mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-02-28 01:01:09 +08:00
Merge remote-tracking branch 'LCTT/master'
This commit is contained in:
commit
d2300de281
189
published/20150708 Choosing a Linux Tracer (2015).md
Normal file
189
published/20150708 Choosing a Linux Tracer (2015).md
Normal file
@ -0,0 +1,189 @@
|
|||||||
|
Linux 跟踪器之选
|
||||||
|
======
|
||||||
|
|
||||||
|
[![][1]][2]
|
||||||
|
|
||||||
|
> Linux 跟踪很神奇!
|
||||||
|
|
||||||
|
<ruby>跟踪器<rt>tracer</rt></ruby>是一个高级的性能分析和调试工具,如果你使用过 `strace(1)` 或者 `tcpdump(8)`,你不应该被它吓到 ... 你使用的就是跟踪器。系统跟踪器能让你看到很多的东西,而不仅是系统调用或者数据包,因为常见的跟踪器都可以跟踪内核或者应用程序的任何东西。
|
||||||
|
|
||||||
|
有大量的 Linux 跟踪器可供你选择。由于它们中的每个都有一个官方的(或者非官方的)的吉祥物,我们有足够多的选择给孩子们展示。
|
||||||
|
|
||||||
|
你喜欢使用哪一个呢?
|
||||||
|
|
||||||
|
我从两类读者的角度来回答这个问题:大多数人和性能/内核工程师。当然,随着时间的推移,这也可能会发生变化,因此,我需要及时去更新本文内容,或许是每年一次,或者更频繁。(LCTT 译注:本文最后更新于 2015 年)
|
||||||
|
|
||||||
|
### 对于大多数人
|
||||||
|
|
||||||
|
大多数人(开发者、系统管理员、运维人员、网络可靠性工程师(SRE)…)是不需要去学习系统跟踪器的底层细节的。以下是你需要去了解和做的事情:
|
||||||
|
|
||||||
|
#### 1. 使用 perf_events 进行 CPU 剖析
|
||||||
|
|
||||||
|
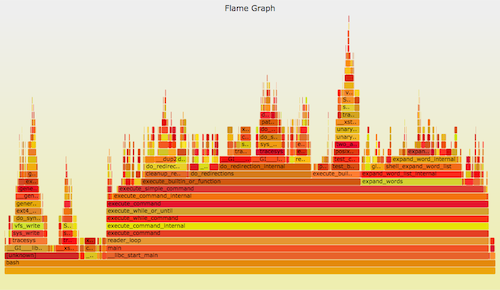
可以使用 perf_events 进行 CPU <ruby>剖析<rt>profiling</rt></ruby>。它可以用一个 [火焰图][3] 来形象地表示。比如:
|
||||||
|
|
||||||
|
```
|
||||||
|
git clone --depth 1 https://github.com/brendangregg/FlameGraph
|
||||||
|
perf record -F 99 -a -g -- sleep 30
|
||||||
|
perf script | ./FlameGraph/stackcollapse-perf.pl | ./FlameGraph/flamegraph.pl > perf.svg
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
Linux 的 perf_events(即 `perf`,后者是它的命令)是官方为 Linux 用户准备的跟踪器/分析器。它位于内核源码中,并且维护的非常好(而且现在它的功能还在快速变强)。它一般是通过 linux-tools-common 这个包来添加的。
|
||||||
|
|
||||||
|
`perf` 可以做的事情很多,但是,如果我只能建议你学习其中的一个功能的话,那就是 CPU 剖析。虽然从技术角度来说,这并不是事件“跟踪”,而是<ruby>采样<rt>sampling</rt></ruby>。最难的部分是获得完整的栈和符号,这部分在我的 [Linux Profiling at Netflix][4] 中针对 Java 和 Node.js 讨论过。
|
||||||
|
|
||||||
|
#### 2. 知道它能干什么
|
||||||
|
|
||||||
|
正如一位朋友所说的:“你不需要知道 X 光机是如何工作的,但你需要明白的是,如果你吞下了一个硬币,X 光机是你的一个选择!”你需要知道使用跟踪器能够做什么,因此,如果你在业务上确实需要它,你可以以后再去学习它,或者请会使用它的人来做。
|
||||||
|
|
||||||
|
简单地说:几乎任何事情都可以通过跟踪来了解它。内部文件系统、TCP/IP 处理过程、设备驱动、应用程序内部情况。阅读我在 lwn.net 上的 [ftrace][5] 的文章,也可以去浏览 [perf_events 页面][6],那里有一些跟踪(和剖析)能力的示例。
|
||||||
|
|
||||||
|
#### 3. 需要一个前端工具
|
||||||
|
|
||||||
|
如果你要购买一个性能分析工具(有许多公司销售这类产品),并要求支持 Linux 跟踪。想要一个直观的“点击”界面去探查内核的内部,以及包含一个在不同堆栈位置的延迟热力图。就像我在 [Monitorama 演讲][7] 中描述的那样。
|
||||||
|
|
||||||
|
我创建并开源了我自己的一些前端工具,虽然它是基于 CLI 的(不是图形界面的)。这样可以使其它人使用跟踪器更快更容易。比如,我的 [perf-tools][8],跟踪新进程是这样的:
|
||||||
|
|
||||||
|
```
|
||||||
|
# ./execsnoop
|
||||||
|
Tracing exec()s. Ctrl-C to end.
|
||||||
|
PID PPID ARGS
|
||||||
|
22898 22004 man ls
|
||||||
|
22905 22898 preconv -e UTF-8
|
||||||
|
22908 22898 pager -s
|
||||||
|
22907 22898 nroff -mandoc -rLL=164n -rLT=164n -Tutf8
|
||||||
|
[...]
|
||||||
|
```
|
||||||
|
|
||||||
|
在 Netflix 公司,我正在开发 [Vector][9],它是一个实例分析工具,实际上它也是一个 Linux 跟踪器的前端。
|
||||||
|
|
||||||
|
### 对于性能或者内核工程师
|
||||||
|
|
||||||
|
一般来说,我们的工作都非常难,因为大多数人或许要求我们去搞清楚如何去跟踪某个事件,以及因此需要选择使用哪个跟踪器。为完全理解一个跟踪器,你通常需要花至少一百多个小时去使用它。理解所有的 Linux 跟踪器并能在它们之间做出正确的选择是件很难的事情。(我或许是唯一接近完成这件事的人)
|
||||||
|
|
||||||
|
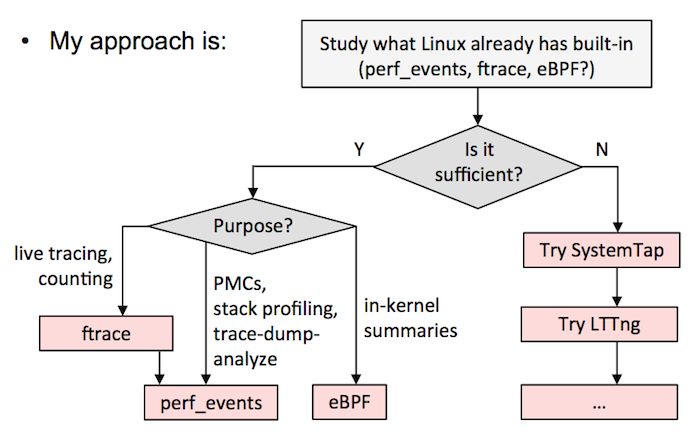
在这里我建议选择如下,要么:
|
||||||
|
|
||||||
|
A)选择一个全能的跟踪器,并以它为标准。这需要在一个测试环境中花大量的时间来搞清楚它的细微差别和安全性。我现在的建议是 SystemTap 的最新版本(例如,从 [源代码][10] 构建)。我知道有的公司选择的是 LTTng ,尽管它并不是很强大(但是它很安全),但他们也用的很好。如果在 `sysdig` 中添加了跟踪点或者是 kprobes,它也是另外的一个候选者。
|
||||||
|
|
||||||
|
B)按我的 [Velocity 教程中][11] 的流程图。这意味着尽可能使用 ftrace 或者 perf_events,eBPF 已经集成到内核中了,然后用其它的跟踪器,如 SystemTap/LTTng 作为对 eBPF 的补充。我目前在 Netflix 的工作中就是这么做的。
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
以下是我对各个跟踪器的评价:
|
||||||
|
|
||||||
|
#### 1. ftrace
|
||||||
|
|
||||||
|
我爱 [ftrace][12],它是内核黑客最好的朋友。它被构建进内核中,它能够利用跟踪点、kprobes、以及 uprobes,以提供一些功能:使用可选的过滤器和参数进行事件跟踪;事件计数和计时,内核概览;<ruby>函数流步进<rt>function-flow walking</rt></ruby>。关于它的示例可以查看内核源代码树中的 [ftrace.txt][13]。它通过 `/sys` 来管理,是面向单一的 root 用户的(虽然你可以使用缓冲实例以让其支持多用户),它的界面有时很繁琐,但是它比较容易<ruby>调校<rt>hackable</rt></ruby>,并且有个前端:ftrace 的主要创建者 Steven Rostedt 设计了一个 trace-cmd,而且我也创建了 perf-tools 集合。我最诟病的就是它不是<ruby>可编程的<rt>programmable</rt></ruby>,因此,举个例子说,你不能保存和获取时间戳、计算延迟,以及将其保存为直方图。你需要转储事件到用户级以便于进行后期处理,这需要花费一些成本。它也许可以通过 eBPF 实现可编程。
|
||||||
|
|
||||||
|
#### 2. perf_events
|
||||||
|
|
||||||
|
[perf_events][14] 是 Linux 用户的主要跟踪工具,它的源代码位于 Linux 内核中,一般是通过 linux-tools-common 包来添加的。它又称为 `perf`,后者指的是它的前端,它相当高效(动态缓存),一般用于跟踪并转储到一个文件中(perf.data),然后可以在之后进行后期处理。它可以做大部分 ftrace 能做的事情。它不能进行函数流步进,并且不太容易调校(而它的安全/错误检查做的更好一些)。但它可以做剖析(采样)、CPU 性能计数、用户级的栈转换、以及使用本地变量利用<ruby>调试信息<rt>debuginfo</rt></ruby>进行<ruby>行级跟踪<rt>line tracing</rt></ruby>。它也支持多个并发用户。与 ftrace 一样,它也不是内核可编程的,除非 eBPF 支持(补丁已经在计划中)。如果只学习一个跟踪器,我建议大家去学习 perf,它可以解决大量的问题,并且它也相当安全。
|
||||||
|
|
||||||
|
#### 3. eBPF
|
||||||
|
|
||||||
|
<ruby>扩展的伯克利包过滤器<rt>extended Berkeley Packet Filter</rt></ruby>(eBPF)是一个<ruby>内核内<rt>in-kernel</rt></ruby>的虚拟机,可以在事件上运行程序,它非常高效(JIT)。它可能最终为 ftrace 和 perf_events 提供<ruby>内核内编程<rt>in-kernel programming</rt></ruby>,并可以去增强其它跟踪器。它现在是由 Alexei Starovoitov 开发的,还没有实现完全的整合,但是对于一些令人印象深刻的工具,有些内核版本(比如,4.1)已经支持了:比如,块设备 I/O 的<ruby>延迟热力图<rt>latency heat map</rt></ruby>。更多参考资料,请查阅 Alexei 的 [BPF 演示][15],和它的 [eBPF 示例][16]。
|
||||||
|
|
||||||
|
#### 4. SystemTap
|
||||||
|
|
||||||
|
[SystemTap][17] 是一个非常强大的跟踪器。它可以做任何事情:剖析、跟踪点、kprobes、uprobes(它就来自 SystemTap)、USDT、内核内编程等等。它将程序编译成内核模块并加载它们 —— 这是一种很难保证安全的方法。它开发是在内核代码树之外进行的,并且在过去出现过很多问题(内核崩溃或冻结)。许多并不是 SystemTap 的过错 —— 它通常是首次对内核使用某些跟踪功能,并率先遇到 bug。最新版本的 SystemTap 是非常好的(你需要从它的源代码编译),但是,许多人仍然没有从早期版本的问题阴影中走出来。如果你想去使用它,花一些时间去测试环境,然后,在 irc.freenode.net 的 #systemtap 频道与开发者进行讨论。(Netflix 有一个容错架构,我们使用了 SystemTap,但是我们或许比起你来说,更少担心它的安全性)我最诟病的事情是,它似乎假设你有办法得到内核调试信息,而我并没有这些信息。没有它我实际上可以做很多事情,但是缺少相关的文档和示例(我现在自己开始帮着做这些了)。
|
||||||
|
|
||||||
|
#### 5. LTTng
|
||||||
|
|
||||||
|
[LTTng][18] 对事件收集进行了优化,性能要好于其它的跟踪器,也支持许多的事件类型,包括 USDT。它的开发是在内核代码树之外进行的。它的核心部分非常简单:通过一个很小的固定指令集写入事件到跟踪缓冲区。这样让它既安全又快速。缺点是做内核内编程不太容易。我觉得那不是个大问题,由于它优化的很好,可以充分的扩展,尽管需要后期处理。它也探索了一种不同的分析技术。很多的“黑匣子”记录了所有感兴趣的事件,以便可以在 GUI 中以后分析它。我担心该记录会错失之前没有预料的事件,我真的需要花一些时间去看看它在实践中是如何工作的。这个跟踪器上我花的时间最少(没有特别的原因)。
|
||||||
|
|
||||||
|
#### 6. ktap
|
||||||
|
|
||||||
|
[ktap][19] 是一个很有前途的跟踪器,它在内核中使用了一个 lua 虚拟机,不需要调试信息和在嵌入时设备上可以工作的很好。这使得它进入了人们的视野,在某个时候似乎要成为 Linux 上最好的跟踪器。然而,由于 eBPF 开始集成到了内核,而 ktap 的集成工作被推迟了,直到它能够使用 eBPF 而不是它自己的虚拟机。由于 eBPF 在几个月过去之后仍然在集成过程中,ktap 的开发者已经等待了很长的时间。我希望在今年的晚些时间它能够重启开发。
|
||||||
|
|
||||||
|
#### 7. dtrace4linux
|
||||||
|
|
||||||
|
[dtrace4linux][20] 主要由一个人(Paul Fox)利用业务时间将 Sun DTrace 移植到 Linux 中的。它令人印象深刻,一些<ruby>供应器<rt>provider</rt></ruby>可以工作,还不是很完美,它最多应该算是实验性的工具(不安全)。我认为对于许可证的担心,使人们对它保持谨慎:它可能永远也进入不了 Linux 内核,因为 Sun 是基于 CDDL 许可证发布的 DTrace;Paul 的方法是将它作为一个插件。我非常希望看到 Linux 上的 DTrace,并且希望这个项目能够完成,我想我加入 Netflix 时将花一些时间来帮它完成。但是,我一直在使用内置的跟踪器 ftrace 和 perf_events。
|
||||||
|
|
||||||
|
#### 8. OL DTrace
|
||||||
|
|
||||||
|
[Oracle Linux DTrace][21] 是将 DTrace 移植到 Linux (尤其是 Oracle Linux)的重大努力。过去这些年的许多发布版本都一直稳定的进步,开发者甚至谈到了改善 DTrace 测试套件,这显示出这个项目很有前途。许多有用的功能已经完成:系统调用、剖析、sdt、proc、sched、以及 USDT。我一直在等待着 fbt(函数边界跟踪,对内核的动态跟踪),它将成为 Linux 内核上非常强大的功能。它最终能否成功取决于能否吸引足够多的人去使用 Oracle Linux(并为支持付费)。另一个羁绊是它并非完全开源的:内核组件是开源的,但用户级代码我没有看到。
|
||||||
|
|
||||||
|
#### 9. sysdig
|
||||||
|
|
||||||
|
[sysdig][22] 是一个很新的跟踪器,它可以使用类似 `tcpdump` 的语法来处理<ruby>系统调用<rt>syscall</rt></ruby>事件,并用 lua 做后期处理。它也是令人印象深刻的,并且很高兴能看到在系统跟踪领域的创新。它的局限性是,它的系统调用只能是在当时,并且,它转储所有事件到用户级进行后期处理。你可以使用系统调用来做许多事情,虽然我希望能看到它去支持跟踪点、kprobes、以及 uprobes。我也希望看到它支持 eBPF 以查看内核内概览。sysdig 的开发者现在正在增加对容器的支持。可以关注它的进一步发展。
|
||||||
|
|
||||||
|
### 深入阅读
|
||||||
|
|
||||||
|
我自己的工作中使用到的跟踪器包括:
|
||||||
|
|
||||||
|
- **ftrace** : 我的 [perf-tools][8] 集合(查看示例目录);我的 lwn.net 的 [ftrace 跟踪器的文章][5]; 一个 [LISA14][8] 演讲;以及帖子: [函数计数][23]、 [iosnoop][24]、 [opensnoop][25]、 [execsnoop][26]、 [TCP retransmits][27]、 [uprobes][28] 和 [USDT][29]。
|
||||||
|
- **perf_events** : 我的 [perf_events 示例][6] 页面;在 SCALE 的一个 [Linux Profiling at Netflix][4] 演讲;和帖子:[CPU 采样][30]、[静态跟踪点][31]、[热力图][32]、[计数][33]、[内核行级跟踪][34]、[off-CPU 时间火焰图][35]。
|
||||||
|
- **eBPF** : 帖子 [eBPF:一个小的进步][36],和一些 [BPF-tools][37] (我需要发布更多)。
|
||||||
|
- **SystemTap** : 很久以前,我写了一篇 [使用 SystemTap][38] 的文章,它有点过时了。最近我发布了一些 [systemtap-lwtools][39],展示了在没有内核调试信息的情况下,SystemTap 是如何使用的。
|
||||||
|
- **LTTng** : 我使用它的时间很短,不足以发布什么文章。
|
||||||
|
- **ktap** : 我的 [ktap 示例][40] 页面包括一行程序和脚本,虽然它是早期的版本。
|
||||||
|
- **dtrace4linux** : 在我的 [系统性能][41] 书中包含了一些示例,并且在过去我为了某些事情开发了一些小的修补,比如, [timestamps][42]。
|
||||||
|
- **OL DTrace** : 因为它是对 DTrace 的直接移植,我早期 DTrace 的工作大多与之相关(链接太多了,可以去 [我的主页][43] 上搜索)。一旦它更加完美,我可以开发很多专用工具。
|
||||||
|
- **sysdig** : 我贡献了 [fileslower][44] 和 [subsecond offset spectrogram][45] 的 chisel。
|
||||||
|
- **其它** : 关于 [strace][46],我写了一些告诫文章。
|
||||||
|
|
||||||
|
不好意思,没有更多的跟踪器了! … 如果你想知道为什么 Linux 中的跟踪器不止一个,或者关于 DTrace 的内容,在我的 [从 DTrace 到 Linux][47] 的演讲中有答案,从 [第 28 张幻灯片][48] 开始。
|
||||||
|
|
||||||
|
感谢 [Deirdre Straughan][49] 的编辑,以及跟踪小马的创建(General Zoi 是小马的创建者)。
|
||||||
|
|
||||||
|
--------------------------------------------------------------------------------
|
||||||
|
|
||||||
|
via: http://www.brendangregg.com/blog/2015-07-08/choosing-a-linux-tracer.html
|
||||||
|
|
||||||
|
作者:[Brendan Gregg][a]
|
||||||
|
译者:[qhwdw](https://github.com/qhwdw)
|
||||||
|
校对:[wxy](https://github.com/wxy)
|
||||||
|
|
||||||
|
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||||
|
|
||||||
|
[a]:http://www.brendangregg.com
|
||||||
|
[1]:http://www.brendangregg.com/blog/images/2015/tracing_ponies.png
|
||||||
|
[2]:http://www.slideshare.net/brendangregg/velocity-2015-linux-perf-tools/105
|
||||||
|
[3]:http://www.brendangregg.com/FlameGraphs/cpuflamegraphs.html
|
||||||
|
[4]:http://www.brendangregg.com/blog/2015-02-27/linux-profiling-at-netflix.html
|
||||||
|
[5]:http://lwn.net/Articles/608497/
|
||||||
|
[6]:http://www.brendangregg.com/perf.html
|
||||||
|
[7]:http://www.brendangregg.com/blog/2015-06-23/netflix-instance-analysis-requirements.html
|
||||||
|
[8]:http://www.brendangregg.com/blog/2015-03-17/linux-performance-analysis-perf-tools.html
|
||||||
|
[9]:http://techblog.netflix.com/2015/04/introducing-vector-netflixs-on-host.html
|
||||||
|
[10]:https://sourceware.org/git/?p=systemtap.git;a=blob_plain;f=README;hb=HEAD
|
||||||
|
[11]:http://www.slideshare.net/brendangregg/velocity-2015-linux-perf-tools
|
||||||
|
[12]:http://lwn.net/Articles/370423/
|
||||||
|
[13]:https://www.kernel.org/doc/Documentation/trace/ftrace.txt
|
||||||
|
[14]:https://perf.wiki.kernel.org/index.php/Main_Page
|
||||||
|
[15]:http://www.phoronix.com/scan.php?page=news_item&px=BPF-Understanding-Kernel-VM
|
||||||
|
[16]:https://github.com/torvalds/linux/tree/master/samples/bpf
|
||||||
|
[17]:https://sourceware.org/systemtap/wiki
|
||||||
|
[18]:http://lttng.org/
|
||||||
|
[19]:http://ktap.org/
|
||||||
|
[20]:https://github.com/dtrace4linux/linux
|
||||||
|
[21]:http://docs.oracle.com/cd/E37670_01/E38608/html/index.html
|
||||||
|
[22]:http://www.sysdig.org/
|
||||||
|
[23]:http://www.brendangregg.com/blog/2014-07-13/linux-ftrace-function-counting.html
|
||||||
|
[24]:http://www.brendangregg.com/blog/2014-07-16/iosnoop-for-linux.html
|
||||||
|
[25]:http://www.brendangregg.com/blog/2014-07-25/opensnoop-for-linux.html
|
||||||
|
[26]:http://www.brendangregg.com/blog/2014-07-28/execsnoop-for-linux.html
|
||||||
|
[27]:http://www.brendangregg.com/blog/2014-09-06/linux-ftrace-tcp-retransmit-tracing.html
|
||||||
|
[28]:http://www.brendangregg.com/blog/2015-06-28/linux-ftrace-uprobe.html
|
||||||
|
[29]:http://www.brendangregg.com/blog/2015-07-03/hacking-linux-usdt-ftrace.html
|
||||||
|
[30]:http://www.brendangregg.com/blog/2014-06-22/perf-cpu-sample.html
|
||||||
|
[31]:http://www.brendangregg.com/blog/2014-06-29/perf-static-tracepoints.html
|
||||||
|
[32]:http://www.brendangregg.com/blog/2014-07-01/perf-heat-maps.html
|
||||||
|
[33]:http://www.brendangregg.com/blog/2014-07-03/perf-counting.html
|
||||||
|
[34]:http://www.brendangregg.com/blog/2014-09-11/perf-kernel-line-tracing.html
|
||||||
|
[35]:http://www.brendangregg.com/blog/2015-02-26/linux-perf-off-cpu-flame-graph.html
|
||||||
|
[36]:http://www.brendangregg.com/blog/2015-05-15/ebpf-one-small-step.html
|
||||||
|
[37]:https://github.com/brendangregg/BPF-tools
|
||||||
|
[38]:http://dtrace.org/blogs/brendan/2011/10/15/using-systemtap/
|
||||||
|
[39]:https://github.com/brendangregg/systemtap-lwtools
|
||||||
|
[40]:http://www.brendangregg.com/ktap.html
|
||||||
|
[41]:http://www.brendangregg.com/sysperfbook.html
|
||||||
|
[42]:https://github.com/dtrace4linux/linux/issues/55
|
||||||
|
[43]:http://www.brendangregg.com
|
||||||
|
[44]:https://github.com/brendangregg/sysdig/commit/d0eeac1a32d6749dab24d1dc3fffb2ef0f9d7151
|
||||||
|
[45]:https://github.com/brendangregg/sysdig/commit/2f21604dce0b561407accb9dba869aa19c365952
|
||||||
|
[46]:http://www.brendangregg.com/blog/2014-05-11/strace-wow-much-syscall.html
|
||||||
|
[47]:http://www.brendangregg.com/blog/2015-02-28/from-dtrace-to-linux.html
|
||||||
|
[48]:http://www.slideshare.net/brendangregg/from-dtrace-to-linux/28
|
||||||
|
[49]:http://www.beginningwithi.com/
|
||||||
@ -0,0 +1,129 @@
|
|||||||
|
Linux 容器安全的 10 个层面
|
||||||
|
======
|
||||||
|
|
||||||
|
> 应用这些策略来保护容器解决方案的各个层面和容器生命周期的各个阶段的安全。
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
容器提供了打包应用程序的一种简单方法,它实现了从开发到测试到投入生产系统的无缝传递。它也有助于确保跨不同环境的连贯性,包括物理服务器、虚拟机、以及公有云或私有云。这些好处使得一些组织为了更方便地部署和管理为他们提升业务价值的应用程序,而快速地采用了容器技术。
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
企业需要高度安全,在容器中运行核心服务的任何人都会问,“容器安全吗?”以及“我们能信任运行在容器中的应用程序吗?”
|
||||||
|
|
||||||
|
对容器进行安全保护就像是对运行中的进程进行安全保护一样。在你部署和运行你的容器之前,你需要去考虑整个解决方案各个层面的安全。你也需要去考虑贯穿了应用程序和容器整个生命周期的安全。
|
||||||
|
|
||||||
|
请尝试从这十个关键的因素去确保容器解决方案栈不同层面、以及容器生命周期的不同阶段的安全。
|
||||||
|
|
||||||
|
### 1. 容器宿主机操作系统和多租户环境
|
||||||
|
|
||||||
|
由于容器将应用程序和它的依赖作为一个单元来处理,使得开发者构建和升级应用程序变得更加容易,并且,容器可以启用多租户技术将许多应用程序和服务部署到一台共享主机上。在一台单独的主机上以容器方式部署多个应用程序、按需启动和关闭单个容器都是很容易的。为完全实现这种打包和部署技术的优势,运营团队需要运行容器的合适环境。运营者需要一个安全的操作系统,它能够在边界上保护容器安全、从容器中保护主机内核,以及保护容器彼此之间的安全。
|
||||||
|
|
||||||
|
容器是隔离而资源受限的 Linux 进程,允许你在一个共享的宿主机内核上运行沙盒化的应用程序。保护容器的方法与保护你的 Linux 中运行的任何进程的方法是一样的。降低权限是非常重要的,也是保护容器安全的最佳实践。最好使用尽可能小的权限去创建容器。容器应该以一个普通用户的权限来运行,而不是 root 权限的用户。在 Linux 中可以使用多个层面的安全加固手段,Linux 命名空间、安全强化 Linux([SELinux][1])、[cgroups][2] 、capabilities(LCTT 译注:Linux 内核的一个安全特性,它打破了传统的普通用户与 root 用户的概念,在进程级提供更好的安全控制)、以及安全计算模式( [seccomp][3] ),这五种 Linux 的安全特性可以用于保护容器的安全。
|
||||||
|
|
||||||
|
### 2. 容器内容(使用可信来源)
|
||||||
|
|
||||||
|
在谈到安全时,首先要考虑你的容器里面有什么?例如 ,有些时候,应用程序和基础设施是由很多可用组件所构成的。它们中的一些是开源的软件包,比如,Linux 操作系统、Apache Web 服务器、Red Hat JBoss 企业应用平台、PostgreSQL,以及 Node.js。这些软件包的容器化版本已经可以使用了,因此,你没有必要自己去构建它们。但是,对于你从一些外部来源下载的任何代码,你需要知道这些软件包的原始来源,是谁构建的它,以及这些包里面是否包含恶意代码。
|
||||||
|
|
||||||
|
### 3. 容器注册(安全访问容器镜像)
|
||||||
|
|
||||||
|
你的团队的容器构建于下载的公共容器镜像,因此,访问和升级这些下载的容器镜像以及内部构建镜像,与管理和下载其它类型的二进制文件的方式是相同的,这一点至关重要。许多私有的注册库支持容器镜像的存储。选择一个私有的注册库,可以帮你将存储在它的注册中的容器镜像实现策略自动化。
|
||||||
|
|
||||||
|
### 4. 安全性与构建过程
|
||||||
|
|
||||||
|
在一个容器化环境中,软件构建过程是软件生命周期的一个阶段,它将所需的运行时库和应用程序代码集成到一起。管理这个构建过程对于保护软件栈安全来说是很关键的。遵守“一次构建,到处部署”的原则,可以确保构建过程的结果正是生产系统中需要的。保持容器的恒定不变也很重要 — 换句话说就是,不要对正在运行的容器打补丁,而是,重新构建和部署它们。
|
||||||
|
|
||||||
|
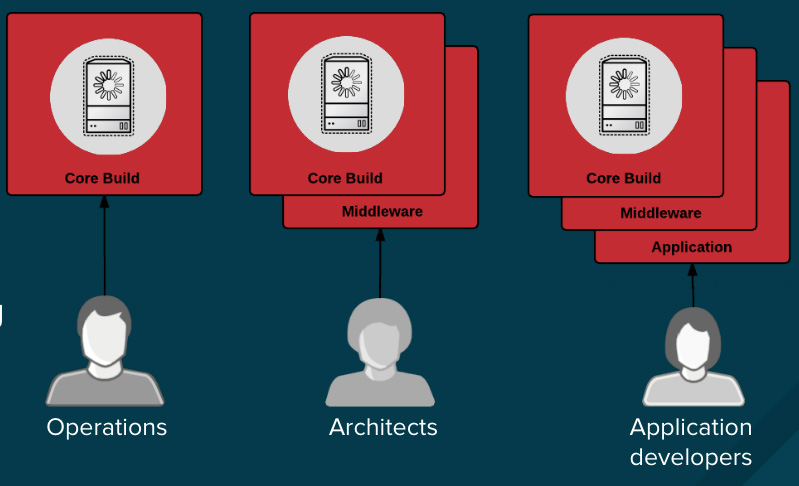
不论是因为你处于一个高强度监管的行业中,还是只希望简单地优化你的团队的成果,设计你的容器镜像管理以及构建过程,可以使用容器层的优势来实现控制分离,因此,你应该去这么做:
|
||||||
|
|
||||||
|
* 运营团队管理基础镜像
|
||||||
|
* 架构师管理中间件、运行时、数据库,以及其它解决方案
|
||||||
|
* 开发者专注于应用程序层面,并且只写代码
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
最后,标记好你的定制构建容器,这样可以确保在构建和部署时不会搞混乱。
|
||||||
|
|
||||||
|
### 5. 控制好在同一个集群内部署应用
|
||||||
|
|
||||||
|
如果是在构建过程中出现的任何问题,或者在镜像被部署之后发现的任何漏洞,那么,请在基于策略的、自动化工具上添加另外的安全层。
|
||||||
|
|
||||||
|
我们来看一下,一个应用程序的构建使用了三个容器镜像层:内核、中间件,以及应用程序。如果在内核镜像中发现了问题,那么只能重新构建镜像。一旦构建完成,镜像就会被发布到容器平台注册库中。这个平台可以自动检测到发生变化的镜像。对于基于这个镜像的其它构建将被触发一个预定义的动作,平台将自己重新构建应用镜像,合并该修复的库。
|
||||||
|
|
||||||
|
一旦构建完成,镜像将被发布到容器平台的内部注册库中。在它的内部注册库中,会立即检测到镜像发生变化,应用程序在这里将会被触发一个预定义的动作,自动部署更新镜像,确保运行在生产系统中的代码总是使用更新后的最新的镜像。所有的这些功能协同工作,将安全功能集成到你的持续集成和持续部署(CI/CD)过程和管道中。
|
||||||
|
|
||||||
|
### 6. 容器编配:保护容器平台安全
|
||||||
|
|
||||||
|
当然了,应用程序很少会以单一容器分发。甚至,简单的应用程序一般情况下都会有一个前端、一个后端、以及一个数据库。而在容器中以微服务模式部署的应用程序,意味着应用程序将部署在多个容器中,有时它们在同一台宿主机上,有时它们是分布在多个宿主机或者节点上,如下面的图所示:
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
在大规模的容器部署时,你应该考虑:
|
||||||
|
|
||||||
|
* 哪个容器应该被部署在哪个宿主机上?
|
||||||
|
* 那个宿主机应该有什么样的性能?
|
||||||
|
* 哪个容器需要访问其它容器?它们之间如何发现彼此?
|
||||||
|
* 你如何控制和管理对共享资源的访问,像网络和存储?
|
||||||
|
* 如何监视容器健康状况?
|
||||||
|
* 如何去自动扩展性能以满足应用程序的需要?
