mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-03-24 02:20:09 +08:00
commit
aff39edee1
published
20140910 With Apple Watch Unveiled, Could an Ubuntu Smartwatch Be Next.md20140912 What' s wrong with IPv4 and Why we are moving to IPv6.md20140915 10 Open Source Cloning Software For Linux Users.md20141013 How to configure peer-to-peer VPN on Linux.md20141023 How to turn your CentOS box into a BGP router using Quagga.md20141023 What are useful Bash aliases and functions.md
201411
20141106 5 Awesome Open Source Backup Software For Linux and Unix-like Systems.md20141115 How to perform system backup with backup-manager on Linux.md201412
20140818 What are useful CLI tools for Linux system admins.md20140818 Why Your Company Needs To Write More Open Source Software.md20140818 Will Linux ever be able to give consumers what they want.md20140826 20 Postfix Interview Questions and Answers.md20140901 How to use on-screen virtual keyboard on Linux.md20140910 How to create a cloud-based encrypted file system on Linux.md20140910 Why Do Some Old Programming Languages Never Die.md20140915 Make Downloading Files Effortless.md20141004 Practical Lessons in Peer Code Review.md20141008 How To Use Steam Music Player on Ubuntu Desktop.md20141009 How to set up RAID 10 for high performance and fault tolerant disk I or O on Linux.md20141013 Manage Multiple Logical Volume Management Disks using Striping I O--Part V.md20141013 Migrating LVM Partitions to New Logical Volume (Drive)--Part VI.md20141017 How to check hard disk health on Linux using smartmontools.md20141017 How to verify the authenticity and integrity of a downloaded file on Linux.md20141017 Linux ss Tool to Identify Sockets or Network Connections with Examples.md20141017 UbuTricks--Script to install the latest versions of several games and applications in Ubuntu.md20141021 Configuring layer-two peer-to-peer VPN using n2n.md20141021 How to create and use Python CGI scripts.md20141021 How to monitor a log file on Linux with logwatch.md20141022 Linux FAQs with Answers--How to fix sshd error--could not load host key.md20141023 What is a good command-line calculator on Linux.md20141024 Amazing 25 Linux Performance Monitoring Tools.md20141027 How to encrypt files and directories with eCryptFS on Linux.md20141029 Shell Scripting--Checking Conditions with if.md20141030 8 Tips to Solve Linux and Unix Systems Hard Disk Problmes Like Disk Full Or Can't Write to the Disk.md20141030 How to run SQL queries against Apache log files on Linux.md20141030 rsync Command to Exclude a List of Files and Directories in Linux.md20141104 Pitivi 0.94 Uses GTK HeaderBar, Squashes Umpteen Bugs.md20141112 How to Remove Music Players from Ubuntu Sound Menu.md20141112 Intro to Systemd Runlevels and Service Management Commands.md20141118 Linux FAQs with Answers--How to convert a text file to PDF format on Linux.md20141118 Linux FAQs with Answers--How to install phpMyAdmin on CentOS.md20141119 10 SCP Commands to Transfer Files or Folders in Linux.md20141119 How To Make Raspberry Pi Boot In To GUI By Default.md20141119 Qshutdown--An avanced shutdown tool.md20141119 When Microsoft Went A-Courting.md20141120 5 Best Open Source Web Browser Security Apps.md20141120 How to visualize memory usage on Linux.md20141120 Postfix tips and Troubleshooting Commands.md20141124 15 pwd (Print Working Directory) Command Examples in Linux.md20141125 Linux FAQs with Answers--How to access a NAT guest from host with VirtualBox.md20141125 Linux FAQs with Answers--How to fix ImportError--No module named scapy.all.md20141127 Some Sentences about Java.md20141127 What Makes a Good Programmer.md20141204 How To Drop Database In Oracle 11 Without Using DBCA.md20141204 Official Ubuntu 14.10 Utopic Unicorn T-Shirts Now Available to Buy.md20141204 Readers' Choice Awards 2014--Linux Journal.md20141208 Linux FAQs with Answers--How to crop an image from the command line on Linux.md20141208 Nathive--A libre software image editor.md20141211 Linux Kernel 3.18 Released, This Is What' s New.md20141211 Was 2014 The Year of Linux Desktop.md20141219 Attic--Deduplicating backup program.md20141219 The 'grinch' isn't a Linux vulnerability, Red Hat says.md20141222 How to use Rsync Command In Linux With Examples.md20141222 Linus Torvalds Launches Linux Kernel 3.19 RC1, One of the Biggest So Far.md20141224 Linux FAQs with Answers--How to install non-free packages on Debian.md20141230 Second Edition of Ubuntu Manual 14.04 LTS Is Ou.md
20141208 U.S. Marine Corps Wants to Change OS for Radar System from Windows XP to Linux.md20141211 Yes, This Trojan Infects Linux. No, It' s Not The Tuxpocalypse.md20141224 Linux FAQs with Answers--How to check SSH protocol version on Linux.mdsources
news
20141208 U.S. Marine Corps Wants to Change OS for Radar System from Windows XP to Linux.md20141211 Yes, This Trojan Infects Linux. No, It' s Not The Tuxpocalypse.md
share
20140701 Easy File Comparisons With These Great Free Diff Tools.md20141106 5 Awesome Open Source Backup Software For Linux and Unix-like Systems.md20141106 Flow' N Play Movie Player Has a Stylish Interface Ubuntu Installation.md20141106 Tomahawk Music Player Returns With New Look, Features.md20141224 Calife--A lightweight alternative to sudo.md20141226 How to Download Music from Grooveshark with a Linux OS.md20141229 2 Ways To Fix The UEFI Bootloader When Dual Booting Windows And Ubuntu.md20150106 This App Can Write a Single ISO to 20 USB Drives Simultaneously.md
talk
20141219 2015 will be the year Linux takes over the enterprise and other predictions.md20141222 A brief history of Linux malware.md20141226 The Good The Bad And The Ugly Of Linux In 2014.md20150106 2015--Open Source Has Won, But It Isn't Finished.md
The history of Android
tech
20100105 How to Backup and Restore Your Apps and PPAs in Ubuntu Using Aptik.md20141008 How to configure HTTP load balancer with HAProxy on Linux.md20141027 ntpq -p output.md20141120 How to install Xen hypervisor on unused old hardware.md20141125 How to install Cacti (Monitoring tool) on ubuntu 14.10 server.md20141127 Quick systemd-nspawn guide.md20141211 How to use matplotlib for scientific plotting on Linux.md20141217 Create Centralized Secure Storage using iSCSI Target on RHEL or CentOS or Fedora Part -I.md20141217 How to Create and Setup LUNs using LVM in 'iSCSI Target Server' on RHEL or CentOS or Fedora -Part II.md20141224 Linux FAQs with Answers--How to install Kingsoft Office on Linux.md20141229 4 Steps to Setup Local Repository in Ubuntu using APT-mirror.md20141229 5 User Space Debugging Tools in Linux.md20150104 Auditd--Tool for Security Auditing on Linux Server.md20150104 How to configure fail2ban to protect Apache HTTP server.md20150104 How to debug a C or C++ program with Nemiver debugger.md
@ -0,0 +1,72 @@
|
||||
Apple Watch之后,下一个智能手表会是Ubuntu吗?
|
||||
===
|
||||
|
||||
**苹果借助‘Apple Watch’的发布,证实了其进军穿戴式电子设备市场的长期传言**
|
||||
|
||||

|
||||
|
||||
Ubuntu智能手表 - 好主意?
|
||||
|
||||
拥有一系列稳定功能、硬件解决方案和应用合作伙伴关系的支持,手腕穿戴设备被许多公司预示为“人与技术关系的新篇章”。
|
||||
|
||||
它的到来,以及用户兴趣的提升,有可能意味着Ubuntu需要跟进一个为智能手表定制的Ubuntu版本。
|
||||
|
||||
### 大的方面还是成功的 ###
|
||||
|
||||
苹果在正确的时间加入了快速发展的智能手表行列。手腕穿戴设备功能的界限并不是一成不变。失败的设计、简陋的用户界面以及主流用户使用穿戴技术功能的弱定制化,这些都见证了硬件类产品仍然很脆弱 - 这一因素使得Cupertino把时间花费在Apple Watch上。
|
||||
|
||||
> ‘分析师说:超过2200万的智能手表将在今年销售’
|
||||
|
||||
去年全球范围内可穿戴设备的销售数量(包括健身追踪器)仅仅1000万。今年,分析师希望设备的销量可以超过2200万 - 不包括苹果手表,因为其直到2015年初才开始零售。
|
||||
|
||||
其实,我们很容易就可以看出增长的来源。今年九月初柏林举办的IFA 2014展览会,展示了一系列来自主要制造商们的可穿戴设备,包括索尼和华硕。大多数搭载着Google最新发布的安卓穿戴平台。
|
||||
|
||||
更成熟的一个表现是:安卓穿戴设备打破了与形式因素保持一致的新奇争论,进而呈现出一致且令人信服的用户方案。和新的苹果手表一样,它紧密地连接在一个现存的智能手机生态系统上。
|
||||
|
||||
但Ubuntu手腕穿戴系统是否能与之匹配,成为一个实用案例,目前还不清楚。
|
||||
|
||||
#### 目前还没有Ubuntu智能手表的计划 ####
|
||||
|
||||
Ubuntu操作系统的通用性将多种设备的严格标准与统一的未来目标联合在一起,Canonical已经将目标指向了智能电视,平板电脑和智能手机。公司自家的显示服务Mir,甚至被用来为所有尺寸的屏幕提供驱动接口(虽然不是公认1.5"的)。
|
||||
|
||||
今年年初,Canonical社区负责人Jono Bacon被问到是否有制作Ubuntu智能手表的打算。Bacon提供了他对这个问题的看法:“为[Ubuntu触摸设备]路线增加额外的形式因素只会减缓现有的进度”。
|
||||
|
||||
在Ubuntu手机发布两周年之际,我们还是挺赞同他的想法的。
|
||||
|
||||
###除了A面还有B面!###
|
||||
|
||||
但是并不是没有希望的。在[几个月之后的一次电话采访][1]中,Ubuntu创始人Mark Shuttleworth提到,可穿戴技术和智能电视、平板电脑、智能手机一样,都在公司计划当中。
|
||||
|
||||
> “Ubuntu因其在电话中的完美设计变得独一无二,但同时它的设计也能够满足其他生态系统,从穿戴设备到PC机。”
|
||||
|
||||
然而这还没得到具体的证实,它更像一个指针,在某个方向给我们提供一个乐观的指引。
|
||||
|
||||
#### 不大可能 — 但这就是原因所在 ####
|
||||
|
||||
Canonical并不反对利用牢固的专利进军市场。事实上,它恰恰是公司DNA基因的一部分 — 犹如服务器端的RHEL,桌面端的Windows,智能手机上的安卓...
|
||||
|
||||
设备上的Ubuntu系统被制作成可以在更小的屏幕上扩展和适配运行,甚至在小如手表一样的屏幕上。当普通的代码基础已经在手机、平板电脑、桌面和TV上准备就绪,在同样的方向上,如果看不到社区的努力是十分令人吃惊的。
|
||||
|
||||
但是我之所以不认为它会从Canonical发生,至少目前还没有,是基于今年早些时候Jono Bacon的个人思想得出的结论:时间和努力。
|
||||
|
||||
Tim Cook在他的主题演讲中说道:“*我们并没有追随iPhone,也没有缩水用户界面,将其强硬捆绑在你的手腕上。*”这是一个很明显的陈述。为如此小的屏幕设计UI和UX模型、通过交互原则工作、对硬件和输入模式的推崇,这些都不是容易的事。
|
||||
|
||||
可穿戴技术仍然是一个新兴的市场。在这个阶段,Canonical可能会在探寻的过程中浪费一些发展、设计和商业上的机会。如果在一些更为紧迫的领域落后了,造成的后果远比眼前利益的损失更严重。
|
||||
|
||||
打一场持久战,耐心等待,看哪些努力成功哪些会失败,这是一条更难的路线,但是却更适合Ubuntu,就如同今天它做的一样。在新产品出现之前,Canonical把力量用在现存的产品上是更好的选择(这是一些已经来迟的理论)
|
||||
|
||||
想更进一步了解什么是Ubuntu智能手表,点击下面的[视频][2],里面展示了一个交互的Unity主题皮肤Tizen(它已经支持Samsung Galaxy Gear智能手表)。
|
||||
|
||||
---
|
||||
|
||||
via: http://www.omgubuntu.co.uk/2014/09/ubuntu-smartwatch-apple-iwatch
|
||||
|
||||
作者:[Joey-Elijah Sneddon][a]
|
||||
译者:[su-kaiyao](https://github.com/su-kaiyao)
|
||||
校对:[Mr小眼儿](https://github.com/tinyeyeser)
|
||||
|
||||
本文由[LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://plus.google.com/117485690627814051450/?rel=author
|
||||
[1]:http://www.omgubuntu.co.uk/2014/03/ubuntu-tablets-coming-year
|
||||
[2]:https://www.youtube.com/embed/8Zf5dktXzEs?feature=oembed
|
||||
@ -1,8 +1,7 @@
|
||||
IPv6:IPv4犯的罪,为什么要我来弥补
|
||||
IPv6:IPv4犯的错,为什么要我来弥补
|
||||
================================================================================
|
||||
(LCTT:标题党了一把,哈哈哈好过瘾,求不拍砖)
|
||||
|
||||
在过去的十年间,IPv6 本来应该得到很大的发展,但事实上这种好事并没有降临。由此导致了一个结果,那就是大部分人都不了解 IPv6 的一些知识:它是什么,怎么使用,以及,为什么它会存在?(LCTT:这是要回答蒙田的“我是谁”哲学思考题吗?)
|
||||
在过去的十年间,IPv6 本来应该得到很大的发展,但事实上这种好事并没有降临。由此导致了一个结果,那就是大部分人都不了解 IPv6 的一些知识:它是什么,怎么使用,以及,为什么它会存在?
|
||||
|
||||

|
||||
|
||||
@ -12,15 +11,15 @@ IPv4 和 IPv6 的区别
|
||||
|
||||
自从1981年发布了 RFC 791 标准以来我们就一直在使用 **IPv4**。在那个时候,电脑又大又贵还不多见,而 IPv4 号称能提供**40亿条 IP 地址**,在当时看来,这个数字好大好大。不幸的是,这么多的 IP 地址并没有被充分利用起来,地址与地址之间存在间隙。举个例子,一家公司可能有**254(2^8-2)**条地址,但只使用其中的25条,剩下的229条被空占着,以备将来之需。于是这些空闲着的地址不能服务于真正需要它们的用户,原因就是网络路由规则的限制。最终的结果是在1981年看起来那个好大好大的数字,在2014年看起来变得好小好小。
|
||||
|
||||
互联网工程任务组(**IETF**)在90年代指出了这个问题,并提供了两套解决方案:无类型域间选路(**CIDR**)以及私有地址。在 CIDR 出现之前,你只能选择三种网络地址长度:**24 位** (共可用16,777,214个地址), **20位** (共可用1,048,574个地址)以及**16位** (共可用65,534个地址)。CIDR 出现之后,你可以将一个网络再划分成多个子网。
|
||||
互联网工程任务组(**IETF**)在90年代初指出了这个问题,并提供了两套解决方案:无类型域间选路(**CIDR**)以及私有IP地址。在 CIDR 出现之前,你只能选择三种网络地址长度:**24 位** (共16,777,214个可用地址), **20位** (共1,048,574个可用地址)以及**16位** (共65,534个可用地址)。CIDR 出现之后,你可以将一个网络再划分成多个子网。
|
||||
|
||||
举个例子,如果你需要**5个 IP 地址**,你的 ISP 会为你提供一个子网,里面的主机地址长度为3位,也就是说你最多能得到**6个地址**(LCTT:抛开子网的网络号,3位主机地址长度可以表示0~7共8个地址,但第0个和第7个有特殊用途,不能被用户使用,所以你最多能得到6个地址)。这种方法让 ISP 能尽最大效率分配 IP 地址。“私有地址”这套解决方案的效果是,你可以自己创建一个网络,里面的主机可以访问外网的主机,但外网的主机很难访问到你创建的那个网络上的主机,因为你的网络是私有的、别人不可见的。你可以创建一个非常大的网络,因为你可以使用16,777,214个主机地址,并且你可以将这个网络分割成更小的子网,方便自己管理。
|
||||
|
||||
也许你现在正在使用私有地址。看看你自己的 IP 地址,如果这个地址在这些范围内:**10.0.0.0 – 10.255.255.255**、**172.16.0.0 – 172.31.255.255**或**192.168.0.0 – 192.168.255.255**,就说明你在使用私有地址。这两套方案有效地将“IP 地址用尽”这个灾难延迟了好长时间,但这毕竟只是权宜之计,现在我们正面临最终的审判。
|
||||
|
||||
**IPv4** 还有另外一个问题,那就是这个协议的消息头长度可变。如果数据通过软件来路由,这个问题还好说。但现在路由器功能都是由硬件提供的,处理变长消息头对硬件来说是一件困难的事情。一个大的路由器需要处理来自世界各地的大量数据包,这个时候路由器的负载是非常大的。所以很明显,我们需要固定消息头的长度。
|
||||
**IPv4** 还有另外一个问题,那就是这个协议的消息头长度可变。如果数据的路由通过软件来实现,这个问题还好说。但现在路由器功能都是由硬件提供的,处理变长消息头对硬件来说是一件困难的事情。一个大的路由器需要处理来自世界各地的大量数据包,这个时候路由器的负载是非常大的。所以很明显,我们需要固定消息头的长度。
|
||||
|
||||
还有一个问题,在分配 IP 地址的时候,美国人发了因特网(LCTT:这个万恶的资本主义国家占用了大量 IP 地址)。其他国家只得到了 IP 地址的碎片。我们需要重新定制一个架构,让连续的 IP 地址能在地理位置上集中分布,这样一来路由表可以做的更小(LCTT:想想吧,网速肯定更快)。
|
||||
在分配 IP 地址的同时,还有一个问题,因特网是美国人发明的(LCTT:这个万恶的资本主义国家占用了大量 IP 地址)。其他国家只得到了 IP 地址的碎片。我们需要重新定制一个架构,让连续的 IP 地址能在地理位置上集中分布,这样一来路由表可以做的更小(LCTT:想想吧,网速肯定更快)。
|
||||
|
||||
还有一个问题,这个问题你听起来可能还不大相信,就是 IPv4 配置起来比较困难,而且还不好改变。你可能不会碰到这个问题,因为你的路由器为你做了这些事情,不用你去操心。但是你的 ISP 对此一直是很头疼的。
|
||||
|
||||
@ -28,10 +27,10 @@ IPv4 和 IPv6 的区别
|
||||
|
||||
### IPv6 和它的优点 ###
|
||||
|
||||
**IETF** 在1995年12月公布了下一代 IP 地址标准,名字叫 IPv6,为什么不是 IPv5?因为某个错误原因,“版本5”这个编号被其他项目用去了。IPv6 的优点如下:
|
||||
**IETF** 在1995年12月公布了下一代 IP 地址标准,名字叫 IPv6,为什么不是 IPv5?→_→ 因为某个错误原因,“版本5”这个编号被其他项目用去了。IPv6 的优点如下:
|
||||
|
||||
- 128位地址长度(共有3.402823669×10³⁸个地址)
|
||||
- 这个架构下的地址在逻辑上聚合
|
||||
- 其架构下的地址在逻辑上聚合
|
||||
- 消息头长度固定
|
||||
- 支持自动配置和修改你的网络。
|
||||
|
||||
@ -43,7 +42,7 @@ IPv4 和 IPv6 的区别
|
||||
|
||||
#### 聚合 ####
|
||||
|
||||
有这么多的地址,这个地址可以被稀稀拉拉地分配给主机,从而更高效地路由数据包。算一笔帐啊,你的 ISP 拿到一个**80位**地址长度的网络空间,其中16位是 ISP 的子网地址,剩下64位分给你作为主机地址。这样一来,你的 ISP 可以分配65,534个子网。
|
||||
有这么多的地址,这些地址可以被稀稀拉拉地分配给主机,从而更高效地路由数据包。算一笔帐啊,你的 ISP 拿到一个**80位**地址长度的网络空间,其中16位是 ISP 的子网地址,剩下64位分给你作为主机地址。这样一来,你的 ISP 可以分配65,534个子网。
|
||||
|
||||
然而,这些地址分配不是一成不变地,如果 ISP 想拥有更多的小子网,完全可以做到(当然,土豪 ISP 可能会要求再来一个80位网络空间)。最高的48位地址是相互独立地,也就是说 ISP 与 ISP 之间虽然可能分到相同地80位网络空间,但是这两个空间是相互隔离的,好处就是一个网络空间里面的地址会聚合在一起。
|
||||
|
||||
@ -51,25 +50,25 @@ IPv4 和 IPv6 的区别
|
||||
|
||||
**IPv4** 消息头长度可变,但 **IPv6** 消息头长度被固定为40字节。IPv4 会由于额外的参数导致消息头变长,IPv6 中,如果有额外参数,这些信息会被放到一个紧挨着消息头的地方,不会被路由器处理,当消息到达目的地时,这些额外参数会被软件提取出来。
|
||||
|
||||
IPv6 消息头有一个部分叫“flow”,是一个20位伪随机数,用于简化路由器对数据包地路由过程。如果一个数据包存在“flow”,路由器就可以根据这个值作为索引查找路由表,不必慢吞吞地遍历整张路由表来查询路由路径。这个优点使 **IPv6** 更容易被路由。
|
||||
IPv6 消息头有一个部分叫“flow”,是一个20位伪随机数,用于简化路由器对数据包的路由过程。如果一个数据包存在“flow”,路由器就可以根据这个值作为索引查找路由表,不必慢吞吞地遍历整张路由表来查询路由路径。这个优点使 **IPv6** 更容易被路由。
|
||||
|
||||
#### 自动配置 ####
|
||||
|
||||
**IPv6** 中,当主机开机时,会检查本地网络,看看有没有其他主机使用了自己的 IP 地址。如果地址没有被使用,就接着查询本地的 IPv6 路由器,找到后就向它请求一个 IPv6 地址。然后这台主机就可以连上互联网了 —— 它有自己的 IP 地址,和自己的默认路由器。
|
||||
|
||||
如果这台默认路由器当机,主机就会接着找其他路由器,作为备用路由器。这个功能在 IPv4 协议里实现起来非常困难。同样地,假如路由器想改变自己的地址,自己改掉就好了。主机会自动搜索路由器,并自动更新路由器地址。路由器会同时保存新老地址,直到所有主机都把自己地路由器地址更新成新地址。
|
||||
如果这台默认路由器宕机,主机就会接着找其他路由器,作为备用路由器。这个功能在 IPv4 协议里实现起来非常困难。同样地,假如路由器想改变自己的地址,自己改掉就好了。主机会自动搜索路由器,并自动更新路由器地址。路由器会同时保存新老地址,直到所有主机都把自己地路由器地址更新成新地址。
|
||||
|
||||
IPv6 自动配置还不是一个完整地解决方案。想要有效地使用互联网,一台主机还需要另外的东西:域名服务器、时间同步服务器、或者还需要一台文件服务器。于是 **dhcp6** 出现了,提供与 dhcp 一样的服务,唯一的区别是 dhcp6 的机器可以在可路由的状态下启动,一个 dhcp 进程可以为大量网络提供服务。
|
||||
|
||||
#### 唯一的大问题 ####
|
||||
|
||||
如果 IPv6 真的比 IPv4 好那么多,为什么它还没有被广泛使用起来(Google 在**2014年5月份**估计 IPv6 的市场占有率为**4%**)?一个最基本的原因是“先有鸡还是先有蛋”问题,用户需要让自己的服务器能为尽可能多的客户提供服务,这就意味着他们必须部署一个 **IPv4** 地址。
|
||||
如果 IPv6 真的比 IPv4 好那么多,为什么它还没有被广泛使用起来(Google 在**2014年5月份**估计 IPv6 的市场占有率为**4%**)?一个最基本的原因是“先有鸡还是先有蛋”。服务商想让自己的服务器为尽可能多的客户提供服务,这就意味着他们必须部署一个 **IPv4** 地址。
|
||||
|
||||
当然,他们可以同时使用 IPv4 和 IPv6 两套地址,但很少有客户会用到 IPv6,并且你还需要对你的软件做一些小修改来适应 IPv6。另外比较头疼的一点是,很多家庭的路由器压根不支持 IPv6。还有就是 ISP 也不愿意支持 IPv6,我问过我的 ISP 这个问题,得到的回答是:只有客户明确指出要部署这个时,他们才会用 IPv6。然后我问了现在有多少人有这个需求,答案是:包括我在内,共有1个。
|
||||
|
||||
与这种现实状况呈明显对比的是,所有主流操作系统:Windows、OS X、Linux 都默认支持 IPv6 好多年了。这些操作系统甚至提供软件让 IPv6 的数据包披上 IPv4 的皮来骗过那些会丢弃 IPv6 数据包的主机,从而达到传输数据的目的(LCTT:呃,这是高科技偷渡?)。
|
||||
与这种现实状况呈明显对比的是,所有主流操作系统:Windows、OS X、Linux 都默认支持 IPv6 好多年了。这些操作系统甚至提供软件让 IPv6 的数据包披上 IPv4 的皮来骗过那些会丢弃 IPv6 数据包的主机,从而达到传输数据的目的。
|
||||
|
||||
#### 总结 ####
|
||||
### 总结 ###
|
||||
|
||||
IPv4 已经为我们服务了好长时间。但是它的缺陷会在不远的将来遭遇不可克服的困难。IPv6 通过改变地址分配规则、简化数据包路由过程、简化首次加入网络时的配置过程等策略,可以完美解决这个问题。
|
||||
|
||||
@ -81,7 +80,7 @@ via: http://www.tecmint.com/ipv4-and-ipv6-comparison/
|
||||
|
||||
作者:[Jeff Silverman][a]
|
||||
译者:[bazz2](https://github.com/bazz2)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[Mr小眼儿](https://github.com/tinyeyeser)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,20 +1,19 @@
|
||||
为 Linux 用户准备的 10 个开源克隆软件
|
||||
给 Linux 用户的 10 个开源克隆软件
|
||||
================================================================================
|
||||
> 这些克隆软件会读取整个磁盘的数据,将它们转换成一个 .img 文件,之后你可以将它复制到其他硬盘上。
|
||||
|
||||

|
||||
|
||||
磁盘克隆意味着从一个硬盘复制数据到另一个硬盘上,而且你可以通过简单的复制粘贴来做到。但是你却不能复制隐藏文件和文件夹,以及正在使用中的文件。这便是一个克隆软件可以通过保存一份文件和文件夹的镜像来帮助你的地方。克隆软件会读取整个磁盘的数据,将它们转换成一个 .img 文件,之后你可以将它复制到其他硬盘上。现在我们将要向你介绍最优秀的 10 个开源的克隆软件:
|
||||
磁盘克隆的意思是说从一个硬盘复制数据到另一个硬盘上。虽然你可以通过简单的复制粘贴来做到这一点,但是你却不能复制隐藏文件和文件夹,以及正在使用中的文件。这便是一个克隆软件可以通过保存一份文件和文件夹的镜像来做到的。克隆软件会读取整个磁盘的数据,将它们转换成一个 .img 文件,之后你可以将它复制到其他硬盘上。现在我们将要向你介绍最优秀的 10 个开源的克隆软件:
|
||||
|
||||
### 1. [Clonezilla][1]:###
|
||||
|
||||
Clonezilla 是一个基于 Ubuntu 和 Debian 的 Live CD。它可以像 Windows 里的诺顿 Ghost 一样克隆你的磁盘数据和做备份,不过它更有效率。Clonezilla 支持包括 ext2、ext3、ext4、btrfs 和 xfs 在内的很多文件系统。它还支持 BIOS、UEFI、MBR 和 GPT 分区。
|
||||
Clonezilla 是一个基于 Ubuntu 和 Debian 的 Live CD。它可以像 Windows 里的 Ghost 一样克隆你的磁盘数据和做备份,不过它更有效率。Clonezilla 支持包括 ext2、ext3、ext4、btrfs 和 xfs 在内的很多文件系统。它还支持 BIOS、UEFI、MBR 和 GPT 分区。
|
||||
|
||||

