mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-01-16 22:42:21 +08:00
Merge remote-tracking branch 'LCTT/master'
This commit is contained in:
commit
d960542025
197
published/20180118 Getting Started with ncurses.md
Normal file
197
published/20180118 Getting Started with ncurses.md
Normal file
@ -0,0 +1,197 @@
|
||||
ncurses 入门指南
|
||||
======
|
||||
|
||||
> 怎样使用curses来绘制终端屏幕?
|
||||
|
||||
虽然图形界面非常酷,但是不是所有的程序都需要点击式的界面。例如,令人尊敬的 Vi 编辑器在第一个 GUI 出现之前在纯文本终端运行了很久。
|
||||
|
||||
Vi 编辑器是一个在“文本”模式下绘制的<ruby>面向屏幕<rt>screen-oriented</rt></ruby>程序的例子。它使用了一个叫 curses 的库。这个库提供了一系列的编程接口来操纵终端屏幕。curses 库产生于 BSD UNIX,但是 Linux 系统通过 ncurses 库提供这个功能。
|
||||
|
||||
[要了解 ncurses “过去曾引起的风暴”,参见 [ncurses: Portable Screen-Handling for Linux][1], September 1, 1995, by Eric S. Raymond.]
|
||||
|
||||
使用 curses 创建程序实际上非常简单。在这个文章中,我展示了一个利用 curses 来在终端屏幕上绘图的示例程序。
|
||||
|
||||
### 谢尔宾斯基三角形
|
||||
|
||||
简单展示一些 curses 函数的一个方法是生成<ruby>谢尔宾斯基三角形<rt>Sierpinski's Triangle</rt></ruby>。如果你对生成谢尔宾斯基三角形的这种方法不熟悉的话,这里是一些产生谢尔宾斯基三角形的规则:
|
||||
|
||||
1. 设置定义三角形的三个点。
|
||||
2. 随机选择任意的一个点 `(x,y)`。
|
||||
|
||||
然后:
|
||||
|
||||
1. 在三角形的顶点中随机选择一个点。
|
||||
2. 将新的 `x,y` 设置为先前的 `x,y` 和三角顶点的中间点。
|
||||
3. 重复(上述步骤)。
|
||||
|
||||
所以我按照这些指令写了这个程序,程序使用 curses 函数来向终端屏幕绘制谢尔宾斯基三角形:
|
||||
|
||||
```
|
||||
/* triangle.c */
|
||||
|
||||
#include <curses.h>
|
||||
#include <stdlib.h>
|
||||
|
||||
#include "getrandom_int.h"
|
||||
|
||||
#define ITERMAX 10000
|
||||
|
||||
int main(void)
|
||||
{
|
||||
long iter;
|
||||
int yi, xi;
|
||||
int y[3], x[3];
|
||||
int index;
|
||||
int maxlines, maxcols;
|
||||
|
||||
/* initialize curses */
|
||||
|
||||
initscr();
|
||||
cbreak();
|
||||
noecho();
|
||||
|
||||
clear();
|
||||
|
||||
/* initialize triangle */
|
||||
|
||||
maxlines = LINES - 1;
|
||||
maxcols = COLS - 1;
|
||||
|
||||
y[0] = 0;
|
||||
x[0] = 0;
|
||||
|
||||
y[1] = maxlines;
|
||||
x[1] = maxcols / 2;
|
||||
|
||||
y[2] = 0;
|
||||
x[2] = maxcols;
|
||||
|
||||
mvaddch(y[0], x[0], '0');
|
||||
mvaddch(y[1], x[1], '1');
|
||||
mvaddch(y[2], x[2], '2');
|
||||
|
||||
/* initialize yi,xi with random values */
|
||||
|
||||
yi = getrandom_int() % maxlines;
|
||||
xi = getrandom_int() % maxcols;
|
||||
|
||||
mvaddch(yi, xi, '.');
|
||||
|
||||
/* iterate the triangle */
|
||||
|
||||
for (iter = 0; iter < ITERMAX; iter++) {
|
||||
index = getrandom_int() % 3;
|
||||
|
||||
yi = (yi + y[index]) / 2;
|
||||
xi = (xi + x[index]) / 2;
|
||||
|
||||
mvaddch(yi, xi, '*');
|
||||
refresh();
|
||||
}
|
||||
|
||||
/* done */
|
||||
|
||||
mvaddstr(maxlines, 0, "Press any key to quit");
|
||||
|
||||
refresh();
|
||||
|
||||
getch();
|
||||
endwin();
|
||||
|
||||
exit(0);
|
||||
}
|
||||
```
|
||||
|
||||
让我一边解释一边浏览这个程序。首先,`getrandom_int()` 函数是我对 Linux 系统调用 `getrandom()` 的包装器。它保证返回一个正整数(`int`)值。(LCTT 译注:`getrandom()` 系统调用按照字节返回随机值到一个变量中,值是随机的,不保证正负,使用 `stdlib.h` 的 `random()` 函数可以达到同样的效果)另外,按照上面的规则,你应该能够辨认出初始化和迭代谢尔宾斯基三角形的代码。除此之外,我们来看看我用来在终端上绘制三角形的 curses 函数。
|
||||
|
||||
大多数 curses 程序以这四条指令开头。 `initscr()` 函数获取包括大小和特征在内的终端类型,并设置终端支持的 curses 环境。`cbreak()` 函数禁用行缓冲并设置 curses 每次只接受一个字符。`noecho()` 函数告诉 curses 不要把输入回显到屏幕上。而 `clear()` 函数清空了屏幕:
|
||||
|
||||
```
|
||||
initscr();
|
||||
cbreak();
|
||||
noecho();
|
||||
|
||||
clear();
|
||||
```
|
||||
|
||||
之后程序设置了三个定义三角的顶点。注意这里使用的 `LINES` 和 `COLS`,它们是由 `initscr()` 来设置的。这些值告诉程序在终端的行数和列数。屏幕坐标从 `0` 开始,所以屏幕左上角是 `0` 行 `0` 列。屏幕右下角是 `LINES - 1` 行,`COLS - 1` 列。为了便于记忆,我的程序里把这些值分别设为了变量 `maxlines` 和 `maxcols`。
|
||||
|
||||
在屏幕上绘制文字的两个简单方法是 `addch()` 和 `addstr()` 函数。也可以使用相关的 `mvaddch()` 和 `mvaddstr()` 函数可以将字符放到一个特定的屏幕位置。我的程序在很多地方都用到了这些函数。首先程序绘制三个定义三角的点并标记为 `'0'`,`'1'` 和 `'2'`:
|
||||
|
||||
```
|
||||
mvaddch(y[0], x[0], '0');
|
||||
mvaddch(y[1], x[1], '1');
|
||||
mvaddch(y[2], x[2], '2');
|
||||
```
|
||||
|
||||
为了绘制任意的一个初始点,程序做了类似的一个调用:
|
||||
|
||||
```
|
||||
mvaddch(yi, xi, '.');
|
||||
```
|
||||
|
||||
还有为了在谢尔宾斯基三角形递归中绘制连续的点:
|
||||
|
||||
```
|
||||
mvaddch(yi, xi, '*');
|
||||
```
|
||||
|
||||
当程序完成之后,将会在屏幕左下角(在 `maxlines` 行,`0` 列)显示一个帮助信息:
|
||||
|
||||
```
|
||||
mvaddstr(maxlines, 0, "Press any key to quit");
|
||||
```
|
||||
|
||||
注意 curses 在内存中维护了一个版本的屏幕显示,并且只有在你要求的时候才会更新这个屏幕,这很重要。特别是当你想要向屏幕显示大量的文字的时候,这样程序会有更好的性能表现。这是因为 curses 只能更新在上次更新之后改变的这部分屏幕。想要让 curses 更新终端屏幕,请使用 `refresh()` 函数。
|
||||
|
||||
在我的示例程序中,我选择在“绘制”每个谢尔宾斯基三角形中的连续点时更新屏幕。通过这样做,用户可以观察三角形中的每次迭代。(LCTT 译注:由于 CPU 太快,迭代过程执行就太快了,所以其实很难直接看到迭代过程)
|
||||
|
||||
在退出之前,我使用 `getch()` 函数等待用户按下一个键。然后我调用 `endwin()` 函数退出 curses 环境并返回终端程序到一般控制。
|
||||
|
||||
```
|
||||
getch();
|
||||
endwin();
|
||||
```
|
||||
|
||||
### 编译和示例输出
|
||||
|
||||
现在你已经有了你的第一个 curses 示例程序,是时候编译运行它了。记住 Linux 操作系统通过 ncurses 库来实现 curses 功能,所以你需要在编译的时候通过 `-lncurses`来链接——例如:
|
||||
|
||||
```
|
||||
$ ls
|
||||
getrandom_int.c getrandom_int.h triangle.c
|
||||
|
||||
$ gcc -Wall -lncurses -o triangle triangle.c getrandom_int.c
|
||||
```
|
||||
|
||||
(LCTT 译注:此处命令行有问题,`-lncurses` 选项在我的 Ubuntu 16.04 系统 + gcc 4.9.3 环境下,必须放在命令行最后,否则找不到库文件,链接时会出现未定义的引用。)
|
||||
|
||||
在标准的 80x24 终端运行这个 `triangle` 程序并没什么意思。在那样的分辨率下你不能看见谢尔宾斯基三角形的很多细节。如果你运行终端窗口并设置非常小的字体大小,你可以更加容易地看到谢尔宾斯基三角形的不规则性质。在我的系统上,输出如图 1。
|
||||
|
||||

|
||||
|
||||
*图 1. triangle 程序的输出*
|
||||
|
||||
虽然迭代具有随机性,但是每次谢尔宾斯基三角形的运行看起来都会很一致。唯一的不同是最初绘制到屏幕的一些点的位置不同。在这个例子中,你可以看到三角形开始的一个小圆点,在点 1 附近。看起来程序接下来选择了点 2,然后你可以看到在圆点和“2”之间的星号。并且看起来程序随机选择了点 2 作为下一个随机数,因为你可以看到在第一个星号和“2”之间的星号。从这里开始,就不能继续分辨三角形是怎样被画出来的了,因为所有的连续点都属于三角形区域。
|
||||
|
||||
### 开始学习 ncurses
|
||||
|
||||
这个程序是一个怎样使用 curses 函数绘制字符到屏幕的简单例子。按照你的程序的需要,你可以通过 curses 做得更多。在下一篇文章中,我将会展示怎样使用 curses 让用户和屏幕交互。如果你对于学习 curses 有兴趣,我建议你去读位于 <ruby>[Linux 文档计划](http://www.tldp.org)<rt>Linux Documentation Project</rt></ruby>的 Pradeep Padala 写的 [NCURSES Programming HOWTO][2]。
|
||||
|
||||
### 关于作者
|
||||
|
||||
Jim Hall 是一个自由及开源软件的倡议者,他最有名的工作是 FreeDOS 计划,也同样致力于开源软件的可用性。Jim 是在明尼苏达州的拉姆齐县的首席信息官。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linuxjournal.com/content/getting-started-ncurses
|
||||
|
||||
作者:[Jim Hall][a]
|
||||
译者:[leemeans](https://github.com/leemeans)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.linuxjournal.com/users/jim-hall
|
||||
[1]:http://www.linuxjournal.com/article/1124
|
||||
[2]:http://tldp.org/HOWTO/NCURSES-Programming-HOWTO
|
||||
59
published/20180202 Which Linux Kernel Version Is Stable.md
Normal file
59
published/20180202 Which Linux Kernel Version Is Stable.md
Normal file
@ -0,0 +1,59 @@
|
||||
哪个 Linux 内核版本是 “稳定的”?
