mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-02-03 23:40:14 +08:00
commit
b75ec3288b
@ -1,33 +1,33 @@
|
||||
中心化存储(iSCSI)- “初始器客户端” 在RHEL/CentOS/Fedora上的设置 - 第三部分
|
||||
================================================================================
|
||||
**iSCSI** 初始化器是一种用于与iSCSI target服务器认证并访问服务器上共享的的LUN的客户端。我们可以在本地挂载的硬盘上部署任何操作系统,只需要安装一个包来与target服务器验证。
|
||||
设置iSCSI的发起程序(客户端)(三)
|
||||
============================
|
||||
|
||||
**iSCSI** 发起程序是一种用于同 iSCSI 目标器认证并访问服务器上共享的LUN的客户端。我们可以在本地挂载的硬盘上部署任何操作系统,只需要安装一个包来与目标器验证。
|
||||
|
||||

|
||||
|
||||
初始器客户端设置
|
||||
*初始器客户端设置*
|
||||
|
||||
#### 功能 ####
|
||||
### 功能 ###
|
||||
|
||||
- 可以处理本地挂载磁盘上的任意文件系统
|
||||
- 在使用fdisk命令后不需要重启系统
|
||||
- 在使用fdisk命令分区后不需要重启系统
|
||||
|
||||
#### 要求 ####
|
||||
### 前置阅读 ###
|
||||
|
||||
- [使用iSCSI Target创建集中化安全存储- 第一部分][1]
|
||||
- [在Target服务器中使用LVM创建LUN - 第二部分][2]
|
||||
- [使用iSCSI Target创建集中式安全存储(一)][1]
|
||||
- [在 iSCSI Target 服务器中使用LVM创建和设置LUN(二)][2]
|
||||
|
||||
#### 我的客户端设置 ####
|
||||
|
||||
- 操作系统 – CentOS release 6.5 (最终版)
|
||||
- iSCSI Target IP – 192.168.0.50
|
||||
- 操作系统 – CentOS 6.5 (Final)
|
||||
- iSCSI 目标器 IP – 192.168.0.50
|
||||
- 使用的端口 : TCP 3260
|
||||
|
||||
**Warning**: Never stop the service while LUNs Mounted in Client machines (Initiator).
|
||||
**Warning**:永远不要在使用LUN的时候在客户端中(初始化器)停止服务。
|
||||
**警告**:永远不要在LUN还挂载在客户端(发起程序)时停止服务。
|
||||
|
||||
### 客户端设置 ###
|
||||
|
||||
**1.** 在客户端,我们需要安装包‘**iSCSI-initiator-utils**‘,用下面的命令搜索包。
|
||||
**1.** 在客户端,我们需要安装包‘**iSCSI-initiator-utils**’,用下面的命令搜索包。
|
||||
|
||||
# yum search iscsi
|
||||
|
||||
@ -37,29 +37,29 @@
|
||||
iscsi-initiator-utils.x86_64 : iSCSI daemon and utility programs
|
||||
iscsi-initiator-utils-devel.x86_64 : Development files for iscsi-initiator-utils
|
||||
|
||||
**2.** 一旦定位了包,就用下面的yum命令安装初始化包。
|
||||
**2.** 找到了包,就用下面的yum命令安装初始化包。
|
||||
|
||||
# yum install iscsi-initiator-utils.x86_64
|
||||
|
||||
**3.** 安装完毕后,我们需要发现**Target 服务器**上的共享。客户端的命令有点难记,因此我们使用man来的到需要运行的命令列表
|
||||
**3.** 安装完毕后,我们需要发现**目标器**上的共享。客户端的命令有点难记,因此我们使用man找到需要运行的命令列表。
|
||||
|
||||
# man iscsiadm
|
||||
|
||||

|
||||
|
||||
man iscsiadm
|
||||
*man iscsiadm*
|
||||
|
||||
**4.** 按下**SHIFT+G** 进入man页的底部并且稍微向上滚动来的到登录的示例命令。下面的发现命令中,需要用我们的**服务器IP地址**来替换。
|
||||
**4.** 按下**SHIFT+G** 进入man页的底部并且稍微向上滚动找到示例的登录命令。下面的发现命令中,需要用我们的**服务器IP地址**来替换。
|
||||
|
||||
# iscsiadm --mode discoverydb --type sendtargets --portal 192.168.0.200 --discover
|
||||
|
||||
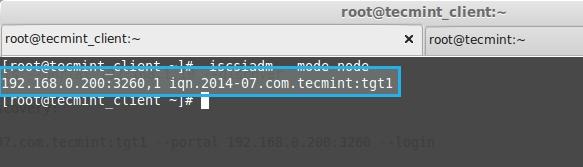
**5.** 这里我们从下面的命令中得到了iSCSIi限定名(iqn)。
|
||||
**5.** 这里我们从下面的命令输出中找到了iSCSI的限定名(iqn)。
|
||||
|
||||
192.168.0.200:3260,1 iqn.2014-07.com.tecmint:tgt1
|
||||
|
||||

|
||||
|
||||
发现服务器
|
||||
*发现服务器*
|
||||
|
||||
**6.** 要登录就用下面的命令来连接一台LUN到我们本地系统中,这会与服务器验证并允许我们登录LUN。
|
||||
|
||||
@ -67,7 +67,7 @@ man iscsiadm
|
||||
|
||||

|
||||
|
||||
登录到服务器
|
||||
*登录到服务器*
|
||||
|
||||
**注意**:登出使用登录命令并在命令的最后使用logout来替换。
|
||||
|
||||
@ -75,15 +75,15 @@ man iscsiadm
|
||||
|
||||

|
||||
|
||||
等出服务器
|
||||
*登出服务器*
|
||||
|
||||
**7.** 登录服务器后,使用下面的命令列出节点的记录。
|
||||
**7.** 登录服务器后,使用下面的命令列出节点的记录行。
|
||||
|
||||
# iscsiadm --mode node
|
||||
|
||||
|
||||
|
||||
列出节点
|
||||
*列出节点*
|
||||
|
||||
**8.** 显示特定节点的所有数据
|
||||
|
||||
@ -109,7 +109,7 @@ man iscsiadm
|
||||
iface.linklocal_autocfg = <empty>
|
||||
....
|
||||
|
||||
**9.** 接着列出使用的磁盘,fdisk会列出所有的认证过的磁盘。
|
||||
**9.** 接着列出使用的磁盘,fdisk会列出所有的登录认证过的磁盘。
|
||||
|
||||
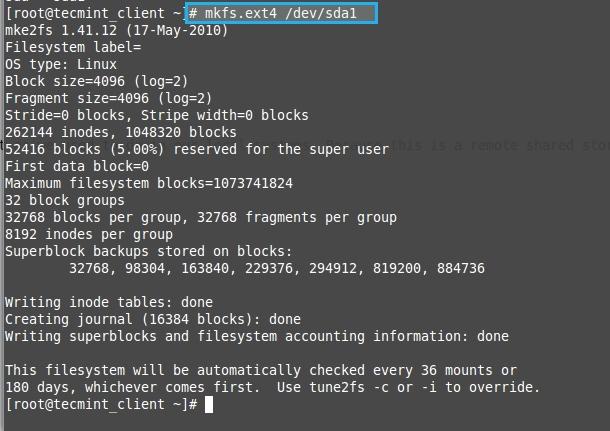
# fdisk -l /dev/sda
|
||||
|
||||
@ -123,7 +123,7 @@ man iscsiadm
|
||||
|
||||

|
||||
|
||||
创建新分区
|
||||
*创建新分区*
|
||||
|
||||
**注意**:在使用fdisk创建新分区之后,我们无需重启,就像使用我们本地的文件系统一样就行。因为这个将远程共享存储挂载到本地了。
|
||||
|
||||
@ -133,7 +133,7 @@ man iscsiadm
|
||||
|
||||
|
||||
|
||||
格式化新分区
|
||||
*格式化新分区*
|
||||
|
||||
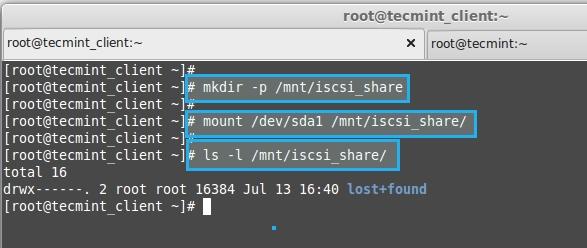
**12.** 创建一个目录来挂载新创建的分区
|
||||
|
||||
@ -143,20 +143,20 @@ man iscsiadm
|
||||
|
||||
|
||||
|
||||
挂载新分区
|
||||
*挂载新分区*
|
||||
|
||||
**13.** 列出挂载点
|
||||
|
||||
# df -Th
|
||||
|
||||
- **-T** – Prints files system types.
|
||||
- **-h** – Prints in human readable format eg : Megabyte or Gigabyte.
|
||||
- **-T** – 输出文件系统类型
|
||||
- **-h** – 以易读的方式显示大小
|
||||
|
||||

|
||||
|
||||
列出新分区
|
||||
*列出新分区*
|
||||
|
||||
**14.** 如果需要永久挂在使用fdtab文件
|
||||
**14.** 如果需要永久挂载,使用fdtab文件
|
||||
|
||||
# vim /etc/fstab
|
||||
|
||||
@ -168,18 +168,18 @@ man iscsiadm
|
||||
|
||||

|
||||
|
||||
自动挂载分区
|
||||
*自动挂载分区*
|
||||
|
||||
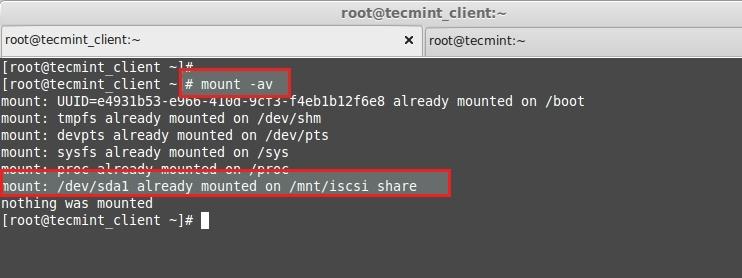
**16.** 最后检查我们fstab文件是否有错误。
|
||||
|
||||
# mount -av
|
||||
|
||||
- **-a** – 所有挂载点
|
||||
- **-v** – 繁琐模式
|
||||
- **-v** – 冗余模式
|
||||
|
||||
|
||||
|
||||
验证fstab文件
|
||||
*验证fstab文件*
|
||||
|
||||
我们已经成功完成了我们的客户端配置。现在让我们像本地磁盘一样使用它吧。
|
||||
|
||||
@ -189,10 +189,10 @@ via: http://www.tecmint.com/iscsi-initiator-client-setup/
|
||||
|
||||
作者:[Babin Lonston][a]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.tecmint.com/author/babinlonston/
|
||||
[1]:http://www.tecmint.com/create-centralized-secure-storage-using-iscsi-targetin-linux/
|
||||
[2]:http://www.tecmint.com/create-luns-using-lvm-in-iscsi-target/
|
||||
[1]:http://linux.cn/article-4971-1.html
|
||||
[2]:http://linux.cn/article-4972-1.html
|
||||
@ -1,46 +1,47 @@
|
||||
在RHEL/CentOS/Fedora上使用iSCSI Target创建集中式安全存储 - 第一部分
|
||||
使用iSCSI Target创建集中式安全存储(一)
|
||||
================================================================================
|
||||
**iSCSI** 是一种就块级别协议,用于通过TCP/IP网络共享**原始存储设备**,可以用已经存在的IP和以太网如网卡、交换机、路由器等通过iSCSI协议共享和访问存储。iSCSI target是一种远程iSCSI服务器或者taget上的远程硬盘。
|
||||
**iSCSI** 是一种块级别的协议,用于通过TCP/IP网络共享**原始存储设备**,可以用已经存在的IP和以太网如网卡、交换机、路由器等通过iSCSI协议共享和访问存储。iSCSI target是一种由远程iSCSI服务器(target)提供的远程硬盘。
|
||||
|
||||
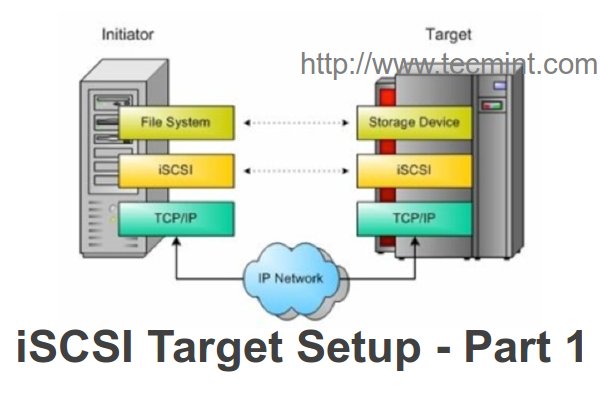
|
||||
在Linux中安装iSCSI Target
|
||||
|
||||
我们不需要在客户端为了稳定的连接和性能而占用很大的资源。iSCSI服务器称为Target,它共享存储。iSCSI客户端称为Initiator,它访问Target服务器行的存储。市场中有用于大型存储服务如SAN的iSCSI适配器。
|
||||
*在Linux中安装iSCSI Target*
|
||||
|
||||
我们不需要占用很大的资源就可以为客户端提供稳定的连接和性能。iSCSI服务器称为“Target(目标器)”,它提供服务器上的存储共享。iSCSI客户端称为“Initiator(发起程序)”,它访问目标器共享的存储。市场中有卖的用于大型存储服务如SAN的iSCSI适配器。
|
||||
|
||||
**我们为什么要在大型存储领域中使用iSCSI适配器**
|
||||
|
||||
以太网适配器(NIC)被设计用于在系统、服务器和存储设备如NAS间传输分组数据,它不适合在Internet中传输块级别数据。
|
||||
以太网适配器(NIC)被设计用于在系统、服务器和存储设备如NAS间传输分组数据,它不适合在Internet中传输块级数据。
|
||||
|
||||
### iSCSI Target的功能 ###
|
||||
|
||||
- 可以在一台机器上运行几个iSCSI target
|
||||
- 一台机器的多个iSCSI target可以在iSCSI中访问
|
||||
- 一个target就是一块存储,并且可以通过网络被初始化器(客户端)访问
|
||||
- 可以在一台机器上运行几个iSCSI 目标器
|
||||
- 一台机器可以提供多个iSCSI 目标器用于iSCSI SAN访问
|
||||
- 一个目标器就是一块存储,并且可以通过网络被发起程序(客户端)访问
|
||||
- 把这些存储汇聚在一起让它们在网络中可以访问的是iSCSI LUN(逻辑单元号)
|
||||
- iSCSI支持在同一个会话中含有多个连接
|
||||
- iSCSI初始化器在网络中发现目标接着用LUN验证并登录,这样就可以本地访问远程存储。
|
||||
- 我们了一在本地挂载的LUN上安装任何操作系统,就像我们安装我们本地的操作系统一样。
|
||||
- iSCSI支持在同一个会话中使用多个连接
|
||||
- iSCSI发起程序在网络中发现目标接着用LUN验证并登录,这样就可以本地访问远程存储。
|
||||
- 我们可以在本地挂载的LUN上安装任何操作系统,就像我们安装我们本地的操作系统一样。
|
||||
|
||||
### 为什么需要iSCSI? ###
|
||||
|
||||
在虚拟化中,我们需要存储拥有高度的冗余性、稳定性,iSCSI以低成本的方式提供了这些特性。与使用光纤通道的SAN比起来,我们可以使用已经存在的设备比如NIC、以太网交换机等建造一个低成本的SAN。
|
||||
|
||||
现在我开始使用iSCSI Target安装并配置安全存储。本篇中,我们遵循下面的步骤
|
||||
现在我开始使用iSCSI 目标器安装并配置安全存储。本篇中,我们遵循下面的步骤:
|
||||
|
||||
- 我们需要隔离一个系统来设置iSCSI Target服务器和初始化器(客户端)。
|
||||
- 可以在大型存储环境中添加多个硬盘,但是我们除了基本的安装盘之外只使用一个额外的驱动器。
|
||||
- 现在我们只使用2块硬盘,一个用于基本的服务器安装,另外一个用于存储(LUN),这个我们会在这个系列的第二篇描述。
|
||||
- 我们需要隔离一个系统来设置iSCSI Target服务器和发起程序(客户端)。
|
||||
- 在大型存储环境中可以添加多个硬盘,但是这里我们除了基本的安装盘之外只使用了一个额外的驱动器。
|
||||
- 这里我们只使用了2块硬盘,一个用于基本的服务器安装,另外一个用于存储(LUN),这个我们会在这个系列的第二篇描述。
|
||||
|
||||
#### 主服务器设置 ####
|
||||
|
||||
- 操作系统 – CentOS release 6.5 (最终版)
|
||||
- iSCSI Target IP – 192.168.0.200
|
||||
- 操作系统 – CentOS 6.5 (Final)
|
||||
- iSCSI 目标器 IP – 192.168.0.200
|
||||
- 使用的端口 : TCP 860, 3260
|
||||
- 配置文件 : /etc/tgt/targets.conf
|
||||
|
||||
## 安装 iSCSI Target ##
|
||||
### 安装 iSCSI Target ###
|
||||
|
||||
打开终端并使用yum命令来搜索我们需要在iscsi target上安装的包名。
|
||||
打开终端并使用yum命令来搜索需要在iscsi 目标器上安装的包名。
|
||||
|
||||
# yum search iscsi
|
||||
|
||||
@ -52,21 +53,21 @@
|
||||
lsscsi.x86_64 : List SCSI devices (or hosts) and associated information
|
||||
scsi-target-utils.x86_64 : The SCSI target daemon and utility programs
|
||||
|
||||
We got the search result as above, choose the **Target** package and install to play around.
|
||||
你会的到上面的那些结果,选择**Target**包来安装
|
||||
你会的到上面的那些结果,选择**Target**包来安装。
|
||||
|
||||
# yum install scsi-target-utils -y
|
||||
|
||||

|
||||
安装iSCSI工具
|
||||
|
||||
列出安装的包来了解默认的配置、服务和man页面的位置
|
||||
*安装iSCSI工具*
|
||||
|
||||
列出安装的包里面的内容来了解默认的配置、服务和man页面的位置。
|
||||
|
||||
# rpm -ql scsi-target-utils.x86_64
|
||||
|
||||

|
||||
|
||||
列出所有的iSCSI文件
|
||||
*列出所有的iSCSI包里面的文件*
|
||||
|
||||
让我们启动iSCSI服务,并检查服务运行的状态,iSCSI的服务名是**tgtd**。
|
||||
|
||||
@ -75,7 +76,7 @@ We got the search result as above, choose the **Target** package and install to
|
||||
|
||||

|
||||
|
||||
启动iSCSI服务
|
||||
*启动iSCSI服务*
|
||||
|
||||
现在我们需要配置开机自动启动。
|
||||
|
||||
@ -87,53 +88,53 @@ We got the search result as above, choose the **Target** package and install to
|
||||
|
||||

|
||||
|
||||
开机启动iSCSI
|
||||
*开机启动iSCSI*
|
||||
|
||||
现在使用**tgtadm**来列出在我们的服务器上已经配置了哪些target和LUN。
|
||||
现在使用**tgtadm**来列出在我们的服务器上已经配置了哪些目标器和LUN。
|
||||
|
||||
# tgtadm --mode target --op show
|
||||
|
||||
**tgtd**已经安装并在运行了,但是上面的命令没有**输出**因为我们还没有在Target服务器上定义LUN。要查看手册,运行‘**man**‘命令。
|
||||
**tgtd**已经安装并在运行了,但是上面的命令没有**输出**因为我们还没有在目标器上定义LUN。要查看手册,可以运行‘**man**‘命令。
|
||||
|
||||
# man tgtadm
|
||||
|
||||

|
||||
|
||||
iSCSI Man 页面
|
||||
*iSCSI Man 页面*
|
||||
|
||||
最终我们需要为iSCSI添加iptable规则,如果你的target服务器上存在iptable的话。首先使用netstat命令找出iscsi target的端口号,target总是监听TCP端口3260。
|
||||
如果你的target服务器上有iptable的话,那么我们需要为iSCSI添加iptable规则。首先使用netstat命令找出iscsi target的端口号,target总是监听TCP端口3260。
|
||||
|
||||
# netstat -tulnp | grep tgtd
|
||||
|
||||

|
||||
|
||||
找出iSCSI端口
|
||||
*找出iSCSI端口*
|
||||
|
||||
下面加入如下规则让iptable允许广播iSCSI target发现包。
|
||||
下面加入如下规则让iptable允许广播iSCSI 目标器发现包。
|
||||
|
||||
# iptables -A INPUT -i eth0 -p tcp --dport 860 -m state --state NEW,ESTABLISHED -j ACCEPT
|
||||
# iptables -A INPUT -i eth0 -p tcp --dport 3260 -m state --state NEW,ESTABLISHED -j ACCEPT
|
||||
|
||||

|
||||
|
||||
打开iSCSI端口
|
||||
*打开iSCSI端口*
|
||||
|
||||

|
||||
|
||||
添加iSCSI端口到iptable中
|
||||
*添加iSCSI端口到iptable中*
|
||||
|
||||
**注意**: 规则可能根据你的 **默认链策略**而不同。接着保存iptable并重启。
|
||||
**注意**: 规则可能根据你的 **默认链策略**而不同。接着保存iptable并重启该服务。
|
||||
|
||||
# iptables-save
|
||||
# /etc/init.d/iptables restart
|
||||
|
||||

