mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-03-27 02:30:10 +08:00
20131219-1 选题 The Linux Kernel 新增4篇
This commit is contained in:
parent
fd93e9b008
commit
b4984193a4
@ -0,0 +1,139 @@
|
||||
24 The Linux Kernel: Configuring the Kernel Part 20
|
||||
================================================================================
|
||||
|
||||
|
||||
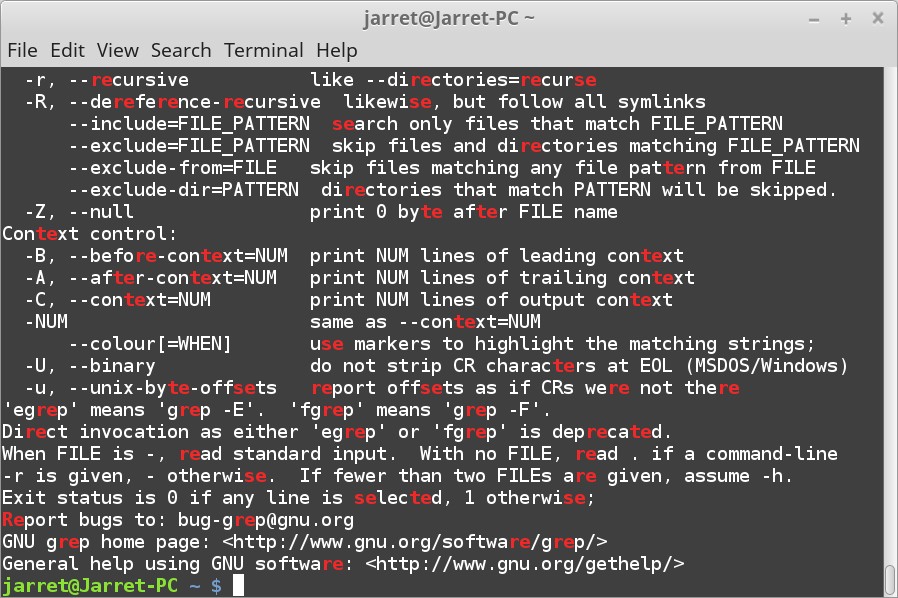
Aloha and welcome to the next Linux kernel article! In this article, we will continue configuring filesystem support.
|
||||
|
||||
First, we can enable "General filesystem local caching manager" which allows the kernel to store filesystem cache. This can enhance performance at the cost of storage space.
|
||||
|
||||
The caching system can be monitored with statistical information used for debugging purposes (Gather statistical information on local caching). Generally, this feature should only be enabled if you plan to debug the caching system.
|
||||
|
||||
|
||||
|
||||
This next feature is a lot like the above, but this feature stores latency information (Gather latency information on local caching). Again, this is a debugging feature.
|
||||
|
||||
The "Debug FS-Cache" driver offers many other debugging abilities for the cache system.
|
||||
|
||||
The next cache debugging tool keeps a global list (any process can access the list) of filesystem cache objects (Maintain global object list for debugging purposes).
|
||||
|
||||
To enhance the speed of network filesystems, enable this next driver (Filesystem caching on files). This feature allows a whole local filesystem to be used as cache for remote filesystem and storage units. The Linux kernel will manage this partition.
|
||||
|
||||
Two different debugging drivers exist for this local cache system for remote filesystems (Debug CacheFiles) and (Gather latency information on CacheFiles).
|
||||
|
||||
The most common optical disc filesystem is ISO-9660 which is ISO standard 9660, hence the name (ISO 9660 CDROM file system support). This driver is needed to read/write the major of optical discs.
|
||||
|
||||
When reading an optical disc with files using long Unicode filenames or writing such files, this driver is required (Microsoft Joliet CDROM extensions). This is an extension to the ISO-9660 filesystem.
|
||||
|
||||
The "Transparent decompression extension" allows data to be written to a disc in a compressed form and read off the disc and decompressed transparently. This will allow more data to be placed on the disc.
|
||||
|
||||
"UDF file system support" allows the kernel to read/write rewritable-optical-discs that are using the UDF filesystem. UDF is designed to manage incremental writes. UDF allows the rewritable optical disc to be used more like flash drives. The system can write and update the optical disc's data more quickly than regular writing on ISO-9660 filesystems. However, this is not faster than using flash drives.
|
||||
|
||||
As many of you know, Windows is a very popular system, so many storage units are using the FAT filesystem of NTFS. Thankfully, Linux supports such filesystems. The "MSDOS fs support" driver is a general driver for MS-DOS filesystems. This will increase the kernel size significantly, but since the FAT filesystems are very common, this size increase is usually worth the cost. [http://www.linux.org/threads/file-allocation-table-fat.4472/][1]
|
||||
|
||||
To support the FAT filesystems, enable this driver (VFAT (Windows-95) fs support). At the time this article was written, this driver does not support FAT64 (commonly called exFAT).
|
||||
|
||||
|
||||
|
||||
The size of the codepage can be set here (Default codepage for FAT).
|
||||
|
||||
After that, the default character set is configured for the FAT filesystems (Default iocharset for FAT).
|
||||
|
||||
The NTFS file system is offered with this driver (NTFS file system support). The driver provides read-only abilities. To write to NTFS, enable this driver (NTFS write support).
|
||||
|
||||
The Linux kernel offers debugging tools for the NTFS filesystem (NTFS debugging support).
