mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-03-21 02:10:11 +08:00
Merge branch 'master' of https://github.com/LCTT/TranslateProject
Conflicts: sources/13 Linux Cat Command Examples To Manage (Display,Sort,Create etc) Files.md
This commit is contained in:
commit
b25bb7d5ae
@ -0,0 +1,42 @@
|
||||
Ubuntu每日小贴士 - 在Ubuntu下创建虚拟网卡
|
||||
================================================================================
|
||||
|
||||
这个教程是为那些想用Ubuntu做点小实验的用户准备的。这并不适用于所有人,尤其是那些在(正式环境中)使用生产机器的用户。
|
||||
|
||||
如果你对网络运行和IP网络有所了解,你应该知道在大多数情况下,每个网卡只会分配一个IP地址。我们习惯认为这是一对一的事物。
|
||||
|
||||
一个网卡对应一个IP地址,你在一台机器上的一个网卡及其IP地址只能绑定或运行单一的网络服务/端口。例如,如果你想在80端口运行一个web服务器,而一个IP地址和端口号只能由一个web服务器监听。这是这样设计的。
|
||||
|
||||
所以,网卡和IP地址并不是一对一的关系,你可以创建可以单独分配IP地址的虚拟网卡。因此,单一的物理网卡可以群集无限的子网卡或虚拟网卡。每一个都能分配它自己IP地址到对应的端口。
|
||||
|
||||
这个简短的教程将展示给你如何在Ubuntu上做到这些。这是在一台电脑上用一张物理网卡和单一的端口号运行及测试多个网络服务的好方式。
|
||||
|
||||
动手吧,运行下列命令打开网络接口文件。
|
||||
|
||||
sudo gedit /etc/network/interfaces
|
||||
|
||||
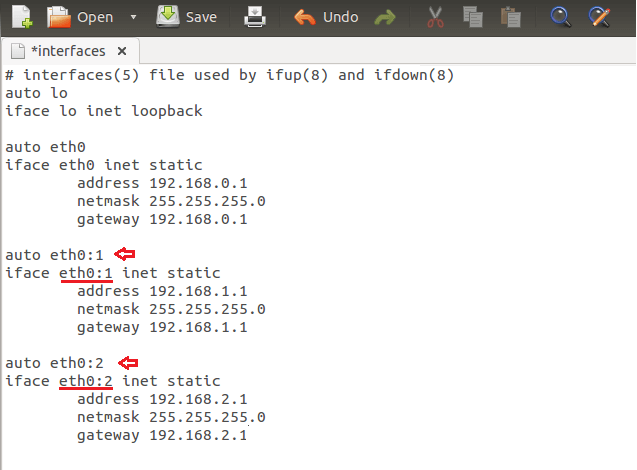
然后按照下图中的步骤,添加你想要的任意多的虚拟网卡。默认情况下,Linux会给第一张网卡分配eth0的名称,所以如果你的机子只有一张网卡,那么它会被命名为eth0。
|
||||
|
||||
添加虚拟网卡,创建多个静态网卡并命名为eth0:1、eth0:2、eth0:3等等(eth0后面紧跟冒号和数字)。
|
||||
|
||||
|
||||
|
||||
对于你创建的每一个网卡,也要确保网络都是不同的子网,这是网络常识(译注:事实上并非如此,虚拟网卡完全可以是相同子网的IP地址,只要你需要)
|
||||
|
||||
完成以后,保存文件并用下列命令重启网络服务。
|
||||
|
||||
sudo service networking restart
|
||||
|
||||
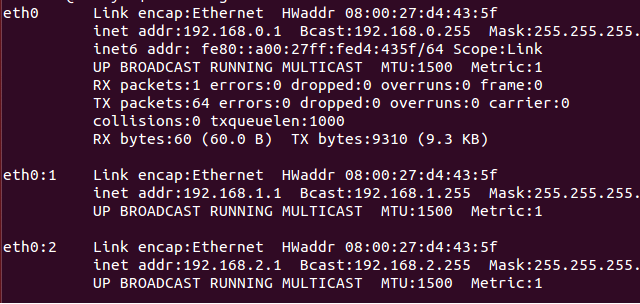
就是这样!
|
||||
|
||||
|
||||
|
||||
玩得开心!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.liberiangeek.net/2013/11/daily-ubuntu-tips-create-virtual-network-cards-in-ubuntu-linux/
|
||||
|
||||
译者:[Luoxcat](https://github.com/Luoxcat) 校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
68
published/Five Examples Of The ping Utility.md
Normal file
68
published/Five Examples Of The ping Utility.md
Normal file
@ -0,0 +1,68 @@
|
||||
五个 ping 工具的使用实例
|
||||
================================================================================
|
||||
|
||||
### 什么是 ping 工具###
|
||||
|
||||
在讲述一些关于ping工具真实直观的使用实例前,先让我来介绍一下这个命令行工具及其目的。ping工具通常用来测试一台主机在互联网协议(IP)网络内的可达性。其名字源于主动声纳法——在水下创建一个脉冲声音信号(ping)并侦听周围物体的返回信号。该方法同样生动描述了ping网络工具的工作原理。ping工具对一台主机发送回应请求然后等待ICMP响应。
|
||||
|
||||
实践中的ping工具的一些例子:
|
||||
|
||||
### 查询主机的IP地址 ###
|
||||
|
||||
有时候你需要得到某一台主机的IP地址,如图一。只需要键入ping命令后面跟上要查询的主机名。
|
||||
|
||||
ping www.omgubuntu.com
|
||||
|
||||

|
||||
|
||||
### 查询正在使用的ping工具的版本信息 ###
|
||||
|
||||
用 -V 选项可以用来查询你手头上ping工具的版本信息。键入下列命令显示正在使用的ping工具的版本信息。
|
||||
|
||||
ping -V
|
||||
|
||||
正如你从图二见到的,我正在使用的是“ping utility,iputils-sss20101006”
|
||||
|
||||

|
||||
|
||||
### 自动退出 ping ###
|
||||
|
||||
当你用‘ping 主机’命令ping一台机器时,ping自己无法停止,你必需按下CTRL+C强行退出,或者你可以用 -c (count)选项指定发送包的数量。使用-c选项,当网络管理员(其实普通用户也可以)发送完指定数量的包之后,无需按CTRL+C,ping进程就会自动停止。
|
||||
|
||||
ping -c 13 127.0.0.1
|
||||
|
||||
上列的命令发送了13个包到我的本地主机上。
|
||||
|
||||

|
||||
|
||||
正如你从图三看到的,我并没有按CTRL+C,而ping自动退出了。
|
||||
|
||||
### 指定数据包之间的时间间隔 ###
|
||||
|
||||
你知道ping每秒钟发送一个数据包吗?你喜欢快一点还是慢一点?用 -i 选项能指定包之间的时间间隔。用下列命令快速发送或慢速发送包。
|
||||
|
||||
### 每0.13秒发送一个包 ###
|
||||
|
||||
ping -i 0.13
|
||||
|
||||

|
||||
|
||||
### 每13秒发送一个包 ###
|
||||
|
||||
ping -i 13
|
||||
|
||||
### 结合 -i 选项和 -c 选项 ###
|
||||
|
||||
ping -c 13 -i 3
|
||||
|
||||
总共花费39秒发出13个数据包,数据包的时间间隔为三秒。
|
||||
|
||||

|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.unixmen.com/five-examples-ping-utility/
|
||||
|
||||
译者:[Luoxcat](https://github.com/Luoxcat) 校对:[Mr小眼儿](http://blog.csdn.net/tinyeyeser)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
@ -0,0 +1,33 @@
|
||||
Mark Shuttleworth为“茶派”及其他错误认错
|
||||
================================================================================
|
||||
**Canonical公司的创始人Mark Shuttleworth他澄清了他的[“茶派”论调][4],为他的言论而表示歉意。**
|
||||
|
||||

|
||||
|
||||
我们并不是每天都能看到Mark Shuttleworth连续道歉两次,很有可能这是第一次。
|
||||
|
||||
[第一个道歉][1]是对收到了Canonical公司法律团队邮件的fixubuntu.com的站长Micah F. Lee,他写了一篇广泛传播的关于这些问题的博客,并且在许多论坛和网站引起了热议。
|
||||
|
||||
Mark Shuttleworth首先在Google+向他道歉,接着他在其个人博客上写了正式的道歉文章,他的博客通常都是用于宣布重要事情的地方。
|
||||
|
||||
这个道歉之后,他又花了一些时间说,他为带来了很多抨击的[“茶派”][2]的说法而后悔,这个事情甚至比他原来认为的还要糟糕。
|
||||
|
||||
“另一方面,从个人角度看,我自己犯了一个错误,当我使用标签“开源茶派”来指那些对Canonical做的事情的非技术评论家。这是不对的,并且的确可能冒犯了真的茶派(注意这里!)以及那些非技术批评家(再看这儿!)。”
|
||||
|
||||
“这并不是说我建议我不需要这样技术反馈,而是一些假定我拒绝了包括技术反馈在内的所有反馈。我没有——我在说对软件的评价,并不是软件本身的中心,而是开发软件的人需求的综合,或者是某个自由软件协议下发布,或者是公司的策略、或者是公司后面的国家”,Mark Shuttleworth[说道][3]。
|
||||
|
||||
|
||||
希望结束在这个事件上的所有的讨论,人们最终将能够接受引发了这次讨论的Mir。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://news.softpedia.com/news/Mark-Shuttleworth-Regrets-the-quot-Tea-Party-quot-Remarks-and-Other-Canonical-Mistakes-398819.shtml
|
||||
|
||||
译者:[Vito](https://github.com/vito-L) 校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://news.softpedia.com/news/Mark-Shuttleworth-Apologizes-for-the-Trademark-Infringement-Letter-Sent-to-Fixubuntu-com-398583.shtml
|
||||
[2]:http://news.softpedia.com/news/Mark-Shuttleworth-Says-That-Mir-Opponents-Have-Formed-the-Open-Source-Tea-Party-392793.shtml
|
||||
[3]:http://www.markshuttleworth.com/archives/1299
|
||||
[4]:http://linux.cn/article-2283-1.html
|
||||
@ -1,4 +1,9 @@
|
||||
<<<<<<< HEAD
|
||||
NearTan认领
|
||||
=======
|
||||
hongchuntang wc
|
||||
|
||||
>>>>>>> 181b97c7467f6f6c937d208d0fa78a6de06d42e7
|
||||
13 Linux Cat Command Examples To Manage (Display,Sort,Create etc) Files
|
||||
================================================================================
|
||||

