mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-01-19 22:51:41 +08:00
Merge remote-tracking branch 'LCTT/master'
This commit is contained in:
commit
ce1e9bbda3
124
sources/talk/20181031 3 scary sysadmin stories.md
Normal file
124
sources/talk/20181031 3 scary sysadmin stories.md
Normal file
@ -0,0 +1,124 @@
|
||||
3 scary sysadmin stories
|
||||
======
|
||||
|
||||
Terrifying ghosts are hanging around every data center, just waiting to haunt the unsuspecting sysadmin.
|
||||
|
||||

|
||||
|
||||
> "It's all just a bunch of hocus pocus!" — Max in [Hocus Pocus][1]
|
||||
|
||||
Over my many years as a system administrator, I've heard many horror stories about the different ghosts that have haunted new admins due to their inexperience.
|
||||
|
||||
Here are three of the stories that stand out to me the most in helping build my character as a good sysadmin.
|
||||
|
||||
### The ghost of the failed restore
|
||||
|
||||
In a well-known data center (whose name I do not want to remember), one cold October night we had a production outage in which thousands of web servers stopped responding due to downtime in the main database. The database administrator asked me, the rookie sysadmin, to recover the database's last full backup and restore it to bring the service back online.
|
||||
|
||||
But, at the end of the process, the database was still broken. I didn't worry, because there were other full backup files in stock. However, even after doing the process several times, the result didn't change.
|
||||
|
||||
With great fear, I asked the senior sysadmin what to do to fix this behavior.
|
||||
|
||||
"You remember when I showed you, a few days ago, how the full backup script was running? Something about how important it was to validate the backup?" responded the sysadmin.
|
||||
|
||||
"Of course! You told me that I had to stay a couple of extra hours to perform that task," I answered.
|
||||
|
||||
"Exactly! But you preferred to leave early without finishing that task," he said.
|
||||
|
||||
"Oh my! I thought it was optional!" I exclaimed.
|
||||
|
||||
"It was, it was…"
|
||||
|
||||
**Moral of the story:** Even with the best solution that promises to make the most thorough backups, the ghost of the failed restoration can appear, darkening our job skills, if we don't make a habit of validating the backup every time.
|
||||
|
||||
### The dark window
|
||||
|
||||
Once upon a night watch, reflecting I was, lonely and tired,
|
||||
Looking at the file window on my screen.
|
||||
Clicking randomly, nearly napping, suddenly came a beeping
|
||||
From some server, sounding gently, sounding on my pager.
|
||||
"It's just a warning," I muttered, "sounding on my pager—
|
||||
Only this and nothing more."
|
||||
Soon again I heard a beeping somewhat louder than before.
|
||||
Opening my pager with great disdain,
|
||||
There was the message from a server of the saintly days of yore:
|
||||
"The legacy application, it's down, doesn't respond," and nothing more.
|
||||
There were many stories of this server,
|
||||
Incredibly, almost terrified,
|
||||
I went down to the data center to review it.
|
||||
I sat engaged in guessing, what would be the console to restart it
|
||||
Without keyboard, mouse, or monitor?
|
||||
"The task level up"—I think—"only this and nothing more."
|
||||
Then, thinking, "In another rack, I saw a similar server,
|
||||
I'll take its monitor and keyboard, nothing bad."
|
||||
Suddenly, this server shut down, and my pager beeped again:
|
||||
"The legacy application, it's down, doesn't respond", and nothing more.
|
||||
Bemused, I sat down to call my sysadmin mentor:
|
||||
"I wanted to use the console of another server, and now both are out."
|
||||
"Did you follow my advice? Don't use the graphics console, the terminal is better."
|
||||
Of course, I remember, it was last December;
|
||||
I felt fear, a horror that I had never felt before;
|
||||
"It is a tool of the past and nothing more."
|
||||
With great shame I understood my mistake:
|
||||
"Master," I said, "truly, your forgiveness I implore;
|
||||
but the fact is I thought it was not used anymore.
|
||||
A dark window and nothing more."
|
||||
"Learn it well, little kid," he spoke.
|
||||
"In the terminal you can trust, it's your friend and much, much more."
|
||||
Step by step, my master showed me to connect with the terminal,
|
||||
And restarting each one
|
||||
With infinite patience, he taught me
|
||||
That from that dark window I should not separate
|
||||
Never, nevermore.
|
||||
|
||||
**Moral of the story:** Fluency in the command-line terminal is a skill often abandoned and considered archaic by newer generations, but it improves your flexibility and productivity as a sysadmin in obvious and subtle ways.
|
||||
|
||||
### Troll bridge
|
||||
|
||||
I'd been a sysadmin for three or four years when one of my old mentors was removed from work. The older man was known for making fun of the new guys in the group—the ones who brought from the university the desire to improve processes with the newly released community operating system. My manager assigned me the older man's office, a small space under the access stairs to the data center—"Troll Bridge," they called it—and the few legacy servers he still managed.
|
||||
|
||||
While reviewing those legacy servers, I realized most of them had many scripts that did practically all the work. I just had to check that they did not go offline due to an electrical failure. I started using those methods, adapting them so my own servers would work the same way, making my tasks more efficient and, at the same time, requiring less of my time to complete them. My day soon became surfing the internet, watching funny videos, and even participating in internet forums.
|
||||
|
||||
A couple of years went by, and I maintained my work in the same way. When a new server arrived, I automated its tasks so I could free myself and continue with my usual participation in internet forums. One day, when I shared one of my scripts in the internet forum, a new admin told me I could simplify it using one novelty language, a new trend that was becoming popular among the new folks.
|
||||
|
||||
"I am a sysadmin, not a programmer," I answered. "They will never be the same."
|
||||
|
||||
From that day on, I dedicated myself to ridiculing the kids who told me I should program in the new languages.
|
||||
|
||||
"You do not know, newbie," I answered every time, "this job will never change."
|
||||
|
||||
A few years later, my responsibilities increased, and my manager wanted me to modify the code of the applications hosted on my server.
|
||||
|
||||
"That's what the job is about now," said my manager. "Development and operations are joining; if you're not willing to do it, we'll bring in some guy who does."
|
||||
|
||||
"I will never do it, it's not my role," I said.
|
||||
|
||||
"Well then…" he said, looking at me harshly.
|
||||
|
||||
I've been here ever since. Hiding. Waiting. Under my bridge.
|
||||
|
||||
I watch from the shadows as the people pass: up the stairs, muttering, or talking about the things the new applications do. Sometimes people pause beneath my bridge, to talk, or share code, or make plans. And I watch them, but they don't see me.
|
||||
|
||||
I'm just going to stay here, in the darkness under the bridge. I can hear you all out there, everything you say.
|
||||
|
||||
Oh yes, I can hear you.
|
||||
But I'm not coming out.
|
||||
|
||||
**Moral of the story:** "The lazy sysadmin is the best sysadmin" is a well-known phrase that means if we are proactive enough to automate all our processes properly, we will have a lot of free time. The best sysadmins never seem to be very busy; they prefer to be relaxed and let the system do the work for them. "Work smarter not harder." However, if we don't use this free time productively, we can fall into obsoleteness and become something we do not want. The best sysadmins reinvent themselves constantly; they are always researching and learning.
|
||||
|
||||
Following these stories' morals—and continually learning from my mistakes—helped me improve my management skills and create the good habits necessary for the sysadmin job.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/10/3-scary-sysadmin-stories
|
||||
|
||||
作者:[Alex Callejas][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/darkaxl
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://en.wikipedia.org/wiki/Hocus_Pocus_(1993_film)
|
||||
@ -0,0 +1,84 @@
|
||||
How open source hardware increases security
|
||||
======
|
||||
Want to boost cybersecurity at your organization? Switch to open source hardware.
|
||||

|
||||
|
||||
Hardware hacks are particularly scary because they trump any software security safeguards—for example, they can render all accounts on a server password-less.
|
||||
|
||||
Fortunately, we can benefit from what the software industry has learned from decades of fighting prolific software hackers: Using open source techniques can, perhaps counterintuitively, [make a system more secure][1]. Open source hardware and distributed manufacturing can provide protection from future attacks.
