mirror of
https://github.com/LCTT/TranslateProject.git
synced 2024-12-23 21:20:42 +08:00
Merge pull request #11000 from FSSlc/master
[Translated] 20181030 How To Analyze And Explore The Contents Of Docker Images.md
This commit is contained in:
commit
b5adb4a595
@ -1,100 +0,0 @@
|
||||
FSSlc translating
|
||||
|
||||
How To Analyze And Explore The Contents Of Docker Images
|
||||
======
|
||||

|
||||
|
||||
As you may already know, a Docker container image is a lightweight, standalone, executable package of software that has everything required to run an application. That’s why container images are often used by developers for building and distributing applications. If you’re curious to know what is in a Docker image, this brief guide might help you. Today, we are going to learn to analyze and explore the contents of Docker images layer by layer using a tool named **“Dive”**. By analyzing a Docker image, we can discover possible duplicate files across the layers and remove them to reduce the size of the docker image. The Dive utility is not just a Docker Image analyzer, but also helps us to build one.
|
||||
|
||||
### Installing Dive
|
||||
|
||||
Get the latest version from the [**releases page**][1] and install it as shown below depending upon the distribution you use.
|
||||
|
||||
If you’re on **Debian** or **Ubuntu** , run the following commands to download and install it.
|
||||
|
||||
```
|
||||
$ wget https://github.com/wagoodman/dive/releases/download/v0.0.8/dive_0.0.8_linux_amd64.deb
|
||||
|
||||
$ sudo apt install ./dive_0.0.8_linux_amd64.deb
|
||||
```
|
||||
|
||||
**On RHEL/CentOS:**
|
||||
|
||||
```
|
||||
$ wget https://github.com/wagoodman/dive/releases/download/v0.0.8/dive_0.0.8_linux_amd64.rpm
|
||||
|
||||
$ sudo rpm -i dive_0.0.8_linux_amd64.rpm
|
||||
```
|
||||
|
||||
Dive can also installed using [**Linuxbrew**][2] package manager.
|
||||
|
||||
```
|
||||
$ brew tap wagoodman/dive
|
||||
|
||||
$ brew install dive
|
||||
```
|
||||
|
||||
For other installation methods, refer the project’s GitHub page given at the end of this guide.
|
||||
|
||||
### Analyze And Explore The Contents Of Docker Images
|
||||
|
||||
To analyze a Docker image, simply run dive command with Docker “Image ID”. You can get your Docker images’ IDs using “sudo docker images” command.
|
||||
|
||||
```
|
||||
$ sudo dive ea4c82dcd15a
|
||||
```
|
||||
|
||||
Here, **ea4c82dcd15a** is Docker image id.
|
||||
|
||||
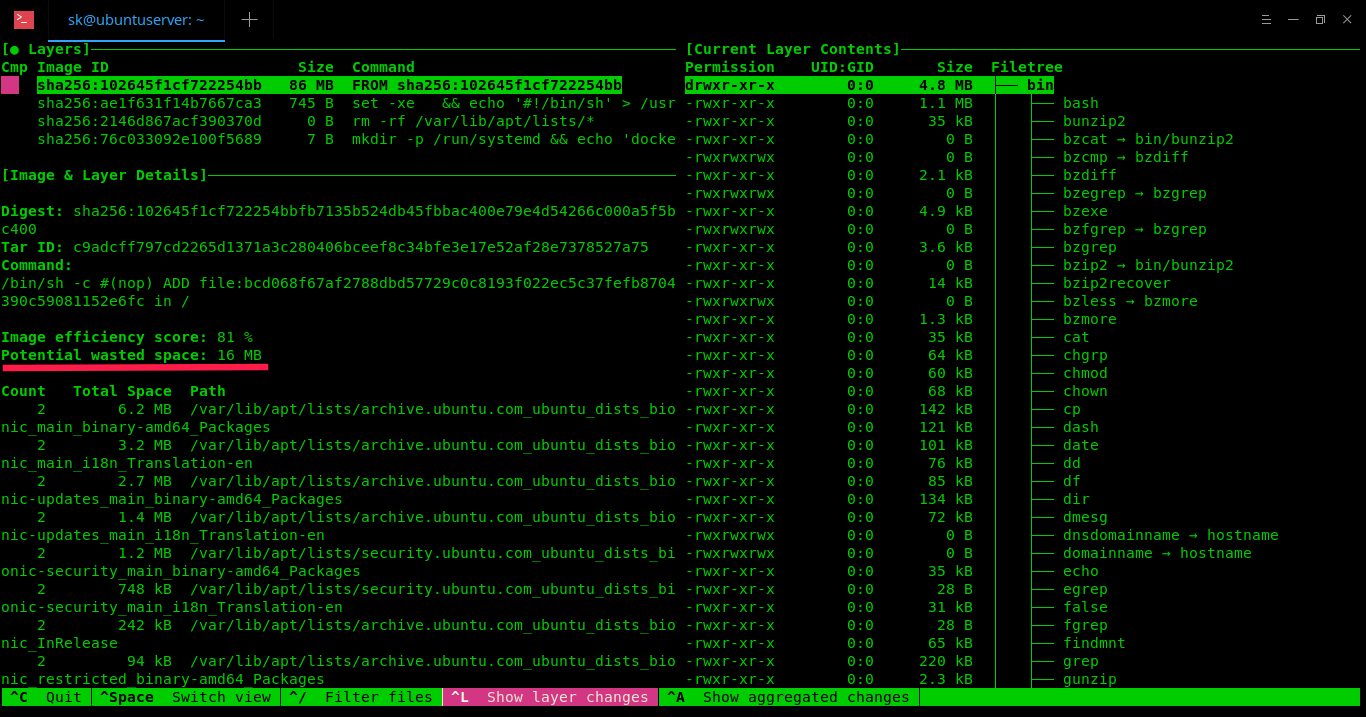
The Dive command will quickly analyze the given Docker image and display its contents in the Terminal.
