_system
|
||||
|
||||
@ -151,17 +150,18 @@ Linux下有多种方法新建文件. 其中使用cat就是方法之一.
|
||||
Windows
|
||||
MacOS
|
||||
|
||||
当你输入cat > operating_system,它会生成一个operating_system的文件. 然后下面会显示空行. 此时你可输入内容.比如我们输入Unix, Linux, Windows and MacOS. 输入完成后, **按Ctrl-D**存盘退出cat. 此时你会发现当前文件夹下会生成一个包含你刚才输入内容的叫 **operating_system**的文件.
|
||||
当你输入cat > operating_system,它会生成一个operating_system的文件。然后下面会显示空行。此时你可输入内容。比如我们输入Unix, Linux, Windows 和 MacOS, 输入完成后,按**Ctrl-D**存盘退出cat。此时你会发现当前文件夹下会生成一个包含你刚才输入内容的叫 **operating_system**的文件。
|
||||
|
||||
### 12.向文件中追加内容 ###
|
||||
|
||||
当你两次使用 >符时, 会将第一个文件中的内容追加到第二个文件的末尾. 举例 :
|
||||
当你使用两个 > 符时, 会将第一个文件中的内容追加到第二个文件的末尾。 举例 :
|
||||
|
||||
# cat /root/linux >> /root/desktop
|
||||
|
||||
# cat /root/desktop
|
||||
|
||||
它会将 /root/linux的内容追加到/root/desktop文件的末尾
|
||||
它会将 /root/linux的内容追加到/root/desktop文件的末尾。
|
||||
|
||||
第二个文件的内容将会变成这样:
|
||||
|
||||
gnome
|
||||
@ -181,7 +181,7 @@ Linux下有多种方法新建文件. 其中使用cat就是方法之一.
|
||||
|
||||
# cat < /root/linux
|
||||
|
||||
上面命令表示 /root/linux中的内容作为cat的输入. 屏幕上显示如下 :
|
||||
上面命令表示 /root/linux中的内容作为cat的输入。屏幕上显示如下 :
|
||||
|
||||
ubuntu
|
||||
centos
|
||||
145
published/How To Display And Set Hostname in Linux.md
Normal file
145
published/How To Display And Set Hostname in Linux.md
Normal file
@ -0,0 +1,145 @@
|
||||
如何在Linux中显示和设置主机名
|
||||
================================================================================
|
||||

|
||||
|
||||
随着连接到网络的计算机数量越来越多,每一台计算机都需要有一个属性来区别于其它计算机。和现实世界中的人一样,计算机也有一个叫做hostname(主机名)的属性。
|
||||
|
||||
### 什么是hostname ###
|
||||
|
||||
从它的操作手册来看,hostname是用来显示系统的DNS名字以及为了显示和设置它的主机名或者NIS域名名字。所以hostname依赖于DNS(Domain Name System域名系统)或者NIS(Network Information System网络信息系统)。
|
||||
|
||||
|
||||
### 怎么显示hostname ###
|
||||
|
||||
hostname是为每一个linux发行版的预安装命令。通过在控制台输入hostname,可以显示你的机器的hostname。这里有一个有个简单的命令及其输出。
|
||||
|
||||
|
||||
$ hostname
|
||||
ubuntu
|
||||
|
||||
上面的命令将会告诉你,计算机的名字是**ubuntu** 。
|
||||
|
||||
|
||||
### 如何设置hostname ###
|
||||
|
||||
Hostname是在你第一次安装Linux的时候设置。其中有一个步骤Linux会让你输入主机名称的信息。不过,如果你愿意的话,你在之后设置也可以。
|
||||
|
||||
设置你的hostname,你可以使用下面的命令:
|
||||
|
||||
# hostname dev-machine
|
||||
|
||||
$ hostname
|
||||
dev-machine
|
||||
|
||||
你**需要使用root权限**,或者等同root的权限来设置/修改你计算机的主机名。“#”标识证明你是root用户。上述命令把你的计算机主机名设置成为**dev-machine**。如果你没有收到任何报错信息,那么你的hostname已经改变了。再一次使用hostname命令检查,看看结果。
|
||||
|
||||
使用hostname命令设置你的hostname **不是永久的** 。当你重启你的计算机,你的设定将会失效。 **为了永久改变** ,你必须手动修改hostname配置文件。
|
||||
|
||||
**Debian / Ubuntu系的Linux**
|
||||
|
||||
你可以在 **/etc/hostname** 和 **/etc/hosts** 文件夹中找到这个文件
|
||||
|
||||
下面是每一个文件的内容
|
||||
|
||||
**/etc/hostname**
|
||||
|
||||
# vi /etc/hostname
|
||||
dev-machine
|
||||
|
||||
**/etc/hosts**
|
||||
|
||||
# vi /etc/hosts
|
||||
127.0.0.1 localhost
|
||||
127.0.0.1 dev-machine
|
||||
|
||||
你将会发现不用重启你的linux它就即刻生效。
|
||||
|
||||
**RedHat / CentOS系的Linux**
|
||||
|
||||
你可以在 **/etc/hosts** 和 **/etc/sysconfig/networks** 文件夹中找到这个文件。
|
||||
|
||||
下面是每一个文件的内容
|
||||
|
||||
**/etc/hosts**
|
||||
|
||||
127.0.0.1 localhost.localdomain localhost dev-machine
|
||||
::localhost 127.0.0.1
|
||||
|
||||
**/etc/sysconfig/network**
|
||||
|
||||
NETWORKING=yes
|
||||
NETWORKING_IPV6=no
|
||||
HOSTNAME=dev-machine
|
||||
|
||||
### 怎么显示DNS域名 ###
|
||||
|
||||
来自上面的hostname的定义,hostname也可以显示你的Linux的DNS名字。如果你的hostname命令会显示你的hostname,那么dnsdomainname命令也就会显示你的域名。来看看这个简单的例子。
|
||||
|
||||
$ dnsdomainname
|
||||
bris.co.id
|
||||
|
||||
在本篇文章,dnsdomainname命令的结果是 **bris.co.id**。
|
||||
|
||||
如果你看见结果是 (**none**),那么你的机器**没有配置FQDN(Fully Qualified Domain Name 完全符合标准的域名)** 。dnsdomainname命令摘取来自**/etc/hosts**文件的信息。你应该配置它为FQDN格式。下面是一个简单的例子:
|
||||
|
||||
**/etc/hosts**
|
||||
|
||||
127.0.0.1 localhost.localdomain localhost dev-machine
|
||||
::localhost 127.0.0.1
|
||||
192.168.0.104 dev-machine.bris.co.id dev-machine
|
||||
|
||||
为了显示更多的细节,你可以使用参数**-v**
|
||||
|
||||
$ dnsdomainname -v
|
||||
gethostname()=’dev-machine.bris.co.id’
|
||||
Resolving ‘dev-machine.bris.co.id’ …
|
||||
Result: h_name=’dev-machine.bris.co.id’
|
||||
Result: h_aliases=’dev-machine’
|
||||
Result: h_addr_list=’192.168.0.104’
|
||||
|
||||
### 如何显示hostname的更多细节信息###
|
||||
|
||||
Hostname命令可以使用多个参数和一些别名,比如dnsdomainname命令就是它的一个别名。这些参数在每日操作中是有用的。下面这些命令的结果是基于**/etc/hosts**的上述配置。
|
||||
|
||||
**显示IP地址**
|
||||
|
||||
$ hostname -i
|
||||
192.168.0.104
|
||||
|
||||
**显示域名**
|
||||
|
||||
$ hostname -d
|
||||
bris.co.id
|
||||
|
||||
**显示短主机名**
|
||||
$ hostname -s
|
||||
dev-machine
|
||||
|
||||
*这个命令将会产生与只输入hostname同样的结果*
|
||||
|
||||
**显示FQDN格式**
|
||||
|
||||
$ hostname -f
|
||||
dev-machine.bris.co.id
|
||||
|
||||
**显示细节信息**
|
||||
|
||||
所有的参数包括上述信息,都可以通过使用参数**-v** 和 **-d** 来概括。让我们来看一个例子。
|
||||
|
||||
$ hostname -v -d
|
||||
gethostname()=’dev-machine.bris.co.id’
|
||||
Resolving ‘dev-machine.bris.co.id’ …
|
||||
Result: h_name=’dev-machine.bris.co.id’
|
||||
Result: h_aliases=’dev-machine’
|
||||
Result: h_addr_list=’192.168.0.104’
|
||||
bris.co.id
|
||||
|
||||
觉得熟悉吗?没错,运行结果与上面提到的 **dnsdomainname -v** 命令式相同的。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/linux-command/display-set-hostname-linux/
|
||||
|
||||
译者:[Vic___](http://blog.csdn.net/Vic___) 校对:[Caroline](https://github.com/carolinewuyan)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
@ -0,0 +1,154 @@
|
||||
如何使用Reaver破解Wi-Fi网络的WPA密码
|
||||
================================================================================
|
||||

|
||||
|
||||
Wi-Fi网络能够让我们便利地访问因特网,但同时,我们又不希望隔壁抠门猥琐男总是蹭我们的网,所以自然要给WiFi加个密码,对吧?于是,好消息是,也许你已经看过我的另一篇文章,“[如何轻易破解WEP密码][1]”,所以你使用了更稳固的WPA安全协议。
|
||||
|
||||
但坏消息是,现在有一款自由开源新工具——[Reaver][2],已经挖掘出了无线路由器的一个漏洞,由此能够破解绝大多数路由器上的密码。今天,我就来一步步介绍,如何使用Reaver破解WPA/WPA2密码。最后我会给出相应的防范对策。
|
||||
|
||||
文章的第一部分,是使用Reaver破解WPA的详细步骤,读者可以看视频,也可以跟着下面的文字一起做。然后,我会解释Reaver的工作原理。最后,介绍如何防范Reaver攻击。
|
||||
|
||||
[http://www.youtube.com/embed/z1c1OIMbmb0?wmode=transparent&rel=0&autohide=1&showinfo=0&enablejsapi=1][3]
|
||||
|
||||
在正式开始之前,我还是要不厌其烦强调一下:知识就是力量,但是拥有力量不代表着可以为所欲为、触犯法律。同样,骑白马的不一定是王子,会开锁的也不一定是小偷。本文只是关于某些技术的实验与验证,只适用于学习。你知道的越多,就能够越好的保护自己。
|
||||
|
||||
###准备工作###
|
||||
|
||||
首先,无需成为一名网络专家,学会使用复杂的命令行工具,你只需要准备一张空白DVD、一台能连接WiFi的电脑,并腾出几个小时时间,这就是我们基本需要的东西。要安装Reaver,可以有很多方法,但是这里我们建议你按照下面的指南来做:
|
||||
|
||||

|
||||
|
||||
- [**The BackTrack 5 Live DVD**][4]。BackTrack是一款支持自启动的Linux发行版,上面集成了大量的网络测试工具。虽然这对于安装、配置Reaver并不是必需的一个条件,但是对于大多数用户却是最简单一个方法。从[BackTrack的下载页面(传送门)][5]下载Live DVD,然后刻盘。这里你也可以下载镜像然后使用VMware安装,如果你不知道VMware是啥,额,那就还是刻盘吧。如图所示,下载的时候,下拉菜单选择BackTrack 5 R3版本、Gnome环境、根据你的CPU选择32或64位系统(如果这里不确定是32还是64,为了保险起见,请选择32位),下载类型选择ISO,然后就可以点击下载了。
|
||||
|
||||
- **配有DVD光驱、支持WiFi的电脑**。BackTrack支持大多数的笔记本无线网卡,这一点对于大多数读者应该没什么问题。同时,你的电脑需要有一个DVD光驱,这样才能从BackTrack光盘启动。我的测试环境是一台用了6年的MacBook Pro。
|
||||
|
||||
- **附近要有采用WPA加密的WiFi网络**。没WiFi网,你破解谁去 =。= ……一会我会在“Reaver的工作原理部分”介绍,WiFi防护设置是如何产生安全漏洞、WPA破解是如何成为可能的。
|
||||
|
||||
- **最后,你还需要一点点的耐心**。这是整个实验的最后一步,使用Reaver破解WPA密码并不难,它采用的是暴力破解,因此,你的电脑将会测试大量不同的密码组合,来尝试破解路由器,直到最终找到正确的密码。我测试的时候,Reaver花了大概两个半小时破解了我的WiFi密码。[Reaver的主页][6]上介绍,一般这个时间在4到10个小时之间,视具体情况而定。
|
||||
|
||||
###让我们开始吧###
|
||||
|
||||
此时,你应该已经把BackTrack的DVD光盘刻录好了,笔记本也应该已经准备就绪。
|
||||
|
||||
####第1步:启动BackTrack####
|
||||
|
||||
要启动BackTrack,只需将DVD放入光驱,电脑从光盘启动。(如果不知道如何使用live CD或DVD启动,请自行Google。)启动过程中,BackTrack会让你选择启动模式,选择默认的“BackTrack Text - Default Boot Text Mode”然后回车。
|
||||
|
||||
最终BackTrack会来到一个命令行界面,键入`startx`,回车,BackTrack就会进入它的图形界面。
|
||||
|
||||
####第2步:安装Reaver####
|
||||
|
||||
(文章更新:Reaver在R3版中已经预装,如果你安装的是BT5的R3版,这一步骤可以忽略,直接跳到第3步。)
|
||||
|
||||
Reaver已经加入了BackTrack的最新版软件包,只是还没有集成到live DVD里,所以,在本文最初撰写的时候,你还需要手动安装Reaver。要安装Reaver,首先设置电脑联网。
|
||||
|
||||
1.点击Applications > Internet > Wicd Network Manager
|
||||
2.选择你的网络并点击Connect,如果需要的话,键入密码,点击OK,然后再次点击Connect。
|
||||
|
||||
连上网以后,安装Reaver。点击菜单栏里的终端按钮(或者依次点击 Applications > Accessories > Terminal)。在终端界面,键入以下命令:
|
||||
|
||||
apt-get update
|
||||
|
||||
更新完成之后,键入:
|
||||
|
||||
apt-get install reaver
|
||||
|
||||
如果一切顺利,Reaver现在应该已经安装好了。如果你刚才的下载安装操作使用的是WiFi上网,那么在继续下面的操作之前,请先断开网络连接,并假装不知道WiFi密码 =。= 接下来我们要准备破解它~
|
||||
|
||||
####第3步:搜集设备信息,准备破解####
|
||||
|
||||
在使用Reaver之前,你需要获取你无线网卡的接口名称、路由的BSSID(BSSID是一个由字母和数字组成的序列,用于作为路由器的唯一标识)、以及确保你的无线网卡处于监控模式。具体参见以下步骤。
|
||||
|
||||
**找到无线网卡:**在终端里,键入:
|
||||
|
||||
iwconfig
|
||||
|
||||
回车。此时你应该看到无线设备的相关信息。一般,名字叫做`wlan0`,但如果你的机子不止一个无线网卡,或者使用的是不常见的网络设备,名字可能会有所不同。
|
||||
|
||||

|
||||
|
||||
**将无线网卡设置为监控模式**:假设你的无线网卡接口名称为`wlan0`,执行下列命令,将无线网卡设置为监控模式:
|
||||
|
||||
airmon-ng start wlan0
|
||||
|
||||
这一命令将会输出监控模式接口的名称,如下图中箭头所示,一般情况下,都叫做`mon0`。
|
||||
|
||||

|
||||
|
||||
**找到你打算破解的路由器的BSSID**:最后,你需要获取路由器的唯一标识,以便Reaver指向要破解的目标。执行以下命令:
|
||||
|
||||
airodump-ng wlan0
|
||||
|
||||
(注意:如果`airodump-ng wlan0`命令执行失败,可以尝试对监控接口执行,例如`airodump-ng mon0`)
|
||||
|
||||
此时,你将看到屏幕上列出周围一定范围内的无线网络,如下图所示:
|
||||
|
||||

|
||||
|
||||
当看到你想要破解的网络时,按下Ctrl+C,停止列表刷新,然后复制该网络的BSSID(图中左侧字母、数字和分号组成的序列)。从ENC这一列可以看出,该网络是WPA或WPA2协议。(如果为WEP协议,可以参考我的[前一篇文章——WEP密码破解指南][7])
|
||||
|
||||
现在,手里有了BSSID和监控接口的名称,万事俱备,只欠破解了。
|
||||
|
||||
####第4步:使用Reaver破解无线网络的WPA密码####
|
||||
|
||||
在终端中执行下列命令,用你实际获取到的BSSID替换命令中的 `bssid` :
|
||||
|
||||
reaver -i moninterface -b bssid -vv
|
||||
|
||||
例如,如果你和我一样,监控接口都叫做 `mon0`,并且你要破解的路由器BSSID是`8D:AE:9D:65:1F:B2`,那么命令应该是下面这个样子:
|
||||
|
||||
reaver -i mon0 -b 8D:AE:9D:65:1F:B2 -vv
|
||||
|
||||
最后,回车!接下来,就是喝喝茶、发发呆,等待Reaver魔法的发生。Reaver将会通过暴力破解,尝试一系列PIN码,这将会持续一段时间,在我的测试中,Reaver花了2个半小时破解网络,得出正确密码。正如前文中提到过的,Reaver的文档号称这个时间一般在4到10个小时之间,因此根据实际情况不同,这个时间也会有所变化。当Reaver的破解完成时,它看起来是下图中这个样子:
|
||||
|
||||

|
||||
|
||||
**一些要强调的事实**:Reaver在我的测试中工作良好,但是并非所有的路由器都能顺利破解(后文会具体介绍)。并且,你要破解的路由器需要有一个相对较强的信号,否则Reaver很难正常工作,可能会出现其他一些意想不到的问题。整个过程中,Reaver可能有时会出现超时、PIN码死循环等问题。一般我都不管它们,只是保持电脑尽量靠近路由器,Reaver最终会自行处理这些问题。
|
||||
|
||||
除此以外,你可以在Reaver运行的任意时候按下Ctrl+C中断工作。这样会退出程序,但是Reaver下次启动的时候会自动恢复继续之前的工作,前提是只要你没有关闭或重启电脑(如果你直接在live DVD里运行,关闭之前的工作都会丢失)。
|
||||
|
||||
###Reaver的工作原理###
|
||||
|
||||
你已经学会了使用Reaver,现在,让我们简单了解一下Reaver的工作原理。它利用了WiFi保护设置(WiFi Protected Setup - 下文中简称为WPS)的一个弱点,WPS是许多路由器上都有的一个功能,可以为用户提供简单的配置过程,它与设备中硬编码保存的一个PIN码绑定在一起。Reaver利用的就是PIN码的一个缺陷,最终的结果就是,只要有足够的时间,它就能破解WPA或WPA2的密码。
|
||||
|
||||
关于这个缺陷的具体细节,参看[Sean Gallagher's excellent post on Ars Technica][8]。
|
||||
|
||||
###如何防范Reaver攻击###
|
||||
|
||||
该缺陷存在于WPS的实现过程中,因此,如果能够关闭WPS,WiFi就是安全的(或者,更好的情况是,你的路由器天生就木有这一功能)。但不幸的是,正如Gallagher[在Ars的文章中所指出的][9],即使在路由器设置中人为关掉了WPS,Reaver仍然能够破解其密码。
|
||||
|
||||
> 在一次电话通话中,Craig Heffner说道,很多路由器即使关闭WPS都无法有效防范攻击。他和同事一起测试过,所有的Linksys和Cisco Valet无线路由器都是如此。“在所有的Linksys路由器上,你甚至无法手动关闭WPS,”他说,尽管Web界面中有关闭WPS配置的按钮,但是“它仍然会自动打开,极易受到攻击”。
|
||||
|
||||
因此,方法一:失败!。也许你可以亲自尝试把你的路由器WPS关闭,然后测试一下Reaver是否还能成功破解。
|
||||
|
||||
你也可以在路由器中设置一下MAC地址过滤(只允许指定的白名单设备连接你的网络),但是有经验的黑客还是能够检测出设备的白名单MAC地址,并使用MAC地址仿冒你的计算机。
|
||||
|
||||
方法二:失败!那到底该怎么办?
|
||||
|
||||
我的建议是,我曾经在我的路由器上安装了开源路由固件[DD-WRT][10],成功防御了Reaver攻击。因为,[DD-WRT天生就是不支持WPS的][11],因此,这成为了又一个我热爱自由软件的原因。如果你也对DD-WRT感兴趣,可以看一下这里的[设备支持列表][12],看是否支持你的路由器设备。除了安全上的升级,DD-WRT还可以[监控网络行为][13],[设置网络驱动器][14],[拦截广告][15],[增强WiFi信号范围][16]等,它完全可以[让你60美刀的路由器发挥出600美刀路由器的水平][17]!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://lifehacker.com/5873407/how-to-crack-a-wi+fi-networks-wpa-password-with-reaver
|
||||
|
||||
译者:[Mr小眼儿](http://blog.csdn.net/tinyeyeser) 校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://lifehacker.com/5305094/how-to-crack-a-wi+fi-networks-wep-password-with-backtrack
|
||||
[2]:http://code.google.com/p/reaver-wps/
|
||||
[3]:http://www.youtube.com/embed/z1c1OIMbmb0?wmode=transparent&rel=0&autohide=1&showinfo=0&enablejsapi=1
|
||||
[4]:http://www.backtrack-linux.org/downloads/
|
||||
[5]:http://www.backtrack-linux.org/downloads/
|
||||
[6]:http://code.google.com/p/reaver-wps/
|
||||
[7]:http://lifehacker.com/5305094/how-to-crack-a-wi+fi-networks-wep-password-with-backtrack
|
||||
[8]:http://arstechnica.com/business/news/2011/12/researchers-publish-open-source-tool-for-hacking-wifi-protected-setup.ars
|
||||
[9]:http://arstechnica.com/business/news/2012/01/hands-on-hacking-wifi-protected-setup-with-reaver.ars
|
||||
[10]:http://dd-wrt.com/
|
||||
[11]:http://code.google.com/p/reaver-wps/issues/detail?id=44
|
||||
[12]:http://dd-wrt.com/wiki/index.php/Supported_Devices
|
||||
[13]:http://lifehacker.com/5821773/how-to-monitor-your-internet-usage-so-you-dont-exceed-your-data-cap
|
||||
[14]:http://lifehacker.com/5756233/get-more-out-of-your-dd+wrt-router-with-an-external-drive?tag=ddwrt
|
||||
[15]:http://lifehacker.com/5680670/turn-your-dd+wrt-enabled-router-into-a-whole-house-ad-blocker?tag=ddwrt
|
||||
[16]:http://lifehacker.com/5563196/turn-your-old-router-into-a-range+boosting-wi+fi-repeater?tag=ddwrt
|
||||
[17]:http://lifehacker.com/178132/hack-attack-turn-your-60-router-into-a-600-router
|
||||
@ -11,6 +11,7 @@
|
||||
不久前,Adobe公司成了网络攻击者的目标。Adobe公司的安全团队发现了一起针对Adobe公司内部网络的复杂攻击,攻击获取了Adobe公司的客户信息并盗取了数个Adobe公司产品的源代码。根据Adobe公司官方博客上的安全告示,攻击者盗取了Adobe用户的账户ID以及登录密码。但是Adobe公司的安全团队并不认为与账户关联的信用卡信息或者资金账户信息会一并被盗取。
|
||||
|
||||
你可以点击[这儿][3]阅读更多相关的安全公告。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.unixmen.com/play-crossword-game-adobes-leaked-passwords/
|
||||
@ -62,19 +62,19 @@ SBackup 可在 Ubuntu、Linux Mint 和 Debian 的默认仓库中获得,所以
|
||||
|
||||