|
||||
|
||||
To have a proc folder in the root, this feature must be enabled (/proc file system support). Some other similar drivers that rely on this one include (/proc/kcore support), (/proc/vmcore support), and (Sysctl support (/proc/sys)). The proc system (short for “process”) uses the proc-filesystem sometimes called procfs. This filesystem is in the hardware's memory and is created when Linux boots up. So, when viewing files in proc, the user is browsing the memory as if it were like other storage units. Proc acts as an interface between userspace and the kernelspace. Proc is in the kernelspace.
|
||||
|
||||
The "Enable /proc page monitoring" driver offers some proc files that monitor the memory utilization of processes.
|
||||
|
||||
The "sysfs file system support" driver creates the /sys/ folder. The sysfs filesystem is in memory and provides an interface to the kernel objects.
|
||||
|
||||
The tmp directory is needed by many applications and Linux itself, so it is strongly recommended that this driver be enabled (Tmpfs virtual memory file system support (former shm fs)). The tmp filesystem maybe stored on the hard-drive or in memory and is used only to store temporary files.
|
||||
|
||||
The "Tmpfs POSIX Access Control Lists" driver offers extra permission features for the files in the tmpfs virtual filesystem.
|
||||
|
||||
The "Tmpfs extended attributes" driver provides more attributes to tmpfs files than what they would normally have without he driver.
|
||||
|
||||
The "HugeTLB file system support" driver provides the hugetlbfs filesystem, which is ramfs based. This virtual filesystem contains HugeTLB pages.
|
||||
|
||||
|
||||
The configfs filesystem is a kernel object manager in the form of a filesystem (Userspace-driven configuration filesystem). It is highly recommended that this driver be enabled. ConfigFS is a lot like sysfs. However, ConfigFS is used to create and delete kernel object while sysfs is used to view and modify kernel objects.
|
||||
|
||||
Next, we can move back to "real" filesystems. That is, the filesystems users themselves use to store their personal files. Next, the kernel can be given the ability to read ADFS filesystems (ADFS file system support).
|
||||
|
||||
The ability to write to ADFS filesystems is provided by a separate and unstable driver (ADFS write support (DANGEROUS)). ADFS stands for Advanced Disc Filing System.
|
||||
|
||||
Linux also supports the Amiga Fast FileSystem (Amiga FFS file system support). [http://www.linux.org/threads/amiga-fast-file-system-affs.4429/][2]
|
||||
|
||||
The "eCrypt filesystem layer support" driver offers a POSIX-compliant cryptographic filesystem layer. This eCrypt can be placed on every and any filesystem no matter what partition table the filesystem resides on. [http://www.linux.org/threads/intro-to-encryption.4376/][3]
|
||||
|
||||
The eCrypt layer can have a device file if this driver is enabled (Enable notifications for userspace key wrap/unwrap). The device path is /dev/ecryptfs.
|
||||
|
||||
Linux also supports HFS and HFS+ (Apple Macintosh file system support) and (Apple Extended HFS file system support). [http://www.linux.org/threads/hierarchical-file-system-hfs.4480/][4] and [http://www.linux.org/threads/hierarchical-file-system-plus-hfs.4493/][5]
|
||||
|
||||
The BeFS filesystem can be used by Linux as a read-only filesystem (BeOS file system (BeFS) support (read only)). Generally, it is easier to program the reading abilities for a filesystem than the writing features.
|
||||
|
||||
Special debugging features exist for BeFS (Debug BeFS).
|
||||
|
||||
EFS is another filesystem that Linux can only read, not write (EFS file system support (read only)). [http://www.linux.org/threads/extent-file-system-efs.4447/][5]
|
||||
|
||||
Some flash drives may use the JFFS2 filesystem (Journalling Flash File System v2 (JFFS2) support). Next, the debugging level can be set (JFFS2 debugging verbosity). [http://www.linux.org/threads/journaling-flash-file-system-version-2-jffs2.4495/][6]
|
||||
|
||||
To use JFFS2 on NAND and NOR flash drives, this driver is needed (JFFS2 write-buffering support).
|
||||
|
||||
This next driver offers better error protection (Verify JFFS2 write-buffer reads).
|
||||
|
||||
JFFS filesystems can be mounted faster with "JFFS2 summary support" enabled. This driver stores information about the filesystem.
|
||||
|
||||
Like the other extended/extra attributes drivers for some filesystems, JFFS2 has such a driver (JFFS2 XATTR support).
|
||||
|
||||
The JFFS2 filesystem supports various transparent compression systems. This allows files to be smaller on JFFS2 filesystems and be read without the user needing to perform any special actions. (Advanced compression options for JFFS2), (JFFS2 ZLIB compression support), (JFFS2 LZO compression support), (JFFS2 RTIME compression support), and (JFFS2 RUBIN compression support). The default compression format can be defined in the following option (JFFS2 default compression mode).
|
||||
|
||||
A successor for JFFS2 exists and is supported by the kernel (UBIFS file system support). The Unsorted Block Image File System (UBIFS) also competes with LogFS.
|
||||
|
||||
The Linux kernel also supports LogFS (LogFS file system).
|
||||
|
||||
ROM-based embedded systems need support for CramFS (Compressed ROM file system support (cramfs)).
|
||||
|
||||
Alternately, embedded systems could use SquashFS which is a read-only compression filesystem (SquashFS 4.0 - Squashed file system support). The Linux kernel also offers extended attributes for SquashFS (Squashfs XATTR support).