|
||||
|
||||
As you can see in the above screenshot, the layers of given docker image and its details, wasted space are shown in the left pane. On the right pane, the contents of each layer in the given Docker image. You can switch between the left and right pane using **Ctrl+SPACEBAR** key and **UP/DOWN** arrow keys to navigate through the directory tree.
|
||||
|
||||
The list of keyboard shortcuts to use “Dive”.
|
||||
|
||||
* **Ctrl+Spacebar** – Switch between left and right panes,
|
||||
* **Spacebar** – Expand/Collapse directory tree,
|
||||
* **Ctrl+A** – Show/hide added files,
|
||||
* **Ctrl+R** – Show/hide removed files,
|
||||
* **Ctrl+M** – Show/hide modified files,
|
||||
* **Ctrl+U** – Show/hide unmodified files,
|
||||
* **Ctrl+ L** – Show layer changes,
|
||||
* **Ctrl+A** – Show layer changes,
|
||||
* **Ctrl+/** – Filter files,
|
||||
* **Ctrl+C** – Exit.
|
||||
|
||||
|
||||
|
||||
In the above example, I have used “sudo” permission, because my Docker images are stored in **/var/lib/docker/** directory. If you have them on your $HOME directory or anywhere not owned “root” user, you need not to use “sudo”.
|
||||
|
||||
You can also build a Docker image and do an immediate analysis with one command: ``
|
||||
|
||||
```
|
||||
$ dive build -t <some-tag>
|
||||
```
|
||||
|
||||
Dive tool is still in beta stage, so there will be bugs. If you came across any bugs, report them in the project’s github page.
|
||||
|
||||
And, that’s all for today. You know now how to explore and analyze the contents of Docker container image and how to build it using Dive tool. Hope this helps.
|
||||
|
||||
More good stuffs to come. Stay tuned!
|
||||
|
||||
Cheers!
|
||||
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.ostechnix.com/how-to-analyze-and-explore-the-contents-of-docker-images/
|
||||
|
||||
作者:[SK][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.ostechnix.com/author/sk/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://github.com/wagoodman/dive/releases
|
||||
[2]: https://www.ostechnix.com/linuxbrew-common-package-manager-linux-mac-os-x/
|
||||
@ -0,0 +1,94 @@
|
||||
如何分析并探索 Docker 容器镜像的内容
|
||||
======
|
||||

|
||||
|
||||
或许你已经了解到 Docker 容器镜像是一个轻量、独立、含有运行某个应用所需全部软件的可执行包,这也是为什么容器镜像会经常被开发者用于构建和分发应用。假如你很好奇一个 Docker 镜像里面包含了什么东西,那么这篇简要的指南或许会帮助到你。今天,我们将学会使用一个名为 **Dive** 的工具来分析和探索 Docker 镜像每层的内容。通过分析 Docker 镜像,我们可以发现在各个层之间可能重复的文件并通过移除它们来减小 Docker 镜像的大小。Dive 工具不仅仅是一个 Docker 镜像分析工具,它还可以帮助我们来构建镜像。Dive 是一个用 Go 编程语言编写的免费开源工具。
|
||||
|
||||
### 安装 Dive
|
||||
|
||||
首先从该项目的 [**发布页**][1] 下载最新版本,然后像下面展示的那样根据你所使用的发行版来安装它。
|
||||
|
||||