|
||||
|
||||
### General ###
|
||||
#### General选项卡 ####
|
||||
|
||||
在 General 选项内,你可以选择多久进行一次完整备份,默认是7天。每7天 SBackup 将会进行一次完整的备份。你也可以选择备份的压缩格式。
|
||||
|
||||

|
||||
|
||||
### Include ###
|
||||
#### Include选项卡 ####
|
||||
|
||||
这个选项不需要解释太多,你可以添加 SBackup 要备份的文件或目录。这里可以选择备份单独的文件或者完整的目录,我删除了所有的目录仅仅保留了“Resume”
|
||||
|
||||

|
||||
|
||||
### Exclude ###
|
||||
#### Exclude选项卡 ####
|
||||
|
||||
如同 Include 选项,我们可以选择备份时排除的文档和目录,只需要选择要排除的文档和目录的路径即可。在默认配置下,/media, /var/run/, /var/cache/, /var/spool/ 和 /vat/tmp/ 目录均被排除
|
||||
|
||||
@ -92,7 +92,7 @@ SBackup 可在 Ubuntu、Linux Mint 和 Debian 的默认仓库中获得,所以
|
||||
|
||||

|
||||
|
||||
### Destination ###
|
||||
#### Destination选项卡 ####
|
||||
|
||||
在这里你可以选择备份存放的路径,正如我之前提到的,你可以把备份的文档或文件夹存放在硬盘或者远程的 FTP 或 NAS。这里我将把备份保存在 /home/sk/My Backup 目录下。
|
||||
|
||||
@ -100,7 +100,7 @@ SBackup 可在 Ubuntu、Linux Mint 和 Debian 的默认仓库中获得,所以
|
||||
|
||||
**提示:** 在备份前确认目录有足够的空间保存备份文件
|
||||
|
||||
### Schedule ###
|
||||
#### Schedule选项卡 ####
|
||||
|
||||
在这个选项中,你可以设定具体的备份时间。点击 **Simple** 选项,可以按每小时、每日、每周、每月来设置你的计划备份时间。
|
||||
|
||||
@ -114,13 +114,13 @@ SBackup 可在 Ubuntu、Linux Mint 和 Debian 的默认仓库中获得,所以
|
||||
|
||||
lrwxrwxrwx 1 root root 33 Nov 8 15:34 /etc/cron.daily/sbackup -> /usr/share/sbackup/sbackup-launch
|
||||
|
||||
### Purging ###
|
||||
#### Purging选项卡 ####
|
||||
|
||||
在这个选项里,可以删除超过一定时间的备份文件。在默认配置下,超过30天的备份文件将被删除。
|
||||
|
||||

|
||||
|
||||
### Report ###
|
||||
#### Report选项卡 ####
|
||||
|
||||
Report 是最后一个选项卡,在这里你可以设置接收备份完成通知的邮箱。输入你的邮箱ID、SMTP服务地址、邮箱用户名、密码后,点击 Test mail settings。需要留意的是,在测试邮箱设置前,点击工具栏中的Save Configuration按钮保存你的配置。
|
||||
|
||||
@ -1,4 +1,3 @@
|
||||
[DONING]BY FingerLiu
|
||||
10 basic examples of linux netstat command
|
||||
================================================================================
|
||||
### Netstat ###
|
||||
|
||||
180
sources/Built in Audit Trail Tool – Last Command in Linux.md
Normal file
180
sources/Built in Audit Trail Tool – Last Command in Linux.md
Normal file
@ -0,0 +1,180 @@
|
||||
Built in Audit Trail Tool – Last Command in Linux
|
||||
================================================================================
|
||||

|
||||
|
||||
If you are working as a server administrator, you may understand that you have to protect your server. Not only from the outside, but you have to protect it from the inside. Linux has one built-in command to see who is the last logged in user into your server.
|
||||
|
||||
The command is **last**. This command is **very useful for audit trail**. Let’s start to see what can last to do for you.
|
||||
|
||||
### What is the function of Last command ###
|
||||
|
||||
**Last** display a list of all user logged in (and out) from **/var/log/wtmp** since the file was created. This file is binary file which cannot view by text editor such as Vi, Joe or another else. This trick is pretty smart because user (or root) can not modify the file as they want.
|
||||
|
||||
Last gives you information the name of all users logged in, its tty, IP Address (if the user doing a remote connection) date – time, and how long the user logged in.
|
||||
|
||||
### How to run Last ###
|
||||
|
||||
You just need to type **last** on your console. Here’s the sample :
|
||||
|
||||
$ last
|
||||
|
||||
leni pts/0 10.0.76.162 Mon Dec 2 12:32 - 13:25 (00:53)
|
||||
pungki tty1 Mon Dec 2 09:31 still logged in
|
||||
reboot system boot 2.6.32-358.23.2 Mon Dec 2 09:20 - 13:25 (04:05)
|
||||
|
||||
Here’s how to read last information :
|
||||
|
||||
- The first column tell who are the user
|
||||
- The second column give us information about how the user is connected
|
||||
|
||||
> pts/0 (pseudo terminal) means that the user connect via remote connections such as SSH or telnet
|
||||
>
|
||||
> tty (teletypewriter) means that the user connect via direct connection to the computer or local terminal
|
||||
>
|
||||
> Exception for reboot activity the status will be shown is system boot
|
||||
|
||||
- The third column **show where the user come from**. If the user connect from remote computer, you will see a hostname or an IP Address. If you see :0.0 or nothing it means that the user is connect via local terminal. Exception for reboot activity, the kernel version will be shown as the status
|
||||
- The remaining columns display **when the log activity has happened**. Numbers in the bracket tell us how many hours and minutes the connection was happened
|
||||
|
||||
### Some examples of Last command on day-to-day operation ###
|
||||
|
||||
#### Limit the number of line shown ####
|
||||
|
||||
When you have a lot of lines to show, you can limit how many lines do you want to see. Use **-n parameter** to do it.
|
||||
|
||||
$ last -n 3
|
||||
|
||||
leni pts/0 10.0.76.162 Mon Dec 2 12:32 - 13:25 (00:53)
|
||||
pungki tty1 Mon Dec 2 09:31 still logged in
|
||||
reboot system boot 2.6.32-358.23.2 Mon Dec 2 09:20 - 13:25 (04:05)
|
||||
|
||||
**-n parameter** will make last command to display 3 lines starting from the current time and backwards
|
||||
|
||||
#### Don’t display the hostname ####
|
||||
|
||||
Use **-R parameter** to do is. Here’s the sample :
|
||||
|
||||
$ last -R
|
||||
|
||||
leni pts/0 Mon Dec 2 12:32 - 13:25 (00:53)
|
||||
pungki tty1 Mon Dec 2 09:31 still logged in
|
||||
reboot system boot Mon Dec 2 09:20 - 13:25 (04:05)
|
||||
|
||||
As you see, now there is no information about hostname or IP Address
|
||||
|
||||
#### Display the hostname in the last column ####
|
||||
|
||||
To do this, we can use **-a parameter**
|
||||
|
||||
$ last -a
|
||||
|
||||
leni pts/0 Mon Dec 2 12:32 - 13:25 (00:53) 10.0.76.162
|
||||
pungki tty1 Mon Dec 2 09:31 still logged in :0.0
|
||||
reboot system boot Mon Dec 2 09:20 - 13:25 (04:05) 2.6.32-358.23.2.el6.i686
|
||||
|
||||
Now the hostname information such as 10.0.76.162 will be placed in the last column.
|
||||
|
||||
#### Print full login and logout time and dates ####
|
||||
|
||||
You can use **-F parameter** for this. Here’s a sample.
|
||||
|
||||
$ last -F
|
||||
|
||||
leni pts/0 10.0.76.162 Mon Dec 2 12:32:24 2013 – Mon Dec 2013 13:25:24 2013 (00:53)
|
||||
|
||||
#### Print specific user name ####
|
||||
|
||||
If you want to trace specific user, you can print it specifically. Put the name of user behind last command.
|
||||
|
||||
$ last leni
|
||||
|
||||
leni tty1 Mon Dec 2 18-42 still logged in
|
||||
leni pts/0 Mon Dec 2 12:32 - 13:25 (00:53) 10.0.76.162
|
||||
|
||||
Or if you want to know when **reboot** is done, you can also display it
|
||||
|
||||
$ last reboot
|
||||
|
||||
reboot system boot Mon Dec 2 09:20 - 16:55 (07:34)
|
||||
reboot system boot Sun Dec 1 04:26 - 04:27 (00:01)
|
||||
reboot system boot Wed Nov 27 20:27 - 01:24 (04:57)
|
||||
reboot system boot Tue Nov 26 21:06 - 06:13 (09:06)
|
||||
|
||||
#### Print spesific tty / pts ####
|
||||
|
||||
Last can also print information about specific tty / pts. Just put the tty name or pty name behind the last command. Here are some sample outputs :
|
||||
|
||||
$ last tty1
|
||||
|
||||
pungki tty1 Mon Dec 2 09:31 still logged in
|
||||
pungki tty1 Mon Dec 2 04:26 – down (00:00)
|
||||
pungki tty1 Mon Dec 2 04:07 – down (00:00)
|
||||
pungki tty1 Sun Dec 1 18:55 – 04:07 (09:12)
|
||||
|
||||
$ last pts/0
|
||||
|
||||
leni pts/0 10.0.76.162 Mon Dec 2 12:32 - 13:25 (00:53)
|
||||
pungki pts/0 :0.0 Wed Nov 27 20:28 – down (04:56)
|
||||
|
||||
When you see **down value** – such as the second line above – , it means that the user was logged in from specific time until the system is reboot or shutdown.
|
||||
|
||||
#### Use another file than /var/log/wtmp ####
|
||||
|
||||
By default, last command will parse information from **/var/log/wtmp**. If you want t**he last command** parse from another file, you can use **-f parameter**. For example, you may rotate the log after a certain condition. Let’s say the previous file is named **/var/log/wtmp.1** . Then the last command will be like this.
|
||||
|
||||
$ last -f /var/log/wtmp.1
|
||||
|
||||
#### Display the run level changes ####
|
||||
|
||||
There is **-x parameter** if you want to display run level changes. Here’s a sample output :
|
||||
|
||||
pungki tty1 Mon Dec 2 19:21 still logged in
|
||||
runlevel (to lvl 3) 2.6.32-358.23.2 Mon Dec 2 19:20 – 19:29 (00:08)
|
||||
reboot system boot 2.6.32-358.23.2 Mon Dec 2 19:20 – 19:29 (00:08)
|
||||
shutdown system down 2.6.32-358.23.2 Mon Dec 2 18:56 – 19:20 (00:23)
|
||||
runlevel (to lvl 0) 2.6.32-358.23.2 Mon Dec 2 18:56 – 18:56 (00:00)
|
||||
leni tty1 Mon Dec 2 18:42 – down (00:00)
|
||||
|
||||
You can see that there are two entries of run level. Runlevel which has **to lvl 3** entry means the system is running on full console mode. No active X Window or GUI. Meanwhile, when the system is **shutdown**, Linux us **run level 0**. That’s why last show you **to lvl 0** entry
|
||||
|
||||
#### View bad logins ####
|
||||
|
||||
While **last** command logs successful logins, then **lastb** command **record failed login attempts**. You **must have root** access to run lastb command. Here’s a sample output from lastb command. Lastb will parse information from /var/log/btmp.
|
||||
|
||||
# lastb
|
||||
|
||||
leni tty1 Mon Dec 2 22:12 – 22:12 (00:00)
|
||||
rahma tty1 Mon Dec 2 22:11 – 22:11 (00:00)
|
||||
|
||||
#### Rotate the logs ####
|
||||
|
||||
Since **/var/log/wtmp** record every single log in activities, the size of the file may grow quickly. By default, Linux will **rotate /var/log/wtmp** every month. The detail of rotation activity is put in /etc/logrotate.conf file. Here’s the content of my **/etc/logrotate.conf** file.
|
||||
|
||||
/var/log/wtmp {
|
||||
monthly
|
||||
create 0664 root umtp
|
||||
minsize 1M
|
||||
rotate 1
|
||||
}
|
||||
|
||||
And for **/var/log/btmp**, here’s default configuration of rotate activity
|
||||
|
||||
/var/log/btmp {
|
||||
missingok
|
||||
monthly
|
||||
create 0600 root umtp
|
||||
minsize 1M
|
||||
rotate 1
|
||||
}
|
||||
|
||||
### Conclusion ###
|
||||
|
||||
You can combine those parameters to custom the output of last and lastb. All parameter **which run on last** command, **also run on** lastb command. For more detail, please visit last manual page by typing **man last** on your console.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/linux-command/linux-last-command/
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
@ -0,0 +1,132 @@
|
||||
CentOS 6.5 desktop installation guide with screenshots
|
||||
================================================================================
|
||||
### CentOS 6.5 released ###
|
||||
|
||||
Following with the release of RHEL 6.5, [CentOS 6.5 has arrived][1] on 1st Dec and its time to play with it. For those who want to update their existing 6.4 systems to 6.5 simply use the "yum update" command and all the magic would be done.
|
||||
|
||||
CentOS 6.5 has received some package updates as well as new features. Check out the [release notes][2] for detailed information.
|
||||
|
||||
### Major updates ###
|
||||
|
||||
> The Precision Time Protocol - previously a technology preview - is now fully supported. The following drivers support network time stamping: bnx2x, tg3, e1000e, igb, ixgbe, and sfc.
|
||||
> OpenSSL has been updated to version 1.0.1.
|
||||
> OpenSSL and NSS now support TLS 1.1 and 1.2.
|
||||
> KVM received various enhancements. These include improved read-only support of VMDK- and VHDX-Files, CPU hot plugging and updated virt-v2v-/virt-p2v-conversion tools.
|
||||
> Hyper-V and VMware drivers have been updated.
|
||||
> Updates to Evolution (2.32) and Libre Office (4.0.4).
|
||||
|
||||
### Download ###
|
||||
|
||||
In this post we shall be installing it on the desktop. Head to either of the following urls
|
||||
|
||||
[http://isoredirect.centos.org/centos-6/6.5/isos/][3]
|
||||
[http://mirror.centos.org/centos/6.5/isos/][4]
|
||||
|
||||
Select your machine architecture and it will then present a list of mirrors. Get into any mirror and then get the torrent file to download or the direct iso download link. There are multiple download options available like LiveCD, LiveDVD, Dvd1+2, Minimal and Netinstall.
|
||||
|
||||
The minimal installer comes with a text based installer that would install CentOS with a shell and minimum software applications. Rest everything has to be installed from yum.
|
||||
|
||||
The LiveCD/LiveDVD provide the desktop and gui installer and installs the CentOS system but does not provide any package selection options.
|
||||
|
||||
The DvD1+2 set provide full set of all applications for those who need it.
|
||||
And the netinstall would actually download the installation image and then install.
|
||||
|
||||
In this post we shall use the LiveCD. It is around 650MB.
|
||||
Although CentOS is used mostly on servers, having a desktop system can help to create a gui based environment with a setup similar to your server. We shall be trying out the minimal and netinstall installation methods in another post.
|
||||
|
||||
### Install ###
|
||||
|
||||
So now, its time to install CentOS onto your desktop system. Use either the LiveDVD or LiveCD to get it up and running fast.
|
||||
|
||||
1. Put in the media and reboot. The boot menu will have many options with self explanatory names. Select Boot to get onto the Live desktop.
|
||||
|
||||
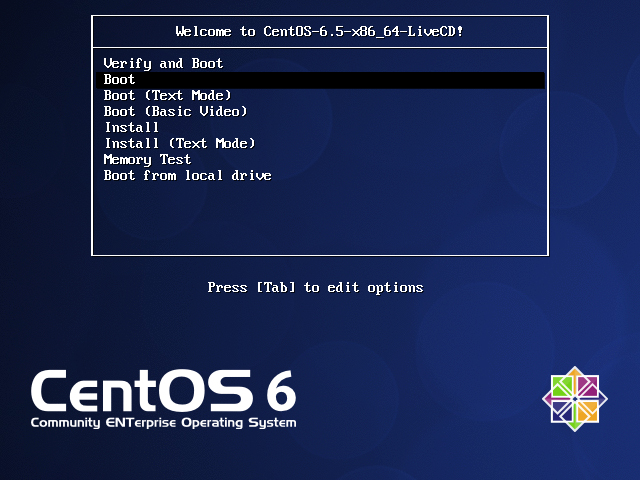
|
||||
|
||||
2. Double clicks the Install icon on the desktop, to start the Anaconda installer.
|
||||
|
||||
|
||||
|
||||
3. Click Next on the installer wizard.
|
||||
|
||||

|
||||
|
||||
4. **Keyboard layout** - The next step would ask you to select the keyboard layout which should be USA for most english users.
|
||||
|
||||

|
||||
|
||||
5. **Storage type** - After the keyboard layout, comes the option select the type of storage on which CentOS is to be installed. For local hard drives, its Basic storage.
|
||||
|
||||

|
||||
|
||||
6. **Hostname** - In the next step the anaconda installer asks for a hostname. So fill it appropriately. If not sure, just enter something like mypc or hplaptop.
|
||||
|
||||

