mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-01-25 23:11:02 +08:00
commit
d4cc79c0eb
@ -1,13 +1,12 @@
|
||||
KevinSJ Translating
|
||||
四大开源版命令行邮件客户端
|
||||
4 个开源的命令行邮件客户端
|
||||
================================================================================
|
||||

|
||||
|
||||
无论你承认与否,email并没有消亡。对依赖命令行的 Linux 高级用户而言,离开 shell 转而使用传统的桌面或网页版邮件客户端并不合适。归根结底,命令行最善于处理文件,特别是文本文件,能使效率倍增。
|
||||
无论你承认与否,email并没有消亡。对那些对命令行至死不渝的 Linux 高级用户而言,离开 shell 转而使用传统的桌面或网页版邮件客户端并不适应。归根结底,命令行最善于处理文件,特别是文本文件,能使效率倍增。
|
||||
|
||||
幸运的是,也有不少的命令行邮件客户端,他们的用户大都乐于帮助你入门并回答你使用中遇到的问题。但别说我没警告过你:一旦你完全掌握了其中一个客户端,要再使用图基于图形界面的客户端将回变得很困难!
|
||||
幸运的是,也有不少的命令行邮件客户端,而它们的用户大都乐于帮助你入门并回答你使用中遇到的问题。但别说我没警告过你:一旦你完全掌握了其中一个客户端,你会发现很难回到基于图形界面的客户端!
|
||||
|
||||
要安装下述四个客户端中的任何一个是非常容易的;主要 Linux 发行版的软件仓库中都提供此类软件,并可通过包管理器进行安装。你也可以再其他的操作系统中寻找并安装这类客户端,但我并未尝试过也没有相关的经验。
|
||||
要安装下述四个客户端中的任何一个是非常容易的;主要的 Linux 发行版的软件仓库中都提供此类软件,并可通过包管理器进行安装。你也可以在其它的操作系统中寻找并安装这类客户端,但我并未尝试过也没有相关的经验。
|
||||
|
||||
### Mutt ###
|
||||
|
||||
@ -17,7 +16,7 @@ KevinSJ Translating
|
||||
|
||||
许多终端爱好者都听说过甚至熟悉 Mutt 和 Alpine, 他们已经存在多年。让我们先看看 Mutt。
|
||||
|
||||
Mutt 支持许多你所期望 email 系统支持的功能:会话,颜色区分,支持多语言,同时还有很多设置选项。它支持 POP3 和 IMAP, 两个主要的邮件传输协议,以及许多邮箱格式。自从1995年诞生以来, Mutt 即拥有一个活跃的开发社区,但最近几年,新版本更多的关注于修复问题和安全更新而非提供新功能。这对大多数 Mutt 用户而言并无大碍,他们钟爱这样的界面,并支持此项目的口号:“所有邮件客户端都很烂,只是这个烂的没那么彻底。”
|
||||
Mutt 支持许多你所期望 email 系统支持的功能:会话,颜色区分,支持多语言,同时还有很多设置选项。它支持 POP3 和 IMAP 这两个主要的邮件传输协议,以及许多邮箱格式。自从1995年诞生以来, Mutt 就拥有了一个活跃的开发社区,但最近几年,新版本更多的关注于修复问题和安全更新而非提供新功能。这对大多数 Mutt 用户而言并无大碍,他们钟爱这样的界面,并支持此项目的口号:“所有邮件客户端都很烂,只是这个烂的没那么彻底。”
|
||||
|
||||
### Alpine ###
|
||||
|
||||
@ -25,13 +24,13 @@ Mutt 支持许多你所期望 email 系统支持的功能:会话,颜色区
|
||||
- [源代码][5]
|
||||
- 授权协议: [Apache 2.0][6]
|
||||
|
||||
Alpine 是另一款知名的终端邮件客户端,它由华盛顿大学开发,初衷是作为 UW 开发的 Pine 的开源,支持unicode的替代版本。
|
||||
Alpine 是另一款知名的终端邮件客户端,它由华盛顿大学开发,设计初衷是作为一个开源的、支持 unicode 的 Pine (也来自华盛顿大学)的替代版本。
|
||||
|
||||
Alpine 不仅容易上手,还为高级用户提供了很多特性,它支持很多协议 —— IMAP, LDAP, NNTP, POP, SMTP 等,同时也支持不同的邮箱格式。Alpine 内置了一款名为 Pico 的可独立使用的简易文本编辑工具,但你也可以使用你常用的文本编辑器: vi, Emacs等。
|
||||
|
||||
尽管Alpine的升级并不频繁,名为re-alpine的分支为不同的开发者提供了开发此项目的机会。
|
||||
尽管 Alpine 的升级并不频繁,不过有个名为 re-alpine 的分支为不同的开发者提供了开发此项目的机会。
|
||||
|
||||
Alpine 支持再屏幕上显示上下文帮助,但一些用户回喜欢 Mutt 式的独立说明手册,但这两种提供了较好的说明。用户可以同时尝试 Mutt 和 Alpine,并由个人喜好作出决定,也可以尝试以下几个比较新颖的选项。
|
||||
Alpine 支持在屏幕上显示上下文帮助,但一些用户会喜欢 Mutt 式的独立说明手册,不过它们两个的文档都很完善。用户可以同时尝试 Mutt 和 Alpine,并由个人喜好作出决定,也可以尝试以下的几个新选择。
|
||||
|
||||
### Sup ###
|
||||
|
||||
@ -39,10 +38,9 @@ Alpine 支持再屏幕上显示上下文帮助,但一些用户回喜欢 Mutt
|
||||
- [源代码][8]
|
||||
- 授权协议: [GPLv2][9]
|
||||
|
||||
Sup 是我们列表中能被称为“大容量邮件客户端”的两个之一。自称“为邮件较多的人设计的命令行客户端”,Sup 的目标是提供一个支持层次化设计并允许再为会话添加标签进行简单整理的界面。
|
||||
Sup 是我们列表中能被称为“大容量邮件客户端”的二者之一。自称“为邮件较多的人设计的命令行客户端”,Sup 的目标是提供一个支持层次化设计并允许为会话添加标签进行简单整理的界面。
|
||||
|
||||
由于采用 Ruby 编写,Sup 能提供十分快速的搜索并能自动管理联系人列表,同时还允许自定义插件。对于使用 Gmail 作为网页邮件客户端的人们,这些功能都是耳熟能详的,这就使得 Sup 成为一种比较现代的命令行邮件管理方式。
|
||||
Written in Ruby, Sup provides exceptionally fast searching, manages your contact list automatically, and allows for custom extensions. For people who are used to Gmail as a webmail interface, these features will seem familiar, and Sup might be seen as a more modern approach to email on the command line.
|
||||
|
||||
### Notmuch ###
|
||||
|
||||
@ -52,16 +50,17 @@ Written in Ruby, Sup provides exceptionally fast searching, manages your contact
|
||||
|
||||
"Sup? Notmuch." Notmuch 作为 Sup 的回应,最初只是重写了 Sup 的一小部分来提高性能。最终,这个项目逐渐变大并成为了一个独立的邮件客户端。
|
||||
|
||||
Notmuch是一款相当精简的软件。它并不能独立的收发邮件,启用 Notmuch 的快速搜索功能的代码实际上是一个需要调用的独立库。但这样的模块化设计也使得你能使用你最爱的工具进行写信,发信和收信,集中精力做好一件事情并有效浏览和管理你的邮件。
|
||||
Notmuch 是一款相当精简的软件。它并不能独立的收发邮件,启用 Notmuch 的快速搜索功能的代码实际上是设计成一个程序可以调用的独立库。但这样的模块化设计也使得你能使用你最爱的工具进行写信,发信和收信,集中精力做好一件事情并有效浏览和管理你的邮件。
|
||||
|
||||
这个列表并不完整,还有很多 email 客户端,它们或许才是你的最佳选择。你喜欢什么客户端呢?
|
||||
|
||||
这个列表并不完整,还有很多 email 客户端,他们或许才是你的最佳选择。你喜欢什么客户端呢?
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://opensource.com/life/15/8/top-4-open-source-command-line-email-clients
|
||||
|
||||
作者:[Jason Baker][a]
|
||||
译者:[KevinSJ](https://github.com/KevinSj)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
@ -0,0 +1,77 @@
|
||||
如何在 Ubuntu 15.04 下创建一个可供 Android/iOS 连接的 AP
|
||||
================================================================================
|
||||
我成功地在 Ubuntu 15.04 下用 Gnome Network Manager 创建了一个无线AP热点。接下来我要分享一下我的步骤。请注意:你必须要有一个可以用来创建AP热点的无线网卡。如果你不知道如何确认它的话,在终端(Terminal)里输入`iw list`。
|
||||
|
||||
如果你没有安装`iw`的话, 在Ubuntu下你可以使用`sudo apt-get install iw`进行安装.
|
||||
|
||||
在你键入`iw list`之后, 查看“支持的接口模式”, 你应该会看到类似下面的条目中看到 AP:
|
||||
|
||||
Supported interface modes:
|
||||
|
||||
* IBSS
|
||||
* managed
|
||||
* AP
|
||||
* AP/VLAN
|
||||
* monitor
|
||||
* mesh point
|
||||
|
||||
让我们一步步看:
|
||||
|
||||
1、 断开WIFI连接。使用有线网络接入你的笔记本。
|
||||
|
||||
2、 在顶栏面板里点击网络的图标 -> Edit Connections(编辑连接) -> 在弹出窗口里点击Add(新增)按钮。
|
||||
|
||||
3、 在下拉菜单内选择Wi-Fi。
|
||||
|
||||
4、 接下来:
|
||||
|
||||
a、 输入一个链接名 比如: Hotspot 1
|
||||
|
||||
b、 输入一个 SSID 比如: Hotspot 1
|
||||
|
||||
c、 选择模式(mode): Infrastructure (基础设施)
|
||||
|
||||
d、 设备 MAC 地址: 在下拉菜单里选择你的无线设备
|
||||
|
||||

