mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-01-28 23:20:10 +08:00
Merge remote-tracking branch 'LCTT/master' into 20171111-A-CEOs-Guide-to-Emacs
This commit is contained in:
commit
ccd7c624d0
@ -0,0 +1,240 @@
|
||||
我的个人电子邮件系统设置:notmuch、mbsync、Postfix 和 dovecot
|
||||
======
|
||||
|
||||
我使用个人电子邮件系统已经相当长的时间了,但是一直没有记录过文档。最近我换了我的笔记本电脑(职业变更导致的变动),我在试图重新创建本地邮件系统时迷茫了。所以这篇文章是一个给自己看的文档,这样我就不用费劲就能再次搭建出来。
|
||||
|
||||
### 服务器端
|
||||
|
||||
我运行自己的邮件服务器,并使用 Postfix 作为 SMTP 服务器,用 Dovecot 实现 IMAP。我不打算详细介绍如何配置这些设置,因为我的设置主要是通过使用 Jonas 为 Redpill 基础架构创建的脚本完成的。什么是 Redpill?(用 Jonas 自己的话说):
|
||||
|
||||
> \<jonas> Redpill 是一个概念:一种设置 Debian hosts 去跨组织协作的方式
|
||||
>
|
||||
> \<jonas> 我发展了这个概念,并将其首次用于 Redpill 网中网:redpill.dk,其中涉及到了我自己的网络(jones.dk),我的主要客户的网络(homebase.dk),一个包括 Skolelinux Germany(free-owl.de)的在德国的网络,和 Vasudev 的网络(copyninja.info)
|
||||
|
||||
除此之外, 我还有一个 dovecot sieve 过滤,根据邮件的来源,对邮件进行高级分类,将其放到各种文件夹中。所有的规则都存在于每个有邮件地址的账户下的 `~/dovecot.sieve` 文件中。
|
||||
|
||||
再次,我不会详细介绍如何设置这些东西,因为这不是我这个帖子的目标。
|
||||
|
||||
### 在我的笔记本电脑上
|
||||
|
||||
在我的笔记本电脑上,我已经按照 4 个部分设置
|
||||
|
||||
1. 邮件同步:使用 `mbsync` 命令完成
|
||||
2. 分类:使用 notmuch 完成
|
||||
3. 阅读:使用 notmuch-emacs 完成
|
||||
4. 邮件发送:使用作为中继服务器和 SMTP 客户端运行的 Postfix 完成。
|
||||
|
||||
### 邮件同步
|
||||
|
||||
邮件同步是使用 `mbsync` 工具完成的, 我以前是 OfflineIMAP 的用户,最近切换到 `mbsync`,因为我觉得它比 OfflineIMAP 的配置更轻量、更简单。该命令是由 isync 包提供的。
|
||||
|
||||
配置文件是 `~/.mbsyncrc`。下面是我的例子与一些个人设置。
|
||||
|
||||
```
|
||||
IMAPAccount copyninja
|
||||
Host imap.copyninja.info
|
||||
User vasudev
|
||||
PassCmd "gpg -q --for-your-eyes-only --no-tty --exit-on-status-write-error --batch --passphrase-file ~/path/to/passphrase.txt -d ~/path/to/mailpass.gpg"
|
||||
SSLType IMAPS
|
||||
SSLVersion TLSv1.2
|
||||
CertificateFile /etc/ssl/certs/ca-certificates.crt
|
||||
|
||||
|
||||
IMAPAccount gmail-kamathvasudev
|
||||
Host imap.gmail.com
|
||||
User kamathvasudev@gmail.com
|
||||
PassCmd "gpg -q --for-your-eyes-only --no-tty --exit-on-status-write-error --batch --passphrase-file ~/path/to/passphrase.txt -d ~/path/to/mailpass.gpg"
|
||||
SSLType IMAPS
|
||||
SSLVersion TLSv1.2
|
||||
CertificateFile /etc/ssl/certs/ca-certificates.crt
|
||||
|
||||
IMAPStore copyninja-remote
|
||||
Account copyninja
|
||||
|
||||
IMAPStore gmail-kamathvasudev-remote
|
||||
Account gmail-kamathvasudev
|
||||
|
||||
MaildirStore copyninja-local
|
||||
Path ~/Mail/vasudev-copyninja.info/
|
||||
Inbox ~/Mail/vasudev-copyninja.info/INBOX
|
||||
|
||||
MaildirStore gmail-kamathvasudev-local
|
||||
Path ~/Mail/Gmail-1/
|
||||
Inbox ~/Mail/Gmail-1/INBOX
|
||||
|
||||
Channel copyninja
|
||||
Master :copyninja-remote:
|
||||
Slave :copyninja-local:
|
||||
Patterns *
|
||||
Create Both
|
||||
SyncState *
|
||||
Sync All
|
||||
|
||||
Channel gmail-kamathvasudev
|
||||
Master :gmail-kamathvasudev-remote:
|
||||
Slave :gmail-kamathvasudev-local:
|
||||
# Exclude everything under the internal [Gmail] folder, except the interesting folders
|
||||
Patterns * ![Gmail]*
|
||||
Create Both
|
||||
SyncState *
|
||||
Sync All
|
||||
```
|
||||
|
||||
对上述配置中的一些有趣部分进行一下说明。一个是 PassCmd,它允许你提供 shell 命令来获取帐户的密码。这样可以避免在配置文件中填写密码。我使用 gpg 的对称加密,并在我的磁盘上存储密码。这当然是由 Unix ACL 保护安全的。
|
||||
|
||||
实际上,我想使用我的公钥来加密文件,但当脚本在后台或通过 systemd 运行时,解锁文件看起来很困难 (或者说几乎不可能)。如果你有更好的建议,我洗耳恭听:-)。
|
||||
|
||||
下一个指令部分是 Patterns。这使你可以有选择地同步来自邮件服务器的邮件。这对我来说真的很有帮助,可以排除所有的 “[Gmail]/ folders” 垃圾目录。
|
||||
|
||||
### 邮件分类
|
||||
|
||||
一旦邮件到达你的本地设备,我们需要一种方法来轻松地在邮件读取器中读取邮件。我最初的设置使用本地 dovecot 实例提供同步的 Maildir,并在 Gnus 中阅读。这种设置相比于设置所有的服务器软件是有点大题小作,但 Gnus 无法很好地应付 Maildir 格式,这是最好的方法。这个设置也有一个缺点,那就是在你快速搜索邮件时,要搜索大量邮件。而这就是 notmuch 的用武之地。
|
||||
|
||||
notmuch 允许我轻松索引上千兆字节的邮件档案而找到我需要的东西。我已经创建了一个小脚本,它结合了执行 `mbsync` 和 `notmuch`。我使用 dovecot sieve 来基于实际上创建在服务器端的 Maildirs 标记邮件。下面是我的完整 shell 脚本,它执行同步分类和删除垃圾邮件的任务。
|
||||
|
||||
```
|
||||
#!/bin/sh
|
||||
|
||||
MBSYNC=$(pgrep mbsync)
|
||||
NOTMUCH=$(pgrep notmuch)
|
||||
|
||||
if [ -n "$MBSYNC" -o -n "$NOTMUCH" ]; then
|
||||
echo "Already running one instance of mail-sync. Exiting..."
|
||||
exit 0
|
||||
fi
|
||||
|
||||
echo "Deleting messages tagged as *deleted*"
|
||||
notmuch search --format=text0 --output=files tag:deleted |xargs -0 --no-run-if-empty rm -v
|
||||
|
||||
echo "Moving spam to Spam folder"
|
||||
notmuch search --format=text0 --output=files tag:Spam and \
|
||||
to:vasudev@copyninja.info | \
|
||||
xargs -0 -I {} --no-run-if-empty mv -v {} ~/Mail/vasudev-copyninja.info/Spam/cur
|
||||
notmuch search --format=text0 --output=files tag:Spam and
|
||||
to:vasudev-debian@copyninja.info | \
|
||||
xargs -0 -I {} --no-run-if-empty mv -v {} ~/Mail/vasudev-copyninja.info/Spam/cur
|
||||
|
||||
|
||||
MDIR="vasudev-copyninja.info vasudev-debian Gmail-1"
|
||||
mbsync -Va
|
||||
notmuch new
|
||||
|
||||
for mdir in $MDIR; do
|
||||
echo "Processing $mdir"
|
||||
for fdir in $(ls -d /home/vasudev/Mail/$mdir/*); do
|
||||
if [ $(basename $fdir) != "INBOX" ]; then
|
||||
echo "Tagging for $(basename $fdir)"
|
||||
notmuch tag +$(basename $fdir) -inbox -- folder:$mdir/$(basename $fdir)
|
||||
fi
|
||||
done
|
||||
done
|
||||
```
|
||||
|
||||
因此,在运行 `mbsync` 之前,我搜索所有标记为“deleted”的邮件,并将其从系统中删除。接下来,我在我的帐户上查找标记为“Spam”的邮件,并将其移动到“Spam”文件夹。你没看错,这些邮件逃脱了垃圾邮件过滤器进入到我的收件箱,并被我亲自标记为垃圾邮件。
|
||||
|
||||
运行 `mbsync` 后,我基于它们的文件夹标记邮件(搜索字符串 `folder:`)。这让我可以很容易地得到一个邮件列表的内容,而不需要记住列表地址。
|
||||
|
||||
### 阅读邮件
|
||||
|
||||
现在,我们已经实现同步和分类邮件,是时候来设置阅读部分。我使用 notmuch-emacs 界面来阅读邮件。我使用 emacs 的 Spacemacs 风格,所以我花了一些时间写了一个私有层,它将我所有的快捷键和分类集中在一个地方,而不会扰乱我的整个 `.spacemacs` 文件。你可以在 [notmuch-emacs-layer 仓库][1] 找到我的私有层的代码。
|
||||
|
||||
### 发送邮件
|
||||
|
||||
能阅读邮件这还不够,我们也需要能够回复邮件。而这是最近是我感到迷茫的一个略显棘手的部分,以至于不得不写这篇文章,这样我就不会再忘记了。(当然也不必在网络上参考一些过时的帖子。)
|
||||
|
||||
我的系统发送邮件使用 Postfix 作为 SMTP 客户端,使用我自己的 SMTP 服务器作为它的中继主机。中继的问题是,它不能是具有动态 IP 的主机。有两种方法可以允许具有动态 IP 的主机使用中继服务器, 一种是将邮件来源的 IP 地址放入 `my_network` 或第二个使用 SASL 身份验证。
|
||||
|
||||
我的首选方法是使用 SASL 身份验证。为此,我首先要为每台机器创建一个单独的账户,它将把邮件中继到我的主服务器上。想法是不使用我的主帐户 SASL 进行身份验证。(最初我使用的是主账户,但 Jonas 给出了可行的按账户的想法)
|
||||
|
||||
```
|
||||
adduser <hostname>_relay
|
||||
```
|
||||
|
||||
这里替换 `<hostname>` 为你的笔记本电脑的名称或任何你正在使用的设备。现在我们需要调整 Postfix 作为中继服务器。因此,在 Postfix 配置中添加以下行:
|
||||
|
||||
```
|
||||
# SASL authentication
|
||||
smtp_sasl_auth_enable = yes
|
||||
smtp_tls_security_level = encrypt
|
||||
smtp_sasl_tls_security_options = noanonymous
|
||||
relayhost = [smtp.copyninja.info]:submission
|
||||
smtp_sasl_password_maps = hash:/etc/postfix/sasl_passwd
|
||||
```
|
||||
|
||||
因此, 这里的 `relayhost` 是用于将邮件转发到互联网的 Postfix 实例的服务器名称。`submission` 的部分 Postfix 将邮件转发到端口 587(安全端口)。`smtp_sasl_tls_security_options` 设置为不允许匿名连接。这是必须的,以便中继服务器信任你的移动主机,并同意为你转发邮件。
|
||||
|
||||
`/etc/postfix/sasl_passwd` 是你需要存储用于服务器 SASL 身份验证的帐户密码的文件。将以下内容放入其中。
|
||||
|
||||
```
|
||||
[smtp.example.com]:submission user:password
|
||||
```
|
||||
|
||||
用你已放入 `relayhost` 配置的 SMTP 服务器名称替换 `smtp.example.com`。用你创建的 `<hostname>_relay` 用户及其密码替换 `user` 和 `passwd`。
|
||||
|
||||
若要保护 `sasl_passwd` 文件,并为 Postfix 创建它的哈希文件,使用以下命令。
|
||||
|
||||
```
|
||||
chown root:root /etc/postfix/sasl_passwd
|
||||
chmod 0600 /etc/postfix/sasl_passwd
|
||||
postmap /etc/postfix/sasl_passwd
|
||||
```
|
||||
|
||||
最后一条命令将创建 `/etc/postfix/sasl_passwd.db` 文件,它是你的文件的 `/etc/postfix/sasl_passwd` 的哈希文件,具有相同的所有者和权限。现在重新加载 Postfix,并使用 `mail` 命令检查邮件是否从你的系统中发出。
|
||||
|
||||
### Bonus 的部分
|
||||
|
||||
好吧,因为我有一个脚本创建以上结合了邮件的同步和分类。我继续创建了一个 systemd 计时器,以定期同步后台的邮件。就我而言,每 10 分钟一次。下面是 `mailsync.timer` 文件。
|
||||
|
||||
```
|
||||
[Unit]
|
||||
Description=Check Mail Every 10 minutes
|
||||
RefuseManualStart=no
|
||||
RefuseManualStop=no
|
||||
|
||||
[Timer]
|
||||
Persistent=false
|
||||
OnBootSec=5min
|
||||
OnUnitActiveSec=10min
|
||||
Unit=mailsync.service
|
||||
|
||||
[Install]
|
||||
WantedBy=default.target
|
||||
```
|
||||
|
||||
下面是 mailsync.service 服务,这是 mailsync.timer 执行我们的脚本所需要的。
|
||||
|
||||
```
|
||||
[Unit]
|
||||
Description=Check Mail
|
||||
RefuseManualStart=no
|
||||
RefuseManualStop=yes
|
||||
|
||||
[Service]
|
||||
Type=oneshot
|
||||
ExecStart=/usr/local/bin/mail-sync
|
||||
StandardOutput=syslog
|
||||
StandardError=syslog
|
||||
```
|
||||
|
||||
将这些文件置于 `/etc/systemd/user` 目录下并运行以下代码去开启它们:
|
||||
|
||||
```
|
||||
systemctl enable --user mailsync.timer
|
||||
systemctl enable --user mailsync.service
|
||||
systemctl start --user mailsync.timer
|
||||
```
|
||||
|
||||
这就是我从系统同步和发送邮件的方式。我从 Jonas Smedegaard 那里了解到了 afew,他审阅了这篇帖子。因此, 下一步, 我将尝试使用 afew 改进我的 notmuch 配置,当然还会有一个后续的帖子:-)。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://copyninja.info/blog/email_setup.html
|
||||
|
||||
作者:[copyninja][a]
|
||||
译者:[lixinyuxx](https://github.com/lixinyuxx)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://copyninja.info
|
||||
[1]:https://source.copyninja.info/notmuch-emacs-layer.git/
|
||||
@ -1,51 +1,58 @@
|
||||
用户,组和其他 Linux 用户
|
||||
用户、组及其它 Linux 特性
|
||||
======
|
||||
|
||||
> Linux 和其他类 Unix 操作系统依赖于用户组,而不是逐个为用户分配权限和特权。一个组就是你想象的那样:一群在某种程度上相关的用户。
|
||||
|
||||

|
||||
|
||||
到这个阶段,[在看到如何操作目录或文件夹之后][1],但在让自己一头扎进文件之前,我们必须重新审视 _权限_, _users_ 和 _group_。幸运的是,[有一个网站上已经有了一个优秀而全面的教程,包括了权限][2],所以你应该去立刻阅读它。简而言之,你使用权限来确定谁可以对文件和目录执行操作,以及他们可以对每个文件和目录执行什么操作 -- 从中读取,写入,擦除等等。
|
||||
到这个阶段,[在看到如何操作目录或文件夹之后][1],但在让自己一头扎进文件之前,我们必须重新审视 _权限_、_用户_ 和 _组_。幸运的是,[有一个网站上已经有了一个优秀而全面的教程,讲到了权限][2],所以你应该去立刻阅读它。简而言之,你使用权限来确定谁可以对文件和目录执行操作,以及他们可以对每个文件和目录执行什么操作 —— 从中读取、写入、移动、擦除等等。
|
||||
|
||||
要尝试本教程涵盖的所有内容,你需要在系统上创建新用户。让我们实践起来,为每一个需要借用你电脑的人创建一个用户,我们称之为 _guest 账户_。
|
||||
要尝试本教程涵盖的所有内容,你需要在系统上创建新用户。让我们实践起来,为每一个需要借用你电脑的人创建一个用户,我们称之为 `guest` 账户。
|
||||
|
||||
**警告:** _例如,如果你错误地删除了自己的用户和目录,那么创建,特别是删除用户以及主目录会严重损坏系统。你可能不想在你日常的工作机中练习,那么请在另一台机器或者虚拟机上练习。无论你是否想要安全地练习,经常备份你的东西总是一个好主意。检查备份是否正常工作,为你自己以后避免很多咬牙切齿的事情。_
|
||||
**警告:** 例如,如果你错误地删除了自己的用户和目录,那么创建用户,特别是删除用户以及主目录会严重损坏系统。你可能不想在你日常的工作机中练习,那么请在另一台机器或者虚拟机上练习。无论你是否想要安全地练习,经常备份你的东西总是一个好主意。检查备份是否正常工作,为你自己以后避免很多咬牙切齿的事情。
|
||||
|
||||
### 一个新用户
|
||||
|
||||
你可以使用 `useradd` 命令来创建一个新用户。使用超级用户或 root 权限运行 `useradd`,即使用 `sudo` 或 `su`,这具体取决于你的系统,你可以:
|
||||
|
||||
```
|
||||
sudo useradd -m guest
|
||||
```
|
||||
|
||||
然后输入你的密码。或者也可以这样:
|
||||
|
||||
```
|
||||
su -c "useradd -m guest"
|
||||
```
|
||||
|
||||
然后输入 root 或超级用户的密码。
|
||||
|
||||
(_为了简洁起见,我们将从现在开始假设你使用 `sudo` 获得超级用户或 root 权限。_)
|
||||
( _为了简洁起见,我们将从现在开始假设你使用 `sudo` 获得超级用户或 root 权限。_ )
|
||||
|
||||
通过使用 `-m` 参数,`useradd` 将为新用户创建一个主目录。你可以通过列出 _/home/guest_ 来查看其内容。
|
||||
通过使用 `-m` 参数,`useradd` 将为新用户创建一个主目录。你可以通过列出 `/home/guest` 来查看其内容。
|
||||
|
||||
然后你可以使用以下命令来为新用户设置密码:
|
||||
|
||||
```
|
||||
sudo passwd guest
|
||||
```
|
||||
|
||||
或者你也可以使用 `adduser`,这是一个交互式的命令,它会询问你一些问题,包括你要为用户分配的 shell(是的,不止一个),你希望其主目录在哪里,你希望他们属于哪些组(有关这点稍后会讲到)等等。在运行 `adduser` 结束时,你可以设置密码。注意,默认情况下,在许多发行版中都没有安装 `adduser`,但安装了 `useradd`。
|
||||
或者你也可以使用 `adduser`,这是一个交互式的命令,它会询问你一些问题,包括你要为用户分配的 shell(是的,shell 有不止一种),你希望其主目录在哪里,你希望他们属于哪些组(有关这点稍后会讲到)等等。在运行 `adduser` 结束时,你可以设置密码。注意,默认情况下,在许多发行版中都没有安装 `adduser`,但安装了 `useradd`。
|
||||
|
||||
顺便说一下,你可以使用 `userdel` 来移除一个用户:
|
||||
|
||||
```
|
||||
sudo userdel -r guest
|
||||
```
|
||||
|
||||
使用 `-r` 选项,`userdel` 不仅删除了 _guest_ 用户,还删除了他们的主目录和邮件中的条目(如果有的话)。
|
||||
使用 `-r` 选项,`userdel` 不仅删除了 `guest` 用户,还删除了他们的主目录和邮件中的条目(如果有的话)。
|
||||
|
||||
### home 中的内容
|
||||
### 主目录中的内容
|
||||
|
||||
谈到用户的主目录,它依赖于你所使用的发行版。你可能已经注意到,当你使用 `-m` 选项时,`useradd` 使用子目录填充用户的目录,包括音乐,文档和诸如此类的内容以及各种各样的隐藏文件。要查看 guest 主目录中的所有内容,运行 `sudo ls -la /home/guest`。
|
||||
谈到用户的主目录,它依赖于你所使用的发行版。你可能已经注意到,当你使用 `-m` 选项时,`useradd` 使用子目录填充用户的目录,包括音乐、文档和诸如此类的内容以及各种各样的隐藏文件。要查看 `guest` 主目录中的所有内容,运行 `sudo ls -la /home/guest`。
|
||||
|
||||
进入新用户目录的内容通常是由 `/etc/skel` 架构目录确定的。有时它可能是一个不同的目录。要检查正在使用的目录,运行:
|
||||
|
||||
进入新用户目录的内容通常是由 _/etc/skel_ 架构目录确定的。有时它可能是一个不同的目录。要检查正在使用的目录,运行:
|
||||
```
|
||||
useradd -D
|
||||
GROUP=100
|
||||
@ -57,31 +64,36 @@ SKEL=/etc/skel
|
||||
CREATE_MAIL_SPOOL=no
|
||||
```
|
||||
|
||||
这给你一些额外的有趣信息,但你现在感兴趣的是 `SKEL=/etc/skel` 这一行,在这种情况下,按照惯例,它指向 _/etc/skel/_。
|
||||
这会给你一些额外的有趣信息,但你现在感兴趣的是 `SKEL=/etc/skel` 这一行,在这种情况下,按照惯例,它指向 `/etc/skel/`。
|
||||
|
||||
由于 Linux 中的所有东西都是可定制的,因此你可以更改那些放入新创建的用户目录的内容。试试这样做:在 `/etc/skel/` 中创建一个新目录:
|
||||
|
||||
由于 Linux 中的所有东西都是可定制的,因此你可以更改那些放入新创建的用户目录的内容。试试这样做:在 _/etc/skel/_ 中创建一个新目录:
|
||||
```
|
||||
sudo mkdir /etc/skel/Documents
|
||||
```
|
||||
|
||||
然后创建一个包含欢迎消息的文件,并将其复制过来:
|
||||
|
||||
```
|
||||
sudo cp welcome.txt /etc/skel/Documents
|
||||
```
|
||||
|
||||
现在删除 guest 账户:
|
||||
现在删除 `guest` 账户:
|
||||
|
||||
```
|
||||
sudo userdel -r guest
|
||||
```
|
||||
|
||||
再次创建:
|
||||
|
||||
```
|
||||
sudo useradd -m guest
|
||||
```
|
||||
|
||||
嘿 presto!(to 校正:这个 presto 是什么?)你的 _Documents/_ 目录和 _welcome.txt_ 文件神奇地出现在了 guest 的主目录中。
|
||||
嘿!你的 `Documents/` 目录和 `welcome.txt` 文件神奇地出现在了 `guest` 的主目录中。
|
||||
|
||||
你还可以在创建用户时通过编辑 `/etc/default/useradd` 来修改其他内容。我的看起来像这样:
|
||||
|
||||
你还可以在创建用户时通过编辑 _/etc/default/useradd_ 来修改其他内容。我的看起来像这样:
|
||||
```
|
||||
GROUP=users
|
||||
HOME=/home
|
||||
@ -96,11 +108,12 @@ CREATE_MAIL_SPOOL=no
|
||||
|
||||
### 群组心态
|
||||
|
||||
Linux 和其他类 Unix 操作系统依赖于 _groups_,而不是逐个为用户分配权限和特权。一个组就是你想象的那样:一群在某种程度上相关的用户。在你的系统上可能有一组允许使用打印机的用户,他们属于 _lp_(即 "_line printer_")组。传统上 _wheel_ 组的成员是唯一可以通过使用 _su_ 成为超级用户或 root 的成员。_network_ 用户组可以启动或关闭网络。还有许多诸如此类的。
|
||||
Linux 和其他类 Unix 操作系统依赖于用户组,而不是逐个为用户分配权限和特权。一个组就是你想象的那样:一群在某种程度上相关的用户。在你的系统上可能有一组允许使用打印机的用户,他们属于 `lp`(即 “_line printer_”)组。传统上 `wheel` 组的成员是唯一可以通过使用 `su` 成为超级用户或 root 的成员。`network` 用户组可以启动或关闭网络。还有许多诸如此类的。
|
||||
|
||||
不同的发行版有不同的组,具有相同或相似名称的组具有不同的权限,这也取决于你使用的发行版。因此,如果你在前一段中读到的内容与你系统中的内容不匹配,不要感到惊讶。
|
||||
|
||||
不管怎样g,要查看系统中有哪些组,你可以使用:
|
||||
不管怎样,要查看系统中有哪些组,你可以使用:
|
||||
|
||||
```
|
||||
getent group
|
||||
```
|
||||
@ -108,18 +121,20 @@ getent group
|
||||
`getent` 命令列出了某些系统数据库的内容。
|
||||
|
||||
要查找当前用户所属的组,尝试:
|
||||
|
||||
```
|
||||
groups
|
||||
```
|
||||
|
||||
当你使用 `useradd` 创建新用户时,除非你另行指定,否则用户讲只属于一个组:他们自己。一个 _guest_ 用户属于 _guest_ 组。组使用户有权管理自己的东西,仅此而已。
|
||||
当你使用 `useradd` 创建新用户时,除非你另行指定,否则用户将只属于一个组:他们自己。`guest` 用户属于 `guest` 组。组使用户有权管理自己的东西,仅此而已。
|
||||
|
||||
你可以使用 `groupadd` 命令创建新组,然后添加用户:
|
||||
|
||||
```
|
||||
sudo groupadd photos
|
||||
```
|
||||
|
||||
例如,这将创建 _photos_ 组。下一次,我们将使用它来构建一个共享目录,该组的所有成员都可以读取和写入,我们将更多地了解权限和特权。敬请关注!
|
||||
例如,这将创建 `photos` 组。下一次,我们将使用它来构建一个共享目录,该组的所有成员都可以读取和写入,我们将更多地了解权限和特权。敬请关注!
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
@ -129,11 +144,11 @@ via: https://www.linux.com/learn/intro-to-linux/2018/7/users-groups-and-other-li
|
||||
作者:[Paul Brown][a]
|
||||
选题:[lujun9972](https://github.com/lujun9972)
|
||||
译者:[MjSeven](https://github.com/MjSeven)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://www.linux.com/users/bro66
|
||||
[1]:https://www.linux.com/blog/learn/2018/5/manipulating-directories-linux
|
||||
[1]:https://linux.cn/article-10066-1.html
|
||||
[2]:https://www.linux.com/learn/understanding-linux-file-permissions
|
||||
[3]:https://training.linuxfoundation.org/linux-courses/system-administration-training/introduction-to-linux
|
||||
@ -0,0 +1,142 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-10375-1.html)
|
||||
[#]: subject: (11 Uses for a Raspberry Pi Around the Office)
|
||||
[#]: via: (https://blog.dxmtechsupport.com.au/11-uses-for-a-raspberry-pi-around-the-office/)
|
||||
[#]: author: (James Mawson https://blog.dxmtechsupport.com.au/author/james-mawson/)
|
||||
|
||||
树莓派在办公室的 11 种用法
|
||||
======
|
||||
|
||||
我知道你在想什么:树莓派只能用在修修补补、原型设计和个人爱好中。它实际不能用在业务中。
|
||||
|
||||
毫无疑问,这台电脑的处理能力相对较低、易损坏的 SD 卡、缺乏电池备份以及支持的 DIY 性质,这意味着它不会是一个能在任何时候执行最关键的操作的[专业的、已安装好、配置好的商业服务器][1]的可行替代品。
|
||||
|
||||
但是它电路板便宜、功耗很小、小到几乎适合任何地方、无限灵活 —— 这实际上是处理办公室一些基本任务的好方法。
|
||||
|
||||
而且,更好的是,已经有一些人完成了这些项目并很乐意分享他们是如何做到的。
|
||||
|
||||
### DNS 服务器
|
||||
|
||||
每次在浏览器中输入网站地址或者点击链接时,都需要将域名转换为数字 IP 地址,然后才能显示内容。
|
||||
|
||||
通常这意味着向互联网上某处 DNS 服务器发出请求 —— 但你可以通过本地处理来加快浏览速度。
|
||||
|
||||
你还可以分配自己的子域,以便本地访问办公室中的计算机。
|
||||
|
||||
[这里了解它是如何工作的。][2]
|
||||
|
||||
### 厕所占用标志
|
||||
|
||||
在厕所排过队吗?
|
||||
|
||||
这对于那些等待的人来说很烦人,花在处理它上面的时间会耗费你在办公室的工作效率。
|
||||
|
||||
我想你希望在办公室里也悬挂飞机上那个厕所有人的标志。
|
||||
|
||||
[Occu-pi][3] 是一个非常简单的解决方案,使用磁性开关和树莓派来判断螺栓何时关闭,并在 Slack 频道中更新“厕所在使用中” —— 这意味着整个办公室的人都可以看一眼电脑或者移动设备知道是否有空闲的隔间。
|
||||
|
||||
### 针对黑客的蜜罐陷阱
|
||||
|
||||
黑客破坏了网络的第一个线索是一些事情变得糟糕,这应该会吓到大多数企业主。
|
||||
|
||||
这就是可以用到蜜罐的地方:一台没有任何服务的计算机位于你的网络,将特定端口打开,伪装成黑客喜欢的目标。
|
||||
|
||||
安全研究人员经常在网络外部部署蜜罐,以收集攻击者正在做的事情的数据。
|
||||
|
||||
但对于普通的小型企业来说,这些作为一种绊脚石部署在内部更有用。因为普通用户没有真正的理由想要连接到蜜罐,所以任何发生的登录尝试都是正在进行捣乱的非常好的指示。
|
||||
|
||||
这可以提供对外部人员入侵的预警,并且也可以提供对值得信赖的内部人员的预警。
|
||||
|
||||
在较大的客户端/服务器网络中,将它作为虚拟机运行可能更为实用。但是在无线路由器上运行的点对点的小型办公室/家庭办公网络中,[HoneyPi][4] 之类的东西是一个很小的防盗报警器。
|
||||
|
||||
### 打印服务器
|
||||
|
||||
联网打印机更方便。
|
||||
|
||||
但更换所有打印机可能会很昂贵 —— 特别是如果你对现有的打印机感到满意的话。
|
||||
|
||||
[将树莓派设置为打印服务器][5]可能会更有意义。
|
||||
|
||||
### 网络附加存储(NAS)
|
||||
|
||||
将硬盘变为 NAS 是树莓派最早的实际应用之一,并且它仍然是最好的之一。
|
||||
|
||||
[这是如何使用树莓派创建 NAS。][6]
|
||||
|
||||
### 工单服务器
|
||||
|
||||
想要在预算不足的情况下在服务台中支持工单?
|
||||
|
||||
有一个名为 osTicket 的完全开源的工单程序,它可以安装在你的树莓派上,它甚至还有[随时可用的 SD 卡镜像][7]。
|
||||
|
||||
### 数字标牌
|
||||
|
||||
无论是用于活动、广告、菜单还是其他任何东西,许多企业都需要一种显示数字标牌的方式 —— 而树莓派的廉价和省电使其成为一个非常有吸引力的选择。
|
||||
|
||||
[这有很多可供选择的选项。] [8]
|
||||
|
||||
### 目录和信息亭
|
||||
|
||||
[FullPageOS][9] 是一个基于 Raspbian 的 Linux 发行版,它直接引导到 Chromium 的全屏版本 —— 这非常适合导购、图书馆目录等。
|
||||
|
||||
### 基本的内联网 Web 服务器
|
||||
|
||||
对于托管一个面向公众的网站,你最好有一个托管帐户。树莓派不适合面对真正的网络流量。
|
||||
|
||||
但对于小型办公室,它可以托管内部业务维基或基本的公司内网。它还可以用作沙箱环境,用于试验代码和服务器配置。
|
||||
|
||||
[这里是如何在树莓派上运行 Apache、MySQL 和 PHP。][10]
|
||||
|
||||
### 渗透测试器
|
||||
|
||||
Kali Linux 是专为探测网络安全漏洞而构建的操作系统。通过将其安装在树莓派上,你就拥有了一个超便携式穿透测试器,其中包含 600 多种工具。
|
||||
|
||||
[你可以在这里找到树莓派镜像的种子链接。][11]
|
||||
|
||||
绝对要小心只在你自己的网络或你有权对它安全审计的网络中使用它 —— 使用此方法来破解其他网络是严重的犯罪行为。
|
||||
|
||||
### VPN 服务器
|
||||
|
||||
当你外出时,依靠的是公共无线互联网,你无法控制还有谁在网络中、谁在窥探你的所有流量。这就是为什么通过 VPN 连接加密所有内容可以让人放心。
|
||||
|
||||
你可以订阅任意数量的商业 VPN 服务,并且你可以在云中安装自己的服务,但是在办公室运行一个 VPN,这样你也可以从任何地方访问本地网络。
|
||||
|
||||
对于轻度使用 —— 比如偶尔的商务旅行 —— 树莓派是一种强大的,节约能源的设置 VPN 服务器的方式。(首先要检查一下你的路由器是不是不支持这个功能,许多路由器是支持的。)
|
||||
|
||||
[这是如何在树莓派上安装 OpenVPN。][12]
|
||||
|
||||
### 无线咖啡机
|
||||
|
||||
啊,美味:好喝的饮料是神赐之物,也是公司内工作效率的支柱。
|
||||
|
||||
那么,为什么不[将办公室的咖啡机变成可以精确控制温度和无线连接的智能咖啡机呢?][13]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://blog.dxmtechsupport.com.au/11-uses-for-a-raspberry-pi-around-the-office/
|
||||
|
||||
作者:[James Mawson][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://blog.dxmtechsupport.com.au/author/james-mawson/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://dxmtechsupport.com.au/server-configuration
|
||||
[2]: https://www.1and1.com/digitalguide/server/configuration/how-to-make-your-raspberry-pi-into-a-dns-server/
|
||||
[3]: https://blog.usejournal.com/occu-pi-the-bathroom-of-the-future-ed69b84e21d5
|
||||
[4]: https://trustfoundry.net/honeypi-easy-honeypot-raspberry-pi/
|
||||
[5]: https://opensource.com/article/18/3/print-server-raspberry-pi
|
||||
[6]: https://howtoraspberrypi.com/create-a-nas-with-your-raspberry-pi-and-samba/
|
||||
[7]: https://everyday-tech.com/a-raspberry-pi-ticketing-system-image-with-osticket/
|
||||
[8]: https://blog.capterra.com/7-free-and-open-source-digital-signage-software-options-for-your-next-event/
|
||||
[9]: https://github.com/guysoft/FullPageOS
|
||||
[10]: https://maker.pro/raspberry-pi/projects/raspberry-pi-web-server
|
||||
[11]: https://www.offensive-security.com/kali-linux-arm-images/
|
||||
[12]: https://medium.freecodecamp.org/running-your-own-openvpn-server-on-a-raspberry-pi-8b78043ccdea
|
||||
[13]: https://www.techradar.com/au/how-to/how-to-build-your-own-smart-coffee-machine
|
||||
@ -0,0 +1,61 @@
|
||||
认识存储:块、文件和对象
|
||||
======
|
||||
> 今天产生的大量数据带来了新的存储挑战。在本文中了解各种存储类型以及它们的使用方式。
|
||||
|
||||

|
||||
|
||||
现在,对于那些创建或消费数据的公司来说,处理数量巨大的生成数据是个非常大的挑战。而对于那些解决存储相关问题的科技公司来说,也是一个挑战。
|
||||
|
||||
Red Hat 存储首席产品营销经理 Michael St. Jean 说,“数据每年呈几何级增长,而我们发现数据大量增长的主要原因是由于消费增长和为拓展价值而进行的产业转型,毫无疑问,物联网对数据增长的贡献很大,但对软件定义存储来说最重要的挑战是,如何处理用户场景相关的数据增长。“
|
||||
|
||||
任何挑战都意味着机遇。Azure 存储、介质和边缘计算总经理 Tad Brockway 说,“今天,新旧数据源产生的海量数据为我们满足客户在规模、性能、灵活性、治理方面急剧增长的需求提供了一个机遇。”
|
||||
|
||||
### 现代软件定义存储的三种类型
|
||||
|
||||
这里有三个不同类型的存储解决方案 —— 块、文件、和对象 —— 虽然它们每个都可以与其它的共同工作,但它们每个都有不同的用途。
|
||||
|
||||
块存储是数据存储的最古老形式,数据都存储在固定长度的块或多个块中。块存储适用于企业存储环境,并且通常使用光纤通道或 iSCSI 接口。根据 SUSE 的软件定义存储高级产品经理 Larry Morris 的说法,“块存储要求一个应用去映射存储设备上存储数据块的位置。”
|
||||
|
||||
块存储在存储区域网和软件定义存储系统中是虚拟的,它是处于一个共享的硬件基础设施上的抽象逻辑设备,其创建和存在于服务器、虚拟服务器、或运行在基于像 SCSI、SATA、SAS、FCP、FCoE、或 iSCSI 这样的协议的系统管理程序上。
|
||||
|
||||
St. Jean 说“块存储将单个的存储卷(如一个虚拟或云存储节点、或一个老式硬盘)分割成单独的被称为块的实体。”
|
||||
|
||||
每个块独立存在,并且能够用它自己的数据传输协议和操作系统格式化 —— 给用户完全的配置自主权。由于块存储系统并不负责像文件存储系统那样的文件查找职责,所以,块存储是一个非常快的存储系统。由于同时具备速度和配置灵活性,使得块存储非常适合原始服务器存储或富媒体数据库。
|
||||
|
||||
块存储适合于宿主机操作系统、应用程序、数据库、完整虚拟机和容器。传统上,块存储仅能够被独立的机器访问,或呈现给集群中的机器访问。
|
||||
|
||||
### 基于文件的存储
|
||||
|
||||
基于文件的存储使用一个文件系统去映射存储设备上数据的存储位置。这种技术在直连或网络附加存储系统应用领域中处于支配地位。它需要做两件事情:组织数据并呈现给用户。St. Jean 说,”使用文件存储时,数据在服务器侧的存储方式与客户端用户所看到的是完全相同的。这就允许用户通过一些唯一标识符(像文件名、位置、或 URL)去请求一个文件,使用特定的数据传输协议与存储系统沟通。
|
||||
|
||||
其结果就是一种能够从上到下进行浏览的分层的文件结构。文件存储处于块存储之上,允许用户去查看和访问文件、文件夹这样的数据,但是被限制访问处于这些文件和文件夹之下的数据块。
|
||||
|
||||
Brockway 解释说,“文件存储一般用于像 NFS 和 CIFS/SMB 这种很多服务器基于 IP 网络进行访问的共享文件系统上。访问控制通过用户和组的权限实现在文件、目录和导出级别上。基于文件的存储可用于被多个用户和机器、二进制应用程序、数据库、虚拟机所需要的文件的存储上,以及容器上。“
|
||||
|
||||
### 对象存储
|
||||
|
||||
对象存储是最新的数据存储形式,它为非结构化数据提供一个仓库,它将内容从索引中分离出来,并允许多个文件连接到一个对象上。一个对象就是与任何相关元数据配对的一个数据块,这些元数据提供对象中包含的字节的上下文(比如数据创建时间和数据大小等)。也就是说这两样东西 —— 数据和元数据 —— 构成了一个对象。
|
||||
|
||||
对象存储的一个好处是每个数据块都关联了一个唯一标识符。访问数据需要唯一标识符,并且不需要应用程序或用户知道数据的真实存储位置。对象数据是通过 API 来访问的。
|
||||
|
||||
St. Jean 说,“对象中存储的数据是没有压缩和加密的,对象本身被组织在对象存储(一个填满其它对象的中心库)中或容器(包含应用程序运行所需要的所有文件的一个包)中。与文件存储系统的层次结构相比,对象、对象存储和容器在本质上是平面的 —— 这使得它们在存储规模巨大时访问速度很快。”
|
||||
|
||||
对象存储可以扩展到很多 PB 字节大小,以适应巨大的数据集,因此它是图像、音频、视频、日志、备份、和分析服务所使用的数据存储的最佳选择。
|
||||
|
||||
### 结论
|
||||
|
||||
现在你已经知道了各种类型的存储以及它们的用处。后面我们将继续研究这个主题的更多内容,敬请关注。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.linux.com/blog/2018/9/know-your-storage-block-file-object
|
||||
|
||||
作者:[Swapnil Bhartiya][a]
|
||||
选题:[lujun9972](https://github.com/lujun9972)
|
||||
译者:[qhwdw](https://github.com/qhwdw)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.linux.com/users/arnieswap
|
||||
[1]: https://events.linuxfoundation.org/events/elc-openiot-europe-2018/
|
||||
@ -1,31 +1,33 @@
|
||||
持续集成与部署的3个最佳实践
|
||||
持续集成与部署的 3 个最佳实践
|
||||
======
|
||||
了解自动化,使用 Git 存储库以及参数化 Jenkins 管道。
|
||||
|
||||
> 了解自动化,使用 Git 存储库以及参数化 Jenkins 管道。
|
||||
|
||||

|
||||
|
||||
本文涵盖了三个关键主题:自动化 CI/CD 配置、使用 Git 存储库处理常见的 CI/CD 工件、参数化 Jenkins 管道。
|
||||
|
||||
### 术语
|
||||
|
||||
首先,我们定义一些术语。**CI/CD** 是允许团队快速自动化测试、打包、部署其应用程序的实践。它通常通过利用名为 **[Jenkins][1]** 的服务器来实现,该服务器充当 CI/CD 协调器。Jenkins 侦听特定输入(通常是代码签入后的 Git hook),并在触发时启动管道。
|
||||
首先,我们定义一些术语。**CI/CD** 是允许团队快速自动化测试、打包、部署其应用程序的实践。它通常通过利用名为 [Jenkins][1] 的服务器来实现,该服务器充当 CI/CD 协调器。Jenkins 侦听特定输入(通常是代码签入后的 Git 挂钩),并在触发时启动一个管道。
|
||||
|
||||
**pipeline** 由开发和/或运营团队编写的代码组成,这些代码指导 Jenkins 在 CI/CD 过程中采取哪些操作。这个流水线通常类似于“构建我的代码,然后测试我的代码,如果这些测试通过,则把我的应用程序部署到下一个最高环境(通常是开发、测试或生产环境)”。组织通常具有更复杂的流水线,并入了诸如工件存储库和代码分析器之类的工具,但是这提供了一个高级示例。
|
||||
<ruby>管道<rt>pipeline</rt></ruby> 由开发和/或运营团队编写的代码组成,这些代码指导 Jenkins 在 CI/CD 过程中采取哪些操作。这个流水线通常类似于“构建我的代码,然后测试我的代码,如果这些测试通过,则把我的应用程序部署到下一个最高环境(通常是开发、测试或生产环境)”。组织通常具有更复杂的管道,并入了诸如工件存储库和代码分析器之类的工具,这里提供了一个高级示例。
|
||||
|
||||
现在我们了解了关键术语,让我们深入研究一些最佳实践。
|
||||
|
||||
### 1\. 自动化是关键
|
||||
### 1、自动化是关键
|
||||
|
||||
要在 PaaS 上运行 CI/CD,需要在集群上配置适当的基础设施。在这个例子中,我将使用 [OpenShift][2]。
|
||||
|
||||
"Hello, World" 的实现很容易实现。简单地运行 **oc new-app jenkins- <persistent/ephemeral>** 和 voilà, 你已经准备好运行 Jenkins 服务器了。然而,在企业中的使用要复杂得多。除了 Jenkins 服务器之外,管理员通常还需要部署代码分析工具(如 SonarQube)和构件库(如 Nexus)。然后,它们必须创建管道来执行 CI/CD 和 Jenkins 从服务器,以减少主服务器的负载。这些实体中的大多数都由 OpenShift 资源支持,需要创建这些资源来部署所需的 CI/CD 基础设施。
|
||||
“Hello, World” 的实现很容易实现。简单地运行 `oc new-app jenkins-<persistent/ephemeral>`,然后,你就有了一个已经就绪的运行中的 Jenkins 服务器了。然而,在企业中的使用要复杂得多。除了 Jenkins 服务器之外,管理员通常还需要部署代码分析工具(如 SonarQube)和工件库(如 Nexus)。然后,它们必须创建管道来执行 CI/CD 和 Jenkins 从服务器,以减少主服务器的负载。这些实体中的大多数都由 OpenShift 资源支持,需要创建这些资源来部署所需的 CI/CD 基础设施。
|
||||
|
||||
最后,部署 CI/CD 组件所需要的手动步骤可能是需要被重复的,并且你可能不想成为执行那些重复步骤的人。为了确保结果能够像以前一样快速、无错误和准确地产生,应该在创建基础设施的方式中结合自动化方法。这可以是一个 Ansible 剧本、一个 Bash 脚本,或者任何您希望自动化 CI/CD 基础设施部署的其他方式。我已经使用 [Ansible][3] 和 [OpenShift-Applier][4] 角色来自动化我的实现。您可能会发现这些工具很有价值,或者您可能会发现其他一些对您和组织更有效的工具。无论哪种方式,您都将发现自动化显著地减少了重新创建 CI/CD 组件所需的工作量。
|
||||
最后,部署 CI/CD 组件所需要的手动步骤可能是需要重复进行的,而且你可能不想成为执行那些重复步骤的人。为了确保结果能够像以前一样快速、无错误和准确地产生,应该在创建基础设施的方式中结合自动化方法。这可以是一个 Ansible 剧本、一个 Bash 脚本,或者任何您希望自动化 CI/CD 基础设施部署的其它方式。我已经使用 [Ansible][3] 和 [OpenShift-Applier][4] 角色来自动化我的实现。您可能会发现这些工具很有价值,或者您可能会发现其他一些对您和组织更有效的工具。无论哪种方式,您都将发现自动化显著地减少了重新创建 CI/CD 组件所需的工作量。
|
||||
|
||||
#### 配置Jenkins主服务器
|
||||
#### 配置 Jenkins 主服务器
|
||||
|
||||
除了一般的“自动化”之外,我想单独介绍一下 Jenkins 主服务器,并讨论管理员如何利用 OpenShift 来自动化配置 Jenkins。来自 [Red Hat Container Catalog][5] 的 Jenkins 映像已经安装了 [OpenShift-Sync plugin][6]。在 [视频][7] 中,我们将讨论如何使用这个插件来创建 Jenkins 管道和从设备。
|
||||
除了一般的“自动化”之外,我想单独介绍一下 Jenkins 主服务器,并讨论管理员如何利用 OpenShift 来自动化配置 Jenkins。来自 [Red Hat Container Catalog][5] 的 Jenkins 镜像已经安装了 [OpenShift-Sync plugin][6]。在 [该视频][7] 中,我们将讨论如何使用这个插件来创建 Jenkins 管道和从设备。
|
||||
|
||||
要创建 Jenkins 流水线,请创建一个类似于下面的 OpenShift BuildConfig:
|
||||
要创建 Jenkins 管道,请创建一个类似于下面的 OpenShift BuildConfig:
|
||||
|
||||
```
|
||||
apiVersion: v1
|
||||
@ -43,7 +45,7 @@ spec:
|
||||
type: JenkinsPipeline
|
||||
```
|
||||
|
||||
OpenShift-Sync 插件将注意到已经创建了带有 **jenkinsPipelineStrategy** 策略的 BuildConfig,并将其转换为 Jenkins 管道,从 Git 源指定的 Jenkins 文件中提取。也可以使用内联 Jenkinsfile,而不是从 Git 存储库中提取。有关更多信息,请参阅[文档][8]。
|
||||
OpenShift-Sync 插件将注意到已经创建了带有 `jenkinsPipelineStrategy` 策略的 BuildConfig,并将其转换为 Jenkins 管道,从 Git 源指定的 Jenkinsfile 中提取。也可以使用内联 Jenkinsfile,而不是从 Git 存储库中提取。有关更多信息,请参阅[文档][8]。
|
||||
|
||||
要创建 Jenkins 从站,请创建一个 OpenShift ImageStream,它从以下定义开始:
|
||||
|
||||
@ -55,12 +57,12 @@ metadata:
|
||||
slave-label: jenkins-slave
|
||||
labels:
|
||||
role: jenkins-slave
|
||||
…
|
||||
...
|
||||
```
|
||||
|
||||
注意在这个 ImageStream 中定义的元数据。OpenShift-Sync 插件将把带有标签 **role: jenkins-slave** 的任何ImageStream 转换为 Jenkins 从站。Jenkins 从站将以 **slave-label** 注释中的值命名。
|
||||
注意在这个 ImageStream 中定义的元数据。OpenShift-Sync 插件将把带有标签 `role: jenkins-slave` 的任何 ImageStream 转换为 Jenkins 从站。Jenkins 从站将以 `slave-label` 注释中的值命名。
|
||||
|
||||
ImageStreams 对于简单的 Jenkins 从属配置工作得很好,但是一些团队会发现有必要配置一些细节详情,比如资源限制、准备就绪和活动性探测,以及实例帽。这就是 ConfigMap 发挥作用的地方:
|
||||
ImageStreams 对于简单的 Jenkins 从属配置工作得很好,但是一些团队会发现有必要配置一些细节详情,比如资源限制、准备就绪和活动性探测,以及实例上限。这就是 ConfigMap 发挥作用的地方:
|
||||
|
||||
```
|
||||
apiVersion: v1
|
||||
@ -74,21 +76,21 @@ data:
|
||||
<Kubernetes pod template>
|
||||
```
|
||||
|
||||
注意,仍然需要角色:jenkins-slave 标签来将 ConfigMap 转换为 Jenkins slave。Kubernetes pod 模板由一长段 XML 组成,它将根据组织的喜好配置每个细节。要查看此 XML,以及有关将 ImageStreams 和 ConfigMaps 转换为 Jenkins 从属的更多信息,请参阅[文档][9]。
|
||||
注意,仍然需要角色:`jenkins-slave` 标签来将 ConfigMap 转换为 Jenkins 从站。Kubernetes pod 模板由一长段 XML 组成,它将根据组织的喜好配置每个细节。要查看此 XML,以及有关将 ImageStreams 和 ConfigMaps 转换为 Jenkins 从站的更多信息,请参阅[文档][9]。
|
||||
|
||||
请注意上面所示的三个示例,其中没有一个操作需要管理员对 Jenkins 控制台进行手动更改。通过使用 OpenShift 资源,可以简单的自动化方式配置 Jenkins。
|
||||
|
||||
### 2\. 分享就是关心
|
||||
### 2、分享就是关爱
|
||||
|
||||
第二个最佳实践是维护一个公共 CI/CD 工件的 Git 存储库。主要思想是防止团队重新发明轮子。假设您的团队需要执行到 OpenShift 环境的蓝色/绿色部署,作为管道 CD 阶段的一部分。负责编写流水线的团队成员可能不是 OpenShift 专家,也不可能具有从头开始编写此功能的能力。幸运的是,有人已经编写了一个将此功能合并到一个公共 CI/CD 存储库中的函数,因此您的团队可以使用该函数而不是花时间编写一个函数。
|
||||
第二个最佳实践是维护一个公共 CI/CD 工件的 Git 存储库。主要思想是防止团队重新发明轮子。假设您的团队需要执行到 OpenShift 环境的蓝/绿部署,作为管道 CD 阶段的一部分。负责编写管道的团队成员可能不是 OpenShift 专家,也不可能具有从头开始编写此功能的能力。幸运的是,有人已经编写了一个将此功能合并到一个公共 CI/CD 存储库中的函数,因此您的团队可以使用该函数而不是花时间编写一个函数。
|
||||
|
||||
为了更进一步,您的组织可能决定维护整个管道。您可能会发现团队正在编写具有相似功能的流水线。对于那些团队来说,使用来自公共存储库的参数化管道要比从头开始编写自己的管道更有效。
|
||||
为了更进一步,您的组织可能决定维护整个管道。您可能会发现团队正在编写具有相似功能的管道。对于那些团队来说,使用来自公共存储库的参数化管道要比从头开始编写自己的管道更有效。
|
||||
|
||||
### 3\. 少即是多
|
||||
### 3、少即是多
|
||||
|
||||
正如我在前一节中提到的,第三个也是最后一个最佳实践是参数化您的 CI/CD 管道。参数化将防止过多的管道,使您的 CI/CD 系统更容易维护。假设我有多个区域可以部署应用程序。如果没有参数化,我需要为每个区域设置单独的管道。
|
||||
|
||||
要参数化作为 OpenShift 构建配置编写的管道,请将 **env** 节添加到配置:
|
||||
要参数化一个作为 OpenShift 构建配置编写的管道,请将 `env` 节添加到配置:
|
||||
|
||||
```
|
||||
...
|
||||
@ -103,9 +105,9 @@ spec:
|
||||
type: JenkinsPipeline
|
||||
```
|
||||
|
||||
使用此配置,我可以传递 **REGION** 参数管道以将我的应用程序部署到指定区域。
|
||||
使用此配置,我可以传递 `REGION` 参数给管道以将我的应用程序部署到指定区域。
|
||||
|
||||
这有一个[视频][7]提供了一个更实质性的情况,其中参数化是必须的。一些组织决定把他们的 CI/CD 管道分割成单独的 CI 和 CD 管道,通常是因为在部署之前有一些审批过程。假设我有四个映像和三个不同的环境要部署。如果没有参数化,我需要12个 CD 管道来允许所有部署可能性。这会很快失去控制。为了使 CD 流水线的维护更容易,组织会发现将映像和环境参数化以便允许一个流水线执行多个流水线的工作会更好。
|
||||
这有一个[视频][7]提供了一个更实质性的情况,其中参数化是必须的。一些组织决定把他们的 CI/CD 管道分割成单独的 CI 和 CD 管道,通常是因为在部署之前有一些审批过程。假设我有四个镜像和三个不同的环境要部署。如果没有参数化,我需要 12 个 CD 管道来允许所有部署可能性。这会很快失去控制。为了使 CD 流水线的维护更容易,组织会发现将镜像和环境参数化以便允许一个流水线执行多个流水线的工作会更好。
|
||||
|
||||
### 总结
|
||||
|
||||
@ -120,7 +122,7 @@ via: https://opensource.com/article/18/11/best-practices-cicd
|
||||
作者:[Austin Dewey][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[ChiZelin](https://github.com/ChiZelin)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,29 +1,30 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: subject: (SMPlayer in Linux: Features, Download and Installation)
|
||||
[#]: via: (https://itsfoss.com/smplayer/)
|
||||
[#]: author: (Aquil Roshan;Abhishek Prakash https://itsfoss.com/author/aquil/)
|
||||
[#]: url: ( )
|
||||
[#]: url: (https://linux.cn/article-10365-1.html)
|
||||
|
||||
Linux 中的 SMPlayer:功能,下载和安装
|
||||
SMPlayer:增强版的媒体播放器
|
||||
======
|
||||
|
||||
当你要播放视频时,你会在[全新安装的 Ubuntu][1],或其他许多发行版中,会注意到一个消息:
|
||||
|
||||
![][2]
|
||||
默认媒体播放器没有适合的编解码器
|
||||
|
||||
这意味着系统上没有安装播放媒体的[所需编解码器][3]。现在,由于某些版权问题,某些基于 Linux 的操作系统无法在安装介质中预先打包编解码器。但是它们能让你只需点击即可下载和安装编解码器,或者你可以安装拥有所有媒体编解码器的媒体播放器。了解一下 [SMPlayer][4]。
|
||||
*默认媒体播放器没有适合的编解码器*
|
||||
|
||||
这意味着系统上没有安装播放媒体的[所需编解码器][3]。现在,由于某些版权问题,某些基于 Linux 的操作系统无法在安装介质中预先打包编解码器。但是它们能让你只需点击即可下载和安装编解码器,或者你可以安装拥有所有媒体编解码器的媒体播放器。让我们了解一下 [SMPlayer][4]。
|
||||
|
||||
### 认识 SMPlayer:适用于 Linux 的更好的媒体播放器
|
||||
|
||||
SMPlayer 是一款免费的开源媒体播放器,它基于强大的 [MPlayer][5] 媒体引擎。SMPlayer 能够播放 avi、mp4、mkv、mpeg、mov、divx、h.264 以及其他任何主要媒体格式。锦上添花的是,它也可以播放 [YouTube][6] 视频,并且无广告。
|
||||
SMPlayer 是一款自由开源媒体播放器,它基于强大的 [MPlayer][5] 媒体引擎。SMPlayer 能够播放 avi、mp4、mkv、mpeg、mov、divx、h.264 以及其他任何主要媒体格式。锦上添花的是,它也可以播放 [YouTube][6] 视频,并且无广告。
|
||||
|
||||
![SMPlayer default interface][7]
|
||||
|
||||
SMPlayer 是一个完整的媒体解决方案。它是跨平台的,因此可在所有操作系统上使用。如果你是双启动,则可以将其安装在 Windows 和 Linux 操作系统上,以便在两个系统上获得统一的体验。它还支持带触摸的可变形笔记本。
|
||||
SMPlayer 是一个完整的媒体解决方案。它是跨平台的,因此可在所有操作系统上使用。如果你是双启动系统,则可以将其安装在 Windows 和 Linux 操作系统上,以便在两个系统上获得统一的体验。它还支持带触摸的可变形笔记本。
|
||||
|
||||
你也可以在 SMPlayer 上播放 YouTube。我知道每次复制粘贴视频 URL 并在外部播放器上播放是不切实际的。但是当你观看相对较长的视频时,SMPlayer 特别有用。SMPlayer 以相当好的质量播放 YouTube 视频,我觉得比在浏览器中播放得更好。通过在 SMPlayer 上播放较长的视频,你可以远离视频中间弹出的插播广告。
|
||||
|
||||
@ -51,7 +52,7 @@ SMPlayer 应该可在所有主要 Linux 发行版的软件中心获取。你可
|
||||
sudo apt install smplayer
|
||||
```
|
||||
|
||||
或者,你可以在[这里][11]下载 Fedora、Arch Linux、OpenSUSE 和 Debian 的软件包
|
||||
或者,你可以在[这里][11]下载 Fedora、Arch Linux、OpenSUSE 和 Debian 的软件包。
|
||||
|
||||
### 总结
|
||||
|
||||
@ -66,7 +67,7 @@ via: https://itsfoss.com/smplayer/
|
||||
作者:[Aquil Roshan;Abhishek Prakash][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
@ -83,4 +84,4 @@ via: https://itsfoss.com/smplayer/
|
||||
[9]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2018/11/SMPlayer-icon-packs.jpg?fit=800%2C450&ssl=1
|
||||
[10]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2018/11/SMPlayer-theme.jpg?fit=800%2C450&ssl=1
|
||||
[11]: https://software.opensuse.org/download.html?project=home%3Asmplayerdev&package=smplayer
|
||||
[12]: https://itsfoss.com/essential-linux-applications/
|
||||
[12]: https://itsfoss.com/essential-linux-applications/
|
||||
@ -1,28 +1,30 @@
|
||||
Bash 环境变量的那些事
|
||||
======
|
||||
> 初学者可以在此教程中了解环境变量。
|
||||
|
||||

|
||||
|
||||
bash 变量,尤其是讨厌的环境变量,已经是一个老生常谈的话题了。我们也更应该对它有一个详细的了解,让它为我们所用。
|
||||
bash 变量,尤其是讨厌的*环境变量*,已经是一个老生常谈的话题了。我们也更应该对它有一个详细的了解,让它为我们所用。
|
||||
|
||||
下面就打开终端,开始吧。
|
||||
|
||||
### 环境变量
|
||||
|
||||
`HOME` 除了是你脱下帽子惬意休息的地方,同时也是 Linux 中的一个变量,它是当前用户主目录的路径:
|
||||
`HOME` (LCTT 译注:双关语)除了是你脱下帽子惬意休息的地方,同时也是 Linux 中的一个变量,它是当前用户主目录的路径:
|
||||
|
||||
```
|
||||
echo $HOME
|
||||
```
|
||||
|
||||
以上这个命令会显示当前用户的主目录路径,通常都在 `/home/` 下。
|
||||
以上这个命令会显示当前用户的主目录路径,通常都在 `/home/<your username>` 下。
|
||||
|
||||
顾名思义,一个变量的值并不是固定的。实际上,Linux 系统中每一个用户的 `HOME` 变量都是不一样的,当然你也可以这样自行更改 `HOME` 变量的值:
|
||||
顾名思义,变量的值是可以根据上下文变化的。实际上,Linux 系统中每一个用户的 `HOME` 变量都是不一样的,当然你也可以这样自行更改 `HOME` 变量的值:
|
||||
|
||||
```
|
||||
HOME=/home/<your username>/Documents
|
||||
```
|
||||
|
||||
以上这个命令将会把 `HOME` 变量设置为 `/home/<your username>/Documents` 目录。
|
||||
以上这个命令将会把 `HOME` 变量设置为你的 `Documents` 目录。
|
||||
|
||||
其中有三点需要留意:
|
||||
|
||||
@ -45,7 +47,7 @@ $ echo $PATH
|
||||
/usr/local/sbin:/usr/local/bin:/usr/bin:/usr/sbin:/bin:/sbin
|
||||
```
|
||||
|
||||
每两个目录之间使用冒号(`:`)分隔。如果某个应用程序的所在目录不在 `PATH` 变量中,那么运行的时候就需要声明应用程序的目录让 shell 能够找到。
|
||||
每两个目录之间使用冒号 `:` 分隔。如果某个应用程序的所在目录不在 `PATH` 变量中,那么运行的时候就需要声明应用程序的目录让 shell 能够找到。
|
||||
|
||||
```
|
||||
/home/<user name>/bin/my_program.sh
|
||||
@ -67,9 +69,9 @@ PATH=$PATH:$HOME/bin
|
||||
|
||||
然后 `/home/<user name>/bin/` 目录就会出现在 `PATH` 变量中了。但正如之前所说,这个变更只会在当前的 shell 生效,当前的 shell 一旦关闭,环境变量的值就又恢复原状了。
|
||||
|
||||
如果要让变更对当前用户持续生效,就不能在 shell 中直接执行对应的变更,而是应该将这些变更操作卸载每次启动 shell 时都会运行的文件当中。这个文件就是当前用户主目录中的 `.bashrc` 文件。文件名前面的点号表明这是一个隐藏文件,执行普通的 `ls` 命令是不会将这个文件显示出来的,但只要在 `ls` 命令中加入 `-a` 参数就可以看到这个文件了。
|
||||
如果要让变更对当前用户持续生效,就不能在 shell 中直接执行对应的变更,而是应该将这些变更操作写在每次启动 shell 时都会运行的文件当中。这个文件就是当前用户主目录中的 `.bashrc` 文件。文件名前面的点号表明这是一个隐藏文件,执行普通的 `ls` 命令是不会将这个文件显示出来的,但只要在 `ls` 命令中加入 `-a` 参数就可以看到这个文件了。
|
||||
|
||||
你可以使用诸如 [kate][1]、[gedit][2]、[nano][3] 或者 [vim][4] 这些文本编辑器来打开 `.bashrc` 文件(但不要用 LibreOffice Writer,它是一个文字处理软件,跟前面几个文字编辑器并不一个量级的东西)。打开 `.bashrc` 文件之后,你会看见里面放置了一些 shell 命令,是用于为当前用户设置环境的。
|
||||
你可以使用诸如 [kate][1]、[gedit][2]、[nano][3] 或者 [vim][4] 这些文本编辑器来打开 `.bashrc` 文件(但不要用 LibreOffice Writer,它是一个文字处理软件,跟前面几个文字编辑器完全不同)。打开 `.bashrc` 文件之后,你会看见里面放置了一些 shell 命令,是用于为当前用户设置环境的。
|
||||
|
||||
在文件的末尾添加新行并输入以下内容:
|
||||
|
||||
@ -97,13 +99,13 @@ source .bashrc
|
||||
new_variable="Hello"
|
||||
```
|
||||
|
||||
然后可以用一下的方式读取到已定义变量的值:
|
||||
然后可以用以下的方式读取到已定义变量的值:
|
||||
|
||||
```
|
||||
echo $new_variable
|
||||
```
|
||||
|
||||
程序的正常工作离不开各种变量,例如要将某个选项设置为 on,又或者让程序找到所需的代码库,都需要使用变量。在 bash 中运行程序的时候会生成一个子 shell,这个子 shell 和执行原程序的父 shell 并不是完全一样的,只是继承了父 shell 的部分内容,而且默认是不继承父 shell 中的变量的。因为变量默认情况下是局部变量,出于安全原因,一个 shell 中的局部变量不会被另一个 shell 读取到,即使是子 shell 也不可以。
|
||||
程序的正常工作离不开各种变量,例如要将某个选项设置为打开,又或者让程序找到所需的代码库,都需要使用变量。在 bash 中运行程序的时候会生成一个子 shell,这个子 shell 和执行原程序的父 shell 并不是完全一样的,只是继承了父 shell 的部分内容,而且默认是不继承父 shell 中的变量的。因为变量默认情况下是局部变量,出于安全原因,一个 shell 中的局部变量不会被另一个 shell 读取到,即使是子 shell 也不可以。
|
||||
|
||||
下面举一个例子。首先定义一个变量:
|
||||
|
||||
@ -198,7 +200,7 @@ via: https://www.linux.com/blog/learn/2018/12/bash-variables-environmental-and-o
|
||||
作者:[Paul Brown][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[HankChow](https://github.com/HankChow)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,11 +1,11 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: subject: (How To Fix Broken Ubuntu OS Without Reinstalling It)
|
||||
[#]: via: (https://www.ostechnix.com/how-to-fix-broken-ubuntu-os-without-reinstalling-it/)
|
||||
[#]: author: (SK https://www.ostechnix.com/author/sk/)
|
||||
[#]: url: ( )
|
||||
[#]: url: (https://linux.cn/article-10367-1.html)
|
||||
|
||||
如何不重装修复损坏的 Ubuntu 系统
|
||||
======
|
||||
@ -18,29 +18,20 @@
|
||||
|
||||
首先,尝试使用 live cd 登录并**在外部驱动器中备份数据**。以防这个方法没用,你仍然可以获取数据并重新安装系统!