|
||||
|
||||
7. **Timezone** - Then comes the timezone selection
|
||||
|
||||
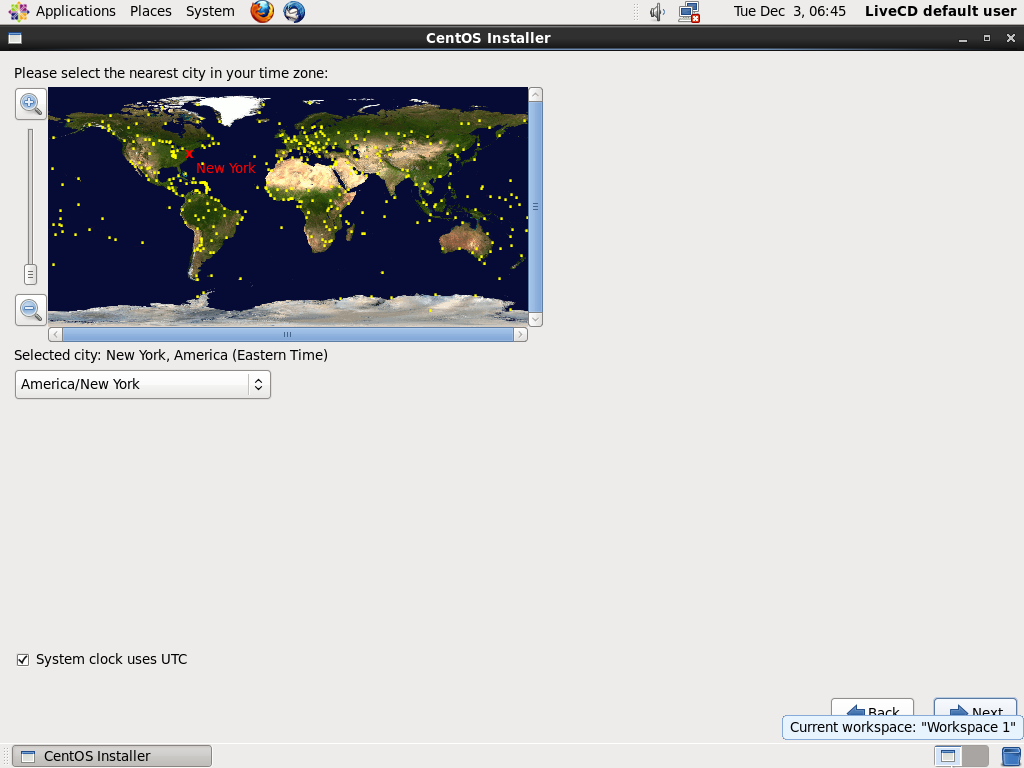
|
||||
|
||||
8. **Root Password** - Next in turn is the root password which, as you know should be a strong one.
|
||||
|
||||
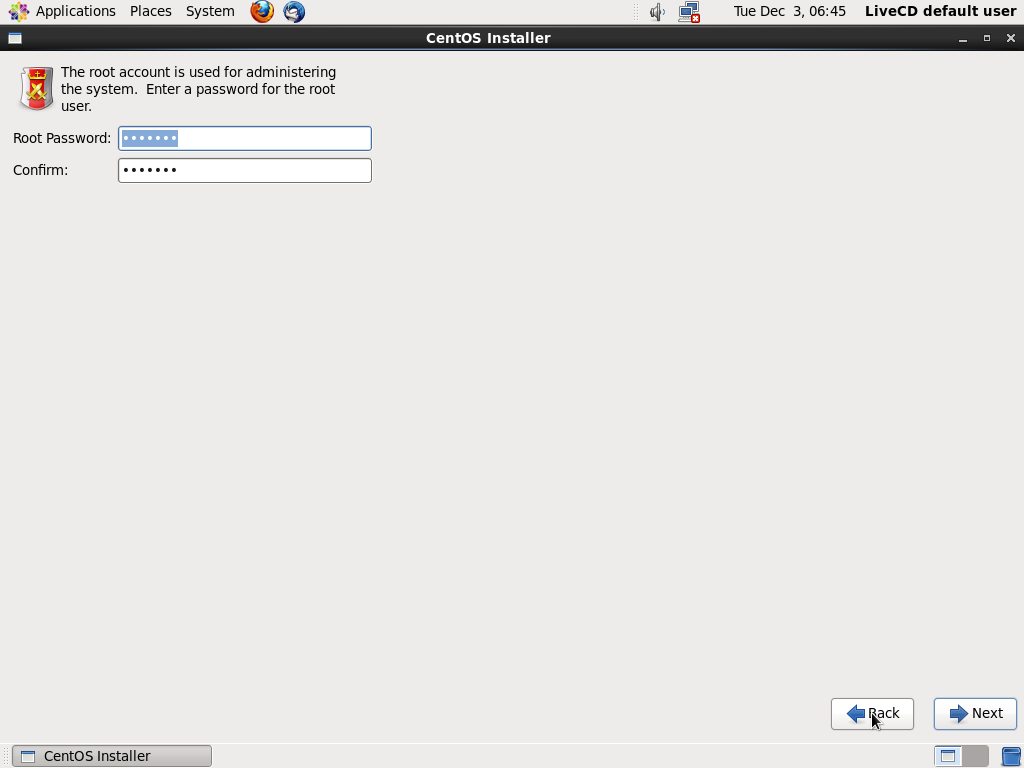
|
||||
|
||||
9. **Formatting** - Now the wizard would like to know, how you wan't to format the storage device. If you want to format the drive yourself, then select "Custom Layout" and create partitions as needed. For the sake of this tutorial we are selecting the first option, that is to use the entire device and let CentOS format it as it likes.
|
||||
|
||||
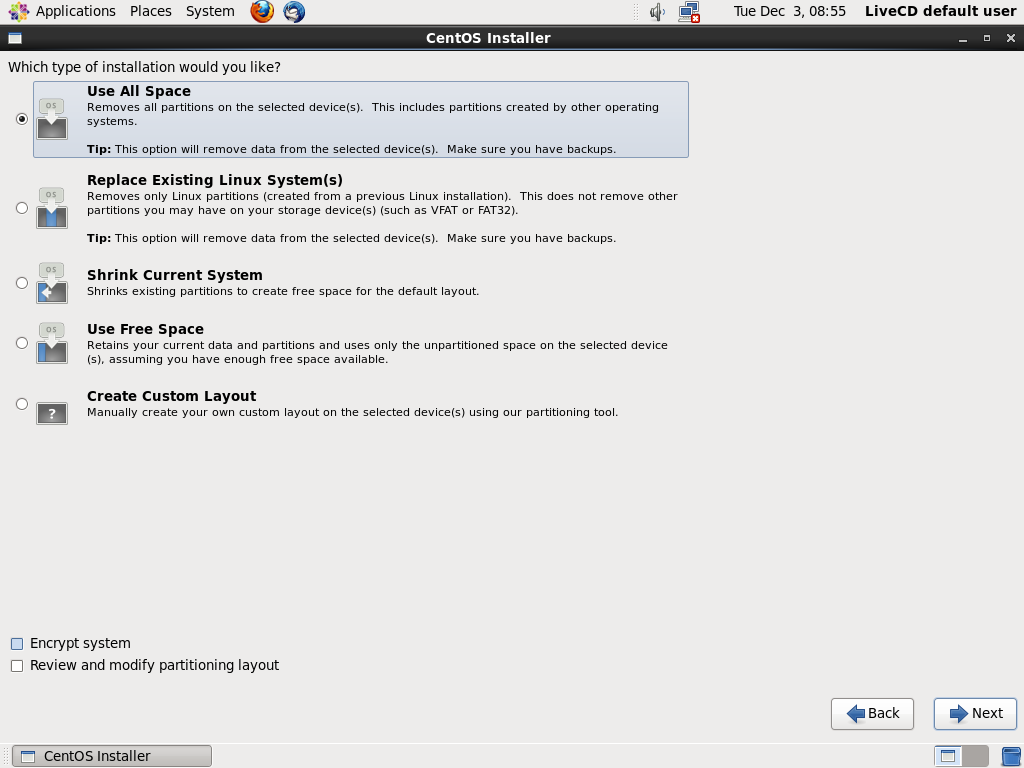
|
||||
|
||||
10. **Copying files** - Now the installer will start copying files. Nothing to do here except wait and watch. The LiveCD installer basically copies the CD image to the hard drive. You do not get any option to select packages to install or omit. Also the liveCD somes with a minimal collection of software and applications.
|
||||
|
||||

|
||||
|
||||
### Post install configuration ###
|
||||
|
||||
11. After the installation completes and reboots, the welcome wizard would come up which would further configure the system.
|
||||
|
||||

|
||||
|
||||
12. License Agreement - Like all software centos too comes with a license that is very minimal and only a few lines. So accept it.
|
||||
|
||||
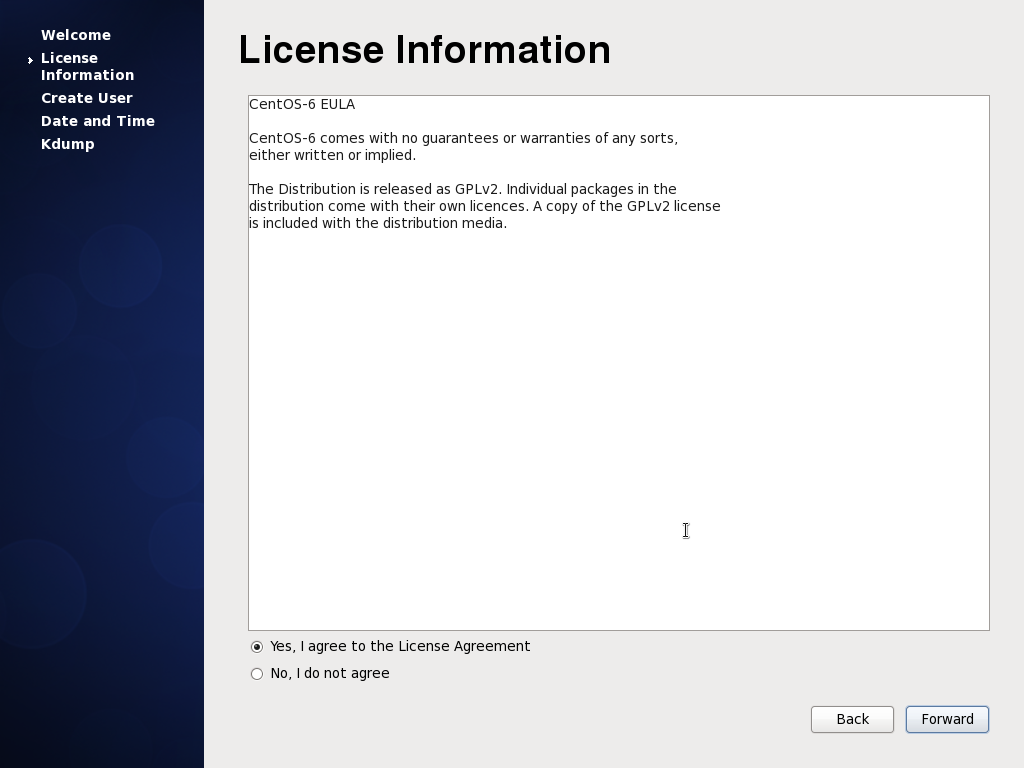
|
||||
|
||||
13. **Create User** - Now its time to create a user account for yourself to be able to use the system.
|
||||
|
||||
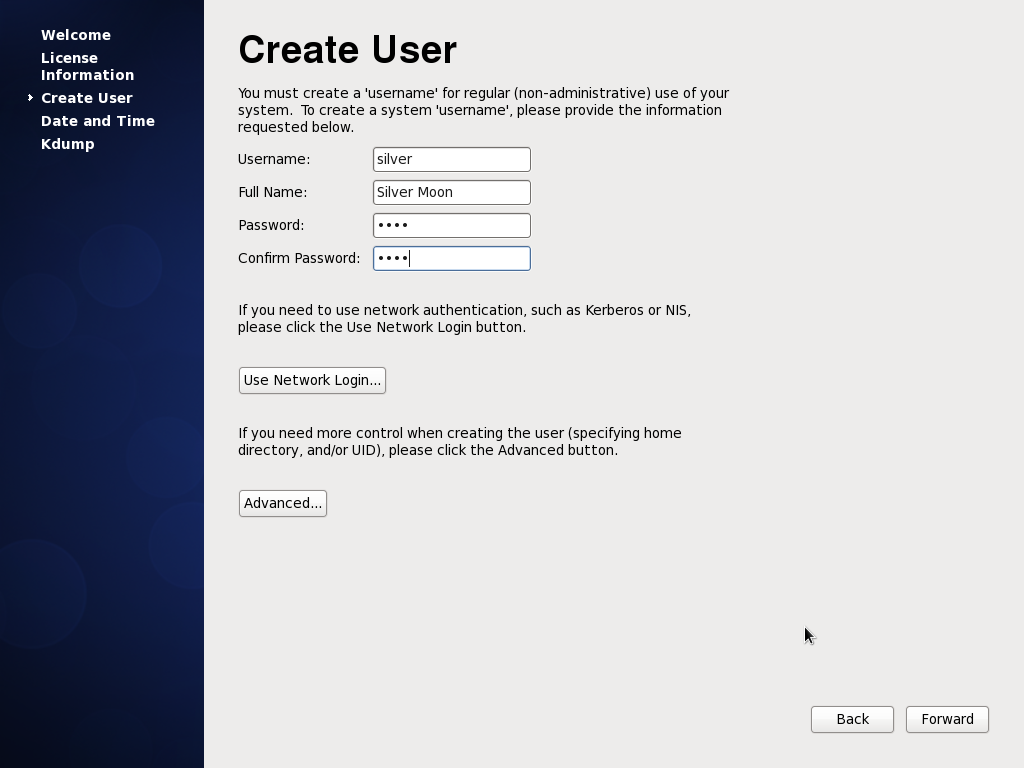
|
||||
|
||||
14. **Current date & time** - Now input the current date and time and select the option to synchronize over the network.
|
||||
|
||||
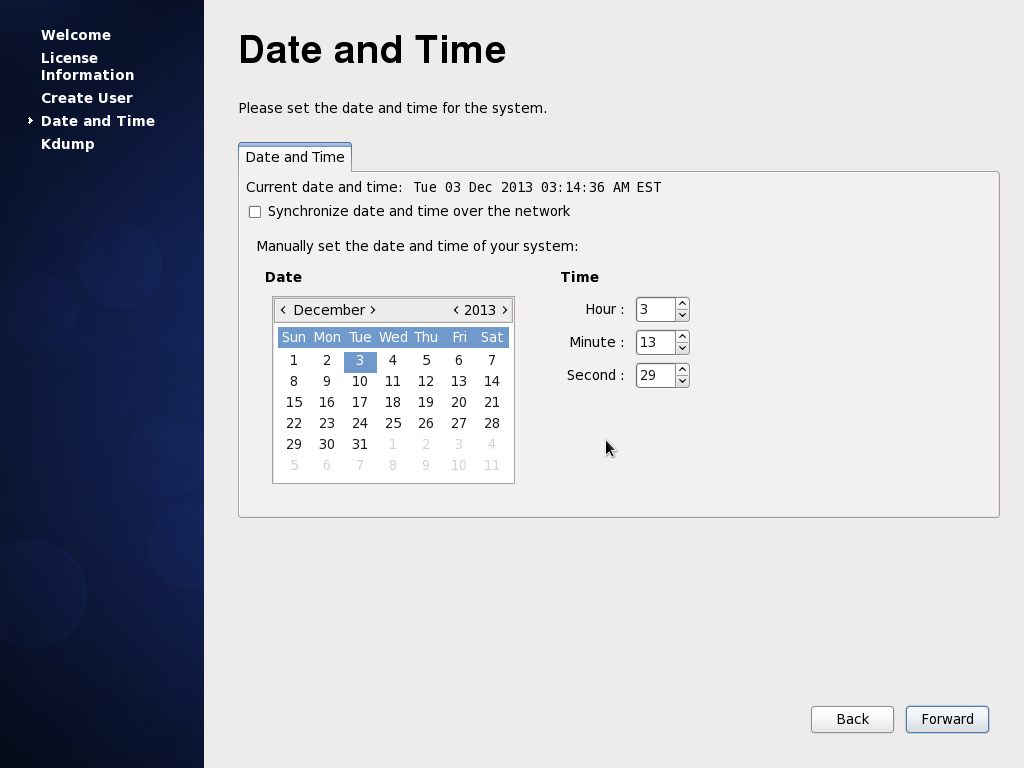
|
||||
|
||||
15. **Kdump** - This is the last step of the welcome wizard that asks whether kdump should be enabled or not. It is a good idea to enable it.
|
||||
|
||||
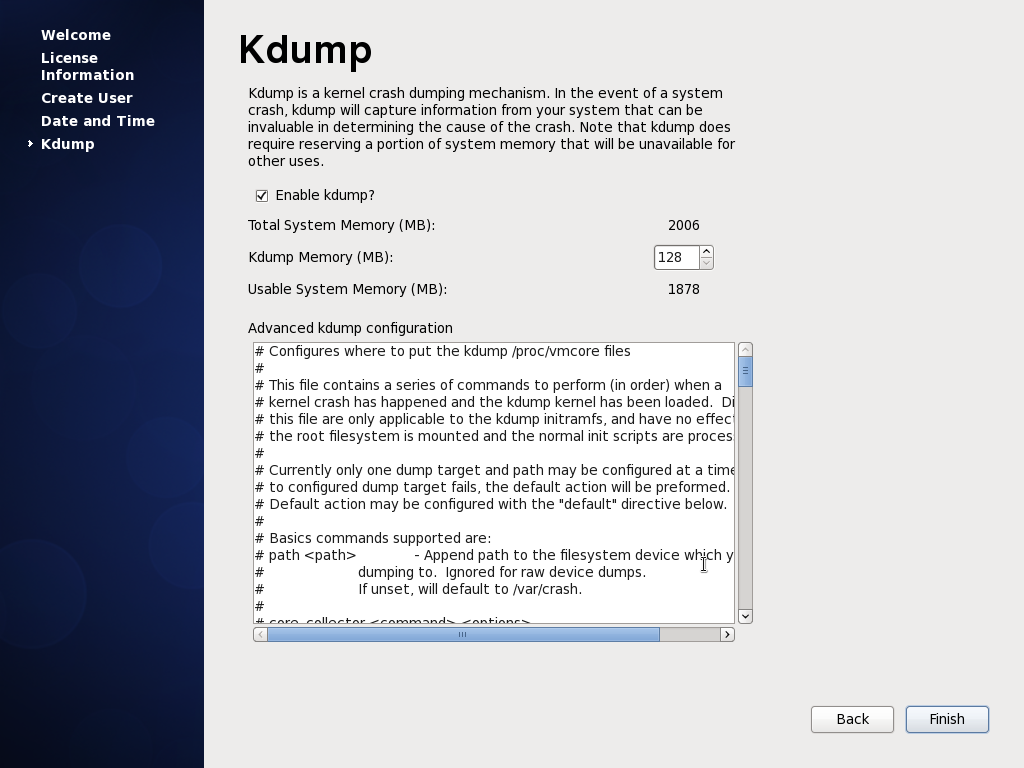
|
||||
|
||||
### Start CentOS 6.5 ###
|
||||
|
||||
After the previous step, the system would be rebooted, and finally comes the login page.
|
||||
|
||||
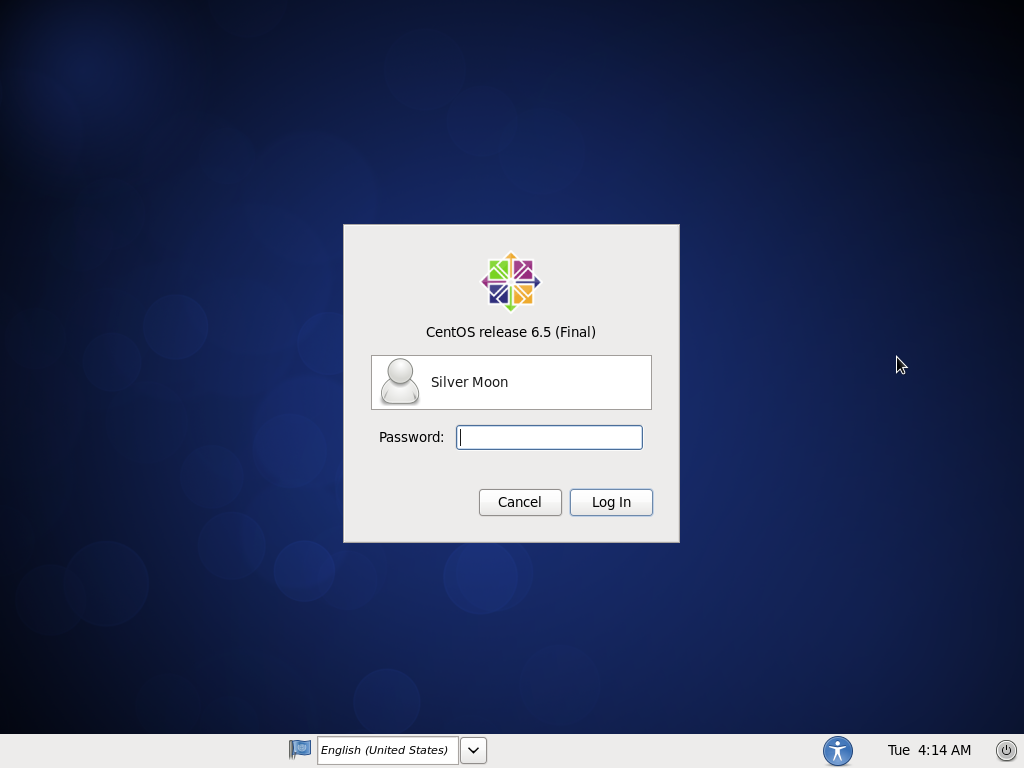
|
||||
|
||||
And after login comes the shiny new CentOS 6.5 desktop
|
||||
|
||||
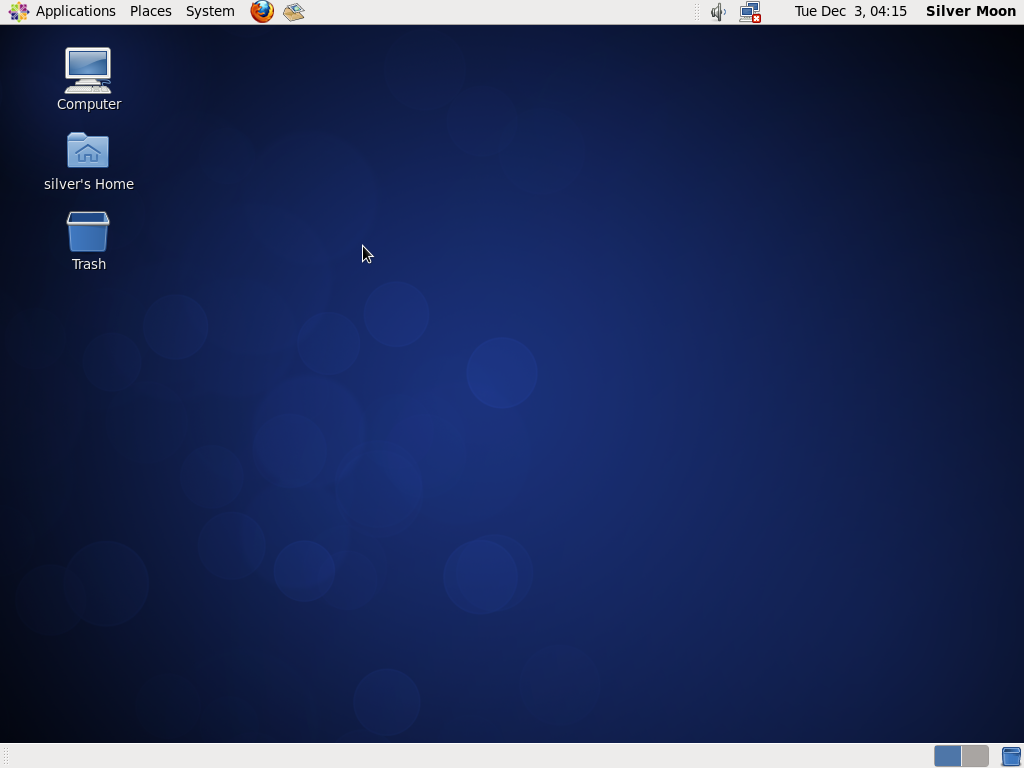
|
||||
|
||||
Hope you enjoyed reading the installation guide. Leave your comments and questions below.
|
||||
|
||||
### Resource ###
|
||||
|
||||
CentOS 6.5 release notes
|
||||
[http://wiki.centos.org/Manuals/ReleaseNotes/CentOS6.5][5]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.binarytides.com/centos-6-5-installation-screenshots/
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://lists.centos.org/pipermail/centos-announce/2013-December/020032.html
|
||||
[2]:http://wiki.centos.org/Manuals/ReleaseNotes/CentOS6.5
|
||||
[3]:http://isoredirect.centos.org/centos-6/6.5/isos/
|
||||
[4]:http://mirror.centos.org/centos/6.5/isos/
|
||||
[5]:http://wiki.centos.org/Manuals/ReleaseNotes/CentOS6.5
|
||||
@ -0,0 +1,72 @@
|
||||
Configure Your Browser To Use Tor On Ubuntu/Debian/Linux Mint
|
||||
================================================================================
|
||||
**Tor**, **T**he **O**nion **R**outer, is a network of Virtual Tunnels that allows users to communicate securely and as well as anonymously over Internet. Tor allows organizations and individuals to share information over public networks without compromising their privacy. We can use Tor to keep websites from tracking us and also our family members, or to connect to news sites, instant messaging services, or the websites which are blocked by the Internet providers and Network Administrators.
|
||||
|
||||
Tor was originally designed, implemented, and deployed as a third-generation [onion routing project of the U.S. Naval Research Laboratory][1]. It was originally developed with the U.S. Navy in mind, for the primary purpose of protecting government communications. Today, it is used every day for a wide variety of purposes by normal people, the military, journalists, law enforcement officers, activists, and many others.
|
||||
|
||||
In this quick how-to let us learn how to use Tor with our browsers. The steps provided here were tested on Ubuntu 13.04 Desktop, but it should work on all Debian/Ubuntu and its derivatives.
|
||||
|
||||
### Install Tor & Vidalia On Ubuntu / Debian / Linux Mint ###
|
||||
|
||||
Tor is available in the default repositories of Debian/Ubuntu, but they might be bit outdated. So add Tor repository to your distribution source lists.
|
||||
|
||||
Edit file **/etc/apt/sources.list**,
|
||||
|
||||
$ sudo nano /etc/apt/sources.list
|
||||
|
||||
Add the following lines depending upon your distribution version. As i am testing this on my Ubuntu 13.04 desktop, i added the following lines.
|
||||
|
||||
[...]
|
||||
deb http://deb.torproject.org/torproject.org raring main
|
||||
|
||||
Save and close the file. If you’re using Ubuntu 13.10, then the lines should be,
|
||||
|
||||
deb http://deb.torproject.org/torproject.org saucy main
|
||||
|
||||
For Debian 7 Wheezy,
|
||||
|
||||
deb http://deb.torproject.org/torproject.org wheezy main
|
||||
|
||||
Add the gpg key using following commands:
|
||||
|
||||
$ gpg --keyserver keys.gnupg.net --recv 886DDD89
|
||||
$ gpg --export A3C4F0F979CAA22CDBA8F512EE8CBC9E886DDD89 | sudo apt-key add -
|
||||
|
||||
Update the repository list and install vidalia using commands:
|
||||
|
||||
$ sudo apt-get update
|
||||
$ sudo apt-get install tor vidalia deb.torproject.org-keyring
|
||||
|
||||
During installation, you’ll be asked which user should be able to control Tor service. Select the user and click Ok.
|
||||
|
||||

