mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-02-28 01:01:09 +08:00
Finish translate
file: 20140709 How to set up two-factor authentication for SSH login on Linux
This commit is contained in:
parent
73b6e3e4f4
commit
d7fc2dbd9f
@ -1,111 +0,0 @@
|
||||
nd0104 is translating
|
||||
How to set up two-factor authentication for SSH login on Linux
|
||||
================================================================================
|
||||
With many high-profile password leaks nowadays, there is a lot of buzz in the industry on "multi-factor" authentication. In a multi-factor authentication system, users are required to go through two distinct authentication procedures: providing something they know (e.g., username/password), and leveraging something they have "physical" access to (e.g., one-time passcode generated by their mobile phone). This scheme is also commonly known as two-factor authentication or two-step verification.
|
||||
|
||||
To encourage the wide adoption of two-factor authentication, Google released [Google Authenticator][1], an open-source application that can generate one-time passcode based on open standards (e.g., HMAP/time-based). It is available on multiple platforms including Linux, [Android][2], [iOS][3]. Google also offers a pluggable authentication module (PAM) for Google Authenticator, allowing it to be integrated with other PAM-enabled applications such as OpenSSH.
|
||||
|
||||
In this tutorial, I will describe **how to set up two-factor authentication for an SSH server** by integrating Google Authenticator with OpenSSH. I am going to use a [Android][4] device to generate one-time passcode. In this tutorial, you will need two things: (1) a Linux host where OpenSSH server is running, and (2) an Android device.
|
||||
|
||||
### Install Google Authenticator on Linux ###
|
||||
|
||||
The first step is to install Google Authenticator on the Linux host where OpenSSH server is running. Follow [this guide][5] to install Google Authenticator and its PAM module on your system.
|
||||
|
||||
Once Google Authenticator is ready, you need to go through one-time configuration which involves creating an authentication key from this Linux host, and registering it with an Android device. This will be explained next.
|
||||
|
||||
### Generate an Authentication Key ###
|
||||
|
||||
To start, simply run Google Authenticator on the Linux server host.
|
||||
|
||||
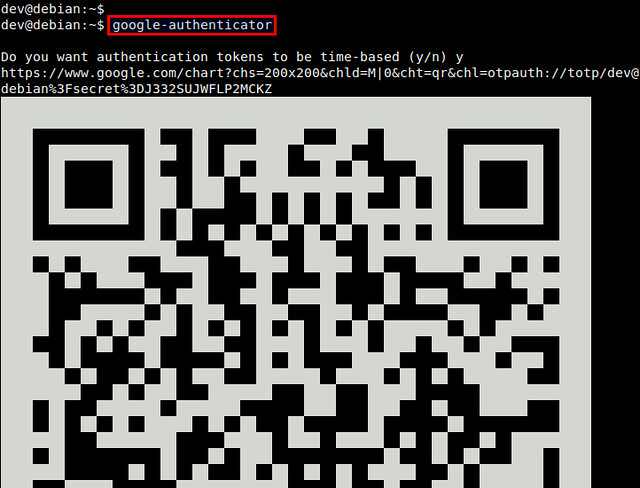
$ google-authenticator
|
||||
|
||||
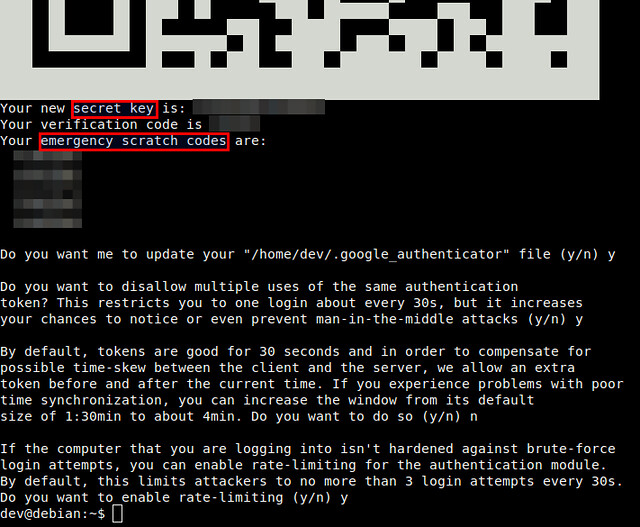