|
||||
|
||||
在登录页上,按下 **CTRL+ALT+F1** 切换到 **tty1**。你可以在[**此处**][1]了解有关在 TTY 之间切换的更多信息。
|
||||
在登录页上,按下 `CTRL+ALT+F1` 切换到 tty1。你可以在[此处][1]了解有关在 TTY 之间切换的更多信息。
|
||||
|
||||
现在,逐个输入以下命令来修复损坏的 Ubuntu Linux。
|
||||
|
||||
```
|
||||
$ sudo rm /var/lib/apt/lists/lock
|
||||
|
||||
$ sudo rm /var/lib/dpkg/lock
|
||||
|
||||
$ sudo rm /var/lib/dpkg/lock-frontend
|
||||
|
||||
$ sudo dpkg --configure -a
|
||||
|
||||
$ sudo apt clean
|
||||
|
||||
$ sudo apt update --fix-missing
|
||||
|
||||
$ sudo apt install -f
|
||||
|
||||
$ sudo dpkg --configure -a
|
||||
|
||||
$ sudo apt upgrade
|
||||
|
||||
$ sudo apt dist-upgrade
|
||||
```
|
||||
|
||||
@ -52,7 +43,7 @@ $ sudo reboot
|
||||
|
||||
你现在可以像往常一样登录到你的 Ubuntu 系统。
|
||||
|
||||
我做完这些步骤后,我 Ubuntu 18.04 测试系统中的所有数据都还在,一切都之前的一样。此方法可能不适用于所有人。但是,这个小小的贴士对我有用,并且比重装节省了一些时间。如果你了解其他更好的方法,请在评论区告诉我。我也会在本指南中添加它们。
|
||||
我做完这些步骤后,我 Ubuntu 18.04 测试系统中的所有数据都还在,一切都之前的一样。此方法可能不适用于所有人。但是,这个小小的技巧对我有用,并且比重装节省了一些时间。如果你了解其他更好的方法,请在评论区告诉我。我也会在本指南中添加它们。
|
||||
|
||||
这是这些了。希望这篇文章有用。
|
||||
|
||||
@ -69,10 +60,10 @@ via: https://www.ostechnix.com/how-to-fix-broken-ubuntu-os-without-reinstalling-
|
||||
作者:[SK][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.ostechnix.com/author/sk/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.ostechnix.com/how-to-switch-between-ttys-without-using-function-keys-in-linux/
|
||||
[1]: https://www.ostechnix.com/how-to-switch-between-ttys-without-using-function-keys-in-linux/
|
||||
@ -1,8 +1,8 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-10373-1.html)
|
||||
[#]: subject: (How to Install Putty on Ubuntu and Other Linux Distributions)
|
||||
[#]: via: (https://itsfoss.com/putty-linux/)
|
||||
[#]: author: (Abhishek Prakash https://itsfoss.com/author/abhishek/)
|
||||
@ -10,11 +10,11 @@
|
||||
如何在 Ubuntu 和其他 Linux 发行版上安装 Putty
|
||||
======
|
||||
|
||||
如果我没错,[Putty][1] 可能是 Windows 最受欢迎的 SSH 客户端。
|
||||
如果我没弄错,[Putty][1] 可能是 Windows 最受欢迎的 SSH 客户端。
|
||||
|
||||
I在 IT 公司中,开发环境通常在远程 Linux 系统上,而开发人员则使用 Windows 作为本地系统。Putty 用于从 Windows 机器连接到远程 Linux 系统。
|
||||
在 IT 公司中,开发环境通常在远程 Linux 系统上,而开发人员则使用 Windows 作为本地系统。Putty 用于从 Windows 机器连接到远程 Linux 系统。
|
||||
|
||||
Putty 不仅限于 Windows。你也可以在 Linux 和 macOS 上使用此开源软件。
|
||||
Putty 不是限定于 Windows 的。你也可以在 Linux 和 macOS 上使用此开源软件。
|
||||
|
||||
但是等等!当你已经拥有“真正的” Linux 终端时,为什么要在 Linux 上使用单独的 SSH 客户端?这有几个想在 Linux 上使用 Putty 的原因。
|
||||
|
||||
@ -22,8 +22,6 @@ Putty 不仅限于 Windows。你也可以在 Linux 和 macOS 上使用此开源
|
||||
* 你发现很难手动编辑 SSH 配置文件以保存各种 SSH 会话。你更喜欢 Putty 图形化保存 SSH 连接的方式。
|
||||
* 你想通过连接到原始套接字和串口进行调试。
|
||||
|
||||
|
||||
|
||||
无论是什么原因,如果你想在 Ubuntu 或任何其他 Linux 上使用 Putty,你当然可以这样做。让我告诉你如何做到。
|
||||
|
||||
### 在 Ubuntu Linux 上安装 Putty
|
||||
@ -38,7 +36,7 @@ Putty 不仅限于 Windows。你也可以在 Linux 和 macOS 上使用此开源
|
||||
sudo add-apt-repository universe
|
||||
```
|
||||
|
||||
启用 universe 存储库后,应使用以下命令更新 Ubuntu:
|
||||
启用 universe 仓库后,应使用以下命令更新 Ubuntu:
|
||||
|
||||
```
|
||||
sudo apt update
|
||||
@ -56,13 +54,13 @@ sudo apt install putty
|
||||
|
||||
![Putty in Linux][3]
|
||||
|
||||
当你输入远程系统的[主机名][4]或 IP 地址并连接到它时,Putty 将使用你主目录中已保存的 SSH 密钥。
|
||||
当你输入远程系统的[主机名][4]或 IP 地址并连接到它时,Putty 将使用你已保存在主目录中的 SSH 密钥。
|
||||
|
||||
![Using Putty in Ubuntu Linux][5]
|
||||
|
||||
### 在其他 Linux 发行版上安装 Putty
|
||||
|
||||
[Putty 可用于 Debian][6],所以你只需要使用 apt-get 或 aptitude 来安装它。
|
||||
[Putty 可用于 Debian][6],所以你只需要使用 `apt-get` 或 `aptitude` 来安装它。
|
||||
|
||||
```
|
||||
sudo apt-get install putty
|
||||
@ -82,7 +80,7 @@ sudo pacman -S putty
|
||||
|
||||
请记住,Putty 是一款开源软件。如果你真的想要,你也可以通过源代码安装它。你可以从下面的链接获取 Putty 的源代码。
|
||||
|
||||
[下载 Putty 源代码][8]
|
||||
- [下载 Putty 源代码][8]
|
||||
|
||||
我一直喜欢原生 Linux 终端而不是像 Putty 这样的 SSH 客户端。我觉得 GNOME 终端或 [Terminator][7] 更有家的感觉。但是,在 Linux 中使用默认终端或 Putty 是个人选择。
|
||||
|
||||
@ -95,7 +93,7 @@ via: https://itsfoss.com/putty-linux/
|
||||
作者:[Abhishek Prakash][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
@ -108,4 +106,4 @@ via: https://itsfoss.com/putty-linux/
|
||||
[5]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2018/12/putty-interface-ubuntu-1.jpeg?resize=800%2C430&ssl=1
|
||||
[6]: https://packages.debian.org/jessie/putty
|
||||
[7]: https://launchpad.net/terminator
|
||||
[8]: https://www.chiark.greenend.org.uk/~sgtatham/putty/latest.html
|
||||
[8]: https://www.chiark.greenend.org.uk/~sgtatham/putty/latest.html
|
||||
@ -0,0 +1,58 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Patch into The Matrix at the Linux command line)
|
||||
[#]: via: (https://opensource.com/article/18/12/linux-toy-cmatrix)
|
||||
[#]: author: (Jason Baker https://opensource.com/users/jason-baker)
|
||||
|
||||
在命令行中步入黑客帝国
|
||||
======
|
||||
|
||||
> 使用 cmatrix 重建每个人都喜欢的 20 世纪 90 年代科幻电影中滚动代码的经典外观。
|
||||
|
||||
|
||||
|
||||
这是今天的命令行玩具日历推荐项目。如果这是你第一次访问该系列,你可能想知道什么是命令行玩具?它可以是在命令行中任何可以娱乐的东西,可以是一个游戏,一个有趣的工具,或者一个消遣的东西。
|
||||
|
||||
其中一些是经典,有些是全新的(至少对我而言),但我希望你们所有人都能在这个系列中找到你喜欢的东西。
|
||||
|
||||
在我们在接近下一年的时候,现在是回顾和期待的好时机。2019 年会为你带来什么?2019 年意味着什么?
|
||||
|
||||
我想起 2019 年将是我青少年时期最喜欢的科幻电影之一[黑客帝国][1]的二十周年纪念日,它当时让我思考了未来将会发生什么。对于像我这样的痴迷计算机小孩来说,这是一个电脑程序员通过利用自己思维的力量崛起并成为虚拟宇宙中的动作英雄的终极故事。
|
||||
|
||||
当时,对我来说没有比这部电影更具未来感了。无论是故事本身,还是迷人的特效。即使意识到它是在二十多年前拍摄的也并没有改变我的想法。
|
||||
|
||||
今天将它带回我们的命令行玩具,让我们在终端用 `cmatrix` 重建黑客帝国中那向下滚动的代码流。 `cmatrix` 很容易安装,它在 Fedora 中被打包了,所以安装它只需:
|
||||
|
||||
```
|
||||
$ dnf install cmatrix
|
||||
```
|
||||
|
||||
接着,只需在你的终端输入 `cmatrix` 即可运行。
|
||||
|
||||
|
||||
|
||||
你可以在 [GitHub][2] 上找到使用 GPL 许可的 `cmatrix` 的源代码。
|
||||
|
||||
你有特别喜欢的命令行小玩具需要我介绍的吗?这个系列要介绍的小玩具大部分已经有了落实,但还预留了几个空位置。评论留言让我知道,我会查看的。如果还有空位置,我会考虑介绍它的。如果没有,但如果我得到了一些很好的意见,我会在最后做一些有价值的提及。
|
||||
|
||||
了解一下昨天的玩具,[在 Linux 中让 Bash 提示符变得像冬天][2],还有记得明天再来!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/12/linux-toy-cmatrix
|
||||
|
||||
作者:[Jason Baker][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/jason-baker
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://en.wikipedia.org/wiki/The_Matrix
|
||||
[2]: https://github.com/abishekvashok/cmatrix
|
||||
[3]: https://opensource.com/article/18/12/linux-toy-bash-prompt
|
||||
@ -1,3 +1,5 @@
|
||||
Translating by wwhio
|
||||
|
||||
The Ruby Story
|
||||
======
|
||||
Ruby has always been one of my favorite languages, though I’ve sometimes found it hard to express why that is. The best I’ve been able to do is this musical analogy: Whereas Python feels to me like punk rock—it’s simple, predictable, but rigid—Ruby feels like jazz. Ruby gives programmers a radical freedom to express themselves, though that comes at the cost of added complexity and can lead to programmers writing programs that don’t make immediate sense to other people.
|
||||
|
||||
@ -1,3 +1,4 @@
|
||||
translated by lixinyuxx
|
||||
6 common questions about agile development practices for teams
|
||||
======
|
||||
|
||||
|
||||
@ -1,3 +1,4 @@
|
||||
translated by lixinyuxx
|
||||
5 guiding principles you should know before you design a microservice
|
||||
======
|
||||
|
||||
|
||||
@ -1,72 +0,0 @@
|
||||
Translating by wwhio
|
||||
|
||||
|
||||
The IBM 029 Card Punch
|
||||
======
|
||||
Lines of code longer than 80 characters drive me crazy. I appreciate that this is pedantic. I’ve seen people on the internet make good arguments for why the 80-character limit ought to be respected even on our modern Retina-display screens, but those arguments hardly justify the visceral hatred I feel for even that one protruding 81st character.
|
||||
|
||||
There was once a golden era in which it was basically impossible to go over the 80-character limit. The 80-character limit was a physical reality, because there was no 81st column for an 81st character to fit in. Any programmers attempting to name a function something horrendously long and awful would discover, in a moment of delicious, slow-dawning horror, that there literally isn’t room for their whole declaration.
|
||||
|
||||
This golden era was the era of punch card programming. By the 1960s, IBM’s punch cards had set the standard and the standard was that punch cards had 80 columns. The 80-column standard survived into the teletype and dumb terminal era and from there embedded itself into the nooks and crannies of our operating systems. Today, when you launch your terminal emulator and open a new window, odds are it will be 80 characters wide, even though we now have plenty of screen real estate and tend to favor longer identifiers over inscrutable nonsense like `iswcntrl()`.
|
||||
|
||||
If questions on Quora are any indication, many people have trouble imagining what it must have been like to program computers using punch cards. I will admit that for a long time I also didn’t understand how punch card programming could have worked, because it struck me as awfully labor-intensive to punch all those holes. This was a misunderstanding; programmers never punched holes in cards the same way a train conductor does. They had card punch machines (also known as key punches), which allowed them to punch holes in cards using a typewriter-style keyboard. And card punches were hardly new technology—they were around as early as the 1890s.
|
||||
|
||||
One of the most widely used card punch machines was the IBM 029. It is perhaps the best remembered card punch today.
|
||||
|
||||
![][1]
|
||||
|
||||
The IBM 029 was released in 1964 as part of IBM’s System/360 rollout. System/360 was a family of computing systems and peripherals that would go on to dominate the mainframe computing market in the late 1960s. Like many of the other System/360 machines, the 029 was big. This was an era when the distinction between computing machinery and furniture was blurry—the 029 was not something you put on a table but an entire table in itself. The 029 improved upon its predecessor, the 026, by supporting new characters like parentheses and by generally being quieter. It had cool electric blue highlights and was flat and angular whereas the 026 had a 1940s rounded, industrial look. Another of its big selling points was that it could automatically left-pad numeric fields with zeros, demonstrating that JavaScript programmers were not the first programmers too lazy to do their own left-padding.
|
||||
|
||||
But wait, you might say—IBM released a brand-new card punch in 1964? What about that photograph of the Unix gods at Bell Labs using teletype machines in, like, 1970? Weren’t card punching machines passé by the mid- to late-1960s? Well, it might surprise you to know that the 029 was available in IBM’s catalog until as late as 1984. In fact, most programmers programmed using punch cards until well into the 1970s. This doesn’t make much sense given that there were people using teletype machines during World War II. Indeed, the teletype is almost of the same vintage as the card punch. The limiting factor, it turns out, was not the availability of teletypes but the availability of computing time. What kept people from using teletypes was that teletypes assumed an interactive, “online” model of communication with the computer. Before Unix and the invention of timesharing operating systems, your interactive session with a computer would have stopped everyone else from using it, a delay potentially costing thousands of dollars. So programmers instead wrote their programs offline using card punch machines and then fed them into mainframe computers later as batch jobs. Punch cards had the added benefit of being a cheap data store in an era where cheap, reliable data storage was hard to come by. Your programs lived in stacks of cards on your shelves rather than in files on your hard drive.
|
||||
|
||||
So what was it actually like using an IBM 029 card punch? That’s hard to explain without first taking a look at the cards themselves. A typical punch card had 12 rows and 80 columns. The bottom nine rows were the digit rows, numbered one through nine. These rows had the appropriate digit printed in each column. The top three rows, called the “zone” rows, consisted of two blank rows and usually a zero row. Row 12 was at the very top of the card, followed by row 11, then rows zero through nine. This somewhat confusing ordering meant that the top edge of the card was called the 12 edge while the bottom was called the nine edge. A corner of each card was usually clipped to make it easier to keep a stack of cards all turned around the right way.
|
||||
|
||||
![][2]
|
||||
|
||||
When they were first invented, punch cards were meant to be punched with circular holes, but IBM eventually realized that they could fit more columns on a card if the holes were narrow rectangles. Different combinations of holes in a column represented different characters. For human convenience, card punches like the 029 would print each column’s character at the top of the card at the same time as punching the necessary holes. Digits were represented by one punched hole in the appropriate digit row. Alphabetical and symbolic characters were represented by a hole in a zone row and then a combination of one or two holes in the digit rows. The letter A, for example, was represented by a hole in the 12 zone row and another hole in the one row. This was an encoding of sorts, sometimes called the Hollerith code, after the original inventor of the punch card machine. The encoding allowed for only a relatively small character set; lowercase letters, for example, were not represented. Some clever engineer today might wonder why punch cards didn’t just use a binary encoding—after all, with 12 rows, you could encode over 4000 characters. The Hollerith code was used instead because it ensured that no more than three holes ever appeared in a single column. This preserved the structural integrity of the card. A binary encoding would have entailed so many holes that the card would have fallen apart.
|
||||
|
||||
Cards came in different flavors. By the 1960s, 80 columns was the standard, but those 80 columns could be used to represent different things. The basic punch card was unlabeled, but cards meant for COBOL programming, for example, divided the 80 columns into fields. On a COBOL card, the last eight columns were reserved for an identification number, which could be used to automatically sort a stack of cards if it were dropped (apparently a perennial hazard). Another column, column seven, could be used to indicate that the statement on this card was a continuation of a statement on a previous card. This meant that if you were truly desperate you could circumvent the 80-character limit, though whether a two-card statement counts as one long line or just two is unclear. FORTRAN cards were similar but had different fields. Universities often watermarked the punch cards handed out by their computing centers, while other kinds of designs were introduced for special occasions like the [1976 bicentennial][3].
|
||||
|
||||
Ultimately the cards had to be read and understood by a computer. IBM sold a System/360 peripheral called the IBM 2540 which could read up to 1000 cards per minute. The IBM 2540 ran electrical brushes across the surface of each card which made contact with a plate behind the cards wherever there was a hole. Once read, the System/360 family of computers represented the characters on each punch card using an 8-bit encoding called EBCDIC, which stood for Extended Binary Coded Decimal Interchange Code. EBCDIC was a proper binary encoding, but it still traced its roots back to the punch card via an earlier encoding called BCDIC, a 6-bit encoding which used the low four bits to represent a punch card’s digit rows and the high two bits to represent the zone rows. Punch card programmers would typically hand their cards to the actual computer operators, who would feed the cards into the IBM 2540 and then hand the printed results back to the programmer. The programmer usually didn’t see the computer at all.
|
||||
|
||||
What the programmer did see a lot of was the card punch. The 029 was not a computer, but that doesn’t mean that it wasn’t a complicated machine. The best way to understand what it was like using the 029 is to watch [this instructional video][4] made by the computing center at the University of Michigan in 1967. I’m going to do my best to summarize it here, but if you don’t watch the video you will miss out on all the wonderful clacking and whooshing.
|
||||
|
||||
The 029 was built around a U-shaped track that the punch cards traveled along. On the right-hand side, at the top of the U, was the card hopper, which you would typically load with a fresh stack of cards before using the machine. The IBM 029 worked primarily with 80-column cards, but the card hopper could accommodate smaller cards if needed. Your punch cards would start in the card hopper, travel along the line of the U, and then end up in the stacker, at the top of the U on the left-hand side. The cards would accumulate there in the order that you punched them.
|
||||
|
||||
To turn the machine on, you flipped a switch under the desk at about the height of your knees. You then pressed the “FEED” key twice to get cards loaded into the machine. The business part of the card track, the bottom of the U, was made up of three separate stations: On the right was a kind of waiting area, in the middle was the punching station, and on the left was the reading station. Pressing the “FEED” key twice loaded one card into the punching station and one card into the waiting area behind it. A column number indicator right above the punching station told you which column you were currently punching. With every keystroke, the machine would punch the requisite holes, print the appropriate character at the top of the card, and then advance the card through the punching station by one column. If you punched all 80 columns, the card would automatically be released to the reading station and a new card would be loaded into the punching station. If you wanted this to happen before you reached the 80th column, you could press the “REL” key (for “release”).
|
||||
|
||||
The printed characters made it easy to spot a mistake. But fixing a mistake, as the University of Michigan video warns, is not as easy as whiting out the printed character at the top of the card and writing in a new one. The holes are all that the computer will read. Nor is it as easy as backspacing one space and typing in a new character. The holes have already been punched in the column, after all, and cannot be unpunched. Punching more holes will only produce an invalid combination not associated with any character. The IBM 029 did have a backspace button that moved the punched card backward one column, but the button was placed on the face of the machine instead of on the keyboard. This was probably done to discourage its use, since backspacing was so seldom what the user actually wanted to do.
|
||||
|
||||
Instead, the only way to correct a mistake was scrap the incorrect card and punch a new one. This is where the reading station came in handy. Say you made a mistake in the 68th column of a card. To fix your mistake, you could carefully repunch the first 67 columns of a new card and then punch the correct character in the 68th column. Alternatively, you could release the incorrect card to the reading station, load a new card into the punching station, and hold down the “DUP” key (for duplicate) until the column number indicator reads 68. You could then correct your mistake by punching the correct character. The reading station and the “DUP” key together allowed IBM 029 operators to easily copy the contents of one card to the next. There were all sorts of reasons to do this, but correcting mistakes was the most common.
|
||||
|
||||
The “DUP” key allowed the 029’s operator to invoke the duplicate functionality manually. But the 029 could also duplicate automatically where necessary. This was particularly useful when punched cards were used to record data rather than programs. For example, you might be using each card to record information about a single undergraduate university student. On each card, you might have a field that contains the name of that student’s residence hall. Perhaps you find yourself entering data for all the students in one residence hall at one time. In that case, you’d want the 029 to automatically copy over the previous card’s residence hall field every time you reached the first column of the field.
|
||||
|
||||
Automated behavior like this could be programmed into the 029 by using the program drum. The drum sat upright in the middle of the U above the punching station. You programmed the 029 by punching holes in a card and wrapping that card around the program drum. The punched card allowed you to specify the automatic behavior you expected from the machine at each column of the card currently in the punching station. You could specify that a column should automatically be copied from the previous card, which is how an 029 operator might more quickly enter student records. You could also specify, say, that a particular field should contain numeric or alphabetic characters, or that a given field should be left blank and skipped altogether. The program drum made it much easier to punch schematized cards where certain column ranges had special meanings. There is another [“advanced” instructional video][5] produced by the University of Michigan that covers the program drum that is worth watching, provided, of course, that you have already mastered the basics.
|
||||
|
||||
Watching either of the University of Michigan videos today, what’s surprising is how easy the card punch is to operate. Correcting mistakes is tedious, but otherwise the machine seems to be less of an obstacle than I would have expected. Moving from one card to the next is so seamless that I can imagine COBOL or FORTRAN programmers forgetting that they are creating separate cards rather than one long continuous text file. On the other hand, it’s interesting to consider how card punches, even though they were only an input tool, probably limited how early programming languages evolved. Structured programming would eventually come along and encourage people to think of entire blocks of code as one unit, but I can see how punch card programming’s emphasis on each line made structured programming hard to conceive of. It’s no wonder that punch card programmers were not the ones that decided to enclose blocks with single curly braces entirely on their own lines. How wasteful that would have seemed!
|
||||
|
||||
So even though nobody programs using punch cards anymore, every programmer ought to [try it][6] at least once—if only to understand why COBOL and FORTRAN look the way they do, or how 80 characters somehow became everybody’s favorite character limit.
|
||||
|
||||
If you enjoyed this post, more like it come out every two weeks! Follow [@TwoBitHistory][7] on Twitter or subscribe to the [RSS feed][8] to make sure you know when a new post is out.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://twobithistory.org/2018/06/23/ibm-029-card-punch.html
|
||||
|
||||
作者:[Two-Bit History][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://twobithistory.org
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://twobithistory.org/images/ibm029_front.jpg
|
||||
[2]: https://twobithistory.org/images/card.png
|
||||
[3]: http://www.jkmscott.net/data/Punched%20card%20013.jpg
|
||||
[4]: https://www.youtube.com/watch?v=kaQmAybWn-w
|
||||
[5]: https://www.youtube.com/watch?v=SWD1PwNxpoU
|
||||
[6]: http://www.masswerk.at/keypunch/
|
||||
[7]: https://twitter.com/TwoBitHistory
|
||||
[8]: https://twobithistory.org/feed.xml
|
||||
@ -0,0 +1,64 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (5 resolutions for open source project maintainers)
|
||||
[#]: via: (https://opensource.com/article/18/12/resolutions-open-source-project-maintainers)
|
||||
[#]: author: (Ben Cotton https://opensource.com/users/bcotton)
|
||||
|
||||
5 resolutions for open source project maintainers
|
||||
======
|
||||
No matter how you say it, good communication is essential to strong open source communities.
|
||||

|
||||
|
||||
I'm generally not big on New Year's resolutions. I have no problem with self-improvement, of course, but I tend to anchor around other parts of the calendar. Even so, there's something about taking down this year's free calendar and replacing it with next year's that inspires some introspection.
|
||||
|
||||
In 2017, I resolved to not share articles on social media until I'd read them. I've kept to that pretty well, and I'd like to think it has made me a better citizen of the internet. For 2019, I'm thinking about resolutions to make me a better open source software maintainer.
|
||||
|
||||
Here are some resolutions I'll try to stick to on the projects where I'm a maintainer or co-maintainer.
|
||||
|
||||
### 1\. Include a code of conduct
|
||||
|
||||
Jono Bacon included "not enforcing the code of conduct" in his article "[7 mistakes you're probably making][1]." Of course, to enforce a code of conduct, you must first have a code of conduct. I plan on defaulting to the [Contributor Covenant][2], but you can use whatever you like. As with licenses, it's probably best to use one that's already written instead of writing your own. But the important thing is to find something that defines how you want your community to behave, whatever that looks like. Once it's written down and enforced, people can decide for themselves if it looks like the kind of community they want to be a part of.
|
||||
|
||||
### 2\. Make the license clear and specific
|
||||
|
||||
You know what really stinks? Unclear licenses. "This software is licensed under the GPL" with no further text doesn't tell me much. Which version of the [GPL][3]? Do I get to pick? For non-code portions of a project, "licensed under a Creative Commons license" is even worse. I love the [Creative Commons licenses][4], but there are several different licenses with significantly different rights and obligations. So, I will make it very clear which variant and version of a license applies to my projects. I will include the full text of the license in the repo and a concise note in the other files.
|
||||
|
||||
Sort of related to this is using an [OSI][5]-approved license. It's tempting to come up with a new license that says exactly what you want it to say, but good luck if you ever need to enforce it. Will it hold up? Will the people using your project understand it?
|
||||
|
||||
### 3\. Triage bug reports and questions quickly
|
||||
|
||||
Few things in technology scale as poorly as open source maintainers. Even on small projects, it can be hard to find the time to answer every question and fix every bug. But that doesn't mean I can't at least acknowledge the person. It doesn't have to be a multi-paragraph reply. Even just labeling the GitHub issue shows that I saw it. Maybe I'll get to it right away. Maybe I'll get to it a year later. But it's important for the community to see that, yes, there is still someone here.
|
||||
|
||||
### 4\. Don't push features or bug fixes without accompanying documentation
|
||||
|
||||
For as much as my open source contributions over the years have revolved around documentation, my projects don't reflect the importance I put on it. There aren't many commits I can push that don't require some form of documentation. New features should obviously be documented at (or before!) the time they're committed. But even bug fixes should get an entry in the release notes. If nothing else, a push is a good opportunity to also make a commit to improving the docs.
|
||||
|
||||
### 5\. Make it clear when I'm abandoning a project
|
||||
|
||||
I'm really bad at saying "no" to things. I told the editors I'd write one or two articles for [Opensource.com][6] and here I am almost 60 articles later. Oops. But at some point, the things that once held my interests no longer do. Maybe the project is unnecessary because its functionality got absorbed into a larger project. Maybe I'm just tired of it. But it's unfair to the community (and potentially dangerous, as the recent [event-stream malware injection][7] showed) to leave a project in limbo. Maintainers have the right to walk away whenever and for whatever reason, but it should be clear that they have.
|
||||
|
||||
Whether you're an open source maintainer or contributor, if you know other resolutions project maintainers should make, please share them in the comments.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/12/resolutions-open-source-project-maintainers
|
||||
|
||||
作者:[Ben Cotton][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/bcotton
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/article/17/8/mistakes-open-source-avoid
|
||||
[2]: https://www.contributor-covenant.org/
|
||||
[3]: https://opensource.org/licenses/gpl-license
|
||||
[4]: https://creativecommons.org/share-your-work/licensing-types-examples/
|
||||
[5]: https://opensource.org/
|
||||
[6]: http://Opensource.com
|
||||
[7]: https://arstechnica.com/information-technology/2018/11/hacker-backdoors-widely-used-open-source-software-to-steal-bitcoin/
|
||||
@ -0,0 +1,111 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (8 tips to help non-techies move to Linux)
|
||||
[#]: via: (https://opensource.com/article/18/12/help-non-techies)
|
||||
[#]: author: (Scott Nesbitt https://opensource.com/users/scottnesbitt)
|
||||
|
||||
8 tips to help non-techies move to Linux
|
||||
======
|
||||
Help your friends dump their proprietary operating systems and make the move to open source.
|
||||

|
||||
|
||||
Back in 2016, I took down the shingle for my technology coaching business. Permanently. Or so I thought.
|
||||
|
||||
Over the last 10 months, a handful of friends and acquaintances have pulled me back into that realm. How? With their desire to dump That Other Operating System™ and move to Linux.
|
||||
|
||||
This has been an interesting experience, in no small part because most of the people aren't at all technical. They know how to use a computer to do what they need to do. Beyond that, they're not interested in delving deeper. That said, they were (and are) attracted to Linux for a number of reasons—probably because I constantly prattle on about it.
|
||||
|
||||
While bringing them to the Linux side of the computing world, I learned a few things about helping non-techies move to Linux. If someone asks you to help them make the jump to Linux, these eight tips can help you.
|
||||
|
||||
### 1\. Be honest about Linux.
|
||||
|
||||
Linux is great. It's not perfect, though. It can be perplexing and sometimes frustrating for new users. It's best to prepare the person you're helping with a short pep talk.
|
||||
|
||||
What should you talk about? Briefly explain what Linux is and how it differs from other operating systems. Explain what you can and _can't_ do with it. Let them know some of the pain points they might encounter when using Linux daily.
|
||||
|
||||
If you take a bit of time to [ease them into][1] Linux and open source, the switch won't be as jarring.
|
||||
|
||||
### 2\. It's not about you.
|
||||
|
||||
It's easy to fall into what I call the _power user fallacy_ : the idea that everyone uses technology the same way you do. That's rarely, if ever, the case.
|
||||
|
||||
This isn't about you. It's not about your needs or how you use a computer. It's about the person you're helping's needs and intentions. Their needs, especially if they're not particularly technical, will be different from yours.
|
||||
|
||||
It doesn't matter if Ubuntu or Elementary or Manjaro aren't your distros of choice. It doesn't matter if you turn your nose up at window managers like GNOME, KDE, or Pantheon in favor of i3 or Ratpoison. The person you're helping might think otherwise.
|
||||
|
||||
Put your needs and prejudices aside and help them find the right Linux distribution for them. Find out what they use their computer for and tailor your recommendations for a distribution or three based on that.
|
||||
|
||||
### 3\. Not everyone's a techie.
|
||||
|
||||
And not everyone wants to be. Everyone I've helped move to Linux in the last 10 months has no interest in compiling kernels or code nor in editing and tweaking configuration files. Most of them will never crack open a terminal window. I don't expect them to be interested in doing any of that in the future, either.
|
||||
|
||||
Guess what? There's nothing wrong with that. Maybe they won't _get the most out of_ Linux (whatever that means) by not embracing their inner geeks. Not everyone will want to take on challenges of, say, installing and configuring Slackware or Arch. They need something that will work out of the box.
|
||||
|
||||
### 4\. Take stock of their hardware.
|
||||
|
||||
In an ideal world, we'd all have tricked-out, high-powered laptops or desktops with everything maxed out. Sadly, that world doesn't exist.
|
||||
|
||||
That probably includes the person you're helping move to Linux. They may have slightly (maybe more than slightly) older hardware that they're comfortable with and that works for them. Hardware that they might not be able to afford to upgrade or replace.
|
||||
|
||||
Also, remember that not everyone needs a system for heavy-duty development or gaming or audio and video production. They just need a computer for browsing the web, editing photos, running personal productivity software, and the like.
|
||||
|
||||
One person I recently helped adopt Linux had an Acer Aspire 1 laptop with 4GB of RAM and a 64GB SSD. That helped inform my recommendations, which revolved around a few lightweight Linux distributions.
|
||||
|
||||
### 5\. Help them test-drive some distros.
|
||||
|
||||
The [DistroWatch][2] database contains close to 900 Linux distributions. You should be able to find three to five Linux distributions to recommend. Make a short list of the distributions you think would be a good fit for them. Also, point them to reviews so they can get other perspectives on those distributions.
|
||||
|
||||
When it comes time to take those Linux distributions for a spin, don't just hand someone a bunch of flash drives and walk away. You might be surprised to learn that most people have never run a live Linux distribution or installed an operating system. Any operating system. Beyond plugging the flash drives in, they probably won't know what to do.
|
||||
|
||||
Instead, show them how to [create bootable flash drives][3] and set up their computer's BIOS to start from those drives. Then, let them spend some time running the distros off the flash drives. That will give them a rudimentary feel for the distros and their window managers' quirks.
|
||||
|
||||
### 6\. Walk them through an installation.
|
||||
|
||||
Running a live session with a flash drive tells someone only so much. They need to work with a Linux distribution for a couple or three weeks to really form an opinion of it and to understand its quirks and strengths.
|
||||
|
||||
There's a myth that Linux is difficult to install. That might have been true back in the mid-1990s, but today most Linux distributions are easy to install. You follow a few graphical prompts and let the software do the rest.
|
||||
|
||||
For someone who's never installed any operating system, installing Linux can be a bit daunting. They might not know what to choose when, say, they're asked which filesystem to use or whether or not to encrypt their hard disk.
|
||||
|
||||
Guide them through at least one installation. While you should let them do most of the work, be there to answer questions.
|
||||
|
||||
### 7\. Be prepared to do a couple of installs.
|
||||
|
||||
As I mentioned a paragraph or two ago, using a Linux distribution for two weeks gives someone ample time to regularly interact with it and see if it can be their daily driver. It often works out. Sometimes, though, it doesn't.
|
||||
|
||||
Remember the person with the Acer Aspire 1 laptop? She thought Xubuntu was the right distribution for her. After a few weeks of working with it, that wasn't the case. There wasn't a technical reason—Xubuntu ran smoothly on her laptop. It was just a matter of feel. Instead, she switched back to the first distro she test drove: [MX Linux][4]. She's been happily using MX ever since.
|
||||
|
||||
### 8\. Teach them to fish.
|
||||
|
||||
You can't always be there to be the guiding hand. Or to be the mechanic or plumber who can fix any problems the person encounters. You have a life, too.
|
||||
|
||||
Once they've settled on a Linux distribution, explain that you'll offer a helping hand for two or three weeks. After that, they're on their own. Don't completely abandon them. Be around to help with big problems, but let them know they'll have to learn to do things for themselves.
|
||||
|
||||
Introduce them to websites that can help them solve their problems. Point them to useful articles and books. Doing that will help make them more confident and competent users of Linux—and of computers and technology in general.
|
||||
|
||||
### Final thoughts
|
||||
|
||||
Helping someone move to Linux from another, more familiar operating system can be a challenge—a challenge for them and for you. If you take it slowly and follow the advice in this article, you can make the process smoother.
|
||||
|
||||
Do you have other tips for helping a non-techie switch to Linux? Feel free to share them by leaving a comment.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/12/help-non-techies
|
||||
|
||||
作者:[Scott Nesbitt][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/scottnesbitt
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/business/15/2/ato2014-lightning-talks-scott-nesbitt
|
||||
[2]: https://distrowatch.com
|
||||
[3]: https://opensource.com/article/18/7/getting-started-etcherio
|
||||
[4]: https://opensource.com/article/18/2/mx-linux-17-distro-beginners
|
||||
146
sources/talk/20181218 The Rise and Demise of RSS.md
Normal file
146
sources/talk/20181218 The Rise and Demise of RSS.md
Normal file
@ -0,0 +1,146 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (The Rise and Demise of RSS)
|
||||
[#]: via: (https://twobithistory.org/2018/12/18/rss.html)
|
||||
[#]: author: (Two-Bit History https://twobithistory.org)
|
||||
|
||||
The Rise and Demise of RSS
|
||||
======
|
||||
|
||||
This post was originally published on [September 16th, 2018][1]. What follows is a revision that includes additional information gleaned from interviews with Ramanathan Guha, Ian Davis, Dan Libby, and Kevin Werbach.
|
||||
|
||||
About a decade ago, the average internet user might well have heard of RSS. Really Simple Syndication, or Rich Site Summary—what the acronym stands for depends on who you ask—is a standard that websites and podcasts can use to offer a feed of content to their users, one easily understood by lots of different computer programs. Today, though RSS continues to power many applications on the web, it has become, for most people, an obscure technology.
|
||||
|
||||
The story of how this happened is really two stories. The first is a story about a broad vision for the web’s future that never quite came to fruition. The second is a story about how a collaborative effort to improve a popular standard devolved into one of the most contentious forks in the history of open-source software development.
|
||||
|
||||
In the late 1990s, in the go-go years between Netscape’s IPO and the Dot-com crash, everyone could see that the web was going to be an even bigger deal than it already was, even if they didn’t know exactly how it was going to get there. One theory was that the web was about to be revolutionized by syndication. The web, originally built to enable a simple transaction between two parties—a client fetching a document from a single host server—would be broken open by new standards that could be used to repackage and redistribute entire websites through a variety of channels. Kevin Werbach, writing for Release 1.0, a newsletter influential among investors in the 1990s, predicted that syndication “would evolve into the core model for the Internet economy, allowing businesses and individuals to retain control over their online personae while enjoying the benefits of massive scale and scope.”
|
||||
|
||||
He invited his readers to imagine a future in which fencing aficionados, rather than going directly to an “online sporting goods site” or “fencing equipment retailer,” could buy a new épée directly through e-commerce widgets embedded into their favorite website about fencing. Just like in the television world, where big networks syndicate their shows to smaller local stations, syndication on the web would allow businesses and publications to reach consumers through a multitude of intermediary sites. This would mean, as a corollary, that consumers would gain significant control over where and how they interacted with any given business or publication on the web.
|
||||
|
||||
RSS was one of the standards that promised to deliver this syndicated future. To Werbach, RSS was “the leading example of a lightweight syndication protocol.” Another contemporaneous article called RSS the first protocol to realize the potential of XML. It was going to be a way for both users and content aggregators to create their own customized channels out of everything the web had to offer. And yet, two decades later, after the rise of social media and Google’s decision to shut down Google Reader, RSS appears to be [a slowly dying technology][2], now used chiefly by podcasters, programmers with tech blogs, and the occasional journalist. Though of course some people really do still rely on RSS readers, stubbornly adding an RSS feed to your blog, even in 2018, is a political statement. That little tangerine bubble has become a wistful symbol of defiance against a centralized web increasingly controlled by a handful of corporations, a web that hardly resembles the syndicated web of Werbach’s imagining.
|
||||
|
||||
The future once looked so bright for RSS. What happened? Was its downfall inevitable, or was it precipitated by the bitter infighting that thwarted the development of a single RSS standard?
|
||||
|
||||
### Muddied Water
|
||||
|
||||
RSS was invented twice. This meant it never had an obvious owner, a state of affairs that spawned endless debate and acrimony. But it also suggests that RSS was an important idea whose time had come.
|
||||
|
||||
In 1998, Netscape was struggling to envision a future for itself. Its flagship product, the Netscape Navigator web browser—once preferred by over 80 percent of web users—was quickly losing ground to Microsoft’s Internet Explorer. So Netscape decided to compete in a new arena. In May, a team was brought together to start work on what was known internally as “Project 60.” Two months later, Netscape announced “My Netscape,” a web portal that would fight it out with other portals like Yahoo, MSN, and Excite.
|
||||
|
||||
The following year, in March, Netscape announced an addition to the My Netscape portal called the “My Netscape Network.” My Netscape users could now customize their My Netscape page so that it contained “channels” featuring the most recent headlines from sites around the web. As long as your favorite website published a special file in a format dictated by Netscape, you could add that website to your My Netscape page, typically by clicking an “Add Channel” button that participating websites were supposed to add to their interfaces. A little box containing a list of linked headlines would then appear.
|
||||
|
||||
![A My Netscape Network Channel][3] A My Netscape Network channel for Mozilla.org, as it might look to users
|
||||
about to add it to their My Netscape page.
|
||||
|
||||
The special file that participating websites had to publish was an RSS file. In the My Netscape Network announcement, Netscape explained that RSS stood for “RDF Site Summary.” This was somewhat of a misnomer. RDF, or the Resource Description Framework, is basically a grammar for describing certain properties of arbitrary resources. (See [my article about the Semantic Web][4] if that sounds really exciting to you.) In 1999, a draft specification for RDF was being considered by the World Wide Web Consortium (W3C), the web’s main standards body. Though RSS was supposed to be based on RDF, the example RSS document Netscape actually released didn’t use any RDF tags at all. In a document that accompanied the Netscape RSS specification, Dan Libby, one of the specification’s authors, explained that “in this release of MNN, Netscape has intentionally limited the complexity of the RSS format.” The specification was given the 0.90 version number, the idea being that subsequent versions would bring RSS more in line with the W3C’s XML specification and the evolving draft of the RDF specification.
|
||||
|
||||
RSS had been created by Libby and two other Netscape employees, Eckart Walther and Ramanathan Guha. According to an email to me from Guha, he and Walther cooked up RSS in the beginning with some input from Libby; after AOL bought Netscape in 1998, he and Walther left and it became Libby’s responsibility. Before Netscape, Guha had worked for Apple, where he came up with something called the Meta Content Framework. MCF was a format for representing metadata about anything from web pages to local files. Guha demonstrated its power by developing an application called [HotSauce][5] that visualized relationships between files as a network of nodes suspended in 3D space. Immediately after leaving Apple for Netscape, Guha worked with a Netscape consultant named Tim Bray, who in a post on his blog said that he and Guha eventually produced an XML-based version of MCF that in turn became the foundation for the W3C’s RDF draft. It’s no surprise, then, that Guha, Walther, and Libby were keen to build on Guha’s prior work and incorporate RDF into RSS. But Libby later wrote that the original vision for an RDF-based RSS was pared back because of time constraints and the perception that RDF was “‘too complex’ for the ‘average user.’”
|
||||
|
||||
While Netscape was trying to win eyeballs in what became known as the “portal wars,” elsewhere on the web a new phenomenon known as “weblogging” was being pioneered. One of these pioneers was Dave Winer, CEO of a company called UserLand Software, which developed early content management systems that made blogging accessible to people without deep technical fluency. Winer ran his own blog, [Scripting News][6], which today is one of the oldest blogs on the internet. More than a year before Netscape announced My Netscape Network, on December 15, 1997, Winer published a post announcing that the blog would now be available in XML as well as HTML.
|
||||
|
||||
Dave Winer’s XML format became known as the Scripting News format. It was supposedly similar to Microsoft’s Channel Definition Format (a “push technology” standard submitted to the W3C in March, 1997), but I haven’t been able to find a file in the original format to verify that claim. Like Netscape’s RSS, it structured the content of Winer’s blog so that it could be understood by other software applications. When Netscape released RSS 0.90, Winer and UserLand Software began to support both formats. But Winer believed that Netscape’s format was “woefully inadequate” and “missing the key thing web writers and readers need.” It could only represent a list of links, whereas the Scripting News format could represent a series of paragraphs, each containing one or more links.
|
||||
|
||||
In June 1999, two months after Netscape’s My Netscape Network announcement, Winer introduced a new version of the Scripting News format, called ScriptingNews 2.0b1. Winer claimed that he decided to move ahead with his own format only after trying but failing to get anyone at Netscape to care about RSS 0.90’s deficiencies. The new version of the Scripting News format added several items to the `<header>` element that brought the Scripting News format to parity with RSS. But the two formats continued to differ in that the Scripting News format, which Winer nicknamed the “fat” syndication format, could include entire paragraphs and not just links.
|
||||
|
||||
Netscape got around to releasing RSS 0.91 the very next month. The updated specification was a major about-face. RSS no longer stood for “RDF Site Summary”; it now stood for “Rich Site Summary.” All the RDF—and there was almost none anyway—was stripped out. Many of the Scripting News tags were incorporated. In the text of the new specification, Libby explained:
|
||||
|
||||
> RDF references removed. RSS was originally conceived as a metadata format providing a summary of a website. Two things have become clear: the first is that providers want more of a syndication format than a metadata format. The structure of an RDF file is very precise and must conform to the RDF data model in order to be valid. This is not easily human-understandable and can make it difficult to create useful RDF files. The second is that few tools are available for RDF generation, validation and processing. For these reasons, we have decided to go with a standard XML approach.
|
||||
|
||||
Winer was enormously pleased with RSS 0.91, calling it “even better than I thought it would be.” UserLand Software adopted it as a replacement for the existing ScriptingNews 2.0b1 format. For a while, it seemed that RSS finally had a single authoritative specification.
|
||||
|
||||
### The Great Fork
|
||||
|
||||
A year later, the RSS 0.91 specification had become woefully inadequate. There were all sorts of things people were trying to do with RSS that the specification did not address. There were other parts of the specification that seemed unnecessarily constraining—each RSS channel could only contain a maximum of 15 items, for example.
|
||||
|
||||
By that point, RSS had been adopted by several more organizations. Other than Netscape, which seems to have lost interest after RSS 0.91, the big players were Dave Winer’s UserLand Software; O’Reilly Net, which ran an RSS aggregator called Meerkat; and Moreover.com, which also ran an RSS aggregator focused on news. Via mailing list, representatives from these organizations and others regularly discussed how to improve on RSS 0.91. But there were deep disagreements about what those improvements should look like.
|
||||
|
||||
The mailing list in which most of the discussion occurred was called the Syndication mailing list. [An archive of the Syndication mailing list][7] is still available. It is an amazing historical resource. It provides a moment-by-moment account of how those deep disagreements eventually led to a political rupture of the RSS community.
|
||||
|
||||
On one side of the coming rupture was Winer. Winer was impatient to evolve RSS, but he wanted to change it only in relatively conservative ways. In June, 2000, he published his own RSS 0.91 specification on the UserLand website, meant to be a starting point for further development of RSS. It made no significant changes to the 0.91 specification published by Netscape. Winer claimed in a blog post that accompanied his specification that it was only a “cleanup” documenting how RSS was actually being used in the wild, which was needed because the Netscape specification was no longer being maintained. In the same post, he argued that RSS had succeeded so far because it was simple, and that by adding namespaces (a way to explicitly distinguish between different RSS vocabularies) or RDF back to the format—some had suggested this be done in the Syndication mailing list—it “would become vastly more complex, and IMHO, at the content provider level, would buy us almost nothing for the added complexity.” In a message to the Syndication mailing list sent around the same time, Winer suggested that these issues were important enough that they might lead him to create a fork:
|
||||
|
||||
> I’m still pondering how to move RSS forward. I definitely want ICE-like stuff in RSS2, publish and subscribe is at the top of my list, but I am going to fight tooth and nail for simplicity. I love optional elements. I don’t want to go down the namespaces and schema road, or try to make it a dialect of RDF. I understand other people want to do this, and therefore I guess we’re going to get a fork. I have my own opinion about where the other fork will lead, but I’ll keep those to myself for the moment at least.
|
||||
|
||||
Arrayed against Winer were several other people, including Rael Dornfest of O’Reilly, Ian Davis (responsible for a search startup called Calaba), and a precocious, 14-year-old Aaron Swartz. This is the same Aaron Swartz that would later co-found Reddit and become famous for his hacktivism. (In 2000, according to an email to me from Davis, his dad often accompanied him to technology meetups.) Dornfest, Davis, and Swartz all thought that RSS needed namespaces in order to accommodate the many different things everyone wanted to do with it. On another mailing list hosted by O’Reilly, Davis proposed a namespace-based module system, writing that such a system would “make RSS as extensible as we like rather than packing in new features that over-complicate the spec.” The “namespace camp” believed that RSS would soon be used for much more than the syndication of blog posts, so namespaces, rather than being a complication, were the only way to keep RSS from becoming unmanageable as it supported more and more use cases.
|
||||
|
||||
At the root of this disagreement about namespaces was a deeper disagreement about what RSS was even for. Winer had invented his Scripting News format to syndicate the posts he wrote for his blog. Netscape had released RSS as “RDF Site Summary” because it was a way of recreating a site in miniature within the My Netscape online portal. Some people felt that Netscape’s original vision should be honored. Writing to the Syndication mailing list, Davis explained his view that RSS was “originally conceived as a way of building mini sitemaps,” and that now he and others wanted to expand RSS “to encompass more types of information than simple news headlines and to cater for the new uses of RSS that have emerged over the last 12 months.” This was a sensible point to make because the goal of the Netscape RSS project in the beginning was even loftier than Davis suggests: Guha told me that he wanted to create a technology that could support not just website channels but feeds about arbitrary entities such as, for example, Madonna. Further developing RSS so that it could do this would indeed be in keeping with that original motivation. But Davis’ argument also overstates the degree to which there was a unified vision at Netscape by the time the RSS specification was published. According to Libby, who I talked to via email, there was eventually contention between a “Let’s Build the Semantic Web” group and “Let’s Make This Simple for People to Author” group even within Netscape.
|
||||
|
||||
For his part, Winer argued that Netscape’s original goals were irrelevant because his Scripting News format was in fact the first RSS and it had been meant for a very different purpose. Given that the people most involved in the development of RSS disagreed about who had created RSS and why, a fork seems to have been inevitable.
|
||||
|
||||
The fork happened after Dornfest announced a proposed RSS 1.0 specification and formed the RSS-DEV Working Group—which would include Davis, Swartz, and several others but not Winer—to get it ready for publication. In the proposed specification, RSS once again stood for “RDF Site Summary,” because RDF had been added back in to represent metadata properties of certain RSS elements. The specification acknowledged Winer by name, giving him credit for popularizing RSS through his “evangelism.” But it also argued that RSS could not be improved in the way that Winer was advocating. Just adding more elements to RSS without providing for extensibility with a module system would “sacrifice scalability.” The specification went on to define a module system for RSS based on XML namespaces.
|
||||
|
||||
Winer felt that it was “unfair” that the RSS-DEV Working Group had arrogated the “RSS 1.0” name for themselves. In another mailing list about decentralization, he wrote that he had “recently had a standard stolen by a big name,” presumably meaning O’Reilly, which had convened the RSS-DEV Working Group. Other members of the Syndication mailing list also felt that the RSS-DEV Working Group should not have used the name “RSS” without unanimous agreement from the community on how to move RSS forward. But the Working Group stuck with the name. Dan Brickley, another member of the RSS-DEV Working Group, defended this decision by arguing that “RSS 1.0 as proposed is solidly grounded in the original RSS vision, which itself had a long heritage going back to MCF (an RDF precursor) and related specs (CDF etc).” He essentially felt that the RSS 1.0 effort had a better claim to the RSS name than Winer did, since RDF had originally been a part of RSS. The RSS-DEV Working Group published a final version of their specification in December. That same month, Winer published his own improvement to RSS 0.91, which he called RSS 0.92, on UserLand’s website. RSS 0.92 made several small optional improvements to RSS, among which was the addition of the `<enclosure>` tag soon used by podcasters everywhere. RSS had officially forked.
|
||||
|
||||
The fork might have been avoided if a better effort had been made to include Winer in the RSS-DEV Working Group. He obviously belonged there. He was a prominent contributor to the Syndication mailing list and responsible for much of RSS’ popularity, as the members of the Working Group themselves acknowledged. But, as Davis wrote in an email to me, Winer “wanted control and wanted RSS to be his legacy so was reluctant to work with us.” Tim O’Reilly, founder and CEO of O’Reilly, explained in a UserLand discussion group in September, 2000 that Winer basically refused to participate:
|
||||
|
||||
> A group of people involved in RSS got together to start thinking about its future evolution. Dave was part of the group. When the consensus of the group turned in a direction he didn’t like, Dave stopped participating, and characterized it as a plot by O’Reilly to take over RSS from him, despite the fact that Rael Dornfest of O’Reilly was only one of about a dozen authors of the proposed RSS 1.0 spec, and that many of those who were part of its development had at least as long a history with RSS as Dave had.
|
||||
|
||||
To this, Winer said:
|
||||
|
||||
> I met with Dale [Dougherty] two weeks before the announcement, and he didn’t say anything about it being called RSS 1.0. I spoke on the phone with Rael the Friday before it was announced, again he didn’t say that they were calling it RSS 1.0. The first I found out about it was when it was publicly announced.
|
||||
>
|
||||
> Let me ask you a straight question. If it turns out that the plan to call the new spec “RSS 1.0” was done in private, without any heads-up or consultation, or for a chance for the Syndication list members to agree or disagree, not just me, what are you going to do?
|
||||
>
|
||||
> UserLand did a lot of work to create and popularize and support RSS. We walked away from that, and let your guys have the name. That’s the top level. If I want to do any further work in Web syndication, I have to use a different name. Why and how did that happen Tim?
|
||||
|
||||
I have not been able to find a discussion in the Syndication mailing list about using the RSS 1.0 name prior to the announcement of the RSS 1.0 proposal. Winer, in a message to me, said that he was not trying to control RSS and just wanted to use it in his products.
|
||||
|
||||
RSS would fork again in 2003, when several developers frustrated with the bickering in the RSS community sought to create an entirely new format. These developers created Atom, a format that did away with RDF but embraced XML namespaces. Atom would eventually be specified by [a proposed IETF standard][8]. After the introduction of Atom, there were three competing versions of RSS: Winer’s RSS 0.92 (updated to RSS 2.0 in 2002 and renamed “Really Simple Syndication”), the RSS-DEV Working Group’s RSS 1.0, and Atom.
|
||||
|
||||
### Decline
|
||||
|
||||
The proliferation of competing RSS specifications may have hampered RSS in other ways that I’ll discuss shortly. But it did not stop RSS from becoming enormously popular during the 2000s. By 2004, the New York Times had started offering its headlines in RSS and had written an article explaining to the layperson what RSS was and how to use it. Google Reader, the RSS aggregator ultimately used by millions, was launched in 2005. By 2013, RSS seemed popular enough that the New York Times, in its obituary for Aaron Swartz, called the technology “ubiquitous.” For a while, before a third of the planet had signed up for Facebook, RSS was simply how many people stayed abreast of news on the internet.
|
||||
|
||||
The New York Times published Swartz’ obituary in January 2013. By that point, though, RSS had actually turned a corner and was well on its way to becoming an obscure technology. Google Reader was shut down in July 2013, ostensibly because user numbers had been falling “over the years.” This prompted several articles from various outlets declaring that RSS was dead. But people had been declaring that RSS was dead for years, even before Google Reader’s shuttering. Steve Gillmor, writing for TechCrunch in May 2009, advised that “it’s time to get completely off RSS and switch to Twitter” because “RSS just doesn’t cut it anymore.” He pointed out that Twitter was basically a better RSS feed, since it could show you what people thought about an article in addition to the article itself. It allowed you to follow people and not just channels. Gillmor told his readers that it was time to let RSS recede into the background. He ended his article with a verse from Bob Dylan’s “Forever Young.”
|
||||
|
||||
Today, RSS is not dead. But neither is it anywhere near as popular as it once was. Lots of people have offered explanations for why RSS lost its broad appeal. Perhaps the most persuasive explanation is exactly the one offered by Gillmor in 2009. Social networks, just like RSS, provide a feed featuring all the latest news on the internet. Social networks took over from RSS because they were simply better feeds. They also provide more benefits to the companies that own them. Some people have accused Google, for example, of shutting down Google Reader in order to encourage people to use Google+. Google might have been able to monetize Google+ in a way that it could never have monetized Google Reader. Marco Arment, the creator of Instapaper, wrote on his blog in 2013:
|
||||
|
||||
> Google Reader is just the latest casualty of the war that Facebook started, seemingly accidentally: the battle to own everything. While Google did technically “own” Reader and could make some use of the huge amount of news and attention data flowing through it, it conflicted with their far more important Google+ strategy: they need everyone reading and sharing everything through Google+ so they can compete with Facebook for ad-targeting data, ad dollars, growth, and relevance.
|
||||
|
||||
So both users and technology companies realized that they got more out of using social networks than they did out of RSS.
|
||||
|
||||
Another theory is that RSS was always too geeky for regular people. Even the New York Times, which seems to have been eager to adopt RSS and promote it to its audience, complained in 2006 that RSS is a “not particularly user friendly” acronym coined by “computer geeks.” Before the RSS icon was designed in 2004, websites like the New York Times linked to their RSS feeds using little orange boxes labeled “XML,” which can only have been intimidating. The label was perfectly accurate though, because back then clicking the link would take a hapless user to a page full of XML. [This great tweet][9] captures the essence of this explanation for RSS’ demise. Regular people never felt comfortable using RSS; it hadn’t really been designed as a consumer-facing technology and involved too many hurdles; people jumped ship as soon as something better came along.
|
||||
|
||||
RSS might have been able to overcome some of these limitations if it had been further developed. Maybe RSS could have been extended somehow so that friends subscribed to the same channel could syndicate their thoughts about an article to each other. Maybe browser support could have been improved. But whereas a company like Facebook was able to “move fast and break things,” the RSS developer community was stuck trying to achieve consensus. When they failed to agree on a single standard, effort that could have gone into improving RSS was instead squandered on duplicating work that had already been done. Davis told me, for example, that Atom would not have been necessary if the members of the Syndication mailing list had been able to compromise and collaborate, and “all that cleanup work could have been put into RSS to strengthen it.” So if we are asking ourselves why RSS is no longer popular, a good first-order explanation is that social networks supplanted it. If we ask ourselves why social networks were able to supplant it, then the answer may be that the people trying to make RSS succeed faced a problem much harder than, say, building Facebook. As Dornfest wrote to the Syndication mailing list at one point, “currently it’s the politics far more than the serialization that’s far from simple.”
|
||||
|
||||
So today we are left with centralized silos of information. Even so, the syndicated web that Werbach foresaw in 1999 has been realized, just not in the way he thought it would be. After all, The Onion is a publication that relies on syndication through Facebook and Twitter the same way that Seinfeld relied on syndication to rake in millions after the end of its original run. I asked Werbach what he thinks about this and he more or less agrees. He told me that RSS, on one level, was clearly a failure, because it isn’t now “a technology that is really the core of the whole blogging world or content world or world of assembling different elements of things into sites.” But, on another level, “the whole social media revolution is partly about the ability to aggregate different content and resources” in a manner reminiscent of RSS and his original vision for a syndicated web. To Werbach, “it’s the legacy of RSS, even if it’s not built on RSS.”
|
||||
|
||||
Unfortunately, syndication on the modern web still only happens through one of a very small number of channels, meaning that none of us “retain control over our online personae” the way that Werbach imagined we would. One reason this happened is garden-variety corporate rapaciousness—RSS, an open format, didn’t give technology companies the control over data and eyeballs that they needed to sell ads, so they did not support it. But the more mundane reason is that centralized silos are just easier to design than common standards. Consensus is difficult to achieve and it takes time, but without consensus spurned developers will go off and create competing standards. The lesson here may be that if we want to see a better, more open web, we have to get better at not screwing each other over.
|
||||
|
||||
If you enjoyed this post, more like it come out every four weeks! Follow [@TwoBitHistory][10] on Twitter or subscribe to the [RSS feed][11] to make sure you know when a new post is out.
|
||||
|
||||
Previously on TwoBitHistory…
|
||||
|
||||
> I've long wondered if the Unix commands on my Macbook are built from the same code that they were built from 20 or 30 years ago. The answer, it turns, out, is "kinda"!
|
||||
>
|
||||
> My latest post, on how the implementation of cat has changed over the years:<https://t.co/dHizjK50ES>
|
||||
>
|
||||
> — TwoBitHistory (@TwoBitHistory) [November 12, 2018][12]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://twobithistory.org/2018/12/18/rss.html
|
||||
|
||||
作者:[Two-Bit History][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://twobithistory.org
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://twobithistory.org/2018/09/16/the-rise-and-demise-of-rss.html
|
||||
[2]: https://trends.google.com/trends/explore?date=all&geo=US&q=rss
|
||||
[3]: https://twobithistory.org/images/mnn-channel.gif
|
||||
[4]: https://twobithistory.org/2018/05/27/semantic-web.html
|
||||
[5]: http://web.archive.org/web/19970703020212/http://mcf.research.apple.com:80/hs/screen_shot.html
|
||||
[6]: http://scripting.com
|
||||
[7]: https://groups.yahoo.com/neo/groups/syndication/info
|
||||
[8]: https://tools.ietf.org/html/rfc4287
|
||||
[9]: https://twitter.com/mgsiegler/status/311992206716203008
|
||||
[10]: https://twitter.com/TwoBitHistory
|
||||
[11]: https://twobithistory.org/feed.xml
|
||||
[12]: https://twitter.com/TwoBitHistory/status/1062114484209311746?ref_src=twsrc%5Etfw
|
||||
@ -1,3 +1,4 @@
|
||||
zjon is translating
|
||||
7 Best eBook Readers for Linux
|
||||
======
|
||||
**Brief:** In this article, we are covering some of the best ebook readers for Linux. These apps give a better reading experience and some will even help in managing your ebooks.
|
||||
|
||||
@ -1,237 +0,0 @@
|
||||
translating by lixinyuxx
|
||||
|
||||
My personal Email setup - Notmuch, mbsync, postfix and dovecot
|
||||
======
|
||||
I've been using personal email setup for quite long and have not documented it anywhere. Recently when I changed my laptop (a post is pending about it) I got lost trying to recreate my local mail setup. So this post is a self documentation so that I don't have to struggle again to get it right.