|
||||
|
||||
### 2. [Redo Backup][2]:###
|
||||
### 2. [Redo Backup][2]:###
|
||||
|
||||
Redo Backup 是另一个用来方便地克隆磁盘的 Live CD。它是自由和开源的软件,使用 GPL 3 许可协议授权。它的主要功能和特点包括从 CD 引导的简单易用的 GUI、无需安装,可以恢复 Linux 和 Windows 等系统、无需登陆访问文件,以及已删除的文件等。
|
||||
Redo Backup 是另一个用来方便地克隆磁盘的 Live CD。它是自由和开源的软件,使用 GPL 3 许可协议授权。它的主要功能和特点包括从 CD 引导的简单易用的 GUI、无需安装,可以恢复 Linux 和 Windows 等系统,无需登陆访问文件,以及已删除的文件等。
|
||||
|
||||

|
||||
|
||||
@ -26,7 +25,7 @@ Mondo 和其他的软件不大一样,它并不将你的磁盘数据转换为
|
||||
|
||||
### 4. [Partimage][4]:###
|
||||
|
||||
这是一个开源的备份软件,默认情况下在 Linux 系统里工作。在大多数发行版中,你都可以从发行版自带的软件包管理工具中安装。如果你没有 Linux 系统,你也可以使用“SystemRescueCd”。它是一个默认包括 Partimage 的 Live CD,可以为你完成备份工作。Partimage 在克隆硬盘方面的性能非常出色。
|
||||
这是一个开源的备份软件,默认工作在 Linux 系统下。在大多数发行版中,你都可以从发行版自带的软件包管理工具中安装。如果你没有 Linux 系统,你也可以使用“SystemRescueCd”。它是一个默认包含了 Partimage 的 Live CD,可以为你完成备份工作。Partimage 在克隆硬盘方面的性能非常出色。
|
||||
|
||||

|
||||
|
||||
@ -71,7 +70,7 @@ via: http://www.efytimes.com/e1/fullnews.asp?edid=148039
|
||||
|
||||
作者:Sanchari Banerjee
|
||||
译者:[felixonmars](https://github.com/felixonmars)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
@ -95,7 +95,7 @@ via: http://xmodulo.com/configure-peer-to-peer-vpn-linux.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[felixonmars](https://github.com/felixonmars)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
@ -0,0 +1,324 @@
|
||||
使用 Quagga 将你的 CentOS 系统变成一个 BGP 路由器
|
||||
================================================================================
|
||||
|
||||
在[之前的教程中][1],我对如何简单地使用Quagga把CentOS系统变成一个不折不扣地OSPF路由器做了一些介绍。Quagga是一个开源路由软件套件。在这个教程中,我将会重点讲讲**如何把一个Linux系统变成一个BGP路由器,还是使用Quagga**,演示如何建立BGP与其它BGP路由器对等。
|
||||
|
||||
在我们进入细节之前,一些BGP的背景知识还是必要的。边界网关协议(即BGP)是互联网的域间路由协议的实际标准。在BGP术语中,全球互联网是由成千上万相关联的自治系统(AS)组成,其中每一个AS代表每一个特定运营商提供的一个网络管理域([据说][2],美国前总统乔治.布什都有自己的 AS 编号)。
|
||||
|
||||
为了使其网络在全球范围内路由可达,每一个AS需要知道如何在英特网中到达其它的AS。这时候就需要BGP出来扮演这个角色了。BGP是一个AS去与相邻的AS交换路由信息的语言。这些路由信息通常被称为BGP线路或者BGP前缀。包括AS号(ASN;全球唯一号码)以及相关的IP地址块。一旦所有的BGP线路被当地的BGP路由表学习和记录,每一个AS将会知道如何到达互联网的任何公网IP。
|
||||
|
||||
在不同域(AS)之间路由的能力是BGP被称为外部网关协议(EGP)或者域间协议的主要原因。就如一些路由协议,例如OSPF、IS-IS、RIP和EIGRP都是内部网关协议(IGPs)或者域内路由协议,用于处理一个域内的路由.
|
||||
|
||||
### 测试方案 ###
|
||||
|
||||
在这个教程中,让我们来使用以下拓扑。
|
||||
|
||||
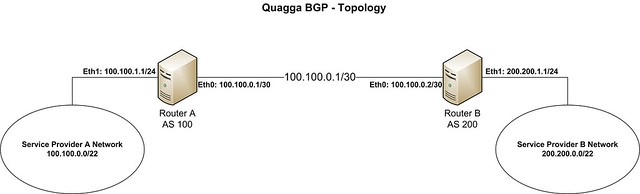
|
||||
|
||||
我们假设运营商A想要建立一个BGP来与运营商B对等交换路由。它们的AS号和IP地址空间的细节如下所示:
|
||||
|
||||
- **运营商 A**: ASN (100), IP地址空间 (100.100.0.0/22), 分配给BGP路由器eth1网卡的IP地址(100.100.1.1)
|
||||
|
||||
- **运营商 B**: ASN (200), IP地址空间 (200.200.0.0/22), 分配给BGP路由器eth1网卡的IP地址(200.200.1.1)
|
||||
|
||||
路由器A和路由器B使用100.100.0.0/30子网来连接到对方。从理论上来说,任何子网从运营商那里都是可达的、可互连的。在真实场景中,建议使用掩码为30位的公网IP地址空间来实现运营商A和运营商B之间的连通。
|
||||
|
||||
### 在 CentOS中安装Quagga ###
|
||||
|
||||
如果Quagga还没安装好,我们可以使用yum来安装Quagga。
|
||||
|
||||
# yum install quagga
|
||||
|
||||
如果你正在使用的是CentOS7系统,你需要应用一下策略来设置SELinux。否则,SElinux将会阻止Zebra守护进程写入它的配置目录。如果你正在使用的是CentOS6,你可以跳过这一步。
|
||||
|
||||
# setsebool -P zebra_write_config 1
|
||||
|
||||
Quagga软件套件包含几个守护进程,这些进程可以协同工作。关于BGP路由,我们将把重点放在建立以下2个守护进程。
|
||||
|
||||
- **Zebra**:一个核心守护进程用于内核接口和静态路由.
|
||||
- **BGPd**:一个BGP守护进程.
|
||||
|
||||
### 配置日志记录 ###
|
||||
|
||||
在Quagga被安装后,下一步就是配置Zebra来管理BGP路由器的网络接口。我们通过创建一个Zebra配置文件和启用日志记录来开始第一步。
|
||||
|
||||
# cp /usr/share/doc/quagga-XXXXX/zebra.conf.sample /etc/quagga/zebra.conf
|
||||
|
||||
在CentOS6系统中:
|
||||
|
||||
# service zebra start
|
||||
# chkconfig zebra on
|
||||
|
||||
在CentOS7系统中:
|
||||
|
||||
# systemctl start zebra
|
||||
# systemctl enable zebra
|
||||
|
||||
Quagga提供了一个叫做vtysh特有的命令行工具,你可以输入与路由器厂商(例如Cisco和Juniper)兼容和支持的命令。我们将使用vtysh shell来配置BGP路由在教程的其余部分。
|
||||
|
||||
启动vtysh shell 命令,输入:
|
||||
|
||||
# vtysh
|
||||
|
||||
提示将被改成该主机名,这表明你是在vtysh shell中。
|
||||
|
||||
Router-A#
|
||||
|
||||
现在我们将使用以下命令来为Zebra配置日志文件:
|
||||
|
||||
Router-A# configure terminal
|
||||
Router-A(config)# log file /var/log/quagga/quagga.log
|
||||
Router-A(config)# exit
|
||||
|
||||
永久保存Zebra配置:
|
||||
|
||||
Router-A# write
|
||||
|
||||
在路由器B操作同样的步骤。
|
||||
|
||||
### 配置对等的IP地址 ###
|
||||
|
||||
下一步,我们将在可用的接口上配置对等的IP地址。
|
||||
|
||||
Router-A# show interface #显示接口信息
|
||||
|
||||
----------
|
||||
|
||||
Interface eth0 is up, line protocol detection is disabled
|
||||
. . . . .
|
||||
Interface eth1 is up, line protocol detection is disabled
|
||||
. . . . .
|
||||
|
||||
配置eth0接口的参数:
|
||||
|
||||
site-A-RTR# configure terminal
|
||||
site-A-RTR(config)# interface eth0
|
||||
site-A-RTR(config-if)# ip address 100.100.0.1/30
|
||||
site-A-RTR(config-if)# description "to Router-B"
|
||||
site-A-RTR(config-if)# no shutdown
|
||||
site-A-RTR(config-if)# exit
|
||||
|
||||
|
||||
继续配置eth1接口的参数:
|
||||
|
||||
site-A-RTR(config)# interface eth1
|
||||
site-A-RTR(config-if)# ip address 100.100.1.1/24
|
||||
site-A-RTR(config-if)# description "test ip from provider A network"
|
||||
site-A-RTR(config-if)# no shutdown
|
||||
site-A-RTR(config-if)# exit
|
||||
|
||||
现在确认配置:
|
||||
|
||||
Router-A# show interface
|
||||
|
||||
----------
|
||||
|
||||
Interface eth0 is up, line protocol detection is disabled
|
||||
Description: "to Router-B"
|
||||
inet 100.100.0.1/30 broadcast 100.100.0.3
|
||||
Interface eth1 is up, line protocol detection is disabled
|
||||
Description: "test ip from provider A network"
|
||||
inet 100.100.1.1/24 broadcast 100.100.1.255
|
||||
|
||||
----------
|
||||
|
||||
Router-A# show interface description #显示接口描述
|
||||
|
||||
----------
|
||||
|
||||
Interface Status Protocol Description
|
||||
eth0 up unknown "to Router-B"
|
||||
eth1 up unknown "test ip from provider A network"
|
||||
|
||||
|
||||
如果一切看起来正常,别忘记保存配置。
|
||||
|
||||
Router-A# write
|
||||
|
||||
同样地,在路由器B重复一次配置。
|
||||
|
||||
在我们继续下一步之前,确认下彼此的IP是可以ping通的。
|
||||
|
||||
Router-A# ping 100.100.0.2
|
||||
|
||||
----------
|
||||
|
||||
PING 100.100.0.2 (100.100.0.2) 56(84) bytes of data.
|
||||
64 bytes from 100.100.0.2: icmp_seq=1 ttl=64 time=0.616 ms
|
||||
|
||||
下一步,我们将继续配置BGP对等和前缀设置。
|
||||
|
||||
### 配置BGP对等 ###
|
||||
|
||||
Quagga守护进程负责BGP的服务叫bgpd。首先我们来准备它的配置文件。
|
||||
|
||||
# cp /usr/share/doc/quagga-XXXXXXX/bgpd.conf.sample /etc/quagga/bgpd.conf
|
||||
|
||||
在CentOS6系统中:
|
||||
|
||||
# service bgpd start
|
||||
# chkconfig bgpd on
|
||||
|
||||
在CentOS7中:
|
||||
|
||||
# systemctl start bgpd
|
||||
# systemctl enable bgpd
|
||||
|
||||
现在,让我们来进入Quagga 的shell。
|
||||
|
||||
# vtysh
|
||||
|
||||
第一步,我们要确认当前没有已经配置的BGP会话。在一些版本,我们可能会发现一个AS号为7675的BGP会话。由于我们不需要这个会话,所以把它移除。
|
||||
|
||||
Router-A# show running-config
|
||||
|
||||
----------
|
||||
|
||||
... ... ...
|
||||
router bgp 7675
|
||||
bgp router-id 200.200.1.1
|
||||
... ... ...
|
||||
|
||||
我们将移除一些预先配置好的BGP会话,并建立我们所需的会话取而代之。
|
||||
|
||||
Router-A# configure terminal
|
||||
Router-A(config)# no router bgp 7675
|
||||
Router-A(config)# router bgp 100
|
||||
Router-A(config)# no auto-summary
|
||||
Router-A(config)# no synchronizaiton
|
||||
Router-A(config-router)# neighbor 100.100.0.2 remote-as 200
|
||||
Router-A(config-router)# neighbor 100.100.0.2 description "provider B"
|
||||
Router-A(config-router)# exit
|
||||
Router-A(config)# exit
|
||||
Router-A# write
|
||||
|
||||
路由器B将用同样的方式来进行配置,以下配置提供作为参考。
|
||||
|
||||
Router-B# configure terminal
|
||||
Router-B(config)# no router bgp 7675
|
||||
Router-B(config)# router bgp 200
|
||||
Router-B(config)# no auto-summary
|
||||
Router-B(config)# no synchronizaiton
|
||||
Router-B(config-router)# neighbor 100.100.0.1 remote-as 100
|
||||
Router-B(config-router)# neighbor 100.100.0.1 description "provider A"
|
||||
Router-B(config-router)# exit
|
||||
Router-B(config)# exit
|
||||
Router-B# write
|
||||
|
||||
|
||||
当相关的路由器都被配置好,两台路由器之间的对等将被建立。现在让我们通过运行下面的命令来确认:
|
||||
|
||||
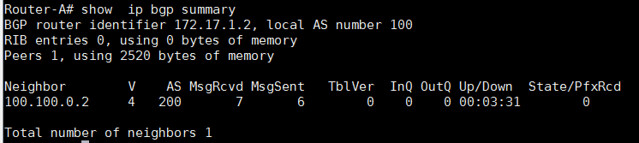
Router-A# show ip bgp summary
|
||||
|
||||
|
||||
|
||||
|
||||
从输出中,我们可以看到"State/PfxRcd"部分。如果对等关闭,输出将会显示"Idle"或者"Active'。请记住,单词'Active'这个词在路由器中总是不好的意思。它意味着路由器正在积极地寻找邻居、前缀或者路由。当对等是up状态,"State/PfxRcd"下的输出状态将会从特殊邻居接收到前缀号。
|
||||
|
||||
在这个例子的输出中,BGP对等只是在AS100和AS200之间呈up状态。因此没有前缀被更改,所以最右边列的数值是0。
|
||||
|
||||
### 配置前缀通告 ###
|
||||
|
||||
正如一开始提到,AS 100将以100.100.0.0/22作为通告,在我们的例子中AS 200将同样以200.200.0.0/22作为通告。这些前缀需要被添加到BGP配置如下。
|
||||
|
||||
在路由器-A中:
|
||||
|
||||
Router-A# configure terminal
|
||||
Router-A(config)# router bgp 100
|
||||
Router-A(config)# network 100.100.0.0/22
|
||||
Router-A(config)# exit
|
||||
Router-A# write
|
||||
|
||||
在路由器-B中:
|
||||
|
||||
Router-B# configure terminal
|
||||
Router-B(config)# router bgp 200
|
||||
Router-B(config)# network 200.200.0.0/22
|
||||
Router-B(config)# exit
|
||||
Router-B# write
|
||||
|
||||
在这一点上,两个路由器会根据需要开始通告前缀。
|
||||
|
||||
### 测试前缀通告 ###
|
||||
|
||||
首先,让我们来确认前缀的数量是否被改变了。
|
||||
|
||||
Router-A# show ip bgp summary
|
||||
|
||||
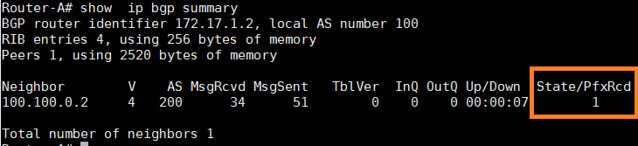
|
||||
|
||||
为了查看所接收的更多前缀细节,我们可以使用以下命令,这个命令用于显示邻居100.100.0.2所接收到的前缀总数。
|
||||
|
||||
Router-A# show ip bgp neighbors 100.100.0.2 advertised-routes
|
||||
|
||||
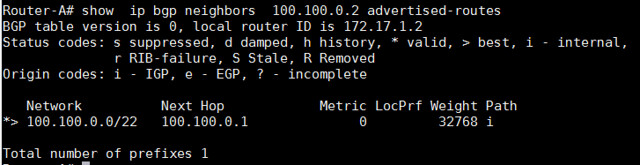
|
||||
|
||||
查看哪一个前缀是我们从邻居接收到的:
|
||||
|
||||
Router-A# show ip bgp neighbors 100.100.0.2 routes
|
||||
|
||||
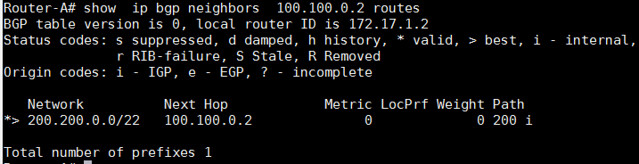
|
||||
|
||||
我们也可以查看所有的BGP路由器:
|
||||
|
||||
Router-A# show ip bgp
|
||||
|
||||
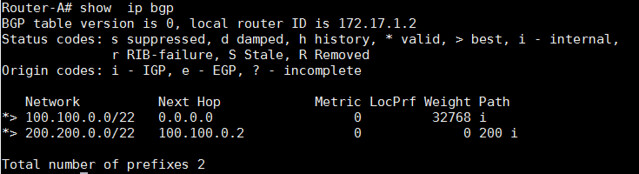
|
||||
|
||||
|
||||
以上的命令都可以被用于检查哪个路由器通过BGP在路由器表中被学习到。
|
||||
|
||||
Router-A# show ip route
|
||||
|
||||
----------
|
||||
|
||||
代码: K - 内核路由, C - 已链接 , S - 静态 , R - 路由信息协议 , O - 开放式最短路径优先协议,
|
||||
|
||||
I - 中间系统到中间系统的路由选择协议, B - 边界网关协议, > - 选择路由, * - FIB 路由
|
||||
|
||||
C>* 100.100.0.0/30 is directly connected, eth0
|
||||
C>* 100.100.1.0/24 is directly connected, eth1
|
||||
B>* 200.200.0.0/22 [20/0] via 100.100.0.2, eth0, 00:06:45
|
||||
|
||||
----------
|
||||
|
||||
Router-A# show ip route bgp
|
||||
|
||||
----------
|
||||
|
||||
B>* 200.200.0.0/22 [20/0] via 100.100.0.2, eth0, 00:08:13
|
||||
|
||||
|
||||
BGP学习到的路由也将会在Linux路由表中出现。
|
||||
|
||||
[root@Router-A~]# ip route
|
||||
|
||||
----------
|
||||
|
||||
100.100.0.0/30 dev eth0 proto kernel scope link src 100.100.0.1
|
||||
100.100.1.0/24 dev eth1 proto kernel scope link src 100.100.1.1
|
||||
200.200.0.0/22 via 100.100.0.2 dev eth0 proto zebra
|
||||
|
||||
|
||||
最后,我们将使用ping命令来测试连通。结果将成功ping通。
|
||||
|
||||
[root@Router-A~]# ping 200.200.1.1 -c 2
|
||||
|
||||
|
||||
总而言之,本教程将重点放在如何在CentOS系统中运行一个基本的BGP路由器。这个教程让你开始学习BGP的配置,一些更高级的设置例如设置过滤器、BGP属性调整、本地优先级和预先路径准备等,我将会在后续的教程中覆盖这些主题。
|
||||
|
||||
希望这篇教程能给大家一些帮助。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/centos-bgp-router-quagga.html
|
||||
|
||||
作者:[Sarmed Rahman][a]
|
||||
译者:[disylee](https://github.com/disylee)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/sarmed
|
||||
[1]:http://linux.cn/article-4232-1.html
|
||||
[2]:http://weibo.com/3181671860/BngyXxEUF
|
||||
@ -1,72 +1,79 @@
|
||||
什么是有用的bash别名和函数
|
||||
一大波有用的 bash 别名和函数
|
||||
================================================================================
|
||||
作为一个命令行探索者,你或许发现你自己一遍又一遍. 如果你总是用ssh进入到同一台电脑, 同时你总是管道关联相同的命令,或者如果你时常用一些参数运行一个程序,你应该想要拯救你人生中的这个珍贵的助手。你一遍又一遍花费着重复相同的动作.
|
||||
解决方案是使用一个别名.正如你可能知道的,别名用一种方式告诉你的shell记住详细的命令并且给它一个新的名字:别名,的方式。不管怎么样,别名是即时有效的,同样地它只是shell命令的快捷方式,没有能力传递或者控制参数.所以补充时,bash也允许你创建你自己的函数,那样可能更漫长和复杂,并且也允许任意数量的参数.
|
||||
当然,当你有一个好的食谱-像汤,你要分享它.因此这里有一个列表,用一些最有用bash别名和函数的.注意"最有用的"是随意的定义,当然别名的有益依赖在于你每天shell的使用性
|
||||
在你用别名开始试验之前, 这里有一个便于使用的小技巧:如果你给予别名相同的名字作为常规命令,你可以选择开始原始的命令并且用技巧忽略别名
|
||||
|
||||
作为一个命令行探索者,你或许发现你自己一遍又一遍重复同样的命令。如果你总是用ssh进入到同一台电脑,如果你总是将一连串命令连接起来,如果你总是用同样的参数运行一个程序,你也许希望在这种不断的重复中为你的生命节约下几秒钟。
|
||||
|
||||
解决方案是使用一个别名(alias)。正如你可能知道的,别名用一种让你的shell记住一个特定的命令并且给它一个新的名字的方式。不管怎么样,别名有一些限制,它只是shell命令的快捷方式,不能传递或者控制其中的参数。所以作为补充,bash 也允许你创建你自己的函数,这可能更长一些和复杂一点,它允许任意数量的参数。
|
||||
|
||||
当然,当你有美食时,比如某种汤,你要分享它给大家。我这里有一个列表,列出了一些最有用bash别名和函数的。注意“最有用的”只是个说法,别名的是否有用要看你是否每天都需要在 shell 里面用它。
|
||||
|
||||
在你开始你的别名体验之旅前,这里有一个便于使用的小技巧:如果你的别名和原本的命令名字相同,你可以用如下技巧来访问原本的命令(LCTT 译注:你也可以直接原本命令的完整路径来访问它。)
|
||||
|
||||
\command
|
||||
例如,第一个别名在下面替换ls命令。如果你想使用常规的ls命令而不是别名,通过调用它:
|
||||
|
||||
例如,如果有一个替换了ls命令的别名 ls。如果你想使用原本的ls命令而不是别名,通过调用它:
|
||||
|
||||
\ls
|
||||
|
||||
### Productivity ###
|
||||
### 提升生产力 ###
|
||||
|
||||
这些别名真的很简单并且真的很短,但他们大多数主要是以主题为依据,那样无论何时倘若你第二次保存一小部分,它允许在多年以后再结束.也许不会.
|
||||
这些别名真的很简单并且真的很短,但他们大多数是为了给你的生命节省几秒钟,最终也许为你这一辈子节省出来几年,也许呢。
|
||||
|
||||
alias ls="ls --color=auto"
|
||||
|
||||
简单但非常重要.使ls命令带着彩色输出
|
||||
简单但非常重要。使ls命令带着彩色输出。
|
||||
|
||||
alias ll = "ls --color -al"
|
||||
alias ll="ls --color -al"
|
||||
|
||||
从一个目录采用列表格式快速显示全部文件.
|
||||
以彩色的列表方式列出目录里面的全部文件。
|
||||
|
||||
alias grep='grep --color=auto'
|
||||
|
||||
相同地,把一些颜色在grep里输出
|
||||
类似,只是在grep里输出带上颜色。
|
||||
|
||||
mcd() { mkdir -p "$1"; cd "$1";}
|
||||
|
||||
我的最爱之一. 制造一个目录采用一个命令mcd[名字]和cd命令进入到目录里面
|
||||
我的最爱之一。创建一个目录并进入该目录里: mcd [目录名]。
|
||||
|
||||
cls() { cd "$1"; ls;}
|
||||
|
||||
类似于前面的功能,cd命令进入一个目录别且列出它的的内容:cls[名字]
|
||||
类似上一个函数,进入一个目录并列出它的的内容:cls[目录名]。
|
||||
|
||||
backup() { cp "$1"{,.bak};}
|
||||
|
||||
简单的方法,使文件有一个备份: backup [文件]将会在相同的目录创建[文件].bak.
|
||||
简单的给文件创建一个备份: backup [文件] 将会在同一个目录下创建 [文件].bak。
|
||||
|
||||
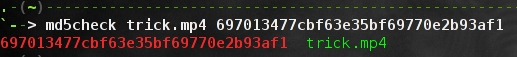
md5check() { md5sum "$1" | grep "$2";}
|
||||
|
||||
因为我讨厌通过手工比较文件的md5算法,这个函数计算它并且计算它使用grep:md5check[文件][钥匙]
|
||||
因为我讨厌通过手工比较文件的md5校验值,这个函数会计算它并进行比较:md5check[文件][校验值]。
|
||||
|
||||
|
||||
|
||||
alias makescript="fc -rnl | head -1 >"
|
||||
|
||||
很容易地制造上个命令的脚本输出,你运行makescript[脚本名字.sh]
|
||||
很容易用你上一个运行的命令创建一个脚本:makescript [脚本名字.sh]
|
||||
|
||||
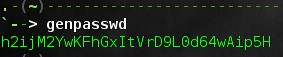
alias genpasswd="strings /dev/urandom | grep -o '[[:alnum:]]' | head -n 30 | tr -d '\n'; echo"
|
||||
|
||||
只是瞬间产生一个强壮的密码
|
||||
只是瞬间产生一个强壮的密码。
|
||||
|
||||
|
||||
|
||||
alias c="clear"
|
||||
|
||||
不能较为简单的清除你终端的屏幕
|
||||
清除你终端屏幕不能更简单了吧?
|
||||
|
||||
alias histg="history | grep"
|
||||
|
||||
通过你的命令历史:histg[关键字]快速地搜索
|
||||
快速搜索你的命令输入历史:histg [关键字]
|
||||
|
||||
alias ..='cd ..'
|
||||
|
||||
不需要写cd命令到上层目录
|
||||
回到上层目录还需要输入 cd 吗?
|
||||
|
||||
alias ...='cd ../..'
|
||||
|
||||
类似地,去到上两个目录
|
||||
自然,去到上两层目录。
|
||||
|
||||
extract() {
|
||||
if [ -f $1 ] ; then
|
||||
@ -89,98 +96,93 @@
|
||||
fi
|
||||
}
|
||||
|
||||
很长,但是也是最有用的。解压任何的文档类型:extract:[文档文件]
|
||||
|
||||
很长,但是也是最有用的。解压任何的文档类型:extract: [压缩文件]
|
||||
|
||||
### 系统信息 ###
|
||||
|
||||
想尽快地知道一切关于你的系统?
|
||||
想尽快地知道关于你的系统一切信息?
|
||||
|
||||
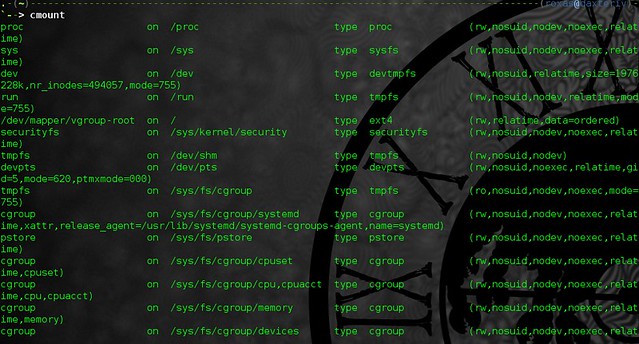
alias cmount="mount | column -t"
|
||||
|
||||
mount到列队中的格式输出
|
||||
按列格式化输出mount信息。
|
||||
|
||||
|
||||
|
||||
alias tree="ls -R | grep ":$" | sed -e 's/:$//' -e 's/[^-][^\/]*\//--/g' -e 's/^/ /' -e 's/-/|/'"
|
||||
|
||||
递归树格式显示目录结构.
|
||||
以树形结构递归地显示目录结构。
|
||||
|
||||
sbs() { du -b --max-depth 1 | sort -nr | perl -pe 's{([0-9]+)}{sprintf "%.1f%s", $1>=2**30? ($1/2**30, "G"): $1>=2**20? ($1/2**20, "M"): $1>=2**10? ($1/2**10, "K"): ($1, "")}e';}
|
||||
|
||||
在当前目录里“按大小排序”显示列表的文件,排序按它们在磁盘上的大小
|
||||
安装文件在磁盘存储的大小排序,显示当前目录的文件列表。
|
||||
|
||||
alias intercept="sudo strace -ff -e trace=write -e write=1,2 -p"
|
||||
|
||||
intercept[一些PID]阻止进程的标准输入输出文件和标准错误文件。注意你需要看着安装完成
|
||||
接管某个进程的标准输出和标准错误。注意你需要安装了 strace。
|
||||
|
||||
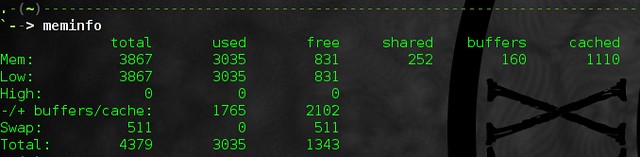
alias meminfo='free -m -l -t'
|
||||
|
||||
查看你还有剩下多少内存
|
||||
查看你还有剩下多少内存。
|
||||
|
||||
|
||||
|
||||
alias ps? = "ps aux | grep"
|
||||
|
||||
ps?[名字]很容易地发现,这个任何进程的
|
||||
可以很容易地找到某个进程的PID:ps? [名字]。
|
||||
|
||||
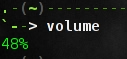
alias volume="amixer get Master | sed '1,4 d' | cut -d [ -f 2 | cut -d ] -f 1"
|
||||
|
||||
显示现在声音的音量.
|
||||
显示当前音量设置。
|
||||
|
||||
|
||||
|
||||
### 网络 ###
|
||||
|
||||
对于所有涉及互联网和你本地网络的命令,也有奇特的别名给它们
|
||||
|
||||
对于所有用在互联网和本地网络的命令,也有一些神奇的别名给它们。
|
||||
|
||||
alias websiteget="wget --random-wait -r -p -e robots=off -U mozilla"
|
||||
|
||||
websiteget[指定的位置]下载完整的网站地址
|
||||
下载整个网站:websiteget [URL]。
|
||||
|
||||
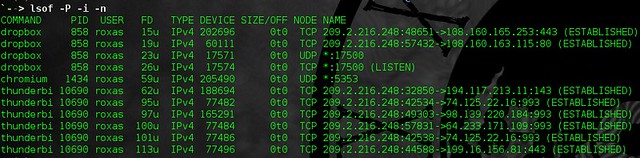
alias listen="lsof -P -i -n"
|
||||
|
||||
显示出哪个应用程序连接到网络
|
||||
显示出哪个应用程序连接到网络。
|
||||
|
||||
|
||||
|
||||
alias port='netstat -tulanp'
|
||||
|
||||
显示出活动的端口
|
||||
显示出活动的端口。
|
||||
|
||||
gmail() { curl -u "$1" --silent "https://mail.google.com/mail/feed/atom" | sed -e 's/<\/fullcount.*/\n/' | sed -e 's/.*fullcount>//'}
|
||||
|
||||
gmail:[用户名]大概的显示你的谷歌邮件里未读邮件的数量
|
||||
|
||||
大概的显示你的谷歌邮件里未读邮件的数量:gmail [用户名]
|
||||
|
||||
alias ipinfo="curl ifconfig.me && curl ifconfig.me/host"
|
||||
|
||||
获得你的公共IP地址和主机
|
||||
获得你的公网IP地址和主机名。
|
||||
|
||||
getlocation() { lynx -dump http://www.ip-adress.com/ip_tracer/?QRY=$1|grep address|egrep 'city|state|country'|awk '{print $3,$4,$5,$6,$7,$8}'|sed 's\ip address flag \\'|sed 's\My\\';}
|
||||
|
||||
以你的IP地址为基础返回你现在的位置
|
||||
返回你的当前IP地址的地理位置。
|
||||
|
||||
### 没用的 ###
|
||||
|
||||
所以呢,如果一些别名是不是全部具有使用价值?它们可能仍然有趣
|
||||
### 也许无用 ###
|
||||
|
||||
所以呢,如果一些别名并不是全都具有使用价值?它们可能仍然有趣。
|
||||
|
||||
kernelgraph() { lsmod | perl -e 'print "digraph \"lsmod\" {";<>;while(<>){@_=split/\s+/; print "\"$_[0]\" -> \"$_\"\n" for split/,/,$_[3]}print "}"' | dot -Tpng | display -;}
|
||||
|
||||
要绘制内核模块依赖曲线图。需要镜像阅读器
|
||||
绘制内核模块依赖曲线图。需要可以查看图片。
|
||||
|
||||
alias busy="cat /dev/urandom | hexdump -C | grep "ca fe""
|
||||
alias busy="cat /dev/urandom | hexdump -C | grep 'ca fe'"
|
||||
|
||||
在非技术人员的眼里你看起来都在忙和构思
|
||||
在那些非技术人员的眼里你看起来是总是那么忙和神秘。
|
||||
|
||||