|
||||
|
||||
### Trust—but verify
|
||||
|
||||
Imagine you are a 007 agent holding classified documents. Would you feel more secure locking them in a safe whose manufacturer keeps the workings of the locks secret, or in a safe whose design is published openly so that everyone (including thieves) can judge its quality—thus enabling you to rely exclusively on technical complexity for protection?
|
||||
|
||||
The former approach might be perfectly secure—you simply don’t know. But why would you trust any manufacturer that could be compromised now or in the future? In contrast, the open system is almost certain to be secure, especially if enough time has passed for it to be tested by multiple companies, governments, and individuals.
|
||||
|
||||
To a large degree, the software world has seen the benefits of moving to free and open source software. That's why open source is run on all [supercomputers][2], [90% of the cloud, 82% of the smartphone market, and 62% of the embedded systems market][3]. Open source appears poised to dominate the future, with over [70% of the IoT][4].
|
||||
|
||||
In fact, security is one of the core benefits of [open source][5]. While open source is not inherently more secure, it allows you to verify security yourself (or pay someone more qualified to do so). With closed source programs, you must trust, without verification, that a program works properly. To quote President Reagan: "Trust—but verify." The bottom line is that open source allows users to make more informed choices about the security of a system—choices that are based on their own independent judgment.
|
||||
|
||||
### Open source hardware
|
||||
|
||||
This concept also holds true for electronic devices. Most electronics customers have no idea what is in their products, and even technically sophisticated companies like Amazon may not know exactly what is in the hardware that runs their servers because they use proprietary products that are made by other companies.
|
||||
|
||||
In the incident mentioned above, Chinese spies recently used a tiny microchip, not much bigger than a grain of rice, to infiltrate hardware made by SuperMicro (the Microsoft of the hardware world). These chips enabled outside infiltrators to access the core server functions of some of America’s leading companies and government operations, including DOD data centers, CIA drone operations, and the onboard networks of Navy warships. Operatives from the People’s Liberation Army or similar groups could have reverse-engineered or made identical or disguised modules (in this case, the chips looked like signal-conditioning couplers, a common motherboard component, rather than the spy devices they were).
|
||||
|
||||
Having the source available helps customers much more than hackers, as most customers do not have the resources to reverse-engineer the electronics they buy. Without the device's source, or design, it's difficult to determine whether or not hardware has been hacked.
|
||||
|
||||
Enter [open source hardware][6]: hardware design that is publicly available so that anyone can study, modify, test, distribute, make, or sell it, or hardware based on it. The hardware’s source is available to everyone.
|
||||
|
||||
### Distributed manufacturing for cybersecurity
|
||||
|
||||
Open source hardware and distributed manufacturing could have prevented the Chinese hack that rightfully terrified the security world. Organizations that require tight security, such as military groups, could then check the product's code and bring production in-house if necessary.
|
||||
|
||||
This open source future may not be far off. Recently I co-authored, with Shane Oberloier, an [article][7] that discusses a low-cost open source benchtop device that enables anyone to make a wide range of open source electronic products. The number of open source electronics designs is proliferating on websites like [Hackaday][8], [Open Electronics][9], and the [Open Circuit Institute][10], as are communities based on specific products like [Arduino][11] and around companies like [Adafruit Industries][12] and [SparkFun Electronics][13].
|
||||
|
||||
Every level of manufacturing that users can do themselves increases the security of the device. Not long ago, you had to be an expert to make even a simple breadboard design. Now, with open source mills for boards and electronics repositories, small companies and even individuals can make reasonably sophisticated electronic devices. While most builders are still using black-box chips on their devices, this is also changing as [open source chips gain traction][14].
|
||||
|
||||
|
||||
|
||||
Creating electronics that are open source all the way down to the chip is certainly possible—and the more besieged we are by hardware hacks, perhaps it is even inevitable. Companies, governments, and other organizations that care about cybersecurity should strongly consider moving toward open source—perhaps first by establishing purchasing policies for software and hardware that makes the code accessible so they can test for security weaknesses.
|
||||
|
||||
Although every customer and every manufacturer of an open source hardware product will have different standards of quality and security, this does not necessarily mean weaker security. Customers should choose whatever version of an open source product best meets their needs, just as users can choose their flavor of Linux. For example, do you run [Fedora][15] for free, or do you, like [90% of Fortune Global 500 companies][16], pay Red Hat for its version and support?
|
||||
|
||||
Red Hat makes billions of dollars a year for the service it provides, on top of a product that can ostensibly be downloaded for free. Open source hardware can follow the [same business model][17]; it is just a less mature field, lagging [open source software by about 15 years][18].
|
||||
|
||||
The core source code for hardware devices would be controlled by their manufacturer, following the "[benevolent dictator for life][19]" model. Code of any kind (infected or not) is screened before it becomes part of the root. This is true for hardware, too. For example, Aleph Objects manufacturers the popular [open source LulzBot brand of 3D printer][20], a commercial 3D printer that's essentially designed to be hacked. Users have made [dozens of modifications][21] (mods) to the printer, and while they are available, Aleph uses only the ones that meet its QC standards in each subsequent version of the printer. Sure, downloading a mod could mess up your own machine, but infecting the source code of the next LulzBot that way would be nearly impossible. Customers are also able to more easily check the security of the machines themselves.
|
||||
|
||||
While [challenges certainly remain for the security of open source products][22], the open hardware model can help enhance cybersecurity—from the Pentagon to your living room.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/10/cybersecurity-demands-rapid-switch-open-source-hardware
|
||||
|
||||
作者:[Joshua Pearce][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/jmpearce
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://dl.acm.org/citation.cfm?id=1188921
|
||||
[2]: https://www.zdnet.com/article/supercomputers-all-linux-all-the-time/
|
||||
[3]: https://www.serverwatch.com/server-news/linux-foundation-on-track-for-best-year-ever-as-open-source-dominates.html
|
||||
[4]: https://www.itprotoday.com/iot/survey-shows-linux-top-operating-system-internet-things-devices
|
||||
[5]: https://www.infoworld.com/article/2985242/linux/why-is-open-source-software-more-secure.html
|
||||
[6]: https://www.oshwa.org/definition/
|
||||
[7]: https://www.mdpi.com/2411-5134/3/3/64/htm
|
||||
[8]: https://hackaday.io/
|
||||
[9]: https://www.open-electronics.org/
|
||||
[10]: http://opencircuitinstitute.org/
|
||||
[11]: https://www.arduino.cc/
|
||||
[12]: http://www.adafruit.com/
|
||||
[13]: https://www.sparkfun.com/
|
||||
[14]: https://www.wired.com/story/using-open-source-designs-to-create-more-specialized-chips/
|
||||
[15]: https://getfedora.org/
|
||||
[16]: https://www.redhat.com/en/technologies/linux-platforms/enterprise-linux
|
||||
[17]: https://openhardware.metajnl.com/articles/10.5334/joh.4/
|
||||
[18]: https://www.mdpi.com/2411-5134/3/3/44/htm
|
||||
[19]: https://www.theatlantic.com/technology/archive/2014/01/on-the-reign-of-benevolent-dictators-for-life-in-software/283139/
|
||||
[20]: https://www.lulzbot.com/
|
||||
[21]: https://forum.lulzbot.com/viewtopic.php?t=2378
|
||||
[22]: https://ieeexplore.ieee.org/abstract/document/8250205
|
||||
@ -1,3 +1,5 @@
|
||||
translating---geekpi
|
||||
|
||||
Joplin: Encrypted Open Source Note Taking And To-Do Application
|
||||
======
|
||||
**[Joplin][1] is a free and open source note taking and to-do application available for Linux, Windows, macOS, Android and iOS. Its key features include end-to-end encryption, Markdown support, and synchronization via third-party services like NextCloud, Dropbox, OneDrive or WebDAV.**
|
||||
|
||||
@ -1,4 +1,3 @@
|
||||
Translating by z52527
|
||||
Publishing Markdown to HTML with MDwiki
|
||||
======
|
||||
|
||||
|
||||
@ -1,69 +0,0 @@
|
||||
translating---geekpi
|
||||
|
||||
6 open source tools for writing a book
|
||||
======
|
||||
|
||||

|
||||
|
||||
I first used and contributed to free and open source software in 1993, and since then I've been an open source software developer and evangelist. I've written or contributed to dozens of open source software projects, although the one that I'll be remembered for is the [FreeDOS Project][1], an open source implementation of the DOS operating system.
