mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-03-24 02:20:09 +08:00
Merge branch 'master' of https://github.com/LCTT/TranslateProject
要提交了,先合并
This commit is contained in:
commit
d18cade82f
@ -1,3 +1,4 @@
|
||||
[bazz222]
|
||||
How to set up networking between Docker containers
|
||||
================================================================================
|
||||
As you may be aware, Docker container technology has emerged as a viable lightweight alternative to full-blown virtualization. There are a growing number of use cases of Docker that the industry adopted in different contexts, for example, enabling rapid build environment, simplifying configuration of your infrastructure, isolating applications in multi-tenant environment, and so on. While you can certainly deploy an application sandbox in a standalone Docker container, many real-world use cases of Docker in production environments may involve deploying a complex multi-tier application in an ensemble of multiple containers, where each container plays a specific role (e.g., load balancer, LAMP stack, database, UI).
|
||||
@ -157,4 +158,4 @@ via: http://xmodulo.com/networking-between-docker-containers.html
|
||||
[2]:http://xmodulo.com/recommend/dockerbook
|
||||
[3]:http://xmodulo.com/manage-linux-containers-docker-ubuntu.html
|
||||
[4]:http://xmodulo.com/docker-containers-centos-fedora.html
|
||||
[5]:http://zettio.github.io/weave/features.html
|
||||
[5]:http://zettio.github.io/weave/features.html
|
||||
|
||||
@ -1,181 +0,0 @@
|
||||
[bazz222222222]
|
||||
How to secure SSH login with one-time passwords on Linux
|
||||
================================================================================
|
||||
As someone says, security is a not a product, but a process. While SSH protocol itself is cryptographically secure by design, someone can wreak havoc on your SSH service if it is not administered properly, be it weak passwords, compromised keys or outdated SSH client.
|
||||
|
||||
As far as SSH authentication is concerned, [public key authentication][1] is in general considered more secure than password authentication. However, key authentication is actually not desirable or even less secure if you are logging in from a public or shared computer, where things like stealth keylogger or memory scraper can always a possibility. If you cannot trust the local computer, it is better to use something else. This is when "one-time passwords" come in handy. As the name implies, each one-time password is for single-use only. Such disposable passwords can be safely used in untrusted environments as they cannot be re-used even when they are stolen.
|
||||
|
||||
One way to generate disposable passwords is [Google Authenticator][2]. In this tutorial, I am going to demonstrate another way to create one-time passwords for SSH login: [OTPW][3], a one-time password login package. Unlike Google Authenticator, you do not rely on any third party for one-time password generation and verification.
|
||||
|
||||
### What is OTPW? ###
|
||||
|
||||
OTPW consists of one-time password generator and PAM-integrated verification routines. In OTPW, one-time passwords are generated apriori with the generator, and carried by a user securely (e.g., printed in a paper sheet). Cryptographic hash of the generated passwords are then stored in the SSH server host. When a user logs in with a one-time password, OTPW's PAM module verifies the password, and invalidates it to prevent re-use.
|
||||
|
||||
### Step One: Install and Configure OTPW on Linux ###
|
||||
|
||||
#### Debian, Ubuntu or Linux Mint ####
|
||||
|
||||
Install OTPW packages with apt-get.
|
||||
|
||||
$ sudo apt-get install libpam-otpw otpw-bin
|
||||
|
||||
Open a PAM configuration file for SSH (/etc/pam.d/sshd) with a text editor, and comment out the following line (to disable password authentication).
|
||||
|
||||
#@include common-auth
|
||||
|
||||
and add the following two lines (to enable one-time password authentication):
|
||||
|
||||
auth required pam_otpw.so
|
||||
session optional pam_otpw.so
|
||||
|
||||

|
||||
|
||||
#### Fedora or CentOS/RHEL ####
|
||||
|
||||
OTPW is not available as a prebuilt package on Red Hat based systems. So let's install OTPW by building it from the source.
|
||||
|
||||
First, install prerequites:
|
||||
|
||||
$ sudo yum git gcc pam-devel
|
||||
$ git clone https://www.cl.cam.ac.uk/~mgk25/git/otpw
|
||||
$ cd otpw
|
||||
|
||||
Open Makefile with a text editor, and edit a line that starts with "PAMLIB=" as follows.
|
||||
|
||||
On 64-bit system:
|
||||
|
||||
PAMLIB=/usr/lib64/security
|
||||
|
||||
On 32-bit system:
|
||||
|
||||
PAMLIB=/usr/lib/security
|
||||
|
||||
Compile and install it. Note that installation will automatically restart an SSH server. So be ready to be disconnected if you are on an SSH connection.
|
||||
|
||||
$ make
|
||||
$ sudo make install
|
||||
|
||||
Now you need to update SELinux policy since /usr/sbin/sshd tries to write to user's home directory, which is not allowed by default SELinux policy. The following commands will do. If you are not using SELinux, skip this step.
|
||||
|
||||
$ sudo grep sshd /var/log/audit/audit.log | audit2allow -M mypol
|
||||
$ sudo semodule -i mypol.pp
|
||||
|
||||
Next, open a PAM configuration file for SSH (/etc/pam.d/sshd) with a text editor, and comment out the following line (to disable password authentication).
|
||||
|
||||
#auth substack password-auth
|
||||
|
||||
and add the following two lines (to enable one-time password authentication):
|
||||
|
||||
auth required pam_otpw.so
|
||||
session optional pam_otpw.so
|
||||
|
||||
#### Step Two: Configure SSH Server for One-time Passwords ####
|
||||
|
||||
The next step is to configure an SSH server to accept one-time passwords.