|
||||||
|
* 如何在满足安全需求的同时启用开发者的自助服务?
|
||||||
|
|
||||||
|
考虑到开发者和运营者的能力,提供基于角色的访问控制是容器平台的关键要素。例如,编配管理服务器是中心访问点,应该接受最高级别的安全检查。API 是规模化的自动容器平台管理的关键,可以用于为 pod、服务,以及复制控制器验证和配置数据;在入站请求上执行项目验证;以及调用其它主要系统组件上的触发器。
|
||||||
|
|
||||||
|
### 7. 网络隔离
|
||||||
|
|
||||||
|
在容器中部署现代微服务应用,经常意味着跨多个节点在多个容器上部署。考虑到网络防御,你需要一种在一个集群中的应用之间的相互隔离的方法。一个典型的公有云容器服务,像 Google 容器引擎(GKE)、Azure 容器服务,或者 Amazon Web 服务(AWS)容器服务,是单租户服务。他们让你在你初始化建立的虚拟机集群上运行你的容器。对于多租户容器的安全,你需要容器平台为你启用一个单一集群,并且分割流量以隔离不同的用户、团队、应用、以及在这个集群中的环境。
|
||||||
|
|
||||||
|
使用网络命名空间,容器内的每个集合(即大家熟知的 “pod”)都会得到它自己的 IP 和绑定的端口范围,以此来从一个节点上隔离每个 pod 网络。除使用下面所述的方式之外,默认情况下,来自不同命名空间(项目)的 pod 并不能发送或者接收其它 pod 上的包和不同项目的服务。你可以使用这些特性在同一个集群内隔离开发者环境、测试环境,以及生产环境。但是,这样会导致 IP 地址和端口数量的激增,使得网络管理更加复杂。另外,容器是被设计为反复使用的,你应该在处理这种复杂性的工具上进行投入。在容器平台上比较受欢迎的工具是使用 [软件定义网络][4] (SDN) 提供一个定义的网络集群,它允许跨不同集群的容器进行通讯。
|
||||||
|
|
||||||
|
### 8. 存储
|
||||||
|
|
||||||
|
容器即可被用于无状态应用,也可被用于有状态应用。保护外加的存储是保护有状态服务的一个关键要素。容器平台对多种受欢迎的存储提供了插件,包括网络文件系统(NFS)、AWS 弹性块存储(EBS)、GCE 持久磁盘、GlusterFS、iSCSI、 RADOS(Ceph)、Cinder 等等。
|
||||||
|
|
||||||
|
一个持久卷(PV)可以通过资源提供者支持的任何方式装载到一个主机上。提供者有不同的性能,而每个 PV 的访问模式被设置为特定的卷支持的特定模式。例如,NFS 能够支持多路客户端同时读/写,但是,一个特定的 NFS 的 PV 可以在服务器上被发布为只读模式。每个 PV 有它自己的一组反应特定 PV 性能的访问模式的描述,比如,ReadWriteOnce、ReadOnlyMany、以及 ReadWriteMany。
|
||||||
|
|
||||||
|
### 9. API 管理、终端安全、以及单点登录(SSO)
|
||||||
|
|
||||||
|
保护你的应用安全,包括管理应用、以及 API 的认证和授权。
|
||||||
|
|
||||||
|
Web SSO 能力是现代应用程序的一个关键部分。在构建它们的应用时,容器平台带来了开发者可以使用的多种容器化服务。
|
||||||
|
|
||||||
|
API 是微服务构成的应用程序的关键所在。这些应用程序有多个独立的 API 服务,这导致了终端服务数量的激增,它就需要额外的管理工具。推荐使用 API 管理工具。所有的 API 平台应该提供多种 API 认证和安全所需要的标准选项,这些选项既可以单独使用,也可以组合使用,以用于发布证书或者控制访问。
|
||||||
|
|
||||||
|
这些选项包括标准的 API key、应用 ID 和密钥对,以及 OAuth 2.0。
|
||||||
|
|
||||||
|
### 10. 在一个联合集群中的角色和访问管理
|
||||||
|
|
||||||
|
在 2016 年 7 月份,Kubernetes 1.3 引入了 [Kubernetes 联合集群][5]。这是一个令人兴奋的新特性之一,它是在 Kubernetes 上游、当前的 Kubernetes 1.6 beta 中引用的。联合是用于部署和访问跨多集群运行在公有云或企业数据中心的应用程序服务的。多个集群能够用于去实现应用程序的高可用性,应用程序可以跨多个可用区域,或者去启用部署公共管理,或者跨不同的供应商进行迁移,比如,AWS、Google Cloud、以及 Azure。
|
||||||
|
|
||||||
|
当管理联合集群时,你必须确保你的编配工具能够提供你所需要的跨不同部署平台的实例的安全性。一般来说,认证和授权是很关键的 —— 不论你的应用程序运行在什么地方,将数据安全可靠地传递给它们,以及管理跨集群的多租户应用程序。Kubernetes 扩展了联合集群,包括对联合的秘密数据、联合的命名空间、以及 Ingress objects 的支持。
|
||||||
|
|
||||||
|
### 选择一个容器平台
|
||||||
|
|
||||||
|
当然,它并不仅关乎安全。你需要提供一个你的开发者团队和运营团队有相关经验的容器平台。他们需要一个安全的、企业级的基于容器的应用平台,它能够同时满足开发者和运营者的需要,而且还能够提高操作效率和基础设施利用率。
|
||||||
|
|
||||||
|
想从 Daniel 在 [欧盟开源峰会][7] 上的 [容器安全的十个层面][6] 的演讲中学习更多知识吗?这个峰会已于 10 月 23 - 26 日在 Prague 举行。
|
||||||
|
|
||||||
|
### 关于作者
|
||||||
|
|
||||||
|
Daniel Oh;Microservives;Agile;Devops;Java Ee;Container;Openshift;Jboss;Evangelism
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
--------------------------------------------------------------------------------
|
||||||
|
|
||||||
|
via: https://opensource.com/article/17/10/10-layers-container-security
|
||||||
|
|
||||||
|
作者:[Daniel Oh][a]
|
||||||
|
译者:[qhwdw](https://github.com/qhwdw)
|
||||||
|
校对:[wxy](https://github.com/wxy)
|
||||||
|
|
||||||
|
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||||
|
|
||||||
|
[a]:https://opensource.com/users/daniel-oh
|
||||||
|
[1]:https://en.wikipedia.org/wiki/Security-Enhanced_Linux
|
||||||
|
[2]:https://en.wikipedia.org/wiki/Cgroups
|
||||||
|
[3]:https://en.wikipedia.org/wiki/Seccomp
|
||||||
|
[4]:https://en.wikipedia.org/wiki/Software-defined_networking
|
||||||
|
[5]:https://kubernetes.io/docs/concepts/cluster-administration/federation/
|
||||||
|
[6]:https://osseu17.sched.com/mobile/#session:f2deeabfc1640d002c1d55101ce81223
|
||||||
|
[7]:http://events.linuxfoundation.org/events/open-source-summit-europe
|
||||||
@ -1,45 +1,44 @@
|
|||||||
# 让 “rm” 命令将文件移动到“垃圾桶”,而不是完全删除它们
|
给 “rm” 命令添加个“垃圾桶”
|
||||||
|
============
|
||||||
|
|
||||||
人类犯错误是因为我们不是一个可编程设备,所以,在使用 `rm` 命令时要额外注意,不要在任何时候使用 `rm -rf * `。当你使用 rm 命令时,它会永久删除文件,不会像文件管理器那样将这些文件移动到 `垃圾箱`。
|
人类犯错误是因为我们不是一个可编程设备,所以,在使用 `rm` 命令时要额外注意,不要在任何时候使用 `rm -rf *`。当你使用 `rm` 命令时,它会永久删除文件,不会像文件管理器那样将这些文件移动到 “垃圾箱”。
|
||||||
|
|
||||||
有时我们会将不应该删除的文件删除掉,所以当错误的删除文件时该怎么办? 你必须看看恢复工具(Linux 中有很多数据恢复工具),但我们不知道是否能将它百分之百恢复,所以要如何解决这个问题?
|
有时我们会将不应该删除的文件删除掉,所以当错误地删除了文件时该怎么办? 你必须看看恢复工具(Linux 中有很多数据恢复工具),但我们不知道是否能将它百分之百恢复,所以要如何解决这个问题?
|
||||||
|
|
||||||
我们最近发表了一篇关于 [Trash-Cli][1] 的文章,在评论部分,我们从用户 Eemil Lgz 那里获得了一个关于 [saferm.sh][2] 脚本的更新,它可以帮助我们将文件移动到“垃圾箱”而不是永久删除它们。
|
我们最近发表了一篇关于 [Trash-Cli][1] 的文章,在评论部分,我们从用户 Eemil Lgz 那里获得了一个关于 [saferm.sh][2] 脚本的更新,它可以帮助我们将文件移动到“垃圾箱”而不是永久删除它们。
|
||||||
|
|
||||||
将文件移动到“垃圾桶”是一个好主意,当你无意中运行 rm 命令时,可以节省你的时间,但是很少有人会说这是一个坏习惯,如果你不注意“垃圾桶”,它可能会在一定的时间内被文件和文件夹堆积起来。在这种情况下,我建议你按照你的意愿去做一个定时任务。
|
将文件移动到“垃圾桶”是一个好主意,当你无意中运行 `rm` 命令时,可以拯救你;但是很少有人会说这是一个坏习惯,如果你不注意“垃圾桶”,它可能会在一定的时间内被文件和文件夹堆积起来。在这种情况下,我建议你按照你的意愿去做一个定时任务。
|
||||||
|
|
||||||
这适用于服务器和桌面两种环境。 如果脚本检测到 **GNOME 、KDE、Unity 或 LXDE** 桌面环境(DE),则它将文件或文件夹安全地移动到默认垃圾箱 **\$HOME/.local/share/Trash/files**,否则会在您的主目录中创建垃圾箱文件夹 **$HOME/Trash**。
|
这适用于服务器和桌面两种环境。 如果脚本检测到 GNOME 、KDE、Unity 或 LXDE 桌面环境(DE),则它将文件或文件夹安全地移动到默认垃圾箱 `$HOME/.local/share/Trash/files`,否则会在您的主目录中创建垃圾箱文件夹 `$HOME/Trash`。
|
||||||
|
|
||||||
|
`saferm.sh` 脚本托管在 Github 中,可以从仓库中克隆,也可以创建一个名为 `saferm.sh` 的文件并复制其上的代码。
|
||||||
|
|
||||||
saferm.sh 脚本托管在 Github 中,可以从 repository 中克隆,也可以创建一个名为 saferm.sh 的文件并复制其上的代码。
|
|
||||||
```
|
```
|
||||||
$ git clone https://github.com/lagerspetz/linux-stuff
|
$ git clone https://github.com/lagerspetz/linux-stuff
|
||||||
$ sudo mv linux-stuff/scripts/saferm.sh /bin
|
$ sudo mv linux-stuff/scripts/saferm.sh /bin
|
||||||
$ rm -Rf linux-stuff
|
$ rm -Rf linux-stuff
|
||||||
|
|
||||||
```
|
```
|
||||||
|
|
||||||
在 `bashrc` 文件中设置别名,
|
在 `.bashrc` 文件中设置别名,
|
||||||
|
|
||||||
```
|
```
|
||||||
alias rm=saferm.sh
|
alias rm=saferm.sh
|
||||||
|
|
||||||
```
|
```
|
||||||
|
|
||||||
执行下面的命令使其生效,
|
执行下面的命令使其生效,
|
||||||
|
|
||||||
```
|
```
|
||||||
$ source ~/.bashrc
|
$ source ~/.bashrc
|
||||||
|
|
||||||
```
|
```
|
||||||
|
|
||||||
一切就绪,现在你可以执行 rm 命令,自动将文件移动到”垃圾桶”,而不是永久删除它们。
|
一切就绪,现在你可以执行 `rm` 命令,自动将文件移动到”垃圾桶”,而不是永久删除它们。
|
||||||
|
|
||||||
|
测试一下,我们将删除一个名为 `magi.txt` 的文件,命令行明确的提醒了 `Moving magi.txt to $HOME/.local/share/Trash/file`。
|
||||||
|
|
||||||
测试一下,我们将删除一个名为 `magi.txt` 的文件,命令行显式的说明了 `Moving magi.txt to $HOME/.local/share/Trash/file`
|
|
||||||
|
|
||||||
```
|
```
|
||||||
$ rm -rf magi.txt
|
$ rm -rf magi.txt
|
||||||
Moving magi.txt to /home/magi/.local/share/Trash/files
|
Moving magi.txt to /home/magi/.local/share/Trash/files
|
||||||
|
|
||||||
```
|
```
|
||||||
|
|
||||||
也可以通过 `ls` 命令或 `trash-cli` 进行验证。
|
也可以通过 `ls` 命令或 `trash-cli` 进行验证。
|
||||||
@ -48,46 +47,15 @@ Moving magi.txt to /home/magi/.local/share/Trash/files
|
|||||||
$ ls -lh /home/magi/.local/share/Trash/files
|
$ ls -lh /home/magi/.local/share/Trash/files
|
||||||
Permissions Size User Date Modified Name
|
Permissions Size User Date Modified Name
|
||||||
.rw-r--r-- 32 magi 11 Oct 16:24 magi.txt
|
.rw-r--r-- 32 magi 11 Oct 16:24 magi.txt
|
||||||
|
|
||||||
```
|
```
|
||||||
|
|
||||||
或者我们可以通过文件管理器界面中查看相同的内容。
|
或者我们可以通过文件管理器界面中查看相同的内容。
|
||||||
|
|
||||||
![![][3]][4]
|
![![][3]][4]
|
||||||
|
|
||||||
创建一个定时任务,每天清理一次“垃圾桶”,( LCTT 注:原文为每周一次,但根据下面的代码,应该是每天一次)
|
(LCTT 译注:原文此处混淆了部分 trash-cli 的内容,考虑到文章衔接和逻辑,此处略。)
|
||||||
|
|
||||||
```
|
要了解 `saferm.sh` 的其他选项,请查看帮助。
|
||||||
$ 1 1 * * * trash-empty
|
|
||||||
|
|
||||||
```
|
|
||||||
|
|
||||||
`注意` 对于服务器环境,我们需要使用 rm 命令手动删除。
|
|
||||||
|
|
||||||
```
|
|
||||||
$ rm -rf /root/Trash/
|
|
||||||
/root/Trash/magi1.txt is on . Unsafe delete (y/n)? y
|
|
||||||
Deleting /root/Trash/magi1.txt
|
|
||||||
|
|
||||||
```
|
|
||||||
|
|
||||||
对于桌面环境,trash-put 命令也可以做到这一点。
|
|
||||||
|
|
||||||
在 `bashrc` 文件中创建别名,
|
|
||||||
|
|
||||||
```
|
|
||||||
alias rm=trash-put
|
|
||||||
|
|
||||||
```
|
|
||||||
|
|
||||||
执行下面的命令使其生效。
|
|
||||||
|
|
||||||
```
|
|
||||||
$ source ~/.bashrc
|
|
||||||
|
|
||||||
```
|
|
||||||
|
|
||||||
要了解 saferm.sh 的其他选项,请查看帮助。
|
|
||||||
|
|
||||||
```
|
```
|
||||||
$ saferm.sh -h
|
$ saferm.sh -h
|
||||||
@ -112,7 +80,7 @@ via: https://www.2daygeek.com/rm-command-to-move-files-to-trash-can-rm-alias/
|
|||||||
|
|
||||||
作者:[2DAYGEEK][a]
|
作者:[2DAYGEEK][a]
|
||||||
译者:[amwps290](https://github.com/amwps290)
|
译者:[amwps290](https://github.com/amwps290)
|
||||||
校对:[校对者ID](https://github.com/校对者ID)
|
校对:[wxy](https://github.com/wxy)
|
||||||
|
|
||||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||||
|
|
||||||
@ -0,0 +1,138 @@
|
|||||||
|
Linux 下最好的图片截取和视频截录工具
|
||||||
|
======
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
可能有一个困扰你多时的问题,当你想要获取一张屏幕截图向开发者反馈问题,或是在 Stack Overflow 寻求帮助时,你可能缺乏一个可靠的屏幕截图工具去保存和发送截图。在 GNOME 中有一些这种类型的程序和 shell 拓展工具。这里介绍的是 Linux 最好的屏幕截图工具,可以供你截取图片或截录视频。
|
||||||
|
|
||||||
|
### 1. Shutter
|
||||||
|
|
||||||
|
[][2]
|
||||||
|
|
||||||
|
[Shutter][3] 可以截取任意你想截取的屏幕,是 Linux 最好的截屏工具之一。得到截屏之后,它还可以在保存截屏之前预览图片。它也有一个扩展菜单,展示在 GNOME 顶部面板,使得用户进入软件变得更人性化,非常方便使用。
|
||||||
|
|
||||||
|
你可以截取选区、窗口、桌面、当前光标下的窗口、区域、菜单、提示框或网页。Shutter 允许用户直接上传屏幕截图到设置内首选的云服务商。它同样允许用户在保存截图之前编辑器图片;同时提供了一些可自由添加或移除的插件。
|
||||||
|
|
||||||
|
终端内键入下列命令安装此工具:
|
||||||
|
|
||||||
|
```
|
||||||
|
sudo add-apt-repository -y ppa:shutter/ppa
|
||||||
|
sudo apt-get update && sudo apt-get install shutter
|
||||||
|
```
|
||||||
|
|
||||||
|
### 2. Vokoscreen
|
||||||
|
|
||||||
|
[][4]
|
||||||
|
|
||||||
|
[Vokoscreen][5] 是一款允许你记录和叙述屏幕活动的一款软件。它易于使用,有一个简洁的界面和顶部面板的菜单,方便用户录制视频。
|
||||||
|
|
||||||
|
你可以选择记录整个屏幕,或是记录一个窗口,抑或是记录一个选区。自定义记录可以让你轻松得到所需的保存类型,你甚至可以将屏幕录制记录保存为 gif 文件。当然,你也可以使用网络摄像头记录自己的情况,用于你写作教程吸引学习者。记录完成后,你还可以在该应用程序中回放视频记录,这样就不必到处去找你记录的内容。
|
||||||
|
|
||||||
|
[][6]
|
||||||
|
|
||||||
|
你可以从你的发行版仓库安装 Vocoscreen,或者你也可以在 [pkgs.org][7] 选择下载你需要的版本。
|
||||||
|
|
||||||
|
```
|
||||||
|
sudo dpkg -i vokoscreen_2.5.0-1_amd64.deb
|
||||||
|
```
|
||||||
|
|
||||||
|
### 3. OBS
|
||||||
|
|
||||||
|
[][8]
|
||||||
|
|
||||||
|
[OBS][9] 可以用来录制自己的屏幕亦可用来录制互联网上的流媒体。它允许你看到自己所录制的内容或你叙述的屏幕录制。它允许你根据喜好选择录制视频的品质;它也允许你选择文件的保存类型。除了视频录制功能之外,你还可以切换到 Studio 模式,不借助其他软件进行视频编辑。要在你的 Linux 系统中安装 OBS,你必须确保你的电脑已安装 FFmpeg。ubuntu 14.04 或更早的版本安装 FFmpeg 可以使用如下命令:
|
||||||
|
|
||||||
|
```
|
||||||
|
sudo add-apt-repository ppa:kirillshkrogalev/ffmpeg-next
|
||||||
|
|
||||||
|
sudo apt-get update && sudo apt-get install ffmpeg
|
||||||
|
```
|
||||||
|
|
||||||
|
ubuntu 15.04 以及之后的版本,你可以在终端中键入如下命令安装 FFmpeg:
|
||||||
|
|
||||||
|
```
|
||||||
|
sudo apt-get install ffmpeg
|
||||||
|
```
|
||||||
|
|
||||||
|
如果 FFmpeg 安装完成,在终端中键入如下安装 OBS:
|
||||||
|
|
||||||
|
```
|
||||||
|
sudo add-apt-repository ppa:obsproject/obs-studio
|
||||||
|
|
||||||
|
sudo apt-get update
|
||||||
|
|
||||||
|
sudo apt-get install obs-studio
|
||||||
|
```
|
||||||
|
|
||||||
|
### 4. Green Recorder
|
||||||
|
|
||||||
|
[][10]
|
||||||
|
|
||||||
|
[Green recorder][11] 是一款界面简单的程序,它可以让你记录屏幕。你可以选择包括视频和单纯的音频在内的录制内容,也可以显示鼠标指针,甚至可以跟随鼠标录制视频。同样,你可以选择记录窗口或是屏幕上的选区,以便于只在自己的记录中保留需要的内容;你还可以自定义最终保存的视频的帧数。如果你想要延迟录制,它提供给你一个选项可以设置出你想要的延迟时间。它还提供一个录制结束后的命令运行选项,这样,就可以在视频录制结束后立即运行。
|
||||||
|
|
||||||
|
在终端中键入如下命令来安装 green recorder:
|
||||||
|
|
||||||
|
```
|
||||||
|
sudo add-apt-repository ppa:fossproject/ppa
|
||||||
|
|
||||||
|
sudo apt update && sudo apt install green-recorder
|
||||||
|
```
|
||||||
|
|
||||||
|
### 5. Kazam
|
||||||
|
|
||||||
|
[][12]
|
||||||
|
|
||||||
|
[Kazam][13] 在几乎所有使用截图工具的 Linux 用户中都十分流行。这是一款简单直观的软件,它可以让你做一个屏幕截图或是视频录制,也同样允许在屏幕截图或屏幕录制之前设置延时。它可以让你选择录制区域,窗口或是你想要抓取的整个屏幕。Kazam 的界面接口安排的非常好,和其它软件相比毫无复杂感。它的特点,就是让你优雅的截图。Kazam 在系统托盘和菜单中都有图标,无需打开应用本身,你就可以开始屏幕截图。
|
||||||
|
|
||||||
|
终端中键入如下命令来安装 Kazam:
|
||||||
|
|
||||||
|
```
|
||||||
|
sudo apt-get install kazam
|
||||||
|
```
|
||||||
|
|
||||||
|
如果没有找到该 PPA,你需要使用下面的命令安装它:
|
||||||
|
|
||||||
|
```
|
||||||
|
sudo add-apt-repository ppa:kazam-team/stable-series
|
||||||
|
|
||||||
|
sudo apt-get update && sudo apt-get install kazam
|
||||||
|
```
|
||||||
|
|
||||||
|
### 6. GNOME 扩展截屏工具
|
||||||
|
|
||||||
|
[][1]
|
||||||
|
|
||||||
|
GNOME 的一个扩展软件就叫做 screenshot tool,它常驻系统面板,如果你没有设置禁用它的话。由于它是常驻系统面板的软件,所以它会一直等待你的调用,获取截图,方便和容易获取是它最主要的特点,除非你在调整工具中禁用,否则它将一直在你的系统面板中。这个工具也有用来设置首选项的选项窗口。在 extensions.gnome.org 中搜索 “_Screenshot Tool_”,在你的 GNOME 中安装它。
|
||||||
|
|
||||||
|
你需要安装 gnome 扩展的 chrome 扩展组件和 GNOME 调整工具才能使用这个工具。
|
||||||
|
|
||||||
|
[][14]
|
||||||
|
|
||||||
|
当你碰到一个问题,不知道怎么处理,想要在 [Linux 社区][15] 或者其他开发社区分享、寻求帮助的的时候, **Linux 截图工具** 尤其合适。学习开发、程序或者其他任何事物都会发现这些工具在分享截图的时候真的很实用。Youtube 用户和教程制作爱好者会发现视频截录工具真的很适合录制可以发表的教程。
|
||||||
|
|
||||||
|
--------------------------------------------------------------------------------
|
||||||
|
|
||||||
|
via: http://www.linuxandubuntu.com/home/best-linux-screenshot-screencasting-tools
|
||||||
|
|
||||||
|
作者:[linuxandubuntu][a]
|
||||||
|
译者:[CYLeft](https://github.com/CYLeft)
|
||||||
|
校对:[wxy](https://github.com/wxy)
|
||||||
|
|
||||||
|
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||||
|
|
||||||
|
[a]:http://www.linuxandubuntu.com
|
||||||
|
[1]:http://www.linuxandubuntu.com/uploads/2/1/1/5/21152474/gnome-screenshot-extension-compressed_orig.jpg
|
||||||
|
[2]:http://www.linuxandubuntu.com/uploads/2/1/1/5/21152474/shutter-linux-screenshot-taking-tools_orig.jpg
|
||||||
|
[3]:http://shutter-project.org/
|
||||||
|
[4]:http://www.linuxandubuntu.com/uploads/2/1/1/5/21152474/vokoscreen-screencasting-tool-for-linux_orig.jpg
|
||||||
|
[5]:https://github.com/vkohaupt/vokoscreen
|
||||||
|
[6]:http://www.linuxandubuntu.com/uploads/2/1/1/5/21152474/vokoscreen-preferences_orig.jpg
|
||||||
|
[7]:https://pkgs.org/download/vokoscreen
|
||||||
|
[8]:http://www.linuxandubuntu.com/uploads/2/1/1/5/21152474/obs-linux-screencasting-tool_orig.jpg
|
||||||
|
[9]:https://obsproject.com/
|
||||||
|
[10]:http://www.linuxandubuntu.com/uploads/2/1/1/5/21152474/green-recording-linux-tool_orig.jpg
|
||||||
|
[11]:https://github.com/foss-project/green-recorder
|
||||||
|
[12]:http://www.linuxandubuntu.com/uploads/2/1/1/5/21152474/kazam-screencasting-tool-for-linux_orig.jpg
|
||||||
|
[13]:https://launchpad.net/kazam
|
||||||
|
[14]:http://www.linuxandubuntu.com/uploads/2/1/1/5/21152474/gnome-screenshot-extension-preferences_orig.jpg
|
||||||
|
[15]:http://www.linuxandubuntu.com/home/top-10-communities-to-help-you-learn-linux
|
||||||
@ -1,21 +1,21 @@
|
|||||||
Partclone - 多功能的分区和克隆免费软件
|
Partclone:多功能的分区和克隆的自由软件
|
||||||
======
|
======
|
||||||
|
|
||||||
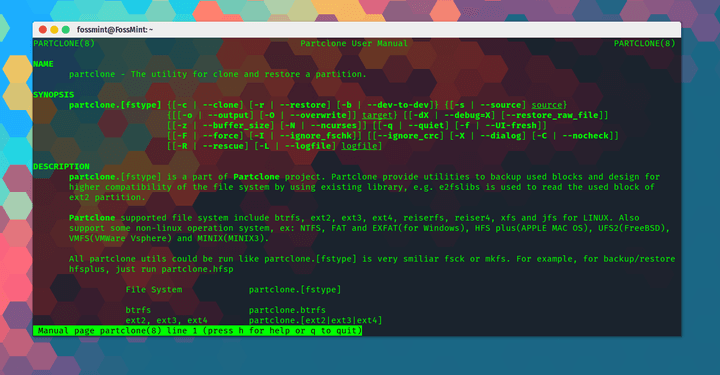
|

|
||||||
|
|
||||||
**[Partclone][1]** 是由 **Clonezilla** 开发者开发的免费开源的用于创建和克隆分区镜像的软件。实际上,**Partclone** 是基于 **Clonezilla** 的工具之一。
|
[Partclone][1] 是由 Clonezilla 的开发者们开发的用于创建和克隆分区镜像的自由开源软件。实际上,Partclone 是 Clonezilla 所基于的工具之一。
|
||||||
|
|
||||||
它为用户提供了备份与恢复占用的分区块工具,并与多个文件系统的高度兼容,这要归功于它能够使用像 **e2fslibs** 这样的现有库来读取和写入分区,例如 **ext2**。
|
它为用户提供了备份与恢复已用分区的工具,并与多个文件系统高度兼容,这要归功于它能够使用像 e2fslibs 这样的现有库来读取和写入分区,例如 ext2。
|
||||||
|
|
||||||
它最大的优点是支持各种格式,包括 ext2、ext3、ext4、hfs +、reiserfs、reiser4、btrfs、vmfs3、vmfs5、xfs、jfs、ufs、ntfs、fat(12/16/32)、exfat、f2fs 和 nilfs。
|
它最大的优点是支持各种格式,包括 ext2、ext3、ext4、hfs+、reiserfs、reiser4、btrfs、vmfs3、vmfs5、xfs、jfs、ufs、ntfs、fat(12/16/32)、exfat、f2fs 和 nilfs。
|
||||||
|
|
||||||
它还有许多的程序,包括 **partclone.ext2**ext3&ext4)、partclone.ntfs、partclone.exfat、partclone.hfsp 和 partclone.vmfs(v3和v5) 等等。
|
它还有许多的程序,包括 partclone.ext2(ext3&ext4)、partclone.ntfs、partclone.exfat、partclone.hfsp 和 partclone.vmfs(v3和v5) 等等。
|
||||||
|
|
||||||
### Partclone中的功能
|
### Partclone中的功能
|
||||||
|
|
||||||
* **免费软件:** **Partclone**免费供所有人下载和使用。
|
* 免费软件: Partclone 免费供所有人下载和使用。
|
||||||
* **开源:** **Partclone**是在 GNU GPL 许可下发布的,并在 [GitHub][2] 上公开。
|
* 开源: Partclone 是在 GNU GPL 许可下发布的,并在 [GitHub][2] 上公开。
|
||||||
* **跨平台**:适用于 Linux、Windows、MAC、ESX 文件系统备份/恢复和 FreeBSD。
|
* 跨平台:适用于 Linux、Windows、MAC、ESX 文件系统备份/恢复和 FreeBSD。
|
||||||
* 一个在线的[文档页面][3],你可以从中查看帮助文档并跟踪其 GitHub 问题。
|
* 一个在线的[文档页面][3],你可以从中查看帮助文档并跟踪其 GitHub 问题。
|
||||||
* 为初学者和专业人士提供的在线[用户手册][4]。
|
* 为初学者和专业人士提供的在线[用户手册][4]。
|
||||||
* 支持救援。
|
* 支持救援。
|
||||||
@ -25,55 +25,53 @@ Partclone - 多功能的分区和克隆免费软件
|
|||||||
* 支持 raw 克隆。
|
* 支持 raw 克隆。
|
||||||
* 显示传输速率和持续时间。
|
* 显示传输速率和持续时间。
|
||||||
* 支持管道。
|
* 支持管道。
|
||||||
* 支持 crc32。
|
* 支持 crc32 校验。
|
||||||
* 支持 ESX vmware server 的 vmfs 和 FreeBSD 的文件系统 ufs。
|
* 支持 ESX vmware server 的 vmfs 和 FreeBSD 的文件系统 ufs。
|
||||||
|
|
||||||
|
Partclone 中还捆绑了更多功能,你可以在[这里][5]查看其余的功能。
|
||||||
|
|
||||||
|
- [下载 Linux 中的 Partclone][6]
|
||||||
**Partclone** 中还捆绑了更多功能,你可以在[这里][5]查看其余的功能。
|
|
||||||
|
|
||||||
[下载 Linux 中的 Partclone][6]
|
|
||||||
|
|
||||||
### 如何安装和使用 Partclone
|
### 如何安装和使用 Partclone
|
||||||
|
|
||||||
在 Linux 上安装 Partclone。
|
在 Linux 上安装 Partclone。
|
||||||
|
|
||||||
```
|
```
|
||||||
$ sudo apt install partclone [On Debian/Ubuntu]
|
$ sudo apt install partclone [On Debian/Ubuntu]
|
||||||
$ sudo yum install partclone [On CentOS/RHEL/Fedora]
|
$ sudo yum install partclone [On CentOS/RHEL/Fedora]
|
||||||
|
|
||||||
```
|
```
|
||||||
|
|
||||||
克隆分区为镜像。
|
克隆分区为镜像。
|
||||||
|
|
||||||
```
|
```
|
||||||
# partclone.ext4 -d -c -s /dev/sda1 -o sda1.img
|
# partclone.ext4 -d -c -s /dev/sda1 -o sda1.img
|
||||||
|
|
||||||
```
|
```
|
||||||
|
|
||||||
将镜像恢复到分区。
|
将镜像恢复到分区。
|
||||||
|
|
||||||
```
|
```
|
||||||
# partclone.ext4 -d -r -s sda1.img -o /dev/sda1
|
# partclone.ext4 -d -r -s sda1.img -o /dev/sda1
|
||||||
|
|
||||||
```
|
```
|
||||||
|
|
||||||
分区到分区克隆。
|
分区到分区克隆。
|
||||||
|
|
||||||
```
|
```
|
||||||
# partclone.ext4 -d -b -s /dev/sda1 -o /dev/sdb1
|
# partclone.ext4 -d -b -s /dev/sda1 -o /dev/sdb1
|
||||||
|
|
||||||
```
|
```
|
||||||
|
|
||||||
显示镜像信息。
|
显示镜像信息。
|
||||||
|
|
||||||
```
|
```
|
||||||
# partclone.info -s sda1.img
|
# partclone.info -s sda1.img
|
||||||
|
|
||||||
```
|
```
|
||||||
|
|
||||||
检查镜像。
|
检查镜像。
|
||||||
|
|
||||||
```
|
```
|
||||||
# partclone.chkimg -s sda1.img
|
# partclone.chkimg -s sda1.img
|
||||||
|
|
||||||
```
|
```
|
||||||
|
|
||||||
你是 **Partclone** 的用户吗?我最近在 [**Deepin Clone**][7] 上写了一篇文章,显然,Partclone 有擅长处理的任务。你使用其他备份和恢复工具的经验是什么?