|
||||
|
||||
I recently wrote a book about FreeDOS. [_Using FreeDOS_][2] is my celebration of the 24th anniversary of FreeDOS. It is a collection of how-to's about installing and using FreeDOS, essays about my favorite DOS applications, and quick-reference guides to the DOS command line and DOS batch programming. I've been working on this book for the last few months, with the help of a great professional editor.
|
||||
|
||||
_Using FreeDOS_ is available under the Creative Commons Attribution (cc-by) International Public License. You can download the EPUB and PDF versions at no charge from the [FreeDOS e-books][2] website. (I'm also planning a print version, for those who prefer a bound copy.)
|
||||
|
||||
The book was produced almost entirely with open source software. I'd like to share a brief insight into the tools I used to create, edit, and produce _Using FreeDOS_.
|
||||
|
||||
### Google Docs
|
||||
|
||||
[Google Docs][3] is the only tool I used that isn't open source software. I uploaded my first drafts to Google Docs so my editor and I could collaborate. I'm sure there are open source collaboration tools, but Google Doc's ability to let two people edit the same document at the same time, make comments, edit suggestions, and change tracking—not to mention its use of paragraph styles and the ability to download the finished document—made it a valuable part of the editing process.
|
||||
|
||||
### LibreOffice
|
||||
|
||||
I started on [LibreOffice][4] 6.0 but I finished the book using LibreOffice 6.1. I love LibreOffice's rich support of styles. Paragraph styles made it easy to apply a style for titles, headers, body text, sample code, and other text. Character styles let me modify the appearance of text within a paragraph, such as inline sample code or a different style to indicate a filename. Graphics styles let me apply certain styling to screenshots and other images. And page styles allowed me to easily modify the layout and appearance of the page.
|
||||
|
||||
### GIMP
|
||||
|
||||
My book includes a lot of DOS program screenshots, website screenshots, and FreeDOS logos. I used [GIMP][5] to modify these images for the book. Usually, this was simply cropping or resizing an image, but as I prepare the print edition of the book, I'm using GIMP to create a few images that will be simpler for print layout.
|
||||
|
||||
### Inkscape
|
||||
|
||||
Most of the FreeDOS logos and fish mascots are in SVG format, and I used [Inkscape][6] for any image tweaking here. And in preparing the PDF version of the ebook, I wanted a simple blue banner at top of the page, with the FreeDOS logo in the corner. After some experimenting, I found it easier to create an SVG image in Inkscape that looked like the banner I wanted, and I pasted that into the header.
|
||||
|
||||
### ImageMagick
|
||||
|
||||
While it's great to use GIMP to do the fine work, sometimes it's faster to run an [ImageMagick][7] command over a set of images, such as to convert into PNG format or to resize images.
|
||||
|
||||
### Sigil
|
||||
|
||||
LibreOffice can export directly to EPUB format, but it wasn't a great transfer. I haven't tried creating an EPUB with LibreOffice 6.1, but LibreOffice 6.0 didn't include my images. It also added styles in a weird way. I used [Sigil][8] to tweak the EPUB file and make everything look right. Sigil even has a preview function so you can see what the EPUB will look like.
|
||||
|
||||
### QEMU
|
||||
|
||||
Because this book is about installing and running FreeDOS, I needed to actually run FreeDOS. You can boot FreeDOS inside any PC emulator, including VirtualBox, QEMU, GNOME Boxes, PCem, and Bochs. But I like the simplicity of [QEMU][9]. And the QEMU console lets you issue a screen dump in PPM format, which is ideal for grabbing screenshots to include in the book.
|
||||
|
||||
Of course, I have to mention running [GNOME][10] on [Linux][11]. I use the [Fedora][12] distribution of Linux.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/9/writing-book-open-source-tools
|
||||
|
||||
作者:[Jim Hall][a]
|
||||
选题:[lujun9972](https://github.com/lujun9972)
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/jim-hall
|
||||
[1]: http://www.freedos.org/
|
||||
[2]: http://www.freedos.org/ebook/
|
||||
[3]: https://www.google.com/docs/about/
|
||||
[4]: https://www.libreoffice.org/
|
||||
[5]: https://www.gimp.org/
|
||||
[6]: https://inkscape.org/
|
||||
[7]: https://www.imagemagick.org/
|
||||
[8]: https://sigil-ebook.com/
|
||||
[9]: https://www.qemu.org/
|
||||
[10]: https://www.gnome.org/
|
||||
[11]: https://www.kernel.org/
|
||||
[12]: https://getfedora.org/
|
||||
@ -1,3 +1,5 @@
|
||||
Translating by jlztan
|
||||
|
||||
KeeWeb – An Open Source, Cross Platform Password Manager
|
||||
======
|
||||
|
||||
|
||||
@ -0,0 +1,69 @@
|
||||
Create animated, scalable vector graphic images with MacSVG
|
||||
======
|
||||
|
||||
Open source SVG: The writing is on the wall
|
||||
|
||||
|
||||
|
||||
The Neo-Babylonian regent [Belshazzar][1] did not heed [the writing on the wall][2] that magically appeared during his great feast. However, if he had had a laptop and a good internet connection in 539 BC, he might have staved off those pesky Persians by reading the SVG on the browser.
|
||||
|
||||
Animating text and objects on web pages is a great way to build user interest and engagement. There are several ways to achieve this, such as a video embed, an animated GIF, or a slideshow—but you can also use [scalable vector graphics][3] (SVG).
|
||||
|
||||
An SVG image is different from, say, a JPG, because it is scalable without losing its resolution. A vector image is created by points, not dots, so no matter how large it gets, it will not lose its resolution or pixelate. An example of a good use of scalable, static images would be logos on websites.
|
||||
|
||||
### Move it, move it
|
||||
|
||||
You can create SVG images with several drawing programs, including open source [Inkscape][4] and Adobe Illustrator. Getting your images to “do something” requires a bit more effort. Fortunately, there are open source solutions that would get even Belshazzar’s attention.
|
||||
|
||||
[MacSVG][5] is one tool that will get your images moving. You can find the source code on [GitHub][6].
|
||||
|
||||
Developed by Douglas Ward of Conway, Arkansas, MacSVG is an “open source Mac OS app for designing HTML5 SVG art and animation,” according to its [website][5].
|
||||
|
||||
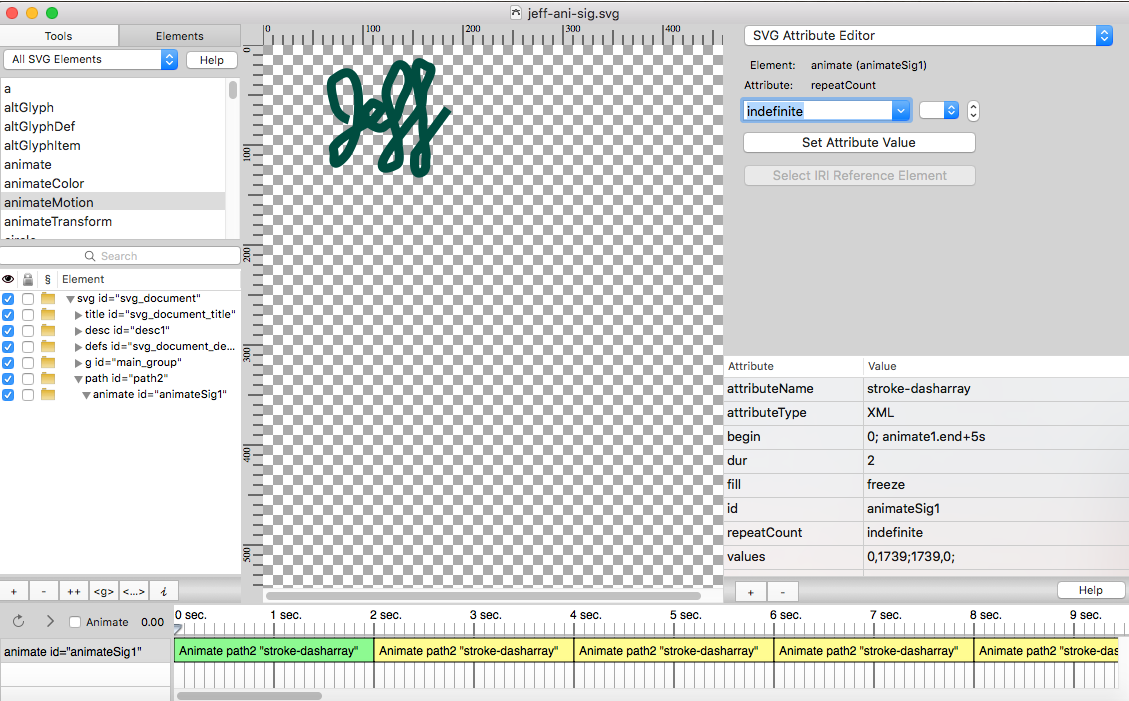
I was interested in using MacSVG to create an animated signature. I admit that I found the process a bit confusing and failed at my first attempts to create an actual animated SVG image.