|
||||
|
||||
Open /etc/ssh/sshd_config with a text editor, and set the following three parameters. Make sure that you do not add these lines more than once, because that will cause an SSH server to fail.
|
||||
|
||||
UsePrivilegeSeparation yes
|
||||
ChallengeResponseAuthentication yes
|
||||
UsePAM yes
|
||||
|
||||
You also need to disable default password authentication. Optionally, enable public key authentication, so that you can fall back to key-based authentication in case you do not have one-time passwords.
|
||||
|
||||
PubkeyAuthentication yes
|
||||
PasswordAuthentication no
|
||||
|
||||
Now restart SSH server.
|
||||
|
||||
Debian, Ubuntu or Linux Mint:
|
||||
|
||||
$ sudo service ssh restart
|
||||
|
||||
Fedora or CentOS/RHEL 7:
|
||||
|
||||
$ sudo systemctl restart sshd
|
||||
|
||||
#### Step Three: Generate One-time Passwords with OTPW ####
|
||||
|
||||
As mentioned earlier, you need to create one-time passwords beforehand, and have them stored on the remote SSH server host. For this, run otpw-gen tool as the user you will be logging in as.
|
||||
|
||||
$ cd ~
|
||||
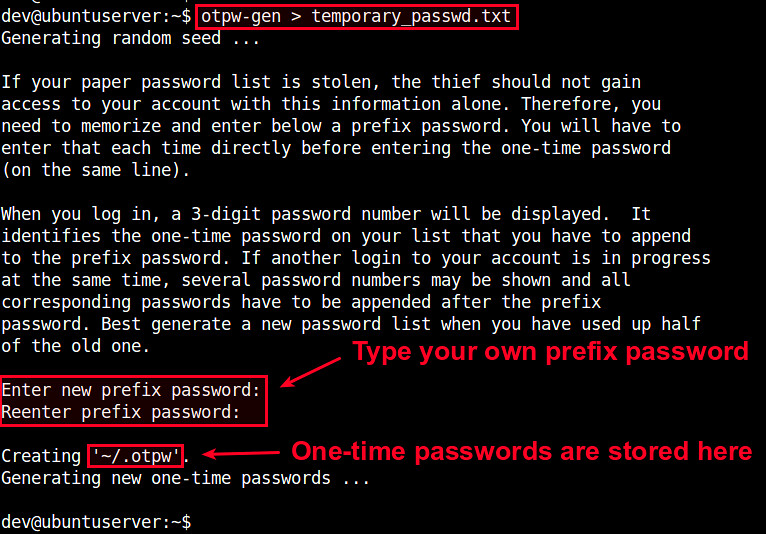
$ otpw-gen > temporary_password.txt
|
||||
|
||||
|
||||
|
||||
It will ask you to set a prefix password. When you later log in, you need to type this prefix password AND one-time password. Essentially the prefix password is another layer of protection. Even if the password sheet falls into the wrong hands, the prefix password forces them to brute-force.
|
||||
|
||||
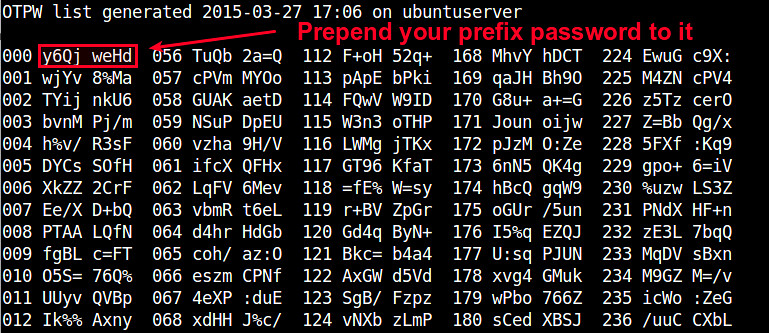
Once the prefix password is set, the command will generate 280 one-time passwords, and store them in the output text file (e.g., temporary_password.txt). Each password (length of 8 characters by default) is preceded by a three-digit index number. You are supposed to print the file in a sheet and carry it with you.
|
||||
|
||||
|
||||
|
||||
You will also see ~/.otpw file created, where cryptographic hashs of these passwords are stored. The first three digits in each line indicate the index number of the password that will be used for SSH login.
|
||||
|
||||
$ more ~/.otpw
|
||||
|
||||
----------
|
||||
|
||||
OTPW1
|
||||
280 3 12 8
|
||||
191ai+:ENwmMqwn
|
||||
218tYRZc%PIY27a
|
||||
241ve8ns%NsHFmf
|
||||
055W4/YCauQJkr:
|
||||
102ZnJ4VWLFrk5N
|
||||
2273Xww55hteJ8Y
|
||||
1509d4b5=A64jBT
|
||||
168FWBXY%ztm9j%
|
||||
000rWUSdBYr%8UE
|
||||
037NvyryzcI+YRX
|
||||
122rEwA3GXvOk=z
|
||||
|
||||
### Test One-time Passwords for SSH Login ###
|
||||
|
||||
Now let's login to an SSH server in a usual way:
|
||||
|
||||
$ ssh user@remote_host
|
||||
|
||||
If OTPW is successfully set up, you will see a slightly different password prompt:
|
||||
|
||||
Password 191:
|
||||
|
||||
Now open up your password sheet, and look for index number "191" in the sheet.
|
||||
|
||||
023 kBvp tq/G 079 jKEw /HRM 135 oW/c /UeB 191 fOO+ PeiD 247 vAnZ EgUt
|
||||
|
||||
According to sheet above, the one-time password for number "191" is "fOO+PeiD". You need to prepend your prefix password to it. For example, if your prefix password is "000", the actual one-time password you need to type is "000fOO+PeiD".