|
你是 Partclone 的用户吗?我最近在 [Deepin Clone][7] 上写了一篇文章,显然,Partclone 有擅长处理的任务。你使用其他备份和恢复工具的经验是什么?
|
||||||
|
|
||||||
请在下面的评论区与我们分享你的想法和建议。
|
请在下面的评论区与我们分享你的想法和建议。
|
||||||
|
|
||||||
@ -81,13 +79,13 @@ $ sudo yum install partclone [On CentOS/RHEL/Fedora]
|
|||||||
|
|
||||||
via: https://www.fossmint.com/partclone-linux-backup-clone-tool/
|
via: https://www.fossmint.com/partclone-linux-backup-clone-tool/
|
||||||
|
|
||||||
作者:[Martins D. Okoi;View All Posts;Peter Beck;Martins Divine Okoi][a]
|
作者:[Martins D. Okoi][a]
|
||||||
译者:[geekpi](https://github.com/geekpi)
|
译者:[geekpi](https://github.com/geekpi)
|
||||||
校对:[校对者ID](https://github.com/校对者ID)
|
校对:[wxy](https://github.com/wxy)
|
||||||
|
|
||||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||||
|
|
||||||
[a]:
|
[a]:https://www.fossmint.com/author/dillivine/
|
||||||
[1]:https://partclone.org/
|
[1]:https://partclone.org/
|
||||||
[2]:https://github.com/Thomas-Tsai/partclone
|
[2]:https://github.com/Thomas-Tsai/partclone
|
||||||
[3]:https://partclone.org/help/
|
[3]:https://partclone.org/help/
|
||||||
@ -1,3 +1,5 @@
|
|||||||
|
lontow Translating
|
||||||
|
|
||||||
Evolutional Steps of Computer Systems
|
Evolutional Steps of Computer Systems
|
||||||
======
|
======
|
||||||
Throughout the history of the modern computer, there were several evolutional steps related to the way we interact with the system. I tend to categorize those steps as following:
|
Throughout the history of the modern computer, there were several evolutional steps related to the way we interact with the system. I tend to categorize those steps as following:
|
||||||
|
|||||||
@ -1,75 +0,0 @@
|
|||||||
translatng---geekpi
|
|
||||||
|
|
||||||
5 of the Best Linux Dark Themes that Are Easy on the Eyes
|
|
||||||
======
|
|
||||||
|
|
||||||

|
|
||||||
|
|
||||||
There are several reasons people opt for dark themes on their computers. Some find them easy on the eye while others prefer them because of their medical condition. Programmers, especially, like dark themes because they reduce glare on the eyes.
|
|
||||||
|
|
||||||
If you are a Linux user and a dark theme lover, you are in luck. Here are five of the best dark themes for Linux. Check them out!
|
|
||||||
|
|
||||||
### 1. OSX-Arc-Shadow
|
|
||||||
|
|
||||||
![OSX-Arc-Shadow Theme][1]
|
|
||||||
|
|
||||||
As its name implies, this theme is inspired by OS X. It is a flat theme based on Arc. The theme supports GTK 3 and GTK 2 desktop environments, so Gnome, Cinnamon, Unity, Manjaro, Mate, and XFCE users can install and use the theme. [OSX-Arc-Shadow][2] is part of the OSX-Arc theme collection. The collection has several other themes (dark and light) included. You can download the whole collection and just use the dark variants.
|
|
||||||
|
|
||||||
Debian- and Ubuntu-based distro users have the option of installing the stable release using the .deb files found on this [page][3]. The compressed source files are also on the same page. Arch Linux users, check out this [AUR link][4]. Finally, to install the theme manually, extract the zip content to the "~/.themes" folder and set it as your current theme, controls, and window borders.
|
|
||||||
|
|
||||||
### 2. Kiss-Kool-Red version 2
|
|
||||||
|
|
||||||
![Kiss-Kool-Red version 2 ][5]
|
|
||||||
|
|
||||||
The theme is only a few days old. It has a darker look compared to OSX-Arc-Shadow and red selection outlines. It is especially appealing to those who want more contrast and less glare from the computer screen. Hence, It reduces distraction when used at night or in places with low lights. It supports GTK 3 and GTK2.
|
|
||||||
|
|
||||||
Head to [gnome-looks][6] to download the theme under the "Files" menu. The installation procedure is simple: extract the theme into the "~/.themes" folder and set it as your current theme, controls, and window borders.
|
|
||||||
|
|
||||||
### 3. Equilux
|
|
||||||
|
|
||||||
![Equilux][7]
|
|
||||||
|
|
||||||
Equilux is another simple dark theme based on Materia Theme. It has a neutral dark color tone and is not overly fancy. The contrast between the selection outlines is also minimal and not as sharp as the red color in Kiss-Kool-Red. The theme is truly made with reduction of eye strain in mind.
|
|
||||||
|
|
||||||
[Download the compressed file][8] and unzip it into your "~/.themes" folder. Then, you can set it as your theme. You can check [its GitHub page][9] for the latest additions.
|
|
||||||
|
|
||||||
### 4. Deepin Dark
|
|
||||||
|
|
||||||
![Deepin Dark][10]
|
|
||||||
|
|
||||||
Deepin Dark is a completely dark theme. For those who like a little more darkness, this theme is definitely one to consider. Moreover, it also reduces the amount of glare from the computer screen. Additionally, it supports Unity. [Download Deepin Dark here][11].
|
|
||||||
|
|
||||||
### 5. Ambiance DS BlueSB12
|
|
||||||
|
|
||||||
![Ambiance DS BlueSB12 ][12]
|
|
||||||
|
|
||||||
Ambiance DS BlueSB12 is a simple dark theme, so it makes the important details stand out. It helps with focus as is not unnecessarily fancy. It is very similar to Deepin Dark. Especially relevant to Ubuntu users, it is compatible with Ubuntu 17.04. You can download and try it from [here][13].
|
|
||||||
|
|
||||||
### Conclusion
|
|
||||||
|
|
||||||
If you use a computer for a very long time, dark themes are a great way to reduce the strain on your eyes. Even if you don't, dark themes can help you in many other ways like improving your focus. Let us know which is your favorite.
|
|
||||||
|
|
||||||
--------------------------------------------------------------------------------
|
|
||||||
|
|
||||||
via: https://www.maketecheasier.com/best-linux-dark-themes/
|
|
||||||
|
|
||||||
作者:[Bruno Edoh][a]
|
|
||||||
译者:[译者ID](https://github.com/译者ID)
|
|
||||||
校对:[校对者ID](https://github.com/校对者ID)
|
|
||||||
|
|
||||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
|
||||||
|
|
||||||
[a]:https://www.maketecheasier.com
|
|
||||||
[1]:https://www.maketecheasier.com/assets/uploads/2017/12/osx-arc-shadow.png (OSX-Arc-Shadow Theme)
|
|
||||||
[2]:https://github.com/LinxGem33/OSX-Arc-Shadow/
|
|
||||||
[3]:https://github.com/LinxGem33/OSX-Arc-Shadow/releases
|
|
||||||
[4]:https://aur.archlinux.org/packages/osx-arc-shadow/
|
|
||||||
[5]:https://www.maketecheasier.com/assets/uploads/2017/12/Kiss-Kool-Red.png (Kiss-Kool-Red version 2 )
|
|
||||||
[6]:https://www.gnome-look.org/p/1207964/
|
|
||||||
[7]:https://www.maketecheasier.com/assets/uploads/2017/12/equilux.png (Equilux)
|
|
||||||
[8]:https://www.gnome-look.org/p/1182169/
|
|
||||||
[9]:https://github.com/ddnexus/equilux-theme
|
|
||||||
[10]:https://www.maketecheasier.com/assets/uploads/2017/12/deepin-dark.png (Deepin Dark )
|
|
||||||
[11]:https://www.gnome-look.org/p/1190867/
|
|
||||||
[12]:https://www.maketecheasier.com/assets/uploads/2017/12/ambience.png (Ambiance DS BlueSB12 )
|
|
||||||
[13]:https://www.gnome-look.org/p/1013664/
|
|
||||||
@ -1,195 +0,0 @@
|
|||||||
translated by cyleft
|
|
||||||
|
|
||||||
Migrating to Linux: The Command Line
|
|
||||||
======
|
|
||||||
|
|
||||||

|
|
||||||
|
|
||||||
This is the fourth article in our series on migrating to Linux. If you missed the previous installments, we've covered [Linux for new users][1], [files and filesystems][2], and [graphical environments][3]. Linux is everywhere. It's used to run most Internet services like web servers, email servers, and others. It's also used in your cell phone, your car console, and a whole lot more. So, you might be curious to try out Linux and learn more about how it works.
|
|
||||||
|
|
||||||
Under Linux, the command line is very useful. On desktop Linux systems, although the command line is optional, you will often see people have a command line window open alongside other application windows. On Internet servers, and when Linux is running in a device, the command line is often the only way to interact directly with the system. So, it's good to know at least some command line basics.
|
|
||||||
|
|
||||||
In the command line (often called a shell in Linux), everything is done by entering commands. You can list files, move files, display the contents of files, edit files, and more, even display web pages, all from the command line.
|
|
||||||
|
|
||||||
If you are already familiar with using the command line in Windows (either CMD.EXE or PowerShell), you may want to jump down to the section titled Familiar with Windows Command Line? and read that first.
|
|
||||||
|
|
||||||
### Navigating
|
|
||||||
|
|
||||||
In the command line, there is the concept of the current working directory (Note: A folder and a directory are synonymous, and in Linux they're usually called directories). Many commands will look in this directory by default if no other directory path is specified. For example, typing ls to list files, will list files in this working directory. For example:
|
|
||||||
```
|
|
||||||
$ ls
|
|
||||||
Desktop Documents Downloads Music Pictures README.txt Videos
|
|
||||||
```
|
|
||||||
|
|
||||||
The command, ls Documents, will instead list files in the Documents directory:
|
|
||||||
```
|
|
||||||
$ ls Documents
|
|
||||||
report.txt todo.txt EmailHowTo.pdf
|
|
||||||
```
|
|
||||||
|
|
||||||
You can display the current working directory by typing pwd. For example:
|
|
||||||
```
|
|
||||||
$ pwd
|
|
||||||
/home/student
|
|
||||||
```
|
|
||||||
|
|
||||||
You can change the current directory by typing cd and then the directory you want to change to. For example:
|
|
||||||
```
|
|
||||||
$ pwd
|
|
||||||
/home/student
|
|
||||||
$ cd Downloads
|
|
||||||
$ pwd
|
|
||||||
/home/student/Downloads
|
|
||||||
```
|
|
||||||
|
|
||||||
A directory path is a list of directories separated by a / (slash) character. The directories in a path have an implied hierarchy, for example, where the path /home/student expects there to be a directory named home in the top directory, and a directory named student to be in that directory home.
|
|
||||||
|
|
||||||
Directory paths are either absolute or relative. Absolute directory paths start with the / character.
|
|
||||||
|
|
||||||
Relative paths start with either . (dot) or .. (dot dot). In a path, a . (dot) means the current directory, and .. (dot dot) means one directory up from the current one. For example, ls ../Documents means look in the directory up one from the current one and show the contents of the directory named Documents in there:
|
|
||||||
```
|
|
||||||
$ pwd
|
|
||||||
/home/student
|
|
||||||
$ ls
|
|
||||||
Desktop Documents Downloads Music Pictures README.txt Videos
|
|
||||||
$ cd Downloads
|
|
||||||
$ pwd
|
|
||||||
/home/student/Downloads
|
|
||||||
$ ls ../Documents
|
|
||||||
report.txt todo.txt EmailHowTo.pdf
|
|
||||||
```
|
|
||||||
|
|
||||||
When you first open a command line window on a Linux system, your current working directory is set to your home directory, usually: /home/<your login name here>. Your home directory is dedicated to your login where you can store your own files.
|
|
||||||
|
|
||||||
The environment variable $HOME expands to the directory path to your home directory. For example:
|
|
||||||
```
|
|
||||||
$ echo $HOME
|
|
||||||
/home/student
|
|
||||||
```
|
|
||||||
|
|
||||||
The following table shows a summary of some of the common commands used to navigate directories and manage simple text files.
|
|
||||||
|
|
||||||
### Searching
|
|
||||||
|
|
||||||
Sometimes I forget where a file resides, or I forget the name of the file I am looking for. There are a couple of commands in the Linux command line that you can use to help you find files and search the contents of files.
|
|
||||||
|
|
||||||
The first command is find. You can use find to search for files and directories by name or other attribute. For example, if I forgot where I kept my todo.txt file, I can run the following:
|
|
||||||
```
|
|
||||||
$ find $HOME -name todo.txt
|
|
||||||
/home/student/Documents/todo.txt
|
|
||||||
```
|
|
||||||
|
|
||||||
The find program has a lot of features and options. A simple form of the command is:
|
|
||||||
find <directory to search> -name <filename>
|
|
||||||
|
|
||||||
If there is more than one file named todo.txt from the example above, it will show me all the places where it found a file by that name. The find command has many options to search by type (file, directory, or other), by date, newer than date, by size, and more. You can type:
|
|
||||||
```
|
|
||||||
man find
|
|
||||||
```
|
|
||||||
|
|
||||||
to get help on how to use the find command.
|
|
||||||
|
|
||||||
You can also use a command called grep to search inside files for specific contents. For example:
|
|
||||||
```
|
|
||||||
grep "01/02/2018" todo.txt
|
|
||||||
```
|
|
||||||
|
|
||||||
will show me all the lines that have the January 2, 2018 date in them.
|
|
||||||
|
|
||||||
### Getting Help
|
|
||||||
|
|
||||||
There are a lot of commands in Linux, and it would be too much to describe all of them here. So the next best step to show how to get help on commands.
|
|
||||||
|
|
||||||
The command apropos helps you find commands that do certain things. Maybe you want to find out all the commands that operate on directories or get a list of open files, but you don't know what command to run. So, you can try:
|
|
||||||
```
|
|
||||||
apropos directory
|
|
||||||
```
|
|
||||||
|
|
||||||
which will give a list of commands and have the word "directory" in their help text. Or, you can do:
|
|
||||||
```
|
|
||||||
apropos "list open files"
|
|
||||||
```
|
|
||||||
|
|
||||||
which will show one command, lsof, that you can use to list open files.
|
|
||||||
|
|
||||||
If you know the command you need to use but aren't sure which options to use to get it to behave the way you want, you can use the command called man, which is short for manual. You would use man <command>, for example:
|
|
||||||
```
|
|
||||||
man ls
|
|
||||||
```
|
|
||||||
|
|
||||||
You can try man ls on your own. It will give several pages of information.
|
|
||||||
|
|
||||||
The man command explains all the options and parameters you can give to a command, and often will even give an example.
|
|
||||||
|
|
||||||
Many commands often also have a help option (e.g., ls --help), which will give information on how to use a command. The man pages are usually more detailed, while the --help option is useful for a quick lookup.
|
|
||||||
|
|
||||||
### Scripts
|
|
||||||
|
|
||||||
One of the best things about the Linux command line is that the commands that are typed in can be scripted, and run over and over again. Commands can be placed as separate lines in a file. You can put #!/bin/sh as the first line in the file, followed by the commands. Then, once the file is marked as executable, you can run the script as if it were its own command. For example,
|
|
||||||
```
|
|
||||||
--- contents of get_todays_todos.sh ---
|
|
||||||
#!/bin/sh
|
|
||||||
todays_date=`date +"%m/%d/%y"`
|
|
||||||
grep $todays_date $HOME/todos.txt
|
|
||||||
```
|
|
||||||
|
|
||||||
Scripts help automate certain tasks in a set of repeatable steps. Scripts can also get very sophisticated if needed, with loops, conditional statements, routines, and more. There's not space here to go into detail, but you can find more information about Linux bash scripting online.
|
|
||||||
|
|
||||||
Familiar with Windows Command Line?
|
|
||||||
|
|
||||||
If you are familiar with the Windows CMD or PowerShell program, typing commands at a command prompt should feel familiar. However, several things work differently in Linux and if you don't understand those differences, it may be confusing.
|
|
||||||
|
|
||||||
First, under Linux, the PATH environment variable works different than it does under Windows. In Windows, the current directory is assumed to be the first directory on the path, even though it's not listed in the list of directories in PATH. Under Linux, the current directory is not assumed to be on the path, and it is not explicitly put on the path either. Putting . in the PATH environment variable is considered to be a security risk under Linux. In Linux, to run a program in the current directory, you need to prefix it with ./ (which is the file's relative path from the current directory). This trips up a lot of CMD users. For example:
|
|
||||||
```
|
|
||||||
./my_program
|
|
||||||
```
|
|
||||||
|
|
||||||
rather than
|
|
||||||
```
|
|
||||||
my_program
|
|
||||||
```
|
|
||||||
|
|
||||||
In addition, in Windows paths are separated by a ; (semicolon) character in the PATH environment variable. On Linux, in PATH, directories are separated by a : (colon) character. Also in Linux, directories in a single path are separated by a / (slash) character while under Windows directories in a single path are separated by a \ (backslash) character. So a typical PATH environment variable in Windows might look like:
|
|
||||||
```
|
|
||||||
PATH="C:\Program Files;C:\Program Files\Firefox;"
|
|
||||||
while on Linux it might look like:
|
|
||||||
PATH="/usr/bin:/opt/mozilla/firefox"
|
|
||||||
```
|
|
||||||
|
|
||||||
Also note that environment variables are expanded with a $ on Linux, so $PATH expands to the contents of the PATH environment variable whereas in Windows you need to enclose the variable in percent symbols (e.g., %PATH%).
|
|
||||||
|
|
||||||
In Linux, options are commonly passed to programs using a - (dash) character in front of the option, while under Windows options are passed by preceding options with a / (slash) character. So, under Linux, you would do:
|
|
||||||
```
|
|
||||||
a_prog -h
|
|
||||||
```
|
|
||||||
|
|
||||||
rather than
|
|
||||||
```
|
|
||||||
a_prog /h
|
|
||||||
```
|
|
||||||
|
|
||||||
Under Linux, file extensions generally don't signify anything. For example, renaming myscript to myscript.bat doesn't make it executable. Instead to make a file executable, the file's executable permission flag needs to be set. File permissions are covered in more detail next time.
|
|
||||||
|
|
||||||
Under Linux when file and directory names start with a . (dot) character they are hidden. So, for example, if you're told to edit the file, .bashrc, and you don't see it in your home directory, it probably really is there. It's just hidden. In the command line, you can use option -a on the command ls to see hidden files. For example:
|
|
||||||
```
|
|
||||||
ls -a
|
|
||||||
```
|
|
||||||
|
|
||||||
Under Linux, common commands are also different from those in the Windows command line. The following table that shows a mapping from common items used under CMD and the alternative used under Linux.
|
|
||||||
|
|
||||||

|
|
||||||
|
|
||||||
--------------------------------------------------------------------------------
|
|
||||||
|
|
||||||
via: https://www.linux.com/blog/learn/2018/1/migrating-linux-command-line
|
|
||||||
|
|
||||||
作者:[John Bonesio][a]
|
|
||||||
译者:[译者ID](https://github.com/译者ID)
|
|
||||||
校对:[校对者ID](https://github.com/校对者ID)
|
|
||||||
|
|
||||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
|
||||||
|
|
||||||
[a]:https://www.linux.com/users/johnbonesio
|
|
||||||
[1]:https://www.linux.com/blog/learn/intro-to-linux/2017/10/migrating-linux-introduction
|
|
||||||
[2]:https://www.linux.com/blog/learn/intro-to-linux/2017/11/migrating-linux-disks-files-and-filesystems
|
|
||||||
[3]:https://www.linux.com/blog/learn/2017/12/migrating-linux-graphical-environments
|
|
||||||
@ -1,3 +1,4 @@
|
|||||||
|
Translating by qhwdw
|
||||||
BUILDING A FULL-TEXT SEARCH APP USING DOCKER AND ELASTICSEARCH
|
BUILDING A FULL-TEXT SEARCH APP USING DOCKER AND ELASTICSEARCH
|
||||||
============================================================
|
============================================================
|
||||||
|
|
||||||
|
|||||||
@ -1,3 +1,5 @@
|
|||||||
|
translating---geekpi
|
||||||
|
|
||||||
A File Transfer Utility To Download Only The New Parts Of A File
|
A File Transfer Utility To Download Only The New Parts Of A File
|
||||||
======
|
======
|
||||||
|
|
||||||
|
|||||||
@ -1,3 +1,4 @@
|
|||||||
|
Translating by qhwdw
|
||||||
Manage printers and printing
|
Manage printers and printing
|
||||||
======
|
======
|
||||||
|
|
||||||
|
|||||||
@ -0,0 +1,203 @@
|
|||||||
|
How to clone, modify, add, and delete files in Git
|
||||||
|
======
|
||||||
|

|
||||||
|
|
||||||
|
In the [first article in this series][1] on getting started with Git, we created a simple Git repo and added a file to it by connecting it with our computer. In this article, we will learn a handful of other things about Git, namely how to clone (download), modify, add, and delete files in a Git repo.
|
||||||
|
|
||||||
|
### Let's make some clones
|
||||||
|
|
||||||
|
Say you already have a Git repo on GitHub and you want to get your files from it—maybe you lost the local copy on your computer or you're working on a different computer and want access to the files in your repository. What should you do? Download your files from GitHub? Exactly! We call this "cloning" in Git terminology. (You could also download the repo as a ZIP file, but we'll explore the clone method in this article.)
|
||||||
|
|
||||||
|
Let's clone the repo, called Demo, we created in the last article. (If you have not yet created a Demo repo, jump back to that article and do those steps before you proceed here.) To clone your file, just open your browser and navigate to `https://github.com/<your_username>/Demo` (where `<your_username>` is the name of your own repo. For example, my repo is `https://github.com/kedark3/Demo`). Once you navigate to that URL, click the "Clone or download" button, and your browser should look something like this:
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
As you can see above, the "Clone with HTTPS" option is open. Copy your repo's URL from that dropdown box (`https://github.com/<your_username>/Demo.git`). Open the terminal and type the following command to clone your GitHub repo to your computer:
|
||||||
|
```
|
||||||
|
git clone https://github.com/<your_username>/Demo.git
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
Then, to see the list of files in the `Demo` directory, enter the command:
|
||||||
|
```
|
||||||
|
ls Demo/
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
Your terminal should look like this:
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
### Modify files
|
||||||
|
|
||||||
|
Now that we have cloned the repo, let's modify the files and update them on GitHub. To begin, enter the commands below, one by one, to change the directory to `Demo/`, check the contents of `README.md`, echo new (additional) content to `README.md`, and check the status with `git status`:
|
||||||
|
```
|
||||||
|
cd Demo/
|
||||||
|
|
||||||
|
ls
|
||||||
|
|
||||||
|
cat README.md
|
||||||
|
|
||||||
|
echo "Added another line to REAMD.md" >> README.md
|
||||||
|
|
||||||
|
cat README.md
|
||||||
|
|
||||||
|
git status
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
This is how it will look in the terminal if you run these commands one by one:
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
Let's look at the output of `git status` and walk through what it means. Don't worry about the part that says:
|
||||||
|
```
|
||||||
|
On branch master
|
||||||
|
|
||||||
|
Your branch is up-to-date with 'origin/master'.".
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
because we haven't learned it yet. The next line says: `Changes not staged for commit`; this is telling you that the files listed below it aren't marked ready ("staged") to be committed. If you run `git add`, Git takes those files and marks them as `Ready for commit`; in other (Git) words, `Changes staged for commit`. Before we do that, let's check what we are adding to Git with the `git diff` command, then run `git add`.
|
||||||
|
|
||||||
|
Here is your terminal output:
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
Let's break this down:
|
||||||
|
|
||||||
|
* `diff --git a/README.md b/README.md` is what Git is comparing (i.e., `README.md` in this example).
|
||||||
|
* `--- a/README.md` would show anything removed from the file.
|
||||||
|
* `+++ b/README.md` would show anything added to your file.
|
||||||
|
* Anything added to the file is printed in green text with a + at the beginning of the line.
|
||||||
|
* If we had removed anything, it would be printed in red text with a - sign at the beginning.
|
||||||
|
* Git status now says `Changes to be committed:` and lists the filename (i.e., `README.md`) and what happened to that file (i.e., it has been `modified` and is ready to be committed).
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
Tip: If you have already run `git add`, and now you want to see what's different, the usual `git diff` won't yield anything because you already added the file. Instead, you must use `git diff --cached`. It will show you the difference between the current version and previous version of files that Git was told to add. Your terminal output would look like this:
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
### Upload a file to your repo
|
||||||
|
|
||||||
|
We have modified the `README.md` file with some new content and it's time to upload it to GitHub.
|
||||||
|
|
||||||
|
Let's commit the changes and push those to GitHub. Run:
|
||||||
|
```
|
||||||
|
git commit -m "Updated Readme file"
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
This tells Git that you are "committing" to changes that you have "added" to it. You may recall from the first part of this series that it's important to add a message to explain what you did in your commit so you know its purpose when you look back at your Git log later. (We will look more at this topic in the next article.) `Updated Readme file` is the message for this commit—if you don't think this is the most logical way to explain what you did, feel free to write your commit message differently.
|
||||||
|
|
||||||
|
Run `git push -u origin master`. This will prompt you for your username and password, then upload the file to your GitHub repo. Refresh your GitHub page, and you should see the changes you just made to `README.md`.
|
||||||
|
|
||||||
|
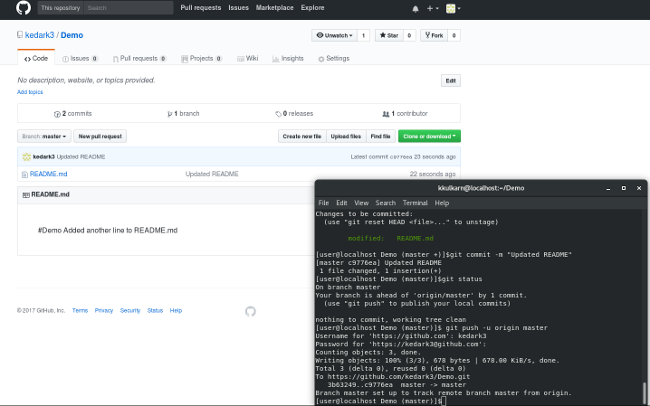
|
||||||
|
|
||||||
|
The bottom-right corner of the terminal shows that I committed the changes, checked the Git status, and pushed the changes to GitHub. Git status says:
|
||||||
|
```
|
||||||
|
Your branch is ahead of 'origin/master' by 1 commit
|
||||||
|
|
||||||
|
(use "git push" to publish your local commits)
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
The first line indicates there is one commit in the local repo but not present in origin/master (i.e., on GitHub). The next line directs us to push those changes to origin/master, and that is what we did. (To refresh your memory on what "origin" means in this case, refer to the first article in this series. I will explain what "master" means in the next article, when we discuss branching.)
|
||||||
|
|
||||||
|
### Add a new file to Git
|
||||||
|
|
||||||
|
Now that we have modified a file and updated it on GitHub, let's create a new file, add it to Git, and upload it to GitHub. Run:
|
||||||
|
```
|
||||||
|
echo "This is a new file" >> file.txt
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
This will create a new file named `file.txt`.
|
||||||
|
|
||||||
|
If you `cat` it out:
|
||||||
|
```
|
||||||
|
cat file.txt
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
You should see the contents of the file. Now run:
|
||||||
|
```
|
||||||
|
git status
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
Git reports that you have an untracked file (named `file.txt`) in your repository. This is Git's way of telling you that there is a new file in the repo directory on your computer that you haven't told Git about, and Git is not tracking that file for any changes you make.
|
||||||
|
|
||||||
|
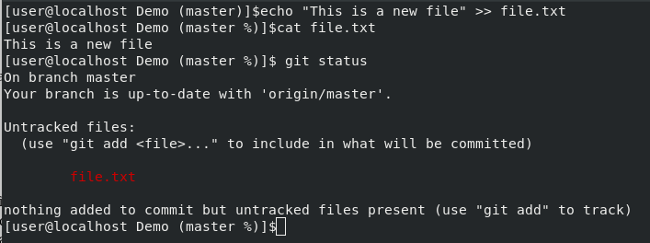
|
||||||
|
|
||||||
|
We need to tell Git to track this file so we can commit it and upload it to our repo. Here's the command to do that:
|
||||||
|
```
|
||||||
|
git add file.txt
|
||||||
|
|
||||||
|
git status
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
Your terminal output is:
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
Git status is telling you there are changes to `file.txt` to be committed, and that it is a `new file` to Git, which it was not aware of before this. Now that we have added `file.txt` to Git, we can commit the changes and push it to origin/master.