|
||||
============================================================
|
||||
|
||||

|
||||
|
||||
> Konstantin Ryabitsev 为你讲解哪个 Linux 内核版本可以被视作“稳定版”,以及你应该如何选择一个适用你的内核版本。
|
||||
|
||||
每次 Linus Torvalds 发布 [一个新 Linux 内核的主线版本][4],几乎都会引起这种困惑,那就是到底哪个内核版本才是最新的“稳定版”?是新的那个 X.Y,还是前面的那个 X.Y-1.Z ?最新的内核版本是不是太“新”了?你是不是应该坚持使用以前的版本?
|
||||
|
||||
[kernel.org][5] 网页上的信息并不会帮你解开这个困惑。目前,在该页面的最顶部,我们看到是最新稳定版内核是 4.15 — 但是在这个表格的下面,4.14.16 也被列为“<ruby>稳定版<rt>stable</rt></ruby>”,而 4.15 被列为“<ruby>主线版本<rt>mainline</rt></ruby>”,很困惑,是吧?
|
||||
|
||||
不幸的是,这个问题并不好回答。我们在这里使用“稳定”这个词有两个不同的意思:一是,作为最初发布的 Git 树的名字,二是,表示这个内核可以被视作“稳定版”,用在“生产系统”。
|
||||
|
||||
由于 Git 的分布式特性,Linux 的开发工作在许多 [不同的分叉仓库中][6] 进行。所有的 bug 修复和新特性也是首先由各个子系统维护者收集和准备的,然后提交给 Linus Torvalds,由 Linus Torvalds 包含进 [他自己的 Linux 树][7] 中,他的 Git 树被认为是 Git 仓库的 “master”。我们称这个树为 “主线” Linux 树。
|
||||
|
||||
### 候选发布版(RC)
|
||||
|
||||
在每个新的内核版本发布之前,它都要经过几轮的“候选发布”,它由开发者进行测试并“打磨”所有的这些很酷的新特性。基于他们这几轮测试的反馈,Linus 决定最终版本是否已经准备就绪。通常有 7 个每周预发布版本,但是,这个数字经常走到 -rc8,并且有时候甚至达到 -rc9 及以上。当 Linus 确信那个新内核已经没有问题了,他就制作最终发行版,我们称这个版本为“稳定版”,表示它不再是一个“候选发布版”。
|
||||
|
||||
### Bug 修复
|
||||
|
||||
就像任何一个由不是十全十美的人所写的复杂软件一样,任何一个 Linux 内核的新版本都包含 bug,并且这些 bug 必须被修复。Linux 内核的 bug 修复规则非常简单:所有修复必须首先进入到 Linus 的树。一旦主线仓库中的 bug 被修复后,它接着会被应用到内核开发社区仍在维护的已发布内核中。在它们被考虑回迁到已发布的稳定版本之前,所有的 bug 修复必须满足 [一套重要的标准][8] — 标准的其中之一是,它们 “必须已经存在于 Linus 的树中”。这是一个 [独立的 Git 仓库][9],维护它的用途是回迁 bug 修复,而它也被称为“稳定”树 —— 因为它用于跟踪以前发布的稳定内核。这个树由 Greg Kroah-Hartman 策划和维护。
|
||||
|
||||
### 最新的稳定内核
|
||||
|
||||
因此,无论在什么时候,为了查看最新的稳定内核而访问 kernel.org 网站时,你应该去使用那个在大黄色按钮所说的“最新的稳定内核”。
|
||||
|
||||

|
||||
|
||||
但是,你可能会惊奇地发现 —— 4.15 和 4.14.16 都是稳定版本,那么到底哪一个更“稳定”呢?有些人不愿意使用 “.0” 的内核发行版,因为他们认为这个版本并不足够“稳定”,直到最新的是 ".1" 的为止。很难证明或者反驳这种观点的对与错,并且这两种观点都有赞成或者反对的理由,因此,具体选择哪一个取决于你的喜好。
|
||||
|
||||
一方面,任何一个进入到稳定树的发行版都必须首先被接受进入主线内核版本中,并且随后会被回迁到已发行版本中。这意味着内核的主线版本相比稳定树中的发行版本来说,总包含有最新的 bug 修复,因此,如果你想使用的发行版包含的“**已知 bug**”最少,那么使用 “.0” 的主线发行版是最佳选择。
|
||||
|
||||
另一方面,主线版本增加了所有很酷的新特性 —— 而新特性也给它们带来了**数量未知的“新 bug”**,而这些“新 bug”在老的稳定版中是**不会存在**的。而新的、未知的 bug 是否比旧的、已知的但尚未修复的 bug 更加令人担心呢? —— 这取决于你的选择。不过需要说明的一点是,许多 bug 修复只对内核的主线版本进行了彻底的测试。当补丁回迁到旧内核时,它们**可能**会工作的很好,但是它们**很少**做与旧内核的集成测试工作。通常都假定,“以前的稳定版本”足够接近当前的确信可用于生产系统的主线版本。而实际上也确实是这样的,当然,这也更加说明了为什么选择“哪个内核版本更稳定”是件**非常困难**的事情了。
|
||||
|
||||
因此,从根本上说,我们并没有定量的或者定性的手段去明确的告诉你哪个内核版本更加稳定 —— 4.15 还是 4.14.16?我们能够做到的只是告诉你,它们具有“**不同的**稳定性”,(这个答案可能没有帮到你,但是,至少你明白了这些版本的差别是什么?)。
|
||||
|
||||
_学习更多的 Linux 的知识,可以通过来自 Linux 基金会和 edX 的免费课程 ["认识 Linux" ][3]。_
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.linux.com/blog/learn/2018/2/which-linux-kernel-version-stable
|
||||
|
||||
作者:[KONSTANTIN RYABITSEV][a]
|
||||
译者:[qhwdw](https://github.com/qhwdw)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://www.linux.com/users/mricon
|
||||
[1]:https://www.linux.com/licenses/category/creative-commons-zero
|
||||
[2]:https://www.linux.com/files/images/apple1jpg
|
||||
[3]:https://training.linuxfoundation.org/linux-courses/system-administration-training/introduction-to-linux
|
||||
[4]:https://linux.cn/article-9328-1.html
|
||||
[5]:https://www.kernel.org/
|
||||
[6]:https://git.kernel.org/pub/scm/linux/kernel/git/
|
||||
[7]:https://git.kernel.org/torvalds/c/v4.15
|
||||
[8]:https://www.kernel.org/doc/html/latest/process/stable-kernel-rules.html
|
||||
[9]:https://git.kernel.org/stable/linux-stable/c/v4.14.16
|
||||
@ -0,0 +1,79 @@
|
||||
Can anonymity and accountability coexist?
|
||||
=========================================
|
||||
|
||||
Anonymity might be a boon to more open, meritocratic organizational cultures. But does it conflict with another important value: accountability?
|
||||
|
||||

|
||||
|
||||
Image by :opensource.com
|
||||
|
||||
### Get the newsletter
|
||||
|
||||
Join the 85,000 open source advocates who receive our giveaway alerts and article roundups.
|
||||
|
||||
Whistleblowing protections, crowdsourcing, anonymous voting processes, and even Glassdoor reviews—anonymous speech may take many forms in organizations.
|
||||
|
||||
As well-established and valued as these anonymous feedback mechanisms may be, anonymous speech becomes a paradoxical idea when one considers how to construct a more open organization. While an inability to discern speaker identity seems non-transparent, an opportunity for anonymity may actually help achieve a _more inclusive and meritocratic_ environment.
|
||||
|
||||
More about open organizations
|
||||
|
||||
* [Download free Open Org books](https://opensource.com/open-organization/resources/book-series?src=too_resource_menu1a)
|
||||
* [What is an Open Organization?](https://opensource.com/open-organization/resources/open-org-definition?src=too_resource_menu2a)
|
||||
* [How open is your organization?](https://opensource.com/open-organization/resources/open-org-maturity-model?src=too_resource_menu3a)
|
||||
* [What is an Open Decision?](https://opensource.com/open-organization/resources/open-decision-framework?src=too_resource_menu4a)
|
||||
* [The Open Org two years later](https://www.redhat.com/en/about/blog/open-organization-two-years-later-and-going-strong?src=too_resource_menu4b&intcmp=70160000000h1s6AAA)
|
||||
|
||||
But before allowing outlets for anonymous speech to propagate, however, leaders of an organization should carefully reflect on whether an organization's "closed" practices make anonymity the unavoidable alternative to free, non-anonymous expression. Though some assurance of anonymity is necessary in a few sensitive and exceptional scenarios, dependence on anonymous feedback channels within an organization may stunt the normalization of a culture that encourages diversity and community.
|
||||
|
||||
### The benefits of anonymity
|
||||
|
||||
In the case of [_Talley v. California (1960)_](https://supreme.justia.com/cases/federal/us/362/60/case.html), the Supreme Court voided a city ordinance prohibiting the anonymous distribution of handbills, asserting that "there can be no doubt that such an identification requirement would tend to restrict freedom to distribute information and thereby freedom of expression." Our judicial system has legitimized the notion that the protection of anonymity facilitates the expression of otherwise unspoken ideas. A quick scroll through any [subreddit](https://www.reddit.com/reddits/) exemplifies what the Court has codified: anonymity can foster [risk-taking creativity](https://www.reddit.com/r/sixwordstories/) and the [inclusion and support of marginalized voices](https://www.reddit.com/r/MyLittleSupportGroup/). Anonymity empowers individuals by granting them the safety to speak without [detriment to their reputations or, more importantly, their physical selves.](https://www.psychologytoday.com/blog/the-compassion-chronicles/201711/why-dont-victims-sexual-harassment-come-forward-sooner)
|
||||
|
||||
For example, an anonymous suggestion program to garner ideas from members or employees in an organization may strengthen inclusivity and enhance the diversity of suggestions the organization receives. It would also make for a more meritocratic decision-making process, as anonymity would ensure that the quality of the articulated idea, rather than the rank and reputation of the articulator, is what's under evaluation. Allowing members to anonymously vote for anonymously-submitted ideas would help curb the influence of office politics in decisions affecting the organization's growth.