|
||||
|
||||
Once you successfully log in, the password used is automatically invalidated. If you check ~/.otpw, you will notice that the first line is replaced with "---------------", meaning that password "191" has been voided.
|
||||
|
||||
OTPW1
|
||||
280 3 12 8
|
||||
---------------
|
||||
218tYRZc%PIY27a
|
||||
241ve8ns%NsHFmf
|
||||
055W4/YCauQJkr:
|
||||
102ZnJ4VWLFrk5N
|
||||
2273Xww55hteJ8Y
|
||||
1509d4b5=A64jBT
|
||||
168FWBXY%ztm9j%
|
||||
000rWUSdBYr%8UE
|
||||
037NvyryzcI+YRX
|
||||
122rEwA3GXvOk=z
|
||||
|
||||
### Conclusion ###
|
||||
|
||||
In this tutorial, I demonstrated how to set up one-time password login for SSH using OTPW package. You may realized that a print sheet can be considered a less fancy version of security token in two-factor authentication. Yet, it is simpler and you do not rely on any third-party for its implementation. Whatever mechanism you are using to create disposable passwords, they can be helpful when you need to log in to an SSH server from an untrusted public computer. Feel free to share your experience or opinion on this topic.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/secure-ssh-login-one-time-passwords-linux.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/nanni
|
||||
[1]:http://xmodulo.com/how-to-force-ssh-login-via-public-key-authentication.html
|
||||
[2]:http://xmodulo.com/two-factor-authentication-ssh-login-linux.html
|
||||
[3]:http://www.cl.cam.ac.uk/~mgk25/otpw.html
|
||||
@ -1,3 +1,4 @@
|
||||
translating wi-cuckoo
|
||||
Docker 1.6 Released - How to Upgrade on Fedora / CentOS
|
||||
================================================================================
|
||||
Docker, a popular open source container platform for packaging applications, has a new release 1.6 with lot of new features in it. This version has updates to Docker Registry, Engine, Swarm, Compose and Machine. The release aims at improvements in performance, developer and system administrator experiences. Let us take a quick look at the new features available.
|
||||
@ -164,4 +165,4 @@ via: http://linoxide.com/linux-how-to/docker-1-6-features-upgrade-fedora-centos/
|
||||
[17]:
|
||||
[18]:
|
||||
[19]:
|
||||
[20]:
|
||||
[20]:
|
||||
|
||||
@ -0,0 +1,82 @@
|
||||
安卓编年史
|
||||
================================================================================
|
||||
### 语音操作——口袋里的超级电脑 ###
|
||||
|
||||
2010年8月,作为语音搜索应用的一项新功能,“[语音命令][1]”登陆了安卓市场。语音命令允许用户向他们的手机发出语音命令,然后安卓会试着去理解他们并完成任务。像“导航至[地址]”这样的命令会打开谷歌地图并且开始逐向导航至你所陈述的目的地。你还可以仅仅通过语音来发送短信或电子邮件,拨打电话,打开网站,获取方向,或是在地图上查看一个地点。
|
||||
|
||||
注:youtube视频地址
|
||||
<iframe width="500" height="281" frameborder="0" src="http://www.youtube-nocookie.com/embed/gGbYVvU0Z5s?start=0&wmode=transparent" type="text/html" style="display:block"></iframe>
|
||||
|
||||