|
||||
|
||||
最后,这些别名和函数的很大一部分来自于我个人的.bashrc.这些令人敬畏的网站 [alias.sh][1]和[commandlinefu.com][2]我早已经展示在我的[best online tools for Linux][3].当然去检测它们的输出,让你拥有特有的秘诀。如果你真的同意,在注释里分享你的智慧,
|
||||
最后,这些别名和函数的很大一部分来自于我个人的.bashrc。而那些令人点赞的网站 [alias.sh][1]和[commandlinefu.com][2]我早已在我的帖子[best online tools for Linux][3] 里面介绍过。你可以去看看,如果你愿意,也可以分享下你的。也欢迎你在这里评论,分享一下你的智慧。
|
||||
|
||||
|
||||
做为奖励,这里有我提到的全部别名和函数的纯文本版本,随时可以复制粘贴到你的.bashrc.
|
||||
做为奖励,这里有我提到的全部别名和函数的纯文本版本,随时可以复制粘贴到你的.bashrc。(如果你已经一行一行的复制到这里了,哈哈,你发现你又浪费了生命的几秒钟~)
|
||||
|
||||
#Productivity
|
||||
alias ls="ls --color=auto"
|
||||
@ -243,8 +245,8 @@ gmail:[用户名]大概的显示你的谷歌邮件里未读邮件的数量
|
||||
via: http://xmodulo.com/useful-bash-aliases-functions.html
|
||||
|
||||
作者:[Adrien Brochard][a]
|
||||
译者:[译者luoyutiantang](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
译者:[luoyutiantang](https://github.com/luoyutiantang)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
@ -0,0 +1,174 @@
|
||||
Linux 和类 Unix 系统上5个最佳开源备份工具
|
||||
================================================================================
|
||||
一个好的备份最基本的目的就是为了能够从一些错误中恢复:
|
||||
|
||||
- 人为的失误
|
||||
- 磁盘阵列或是硬盘故障
|
||||
- 文件系统崩溃
|
||||
- 数据中心被破坏等等。
|
||||
|
||||
所以,我为大家罗列了一些开源的软件备份工具。
|
||||
|
||||
### 当为一个企业选择备份工具的时候,你都考虑什么呢? ###
|
||||
|
||||
确定你正在部署的软件具有下面的特性
|
||||
|
||||
1. **开源软件** - 你务必要选择那些源码可以免费获得,并且可以修改的软件。确信可以恢复你的数据,即使是软件供应商/项目停止继续维护这个软件,或者是拒绝继续为这个软件提供补丁。
|
||||
|
||||
2. **跨平台支持** - 确定备份软件可以很好的运行各种需要部署的桌面操作系统和服务器系统。
|
||||
|
||||
3. **数据格式** - 一种开放的数据格式可以让你能够恢复数据,即使是供应商或是项目停止对软件的支持。
|
||||
|
||||
4. **自动转换** - 自动转换本来是没什么,除了对于各种备份设备,包括图书馆,近线存储和自动加载,自动转换可以自动完成一些任务,包括加载,挂载和标签备份像磁带这些媒体设备。
|
||||
|
||||
5. **备份介质** - 确定你可以备份到磁带,硬盘,DVD 和像 AWS 这样的云存储。
|
||||
|
||||
6. **加密数据流** - 确定所有客户端到服务器的传输都被加密,保证在 LAN/WAN/Internet 中传输的安全性。
|
||||
|
||||
7. **数据库支持** - 确定备份软件可以备份到数据库,像MySQL 或是 Oracle。
|
||||
|
||||
8. **备份可以跨越多个卷** - 备份软件(转储文件时)可以把每个备份文件分成几个部分,允许将每个部分存在于不同的卷。这样可以保证一些数据量很大的备份(像100TB的文件)可以被存储在一些单个容量较小的设备中,比如说像硬盘和磁盘卷。
|
||||
|
||||
9. **VSS (卷影复制)** - 这是[微软的卷影复制服务(VSS)][1],通过创建数据的快照来备份。确定备份软件支持VSS的MS-Windows 客户端/服务器。
|
||||
|
||||
10. **重复数据删除** - 这是一种数据压缩技术,用来消除重复数据的副本(比如,图片)。
|
||||
|
||||
11. **许可证和成本** - 确定你对备份软件所用的[许可证了解和明白其使用方式][3]。
|
||||
|
||||
12. **商业支持** - 开源软件可以提供社区支持(像邮件列表和论坛)和专业的支持(如发行版提供额外的付费支持)。你可以使用付费的专业支持为你提供培训和咨询。
|
||||
|
||||
13. **报告和警告** - 最后,你必须能够看到备份的报告,当前的工作状态,也能够在备份出错的时候提供警告。
|
||||
|
||||
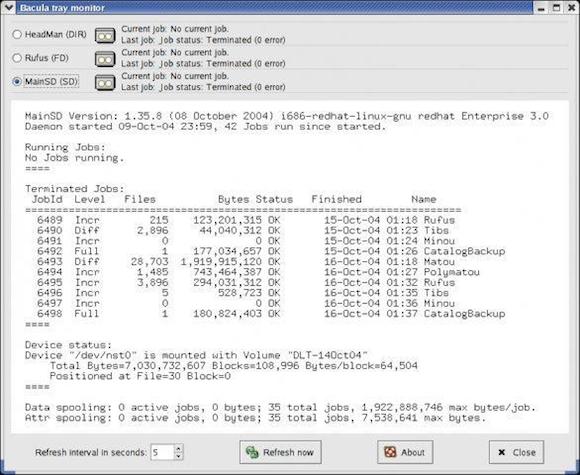
### Bacula - 一个应用于多元化异构网络的客户端服务器备份工具 ###
|
||||
|
||||
我个人应用这个软件来管理备份和通过网络来恢复系统,包括Linux, OSX, 和Windows。你可以通过CLI, GUI, 或者Web界面来配置Bacula。
|
||||
|
||||
|
||||
|
||||
- 操作系统:支持跨平台运行。
|
||||
- 备份级别:完全,差异,增量,合并。
|
||||
- 数据格式:支持自定义且完全开放。
|
||||
- 自动转换:支持。
|
||||
- 备份介质:支持磁带,磁盘和DVD。
|
||||
- 加密数据流:支持。
|
||||
- 数据库:支持MSSQL、PostgreSQL、Oracle 。
|
||||
- 跨卷备份:支持
|
||||
- VSS(卷影复制):支持。
|
||||
- 许可:Affero General Public License v3.0。
|
||||
- 下载链接:[bacula.org][4]
|
||||
|
||||
### Amanda - 又一个客户端服务器备份工具 ###
|
||||
|
||||
AMANDA 是 Advanced Maryland Automatic Network Disk Archiver 的缩写。它允许系统管理员创建一个单独的备份服务器来将网络上的其他主机的数据备份到磁带驱动器、硬盘或者是自动换盘器。
|
||||
|
||||
- 操作系统:支持跨平台运行。
|
||||
- 备份级别:完全,差异,增量,合并。
|
||||
- 数据格式:开放(可以通过tar等工具恢复)。
|
||||
- 自动转换:支持。
|
||||
- 备份介质:支持磁带,磁盘和DVD。
|
||||
- 加密数据流:支持。
|
||||
- 数据库:支持MSSQL, Oracle。
|
||||
- 跨卷备份:支持。
|
||||
- VSS(卷影复制):支持。
|
||||
- 许可:GPL, LGPL, Apache, Amanda License。
|
||||
- 下载链接:[amanda.org][5]
|
||||
|
||||
### Backupninja - 轻量级备份系统 ###
|
||||
|
||||
Backupninja 是一个简单易用的备份系统。你可以简单的拖放一个配置文件到 /etc/backup.d/ 目录来备份到多个主机。
|
||||
|
||||
|
||||
|
||||
- 操作系统:支持Linux,Unix。
|
||||
- 备份级别:支持完全,差异备份(rsync + hard 链接)
|
||||
- 数据格式:开放
|
||||
- 自动转换:N/A。(注:N/A = Not Applicable)。
|
||||
- 备份介质:磁盘,DVD,CD,ISO 镜像。
|
||||
- 加密数据流:支持(ssh)和[通过duplicity远程加密备份][6]。
|
||||
- 数据库:支持MySQL,PostgreSQL,OpenLDAP 和subversion 或trac。
|
||||
- 跨卷备份:??
|
||||
- VSS(卷影复制):??
|
||||
- 许可:GPL
|
||||
- 下载链接:[riseup.net][7]
|
||||
|
||||
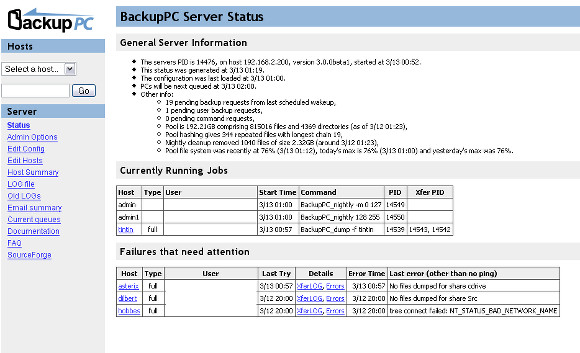
### Backuppc - 高效的客户端服务器备份工具###
|
||||
|
||||
Backuppc 可以用来备份基于Linux 和Windows 系统的主服务器硬盘。它配备了一个巧妙的池计划来最大限度的减少磁盘储存、磁盘 I/O 和网络I/O。
|
||||
|
||||
|
||||
|
||||
- 操作系统:支持Linux,Unix 和Windows。
|
||||
- 备份级别:支持完全和增量备份(rsync +hard 链接和pooling 计划)
|
||||
- 数据格式:开放。
|
||||
- 自动转换:N/A。
|
||||
- 备份介质:磁盘和磁盘阵列。
|
||||
- 加密数据流:支持。
|
||||
- 数据库:支持(通过Shell 脚本)
|
||||
- 跨卷备份:??
|
||||
- VSS(卷影复制):??
|
||||
- 许可:GPL。
|
||||
- 下载链接:[backuppc.sourceforge.net][8]
|
||||
|
||||
### UrBackup - 最容易配置的客户端服务器系统 ###
|
||||
|
||||
UrBackup 是一个非常容易配置的开源客户端服务器备份系统,通过镜像 方式和文件备份的组合完成了数据安全性和快速的恢复。磁盘卷备份可以使用可引导 CD 或U盘,通过Web界面或Windows资源管理器来恢复你的文件(硬恢复)。一个 Web 界面使得配置你自己的备份服务变得非常简单。
|
||||
|
||||
|
||||
|
||||
- 操作系统:支持Linux,FreeBSD,Unix,Windows 和少数基于NAS 的Linux操作系统,客户端只支持Linux 和Windows 操作系统。
|
||||
- 备份级别:支持完全和增量备份。
|
||||
- 数据格式:开放。
|
||||
- 自动转换:N/A。
|
||||
- 备份介质:磁盘,磁盘阵列和DVD。
|
||||
- 加密数据流:支持。
|
||||
- 数据库:??
|
||||
- 跨卷备份:??
|
||||
- VSS(卷影复制):??
|
||||
- 许可:GPL v3+
|
||||
- 下载链接:[urbackup.org][9]
|
||||
|
||||
### 其他供你考虑的一些极好用的开源备份软件 ###
|
||||
|
||||
Amanda,Bacula 和上面所提到的这些软件功能都很丰富,但是对于一些小的网络或者是单独的服务器来说配置比较复杂。我建议你学习和使用一下的下面这些备份软件:
|
||||
|
||||
1. [Rsnapshot][10] - 我建议用这个作为对本地和远程的文件系统快照工具。看看[在Debian 和Ubuntu linux][11]和[基于CentOS,RHEL 的操作系统][12]怎么设置和使用这个工具。
|
||||
2. [rdiff-backup][13] - 另一个好用的类Unix 远程增量备份工具。
|
||||
3. [Burp][14] - Burp 是一个网络备份和恢复程序。它使用了librsync来节省网络流量和节省每个备份占用的空间。它也使用了VSS(卷影复制服务),在备份Windows计算机时进行快照。
|
||||
4. [Duplicity][15] - 伟大的加密和高效的备份类Unix操作系统。查看如何[安装Duplicity来加密云备份][16]来获取更多的信息。
|
||||
5. [SafeKeep][17] - SafeKeep是一个中心化的、易于使用的备份应用程序,结合了镜像和增量备份最佳功能的备份应用程序。
|
||||
6. [DREBS][18] - DREBS 是EBS定期快照的工具。它被设计成在EBS快照所连接的EC2主机上运行。
|
||||
7. 古老的unix 程序,像rsync, tar, cpio, mt 和dump。
|
||||
|
||||
###结论###
|
||||
|
||||
我希望你会发现这篇有用的文章来备份你的数据。不要忘了验证你的备份和创建多个数据备份。注意,磁盘阵列并不是一个备份解决方案!使用任何一个上面提到的程序来备份你的服务器、桌面和笔记本电脑和私人的移动设备。如果你知道其他任何开源的备份软件我没有提到的,请分享在评论里。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.cyberciti.biz/open-source/awesome-backup-software-for-linux-unix-osx-windows-systems/
|
||||
|
||||
作者:[nixCraft][a]
|
||||
译者:[barney-ro](https://github.com/barney-ro)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.cyberciti.biz/tips/about-us
|
||||
[1]:http://technet.microsoft.com/en-us/library/cc785914(v=ws.10).aspx
|
||||
[2]:http://en.wikipedia.org/wiki/Data_deduplication
|
||||
[3]:http://opensource.org/licenses
|
||||
[4]:http://www.bacula.org/
|
||||
[5]:http://www.amanda.org/
|
||||
[6]:http://www.cyberciti.biz/faq/duplicity-installation-configuration-on-debian-ubuntu-linux/
|
||||
[7]:https://labs.riseup.net/code/projects/backupninja
|
||||
[8]:http://backuppc.sourceforge.net/
|
||||
[9]:http://www.urbackup.org/
|
||||
[10]:http://www.rsnapshot.org/
|
||||
[11]:http://www.cyberciti.biz/faq/linux-rsnapshot-backup-howto/
|
||||
[12]:http://www.cyberciti.biz/faq/redhat-cetos-linux-remote-backup-snapshot-server/
|
||||
[13]:http://www.nongnu.org/rdiff-backup/
|
||||
[14]:http://burp.grke.org/
|
||||
[15]:http://www.cyberciti.biz/open-source/awesome-backup-software-for-linux-unix-osx-windows-systems/
|
||||
[16]:http://www.cyberciti.biz/faq/duplicity-installation-configuration-on-debian-ubuntu-linux/
|
||||
[17]:http://safekeep.sourceforge.net/
|
||||
[18]:https://github.com/dojo4/drebs
|
||||
@ -1,8 +1,8 @@
|
||||
Linux上使用备份管理器进行系统备份
|
||||
Linux 上使用 backup-manager 进行系统备份
|
||||
================================================================================
|
||||
无论简单与否,我们都有机会去了解这么一件事,那就是备份的重要性从来都不可以被低估。考虑到备份的方法真的多如牛毛,你可能想要知道怎样来有效地为你的系统选择正确的工具和和合适的策略。
|
||||
|
||||
在本文中,我将为你介绍[备份管理器][1],一个简单易用的命令行备份工具,在大多数的Linux发行版的标准软件库中都能见到它的身影。
|
||||
在本文中,我将为你介绍[backup-manager][1],一个简单易用的命令行备份工具,在大多数的Linux发行版的标准软件库中都能见到它的身影。
|
||||
|
||||
是什么让备份管理器在众多的备份工具或备份策略中脱颖而出呢?让我来简单介绍一些它的与众不同的特性吧:
|
||||
|
||||
@ -28,7 +28,7 @@ Linux上使用备份管理器进行系统备份
|
||||
|
||||
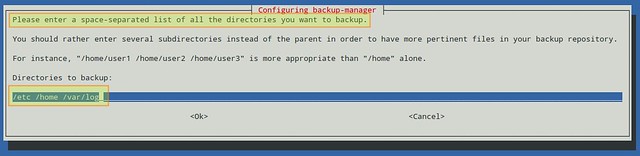
在下一步中,会询问你要备份的所有目录(用空格分隔)。建议,但不是严格要求,列出同一父目录中的几个子目录,而不要仅仅输入父目录。
|
||||
|
||||
你可以跳过该步骤并在以后对配置文件中BM_TARBALL_DIRECTORIESb变量进行设置。否则的话,就请尽可能多地添加你想要的目录,然后选择OK:
|
||||
你可以跳过该步骤并在以后对配置文件中BM\_TARBALL\_DIRECTORIESb变量进行设置。否则的话,就请尽可能多地添加你想要的目录,然后选择OK:
|
||||
|
||||
|
||||
|
||||
@ -115,11 +115,11 @@ Linux上使用备份管理器进行系统备份
|
||||
|
||||
# backup-manager
|
||||
|
||||
BM_TARBALL_DIRECTORIES列出的目录将作为tarball备份到BM_REPOSITORY_ROOT目录,然后通过SSH传输到BM_UPLOAD_SSH_DESTINATION指定的主机dev1和dev3。
|
||||
BM\_TARBALL\_DIRECTORIES列出的目录将作为tarball备份到BM\_REPOSITORY\_ROOT目录,然后通过SSH传输到BM\_UPLOAD\_SSH_DESTINATION指定的主机dev1和dev3。
|
||||
|
||||

|
||||
|
||||
正如你在上面图片中看到的那样,备份管理器在运行的时候创建了一个名为/root/.back-manager_my.cnf的文件,MySQL密码通过BM_MYSQL_ ADMINPASS指定。那样,mysqldump可以验证到MySQL服务器,而不必在命令行以明文格式接受密码,那样会有安全风险。
|
||||
正如你在上面图片中看到的那样,备份管理器在运行的时候创建了一个名为/root/.back-manager\_my.cnf的文件,MySQL密码通过BM\_MYSQL\_ADMINPASS指定。那样,mysqldump可以验证到MySQL服务器,而不必在命令行以明文格式接受密码,那样会有安全风险。
|
||||
|
||||
### 通过cron运行备份管理器 ###
|
||||
|
||||
@ -145,7 +145,7 @@ via: http://xmodulo.com/linux-backup-manager.html
|
||||
|
||||
作者:[Gabriel Cánepa][a]
|
||||
译者:[GOLinux](https://github.com/GOLinux)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,12 +1,12 @@
|
||||
Linus Torvalds发布了Linux 3.19 RC1,目前为止最大的更新
|
||||
Linus Torvalds发布了Linux 3.19 RC1,这是目前为止最大的RC1
|
||||
================================================================================
|
||||
> 新的内核开发周期开始了
|
||||
|
||||

|
||||
|
||||
**首个内核候选版本在3.19分支上发布了,它看上去像目前最大的更新。这个早先发布让众人惊喜,但是很容易理解为什么。**
|
||||
**首个内核候选版本在3.19分支上发布了,它看上去像目前最大的一个 RC1。Linus Torvalds很惊奇这么多人提交了,其实不过也很好理解。**
|
||||
|
||||
内核开发周期被新的3.19的发布而刷新了。事实是3.18分支才几周前才发布,今天的发布并不是完全在预期中。假期要来了,很多开发者和维护任何可能会休息。一般来说RC版本每周发布一次,但是用户可能会看到轻微的延误。
|
||||
内核开发周期因新的3.19的发布而刷新了。事实是3.18分支才几周前才发布,今天的发布并不是完全在预期中。假期要来了,很多开发者和维护人员可能会休息。一般来说RC版本每周发布一次,但是用户可能会看到一点的延误。
|
||||
|
||||
这个版本没有提到在Linux 3.18中确认的回归问题,但是可以确定的是,开发人员仍在努力修复中。另一方面,Linus说这是一个很大的更新,事实上这是目前为止最大的更新。很有可能是许多开发者想要在节日之前推送他们的补丁,因此,下一个RC版本会小一些。
|
||||
|
||||
@ -14,10 +14,9 @@ Linus Torvalds发布了Linux 3.19 RC1,目前为止最大的更新
|
||||
|
||||
发布版本的大小随着更新的频率正在增加。内核的开发周期通常大约8到10周,并且很少多于这个,这给项目一个很好的预测。
|
||||
|
||||
[阅读][1] Linus Torvalds的发布声明中说:“也就是说,也许没有真正的落后者,并且从rc1的大小来看,真的已经不多了。我不仅觉得下一个版本有更多的提交,并且比历史上的rc1更多(知道在提交数量上)。我们已经有比较大的版本(3.10和3.15的都有很大的很并窗口导致的),但是这明显不是一个小的合并窗口。”
|
||||
|
||||
“在这个在蓝图下,这看上去只是一个常规发布。大约三分之二的驱动更新,这剩下的一半是架构的更新(新的nios2补丁还没有优势,它只有ARM一半的性能,新的niso2支持小于整体架构更新的10%)。”
|
||||
[阅读][1] Linus Torvalds的发布声明中说:“也就是说,也许没有谁在拖后腿,并且从rc1的大小来看,真的也不能再多了。我不仅觉得下一个版本会有更多的提交,并且这是历史上最大的一个rc1(在提交数量上)。我们有比它大的版本(3.10和3.15的都是由很大的合并窗口产生的),但是这明显这个合并窗口也不小。”
|
||||
|
||||
“按照蓝图,这看上去只是一个常规发布。大约三分之二的驱动更新,这剩下的一半是架构的更新(新的nios2补丁还没有优势,它只有ARM一半的性能,新的niso2支持小于整体架构更新的10%)。”
|
||||
|
||||
具体关于这个RC的细节可以在官方邮件列表中找到。
|
||||
|
||||
@ -32,9 +31,9 @@ Linus Torvalds发布了Linux 3.19 RC1,目前为止最大的更新
|
||||
|
||||
via: http://news.softpedia.com/news/Linus-Torvalds-Launches-Linux-kernel-3-19-RC1-One-of-the-Biggest-So-Far-468043.shtml
|
||||
|
||||
作者:[Silviu Stahie ][a]
|
||||
作者:[Silviu Stahie][a]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
@ -0,0 +1,36 @@
|
||||
Ubuntu参考手册14.04 LTS第二版正式发布
|
||||
==============================================
|
||||
|
||||
> 初学者可以在手册里获得很有用的信息
|
||||
|
||||
### Ubuntu参考手册团队表示第二版手册现在已经发布并且可以免费下载 ###
|
||||
|
||||
|
||||
|
||||
Ubuntu手册按照惯例会对应相应的LTS发行版本,那么唯一合理的解释就是,现在发布的手册对应于6个月前发布的Ubuntu 14.04 LTS(Trusty Tahr)。与其他书籍一样,特别是大型书籍,手册内容总会出现各种错误或者也许已经和现状不匹配。不过不管怎样,电子书的修正和更新总要方便一些。
|
||||
|
||||
你也许会觉得奇怪,一个方便上手的免费操作系统竟然会有一个参考手册,或许一个社区就已经足够了。但是,总是有一些新用户连基本的操作都不懂,因此,有一本可以指明最基本的东西的手册拿在手里总是一个很好不过的事情。
|
||||
|
||||
### 这是“Ubuntu 14.04 LTS入门”手册的第二个版本 ###
|
||||
|
||||
使用Ubuntu操作系统的用户会发现,它和之前用过的其他操作系统有很大的差异,例如Windows和Max OS X。这很正常,并且你也不是任何时候都可以在网上找到一个特定的功能或者组件的相关资源和信息。有一个可以说明Ubuntu 14.04 LTS基本特性的手册可以提供一些帮助。
|
||||
|
||||
“《Ubuntu 14.04 入门 E2》对于Ubuntu操作系统而言,是一个很全面的初学者指南手册。它采用的是开源许可协议,你可以自由下载、阅读、修改以及共享。这个手册可以帮助你熟悉如何处理日常的工作,例如上网、听音乐或者扫描文档等等。尤其值得一提的是,这个文档浅显易懂,适合各个层次的用户。”
|
||||
|
||||
“这个快速入门手册可以让你很容易的利用你的计算机做一些事情,而不会陷入技术细节当中。在手册的帮助下,新用户可以很快的熟悉Unity桌面,”更多信息参考[官方网站][1]。
|
||||
|
||||
这是该参考手册的第二版,制作手册的团队具有丰富的经验。就算你已经是一个Ubuntu用户,看一看这个手册也没有什么坏处,因为你总能从其中学到一些东西。你可以在Softpedia[下载Ubuntuy参考手册14.04第二版][2]。
|
||||
|
||||
----
|
||||
|
||||
via: http://news.softpedia.com/news/Second-Edition-of-Ubuntu-Manual-14-04-LTS-Is-Out-468395.shtml
|
||||
|
||||
作者:[Silviu Stahie][a]
|
||||
译者:[zhouj-sh](https://github.com/zhouj-sh)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://news.softpedia.com/editors/browse/silviu-stahie
|
||||
[1]:http://ubuntu-manual.org/
|
||||
[2]:http://linux.softpedia.com/get/Documentation/Ubuntu-Manual-53530.shtml
|
||||
@ -0,0 +1,47 @@
|
||||
美国海军陆战队要把雷达操作系统从Windows XP换成Linux
|
||||
================================================================================
|
||||
**一个新的雷达系统已经被送回去升级了**
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||