|
||||
|
||||
重启iptable
|
||||
*重启iptable*
|
||||
|
||||
现在我们已经部署了一个target服务器来共享LUN给通过TCP/IP认证的初始化器。这也适用于从小到大规模的生产环境。
|
||||
现在我们已经部署了一个目标器来共享LUN给通过TCP/IP认证的发起程序。这也适用于从小到大规模的生产环境。
|
||||
|
||||
在我的下篇文章中,我会展示如何[在Target服务器中使用LVM创建LUN][1],并且如何在客户端中共享LUN,在此之前请继续关注TecMint获取更多的更新,并且不要忘记留下有价值的评论。
|
||||
在我的下篇文章中,我会展示如何[在目标器中使用LVM创建LUN][1],并且如何在客户端中共享LUN,不要忘记留下有价值的评论。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
@ -141,7 +142,7 @@ via: http://www.tecmint.com/create-centralized-secure-storage-using-iscsi-target
|
||||
|
||||
作者:[Babin Lonston][a]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,47 +1,47 @@
|
||||
如何在RHEL/CentOS/Fedora中使用LVM创建和设置LUN- 第二部分
|
||||
在 iSCSI Target 服务器中使用LVM创建和设置LUN(二)
|
||||
================================================================================
|
||||
LUN是逻辑单元号,它与iSCSI存储服务器共享。物理iSCSI target服务器共享它的驱动器来初始化TCP/IP网络。驱动器的集合称作LUN来幸存一个大型存储也就是SAN(Storage Area Network)。在真实环境中LUN在LVM中定义,因此它可以按需扩展。
|
||||
LUN是逻辑单元号,它与iSCSI存储服务器共享。iSCSI 目标器通过TCP/IP网络共享它的物理驱动器给发起程序(initiator)。这些来自一个大型存储(SAN:Storage Area Network)的驱动器集合称作LUN。在真实环境中LUN是在LVM中定义的,因为它可以按需扩展。
|
||||
|
||||

|
||||
Create LUNS using LVM in Target Server
|
||||
|
||||
*在目标器中使用 LVM 创建 LUN*
|
||||
|
||||
### 为什么使用LUN? ###
|
||||
|
||||
LUN用于存储,SAN存储大多数有LUN的集群来组成池,LUN由几块物理驱动器组成。我们可以使用LUN作为系统物理驱动器来安装操作系统,LUN在集群、虚拟服务器、SAN中使用。在虚拟服务器中使用LUN的目的是作为系统存储。LUN的性能和可靠性根据在创建目标存储服务器时所使用的驱动器决定。
|
||||
LUN用于存储,SAN存储大多数由LUN的集群来组成存储池,LUN由目标器的几块物理驱动器组成。我们可以使用LUN作为系统物理驱动器来安装操作系统,LUN可以用在集群、虚拟服务器、SAN中。在虚拟服务器中使用LUN的主要用途是作为操作系统的存储。LUN的性能和可靠性根据在创建目标存储服务器时所使用的驱动器决定。
|
||||
|
||||
### 需求 ###
|
||||
### 前置阅读 ###
|
||||
|
||||
要了解创建iSCSI target服务器点击下面的链接。
|
||||
要了解创建iSCSI 目标器,点击下面的链接。
|
||||
|
||||
- [使用iSCSI target创建爱你集中话安全存储][1]
|
||||
- [使用iSCSI Target创建集中式安全存储(一)][1]
|
||||
|
||||
#### 主服务器设置 ####
|
||||
|
||||
系统信息和网络设置部分与已经写的iSCSI Target服务相同 - 我们在相同的服务器上定义LUN。
|
||||
系统信息和网络设置部分与前文的iSCSI 目标器相同 - 我们在相同的服务器上定义LUN。
|
||||
|
||||
|
||||
- 操作系统 – CentOS release 6.5 (最终版)
|
||||
- iSCSI Target IP – 192.168.0.200
|
||||
- 操作系统 – CentOS 6.5 (Final)
|
||||
- iSCSI 目标器 IP – 192.168.0.200
|
||||
- 使用的端口 : TCP 860, 3260
|
||||
- 配置文件 : /etc/tgt/targets.conf
|
||||
|
||||
## 在iSCSI Target Server使用LVM创建LUN ##
|
||||
### 在iSCSI 目标器使用LVM创建LUN ###
|
||||
|
||||
首先,用**fdisk -l**命令找出驱动器的列表,这会列出系统中所有分区的列表。
|
||||
|
||||
# fdisk -l
|
||||
|
||||
上面的命令只会给出基本系统的驱动器信息。为了个到存储设备的信息,使用下面的命令来的到存储设备的列表。
|
||||
上面的命令只会给出基本系统的驱动器信息。为了得到存储设备的信息,使用下面的命令来得到存储设备的列表。
|
||||
|
||||
# fdisk -l /dev/vda && fdisk -l /dev/sda
|
||||
|
||||
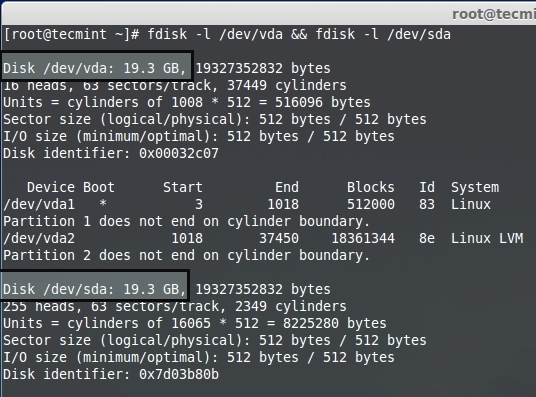
|
||||
|
||||
列出存储设备
|
||||
*列出存储设备*
|
||||
|
||||
**注意**:这里**vda**是虚拟机硬盘,因为我使用的是虚拟机来用于演示,**/dev/sda** 是额外加入的存储。
|
||||
|
||||
### 第一步: 创建用于LUN的LVM ###
|
||||
### 第一步: 创建用于LUN的LVM驱动器 ###
|
||||
|
||||
我们使用**/dev/sda**驱动器来创建LVM。
|
||||
|
||||
@ -49,14 +49,14 @@ LUN用于存储,SAN存储大多数有LUN的集群来组成池,LUN由几块
|
||||
|
||||

|
||||
|
||||
列出LVM驱动器
|
||||
*列出LVM驱动器*
|
||||
|
||||
现在让我们如下使用fdisk命令列出驱动器分区。
|
||||
现在让我们使用如下fdisk命令列出驱动器分区。
|
||||
|
||||
# fdisk -cu /dev/sda
|
||||
|
||||
- The option ‘**-c**‘ 关闭DOS兼容模式。
|
||||
- The option ‘**-u**‘ 用于列出分区表,给出扇区而不是柱面的大小。
|
||||
- 选项 ‘**-c**’ 关闭DOS兼容模式。
|
||||
- 选项 ‘**-u**’ 用于列出分区表时给出扇区而不是柱面的大小。
|
||||
|
||||
使用**n**创建新的分区。
|
||||
|
||||
@ -109,7 +109,7 @@ LUN用于存储,SAN存储大多数有LUN的集群来组成池,LUN由几块
|
||||
|
||||

|
||||
|
||||
创建LVM分区
|
||||
*创建LVM分区*
|
||||
|
||||
系统重启后,使用fdisk命令列出分区表。
|
||||
|
||||
@ -117,7 +117,7 @@ LUN用于存储,SAN存储大多数有LUN的集群来组成池,LUN由几块
|
||||
|
||||

|
||||
|
||||
验证LVM分区
|
||||
*验证LVM分区*
|
||||
|
||||
### 第二步: 为LUN创建逻辑卷 ###
|
||||
|
||||
@ -125,7 +125,7 @@ LUN用于存储,SAN存储大多数有LUN的集群来组成池,LUN由几块
|
||||
|
||||
# pvcreate /dev/sda1
|
||||
|
||||
用iSCSI的名字创建卷组来区分组。
|
||||
用iSCSI的名字创建卷组来区分这个卷组。
|
||||
|
||||
# vgcreate vg_iscsi /dev/sda1
|
||||
|
||||
@ -148,17 +148,17 @@ LUN用于存储,SAN存储大多数有LUN的集群来组成池,LUN由几块
|
||||
|
||||

|
||||
|
||||
创建LVM逻辑卷
|
||||
*创建LVM逻辑卷*
|
||||
|
||||

|
||||
|
||||
验证LVM逻辑卷
|
||||
*验证LVM逻辑卷*
|
||||
|
||||
### 第三步: 在Target Server中定义LUN ###
|
||||
### 第三步: 在目标器中定义LUN ###
|
||||
|
||||
我们已经创建了逻辑卷并准备使用LUN,现在我们在target配置中定义LUN,如果这样那么它只能用在客户机中(启动器)。
|
||||
我们已经创建了逻辑卷并准备使用LUN,现在我们在目标器配置中定义LUN,只有这样做它才能用在客户机中(发起程序)。
|
||||
|
||||
用你选择的编辑器打开位于‘/etc/tgt/targets.conf’的target配置文件。
|
||||
用你选择的编辑器打开位于‘/etc/tgt/targets.conf’的目标器配置文件。
|
||||
|
||||
# vim /etc/tgt/targets.conf
|
||||
|
||||
@ -179,20 +179,22 @@ LUN用于存储,SAN存储大多数有LUN的集群来组成池,LUN由几块
|
||||
|
||||
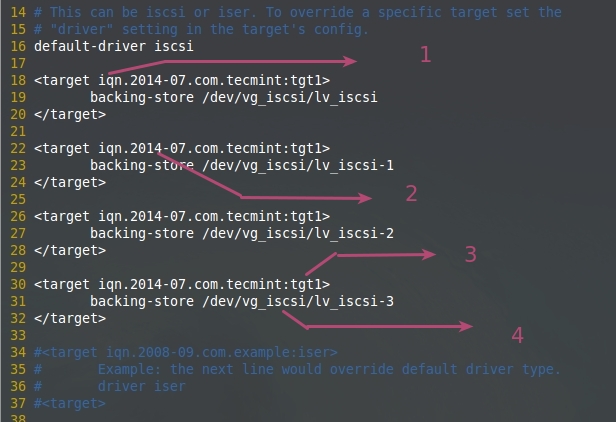
|
||||
|
||||
在target中配置LUN
|
||||
*在target中配置LUN*
|
||||
|
||||
- iSCSI 限定名 (iqn.2014-07.com.tecmint:tgt1).
|
||||
- 随你怎么使用
|
||||
- 确定使用目标, 这台服务器中的第一个目标
|
||||
- 4. LVM共享特定的LUN。
|
||||
上图的解释:
|
||||
|
||||
接下来使用下面命令重载**tgd**服务配置。
|
||||
1. iSCSI 采取限定名 (iqn.2014-07.com.tecmint:tgt1).
|
||||
2. 名称随便你
|
||||
3. 用于确定目标名, 这是这台服务器中的第一个目标
|
||||
4. LVM共享特定的LUN。
|
||||
|
||||
接下来使用下面的命令重载**tgd**服务配置。
|
||||
|
||||
# /etc/init.d/tgtd reload
|
||||
|
||||

|
||||
|
||||
重载配置
|
||||
*重载配置*
|
||||
|
||||
接下来使用下面的命令验证可用的LUN。
|
||||
|
||||
@ -200,23 +202,22 @@ LUN用于存储,SAN存储大多数有LUN的集群来组成池,LUN由几块
|
||||
|
||||

|
||||
|
||||
列出可用LUN
|
||||
*列出可用LUN*
|
||||
|
||||

|
||||
|
||||
LUN信息
|
||||
*LUN信息*
|
||||
|
||||
The above command will give long list of available LUNs with following information.
|
||||
上面的命令会列出可用LUN的下面这些信息
|
||||
|
||||
- iSCSI 限定名
|
||||
- iSCSI 准备使用
|
||||
- 默认LUN 0被控制器保留
|
||||
- LUN 1是我们定义的target服务器
|
||||
- 这里我为每个LUN都定义了4GB
|
||||
- 在线: 是的,这就是可以使用的LUN
|
||||
1. iSCSI 限定名
|
||||
2. iSCSI 已经准备好
|
||||
3. 默认LUN 0被控制器所保留
|
||||
4. LUN 1是我们定义的目标器
|
||||
5. 这里我为每个LUN都定义了4GB
|
||||
6. 在线: 是的,这就是可以使用的LUN
|
||||
|
||||
现在我们已经使用LVM为target服务器定义了LUN,这可扩展并且支持很多特性,如快照。我们将会在第三部分了解如何用target服务器授权,并且本地挂载远程存储。
|
||||
现在我们已经使用LVM为目标器定义了LUN,这可扩展并且支持很多特性,如快照。我们将会在第三部分了解如何用目标器授权,并且本地挂载远程存储。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
@ -224,9 +225,9 @@ via: http://www.tecmint.com/create-luns-using-lvm-in-iscsi-target/
|
||||
|
||||
作者:[Babin Lonston][a]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.tecmint.com/author/babinlonston/
|
||||
[1]:http://www.tecmint.com/create-centralized-secure-storage-using-iscsi-targetin-linux/
|
||||
[1]:http://linux.cn/article-4971-1.html
|
||||
@ -1,11 +1,11 @@
|
||||
|
||||
怎样在废旧的硬件上安装 Xen 虚拟机监视器
|
||||
================================================================================
|
||||
Xen 是一个直接运行在硬件上的虚拟机监视器,这意味着你必须准备一个裸机来安装和运行 Xen。KVM 和 Xen 有一些不同 —— 你可以把它安装在任何已经正在运行 Linux 的机器上。本教程描述了如何在废旧的硬件上安装和配置 Xen 虚拟机监视器。
|
||||
Xen 是一个直接运行在硬件上的虚拟机监视器,这意味着你必须准备一个裸机来安装和运行 Xen。而 KVM 则和 Xen 有一些不同 —— 你可以把它添加到任何已经正在运行 Linux 的机器上。本教程描述了如何在废旧的硬件上安装和配置 Xen 虚拟机监视器。
|
||||
|
||||
整个安装过程使用 Debian Jessie(Debian 的测试发行版)作为宿主机操作系统(也称作 [Dom0][1])。Jessie 并不是唯一的选择 —— Xen 的支持是内建在 Linux 内核中的,[许多 Linux 发行版][2] 都包含支持 Xen 的内核。
|
||||
|
||||
### 找点废旧的硬件 ###
|
||||
|
||||
首先,找一个可以格式化的合适的工作站,比如一台旧的笔记本或者台式机。旧的硬件可能不适合玩游戏,但是足够安装一个宿主机和一些客户机了。一个满足下面这些要求的 PC 机就可以了。
|
||||
|
||||
- 一个双核 CPU(64 位)
|
||||
@ -14,7 +14,7 @@ Xen 是一个直接运行在硬件上的虚拟机监视器,这意味着你必
|
||||
- 能够从 CD,DVD 或者 USB 引导启动
|
||||
- 一块网卡
|
||||
|
||||
注意 CPU 必须是 64 位的,因为 Debian 已经不再支持 32 位的 Xen 安装包。如果你没有空余的硬件,你可以花点钱投资一台旧机器。2010 年值 $1000 的旗舰级笔记本现在只需要 $100。从 eBay 买台二手笔记本并升级下内存也可以满足需求。
|
||||
注意 **CPU 必须是 64 位的,因为 Debian 已经不再支持 32 位的 Xen 安装包**。如果你没有空余的硬件,你可以花点钱买一台旧机器。2010 年值 $1000 的旗舰级笔记本现在只需要 $100。从 eBay 买台二手笔记本并升级下内存也可以满足需求。
|
||||
|
||||
### 刻录一个引导 CD/USB ###
|
||||
|
||||
@ -41,19 +41,19 @@ Xen 是一个直接运行在硬件上的虚拟机监视器,这意味着你必
|
||||
这里的设置使用了四个分区。自动安装时通常会创建一个包含逻辑分区的扩展分区。像下面这样给硬盘分四个区。
|
||||
|
||||
- sda1 挂载至 /boot,200MB
|
||||
- sda2 /, 20GB, Ubuntu 占用 4GB
|
||||
- sda3 swap, 6GB (4GB x 1.5 = 6)
|
||||
- sda2 做为 /, 20GB, Ubuntu 占用 4GB
|
||||
- sda3 做为 swap, 6GB (4GB x 1.5 = 6)
|
||||
- sda4 保留用作 LVM, 不挂载,大小为剩余的硬盘大小
|
||||
|
||||
### 安装基本的系统 ###
|
||||
|
||||
这里尽可能的让系统的安装更简单快速一些。一个基本的工作用系统可以稍后再添加。Debian 的 APT(Advanced Package Tool)使得添加软件非常的简单。在一个工作站上安装 Deibian 可能会有一些很浪费时间的问题。可能显卡驱动与内核不监控或者可能老旧的 CD-ROM 驱动器只能间歇性的工作。
|
||||
这里尽可能的让系统的安装更简单快速一些。一个基本的工作用系统可以稍后再添加。Debian 的 APT(Advanced Package Tool)使得添加软件非常的简单。在机器上安装 Debian 可能会有一些很浪费时间的问题。可能显卡驱动与内核不监控或者可能老旧的 CD-ROM 驱动器只能间歇性的工作。
|
||||
|
||||
当选择安装软件时,选择安装一个 SSH 服务器,不要安装桌面环境如 Gnome。
|
||||
|
||||
|
||||
|
||||
安装一个图形桌面需要安装成百上千的包 —— 这些额外的工作可以稍后再进行。如果你遇到问题了,等到图形桌面的安装会浪费很多事件。同时,没有桌面组件,系统的启动可以更快一些 —— 只需要几十秒而不是几分钟。整个安装过程会需要重启几次,因此这样做可以节省不少时间。
|
||||
安装一个图形桌面需要安装成百上千的包 —— 这些额外的工作可以稍后再进行。如果你遇到问题了,等待图形桌面的安装会浪费很多时间。同时,没有桌面组件,系统的启动可以更快一些 —— 只需要几十秒而不是几分钟。整个安装过程会需要重启几次,因此这样做可以节省不少时间。
|
||||
|
||||
一个 SSH 服务器可以让你从另一台电脑来配置这台工作站。这可以避免一些旧硬件的问题 —— 可能旧机器的键盘少了几个键,LCD 屏幕有坏点或者触摸板没有反应等等。
|
||||
|
||||
@ -79,9 +79,9 @@ Xen 是一个直接运行在硬件上的虚拟机监视器,这意味着你必
|
||||
|
||||
检查 LVM 状态。
|
||||
|
||||
# pvs (to view information about physical volumes)
|
||||
# vgs (to view information about volume groups)
|
||||
# lvs (to view information about logical volumes)
|
||||
# pvs (查看物理卷的信息)
|
||||
# vgs (查看卷组的信息)
|
||||
# lvs (查看逻辑卷的信息)
|
||||
|
||||
### 添加一个 Linux 网桥 ###
|
||||
|
||||
@ -92,7 +92,6 @@ Xen 是一个直接运行在硬件上的虚拟机监视器,这意味着你必
|
||||
# apt-get install bridge-utils
|
||||
|
||||
查看在哪块网卡配置桥接。
|
||||
See what interfaces are configured.
|
||||
|
||||
# ip addr
|
||||
|
||||
@ -156,13 +155,13 @@ See what interfaces are configured.
|
||||
|
||||
|
||||
|
||||
第一个选项会在 5 秒钟内自动启动(在 /etc/default/grub 的 GRUB_TIMEOUT 这行设置),因此这点时间还来不及喝咖啡的。
|
||||
第一个选项会在 5 秒钟内自动启动(在 /etc/default/grub 的 GRUB_TIMEOUT 这行设置),因此这点时间可来不及喝咖啡。
|
||||
|
||||
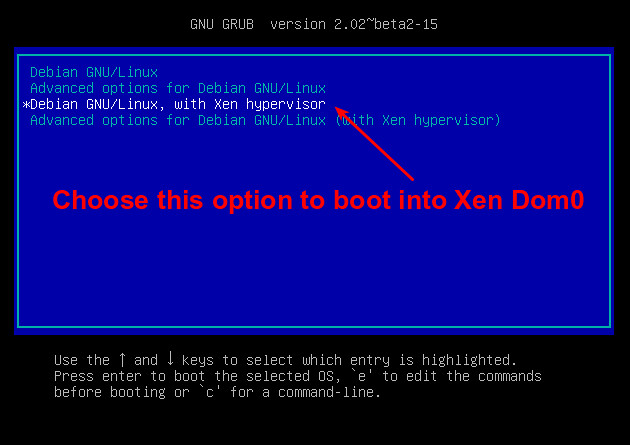
按下方向键选择 "Debian GNU/Linux, with Xen hypervisor" 这个选项,然后按回车。这时屏幕会出现很多行信息,接着是正常的登录界面。
|
||||
|
||||
### 检查 Xen 工作是否正常 ###
|
||||
|
||||
Xen 虚拟机监视器嗲有一个管理 Xen 的命令行工序叫做 xl,可以用来创建和管理 Xen 虚拟机。使用 xl 命令来检查 Xen 是否成功安装了。
|
||||
Xen 虚拟机监视器带有一个管理 Xen 的命令行程序叫做 xl,可以用来创建和管理 Xen 虚拟机。使用 xl 命令来检查 Xen 是否成功安装了。
|
||||
|
||||
以 root 用户登录,执行:
|
||||
|
||||
@ -206,9 +205,11 @@ Xen 虚拟机监视器嗲有一个管理 Xen 的命令行工序叫做 xl,可
|
||||
|
||||
### 最后 ###
|
||||
|
||||
如果你使用这台主机作为你的工作站,可以安装一个图形桌面。Debian 包好几种[桌面环境][6]。如果你想要一个包含所有东西的图形桌面,那么安装 Gnome 吧。如果图形效果并不是你的菜,试试 Awesome 吧。
|
||||
如果你使用这台主机作为你的工作站,可以安装一个图形桌面。Debian 包括好几种[桌面环境][6]。如果你想要一个包含所有东西的图形桌面,那么安装 Gnome 吧。如果它的图形效果并不是你的菜,试试 Awesome 吧。
|
||||
|
||||
注意 Debian 的默认 Gnome 环境有大量的额外应用程序包括办公套件 LibreOffice,Iceweasel 浏览器和 Rhythmbox 音乐播放器。安装命令 "apt-get install gnome" 会安装 1,000 多个包并需要将近 2GB 的硬盘空间。运行这个重量级的桌面环境需要占用 1GB 的内存。
|
||||
注意 Debian 的默认 Gnome 环境有大量的额外应用程序包括办公套件 LibreOffice,Iceweasel 浏览器和 Rhythmbox 音乐播放器。安装命令 "apt-get install gnome" 会安装 1,000 多个包并需要将近 2GB 的硬盘空间。运行这个重量级的桌面环境需要占用 1GB 的内存。
|
||||
|
||||
(LCTT 译注:本文没有涉及如何安装 guest 虚拟机,请关注后继文章)
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
@ -216,7 +217,7 @@ via: http://xmodulo.com/install-xen-hypervisor.html
|
||||
|
||||
作者:[Nick Hardiman][a]
|
||||
译者:[Liao](https://github.com/liaoishere)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,12 +1,12 @@
|
||||
Cutegram: 一个GNU/Linux下更好的Telegram客户端
|
||||
Cutegram: 一个GNU/Linux下不错的Telegram客户端
|
||||
================================================================================
|
||||
不需要再介绍**Telegram**了,对吧。Telegram是一款流行的免费即时通信工具,帮助在全球与你的朋友聊天。不像Whatsapp,Telegram是永久免费、没有广告、没有订阅费用。并且Telegram客户端也是开源的。Telegram在许多不同的平台中都有,包括Linux、Android、iOS、Windows Phone和Mac OS X。使用telegram发送的消失是高度加密且会自我毁灭。它很安全,并且没有对你媒体和聊天的大小作限制。
|
||||
不需要再介绍**Telegram**了,对吧。Telegram是一款流行的免费即时通信工具,帮助你在全球与朋友聊天。不像Whatsapp,Telegram是永久免费、没有广告、没有订阅费用的。并且Telegram客户端也是开源的。Telegram在许多不同的平台中都有,包括Linux、Android、iOS、Windows Phone和Mac OS X。使用telegram发送的消息是高度加密且会自我销毁。它很安全,并且没有对你的多媒体和聊天的大小作限制。
|
||||
|
||||
在[先前的教程][1]中我们已经提到你可以在Ubuntu/Debian中安装Telegram。然而,一个新的Telegram客户端叫**Cutegram**出现了,可以使你的聊天体验更加有趣和简单。
|
||||
在[先前的教程][1]中我们已经提到你可以在Ubuntu/Debian中安装Telegram。然而,有一个新的Telegram客户端叫**Cutegram**出现了,可以使你的聊天体验更加有趣和简单。
|
||||
|
||||
### Cutegram是什么? ###
|
||||
|
||||
Cutegram是一款GNU/Linux中专注于用户友好、与LInux桌面环境兼容和易于使用的开源telegram客户端。Cutegram使用Qt5、QML、libqtelegram、libappindication、AsemanQtTools技术和Faenzatu图标和Twitter emojies图片集。它在GPLv3许可证下免费发布。
|
||||
Cutegram是一款专注于用户友好、与Linux桌面环境兼容和易于使用的开源 telegram 的 GNU/Linux客户端。Cutegram使用Qt5、QML、libqtelegram、libappindication、AsemanQtTools技术和Faenzatu图标和Twitter emojie图片集。它在GPLv3许可证下免费发布。
|
||||
|
||||
### 安装 Cutegram ###
|
||||
|
||||
@ -31,7 +31,7 @@ Cutegram是一款GNU/Linux中专注于用户友好、与LInux桌面环境兼容
|
||||
|
||||
设置执行权限:
|
||||
|
||||
chmod + cutegram-1.0.2-linux*.run
|
||||
chmod a+x cutegram-1.0.2-linux*.run
|
||||
|
||||
如下进行安装。
|
||||
|
||||
@ -41,22 +41,21 @@ Cutegram是一款GNU/Linux中专注于用户友好、与LInux桌面环境兼容
|
||||
|
||||
在菜单或者Unity dash中启动Cutegram。在登录界面,选择你的国家并输入电话号码,最好点击**Login**
|
||||
|
||||