You will see a QR code, as well as a secret key underneath it. The displayed QR code simply represents the numeric secret key. You will need either information to finalize configuration with an Android device.
|
||||
|
||||
|
||||
|
||||
|
||||
Google Authenticator will ask you several questions. If you are not sure, you an answer "Yes" to all questions. The emergency scratch codes can be used to regain access to the SSH server in case you lose your Android device, and so cannot generate one-time passcode. So it's better to write them down somewhere.
|
||||
|
||||
### Run Google Authenticator on Android ###
|
||||
|
||||
As we are going to use an Android device for two-factor authentication, you will need to install [Google Authenticator app][6] on Android. Go to Google Play to install it on Android.
|
||||
|
||||
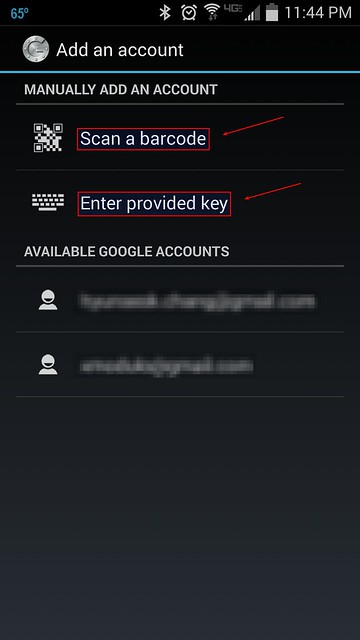
When you start Google Authenticator on Android, you will see the following configuration menu.
|
||||
|
||||
|
||||
|
||||
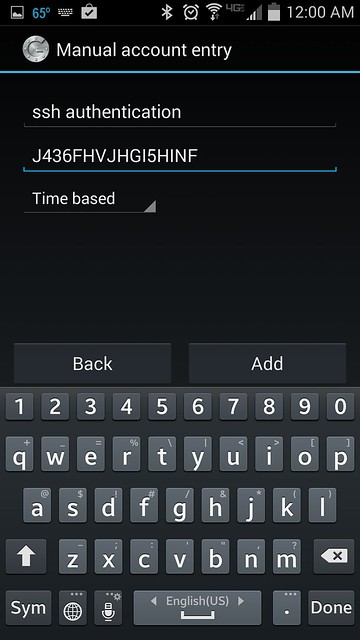
You can choose either "Scan a barcode" or "Enter provided key" option. The first option allows you to enter the security key, simply by scanning the generated QR code. In this case, you will need to install [Barcode Scanner app][7] first. If you choose the second option, you can type the security key using Android keyboard as follows.
|
||||
|
||||
|
||||
|
||||
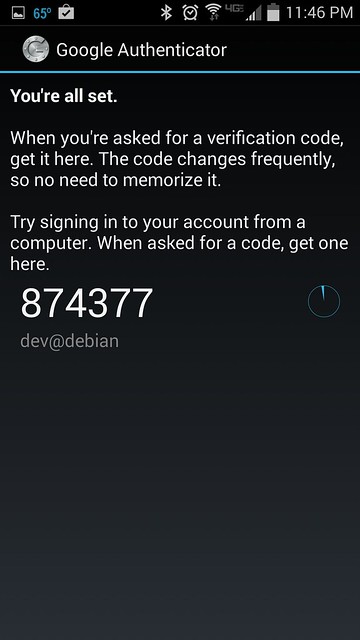
Once you register a secret key either way, you will see the following screen on Android.
|
||||
|
||||
|
||||
|
||||
### Enable Google Authenticator on SSH Server ###
|
||||
|
||||
The final step is to integrate Google Authenticator with OpenSSH server. For that, you need to edit two files.
|
||||
|
||||
First, edit a PAM configuration file, and append the line below.
|
||||
|
||||
$ sudo vi /etc/pam.d/sshd
|
||||
|
||||
----------
|
||||
|
||||
auth required pam_google_authenticator.so
|
||||
|
||||
Then open an SSH server config file, search for ChallengeResponseAuthentication, and enable it.
|
||||
|
||||
$ sudo vi /etc/ssh/sshd_config
|
||||
|
||||
----------
|
||||
|
||||
ChallengeResponseAuthentication yes
|
||||
|
||||
Finally, restart SSH server.
|
||||
|
||||
On Ubuntu, Debian or Linux Mint:
|
||||
|
||||
$ sudo service ssh restart
|
||||
|
||||
On Fedora:
|
||||
|
||||
$ sudo systemctl restart sshd
|
||||
|
||||
On CentOS or RHEL:
|
||||
|
||||
$ sudo service sshd restart
|
||||
|
||||
### Test Two-factor Authentication ###
|
||||
|
||||
Here is how you use two-factor authentication for SSH logins.
|
||||
|
||||
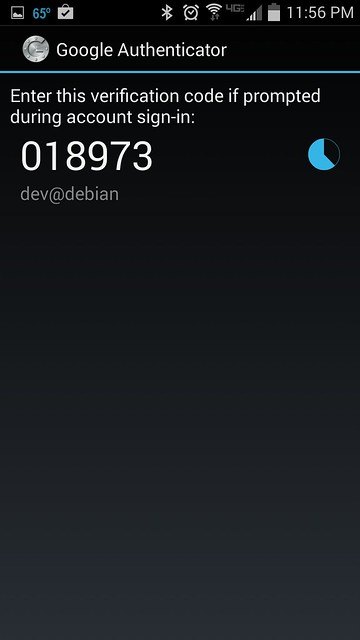