|
||||
|
||||

|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
>一谈到稳定性和性能,没什么能真的比得过Linux。这就是为什么美国海军陆战队的领导们已经决定让Northrop Grumman Corp. Electronic Systems把新送到的地面/空中任务导向雷达(G/ATOR)的操作系统从Windows XP换成Linux。
|
||||
|
||||
地面/空中任务导向雷达(G/ATOR)系统已经研制了很多年。很可能在这项工程启动的时候Windows XP被认为是合理的选择。但在研制的这段时间,事情发生了变化。微软已经撤销了对Windows XP的支持而且只有极少的几个组织会使用它。操作系统要么升级要么被换掉。在这种情况下,Linux成了合理的选择。特别是当替换的费用很可能远远少于更新的费用。
|
||||
|
||||
有个很有趣的地方值得注意一下。地面/空中任务导向雷达(G/ATOR)才刚刚送到美国海军陆战队,但是制造它的公司却还是选择了保留这个过时的操作系统。一定有人注意到的这样一个事实。这是一个糟糕的决定,并且指挥系统已经被告知了可能出现的问题了。
|
||||
|
||||
### G/ATOR雷达的软件将是基于Linux的 ###
|
||||
|
||||
Unix类系统,比如基于BSD或者基于Linux的操作系统,通常会出现在条件苛刻的领域,或者任何情况下都不允许失败的的技术中。例如,这就是为什么大多数的服务器都运行着Linux。一个雷达系统配上一个几乎不可能崩溃的操作系统看起来非常相配。
|
||||
|
||||
“弗吉尼亚州Quantico海军基地海军陆战队系统司令部的官员,在周三宣布了一项与Northrop Grumman Corp. Electronic Systems在林西科姆高地的部分的总经理签订的价值1020万美元的修正合同。这个合同的修改将包括这样一项,把G/ATOR的控制电脑从微软的Windows XP操作系统换成与国防信息局(DISA)兼容的Linux操作系统。”
|
||||
|
||||
‘G/ATOR是一个远征三维中短距离多用途雷达系统。这个系统被设计成能够探测拥有低雷达截面的低可观测目标,比如火箭弹,火炮,迫击炮,巡航导弹以及无人机。”这些内容可以在[militaryaerospace.com][1]看到。
|
||||
|
||||
这项军用科技,即地面/空中任务导向雷达(G/ATOR),早在2005年就与Northrop Grumman签订了第一次合同。所以不难理解为什么美国海军可能想把这件事快点弄完。这次更换的时间限制还没有被提议。
|
||||
|
||||
视频链接:[http://youtu.be/H2ppl4x-eu8][2]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://news.softpedia.com/news/U-S-Marine-Corps-Want-to-Change-OS-for-Radar-System-from-Windows-XP-to-Linux-466756.shtml
|
||||
|
||||
作者:[Silviu Stahie][a]
|
||||
译者:[H-mudcup](https://github.com/H-mudcup)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://news.softpedia.com/editors/browse/silviu-stahie
|
||||
[1]:http://www.militaryaerospace.com/articles/2014/12/gator-linux-software.html
|
||||
[2]:http://youtu.be/H2ppl4x-eu8
|
||||
@ -0,0 +1,76 @@
|
||||
没错,Linux是感染了木马!但,这并非企鹅的末日。
|
||||
================================================================================
|
||||

|
||||
|
||||
译注:原文标题中Tuxpocalypse是作者造的词,由Tux和apocalypse组合而来。Tux是Linux的LOGO中那只企鹅的名字,apocalypse意为末世、大灾变,这里翻译成企鹅的末日。
|
||||
|
||||
你被监视了吗?
|
||||
|
||||
带上一箱罐头,挖一个深坑碉堡,准备进入一个完全不同的新世界吧:[一个强大的木马已经在Linux中被发现][1]。
|
||||
|
||||
没错,迄今为止最牢不可破的计算机世外桃源已经被攻破了,安全专家们都已成惊弓之鸟。
|
||||
|
||||
关掉电脑,拔掉键盘,然后再买只猫(忘掉YouTube吧)。企鹅末日已经降临,我们的日子不多了。
|
||||
|
||||
我去?这是真的吗?依我看,不一定吧~
|
||||
|
||||
### 一次可怕的异常事件! ###
|
||||
|
||||
先声明,**我并没有刻意轻视此次威胁(人们给这个木马起名为‘Turla’)的严重性**,为了避免质疑,我要强调的是,作为Linux用户,我们不应该为此次事件过分担心。
|
||||
|
||||
此次发现的木马能够在人们毫无察觉的情况下感染Linux系统,这是非常可怕的。事实上,它的主要工作是搜寻并向外发送各种类型的敏感信息,这一点同样令人感到恐惧。据了解,它已经存在至少4年时间,而且无需root权限就能完成这些工作。呃,这是要把人吓尿的节奏吗?
|
||||
|
||||
But - 但是 - 新闻稿里常常这个时候该出现‘but’了 - 要说恐慌正在横扫桌面Linux的粉丝,那就有点断章取义、甚至不着边际了。
|
||||
|
||||
对我们中的有些人来说,计算机安全隐患的确是一种新鲜事物,然而我们应该对其审慎对待:对桌面用户来说,Linux仍然是一个天生安全的操作系统。一次瑕疵不应该否定它的一切,我们没有必要慌忙地割断网线。
|
||||
|
||||
### 国家资助,目标政府 ###
|
||||
|
||||

|
||||
|
||||
企鹅和蛇的组合该叫‘企蛇’还是‘蛇鹅’?
|
||||
|
||||
‘Turla’木马是一个复杂、高级的持续威胁,四年多来,它以政府、大使馆以及制药公司的系统为目标,其使用的攻击方式所基于的代码[至少在14年前][2]就已存在了。
|
||||
|
||||
在Windows系统中,安全研究领域来自赛门铁克和卡巴斯基实验室的超级英雄们首先发现了这条黏黏的蛇,他们发现Turla及其组件已经**感染了45个国家的数百台个人电脑**,其中许多都是通过未打补丁的0day漏洞感染的。
|
||||
|
||||
*微软,干得漂亮。*
|
||||
|
||||
经过卡巴斯基实验室的进一步努力,他们发现,同样的木马出现在了Linux上。
|
||||
|
||||
这款木马无需高权限就可以“拦截传入的数据包,在系统中执行传入的命令”,但是它的触角到底有多深,有多少Linux系统被感染,它的完整功能都有哪些,这些目前都暂时还不明朗。
|
||||
|
||||
根据它选定的目标,我们推断“Turla”(及其变种)是由某些民族的国家资助的。美国和英国的读者不要想当然以为这些国家就是“那些国家”。不要忘了我们自己的政府也很乐于趟这摊浑水。
|
||||
|
||||
#### 观点 与 责任 ####
|
||||
|
||||
这次的发现从情感上、技术上、伦理上,都是一次严重的失利,但它远没有达到说我们已经进入一个病毒和恶意软件针对桌面自由肆虐的时代。
|
||||
|
||||
**Turla 并不是那种用户关注的“我想要你的信用卡”病毒**,那些病毒往往绑定在一个伪造的软件下载链接中。Turla是一种复杂的、经过巧妙处理的、具有高度适应性的威胁,它时刻都具有着特定的目标(因此它绝不仅仅满足于搜集一些卖萌少女的网站账户密码,sorry 绿茶婊们!)。
|
||||
|
||||
卡巴斯基实验室是这样介绍的:
|
||||
|
||||
> “Linux上的Turla模块是一个链接多个静态库的C/C++可执行文件,这大大增加了它的文件体积。但它并没有着重减小自身的文件体积,而是剥离了自身的符号信息,这样就增加了对它逆向分析的难度。它的功能主要包括隐藏网络通信、远程执行任意命令以及远程管理等等。它的大部分代码都基于公开源码。”
|
||||
|
||||
不管它的影响和感染率如何,它的技术优势都将不断给那些号称聪明的专家们留下一个又一个问题,就让他们花费大把时间去追踪、分析、解决这些问题吧。
|
||||
|
||||
我不是一个计算机安全专家,但我是一个理智的网络脑残粉,要我说,这次事件应该被看做是一个通(jing)报(gao),而并非有些网站所标榜的洪(shi)水(jie)猛(mo)兽(ri)。
|
||||
|
||||
在更多细节披露之前,我们都不必恐慌。只需继续计算机领域的安全实践,避免从不信任的网站或PPA源下载运行脚本、app或二进制文件,更不要冒险进入web网络的黑暗领域。
|
||||
|
||||
如果你仍然十分担心,你可以前往[卡巴斯基的博客][1]查看更多细节,以确定自己是否感染。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.omgubuntu.co.uk/2014/12/government-spying-turla-linux-trojan-found
|
||||
|
||||
作者:[Joey-Elijah Sneddon][a]
|
||||
译者:[Mr小眼儿](http://blog.csdn.net/tinyeyeser)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://plus.google.com/117485690627814051450/?rel=author
|
||||
[1]:https://securelist.com/blog/research/67962/the-penquin-turla-2/
|
||||
[2]:https://twitter.com/joernchen/status/542060412188262400
|
||||
[3]:https://securelist.com/blog/research/67962/the-penquin-turla-2/
|
||||
@ -1,8 +1,7 @@
|
||||
Linux有问必答-- 如何在Linux上检查SSH的版本
|
||||
Linux有问必答:如何在Linux上检查SSH的版本
|
||||
================================================================================
|
||||
> **Question**:我想到SSH存在1和2两个版本(SSH1和SSH2)。这两者之间有什么不同?还有我该怎么在Linux上检查SSH协议的版本?
|
||||
|
||||
Secure Shell (SSH) is a network protocol that enables remote login or remote command execution between two hosts over a cryptographically secure communication channel. SSH was designed to replace insecure clear-text protocols such as telnet, rsh or rlogin. SSH provides a number of desirable features such as authentication, encryption, data integrity, authorization, and forwarding/tunneling.
|
||||
安全Shell(SSH)通过加密的安全通信通道来远程登录或者远程执行命令。SSH被设计来替代不安全的明文协议,如telnet、rsh和rlogin。SSH提供了大量需要的特性,如认证、加密、数据完整性、授权和转发/通道。
|
||||
|
||||
### SSH1 vs. SSH2 ###
|
||||
@ -11,8 +10,7 @@ SSH协议规范存在一些小版本的差异,但是有两个主要的大版
|
||||
|
||||
事实上,SSH1和SSH2是两个完全不同互不兼容的协议。SSH2明显地提升了SSH1中的很多方面。首先,SSH是宏设计,几个不同的功能(如:认证、传输、连接)被打包进一个单一的协议,SSH2带来了比SSH1更强大的安全特性,如基于MAC的完整性检查,灵活的会话密钥更新、充分协商的加密算法、公钥证书等等。
|
||||
|
||||
SSH2 is standardized by IETF, and as such its implementation is widely deployed and accepted in the industry. Due to SSH2's popularity and cryptographic superiority over SSH1, many products are dropping support for SSH1. As of this writing, OpenSSH still [supports][1] both SSH1 and SSH2, while on all modern Linux distributions, OpenSSH server comes with SSH1 disabled by default.
|
||||
SSH2由IETF标准化,且它的实现在业界被广泛部署和接受。由于SSH2对于SSH1的流行和加密优势,许多产品对SSH1放弃了支持。在写这篇文章的时候,OpenSSH仍旧[支持][1]SSH1和SSH2,然而在所有的现代Linux发行版中,OpenSSH服务器默认禁用了SSH1。
|
||||
SSH2由IETF标准化,且它的实现在业界被广泛部署和接受。由于SSH2对于SSH1的流行和加密优势,许多产品对SSH1放弃了支持。在写这篇文章的时候,OpenSSH仍旧[支持][1]SSH1和SSH2,然而在所有的现代Linux发行版中,OpenSSH服务器默认禁用了SSH1。
|
||||
|
||||
### 检查支持的SSH协议版本 ###
|
||||
|
||||
@ -69,7 +67,7 @@ SSH2由IETF标准化,且它的实现在业界被广泛部署和接受。由于
|
||||
via: http://ask.xmodulo.com/check-ssh-protocol-version-linux.html
|
||||
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,47 +0,0 @@
|
||||
U.S. Marine Corps Wants to Change OS for Radar System from Windows XP to Linux
|
||||
================================================================================
|
||||
**A new radar system has been sent back for upgrade**
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||

|
||||
|
||||

|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
> When it comes to stability and performance, nothing can really beat Linux. This is why the U.S. Marine Corps leaders have decided to ask Northrop Grumman Corp. Electronic Systems to change the operating system of the newly delivered Ground/Air Task-Oriented Radar (G/ATOR) from Windows XP to Linux.
|
||||
|
||||
The Ground/Air Task-Oriented Radar (G/ATOR) system has been in the works for many years and it's very likely that when the project was started, Windows XP could have been considered the logical choice. In the mean time, things changed. Microsoft has pulled the support for Windows XP and very few entities still use it. The operating system is either upgraded or replaced. In this case, Linux is the logical choice, especially since the replacement cost are probably much smaller than an eventual upgrade.
|
||||
|
||||
It's interesting to note that the Ground/Air Task-Oriented Radar (G/ATOR) was just delivered to the U.S. Marine Corps, but the company that built it chose to keep that aging operating system. Someone must have noticed the fact that it was a poor decision and the chain of command was informed of the problems that might have appeared.
|
||||
|
||||
### G/ATOR radar software will be Linux-based ###
|
||||
|
||||
Unix systems, like BSD-based or Linux-based OSes, are usually found in critical areas and technologies that can't fail, under any circumstances. That's why most of the servers out there are running Linux servers, for example. Having a radar system with an operating systems that is very unlikely to crash seems to fit the bill perfectly.
|
||||
|
||||
"Officials of the Marine Corps Systems Command at Quantico Marine Base, Va., announced a $10.2 million contract modification Wednesday to the Northrop Grumman Corp. Electronic Systems segment in Linthicum Heights, Md., to convert the Ground/Air Task-Oriented Radar (G/ATOR) operator command and control computer from Windows XP to Linux. The contract modification will incorporate a change order to switch the G/ATOR control computer from the Microsoft Windows XP operating system to a Defense Information Systems Agency (DISA)-compliant Linux operating system."
|
||||
|
||||
'G/ATOR is an expeditionary, three-dimensional, short-to-medium-range multi-role radar system designed to detect low-observable targets with low radar cross sections such as rockets, artillery, mortars, cruise missiles, and UAVs," reads the entry on [militaryaerospace.com][1].
|
||||
|
||||
This piece of military technology, the Ground/Air Task-Oriented Radar (G/ATOR) was first contracted from the Northrop Grumman Corp. back in 2005, so it's easy to understand why the US Marines might want to hurry this up. No time frame has been proposed for the switch.
|
||||
|
||||
视频链接:[http://youtu.be/H2ppl4x-eu8][2]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://news.softpedia.com/news/U-S-Marine-Corps-Want-to-Change-OS-for-Radar-System-from-Windows-XP-to-Linux-466756.shtml
|
||||
|
||||
作者:[Silviu Stahie][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://news.softpedia.com/editors/browse/silviu-stahie
|
||||
[1]:http://www.militaryaerospace.com/articles/2014/12/gator-linux-software.html
|
||||
[2]:http://youtu.be/H2ppl4x-eu8
|
||||
@ -1,74 +0,0 @@
|
||||
Yes, This Trojan Infects Linux. No, It’s Not The Tuxpocalypse
|
||||
================================================================================
|
||||

|
||||
|
||||
Is something watching you?
|
||||
|
||||
Grab a crate of canned food, start digging a deep underground bunker and prepare to settle into a world that will never be the same again: [a powerful trojan has been uncovered on Linux][1].
|
||||
|
||||
Yes, the hitherto impregnable fortress of computing nirvana has been compromised in a way that has left security experts a touch perturbed.
|
||||
|
||||
Unplug your PC, disinfect your keyboard and buy a cat (no more YouTube ). The Tuxpocalypse is upon us. We’ve reached the end of days.
|
||||
|
||||
Right? RIGHT? Nah, not quite.
|
||||
|
||||
### A Terrifying Anomalous Thing! ###
|
||||
|
||||
Let me set off by saying that **I am not underplaying the severity of this threat (known by the nickname ‘Turla’)** nor, for the avoidance of doubt, am I suggesting that we as Linux users shouldn’t be concerned by the implications.
|
||||
|
||||
The discovery of a silent trojan infecting Linux systems is terrifying. The fact it was tasked with sucking up and sending off all sorts of sensitive information is horrific. And to learn it’s been doing this for at least four years and doesn’t require root privileges? My seat is wet. I’m sorry.
|
||||
|
||||
But — and along with hyphens and typos, there’s always a ‘but’ on this site — the panic currently sweeping desktop Linux fans, Mexican wave style, is a little out of context.
|
||||
|
||||
Vulnerability may be a new feeling for some of us, yet let’s keep it in check: Linux remains an inherently secure operating system for desktop users. One clever workaround does not negate that and shouldn’t send you scurrying offline.
|
||||
|
||||
### State Sponsored, Targeting Governments ###
|
||||
|
||||

|
||||
|
||||
Is a penguin snake a ‘Penguake’ or a ‘Snaguin’?
|
||||
|
||||
‘Turla’ is a complex APT (Advanced Persistent Threat) that has (thus far) targeted government, embassy and pharmaceutical companies’ systems for around four years using a method based on [14 year old code, no less][2].
|
||||
|
||||
On Windows, where the superhero security researchers at Symantec and Kaspersky Lab first sighted the slimy snake, Turla and components of it were found to have **infected hundreds (100s) of PCs across 45 countries**, many through unpatched zero-day exploits.
|
||||
|
||||
*Nice one Microsoft.*
|
||||
|
||||
Further diligence by Kaspersky Lab has now uncovered that parts of the same trojan have also been active on Linux for some time.
|
||||
|
||||
The Trojan doesn’t require elevated privileges and can “intercept incoming packets and run incoming commands on the system”, but it’s not yet clear how deep its tentacles reach or how many Linux systems are infected, nor is the full extent of its capabilities known.
|
||||
|
||||
“Turla” (and its children) are presumed to be nation-state sponsored due to its choice of targets. US and UK readers shouldn’t assume it’s “*them*“, either. Our own governments are just as happy to play in the mud, too.
|
||||
|
||||
#### Perspective and Responsibility ####
|
||||
|
||||
As terrible a breach as this discovery is emotionally, technically and ethically it remains far, far, far away from being an indication that we’re entering a new “free for all” era of viruses and malware aimed at the desktop.
|
||||
|
||||
**Turla is not a user-focused “i wantZ ur CredIt carD” virus** bundled inside a faux software download. It’s a complex, finessed and adaptable threat with specific targets in mind (ergo grander ambitions than collecting a bunch of fruity tube dot com passwords, sorry ego!).
|
||||
|
||||
Kaspersky Lab explains:
|
||||
|
||||
> “The Linux Turla module is a C/C++ executable statically linked against multiple libraries, greatly increasing its file size. It was stripped of symbol information, more likely intended to increase analysis effort than to decrease file size. Its functionality includes hidden network communications, arbitrary remote command execution, and remote management. Much of its code is based on public sources.”
|
||||
|
||||
Regardless of impact or infection rate its precedes will still raise big, big questions that clever, clever people will now spend time addressing, analysing and (importantly) solving.
|
||||
|
||||
IANACSE (I am not a computer security expert) but IAFOA (I am a fan of acronyms), and AFAICT (as far as I can tell) this news should be viewed as as a cautionary PSA or FYI than the kind of OMGGTFO that some sites are painting it as.
|
||||
|
||||
Until more details are known none of us should panic. Let’s continue to practice safe computing. Avoid downloading/running scripts, apps, or binaries from untrusted sites or PPAs, and don’t venture into dodgy dark parts of the web.
|
||||
|
||||
If you remain super concerned you can check out the [Kaspersky blog][1] for details on how to check that you’re not infected.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.omgubuntu.co.uk/2014/12/government-spying-turla-linux-trojan-found
|
||||
|
||||
作者:[Joey-Elijah Sneddon][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://plus.google.com/117485690627814051450/?rel=author
|
||||
[1]:https://securelist.com/blog/research/67962/the-penquin-turla-2/
|
||||
[2]:https://twitter.com/joernchen/status/542060412188262400
|
||||
[3]:https://securelist.com/blog/research/67962/the-penquin-turla-2/
|
||||
@ -1,3 +1,5 @@
|
||||
Translating By H-mudcup
|
||||
|
||||
Easy File Comparisons With These Great Free Diff Tools
|
||||
================================================================================
|
||||
by Frazer Kline
|
||||
@ -163,4 +165,4 @@ via: http://www.linuxlinks.com/article/2014062814400262/FileComparisons.html
|
||||
[2]:https://sourcegear.com/diffmerge/
|
||||
[3]:http://furius.ca/xxdiff/
|
||||
[4]:http://diffuse.sourceforge.net/
|
||||
[5]:http://www.caffeinated.me.uk/kompare/
|
||||
[5]:http://www.caffeinated.me.uk/kompare/
|
||||
|
||||
@ -1,162 +0,0 @@
|
||||
5 Awesome Open Source Backup Software For Linux and Unix-like Systems
|
||||
================================================================================
|
||||
A good backup plan is essential in order to have the ability to recover from
|
||||
|
||||
- Human errors
|
||||
- RAID or disk failure
|
||||
- File system corruption
|
||||
- Data center destruction and more.
|
||||
|
||||
In this post I'm going to list amazingly awesome open source Backup software for you.
|
||||
|
||||
### What to look for when choosing backup software for an enterprise? ###
|
||||
|
||||
Make sure the following features are supported backup software you deploy:
|
||||
|
||||
1. **Open source software** - You must use software for which the original source code is made freely available and may be and modified. This ensures that you can recover your data in case vendor/project stopped working on software or refused to provide patches.
|
||||
1. **Cross-platform support** - Make sure backup software works well on the OS deployed on all desktop and server operating systems.
|
||||
1. **Data format** - Open data format ensures that you can recover data in case vendor or project stopped working on software.
|
||||
1. **Autochangers** - Autochangers are nothing but a variety of backup devices, including library, near-line storage, and autoloader. Autochangers allows you to automate the task of loading, mounting, and labeling backup media such as tape.
|
||||
1. **Backup media** - Make sure you can backup data on tape, disk, DVD and in cloud storage such as AWS.
|
||||
1. **Encryption datastream** - Make sure all client-to-server traffic will be encrypted to ensure transmission integrity over the LAN/WAN/Internet.
|
||||
1. **Database support** - Make sure backup software can backup database server such as MySQL or Oracle.
|
||||
1. **Backup span multiple volumes** - Backup software can split each backup (dumpfile) into a series of parts, allowing for different parts to existing on different volumes. This ensures that large backups (such as 100TB file) can be stored on larger than a single backup device such as disk or tape volume.
|
||||
1. **VSS (Volume Shadow Copy)** - It is [Microsoft's Volume Shadow Copy Service (VSS)][1] and it is used to create snapshots of data that is to be backed up. Make sure backup software support VSS for MS-Windows client/server.
|
||||
1. **[Deduplication][2]** - It is a data compression technique for eliminating duplicate copies of repeating data (for example, images).
|
||||
1. **License and cost** - Make sure you [understand and use of open source license][3] under which the original backup software is made available to you.
|
||||
1. **Commercial support** - Open source software can provide community based (such as email list or fourm) or professional (such as subscriptions provided at additional cost) based support. You can use paid professional support for training and consulting purpose.
|
||||
1. **Reports and alerts** - Finally, you must able to see backup reports, current job status, and get alert when something goes wrong while making backups.
|
||||
|
||||
### Bacula - Client/server backup tool for heterogeneous networks ###
|
||||
|
||||
I personally use this software to manage backup and recovery across a network of computers including Linux, OSX and Windows. You can configure it via a CLI, GUI or web interface.
|
||||
|
||||

|
||||
|
||||
- Operating system : Cross-platform
|
||||
- Backup Levels : Full, differential, incremental, and consolidation.
|
||||
- Data format: Custom but fully open.
|
||||
- Autochangers: Yes
|
||||
- Backup media: Tape/Disk/DVD
|
||||
- Encryption datastream: Yes
|
||||
- Database support: MSSQL/PostgreSQL/Oracle/
|
||||
- Backup span multiple volumes: Yes
|
||||
- VSS: Yes
|
||||
- License : Affero General Public License v3.0
|
||||
- Download url : [bacula.org][4]
|
||||
|
||||
### Amanda - Another good client/server backup tool ###
|
||||
|
||||
AMANDA is an acronym for Advanced Maryland Automatic Network Disk Archiver. It allows the sysadmin to set up a single backup server to back up other hosts over network to tape drives or disk or authchangers.
|
||||
|
||||
- Operating system : Cross-platform
|
||||
- Backup Levels : Full, differential, incremental, and consolidation.
|
||||
- Data format: Open (can be recovered using tool such as tar).
|
||||
- Autochangers: Yes
|
||||
- Backup media: Tape/Disk/DVD
|
||||
- Encryption datastream: Yes
|
||||
- Database support: MSSQL/Oracle
|
||||
- Backup span multiple volumes: Yes
|
||||
- VSS: Yes
|
||||
- License : GPL, LGPL, Apache, Amanda License
|
||||
- Download url : [amanda.org][5]
|
||||
|
||||
### Backupninja - Lightweight backup system ###
|
||||
|
||||
Backupninja is a simple and easy to use backup system. You can simply drop a config files into /etc/backup.d/ to backup multiple hosts.
|
||||
|
||||