|
||||
|
||||
Now Vidalia is installed and running.
|
||||
|
||||
### Configure Firefox Browser ###
|
||||
|
||||
Open your browser. Go to **Edit -> Preferences -> Advanced -> Network ->Settings**. Select manual Proxy Configuration. In the SOCKS Host column, enter **localhost** or **127.0.0.1** and in the port column enter **9050** as shown in the below screenshot.
|
||||
|
||||

|
||||
|
||||
Now point your browser with URL **https://check.torproject.org/**. You will see a green message that indicates: “**Congratulations. This browser is configured to use Tor**”. Red message indicate that Tor is not setup. Refer the following screenshot.
|
||||
|
||||

|
||||
|
||||
The same settings are applicable for all browsers, just open the Browser settings/preferences window, find the Network settings, Enter **127.0.0.1** in proxy server column and **9050** in port box. To disable Tor, Select **Use System Proxy settings** on browser settings.
|
||||
|
||||
**Note**: If you want to use Tor for anonymous web browsing, please read our article about [Tor Browser Bundle][2]. It comes with readily configured Tor and a browser patched for better anonymity. To use SOCKS directly (for instant messaging, Jabber, IRC, etc), you can point your application directly at Tor (localhost port 9050), but see [this FAQ entry][3] for why this may be dangerous.
|
||||
|
||||
That’s it. Good Luck! Stay Safe!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.unixmen.com/configure-browser-use-tor-ubuntu-debian-linux-mint/
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.onion-router.net/
|
||||
[2]:http://www.unixmen.com/protect-your-online-privacy-with-tor-browser/
|
||||
[3]:https://trac.torproject.org/projects/tor/wiki/doc/TorFAQ#SOCKSAndDNS
|
||||
@ -1,4 +1,3 @@
|
||||
occupied by rogetfan
|
||||
Daily Ubuntu Tips–Change The Language You Use In Ubuntu
|
||||
================================================================================
|
||||
Ubuntu, a modern and powerful operating system also allows you to use your desktop in dozens of other languages. By default, there are few language packs installed when you first setup Ubuntu. If you want Ubuntu to support more languages, you must install additional language packs. Not all languages are support, but most languages that are in used and written are supported. This brief tutorial is going to show you how to make this happen.
|
||||
|
||||
@ -1,156 +0,0 @@
|
||||
翻译中 by小眼儿
|
||||
|
||||
How to Crack a Wi-Fi Network's WPA Password with Reaver
|
||||
================================================================================
|
||||

|
||||
|
||||
Your Wi-Fi network is your conveniently wireless gateway to the internet, and since you're not keen on sharing your connection with any old hooligan who happens to be walking past your home, you secure your network with a password, right? Knowing, as you might, how [easy it is to crack a WEP password][1], you probably secure your network using the more bulletproof WPA security protocol.
|
||||
|
||||
Here's the bad news: A new, free, open-source tool called [Reaver][2] exploits a security hole in wireless routers and can crack most routers' current passwords with relative ease. Here's how to crack a WPA or WPA2 password, step by step, with Reaver—and how to protect your network against Reaver attacks.
|
||||
|
||||
In the first section of this post, I'll walk through the steps required to crack a WPA password using Reaver. You can follow along with either the video or the text below. After that, I'll explain how Reaver works, and what you can do to protect your network against Reaver attacks.
|
||||
|
||||
[http://www.youtube.com/embed/z1c1OIMbmb0?wmode=transparent&rel=0&autohide=1&showinfo=0&enablejsapi=1][3]
|
||||
|
||||
First, a quick note: As we remind often remind readers when we discuss topics that appear potentially malicious: Knowledge is power, but power doesn't mean you should be a jerk, or do anything illegal. Knowing how to pick a lock doesn't make you a thief. Consider this post educational, or a proof-of-concept intellectual exercise. The more you know, the better you can protect yourself.
|
||||
|
||||
### What You'll Need ###
|
||||
|
||||
You don't have to be a networking wizard to use Reaver, the command-line tool that does the heavy lifting, and if you've got a blank DVD, a computer with compatible Wi-Fi, and a few hours on your hands, you've got basically all you'll need. There are a number of ways you could set up Reaver, but here are the specific requirements for this guide:
|
||||
|
||||

|
||||
|
||||
- [**The BackTrack 5 Live DVD**][4]. BackTrack is a bootable Linux distribution that's filled to the brim with network testing tools, and while it's not strictly required to use Reaver, it's the easiest approach for most users. Download the Live DVD [from BackTrack's download page][5] and burn it to a DVD. You can alternately download a virtual machine image if you're using VMware, but if you don't know what VMware is, just stick with the Live DVD. As of this writing, that means you should select BackTrack 5 R3 from the Release drop-down, select Gnome, 32- or 64-bit depending on your CPU (if you don't know which you have, 32 is a safe bet), ISO for image, and then download the ISO.
|
||||
|
||||
- **A computer with Wi-Fi and a DVD drive**. BackTrack will work with the wireless card on most laptops, so chances are your laptop will work fine. However, BackTrack doesn't have a full compatibility list, so no guarantees. You'll also need a DVD drive, since that's how you'll boot into BackTrack. I used a six-year-old MacBook Pro.
|
||||
|
||||
- **A nearby WPA-secured Wi-Fi network**. Technically, it will need to be a network using WPA security with the WPS feature enabled. I'll explain in more detail in the "How Reaver Works" section how WPS creates the security hole that makes WPA cracking possible.
|
||||
|
||||
- **A little patience**. This is a 4-step process, and while it's not terribly difficult to crack a WPA password with Reaver, it's a brute-force attack, which means your computer will be testing a number of different combinations of cracks on your router before it finds the right one. When I tested it, Reaver took roughly 2.5 hours to successfully crack my password. The [Reaver home page][6] suggests it can take anywhere from 4-10 hours. Your mileage may vary.
|
||||
|
||||
### Let's Get Crackin' ###
|
||||
|
||||
At this point you should have BackTrack burned to a DVD, and you should have your laptop handy.
|
||||
|
||||
#### Step 1: Boot into BackTrack ####
|
||||
|
||||
To boot into BackTrack, just put the DVD in your drive and boot your machine from the disc. (Google around if you don't know anything about live CDs/DVDs and need help with this part.) During the boot process, BackTrack will prompt you to to choose the boot mode. Select "BackTrack Text - Default Boot Text Mode" and press Enter.
|
||||
|
||||
Eventually BackTrack will boot to a command line prompt. When you've reached the prompt, type `startx` and press Enter. BackTrack will boot into its graphical interface.
|
||||
|
||||
#### Step 2: Install Reaver ####
|
||||
|
||||
Update: This step is no longer necessary, as Reaver comes pre-installed on Backtrack 5 R3. Skip down to Step 3.
|
||||
|
||||
Reaver has been added to the bleeding edge version of BackTrack, but it's not yet incorporated with the live DVD, so as of this writing, you need to install Reaver before proceeding. (Eventually, Reaver will simply be incorporated with BackTrack by default.) To install Reaver, you'll first need to connect to a Wi-Fi network that you have the password to.
|
||||
|
||||
1. Click Applications > Internet > Wicd Network Manager
|
||||
1. Select your network and click Connect, enter your password if necessary, click OK, and then click Connect a second time.
|
||||
|
||||
Now that you're online, let's install Reaver. Click the Terminal button in the menu bar (or click Applications > Accessories > Terminal). At the prompt, type:
|
||||
|
||||
apt-get update
|
||||
|
||||
And then, after the update completes:
|
||||
|
||||
apt-get install reaver
|
||||
|
||||
If all went well, Reaver should now be installed. It may seem a little lame that you need to connect to a network to do this, but it will remain installed until you reboot your computer. At this point, go ahead and disconnect from the network by opening Wicd Network Manager again and clicking Disconnect. (You may not strictly need to do this. I did just because it felt like I was somehow cheating if I were already connected to a network.)
|
||||
|
||||
#### Step 3: Gather Your Device Information, Prep Your Crackin' ####
|
||||
|
||||
In order to use Reaver, you need to get your wireless card's interface name, the BSSID of the router you're attempting to crack (the BSSID is a unique series of letters and numbers that identifies a router), and you need to make sure your wireless card is in monitor mode. So let's do all that.
|
||||
|
||||
**Find your wireless card:** Inside Terminal, type:
|
||||
|
||||
iwconfig
|
||||
|
||||
Press Enter. You should see a wireless device in the subsequent list. Most likely, it'll be named `wlan0`, but if you have more than one wireless card, or a more unusual networking setup, it may be named something different.
|
||||
|
||||

|
||||
|
||||
**Put your wireless card into monitor mode**: Assuming your wireless card's interface name is `wlan0`, execute the following command to put your wireless card into monitor mode:
|
||||
|
||||
airmon-ng start wlan0
|
||||
|
||||
This command will output the name of monitor mode interface, which you'll also want to make note of. Most likely, it'll be `mon0`, like in the screenshot below. Make note of that.
|
||||
|
||||

|
||||
|
||||
**Find the BSSID of the router you want to crack**: Lastly, you need to get the unique identifier of the router you're attempting to crack so that you can point Reaver in the right direction. To do this, execute the following command:
|
||||
|
||||
airodump-ng wlan0
|
||||
|
||||
(Note: If `airodump-ng wlan0` doesn't work for you, you may want to try the monitor interface instead—e.g., `airodump-ng mon0`.)
|
||||
|
||||
You'll see a list of the wireless networks in range—it'll look something like the screenshot below:
|
||||
|
||||

|
||||
|
||||
When you see the network you want, press Ctrl+C to stop the list from refreshing, then copy that network's BSSID (it's the series of letters, numbers, and colons on the far left). The network should have WPA or WPA2 listed under the ENC column. (If it's WEP, use our [previous guide to cracking WEP passwords][7].)
|
||||
|
||||
Now, with the BSSID and monitor interface name in hand, you've got everything you need to start up Reaver.
|
||||
|
||||
#### Step 4: Crack a Network's WPA Password with Reaver ####
|
||||
|
||||
Now execute the following command in the Terminal, replacing `bssid` and moninterface with the BSSID and monitor interface and you copied down above:
|
||||
|
||||
reaver -i moninterface -b bssid -vv
|
||||
|
||||
For example, if your monitor interface was `mon0` like mine, and your BSSID was `8D:AE:9D:65:1F:B2` (a BSSID I just made up), your command would look like:
|
||||
|
||||
reaver -i mon0 -b 8D:AE:9D:65:1F:B2 -vv
|
||||
|
||||
Press Enter, sit back, and let Reaver work its disturbing magic. Reaver will now try a series of PINs on the router in a brute force attack, one after another. This will take a while. In my successful test, Reaver took 2 hours and 30 minutes to crack the network and deliver me with the correct password. As mentioned above, the Reaver documentation says it can take between 4 and 10 hours, so it could take more or less time than I experienced, depending. When Reaver's cracking has completed, it'll look like this:
|
||||
|
||||

