mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-02-03 23:40:14 +08:00
20170521-7 选题
This commit is contained in:
parent
e0dc4c758e
commit
cc95c7c651
@ -0,0 +1,91 @@
|
||||
WPSeku – A Vulnerability Scanner to Find Security Issues in WordPress
|
||||
============================================================
|
||||
|
||||
by [Aaron Kili][9] | Published: May 5, 2017 | Last Updated: May 5, 2017
|
||||
|
||||
Download Your Free eBooks NOW - [10 Free Linux eBooks for Administrators][10] | [4 Free Shell Scripting eBooks][11]
|
||||
|
||||
WordPress is a free and open-source, highly customizable content management system (CMS) that is being used by millions around the world to run blogs and fully functional websites. Because it is the most used CMS out there, there are so many potential WordPress security issues/vulnerabilities to be concerned about.
|
||||
|
||||
However, these security issues can be dealt with, if we follow common WordPress security best practices. In this article, we will show you how to use WPSeku, a WordPress vulnerability scanner in Linux, that can be used to find security holes in your WordPress installation and block potential threats.
|
||||
|
||||
WPSeku is a simple WordPress vulnerability scanner written using Python, it can be used to scan local and remote WordPress installations to find security issues.
|
||||
|
||||
### How to Install WPSeku – WordPress Vulnerability Scanner in Linux
|
||||
|
||||
To install WPSeku in Linux, you need to clone the most recent version of WPSeku from its Github repository as shown.
|
||||
|
||||
```
|
||||
$ cd ~
|
||||
$ git clone https://github.com/m4ll0k/WPSeku
|
||||
```
|
||||
|
||||
Once you have obtained it, move into the WPSeku directory and run it as follows.
|
||||
|
||||
```
|
||||
$ cd WPSeku
|
||||
```
|
||||
|
||||
Now run the WPSeku using the `-u` option to specify your WordPress installation URL like this.
|
||||
|
||||
```
|
||||
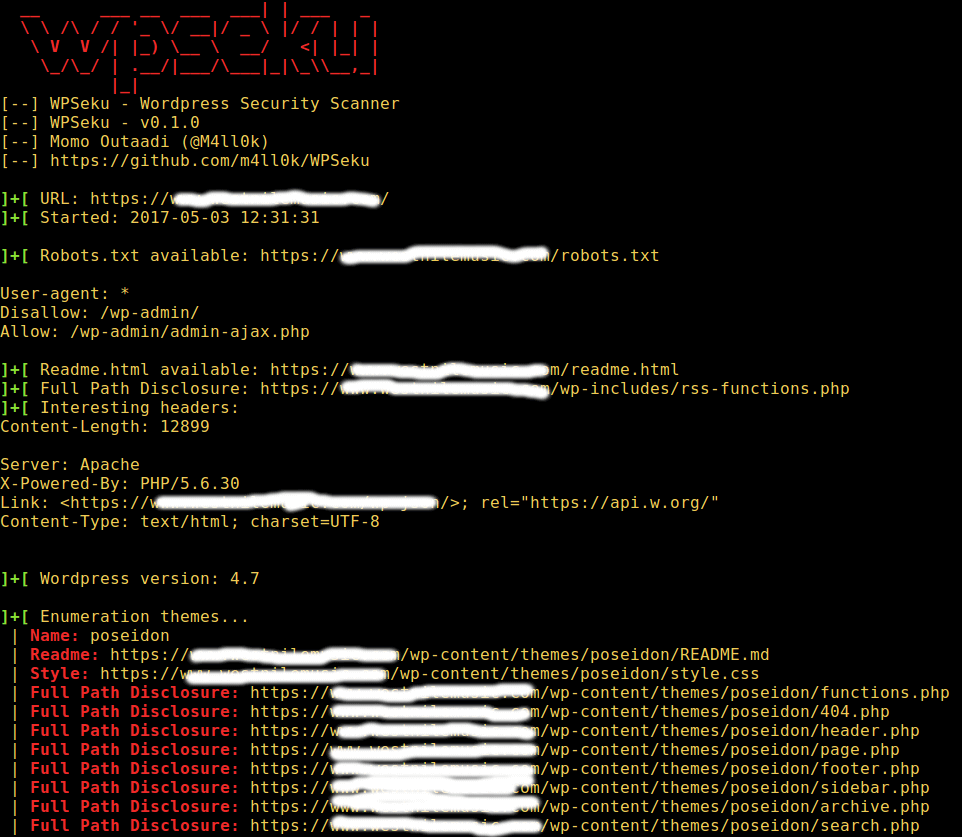
$ ./wpseku.py -u http://yourdomain.com
|
||||
```
|
||||
[][1]
|
||||
|
||||
WordPress Vulnerability Scanner
|
||||
|
||||
The command below will search for cross site scripting, local file inclusion, and SQL injection vulnerabilities in your WordPress plugins using the `-p` option, you need to specify the location of plugins in the URL:
|
||||
|
||||
```
|
||||
$ ./wpseku.py -u http://yourdomain.com/wp-content/plugins/wp/wp.php?id= -p [x,l,s]
|
||||
```
|
||||
|
||||
The following command will execute a brute force password login and password login via XML-RPC using the option `-b`. Also, you can set a username and wordlist using the `--user` and `--wordlist` options respectively as shown below.