|
||||
|
||||
5、 进入Wi-Fi安全选项卡,选择 WPA & WPA2 Personal 并且输入密码。
|
||||
6、 进入IPv4设置选项卡,在Method(方法)下拉菜单里,选择Shared to other computers(共享至其他电脑)。
|
||||
|
||||

|
||||
|
||||
7、 进入IPv6选项卡,在Method(方法)里设置为忽略ignore (只有在你不使用IPv6的情况下这么做)
|
||||
8、 点击 Save(保存) 按钮以保存配置。
|
||||
9、 从 menu/dash 里打开Terminal。
|
||||
10、 修改你刚刚使用 network settings 创建的连接。
|
||||
|
||||
使用 VIM 编辑器:
|
||||
|
||||
sudo vim /etc/NetworkManager/system-connections/Hotspot
|
||||
|
||||
或使用Gedit 编辑器:
|
||||
|
||||
gksu gedit /etc/NetworkManager/system-connections/Hotspot
|
||||
|
||||
把名字 Hotspot 用你在第4步里起的连接名替换掉。
|
||||
|
||||

|
||||
|
||||
a、 把 `mode=infrastructure` 改成 `mode=ap` 并且保存文件。
|
||||
b、 一旦你保存了这个文件,你应该能在 Wifi 菜单里看到你刚刚建立的AP了。(如果没有的话请再顶栏里 关闭/打开 Wifi 选项一次)
|
||||
|
||||

|
||||
|
||||
11、你现在可以把你的设备连上Wifi了。已经过 Android 5.0的小米4测试。(下载了1GB的文件以测试速度与稳定性)
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linuxveda.com/2015/08/23/how-to-create-an-ap-in-ubuntu-15-04-to-connect-to-androidiphone/
|
||||
|
||||
作者:[Sayantan Das][a]
|
||||
译者:[jerryling315](https://github.com/jerryling315)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.linuxveda.com/author/sayantan_das/
|
||||
@ -0,0 +1,63 @@
|
||||
FISH:Linux 的一个智能易用的 Shell
|
||||
================================================================================
|
||||
|
||||
FISH(friendly interactive shell)是一个用户友好的命令行 shell,主要是用来进行交互式使用。shell 就是一个用来执行其他程序的程序。
|
||||
|
||||
### FISH 特性 ###
|
||||
|
||||
#### 自动建议 ####
|
||||
|
||||
fish 会根据你的历史输入和补完来提供命令建议,就像一个网络浏览器一样。注意了,就是Netscape Navigator 4.0!
|
||||
|
||||

|
||||
|
||||
#### 漂亮的VGA 色彩 ####
|
||||
|
||||
fish 原生支持 term256, 它就是一个终端技术的艺术国度。 你将可以拥有一个难以置信的、256 色的shell 来使用。
|
||||
|
||||
#### 理智的脚本 ####
|
||||
|
||||
fish 是完全可以通过脚本控制的,而且它的语法又是那么的简单、干净,而且一致。你甚至不需要去重写。
|
||||
|
||||
#### 基于 web 的配置 ####
|
||||
|
||||
对于少数能使用图形计算机的幸运儿, 你们可以在网页上配置你们自己的色彩方案,以及查看函数、变量和历史记录。
|
||||
|
||||
#### 帮助手册补全 ####
|
||||
|
||||
其它的 shell 支持可配置的补全, 但是只有 fish 可以通过自动转换你安装好的 man 手册来实现补全功能。
|
||||
|
||||
#### 开箱即用 ####
|
||||
|
||||
fish 将会通过 tab 补全和语法高亮使你非常愉快的使用shell, 同时不需要太多的学习或者配置。
|
||||
|
||||
### 在ubuntu 15.04 上安装FISH
|
||||
|
||||
打开终端,运行下列命令:
|
||||
|
||||
sudo apt-add-repository ppa:fish-shell/release-2
|
||||
sudo apt-get update
|
||||
sudo apt-get install fish
|
||||
|
||||
###使用FISH###
|
||||
|
||||
打开终端,运行下列命令来启动FISH:
|
||||
|
||||
fish
|
||||
|
||||
欢迎来到 fish,友好的交互式shell,输入指令 help 来了解怎么使用fish。
|
||||
|
||||
阅读[FISH 文档][1] ,掌握使用方法。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.ubuntugeek.com/fish-a-smart-and-user-friendly-command-line-shell-for-linux.html
|
||||
|
||||
作者:[ruchi][a]
|
||||
译者:[oska874](https://github.com/oska874)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.ubuntugeek.com/author/ubuntufix
|
||||
[1]:http://fishshell.com/docs/current/index.html#introduction
|
||||
@ -1,3 +1,4 @@
|
||||
ictlyh Translating
|
||||
Do Simple Math In Ubuntu And elementary OS With NaSC
|
||||
================================================================================
|
||||

|
||||
|
||||
@ -1,3 +1,4 @@
|
||||
ictlyh Translating
|
||||
How To Manage Log Files With Logrotate On Ubuntu 12.10
|
||||
================================================================================
|
||||
#### About Logrotate ####
|
||||
|
||||
219
sources/tech/20150906 How to Configure OpenNMS on CentOS 7.x.md
Normal file
219
sources/tech/20150906 How to Configure OpenNMS on CentOS 7.x.md
Normal file
@ -0,0 +1,219 @@
|
||||
How to Configure OpenNMS on CentOS 7.x
|
||||
================================================================================
|
||||
Systems management and monitoring services are very important that provides information to view important systems management information that allow us to to make decisions based on this information. To make sure the network is running at its best and to minimize the network downtime we need to improve application performance. So, in this article we will make you understand the step by step procedure to setup OpenNMS in your IT infrastructure. OpenNMS is a free open source enterprise level network monitoring and management platform that provides information to allow us to make decisions in regards to future network and capacity planning.
|
||||
|
||||
OpenNMS designed to manage tens of thousands of devices from a single server as well as manage unlimited devices using a cluster of servers. It includes a discovery engine to automatically configure and manage network devices without operator intervention. It is written in Java and is published under the GNU General Public License. OpenNMS is known for its scalability with its main functional areas in services monitoring, data collection using SNMP and event management and notifications.
|
||||
|
||||
### Installing OpenNMS RPM Repository ###
|
||||
|
||||
We will start from the installation of OpenNMS RPM for our CentOs 7.1 operating system as its available for most of the RPM-based distributions through Yum at their official link http://yum.opennms.org/ .
|
||||
|
||||

|
||||
|
||||
Then open your command line interface of CentOS 7.1 and login with root credentials to run the below command with “wget” to get the required RPM.
|
||||
|
||||
[root@open-nms ~]# wget http://yum.opennms.org/repofiles/opennms-repo-stable-rhel7.noarch.rpm
|
||||
|
||||

|
||||
|
||||
Now we need to install this repository so that the OpenNMS package information could be available through yum for installation. Let’s run the command below with same root level credentials to do so.
|
||||
|
||||
[root@open-nms ~]# rpm -Uvh opennms-repo-stable-rhel7.noarch.rpm
|
||||
|
||||

|
||||
|
||||
### Installing Prerequisite Packages for OpenNMS ###
|
||||
|
||||
Now before we start installation of OpenNMS, let’s make sure you’ve done the following prerequisites.
|
||||
|
||||
**Install JDK 7**
|
||||
|
||||
Its recommended that you install the latest stable Java 7 JDK from Oracle for the best performance to integrate JDK in our YUM repository as a fallback. Let’s go to the Oracle Java 7 SE JDK download page, accept the license if you agree, choose the platform and architecture. Once it has finished downloading, execute it from the command-line and then install the resulting JDK rpm.
|
||||
|
||||
Else run the below command to install using the Yum from the the available system repositories.
|
||||
|
||||
[root@open-nms ~]# yum install java-1.7.0-openjdk-1.7.0.85-2.6.1.2.el7_1
|
||||
|
||||
Once you have installed the Java you can confirm its installation using below command and check its installed version.
|
||||
|
||||
[root@open-nms ~]# java -version
|
||||
|
||||

|
||||
|
||||
**Install PostgreSQL**
|
||||
|
||||
Now we will install the PostgreSQL that is a must requirement to setup the database for OpenNMS. PostgreSQL is included in all of the major YUM-based distributions. To install, simply run the below command.
|
||||
|
||||
[root@open-nms ~]# yum install postgresql postgresql-server
|
||||
|
||||

|
||||
|
||||
### Prepare the Database for OpenNMS ###
|
||||
|
||||
Once you have installed PostgreSQL, now you'll need to make sure that PostgreSQL is up and active. Let’s run the below command to first initialize the database and then start its services.
|
||||
|
||||
[root@open-nms ~]# /sbin/service postgresql initdb
|
||||
[root@open-nms ~]# /sbin/service postgresql start
|
||||
|
||||

|
||||
|
||||
Now to confirm the status of your PostgreSQL database you can run the below command.
|
||||
|
||||
[root@open-nms ~]# service postgresql status
|
||||
|
||||