|
||||
|
||||
**A few important factors to consider**: Reaver worked exactly as advertised in my test, but it won't necessarily work on all routers (see more below). Also, the router you're cracking needs to have a relatively strong signal, so if you're hardly in range of a router, you'll likely experience problems, and Reaver may not work. Throughout the process, Reaver would sometimes experience a timeout, sometimes get locked in a loop trying the same PIN repeatedly, and so on. I just let it keep on running, and kept it close to the router, and eventually it worked its way through.
|
||||
|
||||
Also of note, you can also pause your progress at any time by pressing Ctrl+C while Reaver is running. This will quit the process, but Reaver will save any progress so that next time you run the command, you can pick up where you left off-as long as you don't shut down your computer (which, if you're running off a live DVD, will reset everything).
|
||||
|
||||
### How Reaver Works ###
|
||||
|
||||
Now that you've seen how to use Reaver, let's take a quick overview of how Reaver works. The tool takes advantage of a vulnerability in something called Wi-Fi Protected Setup, or WPS. It's a feature that exists on many routers, intended to provide an easy setup process, and it's tied to a PIN that's hard-coded into the device. Reaver exploits a flaw in these PINs; the result is that, with enough time, it can reveal your WPA or WPA2 password.
|
||||
|
||||
Read more details about the vulnerability at [Sean Gallagher's excellent post on Ars Technica][8].
|
||||
|
||||
### How to Protect Yourself Against Reaver Attacks ###
|
||||
|
||||
Since the vulnerability lies in the implementation of WPS, your network should be safe if you can simply turn off WPS (or, even better, if your router doesn't support it in the first place). Unfortunately, as Gallagher [points out as Ars][9], even with WPS manually turned off through his router's settings, Reaver was still able to crack his password.
|
||||
|
||||
> In a phone conversation, Craig Heffner said that the inability to shut this vulnerability down is widespread. He and others have found it to occur with every Linksys and Cisco Valet wireless access point they've tested. "On all of the Linksys routers, you cannot manually disable WPS," he said. While the Web interface has a radio button that allegedly turns off WPS configuration, "it's still on and still vulnerable.
|
||||
|
||||
So that's kind of a bummer. You may still want to try disabling WPS on your router if you can, and test it against Reaver to see if it helps.
|
||||
|
||||
You could also set up MAC address filtering on your router (which only allows specifically whitelisted devices to connect to your network), but a sufficiently savvy hacker could detect the MAC address of a whitelisted device and use MAC address spoofing to imitate that computer.
|
||||
|
||||
Double bummer. So what will work?
|
||||
|
||||
I have the open-source router firmware [DD-WRT][10] installed on my router and I was unable to use Reaver to crack its password. As it turns out, [DD-WRT does not support WPS][11], so there's yet another reason to love the free router-booster. If that's got you interested in DD-WRT, check their [supported devices list][12] to see if your router's supported. It's a good security upgrade, and DD-WRT can also do cool things like [monitor your internet usage][13], [set up a network hard drive][14], act as a [whole-house ad blocker][15], [boost the range of your Wi-Fi network][16], and more. It essentially [turns your $60 router into a $600 router][17].
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://lifehacker.com/5873407/how-to-crack-a-wi+fi-networks-wpa-password-with-reaver
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://lifehacker.com/5305094/how-to-crack-a-wi+fi-networks-wep-password-with-backtrack
|
||||
[2]:http://go.redirectingat.com/?id=33330X911647&site=lifehacker.com&xs=1&isjs=1&url=http%3A%2F%2Fcode.google.com%2Fp%2Freaver-wps%2F&xguid=&xcreo=0&sref=http%3A%2F%2Flifehacker.com%2F5873407%2Fhow-to-crack-a-wi%2Bfi-networks-wpa-password-with-reaver&pref=http%3A%2F%2Flifehacker.com%2F5953047%2Fhow-to-crack-wep-and-wpa-wi%2Bfi-passwords&xtz=-480&abp=1
|
||||
[3]:http://www.youtube.com/embed/z1c1OIMbmb0?wmode=transparent&rel=0&autohide=1&showinfo=0&enablejsapi=1
|
||||
[4]:http://go.redirectingat.com/?id=33330X911647&site=lifehacker.com&xs=1&isjs=1&url=http%3A%2F%2Fwww.backtrack-linux.org%2Fdownloads%2F&xguid=&xcreo=0&sref=http%3A%2F%2Flifehacker.com%2F5873407%2Fhow-to-crack-a-wi%2Bfi-networks-wpa-password-with-reaver&pref=http%3A%2F%2Flifehacker.com%2F5953047%2Fhow-to-crack-wep-and-wpa-wi%2Bfi-passwords&xtz=-480&abp=1
|
||||
[5]:http://go.redirectingat.com/?id=33330X911647&site=lifehacker.com&xs=1&isjs=1&url=http%3A%2F%2Fwww.backtrack-linux.org%2Fdownloads%2F&xguid=&xcreo=0&sref=http%3A%2F%2Flifehacker.com%2F5873407%2Fhow-to-crack-a-wi%2Bfi-networks-wpa-password-with-reaver&pref=http%3A%2F%2Flifehacker.com%2F5953047%2Fhow-to-crack-wep-and-wpa-wi%2Bfi-passwords&xtz=-480&abp=1
|
||||
[6]:http://go.redirectingat.com/?id=33330X911647&site=lifehacker.com&xs=1&isjs=1&url=http%3A%2F%2Fcode.google.com%2Fp%2Freaver-wps%2F&xguid=&xcreo=0&sref=http%3A%2F%2Flifehacker.com%2F5873407%2Fhow-to-crack-a-wi%2Bfi-networks-wpa-password-with-reaver&pref=http%3A%2F%2Flifehacker.com%2F5953047%2Fhow-to-crack-wep-and-wpa-wi%2Bfi-passwords&xtz=-480&abp=1
|
||||
[7]:http://lifehacker.com/5305094/how-to-crack-a-wi+fi-networks-wep-password-with-backtrack
|
||||
[8]:http://go.redirectingat.com/?id=33330X911647&site=lifehacker.com&xs=1&isjs=1&url=http%3A%2F%2Farstechnica.com%2Fbusiness%2Fnews%2F2011%2F12%2Fresearchers-publish-open-source-tool-for-hacking-wifi-protected-setup.ars&xguid=&xcreo=0&sref=http%3A%2F%2Flifehacker.com%2F5873407%2Fhow-to-crack-a-wi%2Bfi-networks-wpa-password-with-reaver&pref=http%3A%2F%2Flifehacker.com%2F5953047%2Fhow-to-crack-wep-and-wpa-wi%2Bfi-passwords&xtz=-480&abp=1
|
||||
[9]:http://go.redirectingat.com/?id=33330X911647&site=lifehacker.com&xs=1&isjs=1&url=http%3A%2F%2Farstechnica.com%2Fbusiness%2Fnews%2F2012%2F01%2Fhands-on-hacking-wifi-protected-setup-with-reaver.ars&xguid=&xcreo=0&sref=http%3A%2F%2Flifehacker.com%2F5873407%2Fhow-to-crack-a-wi%2Bfi-networks-wpa-password-with-reaver&pref=http%3A%2F%2Flifehacker.com%2F5953047%2Fhow-to-crack-wep-and-wpa-wi%2Bfi-passwords&xtz=-480&abp=1
|
||||
[10]:http://go.redirectingat.com/?id=33330X911647&site=lifehacker.com&xs=1&isjs=1&url=http%3A%2F%2Fdd-wrt.com%2F&xguid=&xcreo=0&sref=http%3A%2F%2Flifehacker.com%2F5873407%2Fhow-to-crack-a-wi%2Bfi-networks-wpa-password-with-reaver&pref=http%3A%2F%2Flifehacker.com%2F5953047%2Fhow-to-crack-wep-and-wpa-wi%2Bfi-passwords&xtz=-480&abp=1
|
||||
[11]:http://go.redirectingat.com/?id=33330X911647&site=lifehacker.com&xs=1&isjs=1&url=http%3A%2F%2Fcode.google.com%2Fp%2Freaver-wps%2Fissues%2Fdetail%3Fid%3D44&xguid=&xcreo=0&sref=http%3A%2F%2Flifehacker.com%2F5873407%2Fhow-to-crack-a-wi%2Bfi-networks-wpa-password-with-reaver&pref=http%3A%2F%2Flifehacker.com%2F5953047%2Fhow-to-crack-wep-and-wpa-wi%2Bfi-passwords&xtz=-480&abp=1
|
||||
[12]:http://go.redirectingat.com/?id=33330X911647&site=lifehacker.com&xs=1&isjs=1&url=http%3A%2F%2Fdd-wrt.com%2Fwiki%2Findex.php%2FSupported_Devices&xguid=&xcreo=0&sref=http%3A%2F%2Flifehacker.com%2F5873407%2Fhow-to-crack-a-wi%2Bfi-networks-wpa-password-with-reaver&pref=http%3A%2F%2Flifehacker.com%2F5953047%2Fhow-to-crack-wep-and-wpa-wi%2Bfi-passwords&xtz=-480&abp=1
|
||||
[13]:http://lifehacker.com/5821773/how-to-monitor-your-internet-usage-so-you-dont-exceed-your-data-cap
|
||||
[14]:http://lifehacker.com/5756233/get-more-out-of-your-dd+wrt-router-with-an-external-drive?tag=ddwrt
|
||||
[15]:http://lifehacker.com/5680670/turn-your-dd+wrt-enabled-router-into-a-whole-house-ad-blocker?tag=ddwrt
|
||||
[16]:http://lifehacker.com/5563196/turn-your-old-router-into-a-range+boosting-wi+fi-repeater?tag=ddwrt
|
||||
[17]:http://lifehacker.com/178132/hack-attack-turn-your-60-router-into-a-600-router
|
||||
@ -1,39 +0,0 @@
|
||||
How to Install Linux Kernel 3.12 in Ubuntu 13.10
|
||||
================================================================================
|
||||
Ubuntu 13.10 users don't have to look with envy at the new Linux kernels that are released, and they can update their systems with relative ease.
|
||||
|
||||
Canonical is usually sticking with one Linux kernel for an entire development cycle. For example, Ubuntu 13.10 is based on Linux kernel 3.11, but now a new stable Linux kernel, 3.12, has been launched.
|
||||
|
||||
Ubuntu users will have to wait until the release of the 14.04 LTS to get a newer Linux kernel, but they can also install, until then, new versions.
|
||||
|
||||
We have to warn you from the get-go. Canonical does not recommend updating your Linux kernel to other versions than the ones provided on official channels. This is not a totally safe procedure and you might have problems afterwards, even system failures. On the other hand, you might get better performance from your system.
|
||||
|
||||
The kernel you are about to download is from Canonical, which means that it is already in a .deb format. You won't have to compile it yourself. Open a terminal, navigate to the Downloads folder, and enter the following commands:
|
||||
|
||||
wget http://kernel.ubuntu.com/~kernel-ppa/mainline/v3.12-saucy/linux-image-3.12.0-031200-generic_3.12.0-031200.201311031935_amd64.deb
|
||||
|
||||
wget http://kernel.ubuntu.com/~kernel-ppa/mainline/v3.12-saucy/linux-headers-3.12.0-031200-generic_3.12.0-031200.201311031935_amd64.deb
|
||||
|
||||
You can also download the 32-bit version, if you have a 32-bit operating system. Just replace the 64-bit links with the ones for 32-bit, which can be found [here][1].
|
||||
|
||||
Now you will have to run those .deb, just like any other program. In the same terminal that you used to download the packages, write the following commands (you will need root access to make this work):
|
||||
|
||||
sudo dpkg -i linux-image-3.12.0-031200-generic_3.12.0-031200.201311031935_amd64.deb
|
||||
sudo dpkg -i linux-headers-3.12.0-031200-generic_3.12.0-031200.201311031935_amd64.deb
|
||||
|
||||
After the process is finished, you will have to restart the system and voila, the new Linux kernels are in place. The good news is that the old ones are still there and, if you need to delete 3.12, all you have to do is use a very well-known command.
|
||||
|
||||
sudo apt-get purge linux-image-3.12.0-031200-generic_3.12.0-031200.201311031935_amd64.deb
|
||||
sudo apt-get linux-headers-3.12.0-031200-generic_3.12.0-031200.201311031935_amd64.deb
|
||||
|
||||
One thing you have to remember. The names of the files shown above will change pretty soon. If the downloads are not working, you will have to update the new links. Enjoy Linux kernel 3.12!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://news.softpedia.com/news/How-to-Install-Linux-Kerrnel-3-12-in-Ubuntu-13-10-397013.shtml
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://kernel.ubuntu.com/~kernel-ppa/mainline/v3.12-saucy/
|
||||
@ -0,0 +1,273 @@
|
||||
How to Install and Configure UFW – An Un-complicated FireWall in Debian/Ubuntu
|
||||
================================================================================
|
||||
Since computers are connected to each other, services are growing fast. **Email, Social Media, Online Shop, Chat** until **Web Conferencing** are services that used by user. But on the other side this connectivity just likes a double-side knife. It’s also possible to send bad messages to those computers like **Virus, malware, trojan-apps** are one of them.
|
||||
|
||||

|
||||
|
||||
*Install UFW Firewall*
|
||||
|
||||
The Internet, as the biggest computer network is not always fill with good people. In order to make sure our computers / servers are safe, we need to protect it.
|
||||
|
||||
One of the must have component on your computer / servers is **Firewall**. From **Wikipedia**, a definition is:
|
||||
|
||||
> In computing, a firewall is a software or hardware-based network security system that controls the incoming and outgoing network traffic by analysing the data packets and determining whether they should be allowed through or not, based on applied rule set.
|
||||
|
||||
**Iptables** is one of the firewall that widely used by servers. It is a program used to manage incoming and outgoing traffic in the server based on a set of rules. Generally, only trusted connection is allowed to enter the server. But **IPTables** is running at console mode and it’s complicated. Those who’re familiar with iptables rules and commands, they can read the following article that describes how to use iptables firewall.
|
||||
|
||||
- [Basic IPTables (Linux Firewall) Guide][1]
|
||||
|
||||
### Installation of UFW Firewall in Debian/Ubuntu ###
|
||||
|
||||
To reduce the complexity of how-to setting **IPTables**, there is a lot of fronted. If you’re running **Ubuntu** Linux, you will find **ufw** as a default firewall tool. Lets start to explore about **ufw** firewall.
|
||||
|
||||
### What is ufw ###
|
||||
|
||||
The **ufw (Uncomplicated Firewall)** is an frontend for most widely used **iptables firewall** and it is well comfortable for host-based firewalls. ufw gives a framework for managing **netfilter**, as well as provides a command-line interface for controlling the firewall. It provides user friendly and easy to use interface for Linux newbies who are not much familiar with firewall concepts.
|
||||
|
||||
While, on the other side same complicated commands helps administrators it set complicated rules using command line interface. The **ufw** is an upstream for other distributions such as **Debian, Ubuntu** and **Linux Mint**.
|
||||
|
||||
#### Basic Usage ufw ####
|
||||
|
||||
First, check if **ufw** is installed using following command.
|
||||
|
||||
$ sudo dpkg --get-selection | grep ufw
|
||||
|
||||
ufw install
|
||||
|
||||
If it’s not installed, you can install it using **apt** command as shown below.
|
||||
|
||||
$ sudo apt-get install ufw
|
||||
|
||||
Before you use, you should check whether **ufw** is running or not. Use the following command to check it.
|
||||
|
||||
$ sudo ufw status
|
||||
|
||||
If you found Status: **inactive**, it mean it’s not active or disable.
|
||||
|
||||
#### Enabling / Disabling ufw ####
|
||||
|
||||
To enable it, you just need to type the following command at the terminal.
|
||||
|
||||
$ sudo ufw enable
|
||||
|
||||
Firewall is active and enabled on system startup
|
||||
|
||||
To disable it, just type.
|
||||
|
||||
$ sudo ufw disable
|
||||
|
||||
#### List the current ufw rules ####
|
||||
|
||||
After the firewall is activated you can add your rules into it. If you want to see what are the default rules, you can type.
|
||||
|
||||
$ sudo status verbose
|
||||
|
||||
##### Sample Output #####
|
||||
|
||||
Status: active
|
||||
Logging: on (low)
|
||||
Default: deny (incoming), allow (outgoing)
|
||||
New profiles: skip
|
||||
$
|
||||
|
||||
#### How to Add ufw rules ####
|
||||
|
||||
As you see, by default every incoming connection is denied. If you want to remote your machine then you have to allow proper port. For example you want to allow ssh connection. Here’s the command to allow it.
|
||||
|
||||
#### Allow Access ####
|
||||
|
||||
$ sudo ufw allow ssh
|
||||
|
||||
[sudo] password for pungki :
|
||||
Rule added
|
||||
Rule added (v6)
|
||||
$
|
||||
|
||||
If you check the status again, you will see an output like this.
|
||||
|
||||
$ sudo ufw status
|
||||
|
||||
To Action From
|
||||
-- ----------- ------
|
||||
22 ALLOW Anywhere
|
||||
22 ALLOW Anywhere (v6)
|
||||
|
||||
If you have a lot of rules, and want to put numbers on every rules on the fly, use parameter numbered.
|
||||
|
||||
$ sudo ufw status numbered
|
||||
|
||||
To Action From
|
||||
------ ----------- ------
|
||||
[1] 22 ALLOW Anywhere
|
||||
[2] 22 ALLOW Anywhere (v6)
|
||||
|
||||
The first rule says that incoming connection to **port 22** from **Anywhere**, both **tcp** or **udp** packets is allowed. What if you want to allow **tcp** packet only? Then you can add the parameter **tcp** after the **port** number. Here’s an example with sample output.
|
||||
|
||||
$ sudo ufw allow ssh/tcp
|
||||
|
||||
To Action From
|
||||
------ ----------- ------
|
||||
22/tcp ALLOW Anywhere
|
||||
22/tcp ALLOW Anywhere (v6)
|
||||
|
||||
#### Deny Access ####
|
||||
|
||||
The same tricks is applied to Deny rule. Let say you want to deny ftp rule. So you only have to type.
|
||||
|
||||
$ sudo ufw deny ftp
|
||||
|
||||
To Action From
|
||||
------ ----------- ------
|
||||
21/tcp DENY Anywhere
|
||||
21/tcp DENY Anywhere (v6)
|
||||
|
||||
### Adding Specific Port ###
|
||||
|
||||
Sometimes we have a custom port which is not follow any standards. Let’s say we change the **ssh** port on our machine from **22**, into **2290**. Then to allow port **2290**, we can add it like this.
|
||||
|
||||
$ sudo ufw allow
|
||||
|
||||
To Action From
|
||||
-- ----------- ------
|
||||
2290 ALLOW Anywhere
|
||||
2290 ALLOW Anywhere (v6)
|
||||
|
||||
It also possible for you to add **port-range** into the rule. If we want to open port from **2290 – 2300** with **tcp** protocol, then the command will be like this.
|
||||
|
||||
$ sudo ufw allow 2290:2300/tcp
|
||||
|
||||
To Action From
|
||||
------ ----------- ------
|
||||
2290:2300/tcp ALLOW Anywhere
|
||||
2290:2300/tcp ALLOW Anywhere (v6)
|
||||
|
||||
while if you want to use **udp**, just use the following command.
|
||||
|
||||
$ sudo ufw allow 2290:2300/udp
|
||||
|
||||
To Action From
|
||||
------ ----------- ------
|
||||
2290:2300/udp ALLOW Anywhere
|
||||
2290:2300/udp ALLOW Anywhere (v6)
|
||||
|
||||
Please remember that you have to put ‘**tcp**’ or ‘**udp**’ explicitly otherwise you will get an error message similar to below.
|
||||
|
||||
ERROR: Must specify ‘tcp’ or ‘udp’ with multiple ports
|
||||
|
||||
### Adding Specific IP ###
|
||||
|
||||
Previously we have added rules based on **service** or **port**. Ufw also allow you to add rules based on **IP Address**. Here’s the sample command.
|
||||
|
||||
$ sudo ufw allow from 192.168.0.104
|
||||
|
||||
You can also use a subnet mask to wider the range.
|
||||
|
||||
$ sudo ufw allow form 192.168.0.0/24
|
||||
|
||||
To Action From
|
||||
-- ----------- ------
|
||||
Anywhere ALLOW 192.168.0.104
|
||||
Anywhere ALLOW 192.168.0.0/24
|
||||
|
||||
As you can see, from parameter will only limit the source of connection. While the destination – which is represented by **To** column – is **Anywhere**. You can also manage the destination using ‘**To**‘ parameter. Let’s see the sample to allow access to **port 22 (ssh)**.
|
||||
|
||||
$ sudo ufw allow to any port 22
|
||||
|
||||
The above command will allow access from anywhere and from any protocol to **port 22**.
|
||||
|
||||
### Combining Parameters ###
|
||||
|
||||
For more specific rules, you can also combining IP Address, **protocol** and **port**. Let’s say we want to create rule that limit the connection only from IP 192.168.0.104, only protocol **tcp** and to port **22**. Then the command will be like below.
|
||||
|
||||
$ sudo ufw allow from 192.168.0.104 proto tcp to any port 22
|
||||
|
||||
Syntax to create deny rule is similar with allow rule. You only need to change parameter from **allow** to **deny**.
|
||||
|
||||
### Deleting Rules ###
|
||||
|
||||
Sometime you may need to delete your existing rule. Once again with **ufw** it is easy to delete rules. From above sample, you have a rule below and you want to delete it.
|
||||
|
||||
To Action From
|
||||
-- ----------- ------
|
||||
22/tcp ALLOW 192.168.0.104
|
||||
21/tcp ALLOW Anywhere
|
||||
21/tcp ALLOW Anywhere (v6)
|
||||
|
||||
There are two methods of deleting rules.
|
||||
|
||||
**Method 1**
|
||||
|
||||
The below command will **delete** rules that match service **ftp**. So the **21/tcp** which mean **ftp** port will be deleted.
|
||||
|
||||
$ sudo ufw delete allow ftp
|
||||
|
||||
**Method 2**
|
||||
|
||||
But when you tried to delete the first rule at the above example using below command.
|
||||
|
||||
$ sudo ufw delete allow ssh
|
||||
|
||||
Or
|
||||
|
||||
$ sudo ufw delete allow 22/tcp
|
||||
|
||||
You may find an error message such as.
|
||||
|
||||
Could not delete non-existent rule
|
||||
Could not delete non-existent rule (v6)
|
||||
|
||||
Then you can do this trick. As we mentioned above, you can show the number of rule to indicate which rule that we want to delete. Let we show it to you.
|
||||
|
||||
$ sudo ufw status numbered
|
||||
|
||||
To Action From
|
||||
-- ----------- ------
|
||||
[1] 22/tcp ALLOW 192.168.0.104
|
||||
[2] 21/tcp ALLOW Anywhere
|
||||
[3] 21/tcp ALLOW Anywhere (v6)
|
||||
|
||||
Then you can delete the first rule using. Press “**y**” will permanently delete the rule.
|
||||
|
||||
$ sudo ufw delete 1
|
||||
|
||||
Deleting :
|
||||
Allow from 192.168.0.104 to any port 22 proto tcp
|
||||
Proceed with operation (y|n)? y
|
||||
|
||||
From those methods you will see the difference. **Method 2** will ask **user confirmation** before deleting the rule while **method 1** is not.
|
||||
|
||||
### How to Reset Rules ###
|
||||
|
||||
In some situation, you may want to **delete / reset** all rules. You can do it by typing.
|
||||
|
||||
$ sudo ufw reset
|
||||
|
||||
Resetting all rules to installed defaults. Proceed with operation (y|n)? y
|
||||
|
||||
If you press “**y**”, then **ufw** will backup all existing rules before doing the reset your ufw. Resetting the rules will also disable your firewall. You need to enabled it again if you want to use it.
|
||||
|
||||
### Advanced Functionality ###
|
||||
|
||||
As I stated above, the ufw firewall can able to do whatever that iptables can do. This is accomplished by using various sets of rules files, which are nothing more than **iptables-restore** appropriate text files. Fine tuning ufw and/or placing additional iptables commands not allowed via the ufw command is a matter of editing several text files.
|
||||
|
||||
- /etc/default/ufw: The main configuration for default policies, IPv6 support and kernel modules.
|
||||
- /etc/ufw/before[6].rules: rules in these files are calculate before any rules added via the ufw command.
|
||||
- /etc/ufw/after[6].rules: rules in these files are calculate after any rules added via the ufw command.
|
||||
- /etc/ufw/sysctl.conf: kernel network tunables.
|
||||
- /etc/ufw/ufw.conf: sets whether or not ufw is enabled on boot and sets the LOGLEVEL.
|
||||
|
||||
### Conclusion ###
|
||||
|
||||
**UFW** as a front-end to iptables surely make an easy interface to user. User don’t need to remember complicated iptables syntax. **UFW** also use ‘**plain english**‘ as its parameter.
|
||||
|
||||
**Allow, deny, reset** are one of them. I believe that there are many more iptables front-end out there. But definitely ufw is one of the best alternative for users who want to setup their firewall fast, easy and of course secure. Please visit **ufw manual page** by typing **man ufw** for more detail.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.tecmint.com/how-to-install-and-configure-ufw-firewall/
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.tecmint.com/basic-guide-on-iptables-linux-firewall-tips-commands/
|
||||
@ -1,4 +1,3 @@
|
||||
(translating by runningwater)
|
||||
Interview with Ding Zhou of Ubuntu Tweak
|
||||
================================================================================
|
||||
[Ubuntu tweak][1] is a well known application which allows Ubuntu users to tweak various aspects of their system. The founder of the project, Ding Zhou aka Tualatrix Chou, is talking to us about the nature and the usability of Ubuntu Tweak, the relation with Canonical and the future plans of the project. Enjoy
|
||||
@ -89,6 +88,6 @@ via: http://www.unixmen.com/interview-with-ding-zhou-of-ubuntu-tweak/
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
译者:[runningwater](https://github.com/runningwater) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
[1]:http://ubuntu-tweak.com/
|
||||
@ -1,4 +1,3 @@
|
||||
(translating by flyingwitholdlady)
|
||||
KDE vs GNOME: Settings, Apps, Widgets
|
||||
=====================================
|
||||
|
||||
|
||||
@ -1,39 +0,0 @@
|
||||
LinuxCon/CloudOpen Goose Chase Ends in Tie for Grand Prize
|
||||
================================================================================
|
||||
Hundreds of people raced to the finish in the first-ever LinuxCon/CloudOpen Goose Chase. From showing your cowsay to the coffee cup that fuels your Linux work, you - the community - showcased your competitive nature and passion for having fun. The competiton was fierce through the end, which resulted in a tie for Grand Prize for Round Two (round one wrapped up in October, and the [winners were announced][1] at LinuxCon and CloudOpen North America). Because there are two Grand Prize winners, we will not be awarding a First Prize.
|
||||
|
||||
The winners of Round Two are:
|
||||
|
||||
**Grand Prize: $500 Amazon Gift Card**
|
||||
|
||||
**Daniel German**, Canada
|
||||
|
||||
**Joao Paulo Rechi Vita**, Brazil
|
||||
|
||||