|
||||
|
||||
### The harmful consequences of anonymity
|
||||
|
||||
Yet anonymity and the open value of _accountability_ may come into conflict with one another. For instance, when establishing anonymous programs to drive greater diversity and more meritocratic evaluation of ideas, organizations may need to sacrifice the ability to hold speakers accountable for the opinions they express.
|
||||
|
||||
Reliance on anonymous speech for serious organizational decision-making may also contribute to complacency in an organizational culture that falls short of openness. Outlets for anonymous speech may be as similar to open as crowdsourcing is—or rather, is not. [Like efforts to crowdsource creative ideas](https://opensource.com/business/10/4/why-open-source-way-trumps-crowdsourcing-way), anonymous suggestion programs may create an organizational environment in which diverse perspectives are only valued when an organization's leaders find it convenient to take advantage of members' ideas.
|
||||
|
||||
Anonymity and the open value of accountability may come into conflict with one another.
|
||||
|
||||
A similar concern holds for anonymous whistle-blowing or concern submission. Though anonymity is important for sexual harassment and assault reporting, regularly redirecting member concerns and frustrations to a "complaints box" makes it more difficult for members to hold their organization's leaders accountable for acting on concerns. It may also hinder intra-organizational support networks and advocacy groups from forming around shared concerns, as members would have difficulty identifying others with similar experiences. For example, many working mothers might anonymously submit requests for a lactation room in their workplace, then falsely attribute a lack of action from leaders to a lack of similar concerns from others.
|
||||
|
||||
### An anonymity checklist
|
||||
|
||||
Organizations in which anonymous speech is the primary mode of communication, like subreddits, have generated innovative works and thought-provoking discourse. These anonymous networks call attention to the potential for anonymity to help organizations pursue open values of diversity and meritocracy. Organizations in which anonymous speech is _not_ the main form of communication should acknowledge the strengths of anonymous speech, but carefully consider whether anonymity is the wisest means to the goal of sustainable openness.
|
||||
|
||||
Leaders may find reflecting on the following questions useful prior to establishing outlets for anonymous feedback within their organizations:
|
||||
|
||||
1\. _Availability of additional communication mechanisms_: Rather than investing time and resources into establishing a new, anonymous channel for communication, can the culture or structure of existing avenues of communication be reconfigured to achieve the same goal? This question echoes the open source affinity toward realigning, rather than reinventing, the wheel.
|
||||
|
||||
2\. _Failure of other communication avenues:_ How and why is the organization ill-equipped to handle the sensitive issue/situation at hand through conventional (i.e. non-anonymous) means of communication?
|
||||
|
||||
Careful deliberation on these questions may help prevent outlets for anonymous speech from leading to a dangerous sense of complacency.
|
||||
|
||||
3\. _Consequences of anonymity:_ If implemented, could the anonymous mechanism stifle the normalization of face-to-face discourse about issues important to the organization's growth? If so, how can leaders ensure that members consider the anonymous communication channel a "last resort," without undermining the legitimacy of the anonymous system?
|
||||
|
||||
4\. _Designing the anonymous communication channel:_ How can accountability be promoted in anonymous communication without the ability to determine the identity of speakers?
|
||||
|
||||
5\. _Long-term considerations_: Is the anonymous feedback mechanism sustainable, or a temporary solution to a larger organizational issue? If the latter, is [launching a campaign](https://opensource.com/open-organization/16/6/8-steps-more-open-communications) to address overarching problems with the organization's communication culture feasible?
|
||||
|
||||
These five points build off of one another to help leaders recognize the tradeoffs involved in legitimizing anonymity within their organization. Careful deliberation on these questions may help prevent outlets for anonymous speech from leading to a dangerous sense of complacency with a non-inclusive organizational structure.
|
||||
|
||||
About the author
|
||||
----------------
|
||||
|
||||
[](https://opensource.com/users/susiechoi)
|
||||
|
||||
Susie Choi - Susie is an undergraduate student studying computer science at Duke University. She is interested in the implications of technological innovation and open source principles for issues relating to education and socioeconomic inequality.
|
||||
|
||||
[More about me](https://opensource.com/users/susiechoi)
|
||||
|
||||
* * *
|
||||
|
||||
via: [https://opensource.com/open-organization/18/1/balancing-accountability-and-anonymity](https://opensource.com/open-organization/18/1/balancing-accountability-and-anonymity)
|
||||
|
||||
作者: [Susie Choi](https://opensource.com/users/susiechoi) 选题者: [@lujun9972](https://github.com/lujun9972) 译者: [译者ID](https://github.com/译者ID) 校对: [校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
@ -0,0 +1,257 @@
|
||||
How to Encrypt Files with Tomb on Ubuntu 16.04 LTS
|
||||
==================================================
|
||||
|
||||
Most people regard file encryption as a necessity nowadays, even on Linux systems. If, like me, you were originally attracted to Ubuntu because of the enhanced security of Linux systems, I’m afraid I’ve got bad news for you: Linux has become a victim of its own success. The vast increase in the number of users over recent years has led to attacks and theft on such systems growing exponentially.
|
||||
|
||||
There used to be a pretty easy solution to encrypting files on Linux systems like Ubuntu: it was called [Truecrypt](https://www.fossmint.com/secure-encrypt-files-folders-with-truecrypt-in-linux/). Up until 2015, it offered varying levels of military-grade encryption, and worked well with most Linux systems. Unfortunately, it has since been discontinued, and has therefore become pretty insecure.
|
||||
|
||||
### The Alternatives
|
||||
|
||||
Luckily, there are a few alternatives to Truecrypt. The direct successor of Truecrypt was [Veracrypt](https://www.fossmint.com/veracrypt-is-a-secure-alternative-encryption-tool-to-truecrypt-for-linux/), made by a group of developers who took the source code from Truecrypt and kept it updated.
|
||||
|
||||
The project has since grown into an impressive standalone system, but is now showing its age. Old systems, and especially those that deal with security, can only be updated so many times without introducing vulnerabilities.
|
||||
|
||||
For this reason, among many others, it’s worth looking a bit further afield for encryption software. My choice would be Tomb.
|
||||
|
||||
### Why Tomb?
|
||||
|
||||
In some ways, Tomb is pretty similar to other encryption software. It stores encrypted files in dedicated “Tomb Folders”, allowing you to quickly see which files you have encrypted.
|
||||
|
||||
It also uses a similar encryption standard to Veracrypt, [AES-256](https://www.dyne.org/software/tomb/). This standard is Applied by everyone from the NSA to Microsoft to Apple, and is regarded as one of the most secure encryption ciphers available. If you’re new to encryption, it’s worth reading a bit of [the background behind the technology](https://thebestvpn.com/advanced-encryption-standard-aes/), but if you just want fast, secure encryption, don’t worry: Tomb will deliver.
|
||||
|
||||
There are a couple of big differences with Tomb. The first is that it has been developed specifically for GNU/Linux systems, cutting out some of the compatibility issues of broader encryption software.
|
||||
|
||||
The second is that, although Tomb is open source, it makes use of statically linked libraries so that its source code is hard to audit. That means that it is not considered free by some OS distributors, but when it comes to security software this is actually a good thing: it means that Tomb is less likely to be hacked than completely “free” software.
|
||||
|
||||
Lastly, it has several advanced features like **steganography**, which allows you to hide your key files within another file. And though Tomb is primarily a command-line tool, it also comes with a GUI interface, gtomb, which allows beginners to use it graphically.
|
||||
|
||||
Sold? Well, before I take you through how to use Tomb, it’s worth noting that no encryption software can offer total protection. Tomb will not hide your online computing from your ISP, and nor does it protect files stored in the cloud. If you want to fully encrypt cloud storage, you’ll need to log into your preferred storage service using the Tor browser and a zero-logging VPN. There are plenty of options available here, but [Trust Zone](https://privacyaustralia.org/trust-zone-vpn-review/) is a good browser, and [Tinc](https://www.howtoforge.com/tutorial/how-to-properly-set-up-tinc-vpn-on-ubuntu-linux/) is a good VPN tool.
|
||||
|
||||
All that said, if you are looking for fast, easy, secure encryption for Ubuntu 16.04, Tomb is undoubtedly the way to go. Let’s get you started.
|
||||
|
||||
### Installing Tomb on Ubuntu 16.04
|
||||
|
||||
Because Tomb was made especially for Linux, install is super easy.
|
||||
|
||||
A couple of years back, the guys over at SparkyLinux (which is a pretty good Debian derivative in its own right) added Tomb to their official repositories. You can install it on your Ubuntu system by adding these repositories.
|
||||
|
||||
To do this, open a terminal and add a repository file:
|
||||
|
||||
`sudo vi /etc/apt/sources.list.d/sparky-repo.list`
|
||||
|
||||
And then add the following lines to the file:
|
||||
|
||||
```
|
||||
deb https://sparkylinux.org/repo stable main
|
||||
deb-src https://sparkylinux.org/repo stable main
|
||||
deb https://sparkylinux.org/repo testing main
|
||||
deb-src https://sparkylinux.org/repo testing main
|
||||
|
||||
```
|
||||
|
||||
Save and close that file.
|
||||
|
||||
You now need to install the Sparky public key, using either:
|
||||
|
||||
```
|
||||
sudo apt-get install sparky-keyring
|
||||
|
||||
```
|
||||
|
||||
Or:
|
||||
|
||||
```
|
||||
wget -O - https://sparkylinux.org/repo/sparkylinux.gpg.key | sudo apt-key add -
|
||||
|
||||
```
|
||||
|
||||
You then need to update your repositories, using the standard command:
|
||||
|
||||
```
|
||||
sudo apt-get update
|
||||
|
||||
```
|
||||
|
||||
And then simply install Tomb using apt:
|
||||
|
||||
```
|
||||
sudo apt-get install tomb
|
||||
|
||||
```
|
||||
|
||||
If you want the GUI, install is just as easy. Just use apt to install gtomb:
|
||||
|
||||
```
|
||||
sudo apt-get install gtomb
|
||||
|
||||
```
|
||||
|
||||
And that’s it: you should now have a working version of Tomb installed. Let’s look at how to use it.
|
||||
|
||||
### Using Tomb
|
||||
|
||||
#### Using Tomb Through The Command Line
|
||||
|
||||
Tomb is primarily a command line tool, so I’ll cover this usage first. If you are not comfortable with using a terminal, you can skip this section and look below.
|
||||
|
||||
Actually, scratch that. If you’ve never used the command line before, Tomb is a great place to start, because it uses simple commands and there is little chance of you messing something up as long as you are careful.
|
||||
|
||||
Tomb actually uses a pretty amusing set of commands, all graveyard-themed. Each encrypted folder is referred to as a “tomb”, and (as I’ll come to shortly) they can be worked with using similarly Gothic commands.
|
||||
|
||||
First, let’s make a new tomb. You can specify the name and the size of your new tomb, so let’s use “Tomb1”, and make it 100mb.