|
||||
|
||||
### Server Side
|
||||
|
||||
I run my own mail server and I use postfix as SMTP server and Dovecot for the IMAP purpose. I'm not going into detail of setting those up as my setup was mostly done by using scripts created by Jonas for Redpill infrastructure. What redpill is?. (In jonas's own words)
|
||||
|
||||
> <jonas> Redpill is a concept - a way to setup Debian hosts to collaborate across organisations <jonas> I develop the concept, and use it for the first ever Redpill network-of-networks redpill.dk, involving my own network (jones.dk), my main client's network (homebase.dk), a network in Germany including Skolelinux Germany (free-owl.de), and Vasudev's network (copyninja.info)
|
||||
|
||||
Along with that I have a dovecot sieve filtering to classify on high level mails into various folders depending on from where they originate. All the rules live in the ~/dovecot.sieve file under every account which has a mail address.
|
||||
|
||||
Again I'm not going into detail of how to set these things up, as its not goal of my this post.
|
||||
|
||||
### On my Laptop
|
||||
|
||||
On my laptop I've following 4 parts setup
|
||||
|
||||
1. Mail syncing : Done using mbsync command
|
||||
2. Classification: Done using notmuch
|
||||
3. Reading: Done using notmuch-emacs
|
||||
4. Mail sending: Done using postfix running as relay server and SMTP client.
|
||||
|
||||
|
||||
|
||||
### Mail Syncing
|
||||
|
||||
Mail syncing is done using mbsync tool, I was previously user of offlineimap and recently switched to mbsync as I felt it more lighter and simpler to configure than offlineimap. mbsync command is provided by package isync.
|
||||
|
||||
Configuration file is ~/.mbsyncrc. Below is my sample content with some private things redacted.
|
||||
|
||||
```
|
||||
IMAPAccount copyninja
|
||||
Host imap.copyninja.info
|
||||
User vasudev
|
||||
PassCmd "gpg -q --for-your-eyes-only --no-tty --exit-on-status-write-error --batch --passphrase-file ~/path/to/passphrase.txt -d ~/path/to/mailpass.gpg"
|
||||
SSLType IMAPS
|
||||
SSLVersion TLSv1.2
|
||||
CertificateFile /etc/ssl/certs/ca-certificates.crt
|
||||
|
||||
|
||||
IMAPAccount gmail-kamathvasudev
|
||||
Host imap.gmail.com
|
||||
User kamathvasudev@gmail.com
|
||||
PassCmd "gpg -q --for-your-eyes-only --no-tty --exit-on-status-write-error --batch --passphrase-file ~/path/to/passphrase.txt -d ~/path/to/mailpass.gpg"
|
||||
SSLType IMAPS
|
||||
SSLVersion TLSv1.2
|
||||
CertificateFile /etc/ssl/certs/ca-certificates.crt
|
||||
|
||||
IMAPStore copyninja-remote
|
||||
Account copyninja
|
||||
|
||||
IMAPStore gmail-kamathvasudev-remote
|
||||
Account gmail-kamathvasudev
|
||||
|
||||
MaildirStore copyninja-local
|
||||
Path ~/Mail/vasudev-copyninja.info/
|
||||
Inbox ~/Mail/vasudev-copyninja.info/INBOX
|
||||
|
||||
MaildirStore gmail-kamathvasudev-local
|
||||
Path ~/Mail/Gmail-1/
|
||||
Inbox ~/Mail/Gmail-1/INBOX
|
||||
|
||||
Channel copyninja
|
||||
Master :copyninja-remote:
|
||||
Slave :copyninja-local:
|
||||
Patterns *
|
||||
Create Both
|
||||
SyncState *
|
||||
Sync All
|
||||
|
||||
Channel gmail-kamathvasudev
|
||||
Master :gmail-kamathvasudev-remote:
|
||||
Slave :gmail-kamathvasudev-local:
|
||||
# Exclude everything under the internal [Gmail] folder, except the interesting folders
|
||||
Patterns * ![Gmail]*
|
||||
Create Both
|
||||
SyncState *
|
||||
Sync All
|
||||
```
|
||||
|
||||
Explanation for some interesting part in above configuration. One is the PassCmd which allows you to provide shell command to obtain the password for the account. This avoids filling in the password in configuration file. I'm using symmetric encryption with gpg and storing password some where on my disk. Which is of course just safe guarded by Unix ACL.
|
||||
|
||||
I actually wanted to use my public key to encrypt the file but unlocking the file when script is run in background or via systemd looks difficult (or looked nearly impossible). If you have better suggestion I'm all ears :-).
|
||||
|
||||
Next instruction part is Patterns. This allows you to selectively sync mail from your mail server. This was really helpful for me to exclude all crappy [Gmail]/ folders.
|
||||
|
||||
### Mail Classification
|
||||
|
||||
Once mail is locally on your device, we need a way to read the mails easily in a mail reader. My original setup was serving synced Maildir using local dovecot instance and read it in Gnus. This setup was bit of a over kill with all server software setups but inability of Gnus to not cope well with Maildir format this was best way to do it. This setup also has a disadvantage, that is searching a mail quickly when you have huge pile of mail to go through. This is where notmuch comes into picture.
|
||||
|
||||
notmuch allows me to easily index through Gigabytes of my mail archives and get what I need very easily. I've created a small script which combines executing of mbsync and notmuch execution. I tag mails based on the Maildirs which are actually created on server side using dovecot sieve. Below is my full shell script which is doing task of syncing classification and deleting of spams.
|
||||
|
||||
```
|
||||
#!/bin/sh
|
||||
|
||||
MBSYNC=$(pgrep mbsync)
|
||||
NOTMUCH=$(pgrep notmuch)
|
||||
|
||||
if [ -n "$MBSYNC" -o -n "$NOTMUCH" ]; then
|
||||
echo "Already running one instance of mail-sync. Exiting..."
|
||||
exit 0
|
||||
fi
|
||||
|
||||
echo "Deleting messages tagged as *deleted*"
|
||||
notmuch search --format=text0 --output=files tag:deleted |xargs -0 --no-run-if-empty rm -v
|
||||
|
||||
echo "Moving spam to Spam folder"
|
||||
notmuch search --format=text0 --output=files tag:Spam and \
|
||||
to:vasudev@copyninja.info | \
|
||||
xargs -0 -I {} --no-run-if-empty mv -v {} ~/Mail/vasudev-copyninja.info/Spam/cur
|
||||
notmuch search --format=text0 --output=files tag:Spam and
|
||||
to:vasudev-debian@copyninja.info | \
|
||||
xargs -0 -I {} --no-run-if-empty mv -v {} ~/Mail/vasudev-copyninja.info/Spam/cur
|
||||
|
||||
|
||||
MDIR="vasudev-copyninja.info vasudev-debian Gmail-1"
|
||||
mbsync -Va
|
||||
notmuch new
|
||||
|
||||
for mdir in $MDIR; do
|
||||
echo "Processing $mdir"
|
||||
for fdir in $(ls -d /home/vasudev/Mail/$mdir/*); do
|
||||
if [ $(basename $fdir) != "INBOX" ]; then
|
||||
echo "Tagging for $(basename $fdir)"
|
||||
notmuch tag +$(basename $fdir) -inbox -- folder:$mdir/$(basename $fdir)
|
||||
fi
|
||||
done
|
||||
done
|
||||
```
|
||||
|
||||
So before running mbsync I search for all mails tagged as deleted and delete them from system. Next I look for mails tagged as Spam on both my accounts and move it to Spam folder. Yeah you got it right these are mails escaping the spam filter and landing in my inbox and personally marked as Spam.
|
||||
|
||||
After running mbsync I tag mails based on their folder (searching string folder:). This allows me easily get contents of lets say a mailing list without remembering the list address.
|
||||
|
||||
### Reading Mails
|
||||
|
||||
Now that we have synced and classified mail its time to setup the reading part. I use notmuch-emacs interface to read the mails. I use Spacemacs flavor of emacs so I took some time to write down the a private layer which brings together all my keybindings and classification in one place and does not clutter my entire .spacemacs file. You can find the code for my private layer in [notmuch-emacs-layer repository][1]
|
||||
|
||||
### Sending Mails
|
||||
|
||||
Well its not sufficient that if we can read mails, we need to be able to reply to mail. And this was the slightly tricky part where I recently got lost and had to write this post so that I don't forget it again. (And of course don't have to refer some outdated posts on web).
|
||||
|
||||
My setup to send mails is using postfix as SMTP client with my own SMTP server as relayhost for it. The problem of relaying is it's not for the hosts with dynamic IP. There are couple of ways to allow hosts with dynamic IP to use relay servers, one is put the IP address from where mail will originate into my_network or second use SASL authentication.
|
||||
|
||||
My preferred way is use of SASL authentication. For this I first had to create a separate account one for each machine which is going to relay the mails to my main server. Idea is to not use my primary account for SASL authentication. (Originally I was using primary account, but Jonas gave this idea of account per road runner).
|
||||
```
|
||||
adduser <hostname>_relay
|
||||
|
||||
```
|
||||
|
||||
Here replace <hostname> with name of your laptop/desktop or whatever you are using. Now we need to adjust postfix to act as relaying server. So add following lines to postfix configuration
|
||||
```
|
||||
# SASL authentication
|
||||
smtp_sasl_auth_enable = yes
|
||||
smtp_tls_security_level = encrypt
|
||||
smtp_sasl_tls_security_options = noanonymous
|
||||
relayhost = [smtp.copyninja.info]:submission
|
||||
smtp_sasl_password_maps = hash:/etc/postfix/sasl_passwd
|
||||
```
|
||||
|
||||
So here relayhost is the server name which your postfix instance will be using to relay mails forward into internet. :submission part tells postfix to forward mail on to port 587 (secure). smtp_sasl_tls_security_options is set to disallow anonymous connection. This is must so that relay server trusts your mobile host and agrees to forward the mail for you.
|
||||
|
||||
/etc/postfix/sasl_passwd is the file where you need to store password for account to be used for SASL authentication with server. Put following content into it.
|
||||
```
|
||||
[smtp.example.com]:submission user:password
|
||||
|
||||
```
|
||||
|
||||
Replace smtp.example.com with your SMTP server name which you have put in relayhost configuration. Replace user with <hostname>_relay user you created and its password.
|
||||
|
||||
To secure the sasl_passwd file and create a hash of it for postfix use following command.
|
||||
```
|
||||
chown root:root /etc/postfix/sasl_passwd
|
||||
chmod 0600 /etc/postfix/sasl_passwd
|
||||
postmap /etc/postfix/sasl_passwd
|
||||
```
|
||||
|
||||
The last command will create /etc/postfix/sasl_passwd.db file which is hash of your file /etc/postfix/sasl_passwd with same owner and permission. Now reload the postfix and check if mail makes out of your system using mail command.
|
||||
|
||||
### Bonus Part
|
||||
|
||||
Well since I've a script created above bringing together mail syncing and classification. I went ahead and created a systemd timer to periodically sync mails in the background. In my case every 10 minutes. Below is mailsync.timer file.
|
||||
```
|
||||
[Unit]
|
||||
Description=Check Mail Every 10 minutes
|
||||
RefuseManualStart=no
|
||||
RefuseManualStop=no
|
||||
|
||||
[Timer]
|
||||
Persistent=false
|
||||
OnBootSec=5min
|
||||
OnUnitActiveSec=10min
|
||||
Unit=mailsync.service
|
||||
|
||||
[Install]
|
||||
WantedBy=default.target
|
||||
```
|
||||
|
||||
Below is mailsync.service which is needed by mailsync.timer to execute our scripts.
|
||||
|
||||
```
|
||||
[Unit]
|
||||
Description=Check Mail
|
||||
RefuseManualStart=no
|
||||
RefuseManualStop=yes
|
||||
|
||||
[Service]
|
||||
Type=oneshot
|
||||
ExecStart=/usr/local/bin/mail-sync
|
||||
StandardOutput=syslog
|
||||
StandardError=syslog
|
||||
```
|
||||
|
||||
Put these files under /etc/systemd/user and run below command to enable them.
|
||||
```
|
||||
systemctl enable --user mailsync.timer
|
||||
systemctl enable --user mailsync.service
|
||||
systemctl start --user mailsync.timer
|
||||
```
|
||||
|
||||
So that's how I've sync and send mail from my system. I came to know about afew from Jonas Smedegaard who also proof read this post. So next step I will try to improve my notmuch configuration using afew and of course a post will follow after that :-).
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://copyninja.info/blog/email_setup.html
|
||||
|
||||
作者:[copyninja][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://copyninja.info
|
||||
[1]:https://source.copyninja.info/notmuch-emacs-layer.git/
|
||||
@ -1,113 +0,0 @@
|
||||
translating by lixinyuxx
|
||||
|
||||
27 open solutions to everything in education
|
||||
======
|
||||

|
||||
|
||||
Openness (from open source software, to open hardware, to open principles) is changing the paradigm of education. So, to celebrate all that's gone on this year, I collected 27 of the best articles published on Opensource.com in 2017 on the subject. I divided them into broad themes, rather than ordering them by popularity. And, if these 27 stories don't satisfy your appetite for information about open source in education, check out our companion article on how [education is leveraging Raspberry Pi and Linux][30].
|
||||
|
||||
### Open is better for everyone
|
||||
|
||||
1. [Book review: 'OPEN' explores broad cultural implications of openness][1]: Scott Nesbitt reviews David Price's book OPEN, which explores the idea that "open" isn't just a technological shift, rather it's "how we'll work, live, and learn in the future."
|
||||
|
||||
2. [Jump-start your career with open source skills][2]: VM (Vicky) Brasseur points out how to get ahead in the workforce by learning open source. This advice isn't just for programmers; designers, writers, marketers, and other creative professionals are also essential to the success of open source.
|
||||
|
||||
3. [A graduate degree could springboard you into an open source job][3]: Citing research that shows that Linux skills lead to higher pay, Joshua Pearce makes the case that open source proficiency and a graduate degree are an unbeatable career combination.
|
||||
|
||||
4. [These 3 practices revolutionized Penn Manor's school culture][4]: Charlie Reisinger shows us how open practices are creating a more inclusive, agile, and open culture in a Pennsylvania school district. Charlie says it's not just about saving money; the district also gains from "open leadership principles that foster innovation among teachers and students, help to better engage the community, and create a more vibrant and inclusive learning community."
|
||||
|
||||
5. [15 ways to empower students with open source tools][5]: I write how open source gives students the freedom to explore, tinker, and learn, whether they're learning basic digital literacy or expanding on those skills with fun projects.
|
||||
|
||||
6. [Developer opportunities to code for good][6]: Open source is often the backbone of socially beneficial projects. As Ahn Bui, vice president of Benetech Labs, states in this interview: "Establishing open data standards is an integral step in breaking down data silos. Those open standards will provide the foundation for interoperability and in turn, translate to more organizations building together, often more cost effectively. The ultimate goal is to serve more people at the same cost or even less."
|
||||
|
||||
### Open education resources for remixing and reusing
|
||||
|
||||
1. [Can academic faculty members teach with Wikipedia?][7] LiAnna Davis, director of programs for Wiki Ed, discusses how open educational resources (OERs), such as Wiki Ed, are providing high-quality and affordable open source learning resources as classroom teaching tools.
|
||||
|
||||
2. [Are textbooks in or out? The state of open educational resources][8]: Cable Green, director of open education for Creative Commons, shares how the face of education is changing in higher education and what Creative Commons is doing to facilitate it.
|
||||
|
||||
3. [School systems desperate for standards-aligned curricula find hope][9]: Karen Vaites, community evangelist and chief marketing officer of Open Up Resources, talks about the nonprofit organization's efforts to provide open, standards-aligned curricula for K-12 schools.
|
||||
|
||||
4. [How the University of Hawaii is solving today's higher ed problems][10]: Billy Meinke, educational technologist at the University of Hawaii at Manoa, says that transitioning to OER in college courses will "empower faculty to take control of what content they teach with, which we expect will result in their saving students money."
|
||||
|
||||
5. [How open courses are slashing the cost of higher education][11]: Saylor Academy's director of education Devon Ritter reports how Saylor is building its college credit-eligible courses on openly licensed content, with the goal of making higher education affordable and accessible to more people.
|
||||
|
||||
6. [Open educational resources movement gains speed][12]: Alexis Clifton, executive director of the State University of New York OER Services, describes how New York's US$ 8 million investment is spurring growth in open education and making college more affordable.
|
||||
|
||||
7. [Open project collaboration from elementary to university classrooms][13]: Aria F. Chernik from Duke University explores OSPRI (Open Source Pedagogy Research and Innovation), a collaboration between Duke and Red Hat that's building a 21st-century, preK-12 learning ecosystem that is open by design.
|
||||
|
||||
8. [Perma.cc stops scholarly link rot][14]: Virginia Tech's Phillip Young writes about Perma.cc, a solution to "link rot," which is the high probability that hyperlinks in academic papers will disappear or change over time.
|
||||
|
||||
9. [Open education: How students save money by creating open textbooks][15]: OER pioneer Robin DeRosa talks about "the freedom that the openly licensed textbook introduced, and the overarching idea that education and learning should be contextualized in inclusive ecosystems that enhance the public good."
|
||||
|
||||
### Open source tools in the classroom
|
||||
|
||||
1. [How an open source board game is saving the planet][16]: Joshua Pearce writes about Save the Planet, a board game that empowers students to solve environmental problems while having fun and contributing to the maker community.
|
||||
|
||||
2. [A new Android app for teaching kids how to read][17]: Michael Hall talks about Phoenicia, a children's literacy app he developed after his son was diagnosed with autism, the value of coding for good, and why user testing matters more than you think.
|
||||
|
||||
3. [8 open source Android apps for education][18]: Joshua Allen Holm challenges us to use our smartphones as learning tools by recommending eight open source apps from the F-Droid repository to try.
|
||||
|
||||
4. [3 open source alternatives to MATLAB][19]: Jason Baker's update to his 2016 survey of open source mathematical computing software presents alternatives to MATLAB, the expensive, proprietary solution nearly ubiquitous in mathematics, physical sciences, engineering, and economics.
|
||||
|
||||
5. [What does SVG have to do with teaching kids to code?][20] Retired engineer Jay Nick talks about how he uses art as a creative way to introduce students to coding. He volunteers in schools, using Scalable Vector Graphics (SVG) to teach an approach to coding that combines principles of mathematics and art.
|
||||
|
||||
6. [5 myths busted: Using open source in higher education][21]: Kyle Conway, who holds a PhD in fine arts from Texas Tech, shares his experience using open source tools in a world ruled by proprietary solutions. Kyle says there's a bias against using open source in disciplines outside of computer science: "Many people think non-technical students can't use Linux, and they make a lot of assumptions about people who use it in their advanced degree programs. … Well, it is possible, and I'm proof."
|
||||
|
||||
7. [A list of open source tools for college][22]: Aaron Cocker outlines the open source tools (including presentation, backup, and programming software) he uses while working on his undergraduate degree in computer science.
|
||||
|
||||
8. [5 great KDE apps to help you study][23]: Zsolt Szakács offers five KDE applications that help anyone who wants to learn new skills or cultivate existing ones.
|
||||
|
||||
### Coding in the classroom
|
||||
|
||||
1. [How to get the next generation coding early][24]: Bryson Payne says we need to teach kids to code before high school: By ninth grade 80% of girls and 60% of boys have already self-selected out of a STEM career. But it's not only about jobs and closing the IT skills gap, he suggests. "Teaching a young person to code could be the single most life-changing skill you can give them. And it's not just a career-enhancer. Coding is about problem-solving, it's about creativity, and more importantly, it's about empowerment."
|
||||
|
||||
2. [Kids can't code without computers][25]: Patrick Masson introduces the FLOSS Desktops for Kids program, which teaches students at underserved schools to repurpose older computers with open source software, such as Linux, LibreOffice, and GIMP. Not only is the program breathing new life into broken or decommissioned hardware, it's also giving students important skills that may translate into future careers.
|
||||
|
||||
3. [Is Scratch today like the Logo of the '80s for teaching kids to code?][26] Anderson Silva offers suggestions for using [Scratch][27] to spark kids' interest in programming, just as LOGO did when he started using it in the 1980s.
|
||||
|
||||
4. [Learn Android development with this drag-and-drop framework][28]: Eric Eslinger describes App Inventor, a programming framework for building Android applications using a visual blocks language (similar to Scratch or [Snap][29]).
|
||||
|
||||
Throughout the year we learned that there is an open solution to everything in education, and I expect this theme to continue in 2018 and beyond. Are there open education topics you'd like Opensource.com to cover in the coming year? If so, please share your ideas in the comments.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/1/best-open-education
|
||||
|
||||
作者:[Don Watkins][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://opensource.com/users/don-watkins
|
||||
[1]:https://opensource.com/article/17/7/book-review-open
|
||||
[2]:https://opensource.com/article/17/8/jump-start-your-career
|
||||
[3]:https://opensource.com/article/17/1/grad-school-open-source-academic-lab
|
||||
[4]:https://opensource.com/article/17/7/open-school-leadership
|
||||
[5]:https://opensource.com/article/17/7/empower-students-open-source-tools
|
||||
[6]:https://opensource.com/article/17/3/interview-anh-bui-benetech-labs
|
||||
[7]:https://opensource.com/article/17/1/Wiki-Education-Foundation
|
||||
[8]:https://opensource.com/article/17/2/future-textbooks-cable-green-creative-commons
|
||||
[9]:https://opensource.com/article/17/1/open-up-resources
|
||||
[10]:https://opensource.com/article/17/2/interview-education-billy-meinke
|
||||
[11]:https://opensource.com/article/17/7/college-alternatives
|
||||
[12]:https://opensource.com/article/17/10/open-educational-resources-alexis-clifton
|
||||
[13]:https://opensource.com/article/17/3/education-should-be-open-design
|
||||
[14]:https://opensource.com/article/17/9/stop-link-rot-permacc
|
||||
[15]:https://opensource.com/article/17/11/creating-open-textbooks
|
||||
[16]:https://opensource.com/article/17/7/save-planet-board-game
|
||||
[17]:https://opensource.com/article/17/4/phoenicia-education-software
|
||||
[18]:https://opensource.com/article/17/8/8-open-source-android-apps-education
|
||||
[19]:https://opensource.com/alternatives/matlab
|
||||
[20]:https://opensource.com/article/17/5/coding-scalable-vector-graphics-make-steam
|
||||
[21]:https://opensource.com/article/17/5/how-linux-higher-education
|
||||
[22]:https://opensource.com/article/17/6/open-source-tools-university-student
|
||||
[23]:https://opensource.com/article/17/6/kde-education-software
|
||||
[24]:https://opensource.com/article/17/8/teach-kid-code-change-life
|
||||
[25]:https://opensource.com/article/17/9/floss-desktops-kids
|
||||
[26]:https://opensource.com/article/17/3/logo-scratch-teach-programming-kids
|
||||
[27]:https://scratch.mit.edu/
|
||||
[28]:https://opensource.com/article/17/8/app-inventor-android-app-development
|
||||
[29]:http://snap.berkeley.edu/
|
||||
[30]:https://opensource.com/article/17/12/best-opensourcecom-linux-and-raspberry-pi-education
|
||||
@ -1,180 +0,0 @@
|
||||
robsean translating
|
||||
Graphics and music tools for game development
|
||||
======
|
||||
|
||||

|
||||
|
||||
In early October, our club, [Geeks and Gadgets][1] from Marshall University, participated in the inaugural [Open Jam][2], a game jam that celebrated the best of open source tools. Game jams are events where participants work as teams to develop computer games for fun. Jams tend to be very short--only three days long--and very exhausting. Opensource.com [announced][3] Open Jam in late August, and more than [three dozen games][4] were entered into the competition.
|
||||
|
||||
Our club likes to create and use open source software in our projects, so Open Jam was naturally the jam we wanted to participate in. Our submission was an experimental game called [Mark My Words][5]. We used a variety of free and open source (FOSS) tools to develop it; in this article we'll discuss some of the tools we used and potential stumbling blocks to be aware of.
|
||||
|
||||
### Audio tools
|
||||
|
||||
#### MilkyTracker
|
||||
|
||||
[MilkyTracker][6] is one of the best software packages available for composing old-style video game music. It is an example of a [music tracker][7], a powerful MOD and XM file creator with a characteristic grid-based pattern editor. We used it to compose most of the musical pieces in our game. One of the great things about this program is that it consumed much less disk space and RAM than most of our other tools. Even so, MilkyTracker is still extremely powerful.
|
||||
|
||||
|
||||
|
||||
The user interface took a while to get used to, so here are some pointers for any musician who wants to try out MilkyTracker:
|
||||
|
||||
* Go to Config > Misc. and set the edit mode control style to "MilkyTracker." This will give you modern keyboard shortcuts for almost everything
|
||||
* Undo with Ctrl+Z
|
||||
* Redo with Ctrl+Y
|
||||
* Toggle pattern-edit mode with the Spacebar
|
||||
* Delete the previous note with the Backspace key
|
||||
* Insert a row with the Insert key
|
||||
* By default, a note will continue playing until it is replaced on that channel. You can end a note explicitly by inserting a KeyOff note with the backquote (`) key
|
||||
* You will have to create or find samples before you can start composing. We recommend finding [Creative Commons][8] licensed samples at websites such as [Freesound][9] or [ccMixter][10]
|
||||
|
||||
|
||||
|
||||
In addition, keep the [MilkyTracker documentation page][11] handy. It contains links to numerous tutorials and manuals. A good starting point is the [MilkyTracker Guide][12] on the project's wiki.
|
||||
|
||||
#### LMMS
|
||||
|
||||
Two of our musicians used the versatile and modern music creation tool [LMMS][13]. It comes with a library of cool samples and effects, plus a variety of flexible plugins for generating unique sounds. The learning curve for LMMS was surprisingly low, in part due to the nice beat/bassline editor.
|
||||
|
||||
|
||||
|
||||
We have one suggestion for musicians trying out LMMS: Use the plugins. For [chiptune][14]-style music, we recommend [sfxr][15], [BitInvader][16], and [FreeBoy][17]. For other styles, [ZynAddSubFX][18] is a good choice. It comes with a wide range of synthesized instruments that can be altered however you see fit.
|
||||
|
||||
### Graphics tools
|
||||
|
||||
#### Tiled
|
||||
|
||||
[Tiled][19] is a popular tilemap editor in open source game development. We used it to assemble consistent, retro-looking backgrounds for our in-game scenes.
|
||||
|
||||
|
||||
|
||||
Tiled can export maps as XML, JSON, or as flattened images. It is stable and cross-platform.
|
||||
|
||||
One of Tiled's features, which we did not use during the jam, allows you to define and place arbitrary game objects, such as coins and powerups, onto the map. All you have to do is load the object's graphics as a tileset, then place them using Insert Tile.
|
||||
|
||||
Overall, Tiled is a stellar piece of software that we recommend for any project that needs a map editor.
|
||||
|
||||
#### Piskel
|
||||
|
||||
[Piskel][20] is a pixel art editor whose source code is licensed under the [Apache License, Version 2.0][21]. We used Piskel for almost all our graphical assets during the jam, and we will certainly be using it in future projects as well.
|
||||
|
||||
Two features of Piskel that helped us immensely during the jam are onion skin and spritesheet exporting.
|
||||
|
||||
##### Onion skin
|
||||
|
||||
The onion skin feature will make Piskel show a ghostly overlay of the previous and next frames of your animation as you edit, like this:
|
||||
|
||||
|
||||
|
||||
Onion skin is handy because it serves as a drawing guide and helps you maintain consistent shapes and volumes on your characters throughout the animation process. To enable it, just click the onion-shaped icon underneath the preview window on the top-right of the screen.
|
||||
|
||||
|
||||
|
||||
##### Spritesheet exporting
|
||||
|
||||
Piskel's ability to export animations as a spritesheet was also very helpful. A spritesheet is a single raster image that contains all the frames of an animation. For example, here is a spritesheet we exported from Piskel:
|
||||
|
||||

|
||||
|
||||
The spritesheet consists of two frames. One frame is in the top half of the image and the other frame is in the bottom half of the image. Spritesheets greatly simplify a game's code by enabling an entire animation to be loaded from a single file. Here is an animated version of the above spritesheet:
|
||||
|
||||

|
||||
|
||||
##### Unpiskel.py
|
||||
|
||||
There were several times during the jam when we wanted to batch convert Piskel files into PNGs. Since the Piskel file format is based on JSON, we wrote a small GPLv3-licensed Python script called [unpiskel.py][22] to do the conversion.
|
||||
|
||||
It is invoked like this:
|
||||
```
|
||||
|
||||
|
||||
python unpiskel.py input.piskel
|
||||
```
|
||||
|
||||
The script will extract the PNG data frames and layers from a Piskel file (here `input.piskel`) and store them in their own files. The files follow the pattern `NAME_XX_YY.png` where `NAME` is the truncated name of the Piskel file, `XX` is the frame number, and `YY` is the layer number.
|
||||
|
||||
Because the script can be invoked from a shell, it can be used on a whole list of files.
|
||||
```
|
||||
for f in *.piskel; do python unpiskel.py "$f"; done
|
||||
```
|
||||
|
||||
### Python, Pygame, and cx_Freeze
|
||||
|
||||
#### Python and Pygame
|
||||
|
||||
We used the [Python][23] language to make our game. It is a scripting language that is commonly used for text processing and desktop app development. It can also be used for game development, as projects like [Angry Drunken Dwarves][24] and [Ren'Py][25] have shown. Both of these projects use a Python library called [Pygame][26] to display graphics and produce sound, so we decided to use this library in Open Jam, too.
|
||||
|
||||
Pygame turned out to be both stable and featureful, and it was great for the arcade-style game we were creating. The library's speed was fast enough at low resolutions, but its CPU-only rendering starts to slow down at higher resolutions. This is because Pygame does not use hardware-accelerated rendering. However, the infrastructure is there for developers to take full advantage of OpenGL.
|
||||
|
||||
If you're looking for a good 2D game programming library, Pygame is one to keep your eye on. Its website has [a good tutorial][27] to get started. Be sure to check it out!
|
||||
|
||||
#### cx_Freeze
|
||||
|
||||
Prepping our game for distribution was interesting. We knew that Windows users were unlikely to have a Python installation, and asking them to install it would have been too much. On top of that, they would have had to also install Pygame, which is not an intuitive task on Windows.
|
||||
|
||||
One thing was clear: We had to put our game into a more convenient form. Many of the other Open Jam participants used the proprietary game engine Unity, which enabled their games to be played in the web browser. This made them extremely convenient to play. Convenience was one thing our game didn't have even a sliver of. But, thanks to a vibrant Python ecosystem, we had options. Tools exist to help Python programmers prepare their programs for distribution on Windows. The two that we considered were [cx_Freeze][28] and [Pygame2exe][29] (which uses [py2exe][30]). We decided on cx_Freeze because it was cross-platform.
|
||||
|
||||
In cx_Freeze, you can pack a single-script game for distribution just by running a command like this in the shell:
|
||||
```
|
||||
cxfreeze main.py --target-dir dist
|
||||
```
|
||||
|
||||
This invocation of `cxfreeze` will take your script (here `main.py`) and the Python interpreter on your system and bundle them up into the `dist` directory. Once this is done, all you have to do is manually copy your game's data files into the `dist` directory. You will find that the `dist` directory contains an executable file that can be run to start your game.
|
||||
|
||||
There is a more involved way to use cx_Freeze that allows you to automate the copying of data files, but we found the straightforward invocation of `cxfreeze` to be good enough for our needs. Thanks to this tool, we made our game a little more convenient to play.
|
||||
|
||||
### Celebrating open source
|
||||
|
||||
Open Jam is important because it celebrates the open source model of software development. This is an opportunity to analyze the current state of open source tools and what we need to work on in the future. Game jams are perhaps the best time for game devs to try to push their tools to the limit, to learn what must be improved for the good of future game devs.
|
||||
|
||||
Open source tools enable people to explore their creativity without compromising their freedom and without investing money upfront. Although we might not become professional game developers, we were still able to get a small taste of it with our short, experimental game called [Mark My Words][5]. It is a linguistically themed game that depicts the evolution of a fictional writing system throughout its history. There were many other delightful submissions to Open Jam, and they are all worth checking out. Really, [go look][31]!
|
||||
|
||||
Before closing, we would like to thank all the [club members who participated][32] and made this experience truly worthwhile. We would also like to thank [Michael Clayton][33], [Jared Sprague][34], and [Opensource.com][35] for hosting Open Jam. It was a blast.
|
||||
|
||||
Now, we have some questions for readers. Are you a FOSS game developer? What are your tools of choice? Be sure to leave a comment below!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/1/graphics-music-tools-game-dev
|
||||
|
||||
作者:[Charlie Murphy][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://opensource.com/users/rsg167
|
||||
[1]:http://mugeeks.org/
|
||||
[2]:https://itch.io/jam/open-jam-1
|
||||
[3]:https://opensource.com/article/17/8/open-jam-announcement
|
||||
[4]:https://opensource.com/article/17/11/open-jam
|
||||
[5]:https://mugeeksalpha.itch.io/mark-omy-words
|
||||
[6]:http://milkytracker.titandemo.org/
|
||||
[7]:https://en.wikipedia.org/wiki/Music_tracker
|
||||
[8]:https://creativecommons.org/
|
||||
[9]:https://freesound.org/
|
||||
[10]:http://ccmixter.org/view/media/home
|
||||
[11]:http://milkytracker.titandemo.org/documentation/
|
||||
[12]:https://github.com/milkytracker/MilkyTracker/wiki/MilkyTracker-Guide
|
||||
[13]:https://lmms.io/
|
||||
[14]:https://en.wikipedia.org/wiki/Chiptune
|
||||
[15]:https://github.com/grimfang4/sfxr
|
||||
[16]:https://lmms.io/wiki/index.php?title=BitInvader
|
||||
[17]:https://lmms.io/wiki/index.php?title=FreeBoy
|
||||
[18]:http://zynaddsubfx.sourceforge.net/
|
||||
[19]:http://www.mapeditor.org/
|
||||
[20]:https://www.piskelapp.com/
|
||||
[21]:https://github.com/piskelapp/piskel/blob/master/LICENSE
|
||||
[22]:https://raw.githubusercontent.com/MUGeeksandGadgets/MarkMyWords/master/tools/unpiskel.py
|
||||
[23]:https://www.python.org/
|
||||
[24]:https://www.sacredchao.net/~piman/angrydd/
|
||||
[25]:https://renpy.org/
|
||||
[26]:https://www.Pygame.org/
|
||||
[27]:http://Pygame.org/docs/tut/PygameIntro.html
|
||||
[28]:https://anthony-tuininga.github.io/cx_Freeze/
|
||||
[29]:https://Pygame.org/wiki/Pygame2exe
|
||||
[30]:http://www.py2exe.org/
|
||||
[31]:https://itch.io/jam/open-jam-1/entries
|
||||
[32]:https://github.com/MUGeeksandGadgets/MarkMyWords/blob/3e1e8aed12ebe13acccf0d87b06d4f3bd124b9db/README.md#credits
|
||||
[33]:https://twitter.com/mwcz
|
||||
[34]:https://twitter.com/caramelcode
|
||||
[35]:https://opensource.com/
|
||||
@ -1,167 +0,0 @@
|
||||
Protecting Code Integrity with PGP — Part 4: Moving Your Master Key to Offline Storage
|
||||
======
|
||||
|
||||

|
||||
In this tutorial series, we're providing practical guidelines for using PGP. You can catch up on previous articles here:
|
||||
|
||||
[Part 1: Basic Concepts and Tools][1]
|
||||
|
||||
[Part 2: Generating Your Master Key][2]
|
||||
|
||||
[Part 3: Generating PGP Subkeys][3]
|
||||
|
||||
Here in part 4, we continue the series with a look at how and why to move your master key from your home directory to offline storage. Let's get started.
|
||||
|
||||
### Checklist
|
||||
|
||||
* Prepare encrypted detachable storage (ESSENTIAL)
|
||||
|
||||
* Back up your GnuPG directory (ESSENTIAL)
|
||||
|
||||
* Remove the master key from your home directory (NICE)
|
||||
|
||||
* Remove the revocation certificate from your home directory (NICE)
|
||||
|
||||
|
||||
|
||||
|
||||
#### Considerations
|
||||
|
||||
Why would you want to remove your master [C] key from your home directory? This is generally done to prevent your master key from being stolen or accidentally leaked. Private keys are tasty targets for malicious actors -- we know this from several successful malware attacks that scanned users' home directories and uploaded any private key content found there.
|
||||
|
||||
It would be very damaging for any developer to have their PGP keys stolen -- in the Free Software world, this is often tantamount to identity theft. Removing private keys from your home directory helps protect you from such events.
|
||||
|
||||
##### Back up your GnuPG directory
|
||||
|
||||
**!!!Do not skip this step!!!**
|
||||
|
||||
It is important to have a readily available backup of your PGP keys should you need to recover them (this is different from the disaster-level preparedness we did with paperkey).
|
||||
|
||||
##### Prepare detachable encrypted storage
|
||||
|
||||
Start by getting a small USB "thumb" drive (preferably two!) that you will use for backup purposes. You will first need to encrypt them:
|
||||
|
||||
For the encryption passphrase, you can use the same one as on your master key.
|
||||
|
||||
##### Back up your GnuPG directory
|
||||
|
||||
Once the encryption process is over, re-insert the USB drive and make sure it gets properly mounted. Find out the full mount point of the device, for example by running the mount command (under Linux, external media usually gets mounted under /media/disk, under Mac it's /Volumes).
|
||||
|
||||
Once you know the full mount path, copy your entire GnuPG directory there:
|
||||
```
|
||||
$ cp -rp ~/.gnupg [/media/disk/name]/gnupg-backup
|
||||
|
||||
```
|
||||
|
||||
(Note: If you get any Operation not supported on socket errors, those are benign and you can ignore them.)
|
||||
|
||||
You should now test to make sure everything still works:
|
||||
```
|
||||
$ gpg --homedir=[/media/disk/name]/gnupg-backup --list-key [fpr]
|
||||
|
||||
```
|
||||
|
||||
If you don't get any errors, then you should be good to go. Unmount the USB drive and distinctly label it, so you don't blow it away next time you need to use a random USB drive. Then, put in a safe place -- but not too far away, because you'll need to use it every now and again for things like editing identities, adding or revoking subkeys, or signing other people's keys.
|
||||
|
||||
##### Remove the master key
|
||||
|
||||
The files in our home directory are not as well protected as we like to think. They can be leaked or stolen via many different means:
|
||||
|
||||
* By accident when making quick homedir copies to set up a new workstation
|
||||
|
||||
* By systems administrator negligence or malice
|
||||
|
||||
* Via poorly secured backups
|
||||
|
||||
* Via malware in desktop apps (browsers, pdf viewers, etc)
|
||||
|
||||
* Via coercion when crossing international borders
|
||||
|
||||
|
||||
|
||||
|
||||
Protecting your key with a good passphrase greatly helps reduce the risk of any of the above, but passphrases can be discovered via keyloggers, shoulder-surfing, or any number of other means. For this reason, the recommended setup is to remove your master key from your home directory and store it on offline storage.
|
||||
|
||||
###### Removing your master key
|
||||
|
||||
Please see the previous section and make sure you have backed up your GnuPG directory in its entirety. What we are about to do will render your key useless if you do not have a usable backup!
|
||||
|
||||
First, identify the keygrip of your master key:
|
||||
```
|
||||
$ gpg --with-keygrip --list-key [fpr]
|
||||
|
||||
```
|
||||
|
||||
The output will be something like this:
|
||||
```
|
||||
pub rsa4096 2017-12-06 [C] [expires: 2019-12-06]
|
||||
111122223333444455556666AAAABBBBCCCCDDDD
|
||||
Keygrip = AAAA999988887777666655554444333322221111
|
||||
uid [ultimate] Alice Engineer <alice@example.org>
|
||||
uid [ultimate] Alice Engineer <allie@example.net>
|
||||
sub rsa2048 2017-12-06 [E]
|
||||
Keygrip = BBBB999988887777666655554444333322221111
|
||||
sub rsa2048 2017-12-06 [S]
|
||||
Keygrip = CCCC999988887777666655554444333322221111
|
||||
|
||||
```
|
||||
|
||||
Find the keygrip entry that is beneath the pub line (right under the master key fingerprint). This will correspond directly to a file in your home .gnupg directory:
|
||||
```
|
||||
$ cd ~/.gnupg/private-keys-v1.d
|
||||
$ ls
|
||||
AAAA999988887777666655554444333322221111.key
|
||||
BBBB999988887777666655554444333322221111.key
|
||||
CCCC999988887777666655554444333322221111.key
|
||||
|
||||
```
|
||||
|
||||
All you have to do is simply remove the .key file that corresponds to the master keygrip:
|
||||
```
|
||||
$ cd ~/.gnupg/private-keys-v1.d
|
||||
$ rm AAAA999988887777666655554444333322221111.key
|
||||
|
||||
```
|
||||
|
||||
Now, if you issue the --list-secret-keys command, it will show that the master key is missing (the # indicates it is not available):
|
||||
```
|
||||
$ gpg --list-secret-keys
|
||||
sec# rsa4096 2017-12-06 [C] [expires: 2019-12-06]
|
||||
111122223333444455556666AAAABBBBCCCCDDDD
|
||||
uid [ultimate] Alice Engineer <alice@example.org>
|
||||
uid [ultimate] Alice Engineer <allie@example.net>
|
||||
ssb rsa2048 2017-12-06 [E]
|
||||
ssb rsa2048 2017-12-06 [S]
|
||||
|
||||
```
|
||||
|
||||
##### Remove the revocation certificate
|
||||
|
||||
Another file you should remove (but keep in backups) is the revocation certificate that was automatically created with your master key. A revocation certificate allows someone to permanently mark your key as revoked, meaning it can no longer be used or trusted for any purpose. You would normally use it to revoke a key that, for some reason, you can no longer control -- for example, if you had lost the key passphrase.
|
||||
|
||||
Just as with the master key, if a revocation certificate leaks into malicious hands, it can be used to destroy your developer digital identity, so it's better to remove it from your home directory.
|
||||
```
|
||||
cd ~/.gnupg/openpgp-revocs.d
|
||||
rm [fpr].rev
|
||||
|
||||
```
|
||||
|
||||
Next time, you'll learn how to secure your subkeys as well. Stay tuned.
|
||||
|
||||
Learn more about Linux through the free ["Introduction to Linux" ][4]course from The Linux Foundation and edX.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.linux.com/blog/learn/pgp/2018/3/protecting-code-integrity-pgp-part-4-moving-your-master-key-offline-storage
|
||||
|
||||
作者:[Konstantin Ryabitsev][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://www.linux.com/users/mricon
|
||||
[1]:https://www.linux.com/blog/learn/2018/2/protecting-code-integrity-pgp-part-1-basic-pgp-concepts-and-tools
|
||||
[2]:https://www.linux.com/blog/learn/pgp/2018/2/protecting-code-integrity-pgp-part-2-generating-and-protecting-your-master-pgp-key
|
||||
[3]:https://www.linux.com/blog/learn/pgp/2018/2/protecting-code-integrity-pgp-part-3-generating-pgp-subkeys
|
||||
[4]:https://training.linuxfoundation.org/linux-courses/system-administration-training/introduction-to-linux
|
||||
@ -1,303 +0,0 @@
|
||||
Protecting Code Integrity with PGP — Part 5: Moving Subkeys to a Hardware Device
|
||||
======
|
||||
|
||||

|
||||
|
||||
In this tutorial series, we're providing practical guidelines for using PGP. If you missed the previous article, you can catch up with the links below. But, in this article, we'll continue our discussion about securing your keys and look at some tips for moving your subkeys to a specialized hardware device.
|
||||
|
||||
[Part 1: Basic Concepts and Tools][1]
|
||||
|
||||
[Part 2: Generating Your Master Key][2]
|
||||
|
||||
[Part 3: Generating PGP Subkeys][3]
|
||||
|
||||
[Part 4: Moving Your Master Key to Offline Storage][4]
|
||||
|
||||
### Checklist
|
||||
|
||||
* Get a GnuPG-compatible hardware device (NICE)
|
||||
|
||||
* Configure the device to work with GnuPG (NICE)
|
||||
|
||||
* Set the user and admin PINs (NICE)
|
||||
|
||||
* Move your subkeys to the device (NICE)
|
||||
|
||||
|
||||
|
||||
|
||||
### Considerations
|
||||
|
||||
Even though the master key is now safe from being leaked or stolen, the subkeys are still in your home directory. Anyone who manages to get their hands on those will be able to decrypt your communication or fake your signatures (if they know the passphrase). Furthermore, each time a GnuPG operation is performed, the keys are loaded into system memory and can be stolen from there by sufficiently advanced malware (think Meltdown and Spectre).
|
||||
|
||||
The best way to completely protect your keys is to move them to a specialized hardware device that is capable of smartcard operations.
|
||||
|
||||
#### The benefits of smartcards
|
||||
|
||||
A smartcard contains a cryptographic chip that is capable of storing private keys and performing crypto operations directly on the card itself. Because the key contents never leave the smartcard, the operating system of the computer into which you plug in the hardware device is not able to retrieve the private keys themselves. This is very different from the encrypted USB storage device we used earlier for backup purposes -- while that USB device is plugged in and decrypted, the operating system is still able to access the private key contents. Using external encrypted USB media is not a substitute to having a smartcard-capable device.
|
||||
|
||||
Some other benefits of smartcards:
|
||||
|
||||
* They are relatively cheap and easy to obtain
|
||||
|
||||
* They are small and easy to carry with you
|
||||
|
||||
* They can be used with multiple devices
|
||||
|
||||
* Many of them are tamper-resistant (depends on manufacturer)
|
||||
|
||||
|
||||
|
||||
|
||||
#### Available smartcard devices
|
||||
|
||||
Smartcards started out embedded into actual wallet-sized cards, which earned them their name. You can still buy and use GnuPG-capable smartcards, and they remain one of the cheapest available devices you can get. However, actual smartcards have one important downside: they require a smartcard reader, and very few laptops come with one.
|
||||
|
||||
For this reason, manufacturers have started providing small USB devices, the size of a USB thumb drive or smaller, that either have the microsim-sized smartcard pre-inserted, or that simply implement the smartcard protocol features on the internal chip. Here are a few recommendations:
|
||||
|
||||
* [Nitrokey Start][5]: Open hardware and Free Software: one of the cheapest options for GnuPG use, but with fewest extra security features
|
||||
|
||||
* [Nitrokey Pro][6]: Similar to the Nitrokey Start, but is tamper-resistant and offers more security features (but not U2F, see the Fido U2F section of the guide)
|
||||
|
||||
* [Yubikey 4][7]: Proprietary hardware and software, but cheaper than Nitrokey Pro and comes available in the USB-C form that is more useful with newer laptops; also offers additional security features such as U2F
|
||||
|
||||
|
||||
|
||||
|
||||
Our recommendation is to pick a device that is capable of both smartcard functionality and U2F, which, at the time of writing, means a Yubikey 4.
|
||||
|
||||
#### Configuring your smartcard device
|
||||
|
||||
Your smartcard device should Just Work (TM) the moment you plug it into any modern Linux or Mac workstation. You can verify it by running:
|
||||
```
|
||||
$ gpg --card-status
|
||||
|
||||
```
|
||||
|
||||
If you didn't get an error, but a full listing of the card details, then you are good to go. Unfortunately, troubleshooting all possible reasons why things may not be working for you is way beyond the scope of this guide. If you are having trouble getting the card to work with GnuPG, please seek support via your operating system's usual support channels.
|
||||
|
||||
##### PINs don't have to be numbers
|
||||
|
||||
Note, that despite having the name "PIN" (and implying that it must be a "number"), neither the user PIN nor the admin PIN on the card need to be numbers.
|
||||
|
||||
Your device will probably have default user and admin PINs set up when it arrives. For Yubikeys, these are 123456 and 12345678, respectively. If those don't work for you, please check any accompanying documentation that came with your device.
|
||||
|
||||
##### Quick setup
|
||||
|
||||
To configure your smartcard, you will need to use the GnuPG menu system, as there are no convenient command-line switches:
|
||||
```
|
||||
$ gpg --card-edit
|
||||
[...omitted...]
|
||||
gpg/card> admin
|
||||
Admin commands are allowed
|
||||
gpg/card> passwd
|
||||
|
||||
```
|
||||
|
||||
You should set the user PIN (1), Admin PIN (3), and the Reset Code (4). Please make sure to record and store these in a safe place -- especially the Admin PIN and the Reset Code (which allows you to completely wipe the smartcard). You so rarely need to use the Admin PIN, that you will inevitably forget what it is if you do not record it.
|
||||
|
||||
Getting back to the main card menu, you can also set other values (such as name, sex, login data, etc), but it's not necessary and will additionally leak information about your smartcard should you lose it.
|
||||
|
||||
#### Moving the subkeys to your smartcard
|
||||
|
||||
Exit the card menu (using "q") and save all changes. Next, let's move your subkeys onto the smartcard. You will need both your PGP key passphrase and the admin PIN of the card for most operations. Remember, that [fpr] stands for the full 40-character fingerprint of your key.
|
||||
```
|
||||
$ gpg --edit-key [fpr]
|
||||
|
||||
Secret subkeys are available.
|
||||
|
||||
pub rsa4096/AAAABBBBCCCCDDDD
|
||||
created: 2017-12-07 expires: 2019-12-07 usage: C
|
||||
trust: ultimate validity: ultimate
|
||||
ssb rsa2048/1111222233334444
|
||||
created: 2017-12-07 expires: never usage: E
|
||||
ssb rsa2048/5555666677778888
|
||||
created: 2017-12-07 expires: never usage: S
|
||||
[ultimate] (1). Alice Engineer <alice@example.org>
|
||||
[ultimate] (2) Alice Engineer <allie@example.net>
|
||||
|
||||
gpg>
|
||||
|
||||
```
|
||||
|
||||
Using --edit-key puts us into the menu mode again, and you will notice that the key listing is a little different. From here on, all commands are done from inside this menu mode, as indicated by gpg>.
|
||||
|
||||
First, let's select the key we'll be putting onto the card -- you do this by typing key 1 (it's the first one in the listing, our [E] subkey):
|
||||
```
|
||||
gpg> key 1
|
||||
|
||||
```
|
||||
|
||||
The output should be subtly different:
|
||||
```
|
||||
pub rsa4096/AAAABBBBCCCCDDDD
|
||||
created: 2017-12-07 expires: 2019-12-07 usage: C
|
||||
trust: ultimate validity: ultimate
|
||||
ssb* rsa2048/1111222233334444
|
||||
created: 2017-12-07 expires: never usage: E
|
||||
ssb rsa2048/5555666677778888
|
||||
created: 2017-12-07 expires: never usage: S
|
||||
[ultimate] (1). Alice Engineer <alice@example.org>
|
||||
[ultimate] (2) Alice Engineer <allie@example.net>
|
||||
|
||||
```
|
||||
|
||||
Notice the * that is next to the ssb line corresponding to the key -- it indicates that the key is currently "selected." It works as a toggle, meaning that if you type key 1 again, the * will disappear and the key will not be selected any more.
|
||||
|
||||
Now, let's move that key onto the smartcard:
|
||||
```
|
||||
gpg> keytocard
|
||||
Please select where to store the key:
|
||||
(2) Encryption key
|
||||
Your selection? 2
|
||||
|
||||
```
|
||||
|
||||
Since it's our [E] key, it makes sense to put it into the Encryption slot. When you submit your selection, you will be prompted first for your PGP key passphrase, and then for the admin PIN. If the command returns without an error, your key has been moved.
|
||||
|
||||
**Important:** Now type key 1 again to unselect the first key, and key 2 to select the [S] key:
|
||||
```
|
||||
gpg> key 1
|
||||
gpg> key 2
|
||||
gpg> keytocard
|
||||
Please select where to store the key:
|
||||
(1) Signature key
|
||||
(3) Authentication key
|
||||
Your selection? 1
|
||||
|
||||
```
|
||||
|
||||
You can use the [S] key both for Signature and Authentication, but we want to make sure it's in the Signature slot, so choose (1). Once again, if your command returns without an error, then the operation was successful.
|
||||
|
||||
Finally, if you created an [A] key, you can move it to the card as well, making sure first to unselect key 2. Once you're done, choose "q":
|
||||
```
|
||||
gpg> q
|
||||
Save changes? (y/N) y
|
||||
|
||||
```
|
||||
|
||||
Saving the changes will delete the keys you moved to the card from your home directory (but it's okay, because we have them in our backups should we need to do this again for a replacement smartcard).
|
||||
|
||||
##### Verifying that the keys were moved
|
||||
|
||||
If you perform --list-secret-keys now, you will see a subtle difference in the output:
|
||||
```
|
||||
$ gpg --list-secret-keys
|
||||
sec# rsa4096 2017-12-06 [C] [expires: 2019-12-06]
|
||||
111122223333444455556666AAAABBBBCCCCDDDD
|
||||
uid [ultimate] Alice Engineer <alice@example.org>
|
||||
uid [ultimate] Alice Engineer <allie@example.net>
|
||||
ssb> rsa2048 2017-12-06 [E]
|
||||
ssb> rsa2048 2017-12-06 [S]
|
||||
|
||||
```
|
||||
|
||||
The > in the ssb> output indicates that the subkey is only available on the smartcard. If you go back into your secret keys directory and look at the contents there, you will notice that the .key files there have been replaced with stubs:
|
||||
```
|
||||
$ cd ~/.gnupg/private-keys-v1.d
|
||||
$ strings *.key
|
||||
|
||||
```
|
||||
|
||||
The output should contain shadowed-private-key to indicate that these files are only stubs and the actual content is on the smartcard.
|
||||
|
||||
#### Verifying that the smartcard is functioning
|
||||
|
||||
To verify that the smartcard is working as intended, you can create a signature:
|
||||
```
|
||||
$ echo "Hello world" | gpg --clearsign > /tmp/test.asc
|
||||
$ gpg --verify /tmp/test.asc
|
||||
|
||||
```
|
||||
|
||||
This should ask for your smartcard PIN on your first command, and then show "Good signature" after you run gpg --verify.
|
||||
|
||||
Congratulations, you have successfully made it extremely difficult to steal your digital developer identity!
|
||||
|
||||
### Other common GnuPG operations
|
||||
|
||||
Here is a quick reference for some common operations you'll need to do with your PGP key.
|
||||
|
||||
In all of the below commands, the [fpr] is your key fingerprint.
|
||||
|
||||
#### Mounting your master key offline storage
|
||||
|
||||
You will need your master key for any of the operations below, so you will first need to mount your backup offline storage and tell GnuPG to use it. First, find out where the media got mounted, for example, by looking at the output of the mount command. Then, locate the directory with the backup of your GnuPG directory and tell GnuPG to use that as its home:
|
||||
```
|
||||
$ export GNUPGHOME=/media/disk/name/gnupg-backup
|
||||
$ gpg --list-secret-keys
|
||||
|
||||
```
|
||||
|
||||
You want to make sure that you see sec and not sec# in the output (the # means the key is not available and you're still using your regular home directory location).
|
||||
|
||||
##### Updating your regular GnuPG working directory
|
||||
|
||||
After you make any changes to your key using the offline storage, you will want to import these changes back into your regular working directory:
|
||||
```
|
||||
$ gpg --export | gpg --homedir ~/.gnupg --import
|
||||
$ unset GNUPGHOME
|
||||
|
||||
```
|
||||
|
||||
#### Extending key expiration date
|
||||
|
||||
The master key we created has the default expiration date of 2 years from the date of creation. This is done both for security reasons and to make obsolete keys eventually disappear from keyservers.
|
||||
|
||||
To extend the expiration on your key by a year from current date, just run:
|
||||
```
|
||||
$ gpg --quick-set-expire [fpr] 1y
|
||||
|
||||
```
|
||||
|
||||
You can also use a specific date if that is easier to remember (e.g. your birthday, January 1st, or Canada Day):
|
||||
```
|
||||
$ gpg --quick-set-expire [fpr] 2020-07-01
|
||||
|
||||
```
|
||||
|
||||
Remember to send the updated key back to keyservers:
|
||||
```
|
||||
$ gpg --send-key [fpr]
|
||||
|
||||
```
|
||||
|
||||
#### Revoking identities
|
||||
|
||||
If you need to revoke an identity (e.g., you changed employers and your old email address is no longer valid), you can use a one-liner:
|
||||
```
|
||||
$ gpg --quick-revoke-uid [fpr] 'Alice Engineer <aengineer@example.net>'
|
||||
|
||||
```
|
||||
|
||||
You can also do the same with the menu mode using gpg --edit-key [fpr].
|
||||
|
||||
Once you are done, remember to send the updated key back to keyservers:
|
||||
```
|
||||
$ gpg --send-key [fpr]
|
||||
|
||||
```
|
||||
|
||||
Next time, we'll look at how Git supports multiple levels of integration with PGP.
|
||||
|
||||
Learn more about Linux through the free ["Introduction to Linux" ][8]course from The Linux Foundation and edX.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.linux.com/blog/learn/pgp/2018/3/protecting-code-integrity-pgp-part-5-moving-subkeys-hardware-device
|
||||
|
||||
作者:[KONSTANTIN RYABITSEV][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://www.linux.com/users/mricon
|
||||
[1]:https://www.linux.com/blog/learn/2018/2/protecting-code-integrity-pgp-part-1-basic-pgp-concepts-and-tools
|
||||
[2]:https://www.linux.com/blog/learn/pgp/2018/2/protecting-code-integrity-pgp-part-2-generating-and-protecting-your-master-pgp-key
|
||||
[3]:https://www.linux.com/blog/learn/pgp/2018/2/protecting-code-integrity-pgp-part-3-generating-pgp-subkeys
|
||||
[4]:https://www.linux.com/blog/learn/pgp/2018/3/protecting-code-integrity-pgp-part-4-moving-your-master-key-offline-storage
|
||||
[5]:https://shop.nitrokey.com/shop/product/nitrokey-start-6
|
||||
[6]:https://shop.nitrokey.com/shop/product/nitrokey-pro-3
|
||||
[7]:https://www.yubico.com/product/yubikey-4-series/
|
||||
[8]:https://training.linuxfoundation.org/linux-courses/system-administration-training/introduction-to-linux
|
||||
@ -1,318 +0,0 @@
|
||||
Protecting Code Integrity with PGP — Part 6: Using PGP with Git
|
||||
======
|
||||
|
||||

|
||||
In this tutorial series, we're providing practical guidelines for using PGP, including basic concepts and generating and protecting your keys. If you missed the previous articles, you can catch up below. In this article, we look at Git's integration with PGP, starting with signed tags, then introducing signed commits, and finally adding support for signed pushes.
|
||||
|
||||
[Part 1: Basic Concepts and Tools][1]
|
||||
|
||||
[Part 2: Generating Your Master Key][2]
|
||||
|
||||
[Part 3: Generating PGP Subkeys][3]
|
||||
|
||||
[Part 4: Moving Your Master Key to Offline Storage][4]
|
||||
|
||||
[Part 5: Moving Subkeys to a Hardware Device][5]
|
||||
|
||||
One of the core features of Git is its decentralized nature -- once a repository is cloned to your system, you have full history of the project, including all of its tags, commits and branches. However, with hundreds of cloned repositories floating around, how does anyone verify that the repository you downloaded has not been tampered with by a malicious third party? You may have cloned it from GitHub or some other official-looking location, but what if someone had managed to trick you?
|
||||
|
||||
Or what happens if a backdoor is discovered in one of the projects you've worked on, and the "Author" line in the commit says it was done by you, while you're pretty sure you had [nothing to do with it][6]?
|
||||
|
||||
To address both of these issues, Git introduced PGP integration. Signed tags prove the repository integrity by assuring that its contents are exactly the same as on the workstation of the developer who created the tag, while signed commits make it nearly impossible for someone to impersonate you without having access to your PGP keys.
|
||||
|
||||
### Checklist
|
||||
|
||||
* Understand signed tags, commits, and pushes (ESSENTIAL)
|
||||
|
||||
* Configure git to use your key (ESSENTIAL)
|
||||
|
||||
* Learn how tag signing and verification works (ESSENTIAL)
|
||||
|
||||
* Configure git to always sign annotated tags (NICE)
|
||||
|
||||
* Learn how commit signing and verification works (ESSENTIAL)
|
||||
|
||||
* Configure git to always sign commits (NICE)
|
||||
|
||||
* Configure gpg-agent options (ESSENTIAL)
|
||||
|
||||
|
||||
|
||||
|
||||
### Considerations
|
||||
|
||||
Git implements multiple levels of integration with PGP, first starting with signed tags, then introducing signed commits, and finally adding support for signed pushes.
|
||||
|
||||
#### Understanding Git Hashes
|
||||
|
||||
Git is a complicated beast, but you need to know what a "hash" is in order to have a good grasp on how PGP integrates with it. We'll narrow it down to two kinds of hashes: tree hashes and commit hashes.
|
||||
|
||||
##### Tree hashes
|
||||
|
||||
Every time you commit a change to a repository, git records checksum hashes of all objects in it -- contents (blobs), directories (trees), file names and permissions, etc, for each subdirectory in the repository. It only does this for trees and blobs that have changed with each commit, so as not to re-checksum the entire tree unnecessarily if only a small part of it was touched.
|
||||
|
||||
Then it calculates and stores the checksum of the toplevel tree, which will inevitably be different if any part of the repository has changed.
|
||||
|
||||
##### Commit hashes
|
||||
|
||||
Once the tree hash has been created, git will calculate the commit hash, which will include the following information about the repository and the change being made:
|
||||
|
||||
* The checksum hash of the tree
|
||||
|
||||
* The checksum hash of the tree before the change (parent)
|
||||
|
||||
* Information about the author (name, email, time of authorship)
|
||||
|
||||
* Information about the committer (name, email, time of commit)
|
||||
|
||||
* The commit message
|
||||
|
||||
|
||||
|
||||
|
||||
##### Hashing function
|
||||
|
||||
At the time of writing, git still uses the SHA1 hashing mechanism to calculate checksums, though work is under way to transition to a stronger algorithm that is more resistant to collisions. Note, that git already includes collision avoidance routines, so it is believed that a successful collision attack against git remains impractical.
|
||||
|
||||
#### Annotated tags and tag signatures
|
||||
|
||||
Git tags allow developers to mark specific commits in the history of each git repository. Tags can be "lightweight" \-- more or less just a pointer at a specific commit, or they can be "annotated," which becomes its own object in the git tree. An annotated tag object contains all of the following information:
|
||||
|
||||
* The checksum hash of the commit being tagged
|
||||
|
||||
* The tag name
|
||||
|
||||
* Information about the tagger (name, email, time of tagging)
|
||||
|
||||
* The tag message
|
||||
|
||||
|
||||
|
||||
|
||||
A PGP-signed tag is simply an annotated tag with all these entries wrapped around in a PGP signature. When a developer signs their git tag, they effectively assure you of the following:
|
||||
|
||||
* Who they are (and why you should trust them)
|
||||
|
||||
* What the state of their repository was at the time of signing:
|
||||
|
||||
* The tag includes the hash of the commit
|
||||
|
||||
* The commit hash includes the hash of the toplevel tree
|
||||
|
||||
* Which includes hashes of all files, contents, and subtrees
|
||||
* It also includes all information about authorship
|
||||
|
||||
* Including exact times when changes were made
|
||||
|
||||
|
||||
|
||||
|
||||
When you clone a git repository and verify a signed tag, that gives you cryptographic assurance that all contents in the repository, including all of its history, are exactly the same as the contents of the repository on the developer's computer at the time of signing.
|
||||
|
||||
#### Signed commits
|
||||
|
||||
Signed commits are very similar to signed tags -- the contents of the commit object are PGP-signed instead of the contents of the tag object. A commit signature also gives you full verifiable information about the state of the developer's tree at the time the signature was made. Tag signatures and commit PGP signatures provide exact same security assurances about the repository and its entire history.
|
||||
|
||||
#### Signed pushes
|
||||
|
||||
This is included here for completeness' sake, since this functionality needs to be enabled on the server receiving the push before it does anything useful. As we saw above, PGP-signing a git object gives verifiable information about the developer's git tree, but not about their intent for that tree.