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
Git has now uploaded this new file to GitHub; if you refresh your GitHub page, you should see the new file, `file.txt`, in your Git repo on GitHub.
|
||||||
|
|
||||||
|
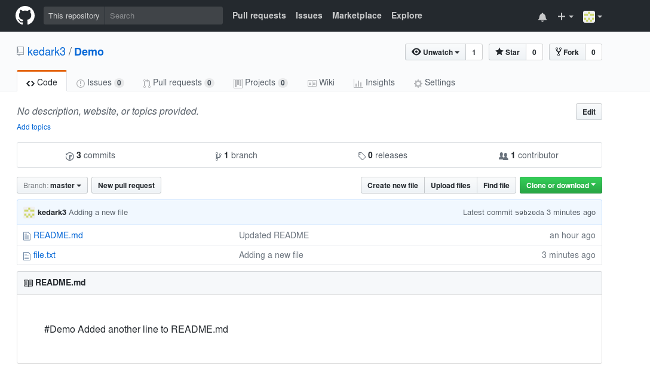
|
||||||
|
|
||||||
|
With these steps, you can create as many files as you like, add them to Git, and commit and push them up to GitHub.
|
||||||
|
|
||||||
|
### Delete a file from Git
|
||||||
|
|
||||||
|
What if we discovered we made an error and need to delete `file.txt` from our repo. One way is to remove the file from our local copy of the repo with this command:
|
||||||
|
```
|
||||||
|
rm file.txt
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
If you do `git status` now, Git says there is a file that is `not staged for commit` and it has been `deleted` from the local copy of the repo. If we now run:
|
||||||
|
```
|
||||||
|
git add file.txt
|
||||||
|
|
||||||
|
git status
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
I know we are deleting the file, but we still run `git add` ** because we need to tell Git about the **change** we are making. `git add` ** can be used when we are adding a new file to Git, modifying contents of an existing file and adding it to Git, or deleting a file from a Git repo. Effectively, `git add` takes all the changes into account and stages those changes for commit. If in doubt, carefully look at output of each command in the terminal screenshot below.
|
||||||
|
|
||||||
|
Git will tell us the deleted file is staged for commit. As soon as you commit this change and push it to GitHub, the file will be removed from the repo on GitHub as well. Do this by running:
|
||||||
|
```
|
||||||
|
git commit -m "Delete file.txt"
|
||||||
|
|
||||||
|
git push -u origin master
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
Now your terminal looks like this:
|
||||||
|
|
||||||
|
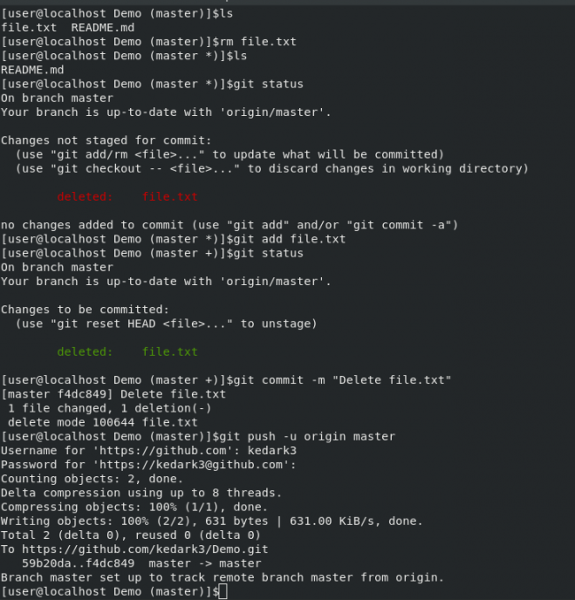
|
||||||
|
|
||||||
|
And your GitHub looks like this:
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
Now you know how to clone, add, modify, and delete Git files from your repo. The next article in this series will examine Git branching.
|
||||||
|
|
||||||
|
--------------------------------------------------------------------------------
|
||||||
|
|
||||||
|
via: https://opensource.com/article/18/2/how-clone-modify-add-delete-git-files
|
||||||
|
|
||||||
|
作者:[Kedar Vijay Kulkarni][a]
|
||||||
|
译者:[译者ID](https://github.com/译者ID)
|
||||||
|
校对:[校对者ID](https://github.com/校对者ID)
|
||||||
|
|
||||||
|
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||||
|
|
||||||
|
[a]:https://opensource.com/users/kkulkarn
|
||||||
|
[1]:https://opensource.com/article/18/1/step-step-guide-git
|
||||||
@ -1,163 +0,0 @@
|
|||||||
The List Of Useful Bash Keyboard Shortcuts
|
|
||||||
======
|
|
||||||
translating by heart4lor
|
|
||||||
|
|
||||||

|
|
||||||
|
|
||||||
Nowadays, I spend more time in Terminal, trying to accomplish more in CLI than GUI. I learned many BASH tricks over time. And, here is the list of useful of BASH shortcuts that every Linux users should know to get things done faster in their BASH shell. I won’t claim that this list is a complete list of BASH shortcuts, but just enough to move around your BASH shell faster than before. Learning how to navigate faster in BASH Shell not only saves some time, but also makes you proud of yourself for learning something worth. Well, let’s get started.
|
|
||||||
|
|
||||||
### List Of Useful Bash Keyboard Shortcuts
|
|
||||||
|
|
||||||
#### ALT key shortcuts
|
|
||||||
|
|
||||||
1\. **ALT+A** – Go to the beginning of a line.
|
|
||||||
|
|
||||||
2\. **ALT+B** – Move one character before the cursor.
|
|
||||||
|
|
||||||
3\. **ALT+C** – Suspends the running command/process. Same as CTRL+C
|
|
||||||
|
|
||||||
4\. **ALT+D** – Closes the empty Terminal (I.e it closes the Terminal when there is nothing typed). Also deletes all chracters after the cursor.
|
|
||||||
|
|
||||||
5\. **ALT+F** – Move forward one character.
|
|
||||||
|
|
||||||
6\. **ALT+T** – Swaps the last two words.
|
|
||||||
|
|
||||||
7\. **ALT+U** – Capitalize all characters in a word after the cursor.
|
|
||||||
|
|
||||||
8\. **ALT+L** – Uncaptalize all characters in a word after the cursor.
|
|
||||||
|
|
||||||
9\. **ALT+R** – Undo any changes to a command that you have brought from the history if you’ve edited it.
|
|
||||||
|
|
||||||
As you see in the above output, I have pulled a command using reverse search and changed the last characters in that command and revert the changes using **ALT+R**.
|
|
||||||
|
|
||||||
10\. **ALT+.** (note the dot at the end) – Use the last word of the previous command.
|
|
||||||
|
|
||||||
If you want to use the same options for multiple commands, you can use this shortcut to bring back the last word of previous command. For instance, I need to short the contents of a directory using “ls -r” command. Also, I want to view my Kernel version using “uname -r”. In both commands, the common word is “-r”. This is where ALT+. shortcut comes in handy. First run, ls -r command to do reverse shorting and use the last word “-r” in the nex command i.e uname.
|
|
||||||
|
|
||||||
#### CTRL key shortcuts
|
|
||||||
|
|
||||||
1\. **CTRL+A** – Quickly move to the beginning of line.
|
|
||||||
|
|
||||||
Let us say you’re typing a command something like below. While you’re at the N’th line, you noticed there is a typo in the first character
|
|
||||||
```
|
|
||||||
$ gind . -mtime -1 -type
|
|
||||||
|
|
||||||
```
|
|
||||||
|
|
||||||
Did you notice? I typed “gind” instead of “find” in the above command. You can correct this error by pressing the left arrow all the way to the first letter and replace “g” with “f”. Alternatively, just hit the **CTRL+A** or **Home** key to instantly go to the beginning of the line and replace the misspelled character. This will save you a few seconds.
|
|
||||||
|
|
||||||
2\. **CTRL+B** – To move backward one character.
|
|
||||||
|
|
||||||
This shortcut key can move the cursor backward one character i.e one character before the cursor. Alternatively, you can use LEFT arrow to move backward one character.
|
|
||||||
|
|
||||||
3\. **CTRL+C** – Stop the currently running command
|
|
||||||
|
|
||||||
If a command takes too long to complete or if you mistakenly run it, you can forcibly stop or quit the command by using **CTRL+C**.
|
|
||||||
|
|
||||||
4\. **CTRL+D** – Delete one character backward.
|
|
||||||
|
|
||||||
If you have a system where the BACKSPACE key isn’t working, you can use **CTRL+D** to delete one character backward. This shortcut also lets you logs out of the current session, similar to exit.
|
|
||||||
|
|
||||||
5\. **CTRL+E** – Move to the end of line
|
|
||||||
|
|
||||||
After you corrected any misspelled word in the start of a command or line, just hit **CTRL+E** to quickly move to the end of the line. Alternatively, you can use END key in your keyboard.
|
|
||||||
|
|
||||||
6\. **CTRL+F** – Move forward one character
|
|
||||||
|
|
||||||
If you want to move the cursor forward one character after another, just press **CTRL+F** instead of RIGHT arrow key.
|
|
||||||
|
|
||||||
7\. **CTRL+G** – Leave the history searching mode without running the command.
|
|
||||||
|
|
||||||
As you see in the above screenshot, I did the reverse search, but didn’t execute the command and left the history searching mode.
|
|
||||||
|
|
||||||
8\. **CTRL+H** – Delete the characters before the cursor, same as BASKSPACE.
|
|
||||||
|
|
||||||
9\. **CTRL+J** – Same as ENTER/RETURN key.
|
|
||||||
|
|
||||||
ENTER key is not working? No problem! **CTRL+J** or **CTRL+M** can be used as an alternative to ENTER key.
|
|
||||||
|
|
||||||
10\. **CTRL+K** – Delete all characters after the cursor.
|
|
||||||
|
|
||||||
You don’t have to keep hitting the DELETE key to delete the characters after the cursor. Just press **CTRL+K** to delete all characters after the cursor.
|
|
||||||
|
|
||||||
11\. **CTRL+L** – Clears the screen and redisplay the line.
|
|
||||||
|
|
||||||
Don’t type “clear” to clear the screen. Just press CTRL+L to clear and redisplay the currently typed line.
|
|
||||||
|
|
||||||
12\. **CTRL+M** – Same as CTRL+J or RETURN.
|
|
||||||
|
|
||||||
13\. **CTRL+N** – Display next line in command history.
|
|
||||||
|
|
||||||
You can also use DOWN arrow.
|
|
||||||
|
|
||||||
14\. **CTRL+O** – Run the command that you found using reverse search i.e CTRL+R.
|
|
||||||
|
|
||||||
15\. **CTRL+P** – Displays the previous line in command history.
|
|
||||||
|
|
||||||
You can also use UP arrow.
|
|
||||||
|
|
||||||
16\. **CTRL+R** – Searches the history backward (Reverse search).
|
|
||||||
|
|
||||||
17\. **CTRL+S** – Searches the history forward.
|
|
||||||
|
|
||||||
18\. **CTRL+T** – Swaps the last two characters.
|
|
||||||
|
|
||||||
This is one of my favorite shortcut. Let us say you typed “sl” instead of “ls”. No problem! This shortcut will transposes the characters as in the below screenshot.
|
|
||||||
|
|
||||||
![][2]
|
|
||||||
|
|
||||||
19\. **CTRL+U** – Delete all characters before the cursor (Kills backward from point to the beginning of line).
|
|
||||||
|
|
||||||
This shortcut will delete all typed characters backward at once.
|
|
||||||
|
|
||||||
20\. **CTRL+V** – Makes the next character typed verbatim
|
|
||||||
|
|
||||||
21\. **CTRL+W** – Delete the words before the cursor.
|
|
||||||
|
|
||||||
Don’t confuse it with CTRL+U. CTRL+W won’t delete everything behind a cursor, but a single word.
|
|
||||||
|
|
||||||
![][3]
|
|
||||||
|
|
||||||
22\. **CTRL+X** – Lists the possible filename completions of the current word.
|
|
||||||
|
|
||||||
23\. **CTRL+XX** – Move between start of command line and current cursor position (and back again).
|
|
||||||
|
|
||||||
24\. **CTRL+Y** – Retrieves last item that you deleted or cut.
|
|
||||||
|
|
||||||
Remember, we deleted a word “-al” using CTRL+W in the 21st command. You can retrieve that word instantly using CTRL+Y.
|
|
||||||
|
|
||||||
![][4]
|
|
||||||
|
|
||||||
See? I didn’t type “-al”. Instead, I pressed CTRL+Y to retrieve it.
|
|
||||||
|
|
||||||
25\. **CTRL+Z** – Stops the current command.
|
|
||||||
|
|
||||||
You may very well know this shortcut. It kills the currently running command. You can resume it with **fg** in the foreground or **bg** in the background.
|
|
||||||
|
|
||||||
26\. **CTRL+[** – Equivalent to ESC key.
|
|
||||||
|
|
||||||
#### Miscellaneous
|
|
||||||
|
|
||||||
1\. **!!** – Repeats the last command.
|
|
||||||
|
|
||||||
2\. **ESC+t** – Swaps the last tow words.
|
|
||||||
|
|
||||||
That’s all I have in mind now. I will keep adding more if I came across any Bash shortcut keys in future. If you think there is a mistake in this article, please do notify me in the comments section below. I will update it asap.
|
|
||||||
|
|
||||||
Cheers!
|
|
||||||
|
|
||||||
|
|
||||||
--------------------------------------------------------------------------------
|
|
||||||
|
|
||||||
via: https://www.ostechnix.com/list-useful-bash-keyboard-shortcuts/
|
|
||||||
|
|
||||||
作者:[SK][a]
|
|
||||||
译者:[译者ID](https://github.com/译者ID)
|
|
||||||
校对:[校对者ID](https://github.com/校对者ID)
|
|
||||||
|
|
||||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
|
||||||
|
|
||||||
[a]:https://www.ostechnix.com/author/sk/
|
|
||||||
[2]:http://www.ostechnix.com/wp-content/uploads/2018/02/CTRLT-1.gif
|
|
||||||
[3]:http://www.ostechnix.com/wp-content/uploads/2018/02/CTRLW-1.gif
|
|
||||||
[4]:http://www.ostechnix.com/wp-content/uploads/2018/02/CTRLY-1.gif
|
|
||||||
@ -1,177 +0,0 @@
|
|||||||
translating by kimii
|
|
||||||
Protecting Code Integrity with PGP — Part 2: Generating Your Master Key
|
|
||||||
======
|
|
||||||
|
|
||||||

|
|
||||||
|
|
||||||
In this article series, we're taking an in-depth look at using PGP and provide practical guidelines for developers working on free software projects. In the previous article, we provided an introduction to [basic tools and concepts][1]. In this installment, we show how to generate and protect your master PGP key.
|
|
||||||
|
|
||||||
### Checklist
|
|
||||||
|
|
||||||
1. Generate a 4096-bit RSA master key (ESSENTIAL)
|
|
||||||
|
|
||||||
2. Back up the master key using paperkey (ESSENTIAL)
|
|
||||||
|
|
||||||
3. Add all relevant identities (ESSENTIAL)
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
### Considerations
|
|
||||||
|
|
||||||
#### Understanding the "Master" (Certify) key
|
|
||||||
|
|
||||||
In this and next section we'll talk about the "master key" and "subkeys." It is important to understand the following:
|
|
||||||
|
|
||||||
1. There are no technical differences between the "master key" and "subkeys."
|
|
||||||
|
|
||||||
2. At creation time, we assign functional limitations to each key by giving it specific capabilities.
|
|
||||||
|
|
||||||
3. A PGP key can have four capabilities.
|
|
||||||
|
|
||||||
* [S] key can be used for signing
|
|
||||||
|
|
||||||
* [E] key can be used for encryption
|
|
||||||
|
|
||||||
* [A] key can be used for authentication
|
|
||||||
|
|
||||||
* [C] key can be used for certifying other keys
|
|
||||||
|
|
||||||
4. A single key may have multiple capabilities.
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
The key carrying the [C] (certify) capability is considered the "master" key because it is the only key that can be used to indicate relationship with other keys. Only the [C] key can be used to:
|
|
||||||
|
|
||||||
* Add or revoke other keys (subkeys) with S/E/A capabilities
|
|
||||||
|
|
||||||
* Add, change or revoke identities (uids) associated with the key
|
|
||||||
|
|
||||||
* Add or change the expiration date on itself or any subkey
|
|
||||||
|
|
||||||
* Sign other people's keys for the web of trust purposes
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
In the Free Software world, the [C] key is your digital identity. Once you create that key, you should take extra care to protect it and prevent it from falling into malicious hands.
|
|
||||||
|
|
||||||
#### Before you create the master key
|
|
||||||
|
|
||||||
Before you create your master key you need to pick your primary identity and your master passphrase.
|
|
||||||
|
|
||||||
##### Primary identity
|
|
||||||
|
|
||||||
Identities are strings using the same format as the "From" field in emails:
|
|
||||||
```
|
|
||||||
Alice Engineer <alice.engineer@example.org>
|
|
||||||
|
|
||||||
```
|
|
||||||
|
|
||||||
You can create new identities, revoke old ones, and change which identity is your "primary" one at any time. Since the primary identity is shown in all GnuPG operations, you should pick a name and address that are both professional and the most likely ones to be used for PGP-protected communication, such as your work address or the address you use for signing off on project commits.
|
|
||||||
|
|
||||||
##### Passphrase
|
|
||||||
|
|
||||||
The passphrase is used exclusively for encrypting the private key with a symmetric algorithm while it is stored on disk. If the contents of your .gnupg directory ever get leaked, a good passphrase is the last line of defense between the thief and them being able to impersonate you online, which is why it is important to set up a good passphrase.
|
|
||||||
|
|
||||||
A good guideline for a strong passphrase is 3-4 words from a rich or mixed dictionary that are not quotes from popular sources (songs, books, slogans). You'll be using this passphrase fairly frequently, so it should be both easy to type and easy to remember.
|
|
||||||
|
|
||||||
##### Algorithm and key strength
|
|
||||||
|
|
||||||
Even though GnuPG has had support for Elliptic Curve crypto for a while now, we'll be sticking to RSA keys, at least for a little while longer. While it is possible to start using ED25519 keys right now, it is likely that you will come across tools and hardware devices that will not be able to handle them correctly.
|
|
||||||
|
|
||||||
You may also wonder why the master key is 4096-bit, if later in the guide we state that 2048-bit keys should be good enough for the lifetime of RSA public key cryptography. The reasons are mostly social and not technical: master keys happen to be the most visible ones on the keychain, and some of the developers you interact with will inevitably judge you negatively if your master key has fewer bits than theirs.
|
|
||||||
|
|
||||||
#### Generate the master key
|
|
||||||
|
|
||||||
To generate your new master key, issue the following command, putting in the right values instead of "Alice Engineer:"
|
|
||||||
```
|
|
||||||
$ gpg --quick-generate-key 'Alice Engineer <alice@example.org>' rsa4096 cert
|
|
||||||
|
|
||||||
```
|
|
||||||
|
|
||||||
A dialog will pop up asking to enter the passphrase. Then, you may need to move your mouse around or type on some keys to generate enough entropy until the command completes.
|
|
||||||
|
|
||||||
Review the output of the command, it will be something like this:
|
|
||||||
```
|
|
||||||
pub rsa4096 2017-12-06 [C] [expires: 2019-12-06]
|
|
||||||
111122223333444455556666AAAABBBBCCCCDDDD
|
|
||||||
uid Alice Engineer <alice@example.org>
|
|
||||||
|
|
||||||
```
|
|
||||||
|
|
||||||
Note the long string on the second line -- that is the full fingerprint of your newly generated key. Key IDs can be represented in three different forms:
|
|
||||||
|
|
||||||
* Fingerprint, a full 40-character key identifier
|
|
||||||
|
|
||||||
* Long, last 16-characters of the fingerprint (AAAABBBBCCCCDDDD)
|
|
||||||
|
|
||||||
* Short, last 8 characters of the fingerprint (CCCCDDDD)
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
You should avoid using 8-character "short key IDs" as they are not sufficiently unique.
|
|
||||||
|
|
||||||
At this point, I suggest you open a text editor, copy the fingerprint of your new key and paste it there. You'll need to use it for the next few steps, so having it close by will be handy.
|
|
||||||
|
|
||||||
#### Back up your master key
|
|
||||||
|
|
||||||
For disaster recovery purposes -- and especially if you intend to use the Web of Trust and collect key signatures from other project developers -- you should create a hardcopy backup of your private key. This is supposed to be the "last resort" measure in case all other backup mechanisms have failed.
|
|
||||||
|
|
||||||
The best way to create a printable hardcopy of your private key is using the paperkey software written for this very purpose. Paperkey is available on all Linux distros, as well as installable via brew install paperkey on Macs.
|
|
||||||
|
|
||||||
Run the following command, replacing [fpr] with the full fingerprint of your key:
|
|
||||||
```
|
|
||||||
$ gpg --export-secret-key [fpr] | paperkey -o /tmp/key-backup.txt
|
|
||||||
|
|
||||||
```
|
|
||||||
|
|
||||||
The output will be in a format that is easy to OCR or input by hand, should you ever need to recover it. Print out that file, then take a pen and write the key passphrase on the margin of the paper. This is a required step because the key printout is still encrypted with the passphrase, and if you ever change the passphrase on your key, you will not remember what it used to be when you had first created it -- guaranteed.
|
|
||||||
|
|
||||||
Put the resulting printout and the hand-written passphrase into an envelope and store in a secure and well-protected place, preferably away from your home, such as your bank vault.
|
|
||||||
|
|
||||||
**Note on printers:** Long gone are days when printers were dumb devices connected to your computer's parallel port. These days they have full operating systems, hard drives, and cloud integration. Since the key content we send to the printer will be encrypted with the passphrase, this is a fairly safe operation, but use your best paranoid judgement.
|
|
||||||
|
|
||||||
#### Add relevant identities
|
|
||||||
|
|
||||||
If you have multiple relevant email addresses (personal, work, open-source project, etc), you should add them to your master key. You don't need to do this for any addresses that you don't expect to use with PGP (e.g., probably not your school alumni address).
|
|
||||||
|
|
||||||
The command is (put the full key fingerprint instead of [fpr]):
|
|
||||||
```
|
|
||||||
$ gpg --quick-add-uid [fpr] 'Alice Engineer <allie@example.net>'
|
|
||||||
|
|
||||||
```
|
|
||||||
|
|
||||||
You can review the UIDs you've already added using:
|
|
||||||
```
|
|
||||||
$ gpg --list-key [fpr] | grep ^uid
|
|
||||||
|
|
||||||
```
|
|
||||||
|
|
||||||
##### Pick the primary UID
|
|
||||||
|
|
||||||
GnuPG will make the latest UID you add as your primary UID, so if that is different from what you want, you should fix it back:
|
|
||||||
```
|
|
||||||
$ gpg --quick-set-primary-uid [fpr] 'Alice Engineer <alice@example.org>'
|
|
||||||
|
|
||||||
```
|
|
||||||
|
|
||||||
Next time, we'll look at generating PGP subkeys, which are the keys you'll actually be using for day-to-day work.
|
|
||||||
|
|
||||||
Learn more about Linux through the free ["Introduction to Linux" ][2]course from The Linux Foundation and edX.
|
|
||||||
|
|
||||||
--------------------------------------------------------------------------------
|
|
||||||
|
|
||||||
via: https://www.linux.com/blog/learn/PGP/2018/2/protecting-code-integrity-pgp-part-2-generating-and-protecting-your-master-pgp-key
|
|
||||||
|
|
||||||
作者:[KONSTANTIN RYABITSEV][a]
|
|
||||||
译者:[译者ID](https://github.com/译者ID)
|
|
||||||
校对:[校对者ID](https://github.com/校对者ID)
|
|
||||||
|
|
||||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
|
||||||
|
|
||||||
[a]:https://www.linux.com/users/mricon
|
|
||||||
[1]:https://www.linux.com/blog/learn/2018/2/protecting-code-integrity-pgp-part-1-basic-pgp-concepts-and-tools
|
|
||||||
[2]:https://training.linuxfoundation.org/linux-courses/system-administration-training/introduction-to-linux
|
|
||||||
@ -1,103 +0,0 @@
|
|||||||
Linux LAN Routing for Beginners: Part 1
|
|
||||||
======
|
|
||||||
|
|
||||||

|
|
||||||
Once upon a time we learned about [IPv6 routing][1]. Now we're going to dig into the basics of IPv4 routing with Linux. We'll start with an overview of hardware and operating systems, and IPv4 addressing basics, and next week we'll setup and test routing.
|
|
||||||
|
|
||||||
### LAN Router Hardware
|
|
||||||
|
|
||||||
Linux is a real networking operating system, and always has been, with network functionality built-in from the beginning. Building a LAN router is simple compared to building a gateway router that connects your LAN to the Internet. You don't have to hassle with security or firewall rules, which are still complicated by having to deal with NAT, network address translation, an affliction of IPv4. Why do we not drop IPv4 and migrate to IPv6? The life of the network administrator would be ever so much simpler.
|
|
||||||
|
|
||||||
But I digress. Ideally, your Linux router is a small machine with at least two network interfaces. Linux Gizmos has a great roundup of single-board computers here: [Catalog of 98 open-spec, hacker friendly SBCs][2]. You could use an old laptop or desktop PC. You could use a compact computer, like the ZaReason Zini or the System76 Meerkat, though these are a little pricey at nearly $600. But they are stout and reliable, and you're not wasting money on a Windows license.
|
|
||||||
|
|
||||||
The Raspberry Pi 3 Model B is great for lower-demand routing. It has a single 10/100 Ethernet port, onboard 2.4GHz 802.11n wireless, and four USB ports, so you can plug in more USB network interfaces. USB 2.0 and the slower onboard network interfaces make the Pi a bit of a network bottleneck, but you can't beat the price ($35 without storage or power supply). It supports a couple dozen Linux flavors, so chances are you can have your favorite. The Debian-based Raspbian is my personal favorite.
|
|
||||||
|
|
||||||
### Operating System
|
|
||||||
|
|
||||||
You might as well stuff the smallest version of your favorite Linux on your chosen hardware thingy, because the specialized router operating systems such as OpenWRT, Tomato, DD-WRT, Smoothwall, Pfsense, and so on all have their own non-standard interfaces. In my admirable opinion this is an unnecessary complication that gets in the way rather than helping. Use the standard Linux tools and learn them once.
|
|
||||||
|
|
||||||
The Debian net install image is about 300MB and supports multiple architectures, including ARM, i386, amd64, and armhf. Ubuntu's server net installation image is under 50MB, giving you even more control over what packages you install. Fedora, Mageia, and openSUSE all offer compact net install images. If you need inspiration browse [Distrowatch][3].
|
|
||||||
|
|
||||||
### What Routers Do
|
|
||||||
|
|
||||||
Why do we even need network routers? A router connects different networks. Without routing every network space is isolated, all sad and alone with no one to talk to but the same boring old nodes. Suppose you have a 192.168.1.0/24 and a 192.168.2.0/24 network. Your two networks cannot talk to each other without a router connecting them. These are Class C private networks with 254 usable addresses each. Use ipcalc to get nice visual information about them:
|
|
||||||
```
|
|
||||||
$ ipcalc 192.168.1.0/24
|
|
||||||
Address: 192.168.1.0 11000000.10101000.00000001. 00000000
|
|
||||||
Netmask: 255.255.255.0 = 24 11111111.11111111.11111111. 00000000
|
|
||||||
Wildcard: 0.0.0.255 00000000.00000000.00000000. 11111111
|
|
||||||
=>
|
|
||||||
Network: 192.168.1.0/24 11000000.10101000.00000001. 00000000
|
|
||||||
HostMin: 192.168.1.1 11000000.10101000.00000001. 00000001
|
|
||||||
HostMax: 192.168.1.254 11000000.10101000.00000001. 11111110
|
|
||||||
Broadcast: 192.168.1.255 11000000.10101000.00000001. 11111111
|
|
||||||
Hosts/Net: 254 Class C, Private Internet
|
|
||||||
|
|
||||||
```
|
|
||||||
|
|
||||||
I like that ipcalc's binary output makes a visual representation of how the netmask works. The first three octets are the network address, and the fourth octet is the host address, so when you are assigning host addresses you "mask" out the network portion and use the leftover. Your two networks have different network addresses, and that is why they cannot communicate without a router in between them.
|
|
||||||
|
|
||||||
Each octet is 256 bytes, but that does not give you 256 host addresses because the first and last values, 0 and 255, are reserved. 0 is the network identifier, and 255 is the broadcast address, so that leaves 254 host addresses. ipcalc helpfully spells all of this out.
|
|
||||||
|
|
||||||
This does not mean that you never have a host address that ends in 0 or 255. Suppose you have a 16-bit prefix:
|
|
||||||
```
|
|
||||||
$ ipcalc 192.168.0.0/16
|
|
||||||
Address: 192.168.0.0 11000000.10101000. 00000000.00000000
|
|
||||||
Netmask: 255.255.0.0 = 16 11111111.11111111. 00000000.00000000
|
|
||||||
Wildcard: 0.0.255.255 00000000.00000000. 11111111.11111111
|
|
||||||
=>
|
|
||||||
Network: 192.168.0.0/16 11000000.10101000. 00000000.00000000
|
|
||||||
HostMin: 192.168.0.1 11000000.10101000. 00000000.00000001
|
|
||||||
HostMax: 192.168.255.254 11000000.10101000. 11111111.11111110
|
|
||||||
Broadcast: 192.168.255.255 11000000.10101000. 11111111.11111111
|
|
||||||
Hosts/Net: 65534 Class C, Private Internet
|
|
||||||
|
|
||||||
```
|
|
||||||
|
|
||||||
ipcalc lists your first and last host addresses, 192.168.0.1 and 192.168.255.254. You may have host addresses that end in 0 and 255, for example 192.168.1.0 and 192.168.0.255, because those fall in between the HostMin and HostMax.
|
|
||||||
|
|
||||||
The same principles apply regardless of your address blocks, whether they are private or public, and don't be shy about using ipcalc to help you understand.
|
|
||||||
|
|
||||||
### CIDR
|
|
||||||
|
|
||||||
CIDR (Classless Inter-Domain Routing) was created to extend IPv4 by providing variable-length subnet masking. CIDR allows finer slicing-and-dicing of your network space. Let ipcalc demonstrate:
|
|
||||||
```
|
|
||||||
$ ipcalc 192.168.1.0/22
|
|
||||||
Address: 192.168.1.0 11000000.10101000.000000 01.00000000
|
|
||||||
Netmask: 255.255.252.0 = 22 11111111.11111111.111111 00.00000000
|
|
||||||
Wildcard: 0.0.3.255 00000000.00000000.000000 11.11111111
|
|
||||||
=>
|
|
||||||
Network: 192.168.0.0/22 11000000.10101000.000000 00.00000000
|
|
||||||
HostMin: 192.168.0.1 11000000.10101000.000000 00.00000001
|
|
||||||
HostMax: 192.168.3.254 11000000.10101000.000000 11.11111110
|
|
||||||
Broadcast: 192.168.3.255 11000000.10101000.000000 11.11111111
|
|
||||||
Hosts/Net: 1022 Class C, Private Internet
|
|
||||||
|
|
||||||
```
|
|
||||||
|
|
||||||
The netmask is not limited to whole octets, but rather crosses the boundary between the third and fourth octets, and the subnet portion ranges from 0 to 3, and not from 0 to 255. The number of available hosts is not a multiple of 8 as it is when the netmask is defined by whole octets.
|
|
||||||
|
|
||||||
Your homework is to review CIDR and how the IPv4 address space is allocated between public, private, and reserved blocks, as this is essential to understanding routing. Setting up routes is not complicated as long as you have a good knowledge of addressing.
|
|
||||||
|
|
||||||
Start with [Understanding IP Addressing and CIDR Charts][4], [IPv4 Private Address Space and Filtering][5], and [IANA IPv4 Address Space Registry][6]. Then come back next week to learn how to create and manage routes.
|
|
||||||
|
|
||||||
Learn more about Linux through the free ["Introduction to Linux" ][7]course from The Linux Foundation and edX.
|
|
||||||
|
|
||||||
--------------------------------------------------------------------------------
|
|
||||||
|
|
||||||
via: https://www.linux.com/learn/intro-to-linux/2018/2/linux-lan-routing-beginners-part-1
|
|
||||||
|
|
||||||
作者:[Carla Schroder][a]
|
|
||||||
译者:[译者ID](https://github.com/译者ID)
|
|
||||||
校对:[校对者ID](https://github.com/校对者ID)
|
|
||||||
|
|
||||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
|
||||||
|
|
||||||
[a]:https://www.linux.com/users/cschroder
|
|
||||||
[1]:https://www.linux.com/learn/intro-to-linux/2017/7/practical-networking-linux-admins-ipv6-routing
|
|
||||||
[2]:http://linuxgizmos.com/catalog-of-98-open-spec-hacker-friendly-sbcs/#catalog
|
|
||||||
[3]:http://distrowatch.org/
|
|
||||||
[4]:https://www.ripe.net/about-us/press-centre/understanding-ip-addressing
|
|
||||||
[5]:https://www.arin.net/knowledge/address_filters.html
|
|
||||||
[6]:https://www.iana.org/assignments/ipv4-address-space/ipv4-address-space.xhtml
|
|
||||||
[7]:https://training.linuxfoundation.org/linux-courses/system-administration-training/introduction-to-linux
|
|
||||||
@ -1,118 +0,0 @@
|
|||||||
Linux LAN Routing for Beginners: Part 2
|
|
||||||
======
|
|
||||||
|
|
||||||

|
|
||||||
|
|
||||||
Last week [we reviewed IPv4 addressing][1] and using the network admin's indispensible ipcalc tool: Now we're going to make some nice LAN routers.
|
|
||||||
|
|
||||||
VirtualBox and KVM are wonderful for testing routing, and the examples in this article are all performed in KVM. If you prefer to use physical hardware, then you need three computers: one to act as the router, and the other two to represent two different networks. You also need two Ethernet switches and cabling.
|
|
||||||
|
|
||||||
The examples assume a wired Ethernet LAN, and we shall pretend there are some bridged wireless access points for a realistic scenario, although we're not going to do anything with them. (I have not yet tried all-WiFi routing and have had mixed success with connecting a mobile broadband device to an Ethernet LAN, so look for those in a future installment.)
|
|
||||||
|
|
||||||
### Network Segments
|
|
||||||
|
|
||||||
The simplest network segment is two computers in the same address space connected to the same switch. These two computers do not need a router to communicate with each other. A useful term is _broadcast domain_ , which describes a group of hosts that are all in the same network. They may be all connected to a single Ethernet switch, or multiple switches. A broadcast domain may include two different networks connected by an Ethernet bridge, which makes the two networks behave as a single network. Wireless access points are typically bridged to a wired Ethernetwork.
|
|
||||||
|
|
||||||
A broadcast domain can talk to a different broadcast domain only when they are connected by a network router.
|
|
||||||
|
|
||||||
### Simple Network
|
|
||||||
|
|
||||||
The following example commands are not persistent, and your changes will vanish with a restart.
|
|
||||||
|
|
||||||
A broadcast domain needs a router to talk to other broadcast domains. Let's illustrate this with two computers and the `ip` command. Our two computers are 192.168.110.125 and 192.168.110.126, and they are plugged into the same Ethernet switch. In VirtualBox or KVM, you automatically create a virtual switch when you configure a new network, so when you assign a network to a virtual machine it's like plugging it into a switch. Use `ip addr show` to see your addresses and network interface names. The two hosts can ping each other.