|
||||
|
||||
```
|
||||
$ ./wpseku.py -u http://yourdomian.com --user username --wordlist wordlist.txt -b [l,x]
|
||||
```
|
||||
|
||||
To view all WPSeku usage options, type.
|
||||
|
||||
```
|
||||
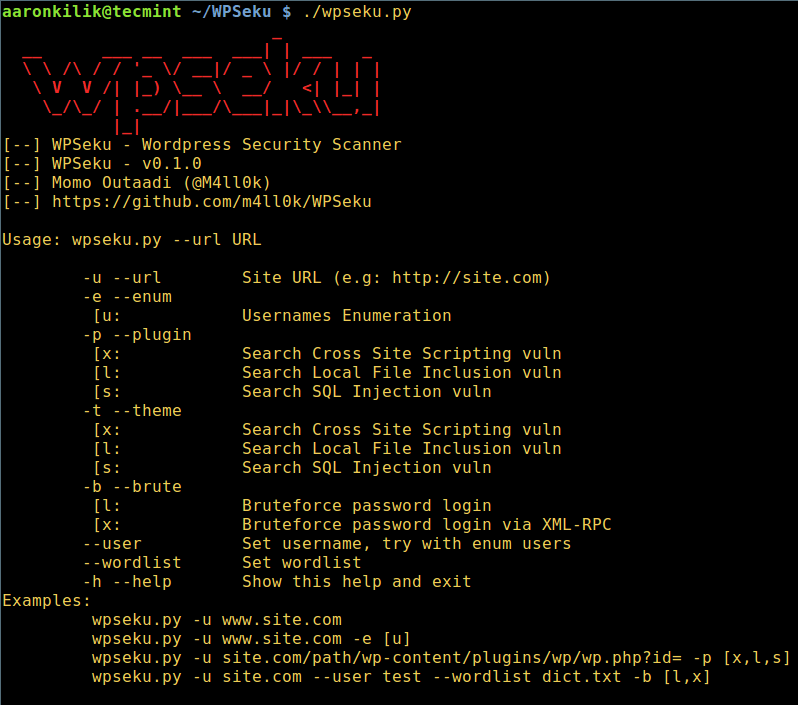
$ ./wpseku.py --help
|
||||
```
|
||||
[][2]
|
||||
|
||||
WPSeku WordPress Vulnerability Scanner Help
|
||||
|
||||
WPSeku Github repository: [https://github.com/m4ll0k/WPSeku][3]
|
||||
|
||||
That’s it! In this article, we showed you how to get and use WPSeku for WordPress vulnerability scanning in Linux. WordPress is secure but only if we follow WordPress security best practices. Do you have any thoughts to share? If yes, then use the comment section below.
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
作者简介:
|
||||
|
||||
Aaron Kili is a Linux and F.O.S.S enthusiast, an upcoming Linux SysAdmin, web developer, and currently a content creator for TecMint who loves working with computers and strongly believes in sharing knowledge.
|
||||
|
||||
------------------
|
||||
|
||||
via: https://www.tecmint.com/wpseku-wordpress-vulnerability-security-scanner/
|
||||
|
||||
作者:[Aaron Kili ][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://www.tecmint.com/author/aaronkili/
|
||||
[1]:https://www.tecmint.com/wp-content/uploads/2017/05/WordPress-Vulnerability-Scanner.png
|
||||
[2]:https://www.tecmint.com/wp-content/uploads/2017/05/WPSeku-WordPress-Vulnerability-Scanner-Help.png
|
||||
[3]:https://github.com/m4ll0k/WPSeku
|
||||
[4]:https://www.tecmint.com/wpseku-wordpress-vulnerability-security-scanner/#
|
||||
[5]:https://www.tecmint.com/wpseku-wordpress-vulnerability-security-scanner/#
|
||||
[6]:https://www.tecmint.com/wpseku-wordpress-vulnerability-security-scanner/#
|
||||
[7]:https://www.tecmint.com/wpseku-wordpress-vulnerability-security-scanner/#
|
||||
[8]:https://www.tecmint.com/wpseku-wordpress-vulnerability-security-scanner/#comments
|
||||
[9]:https://www.tecmint.com/author/aaronkili/
|
||||
[10]:https://www.tecmint.com/10-useful-free-linux-ebooks-for-newbies-and-administrators/
|
||||
[11]:https://www.tecmint.com/free-linux-shell-scripting-books/
|
||||
Loading…
Reference in New Issue
Block a user