|
||||
@ -208,4 +213,4 @@ via: http://linoxide.com/linux-command/13-cat-command-examples/
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,41 +0,0 @@
|
||||
Canonical Dev Calls Linux Mint ‘Vulnerable’, Wouldn’t Use it For Online Banking
|
||||
================================================================================
|
||||
**Users of the popular Ubuntu-based operating system Linux Mint should not use it for online banking, a Canonical [engineer has advised][1].**
|
||||
|
||||
Mint’s decision to prevent packages with known security issues from updating – from the kernel and browser to the boot-loader and Xorg display server – leaves its users with a “vulnerable system”, says Oliver Grawert.
|
||||
|
||||
> “Instead of just integrating changes properly with the packages in the ubuntu archive they instead suppress doing (security) updates at all for them. i would say forcefully keeping a vulnerable kernel browser or xorg in place instead of allowing the provided security updates to be installer makes it a vulnerable system, (sic)”.
|
||||
>
|
||||
> “I personally wouldn’t do online banking with it.”
|
||||
|
||||
Grawert certainly isn’t alone in considering Mint a sub-par choice for the security conscious. Mozilla contributor and former Ubuntu member **Benjamin Kerensa*** feels the same:
|
||||
|
||||
> “It is unclear why Linux Mint disables all of their security updates. I can say that it took them many months to get a fixed version of Firefox packaged while Ubuntu and Debian had already had security fixes in their package.
|
||||
>
|
||||
> This puts Linux Mint users at risk and is one of the key reasons I never suggest Linux Mint to anyone as an alternative to Ubuntu.”
|
||||
|
||||
Oliver Grawert is no fly-by-night contributor. As one of Canonical’s Ubuntu Engineering bods he’s better placed than most to know what he’s talking about.
|
||||
|
||||
**‘But are Mint users in actual risk? Yes and no…’**
|
||||
|
||||
But are Mint users in actual risk?
|
||||
|
||||
Yes and no. The majority of security “holes” (for want of a better word) of the kind present in the packages that Mint’s developers steadfastly refuse to update are both documented and known, but rarely exploited by those of a nefarious breed. As such the “actual threat” posed to users remains, at least for now, largely a theoretical one.
|
||||
|
||||
That’s to say that there are no known incidents of identify theft or worse resulting from use of Mint (or any other Ubuntu-based distribution with unpatched packages) through any of the exploits referenced by Grawert on the Ubuntu Dev Mailing List.
|
||||
|
||||
But just because no-one has entered through the window left ajar thus far, isn’t to say someone won’t ever do it.
|
||||
|
||||
**After seeing Ubuntu given a long and sustained kicking about its own (largely theoretical) privacy issues, it will be interesting to see if, now the boot is placed firmly on the other foot, the vehement concern for users’ wellbeing will extend to other distributions. **
|
||||
|
||||
*Notice: We reached out to Linux Mint for comment & clarification but received no reply.*
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.omgubuntu.co.uk/2013/11/canonical-dev-dont-use-linux-mint-online-banking-unsecure
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:https://lists.ubuntu.com/archives/ubuntu-devel-discuss/2013-November/014770.html
|
||||
@ -1,292 +0,0 @@
|
||||
Translating-------------geekpi
|
||||
|
||||
|
||||
Core algorithms deployed
|
||||
================================================================================
|
||||
Algorithms that are the main driver behind a system are, in my opinion, easier to find in non-algorithms courses for the same reason theorems with immediate applications are easier to find in applied mathematics rather than pure mathematics courses. It is rare for a practical problem to have the exact structure of the abstract problem in a lecture. To be argumentative, I see no reason why fashionable algorithms course material such as Strassen's multiplication, the AKS primality test, or the Moser-Tardos algorithm is relevant for low-level practical problems of implementing a video database, an optimizing compiler, an operating system, a network congestion control system or any other system. The value of these courses is learning that there are intricate ways to exploit the structure of a problem to find efficient solutions. Advanced algorithms is also where one meets simple algorithms whose analysis is non-trivial. For this reason, I would not dismiss simple randomized algorithms or PageRank.
|
||||
|
||||
I think you can choose any large piece of software and find basic and advanced algorithms implemented in it. As a case study, I've done this for the Linux kernel, and shown a few examples from Chromium.
|
||||
|
||||
### Basic Data Structures and Algorithms in the Linux kernel ###
|
||||
|
||||
Links are to the [source code on github][1].
|
||||
|
||||
1.[Linked list][2], [doubly linked list][3], [lock-free linked list][4].
|
||||
|
||||
2.[B+ Trees][5] with comments telling you what you can't find in the textbooks.
|
||||
|
||||
> A relatively simple B+Tree implementation. I have written it as a learning exercise to understand how B+Trees work. Turned out to be useful as well.
|
||||
>
|
||||
> ...
|
||||
>
|
||||
> A tricks was used that is not commonly found in textbooks. The lowest values are to the right, not to the left. All used slots within a node are on the left, all unused slots contain NUL values. Most operations simply loop once over all slots and terminate on the first NUL.
|
||||
|
||||
3.[Priority sorted lists][6] used for [mutexes][7], [drivers][8], etc.
|
||||
|
||||
4.[Red-Black trees][9] are [used][10] for scheduling, virtual memory management, to track file descriptors and directory entries,etc.
|
||||
|
||||
5.[Interval trees][11]
|
||||
|
||||
6.[Radix trees][12], are used for [memory management][13], NFS related lookups and networking related functionality.
|
||||
|
||||
> A common use of the radix tree is to store pointers to struct pages;
|
||||
|
||||
7.[Priority heap][14], which is literally, a textbook implementation, used in the [control group system][15].
|
||||
|
||||
> Simple insertion-only static-sized priority heap containing pointers, based on CLR, chapter 7
|
||||
|
||||
8.[Hash functions][16], with a reference to Knuth and to a paper.
|
||||
|
||||
> Knuth recommends primes in approximately golden ratio to the maximum integer representable by a machine word for multiplicative hashing. Chuck Lever verified the effectiveness of this technique:
|
||||
>
|
||||
> [http://www.citi.umich.edu/techreports/reports/citi-tr-00-1.pdf][17]
|
||||
>
|
||||
> These primes are chosen to be bit-sparse, that is operations on them can use shifts and additions instead of multiplications for machines where multiplications are slow.
|
||||
|
||||
9.Some parts of the code, such as [this driver][18], implement their own hash function.
|
||||
|
||||
> hash function using a Rotating Hash algorithm
|
||||
>
|
||||
> Knuth, D. The Art of Computer Programming, Volume 3: Sorting and Searching, Chapter 6.4. Addison Wesley, 1973
|
||||
|
||||
10.[Hash tables][19] used to implement [inodes][20], f[ile system integrity checks][21] etc.
|
||||
|
||||
11.[Bit arrays][22], which are used for dealing with flags, interrupts, etc. and are featured in Knuth Vol. 4.
|
||||
|
||||
12.[Semaphores][23] and [spin locks][24]
|
||||
|
||||
13.[Binary search][25] is used for [interrupt handling][26], [register cache lookup][27], etc.
|
||||
|
||||
14.[Binary search with B-trees][28]
|
||||
|
||||
15.[Depth first search][29] and variant used in [directory configuration][30].
|
||||
|
||||
> Performs a modified depth-first walk of the namespace tree, starting (and ending) at the node specified by start_handle. The callback function is called whenever a node that matches the type parameter is found. If the callback function returns a non-zero value, the search is terminated immediately and this value is returned to the caller.
|
||||
|
||||
16.[Breadth first search][31] is used to check correctness of locking at runtime.
|
||||
|
||||
17.[Merge sort][32] on linked lists is used for [garbage collection][33], [file system management][34], etc.
|
||||
|
||||
18.[Bubble sort][35] is amazingly implemented too, in a driver library.
|
||||
|
||||
19.[Knuth-Morris-Pratt string matching][36],
|
||||
|
||||
> Implements a linear-time string-matching algorithm due to Knuth, Morris, and Pratt [1]. Their algorithm avoids the explicit computation of the transition function DELTA altogether. Its matching time is O(n), for n being length(text), using just an auxiliary function PI[1..m], for m being length(pattern), precomputed from the pattern in time O(m). The array PI allows the transition function DELTA to be computed efficiently "on the fly" as needed. Roughly speaking, for any state "q" = 0,1,...,m and any character "a" in SIGMA, the value PI["q"] contains the information that is independent of "a" and is needed to compute DELTA("q", "a") 2. Since the array PI has only m entries, whereas DELTA has O(m|SIGMA|) entries, we save a factor of |SIGMA| in the preprocessing time by computing PI rather than DELTA.
|
||||
>
|
||||
> [1] Cormen, Leiserson, Rivest, Stein Introdcution to Algorithms, 2nd Edition, MIT Press
|
||||
>
|
||||
> [2] See finite automation theory
|
||||
|
||||
20.[Boyer-Moore pattern matching][37] with references and recommendations for when to prefer the alternative.
|
||||
|
||||
> Implements Boyer-Moore string matching algorithm:
|
||||
>
|
||||
> [1] A Fast String Searching Algorithm, R.S. Boyer and Moore. Communications of the Association for Computing Machinery, 20(10), 1977, pp. 762-772. [http://www.cs.utexas.edu/users/moore/publications/fstrpos.pdf][38]
|
||||
>
|
||||
> [2] Handbook of Exact String Matching Algorithms, Thierry Lecroq, 2004 [http://www-igm.univ-mlv.fr/~lecroq/string/string.pdf][39]
|
||||
>
|
||||
> Note: Since Boyer-Moore (BM) performs searches for matchings from right to left, it's still possible that a matching could be spread over multiple blocks, in that case this algorithm won't find any coincidence.
|
||||
>
|
||||
> If you're willing to ensure that such thing won't ever happen, use the Knuth-Pratt-Morris (KMP) implementation instead. In conclusion, choose the proper string search algorithm depending on your setting.
|
||||
>
|
||||
> Say you're using the textsearch infrastructure for filtering, NIDS or
|
||||
> any similar security focused purpose, then go KMP. Otherwise, if you really care about performance, say you're classifying packets to apply Quality of Service (QoS) policies, and you don't mind about possible matchings spread over multiple fragments, then go BM.
|
||||
|
||||
### Data Structures and Algorithms in the Chromium Web Browser ###
|
