mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-01-28 23:20:10 +08:00
commit
d2e2aacffb
@ -1,20 +1,20 @@
|
||||
GNOME控制中心3.14 RC1修复大量潜在崩溃因素
|
||||
GNOME控制中心3.14 RC1修复了大量潜在崩溃问题
|
||||
================================================================================
|
||||

|
||||
|
||||
Arch Linux下的GNOME控制中心
|
||||
|
||||
**GNOME控制中心,GNOME中更改你的桌面各个方面设置的主界面,已经升级至3.14 RC1,伴随而来的是大量来自GNOME stack的包。**
|
||||
**GNOME控制中心,可以在GNOME中更改你的桌面各个方面设置的主界面,已经升级至3.14 RC1,伴随而来的是大量来自GNOME stack的包。**
|
||||
|
||||
GNOME控制中心是在GNOME生态系统中十分重要的软件之一,尽管不是所有的用户意识到了它的存在。GNOME控制中心是管理由GNOME驱动的操作系统中所有设置的部分,就像你从截图里看到的那样。
|
||||
|
||||
GNOME控制中心不是很经常被宣传,它实际上是GNOME stack中为数不多的作为源包以及工具时,拥有不同名字的包之一。源包为称为GNOME控制中心,但用户经常看到的是设置或系统设置,取决于开发者的选择。
|
||||
GNOME控制中心不是很经常被宣传,它实际上是GNOME stack中为数不多的源代码包和安装后的应用名称不同的软件包。源代码包的名字为GNOME控制中心,但用户经常看到的应用名称是“设置”或“系统设置”,取决于开发者的选择。
|
||||
|
||||
### GNOME控制中心 3.14 RC1 带来哪些新东西 ###
|
||||
|
||||
通过更新日志可以得知,libgd得到了升级以修复GdNotification主题,切换视图时背景选择对话框不能够自适应大小,一个带有树状视图的堆叠现在被用于选择对话框,修复Flickr支持中的一个内存泄漏,硬编码字体大小不再用于日期和时间,修复WM改变(或重启)时引起的崩溃,更改无线网络启用时可能引起的崩溃也已被修复,以及纠正了更多可能的WWAN潜在崩溃因素。
|
||||
通过更新日志可以得知,升级了libgd以修复GdNotification主题,切换视图时背景选择对话框不再重新调整大小,选择对话框由三个不同视图组合而成,修复Flickr支持中的一个内存泄漏,在“日期和时间”中不再使用硬编码的字体大小,修复改换窗口管理器(或重启)时引起的崩溃,更改无线网络启用时可能引起的崩溃也已被修复,以及纠正了更多可能的WWAN潜在崩溃因素。
|
||||
|
||||
同时,现在热点仅在设备活动时运行,所有虚拟桥接现在是隐藏的,VPN连接的底层设备不再显示,空文件夹列表不再默认显示,不同的UI填充问题已经得到解决,焦点现在重新回到了账户对话框,将年份设置为0时导致的崩溃已修复,“Wi-Fi热点”属性居中,打开并启用热点时弹出警告已修复,以及现在打开热点失败时将弹出错误信息。
|
||||
此外,现在热点仅在设备活动时运行,所有虚拟桥接现在是隐藏的,不再显示VPN连接的底层设备,默认不显示空文件夹列表,解决了几个UI填充问题,输入焦点现在重新回到了账户对话框,将年份设置为0时导致的崩溃已修复,“Wi-Fi热点”属性居中,修复了打开启用热点时弹出警告的问题,以及现在打开热点失败时将弹出错误信息。
|
||||
|
||||
完整的变动,更新以及bug修复,参见官方[更新日志][1]。
|
||||
|
||||
@ -31,7 +31,7 @@ via: http://news.softpedia.com/news/GNOME-Control-Center-3-14-RC1-Correct-Lots-o
|
||||
|
||||
作者:[Silviu Stahie][a]
|
||||
译者:[alim0x](https://github.com/alim0x)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
@ -0,0 +1,36 @@
|
||||
欧洲现在很流行拥抱开源
|
||||
================================================================================
|
||||

|
||||
|
||||
看来拥抱[开源][1]最近在欧洲的国家很流行。上个月我们我只听说[都灵成为意大利首个官方接受开源产品的城市][2]。另一个意大利西北部城市,[乌迪内][3],已经宣布他们正在抛弃微软Office转而迁移到[OpenOffice][4]。
|
||||
|
||||
乌迪内有100,000的人口并且行政部门有大约900台电脑,它们都运行着微软Windows以及它的默认产品套装。根据[预算文档][5],迁移将在大约12月份时进行,从80台新电脑开始。接着将会是旧电脑迁移到OpenOffice。
|
||||
|
||||
迁移估计会节省一笔授权费用,不然将会每台电脑花费大约400欧元,总计360,000欧元。但是节约成本并不是迁移的唯一目的,获得常规的软件升级也是其中一个因素。
|
||||
|
||||
当然从微软的Office到OpenOfifice不会太顺利。不过,全市的培训计划是先让少数员工使用安装了OpenOffice的电脑。
|
||||
|
||||
如我先前说明的,这似乎在欧洲是一个趋势。在今年早些时候在[西班牙的加那利群岛][7]之后[法国城市图卢兹也使用了LibreOffice中从而节省了100万欧元][6]。相邻的法国城市[日内瓦也有开源方面的迹象][8]。在世界的另一边,政府机构[泰米尔纳德邦][9]和印度喀拉拉邦省也抛弃了微软而使用开源软件。
|
||||
|
||||
伴随着经济的萧条,我觉得Windows XP的死亡一直是开源的福音。无论是什么原因,我很高兴看到这份名单越来越大。你看呢?
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://itsfoss.com/udine-open-source/
|
||||
|
||||
作者:[Abhishek][a]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://itsfoss.com/author/Abhishek/
|
||||
[1]:http://itsfoss.com/category/open-source-software/
|
||||
[2]:http://linux.cn/article-3602-1.html
|
||||
[3]:http://en.wikipedia.org/wiki/Udine
|
||||
[4]:https://www.openoffice.org/
|
||||
[5]:http://www.comune.udine.it/opencms/opencms/release/ComuneUdine/comune/Rendicontazione/PEG/PEG_2014/index.html?lang=it&style=1&expfolder=???+NavText+???
|
||||
[6]:http://linux.cn/article-3575-1.html
|
||||
[7]:http://itsfoss.com/canary-islands-saves-700000-euro-open-source/
|
||||
[8]:http://itsfoss.com/170-primary-public-schools-geneva-switch-ubuntu/
|
||||
[9]:http://linux.cn/article-2744-1.html
|
||||
@ -4,25 +4,17 @@
|
||||
|
||||