|
||||
|
||||
For example, you can be working on an experimental branch in your own git fork trying out a promising cool feature, but after you submit your work for review, someone finds a nasty bug in your code. Since your commits are properly signed, someone can take the branch containing your nasty bug and push it into master, introducing a vulnerability that was never intended to go into production. Since the commit is properly signed with your key, everything looks legitimate and your reputation is questioned when the bug is discovered.
|
||||
|
||||
Ability to require PGP-signatures during git push was added in order to certify the intent of the commit, and not merely verify its contents.
|
||||
|
||||
#### Configure git to use your PGP key
|
||||
|
||||
If you only have one secret key in your keyring, then you don't really need to do anything extra, as it becomes your default key.
|
||||
|
||||
However, if you happen to have multiple secret keys, you can tell git which key should be used ([fpr] is the fingerprint of your key):
|
||||
```
|
||||
$ git config --global user.signingKey [fpr]
|
||||
|
||||
```
|
||||
|
||||
NOTE: If you have a distinct gpg2 command, then you should tell git to always use it instead of the legacy gpg from version 1:
|
||||
```
|
||||
$ git config --global gpg.program gpg2
|
||||
|
||||
```
|
||||
|
||||
#### How to work with signed tags
|
||||
|
||||
To create a signed tag, simply pass the -s switch to the tag command:
|
||||
```
|
||||
$ git tag -s [tagname]
|
||||
|
||||
```
|
||||
|
||||
Our recommendation is to always sign git tags, as this allows other developers to ensure that the git repository they are working with has not been maliciously altered (e.g. in order to introduce backdoors).
|
||||
|
||||
##### How to verify signed tags
|
||||
|
||||
To verify a signed tag, simply use the verify-tag command:
|
||||
```
|
||||
$ git verify-tag [tagname]
|
||||
|
||||
```
|
||||
|
||||
If you are verifying someone else's git tag, then you will need to import their PGP key. Please refer to the "Trusted Team communication" document in the same repository for guidance on this topic.
|
||||
|
||||
##### Verifying at pull time
|
||||
|
||||
If you are pulling a tag from another fork of the project repository, git should automatically verify the signature at the tip you're pulling and show you the results during the merge operation:
|
||||
```
|
||||
$ git pull [url] tags/sometag
|
||||
|
||||
```
|
||||
|
||||
The merge message will contain something like this:
|
||||
```
|
||||
Merge tag 'sometag' of [url]
|
||||
|
||||
[Tag message]
|
||||
|
||||
# gpg: Signature made [...]
|
||||
# gpg: Good signature from [...]
|
||||
|
||||
```
|
||||
|
||||
#### Configure git to always sign annotated tags
|
||||
|
||||
Chances are, if you're creating an annotated tag, you'll want to sign it. To force git to always sign annotated tags, you can set a global configuration option:
|
||||
```
|
||||
$ git config --global tag.forceSignAnnotated true
|
||||
|
||||
```
|
||||
|
||||
Alternatively, you can just train your muscle memory to always pass the -s switch:
|
||||
```
|
||||
$ git tag -asm "Tag message" tagname
|
||||
|
||||
```
|
||||
|
||||
#### How to work with signed commits
|
||||
|
||||
It is easy to create signed commits, but it is much more difficult to incorporate them into your workflow. Many projects use signed commits as a sort of "Committed-by:" line equivalent that records code provenance -- the signatures are rarely verified by others except when tracking down project history. In a sense, signed commits are used for "tamper evidence," and not to "tamper-proof" the git workflow.
|
||||
|
||||
To create a signed commit, you just need to pass the -S flag to the git commit command (it's capital -S due to collision with another flag):
|
||||
```
|
||||
$ git commit -S
|
||||
|
||||
```
|
||||
|
||||
Our recommendation is to always sign commits and to require them of all project members, regardless of whether anyone is verifying them (that can always come at a later time).
|
||||
|
||||
##### How to verify signed commits
|
||||
|
||||
To verify a single commit you can use verify-commit:
|
||||
```
|
||||
$ git verify-commit [hash]
|
||||
|
||||
```
|
||||
|
||||
You can also look at repository logs and request that all commit signatures are verified and shown:
|
||||
```
|
||||
$ git log --pretty=short --show-signature
|
||||
|
||||
```
|
||||
|
||||
##### Verifying commits during git merge
|
||||
|
||||
If all members of your project sign their commits, you can enforce signature checking at merge time (and then sign the resulting merge commit itself using the -S flag):
|
||||
```
|
||||
$ git merge --verify-signatures -S merged-branch
|
||||
|
||||
```
|
||||
|
||||
Note, that the merge will fail if there is even one commit that is not signed or does not pass verification. As it is often the case, technology is the easy part -- the human side of the equation is what makes adopting strict commit signing for your project difficult.
|
||||
|
||||
##### If your project uses mailing lists for patch management
|
||||
|
||||
If your project uses a mailing list for submitting and processing patches, then there is little use in signing commits, because all signature information will be lost when sent through that medium. It is still useful to sign your commits, just so others can refer to your publicly hosted git trees for reference, but the upstream project receiving your patches will not be able to verify them directly with git.
|
||||
|
||||
You can still sign the emails containing the patches, though.
|
||||
|
||||
#### Configure git to always sign commits
|
||||
|
||||
You can tell git to always sign commits:
|
||||
```
|
||||
git config --global commit.gpgSign true
|
||||
|
||||
```
|
||||
|
||||
Or you can train your muscle memory to always pass the -S flag to all git commit operations (this includes --amend).
|
||||
|
||||
#### Configure gpg-agent options
|
||||
|
||||
The GnuPG agent is a helper tool that will start automatically whenever you use the gpg command and run in the background with the purpose of caching the private key passphrase. This way you only have to unlock your key once to use it repeatedly (very handy if you need to sign a bunch of git operations in an automated script without having to continuously retype your passphrase).
|
||||
|
||||
There are two options you should know in order to tweak when the passphrase should be expired from cache:
|
||||
|
||||
* default-cache-ttl (seconds): If you use the same key again before the time-to-live expires, the countdown will reset for another period. The default is 600 (10 minutes).
|
||||
|
||||
* max-cache-ttl (seconds): Regardless of how recently you've used the key since initial passphrase entry, if the maximum time-to-live countdown expires, you'll have to enter the passphrase again. The default is 30 minutes.
|
||||
|
||||
|
||||
|
||||
|
||||
If you find either of these defaults too short (or too long), you can edit your ~/.gnupg/gpg-agent.conf file to set your own values:
|
||||
```
|
||||
# set to 30 minutes for regular ttl, and 2 hours for max ttl
|
||||
default-cache-ttl 1800
|
||||
max-cache-ttl 7200
|
||||
|
||||
```
|
||||
|
||||
##### Bonus: Using gpg-agent with ssh
|
||||
|
||||
If you've created an [A] (Authentication) key and moved it to the smartcard, you can use it with ssh for adding 2-factor authentication for your ssh sessions. You just need to tell your environment to use the correct socket file for talking to the agent.
|
||||
|
||||
First, add the following to your ~/.gnupg/gpg-agent.conf:
|
||||
```
|
||||
enable-ssh-support
|
||||
|
||||
```
|
||||
|
||||
Then, add this to your .bashrc:
|
||||
```
|
||||
export SSH_AUTH_SOCK=$(gpgconf --list-dirs agent-ssh-socket)
|
||||
|
||||
```
|
||||
|
||||
You will need to kill the existing gpg-agent process and start a new login session for the changes to take effect:
|
||||
```
|
||||
$ killall gpg-agent
|
||||
$ bash
|
||||
$ ssh-add -L
|
||||
|
||||
```
|
||||
|
||||
The last command should list the SSH representation of your PGP Auth key (the comment should say cardno:XXXXXXXX at the end to indicate it's coming from the smartcard).
|
||||
|
||||
To enable key-based logins with ssh, just add the ssh-add -L output to ~/.ssh/authorized_keys on remote systems you log in to. Congratulations, you've just made your ssh credentials extremely difficult to steal.
|
||||
|
||||
As a bonus, you can get other people's PGP-based ssh keys from public keyservers, should you need to grant them ssh access to anything:
|
||||
```
|
||||
$ gpg --export-ssh-key [keyid]
|
||||
|
||||
```
|
||||
|
||||
This can come in super handy if you need to allow developers access to git repositories over ssh. Next time, we'll provide tips for protecting your email accounts as well as your PGP keys.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.linux.com/blog/learn/pgp/2018/3/protecting-code-integrity-pgp-part-6-using-pgp-git
|
||||
|
||||
作者:[KONSTANTIN RYABITSEV][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://www.linux.com/users/mricon
|
||||
[1]:https://www.linux.com/blog/learn/2018/2/protecting-code-integrity-pgp-part-1-basic-pgp-concepts-and-tools
|
||||
[2]:https://www.linux.com/blog/learn/pgp/2018/2/protecting-code-integrity-pgp-part-2-generating-and-protecting-your-master-pgp-key
|
||||
[3]:https://www.linux.com/blog/learn/pgp/2018/2/protecting-code-integrity-pgp-part-3-generating-pgp-subkeys
|
||||
[4]:https://www.linux.com/blog/learn/pgp/2018/3/protecting-code-integrity-pgp-part-4-moving-your-master-key-offline-storage
|
||||
[5]:https://www.linux.com/blog/learn/pgp/2018/3/protecting-code-integrity-pgp-part-5-moving-subkeys-hardware-device
|
||||
[6]:https://github.com/jayphelps/git-blame-someone-else
|
||||
@ -1,3 +1,4 @@
|
||||
translated by lixinyuxx
|
||||
4 Firefox extensions worth checking out
|
||||
======
|
||||
|
||||
|
||||
@ -1,3 +1,4 @@
|
||||
translated by lixinyuxx
|
||||
The life cycle of a software bug
|
||||
======
|
||||
|
||||
|
||||
@ -1,3 +1,4 @@
|
||||
Translating by MjSeven
|
||||
Users, Groups and Other Linux Beasts: Part 2
|
||||
======
|
||||

|
||||
|
||||
@ -1,142 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (11 Uses for a Raspberry Pi Around the Office)
|
||||
[#]: via: (https://blog.dxmtechsupport.com.au/11-uses-for-a-raspberry-pi-around-the-office/)
|
||||
[#]: author: (James Mawson https://blog.dxmtechsupport.com.au/author/james-mawson/)
|
||||
|
||||
11 Uses for a Raspberry Pi Around the Office
|
||||
======
|
||||
|
||||
Look, I know what you’re thinking: a Raspberry Pi is really just for tinkering, prototyping and hobby use. It’s not actually meant for running a business on.
|
||||
|
||||
And it’s definitely true that this computer’s relatively low processing power, corruptible SD card, lack of battery backup and the DIY nature of the support means it’s not going to be a viable replacement for a [professionally installed and configured business server][1] for your most mission-critical operations any time soon.
|
||||
|
||||
But the board is affordable, incredibly frugal with power, small enough to fit just about anywhere and endlessly flexible – it’s actually a pretty great way to handle some basic tasks around the office.
|
||||
|
||||
And, even better, there’s a whole world of people out there who have done these projects before and are happy to share how they did it.
|
||||
|
||||
### DNS Server
|
||||
|
||||
Every time you type a website address or click a link in your browser, it needs to convert the domain name into a numeric IP address before it can show you anything.
|
||||
|
||||
Normally this means a request to a DNS server somewhere on the internet – but you can speed up your browsing by handling this locally.
|
||||
|
||||
You can also assign your own subdomains for local access to machines around the office.
|
||||
|
||||
[Here’s how to get this working.][2]
|
||||
|
||||
### Toilet Occupied Sign
|
||||
|
||||
Ever get queues at the loos?
|
||||
|
||||
That’s annoying for those left waiting and the time spent dealing with it is a drain on your whole office’s productivity.
|
||||
|
||||
I guess you could always hang those signs they have on airplanes all through your office.
|
||||
|
||||
[Occu-pi][3] is a much simpler solution, using a magnetic switch and a Raspberry Pi to tell when the bolt is closed and update a Slack channel as to when it’s in use – meaning that the whole office can tell at a glance of their computer or mobile device whether there’s a cubicle free.
|
||||
|
||||
### Honeypot Trap for Hackers
|
||||
|
||||
It should scare most business owners just a little bit that their first clue that a hacker’s breached the network is when something goes badly wrong.
|
||||
|
||||
That’s where it can help to have a honeypot: a computer that serves no purpose except to sit on your network with certain ports open to masquerade as a juicy target to hackers.
|
||||
|
||||
Security researchers often deploy honeypots on the exterior of a network, to collect data on what attackers are doing.
|
||||
|
||||
But for the average small business, these are more usefully deployed in the interior, to serve as kind of a tripwire. Because no ordinary user has any real reason to want to connect to the honeypot, any login attempts that occur are a very good indicator that mischief is afoot.
|
||||
|
||||
This can provide early warning of outsider intrusion, and of trusted insiders up to no good.
|
||||
|
||||
In larger, client/server networks, it might be more practical to run something like this as a virtual machine. But in small-office/home-office situations with a peer-to-peer network running on a wireless router, something like [HoneyPi][4] is a great little burglar alarm.
|
||||
|
||||
### Print Server
|
||||
|
||||
Network-attached printers are so much more convenient.
|
||||
|
||||
But it can be expensive to replace all your printers- especially if you’re otherwise happy with them.
|
||||
|
||||
It might make a lot more sense to [set up a Raspberry Pi as a print server][5].
|
||||
|
||||
### Network Attached Storage
|
||||
|
||||
Turning simple hard drives into network attached storage was one of the earliest practical uses for a Raspberry Pi, and it’s still one of the best.
|
||||
|
||||
[Here’s how to create a NAS with your Raspberry Pi.][6]
|
||||
|
||||
### Ticketing Server
|
||||
|
||||
Looking for a way to manage the support tickets for your help desk on a shoestring budget?
|
||||
|
||||
There’s a totally open source ticketing program called osTicket that you can install on your Pi, and it’s even available as [a ready-to-go SD card image][7].
|
||||
|
||||
### Digital Signage
|
||||
|
||||
Whether it’s for events, advertising, a menu, or something else entirely, a lot of businesses need a way to display digital signage – and the Pi’s affordability and frugal electricity needs make it a very attractive choice.
|
||||
|
||||
[There are a wealth of options to choose from here.][8]
|
||||
|
||||
### Directories and Kiosks
|
||||
|
||||
[FullPageOS][9] is a Linux distribution based on Raspbian that boots straight into a full screen version of Chromium – ideal for shopping directoriers, library catalogues and so on.
|
||||
|
||||
### Basic Intranet Web Server
|
||||
|
||||
For hosting a public-facing website, you’re really much better off just getting a hosting account. A Raspberry Pi is not really built to serve any real volume of web traffic.
|
||||
|
||||
But for small offices, it can host an internal business wiki or basic company intranet. It can also work as a sandbox environment for experimenting with code and server configurations.
|
||||
|
||||
[Here’s how to get Apache, MySQL and PHP running on a Pi.][10]
|
||||
|
||||
### Penetration Tester
|
||||
|
||||
Kali Linux is an operating system built specifically to probe networks for security vulnerabilities. By installing it on a Pi, you’ve got a super portable penetration tester with more than 600 tools included.
|
||||
|
||||
[You can find a torrent link for the Raspberry Pi image here.][11]
|
||||
|
||||
Be absolutely scrupulous to only use this on your own network or networks you’ve got permission to perform a security audit on – using this to hack other networks is a serious crime.
|
||||
|
||||
### VPN Server
|
||||
|
||||
When you’re out on the road, relying on public wireless internet, you’ve not really any say in who else might be on the network, snooping on all your traffic. That’s why it can be reassuring to encrypt everything with a VPN connection.
|
||||
|
||||
There are any number of commercial VPN services you can subscribe to – and you can install your own in the cloud – but by running one from your office, you can also access the local network from anywhere.
|
||||
|
||||
For light use – say, the occasional bit of business travel – a Raspberry Pi is a great, power-efficient way to set up a VPN server. (It’s also worth checking first that your router doesn’t offer this functionality already – very many do.)
|
||||
|
||||
[Here’s how to install OpenVPN on a Raspberry Pi.][12]
|
||||
|
||||
### Wireless Coffee Machine
|
||||
|
||||
Ahh, ambrosia: sweet nectar of the gods and the backbone of all productive enterprise.
|
||||
|
||||
So why not [hack the office coffee machine into a smart coffee machine][13] for precision temperature control and wireless network connectivity?
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://blog.dxmtechsupport.com.au/11-uses-for-a-raspberry-pi-around-the-office/
|
||||
|
||||
作者:[James Mawson][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://blog.dxmtechsupport.com.au/author/james-mawson/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://dxmtechsupport.com.au/server-configuration
|
||||
[2]: https://www.1and1.com/digitalguide/server/configuration/how-to-make-your-raspberry-pi-into-a-dns-server/
|
||||
[3]: https://blog.usejournal.com/occu-pi-the-bathroom-of-the-future-ed69b84e21d5
|
||||
[4]: https://trustfoundry.net/honeypi-easy-honeypot-raspberry-pi/
|
||||
[5]: https://opensource.com/article/18/3/print-server-raspberry-pi
|
||||
[6]: https://howtoraspberrypi.com/create-a-nas-with-your-raspberry-pi-and-samba/
|
||||
[7]: https://everyday-tech.com/a-raspberry-pi-ticketing-system-image-with-osticket/
|
||||
[8]: https://blog.capterra.com/7-free-and-open-source-digital-signage-software-options-for-your-next-event/
|
||||
[9]: https://github.com/guysoft/FullPageOS
|
||||
[10]: https://maker.pro/raspberry-pi/projects/raspberry-pi-web-server
|
||||
[11]: https://www.offensive-security.com/kali-linux-arm-images/
|
||||
[12]: https://medium.freecodecamp.org/running-your-own-openvpn-server-on-a-raspberry-pi-8b78043ccdea
|
||||
[13]: https://www.techradar.com/au/how-to/how-to-build-your-own-smart-coffee-machine
|
||||
@ -1,202 +0,0 @@
|
||||
Translating by ScarboroughCoral
|
||||
How to turn on an LED with Fedora IoT
|
||||
======
|
||||
|
||||

|
||||
|
||||
Do you enjoy running Fedora, containers, and have a Raspberry Pi? What about using all three together to play with LEDs? This article introduces Fedora IoT and shows you how to install a preview image on a Raspberry Pi. You’ll also learn how to interact with GPIO in order to light up an LED.
|
||||
|
||||
### What is Fedora IoT?
|
||||
|
||||
Fedora IoT is one of the current Fedora Project objectives, with a plan to become a full Fedora Edition. The result will be a system that runs on ARM (aarch64 only at the moment) devices such as the Raspberry Pi, as well as on the x86_64 architecture.
|
||||
|
||||
![][1]
|
||||
|
||||
Fedora IoT is based on OSTree, like [Fedora Silverblue][2] and the former [Atomic Host][3].
|
||||
|
||||
### Download and install Fedora IoT
|
||||
|
||||
The official Fedora IoT images are coming with the Fedora 29 release. However, in the meantime you can download a [Fedora 28-based image][4] for this experiment.
|
||||
|
||||
You have two options to install the system: either flash the SD card using a dd command, or use a fedora-arm-installer tool. The Fedora Wiki offers more information about [setting up a physical device][5] for IoT. Also, remember that you might need to resize the third partition.
|
||||
|
||||
Once you insert the SD card into the device, you’ll need to complete the installation by creating a user. This step requires either a serial connection, or a HDMI display with a keyboard to interact with the device.
|
||||
|
||||
When the system is installed and ready, the next step is to configure a network connection. Log in to the system with the user you have just created choose one of the following options:
|
||||
|
||||
* If you need to configure your network manually, run a command similar to the following. Remember to use the right addresses for your network:
|
||||
```
|
||||
$ nmcli connection add con-name cable ipv4.addresses \
|
||||
192.168.0.10/24 ipv4.gateway 192.168.0.1 \
|
||||
connection.autoconnect true ipv4.dns "8.8.8.8,1.1.1.1" \
|
||||
type ethernet ifname eth0 ipv4.method manual
|
||||
|
||||
```
|
||||
|
||||
* If there’s a DHCP service on your network, run a command like this:
|
||||
|
||||
```
|
||||
$ nmcli con add type ethernet con-name cable ifname eth0
|
||||
```
|
||||
|
||||
|
||||
|
||||
|
||||
### **The GPIO interface in Fedora**
|
||||
|
||||
Many tutorials about GPIO on Linux focus on a legacy GPIO sysfis interface. This interface is deprecated, and the upstream Linux kernel community plan to remove it completely, due to security and other issues.
|
||||
|
||||
The Fedora kernel is already compiled without this legacy interface, so there’s no /sys/class/gpio on the system. This tutorial uses a new character device /dev/gpiochipN provided by the upstream kernel. This is the current way of interacting with GPIO.
|
||||
|
||||
To interact with this new device, you need to use a library and a set of command line interface tools. The common command line tools such as echo or cat won’t work with this device.
|
||||
|
||||
You can install the CLI tools by installing the libgpiod-utils package. A corresponding Python library is provided by the python3-libgpiod package.
|
||||
|
||||
### **Creating a container with Podman**
|
||||
|
||||
[Podman][6] is a container runtime with a command line interface similar to Docker. The big advantage of Podman is it doesn’t run any daemon in the background. That’s especially useful for devices with limited resources. Podman also allows you to start containerized services with systemd unit files. Plus, it has many additional features.
|
||||
|
||||
We’ll create a container in these two steps:
|
||||
|
||||
1. Create a layered image containing the required packages.
|
||||
2. Create a new container starting from our image.
|
||||
|
||||
|
||||
|
||||
First, create a file Dockerfile with the content below. This tells podman to build an image based on the latest Fedora image available in the registry. Then it updates the system inside and installs some packages:
|
||||
|
||||
```
|
||||
FROM fedora:latest
|
||||
RUN dnf -y update
|
||||
RUN dnf -y install libgpiod-utils python3-libgpiod
|
||||
|
||||
```
|
||||
|
||||
You have created a build recipe of a container image based on the latest Fedora with updates, plus packages to interact with GPIO.
|
||||
|
||||
Now, run the following command to build your base image:
|
||||
|
||||
```
|
||||
$ sudo podman build --tag fedora:gpiobase -f ./Dockerfile
|
||||
|
||||
```
|
||||
|
||||
You have just created your custom image with all the bits in place. You can play with this base container images as many times as you want without installing the packages every time you run it.
|
||||
|
||||
### Working with Podman
|
||||
|
||||
To verify the image is present, run the following command:
|
||||
|
||||
```
|
||||
$ sudo podman images
|
||||
REPOSITORY TAG IMAGE ID CREATED SIZE
|
||||
localhost/fedora gpiobase 67a2b2b93b4b 10 minutes ago 488MB
|
||||
docker.io/library/fedora latest c18042d7fac6 2 days ago 300MB
|
||||
|
||||
```
|
||||
|
||||
Now, start the container and do some actual experiments. Containers are normally isolated and don’t have an access to the host system, including the GPIO interface. Therefore, you need to mount it inside while starting the container. To do this, use the –device option in the following command:
|
||||
|
||||
```
|
||||
$ sudo podman run -it --name gpioexperiment --device=/dev/gpiochip0 localhost/fedora:gpiobase /bin/bash
|
||||
|
||||
```
|
||||
|
||||
You are now inside the running container. Before you move on, here are some more container commands. For now, exit the container by typing exit or pressing **Ctrl+D**.
|
||||
|
||||
To list the the existing containers, including those not currently running, such as the one you just created, run:
|
||||
|
||||
```
|
||||
$ sudo podman container ls -a
|
||||
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
|
||||
64e661d5d4e8 localhost/fedora:gpiobase /bin/bash 37 seconds ago Exited (0) Less than a second ago gpioexperiment
|
||||
|
||||
```
|
||||
|
||||
To create a new container, run this command:
|
||||
|
||||
```
|
||||
$ sudo podman run -it --name newexperiment --device=/dev/gpiochip0 localhost/fedora:gpiobase /bin/bash
|
||||
|
||||
```
|
||||
|
||||
Delete it with the following command:
|
||||
|
||||
```
|
||||
$ sudo podman rm newexperiment
|
||||
|
||||
```
|
||||
|
||||
### **Turn on an LED**
|
||||
|
||||
Now you can use the container you already created. If you exited from the container, start it again with this command:
|
||||
|
||||
```
|
||||
$ sudo podman start -ia gpioexperiment
|
||||
|
||||
```
|
||||
|
||||
As already discussed, you can use the CLI tools provided by the libgpiod-utils package in Fedora. To list the available GPIO chips, run:
|
||||
|
||||
```
|
||||
$ gpiodetect
|
||||
gpiochip0 [pinctrl-bcm2835] (54 lines)
|
||||
|
||||
```
|
||||
|
||||
To get the list of the lines exposed by a specific chip, run:
|
||||
|
||||
```
|
||||
$ gpioinfo gpiochip0
|
||||
|
||||
```
|
||||
|
||||
Notice there’s no correlation between the number of physical pins and the number of lines printed by the previous command. What’s important is the BCM number, as shown on [pinout.xyz][7]. It is not advised to play with the lines that don’t have a corresponding BCM number.
|
||||
|
||||
Now, connect an LED to the physical pin 40, that is BCM 21. Remember: the shorter leg of the LED (the negative leg, called the cathode) must be connected to a GND pin of the Raspberry Pi with a 330 ohm resistor, and the long leg (the anode) to the physical pin 40.
|
||||
|
||||
To turn the LED on, run the following command. It will stay on until you press **Ctrl+C** :
|
||||
|
||||
```
|
||||
$ gpioset --mode=wait gpiochip0 21=1
|
||||
|
||||
```
|
||||
|
||||
To light it up for a certain period of time, add the -b (run in the background) and -s NUM (how many seconds) parameters, as shown below. For example, to light the LED for 5 seconds, run:
|
||||
|
||||
```
|
||||
$ gpioset -b -s 5 --mode=time gpiochip0 21=1
|
||||
|
||||
```
|
||||
|
||||
Another useful command is gpioget. It gets the status of a pin (high or low), and can be useful to detect buttons and switches.
|
||||
|
||||
![Closeup of LED connection with GPIO][8]
|
||||
|
||||
### **Conclusion**
|
||||
|
||||
You can also play with LEDs using Python — [there are some examples here][9]. And you can also use the i2c devices inside the container as well. In addition, Podman is not strictly related to this Fedora edition. You can install it on any existing Fedora Edition, or try it on the two new OSTree-based systems in Fedora: [Fedora Silverblue][2] and [Fedora CoreOS][10].
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://fedoramagazine.org/turnon-led-fedora-iot/
|
||||
|
||||
作者:[Alessio Ciregia][a]
|
||||
选题:[lujun9972](https://github.com/lujun9972)
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: http://alciregi.id.fedoraproject.org/
|
||||
[1]: https://fedoramagazine.org/wp-content/uploads/2018/08/oled-1024x768.png
|
||||
[2]: https://teamsilverblue.org/
|
||||
[3]: https://www.projectatomic.io/
|
||||
[4]: https://kojipkgs.fedoraproject.org/compose/iot/latest-Fedora-IoT-28/compose/IoT/
|
||||
[5]: https://fedoraproject.org/wiki/InternetOfThings/GettingStarted#Setting_up_a_Physical_Device
|
||||
[6]: https://github.com/containers/libpod
|
||||
[7]: https://pinout.xyz/
|
||||
[8]: https://fedoramagazine.org/wp-content/uploads/2018/08/breadboard-1024x768.png
|
||||
[9]: https://github.com/brgl/libgpiod/tree/master/bindings/python/examples
|
||||
[10]: https://coreos.fedoraproject.org/
|
||||
@ -1,5 +1,5 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: translator: ( Auk7F7)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: subject: (Arch-Audit : A Tool To Check Vulnerable Packages In Arch Linux)
|
||||
@ -7,6 +7,7 @@
|
||||
[#]: author: (Prakash Subramanian https://www.2daygeek.com/author/prakash/)
|
||||
[#]: url: ( )
|
||||
|
||||
|
||||
Arch-Audit : A Tool To Check Vulnerable Packages In Arch Linux
|
||||
======
|
||||
|
||||
|
||||
169
sources/tech/20181204 4 Unique Terminal Emulators for Linux.md
Normal file
169
sources/tech/20181204 4 Unique Terminal Emulators for Linux.md
Normal file
@ -0,0 +1,169 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (4 Unique Terminal Emulators for Linux)
|
||||
[#]: via: (https://www.linux.com/blog/learn/2018/12/4-unique-terminals-linux)
|
||||
[#]: author: (Jack Wallen https://www.linux.com/users/jlwallen)
|
||||
|
||||
4 Unique Terminal Emulators for Linux
|
||||
======
|
||||

|
||||
Let’s face it, if you’re a Linux administrator, you’re going to work with the command line. To do that, you’ll be using a terminal emulator. Most likely, your distribution of choice came pre-installed with a default terminal emulator that gets the job done. But this is Linux, so you have a wealth of choices to pick from, and that ideology holds true for terminal emulators as well. In fact, if you open up your distribution’s GUI package manager (or search from the command line), you’ll find a trove of possible options. Of those, many are pretty straightforward tools; however, some are truly unique.
|
||||
|
||||
In this article, I’ll highlight four such terminal emulators, that will not only get the job done, but do so while making the job a bit more interesting or fun. So, let’s take a look at these terminals.
|
||||
|
||||
### Tilda
|
||||
|
||||
[Tilda][1] is designed for Gtk and is a member of the cool drop-down family of terminals. That means the terminal is always running in the background, ready to drop down from the top of your monitor (such as Guake and Yakuake). What makes Tilda rise above many of the others is the number of configuration options available for the terminal (Figure 1).
|
||||

|
||||
|
||||
Tilda can be installed from the standard repositories. On a Ubuntu- (or Debian-) based distribution, the installation is as simple as:
|
||||
|
||||
```
|
||||
sudo apt-get install tilda -y
|
||||
```
|
||||
|
||||
Once installed, open Tilda from your desktop menu, which will also open the configuration window. Configure the app to suit your taste and then close the configuration window. You can then open and close Tilda by hitting the F1 hotkey. One caveat to using Tilda is that, after the first run, you won’t find any indication as to how to reach the configuration wizard. No worries. If you run the command tilda -C it will open the configuration window, while still retaining the options you’ve previously set.
|
||||
|
||||
Available options include:
|
||||
|
||||
* Terminal size and location
|
||||
|
||||
* Font and color configurations
|
||||
|
||||
* Auto Hide
|
||||
|
||||
* Title
|
||||
|
||||
* Custom commands
|
||||
|
||||
* URL Handling
|
||||
|
||||
* Transparency
|
||||
|
||||
* Animation
|
||||
|
||||
* Scrolling
|
||||
|
||||
* And more
|
||||
|
||||
|
||||
|
||||
|
||||
What I like about these types of terminals is that they easily get out of the way when you don’t need them and are just a button click away when you do. For those that hop in and out of the terminal, a tool like Tilda is ideal.
|
||||
|
||||
### Aterm
|
||||
|
||||
Aterm holds a special place in my heart, as it was one of the first terminals I used that made me realize how flexible Linux was. This was back when AfterStep was my window manager of choice (which dates me a bit) and I was new to the command line. What Aterm offered was a terminal emulator that was highly customizable, while helping me learn the ins and outs of using the terminal (how to add options and switches to a command). “How?” you ask. Because Aterm never had a GUI for customization. To run Aterm with any special options, it had to run as a command. For example, say you want to open Aterm with transparency enabled, green text, white highlights, and no scroll bar. To do this, issue the command:
|
||||
|
||||
```
|
||||
aterm -tr -fg green -bg white +xb
|
||||
```
|
||||
|
||||
The end result (with the top command running for illustration) would look like that shown in Figure 2.
|
||||
|
||||
![Aterm][3]
|
||||
|
||||
Figure 2: Aterm with a few custom options.
|
||||
|
||||
[Used with permission][4]
|
||||
|
||||
Of course, you must first install Aterm. Fortunately, the application is still found in the standard repositories, so installing on the likes of Ubuntu is as simple as:
|
||||
|
||||
```
|
||||
sudo apt-get install aterm -y
|
||||
```
|
||||
|
||||
If you want to always open Aterm with those options, your best bet is to create an alias in your ~/.bashrc file like so:
|
||||
|
||||
```
|
||||
alias=”aterm -tr -fg green -bg white +sb”
|
||||
```
|
||||
|
||||
Save that file and, when you issue the command aterm, it will always open with those options. For more about creating aliases, check out [this tutorial][5].
|
||||
|
||||
### Eterm
|
||||
|
||||
Eterm is the second terminal that really showed me how much fun the Linux command line could be. Eterm is the default terminal emulator for the Enlightenment desktop. When I eventually migrated from AfterStep to Enlightenment (back in the early 2000s), I was afraid I’d lose out on all those cool aesthetic options. That turned out to not be the case. In fact, Eterm offered plenty of unique options, while making the task easier with a terminal toolbar. With Eterm, you can easily select from a large number of background images (should you want one - Figure 3) by selecting from the Background > Pixmap menu entry.
|
||||
|
||||
![Eterm][7]
|
||||
|
||||
Figure 3: Selecting from one of the many background images for Eterm.
|
||||
|
||||
[Used with permission][4]
|
||||
|
||||
There are a number of other options to configure (such as font size, map alerts, toggle scrollbar, brightness, contrast, and gamma of background images, and more). The one thing you want to make sure is, after you’ve configured Eterm to suit your tastes, to click Eterm > Save User Settings (otherwise, all settings will be lost when you close the app).
|
||||
|
||||
Eterm can be installed from the standard repositories, with a command such as:
|
||||
|
||||
```
|
||||
sudo apt-get install eterm
|
||||
```
|
||||
|
||||
### Extraterm
|
||||
|
||||
[Extraterm][8] should probably win a few awards for coolest feature set of any terminal window project available today. The most unique feature of Extraterm is the ability to wrap commands in color-coded frames (blue for successful commands and red for failed commands - Figure 4).
|
||||
|
||||
![Extraterm][10]
|
||||
|
||||
Figure 4: Extraterm showing two failed command frames.
|
||||
|
||||
[Used with permission][4]
|
||||
|
||||
When you run a command, Extraterm will wrap the command in an isolated frame. If the command succeeds, the frame will be outlined in blue. Should the command fail, the frame will be outlined in red.
|
||||
|
||||
Extraterm cannot be installed via the standard repositories. In fact, the only way to run Extraterm on Linux (at the moment) is to [download the precompiled binary][11] from the project’s GitHub page, extract the file, change into the newly created directory, and issue the command ./extraterm.
|
||||
|
||||
Once the app is running, to enable frames you must first enable bash integration. To do that, open Extraterm and then right-click anywhere in the window to reveal the popup menu. Scroll until you see the entry for Inject Bash shell Integration (Figure 5). Select that entry and you can then begin using the frames option.
|
||||
|
||||
![Extraterm][13]
|
||||
|
||||
Figure 5: Injecting Bash integration for Extraterm.
|
||||
|
||||
[Used with permission][4]
|
||||
|
||||
If you run a command, and don’t see a frame appear, you probably have to create a new frame for the command (as Extraterm only ships with a few default frames). To do that, click on the Extraterm menu button (three horizontal lines in the top right corner of the window), select Settings, and then click the Frames tab. In this window, scroll down and click the New Rule button. You can then add a command you want to work with the frames option (Figure 6).
|
||||
|
||||
![frames][15]
|
||||
|
||||
Figure 6: Adding a new rule for frames.
|
||||
|
||||
[Used with permission][4]
|
||||
|
||||
If, after this, you still don’t see frames appearing, download the extraterm-commands file from the [Download page][11], extract the file, change into the newly created directory, and issue the command sh setup_extraterm_bash.sh. That should enable frames for Extraterm.
|
||||
There’s plenty more options available for Extraterm. I’m convinced, once you start playing around with this new take on the terminal window, you won’t want to go back to the standard terminal. Hopefully the developer will make this app available to the standard repositories soon (as it could easily become one of the most popular terminal windows in use).
|
||||
|
||||
### And Many More
|
||||
|
||||
As you probably expected, there are quite a lot of terminals available for Linux. These four represent (at least for me) four unique takes on the task, each of which do a great job of helping you run the commands every Linux admin needs to run. If you aren’t satisfied with one of these, give your package manager a look to see what’s available. You are sure to find something that works perfectly for you.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.linux.com/blog/learn/2018/12/4-unique-terminals-linux
|
||||
|
||||
作者:[Jack Wallen][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.linux.com/users/jlwallen
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: http://tilda.sourceforge.net/tildadoc.php
|
||||
[2]: https://www.linux.com/files/images/terminals2jpg
|
||||
[3]: https://www.linux.com/sites/lcom/files/styles/rendered_file/public/terminals_2.jpg?itok=gBkRLwDI (Aterm)
|
||||
[4]: https://www.linux.com/licenses/category/used-permission
|
||||
[5]: https://www.linux.com/blog/learn/2018/12/aliases-diy-shell-commands
|
||||
[6]: https://www.linux.com/files/images/terminals3jpg
|
||||
[7]: https://www.linux.com/sites/lcom/files/styles/rendered_file/public/terminals_3.jpg?itok=RVPTJAtK (Eterm)
|
||||
[8]: http://extraterm.org
|
||||
[9]: https://www.linux.com/files/images/terminals4jpg
|
||||
[10]: https://www.linux.com/sites/lcom/files/styles/rendered_file/public/terminals_4.jpg?itok=2n01qdwO (Extraterm)
|
||||
[11]: https://github.com/sedwards2009/extraterm/releases
|
||||
[12]: https://www.linux.com/files/images/terminals5jpg
|
||||
[13]: https://www.linux.com/sites/lcom/files/styles/rendered_file/public/terminals_5.jpg?itok=FdaE1Mpf (Extraterm)
|
||||
[14]: https://www.linux.com/files/images/terminals6jpg
|
||||
[15]: https://www.linux.com/sites/lcom/files/styles/rendered_file/public/terminals_6.jpg?itok=lQ1Zv5wq (frames)
|
||||
@ -1,5 +1,5 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
|
||||
@ -1,5 +1,5 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
|
||||
@ -1,54 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Patch into The Matrix at the Linux command line)
|
||||
[#]: via: (https://opensource.com/article/18/12/linux-toy-cmatrix)
|
||||
[#]: author: (Jason Baker https://opensource.com/users/jason-baker)
|
||||
|
||||
Patch into The Matrix at the Linux command line
|
||||
======
|
||||
Recreate the classic look and feel of everyone's favorite 1990s sci-fi movie code scroller with cmatrix.
|
||||

|
||||
|
||||
You've found your way to today's entry from the Linux command-line toys advent calendar. If this is your first visit to the series, you might be wondering what a command-line toy even is? It's anything that's an entertaining diversion at the terminal, be it a game, a fun utility, or a simple distraction.
|
||||
|
||||
Some of these are classics, and some are completely new (at least to me), but I hope all of you find something you enjoy in this series.
|
||||
|
||||
As we come to the close of another year, it's a good time for looking back, and looking forward. What will 2019 hold for you? What does it mean to be 2019?
|
||||
|
||||
I'm reminded that 2019 will mark the twentieth anniversary of one of my favorite science fiction movies from my teenage years, that at the time had me thinking a lot about what the future would hold: [The Matrix][1]. For a computer nerd kid like me, it was the ultimate story of a computer programmer rising up and becoming an action hero in a virtual universe by tapping into the power of his mind.
|
||||
|
||||
At the time, there was no movie that seemed more futuristic to me; both in the story itself, and in the mesmerizing special effects. Realizing that it was filmed over twenty years ago doesn't change that in my mind.
|
||||
|
||||
Bringing it back to our command-line toy for today, let's recreate the downward flowing code of the Matrix at our terminal with **cmatrix**. **cmatrix** was an easy install for me, packaged for Fedora, so installing it took simply:
|
||||
|
||||
```
|
||||
$ dnf install cmatrix
|
||||
```
|
||||
|
||||
Then, just type **cmatrix **at your terminal to run.
|
||||

|
||||
You can find the source code for **** **cmatrix** [on GitHub][2] under a GPL license.
|
||||
|
||||
Do you have a favorite command-line toy that you think I ought to include? The calendar for this series is mostly filled out but I've got a few spots left. Let me know in the comments below, and I'll check it out. If there's space, I'll try to include it. If not, but I get some good submissions, I'll do a round-up of honorable mentions at the end.
|
||||
|
||||
Check out yesterday's toy, [Winterize your Bash prompt in Linux][3], and check back tomorrow for another!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/12/linux-toy-cmatrix
|
||||
|
||||
作者:[Jason Baker][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/jason-baker
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://en.wikipedia.org/wiki/The_Matrix
|
||||
[2]: https://github.com/abishekvashok/cmatrix
|
||||
[3]: https://opensource.com/article/18/12/linux-toy-bash-prompt
|
||||
@ -0,0 +1,745 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (TLP – An Advanced Power Management Tool That Improve Battery Life On Linux Laptop)
|
||||
[#]: via: (https://www.2daygeek.com/tlp-increase-optimize-linux-laptop-battery-life/)
|
||||
[#]: author: (Magesh Maruthamuthu https://www.2daygeek.com/author/magesh/)
|
||||
|
||||
TLP – An Advanced Power Management Tool That Improve Battery Life On Linux Laptop
|
||||
======
|
||||
|
||||
Laptop battery is highly optimized for Windows OS, that i had realized when i was using Windows OS in my laptop but it’s not same for Linux.
|
||||
|
||||
Over the years Linux has improved a lot for battery optimization but still we need make some necessary things to improve laptop battery life in Linux.
|
||||
|
||||
When i think about battery life, i got few options for that but i felt TLP is a better solutions for me so, i’m going with it.
|
||||
|
||||
In this tutorial we are going to discuss about TLP in details to improve battery life.
|
||||
|
||||
We had written three articles previously in our site about **[laptop battery saving utilities][1]** for Linux **[PowerTOP][2]** and **[Battery Charging State][3]**.
|
||||
|
||||
### What is TLP?
|
||||
|
||||
[TLP][4] is a free opensource advanced power management tool that improve your battery life without making any configuration change.
|
||||
|
||||
Since it comes with a default configuration already optimized for battery life, so you may just install and forget it.
|
||||
|
||||
Also, it is highly customizable to fulfill your specific requirements. TLP is a pure command line tool with automated background tasks. It does not contain a GUI.
|
||||
|
||||
TLP runs on every laptop brand. Setting the battery charge thresholds is available for IBM/Lenovo ThinkPads only.
|
||||
|
||||
All TLP settings are stored in `/etc/default/tlp`. The default configuration provides optimized power saving out of the box.
|
||||
|
||||
The following TLP settings is available for customization and you need to make the necessary changes accordingly if you want it.
|
||||
|
||||
### TLP Features
|
||||
|
||||
* Kernel laptop mode and dirty buffer timeouts
|
||||
* Processor frequency scaling including “turbo boost” / “turbo core”
|
||||
* Limit max/min P-state to control power dissipation of the CPU
|
||||
* HWP energy performance hints
|
||||
* Power aware process scheduler for multi-core/hyper-threading
|
||||
* Processor performance versus energy savings policy (x86_energy_perf_policy)
|
||||
* Hard disk advanced power magement level (APM) and spin down timeout (per disk)
|
||||
* AHCI link power management (ALPM) with device blacklist
|
||||
* PCIe active state power management (PCIe ASPM)
|
||||
* Runtime power management for PCI(e) bus devices
|
||||
* Radeon graphics power management (KMS and DPM)
|
||||
* Wifi power saving mode
|
||||
* Power off optical drive in drive bay
|
||||
* Audio power saving mode
|
||||
* I/O scheduler (per disk)
|
||||
* USB autosuspend with device blacklist/whitelist (input devices excluded automatically)
|
||||
* Enable or disable integrated wifi, bluetooth or wwan devices upon system startup and shutdown
|
||||
* Restore radio device state on system startup (from previous shutdown).
|
||||
* Radio device wizard: switch radios upon network connect/disconnect and dock/undock
|
||||
* Disable Wake On LAN
|
||||
* Integrated WWAN and bluetooth state is restored after suspend/hibernate
|
||||
* Untervolting of Intel processors – requires kernel with PHC-Patch
|
||||
* Battery charge thresholds – ThinkPads only
|
||||
* Recalibrate battery – ThinkPads only
|
||||
|
||||
|
||||
|
||||
### How to Install TLP in Linux
|
||||
|
||||
TLP package is available in most of the distributions official repository so, use the distributions **[Package Manager][5]** to install it.
|
||||
|
||||
For **`Fedora`** system, use **[DNF Command][6]** to install TLP.
|
||||
|
||||
```
|
||||
$ sudo dnf install tlp tlp-rdw
|
||||
```
|
||||
|
||||
ThinkPads require an additional packages.
|
||||
|
||||
```
|
||||
$ sudo dnf install https://download1.rpmfusion.org/free/fedora/rpmfusion-free-release-$(rpm -E %fedora).noarch.rpm
|
||||
$ sudo dnf install http://repo.linrunner.de/fedora/tlp/repos/releases/tlp-release.fc$(rpm -E %fedora).noarch.rpm
|
||||
$ sudo dnf install akmod-tp_smapi akmod-acpi_call kernel-devel
|
||||
```
|
||||
|
||||
Install smartmontool to display S.M.A.R.T. data in tlp-stat.
|
||||
|
||||
```
|
||||
$ sudo dnf install smartmontools
|
||||
```
|
||||
|
||||
For **`Debian/Ubuntu`** systems, use **[APT-GET Command][7]** or **[APT Command][8]** to install TLP.
|
||||
|
||||
```
|
||||
$ sudo apt install tlp tlp-rdw
|
||||
```
|
||||
|
||||
ThinkPads require an additional packages.
|
||||
|
||||
```
|
||||
$ sudo apt-get install tp-smapi-dkms acpi-call-dkms
|
||||
```
|
||||
|
||||
Install smartmontool to display S.M.A.R.T. data in tlp-stat.
|
||||
|
||||
```
|
||||
$ sudo apt-get install smartmontools
|
||||
```
|
||||
|
||||
When the official package becomes outdated for Ubuntu based systems then use the following PPA repository which provides an up-to-date version. Run the following commands to install TLP using the PPA.
|
||||
|
||||
```
|
||||
$ sudo apt-get install tlp tlp-rdw
|
||||
```
|
||||
|
||||
For **`Arch Linux`** based systems, use **[Pacman Command][9]** to install TLP.
|
||||
|
||||
```
|
||||
$ sudo pacman -S tlp tlp-rdw
|
||||
```
|
||||
|
||||
ThinkPads require an additional packages.
|
||||
|
||||
```
|
||||
$ pacman -S tp_smapi acpi_call
|
||||
```
|
||||
|
||||
Install smartmontool to display S.M.A.R.T. data in tlp-stat.
|
||||
|
||||
```
|
||||
$ sudo pacman -S smartmontools
|
||||
```
|
||||
|
||||
Enable TLP & TLP-Sleep service on boot for Arch Linux based systems.
|
||||
|
||||
```
|
||||
$ sudo systemctl enable tlp.service
|
||||
$ sudo systemctl enable tlp-sleep.service
|
||||
```
|
||||
|
||||
You should also mask the following services to avoid conflicts and assure proper operation of TLP’s radio device switching options for Arch Linux based systems.
|
||||
|
||||
```
|
||||
$ sudo systemctl mask systemd-rfkill.service
|
||||
$ sudo systemctl mask systemd-rfkill.socket
|
||||
```
|
||||
|
||||
For **`RHEL/CentOS`** systems, use **[YUM Command][10]** to install TLP.
|
||||
|
||||
```
|
||||
$ sudo yum install tlp tlp-rdw
|
||||
```
|
||||
|
||||
Install smartmontool to display S.M.A.R.T. data in tlp-stat.
|
||||
|
||||
```
|
||||
$ sudo yum install smartmontools
|
||||
```
|
||||
|
||||
For **`openSUSE Leap`** system, use **[Zypper Command][11]** to install TLP.
|
||||
|
||||
```
|
||||
$ sudo zypper install TLP
|
||||
```
|
||||
|
||||
Install smartmontool to display S.M.A.R.T. data in tlp-stat.
|
||||
|
||||
```
|
||||
$ sudo zypper install smartmontools
|
||||
```
|
||||
|
||||
After successfully TLP installed, use the following command to start the service.
|
||||
|
||||
```
|
||||
$ systemctl start tlp.service
|
||||
```
|
||||
|
||||
To show battery information.
|
||||
|
||||
```
|
||||
$ sudo tlp-stat -b
|
||||
or
|
||||
$ sudo tlp-stat --battery
|
||||
|
||||
--- TLP 1.1 --------------------------------------------
|
||||
|
||||
+++ Battery Status
|
||||
/sys/class/power_supply/BAT0/manufacturer = SMP
|
||||
/sys/class/power_supply/BAT0/model_name = L14M4P23
|
||||
/sys/class/power_supply/BAT0/cycle_count = (not supported)
|
||||
/sys/class/power_supply/BAT0/energy_full_design = 60000 [mWh]
|
||||
/sys/class/power_supply/BAT0/energy_full = 48850 [mWh]
|
||||
/sys/class/power_supply/BAT0/energy_now = 48850 [mWh]
|
||||
/sys/class/power_supply/BAT0/power_now = 0 [mW]
|
||||
/sys/class/power_supply/BAT0/status = Full
|
||||
|
||||
Charge = 100.0 [%]
|
||||
Capacity = 81.4 [%]
|
||||
```
|
||||
|
||||
To show disk information.
|
||||
|
||||
```
|
||||
$ sudo tlp-stat -d
|
||||
or
|
||||
$ sudo tlp-stat --disk
|
||||
|
||||
--- TLP 1.1 --------------------------------------------
|
||||
|
||||
+++ Storage Devices
|
||||
/dev/sda:
|
||||
Model = WDC WD10SPCX-24HWST1
|
||||
Firmware = 02.01A02
|
||||
APM Level = 128
|
||||
Status = active/idle
|
||||
Scheduler = mq-deadline
|
||||
|
||||
Runtime PM: control = on, autosuspend_delay = (not available)
|
||||
|
||||
SMART info:
|
||||
4 Start_Stop_Count = 18787
|
||||
5 Reallocated_Sector_Ct = 0
|
||||
9 Power_On_Hours = 606 [h]
|
||||
12 Power_Cycle_Count = 1792
|
||||
193 Load_Cycle_Count = 25775
|
||||
194 Temperature_Celsius = 31 [°C]
|
||||
|
||||
|
||||
+++ AHCI Link Power Management (ALPM)
|
||||
/sys/class/scsi_host/host0/link_power_management_policy = med_power_with_dipm
|
||||
/sys/class/scsi_host/host1/link_power_management_policy = med_power_with_dipm
|
||||
/sys/class/scsi_host/host2/link_power_management_policy = med_power_with_dipm
|
||||
/sys/class/scsi_host/host3/link_power_management_policy = med_power_with_dipm
|
||||
|
||||
+++ AHCI Host Controller Runtime Power Management
|
||||
/sys/bus/pci/devices/0000:00:17.0/ata1/power/control = on
|
||||
/sys/bus/pci/devices/0000:00:17.0/ata2/power/control = on
|
||||
/sys/bus/pci/devices/0000:00:17.0/ata3/power/control = on
|
||||
/sys/bus/pci/devices/0000:00:17.0/ata4/power/control = on
|
||||
```
|
||||
|
||||
To show PCI device information.
|
||||
|
||||
```
|
||||
$ sudo tlp-stat -e
|
||||
or
|
||||
$ sudo tlp-stat --pcie
|
||||
|
||||
--- TLP 1.1 --------------------------------------------
|
||||
|
||||
+++ Runtime Power Management
|
||||
Device blacklist = (not configured)
|
||||
Driver blacklist = amdgpu nouveau nvidia radeon pcieport
|
||||
|
||||
/sys/bus/pci/devices/0000:00:00.0/power/control = auto (0x060000, Host bridge, skl_uncore)
|
||||
/sys/bus/pci/devices/0000:00:01.0/power/control = auto (0x060400, PCI bridge, pcieport)
|
||||
/sys/bus/pci/devices/0000:00:02.0/power/control = auto (0x030000, VGA compatible controller, i915)
|
||||
/sys/bus/pci/devices/0000:00:14.0/power/control = auto (0x0c0330, USB controller, xhci_hcd)
|
||||
/sys/bus/pci/devices/0000:00:16.0/power/control = auto (0x078000, Communication controller, mei_me)
|
||||
/sys/bus/pci/devices/0000:00:17.0/power/control = auto (0x010601, SATA controller, ahci)
|
||||
/sys/bus/pci/devices/0000:00:1c.0/power/control = auto (0x060400, PCI bridge, pcieport)
|
||||
/sys/bus/pci/devices/0000:00:1c.2/power/control = auto (0x060400, PCI bridge, pcieport)
|
||||
/sys/bus/pci/devices/0000:00:1c.3/power/control = auto (0x060400, PCI bridge, pcieport)
|
||||
/sys/bus/pci/devices/0000:00:1d.0/power/control = auto (0x060400, PCI bridge, pcieport)
|
||||
/sys/bus/pci/devices/0000:00:1f.0/power/control = auto (0x060100, ISA bridge, no driver)
|
||||
/sys/bus/pci/devices/0000:00:1f.2/power/control = auto (0x058000, Memory controller, no driver)
|
||||
/sys/bus/pci/devices/0000:00:1f.3/power/control = auto (0x040300, Audio device, snd_hda_intel)
|
||||
/sys/bus/pci/devices/0000:00:1f.4/power/control = auto (0x0c0500, SMBus, i801_smbus)
|
||||
/sys/bus/pci/devices/0000:01:00.0/power/control = auto (0x030200, 3D controller, nouveau)
|
||||
/sys/bus/pci/devices/0000:07:00.0/power/control = auto (0x080501, SD Host controller, sdhci-pci)
|
||||
/sys/bus/pci/devices/0000:08:00.0/power/control = auto (0x028000, Network controller, iwlwifi)
|
||||
/sys/bus/pci/devices/0000:09:00.0/power/control = auto (0x020000, Ethernet controller, r8168)
|
||||
/sys/bus/pci/devices/0000:0a:00.0/power/control = auto (0x010802, Non-Volatile memory controller, nvme)
|
||||
```
|
||||
|
||||
To show graphics card information.
|
||||
|
||||
```
|
||||
$ sudo tlp-stat -g
|
||||
or
|
||||
$ sudo tlp-stat --graphics
|
||||
|
||||
--- TLP 1.1 --------------------------------------------
|
||||
|
||||
+++ Intel Graphics
|
||||
/sys/module/i915/parameters/enable_dc = -1 (use per-chip default)
|
||||
/sys/module/i915/parameters/enable_fbc = 1 (enabled)
|
||||
/sys/module/i915/parameters/enable_psr = 0 (disabled)
|
||||
/sys/module/i915/parameters/modeset = -1 (use per-chip default)
|
||||
```
|
||||
|
||||
To show Processor information.
|
||||
|
||||
```
|
||||
$ sudo tlp-stat -p
|
||||
or
|
||||
$ sudo tlp-stat --processor
|
||||
|
||||
--- TLP 1.1 --------------------------------------------
|
||||
|
||||
+++ Processor
|
||||
CPU model = Intel(R) Core(TM) i7-6700HQ CPU @ 2.60GHz
|
||||
|
||||
/sys/devices/system/cpu/cpu0/cpufreq/scaling_driver = intel_pstate
|
||||
/sys/devices/system/cpu/cpu0/cpufreq/scaling_governor = powersave
|
||||
/sys/devices/system/cpu/cpu0/cpufreq/scaling_available_governors = performance powersave
|
||||
/sys/devices/system/cpu/cpu0/cpufreq/scaling_min_freq = 800000 [kHz]
|
||||
/sys/devices/system/cpu/cpu0/cpufreq/scaling_max_freq = 3500000 [kHz]
|
||||
/sys/devices/system/cpu/cpu0/cpufreq/energy_performance_preference = balance_power
|
||||
/sys/devices/system/cpu/cpu0/cpufreq/energy_performance_available_preferences = default performance balance_performance balance_power power
|
||||
|
||||
/sys/devices/system/cpu/cpu1/cpufreq/scaling_driver = intel_pstate
|
||||
/sys/devices/system/cpu/cpu1/cpufreq/scaling_governor = powersave
|
||||
/sys/devices/system/cpu/cpu1/cpufreq/scaling_available_governors = performance powersave
|
||||
/sys/devices/system/cpu/cpu1/cpufreq/scaling_min_freq = 800000 [kHz]
|
||||
/sys/devices/system/cpu/cpu1/cpufreq/scaling_max_freq = 3500000 [kHz]
|
||||
/sys/devices/system/cpu/cpu1/cpufreq/energy_performance_preference = balance_power
|
||||
/sys/devices/system/cpu/cpu1/cpufreq/energy_performance_available_preferences = default performance balance_performance balance_power power
|
||||
|
||||
/sys/devices/system/cpu/cpu2/cpufreq/scaling_driver = intel_pstate
|
||||
/sys/devices/system/cpu/cpu2/cpufreq/scaling_governor = powersave
|
||||
/sys/devices/system/cpu/cpu2/cpufreq/scaling_available_governors = performance powersave
|
||||
/sys/devices/system/cpu/cpu2/cpufreq/scaling_min_freq = 800000 [kHz]
|
||||
/sys/devices/system/cpu/cpu2/cpufreq/scaling_max_freq = 3500000 [kHz]
|
||||
/sys/devices/system/cpu/cpu2/cpufreq/energy_performance_preference = balance_power
|
||||
/sys/devices/system/cpu/cpu2/cpufreq/energy_performance_available_preferences = default performance balance_performance balance_power power
|
||||
|
||||
/sys/devices/system/cpu/cpu3/cpufreq/scaling_driver = intel_pstate
|
||||
/sys/devices/system/cpu/cpu3/cpufreq/scaling_governor = powersave
|
||||
/sys/devices/system/cpu/cpu3/cpufreq/scaling_available_governors = performance powersave
|
||||
/sys/devices/system/cpu/cpu3/cpufreq/scaling_min_freq = 800000 [kHz]
|
||||
/sys/devices/system/cpu/cpu3/cpufreq/scaling_max_freq = 3500000 [kHz]
|
||||
/sys/devices/system/cpu/cpu3/cpufreq/energy_performance_preference = balance_power
|
||||
/sys/devices/system/cpu/cpu3/cpufreq/energy_performance_available_preferences = default performance balance_performance balance_power power
|
||||
|
||||
/sys/devices/system/cpu/cpu4/cpufreq/scaling_driver = intel_pstate
|
||||
/sys/devices/system/cpu/cpu4/cpufreq/scaling_governor = powersave
|
||||
/sys/devices/system/cpu/cpu4/cpufreq/scaling_available_governors = performance powersave
|
||||
/sys/devices/system/cpu/cpu4/cpufreq/scaling_min_freq = 800000 [kHz]
|
||||
/sys/devices/system/cpu/cpu4/cpufreq/scaling_max_freq = 3500000 [kHz]
|
||||
/sys/devices/system/cpu/cpu4/cpufreq/energy_performance_preference = balance_power
|
||||
/sys/devices/system/cpu/cpu4/cpufreq/energy_performance_available_preferences = default performance balance_performance balance_power power
|
||||
|
||||
/sys/devices/system/cpu/cpu5/cpufreq/scaling_driver = intel_pstate
|
||||
/sys/devices/system/cpu/cpu5/cpufreq/scaling_governor = powersave
|
||||
/sys/devices/system/cpu/cpu5/cpufreq/scaling_available_governors = performance powersave
|
||||
/sys/devices/system/cpu/cpu5/cpufreq/scaling_min_freq = 800000 [kHz]
|
||||
/sys/devices/system/cpu/cpu5/cpufreq/scaling_max_freq = 3500000 [kHz]
|
||||
/sys/devices/system/cpu/cpu5/cpufreq/energy_performance_preference = balance_power
|
||||
/sys/devices/system/cpu/cpu5/cpufreq/energy_performance_available_preferences = default performance balance_performance balance_power power
|
||||
|
||||
/sys/devices/system/cpu/cpu6/cpufreq/scaling_driver = intel_pstate
|
||||
/sys/devices/system/cpu/cpu6/cpufreq/scaling_governor = powersave
|
||||
/sys/devices/system/cpu/cpu6/cpufreq/scaling_available_governors = performance powersave
|
||||
/sys/devices/system/cpu/cpu6/cpufreq/scaling_min_freq = 800000 [kHz]
|
||||
/sys/devices/system/cpu/cpu6/cpufreq/scaling_max_freq = 3500000 [kHz]
|
||||
/sys/devices/system/cpu/cpu6/cpufreq/energy_performance_preference = balance_power
|
||||
/sys/devices/system/cpu/cpu6/cpufreq/energy_performance_available_preferences = default performance balance_performance balance_power power
|
||||
|
||||
/sys/devices/system/cpu/cpu7/cpufreq/scaling_driver = intel_pstate
|
||||
/sys/devices/system/cpu/cpu7/cpufreq/scaling_governor = powersave
|
||||
/sys/devices/system/cpu/cpu7/cpufreq/scaling_available_governors = performance powersave
|
||||
/sys/devices/system/cpu/cpu7/cpufreq/scaling_min_freq = 800000 [kHz]
|
||||
/sys/devices/system/cpu/cpu7/cpufreq/scaling_max_freq = 3500000 [kHz]
|
||||
/sys/devices/system/cpu/cpu7/cpufreq/energy_performance_preference = balance_power
|
||||
/sys/devices/system/cpu/cpu7/cpufreq/energy_performance_available_preferences = default performance balance_performance balance_power power
|
||||
|
||||
/sys/devices/system/cpu/intel_pstate/min_perf_pct = 22 [%]
|
||||
/sys/devices/system/cpu/intel_pstate/max_perf_pct = 100 [%]
|
||||
/sys/devices/system/cpu/intel_pstate/no_turbo = 0
|
||||
/sys/devices/system/cpu/intel_pstate/turbo_pct = 33 [%]
|
||||
/sys/devices/system/cpu/intel_pstate/num_pstates = 28
|
||||
|
||||
x86_energy_perf_policy: program not installed.
|
||||
|
||||
/sys/module/workqueue/parameters/power_efficient = Y
|
||||
/proc/sys/kernel/nmi_watchdog = 0
|
||||
|
||||
+++ Undervolting
|
||||
PHC kernel not available.
|
||||
```
|
||||
|
||||
To show system data information.
|
||||
|
||||
```
|
||||
$ sudo tlp-stat -s
|
||||
or
|
||||
$ sudo tlp-stat --system
|
||||
|
||||
--- TLP 1.1 --------------------------------------------
|
||||
|
||||
+++ System Info
|
||||
System = LENOVO Lenovo ideapad Y700-15ISK 80NV
|
||||
BIOS = CDCN35WW
|
||||
Release = "Manjaro Linux"
|
||||
Kernel = 4.19.6-1-MANJARO #1 SMP PREEMPT Sat Dec 1 12:21:26 UTC 2018 x86_64
|
||||
/proc/cmdline = BOOT_IMAGE=/boot/vmlinuz-4.19-x86_64 root=UUID=69d9dd18-36be-4631-9ebb-78f05fe3217f rw quiet resume=UUID=a2092b92-af29-4760-8e68-7a201922573b
|
||||
Init system = systemd
|
||||
Boot mode = BIOS (CSM, Legacy)
|
||||
|
||||
+++ TLP Status
|
||||
State = enabled
|
||||
Last run = 11:04:00 IST, 596 sec(s) ago
|
||||
Mode = battery
|
||||
Power source = battery
|
||||
```
|
||||
|
||||
To show temperatures and fan speed information.
|
||||
|
||||
```
|
||||
$ sudo tlp-stat -t
|
||||
or
|
||||
$ sudo tlp-stat --temp
|
||||
|
||||
--- TLP 1.1 --------------------------------------------
|
||||
|
||||
+++ Temperatures
|
||||
CPU temp = 36 [°C]
|
||||
Fan speed = (not available)
|
||||
```
|
||||
|
||||
To show USB device data information.