|
||||

|
||||
|
||||
A code will be sent to your mobile number. Enter the code and click **Sign in**.
|
||||
一个验证码将会发送到你手机上。输入验证码病点击****
|
||||
一个验证码将会发送到你手机上。输入验证码并点击**Sign in**
|
||||
|
||||

|
||||

|
||||
|
||||
你会看到
|
||||
|
||||

|
||||

|
||||
|
||||
开始聊天吧!
|
||||
|
||||

|
||||

|
||||
|
||||
接着,你可以设置头像,开始新的聊天/群聊,或者使用左边面板的按钮开始秘密聊天。
|
||||
接着,你可以设置头像,开始新的聊天/群聊,或者使用左边面板的按钮开始秘密聊天。
|
||||
|
||||
玩得开心!干杯!!
|
||||
|
||||
@ -68,7 +67,7 @@ via: http://www.unixmen.com/cutegram-better-telegram-client-gnulinux/
|
||||
|
||||
作者:[SK][a]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,156 +0,0 @@
|
||||
Translating by FSSlc
|
||||
|
||||
11 Useful Utilities To Supercharge Your Ubuntu Experience
|
||||
================================================================================
|
||||
**Whether you’re a relative novice or a seasoned pro, we all want to get the most from our operating system. Ubuntu, like most modern OSes, has more to offer than what is presented at first blush.**
|
||||
|
||||
From tweaking and refining the look, behaviour and performance of the Unity desktop to performing system maintenance, there are a huge array of useful utilities and apps that can help **tune Ubuntu to meet your needs in no time**.
|
||||
|
||||
Caveat time: Ubuntu has always shipped with ‘sane defaults’ — options that just work — out of the box. These defaults are well suited for the majority of people. They’re tested, accepted and recommended.
|
||||
|
||||
But one size doesn’t fit all. For the tinkerers and experimenters among us the default experience is a starting point from which to tailor.
|
||||
|
||||
So, without any more waffle, here is a set of 11 nifty utilities to help you supercharge your Ubuntu experience.
|
||||
|
||||
### Unity Tweak Tool ###
|
||||
|
||||

|
||||
|
||||
I’ll kick off this list with the big one: **Unity Tweak** Tool. The kitchen sink of customisation, Unity Tweak Tool offers a comprehensive set of system tweaks tuned for Ubuntu and the Unity desktop.
|
||||
|
||||
It’s stuffed full of switches, toggles and control, letting you configure everything from the way Unity looks to the way it behaves. Use it to **quickly and easily change the GTK theme and icon set**, set up hot corners, adjust launcher size, add or remove workspaces, and — notably — enable Unity’s elusive ‘minimise on click’ feature.
|
||||
|
||||
Free and readily available from the Software Center, Unity Tweak Tool is one well worth keeping in your back pocket.
|
||||
|
||||
### Unity Privacy Indicator ###
|
||||
|
||||

|
||||
|
||||
Privacy. A big, big issue and rightly so. But the topic is often shaded rather than binary; you may be happy to let some data or habits, say apps you frequently open, be logged locally, but not be ok with the searches you make in the Dash being ferried to a third-party server (however anonymous that data may be).
|
||||
|
||||
[Privacy Indicator][1] is a useful tool to help you stay abreast of what files, folders and services are being accessed, logged and recce’d on the Ubuntu desktop.
|
||||
|
||||
With a quick click on the ‘eye’ icon added to the desktop panel you can:
|
||||
|
||||
- Toggle Online Search Results, Zeitgeist, HUD Logging & GeoIP
|
||||
- Quick access to clean Zeitgeist, F2, Recent Files, etc.
|
||||
- Options to show/hide desktop icons and name in the panel
|
||||
|
||||
The latter two options may seem a little misplaced in this app but have less obvious privacy implications for those who take screenshots or screen share.
|
||||
|
||||
- [Download Indicator Privacy (.deb)][2]
|
||||
|
||||
### Unity Folders ###
|
||||
|
||||
|
||||
|
||||
**Android, iOS, OS X, Chrome OS, and GNOME Shell have app folders, and so can Unity with a nifty third-party app. **
|
||||
|
||||
“Unity Folders” allows you to organise apps on the Unity Launcher into handy folders — think ‘games’, ‘office’, ‘social‘, etc. You get quick access to your favourite apps without needing to open the Dash, which may suit your workflow.
|
||||
|
||||
Each ‘folder’ is, actually, an application that opens up and positions itself near the origin point. But the overall effect is one that looks like an OS X style stack or an Android folder popover.
|
||||
|
||||
Folder icons can be customised or auto-generated based on the applications tucked up inside. Existing folders can be edited, rearranged, rename and re-other stuff, too.
|
||||
|
||||
- Create as many folders as you like
|
||||
- Choose custom or auto-generated folder icon
|
||||
- 3 folder layouts to choose from
|
||||
- Set custom icons for apps added to folders
|
||||
- Edit existing folders
|
||||
|
||||
- Unity Folders Website
|
||||
|
||||
### Caffeine ###
|
||||
|
||||
A staple for many of us, and not just in our drinks, Caffeine offers a fast, silent way to stop your screensaver or lock-screen kicking in. The degree of usefulness will depend on your circumstances (read: quirks of your system), and though it’s not quite as user friendly as it once was, it’s still worth [checking out][3].
|
||||
|
||||
### System Monitor Indicator ###
|
||||
|
||||

|
||||
|
||||
If you’re a stat hound who likes to keep tabs on apps, processes and hardware status, Linux makes it easy. From Conky Configs to Terminal Commands — there’s no shortage of ways to monitor your CPU usage, network traffic or GPU temperature.
|
||||
|
||||
But by far my favourite is System **Monitor Indicator** – also known as indicator-multiload — available from the Ubuntu Software Center. It has a host of configuration options, too.
|
||||
|
||||
- [Click to Install ‘System Load Indicator’ on Ubuntu][4]
|
||||
|
||||
### Power Saving Tools for Linux Laptops ###
|
||||
|
||||