|
||||
|
||||
- Operating system : Linux/Unix
|
||||
- Backup Levels : Full and incremental (rsync+hard links)
|
||||
- Data format: Open
|
||||
- Autochangers: N/A
|
||||
- Backup media: Disk/DVD/CD/ISO images
|
||||
- Encryption datastream: Yes (ssh) and [encrypted remote backups via duplicity][6]
|
||||
- Database support: MySQL/PostgreSQL/OpenLDAP and subversion or trac repositories.
|
||||
- Backup span multiple volumes: ??
|
||||
- VSS: ??
|
||||
- License : GPL
|
||||
- Download url : [riseup.net][7]
|
||||
|
||||
### Backuppc - High-performance client/server tool ###
|
||||
|
||||
Backuppc is can be used to backup Linux and Windows based systems to a master server's disk. It comes with a clever pooling scheme minimizes disk storage, disk I/O and network I/O.
|
||||
|
||||

|
||||
|
||||
- Operating system : Linux/Unix and Windows
|
||||
- Backup Levels : Full and incremental (rsync+hard links and pooling scheme)
|
||||
- Data format: Open
|
||||
- Autochangers: N/A
|
||||
- Backup media: Disk/RAID storage
|
||||
- Encryption datastream: Yes
|
||||
- Database support: Yes (via custom shell scripts)
|
||||
- Backup span multiple volumes: ??
|
||||
- VSS: ??
|
||||
- License : GPL
|
||||
- Download url : [backuppc.sourceforge.net][8]
|
||||
|
||||
### UrBackup - Easy to setup client/server system ###
|
||||
|
||||
It is an easy to setup open source client/server backup system, that through a combination of image and file backups accomplishes both data safety and a fast restoration time. Your files can be restored through the web interface or the Windows Explorer while the backups of drive volumes can be restored with a bootable CD or USB-Stick (bare metal restore). A web interface makes setting up your own backup server really easy.
|
||||
|
||||

|
||||
|
||||
- Operating system : Linux/FreeBSD/Unix/Windows/several Linux based NAS operating systems. Client only runs on Linux and Windows.
|
||||
- Backup Levels : Full and incremental
|
||||
- Data format: Open
|
||||
- Autochangers: N/A
|
||||
- Backup media: Disk/Raid storage/DVD
|
||||
- Encryption datastream: Yes
|
||||
- Database support: ??
|
||||
- Backup span multiple volumes: ??
|
||||
- VSS: ??
|
||||
- License : GPL v3+
|
||||
- Download url : [urbackup.org][9]
|
||||
|
||||
### Other awesome open source backup software for your consideration ###
|
||||
|
||||
The Amanda, Bacula and above-mentioned software are feature rich but can be complicated to set for small network or a single server. I recommend that you study and use the following backup software:
|
||||
|
||||
1. [Rsnapshot][10] - I recommend this tool for local and remote filesystem snapshot utility. See how to set and use [this tool on Debian/Ubuntu Linux][11] and [CentOS/RHEL based systems][12].
|
||||
1. [rdiff-backup][13] - Another great remote incremental backup tool for Unix-like systems.
|
||||
1. [Burp][14] - Burp is a network backup and restore program. It uses librsync in order to save network traffic and to save on the amount of space that is used by each backup. It also uses VSS (Volume Shadow Copy Service) to make snapshots when backing up Windows computers.
|
||||
1. [Duplicity][15] - Great encrypted bandwidth-efficient backup for Unix-like system. See how to [Install Duplicity for encrypted backup in cloud][16] for more infomation.
|
||||
1. [SafeKeep][17] - SafeKeep is a centralized and easy to use backup application that combines the best features of a mirror and an incremental backup.
|
||||
1. [DREBS][18] - DREBS is a tool for taking periodic snapshots of EBS volumes. It is designed to be run on the EC2 host which the EBS volumes to be snapshoted are attached.
|
||||
1. Old good unix programs like rsync, tar, cpio, mt and dump.
|
||||
|
||||
### Conclusion ###
|
||||
|
||||
I hope you will find this post useful to backup your important data. Do not forgot to verify your backups and make multiple backup copies of your data. Also, RAID is not a backup solution. Use any one of the above-mentioned programs to backup your servers, desktop/laptop and personal mobile devices. If you know of any other open source backup software I didn't mention, share them in the comments below.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.cyberciti.biz/open-source/awesome-backup-software-for-linux-unix-osx-windows-systems/
|
||||
|
||||
作者:[nixCraft][a]
|
||||
译者:[barney-ro](https://github.com/barney-ro)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.cyberciti.biz/tips/about-us
|
||||
[1]:http://technet.microsoft.com/en-us/library/cc785914(v=ws.10).aspx
|
||||
[2]:http://en.wikipedia.org/wiki/Data_deduplication
|
||||
[3]:http://opensource.org/licenses
|
||||
[4]:http://www.bacula.org/
|
||||
[5]:http://www.amanda.org/
|
||||
[6]:http://www.cyberciti.biz/faq/duplicity-installation-configuration-on-debian-ubuntu-linux/
|
||||
[7]:https://labs.riseup.net/code/projects/backupninja
|
||||
[8]:http://backuppc.sourceforge.net/
|
||||
[9]:http://www.urbackup.org/
|
||||
[10]:http://www.rsnapshot.org/
|
||||
[11]:http://www.cyberciti.biz/faq/linux-rsnapshot-backup-howto/
|
||||
[12]:http://www.cyberciti.biz/faq/redhat-cetos-linux-remote-backup-snapshot-server/
|
||||
[13]:http://www.nongnu.org/rdiff-backup/
|
||||
[14]:http://burp.grke.org/
|
||||
[15]:http://www.cyberciti.biz/open-source/awesome-backup-software-for-linux-unix-osx-windows-systems/
|
||||
[16]:http://www.cyberciti.biz/faq/duplicity-installation-configuration-on-debian-ubuntu-linux/
|
||||
[17]:http://safekeep.sourceforge.net/
|
||||
[18]:https://github.com/dojo4/drebs
|
||||
@ -1,55 +0,0 @@
|
||||
Flow ‘N Play Movie Player Has a Stylish Interface [Ubuntu Installation]
|
||||
================================================================================
|
||||
**Flow ‘N Play** is a new video player written in Qt which features a pretty slick and simple interface which provides only the basic features for playing movies.
|
||||
|
||||
|
||||
|
||||
[Flow ‘N Play][1] is relatively new video player (the first release was made earlier this year in March) with a beautiful interface and a pretty simple approach, with one of the features being the possibility to slide over the list of movies by dragging the mouse. The player comes with basic functionality, a search function, support for colored themes.
|
||||
|
||||
Opening a new video – you can also choose a custom cover in the same dialog:
|
||||
|
||||
|
||||
|
||||
The Settings dialog – customize some basic options here:
|
||||
|
||||
|
||||
|
||||
Flow ‘N Play is still in early development though, and as such it has a few downsides over more advanced players. There are few options to customize it, no support for subtitles or video and audio filters. Currently there seems to be either a bug or strange behavior upon opening a new movie, which doesn’t always start automatically.
|
||||
|
||||
I believe a few more features could be added before it gets to being usable as a decent alternative to other players, but given the time, Flow ‘N Play looks really promising.
|
||||
|
||||
### Install Flow ‘N Play 0.922 in Ubuntu 14.04 ###
|
||||
|
||||
There are several different ways to install Flow N’ Play in Ubuntu. There are DEB packages, RUN Bash installers, and standalone binaries available on the [Qt-Apps page][2].
|
||||
|
||||
To install Flow ‘N Play first get the dependencies:
|
||||
|
||||
sudo apt-get install libqt5multimediaquick-p5 qtdeclarative5-controls-plugin qtdeclarative5 qtmultimedia-plugin qtdeclarative5-qtquick2-plugin qtdeclarative5-quicklayouts-plugin
|
||||
|
||||
Then download the DEB package and either double click it or change the working directory to the one where you saved it and type the following in a terminal (for 64-bit, replace the DEB file for 32-bit):
|
||||
|
||||
sudo dpkg -i flow-n-play_v0.926_qt-5.3.2_x64.deb
|
||||
|
||||
Then type **flow-n-play** in a terminal to run it. Notice that in case you get dependency errors when trying to install the DEB file, you can run **sudo apt-get -f install**, which will fetch the missing dependencies automatically and will install Flow ‘N Play as well.
|
||||
|
||||
To install Flow ‘N Play using the RUN script, install the dependencies mentioned above and then run the script:
|
||||
|
||||
wget -O http://www.prest1ge-c0ding.24.eu/programs/Flow-N-Play/v0.926/bin/flow-n-play_v0.926_qt-5.3.2_x64.run
|
||||
sudo ./flow-n-play_v0.926_qt-5.3.2_x64.run
|
||||
|
||||
The third method is to install it manually to a location of your choice (just download the binary provided after installing the dependencies) e.g. for 32-bit:
|
||||
|
||||
wget -O http://www.prest1ge-c0ding.24.eu/programs/Flow-N-Play/v0.926/bin/Flow-N-Play_v0.926_Qt-5.3.2_x86
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.tuxarena.com/2014/11/flow-n-play-movie-player-has-a-stylish-interface-ubuntu-installation/
|
||||
|
||||
作者:Craciun Dan
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.prest1ge-c0ding.24.eu/programme-php/app-flow_n_play.php?lang=en
|
||||
[2]:http://qt-apps.org/content/show.php/Flow+%27N+Play?content=167736
|
||||
@ -1,62 +0,0 @@
|
||||
Tomahawk Music Player Returns With New Look, Features
|
||||
================================================================================
|
||||
**After a quiet year Tomahawk, the Swiss Army knife of music players, is back with a brand new release to sing about. **
|
||||
|
||||

|
||||
|
||||
Version 0.8 of the open-source and cross-platform app adds **support for more online services**, refreshes its appearance, and doubles down on making sure its innovative social features work flawlessly.
|
||||
|
||||
### Tomahawk — The Best of Both Worlds ###
|
||||
|
||||
Tomahawk marries a traditional app structure with the modernity of our “on demand” culture. It can browse and play music from local libraries as well as online services like Spotify, Grooveshark, and SoundCloud. In its latest release it adds Google Play Music and Beats Music to its roster.
|
||||
|
||||
That may sound cumbersome or confusing on paper but in practice it all works fantastically.
|
||||
|
||||
When you want to play a song, and don’t care where it’s played back from, you just tell Tomahawk the track title and artist and it automatically finds a high-quality version from enabled sources — you don’t need to do anything.
|
||||
|
||||

|
||||
|
||||
The app also sports some additional features, like EchoNest profiling, Last.fm suggestions, and Jabber support so you can ‘play’ friends’ music. There’s also a built-in messaging service so you can quickly share playlists and tracks with others.
|
||||
|
||||
> “This fundamentally different approach to music enables a range of new music consumption and sharing experiences previously not possible,” the project says on its website. And with little else like it, it’s not wrong.
|
||||
|
||||
|
||||
|
||||
Tomahawk supports the Sound Menu
|
||||
|
||||
### Tomahawk 0.8 Release Highlights ###
|
||||
|
||||
- New UI
|
||||
- Support for Beats Music support
|
||||
- Support for Google Play Music (stored and Play All Access)
|
||||
- Support for drag and drop iTunes, Spotify, etc. web links
|
||||
- Now Playing notifications
|
||||
- Android app (beta)
|
||||
- Inbox improvements
|
||||
|
||||
### Install Tomahawk 0.8 in Ubuntu ###
|
||||
|
||||
As a big music streaming user I’ll be using the app over the next few days to get a fuller appreciation of the changes on offer. In the mean time, to go hands on for yourself, you can.
|
||||
|
||||
Tomahawk 0.8 is available for Ubuntu 14.04 LTS and Ubuntu 14.10 via an official PPA.
|
||||
|
||||
sudo add-apt-repository ppa:tomahawk/ppa
|
||||
|
||||
sudo apt-get update && sudo apt-get install tomahawk
|
||||
|
||||
Standalone installers, and more information, can be found on the official project website.
|
||||
|
||||
- [Visit the Official Tomahawk Website][1]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.omgubuntu.co.uk/2014/11/tomahawk-media-player-returns-new-look-features
|
||||
|
||||
作者:[Joey-Elijah Sneddon][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://plus.google.com/117485690627814051450/?rel=author
|
||||
[1]:http://gettomahawk.com/
|
||||
@ -1,70 +0,0 @@
|
||||
Calife – A lightweight alternative to sudo
|
||||
================================================================================
|
||||
Calife requests user's own password for becoming login (or root, if no login is provided), and switches to that user and group ID after verifying proper rights to do so. A shell is then executed. If calife is executed by root, no password is requested and a shell with the appropriate user ID is executed.
|
||||
|
||||
The invoked shell is the user's own except when a shell is specified in the configuration file calife.auth.
|
||||
|
||||
If "-" is specified on the command line, user's profile files are read as if it was a login shell.
|
||||
|
||||
This is not the traditional behavior of su.
|
||||
|
||||
Only users specified in calife.auth can use calife to become another one with this method.
|
||||
|
||||
calife.auth is installed as /etc/calife.auth
|
||||
|
||||
### Calife Features ###
|
||||
|
||||
Here is an extensive list of features:
|
||||
|
||||
you keep your environment variables and shell aliases intact
|
||||
it has start and end of session logging
|
||||
you can have a list of all permitted logins for each calife user. That way, you can give a user newsmaster’s rights without giving out the root password
|
||||
you can specify a group in the configuration file instead of the logins of all administrators: Juste use @staff or %staff and all members of the staff group will have access to calife
|
||||
calife can also be used to become users even if they have no home directory or even no shell. That’s very practical if you want to become uucp or even bin
|
||||
you can make calife runs a specific system-wide script at the end of the session (to send a mailabout what was done as root for example)
|
||||
|
||||
### Install calife in ubuntu ###
|
||||
|
||||
Open the terminal and run the following command
|
||||
|
||||
sudo apt-get install calife
|
||||
|
||||
### Using Calife ###
|
||||
|
||||
### Syntax ###
|
||||
|
||||
calife [-] [login]
|
||||
|
||||
Check calife manpage for more details
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.ubuntugeek.com/calife-a-lightweight-alternative-to-sudo.html
|
||||
|
||||
作者:[ruchi][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.ubuntugeek.com/author/ubuntufix
|
||||
[1]:
|
||||
[2]:
|
||||
[3]:
|
||||
[4]:
|
||||
[5]:
|
||||
[6]:
|
||||
[7]:
|
||||
[8]:
|
||||
[9]:
|
||||
[10]:
|
||||
[11]:
|
||||
[12]:
|
||||
[13]:
|
||||
[14]:
|
||||
[15]:
|
||||
[16]:
|
||||
[17]:
|
||||
[18]:
|
||||
[19]:
|
||||
[20]:
|
||||
@ -1,47 +0,0 @@
|
||||
How to Download Music from Grooveshark with a Linux OS
|
||||
================================================================================
|
||||
> The solution is actually much simpler than you think
|
||||
|
||||

|
||||
|
||||
**Grooveshark is a great online platform for people who want to listen to music, and there are a number of ways to download music from there. Groovesquid is just one of the applications that let users get music from Grooveshark, and it's multiplatform.**
|
||||
|
||||
If there is a service that streams something online, then there is a way to download the stuff that you are just watching or listening. As it turns out, it's not that difficult and there are a ton of solutions, no matter the platform. For example, there are dozens of YouTube downloaders and it stands to reason that it's not all that difficult to get stuff from Grooveshark either.
|
||||
|
||||
Now, there is the problem of legality. Like many other applications out there, Groovesquid is not actually illegal. It's the user's fault if they do something illegal with an application. The same reasoning can be applied to apps like utorrent or Bittorrent. As long as you don't touch copyrighted material, there are no problems in using Groovesquid.
|
||||
|
||||
### Groovesquid is fast and efficient ###
|
||||
|
||||
The only problem that you could find with Groovesquid is the fact that it's based on Java and that's never a good sign. This is a good way to ensure that an application runs on all the platforms, but it's an issue when it comes to the interface. It's not great, but it doesn't really matter all that much for users, especially since the app is doing a great job.
|
||||
|
||||
There is one caveat though. Groovesquid is a free application, but in order to remain free, it has to display an ad on the right side of the menu. This shouldn't be a problem for most people, but it's a good idea to mention that right from the start.
|
||||
|
||||
From a usability point of view, the application is pretty straightforward. Users can download a single song by entering the link in the top field, but the purpose of that field can be changed by accessing the small drop-down menu to its left. From there, it's possible to change to Song, Popular, Albums, Playlist, and Artist. Some of the options provide access to things like the most popular song on Grooveshark and other options allow you to download an entire playlist, for example.
|
||||
|
||||
You can download Groovesquid 0.7.0
|
||||
|
||||
- [jar][1] File size: 3.8 MB
|
||||
- [tar.gz][2] File size: 549 KB
|
||||
|
||||
You will get a Jar file and all you have to do is to make it executable and let Java do the rest.
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||

|
||||
|
||||

|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://news.softpedia.com/news/How-to-Download-Music-from-Grooveshark-with-a-Linux-OS-468268.shtml
|
||||
|
||||
作者:[Silviu Stahie][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://news.softpedia.com/editors/browse/silviu-stahie
|
||||
[1]:https://github.com/groovesquid/groovesquid/releases/download/v0.7.0/Groovesquid.jar
|
||||
[2]:https://github.com/groovesquid/groovesquid/archive/v0.7.0.tar.gz
|
||||
@ -0,0 +1,104 @@
|
||||
[zhouj-sh translating...]
|
||||
2 Ways To Fix The UEFI Bootloader When Dual Booting Windows And Ubuntu
|
||||
================================================================================
|
||||
The main problem that users experience after following my [tutorials for dual booting Ubuntu and Windows 8][1] is that their computer continues to boot directly into Windows 8 with no option for running Ubuntu.
|
||||
|
||||
Here are two ways to fix the EFI boot loader to get the Ubuntu portion to boot correctly.
|
||||
|
||||

|
||||
|
||||
### 1. Make GRUB The Active Bootloader ###
|
||||
|
||||
There are a few things that may have gone wrong during the installation.
|
||||
|
||||
In theory if you have managed to install Ubuntu in the first place then you will have [turned off fast boot][2].
|
||||
|
||||
Hopefully you [followed this guide to create a bootable UEFI Ubuntu USB drive][3] as this installs the correct UEFI boot loader.
|
||||
|
||||
If you have done both of these things as part of the installation, the bit that may have gone wrong is the part where you set GRUB2 as the boot manager.
|
||||
|
||||
To set GRUB2 as the default bootloader follow these steps:
|
||||
|
||||
1.Login to Windows 8
|
||||
2.Go to the desktop
|
||||
3.Right click on the start button and choose administrator command prompt
|
||||
4.Type mountvol g: /s (This maps your EFI folder structure to the G drive).
|
||||
5.Type cd g:\EFI
|
||||
6.When you do a directory listing you will see a folder for Ubuntu. Type dir.
|
||||
7.There should be options for grubx64.efi and shimx64.efi
|
||||
8.Run the following command to set grubx64.efi as the bootloader:
|
||||
|
||||
bcdedit /set {bootmgr} path \EFI\ubuntu\grubx64.efi
|
||||
|
||||
9:Reboot your computer
|
||||
10:You should now have a GRUB menu appear with options for Ubuntu and Windows.
|
||||
11:If your computer still boots straight to Windows repeat steps 1 through 7 again but this time type:
|
||||
|
||||
bcdedit /set {bootmgr} path \EFI\ubuntu\shimx64.efi
|
||||
|
||||
12:Reboot your computer
|
||||
|
||||
What you are doing here is logging into the Windows administration command prompt, mapping a drive to the EFI partition so that you can see where the Ubuntu bootloaders are installed and then either choosing grubx64.efi or shimx64.efi as the bootloader.
|
||||
|
||||
So [what is the difference between grubx64.efi and shimx64.efi][4]? You should choose grubx64.efi if secureboot is turned off. If secureboot is turned on you should choose shimx64.efi.
|
||||
|
||||
In my steps above I have suggested trying one and then trying another. The other option is to install one and then turn secure boot on or off within the UEFI firmware for your computer depending on the bootloader you chose.
|
||||
|
||||
### 2. Use rEFInd To Dual Boot Windows 8 And Ubuntu ###
|
||||
The [rEFInd boot loader][5] works by listing all of your operating systems as icons. You will therefore be able to boot Windows, Ubuntu and operating systems from USB drives simply by clicking the appropriate icon.
|
||||
|
||||
To download rEFInd for Windows 8 [click here][6].
|
||||
|
||||
After you have downloaded the file extract the zip file.
|
||||
|
||||
Now follow these steps to install rEFInd.
|
||||
|
||||
1.Go to the desktop
|
||||
2.Right click on the start button and choose administrator command prompt
|
||||
3.Type mountvol g: /s (This maps your EFI folder structure to the G drive)
|
||||
4.Navigate to the extracted rEFInd folder. For example:
|
||||
|
||||
cd c:\users\gary\downloads\refind-bin-0.8.4\refind-bin-0.8.4
|
||||
|
||||
When you type dir you should see a folder for refind
|
||||
5.Type the following to copy refind to the EFI partition:
|
||||
|
||||
xcopy /E refind g:\EFI\refind\
|
||||
|
||||
6.Type the following to navigate to the refind folder
|
||||
|
||||
cd g:\EFI\refind
|
||||
|
||||
7.Rename the sample configuration file:
|
||||
|
||||
rename refind.conf-sample refind.conf
|
||||
8.Run the following command to set rEFInd as the bootloader
|
||||
|
||||
bcdedit /set {bootmgr} path \EFI\refind\refind_x64.efi
|
||||
|
||||
9.Reboot your computer
|
||||
10.You should now have a menu similar to the image above with options to boot Windows and Ubuntu
|
||||
|
||||
This process is fairly similar to choosing the GRUB bootloader.
|
||||
|
||||
Basically it involves downloading rEFInd, extracting the files. copying the files to the EFI partition, renaming the configuration file and then setting rEFInd as the boot loader.
|
||||
|
||||
### Summary ###
|
||||
|
||||
Hopefully this guide has solved the issues that some of you have been having with dual booting Ubuntu and Windows 8.1. If you are still having issues feel free to get back in touch using the email link above.
|
||||
|
||||
|
||||
作者:[Gary Newell][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
via:http://linux.about.com/od/LinuxNewbieDesktopGuide/tp/3-Ways-To-Fix-The-UEFI-Bootloader-When-Dual-Booting-Windows-And-Ubuntu.htm
|
||||
[a]:http://linux.about.com/bio/Gary-Newell-132058.htm
|
||||
[1]:http://linux.about.com/od/LinuxNewbieDesktopGuide/ss/The-Ultimate-Windows-81-And-Ubuntu-
|
||||
[2]:http://linux.about.com/od/howtos/ss/How-To-Create-A-UEFI-Bootable-Ubuntu-USB-Drive-Using-Windows_3.htm#step-heading
|
||||
[3]:http://linux.about.com/od/howtos/ss/How-To-Create-A-UEFI-Bootable-Ubuntu-USB-Drive-Using-Windows.htm
|
||||
[4]:https://wiki.ubuntu.com/SecurityTeam/SecureBoot
|
||||
[5]:http://www.rodsbooks.com/refind/installing.html#windows
|
||||
[6]:http://sourceforge.net/projects/refind/files/0.8.4/refind-bin-0.8.4.zip/download
|
||||
@ -0,0 +1,59 @@
|
||||
This App Can Write a Single ISO to 20 USB Drives Simultaneously
|
||||
================================================================================
|
||||
**If I were to ask you to burn a single Linux ISO to 17 USB thumb drives how would you go about doing it?**
|
||||
|
||||
Code savvy folks would write a little bash script to automate the process, and a large number would use a GUI tool like the USB Startup Disk Creator to burn the ISO to each drive in turn, one by one. But the rest of us would fast conclude that neither method is ideal.
|
||||
|
||||
### Problem > Solution ###
|
||||
|
||||
|
||||
|
||||
GNOME MultiWriter in action
|
||||
|
||||
Richard Hughes, a GNOME developer, faced a similar dilemma. He wanted to create a number of USB drives pre-loaded with an OS, but wanted a tool simple enough for someone like his dad to use.
|
||||
|
||||
His response was to create a **brand new app** that combines both approaches into one easy to use tool.
|
||||
|
||||
It’s called “[GNOME MultiWriter][1]” and lets you write a single ISO or IMG to multiple USB drives at the same time.
|
||||
|
||||
It nixes the need to customize or create a command line script and relinquishes the need to waste an afternoon performing an identical set of actions on repeat.
|
||||
|
||||
All you need is this app, an ISO, some thumb-drives and lots of empty USB ports.
|
||||
|
||||
### Use Cases and Installing ###
|
||||
|
||||

|
||||
|
||||
The app can be installed on Ubuntu
|
||||
|
||||
The app has a pretty defined usage scenario, that being situations where USB sticks pre-loaded with an OS or live image are being distributed.
|
||||
|
||||
That being said, it should work just as well for anyone wanting to create a solitary bootable USB stick, too — and since I’ve never once successfully created a bootable image from Ubuntu’s built-in disk creator utility, working alternatives are welcome news to me!
|
||||
|
||||
Hughes, the developer, says it **supports up to 20 USB drives**, each being between 1GB and 32GB in size.
|
||||
|
||||
The drawback (for now) is that GNOME MultiWriter is not a finished, stable product. It works, but at this early blush there are no pre-built binaries to install or a PPA to add to your overstocked software sources.
|
||||
|
||||
If you know your way around the usual configure/make process you can get it up and running in no time. On Ubuntu 14.10 you may also need to install the following packages first:
|
||||
|
||||
sudo apt-get install gnome-common yelp-tools libcanberra-gtk3-dev libudisks2-dev gobject-introspection
|
||||
|
||||
If you get it up and running, give it a whirl and let us know what you think!
|
||||
|
||||
Bugs and pull requests can be longed on the GitHub page for the project, which is where you’ll also found tarball downloads for manual installation.
|
||||
|
||||
- [GNOME MultiWriter on Github][2]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.omgubuntu.co.uk/2015/01/gnome-multiwriter-iso-usb-utility
|
||||
|
||||
作者:[Joey-Elijah Sneddon][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://plus.google.com/117485690627814051450/?rel=author
|
||||
[1]:https://github.com/hughsie/gnome-multi-writer/
|
||||
[2]:https://github.com/hughsie/gnome-multi-writer/
|
||||
@ -1,3 +1,5 @@
|
||||
translating by barney-ro
|
||||
|
||||
2015 will be the year Linux takes over the enterprise (and other predictions)
|
||||
================================================================================
|
||||
> Jack Wallen removes his rose-colored glasses and peers into the crystal ball to predict what 2015 has in store for Linux.
|
||||
@ -62,7 +64,7 @@ What are your predictions for Linux and open source in 2015? Share your thoughts
|
||||
via: http://www.techrepublic.com/article/2015-will-be-the-year-linux-takes-over-the-enterprise-and-other-predictions/
|
||||
|
||||
作者:[Jack Wallen][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
译者:[barney-ro](https://github.com/barney-ro)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,3 +1,4 @@
|
||||
[translating by KayGuoWhu]
|
||||
A brief history of Linux malware
|
||||
================================================================================
|
||||
A look at some of the worms and viruses and Trojans that have plagued Linux throughout the years.
|
||||
|
||||
@ -1,100 +0,0 @@
|
||||
The Good, The Bad And The Ugly Of Linux In 2014
|
||||
================================================================================
|
||||

|
||||
|
||||
Year 2014 is coming to an end and this is the time to summarize some of the **biggest Linux stories in year 2014**. All year round we have followed some good, some bad and some ugly stories related to Linux and Open Source. Let’ have a quick recap on how was the year 2014 for Linux.
|
||||
|
||||
### The Good ###
|
||||
|
||||
First and foremost, let’s see what were the positive stories for Linux lovers in 2014.
|
||||
|
||||
#### Netflix on Linux ####
|
||||
|
||||