||||
|
||||
Links are to the [source code on Google code][40]. I'm only going to list a few. I would suggest using the search feature to look up your favourite algorithm or data structure.
|
||||
|
||||
1.[Splay trees][41].
|
||||
|
||||
> The tree is also parameterized by an allocation policy (Allocator). The policy is used for allocating lists in the C free store or the zone; see zone.h.
|
||||
|
||||
2.[Voronoi diagrams][42] are used in a demo.
|
||||
|
||||
3.[Tabbing based on Bresenham's algorithm][43].
|
||||
|
||||
There are also such data structures and algorithms in the third-party code included in the Chromium code.
|
||||
|
||||
1.[Binary trees][44]
|
||||
2.[Red-Black trees][45]
|
||||
|
||||
> Conclusion of Julian Walker
|
||||
>
|
||||
> Red black trees are interesting beasts. They're believed to be simpler than AVL trees (their direct competitor), and at first glance this seems to be the case because insertion is a breeze. However, when one begins to play with the deletion algorithm, red black trees become very tricky. However, the counterweight to this added complexity is that both insertion and deletion can be implemented using a single pass, top-down algorithm. Such is not the case with AVL trees, where only the insertion algorithm can be written top-down. Deletion from an AVL tree requires a bottom-up algorithm.
|
||||
>
|
||||
> ...
|
||||
>
|
||||
> Red black trees are popular, as most data structures with a whimsical name. For example, in Java and C++, the library map structures are typically implemented with a red black tree. Red black trees are also comparable in speed to AVL trees. While the balance is not quite as good, the work it takes to maintain balance is usually better in a red black tree. There are a few misconceptions floating around, but for the most part the hype about red black trees is accurate.
|
||||
|
||||
3.[AVL trees][46]
|
||||
|
||||
4.[Rabin-Karp string matching][47] is used for compression.
|
||||
|
||||
5.[Compute the suffixes of an automaton][48].
|
||||
|
||||
6.[Bloom filter][49] implemented by Apple Inc.
|
||||
|
||||
7.[Bresenham's algorithm][50].
|
||||
|
||||
### Programming Language Libraries ###
|
||||
|
||||
I think they are worth considering. The programming languages designers thought it was worth the time and effort of some engineers to implement these data structures and algorithms so others would not have to. The existence of libraries is part of the reason we can find basic data structures reimplemented in software that is written in C but less so for Java applications.
|
||||
|
||||
1.The [C++ STL][51] includes lists, stacks, queues, maps, vectors, and algorithms for [sorting][52], [searching and heap manipulation][53].
|
||||
|
||||
2.[The Java API][54] is very extensive and covers much more.
|
||||
|
||||
3.The [Boost C++ library][55] includes algorithms like Boyer-Moore and Knuth-Morris-Pratt string matching algorithms.
|
||||
|
||||
### Allocation and Scheduling Algorithms ###
|
||||
|
||||
I find these interesting because even though they are called heuristics, the policy you use dictates the type of algorithm and data structure that are required, so one need to know about stacks and queues.
|
||||
|
||||
1.Least Recently Used can be implemented in multiple ways. A [list-based implementation][56] in the Linux kernel.
|
||||
|
||||
2.Other possibilities are First In First Out, Least Frequently Used, and Round Robin.
|
||||
|
||||
3.A variant of FIFO was used by the VAX/VMS system.
|
||||
|
||||
4.[The Clock algorithm][57] by [Richard Carr][58] is used for page frame replacement in Linux.
|
||||
|
||||
5.he Intel i860 processor used a random replacement policy.
|
||||
|
||||
6.[Adaptive Replacement Cache][59] is used in some IBM storage controllers, and was used in PostgreSQL though [only briefly due to patent concerns][60].
|
||||
|
||||
7.The [Buddy memory allocation algorithm][61], which is discussed by Knuth in TAOCP Vol. 1 is used in the Linux kernel, and the jemalloc concurrent allocator used by FreeBSD and in [facebook][62].
|
||||
|
||||
### Core utils in *nix systems ###
|
||||
|
||||
1.*grep* and awk both implement the Thompson-McNaughton-Yamada construction of NFAs from regular expressions, which apparently [even beats the Perl implementation][63].
|
||||
|
||||
2.*tsort* implements topological sort.
|
||||
|
||||
3.*fgrep* implements the [Aho-Corasick string matching algorithm][64].
|
||||
|
||||
4.*GNU grep*, [implements the Boyer-Moore algorithm][65] according to the author Mike Haertel.
|
||||
|
||||
5.crypt(1) on Unix implemented a variant of the encryption algorithm in the Enigma machine.
|
||||
|
||||
6.[*Unix diff*][66] implemented by Doug McIllroy, based on a prototype co-written with James Hunt, performs better than the standard dynamic programming algorithm used to compute Levenshtein distances. The [Linux version][67] computes the shortest edit distance.
|
||||
|
||||
### Cryptographic Algorithms ###
|
||||
|
||||
This could be a very long list. Cryptographic algorithms are implemented in all software that can perform secure communications or transactions.
|
||||
|
||||
1.[Merkle trees][68], specifically the Tiger Tree Hash variant, were used in peer-to-peer applications such as [GTK Gnutella][69] and [LimeWire][70].
|
||||
|
||||
2.[MD5][71] is used to provide a checksum for software packages and is used for integrity checks on *nix systems ([Linux implementation][72]) and is also supported on Windows and OS X.
|
||||
|
||||
3.[OpenSSL][73] implements many cryptographic algorithms including AES, Blowfish, DES, SHA-1, SHA-2, RSA, DES, etc.
|
||||
|
||||
### Compilers ###
|
||||
|
||||
1.[LALR parsing][74] is implemented by yacc and bison.
|
||||
|
||||
2.Dominator algorithms are used in most optimizing compilers based on SSA form.
|
||||
|
||||
3.lex and flex compile regular expressions into NFAs.
|
||||
|
||||
### Compression and Image Processing ###
|
||||
|
||||
1.[The Lempel-Ziv][75] algorithms for the GIF image format are implemented in image manipulation programs, starting from the *nix utility convert to complex programs.
|
||||
|
||||
2.Run length encoding is used to generate PCX files (used by the original Paintbrush program), compressed BMP files and TIFF files.
|
||||
|
||||
3.Wavelet compression is the basis for JPEG 2000 so all digital cameras that produce JPEG 2000 files will be implementing this algorithm.
|
||||
|
||||
4.Reed-Solomon error correction is implemented in [the Linux kernel][76], CD drives, barcode readers and was combined with convolution for image transmission from Voyager.
|
||||
|
||||
### ###Conflict Driven Clause Learning
|
||||
|
||||
Since the year 2000, the running time of SAT solvers on industrial benchmarks (usually from the hardware industry, though though other sources are used too) has decreased nearly exponentially every year. A very important part of this development is the Conflict Driven Clause Learning algorithm that combines the Boolean Constraint Propagation algorithm in the original paper of Davis Logemann and Loveland with the technique of clause learning that originated in constraint programming and artificial intelligence research. For specific, industrial modelling, SAT is considered an easy problem ([see this discussion][77]). To me, this is one of the greatest success stories in recent times because it combines algorithmic advances spread over several years, clever engineering ideas, experimental evaluation, and a concerted communal effort to solve the problem. The [CACM article by Malik and Zhang][78] is a good read. This algorithm is taught in many universities (I have attended four where it was the case) but typically in a logic or formal methods class.
|
||||
|
||||
Applications of SAT solvers are numerous. IBM, Intel and many other companies have their own SAT solver implementations. The [package manager][78] in OpenSUSE also uses a SAT solver.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://cstheory.stackexchange.com/questions/19759/core-algorithms-deployed/19773#19773
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:https://github.com/mirrors/linux-2.6
|
||||
[2]:https://github.com/mirrors/linux-2.6/blob/master/lib/llist.c
|
||||
[3]:https://github.com/mirrors/linux-2.6/blob/master/include/linux/list.h
|
||||
[4]:https://github.com/mirrors/linux-2.6/blob/master/include/linux/llist.h
|
||||
[5]:https://github.com/mirrors/linux-2.6/blob/39caa0916ef27cf1da5026eb708a2b8413156f75/lib/btree.c
|
||||
[6]:https://github.com/mirrors/linux-2.6/blob/master/include/linux/plist.h
|
||||
[7]:https://github.com/mirrors/linux-2.6/blob/b3a3a9c441e2c8f6b6760de9331023a7906a4ac6/include/linux/rtmutex.h
|
||||
[8]:https://github.com/mirrors/linux-2.6/blob/f0d55cc1a65852e6647d4f5d707c1c9b5471ce3c/drivers/powercap/intel_rapl.c
|
||||
[9]:https://github.com/mirrors/linux-2.6/blob/master/include/linux/rbtree.h
|
||||
[10]:http://lwn.net/Articles/184495/
|
||||
[11]:https://github.com/mirrors/linux-2.6/blob/master/include/linux/interval_tree.h
|
||||
[12]:https://github.com/mirrors/linux-2.6/blob/master/include/linux/radix-tree.h
|
||||
[13]:http://lwn.net/Articles/175432/
|
||||
[14]:https://github.com/mirrors/linux-2.6/blob/b3a3a9c441e2c8f6b6760de9331023a7906a4ac6/include/linux/prio_heap.h
|
||||
[15]:https://github.com/mirrors/linux-2.6/blob/42a2d923cc349583ebf6fdd52a7d35e1c2f7e6bd/include/linux/cgroup.h
|
||||
[16]:https://github.com/mirrors/linux-2.6/blob/b3a3a9c441e2c8f6b6760de9331023a7906a4ac6/include/linux/hash.h
|
||||
[17]:ttp://www.citi.umich.edu/techreports/reports/citi-tr-00-1.pdf
|
||||
[18]:https://github.com/mirrors/linux-2.6/blob/0b1e73ed225d8f7aeef96b74147215ca8b990dce/drivers/staging/lustre/lustre/lov/lov_pool.c
|
||||
[19]:https://github.com/mirrors/linux-2.6/blob/master/include/linux/hashtable.h
|
||||
[20]:https://github.com/mirrors/linux-2.6/blob/42a2d923cc349583ebf6fdd52a7d35e1c2f7e6bd/fs/inode.c
|
||||
[21]:https://github.com/mirrors/linux-2.6/blob/ff812d724254b95df76b7775d1359d856927a840/fs/btrfs/check-integrity.c
|
||||
[22]:https://github.com/mirrors/linux-2.6/blob/master/include/linux/bitmap.h
|
||||
[23]:https://github.com/mirrors/linux-2.6/blob/master/include/linux/semaphore.h
|
||||
[24]:https://github.com/mirrors/linux-2.6/blob/master/include/linux/spinlock.h
|
||||
[25]:https://github.com/mirrors/linux-2.6/blob/master/lib/bsearch.c
|
||||
[26]:https://github.com/mirrors/linux-2.6/blob/b3a3a9c441e2c8f6b6760de9331023a7906a4ac6/drivers/sh/intc/chip.c
|
||||
[27]:https://github.com/mirrors/linux-2.6/blob/10d0c9705e80bbd3d587c5fad24599aabaca6688/drivers/base/regmap/regcache.c
|
||||
[28]:https://github.com/mirrors/linux-2.6/blob/b3a3a9c441e2c8f6b6760de9331023a7906a4ac6/fs/befs/btree.c
|
||||
[29]:https://github.com/mirrors/linux-2.6/blob/a9238741987386bb549d61572973c7e62b2a4145/drivers/acpi/acpica/nswalk.c
|
||||