|
||||
|
||||
**和其他项目一样,Canonical也在开发Unity桌面环境与Mir显示服务。开发团队刚刚发布了一个小的更新来据此让我们知道发生了些什么**
|
||||
**和其他项目一样,Canonical也在开发Unity桌面环境与Mir显示服务。开发团队刚刚发布了一个小的更新,据此我们可以知道都有些什么进展**
|
||||
|
||||
Ubuntu开发者可能刚刚集中精力在一些重要的发布上,就像接下来的Ubuntu 14.10(Utopic Unicorn) 或者是新的面向移动设备的Ubuntu Touch,但是他们同样也涉及想Mir以及Unity 8这样的项目。
|
||||
Ubuntu开发者可能刚刚集中精力在一些重要的发布上,就像接下来的Ubuntu 14.10(Utopic Unicorn) 或者是新的面向移动设备的Ubuntu Touch,但是他们同样也涉及像Mir以及Unity 8这样的项目。
|
||||
|
||||
目前这代Ubuntu系统使用的是Unity 7桌面环境,但是新一代已经酝酿了很长一段时间。与新的显示服务一起,已经在Ubuntu的移动版中了,但最终也要将它带到桌面上。
|
||||
目前这代Ubuntu系统使用的是Unity 7桌面环境,但是新一代已经酝酿了很长一段时间。它与新的显示服务一起,已经在Ubuntu的移动版中了,但最终也要将它带到桌面上。
|
||||
|
||||
这两个项目的领导Kevin Gunn经常发布一些来自开发者的进度信息以及这周以来的一些改变,虽然这些都很粗略。
|
||||
|
||||
根据 [开发团队][1]的消息, 一些关于触摸/高难度的问题已经修正了,几个翻译问题也已经修复了,一些Dash UI相关的问题已经修复了,目前 团队在开发Mir 0.8,Mir 0.7.2已经推广了,同时一些高优先级的bug也在进行中。
|
||||
根据 [开发团队][1]的消息, 一些关于触摸/触发角的问题已经修正了,也修复了几个翻译问题,一些Dash UI相关的问题已经修复了,目前 团队在开发Mir 0.8,Mir 0.7.2将被升级,同时一些高优先级的bug处理也在进行中。
|
||||
|
||||
你可以下载 Ubuntu Next
|
||||
|
||||
- [Ubuntu 14.10 Daily Build (ISO) 64-bit][2]
|
||||
- [Ubuntu 14.10 Daily Build (ISO) 32-bit][3]
|
||||
- [Ubuntu 14.10 Daily Build (ISO) 64-bit Mac][4]
|
||||
- [Ubuntu Desktop Next 14.10 Daily Build (ISO) 64-bit][5]
|
||||
- [Ubuntu Desktop Next 14.10 Daily Build (ISO) 32-bit][6]
|
||||
|
||||
这个的特性是新的Unity 8以及Mir,但是还不完全。直到有一个明确的方向之前,它还会持续一会。
|
||||
你可以[下载 Ubuntu Next][7]来体验新的Unity 8以及Mir的特性,但是还不够稳定。要等到成熟还需要一些时间。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
@ -30,7 +22,7 @@ via: http://news.softpedia.com/news/Mir-and-Unity-8-Update-Arrive-from-Ubuntu-De
|
||||
|
||||
作者:[Silviu Stahie][a]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
@ -0,0 +1,48 @@
|
||||
Netflix支持 Ubuntu 上原生回放
|
||||
================================================================================
|
||||
|
||||
|
||||
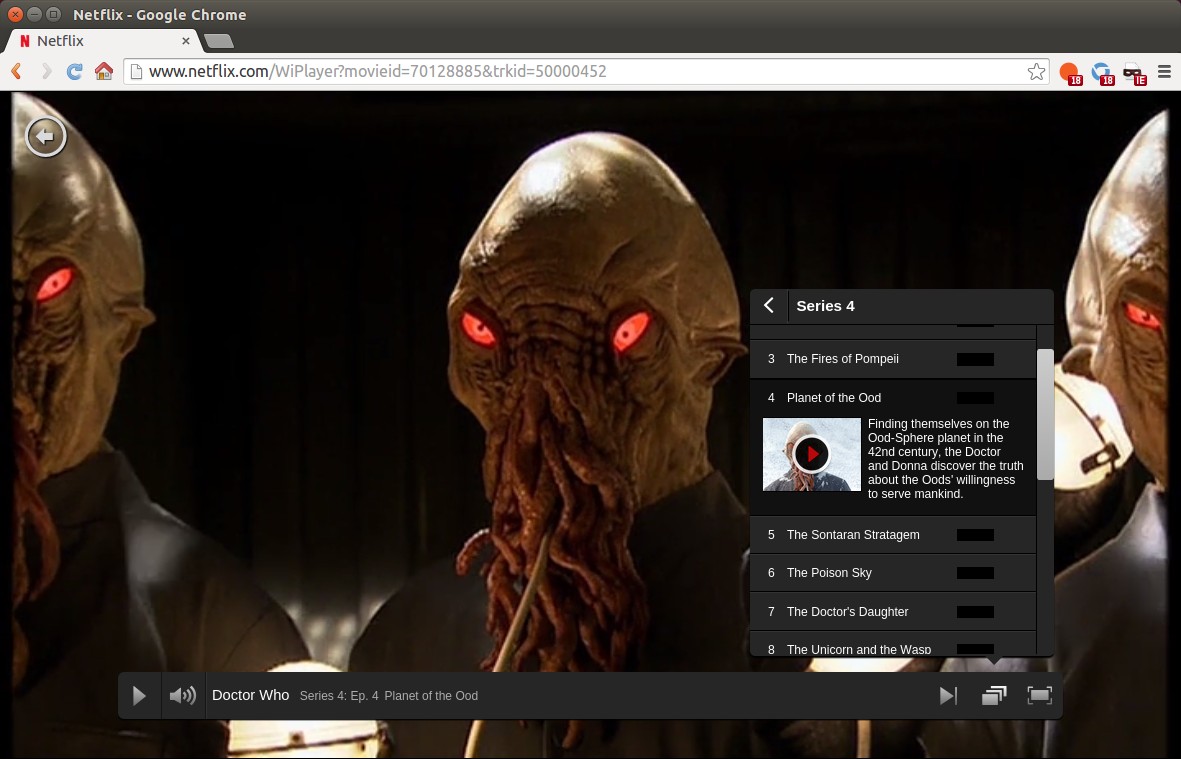
**我们[上个月说的Netflix 的原生Linux支持很接近了][1],现在终于有了,我们只需几个简单的步骤就可以在Ubuntu桌面上启用HTML 5视频流了。
|
||||
|
||||
现在Netflix更近一步提供了支持。它希望给Ubuntu带来真正的开箱即用的Netflix回放。现在只需要更新**网络安全(Network Security Services,NSS)**服务库就行。
|
||||
|
||||
### 原生Netflix? Neato. ###
|
||||
|
||||
在一封发给Ubuntu开发者邮件列表的[邮件中][2],Netflix的Paul Adolph解释了现在的情况:
|
||||
|
||||
> “如果NSS的版本是3.16.2或者更高的话,Netflix可以在Ubuntu 14.04的稳定版Chrome中播放。如果版本超过了14.04,Netflix会作出一些调整,以避免用户必须对浏览器的 User-Agent 参数进行一些修改才能播放。”
|
||||
|
||||
[LCTT 译注:此处原文是“14.02”,疑是笔误,应该是指Ubuntu 14.04。]
|
||||
|
||||
很快要发布的Ubuntu 14.10提供了更新的[NSS v3.17][3], 而目前大多数用户使用的版本 Ubuntu 14.04 LTS 提供的是 v3.15.x。
|
||||
|
||||
NSS是一系列支持多种安全功能的客户端和服务端应用的库,包括SSL,TLS,PKCS和其他安全标准。为了让Ubuntu LTS用户可以尽快用上原生的HTML5 Netflix, Paul 问道:
|
||||
|
||||
>”让一个新的NSS版本进入更新流的过程是什么?或者有人可以给我提供正确的联系方式么?“
|
||||
|
||||
Netflix今年早期时在Windows 8.1和OSX Yosemite上提供了HTML5视频回放,而不需要任何额外的下载或者插件。现在可以通过[加密媒体扩展][4]特性来使用。
|
||||
|
||||
虽然我们等待这讨论取得进展(并且希望可以完全解决),但是你仍可以在Ubuntu上[下面的指导来][5]修改HTML5 Netflix。
|
||||
|
||||
更新:9/19
|
||||
|
||||
本文发表后,Canonical 已经确认所需版本的NSS 库会按计划在下个“安全更新”中更新,预计 Ubuntu 14.04 LTS 将在两周内得到更新。
|
||||
|
||||
这个新闻让 Netflix 的Paul Adolph 很高兴,作为回应,他说当软件包更新后,他将“去掉 Chrome 中回放 Netflix HTML5 视频时的User-Agent 过滤,不再需要修改UA 了”。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.omgubuntu.co.uk/2014/09/netflix-linux-html5-nss-change-request
|
||||
|
||||
作者:[Joey-Elijah Sneddon][a]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://plus.google.com/117485690627814051450/?rel=author
|
||||
[1]:http://www.omgubuntu.co.uk/2014/08/netflix-linux-html5-support-plugins
|
||||
[2]:https://lists.ubuntu.com/archives/ubuntu-devel-discuss/2014-September/015048.html
|
||||
[3]:https://developer.mozilla.org/en-US/docs/Mozilla/Projects/NSS/NSS_3.17_release_notes
|
||||
[4]:http://en.wikipedia.org/wiki/Encrypted_Media_Extensions
|
||||
[5]:http://www.omgubuntu.co.uk/2014/08/netflix-linux-html5-support-plugins
|
||||
@ -1,40 +0,0 @@
|
||||
2q1w2007翻译中
|
||||
One of the Smallest Distros in the World, Tiny Core, Gets a Fresh Update
|
||||
================================================================================
|
||||

|
||||
|
||||
Tiny Core desktop
|
||||
|
||||
**Robert Shingledecker has announced the immediate availability for download of the final version of the Tiny Core 5.4 Linux operating system, which also happens to be one the smaller operating systems in the world.**
|
||||
|
||||
The name of the distro says pretty much everything about the operating system, but the developers have integrated some interesting packages and a very light desktop to match it. This latest iteration only had a single Release Candidate and it's one of the quietest releases made so far.
|
||||
|
||||
"Tiny Core is simply an example of what the Core Project can produce, an 12MB FLTK/FLWM desktop. The user has complete control over which applications and/or additional hardware to have supported, be it for a desktop, a netbook, an appliance, or server, selectable by the user by installing additional applications from online repositories, or easily compiling most anything you desire using tools provided," says the dev on the official website.
|
||||
|
||||
According to the changelog, entries for nfs server have been added, 'Done' is now printed in a new lin, and udev has been updated to version 174 to fix a race condition.
|
||||
|
||||
A complete list of updates and changes can be found in the official [announcement][1].
|
||||
|
||||
You can download Tiny Core Linux 5.4.
|
||||
|
||||
- [Tiny Core Linux 5.4 (ISO)][2][iso] [14 MB]
|
||||
- [Tiny Core Plus 5.4 (ISO)][3][iso] [72 MB]
|
||||
- [Core 5.4 (ISO)][4][iso] [8.90 MB]
|
||||
|
||||
The distribution is Live, so you can test it before installing it.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://news.softpedia.com/news/One-of-the-Smallest-Distros-in-the-World-Tiny-Core-Gets-a-Fresh-Update-458785.shtml
|
||||
|
||||
作者:[Silviu Stahie][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://news.softpedia.com/editors/browse/silviu-stahie
|
||||
[1]:http://forum.tinycorelinux.net/index.php/topic,17487.0.html
|
||||
[2]:http://distro.ibiblio.org/pub/linux/distributions/tinycorelinux/5.x/x86/release/TinyCore-5.4.iso
|
||||
[3]:http://repo.tinycorelinux.net/5.x/x86/release/CorePlus-5.4.iso
|
||||
[4]:http://distro.ibiblio.org/tinycorelinux/5.x/x86/release/Core-current.iso
|
||||
@ -1,36 +0,0 @@
|
||||
Another Italian City Says Goodbye To Microsoft Office, Will Switch To OpenOffice Soon
|
||||
================================================================================
|
||||

