mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-01-13 22:30:37 +08:00
Merge pull request #1814 from GOLinux/master
[Translated] 20141008 How to configure a host intrusion detection system on CentOS.md
This commit is contained in:
commit
cd8d87ce91
@ -1,126 +0,0 @@
|
||||
Translating by GOLinux!
|
||||
How to configure a host intrusion detection system on CentOS
|
||||
================================================================================
|
||||
One of the first safety measures that any sysadmin may want to implement in their production servers is a mechanism to detect file tampering - not only the content of files, but also their attributes.
|
||||
|
||||
[AIDE][1] (short for "Advanced Intrusion Detection Environment") is an open source host-based intrusion detection system. AIDE checks the integrity of system binaries and essential configuration files by checking for inconsistencies in a number of file attributes, including permissions, file type, inode, number of links, link name, user, group, file size, block count, mtime, atime, ctime, acl, SELinux security context, xattrs, and md5/sha checksums.
|
||||
|
||||
AIDE builds a database of file attributes by scanning the file system of a (untampered) Linux server. It then checks the server's file attributes against the database, and alerts of any changes made to the indexed files while the server is running. For this very reason, AIDE must reindex protected files every time the system is updated or configuration files are changed for legitimate reasons.
|
||||
|
||||
For some clients, their security policies may mandate some sort of IDS installed on their servers. But whether a client requires it or not, it's a good sysadmin practice to have IDS in place.
|
||||
|
||||
### Installing AIDE on CentOS or RHEL ###
|
||||
|
||||
An initial installation (along with the first run) of AIDE is best performed in a system where the operating system has just been installed, and none of the services is exposed to the Internet or even to a local area network. At this early stage, we can minimize the risk of any break-ins and tampering attempts coming from outside. In fact, it is the only way to ensure that the system is clean at the time AIDE builds its initial database.
|
||||
|
||||
For that reason, after we install AIDE using:
|
||||
|
||||
# yum install aide
|
||||
|
||||
we need to unplug our machine from the network, and perform some basic configuration tasks as described next.
|
||||
|
||||
### Configuring AIDE ###
|
||||
|
||||
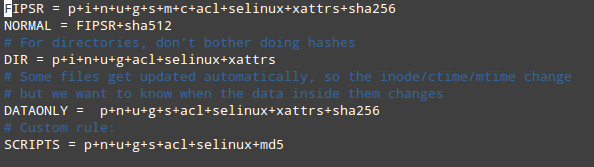
The default configuration file can be found in /etc/aide.conf. This file presents several example protection rules (e.g., FIPSR, NORMAL, DIR, DATAONLY), each of which is followed by an equal sign and a list of file attributes to check for, or any predefined rules (delimited by a plus sign). You can also define any custom rules using this format.
|
||||
|
||||
|
||||
|
||||
FIPSR = p+i+n+u+g+s+m+c+acl+selinux+xattrs+sha256
|
||||
NORMAL = FIPSR+sha512
|
||||
|
||||
For example, the above means that NORMAL rule will check for inconsistencies in the following attributes: permissions (p), inode (i), number of links (n), user (u), group (g), size (s), mtime (m), ctime (c), ACL (acl), SELinux (selinux), xattrs (xattr), SHA256/SHA512 checksums (sha256 and sha512).
|
||||
|
||||
The defined rules can be used for different directories and files (denoted with regular expressions) flexibly.
|
||||
|
||||
|
||||
|
||||
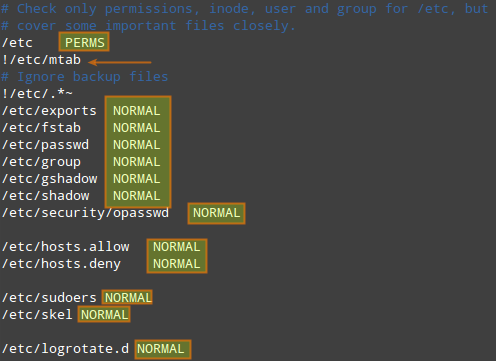
An exclamation sign (!) preceding an entry tells AIDE to ignore a subdirectory (or files inside a directory) for which another rule can be defined.
|
||||
|
||||
In the above example, PERMS is the default rule for /etc and its subdirectories and files. However, no rule will be applied to backup files in /etc (i.e., /etc/.*~) nor to /etc/mtab file. For some selective subdirectories or files in /etc, NORMAL rule is applied instead, overriding the default rule PERMS.
|
||||
|
||||
Defining and applying the right rules to the right locations in your system is perhaps the most difficult part of using AIDE, but using a good judgement is a nice start. As a rule of thumb, do not check for more attributes than necessary. For example, checking mtime for files inside /var/log or /var/spool will certainly result in a lot of false positives because there are many applications and daemons often writing to these locations, which is perfectly fine. In addition, checking for multiple checksums may enhance security at the expense of AIDE's increased running time.
|
||||
|
||||
Optionally, you can have the results of the check mailed to you if you specify your email address with the MAILTO variable. Place the following line anywhere in /etc/aide.conf.
|
||||
|
||||
MAILTO=root@localhost
|
||||
|
||||
### Running AIDE for the First Time ###
|
||||
|
||||
Run the following command to initialize the AIDE database:
|
||||
|
||||
# aide --init
|
||||
|
||||
|
||||
|
||||
The /var/lib/aide/aide.db.new.gz file, as per /etc/aide.conf, needs to be renamed to /var/lib/aide/aide.db.gz, so as to enable AIDE to read it:
|
||||
|
||||
# mv /var/lib/aide/aide.db.new.gz /var/lib/aide.db.gz
|
||||
|
||||
Now it's time to perform our first system check against the database. For that, simply run:
|
||||
|
||||
# aide
|
||||
|
||||
When called with no options, AIDE assumes --check.
|
||||
|
||||
If no change was made since the database had been created, AIDE will finish with an OK message.
|
||||
|
||||