|
||||
|
||||
|
||||
|
||||
It is important to first learn what makes “the writing on the wall” actually write.
|
||||
|
||||
The attribute behind the animated writing is [stroke-dasharray][7]. Breaking the term into three words helps explain what is happening: Stroke refers to the line or stroke you would make with a pen, whether physical or digital. Dash means breaking the stroke down into a series of dashes. Array means producing the whole thing into an array. That’s a simple overview, but it helped me understand what was supposed to happen and why.
|
||||
|
||||
With MacSVG, you can import a graphic (.PNG) and use the pen tool to trace the path of the writing. I used a cursive representation of my first name. Then it was just a matter of applying the attributes to animate the writing, increase and decrease the thickness of the stroke, change its color, and so on. Once completed, the animated writing was exported as an .SVG file and was ready for use on the web. MacSVG can be used for many different types of SVG animation in addition to handwriting.
|
||||
|
||||
### The writing is on the WordPress
|
||||
|
||||
I was ready to upload and share my SVG example on my [WordPress][8] site, but I discovered that WordPress does not allow for SVG media imports. Fortunately, I found a handy plugin: Benbodhi’s [SVG Support][9] allowed a quick, easy import of my SVG the same way I would import a JPG to my Media Library. I was able to showcase my [writing on the wall][10] to Babylonians everywhere.
|
||||
|
||||
I opened the source code of my SVG in [Brackets][11], and here are the results:
|
||||
|
||||
```
|
||||
<?xml version="1.0" encoding="utf-8" standalone="yes"?>
|
||||
<!DOCTYPE svg PUBLIC "-//W3C//DTD SVG 1.1//EN" "http://www.w3.org/Graphics/SVG/1.1/DTD/svg11.dtd">
|
||||
<svg xmlns="http://www.w3.org/2000/svg" xmlns:xlink="http://www.w3.org/1999/xlink" xmlns:dc="http://purl.org/dc/elements/1.1/" xmlns:cc="http://web.resource.org/cc/" xmlns:rdf="http://www.w3.org/1999/02/22-rdf-syntax-ns#" xmlns:sodipodi="http://sodipodi.sourceforge.net/DTD/sodipodi-0.dtd" xmlns:inkscape="http://www.inkscape.org/namespaces/inkscape" height="360px" style="zoom: 1;" cursor="default" id="svg_document" width="480px" baseProfile="full" version="1.1" preserveAspectRatio="xMidYMid meet" viewBox="0 0 480 360"><title id="svg_document_title">Path animation with stroke-dasharray</title><desc id="desc1">This example demonstrates the use of a path element, an animate element, and the stroke-dasharray attribute to simulate drawing.</desc><defs id="svg_document_defs"></defs><g id="main_group"></g><path stroke="#004d40" id="path2" stroke-width="9px" d="M86,75 C86,75 75,72 72,61 C69,50 66,37 71,34 C76,31 86,21 92,35 C98,49 95,73 94,82 C93,91 87,105 83,110 C79,115 70,124 71,113 C72,102 67,105 75,97 C83,89 111,74 111,74 C111,74 119,64 119,63 C119,62 110,57 109,58 C108,59 102,65 102,66 C102,67 101,75 107,79 C113,83 118,85 122,81 C126,77 133,78 136,64 C139,50 147,45 146,33 C145,21 136,15 132,24 C128,33 123,40 123,49 C123,58 135,87 135,96 C135,105 139,117 133,120 C127,123 116,127 120,116 C124,105 144,82 144,81 C144,80 158,66 159,58 C160,50 159,48 161,43 C163,38 172,23 166,22 C160,21 155,12 153,23 C151,34 161,68 160,78 C159,88 164,108 163,113 C162,118 165,126 157,128 C149,130 152,109 152,109 C152,109 185,64 185,64 " fill="none" transform=""><animate values="0,1739;1739,0;" attributeType="XML" begin="0; animate1.end+5s" id="animateSig1" repeatCount="indefinite" attributeName="stroke-dasharray" fill="freeze" dur="2"></animate></path></svg>
|
||||
```
|
||||
|
||||
What would you use MacSVG for?
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/10/macsvg-open-source-tool-animation
|
||||
|
||||
作者:[Jeff Macharyas][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/rikki-endsley
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://en.wikipedia.org/wiki/Belshazzar
|
||||
[2]: https://en.wikipedia.org/wiki/Belshazzar%27s_feast
|
||||
[3]: https://en.wikipedia.org/wiki/Scalable_Vector_Graphics
|
||||
[4]: https://inkscape.org/
|
||||
[5]: https://macsvg.org/
|
||||
[6]: https://github.com/dsward2/macSVG
|
||||
[7]: https://gist.github.com/mbostock/5649592
|
||||
[8]: https://macharyas.com/
|
||||
[9]: https://wordpress.org/plugins/svg-support/
|
||||
[10]: https://macharyas.com/index.php/2018/10/14/open-source-svg/
|
||||
[11]: http://brackets.io/
|
||||
@ -1,3 +1,5 @@
|
||||
FSSlc translating
|
||||
|
||||
How To Analyze And Explore The Contents Of Docker Images
|
||||
======
|
||||

|
||||
|
||||
@ -0,0 +1,60 @@
|
||||
8 creepy commands that haunt the terminal | Opensource.com
|
||||
======
|
||||
|
||||
Welcome to the spookier side of Linux.
|
||||
|
||||

|
||||
|
||||
It’s that time of year again: The weather gets chilly, the leaves change colors, and kids everywhere transform into tiny ghosts, goblins, and zombies. But did you know that Unix (and Linux) and its various offshoots are also chock-full of creepy crawly things? Let’s take a quick look at some of the spookier aspects of the operating system we all know and love.
|
||||
|
||||
### daemon
|
||||
|
||||
Unix just wouldn’t be the same without all the various daemons that haunt the system. A `daemon` is a process that runs in the background and provides useful services to both the user and the operating system itself. Think SSH, FTP, HTTP, etc.
|
||||
|
||||
### zombie
|
||||
|
||||
Every now and then a zombie, a process that has been killed but refuses to go away, shows up. When this happens, you have no choice but to dispatch it using whatever tools you have available. A zombie usually indicates that something is wrong with the process that spawned it.
|
||||
|
||||
### kill
|
||||
|
||||
Not only can you use the `kill` command to dispatch a zombie, but you can also use it to kill any process that’s adversely affecting your system. Have a process that’s using too much RAM or CPU cycles? Dispatch it with the `kill` command.
|
||||
|
||||
### cat
|
||||
|
||||
The `cat` command has nothing to do with felines and everything to do with combining files: `cat` is short for "concatenate." You can even use this handy command to view the contents of a file.
|
||||
|
||||
|
||||
### tail
|
||||
|
||||
|
||||
The `tail` command is useful when you want to see last n number of lines in a file. It’s also great when you want to monitor a file.
|
||||
|
||||
### which
|
||||
|
||||
No, not that kind of witch, but the command that prints the location of the files associated with any command passed to it. `which python`, for example, will print the locations of every version of Python on your system.