|
||||
|
||||
It seems [Open Source][1] adoption is the latest fad in European countries. Last month only we heard that [Turin became the first Italian city to officially opt for Open Source product][2]. Another city in north-west Italy, [Udine][3], has also announced that it is ditching Microsoft office and will migrate to [OpenOffice][4].
|
||||
|
||||
Udine has a population of 100,000 and the administration has around 900 computers which are running Microsoft Windows as their default productivity suite. As per the [budget document][5], the migration will start somewhere around December with 80 new computers. It will be followed by the migration of older computers to OpenOffice.
|
||||
|
||||
The migration is estimated to save licensing fee which otherwise would have cost around Euro 400 per computer, which makes a total of Euro 360,000. But saving money is not the only goal of this migration, getting regular software update is also one of the factors.
|
||||
|
||||
Of course the transition from Microsoft Office to OpenOffice won’t be smooth. Keeping this in mind, the municipality is planning training sessions for at least first few employees who will get the new machines with OpenOffice.
|
||||
|
||||
As I stated earlier, this seems to be a trend in Europe. [French city Toulouse saved a million euro with LibreOffice][6] earlier this year along with [Canary Islands in Spain][7]. Neighboring Spanish city [Geneva also showed sign of Open Source adoption][8]. In other part of the world, government organizations in [Tamil Nadu][9] and Kerala provinces of India also ditched Microsoft for Open Source.
|
||||
|
||||
I think demise of Windows XP has been a boon for Open Source, along with sluggish economy. Whatever may be the reason, I am happy to see this list growing. What about you?
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://itsfoss.com/udine-open-source/
|
||||
|
||||
作者:[Abhishek][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://itsfoss.com/author/Abhishek/
|
||||
[1]:http://itsfoss.com/category/open-source-software/
|
||||
[2]:http://itsfoss.com/italian-city-turin-open-source/
|
||||
[3]:http://en.wikipedia.org/wiki/Udine
|
||||
[4]:https://www.openoffice.org/
|
||||
[5]:http://www.comune.udine.it/opencms/opencms/release/ComuneUdine/comune/Rendicontazione/PEG/PEG_2014/index.html?lang=it&style=1&expfolder=???+NavText+???
|
||||
[6]:http://itsfoss.com/french-city-toulouse-saved-1-million-euro-libreoffice/
|
||||
[7]:http://itsfoss.com/canary-islands-saves-700000-euro-open-source/
|
||||
[8]:http://itsfoss.com/170-primary-public-schools-geneva-switch-ubuntu/
|
||||
[9]:http://itsfoss.com/tamil-nadu-switches-linux/
|
||||
@ -1,106 +0,0 @@
|
||||
[translating by KayGuoWhu]
|
||||
How to Encrypt Email in Linux
|
||||
================================================================================
|
||||
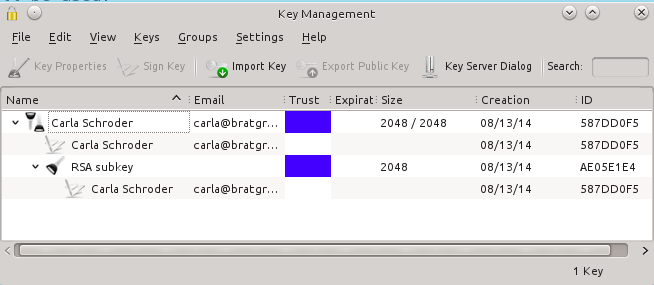
|
||||
Kgpg provides a nice GUI for creating and managing your encryption keys.
|
||||
|
||||
If you've been thinking of encrypting your email, it is a rather bewildering maze to sort through thanks to the multitude of email services and mail clients. There are two levels of encryption to consider: SSL/TLS encryption protects your login and password to your mailserver. [GnuPG][1] is the standard strong Linux encryption tool, and it encrypts and authenticates your messages. It is best if you manage your own GPG encryption and not leave it up to third parties, which we will discuss in a moment.
|
||||
|
||||
Encrypting messages still leaves you vulnerable to traffic analysis, as message headers must be in the clear. So that necessitates yet another tool such as the [Tor network][2] for hiding your Internet footprints. Let's look at various mail services and clients, and the pitfalls and benefits therein.
|
||||
|
||||
### Forget Webmail ###
|
||||
|
||||
If you use GMail, Yahoo, Hotmail, or another Web mail provider, forget about it. Anything you type in a Web browser is vulnerable to JavaScript attacks, and whatever mischiefs the service provider engages in. GMail, Yahoo, and Hotmail all offer SSL/TLS encryption to protect your messages from wiretapping. But they offer no protections from their own data-mining habits, so they don't offer end-to-end encryption. Yahoo and Google both claim they're going to roll out end-to-end encryption next year. Color me skeptical, because they will wither and die if anything interferes with the data-mining that is their core business.
|
||||
|
||||
There are various third-party email security services such as [Virtru][3] and [SafeMess][4] that claim to offer secure encryption for all types of email. Again I am skeptical, because whoever holds your encryption keys has access to your messages, so you're still depending on trust rather than technology.
|
||||
|
||||
Peer messaging avoids many of the pitfalls of using centralized services. [RetroShare][5] and [Bitmessage][6] are two popular examples of this. I don't know if they live up to their claims, but the concept certainly has merit.
|
||||
|
||||
What about Android and iOS? It's safest to assume that the majority of Android and iOS apps are out to get you. Don't take my word for it-- read their terms of service and examine the permissions they require to install on your devices. And even if their terms are acceptable when you first install them, unilateral TOS changes are industry standard, so it is safest to assume the worst.
|
||||
|
||||
### Zero Knowledge ###
|
||||
|
||||
[Proton Mail][7] is a new email service that claims zero-knowledge message encryption. Authentication and message encryption are two separate steps, Proton is under Swiss privacy laws, and they do not log user activity. Zero knowledge encryption offers real security. This means that only you possess your encryption keys, and if you lose them your messages are not recoverable.
|
||||
|
||||
There are many encrypted email services that claim to protect your privacy. Read the fine print carefully and look for red flags such as limited user data collection, sharing with partners, and cooperation with law enforcement. These indicate that they collect and share user data, and have access to your encryption keys and can read your messages.
|
||||
|
||||
### Linux Mail Clients ###
|
||||
|
||||
A standalone open source mail client such as KMail, Thunderbird, Mutt, Claws, Evolution, Sylpheed, or Alpine, set up with your own GnuPG keys that you control gives you the most protection. (The easiest way to set up more secure email and Web surfing is to run the TAILS live Linux distribution. See [Protect Yourself Online With Tor, TAILS, and Debian][8].)
|
||||
|
||||
Whether you use TAILS or a standard Linux distro, managing GnuPG is the same, so let's learn how to encrypt messages with GnuPG.
|
||||
|
||||
### How to Use GnuPG ###
|
||||
|
||||
First, a quick bit of terminology. OpenPGP is an open email encryption and authentication protocol, based on Phil Zimmerman's Pretty Good Privacy (PGP). GNU Privacy Guard (GnuPG or GPG) is the GPL implementation of OpenPGP. GnuPG uses symmetric public key cryptography. This means that you create pairs of keys: a public key that anyone can use to encrypt messages to send to you, and a private key that only you possess to decrypt them. GnuPG performs two separate functions: digitally-signing messages to prove they came from you, and encrypting messages. Anyone can read your digitally-signed messages, but only people you have exchanged keys with can read your encrypted messages. Remember, never share your private keys! Only public keys.
|
||||
|
||||
Seahorse is GNOME's graphical front-end to GnuPG, and KGpg is KDE's graphical GnuPG tool.
|
||||
|
||||
Now let's run through the basic steps of creating and managing GnuPG keys. This command creates a new key:
|
||||
|
||||
$ gpg --gen-key
|
||||
|
||||
This is a multi-step process; just answer all the questions, and the defaults are fine for most people. When you create your passphrase, write it down and keep it in a secure place because if you lose it you cannot decrypt anything. All that advice about never writing down your passwords is wrong. Most of us have dozens of logins and passwords to track, including some that we rarely use, so it's not realistic to remember all of them. You know what happens when people don't write down their passwords? They create simple passwords and re-use them. Anything you store on your computer is potentially vulnerable; a nice little notebook kept in a locked drawer is impervious to everything but a physical intrusion, if an intruder even knew to look for it.
|
||||
|
||||
I must leave it as your homework to figure out how to configure your mail client to use your new key, as every one is different. You can list your key or keys:
|
||||
|
||||
$ gpg --list-keys
|
||||
/home/carla/.gnupg/pubring.gpg
|
||||
------------------------------
|
||||
pub 2048R/587DD0F5 2014-08-13
|
||||
uid Carla Schroder (my gpg key)
|
||||
sub 2048R/AE05E1E4 2014-08-13
|
||||
|
||||
This is a fast way to grab necessary information like the location of your keys, and your key name, which is the UID. Suppose you want to upload your public key to a keyserver; this is how it looks using my example key:
|
||||
|
||||
$ gpg --send-keys 'Carla Schroder' --keyserver http://example.com
|
||||
|
||||
When you create a new key for upload to public key servers, you should also create a revocation certificate. Don't do it later-- create it when you create your new key. You can give it any arbitrary name, so instead of revoke.asc you could give it a descriptive name like mycodeproject.asc:
|
||||
|
||||
$ gpg --output revoke.asc --gen-revoke 'Carla Schroder'
|
||||
|
||||
Now if your key ever becomes compromised you can revoke it by first importing the revocation certificate into your keyring:
|
||||
|
||||
$ gpg --import ~/.gnupg/revoke.asc
|
||||
|
||||
Then create and upload a new key to replace it. Any users of your old key will be notified as they refresh their key databases.
|
||||
|
||||
You must guard your revocation certificate just as zealously as your private key. Copy it to a CD or USB stick and lock it up, and delete it from your computer. It is a plain-text key, so you could even print it on paper.
|
||||
|
||||
If you ever need a copy-and-paste key, for example on public keyrings that allow pasting your key into a web form, or if you want to post your public key on your Web site, then you must create an ASCII-armored version of your public key:
|
||||
|
||||
$ gpg --output carla-pubkey.asc --export -a 'Carla Schroder'
|
||||
|
||||
This creates the familiar plain-text public key you've probably seen, like this shortened example:
|
||||
|
||||
-----BEGIN PGP PUBLIC KEY BLOCK-----
|
||||
Version: GnuPG v1
|
||||
mQENBFPrn4gBCADeEXKdrDOV3AFXL7QQQ+i61rMOZKwFTxlJlNbAVczpawkWRC3l
|
||||
IrWeeJiy2VyoMQ2ZXpBLDwGEjVQ5H7/UyjUsP8h2ufIJt01NO1pQJMwaOMcS5yTS
|
||||
[...]
|
||||
I+LNrbP23HEvgAdNSBWqa8MaZGUWBietQP7JsKjmE+ukalm8jY8mdWDyS4nMhZY=
|
||||
=QL65
|
||||
-----END PGP PUBLIC KEY BLOCK-----
|
||||
|
||||