|
||||
|
||||
There are three different compression formats supported by SquashFS - (Include support for ZLIB compressed file systems), (Include support for LZO compressed file systems), and (Include support for XZ compressed file systems). The block size for SquashFS can be set to four kilobytes (Use 4K device block size?). Also, the cache size can be set (Additional option for memory-constrained systems).
|
||||
|
||||
The Linux kernel supports FreeVxFS (FreeVxFS file system support (VERITAS VxFS(TM) compatible)), Minix (Minix file system support), MPEG filesystem (SonicBlue Optimized MPEG File System support), HPFS (OS/2 HPFS file system support), QNX4 (QNX4 file system support (read only)), QNX6 (QNX6 file system support (read only)), and the ROM filesystem (ROM file system support). [http://www.linux.org/threads/qnx-file-systems.4577/][8] and [http://www.linux.org/threads/minix-mini-unix-file-system.4545/][9]
|
||||
|
||||
"RomFS backing stores (Block device-backed ROM file system support)" offers a list of various ROMfs extra features and abilities.
|
||||
|
||||
The "Persistent store support" driver provides support for the pstore filesystem which allows access to platform level persistent storage.
|
||||
|
||||
The pstore filesystem can store kernel logs/messages (Log kernel console messages).
|
||||
|
||||
When a kernel panic takes place (equivalent to the "Blue-Screen-of-Death" on Windows), the "Log panic/oops to a RAM buffer" driver will store a log in the RAM.
|
||||
|
||||
This next single driver offers support for the Xenix, Coherent, Version 7, and System V filesystems (System V/Xenix/V7/Coherent file system support).
|
||||
|
||||
The Linux kernel also supports UFS (UFS file system support (read only)), (UFS file system write support (DANGEROUS)), and (UFS debugging).
|
||||
|
||||
exofs is also supported by the kernel (exofs: OSD based file system support).
|
||||
|
||||
The Flash-Friendly FileSystem is a special filesystem for flash drives (F2FS filesystem support (EXPERIMENTAL)), (F2FS Status Information ), (F2FS extended attributes), and (F2FS Access Control Lists). [http://www.linux.org/threads/flash-friendly-file-system-f2fs.4477/][10]
|
||||
|
||||
In the next article, we will configure network filesystems. Mahalo!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linux.org/threads/the-linux-kernel-configuring-the-kernel-part-20.4957/
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.linux.org/threads/file-allocation-table-fat.4472/
|
||||
[2]:http://www.linux.org/threads/amiga-fast-file-system-affs.4429/
|
||||
[3]:http://www.linux.org/threads/intro-to-encryption.4376/
|
||||
[4]:http://www.linux.org/threads/hierarchical-file-system-hfs.4480/
|
||||
[5]:http://www.linux.org/threads/hierarchical-file-system-plus-hfs.4493/
|
||||
[6]:http://www.linux.org/threads/extent-file-system-efs.4447/
|
||||
[7]:http://www.linux.org/threads/journaling-flash-file-system-version-2-jffs2.4495/
|
||||
[8]:http://www.linux.org/threads/qnx-file-systems.4577/
|
||||
[9]:http://www.linux.org/threads/minix-mini-unix-file-system.4545/
|
||||
[10]:http://www.linux.org/threads/flash-friendly-file-system-f2fs.4477/
|
||||
@ -0,0 +1,120 @@
|
||||
25 The Linux Kernel: Configuring the Kernel Part 21
|
||||
================================================================================
|
||||
|
||||
|
||||
Aloha! In this next article, we will configure network filesystem support for the Linux kernel. A network filesystem is a remote filesystem that computers access via the network.
|
||||
|
||||
First, the "NFS client support" driver allows the Linux system to use the NFS network filesystem. There are also three other drivers for different versions of NFS - (NFS client support for NFS version 2), (NFS client support for NFS version 3), (NFS client support for NFS version 4), and (NFS client support for NFSv4.1). If you have a network that possess NFS, either figure out what version of NFS you are using, or enable all of the NFS drivers.
|
||||
|
||||
Swap space is not required to be on a local storage unit. This driver allows Linux to use NFS support to use remote swap spaces (Provide swap over NFS support).
|
||||
|
||||
The NFS system can be sped up by using a cache system (Provide NFS client caching support). This is local cache.
|
||||
|
||||
Enable this driver to allow DNS to use host-names for NFS servers (Use the legacy NFS DNS resolver).
|
||||
|
||||
"NFS server support" gives the server providing NFS the features it needs to fulfill such a task. Some other NFS drivers include (NFS server support for NFS version 3) and (NFS server support for NFS version 4).
|
||||
|
||||
The "NFS server manual fault injection" driver is a debugging tool that allows developers to make the NFS server think an error occurred with NFS. Specifically, this is used to test how the server handles NFS errors.
|
||||
|
||||
The "Secure RPC: Kerberos V mechanism" is needed to make the RPC calls secure. NFS cannot be added to the kernel without this feature for security reasons.
|
||||
|
||||
There is a special debugging tool for RPC (RPC: Enable dprintk debugging).
|
||||
|
||||
The Linux kernel supports the Ceph filesystem (Ceph distributed file system).
|
||||
|
||||
CIFS is a virtual filesystem used by Samba and Windows servers (CIFS support (advanced network filesystem, SMBFS successor)). CIFS stands for Common Internet FileSystem.
