mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-02-03 23:40:14 +08:00
翻译完成,放到 translated
This commit is contained in:
parent
243529de97
commit
c0a8fa7b54
@ -1,19 +1,14 @@
|
||||
More than 11 Million HTTPS Websites Imperiled by New Decryption Attack
|
||||
|
||||
超过一千万个使用 https 的站点有可能收到新型的加密攻击的影响
|
||||
===========================================================================
|
||||
|
||||
|
||||
|
||||
Low-cost DROWN attack decrypts data in hours, works against TLS e-mail servers, too.
|
||||
|
||||
低成本的淹没攻击会在几个小时内完成解密操作,同时这也不利于采用了 TLS 的邮件服务器。
|
||||
|
||||
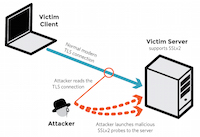
More than 11 million websites and e-mail services protected by the [transport layer security protocol[[1] are vulnerable to a newly discovered, low-cost attack that decrypts sensitive communications in a matter of hours and in some cases almost immediately, an international team of researchers warned Tuesday. More than 81,000 of the top 1 million most popular Web properties are among the vulnerable HTTPS-protected sites.
|
||||
|
||||
一个国际研究小组在周二发出的警告说,超过 1100 万的网站和邮件服务采用了[传输层安全协议][1],以此来保护自己的服务,而这些都是处于一个新发现的、低成本的攻击的威胁之下,这种攻击会在几个小时内解密敏感的通信,在某些情况下甚至是立即解密。 1 百万个最流行的网站中有超过 81,000 个就处于这些受到威胁的 HTTPS 协议保护之下。
|
||||
|
||||
The attack works against TLS-protected communications that rely on the [RSA cryptosystem][2] when the key is exposed even indirectly through SSLv2, a TLS precursor that was retired almost two decades ago because of crippling weaknesses. The vulnerability allows an attacker to decrypt an intercepted TLS connection by repeatedly using SSLv2 to make connections to a server.
|
||||
|
||||
处于 TLS 保护的通信协议,依赖于 [RSA 加密系统][2],如果密钥被泄露了,即使是间接的通过 SSLv2 ——一种在 20 年前就因为自身缺陷而退休了的安全协议,也就是 TLS 的前辈协议——泄露也会处于这种新型攻击的威胁之下。这种危险性在于允许一个入侵者通过反复的使用 SSLv2 来连接到服务器,可以解密一个被中途拦截下来的 TLS 连接。
|
||||
|
||||
Loading…
Reference in New Issue
Block a user