语音命令是谷歌新应用设计哲学的顶峰。语音命令是那时候最先进的语音控制软件,秘密在于谷歌并不在设备上做任运算。一般来说,语音识别是对CPU的密集任务要求。实际上,许多语音识别程序仍然有“速度与准确性”设置,用户可以选择他们愿意为语音识别算法运行等待的时间——更多的CPU处理意味着更加准确。
|
||||
|
||||
谷歌的创新在于没有劳烦手机上能力有限的处理器来进行语音识别运算。当说出一个命令时,用户的声音会被打包并通过互联网发送到谷歌云服务器。在那里,谷歌超算中心的超级计算机分析并解释语音,然后发送回手机。这是很长的一段旅程,但互联网最终还是有足够快的速度在一两秒内完成像这样的任务。
|
||||
|
||||
很多人抛出词语“云计算”来表达“所有东西都被存储在服务器上”,但这才是真正的云计算。谷歌在云端进行这些巨量的运算操作,又因为在这个问题上投入了看似荒唐的CPU资源数目,所以语音识别准确性的唯一限制就是算法本身了。软件不需要由每个用户独立“训练”,因为所有使用语音操作的人无时不刻都在训练它。借助互联网的力量,安卓在你的口袋里放了一部超级电脑,同时相比于已有的解决方案,把语音识别这个工作量从口袋大小的电脑转移到房间大小的电脑上大大提高了准确性。
|
||||
|
||||
语音识别作为谷歌的项目已经有一段时间了,它的出现都是因为一个800号码。[1-800-GOOG-411][2]是个谷歌从2007年4月起开通的免费电话信息服务。它就像411信息服务一样工作了多年——用户可以拨打这个号码询问电话号码——但是谷歌免费提供这项服务。查询过程中没有人工的干预,411服务由语音识别和文本语音转换引擎驱动。语音命令就是人们教谷歌如何去听之后三年才有实现的可能。
|
||||
|
||||
语音识别是谷歌长远思考的极佳范例——公司并不怕在一个可能成不了商业产品的项目上投资多年。今天,语音识别驱动的产品遍布谷歌。它被用在谷歌搜索应用的输入,安卓的语音输入,以及Google.com。同时它还是Google Glass和[Android Wear][3]的默认输入界面。
|
||||
|
||||
谷歌甚至还在输入之外的地方使用语音识别。谷歌的语音识别技术被用在了转述Youtube视频上,它能自动生成字幕供听障用户观看。生成的字幕甚至被谷歌做成了索引,所以你可以搜索某句话在视频的哪里说过。语音是许多产品的未来,并且这项长期计划将谷歌带入了屈指可数的拥有自家语音识别服务的公司行列。大部分其它的语音识别产品,像苹果的Siri和三星设备,被迫使用——并且为其支付了授权费——Nuance的语音识别。
|
||||
|
||||
在计算机听觉系统设立运行之后,谷歌下一步将把这项策略应用到计算机视觉上。这就是为什么像Google Goggles,Google图像搜索和[Project Tango][4]这样的项目存在的原因。就像GOOG-411的那段日子,这些项目还处在早期阶段。当[谷歌的机器人部门][5]造出了机器人,它会需要看和听,谷歌的计算机视觉和听觉项目会给谷歌一个先机。
|
||||
|
||||

|
||||
Nexus S,第一部三星制造的Nexus手机。
|
||||
|
||||
### Android 2.3 Gingerbread——第一次UI大变 ###
|
||||
|
||||
Gingerbread(姜饼人)发布于2010年12月,这已是2.2发布整整七个月之后了。尽管如此,等待是值得的,因为安卓2.3整个系统的每个界面几乎都改变了。这是从安卓0.9最初的样式以来第一次重大的更新。2.3开始了一系列持续的改进,试着将安卓从丑陋的小鸭子变成能承载它自己的合适的样子——从美学角度——来对抗iPhone。
|
||||
|
||||
说到苹果,六个月前,它发布了iPhone 4和iOS 4,新增了多任务处理和Facetime视频聊天。微软同样也终于重返这场游戏。微软在2010年11月发布了Windows Phone 7,也进入了智能手机时代。
|
||||
|
||||
安卓2.3在界面设计上投入了很多精力,但是由于缺乏方向或设计文档,许多应用仅仅止步于获得了一个新的定制主题而已。一些应用用了更扁平的暗色主题,一些用了充满渐变,活泼的暗色主题,其他应用则是高对比度的白色和绿色组合。尽管2.3并没有做到风格统一,Gingerbread还是完成了让系统几乎每个部分变得更现代化的任务。这同样是件好事,因为下一个手机版安卓要在将近一年后才到来。
|
||||
|
||||
Gingerbread的首发设备是Nexus S,谷歌的第二部旗舰设备,并且是第一部由三星生产的Nexus设备。尽管今天我们已经习惯了每年都有更新型号的CPU,那时候可不是这个样子。Nexus S有个1GHz Cortex A8处理器,和Nexus One是一样的。GPU从速度来说略微有所变快。Nexus S稍微比Nexus One大一点,拥有800×480分辨率的AMOLED显示屏。
|
||||
|
||||
从参数上来说,Nexus S看起来只是个平淡无奇的升级,但他确实开了安卓的许多先河。Nexus S是谷歌第一部没有MicroSD卡槽的旗舰,板载16GB存储。Nexus One只有512MB存储空间,但它有MicroSD卡槽。移除SD卡槽为用户简化了存储管理——现在只有一个存储地点了——但是影响了高级用户的扩展能力。它是谷歌第一部带有NFC的手机,手机背面的一个特殊芯片能够在和其他NFC芯片接触时传输数据。Nexus S暂时只能读取NFC标签,而不能发送数据。
|
||||
|
||||
托Gingerbread中一些升级的福,Nexus S是第一部不带有硬件十字方向键或轨迹球安卓手机之一。Nexus S缩减到只有电源,音量以及四个导航键。Nexus S同时还是如今[疯狂的曲面手机][6]的先驱,因为三星给Nexus S配备了一块略微有些弯曲的玻璃。
|
||||
|
||||

|
||||
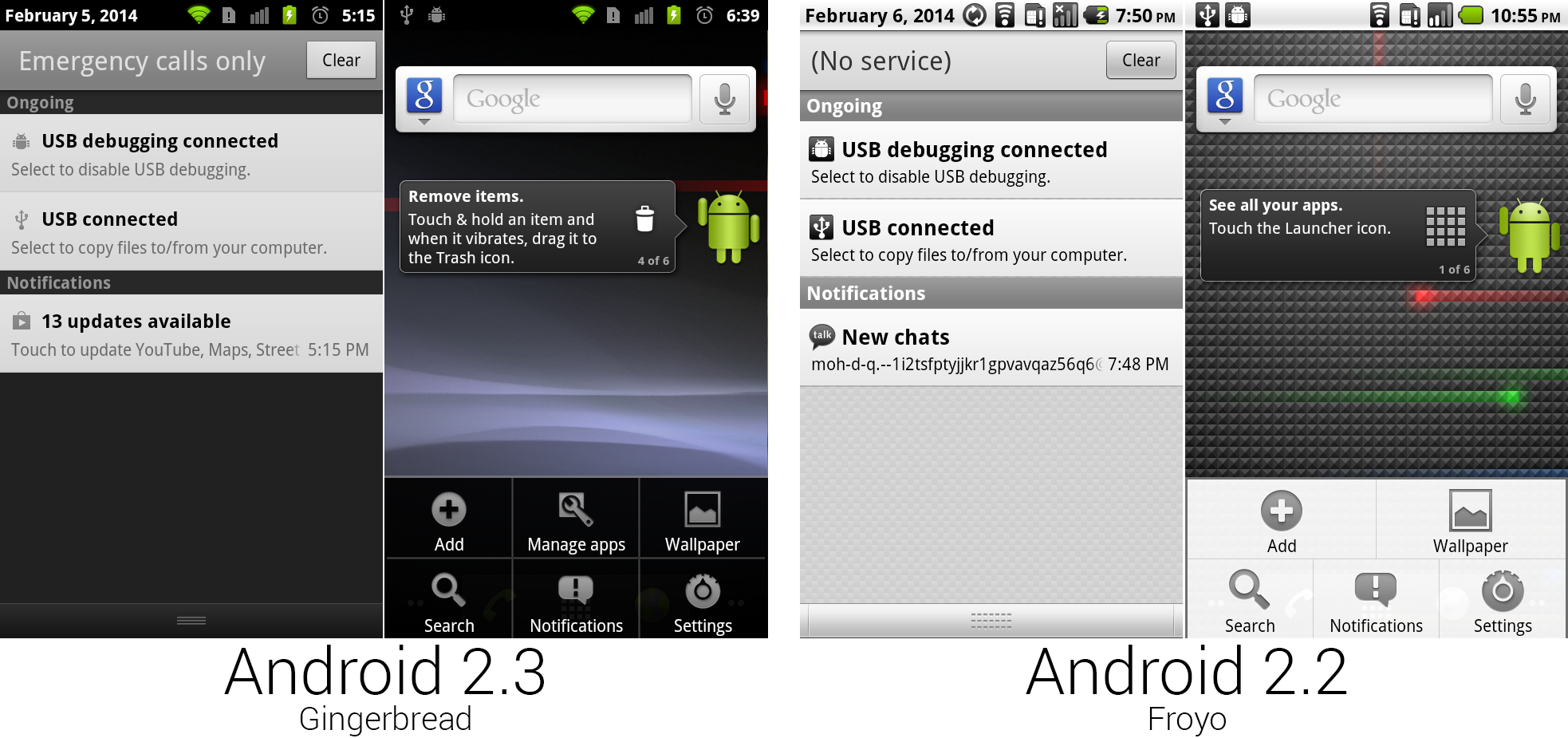
Gingerbread更改了状态栏和壁纸,并且添加了许多新图标。
|
||||
Ron Amadeo供图
|
||||
|
||||
升级过的“Nexus”动态壁纸作为Nexus S的独占发布。这个壁纸基本上和Nexus One的一样,带有带动画轨迹的光点。在Nexus S上,去除了方阵设计,取而代之的是波浪形的蓝/灰色背景。底部dock有了直角和彩色图标。
|
||||
|
||||
|
||||
新通知面板和菜单。
|
||||
Ron Amadeo供图
|
||||
|
||||