|
||||
|
||||
Joao works for the Nokia Institute of Technology. His latest Linux project was adding BlueZ 5 bluetooth support to PulseAudio on the Linux desktop. He's attended LinuxCon in Japan, North America and Europe this year.
|
||||
|
||||
"I participated in the Goose Chase at LinuxCon North America and found it really fun, so when I was showing the pictures to my girlfriend back home I found the {online} Goose Chase and decided to join it as well. And as I expected, {it} was a lot of fun again, specially because this time some of the missions needed quite a bit of creativity to be accomplished."
|
||||
|
||||
**Second Prize, $50 Amazon Gift Card**
|
||||
|
||||
**Madalina-Ioana Alexe**, Romania
|
||||
|
||||
Madalina-Ioana works for Intel Romania on Tizen and attended the Gluster Community Day this week at LinuxCon Europe.
|
||||
|
||||
"I found it is a fun game, which is still suitable for geeks. It was a nice and funny experience and I found out that there are even more geeks like me."
|
||||
|
||||
Congratulations to all our winners and thank you so much for participating in the Goose Chase!
|
||||
|
||||

|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linux.com/news/featured-blogs/185-jennifer-cloer/745263-linuxconcloudopen-goose-chase-ends-in-tie-for-grand-prize/
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.linux.com/news/featured-blogs/200-libby-clark/737969-announcing-goose-chase-contest-winners-more-prizes-for-linuxcon-europe
|
||||
@ -1,26 +0,0 @@
|
||||
New Ubuntu 14.04 LTS Icon Theme Uses Origami Concept
|
||||
================================================================================
|
||||

|
||||
|
||||
**Ubuntu 14.04 LTS has a good chance of getting a new icon theme, but there's one very interesting concept integrated in the design, and that is an origami motif.**
|
||||
|
||||
When designers begin to make original artwork for operating systems, they usually start from scratch or they integrate the current trend in their work. Ubuntu designers have managed to produce something unique, that doesn’t follow the overall trend, and which is inspired by art.
|
||||
|
||||
In the Ubuntu 14.04 icon theme presentation showed during the Ubuntu Developer Summit, visual designer James Matthieu explained that they used an origami concept to illustrate various components.
|
||||
|
||||
“The default file shape represent a sheet of paper using the origami effect to maintain consistency with the style of some of the application icon,” [said][1] James Matthieu during the presentation.
|
||||
|
||||
This is not the first time that a folded corner is used for folders or files, but if you look close enough the folding mark of the “paper” is also present in the final form.
|
||||
|
||||
We hope that the new icon theme will make it because it looks awesome. You can see more details about the new icon in [our original report][2].
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://news.softpedia.com/news/New-Ubuntu-14-04-LTS-Icon-Theme-Uses-Origami-Concept-403061.shtml
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.youtube.com/watch?v=0AEvSIX41lk&feature=share
|
||||
[2]:http://news.softpedia.com/news/Ubuntu-14-04-LTS-to-Get-Stunning-Icon-Theme-and-They-re-Not-Flat-402712.shtml
|
||||
@ -0,0 +1,31 @@
|
||||
Oracle Linux 6.5 Arrives with Unbreakable Enterprise Linux Kernel 3.8
|
||||
================================================================================
|
||||
**Oracle has announced a few days ago that its Oracle Linux operating system has reached version 6.5, bringing lots of new features, updated packages and several improvements over previus releases.**
|
||||
|
||||

|
||||
|
||||
First of all, we should mention that Oracle Linux 6.5 is now powered by three separate kernels, the unbreakable enterprise kernel version 2.6.39-400.211.1.el6uek only for the x86 (32-bit) platform, the unbreakable enterprise kernel version 3.8.13-16.2.1.el6uek for both 64-bit and 32-bit architectures, and the Red Hat compatible kernel 2.6.32-431.el6 for x86 and x86_64.
|
||||
|
||||
Unbreakable Enterprise Kernel Release 3 (UEK R3) introduces major improvements over UEK R2, including integrated DTrace support, device mapper support, Btrfs quota groups, Btrfs send and receive subcommands, support for replacing devices without unmounting in Btrfs, EXT4 quotas, TCP controlled delay management, TCP connection repair, STCP and TCP early retransmit, TCP fast open, and TCP small queue algorithm.
|
||||
|
||||
The loop driver has been update to provide the same I/O functionality as the dm-nfs project, simply by extending the AIO interface to perform direct I/O. Moreover, the secure computing mode feature has been added, and the OpenFabrics Enterprise Distribution (OFED) 2.0 stack supports the following protocols: SRP (SCSI RDMA Protocol), iSER (iSCSI Extensions), RDS (Reliable Datagram Sockets), SDP (Sockets Direct Protocol), EoIB (Ethernet over InfiniBand), IPoIB (IP encapsulation over InfiniBand), and eIPoIB (Ethernet tunneling over InfiniBand).
|
||||
|
||||
The OFED (OpenFabrics Enterprise Distribution) 2.0 stack also supports the following RDS features: AS (Async Send), APM (Automatic Path Migration), QoS (Quality of Service), SRQ (Shared Request Queue), AB (Active Bonding), and NF (Netfilter).
|
||||
|
||||
Last but not least, paravirtualization support has been enabled for Oracle Linux guests on Windows Server 2008 R2 Hyper-V or Windows Server 2008 Hyper-V.
|
||||
|
||||
**Download Oracle Linux 6.5 right now:**
|
||||
|
||||
- [Oracle Enterprise Linux 6.5 (ISO) i386][1][iso] [3 GB]
|
||||
- [Oracle Enterprise Linux 6.5 (ISO) amd64][2][iso] [3.60 GB]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://news.softpedia.com/news/Oracle-Linux-6-5-Arrives-with-Unbreakable-Enterprise-Linux-Kernel-3-8-406093.shtml
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://mirrors.dotsrc.org/oracle-linux/OL6/U5/i386/OracleLinux-R6-U5-Server-i386-dvd.iso
|
||||
[2]:http://mirrors.dotsrc.org/oracle-linux/OL6/U5/x86_64/OracleLinux-R6-U5-Server-x86_64-dvd.iso
|
||||
@ -1,97 +0,0 @@
|
||||
Personality Traits of the Best Software Developers
|
||||
================================================================================
|
||||
I come from the world of corporate software development. It may not be the most glamorous side of software (it’s nowhere near as interesting as [shrinkwrap startups][1] or those fancy-dancy [Web 2.0][2] companies that show up in your browser every time you mistype a domain name), but it’s stable, pays well, and has its own set of challenges that other types of software development know nothing about.
|
||||
|
||||
For example, when was the last time someone working on the next version of Halo spent three weeks trying to gather people from accounting, marketing, product management, and their call center in order to nail down requirements that would likely change in 2 months once they’ve delivered the software?
|
||||
|
||||
Or when was the last time someone at [37Signals][3] sat through back to back weeks of [JAD sessions][4]?
|
||||
|
||||
In this world of corporate development I’ve known a few phenomenal developers. I’m talking about those A people whom you would quit your job for to go start a company. And the the more I looked at what makes them so good, the more I realized they all share a handful of personality traits. Well, not exactly a handful, more like four.
|
||||
|
||||

|
||||
|
||||
### Pessimistic ###
|
||||
|
||||
Admiral Jim Stockdale was the highest ranking US military officer imprisoned in Vietnam. He was held in the “Hanoi Hilton” and repeatedly tortured over 8 years. Stockdale told Jim Collins, author of [Good to Great][5], “You must never confuse faith that you will prevail in the end, which you can never afford to lose, with the discipline to confront the most brutal facts of your current reality, whatever they might be.”
|
||||
|
||||
After his release, Stockdale became the first three-star officer in the history of the navy to wear both aviator wings and the Congressional Medal of Honor.
|
||||
|
||||
Stockdale was a pessimist in the short-term because he faced the brutal facts of his reality, but was an optimist in the long-term because of his confidence that he would prevail in the end.
|
||||
|
||||
No one anticipates a catastrophic system failure by looking on the bright side. The best developers I know are experts at finding points of failure. You’ll often hear them quipping “What could possibly go wrong?” after someone makes a suggestion to handle a critical data transfer via nightly FTP over a dial-up connection. The best developers anticipate headaches that other developers never think of, and do everything within their power to avoid them.
|
||||
|
||||
On the flip side, great developers are optimistic, even downright confident, about their overall success. They know that by being a pessimist in the short-term, their long-term success is ensured. Just like Jim Stockdale, they realize that by confronting the brutal facts of their current reality they will prevail in the end.
|
||||
|
||||
### Angered By Sloppy Code ###
|
||||
|
||||
Paul Graham nailed it when [he said][6] “…people who are great at something are not so much convinced of their own greatness as mystified at why everyone else seems so incompetent.”
|
||||
|
||||
The worst nightmare for a great developer is to see someone else’s software gasping for air while bringing the rest of the system to its knees. It’s downright infuriating. And this isn’t limited to code; it can be bad installation packages, sloppy deployments, or a misspelled column name.
|
||||
|
||||

|
||||
|
||||
Due to the life and death nature of their products, NASA designs zero-defect software systems using a process that has nearly eliminated the possibility for human error. They’ve added layer after layer of checks and balances that have resulted from years of finding mistakes and figuring out the best way to eliminate them. NASA is the poster child for discovering the source of a mistake and modifying their process to eliminate the possibility of that mistake ever happening again. And it works. A quote from [this Fast Company article][7] on NASA’s development process says
|
||||
|
||||
“What makes it remarkable is how well the software works. This software never crashes. It never needs to be re-booted. This software is bug-free. It is perfect, as perfect as human beings have achieved. Consider these stats: the last three versions of the program — each 420,000 lines long-had just one error each. The last 11 versions of this software had a total of 17 errors. Commercial programs of equivalent complexity would have 5,000 errors.”
|
||||
|
||||
I’m not saying we have to develop to this standard, but NASA knows how to find and fix bugs, and the way they do it is to find the source of every problem.
|
||||
|
||||
Someone who fixes a problem but doesn’t take the time to find out what caused it is doomed to never become an expert in their field. Experience is not years on the job, it’s learning to recognize a problem before it occurs, which can only be done by knowing what causes it in the first place.
|
||||
|
||||
Developers who don’t take the time to find the source often create sloppy solutions. For hundreds of examples of sloppy solutions visit [The Daily WTF][8]. Here are a few I’ve seen in my career:
|
||||
|
||||
- An assembly is deleted from a server each time it’s rebooted. You could create a custom script to re-copy that assembly to the server after each reboot, or find out why the assembly is being deleted in the first place.
|
||||
- An image-manipulation script is hogging processor power for minutes at a time when it should run in under 10 seconds. You could make the script run at 2am when no one will notice, or you can take the time to step through the code and figure out where the real problem is.
|
||||
- A shared XML file is being locked by a process, causing other processes to fail when they try to open it. You could make several copies of the XML file so each process has its own, or you could troubleshoot the file access code to find out why it’s locking the file.
|
||||
- And on and on…
|
||||
|
||||
### Long Term Life Planners ###
|
||||
|
||||
This one was a little puzzling for the longest time, but I think I’ve finally put it together.
|
||||
|
||||