|
||||
|
||||
You need root privileges, so open a terminal and type (or copy):
|
||||
|
||||
```
|
||||
sudo tomb dig -s 100 Tomb1.tomb
|
||||
|
||||
```
|
||||
|
||||
This should give you output similar to:
|
||||
|
||||
```
|
||||
tomb . Commanded to dig tomb Tomb1.tomb
|
||||
tomb (*) Creating a new tomb in Tomb1.tomb
|
||||
tomb . Generating Tomb1.tomb of 100MiB
|
||||
100 blocks (100Mb) written.
|
||||
100+0 records in
|
||||
100+0 records out
|
||||
-rw------- 1 Tomb1 Tomb1 100M Jul 4 18:53 Tomb1.tomb
|
||||
tomb (*) Done digging Tomb1
|
||||
tomb . Your tomb is not yet ready, you need to forge a key and lock it:
|
||||
tomb . tomb forge Tomb1.tomb.key
|
||||
tomb . tomb lock Tomb1.tomb -k Tomb1.tomb.key
|
||||
|
||||
```
|
||||
|
||||
As the output helpfully states, you now need to create a keyfile to lock your tomb:
|
||||
|
||||
```
|
||||
sudo tomb forge Tomb1.tomb.key
|
||||
|
||||
```
|
||||
|
||||
If, at this point, you get an error that mentions “an active swap partition”, you need to deactivate all of your active swap partititions:
|
||||
|
||||
```
|
||||
sudo swapoff -a
|
||||
|
||||
```
|
||||
|
||||
And then run the keyfile command above.
|
||||
|
||||
It might take a few minutes to generate a keyfile, depending on the speed of your system. After it is done, however, you’ll be asked to enter a new password to secure the key:
|
||||
|
||||
[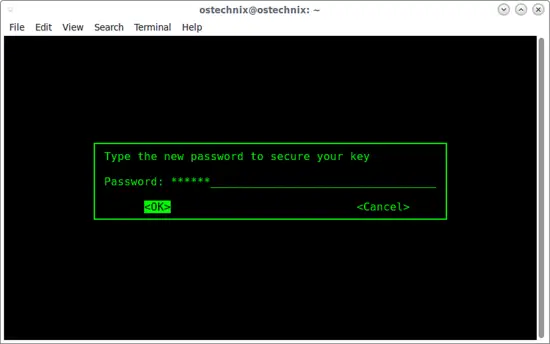](https://www.howtoforge.com/images/how_to_setup_and_install_tomb_on_ubuntu_1604/big/tomb1.png)
|
||||
|
||||
Enter it twice, and your new keyfile will be made.
|
||||
|
||||
You now need to lock your tomb using your new key. You can do this like this:
|
||||
|
||||
```
|
||||
sudo tomb lock Tomb1.tomb -k Tomb1.tomb.key
|
||||
|
||||
```
|
||||
|
||||
You will be asked to enter your password. Do this, and you should get something like the following output:
|
||||
|
||||
```
|
||||
tomb . Commanded to lock tomb Tomb1.tomb
|
||||
|
||||
[sudo] Enter password for user Tomb1 to gain superuser privileges
|
||||
|
||||
tomb . Checking if the tomb is empty (we never step on somebody else's bones).
|
||||
tomb . Fine, this tomb seems empty.
|
||||
tomb . Key is valid.
|
||||
tomb . Locking using cipher: aes-xts-plain64:sha256
|
||||
tomb . A password is required to use key Tomb1.tomb.key
|
||||
tomb . Password OK.
|
||||
tomb (*) Locking Tomb1.tomb with Tomb1.tomb.key
|
||||
tomb . Formatting Luks mapped device.
|
||||
tomb . Formatting your Tomb with Ext3/Ext4 filesystem.
|
||||
tomb . Done locking Tomb1 using Luks dm-crypt aes-xts-plain64:sha256
|
||||
tomb (*) Your tomb is ready in Tomb1.tomb and secured with key Tomb1.tomb.key
|
||||
|
||||
```
|
||||
|
||||
Now everything is set up, you can start using your new tomb.
|
||||
|
||||
A note here: because I’m just showing you what to do, I’ve stored my key and tomb in the same directory (in this case $HOME). You shouldn’t do this – store your key somewhere else, preferably where no-one but you is going to find it.
|
||||
|
||||
You’ll need to remember where you stored it, however, because you need it to unlock your tomb. To do this, enter:
|
||||
|
||||
```
|
||||
sudo tomb open Tomb1.tomb -k path/to/your/Tomb1.tomb.key
|
||||
|
||||
```
|
||||
|
||||
Enter your password, and you should be in. Tomb will generate something like:
|
||||
|
||||
```
|
||||
tomb (*) Success unlocking tomb Tomb1
|
||||
tomb . Checking filesystem via /dev/loop0
|
||||
fsck from util-linux 2.27.1
|
||||
Tomb1: clean, 11/25168 files, 8831/100352 blocks
|
||||
tomb (*) Success opening Tomb1.tomb on /media/Tomb1
|
||||
|
||||
```
|
||||
|
||||
And then you should see your new tomb, mounted in the finder window.
|
||||
|
||||
You can now save and open files from the tomb, but note that you will need root privileges in order to do so.
|
||||
|
||||
To unmount your tomb after you have finished using it, close it by using:
|
||||
|
||||
```
|
||||
sudo tomb close
|
||||
|
||||
```
|
||||
|
||||
Or, if you want to force close all open tombs, you can use:
|
||||
|
||||
```
|
||||
sudo tomb slam all
|
||||
|
||||
```
|
||||
|
||||
#### **Using Tomb Through The GUI**
|
||||
|
||||
If you are uncomfortable using the command line, or simply just want a graphical interface, you can use gtomb. Unlike a lot of GUI wrappers, gtomb is pretty straightforward to use.
|
||||
|
||||
Let’s look at how to set up a new tomb using gtomb. First, launch gtomb from the Menu. It will probably look like this:
|
||||
|
||||
[](https://www.howtoforge.com/images/how_to_setup_and_install_tomb_on_ubuntu_1604/big/tomb2.png)
|
||||
|
||||
Everything is pretty self-explanatory, but for the sake of completeness I’ll run through how to set up your first tomb.
|
||||
|
||||
To start, click on the first option, “dig”. Click OK, and then choose a location.
|
||||
|
||||
Next, enter the size of your tomb:
|
||||
|
||||
[](https://www.howtoforge.com/images/how_to_setup_and_install_tomb_on_ubuntu_1604/big/tomb3.png)
|
||||
|
||||
You’ve now got a new tomb, but you need to make a key before you can use it. To do this, click “forge” from the main menu:
|
||||
|
||||
[](https://www.howtoforge.com/images/how_to_setup_and_install_tomb_on_ubuntu_1604/big/tomb4.png)
|
||||
|
||||
Tomb will ask you to enter a passcode twice, so do that.
|
||||
|
||||
Then lock your tomb using the key by clicking, you’ve guessed it, “lock”. To open it, click “open” and enter your passcode again.
|
||||
|
||||
As you can see from the screenshot above, usage of gtomb is really easy, and you shouldn’t encounter any problems. Most common tasks can be done with a few clicks, and for anything more complicated you can use the command line.
|
||||
|
||||
### Final Thoughts
|
||||
|
||||
That’s it! You should now have your first tomb set up and ready to go. Store anything you want to keep secret and secure in tombs, and this information will be much more secure.
|
||||
|
||||
You can use multiple tombs at the same time, and bind the files in them to your $HOME directory, so your programs don’t get confused.
|
||||
|
||||
I hope this guide has helped you get started. Using your tombs is just like using a standard folder, but for more complex commands you can always check the Tomb [Official Guide](https://www.dyne.org/software/tomb/).
|
||||
|
||||
* * *
|
||||
|
||||
via: [https://www.howtoforge.com/tutorial/how-to-install-and-use-tomb-file-encryption-on-ubuntu-1604/](https://www.howtoforge.com/tutorial/how-to-install-and-use-tomb-file-encryption-on-ubuntu-1604/)
|
||||
|
||||
作者: [Dan Fries](https://www.howtoforge.com/) 选题者: [@lujun9972](https://github.com/lujun9972) 译者: [译者ID](https://github.com/译者ID) 校对: [校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
@ -1,3 +1,4 @@
|
||||
Translating by qhwdw
|
||||
Choosing a Linux Tracer (2015)
|
||||
======
|
||||
[![][1]][2]
|
||||
|
||||
@ -1,3 +1,4 @@
|
||||
Translating by qhwdw
|
||||
Install a Centralized Log Server with Rsyslog in Debian 9
|
||||
======
|
||||
|
||||
|
||||
@ -1,3 +1,4 @@
|
||||
Translating by qhwdw
|
||||
Torrents - Everything You Need to Know
|
||||
======
|
||||
|
||||
|
||||
@ -1,3 +1,4 @@
|
||||
Translating by qhwdw
|
||||
Mail transfer agent (MTA) basics
|
||||
======
|
||||
|
||||
|
||||
@ -1,3 +1,4 @@
|
||||
Translating by qhwdw
|
||||
What’s behind the Intel design flaw forcing numerous patches?
|
||||
============================================================
|
||||
|
||||
|
||||
@ -1,155 +0,0 @@
|
||||
How to install/update Intel microcode firmware on Linux
|
||||
======
|
||||
|
||||
|
||||
I am a new Linux sysadmin. How do I install or update microcode firmware for Intel/AMD CPUs on Linux using the command line option?
|
||||
|
||||
|
||||
A microcode is nothing but CPU firmware provided by Intel or AMD. The Linux kernel can update the CPU's firmware without the BIOS update at boot time. Processor microcode is stored in RAM and kernel update the microcode during every boot. These microcode updates from Intel/AMD needed to fix bugs or apply errata to avoid CPU bugs. This page shows how to install AMD or Intel microcode update using package manager or processor microcode updates supplied by Intel on Linux.
|
||||
|
||||
## How to find out current status of microcode
|
||||
|
||||
|
||||
Run the following command as root user:
|
||||
`# dmesg | grep microcode`
|
||||
Sample outputs:
|
||||
|
||||
[![Verify microcode update on a CentOS RHEL Fedora Ubuntu Debian Linux][1]][1]
|
||||
|
||||
Please note that it is entirely possible that there is no microcode update available for your CPU. In that case it will look as follows:
|
||||
```
|
||||
[ 0.952699] microcode: sig=0x306a9, pf=0x10, revision=0x1c
|
||||
[ 0.952773] microcode: Microcode Update Driver: v2.2.