|
||||
|
||||
### crypt
|
||||
|
||||
The `crypt` command, known these days as `mcrypt`, is handy when you want to scramble (encrypt) the contents of a file so that no one but you can read it. Like most Unix commands, you can use `crypt` standalone or within a system script.
|
||||
|
||||
### shred
|
||||
|
||||
The `shred` command is handy when you not only want to delete a file but you also want to ensure that no one will ever be able to recover it. Using the `rm` command to delete a file isn’t enough. You also need to overwrite the space that the file previously occupied. That’s where `shred` comes in.
|
||||
|
||||
These are just a few of the spooky things you’ll find hiding inside Unix. Do you know more creepy commands? Feel free to let me know.
|
||||
|
||||
Happy Halloween!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/10/spookier-side-unix-linux
|
||||
|
||||
作者:[Patrick H.Mullins][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/pmullins
|
||||
[b]: https://github.com/lujun9972
|
||||
@ -0,0 +1,302 @@
|
||||
Working with data streams on the Linux command line
|
||||
======
|
||||
Learn to connect data streams from one utility to another using STDIO.
|
||||

|
||||
|
||||
**Author’s note:** Much of the content in this article is excerpted, with some significant edits to fit the Opensource.com article format, from Chapter 3: Data Streams, of my new book, [The Linux Philosophy for SysAdmins][1].
|
||||
|
||||
Everything in Linux revolves around streams of data—particularly text streams. Data streams are the raw materials upon which the [GNU Utilities][2], the Linux core utilities, and many other command-line tools perform their work.
|
||||
|
||||
As its name implies, a data stream is a stream of data—especially text data—being passed from one file, device, or program to another using STDIO. This chapter introduces the use of pipes to connect streams of data from one utility program to another using STDIO. You will learn that the function of these programs is to transform the data in some manner. You will also learn about the use of redirection to redirect the data to a file.
|
||||
|
||||
I use the term “transform” in conjunction with these programs because the primary task of each is to transform the incoming data from STDIO in a specific way as intended by the sysadmin and to send the transformed data to STDOUT for possible use by another transformer program or redirection to a file.
|
||||
|
||||
The standard term, “filters,” implies something with which I don’t agree. By definition, a filter is a device or a tool that removes something, such as an air filter removes airborne contaminants so that the internal combustion engine of your automobile does not grind itself to death on those particulates. In my high school and college chemistry classes, filter paper was used to remove particulates from a liquid. The air filter in my home HVAC system removes particulates that I don’t want to breathe.
|
||||
|
||||
Although they do sometimes filter out unwanted data from a stream, I much prefer the term “transformers” because these utilities do so much more. They can add data to a stream, modify the data in some amazing ways, sort it, rearrange the data in each line, perform operations based on the contents of the data stream, and so much more. Feel free to use whichever term you prefer, but I prefer transformers. I expect that I am alone in this.
|
||||
|
||||
Data streams can be manipulated by inserting transformers into the stream using pipes. Each transformer program is used by the sysadmin to perform some operation on the data in the stream, thus changing its contents in some manner. Redirection can then be used at the end of the pipeline to direct the data stream to a file. As mentioned, that file could be an actual data file on the hard drive, or a device file such as a drive partition, a printer, a terminal, a pseudo-terminal, or any other device connected to a computer.
|
||||
|
||||
The ability to manipulate these data streams using these small yet powerful transformer programs is central to the power of the Linux command-line interface. Many of the core utilities are transformer programs and use STDIO.
|
||||
|
||||
In the Unix and Linux worlds, a stream is a flow of text data that originates at some source; the stream may flow to one or more programs that transform it in some way, and then it may be stored in a file or displayed in a terminal session. As a sysadmin, your job is intimately associated with manipulating the creation and flow of these data streams. In this post, we will explore data streams—what they are, how to create them, and a little bit about how to use them.
|
||||
|
||||
### Text streams—a universal interface
|
||||
|
||||
The use of Standard Input/Output (STDIO) for program input and output is a key foundation of the Linux way of doing things. STDIO was first developed for Unix and has found its way into most other operating systems since then, including DOS, Windows, and Linux.
|
||||
|
||||
> “This is the Unix philosophy: Write programs that do one thing and do it well. Write programs to work together. Write programs to handle text streams, because that is a universal interface.”
|
||||
>
|
||||
> — Doug McIlroy, Basics of the Unix Philosophy
|
||||
|
||||
### STDIO
|
||||
|
||||
STDIO was developed by Ken Thompson as a part of the infrastructure required to implement pipes on early versions of Unix. Programs that implement STDIO use standardized file handles for input and output rather than files that are stored on a disk or other recording media. STDIO is best described as a buffered data stream, and its primary function is to stream data from the output of one program, file, or device to the input of another program, file, or device.
|
||||
|
||||
There are three STDIO data streams, each of which is automatically opened as a file at the startup of a program—well, those programs that use STDIO. Each STDIO data stream is associated with a file handle, which is just a set of metadata that describes the attributes of the file. File handles 0, 1, and 2 are explicitly defined by convention and long practice as STDIN, STDOUT, and STDERR, respectively.
|
||||
|
||||
**STDIN, File handle 0** , is standard input which is usually input from the keyboard. STDIN can be redirected from any file, including device files, instead of the keyboard. It is not common to need to redirect STDIN, but it can be done.
|
||||
|
||||
**STDOUT, File handle 1** , is standard output which sends the data stream to the display by default. It is common to redirect STDOUT to a file or to pipe it to another program for further processing.
|
||||
|
||||
**STDERR, File handle 2**. The data stream for STDERR is also usually sent to the display.
|
||||
|
||||
If STDOUT is redirected to a file, STDERR continues to be displayed on the screen. This ensures that when the data stream itself is not displayed on the terminal, that STDERR is, thus ensuring that the user will see any errors resulting from execution of the program. STDERR can also be redirected to the same or passed on to the next transformer program in a pipeline.
|
||||
|
||||
STDIO is implemented as a C library, **stdio.h** , which can be included in the source code of programs so that it can be compiled into the resulting executable.
|
||||
|
||||
### Simple streams
|
||||
|
||||
You can perform the following experiments safely in the **/tmp** directory of your Linux host. As the root user, make **/tmp** the PWD, create a test directory, and then make the new directory the PWD.
|
||||
|
||||
```
|
||||
# cd /tmp ; mkdir test ; cd test
|
||||
```
|
||||
|
||||
Enter and run the following command line program to create some files with content on the drive. We use the `dmesg` command simply to provide data for the files to contain. The contents don’t matter as much as just the fact that each file has some content.
|
||||
|
||||
```
|
||||
# for I in 0 1 2 3 4 5 6 7 8 9 ; do dmesg > file$I.txt ; done
|
||||
```
|
||||
|
||||
Verify that there are now at least 10 files in **/tmp/** with the names **file0.txt** through **file9.txt**.
|
||||
|
||||
```
|
||||
# ll
|
||||
total 1320
|
||||
-rw-r--r-- 1 root root 131402 Oct 17 15:50 file0.txt
|
||||
-rw-r--r-- 1 root root 131402 Oct 17 15:50 file1.txt
|
||||
-rw-r--r-- 1 root root 131402 Oct 17 15:50 file2.txt
|
||||
-rw-r--r-- 1 root root 131402 Oct 17 15:50 file3.txt
|
||||
-rw-r--r-- 1 root root 131402 Oct 17 15:50 file4.txt
|
||||
-rw-r--r-- 1 root root 131402 Oct 17 15:50 file5.txt
|
||||
-rw-r--r-- 1 root root 131402 Oct 17 15:50 file6.txt
|
||||
-rw-r--r-- 1 root root 131402 Oct 17 15:50 file7.txt
|
||||
-rw-r--r-- 1 root root 131402 Oct 17 15:50 file8.txt
|
||||
-rw-r--r-- 1 root root 131402 Oct 17 15:50 file9.txt
|
||||
```
|
||||
|
||||
We have generated data streams using the `dmesg` command, which was redirected to a series of files. Most of the core utilities use STDIO as their output stream and those that generate data streams, rather than acting to transform the data stream in some way, can be used to create the data streams that we will use for our experiments. Data streams can be as short as one line or even a single character, and as long as needed.