|
||||
|
||||
```
|
||||
$ sudo tlp-stat -u
|
||||
or
|
||||
$ sudo tlp-stat --usb
|
||||
|
||||
--- TLP 1.1 --------------------------------------------
|
||||
|
||||
+++ USB
|
||||
Autosuspend = disabled
|
||||
Device whitelist = (not configured)
|
||||
Device blacklist = (not configured)
|
||||
Bluetooth blacklist = disabled
|
||||
Phone blacklist = disabled
|
||||
WWAN blacklist = enabled
|
||||
|
||||
Bus 002 Device 001 ID 1d6b:0003 control = auto, autosuspend_delay_ms = 0 -- Linux Foundation 3.0 root hub (hub)
|
||||
Bus 001 Device 003 ID 174f:14e8 control = auto, autosuspend_delay_ms = 2000 -- Syntek (uvcvideo)
|
||||
Bus 001 Device 002 ID 17ef:6053 control = on, autosuspend_delay_ms = 2000 -- Lenovo (usbhid)
|
||||
Bus 001 Device 004 ID 8087:0a2b control = auto, autosuspend_delay_ms = 2000 -- Intel Corp. (btusb)
|
||||
Bus 001 Device 001 ID 1d6b:0002 control = auto, autosuspend_delay_ms = 0 -- Linux Foundation 2.0 root hub (hub)
|
||||
```
|
||||
|
||||
To show warnings.
|
||||
|
||||
```
|
||||
$ sudo tlp-stat -w
|
||||
or
|
||||
$ sudo tlp-stat --warn
|
||||
|
||||
--- TLP 1.1 --------------------------------------------
|
||||
|
||||
No warnings detected.
|
||||
```
|
||||
|
||||
Status report with configuration and all active settings.
|
||||
|
||||
```
|
||||
$ sudo tlp-stat
|
||||
|
||||
--- TLP 1.1 --------------------------------------------
|
||||
|
||||
+++ Configured Settings: /etc/default/tlp
|
||||
TLP_ENABLE=1
|
||||
TLP_DEFAULT_MODE=AC
|
||||
TLP_PERSISTENT_DEFAULT=0
|
||||
DISK_IDLE_SECS_ON_AC=0
|
||||
DISK_IDLE_SECS_ON_BAT=2
|
||||
MAX_LOST_WORK_SECS_ON_AC=15
|
||||
MAX_LOST_WORK_SECS_ON_BAT=60
|
||||
CPU_HWP_ON_AC=balance_performance
|
||||
CPU_HWP_ON_BAT=balance_power
|
||||
SCHED_POWERSAVE_ON_AC=0
|
||||
SCHED_POWERSAVE_ON_BAT=1
|
||||
NMI_WATCHDOG=0
|
||||
ENERGY_PERF_POLICY_ON_AC=performance
|
||||
ENERGY_PERF_POLICY_ON_BAT=power
|
||||
DISK_DEVICES="sda sdb"
|
||||
DISK_APM_LEVEL_ON_AC="254 254"
|
||||
DISK_APM_LEVEL_ON_BAT="128 128"
|
||||
SATA_LINKPWR_ON_AC="med_power_with_dipm max_performance"
|
||||
SATA_LINKPWR_ON_BAT="med_power_with_dipm max_performance"
|
||||
AHCI_RUNTIME_PM_TIMEOUT=15
|
||||
PCIE_ASPM_ON_AC=performance
|
||||
PCIE_ASPM_ON_BAT=powersave
|
||||
RADEON_POWER_PROFILE_ON_AC=default
|
||||
RADEON_POWER_PROFILE_ON_BAT=low
|
||||
RADEON_DPM_STATE_ON_AC=performance
|
||||
RADEON_DPM_STATE_ON_BAT=battery
|
||||
RADEON_DPM_PERF_LEVEL_ON_AC=auto
|
||||
RADEON_DPM_PERF_LEVEL_ON_BAT=auto
|
||||
WIFI_PWR_ON_AC=off
|
||||
WIFI_PWR_ON_BAT=on
|
||||
WOL_DISABLE=Y
|
||||
SOUND_POWER_SAVE_ON_AC=0
|
||||
SOUND_POWER_SAVE_ON_BAT=1
|
||||
SOUND_POWER_SAVE_CONTROLLER=Y
|
||||
BAY_POWEROFF_ON_AC=0
|
||||
BAY_POWEROFF_ON_BAT=0
|
||||
BAY_DEVICE="sr0"
|
||||
RUNTIME_PM_ON_AC=on
|
||||
RUNTIME_PM_ON_BAT=auto
|
||||
RUNTIME_PM_DRIVER_BLACKLIST="amdgpu nouveau nvidia radeon pcieport"
|
||||
USB_AUTOSUSPEND=0
|
||||
USB_BLACKLIST_BTUSB=0
|
||||
USB_BLACKLIST_PHONE=0
|
||||
USB_BLACKLIST_PRINTER=1
|
||||
USB_BLACKLIST_WWAN=1
|
||||
RESTORE_DEVICE_STATE_ON_STARTUP=0
|
||||
|
||||
+++ System Info
|
||||
System = LENOVO Lenovo ideapad Y700-15ISK 80NV
|
||||
BIOS = CDCN35WW
|
||||
Release = "Manjaro Linux"
|
||||
Kernel = 4.19.6-1-MANJARO #1 SMP PREEMPT Sat Dec 1 12:21:26 UTC 2018 x86_64
|
||||
/proc/cmdline = BOOT_IMAGE=/boot/vmlinuz-4.19-x86_64 root=UUID=69d9dd18-36be-4631-9ebb-78f05fe3217f rw quiet resume=UUID=a2092b92-af29-4760-8e68-7a201922573b
|
||||
Init system = systemd
|
||||
Boot mode = BIOS (CSM, Legacy)
|
||||
|
||||
+++ TLP Status
|
||||
State = enabled
|
||||
Last run = 11:04:00 IST, 684 sec(s) ago
|
||||
Mode = battery
|
||||
Power source = battery
|
||||
|
||||
+++ Processor
|
||||
CPU model = Intel(R) Core(TM) i7-6700HQ CPU @ 2.60GHz
|
||||
|
||||
/sys/devices/system/cpu/cpu0/cpufreq/scaling_driver = intel_pstate
|
||||
/sys/devices/system/cpu/cpu0/cpufreq/scaling_governor = powersave
|
||||
/sys/devices/system/cpu/cpu0/cpufreq/scaling_available_governors = performance powersave
|
||||
/sys/devices/system/cpu/cpu0/cpufreq/scaling_min_freq = 800000 [kHz]
|
||||
/sys/devices/system/cpu/cpu0/cpufreq/scaling_max_freq = 3500000 [kHz]
|
||||
/sys/devices/system/cpu/cpu0/cpufreq/energy_performance_preference = balance_power
|
||||
/sys/devices/system/cpu/cpu0/cpufreq/energy_performance_available_preferences = default performance balance_performance balance_power power
|
||||
|
||||
/sys/devices/system/cpu/cpu1/cpufreq/scaling_driver = intel_pstate
|
||||
/sys/devices/system/cpu/cpu1/cpufreq/scaling_governor = powersave
|
||||
/sys/devices/system/cpu/cpu1/cpufreq/scaling_available_governors = performance powersave
|
||||
/sys/devices/system/cpu/cpu1/cpufreq/scaling_min_freq = 800000 [kHz]
|
||||
/sys/devices/system/cpu/cpu1/cpufreq/scaling_max_freq = 3500000 [kHz]
|
||||
/sys/devices/system/cpu/cpu1/cpufreq/energy_performance_preference = balance_power
|
||||
/sys/devices/system/cpu/cpu1/cpufreq/energy_performance_available_preferences = default performance balance_performance balance_power power
|
||||
|
||||
/sys/devices/system/cpu/cpu2/cpufreq/scaling_driver = intel_pstate
|
||||
/sys/devices/system/cpu/cpu2/cpufreq/scaling_governor = powersave
|
||||
/sys/devices/system/cpu/cpu2/cpufreq/scaling_available_governors = performance powersave
|
||||
/sys/devices/system/cpu/cpu2/cpufreq/scaling_min_freq = 800000 [kHz]
|
||||
/sys/devices/system/cpu/cpu2/cpufreq/scaling_max_freq = 3500000 [kHz]
|
||||
/sys/devices/system/cpu/cpu2/cpufreq/energy_performance_preference = balance_power
|
||||
/sys/devices/system/cpu/cpu2/cpufreq/energy_performance_available_preferences = default performance balance_performance balance_power power
|
||||
|
||||
/sys/devices/system/cpu/cpu3/cpufreq/scaling_driver = intel_pstate
|
||||
/sys/devices/system/cpu/cpu3/cpufreq/scaling_governor = powersave
|
||||
/sys/devices/system/cpu/cpu3/cpufreq/scaling_available_governors = performance powersave
|
||||
/sys/devices/system/cpu/cpu3/cpufreq/scaling_min_freq = 800000 [kHz]
|
||||
/sys/devices/system/cpu/cpu3/cpufreq/scaling_max_freq = 3500000 [kHz]
|
||||
/sys/devices/system/cpu/cpu3/cpufreq/energy_performance_preference = balance_power
|
||||
/sys/devices/system/cpu/cpu3/cpufreq/energy_performance_available_preferences = default performance balance_performance balance_power power
|
||||
|
||||
/sys/devices/system/cpu/cpu4/cpufreq/scaling_driver = intel_pstate
|
||||
/sys/devices/system/cpu/cpu4/cpufreq/scaling_governor = powersave
|
||||
/sys/devices/system/cpu/cpu4/cpufreq/scaling_available_governors = performance powersave
|
||||
/sys/devices/system/cpu/cpu4/cpufreq/scaling_min_freq = 800000 [kHz]
|
||||
/sys/devices/system/cpu/cpu4/cpufreq/scaling_max_freq = 3500000 [kHz]
|
||||
/sys/devices/system/cpu/cpu4/cpufreq/energy_performance_preference = balance_power
|
||||
/sys/devices/system/cpu/cpu4/cpufreq/energy_performance_available_preferences = default performance balance_performance balance_power power
|
||||
|
||||
/sys/devices/system/cpu/cpu5/cpufreq/scaling_driver = intel_pstate
|
||||
/sys/devices/system/cpu/cpu5/cpufreq/scaling_governor = powersave
|
||||
/sys/devices/system/cpu/cpu5/cpufreq/scaling_available_governors = performance powersave
|
||||
/sys/devices/system/cpu/cpu5/cpufreq/scaling_min_freq = 800000 [kHz]
|
||||
/sys/devices/system/cpu/cpu5/cpufreq/scaling_max_freq = 3500000 [kHz]
|
||||
/sys/devices/system/cpu/cpu5/cpufreq/energy_performance_preference = balance_power
|
||||
/sys/devices/system/cpu/cpu5/cpufreq/energy_performance_available_preferences = default performance balance_performance balance_power power
|
||||
|
||||
/sys/devices/system/cpu/cpu6/cpufreq/scaling_driver = intel_pstate
|
||||
/sys/devices/system/cpu/cpu6/cpufreq/scaling_governor = powersave
|
||||
/sys/devices/system/cpu/cpu6/cpufreq/scaling_available_governors = performance powersave
|
||||
/sys/devices/system/cpu/cpu6/cpufreq/scaling_min_freq = 800000 [kHz]
|
||||
/sys/devices/system/cpu/cpu6/cpufreq/scaling_max_freq = 3500000 [kHz]
|
||||
/sys/devices/system/cpu/cpu6/cpufreq/energy_performance_preference = balance_power
|
||||
/sys/devices/system/cpu/cpu6/cpufreq/energy_performance_available_preferences = default performance balance_performance balance_power power
|
||||
|
||||
/sys/devices/system/cpu/cpu7/cpufreq/scaling_driver = intel_pstate
|
||||
/sys/devices/system/cpu/cpu7/cpufreq/scaling_governor = powersave
|
||||
/sys/devices/system/cpu/cpu7/cpufreq/scaling_available_governors = performance powersave
|
||||
/sys/devices/system/cpu/cpu7/cpufreq/scaling_min_freq = 800000 [kHz]
|
||||
/sys/devices/system/cpu/cpu7/cpufreq/scaling_max_freq = 3500000 [kHz]
|
||||
/sys/devices/system/cpu/cpu7/cpufreq/energy_performance_preference = balance_power
|
||||
/sys/devices/system/cpu/cpu7/cpufreq/energy_performance_available_preferences = default performance balance_performance balance_power power
|
||||
|
||||
/sys/devices/system/cpu/intel_pstate/min_perf_pct = 22 [%]
|
||||
/sys/devices/system/cpu/intel_pstate/max_perf_pct = 100 [%]
|
||||
/sys/devices/system/cpu/intel_pstate/no_turbo = 0
|
||||
/sys/devices/system/cpu/intel_pstate/turbo_pct = 33 [%]
|
||||
/sys/devices/system/cpu/intel_pstate/num_pstates = 28
|
||||
|
||||
x86_energy_perf_policy: program not installed.
|
||||
|
||||
/sys/module/workqueue/parameters/power_efficient = Y
|
||||
/proc/sys/kernel/nmi_watchdog = 0
|
||||
|
||||
+++ Undervolting
|
||||
PHC kernel not available.
|
||||
|
||||
+++ Temperatures
|
||||
CPU temp = 42 [°C]
|
||||
Fan speed = (not available)
|
||||
|
||||
+++ File System
|
||||
/proc/sys/vm/laptop_mode = 2
|
||||
/proc/sys/vm/dirty_writeback_centisecs = 6000
|
||||
/proc/sys/vm/dirty_expire_centisecs = 6000
|
||||
/proc/sys/vm/dirty_ratio = 20
|
||||
/proc/sys/vm/dirty_background_ratio = 10
|
||||
|
||||
+++ Storage Devices
|
||||
/dev/sda:
|
||||
Model = WDC WD10SPCX-24HWST1
|
||||
Firmware = 02.01A02
|
||||
APM Level = 128
|
||||
Status = active/idle
|
||||
Scheduler = mq-deadline
|
||||
|
||||
Runtime PM: control = on, autosuspend_delay = (not available)
|
||||
|
||||
SMART info:
|
||||
4 Start_Stop_Count = 18787
|
||||
5 Reallocated_Sector_Ct = 0
|
||||
9 Power_On_Hours = 606 [h]
|
||||
12 Power_Cycle_Count = 1792
|
||||
193 Load_Cycle_Count = 25777
|
||||
194 Temperature_Celsius = 31 [°C]
|
||||
|
||||
|
||||
+++ AHCI Link Power Management (ALPM)
|
||||
/sys/class/scsi_host/host0/link_power_management_policy = med_power_with_dipm
|
||||
/sys/class/scsi_host/host1/link_power_management_policy = med_power_with_dipm
|
||||
/sys/class/scsi_host/host2/link_power_management_policy = med_power_with_dipm
|
||||
/sys/class/scsi_host/host3/link_power_management_policy = med_power_with_dipm
|
||||
|
||||
+++ AHCI Host Controller Runtime Power Management
|
||||
/sys/bus/pci/devices/0000:00:17.0/ata1/power/control = on
|
||||
/sys/bus/pci/devices/0000:00:17.0/ata2/power/control = on
|
||||
/sys/bus/pci/devices/0000:00:17.0/ata3/power/control = on
|
||||
/sys/bus/pci/devices/0000:00:17.0/ata4/power/control = on
|
||||
|
||||
+++ PCIe Active State Power Management
|
||||
/sys/module/pcie_aspm/parameters/policy = powersave
|
||||
|
||||
+++ Intel Graphics
|
||||
/sys/module/i915/parameters/enable_dc = -1 (use per-chip default)
|
||||
/sys/module/i915/parameters/enable_fbc = 1 (enabled)
|
||||
/sys/module/i915/parameters/enable_psr = 0 (disabled)
|
||||
/sys/module/i915/parameters/modeset = -1 (use per-chip default)
|
||||
|
||||
+++ Wireless
|
||||
bluetooth = on
|
||||
wifi = on
|
||||
wwan = none (no device)
|
||||
|
||||
hci0(btusb) : bluetooth, not connected
|
||||
wlp8s0(iwlwifi) : wifi, connected, power management = on
|
||||
|
||||
+++ Audio
|
||||
/sys/module/snd_hda_intel/parameters/power_save = 1
|
||||
/sys/module/snd_hda_intel/parameters/power_save_controller = Y
|
||||
|
||||
+++ Runtime Power Management
|
||||
Device blacklist = (not configured)
|
||||
Driver blacklist = amdgpu nouveau nvidia radeon pcieport
|
||||
|
||||
/sys/bus/pci/devices/0000:00:00.0/power/control = auto (0x060000, Host bridge, skl_uncore)
|
||||
/sys/bus/pci/devices/0000:00:01.0/power/control = auto (0x060400, PCI bridge, pcieport)
|
||||
/sys/bus/pci/devices/0000:00:02.0/power/control = auto (0x030000, VGA compatible controller, i915)
|
||||
/sys/bus/pci/devices/0000:00:14.0/power/control = auto (0x0c0330, USB controller, xhci_hcd)
|
||||
/sys/bus/pci/devices/0000:00:16.0/power/control = auto (0x078000, Communication controller, mei_me)
|
||||
/sys/bus/pci/devices/0000:00:17.0/power/control = auto (0x010601, SATA controller, ahci)
|
||||
/sys/bus/pci/devices/0000:00:1c.0/power/control = auto (0x060400, PCI bridge, pcieport)
|
||||
/sys/bus/pci/devices/0000:00:1c.2/power/control = auto (0x060400, PCI bridge, pcieport)
|
||||
/sys/bus/pci/devices/0000:00:1c.3/power/control = auto (0x060400, PCI bridge, pcieport)
|
||||
/sys/bus/pci/devices/0000:00:1d.0/power/control = auto (0x060400, PCI bridge, pcieport)
|
||||
/sys/bus/pci/devices/0000:00:1f.0/power/control = auto (0x060100, ISA bridge, no driver)
|
||||
/sys/bus/pci/devices/0000:00:1f.2/power/control = auto (0x058000, Memory controller, no driver)
|
||||
/sys/bus/pci/devices/0000:00:1f.3/power/control = auto (0x040300, Audio device, snd_hda_intel)
|
||||
/sys/bus/pci/devices/0000:00:1f.4/power/control = auto (0x0c0500, SMBus, i801_smbus)
|
||||
/sys/bus/pci/devices/0000:01:00.0/power/control = auto (0x030200, 3D controller, nouveau)
|
||||
/sys/bus/pci/devices/0000:07:00.0/power/control = auto (0x080501, SD Host controller, sdhci-pci)
|
||||
/sys/bus/pci/devices/0000:08:00.0/power/control = auto (0x028000, Network controller, iwlwifi)
|
||||
/sys/bus/pci/devices/0000:09:00.0/power/control = auto (0x020000, Ethernet controller, r8168)
|
||||
/sys/bus/pci/devices/0000:0a:00.0/power/control = auto (0x010802, Non-Volatile memory controller, nvme)
|
||||
|
||||
+++ USB
|
||||
Autosuspend = disabled
|
||||
Device whitelist = (not configured)
|
||||
Device blacklist = (not configured)
|
||||
Bluetooth blacklist = disabled
|
||||
Phone blacklist = disabled
|
||||
WWAN blacklist = enabled
|
||||
|
||||
Bus 002 Device 001 ID 1d6b:0003 control = auto, autosuspend_delay_ms = 0 -- Linux Foundation 3.0 root hub (hub)
|
||||
Bus 001 Device 003 ID 174f:14e8 control = auto, autosuspend_delay_ms = 2000 -- Syntek (uvcvideo)
|
||||
Bus 001 Device 002 ID 17ef:6053 control = on, autosuspend_delay_ms = 2000 -- Lenovo (usbhid)
|
||||
Bus 001 Device 004 ID 8087:0a2b control = auto, autosuspend_delay_ms = 2000 -- Intel Corp. (btusb)
|
||||
Bus 001 Device 001 ID 1d6b:0002 control = auto, autosuspend_delay_ms = 0 -- Linux Foundation 2.0 root hub (hub)
|
||||
|
||||
+++ Battery Status
|
||||
/sys/class/power_supply/BAT0/manufacturer = SMP
|
||||
/sys/class/power_supply/BAT0/model_name = L14M4P23
|
||||
/sys/class/power_supply/BAT0/cycle_count = (not supported)
|
||||
/sys/class/power_supply/BAT0/energy_full_design = 60000 [mWh]
|
||||
/sys/class/power_supply/BAT0/energy_full = 51690 [mWh]
|
||||
/sys/class/power_supply/BAT0/energy_now = 50140 [mWh]
|
||||
/sys/class/power_supply/BAT0/power_now = 12185 [mW]
|
||||
/sys/class/power_supply/BAT0/status = Discharging
|
||||
|
||||
Charge = 97.0 [%]
|
||||
Capacity = 86.2 [%]
|
||||
```
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.2daygeek.com/tlp-increase-optimize-linux-laptop-battery-life/
|
||||
|
||||
作者:[Magesh Maruthamuthu][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.2daygeek.com/author/magesh/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.2daygeek.com/check-laptop-battery-status-and-charging-state-in-linux-terminal/
|
||||
[2]: https://www.2daygeek.com/powertop-monitors-laptop-battery-usage-linux/
|
||||
[3]: https://www.2daygeek.com/monitor-laptop-battery-charging-state-linux/
|
||||
[4]: https://linrunner.de/en/tlp/docs/tlp-linux-advanced-power-management.html
|
||||
[5]: https://www.2daygeek.com/category/package-management/
|
||||
[6]: https://www.2daygeek.com/dnf-command-examples-manage-packages-fedora-system/
|
||||
[7]: https://www.2daygeek.com/apt-get-apt-cache-command-examples-manage-packages-debian-ubuntu-systems/
|
||||
[8]: https://www.2daygeek.com/apt-command-examples-manage-packages-debian-ubuntu-systems/
|
||||
[9]: https://www.2daygeek.com/pacman-command-examples-manage-packages-arch-linux-system/
|
||||
[10]: https://www.2daygeek.com/yum-command-examples-manage-packages-rhel-centos-systems/
|
||||
[11]: https://www.2daygeek.com/zypper-command-examples-manage-packages-opensuse-system/
|
||||
@ -0,0 +1,145 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Podman and user namespaces: A marriage made in heaven)
|
||||
[#]: via: (https://opensource.com/article/18/12/podman-and-user-namespaces)
|
||||
[#]: author: (Daniel J Walsh https://opensource.com/users/rhatdan)
|
||||
|
||||
Podman and user namespaces: A marriage made in heaven
|
||||
======
|
||||
Learn how to use Podman to run containers in separate user namespaces.
|
||||

|
||||
|
||||
[Podman][1], part of the [libpod][2] library, enables users to manage pods, containers, and container images. In my last article, I wrote about [Podman as a more secure way to run containers][3]. Here, I'll explain how to use Podman to run containers in separate user namespaces.
|
||||
|
||||
I have always thought of [user namespace][4], primarily developed by Red Hat's Eric Biederman, as a great feature for separating containers. User namespace allows you to specify a user identifier (UID) and group identifier (GID) mapping to run your containers. This means you can run as UID 0 inside the container and UID 100000 outside the container. If your container processes escape the container, the kernel will treat them as UID 100000. Not only that, but any file object owned by a UID that isn't mapped into the user namespace will be treated as owned by "nobody" (65534, kernel.overflowuid), and the container process will not be allowed access unless the object is accessible by "other" (world readable/writable).
|
||||
|
||||
If you have a file owned by "real" root with permissions [660][5], and the container processes in the user namespace attempt to read it, they will be prevented from accessing it and will see the file as owned by nobody.
|
||||
|
||||
### An example
|
||||
|
||||
Here's how that might work. First, I create a file in my system owned by root.
|
||||
|
||||
```
|
||||
$ sudo bash -c "echo Test > /tmp/test"
|
||||
$ sudo chmod 600 /tmp/test
|
||||
$ sudo ls -l /tmp/test
|
||||
-rw-------. 1 root root 5 Dec 17 16:40 /tmp/test
|
||||
```
|
||||
|
||||
Next, I volume-mount the file into a container running with a user namespace map 0:100000:5000.
|
||||
|
||||
```
|
||||
$ sudo podman run -ti -v /tmp/test:/tmp/test:Z --uidmap 0:100000:5000 fedora sh
|
||||
# id
|
||||
uid=0(root) gid=0(root) groups=0(root)
|
||||
# ls -l /tmp/test
|
||||
-rw-rw----. 1 nobody nobody 8 Nov 30 12:40 /tmp/test
|
||||
# cat /tmp/test
|
||||
cat: /tmp/test: Permission denied
|
||||
```
|
||||
|
||||
The **\--uidmap** setting above tells Podman to map a range of 5000 UIDs inside the container, starting with UID 100000 outside the container (so the range is 100000-104999) to a range starting at UID 0 inside the container (so the range is 0-4999). Inside the container, if my process is running as UID 1, it is 100001 on the host
|
||||
|
||||
Since the real UID=0 is not mapped into the container, any file owned by root will be treated as owned by nobody. Even if the process inside the container has **CAP_DAC_OVERRIDE** , it can't override this protection. **DAC_OVERRIDE** enables root processes to read/write any file on the system, even if the process was not owned by root or world readable or writable.
|
||||
|
||||
User namespace capabilities are not the same as capabilities on the host. They are namespaced capabilities. This means my container root has capabilities only within the container—really only across the range of UIDs that were mapped into the user namespace. If a container process escaped the container, it wouldn't have any capabilities over UIDs not mapped into the user namespace, including UID=0. Even if the processes could somehow enter another container, they would not have those capabilities if the container uses a different range of UIDs.
|
||||
|
||||
Note that SELinux and other technologies also limit what would happen if a container process broke out of the container.
|
||||
|
||||
### Using `podman top` to show user namespaces
|
||||
|
||||
We have added features to **podman top** to allow you to examine the usernames of processes running inside a container and identify their real UIDs on the host.
|
||||
|
||||
Let's start by running a sleep container using our UID mapping.
|
||||
|
||||
```
|
||||
$ sudo podman run --uidmap 0:100000:5000 -d fedora sleep 1000
|
||||
```
|
||||
|
||||
Now run **podman top** :
|
||||
|
||||
```
|
||||
$ sudo podman top --latest user huser
|
||||
USER HUSER
|
||||
root 100000
|
||||
|
||||
$ ps -ef | grep sleep
|
||||
100000 21821 21809 0 08:04 ? 00:00:00 /usr/bin/coreutils --coreutils-prog-shebang=sleep /usr/bin/sleep 1000
|
||||
```
|
||||
|
||||
Notice **podman top** reports that the user process is running as root inside the container but as UID 100000 on the host (HUSER). Also the **ps** command confirms that the sleep process is running as UID 100000.
|
||||
|
||||
Now let's run a second container, but this time we will choose a separate UID map starting at 200000.
|
||||
|
||||
```
|
||||
$ sudo podman run --uidmap 0:200000:5000 -d fedora sleep 1000
|
||||
$ sudo podman top --latest user huser
|
||||
USER HUSER
|
||||
root 200000
|
||||
|
||||
$ ps -ef | grep sleep
|
||||
100000 21821 21809 0 08:04 ? 00:00:00 /usr/bin/coreutils --coreutils-prog-shebang=sleep /usr/bin/sleep 1000
|
||||
200000 23644 23632 1 08:08 ? 00:00:00 /usr/bin/coreutils --coreutils-prog-shebang=sleep /usr/bin/sleep 1000
|
||||
```
|
||||
|
||||
Notice that **podman top** reports the second container is running as root inside the container but as UID=200000 on the host.
|
||||
|
||||
Also look at the **ps** command—it shows both sleep processes running: one as 100000 and the other as 200000.
|
||||
|
||||
This means running the containers inside separate user namespaces gives you traditional UID separation between processes, which has been the standard security tool of Linux/Unix from the beginning.
|
||||
|
||||
### Problems with user namespaces
|
||||
|
||||
For several years, I've advocated user namespace as the security tool everyone wants but hardly anyone has used. The reason is there hasn't been any filesystem support or a shifting file system.
|
||||
|
||||
In containers, you want to share the **base** image between lots of containers. The examples above use the Fedora base image in each example. Most of the files in the Fedora image are owned by real UID=0. If I run a container on this image with the user namespace 0:100000:5000, by default it sees all of these files as owned by nobody, so we need to shift all of these UIDs to match the user namespace. For years, I've wanted a mount option to tell the kernel to remap these file UIDs to match the user namespace. Upstream kernel storage developers continue to investigate and make progress on this feature, but it is a difficult problem.
|
||||
|
||||
|
||||
Podman can use different user namespaces on the same image because of automatic [chowning][6] built into [containers/storage][7] by a team led by Nalin Dahyabhai. Podman uses containers/storage, and the first time Podman uses a container image in a new user namespace, container/storage "chowns" (i.e., changes ownership for) all files in the image to the UIDs mapped in the user namespace and creates a new image. Think of this as the **fedora:0:100000:5000** image.
|
||||
|
||||
When Podman runs another container on the image with the same UID mappings, it uses the "pre-chowned" image. When I run the second container on 0:200000:5000, containers/storage creates a second image, let's call it **fedora:0:200000:5000**.
|
||||
|
||||
Note if you are doing a **podman build** or **podman commit** and push the newly created image to a container registry, Podman will use container/storage to reverse the shift and push the image with all files chowned back to real UID=0.
|
||||
|
||||
This can cause a real slowdown in creating containers in new UID mappings since the **chown** can be slow depending on the number of files in the image. Also, on a normal [OverlayFS][8], every file in the image gets copied up. The normal Fedora image can take up to 30 seconds to finish the chown and start the container.
|
||||
|
||||
Luckily, the Red Hat kernel storage team, primarily Vivek Goyal and Miklos Szeredi, added a new feature to OverlayFS in kernel 4.19. The feature is called **metadata only copy-up**. If you mount an overlay filesystem with **metacopy=on** as a mount option, it will not copy up the contents of the lower layers when you change file attributes; the kernel creates new inodes that include the attributes with references pointing at the lower-level data. It will still copy up the contents if the content changes. This functionality is available in the Red Hat Enterprise Linux 8 Beta, if you want to try it out.
|
||||
|
||||
This means container chowning can happen in a couple of seconds, and you won't double the storage space for each container.
|
||||
|
||||
This makes running containers with tools like Podman in separate user namespaces viable, greatly increasing the security of the system.
|
||||
|
||||
### Going forward
|
||||
|
||||
I want to add a new flag, like **\--userns=auto** , to Podman that will tell it to automatically pick a unique user namespace for each container you run. This is similar to the way SELinux works with separate multi-category security (MCS) labels. If you set the environment variable **PODMAN_USERNS=auto** , you won't even need to set the flag.
|
||||
|
||||
Podman is finally allowing users to run containers in separate user namespaces. Tools like [Buildah][9] and [CRI-O][10] will also be able to take advantage of user namespaces. For CRI-O, however, Kubernetes needs to understand which user namespace will run the container engine, and the upstream is working on that.
|
||||
|
||||
In my next article, I will explain how to run Podman as non-root in a user namespace.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/12/podman-and-user-namespaces
|
||||
|
||||
作者:[Daniel J Walsh][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/rhatdan
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://podman.io/
|
||||
[2]: https://github.com/containers/libpod
|
||||
[3]: https://opensource.com/article/18/10/podman-more-secure-way-run-containers
|
||||
[4]: http://man7.org/linux/man-pages/man7/user_namespaces.7.html
|
||||
[5]: https://chmodcommand.com/chmod-660/
|
||||
[6]: https://en.wikipedia.org/wiki/Chown
|
||||
[7]: https://github.com/containers/storage
|
||||
[8]: https://en.wikipedia.org/wiki/OverlayFS
|
||||
[9]: https://buildah.io/
|
||||
[10]: http://cri-o.io/
|
||||
@ -0,0 +1,57 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Relax by the fire at your Linux terminal)
|
||||
[#]: via: (https://opensource.com/article/18/12/linux-toy-aafire)
|
||||
[#]: author: (Jason Baker https://opensource.com/users/jason-baker)
|
||||
|
||||
Relax by the fire at your Linux terminal
|
||||
======
|
||||
Chestnuts roasting on an open command prompt? Why not, with this fun Linux toy.
|
||||
|
||||
|
||||
|
||||
Welcome back. Here we are, just past the halfway mark at day 13 of our 24 days of Linux command-line toys. If this is your first visit to the series, see the link to the previous article at the bottom of this one, and take a look back to learn what it's all about. In short, our command-line toys are anything that's a fun diversion at the terminal.
|
||||
|
||||
Maybe some are familiar, and some aren't. Either way, we hope you have fun.
|
||||
|
||||
If you're in the northern hemisphere outside of the tropics, perhaps winter is starting to rear its frigid face outside. At least it is where I live. And some I'd love nothing more than to curl up by the fire with a cup of tea and my favorite book (or a digital equivalent).
|
||||
|
||||
The bad news is my house lacks a fireplace. The good news is that I can still pretend, thanks to the Linux terminal and today's command-line toy, **aafire**.
|
||||
|
||||
On my system, I found **aafire** packed with **aalib** , a delightful library for converting visual images into the style of ASCII art and making it available at your terminal (or elsewhere). **aalib** enables all sorts of fun graphics at the Linux terminal, so we may revisit a toy or two that make use of it before the end of our series. On Fedora, this meant installation was as simple as:
|
||||
|
||||
```
|
||||
$ sudo dnf install aalib
|
||||
```
|
||||
|
||||
Then, it was simple to launch with the **aafire** command. By default, **aalib** attempted to draw to my GUI, so I had to manually override it to keep my fire in the terminal (this is a command-line series, after all). Fortunately, it comes with a [curses][1] driver, so this meant I just had to run the following to get my fire going:
|
||||
|
||||
```
|
||||
$ aafire -driver curses
|
||||
```
|
||||

|
||||
You can find out more about the **aa-lib** library and download the source on [Sourceforge][2], under an LGPLv2 license.
|
||||
|
||||
Do you have a favorite command-line toy that you think I ought to include? The calendar for this series is mostly filled out but I've got a few spots left. Let me know in the comments below, and I'll check it out. If there's space, I'll try to include it. If not, but I get some good submissions, I'll do a round-up of honorable mentions at the end.
|
||||
|
||||
Check out yesterday's toy, [Patch into The Matrix at the Linux command line][3] , and check back tomorrow for another!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/12/linux-toy-aafire
|
||||
|
||||
作者:[Jason Baker][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/jason-baker
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://en.wikipedia.org/wiki/Curses_(programming_library)
|
||||
[2]: http://aa-project.sourceforge.net/aalib/
|
||||
[3]: https://opensource.com/article/18/12/linux-toy-cmatrix
|
||||
@ -1,5 +1,5 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: translator: (jlztan)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
|
||||
@ -0,0 +1,179 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (How To Install Rust Programming Language In Linux)
|
||||
[#]: via: (https://www.2daygeek.com/how-to-install-rust-programming-language-in-linux/)
|
||||
[#]: author: (Prakash Subramanian https://www.2daygeek.com/author/prakash/)
|
||||
|
||||
How To Install Rust Programming Language In Linux
|
||||
======
|
||||
|
||||
Rust is often called rust-lang.
|
||||
|
||||
Rust is a general-purpose, multi-paradigm, modern, cross-platform, and open source systems programming language sponsored by Mozilla Research.
|
||||
|
||||
It was designed to be achieve a goals such as safety, speed, and concurrency.
|
||||
|
||||
Rust is syntactically similar to C++,[14] but its designers intend it to provide better memory safety while still maintaining performance.
|
||||
|
||||
Rust is currently used in many organization such as Firefox, Chef, Dropbox, Oracle, GNOME, etc,.
|
||||
|
||||
### How to Install Runs Language in Linux?
|
||||
|
||||
There are many ways we can install Rust but below is the officially recommended way to install it.
|
||||
|
||||
```
|
||||
$ curl https://sh.rustup.rs -sSf | sh
|
||||
info: downloading installer
|
||||
|
||||
Welcome to Rust!
|
||||
|
||||
This will download and install the official compiler for the Rust programming
|
||||
language, and its package manager, Cargo.
|
||||
|
||||
It will add the cargo, rustc, rustup and other commands to Cargo's bin
|
||||
directory, located at:
|
||||
|
||||
/home/daygeek/.cargo/bin
|
||||
|
||||
This path will then be added to your PATH environment variable by modifying the
|
||||
profile files located at:
|
||||
|
||||
/home/daygeek/.profile
|
||||
/home/daygeek/.bash_profile
|
||||
|
||||
You can uninstall at any time with rustup self uninstall and these changes will
|
||||
be reverted.
|
||||
|
||||
Current installation options:
|
||||
|
||||
default host triple: x86_64-unknown-linux-gnu
|
||||
default toolchain: stable
|
||||
modify PATH variable: yes
|
||||
|
||||
1) Proceed with installation (default)
|
||||
2) Customize installation
|
||||
3) Cancel installation
|
||||
>1
|
||||
|
||||
info: syncing channel updates for 'stable-x86_64-unknown-linux-gnu'
|
||||
info: latest update on 2018-12-06, rust version 1.31.0 (abe02cefd 2018-12-04)
|
||||
info: downloading component 'rustc'
|
||||
77.7 MiB / 77.7 MiB (100 %) 1.2 MiB/s ETA: 0 s
|
||||
info: downloading component 'rust-std'
|
||||
54.2 MiB / 54.2 MiB (100 %) 1.2 MiB/s ETA: 0 s
|
||||
info: downloading component 'cargo'
|
||||
4.7 MiB / 4.7 MiB (100 %) 1.2 MiB/s ETA: 0 s
|
||||
info: downloading component 'rust-docs'
|
||||
8.5 MiB / 8.5 MiB (100 %) 1.2 MiB/s ETA: 0 s
|
||||
info: installing component 'rustc'
|
||||
info: installing component 'rust-std'
|
||||
info: installing component 'cargo'
|
||||
info: installing component 'rust-docs'
|
||||
info: default toolchain set to 'stable'
|
||||
|
||||
stable installed - rustc 1.31.0 (abe02cefd 2018-12-04)
|
||||
|
||||
|
||||
Rust is installed now. Great!
|
||||
|
||||
To get started you need Cargo's bin directory ($HOME/.cargo/bin) in your PATH
|
||||
environment variable. Next time you log in this will be done automatically.
|
||||
|
||||
To configure your current shell run source $HOME/.cargo/env
|
||||
```
|
||||
|
||||
Run the following command to configure your current shell.
|
||||
|
||||
```
|
||||
$ source $HOME/.cargo/env
|
||||
```
|
||||
|
||||
Run the following command to verify the installed Rust version.
|
||||
|
||||
```
|
||||
$ rustc --version
|
||||
rustc 1.31.0 (abe02cefd 2018-12-04)
|
||||
```
|
||||
|
||||
### How To Test Rust programming language?
|
||||
|
||||
Once you installed Rust follow the below steps to check whether Rust programe language is working fine or not.
|
||||
|
||||
```
|
||||
$ mkdir ~/projects
|
||||
$ cd ~/projects
|
||||
$ mkdir hello_world
|
||||
$ cd hello_world
|
||||
```
|
||||
|
||||
Create a file and add the below code and save the file. Make sure, Rust files always end in a .rs extension.
|
||||
|
||||
```
|
||||
$ vi 2g.rs
|
||||
|
||||
fn main() {
|
||||
println!("Hello, It's 2DayGeek.com - Best Linux Practical Blog!");
|
||||
}
|
||||
```
|
||||
|
||||
Run the following command to compile the rust code.
|
||||
|
||||
```
|
||||
$ rustc 2g.rs
|
||||
```
|
||||
|
||||
The above command will create a executable Rust program file in the same directory.
|
||||
|
||||
```
|
||||
$ ls -lh
|
||||
total 3.9M
|
||||
-rwxr-xr-x 1 daygeek daygeek 3.9M Dec 14 11:09 2g
|
||||
-rw-r--r-- 1 daygeek daygeek 86 Dec 14 11:09 2g.rs
|
||||
```
|
||||
|
||||
Run the Rust executable file to get the output.
|
||||
|
||||
```
|
||||
$ ./2g
|
||||
Hello, It's 2DayGeek.com - Best Linux Practical Blog!
|
||||
```
|
||||
|
||||
Yup! that’s working fine.
|
||||
|
||||
To update Rust to latest version.
|
||||
|
||||
```
|
||||
$ rustup update
|
||||
info: syncing channel updates for 'stable-x86_64-unknown-linux-gnu'
|
||||
info: checking for self-updates
|
||||
|
||||
stable-x86_64-unknown-linux-gnu unchanged - rustc 1.31.0 (abe02cefd 2018-12-04)
|
||||
```
|
||||
|
||||
Run the following command to remove the Rust package from your system.
|
||||
|
||||
```
|
||||
$ rustup self uninstall
|
||||
```
|
||||
|
||||
Once you uninstalled the Rust package, remove the Rust project directory.
|
||||
|
||||
```
|
||||
$ rm -fr ~/projects
|
||||
```
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.2daygeek.com/how-to-install-rust-programming-language-in-linux/
|
||||
|
||||
作者:[Prakash Subramanian][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.2daygeek.com/author/prakash/
|
||||
[b]: https://github.com/lujun9972
|
||||
@ -0,0 +1,66 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (The Linux terminal is no one-trick pony)
|
||||
[#]: via: (https://opensource.com/article/18/12/linux-toy-ponysay)
|
||||
[#]: author: (Jason Baker https://opensource.com/users/jason-baker)
|
||||
|
||||
The Linux terminal is no one-trick pony
|
||||
======
|
||||
Bring the magic of My Little Pony to your Linux command line.
|
||||

|
||||
|
||||
Welcome to another day of the Linux command-line toys advent calendar. If this is your first visit to the series, you might be asking yourself what a command-line toy even is. We’re figuring that out as we go, but generally, it could be a game, or any simple diversion that helps you have fun at the terminal.
|
||||
|
||||
Some of you will have seen various selections from our calendar before, but we hope there’s at least one new thing for everyone.
|
||||
|
||||
Reader [Lori][1] made the suggestion of today's toy in a comment on my previous article on [cowsay][2]:
|
||||
|
||||
"Hmmm, I've been playing with something called ponysay which seems to be a full-color variant on your cowsay."
|
||||
|
||||
Intrigued, I had to check it out, and I was not disappointed with what I found.
|
||||
|
||||
In a nutshell, **[ponysay][3]** is exactly that: a rewrite of **cowsay** that includes many full-color characters from [My Little Pony][4], that you can use to output phrases at the Linux command line. It's actually a really well-done project, that features over 400 characters and character combinations, and is incredibly well documented in a [78-page PDF][5] covering full usage.
|
||||
|
||||
To install **ponysay** , you'll want to check out the project [README][6] to select the installation method that works best for your distribution and situation. Since ponysay didn't appear to be packaged for my distribution, Fedora, I opted to try out the Docker container image, but do what works best for you; installation from source may also work for you.
|
||||
|
||||
I was curious to try out [**podman**][7] as a drop-in replacement for **docker** for a casual container users, and for me at least, it just worked!
|
||||
|
||||
```
|
||||
$ podman run -ti --rm mpepping/ponysay 'Ponytastic'
|
||||
```
|
||||
|
||||
The outputs are amazing, and I challenge you to try it out and let me know your favorite. Here was one of mine:
|
||||
|
||||

|
||||
|
||||
It's developers chose to write the code in [Pony][8]! (Update: Sadly, I was wrong about this. It's written in Python, though GitHub believes it to be Pony because of the file extensions.) Ponysay is licensed under the GPL version 3, and you can pick up its source code [on GitHub][3].
|
||||
|
||||
Do you have a favorite command-line toy that you think I ought to profile? The calendar for this series is mostly filled out but I've got a few spots left. Let me know in the comments below, and I'll check it out. If there's space, I'll try to include it. If not, but I get some good submissions, I'll do a round-up of honorable mentions at the end.
|
||||
|
||||
Check out yesterday's toy, [Relax by the fire at your Linux terminal][9], and check back tomorrow for another!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/12/linux-toy-ponysay
|
||||
|
||||
作者:[Jason Baker][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/jason-baker
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/users/n8chz
|
||||
[2]: https://opensource.com/article/18/12/linux-toy-cowsay
|
||||
[3]: https://github.com/erkin/ponysay
|
||||
[4]: https://en.wikipedia.org/wiki/My_Little_Pony
|
||||
[5]: https://github.com/erkin/ponysay/blob/master/ponysay.pdf?raw=true
|
||||
[6]: https://github.com/erkin/ponysay/blob/master/README.md
|
||||
[7]: https://opensource.com/article/18/10/podman-more-secure-way-run-containers
|
||||
[8]: https://opensource.com/article/18/5/pony
|
||||
[9]: https://opensource.com/article/18/12/linux-toy-aafire
|
||||
@ -0,0 +1,180 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Tips for using Flood Element for performance testing)
|
||||
[#]: via: (https://opensource.com/article/18/12/tips-flood-element-testing)
|
||||
[#]: author: (Nicole van der Hoeven https://opensource.com/users/nicolevanderhoeven)
|
||||
|
||||
Tips for using Flood Element for performance testing
|
||||
======
|
||||
Get started with this powerful, intuitive load testing tool.
|
||||

|
||||
|
||||
In case you missed it, there’s a new performance test tool on the block: [Flood Element][1]. It’s a scalable, browser-based tool that allows you to write scripts in JavaScript that interact with web pages like a real user would.
|
||||
|
||||
Browser Level Users is a [newer approach to load testing][2] that overcomes many of the common challenges we hear about traditional methods of testing. It offers:
|
||||
|
||||
* Scripting that is akin to common functional tools like Selenium and easier to learn
|
||||
* More realistic results that are based on true browser performance rather than API response
|
||||
* The ability to test against all components of your web app, including things like JavaScript that are rendered via the browser
|
||||
|
||||
|
||||
|
||||
Given the above benefits, it’s a no-brainer to check out Flood Element for your web load testing, especially if you have struggled with existing tools like JMeter or HP LoadRunner.
|
||||
|
||||
Pairing Element with [Flood][3] turns it into a pretty powerful load test tool. We have a [great guide here][4] that you can follow if you’d like to get started. I’ve been using and testing Element for several months now, and I’d like to share some tips I’ve learned along the way.
|
||||
|
||||
### Initializing your script
|
||||
|
||||
You can always start from scratch, but the quickest way to get started is to type `element init myfirstelementtest` from your terminal, filling in your preferred project name.
|
||||
|
||||
You’ll then be asked to type the title of your test as well as the URL you’d like to script against. After a minute, you’ll see that a new directory has been created:
|
||||
|
||||
|
||||
|
||||
Element will automatically create a file called **test.ts**. This file contains the skeleton of a script, along with some sample code to help you find a button and then click on it. But before you open it, let’s move on to…
|
||||
|
||||
### Choosing the right text editor
|
||||
|
||||
Scripting in Element is already pretty simple, but two things that help are syntax highlighting and code completion. Syntax highlighting will greatly improve the experience of learning a new test tool like Element, and code completion will make your scripting lightning-fast as you become more experienced. My text editor of choice is [Visual Studio Code][5], which has both of those features. It’s slick and clean, and it does the job.
|
||||
|
||||
Syntax highlighting is when the text editor intelligently changes the font color of your code according to its role in the programming language you’re using. Here’s a screenshot of the **test.ts** file we generated earlier in VS Code to show you what I mean:
|
||||
|
||||
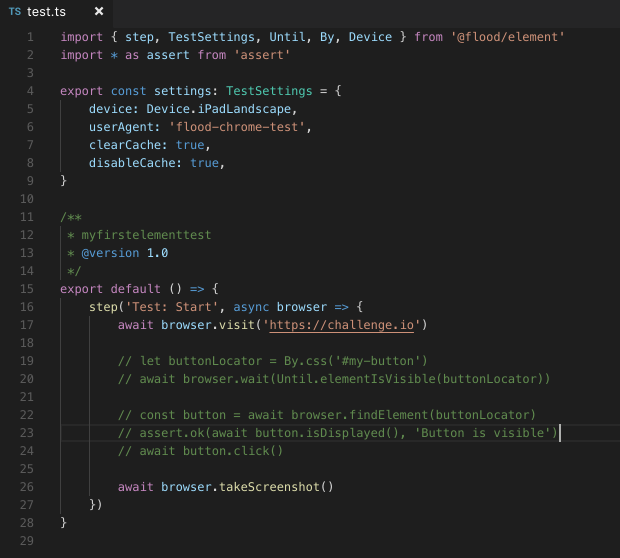
|
||||
|
||||
This makes it easier to make sense of the code at a glance: Comments are in green, values and labels are in orange, etc.
|
||||
|
||||
Code completion is when you start to type something, and VS Code helpfully opens a context menu with suggestions for methods you can use.
|
||||
|
||||
![][6]
|
||||
|
||||
I love this because it means I don’t need to remember the exact name of the method. It also suggests names of variables you’ve already defined and highlights code that doesn’t make sense. This will help to make your tests more maintainable and readable for others, which is a great benefit as you look to scale your testing out in the future.
|
||||
|
||||
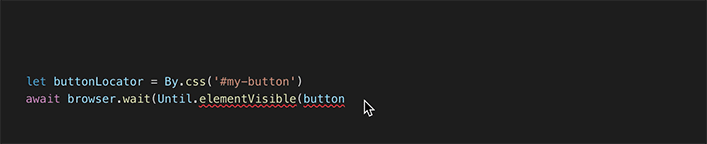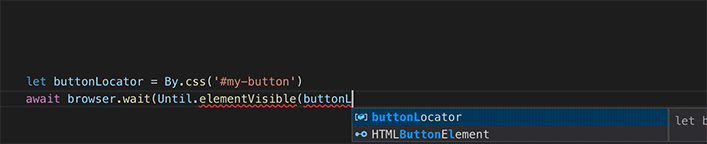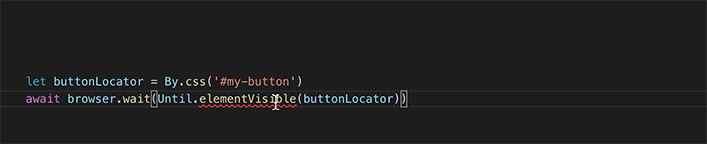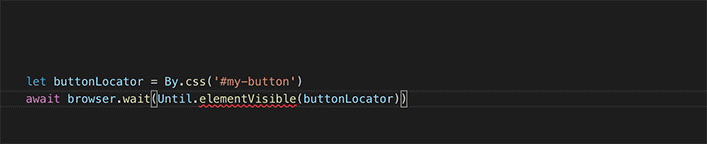
|
||||
|
||||
### Taking screenshots
|
||||
|
||||
One of the most powerful features of Element is its ability to take screenshots. I find it immensely useful when debugging because sometimes it’s just easier to see what’s going on visually. With protocol-based tools, debugging can be a much more involved and technical process.
|
||||
|
||||
There are two ways to take screenshots in Element:
|
||||
|
||||
1. Add a setting to automatically take a screenshot when an error is encountered. You can do this by setting `screenshotOnFailure` to "true" in `TestSettings`:
|
||||
|
||||
|
||||
|
||||
```
|
||||
export const settings: TestSettings = {
|
||||
device: Device.iPadLandscape,
|
||||
userAgent: 'flood-chrome-test',
|
||||
clearCache: true,
|
||||
disableCache: true,
|
||||
screenshotOnFailure: true,
|
||||
}
|
||||
```
|
||||
|
||||
2. Explicitly take a screenshot at a particular point in the script. You can do this by adding
|
||||
|
||||
|
||||
|
||||
```
|
||||
await browser.takeScreenshot()
|
||||
```
|
||||
|
||||
to your code.
|
||||
|
||||
### Viewing screenshots
|
||||
|
||||
Once you’ve taken screenshots within your tests, you will probably want to view them and know that they will be stored for future safekeeping. Whether you are running your test locally on have uploaded it to Flood to run with increased concurrency, Flood Element has you covered.
|
||||
|
||||
**Locally run tests**
|
||||
|
||||
Screenshots will be saved as .jpg files in a timestamped folder corresponding to your run. It should look something like this: **…myfirstelementtest/tmp/element-results/test/2018-11-20T135700.595Z/flood/screenshots/**. The screenshots will be uniquely named so that new screenshots, even for the same step, don’t overwrite older ones.
|
||||
|
||||
However, I rarely need to look up the screenshots in that folder because I prefer to see them in iTerm2 for MacOS. iTerm is an alternative to the terminal that works particularly well with Element. When you take a screenshot, iTerm actually shows it in-line:
|
||||
|
||||
|
||||
|
||||
**Tests run in Flood**
|
||||
|
||||
Running an Element script on Flood is ideal when you need larger concurrency. Rather than accessing your screenshot locally, Flood will centralize the images into your account, so the images remain even after the cloud load injectors are destroyed. You can get to the screenshot files by downloading Archived Results:
|
||||
|
||||
|
||||
|
||||
You can also click on a step on the dashboard to see a filmstrip of your test:
|
||||
|
||||
|
||||
|
||||
### Using logs
|
||||
|
||||
You may need to check out the logs for more technical debugging, especially when the screenshots don’t tell the whole story. Again, whether you are running your test locally or have uploaded it to Flood to run with increased concurrency, Flood Element has you covered.
|
||||
|
||||
**Locally run tests**
|
||||
|
||||
You can print to the console by typing, for example: `console.log('orderValues = ’ + orderValues)`
|
||||
|
||||
This will print the value of the variable `orderValues` at that point in the script. You would see this in your terminal if you’re running Element locally.
|
||||
|
||||
**Tests run in Flood**
|
||||
|
||||
If you’re running the script on Flood, you can either download the log (in the same Archived Results zipped file mentioned earlier) or click on the Logs tab:
|
||||
|
||||
|
||||
|
||||
### Fun with flags
|
||||
|
||||
Element comes with a few flags that give you more control over how the script is run locally. Here are a few of my favorites:
|
||||
|
||||
**Headless flag**
|
||||
|
||||
When in doubt, run Element in non-headless mode to see the script actually opening the web app on Chrome and interacting with the page. This is only possible locally, but there’s nothing like actually seeing for yourself what’s happening in real time instead of relying on screenshots and logs after the fact. To enable this mode, add the flag when running your test:
|
||||
|
||||
```
|
||||
element run myfirstelementtest.ts --no-headless
|
||||
```
|
||||
|
||||
**Watch flag**
|
||||
|
||||
Element will automatically close the browser window when it encounters an error or finishes the iteration. Adding `--watch` will leave the browser window open and then monitor the script. As soon as the script is saved, it will automatically run it in the same window from the beginning. Simply add this flag like the above example:
|
||||
|
||||
```
|
||||
--watch
|
||||
```
|
||||
|
||||
**Dev tools flag**
|
||||
|
||||
This opens a browser instance and runs the script with the Chrome Dev Tools open, allowing you to find locators for the next action you want to script. Simply add this flag as in the first example:
|
||||
|
||||
```
|
||||
--dev-tools
|
||||
```
|
||||
|
||||
For more flags, use `element run --help`.
|
||||
|
||||
### Try Element
|
||||
|
||||
You’ve just gotten a crash course on Flood Element and are ready to get started. [Download Element][1] to start writing functional test scripts and reusing them as load test scripts on Flood. If you don’t have a Flood account, you can easily sign up for a free trial [on the Flood website][7].
|
||||
|
||||
We’re proud to contribute to the open source community and can’t wait to have you try this new addition to the Flood line.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/12/tips-flood-element-testing
|
||||
|
||||
作者:[Nicole van der Hoeven][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/nicolevanderhoeven
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://element.flood.io/
|
||||
[2]: https://flood.io/blog/why-you-should-load-test-with-browsers/
|
||||
[3]: https://flood.io/
|
||||
[4]: https://help.flood.io/getting-started-with-load-testing/step-by-step-guide-flood-element
|
||||
[5]: https://code.visualstudio.com/
|
||||
[6]: https://flood.io/wp-content/uploads/2018/11/vscode-codecompletion2.gif
|
||||
[7]: https://flood.io/load-performance-testing-tool/free-load-testing-trial/
|
||||
@ -0,0 +1,52 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Head to the arcade in your Linux terminal with this Pac-man clone)
|
||||
[#]: via: (https://opensource.com/article/18/12/linux-toy-myman)
|
||||
[#]: author: (Jason Baker https://opensource.com/users/jason-baker)
|
||||
|
||||
Head to the arcade in your Linux terminal with this Pac-man clone
|
||||
======
|
||||
Want to recreate the magic of your favorite arcade game? Today's command-line toy will transport you back in time.
|
||||
|
||||
|
||||
Welcome back to another day of the Linux command-line toys advent calendar. If this is your first visit to the series, you might be asking yourself what command-line toys are all about. Basically, they're games and simple diversions that help you have fun at the terminal.
|
||||
|
||||
Some are new, and some are old classics. We hope you enjoy.
|
||||
|
||||
Today's toy, MyMan, is a fun clone of the classic arcade game [Pac-Man][1]. (You didn't think this was going to be about the [similarly-named][2] Linux package manager, did you?) If you're anything like me, you spent more than your fair share of quarters trying to hit a high score Pac-Man back in the day, and still give it a go whenever you get a chance.
|
||||
|
||||
MyMan isn't the only Pac-Man clone for the Linux terminal, but it's the one I chose to include because 1) I like its visual style, which rings true to the original and 2) it's conveniently packaged for my Linux distribution so it was an easy install. But you should check out your other options as well. Here's [another one][3] that looks like it may be promising, but I haven't tried it.
|
||||
|
||||
Since MyMan was packaged for Fedora, installation was as simple as:
|
||||
|
||||
```
|
||||
$ dnf install myman
|
||||
```
|
||||
|
||||
MyMan is made available under an MIT license and you can check out the source code on [SourceForge][4].
|
||||
|
||||
Do you have a favorite command-line toy that you think I ought to profile? The calendar for this series is mostly filled out but I've got a few spots left. Let me know in the comments below, and I'll check it out. If there's space, I'll try to include it. If not, but I get some good submissions, I'll do a round-up of honorable mentions at the end.
|
||||
|
||||
Check out yesterday's toy, [The Linux terminal is no one-trick pony][5], and check back tomorrow for another!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/12/linux-toy-myman
|
||||
|
||||
作者:[Jason Baker][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/jason-baker
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://en.wikipedia.org/wiki/Pac-Man
|
||||
[2]: https://wiki.archlinux.org/index.php/pacman
|
||||
[3]: https://github.com/YoctoForBeaglebone/pacman4console
|
||||
[4]: https://myman.sourceforge.io/
|
||||
[5]: https://opensource.com/article/18/12/linux-toy-ponysay
|
||||
@ -0,0 +1,62 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Schedule a visit with the Emacs psychiatrist)
|
||||
[#]: via: (https://opensource.com/article/18/12/linux-toy-eliza)
|
||||
[#]: author: (Jason Baker https://opensource.com/users/jason-baker)
|
||||
|
||||
Schedule a visit with the Emacs psychiatrist
|
||||
======
|
||||
Eliza is a natural language processing chatbot hidden inside of one of Linux's most popular text editors.
|
||||
|
||||
|
||||
Welcome to another day of the 24-day-long Linux command-line toys advent calendar. If this is your first visit to the series, you might be asking yourself what a command-line toy even is. We’re figuring that out as we go, but generally, it could be a game, or any simple diversion that helps you have fun at the terminal.
|
||||
|
||||
Some of you will have seen various selections from our calendar before, but we hope there’s at least one new thing for everyone.
|
||||
|
||||
Today's selection is a hidden gem inside of Emacs: Eliza, the Rogerian psychotherapist, a terminal toy ready to listen to everything you have to say.
|
||||
|
||||
A brief aside: While this toy is amusing, your health is no laughing matter. Please take care of yourself this holiday season, physically and mentally, and if stress and anxiety from the holidays are having a negative impact on your wellbeing, please consider seeing a professional for guidance. It really can help.
|
||||
|
||||
To launch [Eliza][1], first, you'll need to launch Emacs. There's a good chance Emacs is already installed on your system, but if it's not, it's almost certainly in your default repositories.
|
||||
|
||||
Since I've been pretty fastidious about keeping this series in the terminal, launch Emacs with the **-nw** flag to keep in within your terminal emulator.
|
||||
|
||||
```
|
||||
$ emacs -nw
|
||||
```
|
||||
|
||||
Inside of Emacs, type M-x doctor to launch Eliza. For those of you like me from a Vim background who have no idea what this means, just hit escape, type x and then type doctor. Then, share all of your holiday frustrations.
|
||||
|
||||
Eliza goes way back, all the way to the mid-1960s a the MIT Artificial Intelligence Lab. [Wikipedia][2] has a rather fascinating look at her history.
|
||||
|
||||
Eliza isn't the only amusement inside of Emacs. Check out the [manual][3] for a whole list of fun toys.
|
||||
|
||||
|
||||
![Linux toy: eliza animated][5]
|
||||
|
||||
Do you have a favorite command-line toy that you think I ought to profile? We're running out of time, but I'd still love to hear your suggestions. Let me know in the comments below, and I'll check it out. And let me know what you thought of today's amusement.
|
||||
|
||||
Be sure to check out yesterday's toy, [Head to the arcade in your Linux terminal with this Pac-man clone][6], and come back tomorrow for another!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/12/linux-toy-eliza
|
||||
|
||||
作者:[Jason Baker][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/jason-baker
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.emacswiki.org/emacs/EmacsDoctor
|
||||
[2]: https://en.wikipedia.org/wiki/ELIZA
|
||||
[3]: https://www.gnu.org/software/emacs/manual/html_node/emacs/Amusements.html
|
||||
[4]: /file/417326
|
||||
[5]: https://opensource.com/sites/default/files/uploads/linux-toy-eliza-animated.gif (Linux toy: eliza animated)
|
||||
[6]: https://opensource.com/article/18/12/linux-toy-myman
|
||||
@ -0,0 +1,93 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (4 cool new projects to try in COPR for December 2018)
|
||||
[#]: via: (https://fedoramagazine.org/4-try-copr-december-2018/)
|
||||
[#]: author: (Dominik Turecek https://fedoramagazine.org)
|
||||
|
||||
4 cool new projects to try in COPR for December 2018
|
||||
======
|
||||

|
||||
|
||||
COPR is a [collection][1] of personal repositories for software that isn’t carried in Fedora. Some software doesn’t conform to standards that allow easy packaging. Or it may not meet other Fedora standards, despite being free and open source. COPR can offer these projects outside the Fedora set of packages. Software in COPR isn’t supported by Fedora infrastructure or signed by the project. However, it can be a neat way to try new or experimental software.
|
||||
|
||||
Here’s a set of new and interesting projects in COPR.
|
||||
|
||||
### MindForger
|
||||
|
||||
[MindForger][2] is a Markdown editor and a notebook. In addition to features you’d expect from a Markdown editor, MindForger lets you split a single file into multiple notes. It’s easy to organize the notes and move them around between files, as well as search through them. I’ve been using MindForger for some time for my study notes, so it’s nice that it’s available through COPR now.![][3]
|
||||
|
||||
#### Installation instructions
|
||||
|
||||
The repo currently provides MindForger for Fedora 29 and Rawhide. To install MindForger, use these commands:
|
||||
|
||||
```
|
||||
sudo dnf copr enable deadmozay/mindforger
|
||||
sudo dnf install mindforger
|
||||
```
|
||||
|
||||
### Clingo
|
||||
|
||||
[Clingo][4] is a program for solving logical problems using [answer set programming][5] (ASP) modeling language. With ASP, you can declaratively describe a problem as a logical program that Clingo then solves. As a result, Clingo produces solutions to the problem in the form of logical models, called answer sets.
|
||||
|
||||
#### Installation instructions
|
||||
|
||||
The repo currently provides Clingo for Fedora 28 and 29. To install Clingo, use these commands:
|
||||
|
||||
```
|
||||
sudo dnf copr enable timn/clingo
|
||||
sudo dnf install clingo
|
||||
```
|
||||
|
||||
### SGVrecord
|
||||
|
||||
[SGVrecord][6] is a simple tool for recording your screen. It allows you to either capture the whole screen or select just a part of it. Furthermore, it is possible to make the record with or without sound. Sgvrecord produces files in WebM format.![][7]
|
||||
|
||||
#### Installation instructions
|
||||
|
||||
The repo currently provides SGVrecord for Fedora 28, 29, and Rawhide. To install SGVrecord, use these commands:
|
||||
|
||||
```
|
||||
sudo dnf copr enable youssefmsourani/sgvrecord
|
||||
sudo dnf install sgvrecord
|
||||
```
|
||||
|
||||
### Watchman
|
||||
|
||||
[Watchman][8] is a service for monitoring and recording when changes are done to files.