|
||||
|
||||
```
|
||||
|
||||
## How to install Intel microcode firmware on Linux using a package manager
|
||||
|
||||
Tool to transform and deploy CPU microcode update for x86/amd64 comes with Linux. The procedure to install AMD or Intel microcode firmware on Linux is as follows:
|
||||
|
||||
1. Open the terminal app
|
||||
2. Debian/Ubuntu Linux user type: **sudo apt install intel-microcode**
|
||||
3. CentOS/RHEL Linux user type: **sudo yum install microcode_ctl**
|
||||
|
||||
|
||||
|
||||
The package names are as follows for popular Linux distros:
|
||||
|
||||
* microcode_ctl and linux-firmware - CentOS/RHEL microcode update package
|
||||
* intel-microcode - Debian/Ubuntu and clones microcode update package for Intel CPUS
|
||||
* amd64-microcode - Debian/Ubuntu and clones microcode firmware for AMD CPUs
|
||||
* linux-firmware - Arch Linux microcode firmware for AMD CPUs (installed by default and no action is needed on your part)
|
||||
* intel-ucode - Arch Linux microcode firmware for Intel CPUs
|
||||
* microcode_ctl and ucode-intel - Suse/OpenSUSE Linux microcode update package
|
||||
|
||||
|
||||
|
||||
**Warning** : In some cases, microcode update may cause boot issues such as server getting hang or resets automatically at the time of boot. The procedure worked for me, and I am an experienced sysadmin. I do not take responsibility for any hardware failures. Do it at your own risk.
|
||||
|
||||
### Examples
|
||||
|
||||
Type the following [apt command][2]/[apt-get command][3] on a Debian/Ubuntu Linux for Intel CPU:
|
||||
|
||||
`$ sudo apt-get install intel-microcode`
|
||||
|
||||
Sample outputs:
|
||||
|
||||
[![How to install Intel microcode firmware Linux][4]][4]
|
||||
|
||||
You [must reboot the box to activate micocode][5] update:
|
||||
|
||||
`$ sudo reboot`
|
||||
|
||||
Verify it after reboot:
|
||||
|
||||
`# dmesg | grep 'microcode'`
|
||||
|
||||
Sample outputs:
|
||||
|
||||
```
|
||||
[ 0.000000] microcode: microcode updated early to revision 0x1c, date = 2015-02-26
|
||||
[ 1.604672] microcode: sig=0x306a9, pf=0x10, revision=0x1c
|
||||
[ 1.604976] microcode: Microcode Update Driver: v2.01 <tigran@aivazian.fsnet.co.uk>, Peter Oruba
|
||||
|
||||
```
|
||||
|
||||
If you are using RHEL/CentOS try installing or updating the following two packages using [yum command][6]:
|
||||
|
||||
```
|
||||
$ sudo yum install linux-firmware microcode_ctl
|
||||
$ sudo reboot
|
||||
$ sudo dmesg | grep 'microcode'
|
||||
```
|
||||
|
||||
## How to update/install microcode downloaded from Intel site
|
||||
|
||||
Only use the following method when recommended by your vendor otherwise stick to Linux packages as described above. Most Linux distro maintainer update microcode via the package manager. Package manager method is safe as tested by many users.
|
||||
|
||||
### How to install Intel processor microcode blob for Linux (20180108 release)
|
||||
|
||||
Ok, first visit AMD or [Intel site][7] to grab the latest microcode firmware. In this example, I have a file named ~/Downloads/microcode-20180108.tgz (don't forget to check for checksum) that suppose to help with meltdown/Spectre. First extract it using the tar command:
|
||||
```
|
||||
$ mkdir firmware
|
||||
$ cd firmware
|
||||
$ tar xvf ~/Downloads/microcode-20180108.tgz
|
||||
$ ls -l
|
||||
```
|
||||
|
||||
Sample outputs:
|
||||
|
||||
```
|
||||
drwxr-xr-x 2 vivek vivek 4096 Jan 8 12:41 intel-ucode
|
||||
-rw-r--r-- 1 vivek vivek 4847056 Jan 8 12:39 microcode.dat
|
||||
-rw-r--r-- 1 vivek vivek 1907 Jan 9 07:03 releasenote
|
||||
|
||||
```
|
||||
|
||||
Make sure /sys/devices/system/cpu/microcode/reload exits:
|
||||
|
||||
`$ ls -l /sys/devices/system/cpu/microcode/reload`
|
||||
|
||||
You must copy all files from intel-ucode to /lib/firmware/intel-ucode/ using the [cp command][8]:
|
||||
|
||||
`$ sudo cp -v intel-ucode/* /lib/firmware/intel-ucode/`
|
||||
|
||||
You just copied intel-ucode directory to /lib/firmware/. Write the reload interface to 1 to reload the microcode files:
|
||||
|
||||
`# echo 1 > /sys/devices/system/cpu/microcode/reload`
|
||||
|
||||
Update an existing initramfs so that next time it get loaded via kernel:
|
||||
|
||||
```
|
||||
$ sudo update-initramfs -u
|
||||
$ sudo reboot
|
||||
```
|
||||
Verifying that microcode got updated on boot or reloaded by echo command:
|
||||
`# dmesg | grep microcode`
|
||||
|
||||
That is all. You have just updated firmware for your Intel CPU.
|
||||
|
||||
## about the author
|
||||
|
||||
The author is the creator of nixCraft and a seasoned sysadmin and a trainer for the Linux operating system/Unix shell scripting. He has worked with global clients and in various industries, including IT, education, defense and space research, and the nonprofit sector. Follow him on [Twitter][9], [Facebook][10], [Google+][11].
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.cyberciti.biz/faq/install-update-intel-microcode-firmware-linux/
|
||||
|
||||
作者:[Vivek Gite][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://www.cyberciti.biz
|
||||
[1]:https://www.cyberciti.biz/media/new/faq/2018/01/Verify-microcode-update-on-a-CentOS-RHEL-Fedora-Ubuntu-Debian-Linux.jpg
|
||||
[2]:https://www.cyberciti.biz/faq/ubuntu-lts-debian-linux-apt-command-examples/ (See Linux/Unix apt command examples for more info)
|
||||
[3]:https://www.cyberciti.biz/tips/linux-debian-package-management-cheat-sheet.html (See Linux/Unix apt-get command examples for more info)
|
||||
[4]:https://www.cyberciti.biz/media/new/faq/2018/01/How-to-install-Intel-microcode-firmware-Linux.jpg
|
||||
[5]:https://www.cyberciti.biz/faq/howto-reboot-linux/
|
||||
[6]:https://www.cyberciti.biz/faq/rhel-centos-fedora-linux-yum-command-howto/ (See Linux/Unix yum command examples for more info)
|
||||
[7]:https://downloadcenter.intel.com/download/27431/Linux-Processor-Microcode-Data-File
|
||||
[8]:https://www.cyberciti.biz/faq/cp-copy-command-in-unix-examples/ (See Linux/Unix cp command examples for more info)
|
||||
[9]:https://twitter.com/nixcraft
|
||||
[10]:https://facebook.com/nixcraft
|
||||
[11]:https://plus.google.com/+CybercitiBiz
|
||||
@ -1,3 +1,4 @@
|
||||
Translating by qhwdw
|
||||
Building a Linux-based HPC system on the Raspberry Pi with Ansible
|
||||
============================================================
|
||||
|
||||
@ -150,4 +151,4 @@ via: https://opensource.com/article/18/1/how-build-hpc-system-raspberry-pi-and-o
|
||||
[28]:https://opensource.com/tags/raspberry-pi
|
||||
[29]:https://opensource.com/tags/programming
|
||||
[30]:https://opensource.com/tags/linux
|
||||
[31]:https://opensource.com/tags/ansible
|
||||
[31]:https://opensource.com/tags/ansible
|
||||
|
||||
@ -1,3 +1,4 @@
|
||||
translated by cyleft
|
||||
Linux rmdir Command for Beginners (with Examples)
|
||||
======
|
||||
|
||||
|
||||
@ -0,0 +1,191 @@
|
||||
Building a Linux-based HPC system on the Raspberry Pi with Ansible
|
||||
==================================================================
|
||||
|
||||
### Create a high-performance computing cluster with low-cost hardware and open source software.
|
||||
|
||||

|
||||
|
||||
Image by :opensource.com
|
||||
|
||||
### Get the newsletter
|
||||
|
||||
Join the 85,000 open source advocates who receive our giveaway alerts and article roundups.
|
||||
|
||||
In my [previous article for Opensource.com](https://opensource.com/article/17/11/openhpc), I introduced the [OpenHPC](https://openhpc.community/) project, which aims to accelerate innovation in high-performance computing (HPC). This article goes a step further by using OpenHPC's capabilities to build a small HPC system. To call it an _HPC system_ might sound bigger than it is, so maybe it is better to say this is a system based on the [Cluster Building Recipes](https://openhpc.community/downloads/) published by the OpenHPC project.
|
||||
|
||||
The resulting cluster consists of two Raspberry Pi 3 systems acting as compute nodes and one virtual machine acting as the master node:
|
||||
|
||||

|
||||
|
||||
My master node is running CentOS on x86_64 and my compute nodes are running a slightly modified CentOS on aarch64.
|
||||
|
||||
This is what the setup looks in real life:
|
||||
|
||||

|
||||
|
||||
To set up my system like an HPC system, I followed some of the steps from OpenHPC's Cluster Building Recipes [install guide for CentOS 7.4/aarch64 + Warewulf + Slurm](https://github.com/openhpc/ohpc/releases/download/v1.3.3.GA/Install_guide-CentOS7-Warewulf-SLURM-1.3.3-aarch64.pdf) (PDF). This recipe includes provisioning instructions using [Warewulf](https://en.wikipedia.org/wiki/Warewulf); because I manually installed my three systems, I skipped the Warewulf parts and created an [Ansible playbook](http://people.redhat.com/areber/openhpc/ansible/) for the steps I took.
|
||||
|
||||
Linux Containers
|
||||
|
||||
* [What are Linux containers?](https://opensource.com/resources/what-are-linux-containers?utm_campaign=containers&intcmp=70160000000h1s6AAA)
|
||||
* [What is Docker?](https://opensource.com/resources/what-docker?utm_campaign=containers&intcmp=70160000000h1s6AAA)
|
||||
* [What is Kubernetes?](https://opensource.com/resources/what-is-kubernetes?utm_campaign=containers&intcmp=70160000000h1s6AAA)
|
||||
* [An introduction to container terminology](https://developers.redhat.com/blog/2016/01/13/a-practical-introduction-to-docker-container-terminology/?utm_campaign=containers&intcmp=70160000000h1s6AAA)
|
||||
|
||||
Once my cluster was set up by the [Ansible](https://www.ansible.com/) playbooks, I could start to submit jobs to my resource manager. The resource manager, [Slurm](https://slurm.schedmd.com/) in my case, is the instance in the cluster that decides where and when my jobs are executed. One possibility to start a simple job on the cluster is:
|
||||
|
||||
```
|
||||
[ohpc@centos01 ~]$ srun hostname
|
||||
|
||||
|
||||
calvin
|
||||
|
||||
```
|
||||
|
||||
If I need more resources, I can tell Slurm that I want to run my command on eight CPUs:
|
||||
|
||||
```
|
||||
[ohpc@centos01 ~]$ srun -n 8 hostname
|
||||
|
||||
|
||||
hobbes
|
||||
|
||||
|
||||
hobbes
|
||||
|
||||
|
||||
hobbes
|
||||
|
||||
|
||||
hobbes
|
||||
|
||||
|
||||
calvin
|
||||
|
||||
|
||||
calvin
|
||||
|
||||
|
||||
calvin
|
||||
|
||||
|
||||
calvin
|
||||
|
||||
```
|
||||
|
||||
In the first example, Slurm ran the specified command (`hostname`) on a single CPU, and in the second example Slurm ran the command on eight CPUs. One of my compute nodes is named `calvin` and the other is named `hobbes`; that can be seen in the output of the above commands. Each of the compute nodes is a Raspberry Pi 3 with four CPU cores.