假如你正在使用 **Debian** 或者 **Ubuntu**,那么可以运行下面的命令来下载并安装它。
|
||||
```
|
||||
$ wget https://github.com/wagoodman/dive/releases/download/v0.0.8/dive_0.0.8_linux_amd64.deb
|
||||
```
|
||||
```
|
||||
$ sudo apt install ./dive_0.0.8_linux_amd64.deb
|
||||
```
|
||||
|
||||
**在 RHEL 或 CentOS 系统中**
|
||||
```
|
||||
$ wget https://github.com/wagoodman/dive/releases/download/v0.0.8/dive_0.0.8_linux_amd64.rpm
|
||||
```
|
||||
```
|
||||
$ sudo rpm -i dive_0.0.8_linux_amd64.rpm
|
||||
```
|
||||
|
||||
Dive 也可以使用 [**Linuxbrew**][2] 包管理器来安装。
|
||||
```
|
||||
$ brew tap wagoodman/dive
|
||||
```
|
||||
```
|
||||
$ brew install dive
|
||||
```
|
||||
|
||||
至于其他的安装方法,请参考 [Dive 项目的 GitHub 网页][3]。
|
||||
|
||||
### 分析并探索 Docker 镜像的内容
|
||||
|
||||
要分析一个 Docker 镜像,只需要运行加上 Docker 镜像 ID的 dive 命令就可以了。你可以使用 `sudo docker images` 来得到 Docker 镜像的 ID。
|
||||
```
|
||||
$ sudo dive ea4c82dcd15a
|
||||
```
|
||||
|
||||
上面命令中的 **ea4c82dcd15a** 是某个镜像的 id。
|
||||
|
||||
然后 Dive 命令将快速地分析给定 Docker 镜像的内容并将它在终端中展示出来。
|
||||
|
||||

|
||||
|
||||
正如你在上面的截图中看到的那样,在终端的左边一栏列出了给定 Docker 镜像的各个层及其详细内容,浪费的空间大小等信息。右边一栏则给出了给定 Docker 镜像每一层的内容。你可以使用 **Ctrl+SPACEBAR** 来在左右栏之间切换,使用 **UP/DOWN** 上下键来在目录树中进行浏览。
|
||||
|
||||
下面是 `Dive` 的快捷键列表:
|
||||
* **Ctrl+Spacebar** – 在左右栏之间切换
|
||||
* **Spacebar** – 展开或收起目录树
|
||||
* **Ctrl+A** – 文件树视图:展示或隐藏增加的文件
|
||||
* **Ctrl+R** – 文件树视图:展示或隐藏被移除的文件
|
||||
* **Ctrl+M** – 文件树视图:展示或隐藏被修改的文件
|
||||
* **Ctrl+U** – 文件树视图:展示或隐藏未修改的文件
|
||||
* **Ctrl+L** – 层视图:展示当前层的变化
|
||||
* **Ctrl+A** – 层视图:展示总的变化
|
||||
* **Ctrl+/** – 筛选文件
|
||||
* **Ctrl+C** – 退出
|
||||
|
||||
在上面的例子中,我使用了 `sudo` 权限,这是因为我的 Docker 镜像存储在 **/var/lib/docker/** 目录中。假如你的镜像保存在你的家目录 `$HOME`或者在其他不属于 `root` 用户的目录,你就没有必要使用 `sudo` 命令。
|
||||
|
||||
你还可以使用下面的单个命令来构建一个 Docker 镜像并立刻分析该镜像:
|
||||
```
|
||||
$ dive build -t <some-tag>
|
||||
```
|
||||
|
||||
Dive 工具仍处于 beta 阶段,所以可能会存在 bug。假如你遇到了 bug,请在该项目的 GitHub 主页上进行报告。
|
||||
|
||||
好了,这就是今天的全部内容。现在你知道如何使用 Dive 工具来探索和分析 Docker 容器镜像的内容以及利用它构建镜像。希望本文对你有所帮助。
|
||||
|
||||
更多精彩内容即将呈现,请保持关注!
|
||||
|
||||
干杯!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.ostechnix.com/how-to-analyze-and-explore-the-contents-of-docker-images/
|
||||
|
||||
作者:[SK][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[FSSlc](https://github.com/FSSlc)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.ostechnix.com/author/sk/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://github.com/wagoodman/dive/releases
|
||||
[2]: https://www.ostechnix.com/linuxbrew-common-package-manager-linux-mac-os-x/
|
||||
[3]: https://github.com/wagoodman/dive
|
||||
Loading…
Reference in New Issue
Block a user