|
||||
You can specify directory trees for Watchman to monitor, as well as define actions
|
||||
that are triggered when specified files are changed.
|
||||
|
||||
#### Installation instructions
|
||||
|
||||
The repo currently provides Watchman for Fedora 29 and Rawhide. To install Watchman, use these commands:
|
||||
|
||||
```
|
||||
sudo dnf copr enable eklitzke/watchman
|
||||
sudo dnf install watchman
|
||||
```
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://fedoramagazine.org/4-try-copr-december-2018/
|
||||
|
||||
作者:[Dominik Turecek][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://fedoramagazine.org
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://copr.fedorainfracloud.org/
|
||||
[2]: https://www.mindforger.com/
|
||||
[3]: https://fedoramagazine.org/wp-content/uploads/2018/12/mindforger.png
|
||||
[4]: https://potassco.org/clingo/
|
||||
[5]: https://en.wikipedia.org/wiki/Answer_set_programming
|
||||
[6]: https://github.com/yucefsourani/sgvrecord
|
||||
[7]: https://fedoramagazine.org/wp-content/uploads/2018/12/SGVrecord.png
|
||||
[8]: https://facebook.github.io/watchman/
|
||||
@ -0,0 +1,78 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (6 tips and tricks for using KeePassX to secure your passwords)
|
||||
[#]: via: (https://opensource.com/article/18/12/keepassx-security-best-practices)
|
||||
[#]: author: (Michael McCune https://opensource.com/users/elmiko)
|
||||
|
||||
6 tips and tricks for using KeePassX to secure your passwords
|
||||
======
|
||||
Get more out of your password manager by following these best practices.
|
||||

|
||||
|
||||
Our increasingly interconnected digital world makes security an essential and common discussion topic. We hear about [data breaches][1] with alarming regularity and are often on our own to make informed decisions about how to use technology securely. Although security is a deep and nuanced topic, there are some easy daily habits you can keep to reduce your attack surface.
|
||||
|
||||
Securing passwords and account information is something that affects anyone today. Technologies like [OAuth][2] help make our lives simpler by reducing the number of accounts we need to create, but we are still left with a staggering number of places where we need new, unique information to keep our records secure. An easy way to deal with the increased mental load of organizing all this sensitive information is to use a password manager like [KeePassX][3].
|
||||
|
||||
In this article, I will explain the importance of keeping your password information secure and offer suggestions for getting the most out of KeePassX. For an introduction to KeePassX and its features, I highly recommend Ricardo Frydman's article "[Managing passwords in Linux with KeePassX][4]."
|
||||
|
||||
### Why are unique passwords important?
|
||||
|
||||
Using a different password for each account is the first step in ensuring that your accounts are not vulnerable to shared information leaks. Generating new credentials for every account is time-consuming, and it is extremely common for people to fall into the trap of using the same password on several accounts. The main problem with reusing passwords is that you increase the number of accounts an attacker could access if one of them experiences a credential breach.
|
||||
|
||||
It may seem like a burden to create new credentials for each account, but the few minutes you spend creating and recording this information will pay for itself many times over in the event of a data breach. This is where password management tools like KeePassX are invaluable for providing convenience and reliability in securing your logins.
|
||||
|
||||
### 3 tips for getting the most out of KeePassX
|
||||
|
||||
I have been using KeePassX to manage my password information for many years, and it has become a primary resource in my digital toolbox. Overall, it's fairly simple to use, but there are a few best practices I've learned that I think are worth highlighting.
|
||||
|
||||
1. Add the direct login URL for each account entry. KeePassX has a very convenient shortcut to open the URL listed with an entry. (It's Control+Shift+U on Linux.) When creating a new account entry for a website, I spend some time to locate the site's direct login URL. Although most websites have a login widget in their navigation toolbars, they also usually have direct pages for login forms. By putting this URL into the URL field on the account entry setup form, I can use the shortcut to directly open the login page in my browser.
|
||||
|
||||
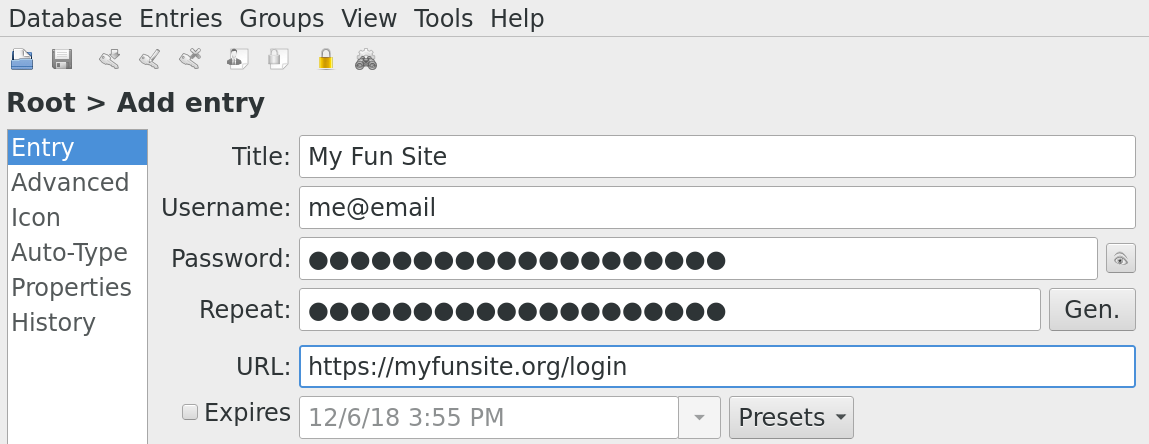
|
||||
|
||||
2. Use the Notes field to record extra security information. In addition to passwords, most websites will ask several questions to create additional authentication factors for an account. I use the Notes sections in my account entries to record these additional factors.
|
||||
|
||||
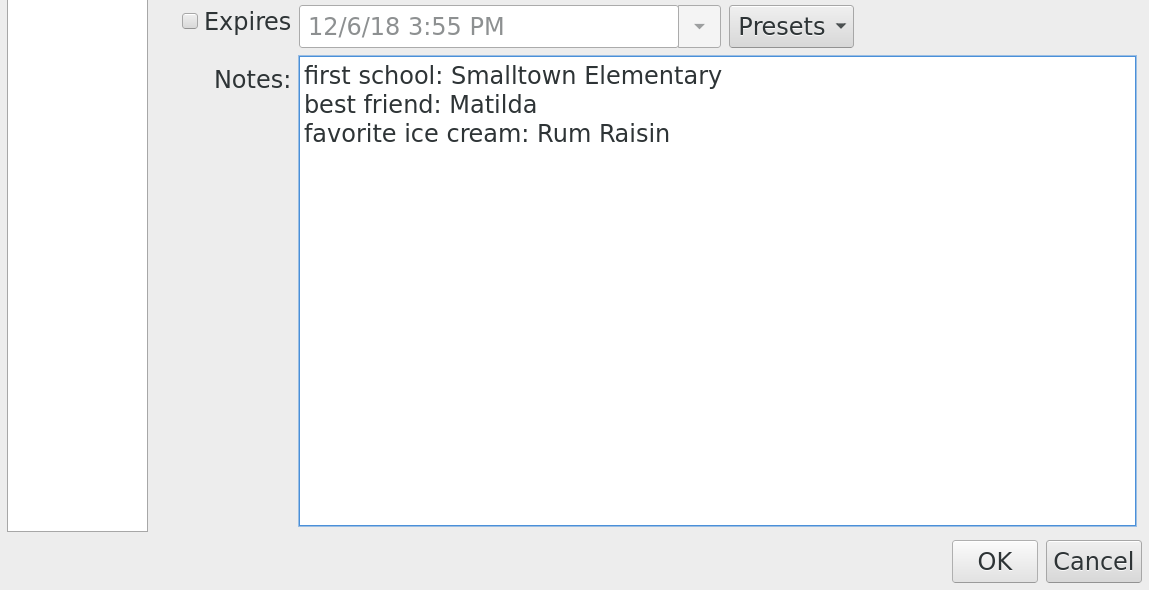
|
||||
|
||||
3. Turn on automatic database locking. In the **Application Settings** under the **Tools** menu, there is an option to lock the database after a period of inactivity. Enabling this option is a good common-sense measure, similar to enabling a password-protected screen lock, that will help ensure your password database is not left open and unprotected if someone else gains access to your computer.
|
||||
|
||||
|
||||
|
||||
### Food for thought
|
||||
|
||||
Protecting your accounts with better password practices and daily habits is just the beginning. Once you start using a password manager, you need to consider issues like protecting the password database file and ensuring you don't forget or lose the master credentials.
|
||||
|
||||
The cloud-native world of disconnected devices and edge computing makes having a central password store essential. The practices and methodologies you adopt will help minimize your risk while you explore and work in the digital world.
|
||||
|
||||
1. Be aware of retention policies when storing your database in the cloud. KeePassX's database has an open format used by several tools on multiple platforms. Sooner or later, you will want to transfer your database to another device. As you do this, consider the medium you will use to transfer the file. The best option is to use some sort of direct transfer between devices, but this is not always convenient. Always think about where the database file might be stored as it winds its way through the information superhighway; an email may get cached on a server, an object store may move old files to a trash folder. Learn about these interactions for the platforms you are using before deciding where and how you will share your database file.
|
||||
|
||||
2. Consider the source of truth for your database while you're making edits. After you share your database file between devices, you might need to create accounts for new services or change information for existing services while using a device. To ensure your information is always correct across all your devices, you need to make sure any edits you make on one device end up in all copies of the database file. There is no easy solution to this problem, but you might think about making all edits from a single device or storing the master copy in a location where all your devices can make edits.
|
||||
|
||||
3. Do you really need to know your passwords? This is more of a philosophical question that touches on the nature of memorable passwords, convenience, and secrecy. I hardly look at passwords as I create them for new accounts; in most cases, I don't even click the "Show Password" checkbox. There is an idea that you can be more secure by not knowing your passwords, as it would be impossible to compel you to provide them. This may seem like a worrisome idea at first, but consider that you can recover or reset passwords for most accounts through alternate verification methods. When you consider that you might want to change your passwords on a semi-regular basis, it almost makes more sense to treat them as ephemeral information that can be regenerated or replaced.
|
||||
|
||||
|
||||
|
||||
|
||||
Here are a few more ideas to consider as you develop your best practices.
|
||||
|
||||
I hope these tips and tricks have helped expand your knowledge of password management and KeePassX. You can find tools that support the KeePass database format on nearly every platform. If you are not currently using a password manager or have never tried KeePassX, I highly recommend doing so now!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/12/keepassx-security-best-practices
|
||||
|
||||
作者:[Michael McCune][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/elmiko
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://vigilante.pw/
|
||||
[2]: https://en.wikipedia.org/wiki/OAuth
|
||||
[3]: https://www.keepassx.org/
|
||||
[4]: https://opensource.com/business/16/5/keepassx
|
||||
@ -0,0 +1,48 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Take a swim at your Linux terminal with asciiquarium)
|
||||
[#]: via: (https://opensource.com/article/18/12/linux-toy-asciiquarium)
|
||||
[#]: author: (Jason Baker https://opensource.com/users/jason-baker)
|
||||
|
||||
Take a swim at your Linux terminal with asciiquarium
|
||||
======
|
||||
Darling it's better, when your command line is wetter, thanks to ASCII.
|
||||

|
||||
|
||||
We're now nearing the end of our 24-day-long Linux command-line toys advent calendar. Just one week left after today! If this is your first visit to the series, you might be asking yourself what a command-line toy even is. We’re figuring that out as we go, but generally, it could be a game, or any simple diversion that helps you have fun at the terminal.
|
||||
|
||||
Some of you will have seen various selections from our calendar before, but we hope there’s at least one new thing for everyone.
|
||||
|
||||
Today's selection is a fishy one. Say hello to **asciiquarium** , an undersea adventure for your terminal. I found **asciiquarium** in my Fedora repositories, so installing it was as simple as:
|
||||
|
||||
```
|
||||
$ sudo dnf install asciiquarium
|
||||
```
|
||||
|
||||
If you're running a different distribution, chances are it's packaged for you too. Just run **asciiquarium** at your terminal to feel happy as a clam. The project has been translated outside of the terminal as well, with screensavers of all of the aquatic pals being made for several non-Linux operating systems, and even an Android live wallpaper version is floating around out there.
|
||||
|
||||
Visit the **asciiquarium** [homepage][1] for more information or to download the Perl source code. The project is open source under a GPL version 2 license. And if you want to learn more about how open source, open data, and open science are making a difference in the actual oceans, take a moment to go learn about the [Ocean Health Index][2].
|
||||
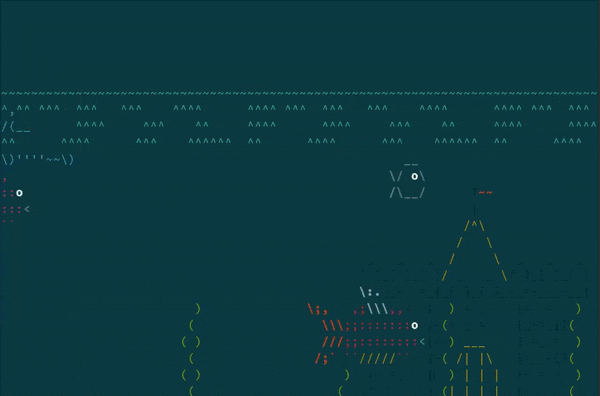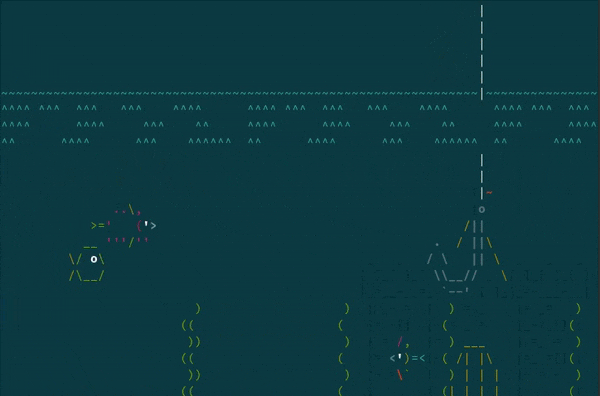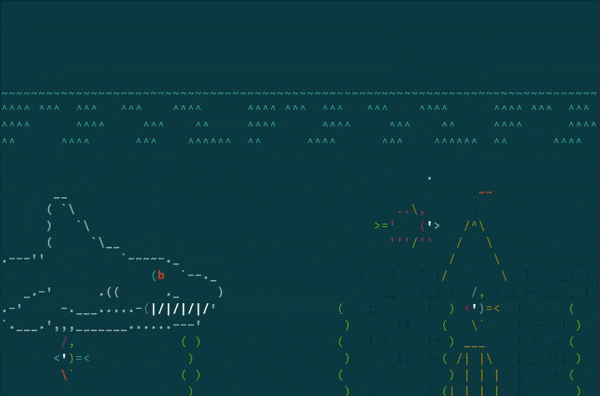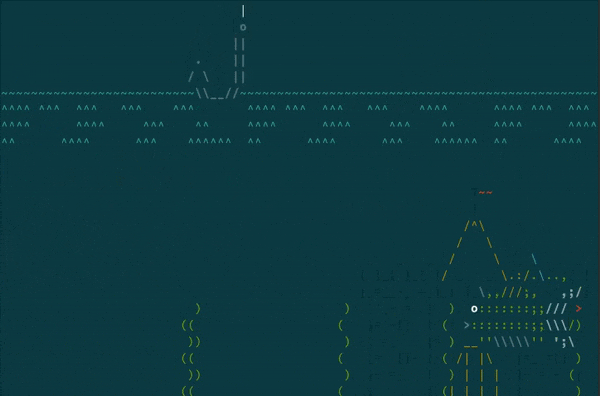
|
||||
Do you have a favorite command-line toy that you think I ought to profile? We're running out of time, but I'd still love to hear your suggestions. Let me know in the comments below, and I'll check it out. And let me know what you thought of today's amusement.
|
||||
|
||||
Be sure to check out yesterday's toy, [Schedule a visit with the Emacs psychiatrist][3], and come back tomorrow for another!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/12/linux-toy-asciiquarium
|
||||
|
||||
作者:[Jason Baker][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/jason-baker
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://robobunny.com/projects/asciiquarium/html/
|
||||
[2]: https://opensource.com/article/18/12/protecting-world-oceans
|
||||
[3]: https://opensource.com/article/18/12/linux-toy-eliza
|
||||
100
sources/tech/20181217 Working with tarballs on Linux.md
Normal file
100
sources/tech/20181217 Working with tarballs on Linux.md
Normal file
@ -0,0 +1,100 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Working with tarballs on Linux)
|
||||
[#]: via: (https://www.networkworld.com/article/3328840/linux/working-with-tarballs-on-linux.html)
|
||||
[#]: author: (Sandra Henry-Stocker https://www.networkworld.com/author/Sandra-Henry_Stocker/)
|
||||
|
||||
Working with tarballs on Linux
|
||||
======
|
||||

|
||||
|
||||
The word “tarball” is often used to describe the type of file used to back up a select group of files and join them into a single file. The name comes from the **.tar** file extension and the **tar** command that is used to group together the files into a single file that is then sometimes compressed to make it smaller for its move to another system.
|
||||
|
||||
Tarballs are often used to back up personal or system files in place to create an archive, especially prior to making changes that might have to be reversed. Linux sysadmins, for example, will often create a tarball containing a series of configuration files before making changes to an application just in case they have to reverse those changes. Extracting the files from a tarball that’s sitting in place will generally be faster than having to retrieve the files from backups.
|
||||
|
||||
### How to create a tarball on Linux
|
||||
|
||||
You can create a tarball and compress it in a single step if you use a command like this one:
|
||||
|
||||
```
|
||||
$ tar -cvzf PDFs.tar.gz *.pdf
|
||||
```
|
||||
|
||||
The result in this case is a compressed (gzipped) file that contains all of the PDF files that are in the current directory. The compression is optional, of course. A slightly simpler command would just put all of the PDF files into an uncompressed tarball:
|
||||
|
||||
```
|
||||
$ tar -cvf PDFs.tar *.pdf
|
||||
```
|
||||
|
||||
Note that it’s the **z** in that list of options that causes the file to be compressed or “zipped”. The **c** specifies that you are creating the file and the **v** (verbose) indicates that you want some feedback while the command is running. Omit the **v** if you don't want to see the files listed.
|
||||
|
||||
Another common naming convention is to give zipped tarballs the extension **.tgz** instead of the double extension **.tar.gz** as shown in this command:
|
||||
|
||||
```
|
||||
$ tar cvzf MyPDFs.tgz *.pdf
|
||||
```
|
||||
|
||||
### How to extract files from a tarball
|
||||
|
||||
To extract all of the files from a gzipped tarball, you would use a command like this:
|
||||
|
||||
```
|
||||
$ tar -xvzf file.tar.gz
|
||||
```
|
||||
|
||||
If you use the .tgz naming convention, that command would look like this:
|
||||
|
||||
```
|
||||
$ tar -xvzf MyPDFs.tgz
|
||||
```
|
||||
|
||||
To extract an individual file from a gzipped tarball, you do almost the same thing but add the file name:
|
||||
|
||||
```
|
||||
$ tar -xvzf PDFs.tar.gz ShenTix.pdf
|
||||
ShenTix.pdf
|
||||
ls -l ShenTix.pdf
|
||||
-rw-rw-r-- 1 shs shs 122057 Dec 14 14:43 ShenTix.pdf
|
||||
```
|
||||
|
||||
You can even delete files from a tarball if the tarball is not compressed. For example, if we wanted to remove tile file that we extracted above from the PDFs.tar.gz file, we would do it like this:
|
||||
|
||||
```
|
||||
$ gunzip PDFs.tar.gz
|
||||
$ ls -l PDFs.tar
|
||||
-rw-rw-r-- 1 shs shs 10700800 Dec 15 11:51 PDFs.tar
|
||||
$ tar -vf PDFs.tar --delete ShenTix.pdf
|
||||
$ ls -l PDFs.tar
|
||||
-rw-rw-r-- 1 shs shs 10577920 Dec 15 11:45 PDFs.tar
|
||||
```
|
||||
|
||||
Notice that we shaved a little space off the tar file while deleting the ShenTix.pdf file. We can then compress the file again if we want:
|
||||
|
||||
```
|
||||
$ gzip -f PDFs.tar
|
||||
ls -l PDFs.tar.gz
|
||||
-rw-rw-r-- 1 shs shs 10134499 Dec 15 11:51 PDFs.tar.gzFlickr / James St. John
|
||||
```
|
||||
|
||||
The versatility of the command line options makes working with tarballs easy and very convenient.
|
||||
|
||||
Join the Network World communities on [Facebook][1] and [LinkedIn][2] to comment on topics that are top of mind.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.networkworld.com/article/3328840/linux/working-with-tarballs-on-linux.html
|
||||
|
||||
作者:[Sandra Henry-Stocker][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.networkworld.com/author/Sandra-Henry_Stocker/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.facebook.com/NetworkWorld/
|
||||
[2]: https://www.linkedin.com/company/network-world
|
||||
@ -0,0 +1,137 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Insync: The Hassleless Way of Using Google Drive on Linux)
|
||||
[#]: via: (https://itsfoss.com/insync-linux-review/)
|
||||
[#]: author: (Abhishek Prakash https://itsfoss.com/author/abhishek/)
|
||||
|
||||
Insync: The Hassleless Way of Using Google Drive on Linux
|
||||
======
|
||||
|
||||
Using Google Drive on Linux is a pain and you probably already know that. There is no official desktop client of Google Drive for Linux. It’s been [more than six years since Google promised Google Drive on Linux][1] but it doesn’t seem to be happening.
|
||||
|
||||
In the absence of the official Google Drive client on Linux, you have no option other than trying the alternatives. I have already discussed a number of [tools that allow you to use Google Drive on Linux][2]. One of those to[ols is][3] Insync, and in my opinion, this is your best bet for a native Google Drive experience on desktop Linux.
|
||||
|
||||
Note that Insync is not an open source software. Heck, it is not even free to use.
|
||||
|
||||
But it has so many features that it becomes an essential tool for those Linux users who rely heavily on Google Drive.
|
||||
|
||||
I briefly discussed Insync in the old article about [Google Drive and Linux][2]. In this article, I’ll discuss Insync features in detail.
|
||||
|
||||
### Insync brings native Google Drive experience to Linux desktop
|
||||
|
||||
![Use insync to access Google Drive in Linux][4]
|
||||
|
||||
The core competency of Insync is syncing your Google Drive, but the app is much more than that. It has features to help you maximize and control your productivity, your Google Drive and your files such as:
|
||||
|
||||
* Cross-platform access (supports Linux, Windows and macOS)
|
||||
* Easy multiple Google Drive accounts access
|
||||
* Choose your syncing location. Sync files to your hard drive, external drives and NAS!
|
||||
* Support for features like file matching, symlink and ignore list
|
||||
|
||||
|
||||
|
||||
Let me show you some of the main features in action:
|
||||
|
||||
#### Cross-platform in true sense
|
||||
|
||||
Insync claims to run the same app across all operating systems i.e., Linux, Windows, and macOS. That means that you can access the same UI across different OSes, making it easy for you to manage your files across multiple machines.
|
||||
|
||||
![The UI of Insync and the default location of the Insync folder.][5]The UI of Insync and the default location of the Insync folder.
|
||||
|
||||
#### Multiple Google account management
|
||||
|
||||
Insync interface allows you to manage multiple Google Drive accounts seamlessly. You can easily switch between several accounts just by clicking your Google account.
|
||||
|
||||
![Switching between multiple Google accounts in Insync][6]Switching between multiple Google accounts
|
||||
|
||||
#### Custom sync folders
|
||||
|
||||
Customize the way you sync your files and folders. You can easily set your syncing destination anywhere on your machine including external drive and network drives.
|
||||
|
||||
![Customize sync location in Insync][7]Customize sync location
|
||||
|
||||
The selective syncing mode also allows you to easily select a number of files and folders you’d want to sync (or unsync) in your local machine. This includes selectively syncing files within folders.
|
||||
|
||||
![Selective synchronization in Insync][8]Selective synchronization
|
||||
|
||||
It has features like file matching and ‘ignore list’ to help you filter files you don’t want to sync or files that you already have on your machine.
|
||||
|
||||
![File matching feature in Insync][9]Avoids duplication of files
|
||||
|
||||
The ‘ignore list’ allows you to set rules to exclude certain type of files from synchronization.
|
||||
|
||||
![Selective syncing based on rules in Insync][10]Selective syncing based on rules
|
||||
|
||||
If you prefer to work out of the desktop, you have an “Add to Insync” feature that will allow you to add any local file to your Drive.
|
||||
|
||||
![Sync files right from your desktop][11]Sync files right from your desktop
|
||||
|
||||
Insync also supports symlinks for those with workflows that use symbolic links. To learn more about Insync and symlinks, you can refer to [this article.][12]
|
||||
|
||||
#### Exclusive features for Linux
|
||||
|
||||
Insync supports the most commonly used 64-bit Linux distributions like **Ubuntu, Debian and Fedora**. You can check out the full list of distribution support [here][13].
|
||||
|
||||
Insync also has [headless][14] support for those looking to sync through the command line interface. This is perfect if you use a distro that is not fully supported by the GUI app or if you are working with servers or if you simply prefer the CLI.
|
||||
|
||||
![Insync CLI][15]Command Line Interface
|
||||
|
||||
You can learn more about installing and running Insync headless [here][16].
|
||||
|
||||
### Insync pricing and special discount
|
||||
|
||||
Insync is a premium tool and it comes with a [price tag][17]. You have 2 licenses to choose from:
|
||||
|
||||
* **Prime** is priced at $29.99 per Google account. You’ll get access to: cross-platform syncing, multiple accounts access and **support**.
|
||||
* **Teams** is priced at $49.99 per Google account. You’ll be able to access all the Prime features + Team Drives syncing
|
||||
|
||||
|
||||
|
||||
It’s a one-time fee which means once you buy it, you don’t have to pay it again. In a world where everything is paid monthly, it’s refreshing to pay for software that is still one-time!
|
||||
|
||||
Each Google account has a 15-day free trial that will allow you to test the full suite of features, including [Team Drives][18] syncing.
|
||||
|
||||
If you think it’s a bit expensive for your budget, I have good news for you. As an It’s FOSS reader, you get Insync at 25% discount.
|
||||
|
||||
Just use the code ITSFOSS25 at checkout time and you will get 25% immediate discount on any license. Isn’t it cool?
|
||||
|
||||
If you are not certain yet, you can try Insync free for 15 days. And if you think it’s worth the money, purchase the license with **ITSFOSS25** coupon code.
|
||||
|
||||
You can download Insync from their website.
|
||||
|
||||
I have used Insync from the time when it was available for free and I have always liked it. They have added more features over the time and improved its UI and performance. Overall, it’s a nice-to-have application if you use Google Drive a lot and do not mind paying for the efforts of the developers.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://itsfoss.com/insync-linux-review/
|
||||
|
||||
作者:[Abhishek Prakash][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://itsfoss.com/author/abhishek/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://abevoelker.github.io/how-long-since-google-said-a-google-drive-linux-client-is-coming/
|
||||
[2]: https://itsfoss.com/use-google-drive-linux/
|
||||
[3]: https://www.insynchq.com
|
||||
[4]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2018/12/google-drive-linux-insync.jpeg?resize=800%2C450&ssl=1
|
||||
[5]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2018/11/insync_interface.jpeg?fit=800%2C501&ssl=1
|
||||
[6]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2018/11/insync_multiple_google_account.jpeg?ssl=1
|
||||
[7]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2018/11/insync_folder_settings.png?ssl=1
|
||||
[8]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2018/11/insync_selective_sync.png?ssl=1
|
||||
[9]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2018/11/insync_file_matching.jpeg?ssl=1
|
||||
[10]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2018/11/insync_ignore_list_1.png?ssl=1
|
||||
[11]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2018/11/add-to-insync-shortcut.jpeg?ssl=1
|
||||
[12]: https://help.insynchq.com/key-features-and-syncing-explained/syncing-superpowers/using-symlinks-on-google-drive-with-insync
|
||||
[13]: https://www.insynchq.com/downloads
|
||||
[14]: https://en.wikipedia.org/wiki/Headless_software
|
||||
[15]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2018/11/insync_cli.jpeg?fit=800%2C478&ssl=1
|
||||
[16]: https://help.insynchq.com/installation-on-windows-linux-and-macos/advanced/linux-controlling-insync-via-command-line-cli
|
||||
[17]: https://www.insynchq.com/pricing
|
||||
[18]: https://gsuite.google.com/learning-center/products/drive/get-started-team-drive/#!/
|
||||
@ -0,0 +1,170 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Termtosvg – Record Your Terminal Sessions As SVG Animations In Linux)
|
||||
[#]: via: (https://www.2daygeek.com/termtosvg-record-your-terminal-sessions-as-svg-animations-in-linux/)
|
||||
[#]: author: (Magesh Maruthamuthu https://www.2daygeek.com/author/magesh/)
|
||||
|
||||
Termtosvg – Record Your Terminal Sessions As SVG Animations In Linux
|
||||
======
|
||||
|
||||
By default everyone prefer history command to review/recall the previously entered commands in terminal.
|
||||
|
||||
But unfortunately, that shows only the commands that we ran and doesn’t shows the commands output which was performed previously.
|
||||
|
||||
There are many utilities available in Linux to record the terminal session activity.
|
||||
|
||||
This tool will help us to record the users terminal activity, also will help us to identify other useful information from the output.
|
||||
|
||||
Also, we had written about few utilities in the past and today also we are going to discuss about the same kind of topic.
|
||||
|
||||
If you would like to check other utilities to record your Linux terminal session activity then you can give a try to **[Script Command][1]** and **[Terminalizer Tool][2]**.
|
||||
|
||||
But if you are looking for **[GIF Recorder][3]** then try **[Gifine][4]** , **[Kgif][5]** and **[Peek][6]** utilities.
|
||||
|
||||
Script is one of the best utility to record your terminal session on headless server.
|
||||
|
||||
Script is a Unix command line utility that records a terminal session (in other terms, It’s record everything displayed on your terminal).
|
||||
|
||||
It stores the output in the current directory as a text file and the default file name is typescript.
|
||||
|
||||
### What is Termtosvg
|
||||
|
||||
Termtosvg is a Unix terminal recorder written in Python that renders your command line sessions as standalone SVG animations.
|
||||
|
||||
### Termtosvg Features
|
||||
|
||||
* Produce lightweight and clean looking animations embeddable on a project page.
|
||||
* Custom color themes, terminal UI and animation controls via SVG templates.
|
||||
* Compatible with asciinema recording format.
|
||||
* It requires Python >= 3.5
|
||||
|
||||
|
||||
|
||||
### How to Install Termtosvg In Linux
|
||||
|
||||
It was written in Python and pip installation is a recommended method to install Termtosvg on Linux.
|
||||
|
||||
Make sure you should have installed python-pip package on your system. If no, use the following command to install it.
|
||||
|
||||
For Debian/Ubuntu users, use **[Apt Command][7]** or **[Apt-Get Command][8]** to install pip package.
|
||||
|
||||
```
|
||||
$ sudo apt install python-pip
|
||||
```
|
||||
|
||||
For Archlinux users, use **[Pacman Command][9]** to install pip package.
|
||||
|
||||
```
|
||||
$ sudo pacman -S python-pip
|
||||
```
|
||||
|
||||
For Fedora users, use **[DNF Command][10]** to install pip package.
|
||||
|
||||
```
|
||||
$ sudo dnf install python-pip
|
||||
```
|
||||
|
||||
For CentOS/RHEL users, use **[YUM Command][11]** to install pip package.
|
||||
|
||||
```
|
||||
$ sudo yum install python-pip
|
||||
```
|
||||
|
||||
For openSUSE users, use **[Zypper Command][12]** to install pip package.
|
||||
|
||||
```
|
||||
$ sudo zypper install python-pip
|
||||
```
|
||||
|
||||
Finally run the following **[pip command][13]** to install Termtosvg tool in Linux.
|
||||
|
||||
```
|
||||
$ sudo pip3 install termtosvg pyte python-xlib svgwrite
|
||||
```
|
||||
|
||||
### How to Record Your Terminal Session Using Termtosvg
|
||||
|
||||
Once you successfully installed Termtosvg. Just run the following command to start recording.
|
||||
|
||||
```
|
||||
$ termtosvg
|
||||
Recording started, enter "exit" command or Control-D to end
|
||||
```
|
||||
|
||||
For testing purpose run few commands and see whether it’s working fine or not.
|
||||
|
||||
```
|
||||
$ uname -a
|
||||
Linux daygeek-Y700 4.19.8-2-MANJARO #1 SMP PREEMPT Sat Dec 8 14:45:36 UTC 2018 x86_64 GNU/Linux
|
||||
$ hostname
|
||||
daygeek-Y700
|
||||
$ cat /etc/*-release
|
||||
Manjaro Linux
|
||||
DISTRIB_ID=ManjaroLinux
|
||||
DISTRIB_RELEASE=18.0
|
||||
DISTRIB_CODENAME=Illyria
|
||||
DISTRIB_DESCRIPTION="Manjaro Linux"
|
||||
Manjaro Linux
|
||||
NAME="Manjaro Linux"
|
||||
ID=manjaro
|
||||
ID_LIKE=arch
|
||||
PRETTY_NAME="Manjaro Linux"
|
||||
ANSI_COLOR="1;32"
|
||||
HOME_URL="https://www.manjaro.org/"
|
||||
SUPPORT_URL="https://www.manjaro.org/"
|
||||
BUG_REPORT_URL="https://bugs.manjaro.org/"
|
||||
$ free -g
|
||||
free: Multiple unit options doesn't make sense.
|
||||
$ free -m
|
||||
free: Multiple unit options doesn't make sense.
|
||||
$ pip3 --version
|
||||
pip 18.1 from /usr/lib/python3.7/site-packages/pip (python 3.7)
|
||||
```
|
||||
|
||||
Once you have done, simple press `CTRL+D` or type `exit` to stop the recording. The result will be saved in `/tmp` folder with a unique name.
|
||||
|
||||
```
|
||||
$ exit
|
||||
exit
|
||||
Recording ended, SVG animation is /tmp/termtosvg_5waorper.svg
|
||||
```
|
||||
|
||||
We can open the SVG file output with help of any web browser.
|
||||
|
||||
```
|
||||
$ firefox /tmp/termtosvg_5waorper.svg
|
||||
```
|
||||
|
||||
![][15]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.2daygeek.com/termtosvg-record-your-terminal-sessions-as-svg-animations-in-linux/
|
||||
|
||||
作者:[Magesh Maruthamuthu][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.2daygeek.com/author/magesh/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.2daygeek.com/script-command-record-save-your-terminal-session-activity-linux/
|
||||
[2]: https://www.2daygeek.com/terminalizer-a-tool-to-record-your-terminal-and-generate-animated-gif-images/
|
||||
[3]: https://www.2daygeek.com/category/gif-recorder/
|
||||
[4]: https://www.2daygeek.com/gifine-create-animated-gif-vedio-recorder-linux-mint-debian-ubuntu/
|
||||
[5]: https://www.2daygeek.com/kgif-create-animated-gif-file-active-window-screen-recorder-capture-arch-linux-mint-fedora-ubuntu-debian-opensuse-centos/
|
||||
[6]: https://www.2daygeek.com/peek-create-animated-gif-screen-recorder-capture-arch-linux-mint-fedora-ubuntu/
|
||||
[7]: https://www.2daygeek.com/apt-command-examples-manage-packages-debian-ubuntu-systems/
|
||||
[8]: https://www.2daygeek.com/apt-get-apt-cache-command-examples-manage-packages-debian-ubuntu-systems/
|
||||
[9]: https://www.2daygeek.com/pacman-command-examples-manage-packages-arch-linux-system/
|
||||
[10]: https://www.2daygeek.com/dnf-command-examples-manage-packages-fedora-system/
|
||||
[11]: https://www.2daygeek.com/yum-command-examples-manage-packages-rhel-centos-systems/
|
||||
[12]: https://www.2daygeek.com/zypper-command-examples-manage-packages-opensuse-system/
|
||||
[13]: https://www.2daygeek.com/install-pip-manage-python-packages-linux/
|
||||
[14]: data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7
|
||||
[15]: https://www.2daygeek.com/wp-content/uploads/2018/12/Termtosvg-Record-Your-Terminal-Sessions-As-SVG-Animations-In-Linux-1.gif
|
||||
@ -0,0 +1,100 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Use your Linux terminal to celebrate a banner year)
|
||||
[#]: via: (https://opensource.com/article/18/12/linux-toy-figlet)
|
||||
[#]: author: (Jason Baker https://opensource.com/users/jason-baker)
|
||||
|
||||
Use your Linux terminal to celebrate a banner year
|
||||
======
|
||||
Need make sure your command is heard? Pipe it to a banner and it won't be missed.
|
||||

|
||||
|
||||
|
||||
Hello again for another installment in our 24-day-long Linux command-line toys advent calendar. If this is your first visit to the series, you might be asking yourself what a command-line toy even is. We’re figuring that out as we go, but generally, it could be a game, or any simple diversion that helps you have fun at the terminal.
|
||||
|
||||
Some of you will have seen various selections from our calendar before, but we hope there’s at least one new thing for everyone.
|
||||
|
||||
Today's toy if **figlet** , a utility for printing text in banner form across your Linux terminal.
|
||||
|
||||
You'll likely find **figlet** packaged in your standard repositories. For me on Fedora, this meant installation was as simple as:
|
||||
|
||||
```
|
||||
$ sudo dnf install figlet
|
||||
```
|
||||
|
||||
After that, simply use the program's name to invoke it. You can either use it interactively, or, pipe some text to it, as below:
|
||||
|
||||
```
|
||||
echo "Hello world" | figlet
|
||||
_ _ _ _ _ _
|
||||
| | | | ___| | | ___ __ _____ _ __| | __| |
|
||||
| |_| |/ _ \ | |/ _ \ \ \ /\ / / _ \| '__| |/ _` |
|
||||
| _ | __/ | | (_) | \ V V / (_) | | | | (_| |
|
||||
|_| |_|\___|_|_|\___/ \_/\_/ \___/|_| |_|\__,_|
|
||||
```
|
||||
|
||||
There are a number of different font options available for **figlet**. To see the options available to you, try the command **showfigfonts**. For me, this displayed over a dozen. I've copied out a few of my favorites below.
|
||||
|
||||
```
|
||||
block :
|
||||
|
||||
_| _| _|
|
||||
_|_|_| _| _|_| _|_|_| _| _|
|
||||
_| _| _| _| _| _| _|_|
|
||||
_| _| _| _| _| _| _| _|
|
||||
_|_|_| _| _|_| _|_|_| _| _|
|
||||
|
||||
|
||||
bubble :
|
||||
_ _ _ _ _ _
|
||||
/ \ / \ / \ / \ / \ / \
|
||||
( b | u | b | b | l | e )
|
||||
\_/ \_/ \_/ \_/ \_/ \_/
|
||||
|
||||
|
||||
lean :
|
||||
|
||||
_/
|
||||
_/ _/_/ _/_/_/ _/_/_/
|
||||
_/ _/_/_/_/ _/ _/ _/ _/
|
||||
_/ _/ _/ _/ _/ _/
|
||||
_/ _/_/_/ _/_/_/ _/ _/
|
||||
|
||||
|
||||
script :
|
||||
|
||||
o
|
||||
, __ ,_ _ _|_
|
||||
/ \_/ / | | |/ \_|
|
||||
\/ \___/ |_/|_/|__/ |_/
|
||||
/|
|
||||
\|
|
||||
```
|
||||
|
||||
You can find out more about **figlet** on the project's [homepage][1]. The version I downloaded was made available as open source under an MIT license.
|
||||
|
||||
You'll find that **figlet** isn't the only banner-printer available for the Linux terminal. Another option that you may choose to check out is [toilet][2], which comes with its own set of ASCII-art style printing options.
|
||||
|
||||
Do you have a favorite command-line toy that you we should have included? Our calendar is basically set for the remainder of the series, but we'd still love to feature some cool command-line toys in the new year. Let me know in the comments below, and I'll check it out. And let me know what you thought of today's amusement.
|
||||
|
||||
Be sure to check out yesterday's toy, [Take a swim at your Linux terminal with asciiquarium][3], and come back tomorrow for another!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/12/linux-toy-figlet
|
||||
|
||||
作者:[Jason Baker][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/jason-baker
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: http://www.figlet.org/
|
||||
[2]: http://caca.zoy.org/wiki/toilet
|
||||
[3]: https://opensource.com/article/18/12/linux-toy-asciiquarium
|
||||
114
sources/tech/20181219 How to open source your Python library.md
Normal file
114
sources/tech/20181219 How to open source your Python library.md
Normal file
@ -0,0 +1,114 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (HankChow)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (How to open source your Python library)
|
||||
[#]: via: (https://opensource.com/article/18/12/tips-open-sourcing-python-libraries)
|
||||
[#]: author: (Moshe Zadka https://opensource.com/users/moshez)
|
||||
|
||||
How to open source your Python library
|
||||
======
|
||||
This 12-step checklist will ensure a successful launch.
|
||||

|
||||
|
||||
You wrote a Python library. I'm sure it's amazing! Wouldn't it be neat if it was easy for people to use it? Here is a checklist of things to think about and concrete steps to take when open sourcing your Python library.
|
||||
|
||||
### 1\. Source
|
||||
|
||||
Put the code up on [GitHub][1], where most open source projects happen and where it is easiest for people to submit pull requests.
|
||||
|
||||
### 2\. License
|
||||
|
||||
Choose an open source license. A good, permissive default is the [MIT License][2]. If you have specific requirements, Creative Common's [Choose a License][3] can guide you through the alternatives. Most importantly, there are three rules to keep in mind when choosing a license:
|
||||
|
||||
* Don't create your own license.
|
||||
* Don't create your own license.
|
||||
* Don't create your own license.
|
||||
|
||||
|
||||
|
||||
### 3\. README
|
||||
|
||||
Put a file called README.rst, formatted with ReStructured Text, at the top of your tree.
|
||||
|
||||
GitHub will render ReStructured Text just as well as Markdown, and ReST plays better with Python's documentation ecosystem.
|
||||
|
||||
### 4\. Tests
|
||||
|
||||
Write tests. This is not useful just for you: it is useful for people who want to make patches that avoid breaking related functionality.
|
||||
|
||||
Tests help collaborators collaborate.
|
||||
|
||||
Usually, it is best if they are runnable with [**pytest**][4]. There are other test runners—but very little reason to use them.
|
||||
|
||||
### 5\. Style
|
||||
|
||||
Enforce style with a linter: PyLint, Flake8, or Black with **\--check**. Unless you use Black, make sure to specify configuration options in a file checked into source control.
|
||||
|
||||
### 6\. API documentation
|
||||
|
||||
Use docstrings to document modules, functions, classes, and methods.
|
||||
|
||||
There are a few styles you can use. I prefer the [Google-style docstrings][5], but [ReST docstrings][6] are an option.
|
||||
|
||||
Both Google-style and ReST docstrings can be processed by Sphinx to integrate API documentation with prose documentation.
|
||||
|
||||
### 7\. Prose documentation
|
||||
|
||||
Use [Sphinx][7]. (Read [our article on it][8].) A tutorial is useful, but it is also important to specify what this thing is, what it is good for, what it is bad for, and any special considerations.
|
||||
|
||||
### 8\. Building
|
||||
|
||||
Use **tox** or **nox** to automatically run your tests and linter and build the documentation. These tools support a "dependency matrix." These matrices tend to explode fast, but try to test against a reasonable sample, such as Python versions, versions of dependencies, and possibly optional dependencies you install.
|
||||
|
||||
### 9\. Packaging
|
||||
|
||||
Use [setuptools][9]. Write a **setup.py** and a **setup.cfg**. If you support both Python 2 and 3, specify universal wheels in the **setup.cfg**.
|
||||
|
||||
One thing **tox** or **nox** should do is build a wheel and run tests against the installed wheel.
|
||||
|
||||
Avoid C extensions. If you absolutely need them for performance or binding reasons, put them in a separate package. Properly packaging C extensions deserves its own post. There are a lot of gotchas!
|
||||
|
||||
### 10\. Continuous integration
|
||||
|
||||
### 11\. Versions
|
||||
|
||||
Use a public continuous integration runner. [TravisCI][10] and [CircleCI][11] offer free tiers for open source projects. Configure GitHub or other repo to require passing checks before merging pull requests, and you'll never have to worry about telling people to fix their tests or their style in code reviews.
|
||||
|
||||
Use either [SemVer][12] or [CalVer][13]. There are many tools to help manage versions: [incremental][14], [bumpversion][15], and [setuptools_scm][16] are all packages on PyPI that help manage versions for you.
|
||||
|
||||
### 12\. Release
|
||||
|
||||
Release by running **tox** or **nox** and using **twine** to upload the artifacts to PyPI. You can do a "test upload" by running [DevPI][17].
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/12/tips-open-sourcing-python-libraries
|
||||
|
||||
作者:[Moshe Zadka][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/moshez
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://github.com/
|
||||
[2]: https://en.wikipedia.org/wiki/MIT_License
|
||||
[3]: https://choosealicense.com/
|
||||
[4]: https://docs.pytest.org/en/latest/
|
||||
[5]: https://github.com/google/styleguide/blob/gh-pages/pyguide.md
|
||||
[6]: https://www.python.org/dev/peps/pep-0287/
|
||||
[7]: http://www.sphinx-doc.org/en/master/
|
||||
[8]: https://opensource.com/article/18/11/building-custom-workflows-sphinx
|
||||
[9]: https://pypi.org/project/setuptools/
|
||||
[10]: https://travis-ci.org/
|
||||
[11]: https://circleci.com/
|
||||
[12]: https://semver.org/
|
||||
[13]: https://calver.org/
|
||||
[14]: https://pypi.org/project/incremental/
|
||||
[15]: https://pypi.org/project/bumpversion/
|
||||
[16]: https://pypi.org/project/setuptools_scm/
|
||||
[17]: https://opensource.com/article/18/7/setting-devpi
|
||||
@ -0,0 +1,54 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Solve a puzzle at the Linux command line with nudoku)
|
||||
[#]: via: (https://opensource.com/article/18/12/linux-toy-nudoku)
|
||||
[#]: author: (Jason Baker https://opensource.com/users/jason-baker)
|
||||
|
||||
Solve a puzzle at the Linux command line with nudoku
|
||||
======
|
||||
Sudokus are simple logic games that can be enjoyed just about anywhere, including in your Linux terminal.
|
||||
|
||||
|
||||
Welcome back to another installment in our 24-day-long Linux command-line toys advent calendar. If this is your first visit to the series, you might be asking yourself what a command-line toy even is. We’re figuring that out as we go, but generally, it could be a game, or any simple diversion that helps you have fun at the terminal.
|
||||
|
||||
Some of you will have seen various selections from our calendar before, but we hope there’s at least one new thing for everyone.
|
||||
|
||||
Every year for Christmas, my mother-in-law gives my wife a Sudoku calendar. It sits on our coffee table for the year to follow. Each day is a separate sheet (except for Saturday and Sunday, that are combined onto one page), with the idea being that you have a new puzzle every day while also having a functioning calendar.
|
||||
|
||||
The problem, in practice, is that it's a great pad of puzzles but not a great calendar because it turns out some days are harder than others and we just don't get through them at the necessary rate of one a day. Then, we may have a week's worth that gets batched on a lazy Sunday.
|
||||
|
||||
Since I've already given you a [calendar][1] as a part of this series, I figure it's only fair to give you a Sudoku puzzle as well, except our command-line versions are decoupled so there's no pressure to complete exactly one a day.
|
||||
|
||||
I found **nudoku** in my default repositories on Fedora, so installing it was as simple as:
|
||||
|
||||
```
|
||||
$ sudo dnf install nudoku
|
||||
```
|
||||
|
||||
Once installed, just invoke **nudoku** by name to launch it, and it should be fairly self-explanatory from there. If you've never played Sudoku before, it's fairly simple: You need to make sure that each row, each column, and each of the nine 3x3 squares that make up the large square each have one of every digit, 1-9.
|
||||
|
||||
You can find **nudoku** 's c source code [on GitHub][2] under a GPLv3 license.
|
||||
|
||||
Do you have a favorite command-line toy that you we should have included? Our calendar is basically set for the remainder of the series, but we'd still love to feature some cool command-line toys in the new year. Let me know in the comments below, and I'll check it out. And let me know what you thought of today's amusement.
|
||||
|
||||
Be sure to check out yesterday's toy, [Use your Linux terminal to celebrate a banner][3] [year][3], and come back tomorrow for another!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/12/linux-toy-nudoku
|
||||
|
||||
作者:[Jason Baker][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/jason-baker
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/article/18/12/linux-toy-cal
|
||||
[2]: https://github.com/jubalh/nudoku
|
||||
[3]: https://opensource.com/article/18/12/linux-toy-figlet
|
||||
166
sources/tech/20181220 Getting started with Prometheus.md
Normal file
166
sources/tech/20181220 Getting started with Prometheus.md
Normal file
@ -0,0 +1,166 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Getting started with Prometheus)
|
||||
[#]: via: (https://opensource.com/article/18/12/introduction-prometheus)
|
||||
[#]: author: (Michael Zamot https://opensource.com/users/mzamot)
|
||||
|
||||
Getting started with Prometheus
|
||||
======
|
||||
Learn to install and write queries for the Prometheus monitoring and alerting system.
|
||||

|
||||
|
||||
[Prometheus][1] is an open source monitoring and alerting system that directly scrapes metrics from agents running on the target hosts and stores the collected samples centrally on its server. Metrics can also be pushed using plugins like **collectd_exporter** —although this is not Promethius' default behavior, it may be useful in some environments where hosts are behind a firewall or prohibited from opening ports by security policy.
|
||||
|
||||
Prometheus, a project of the [Cloud Native Computing Foundation][2], scales up using a federation model, which enables one Prometheus server to scrape another Prometheus server. This allows creation of a hierarchical topology, where a central system or higher-level Prometheus server can scrape aggregated data already collected from subordinate instances.
|
||||
|
||||
Besides the Prometheus server, its most common components are its [Alertmanager][3] and its exporters.
|
||||
|
||||
Alerting rules can be created within Prometheus and configured to send custom alerts to Alertmanager. Alertmanager then processes and handles these alerts, including sending notifications through different mechanisms like email or third-party services like [PagerDuty][4].
|
||||
|
||||
Prometheus' exporters can be libraries, processes, devices, or anything else that exposes the metrics that will be scraped by Prometheus. The metrics are available at the endpoint **/metrics** , which allows Prometheus to scrape them directly without needing an agent. The tutorial in this article uses **node_exporter** to expose the target hosts' hardware and operating system metrics. Exporters' outputs are plaintext and highly readable, which is one of Prometheus' strengths.
|
||||
|
||||
In addition, you can configure [Grafana][5] to use Prometheus as a backend to provide data visualization and dashboarding functions.
|
||||
|
||||
### Making sense of Prometheus' configuration file
|
||||
|
||||
The number of seconds between when **/metrics** is scraped controls the granularity of the time-series database. This is defined in the configuration file as the **scrape_interval** parameter, which by default is set to 60 seconds.
|
||||
|
||||
Targets are set for each scrape job in the **scrape_configs** section. Each job has its own name and a set of labels that can help filter, categorize, and make it easier to identify the target. One job can have many targets.
|
||||
|
||||
### Installing Prometheus
|
||||
|
||||
In this tutorial, for simplicity, we will install a Prometheus server and **node_exporter** with docker. Docker should already be installed and configured properly on your system. For a more in-depth, automated method, I recommend Steve Ovens' article [How to use Ansible to set up system monitoring with Prometheus][6].
|
||||
|
||||
Before starting, create the Prometheus configuration file **prometheus.yml** in your work directory as follows:
|
||||
|
||||
```
|
||||
global:
|
||||
scrape_interval: 15s
|
||||
evaluation_interval: 15s
|
||||
|
||||
scrape_configs:
|
||||
- job_name: 'prometheus'
|
||||
|
||||
static_configs:
|
||||
- targets: ['localhost:9090']
|
||||
|
||||
- job_name: 'webservers'
|
||||
|
||||
static_configs:
|
||||
- targets: ['<node exporter node IP>:9100']
|
||||
```
|
||||
|
||||
Start Prometheus with Docker by running the following command:
|
||||
|
||||
```
|
||||
$ sudo docker run -d -p 9090:9090 -v
|
||||
/path/to/prometheus.yml:/etc/prometheus/prometheus.yml
|
||||
prom/prometheus
|
||||
```
|
||||
|
||||
By default, the Prometheus server will use port 9090. If this port is already in use, you can change it by adding the parameter **\--web.listen-address=" <IP of machine>:<port>"** at the end of the previous command.
|
||||
|
||||
In the machine you want to monitor, download and run the **node_exporter** container by using the following command:
|
||||
|
||||
```
|
||||
$ sudo docker run -d -v "/proc:/host/proc" -v "/sys:/host/sys" -v
|
||||
"/:/rootfs" --net="host" prom/node-exporter --path.procfs
|
||||
/host/proc --path.sysfs /host/sys --collector.filesystem.ignored-
|
||||
mount-points "^/(sys|proc|dev|host|etc)($|/)"
|
||||
```
|
||||
|
||||
For the purposes of this learning exercise, you can install **node_exporter** and Prometheus on the same machine. Please note that it's not wise to run **node_exporter** under Docker in production—this is for testing purposes only.
|
||||
|
||||
To verify that **node_exporter** is running, open your browser and navigate to **http:// <IP of Node exporter host>:9100/metrics**. All the metrics collected will be displayed; these are the same metrics Prometheus will scrape.
|
||||
|
||||
|
||||
|
||||
To verify the Prometheus server installation, open your browser and navigate to <http://localhost:9090>.
|
||||
|
||||
You should see the Prometheus interface. Click on **Status** and then **Targets**. Under State, you should see your machines listed as **UP**.
|
||||
|
||||
|
||||
|
||||
### Using Prometheus queries
|
||||
|
||||
It's time to get familiar with [PromQL][7], Prometheus' query syntax, and its graphing web interface. Go to **<http://localhost:9090/graph>** on your Prometheus server. You will see a query editor and two tabs: Graph and Console.
|
||||
|
||||
Prometheus stores all data as time series, identifying each one with a metric name. For example, the metric **node_filesystem_avail_bytes** shows the available filesystem space. The metric's name can be used in the expression box to select all of the time series with this name and produce an instant vector. If desired, these time series can be filtered using selectors and labels—a set of key-value pairs—for example:
|
||||
|
||||
```
|
||||
node_filesystem_avail_bytes{fstype="ext4"}
|
||||
```
|
||||
|
||||
When filtering, you can match "exactly equal" ( **=** ), "not equal" ( **!=** ), "regex-match" ( **=~** ), and "do not regex-match" ( **!~** ). The following examples illustrate this:
|
||||
|
||||
To filter **node_filesystem_avail_bytes** to show both ext4 and XFS filesystems:
|
||||
|
||||
```
|
||||
node_filesystem_avail_bytes{fstype=~"ext4|xfs"}
|
||||
```
|
||||
|
||||
To exclude a match:
|
||||
|
||||
```
|
||||
node_filesystem_avail_bytes{fstype!="xfs"}
|
||||
```
|
||||
|
||||
You can also get a range of samples back from the current time by using square brackets. You can use **s** to represent seconds, **m** for minutes, **h** for hours, **d** for days, **w** for weeks, and **y** for years. When using time ranges, the vector returned will be a range vector.
|
||||
|
||||
For example, the following command produces the samples from five minutes to the present:
|
||||
|
||||
```
|
||||
node_memory_MemAvailable_bytes[5m]
|
||||
```
|
||||
|
||||
Prometheus also includes functions to allow advanced queries, such as this:
|
||||
|
||||
```
|
||||
100 core.md Dict.md lctt2014.md lctt2016.md lctt2018.md LICENSE published README.md scripts sources translated (1 - avg by(instance)(irate(node_cpu_seconds_total{job='webservers',mode='idle'}[5m])))
|
||||
```
|
||||
|
||||
Notice how the labels are used to filter the job and the mode. The metric **node_cpu_seconds_total** returns a counter, and the **irate()** function calculates the per-second rate of change based on the last two data points of the range interval (meaning the range can be smaller than five minutes). To calculate the overall CPU usage, you can use the idle mode of the **node_cpu_seconds_total** metric. The idle percent of a processor is the opposite of a busy processor, so the **irate** value is subtracted from 1. To make it a percentage, multiply it by 100.
|
||||
|
||||
|
||||
|
||||
### Learn more
|
||||
|
||||
Prometheus is a powerful, scalable, lightweight, and easy to use and deploy monitoring tool that is indispensable for every system administrator and developer. For these and other reasons, many companies are implementing Prometheus as part of their infrastructure.
|
||||
|
||||
To learn more about Prometheus and its functions, I recommend the following resources:
|
||||
|
||||
+ About [PromQL][8]
|
||||
+ What [node_exporters collects][9]
|
||||
+ [Prometheus functions][10]
|
||||
+ [4 open source monitoring tools][11]
|
||||
+ [Now available: The open source guide to DevOps monitoring tools][12]
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/12/introduction-prometheus
|
||||
|
||||
作者:[Michael Zamot][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/mzamot
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://prometheus.io/
|
||||
[2]: https://www.cncf.io/
|
||||
[3]: https://prometheus.io/docs/alerting/alertmanager/
|
||||
[4]: https://en.wikipedia.org/wiki/PagerDuty
|
||||
[5]: https://grafana.com/
|
||||
[6]: https://opensource.com/article/18/3/how-use-ansible-set-system-monitoring-prometheus
|
||||
[7]: https://prometheus.io/docs/prometheus/latest/querying/basics/
|
||||
[8]: https://prometheus.io/docs/prometheus/latest/querying/basics/
|
||||
[9]: https://github.com/prometheus/node_exporter#collectors
|
||||
[10]: https://prometheus.io/docs/prometheus/latest/querying/functions/
|
||||
[11]: https://opensource.com/article/18/8/open-source-monitoring-tools
|
||||
[12]: https://opensource.com/article/18/8/now-available-open-source-guide-devops-monitoring-tools
|
||||
@ -0,0 +1,62 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Let your Linux terminal speak its mind)
|
||||
[#]: via: (https://opensource.com/article/18/12/linux-toy-espeak)
|
||||
[#]: author: (Jason Baker https://opensource.com/users/jason-baker)
|
||||
|
||||
Let your Linux terminal speak its mind
|
||||
======
|
||||
eSpeak is an open source text-to-speech synthesizer that can be invoked from the Linux command line.
|
||||
|
||||
|
||||
Greetings from another day in our 24-day-long Linux command-line toys advent calendar. If this is your first visit to the series, you might be asking yourself what a command-line toy even is. We’re figuring that out as we go, but generally, it could be a game, or any simple diversion that helps you have fun at the terminal.
|
||||
|
||||
We hope that even if you've seen some of these before, there will be something new for everybody in our series.
|
||||
|
||||
Some of you may be too young to remember, but before there was Alexa, Siri, or the Google Assistant, computers still had voices.
|
||||
|
||||
Many of us will never forget HAL 9000 from [2001: A Space Odessey][1] helpfully conversing with the crew (sorry, Dave). But between 1960s science fiction and today, there was a whole generation of speaking computers. Some of them great, most of them, not so great.
|
||||
|
||||
One of my favorites is the open source project [eSpeak][2]. It's available in many forms, including a library version you can use to include speech technology in your own project, but it also coms as a command-line program that you can install and use easily. In my distribution, this was as simple as:
|
||||
|
||||
```
|
||||
$ sudo dnf install espeak
|
||||
```
|
||||
|
||||
Invoking eSpeak then can be invoked either interactively, or by piping text to it using the output of another program or a simple echo command. There are a number of [voice files][3] available for eSpeak, and if you're especially bored over the holidays, you could even create your own.
|
||||
|
||||
A fork of eSpeak called eSpeak NG ("Next Generation") was created in 2015 from some developers who wanted to continue development of the otherwise lightly-updated eSpeak. eSpeak is made available as open source under a GPL version 3 license, and you can find out more about the project and download the source code [on SourceForge][2].
|
||||
|
||||
I'll also throw in a bonus toy today, [cava][4]. Because I've been eager to give each of these articles a unique screenshot as the lead image, and today's toy outputs sound rather than something visual, I needed to find something to fill the space. Short for "console-based audio visualizer for ALSA" (although it supports more than just ALSA now), cava is a nice MIT-licensed terminal audio visualization tool that's fun to watch. Below, is a visualization of eSpeak's output of the following:
|
||||
|
||||
```
|
||||
$ echo "Rudolph, the red-nosed reindeer, had a very shiny nose." | espeak
|
||||
```
|
||||
|
||||
|
||||
|
||||
Do you have a favorite command-line toy that you we should have included? Our calendar is basically set for the remainder of the series, but we'd still love to feature some cool command-line toys in the new year. Let me know in the comments below, and I'll check it out. And let me know what you thought of today's amusement.