|
||||
|
||||
Linux users have been trying several workaround to make Netflix work on Linux from using Wine to [using beta features in Chrome][1]. Good thing is that Netflix finally brought native support on Linux in year 2014 bringing smiles on the faces of Linux users where Netflix is available. People would still have to rely on workaround to [use Netflix outside US][2] (and other countries where Netflix is available officially).
|
||||
|
||||
#### Open Source/Linux adoption in European countries ####
|
||||
|
||||

|
||||
|
||||
Give the credit to economic meltdown, if you want, but Linux and Open Source adoption has been gripping European cities. I am not talking about Linux adoption by individuals but by government and authorities. All year round we heard stories of how [French][3] and [Italian cities saved millions of Euro by switching to Linux][4] and Open Office. And the trend was not limited just to Italy and France, the same could be seen in Spain, [Switzerland][5] and [Germany][6].
|
||||
|
||||
#### Windows 10 takes inspiration from Linux ####
|
||||
|
||||

|
||||
|
||||
The upcoming release of Microsoft’s flagship operating system, Windows will be called Windows 10 (no Windows 9). And Windows 10 boasts of a number of new features. But these ‘new features’ are new to Microsoft world only and most of those have been existing in Linux world for years. Have a look at such [Windows 10 features copied from Linux][7].
|
||||
|
||||
### The Bad ###
|
||||
|
||||
Everything was not rosy for Linux in year 2014. Some events happened that dented the image of Linux/Open Source.
|
||||
|
||||
#### Heartbleed ####
|
||||
|
||||

|
||||
|
||||
In April this year, a vulnerability was detected in [OpenSSL][8]. This bug, named [Heartbleed][9], impacted over half a million ‘secured’ websites including Facebook and Google. The bug actually allowed anyone to read memory of the system and hence giving the access to the key that is used to encrypt the traffic. A [comic at xkcd explains the Heartbleed][10] in easier way. Needless to say that this vulnerability was fixed in an update to OpenSSL.
|
||||
|
||||
#### Shellshock ####
|
||||
|
||||

|
||||
|
||||
As if Heartbleed was not enough, Linux world was further rocked in September with a vulnerability in Bash. The bug, named [Shellshock][11], further put Linux system at risk of remote attacks. The vulnerability was exploited by hackers to launch DDoS attacks. An update to Bash version supposedly fixed the issue.
|
||||
|
||||
#### Ubuntu Phone and Steam Console ####
|
||||
|
||||

|
||||
|
||||
Promises after promises, hopes after hopes. But even in year 2014 no one saw Ubuntu Phone or Steam gaming consoles. Lots of talks were around Ubuntu Phone tough. From February 2014 release to September to December, finally it is (hopefully slotted) for February 2015 release. No information on Steam consoles though. Read more for [Ubuntu Phone specification, price and release date][12].
|
||||
|
||||
### The Ugly ###
|
||||
|
||||
Things turned ugly with war over systemd adoption.
|
||||
|
||||
### systemd controversy ###
|
||||
|
||||

|
||||
|
||||
[init vs systemd][13] dispute is going on for some time. But it turned ugly in 2014 as systemd poised to replace init on several major Linux distribution including Debian, Ubuntu, OpenSUSE, Arch Linux and Fedora. It turned so ugly that it was not just limited to boycottsystemd.org like websites. Lennart Poettering (lead developer and author of systemd) claimed in a [Google Plus post][14] that anti systemd people were “collecting bitcoins to hire a hitman to kill him”. Lennart went on calling Open Source community “a sick place to be in”. People have taken this battle as far as forking Debian to a new OS named [Devuan][15].
|
||||
|
||||
### And the weird ###
|
||||
|
||||
Along with the good, the bad and the ugly comes the weird and that weird is none other than Microsoft.
|
||||
|
||||
#### Microsoft loves Linux ####
|
||||
|
||||

|
||||
|
||||
Yes! You read it right. [Microsoft loves Linux][16]. The same Microsoft whose CEO Steve Ballmer had once said that [Linux is cancer][17]. Change in Microsoft leadership saw some changes in its approach towards Linux and Open Source when the new CEO Satya Nadella announced that Microsoft loves Linux. This new found love for Linux is actually Microsoft’s attempt to make [Azure][18] as a better cloud platform. For this purpose it needs Hyper-V (core of Azure) virtualization to work with Linux. This desperation has made [Microsoft, fifth biggest contributor to Linux kernel][19].
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://itsfoss.com/biggest-linux-stories-2014/
|
||||
|
||||
作者:[Abhishek][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://itsfoss.com/author/Abhishek/
|
||||
[1]:http://itsfoss.com/watch-netflix-in-ubuntu-14-04/
|
||||
[2]:http://itsfoss.com/easiest-watch-netflix-hulu-usa/
|
||||
[3]:http://itsfoss.com/french-city-toulouse-saved-1-million-euro-libreoffice/
|
||||
[4]:http://itsfoss.com/italian-city-turin-open-source/
|
||||
[5]:http://itsfoss.com/170-primary-public-schools-geneva-switch-ubuntu/
|
||||
[6]:http://itsfoss.com/german-town-gummersbach-completes-switch-open-source/
|
||||
[7]:http://itsfoss.com/windows-10-inspired-linux/
|
||||
[8]:http://en.wikipedia.org/wiki/OpenSSL
|
||||
[9]:http://heartbleed.com/
|
||||
[10]:http://xkcd.com/1354/
|
||||
[11]:http://itsfoss.com/linux-shellshock-check-fix/
|
||||
[12]:http://itsfoss.com/ubuntu-phone-specification-release-date-pricing/
|
||||
[13]:http://www.tecmint.com/systemd-replaces-init-in-linux/
|
||||
[14]:https://plus.google.com/+LennartPoetteringTheOneAndOnly/posts/J2TZrTvu7vd
|
||||
[15]:http://debianfork.org/
|
||||
[16]:http://thenewstack.io/microsoft-professes-love-for-linux-adds-support-for-coreos-cloudera-and-host-of-new-features/
|
||||
[17]:http://www.theregister.co.uk/2001/06/02/ballmer_linux_is_a_cancer/
|
||||
[18]:http://azure.microsoft.com/en-us/
|
||||
[19]:http://www.zdnet.com/article/top-five-linux-contributor-microsoft/
|
||||
@ -0,0 +1,47 @@
|
||||
2015: Open Source Has Won, But It Isn't Finished
|
||||
================================================================================
|
||||
> After the wins of 2014, what's next?
|
||||
|
||||
At the beginning of a new year, it's traditional to look back over the last 12 months. But as far as this column is concerned, it's easy to summarise what happened then: open source has won. Let's take it from the top:
|
||||
|
||||
**Supercomputers**. Linux is so dominant on the Top 500 Supercomputers lists it is almost embarrassing. The [November 2014 figures][1] show that 485 of the top 500 systems were running some form of Linux; Windows runs on just one. Things are even more impressive if you look at the numbers of cores involved. Here, Linux is to be found on 22,851,693 of them, while Windows is on just 30,720; what that means is that not only does Linux dominate, it is particularly strong on the bigger systems.
|
||||
|
||||
**Cloud computing**. The Linux Foundation produced an interesting [report][2] last year, which looked at the use of Linux in the cloud by large companies. It found that 75% of them use Linux as their primary platform there, against just 23% that use Windows. It's hard to translate that into market share, since the mix between cloud and non-cloud needs to be factored in; however, given the current popularity of cloud computing, it's safe to say that the use of Linux is high and increasing. Indeed, the same survey found Linux deployments in the cloud have increased from 65% to 79%, while those for Windows have fallen from 45% to 36%. Of course, some may not regard the Linux Foundation as totaly disinterested here, but even allowing for that, and for statistical uncertainties, it's pretty clear which direction things are moving in.
|
||||
|
||||
**Web servers**. Open source has dominated this sector for nearly 20 years - an astonishing record. However, more recently there's been some interesting movement in market share: at one point, Microsoft's IIS managed to overtake Apache in terms of the total number of Web servers. But as Netcraft explains in its most recent [analysis][3], there's more than meets the eye here:
|
||||
|
||||
> This is the second month in a row where there has been a large drop in the total number of websites, giving this month the lowest count since January. As was the case in November, the loss has been concentrated at just a small number of hosting companies, with the ten largest drops accounting for over 52 million hostnames. The active sites and web facing computers metrics were not affected by the loss, with the sites involved being mostly advertising linkfarms, having very little unique content. The majority of these sites were running on Microsoft IIS, causing it to overtake Apache in the July 2014 survey. However the recent losses have resulted in its market share dropping to 29.8%, leaving it now over 10 percentage points behind Apache.
|
||||
|
||||
As that indicates, Microsoft's "surge" was more apparent than real, and largely based on linkfarms with little useful content. Indeed, Netcraft's figures for active sites paints a very different picture: Apache has 50.57% market share, with nginx second on 14.73%; Microsoft IIS limps in with a rather feeble 11.72%. This means that open source has around 65% of the active Web server market - not quite at the supercomputer level, but pretty good.
|
||||
|
||||
**Mobile systems**. Here, the march of open source as the foundation of Android continues. Latest figures show that Android accounted for [83.6%][4] of smartphone shipments in the third quarter of 2014, up from 81.4% in the same quarter the previous year. Apple achieved 12.3%, down from 13.4%. As far as tablets are concerned, Android is following a similar trajectory: for the second quarter of 2014, Android notched up around [75% of global tablet sales][5], while Apple was on 25%.
|
||||
|
||||
**Embedded systems**. Although it's much harder to quantify the market share of Linux in the important embedded system market, but figures from one 2013 study indicated that around [half of planned embedded systems][6] would use it.
|
||||
|
||||
**Internet of Things**. In many ways this is simply another incarnation of embedded systems, with the difference that they are designed to be online, all the time. It's too early to talk of market share, but as I've [discussed][7] recently, AllSeen's open source framework is coming on apace. What's striking by their absence are any credible closed-source rivals; it therefore seems highly likely that the Internet of Things will see supercomputer-like levels of open source adoption.
|
||||
|
||||
Of course, this level of success always begs the question: where do we go from here? Given that open source is approaching saturation levels of success in many sectors, surely the only way is down? In answer to that question, I recommend a thought-provoking essay from 2013 written by Christopher Kelty for the Journal of Peer Production, with the intriguing title of "[There is no free software.][8]" Here's how it begins:
|
||||
|
||||
> Free software does not exist. This is sad for me, since I wrote a whole book about it. But it was also a point I tried to make in my book. Free software—and its doppelganger open source—is constantly becoming. Its existence is not one of stability, permanence, or persistence through time, and this is part of its power.
|
||||
|
||||
In other words, whatever amazing free software 2014 has already brought us, we can be sure that 2015 will be full of yet more of it, as it continues its never-ending evolution.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.computerworlduk.com/blogs/open-enterprise/open-source-has-won-3592314/
|
||||
|
||||
作者:[lyn Moody][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.computerworlduk.com/author/glyn-moody/
|
||||
[1]:http://www.top500.org/statistics/list/
|
||||
[2]:http://www.linuxfoundation.org/publications/linux-foundation/linux-end-user-trends-report-2014
|
||||
[3]:http://news.netcraft.com/archives/2014/12/18/december-2014-web-server-survey.html
|
||||
[4]:http://www.cnet.com/news/android-stays-unbeatable-in-smartphone-market-for-now/
|
||||
[5]:http://timesofindia.indiatimes.com/tech/tech-news/Android-tablet-market-share-hits-70-in-Q2-iPads-slip-to-25-Survey/articleshow/38966512.cms
|
||||
[6]:http://linuxgizmos.com/embedded-developers-prefer-linux-love-android/
|
||||
[7]:http://www.computerworlduk.com/blogs/open-enterprise/allseen-3591023/
|
||||
[8]:http://peerproduction.net/issues/issue-3-free-software-epistemics/debate/there-is-no-free-software/
|
||||
@ -1,85 +0,0 @@
|
||||
The history of Android
|
||||
================================================================================
|
||||
|
||||
The redesigned Dialer and Contacts pages.
|
||||
Photo by Ron Amadeo
|
||||
|
||||
The rounded tabs in the contacts/dialer app were changed to a sharper, more mature-looking design. The dialer changed its name to "Phone" and the dial pad buttons changed from circles to rounded rectangles. Buttons for voicemail, call, and delete were placed at the bottom. This screen is a great example of Android’s lack of design consistency in the pre-3.0 days. Just on this screen, the tabs used sharp-cornered rectangles, the dial pad used rounded rectangles, and the sides of the bottom buttons were complete circles. It was a grab bag of UI widgets where no one ever tried to make anything match anything else.
|
||||
|
||||
One of the new features in Android 2.0 was "Quick Contacts," which took the form of contact thumbnails that were added all over the OS. Tapping on them would bring up a list of shortcuts to contact that person through other apps. This didn't make as much sense in the contacts app, but in something like Google Talk, being able to tap on the contact thumbnail and call the person was very handy.
|
||||
|
||||
|
||||
Photo by Ron Amadeo
|
||||
|
||||
Android 2.0 was finally equipped with all the on-screen buttons needed to answer and hang up a call without needing a hardware button, and the Droid took advantage of this and removed the now-redundant buttons from its design. Android’s solution to accept or reject calls was these left and right pull tabs. They work a lot like slide-to-unlock (and would later be used for slide-to-unlock)—a slide from the green button to the right would answer, and a slide from the red button to the left would reject the call. Once inside a call, it looked a lot like Android 1.6. All the options were still hidden behind the menu button.
|
||||
|
||||
Someone completely phoned-in the art for the dialpad drawer. Instead of redrawing the number "5" button from Android 1.6, they just dropped in bold text that said "Dialpad" and called it a day.
|
||||
|
||||
|
||||
The Calculator and Browser.
|
||||
Photo by Ron Amadeo
|
||||
|
||||
The calculator was revamped for the first time since its introduction in Android 0.9. The black glass balls were replaced with gradiented blue and black buttons. The crazy red on-press highlight of the old calculator was replaced with a more normal looking white outline.
|
||||
|
||||
The browser's tiny website name bar grew into a full, functional address bar, along with a button for bookmarks. To save on screen real estate, the address bar was attached to the page, so the bar scrolled up with the rest of the page and left you with a full screen for reading. Android 1.6's unique magnifying rectangle zoom control and its associated buttons were tossed in favor of a much simpler double-tab-to-zoom gesture, and the browser could once again render arstechnica.com without crashing. There still wasn't pinch zoom.
|
||||
|
||||
|
||||
The camera with the settings drawer open, the flash settings, and the menu over top of the photo review screen.
|
||||
Photo by Ron Amadeo
|
||||
|
||||
The camera app gained an entire drawer on the left side, which opened to reveal a ton of settings. The Motorola Droid was one of the first Android phones with an LED flash, so there was a setting for flash control, along with settings like scene mode, white balance, effects, picture size, and storage location (SD or Internal).
|
||||
|
||||
On the photo review screen, Google pared down the menu button options. They were no longer redundant when compared to the on-screen options. With the extra room in the menu, all the options fit in the menu bar without needing a "more" button.
|
||||
|
||||
|
||||
The “accounts" page of the e-mail app, the new combined inbox, the account & sync page from the system settings, and the auto brightness setting.
|
||||
Photo by Ron Amadeo
|
||||
|
||||
The e-mail app got a big functionality boost. The most important of which is that it finally supported Microsoft Exchange. The Android 2.0 version of Email finally separated the inbox and folder views instead of using the messy mashed-together view introduced in Android 1.0. Email even had a unified inbox that would weave all your messages together from different accounts.
|
||||
|
||||
The inbox view put the generic Email app on even ground with the Gmail app. Combined inbox even trumped Gmail's functionality, which was an extremely rare occurrence. Email still felt like the unwanted stepchild to Gmail, though. It used the Gmail interface to view messages, which meant the inbox and folders used a black theme, and the message view oddly used a light theme.
|
||||
|
||||
The bundled Facebook app had an awesome account sync feature, which would download contact pictures and information from the social network and seamlessly integrate it into the contacts app. Later down the road when Facebook and Google stopped being friends, [Google removed this feature][1]. The company said it didn't like the idea of sharing information with Facebook when Facebook wouldn't share information back, thus a better user experience lost out to company politics.
|
||||
|
||||
(Sadly, we couldn't show off the Facebook app because it is yet another client that died at the hands of OAuth updates. It's no longer possible to sign in from a client this old.)
|
||||
|
||||
The last picture shows the auto brightness control, which Android 2.0 was the first version to support. The Droid was equipped with an ambient light sensor, and tapping on the checkbox would make the brightness slider disappear and allow the device to automatically control the screen brightness.
|
||||
|
||||
As the name would imply, Android 2.0 was Google's biggest update to date. Motorola and Verizon brought Android a slick-looking device with tons of ad dollars behind it, and for a time, “Droid" became a household name.
|
||||
|
||||
### The Nexus One—enter the Google Phone ###
|
||||
|
||||

|
||||
|
||||
In January 2010, the first Nexus device launched, appropriately called the "[Nexus One][2]". The device was a huge milestone for Google. It was the first phone designed and branded by the company, and Google planned to sell the device directly to consumers. The HTC-manufactured Nexus One had a 1GHz, single-core Qualcomm Snapdragon S1 SoC, 512MB of RAM, 512MB of storage, and a 3.7-inch AMOLED display.
|
||||
|
||||
The Nexus One was meant to be a pure Android experience free of carrier meddling and crapware. Google directly controlled the updates. It was able to push software out to users as soon as it was done, rather than having to be approved by carriers, who slowed the process down and were not always eager to improve a phone customers already paid for.
|
||||
|
||||
Google sold the Nexus One [directly over the Web][3], unlocked, contract-free, and at the full retail price of $529.99. While the Nexus One was also sold at T-Mobile stores on-contract for $179.99, Google wanted to change the way the cell phone industry worked in America with its online store. The idea was to pick the phone first and the carrier second, breaking the control the wireless oligarchy had over hardware in the United States.
|
||||
|
||||
Google's retail revolution didn't work out though, and six months after the opening on the online phone store, Google shut the service down. Google cited the primary problem as low sales. In 2010, Internet shopping wasn't the commonplace thing it is today, and consumers weren't ready to spend $530 on a device they couldn’t first hold in their hands. The high price was also a limiting factor; smartphone shoppers were more used to paying $200 up front for devices and agreeing to a two-year contract. There was also the issue of the Motorola Droid, which came out only three months earlier and was not significantly slower. With the Droid’s huge marketing campaign and "iPhone Killer" hype, it already captured much of the same Android enthusiast market that the Nexus One was gunning for.
|
||||
|
||||
While the Nexus One online sales experiment could be considered a failure, Google learned a lot. In 2012, it [relaunched its online store][4] as the "Devices" section on Google Play.
|
||||
|
||||
----------
|
||||
|
||||

|
||||
|
||||
[Ron Amadeo][a] / Ron is the Reviews Editor at Ars Technica, where he specializes in Android OS and Google products. He is always on the hunt for a new gadget and loves to rip things apart to see how they work.
|
||||
|
||||
[@RonAmadeo][t]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://arstechnica.com/gadgets/2014/06/building-android-a-40000-word-history-of-googles-mobile-os/11/
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://techcrunch.com/2011/02/22/google-android-facebook-contacts/
|
||||
[2]:http://arstechnica.com/gadgets/2010/01/nexus-one-review/
|
||||
[3]:http://arstechnica.com/gadgets/2010/01/googles-big-news-today-was-not-a-phone-but-a-url/
|
||||
[4]:http://arstechnica.com/gadgets/2012/04/unlocked-samsung-galaxy-nexus-can-now-be-purchased-from-google/
|
||||
[a]:http://arstechnica.com/author/ronamadeo
|
||||
[t]:https://twitter.com/RonAmadeo
|
||||
@ -0,0 +1,157 @@
|
||||
Mr-Ping 翻译中
|
||||
|
||||
How to Backup and Restore Your Apps and PPAs in Ubuntu Using Aptik
|
||||
================================================================================
|
||||

|
||||
|
||||
If you need to reinstall Ubuntu or if you just want to install a new version from scratch, wouldn’t it be useful to have an easy way to reinstall all your apps and settings? You can easily accomplish this using a free tool called Aptik.
|
||||
|
||||
Aptik (Automated Package Backup and Restore), an application available in Ubuntu, Linux Mint, and other Debian- and Ubuntu-based Linux distributions, allows you to backup a list of installed PPAs (Personal Package Archives), which are software repositories, downloaded packages, installed applications and themes, and application settings to an external USB drive, network drive, or a cloud service like Dropbox.
|
||||
|
||||
NOTE: When we say to type something in this article and there are quotes around the text, DO NOT type the quotes, unless we specify otherwise.
|
||||
|
||||
To install Aptik, you must add the PPA. To do so, press Ctrl + Alt + T to open a Terminal window. Type the following text at the prompt and press Enter.
|
||||
|
||||
sudo apt-add-repository –y ppa:teejee2008/ppa
|
||||
|
||||
Type your password when prompted and press Enter.
|
||||
|
||||

|
||||
|
||||
Type the following text at the prompt to make sure the repository is up-to-date.
|
||||
|
||||
sudo apt-get update
|
||||
|
||||

|
||||
|
||||
When the update is finished, you are ready to install Aptik. Type the following text at the prompt and press Enter.
|
||||
|
||||
sudo apt-get install aptik
|
||||
|
||||
NOTE: You may see some errors about packages that the update failed to fetch. If they are similar to the ones listed on the following image, you should have no problem installing Aptik.
|
||||
|
||||

|
||||
|
||||
The progress of the installation displays and then a message displays saying how much disk space will be used. When asked if you want to continue, type a “y” and press Enter.
|
||||
|
||||

|
||||
|
||||
When the installation if finished, close the Terminal window by typing “Exit” and pressing Enter, or by clicking the “X” button in the upper-left corner of the window.
|
||||
|
||||

|
||||
|
||||
Before running Aptik, you should set up a backup directory on a USB flash drive, a network drive, or on a cloud account, such as Dropbox or Google Drive. For this example, will will use Dropbox.
|
||||
|
||||

|
||||
|
||||
Once your backup directory is set up, click the “Search” button at the top of the Unity Launcher bar.
|
||||
|
||||

|
||||
|
||||
Type “aptik” in the search box. Results of the search display as you type. When the icon for Aptik displays, click on it to open the application.
|
||||
|
||||

|
||||
|
||||
A dialog box displays asking for your password. Enter your password in the edit box and click “OK.”
|
||||
|
||||

|
||||
|
||||
The main Aptik window displays. Select “Other…” from the “Backup Directory” drop-down list. This allows you to select the backup directory you created.
|
||||
|
||||
NOTE: The “Open” button to the right of the drop-down list opens the selected directory in a Files Manager window.
|
||||
|
||||

|
||||
|
||||
On the “Backup Directory” dialog box, navigate to your backup directory and then click “Open.”
|
||||
|
||||
NOTE: If you haven’t created a backup directory yet, or you want to add a subdirectory in the selected directory, use the “Create Folder” button to create a new directory.
|
||||
|
||||

|
||||
|
||||
To backup the list of installed PPAs, click “Backup” to the right of “Software Sources (PPAs).”
|
||||
|
||||

|
||||
|
||||
The “Backup Software Sources” dialog box displays. The list of installed packages and the associated PPA for each displays. Select the PPAs you want to backup, or use the “Select All” button to select all the PPAs in the list.
|
||||
|
||||

|
||||
|
||||
Click “Backup” to begin the backup process.
|
||||
|
||||

|
||||
|
||||
A dialog box displays when the backup is finished telling you the backup was created successfully. Click “OK” to close the dialog box.
|
||||
|
||||
A file named “ppa.list” will be created in the backup directory.
|
||||
|
||||

|
||||
|
||||
The next item, “Downloaded Packages (APT Cache)”, is only useful if you are re-installing the same version of Ubuntu. It backs up the packages in your system cache (/var/cache/apt/archives). If you are upgrading your system, you can skip this step because the packages for the new version of the system will be newer than the packages in the system cache.
|
||||
|
||||
Backing up downloaded packages and then restoring them on the re-installed Ubuntu system will save time and Internet bandwidth when the packages are reinstalled. Because the packages will be available in the system cache once you restore them, the download will be skipped and the installation of the packages will complete more quickly.
|
||||
|
||||
If you are reinstalling the same version of your Ubuntu system, click the “Backup” button to the right of “Downloaded Packages (APT Cache)” to backup the packages in the system cache.
|
||||
|
||||
NOTE: When you backup the downloaded packages, there is no secondary dialog box. The packages in your system cache (/var/cache/apt/archives) are copied to an “archives” directory in the backup directory and a dialog box displays when the backup is finished, indicating that the packages were copied successfully.
|
||||
|
||||

|
||||
|
||||
There are some packages that are part of your Ubuntu distribution. These are not checked, since they are automatically installed when you install the Ubuntu system. For example, Firefox is a package that is installed by default in Ubuntu and other similar Linux distributions. Therefore, it will not be selected by default.
|
||||
|
||||
Packages that you installed after installing the system, such as the [package for the Chrome web browser][1] or the package containing Aptik (yes, Aptik is automatically selected to back up), are selected by default. This allows you to easily back up the packages that are not included in the system when installed.
|
||||
|
||||
Select the packages you want to back up and de-select the packages you don’t want to backup. Click “Backup” to the right of “Software Selections” to back up the selected top-level packages.
|
||||
|
||||
NOTE: Dependency packages are not included in this backup.
|
||||
|
||||

|
||||
|
||||
Two files, named “packages.list” and “packages-installed.list”, are created in the backup directory and a dialog box displays indicating that the backup was created successfully. Click “OK” to close the dialog box.
|
||||
|
||||
NOTE: The “packages-installed.list” file lists all the packages. The “packages.list” file also lists all the packages, but indicates which ones were selected.
|
||||
|
||||

|
||||
|
||||
To backup settings for installed applications, click the “Backup” button to the right of “Application Settings” on the main Aptik window. Select the settings you want to back up and click “Backup”.
|
||||
|
||||
NOTE: Click the “Select All” button if you want to back up all application settings.
|
||||
|
||||

|
||||
|
||||
The selected settings files are zipped into a file called “app-settings.tar.gz”.
|
||||
|
||||

|
||||
|
||||
When the zipping is complete, the zipped file is copied to the backup directory and a dialog box displays telling you that the backups were created successfully. Click “OK” to close the dialog box.
|
||||
|
||||

|
||||
|
||||
Themes from the “/usr/share/themes” directory and icons from the “/usr/share/icons” directory can also be backed up. To do so, click the “Backup” button to the right of “Themes and Icons”. The “Backup Themes” dialog box displays with all the themes and icons selected by default. De-select any themes or icons you don’t want to back up and click “Backup.”
|
||||
|
||||

|
||||
|
||||
The themes are zipped and copied to a “themes” directory in the backup directory and the icons are zipped and copied to an “icons” directory in the backup directory. A dialog box displays telling you that the backups were created successfully. Click “OK” to close the dialog box.
|
||||
|
||||

|
||||
|
||||
Once you’ve completed the desired backups, close Aptik by clicking the “X” button in the upper-left corner of the main window.
|
||||
|
||||

|
||||
|
||||
Your backup files are available in the backup directory you chose.
|
||||
|
||||