|
|
||||||
|
|
||||||
Now add an address in a different network to one of the hosts:
|
|
||||||
```
|
|
||||||
# ip addr add 192.168.120.125/24 dev ens3
|
|
||||||
|
|
||||||
```
|
|
||||||
|
|
||||||
You have to specify the network interface name, which in the example is ens3. It is not required to add the network prefix, in this case /24, but it never hurts to be explicit. Check your work with `ip`. The example output is trimmed for clarity:
|
|
||||||
```
|
|
||||||
$ ip addr show
|
|
||||||
ens3:
|
|
||||||
inet 192.168.110.125/24 brd 192.168.110.255 scope global dynamic ens3
|
|
||||||
valid_lft 875sec preferred_lft 875sec
|
|
||||||
inet 192.168.120.125/24 scope global ens3
|
|
||||||
valid_lft forever preferred_lft forever
|
|
||||||
|
|
||||||
```
|
|
||||||
|
|
||||||
The host at 192.168.120.125 can ping itself (`ping 192.168.120.125`), and that is a good basic test to verify that your configuration is working correctly, but the second computer can't ping that address.
|
|
||||||
|
|
||||||
Now we need to do bit of network juggling. Start by adding a third host to act as the router. This needs two virtual network interfaces and a second virtual network. In real life you want your router to have static IP addresses, but for now we'll let the KVM DHCP server do the work of assigning addresses, so you only need these two virtual networks:
|
|
||||||
|
|
||||||
* First network: 192.168.110.0/24
|
|
||||||
* Second network: 192.168.120.0/24
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
Then your router must be configured to forward packets. Packet forwarding should be disabled by default, which you can check with `sysctl`:
|
|
||||||
```
|
|
||||||
$ sysctl net.ipv4.ip_forward
|
|
||||||
net.ipv4.ip_forward = 0
|
|
||||||
|
|
||||||
```
|
|
||||||
|
|
||||||
The zero means it is disabled. Enable it with this command:
|
|
||||||
```
|
|
||||||
# echo 1 > /proc/sys/net/ipv4/ip_forward
|
|
||||||
|
|
||||||
```
|
|
||||||
|
|
||||||
Then configure one of your other hosts to play the part of the second network by assigning the 192.168.120.0/24 virtual network to it in place of the 192.168.110.0/24 network, and then reboot the two "network" hosts, but not the router. (Or restart networking; I'm old and lazy and don't care what weird commands are required to restart services when I can just reboot.) The addressing should look something like this:
|
|
||||||
|
|
||||||
* Host 1: 192.168.110.125
|
|
||||||
* Host 2: 192.168.120.135
|
|
||||||
* Router: 192.168.110.126 and 192.168.120.136
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
Now go on a ping frenzy, and ping everyone from everyone. There are some quirks with virtual machines and the various Linux distributions that produce inconsistent results, so some pings will succeed and some will not. Not succeeding is good, because it means you get to practice creating a static route. First, view the existing routing tables. The first example is from Host 1, and the second is from the router:
|
|
||||||
```
|
|
||||||
$ ip route show
|
|
||||||
default via 192.168.110.1 dev ens3 proto static metric 100
|
|
||||||
192.168.110.0/24 dev ens3 proto kernel scope link src 192.168.110.164 metric 100
|
|
||||||
|
|
||||||
$ ip route show
|
|
||||||
default via 192.168.110.1 dev ens3 proto static metric 100
|
|
||||||
default via 192.168.120.1 dev ens3 proto static metric 101
|
|
||||||
169.254.0.0/16 dev ens3 scope link metric 1000
|
|
||||||
192.168.110.0/24 dev ens3 proto kernel scope link
|
|
||||||
src 192.168.110.126 metric 100
|
|
||||||
192.168.120.0/24 dev ens9 proto kernel scope link
|
|
||||||
src 192.168.120.136 metric 100
|
|
||||||
|
|
||||||
```
|
|
||||||
|
|
||||||
This shows us that the default routes are the ones assigned by KVM. The 169.* address is the automatic link local address, and we can ignore it. Then we see two more routes, the two that belong to our router. You can have multiple routes, and this example shows how to add a non-default route to Host 1:
|
|
||||||
```
|
|
||||||
# ip route add 192.168.120.0/24 via 192.168.110.126 dev ens3
|
|
||||||
|
|
||||||
```
|
|
||||||
|
|
||||||
This means Host 1 can access the 192.168.110.0/24 network via the router interface 192.168.110.126. See how it works? Host 1 and the router need to be in the same address space to connect, then the router forwards to the other network.
|
|
||||||
|
|
||||||
This command deletes a route:
|
|
||||||
```
|
|
||||||
# ip route del 192.168.120.0/24
|
|
||||||
|
|
||||||
```
|
|
||||||
|
|
||||||
In real life, you're not going to be setting up routes manually like this, but rather using a router daemon and advertising your router via DHCP but understanding the fundamentals is key. Come back next week to learn how to set up a nice easy router daemon that does the work for you.
|
|
||||||
|
|
||||||
Learn more about Linux through the free ["Introduction to Linux" ][2]course from The Linux Foundation and edX.
|
|
||||||
|
|
||||||
--------------------------------------------------------------------------------
|
|
||||||
|
|
||||||
via: https://www.linux.com/learn/intro-to-linux/2018/3/linux-lan-routing-beginners-part-2
|
|
||||||
|
|
||||||
作者:[CARLA SCHRODER][a]
|
|
||||||
译者:[译者ID](https://github.com/译者ID)
|
|
||||||
校对:[校对者ID](https://github.com/校对者ID)
|
|
||||||
|
|
||||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
|
||||||
|
|
||||||
[a]:https://www.linux.com/users/cschroder
|
|
||||||
[1]:https://www.linux.com/learn/intro-to-linux/2018/2/linux-lan-routing-beginners-part-1
|
|
||||||
[2]:https://training.linuxfoundation.org/linux-courses/system-administration-training/introduction-to-linux
|
|
||||||
@ -1,3 +1,5 @@
|
|||||||
|
translated by cyleft
|
||||||
|
|
||||||
Most Useful Linux Commands You Can Run in Windows 10
|
Most Useful Linux Commands You Can Run in Windows 10
|
||||||
======
|
======
|
||||||
|
|
||||||
|
|||||||
@ -1,56 +0,0 @@
|
|||||||
Host your own email with projectx/os and a Raspberry Pi
|
|
||||||
======
|
|
||||||
|
|
||||||

|
|
||||||
|
|
||||||
There are plenty of reasons not to want to hand off the tasks of storing your data and running your services to third-party companies; privacy, ownership, and avoiding abusive "monetization" are some of the top ones. But for most people, the task of running a server is just too time-consuming and requires too much-specialized knowledge. Instead, we compromise. We put aside our worries and just use cloud-hosted corporate services, with all the advertising, data mining and selling, and everything else that comes with them.
|
|
||||||
|
|
||||||
This project aims to eliminate that compromise: [projectx/os][1] makes hosting services at home cheap and nearly as easy as creating a Gmail account. All you need is a $35 Raspberry Pi 3 and a Debian-derived OS image—and very little technical knowledge. There are only four steps:
|
|
||||||
|
|
||||||
1. Unzip a ZIP file onto a Secure Digital memory card.
|
|
||||||
2. Edit a text file on the SD card with your WiFi password (if you're not using wired Ethernet).
|
|
||||||
3. Place the SD card into the slot on the Raspberry Pi 3.
|
|
||||||
4. Use your smartphone to choose a subdomain and install the "email server" app on the Raspberry Pi 3.
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
Server applications (such as email servers) are broken into multiple containers, which can only communicate with the outside world and each other in declaratively specified ways, using fine-grained isolation to improve security. For example, incoming SMTP, [SpamAssassin][2] (anti-spam platform), [Dovecot][3] (secure IMAP server), and webmail are all separate containers that can't see each other's data, so compromising an individual daemon does not compromise the others.
|
|
||||||
|
|
||||||
In addition, stateless containers, such as SpamAssassin and incoming SMTP, can be torn down and recreated after each incoming email, so even if someone finds a bug and exploits it, they can't access previous emails or subsequent emails; they can only access their own exploit email. Fortunately, the services that are most exposed to attack are the easiest to run isolated and stateless.
|
|
||||||
|
|
||||||
All storage is encrypted using [dm-crypt][4]. Non-public services, such as Dovecot (IMAP) or webmail, listen on a private, encrypted overlay network provided by [ZeroTier One][5], so only your devices (phones, laptops, tablets, etc.) can access them.
|
|
||||||
|
|
||||||
While emails aren't encrypted end-to-end (unless you use [PGP][6]), the unencrypted email never crosses a network and is never stored on disk. It is present in plaintext only on the two parties' private mail servers, which are secured in their homes and on their clients (phones, laptops, etc.).
|
|
||||||
|
|
||||||
One other advantage is that personal devices secured with a passcode (not a fingerprint or other biometrics) and devices in your home receive far stronger [Fourth Amendment][7] legal protections in the United States than data on a server in a third-party data center owned by a company that wants to avoid downtime or be seen as uncooperative. Of course, if you email with a Gmail user, for example, Google still gets a copy.
|
|
||||||
|
|
||||||
### Going forward
|
|
||||||
|
|
||||||
Email is the first application I've packaged with projectx/os. Imagine an app store full of server software, packaged up for ease of installation and use. Want a blog? Add a WordPress app! Secure Dropbox replacement? Add a [Seafile][8] app or a [Syncthing][9] backend app. [IPFS][10] node? [Mastodon][11] instance? GitLab server? Various home automation/IoT backend services? There are tons of great open source server software that is as easy to install and use as the proprietary cloud services they replace.
|
|
||||||
|
|
||||||
Nolan Leake will be presenting [A cloud in every home: Host servers at home with 0 sysadmin skills][12] at the [Southern California Linux Expo][12] in Pasadena, March 8-11. To attend and get 50% of your ticket, [register][13] using promo code **OSDC**.
|
|
||||||
|
|
||||||
--------------------------------------------------------------------------------
|
|
||||||
|
|
||||||
via: https://opensource.com/article/18/3/host-your-own-email
|
|
||||||
|
|
||||||
作者:[Nolan Leake][a]
|
|
||||||
译者:[译者ID](https://github.com/译者ID)
|
|
||||||
校对:[校对者ID](https://github.com/校对者ID)
|
|
||||||
|
|
||||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
|
||||||
|
|
||||||
[a]:https://opensource.com/users/nolan
|
|
||||||
[1]:https://git.sigbus.net/projectx/os
|
|
||||||
[2]:http://spamassassin.apache.org/
|
|
||||||
[3]:https://www.dovecot.org/
|
|
||||||
[4]:https://gitlab.com/cryptsetup/cryptsetup/wikis/DMCrypt
|
|
||||||
[5]:https://www.zerotier.com/download.shtml
|
|
||||||
[6]:https://en.wikipedia.org/wiki/Pretty_Good_Privacy
|
|
||||||
[7]:https://simple.wikipedia.org/wiki/Fourth_Amendment_to_the_United_States_Constitution
|
|
||||||
[8]:https://www.seafile.com/en/home/
|
|
||||||
[9]:https://syncthing.net/
|
|
||||||
[10]:https://ipfs.io/
|
|
||||||
[11]:https://github.com/tootsuite/mastodon
|
|
||||||
[12]:https://www.socallinuxexpo.org/scale/16x/presentations/cloud-every-home-host-servers-home-0-sysadmin-skills
|
|
||||||
[13]:https://register.socallinuxexpo.org/reg6/
|
|
||||||
189
translated/20180123 Migrating to Linux- The Command Line.md
Normal file
189
translated/20180123 Migrating to Linux- The Command Line.md
Normal file
@ -0,0 +1,189 @@
|
|||||||
|
迁徙到 Linux:命令行环境
|
||||||
|
======
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
这是关于迁徙到 Linux 系列的第四篇文章了。如果您错过了之前的内容,可以回顾我们之前谈到的内容 [新手之 Linux][1]、[文件和文件系统][2]、和 [图形环境][3]。Linux 无处不在,它可以运行在大部分的网络服务器,如 web、email 和其他服务器;它同样可以在您的手机、汽车控制台和其他很多设备上使用。现在,您可能会开始好奇 Linux 系统,并对学习 Linux 的工作原理萌发兴趣。
|
||||||
|
|
||||||
|
在 Linux 下,命令行非常实用。Linux 的桌面系统中,尽管命令行只是可选操作,但是您依旧能看见很多朋友开着一个命令行窗口和其他应用窗口并肩作战。在运行 Linux 系统的网络服务器中,命令行通常是唯一能直接与操作系统交互的工具。因此,命令行是有必要了解的,至少应当涉猎一些基础命令。
|
||||||
|
|
||||||
|
在命令行(通常称之为 Linux shell)中,所有操作都是通过键入命令完成。您可以执行查看文件列表、移动文件位置、显示文件内容、编辑文件内容等一系列操作,通过命令行,您甚至可以查看网页中的内容。
|
||||||
|
|
||||||
|
如果您在 Windows(CMD 或者 PowerShell) 上已经熟悉关于命令行的使用,您是否想跳转到了解 Windows 命令行的章节上去?先了阅读这些内容吧。
|
||||||
|
|
||||||
|
### 导语
|
||||||
|
|
||||||
|
在命令行中,这里有一个当前工作目录(文件夹和目录是同义词,在 Linux 中它们通常都被称为目录)的概念。如果没有特别指定目录,许多命令的执行会在当前目录下生效。比如,键入 ls 列出文件目录,当前工作目录的文件将会被列举出来。看一个例子:
|
||||||
|
```
|
||||||
|
$ ls
|
||||||
|
Desktop Documents Downloads Music Pictures README.txt Videos
|
||||||
|
```
|
||||||
|
|
||||||
|
`ls Documents` 这条命令将会列出 `Documents` 目录下的文件:
|
||||||
|
```
|
||||||
|
$ ls Documents
|
||||||
|
report.txt todo.txt EmailHowTo.pdf
|
||||||
|
```
|
||||||
|
|
||||||
|
通过 `pwd` 命令可以显示当前您的工作目录。比如:
|
||||||
|
```
|
||||||
|
$ pwd
|
||||||
|
/home/student
|
||||||
|
```
|
||||||
|
|
||||||
|
您可以通过 `cd` 命令改变当前目录并切换到您想要抵达的目录。比如:
|
||||||
|
```
|
||||||
|
$ pwd
|
||||||
|
/home/student
|
||||||
|
$ cd Downloads
|
||||||
|
$ pwd
|
||||||
|
/home/student/Downloads
|
||||||
|
```
|
||||||
|
|
||||||
|
路径中的目录由 `/`(左斜杠)字符分隔。路径中有一个隐含的层次关系,比如 `/home/student` 目录中,home 是顶层目录,而 student 是 home 的子目录。
|
||||||
|
|
||||||
|
路径要么是绝对路径,要么是相对路径。绝对路径由一个 `/` 字符打头。
|
||||||
|
|
||||||
|
相对路径由 `.` 或者 `..` 开始。在一个路径中,一个 `.` 意味着当前目录,`..` 意味着当前目录的上级目录。比如,`ls ../Documents` 意味着在此寻找当前目录的上级名为 `Documets` 的目录:
|
||||||
|
```
|
||||||
|
$ pwd
|
||||||
|
/home/student
|
||||||
|
$ ls
|
||||||
|
Desktop Documents Downloads Music Pictures README.txt Videos
|
||||||
|
$ cd Downloads
|
||||||
|
$ pwd
|
||||||
|
/home/student/Downloads
|
||||||
|
$ ls ../Documents
|
||||||
|
report.txt todo.txt EmailHowTo.pdf
|
||||||
|
```
|
||||||
|
|
||||||
|
当您第一次打开命令行窗口时,您当前的工作目录被设置为您的家目录,通常为 `/home/<您的登录名>`。家目录专用于登陆之后存储您的专属文件。
|
||||||
|
|
||||||
|
设置环境变量 `$HOME` 到您的家目录,比如:
|
||||||
|
```
|
||||||
|
$ echo $HOME
|
||||||
|
/home/student
|
||||||
|
```
|
||||||
|
|
||||||
|
下表显示了用于目录导航和管理简单的文本文件的一些命令摘要。
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
### 搜索
|
||||||
|
|
||||||
|
有时我们会遗忘文件的位置,或者忘记了我要寻找的文件名。Linux 命令行有几个命令可以帮助您搜索到文件。
|
||||||
|
|
||||||
|
第一个命令是 `find`。您可以使用 `find` 命令通过文件名或其他属性搜索文件和目录。举个例子,当您遗忘了 todo.txt 文件的位置,我们可以执行下面的代码:
|
||||||
|
```
|
||||||
|
$ find $HOME -name todo.txt
|
||||||
|
/home/student/Documents/todo.txt
|
||||||
|
```
|
||||||
|
|
||||||
|
`find` 程序有很多功能和选项。一个简单的例子:
|
||||||
|
```
|
||||||
|
find <要寻找的目录> -name <文件名>
|
||||||
|
```
|
||||||
|
|
||||||
|
如果这里有 `todo.txt` 文件且不止一个,它将向我们列出拥有这个名字的所有文件的所有所在位置。`find` 命令有很多便于搜索的选项比如类型(文件或是目录等等)、时间、大小和其他一些选项。更多内容您可以同通过:`man find` 获取关于如何使用 `find` 命令的帮助。
|
||||||
|
|
||||||
|
您还可以使用 `grep` 命令搜索文件的特殊内容,比如:
|
||||||
|
```
|
||||||
|
grep "01/02/2018" todo.txt
|
||||||
|
```
|
||||||
|
这将为您展示 `todo` 文件中 `01/02/2018` 所在行。
|
||||||
|
|
||||||
|
### 获取帮助
|
||||||
|
|
||||||
|
Linux 有很多命令,这里,我们没有办法一一列举。授人以鱼不如授人以渔,所以下一步我们将向您介绍帮助命令。
|
||||||
|
|
||||||
|
`apropos` 命令可以帮助您查找需要使用的命令。也许您想要查找能够操作目录或是获得文件列表的所有命令,但是您并不希望让这些命令执行。您可以这样尝试:
|
||||||
|
```
|
||||||
|
apropos directory
|
||||||
|
```
|
||||||
|
|
||||||
|
要在帮助文档中,得到一个于 `directiory` 关键字的相关命令列表,您可以这样操作:
|
||||||
|
```
|
||||||
|
apropos "list open files"
|
||||||
|
```
|
||||||
|
|
||||||
|
这将提供一个 `lsof` 命令给您,帮助您打开文件列表。
|
||||||
|
|
||||||
|
当您明确您要使用的命令,但是不确定应该使用什么选项完成预期工作,您可以使用 man 命令,它是 manual 的缩写。您可以这样使用:
|
||||||
|
```
|
||||||
|
man ls
|
||||||
|
```
|
||||||
|
|
||||||
|
您可以在自己的设备上尝试这个命令。它会提供给您关于使用这个命令的完整信息。
|
||||||
|
|
||||||
|
通常,很多命令都会有能够给 `help` 选项(比如说,`ls --help`),列出命令使用的提示。`man` 页面的内容通常太繁琐,`--help` 选项可能更适合快速浏览。
|
||||||
|
|
||||||
|
### 脚本
|
||||||
|
|
||||||
|
Linux 命令行中最贴心的功能是能够运行脚本文件,并且能重复运行。Linux 命令可以存储在文本文件中,您可以在文件的开头写入 `#!/bin/sh`,之后追加命令。之后,一旦文件被存储为可执行文件,您就可以像执行命令一样运行脚本文件,比如,
|
||||||
|
```
|
||||||
|
--- contents of get_todays_todos.sh ---
|
||||||
|
#!/bin/sh
|
||||||
|
todays_date=`date +"%m/%d/%y"`
|
||||||
|
grep $todays_date $HOME/todos.txt
|
||||||
|
```
|
||||||
|
|
||||||
|
在一个确定的工作中脚本可以帮助自动化重复执行命令。如果需要的话,脚本也可以很复杂,能够使用循环、判断语句等。限于篇幅,这里不细述,但是您可以在网上查询到相关信息。
|
||||||
|
|
||||||
|
您是否已经熟悉了 Windows 命令行?
|
||||||
|
|
||||||
|
如果您对 Windows CMD 或者 PowerShell 程序很熟悉,在命令行输入命令应该是轻车熟路的。然而,它们之间有很多差异,如果您没有理解它们之间的差异可能会为之困扰。
|
||||||
|
|
||||||
|
首先,在 Linux 下的 PATH 环境于 Windows 不同。在 Windows 中,当前目录被认为是路径中的第一个文件夹,尽管该目录没有在环境变量中列出。而在 Linux 下,当前目录不会在路径中显示表示。Linux 下设置环境变量会被认为是风险操作。在 Linux 的当前目录执行程序,您需要使用 ./(代表当前目录的相对目录表示方式) 前缀。这可能会干扰很多 CMD 用户。比如:
|
||||||
|
```
|
||||||
|
./my_program
|
||||||
|
```
|
||||||
|
|
||||||
|
而不是
|
||||||
|
```
|
||||||
|
my_program
|
||||||
|
```
|
||||||
|
|
||||||
|
另外,在 Windows 环境变量的路径中是以 `;`(分号) 分割的。在 Linux 中,由 `:` 分割环境变量。同样,在 Linux 中路径由 `/` 字符分隔,而在 Windows 目录中路径由 `\` 字符分割。因此 Windows 中典型的环境变量会像这样:
|
||||||
|
```
|
||||||
|
PATH="C:\Program Files;C:\Program Files\Firefox;"
|
||||||
|
while on Linux it might look like:
|
||||||
|
PATH="/usr/bin:/opt/mozilla/firefox"
|
||||||
|
```
|
||||||
|
|
||||||
|
还要注意,在 Linux 中环境变量由 `$` 拓展,而在 Windows 中您需要使用百分号(就是这样: %PATH%)。
|
||||||
|
|
||||||
|
在 Linux 中,通过 `-` 使用命令选项,而在 Windows 中,使用选项要通过 `/` 字符。所以,在 Linux 中您应该:
|
||||||
|
```
|
||||||
|
a_prog -h
|
||||||
|
```
|
||||||
|
|
||||||
|
而不是
|
||||||
|
```
|
||||||
|
a_prog /h
|
||||||
|
```
|
||||||
|
|
||||||
|
在 Linux 下,文件拓展名并没有意义。例如,将 `myscript` 重命名为 `myscript.bat` 并不会因此而可执行,需要设置文件的执行权限。文件执行权限会在下次的内容中覆盖到。
|
||||||
|
|
||||||
|
在 Linux 中,如果文件或者目录名以 `.` 字符开头,意味着它们是隐藏文件。比如,如果您申请编辑 `.bashrc` 文件,您不能在 `home` 目录中找到它,但是它可能真的存在,只不过它是隐藏文件。在命令行中,您可以通过 `ls` 命令的 `-a` 选项查看隐藏文件,比如:
|
||||||
|
```
|
||||||
|
ls -a
|
||||||
|
```
|
||||||
|
|
||||||
|
在 Linux 中,普通的命令与 Windows 的命令不尽相同。下面的表格显示了常用命令中 CMD 命令和 Linux 命令行的差异。
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
--------------------------------------------------------------------------------
|
||||||
|
|
||||||
|
via: https://www.linux.com/blog/learn/2018/1/migrating-linux-command-line
|
||||||
|
|
||||||
|
作者:[John Bonesio][a]
|
||||||
|
译者:[CYLeft](https://github.com/CYLeft)
|
||||||
|
校对:[校对者ID](https://github.com/校对者ID)
|
||||||
|
|
||||||
|
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||||
|
|
||||||
|
[a]:https://www.linux.com/users/johnbonesio
|
||||||
|
[1]:https://www.linux.com/blog/learn/intro-to-linux/2017/10/migrating-linux-introduction
|
||||||
|
[2]:https://www.linux.com/blog/learn/intro-to-linux/2017/11/migrating-linux-disks-files-and-filesystems
|
||||||
|
[3]:https://www.linux.com/blog/learn/2017/12/migrating-linux-graphical-environments
|
||||||
@ -1,192 +0,0 @@
|
|||||||
选择一个 Linux 跟踪器(2015)
|
|
||||||
======
|
|
||||||
[![][1]][2]
|
|
||||||
_Linux 跟踪很神奇!_
|
|
||||||
|
|
||||||
跟踪器是高级的性能分析和调试工具,如果你使用过 strace(1) 或者 tcpdump(8),你不应该被它吓到 ... 你使用的就是跟踪器。系统跟踪器能让你看到很多的东西,而不仅是系统调用或者包,因为常见的跟踪器都可以跟踪内核或者应用程序的任何东西。
|
|
||||||
|
|
||||||
有大量的 Linux 跟踪器可供你选择。由于它们中的每个都有一个官方的(或者非官方的)的吉祥物,我们有足够多的选择给孩子们展示。
|
|
||||||
|
|
||||||
你喜欢使用哪一个呢?
|
|
||||||
|
|
||||||
我从两类读者的角度来回答这个问题:大多数人和性能/内核工程师。当然,随着时间的推移,这也可能会发生变化,因此,我需要及时去更新本文内容,或许是每年一次,或者更频繁。
|
|
||||||
|
|
||||||
## 对于大多数人
|
|
||||||
|
|
||||||
大多数人(开发者、系统管理员、运维人员、网络可靠性工程师(SRE)…)是不需要去学习系统跟踪器的详细内容的。以下是你需要去了解和做的事情:
|
|
||||||
|
|
||||||
### 1. 使用 perf_events 了解 CPU 概要信息
|
|
||||||
|
|
||||||
使用 perf_events 去了解 CPU 的基本情况。它的概要信息可以用一个 [火焰图][3] 来形象地表示。比如:
|
|
||||||
```
|
|
||||||
git clone --depth 1 https://github.com/brendangregg/FlameGraph
|
|
||||||
perf record -F 99 -a -g -- sleep 30
|
|
||||||
perf script | ./FlameGraph/stackcollapse-perf.pl | ./FlameGraph/flamegraph.pl > perf.svg
|
|
||||||
|
|
||||||
```
|
|
||||||
|
|
||||||
Linux 的 perf_events(又称为 "perf",后面用它来表示命令)是官方为 Linux 用户准备的跟踪器/分析器。它在内核源码中,并且维护的非常好(而且现在它的功能还是快速加强)。它一般是通过 linux-tools-common 这个包来添加的。
|
|
||||||
|
|
||||||
perf 可以做的事情很多,但是,如果我建议你只学习其中的一个功能,那就是查看 CPU 概要信息。虽然从技术角度来说,这并不是事件“跟踪”,主要是它很简单。较难的部分是去获得工作的完整栈和符号,这部分的功能在我的 [Linux Profiling at Netflix][4] 中讨论过。
|
|
||||||
|
|
||||||
### 2. 知道它能干什么
|
|
||||||
|
|
||||||
正如一位朋友所说的:“你不需要知道 X 光机是如何工作的,但你需要明白的是,如果你吞下了一个硬币,X 光机是你的一个选择!”你需要知道使用跟踪器能够做什么,因此,如果你在业务上需要它,你可以以后再去学习它,或者请会使用它的人来做。
|
|
||||||
|
|
||||||
简单地说:几乎任何事情都可以通过跟踪来了解它。内部文件系统、TCP/IP 处理过程、设备驱动、应用程序内部情况。阅读我在 lwn.net 上的 [ftrace][5] 的文章,也可以去浏览 [perf_events 页面][6],那里有一些跟踪能力的示例。
|
|
||||||
|
|
||||||
### 3. 请求一个前端
|
|
||||||
|
|
||||||
如果你把它作为一个性能分析工具(有许多公司销售这类产品),并要求支持 Linux 跟踪。希望通过一个“点击”界面去探查内核的内部,包含一个在栈不同位置的延迟的热力图。就像我在 [Monitorama 演讲][7] 中描述的那样。
|
|
||||||
|
|
||||||
我创建并开源了我自己的一些前端,虽然它是基于 CLI 的(不是图形界面的)。这样将使其它人使用跟踪器更快更容易。比如,我的 [perf-tools][8],跟踪新进程是这样的:
|
|
||||||
```
|
|
||||||
# ./execsnoop
|
|
||||||
Tracing exec()s. Ctrl-C to end.
|
|
||||||
PID PPID ARGS
|
|
||||||
22898 22004 man ls
|
|
||||||
22905 22898 preconv -e UTF-8
|
|
||||||
22908 22898 pager -s
|
|
||||||
22907 22898 nroff -mandoc -rLL=164n -rLT=164n -Tutf8
|
|
||||||
[...]