That should get you started learning your way around GnuPG. [The GnuPG manuals][9] have complete details on using GnuPG and all of its options.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linux.com/learn/tutorials/784165-how-to-encrypt-email-in-linux
|
||||
|
||||
作者:[Carla Schroder][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.linux.com/component/ninjaboard/person/3734
|
||||
[1]:http://www.openpgp.org/members/gnupg.shtml
|
||||
[2]:https://www.torproject.org/
|
||||
[3]:https://www.virtru.com/
|
||||
[4]:https://www.safemess.com/
|
||||
[5]:http://retroshare.sourceforge.net/
|
||||
[6]:http://retroshare.sourceforge.net/
|
||||
[7]:https://protonmail.ch/
|
||||
[8]:http://www.linux.com/learn/docs/718398-protect-yourself-online-with-tor-+tails-and-debian
|
||||
[9]:https://www.gnupg.org/documentation/manuals.html
|
||||
@ -1,104 +0,0 @@
|
||||
SPccman is translating
|
||||
How to sniff HTTP traffic from the command line on Linux
|
||||
================================================================================
|
||||
Suppose you want to sniff live HTTP web traffic (i.e., HTTP requests and responses) on the wire for some reason. For example, you may be testing experimental features of a web server. Or you may be debugging a web application or a RESTful service. Or you may be trying to troubleshoot [PAC (proxy auto config)][1] or check for any malware files surreptitiously downloaded from a website. Whatever the reason is, there are cases where HTTP traffic sniffing is helpful, for system admins, developers, or even end users.
|
||||
|
||||
While [packet sniffing tools][2] such as tcpdump are popularly used for live packet dump, you need to set up proper filtering to capture HTTP traffic, and even then, their raw output typically cannot be interpreted on the HTTP protocol level so easily. Real-time web server log parsers such as [ngxtop][3] provide human-readable real-time web traffic traces, but only applicable with a full access to live web server logs.
|
||||
|
||||
What will be nice is to have tcpdump-like traffic sniffing tool, but targeting HTTP traffic only. In fact, [httpry][4] is extactly that: **HTTP packet sniffing tool**. httpry captures live HTTP packets on the wire, and displays their content at the HTTP protocol level in a human-readable format. In this tutorial, let's see how we can sniff HTTP traffic with httpry.
|
||||
|
||||
### Install httpry on Linux ###
|
||||
|
||||
On Debian-based systems (Ubuntu or Linux Mint), httpry is not available in base repositories. So build it from the source:
|
||||
|
||||
$ sudo apt-get install gcc make git libpcap0.8-dev
|
||||
$ git clone https://github.com/jbittel/httpry.git
|
||||
$ cd httpry
|
||||
$ make
|
||||
$ sudo make install
|
||||
|
||||
On Fedora, CentOS or RHEL, you can install httpry with yum as follows. On CentOS/RHEL, enable [EPEL repo][5] before running yum.
|
||||
|
||||
$ sudo yum install httpry
|
||||
|
||||
If you still want to build httpry from the source, you can easily do that by:
|
||||
|
||||
$ sudo yum install gcc make git libpcap-devel
|
||||
$ git clone https://github.com/jbittel/httpry.git
|
||||
$ cd httpry
|
||||
$ make
|
||||
$ sudo make install
|
||||
|
||||
### Basic Usage of httpry ###
|
||||
|
||||
The basic use case of httpry is as follows.
|
||||
|
||||
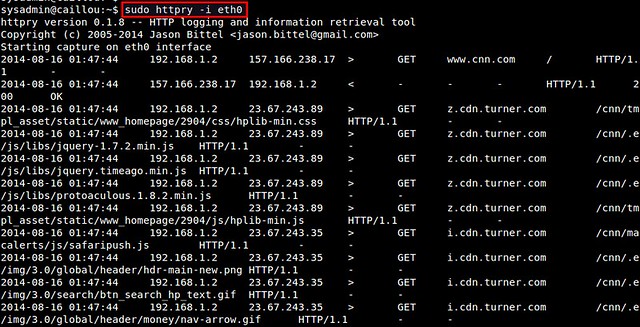
$ sudo httpry -i <network-interface>
|
||||
|
||||
httpry then listens on a specified network interface, and displays captured HTTP requests/responses in real time.
|
||||
|
||||
|
||||
|
||||
In most cases, however, you will be swamped with the fast scrolling output as packets are coming in and out. So you want to save captured HTTP packets for offline analysis. For that, use either '-b' or '-o' options. The '-b' option allows you to save raw HTTP packets into a binary file as is, which then can be replayed with httpry later. On the other hand, '-o' option saves human-readable output of httpry into a text file.
|
||||
|
||||
To save raw HTTP packets into a binary file:
|
||||
|
||||
$ sudo httpry -i eth0 -b output.dump
|
||||
|
||||
To replay saved HTTP packets:
|
||||
|
||||
$ httpry -r output.dump
|
||||
|
||||
Note that when you read a dump file with '-r' option, you don't need root privilege.
|
||||
|
||||
To save httpr's output to a text file:
|
||||
|
||||
$ sudo httpry -i eth0 -o output.txt
|
||||
|
||||
### Advanced Usage of httpry ###
|
||||
|
||||
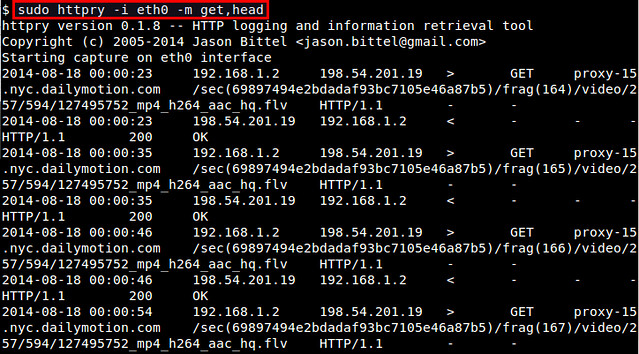
If you want to monitor only specific HTTP methods (e.g., GET, POST, PUT, HEAD, CONNECT, etc), use '-m' option:
|
||||
|
||||
$ sudo httpry -i eth0 -m get,head
|
||||
|
||||
|
||||
|
||||
If you downloaded httpry's source code, you will notice that the source code comes with a collection of Perl scripts which aid in analyzing httpry's output. These scripts are found in httpry/scripts/plugins directory. If you want to write a custom parser for httpry's output, these scripts can be good examples to start from. Some of their capabilities are:
|
||||
|
||||
- **hostnames**: Displays a list of unique host names with counts.
|
||||
- **find_proxies**: Detect web proxies.
|
||||
- **search_terms**: Find and count search terms entered in search services.
|
||||
- **content_analysis**: Find URIs which contain specific keywords.
|
||||
- **xml_output**: Convert output into XML format.
|
||||
- **log_summary**: Generate a summary of log.
|
||||
- **db_dump**: Dump log file data into a database.
|
||||
|
||||
Before using these scripts, first run httpry with '-o' option for some time. Once you obtained the output file, run the scripts on it at once by using this command:
|
||||
|
||||
$ cd httpry/scripts
|
||||
$ perl parse_log.pl -d ./plugins <httpry-output-file>
|
||||
|
||||
You may encounter warnings with several plugins. For example, db_dump plugin may fail if you haven't set up a MySQL database with DBI interface. If a plugin fails to initialize, it will automatically be disabled. So you can ignore those warnings.
|
||||
|
||||
After parse_log.pl is completed, you will see a number of analysis results (*.txt/xml) in httpry/scripts directory. For example, log_summary.txt looks like the following.
|
||||
|
||||
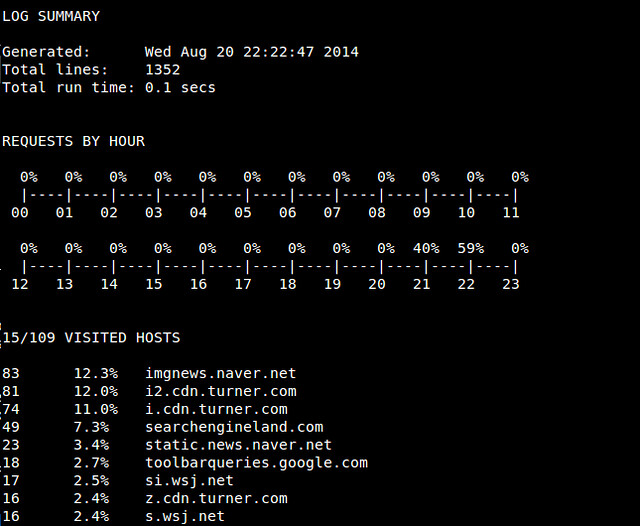
|
||||
|
||||
To conclude, httpry can be a life saver if you are in a situation where you need to interpret live HTTP packets. That might not be so common for average Linux users, but it never hurts to be prepared. What do you think of this tool?
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/2014/08/sniff-http-traffic-command-line-linux.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/nanni
|
||||
[1]:http://xmodulo.com/2012/12/how-to-set-up-proxy-auto-config-on-ubuntu-desktop.html
|
||||
[2]:http://xmodulo.com/2012/11/what-are-popular-packet-sniffers-on-linux.html
|
||||
[3]:http://xmodulo.com/2014/06/monitor-nginx-web-server-command-line-real-time.html
|
||||
[4]:http://dumpsterventures.com/jason/httpry/
|
||||
[5]:http://xmodulo.com/2013/03/how-to-set-up-epel-repository-on-centos.html
|
||||
@ -1,3 +1,4 @@
|
||||
DoubleC is translating
|
||||
How to create a site-to-site IPsec VPN tunnel using Openswan in Linux
|
||||
================================================================================
|
||||
A virtual private network (VPN) tunnel is used to securely interconnect two physically separate networks through a tunnel over the Internet. Tunneling is needed when the separate networks are private LAN subnets with globally non-routable private IP addresses, which are not reachable to each other via traditional routing over the Internet. For example, VPN tunnels are often deployed to connect different NATed branch office networks belonging to the same institution.
|
||||
@ -215,4 +216,4 @@ via: http://xmodulo.com/2014/08/create-site-to-site-ipsec-vpn-tunnel-openswan-li
|
||||
|
||||
[a]:http://xmodulo.com/author/sarmed
|
||||
[1]:http://en.wikipedia.org/wiki/IPsec
|
||||
[2]:https://www.openswan.org/
|
||||
[2]:https://www.openswan.org/
|
||||
|
||||
@ -1,3 +1,5 @@
|
||||
chi1shi2 is translating.
|
||||
|
||||
How to use on-screen virtual keyboard on Linux
|
||||
================================================================================
|
||||
On-screen virtual keyboard is an alternative input method that can replace a real hardware keyboard. Virtual keyboard may be a necessity in various cases. For example, your hardware keyboard is just broken; you do not have enough keyboards for extra machines; your hardware does not have an available port left to connect a keyboard; you are a disabled person with difficulty in typing on a real keyboard; or you are building a touchscreen-based web kiosk.
|
||||
|
||||
@ -1,3 +1,4 @@
|
||||
translating by cvsher
|
||||
20 Useful Commands of ‘Sysstat’ Utilities (mpstat, pidstat, iostat and sar) for Linux Performance Monitoring
|
||||
================================================================================
|
||||
In our last article, we have learned about installing and upgrading the **sysstat** package and understanding briefly about the utilities which comes with the package.
|
||||
@ -401,4 +402,4 @@ via: http://www.tecmint.com/sysstat-commands-to-monitor-linux/
|
||||
|
||||
[a]:http://www.tecmint.com/author/kuldeepsharma47/
|
||||
[1]:http://www.tecmint.com/install-sysstat-in-linux/
|
||||
[2]:http://www.tecmint.com/linux-performance-monitoring-with-vmstat-and-iostat-commands/
|
||||
[2]:http://www.tecmint.com/linux-performance-monitoring-with-vmstat-and-iostat-commands/
|
||||
|
||||
@ -1,111 +0,0 @@
|
||||
[su-kaiyao]翻译中
|
||||
|
||||
Linux FAQs with Answers--How to create a MySQL database from the command line
|
||||
================================================================================
|
||||
> **Question**: I have a MySQL server up and running somewhere. How can I create and populate a MySQL database from the command line?
|
||||
|
||||
To create a MySQL database from the command line, you can use mysql CLI client. Here is a step-by-step procedure to create and populate a MySQL database using mysql client from the command line.
|
||||
|
||||
### Step One: Install MySQL Client ###
|
||||
|
||||
Of course you need to make sure that MySQL client program is installed. If not, you can install it as follows.
|
||||
|
||||
On Debian, Ubuntu or Linux Mint:
|
||||
|
||||
$ sudo apt-get install mysql-client
|
||||
|
||||
On Fedora, CentOS or RHEL:
|
||||
|
||||
$ sudo yum install mysql
|
||||
|
||||
### Step Two: Log in to a MySQL Server ###
|
||||
|
||||
To begin, first log in to your MySQL server as root with the following command:
|
||||
|
||||
$ mysql -u root -h <mysql-server-ip-address> -p
|
||||
|
||||
Note that to be able to log in to a remote MySQL server, you need to [enable remote access on the server][1]. If you are invoking mysql command on the same host where the MySQL server is running, you can omit "-h <mysql-server-ip-address>" as follows.
|
||||
|
||||
$ mysql -u root -p
|
||||
|
||||
You will be then asked for the password of the MySQL root user. If the authentication succeeds, the MySQL prompt will appear.
|
||||
|
||||