|
||||
|
||||
When you re-install your Ubuntu system or install a new version of Ubuntu, install Aptik on the newly installed system and make the backup files you generated available to the system. Run Aptik and use the “Restore” button for each item to restore your PPAs, applications, packages, settings, themes, and icons.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.howtogeek.com/206454/how-to-backup-and-restore-your-apps-and-ppas-in-ubuntu-using-aptik/
|
||||
|
||||
作者:Lori Kaufman
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.howtogeek.com/203768
|
||||
@ -1,273 +0,0 @@
|
||||
How to configure HTTP load balancer with HAProxy on Linux
|
||||
================================================================================
|
||||
Increased demand on web based applications and services are putting more and more weight on the shoulders of IT administrators. When faced with unexpected traffic spikes, organic traffic growth, or internal challenges such as hardware failures and urgent maintenance, your web application must remain available, no matter what. Even modern devops and continuous delivery practices can threaten the reliability and consistent performance of your web service.
|
||||
|
||||
Unpredictability or inconsistent performance is not something you can afford. But how can we eliminate these downsides? In most cases a proper load balancing solution will do the job. And today I will show you how to set up HTTP load balancer using [HAProxy][1].
|
||||
|
||||
### What is HTTP load balancing? ###
|
||||
|
||||
HTTP load balancing is a networking solution responsible for distributing incoming HTTP or HTTPS traffic among servers hosting the same application content. By balancing application requests across multiple available servers, a load balancer prevents any application server from becoming a single point of failure, thus improving overall application availability and responsiveness. It also allows you to easily scale in/out an application deployment by adding or removing extra application servers with changing workloads.
|
||||
|
||||
### Where and when to use load balancing? ###
|
||||
|
||||
As load balancers improve server utilization and maximize availability, you should use it whenever your servers start to be under high loads. Or if you are just planning your architecture for a bigger project, it's a good habit to plan usage of load balancer upfront. It will prove itself useful in the future when you need to scale your environment.
|
||||
|
||||
### What is HAProxy? ###
|
||||
|
||||
HAProxy is a popular open-source load balancer and proxy for TCP/HTTP servers on GNU/Linux platforms. Designed in a single-threaded event-driven architecture, HAproxy is capable of handling [10G NIC line rate][2] easily, and is being extensively used in many production environments. Its features include automatic health checks, customizable load balancing algorithms, HTTPS/SSL support, session rate limiting, etc.
|
||||
|
||||
### What are we going to achieve in this tutorial? ###
|
||||
|
||||
In this tutorial, we will go through the process of configuring a HAProxy-based load balancer for HTTP web servers.
|
||||
|
||||
### Prerequisites ###
|
||||
|
||||
You will need at least one, or preferably two web servers to verify functionality of your load balancer. We assume that backend HTTP web servers are already [up and running][3].
|
||||
|
||||
### Install HAProxy on Linux ###
|
||||
|
||||
For most distributions, we can install HAProxy using your distribution's package manager.
|
||||
|
||||
#### Install HAProxy on Debian ####
|
||||
|
||||
In Debian we need to add backports for Wheezy. To do that, please create a new file called "backports.list" in /etc/apt/sources.list.d, with the following content:
|
||||
|
||||
deb http://cdn.debian.net/debian wheezybackports main
|
||||
|
||||
Refresh your repository data and install HAProxy.
|
||||
|
||||
# apt get update
|
||||
# apt get install haproxy
|
||||
|
||||
#### Install HAProxy on Ubuntu ####
|
||||
|
||||
# apt get install haproxy
|
||||
|
||||
#### Install HAProxy on CentOS and RHEL ####
|
||||
|
||||
# yum install haproxy
|
||||
|
||||
### Configure HAProxy ###
|
||||
|
||||
In this tutorial, we assume that there are two HTTP web servers up and running with IP addresses 192.168.100.2 and 192.168.100.3. We also assume that the load balancer will be configured at a server with IP address 192.168.100.4.
|
||||
|
||||
To make HAProxy functional, you need to change a number of items in /etc/haproxy/haproxy.cfg. These changes are described in this section. In case some configuration differs for different GNU/Linux distributions, it will be noted in the paragraph.
|
||||
|
||||
#### 1. Configure Logging ####
|
||||
|
||||
One of the first things you should do is to set up proper logging for your HAProxy, which will be useful for future debugging. Log configuration can be found in the global section of /etc/haproxy/haproxy.cfg. The following are distro-specific instructions for configuring logging for HAProxy.
|
||||
|
||||
**CentOS or RHEL:**
|
||||
|
||||
To enable logging on CentOS/RHEL, replace:
|
||||
|
||||
log 127.0.0.1 local2
|
||||
|
||||
with:
|
||||
|
||||
log 127.0.0.1 local0
|
||||
|
||||
The next step is to set up separate log files for HAProxy in /var/log. For that, we need to modify our current rsyslog configuration. To make the configuration simple and clear, we will create a new file called haproxy.conf in /etc/rsyslog.d/ with the following content.
|
||||
|
||||
$ModLoad imudp
|
||||
$UDPServerRun 514
|
||||
$template Haproxy,"%msg%\n"
|
||||
local0.=info /var/log/haproxy.log;Haproxy
|
||||
local0.notice /var/log/haproxystatus.log;Haproxy
|
||||
local0.* ~
|
||||
|
||||
This configuration will separate all HAProxy messages based on the $template to log files in /var/log. Now restart rsyslog to apply the changes.
|
||||
|
||||
# service rsyslog restart
|
||||
|
||||
**Debian or Ubuntu:**
|
||||
|
||||
To enable logging for HAProxy on Debian or Ubuntu, replace:
|
||||
|
||||
log /dev/log local0
|
||||
log /dev/log local1 notice
|
||||
|
||||
with:
|
||||
|
||||
log 127.0.0.1 local0
|
||||
|
||||
Next, to configure separate log files for HAProxy, edit a file called haproxy.conf (or 49-haproxy.conf in Debian) in /etc/rsyslog.d/ with the following content.
|
||||
|
||||
$ModLoad imudp
|
||||
$UDPServerRun 514
|
||||
$template Haproxy,"%msg%\n"
|
||||
local0.=info /var/log/haproxy.log;Haproxy
|
||||
local0.notice /var/log/haproxystatus.log;Haproxy
|
||||
local0.* ~
|
||||
|
||||
This configuration will separate all HAProxy messages based on the $template to log files in /var/log. Now restart rsyslog to apply the changes.
|
||||
|
||||
# service rsyslog restart
|
||||
|
||||
#### 2. Setting Defaults ####
|
||||
|
||||
The next step is to set default variables for HAProxy. Find the defaults section in /etc/haproxy/haproxy.cfg, and replace it with the following configuration.
|
||||
|
||||
defaults
|
||||
log global
|
||||
mode http
|
||||
option httplog
|
||||
option dontlognull
|
||||
retries 3
|
||||
option redispatch
|
||||
maxconn 20000
|
||||
contimeout 5000
|
||||
clitimeout 50000
|
||||
srvtimeout 50000
|
||||
|
||||
The configuration stated above is recommended for HTTP load balancer use, but it may not be the optimal solution for your environment. In that case, feel free to explore HAProxy man pages to tweak it.
|
||||
|
||||
#### 3. Webfarm Configuration ####
|
||||
|
||||
Webfarm configuration defines the pool of available HTTP servers. Most of the settings for our load balancer will be placed here. Now we will create some basic configuration, where our nodes will be defined. Replace all of the configuration from frontend section until the end of file with the following code:
|
||||
|
||||
listen webfarm *:80
|
||||
mode http
|
||||
stats enable
|
||||
stats uri /haproxy?stats
|
||||
stats realm Haproxy\ Statistics
|
||||
stats auth haproxy:stats
|
||||
balance roundrobin
|
||||
cookie LBN insert indirect nocache
|
||||
option httpclose
|
||||
option forwardfor
|
||||
server web01 192.168.100.2:80 cookie node1 check
|
||||
server web02 192.168.100.3:80 cookie node2 check
|
||||
|
||||
The line "listen webfarm *:80" defines on which interfaces our load balancer will listen. For the sake of the tutorial, I've set that to "*" which makes the load balancer listen on all our interfaces. In a real world scenario, this might be undesirable and should be replaced with an interface that is accessible from the internet.
|
||||
|
||||
stats enable
|
||||
stats uri /haproxy?stats
|
||||
stats realm Haproxy\ Statistics
|
||||
stats auth haproxy:stats
|
||||
|
||||
The above settings declare that our load balancer statistics can be accessed on http://<load-balancer-IP>/haproxy?stats. The access is secured with a simple HTTP authentication with login name "haproxy" and password "stats". These settings should be replaced with your own credentials. If you don't need to have these statistics available, then completely disable them.
|
||||
|
||||
Here is an example of HAProxy statistics.
|
||||
|
||||
|
||||
|
||||
The line "balance roundrobin" defines the type of load balancing we will use. In this tutorial we will use simple round robin algorithm, which is fully sufficient for HTTP load balancing. HAProxy also offers other types of load balancing:
|
||||
|
||||
- **leastconn**: gives connections to the server with the lowest number of connections.
|
||||
- **source**: hashes the source IP address, and divides it by the total weight of the running servers to decide which server will receive the request.
|
||||
- **uri**: the left part of the URI (before the question mark) is hashed and divided by the total weight of the running servers. The result determines which server will receive the request.
|
||||
- **url_param**: the URL parameter specified in the argument will be looked up in the query string of each HTTP GET request. You can basically lock the request using crafted URL to specific load balancer node.
|
||||
- **hdr(name**): the HTTP header <name> will be looked up in each HTTP request and directed to specific node.
|
||||
|
||||
The line "cookie LBN insert indirect nocache" makes our load balancer store persistent cookies, which allows us to pinpoint which node from the pool is used for a particular session. These node cookies will be stored with a defined name. In our case, I used "LBN", but you can specify any name you like. The node will store its string as a value for this cookie.
|
||||
|
||||
server web01 192.168.100.2:80 cookie node1 check
|
||||
server web02 192.168.100.3:80 cookie node2 check
|
||||
|
||||
The above part is the definition of our pool of web server nodes. Each server is represented with its internal name (e.g., web01, web02). IP address, and unique cookie string. The cookie string can be defined as anything you want. I am using simple node1, node2 ... node(n).
|
||||
|
||||
### Start HAProxy ###
|
||||
|
||||
When you are done with the configuration, it's time to start HAProxy and verify that everything is working as intended.
|
||||
|
||||
#### Start HAProxy on Centos/RHEL ####
|
||||
|
||||
Enable HAProxy to be started after boot and turn it on using:
|
||||
|
||||
# chkconfig haproxy on
|
||||
# service haproxy start
|
||||
|
||||
And of course don't forget to enable port 80 in the firewall as follows.
|
||||
|
||||
**Firewall on CentOS/RHEL 7:**
|
||||
|
||||
# firewallcmd permanent zone=public addport=80/tcp
|
||||
# firewallcmd reload
|
||||
|
||||
**Firewall on CentOS/RHEL 6:**
|
||||
|
||||
Add following line into section ":OUTPUT ACCEPT" of /etc/sysconfig/iptables:
|
||||
|
||||
A INPUT m state state NEW m tcp p tcp dport 80 j ACCEPT
|
||||
|
||||
and restart **iptables**:
|
||||
|
||||
# service iptables restart
|
||||
|
||||
#### Start HAProxy on Debian ####
|
||||
|
||||
#### Start HAProxy with: ####
|
||||
|
||||
# service haproxy start
|
||||
|
||||
Don't forget to enable port 80 in the firewall by adding the following line into /etc/iptables.up.rules:
|
||||
|
||||
A INPUT p tcp dport 80 j ACCEPT
|
||||
|
||||
#### Start HAProxy on Ubuntu ####
|
||||
|
||||
Enable HAProxy to be started after boot by setting "ENABLED" option to "1" in /etc/default/haproxy:
|
||||
|
||||
ENABLED=1
|
||||
|
||||
Start HAProxy:
|
||||
|
||||
# service haproxy start
|
||||
|
||||
and enable port 80 in the firewall:
|
||||
|
||||
# ufw allow 80
|
||||
|
||||
### Test HAProxy ###
|
||||
|
||||
To check whether HAproxy is working properly, we can do the following.
|
||||
|
||||
First, prepare test.php file with the following content:
|
||||
|
||||
<?php
|
||||
header('Content-Type: text/plain');
|
||||
echo "Server IP: ".$_SERVER['SERVER_ADDR'];
|
||||
echo "\nX-Forwarded-for: ".$_SERVER['HTTP_X_FORWARDED_FOR'];
|
||||
?>
|
||||
|
||||
This PHP file will tell us which server (i.e., load balancer) forwarded the request, and what backend web server actually handled the request.
|
||||
|
||||
Place this PHP file in the root directory of both backend web servers. Now use curl command to fetch this PHP file from the load balancer (192.168.100.4).
|
||||
|
||||
$ curl http://192.168.100.4/test.php
|
||||
|
||||
When we run this command multiple times, we should see the following two outputs alternate (due to the round robin algorithm).
|
||||
|
||||
Server IP: 192.168.100.2
|
||||
X-Forwarded-for: 192.168.100.4
|
||||
|
||||
----------
|
||||
|
||||
Server IP: 192.168.100.3
|
||||
X-Forwarded-for: 192.168.100.4
|
||||
|
||||
If we stop one of the two backend web servers, the curl command should still work, directing requests to the other available web server.
|
||||
|
||||
### Summary ###
|
||||
|
||||
By now you should have a fully operational load balancer that supplies your web nodes with requests in round robin mode. As always, feel free to experiment with the configuration to make it more suitable for your infrastructure. I hope this tutorial helped you to make your web projects more resistant and available.
|
||||
|
||||
As most of you already noticed, this tutorial contains settings for only one load balancer. Which means that we have just replaced one single point of failure with another. In real life scenarios you should deploy at least two or three load balancers to cover for any failures that might happen, but that is out of the scope of this tutorial right now.
|
||||
|
||||
If you have any questions or suggestions feel free to post them in the comments and I will do my best to answer or advice.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/haproxy-http-load-balancer-linux.html
|
||||
|
||||
作者:[Jaroslav Štěpánek][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/jaroslav
|
||||
[1]:http://www.haproxy.org/
|
||||
[2]:http://www.haproxy.org/10g.html
|
||||
[3]:http://xmodulo.com/how-to-install-lamp-server-on-ubuntu.html
|
||||
@ -1,301 +0,0 @@
|
||||
“ntpq -p” output
|
||||
================================================================================
|
||||
The [Gentoo][1] (and others?) [incomplete man pages for “ntpq -p”][2] merely give the description: “*Print a list of the peers known to the server as well as a summary of their state.*”
|
||||
|
||||
I had not seen this documented, hence here is a summary that can be used in addition to the brief version of the man page “[man ntpq][3]“. More complete details are given on: “[ntpq – standard NTP query program][4]” (source author), and [other examples of the man ntpq pages][5].
|
||||
|
||||
[NTP][6] is a protocol designed to synchronize the clocks of computers over a ([WAN][7] or [LAN][8]) [udp][9] network. From [Wikipedia – NTP][10]:
|
||||
|
||||
> The Network Time Protocol (NTP) is a protocol and software implementation for synchronizing the clocks of computer systems over packet-switched, variable-latency data networks. Originally designed by David L. Mills of the University of Delaware and still maintained by him and a team of volunteers, it was first used before 1985 and is one of the oldest Internet protocols.
|
||||
|
||||
For an awful lot more than you might ever want to know about time and NTP, see “[The NTP FAQ, Time, what Time?][11]” and the current [RFCs for NTP][12]. The earlier “Network Time Protocol (Version 3) RFC” ([txt][13], or [pdf][14], Appendix E, The NTP Timescale and its Chronometry, p70) includes an interesting explanation of the changes in, and relations between, our timekeeping systems over the past 5000 years or so. Wikipedia gives a broader view in the articles [Time][15] and [Calendar][16].
|
||||
|
||||
The command “ntpq -p” outputs a table such as for example:
|
||||
|
||||
remote refid st t when poll reach delay offset jitter
|
||||
==============================================================================
|
||||
LOCAL(0) .LOCL. 10 l 96h 64 0 0.000 0.000 0.000
|
||||
*ns2.example.com 10.193.2.20 2 u 936 1024 377 31.234 3.353 3.096
|
||||
|
||||
### Further detail: ###
|
||||
|
||||
#### Table headings: ####
|
||||
|
||||
|
||||
- **remote** – The remote peer or server being synced to. “LOCAL” is this local host (included in case there are no remote peers or servers available);
|
||||
- **refid** – Where or what the remote peer or server is itself synchronised to;
|
||||
- **st** – The remote peer or server [Stratum][17]
|
||||
- **t** – Type (u: [unicast][18] or [manycast][19] client, b: [broadcast][20] or [multicast][21] client, l: local reference clock, s: symmetric peer, A: manycast server, B: broadcast server, M: multicast server, see “[Automatic Server Discovery][22]“);
|
||||
- **when** – When last polled (seconds ago, “h” hours ago, or “d” days ago);
|
||||
- **poll** – Polling frequency: [rfc5905][23] suggests this ranges in NTPv4 from 4 (16s) to 17 (36h) (log2 seconds), however observation suggests the actual displayed value is seconds for a much smaller range of 64 (26) to 1024 (210) seconds;
|
||||
- **reach** – An 8-bit left-shift shift register value recording polls (bit set = successful, bit reset = fail) displayed in [octal][24];
|
||||
- **delay** – Round trip communication delay to the remote peer or server (milliseconds);
|
||||
- **offset** – Mean offset (phase) in the times reported between this local host and the remote peer or server ([RMS][25], milliseconds);
|
||||
- **jitter** – Mean deviation (jitter) in the time reported for that remote peer or server (RMS of difference of multiple time samples, milliseconds);
|
||||
|
||||
#### Select Field tally code: ####
|
||||
|
||||
The first character displayed in the table (Select Field tally code) is a state flag (see [Peer Status Word][26]) that follows the sequence ” “, “x”, “-“, “#”, “+”, “*”, “o”:
|
||||
|
||||
|
||||
- ”** **” – No state indicated for:
|
||||
- non-communicating remote machines,
|
||||
- “LOCAL” for this local host,
|
||||
- (unutilised) high stratum servers,
|
||||
- remote machines that are themselves using this host as their synchronisation reference;
|
||||
- “**x**” – Out of tolerance, do not use (discarded by intersection algorithm);
|
||||
- “**-**” – Out of tolerance, do not use (discarded by the cluster algorithm);
|
||||
- “**#**” – Good remote peer or server but not utilised (not among the first six peers sorted by synchronization distance, ready as a backup source);
|
||||
- “**+**” – Good and a preferred remote peer or server (included by the combine algorithm);
|
||||
- “*****” – The remote peer or server presently used as the primary reference;
|
||||
- “**o**” – PPS peer (when the prefer peer is valid). The actual system synchronization is derived from a pulse-per-second (PPS) signal, either indirectly via the PPS reference clock driver or directly via kernel interface.
|
||||
|
||||
See the [Clock Select Algorithm][27].
|
||||
|
||||
#### “refid”: ####
|
||||
|
||||
The **refid** can have the status values:
|
||||
|
||||
|
||||
- An IP address – The [IP address][28] of a remote peer or server;
|
||||
- **.LOCL.** – This local host (a place marker at the lowest stratum included in case there are no remote peers or servers available);
|
||||
- **.PPS.** – “[Pulse Per Second][29]” from a time standard;
|
||||
- **.IRIG.** – [Inter-Range Instrumentation Group][30] time code;
|
||||
- **.ACTS.** – American [NIST time standard][31] telephone modem;
|
||||
- **.NIST.** – American NIST time standard telephone modem;
|
||||
- **.PTB.** – German [PTB][32] time standard telephone modem;
|
||||
- **.USNO.** – American [USNO time standard][33] telephone modem;
|
||||
- **.CHU.** – [CHU][34] ([HF][35], Ottawa, ON, Canada) time standard radio receiver;
|
||||
- **.DCFa.** – [DCF77][36] ([LF][37], Mainflingen, Germany) time standard radio receiver;
|
||||
- **.HBG.** – [HBG][38] (LF Prangins, Switzerland) time standard radio receiver;
|
||||
- **.JJY.** – [JJY][39] (LF Fukushima, Japan) time standard radio receiver;
|
||||
- **.LORC.** – [LORAN][40]-C station ([MF][41]) time standard radio receiver. Note, [no longer operational][42] (superseded by [eLORAN][43]);
|
||||
- **.MSF.** – [MSF][44] (LF, Anthorn, Great Britain) time standard radio receiver;
|
||||
- **.TDF.** – [TDF][45] (MF, Allouis, France) time standard radio receiver;
|
||||
- **.WWV.** – [WWV][46] (HF, Ft. Collins, CO, America) time standard radio receiver;
|
||||
- **.WWVB.** – [WWVB][47] (LF, Ft. Collins, CO, America) time standard radio receiver;
|
||||
- **.WWVH.** – [WWVH][48] (HF, Kauai, HI, America) time standard radio receiver;
|
||||
- **.GOES.** – American [Geosynchronous Orbit Environment Satellite][49];
|
||||
- **.GPS.** – American [GPS][50];
|
||||
- **.GAL.** – [Galileo][51] European [GNSS][52];
|
||||
- **.ACST.** – manycast server;
|
||||
- **.AUTH.** – authentication error;
|
||||
- **.AUTO.** – Autokey sequence error;
|
||||
- **.BCST.** – broadcast server;
|
||||
- **.CRYPT.** – Autokey protocol error;
|
||||
- **.DENY.** – access denied by server;
|
||||
- **.INIT.** – association initialized;
|
||||
- **.MCST.** – multicast server;
|
||||
- **.RATE.** – (polling) rate exceeded;
|
||||
- **.TIME.** – association timeout;
|
||||
- **.STEP.** – step time change, the offset is less than the panic threshold (1000ms) but greater than the step threshold (125ms).
|
||||
|
||||
#### Operation notes ####
|
||||
|
||||
A time server will report time information with no time updates from clients (unidirectional updates), whereas a peer can update fellow participating peers to converge upon a mutually agreed time (bidirectional updates).
|
||||
|
||||
During [initial startup][53]:
|
||||
|
||||
> Unless using the iburst option, the client normally takes a few minutes to synchronize to a server. If the client time at startup happens to be more than 1000s distant from NTP time, the daemon exits with a message to the system log directing the operator to manually set the time within 1000s and restart. If the time is less than 1000s but more than 128s distant, a step correction occurs and the daemon restarts automatically.
|
||||
|
||||
> When started for the first time and a frequency file is not present, the daemon enters a special mode in order to calibrate the frequency. This takes 900s during which the time is not [disciplined][54]. When calibration is complete, the daemon creates the frequency file and enters normal mode to amortize whatever residual offset remains.
|
||||
|
||||
Stratum 0 devices are such as atomic (caesium, rubidium) clocks, GPS clocks, or other time standard radio clocks providing a time signal to the Stratum 1 time servers. NTP reports [UTC][55] (Coordinated Universal Time) only. Client programs/utilities then use [time zone][56] data to report local time from the synchronised UTC.
|
||||
|
||||
The protocol is highly accurate, using a resolution of less than a nanosecond (about 2-32 seconds). The time resolution achieved and other parameters for a host (host hardware and operating system limited) is reported by the command “ntpq -c rl” (see [rfc1305][57] Common Variables and [rfc5905][58]).
|
||||
|
||||
#### “ntpq -c rl” output parameters: ####
|
||||
|
||||
- **precision** is rounded to give the next larger integer power of two. The achieved resolution is thus 2precision (seconds)
|
||||
- **rootdelay** – total roundtrip delay to the primary reference source at the root of the synchronization subnet. Note that this variable can take on both positive and negative values, depending on clock precision and skew (seconds)
|
||||
- **rootdisp** – maximum error relative to the primary reference source at the root of the synchronization subnet (seconds)
|
||||
- **tc** – NTP algorithm [PLL][59] (phase locked loop) or [FLL][60] (frequency locked loop) time constant (log2)
|
||||
- **mintc** – NTP algorithm PLL/FLL minimum time constant or ‘fastest response’ (log2)
|
||||
- **offset** – best and final offset determined by the combine algorithm used to discipline the system clock (ms)
|
||||
- **frequency** – system clock period (log2 seconds)
|
||||
- **sys_jitter** – best and final jitter determined by the combine algorithm used to discipline the system clock (ms)
|
||||
- **clk_jitter** – host hardware(?) system clock jitter (ms)
|
||||
- **clk_wander** – host hardware(?) system clock wander ([PPM][61] – parts per million)
|
||||
|
||||
Jitter (also called timing jitter) refers to short-term variations in frequency with components greater than 10Hz, while wander refers to long-term variations in frequency with components less than 10Hz. (Stability refers to the systematic variation of frequency with time and is synonymous with aging, drift, trends, etc.)
|
||||
|
||||
#### Operation notes (continued) ####
|
||||
|
||||
The NTP software maintains a continuously updated drift correction. For a correctly configured and stable system, a reasonable expectation for modern hardware synchronising over an uncongested internet connection is for network client devices to be synchronised to within a few milliseconds of UTC at the time of synchronising to the NTP service. (What accuracy can be expected between peers on an uncongested Gigabit LAN?)
|
||||
|
||||
Note that for UTC, a [leap second][62] can be inserted into the reported time up to twice a year to allow for variations in the Earth’s rotation. Also beware of the one hour time shifts for when local times are reported for “[daylight savings][63]” times. Also, the clock for a client device will run independently of UTC until resynchronised oncemore, unless that device is calibrated or a drift correction is applied.
|
||||
|
||||
#### [What happens during a Leap Second?][64] ####
|
||||
|
||||