[30]:https://github.com/mirrors/linux-2.6/blob/b3a3a9c441e2c8f6b6760de9331023a7906a4ac6/fs/configfs/dir.c
|
||||
[31]:https://github.com/mirrors/linux-2.6/blob/4fbf888accb39af423f271111d44e8186f053723/kernel/locking/lockdep.c
|
||||
[32]:https://github.com/mirrors/linux-2.6/blob/master/lib/list_sort.c
|
||||
[33]:https://github.com/mirrors/linux-2.6/blob/42a2d923cc349583ebf6fdd52a7d35e1c2f7e6bd/fs/ubifs/gc.c
|
||||
[34]:https://github.com/mirrors/linux-2.6/blob/ff812d724254b95df76b7775d1359d856927a840/fs/btrfs/raid56.c
|
||||
[35]:https://github.com/mirrors/linux-2.6/blob/b3a3a9c441e2c8f6b6760de9331023a7906a4ac6/drivers/media/common/saa7146/saa7146_hlp.c
|
||||
[36]:https://github.com/mirrors/linux-2.6/blob/b3a3a9c441e2c8f6b6760de9331023a7906a4ac6/lib/ts_kmp.c
|
||||
[37]:https://github.com/mirrors/linux-2.6/blob/b3a3a9c441e2c8f6b6760de9331023a7906a4ac6/lib/ts_bm.c
|
||||
[38]:http://www.cs.utexas.edu/users/moore/publications/fstrpos.pdf
|
||||
[39]:http://www-igm.univ-mlv.fr/~lecroq/string/string.pdf
|
||||
[40]:https://code.google.com/p/chromium/
|
||||
[41]:https://code.google.com/p/chromium/codesearch#chromium/src/v8/src/splay-tree.h
|
||||
[42]:https://code.google.com/p/chromium/codesearch#chromium/src/native_client_sdk/src/examples/demo/voronoi/index.html
|
||||
[43]:https://code.google.com/p/chromium/codesearch#chromium/src/chrome/browser/ui/cocoa/tabs/tab_strip_controller.mm
|
||||
[44]:https://code.google.com/p/chromium/codesearch#chromium/src/third_party/bintrees/bintrees/bintree.py
|
||||
[45]:https://code.google.com/p/chromium/codesearch#chromium/src/third_party/bintrees/bintrees/rbtree.py
|
||||
[46]:https://code.google.com/p/chromium/codesearch#chromium/src/third_party/bintrees/bintrees/avltree.py
|
||||
[47]:https://code.google.com/p/chromium/codesearch#chromium/src/third_party/zlib/deflate.c
|
||||
[48]:https://code.google.com/p/chromium/codesearch#chromium/src/native_client/src/trusted/validator_ragel/dfa_traversal.py
|
||||
[49]:https://code.google.com/p/chromium/codesearch#chromium/src/third_party/WebKit/Source/wtf/BloomFilter.h
|
||||
[50]:https://code.google.com/p/chromium/codesearch#chromium/src/third_party/libvpx/source/libvpx/vp8/common/textblit.c
|
||||
[51]:http://www.cplusplus.com/reference/stl/
|
||||
[52]:http://www.cplusplus.com/reference/algorithm/
|
||||
[53]:http://www.cplusplus.com/reference/algorithm/
|
||||
[54]:http://docs.oracle.com/javase/7/docs/api/
|
||||
[55]:http://www.boost.org/doc/libs/1_55_0/libs/algorithm/doc/html/index.html#algorithm.description_and_rationale
|
||||
[56]:https://github.com/mirrors/linux-2.6/blob/master/include/linux/list_lru.h
|
||||
[57]:http://en.wikipedia.org/wiki/Page_replacement_algorithm#Clock
|
||||
[58]:http://dl.acm.org/citation.cfm?id=4750
|
||||
[59]:http://en.wikipedia.org/wiki/Adaptive_Replacement_Cache
|
||||
[60]:http://www.varlena.com/GeneralBits/96.php
|
||||
[61]:http://en.wikipedia.org/wiki/Buddy_memory_allocation
|
||||
[62]:http://www.facebook.com/notes/facebook-engineering/scalable-memory-allocation-using-jemalloc/480222803919
|
||||
[63]:http://swtch.com/~rsc/regexp/regexp1.html
|
||||
[64]:http://en.wikipedia.org/wiki/Aho%E2%80%93Corasick_string_matching_algorithm
|
||||
[65]:http://lists.freebsd.org/pipermail/freebsd-current/2010-August/019310.html
|
||||
[66]:http://www.cs.dartmouth.edu/~doug/diff.pdf
|
||||
[67]:http://linux.die.net/man/3/diff
|
||||
[68]:http://en.wikipedia.org/wiki/Merkle_tree
|
||||
[69]:https://github.com/gtk-gnutella/bitter
|
||||
[70]:http://en.wikibooks.org/wiki/LimeWire
|
||||
[71]:http://en.wikipedia.org/wiki/MD5
|
||||
[72]:https://github.com/mirrors/linux-2.6/blob/b3a3a9c441e2c8f6b6760de9331023a7906a4ac6/crypto/md5.c
|
||||
[73]:http://www.openssl.org/
|
||||
[74]:http://en.wikipedia.org/wiki/LALR_parser
|
||||
[75]:http://en.wikipedia.org/wiki/Lempel_Ziv
|
||||
[76]:https://github.com/mirrors/linux-2.6/blob/b3a3a9c441e2c8f6b6760de9331023a7906a4ac6/lib/reed_solomon/reed_solomon.c
|
||||
[77]:http://rjlipton.wordpress.com/2009/07/13/sat-solvers-is-sat-hard-or-easy/
|
||||
[78]:http://dl.acm.org/citation.cfm?id=1536637
|
||||
[79]:http://en.opensuse.org/Portal%3aLibzypp
|
||||
@ -0,0 +1,41 @@
|
||||
Canonical Dev称Linux Mint“脆弱”,不要将其用于办理在线银行业务
|
||||
================================================================================
|
||||
**一位Canonical公司[工程师建议][1]:基于Ubuntu的流行操作系统Linux Mint用户不应该将其用于在线办理银行业务 。**
|
||||
|
||||
Mint禁止更新那些存在已知安全问题的安装包 - 从内核和浏览器到启动加载器和Xorg显示服务 - 的决定提供给用户一个“脆弱的系统” ,Oliver Grawert说。
|
||||
|
||||
> “不去适当整合Ubuntu中归档包的变化,反而拒绝这些软件包的(安全)更新。不允许安装提供的安全更新,强迫保留一个基于脆弱内核的浏览器或xorg,将使之成为一个易受攻击的系统,(原文如此)”。
|
||||
>
|
||||
> “就我个人而言,我不会用它在线办理银行业务。 ”
|
||||
|
||||
当然不只有Grawert认为Mint在安全意识上的低下。Mozilla贡献者兼前Ubuntu成员 **Benjamin Kerensa** 也有同样的看法:
|
||||
|
||||
> “目前还不清楚为什么Linux Mint禁止所有的安全更新。我可以说,Mint需要花好几个月才能得到一个Firefox的修正版,而Ubuntu和Debian已经同时在他们的包上打了安全补丁。
|
||||
>
|
||||
> 这是使得Linux Mint用户处于危险中的其中一个关键原因,我从来不建议任何人将Linux Mint作为一种替代Ubuntu的系统。”
|
||||
|
||||
Oliver Grawert是一位可靠的撰稿人。作为一位Canonical公司下的Ubuntu工程师,他比大多数人更了解自己在说什么。
|
||||
|
||||
**‘那么Mint的用户存在实际风险么?可以说对也可以说不对…’**
|
||||
|
||||
那么Mint的用户存在实际风险么?
|
||||
|
||||
半对半错。Mint开发商坚决拒绝更新的现有软件包中大部分的安全“漏洞”(一个更好的词)都是有记录和已知的,虽然这些漏洞很少被利用。因此对用户构成的“实际风险”仍然存在,至少现在,在理论上是很有可能的。
|
||||
|
||||
也就是说,没有发生已知的由于使用Mint发行版(或任何其他基于Ubuntu的未打补丁的发行版)并被通过利用Grawert引用的Ubuntu开发邮件列表上的漏洞造成身份盗窃乃至更糟的事故的情况。
|
||||
|
||||
但是,仅仅因为迄今为止没有人曾经钻进这扇半掩的窗户,并不能说明其他人永远不会这么做。
|
||||
|
||||
**看到Ubuntu持续被提及有关自身的(主要是理论上)隐私问题后,现在靴子被牢牢地套在另一只脚上,我们将可喜的看到对用户安全的强烈关注正在延伸至其他发行版上**
|
||||
|
||||
*请注意:我们已经向Linux Mint征求意见及澄清,但还没收到任何答复。*
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.omgubuntu.co.uk/2013/11/canonical-dev-dont-use-linux-mint-online-banking-unsecure
|
||||
|
||||
译者:[whatever1992](https://github.com/whatever1992) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:https://lists.ubuntu.com/archives/ubuntu-devel-discuss/2013-November/014770.html
|
||||
287
translated/Core algorithms deployed.md
Normal file
287
translated/Core algorithms deployed.md
Normal file
@ -0,0 +1,287 @@
|
||||
已部署的核心算法
|
||||
================================================================================
|
||||
在我看来,一个系统背后主要驱动的算法更容易在非算法课程上找到,同理,目前的程序更容易在应用数学而不是理论数学中找到。在讲座中,很少有实际问题有一个抽象问题的精确就够。追根究底地说,我认为没有理由为何流行算法课程资料。诸如Strassen乘法,AKS素性测试、或者Moser-Tardos算法与底层实际问题,如实现视频数据库、优化的编译器、操作系统、网络拥堵控制系统或者其他系统有相关。这些课程的价值是学习利用错综复杂的方法找出问题的结构而找出有效的解决方案。高级算法也满足了一些简单算法,这些分析并不平凡。正是由于这个原因,我不会不理会简单随机算法或者PageRank。
|
||||
|
||||
我想你可以选择任何一个大型软件并会内部实现了发现基础和高级的算法。作为一个研究案例,我选择了Linux内核,并会示例一些Chromium里面的例子。
|
||||
|
||||
### Linux内核中的基本数据结构和算法 ###
|
||||
|
||||
链接在这里([source code on github][1])。
|
||||
|
||||
1.[链表][2], [双向链表][3], [无锁链表][4]。
|
||||
|
||||
2.[B+ 树][5]的注释会告诉你无法在教科书上找到的东西。
|
||||
|
||||
> 一个相对简单的B+树的实现。我把它作为一个学习练习来帮助理解B+树是如何工作的。这同样也被证明是有用的。
|
||||
>
|
||||
> ...
|
||||
>
|
||||
> 一个技巧在教科书中并不常见。最小的值在右侧而不是在左侧。所有在一个节点里用到的槽都在左侧,所有没有用到的槽包含了空值(NUL)。大多数操作只简单地遍历所有的槽一次并在第一个空值时(NUL)终止。
|
||||
|
||||
3.[优先排序列表][6] 用于 [互斥量][7]、[驱动][8]等等。
|
||||
|
||||
4.[红黑树][9][用于][10]调度、虚拟内存管理、追踪文件描述符和目录项等。
|
||||
|
||||
5.[区间树][11]
|
||||
|
||||
6.[根树][12]用于[内存管理][13],NFS相关查询和网络相关功能。
|
||||
|
||||
> 根树一个通用的用处是存储指针到结构页中。
|
||||
|
||||
7.[优先级堆][14],是一个字面上的教科书实现,用于[cgroup][15]。
|
||||
|
||||
> 第七章中,简单的基于CLR的只插入,含有指针的静态大小优先级堆
|
||||
|
||||
8.[哈希函数][16],参考了Knuth和一篇论文。
|
||||
|
||||
> Knuth建议约黄金比例的素数通过对乘法散列机器字的最大整数表示。Chuck Lever验证了该技术的有效性:
|
||||
>
|
||||
> [http://www.citi.umich.edu/techreports/reports/citi-tr-00-1.pdf][17]
|
||||
>
|
||||
> 这些素数的选择是位稀疏的,他们可以通过移位和加法操作,而不必使用乘法器,乘法器是很慢的。
|
||||
|
||||
9.一部分代码,比如[这个驱动][18],实现了他们自己的哈希函数。
|
||||
|
||||
> 哈希函数使用了一种旋转哈希算法
|
||||
>
|
||||
> Knuth, D. 计算机程序设计艺术, 卷 3: 排序与搜索, 第6.7章. Addison Wesley, 1973
|
||||
|
||||
10.[哈希表][19]用于实现[inode][20],[文件系统完整性检测][21]等等。
|
||||
|
||||
11.[位数组][22]用于处理标志位、中断等等。并在Knuth的卷4中阐述。
|
||||
|
||||
12.[信号量][23]和[自旋锁][24]
|
||||
|
||||
13.[二分查找][25]用于[中断处理][26],[寄存器缓存查询][27]等等。
|
||||
|
||||
14.[B树的二分查找][28]。
|
||||
|
||||
15.[深度优先搜索][29]被广泛地用于[目录配置中][30]。
|
||||
|
||||
> 执行一个修改过的遍历深度优先的命名空间树,以指定的start_handle节点开始以及结束。回调函数会在任何一个参数匹配的节点被发现时被调用。如果回调函数返回了一个非0值,搜索将会激励结束并且将返回值给调用者。
|
||||
|
||||
16.[广度有限搜索][31]用于检测运行时锁定的正确性。
|
||||
|
||||
17.链表中的[归并排序][32]用于[垃圾收集][33],[文件系统管理][34]等等。
|
||||
|
||||
18.[冒泡排序][35]在一个驱动库中也是一个令人惊讶的实现。
|
||||
|
||||
19.[Knuth-Morris-Pratt 字符串匹配][36],
|
||||
|
||||
> 根据Knuth、Morris和Pratt [1]实现了一个线性时间的字符串匹配算法。他们的算法避免了转换函数的显式地计算DELTA。对于长度为n的文本,其匹配时间是O(n),对于长度为m的模式(pattern),仅使用一个辅助函数PI[1 . .m],预先计算模式的时间为O(m)。数组PI允许转换函数DELTA被实时有效地计算。粗略地说,对于任何状态"q"= 0,1,…、m和在SIGMA中的任何字符"a",PI["q"]的值包含的信息是独立的"a"并需要计算DELTA("q","a") 2.既然PI只有m个记录,而DELTA有O(m |SIGMA|)个记录,在预处理时间计算PI而不是DELTA的时候,我们可以节省一个因数|SIGMA|
|
||||
>
|
||||
> [1] Cormen, Leiserson, Rivest, Stein,算法介绍,第二版,MIT出版社
|
||||
>
|
||||
> [2] 见有限自动机原理
|
||||
|
||||
20.[Boyer-Moore 模式匹配][37]是在找替代品时的参考和建议。
|
||||
|
||||
> 实现了Boyer-Moore字符串匹配算法:
|
||||
>
|
||||
> [1] 一个快速的字符串搜索算法,R.S. Boyer and Moore.计算机通信协会,20(10), 1977, pp. 762-772. [http://www.cs.utexas.edu/users/moore/publications/fstrpos.pdf][38]
|
||||
>
|
||||
> [2] 准确的字符串匹配算法手册,Thierry Lecroq, 2004 [http://www-igm.univ-mlv.fr/~lecroq/string/string.pdf][39]
|
||||
>
|
||||
> 注:由于Boyer-Moore(BM)从右到左搜索匹配,仍然有可能匹配分布在多个块,在这种情况下该算法不会找到任何巧合。
|
||||
>
|
||||
> 如果你愿意确保这样的事情永远不会发生,那使用Knuth-Pratt-Morris(KMP)实现。总之,根据您的设置适当地选择字符串搜索算法。
|
||||
>
|
||||
> 如果你正在用文本搜索器进行过滤,NIDS或任何类似的注重安全的目的,那么使用KMP。否则,如果你真的关心性能,并且你对数据包进行分类以使用服务质量(QoS)政策,且你不介意匹配可能分布分散,那么用BM。
|
||||
|
||||
### Chromium 浏览器中的数据结构和算法 ###
|
||||
|
||||
链接在这里([source code on Google code][40])。我只会列出一部分。我建议使用搜索来找到你最喜欢的算法或者数据结构。
|
||||
|
||||
1.[伸展树][41]。
|
||||
|
||||
> The tree is also parameterized by an allocation policy (Allocator). The policy is used for allocating lists in the C free store or the zone; see zone.h.
|
||||
|
||||
2.[Voronoi diagrams][42]用于一个示例。
|
||||
|
||||
3.[基于Bresenham的标志算法][43]
|
||||
|
||||
也有这样的第三方的数据结构和算法包含在Chromium代码中。
|
||||
|
||||
1.[二叉树][44]
|
||||
|
||||
2.[红黑树][45]
|
||||
|
||||
> Julian Walker的总结
|
||||
>
|
||||
> 红黑树是有趣的野兽。他们被认为比AVL树(它们的直接竞争对手)简单,乍一看这似乎是由于插入是一项轻松的乐事。然而,当你开始玩删除算法,红黑树变得非常棘手。然而, 平衡物增加了复杂性,插入和删除可以使用单通道,实现自上而下的算法。这与AVL树情况不一样,只能写自顶向下插入算法。删除从AVL树需要自下而上的算法。
|
||||
> ...
|
||||
>
|
||||
> 红黑树是很流行的,因为大多数数据结构都有一个古怪的名字。比如,在Java和c++库映射结构通常用红黑树实现。红黑树的速度也与AVL树相当。而AVL树平衡不是很好,需要保持平衡的工作红黑树通常更好。有一些误解被流传,但在大多数情况下对红黑树的宣传是准确的。
|
||||
|
||||
3.[AVL 树][46]
|
||||
|
||||
4.[Rabin-Karp字符串匹配][47]用于比较。
|
||||
|
||||
5.[计算机器人后缀][48]
|
||||
|
||||
6.由Apple公司实现的[布隆过滤器][49]
|
||||
|
||||
7.[Bresenham 算法][50].
|
||||
|
||||
### 编程语言库 ###
|
||||
|
||||
我想这个问题值得思考。编程语言设计者们认为这值得花一些工程师时间和精力来实现这些数据结构和算法,这样其他人你不必这么做了。库的存在是我们可以在一些用C写的软件,但比Java少,重新实现了基础数据结构的部分原因。
|
||||
|
||||
1.[C++ STL][51]包含了链表、栈、队列、map、向量和对[排序][52]、[搜索和堆操作][53]算法。
|
||||
|
||||
2.[Java API][54]是非常广阔的并且覆盖了更多。
|
||||
3.[Boost C++ 库][55]包含了像 Boyer-Moore以及Knuth-Morris-Pratt字符串匹配算法。
|
||||
|
||||
### 分配和调度算法 ###
|
||||
|
||||
我发现这些很有趣,因为即使他们被称为启发式,您使用的策略规定了算法类型和需要的数据结构,因此,所以需要人们知道栈和队列。
|
||||
|
||||
1.最近最少使用算法可以用不同的方法实现。Linux内核有一种[基于列表的实现][56]。