|
||||
|
||||
### Step Three: Create a MySQL Database ###
|
||||
|
||||
Before you start typing commands at the MySQL prompt, remember that each command must end with a semicolon (otherwise it will not execute). In addition, consider using uppercase letters for commands and lowercase letter for database objects. Note that this is not required but helpful for reading.
|
||||
|
||||
Now, let's create a database named xmodulo_DB:
|
||||
|
||||
mysql> CREATE DATABASE IF NOT EXISTS xmodulo_DB;
|
||||
|
||||

|
||||
|
||||
### Step Four: Create a MySQL Table ###
|
||||
|
||||
For a demonstration purpose, we will create a tabled called posts_tbl where we want to store the following information about posts:
|
||||
|
||||
- Text of article
|
||||
- Author's first name
|
||||
- Author's last name
|
||||
- Whether the post is enabled (visible) or not
|
||||
- Date when article was posted
|
||||
|
||||
This process is actually performed in two steps:
|
||||
|
||||
First, select the database that we want to use:
|
||||
|
||||
mysql> USE xmodulo_DB;
|
||||
|
||||
Then create a new table in the database:
|
||||
|
||||
mysql> CREATE TABLE 'posts_tbl' (
|
||||
'post_id' INT UNSIGNED NOT NULL AUTO_INCREMENT,
|
||||
'content' TEXT,
|
||||
'author_FirstName' VARCHAR(100) NOT NULL,
|
||||
'author_LastName' VARCHAR(50) DEFAULT NULL ,
|
||||
'isEnabled' TINYINT(1) NOT NULL DEFAULT 1,
|
||||
'date' TIMESTAMP NOT NULL DEFAULT CURRENT_TIMESTAMP ,
|
||||
PRIMARY KEY ( 'post_id' )
|
||||
) TYPE = MYISAM;
|
||||
|
||||
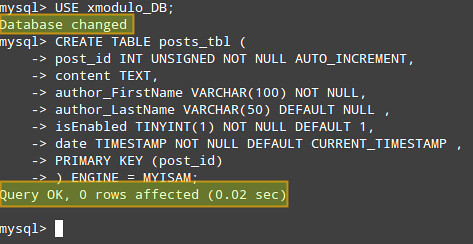
|
||||
|
||||
### Step Five: Create a User Account and Grant Permissions ###
|
||||
|
||||
When it comes to accessing our newly created database and tables, it's a good idea to create a new user account, so it can access that database (and that database only) without full permissions to the whole MySQL server.
|
||||
|
||||
You can create a new user, grant permissions and apply changes in two easy steps as follows:
|
||||
|
||||
mysql> GRANT ALL PRIVILEGES ON xmodulo_DB.* TO 'new_user'@'%' IDENTIFIED BY 'new_password';
|
||||
mysql> FLUSH PRIVILEGES;
|
||||
|
||||
where 'new_user' and 'new_password' refer to the new user account name and its password, respectively. This information will be stored in the mysql.user table, and the password will be encrypted.
|
||||
|
||||
### Step Six: Testing ###
|
||||
|
||||
Let's insert one dummy record to the posts_tbl table:
|
||||
|
||||
mysql> USE xmodulo_DB;
|
||||
mysql> INSERT INTO posts_tbl (content, author_FirstName, author_LastName)
|
||||
VALUES ('Hi! This is some dummy text.', 'Gabriel', 'Canepa');
|
||||
|
||||
Then view all the records in posts_tbl table:
|
||||
|
||||
mysql> SELECT * FROM posts_tbl;
|
||||
|
||||