|
||||
|
||||
There are two features that can be used to debug or monitor the CIFS driver (CIFS statistics) and (Extended statistics).
|
||||
|
||||
|
||||
A special driver is needed to support servers with LANMAN security (Support legacy servers which use weaker LANMAN security). LANMAN or LM hash is a special password hashing function that has some weaknesses.
|
||||
|
||||
CIFS requires that Kerberos tickets be used before mounting to secure servers (Kerberos/SPNEGO advanced session setup). This driver offers the ability for CIFS to use userspace tools which is needed to provide the tickets.
|
||||
|
||||
Like other filesystems, CIFS can have extended abilities (CIFS extended attributes) and (CIFS POSIX Extensions).
|
||||
|
||||
This driver gets the Access Control List (ACL) from the CIFS server (Provide CIFS ACL support).
|
||||
|
||||
CIFS has two other debugging tools (Enable CIFS debugging routines) and (Enable additional CIFS debugging routines).
|
||||
|
||||
CIFS can have "DFS feature support" which allows shares to be accessed even when they are moved. DFS stands for Distributed FileSystem.
|
||||
|
||||
SMB2 is an improved alternative to CIFS (SMB2 network file system support). SMB2 stands for Server Message Block version 2.
|
||||
|
||||
Clients can store CIFS cache with this driver enabled (Provide CIFS client caching support).
|
||||
|
||||
Novell NetWare clients need this driver to access NetWare volumes (NCP file system support (to mount NetWare volumes)). NCP stands for NetWare Core Protocol. NCP is a protocol that allows clients to communicate with the servers hosting NetWare volumes.
|
||||
|
||||
NetWare servers can use NFS namespaces if this driver is enabled (Use NFS namespace if available).
|
||||
|
||||
NetWare servers can use the OS/2 long namespaces if this driver is enabled (Use LONG (OS/2) namespace if available).
|
||||
|
||||
If this driver is enabled, then filenames made by DOS or on storage units owned by a DOS system will be converted to lowercase (Lowercase DOS filenames).
|
||||
|
||||
Many filesystems depend on native language support (Use Native Language Support). Specifically, Native Language Support (NLS) allows the different character-sets to be used in filenames.
|
||||
|
||||
NCP filesystems can support the execute flag and symbolic links with this driver enabled (Enable symbolic links and execute flags).
|
||||
|
||||
The Linux kernel offers support for the Coda filesystem (Coda file system support (advanced network fs)). Coda is one of many network filesystems.
|
||||
|
||||
The Linux kernel can support the Andrew Filesystem (Andrew File System support (AFS)). However, the Linux kernel can only read such filesystems in an insecure manner. This driver is intended to allow Linux systems to access AFS. If your network only contains Linux systems, then select a different network filesystem that the kernel can fully support.
|
||||
|
||||
The Linux kernel has an experimental driver for accessing Plan 9 resources via the 9P2000 protocol (Plan 9 Resource Sharing Support (9P2000)). The kernel also has cache support (Enable 9P client caching support) and control lists (9P POSIX Access Control Lists) for the previously mentioned Plan 9 feature.
|
||||
|
||||
|
||||
|
||||
After the network filesystems have been configured, the next part of the kernel to setup is the "Native Language Support". This whole menu contains the drivers for most or all of the character-sets and encodings. Enabling these encodings allows these character sets to be used by the system and applications. UTF-8 is the most commonly used encoding, but it is not the only one. Most applications and driver need UTF-8, so this encoding is already set to be added to the kernel.
|
||||
|
||||
After that menu, the "Distributed Lock Manager (DLM)" can be configured. A DLM is used to keep shared resources in sync and performing well. This driver manages the userspace and kernelspace applications that access or manipulate shared resources (like network filesystems). Clusters strongly depend on this driver.
|
||||
|
||||
Now that we have finally finished configuring the filesystems and related features, we can now move on to the "Kernel hacking" menu seen on the main (first) screen on the kernel configuration tool (when using the command "make menuconfig"). I am using the ncurses interface (seen in the screenshot) which is initiated with the "make menuconfig" command, so other interfaces may be a little different. Many of the features and settings in the kernel hacking menu contain various settings concerning the kernel itself. Some of these features are debugging tools and some control the kernel's behavior.
|
||||
|
||||
This first setting adds the pritnk time stamps to the syslog system call output (Show timing information on printks).
|
||||
|
||||
The next three features control various debugging features (Default message log level (1-7)), (Enable __deprecated logic), and (Enable __must_check logic).
|
||||
|
||||
|
||||
|
||||
The next feature is a debugging feature that is active at compiling time ((1024) Warn for stack frames larger than (needs gcc 4.4)). If stack frames are larger than the specified amount, then the compiler will warn the user.
|
||||
|
||||
The "Magic SysRq key" driver will enable support for the Magic SysRq key. This allows users to send the kernel special commands when Alt+PrintScreen is pressed. This works in most cases regardless of the kernel's state. However, exceptions exist. It is highly recommended that the Magic SysRq Key be enabled.
|
||||
|
||||
During compilation, the assembler's symbolic links will be removed during a link to reduce the output of get_wchan() (Strip assembler-generated symbols during link).
|
||||
|
||||
This next feature is for debugging purposes (Generate readable assembler code). If enabled, some kernel optimizations will be disabled so some of the assembly code will be human-readable. This will harm the kernel's speed. Only enable this if you have a specific reason for doing so.