|
||||
|
||||
To ensure that PostgreSQL will start after a reboot, use the “systemctl”command to enable start on bootup using below command.
|
||||
|
||||
[root@open-nms ~]# systemctl enable postgresql
|
||||
ln -s '/usr/lib/systemd/system/postgresql.service' '/etc/systemd/system/multi-user.target.wants/postgresql.service'
|
||||
|
||||
### Configure PostgreSQL ###
|
||||
|
||||
Locate the Postgres “data” directory. Often this is located in /var/lib/pgsql/data directory and Open the postgresql.conf file in text editor and configure the following parameters as shown.
|
||||
|
||||
[root@open-nms ~]# vim /var/lib/pgsql/data/postgresql.conf
|
||||
|
||||
----------
|
||||
|
||||
#------------------------------------------------------------------------------
|
||||
# CONNECTIONS AND AUTHENTICATION
|
||||
#------------------------------------------------------------------------------
|
||||
|
||||
listen_addresses = 'localhost'
|
||||
max_connections = 256
|
||||
|
||||
#------------------------------------------------------------------------------
|
||||
# RESOURCE USAGE (except WAL)
|
||||
#------------------------------------------------------------------------------
|
||||
|
||||
shared_buffers = 1024MB
|
||||
|
||||
**User Access to the Database**
|
||||
|
||||
PostgreSQL only allows you to connect if you are logged in to the local account name that matches the PostgreSQL user. Since OpenNMS runs as root, it cannot connect as a "postgres" or "opennms" user by default, so we have to change the configuration to allow user access to the database by opening the below configuration file.
|
||||
|
||||
[root@open-nms ~]# vim /var/lib/pgsql/data/pg_hba.conf
|
||||
|
||||
Update the configuration file as shown below and change the METHOD settings from "ident" to "trust"
|
||||
|
||||

|
||||
|
||||
Write and quit the file to make saved changes and then restart PostgreSQL services.
|
||||
|
||||
[root@open-nms ~]# service postgresql restart
|
||||
|
||||
### Starting OpenNMS Installation ###
|
||||
|
||||
Now we are ready go with installation of OpenNMS as we have almost don with its prerequisites. Using the YUM packaging system will download and install all of the required components and their dependencies, if they are not already installed on your system.
|
||||
So let's riun th belwo command to start OpenNMS installation that will pull everything you need to have a working OpenNMS, including the OpenNMS core, web UI, and a set of common plugins.
|
||||
|
||||
[root@open-nms ~]# yum -y install opennms
|
||||
|
||||

|
||||
|
||||
The above command will ends up with successful installation of OpenNMS and its derivative packages.
|
||||
|
||||
### Configure JAVA for OpenNMS ###
|
||||
|
||||
In order to integrate the default version of Java with OpenNMS we will run the below command.
|
||||
|
||||
[root@open-nms ~]# /opt/opennms/bin/runjava -s
|
||||
|
||||

|
||||
|
||||
### Run the OpenNMS installer ###
|
||||
|
||||
Now it's time to start the OpenNMS installer that will create and configure the OpenNMS database, while the same command will be used in case we want to update it to the latest version. To do so, we will run the following command.
|
||||
|
||||
[root@open-nms ~]# /opt/opennms/bin/install -dis
|
||||
|
||||
The above install command will take many options with following mechanism.
|
||||
|
||||
-d - to update the database
|
||||
-i - to insert any default data that belongs in the database
|
||||
-s - to create or update the stored procedures OpenNMS uses for certain kinds of data access
|
||||
|
||||
==============================================================================
|
||||
OpenNMS Installer
|
||||
==============================================================================
|
||||
|
||||
Configures PostgreSQL tables, users, and other miscellaneous settings.
|
||||
|
||||
DEBUG: Platform is IPv6 ready: true
|
||||
- searching for libjicmp.so:
|
||||
- trying to load /usr/lib64/libjicmp.so: OK
|
||||
- searching for libjicmp6.so:
|
||||
- trying to load /usr/lib64/libjicmp6.so: OK
|
||||
- searching for libjrrd.so:
|
||||
- trying to load /usr/lib64/libjrrd.so: OK
|
||||
- using SQL directory... /opt/opennms/etc
|
||||
- using create.sql... /opt/opennms/etc/create.sql
|
||||
17:27:51.178 [Main] INFO org.opennms.core.schema.Migrator - PL/PgSQL call handler exists
|
||||
17:27:51.180 [Main] INFO org.opennms.core.schema.Migrator - PL/PgSQL language exists
|
||||
- checking if database "opennms" is unicode... ALREADY UNICODE
|
||||
- Creating imports directory (/opt/opennms/etc/imports... OK
|
||||
- Checking for old import files in /opt/opennms/etc... DONE
|
||||
INFO 16/08/15 17:27:liquibase: Reading from databasechangelog
|
||||
Installer completed successfully!
|
||||
|
||||
==============================================================================
|
||||
OpenNMS Upgrader
|
||||
==============================================================================
|
||||
|
||||
OpenNMS is currently stopped
|
||||
Found upgrade task SnmpInterfaceRrdMigratorOnline
|
||||
Found upgrade task KscReportsMigrator
|
||||
Found upgrade task JettyConfigMigratorOffline
|
||||
Found upgrade task DataCollectionConfigMigratorOffline
|
||||
Processing RequisitionsMigratorOffline: Remove non-ip-snmp-primary and non-ip-interfaces from requisitions: NMS-5630, NMS-5571
|
||||
- Running pre-execution phase
|
||||
Backing up: /opt/opennms/etc/imports
|
||||
- Running post-execution phase
|
||||
Removing backup /opt/opennms/etc/datacollection.zip
|
||||
|
||||
Finished in 0 seconds
|
||||
|
||||
Upgrade completed successfully!
|
||||
|
||||
### Firewall configurations to Allow OpenNMS ###
|
||||
|
||||
Here we have to allow OpenNMS management interface port 8980 through firewall or router to access the management web interface from the remote systems. So use the following commands to do so.
|
||||
|
||||
[root@open-nms etc]# firewall-cmd --permanent --add-port=8980/tcp
|
||||
[root@open-nms etc]# firewall-cmd --reload
|
||||
|
||||
### Start OpenNMS and Login to Web Interface ###
|
||||
|
||||
Let's start OpenNMS service and enable to it start at each bootup by using the below command.
|
||||
|
||||
[root@open-nms ~]#systemctl start opennms
|
||||
[root@open-nms ~]#systemctl enable opennms
|
||||
|
||||
Once the services are up are ready to go with its web management interface. Open your web browser and access it with your server's IP address and 8980 port.
|
||||
|
||||
http://servers_ip:8980/
|
||||
|
||||
Give the username and password where as the default username and password is admin/admin.
|
||||
|
||||

|
||||
|
||||
After successful authentication with your provided username and password you will be directed towards the the Home page of OpenNMS where you can configure the new monitoring devices/nodes/services etc.
|
||||
|
||||

|
||||
|
||||
### Conclusion ###
|
||||
|
||||
Congratulations! we have successfully setup OpenNMS on CentOS 7.1. So, at the end of this tutorial, you are now able to install and configure OpenNMS with its prerequisites that included PostgreSQL and JAVA setup. So let's enjoy with the great network monitoring system with open source roots using OpenNMS that provide a bevy of features at no cost than their high-end competitors, and can scale to monitor large numbers of network nodes.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/monitoring-2/install-configure-opennms-centos-7-x/
|
||||
|
||||
作者:[Kashif Siddique][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://linoxide.com/author/kashifs/
|
||||
@ -0,0 +1,174 @@
|
||||
How to Install DNSCrypt and Unbound in Arch Linux
|
||||
================================================================================
|
||||
**DNSCrypt** is a protocol that encrypt and authenticate communications between a DNS client and a DNS resolver. Prevent from DNS spoofing or man in the middle-attack. DNSCrypt are available for most operating system, including Linux, Windows, MacOSX android and iOS. And in this tutorial I'm using archlinux with kernel 4.1.
|
||||
|
||||
Unbound is a DNS cache server used to resolve any DNS query received. If the user requests a new query, then unbound will store it as a cache, and when the user requests the same query for the second time, then unbound would take from the cache that have been saved. This will be faster than the first request query.
|
||||
|
||||
And now I will try to install "DNSCrypt" to secure the dns communication, and make it faster with dns cache "Unbound".
|
||||
|
||||
### Step 1 - Install yaourt ###
|
||||
|
||||
Yaourt is one of AUR(Arch User Repository) helper that make archlinux users easy to install a program from AUR. Yaourt use same syntax as pacman, so you can install the program with yaourt. and this is easy way to install yaourt :
|
||||
|
||||
1. Edit the arch repository configuration file with nano or vi, stored in a file "/etc/pacman.conf".
|
||||
|
||||
$ nano /etc/pacman.conf
|
||||
|
||||
2. Add at the bottom line yaourt repository, just paste script below :
|
||||
|
||||
[archlinuxfr]
|
||||
SigLevel = Never
|
||||
Server = http://repo.archlinux.fr/$arch
|
||||
|
||||
3. Save it with press "Ctrl + x" and then "Y".
|
||||
|
||||
4. Now update the repository database and install yaourt with pacman command :
|
||||
|
||||
$ sudo pacman -Sy yaourt
|
||||
|
||||
### Step 2 - Install DNSCrypt and Unbound ###
|
||||
|
||||
DNSCrypt and unbound available on archlinux repository, then you can install it with pacman command :
|
||||
|
||||
$ sudo pacman -S dnscrypt-proxy unbound
|
||||
|
||||
wait it and press "Y" for proceed with installation.
|
||||
|
||||
### Step 3 - Install dnscrypt-autoinstall ###
|
||||
|
||||
Dnscrypt-autoinstall is A script for installing and automatically configuring DNSCrypt on Linux-based systems. Dnscrypt-autoinstall available in AUR(Arch User Repository), and you must use "yaourt" command to install it :
|
||||
|
||||
$ yaourt -S dnscrypt-autoinstall
|
||||
|
||||
Note :
|
||||
|
||||
-S = it is same as pacman -S to install a software/program.
|
||||
|
||||
### Step 4 - Run dnscrypt-autoinstall ###
|
||||
|
||||
run the command "dnscrypt-autoinstall" with root privileges to configure DNSCrypt automatically :
|
||||
|
||||
$ sudo dnscrypt-autoinstall
|
||||
|
||||
Press "Enter" for the next configuration, and then type "y" and choose the DNS provider you want to use, I'm here use DNSCrypt.eu featured with no logs and DNSSEC.
|
||||
|
||||