|
||||
|
||||
### Exploring the hard drive
|
||||
|
||||
It is now time to do a little exploring. In this experiment, we will look at some of the filesystem structures.
|
||||
|
||||
Let’s start with something simple. You should be at least somewhat familiar with the `dd` command. Officially known as “disk dump,” many sysadmins call it “disk destroyer” for good reason. Many of us have inadvertently destroyed the contents of an entire hard drive or partition using the `dd` command. That is why we will hang out in the **/tmp/test** directory to perform some of these experiments.
|
||||
|
||||
Despite its reputation, `dd` can be quite useful in exploring various types of storage media, hard drives, and partitions. We will also use it as a tool to explore other aspects of Linux.
|
||||
|
||||
Log into a terminal session as root if you are not already. We first need to determine the device special file for your hard drive using the `lsblk` command.
|
||||
|
||||
```
|
||||
[root@studentvm1 test]# lsblk -i
|
||||
NAME MAJ:MIN RM SIZE RO TYPE MOUNTPOINT
|
||||
sda 8:0 0 60G 0 disk
|
||||
|-sda1 8:1 0 1G 0 part /boot
|
||||
`-sda2 8:2 0 59G 0 part
|
||||
|-fedora_studentvm1-pool00_tmeta 253:0 0 4M 0 lvm
|
||||
| `-fedora_studentvm1-pool00-tpool 253:2 0 2G 0 lvm
|
||||
| |-fedora_studentvm1-root 253:3 0 2G 0 lvm /
|
||||
| `-fedora_studentvm1-pool00 253:6 0 2G 0 lvm
|
||||
|-fedora_studentvm1-pool00_tdata 253:1 0 2G 0 lvm
|
||||
| `-fedora_studentvm1-pool00-tpool 253:2 0 2G 0 lvm
|
||||
| |-fedora_studentvm1-root 253:3 0 2G 0 lvm /
|
||||
| `-fedora_studentvm1-pool00 253:6 0 2G 0 lvm
|
||||
|-fedora_studentvm1-swap 253:4 0 10G 0 lvm [SWAP]
|
||||
|-fedora_studentvm1-usr 253:5 0 15G 0 lvm /usr
|
||||
|-fedora_studentvm1-home 253:7 0 2G 0 lvm /home
|
||||
|-fedora_studentvm1-var 253:8 0 10G 0 lvm /var
|
||||
`-fedora_studentvm1-tmp 253:9 0 5G 0 lvm /tmp
|
||||
sr0 11:0 1 1024M 0 rom
|
||||
```
|
||||
|
||||
We can see from this that there is only one hard drive on this host, that the device special file associated with it is **/dev/sda** , and that it has two partitions. The **/dev/sda1** partition is the boot partition, and the **/dev/sda2** partition contains a volume group on which the rest of the host’s logical volumes have been created.
|
||||
|
||||
As root in the terminal session, use the `dd` command to view the boot record of the hard drive, assuming it is assigned to the **/dev/sda** device. The `bs=` argument is not what you might think; it simply specifies the block size, and the `count=` argument specifies the number of blocks to dump to STDIO. The `if=` argument specifies the source of the data stream, in this case, the **/dev/sda** device. Notice that we are not looking at the first block of the partition, we are looking at the very first block of the hard drive.
|
||||
|
||||
```
|
||||
[root@studentvm1 test]# dd if=/dev/sda bs=512 count=1
|
||||
<EFBFBD>c<EFBFBD>#<23>м<EFBFBD><D0BC><EFBFBD>؎<EFBFBD><D88E><EFBFBD>|<7C>#<23>#<23><><EFBFBD>!#<23><>8#u
|
||||
<20><>#<23><><EFBFBD>u<EFBFBD><75>#<23>#<23>#<23>|<7C><><EFBFBD>t#<23>L#<23>#<23>|<7C><><EFBFBD>#<23><><EFBFBD><EFBFBD><EFBFBD>t<C280><74>pt#<23><><EFBFBD>y|1<><31>؎м <20><>d|<<EFBFBD>t#<23><>R<EFBFBD>|1<><31>D#@<40>D<EFBFBD><44>D#<23>##f<>#\|f<>f<EFBFBD>#`|f<>\
|
||||
<20>D#p<>B<EFBFBD>#r<>p<EFBFBD>#<23>K`#<23>#<23><>1<EFBFBD><31><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>#a`<60><><EFBFBD>#f<><66>u#<23><><EFBFBD><EFBFBD>f1<66>f<EFBFBD>TCPAf<41>#f<>#a<>&Z|<7C>#}<7D>#<23>.}<7D>4<EFBFBD>3}<7D>.<2E>#<23><>GRUB GeomHard DiskRead Error
|
||||
<EFBFBD>#<23><>#<23><u<EFBFBD><EFBFBD>ܻޮ<EFBFBD>###<EFBFBD><EFBFBD><EFBFBD> <EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> <EFBFBD>_U<EFBFBD>1+0 records in
|
||||
1+0 records out
|
||||
512 bytes copied, 4.3856e-05 s, 11.7 MB/s
|
||||
```
|
||||
|
||||
This prints the text of the boot record, which is the first block on the disk—any disk. In this case, there is information about the filesystem and, although it is unreadable because it is stored in binary format, the partition table. If this were a bootable device, stage 1 of GRUB or some other boot loader would be located in this sector. The last three lines contain data about the number of records and bytes processed.
|
||||
|
||||
Starting with the beginning of **/dev/sda1** , let’s look at a few blocks of data at a time to find what we want. The command is similar to the previous one, except that we have specified a few more blocks of data to view. You may have to specify fewer blocks if your terminal is not large enough to display all of the data at one time, or you can pipe the data through the less utility and use that to page through the data—either way works. Remember, we are doing all of this as root user because non-root users do not have the required permissions.
|
||||
|
||||
Enter the same command as you did in the previous experiment, but increase the block count to be displayed to 100, as shown below, in order to show more data.
|
||||
|
||||
```
|
||||
[root@studentvm1 test]# dd if=/dev/sda1 bs=512 count=100
|
||||
##33<33><33>#:<3A>##<23><> :o<>[:o<>[#<23><>S<EFBFBD>###<23>q[#
|
||||
#<<EFBFBD>#{5OZh<5A>GJ͞#t<>Ұ##boot/bootysimage/booC<6F>dp<64><70>G'<27>*)<29>#A<>##@
|
||||
#<23>q[
|
||||
<EFBFBD>## ## ###<23>#<23><><EFBFBD>To=###<#8<><38><EFBFBD>#'#<23>###<23>#<23><><EFBFBD><EFBFBD><EFBFBD>#<23>' <><C2A0><EFBFBD><EFBFBD><EFBFBD>#Xi <>#<23><>` qT<71><54><EFBFBD>
|
||||
<<EFBFBD><EFBFBD><EFBFBD>
|
||||
<20> r<C2A0><72><EFBFBD><EFBFBD> ]<5D>#<23>#<23>##<23>##<23>##<23>#<23>##<23>##<23>##<23>#<23>##<23>##<23>#<23><>#<23>#<23>##<23>#<23>##<23>##<23>#<23><>#<23>#<23><><EFBFBD><EFBFBD># <20> <20># <20># <20>#
|
||||
<EFBFBD>
|
||||
<EFBFBD>#
|
||||
<EFBFBD>#
|
||||
<EFBFBD>#
|
||||
<20>
|
||||
<>#
|
||||
<>#
|
||||
<>#
|
||||
<>
|
||||
<20>#
|
||||
<20>#
|
||||
<20>#100+0 records in
|
||||
100+0 records out
|
||||
51200 bytes (51 kB, 50 KiB) copied, 0.00117615 s, 43.5 MB/s
|
||||
```
|
||||
|
||||
Now try this command. I won’t reproduce the entire data stream here because it would take up huge amounts of space. Use **Ctrl-C** to break out and stop the stream of data.