|
||||
|
||||
This setting enables/disables commonly unneeded or obsolete symbols (Enable unused/obsolete exported symbols). However, some modules may need such symbols. Enabling this will increase the kernel's size. It is very unlikely that a Linux user will need such symbols. In general, disable this unless you know for a fact the user needs a symbol for an important module.
|
||||
|
||||
Sanity checks will be performed on user kernel headers if this setting is enabled (Run 'make headers_check' when building vmlinux).
|
||||
|
||||
During compilation, this feature will check for invalid references (Enable full Section mismatch analysis).
|
||||
|
||||
The kernel can be configured to detect soft and hard lockups (Detect Hard and Soft Lockups). When the system is frozen for more than twenty second and other tasks cannot execute, this is called a soft-lockup. If the CPU is in a loop that lasts for more than ten seconds and interrupts fail to get execution time, then this is called a hard-lockup.
|
||||
|
||||
The next to features set the kernel to reboot on hard and soft lockups respectively, (Panic (Reboot) On Hard Lockups) and (Panic (Reboot) On Soft Lockups).
|
||||
|
||||
When the kernel experiences major problems, it can be set to start a kernel panic (Panic on Oops). It is highly recommended that this setting be enabled. This will help to prevent the kernel from causing system damage and data loss.
|
||||
|
||||
The kernel can be set to detect hung tasks (Detect Hung Tasks). This is when a process or application locks-up or is frozen. Specifically, the application becomes uninterruptable. The following setting allows the user to define how much time must pass before a process is deemed "hung" (Default timeout for hung task detection (in seconds)).
|
||||
|
||||
The kernel can be set to restart when a process hangs (Panic (Reboot) On Hung Tasks). Generally, users will not want to enabled this. Would you like your computer to restart every time an application becomes frozen?
|
||||
|
||||
The "Kernel memory leak detector" finds and logs memory leaks.
|
||||
|
||||
The kernel uses frame pointers to help report errors more efficiently and include more information (Compile the kernel with frame pointers). I will skip a lot of the debugging tools because they are self-explanatory.
|
||||
|
||||
As many Linux users know, when the system boots up, the boot messages appear too quickly to be read. This feature sets the delay time which will give users more time to read the messages (Delay each boot printk message by N milliseconds).
|
||||
|
||||
This is a special developmental feature for testing backtrace code (Self test for the backtrace code). Backtrace code is a self-test.
|
||||
|
||||
Block device number can be extended (Force extended block device numbers and spread them). However, this may cause booting issues, so use with caution.
|
||||
|
||||
We will continue to configure the kernel itself in the next article. I hope you have enjoyed this article. Mahalo!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linux.org/threads/the-linux-kernel-configuring-the-kernel-part-21.4988/
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
@ -0,0 +1,119 @@
|
||||
26 The Linux Kernel: Configuring the Kernel Part 22
|
||||
================================================================================
|
||||
|
||||
|
||||
Aloha! In this article, we will continue to configure the kernel hacks and then we will configure the whole security system.
|
||||
|
||||
The next feature to configure is needed by Alpha and s390 processor (Force weak per-cpu definitions). This feature offers a fix for an addressing issue commonly seen in such processors. Other processors do not need this feature enabled.
|
||||
|
||||
Kernel dumps can be tested with this special debugging tool (Linux Kernel Dump Test Tool Module). This software will allow a kernel developer to trigger a fake error that will cause a kernel dump. The kernel developers can then ensure that the dumps complete successfully.
|
||||
|
||||
The kernel offers some different error injection modules that allow kernel developers to test the notifiers (CPU notifier error injection module), (PM notifier error injection module), and (Memory hotplug notifier error injection module). A notifier informs the system that the hardware is present, which is important for hotplugging. These error injection modules trigger an error in this notification system so developers can test the notification system's error handling abilities.
|
||||
|
||||
The "Fault-injection framework" driver offers various tools for testing fault-handling.
|
||||
|
||||
The "Latency measuring infrastructure" driver provides the LatencyTOP tool used to find the userspace object that is blocking/interfering with a kernel execution/task.
|
||||
|
||||
Next, we have a sub-menu titled "Tracers" that contains a list of various tracers. A tracer is a piece of code that watches various kernel functions. Every time a particular function starts, a tracer will be called to watch the function.
|
||||
|
||||
This next module tests the performance of the Red-Black tree library (Red-Black tree test). The Red-Black tree library is a sorting and searching algorithm.
|
||||
|
||||
The next feature is the same except that it tests the interval tree library (Interval tree test).
|
||||
|
||||
The kernel can also debug FireWire on other systems while that particular remote system is booting (Remote debugging over FireWire early on boot) and (Remote debugging over FireWire with firewire-ohci).
|
||||
|
||||
The printk() function can be made to print various debugging messages if this feature is enabled (Enable dynamic printk() support). “printk()” is a commonly discussed system call, so remember that it prints debugging messages about the kernel.
|
||||
|
||||
Here is a Direct Memory Access (DMA) debugging driver (Enable debugging of DMA-API usage).
|
||||
|
||||
The Atomic64 self-tests checks if the system supports atomic operations (Perform an atomic64_t self-test at boot). This is where a 32-bit system performs a 64-bit operation.
|
||||
|
||||
This driver provides a self-test for all of the possible RAID6 recovery systems (Self test for hardware accelerated raid6 recovery).