Run Google Authenticator app on Android to obtain one-time verification code. Once generated, a given passcode is valid for 30 seconds. Once it expires, Google Authenticator will automatically generate a new one.
|
||||
|
||||
|
||||
|
||||
Now log in to the SSH server as you normally do.
|
||||
|
||||
$ ssh user@ssh_server
|
||||
|
||||
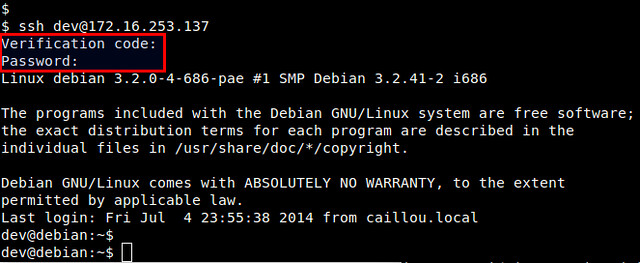
When you are asked to enter "Verification code", type in the verification code generated by Android. After successful verification, then you can type in your SSH login password.
|
||||
|
||||
|
||||
|
||||
To conclude, two-factor authentication can be an effective means to secure password authentication by adding an extra layer of protection. You can use Google Authenticator to secure other logins such as Google account, WordPress.com, Dropbox.com, Outlook.com, etc. Whether you decide to use it or not, it's up to you, but there is a clear industry trend towards the adoption of two-factor authentication.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/2014/07/two-factor-authentication-ssh-login-linux.html
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://code.google.com/p/google-authenticator/
|
||||
[2]:https://play.google.com/store/apps/details?id=com.google.android.apps.authenticator2
|
||||
[3]:https://itunes.apple.com/us/app/google-authenticator/id388497605
|
||||
[4]:http://xmodulo.com/go/android_guide
|
||||
[5]:http://ask.xmodulo.com/install-google-authenticator-linux.html
|
||||
[6]:https://play.google.com/store/apps/details?id=com.google.android.apps.authenticator2
|
||||
[7]:https://play.google.com/store/apps/details?id=com.google.zxing.client.android
|
||||
@ -0,0 +1,90 @@
|
||||
如何为Linux系统中的SSH添加双重认证
|
||||
================================================================================
|
||||
近来很多知名企业都出现了密码泄露,业内对多重认证的呼声也越来越高。在这种多重认证的系统中,用户需要通过两种不同的认证程序:提供他们知道的信息(如 用户名/密码),再借助其他工具提供用户所不知道的信息(如 用手机生成的一次性密码)。这种组合方式常叫做双因子认证或者两阶段验证。
|
||||
为了鼓励广泛采用双因子认证的方式,Google公司发布了[Google Authenticator][1],一款开源的,可基于开放规则(如 HMAP/基于时间)生成一次性密码的软件。这是一款跨平台软件,可运行在Linux, [Android][2], [iOS][3]。Google公司同时也支持插件式鉴别模块PAM(pluggable authentication module),使其能和其他也适用PAM进行验证的工具(如OpenSSH)协同工作。
|
||||
在本教程中,我们将叙述集成OpenSSH和Google提供的认证器实现**如何为SSH服务设置双因子认证**。我将使用一款[Android][4]设备来生成一次性密码,本教程中需要两样兵器:(1)一台运行着OpenSSH服务的Linux终端,(2)一台安卓设备。
|
||||
### 在Linux系统中安装Google Authenticator ###
|
||||
|
||||
第一步需要在运行着OpenSSH服务的Linux主机上安装Google认证器。按照[安装指南] [5]的步骤安装Google认证器及其PAM模块。
|
||||
当Google认证器安装好后,你需要在Linux主机上创建验证密钥,并且在安卓设备上注册,注意这项配置操作是一次性的。我们将详细叙述如何完成这些操作:
|
||||
### 生成验证密钥 ###
|
||||
|
||||
在Linux主机上运行Google认证器
|
||||
$ google-authenticator
|
||||
|
||||
你将看到一个QR码,它使用图形保存了我们数字形态的密钥。一会我们要用到它在安卓设备上完成配置。
|
||||