|
||||
|
||||
### Step 5 - Configure DNSCrypt and Unbound ###
|
||||
|
||||
1. Open the dnscrypt configuration file "/etc/conf.d/dnscrypt-config" and make sure the configuration of "DNSCRYPT_LOCALIP" point to **localhost IP**, and for port configuration "DNSCRYPT_LOCALPORT" it's up to you, I`m here use port **40**.
|
||||
|
||||
$ nano /etc/conf.d/dnscrypt-config
|
||||
|
||||
DNSCRYPT_LOCALIP=127.0.0.1
|
||||
DNSCRYPT_LOCALIP2=127.0.0.2
|
||||
DNSCRYPT_LOCALPORT=40
|
||||
|
||||

|
||||
|
||||
Save and exit.
|
||||
|
||||
2. Now you can edit unbound configuration in "/etc/unbound/". edit the file configuration with nano editor :
|
||||
|
||||
$ nano /etc/unbound/unbound.conf
|
||||
|
||||
3. Add the following script in the end of line :
|
||||
|
||||
do-not-query-localhost: no
|
||||
forward-zone:
|
||||
name: "."
|
||||
forward-addr: 127.0.0.1@40
|
||||
|
||||
Make sure the "**forward-addr**" port is same with "**DNSCRYPT_LOCALPORT**" configuration in DNSCrypt. You can see the I`m use port **40**.
|
||||
|
||||

|
||||
|
||||
and then save and exit.
|
||||
|
||||
### Step 6 - Run DNSCrypt and Unbound, then Add to startup/Boot ###
|
||||
|
||||
Please run DNSCrypt and unbound with root privileges, you can run with systemctl command :
|
||||
|
||||
$ sudo systemctl start dnscrypt-proxy unbound
|
||||
|
||||
Add the service at the boot time/startup. You can do it by running "systemctl enable" :
|
||||
|
||||
$ sudo systemctl enable dnscrypt-proxy unbound
|
||||
|
||||
the command will create the symlink of the service to "/usr/lib/systemd/system/" directory.
|
||||
|
||||
### Step 7 - Configure resolv.conf and restart all services ###
|
||||
|
||||
Resolv.conf is a file used by linux to configure Domain Name Server(DNS) resolver. it is just plain-text created by administrator, so you must edit by root privileges and make it immutable/no one can edit it.
|
||||
|
||||
Edit it with nano editor :
|
||||
|
||||
$ nano /etc/resolv.conf
|
||||
|
||||
and add the localhost IP "**127.0.0.1**". and now make it immutable with "chattr" command :
|
||||
|
||||
$ chattr +i /etc/resolv.conf
|
||||
|
||||
Note :
|
||||
|
||||
If you want to edit it again, make it writable with command "chattr -i /etc/resolv.conf".
|
||||
|
||||
Now yo need to restart the DNSCrypt, unbound and the network :
|
||||
|
||||
$ sudo systemctl restart dnscrypt-proxy unbound netctl
|
||||
|
||||
If you see the error, check your configuration file.
|
||||
|
||||
### Testing ###
|
||||
|
||||
1. Test DNSCrypt
|
||||
|
||||
You can be sure that DNSCrypt had acted correctly by visiting https://dnsleaktest.com/, then click on "Standard Test" or "Extended Test" and wait the process running.
|
||||
|
||||
And now you can see that DNSCrypt is working with DNSCrypt.eu as your DNS provider.
|
||||
|
||||

|
||||
|
||||
And now you can see that DNSCrypt is working with DNSCrypt.eu as your DNS provider.
|
||||
|
||||
2. Test Unbound
|
||||
|
||||
Now you should ensure that the unbound is working correctly with "dig" or "drill" command.
|
||||
|
||||
This is the results for dig command :
|
||||
|
||||
$ dig linoxide.com
|
||||
|
||||
Now see in the results, the "Query time" is "533 msec" :
|
||||
|
||||
;; Query time: 533 msec
|
||||
;; SERVER: 127.0.0.1#53(127.0.0.1)
|
||||
;; WHEN: Sun Aug 30 14:48:19 WIB 2015
|
||||
;; MSG SIZE rcvd: 188
|
||||
|
||||
and try again with the same command. And you will see the "Query time" is "0 msec".
|
||||
|
||||
;; Query time: 0 msec
|
||||
;; SERVER: 127.0.0.1#53(127.0.0.1)
|
||||
;; WHEN: Sun Aug 30 14:51:05 WIB 2015
|
||||
;; MSG SIZE rcvd: 188
|
||||
|
||||

|
||||
|
||||
And in the end DNSCrypt secure communications between the DNS clients and DNS resolver is working perfectly, and then Unbound make it faster if there is the same request in another time by taking the cache that have been saved.
|
||||
|
||||
### Conclusion ###
|
||||
|
||||
DNSCrypt is a protocol that can encrypt data flow between the DNS client and DNS resolver. DNSCrypt can run on various operating systems, either mobile or desktop. Choose DNS provider also includes something important, choose which provide a DNSSEC and no logs. Unbound can be used as a DNS cache, thus speeding up the resolve process resolv, because Unbound will store a request as the cache, then when a client request same query in the next time, then unbound would take from the cache that have been saved. DNSCrypt and Unbound is a powerful combination for the safety and speed.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/tools/install-dnscrypt-unbound-archlinux/
|
||||
|
||||
作者:[Arul][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://linoxide.com/author/arulm/
|
||||
@ -0,0 +1,73 @@
|
||||
translation by strugglingyouth
|
||||
Install Qmmp 0.9.0 Winamp-like Audio Player in Ubuntu
|
||||
================================================================================
|
||||

|
||||
|
||||
Qmmp, Qt-based audio player with winamp or xmms like user interface, now is at 0.9.0 release. PPA updated for Ubuntu 15.10, Ubuntu 15.04, Ubuntu 14.04, Ubuntu 12.04 and derivatives.
|
||||
|
||||
Qmmp 0.9.0 is a big release with many new features, improvements and some translation updates. It added:
|
||||
|
||||
- audio-channel sequence converter;
|
||||
- 9 channels support to equalizer;
|
||||
- album artist tag support;
|
||||
- asynchronous sorting;
|
||||
- sorting by file modification date;
|
||||
- sorting by album artist;
|
||||
- multiple column support;
|
||||
- feature to hide track length;
|
||||
- feature to disable plugins without qmmp.pri modification (qmake only)
|
||||
- feature to remember playlist scroll position;
|
||||
- feature to exclude cue data files;
|
||||
- feature to change user agent;
|
||||
- feature to change window title;
|
||||
- feature to reset fonts;
|
||||
- feature to restore default shortcuts;
|
||||
- default hotkey for the “Rename List” action;
|
||||
- feature to disable fadeout in the gme plugin;
|
||||
- Simple User Interface (QSUI) with the following changes:
|
||||
- added multiple column support;
|
||||
- added sorting by album artist;
|
||||
- added sorting by file modification date;
|
||||
- added feature to hide song length;
|
||||
- added default hotkey for the “Rename List” action;
|
||||
- added “Save List” action to the tab menu;
|
||||
- added feature to reset fonts;
|
||||
- added feature to reset shortcuts;
|
||||
- improved status bar;
|
||||
|
||||
It also improved playlist changes notification, playlist container, sample rate converter, cmake build scripts, title formatter, ape tags support in the mpeg plugin, fileops plugin, reduced cpu usage, changed default skin (to Glare) and playlist separator.
|
||||
|
||||
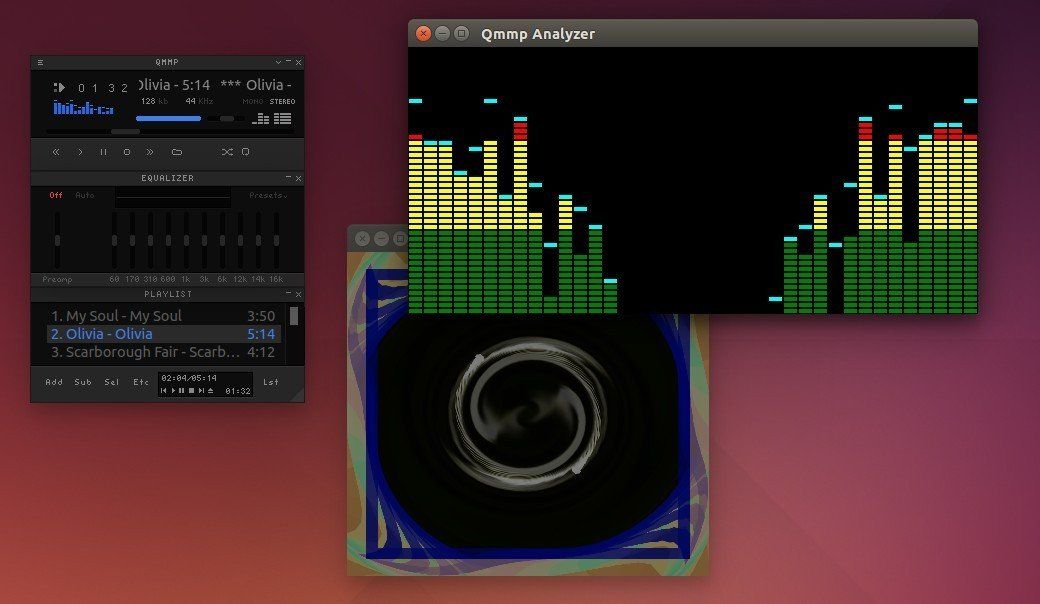
|
||||
|
||||
### Install Qmmp 0.9.0 in Ubuntu: ###
|
||||
|
||||
New release has been made into PPA, available for all current Ubuntu releases and derivatives.
|
||||
|
||||
1. To add the [Qmmp PPA][1].
|
||||
|
||||
Open terminal from the Dash, App Launcher, or via Ctrl+Alt+T shortcut keys. When it opens, run command:
|
||||
|
||||
sudo add-apt-repository ppa:forkotov02/ppa
|
||||
|
||||
|
||||
|
||||
2. After adding the PPA, upgrade Qmmp player through Software Updater. Or refresh system cache and install the software via below commands:
|
||||
|
||||
sudo apt-get update
|
||||
|
||||
sudo apt-get install qmmp qmmp-plugin-pack
|
||||
|
||||
That’s it. Enjoy!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://ubuntuhandbook.org/index.php/2015/09/qmmp-0-9-0-in-ubuntu/
|
||||
|
||||
作者:[Ji m][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://ubuntuhandbook.org/index.php/about/
|
||||
[1]:https://launchpad.net/~forkotov02/+archive/ubuntu/ppa
|
||||
@ -1,4 +1,5 @@
|
||||
Installing NGINX and NGINX Plus With Ansible
|
||||
translation by strugglingyouth
|
||||
nstalling NGINX and NGINX Plus With Ansible
|
||||
================================================================================
|
||||
Coming from a production operations background, I have learned to love all things related to automation. Why do something by hand if a computer can do it for you? But creating and implementing automation can be a difficult task given an ever-changing infrastructure and the various technologies surrounding your environments. This is why I love [Ansible][1]. Ansible is an open source tool for IT configuration management, deployment, and orchestration that is extremely easy to use.
|
||||
|
||||
|
||||
@ -0,0 +1,63 @@
|
||||
ictlyh Translating
|
||||
Make Math Simple in Ubuntu / Elementary OS via NaSC
|
||||
================================================================================
|
||||