|
||||
|
||||
NOTE: Self-tests are low-level tests and detection software that executes before most of the system's hardware and software turns on and executes. Self-tests search for hardware, failing devices, etc. A self-test may also be code an application uses to test itself.
|
||||
|
||||
In the Kernel Hacking menu (if you are using a menu-like interface such as ncurses), there is a sub-menu titled "Sample kernel code". If you make your own personal modules, this is where you can enable them. In a later article, we will discuss how to implement custom/home-made kernel modules. Just remember this is where you enable your module.
|
||||
|
||||
|
||||
|
||||
The Kernel GNU DeBugger (KGDB) has many features that can be enabled or disabled (KGDB: kernel debugger). This debugger only works with two Linux systems plugged into each other via serial connection.
|
||||
|
||||
This feature provides extra boot-up messages for the decompression of the bzimage (Enable verbose x86 bootup info messages). You set the kernel encryption near the beginning of the configuration process.
|
||||
|
||||
Printk() prints various information to the boot-screen of dmesg, but after the serial and console drivers load. Enable this driver to make printk start printing messages sooner (Early printk).
|
||||
|
||||
This next driver is the same as above, but uses the EHCI port (Early printk via EHCI debug port).
|
||||
|
||||
The kernel can be set to watch for stack overflows so the kernel can manage the error better (Check for stack overflows). The kernel will execute more slowly, but overflows will not cause as much damage.
|
||||
|
||||
The page-table for the kernel can be seen on debugfs with this enabled (Export kernel pagetable layout to userspace via debugfs). However, this will slow down the kernel. This is needed for debugging purposes.
|
||||
|
||||
The kernel's written mistakes can be caught with this feature (Write protect kernel read-only data structures). This option turns the kernel's read-only data to write-protected mode. This debugging tool harms the kernel's speed. That debugging tool has a tool to debug itself (Testcase for the DEBUG_RODATA feature).
|
||||
|
||||
To prevent the execution of modules with modified code (due to an error), then enable this protective feature (Set loadable kernel module data as NX and text as RO). The debugging tool for that feature is provided by this driver (Testcase for the NX non-executable stack feature).
|
||||
|
||||
The kernel can be set to flush one of the TLB entries at a time or the whole table using this option (Set upper limit of TLB entries to flush one-by-one).
|
||||
|
||||
The next feature is an IOMMU debugging feature (Enable IOMMU debugging). There is another debugging test that disables some IOMMU features to test for extra stability (Enable IOMMU stress-test mode). The IOMMU stands for input/output memory management unit.
|
||||
|
||||
Enabling this option will make the kernel perform selt-tests on the change_page_attr() system call on thirty second intervals (CPA self-test code). This system call changes page attributes.
|
||||
|
||||
Any kernel code marked as "inline" can not be manipulated as much as it would by GCC than if it were not marked (Allow gcc to uninline functions marked). The GCC compiler adds code that it feels will make the code better (GCC is good at doing so). However, some code is not meant to be manipulated by GCC.
|
||||
|
||||
This next driver offers sanity checks for the "copy_from_user()" system call (Strict copy size checks). copy_from_user() copies a block of userspace data to kernelspace.
|
||||
|
||||
Here is another self-test; this one is for NMI (NMI Selftest).
|
||||
|
||||
Now, we can move on to the "Security Options" which is seen as a sub-menu in the main menu if you are using a menu-based interface, like ncurses. The first option allows access keys and authentication tokens to be stored in the kernel (Enable access key retention support). This is used for many reasons like accessing encrypted filesystems.
|
||||
|
||||
The following option is for creating and sealing/unsealing keys (TRUSTED KEYS). Encrypted keys are encrypted/decrypted using this driver (ENCRYPTED KEYS).
|
||||
|
||||
Keys can be viewed in proc with this feature enabled (Enable the /proc/keys file by which keys may be viewed).
|
||||
|
||||
Extra restrictions can be applied to syslog with this security feature (Restrict unprivileged access to the kernel syslog).
|
||||
|
||||
If this option is enabled, then the user can select different security models (Enable different security models). Otherwise, the defaults will be used. Disable this if you do not fully understand security or if you are fine with your kernel using the defaults.
|
||||
|
||||
The securityfs filesystem is offered by this driver (Enable the securityfs filesystem).
|
||||
|
||||
Hooks are added to networking and socket security when this feature is enabled (Socket and Networking Security Hooks). These hooks are access controls.
|
||||
|
||||
IPSec networking hooks (also called XFRM networking hooks) are implemented when this option is enabled (XFRM (IPSec) Networking Security Hooks). Security hooks are also available for files (Security hooks for pathname based access control).
|
||||
|
||||
The next driver provides support for Intel's Trusted Execution Technology (Enable Intel(R) Trusted Execution Technology (Intel(R) TXT)).
|
||||
|
||||
The user can set the range of memory addresses that cannot be reserved for userspace (Low address space for LSM to protect from user allocation). The starting point is 0. The user types the end point for this option. For most platforms, 65536 is a recommended choice.
|
||||
|
||||
SELinux (mentioned in the Kernel Security article) is one of the popular Linux-Security-Modules (NSA SELinux Support). Many options and features exist for SELinux. The boot parameter determines whether SELinux is started {1} or not started {0} when the kernel executes (NSA SELinux boot parameter). SELinux can be configured with the ability to be temporarily disabled at times when the Root user needs to do so (NSA SELinux runtime disable). Users can develop and test new policies with this feature enabled (NSA SELinux Development Support). AVC statistics are collected and stored by this feature (NSA SELinux AVC Statistics). A default can be set for the checkreqprot flag; a "1" means SELinux will check the application's requested protection and zero will default to the kernel's protection for mmap and mprotect system calls (NSA SELinux checkreqprot default value). Many SELinux policies exist; the user can set the latest version that they wish SELinux not to excede (NSA SELinux maximum supported policy format version).