|
|
||||||
|
|
||||||
```
|
|
||||||
|
|
||||||
在 Netflix 上,我创建了一个 [Vector][9],它是一个实例分析工具,实际上它是一个 Linux 跟踪器的前端。
|
|
||||||
|
|
||||||
## 对于性能或者内核工程师
|
|
||||||
|
|
||||||
一般来说,我们的工作都非常难,因为大多数人或许要求我们去搞清楚如何去跟踪某个事件,以及因此需要选择使用其中一个跟踪器。为完全理解一个跟踪器,你通常需要花至少一百多个小时去使用它。理解所有的 Linux 跟踪器并能在它们之间做出正确的选择是件很难的事情。(我或许是唯一接近完成这件事的人)
|
|
||||||
|
|
||||||
在这里我建议选择如下之一:
|
|
||||||
|
|
||||||
A) 选择一个全能的跟踪器,并以它为标准。这需要在一个测试环境中,花大量的时间来搞清楚它的细微差别和安全性。我现在的建议是 SystemTap 的最新版本(即从这个 [源][10] 构建的)。我知道有的公司选择的是 LTTng ,尽管它并不是很强大(但是它很安全),但他们也用的很好。如果在 sysdig 中添加了跟踪点或者是 kprobes,它也是另外的一个候选者。
|
|
||||||
|
|
||||||
B) 按我的 [Velocity 教程中][11] 的流程图。这意味着可能是使用 ftrace 或者 perf_events,因为 eBPF 是集成在内核中的,然后用其它的跟踪器,如 SystemTap/LTTng 作为对 eBPF 的补充。我目前在 Netflix 的工作中就是这么做的。
|
|
||||||
|
|
||||||
以下是我对各个跟踪器的评价:
|
|
||||||
|
|
||||||
### 1. ftrace
|
|
||||||
|
|
||||||
我爱 [Ftrace][12],它是内核黑客最好的朋友。它被构建进内核中,它能够消费跟踪点、kprobes、以及 uprobes,并且提供一些功能:使用可选的过滤器和参数进行事件跟踪;事件计数和计时,内核概览;函数流步进。关于它的示例可以查看内核源树中的 [ftrace.txt][13]。它通过 /sys 来管理,是面向单 root 用户的(虽然你可以使用缓冲实例来破解它以支持多用户),它的界面有时很繁琐,但是它比较容易破解,并且有前端:Steven Rostedt,ftrace 的主要创建者,他设计了 trace-cmd,并且我已经创建了 perf-tools 集合。我最讨厌的就是它不可编程,因此,你也不能,比如,去保存和获取时间戳,计算延迟,以及保存它的历史。你不需要花成本转储事件到用户级以便于进行后期处理。它通过 eBPF 可以实现可编程。
|
|
||||||
|
|
||||||
### 2. perf_events
|
|
||||||
|
|
||||||
[perf_events][14] 是 Linux 用户的主要跟踪工具,它来源于 Linux 内核,一般是通过 linux-tools-common 包来添加。又称为 "perf",后面的 perf 指的是它的前端,它非常高效(动态缓存),一般用于跟踪并转储到一个文件中(perf.data),然后可以在以后的某个时间进行后期处理。它可以做大部分 ftrace 能做的事情。它实现不了函数流步进,并且不太容易破解(因为它的安全/错误检查做的非常好)。但它可以做概览(采样)、CPU 性能计数、用户级的栈转换、以及消费对行使用本地变量进行跟踪的调试信息。它也支持多个并发用户。与 ftrace 一样,它也是内核不可编程的,或者 eBPF 支持(已经计划了补丁)。如果只学习一个跟踪器,我建议大家去学习 perf,它可以解决大量的问题,并且它也很安全。
|
|
||||||
|
|
||||||
### 3. eBPF
|
|
||||||
|
|
||||||
扩展的伯克利包过滤器(eBPF)是一个内核虚拟机,可以在事件上运行程序,它非常高效(JIT)。它可能最终为 ftrace 和 perf_events 提供内核可编程,并可以去增强其它跟踪器。它现在是由 Alexei Starovoitov 开发,还没有实现全整合,但是对于一些令人印象深刻的工具,有些内核版本(比如,4.1)已经支持了:比如,块设备 I/O 延迟热力图。更多参考资料,请查阅 Alexei 的 [BPF 演示][15],和它的 [eBPF 示例][16]。
|
|
||||||
|
|
||||||
### 4. SystemTap
|
|
||||||
|
|
||||||
[SystemTap][17] 是一个非常强大的跟踪器。它可以做任何事情:概览、跟踪点、kprobes、uprobes(它就来自 SystemTap)、USDT、内核编程等等。它将程序编译成内核模块并加载它们 —— 这是一种很难保证安全的方法。它开发的很怪诞,并且在过去的一段时间内出现了很多问题(恐慌或冻结)。许多并不是 SystemTap 的过错 —— 它通常被内核首先用于某些功能跟踪,并首先遇到运行 bug。最新版本的 SystemTap 是非常好的(你需要从它的源代码编译),但是,许多人仍然没有从早期版本的问题阴影中走出来。如果你想去使用它,花一些时间去测试环境,然后,在 irc.freenode.net 的 #systemtap 频道与开发者进行讨论。(Netflix 有一个容错架构,我们使用了 SystemTap,但是我们或许比起你来说,很少担心它的安全性)我最讨厌的事情是,它假设你有办法得到内核调试信息,而我并没有这些信息。没有它我确实可以做一些事情,但是缺少相关的文档和示例(我现在自己开始帮着做这些了)。
|
|
||||||
|
|
||||||
### 5. LTTng
|
|
||||||
|
|
||||||
[LTTng][18] 对事件收集进行了优化,性能要好于其它的跟踪器,也支持许多的事件类型,包括 USDT。它开发的很怪诞。它的核心部分非常简单:通过一个很小的且很固定的指令集写入事件到跟踪缓冲区。这样让它既安全又快速。缺点是做内核编程不太容易。我觉得那不是个大问题,由于它优化的很好,尽管在需要后期处理的情况下,仍然可以充分的扩展。它也探索了一种不同的分析技术。很多的“黑匣子”记录了全部有趣的事件,可以在以后的 GUI 下学习它。我担心意外的记录丢失事件,我真的需要花一些时间去看看它在实践中是如何工作的。这个跟踪器上我花的时间最少(原因是没有实践过它)。
|
|
||||||
|
|
||||||
### 6. ktap
|
|
||||||
|
|
||||||
[ktap][19] 是一个很有前途的跟踪器,它在内核中使用了一个 lua 虚拟机,它不需要调试信息和嵌入式设备就可以工作的很好。这使得它进入了人们的视野,在某个时候似乎要成为 Linux 上最好的跟踪器。然而,eBPF 开始集成到了内核,而 ktap 的集成工作被推迟了,直到它能够使用 eBPF 而不是它自己的虚拟机。由于 eBPF 在几个月后仍然在集成过程中,使得 ktap 的开发者等待了很长的时间。我希望在今年的晚些时间它能够重启开发。
|
|
||||||
|
|
||||||
### 7. dtrace4linux
|
|
||||||
|
|
||||||
[dtrace4linux][20] 主要由一个人 (Paul Fox) 利用业务时间将 Sun DTrace 移植到 Linux 中的。它令人印象深刻,而一些贡献者的工作,还不是很完美,它最多应该算是实验性的工具(不安全)。我认为对于许可证(license)的担心,使人们对它保持谨慎:它可能永远也进入不了 Linux 内核,因为 Sun 是基于 CDDL 许可证发布的 DTrace;Paul 的方法是将它作为一个插件。我非常希望看到 Linux 上的 DTrace,并且希望这个项目能够完成,我想我加入 Netflix 时将花一些时间来帮它完成。但是,我一直在使用内置的跟踪器 ftrace 和 perf_events。
|
|
||||||
|
|
||||||
### 8. OL DTrace
|
|
||||||
|
|
||||||
[Oracle Linux DTrace][21] 是将 DTrace 移植到 Linux 的一系列努力之一,尤其是 Oracle Linux。过去这些年的许多发行版都一直稳定的进步,开发者甚至谈到了改善 DTrace 测试套件,这显示了这个项目很有前途。许多有用的功能已经完成:系统调用、概览、sdt、proc、sched、以及 USDT。我一直在等待着 fbt(函数边界跟踪,对内核的动态跟踪),它将成为 Linux 内核上非常强大的功能。它最终能否成功取决于能否吸引足够多的人去使用 Oracle Linux(并为支持付费)。另一个羁绊是它并非完全开源的:内核组件是开源的,但用户级代码我没有看到。
|
|
||||||
|
|
||||||
### 9. sysdig
|
|
||||||
|
|
||||||
[sysdig][22] 是一个很新的跟踪器,它可以使用类似 tcpdump 的语法来处理系统调用事件,并用 lua 做后期处理。它也是令人印象深刻的,并且很高兴能看到在系统跟踪空间的创新。它的局限性是,它的系统调用只能是在当时,并且,它不能转储事件到用户级进行后期处理。虽然我希望能看到它去支持跟踪点、kprobes、以及 uprobes,但是你还是可以使用系统调用来做一些事情。我也希望在内核概览方面看到它支持 eBPF。sysdig 的开发者现在增加了对容器的支持。可以关注它的进一步发展。
|
|
||||||
|
|
||||||
## 深入阅读
|
|
||||||
|
|
||||||
我自己的工作中使用到的跟踪器包括:
|
|
||||||
|
|
||||||
**ftrace** : 我的 [perf-tools][8] 集合(查看示例目录);我的 lwn.net 的 [ftrace 跟踪器的文章][5]; 一个 [LISA14][8] 演讲;和文章: [function counting][23], [iosnoop][24], [opensnoop][25], [execsnoop][26], [TCP retransmits][27], [uprobes][28], 和 [USDT][29]。
|
|
||||||
|
|
||||||
**perf_events** : 我的 [perf_events 示例][6] 页面:对于 SCALE 的一个 [Linux Profiling at Netflix][4] 演讲;和文章:[CPU 采样][30],[静态跟踪点][31],[势力图][32],[计数][33],[内核行跟踪][34],[off-CPU 时间火焰图][35]。
|
|
||||||
|
|
||||||
**eBPF** : 文章 [eBPF:一个小的进步][36],和一些 [BPF-tools][37] (我需要发布更多)。
|
|
||||||
|
|
||||||
**SystemTap** : 很久以前,我写了一篇 [使用 SystemTap][38] 的文章,它有点时间了。最近我发布了一些 [systemtap-lwtools][39],展示了在没有内核调试信息的情况下,SystemTap 是如何使用的。
|
|
||||||
|
|
||||||
**LTTng** : 我使用它的时间很短,也没有发布什么文章。
|
|
||||||
|
|
||||||
**ktap** : 我的 [ktap 示例][40] 页面包括一行程序和脚本,虽然它是早期的版本。
|
|
||||||
|
|
||||||
**dtrace4linux** : 在我的 [系统性能][41] 书中包含了一些示例,并且在过去的时间中我为了某些事情开发了一些小的修补,比如, [timestamps][42]。
|
|
||||||
|
|
||||||
**OL DTrace** : 因为它是对 DTrace 的简单移植,我早期 DTrace 的大部分工作都 应该是与它相关的(链接太多了,可以去 [我的主页][43] 上搜索)。一旦它更加完美,我可以开发很多专用工具。
|
|
||||||
|
|
||||||
**sysdig** : 我贡献了 [fileslower][44] 和 [subsecond offset spectrogram][45] chisels。
|
|
||||||
|
|
||||||
**others** : 关于 [strace][46],我写了一些告诫文章。
|
|
||||||
|
|
||||||
不好意思,没有更多的跟踪器了! … 如果你想知道为什么 Linux 中的跟踪器不止一个,或者关于 DTrace 的内容,在我的 [从 DTrace 到 Linux][47] 的演讲中有答案,从 [第 28 张幻灯片][48] 开始。
|
|
||||||
|
|
||||||
感谢 [Deirdre Straughan][49] 的编辑,以及创建了跟踪的小马(General Zoi 是小马的创建者)。
|
|
||||||
|
|
||||||
--------------------------------------------------------------------------------
|
|
||||||
|
|
||||||
via: http://www.brendangregg.com/blog/2015-07-08/choosing-a-linux-tracer.html
|
|
||||||
|
|
||||||
作者:[Brendan Gregg.][a]
|
|
||||||
译者:[qhwdw](https://github.com/qhwdw)
|
|
||||||
校对:[校对者ID](https://github.com/校对者ID)
|
|
||||||
|
|
||||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
|
||||||
|
|
||||||
[a]:http://www.brendangregg.com
|
|
||||||
[1]:http://www.brendangregg.com/blog/images/2015/tracing_ponies.png
|
|
||||||
[2]:http://www.slideshare.net/brendangregg/velocity-2015-linux-perf-tools/105
|
|
||||||
[3]:http://www.brendangregg.com/FlameGraphs/cpuflamegraphs.html
|
|
||||||
[4]:http://www.brendangregg.com/blog/2015-02-27/linux-profiling-at-netflix.html
|
|
||||||
[5]:http://lwn.net/Articles/608497/
|
|
||||||
[6]:http://www.brendangregg.com/perf.html
|
|
||||||
[7]:http://www.brendangregg.com/blog/2015-06-23/netflix-instance-analysis-requirements.html
|
|
||||||
[8]:http://www.brendangregg.com/blog/2015-03-17/linux-performance-analysis-perf-tools.html
|
|
||||||
[9]:http://techblog.netflix.com/2015/04/introducing-vector-netflixs-on-host.html
|
|
||||||
[10]:https://sourceware.org/git/?p=systemtap.git;a=blob_plain;f=README;hb=HEAD
|
|
||||||
[11]:http://www.slideshare.net/brendangregg/velocity-2015-linux-perf-tools
|
|
||||||
[12]:http://lwn.net/Articles/370423/
|
|
||||||
[13]:https://www.kernel.org/doc/Documentation/trace/ftrace.txt
|
|
||||||
[14]:https://perf.wiki.kernel.org/index.php/Main_Page
|
|
||||||
[15]:http://www.phoronix.com/scan.php?page=news_item&px=BPF-Understanding-Kernel-VM
|
|
||||||
[16]:https://github.com/torvalds/linux/tree/master/samples/bpf
|
|
||||||
[17]:https://sourceware.org/systemtap/wiki
|
|
||||||
[18]:http://lttng.org/
|
|
||||||
[19]:http://ktap.org/
|
|
||||||
[20]:https://github.com/dtrace4linux/linux
|
|
||||||
[21]:http://docs.oracle.com/cd/E37670_01/E38608/html/index.html
|
|
||||||
[22]:http://www.sysdig.org/
|
|
||||||
[23]:http://www.brendangregg.com/blog/2014-07-13/linux-ftrace-function-counting.html
|
|
||||||
[24]:http://www.brendangregg.com/blog/2014-07-16/iosnoop-for-linux.html
|
|
||||||
[25]:http://www.brendangregg.com/blog/2014-07-25/opensnoop-for-linux.html
|
|
||||||
[26]:http://www.brendangregg.com/blog/2014-07-28/execsnoop-for-linux.html
|
|
||||||
[27]:http://www.brendangregg.com/blog/2014-09-06/linux-ftrace-tcp-retransmit-tracing.html
|
|
||||||
[28]:http://www.brendangregg.com/blog/2015-06-28/linux-ftrace-uprobe.html
|
|
||||||
[29]:http://www.brendangregg.com/blog/2015-07-03/hacking-linux-usdt-ftrace.html
|
|
||||||
[30]:http://www.brendangregg.com/blog/2014-06-22/perf-cpu-sample.html
|
|
||||||
[31]:http://www.brendangregg.com/blog/2014-06-29/perf-static-tracepoints.html
|
|
||||||
[32]:http://www.brendangregg.com/blog/2014-07-01/perf-heat-maps.html
|
|
||||||
[33]:http://www.brendangregg.com/blog/2014-07-03/perf-counting.html
|
|
||||||
[34]:http://www.brendangregg.com/blog/2014-09-11/perf-kernel-line-tracing.html
|
|
||||||
[35]:http://www.brendangregg.com/blog/2015-02-26/linux-perf-off-cpu-flame-graph.html
|
|
||||||
[36]:http://www.brendangregg.com/blog/2015-05-15/ebpf-one-small-step.html
|
|
||||||
[37]:https://github.com/brendangregg/BPF-tools
|
|
||||||
[38]:http://dtrace.org/blogs/brendan/2011/10/15/using-systemtap/
|
|
||||||
[39]:https://github.com/brendangregg/systemtap-lwtools
|
|
||||||
[40]:http://www.brendangregg.com/ktap.html
|
|
||||||
[41]:http://www.brendangregg.com/sysperfbook.html
|
|
||||||
[42]:https://github.com/dtrace4linux/linux/issues/55
|
|
||||||
[43]:http://www.brendangregg.com
|
|
||||||
[44]:https://github.com/brendangregg/sysdig/commit/d0eeac1a32d6749dab24d1dc3fffb2ef0f9d7151
|
|
||||||
[45]:https://github.com/brendangregg/sysdig/commit/2f21604dce0b561407accb9dba869aa19c365952
|
|
||||||
[46]:http://www.brendangregg.com/blog/2014-05-11/strace-wow-much-syscall.html
|
|
||||||
[47]:http://www.brendangregg.com/blog/2015-02-28/from-dtrace-to-linux.html
|
|
||||||
[48]:http://www.slideshare.net/brendangregg/from-dtrace-to-linux/28
|
|
||||||
[49]:http://www.beginningwithi.com/
|
|
||||||
@ -1,131 +0,0 @@
|
|||||||
Linux 容器安全的 10 个层面
|
|
||||||
======
|
|
||||||

|
|
||||||
|
|
||||||
容器提供了打包应用程序的一种简单方法,它实现了从开发到测试到投入生产系统的无缝传递。它也有助于确保跨不同环境的连贯性,包括物理服务器、虚拟机、以及公有云或私有云。这些好处使得一些组织为了更方便地部署和管理为他们提升业务价值的应用程序,而快速部署容器。
|
|
||||||
|
|
||||||
企业要求存储安全,在容器中运行基础服务的任何人都会问,“容器安全吗?”以及“怎么相信运行在容器中的我的应用程序是安全的?”
|
|
||||||
|
|
||||||
安全的容器就像是许多安全运行的进程。在你部署和运行你的容器之前,你需要去考虑整个解决方案栈~~(致校对,容器是由不同的层堆叠而成,英文原文中使用的stack,可以直译为“解决方案栈”,但是似乎没有这一习惯说法,也可以翻译为解决方案的不同层级,哪个更合适?)~~各个层面的安全。你也需要去考虑应用程序和容器整个生命周期的安全。
|
|
||||||
|
|
||||||
尝试从这十个关键的因素去确保容器解决方案栈不同层面、以及容器生命周期的不同阶段的安全。
|
|
||||||
|
|
||||||
### 1. 容器宿主机操作系统和多租户环境
|
|
||||||
|
|
||||||
由于容器将应用程序和它的依赖作为一个单元来处理,使得开发者构建和升级应用程序变得更加容易,并且,容器可以启用多租户技术将许多应用程序和服务部署到一台共享主机上。在一台单独的主机上以容器方式部署多个应用程序、按需启动和关闭单个容器都是很容易的。为完全实现这种打包和部署技术的优势,运营团队需要运行容器的合适环境。运营者需要一个安全的操作系统,它能够在边界上保护容器安全、从容器中保护主机内核、以及保护容器彼此之间的安全。
|
|
||||||
|
|
||||||
### 2. 容器内容(使用可信来源)
|
|
||||||
|
|
||||||
容器是隔离的 Linux 进程,并且在一个共享主机的内核中,容器内使用的资源被限制在仅允许你运行着应用程序的沙箱中。保护容器的方法与保护你的 Linux 中运行的任何进程的方法是一样的。降低权限是非常重要的,也是保护容器安全的最佳实践。甚至是使用尽可能小的权限去创建容器。容器应该以一个普通用户的权限来运行,而不是 root 权限的用户。在 Linux 中可以使用多级安全,Linux 命名空间、安全强化 Linux( [SELinux][1])、[cgroups][2] 、capabilities(译者注:Linux 内核的一个安全特性,它打破了传统的普通用户与 root 用户的概念,在进程级提供更好的安全控制)、以及安全计算模式( [seccomp][3] ),Linux 的这五种安全特性可以用于保护容器的安全。
|
|
||||||
|
|
||||||
在谈到安全时,首先要考虑你的容器里面有什么?例如 ,有些时候,应用程序和基础设施是由很多可用的组件所构成。它们中的一些是开源的包,比如,Linux 操作系统、Apache Web 服务器、Red Hat JBoss 企业应用平台、PostgreSQL、以及Node.js。这些包的容器化版本已经可以使用了,因此,你没有必要自己去构建它们。但是,对于你从一些外部来源下载的任何代码,你需要知道这些包的原始来源,是谁构建的它,以及这些包里面是否包含恶意代码。
|
|
||||||
|
|
||||||
### 3. 容器注册(安全访问容器镜像)
|
|
||||||
|
|
||||||
你的团队所构建的容器的最顶层的内容是下载的公共容器镜像,因此,管理和下载容器镜像以及内部构建镜像,与管理和下载其它类型的二进制文件的方式是相同的,这一点至关重要。许多私有的注册者支持容器镜像的保存。选择一个私有的注册者,它可以帮你将存储在它的注册中的容器镜像实现策略自动化。
|
|
||||||
|
|
||||||
### 4. 安全性与构建过程
|
|
||||||
|
|
||||||
在一个容器化环境中,构建过程是软件生命周期的一个阶段,它将所需的运行时库和应用程序代码集成到一起。管理这个构建过程对于软件栈安全来说是很关键的。遵守“一次构建,到处部署”的原则,可以确保构建过程的结果正是生产系统中需要的。保持容器的恒定不变也很重要 — 换句话说就是,不要对正在运行的容器打补丁,而是,重新构建和部署它们。
|
|
||||||
|
|
||||||
不论是因为你处于一个高强度监管的行业中,还是只希望简单地优化你的团队的成果,去设计你的容器镜像管理以及构建过程,可以使用容器层的优势来实现控制分离,因此,你应该去这么做:
|
|
||||||
|
|
||||||
* 运营团队管理基础镜像
|
|
||||||
* 设计者管理中间件、运行时、数据库、以及其它解决方案
|
|
||||||
* 开发者专注于应用程序层面,并且只写代码
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
最后,标记好你的定制构建容器,这样可以确保在构建和部署时不会搞混乱。
|
|
||||||
|
|
||||||
### 5. 控制好在同一个集群内部署应用
|
|
||||||
|
|
||||||
如果是在构建过程中出现的任何问题,或者在镜像被部署之后发现的任何漏洞,那么,请在基于策略的、自动化工具上添加另外的安全层。
|
|
||||||
|
|
||||||
我们来看一下,一个应用程序的构建使用了三个容器镜像层:内核、中间件、以及应用程序。如果在内核镜像中发现了问题,那么只能重新构建镜像。一旦构建完成,镜像就会被发布到容器平台注册中。这个平台可以自动检测到发生变化的镜像。对于基于这个镜像的其它构建将被触发一个预定义的动作,平台将自己重新构建应用镜像,合并进修复库。
|
|
||||||
|
|
||||||
在基于策略的、自动化工具上添加另外的安全层。
|
|
||||||
|
|
||||||
一旦构建完成,镜像将被发布到容器平台的内部注册中。在它的内部注册中,会立即检测到镜像发生变化,应用程序在这里将会被触发一个预定义的动作,自动部署更新镜像,确保运行在生产系统中的代码总是使用更新后的最新的镜像。所有的这些功能协同工作,将安全功能集成到你的持续集成和持续部署(CI/CD)过程和管道中。
|
|
||||||
|
|
||||||
### 6. 容器编配:保护容器平台
|
|
||||||
|
|
||||||
一旦构建完成,镜像被发布到容器平台的内部注册中。内部注册会立即检测到镜像的变化,应用程序在这里会被触发一个预定义的动作,自己部署更新,确保运行在生产系统中的代码总是使用更新后的最新的镜像。所有的功能协同工作,将安全功能集成到你的持续集成和持续部署(CI/CD)过程和管道中。~~(致校对:这一段和上一段是重复的,请确认,应该是选题工具造成的重复!!)~~
|
|
||||||
|
|
||||||
当然了,应用程序很少会部署在单一的容器中。甚至,单个应用程序一般情况下都有一个前端、一个后端、以及一个数据库。而在容器中以微服务模式部署的应用程序,意味着应用程序将部署在多个容器中,有时它们在同一台宿主机上,有时它们是分布在多个宿主机或者节点上,如下面的图所示:~~(致校对:图去哪里了???应该是选题问题的问题!)~~
|
|
||||||
|
|
||||||
在大规模的容器部署时,你应该考虑:
|
|
||||||
|
|
||||||
* 哪个容器应该被部署在哪个宿主机上?
|
|
||||||
* 那个宿主机应该有什么样的性能?
|
|
||||||
* 哪个容器需要访问其它容器?它们之间如何发现彼此?
|
|
||||||
* 你如何控制和管理对共享资源的访问,像网络和存储?
|
|
||||||
* 如何监视容器健康状况?
|
|
||||||
* 如何去自动扩展性能以满足应用程序的需要?
|
|
||||||
* 如何在满足安全需求的同时启用开发者的自助服务?
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
考虑到开发者和运营者的能力,提供基于角色的访问控制是容器平台的关键要素。例如,编配管理服务器是中心访问点,应该接受最高级别的安全检查。APIs 是规模化的自动容器平台管理的关键,可以用于为 pods、服务、以及复制控制器去验证和配置数据;在入站请求上执行项目验证;以及调用其它主要系统组件上的触发器。
|
|
||||||
|
|
||||||
### 7. 网络隔离
|
|
||||||
|
|
||||||
在容器中部署现代微服务应用,经常意味着跨多个节点在多个容器上部署。考虑到网络防御,你需要一种在一个集群中的应用之间的相互隔离的方法。一个典型的公有云容器服务,像 Google 容器引擎(GKE)、Azure 容器服务、或者 Amazon Web 服务(AWS)容器服务,是单租户服务。他们让你在你加入的虚拟机集群上运行你的容器。对于多租户容器的安全,你需要容器平台为你启用一个单一集群,并且分割通讯以隔离不同的用户、团队、应用、以及在这个集群中的环境。
|
|
||||||
|
|
||||||
使用网络命名空间,容器内的每个集合(即大家熟知的“pod”)得到它自己的 IP 和绑定的端口范围,以此来从一个节点上隔离每个 pod 网络。除使用下文所述的选项之外,~~(选项在哪里???,请查看原文,是否是选题丢失???)~~默认情况下,来自不同命名空间(项目)的Pods 并不能发送或者接收其它 Pods 上的包和不同项目的服务。你可以使用这些特性在同一个集群内,去隔离开发者环境、测试环境、以及生产环境。但是,这样会导致 IP 地址和端口数量的激增,使得网络管理更加复杂。另外,容器是被反复设计的,你应该在处理这种复杂性的工具上进行投入。在容器平台上比较受欢迎的工具是使用 [软件定义网络][4] (SDN) 去提供一个定义的网络集群,它允许跨不同集群的容器进行通讯。
|
|
||||||
|
|
||||||
### 8. 存储
|
|
||||||
|
|
||||||
容器即可被用于无状态应用,也可被用于有状态应用。保护附加存储是保护有状态服务的一个关键要素。容器平台对多个受欢迎的存储提供了插件,包括网络文件系统(NFS)、AWS 弹性块存储(EBS)、GCE 持久磁盘、GlusterFS、iSCSI、 RADOS(Ceph)、Cinder、等等。
|
|
||||||
|
|
||||||
一个持久卷(PV)可以通过资源提供者支持的任何方式装载到一个主机上。提供者有不同的性能,而每个 PV 的访问模式是设置为被特定的卷支持的特定模式。例如,NFS 能够支持多路客户端同时读/写,但是,一个特定的 NFS 的 PV 可以在服务器上被发布为只读模式。每个 PV 得到它自己的一组反应特定 PV 性能的访问模式的描述,比如,ReadWriteOnce、ReadOnlyMany、以及 ReadWriteMany。
|
|
||||||
|
|
||||||
### 9. API 管理、终端安全、以及单点登陆(SSO)
|
|
||||||
|
|
||||||
保护你的应用包括管理应用、以及 API 的认证和授权。
|
|
||||||
|
|
||||||
Web SSO 能力是现代应用程序的一个关键部分。在构建它们的应用时,容器平台带来了开发者可以使用的多种容器化服务。
|
|
||||||
|
|
||||||
APIs 是微服务构成的应用程序的关键所在。这些应用程序有多个独立的 API 服务,这导致了终端服务数量的激增,它就需要额外的管理工具。推荐使用 API 管理工具。所有的 API 平台应该提供多种 API 认证和安全所需要的标准选项,这些选项既可以单独使用,也可以组合使用,以用于发布证书或者控制访问。
|
|
||||||
|
|
||||||
保护你的应用包括管理应用以及 API 的认证和授权。~~(致校对:这一句话和本节的第一句话重复)~~
|
|
||||||
|
|
||||||
这些选项包括标准的 API keys、应用 ID 和密钥对、 以及 OAuth 2.0。
|
|
||||||
|
|
||||||
### 10. 在一个联合集群中的角色和访问管理
|
|
||||||
|
|
||||||
这些选项包括标准的 API keys、应用 ID 和密钥对、 以及 OAuth 2.0。~~(致校对:这一句和上一节最后一句重复)~~
|
|
||||||
|
|
||||||
在 2016 年 7 月份,Kubernetes 1.3 引入了 [Kubernetes 联合集群][5]。这是一个令人兴奋的新特性之一,它是在 Kubernetes 上游、当前的 Kubernetes 1.6 beta 中引用的。联合是用于部署和访问跨多集群运行在公有云或企业数据中心的应用程序服务的。多个集群能够用于去实现应用程序的高可用性,应用程序可以跨多个可用区域、或者去启用部署公共管理、或者跨不同的供应商进行迁移,比如,AWS、Google Cloud、以及 Azure。
|
|
||||||
|
|
||||||
当管理联合集群时,你必须确保你的编配工具能够提供,你所需要的跨不同部署平台的实例的安全性。一般来说,认证和授权是很关键的 — 不论你的应用程序运行在什么地方,将数据安全可靠地传递给它们,以及管理跨集群的多租户应用程序。Kubernetes 扩展了联合集群,包括对联合的秘密数据、联合的命名空间、以及 Ingress objects 的支持。
|
|
||||||
|
|
||||||
### 选择一个容器平台
|
|
||||||
|
|
||||||
当然,它并不仅关乎安全。你需要提供一个你的开发者团队和运营团队有相关经验的容器平台。他们需要一个安全的、企业级的基于容器的应用平台,它能够同时满足开发者和运营者的需要,而且还能够提高操作效率和基础设施利用率。
|
|
||||||
|
|
||||||
想从 Daniel 在 [欧盟开源峰会][7] 上的 [容器安全的十个层面][6] 的演讲中学习更多知识吗?这个峰会将于10 月 23 - 26 日在 Prague 举行。
|
|
||||||
|
|
||||||
### 关于作者
|
|
||||||
Daniel Oh;Microservives;Agile;Devops;Java Ee;Container;Openshift;Jboss;Evangelism
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
--------------------------------------------------------------------------------
|
|
||||||
|
|
||||||
via: https://opensource.com/article/17/10/10-layers-container-security
|
|
||||||
|
|
||||||
作者:[Daniel Oh][a]
|
|
||||||
译者:[qhwdw](https://github.com/qhwdw)
|
|
||||||
校对:[校对者ID](https://github.com/校对者ID)
|
|
||||||
|
|
||||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
|
||||||
|
|
||||||
[a]:https://opensource.com/users/daniel-oh
|
|
||||||
[1]:https://en.wikipedia.org/wiki/Security-Enhanced_Linux
|
|
||||||
[2]:https://en.wikipedia.org/wiki/Cgroups
|
|
||||||
[3]:https://en.wikipedia.org/wiki/Seccomp
|
|
||||||
[4]:https://en.wikipedia.org/wiki/Software-defined_networking
|
|
||||||
[5]:https://kubernetes.io/docs/concepts/cluster-administration/federation/
|
|
||||||
[6]:https://osseu17.sched.com/mobile/#session:f2deeabfc1640d002c1d55101ce81223
|
|
||||||
[7]:http://events.linuxfoundation.org/events/open-source-summit-europe
|
|
||||||
@ -1,140 +0,0 @@
|
|||||||
Linux 最好的图片截取和视频截录工具
|
|
||||||
======
|
|
||||||

|
|
||||||
|
|
||||||
这里可能有一个困扰你多时的问题,当你想要获取一张屏幕截图向开发者反馈问题,或是在 _Stack Overflow_ 寻求帮助时,你可能缺乏一个可靠的屏幕截图工具去保存和发送集截图。GNOME 有一些形如程序和 shell 拓展的工具。不必担心,这里有 Linux 最好的屏幕截图工具,供你截取图片或截录视频。
|
|
||||||
|
|
||||||
## Linux 最好的图片截取和视频截录工具
|
|
||||||
|
|
||||||
### 1. Shutter
|
|
||||||
|
|
||||||
[][2]
|
|
||||||
|
|
||||||
[Shutter][3] 可以截取任意你想截取的屏幕,是 Linux 最好的截屏工具之一。得到截屏之后,它还可以在保存截屏之前预览图片。GNOME 面板顶部有一个 Shutter 拓展菜单,使得用户进入软件变得更人性化。
|
|
||||||
|
|
||||||
你可以选择性的截取窗口、桌面、光标下的面板、自由内容、菜单、提示框或网页。Shutter 允许用户直接上传屏幕截图到设置内首选的云服务器中。它同样允许用户在保存截图之前编辑器图片;同样提供可自由添加或移除的插件。
|
|
||||||
|
|
||||||
终端内键入下列命令安装此工具:
|
|
||||||
|
|
||||||
```
|
|
||||||
sudo add-apt-repository -y ppa:shutter/ppa
|
|
||||||
sudo apt-get update && sudo apt-get install shutter
|
|
||||||
```
|
|
||||||
|
|
||||||
### 2. Vokoscreen
|
|
||||||
|
|
||||||
[][4]
|
|
||||||
|
|
||||||
|
|
||||||
[Vokoscreen][5] 是一款允许记录和叙述屏幕活动的一款软件。它有一个简洁的界面,界面的顶端包含有一个简明的菜单栏,方便用户开始录制视频。
|
|
||||||
|
|
||||||
你可以选择记录整个屏幕,或是记录一个窗口,抑或是记录一个自由区域,并且自定义保存类型;你甚至可以将屏幕录制记录保存为 gif 文件。当然,你也可以使用网络摄像头记录自己的情况,将自己转换成学习者。一旦你这么做了,你就可以在应用程序中回放视频记录。
|
|
||||||
|
|
||||||
[][6]
|
|
||||||
|
|
||||||
你可以安装自己仓库的 Vocoscreen 发行版,或者你也可以在 [pkgs.org][7] 选择下载你需要的发行版。
|
|
||||||
|
|
||||||
```
|
|
||||||
sudo dpkg -i vokoscreen_2.5.0-1_amd64.deb
|
|
||||||
```
|
|
||||||
|
|
||||||
### 3. OBS
|
|
||||||
|
|
||||||
[][8]
|
|
||||||
|
|
||||||
[OBS][9] 可以用来录制自己的屏幕亦可用来录制互联网上的数据流。它允许你看到自己所录制的内容或者当你叙述时的屏幕录制。它允许你根据喜好选择录制视频的品质;它也允许你选择文件的保存类型。除了视频录制功能之外,你还可以切换到 Studio 模式,不借助其他软件编辑视频。要在你的 Linux 系统中安装 OBS,你必须确保你的电脑已安装 FFmpeg。ubuntu 14.04 或更早的版本安装 FFmpeg 可以使用如下命令:
|
|
||||||
|
|
||||||
```
|
|
||||||
sudo add-apt-repository ppa:kirillshkrogalev/ffmpeg-next
|
|
||||||
|
|
||||||
sudo apt-get update && sudo apt-get install ffmpeg
|
|
||||||
```
|
|
||||||
|
|
||||||
ubuntu 15.04 以及之后的版本,你可以在终端中键入如下命令安装 FFmpeg:
|
|
||||||
|
|
||||||
```
|
|
||||||
sudo apt-get install ffmpeg
|
|
||||||
```
|
|
||||||
|
|
||||||
如果 GGmpeg 安装完成,在终端中键入如下安装 OBS:
|
|
||||||
|
|
||||||
```
|
|
||||||
sudo add-apt-repository ppa:obsproject/obs-studio
|
|
||||||
|
|
||||||
sudo apt-get update
|
|
||||||
|
|
||||||
sudo apt-get install obs-studio
|
|
||||||
```
|
|
||||||
|
|
||||||
### 4. Green Recorder
|
|
||||||
|
|
||||||
[][10]
|
|
||||||
|
|
||||||
[Green recorder][11] 是一款基于接口的简单程序,它可以让你记录屏幕。你可以选择包括视频和单纯的音频在内的录制内容,也可以显示鼠标指针,甚至可以跟随鼠标录制视频。同样,你可以选择记录窗口或是自由区域,以便于在自己的记录中保留需要的内容;你还可以自定义保存视频的帧数。如果你想要延迟录制,它提供给你一个选项可以设置出你想要的延迟时间。它还提供一个录制结束的命令运行选项,这样,就可以在视频录制结束后立即运行。
|
|
||||||
|
|
||||||
在终端中键入如下命令来安装 green recorder:
|
|
||||||
|
|
||||||
```
|
|
||||||
sudo add-apt-repository ppa:fossproject/ppa
|
|
||||||
|
|
||||||
sudo apt update && sudo apt install green-recorder
|
|
||||||
```
|
|
||||||
|
|
||||||
### 5. Kazam
|
|
||||||
|
|
||||||
[][12]
|
|
||||||
|
|
||||||
[Kazam][13] 在几乎所有使用截图工具的 Linux 用户中,都十分流行。这是一款简单直观的软件,它可以让你做一个屏幕截图或是视频录制也同样允许在屏幕截图或屏幕录制之前设置延时。它可以让你选择录制区域,窗口或是你想要抓取的整个屏幕。Kazam 的界面接口部署的非常好,和其他软件相比毫无复杂感。它的特点,就是让你优雅的截图。Kazam 在系统托盘和菜单中都有图标,无需打开应用本身,你就可以开始屏幕截图。
|
|
||||||
|
|
||||||
终端中键入如下命令来安装 Kazam:
|
|
||||||
|
|
||||||
```
|
|
||||||
sudo apt-get install kazam
|
|
||||||
```
|
|
||||||
|
|
||||||
如果没有找到 PPA,你需要使用下面的命令安装它:
|
|
||||||
|
|
||||||
```
|
|
||||||
sudo add-apt-repository ppa:kazam-team/stable-series
|
|
||||||
|
|
||||||
sudo apt-get update && sudo apt-get install kazam
|
|
||||||
```
|
|
||||||
|
|
||||||
### 6. GNOME 拓展截屏工具
|
|
||||||
|
|
||||||
[][1]
|
|
||||||
|
|
||||||
GNOME 的一个拓展软件就叫做 screenshot tool,它常驻系统面板,如果你没有设置禁用它。由于它是常驻系统面板的软件,所以它会一直等待你的调用,获取截图,方便和容易获取是它最主要的特点,除非你在系统工具禁用,否则它将一直在你的系统面板中。这个工具也有用来设置首选项的选项窗口。在 extensions.gnome.org 中搜索“_Screenshot Tool_”,在你的 GNOME 中安装它。
|
|
||||||
|
|
||||||
你需要安装 gnome 拓展,chrome 拓展和 GNOME 调整工具才能使用这个工具。
|
|
||||||
|
|
||||||
[][14]
|
|
||||||
|
|
||||||
当你碰到一个问题,不知道怎么处理,想要在 [the Linux community][15] 或者其他开发社区分享、寻求帮助的的时候, **Linux 截图工具** 尤其合适。学习开发、程序或者其他任何事物都会发现这些工具在分享截图的时候真的很实用。Youtube 用户和教程制作爱好者会发现视频截录工具真的很适合录制可以发表的教程。
|
|
||||||
|
|
||||||
--------------------------------------------------------------------------------
|
|
||||||
|
|
||||||
via: http://www.linuxandubuntu.com/home/best-linux-screenshot-screencasting-tools
|
|
||||||
|
|
||||||
作者:[linuxandubuntu][a]
|
|
||||||
译者:[CYLeft](https://github.com/CYLeft)
|
|
||||||
校对:[校对者ID](https://github.com/校对者ID)
|
|
||||||
|
|
||||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
|
||||||
|
|
||||||
[a]:http://www.linuxandubuntu.com
|
|
||||||
[1]:http://www.linuxandubuntu.com/uploads/2/1/1/5/21152474/gnome-screenshot-extension-compressed_orig.jpg
|
|
||||||
[2]:http://www.linuxandubuntu.com/uploads/2/1/1/5/21152474/shutter-linux-screenshot-taking-tools_orig.jpg
|
|
||||||
[3]:http://shutter-project.org/
|
|
||||||
[4]:http://www.linuxandubuntu.com/uploads/2/1/1/5/21152474/vokoscreen-screencasting-tool-for-linux_orig.jpg
|
|
||||||
[5]:https://github.com/vkohaupt/vokoscreen
|
|
||||||
[6]:http://www.linuxandubuntu.com/uploads/2/1/1/5/21152474/vokoscreen-preferences_orig.jpg
|
|
||||||
[7]:https://pkgs.org/download/vokoscreen
|
|
||||||
[8]:http://www.linuxandubuntu.com/uploads/2/1/1/5/21152474/obs-linux-screencasting-tool_orig.jpg
|
|
||||||
[9]:https://obsproject.com/
|
|
||||||
[10]:http://www.linuxandubuntu.com/uploads/2/1/1/5/21152474/green-recording-linux-tool_orig.jpg
|
|
||||||
[11]:https://github.com/foss-project/green-recorder
|
|
||||||
[12]:http://www.linuxandubuntu.com/uploads/2/1/1/5/21152474/kazam-screencasting-tool-for-linux_orig.jpg
|
|
||||||
[13]:https://launchpad.net/kazam
|
|
||||||
[14]:http://www.linuxandubuntu.com/uploads/2/1/1/5/21152474/gnome-screenshot-extension-preferences_orig.jpg
|
|
||||||
[15]:http://www.linuxandubuntu.com/home/top-10-communities-to-help-you-learn-linux
|
|
||||||
@ -0,0 +1,73 @@
|
|||||||
|
5 个最好的再在视觉上最轻松的黑色主题
|
||||||
|
======
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
人们在电脑上选择黑暗主题有几个原因。有些人觉得对于眼睛轻松,而另一些人因为他们的医学条件选择黑色。特别地,程序员喜欢黑暗的主题,因为可以减少眼睛的眩光。
|
||||||
|
|
||||||
|
如果你是一位 Linux 用户和黑暗的主题爱好者,那么你很幸运。这里有五个最好的 Linux 黑暗主题。去看一下!