|
||||
|
||||
2.其他的还有先入先出、最常使用、和轮循。
|
||||
|
||||
3.FIFO的一个变种用于VAX/VMS系统。
|
||||
|
||||
4.[Richard Carr][58]的[时钟算法][57]用于Linux中的页面替换。
|
||||
|
||||
5.Intel i860处理器是一种随即替代策略。
|
||||
|
||||
6.[自适应置换高速缓存][59]用于一些IBM存储控制器中,也曾经用于PostgreSQL中([虽然仅仅因为一些专利问题][60])。
|
||||
|
||||
7.Knuth在计算机程序设计艺术,卷1中讨论过的[Buddy内存分配算法][61]内用于Linux内核中,jemalloc并发分配器被用于FreeBSD和[facebook][62]中。
|
||||
|
||||
### *nix系统核心工具 ###
|
||||
|
||||
1.*grep*和*awk*同时实从正则表达式中实现NFA的Thompson-McNaughton-Yamada构造,这显然击败了[Perl的实现][63]。
|
||||
|
||||
2.*tsort*实现了拓扑排序。
|
||||
|
||||
3.*fgrep*实现了[Aho-Corasick字符串匹配算法][64]。
|
||||
|
||||
4.*GNU grep*,根据作者Mike Haertel实现了[Boyer-Mooresuan算法][65]。
|
||||
|
||||
5.Unix上的crypt(1)实现了一个在Enigma机器上的不同加密算法。
|
||||
|
||||
6.[*Unix diff*][66]由Doug McIllroy实现,基于和James Hunt合作编写的圆形。它比用于计算Levenshtein距离的标准动态规划算法执行地更好。[Linux 版本][67]计算最短编辑距离。
|
||||
|
||||
### 加密算法 ###
|
||||
|
||||
这可能回事一个非常长的列表。加密算法在所有执行安全通信和交易的程序中都有实现。
|
||||
|
||||
1.[Merkle 树][68],特别是 Tiger Tree Hash变种,被用于点对点应用,比如[GTK Gnutella][69]和[LimeWire][70]。
|
||||
|
||||
2.[MD5][71]被用于提供软件包的校验和并被用于在*nix系统上的完整性检测(([Linux 实现][72])),同样也在Windows和OSX中支持。
|
||||
|
||||
3.[OpenSSL][73]实现了很多加密算法包括AES、Blowfish、DES、SHA-1、SHA-2、RSA、DES等等
|
||||
|
||||
### 编译器 ###
|
||||
|
||||
1.[LALR 解析][74]用yacc和bison实现。
|
||||
|
||||
2.支配算法被用于大多数基于SSA形式的编译器优化。
|
||||
|
||||
3.lex和flex编译正则表达式成为NFA。
|
||||
|
||||
### 压缩和图像处理 ###
|
||||
|
||||
1.用于GIF图片格式的[Lempel-Ziv][75]算法用图形操作程序实现,从*unix工具转化到复杂的程序。
|
||||
|
||||
2.行程长度编码用于产生PCX文件(用于原始的画笔程序),是被压缩的BMP和TIFF文件。
|
||||
|
||||
3.小波压缩是JPEG2000的基础,所以所有生成JPEG2000文件的数码相机会支持这个算法。
|
||||
|
||||
4.Reed-Solomon纠错在[Linux内核][76]、CD驱动器、条形码读取器、结合从Voyager中的卷积图像传输中实现。
|
||||
|
||||
### 冲突驱动语句学习算法 (CDCL) ###
|
||||
|
||||
自2000以来,SAT求解器在工业标准的运行时间(通常是硬件工业,虽然其他地方也被使用)以近乎指数的方式每年下跌。这发展中很重要的一部分是冲突驱动语句学习算法,它结合了Davis Logemann和Loveland在约束规划和人工智能研究中关于语句学习的原始论文中的布尔约束传播算法。特定地,工业造型,SAT被认为是一个简单的问题([见这个讨论][77])。对我而言,这个一个最近最好的成功故事因为它结合了这几年算法的前进推广、聪明的工程理念、实验性的评估、齐心协力地解决一个问题。[Malik and Zhang的CACM文章][78]值得阅读。这个算法在许多大学中教授(我参加了4个地方都是如此),但是通常在一个逻辑或者形式方法课上。
|
||||
|
||||
SAT求解器的应用有很多。IBM,Intel和许多其他公司都有他们的SAT求解器是西安。OpenSuse的[包管理器][78]同样使用了一个SAT求解器。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://cstheory.stackexchange.com/questions/19759/core-algorithms-deployed/19773#19773
|
||||
|
||||
译者:[geekpi](https://github.com/geekpi) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:https://github.com/mirrors/linux-2.6
|
||||
[2]:https://github.com/mirrors/linux-2.6/blob/master/lib/llist.c
|
||||
[3]:https://github.com/mirrors/linux-2.6/blob/master/include/linux/list.h
|
||||
[4]:https://github.com/mirrors/linux-2.6/blob/master/include/linux/llist.h
|
||||
[5]:https://github.com/mirrors/linux-2.6/blob/39caa0916ef27cf1da5026eb708a2b8413156f75/lib/btree.c
|
||||
[6]:https://github.com/mirrors/linux-2.6/blob/master/include/linux/plist.h
|
||||
[7]:https://github.com/mirrors/linux-2.6/blob/b3a3a9c441e2c8f6b6760de9331023a7906a4ac6/include/linux/rtmutex.h
|
||||
[8]:https://github.com/mirrors/linux-2.6/blob/f0d55cc1a65852e6647d4f5d707c1c9b5471ce3c/drivers/powercap/intel_rapl.c
|
||||
[9]:https://github.com/mirrors/linux-2.6/blob/master/include/linux/rbtree.h
|
||||
[10]:http://lwn.net/Articles/184495/
|
||||
[11]:https://github.com/mirrors/linux-2.6/blob/master/include/linux/interval_tree.h
|
||||
[12]:https://github.com/mirrors/linux-2.6/blob/master/include/linux/radix-tree.h
|
||||
[13]:http://lwn.net/Articles/175432/
|
||||
[14]:https://github.com/mirrors/linux-2.6/blob/b3a3a9c441e2c8f6b6760de9331023a7906a4ac6/include/linux/prio_heap.h
|
||||
[15]:https://github.com/mirrors/linux-2.6/blob/42a2d923cc349583ebf6fdd52a7d35e1c2f7e6bd/include/linux/cgroup.h
|
||||
[16]:https://github.com/mirrors/linux-2.6/blob/b3a3a9c441e2c8f6b6760de9331023a7906a4ac6/include/linux/hash.h
|
||||
[17]:ttp://www.citi.umich.edu/techreports/reports/citi-tr-00-1.pdf
|
||||
[18]:https://github.com/mirrors/linux-2.6/blob/0b1e73ed225d8f7aeef96b74147215ca8b990dce/drivers/staging/lustre/lustre/lov/lov_pool.c
|
||||
[19]:https://github.com/mirrors/linux-2.6/blob/master/include/linux/hashtable.h
|
||||
[20]:https://github.com/mirrors/linux-2.6/blob/42a2d923cc349583ebf6fdd52a7d35e1c2f7e6bd/fs/inode.c
|
||||
[21]:https://github.com/mirrors/linux-2.6/blob/ff812d724254b95df76b7775d1359d856927a840/fs/btrfs/check-integrity.c
|
||||
[22]:https://github.com/mirrors/linux-2.6/blob/master/include/linux/bitmap.h
|
||||
[23]:https://github.com/mirrors/linux-2.6/blob/master/include/linux/semaphore.h
|
||||
[24]:https://github.com/mirrors/linux-2.6/blob/master/include/linux/spinlock.h
|
||||
[25]:https://github.com/mirrors/linux-2.6/blob/master/lib/bsearch.c
|
||||
[26]:https://github.com/mirrors/linux-2.6/blob/b3a3a9c441e2c8f6b6760de9331023a7906a4ac6/drivers/sh/intc/chip.c
|
||||
[27]:https://github.com/mirrors/linux-2.6/blob/10d0c9705e80bbd3d587c5fad24599aabaca6688/drivers/base/regmap/regcache.c
|
||||
[28]:https://github.com/mirrors/linux-2.6/blob/b3a3a9c441e2c8f6b6760de9331023a7906a4ac6/fs/befs/btree.c
|
||||
[29]:https://github.com/mirrors/linux-2.6/blob/a9238741987386bb549d61572973c7e62b2a4145/drivers/acpi/acpica/nswalk.c
|
||||
[30]:https://github.com/mirrors/linux-2.6/blob/b3a3a9c441e2c8f6b6760de9331023a7906a4ac6/fs/configfs/dir.c
|
||||
[31]:https://github.com/mirrors/linux-2.6/blob/4fbf888accb39af423f271111d44e8186f053723/kernel/locking/lockdep.c
|
||||
[32]:https://github.com/mirrors/linux-2.6/blob/master/lib/list_sort.c
|
||||
[33]:https://github.com/mirrors/linux-2.6/blob/42a2d923cc349583ebf6fdd52a7d35e1c2f7e6bd/fs/ubifs/gc.c
|
||||
[34]:https://github.com/mirrors/linux-2.6/blob/ff812d724254b95df76b7775d1359d856927a840/fs/btrfs/raid56.c
|
||||
[35]:https://github.com/mirrors/linux-2.6/blob/b3a3a9c441e2c8f6b6760de9331023a7906a4ac6/drivers/media/common/saa7146/saa7146_hlp.c
|
||||
[36]:https://github.com/mirrors/linux-2.6/blob/b3a3a9c441e2c8f6b6760de9331023a7906a4ac6/lib/ts_kmp.c
|
||||
[37]:https://github.com/mirrors/linux-2.6/blob/b3a3a9c441e2c8f6b6760de9331023a7906a4ac6/lib/ts_bm.c
|
||||
[38]:http://www.cs.utexas.edu/users/moore/publications/fstrpos.pdf
|
||||
[39]:http://www-igm.univ-mlv.fr/~lecroq/string/string.pdf
|
||||
[40]:https://code.google.com/p/chromium/
|
||||
[41]:https://code.google.com/p/chromium/codesearch#chromium/src/v8/src/splay-tree.h
|
||||
[42]:https://code.google.com/p/chromium/codesearch#chromium/src/native_client_sdk/src/examples/demo/voronoi/index.html
|
||||
[43]:https://code.google.com/p/chromium/codesearch#chromium/src/chrome/browser/ui/cocoa/tabs/tab_strip_controller.mm
|
||||
[44]:https://code.google.com/p/chromium/codesearch#chromium/src/third_party/bintrees/bintrees/bintree.py
|
||||
[45]:https://code.google.com/p/chromium/codesearch#chromium/src/third_party/bintrees/bintrees/rbtree.py
|
||||
[46]:https://code.google.com/p/chromium/codesearch#chromium/src/third_party/bintrees/bintrees/avltree.py
|
||||
[47]:https://code.google.com/p/chromium/codesearch#chromium/src/third_party/zlib/deflate.c
|
||||
[48]:https://code.google.com/p/chromium/codesearch#chromium/src/native_client/src/trusted/validator_ragel/dfa_traversal.py
|
||||
[49]:https://code.google.com/p/chromium/codesearch#chromium/src/third_party/WebKit/Source/wtf/BloomFilter.h
|
||||
[50]:https://code.google.com/p/chromium/codesearch#chromium/src/third_party/libvpx/source/libvpx/vp8/common/textblit.c
|
||||
[51]:http://www.cplusplus.com/reference/stl/
|
||||
[52]:http://www.cplusplus.com/reference/algorithm/
|
||||
[53]:http://www.cplusplus.com/reference/algorithm/
|
||||
[54]:http://docs.oracle.com/javase/7/docs/api/
|
||||
[55]:http://www.boost.org/doc/libs/1_55_0/libs/algorithm/doc/html/index.html#algorithm.description_and_rationale
|
||||
[56]:https://github.com/mirrors/linux-2.6/blob/master/include/linux/list_lru.h
|
||||
[57]:http://en.wikipedia.org/wiki/Page_replacement_algorithm#Clock
|
||||
[58]:http://dl.acm.org/citation.cfm?id=4750
|
||||
[59]:http://en.wikipedia.org/wiki/Adaptive_Replacement_Cache
|
||||
[60]:http://www.varlena.com/GeneralBits/96.php
|
||||
[61]:http://en.wikipedia.org/wiki/Buddy_memory_allocation
|
||||
[62]:http://www.facebook.com/notes/facebook-engineering/scalable-memory-allocation-using-jemalloc/480222803919
|
||||
[63]:http://swtch.com/~rsc/regexp/regexp1.html
|
||||
[64]:http://en.wikipedia.org/wiki/Aho%E2%80%93Corasick_string_matching_algorithm
|
||||
[65]:http://lists.freebsd.org/pipermail/freebsd-current/2010-August/019310.html
|
||||
[66]:http://www.cs.dartmouth.edu/~doug/diff.pdf
|
||||
[67]:http://linux.die.net/man/3/diff
|
||||
[68]:http://en.wikipedia.org/wiki/Merkle_tree
|
||||
[69]:https://github.com/gtk-gnutella/bitter
|
||||
[70]:http://en.wikibooks.org/wiki/LimeWire
|
||||
[71]:http://en.wikipedia.org/wiki/MD5
|
||||
[72]:https://github.com/mirrors/linux-2.6/blob/b3a3a9c441e2c8f6b6760de9331023a7906a4ac6/crypto/md5.c
|
||||
[73]:http://www.openssl.org/
|
||||
[74]:http://en.wikipedia.org/wiki/LALR_parser
|
||||
[75]:http://en.wikipedia.org/wiki/Lempel_Ziv
|
||||
[76]:https://github.com/mirrors/linux-2.6/blob/b3a3a9c441e2c8f6b6760de9331023a7906a4ac6/lib/reed_solomon/reed_solomon.c
|
||||
[77]:http://rjlipton.wordpress.com/2009/07/13/sat-solvers-is-sat-hard-or-easy/
|
||||
[78]:http://dl.acm.org/citation.cfm?id=1536637
|
||||
[79]:http://en.opensuse.org/Portal%3aLibzypp
|
||||
@ -1,40 +1,39 @@
|
||||
Ubuntu小贴士-改变Samba工作组和计算机名
|
||||
每日Ubuntu小技巧-更改Samba工作组和计算机名
|
||||
================================================================================
|
||||
这里还有另一个Ubuntu新手经常问的问题,答案很简单,但是对于新人来说完全理解需要花费一些时间。
|
||||
这是另一个Ubuntu的新用户问的最多的问题。这个问题的答案很简单,但当你接触新事物时,你需要时间来完全理解它。
|
||||
|
||||
这里有一些我们几天前收到的问题:
|
||||
这是我们前几天收到的问题;
|
||||
|
||||
> 怎样在Ubuntu里改变Samba工作组和计算机名?
|
||||
> 如何更改Samba的工作组名和Ubuntu的计算机名称?
|
||||
|
||||
对于大多数的Ubuntu用户来说,给计算机改一个名字一定会在最低限度完成的列表上,更不用说Samba工作组了,一些少量的高级用户或者也会想轻松地在使用Ubuntu时做到这些。
|
||||
对于大多数Ubuntu用户,改变他们的计算机名称是极少发生的事情,更别说samba工作组了。一些进阶使用者可能要学习如何用Ubuntu很简单的做到这一点。
|
||||
|
||||
如果是在Ubuntu里改变计算机名这个问题的话,我们之前已经写过一个简单的文章了,你真可以在[这里][1]找到。紧紧跟随[在Ubuntu里改变计算机名(changing your computer name in Ubuntu)][1]这篇向导性文章就可以达到你的目标。
|
||||
当涉及到在Ubuntu中更改计算机名时,我们曾写过一个简单的帖子,可以点击这里[这里][1]找到。按照这个简易指南[changing your computer name in Ubuntu][1]来实现要求。
|
||||
|
||||
或许还有别的方法可以在Ubuntu里改变你的计算机名但是这是最简单而快速的方法。对于那些使用Ubuntu服务器的,你可以使用Vi或者Vim编辑hostname和host等文件。使用Vi或者Vim对大多数人有点儿难,所以只有部分由使用这些编辑器的知识的人才会使用它。
|
||||
也许还有其他方法来改变你在Ubuntu中的计算机名,但是这是最简单和最快的。对于那些使用Ubuntu系统的服务器,你可以用vi或vim编辑的主机名和主机文件。那些不了解这些编辑器的人也许很难使用vi或vim。
|
||||
|
||||
要在Ubuntu里改变Samba工作组,按下键盘上的**Ctrl – Alt – T** 打开终端。但它(终端)打开后,运行下面的命令以编辑Samba的配置文件。
|
||||
在键盘上按**Ctrl – Alt – T**打开终端来更改Ubuntu中的Samba工作组。当终端打开时,运行以下命令来编辑的Samba的配置文件。
|
||||
|
||||
sudo gedit /etc/samba/smb.conf
|
||||
|
||||
这个文件打开之后,确定在[global]段的以workgroup开头的行有你想要起给工作组的名字。例如,如果你想要让工作组叫UBGP,将WORKGROUP替换成UBGP然后保存文件。在大多数情况下,你会必须重启计算机以应用这些改变。
|
||||
打开这个文件后,请确保在[global]段中workgroup起始的那行的单词或值是你想要的工作组。例如,如果你希望工作组变成UBGP,将WORKGROUP替换成UBGP,并保存该文件。在大多数情况下,你必须重启动计算机以使之生效。
|
||||
|
||||