|
||||
|
||||
One of the other Linux-Security-Modules (LSM), SMACK, is supported by the kernel (Simplified Mandatory Access Control Kernel Support).
|
||||
|
||||
TOMOYO is another supported LSM (TOMOYO Linux Support). The maximum number of entries permitted to be added during learning-mode is set in the following feature (Default maximal count for learning mode). The amount of log entires can also be set (Default maximal count for audit log). Next, this option allows/disallows TOMOYO to be activated without a policy loader (Activate without calling userspace policy loader). The location of the policy loader is configured here ((/sbin/tomoyo-init) Location of userspace policy loader) and the executable that triggers the execution is set here ((/sbin/init) Trigger for calling userspace policy loader).
|
||||
|
||||
Again, the kernel supports another LSM - AppArmor (AppArmor support). Like with SELinux, the default boot parameter can be set for AppArmor (AppArmor boot parameter default value).
|
||||
|
||||
Yama is another LSM (Yama support). Yama can be used with another LSM if this feature is enabled (Yama stacked with other LSMs).
|
||||
|
||||
This driver gives the kernel the ability to use multiple keyrings for verification processes (Digital signature verification using multiple keyrings).
|
||||
|
||||
Asymmetric keys are supported with this feature (Enable asymmetric keys support).
|
||||
|
||||
The kernel can keep and maintain a list of hashes and important system files (Integrity Measurement Architecture(IMA)). Then, if malware changes an important file, the kernel will know because the hashes are checked before the file or executable are used. It is highly recommended that this feature be enabled.
|
||||
|
||||
Extra security attributes are added to files if this feature is enabled (EVM support). The version can be set using this next option (EVM HMAC version). The two choices are version 1 and 2.
|
||||
|
||||
Remember all of the different Linux Security Modules (LSMs)? Well, the default can be set here (Default security module (AppArmor)).
|
||||
|
||||
In the next article, we can configure the "Cryptographic API". There may be two additional configuration articles left than what I estimated. After that, there are other kernel topics to discuss.
|
||||
|
||||
SNEAK PEAK: After this article, there is one more about the configuration process. Then, we can finally compile and install the kernel.
|
||||
|
||||
MESSAGE TO MY FANS: Feel free to post and/or email suggestions for kernel topics you would like me to cover in the following kernel articles. I still have a list of the suggestions some readers have sent me over the course of this series. Please feel free to send more.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linux.org/threads/the-linux-kernel-configuring-the-kernel-part-22.5017/
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
@ -0,0 +1,114 @@
|
||||
27 The Linux Kernel: Configuring the Kernel Part 23
|
||||
================================================================================
|
||||
|
||||
|
||||
Aloha and welcome to the next kernel configuration article! In this article, we will configure the Cryptographic API, Virtualization, and Library Routines. Cryptography refers to encryption and secure communication between desired computers. Users may encrypt data to ensure only the recipient reads the data instead of hackers that may obtain the data.
|
||||
|
||||
The Linux kernel requires the "Cryptographic algorithm manager" to be enabled in the kernel. This feature provides the software needed to operate the cryptographic abilities of the kernel.
|
||||
|
||||
The userspace can configure the cryptography features when this driver is enabled (Userspace cryptographic algorithm configuration). NOTE: This configuration is referring to the cryptographic setup during kernel runtime, not the tool for making the kernel.
|
||||
|
||||
To enhance performance, enable this feature which stops self-tests on cryptographic algorithms (Disable run-time self tests).
|
||||
|
||||
The "GF(2^128) multiplication functions" is a specific algorithm used by some ciphers. GF stands for Galois field and is a set of finite numbers. These sets are called fields and they come in a variety of sizes.
|
||||
|
||||
"Null algorithms" are algorithms used in IPsec. Null encryption means no encryption, so this driver allows IPsec to use no encryption.
|
||||
|
||||
Arbitrary algorithms can be converted to parallel algorithms (Parallel crypto engine). This feature provides that converter.
|
||||
|
||||
Arbitrary algorithms can also be converted to asynchronous algorithms (Software async crypto daemon).
|
||||
|
||||
"Authenc support" is needed by IPsec. Authenc support stands for Authenticated Encryption and offers multiple encryptions to IPsec.
|
||||
|
||||
CCM stands for "Counter with CBC MAC" and is needed by IPsec (CCM support).
|
||||
|
||||
This driver offers "GCM/GMAC support". GCM is "Galois/Counter Mode" and GMAC is "Galois Message Authentication Code".
|
||||
|
||||
NOTE: I will not be able to explain specifically the use and details of some of these features. Cryptography is a detail field of computers and explaining cryptography is beyond the scope of this article.
|
||||
|
||||
The "Sequence Number IV Generator" is a special number generator used by some cryptography software.
|
||||
|
||||
The Linux kernel supports various cipher algorithms (CBC support), (CTR support), (CTS support), (ECB support), (LRW support), (PCBC support), (XTS support), (HMAC support), (XCBC support), and (VMAC support).