|
||||
|
||||
### Managing AIDE in a Production Environment ###
|
||||
|
||||
After constructing an initial AIDE database, you often need to update a protected server for various legitimate reasons as part of ongoing system administration activities. Every time your server has been updated, you must re-build the AIDE database to incorporate the change in the database. For that, use this command:
|
||||
|
||||
# aide --update
|
||||
|
||||
To protect a production system with AIDE, it is probably best to schedule a cron job for checking for any inconsistencies with AIDE periodically. For example, to schedule AIDE to run and have the result mailed to an email address on a daily basis:
|
||||
|
||||
# crontab -e
|
||||
|
||||
----------
|
||||
|
||||
0 0 * * * /usr/sbin/aide --check | /usr/bin/mail -s "AIDE run for $HOSTNAME" your@email.com
|
||||
|
||||
### Testing AIDE for File Tampering ###
|
||||
|
||||
The following test scenarios will demonstrate how AIDE check the integrity of our files.
|
||||
|
||||
#### Test Scenario 1 ####
|
||||
|
||||
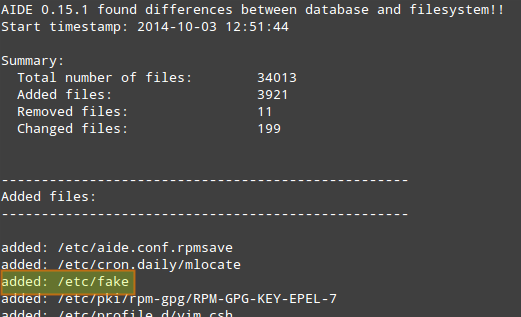
Let's add a new file (e.g., /etc/fake).
|
||||
|
||||
# cat /dev/null > /etc/fake
|
||||
|
||||
|
||||
|
||||
#### Test Scenario 2 ####
|
||||
|
||||
Let's change file permissions, and see if it can be detected.
|
||||
|
||||
# chmod 644 /etc/aide.conf
|
||||
|
||||
#### Test Scenario 3 ####
|
||||
|
||||
Finally, let's change file content (e.g., adding a comment line to /etc/aide.conf)
|
||||
|
||||
echo "#This is a comment" >> /etc/aide.conf
|
||||
|
||||
|
||||
|
||||
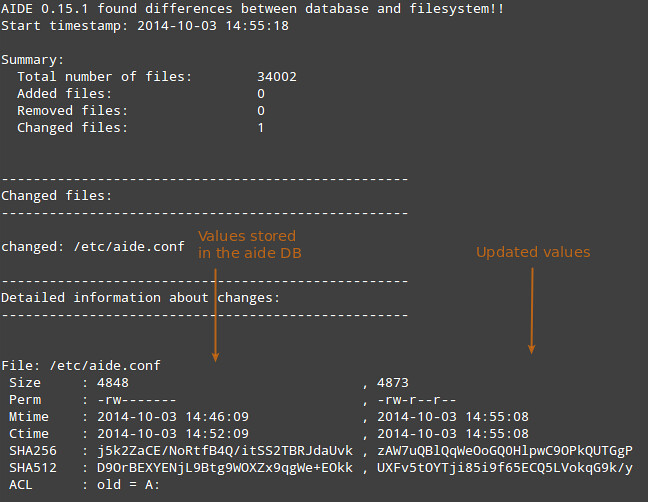
In the screenshot above, the first column shows the file attributes, the second column the values present in the AIDE database, and the third column the updated values for those attributes. An empty space in the third columns indicates that the attribute has not changed (ACL in this example).