|
||||||
|
|
||||||
|
### 1. OSX-Arc-Shadow
|
||||||
|
|
||||||
|
![OSX-Arc-Shadow Theme][1]
|
||||||
|
|
||||||
|
顾名思义,这个主题受 OS X 的启发,它是基于 Arc 的平面主题。该主题支持 GTK 3 和 GTK 2 桌面环境,因此 Gnome、Cinnamon、Unity、Manjaro、Mate 和 XFCE 用户可以安装和使用该主题。[OSX-Arc-Shadow][2] 是 OSX-Arc 主题集合的一部分。集合还包括其他几个主题(黑暗明亮)。你可以下载整个系列并使用黑色主题。
|
||||||
|
|
||||||
|
基于 Debian 和 Ubuntu 的发行版用户可以选择使用此[页面][3]中找到的 .deb 文件来安装稳定版本。压缩的源文件也位于同一页面上。Arch Linux 用户,请查看此[ AUR 链接][4]。最后,要手动安装主题,请将 zip 解压到 “~/.themes” ,并将其设置为当前主题、控件和窗口边框。
|
||||||
|
|
||||||
|
### 2. Kiss-Kool-Red version 2
|
||||||
|
|
||||||
|
![Kiss-Kool-Red version 2 ][5]
|
||||||
|
|
||||||
|
主题发布不久。与 OSX-Arc-Shadow 相比它有更黑的外观和红色选择框。对于那些希望电脑屏幕上有更强对比度和更少眩光的人尤其有吸引力。因此,它可以减少在夜间使用或在光线较暗的地方使用时的注意力分散。它支持 GTK 3 和 GTK2。
|
||||||
|
|
||||||
|
前往 [gnome-looks][6],在“文件”菜单下下载主题。安装过程很简单:将主题解压到 “~/.themes” 中,并将其设置为当前主题、控件和窗口边框。
|
||||||
|
|
||||||
|
### 3. Equilux
|
||||||
|
|
||||||
|
![Equilux][7]
|
||||||
|
|
||||||
|
Equilux 是基于 Materia 主题的另一个简单的黑暗主题。它有一个中性的深色调,并不过分花哨。选择框之间的对比度也很小,并且没有 Kiss-Kool-Red 中红色的锐利。这个主题的确是为减轻眼睛疲劳而做的。
|
||||||
|
|
||||||
|
[下载压缩文件][8]并将其解压缩到你的 “~/.themes” 中。然后,你可以将其设置为你的主题。你可以查看[它的 GitHub 页面][9]了解最新的增加内容。
|
||||||
|
|
||||||
|
### 4. Deepin Dark
|
||||||
|
|
||||||
|
![Deepin Dark][10]
|
||||||
|
|
||||||
|
Deepin Dark 是一个完全黑暗的主题。对于那些喜欢更黑暗的人来说,这个主题绝对是值得考虑的。此外,它还可以减少电脑屏幕的眩光量。另外,它支持 Unity。[在这里下载 Deepin Dark][11]。
|
||||||
|
|
||||||
|
### 5. Ambiance DS BlueSB12
|
||||||
|
|
||||||
|
![Ambiance DS BlueSB12 ][12]
|
||||||
|
|
||||||
|
Ambiance DS BlueSB12 是一个简单的黑暗主题,所以它使重要细节突出。它有助于专注,因为它没必要花哨。它与 Deepin Dark 非常相似。特别与 Ubuntu 用户相关,它与 Ubuntu 17.04 兼容。你可以从[这里][13]下载并尝试。
|
||||||
|
|
||||||
|
### 总结
|
||||||
|
|
||||||
|
如果你长时间使用电脑,黑暗主题是减轻眼睛疲劳的好方法。即使你不这样做,黑暗主题也可以在其他方面帮助你,例如提高专注。让我们知道你最喜欢哪一个。
|
||||||
|
|
||||||
|
--------------------------------------------------------------------------------
|
||||||
|
|
||||||
|
via: https://www.maketecheasier.com/best-linux-dark-themes/
|
||||||
|
|
||||||
|
作者:[Bruno Edoh][a]
|
||||||
|
译者:[geekpi](https://github.com/geekpi)
|
||||||
|
校对:[校对者ID](https://github.com/校对者ID)
|
||||||
|
|
||||||
|
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||||
|
|
||||||
|
[a]:https://www.maketecheasier.com
|
||||||
|
[1]:https://www.maketecheasier.com/assets/uploads/2017/12/osx-arc-shadow.png (OSX-Arc-Shadow Theme)
|
||||||
|
[2]:https://github.com/LinxGem33/OSX-Arc-Shadow/
|
||||||
|
[3]:https://github.com/LinxGem33/OSX-Arc-Shadow/releases
|
||||||
|
[4]:https://aur.archlinux.org/packages/osx-arc-shadow/
|
||||||
|
[5]:https://www.maketecheasier.com/assets/uploads/2017/12/Kiss-Kool-Red.png (Kiss-Kool-Red version 2 )
|
||||||
|
[6]:https://www.gnome-look.org/p/1207964/
|
||||||
|
[7]:https://www.maketecheasier.com/assets/uploads/2017/12/equilux.png (Equilux)
|
||||||
|
[8]:https://www.gnome-look.org/p/1182169/
|
||||||
|
[9]:https://github.com/ddnexus/equilux-theme
|
||||||
|
[10]:https://www.maketecheasier.com/assets/uploads/2017/12/deepin-dark.png (Deepin Dark )
|
||||||
|
[11]:https://www.gnome-look.org/p/1190867/
|
||||||
|
[12]:https://www.maketecheasier.com/assets/uploads/2017/12/ambience.png (Ambiance DS BlueSB12 )
|
||||||
|
[13]:https://www.gnome-look.org/p/1013664/
|
||||||
118
translated/tech/20180213 Getting started with the RStudio IDE.md
Normal file
118
translated/tech/20180213 Getting started with the RStudio IDE.md
Normal file
@ -0,0 +1,118 @@
|
|||||||
|
开始使用 RStudio IDE
|
||||||
|
======
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
从我记事起,我就一直在与数字玩耍。作为 20 世纪 70 年代后期的本科生,我开始上统计学的课程,学习如何检查和分析数据以揭示某些意义。
|
||||||
|
|
||||||
|
那时候,我有一部科学计算器,它让统计计算变得比以前容易很多。在 90 年代早期,作为一名从事 t 检验,相关性以及 [ANOVA][1] 研究的教育心理学研究生,我开始通过精心编写输入 IBM 主机的文本文件来进行计算。这个主机是对我的手持计算器的一个改进,但是一个小的间距错误会使得整个过程无效,而且这个过程仍然有点乏味。
|
||||||
|
|
||||||
|
撰写论文时,尤其是我的毕业论文,我需要一种方法能够根据我的数据来创建图表并将它们嵌入到文字处理文档中。我着迷于 Microsoft Excel 及其数字运算能力以及可以用计算结果创建出的大量图表。但每一步都有成本。在 20 世纪 90 年代,除了 Excel,还有其他专有软件包,比如 SAS 和 SPSS+,但对于我那已经满满的研究生时间表来说,学习曲线是一项艰巨的任务。
|
||||||
|
|
||||||
|
### 快速回到现在
|
||||||
|
|
||||||
|
最近,由于我对数据科学的兴趣浓厚,加上对 Linux 和开源软件的浓厚兴趣,我阅读了大量的数据科学文章,并在 Linux 会议上听了许多数据科学演讲者谈论他们的工作。因此,我开始对编程语言 R(一种开源的统计计算软件)非常感兴趣。
|
||||||
|
|
||||||
|
起初,这只是一个火花。当我和我的朋友 Michael J. Gallagher 博士谈论他如何在他的 [博士论文][2] 研究中使用 R 时,这个火花便增大了。最后,我访问了 [R project][3] 的网站,并了解到我可以轻松地安装 [R for Linux][4]。游戏开始!
|
||||||
|
|
||||||
|
### 安装 R
|
||||||
|
|
||||||
|
根据你的操作系统和分布情况,安装 R 会稍有不同。请参阅 [Comprehensive R Archive Network][5] (CRAN) 网站上的安装指南。CRAN 提供了在 [各种 Linux 发行版][6],[Fedora,RHEL,及其衍生版][7],[MacOS][8] 和 [Windows][9] 上的安装指示。
|
||||||
|
|
||||||
|
我在使用 Ubuntu,则按照 CRAN 的指示,将以下行加入到我的 `/etc/apt/sources.list` 文件中:
|
||||||
|
|
||||||
|
```
|
||||||
|
deb https://<my.favorite.cran.mirror>/bin/linux/ubuntu artful/
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
接着我在终端运行下面命令:
|
||||||
|
|
||||||
|
```
|
||||||
|
$ sudo apt-get update
|
||||||
|
|
||||||
|
$ sudo apt-get install r-base
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
根据 CRAN,“需要从源码编译 R 的用户【如包的维护者,或者任何通过 `install.packages()` 安装包的用户】也应该安装 `r-base-dev` 的包。”
|
||||||
|
|
||||||
|
### 使用 R 和 Rstudio
|
||||||
|
|
||||||
|
安装好了 R,我就准备了解更多关于使用这个强大的工具的信息。Gallagher 博士推荐了 [DataCamp][10] 上的 “Start learning R”,并且我也找到了适用于 R 新手的免费课程。两门课程都帮助我学习 R 的命令和语法。我还参加了 [Udemy][12] 上的 R 在线编程课程,并从 [No Starch Press][14] 上购买了 [Book of R][13]。
|
||||||
|
|
||||||
|
在阅读更多内容并观看 YouTube 视频后,我意识到我还应该安装 [RStudio][15]。Rstudio 是 R 的开源 IDE,易于在 [Debian, Ubuntu, Fedora, 和 RHEL][16] 上安装。它也可以安装在 MacOS 和 Windows 上。
|
||||||
|
|
||||||
|
根据 Rstudio 网站的说明,可以根据你的偏好对 IDE 进行自定义,具体方法是选择工具菜单,然后从中选择全局选项。
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
R 提供了一些很棒的演示例子,可以通过在提示符处输入 `demo()` 从控制台访问。`demo(plotmath)` 和 `demo(perspective)` 选项为 R 强大的功能提供了很好的例证。我尝试过一些简单的 [vectors][17] 并在 R 控制台的命令行中绘制,如下所示。
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
你可能想要开始学习如何将 R 和一些样本数据结合起来使用,然后将这些知识应用到自己的数据上得到描述性统计。我自己没有丰富的数据来分析,但我搜索了可以使用的数据集 [datasets][18];这样一个数据集(我并没有用这个例子)是由圣路易斯联邦储备银行提供的 [经济研究数据][19]。我对一个题为“美国商业航空公司的乘客里程(1937-1960)”很感兴趣,因此我将它导入 RStudio 以测试 IDE 的功能。Rstudio 可以接受各种格式的数据,包括 CSV,Excel,SPSS 和 SAS。
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
数据导入后,我使用 `summary(AirPassengers)` 命令获取数据的一些初始描述性统计信息。按回车键后,我得到了 1949-1960 年的每月航空公司旅客的摘要以及其他数据,包括飞机乘客数量的最小值,最大值,第一四分位数,第三四分位数。中位数以及平均数。
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
我从摘要统计信息中知道航空乘客样本的均值为 280.3。在命令行中输入 `sd(AirPassengers)` 会得到标准偏差,在 RStudio 控制台中可以看到:
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
接下来,我生成了一个数据直方图,通过输入 `hist(AirPassengers);` 得到,这以图形的方式显示此数据集;Rstudio 可以将数据导出为 PNG,PDF,JPEG,TIFF,SVG,EPS 或 BMP。
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
除了生成统计数据和图形数据外,R 还记录了我所有的历史操作。这使得我能够返回先前的操作,并且我可以保存此历史记录以供将来参考。
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
在 RStudio 的脚本编辑器中,我可以编写我发出的所有命令的脚本,然后保存该脚本以便在我的数据更改后能再次运行,或者想重新访问它。
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
### 获得帮助
|
||||||
|
|
||||||
|
在 R 提示符下输入 `help()` 可以很容易找到帮助信息。输入你正在寻找的信息的特定主题可以找到具体的帮助信息,例如 `help(sd)` 可以获得有关标准差的帮助。通过在提示符处输入 `contributors()` 可以获得有关 R 项目贡献者的信息。您可以通过在提示符处输入 `citation()` 来了解如何引用 R。通过在提示符出输入 `license()` 可以很容易地获得 R 的许可证信息。
|
||||||
|
|
||||||
|
R 是在 GNU General Public License(1991 年 6 月的版本 2,或者 2007 年 6 月的版本 3)的条款下发布的。有关 R 许可证的更多信息,请参考 [R Project website][20]。
|
||||||
|
|
||||||
|
另外,RStudio 在 GUI 中提供了完美的帮助菜单。该区域包括 RStudio 备忘单(可作为 PDF 下载),[RStudio][21]的在线学习,RStudio 文档,支持和 [许可证信息][22]。
|
||||||
|
|
||||||
|
--------------------------------------------------------------------------------
|
||||||
|
|
||||||
|
via: https://opensource.com/article/18/2/getting-started-RStudio-IDE
|
||||||
|
|
||||||
|
作者:[Don Watkins][a]
|
||||||
|
译者:[szcf-weiya](https://github.com/szcf-weiya)
|
||||||
|
校对:[校对者ID](https://github.com/校对者ID)
|
||||||
|
|
||||||
|
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||||
|
|
||||||
|
[a]:https://opensource.com/users/don-watkins
|
||||||
|
[1]:https://en.wikipedia.org/wiki/Analysis_of_variance
|
||||||
|
[2]:https://www.michael-j-gallagher.com/high-performance-computing
|
||||||
|
[3]:https://www.r-project.org/
|
||||||
|
[4]:https://cran.r-project.org/index.html
|
||||||
|
[5]:https://cran.r-project.org/
|
||||||
|
[6]:https://cran.r-project.org/bin/linux/
|
||||||
|
[7]:https://cran.r-project.org/bin/linux/redhat/README
|
||||||
|
[8]:https://cran.r-project.org/bin/macosx/
|
||||||
|
[9]:https://cran.r-project.org/bin/windows/
|
||||||
|
[10]:https://www.datacamp.com/onboarding/learn?from=home&technology=r
|
||||||
|
[11]:http://tryr.codeschool.com/levels/1/challenges/1
|
||||||
|
[12]:https://www.udemy.com/r-programming
|
||||||
|
[13]:https://nostarch.com/bookofr
|
||||||
|
[14]:https://opensource.com/article/17/10/no-starch
|
||||||
|
[15]:https://www.rstudio.com/
|
||||||
|
[16]:https://www.rstudio.com/products/rstudio/download/
|
||||||
|
[17]:http://www.r-tutor.com/r-introduction/vector
|
||||||
|
[18]:https://vincentarelbundock.github.io/Rdatasets/datasets.html
|
||||||
|
[19]:https://fred.stlouisfed.org/
|
||||||
|
[20]:https://www.r-project.org/Licenses/
|
||||||
|
[21]:https://www.rstudio.com/online-learning/#R
|
||||||
|
[22]:https://support.rstudio.com/hc/en-us/articles/217801078-What-license-is-RStudio-available-under-
|
||||||
@ -0,0 +1,160 @@
|
|||||||
|
有用的 Bash 快捷键清单
|
||||||
|
======
|
||||||
|

|
||||||
|
|
||||||
|
现如今,我在终端上花的时间更多,尝试在命令行完成比在图形界面更多的工作。随着时间推移,我学了许多 BASH 的技巧。这是一份每个 Linux 用户都应该知道的 BASH 快捷键,这样在终端做事就会快很多。我不会说这是一份完全的 BASH 快捷键清单,但是这足够让你的 BASH shell 比以前更快了。学习更快地使用 BASH 不仅节省了更多时间,也让你因为学到了有用的知识而感到自豪。那么,让我们开始吧。
|
||||||
|
|
||||||
|
### 有用的 Bash 快捷键清单
|
||||||
|
|
||||||
|
#### ALT 快捷键
|
||||||
|
|
||||||
|
1\. **ALT+A** – 移动到行首。
|
||||||
|
|
||||||
|
2\. **ALT+B** – 移动到光标所在单词词首。
|
||||||
|
|
||||||
|
3\. **ALT+C** – 终止正在运行的命令/进程。与 CTRL+C 相同。
|
||||||
|
|
||||||
|
4\. **ALT+D** – 关闭空的终端(也就是他会关闭没有输入的终端)。也删除光标后的全部字符。
|
||||||
|
|
||||||
|
5\. **ALT+F** – 移动到光标所在单词词末。
|
||||||
|
|
||||||
|
6\. **ALT+T** – 交换最后两个单词。
|
||||||
|
|
||||||
|
7\. **ALT+U** – 将单词内光标后的字母转为大写。
|
||||||
|
|
||||||
|
8\. **ALT+L** – 将单词内光标后的字母转为小写。
|
||||||
|
|
||||||
|
9\. **ALT+R** – 撤销对从历史记录中带来的命令的修改。
|
||||||
|
|
||||||
|
正如你在上面输出所见,我使用反向搜索拉取了一个指令,并更改了那个指令的最后一个字母,并使用 **ALT+R** 撤销了更改。
|
||||||
|
|
||||||
|
10\. **ALT+.** (注意末尾的点号) – 使用上一条命令的最后一个单词。
|
||||||
|
|
||||||
|
如果你想要对多个命令进行相同的操作的话,你可以使用这个快捷键来获取前几个指令的最后一个单词。例如,我需要使用 `ls -r` 命令输出以文件名逆序排列的目录内容。同时,我也想使用 `uname -r` 命令来查看我的内核版本。在这两个命令中,相同的单词是 `-r` 。这就是需要 `ALT+.` 的地方。快捷键很顺手。首先运行 `ls -r` 来按文件名逆序输出,然后在其他命令,比如 `uname` 中使用最后一个单词 `-r` 。
|
||||||
|
|
||||||
|
#### CTRL 快捷键
|
||||||
|
|
||||||
|
1\. **CTRL+A** – 快速移动到行首。
|
||||||
|
|
||||||
|
我们假设你输入了像下面这样的命令。当你在第 N 行时,你发现在行首字符有一个输入错误
|
||||||
|
|
||||||
|
```
|
||||||
|
$ gind . -mtime -1 -type
|
||||||
|
```
|
||||||
|
|
||||||
|
注意到了吗?上面的命令中我输入了 `gind` 而不是 `find` 。你可以通过一直按着左箭头键定位到第一个字母然后用 `g` 替换 `f` 。或者,仅通过 **CTRL+A** 或 **home** 键来立刻定位到行首,并替换拼错的单词。这将节省你几秒钟的时间。
|
||||||
|
|
||||||
|
2\. **CTRL+B** – 光标向前移动一个字符。
|
||||||
|
|
||||||
|
这个快捷键可以使光标向前移动一个字符,即光标前的一个字符。或者,你可以使用左箭头键来向前移动一个字符。
|
||||||
|
|
||||||
|
3\. **CTRL+C** – 停止当前运行的命令。
|
||||||
|
|
||||||
|
如果一个命令运行时间过久,或者你误运行了,你可以通过使用 **CTRL+C** 来强制停止或退出。
|
||||||
|
|
||||||
|
4\. **CTRL+D** – 删除光标后的一个字符。
|
||||||
|
|
||||||
|
如果你的系统退格键无法工作的话,你可以使用 **CTRL+D** 来删除光标后的一个字符。这个快捷键也可以让你退出当前会话,和 exit 类似。
|
||||||
|
|
||||||
|
5\. **CTRL+E** – 移动到行末。
|
||||||
|
|
||||||
|
当你修正了行首拼写错误的单词,按下 **CTRL+E** 来快速移动到行末。或者,你也可以使用你键盘上的 END 键。
|
||||||
|
|
||||||
|
6\. **CTRL+F** – 光标向后移动一个字符。
|
||||||
|
|
||||||
|
如果你想将光标向后移动一个字符的话,按 **CTRL+F** 来替代右箭头键。
|
||||||
|
|
||||||
|
7\. **CTRL+G** – 退出历史搜索模式,不运行命令。
|
||||||
|
|
||||||
|
正如你在上面的截图看到的,我进行了反向搜索,但是我执行命令,并退出了历史搜索模式。
|
||||||
|
|
||||||
|
8\. **CTRL+H** – 删除光标签的一个字符,和退格键相同。
|
||||||
|
|
||||||
|
9\. **CTRL+J** – 和 ENTER/RETURN 键相同。
|
||||||
|
|
||||||
|
回车键不工作?没问题! **CTRL+J** 或 **CTRL+M** 可以用来替换回车键。
|
||||||
|
|
||||||
|
10\. **CTRL+K** – 删除光标后的所有字符。
|
||||||
|
|
||||||
|
你不必一直按着删除键来删除光标后的字符。只要按 **CTRL+K** 就能删除光标后的所有字符。
|
||||||
|
|
||||||
|
11\. **CTRL+L** – 清空屏幕并重新显示当前行。
|
||||||
|
|
||||||
|
别输入 `clear` 来清空屏幕了。只需按 **CTRL+M** 即可清空并重新显示当前行。
|
||||||
|
|
||||||
|
12\. **CTRL+M** – 和 **CTRL+J** 或 RETURN键相同。
|
||||||
|
|
||||||
|
13\. **CTRL+N** – 在命令历史中显示下一行。
|
||||||
|
|
||||||
|
你也可以使用下箭头键。
|
||||||
|
|
||||||
|
14\. **CTRL+O** – 运行你使用反向搜索时发现的命令,即 CTRL+R。
|
||||||
|
|
||||||
|
15\. **CTRL+P** – 显示命令历史的上一条命令。
|
||||||
|
|
||||||
|
你也可以使用上箭头键。
|
||||||
|
|
||||||
|
16\. **CTRL+R** – 向后搜索历史记录(反向搜索)。
|
||||||
|
|
||||||
|
17\. **CTRL+S** – 向前搜索历史记录。
|
||||||
|
|
||||||
|
18\. **CTRL+T** – 交换最后两个字符。
|
||||||
|
|
||||||
|
这是我最喜欢的一个快捷键。假设你输入了 `sl` 而不是 `ls` 。没问题!这个快捷键会像下面这张截图一样交换字符。
|
||||||
|
|
||||||
|
![][2]
|
||||||
|
|
||||||
|
19\. **CTRL+U** – 删除光标前的所有字符(从光标后的点删除到行首)。
|
||||||
|
|
||||||
|
这个快捷键立刻删除前面的所有字符。
|
||||||
|
|
||||||
|
20\. **CTRL+V** – 逐字显示输入的下一个字符。
|
||||||
|
|
||||||
|
21\. **CTRL+W** – 删除光标前的一个单词。
|
||||||
|
|
||||||
|
不要和 CTRL+U 弄混了。CTRL+W 不会删除光标前的所有东西,而是只删除一个单词。
|
||||||
|
|
||||||
|
![][3]
|
||||||
|
|
||||||
|
22\. **CTRL+X** – 列出当前单词可能的文件名补全。
|
||||||
|
|
||||||
|
23\. **CTRL+XX** – 移动到行首位置(再移动回来)。
|
||||||
|
|
||||||
|
24\. **CTRL+Y** – 恢复你上一个删除或剪切的条目。
|
||||||
|
|
||||||
|
记得吗,我们在第 21 个命令用 CTRL+W 删除了单词“-al”。你可以使用 CTRL+Y 立刻恢复。
|
||||||
|
|
||||||
|
![][4]
|
||||||
|
|
||||||
|
看见了吧?我没有输入“-al”。取而代之,我按了 CTRL+Y 来恢复它。
|
||||||
|
|
||||||
|
25\. **CTRL+Z** – 停止当前的命令。
|
||||||
|
|
||||||
|
你也许很了解这个快捷键。它终止了当前运行的命令。你可以在前台使用 **fg** 或在后台使用 **bg** 来恢复它。
|
||||||
|
|
||||||
|
26\. **CTRL+[** – 和 ESC 键等同。
|
||||||
|
|
||||||
|
#### 杂项
|
||||||
|
|
||||||
|
1\. **!!** – 重复上一个命令。
|
||||||
|
|
||||||
|
2\. **ESC+t** – 交换最后两个单词。
|
||||||
|
|
||||||
|
这就是我所能想到的了。将来我遇到 Bash 快捷键时我会持续添加的。如果你觉得文章有错的话,请在下方的评论区留言。我会尽快更新。
|
||||||
|
|
||||||
|
Cheers!