|
||||
|
||||
The "CRC32c CRC algorithm" is used specifically with SPARC64 processors.
|
||||
|
||||
"CRC32c INTEL hardware acceleration" is another processor specific algorithm. It works on Intel processors with SSE4.2.
|
||||
|
||||
The kernel also offers many digests, ciphers, and other cryptographic software. Generally, allow the defaults unless you have a specific reason for enabling or disabling features.
|
||||
|
||||
NOTE: A digest (like MD5) generates a hash (sequence of characters) based on a file. Hashes are then used to check files. For example, if you download the Ubuntu installation ISO file from Canonical's website, you may want to know if the file on your hard-drive is an exact replica of the server's file. Users do this because the ISO may become corrupted during the long download. The hash is used to prove that the file is unchanged.
|
||||
|
||||
NOTE: A cipher is an encryption/decryption algorithm. Encryption is the process of making a file unreadable to anyone other than the intended recipients/owners. Decryption is the process used to view an encrypted file.
|
||||
|
||||
The Linux kernel also supports various compression algorithms that users are strongly recommended to enable (Deflate compression algorithm), (Zlib compression algorithm), and (LZO compression algorithm).
|
||||
|
||||
The kernel can generate random numbers which are needed for cryptographic software (Pseudo Random Number Generation for Cryptographic modules), (User-space interface for hash algorithms), and (User-space interface for symmetric key cipher algorithms).
|
||||
|
||||
"Hardware crypto devices" is a sub-menu that contains a list of drivers for hardware-based cryptography tools. This is hardware that has the algorithms in the firmware.
|
||||
|
||||
Various drivers for asymmetric public-keys exist in the "Asymmetric (public-key cryptographic) key type" menu.
|
||||
|
||||
Now, we can move on to the next entry on the main menu of the configuration tool (on menu-based interfaces). Virtualization is the ability to host an operating system. This means Linux (and other systems) can run another operating system as if the guest system is an application.
|
||||
|
||||
"Kernel-based Virtual Machine (KVM) support" allows the kernel itself to manage the guest system. Computers with Intel processors need this driver (KVM for Intel processors support) and AMD processors need (KVM for AMD processors support).
|
||||
|
||||
The memory management unit (MMU) for the Kernel Virtual Machine (KVM) can have an auditing system.
|
||||
|
||||
The guest's network can become faster with this feature enabled (Host kernel accelerator for virtio net).
|
||||
|
||||
After configuring the virtual machine abilities for the kernel, the last menu on the main screen of the configuration tool (when using a menu interface) is the last portion of the kernel to configure. This menu is for the "Library Routines", also called library functions. Parts of the kernel can be used as a linkable library. For example, XZ filters (compression algorithms) can be accessed by external programs. The different libraries are listed below.
|
||||
|
||||
NOTE: The CRC functions are mostly the same but with different features or performance. Generally, it is best to allow the defaults.
|
||||
|
||||
CRC-CCITT functions - The Cyclic Redundancy Check function tests for changes in raw data
|
||||
|
||||
CRC16 functions - The Cyclic Redundancy Check function tests for changes in raw data
|
||||
|
||||
CRC calculation for the T10 Data Integrity Field - The Cyclic Redundancy Check function tests for changes in raw data
|
||||
|
||||
CRC ITU-T V.41 functions - The Cyclic Redundancy Check function tests for changes in raw data
|
||||
|
||||
CRC32/CRC32c functions - The Cyclic Redundancy Check function tests for changes in raw data
|
||||
|
||||
CRC32 perform self test on init - The Cyclic Redundancy Check function tests for changes in raw data
|
||||
|
||||
CRC32 implementation (Slice by 8 bytes) - The Cyclic Redundancy Check function tests for changes in raw data
|
||||
|
||||
CRC7 functions - The Cyclic Redundancy Check function tests for changes in raw data
|
||||
|
||||
CRC32c (Castagnoli, et al) Cyclic Redundancy-Check - The Cyclic Redundancy Check function tests for changes in raw data
|
||||
|
||||
CRC8 function - The Cyclic Redundancy Check function tests for changes in raw data
|
||||
|
||||
* BCJ filter decoder - XZ decoder design for a specific processor where "*" is the processor. The kernel lists a few different architectures.
|
||||
|
||||
XZ decompressor tester - Debug functions for testing the XZ decoder
|
||||
|
||||
Averaging functions - Load average as seen in the output of "uptime"
|
||||
|
||||
CORDIC algorithm - hyperbolic and trigonometry functions
|
||||
|
||||
|
||||
JEDEC DDR data - JEDEC Double Data Rate SD-RAM specification
|
||||
|
||||
|
||||
Guess what? You have finished configuring your kernel. I am sure after twenty-three articles, this is how you feel -
|
||||
|
||||
Video link:[http://www.youtube.com/embed/barWV7RWkq0?wmode=opaque][1]
|
||||
|
||||
Next, we can compile and install.
|
||||
|
||||
In the far distance, I still hear this -
|
||||
|
||||
Video link:[http://www.youtube.com/embed/ELoUppY1esw?wmode=opaque][2]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linux.org/threads/the-linux-kernel-configuring-the-kernel-part-23.5112/
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.youtube.com/embed/barWV7RWkq0?wmode=opaque
|
||||
[2]:http://www.youtube.com/embed/ELoUppY1esw?wmode=opaque
|
||||
Loading…
Reference in New Issue
Block a user