状态栏自0.9的首次登场以来终于得到了重制。状态栏从白色渐变变成纯黑,所有图标重绘成了灰色和绿色。所有东西看起来都更加清爽和现代,这要感谢锐角图标设计和高分辨率。最奇怪的决定可能是从状态栏时钟移除了时间段显示以及信号强度那令人疑惑的灰色。尽管灰色被用在状态栏的许多图标上,而且上面截图有四格灰色信号,安卓实际上指示的是没有信号。绿色格表示信号强度,灰色格指示的是“空”信号格。
|
||||
|
||||
Gingerbread的状态栏图标同时还作为网络连接的状态指示。如果你的设备连接到了谷歌的服务器,图标会变绿,如果没有谷歌的连接,图标会是白色的。这让你可以在外出时轻松了解你的网络连接状态。
|
||||
|
||||
通知面板的设计从安卓1.5的设计改进而来。我们看到UI部分再次从浅色主题变为暗色主题,有个深灰色顶部,黑色背景以及在灰色底色上的黑色文本。
|
||||
|
||||
菜单颜色同样变深了,背景从白色变成了带点透明的黑色。菜单图标和背景的对比并没有它应该有的那么强烈,因为灰色图标的颜色和它们在白色背景上的时候是一样的。要求改变颜色意味着每个开发者都得制作新的图标,所以谷歌在黑色背景上使用了先前就有的灰色。这是系统级别的改变,所以这个新菜单会出现在每个应用中。
|
||||
|
||||
----------
|
||||
|
||||

|
||||
|
||||
[Ron Amadeo][a] / Ron是Ars Technica的评论编缉,专注于安卓系统和谷歌产品。他总是在追寻新鲜事物,还喜欢拆解事物看看它们到底是怎么运作的。
|
||||
|
||||
[@RonAmadeo][t]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://arstechnica.com/gadgets/2014/06/building-android-a-40000-word-history-of-googles-mobile-os/14/
|
||||
|
||||
译者:[alim0x](https://github.com/alim0x) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://arstechnica.com/gadgets/2010/08/google-beefs-up-voice-search-mobile-sync/
|
||||
[2]:http://arstechnica.com/business/2007/04/google-rolls-out-free-411-service/
|
||||
[3]:http://arstechnica.com/gadgets/2014/03/in-depth-with-android-wear-googles-quantum-leap-of-a-smartwatch-os/
|
||||
[4]:http://arstechnica.com/gadgets/2014/02/googles-project-tango-is-a-smartphone-with-kinect-style-computer-vision/
|
||||
[5]:http://arstechnica.com/gadgets/2013/12/google-robots-former-android-chief-will-lead-google-robotics-division/
|
||||
[6]:http://arstechnica.com/gadgets/2013/12/lg-g-flex-review-form-over-even-basic-function/
|
||||
[a]:http://arstechnica.com/author/ronamadeo
|
||||
[t]:https://twitter.com/RonAmadeo
|
||||
@ -0,0 +1,178 @@
|
||||
使用 SSH 和一次性密码安全登录 Linux
|
||||
================================================================================
|
||||
有人说,安全不是一个产品,而是一个过程(LCTT 注:安全公司 McAfee 认为,安全风险管理是一个方法论,而不是安全产品的堆叠)。虽然 SSH 协议被设计成使用加密技术来确保安全,但如果使用不当,别人还是能够破坏你的系统:比如弱密码、密钥泄露、使用的 SSH 客户端过时等,都能引发安全问题。
|
||||
|
||||
在考虑 SSH 认证方案时,大家普遍认为[公钥认证][1]比密码认证更安全。然而,公钥认证技术并不是为公共环境设置的,如果你在一台公用电脑上使用公钥认证登录 SSH 服务器,你的服务器已经毫无安全可言了,公用的电脑可能会记录你的公钥,或从你的内存中读取公钥。如果你不信任本地电脑,那你最好还是使用其他方式登录服务器。现在就是“一次性密码”派上用场的时候了,就像名字所示,一次性密码只能被使用一次。这种一次性密码非常合适在不安全的环境下发挥作用,就算它被窃取,也无法再次使用。
|
||||
|
||||
有个一次性密码方案叫[谷歌认证][2],但在本文中,我要介绍的是另一种 SSH 登录方案:[OTPW][3],它是个一次性密码登录的软件包。不像谷歌认证,OTPW 不需要依赖任何第三方库。
|
||||
|
||||
### OTPW 是什么 ###
|
||||
|
||||
OTPW 由一次性密码生成器和 PAM 认证规则组成。在 OTPW 中一次性密码由生成器事先生成,然后由用户以某种安全的方式获得(比如打印到纸上)。另一方面,这些密码会通过 Hash 加密保存在 SSH 服务器端。当用户使用一次性密码登录系统时,OTPW 的 PAM 模块认证这些密码,并且保证它们不能再次使用。
|
||||
|
||||
### 步骤1:OTPW 的安装和配置 ###
|
||||
|
||||
#### 在 Debian, Ubuntu 或 Linux Mint 发行版上 ####
|
||||
|
||||
使用 apt-get 安装:
|
||||
|
||||
$ sudo apt-get install libpam-otpw otpw-bin
|
||||
|
||||
打开针对 SSH 服务的 PAM 配置文件(/etc/pam.d/sshd),注释掉下面这行(目的是禁用 PAM 的密码认证功能):
|
||||
|
||||
#@include common-auth
|
||||