|
||||
|
||||
Note that MySQL automatically inserted the proper default values in the fields where we defined them earlier (e.g., 'isEnabled' and 'date').
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://ask.xmodulo.com/create-mysql-database-command-line.html
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://xmodulo.com/2012/06/how-to-allow-remote-access-to-mysql.html
|
||||
@ -0,0 +1,40 @@
|
||||
2q1w2007翻译中
|
||||
世界上最小的发行版之一Tiny Core有了新的更新
|
||||
================================================================================
|
||||

|
||||
|
||||
Tiny Core
|
||||
|
||||
**Robert Shingledecker 刚刚发布了最新可用的最终版本的Tiny Core 5.4,这也使它成为世界上最小的发行版之一**
|
||||
|
||||
发行版的名字说明了一切,但是开发者依然集成了一些有意思的包和一个轻量的桌面。这次最新的迭代只有一个候选版本,而且它将会是有史以来最安静的版本。
|
||||
|
||||
官网上的开发者说"Tiny Core是一个简单的例子来示范核心项目可以提供什么。,它提供了一个12MB的FLTK/FLWM桌面。用户对提供的程序和外加的硬件有完整的控制权。你可以把它用在桌面、笔记本或者服务器上,这可以由用户在从在线库中安装附加程序时选择,或者用提供的工具编译大多数你需要的。"
|
||||
|
||||
根据更新日志,NFS的入口被添加,'Done'将在新的一行里显示,udev也升级到174来修复竞态条件问题。
|
||||
|
||||
关于修改和升级的完整内容可以在官方的[声明][1]里找到。
|
||||
|
||||
你可以下载Tiny Core Linux 5.4.
|
||||
|
||||
- [Tiny Core Linux 5.4 (ISO)][2][iso] [14 MB]
|
||||
- [Tiny Core Plus 5.4 (ISO)][3][iso] [72 MB]
|
||||
- [Core 5.4 (ISO)][4][iso] [8.90 MB]
|
||||
|
||||
这些分发都有Live,你可以在安装之前试用。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://news.softpedia.com/news/One-of-the-Smallest-Distros-in-the-World-Tiny-Core-Gets-a-Fresh-Update-458785.shtml
|
||||
|
||||
作者:[Silviu Stahie][a]
|
||||
译者:[2q1w2007](https://github.com/2q1w2007)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://news.softpedia.com/editors/browse/silviu-stahie
|
||||
[1]:http://forum.tinycorelinux.net/index.php/topic,17487.0.html
|
||||
[2]:http://distro.ibiblio.org/pub/linux/distributions/tinycorelinux/5.x/x86/release/TinyCore-5.4.iso
|
||||
[3]:http://repo.tinycorelinux.net/5.x/x86/release/CorePlus-5.4.iso
|
||||
[4]:http://distro.ibiblio.org/tinycorelinux/5.x/x86/release/Core-current.iso
|
||||
@ -1,42 +0,0 @@
|
||||
Netflix与Ubuntu合作带来在Ubuntu上回放Netflix节目的功能
|
||||
================================================================================
|
||||

|
||||
|
||||
**我们[上个月见到Netflix刚关闭了在Linux上的支持][1],现在我们只需几个简单的步骤就可以在Ubuntu桌面上启用HTML 5视频流了。
|
||||
|
||||
现在Netflix想要更近一部。它希望给Ubuntu带来真正的开箱即用的Netflix回放。现在需要的就是更新**网络安全**服务库。
|
||||
|
||||
### 原生Netflix? Neato. ###
|
||||
|
||||
在一封寄给Ubuntu开发者邮件列表的[邮件中][2],Netflix的Paul Adolph解释了现在的情况:
|
||||
|
||||
> “如果NSS的版本是3.16.2或者更高的话,Netflix可以在14.02的稳定版Chrome中播放。如果版本超过了14.02,Netflix会作出一些改变来避免用户不得不对客户端进行一些修改才能播放。”
|
||||
|
||||
很快要发布的Ubuntu 14.10提供了更新的[NSS v3.17][3], Ubuntu 14.04 LTS — 这个被大多数用户使用的版本 — 目前提供v3.15.x。
|
||||
|
||||
|
||||
NSS是一系列的库,支持多种安全功能的客户端和服务端应用,包括SSL,TLS,PKCS和其他安全标准。热终于让Ubuntu LTS用户可以用上原声HTML5 Netflix, Paul 问道:
|
||||
|
||||
>”让一个新的NSS版本进入更新流的过程是什么?或者有人可以给我提供正确的联系么?“
|
||||
|
||||
Netflix began offering HTML5 video playback on Windows 8.1 and OS X Yosemite earlier this year, negating the need for any extra downloads or plugins. The switch has been made possible through the [Encrypted Media Extension][4] spec.
|
||||
Netflix今年早期时在Windows 8.1和OSX Yosemite上提供HTML5视频回放,而否定了任何额外的下载或者插件。现在可以通过[加密媒体扩展][4]特性来使用
|
||||
|
||||
虽然我们等待这讨论取得进展(并且希望可以完全解决),但是你仍可以在Ubuntu上[下面的指导来][5]修改HTML5 Netflix。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.omgubuntu.co.uk/2014/09/netflix-linux-html5-nss-change-request
|
||||
|
||||
作者:[Joey-Elijah Sneddon][a]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://plus.google.com/117485690627814051450/?rel=author
|
||||
[1]:http://www.omgubuntu.co.uk/2014/08/netflix-linux-html5-support-plugins
|
||||
[2]:https://lists.ubuntu.com/archives/ubuntu-devel-discuss/2014-September/015048.html
|
||||
[3]:https://developer.mozilla.org/en-US/docs/Mozilla/Projects/NSS/NSS_3.17_release_notes
|
||||
[4]:http://en.wikipedia.org/wiki/Encrypted_Media_Extensions
|
||||
[5]:http://www.omgubuntu.co.uk/2014/08/netflix-linux-html5-support-plugins
|
||||
105
translated/tech/20140819 How to Encrypt Email in Linux.md
Normal file
105
translated/tech/20140819 How to Encrypt Email in Linux.md
Normal file
@ -0,0 +1,105 @@
|
||||
在Linux中加密邮件
|
||||
================================================================================
|
||||