|
||||
|
||||
**TLP**
|
||||
|
||||
Linux distributions don’t have the best reputation when it comes to power efficiency on portable devices.
|
||||
|
||||
If your own Linux laptop can barely get you from the sofa to the kitchen before needing a recharge, there are some tools you can try.
|
||||
|
||||
TLP is one of the most popular automated background tool promising to prolong battery life of laptops running Linux. It does this by adjusting the settings and behaviour of system processes and hardware, such as enabling Wi-Fi power saving mode, runtime power management of PCI bus devices, and processor frequency scaling.
|
||||
|
||||
It’s available to [install on Ubuntu 14.04 LTS and later using the dedicated TLP PPA][5] and comes with a ‘catch-all’ config to get you started. The more advanced users among you can dive in and manually adjust the settings to suit your own hardware, something that a [thorough guide on the TLP wiki][6] makes easy.
|
||||
|
||||
**Laptop Mode Tools**
|
||||
|
||||
If TLP sounds a little too complex — and there’s no shame if it does — there’s a simpler alternative: **Laptop Mode Tools**. This package is available to install from the Ubuntu Software Center and keeps the tweaks made to a set of sane defaults (Wi-Fi, Bluetooth, etc.).
|
||||
|
||||
Laptop Mode Tools cannot be installed at the same time as TLP.
|
||||
|
||||
- [Laptop Mode Tools in Ubuntu Software Center][7]
|
||||
|
||||
### Intel Graphics Installer ###
|
||||
|
||||
|
||||
|
||||
The Intel Graphics Installer tool is a must-have for those running Intel graphics hardware who want the best performance they can get. It makes finding and installing the latest Intel GPU drivers a painless, fuss-free affair — no PPAs or Terminal kung foo needed.
|
||||
|
||||
- [Download Intel Graphics Installer for Linux 0.7][8]
|
||||
|
||||
### Hardware Stats ###
|
||||
|
||||
|
||||
|
||||
If you plan on upgrading your PC or replacing a worn-out part you’ll need to get some specific hardware details, such as RAM type, CPU socket set or what PCI slots are available.
|
||||
|
||||
**I-Nex** makes unearthing this, and host of other detailed system stats, easy. Use it to find your motherboard model number, RAM stepping, S.M.A.R.T. status and…well, pretty much anything else you can think of!
|
||||
|
||||
- [Learn More About I-Nex on Launchpad][9]
|
||||
|
||||
### Disk Space Visualizer ###
|
||||
|
||||
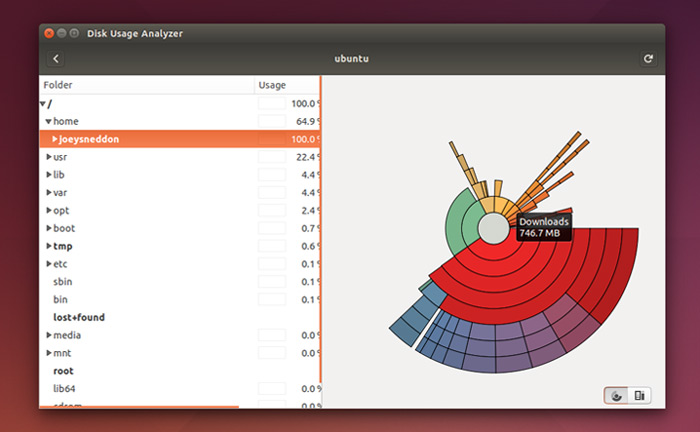
|
||||
|
||||
In this age of 1TB hard drives we might not need to be as prudent with disk space as we once were. But for those of using a smallish SSD, running multiple partitions or working in a virtual machine with a fixed-size virtual disk, there’ll be times when freeing up a bit of extra space is required.
|
||||
|
||||
GNOME Disks, installed in Ubuntu by default, makes finding the biggest space-gobbling culprits easy. Ideal for locating hidden logs, caches, and media files.
|
||||
|
||||
### BleachBit (Cruft Cleaner) ###
|
||||
|
||||
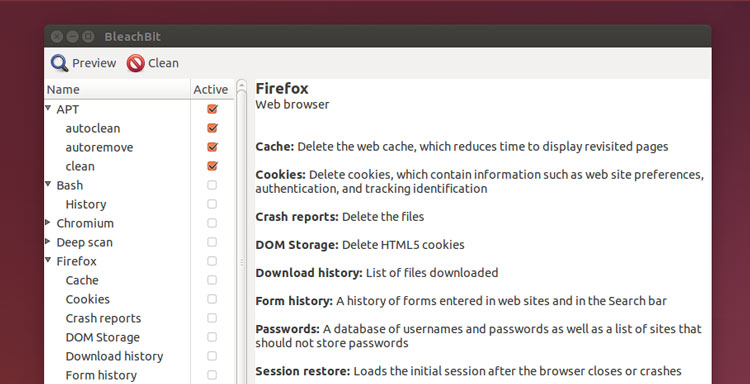
|
||||
|
||||
Windows users will be familiar with applications like CCleaner, which scan for and clean out junk files, empty folders, bloated caches, and obsolete packages. For a a similarly quick and effortless click n’ clean solution on Ubuntu try **BleachBit**.
|
||||
|
||||
It is a powerful tool, so do pay attention to what you’re cleaning. Don’t aimlessly check every box; not everything that it can clean needs to be. Play it smart; when in doubt, leave it out.
|
||||
|
||||
- [Install BleachBit from Ubuntu Software Center][10]
|
||||
|
||||
Got a favourite system utility of your own? Let others know about it in the comments.
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.omgubuntu.co.uk/2014/11/useful-tools-for-ubuntu-do-you-use-them
|
||||
|
||||
作者:[Joey-Elijah Sneddon][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://plus.google.com/117485690627814051450/?rel=author
|
||||
[1]:http://www.florian-diesch.de/software/indicator-privacy/index.html
|
||||
[2]:http://www.florian-diesch.de/software/indicator-privacy/dist/indicator-privacy_0.04-1_all.deb
|
||||
[3]:http://www.omgubuntu.co.uk/2014/05/stop-ubuntu-sleeping-caffeine
|
||||
[4]:apt://indicator-mulitload
|
||||
[5]:https://launchpad.net/~linrunner/+archive/ubuntu/tlp/+packages
|
||||
[6]:http://linrunner.de/en/tlp/docs/tlp-configuration.html
|
||||
[7]:https://apps.ubuntu.com/cat/applications/laptop-mode-tools/
|
||||
[8]:https://01.org/linuxgraphics/downloads/2014/intelr-graphics-installer-linux-1.0.7
|
||||
[9]:https://launchpad.net/i-nex
|
||||
[10]:https://apps.ubuntu.com/cat/applications/bleachbit/
|
||||
@ -1,154 +0,0 @@
|
||||
How to configure a syslog server with rsyslog on Linux
|
||||
================================================================================
|
||||
A syslog server represents a central log monitoring point on a network, to which all kinds of devices including Linux or Windows servers, routers, switches or any other hosts can send their logs over network. By setting up a syslog server, you can filter and consolidate logs from different hosts and devices into a single location, so that you can view and archive important log messages more easily.
|
||||
|
||||
On most Linux distributions, **rsyslog** is the standard syslog daemon that comes pre-installed. Configured in a client/server architecture, **rsyslog** can play both roles; as a syslog server **rsyslog** can gather logs from other devices, and as a syslog client, **rsyslog** can transmit its internal logs to a remote syslog server.
|
||||
|
||||
In this tutorial, we cover how to configure a centralized syslog server using **rsyslog** on Linux. Before we go into the details, it is instructive to go over syslog standard first.
|
||||
|
||||
### Basic of Syslog Standard ###
|
||||
|
||||
When logs are collected with syslog mechanism, three important things must be taken into consideration:
|
||||
|
||||
- **Facility level**: what type of processes to monitor
|
||||
- **Severity (priority) level**: what type of log messages to collect
|
||||
- **Destination**: where to send or record log messages
|
||||
|
||||
Let's take a look at how the configuration is defined in more detail.
|
||||
|
||||
The facility levels define a way to categorize internal system processes. Some of the common standard facilities in Linux are:
|
||||
|
||||
- **auth**: messages related to authentication (login)
|
||||
- **cron**: messages related to scheduled processes or applications
|
||||
- **daemon**: messages related to daemons (internal servers)
|
||||
- **kernel**: messages related to the kernel
|
||||
- **mail**: messages related to internal mail servers
|
||||
- **syslog**: messages related to the syslog daemon itself
|
||||
- **lpr**: messages related to print servers
|
||||
- **local0 - local7**: messages defined by user (local7 is usually used by Cisco and Windows servers)
|
||||
|
||||
The severity (priority) levels are standardized, and defined by using standard abbreviation and an assigned number with number 7 being the highest level of all. These levels are:
|
||||
|
||||
- emerg: Emergency - 0
|
||||
- alert: Alerts - 1
|
||||
- crit: Critical - 2
|
||||
- err: Errors - 3
|
||||
- warn: Warnings - 4
|
||||
- notice: Notification - 5
|
||||
- info: Information - 6
|
||||
- debug: Debugging - 7
|
||||
|
||||
Finally, the destination statement enforces a syslog client to perform one of three following tasks: (1) save log messages on a local file, (2) route them to a remote syslog server over TCP/UDP, or (3) send them to stdout such as a console.
|
||||
|
||||
In rsyslog, syslog configuration is structured based on the following schema.
|
||||
|
||||
[facility-level].[severity-level] [destination]
|
||||
|
||||
### Configure Rsyslog on Linux ###
|
||||
|
||||
Now that we understand syslog, it's time to configure a Linux server as a central syslog server using rsyslog. We will also see how to configure a Windows based system as a syslog client to send internal logs to the syslog server.
|
||||
|
||||
#### Step One: Initial System Requirements ####
|
||||
|
||||
To set up a Linux host as a central log server, we need to create a separate /var partition, and allocate a large enough disk size or create a LVM special volume group. That way, the syslog server will be able to sustain the exponential growth of collected logs over time.
|
||||
|
||||
#### Step Two: Enable Rsyslog Daemon ####
|
||||
|
||||
rsyslog daemon comes pre-installed on modern Linux distributions, but is not enabled by default. To enable rsyslog daemon to receive external messages, edit its configuration file located in /etc/rsyslog.conf.
|
||||
|
||||
Once the file is opened for editing, search and uncomment the below two lines by removing the # sign from the beginning of lines.
|
||||
|
||||
$ModLoad imudp
|
||||
$UDPServerRun 514
|
||||
|
||||
This will enable rsyslog daemon to receive log messages on UDP port 514. UDP is way faster than TCP, but does not provide reliability on data flow the same way as TCP does. If you need to reliable delivery, you can enable TCP by uncommenting the following lines.
|
||||
|
||||
$ModLoad imtcp
|
||||
$InputTCPServerRun 514
|
||||
|
||||
Note that both TCP and UDP can be set on the server simultaneously to listen on TCP/UDP connections.
|
||||
|
||||
#### Step Three: Create a Template for Log Receipt ####
|
||||
|
||||
In the next step we need to create a template for remote messages, and tell rsyslog daemon how to record messages received from other client machines.
|
||||
|
||||
Open /etc/rsyslog.conf with a text editor, and append the following template before the GLOBAL DIRECTIVES block:
|
||||
|
||||
$template RemoteLogs,"/var/log/%HOSTNAME%/%PROGRAMNAME%.log" *
|
||||
*.* ?RemoteLogs
|
||||
& ~
|
||||
|
||||
This template needs a little explanation. The $template RemoteLogs directive ("RemoteLogs" string can be changed to any other descriptive name) forces rsyslog daemon to write log messages to separate local log files in /var/log/, where log file names are defined based on the hostname of the remote sending machine as well as the remote application that generated the logs. The second line ("*.* ?RemoteLogs") implies that we apply RemoteLogs template to all received logs.
|
||||
|
||||
The "& ~" sign represents a redirect rule, and is used to tell rsyslog daemon to stop processing log messages further, and not write them locally. If this redirection is not used, all the remote messages would be also written on local log files besides the log files described above, which means they would practically be written twice. Another consequence of using this rule is that the syslog server's own log messages would only be written to dedicated files named after machine's hostname.
|
||||
|
||||
If you want, you can direct log messages with a specific facility or severity level to this new template using the following schema.
|
||||
|
||||
[facility-level].[severity-level] ?RemoteLogs
|
||||
|
||||
For example:
|
||||
|
||||
Direct all internal authentication messages of all priority levels to RemoteLogs template:
|
||||
|
||||
authpriv.* ?RemoteLogs
|
||||
|
||||
Direct informational messages generated by all system processes, except mail, authentication and cron messages to RemoteLogs template:
|
||||
|
||||
*.info,mail.none,authpriv.none,cron.none ?RemoteLogs
|
||||
|
||||
If we want all received messages from remote clients written to a single file named after their IP address, you can use the following template. We assign a new name "IpTemplate" to this template.
|
||||
|
||||
$template IpTemplate,"/var/log/%FROMHOST-IP%.log"
|
||||
*.* ?IpTemplate
|
||||
& ~
|
||||
|
||||
After we have enabled rsyslog daemon and edited its configuration file, we need to restart the daemon.
|
||||
|
||||
On Debian, Ubuntu or CentOS/RHEL 6:
|
||||
|
||||
$ sudo service rsyslog restart
|
||||
|
||||
On Fedora or CentOS/RHEL 7:
|
||||
|
||||
$ sudo systemctl restart rsyslog
|
||||
|
||||
We can verify that rsyslog daemon is functional by using netstat command.
|
||||
|
||||
$ sudo netstat -tulpn | grep rsyslog
|
||||
|
||||
The output should look like the following in case rsyslog daemon listens on UDP port.
|
||||
|
||||
udp 0 0 0.0.0.0:514 0.0.0.0:* 551/rsyslogd
|
||||
udp6 0 0 :::514 :::* 551/rsyslogd
|
||||
|
||||
If rsyslog daemon is set up to listen on TCP connections, the output should look like this.
|
||||
|
||||
tcp 0 0 0.0.0.0:514 0.0.0.0:* LISTEN 1891/rsyslogd
|
||||
tcp6 0 0 :::514 :::* LISTEN 1891/rsyslogd
|
||||
|
||||
#### Send Windows Logs to a Remote Rsyslog Server ####
|
||||
|
||||
To forward a Windows based client's log messages to our rsyslog server, we need a Windows syslog agent. While there are a multitude of syslog agents that can run on Windows, we can use [Datagram SyslogAgent][1], which is a freeware program.
|
||||
|
||||
After downloading and installing the syslog agent, we need to configure it to run as a service. Specify the protocol though which it will send data, the IP address and port of a remote rsyslog server, and what type of event logs should be transmitted as follows.
|
||||
|
||||
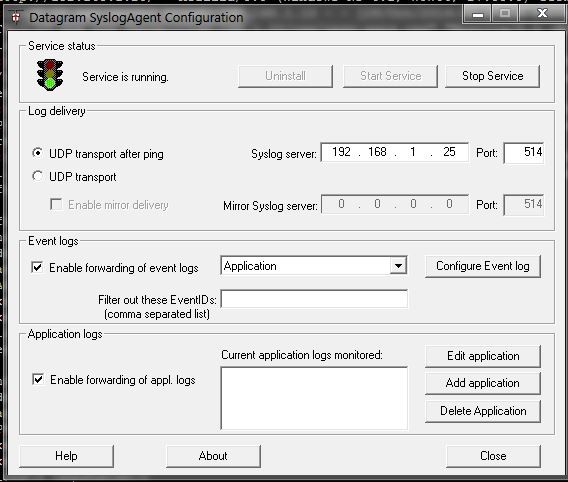
|
||||
|
||||
After we have set up all the configurations, we can start the service and watch the log files on the central rsyslog server using tailf command line utility.
|
||||
|
||||
### Conclusion ###
|
||||
|
||||
By creating a central rsyslog server that can collect log files of local or remote hosts, we can get a better idea on what is going on internally in their systems, and can debug their problems more easily should any of them become unresponsive or crash.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/configure-syslog-server-linux.html
|
||||
|
||||
作者:[Caezsar M][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/caezsar
|
||||
[1]:http://www.syslogserver.com/download.html
|
||||
@ -1,134 +0,0 @@
|
||||
How to set up a cross-platform backup server on Linux with BackupPC
|
||||
================================================================================
|
||||
Just in case you haven't been able to tell from my earlier posts on [backupninja][1] and [backup-manager][2], I am a big backup fan. When it comes to backup, I'd rather have too much than not enough, because if the need arises, you will be grateful that you took the time and effort to generate extra copies of your important data.
|
||||
|
||||
In this post, I will introduce you to [BackupPC][3], a cross-platform backup server software which can perform pull backup of Linux, Windows and MacOS client hosts over network. BackupPC adds a number of features that make managing backups an almost fun thing to do.
|
||||
|
||||
### Features of BackupPC ###
|
||||
|
||||
BackupPC comes with a robust web interface that allows you to collect and manage backups of other remote client hosts in a centralized fashion. Using the web interface, you can examine logs and configuration files, start/cancel/schedule backups of other remote hosts, and visualize current status of backup tasks. You can also browse through archived files and restore individual files or entire jobs from backup archives very easily. To restore individual single files, you can download them from any previous backup directly from the web interface. As if this weren't enough, no special client-side software is needed for client hosts. On Windows clients, the native SMB protocol is used, whereas on *nix clients, you will use `rsync` or tar over SSH, RSH or NFS.
|
||||
|
||||
### Installing BackupPC ###
|
||||
|
||||
On Debian, Ubuntu and their derivatives, run the following command.
|
||||
|
||||
# aptitude install backuppc
|
||||
|
||||
On Fedora, use `yum` command. Note the case sensitive package name.
|
||||
|
||||
On CentOS/RHEL 6, first enable [EPEL repository][4]. On CentOS/RHEL 7, enable [Nux Dextop][5] repository instead. Then go ahead with `yum` command:
|
||||
|
||||
# yum install BackupPC
|
||||
|
||||
As usual, both package management systems will take care of dependency resolution automatically. In addition, as part of the installation process, you may be asked to configure, or reconfigure the web server that will be used for the graphical user interface. The following screenshot is from a Debian system:
|
||||
|
||||
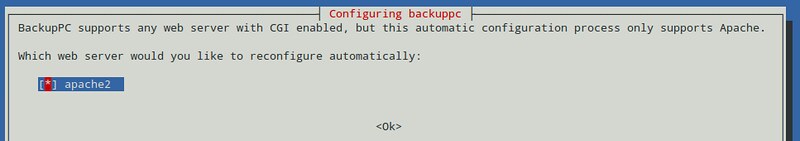
|
||||
|
||||
Select your choice by pressing the space bar, and then move to Ok with the tab key and hit ENTER.
|
||||
|
||||
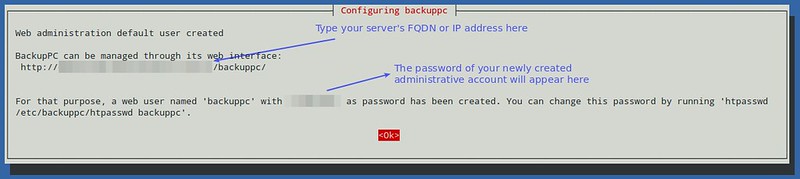
You will then be presented with the following screen informing you that an administrative user account 'backuppc', along with its corresponding password (which can be changed later if desired), has been created to manage BackupPC. Note that both a HTTP user account and a regular Linux account of the same name 'backuppc' will be created with an identical password. The former is needed to access BackupPC's protected web interface, while the latter is needed to perform backup using rsync over SSH.
|
||||
|
||||
|
||||
|
||||
You can change the default password for the HTTP user 'backuppc' with the following command:
|
||||
|
||||
# htpasswd /path/to/hash/file backuppc
|
||||
|
||||
As for a regular 'backuppc' [Linux][6] user account, use passwd command to change its default password.
|
||||
|
||||
# passwd backuppc
|
||||
|
||||
Note that the installation process creates the web and the program's configuration files automatically.
|
||||
|
||||
### Launching BackupPC and Configuring Backups ###
|
||||
|
||||
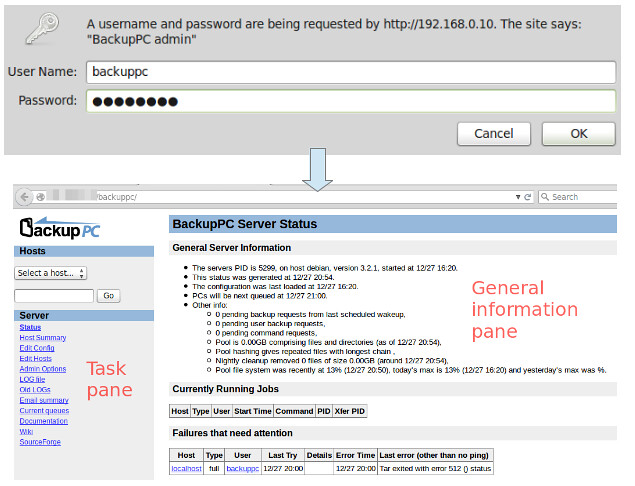
To start, open a browser window and point to http://<server's FQDN or IP address>/backuppc/. When prompted, enter the default HTTP user credentials that were supplied to you earlier. If the authentication succeeds, you will be taken to the main page of the web interface.
|
||||
|
||||
|
||||
|
||||
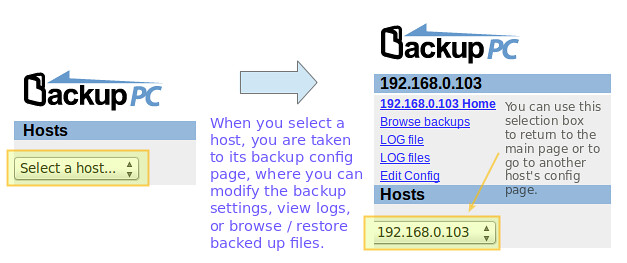
Most likely the first thing that you will want to do is add a new client host to back up. Go to "Edit Hosts" in the Task pane. We will add two client hosts:
|
||||
|
||||
- Host #1: CentOS 7 [IP 192.168.0.17]
|
||||
- Host #2: Windows 7 [IP 192.168.0.103]
|
||||
|
||||
We will back up the CentOS host using rsync over SSH and the Windows host using SMB. Prior to performing the backup, we need to set up [key-based authentication][7] to our CentOS host and a shared folder in our Windows machine.
|
||||
|
||||
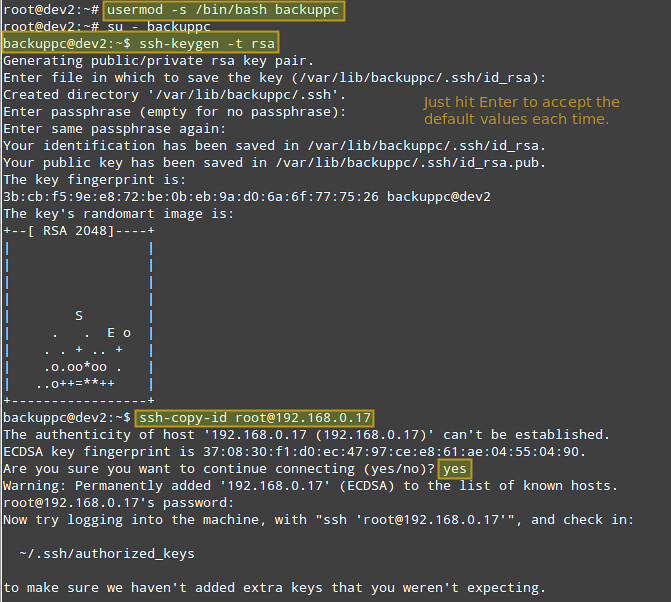
Here are the instructions for setting up key-based authentication for a remote CentOS host. We create the 'backuppc' user's RSA key pair, and transfer its public key to the root account of the CentOS host.
|
||||
|
||||
# usermod -s /bin/bash backuppc
|
||||
# su - backuppc
|
||||
# ssh-keygen -t rsa
|
||||
# ssh-copy-id root@192.168.0.17
|
||||
|
||||
When prompted, type yes and enter root's password for 192.168.0.17.
|
||||
|
||||
|
||||
|
||||
You will need root access for a remote CentOS host to grant write access to all its file system in case of restoring a backup of files or directories owned by root.
|
||||
|
||||
Once the CentOS and Windows hosts are ready, add them to BackupPC using the web interface:
|
||||
|
||||
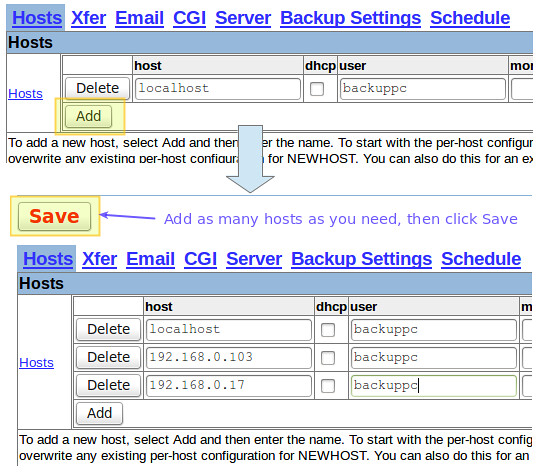
|
||||
|
||||
The next step consists of modifying each host's backup settings:
|
||||
|
||||
|
||||
|
||||
The following image shows the configuration for the backup of the Windows machine:
|
||||
|
||||
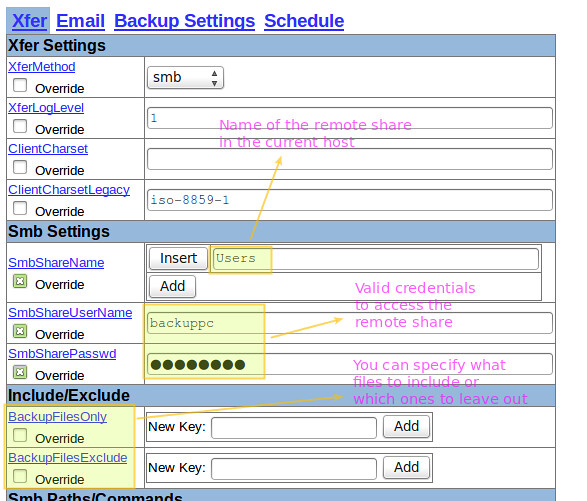
|
||||
|
||||
And the following screenshot shows the settings for the backup of the CentOS box:
|
||||
|
||||
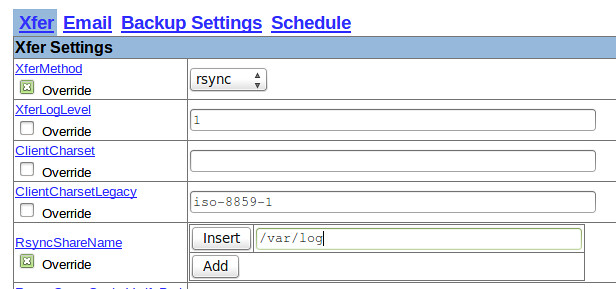
|
||||
|
||||
### Starting a Backup ###
|
||||
|
||||
To start each backup, go to each host's settings, and then click "Start Full Backup":
|
||||
|
||||
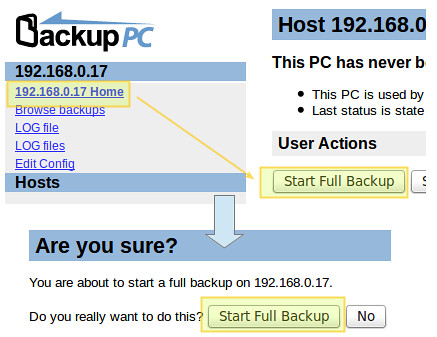
|
||||
|
||||
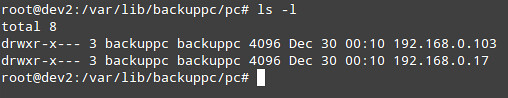
At any time, you can view the status of the process by clicking on the host's home as shown in the image above. If it fails for some reason, a link to a page with the error message(s) will appear in the host menu as well. When a backup completes successfully, a directory with the host's name or IP address is created under /var/lib/backuppc/pc in the server:
|
||||
|
||||
|
||||
|
||||
Feel free to browse those directories for the files from the command line, but there is an easier way to look for those files and restore them.
|
||||
|
||||
### Restoring Backup ###
|
||||
|
||||
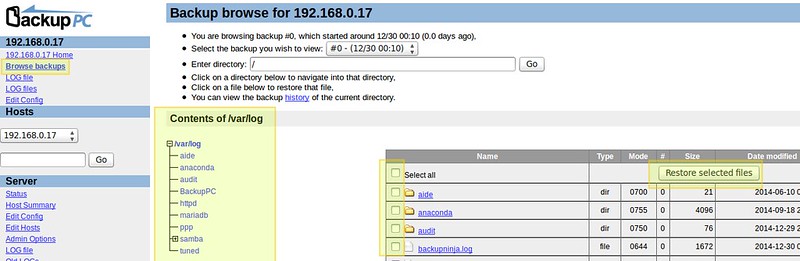
To view the files that have been saved, go to "Browse backups" under each host's main menu. You can visualize the directories and files at a glance, and select those that you want to restore. Alternatively, you can click on files to open them with the default program, or right click and choose Save link as to download it to the machine where you're working at the time:
|
||||
|
||||
|
||||
|
||||
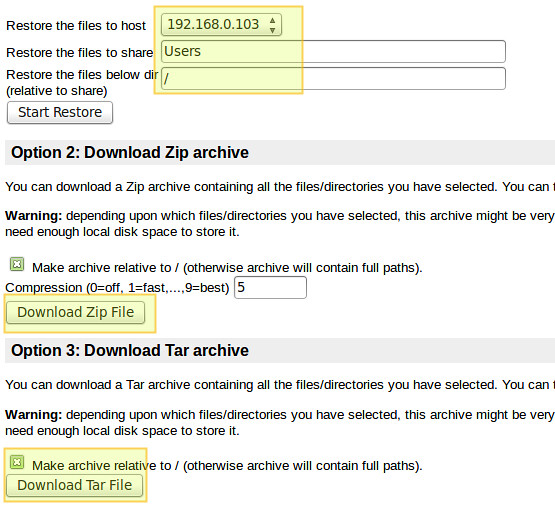
If you want, you can download a zip or tar file containing the backup's contents:
|
||||
|
||||
|
||||
|
||||
or just restore the file(s):
|
||||
|
||||