|
||||
|
||||
Another way to submit jobs to my cluster is the command `sbatch`, which can be used to execute scripts with the output written to a file instead of my terminal.
|
||||
|
||||
```
|
||||
[ohpc@centos01 ~]$ cat script1.sh
|
||||
|
||||
|
||||
#!/bin/sh
|
||||
|
||||
|
||||
date
|
||||
|
||||
|
||||
hostname
|
||||
|
||||
|
||||
sleep 10
|
||||
|
||||
|
||||
date
|
||||
|
||||
|
||||
[ohpc@centos01 ~]$ sbatch script1.sh
|
||||
|
||||
|
||||
Submitted batch job 101
|
||||
|
||||
```
|
||||
|
||||
This will create an output file called `slurm-101.out` with the following content:
|
||||
|
||||
```
|
||||
Mon 11 Dec 16:42:31 UTC 2017
|
||||
|
||||
|
||||
calvin
|
||||
|
||||
|
||||
Mon 11 Dec 16:42:41 UTC 2017
|
||||
|
||||
```
|
||||
|
||||
To demonstrate the basic functionality of the resource manager, simple and serial command line tools are suitable—but a bit boring after doing all the work to set up an HPC-like system.
|
||||
|
||||
A more interesting application is running an [Open MPI](https://www.open-mpi.org/) parallelized job on all available CPUs on the cluster. I'm using an application based on [Game of Life](https://en.wikipedia.org/wiki/Conway%27s_Game_of_Life), which was used in a [video](https://www.youtube.com/watch?v=n8DvxMcOMXk) called "Running Game of Life across multiple architectures with Red Hat Enterprise Linux." In addition to the previously used MPI-based Game of Life implementation, the version now running on my cluster colors the cells for each involved host differently. The following script starts the application interactively with a graphical output:
|
||||
|
||||
```
|
||||
$ cat life.mpi
|
||||
|
||||
|
||||
#!/bin/bash
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
module load gnu6 openmpi3
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
if [[ "$SLURM_PROCID" != "0" ]]; then
|
||||
|
||||
|
||||
exit
|
||||
|
||||
|
||||
fi
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
mpirun ./mpi_life -a -p -b
|
||||
|
||||
```
|
||||
|
||||
I start the job with the following command, which tells Slurm to allocate eight CPUs for the job:
|
||||
|
||||
```
|
||||
$ srun -n 8 --x11 life.mpi
|
||||
|
||||
```
|
||||
|
||||
For demonstration purposes, the job has a graphical interface that shows the current result of the calculation:
|
||||
|
||||
|
||||
|
||||
The position of the red cells is calculated on one of the compute nodes, and the green cells are calculated on the other compute node. I can also tell the Game of Life program to color the cell for each used CPU (there are four per compute node) differently, which leads to the following output:
|
||||
|
||||
|
||||
|
||||
Thanks to the installation recipes and the software packages provided by OpenHPC, I was able to set up two compute nodes and a master node in an HPC-type configuration. I can submit jobs to my resource manager, and I can use the software provided by OpenHPC to start MPI applications utilizing all my Raspberry Pis' CPUs.
|
||||
|
||||
* * *
|
||||
|
||||
_To learn more about using OpenHPC to build a Raspberry Pi cluster, please attend Adrian Reber's talks at [DevConf.cz 2018](https://devconfcz2018.sched.com/event/DJYi/openhpc-introduction), January 26-28, in Brno, Czech Republic, and at the [CentOS Dojo 2018](https://wiki.centos.org/Events/Dojo/Brussels2018), on February 2, in Brussels._
|
||||
|
||||
About the author
|
||||
----------------
|
||||
|
||||
[](https://opensource.com/users/adrianreber)
|
||||
|
||||
Adrian Reber - Adrian is a Senior Software Engineer at Red Hat and is migrating processes at least since 2010. He started to migrate processes in a high performance computing environment and at some point he migrated so many processes that he got a PhD for that and since he joined Red Hat he started to migrate containers. Occasionally he still migrates single processes and is still interested in high performance computing topics.
|
||||
|
||||
[More about me](https://opensource.com/users/adrianreber)
|
||||
|
||||
* * *
|
||||
|
||||
via: [https://opensource.com/article/18/1/how-build-hpc-system-raspberry-pi-and-openhpc](https://opensource.com/article/18/1/how-build-hpc-system-raspberry-pi-and-openhpc)
|
||||
|
||||
作者: [Adrian Reber](https://opensource.com/users/adrianreber) 选题者: [@lujun9972](https://github.com/lujun9972) 译者: [译者ID](https://github.com/译者ID) 校对: [校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
@ -0,0 +1,155 @@
|
||||
如何在 Linux 上安装/更新 Intel 微码固件
|
||||
======
|
||||
|
||||
|
||||
如果你是一个 Linux 系统管理方面的新手,如何在 Linux 上使用命令行选项去安装或者更新 Intel/AMD CPU 的微码固件?
|
||||
|
||||
|
||||
微码只是由 Intel/AMD 提供的 CPU 固件而已。Linux 的内核可以在系统引导时不需要升级 BIOS 的情况下更新 CPU 的固件。处理器微码保存在内存中,在每次启动系统时,内核可以更新这个微码。这些来自 Intel/AMD 的升级微码可以去修复 bug 或者使用补丁来防范 bugs。这篇文章演示了如何使用包管理器去安装 AMD 或者 Intel 微码更新,或者由 lntel 提供的 Linux 上的处理器微码更新。
|
||||
|
||||
## 如何查看当前的微码状态
|
||||
|
||||
|
||||
以 root 用户运行下列命令:
|
||||
`# dmesg | grep microcode`
|
||||
输出如下:
|
||||
|
||||
[![Verify microcode update on a CentOS RHEL Fedora Ubuntu Debian Linux][1]][1]
|
||||
|
||||
请注意,你的 CPU 在这里完全有可能出现没有可用的微码更新的情况。如果是这种情况,它的输出可能是如下图这样的:
|
||||
```
|
||||
[ 0.952699] microcode: sig=0x306a9, pf=0x10, revision=0x1c
|
||||
[ 0.952773] microcode: Microcode Update Driver: v2.2.
|
||||
|
||||
```
|
||||
|
||||
## 如何在 Linux 上使用包管理器去安装微码固件更新
|
||||
|
||||
对于运行在 Linux 系统的 x86/amd64 架构的 CPU 上,Linux 自带了工具去更改或者部署微码固件。在 Linux 上安装 AMD 或者 Intel 的微码固件的过程如下:
|
||||
|
||||
1. 打开终端应用程序
|
||||
2. Debian/Ubuntu Linux 用户推输入:**sudo apt install intel-microcode**
|
||||
3. CentOS/RHEL Linux 用户输入:**sudo yum install microcode_ctl**
|
||||
|
||||
|
||||
|
||||
对于流行的 Linux 发行版,这个包的名字一般如下 :
|
||||
|
||||
* microcode_ctl 和 linux-firmware —— CentOS/RHEL 微码更新包
|
||||
* intel-microcode —— Debian/Ubuntu 和 clones 发行版适用于 Intel CPU 的微码更新包
|
||||
* amd64-microcode —— Debian/Ubuntu 和 clones 发行版适用于 AMD CPU 的微码固件
|
||||
* linux-firmware —— 适用于 AMD CPU 的 Arch Linux 发行版微码固件(你不用做任何操作,它是默认安装的)
|
||||
* intel-ucode —— 适用于 Intel CPU 的 Arch Linux 发行版微码固件
|
||||
* microcode_ctl 和 ucode-intel —— Suse/OpenSUSE Linux 微码更新包
|
||||
|
||||
|
||||
|
||||
**警告 :在某些情况下,更新微码可能会导致引导问题,比如,服务器在引导时被挂起或者自动重置。以下的步骤是在我的机器上运行过的,并且我是一个经验丰富的系统管理员。对于由此引发的任何硬件故障,我不承担任何责任。在做固件更新之前,请充分评估操作风险!**
|
||||
|
||||
### 示例
|
||||
|
||||
在使用 Intel CPU 的 Debian/Ubuntu Linux 系统上,输入如下的 [apt 命令][2]/[apt-get 命令][3]:
|
||||
|
||||
`$ sudo apt-get install intel-microcode`
|
||||
|
||||
示例输出如下:
|
||||
|
||||
[![How to install Intel microcode firmware Linux][4]][4]
|
||||
|
||||