|
||||
|
||||
People who think many years down the road in their personal life have the gift to think down the road during development. Being able to see the impacts of present-day decisions is paramount to building great software. The best developers I know have stable family lives, save for retirement, own their own home, and eat an apple a day (ok, maybe not that last one). People who have spastic home-lives and live paycheck to paycheck can certainly be good developers, but what they lack in life they tend to lack in the office: the ability to be disciplined, and to develop and adhere to a long-term plan.
|
||||
|
||||
### Attention to Detail ###
|
||||
|
||||
I’ve known smart developers who don’t pay attention to detail. The result is misspelled database columns, uncommented code, projects that aren’t checked into source control, software that’s not unit tested, unimplemented features, and so on. All of these can be easily dealt with if you’re building a Google mash-up or a five page website. But in corporate development each of these screw-ups is a death knell.
|
||||
|
||||
So I’ll say it very loud, but I promise I’ll only say it once:
|
||||
|
||||
**I have never, ever, ever seen a great software developer who does not have amazing attention to detail.**
|
||||
|
||||
I worked with a programmer back in school who forced anyone working with him to indent using two spaces instead of tabs. If you gave him code that didn’t use two spaces he would go through it line-by-line and replace your tabs with his spaces. While the value of tabs is not even a question, (I’ve long-chided him for this anal behavior) his attention to such a small detail has served him well in his many years designing chips at Intel.
|
||||
|
||||
### So There You Have It ###
|
||||
|
||||
The next time you’re interviewing a potential developer, determine if she has the four personality traits I’ve listed above. Here are a few methods I’ve found useful:
|
||||
|
||||
- Ask if they’re an optimist or a pessimist
|
||||
- Ask about a time when they found the source of a problem
|
||||
- Find out if they save for retirement (you can work this in during discussions of your company’s retirement plan)
|
||||
- Make an obvious misspelling in a short code sample and ask if they see anything wrong
|
||||
|
||||
We know from [Facts and Fallacies of Software Engineering][9] that the best programmers are up to [28 times better][10] than the worst programmers, making them the best bargains in software. Take these four traits and go find a bargain (or better yet, make yourself into one).
|
||||
|
||||
If you liked this article you’ll also like my article [Timeline and Risk: How to Piss off Your Software Developers][11].
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.softwarebyrob.com/2006/08/20/personality-traits-of-the-best-software-developers/
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.joelonsoftware.com/
|
||||
[2]:http://www.econsultant.com/web2/
|
||||
[3]:http://www.37signals.com/
|
||||
[4]:http://expertanswercenter.techtarget.com/eac/knowledgebaseAnswer/0,295199,sid63_gci986072,00.html
|
||||
[5]:http://www.amazon.com/gp/redirect.html?link_code=ur2&tag=softwarbyrob-20&camp=1789&creative=9325&location=%2Fgp%2Fproduct%2F0060794410%2Fsr%3D8-3%2Fqid%3D1155789849%2Fref%3Dpd_bbs_3%3Fie%3DUTF8
|
||||
[6]:http://www.paulgraham.com/gh.html
|
||||
[7]:http://www.fastcompany.com/online/06/writestuff.html
|
||||
[8]:http://www.thedailywtf.com/
|
||||
[9]:http://www.amazon.com/gp/redirect.html?link_code=ur2&tag=softwarbyrob-20&camp=1789&creative=9325&location=http%3A%2F%2Fwww.amazon.com%2Fgp%2Fproduct%2F0321117425%2Fsr%3D8-1%2Fqid%3D1154642314%2Fref%3Dpd_bbs_1%3Fie%3DUTF8
|
||||
[10]:http://safari.oreilly.com/0321117425/ch01lev1sec1
|
||||
[11]:http://www.softwarebyrob.com/articles/Timeline_and_Risk_Piss_Off_Your_Software_Developers.aspx
|
||||
@ -1,3 +1,4 @@
|
||||
Crowner's crown
|
||||
Setup Apache 2.4 and Php FPM with mod proxy fcgi on Ubuntu 13.10
|
||||
================================================================================
|
||||
### mod_proxy_fcgi ###
|
||||
|
||||
@ -1,3 +1,5 @@
|
||||
translating by zsJacky
|
||||
|
||||
Setup FTP Server On openSUSE 13.1
|
||||
================================================================================
|
||||
**vsftpd** (**V**ery **S**ecure **F**ile **T**ransport **P**rotocol **D**aemon) is a secure, fast FTP server for Unix/Linux systems. In this how-to article, let us see how to setup a basic FTP server using vsftpd on openSUSE 13.1.
|
||||
@ -182,7 +184,7 @@ That’s it for now. Your FTP server is ready to use. Enjoy!
|
||||
|
||||
via: http://www.unixmen.com/setup-ftp-server-opensuse-13-1/
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
译者:[zsJacky](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
|
||||
@ -1,221 +0,0 @@
|
||||
我不入监狱 谁入监狱
|
||||
|
||||
Setup a jailed shell with jailkit on ubuntu
|
||||
================================================================================
|
||||
### Jailed Shell and Jailkit ###
|
||||
|
||||
A jailed shell is a kind of limited shell that provides the user with a very real looking shell but does not allow him to mess with/view/modify any parts of the real file systems. The file system inside the shell is different from the actual file system of the underlying system. Such a functionality is achived through chroot and finds many kinds of applications. For example to setup a linux shell for users to just "play with". Or run some program with full functionality but in a limited environment and so on.
|
||||
|
||||
In this tutorial we are going to talk about setting up a jailed shell quickly with jailkit on ubuntu. Jailkit is helper program that allows to quickly setup a jailed shell, jail users inside it, and configure programs to run from the jailed environment.
|
||||
|
||||
Jailkit can be downloaded from [http://olivier.sessink.nl/jailkit/][1]
|
||||
|
||||
We have already discussed about installing jailkit on ubuntu so check out that post.
|
||||
|
||||
### Setup jailed shell ###
|
||||
|
||||
#### 1. Setup the jail environment ####
|
||||
|
||||
There needs to be a directory where the whole jail environment will be setup. Lets do it in /opt/jail. This can be whatever.
|
||||
|
||||
$ sudo mkdir /opt/jail
|
||||
|
||||
Root should own this directory. So chown it out.
|
||||
|
||||
$ sudo chown root:root /opt/jail
|
||||
|
||||
#### 2. Setup the programs to make available inside the jail ####
|
||||
|
||||
All the programs that need to be available in the jail need to be copied inside it using the jk_init command.
|
||||
|
||||
Example
|
||||
|
||||
$ sudo jk_init -v /jail basicshell
|
||||
$ sudo jk_init -v /jail editors
|
||||
$ sudo jk_init -v /jail extendedshell
|
||||
$ sudo jk_init -v /jail netutils
|
||||
$ sudo jk_init -v /jail ssh
|
||||
$ sudo jk_init -v /jail sftp
|
||||
$ sudo jk_init -v /jail jk_lsh
|
||||
|
||||
Or at one go
|
||||
|
||||
$ sudo jk_init -v /opt/jail netutils basicshell jk_lsh openvpn ssh sftp
|
||||
|
||||
The names like basicshell , editors , netutils are groups that contain multiple programs. Each group is a set of executable files, libraries etc to be copied into the shell. For example, the section **basicshell** provides many programs like bash, ls, cat, chmod, mkdir, cp, cpio, date, dd, echo, egrep etc in the jail.
|
||||
|
||||
For a complete list of sections that can be setup, have a look at /etc/jailkit/jk_init.ini.
|
||||
|
||||
jk_lsh (Jailkit limited shell) - is an important section, and must be added.
|
||||
|
||||
#### 3. Create the user who will be jailed ####
|
||||
|
||||
Need a user to put inside the jail. Lets create one
|
||||
|
||||
$ sudo adduser robber
|
||||
Adding user `robber' ...
|
||||
Adding new group `robber' (1005) ...
|
||||
Adding new user `robber' (1006) with group `robber' ...
|
||||
Creating home directory `/home/robber' ...
|
||||
Copying files from `/etc/skel' ...
|
||||
Enter new UNIX password:
|
||||
Retype new UNIX password:
|
||||
passwd: password updated successfully
|
||||
Changing the user information for robber
|
||||
Enter the new value, or press ENTER for the default
|
||||
Full Name []:
|
||||
Room Number []:
|
||||
Work Phone []:
|
||||
Home Phone []:
|
||||
Other []:
|
||||
Is the information correct? [Y/n] y
|
||||
|
||||
Note that this is a normal user who is created in the actual filesystem and not inside the jail.
|
||||
In the next step this user shall be imprisoned inside the jail.
|
||||
|
||||
At this point if you take a look at /etc/passwd you get to see an entry at the end that looks like this
|
||||
|
||||
robber:x:1006:1005:,,,:/home/robber:/bin/bash
|
||||
|
||||
This is our new user and the last part /bin/bash indicates that the user has a normal shell access on the system, if he logs in.
|
||||
|
||||
#### 4. Jail the user ####
|
||||
|
||||
Now its time to put the user inside the jail.
|
||||
|
||||
$ sudo jk_jailuser -m -j /opt/jail/ robber
|
||||
|
||||
By doing this the user robber has now been jailed.
|
||||
|
||||
Now if you take a look at /etc/passwd the last entry would look like this
|
||||
|
||||
robber:x:1006:1005:,,,:/opt/jail/./home/robber:/usr/sbin/jk_chrootsh
|
||||
|
||||
Note that the last 2 parts that indicate the home user and the shell type have changed. The home directory of the user is now inside the jail environment at /opt/jail. The shell of the user is now a special program called jk_chrootsh that will provide the jailed shell.
|
||||
|
||||
It is this particular shell called jk_chrootsh that takes the user inside the jail, everytime he logs onto the system.
|
||||
|
||||
The jail setup by now is nearly done. But if you try to connect to id from ssh, it will fail like this :
|
||||
|
||||
$ ssh robber@localhost
|
||||
robber@localhost's password:
|
||||
Welcome to Ubuntu 12.04 LTS (GNU/Linux 3.2.0-25-generic x86_64)
|
||||
|
||||
* Documentation: https://help.ubuntu.com/
|
||||
|
||||
13 packages can be updated.
|
||||
0 updates are security updates.
|
||||
|
||||
*** /dev/sda7 will be checked for errors at next reboot ***
|
||||
*** /dev/sda8 will be checked for errors at next reboot ***
|
||||
|
||||
Last login: Sat Jun 23 12:45:13 2012 from localhost
|
||||
Connection to localhost closed.
|
||||
$
|
||||
|
||||
The connection shall close. This happens because the user actually has a limited shell.
|
||||
|
||||
#### 5. Give bash shell to user inside the jail ####
|
||||
|
||||
The next important thing to do is to give the user a proper bash shell, but inside the jail.
|
||||
Open the following file
|
||||
|
||||
/opt/jail/etc/passwd
|
||||
|
||||
Its the password file inside the jail. It would look somewhat like this
|
||||
|
||||
root:x:0:0:root:/root:/bin/bash
|
||||
robber:x:1006:1005:,,,:/home/robber:/usr/sbin/jk_lsh
|
||||
|
||||
Change the /usr/sbin/jk_lsh to /bin/bash
|
||||
|
||||
root:x:0:0:root:/root:/bin/bash
|
||||
robber:x:1006:1005:,,,:/home/robber:/bin/bash
|
||||
|
||||
Save the file and exit.
|
||||
|
||||
#### 6. Login to the jail ####
|
||||
|
||||
So now its time to login into the jail again
|
||||
|
||||
$ ssh robber@localhost
|
||||
robber@localhost's password:
|
||||
Welcome to Ubuntu 12.04 LTS (GNU/Linux 3.2.0-25-generic x86_64)
|
||||
|
||||
* Documentation: https://help.ubuntu.com/
|
||||
|
||||
13 packages can be updated.
|
||||
0 updates are security updates.
|
||||
|
||||
*** /dev/sda7 will be checked for errors at next reboot ***
|
||||
*** /dev/sda8 will be checked for errors at next reboot ***
|
||||
|
||||
Last login: Sat Jun 23 12:46:01 2012 from localhost
|
||||
bash: groups: command not found
|
||||
I have no name!@desktop:~$
|
||||
|
||||
The jail says 'I have no name!' , ha ha. Now we have a fully functional bash shell but inside the jail.
|
||||
|
||||
Now check the environment by moving around. The root / of the jailed environment is /opt/jail of the real file system. But its only we who knows that, not the jailed user.
|
||||
|
||||
I have no name!@desktop:~$ cd /
|
||||
I have no name!@desktop:/$ ls
|
||||
bin dev etc home lib lib64 run usr var
|
||||
I have no name!@desktop:/$
|
||||
|
||||
Also only the commands that were copied via jk_cp sections will be available in this jail.
|
||||
|
||||
If the login fails, then check /var/log/auth.log for error messages.
|
||||
|
||||
Now try running some network command like wget or anything similar.
|
||||
|
||||
$ wget http://www.google.com/
|
||||
|
||||
If you get an error like this :
|
||||
|
||||
$ wget http://www.google.com/
|
||||
--2012-06-23 12:56:43-- http://www.google.com/
|
||||
Resolving www.google.com (www.google.com)... failed: Name or service not known.
|
||||
wget: unable to resolve host address `www.google.com'
|
||||
|
||||
Fix it by running the following 2 commands :
|
||||
|
||||
$ sudo jk_cp -v -j /opt/jail /lib/x86_64-linux-gnu/libnss_files.so.2
|
||||
$ sudo jk_cp -v -j /opt/jail /lib/x86_64-linux-gnu/libnss_dns.so.2
|
||||
|
||||
The exact location of the libnss_files.so and libnss_dns.so can vary so check.
|
||||
|
||||
### Running programs or services in the jail ###
|
||||
|
||||
Now the setup is complete. Jails are useful to run programs or services in a restricted/secure environments. To launch a program or daemon inside the jail use the **jk_chrootlaunch** command.
|
||||
|
||||
$ sudo jk_chrootlaunch -j /opt/jail -u robber -x /some/command/in/jail
|
||||
|
||||
The jk_chrootlaunch utility can be used to launch a particular process inside the jail environment with privileges of the specified user. If the daemon fails to start, check /var/log/syslog for error messages.
|
||||
|
||||
To run the program inside the jail, the program must first be fully copied inside the jail using the jk_cp command.
|
||||
|
||||
jk_cp - a utility to copy files including permissions and libraries into a jail
|
||||
|
||||
For further reading about various jailkit commands, check the documentation at [http://olivier.sessink.nl/jailkit/][1]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.binarytides.com/setup-jailed-shell-jailkit-ubuntu/
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://olivier.sessink.nl/jailkit/
|
||||
[2]:
|
||||
[3]:
|
||||
[4]:
|
||||
[5]:
|
||||
[6]:
|
||||
[7]:
|
||||
[8]:
|
||||
[9]:
|
||||
[10]:
|
||||
[11]:
|
||||
[12]:
|
||||
@ -0,0 +1,41 @@
|
||||
Unvanquished Will Probably Be the Best Free Multiplayer Game on Linux
|
||||
================================================================================
|
||||
**Unvanquished, a free, open-source first-person shooter combining real-time strategy elements with a futuristic and sci-fi setting, has just received its 22nd update. Actually it's 22.1, but who's counting?**
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
Even if Unvanquished is still in its Alpha stages, the developers have added a lot of new features and the game has become a lot more playable.
|
||||
|
||||
The Unvanquished Alpha 22.1 has received a few engine changes, some gameplay changes, a new map, a new version of an existing map, and more.
|
||||
|
||||
Snowstation is the new map integrated in the game. According to the developer, it has a simple layout, essentially a loop, and a snow-covered outside area forming part of that loop.
|
||||
|
||||
“We're now using C++ for all engine code. A few things are a bit different – some commands are changed a little or renamed and some output looks different. One which you'll probably notice while playing is marking for deconstruction – you'll need to rebind that key. The reason is that /if has lost its modifier key support; you'll need to use /modcase instead,” reads the announcement.
|
||||
|
||||
### Highlight of Unvanquished Alpha 22.1: ###
|
||||
|
||||
• The jetpack has been added. Users have to hold down the jump key and fly – but you can't hover anymore and you only have a limited amount of fuel;
|
||||
• The reasons “under attack” messages are reported have been changed;
|
||||
• Human weapons will be refilled or recharged automatically when close to a suitable building and not in use;
|
||||
• Repeaters are now effectively small reactors and they will provide power even when there is no reactor around;
|
||||
• FXAA now works with Mesa in OpenGL 2.1 contexts.
|
||||
|
||||
More details about this amazingly-looking game can be found on the official [website][1]. Keep in mind that this is a work in progress and bugs are bound to appear.
|
||||
|
||||
**Download Unvanquished Alpha 22.1 right now:**
|
||||
|
||||
- [Debian/Ubuntu DEB ALL][2][ubuntu_deb] [0 KB]
|
||||
- [Arch Linux package][2][binary] [0 KB]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://news.softpedia.com/news/Unvanquished-Will-Probably-Be-the-Best-Free-Multiplayer-Game-on-Linux-405956.shtml
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.unvanquished.net/news/111-it-s-release-time-again-alpha-22
|
||||
[2]:http://www.unvanquished.net/download#linux
|
||||
@ -1,6 +1,7 @@
|
||||
10 Lesser Known Effective Linux Commands – Part IV
|
||||
10个鲜为人知的Linux命令(4)
|
||||
================================================================================
|
||||
Continuing the **Lesser Known** series, this fourth article of the series will let you know some useful **funny** and **animated** commands. Here we go into the practical session, without much theory.
|
||||
继续我们的"鲜为人知"系列,本系列的第四篇会让你了解一些**有趣** 又 **动态**的命令。这里我们进入实际的教程,没有很多理论。
|
||||
|
||||

|
||||
|
||||
@ -8,17 +9,17 @@ Continuing the **Lesser Known** series, this fourth article of the series will l
|
||||
- [10 Lesser Known Linux Commands – Part 2][2]
|
||||
- [10 Lesser Known Commands for Linux – Part 3][3]
|
||||
|
||||
In the fourth article of this series which includes few other lesser known Linux commands, worth knowing. Might be you’re already aware of these commands, no doubt you’re an experienced Linux user and loves exploration.
|
||||
本系列的第四篇包含了另外的鲜为人知的Linux命令,这些值得去了解。也许你已经知道了这些命令,毫无疑问你是一个有经验的Linux用户并且乐于探索。
|
||||
|
||||
### 32. strace Command ###
|
||||
|
||||
The **strace** is a debugging tool which is used primarily for troubleshooting purpose in Linux. It might not be installed by default in your system and you may need to **apt** or **yum** the required package.
|
||||
**strace**是一个调试工具并被主要用于Linux的故障排除。它可能在你的系统内没有默认安装,你可能需要**apt** 或者 **yum**安装所需要的包。
|
||||
|
||||
Trace a command execution using strace command:
|
||||
使用strace命令追踪一个命令的执行。
|
||||
|
||||
root@tecmint [~]# strace pwd
|
||||
|
||||
#### Sample Output ####
|
||||
#### 示例输出 ####
|
||||
|
||||
execve("/bin/pwd", ["pwd"], [/* 29 vars */]) = 0
|
||||
brk(0) = 0x728000
|
||||
@ -40,56 +41,56 @@ Trace a command execution using strace command:
|
||||
mmap(NULL, 4096, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7f29b0de6000
|
||||
mmap(NULL, 4096, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7f29b0de5000
|
||||
....
|
||||
**strace**命令接收大量的参数和选项,请参考man页来获取详细信息。
|
||||
|
||||
The **strace** command accepts a lot of arguments and have many options. Refer to man page for detailed information.
|
||||
### 33. disown -a && exit 命令 ###
|
||||
|
||||
### 33. disown -a && exit Command ###
|
||||
大多数系统管理员使用[screen 命令][4]来控制运行在终端后台的作业。让我们假设一下如果你有一个长期运行的作业并想要将它从终端中**分离**,你可以用screen命令来这么做。但是如果你不知道如何使用screen,那么disown可以用来救急。
|
||||
|
||||
Most of the system administrators use [screen command][4] to control jobs running in the terminal background. Let’s say if you having a long running job and want to **detach** from the terminal, you use screen command to do it. But what if you don’t know how to use screen, here comes disown command to rescue.
|
||||
disown命令可以在后台持续运行作业即使你关闭了终端会话。disown命令的语法是:
|
||||
|
||||
The disown command is used to run the jobs continuously in the background even after you closing the terminal session. The syntax of the disown command is:
|
||||
|
||||
root@tecmint [~]# Command; disown -a && exit
|
||||
|
||||
To detach again the long running job in the terminal, use the **jobs** command to find the job number and then use disown **%n** where **n** is the job number. To verify actually the job is running use **ps** or [top command][5]. The **nohup** command is an alternative to the disown command.
|
||||
为了在终端中再次分离长期运行的作业,使用**jobs**命令来找出作业号,接着使用disown **%n**,这里的**%n**是作业号。为了验证作业确实在运行,使用**ps** 或者 [top 命令][5]。**nohup**命令也是一个disown命令的替代品。
|
||||
|
||||
### 34. getconf LONG_BIT Command ###
|
||||
### 34. getconf LONG_BIT 命令 ###
|
||||
|
||||
The above command shows your machine architecture if it is **32** bit or **64** bit?
|
||||
上面的命令能显示你的机器架构是**32** bit 或者 **64** 位?
|
||||
|
||||
root@tecmint [~]# getconf LONG_BIT
|
||||
|
||||
32
|
||||
|
||||
- [Download Linux Command Line Cheat Sheet][5]
|
||||
- [下载Linux命令备忘单][5]
|
||||
|
||||
### 35. Display Date on the Terminal ###
|
||||
### 35. 终端上显示日期 ###
|
||||
|
||||
The below command is a combination of several commands, better say it a script. For a person working at shell or terminal, without GUI seeing current system date is tedious job. You have to type ‘**date**‘ command to check today’s date.
|
||||
下面的命令是几个命令的集合,确切地说是一个脚本。对于在shell或者终端下工作的人来说,没有GUI界面看到当前系统日期是一个乏味的工作。你可以用‘**date**‘命令查看今天的日期。
|
||||
|
||||
Just execute the below command on you prompt and see the **date** and **time** on the above right corner of terminal.
|
||||
只要在提示符后输入如下的命令你就会在终端的右上角看到**日期**和**时间**。
|
||||
|
||||
root@tecmint [~]# while sleep 1;do tput sc;tput cup 0 $(($(tput cols)-29));date;tput rc;done &
|
||||
|
||||

|
||||

|
||||
|
||||
### 36. convert Command ###
|
||||
### 36. convert 命令 ###
|
||||
|
||||
While writing tutorial, I usually need to produce output, many a times in image format. The above command combination does this for me. Say I need the output of tree command (for **/etc/x11** directory) in image format. What I did at terminal was:
|
||||
在写教程的时候,我经常需要生成输出,很多时候是图片格式。上面的命令集合并不适合我。假设我需要tree命令的图片格式的输出(对 **/etc/x11** 目录 )。
|
||||
|
||||
root@tecmint:/etc/X11# tree | convert label:@- /home/avi/tree.png
|
||||
|
||||
The output of the above command can be seen at the specified location (here, home directory of mine) with the file name specified as **tree.png**.
|
||||
上面命令的输出可以在一个特定的位置(这里是我的家目录)下看到,文件名是**tree.png**。
|
||||
|
||||
### 37. watch -t -n1 “date +%T|figlet” ###
|
||||
|
||||
Remember our description of “**figlet**” command in our earlier article “[20 Funny Commands of Linux][7]”. This command was very cool, this time we will be pipelining ‘**figlet**‘ to show animated digital clock in the terminal.
|
||||
记住“**figlet**”命令在我们早期的文章“[20 Funny Commands of Linux][7]”中的描述。这个命令非常酷,这次我们会通过管道输出到‘**figlet**‘而在终端上显示一个动画电子钟。
|
||||
|
||||
Just check-out yourself, remember you must have **figlet** installed on the system, do **apt** or **yum** to install the required package.
|
||||
你自己检查一下,记住你必须已经在系统上安装了**figlet**,用**apt** 或者 **yum**安装所需要的包。
|
||||
|
||||
root@tecmint [~]# watch -t -n1 "date +%T|figlet"
|
||||
|
||||
#### Sample Output ####
|
||||
#### 示例输出 ####
|
||||
|
||||
_ ___ ____ ___ _____ _ _ Fri Nov 29 10:29:34 GMT
|
||||
/ |/ _ \ _|___ \ / _ \ _|___ /| || |
|
||||
@ -97,9 +98,9 @@ Just check-out yourself, remember you must have **figlet** installed on the syst
|
||||
| | |_| |_ / __/ \__, |_ ___) |__ _|
|
||||
|_|\___/(_)_____| /_/(_)____/ |_|
|
||||
|
||||
### 38. host and dig Commands ###
|
||||
### 38. host and dig 命令 ###
|
||||
|
||||
Although “**host**” and “**dig**” command is not that much lesser known, still not very frequently used. The host command is **DNS** lookup utility.
|
||||
虽然“**host**” 和 “**dig**”命令不那么鲜为人知,但是仍并不常被使用。host命令是**DNS**查询工具。
|
||||
|
||||
root@tecmint [~]# host www.google.com
|
||||
|
||||
@ -119,17 +120,17 @@ Although “**host**” and “**dig**” command is not that much lesser known,
|
||||
;; Got answer:
|
||||
;; ->>HEADER<
|
||||
|
||||
### 39. dstat Command ###
|
||||
### 39. dstat 命令 ###
|
||||
|
||||
The **dstat** is a versatile tool, that generates statistics relating to system resource. By default your system might not have ‘**dstat**‘ installed. Do a **apt** or **yum** to install ‘**dstat**‘ before using this very colorful and description system resource generator.
|
||||
**dstat**是一个多用的工具,它会依据系统资源生成统计。默认上你的系统可能没有安装‘**dstat**‘。在使用这个多彩的描述系统信息的生成器前使用**apt** 或者 **yum**来安装。
|
||||
|
||||
root@tecmint [~]# dstat
|
||||
|
||||

|
||||

|
||||
|
||||
### 40. bind -p Command ###
|
||||
### 40. bind -p 命令 ###
|
||||
|
||||
The ‘**bind -p**‘ command will show all the shortcuts available for **BASH** shell.
|
||||
‘**bind -p**‘会显示所有的**BASH** shell可用的快捷方式。
|
||||
|
||||
root@tecmint [~]# bind -p
|
||||
|
||||
@ -160,19 +161,19 @@ The ‘**bind -p**‘ command will show all the shortcuts available for **BASH**
|
||||
|
||||
### 41. touch /forcefsck ###
|
||||
|
||||
The above command will create an empty folder '**forcefsck**', under root directory. This will force Linux System to check the file system on the very next boot.
|
||||
下面的命令会在root目录下创建一个空的文件夹'**forcefsck**'。这会强制Linux系统在下次启动时检查文件系统。
|
||||
|
||||
root@tecmint [~]# touch /forcefsck
|
||||
|
||||
hat’s all for Now. You People are loving these ‘**Lesser Known Commands**‘ and hence we are continuing the series, the next article of this series will be available very soon.
|
||||
今天这些就是全部。因为你们爱‘**鲜为人知的命令**‘ ,因此我们将继续这个系列,本系列的下一篇文章将很快发布。
|
||||
|
||||
Till then stay tuned and connected to **Tecmint**. Don’t forget to give your valuable feedback in our comment section. Do a favor to us, Like and share us and help us spread.
|
||||
不要走开继续关注**Tecmint**。不要忘记在评论栏里留下你们有价值的反馈。帮我们一个忙,喜爱、分享我们的文章,并帮我们传播。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.tecmint.com/10-lesser-known-effective-linux-commands-part-iv/
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
译者:[geekpi](https://github.com/geekpi) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,150 +0,0 @@
|
||||
Linux中如何显示和设置Hostname
|
||||
================================================================================
|
||||