|
||||
|
||||
### Conclusion ###
|
||||
|
||||
If you ever find yourself in a situation where you have good reasons to think that a system has been tampered with, but are unable to determine what might have been changed at first sight, a host-based intrusion detection system like AIDE can be very helpful in that it can help you quickly identify what has changed instead of guessing and wasting valuable time.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/host-intrusion-detection-system-centos.html
|
||||
|
||||
作者:[Gabriel Cánepa][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/gabriel
|
||||
[1]:http://aide.sourceforge.net/
|
||||
@ -0,0 +1,125 @@
|
||||
在CentOS上配置主机入侵检测系统
|
||||
================================================================================
|
||||
所有系统管理员想要在他们生产服务器上部署的第一个安全手段之一,就是检测文件篡改的机制——不仅仅是文件内容,而且也包括它们的属性。
|
||||
|
||||
[AIDE][1] (“高级入侵检测环境”的简称)是一个开源的基于主机的入侵检测系统。AIDE通过检查大量文件属性的不一致性来检查系统二进制文件和基本配置文件的完整性,这些文件属性包括权限、文件类型、索引节点、链接数、链接名、用户、组、文件大小、块计数、修改时间、添加时间、创建时间、acl、SELinux安全上下文、xattrs,以及md5/sha校验和在内。
|
||||
|
||||
AIDE通过扫描一台(未被篡改)的Linux服务器的文件系统来构建文件属性数据库,以后将服务器文件属性与数据库中的进行校对,然后在服务器运行时对修改过的索引的文件发出警告。处于这个原因,AIDE必须在系统更新后或其配置文件进行合法修改后重新对受保护的文件做索引。
|
||||
|
||||
对于某些客户,他们可能会根据他们的安全策略在他们的服务器上强制安装某种入侵检测系统。但是,不管客户是否要求,系统管理员都部署一个入侵检测系统,这通常是一个很好的做法。
|
||||
|
||||
### 安装AIDE到CentOS或RHEL ###
|
||||
|
||||
AIDE的初始安装(同时是首次运行)最好是在系统刚安装完后,并且没有任何服务暴露在互联网,甚至是局域网中。在这个早期阶段,我们可以将来自外部的一切闯入和破坏风险降到最低限度。事实上,这也是确保系统在AIDE构建其初始数据库时保持干净的唯一途径。
|
||||
|
||||
出于上面的原因,在安装完AIDE后,我们可以执行下面的命令:
|
||||
|
||||
# yum install aide
|
||||
|
||||
我们需要将我们的机器从网络断开,并实施下面所述的一些基本配置任务。
|
||||
|
||||
### 配置AIDE ###
|
||||
|
||||
默认配置文件是/etc/aide.conf,该文件介绍了几个示例保护规则(如FIPSR,NORMAL,DIR,DATAONLY),各个规则后面跟着一个等于号以及要检查的文件属性列表,或者某些预定义的规则(由+分隔)。你也可以使用此种格式自定义规则。
|
||||
|
||||