|
||||
|
||||
NaSC (Not a Soulver Clone) is an open source software designed for Elementary OS to do arithmetics. It’s kinda similar to the Mac app [Soulver][1].
|
||||
|
||||
> Its an app where you do maths like a normal person. It lets you type whatever you want and smartly figures out what is math and spits out an answer on the right pane. Then you can plug those answers in to future equations and if that answer changes, so does the equations its used in.
|
||||
|
||||
With NaSC you can for example:
|
||||
|
||||
- Perform calculations with strangers you can define yourself
|
||||
- Change the units and values (in m cm, dollar euro …)
|
||||
- Knowing the surface area of a planet
|
||||
- Solve of second-degree polynomial
|
||||
- and more …
|
||||
|
||||
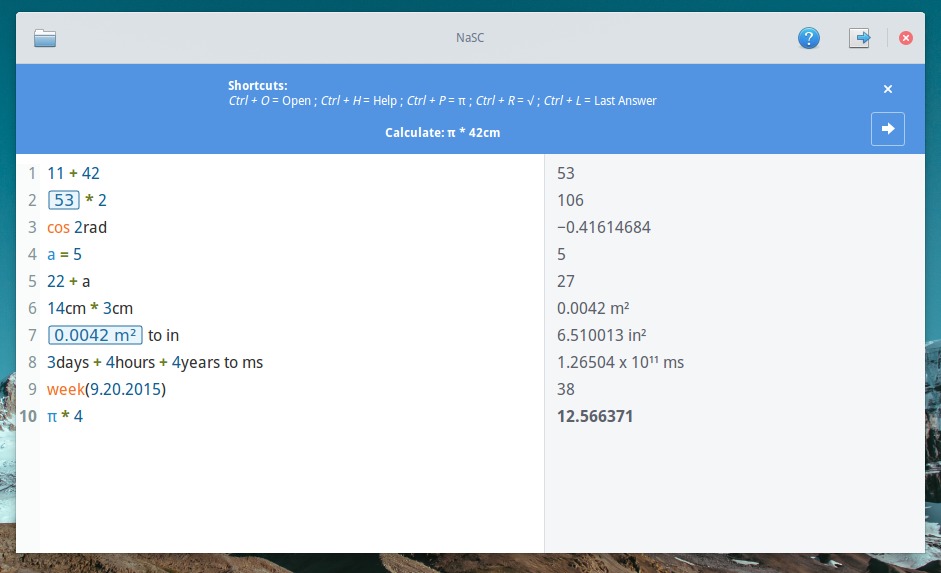
|
||||
|
||||
At the first launch, NaSC offers a tutorial that details possible features. You can later click the help icon on headerbar to get more.
|
||||
|
||||
|
||||
|
||||
In addition, the software allows to save your file in order to continue the work. It can be also shared on Pastebin with a defined time.
|
||||
|
||||
### Install NaSC in Ubuntu / Elementary OS Freya: ###
|
||||
|
||||
For Ubuntu 15.04, Ubuntu 15.10, Elementary OS Freya, open terminal from the Dash, App Launcher and run below commands one by one:
|
||||
|
||||
1. Add the [NaSC PPA][2] via command:
|
||||
|
||||
sudo apt-add-repository ppa:nasc-team/daily
|
||||
|
||||
|
||||
|
||||
2. If you’ve installed Synaptic Package Manager, search for and install `nasc` via it after clicking Reload button.
|
||||
|
||||
Or run below commands to update system cache and install the software:
|
||||
|
||||
sudo apt-get update
|
||||
|
||||
sudo apt-get install nasc
|
||||
|
||||
3. **(Optional)** To remove the software as well as NaSC, run:
|
||||
|
||||
sudo apt-get remove nasc && sudo add-apt-repository -r ppa:nasc-team/daily
|
||||
|
||||
For those who don’t want to add PPA, grab the .deb package directly from [this page][3].
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://ubuntuhandbook.org/index.php/2015/09/make-math-simple-in-ubuntu-elementary-os-via-nasc/
|
||||
|
||||
作者:[Ji m][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://ubuntuhandbook.org/index.php/about/
|
||||
[1]:http://www.acqualia.com/soulver/
|
||||
[2]:https://launchpad.net/~nasc-team/+archive/ubuntu/daily/
|
||||
[3]:http://ppa.launchpad.net/nasc-team/daily/ubuntu/pool/main/n/nasc/
|
||||
@ -1,193 +0,0 @@
|
||||
FSSlc Translating
|
||||
|
||||
RHCSA Series: Firewall Essentials and Network Traffic Control Using FirewallD and Iptables – Part 11
|
||||
================================================================================
|
||||
In simple words, a firewall is a security system that controls the incoming and outgoing traffic in a network based on a set of predefined rules (such as the packet destination / source or type of traffic, for example).
|
||||
|
||||

|
||||
|
||||
RHCSA: Control Network Traffic with FirewallD and Iptables – Part 11
|
||||
|
||||
In this article we will review the basics of firewalld, the default dynamic firewall daemon in Red Hat Enterprise Linux 7, and iptables service, the legacy firewall service for Linux, with which most system and network administrators are well acquainted, and which is also available in RHEL 7.
|
||||
|
||||
### A Comparison Between FirewallD and Iptables ###
|
||||
|
||||
Under the hood, both firewalld and the iptables service talk to the netfilter framework in the kernel through the same interface, not surprisingly, the iptables command. However, as opposed to the iptables service, firewalld can change the settings during normal system operation without existing connections being lost.
|
||||
|
||||
Firewalld should be installed by default in your RHEL system, though it may not be running. You can verify with the following commands (firewall-config is the user interface configuration tool):
|
||||
|
||||
# yum info firewalld firewall-config
|
||||
|
||||

|
||||
|
||||
Check FirewallD Information
|
||||
|
||||
and,
|
||||
|
||||
# systemctl status -l firewalld.service
|
||||
|
||||

|
||||
|
||||
Check FirewallD Status
|
||||
|
||||
On the other hand, the iptables service is not included by default, but can be installed through.
|
||||
|
||||
# yum update && yum install iptables-services
|
||||
|
||||
Both daemons can be started and enabled to start on boot with the usual systemd commands:
|
||||
|
||||
# systemctl start firewalld.service | iptables-service.service
|
||||
# systemctl enable firewalld.service | iptables-service.service
|
||||
|
||||
Read Also: [Useful Commands to Manage Systemd Services][1]
|
||||
|
||||
As for the configuration files, the iptables service uses `/etc/sysconfig/iptables` (which will not exist if the package is not installed in your system). On a RHEL 7 box used as a cluster node, this file looks as follows:
|
||||
|
||||

|
||||
|
||||
Iptables Firewall Configuration
|
||||
|
||||
Whereas firewalld store its configuration across two directories, `/usr/lib/firewalld` and `/etc/firewalld`:
|
||||
|
||||
# ls /usr/lib/firewalld /etc/firewalld
|
||||
|
||||