你 [必须重启服务器以激活微码][5] 更新:
|
||||
|
||||
`$ sudo reboot`
|
||||
|
||||
重启后检查微码状态:
|
||||
|
||||
`# dmesg | grep 'microcode'`
|
||||
|
||||
示例输出如下:
|
||||
|
||||
```
|
||||
[ 0.000000] microcode: microcode updated early to revision 0x1c, date = 2015-02-26
|
||||
[ 1.604672] microcode: sig=0x306a9, pf=0x10, revision=0x1c
|
||||
[ 1.604976] microcode: Microcode Update Driver: v2.01 <tigran@aivazian.fsnet.co.uk>, Peter Oruba
|
||||
|
||||
```
|
||||
|
||||
如果你使用的是 RHEL/CentOS 系统,使用 [yum 命令][6] 尝试去安装或者更新以下两个包:
|
||||
|
||||
```
|
||||
$ sudo yum install linux-firmware microcode_ctl
|
||||
$ sudo reboot
|
||||
$ sudo dmesg | grep 'microcode'
|
||||
```
|
||||
|
||||
## 如何去更新/安装从 Intel 网站上下载的微码
|
||||
|
||||
仅当你的 CPU 制造商建议这么做的时候,才可以使用下列的方法去更新/安装微码,除此之外,都应该使用上面的方法去更新。大多数 Linux 发行版都可以通过包管理器来维护更新微码。使用包管理器的方法是经过测试的,对大多数用户来说是最安全的方式。
|
||||
|
||||
### 如何为 Linux 安装 Intel 处理器微码块(20180108 发布)
|
||||
|
||||
首先通过 AMD 或 [Intel 网站][7] 去获取最新的微码固件。在本示例中,我有一个名称为 ~/Downloads/microcode-20180108.tgz(不要忘了去验证它的检验和),它的用途是去防范 meltdown/Spectre bugs。先使用 tar 命令去提取它:
|
||||
```
|
||||
$ mkdir firmware
|
||||
$ cd firmware
|
||||
$ tar xvf ~/Downloads/microcode-20180108.tgz
|
||||
$ ls -l
|
||||
```
|
||||
|
||||
示例输出如下:
|
||||
|
||||
```
|
||||
drwxr-xr-x 2 vivek vivek 4096 Jan 8 12:41 intel-ucode
|
||||
-rw-r--r-- 1 vivek vivek 4847056 Jan 8 12:39 microcode.dat
|
||||
-rw-r--r-- 1 vivek vivek 1907 Jan 9 07:03 releasenote
|
||||
|
||||
```
|
||||
|
||||
检查一下,确保存在 /sys/devices/system/cpu/microcode/reload 目录:
|
||||
|
||||
`$ ls -l /sys/devices/system/cpu/microcode/reload`
|
||||
|
||||
你必须使用 [cp 命令][8] 拷贝 intel-ucode 目录下的所有文件到 /lib/firmware/intel-ucode/ 下面:
|
||||
|
||||
`$ sudo cp -v intel-ucode/* /lib/firmware/intel-ucode/`
|
||||
|
||||
你只需要将 intel-ucode 这个目录整个拷贝到 /lib/firmware/ 目录下即可。然后在重新加载接口中写入 1 去重新加载微码文件:
|
||||
|
||||
`# echo 1 > /sys/devices/system/cpu/microcode/reload`
|
||||
|
||||
更新现有的 initramfs,以便于下次启动时通过内核来加载:
|
||||
|
||||
```
|
||||
$ sudo update-initramfs -u
|
||||
$ sudo reboot
|
||||
```
|
||||
重启后通过以下的命令验证微码是否已经更新:
|
||||
`# dmesg | grep microcode`
|
||||
|
||||
到此为止,就是更新处理器微码的全部步骤。如果一切顺利的话,你的 Intel CPU 的固件将已经是最新的版本了。
|
||||
|
||||
## 关于作者
|
||||
|
||||
作者是 nixCraft 的创始人、一位经验丰富的系统管理员、Linux/Unix 操作系统 shell 脚本培训师。他与全球的包括 IT、教育、国防和空间研究、以及非盈利组织等各行业的客户一起工作。可以在 [Twitter][9]、[Facebook][10]、[Google+][11] 上关注他。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.cyberciti.biz/faq/install-update-intel-microcode-firmware-linux/
|
||||
|
||||
作者:[Vivek Gite][a]
|
||||
译者:[qhwdw](https://github.com/qhwdw)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://www.cyberciti.biz
|
||||
[1]:https://www.cyberciti.biz/media/new/faq/2018/01/Verify-microcode-update-on-a-CentOS-RHEL-Fedora-Ubuntu-Debian-Linux.jpg
|
||||
[2]:https://www.cyberciti.biz/faq/ubuntu-lts-debian-linux-apt-command-examples/ "See Linux/Unix apt command examples for more info"
|
||||
[3]:https://www.cyberciti.biz/tips/linux-debian-package-management-cheat-sheet.html "See Linux/Unix apt-get command examples for more info"
|
||||
[4]:https://www.cyberciti.biz/media/new/faq/2018/01/How-to-install-Intel-microcode-firmware-Linux.jpg
|
||||
[5]:https://www.cyberciti.biz/faq/howto-reboot-linux/
|
||||
[6]:https://www.cyberciti.biz/faq/rhel-centos-fedora-linux-yum-command-howto/ "See Linux/Unix yum command examples for more info"
|
||||
[7]:https://downloadcenter.intel.com/download/27431/Linux-Processor-Microcode-Data-File
|
||||
[8]:https://www.cyberciti.biz/faq/cp-copy-command-in-unix-examples/ "See Linux/Unix cp command examples for more info"
|
||||
[9]:https://twitter.com/nixcraft
|
||||
[10]:https://facebook.com/nixcraft
|
||||
[11]:https://plus.google.com/+CybercitiBiz
|
||||
@ -1,214 +0,0 @@
|
||||
ncurses入门指南
|
||||
======
|
||||
怎样使用curses来绘制终端屏幕。
|
||||
|
||||
虽然图形界面非常酷,但是不是所有的程序都需要点击式的界面。例如,令人尊敬的vi编辑器在第一个GUI(出现)之前在纯文本终端运行了很久。
|
||||
|
||||
vi编辑器是一个在"文本"模式下绘制的面向屏幕程序的例子。它使用了一个叫curses的库。这个库提供了一系列的编程接口来操纵终端屏幕。curses库产生于BSD UNIX,但是Linux系统通过ncurses库提供这个功能。
|
||||
|
||||
[了解ncurses"过去曾引起的风暴",参见 ["ncurses: Portable Screen-Handling for Linux"][1], September 1, 1995, by Eric S. Raymond.]
|
||||
|
||||
使用curses创建程序实际上非常简单。在这个文章中,我展示了一个利用curses来在终端屏幕上绘图的示例程序。
|
||||
|
||||
### 谢尔宾斯基三角形
|
||||
|
||||
简单展示一些curses函数的一个方法是生成谢尔宾斯基三角形。如果你对生成谢尔宾斯基三角形的这种方法不熟悉的话,这里是一些(产生谢尔宾斯基三角形的)规则:
|
||||
|
||||
1. 设置定义三角形的三个点。
|
||||
|
||||
2. 随机选择任意的一个点(x,y)。
|
||||
|
||||
然后:
|
||||
|
||||
1. 在三角形的顶点中随机选择一个点
|
||||
|
||||
2. 将新的x,y设置为先前的x,y和三角顶点的中间点。
|
||||
|
||||
3. 重复(上述步骤)。
|
||||
|
||||
所以我按照这些指令写了这个程序,程序使用curses函数来向终端屏幕绘制谢尔宾斯基三角形:
|
||||
|
||||
```
|
||||
|
||||
1 /* triangle.c */
|
||||
2
|
||||
3 #include <curses.h>
|
||||
4 #include <stdlib.h>
|
||||
5
|
||||
6 #include "getrandom_int.h"
|
||||
7
|
||||
8 #define ITERMAX 10000
|
||||
9
|
||||
10 int main(void)
|
||||
11 {
|
||||
12 long iter;
|
||||
13 int yi, xi;
|
||||
14 int y[3], x[3];
|
||||
15 int index;
|
||||
16 int maxlines, maxcols;
|
||||
17
|
||||
18 /* 初始化 curses */
|
||||
19
|
||||
20 initscr();
|
||||
21 cbreak();
|
||||
22 noecho();
|
||||
23
|
||||
24 clear();
|
||||
25
|
||||
26 /* 初始化三角形 */
|
||||
27
|
||||
28 maxlines = LINES - 1;
|
||||
29 maxcols = COLS - 1;
|
||||
30
|
||||
31 y[0] = 0;
|
||||
32 x[0] = 0;
|
||||
33
|
||||
34 y[1] = maxlines;
|
||||
35 x[1] = maxcols / 2;
|
||||
36
|
||||
37 y[2] = 0;
|
||||
38 x[2] = maxcols;
|
||||
39
|
||||
40 mvaddch(y[0], x[0], '0');
|
||||
41 mvaddch(y[1], x[1], '1');
|
||||
42 mvaddch(y[2], x[2], '2');
|
||||
43
|
||||
44 /* 将 yi,xi 初始化为随机值 */
|
||||
45
|
||||
46 yi = getrandom_int() % maxlines;
|
||||
47 xi = getrandom_int() % maxcols;
|
||||
48
|
||||
49 mvaddch(yi, xi, '.');
|
||||
50
|
||||
51 /* 迭代(形成)三角形 */
|
||||
52
|
||||
53 for (iter = 0; iter < ITERMAX; iter++) {
|
||||
54 index = getrandom_int() % 3;
|
||||
55
|
||||
56 yi = (yi + y[index]) / 2;
|
||||
57 xi = (xi + x[index]) / 2;
|
||||
58
|
||||
59 mvaddch(yi, xi, '*');
|
||||
60 refresh();
|
||||
61 }
|
||||
62
|
||||
63 /* 完成 */
|
||||
64
|
||||
65 mvaddstr(maxlines, 0, "Press any key to quit");
|
||||
66
|
||||
67 refresh();
|
||||
68
|
||||
69 getch();
|
||||
70 endwin();
|
||||
71
|
||||
72 exit(0);
|
||||
73 }
|
||||
|
||||
```
|
||||
|
||||
让我一边解释一边浏览这个程序。首先,getrandom_int()函数是我对Linux系统调用getrandom()的包装器。它保证返回一个正整数(int)值。(译者注:getrandom()系统按照字节返回随机值到一个变量中,值是随机的,不保证正负,使用stdlib.h的random()函数可以达到同样的效果) 另外,按照上面的规则,你应该能够辨认出初始化和迭代谢尔宾斯基三角形的代码。除此之外,我们来看看我用来在终端上绘制三角形的curses函数。
|
||||
|
||||