|
||||
添加下面两行(用于打开一次性密码认证功能):
|
||||
|
||||
auth required pam_otpw.so
|
||||
session optional pam_otpw.so
|
||||
|
||||

|
||||
|
||||
#### 在 Fedora 或 CentOS/RHEL 发行版上 ####
|
||||
|
||||
在基于 RedHat 的发行版中没有编译好的 OTPW,所以我们需要使用源代码来安装它。
|
||||
|
||||
首先,安装编译环境:
|
||||
|
||||
$ sudo yum git gcc pam-devel
|
||||
$ git clone https://www.cl.cam.ac.uk/~mgk25/git/otpw
|
||||
$ cd otpw
|
||||
|
||||
打开 Makefile 文件,编辑以“PAMLIB=”开头的那行配置:
|
||||
|
||||
64 位系统:
|
||||
|
||||
PAMLIB=/usr/lib64/security
|
||||
|
||||
32 位系统:
|
||||
|
||||
PAMLIB=/usr/lib/security
|
||||
|
||||
编译安装。需要注意的是安装过程会把 SSH 服务重启一下,所以如果你是使用 SSH 连接到服务器,做好被断开连接的准备吧。
|
||||
|
||||
$ make
|
||||
$ sudo make install
|
||||
|
||||
现在你需要更新 SELinux 策略,因为 /usr/sbin/sshd 会往你的 home 目录写数据,而 SELinux 默认是不允许这么做的。如果你使用了 SELinux 服务(LCTT 注:使用 getenforce 命令查看结果,如果是 enforcing,就是打开了 SELinux 服务),如果没有使用 SELinux 服务,请跳过这一步。
|
||||
|
||||
$ sudo grep sshd /var/log/audit/audit.log | audit2allow -M mypol
|
||||
$ sudo semodule -i mypol.pp
|
||||
|
||||
接下来打开 PAM 配置文件(/etc/pam.d/sshd),注释下面这行(为了禁用密码认证):
|
||||
|
||||
#auth substack password-auth
|
||||
|
||||
添加下面两行(用于打开一次性密码认证功能):
|
||||
|
||||
auth required pam_otpw.so
|
||||
session optional pam_otpw.so
|
||||
|
||||
#### 步骤2:配置 SSH 服务器,使用一次性密码 ####
|
||||
|
||||
打开 /etc/ssh/sshd_config 文件,设置下面三个参数。你要确保下面的参数不会重复存在,否则 SSH 服务器可能会出现异常。
|
||||
|
||||
UsePrivilegeSeparation yes
|
||||
ChallengeResponseAuthentication yes
|
||||
UsePAM yes
|
||||
|
||||
你还需要禁用默认的密码认证功能。另外可以选择开启公钥认证功能,那样的话你就可以在没有一次性密码的时候使用公钥进行认证。
|
||||
|
||||
PubkeyAuthentication yes
|
||||
PasswordAuthentication no
|
||||
|
||||
重启 SSH 服务器。
|
||||
|
||||
Debian, Ubuntu 或 Linux Mint 发行版:
|
||||
|
||||
$ sudo service ssh restart
|
||||
|
||||
Fedora 或 CentOS/RHEL 7 发行版:
|
||||
|
||||
$ sudo systemctl restart sshd
|
||||
|
||||
#### 步骤3:使用 OTPW 产生一次性密码 ####
|
||||
|
||||
之前提到过,你需要事先创建一次性密码,并保存起来。使用 otpw-gen 命令创建密码:
|
||||
|
||||
$ cd ~
|
||||
$ otpw-gen > temporary_password.txt
|
||||
|
||||

|
||||
|
||||
这个命令会让你输入密码前缀,当你以后登录的时候,你需要同时输入这个前缀以及一次性密码。密码前缀是另外一层保护,就算你的一次性密码表被泄漏,别人也无法通过暴力破解你的 SSH 密码。
|
||||
|
||||
设置好密码前缀后,这个命令会产生 280 个一次性密码,并将它们保存在一个文本文件中(如 temporary_password.txt)。每个密码(默认是 8 个字符)由一个 3 位十进制数索引。你需要将这个密码表打印出来,并随身携带。
|
||||
|
||||

|
||||
|
||||
查看 ./.otpw 文件,它存放了一次性密码的 HASH 值。头 3 位十进制数与你随身携带的密码表的索引一一对应,在你登录 SSH 服务器的时候会被用到。
|
||||
|
||||
$ more ~/.otpw
|
||||
|
||||
----------
|
||||
|
||||
OTPW1
|
||||
280 3 12 8
|
||||
191ai+:ENwmMqwn
|
||||
218tYRZc%PIY27a
|
||||
241ve8ns%NsHFmf
|
||||
055W4/YCauQJkr:
|
||||
102ZnJ4VWLFrk5N
|
||||
2273Xww55hteJ8Y
|
||||
1509d4b5=A64jBT
|
||||
168FWBXY%ztm9j%
|
||||
000rWUSdBYr%8UE
|
||||
037NvyryzcI+YRX
|
||||
122rEwA3GXvOk=z
|
||||
|
||||
### 测试一次性密码登录 SSH 服务器 ###
|
||||
|
||||
使用普通的方式登录 SSH 服务器:
|
||||
|
||||
$ ssh user@remote_host
|
||||
|
||||
如果 OTPW 成功运行,你会看到一点与平时登录不同的地方:
|
||||
|