|
||||
|
||||
### Conclusion ###
|
||||
|
||||
There is a saying that goes, "the simpler, the better", and that is just what BackupPC has to offer. In BackupPC, you will not only find a backup tool but also a very versatile interface to manage your backups of several operating systems without needing any client-side application. I believe that's more than reason enough for you to give it at least a try.
|
||||
|
||||
Feel free to leave your comments and questions, if you have any, using the form below. I am always happy to hear what readers have to say!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/backuppc-cross-platform-backup-server-linux.html
|
||||
|
||||
作者:[Gabriel Cánepa][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/gabriel
|
||||
[1]:http://xmodulo.com/backup-debian-system-backupninja.html
|
||||
[2]:http://xmodulo.com/linux-backup-manager.html
|
||||
[3]:http://backuppc.sourceforge.net/
|
||||
[4]:http://xmodulo.com/how-to-set-up-epel-repository-on-centos.html
|
||||
[5]:http://ask.xmodulo.com/enable-nux-dextop-repository-centos-rhel.html
|
||||
[6]:http://xmodulo.com/recommend/linuxguide
|
||||
[7]:http://xmodulo.com/how-to-enable-ssh-login-without.html
|
||||
@ -1,3 +1,5 @@
|
||||
FSSlc translating
|
||||
|
||||
How to back up a Debian system using backupninja
|
||||
================================================================================
|
||||
Prudence or experience by disaster can teach every [sysadmin][1] the importance of taking frequent system backups. You can do so by writing good old shell scripts, or using one (or more) of the many backup tools available for the job. Thus the more tools you become acquainted with, the better informed decisions you will make when implementing a backup solution.
|
||||
@ -108,4 +110,4 @@ via: http://xmodulo.com/backup-debian-system-backupninja.html
|
||||
|
||||
[a]:http://xmodulo.com/author/gabriel
|
||||
[1]:http://xmodulo.com/recommend/sysadminbook
|
||||
[2]:https://labs.riseup.net/code/projects/backupninja
|
||||
[2]:https://labs.riseup.net/code/projects/backupninja
|
||||
|
||||
@ -1,187 +0,0 @@
|
||||
10 quick tar command examples to create/extract archives in Linux
|
||||
================================================================================
|
||||
### Tar command on Linux ###
|
||||
|
||||
The tar (tape archive) command is a frequently used command on linux that allows you to store files into an archive.
|
||||
|
||||
The commonly seen file extensions are .tar.gz and .tar.bz2 which is a tar archive further compressed using gzip or bzip algorithms respectively.
|
||||
|
||||
In this tutorial we shall take a look at simple examples of using the tar command to do daily jobs of creating and extracting archives on linux desktops or servers.
|
||||
|
||||
### Using the tar command ###
|
||||
|
||||
The tar command is available by default on most linux systems and you do not need to install it separately.
|
||||
|
||||
> With tar there are 2 compression formats, gzip and bzip. The "z" option specifies gzip and "j" option specifies bzip. It is also possible to create uncompressed archives.
|
||||
|
||||
#### 1. Extract a tar.gz archive ####
|
||||
|
||||
Well, the more common use is to extract tar archives. The following command shall extract the files out a tar.gz archive
|
||||
|
||||
$ tar -xvzf tarfile.tar.gz
|
||||
|
||||
Here is a quick explanation of the parameters used -
|
||||
|
||||
> x - Extract files
|
||||
>
|
||||
> v - verbose, print the file names as they are extracted one by one
|
||||
>
|
||||
> z - The file is a "gzipped" file
|
||||
>
|
||||
> f - Use the following tar archive for the operation
|
||||
|
||||
Those are some of the important options to memorise
|
||||
|
||||
**Extract tar.bz2/bzip archives**
|
||||
|
||||
Files with extension bz2 are compressed with the bzip algorithm and tar command can deal with them as well. Use the j option instead of the z option.
|
||||
|
||||
$ tar -xvjf archivefile.tar.bz2
|
||||
|
||||
#### 2. Extract files to a specific directory or path ####
|
||||
|
||||
To extract out the files to a specific directory, specify the path using the "-C" option. Note that its a capital C.
|
||||
|
||||
$ tar -xvzf abc.tar.gz -C /opt/folder/
|
||||
|
||||
However first make sure that the destination directory exists, since tar is not going to create the directory for you and will fail if it does not exist.
|
||||
|
||||
#### 3. Extract a single file ####
|
||||
|
||||
To extract a single file out of an archive just add the file name after the command like this
|
||||
|
||||
$ tar -xz -f abc.tar.gz "./new/abc.txt"
|
||||
|
||||
More than once file can be specified in the above command like this
|
||||
|
||||
$ tar -xv -f abc.tar.gz "./new/cde.txt" "./new/abc.txt"
|
||||
|
||||
#### 4. Extract multiple files using wildcards ####
|
||||
|
||||
Wildcards can be used to extract out a bunch of files matching the given wildcards. For example all files with ".txt" extension.
|
||||
|
||||
$ tar -xv -f abc.tar.gz --wildcards "*.txt"
|
||||
|
||||
#### 5. List and search contents of the tar archive ####
|
||||
|
||||
If you want to just list out the contents of the tar archive and not extract them, use the "-t" option. The following command prints the contents of a gzipped tar archive,
|
||||
|
||||
$ tar -tz -f abc.tar.gz
|
||||
./new/
|
||||
./new/cde.txt
|
||||
./new/subdir/
|
||||
./new/subdir/in.txt
|
||||
./new/abc.txt
|
||||
...
|
||||
|
||||
Pipe the output to grep to search a file or less command to browse the list. Using the "v" verbose option shall print additional details about each file.
|
||||
|
||||
For tar.bz2/bzip files use the "j" option
|
||||
|
||||
Use the above command in combination with the grep command to search the archive. Simple!
|
||||
|
||||
$ tar -tvz -f abc.tar.gz | grep abc.txt
|
||||
-rw-rw-r-- enlightened/enlightened 0 2015-01-13 11:40 ./new/abc.txt
|
||||
|
||||
#### 6. Create a tar/tar.gz archive ####
|
||||
|
||||
Now that we have learnt how to extract existing tar archives, its time to start creating new ones. The tar command can be told to put selected files in an archive or an entire directory. Here are some examples.
|
||||
|
||||
The following command creates a tar archive using a directory, adding all files in it and sub directories as well.
|
||||
|
||||
$ tar -cvf abc.tar ./new/
|
||||
./new/
|
||||
./new/cde.txt
|
||||
./new/abc.txt
|
||||
|
||||
The above example does not create a compressed archive. Just a plain archive, that puts multiple files together without any real compression.
|
||||
|
||||
In order to compress, use the "z" or "j" option for gzip or bzip respectively.
|
||||
|
||||
$ tar -cvzf abc.tar.gz ./new/
|
||||
|
||||
> The extension of the file name does not really matter. "tar.gz" and tgz are common extensions for files compressed with gzip. ".tar.bz2" and ".tbz" are commonly used extensions for bzip compressed files.
|
||||
|
||||
#### 7. Ask confirmation before adding files ####
|
||||
|
||||
A useful option is "w" which makes tar ask for confirmation for every file before adding it to the archive. This can be sometimes useful.
|
||||
|
||||
Only those files would be added which are given a yes answer. If you do not enter anything, the default answer would be a "No".
|
||||
|
||||
# Add specific files
|
||||
|
||||
$ tar -czw -f abc.tar.gz ./new/*
|
||||
add ‘./new/abc.txt’?y
|
||||
add ‘./new/cde.txt’?y
|
||||
add ‘./new/newfile.txt’?n
|
||||
add ‘./new/subdir’?y
|
||||
add ‘./new/subdir/in.txt’?n
|
||||
|
||||
# Now list the files added
|
||||
$ tar -t -f abc.tar.gz
|
||||
./new/abc.txt
|
||||
./new/cde.txt
|
||||
./new/subdir/
|
||||
|
||||
#### 8. Add files to existing archives ####
|
||||
|
||||
The r option can be used to add files to existing archives, without having to create new ones. Here is a quick example
|
||||
|
||||
$ tar -rv -f abc.tar abc.txt
|
||||
|
||||
> Files cannot be added to compressed archives (gz or bzip). Files can only be added to plain tar archives.
|
||||
|
||||
#### 9. Add files to compressed archives (tar.gz/tar.bz2) ####
|
||||
|
||||
Its already mentioned that its not possible to add files to compressed archives. However it can still be done with a simple trick. Use the gunzip command to uncompress the archive, add file to archive and compress it again.
|
||||
|
||||
$ gunzip archive.tar.gz
|
||||
$ tar -rf archive.tar ./path/to/file
|
||||
$ gzip archive.tar
|
||||
|
||||
For bzip files use the bzip2 and bunzip2 commands respectively.
|
||||
|
||||
#### 10. Backup with tar ####
|
||||
|
||||
A real scenario is to backup directories at regular intervals. The tar command can be scheduled to take such backups via cron. Here is an example -
|
||||
|
||||
$ tar -cvz -f archive-$(date +%Y%m%d).tar.gz ./new/
|
||||
|
||||
Run the above command via cron and it would keep creating backup files with names like -
|
||||
'archive-20150218.tar.gz'.
|
||||
|
||||
Ofcourse make sure that the disk space is not overflown with larger and larger archives.
|
||||
|
||||
#### 11. Verify archive files while creation ####
|
||||
|
||||
The "W" option can be used to verify the files after creating archives. Here is a quick example.
|
||||
|
||||
$ tar -cvW -f abc.tar ./new/
|
||||
./new/
|
||||
./new/cde.txt
|
||||
./new/subdir/
|
||||
./new/subdir/in.txt
|
||||
./new/newfile.txt
|
||||
./new/abc.txt
|
||||
Verify ./new/
|
||||
Verify ./new/cde.txt
|
||||
Verify ./new/subdir/
|
||||
Verify ./new/subdir/in.txt
|
||||
Verify ./new/newfile.txt
|
||||
Verify ./new/abc.txt
|
||||
|
||||
Note that the verification cannot be done on compressed archives. It works only with uncompressed tar archives.
|
||||
|
||||
Thats all for now. For more check out the man page for tar command, with "man tar".
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.binarytides.com/linux-tar-command/
|
||||
|
||||
作者:[Silver Moon][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://plus.google.com/117145272367995638274/posts
|
||||
@ -1,63 +0,0 @@
|
||||
Linux FAQs with Answers--How to install a USB webcam in Raspberry Pi
|
||||
================================================================================
|
||||
> **Question**: Can I use a standard USB-based webcam on Raspberry Pi? How can I check if my USB webcam is compatible with Raspberry Pi, and how can I install it on Raspberry Pi?
|
||||
|
||||
If you want to take pictures or record videos using Raspberry Pi board, you can install [Raspberry Pi camera board][1]. If you do not want to shell out money just for the camera board module, there is yet another way, which is to utilize a commonly found [USB web camera][2]. You may already have one for your PC.
|
||||
|
||||
In this tutorial, we show how to set up a USB web camera on Raspberry Pi board. We assume that you are using Raspbian operation system.
|
||||
|
||||
Before we start, it is better to check if your USB web camera is [one of those][3] which are known to be compatible with Raspberry Pi. If your USB webcam is not found in the compatibility list, don't be discouraged, as there is still a chance that your USB web camera may be detected by Raspberry Pi.
|
||||
|
||||
### Check if a USB Webcam is Compatible with Raspberry Pi ###
|
||||
|
||||
To check whether your USB web camera is detected on Raspberry Pi or not, plug it into the USB port of your Raspberry Pi, and type lsusb command in the terminal.
|
||||
|
||||
$ lsusb
|
||||
|
||||
If the output of the command does not list your webcam, there is a possibility that this is because your Raspberry Pi doesn't supply enough power needed for your USB web camera. In this case, you can try using a separate power line for the USB web camera, such as [USB power hub][4], and then repeat the lsusb command. If the USB webcam is still not recognized, we can only suggest you buy another USB web camera which is supported by Raspberry Pi.
|
||||
|
||||
|
||||
|
||||
In the above screenshot, the USB web camera is detected as "1e4e:0102", but it doesn't show the maker or the name of the web camera. When we try it with Fedora 20 in a laptop, it is successfully detected as "1e4e:0102 Cubeternet GL-UPC822 UVC WebCam."
|
||||
|
||||
Another way to check if your USB web camera is supported by Raspberry Pi is by checking the /dev directory. If there is /dev/video0, this implies that your USB webcam is recognized by Raspberry Pi.
|
||||
|
||||
### Take a Picture with USB Webcam ###
|
||||
|
||||
After your USB webcam is successfully hooked up with Raspberry Pi, the next thing to do is to take some pictures to verify its functionality.
|
||||
|
||||
For this, you can install fswebcam, which is a small webcam application. You can install fswebcam directly from the Raspbian repository as follows.
|
||||
|
||||
$ sudo apt-get install fswebcam
|
||||
|
||||
Once fswebcam is installed, run the following command in a terminal to capture a picture from the USB webcam:
|
||||
|
||||
$ fswebcam --no-banner -r 640x480 image.jpg
|
||||
|
||||
This command will capture a picture with 640x480 resolution, and save it as image.jpg. It will not put any banner in the bottom part of the picture.
|
||||
|
||||
|
||||
|
||||
Here is the result from the fswebcam command with 640x480 resolution.
|
||||
|
||||

|
||||
|
||||
The next example picture is captured without defining the resolution. The picture color is blueish, and the default resolution is only 358x288.
|
||||
|
||||

|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://ask.xmodulo.com/install-usb-webcam-raspberry-pi.html
|
||||
|
||||
作者:[Kristophorus Hadiono][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://ask.xmodulo.com/author/kristophorus
|
||||
[1]:http://xmodulo.com/install-raspberry-pi-camera-board.html
|
||||
[2]:http://xmodulo.com/go/usb_webcam
|
||||
[3]:http://elinux.org/RPi_USB_Webcams
|
||||
[4]:http://xmodulo.com/go/usb_powerhub
|
||||
@ -0,0 +1,296 @@
|
||||
How to Limit the Network Bandwidth Used by Applications in a Linux System with Trickle
|
||||
================================================================================
|
||||
Have you ever encountered situations where one application dominated you all network bandwidth? If you have ever been in a situation where one application ate all your traffic, then you will value the role of the trickle bandwidth shaper application. Either you are a system admin or just a Linux user, you need to learn how to control the upload and download speeds for applications to make sure that your network bandwidth is not burned by a single application.
|
||||
|
||||

|
||||
Install Trickle Bandwidth Limit in Linux
|
||||
|
||||
### What is Trickle? ###
|
||||
|
||||
Trickle is a network bandwidth shaper tool that allows us to manage the upload and download speeds of applications in order to prevent any single one of them to hog all (or most) of the available bandwidth. In few words, trickle lets you control the network traffic rate on a per-application basis, as opposed to per-user control, which is the classic example of bandwidth shaping in a client-server environment, and is probably the setup we are more familiar with.
|
||||
|
||||
### How Trickle Works? ###
|
||||
|
||||
In addition, trickle can help us to define priorities on a per-application basis, so that when overall limits have been set for the entire system, priority apps will still get more bandwidth automatically. To accomplish this task, trickle sets traffic limits to the way in which data is sent to, and received from, sockets using TCP connections. We must note that, other than the data transfer rates, trickle does not modify in any way the behavior of the process it is shaping at any given moment.
|
||||
|
||||
### What Can’t Trickle do? ###
|
||||
|
||||
The only limitation, so to speak, is that trickle will not work with statically linked applications or binaries with the SUID or SGID bits set since it uses dynamic linking and loading to place itself between the shaped process and its associated network socket. Trickle then acts as a proxy between these two software components.
|
||||
|
||||
Since trickle does not require superuser privileges in order to run, users can set their own traffic limits. Since this may not be desirable, we will explore how to set overall limits that system users cannot exceed. In other words, users will still be able to manage their traffic rates, but always within the boundaries set by the system administrator.
|
||||
|
||||
In this article we will explain how to limit the network bandwidth used by applications in a Linux server with trickle. To generate the necessary traffic, we will use ncftpput and ncftpget (both tools are available by installing ncftp) on the client (CentOS 7 server – dev1: 192.168.0.17), and vsftpd on the server (Debian Wheezy 7.5 – dev2: 192.168.0.15) for demonstration purposes. The same instructions also works on RedHat, Fedora and Ubuntu based systems.
|
||||
|
||||
#### Prerequisites ####
|
||||
|
||||
1. For RHEL/CentOS 7/6, [enable the EPEL repository][1]. Extra Packages for Enterprise Linux (EPEL) is a repository of high-quality free and open-source software maintained by the Fedora project and is 100% compatible with its spinoffs, such as Red Hat Enterprise Linux and CentOS. Both trickle and ncftp are made available from this repository.
|
||||
|
||||
2. Install ncftp as follows:
|
||||
|
||||
# yum update && sudo yum install ncftp [On RedHat based systems]
|
||||
# aptitude update && aptitude install ncftp [On Debian based systems]
|
||||
|
||||
3. Set up a FTP server in a separate server. Please note that although FTP is inherently insecure, it is still widely used in cases when security in uploading or downloading files is not needed. We are using it in this article to illustrate the bounties of trickle and because it shows the transfer rates in stdout on the client, and we will leave the discussion of whether it should or should not be used for another date and time :).
|
||||
|
||||
# yum update && yum install vsftpd [On RedHat based systems]
|
||||
# aptitude update && aptitude install vsftpd [On Debian based systems]
|
||||
|
||||
Now, edit the /etc/vsftpd/vsftpd.conf file on the FTP server as follows:
|
||||
|
||||
anonymous_enable=NO
|
||||
local_enable=YES
|
||||
chroot_local_user=YES
|
||||
allow_writeable_chroot=YES
|
||||
|
||||
After that, make sure to start vsftpd for your current session and to enable it for automatic start on future boots:
|
||||
|
||||
# systemctl start vsftpd [For systemd-based systems]
|
||||
# systemctl enable vsftpd
|
||||
# service vsftpd start [For init-based systems]
|
||||
# chkconfig vsftpd on
|
||||
|
||||
4. If you chose to set up the FTP server in a CentOS/RHEL 7 droplet with SSH keys for remote access, you will need a password-protected user account with the appropriate directory and file permissions for uploading and downloading the desired content OUTSIDE root’s home directory.
|
||||
|
||||
You can then browse to your home directory by entering the following URL in your browser. A login window will pop up prompting you for a valid user account and password on the FTP server.
|
||||
|
||||
ftp://192.168.0.15
|
||||
|
||||
If the authentication succeeds, you will see the contents of your home directory. Later in this tutorial you will be able to refresh that page to display the files that have been uploaded during previous steps.
|
||||
|
||||