|
||||
|
||||
随着原来越多的计算机连接上网络,计算机需要有一个属性来与其他计算机区别。如同在真实世界的人,计算机也有自己属性叫hostname(主机名称)
|
||||
|
||||
### 什么是hostname ###
|
||||
|
||||
从它的操作手册来看,hostname是用来显示系统的DNS名字以及为了显示和设置它的主机名或者NIS域名名字。所以hostname是依赖于DNS(Domain Name System域名系统)或者NIS(Network Information System网络信息系统)。
|
||||
|
||||
|
||||
### 怎么显示hostname ###
|
||||
|
||||
hostname是为一个linux发行版的预安装命令。通过在控制台输入hostname,可以显示你的机器的hostname。这里有一个有个简单的命令及其输出。
|
||||
|
||||
|
||||
$ hostname
|
||||
ubuntu
|
||||
|
||||
上面的命令将会告诉你,计算机的名字是**ubuntu** 。
|
||||
|
||||
|
||||
### 如何设置hostname ###
|
||||
|
||||
Hostname当你在第一次安装你的Linux的时候已经设置好了。 就是在你安装你的Linux产品的那步时,将会询问你去填入主机名信息。然而,**你可以稍后填写它**如果你愿意。
|
||||
为了设置你的hostname,你可以使用下面的命令:
|
||||
|
||||
# hostname dev-machine
|
||||
|
||||
$ hostname
|
||||
dev-machine
|
||||
|
||||
你**需要使用root权限**或者同样的权限可以设置/改变你的hostname。#号提示你在使用root用户。上述命令告诉你的计算机设置你的hostname为**dev-machine**。如果你没有收到任何错误消息,那么你的hostname已经改变了。再一次使用hostname命令检查,看看结果。
|
||||
|
||||
使用hostname命令设置你的hostname**不是永久的**。当你重启你的计算机,你的设定将会取消。**为了永久改变**,你必须手动地修改hostname配置文件。
|
||||
|
||||
**On Debian / Ubuntu based Linux**
|
||||
**基于Linux 的 Debian / Ubuntu**
|
||||
|
||||
你可以在下列文件夹找到这个文件,
|
||||
**/etc/hostname**
|
||||
或者
|
||||
**/etc/hosts**
|
||||
|
||||
下面是每一个文件的内容
|
||||
|
||||
**/etc/hostname**
|
||||
|
||||
# vi /etc/hostname
|
||||
dev-machine
|
||||
|
||||
**/etc/hosts**
|
||||
|
||||
# vi /etc/hosts
|
||||
127.0.0.1 localhost
|
||||
127.0.0.1 dev-machine
|
||||
|
||||
你将会发现修改它会立即生效而不用重启你的linux。
|
||||
|
||||
**On RedHat / CentOS based Linux**
|
||||
**基于Linux的 RedHat / CentOS**
|
||||
|
||||
你可以在下列文件夹找到这个文件,
|
||||
**/etc/hosts**
|
||||
或者
|
||||
**/etc/sysconfig/networks**
|
||||
|
||||
下面是每一个文件的内容
|
||||
**/etc/hosts**
|
||||
|
||||
127.0.0.1 localhost.localdomain localhost dev-machine
|
||||
::localhost 127.0.0.1
|
||||
|
||||
/etc/sysconfig/network
|
||||
|
||||
NETWORKING=yes
|
||||
NETWORKING_IPV6=no
|
||||
HOSTNAME=dev-machine
|
||||
|
||||
### 怎么显示DNS域名 ###
|
||||
|
||||
来自上面的hostname的定义,hostname也可以显示你的Linux的DNS名字。如果你的hostname命令会显示你的hostname,那么dnsdomainname命令也就会显示你的域名。来看看这个简单的例子。
|
||||
|
||||
$ dnsdomainname
|
||||
bris.co.id
|
||||
|
||||
在本篇文章,dnsdomainname命令的结果是 **bris.co.id**。
|
||||
|
||||
如果你看见结果是 (**none**),那么你的机器**没有配置完整合格的域名(FQDN(Fully Qualified Domain Name))**。Dnsdomainname命令摘取来自**/etc/hosts**文件的信息。你应该配置它为完整合格的域名格式。接下来一个简单的例子:
|
||||
|
||||
**/etc/hosts**
|
||||
|
||||
127.0.0.1 localhost.localdomain localhost dev-machine
|
||||
::localhost 127.0.0.1
|
||||
192.168.0.104 dev-machine.bris.co.id dev-machine
|
||||
|
||||
为了显示更多的细节,你可以使用参数**-v**
|
||||
|
||||
$ dnsdomainname -v
|
||||
gethostname()=’dev-machine.bris.co.id’
|
||||
Resolving ‘dev-machine.bris.co.id’ …
|
||||
Result: h_name=’dev-machine.bris.co.id’
|
||||
Result: h_aliases=’dev-machine’
|
||||
Result: h_addr_list=’192.168.0.104’
|
||||
|
||||
### 如何显示hostname更多细节信息###
|
||||
|
||||
Hostname命令可以使用多个参数和一些别名如:dnsdomainname命令。这里有一些参数是每日操作中有用的。下面这些命令的结果是基于**/etc/hosts**的上述配置。
|
||||
|
||||
**显示IP地址**
|
||||
|
||||
$ hostname -i
|
||||
192.168.0.104
|
||||
|
||||
**显示域名**
|
||||
|
||||
$ hostname -d
|
||||
bris.co.id
|
||||
|
||||
**显示短主机名**
|
||||
$ hostname -s
|
||||
dev-machine
|
||||
|
||||
* 这个命令将会产生与输入hostname同样的结果 *
|
||||
|
||||
**显示FQDN格式**
|
||||
|
||||
$ hostname -f
|
||||
dev-machine.bris.co.id
|
||||
|
||||
**显示细节信息**
|
||||
|
||||
所有的参数包括上述信息,都可以通过使用参数**-v 和 -d** 来概括。让我们来看一个例子。
|
||||
|
||||
$ hostname -v -d
|
||||
gethostname()=’dev-machine.bris.co.id’
|
||||
Resolving ‘dev-machine.bris.co.id’ …
|
||||
Result: h_name=’dev-machine.bris.co.id’
|
||||
Result: h_aliases=’dev-machine’
|
||||
Result: h_addr_list=’192.168.0.104’
|
||||
bris.co.id
|
||||
|
||||
感到熟悉?是的,这个结果与**dnsdomainname -v**命令是相同的,同样包含上面的内容。
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/linux-command/display-set-hostname-linux/
|
||||
|
||||
译者:[Vic___](http://blog.csdn.net/Vic___) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
@ -1,15 +1,13 @@
|
||||
(translating by whatever1992)
|
||||
Install Oracle Java 7 in Elementary OS ‘Luna’ Via PPA
|
||||
使用PPA在Elementary OS 'Luna'上安装Oracle Java 7
|
||||
================================================================================
|
||||
**Question**: How can I install Oracle Java 7 in Elemetary OS Luna?
|
||||
**问题**: 我该如何在 Elemetary OS Luna 上安装Oracle Java 7?
|
||||
|
||||
**Answer**: To install Java 7 in Elementary OS Luna follow the steps below:
|
||||
**回答**: 在 Elementary OS Luna 安装 Java 7 的步骤如下:
|
||||
由于Elementary OS是基于Ubuntu,所以我们允许使用具有多种Java包的**WEPUD8 PPA**。
|
||||
|
||||
Since Elementary OS is Ubuntu based we are at liberty to use **WEPUD8 PPA** which has various Java packages in it.
|
||||
1. 打开终端。
|
||||
|
||||
1. Open Terminal.
|
||||
|
||||
2. Run the command below to add Java PPA to your repository:
|
||||
2. 运行以下指令添加Java的PPA到你的软件仓:
|
||||
|
||||
$ sudo add-apt-repository ppa:webupd8team/java
|
||||
|
||||
@ -19,7 +17,7 @@ Since Elementary OS is Ubuntu based we are at liberty to use **WEPUD8 PPA** whic
|
||||
More info: https://launchpad.net/~webupd8team/+archive/java
|
||||
Press [ENTER] to continue or ctrl-c to cancel adding it
|
||||
|
||||
3. Press ENTER to continue
|
||||
3. 按回车继续
|
||||
|
||||
gpg: keyring `/tmp/tmpB5WwDG/secring.gpg' created
|
||||
gpg: keyring `/tmp/tmpB5WwDG/pubring.gpg' created
|
||||
@ -30,11 +28,11 @@ Since Elementary OS is Ubuntu based we are at liberty to use **WEPUD8 PPA** whic
|
||||
gpg: imported: 1 (RSA: 1)
|
||||
OK
|
||||
|
||||
4. Now update your system
|
||||
4. 现在更新你的系统
|
||||
|
||||
$ sudo apt-get update
|
||||
|
||||
5. Install Java 7 by running the command below:
|
||||
5. 运行以下命令安装Java 7:
|
||||
|
||||
$ sudo apt-get install oracle-java7-installer
|
||||
|
||||
@ -60,21 +58,21 @@ Since Elementary OS is Ubuntu based we are at liberty to use **WEPUD8 PPA** whic
|
||||
After this operation, 473 kB of additional disk space will be used.
|
||||
Do you want to continue [Y/n]?
|
||||
|
||||
6. Type **Y** for Yes and Press enter to continue installation.
|
||||
6. 输入代表Yes的**Y**以及回车键继续安装。
|
||||
|
||||
7. During the installation, you need to agree to the license to continue. Select **OK**.
|
||||
7. 在安装过程中,你需要同意条款才能继续。选择**OK**。
|
||||
|
||||

|
||||
|
||||
8. Then Select **Yes** to continue.
|
||||
8. 然后选择**Yes**继续。
|
||||
|
||||

|
||||
|
||||
9. Now relax for the packages to be downloaded and installed automatically:
|
||||
9. 现在请等待安装包的下载与自动安装:
|
||||
|
||||

|
||||
|
||||
7. Installation has been completed successfully. You can now check the version of Java from the Terminal:
|
||||
10. 安装完成。你可以在终端上查看Java版本:
|
||||
|
||||
$ java -version
|
||||
java version "1.7.0_45"
|
||||
@ -85,6 +83,6 @@ Since Elementary OS is Ubuntu based we are at liberty to use **WEPUD8 PPA** whic
|
||||
|
||||
via: http://www.unixmen.com/install-oracle-java-7-elementary-os-luna-via-ppa/
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
译者:[whatever1992](https://github.com/whatever1992) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
266
translated/Setup a jailed shell with jailkit on ubuntu.md
Normal file
266
translated/Setup a jailed shell with jailkit on ubuntu.md
Normal file
@ -0,0 +1,266 @@
|
||||
在Ubuntu下用jailkit建立一个被监禁的Shell
|
||||
|
||||
================================================================================
|
||||
|
||||
### Jailkit和jailed Shell ###
|
||||
|
||||
监狱性的shell是一类限制性的shell,提供给用户非常真实的Shell模样,但是不允许它查看和修改真正的文件系统。Shell内的文件系统不同于底层的文件系统。这种功能是通过chroot和其他多种程序实现的。举例来说,建立一个用户的linux shell可能仅仅为了玩耍。或者在一个限定的环境里运行一些程序的所有功能等。
|
||||
|
||||
在这个教程里我们将会探讨在Ubuntu下用jailkit建立一个监禁的shell。Jailkit是辅助程序,允许快速的建立一个监禁的shell,监禁的用户,在受监禁的环境里配置程序并运行。
|
||||
|
||||
Jailkit can be downloaded from [http://olivier.sessink.nl/jailkit/][1]
|
||||
|
||||
我们已经谈论过关于在Ubuntu下安装jailkit,如果有不懂,多看看那篇文章。
|
||||
|
||||
### 配置jailed Shell ###
|
||||
|
||||
#### 配置jail环境 ####
|
||||
|
||||
我们需要建立一个目录来存放所有jail环境的配置。这不是重点,我们可以创建个/opt/jail的目录。
|
||||
|
||||
$ sudo mkdir /opt/jail
|
||||
|
||||
这个目录应为Root所有。所以用chown。
|
||||
|
||||
$ sudo chown root:root /opt/jail
|
||||
|
||||
#### 2. 设置在jail中可用的程序 ####
|
||||
|
||||
任何程序想要在jail中执行则必须用jk_init命令拷贝到目录中。
|
||||
|
||||
例如:
|
||||
|
||||
$ sudo jk_init -v /jail basicshell
|
||||
|
||||
$ sudo jk_init -v /jail editors
|
||||
|
||||
$ sudo jk_init -v /jail extendedshell
|
||||
|
||||
$ sudo jk_init -v /jail netutils
|
||||
|
||||
$ sudo jk_init -v /jail ssh
|
||||
|
||||
$ sudo jk_init -v /jail sftp
|
||||
|
||||
$ sudo jk_init -v /jail jk_lsh
|
||||
|
||||
或一次性解决:
|
||||
|
||||
$ sudo jk_init -v /opt/jail netutils basicshell jk_lsh openvpn ssh sftp
|
||||
|
||||
像basicshell, editors, netutils是一些组名,其中包含多个程序。复制到jail shell中的每个组都是可执行文件,库文件等的集合。比如**basicshell**就在jail提供有bash, ls, cat, chmod, mkdir, cp, cpio, date, dd, echo, egrep等程序。
|
||||
|
||||
完整的程序列表设置,你可以在/etc/jailkit/jk_init.ini中查看。
|
||||
|
||||
jk_lsh (Jailkit limited shell) - is an important section, and must be added.
|
||||
|
||||
#### 3. 创建将被监禁的用户 ####
|
||||
|
||||
需要将用户放入jail里。可以先创建一个
|
||||
|
||||
$ sudo adduser robber
|
||||
|
||||
Adding user `robber' ...
|
||||
|
||||
Adding new group `robber' (1005) ...
|
||||
|
||||
Adding new user `robber' (1006) with group `robber' ...
|
||||
|
||||
Creating home directory `/home/robber' ...
|
||||
|
||||
Copying files from `/etc/skel' ...
|
||||
|
||||
Enter new UNIX password:
|
||||
|
||||
Retype new UNIX password:
|
||||
|
||||
passwd: password updated successfully
|
||||
|
||||
Changing the user information for robber
|
||||
|
||||
Enter the new value, or press ENTER for the default
|
||||
|
||||
Full Name []:
|
||||
|
||||
Room Number []:
|
||||
|
||||
Work Phone []:
|
||||
|
||||
Home Phone []:
|
||||
|
||||
Other []:
|
||||
|
||||
Is the information correct? [Y/n] y
|
||||
|
||||
注意:目前创建的是一个活动在文件系统中的普通用户并没有添加到jail中。
|
||||
|
||||
在下一步这个用户会被监禁在jail里。
|
||||
|
||||
这时候如果你查看/etc/passwd文件,你会在文件最后看到跟下面差不多的一个条目。
|
||||
|
||||
robber:x:1006:1005:,,,:/home/robber:/bin/bash
|
||||
|
||||
这是我们新创建的用户,最后部分的/bin/bash指示了这个用户如果登入了那么它可以在系统上正常的Shell访问
|
||||
|
||||
#### 4. 监禁用户 ####
|
||||
|
||||
现在是时候将用户监禁在jail中
|
||||
|
||||
$ sudo jk_jailuser -m -j /opt/jail/ robber
|
||||
|
||||
执行上列命令后,用户robber将会被监禁。
|
||||
|
||||
如果你现在再观察/etc/passwd文件,会发现类似下面的最后条目。
|
||||
|
||||
robber:x:1006:1005:,,,:/opt/jail/./home/robber:/usr/sbin/jk_chrootsh
|
||||
|
||||
注意:最后两部分表明用户主目录和shell类型已经被改变了。现在用户的主目录在/opt/jail(jail环境)中。用户的Shell是一个名叫jk_chrootsh的特殊程序,会提供jailed Shell。
|
||||
|
||||
jk_chrootsh这是个特殊的shell,每当用户登入系统时,它都会将用户放入jail中。
|
||||
|
||||
到目前为止jail配置已经几乎完成了。但是如果你试图用ssh连接,那么注定会失败,像这样:
|
||||
|
||||
$ ssh robber@localhost
|
||||
|
||||
robber@localhost's password:
|
||||
|
||||
Welcome to Ubuntu 12.04 LTS (GNU/Linux 3.2.0-25-generic x86_64)
|
||||
|
||||
* Documentation: https://help.ubuntu.com/
|
||||
|
||||
13 packages can be updated.
|
||||
|
||||
0 updates are security updates.
|
||||
|
||||
*** /dev/sda7 will be checked for errors at next reboot ***
|
||||
|
||||
*** /dev/sda8 will be checked for errors at next reboot ***
|
||||
|
||||
Last login: Sat Jun 23 12:45:13 2012 from localhost
|
||||
|
||||
Connection to localhost closed.
|
||||
|
||||
$
|
||||
|
||||
连接会立马关闭,这意味着用户已经活动在一个受限制的shell中。
|
||||
|
||||
#### 5. 给在jail中的用户Bash Shell ####
|
||||
|
||||
下个重要的事情是给用户一个正确的bash shell,但是他却在jail中。
|
||||
|
||||
打开下面的文件
|
||||
|
||||
/opt/jail/etc/passwd
|
||||
|
||||
这是个jail中的password文件。类似如下
|
||||
|
||||
root:x:0:0:root:/root:/bin/bash
|
||||
|
||||
robber:x:1006:1005:,,,:/home/robber:/usr/sbin/jk_lsh
|
||||
|
||||
将/usr/sbin/jk_lsh改为/bin/bash
|
||||
|
||||
root:x:0:0:root:/root:/bin/bash
|
||||
|
||||
robber:x:1006:1005:,,,:/home/robber:/bin/bash
|
||||
|
||||
保存文件并退出。
|
||||
|
||||
#### 6. 登入jail ####
|
||||
|
||||
现在让我们再次登入jail
|
||||
|
||||
$ ssh robber@localhost
|
||||
|
||||
robber@localhost's password:
|
||||
|
||||
Welcome to Ubuntu 12.04 LTS (GNU/Linux 3.2.0-25-generic x86_64)
|
||||
|
||||
* Documentation: https://help.ubuntu.com/
|
||||
|
||||
13 packages can be updated.
|
||||
|
||||
0 updates are security updates.
|
||||
|
||||
*** /dev/sda7 will be checked for errors at next reboot ***
|
||||
|
||||
*** /dev/sda8 will be checked for errors at next reboot ***
|
||||
|
||||
Last login: Sat Jun 23 12:46:01 2012 from localhost
|
||||
|
||||
bash: groups: command not found
|
||||
|
||||
I have no name!@desktop:~$
|
||||
|
||||
jail说'I have no name!',哈哈。现在我们在jail中有个完整功能的bash shell。
|
||||
|
||||
现在通过操作检查环境。jail中的root /实际就是真实文件系统中的/opt/jail.但这只有我们自己知道,jail用户并不知情。
|
||||
|
||||
I have no name!@desktop:~$ cd /
|
||||
|
||||
I have no name!@desktop:/$ ls
|
||||
|
||||
bin dev etc home lib lib64 run usr var
|
||||
|
||||
I have no name!@desktop:/$
|
||||
|
||||
也只有我们通过jk_cp拷贝到jail中的命令能使用。
|
||||
|
||||
如果登入失败,请检查一下/var/log/auth.log的错误信息。
|
||||
|
||||
现在尝试运行一些网络命令,类似wget的命令。
|
||||
|
||||
$ wget http://www.google.com/
|
||||
|
||||
如果你获得类似的错误提示:
|
||||
|
||||
$ wget http://www.google.com/
|
||||
|
||||
--2012-06-23 12:56:43-- http://www.google.com/
|
||||
|
||||
Resolving www.google.com (www.google.com)... failed: Name or service not known.
|
||||
|
||||
wget: unable to resolve host address `www.google.com'
|
||||
|
||||
你可以通过运行下列两条命令来解决这个问题:
|
||||
|
||||
$ sudo jk_cp -v -j /opt/jail /lib/x86_64-linux-gnu/libnss_files.so.2
|
||||
|
||||
$ sudo jk_cp -v -j /opt/jail /lib/x86_64-linux-gnu/libnss_dns.so.2
|
||||
|
||||
这样才能正确的定位到libnss_files.so和libnss_dns.so
|
||||
|
||||
### 在jail中运行程序或服务 ###
|
||||
|
||||
此时此刻配置已经完成了。Jails可以在限制/安全的环境里运行程序或服务。用**jk_chrootlaunch**命令在jail中启动一个程序或守护进程。
|
||||
|
||||
$ sudo jk_chrootlaunch -j /opt/jail -u robber -x /some/command/in/jail
|
||||
|
||||
jk_chrootlaunch工具可以在jail环境中启动一个特殊的进程同时指定用户特权。如果守护进程启动失败,请检查/var/log/syslog/错误信息。
|
||||
|
||||
在jail中运行程序之前,该程序必须已经用jk_cp命令复制到jail中。
|
||||
|
||||
jk_cp - 将文件包括权限信息和库文件复制到jail的工具
|
||||
|
||||
进一步阅读有关其他jailkit命令信息,可以阅读文档,[http://olivier.sessink.nl/jailkit/][1]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.binarytides.com/setup-jailed-shell-jailkit-ubuntu/
|
||||
|
||||
译者:[Luoxcat](https://github.com/Luoxcat) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://olivier.sessink.nl/jailkit/
|
||||
[2]:
|
||||
[3]:
|
||||
[4]:
|
||||
[5]:
|
||||
[6]:
|
||||
[7]:
|
||||
[8]:
|
||||
[9]:
|
||||
[10]:
|
||||
[11]:
|
||||
[12]:
|
||||
Loading…
Reference in New Issue
Block a user