||||
Password 191:
|
||||
|
||||
现在打开你的密码表,找到索引号为 191 的密码。
|
||||
|
||||
023 kBvp tq/G 079 jKEw /HRM 135 oW/c /UeB 191 fOO+ PeiD 247 vAnZ EgUt
|
||||
|
||||
从上表可知,191 号密码是“fOO+PeiD”。你需要加上密码前缀,比如你设置的前缀是“000”,则你实际需要输入的密码是“000fOO+PeiD”。
|
||||
|
||||
成功登录后,你这次输入的密码自动失效。查看 ~/.otpw 文件,你会发现第一行变成“---------------”,这表示 191 号密码失效了。
|
||||
|
||||
OTPW1
|
||||
280 3 12 8
|
||||
---------------
|
||||
218tYRZc%PIY27a
|
||||
241ve8ns%NsHFmf
|
||||
055W4/YCauQJkr:
|
||||
102ZnJ4VWLFrk5N
|
||||
2273Xww55hteJ8Y
|
||||
1509d4b5=A64jBT
|
||||
168FWBXY%ztm9j%
|
||||
000rWUSdBYr%8UE
|
||||
037NvyryzcI+YRX
|
||||
122rEwA3GXvOk=z
|
||||
|
||||
### 总结 ###
|
||||
|
||||
在这个教程中,我介绍了如何使用 OTPW 工具来设置一次性登录密码。你也许意识到了在这种两个因子的认证方式中,打印一张密码表让人感觉好 low,但是这种方式是最简单的,并且不用依赖任何第三方软件。无论你用哪种方式创建一次性密码,在你需要在一个不被信任的环境登录 SSH 服务器的时候,它们都很有用。你可以就这个主题来分享你的经验和观点。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/secure-ssh-login-one-time-passwords-linux.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[bazz2](https://github.com/bazz2)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/nanni
|
||||
[1]:http://xmodulo.com/how-to-force-ssh-login-via-public-key-authentication.html
|
||||
[2]:http://xmodulo.com/two-factor-authentication-ssh-login-linux.html
|
||||
[3]:http://www.cl.cam.ac.uk/~mgk25/otpw.html
|
||||
@ -1,61 +1,62 @@
|
||||
Vic020
|
||||
Linux 有问必答 -- 如何在红帽系linux中编译Ixgbe
|
||||
|
||||
Linux FAQs with Answers--How to compile ixgbe driver on CentOS, RHEL or Fedora
|
||||
================================================================================
|
||||
> **Question**: I want to build and install the latest ixgbe 10G NIC driver. How can I compile ixgbe driver on CentOS, Fedora or RHEL?
|
||||
> **提问**:我想要安装最新版的ixgbe 10G网卡驱动。在CentOS, Fedora 或 RHEL中,我应该如何编译ixgbe驱动?
|
||||
|
||||
To use Intel's PCI Express 10G NICs (e.g., 82598, 82599, x540) on your Linux system, you need to install ixgbe driver. While modern Linux distributions come with ixgbe driver pre-installed as a loadable module, the pre-built ixgbe driver is not fully customizable with limited parameters. If you want to enable and customize all available features of the 10G NICs (e.g., RSS, multi-queue, virtual functions, hardware offload), you will need to build the driver from the source.
|
||||
|
||||
Here is how to compile ixgbe driver from the source on Red Hat based platforms (e.g., CentOS, RHEL or Fedora). For Debian based systems, refer to [this guideline][1] instead.
|
||||
想要在linux使用Intel的PCI Express 10G网卡(例如,82598,82599,x540),需要安装Ixgbe驱动。如今的Linux发行版都会欲安装ixgbe作为可加载模块,但是预安装的ixgbe驱动不是完整功能版。如果想要开启和定制所有10G网卡(如,RSS,多)的功能,需要源码编译安装。
|
||||
|
||||
### Step One: Install Prerequisites ###
|
||||
本文基于红帽系平台(如,CentOS,RHEL或Fedora)。Debian系系统,请看[这篇文章][1]
|
||||
|
||||
First, set up necessary developmen environment and install matching kernel headers.