|
||||
|
||||
```
|
||||
[root@studentvm1 test]# dd if=/dev/sda
|
||||
```
|
||||
|
||||
This command produces a stream of data that is the complete content of the hard drive, **/dev/sda** , including the boot record, the partition table, and all of the partitions and their content. This data could be redirected to a file for use as a complete backup from which a bare metal recovery can be performed. It could also be sent directly to another hard drive to clone the first. But do not perform this particular experiment.
|
||||
|
||||
```
|
||||
[root@studentvm1 test]# dd if=/dev/sda of=/dev/sdx
|
||||
```
|
||||
|
||||
You can see that the `dd` command can be very useful for exploring the structures of various types of filesystems, locating data on a defective storage device, and much more. It also produces a stream of data on which we can use the transformer utilities in order to modify or view.
|
||||
|
||||
The real point here is that `dd`, like so many Linux commands, produces a stream of data as its output. That data stream can be searched and manipulated in many ways using other tools. It can even be used for ghost-like backups or disk duplication.
|
||||
|
||||
### Randomness
|
||||
|
||||
It turns out that randomness is a desirable thing in computers—who knew? There are a number of reasons that sysadmins might want to generate a stream of random data. A stream of random data is sometimes useful to overwrite the contents of a complete partition, such as **/dev/sda1** , or even the entire hard drive, as in **/dev/sda**.
|
||||
|
||||
Perform this experiment as a non-root user. Enter this command to print an unending stream of random data to STDIO.
|
||||
|
||||
```
|
||||
[student@studentvm1 ~]$ cat /dev/urandom
|
||||
```
|
||||
|
||||
Use **Ctrl-C** to break out and stop the stream of data. You may need to use **Ctrl-C** multiple times.
|
||||
|
||||
Random data is also used as the input seed to programs that generate random passwords and random data and numbers for use in scientific and statistical calculations. I will cover randomness and other interesting data sources in a bit more detail in Chapter 24: Everything is a file.
|
||||
|
||||
### Pipe dreams
|
||||
|
||||
Pipes are critical to our ability to do the amazing things on the command line, so much so that I think it is important to recognize that they were invented by Douglas McIlroy during the early days of Unix (thanks, Doug!). The Princeton University website has a fragment of an [interview][3] with McIlroy in which he discusses the creation of the pipe and the beginnings of the Unix philosophy.
|
||||
|
||||
Notice the use of pipes in the simple command-line program shown next, which lists each logged-in user a single time, no matter how many logins they have active. Perform this experiment as the student user. Enter the command shown below:
|
||||
|
||||
```
|
||||
[student@studentvm1 ~]$ w | tail -n +3 | awk '{print $1}' | sort | uniq
|
||||
root
|
||||
student
|
||||
[student@studentvm1 ~]$
|
||||
```
|
||||
|
||||
The results from this command produce two lines of data that show that the user's root and student are both logged in. It does not show how many times each user is logged in. Your results will almost certainly differ from mine.
|
||||
|
||||
Pipes—represented by the vertical bar ( | )—are the syntactical glue, the operator, that connects these command-line utilities together. Pipes allow the Standard Output from one command to be “piped,” i.e., streamed from Standard Output of one command to the Standard Input of the next command.
|
||||
|
||||
The |& operator can be used to pipe the STDERR along with STDOUT to STDIN of the next command. This is not always desirable, but it does offer flexibility in the ability to record the STDERR data stream for the purposes of problem determination.
|
||||
|
||||
A string of programs connected with pipes is called a pipeline, and the programs that use STDIO are referred to officially as filters, but I prefer the term “transformers.”
|
||||
|
||||
Think about how this program would have to work if we could not pipe the data stream from one command to the next. The first command would perform its task on the data and then the output from that command would need to be saved in a file. The next command would have to read the stream of data from the intermediate file and perform its modification of the data stream, sending its own output to a new, temporary data file. The third command would have to take its data from the second temporary data file and perform its own manipulation of the data stream and then store the resulting data stream in yet another temporary file. At each step, the data file names would have to be transferred from one command to the next in some way.
|
||||
|
||||
I cannot even stand to think about that because it is so complex. Remember: Simplicity rocks!
|
||||
|
||||
### Building pipelines
|
||||
|
||||
When I am doing something new, solving a new problem, I usually do not just type in a complete Bash command pipeline from scratch off the top of my head. I usually start with just one or two commands in the pipeline and build from there by adding more commands to further process the data stream. This allows me to view the state of the data stream after each of the commands in the pipeline and make corrections as they are needed.
|
||||
|
||||
It is possible to build up very complex pipelines that can transform the data stream using many different utilities that work with STDIO.
|
||||
|
||||
### Redirection
|
||||
|
||||
Redirection is the capability to redirect the STDOUT data stream of a program to a file instead of to the default target of the display. The “greater than” ( > ) character, aka “gt”, is the syntactical symbol for redirection of STDOUT.
|
||||
|
||||
Redirecting the STDOUT of a command can be used to create a file containing the results from that command.
|
||||
|
||||
```
|
||||
[student@studentvm1 ~]$ df -h > diskusage.txt
|
||||
```
|
||||
|
||||
There is no output to the terminal from this command unless there is an error. This is because the STDOUT data stream is redirected to the file and STDERR is still directed to the STDOUT device, which is the display. You can view the contents of the file you just created using this next command:
|
||||
|
||||
```
|
||||
[student@studentvm1 test]# cat diskusage.txt
|
||||
Filesystem Size Used Avail Use% Mounted on
|
||||
devtmpfs 2.0G 0 2.0G 0% /dev
|
||||
tmpfs 2.0G 0 2.0G 0% /dev/shm
|
||||
tmpfs 2.0G 1.2M 2.0G 1% /run
|
||||
tmpfs 2.0G 0 2.0G 0% /sys/fs/cgroup
|
||||
/dev/mapper/fedora_studentvm1-root 2.0G 50M 1.8G 3% /
|
||||
/dev/mapper/fedora_studentvm1-usr 15G 4.5G 9.5G 33% /usr
|
||||
/dev/mapper/fedora_studentvm1-var 9.8G 1.1G 8.2G 12% /var
|
||||
/dev/mapper/fedora_studentvm1-tmp 4.9G 21M 4.6G 1% /tmp
|
||||
/dev/mapper/fedora_studentvm1-home 2.0G 7.2M 1.8G 1% /home
|
||||
/dev/sda1 976M 221M 689M 25% /boot
|
||||
tmpfs 395M 0 395M 0% /run/user/0
|
||||
tmpfs 395M 12K 395M 1% /run/user/1000
|
||||
```
|
||||
|
||||
When using the > symbol to redirect the data stream, the specified file is created if it does not already exist. If it does exist, the contents are overwritten by the data stream from the command. You can use double greater-than symbols, >>, to append the new data stream to any existing content in the file.
|
||||
|
||||
```
|
||||
[student@studentvm1 ~]$ df -h >> diskusage.txt
|
||||
```
|
||||
|
||||
You can use `cat` and/or `less` to view the **diskusage.txt** file in order to verify that the new data was appended to the end of the file.
|
||||
|
||||
The < (less than) symbol redirects data to the STDIN of the program. You might want to use this method to input data from a file to STDIN of a command that does not take a filename as an argument but that does use STDIN. Although input sources can be redirected to STDIN, such as a file that is used as input to grep, it is generally not necessary as grep also takes a filename as an argument to specify the input source. Most other commands also take a filename as an argument for their input source.
|
||||
|
||||
### Just grep’ing around
|
||||
|
||||
The `grep` command is used to select lines that match a specified pattern from a stream of data. `grep` is one of the most commonly used transformer utilities and can be used in some very creative and interesting ways. The `grep` command is one of the few that can correctly be called a filter because it does filter out all the lines of the data stream that you do not want; it leaves only the lines that you do want in the remaining data stream.
|
||||
|
||||
If the PWD is not the **/tmp/test** directory, make it so. Let’s first create a stream of random data to store in a file. In this case, we want somewhat less random data that would be limited to printable characters. A good password generator program can do this. The following program (you may have to install `pwgen` if it is not already) creates a file that contains 50,000 passwords that are 80 characters long using every printable character. Try it without redirecting to the **random.txt** file first to see what that looks like, and then do it once redirecting the output data stream to the file.