|
||||
FTP Directory Tree
|
||||
|
||||
### How to Install Trickle in Linux ###
|
||||
|
||||
1. Install trickle via yum or aptitude.
|
||||
|
||||
To ensure a successful installation, it is considered good practice to make sure the currently installed packages are up-to-date (using yum update) before installing the tool itself.
|
||||
|
||||
# yum -y update && yum install trickle [On RedHat based systems]
|
||||
# aptitude -y update && aptitude install trickle [On Debian based systems]
|
||||
|
||||
2. Verify whether trickle will work with the desired binary.
|
||||
|
||||
As we explained earlier, trickle will only work with binaries using dynamic, or shared, libraries. To verify whether we can use this tool with a certain application, we can use the well-known ldd utility, where ldd stands for list dynamic dependencies. Specifically, we will look for the presence of glibc (the GNU C library) in the list of dynamic dependencies of any given program because it is precisely that library which defines the system calls involved in communication through sockets.
|
||||
|
||||
Run the following command against a given binary to see if trickle can be used to shape its bandwidth:
|
||||
|
||||
# ldd $(which [binary]) | grep libc.so
|
||||
|
||||
For example,
|
||||
|
||||
# ldd $(which ncftp) | grep libc.so
|
||||
|
||||
whose output is:
|
||||
|
||||
# libc.so.6 => /lib64/libc.so.6 (0x00007efff2e6c000)
|
||||
|
||||
The string between brackets in the output may change from system to system and even between subsequent runs of the same command, since it represents the load address of the library in physical memory.
|
||||
|
||||
If the above command does not return any results, it means that the binary it was run against does not use libc and thus trickle cannot be used as bandwidth shaper in that case.
|
||||
|
||||
### Learn How to Use Trickle ###
|
||||
|
||||
The most basic usage of trickle is in standalone mode. Using this approach, trickle is used to explicitly define the download and upload speeds of a given application. As we explained earlier, for the sake of brevity, we will use the same application for download and upload tests.
|
||||
|
||||
#### Running Trickle in Standalone Mode ####
|
||||
|
||||
We will compare the download and upload speeds with and without using trickle. The -d option indicates the download speed in KB/s, while the -u flag tells trickle to limit the upload speed by the same unit. In addition, we will use the -s flag, which specifies that trickle should run in standalone mode.
|
||||
|
||||
The basic syntax to run trickle in standalone mode is as follows:
|
||||
|
||||
# trickle -s -d [download rate in KB/s] -u [upload rate in KB/s]
|
||||
|
||||
In order to perform the following examples on your own, make sure to have trickle and ncftp installed on the client machine (192.168.0.17 in my case).
|
||||
|
||||
**Example 1: Uploading a 2.8 MB PDF file with and without trickle.**
|
||||
|
||||
We are using the freely-distributable Linux Fundamentals PDF file (available from [here][2]) for the following tests.
|
||||
|
||||
You can initially download this file to your current working directory with the following command:
|
||||
|
||||
# wget http://linux-training.be/files/books/LinuxFun.pdf
|
||||
|
||||
The syntax to upload a file to our FTP server without trickle is as follows:
|
||||
|
||||
# ncftpput -u username -p password 192.168.0.15 /remote_directory local-filename
|
||||
|
||||
Where /remote_directory is the path of the upload directory relative to username’s home, and local-filename is a file in your current working directory.
|
||||
|
||||
Specifically, without trickle we get a peak upload speed of 52.02 MB/s (please note that this is not the real average upload speed, but an instant starting peak), and the file gets uploaded almost instantly:
|
||||
|
||||
# ncftpput -u username -p password 192.168.0.15 /testdir LinuxFun.pdf
|
||||
|
||||
Output:
|
||||
|
||||
LinuxFun.pdf: 2.79 MB 52.02 MB/s
|
||||
|
||||
With trickle, we will limit the upload transfer rate at 5 KB/s. Before uploading the file for the second time, we need to delete it from the destination directory; otherwise, ncftp will inform us that the file at the destination directory is the same that we are trying to upload, and will not perform the transfer:
|
||||
|
||||
# rm /absolute/path/to/destination/directory/LinuxFun.pdf
|
||||
|
||||
Then:
|
||||
|
||||
# trickle -s -u 5 ncftpput -u username -p password 111.111.111.111 /testdir LinuxFun.pdf
|
||||
|
||||
Output:
|
||||
|
||||
LinuxFun.pdf: 2.79 MB 4.94 kB/s
|
||||
|
||||
In the example above, we can see that the average upload speed dropped to ~5 KB/s.
|
||||
|
||||
**Example 2: Downloading the same 2.8 MB PDF file with and without trickle**
|
||||
|
||||
First, remember to delete the PDF from the original source directory:
|
||||
|
||||
# rm /absolute/path/to/source/directory/LinuxFun.pdf
|
||||
|
||||
Please note that the following cases will download the remote file to the current directory in the client machine. This fact is indicated by the period (‘.‘) that appears after the IP address of the FTP server.
|
||||
|
||||
Without trickle:
|
||||
|
||||
# ncftpget -u username -p password 111.111.111.111 . /testdir/LinuxFun.pdf
|
||||
|
||||
Output:
|
||||
|
||||
LinuxFun.pdf: 2.79 MB 260.53 MB/s
|
||||
|
||||
With trickle, limiting the download speed at 20 KB/s:
|
||||
|
||||
# trickle -s -d 30 ncftpget -u username -p password 111.111.111.111 . /testdir/LinuxFun.pdf
|
||||
|
||||
Output:
|
||||
|
||||
LinuxFun.pdf: 2.79 MB 17.76 kB/s
|
||||
|
||||
### Running Trickle in Supervised [unmanaged] Mode ###
|
||||
|
||||
Trickle can also run in unmanaged mode, following a series of parameters defined in /etc/trickled.conf. This file defines how trickled (the daemon) behaves and manages trickle.
|
||||
|
||||
In addition, if we want to set global settings to be used, overall, by all applications, we will need to use the trickled command. This command runs the daemon and allows us to define download and upload limits that will be shared by all the applications run through trickle without us needing to specify limits each time.
|
||||
|
||||
For example, running:
|
||||
|
||||
# trickled -d 50 -u 10
|
||||
|
||||
Will cause that the download and upload speeds of any application run through trickle be limited to 30 KB/s and 10 KB/s, respectively.
|
||||
|
||||
Please note that you can check at any time whether trickled is running and with what arguments:
|
||||
|
||||
# ps -ef | grep trickled | grep -v grep
|
||||
|
||||
Output:
|
||||
|
||||
root 16475 1 0 Dec24 ? 00:00:04 trickled -d 50 -u 10
|
||||
|
||||
**Example 3: Uploading a 19 MB mp4 file to our FTP server using with and without trickle.**
|
||||
|
||||
In this example we will use the freely-distributable “He is the gift” video, available for download from [this link][3].
|
||||
|
||||
We will initially download this file to your current working directory with the following command:
|
||||
|
||||
# wget http://media2.ldscdn.org/assets/missionary/our-people-2014/2014-00-1460-he-is-the-gift-360p-eng.mp4
|
||||
|
||||
First off, we will start the trickled daemon with the command listed above:
|
||||
|
||||
# trickled -d 30 -u 10
|
||||
|
||||
Without trickle:
|
||||
|
||||
# ncftpput -u username -p password 192.168.0.15 /testdir 2014-00-1460-he-is-the-gift-360p-eng.mp4
|
||||
|
||||
Output:
|
||||
|
||||
2014-00-1460-he-is-the-gift-360p-eng.mp4: 18.53 MB 36.31 MB/s
|
||||
|
||||
With trickle:
|
||||
|
||||
# trickle ncftpput -u username -p password 192.168.0.15 /testdir 2014-00-1460-he-is-the-gift-360p-eng.mp4
|
||||
|
||||
Output:
|
||||
|
||||
2014-00-1460-he-is-the-gift-360p-eng.mp4: 18.53 MB 9.51 kB/s
|
||||
|
||||
As we can see in the output above, the upload transfer rate dropped to ~10 KB/s.
|
||||
|
||||
**Example 4: Downloading the same video with and without trickle**
|
||||
|
||||
As in Example 2, we will be downloading the file to the current working directory.
|
||||
|
||||
Without trickle:
|
||||
|
||||
# ncftpget -u username -p password 192.168.0.15 . /testdir/2014-00-1460-he-is-the-gift-360p-eng.mp4
|
||||
|
||||
Output:
|
||||
|
||||
2014-00-1460-he-is-the-gift-360p-eng.mp4: 18.53 MB 108.34 MB/s
|
||||
|
||||
With trickle:
|
||||
|
||||
# trickle ncftpget -u username -p password 111.111.111.111 . /testdir/2014-00-1460-he-is-the-gift-360p-eng.mp4
|
||||
|
||||
Output:
|
||||
|
||||
2014-00-1460-he-is-the-gift-360p-eng.mp4: 18.53 MB 29.28 kB/s
|
||||
|
||||
Which is in accordance with the download limit set earlier (30 KB/s).
|
||||
|
||||
**Note:** That once the daemon has been started, there is no need to set individual limits for each application that uses trickle.
|
||||
|
||||
As we mentioned earlier, one can further customize trickle’s bandwidth shaping through trickled.conf. A typical section in this file consists of the following:
|
||||
|
||||
[service]
|
||||
Priority = <value>
|
||||
Time-Smoothing = <value>
|
||||
Length-Smoothing = <value>
|
||||
|
||||
Where,
|
||||
|
||||
- [service] indicates the name of the application whose bandwidth usage we intend to shape.
|
||||
- Priority allows us to specify a service to have a higher priority relative to another, thus not allowing a single application to hog all the bandwidth which the daemon is managing. The lower the number, the more bandwidth that is assigned to [service].
|
||||
- Time-Smoothing [in seconds]: defines with what time intervals trickled will try to let the application transfer and / or receive data. Smaller values (something between the range of 0.1 – 1s) are ideal for interactive applications and will result in a more continuous (smooth) session while slightly larger values (1 – 10 s) are better for applications that need bulk transfer. If no value is specified, the default (5 s) is used.
|
||||
- Length-Smoothing [in KB]: the idea is the same as in Time-Smoothing, but based on the length of an I/O operation. If no value is specified, the default (10 KB) is used.
|
||||
|
||||
Changing the smoothing values will translate into the application specified by [service] using transfer rates within an interval instead of a fixed value. Unfortunately, there is no formula to calculate the lower and upper limits of this interval as it mainly depends of each specific case scenario.
|
||||
|
||||
The following is a trickled.conf sample file in the CentOS 7 client (192.168.0.17):
|
||||
|
||||
[ssh]
|
||||
Priority = 1
|
||||
Time-Smoothing = 0.1
|
||||
Length-Smoothing = 2
|
||||
|
||||
[ftp]
|
||||
Priority = 2
|
||||
Time-Smoothing = 1
|
||||
Length-Smoothing = 3
|
||||
|
||||
Using this setup, trickled will prioritize SSH connections over FTP transfers. Note that an interactive process, such as SSH, uses smaller time-smoothing values, whereas a service that performs bulk data transfers (FTP) uses a greater value. The smoothing values are responsible for the download and upload speeds in our previous example not matching the exact value specified by the trickled daemon but moving in an interval close to it.
|
||||
|
||||
### Conclusion ###
|
||||
|
||||
In this article we have explored how to limit the bandwidth used by applications using trickle on Fedora-based distributions and Debian / derivatives. Other possible use cases include, but are not limited to:
|
||||
|
||||
- Limiting the download speed via a system utility such as [wget][4], or a torrent client, for example.
|
||||
- Limiting the speed at which your system can be updated via `[yum][5]` (or `[aptitude][6]`, if you’re in a Debian-based system), the package management system.
|
||||
- If your server happens to be behind a proxy or firewall (or is the proxy or firewall itself), you can use trickle to set limits on both the download and upload, or communication speed with the clients or the outside.
|
||||
|
||||
Questions and comments are most welcome. Feel free to use the form below to send them our way.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.tecmint.com/manage-and-limit-downloadupload-bandwidth-with-trickle-in-linux/
|
||||
|
||||
作者:[Gabriel Cánepa][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.tecmint.com/author/gacanepa/
|
||||
[1]:http://www.tecmint.com/how-to-enable-epel-repository-for-rhel-centos-6-5/
|
||||
[2]:http://linux-training.be/files/books/LinuxFun.pdf
|
||||
[3]:http://media2.ldscdn.org/assets/missionary/our-people-2014/2014-00-1460-he-is-the-gift-360p-eng.mp4
|
||||
[4]:http://www.tecmint.com/10-wget-command-examples-in-linux/
|
||||
[5]:http://www.tecmint.com/20-linux-yum-yellowdog-updater-modified-commands-for-package-mangement/
|
||||
[6]:http://www.tecmint.com/dpkg-command-examples/
|
||||
@ -0,0 +1,152 @@
|
||||
How to Manage KVM Virtual Environment using Commandline Tools in Linux
|
||||
================================================================================
|
||||
In this 4th part of our [KVM series][1], we are discussing KVM environment management using CLI. We use ‘virt-install’ CL tool to create and configure virtual machines, virsh CL tool to create and configure storage pools and qemu-img CL tool to create and manage disk images.
|
||||
|
||||

|
||||
KVM Management in Linux
|
||||
|
||||
There is nothing new concepts in this article, we just do the previous tasks using command line tools. There is no new prerequisite, just the same procedure, we have discussed in previous parts.
|
||||
|
||||
### Step 1: Configure Storage Pool ###
|
||||
|
||||
Virsh CLI tool is a management user interface for managing virsh guest domains. The virsh program can be used either to run one command by giving the command and its arguments on the shell command line.
|
||||
|
||||
In this section, we will use it to create storage pool for our KVM environment. For more information about the tool, use the following command.
|
||||
|
||||
# man virsh
|
||||
|
||||
**1. Using the command pool-define-as with virsh to define new storage pool, you need also to specify name, type and type’s arguments.**
|
||||
|
||||
In our case, name will be Spool1, type will be dir. By default you could provide five arguments for the type:
|
||||
|
||||
- source-host
|
||||
- source-path
|
||||
- source-dev
|
||||
- source-name
|
||||
- target
|
||||
|
||||
For (Dir) type, we need the last argumet “target” to specify the path of storage pool, for the other arguments we could use “-” to unspecific them.
|
||||
|
||||
# virsh pool-define-as Spool1 dir - - - - "/mnt/personal-data/SPool1/"
|
||||
|
||||

|
||||
Create New Storage Pool
|
||||
|
||||
**2. To check the all storage pools you have in the environment, use the following command.**
|
||||
|
||||
# virsh pool-list --all
|
||||
|
||||

|
||||
List All Storage Pools
|
||||
|
||||
**3. Now it’s time to build the storage pool, which we have defined above with the following command.**
|
||||
|
||||
# virsh pool-build Spool1
|
||||
|
||||

|
||||
Build Storage Pool
|
||||
|
||||
**4. Using the virsh command pool-start to active/enable the storage pool we have just created/built above.**
|
||||
|
||||
# virsh pool-start Spool1
|
||||
|
||||

|
||||
Active Storage Pool
|
||||
|
||||
**5. Check the status of environment storage pools using the following command.**
|
||||
|
||||
# virsh pool-list --all
|
||||
|
||||

|
||||
Check Storage Pool Status
|
||||
|
||||
You will notice that the status of Spool1 converted to active.
|
||||
|
||||
**6. Configure Spool1 to start by libvirtd service every time automaticlly.**
|
||||
|
||||
# virsh pool-autostart Spool1
|
||||
|
||||

|
||||
Configure KVM Storage Pool
|
||||
|
||||
**7. Finally lets display information about our new storage pool.**
|
||||
|
||||
# virsh pool-info Spool1
|
||||
|
||||

|
||||
Check KVM Storage Pool Information
|
||||
|
||||
Congratulations, Spool1 is ready to be used lets try to create storage volumes using it.
|
||||
|
||||
### Step 2: Configure Storage Volumes/Disk Images ###
|
||||
|
||||
Now it is disk image’s turn, using qemu-img to create new disk image from Spool1. For more details about qemy-img, use the man page.
|
||||
|
||||
# man qemu-img
|
||||
|
||||
**8. We should specify the qemu-img command “create, check,….etc”, disk image format, the path of disk image you want to create and the size.**
|
||||
|
||||
# qemu-img create -f raw /mnt/personal-data/SPool1/SVol1.img 10G
|
||||
|
||||

|
||||
Create Storage Volume
|
||||
|
||||
**9. By using qemu-img command info, you could get information about your new disk image.**
|
||||
|
||||

|
||||
Check Storage Volume Information
|
||||
|
||||
**Warning**: Never use qemu-img to modify images in use by a running virtual machine or any other process; this may destroy the image.
|
||||
|
||||
Now its time to create virtual machines in the next step.
|
||||
|
||||
### Step 3: Create Virtual Machines ###
|
||||
|
||||
10. Now with the last and latest part, we will create virtual machines using virt-istall. The virt-install is a command line tool for creating new KVM virtual machines using the “libvirt” hypervisor management library. For more details about it, use:
|
||||
|
||||
# man virt-install
|
||||
|
||||
To create new KVM virtual machine, you need to use the following command with all the details like shown in the below.
|
||||
|
||||
- Name: Virtual Machine’s name.
|
||||
- Disk Location: Location of disk image.
|
||||
- Graphics : How to connect to VM “Usually be SPICE”.
|
||||
- vcpu : Number of virtual CPU’s.
|
||||
- ram : Amount of allocated memory in megabytes.
|
||||
- Location : Specify the installation source path.
|
||||
- Network : Specify the virtual network “Usually be vibr00 bridge”.
|
||||
|
||||
# virt-install --name=rhel7 --disk path=/mnt/personal-data/SPool1/SVol1.img --graphics spice --vcpu=1 --ram=1024 --location=/run/media/dos/9e6f605a-f502-4e98-826e-e6376caea288/rhel-server-7.0-x86_64-dvd.iso --network bridge=virbr0
|
||||
|
||||

|
||||
Create New Virtual Machine
|
||||
|
||||
**11. You will find also a pop-up virt-vierwer window appears to communicate with virtual machine through it.**
|
||||
|
||||

|
||||
Booting Virtual Machine
|
||||
|
||||

|
||||
Installation of Virtual Machine
|
||||
|
||||
### Conclusion ###
|
||||
|
||||
This is the latest part of our KVM tutorial, we haven’t covered everything of course. It a shot to scratch the KVM environment so its your turn to search and keep hands dirty using this nice resources.
|
||||
|
||||
- [KVM Getting Started Guide][2]
|
||||
- [KVM Virtualization Deployment and Administration Guide][3]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.tecmint.com/kvm-management-tools-to-manage-virtual-machines/
|
||||
|
||||
作者:[Mohammad Dosoukey][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.tecmint.com/author/dos2009/
|
||||
[1]:http://www.tecmint.com/install-and-configure-kvm-in-linux/
|
||||
[2]:https://access.redhat.com/site/documentation/en-US/Red_Hat_Enterprise_Linux/7/html/Virtualization_Getting_Started_Guide/index.html
|
||||
[3]:https://access.redhat.com/site/documentation/en-US/Red_Hat_Enterprise_Linux/7/html/Virtualization_Deployment_and_Administration_Guide/index.html
|
||||
@ -0,0 +1,85 @@
|
||||
How to Setup Passwordless SSH Logon to Ubuntu 14.04
|
||||
================================================================================
|
||||
Hi all, today we'll gonna learn how we can setup Passwordless SSH Logon to Ubuntu 14.04 "Trusty". Only the workstations having the correct matching key pair (private and public) will be allowed to logon to the SSH server, without the key paring, access will not be allowed.
|
||||
|
||||
Usually, we need to enter username and password combination to connect to an SSH console. If the combination is correct to that of the system's then, we get access to the server else we are denied from the access. But, there is something more secure than Password logon, we have passwordless SSH logon using the encrypted keys.
|
||||
|
||||
If you want to enable this secured option, we can simply disable password-logon and only allow logon using an encryption key. When using encryption keys option, the client computer generates a private and public key pair. The client then must upload the public key to the SSH server authorized_key file. Before access is granted, the server and client computer validate the key pair. If the public key on the server matches the private key submitted via the client then access will be granted else will be denied.
|
||||
|
||||
This is a very secure way authenticating to a SSH server and it’s a recommended method if you wish to implement secure logon with single user SSH logon. Here's a quick step-wise process on how to enable Passwordless SSH logon.
|
||||
|
||||
### 1. Installing Openssh Server ###
|
||||
|
||||
First off all, we'll need to update our local repository index. To do so, we'll first need to run apt-get update as shown below.
|
||||
|
||||
$ sudo apt-get update
|
||||
|
||||

|
||||
|
||||
Now, we can install openssh-server by running following command.
|
||||
|
||||
$ sudo apt-get install openssh-server
|
||||
|
||||

|
||||
|
||||
### 2. Enabling Openssh Server ###
|
||||
|
||||
Now, we'll want to enable OpenSSH server after we successfully installed it on our Ubuntu 14.04 Operating System. The command to enable/start the server is given as follows.
|
||||
|
||||
$ sudo service ssh start
|
||||
|
||||
OR
|
||||
|
||||
$ sudo /etc/init.d/ssh start
|
||||
|
||||
### 3. Configuring Key Pair ###
|
||||
|
||||
After we have installed our OpenSSH Server and enabled it. We'll now finally wanna go for generating our Public and Private Key Pair. To do that, run the following command in a terminal or console.
|
||||
|
||||
$ ssh-keygen -t rsa
|
||||
|
||||
After running the above command, we'll be prompted to complete a series of tasks. The first will be where to save the keys, press Enter to choose the default location which is in a hidden .ssh folder in the home directory. The next prompt will be to enter the Paraphrase. I personally leave this blank (just press enter) to continue. It will then create the key pair and we’re done.
|
||||
|
||||

|
||||
|
||||
After generation of the key pair, we will need to **copy the client’s public key to the SSH server** or host inorder to create trusted relationship with it. We'll need to run the commands below to copy the client public key to the server.
|
||||
|
||||
$ ssh-copy-id user@ip_address
|
||||
|
||||
After the public key is copied to the server, we can now go and disable password logon via SSH. To do that, we'll need to open **/etc/ssh/ssh_config** via a text editor by run the commands below.
|
||||
|
||||
$ sudo nano /etc/ssh/sshd_config
|
||||
|
||||
Now, we'll need to uncomment the lines and set the values as shown below.
|
||||
|
||||

|
||||
|
||||
### 4. Restarting the SSH Server ###
|
||||
|
||||
Finally, after we are done configuring SSH Server, we'll want to restart our SSH Server so that all the changes will take affect. To restart one can run the following command in a terminal or the console.
|
||||
|
||||
$ sudo service ssh restart
|
||||
|
||||
OR
|
||||
|
||||
$ sudo /etc/init.d/ssh restart
|
||||
|
||||

|
||||
|
||||
Finally, we can now ssh in to the server without a password and only from the client having the same key pair not the password.
|
||||
|
||||
### Conclusion ###
|
||||
|
||||
Hurray! We have successfully enabled Passwordless SSH logon. It is a lot secure to enable Encrypted Key Pair SSH logon . This is a very secure way authenticating to a SSH server and it’s a recommended method if you wish to implement secure logon with single user SSH logon. So, if you have any questions, suggestions, feedback please write them in the comment box below. Thank you ! Enjoy Encrypted Secure SSH Login :-)
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/ubuntu-how-to/setup-passwordless-ssh-logon-ubuntu-14-04/
|
||||
|
||||
作者:[Arun Pyasi][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://linoxide.com/author/arunp/
|
||||
@ -0,0 +1,155 @@
|
||||
11 个 增强你的 Ubuntu 使用体验的实用工具
|
||||
================================================================================
|
||||
**无论你是一个相对的新手还是经验丰富的专家,我们都想从我们的操作系统中得到更多的东西。正如大多数现代的操作系统,相比于乍一看呈现出的内容,Ubuntu 有更多东西可以向我们提供。**
|
||||
|
||||
从调整和优化 Unity 桌面的外观、行为、性能 到 执行系统维护,有着大量的实用工具和应用可以帮助你 **调整 Ubuntu 来无时不刻地满足你的需求**。
|
||||
|
||||
注意时刻: Ubuntu 一直都配备了‘合理的默认设置---即工作良好的选项---’,以达到开箱即用,这些默认设置适合大多数人,并且它们都是经过了测试,采用及推荐等过程的。
|
||||
|
||||
但一个尺寸并不适合所有。对于我们当中的能工巧匠和实验主义者来说,默认设置只是他们定制系统的起点。
|
||||
|
||||
所以,无需更多的唠叨, 这里有 11 个极好的实用工具来帮助你增强你的 Ubuntu 使用体验。
|
||||
|
||||
### Unity Tweak Tool ###
|
||||
|
||||