|
||||

|
||||
|
||||
Google认证器会问一些问题,如果你不确定,就回答"Yes"。这个应急备用验证码(图中 emergency scratch codes)可以在你丢失被绑定的安卓设备的情况下恢复访问,并且设备也不再生成一次性密码。所以最好将应急备用验证码妥善保存。
|
||||
### 在安卓设备上运行Google认证器 ###
|
||||
|
||||
我们需要在安卓设备上安装[Google Authenticator app][6]才能完成双因子认证,到Google Play下载并安装一个。
|
||||
在安卓设备上运行Google认证器,找到下图所示中的配置菜单。
|
||||

|
||||
|
||||
你可以选择"Scan a barcode" 或者"Enter provided key"选项。"Scan a barcode"允许你扫描QR码来完成密钥的输入,在此可能需要先安装扫描软件[Barcode Scanner app][7]。如果选择"Enter provided key"选项,你可以使用键盘输入验证密钥,如下图所示:
|
||||

|
||||
|
||||
无论采用上述两种选项的任何方式,一旦成功,你将看到注册成功提示和一次性密码,如下图所示:
|
||||

|
||||
|
||||
### 为SSH服务器用Google认证器 ###
|
||||
|
||||
最终我们需要修改两个文件来完成集成Google认证器和OpenSSH服务这临门一脚。
|
||||
首先,修改PAM配置文件,命令和需添加的内容如下:
|
||||
$ sudo vi /etc/pam.d/sshd
|
||||
|
||||
----------
|
||||
|
||||
auth required pam_google_authenticator.so
|
||||
|
||||
然后打开SSH配置文件,找到参数ChallengeResponseAuthentication,并启用它。
|
||||
$ sudo vi /etc/ssh/sshd_config
|
||||
|
||||
----------
|
||||
|
||||
ChallengeResponseAuthentication yes
|
||||
|
||||
Finally, restart SSH server.
|
||||
最后,重启SSH服务。
|
||||
在 Ubuntu, Debian, Linux Mint:
|
||||
|
||||
$ sudo service ssh restart
|
||||
|
||||
在Fedora:
|
||||
|
||||
$ sudo systemctl restart sshd
|
||||
|
||||
在CentOS 或 RHEL:
|
||||
|
||||
$ sudo service sshd restart
|
||||
|
||||
### 验证双因子认证 ###
|
||||
|
||||
在绑定的安卓设备上运行Google认证器,获得一个一次性验证码,该验证码30秒内有效,一旦过期,将重新生成一个新的验证码。
|
||||

|
||||
|
||||
Now log in to the SSH server as you normally do.
|
||||
现在和往常一样,使用SSH登录终端
|
||||
$ ssh user@ssh_server
|
||||
|
||||
当提示你输入验证码的时候,输入我们刚获得的验证码。验证成功后,再输入SSH的登录密码。
|
||||

|
||||
|
||||
双因子认证通过在用户密码前新增一层来有效的保护我们脆弱的用户密码。你可以使用Google认证器来保护我们其他的密码,如Google账户, WordPress.com, Dropbox.com, Outlook.com等等。是否使用这项技术,取决于我们自己,但采用双因子认证已经是行业的大趋势了。
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/2014/07/two-factor-authentication-ssh-login-linux.html
|
||||
|
||||
译者:[nd0104](https://github.com/nd0104) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://code.google.com/p/google-authenticator/
|
||||
[2]:https://play.google.com/store/apps/details?id=com.google.android.apps.authenticator2
|
||||
[3]:https://itunes.apple.com/us/app/google-authenticator/id388497605
|
||||
[4]:http://xmodulo.com/go/android_guide
|
||||
[5]:http://ask.xmodulo.com/install-google-authenticator-linux.html
|
||||
[6]:https://play.google.com/store/apps/details?id=com.google.android.apps.authenticator2
|
||||
[7]:https://play.google.com/store/apps/details?id=com.google.zxing.client.android
|
||||
Loading…
Reference in New Issue
Block a user