|
||||
|
||||
这就是怎样在Unbuntu里改变你的计算机的名字和它的工作组。切记,如果你想做这些以分享或者访问Windows的文件或者文件夹,你必须安装Samba。离了Samba,和Windows共享文件会很难。
|
||||
以上就是如何在Ubuntu中更改你的计算机名以及工作组的方法。记住,如果你这样做是为了共享或访问Windows文件和文件夹,还必须安装Samba。没有Samba,你将难以与Windows共享文件。
|
||||
|
||||
运行以下命令以安装Samba。
|
||||
To install Samba, run the commands below.
|
||||
|
||||
运行下面的命令安装Samba。
|
||||
|
||||
sudo apt-get install samba
|
||||
|
||||
欢迎回来掌握更多的Ubuntu小技巧。
|
||||
|
||||
请继续关注和访问更多关于Ubuntu的小贴士。
|
||||
尽情享受吧!
|
||||
=======
|
||||
|
||||
尽情享受吧!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.liberiangeek.net/2013/11/daily-ubuntu-tips-change-samba-workgroup-and-computer-name/
|
||||
|
||||
译者:[crowner](https://github.com/crowner) 校对:[wxy](https://github.com/校对者ID)
|
||||
译者:[crowner](https://github.com/crowner),[whatever1992](https://github.com/whatever1992) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
|
||||
@ -1,43 +0,0 @@
|
||||
Ubuntu每日小贴士 - 在Ubuntu下创建虚拟网卡
|
||||
|
||||
================================================================================
|
||||
|
||||
这个教程是为那些想用Ubuntu做点小实验的用户准备的.这并不适用于所有人,尤其是那些正在使用生产机器的用户.
|
||||
|
||||
如果你对网络运行和IP网络有所了解,你应该知道在大多数情况下,每个网卡只会分配一个IP地址.我们习惯认为这是一对一的事物.
|
||||
|
||||
一个网卡对应一个IP地址,你在一台机器用一个网卡和IP地址只能绑定或运行单一的网络服务/端口.例如,如果你想在80端口运行一个web服务器,只有一个web服务器将监听一个IP地址和端口#.这就是它如何工作的.
|
||||
|
||||
所以,网卡和IP地址并不是一对一的关系,你可以创建可以单独分配IP地址的虚拟网卡.因此,单一的物理网卡可以群集无限的子网卡或虚拟网卡.每一个都能分配它自己IP地址到对应的端口.
|
||||
|
||||
这个简短的教程将展示给你如何在Ubuntu做到这些.这是极好的方式在一台电脑上用一张物理网卡和单一的端口#运行和测试多个网络服务.
|
||||
|
||||
动手吧,运行下列命令打开网络接口文件.
|
||||
|
||||
sudo gedit /etc/network/interfaces
|
||||
|
||||
然后按照下图中的步骤吗,尽可能多的添加你想要的虚拟网卡.默认情况下,Linux会给第一张网卡分配eth0的名称.所以如果你的机子只有一张网卡,那么它会被命名为eth0
|
||||
|
||||
添加虚拟网卡,创建多个静态网卡并命名为eth0:1,eth0:2,eth0:3, etc.(eth0后面紧跟冒号和数字).
|
||||
|
||||