|
||||
|
||||
FirewallD Configuration
|
||||
|
||||
We will examine these configuration files further later in this article, after we add a few rules here and there. By now it will suffice to remind you that you can always find more information about both tools with.
|
||||
|
||||
# man firewalld.conf
|
||||
# man firewall-cmd
|
||||
# man iptables
|
||||
|
||||
Other than that, remember to take a look at [Reviewing Essential Commands & System Documentation – Part 1][2] of the current series, where I described several sources where you can get information about the packages installed on your RHEL 7 system.
|
||||
|
||||
### Using Iptables to Control Network Traffic ###
|
||||
|
||||
You may want to refer to [Configure Iptables Firewall – Part 8][3] of the Linux Foundation Certified Engineer (LFCE) series to refresh your memory about iptables internals before proceeding further. Thus, we will be able to jump in right into the examples.
|
||||
|
||||
**Example 1: Allowing both incoming and outgoing web traffic**
|
||||
|
||||
TCP ports 80 and 443 are the default ports used by the Apache web server to handle normal (HTTP) and secure (HTTPS) web traffic. You can allow incoming and outgoing web traffic through both ports on the enp0s3 interface as follows:
|
||||
|
||||
# iptables -A INPUT -i enp0s3 -p tcp --dport 80 -m state --state NEW,ESTABLISHED -j ACCEPT
|
||||
# iptables -A OUTPUT -o enp0s3 -p tcp --sport 80 -m state --state ESTABLISHED -j ACCEPT
|
||||
# iptables -A INPUT -i enp0s3 -p tcp --dport 443 -m state --state NEW,ESTABLISHED -j ACCEPT
|
||||
# iptables -A OUTPUT -o enp0s3 -p tcp --sport 443 -m state --state ESTABLISHED -j ACCEPT
|
||||
|
||||
**Example 2: Block all (or some) incoming connections from a specific network**
|
||||
|
||||
There may be times when you need to block all (or some) type of traffic originating from a specific network, say 192.168.1.0/24 for example:
|
||||
|
||||
# iptables -I INPUT -s 192.168.1.0/24 -j DROP
|
||||
|
||||
will drop all packages coming from the 192.168.1.0/24 network, whereas,
|
||||
|
||||
# iptables -A INPUT -s 192.168.1.0/24 --dport 22 -j ACCEPT
|
||||
|
||||
will only allow incoming traffic through port 22.
|
||||
|
||||
**Example 3: Redirect incoming traffic to another destination**
|
||||
|
||||
If you use your RHEL 7 box not only as a software firewall, but also as the actual hardware-based one, so that it sits between two distinct networks, IP forwarding must have been already enabled in your system. If not, you need to edit `/etc/sysctl.conf` and set the value of net.ipv4.ip_forward to 1, as follows:
|
||||
|
||||
net.ipv4.ip_forward = 1
|
||||
|
||||
then save the change, close your text editor and finally run the following command to apply the change:
|
||||
|
||||
# sysctl -p /etc/sysctl.conf
|
||||
|
||||
For example, you may have a printer installed at an internal box with IP 192.168.0.10, with the CUPS service listening on port 631 (both on the print server and on your firewall). In order to forward print requests from clients on the other side of the firewall, you should add the following iptables rule:
|
||||
|
||||
# iptables -t nat -A PREROUTING -i enp0s3 -p tcp --dport 631 -j DNAT --to 192.168.0.10:631
|
||||
|
||||
Please keep in mind that iptables reads its rules sequentially, so make sure the default policies or later rules do not override those outlined in the examples above.
|
||||
|
||||
### Getting Started with FirewallD ###
|
||||
|
||||
One of the changes introduced with firewalld are zones. This concept allows to separate networks into different zones level of trust the user has decided to place on the devices and traffic within that network.
|
||||
|
||||
To list the active zones:
|
||||
|
||||
# firewall-cmd --get-active-zones
|
||||
|
||||
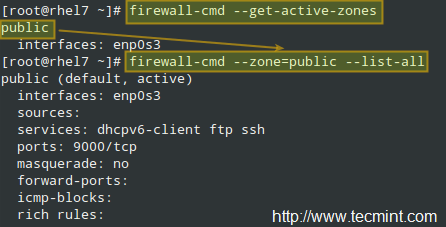
In the example below, the public zone is active, and the enp0s3 interface has been assigned to it automatically. To view all the information about a particular zone:
|
||||
|
||||
# firewall-cmd --zone=public --list-all
|
||||
|
||||
|
||||
|
||||
List all FirewallD Zones
|
||||
|
||||
Since you can read more about zones in the [RHEL 7 Security guide][4], we will only list some specific examples here.
|
||||
|
||||
**Example 4: Allowing services through the firewall**
|
||||
|
||||
To get a list of the supported services, use.
|
||||
|
||||
# firewall-cmd --get-services
|
||||
|
||||

|
||||
|
||||
List All Supported Services
|
||||
|
||||
To allow http and https web traffic through the firewall, effective immediately and on subsequent boots:
|
||||
|
||||
# firewall-cmd --zone=MyZone --add-service=http
|
||||
# firewall-cmd --zone=MyZone --permanent --add-service=http
|
||||
# firewall-cmd --zone=MyZone --add-service=https
|
||||
# firewall-cmd --zone=MyZone --permanent --add-service=https
|
||||
# firewall-cmd --reload
|
||||
|
||||
If code>–zone is omitted, the default zone (you can check with firewall-cmd –get-default-zone) is used.
|
||||
|
||||
To remove the rule, replace the word add with remove in the above commands.
|
||||
|
||||
**Example 5: IP / Port forwarding**
|
||||
|
||||
First off, you need to find out if masquerading is enabled for the desired zone:
|
||||
|
||||
# firewall-cmd --zone=MyZone --query-masquerade
|
||||
|
||||
In the image below, we can see that masquerading is enabled for the external zone, but not for public:
|
||||
|
||||

|
||||
|
||||
Check Masquerading Status
|
||||
|
||||
You can either enable masquerading for public:
|
||||
|
||||
# firewall-cmd --zone=public --add-masquerade
|
||||
|
||||
or use masquerading in external. Here’s what we would do to replicate Example 3 with firewalld:
|
||||
|
||||
# firewall-cmd --zone=external --add-forward-port=port=631:proto=tcp:toport=631:toaddr=192.168.0.10
|
||||
|
||||
And don’t forget to reload the firewall.
|
||||
|
||||
You can find further examples on [Part 9][5] of the RHCSA series, where we explained how to allow or disable the ports that are usually used by a web server and a ftp server, and how to change the corresponding rule when the default port for those services are changed. In addition, you may want to refer to the firewalld wiki for further examples.
|
||||
|
||||
Read Also: [Useful FirewallD Examples to Configure Firewall in RHEL 7][6]
|
||||
|
||||
### Conclusion ###
|
||||
|
||||
In this article we have explained what a firewall is, what are the available services to implement one in RHEL 7, and provided a few examples that can help you get started with this task. If you have any comments, suggestions, or questions, feel free to let us know using the form below. Thank you in advance!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.tecmint.com/firewalld-vs-iptables-and-control-network-traffic-in-firewall/
|
||||
|
||||
作者:[Gabriel Cánepa][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.tecmint.com/author/gacanepa/
|
||||
[1]:http://www.tecmint.com/manage-services-using-systemd-and-systemctl-in-linux/
|
||||
[2]:http://www.tecmint.com/rhcsa-exam-reviewing-essential-commands-system-documentation/
|
||||
[3]:http://www.tecmint.com/configure-iptables-firewall/
|
||||
[4]:https://access.redhat.com/documentation/en-US/Red_Hat_Enterprise_Linux/7/html/Security_Guide/sec-Using_Firewalls.html
|
||||
[5]:http://www.tecmint.com/rhcsa-series-install-and-secure-apache-web-server-and-ftp-in-rhel/
|
||||
[6]:http://www.tecmint.com/firewalld-rules-for-centos-7/
|
||||
@ -1,3 +1,5 @@
|
||||
FSSlc translating
|
||||
|
||||
RHCSA Series: Automate RHEL 7 Installations Using ‘Kickstart’ – Part 12
|
||||
================================================================================
|
||||
Linux servers are rarely standalone boxes. Whether it is in a datacenter or in a lab environment, chances are that you have had to install several machines that will interact one with another in some way. If you multiply the time that it takes to install Red Hat Enterprise Linux 7 manually on a single server by the number of boxes that you need to set up, this can lead to a rather lengthy effort that can be avoided through the use of an unattended installation tool known as kickstart.
|
||||
|
||||
@ -1,74 +0,0 @@
|
||||
如何在 Ubuntu 15.04 下创建连接至 Android/iOS 的 AP
|
||||
================================================================================
|
||||
我成功地在 Ubuntu 15.04 下用 Gnome Network Manager 创建了一个无线AP热点. 接下来我要分享一下我的步骤. 请注意: 你必须要有一个可以用来创建AP热点的无线网卡. 如果你不知道如何找到连上了的设备的话, 在终端(Terminal)里输入`iw list`.
|
||||
|
||||
如果你没有安装`iw`的话, 在Ubuntu下你可以使用`udo apt-get install iw`进行安装.
|
||||
|
||||
在你键入`iw list`之后, 寻找可用的借口, 你应该会看到类似下列的条目:
|
||||
|
||||
Supported interface modes:
|
||||
|
||||
* IBSS
|
||||
* managed
|
||||
* AP
|
||||
* AP/VLAN
|
||||
* monitor
|
||||
* mesh point
|
||||
|
||||
让我们一步步看
|
||||
|
||||
1. 断开WIFI连接. 使用有线网络接入你的笔记本.
|
||||
1. 在顶栏面板里点击网络的图标 -> Edit Connections(编辑连接) -> 在弹出窗口里点击Add(新增)按钮.
|
||||
1. 在下拉菜单内选择Wi-Fi.
|
||||
1. 接下来,
|
||||
|
||||
a. 输入一个链接名 比如: Hotspot
|
||||
|
||||
b. 输入一个 SSID 比如: Hotspot
|
||||
|
||||
c. 选择模式(mode): Infrastructure
|
||||
|
||||
d. 设备 MAC 地址: 在下拉菜单里选择你的无线设备
|
||||
|
||||

|
||||
|
||||
1. 进入Wi-Fi安全选项卡, 选择 WPA & WPA2 Personal 并且输入密码.
|
||||
1. 进入IPv4设置选项卡, 在Method(方法)下拉菜单里, 选择Shared to other computers(共享至其他电脑).
|
||||
|
||||