|
||||
Kgpg为了创建了管理加密秘钥提供了一个很好的GUI界面.
|
||||
|
||||
如果你一直在考虑如何加密电子邮件,那么在众多的邮件服务和邮件客户端中挑来挑去一定是件头痛的事情.可以考虑两种加密方法:SSL或TLS加密会保护发送到邮件服务器的登录名和密码.[Gunpg][1]是一款标准有用的Linux加密工具,可以加密和认证消息.如果你可以管理自己的GPG加密,并不考虑第三方工具,那它就够了,其它的我们将在稍后讨论.
|
||||
|
||||
即便加密了消息,你仍然会暴露在流量分析中,因为消息头部必须是明文形式.所以需要另一款比如[Tor network][2]来隐藏你在互联网上的足迹.我们会看看各种邮件服务和客户端,以及其中的利弊.
|
||||
|
||||
### 忘掉Web邮件 ###
|
||||
|
||||
如果你使用过GMail, Yahoo,Hotmail或者其它Web邮件提供商的邮件服务,那就忘掉它们吧.你在Web浏览器里输入的任何信息都会暴露在JavaScript攻击中,而且无论服务提供商提供什么保障都是过眼云烟(译者注:此说法靠谱否?).GMail,Yahoo和Hotmail均提供SSL/TLS加密来防止消息被窃听.但是它们不会提供任何保护来阻碍它们自己的数据挖掘,因此并不会提供端到端的加密.Yahoo和Google都声称将在明年推出端到端的加密.对此我持怀疑态度,因为如果一旦它们的核心业务数据挖掘受到干预,它们就什么都干不了了.
|
||||
|
||||
市面上也有各式各样的声称可以为所有类型的电子邮件都能提供安全加密的第三方邮件加密服务,比如[Virtru][3]和[SafeMess][4].对此我依旧表示怀疑,因为无论是谁,只要持有加密秘钥就可以访问你的消息,所以你还是要依赖于可信而不是技术.
|
||||
|
||||
对等消息可以避免许多使用集中化服务中的缺陷.[RetroShare][5]和[Bitmessage][6]是两种流行的范例.我不知道它们是否如实所述,但这么说肯定由可取之处.
|
||||
|
||||
那Anddroid和iOS又如何呢?假设大部分的Android和iOS应用都没有权限获取你的消息的话,那就是最安全的.不要照搬我说的 -- 在应用将要安装到你的设备上时麻烦读读相关的服务条款并检查所要求的权限.即便在初次安装时它们的条款是可接受的,也记得单方面的条款改变是行业的标准,所以做最坏的打算是最安全的.
|
||||
|
||||
### 零基础知识 ###
|
||||
|
||||
[Proton Mail][7]是一款全新的邮件服务,声称无需任何基础就可以实现消息加密.认证和消息加密分为两个单独的步骤,Proton受到Swiss隐私条款的保护,它们不会通过日志记录用户的活动.零基础知识加密提供真正的安全.这代表只有你拥有你的加密秘钥,如果你丢了它们,你的消息就无法恢复了.
|
||||
|
||||
也有许多加密电子邮件服务声称可以保护你的隐私.认真阅读细则,查看红色标注的地方,比如受限的用户数据采集,与好友分享,与执法部门的合作等.这些条款暗示它们会收集和共享用户数据,拥有权限获取你的加密秘钥,并读取你的消息.
|
||||
|
||||
### Linux邮件客户端 ###
|
||||
|
||||
一款独立的开源邮件客户端,比如, Mutt, Claws, Evolution, Sylpheed和Alpine,可建立你自己控制的GnuPG秘钥,给你大部分的保护.(建立更安全的电子邮件和Web浏览的最容易的方式是运行TAILS live的Linux发行版.详情查看[Protect Yourself Online With Tor, TAILS, and Debian][8].)
|
||||
|
||||
无论你使用的是TAILS还是一款标准Linux发行版,管理GnuPG的方法是相同的,所以下面来学习如何使用GnuPG加密消息.
|
||||
|
||||
### 使用GnuPG ###
|
||||
|
||||
首先,熟悉一下相关术语。OpenPGP是一种开放的电子邮件加密和认证协议,基于菲利普·齐默曼的Pretty Good Privacy (PGP)。GNU Privacy Guard (GnuPG or GPG)是OpenPGP的GPL实现。GnuPG使用对称公钥加密算法,也就是说会生成一堆密钥:一个任何人都可以用来加密发送给你的消息的公钥和一个只有你自己拥有用来解密消息的的私钥。GnuPG执行两个分开的函数:数字化签名消息以证明消息来自你和加密消息。任何人都可以读到你的数字签名消息,但只有那些与你交换密钥的人才可以读取加密消息。切记千万不要与他人分享你的密钥!只能分享公钥。
|
||||
|
||||
Seahorse是GnuPG对应的GNOME图形化前端,KGpg是KDE图形化的GnuPG工具。
|
||||
|
||||
现在我们执行生成和管理GunPG密钥的基本步骤。这个命令生成一个新的密钥:
|
||||
|
||||
$ gpg --gen-key
|
||||
|
||||
这个过程有许多步骤;对于大部分人来说,只需要回答所有的问题,遵循默认设置就好。当你生成你的密钥时,记下来并将其保存在一个安全的地方,因为如果你丢掉了它,你就不能解密任何消息了。任何关于不要写下密码的建议都是错误的。我们中的大部分人要记住许多登录名和密码,包括那些我们几乎从来不会用到的,所以全部记住它们是不现实的。你知道当人们不写下他们的密码时会发生什么吗?他们会选择生成简单的密码并不断重复使用。你存储在电脑里的任何东西都潜在地会被攻击窃取;一个保存在上锁的柜子里的小本是无法通过渗透获取的,除了物理的入侵,当然入侵者要知道如何去寻找它。
|
||||
|
||||
我必须叮嘱你们去弄清楚如何使用新密钥去配置邮件客户端,因为每一个都不同。你可以按照如下操作列出你的密钥:
|
||||
|
||||
$ gpg --list-keys
|
||||
/home/carla/.gnupg/pubring.gpg
|
||||
------------------------------
|
||||
pub 2048R/587DD0F5 2014-08-13
|
||||
uid Carla Schroder (my gpg key)
|
||||
sub 2048R/AE05E1E4 2014-08-13
|
||||
|
||||
这能快速地获知像密钥的位置、名称(也就是UID)等必要信息。假设你想要把公钥上传到密钥服务器,可以参考实例操作:
|
||||
|
||||
$ gpg --send-keys 'Carla Schroder' --keyserver http://example.com
|
||||
|
||||
当你为上传到公钥服务器生成了一个新的密钥,你也应该生成一个撤销证书。不要推迟到以后做———当你生成新密钥时就生成它。你可以给它取任意的名称,比如使用一个像mycodeproject.asc的描述性名称来代替revoke.asc:
|
||||
|
||||
$ gpg --output revoke.asc --gen-revoke 'Carla Schroder'
|
||||
|
||||
如果你的密钥缺乏抵抗力,你可以通过向keyring导入撤销证书来撤销它:
|
||||
|
||||
$ gpg --import ~/.gnupg/revoke.asc
|
||||
|
||||
然后生成并上传一个新的密钥来取代它。当它们更新到密钥数据库时,所有使用旧密钥的用户都会被通知。
|
||||
|
||||
你必须像保护私钥一样保护撤销证书。将它拷贝到CD或USB存储器中,并加锁,然后从电脑中删除。这是明文密钥,所以你甚至可以将它打印出来。
|
||||
|
||||
如果你需要一份复制粘贴的密钥,比如在允许将密钥粘贴到网页表格中的公用keyring中,或者是想将公钥发布到个人站点上,那么你必须生成一份公钥的ASCII-armored版本:
|
||||
|
||||
$ gpg --output carla-pubkey.asc --export -a 'Carla Schroder'
|
||||
|
||||
这会生成可见的明文公钥,就像下面这个小例子:
|
||||
|
||||
-----BEGIN PGP PUBLIC KEY BLOCK-----
|
||||
Version: GnuPG v1
|
||||
mQENBFPrn4gBCADeEXKdrDOV3AFXL7QQQ+i61rMOZKwFTxlJlNbAVczpawkWRC3l
|
||||
IrWeeJiy2VyoMQ2ZXpBLDwGEjVQ5H7/UyjUsP8h2ufIJt01NO1pQJMwaOMcS5yTS
|
||||
[...]
|
||||
I+LNrbP23HEvgAdNSBWqa8MaZGUWBietQP7JsKjmE+ukalm8jY8mdWDyS4nMhZY=
|
||||
=QL65
|
||||
-----END PGP PUBLIC KEY BLOCK-----
|
||||
|
||||
相信上面的教程应该使你学会如何使用GnuPG。如果不够,[The GnuPG manuals][9]上有使用GnuPG和相关全部配置的详细信息。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linux.com/learn/tutorials/784165-how-to-encrypt-email-in-linux
|
||||
|
||||
作者:[Carla Schroder][a]
|
||||
译者:[KayGuoWhu](https://github.com/KayGuoWhu)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.linux.com/component/ninjaboard/person/3734
|
||||
[1]:http://www.openpgp.org/members/gnupg.shtml
|
||||
[2]:https://www.torproject.org/
|
||||
[3]:https://www.virtru.com/
|
||||
[4]:https://www.safemess.com/
|
||||
[5]:http://retroshare.sourceforge.net/
|
||||
[6]:http://retroshare.sourceforge.net/
|
||||
[7]:https://protonmail.ch/
|
||||
[8]:http://www.linux.com/learn/docs/718398-protect-yourself-online-with-tor-+tails-and-debian
|
||||
[9]:https://www.gnupg.org/documentation/manuals.html
|
||||
@ -0,0 +1,116 @@
|
||||
数据库常见问题答案--如何使用命令行创建一个MySQL数据库
|
||||
===
|
||||
|
||||
> **问题**:在一个某处运行的MySQL服务器上,我该怎样通过命令行创建和安装一个MySQL数据库呢?
|
||||
|
||||
|
||||
为了能通过命令行创建一个MySQL数据库,你可以使用mysql命令行客户端。下面是通过mysql命令行客户端创建和安装MySQL的步骤。
|
||||
|
||||
### 第一步:安装MySQL客户端 ###
|
||||
|
||||
当然你得确保MySQL客户端已经安装完毕。如果没有的话,可以按照下面的方法。
|
||||
|
||||
在Debian,Ubuntu 或者 Linux Mint上:
|
||||
|
||||
$ sudo apt-get install mysql-client
|
||||
|
||||
在Fedora,CentOS 或者 RHEL上:
|
||||
|
||||
$ sudo apt-get install mysql
|
||||
|
||||
### 第二步:登陆到MySQL服务器 ###
|
||||
|
||||
首先,你需要使用root用户登陆进你的MySQL数据库,如下:
|
||||
|
||||
$ mysql -u root -h <mysql-server-ip-address> -p
|
||||
|
||||
请注意:为了能登进远程的MySQL服务器,你需要[开启服务器上的远程访问][1],如果你想调用同一主机上的MySQL服务器,你可以省略 "-h <mysql-server-ip-address>" 参数
|
||||
|
||||
$ mysql -u root -p
|
||||
|
||||
你将需要输入MySQL服务器的密码,如果认证成功,MySQL提示将会出现。
|
||||
|
||||

|
||||
|
||||
### 第三步:创建一个MySQL数据库 ###
|
||||
|
||||
在MySQL提示中输入命令之前,请记住所有的命令都是以分号结束的(否则将不会执行)。另外,考虑输入命令的时候使用大些字母,输入数据库对象使用小写字母。但那不是必须的,只是方便你的阅读。
|
||||
|
||||
现在,让我们创建一个叫做xmodulo_DB的数据库:
|
||||
|
||||
mysql> CREATE DATABASE IF NOT EXISTS xmodulo_DB;
|
||||
|
||||