|
||||
|
||||
对于你创建的每一个网卡,也要确保网络都是不同的子网 ..
|
||||
|
||||
完成以后,保存文件并用下列命令重置网络服务.
|
||||
|
||||
sudo service networking restart
|
||||
|
||||
就是这样!
|
||||
|
||||

|
||||
|
||||
玩得开心!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.liberiangeek.net/2013/11/daily-ubuntu-tips-create-virtual-network-cards-in-ubuntu-linux/
|
||||
|
||||
译者:[Luoxcat](https://github.com/Luoxcat) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
@ -1,69 +0,0 @@
|
||||
五个 ping 工具的实例
|
||||
|
||||
================================================================================
|
||||
|
||||
### 什么是 ping 工具###
|
||||
|
||||
在传授一些关于ping工具真实大观的实例前,先让我来介绍一下这个命令行工具及其目的.ping工具通常用来测试一台主机在互联网协议(IP)网络内的可达性.其名字源于主动声纳法——在水下创建一个脉冲声音信号(ping)并侦听周围物体的返回信号.该方法同样生动描述了ping网络工具的工作原理.ping工具对一台主机发送回应请求然后等待ICMP响应.
|
||||
|
||||
用于实践ping工具的一些例子:
|
||||
|
||||
### 查询主机的IP地址 ###
|
||||
|
||||
有时候你需要得到某一台主机的IP地址,如图一.只需要键入ping命令后面跟上要查询的主机名.
|
||||
|
||||
ping www.omgubuntu.com
|
||||
|
||||