|
||||
|
||||
Be sure to check out yesterday's toy, [Solve a puzzle at the Linux command line with nudoku][5], and come back tomorrow for another!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/12/linux-toy-espeak
|
||||
|
||||
作者:[Jason Baker][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/jason-baker
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://en.wikipedia.org/wiki/2001:_A_Space_Odyssey_(film)
|
||||
[2]: http://espeak.sourceforge.net/
|
||||
[3]: http://espeak.sourceforge.net/voices.html
|
||||
[4]: https://github.com/karlstav/cava
|
||||
[5]: https://opensource.com/article/18/12/linux-toy-nudoku
|
||||
71
translated/talk/20180623 The IBM 029 Card Punch.md
Normal file
71
translated/talk/20180623 The IBM 029 Card Punch.md
Normal file
@ -0,0 +1,71 @@
|
||||
IBM 029 型打孔机
|
||||
======
|
||||
我知道这很学院派,可一行超过 80 个字符的代码还是让我抓狂。我也在网上见过不少人认为即在现代视网膜屏幕下也应当采用行长度为 80 个字符的标准,可他们都不理解我对破坏这一标准的怒火,就算 1 个字符也不行。
|
||||
|
||||
在这一标准的黄金时期,一行代码的长度几乎不会超过 80 个字符的限制。在那时,这一限制是物理的,没有第 81 列用于存放第 81 个字符。每一个试图把函数名起的又长又臭的程序员都会在短暂的愉悦后迎来更多的麻烦,而这仅仅时因为没有足够的空间放下整个函数的声明。
|
||||
|
||||
这一黄金时期也是打孔卡编程时期。在 20 世纪 60 年代, IBM 打孔卡的特性,也就是打孔卡的长度为 80 个字符成为了打孔卡的标准。这一标准在后来的电传打字机和哑终端时期得以延续,并逐渐成为操作系统中隐藏的细节。时至今日,即使我们用上了更大、更好的屏幕,偏向于使用更长的标识符而不是类似 `iswcntrl()` 这样令人难以猜测的函数名,可当你打开新的终端模拟器窗口时,默认的宽度依然是 80 个字符。
|
||||
|
||||
从 Quora 上的很多问题中可以发现,很多人并不能想象如何使用打孔卡给计算机编程。我承认,在很长的一段时间里我也不能理解卡编程成是如何工作的,因为这让我想到有很多劳工不停的给这些打孔卡打孔。当然,这是一个误解,程序员不需要亲自给打孔卡打孔,就像是火车调度员不用亲自扳道岔。程序员们有打孔机(也被称为<ruby>键控打孔机<rt>key punches</rt></ruby>),这让他们可以使用打字机式的键盘给打孔卡打孔。这样的设备在 19 世纪 90 年代时就已经不是什么新技术了。
|
||||
|
||||
那时,最为广泛使用的打孔机之一便是 IBM 029 型打孔机。就算在今天,它也许是最棒的打孔机。
|
||||
|
||||
![][1]
|
||||
|
||||
IBM 029 型打孔机在 1964 年作为 IBM 的 System/360 大型电脑的配件发售的。 System/360 是计算系统与外设所组成的一个系列,在 20 世纪 60 年代晚期,它几乎垄断了整个大型计算机市场。就像其它 System/360 外设一样, 029 型打孔机也是个大块头。那时,计算机和家具的界限还很模糊,但 029 型打孔机可不是那种会占领你的整张桌子的机器。它改进自 026 型打孔机,增加了新的字符支持,如括号,总体上也更加安静。与前辈 026 型所展出 20 世纪 40 年代的圆形按钮与工业化的样貌相比, 029 型的按键方正扁平、功能按键还有酷炫的蓝色高亮提示。它的另一个重要买点是它能够在<ruby>数字区<rt>numeric fields</rt></ruby>左侧自动的填充 0 ,这证明了 JavaScript 程序员不是第一批懒得自己做<ruby>左填充<rt>left-padding</rt></ruby>的程序员。
|
||||
(译者注:这项功能需要额外的 4 张 [<ruby>标准模块系统卡<rt>SMS card</rt></ruby>](https://en.wikipedia.org/wiki/IBM_Standard_Modular_System)才能使用。例如设置数字区域长度为 6 列时,操作员只需要输入 73 ,打孔机会自动填充起始位置上的 4 个 0 ,故最终输出 000073。[更多信息](https://en.wikipedia.org/wiki/Keypunch#IBM_029_Card_Punch))
|
||||
|
||||
等等!你说的是 IBM 在 1964 年发布了全新的打孔机?你知道那张在贝尔实验室拍摄的 Unix 之父正在使用电传打字机的照片吗?那是哪一年的来着?1970?打孔机不是应该在 20 世纪 60 年代中期到晚期时就过时了吗?是的,你也许会奇怪,为什么直到 1984 年, IBM 的产品目录中才出现 029 型打孔机的身影。事实上,直到 20 世纪 70 年代,大多数程序员仍然在使用打孔卡编程。其实二战期间就已经有人在用电传打字机了,可那时并没能普及。客观的讲,电传打字机几乎和打孔卡一样古老。也许和你想象的恰恰相反,并不是电传打字机本身限制了他的普及,而是计算时间。人们拒绝使用电传打字机的原因是,它是可交互的,它和计算机使用<ruby>“在线”的传输方式<rt>"online" mode of communication</rt></ruby>。在以 Unix 为代表的分时操作系统被发明前,你和电脑的交互会被任何人的使用而打断,而这一点延迟通常意味着几千美元的损失。所以程序员们普遍选择离线地使用打孔机编程,再将打孔卡放入大型计算机中,作为<ruby>批任务<rt>batch job</rt></ruby>执行。在那时,还没有即廉价又可靠的存储设备,可打孔卡的廉价优势已经足够让他成为那时最流行的数据存储方式了。那时的程序是书架上一落的打孔卡而不是硬盘里的一堆文件。
|
||||
|
||||
那么实际使用 IBM 029 型打孔机是个什么样子呢?这很难向没有实际看过打孔卡的人解释。一张打孔卡通常有12行80列。打孔卡下面是从 1 到 9 的<ruby>数字行<rt>digit rows</rt></ruby>,打孔卡上的每一列都有这些行所对应的数字。最上面的三行是<ruby>空间行<rt>"zone" rows</rt></ruby>,通常由两行空白行和一行 0 行组成。第 12 行是打孔卡最顶层的行,接下来是 11 行,随后是从数字 0 到 9 所在的行。这个有点让人感到困惑的顺序的原因是打孔卡的上边缘被称为<ruby>12 边<rt>12 edge</rt></ruby>、下边缘被称为 <ruby>9 边<rt>9 edge</rt></ruby>。那时,为了让打孔卡便于整理,常常会剪去打孔卡的一个角。
|
||||
|
||||
![][2]
|
||||
(译者注:可参考[EBCDIC 编码](https://zh.wikipedia.org/wiki/EBCDIC))
|
||||
|
||||
在打孔卡发明之初,孔洞的形状是圆形的,但是 IBM 最终意识到如果使用窄长方形作为孔洞,一张卡就可以放下更多的列了。每一列中孔洞的不同组合就可以表达不同的字符。像 029 型这样的拥有人性化设计的打孔机除了完成本质的打孔任务外,还会在打孔卡最上方打印出每一列所对应的字符。输入是数字就在对应的数字行上打孔。输入的是字母或符号就用一个在空间列的孔和一或俩个在数字列的孔的组合表示,例如字母 A 就用一个在第 12 空间行的空和一个数字 1 所在行的孔表示。这是一种顺序编码,在第一台打孔机被发明后,也叫 Hollerith 编码。这种编码只能表示相对较小的一套字符集,小写字母就没有包含在这套字符集中,但它的优势在于保留了打孔卡的结构强度。如果直接使用二进制编码,打孔卡可能会因为孔洞过于密集而断裂。
|
||||
|
||||
打孔卡也有不同。在 20 世纪 60 年代,80 列虽然是标准,但表达的方式不一定相同。基础打孔卡是无标注的,但用于 COBOL 编程的打孔卡会把最后的 8 列保留,供标识数保存使用。这一标识数可以在打孔卡被打乱 (例如一叠打孔卡掉在地上了) 后用于自动排序。此外,第 7 列被用于表示本张打孔卡上的是否是上一张打孔卡一起构成一条语句。也就是说当你真的对 80 字符的限制感到绝望的时候,还可以用两张卡甚至更多的卡拼接成一条长语句。用于 FORTRAN 编程的打孔卡和 COBOL 打孔卡类似,但是定义的列不同。大学里使用的打孔卡通常会由其计算机中心加上水印,其他的设计则会在如 [1976 年美国独立 200 周年][3] 的特殊场合才会加入。
|
||||
|
||||
最终,这些打孔卡都要被计算机读取和计算。 IBM 出售的 System/360 大型计算机的外设 IBM 2540 可以以每分钟 1000 张打孔卡的速度读取这些卡片。IBM 2540 使用电刷扫过每张打孔卡,电刷通过孔洞就可以接触到卡片后面的金属板完成一次读取。一旦读取完毕, System/360 大型计算机就会把每张打孔卡上的数据使用一种定长的 8 位编码保存,这种编码是<ruby>扩展的二进制十数交换码<rt>Extended Binary Coded Decimal Interchange Code</rt></ruby>,简写为 EBCDIC 编码。它的源自于早期打孔卡所使用的 BCDIDC 编码,这一 6 位编码使用低 4 位表示数字行,高 2 位表示空间行。程序员们在打孔卡上编写玩程序后,会把卡片们交给计算机操作员,操作员们会把这些卡片放入 IBM 2540 ,再把打印结果交给程序员。那时的程序员大多都没有见过计算机长什么样。
|
||||
|
||||
程序员们真正能见到的是很多打孔机。 029 型打孔机虽然不是计算机,但这并不意味着它不是一台复杂的机器。看看这个由<ruby>密歇根大学<rt>University of Michigan</rt></ruby>在 1967 年制作的[教学视频][4],你就能更好的理解使用一台 029 型打孔机是什么情形了。我会尽可能在这里总结这段视频,但如果你不去亲自看看的话,你会错过许多惊奇和感叹。
|
||||
|
||||
029 型打孔机的结构围绕着一个打孔卡穿过机器的 U 形轨道开始。使用打孔机时,右手边也就是 U 形轨道的右侧顶部是<ruby>进卡卡槽<rt>hopper</rt></ruby>,使用前通常在里面放入一叠未使用的打孔卡。虽然 029 型打孔机主要使用 80 列打孔卡,但在需要的情况下也可以使用更小号的打孔卡。在打孔机的使用过程中,打孔卡离开轨道右上端的进卡卡槽,顺着 U 形轨道移动并最终进入左上端的<ruby>出卡卡槽<rt>stacker</rt></ruby>。这一流程可以保证出卡卡槽中的打孔卡按打孔时的先后顺序排列。
|
||||
|
||||
029 型打孔机的开关在桌面下膝盖高度的位置。在开机后,连按两次 “<ruby>装入<rt>FEED</rt></ruby>” 键让机器自动将打孔卡从进卡卡槽中取出并移动到机器内。 U 形轨道的底部是打孔机的核心区域,它由三个部分组成:右侧是等待区,中间是打孔操作区,左侧是阅读区。连按两次 “装入” 键,机器就会把一张打孔卡装入打孔机的打孔操作区,另一张打孔卡进入等待区。在打孔操作区上方有一个列数指示器来显示当前打孔所在的列的位置。这时,每按下一个按键,机器就会在打孔卡对应的位置打孔并在卡片的顶部打印按键对应的字符,随后将打孔卡向左移动一列。如果一张卡片的 80 列全部被打上了数据,这张卡片会被打孔操作区自动释放并进入阅读区,同时,一张新的打孔卡会被装入打孔操作区。如果没有打完全部的 80 列,可以使用 “<ruby>释放<rt>REL (for release)</rt></ruby>” 键完成上面的操作。
|
||||
|
||||
在打孔卡上打印对应的字符这一设计让人很容易分辨出错误。但就像密歇根大学的视频中警告的那样,打孔卡上修正一个错误可不像擦掉一个打印的字符然后再写上一个新的那样容易,因为计算机只会根据卡片上的孔来读取信息。因为被打出的孔不能被<ruby>复原<rt>unpunched</rt></ruby>,所以并不能直接退回一列然后再打上一个新的字符。打出更多的孔也只能让这一列的组合变成一个无效字符。 IBM 029 型打孔机上虽然有一个可以让打孔卡回退一列的退格按键,但这个按键被放置在机器上而非在键盘上。这样的设计也许是为了阻止这个按键的使用,因为实际上很少有用户需要这个功能。
|
||||
|
||||
实际上,只有废弃错误的打孔卡再在新的打孔卡上重新打孔这一种修正错误的方式。这就是阅读区的用武之处了。当你发现打孔卡上的第 68 列出错时,你需要在新的打孔卡上小心的给前 67 列打孔,然后给第 68 列打上正确的字母。另一种操作方式是把带有错误信息的打孔卡放在阅读区,同时在打孔操作区载入一张新的打孔卡,然后按下 “<ruby>重复<rt>DUP (for duplicate)</rt></ruby>” 按键直到列数指示器显示 68 列。这时按下正确的字符来修正错误。阅读区和重复按键使得 029 型打孔机很容易复制打孔卡上的内容。当然,这一功能的使用可能有各种各样的原因,但改错是最常见的。
|
||||
|
||||
“重复”按键允许 029 型打孔机的操作员手动调用重复的函数。但是 029 型打孔机还可以设置为自动重复。当用于记录数据而不是编程时,这项功能十分有效。举个例子,当用打孔卡来记录大学生的信息时,每张卡片上都需要输入学生的宿舍楼的名字,如果发现所输入信息的学生都在同一栋楼,就可以使用 029 型打孔机的自动重复功能来完成宿舍楼名称的填写。
|
||||
|
||||
像这样的自动化操作可以通过打孔卡给 029 型打孔机编程控制。安装打孔卡的<ruby>圆柱形装置<rt>drum</rt></ruby>就在 U 形轨道中间部分的右上角。通过使用 029 型在打孔卡上写下程序,然后把打孔卡的装入圆柱形装置,再将其安装到打孔机内后,就完成了一次给 029 型打孔机的编程任务。用户可以通过这种方式对打孔卡的每一列都按需要定义不同的自动化操作。029 型打孔机允许指定某些列重复上一张打孔卡相同位置的字符,这就是它能更快的输入学生信息的理由。它还允许指定某些列只能输入数字或者字母,指定特定的列为空或者到某一列时就直接跳过一整张打孔卡。这样的可编程特性使它在输入拥有固定格式的数据时效率很高。密歇根大学制作的[进阶教学视频][5]包括了给 029 型打孔机编程的过程,如果你已经掌握了它的基础操作,就快去看看吧。
|
||||
|
||||
这会儿,无论你是否看了密歇根大学制作的视频,都会感叹打孔机的操作之简便。虽然修正错误的过程很乏味,但除此之外,操作一台打孔机并不像想象的那样复杂。我甚至可以想象打孔卡之间的无缝切换让 COBOL 和 FORTRAN 程序员忘记了他们的程序是打在不同的打孔卡上而不是写在一个连续的文本文件内。另一方面,思考一下打孔机是如何影响编程语言的发展也是很有趣的,虽然它仅仅是一台输入设备。结构化编程最终会出现并鼓励程序员把整个代码块视为一个整体,但可以想象打孔卡程序员们强调每一行的作用且难以认同结构化编程的场景。同时你能够理解他们为什么不把代码块闭合所使用的括号放在单独的一行,只是因为这样会浪费打孔卡。
|
||||
|
||||
现在,虽然没有人再使用打孔卡编程了,每个程序员都该试试[这个][6],哪怕一次也好。或许你因此能够更好的理解 COBOL 和 FORTRAN 的历史,或许你就能体会到为什么每个人把 80 个字符作为长度限制的标注。
|
||||
|
||||
喜欢吗?这里每两周都会发表一篇这样的文章。请在推特上关注我们 [@TwoBitHistory][7] 或者订阅我们的 [RSS][8],这样你就能在第一时间收到新文章的通知。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://twobithistory.org/2018/06/23/ibm-029-card-punch.html
|
||||
|
||||
作者:[Two-Bit History][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[wwhio](https://github.com/wwhio)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://twobithistory.org
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://twobithistory.org/images/ibm029_front.jpg
|
||||
[2]: https://twobithistory.org/images/card.png
|
||||
[3]: http://www.jkmscott.net/data/Punched%20card%20013.jpg
|
||||
[4]: https://www.youtube.com/watch?v=kaQmAybWn-w
|
||||
[5]: https://www.youtube.com/watch?v=SWD1PwNxpoU
|
||||
[6]: http://www.masswerk.at/keypunch/
|
||||
[7]: https://twitter.com/TwoBitHistory
|
||||
[8]: https://twobithistory.org/feed.xml
|
||||
@ -7,138 +7,136 @@
|
||||
[#]: author: (Abhishek Prakash https://itsfoss.com/author/abhishek/)
|
||||
[#]: url: ( )
|
||||
|
||||
Celebrate Christmas In Linux Way With These Wallpapers
|
||||
使用这些壁纸以 Linux 的方式庆祝圣诞节
|
||||
======
|
||||
|
||||
It’s the holiday season and many of you might be celebrating Christmas already. From the team of It’s FOSS, I would like to wish you a Merry Christmas and a happy new year.
|
||||
当前正是假日季节,很多人可能已经在庆祝圣诞节了。我代表 It's FOSS 团队祝你圣诞快乐,新年快乐。
|
||||
|
||||
To continue the festive mood, I’ll show you some really awesome [Linux wallpapers][1] on Christmas theme. But before we see that, how about a Christmas Tree in Linux terminal.
|
||||
为了延续节日氛围,我将向你展示一些非常棒的圣诞主题 [Linux壁纸][1]。在呈现这些壁纸之前,先来看一棵 Linux 终端下的圣诞树。
|
||||
|
||||
### Display Christmas Tree in Linux Terminal
|
||||
### 在 Linux 终端下显示圣诞树
|
||||
|
||||
<https://giphy.com/embed/xUNda6KphvbpYxL3tm>
|
||||
圣诞树的效果如 [这个页面](https://giphy.com/embed/xUNda6KphvbpYxL3tm) 所示。
|
||||
|
||||
If you want to display an animated Christmas tree in the terminal, you can use the command below:
|
||||
使用以下命令在终端中显示一棵动画圣诞树:
|
||||
|
||||
```
|
||||
curl https://raw.githubusercontent.com/sergiolepore/ChristBASHTree/master/tree-EN.sh | bash
|
||||
```
|
||||
|
||||
If you don’t want to get it from the internet all the time, you can get the shell script from its GitHub repository, change the permission and run it like a normal shell script.
|
||||
要是不想一直从互联网上获取这棵圣诞树,也可以从它的 [GitHub 仓库][2] 中获取对应的 shell 脚本,更改权限之后按照运行普通 shell 脚本的方式运行它。
|
||||
|
||||
[ChristBASHTree][2]
|
||||
|
||||
### Display Christmas Tree in Linux terminal using Perl
|
||||
### 使用 Perl 在 Linux 终端下显示圣诞树
|
||||
|
||||
[![Christmas Tree in Linux terminal by NixCraft][3]][4]
|
||||
|
||||
This trick was originally shared by [NixCraft][5]. You’ll need to install a Perl module for this.
|
||||
这个技巧最初由 [NixCraft][5] 分享,你需要为此安装 Perl 模块。
|
||||
|
||||
To be honest, I don’t like using Perl modules because uninstalling them is a real pain. So **use this Perl module knowing that you’ll have to manually remove it**.
|
||||
说实话,我不喜欢使用 Perl 模块,因为卸载它们真的很痛苦。所以使用这个 Perl 模块时需谨记,你必须手动移除它。
|
||||
|
||||
```
|
||||
perl -MCPAN -e 'install Acme::POE::Tree'
|
||||
```
|
||||
|
||||
You can read the original article [here][5] to know more about it.
|
||||
你可以阅读 [原文][5] 来了解更多信息。
|
||||
|
||||
## Download Linux Christmas Wallpapers
|
||||
## 下载 Linux 圣诞主题壁纸
|
||||
|
||||
All these Linux Christmas wallpapers are created by Mark Riedesel and you can find plenty of other artwork on [his website][6].
|
||||
所有这些 Linux 圣诞主题壁纸都是由 Mark Riedesel 制作的,你可以在 [他的网站][6] 上找到很多其他艺术品。
|
||||
|
||||
He has been making such wallpapers almost every year since 2002. Quite understandably some of the earliest wallpapers don’t have modern aspect ratio. I have put them up in reverse chronological order.
|
||||
自 2002 年以来,他几乎每年都在制作这样的壁纸。可以理解的是,最早的一些壁纸不具有现代的宽高比。我把它们按时间倒序排列。
|
||||
|
||||
One tiny note. The images displayed here are highly compressed so download the wallpapers from the provided link only.
|
||||
注意一个小地方,这里显示的图片都是高度压缩的,因此你要通过图片下方提供的链接进行下载。
|
||||
|
||||
![Christmas Linux Wallpaper][7]
|
||||
|
||||
[Download This Wallpaper][8]
|
||||
[下载此壁纸][8]
|
||||
|
||||
[![Christmas Linux Wallpapers][9]][10]
|
||||
|
||||
[Download This Wallpaper][11]
|
||||
[下载此壁纸][11]
|
||||
|
||||
[![Christmas Linux Wallpapers][12]][13]
|
||||
|
||||
[Download This Wallpaper][14]
|
||||
[下载此壁纸][14]
|
||||
|
||||
[![Christmas Linux Wallpapers][15]][16]
|
||||
|
||||
[Download This Wallpaper][17]
|
||||
[下载此壁纸][17]
|
||||
|
||||
[![Christmas Linux Wallpapers][18]][19]
|
||||
|
||||
[Download This Wallpaper][20]
|
||||
[下载此壁纸][20]
|
||||
|
||||
[![Christmas Linux Wallpapers][21]][22]
|
||||
|
||||
[Download This Wallpaper][23]
|
||||
[下载此壁纸][23]
|
||||
|
||||
[![Christmas Linux Wallpapers][24]][25]
|
||||
|
||||
[Download This Wallpaper][26]
|
||||
[下载此壁纸][26]
|
||||
|
||||
[![Christmas Linux Wallpapers][27]][28]
|
||||
|
||||
[Download This Wallpaper][29]
|
||||
[下载此壁纸][29]
|
||||
|
||||
[![Christmas Linux Wallpapers][30]][31]
|
||||
|
||||
[Download This Wallpaper][32]
|
||||
[下载此壁纸][32]
|
||||
|
||||
[![Christmas Linux Wallpapers][33]][34]
|
||||
|
||||
[Download This Wallpaper][35]
|
||||
[下载此壁纸][35]
|
||||
|
||||
[![Christmas Linux Wallpapers][36]][37]
|
||||
|
||||
[Download This Wallpaper][38]
|
||||
[下载此壁纸][38]
|
||||
|
||||
[![Christmas Linux Wallpapers][39]][40]
|
||||
|
||||
[Download This Wallpaper][41]
|
||||
[下载此壁纸][41]
|
||||
|
||||
[![Christmas Linux Wallpapers][42]][43]
|
||||
|
||||
[Download This Wallpaper][44]
|
||||
[下载此壁纸][44]
|
||||
|
||||
[![Christmas Linux Wallpapers][45]][46]
|
||||
|
||||
[Download This Wallpaper][47]
|
||||
[下载此壁纸][47]
|
||||
|
||||
[![Christmas Linux Wallpapers][48]][49]
|
||||
|
||||
[Download This Wallpaper][50]
|
||||
[下载此壁纸][50]
|
||||
|
||||
### Bonus: Linux Christmas carols
|
||||
### 福利:Linux 圣诞颂歌
|
||||
|
||||
Here is a bonus for you. Christmas carols Linuxified for Linux lovers like us.
|
||||
这是给你的一份福利,给像我们一样的 Linux 爱好者的关于 Linux 的圣诞颂歌。
|
||||
|
||||
In [an article on Computer World][51], [Sandra Henry-Stocker][52] shared such Christmas carols. An excerpt:
|
||||
在 [计算机世界的一篇文章][51] 中,[Sandra Henry-Stocker][52] 分享了这些圣诞颂歌。摘录片段如下:
|
||||
|
||||
To the tune of: [Chestnuts Roasting on an Open Fire][53]
|
||||
这一段用的 [Chestnuts Roasting on an Open Fire][53] 的曲调:
|
||||
|
||||
> Running merrily on open source
|
||||
> With users happy as can be
|
||||
> We’re using Linux and getting lots done
|
||||
> And happy everything is free
|
||||
|
||||
To the tune of: [The Twelve Days of Christmas][54]
|
||||
这一段用的 [The Twelve Days of Christmas][54] 的曲调:
|
||||
|
||||
> On my first day with Linux, my admin gave to me a password and a login ID
|
||||
> On my second day with Linux my admin gave to me two new commands and a password and a login ID
|
||||
|
||||
You can read full carols [here][51].
|
||||
在 [这里][51] 阅读完整的颂歌。
|
||||
|
||||
Merry Linux to you!!
|
||||
祝你享受 Linux!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
------
|
||||
|
||||
via: https://itsfoss.com/christmas-linux-wallpaper/
|
||||
|
||||
作者:[Abhishek Prakash][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
译者:[jlztan](https://github.com/jlztan)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
@ -0,0 +1,110 @@
|
||||
27个解决教学问题的开放式方法
|
||||
======
|
||||

|
||||
|
||||
开放式理念 (从开源软件到开放硬件, 再到开放原则) 正在改变教育的范式。因此, 为了庆祝今年发生的一切, 我收集了2017年在 Opensource.com 上发表的27篇关于这个主题的最好的文章。我把它们分成明确的主题, 而不是按人气来分类。而且, 如果这27个故事不能满足你对教育公开信息的胃口, 那就看看我们的合作文章吧 “ [education is leveraging Raspberry Pi and Linux][30]”
|
||||
|
||||
### 开放对每个人都有好处
|
||||
|
||||
1. [Book review: 'OPEN' explores broad cultural implications of openness][1]: Scott Nesbitt 评价David Price 的书 'OPEN' ,该书探讨了 “开放” 不仅仅是技术转变的观点, 而是 “我们未来将如何工作、生活和学习”。
|
||||
|
||||
2. [Jump-start your career with open source skills][2]: VM (Vicky) Brasseur 指出了如何利用开放式学习在工作群体中脱颖而出。 这个建议不仅仅是针对程序员的, 而是针对程序员的。设计师、作家、营销人员和其他创意专业人士也是开放式成功的关键。
|
||||
|
||||
3. [A graduate degree could springboard you into an open source job][3]: 引用的研究表明会 Linux 技能会带来更高的薪水, Joshua Pearce 说对开源的熟练和研究生学位是无与伦比的职业技能组合。
|
||||
|
||||
4. [These 3 practices revolutionized Penn Manor's school culture][4]: Charlie Reisinger 向我们展示了开放的做法是如何在宾夕法尼亚州的一个学区创造一种更具包容性、敏捷性和开放性的文化的。 Charlie 说, 这不仅仅是为了省钱;该区还受益于 “开放式领导原则, 促进师生创新, 帮助更好地吸引社区, 创造一个更有活力和包容性的学习社区”。
|
||||
|
||||
5. [15 ways to empower students with open source tools][5]: 我写开源是如何让学生自由探索、补拙和学习的, 不管他们是在学习基本的数字化素养, 还是通过有趣的项目来扩展这些技能。
|
||||
|
||||
6. [Developer opportunities to code for good][6]: 开源往往是对社会有益的项目的支柱。正如 Benetech Labs 副总裁 Ahn Bui 在这次采访中指出的那样: “建立开放数据标准是打破数据孤岛不可或缺的一步。这些开放标准将为互操作性提供基础, 进而转化为更多的组织共同建设, 往往更具成本效益。最终目标是以同样的成本甚至更低的成本为更多的人服务。”
|
||||
|
||||
### 用于再融合和再利用的开放式教育资源
|
||||
|
||||
1. [Can academic faculty members teach with Wikipedia?][7] LiAnna Davis,Wiki Ed 的, 项目总监,讨论开放教育资源 (OERs) ,如 Wiki Ed,如何提供高质量且经济实惠的开源学习资源作为课堂教学工具。
|
||||
|
||||
2. [Are textbooks in or out? The state of open educational resources][8]: Cable Green,是 Creative Common 开放教育主任,分享高等教育中教育面貌是如何变化的, 以及 Creative Common 正在采取哪些措施来促进教育。
|
||||
|
||||
3. [School systems desperate for standards-aligned curricula find hope][9]: Karen Vaites,是 Open Up Resources 社区的福音传教士和首席营销官, 谈论非营利组织努力为 K-12 学校提供开放的, 标准一致的课程。
|
||||
|
||||
4. [How the University of Hawaii is solving today's higher ed problems][10]: Billy Meinke , Hawaii 大学 Manoa 分校的教育技术专家,他说, 在大学课程中过渡到 ORE 将 “使教师能够控制他们教授的内容, 我们预计这将为他们节省学生的费用。”
|
||||
|
||||
5. [How open courses are slashing the cost of higher education][11]: Saylor Academy 的教育主任 Devon Ritter 报告了 Saylor 是如何建立以公开许可内容为基础的大学学分课程, 目的是使更多的人能够负担得起和获得高等教育。
|
||||
|
||||
6. [Open educational resources movement gains speed][12]: Alexis Clifton,State University of New York 的 OER 服务的执行主任, 描述了纽约800万美元的投资如何刺激开放教育的增长, 并使大学更实惠。
|
||||
|
||||
7. [Open project collaboration from elementary to university classrooms][13]: Aria F. Chernik 在Duke University 探索 OSPRI (Open Source Pedagogy Research and Innovation,开源教育学的研究与创新), 在 Duke 和 Red Hat 的联合合作这是建立一个21世纪的, preK-12 学习生态系统, 是开放的设计。
|
||||
|
||||
8. [Perma.cc stops scholarly link rot][14]: Virginia Tech 的 Phillip Young 写关于 Perma.cc, “link rot”(链接失效) 的解决方案 很大可能在学术论文中的超链接随着时间的推移而消失或变化。
|
||||
|
||||
9. [Open education: How students save money by creating open textbooks][15]: OER 先驱 Robin DeRosa 谈到 “公开许可教科书引入的自由, 以及教育和学习应结合包容性生态系统, 以增强公益的总体理念”。
|
||||
|
||||
### 课堂上的开源工具
|
||||
|
||||
1. [How an open source board game is saving the planet][16]: Joshua Pearce 写的关于拯救地球的一个棋盘游戏, 使学生能够解决环境问题, 同时有乐趣, 并为制造商社区作出贡献。
|
||||
|
||||
2. [A new Android app for teaching kids how to read][17]: Michael Hall 谈到他的儿子 Phoenicia,他在儿子被诊断为自闭症后开发的儿童识字应用, 为了产生更好的编码价值, 以及为什么用户测试比你想象的更重要。
|
||||
|
||||
3. [8 open source Android apps for education][18]: Joshua Allen Holm 通过推荐 F-Droid 存储库中的8个开源应用来尝试, 这将挑战我们将智能手机用作学习工具。
|
||||
|
||||
4. [3 open source alternatives to MATLAB][19]: Jason Baker's 更新了他2016年的开源数学计算软件调查, 提出了 MATLAB 的替代方案, 这是数学、物理科学、工程和经济学中几乎无处不在的昂贵的专用解决方案。
|
||||
|
||||
5. [What does SVG have to do with teaching kids to code?][20] 退休工程师 Jay Nick 谈论他如何使用艺术作为一种创造性的方式, 向学生介绍编码。他在学校做志愿者, 使用可缩放矢量图形 (SVG,Scalable Vector Graphics) 教授一种结合数学和艺术原理的编码方法。
|
||||
|
||||
6. [5 myths busted: Using open source in higher education][21]: Kyle Conway, 在 Texas Tech 拥有美术博士学位分享他在单一解决方案统治的世界中使用开源工具的经验。 Kyle 说有一种偏见, 反对在计算机科学以外的学科中使用开源:“很多人认为非技术专业的学生不能使用 Linux, 他们对在高级学位课程中使用 Linux 的人做出了很多假设。...嗯, 这是有可能的, 我就是证明。”
|
||||
|
||||
7. [A list of open source tools for college][22]: Aaron Cocker 概述了他在攻读计算机科学本科学位时使用的开源工具 (包括演示、备份和编程软件)。
|
||||
|
||||
8. [5 great KDE apps to help you study][23]: Zsolt Szakács 提供五个 KDE 应用程序, 帮助任何想要学习新技能或培养现有技能的人。
|
||||
|
||||
### 在教室编码
|
||||
|
||||
1. [How to get the next generation coding early][24]: Bryson Payne 说我们需要教孩子们在高中前编码: 到了九年级, 80% 的女孩和60% 的男孩已经从 STEM 职业中自选。但他建议, 这不仅仅是就业和缩小 IT 技能差距的问题。“教一个年轻人编写代码可能是你能给他们的最改变生活的技能。而且这不仅仅是一个职业提升者。编码是关于解决问题, 它是关于创造力, 更重要的是, 它是关于授权。
|
||||
|
||||
2. [Kids can't code without computers][25]: Patrick Masson 推出了 FLOSS 儿童桌面计划, 该计划教授服务不足学校的学生使用开源软件 (如 Linux、LibreOffice 和 GIMP) 重新设计较旧的计算机。该计划不仅为破旧或退役的硬件注入新的生命, 还为学生提供了重要的技能, 这些技能可能会利于转化为未来的职业。
|
||||
|
||||
3. [Is Scratch today like the Logo of the '80s for teaching kids to code?][26] Anderson Silva 提出 [Scratch][27] 的使用建议以激发孩子们对编程的兴趣, 就像 LOGO 在20世纪80年代开始使用它时一样。
|
||||
|
||||
4. [Learn Android development with this drag-and-drop framework][28]: Eric Eslinger 描述应用发明者, 一个编程框架, 用于构建 Android 应用程序使用可视块语言 (类似 Scratch 或者[Snap][29]).
|
||||
|
||||
在这一年里, 我们了解到, 教育领域的一切都有一个开放的解决方案, 我预计这一主题将在2018年及以后继续下去。在未来的一年里, 你是否希望 Opensource.com 涵盖开放式的教育主题?如果是, 请在评论中分享你的想法。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/1/best-open-education
|
||||
|
||||
作者:[Don Watkins][a]
|
||||
译者:[lixinyuxx](https://github.com/lixinyuxx)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://opensource.com/users/don-watkins
|
||||
[1]:https://opensource.com/article/17/7/book-review-open
|
||||
[2]:https://opensource.com/article/17/8/jump-start-your-career
|
||||
[3]:https://opensource.com/article/17/1/grad-school-open-source-academic-lab
|
||||
[4]:https://opensource.com/article/17/7/open-school-leadership
|
||||
[5]:https://opensource.com/article/17/7/empower-students-open-source-tools
|
||||
[6]:https://opensource.com/article/17/3/interview-anh-bui-benetech-labs
|
||||
[7]:https://opensource.com/article/17/1/Wiki-Education-Foundation
|
||||
[8]:https://opensource.com/article/17/2/future-textbooks-cable-green-creative-commons
|
||||
[9]:https://opensource.com/article/17/1/open-up-resources
|
||||
[10]:https://opensource.com/article/17/2/interview-education-billy-meinke
|
||||
[11]:https://opensource.com/article/17/7/college-alternatives
|
||||
[12]:https://opensource.com/article/17/10/open-educational-resources-alexis-clifton
|
||||
[13]:https://opensource.com/article/17/3/education-should-be-open-design
|
||||
[14]:https://opensource.com/article/17/9/stop-link-rot-permacc
|
||||
[15]:https://opensource.com/article/17/11/creating-open-textbooks
|
||||
[16]:https://opensource.com/article/17/7/save-planet-board-game
|
||||
[17]:https://opensource.com/article/17/4/phoenicia-education-software
|
||||
[18]:https://opensource.com/article/17/8/8-open-source-android-apps-education
|
||||
[19]:https://opensource.com/alternatives/matlab
|
||||
[20]:https://opensource.com/article/17/5/coding-scalable-vector-graphics-make-steam
|
||||
[21]:https://opensource.com/article/17/5/how-linux-higher-education
|
||||
[22]:https://opensource.com/article/17/6/open-source-tools-university-student
|
||||
[23]:https://opensource.com/article/17/6/kde-education-software
|
||||
[24]:https://opensource.com/article/17/8/teach-kid-code-change-life
|
||||
[25]:https://opensource.com/article/17/9/floss-desktops-kids
|
||||
[26]:https://opensource.com/article/17/3/logo-scratch-teach-programming-kids
|
||||
[27]:https://scratch.mit.edu/
|
||||
[28]:https://opensource.com/article/17/8/app-inventor-android-app-development
|
||||
[29]:http://snap.berkeley.edu/
|
||||
@ -0,0 +1,177 @@
|
||||
用于游戏开发的图形和音乐工具
|
||||
======
|
||||
|
||||

|
||||
|
||||
在十月初,我们的俱乐部,来自马歇尔大学的 [Geeks and Gadgets][1] , 参加就职 [Open Jam][2], 一个游戏 jam ,庆祝最好的开源工具。游戏 jams 是参与者为娱乐像团队协作的来开发计算机游戏的事件。Jams 倾向于非常简短--仅三天时间长--并非常让人精疲力尽。Opensource.com 在八月下旬 [宣布][3] Open Jam ,更多 [three dozen games][4] 进入到竞赛中。
|
||||
|
||||
我们的俱乐部希望在我们的工程中创建和使用开放源码软件,所以 Open Jam 自然是我们想要参与的 jam 。我们的提交的文件是一个实验性的名称为 [Mark My Words][5] 的游戏。我们使用多种自由和开放源码 (FOSS) 工具来开发它;在这篇文章中,我们将讨论一些我们使用和意识到有潜在的障碍物的工具。
|
||||
|
||||
### 音频工具
|
||||
|
||||
#### MilkyTracker
|
||||
|
||||
[MilkyTracker][6] 是最好的可用于构成旧样式电子游戏音乐的软件包中的一个。它是一个 [music tracker][7] 的一个示例,一个强大的带有特殊的基于网格的图形编辑器的 MOD 和 XM 文件创建器。在我们的游戏中,我们使用它来构成大多数的音乐片段。这个程序最好的特点是,它比我们其它的大多数工具消耗更少的硬盘空间和 RAM 。虽然如此,MilkyTracker 仍然非常强大。
|
||||
|
||||

|
||||
|
||||
用户界面需要一会来习惯,这里有对一些想试用MilkyTracker的音乐家的一些提示:
|
||||
|
||||
* 转到 Config > Misc. ,设置 edit 模式控制样式为 "MilkyTracker." 这将给你几乎所有的现代键盘快捷方式
|
||||
* 撤销 Ctrl+Z
|
||||
* 重做 Ctrl+Y
|
||||
* 切换 pattern-edit 模式 空格键
|
||||
* 删除先前的注释 退格键
|
||||
* 插入一行 Insert键
|
||||
* 默认情况下,一个注释将持续作用,直到它在这频道上被替换。你可以明确地结束一个注释,通过使用一个反引号 (`) 键插入一个 KeyOff 注释
|
||||
* 在你开始谱写乐曲前,你将不得不创建或查找示例。我们建议在网站上查找 [Creative Commons][8] 协议的示例,例如 [Freesound][9] 或 [ccMixter][10]
|
||||
|
||||
|
||||
|
||||
另外,保持 [MilkyTracker 文档页面][11] 在手边。它含有数不清的教程和手册的链接。一个好的开始点是在该项目 wiki 上的 [MilkyTracker 指南][12] 。
|
||||
|
||||
#### LMMS
|
||||
|
||||
我们中的两个音乐家使用多用途和现代音乐创建工具 [LMMS][13] 。它带来一个绝妙的示例和效果库,加一个灵活的多种多样的插件来生成独特的声音。 The learning curve for LMMS 的学习曲线令人吃惊的低,在某种程度上是因为友好的节拍/低音线编辑器。
|
||||
|
||||

|
||||
|
||||
我们对音乐家有一个建议,尝试 LMMS:使用插件。 对于 [chiptune][14]-样式音乐,我们推荐 [sfxr][15] ,[BitInvader][16] ,和 [FreeBoy][17] 。对于其它样式, [ZynAddSubFX][18] 是一个好的选择。它带来一个宽波段的可以被你任意更改的人工合成工具。
|
||||
|
||||
### 图形工具
|
||||
|
||||
#### Tiled
|
||||
|
||||
在开放源码游戏开发中,[Tiled][19] 是一个流行的组件地图类(tilemap)编辑器。我们使用它为来为我们在游戏场景中组合连续的,复古的背景。
|
||||
|
||||

|
||||
|
||||
Tiled 可以导出地图为 XM L,JSON ,或平坦的图像。它是稳定的和跨平台的。
|
||||
|
||||
Tiled 的特征一,在 jam 期间,我们不能使用, 允许你定义和随意的放置游戏对象,例如硬币和永久能力提升道具到地图上。你需要做的全部是加载对象的图像为一个平铺显示集,然后使用插入平铺显示放置它们。
|
||||
|
||||
一般来说,对于一些需要一个地图编辑器的工程,Tiled 是我们建议软件的一个主要的部分。
|
||||
|
||||
#### Piskel
|
||||
|
||||
[Piskel][20] 是一个像素艺术编辑器,它的源文件代码是在 [Apache 协议, 版本 2.0][21] 协议下。在 jam 期间,我们对我们的大多数的图像资源使用 Piskel ,我们当然也将在未来的工程中使用它。
|
||||
|
||||
Piskel 的特征二,在 jam 的 onion skin和Spritesheet导出期间极大地帮助我们。
|
||||
|
||||
##### Onion skin
|
||||
|
||||
onion skin 特征将使 Piskel 显示你编辑的动画的前一帧和后一帧的一个幽灵似的覆盖物,像这样:
|
||||
|
||||

|
||||
|
||||
Onion skin 是便于使用的,因为它适合作为一个绘制指南和在动画进程期间帮助你维护在你的角色上连续的图形和声音。为启用它,只需要在屏幕的右上方预览窗体的下面单击 onion-shaped 图标。
|
||||
|
||||

|
||||
|
||||
##### Spritesheet 导出
|
||||
|
||||
Piskel 的能力是导出动画为一个 spritesheet ,也是非常有用的。一个 spritesheet 是一个单个光栅图象,它包含一个动画的所有的帧。例如,这是一个我们从 Piskel 导出的 spritesheet :
|
||||
|
||||

|
||||
|
||||
spritesheet 包含两幅帧。一幅帧是图像的上半部分,另一帧是图像的下半部分。Spritesheets 通过启用一个完整的动画来从单个文件加载,大大地简化一个游戏的代码。这是上面的 spritesheet 的一个动画版本:
|
||||
|
||||

|
||||
|
||||
##### Unpiskel.py
|
||||
|
||||
在 jam 期间,我们很多次想批量转换 Piskel 文件到 PNG 文件。尽管 Piskel 文件格式基于 JSON ,我们写一个小的 GPLv3 协议的称为 [unpiskel.py][22] 的 Python 脚本来做转换。
|
||||
|
||||
它像这样被引用:
|
||||
```
|
||||
python unpiskel.py input.piskel
|
||||
```
|
||||
|
||||
这个脚本将从一个 Piskel 文件(这里 `input.piskel`)中提取 PNG 数据帧和层,并存储它们在它们拥有的文件中。这些文件采用模式 `NAME_XX_YY.png` ,在这里 `NAME` 是 Piskel 文件的缩减名称,`XX` 是帧的编号,`YY` 是层的编号。
|
||||
|
||||
因为脚本可以从一个 shell 中引用,它可以被使用在文件的整个列表中。
|
||||
```
|
||||
for f in *.piskel; do python unpiskel.py "$f"; done
|
||||
```
|
||||
|
||||
### Python, Pygame, 和 cx_Freeze
|
||||
|
||||
#### Python 和 Pygame
|
||||
|
||||
我们使用 [Python][23] 语言来自制作我们的游戏。它是一个脚本语言,通常被用于文本处理和桌面应用程序开发。它也可以用于游戏开发,例如工程,像 [Angry Drunken Dwarves][24] 和 [Ren'Py][25] 已经显示。这两个工程都使用一个称为 [Pygame][26] 的 Python 库来显示图形和产生声音,所以我们也决定在 Open Jam 中使用这个库。
|
||||
|
||||
Pygame 被证明是既稳定又富有特色,并且它对我们创建的街机游戏来说是优秀的。在低分辨率时,库的速度足够快的,但是在高分辨率时,它的仅 CPU 渲染开始变慢。这是因为 Pygame 不使用硬件加速渲染。然而,开发者可以充分利用 OpenGL 基础设施。
|
||||
|
||||
如果你正在寻找一个好的 2D 游戏编程库,Pygame 是值得密切注意的一个。它的网站有 [一个好的教程][27] 来开始。务必看看它!
|
||||
|
||||
#### cx_Freeze
|
||||
|
||||
准备发行我们的游戏是有趣的。我们知道,Windows 用户不喜欢有一个 Python 安装,并且要求他们来安装它可能很过分。除此之外,他们也可能不得不安装 Pygame ,在 Windows 上,这不是一个简单的工作。
|
||||
|
||||
有一件事很清楚:我们不得不放置我们的游戏到一个更方便的结构中。很多其他的 Open Jam 参与者使用专有的游戏引擎 Unity ,它能够使它们的游戏在网页浏览器中来玩。这使得它们非常方便地来玩。便利性是一个我们的游戏恰巧一丝的都没有的东西。但是,感谢生机勃勃的 Python 生态系统,我们有选择。在 Windows 上现有的工具帮助 Python 程序员准备发行他们的游戏。我们考虑的两个是 [cx_Freeze][28] 和 [Pygame2exe][29] (它使用 [py2exe][30])。我们下决心在 cx_Freeze 上,因为它是跨平台的。
|
||||
|
||||
在 cx_Freeze 中,你可以为发行版打包一个单个脚本游戏,只要在shell运行一个命令,像这样:
|
||||
```
|
||||
cxfreeze main.py --target-dir dist
|
||||
```
|
||||
|
||||
`cxfreeze` 的这个调用将拿你的脚本(这里 `main.py`) 和在你系统上的 Python 解释器,并捆绑定它们到 `dist` 目录。一旦完成它,你需要做的是手动复制你的游戏的数据文件到 `dist` 目录。你将发现,`dist` 目录包含一个可以运行来开始你的游戏的可执行文件。
|
||||
|
||||
这里有更复杂难解的方法来使用 cx_Freeze ,允许你自动地复制数据文件,但是我们发现简单的调用 `cxfreeze` 足够我们的需要。感谢这个工具,我们使我们的游戏稍微便利的运行。
|
||||
|
||||
### 庆祝开放源码
|
||||
|
||||
Open Jam 是重要的,因为它庆祝软件开发的开放源码模式。这是来分析开放源码工具的当前状态和我们在未来工作中需求的一个机会。,对于游戏开发者来设法推动它们的工具的使用范围,学习必需提高未来游戏开发者的益处,游戏 jams 或许是最好的时间。
|
||||
|
||||
开放源码工具使人们能够探索他们的创造性,而不妥协他们的自由和前期的投资。尽管我们可能不能成为专业的游戏开发者,我们仍然能获取它的一段小的体验,使用我们简短的,实验性的称为 [Mark My Words][5] 的游戏。它是一个语言学方面地的有特定主题的游戏,它描述一个小说写作系统在它历史期间的演化。Open Jam 有一些令人愉快的提交,并且它们是值得校核。真的, [去看看][31] !
|
||||
|
||||
在结束前,我们想要感谢所有的 [参加俱乐部的成员][32],使这次经历真正的有价值。我们也想要感谢 [Michael Clayton][33],[Jared Sprague][34] 和 [Opensource.com][35] 主办 open Jam。它是一次欢乐。
|
||||
|
||||
现在,我们对读者有一些问题。你是一个 FOSS 游戏开发者吗?你选择的工具是什么?务必在下面留下一个评论!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/1/graphics-music-tools-game-dev
|
||||
|
||||
作者:[Charlie Murphy][a]
|
||||
译者:[robsean](https://github.com/robsean)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://opensource.com/users/rsg167
|
||||
[1]:http://mugeeks.org/
|
||||
[2]:https://itch.io/jam/open-jam-1
|
||||
[3]:https://opensource.com/article/17/8/open-jam-announcement
|
||||
[4]:https://opensource.com/article/17/11/open-jam
|
||||
[5]:https://mugeeksalpha.itch.io/mark-omy-words
|
||||
[6]:http://milkytracker.titandemo.org/
|
||||
[7]:https://en.wikipedia.org/wiki/Music_tracker
|
||||
[8]:https://creativecommons.org/
|
||||
[9]:https://freesound.org/
|
||||
[10]:http://ccmixter.org/view/media/home
|
||||
[11]:http://milkytracker.titandemo.org/documentation/
|
||||
[12]:https://github.com/milkytracker/MilkyTracker/wiki/MilkyTracker-Guide
|
||||
[13]:https://lmms.io/
|
||||
[14]:https://en.wikipedia.org/wiki/Chiptune
|
||||
[15]:https://github.com/grimfang4/sfxr
|
||||
[16]:https://lmms.io/wiki/index.php?title=BitInvader
|
||||
[17]:https://lmms.io/wiki/index.php?title=FreeBoy
|
||||
[18]:http://zynaddsubfx.sourceforge.net/
|
||||
[19]:http://www.mapeditor.org/
|
||||
[20]:https://www.piskelapp.com/
|
||||
[21]:https://github.com/piskelapp/piskel/blob/master/LICENSE
|
||||
[22]:https://raw.githubusercontent.com/MUGeeksandGadgets/MarkMyWords/master/tools/unpiskel.py
|
||||
[23]:https://www.python.org/
|
||||
[24]:https://www.sacredchao.net/~piman/angrydd/
|
||||
[25]:https://renpy.org/
|
||||
[26]:https://www.Pygame.org/
|
||||
[27]:http://Pygame.org/docs/tut/PygameIntro.html
|
||||
[28]:https://anthony-tuininga.github.io/cx_Freeze/
|
||||
[29]:https://Pygame.org/wiki/Pygame2exe
|
||||
[30]:http://www.py2exe.org/
|
||||
[31]:https://itch.io/jam/open-jam-1/entries
|
||||
[32]:https://github.com/MUGeeksandGadgets/MarkMyWords/blob/3e1e8aed12ebe13acccf0d87b06d4f3bd124b9db/README.md#credits
|
||||
[33]:https://twitter.com/mwcz
|
||||
[34]:https://twitter.com/caramelcode
|
||||
[35]:https://opensource.com/
|
||||
@ -0,0 +1,167 @@
|
||||
用 PGP 保护代码完整性(四):将主密钥移到离线存储中
|
||||
======
|
||||
|
||||

|
||||
在本系列教程中,我们为使用 PGP 提供了一个实用指南。你可以从下面的链接中查看前面的文章:
|
||||
|
||||
[第一部分:基本概念和工具][1]
|
||||
|
||||
[第二部分:生成你的主密钥][2]
|
||||
|
||||
[第三部分:生成 PGP 子密钥][3]
|
||||
|
||||
这是本系列教程的第四部分,我们继续本教程,我们将谈一谈如何及为什么要将主密钥从你的 Home 目录移到离线存储中。现在开始我们的教程。
|
||||
|
||||
### 清单
|
||||
|
||||
* 准备一个加密的可移除的存储(必要)
|
||||
|
||||
* 备份你的 GnuPG 目录(必要)
|
||||
|
||||
* 从你的 Home 目录中删除主密钥(推荐)
|
||||
|
||||
* 从你的 Home 目录中删除吊销证书(推荐)
|
||||
|
||||
|
||||
|
||||
|
||||
#### Considerations
|
||||
|
||||
为什么要从你的 Home 目录中删除你的主密钥 [C] ?这样做的主要原因是防止你的主密钥失窃或意外泄露。对于心怀不轨的人来说,私钥对他们具有很大的诱惑力 —— 我们知道有几个恶意软件成功地实现了扫描用户的 Home 目录并将发现的任何私钥内容上传。
|
||||
|
||||
对于任何开发者来说,私钥失窃是非常危险的事情 —— 在自由软件的世界中,这无疑是身份证明失窃。从你的 Home 目录中删除私钥将帮你防范这类事件的发生。
|
||||
|
||||
##### 备份你的 GnuPG 目录
|
||||
|
||||
**!!!绝对不要跳过这一步!!!**
|
||||
|
||||
备份你的 PGP 密钥将让你在需要的时候很容易地恢复它们,这很重要!(这与我们做的使用 paperkey 的灾难级备份是不一样的)。
|
||||
|
||||
##### 准备可移除的加密存储
|
||||
|
||||
我们从取得一个(最好是两个)小型的 USB “拇指“ 驱动器(可加密 U 盘)开始,我们将用它来做备份。你首先需要去加密它们:
|
||||
|
||||
加密密码可以使用与主密钥相同的密码。
|
||||
|
||||
##### 备份你的 GnuPG 目录
|
||||
|
||||
加密过程结束之后,重新插入 USB 驱动器并确保它能够正常挂载。你可以通过运行 `mount` 命令去找到设备挂载点的完全路径。(在 Linux 下,外置介质一般挂载在 /media/disk 下,Mac 一般在它的 /Volumes 下)
|
||||
|
||||
你知道了挂载点的全路径后,将你的整个 GnuPG 的目录复制进去:
|
||||
```
|
||||
$ cp -rp ~/.gnupg [/media/disk/name]/gnupg-backup
|
||||
|
||||
```
|
||||
|
||||
(注意:如果出现任何套接字不支持的错误,没有关系,直接忽略它们。)
|
||||
|
||||
现在,用如下的命令去测试一下,确保它们能够正常地工作:
|
||||
```
|
||||
$ gpg --homedir=[/media/disk/name]/gnupg-backup --list-key [fpr]
|
||||
|
||||
```
|
||||
|
||||
如果没有出现任何错误,说明一切正常。弹出这个 USB 驱动器并给它粘上一个明确的标签,以便于你下次需要它时能够很快找到它。接着,将它放到一个安全的 —— 但不要太远 —— 的地方,因为从现在起,你需要偶尔使用它来做一些像编辑身份信息、添加或吊销子证书、或签署其它人的密钥这样的事情。
|
||||
|
||||
##### 删除主密钥
|
||||
|
||||
我们 Home 目录中的文件并没有像我们所想像的那样受到保护。它们可能会通过许多不同的方式被泄露或失窃:
|
||||
|
||||
* 通过快速复制来配置一个新工作站时的偶尔事故
|
||||
|
||||
* 通过系统管理员的疏忽或恶意操作
|
||||
|
||||
* 通过安全性欠佳的备份
|
||||
|
||||
* 通过桌面应用中的恶意软件(浏览器、pdf 查看器等等)
|
||||
|
||||
* 通过跨境胁迫
|
||||
|
||||
|
||||
|
||||
|
||||
使用一个很好的密码来保护你的密钥是降低上述风险的一个很好方法,但是密码能够通过键盘记录器、背后窥视、或其它方式被发现。基于以上原因,我们建议去配置一个从你的 Home 目录上可移除的主密钥,将它保存在一个离线存储中。
|
||||
|
||||
###### 删除主密钥
|
||||
|
||||
**请查看前面的节,确保你有完整的你的 GnuPG 目录的一个备份。如果你没有一个可用的备份,下面所做的操作将会使你的主密钥失效!!!**
|
||||
|
||||
首先,识别你的主密钥的 keygrip:
|
||||
```
|
||||
$ gpg --with-keygrip --list-key [fpr]
|
||||
|
||||
```
|
||||
|
||||
它的输出应该像下面这样:
|
||||
```
|
||||
pub rsa4096 2017-12-06 [C] [expires: 2019-12-06]
|
||||
111122223333444455556666AAAABBBBCCCCDDDD
|
||||
Keygrip = AAAA999988887777666655554444333322221111
|
||||
uid [ultimate] Alice Engineer <alice@example.org>
|
||||
uid [ultimate] Alice Engineer <allie@example.net>
|
||||
sub rsa2048 2017-12-06 [E]
|
||||
Keygrip = BBBB999988887777666655554444333322221111
|
||||
sub rsa2048 2017-12-06 [S]
|
||||
Keygrip = CCCC999988887777666655554444333322221111
|
||||
|
||||
```
|
||||
|
||||
找到 pub 行下方的 keygrip 条目(就在主密钥指纹的下方)。它与你的 Home 目录下 `.gnupg` 目录下的一个文件是一致的:
|
||||
```
|
||||
$ cd ~/.gnupg/private-keys-v1.d
|
||||
$ ls
|
||||
AAAA999988887777666655554444333322221111.key
|
||||
BBBB999988887777666655554444333322221111.key
|
||||
CCCC999988887777666655554444333322221111.key
|
||||
|
||||
```
|
||||
|
||||
现在你做的全部操作就是简单地删除与主密钥 keygrip 一致的 `.key` 文件:
|
||||
```
|
||||
$ cd ~/.gnupg/private-keys-v1.d
|
||||
$ rm AAAA999988887777666655554444333322221111.key
|
||||
|
||||
```
|
||||
|
||||
现在,如果运行 --list-secret-keys 命令将出现问题,它将显示主密钥丢失(# 表示不可用):
|
||||
```
|
||||
$ gpg --list-secret-keys
|
||||
sec# rsa4096 2017-12-06 [C] [expires: 2019-12-06]
|
||||
111122223333444455556666AAAABBBBCCCCDDDD
|
||||
uid [ultimate] Alice Engineer <alice@example.org>
|
||||
uid [ultimate] Alice Engineer <allie@example.net>
|
||||
ssb rsa2048 2017-12-06 [E]
|
||||
ssb rsa2048 2017-12-06 [S]
|
||||
|
||||
```
|
||||
|
||||
##### 删除吊销证书
|
||||
|
||||
你应该去删除的另一个文件是吊销证书(**删除之前,确保你的备份中有它**),它是使用你的主密钥自动创建的。吊销证书允许一些人去永久标记你的证书为吊销状态,这意味着它无论在任何用途中将不再被使用或信任。一般是使用它来吊销由于某些原因不再受控的一个密钥 —— 比如,你丢失了密钥密码。
|
||||
|
||||
与使用主密钥一样,如果一个吊销证书泄露到恶意者手中,他们能够使用它去破坏你的开发者数字身份,因此,最好是从你的 Home 目录中删除它。
|
||||
```
|
||||
cd ~/.gnupg/openpgp-revocs.d
|
||||
rm [fpr].rev
|
||||
|
||||
```
|
||||
|
||||
在下一篇文章中,你将学习如何保护你的子密钥。敬请期待。
|
||||
|
||||
从来自 Linux 基金会和 edX 的免费课程 [“Linux 入门" ][4] 中学习更多 Linux 知识。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.linux.com/blog/learn/pgp/2018/3/protecting-code-integrity-pgp-part-4-moving-your-master-key-offline-storage
|
||||
|
||||
作者:[Konstantin Ryabitsev][a]
|
||||
译者:[qhwdw](https://github.com/qhwdw)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://www.linux.com/users/mricon
|
||||
[1]:https://www.linux.com/blog/learn/2018/2/protecting-code-integrity-pgp-part-1-basic-pgp-concepts-and-tools
|
||||
[2]:https://www.linux.com/blog/learn/pgp/2018/2/protecting-code-integrity-pgp-part-2-generating-and-protecting-your-master-pgp-key
|
||||
[3]:https://www.linux.com/blog/learn/pgp/2018/2/protecting-code-integrity-pgp-part-3-generating-pgp-subkeys
|
||||
[4]:https://training.linuxfoundation.org/linux-courses/system-administration-training/introduction-to-linux
|
||||
@ -0,0 +1,304 @@
|
||||
用 PGP 保护代码完整性(五):将子密钥移到一个硬件设备中
|
||||
======
|
||||
|
||||

|
||||
|
||||
在本系列教程中,我们将提供一个使用 PGP 的实用指南。如果你没有看过前面的文章,你可以通过下面的链接去查看。在这篇文章中,我们将继续讨论如何保护你的密钥,谈一谈将你的子密钥移到一个专门的硬件设备中的一些技巧。
|
||||
|
||||
[第一部分:基本概念和工具][1]
|
||||
|
||||
[第二部分:生成你的主密钥][2]
|
||||
|
||||
[第三部分:生成 PGP 子密钥][3]
|
||||
|
||||
[第四部分:将主密钥移到离线存储中][4]
|
||||
|
||||
### 清单
|
||||
|
||||
* 取得一个 GnuPG 兼容的硬件设备(必要)
|
||||
|
||||
* 配置 GnuPG 在设备上工作(必要)
|
||||
|
||||
* 设置 user 和 admin 的 PIN(必要)
|
||||
|
||||
* 移动子密钥到设备中(必要)
|
||||
|
||||
|
||||
|
||||
|
||||
### 考虑事项
|
||||
|
||||
虽然现在主密钥已经不用担心泄露或失窃了,但子密钥仍然在你的 Home 目录中。任何得到它的人都能够解密你的通讯或假冒你的签名(如果他们知道密钥的密码)。并且,每次执行一个 GnuPG 操作都要将密钥加载到操作系统内存中,这将使一些更高级的恶意软件有机会得到你的密钥(想想 Meltdown 和 Spectre)。
|
||||
|
||||
完全保护密钥的最好方式就是,将它移到一个专门的硬件设备中,这种硬件设备是一个可操作的智能卡。
|
||||
|
||||
#### 智能卡的好处
|
||||
|
||||
一个智能卡包含一个加密芯片,它能够存储私钥,并且直接在智能卡内部执行秘密操作。因为密钥内容从来没有离开过智能卡,计算机操作系统并不能检索你插入的智能卡上的私钥。这与前面用于备份目的的加密 USB 存储是不同的 —— 虽然 USB 设备也是插入并解密的,但操作系统是能够去访问私钥内容的。使用外置的加密 USB 介质并不能代替智能卡设备的功能。
|
||||
|
||||
智能卡的一些其它好处:
|
||||
|
||||
* 它们很便宜且易于获得
|
||||
|
||||
* 它们小巧且易于携带
|
||||
|
||||
* 它们可以用于多种设备上
|
||||
|
||||
* 它们中的很多都具有防篡改功能(取决于制造商)
|
||||
|
||||
|
||||
|
||||
|
||||
#### 可用的智能卡设备
|
||||
|
||||
智能卡最初是嵌入到真实钱包大小的卡中,故而得名智能卡。你总是可以买到并使用 GnuPG 功能的智能卡,并且它们是你能得到的最便宜的可用设备之一。但是,事实上智能卡有一个很重要的缺点:它们需要一个智能卡读卡器,只有极小数的笔记本电脑上有这种读卡器。
|
||||
|
||||
由于这个原因,制造商开始推出小型 USB 设备,它的大小和 U 盘类似,内置有微型智能卡,并且在芯片上简单地实现了智能卡协议特性。下面推荐几个这样的设备:
|
||||
|
||||
* [Nitrokey Start][5]:开源硬件和自由软件,可用于 GnuPG 的最便宜的选择之一,但是额外的安全特性很少。
|
||||
|
||||
* [Nitrokey Pro][6]:类似于 Nitrokey Start,它提供防篡改及更多的安全特性(但没有 U2F,具体查看指南的 U2F 节)。
|
||||
|
||||
* [Yubikey 4][7]:专利硬件和软件,但比 Nitrokey Pro 便宜,并且可以用在最新的笔记本电脑上的 USB-C 接口;也提供像 U2F 这样的额外的安全特性。
|
||||
|
||||
|
||||
|
||||
|
||||
我们推荐选一个同时具备智能卡功能和 U2F 的设备,在写这篇文章时,只能选择 Yubikey 4。
|
||||
|
||||
#### 配置智能卡设备
|
||||
|
||||
你的智能卡设备插入任何一台现代的 Linux 或 Mac 工作站上都应该能正常工作。你可以通过运行如下的命令去验证它:
|
||||
```
|
||||
$ gpg --card-status
|
||||
|
||||
```
|
||||
|
||||
如果你没有收到错误,有一个完整的卡列表,就表示一切正常。不幸的是,排除为什么设备不能正常工作的所有可能原因,已经超出了本指南的范围。如果你的智能卡使用 GnuPG 时有问题,请通过你的操作系统的常见支持通道寻求支持。
|
||||
|
||||
##### PIN 不一定是数字
|
||||
|
||||
注意,尽管名为 “PIN”(暗示你它必须是一个“数字”),不论是 user PIN 还是 admin PIN 都不必非要是数字。
|
||||
|
||||
当你收到一个新设备时,它可能设置有一个默认的 user 和 admin PIN,对于 Yubikeys,它分别是 123456 和 12345678。如果它们的 PIN 不是默认的,请查看设备附带的说明书。
|
||||
|
||||
##### 快速设置
|
||||
|
||||
为配置你的智能卡,你需要使用 GnuPG 菜单系统,因此这里并没有更方便的命令行开关:
|
||||
```
|
||||
$ gpg --card-edit
|
||||
[...omitted...]
|
||||
gpg/card> admin
|
||||
Admin commands are allowed
|
||||
gpg/card> passwd
|
||||
|
||||
```
|
||||
|
||||
你应该去设置 user PIN (1)、admin PIN (3)、和 Reset Code (4)。请确保把它们记录并保存到一个安全的地方 —— 尤其是 Admin PIN 和 Reset Code(它允许你去擦除整个智能卡内容)。你很少使用到 Admin PIN,因此如果你不记录下来,很可能会忘掉它。
|
||||
|
||||
返回到智能卡主菜单,你也可以设置其它值(比如名字、性别、登入日期、等等),但是这些都不是必需的,一旦你的智能卡丢失了,将导致额外的信息泄露。
|
||||
|
||||
#### 将子密钥移到你的智能卡中
|
||||
|
||||
退出卡菜单(使用 “q” 命令)保存所有更改。接下来,我们将你的子密钥移到智能卡中。将需要用到你的 PGP 密钥的密码,在大多数的智能卡操作中都将用到 admin PIN。记住,那个 [fpr] 表示你的密钥的完整的 40 个字符的指纹。
|
||||
```
|
||||
$ gpg --edit-key [fpr]
|
||||
|
||||
Secret subkeys are available.