|
||||
|
||||
### 第一步: 安装依赖 ###
|
||||
|
||||
首先,安装必要的开发环境和安装匹配的内核头
|
||||
|
||||
$ sudo yum install gcc make
|
||||
$ sudo yum install kernel-devel
|
||||
|
||||
### Step Two: Compile Ixgbe Driver ###
|
||||
### 第二步: 编译Ixgbe ###
|
||||
|
||||
Download the latest ixgbe source code from the [official site][2].
|
||||
从[官方页面][2]下载最新Ixgbe源码
|
||||
|
||||
$ wget http://downloads.sourceforge.net/project/e1000/ixgbe%20stable/3.23.2/ixgbe-3.23.2.tar.gz
|
||||
|
||||
Be sure to check supported kernel versions. For example, the ixgbe driver 3.23.2 supports Linux kernel versions 2.6.18 up to 3.18.1.
|
||||
确保检查支持内核版本。例如,Ixgbe3.23.2版本支持Linux内核版本2.6.18以上到3.18.1.
|
||||
|
||||
Extract the tarball and compile it.
|
||||
提取压缩包并编译
|
||||
|
||||
$ tar -xvf ixgbe-3.23.2.tar.gz
|
||||
$ cd ixgbe-3.23.2/src
|
||||
$ make
|
||||
|
||||
If successful, the compiled driver (ixgbe.ko) will be found in the current directory.
|
||||
如果成功,编译完成的驱动(ixgbe.ko)可以在当前目录找到。
|
||||
|
||||
You can check the information of the compiled driver by running:
|
||||
可以运行这个命令来查看编译信息:
|
||||
|
||||
$ modinfo ./ixgbe.ko
|
||||
|
||||
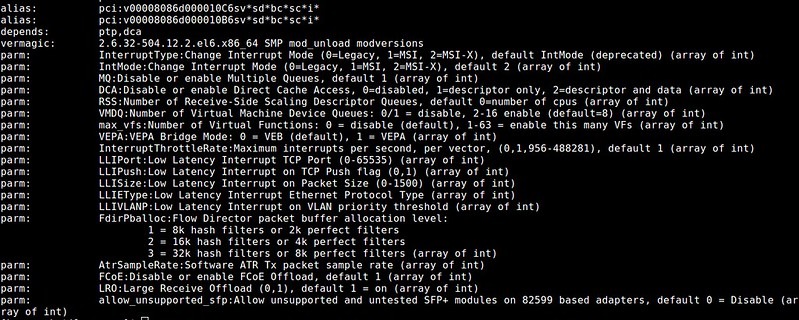
The output will show a list of available parameters of the ixgbe driver.
|
||||
将会输出一个Ixgbe驱动的可用参数列表
|
||||
|
||||
|
||||
|
||||
### Step Three: Load Ixgbe Driver ###
|
||||
### 第三步: 加载 Ixgbe 驱动 ###
|
||||
|
||||
Now you are ready to load the compiled ixgbe driver.
|
||||
这步准备加载已经编译好的驱动。
|
||||
|
||||
If the stock ixgbe driver is already loaded on your system, you need to unload it first. Otherwise, you won't be able to load the new ixgbe driver.
|
||||
如果系统已经加载了Ixgbe驱动,首先需要卸载掉老版本。否者,新版本不能够加载。
|
||||
|
||||
$ sudo rmmod ixgbe.ko
|
||||
|
||||
Then insert the compiled driver in the kernel by running:
|
||||
然后插入编译完成的驱动到内核中:
|
||||
|
||||
$ sudo insmod ./ixgbe.ko
|
||||
|
||||
Optionally, you can supply any parameters while loading the driver.
|
||||
同时,你可以设置启动参数
|
||||
|
||||
$ sudo insmod ./ixgbe.ko FdirPballoc=3 RSS=16
|
||||
|
||||
To verify that the driver is loaded successfully, check the output of dmesg command.
|
||||
验证驱动是否加载成功,使用dmesg命令,查看其输出
|
||||
|
||||
$ dmesg
|
||||
|
||||
@ -167,17 +168,17 @@ To verify that the driver is loaded successfully, check the output of dmesg comm
|
||||
eth3: no IPv6 routers present
|
||||
eth4: no IPv6 routers present
|
||||
|
||||
### Step Four: Install Ixgbe Driver ###
|
||||
### 第四步: 安装Ixgbe驱动 ###
|
||||
|
||||
Once you have checked that the driver is loaded successfully, go ahead and install the driver on your system.
|
||||
当确认驱动已经加载后,就可以安装驱动到系统中了
|
||||
|
||||
$ sudo make install
|
||||
|
||||
ixgbe.ko will be installed in the following location.
|
||||
ixgbe.ko将会安装在下列目录
|
||||
|
||||
/lib/modules/<kernel-version>/kernel/drivers/net/ixgbe
|
||||
|
||||
At this point, the compiled driver will be loaded automatically upon boot, or you can load it by running:
|
||||
此时,编译完蛋程序将在启动时自动加载,也可以通过运行命令加载它:
|
||||
|
||||
$ sudo modprobe ixgbe
|
||||
|
||||
@ -188,7 +189,7 @@ At this point, the compiled driver will be loaded automatically upon boot, or yo
|
||||
via: http://ask.xmodulo.com/compile-ixgbe-driver-centos-rhel-fedora.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
译者:[Vic020](http://vicyu.net)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
Loading…
Reference in New Issue
Block a user