|
||||
|
||||
### 查询正在使用的ping工具的版本信息 ###
|
||||
|
||||
用 -V 选项可以用来查询你手头上ping工具的版本信息.键入下列命令显示正在使用的ping工具的版本信息.
|
||||
|
||||
ping -V
|
||||
|
||||
正如你从图二见到的,我正在使用的是“ping utility,iputils-sss20101006”
|
||||
|
||||

|
||||
|
||||
### 自动退出 ping ###
|
||||
|
||||
当你用‘ping 主机’命令ping一台机器时,ping自己无法停止,你必需按下CTRL+C强行退出,或者你可以用 -c (count)选项指定发送包的数量.使用-c选项,当网络管理员(其实普通用户也可以)发送完指定数量的包之后,无需按CTRL+C,ping进程就会自动停止.
|
||||
|
||||
ping -c 13 127.0.0.1
|
||||
|
||||
上列的命令发送了13个包到我的本地主机上.
|
||||
|
||||

|
||||
|
||||
正如你从图三看到的,我并没有按CTRL+C,而ping自动退出了.
|
||||
|
||||
### 指定数据包之间的时间间隔 ###
|
||||
|
||||
你知道ping每秒钟发送一个数据包吗?你喜欢快一点还是慢一点?用 -i 选项能指定包之间的时间间隔.用下列命令快速发送或慢速发送包.
|
||||
|
||||
### 每0.13秒发送一个包 ###
|
||||
|
||||
ping -i 0.13
|
||||
|
||||

|
||||
|
||||
### 每13秒发送一个包 ###
|
||||
|
||||
ping -i 13
|
||||
|
||||
### 结合 -i 选项和 -c 选项 ###
|
||||
|
||||
ping -c 13 -i 3
|
||||
|
||||
总共花费39秒发出13个数据包,数据包的时间间隔为三秒.
|
||||
|
||||

|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.unixmen.com/five-examples-ping-utility/
|
||||
|
||||
译者:[Luoxcat](https://github.com/Luoxcat) 校对:[Mr小眼儿](http://blog.csdn.net/tinyeyeser)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
@ -1,32 +0,0 @@
|
||||
Mark Shuttleworth后悔“茶派”笔谈以及其他典型错误
|
||||
================================================================================
|
||||
**Mark Shuttleworth, Canonical公司的创始人,他澄清了他的“茶派”言论和为个人言论而表示歉意。**
|
||||
|
||||

|
||||
|
||||
我们看到Mark Shuttleworth不是每天连续道歉两次, 很有可能这是他第一次发生这样的事情。
|
||||
|
||||
[第一个道歉][1] 来自fixubuntu.com的主人,他是一封来自Canonical公司法律团队的收件人。Micah F. Lee,该网站背后的家伙,写了一篇关于这些问题以及在许多论坛和网站对此事进行了长时间讨论。
|
||||
|
||||
Mark Shuttleworth首先在Google+向他道歉,但是他同样在他的个人博客上写了很多正式文本,这通常是保留了有重要意义的事情。
|
||||
|
||||
由于他道歉,他同样花时间去说他后悔[“茶派”][2]解释惹来了许多压力对Canonical公司,他为可能甚至超过最初的问题生气。
|
||||
|
||||
“另一面,个人角度,我自己也犯了一个错误,当我使用标签‘open source tea party’指的是工作的非技术的批评。这是不必要的并且的确可能一样冒犯真的茶派成员(嗨,这里!)以及人民非技术工作的批评(hello,这儿!)。”
|
||||
“On another, more personal note, I made a mistake myself when I used the label ‘open source tea party’ to refer to the vocal non-technical critics of work that Canonical does. That was unnecessary and quite possibly equally offensive to members of the real Tea Party (hi there!) and the people with vocal non-technical criticism of work that Canonical does (hello there!).”
|
||||
|
||||
“没有什么我说的建议,我不欢迎像这样的技术反馈,但是一些假定我拒绝了所有的反馈包括技术评论。我没有 – 我谈论软件的批评在软件本身没有中心, 而是一些动机的组合的人写的,或依据它所公布的特定的自由软件许可证,或公司的政策,或公司背后国家的政策,”Mark Shuttleworth说道。
|
||||
“There isn’t anything in what I said to suggest that I don’t welcome such technical feedback, but some assumed I was rejecting all feedback including technical commentary. I was not – I was talking about criticism of software which does not centre on the software itself, but rather on some combination of the motivations of the people who wrote it, or the particular free software license under which it is published, or the policies of the company, or the nationality of the company behind it,” said Mark Shuttleworth.
|
||||
|
||||
希望结束在这个事件上的所有的讨论以及人们最终将能够一起在Mir显示服务器上工作, 实际上是崩溃的根源。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://news.softpedia.com/news/Mark-Shuttleworth-Regrets-the-quot-Tea-Party-quot-Remarks-and-Other-Canonical-Mistakes-398819.shtml
|
||||
|
||||
译者:[Vito](https://github.com/vito-L) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://news.softpedia.com/news/Mark-Shuttleworth-Apologizes-for-the-Trademark-Infringement-Letter-Sent-to-Fixubuntu-com-398583.shtml
|
||||
[2]:http://news.softpedia.com/news/Mark-Shuttleworth-Says-That-Mir-Opponents-Have-Formed-the-Open-Source-Tea-Party-392793.shtml
|
||||
Loading…
Reference in New Issue
Block a user