|
||||||
|
|
||||||
|
--------------------------------------------------------------------------------
|
||||||
|
|
||||||
|
via: https://www.ostechnix.com/list-useful-bash-keyboard-shortcuts/
|
||||||
|
|
||||||
|
作者:[SK][a]
|
||||||
|
译者:[heart4lor](https://github.com/heart4lor)
|
||||||
|
校对:[校对者ID](https://github.com/校对者ID)
|
||||||
|
|
||||||
|
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||||
|
|
||||||
|
[a]:https://www.ostechnix.com/author/sk/
|
||||||
|
[2]:http://www.ostechnix.com/wp-content/uploads/2018/02/CTRLT-1.gif
|
||||||
|
[3]:http://www.ostechnix.com/wp-content/uploads/2018/02/CTRLW-1.gif
|
||||||
|
[4]:http://www.ostechnix.com/wp-content/uploads/2018/02/CTRLY-1.gif
|
||||||
@ -0,0 +1,176 @@
|
|||||||
|
用 PGP 保护代码完整性 - 第二部分:生成你的主密钥
|
||||||
|
======
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
在本系列文章中,我们将深度探讨如何使用 PGP 以及为工作于自由软件项目的开发者提供实用指南。在前一篇文章中,我们介绍了[基本工具和概念][1]。在本文中,我们将展示如何生成和保护你的 PGP 主密钥。
|
||||||
|
|
||||||
|
### 清单
|
||||||
|
|
||||||
|
1. 生成一个 4096 位的 RSA 主密钥 (ESSENTIAL)
|
||||||
|
|
||||||
|
2. 使用 paperkey 备份你的 RSA 主密钥 (ESSENTIAL)
|
||||||
|
|
||||||
|
3. 添加所有相关的身份 (ESSENTIAL)
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
### 考虑事项
|
||||||
|
|
||||||
|
#### 理解“主”(认证)密钥
|
||||||
|
|
||||||
|
在本节和下一节中,我们将讨论“主密钥”和“子密钥”。理解以下内容很重要:
|
||||||
|
|
||||||
|
1. 在“主密钥”和“子密钥”之间没有技术上的区别。
|
||||||
|
|
||||||
|
2. 在创建时,我们赋予每个密钥特定的能力来分配功能限制
|
||||||
|
|
||||||
|
3. 一个 PGP 密钥有四项能力
|
||||||
|
|
||||||
|
* [S] 密钥可以用于签名
|
||||||
|
|
||||||
|
* [E] 密钥可以用于加密
|
||||||
|
|
||||||
|
* [A] 密钥可以用于身份认证
|
||||||
|
|
||||||
|
* [C] 密钥可以用于认证其他密钥
|
||||||
|
|
||||||
|
4. 一个密钥可能有多种能力
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
带有[C] (认证)能力的密钥被认为是“主”密钥,因为它是唯一可以用来表明与其他密钥关系的密钥。只有[C]密钥可以被用于:
|
||||||
|
|
||||||
|
* 添加或撤销其他密钥(子密钥)的 S/E/A 能力
|
||||||
|
|
||||||
|
* 添加,更改或撤销密钥关联的身份(uids)
|
||||||
|
|
||||||
|
* 添加或更改本身或其他子密钥的到期时间
|
||||||
|
|
||||||
|
* 为了网络信任目的为其它密钥签名
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
在自由软件的世界里,[C]密钥就是你的数字身份。一旦你创建该密钥,你应该格外小心地保护它并且防止它落入坏人的手中。
|
||||||
|
|
||||||
|
#### 在你创建主密钥前
|
||||||
|
|
||||||
|
在你创建的你的主密钥前,你需要选择你的主要身份和主密码。
|
||||||
|
|
||||||
|
##### 主要身份
|
||||||
|
|
||||||
|
身份使用邮件中发件人一栏相同格式的字符串:
|
||||||
|
```
|
||||||
|
Alice Engineer <alice.engineer@example.org>
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
你可以在任何时候创建新的身份,取消旧的,并且更改你的“主要”身份。由于主要身份在所有 GnuPG 操作中都展示,你应该选择正式的和最有可能用于 PGP 保护通信的名字和邮件地址,比如你的工作地址或者用于在项目提交(commit)时签名的地址。
|
||||||
|
|
||||||
|
##### 密码
|
||||||
|
|
||||||
|
密码(passphrase)专用于在存储在磁盘上时使用对称加密算法对私钥进行加密。如果你的 .gnupg 目录的内容被泄露,那么一个好的密码就是小偷能够在线模拟你的最后一道防线,这就是为什么设置一个好的密码很重要的原因。
|
||||||
|
|
||||||
|
一个强密码的好的指导是用丰富或混合的词典的 3-4 个词,而不引用自流行来源(歌曲,书籍,口号)。由于你将相当频繁地使用该密码,所以它应当易于 输入和记忆。
|
||||||
|
|
||||||
|
##### 算法和密钥强度
|
||||||
|
|
||||||
|
尽管现在 GnuPG 已经支持椭圆曲线加密一段时间了,我们仍坚持使用 RSA 密钥,至少稍长一段时间。虽然现在就可以开始使用 ED25519 密钥,但你可能会碰到无法正确处理它们的工具和硬件设备。
|
||||||
|
|
||||||
|
如果后续的指南中我们说 2048 位的密钥对 RSA 公钥加密的生命周期已经足够,你可能也会好奇主密钥为什么是 4096 位。 原因很大程度是由于社会因素而非技术上的:主密钥在密钥链上恰好是最明显的,同时如果你的主密钥位数比一些你交互的开发者的少,他们将不可避免地负面评价你。
|
||||||
|
|
||||||
|
#### 生成主密钥
|
||||||
|
|
||||||
|
为了生成你的主密钥,请使用以下命令,并且将“Alice Engineer:”替换为正确值
|
||||||
|
```
|
||||||
|
$ gpg --quick-generate-key 'Alice Engineer <alice@example.org>' rsa4096 cert
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
一个要求输入密码的对话框将弹出。然后,你可能需要移动鼠标或输入一些密钥才能生成足够的熵,直到命令完成。
|
||||||
|
|
||||||
|
查看命令输出,它就像这样:
|
||||||
|
```
|
||||||
|
pub rsa4096 2017-12-06 [C] [expires: 2019-12-06]
|
||||||
|
111122223333444455556666AAAABBBBCCCCDDDD
|
||||||
|
uid Alice Engineer <alice@example.org>
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
注意第二行的长字符串 -- 它是你新生成的密钥的完整指纹。密钥 ID(key IDs)可以用以下三种不同形式表达:
|
||||||
|
|
||||||
|
* Fingerprint,一个完整的 40 个字符的密钥标识符
|
||||||
|
|
||||||
|
* Long,指纹的最后 16 个字符(AAAABBBBCCCCDDDD)
|
||||||
|
|
||||||
|
* Short,指纹的最后 8 个字符(CCCCDDDD)
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
你应该避免使用 8 个字符的短密钥 ID(short key IDs),因为它们不足够唯一。
|
||||||
|
|
||||||
|
这里,我建议你打开一个文本编辑器,复制你新密钥的指纹并粘贴。你需要在接下来几步中用到它,所以将它放在旁边会很方便。
|
||||||
|
|
||||||
|
#### 备份你的主密钥
|
||||||
|
|
||||||
|
出于灾后恢复的目的 -- 同时特别的如果你试图使用 Web of Trust 并且收集来自其他项目开发者的密钥签名 -- 你应该创建你的私钥的 硬拷贝备份。万一所有其它的备份机制都失败了,这应当是最后的补救措施。
|
||||||
|
|
||||||
|
创建一个你的私钥的可打印的硬拷贝的最好方法是使用为此而写的软件 paperkey。Paperkey 在所有 Linux 发行版上可用,在 Mac 上也可以通过 brew 安装 paperkey。
|
||||||
|
|
||||||
|
运行以下命令,用你密钥的完整指纹替换[fpr]:
|
||||||
|
```
|
||||||
|
$ gpg --export-secret-key [fpr] | paperkey -o /tmp/key-backup.txt
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
输出将采用易于 OCR 或手动输入的格式,以防如果你需要恢复它的话。打印出该文件,然后拿支笔,并在纸的边缘写下密钥的密码。这是必要的一步,因为密钥输出仍然使用密码加密,并且如果你更改了密钥的密码,你不会记得第一次创建的密钥是什么 -- 我保证。
|
||||||
|
|
||||||
|
将打印结果和手写密码放入信封中,并存放在一个安全且保护好的地方,最好远离你家,例如银行保险库。
|
||||||
|
|
||||||
|
**打印机注意事项** 打印机连接到计算机的并行端口的时代已经过去了。现在他们拥有完整的操作系统,硬盘驱动器和云集成。由于我们发送给打印机的关键内容将使用密码进行加密,因此这是一项相当安全的操作,但请使用您最好的偏执判断。
|
||||||
|
|
||||||
|
#### 添加相关身份
|
||||||
|
|
||||||
|
如果你有多个相关的邮件地址(个人,工作,开源项目等),你应该将其添加到主密钥中。你不需要为任何你不希望用于 PGP 的地址(例如,可能不是你的校友地址)这样做。
|
||||||
|
|
||||||
|
该命令是(用你完整的密钥指纹替换[fpr]):
|
||||||
|
```
|
||||||
|
$ gpg --quick-add-uid [fpr] 'Alice Engineer <allie@example.net>'
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
你可以查看你已经使用的 UIDs:
|
||||||
|
```
|
||||||
|
$ gpg --list-key [fpr] | grep ^uid
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
##### 选择主 UID
|
||||||
|
|
||||||
|
GnuPG 将会把你最近添加的 UID 作为你的主 UID,如果这与你想的不同,你应该改回来:
|
||||||
|
```
|
||||||
|
$ gpg --quick-set-primary-uid [fpr] 'Alice Engineer <alice@example.org>'
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
下次,我们将介绍如何生成 PGP 子密钥,它是你实际用于日常工作的密钥。
|
||||||
|
|
||||||
|
通过 Linux 基金会和 edX 的免费[“Introduction to Linux” ][2]课程了解关于 Linux 的更多信息。
|
||||||
|
|
||||||
|
--------------------------------------------------------------------------------
|
||||||
|
|
||||||
|
via: https://www.linux.com/blog/learn/PGP/2018/2/protecting-code-integrity-pgp-part-2-generating-and-protecting-your-master-pgp-key
|
||||||
|
|
||||||
|
作者:[KONSTANTIN RYABITSEV][a]
|
||||||
|
译者:[kimii](https://github.com/kimii)
|
||||||
|
校对:[校对者ID](https://github.com/校对者ID)
|
||||||
|
|
||||||
|
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||||
|
|
||||||
|
[a]:https://www.linux.com/users/mricon
|
||||||
|
[1]:https://www.linux.com/blog/learn/2018/2/protecting-code-integrity-pgp-part-1-basic-pgp-concepts-and-tools
|
||||||
|
[2]:https://training.linuxfoundation.org/linux-courses/system-administration-training/introduction-to-linux
|
||||||
@ -0,0 +1,103 @@
|
|||||||
|
Linux 局域网路由新手指南:第 1 部分
|
||||||
|
======
|
||||||
|
|
||||||
|

|
||||||
|
前面我们学习了 [IPv6 路由][1]。现在我们继续深入学习 Linux 中的 IPv4 路由的基础知识。我们从硬件概述、操作系统和 IPv4 地址的基础知识开始,下周我们将继续学习它们如何配置,以及测试路由。
|
||||||
|
|
||||||
|
### 局域网路由器硬件
|
||||||
|
|
||||||
|
Linux 实际上是一个网络操作系统,一直都是,从一开始它就有内置的网络功能。为将你的局域网连入因特网,构建一个局域网路由器比起构建网关路由器要简单的多。你不要太过于执念安全或者防火墙规则,对于处理 NAT 它还是比较复杂的,网络地址转换是 IPv4 的一个痛点。我们为什么不放弃 IPv4 去转到 IPv6 呢?这样将使网络管理员的工作更加简单。
|
||||||
|
|
||||||
|
有点跑题了。从理论上讲,你的 Linux 路由器是一个至少有两个网络接口的小型机器。Linux Gizmos 是一个单片机的综合体:[98 个开放规格的目录,黑客友好的 SBCs][2]。你能够使用一个很老的笔记本电脑或者台式计算机。你也可以使用一个精简版计算机,像 ZaReason Zini 或者 System76 Meerkat 一样,虽然这些有点贵,差不多要 $600。但是它们又结实又可靠,并且你不用在 Windows 许可证上浪费钱。
|
||||||
|
|
||||||
|
如果对路由器的要求不高,使用树莓派 3 Model B 作为路由器是一个非常好的选择。它有一个 10/100 以太网端口,板载 2.4GHz 的 802.11n 无线网卡,并且它还有四个 USB 端口,因此你可以插入多个 USB 网卡。USB 2.0 和低速板载网卡可能会让树莓派变成你的网络上的瓶颈,但是,你不能对它期望太高(毕竟它只有 $35,既没有存储也没有电源)。它支持很多种风格的 Linux,因此你可以选择使用你喜欢的版本。基于 Debian 的树莓派是我的最爱。
|
||||||
|
|
||||||
|
### 操作系统
|
||||||
|
|
||||||
|
你可以在你选择的硬件上安装将你喜欢的 Linux 的简化版,因为定制的路由器操作系统,比如 OpenWRT、 Tomato、DD-WRT、Smoothwall、Pfsense 等等,都有它们自己的非标准界面。我的观点是,没有必要这么麻烦,它们对你并没有什么帮助。尽量使用标准的 Linux 工具,因为你只需要学习它们一次就够了。
|
||||||
|
|
||||||
|
Debian 的网络安装镜像大约有 300MB 大小,并且支持多种架构,包括 ARM、i386、amd64、和 armhf。Ubuntu 的服务器网络安装镜像也小于 50MB,这样你就可以控制你要安装哪些包。Fedora、Mageia、和 openSUSE 都提供精简的网络安装镜像。如果你需要创意,你可以浏览 [Distrowatch][3]。
|
||||||
|
|
||||||
|
### 路由器能做什么
|
||||||
|
|
||||||
|
我们需要网络路由器做什么?一个路由器连接不同的网络。如果没有路由,那么每个网络都是相互隔离的,所有的悲伤和孤独都没有人与你分享,所有节点只能孤独终老。假设你有一个 192.168.1.0/24 和一个 192.168.2.0/24 网络。如果没有路由器,你的两个网络之间不能相互沟通。这些都是 C 类的私有地址,它们每个都有 254 个可用网络地址。使用 ipcalc 可以非常容易地得到它们的这些信息:
|
||||||
|
```
|
||||||
|
$ ipcalc 192.168.1.0/24
|
||||||
|
Address: 192.168.1.0 11000000.10101000.00000001. 00000000
|
||||||
|
Netmask: 255.255.255.0 = 24 11111111.11111111.11111111. 00000000
|
||||||
|
Wildcard: 0.0.0.255 00000000.00000000.00000000. 11111111
|
||||||
|
=>
|
||||||
|
Network: 192.168.1.0/24 11000000.10101000.00000001. 00000000
|
||||||
|
HostMin: 192.168.1.1 11000000.10101000.00000001. 00000001
|
||||||
|
HostMax: 192.168.1.254 11000000.10101000.00000001. 11111110
|
||||||
|
Broadcast: 192.168.1.255 11000000.10101000.00000001. 11111111
|
||||||
|
Hosts/Net: 254 Class C, Private Internet
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
我喜欢 ipcalc 的二进制输出信息,它更加可视地表示了掩码是如何工作的。前三个八位组表示了网络地址,第四个八位组是主机地址,因此,当你分配主机地址时,你将 “掩盖” 掉网络地址部分,只使用剩余的主机部分。你的两个网络有不同的网络地址,而这就是如果两个网络之间没有路由器它们就不能互相通讯的原因。
|
||||||
|
|
||||||
|
每个八位组一共有 256 字节,但是它们并不能提供 256 个主机地址,因为第一个和最后一个值 ,也就是 0 和 255,是被保留的。0 是网络标识,而 255 是广播地址,因此,只有 254 个主机地址。ipcalc 可以帮助你很容易地计算出这些。
|
||||||
|
|
||||||
|
当然,这并不意味着你不能有一个结尾是 0 或者 255 的主机地址。假设你有一个 16 位的前缀:
|
||||||
|
```
|
||||||
|
$ ipcalc 192.168.0.0/16
|
||||||
|
Address: 192.168.0.0 11000000.10101000. 00000000.00000000
|
||||||
|
Netmask: 255.255.0.0 = 16 11111111.11111111. 00000000.00000000
|
||||||
|
Wildcard: 0.0.255.255 00000000.00000000. 11111111.11111111
|
||||||
|
=>
|
||||||
|
Network: 192.168.0.0/16 11000000.10101000. 00000000.00000000
|
||||||
|
HostMin: 192.168.0.1 11000000.10101000. 00000000.00000001
|
||||||
|
HostMax: 192.168.255.254 11000000.10101000. 11111111.11111110
|
||||||
|
Broadcast: 192.168.255.255 11000000.10101000. 11111111.11111111
|
||||||
|
Hosts/Net: 65534 Class C, Private Internet
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
ipcalc 列出了你的第一个和最后一个主机地址,它们是 192.168.0.1 和 192.168.255.254。你是可以有以 0 或者 255 结尾的主机地址的,例如,192.168.1.0 和 192.168.0.255,因为它们都在最小主机地址和最大主机地址之间。
|
||||||
|
|
||||||
|
不论你的地址块是私有的还是公共的,这个原则同样都是适用的。不要羞于使用 ipcalc 来帮你计算地址。
|
||||||
|
|
||||||
|
### CIDR
|
||||||
|
|
||||||
|
CIDR(无类域间路由)就是通过可变长度的子网掩码来扩展 IPv4 的。CIDR 允许对网络空间进行更精细地分割。我们使用 ipcalc 来演示一下:
|
||||||
|
```
|
||||||
|
$ ipcalc 192.168.1.0/22
|
||||||
|
Address: 192.168.1.0 11000000.10101000.000000 01.00000000
|
||||||
|
Netmask: 255.255.252.0 = 22 11111111.11111111.111111 00.00000000
|
||||||
|
Wildcard: 0.0.3.255 00000000.00000000.000000 11.11111111
|
||||||
|
=>
|
||||||
|
Network: 192.168.0.0/22 11000000.10101000.000000 00.00000000
|
||||||
|
HostMin: 192.168.0.1 11000000.10101000.000000 00.00000001
|
||||||
|
HostMax: 192.168.3.254 11000000.10101000.000000 11.11111110
|
||||||
|
Broadcast: 192.168.3.255 11000000.10101000.000000 11.11111111
|
||||||
|
Hosts/Net: 1022 Class C, Private Internet
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
网络掩码并不局限于整个八位组,它可以跨越第三和第四个八位组,并且子网部分的范围可以是从 0 到 3,而不是非得从 0 到 255。可用主机地址的数量并不一定是 8 的倍数,因为它是由整个八位组定义的。
|
||||||
|
|
||||||
|
给你留一个家庭作业,复习 CIDR 和 IPv4 地址空间是如何在公共、私有和保留块之间分配的,这个作业有助你更好地理解路由。一旦你掌握了地址的相关知识,配置路由器将不再是件复杂的事情了。
|
||||||
|
|
||||||
|
从 [理解 IP 地址和 CIDR 图表][4]、[IPv4 私有地址空间和过滤][5]、以及 [IANA IPv4 地址空间注册][6] 开始。接下来的我们将学习如何创建和管理路由器。
|
||||||
|
|
||||||
|
通过来自 Linux 基金会和 edX 的免费课程 ["Linux 入门" ][7]学习更多 Linux 知识。
|
||||||
|
|
||||||
|
--------------------------------------------------------------------------------
|
||||||
|
|
||||||
|
via: https://www.linux.com/learn/intro-to-linux/2018/2/linux-lan-routing-beginners-part-1
|
||||||
|
|
||||||
|
作者:[Carla Schroder][a]
|
||||||
|
译者:[qhwdw](https://github.com/qhwdw)
|
||||||
|
校对:[校对者ID](https://github.com/校对者ID)
|
||||||
|
|
||||||
|
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||||
|
|
||||||
|
[a]:https://www.linux.com/users/cschroder
|
||||||
|
[1]:https://www.linux.com/learn/intro-to-linux/2017/7/practical-networking-linux-admins-ipv6-routing
|
||||||
|
[2]:http://linuxgizmos.com/catalog-of-98-open-spec-hacker-friendly-sbcs/#catalog
|
||||||
|
[3]:http://distrowatch.org/
|
||||||
|
[4]:https://www.ripe.net/about-us/press-centre/understanding-ip-addressing
|
||||||
|
[5]:https://www.arin.net/knowledge/address_filters.html
|
||||||
|
[6]:https://www.iana.org/assignments/ipv4-address-space/ipv4-address-space.xhtml
|
||||||
|
[7]:https://training.linuxfoundation.org/linux-courses/system-administration-training/introduction-to-linux
|
||||||
@ -0,0 +1,118 @@
|
|||||||
|
Linux 局域网路由新手指南:第 2 部分
|
||||||
|
======
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
上周 [我们学习了 IPv4 地址][1] 和如何使用管理员不可或缺的工具 —— ipcalc,今天我们继续学习更精彩的内容:局域网路由器。
|
||||||
|
|
||||||
|
VirtualBox 和 KVM 是测试路由的好工具,在本文中的所有示例都是在 KVM 中执行的。如果你喜欢使用物理硬件去做测试,那么你需要三台计算机:一台用作路由器,另外两台用于表示两个不同的网络。你也需要两台以太网交换机和相应的线缆。
|
||||||
|
|
||||||
|
我们假设示例是一个有线以太局域网,为了更符合真实使用场景,我们将假设有一些桥接的无线接入点,当然我并不会使用这些无线接入点做任何事情。(我也不会去尝试所有的无线路由器,以及使用一个移动宽带设备连接到以太网的局域网口进行混合组网,因为它们需要进一步的安装和设置)
|
||||||
|
|
||||||
|
### 网段
|
||||||
|
|
||||||
|
最简单的网段是两台计算机连接在同一个交换机上的相同地址空间中。这样两台计算机不需要路由器就可以相互通讯。这就是我们常说的术语 —— “广播域”,它表示所有在相同的网络中的一组主机。它们可能连接到一台单个的以太网交换机上,也可能是连接到多台交换机上。一个广播域可以包括通过以太网桥连接的两个不同的网络,通过网桥可以让两个网络像一个单个网络一样运转。无线访问点一般是桥接到有线以太网上。
|
||||||
|
|
||||||
|
一个广播域仅当在它们通过一台网络路由器连接的情况下,才可以与不同的广播域进行通讯。
|
||||||
|
|
||||||
|
### 简单的网络
|
||||||
|
|
||||||
|
以下示例的命令并不是永久生效的,重启之后你所做的改变将会消失。
|
||||||
|
|
||||||
|
一个广播域需要一台路由器才可以与其它广播域通讯。我们使用两台计算机和 `ip` 命令来解释这些。我们的两台计算机是 192.168.110.125 和 192.168.110.126,它们都插入到同一台以太网交换机上。在 VirtualBox 或 KVM 中,当你配置一个新网络的时候会自动创建一个虚拟交换机,因此,当你分配一个网络到虚拟虚拟机上时,就像是插入一个交换机一样。使用 `ip addr show` 去查看你的地址和网络接口名字。现在,这两台主机可以互 ping 成功。
|
||||||
|
|
||||||
|
现在,给其中一台主机添加一个不同网络的地址:
|
||||||
|
```
|
||||||
|
# ip addr add 192.168.120.125/24 dev ens3
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
你可以指定一个网络接口名字,在示例中它的名字是 ens3。这不需要去添加一个网络前缀,在本案例中,它是 /24,但是显式地添加它并没有什么坏处。你可以使用 `ip` 命令去检查你的配置。下面的示例输出为了清晰其见进行了删减:
|
||||||
|
```
|
||||||
|
$ ip addr show
|
||||||
|
ens3:
|
||||||
|
inet 192.168.110.125/24 brd 192.168.110.255 scope global dynamic ens3
|
||||||
|
valid_lft 875sec preferred_lft 875sec
|
||||||
|
inet 192.168.120.125/24 scope global ens3
|
||||||
|
valid_lft forever preferred_lft forever
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
主机在 192.168.120.125 上可以 ping 它自己(`ping 192.168.120.125`),这是对你的配置是否正确的一个基本校验,这个时候第二台计算机就已经不能 ping 通那个地址了。
|
||||||
|
|
||||||
|
现在我们需要做一些网络变更。添加第三台主机作为路由器。它需要两个虚拟网络接口并添加第二个虚拟网络。在现实中,你的路由器必须使用一个静态 IP 地址,但是现在,我们可以让 KVM 的 DHCP 服务器去为它分配地址,所以,你仅需要两个虚拟网络:
|
||||||
|
|
||||||
|
* 第一个网络:192.168.110.0/24
|
||||||
|
* 第二个网络:192.168.120.0/24
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
接下来你的路由器必须配置去转发数据包。数据包转发默认是禁用的,你可以使用 `sysctl` 命令去检查它的配置:
|
||||||
|
```
|
||||||
|
$ sysctl net.ipv4.ip_forward
|
||||||
|
net.ipv4.ip_forward = 0
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
0 意味着禁用,使用如下的命令去启用它:
|
||||||
|
```
|
||||||
|
# echo 1 > /proc/sys/net/ipv4/ip_forward
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
接下来配置你的另一台主机做为第二个网络的一部分,你可以通过将原来在 192.168.110.0/24 的网络中的一台主机分配到 192.168.120.0/24 虚拟网络中,然后重新启动两个 “网络” 主机,注意不是路由器。(或者重启动网络;我年龄大了还有点懒,我记不住那些重启服务的奇怪命令,还不如重启网络来得干脆。)重启后各台机器的地址应该如下所示:
|
||||||
|
|
||||||
|
* 主机 1: 192.168.110.125
|
||||||
|
* 主机 2: 192.168.120.135
|
||||||
|
* 路由器: 192.168.110.126 and 192.168.120.136
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
现在可以去随意 ping 它们,可以从任何一台计算机上 ping 到任何一台其它计算机上。使用虚拟机和各种 Linux 发行版做这些事时,可能会产生一些意想不到的问题,因此,有时候 ping 的通,有时候 ping 不通。不成功也是一件好事,这意味着你需要动手去创建一条静态路由。首先,查看已经存在的路由表。主机 1 和主机 2 的路由表如下所示:
|
||||||
|
```
|
||||||
|
$ ip route show
|
||||||
|
default via 192.168.110.1 dev ens3 proto static metric 100
|
||||||
|
192.168.110.0/24 dev ens3 proto kernel scope link src 192.168.110.164 metric 100
|
||||||
|
|
||||||
|
$ ip route show
|
||||||
|
default via 192.168.110.1 dev ens3 proto static metric 100
|
||||||
|
default via 192.168.120.1 dev ens3 proto static metric 101
|
||||||
|
169.254.0.0/16 dev ens3 scope link metric 1000
|
||||||
|
192.168.110.0/24 dev ens3 proto kernel scope link
|
||||||
|
src 192.168.110.126 metric 100
|
||||||
|
192.168.120.0/24 dev ens9 proto kernel scope link
|
||||||
|
src 192.168.120.136 metric 100
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
这显示了我们使用的由 KVM 分配的缺省路由。169.* 地址是自动链接的本地地址,我们不去管它。接下来我们看两条路由,这两条路由指向到我们的路由器。你可以有多条路由,在这个示例中我们将展示如何在主机 1 上添加一个非默认路由:
|
||||||
|
```
|
||||||
|
# ip route add 192.168.120.0/24 via 192.168.110.126 dev ens3
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
这意味着主机1 可以通过路由器接口 192.168.110.126 去访问 192.168.110.0/24 网络。看一下它们是如何工作的?主机1 和路由器需要连接到相同的地址空间,然后路由器转发到其它的网络。
|
||||||
|
|
||||||
|
以下的命令去删除一条路由:
|
||||||
|
```
|
||||||
|
# ip route del 192.168.120.0/24
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
在真实的案例中,你不需要像这样手动配置一台路由器,而是使用一个路由器守护程序,并通过 DHCP 做路由器通告,但是理解基本原理很重要。接下来我们将学习如何去配置一个易于使用的路由器守护程序来为你做这些事情。
|
||||||
|
|
||||||
|
通过来自 Linux 基金会和 edX 的免费课程 ["Linux 入门" ][2] 来学习更多 Linux 的知识。
|
||||||
|
|
||||||
|
--------------------------------------------------------------------------------
|
||||||
|
|
||||||
|
via: https://www.linux.com/learn/intro-to-linux/2018/3/linux-lan-routing-beginners-part-2
|
||||||
|
|
||||||
|
作者:[CARLA SCHRODER][a]
|
||||||
|
译者:[qhwdw](https://github.com/qhwdw)
|
||||||
|
校对:[校对者ID](https://github.com/校对者ID)
|
||||||
|
|
||||||
|
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||||
|
|
||||||
|
[a]:https://www.linux.com/users/cschroder
|
||||||
|
[1]:https://www.linux.com/learn/intro-to-linux/2018/2/linux-lan-routing-beginners-part-1
|
||||||
|
[2]:https://training.linuxfoundation.org/linux-courses/system-administration-training/introduction-to-linux
|
||||||
@ -0,0 +1,56 @@
|
|||||||
|
使用一个树莓派和 projectx/os 托管你自己的电子邮件
|
||||||
|
======
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
现在有大量的理由,不能再将存储你的数据的任务委以他人之手,也不能在第三方公司运行你的服务;隐私、所有权、以及防范任何人拿你的数据去“赚钱”。但是对于大多数人来说,自己去运行一个服务器,是件即费时间又需要太多的专业知识的事情。不得已,我们只能妥协。抛开这些顾虑,使用某些公司的云服务,随之而来的就是广告、数据挖掘和售卖、以及其它可能的任何东西。
|
||||||
|
|
||||||
|
[projectx/os][1] 项目就是要去除这种顾虑,它可以在家里毫不费力地做服务托管,并且可以很容易地创建一个类似于 Gmail 的帐户。实现上述目标,你只需一个 $35 的树莓派 3 和一个基于 Debian 的操作系统镜像 —— 并且不需要很多的专业知识。仅需要四步就可以实现:
|
||||||
|
|
||||||
|
1. 解压缩一个 ZIP 文件到 SD 存储卡中。
|
||||||
|
2. 编辑 SD 上的一个文本文件以便于它连接你的 WiFi(如果你不使用有线网络的话)。
|
||||||
|
3. 将这个 SD 卡插到树莓派 3 中。
|
||||||
|
4. 使用你的智能手机在树莓派 3 上安装 "email 服务器“ 应用并选择一个二级域。
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
服务器应用程序(比如电子邮件服务器)被分解到多个容器中,它们中的每个都只能够使用指定的方式与外界通讯,它们使用了管理粒度非常细的隔离措施以提高安全性。例如,入站 SMTP,[SpamAssassin][2](防垃圾邮件平台),[Dovecot][3] (安全 IMAP 服务器),并且 webmail 都使用了独立的容器,它们之间相互不能看到对方的数据,因此,单个守护进程出现问题不会波及其它的进程。
|
||||||
|
|
||||||
|
另外,它们都是无状态容器,比如 SpamAssassin 和入站 SMTP,每次收到电子邮件之后,它们的连接都会被拆除并重建,因此,即便是有人找到了 bug 并利用了它,他们也不能访问以前的电子邮件或者接下来的电子邮件;他们只能访问他们自己挖掘出漏洞的那封电子邮件。幸运的是,大多数对外发布的、最容易受到攻击的服务都是隔离的和无状态的。
|
||||||
|
|
||||||
|
所有存储的数据都使用 [dm-crypt][4] 进行加密。非公开服务,比如 Dovecot(IMAP)或者 webmail,都是在内部监听,并使用 [ZeroTier One][5] 加密整个网络,因此只有你的设备(智能手机、笔记本电脑、平板等等)才能访问它们。
|
||||||
|
|
||||||
|
虽然电子邮件并不是端到端加密的(除非你使用了 [PGP][6]),但是非加密的电子邮件绝不会跨越网络,并且也不会存储在磁盘上。现在明文的电子邮件只存在于双方的私有邮件服务器上,它们都在他们的家中受到很好的安全保护并且只能通过他们的客户端访问(智能手机、笔记本电脑、平板等等)。
|
||||||
|
|
||||||
|
另一个好处就是,个人设备都使用一个密码保护(不是指纹或者其它生物识别技术),而且在你家中的设备都受到美国的 [第四宪法修正案][7] 的保护,比起由公司所有的第三方数据中心,它们受到更强的法律保护。当然,如果你的电子邮件使用的是 Gmail,Google 还保存着你的电子邮件的拷贝。
|
||||||
|
|
||||||
|
### 展望
|
||||||
|
|
||||||
|
电子邮件是我使用 project/os 项目打包的第一个应用程序。想像一下,一个应用程序商店有全部的服务器软件,为易于安装和使用将它们打包到一起。想要一个博客?添加一个 WordPress 应用程序!想替换安全的 Dropbox ?添加一个 [Seafile][8] 应用程序或者一个 [Syncthing][9] 后端应用程序。 [IPFS][10] 节点? [Mastodon][11] 实例?GitLab 服务器?各种家庭自动化/物联网后端服务?这里有大量的非常好的开源服务器软件 ,它们都非常易于安装,并且可以使用它们来替换那些有专利的云服务。
|
||||||
|
|
||||||
|
Nolan Leake 的 [在每个家庭中都有一个云:0 系统管理员技能就可以在家里托管服务器][12] 将在三月 8 - 11日的 [Southern California Linux Expo][12] 进行。使用折扣代码 **OSDC** 去注册可以 50% 的价格得到门票。
|
||||||
|
|
||||||
|
--------------------------------------------------------------------------------
|
||||||
|
|
||||||
|
via: https://opensource.com/article/18/3/host-your-own-email
|
||||||
|
|
||||||
|
作者:[Nolan Leake][a]
|
||||||
|
译者:[qhwdw](https://github.com/qhwdw)
|
||||||
|
校对:[校对者ID](https://github.com/校对者ID)
|
||||||
|
|
||||||
|
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||||
|
|
||||||
|
[a]:https://opensource.com/users/nolan
|
||||||
|
[1]:https://git.sigbus.net/projectx/os
|
||||||
|
[2]:http://spamassassin.apache.org/
|
||||||
|
[3]:https://www.dovecot.org/
|
||||||
|
[4]:https://gitlab.com/cryptsetup/cryptsetup/wikis/DMCrypt
|
||||||
|
[5]:https://www.zerotier.com/download.shtml
|
||||||
|
[6]:https://en.wikipedia.org/wiki/Pretty_Good_Privacy
|
||||||
|
[7]:https://simple.wikipedia.org/wiki/Fourth_Amendment_to_the_United_States_Constitution
|
||||||
|
[8]:https://www.seafile.com/en/home/
|
||||||
|
[9]:https://syncthing.net/
|
||||||
|
[10]:https://ipfs.io/
|
||||||
|
[11]:https://github.com/tootsuite/mastodon
|
||||||
|
[12]:https://www.socallinuxexpo.org/scale/16x/presentations/cloud-every-home-host-servers-home-0-sysadmin-skills
|
||||||
|
[13]:https://register.socallinuxexpo.org/reg6/
|
||||||
Loading…
Reference in New Issue
Block a user