|
||||
|
||||
我将以这个列表中最重要的一个工具: **Unity Tweak Tool** 来开始这次的介绍。定制的厨房水槽(注:不知该如何翻译,感觉意思是:水槽之于厨房的重要性相当于该软件之于定制 Ubuntu 的重要性), Unity Tweak Tool 提供了一系列针对 Ubuntu 和 Unity 桌面的系统综合调整功能。
|
||||
|
||||
它被各种开关,切换和控制塞得满满的,使得你可以任意设置从 Unity 桌面的外观到 Unity 的行为之类的任何东西。你可以使用它 **快速简便地改变 GTK 主题和图标集**、设置热区、调整启动器图标尺寸、增加或移除工作区,以及 ---特别地---开启 Unity 桌面中被巧妙隐藏的“通过点击最小化”的特点。
|
||||
|
||||
免费并可直接从 Ubuntu 软件中心里找到, Unity Tweak Tool 是非常值得保留在你的口袋里的工具之一。
|
||||
|
||||
### Unity Privacy Indicator ###
|
||||
|
||||

|
||||
|
||||
隐私是一个非常,非常重要的事,事实也恰恰如此。但这个话题总是被隐藏在二进制之下(注:感觉这里翻译有误,不太确定)。让一些数据或习惯,比如说你经常打开的应用,在本地被记录下来,这或许会让你感到高兴,但对于 你在 Dash 中的搜索数据被发送带第三方服务机构(尽管这些数据或许是匿名的)这类事情,你就高兴不起来了。
|
||||
|
||||
[Privacy Indicator][1] 是一个帮助你时刻跟踪 Ubuntu桌面系统中哪些文件、目录和服务正被获取、记录及搜索的实用工具。
|
||||
|
||||
通过快速的点击被添加到桌面面板上的‘眼睛’图标,你可以:
|
||||
|
||||
- 开启或关闭在线搜索结果,Zeitgeist(注:根据图片看,Zeitgeist 指的是 record activity), HUD 记录 和 GeoIP 服务
|
||||
- 快速的启用 清理 Zeitgeist,F2(注:根据图片看,F2 指的是 通过 Alt-F2 执行的命令),当前文件等等的记录数据
|
||||
- 展示或隐藏桌面图标以及它们在桌面面板上的名称
|
||||
|
||||
上面的最后两个选项在这个应用中似乎有点被放错了位置,但对于那些要分享截图或截屏的人来说,将会泄露更少的隐私。
|
||||
|
||||
- [从这里下载 Indicator Privacy (.deb)][2]
|
||||
|
||||
### Unity Folders ###
|
||||
|
||||

|
||||
|
||||
**Android, iOS, OS X, Chrome OS, 和 GNOME Shell 都有应用橱窗, 借助一个极好的第三方应用,Unity 也可以实现类似功能。**
|
||||
|
||||
“Unity Folders” 允许你组织位于 Unity 启动器中的应用到实用的橱窗中,--- 如 游戏,办公,社交等。不必打开 Dash,你就可以快速启动你喜爱的应用,这非常适合你的工作流。
|
||||
|
||||
每一个 ‘橱窗’其实一个打开 ,但总体效果看上去就像是一个 OS X 的风格栈 或 Android 的切换框(注:这里的翻译我拿不准)。
|
||||
|
||||
橱窗的图标可以自定义或根据橱窗内的应用来自动生成。已经存在的橱窗可以被编辑,重新组织,重命名以及如下的更多选择:
|
||||
|
||||
- 根据你的喜好创建任意多的橱窗
|
||||
- 选择自定义或自动生成橱窗图标
|
||||
- 可选择 3 种橱窗样式
|
||||
- 为添加到橱窗中的应用设定自定义图标
|
||||
- 编辑现有橱窗
|
||||
|
||||
[Unity Folders 的网址](http://unity-folders.exceptionfound.com/)
|
||||
(注:根据原文来看,这里应该有链接,转换为 md 文档时没有加上链接)
|
||||
|
||||
### 咖啡因 ###
|
||||
|
||||
对于我们中的许多人来说,咖啡因是主食,它并不只存在于饮料之中。咖啡因提供了一个快速,温和的方式来阻止你的屏保或锁屏起作用。有用的程度将取决于你的环境(即你系统的怪癖) (注:这一句我没有完全理解原文的意思),并且尽管它不像以前那样对用户友好,它仍然值得你[尝试一下][3]。
|
||||
|
||||
### 系统状态指示器 (System Monitor Indicator) ###
|
||||
|
||||

|
||||
|
||||
假如你是一个状态迷,即一个喜欢密切关注程序,进程和硬件的状态的人, Linux 很容易满足你的需求。从 Conky 的配置到终端命令,并不缺少监视你的 CPU 使用情况、网络流量或 GPU 温度的方法。
|
||||
|
||||
但至今为止,我最喜爱的应用是 系统**监视指示器**,---也被叫做多负载指示器---它可从 Ubuntu 软件中心获得。它也有着大量的配置选项。
|
||||
|
||||
- [点击这个链接,在 Ubuntu 中 下载 ‘System Load Indicator’][4]
|
||||
|
||||
### 针对 Linux 笔记本电脑的省电工具 ###
|
||||
|
||||

|
||||
|
||||
**TLP**
|
||||
|
||||
当提到便携式设备上的电池使用效率时,Linux 发行版本并没有最好的声誉。
|
||||
|
||||
如果你自己的 Linux 笔记本可以勉强在再次充电之前,让你从沙发到厨房,那么这里有几个你可以试试的工具。
|
||||
|
||||
TLP 是最受欢迎的确保延长 Linux 笔记本的电池寿命的自动化后台工具之一,它是通过调整系统进程和硬件的设置及行为来达到此目的的,例如 启动 Wi-Fi 省电模式, PCI 总线设备的实时电量管理和处理器的频率缩放调整。
|
||||
|
||||
在 Ubuntu 14.04 LTS 以及后续发行版本中可以使用 TLP 专用的 PPA 来安装它。且它只带了‘包罗万象’的设置来使你踏上配置它的旅程。 在我们之中的高级用户可以潜心研究并根据你自己的硬件来调整设置,一个 [关于 TLP 的完整指导 wiki][6] 使得设置更加容易。
|
||||
|
||||
**Laptop Mode Tools**
|
||||
|
||||
假如 TLP 听起来有一点复杂 --这也并没有什么可羞耻的--这里有一个更简单的替代品: **Laptop Mode Tools**。 这个软件包可从 Ubuntu 软件中心直接安装,且本身设置好了一系列合理的默认设置(Wi-Fi,蓝牙等等)。
|
||||
|
||||
Laptop Mode Tools 不能和 TLP 同时被安装在电脑中。
|
||||
|
||||
- [Ubuntu 软件中心里的 Laptop Mode Tools ][7]
|
||||
|
||||
### Intel 显卡驱动安装工具 ###
|
||||
|
||||

|
||||
|
||||
对于那些运行 Intel 显卡硬件,并想使得这些硬件发挥出最佳性能的人来说,Intel 显卡安装工具是必须拥有的。 它使得 查找并安装最新的 Intel GPU 驱动变得不再是一件痛苦和大费周折的事 ---因为这无需 PPA 或任何的终端使用知识。
|
||||
|
||||
- [下载针对 Linux平台的 Intel 图形安装器 0.7 版本][8]
|
||||
|
||||
### Hardware Stats ###
|
||||
|
||||

|
||||
|
||||
假如你计划 升级你的 PC 或替换一个坏掉的零部件,你需要知道一些特定的硬件信息,例如 RAM 类型,CPU插座类型 或 查看那个PCI 槽是可用的等信息。
|
||||
|
||||
**I-Nex**可以使得 发掘出以上的信息以及其他的系统具体状态变得更加容易。使用它来查找你的主板型号、S.M.A.R.T.(注:为 Self-Monitoring, Analysis and Reporting Technology 的缩写,经常写为 SMART ) 状态,以及你想得出的很多东西!
|
||||
|
||||
- [可从 Launchpad 了解到更多关于 I-Nex 的信息][9]
|
||||
|
||||
### 磁盘空间可视化程序(Disk Space Visualizer) ###
|
||||
|
||||

|
||||
|
||||
在这个硬盘以 1TB 计数的时代,我们或许不必同以前一样对硬盘空间的使用三思而后行。但对于那些使用小容量的 SSD,运行多个分区或在一个拥有固定虚拟磁盘大小的虚拟机上工作,总有感觉 释放一些额外空间是必要的 这种想法的时候。
|
||||
|
||||
GNOME Disks,在 Ubuntu 中被默认安装,使得查找占用最大磁盘空间的罪魁祸首变得容易。对于定位隐藏的日志、缓存和视频文件,它是非常完美的工具。
|
||||
|
||||
### BleachBit (Cruft Cleaner) ###
|
||||
|
||||

|
||||
|
||||
Windows 用户可能对像 CCleaner 之类的应用很熟悉,它可以扫描并清理垃圾文件、空白文件夹、臃肿的缓存以及陈旧的软件包。在 Ubuntu 上,一个相似的快速且毫不费力的一键式清理方法可以试试 **BleachBit** 。
|
||||
|
||||
它是一个强大的工具,所以一定要注意你正在清理什么。不要漫无目的地确认每个选项框;不是所有的东西它都可以清理。所以请合理地使用它,当你对某个选项有疑问时,就跳过它。
|
||||
|
||||
- [Install BleachBit from Ubuntu Software Center][10]
|
||||
|
||||
你已经有了自己最喜欢的系统实用工具了吗?可以在下面的评论中让其他人知晓它。
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.omgubuntu.co.uk/2014/11/useful-tools-for-ubuntu-do-you-use-them
|
||||
|
||||
作者:[Joey-Elijah Sneddon][a]
|
||||
译者:[FSSlc](https://github.com/FSSlc)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://plus.google.com/117485690627814051450/?rel=author
|
||||
[1]:http://www.florian-diesch.de/software/indicator-privacy/index.html
|
||||
[2]:http://www.florian-diesch.de/software/indicator-privacy/dist/indicator-privacy_0.04-1_all.deb
|
||||
[3]:http://www.omgubuntu.co.uk/2014/05/stop-ubuntu-sleeping-caffeine
|
||||
[4]:apt://indicator-mulitload
|
||||
[5]:https://launchpad.net/~linrunner/+archive/ubuntu/tlp/+packages
|
||||
[6]:http://linrunner.de/en/tlp/docs/tlp-configuration.html
|
||||
[7]:https://apps.ubuntu.com/cat/applications/laptop-mode-tools/
|
||||
[8]:https://01.org/linuxgraphics/downloads/2014/intelr-graphics-installer-linux-1.0.7
|
||||
[9]:https://launchpad.net/i-nex
|
||||
[10]:https://apps.ubuntu.com/cat/applications/bleachbit/
|
||||
@ -0,0 +1,166 @@
|
||||
如何在linux上通过rsyslog来配置一个syslog服务器
|
||||
========================================================================
|
||||
syslog服务器表示一个用来监控一个网络中的端点--所有能够通过网络来发送日志的设施(包含了Linux或Windows服务器,路由器,交换机以及其他主机)--的中央日志。 通过设置一个syslog服务器,可以将不同设施/主机发送的日志,过滤和合并到一个独立的位置,这样使得你更容易地查看和获取重要的日志消息。
|
||||
|
||||
**rsyslog** 被作为标准的syslog守护进程预装在了大多数的Linux发行版中。在客户端/服务器架构的配置下,**rsyslog**同时扮演了两种角色:1.作为一个syslog服务器,**rsyslog**可以收集来自其他设施的日志信息;2.作为一个syslog客户端,**rsyslog**可以将其内部的日志信息传输到远程的syslog服务器。
|
||||
|
||||
|
||||
在此,我们演示了在linux上如何通过**rsyslog**来配置一个中心化syslog服务器。 在进入详解之前,先温习一下syslog标准。
|
||||
|
||||
### syslog标准基础###
|
||||
|
||||
当通过syslog机制来收集日志时,有3个必须要考虑到的重要事情:
|
||||
|
||||
- **设施层级**: 监听何种类型的进程
|
||||
- **严重性 (优先) 级别**: 收集何种类型的日志消息
|
||||
- **目标**: 发送或记录日志消息到何处
|
||||
|
||||
现在我们更加深入地了解一下配置是如何定义的。
|
||||
|
||||
|
||||
设施层级定义了一种用来对内部系统进程进行分类的方法,linux中的一些常见的设施包括:
|
||||
|
||||
- **auth**: 身份验证相关的消息(登录时)
|
||||
- **cron**: 进程或应用调度相关的消息
|
||||
- **daemon**: 守护进程相关的消息(内部服务器)
|
||||
- **kernel**: 内核相关的消息
|
||||
- **mail**: 内部邮件服务器相关的消息
|
||||
- **syslog**: syslog 守护进程本身相关的消息
|
||||
- **lpr**: 打印服务相关的消息
|
||||
- **local0 - local7**: 用户自定义的消息 (local7 通常被Cisco 和 Windows 服务器 使用)
|
||||
|
||||
严重性(优先)级别是通过标准的缩写和赋予的数字来进行定义和标准化的,其中的数字7具有最高的级别,这些级别包含了:
|
||||
|
||||
- emerg: Emergency(紧急)- 0
|
||||
- alert: Alerts (报警)- 1
|
||||
- crit: Critical (关键)- 2
|
||||
- err: Errors (错误)- 3
|
||||
- warn: Warnings (警告)- 4
|
||||
- notice: Notification (通知)- 5
|
||||
- info: Information (消息)- 6
|
||||
- debug: Debugging (调试)- 7
|
||||
|
||||
最后,目标语句迫使一个syslog客户端来执行以下3个任务中的一个:1.保存日志消息到一个本地文件;2. 通过TCP/UDP将消息路由到远程的syslog服务器中
|
||||
;3.将其发送到一个标准输出中,例如控制台。
|
||||
|
||||
在rsyslog, syslog配置是基于以下模式进行结构化的。
|
||||
|
||||
[facility-level].[severity-level] [destination]
|
||||
|
||||
### Configure Rsyslog on Linux ###
|
||||
### 在Linux中配置Rsyslog###
|
||||
|
||||
在我们理解syslog之后,现在是时候来通过rsyslog来将一个Linux服务器配置为一个中心syslog服务器了,另外我们也将看到如何将基于Windows的系统配置为一个syslog客户端来发送内部日志到该syslog服务器中。
|
||||
|
||||
### 第1步: 初始化系统需求 ###
|
||||
|
||||
为了将linux主机设置为一个中央日志服务器, 我们需要创建一个隔离的/var 分区,并分配足够大的磁盘空间或者创建一个特殊的LVM卷组。这样就会使得syslog服务器能够承担在日积月累收集日志所带来的潜在增长。
|
||||
|
||||
|
||||
### 第2步: 让rsyslog 后台进程生效 ###
|
||||
|
||||
rsyslog守护进程来自于当前的linux发布版本的预装模块,但是默认并没有启动。为了能够让rsyslog守护进程能够接受外部的消息,需要编辑其配置文件/etc/rsyslog.conf.
|
||||
|
||||
如果已经准备好打开文件进行编辑,查找到下面的两行所在的位置,通过删除其行首的#字符来取消其注释。
|
||||
|
||||
$ModLoad imudp
|
||||
$UDPServerRun 514
|
||||
|
||||
这会使得rsysolog守护进程能够在UDP端口514上接受日志消息了---UDP是一种比TCP速度快,但是并不具有TCP一样的数据流程的可靠性。所以如果你需要使用可靠的传送机制,就可以通过取消以下行的注释。
|
||||
|
||||
$ModLoad imtcp
|
||||
$InputTCPServerRun 514
|
||||
|
||||
需要注意的是,TCP和UDP可以被同时生效来监听TCP/UDP 连接。
|
||||
|
||||
### 第3步:创建日志接受模板###
|
||||
|
||||
接下来的这步,需要我们来为远程消息创建模板,并告知rsyslog守护进程如何记录从其他客户端机器所接受到的消息。
|
||||
|
||||
|
||||
使用文本编辑器来打开 /etc/rsyslog.conf,然后在GLOBAL DIRECTIVE块前追加以下的模板。
|
||||
|
||||
$template RemoteLogs,"/var/log/%HOSTNAME%/%PROGRAMNAME%.log" *
|
||||
*.* ?RemoteLogs
|
||||
& ~
|
||||
|
||||
在此对该模板进行简单解释,$template RemoteLogs(“RemoteLogs” 字符串可以为任何其他的指令名称)指令强制rsyslog后台进程将日志消息写道/var/log下的分开的本地日志文件中,其中日志文件的名称是基于远程日志发送机器的主机名以及生成该日志的应用程序名进行定义的。其中第二行暗示了我们将RemoteLogs模板应用到所有接受到的日志上。
|
||||
|
||||
|
||||
符号"& ~"表示了一个重定向规则,被用来告知rsyslog守护进程停止对日志消息的进一步处理,并且不要在本地写入。如果该重定向规则没有使用,那么所有的远程消息都会在写入上述描述的日志文件之外同时被写入到本地日志文件,这就意味着日志消息实际上被写了两次。使用该规则的另外一个结果就是syslog服务器本身的日志消息只会被以该机器主机名命名的专有文件中。
|
||||
|
||||
|
||||
如果你想要的话,也可以使用下面的模式对特定的设备或严重性级别使用新的模板直接来记录日志消息。
|
||||
|
||||
|
||||
[facility-level].[severity-level] ?RemoteLogs
|
||||
|
||||
例如:
|
||||
|
||||
将所有内部的所有优先级别的用户验证消息指定为RemoteLogs模板:
|
||||
|
||||
authpriv.* ?RemoteLogs
|
||||
|
||||
将所有系统进程中除开mail,用户验证和cron消息之外的进程产生的消息级别的日志指定为RemoteLogs模板:
|
||||
|
||||
|
||||
*.info,mail.none,authpriv.none,cron.none ?RemoteLogs
|
||||
|
||||
如果我们想要将所有从远程客户端接受到的消息写入到一个以它们的IP地址命名的单个文件中,可以使用以下的模板。在此我们为该模板赋予了“IPTemplate”名称。
|
||||
|
||||
$template IpTemplate,"/var/log/%FROMHOST-IP%.log"
|
||||
*.* ?IpTemplate
|
||||
& ~
|
||||
|
||||
在我们生效rsyslog守护进程以及编辑其配置文件之后,需要重启该守护进程。
|
||||
|
||||
在 Debian,Ubuntu 或 CentOS/RHEL 6中:
|
||||
|
||||
$ sudo service rsyslog restart
|
||||
|
||||
在 Fedora 或 CentOS/RHEL 7中:
|
||||
|
||||
$ sudo systemctl restart rsyslog
|
||||
|
||||
我们可以通过netstat命令来验证rsyslog守护进程是否正常工作。
|
||||
|
||||
$ sudo netstat -tulpn | grep rsyslog
|
||||
|
||||
在UDP监听端口下工作的rsyslog守护进程会有类似下面的输出。
|
||||
|
||||
udp 0 0 0.0.0.0:514 0.0.0.0:* 551/rsyslogd
|
||||
udp6 0 0 :::514 :::* 551/rsyslogd
|
||||
|
||||
如果rsyslog守护进程被设置在TCP连接端口,那么应该有类似下面所示的输出。
|
||||
|
||||
tcp 0 0 0.0.0.0:514 0.0.0.0:* LISTEN 1891/rsyslogd
|
||||
tcp6 0 0 :::514 :::* LISTEN 1891/rsyslogd
|
||||
|
||||
### 发送Windows日志到一个远程的rsyslog服务器###
|
||||
|
||||
为了将一个Windows客户端的日志消息转发到我们的rsyslog服务器,需要一个Windows syslog 代理。当然,有许多的syslog代理可以在windows上运行,在此我们可以使用一个自由软件程序 [Datagram SyslogAgent][1].
|
||||
|
||||
|
||||
|
||||
在下载安装该syslog代理后,需要将其配置为作为服务运行。指定使用何种协议来发送数据,以及远程rsyslog服务器的IP地址和端口,最后指定应该传输的事件日志类型,如下所示。
|
||||
|
||||