|
||||
|
||||
1. 进入IPv6选项卡, 在Method(方法)里设置为忽略ignore (只有在你不使用IPv6的情况下这么做)
|
||||
1. 点击 Save(保存) 按钮以保存配置.
|
||||
1. 从 menu/dash 里打开Terminal.
|
||||
1. 修改你刚刚使用 network settings 创建的连接.
|
||||
|
||||
使用 VIM 编辑器:
|
||||
|
||||
sudo vim /etc/NetworkManager/system-connections/Hotspot
|
||||
|
||||
使用Gedit 编辑器:
|
||||
|
||||
gksu gedit /etc/NetworkManager/system-connections/Hotspot
|
||||
|
||||
把名字 Hotspot 用你在第4步里起的连接名替换掉.
|
||||
|
||||

|
||||
|
||||
1. 把 `mode=infrastructure` 改成 `mode=ap` 并且保存文件
|
||||
1. 一旦你保存了这个文件, 你应该能在 Wifi 菜单里看到你刚刚建立的AP了. (如果没有的话请再顶栏里 关闭/打开 Wifi 选项一次)
|
||||
|
||||

|
||||
|
||||
1. 你现在可以把你的设备连上Wifi了. 已经过 Android 5.0的小米4测试.(下载了1GB的文件以测试速度与稳定性)
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linuxveda.com/2015/08/23/how-to-create-an-ap-in-ubuntu-15-04-to-connect-to-androidiphone/
|
||||
|
||||
作者:[Sayantan Das][a]
|
||||
译者:[jerryling315](https://github.com/jerryling315)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.linuxveda.com/author/sayantan_das/
|
||||
@ -0,0 +1,113 @@
|
||||
如何在Ubuntu中安装QGit浏览器
|
||||
================================================================================
|
||||
QGit是一款Marco Costalba用Qt和C++写的开源GUI Git浏览器。它是一款在GUI环境下更好地提供浏览历史记录、提交记录和文件补丁的浏览器。它利用git命令行来执行并显示输出。它有一些常规的功能像浏览历史、比较、文件历史、文件标注、档案树。我们可以格式化并用选中的提交应用补丁,在两个实例之间拖拽并提交等等。它允许我们创建自定义的按钮来用它内置的生成器来执行特定的命令。
|
||||
|
||||
这里有简单的几步在Ubuntu 14.04 LTS "Trusty"中编译并安装QGit浏览器。
|
||||
|
||||
### 1. 安装 QT4 库 ###
|
||||
|
||||
首先在ubuntu中运行QGit需要先安装QT4库。由于apt是ubuntu默认的包管理器,同时qt4也在官方的仓库中,因此我们直接用下面的apt-get命令来安装qt4。
|
||||
|
||||
$ sudo apt-get install qt4-default
|
||||
|
||||
### 2. 下载QGit压缩包 ###
|
||||
|
||||
安装完Qt4之后,我们要安装git,这样我们才能在QGit中克隆git仓库。运行下面的apt-get命令。
|
||||
|
||||
$ sudo apt-get install git
|
||||
|
||||
现在,我们要使用下面的git命令来克隆仓库。
|
||||
|
||||
$ git clone git://repo.or.cz/qgit4/redivivus.git
|
||||
|
||||
Cloning into 'redivivus'...
|
||||
remote: Counting objects: 7128, done.
|
||||
remote: Compressing objects: 100% (2671/2671), done.
|
||||
remote: Total 7128 (delta 5464), reused 5711 (delta 4438)
|
||||
Receiving objects: 100% (7128/7128), 2.39 MiB | 470.00 KiB/s, done.
|
||||
Resolving deltas: 100% (5464/5464), done.
|
||||
Checking connectivity... done.
|
||||
|
||||
### 3. 编译 QGit ###
|
||||
|
||||
克隆之后,我们现在进入redivivus的目录,并创建我们编译需要的makefile文件。因此,要进入目录,我们要运行下面的命令。
|
||||
|
||||
$ cd redivivus
|
||||
|
||||
接下来,我们运行下面的命令从qmake项目也就是qgit.pro来生成新的Makefile。
|
||||
|
||||
$ qmake qgit.pro
|
||||
|
||||
生成Makefile之后,我们现在终于要编译qgit的源代码并得到二进制的输出。首先我们要安装make和g++包用于编译,因为这是一个用C++写的程序。
|
||||
|
||||
$ sudo apt-get install make g++
|
||||
|
||||
现在,我们要用make命令来编译代码了
|
||||
|
||||
$ make
|
||||
|
||||
### 4. 安装 QGit ###
|
||||
|
||||
成功编译QGit的源码之后,我们就要在Ubuntu 14.04中安装它了,这样就可以在系统中执行它。因此我们将运行下面的命令、
|
||||
|
||||
$ sudo make install
|
||||
|
||||
cd src/ && make -f Makefile install
|
||||
make[1]: Entering directory `/home/arun/redivivus/src'
|
||||
make -f Makefile.Release install
|
||||
make[2]: Entering directory `/home/arun/redivivus/src'
|
||||
install -m 755 -p "../bin/qgit" "/usr/lib/x86_64-linux-gnu/qt4/bin/qgit"
|
||||
strip "/usr/lib/x86_64-linux-gnu/qt4/bin/qgit"
|
||||
make[2]: Leaving directory `/home/arun/redivivus/src'
|
||||
make[1]: Leaving directory `/home/arun/redivivus/src'
|
||||
|
||||
接下来,我们需要从bin目录下复制qgit的二进制文件到/usr/bin/,这样我们就可以全局运行它了。
|
||||
|
||||
$ sudo cp bin/qgit /usr/bin/
|
||||
|
||||
### 5. 创建桌面文件 ###
|
||||
|
||||
既然我们已经在ubuntu中成功安装了qgit,我们来创建一个桌面文件,这样QGit就可以在我们桌面环境中的菜单或者启动器中找到了。要做到这点,我们要在/usr/share/applications/创建一个新文件叫qgit.desktop。
|
||||
|
||||
$ sudo nano /usr/share/applications/qgit.desktop
|
||||
|
||||
接下来复制下面的行到文件中。
|
||||
|
||||
[Desktop Entry]
|
||||
Name=qgit
|
||||
GenericName=git GUI viewer
|
||||
Exec=qgit
|
||||
Icon=qgit
|
||||
Type=Application
|
||||
Comment=git GUI viewer
|
||||
Terminal=false
|
||||
MimeType=inode/directory;
|
||||
Categories=Qt;Development;RevisionControl;
|
||||
|
||||
完成之后,保存并退出。
|
||||
|
||||
### 6. 运行 QGit 浏览器 ###
|
||||
|
||||
QGit安装完成之后,我们现在就可以从任何启动器或者程序菜单中启动它了。要在终端下面运行QGit,我们可以像下面那样。
|
||||
|
||||
$ qgit
|
||||
|
||||
这会打开基于Qt4框架GUI模式的QGit。
|
||||
|
||||

|
||||
|
||||
### 总结 ###
|
||||
|
||||
QGit是一个很棒的基于QT的git浏览器。它可以在Linux、MAC OSX和 Microsoft Windows所有这三个平台中运行。它帮助我们很容易地浏览历史、版本、分支等等git仓库提供的信息。它减少了使用命令行的方式去执行诸如浏览版本、历史、比较功能的需求,并用图形化的方式来简化了这些任务。最新的qgit版本也在默认仓库中,你可以使用 **apt-get install qgit** 命令来安装。因此。qgit用它简单的GUI使得我们的工作更加简单和快速。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/ubuntu-how-to/install-qgit-viewer-ubuntu-14-04/
|
||||
|
||||
作者:[Arun Pyasi][a]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://linoxide.com/author/arunp/
|
||||
@ -0,0 +1,193 @@
|
||||
RHCSA 系列: 防火墙简要和使用 FirewallD 和 Iptables 来控制网络流量 – Part 11
|
||||
================================================================================
|
||||
|
||||
简单来说,防火墙就是一个基于一系列预先定义的规则(例如流量包的目的地或来源,流量的类型等)的安全系统,它控制着一个网络中的流入和流出流量。
|
||||
|
||||

|
||||
|
||||
RHCSA: 使用 FirewallD 和 Iptables 来控制网络流量 – Part 11
|
||||
|
||||
在本文中,我们将回顾 firewalld 和 iptables 的基础知识。前者是 RHEL 7 中的默认动态防火墙守护进程,而后者则是针对 Linux 的传统的防火墙服务,大多数的系统和网络管理员都非常熟悉它,并且在 RHEL 7 中也可以获取到。
|
||||
|
||||
### FirewallD 和 Iptables 的一个比较 ###
|
||||
|
||||
在后台, firewalld 和 iptables 服务都通过相同的接口来与内核中的 netfilter 框架相交流,这不足为奇,即它们都通过 iptables 命令来与 netfilter 交互。然而,与 iptables 服务相反, firewalld 可以在不丢失现有连接的情况下,在正常的系统操作期间更改设定。
|
||||
|
||||
在默认情况下, firewalld 应该已经安装在你的 RHEL 系统中了,尽管它可能没有在运行。你可以使用下面的命令来确认(firewall-config 是用户界面配置工具):
|
||||
|
||||
# yum info firewalld firewall-config
|
||||
|
||||

|
||||
|
||||
检查 FirewallD 的信息
|
||||
|
||||
以及,
|
||||
|
||||
# systemctl status -l firewalld.service
|
||||
|
||||