大多数curses程序以这四条指令开头。1)initscr()函数获取包括大小和特征在内的终端类型,并设置终端支持的curses环境。cbreak()函数禁用行缓冲并设置curses每次只接受一个字符。noecho()函数告诉curses不要把输入回显到屏幕上。而clear()函数清空了屏幕():
|
||||
|
||||
```
|
||||
|
||||
20 initscr();
|
||||
21 cbreak();
|
||||
22 noecho();
|
||||
23
|
||||
24 clear();
|
||||
|
||||
```
|
||||
|
||||
之后程序设置了三个定义三角的顶点。注意这里使用的LINES和COLS,它们是由initscr()来设置的。这些值告诉程序在终端的行数和列数。屏幕坐标从0开始,所以屏幕左上角是0行0列。屏幕右下角是LINES - 1行,COLS - 1列。为了便于记忆,我的程序里把这些值分别设为了变量maxlines和maxcols。
|
||||
|
||||
在屏幕上绘制文字的两个简单方法是addch()和addstr()函数。也可以使用相关的mvaddch()和mvaddstr()函数可以将字符放到一个特定的屏幕位置。我的程序在很多地方都用到了这些函数。首先程序绘制三个定义三角的点并标记为"0","1"和"2":
|
||||
|
||||
```
|
||||
|
||||
40 mvaddch(y[0], x[0], '0');
|
||||
41 mvaddch(y[1], x[1], '1');
|
||||
42 mvaddch(y[2], x[2], '2');
|
||||
|
||||
```
|
||||
|
||||
为了绘制任意的一个初始点,程序做了类似的一个调用:
|
||||
|
||||
```
|
||||
|
||||
49 mvaddch(yi, xi, '.');
|
||||
|
||||
```
|
||||
|
||||
还有为了在谢尔宾斯基三角形递归中绘制连续的点:
|
||||
|
||||
```
|
||||
|
||||
59 mvaddch(yi, xi, '*');
|
||||
|
||||
```
|
||||
|
||||
当程序完成之后,将会在屏幕左下角(在maxlines行,0列)显示一个帮助信息:
|
||||
|
||||
```
|
||||
|
||||
65 mvaddstr(maxlines, 0, "Press any key to quit");
|
||||
|
||||
```
|
||||
|
||||
注意curses在内存中维护了一个版本的屏幕并且只有在你要求的时候才会更新这个屏幕,这很重要。特别是当你想要向屏幕显示大量的文字的时候,这样(程序会有)更好的表现。这是因为curses只能更新在上次更新之后可以被改变的这部分屏幕。想要引得curses更新终端屏幕,请使用refresh()函数。
|
||||
|
||||
在我的示例程序中,我选择在"绘制"每个谢尔宾斯基三角形中的连续点时更新屏幕。通过这样做,用户可以观察三角形中的每次迭代。(译者注:迭代过程执行太快了,所以其实很难直接看到迭代过程)
|
||||
|
||||
在退出之前,我使用getch()函数等待用户按下一个键。然后我调用endwin()函数退出curses环境并返回终端程序到一般控制。
|
||||
|
||||
```
|
||||
|
||||
69 getch();
|
||||
70 endwin();
|
||||
|
||||
```
|
||||
|
||||
### 编译和示例输出
|
||||
|
||||
现在你已经有了你的第一个curses示例程序,是时候编译运行它了。记住Linux操作系统通过ncurses库来实现curses功能,所以你需要在编译的时候通过-lncurses来链接--例如:
|
||||
|
||||
```
|
||||
|
||||
$ ls
|
||||
getrandom_int.c getrandom_int.h triangle.c
|
||||
|
||||
$ gcc -Wall -lncurses -o triangle triangle.c getrandom_int.c
|
||||
|
||||
```
|
||||
|
||||
译注:此处命令行有问题,`-lncurses`选项在我的Ubuntu16.04系统+gcc 4.9.3 环境下,必须放在命令行最后,否则找不到库文件,链接时会出现未定义的引用。
|
||||
|
||||
在标准的80x24终端运行这个triangle程序并没什么意思。在那样的分辨率下你不能看见谢尔宾斯基三角形的很多细节。如果你运行终端窗口并设置非常小的字体大小,你可以更加容易地看到谢尔宾斯基三角形的不规则性质。在我的系统上,输出如图1。
|
||||
|
||||

|
||||
|
||||
图 1. triangle程序的输出
|
||||
|
||||
虽然迭代具有随机性,但是每次谢尔宾斯基三角形的运行看起来都会很一致。唯一的不同是最初绘制到屏幕的一些点。在这个例子中,你可以看到开创三角形的一个小圆点,在点1附近。看起来程序接下来选择了点2,然后你可以看到在圆点和"2"之间的星号。并且看起来程序随机选择了点2作为下一个随机数,因为你可以看到在第一个星号和"2"之间的星号。从这里开始,就不能继续分辨三角形是怎样被画出来的了,因为所有的连续点都属于三角形区域。
|
||||
|
||||
### 开始学习ncurses
|
||||
|
||||
这个程序是一个怎样使用curses函数绘制字符到屏幕的简单例子。按照你的程序的需要,你可以通过curses做得更多。在下一篇文章中,我将会展示怎样使用curses让用户和屏幕交互。如果你对于在curses有一个良好开端有兴趣,我支持你去读位于Linux文档中Pradeep Padala的 ["NCURSES Programming HOWTO"][2]
|
||||
|
||||
### 关于作者
|
||||
|
||||
Jim Hall是一个免费和开源软件的倡议者,他最有名的工作是FreeDOS计划,也同样致力于开源软件的可用性。Jim是在明尼苏达州的拉姆齐县的首席资讯长。
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linuxjournal.com/content/getting-started-ncurses
|
||||
|
||||
作者:[Jim Hall][a]
|
||||
译者:[leemeans](https://github.com/leemeans)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.linuxjournal.com/users/jim-hall
|
||||
[1]:http://www.linuxjournal.com/article/1124
|
||||
[2]:http://tldp.org/HOWTO/NCURSES-Programming-HOWTO
|
||||
@ -1,59 +0,0 @@
|
||||
哪个 Linux 内核版本是 “稳定的”?
|
||||
============================================================
|
||||
|
||||
|
||||

|
||||
Konstantin Ryabitsev 为你讲解哪个 Linux 内核版本将被考虑作为“稳定版”,以及你如何选择一个适用你的内核版本。[Creative Commons Zero][1]
|
||||
|
||||
每次 Linus Torvalds 发布 [一个新 Linux 内核的主线版本][4],几乎都会引起这种困惑,那就是到底哪个内核版本才是最新的“稳定版”?是新的那个 X.Y,还是前面的那个 X.Y-1.Z ?最新的内核版本是不是太“新”了?你是不是应该坚持使用以前的版本?
|
||||
|
||||
[kernel.org][5] 网页上的信息并不会帮你解开这个困惑。目前,在页面的最顶部,我们看到是最新稳定版内核是 4.15 — 但是在这个表格的下面,4.14.16 也被列为“稳定版”,而 4.15 被列为“主线版本”,很困惑,是吧?
|
||||
|
||||
不幸的是,这个问题并不好回答。我们在这里使用“稳定”这个词有两个不同的意思:一是,作为最初发布的 Git 树的名字,二是,表示这个内核已经被考虑为“稳定版”,可以作为“生产系统”使用了。
|
||||
|
||||
由于 Git 的分布式特性,Linux 的开发工作在许多 [不同的 fork 仓库中][6] 进行。所有的 bug 修复和新特性也是由子系统维护者首次收集和准备的,然后提交给 Linus Torvalds,由 Linus Torvalds 包含进 [他的 Linux 树][7] 中,它的 Git 树被认为是 Git 仓库的 “master”。我们称这个树为 ”主线" Linux 树。
|
||||
|
||||
### 候选发布版
|
||||
|
||||
在每个新的内核版本发布之前,它都要经过几轮的“候选发布”,它由开发者进行测试并“打磨”所有的这些很酷的新特性。基于他们这几轮测试的反馈,Linus 决定最终版本是否准备就绪。通常每周发布一个候选版本,但是,这个数字经常走到 -rc8,并且有时候甚至达到 -rc9 及以上。当 Linus 确信那个新内核已经没有问题了,他就制作最终发行版,我们称这个版本为“稳定版”,表示它不再是一个“候选发布版”。
|
||||
|
||||
### Bug 修复
|
||||
|
||||
就像任何一个由不是十全十美的人所写的复杂软件一样,任何一个 Linux 内核的新版本都包含 bug,并且这些 bug 必须被修复。Linux 内核的 bug 修复规则是非常简单的:所有修复必须首先进入到 Linus 的树。一旦在主线仓库中 bug 被修复后,它接着会被应用到由内核开发社区仍然在维护的已发布的内核中。在它们被考虑回迁到已发布的稳定版本之前,所有的 bug 修复必须满足 [一套重要的标准][8] — 标准的其中之一是,它们 “必须已经存在于 Linus 的树中”。这是一个 [独立的 Git 仓库][9],维护它的用途是回迁 bug 修复,而它也被称为“稳定”树 — 因为它用于跟踪以前发布的稳定内核。这个树由 Greg Kroah-Hartman 策划和维护。
|
||||
|
||||
### 最新的稳定内核
|
||||
|
||||
因此,无论在什么时候,为了查看最新的稳定内核而访问 kernel.org 网站时,你应该去使用那个在大黄色按钮所说的“最新的稳定内核”。
|
||||
|
||||

|
||||
|
||||
但是,你可能会惊奇地发现 -- 4.15 和 4.14.16 都是稳定版本,那么到底哪一个更“稳定”呢?有些人不愿意使用 ".0" 的内核发行版,因为他们认为这个版本并不足够“稳定”,直到最新的是 ".1" 的为止。很难证明或者反驳这种观点的对与错,并且这两种观点都有赞成或者反对的理由,因此,具体选择哪一个取决于你的喜好。
|
||||
|
||||
一方面,任何一个进入到稳定树的发行版都必须首先被接受进入主线内核版本中,并且随后会被回迁到已发行版本中。这意味着内核的主线版本相比稳定树中的发行版本来说,总包含有最新的 bug 修复,因此,如果你想使用的发行版包含的“**已知 bug**”最少,那么使用 “.0” 的主线发行版是最佳选择。
|
||||
|
||||
另一方面,主线版本增加了所有很酷的新特性 — 而新特性也给它们带来了**数量未知的“新 bug”**,而这些“新 bug”在老的稳定版中是**不会存在**的。而新的、未知的 bug 是否比旧的、已知的但尚未修复的 bug 更加令人担心呢? -- 这取决于你的选择。不过需要说明的一点是,许多 bug 修复仅对内核的主线版本进行了彻底的测试。当补丁回迁到旧内核时,它们**可能**会工作的很好,但是它们**很少**做与旧内核的集成测试工作。通常都假定,“以前的稳定版本”足够接近当前的确信可用于生产系统的主线版本。而实际上也确实是这样做的,当然,这也更加说明了为什么选择”哪个内核版本更稳定“是件**非常困难**的事情了。
|
||||
|
||||
因此,从根本上说,我们并没有定量的或者定性的手段去明确的告诉你哪个内核版本更加稳定 -- 4.15 还是 4.14.16?我们能够做到的只是告诉你,它们具有”**不同的**稳定性“,(这个答案可能没有帮到你,但是,至少你明白了这些版本的差别是什么?)。
|
||||
|
||||
_学习更多的 Linux 的知识,可以通过来自 Linux 基金会和 edX 的免费课程 ["认识 Linux" ][3]。_
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.linux.com/blog/learn/2018/2/which-linux-kernel-version-stable
|
||||
|
||||
作者:[KONSTANTIN RYABITSEV ][a]
|
||||
译者:[qhwdw](https://github.com/qhwdw)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://www.linux.com/users/mricon
|
||||
[1]:https://www.linux.com/licenses/category/creative-commons-zero
|
||||
[2]:https://www.linux.com/files/images/apple1jpg
|
||||
[3]:https://training.linuxfoundation.org/linux-courses/system-administration-training/introduction-to-linux
|
||||
[4]:https://www.linux.com/blog/intro-to-linux/2018/1/linux-kernel-415-unusual-release-cycle
|
||||
[5]:https://www.kernel.org/
|
||||
[6]:https://git.kernel.org/pub/scm/linux/kernel/git/
|
||||
[7]:https://git.kernel.org/torvalds/c/v4.15
|
||||
[8]:https://www.kernel.org/doc/html/latest/process/stable-kernel-rules.html
|
||||
[9]:https://git.kernel.org/stable/linux-stable/c/v4.14.16
|
||||
Loading…
Reference in New Issue
Block a user