|
||||
|
||||
### 第四步:创建一个数据库表 ###
|
||||
|
||||
为了达到演示的目的,我们将会创建一个叫做posts_tbl的表,表里会存储关于文章的如下信息:
|
||||
|
||||
- 文章的标题
|
||||
- 作者的第一个名字
|
||||
- 作者的最后一个名字
|
||||
- 文章可用或者不可用
|
||||
- 文章创建的日期
|
||||
|
||||
这个过程分两步执行:
|
||||
|
||||
首先,选择我们需要使用的数据库:
|
||||
|
||||
mysql> USE xmodulo_DB;
|
||||
|
||||
然后,在数据库中创建新表:
|
||||
|
||||
mysql> CREATE TABLE 'posts_tbl' (
|
||||
'post_id' INT UNSIGNED NOT NULL AUTO_INCREMENT,
|
||||
'content' TEXT,
|
||||
'author_FirstName' VARCHAR(100) NOT NULL,
|
||||
'author_LastName' VARCHAR(50) DEFAULT NULL ,
|
||||
'isEnabled' TINYINT(1) NOT NULL DEFAULT 1,
|
||||
'date' TIMESTAMP NOT NULL DEFAULT CURRENT_TIMESTAMP ,
|
||||
PRIMARY KEY ( 'post_id' )
|
||||
) TYPE = MYISAM;
|
||||
|
||||

|
||||
|
||||
### 第五步:创建一个用户,并授予权限 ###
|
||||
|
||||
当涉及到访问我们新创的数据库和表的时候,创建一个新用户是一个很好的主意。这样做就可以让用户在没有整个MySQL服务器权限的情况下,去访问那个数据库(而且只能是那个数据库)
|
||||
|
||||
你可以创建新用户,授予权限,并且使改变生效:
|
||||
|
||||
mysql> GRANT ALL PRIVILEGES ON xmodulo_DB.* TO 'new_user'@'%' IDENTIFIED BY 'new_password';
|
||||
mysql> FLUSH PRIVILEGES;
|
||||
|
||||
'new_user'和'new_password'分别指的是新的用户名和他的密码。这条信息将会被保存在mysql.user表中,而且密码会被加密。
|
||||
|
||||
### 第六步:测试 ###
|
||||
|
||||
让我们插入一个虚拟的记录到posts_tbl表:
|
||||
|
||||
mysql> USE xmodulo_DB;
|
||||
mysql> INSERT INTO posts_tbl (content, author_FirstName, author_Las tName)
|
||||
VALUES ('Hi! This is some dummy text.', 'Gabriel', 'Canepa');
|
||||
|
||||
然后查看posts_tbl表中的所有记录:
|
||||
|
||||
mysql> SELECT * FROM posts_tbl;
|
||||
|
||||

|
||||
|
||||
注意:MySQL会在我们先前定义的地方自动插入适当的默认值(比如,'isEnabled'和'date')。
|
||||
|
||||
---
|
||||
|
||||
via: http://ask.xmodulo.com/create-mysql-database-command-line.html
|
||||
|
||||
译者:[su-kaiyao](https://github.com/su-kaiyao)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linu
|
||||
x中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://xmodulo.com/2012/06/how-to-allow-remote-access-to-mysql.html
|
||||
|
||||
|
||||
|
||||
|
||||
@ -0,0 +1,103 @@
|
||||
使用Linux命令行嗅探HTTP流量
|
||||
================================================================================
|
||||
假设由于某种原因,你需要嗅探HTTP站点的流量(如HTTP请求与响应)。举个例子,你可能在测试一个web服务器的实验性功能,或者 你在为某个web应用或RESTful服务排错,又或者你正在为PAC排错或寻找某个站点下载的恶意软件。不论什么原因,在这些情况下,进行HTTP流量嗅探对于系统管理、开发者、甚至最终用户来说都是很有帮助的。
|
||||
|
||||
数据包嗅工具tcpdump被广泛用于实时数据包的导出,但是你需要设置过滤规则来捕获HTTP流量,甚至它的原始输出通常不能方便的停 在HTTP协议层。实时web服务器日志解析器如[ngxtop][3]提供可读的实时web流量跟踪痕迹,但这仅适用于可完全访问live web服务器日志的情况。
|
||||
|
||||
要是有一个仅用于抓取HTTP流量的类tcpdump的数据包嗅探工具就非常好了。事实上,[httpry][4]就是:**HTTP包嗅探工具**。httpry捕获HTTP数据包,并且将HTTP协议层的数据内容以可读形式列举出来。通过这篇指文章,让我们了解如何使用httpry工具嗅探HTTP流 量。
|
||||
|
||||
###在Linux上安装httpry###
|
||||
|
||||
在基于Debian系统(Ubuntu 或 LinuxMint),基础仓库中没有httpry安装包(译者注:本人ubuntu14.04,仓库中已有包,可直接安装)。所以我们需要通过源码安装:
|
||||
|
||||
$ sudo apt-get install gcc make git libpcap0.8-dev
|
||||
$ git clone https://github.com/jbittel/httpry.git
|
||||
$ cd httpry
|
||||
$ make
|
||||
$ sudo make install
|
||||
|
||||
在Fedora,CentOS 或 RHEL系统,可以使用如下yum命令安装httpry。在CentOS/RHEL系统上,运行yum之前使能[EPEL repo][5]。
|
||||
|
||||
$ sudo yum install httpry
|
||||
|
||||
如果逆向通过源码来构httpry的话,你可以通过这几个步骤实现:
|
||||
|
||||
$ sudo yum install gcc make git libpcap-devel
|
||||
$ git clone https://github.com/jbittel/httpry.git
|
||||
$ cd httpry
|
||||
$ make
|
||||
$ sudo make install
|
||||
|
||||
###httpry的基本用法###
|
||||
|
||||
以下是httpry的基本用法
|
||||
|
||||
$ sudo httpry -i <network-interface>
|
||||
|
||||
httpry就会监听指定的网络接口,并且实时的显示捕获到的HTTP 请求/响。
|
||||
|
||||

|
||||
|
||||
在大多数情况下,由于发送与接到的数据包过多导致刷屏很快,难以分析。这时候你肯定想将捕获到的数据包保存下来以离线分析。可以使用'b'或'-o'选项保存数据包。'-b'选项将数据包以二进制文件的形式保存下来,这样可以使用httpry软件打开文件以浏览。另 一方面,'-o'选项将数据以可读的字符文件形式保存下来。
|
||||
|
||||
以二进制形式保存文件:
|
||||
|
||||
$ sudo httpry -i eth0 -b output.dump
|
||||
|
||||
浏览所保存的HTTP数据包文件:
|
||||
|
||||
$ httpry -r output.dump
|
||||
|
||||
注意,不需要根用户权限就可以使用'-r'选项读取数据文件。
|
||||
|
||||
将httpry数据以字符文件保存:
|
||||
|
||||
$ sudo httpry -i eth0 -o output.txt
|
||||
|
||||
###httpry 的高级应用###
|
||||
|
||||
如果你想监视指定的HTTP方法(如:GET,POST,PUT,HEAD,CONNECT等),使用'-m'选项:
|
||||
|
||||
$ sudo httpry -i eth0 -m get,head
|
||||
|
||||

|
||||
|
||||
如果你下载了httpry的源码,你会发现源码下有一系Perl脚本,这些脚本用于分析httpry输出。脚本位于目录httpry/scripts/plugins。如果你想写一个定制的httpry输出分析器,则这些脚可以作为很好的例子。其中一些有如下的功能:
|
||||
|
||||
- **hostnames**: 显示唯一主机名列表.
|
||||
- **find_proxies**: 探测web代理.
|
||||
- **search_terms**: 查找及计算输入检索服务的检索词。
|
||||
- **content_analysis**: 查找含有指定关键的URL。
|
||||
- **xml_output**: 将输出转换为XML形式。
|
||||
- **log_summary**: 生成日志摘要。
|
||||
- **db_dump**: 将日志文件数据保存数据库。
|
||||
|
||||
在使用这些脚本之前,首先使用'-o'选项运行httpry。当获取到输出文件后,立即使用如下命令执行脚本:
|
||||
|
||||
$ cd httpry/scripts
|
||||
$ perl parse_log.pl -d ./plugins <httpry-output-file>
|
||||
|
||||
你可能在使用插件的时候遇到警告。比如,如果你没有安装带有DBI接口的MySQL数据库那么使用db_dump插件时可能会失败。如果一个 插件初始化失败的话,那么这个插件不能使用。所以你可以忽略那些警告。
|
||||
|
||||
当parse_log.pl完成后,你将在httpry/scripts 目录下看到数个分析结果。例如,log_summary.txt 与如下内容类似。
|
||||
|
||||

|
||||
|
||||
总结,当你要分析HTTP数据包的时候,httpry非常有用。它可能并不被大多Linux使用着所熟知,但会用总是有好处的。你对这个工具有什么看法呢?
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/2014/08/sniff-http-traffic-command-line-linux.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[DoubleC](https://github.com/DoubleC)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/nanni
|
||||
[1]:http://xmodulo.com/2012/12/how-to-set-up-proxy-auto-config-on-ubuntu-desktop.html
|
||||
[2]:http://xmodulo.com/2012/11/what-are-popular-packet-sniffers-on-linux.html
|
||||
[3]:http://xmodulo.com/2014/06/monitor-nginx-web-server-command-line-real-time.html
|
||||
[4]:http://dumpsterventures.com/jason/httpry/
|
||||
[5]:http://xmodulo.com/2013/03/how-to-set-up-epel-repository-on-centos.html
|
||||
Loading…
Reference in New Issue
Block a user