|
||||
|
||||
在我们完成所有的这些配置之后,我们就可以启动该服务并且在中央rsyslog服务器中使用命令行工具tailf来查看日志文件了。
|
||||
|
||||
### 总结###
|
||||
|
||||
通过创建一个可以收集本地和远程主机的中央rsyslog服务器,我们可以更好地了解在这些系统内部究竟发生着什么,而且可以更加容易地调试他们的问题,是否在他们之间有任何缓慢或崩溃存在。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/configure-syslog-server-linux.html
|
||||
|
||||
作者:[Caezsar M][a]
|
||||
译者:[theo-l](https://github.com/theo-l)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/caezsar
|
||||
[1]:http://www.syslogserver.com/download.html
|
||||
@ -0,0 +1,133 @@
|
||||
如何在 Linux 上使用 BackupPC 来设置一个跨平台的备份服务器
|
||||
================================================================================
|
||||
为了防止你不能分辨这篇教程和我先前关于[backupninja][1] 和 [backup-manager][2] 的帖子,=== 我是一个积极的备份迷。当提到备份,我宁愿备份的太多而不希望备份不足,因为如果我们有需要的话,你将会感激你花费了时间和精力来为你的重要数据生成额外的拷贝。
|
||||
|
||||
在这篇帖子中,我将向你介绍 [BackupPC][3],一个跨平台的备份服务器软件,它可以通过网络为 Linux,Windows 和 MacOS 等系统上的客户端主机拉取备份。BackupPC 添加了一系列的特点使得管理备份变为一件快乐的事。
|
||||
|
||||
### BackupPC 的特点 ###
|
||||
|
||||
BackupPC 自带有一个健壮的 Web 界面,允许你以集中的方式来收集和管理其他远程客户端主机上的备份。通过使用它的 Web 界面,你可以检查日志和配置文件、为其他远程主机启动/取消/安排备份任务以及可视化备份任务的当前状态。你也可以非常容易地浏览归档的文件以及从备份的归档中恢复个人文件或整个作业。为了恢复单一的个人文件,你可以直接通过 Web 界面来下载任何先前备份的文件。若如这还不够,针对客户端主机,没有特别的客户端软件需要安装。在 Windows 客户端上, 本机 SMB 协议将被使用,而对于 *nix 客户端,你将使用 `rsync` 或 通过 SSH, RSH 或 NFS 来使用 `tar` 。
|
||||
|
||||
### 安装 BackupPC ###
|
||||
|
||||
在 Debian,Ubuntu 和它们的衍生版本上,运行下面的命令:
|
||||
|
||||
# aptitude install backuppc
|
||||
|
||||
在 Fedora上, 使用 `yum` 命令。请注意软件包名字对大小写敏感。
|
||||
|
||||
在 CentOS/RHEL 6 上,首先要启用 [EPEL 软件仓库][4]。在 CentOS/RHEL 7 上,请替代启用 [Nux Dextop][5] 软件仓库。然后接着使用 `yum` 命令:
|
||||
|
||||
# yum install BackupPC
|
||||
|
||||
同往常一样,这两种包管理系统都会自动地对依赖问题进行解决。另外,作为安装过程中的一部分,你可能会被要求去配置或重新配置用于图形用户界面的 Web 服务器。下面的截图来自于 Debian 系统:
|
||||
|
||||

|
||||
|
||||
通过空格键来确定你的选择,然后使用 tab 键移动到 Ok 选项并敲回车键。
|
||||
|
||||
接着类似于下面的截屏将会呈现在你眼前,通知你一个用来管理 BackupPC 的名为 ‘backuppc’的管理员用户以及相应的密码(这个密码可以在以后被更改,如果你希望的话)已经被创建。这里需要注意的是:同样名为 ‘backuppc’的一个 HTTP 账户和一个常规的 Linux 账户将会被创建,它们使用同一个密码。需要前者的目的是来访问受保护的 BackupPC 的 Web 界面,而后者则是为了通过 SSH 来使用 `rsync` 来执行备份任务。
|
||||
|
||||

|
||||
|
||||
你可以使用下面的命令来更改 HTTP 账户 ‘backuppc’ 的默认密码:
|
||||
|
||||
# htpasswd /path/to/hash/file backuppc
|
||||
|
||||
至于常规的 ‘backuppc’ [Linux][6]账户,可以使用 `passwd`命令来更改它的默认密码:
|
||||
|
||||
# passwd backuppc
|
||||
|
||||
需要提及的是:安装过程中会自动创建 Web 和程序的配置文件。
|
||||
|
||||
### 启动 BackupPC 并设置备份 ###
|
||||
|
||||
首先,打开一个浏览器窗口并指向 http://<server's FQDN or IP address>/backuppc/ 。当弹出提示框时,输入先前向你提供的默认 HTTP 用户凭据(注:即用户名 backuppc 和相应的默认密码)。假如认证成功,你就会被带入到 Web 界面的主页:
|
||||
|
||||

|
||||
|
||||
你想做的第一件事最有可能是通过新增一个客户端主机来备份。进入任务窗格中的 “编辑主机”选项。我们将添加两个客户端主机:
|
||||
|
||||
- Host #1: CentOS 7 [IP 192.168.0.17]
|
||||
- Host #2: Windows 7 [IP 192.168.0.103]
|
||||
|
||||
我们将通过 SSH 使用 `rsync`来备份 CentOS 主机,使用 SMB 来备份 Windows 主机。在执行备份之前,我们需要向我们的 CentOS 主机设置 [基于密码认证][7](注:这里我不知如何翻译,根据链接,感觉是无需密码来连接主机)以及在我们的 Windows 主机中设置一个共享目录。
|
||||
|
||||
下面是关于如何为一个远程 CentOS 主机设置 key-based authentication 的指导。我们创建 ‘backuppc’ 用户的 RSA 密钥对,并向 CentOS 主机上的 root 账户传递它的公共密钥。
|
||||
|
||||
# usermod -s /bin/bash backuppc
|
||||
# su - backuppc
|
||||
# ssh-keygen -t rsa
|
||||
# ssh-copy-id root@192.168.0.17
|
||||
|
||||
当弹出提示框时,键入 yes 并为 192.168.0.17 键入 root 用户的密码:
|
||||
|
||||

|
||||
|
||||
你需要一个远程的 CentOS 主机的 root 权限来在该主机中的文件系统中发放写权限,以防要恢复的备份文件或目录的所有者为 root 账户。
|
||||
|
||||
一旦 CentOS 和 Windows 主机都准备完毕,使用 Web 界面将它们添加到 BackupPC:
|
||||
|
||||

|
||||
|
||||
下一步的内容由更改每个主机的备份设置组成:
|
||||
|
||||

|
||||
|
||||
接下来的图片展示了 Windows 主机的备份设置:
|
||||
|
||||

|
||||
|
||||
而接着的截图展示了 CentOS 主机的备份设置:
|
||||
|
||||

|
||||
|
||||
### 开始一个备份任务 ###
|
||||
|
||||
为了开始备份,到每个主机的设定选项,然后点击“开始全备份”:
|
||||
|
||||

|
||||
|
||||
在任何时候,你都可以通过点击如上图展示的每个主机的备份主页来查看备份任务的状态。假如因为某些原因备份失败,在主机菜单中将会出现一个指向包含错误信息的网页的链接。当一个备份任务被成功地完成,一个被命名为主机名或 IP 地址的目录将会在服务器的 /var/lib/backuppc/pc 目录下被创建。
|
||||
|
||||

|
||||
|
||||
我们也可以随意地在命令行中浏览这个目录中的文件,但存在一个更加简单的方式来查找和恢复这些文件。
|
||||
|
||||
### 恢复备份 ###
|
||||
|
||||
为了浏览已经保存过的文件。进入每个主机的主菜单下的 “浏览备份”选项,你可以一目了然地看到目录和文件,并选择那些你想恢复的文件。另外,你还可以通过点击文件来使用默认程序打开文件或右击文件并选择“另存为”来下载该文件到你正在工作的机器上:
|
||||
|
||||

|
||||
|
||||
如若你想,你可以下载一个包含所有你想备份的内容的 zip 或 tar 文件:
|
||||
|
||||

|
||||
|
||||
或只是恢复文件:
|
||||
|
||||

|
||||
|
||||
### 总结 ###
|
||||
|
||||
有句俗话说,"越简单,越好",而这正是 BackupPC 所提供的东西。在 BackupPC 中,你将不仅找到了一个备份工具,而且还找到了一个无需任何客户端应用来在几个不同的操作系统中管理你的备份的方法。我相信这就有足够的理由让你去尝试一下。
|
||||
|
||||
欢迎使用下面的评论框来留下你的评论和问题,假如你有的话。我总是乐于听取读者想说的话!
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/backuppc-cross-platform-backup-server-linux.html
|
||||
|
||||
作者:[Gabriel Cánepa][a]
|
||||
译者:[FSSlc](https://github.com/FSSlc)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/gabriel
|
||||
[1]:http://xmodulo.com/backup-debian-system-backupninja.html
|
||||
[2]:http://xmodulo.com/linux-backup-manager.html
|
||||
[3]:http://backuppc.sourceforge.net/
|
||||
[4]:http://xmodulo.com/how-to-set-up-epel-repository-on-centos.html
|
||||
[5]:http://ask.xmodulo.com/enable-nux-dextop-repository-centos-rhel.html
|
||||
[6]:http://xmodulo.com/recommend/linuxguide
|
||||
[7]:http://xmodulo.com/how-to-enable-ssh-login-without.html
|
||||
@ -0,0 +1,191 @@
|
||||
linux中创建和解压文档的10个快速tar命令样例
|
||||
================================================================================
|
||||
### linux中的tar命令###
|
||||
|
||||
tar(磁带归档)命令是linux系统中被经常用来将文件存入到一个归档文件中的命令。
|
||||
|
||||
常见的文件扩展包括:.tar.gz 和 .tar.bz2, 分别表示通过gzip或bzip算法进一步压缩的磁带归档文件扩展。
|
||||
|
||||
|
||||
在该教程中我们会窥探一下在linux桌面或服务器版本中使用tar命令来处理一些日常创建和解压归档文件的工作样例。
|
||||
### 使用tar命令###
|
||||
|
||||
tar命令在大部分linux系统默认情况下都是可用的,所以你不用单独安装该软件。
|
||||
|
||||
> tar命令具有两个压缩格式,gzip和bzip,该命令的“z”选项用来指定gzip,“j”选项用来指定bzip。同时也可哟用来创建非压缩归档文件。
|
||||
|
||||
#### 1.解压一个tar.gz归档 ####
|
||||
|
||||
一般常见的用法是用来解压归档文件,下面的命令将会把文件从一个tar.gz归档文件中解压出来。
|
||||
|
||||
|
||||
$ tar -xvzf tarfile.tar.gz
|
||||
|
||||
这里对这些参数做一个简单解释-
|
||||
|
||||
> x - 解压文件
|
||||
|
||||
> v - 繁琐,在解压每个文件时打印出文件的名称。
|
||||
|
||||
> z - 该文件是一个使用 gzip压缩的文件。
|
||||
|
||||
> f - 使用接下来的tar归档来进行操作。
|
||||
|
||||
这些就是一些需要记住的重要选项。
|
||||
|
||||
**解压 tar.bz2/bzip 归档文件 **
|
||||
|
||||
具有bz2扩展名的文件是使用bzip算法进行压缩的,但是tar命令也可以对其进行处理,但是是通过使用“j”选项来替换“z”选项。
|
||||
|
||||
$ tar -xvjf archivefile.tar.bz2
|
||||
|
||||
#### 2.将文件解压到一个指定的目录或路径 ####
|
||||
|
||||
为了将文件解压到一个指定的目录中,使用“-C”选项来指定路径,此处的“C”是大写“C”。
|
||||
|
||||
$ tar -xvzf abc.tar.gz -C /opt/folder/
|
||||
|
||||
然后,首先需要确认目标目录是否存在,毕竟tar命令并不会为你创建目录,所以如果目标目录不存在的情况下该命令会失败。
|
||||
|
||||
####3. 解压出单个文件 ####
|
||||
|
||||
为了从一个归档文件中解压出单个文件,只需要将文件名按照以下方式将其放置在命令后面。
|
||||
|
||||
$ tar -xz -f abc.tar.gz "./new/abc.txt"
|
||||
|
||||
在上述命令中,可以按照以下方式来指定多个文件。
|
||||
|
||||
$ tar -xv -f abc.tar.gz "./new/cde.txt" "./new/abc.txt"
|
||||
|
||||
#### 4.使用通配符来解压多个文件 ####
|
||||
|
||||
通配符可以用来解压于给定通配符匹配的一批文件,例如所有以".txt"作为扩展名的文件。
|
||||
|
||||
$ tar -xv -f abc.tar.gz --wildcards "*.txt"
|
||||
|
||||
#### 5. 列出并检索tar归档文件中的内容 ####
|
||||
|
||||
如果你仅仅想要列出而不是解压tar归档文件的中的内容,使用“-t”选项, 下面的命令用来打印一个使用gzip压缩过的tar归档文件中的内容。
|
||||
|
||||
$ tar -tz -f abc.tar.gz
|
||||
./new/
|
||||
./new/cde.txt
|
||||
./new/subdir/
|
||||
./new/subdir/in.txt
|
||||
./new/abc.txt
|
||||
...
|
||||
|
||||
将输出通过管道定向到grep来搜索一个文件或者定向到less命令来浏览内容列表。 使用"v"繁琐选项将会打印出每个文件的额外详细信息。
|
||||
|
||||
对于 tar.bz2/bzip文件,需要使用"j"选项。
|
||||
|
||||
结合上述的命令和grep命令来检索归档文件,如下所示。简单吧!
|
||||
|
||||
$ tar -tvz -f abc.tar.gz | grep abc.txt
|
||||
-rw-rw-r-- enlightened/enlightened 0 2015-01-13 11:40 ./new/abc.txt
|
||||
|
||||
#### 6.创建一个tar/tar.gz归档文件 ####
|
||||
|
||||
现在我们已经学过了如何解压一个tar归档文件,是时候开始创建一个新的tar归档文件了。tar命令可以用来将所选的文件或整个目录放入到一个归档文件中,以下是相应的样例。
|
||||
|
||||
|
||||
下面的命令使用一个目录来创建一个tar归档文件,它会将该目录中所有的文件和子目录都加入到归档文件中。
|
||||
|
||||
$ tar -cvf abc.tar ./new/
|
||||
./new/
|
||||
./new/cde.txt
|
||||
./new/abc.txt
|
||||
|
||||
上述命令不会创建一个压缩的的归档文件,只是一个普通的归档文件,只是将多个文件放入到一个归档文件中并没有真正地压缩每个文件。
|
||||
|
||||
为了使用压缩,可以分别使用“z”或“j”选项进行gzip或bzip压缩算法。
|
||||
|
||||
$ tar -cvzf abc.tar.gz ./new/
|
||||
|
||||
> 文件的扩展名其实并不真正有什么影响。“tar.gz” 和tgz是gzip压缩算法压缩文件的常见扩展名。 “tar.bz2”和“tbz”是bzip压缩算法压缩文件的常见扩展名。
|
||||
|
||||
|
||||
#### 7. 在添加文件之前进行确认 ####
|
||||
|
||||
一个有用的选项是“w”,该选项使得tar命令在添加每个文件到归档文件之前来让用户进行确认,有时候这会很有用。
|
||||
|
||||
使用该选项时,只有用户输入yes时的文件才会被加入到归档文件中,如果你输入任何东西,默认的回答是一个“No”。
|
||||
|
||||
# 添加指定文件
|
||||
|
||||
$ tar -czw -f abc.tar.gz ./new/*
|
||||
add ‘./new/abc.txt’?y
|
||||
add ‘./new/cde.txt’?y
|
||||
add ‘./new/newfile.txt’?n
|
||||
add ‘./new/subdir’?y
|
||||
add ‘./new/subdir/in.txt’?n
|
||||
|
||||
#现在列出所有被加入的文件
|
||||
|
||||
$ tar -t -f abc.tar.gz
|
||||
./new/abc.txt
|
||||
./new/cde.txt
|
||||
./new/subdir/
|
||||
|
||||
#### 8. 加入文件到存在的归档文件中 ####
|
||||
|
||||
“r”选项可以被用来将文件加入到已存在的归档文件中,而不用创建一个新的归档文件,下面是一个简单的样例:
|
||||
|
||||
$ tar -rv -f abc.tar abc.txt
|
||||
|
||||
> 文件并不能加入到已压缩的归档文件中(gz 或 bzip)。文件只能被加入到普通的归档文件中。
|
||||
|
||||
#### 9. 将文件加入到压缩的归档文件中(tar.gz/tar.bz2) ####
|
||||
|
||||
之前已经提到了不可能将文件加入到已压缩的归档文件中,然和依然可以通过简单的一些把戏来完成。使用gunzip命令来解压缩归档文件,然后将文件加入到归档文件中后重新进行压缩。
|
||||
|
||||
$ gunzip archive.tar.gz
|
||||
$ tar -rf archive.tar ./path/to/file
|
||||
$ gzip archive.tar
|
||||
|
||||
对于bzip文件分别使用bzip2和bunzip2。
|
||||
|
||||
#### 10.通过tar来进行备份 ####
|
||||
|
||||
一个真实的场景是在规则的间隔内来备份目录,tar命令可以通过cron调度来实现这样的一个备份,以下是一个样例 -
|
||||
|
||||
$ tar -cvz -f archive-$(date +%Y%m%d).tar.gz ./new/
|
||||
|
||||
使用cron来运行上述的命令会保持创建类似以下名称的备份文件 -
|
||||
'archive-20150218.tar.gz'.
|
||||
|
||||
当然,需要确保日益增长的归档文件不会导致磁盘空间的溢出。
|
||||
|
||||
#### 11. 在创建归档文件是进行验证 ####
|
||||
|
||||
"W"选项可以用来在创建归档文件之后进行验证,以下是一个简单例子。
|
||||
|
||||
$ tar -cvW -f abc.tar ./new/
|
||||
./new/
|
||||
./new/cde.txt
|
||||
./new/subdir/
|
||||
./new/subdir/in.txt
|
||||
./new/newfile.txt
|
||||
./new/abc.txt
|
||||
Verify ./new/
|
||||
Verify ./new/cde.txt
|
||||
Verify ./new/subdir/
|
||||
Verify ./new/subdir/in.txt
|
||||
Verify ./new/newfile.txt
|
||||
Verify ./new/abc.txt
|
||||
|
||||
需要注意的是验证动作不能呢该在压缩过的归档文件上进行,只能在非压缩的tar归档文件上执行。
|
||||
|
||||
现在就先到此为止,可以通过“man tar”命令来查看tar命令的的手册。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.binarytides.com/linux-tar-command/
|
||||
|
||||
作者:[Silver Moon][a]
|
||||
译者:[theo-l](https://github.com/theo-l)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://plus.google.com/117145272367995638274/posts
|
||||
@ -0,0 +1,63 @@
|
||||
Linux有问必答 -- 如何在树莓派上安装USB网络摄像头
|
||||
================================================================================
|
||||
> **Question**: 我可以在树莓派上使用标准的USB网络摄像头么?我该如何检查USB网络摄像头与树莓派是否兼容?另外我该如何在树莓派上安装它?
|
||||
|
||||
如果你想在树莓上拍照或者录影,你可以安装[树莓派的摄像头板][1]。如果你不想要为摄像头模块花费额外的金钱,那有另外一个方法,就是你常见的[USB 摄像头][2]。你可能已经在PC上安装了。
|
||||
|
||||
本教程中,我会展示如何在树莓派上设置摄像头。我们假设你使用的系统是Raspbian。
|
||||
|
||||
在此之前,你最好检查一下你的摄像头是否在[这些][3]已知与树莓派兼容的摄像头之中。如果你的摄像头不在这个兼容列表中,不要丧气,仍然有可能你的摄像头被树莓派检测到。
|
||||
|
||||
### 检查USB摄像头是否雨树莓派兼容 ###
|
||||
|
||||
要检查你的摄像头是否可以被树莓派检测到,将它插入到树莓派的USB口中,然后输入下面的命令。
|
||||
|
||||
$ lsusb
|
||||
|
||||
如果输出中没有你的摄像头,那么有可能你的树莓派的电源无法供应足够的电力给你的摄像头。这时你可以给你的摄像头用独立的电源线,比如[有源USB hub][4],并重新输入lsusb命令。如果摄像头还是不能被识别,我们只有建议你购买其他树莓派支持的摄像头了。
|
||||
|
||||

|
||||
|
||||
在上面的截屏中,USB摄像头被识别为“1e4e:0102”,但是没有显示摄像头的制造商。当你在笔记本的Fedora 20中使用它时,它可以成功的检测到“1e4e:0102 Cubeternet GL-UPC822 UVC WebCam”。
|
||||
|
||||
另外一个可以检查摄像头是否被树莓派支持的方法是检查/dev目录。如果有/dev/video0,那么这暗示树莓派支持你的摄像头。
|
||||
|
||||
### 用USB Webcam拍照片 ###
|
||||
|
||||
当USB摄像头成功挂载到树莓派上之后,下一步就是拍一些照片来验证它的功能了。
|
||||
|
||||
要想拍摄照片,你要安装fswebcam,这是一款小型摄像头程序。你可以直接通过Raspbian的仓库来安装fswebcam。
|
||||
|
||||
$ sudo apt-get install fswebcam
|
||||
|
||||
fswebcam安装完成后,在终端中运行下面的命令来抓去一张来自摄像头的照片:
|
||||
|
||||
$ fswebcam --no-banner -r 640x480 image.jpg
|
||||
|
||||
这条命令可以抓取一张640x480分辨率的照片,并且用jpg格式保存。它不会在照片的地步留下任何标志.
|
||||
|
||||

|
||||
|
||||
这就是fswebcam下640x480分辨率的结果。
|
||||
|
||||

|
||||
|
||||
下面的例子是没有定义分辨率的照片。图片是偏蓝的,并且默认的分辨率是358x288。
|
||||
|
||||

|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://ask.xmodulo.com/install-usb-webcam-raspberry-pi.html
|
||||
|
||||
作者:[Kristophorus Hadiono][a]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://ask.xmodulo.com/author/kristophorus
|
||||
[1]:http://xmodulo.com/install-raspberry-pi-camera-board.html
|
||||
[2]:http://xmodulo.com/go/usb_webcam
|
||||
[3]:http://elinux.org/RPi_USB_Webcams
|
||||
[4]:http://xmodulo.com/go/usb_powerhub
|
||||
Loading…
Reference in New Issue
Block a user