|
||||
|
||||
FIPSR = p+i+n+u+g+s+m+c+acl+selinux+xattrs+sha256
|
||||
NORMAL = FIPSR+sha512
|
||||
|
||||
例如,上面的例子说明,NORMAL规则将检查下列属性的不一致性:权限(p)、索引节点(i)、链接数(n)、用户(u)、组(g)、大小(s)、修改时间(m)、创建时间(c)、ACL(acl)、SELinux(selinux)、xattrs(xattr)、SHA256/SHA512校验和(sha256和sha512)。
|
||||
|
||||
定义的规则可灵活地用于不同的目录和文件(用正则表达式表示)。
|
||||
|
||||

|
||||
|
||||
条目之前的感叹号(!)告诉AIDE忽略子目录(或目录中的文件),对于这些可以另外定义规则。
|
||||
|
||||
在上面的例子中,PERMS是用于/etc机器子目录和文件的默认规则。然而,没有规则将用于/etc中的备份文件(如/etc/.*~),也没有规则用于/etc/mtab文件。对于/etc中的一些选择性的子目录或文件,NORMAL规则会被应用,覆盖默认规则PERMS。
|
||||
|
||||
定义并应用正确的规则到系统中正确的位置,是使用AIDE最难的一部分,但作出好的判断是一个良好的开始。作为首要的一条规则,不要检查不必要的属性。例如,检查/var/log或/var/spool里头的文件的修改时间将导致大量误报,因为许多的应用程序和守护进程经常会写入内容到该位置,而这些内容都没有问题。此外,检查多个校验和可能加强安全性,但随之而来的是AIDE的运行时间的增加。
|
||||
|
||||
你可以选择将检查结果发送到你的邮箱,如果你使用MAILTO变量指定了电子邮件地址。将下面这一行放到/etc/aide.conf中的任何位置即可。
|
||||
|
||||
MAILTO=root@localhost
|
||||
|
||||
### 首次运行AIDE ###
|
||||
|
||||
运行以下命令来初始化AIDE数据库:
|
||||
|
||||
# aide --init
|
||||
|
||||

|
||||
|
||||
根据/etc/aide.conf生成的/var/lib/aide/aide.db.new.gz文件需要被重命名为/var/lib/aide/aide.db.gz,以便AIDE能读取它:
|
||||
|
||||
# mv /var/lib/aide/aide.db.new.gz /var/lib/aide.db.gz
|
||||
|
||||
现在,是时候来将我们的系统与数据库进行第一次校对了。任务很简单,只需运行:
|
||||
|
||||
# aide
|
||||
|
||||
在没有选项时,AIDE假定使用了--check选项。
|
||||
|
||||
如果在数据库创建后没有对系统做过任何修改,AIDE将会以OK信息来结束本次校对。
|
||||
|
||||

|
||||
|
||||
### 生产环境中管理AIDE ###
|
||||
|
||||
在构建了一个初始AIDE数据库后,作为不断推进的系统管理活动,你常常需要处于某些合法的理由更新受保护的服务器。每次服务器更新后,你必须重新构建AIDE数据库,以更新数据库内容。要完成该任务,请执行以下命令:
|
||||
|
||||
# aide --update
|
||||
|
||||
要使用AIDE保护生产系统,可能最好通过任务计划调用AIDE来周期性检查不一致性。例如,要让AIDE每天运行一次,并将结果发送到邮箱:
|
||||
|
||||
# crontab -e
|
||||
|
||||
----------
|
||||
|
||||
0 0 * * * /usr/sbin/aide --check | /usr/bin/mail -s "AIDE run for $HOSTNAME" your@email.com
|
||||
|
||||
### 测试AIDE检查文件篡改 ###
|
||||
|
||||
下面的测试环境将演示AIDE是如何来检查文件的完整性的。
|
||||
|
||||
#### 测试环境 1 ####
|
||||
|
||||
让我们添加一个新文件(如/etc/fake)。
|
||||
|
||||
# cat /dev/null > /etc/fake
|
||||
|
||||

|
||||
|
||||
#### 测试环境 2 ####
|
||||
|
||||
让我们修改文件权限,然后看看它是否被检测到。
|
||||
|
||||
# chmod 644 /etc/aide.conf
|
||||
|
||||
#### 测试环境 3 ####
|
||||
|
||||
最后,让我们修改文件内容(如,添加一个注释行到/etc/aide.conf)。
|
||||
|
||||
echo "#This is a comment" >> /etc/aide.conf
|
||||
|
||||

|
||||
|
||||
上面的截图中,第一栏显示了文件的属性,第二栏是AIDE数据库中的值,而第三栏是更新后的值。第三栏中空白部分表示该属性没有改动(如本例中的ACL)。
|
||||
|
||||
### 结尾 ###
|
||||
|
||||
如果你曾经发现你自己有很好的理由相信系统被入侵了,但是第一眼又不能确定到底哪些东西被改动了,那么像AIDE这样一个基于主机的入侵检测系统就会很有帮助了,因为它可以帮助你很快识别出哪些东西被改动过,而不是通过猜测来浪费宝贵的时间。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/host-intrusion-detection-system-centos.html
|
||||
|
||||
作者:[Gabriel Cánepa][a]
|
||||
译者:[GOLinux](https://github.com/GOLinux)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/gabriel
|
||||
[1]:http://aide.sourceforge.net/
|
||||
Loading…
Reference in New Issue
Block a user