|
||||
|
||||
检查 FirewallD 的状态
|
||||
|
||||
另一方面, iptables 服务在默认情况下没有被包含在 RHEL 系统中,但可以被安装上。
|
||||
|
||||
# yum update && yum install iptables-services
|
||||
|
||||
这两个守护进程都可以使用常规的 systemd 命令来在开机时被启动和开启:
|
||||
|
||||
# systemctl start firewalld.service | iptables-service.service
|
||||
# systemctl enable firewalld.service | iptables-service.service
|
||||
|
||||
另外,请阅读:[管理 Systemd 服务的实用命令][1] (注: 本文已被翻译发表,在 https://linux.cn/article-5926-1.html)
|
||||
|
||||
至于配置文件, iptables 服务使用 `/etc/sysconfig/iptables` 文件(假如这个软件包在你的系统中没有被安装,则这个文件将不存在)。在一个被用作集群节点的 RHEL 7 机子上,这个文件长得像这样:
|
||||
|
||||

|
||||
|
||||
Iptables 防火墙配置文件
|
||||
|
||||
而 firewalld 则在两个目录中存储它的配置文件,即 `/usr/lib/firewalld` 和 `/etc/firewalld`:
|
||||
|
||||
# ls /usr/lib/firewalld /etc/firewalld
|
||||
|
||||

|
||||
|
||||
FirewallD 的配置文件
|
||||
|
||||
在这篇文章中后面,我们将进一步查看这些配置文件,在那之后,我们将在各处添加一些规则。
|
||||
现在,是时候提醒你了,你总可以使用下面的命令来找到更多有关这两个工具的信息。
|
||||
|
||||
# man firewalld.conf
|
||||
# man firewall-cmd
|
||||
# man iptables
|
||||
|
||||
除了这些,记得查看一下当前系列的第一篇 [RHCSA 系列(一): 回顾基础命令及系统文档][2](注: 本文已被翻译发表,在 https://linux.cn/article-6133-1.html ),在其中我描述了几种渠道来得到安装在你的 RHEL 7 系统上的软件包的信息。
|
||||
|
||||
### 使用 Iptables 来控制网络流量 ###
|
||||
|
||||
在进一步深入之前,或许你需要参考 Linux 基金会认证工程师(Linux Foundation Certified Engineer,LFCE) 系列中的 [配置 Iptables 防火墙 – Part 8][3] 来复习你脑中有关 iptables 的知识。
|
||||
|
||||
**例 1:同时允许流入和流出的网络流量**
|
||||
|
||||
TCP 端口 80 和 443 是 Apache web 服务器使用的用来处理常规(HTTP) 和安全(HTTPS)网络流量的默认端口。你可以像下面这样在 enp0s3 接口上允许流入和流出网络流量通过这两个端口:
|
||||
|
||||
# iptables -A INPUT -i enp0s3 -p tcp --dport 80 -m state --state NEW,ESTABLISHED -j ACCEPT
|
||||
# iptables -A OUTPUT -o enp0s3 -p tcp --sport 80 -m state --state ESTABLISHED -j ACCEPT
|
||||
# iptables -A INPUT -i enp0s3 -p tcp --dport 443 -m state --state NEW,ESTABLISHED -j ACCEPT
|
||||
# iptables -A OUTPUT -o enp0s3 -p tcp --sport 443 -m state --state ESTABLISHED -j ACCEPT
|
||||
|
||||
**例 2:从某个特定网络中阻挡所有(或某些)流入连接**
|
||||
|
||||
或许有时你需要阻挡来自于某个特定网络的所有(或某些)类型的来源流量,比方说 192.168.1.0/24:
|
||||
|
||||
# iptables -I INPUT -s 192.168.1.0/24 -j DROP
|
||||
|
||||
上面的命令将丢掉所有来自 192.168.1.0/24 网络的网络包,而
|
||||
|
||||
# iptables -A INPUT -s 192.168.1.0/24 --dport 22 -j ACCEPT
|
||||
|
||||
将只允许通过端口 22 的流入流量。
|
||||
|
||||
**例 3:将流入流量重定向到另一个目的地**
|
||||
|
||||
假如你不仅使用你的 RHEL 7 机子来作为一个软件防火墙,而且还将它作为一个硬件防火墙,使得它位于两个不同的网络之间,则在你的系统 IP 转发一定已经被开启了。假如没有开启,你需要编辑 `/etc/sysctl.conf` 文件并将 `net.ipv4.ip_forward` 的值设为 1,即:
|
||||
|
||||
net.ipv4.ip_forward = 1
|
||||
|
||||
接着保存更改,关闭你的文本编辑器,并最终运行下面的命令来应用更改:
|
||||
|
||||
# sysctl -p /etc/sysctl.conf
|
||||
|
||||
例如,你可能在一个内部的机子上安装了一个打印机,它的 IP 地址为 192.168.0.10,CUPS 服务在端口 631 上进行监听(同时在你的打印服务器和你的防火墙上)。为了从防火墙另一边的客户端传递打印请求,你应该添加下面的 iptables 规则:
|
||||
|
||||
# iptables -t nat -A PREROUTING -i enp0s3 -p tcp --dport 631 -j DNAT --to 192.168.0.10:631
|
||||
|
||||
请记住 iptables 逐条地读取它的规则,所以请确保默认的策略或后面的规则不会重载上面例子中那些有下划线的规则。
|
||||
|
||||
### FirewallD 入门 ###
|
||||
|
||||
引入 firewalld 的一个改变是区域(zone) (注:翻译参考了 https://fedoraproject.org/wiki/FirewallD/zh-cn) 的概念。它允许将网路划分为拥有不同信任级别的区域,由用户决定将设备和流量放置到哪个区域。
|
||||
|
||||
要获取活动的区域,使用:
|
||||
|
||||
# firewall-cmd --get-active-zones
|
||||
|
||||
在下面的例子中,公用区域被激活了,并且 enp0s3 接口被自动地分配到了这个区域。要查看有关一个特定区域的所有信息,可使用:
|
||||
|
||||
# firewall-cmd --zone=public --list-all
|
||||
|
||||

|
||||
|
||||
列出所有的 Firewalld 区域
|
||||
|
||||
由于你可以在 [RHEL 7 安全指南][4] 中阅读到更多有关区域的知识,这里我们将仅列出一些特别的例子。
|
||||
|
||||
**例 4:允许服务通过防火墙**
|
||||
|
||||
要获取受支持的服务的列表,可以使用:
|
||||
|
||||
# firewall-cmd --get-services
|
||||
|
||||

|
||||
|
||||
列出所有受支持的服务
|
||||
|
||||
要立刻且在随后的开机中使得 http 和 https 网络流量通过防火墙,可以这样:
|
||||
|
||||
# firewall-cmd --zone=MyZone --add-service=http
|
||||
# firewall-cmd --zone=MyZone --permanent --add-service=http
|
||||
# firewall-cmd --zone=MyZone --add-service=https
|
||||
# firewall-cmd --zone=MyZone --permanent --add-service=https
|
||||
# firewall-cmd --reload
|
||||
|
||||
假如 code>–zone 被忽略,则默认的区域(你可以使用 `firewall-cmd –get-default-zone`来查看)将会被使用。
|
||||
|
||||
若要移除这些规则,可以在上面的命令中将 `add` 替换为 `remove`。
|
||||
|
||||
**例 5:IP 转发或端口转发**
|
||||
|
||||
首先,你需要查看在目标区域中,伪装是否被开启:
|
||||
|
||||
# firewall-cmd --zone=MyZone --query-masquerade
|
||||
|
||||
在下面的图片中,我们可以看到对于外部区域,伪装已被开启,但对于公用区域则没有:
|
||||
|
||||

|
||||
|
||||
查看伪装状态
|
||||
|
||||
你可以为公共区域开启伪装:
|
||||
|
||||
# firewall-cmd --zone=public --add-masquerade
|
||||
|
||||
或者在外部区域中使用伪装。下面是使用 firewalld 来重复例 3 中的任务所需的命令:
|
||||
|
||||
# firewall-cmd --zone=external --add-forward-port=port=631:proto=tcp:toport=631:toaddr=192.168.0.10
|
||||
|
||||
并且别忘了重新加载防火墙。
|
||||
|
||||
在 RHCSA 系列的 [Part 9][5] 你可以找到更深入的例子,在那篇文章中我们解释了如何允许或禁用通常被 web 服务器和 ftp 服务器使用的端口,以及在针对这两个服务所使用的默认端口被改变时,如何更改相应的规则。另外,你或许想参考 firewalld 的 wiki 来查看更深入的例子。
|
||||
|
||||
Read Also: [在 RHEL 7 中配置防火墙的几个实用的 firewalld 例子][6]
|
||||
|
||||
### 总结 ###
|
||||
|
||||
在这篇文章中,我们已经解释了防火墙是什么,介绍了在 RHEL 7 中用来实现防火墙的几个可用的服务,并提供了可以帮助你入门防火墙的几个例子。假如你有任何的评论,建议或问题,请随意使用下面的评论框来让我们知晓。这里就事先感谢了!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.tecmint.com/firewalld-vs-iptables-and-control-network-traffic-in-firewall/
|
||||
|
||||
作者:[Gabriel Cánepa][a]
|
||||
译者:[FSSlc](https://github.com/FSSlc)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.tecmint.com/author/gacanepa/
|
||||
[1]:http://www.tecmint.com/manage-services-using-systemd-and-systemctl-in-linux/
|
||||
[2]:http://www.tecmint.com/rhcsa-exam-reviewing-essential-commands-system-documentation/
|
||||
[3]:http://www.tecmint.com/configure-iptables-firewall/
|
||||
[4]:https://access.redhat.com/documentation/en-US/Red_Hat_Enterprise_Linux/7/html/Security_Guide/sec-Using_Firewalls.html
|
||||
[5]:http://www.tecmint.com/rhcsa-series-install-and-secure-apache-web-server-and-ftp-in-rhel/
|
||||
[6]:http://www.tecmint.com/firewalld-rules-for-centos-7/
|
||||
Loading…
Reference in New Issue
Block a user