|
||||
|
||||
```
|
||||
$ pwgen -sy 80 50000 > random.txt
|
||||
```
|
||||
|
||||
Considering that there are so many passwords, it is very likely that some character strings in them are the same. First, `cat` the **random.txt** file, then use the `grep` command to locate some short, randomly selected strings from the last ten passwords on the screen. I saw the word “see” in one of those ten passwords, so my command looked like this: `grep see random.txt`, and you can try that, but you should also pick some strings of your own to check. Short strings of two to four characters work best.
|
||||
|
||||
```
|
||||
$ grep see random.txt
|
||||
R=p)'s/~0}wr~2(OqaL.S7DNyxlmO69`"12u]h@rp[D2%3}1b87+>Vk,;4a0hX]d7see;1%9|wMp6Yl.
|
||||
bSM_mt_hPy|YZ1<TY/Hu5{g#mQ<u_(@8B5Vt?w%i-&C>NU@[;zV2-see)>(BSK~n5mmb9~h)yx{a&$_e
|
||||
cjR1QWZwEgl48[3i-(^x9D=v)seeYT2R#M:>wDh?Tn$]HZU7}j!7bIiIr^cI.DI)W0D"'vZU@.Kxd1E1
|
||||
z=tXcjVv^G\nW`,y=bED]d|7%s6iYT^a^Bvsee:v\UmWT02|P|nq%A*;+Ng[$S%*s)-ls"dUfo|0P5+n
|
||||
```
|
||||
|
||||
### Summary
|
||||
|
||||
It is the use of pipes and redirection that allows many of the amazing and powerful tasks that can be performed with data streams on the Linux command line. It is pipes that transport STDIO data streams from one program or file to another. The ability to pipe streams of data through one or more transformer programs supports powerful and flexible manipulation of data in those streams.
|
||||
|
||||
Each of the programs in the pipelines demonstrated in the experiments is small, and each does one thing well. They are also transformers; that is, they take Standard Input, process it in some way, and then send the result to Standard Output. Implementation of these programs as transformers to send processed data streams from their own Standard Output to the Standard Input of the other programs is complementary to, and necessary for, the implementation of pipes as a Linux tool.
|
||||
|
||||
STDIO is nothing more than streams of data. This data can be almost anything from the output of a command to list the files in a directory, or an unending stream of data from a special device like **/dev/urandom** , or even a stream that contains all of the raw data from a hard drive or a partition.
|
||||
|
||||
Any device on a Linux computer can be treated like a data stream. You can use ordinary tools like `dd` and `cat` to dump data from a device into a STDIO data stream that can be processed using other ordinary Linux tools.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/10/linux-data-streams
|
||||
|
||||
作者:[David Both][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/dboth
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.apress.com/us/book/9781484237298
|
||||
[2]: https://www.gnu.org/software/coreutils/coreutils.html
|
||||
[3]: https://www.princeton.edu/~hos/mike/transcripts/mcilroy.htm
|
||||
@ -0,0 +1,67 @@
|
||||
6 个用于写书的开源工具
|
||||
======
|
||||
|
||||

|
||||
|
||||
我在 1993 年首次使用并贡献了免费和开源软件,从那时起我一直是一名开源软件开发人员和传播者。尽管我一个被记住的项目是[ FreeDOS 项目][1], 一个 DOS 操作系统的开源实现,但我已经编写或者贡献了数十个开源软件项目。
|
||||
|
||||
我最近写了一本关于 FreeDOS 的书。 [_使用 FreeDOS_][2]是我庆祝 FreeDOS 出现 24 周年。它是关于安装和使用 FreeDOS、关于我最喜欢的 DOS 程序的文章,以及 DOS 命令行和 DOS 批处理编程的快速参考指南的集合。在一位出色的专业编辑的帮助下,我在过去的几个月里一直在编写这本书。
|
||||
|
||||
_使用 FreeDOS_ 可在知识共享署名(cc-by)国际公共许可证下获得。你可以从[FreeDO S电子书][2]网站免费下载 EPUB 和 PDF 版本。(我也计划为那些喜欢纸质的人提供打印版本。)
|
||||
|
||||
这本书几乎完全是用开源软件制作的。我想分享一下对用来创建、编辑和生成_使用 FreeDOS_的工具的看法。
|
||||
|
||||
### Google 文档
|
||||
|
||||
[Google 文档][3]是我使用的唯一不是开源软件的工具。我将我的第一份草稿上传到 Google 文档,这样我就能与编辑器进行协作。我确信有开源协作工具,但 Google 文档能够让两个人同时编辑同一个文档、发表评论、编辑建议和更改跟踪 - 更不用说它使用段落样式和能够下载完成的文档 - 这使其成为编辑过程中有价值的一部分。
|
||||
|
||||
### LibreOffice
|
||||
|
||||
我开始使用 [LibreOffice][4] 6.0,但我最终使用 LibreOffice 6.1 完成了这本书。我喜欢 LibreOffice 对样式的丰富支持。段落样式可以轻松地为标题、页眉、正文、示例代码和其他文本应用样式。字符样式允许我修改段落中文本的外观,例如内联示例代码或用不同的样式代表文件名。图形样式让我可以将某些样式应用于截图和其他图像。页面样式允许我轻松修改页面的布局和外观。
|
||||
|
||||
### GIMP
|
||||
|
||||
我的书包括很多 DOS 程序截图,网站截图和 FreeDOS logo。我用 [GIMP][5] 修改了这本书的图像。通常,只是裁剪或调整图像大小,但在我准备本书的印刷版时,我使用 GIMP 创建了一些更易于打印布局的图像。
|
||||
|
||||
### Inkscape
|
||||
|
||||
大多数 FreeDOS logo 和小鱼吉祥物都是 SVG 格式,我使用 [Inkscape][6]来调整它们。在准备电子书的 PDF 版本时,我想在页面顶部放置一个简单的蓝色横幅,角落里有 FreeDOS logo。实验后,我发现在 Inkscape 中创建一个我想要的横幅 SVG 图案更容易,然后我将其粘贴到页眉中。
|
||||
|
||||
### ImageMagick
|
||||
|
||||
虽然使用 GIMP 来完成这项工作也很好,但有时在一组图像上运行 [ImageMagick][7] 命令会更快,例如转换为 PNG 格式或调整图像大小。
|
||||
|
||||
### Sigil
|
||||
|
||||
LibreOffice 可以直接导出到 EPUB 格式,但它不是个好的转换器。我没有尝试使用 LibreOffice 6.1 创建 EPUB,但 LibreOffice 6.0 没有包含我的图像。它还以奇怪的方式添加了样式。我使用 [Sigil][8] 来调整 EPUB 并使一切看起来正常。Sigil 甚至还有预览功能,因此你可以看到 EPUB 的样子。
|
||||
|
||||
### QEMU
|
||||
|
||||
因为本书是关于安装和运行 FreeDOS 的,所以我需要实际运行 FreeDOS。你可以在任何 PC 模拟器中启动 FreeDOS,包括 VirtualBox、QEMU、GNOME Boxes、PCem 和 Bochs。但我喜欢 [QEMU] [9] 的简单性。QEMU 控制台允许你以 PPM 转储屏幕,这非常适合抓取截图来包含在书中。
|
||||
|
||||
当然,我不得不提到在 [Linux][11] 上运行 [GNOME][10]。我使用 Linux 的 [Fedora][12] 发行版。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/9/writing-book-open-source-tools
|
||||
|
||||
作者:[Jim Hall][a]
|
||||
选题:[lujun9972](https://github.com/lujun9972)
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/jim-hall
|
||||
[1]: http://www.freedos.org/
|
||||
[2]: http://www.freedos.org/ebook/
|
||||
[3]: https://www.google.com/docs/about/
|
||||
[4]: https://www.libreoffice.org/
|
||||
[5]: https://www.gimp.org/
|
||||
[6]: https://inkscape.org/
|
||||
[7]: https://www.imagemagick.org/
|
||||
[8]: https://sigil-ebook.com/
|
||||
[9]: https://www.qemu.org/
|
||||
[10]: https://www.gnome.org/
|
||||
[11]: https://www.kernel.org/
|
||||
[12]: https://getfedora.org/
|
||||
Loading…
Reference in New Issue
Block a user