|
||||
|
||||
pub rsa4096/AAAABBBBCCCCDDDD
|
||||
created: 2017-12-07 expires: 2019-12-07 usage: C
|
||||
trust: ultimate validity: ultimate
|
||||
ssb rsa2048/1111222233334444
|
||||
created: 2017-12-07 expires: never usage: E
|
||||
ssb rsa2048/5555666677778888
|
||||
created: 2017-12-07 expires: never usage: S
|
||||
[ultimate] (1). Alice Engineer <alice@example.org>
|
||||
[ultimate] (2) Alice Engineer <allie@example.net>
|
||||
|
||||
gpg>
|
||||
|
||||
```
|
||||
|
||||
使用 --edit-key 再次进入到菜单模式,你将注意到那个密钥清单有一点小差别。从现在开始,所有的命令都是在这个菜单模式下运行,它用 gpg> 提示符来表示。
|
||||
|
||||
首先,我们来选择移到智能卡中的密钥 —— 你可以通过键入 `key 1`(它表示选择清单中的第一个密钥)来实现:
|
||||
```
|
||||
gpg> key 1
|
||||
|
||||
```
|
||||
|
||||
这个输出会有一点细微的差别:
|
||||
```
|
||||
pub rsa4096/AAAABBBBCCCCDDDD
|
||||
created: 2017-12-07 expires: 2019-12-07 usage: C
|
||||
trust: ultimate validity: ultimate
|
||||
ssb* rsa2048/1111222233334444
|
||||
created: 2017-12-07 expires: never usage: E
|
||||
ssb rsa2048/5555666677778888
|
||||
created: 2017-12-07 expires: never usage: S
|
||||
[ultimate] (1). Alice Engineer <alice@example.org>
|
||||
[ultimate] (2) Alice Engineer <allie@example.net>
|
||||
|
||||
```
|
||||
|
||||
注意与密钥对应的 ssb 行旁边的 `*` —— 它表示这是当前选定的密钥。它是可切换的,意味着如果你再次输入 `key 1`,这个 `*` 将消失,这个密钥将不再被选中。
|
||||
|
||||
现在,我们来将密钥移到智能卡中:
|
||||
```
|
||||
gpg> keytocard
|
||||
Please select where to store the key:
|
||||
(2) Encryption key
|
||||
Your selection? 2
|
||||
|
||||
```
|
||||
|
||||
由于它是我们的 [E] 密钥,把它移到加密区中是有很有意义的。当你提交了你的选择之后,将会被提示输入你的 PGP 密钥的保护密码,接下来输入智能卡的 admin PIN。如果命令没有返回错误,表示你的密钥已经被移到智能卡中了。
|
||||
|
||||
**重要:** 现在再次输入 `key 1` 去取消选中第一个密钥,并输入 `key 2` 去选择 [S] 密钥:
|
||||
|
||||
```
|
||||
gpg> key 1
|
||||
gpg> key 2
|
||||
gpg> keytocard
|
||||
Please select where to store the key:
|
||||
(1) Signature key
|
||||
(3) Authentication key
|
||||
Your selection? 1
|
||||
|
||||
```
|
||||
|
||||
你可以使用 [S] 密钥同时做签名和验证,但是我们希望确保它在签名区,因此,我们选择 (1)。完成后,如果你的命令没有返回错误,表示操作已成功。
|
||||
|
||||
最后,如果你创建了一个 [A] 密钥,你也可以将它移到智能卡中,但是你需要先取消选中 `key 2`。完成后,选择 “q":
|
||||
```
|
||||
gpg> q
|
||||
Save changes? (y/N) y
|
||||
|
||||
```
|
||||
|
||||
保存变更将把你的子密钥移到智能卡后,把你的 Home 目录中的相应子密钥删除(没有关系,因为我们的备份中还有,如果更换了智能卡,你需要再做一遍)。
|
||||
|
||||
##### 验证移动后的密钥
|
||||
|
||||
现在,如果你执行一个` --list-secret-keys` 操作,你将看到一个稍有不同的输出:
|
||||
```
|
||||
$ gpg --list-secret-keys
|
||||
sec# rsa4096 2017-12-06 [C] [expires: 2019-12-06]
|
||||
111122223333444455556666AAAABBBBCCCCDDDD
|
||||
uid [ultimate] Alice Engineer <alice@example.org>
|
||||
uid [ultimate] Alice Engineer <allie@example.net>
|
||||
ssb> rsa2048 2017-12-06 [E]
|
||||
ssb> rsa2048 2017-12-06 [S]
|
||||
|
||||
```
|
||||
|
||||
在 ssb> 的输出中的 `>` 表示子密钥仅在智能卡上有效。如果你进入到你的密钥目录中,查看目录的内容,你将会看到那个 `.key` 文件已经被存根替换:
|
||||
```
|
||||
$ cd ~/.gnupg/private-keys-v1.d
|
||||
$ strings *.key
|
||||
|
||||
```
|
||||
|
||||
这个输出将包含一个影子私钥,它表示那个文件仅是个存根,真正的内容在智能卡中。
|
||||
|
||||
#### 验证智能卡的功能
|
||||
|
||||
验证智能卡能否如期正常运行,你可以通过创建一个签名来验证:
|
||||
```
|
||||
$ echo "Hello world" | gpg --clearsign > /tmp/test.asc
|
||||
$ gpg --verify /tmp/test.asc
|
||||
|
||||
```
|
||||
|
||||
首次运行这个命令时将询问你智能卡的 PIN,在你运行 `gpg —verify` 之后,它将显示 "Good signature”。
|
||||
|
||||
祝贺你,你已经成功将窃取你的开发者数字身份变得更加困难了!
|
||||
|
||||
### 其它常见 GnuPG 操作
|
||||
|
||||
下面是使用你的 PGP 密钥需要做的一些常见操作的快速指南。
|
||||
|
||||
在下面的所有命令中,[fpr] 表示你的密钥指纹。
|
||||
|
||||
#### 挂载主密钥离线存储
|
||||
|
||||
下面的一些操作将需要你的主密钥,因此首先需要去挂载你的主密钥离线存储,并告诉 GnuPG 去使用它。首先,找出介质挂载路径,可以通过查看 mount 命令的输出找到它。接着,设置你的 GnuPG 目录为你的介质上备份的目录,并告诉 GnuPG 将那个目录做为它的 Home:
|
||||
```
|
||||
$ export GNUPGHOME=/media/disk/name/gnupg-backup
|
||||
$ gpg --list-secret-keys
|
||||
|
||||
```
|
||||
|
||||
确保你在输出中看到的是 `sec` 而不是 `sec#`(这个 `#` 表示密钥不可用,仍然使用的是惯常的那个 Home 目录)。
|
||||
|
||||
##### 更新你惯常使用的那个 GnuPG 工作目录
|
||||
|
||||
在你的离线存储上做了任何更改之后,你应该将这些更改同步应用到你惯常使用的工作目录中:
|
||||
```
|
||||
$ gpg --export | gpg --homedir ~/.gnupg --import
|
||||
$ unset GNUPGHOME
|
||||
|
||||
```
|
||||
|
||||
#### 延长密钥过期日期
|
||||
|
||||
我们创建的主密钥的默认过期日期是自创建之日起两年后。这样做都是为安全考虑,这样将使淘汰密钥最终从密钥服务器上消失。
|
||||
|
||||
延长你的密钥过期日期,从当前日期延长一年,只需要运行如下命令:
|
||||
```
|
||||
$ gpg --quick-set-expire [fpr] 1y
|
||||
|
||||
```
|
||||
|
||||
如果为了好记住,你也可以使用一个特定日期(比如,你的生日、1 月 1 日、或加拿大国庆日):
|
||||
```
|
||||
$ gpg --quick-set-expire [fpr] 2020-07-01
|
||||
|
||||
```
|
||||
|
||||
记得将更新后的密钥发送到密钥服务器:
|
||||
```
|
||||
$ gpg --send-key [fpr]
|
||||
|
||||
```
|
||||
|
||||
#### 吊销身份
|
||||
|
||||
如果你需要吊销一个身份(比如,你换了雇主并且旧的邮件地址不再有效了),你可以使用一行命令搞定:
|
||||
```
|
||||
$ gpg --quick-revoke-uid [fpr] 'Alice Engineer <aengineer@example.net>'
|
||||
|
||||
```
|
||||
|
||||
你也可以通过使用 `gpg --edit-key [fpr]` 在菜单模式下完成同样的事情。
|
||||
|
||||
完成后,记得将更新后的密钥发送到密钥服务器上:
|
||||
```
|
||||
$ gpg --send-key [fpr]
|
||||
|
||||
```
|
||||
|
||||
下一篇文章中,我们将谈谈 Git 如何支持 PGP 的多级别集成。
|
||||
|
||||
通过来自 Linux 基金会和 edX 的免费课程 [“Linux 入门" ][8]学习更多 Linux 知识。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.linux.com/blog/learn/pgp/2018/3/protecting-code-integrity-pgp-part-5-moving-subkeys-hardware-device
|
||||
|
||||
作者:[KONSTANTIN RYABITSEV][a]
|
||||
译者:[qhwdw](https://github.com/qhwdw)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://www.linux.com/users/mricon
|
||||
[1]:https://www.linux.com/blog/learn/2018/2/protecting-code-integrity-pgp-part-1-basic-pgp-concepts-and-tools
|
||||
[2]:https://www.linux.com/blog/learn/pgp/2018/2/protecting-code-integrity-pgp-part-2-generating-and-protecting-your-master-pgp-key
|
||||
[3]:https://www.linux.com/blog/learn/pgp/2018/2/protecting-code-integrity-pgp-part-3-generating-pgp-subkeys
|
||||
[4]:https://www.linux.com/blog/learn/pgp/2018/3/protecting-code-integrity-pgp-part-4-moving-your-master-key-offline-storage
|
||||
[5]:https://shop.nitrokey.com/shop/product/nitrokey-start-6
|
||||
[6]:https://shop.nitrokey.com/shop/product/nitrokey-pro-3
|
||||
[7]:https://www.yubico.com/product/yubikey-4-series/
|
||||
[8]:https://training.linuxfoundation.org/linux-courses/system-administration-training/introduction-to-linux
|
||||
@ -0,0 +1,318 @@
|
||||
保护代码完整性(六):在 Git 上使用 PGP
|
||||
======
|
||||
|
||||

|
||||
在本系列教程中,我们提供了一个使用 PGP 的实用指南,包括基本概念和工具、生成和保护你的密钥。如果你错过了前面的文章,你可以查看下面的链接。在这篇文章中,我们谈一谈在 Git 中如何集成 PGP、使用签名的标签,然后介绍签名提交,最后添加签名推送的支持。
|
||||
|
||||
[第一部分:基本概念和工具][1]
|
||||
|
||||
[第二部分:生成你的主密钥][2]
|
||||
|
||||
[第三部分:生成 PGP 子密钥][3]
|
||||
|
||||
[第四部分:将主密钥移到离线存储中][4]
|
||||
|
||||
[第五部分:将子密钥移到硬件设备中][5]
|
||||
|
||||
Git 的核心特性之一就是它的去中心化本质 —— 一旦仓库克隆到你的本地系统,你就拥有了项目的完整历史,包括所有的标签、提交和分支。然而由于存在着成百上千的克隆仓库,如何才能验证你下载的仓库没有被恶意的第三方做过篡改?你可以从 GitHub 或一些貌似官方的位置来克隆它们,但是如果有些人故意欺骗了你怎么办?
|
||||
|
||||
或者在你参与的一些项目上发现了后门,而 "Author" 行显示是你干的,然而你很确定 [不是你干的][6],会发生什么情况?
|
||||
|
||||
为解决上述问题,Git 添加了 PGP 集成。签名的标签通过确认它的内容与创建这个标签的开发者的工作站上的内容完全一致来证明仓库的完整性,而签名的提交几乎是不可能在不访问你的 PGP 密钥的情况下能够假冒你。
|
||||
|
||||
### 清单
|
||||
|
||||
* 了解签名的标签、提交、和推送(必要)
|
||||
|
||||
* 配置 git 使用你的密钥(必要)
|
||||
|
||||
* 学习如何签名标签和验证工作(必要)
|
||||
|
||||
* 配置 git 总是签名注释的标签(推荐)
|
||||
|
||||
* 学习如何签名提交和验证工作(必要)
|
||||
|
||||
* 配置 git 总是签名提交(推荐)
|
||||
|
||||
* 配置 gpg-agent 选项(必要)
|
||||
|
||||
|
||||
|
||||
|
||||
### 考虑事项
|
||||
|
||||
Git 实现了 PGP 的多级集成,首先从签名标签开始,接着介绍签名提交,最后添加签名推送的支持。
|
||||
|
||||
#### 了解 Git 哈希
|
||||
|
||||
Git 是一个复杂的东西,为了你能够更好地掌握它如何集成 PGP,你需要了解什么是”哈希“。我们将它归纳为两种类型的哈希:树哈希和提交哈希。
|
||||
|
||||
##### 树哈希
|
||||
|
||||
每次你向仓库提交一个变更,对于仓库中的每个子目录,git 都会记录它里面所有对象的校验和哈希 —— 内容(blobs)、目录(trees)、文件名和许可等等。它只对每次提交中发生变更的树和内容做此操作,这样在只变更树的一小部分时就不必去重新计算整个树的校验和。
|
||||
|
||||
然后再计算和存储处于顶级的树的校验和,这样如果仓库的任何一部分发生变化,校验和将不可避免地发生变化。
|
||||
|
||||
##### 提交哈希
|
||||
|
||||
一旦创建了树哈希,git 将计算提交哈希,它将包含有关仓库和变更的下列信息:
|
||||
|
||||
* 树哈希的校验和
|
||||
|
||||
* 变更前树哈希的校验和(父级)
|
||||
|
||||
* 有关作者的信息(名字、email、创作时间)
|
||||
|
||||
* 有关提交者的信息(名字、email、提交时间)
|
||||
|
||||
* 提交信息
|
||||
|
||||
|
||||
|
||||
|
||||
##### 哈希函数
|
||||
|
||||
在写这篇文章时,虽然研究一种更强大的、抗碰撞的算法的工作正在进行,但 git 仍然使用的是 SHA1 哈希机制去计算校验和。注意,git 已经包含了碰撞防范程序,因此认为对 git 成功进行碰撞攻击仍然是不可行的。
|
||||
|
||||
#### 注释的标签和标签签名
|
||||
|
||||
在每个 Git 仓库中,标签允许开发者标记特定的提交。标签可以是 “轻量级的” —— 几乎只是一个特定提交上的指针,或者它们可以是 “注释的”,它成为 git 树中自己的项目。一个注释的标签对象包含所有下列的信息:
|
||||
|
||||
* 成为标签的提交哈希的校验和
|
||||
|
||||
* 标签名字
|
||||
|
||||
* 关于打标签的人的信息(名字、email、打标签时间)
|
||||
|
||||
* 标签信息
|
||||
|
||||
|
||||
|
||||
|
||||
一个 PGP 签名的标签是一个带有将所有这些条目封装进一个 PGP 签名的注释标签。当开发者签名他们的 git 标签时,他们实际上是向你保证了如下的信息:
|
||||
|
||||
* 他们是谁(以及他们为什么应该被信任)
|
||||
|
||||
* 他们在签名时的仓库状态是什么样:
|
||||
|
||||
* 标签包含提交的哈希
|
||||
|
||||
* 提交哈希包含了顶级树的哈希
|
||||
|
||||
* 顶级哈希包含了所有文件、内容和子树的哈希
|
||||
* 它也包含有关作者的所有信息
|
||||
|
||||
* 包含变更发生时的精确时间
|
||||
|
||||
|
||||
|
||||
|
||||
当你克隆一个仓库并验证一个签名标签时,就是向你以密码方式保证仓库中的所有内容、包括所有它的历史,与开发者签名时在它的计算机上的仓库完全一致。
|
||||
|
||||
#### 签名的提交
|
||||
|
||||
签名的提交与签名的标签非常类似 —— 提交对象的内容是 PGP 签名过的,而不是标签对象的内容。一个提交签名也给你提供了开发者签名时,开发者树上的全部可验证信息。标签签名和提交 PGP 签名提供了有关仓库和它的完整历史的完全一致的安全保证。
|
||||
|
||||
#### 签名的推送
|
||||
|
||||
为了完整起见,在这里包含了签名的推送这一功能,因为在你使用这个功能之前,需要在接收推送的服务器上先启用它。正如我们在上面所说过的,PGP 签名一个 git 对象就是提供了开发者的 git 树当时的可验证信息,但不提供开发者对那个树意图相关的信息。
|
||||
|
||||
比如,你可以在你自己 fork 的 git 仓库的一个实验分支上尝试一个很酷的特性,为了评估它,你提交了你的工作,但是有人在你的代码中发现了一个恶意的 bug。由于你的提交是经过正确签名的,因此有人可能将包含有恶意 bug 的分支推入到 master 分支中,从而在生产系统中引入一个漏洞。由于提交是经过你的密钥正确签名的,所以一切看起来都是合理合法的,而当 bug 被发现时,你的声誉就会因此而受到影响。
|
||||
|
||||
在 `git push` 时,为了验证提交的意图而不仅仅是验证它的内容,添加了要求 PGP 推送签名的功能。
|
||||
|
||||
#### 配置 git 使用你的 PGP 密钥
|
||||
|
||||
如果在你的钥匙环上只有一个密钥,那么你就不需要再做额外的事了,因为它是你的默认密钥。
|
||||
|
||||
然而,如果你有多个密钥,那么你必须要告诉 git 去使用哪一个密钥。([fpr] 是你的密钥的指纹):
|
||||
```
|
||||
$ git config --global user.signingKey [fpr]
|
||||
|
||||
```
|
||||
|
||||
注意:如果你有一个不同的 gpg2 命令,那么你应该告诉 git 总是去使用它,而不是传统的版本 1 的 gpg:
|
||||
```
|
||||
$ git config --global gpg.program gpg2
|
||||
|
||||
```
|
||||
|
||||
#### 如何使用签名标签
|
||||
|
||||
创建一个签名的标签,只要传递一个简单地 -s 开关给 tag 命令即可:
|
||||
```
|
||||
$ git tag -s [tagname]
|
||||
|
||||
```
|
||||
|
||||
我们建议始终对 git 标签签名,这样让其它的开发者确信他们使用的 git 仓库没有被恶意地修改过(比如,引入后门):
|
||||
|
||||
##### 如何验证签名的标签
|
||||
|
||||
验证一个签名的标签,只需要简单地使用 verify-tag 命令即可:
|
||||
```
|
||||
$ git verify-tag [tagname]
|
||||
|
||||
```
|
||||
|
||||
如果你要验证其他人的 git 标签,那么就需要你导入他的 PGP 公钥。请参考 “可信任的团队沟通” 一文中关于此主题的指导。
|
||||
|
||||
##### 在拉取时验证
|
||||
|
||||
如果你从项目仓库的其它 fork 中拉取一个标签,git 将自动验证签名,并在合并操作时显示结果:
|
||||
```
|
||||
$ git pull [url] tags/sometag
|
||||
|
||||
```
|
||||
|
||||
合并信息将包含类似下面的内容:
|
||||
```
|
||||
Merge tag 'sometag' of [url]
|
||||
|
||||
[Tag message]
|
||||
|
||||
# gpg: Signature made [...]
|
||||
# gpg: Good signature from [...]
|
||||
|
||||
```
|
||||
|
||||
#### 配置 git 始终签名注释的标签
|
||||
|
||||
很可能的是,你正在创建一个带注释的标签,你应该去签名它。强制 git 始终签名带注释的标签,你可以设置一个全局配置选项:
|
||||
```
|
||||
$ git config --global tag.forceSignAnnotated true
|
||||
|
||||
```
|
||||
|
||||
或者,你始终记得每次都传递一个 -s 开关:
|
||||
```
|
||||
$ git tag -asm "Tag message" tagname
|
||||
|
||||
```
|
||||
|
||||
#### 如何使用签名提交
|
||||
|
||||
创建一个签名提交很容易,但是将它纳入到你的工作流中却很困难。许多项目使用签名提交作为一种 "Committed-by:” 的等价行,它记录了代码来源 —— 除了跟踪项目历史外,签名很少有人去验证。在某种意义上,签名的提交用于 ”篡改证据“,而不是 git 工作流的 ”篡改证明“。
|
||||
|
||||
为创建一个签名的提交,你只需要 `git commit` 命令传递一个 -S 标志即可(由于它与另一个标志冲突,所以改为大写的 -S):
|
||||
```
|
||||
$ git commit -S
|
||||
|
||||
```
|
||||
|
||||
我们建议始终使用签名提交,并要求项目所有成员都这样做,这样其它人就可以验证它们(下面就讲到如何验证)。
|
||||
|
||||
##### 如何去验证签名的提交
|
||||
|
||||
验证签名的提交需要使用 verify-commit 命令:
|
||||
```
|
||||
$ git verify-commit [hash]
|
||||
|
||||
```
|
||||
|
||||
你也可以查看仓库日志,要求所有提交签名是被验证和显示的:
|
||||
```
|
||||
$ git log --pretty=short --show-signature
|
||||
|
||||
```
|
||||
|
||||
##### 在 git merge 时验证提交
|
||||
|
||||
如果项目的所有成员都签名了他们的提交,你可以在合并时强制进行签名检查(然后使用 -S 标志对合并操作本身进行签名):
|
||||
```
|
||||
$ git merge --verify-signatures -S merged-branch
|
||||
|
||||
```
|
||||
|
||||
注意,如果有一个提交没有签名或验证失败,将导致合并操作失败。通常情况下,技术是最容易的部分 —— 而人的因素使得项目中很难采用严格的提交验证。
|
||||
|
||||
##### 如果你的项目在补丁管理上采用邮件列表
|
||||
|
||||
如果你的项目在提交和处理补丁时使用一个邮件列表,那么一般很少使用签名提交,因为通过那种方式发送时,签名信息将会丢失。对提交进行签名仍然是非常有用的,这样引用你托管在公开 git 树的其他人就能以它作为参考,但是上游项目接收你的补丁时,仍然不能直接使用 git 去验证它们。
|
||||
|
||||
尽管,你仍然可以签名包含补丁的电子邮件。
|
||||
|
||||
#### 配置 git 始终签名提交
|
||||
|
||||
你可以告诉 git 总是签名提交:
|
||||
```
|
||||
git config --global commit.gpgSign true
|
||||
|
||||
```
|
||||
|
||||
或者你每次都记得给 `git commit` 操作传递一个 -S 标志(包括 —amend)。
|
||||
|
||||
#### 配置 gpg-agent 选项
|
||||
|
||||
GnuPG agent 是一个守护工具,它能在你使用 gpg 命令时随时自动启动,并运行在后台来缓存私钥的密码。这种方式让你只需要解锁一次密钥就可以重复地使用它(如果你需要在一个自动脚本中签署一组 git 操作,而不需要重复输入密钥,这种方式就很方便)。
|
||||
|
||||
为了调整缓存中的密钥过期时间,你应该知道这两个选项:
|
||||
|
||||
* default-cache-ttl(秒):如果在 time-to-live 过期之前再次使用同一个密钥,这个倒计时将重置成另一个倒计时周期。缺省值是 600(10 分钟)。
|
||||
|
||||
* max-cache-ttl(秒):自首次密钥输入以后,不论最近一次使用密钥是什么时间,只要最大值的 time-to-live 倒计时过期,你将被要求再次输入密码。它的缺省值是 30 分钟。
|
||||
|
||||
|
||||
|
||||
|
||||
如果你认为这些缺省值过短(或过长),你可以编辑 ~/.gnupg/gpg-agent.conf 文件去设置你自己的值:
|
||||
```
|
||||
# set to 30 minutes for regular ttl, and 2 hours for max ttl
|
||||
default-cache-ttl 1800
|
||||
max-cache-ttl 7200
|
||||
|
||||
```
|
||||
|
||||
##### 额外好处:与 ssh 一起使用 gpg-agent
|
||||
|
||||
如果你创建了一个 [A](验证)密钥,并将它移到了智能卡,你可以将它用到 ssh 上,为你的 ssh 会话添加一个双因子验证。为了与 agent 沟通你只需要告诉你的环境去使用正确的套接字文件即可。
|
||||
|
||||
首先,添加下列行到你的 ~/.gnupg/gpg-agent.conf 文件中:
|
||||
```
|
||||
enable-ssh-support
|
||||
|
||||
```
|
||||
|
||||
接着,添加下列行到你的 .bashrc 文件中:
|
||||
```
|
||||
export SSH_AUTH_SOCK=$(gpgconf --list-dirs agent-ssh-socket)
|
||||
|
||||
```
|
||||
|
||||
为了让改变生效,你需要 kill 掉正在运行的 gpg-agent 进程,并重新启动一个新的登入会话:
|
||||
```
|
||||
$ killall gpg-agent
|
||||
$ bash
|
||||
$ ssh-add -L
|
||||
|
||||
```
|
||||
|
||||
最后的命令将列出代表你的 PGP Auth 密钥的 SSH(注释应该会在结束的位置显示: cardno:XXXXXXXX,表示它来自智能卡)。
|
||||
|
||||
为了启用 ssh 的基于密钥的登入,只需要在你要登入的远程系统上添加 `ssh-add -L` 的输出到 ~/.ssh/authorized_keys 中。祝贺你,这将使你的 SSH 登入凭据更难以窃取。
|
||||
|
||||
作为一个福利,你可以从公共密钥服务器上下载其它人的基于 PGP 的 ssh 公钥,这样就可以赋予他登入 ssh 的权利:
|
||||
```
|
||||
$ gpg --export-ssh-key [keyid]
|
||||
|
||||
```
|
||||
|
||||
如果你有让开发人员通过 ssh 来访问 git 仓库的需要,这将让你非常方便。下一篇文章,我们将提供像保护你的密钥那样保护电子邮件帐户的小技巧。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.linux.com/blog/learn/pgp/2018/3/protecting-code-integrity-pgp-part-6-using-pgp-git
|
||||
|
||||
作者:[KONSTANTIN RYABITSEV][a]
|
||||
译者:[qhwdw](https://github.com/qhwdw)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://www.linux.com/users/mricon
|
||||
[1]:https://www.linux.com/blog/learn/2018/2/protecting-code-integrity-pgp-part-1-basic-pgp-concepts-and-tools
|
||||
[2]:https://www.linux.com/blog/learn/pgp/2018/2/protecting-code-integrity-pgp-part-2-generating-and-protecting-your-master-pgp-key
|
||||
[3]:https://www.linux.com/blog/learn/pgp/2018/2/protecting-code-integrity-pgp-part-3-generating-pgp-subkeys
|
||||
[4]:https://www.linux.com/blog/learn/pgp/2018/3/protecting-code-integrity-pgp-part-4-moving-your-master-key-offline-storage
|
||||
[5]:https://www.linux.com/blog/learn/pgp/2018/3/protecting-code-integrity-pgp-part-5-moving-subkeys-hardware-device
|
||||
[6]:https://github.com/jayphelps/git-blame-someone-else
|
||||
@ -1,60 +0,0 @@
|
||||
认识存储:块、文件和对象
|
||||
======
|
||||
|
||||

|
||||
|
||||
现在,对于那些创建或消费数据的公司来说,处理生成的数量巨大的数据是个非常大的挑战。而对于那些解决存储相关问题的科技公司来说,也是一个挑战。
|
||||
|
||||
Red Hat 存储首席产品营销经理 Michael St. Jean 说,“数据每年呈几何级增长,而我们发现数据大量增长的主要原因是由于消费增长和为拓展价值而进行的产业转型,毫无疑问,物联网对数据增长的贡献很大,但对软件定义存储来说最重要的挑战是,如何处理用户场景相关的数据增长。“
|
||||
|
||||
任何挑战都意味着机遇。Azure 存储、介质和边缘总经理 Tad Brockway 说,“今天,新旧数据源产生的海量数据为我们满足客户在规模、性能、灵活性、治理方面急剧增长的需求提供了一个机遇。”
|
||||
|
||||
### 现代软件定义存储的三种类型
|
||||
|
||||
这里有三个不同类型的存储解决方案 — 块、文件、和对象 — 虽然它们每个都可以与其它的共同工作,但它们每个都有不同的用途。
|
||||
|
||||
块存储是数据存储的最古老形式,数据都存储在固定长度的块或多个块中。块存储适用于企业存储环境,并且通常使用光纤通道或 iSCSI 接口。根据 SUSE 软件定义存储高级产品经理 Larry Morris 的说法,“块存储要求一个应用去映射存储设备上存储数据块的位置”。
|
||||
|
||||
块存储在存储区域网和软件定义存储系统中是虚拟的,它是处于一个共享的硬件基础设施上的抽象逻辑设备,它创建和存在于服务器、虚拟服务器、或运行在基于像 SCSI、SATA、SAS、FCP、FCoE、或 iSCSI 这样的协议的系统管理程序上。
|
||||
|
||||
St. Jean 说“块存储将单个的存储卷(像一个虚拟或云存储节点、或一个老式硬盘)分割成单独的被称为块的实体。“
|
||||
|
||||
每个块独立存在,并且能够用它自己的数据传输协议和操作系统格式化 — 给用户完全的配置自主权。由于块存储系统并不负责像文件存储系统那样的文件查找职责,所以,块存储是一个非常快的存储系统。由于同时具备速度和配置灵活性,使得块存储非常适合原始服务器存储或富媒体数据库。
|
||||
|
||||
块存储适合于宿主机操作系统、应用程序、数据库、完整虚拟机和容器。传统上,块存储仅能够被独立的机器、或集群中呈现出的机器访问。
|
||||
|
||||
### 基于文件的存储
|
||||
|
||||
基于文件的存储使用一个文件系统去映射存储设备上数据的存储位置。这种技术在直接或网络附加存储系统应用领域中处于支配地位。它需要做两件事情:组织数据并呈现给用户。 St. Jean 说,”使用文件存储时,数据在服务器侧的排列格式与客户端用户所看到的是完全相同的。这就允许用户通过一些唯一标识符(像文件名、位置、或 URL)去请求一个文件,使用特定的数据传输协议与存储系统沟通。
|
||||
|
||||
最终成为了一种能够从上到下进行浏览的分层的文件结构。文件存储处于块存储之上,允许用户去查看和访问文件、文件夹这样的数据,但是限制访问处于这些文件和文件夹之下的数据块。
|
||||
|
||||
Brockway 解释说,“文件存储一般用于像 NFS 和 CIFS/SMB 这种很多服务器基于 IP 网络进行访问的共享文件系统上。访问控制通过用户和组的权限实现在文件、目录、和导出级别上。基于文件的存储可用于被多个用户和机器、二进制应用程序、数据库、虚拟机所需要的文件的存储上,以及容器上。“
|
||||
|
||||
### 对象存储
|
||||
|
||||
对象存储是最新的数据存储形式,它为非结构化数据提供一个库,它将内容从索引中分离出来,并允许多个文件连接到一个对象上。一个对象就是与任何相关元数据配对的一个数据块,这些元数据提供对象中包含的字节的上下文(比如数据创建时间和数据大小等)。也就是说这两样东西 — 数据和元数据 — 构成了一个对象。
|
||||
|
||||
对象存储的一个好处是每个数据块都关联了一个唯一标识符。访问数据需要唯一标识符,并且不需要应用程序或用户知道数据的真实存储位置。对象数据是通过 API 来访问的。
|
||||
|
||||
St. Jean 说,“对象中存储的数据是没有压缩和加密的,对象本身被安排在对象存储(一个填满其它对象的中心库)中或容器(包含应用程序运行所需要的所有文件的一个包)中。与文件存储系统的层次结构相比,对象、对象存储和容器在本质上是平面的 — 这使得它们在存储规模巨大时访问速度很快。”
|
||||
|
||||
对象存储可以扩展到很多 PB 字节大小,以适应巨大的数据集,因此它是图像、音频、视频、日志、备份、和分析服务所使用的数据存储的最佳选择。
|
||||
|
||||
### 结论
|
||||
|
||||
现在你已经知道了各种类型的存储以及它们的用处。后面我们将继续研究这个主题的更多内容,敬请关注。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.linux.com/blog/2018/9/know-your-storage-block-file-object
|
||||
|
||||
作者:[Swapnil Bhartiya][a]
|
||||
选题:[lujun9972](https://github.com/lujun9972)
|
||||
译者:[qhwdw](https://github.com/qhwdw)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.linux.com/users/arnieswap
|
||||
[1]: https://events.linuxfoundation.org/events/elc-openiot-europe-2018/
|
||||
@ -0,0 +1,201 @@
|
||||
# 如何使用 Fedora IoT 开启 LED 灯
|
||||
|
||||

|
||||
|
||||
你喜欢 Fedora、容器和树莓派吗?这三者结合操控 LED 会怎么样?本文介绍的是 Fedora IoT,将展示如何在树莓派上安装预览镜像。还将学习如何与 GPIO 交互以开启 LED。
|
||||
|
||||
### 什么是 Fedora IoT?
|
||||
|
||||
Fedora IoT 是当前 Fedora 项目的目标之一,计划成为一个完整的 Fedora 版本。Fedora IoT 将是一个在ARM(目前仅限 aarch64)例如树莓派,以及 x86_64 架构设备上运行的系统。
|
||||
|
||||
![][1]
|
||||
|
||||
Fedora IoT 基于 OSTree 开发, 就像[Fedora Silverblue][2] 和以往的 [Atomic Host][3].
|
||||
|
||||
### 下载和安装 Fedora IoT
|
||||
|
||||
官方 Fedora IoT 镜像将和 Fedora 29 一起发布。但是在此期间你可以下载 [Fedora 28-based 镜像][4] 来进行这个实验。
|
||||
|
||||
你有两种方法来安装这个系统:使用 dd 命令闪存SD卡,或者使用 fedora-arm-installer 工具。Fedora 的 Wiki 里面提供了更多关于[设置物理设备][5] 的信息来开发 IoT。另外,你可能需要调整第三个分区的大小。
|
||||
|
||||
把 SD 卡插入到设备并运行,需要创建一个用户来完成安装。这个步骤需要串行连接或带键盘的 HDMI 显示器来与设备进行交互。
|
||||
|
||||
当系统安装完成后,下一步就是要设置网络连接。使用你刚才创建的用户登录系统,可以使用下列方式之一完成网络连接设置:
|
||||
|
||||
- 如果你需要手动配置你的网络,可能需要执行类似如下命令,需要保证设置正确的网络地址:
|
||||
|
||||
```
|
||||
$ nmcli connection add con-name cable ipv4.addresses \
|
||||
192.168.0.10/24 ipv4.gateway 192.168.0.1 \
|
||||
connection.autoconnect true ipv4.dns "8.8.8.8,1.1.1.1" \
|
||||
type ethernet ifname eth0 ipv4.method manual
|
||||
|
||||
```
|
||||
|
||||
- 如果你网络上运行着 DHCP 服务,可能需要类似如下命令:
|
||||
|
||||
```
|
||||
$ nmcli con add type ethernet con-name cable ifname eth0
|
||||
```
|
||||
|
||||
|
||||
|
||||
### **Fedora 中的 GPIO 接口**
|
||||
|
||||
许多关于 Linux 上 GPIO 的教程都关注传统的 GPIO sysfis 接口。这个接口已经不推荐使用了,并且上游 Linux 内核社区由于安全和其他问题的缘故打算完全删除它。
|
||||
|
||||
Fedora 已经不将这个传统的接口编译到内核了,因此在系统上没有 /sys/class/gpio 这个文件。此教程使用一个上游内核提供的一个新的字符设备 /dev/gpiochipN 。这是目前和 GPIO 交互的方式。
|
||||
|
||||
为了和这个新设备进行交互,你需要使用一个库和一系列命令行界面工具。公共命令行工具比如说 echo 和 cat 在此设备上无法正常工作。
|
||||
|
||||
你可以通过安装 libgpiod-utils 包来安装命令行界面工具。python3-libgpiod 包提供了相应的 Python 库。
|
||||
|
||||
### **使用 Podman 来创建一个容器**
|
||||
|
||||
[Podman][6] 是一个容器运行环境,其命令行界面类似于Docker。Podman的一大优势是它不会在后台运行任何守护进程。这对于资源有限的设备尤其有用。Podman 还允许您使用 systemd 单元文件启动容器化服务。此外,它还有许多其他功能。
|
||||
|
||||
我们使用如下两步来创建一个容器:
|
||||
|
||||
```
|
||||
1. 创建包含所需包的分层镜像。
|
||||
2. 使用分层镜像创建一个新容器。
|
||||
```
|
||||
|
||||
|
||||
|
||||
首先创建一个 Dockerfile 文件,内容如下。这些内容告诉 podman 基于可使用的最新 Fedora 镜像来构建我们的分层镜像。然后就是更新系统和安装一些软件包:
|
||||
|
||||
```
|
||||
FROM fedora:latest
|
||||
RUN dnf -y update
|
||||
RUN dnf -y install libgpiod-utils python3-libgpiod
|
||||
|
||||
```
|
||||
|
||||
这样你就完成了镜像的生成前的配置工作,这个镜像基于最新的 Fedora,而且包含了和 GPIO 交互的软件包。
|
||||
|
||||
现在你就可以运行下方命令来构建你的基本镜像了:
|
||||
|
||||
```
|
||||
$ sudo podman build --tag fedora:gpiobase -f ./Dockerfile
|
||||
|
||||
```
|
||||
|
||||
你已经成功创建了你的自定义镜像。这样以后你就可以不用每次都重新搭建环境了,而是基于你创建的镜像来完成工作。
|
||||
|
||||
### 使用 Podman 完成工作
|
||||
|
||||
为了确认当前的镜像,可以运行下方命令:
|
||||
|
||||
```
|
||||
$ sudo podman images
|
||||
REPOSITORY TAG IMAGE ID CREATED SIZE
|
||||
localhost/fedora gpiobase 67a2b2b93b4b 10 minutes ago 488MB
|
||||
docker.io/library/fedora latest c18042d7fac6 2 days ago 300MB
|
||||
|
||||
```
|
||||
|
||||
现在,启动容器并进行一些实际的实验。 容器通常是隔离的,无法访问主机系统,包括GPIO接口。 因此需要在启动容器时将其挂载在容器内。 可以使用以下命令中的 -device 选项来解决:
|
||||
|
||||
```
|
||||
$ sudo podman run -it --name gpioexperiment --device=/dev/gpiochip0 localhost/fedora:gpiobase /bin/bash
|
||||
|
||||
```
|
||||
|
||||
运行之后就进入了正在运行的容器中。 在继续之前,这里有一些容器命令。 输入 exit 或者按下 **Ctrl+D** 来退出容器。
|
||||
|
||||
显示所有存在的容器可以运行如下命令:
|
||||
|
||||
```
|
||||
$ sudo podman container ls -a
|
||||
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
|
||||
64e661d5d4e8 localhost/fedora:gpiobase /bin/bash 37 seconds ago Exited (0) Less than a second ago gpioexperiment
|
||||
|
||||
```
|
||||
|
||||
使用如下命令创建一个新的容器:
|
||||
|
||||
```
|
||||
$ sudo podman run -it --name newexperiment --device=/dev/gpiochip0 localhost/fedora:gpiobase /bin/bash
|
||||
|
||||
```
|
||||
|
||||
如果想删除容器可以使用如下命令:
|
||||
|
||||
```
|
||||
$ sudo podman rm newexperiment
|
||||
|
||||
```
|
||||
|
||||
### **开启 LED 灯**
|
||||
|
||||
现在可以使用已创建的容器。 如果容器已经退出,请使用以下命令再次启动它:
|
||||
|
||||
```
|
||||
$ sudo podman start -ia gpioexperiment
|
||||
|
||||
```
|
||||
|
||||
如前所述,可以使用 Fedora 中 libgpiod-utils 包提供的 CLI 工具。 要列出可用的 GPIO 芯片可以使用如下命令:
|
||||
|
||||
```
|
||||
$ gpiodetect
|
||||
gpiochip0 [pinctrl-bcm2835] (54 lines)
|
||||
|
||||
```
|
||||
|
||||
要获取特定芯片的公开列表,请运行:
|
||||
|
||||
```
|
||||
$ gpioinfo gpiochip0
|
||||
|
||||
```
|
||||
|
||||
请注意,物理引脚数与前一个命令打印的行数之间没有相关性。 重要的是 BCM 编号,如 [pinout.xyz][7] 所示。 建议不要使用没有相应 BCM 编号的线路。
|
||||
|
||||
现在,将 LED 连接到物理引脚40,也就是 BCM 21。请记住:LED的短腿(负极,称为阴极)必须连接到带有330欧姆电阻的树莓派的 GND 引脚, 并且长腿(阳极)到物理引脚40。
|
||||
|
||||
运行以下命令打开LED。,按下 **Ctrl + C ** 关闭:
|
||||
|
||||
```
|
||||
$ gpioset --mode=wait gpiochip0 21=1
|
||||
|
||||
```
|
||||
|
||||
要点亮一段时间,请添加 -b(在后台运行)和 -s NUM(多少秒)参数,如下所示。 例如,要点亮 LED 5秒钟,运行如下命令:
|
||||
|
||||
```
|
||||
$ gpioset -b -s 5 --mode=time gpiochip0 21=1
|
||||
|
||||
```
|
||||
|
||||
另一个有用的命令是 gpioget。 它可以获得引脚的状态(高或低),可用于检测按钮和开关。
|
||||
|
||||
![Closeup of LED connection with GPIO][8]
|
||||
|
||||
### **总结**
|
||||
|
||||
你也可以使用 Python 操控 LED - [这里有一些例子][9]。 也可以在容器内使用 i2c 设备。 此外,Podman 与此 Fedora 版本并不严格相关。 你可以在任何现有的 Fedora Edition 上安装它,或者在 Fedora 中使用两个基于 OSTree 的新系统进行尝试:[Fedora Silverblue][2] 和 [Fedora CoreOS][10]。
|
||||
|
||||
------
|
||||
|
||||
via: https://fedoramagazine.org/turnon-led-fedora-iot/
|
||||
|
||||
作者:[Alessio Ciregia][a]
|
||||
选题:[lujun9972](https://github.com/lujun9972)
|
||||
译者:[ScarboroughCoral](https://github.com/ScarboroughCoral)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: http://alciregi.id.fedoraproject.org/
|
||||
[1]: https://fedoramagazine.org/wp-content/uploads/2018/08/oled-1024x768.png
|
||||
[2]: https://teamsilverblue.org/
|
||||
[3]: https://www.projectatomic.io/
|
||||
[4]: https://kojipkgs.fedoraproject.org/compose/iot/latest-Fedora-IoT-28/compose/IoT/
|
||||
[5]: https://fedoraproject.org/wiki/InternetOfThings/GettingStarted#Setting_up_a_Physical_Device
|
||||
[6]: https://github.com/containers/libpod
|
||||
[7]: https://pinout.xyz/
|
||||
[8]: https://fedoramagazine.org/wp-content/uploads/2018/08/breadboard-1024x768.png
|
||||
[9]: https://github.com/brgl/libgpiod/tree/master/bindings/python/examples
|
||||
[10]: https://coreos.fedoraproject.org/
|
||||
@ -1,28 +1,28 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: translator: (qhwdw)
|
||||
[#]: reviewer: ()
|
||||
[#]: publisher: ()
|
||||
[#]: url: ()
|
||||
[#]: subject: (How to Build a Netboot Server, Part 2)
|
||||
[#]: via: (https://fedoramagazine.org/how-to-build-a-netboot-server-part-2/)
|
||||
[#]: author: (Gregory Bartholomew https://fedoramagazine.org/author/glb/)
|
||||
|
||||
How to Build a Netboot Server, Part 2
|
||||
如何构建一台网络引导服务器(第二部分)
|
||||
======
|
||||
|
||||
|
||||
|
||||
The article [How to Build a Netboot Server, Part 1][1] showed you how to create a netboot image with a “liveuser” account whose home directory lives in volatile memory. Most users probably want to preserve files and settings across reboots, though. So this second part of the netboot series shows how to reconfigure the netboot image from part one so that [Active Directory][2] user accounts can log in and their home directories can be automatically mounted from a NFS server.
|
||||
在 [如何构建一台网络引导服务器(第一部分)][1] 的文章中,我们展示了如何创建一个网络引导镜像,在那个镜像中使用了一个名为 “liveuser” 帐户,它的 home 目录位于内存中,重启后 home 中的内容将全部消失。然而很多用户都希望机器重启后保存他们的文件和设置。因此,在本系列的第二部分,我们将向你展示如何在第一部分的基础上,重新配置网络引导镜像,使它能够使用 [活动目录][2] 中的用户帐户进行登陆,然后能够从一个 NFS 服务器上自动挂载他们的 home 目录。
|
||||
|
||||
Part 3 of this series will show how to make an interactive and centrally-configurable iPXE boot menu for the netboot clients.
|
||||
本系列的第三部分,我们将向你展示网络引导客户端如何与中心化配置的 iPXE 引导菜单进行交互。
|
||||
|
||||
### Setup NFS4 Home Directories with KRB5 Authentication
|
||||
### 设置使用 KRB5 认证的 NFS4 Home 目录
|
||||
|
||||
Follow the directions from the previous post “[Share NFS Home Directories Securely with Kerberos][3],” then return here.
|
||||
按以前的文章 “[使用 Kerberos 强化共享的 NFS Home 目录安全性][3]” 的指导来做这个设置。
|
||||
|
||||
### Remove the Liveuser Account
|
||||
### 删除 Liveuser 帐户
|
||||
|
||||
Remove the “liveuser” account created in part one of this series:
|
||||
删除本系列文章第一部分中创建的 “liveuser” 帐户:
|
||||
|
||||
```
|
||||
$ sudo -i
|
||||
@ -31,9 +31,9 @@ $ sudo -i
|
||||
# for i in passwd shadow group gshadow; do sed -i '/^liveuser:/d' /fc28/etc/$i; done
|
||||
```
|
||||
|
||||
### Configure NTP, KRB5 and SSSD
|
||||
### 配置 NTP、KRB5 和 SSSD
|
||||
|
||||
Next, we will need to duplicate the NTP, KRB5, and SSSD configuration that we set up on the server in the client image so that the same accounts will be available:
|
||||
接下来,我们需要将 NTP、KRB5、和 SSSD 的配置文件复制进客户端使用的镜像中,以便于它们能够使用同一个帐户:
|
||||
|
||||
```
|
||||
# MY_HOSTNAME=$(</etc/hostname)
|
||||
@ -45,27 +45,27 @@ Next, we will need to duplicate the NTP, KRB5, and SSSD configuration that we se
|
||||
# cp /etc/sssd/sssd.conf /fc28/etc/sssd
|
||||
```
|
||||
|
||||
Reconfigure sssd to provide authentication services, in addition to the identification service already configured:
|
||||
重新配置 sssd 在已配置的识别服务的基础上去提供认证服务:
|
||||
|
||||
```
|
||||
# sed -i '/services =/s/$/, pam/' /fc28/etc/sssd/sssd.conf
|
||||
```
|
||||
|
||||
Also, ensure none of the clients attempt to update the computer account password:
|
||||
另外,配置成确保客户端不能更改这个帐户密码:
|
||||
|
||||
```
|
||||
# sed -i '/id_provider/a \ \ ad_maximum_machine_account_password_age = 0' /fc28/etc/sssd/sssd.conf
|
||||
```
|
||||
|
||||
Also, copy the nfsnobody definitions:
|
||||
另外,复制 nfsnobody 的定义:
|
||||
|
||||
```
|
||||
# for i in passwd shadow group gshadow; do grep "^nfsnobody:" /etc/$i >> /fc28/etc/$i; done
|
||||
```
|
||||
|
||||
### Join Active Directory
|
||||
### 连接活动目录
|
||||
|
||||
Next, you’ll perform a chroot to join the client image to Active Directory. Begin by deleting any pre-existing computer account with the same name your netboot image will use:
|
||||
接下来,你将执行一个 chroot 将客户端镜像连接到活动目录。从删除预置在网络引导镜像中相同的计算机帐户开始:
|
||||
|
||||
```
|
||||
# MY_USERNAME=jsmith
|
||||
@ -73,20 +73,20 @@ Next, you’ll perform a chroot to join the client image to Active Directory. Be
|
||||
# adcli delete-computer "${MY_CLIENT_HOSTNAME%%.*}" -U "$MY_USERNAME"
|
||||
```
|
||||
|
||||
Also delete the krb5.keytab file from the netboot image if it exists:
|
||||
在网络引导镜像中如果有 krb5.keytab 文件,也删除它:
|
||||
|
||||
```
|
||||
# rm -f /fc28/etc/krb5.keytab
|
||||
```
|
||||
|
||||
Perform a chroot into the netboot image:
|
||||
在网络引导镜像中执行一个 chroot 操作:
|
||||
|
||||
```
|
||||
# for i in dev dev/pts dev/shm proc sys run; do mount -o bind /$i /fc28/$i; done
|
||||
# chroot /fc28 /usr/bin/bash --login
|
||||
```
|
||||
|
||||
Perform the join:
|
||||
执行一个 join 操作:
|
||||
|
||||
```
|
||||
# MY_USERNAME=jsmith
|
||||
@ -97,7 +97,7 @@ Perform the join:
|
||||
# adcli join $MY_DOMAIN --login-user="$MY_USERNAME" --computer-name="${MY_HOSTNAME%%.*}" --host-fqdn="$MY_HOSTNAME" --user-principal="host/$MY_HOSTNAME@$MY_REALM" --domain-ou="$MY_OU"
|
||||
```
|
||||
|
||||
Now log out of the chroot and clear the root user’s command history:
|
||||
现在登出 chroot,并清除命令历史:
|
||||
|
||||
```
|
||||
# logout
|
||||
@ -105,9 +105,9 @@ Now log out of the chroot and clear the root user’s command history:
|
||||
# > /fc28/root/.bash_history
|
||||
```
|
||||
|
||||
### Install and Configure PAM Mount
|
||||
### 安装和配置 PAM Mount
|
||||
|
||||
We want our clients to automatically mount the user’s home directory when they log in. To accomplish this, we’ll use the “pam_mount” module. Install and configure pam_mount:
|
||||
我们希望客户端登入后自动挂载它的 home 目录。为实现这个目的,我们将要使用 “pam_mount” 模块。安装和配置 pam_mount:
|
||||
|
||||
```
|
||||
# dnf install -y --installroot=/fc28 pam_mount
|
||||
@ -123,7 +123,7 @@ We want our clients to automatically mount the user’s home directory when they
|
||||
END
|
||||
```
|
||||
|
||||
Reconfigure PAM to use pam_mount:
|
||||
重新配置 PAM 去使用 pam_mount:
|
||||
|
||||
```
|
||||
# dnf install -y patch
|
||||
@ -152,24 +152,24 @@ END
|
||||
# chroot /fc28 authselect select custom/sssd with-pammount --force
|
||||
```
|
||||
|
||||
Also ensure the NFS server’s hostname is always resolvable from the client:
|
||||
另外,要确保从客户端上总是可解析 NFS 服务器的主机名:
|
||||
|
||||
```
|
||||
# MY_IP=$(host -t A $MY_HOSTNAME | awk '{print $4}')
|
||||
# echo "$MY_IP $MY_HOSTNAME ${MY_HOSTNAME%%.*}" >> /fc28/etc/hosts
|
||||
```
|
||||
|
||||
Optionally, allow all users to run sudo:
|
||||
可选,允许所有用户去使用 sudo:
|
||||
|
||||
```
|
||||
# echo '%users ALL=(ALL) NOPASSWD: ALL' > /fc28/etc/sudoers.d/users
|
||||
```
|
||||
|
||||
### Convert the NFS Root to an iSCSI Backing-Store
|
||||
### 转换 NFS Root 到一个 iSCSI 背后的存储
|
||||
|
||||
Current versions of nfs-utils may have difficulty establishing a second connection from the client back to the NFS server for home directories when an nfsroot connection is already established. The client hangs when attempting to access the home directory. So, we will work around the problem by using a different protocol (iSCSI) for sharing our netboot image.
|
||||
在一个 nfsroot 连接建立之后,目前版本的 nfs-utils 可能很难为 home 目录维护一个从客户端到 NFS 服务器的二次连接。当尝试去访问 home 目录时,客户端将被挂住。因此,为了网络引导镜像可共享使用,我们将使用一个不同的协议(iSCSI)来解决这个问题。
|
||||
|
||||
First chroot into the image to reconfigure its initramfs for booting from an iSCSI root:
|
||||
首先 chroot 到镜像中,去重新配置它的 initramfs,让它从一个 iSCSI root 中去引导:
|
||||
|
||||
```
|
||||
# for i in dev dev/pts dev/shm proc sys run; do mount -o bind /$i /fc28/$i; done
|
||||
@ -186,18 +186,18 @@ First chroot into the image to reconfigure its initramfs for booting from an iSC
|
||||
# > /fc28/root/.bash_history
|
||||
```
|
||||
|
||||
The qedi driver broke iscsi during testing, so it’s been disabled here.
|
||||
在测试时,qedi 驱动会破坏 iscsi,因此我们将它禁用。
|
||||
|
||||
Next, create a fc28.img [sparse file][4]. This file serves as the iSCSI target’s backing store:
|
||||
接着,创建一个 fc28.img 的 [稀疏文件][4]。这个稀疏文件代表 iSCSI 目标的背后存储:
|
||||
|
||||
```
|
||||
# FC28_SIZE=$(du -ms /fc28 | cut -f 1)
|
||||
# dd if=/dev/zero of=/fc28.img bs=1MiB count=0 seek=$(($FC28_SIZE*2))
|
||||
```
|
||||
|
||||
(If you have one available, a separate partition or disk drive can be used instead of creating a file.)
|
||||
(如果你有一个可使用的稀疏文件、一个单独的分区或磁盘驱动器,就可以代替它了,不用再去创建这个稀疏文件了。)
|
||||
|
||||
Next, format the image with a filesystem, mount it, and copy the netboot image into it:
|
||||
接着,使用一个文件系统去格式化镜像、挂载它、然后将网络引导镜像复制进去:
|
||||
|
||||
```
|
||||
# mkfs -t xfs -L NETROOT /fc28.img
|
||||
@ -207,19 +207,19 @@ Next, format the image with a filesystem, mount it, and copy the netboot image i
|
||||
# umount $TEMP_MNT
|
||||
```
|
||||
|
||||
During testing using SquashFS, the client would occasionally stutter. It seems that SquashFS does not perform well when doing random I/O from a multiprocessor client. (See also [The curious case of stalled squashfs reads][5].) If you want to improve throughput performance with filesystem compression, [ZFS][6] is probably a better option.
|
||||
在使用 SquashFS 测试时,客户端偶尔会出现小状况。似乎是因为 SquashFS 在多处理器客户端上没法执行一个随机 I/O。(更多内容见 [squashfs 读取卡顿的奇怪案例][5])。如果你希望使用一个压缩文件系统来提升吞吐性能,[ZFS][6] 或许是个很好的选择。
|
||||
|
||||
If you need extremely high throughput from the iSCSI server (say, for hundreds of clients), it might be possible to [load balance][7] a [Ceph][8] cluster. For more information, see [Load Balancing Ceph Object Gateway Servers with HAProxy and Keepalived][9].
|
||||
如果你对 iSCSI 服务器的吞吐性能要求非常高(比如,成百上千的客户端要连接它),可能需要使用带 [负载均衡][7] 的 [Ceph][8] 集群了。更多相关内容,请查看 [使用 HAProxy 和 Keepalived 负载均衡的 Ceph 对象网关][9]。
|
||||
|
||||
### Install and Configure iSCSI
|
||||
### 安装和配置 iSCSI
|
||||
|
||||
Install the scsi-target-utils package which will provide the iSCSI daemon for serving our image out to our clients:
|
||||
为了给我们的客户端提供网络引导镜像,安装 scsi-target-utils 包:
|
||||
|
||||
```
|
||||
# dnf install -y scsi-target-utils
|
||||
```
|
||||
|
||||
Configure the iSCSI daemon to serve the fc28.img file:
|
||||
配置 iSCSI 守护程序去提供 fc28.img 文件:
|
||||
|
||||
```
|
||||
# MY_REVERSE_HOSTNAME=$(echo $MY_HOSTNAME | tr '.' "\n" | tac | tr "\n" '.' | cut -b -${#MY_HOSTNAME})
|
||||
@ -231,9 +231,9 @@ Configure the iSCSI daemon to serve the fc28.img file:
|
||||
END
|
||||
```
|
||||
|
||||
The leading iqn. is expected by /usr/lib/dracut/modules.d/40network/net-lib.sh.
|
||||
通过 /usr/lib/dracut/modules.d/40network/net-lib.sh 来指示预期的 iqn。
|
||||
|
||||
Add an exception to the firewall and enable and start the service:
|
||||
添加一个防火墙例外,并启用和启动这个服务:
|
||||
|
||||
```
|
||||
# firewall-cmd --add-service=iscsi-target
|
||||
@ -242,13 +242,13 @@ Add an exception to the firewall and enable and start the service:
|
||||
# systemctl start tgtd.service
|
||||
```
|
||||
|
||||
You should now be able to see the image being shared with the tgtadm command:
|
||||
你现在应该能够使用 tatadm 命令看到这个共享后的镜像:
|
||||
|
||||
```
|
||||
# tgtadm --mode target --op show
|
||||
```
|
||||
|
||||
The above command should output something similar to the following:
|
||||
上述命令的输出应该类似如下的内容:
|
||||
|
||||
```
|
||||
Target 1: iqn.edu.example.server-01:fc28
|
||||
@ -290,7 +290,7 @@ Target 1: iqn.edu.example.server-01:fc28
|
||||
ALL
|
||||
```
|
||||
|
||||
We can now remove the NFS share that we created in part one of this series:
|
||||
现在,我们可以去删除本系列文章的第一部分中创建的 NFS 共享了:
|
||||
|
||||
```
|
||||
# rm -f /etc/exports.d/fc28.exports
|
||||
@ -300,11 +300,11 @@ We can now remove the NFS share that we created in part one of this series:
|
||||
# sed -i '/^\/fc28 /d' /etc/fstab
|
||||
```
|
||||
|
||||
You can also delete the /fc28 filesystem, but you may want to keep it for performing future updates.
|
||||
你也可以删除 /fc28 文件系统,但为了以后进一步更新,你可能需要保留它。
|
||||
|
||||
### Update the ESP to use the iSCSI Kernel
|
||||
### 更新 ESP 去使用 iSCSI 内核
|
||||
|
||||
Ipdate the ESP to contain the iSCSI-enabled initramfs:
|
||||
更新 ESP 去包含启用了 iSCSI 的 initramfs:
|
||||
|
||||
```
|
||||
$ rm -vf $HOME/esp/linux/*.fc28.*
|
||||
@ -313,7 +313,7 @@ $ cp $(find /fc28/lib/modules -maxdepth 2 -name 'vmlinuz' | grep -m 1 $MY_KRNL)
|
||||
$ cp $(find /fc28/boot -name 'init*' | grep -m 1 $MY_KRNL) $HOME/esp/linux/initramfs-$MY_KRNL.img
|
||||
```
|
||||
|
||||
Update the boot.cfg file to pass the new root and netroot parameters:
|
||||
更新 boot.cfg 文件去传递新的 root 和 netroot 参数:
|
||||
|
||||
```
|
||||
$ MY_NAME=server-01.example.edu
|
||||
@ -322,52 +322,52 @@ $ MY_ADDR=$(host -t A $MY_NAME | awk '{print $4}')
|
||||
$ sed -i "s! root=[^ ]*! root=/dev/disk/by-path/ip-$MY_ADDR:3260-iscsi-iqn.$MY_EMAN:fc28-lun-1 netroot=iscsi:$MY_ADDR::::iqn.$MY_EMAN:fc28!" $HOME/esp/linux/boot.cfg
|
||||
```
|
||||
|
||||
Now you just need to copy the updated files from your $HOME/esp/linux directory out to the ESPs of all your client systems. You should see results similar to what is shown in the below screenshot:
|
||||
现在,你只需要从 $HOME/esp/linux 目录中复制更新后的文件到所有客户端系统的 ESP 中。你应该会看到类似下面屏幕截图的结果:
|
||||
|
||||
![][10]
|
||||
|
||||
### Upgrading the Image
|
||||
### 更新镜像
|
||||
|
||||
First, make a copy of the current image:
|
||||
首先,复制出一个当前镜像的副本:
|
||||
|
||||
```
|
||||
# cp -a /fc28 /fc29
|
||||
```
|
||||
|
||||
Chroot into the new copy of the image:
|
||||
Chroot 进入到镜像的新副本:
|
||||
|
||||
```
|
||||
# for i in dev dev/pts dev/shm proc sys run; do mount -o bind /$i /fc29/$i; done
|
||||
# chroot /fc29 /usr/bin/bash --login
|
||||
```
|
||||
|
||||
Allow updating the kernel:
|
||||
允许更新内核:
|
||||
|
||||
```
|
||||
# sed -i 's/^exclude=kernel-\*$/#exclude=kernel-*/' /etc/dnf/dnf.conf
|
||||
```
|
||||
|
||||
Perform the upgrade:
|
||||
执行升级:
|
||||
|
||||
```
|
||||
# dnf distro-sync -y --releasever=29
|
||||
```
|
||||
|
||||
Prevent the kernel from being updated:
|
||||
阻止更新过的内核被再次更新:
|
||||
|
||||
```
|
||||
# sed -i 's/^#exclude=kernel-\*$/exclude=kernel-*/' /etc/dnf/dnf.conf
|
||||
```
|
||||
|
||||
The above command is optional, but saves you from having to copy a new kernel out to the clients if you add or update a few packages in the image at some future time.
|
||||
上述命令是可选的,但是在以后,如果在镜像中添加和更新了几个包,在你的客户端之外保存有一个最新内核的副本,会在关键时刻对你非常有帮助。
|
||||
|
||||
Clean up dnf’s package cache:
|
||||
清理 dnf 的包缓存:
|
||||
|
||||
```
|
||||
# dnf clean all
|
||||
```
|
||||
|
||||
Exit the chroot and clear root’s command history:
|
||||
退出 chroot 并清理 root 的命令历史:
|
||||
|
||||
```
|
||||
# logout
|
||||
@ -375,7 +375,7 @@ Exit the chroot and clear root’s command history:
|
||||
# > /fc29/root/.bash_history
|
||||
```
|
||||
|
||||
Create the iSCSI image:
|
||||
创建 iSCSI 镜像:
|
||||
|
||||
```
|
||||
# FC29_SIZE=$(du -ms /fc29 | cut -f 1)
|
||||
@ -387,7 +387,7 @@ Create the iSCSI image:
|
||||
# umount $TEMP_MNT
|
||||
```
|
||||
|
||||
Define a new iSCSI target that points to our new image and export it:
|
||||
定义一个新的 iSCSI 目标,指向到新的镜像并导出它:
|
||||
|
||||
```
|
||||
# MY_HOSTNAME=$(</etc/hostname)
|
||||
@ -401,7 +401,7 @@ END
|
||||
# tgt-admin --update ALL
|
||||
```
|
||||
|
||||
Add the new kernel and initramfs to the ESP:
|
||||
添加新内核并 initramfs 到 ESP:
|
||||
|
||||
```
|
||||
$ MY_KRNL=$(ls -c /fc29/lib/modules | head -n 1)
|
||||
@ -409,7 +409,7 @@ $ cp $(find /fc29/lib/modules -maxdepth 2 -name 'vmlinuz' | grep -m 1 $MY_KRNL)
|
||||
$ cp $(find /fc29/boot -name 'init*' | grep -m 1 $MY_KRNL) $HOME/esp/linux/initramfs-$MY_KRNL.img
|
||||
```
|
||||
|
||||
Update the boot.cfg in the ESP:
|
||||
更新 ESP 的 boot.cfg:
|
||||
|
||||
```
|
||||
$ MY_DNS1=192.0.2.91
|
||||
@ -426,8 +426,7 @@ boot || exit
|
||||
END
|
||||
```
|
||||
|
||||
Finally, copy the files from your $HOME/esp/linux directory out to the ESPs of all your client systems and enjoy!
|
||||
|
||||
最后,从我的 $HOME/esp/linux 目录中复制文件到所有客户端系统的 ESP 中去使用它吧!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
@ -435,7 +434,7 @@ via: https://fedoramagazine.org/how-to-build-a-netboot-server-part-2/
|
||||
|
||||
作者:[Gregory Bartholomew][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
译者:[qhwdw](https://github.com/qhwdw)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
Loading…
Reference in New Issue
Block a user