> During a leap second, either one second is removed from the current day, or a second is added. In both cases this happens at the end of the UTC day. If a leap second is inserted, the time in UTC is specified as 23:59:60. In other words, it takes two seconds from 23:59:59 to 0:00:00 instead of one. If a leap second is deleted, time will jump from 23:59:58 to 0:00:00 in one second instead of two. See also [The Kernel Discipline][65].
|
||||
|
||||
So… What actually is the value for the step threshold: 125ms or 128ms? And what are the PLL/FLL tc units (log2 s? ms?)? And what accuracy can be expected between peers on an uncongested Gigabit LAN?
|
||||
|
||||
|
||||
|
||||
Thanks for comments from Camilo M and Chris B. Corrections and further details welcomed.
|
||||
|
||||
Cheers,
|
||||
Martin
|
||||
|
||||
### Apocrypha: ###
|
||||
|
||||
- The [epoch for NTP][66] starts in year 1900 while the epoch in UNIX starts in 1970.
|
||||
- [Time corrections][67] are applied gradually, so it may take up to three hours until the frequency error is compensated.
|
||||
- [Peerstats and loopstats][68] can be logged to [summarise/plot time offsets and errors][69]
|
||||
- [RMS][70] – Root Mean Square
|
||||
- [PLL][71] – Phase locked loop
|
||||
- [FLL][72] – Frequency locked loop
|
||||
- [PPM][73] – Parts per million, used here to describe rate of time drift
|
||||
- [man ntpq (Gentoo brief version)][74]
|
||||
- [man ntpq (long version)][75]
|
||||
- [man ntpq (Gentoo long version)][76]
|
||||
|
||||
### See: ###
|
||||
|
||||
- [ntpq – standard NTP query program][77]
|
||||
- [The Network Time Protocol (NTP) Distribution][78]
|
||||
- A very brief [history][79] of NTP
|
||||
- A more detailed brief history: “Mills, D.L., A brief history of NTP time: confessions of an Internet timekeeper. Submitted for publication; please do not cite or redistribute” ([pdf][80])
|
||||
- [NTP RFC][81] standards documents
|
||||
- Network Time Protocol (Version 3) RFC – [txt][82], or [pdf][83]. Appendix E, The NTP Timescale and its Chronometry, p70, includes an interesting explanation of the changes in, and relations between, our timekeeping systems over the past 5000 years or so
|
||||
- Wikipedia: [Time][84] and [Calendar][85]
|
||||
- [John Harrison and the Longitude problem][86]
|
||||
- [Clock of the Long Now][87] – The 10,000 Year Clock
|
||||
- John C Taylor – [Chronophage][88]
|
||||
- [Orders of magnitude of time][89]
|
||||
- The [Greenwich Time Signal][90]
|
||||
|
||||
### Others: ###
|
||||
|
||||
SNTP (Simple Network Time Protocol, [RFC 4330][91]) is basically also NTP, but lacks some internal algorithms for servers where the ultimate performance of a full NTP implementation based on [RFC 1305][92] is neither needed nor justified.
|
||||
|
||||
The W32Time [Windows Time Service][93] is a non-standard implementation of SNTP, with no accuracy guarantees, and an assumed accuracy of no better than about a 1 to 2 second range. (Is that due to there being no system clock drift correction and a time update applied only once every 24 hours assumed for a [PC][94] with typical clock drift?)
|
||||
|
||||
There is also the [PTP (IEEE 1588)][95] Precision Time Protocol. See Wikipedia: [Precision Time Protocol][96]. A software demon is [PTPd][97]. The significant features are that it is intended as a [LAN][98] high precision master-slave synchronisation system synchronising at the microsecond scale to a master clock for [International Atomic Time][99] (TAI, [monotonic][100], no leap seconds). Data packet timestamping can be appended by hardware at the physical layer by a network interface card or switch for example. Network kit supporting PTP can timestamp data packets in and out in a way that removes the delay effect of processing within the switch/router. You can run PTP without hardware timestamping but it might not synchronise if the time errors introduced are too great. Also it will struggle to work through a router (large delays) for the same reason.
|
||||
|
||||
### Older time synchronization protocols: ###
|
||||
|
||||
- DTSS – Digital Time Synchronisation Service by Digital Equipment Corporation, superseded by NTP. See an example of [DTSS VMS C code c2000][101]. (Any DTSS articles/documentation anywhere?)
|
||||
- [DAYTIME protocol][102], synchronization protocol using [TCP][103] or [UDP][104] port 13
|
||||
- [ICMP Timestamp][105] and [ICMP Timestamp Reply][106], synchronization protocol using [ICMP][107]
|
||||
- [Time Protocol][108], synchronization protocol using TCP or UDP port 37
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://nlug.ml1.co.uk/2012/01/ntpq-p-output/831
|
||||
|
||||
作者:Martin L
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.gentoo.org/
|
||||
[2]:http://nlug.ml1.co.uk/2012/01/man-ntpq-gentoo-brief-version/853
|
||||
[3]:http://www.thelinuxblog.com/linux-man-pages/1/ntpq
|
||||
[4]:http://www.eecis.udel.edu/~mills/ntp/html/ntpq.html
|
||||
[5]:http://linux.die.net/man/8/ntpq
|
||||
[6]:http://www.ntp.org/
|
||||
[7]:http://en.wikipedia.org/wiki/Wide_area_network
|
||||
[8]:http://en.wikipedia.org/wiki/Local_area_network
|
||||
[9]:http://en.wikipedia.org/wiki/User_Datagram_Protocol
|
||||
[10]:http://en.wikipedia.org/wiki/Network_Time_Protocol
|
||||
[11]:http://www.ntp.org/ntpfaq/NTP-s-time.htm
|
||||
[12]:http://www.ntp.org/rfc.html
|
||||
[13]:http://www.ietf.org/rfc/rfc1305.txt
|
||||
[14]:http://www.rfc-editor.org/rfc/rfc1305.pdf
|
||||
[15]:http://en.wikipedia.org/wiki/Time
|
||||
[16]:http://en.wikipedia.org/wiki/Calendar
|
||||
[17]:http://en.wikipedia.org/wiki/Network_Time_Protocol#Clock_strata
|
||||
[18]:http://en.wikipedia.org/wiki/Unicast
|
||||
[19]:http://www.eecis.udel.edu/~mills/ntp/html/manyopt.html#mcst
|
||||
[20]:http://en.wikipedia.org/wiki/Broadcasting_%28computing%29
|
||||
[21]:http://en.wikipedia.org/wiki/Multicast
|
||||
[22]:http://www.eecis.udel.edu/~mills/ntp/html/manyopt.html
|
||||
[23]:http://www.ietf.org/rfc/rfc5905.txt
|
||||
[24]:http://en.wikipedia.org/wiki/Octal#In_computers
|
||||
[25]:http://en.wikipedia.org/wiki/Root_mean_square
|
||||
[26]:http://www.eecis.udel.edu/~mills/ntp/html/decode.html#peer
|
||||
[27]:http://www.eecis.udel.edu/~mills/ntp/html/select.html
|
||||
[28]:http://en.wikipedia.org/wiki/Ip_address
|
||||
[29]:http://en.wikipedia.org/wiki/Pulse_per_second
|
||||
[30]:http://en.wikipedia.org/wiki/Inter-Range_Instrumentation_Group
|
||||
[31]:http://en.wikipedia.org/wiki/Standard_time_and_frequency_signal_service
|
||||
[32]:http://www.ptb.de/index_en.html
|
||||
[33]:http://en.wikipedia.org/wiki/United_States_Naval_Observatory#Time_service
|
||||
[34]:http://en.wikipedia.org/wiki/CHU_%28radio_station%29
|
||||
[35]:http://en.wikipedia.org/wiki/High_frequency
|
||||
[36]:http://en.wikipedia.org/wiki/DCF77
|
||||
[37]:http://en.wikipedia.org/wiki/Low_frequency
|
||||
[38]:http://en.wikipedia.org/wiki/HBG_%28time_signal%29
|
||||
[39]:http://en.wikipedia.org/wiki/JJY#Time_standards
|
||||
[40]:http://en.wikipedia.org/wiki/LORAN#Timing_and_synchronization
|
||||
[41]:http://en.wikipedia.org/wiki/Medium_frequency
|
||||
[42]:http://en.wikipedia.org/wiki/LORAN#The_future_of_LORAN
|
||||
[43]:http://en.wikipedia.org/wiki/LORAN#eLORAN
|
||||
[44]:http://en.wikipedia.org/wiki/Time_from_NPL#The_.27MSF_signal.27_and_the_.27Rugby_clock.27
|
||||
[45]:http://en.wikipedia.org/wiki/T%C3%A9l%C3%A9_Distribution_Fran%C3%A7aise
|
||||
[46]:http://en.wikipedia.org/wiki/WWV_%28radio_station%29#Time_signals
|
||||
[47]:http://en.wikipedia.org/wiki/WWVB
|
||||
[48]:http://en.wikipedia.org/wiki/WWVH
|
||||
[49]:http://en.wikipedia.org/wiki/GOES#Further_reading
|
||||
[50]:http://en.wikipedia.org/wiki/Gps#Timekeeping
|
||||
[51]:http://en.wikipedia.org/wiki/Galileo_%28satellite_navigation%29#The_concept
|
||||
[52]:http://en.wikipedia.org/wiki/Gnss
|
||||
[53]:http://www.eecis.udel.edu/~mills/ntp/html/debug.html
|
||||
[54]:http://www.ntp.org/ntpfaq/NTP-s-algo-kernel.htm
|
||||
[55]:http://en.wikipedia.org/wiki/Coordinated_Universal_Time
|
||||
[56]:http://en.wikipedia.org/wiki/Time_zone
|
||||
[57]:http://www.ietf.org/rfc/rfc1305.txt
|
||||
[58]:http://www.ietf.org/rfc/rfc5905.txt
|
||||
[59]:http://en.wikipedia.org/wiki/PLL
|
||||
[60]:http://en.wikipedia.org/wiki/Frequency-locked_loop
|
||||
[61]:http://en.wikipedia.org/wiki/Parts_per_million
|
||||
[62]:http://en.wikipedia.org/wiki/Leap_second
|
||||
[63]:http://en.wikipedia.org/wiki/Daylight_saving_time
|
||||
[64]:http://www.ntp.org/ntpfaq/NTP-s-time.htm#Q-TIME-LEAP-SECOND
|
||||
[65]:http://www.ntp.org/ntpfaq/NTP-s-algo-kernel.htm
|
||||
[66]:http://www.ntp.org/ntpfaq/NTP-s-algo.htm#AEN1895
|
||||
[67]:http://www.ntp.org/ntpfaq/NTP-s-algo.htm#Q-ACCURATE-CLOCK
|
||||
[68]:http://www.ntp.org/ntpfaq/NTP-s-trouble.htm#Q-TRB-MON-STATFIL
|
||||
[69]:http://www.ntp.org/ntpfaq/NTP-s-trouble.htm#AEN5086
|
||||
[70]:http://en.wikipedia.org/wiki/Root_mean_square
|
||||
[71]:http://en.wikipedia.org/wiki/PLL
|
||||
[72]:http://en.wikipedia.org/wiki/Frequency-locked_loop
|
||||
[73]:http://en.wikipedia.org/wiki/Parts_per_million
|
||||
[74]:http://nlug.ml1.co.uk/2012/01/man-ntpq-gentoo-brief-version/853
|
||||
[75]:http://nlug.ml1.co.uk/2012/01/man-ntpq-long-version/855
|
||||
[76]:http://nlug.ml1.co.uk/2012/01/man-ntpq-gentoo-long-version/856
|
||||
[77]:http://www.eecis.udel.edu/~mills/ntp/html/ntpq.html
|
||||
[78]:http://www.eecis.udel.edu/~mills/ntp/html/index.html
|
||||
[79]:http://www.ntp.org/ntpfaq/NTP-s-def-hist.htm
|
||||
[80]:http://www.eecis.udel.edu/~mills/database/papers/history.pdf
|
||||
[81]:http://www.ntp.org/rfc.html
|
||||
[82]:http://www.ietf.org/rfc/rfc1305.txt
|
||||
[83]:http://www.rfc-editor.org/rfc/rfc1305.pdf
|
||||
[84]:http://en.wikipedia.org/wiki/Time
|
||||
[85]:http://en.wikipedia.org/wiki/Calendar
|
||||
[86]:http://www.rmg.co.uk/harrison
|
||||
[87]:http://longnow.org/clock/
|
||||
[88]:http://johnctaylor.com/
|
||||
[89]:http://en.wikipedia.org/wiki/Orders_of_magnitude_%28time%29
|
||||
[90]:http://en.wikipedia.org/wiki/Greenwich_Time_Signal
|
||||
[91]:http://tools.ietf.org/html/rfc4330
|
||||
[92]:http://tools.ietf.org/html/rfc1305
|
||||
[93]:http://en.wikipedia.org/wiki/Network_Time_Protocol#Microsoft_Windows
|
||||
[94]:http://en.wikipedia.org/wiki/Personal_computer
|
||||
[95]:http://www.nist.gov/el/isd/ieee/ieee1588.cfm
|
||||
[96]:http://en.wikipedia.org/wiki/IEEE_1588
|
||||
[97]:http://ptpd.sourceforge.net/
|
||||
[98]:http://en.wikipedia.org/wiki/Local_area_network
|
||||
[99]:http://en.wikipedia.org/wiki/International_Atomic_Time
|
||||
[100]:http://en.wikipedia.org/wiki/Monotonic_function
|
||||
[101]:http://antinode.info/ftp/dtss_ntp/
|
||||
[102]:http://en.wikipedia.org/wiki/DAYTIME
|
||||
[103]:http://en.wikipedia.org/wiki/Transmission_Control_Protocol
|
||||
[104]:http://en.wikipedia.org/wiki/User_Datagram_Protocol
|
||||
[105]:http://en.wikipedia.org/wiki/ICMP_Timestamp
|
||||
[106]:http://en.wikipedia.org/wiki/ICMP_Timestamp_Reply
|
||||
[107]:http://en.wikipedia.org/wiki/Internet_Control_Message_Protocol
|
||||
[108]:http://en.wikipedia.org/wiki/Time_Protocol
|
||||
@ -1,228 +0,0 @@
|
||||
How to install Xen hypervisor on unused old hardware
|
||||
================================================================================
|
||||
Xen is a bare metal hypervisor, meaning that you must prepare a bare machine to install and run Xen. KVM is a little different - you can add it to any machine already running Linux. This tutorial describes how to install and configure Xen hypervisor on unused hardware.
|
||||
|
||||
This procedure uses Debian Jessie (their testing distribution) as the host OS (also known as [Dom0][1]). Jessie is not the only choice - Xen support is built into the Linux kernel, and [plenty of Linux distributions][2] include one of these Xen-enabled kernels.
|
||||
|
||||
### Find unused hardware ###
|
||||
|
||||
As a start, find a suitable workstation which can be wiped out, such as an old laptop or desktop. Older hardware may not be good for gaming, but it is good enough for a host OS and a couple of guests. A PC with these specifications works fine.
|
||||
|
||||
- 1 CPU with 2 cores (64-bit)
|
||||
- 4GB memory
|
||||
- 80GB hard disk
|
||||
- ability to boot from CD, DVD or USB
|
||||
- a network interface
|
||||
|
||||
Note that the CPU must be a 64-bit processor since Debian dropped support for 32-bit Xen packages. If you don't have spare hardware, you could invest in an old machine. 2010's $1000 flagship laptop is today's $100 bargain. A second-hand laptop from eBay and a memory upgrade will do fine.
|
||||
|
||||
### Burn a bootable CD/USB ###
|
||||
|
||||
Download the ISO image for Debian Jessie. The small netinst image available from the [official Debian website][3] works fine.
|
||||
|
||||
$ wget http://cdimage.debian.org/cdimage/jessie_di_beta_2/amd64/iso-cd/debian-jessie-DI-b2-amd64-netinst.iso
|
||||
|
||||
Next, identify the device name assigned to your [CD/DVD][4] or [USB drive][5] (e.g., /dev/sdc).
|
||||
|
||||
Burn the downloaded ISO image into a bootable CD or a USB using dd command. Replace /dev/sdc with the device name you identified above.
|
||||
|
||||
$ sudo dd if=debian-jessie-DI-b2-amd64-netinst.iso of=/dev/sdc
|
||||
|
||||
### Start the installation ###
|
||||
|
||||
To start the installation, boot with the Debian installer CD/USB.
|
||||
|
||||
It's a good idea to use a wired connection, not WiFi. If the WiFi won't connect because firmware or driver software is missing, you won't get very far.
|
||||
|
||||
|
||||
|
||||
### Partition the disk ###
|
||||
|
||||
This setup uses four primary disk partitions. Automatic OS installers usually set up an extended partition that contains logical partitions. Set up the four partitions like this.
|
||||
|
||||
- sda1 mount on /boot, 200MB
|
||||
- sda2 /, 20GB, Ubuntu uses 4GB
|
||||
- sda3 swap, 6GB (4GB of memory x 1.5 = 6)
|
||||
- sda4 reserved for LVM, not mounted, all the rest of the disk space
|
||||
|
||||
### Install the base system ###
|
||||
|
||||
It's a good idea to make the install as simple and short as possible. A basic working system can always be added to later. Debian's APT (Advanced Package Tool) makes adding software easy. Installing Debian on a workstation can cause pretty obscure time-wasting issues. Perhaps a graphics driver does not agree with the kernel or maybe the old CD-ROM drive only works intermittently.
|
||||
|
||||
When it comes to choosing what to install, do install an SSH server and don't install a desktop like Gnome.
|
||||
|
||||
|
||||
|
||||
A graphical desktop requires hundreds of package installs - it's a lot of extra work that can be done later. If you run into problems, waiting for that desktop install is a waste of time. Also, without desktop component, the system boot will be much quicker - seconds rather than minutes. This procedure requires a few reboots, so that's a handy time-saver.
|
||||
|
||||
An SSH server lets you configure the workstation from another computer. This allows you to avoid some of the problems with old hardware - perhaps the old machine's keyboard is missing keys, the LCD screen has dead pixels or the trackpad is unresponsive etc.
|
||||
|
||||
### Add LVM (Logical Volume Manager) ###
|
||||
|
||||
Install the LVM tools as the root.
|
||||
|
||||
# apt-get update
|
||||
# apt-get install lvm2
|
||||
|
||||
Pick a physical volume to work with.
|
||||
|
||||
# pvcreate /dev/sda4
|
||||
|
||||
Create a volume group.
|
||||
|
||||
# vgcreate vg0 /dev/sda4
|
||||
|
||||
You don't need to create a logical volume. If you want to test LVM works, create a volume then delete it.
|
||||
|
||||
# lvcreate -nmytempvol -L10G vg0
|
||||
# lvremove /dev/vg0/mytempvol
|
||||
|
||||
Check LVM status.
|
||||
|
||||
# pvs (to view information about physical volumes)
|
||||
# vgs (to view information about volume groups)
|
||||
# lvs (to view information about logical volumes)
|
||||
|
||||
### Add a Linux Ethernet bridge ###
|
||||
|
||||
We are going to set up a Linux bridge so that all Xen's guest domains can be connected to, and communicate through the bridge.
|
||||
|
||||
Install the bridge tools.
|
||||
|
||||
# apt-get install bridge-utils
|
||||
|
||||
See what interfaces are configured.
|
||||
|
||||
# ip addr
|
||||
|
||||
|
||||
|
||||
In this example, we have one primary interface assigned eth0. We are going to add eth0 to the Linux bridge by editing the network configuration file (/etc/network/interfaces).
|
||||
|
||||
Before making any change, back up the network configuration file to keep the original working configuration safe.
|
||||
|
||||
# cd /etc/network/
|
||||
# cp interfaces interfaces.backup
|
||||
# vi /etc/network/interfaces
|
||||
|
||||
The file contents look something like this.
|
||||
|
||||
auto lo
|
||||
iface lo inet loopback
|
||||
|
||||
allow-hotplug eth0
|
||||
iface eth0 inet dhcp
|
||||
|
||||
Change the file to this.
|
||||
|
||||
auto lo
|
||||
iface lo inet loopback
|
||||
|
||||
auto eth0
|
||||
iface eth0 inet manual
|
||||
|
||||
auto xenbr0
|
||||
iface xenbr0 inet dhcp
|
||||
bridge_ports eth0
|
||||
|
||||
Activate the network configuration change:
|
||||
|
||||
# systemctl restart networking
|
||||
|
||||
### Verify networking settings ###
|
||||
|
||||
Verify that a Linux bridge xenbr0 is created successfully.
|
||||
|
||||
# ip addr show xenbr0
|
||||
|
||||
Also check that the primary interface eth0 is successfully added to the bridge.
|
||||
|
||||
# brctl show
|
||||
|
||||
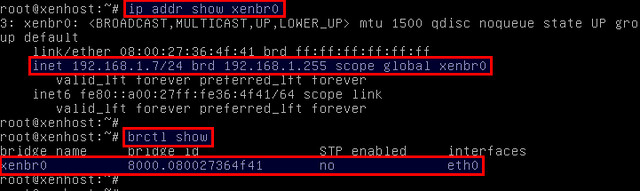
|
||||
|
||||
You now have a working machine with Jessie installed. Xen is not yet installed at this point. Let's proceed to install Xen next.
|
||||
|
||||
### Install the Xen hypervisor ###
|
||||
|
||||
Install Xen and QEMU packages, and update the GRUB bootloader.
|
||||
|
||||
# apt-get install xen-linux-system
|
||||
|
||||
Reboot.
|
||||
|
||||
When the GRUB screen appears, you can see extra booting options listed.
|
||||
|
||||
|
||||
|
||||
The first option will boot automatically in five seconds (see the GRUB_TIMEOUT line in /etc/default/grub), so this is not the time to get a coffee.
|
||||
|
||||
Press the down arrow to highlight the option "Debian GNU/Linux, with Xen hypervisor", and press RETURN. Many lines of information appear, followed by the usual login screen.
|
||||
|
||||
### Check Xen works ###
|
||||
|
||||
Xen hypervisor comes with Xen management command-line tool called xl, which can be used to create and manage Xen guest domains. Let's use xl command to check if Xen is successfully installed.
|
||||
|
||||
Log in as root, and run:
|
||||
|
||||
# xl info
|
||||
|
||||
which will display various information about Xen host.
|
||||
|
||||
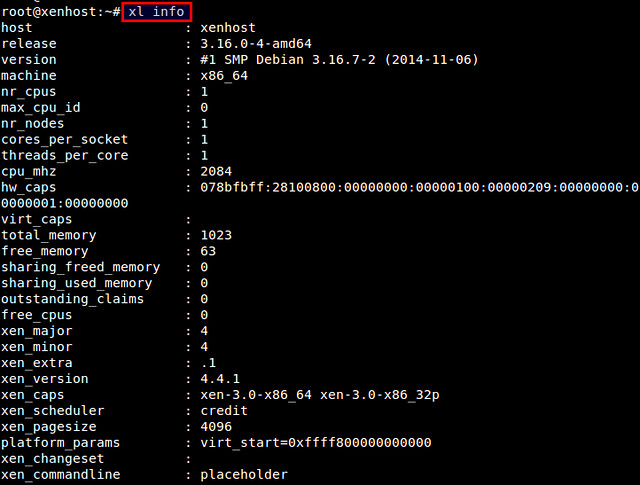
|
||||
|
||||
To see a list of existing Xen domains:
|
||||
|
||||
# xl list
|
||||
|
||||
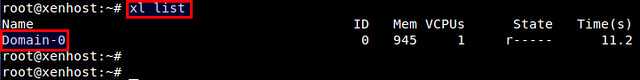
|
||||
|
||||
A little table of domains appears. Without any Xen guest domain created, the only entry should be Domain-0, your Debian installation.
|
||||
|
||||
### Change the boot order ###
|
||||
|
||||
When you reach this point, the Xen install is complete. There is one more thing to fix - the default boot will not load Xen. GRUB chooses the first item in the boot menu (Debian GNU/Linux), not the third (Debian GNU/Linux, with Xen hypervisor).
|
||||
|
||||
The default option in the boot menu is defined in the grub configuration file /boot/grub/grub.cfg. To change the default option, don't edit that file, but edit /etc/default/grub instead. A little helper program called grub-mkconfig reads in this default configuration file and all the templates in /etc/grub.d/, then writes the grub.cfg file.
|
||||
|
||||
Edit Debian's configuration file for grub-mkconfig.
|
||||
|
||||
# vi /etc/default/grub
|
||||
|
||||
Change the line:
|
||||
|
||||
GRUB_DEFAULT=0
|
||||
|
||||
to
|
||||
|
||||
GRUB_DEFAULT='Debian GNU/Linux, with Xen hypervisor'
|
||||
|
||||
Then update the grub configuration file.
|
||||
|
||||
# grub-mkconfig -o /boot/grub/grub.cfg
|
||||
|
||||
Finally reboot. After a few seconds, the grub boot menu appears. Check that the third option "Debian GNU/Linux, with Xen hypervisor" is highlighted automatically.
|
||||
|
||||
### Final note ###
|
||||
|
||||
If you use this machine as your hands-on workstation, install a graphical desktop. The Debian library includes a few [desktop environments][6]. If you want a graphical desktop that includes everything and the kitchen sink, go for Gnome. If graphics just get in your way, try Awesome.
|
||||
|
||||
Note that the Debian Jessie default environment Gnome comes with a huge amount of extra applications including the productivity suite LibreOffice, the Iceweasel web browser and the Rhythmbox music player. The install command "apt-get install gnome" adds 1,000 packages and takes up nearly 2GB of disk space. Running this heavyweight desktop takes up 1GB of memory.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/install-xen-hypervisor.html
|
||||
|
||||
作者:[Nick Hardiman][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/nick
|
||||
[1]:http://wiki.xen.org/wiki/Dom0
|
||||
[2]:http://wiki.xen.org/wiki/Dom0_Kernels_for_Xen
|
||||
[3]:https://www.debian.org/devel/debian-installer/
|
||||
[4]:http://ask.xmodulo.com/detect-dvd-writer-device-name-writing-speed-command-line-linux.html
|
||||
[5]:http://ask.xmodulo.com/find-device-name-usb-drive-linux.html
|
||||
[6]:https://wiki.debian.org/DesktopEnvironment
|
||||
@ -1,129 +0,0 @@
|
||||
How to install Cacti (Monitoring tool) on ubuntu 14.10 server
|
||||
================================================================================
|
||||
Cacti is a complete network graphing solution designed to harness the power of RRDTool's data storage and graphing functionality. Cacti provides a fast poller, advanced graph templating, multiple data acquisition methods, and user management features out of the box. All of this is wrapped in an intuitive, easy to use interface that makes sense for LAN-sized installations up to complex networks with hundreds of devices.
|
||||
|
||||
### Features ###
|
||||
|
||||
#### Graphs ####
|
||||
|
||||
Unlimited number of graph items can be defined for each graph optionally utilizing CDEFs or data sources from within cacti.
|
||||
|
||||
Automatic grouping of GPRINT graph items to AREA, STACK, and LINE[1-3] to allow for quick re-sequencing of graph items.
|
||||
|
||||
Auto-Padding support to make sure graph legend text lines up.
|
||||
|
||||
Graph data can be manipulated using the CDEF math functions built into RRDTool. These CDEF functions can be defined in cacti and can be used globally on each graph.
|
||||
|
||||
Support for all of RRDTool's graph item types including AREA, STACK, LINE[1-3], GPRINT, COMMENT, VRULE, and HRULE.
|
||||
|
||||
#### Data Sources ####
|
||||
|
||||
Data sources can be created that utilize RRDTool's "create" and "update" functions. Each data source can be used to gather local or remote data and placed on a graph.
|
||||
|
||||
Supports RRD files with more than one data source and can use an RRD file stored anywhere on the local file system.
|
||||
Round robin archive (RRA) settings can be customized giving the user the ability to gather data on non-standard timespans while store varying amounts of data.
|
||||
|
||||
#### Data Gathering ####
|
||||
|
||||
Contains a "data input" mechanism which allows users to define custom scripts that can be used to gather data. Each script can contain arguments that must be entered for each data source created using the script (such as an IP address).
|
||||
|
||||
Built in SNMP support that can use php-snmp, ucd-snmp, or net-snmp.
|
||||
|
||||
Ability to retrieve data using SNMP or a script with an index. An example of this would be populating a list with IP interfaces or mounted partitions on a server. Integration with graph templates can be defined to enable one click graph creation for hosts.
|
||||
|
||||
A PHP-based poller is provided to execute scripts, retrieve SNMP data, and update your RRD files.
|
||||
|
||||
#### Templates ####
|
||||
|
||||
Graph templates enable common graphs to be grouped together by templating. Every field for a normal graph can be templated or specified on a per-graph basis.
|
||||
|
||||
Data source templates enable common data source types to be grouped together by templating. Every field for a normal data source can be templated or specified on a per-data source basis.
|
||||
|
||||
Host templates are a group of graph and data source templates that allow you to define common host types. Upon the creation of a host, it will automatically take on the properties of its template.
|
||||
|
||||
#### Graph Display ####
|
||||
|
||||
The tree view allows users to create "graph hierarchies" and place graphs on the tree. This is an easy way to manage/organize a large number of graphs.
|
||||
|
||||
The list view lists the title of each graph in one large list which links the user to the actual graph.
|
||||
The preview view displays all of the graphs in one large list format. This is similar to the default view for the 14all cgi script for RRDTool/MRTG.
|
||||
|
||||
#### User Management ####
|
||||
|
||||
User based management allows administrators to create users and assign different levels of permissions to the cacti interface.
|
||||
|
||||
Permissions can be specified per-graph for each user, making cacti suitable for co location situations.
|
||||
Each user can keep their own graph settings for varying viewing preferences.
|
||||
|
||||
#### Preparing your system ####
|
||||
|
||||
Before installing cacti you need to make sure you have installed [Ubuntu 14.10 LAMP server][1].
|
||||
|
||||
#### Install Cacti on ubuntu 14.10 server ####
|
||||
|
||||
Open the terminal and run the following command
|
||||
|
||||
sudo apt-get install cacti-spine
|
||||
|
||||
The above command starts the cacti installation and you should see the first as php path change select ok and press enter
|
||||
|
||||
|
||||
|
||||
Now select the webserver you want to use (in my case it is apache2)
|
||||
|
||||

|
||||
|
||||
Cacti database configurations select yes
|
||||
|
||||

|
||||
|
||||
Enter database admin user password
|
||||
|
||||
|
||||
|
||||
Mysql application password for cacti
|
||||
|
||||

|
||||
|
||||
confirm the password
|
||||
|
||||

|
||||
|
||||
Now that Cacti is installed, we can start the configuration process on it.
|
||||
|
||||
#### Configuring cacti ####
|
||||
|
||||
Point your web browser towards http://YOURSERVERIP/cacti/install/ to start the initial setup and click next
|
||||
|
||||

|
||||
|
||||
Select new install option and click next
|
||||
|
||||

|
||||
|
||||
In the following screen you need to make sure you have all the required paths are correct and click on finish
|
||||
|
||||

|
||||
|
||||
Now login to Cacti with the default admin/admin, and change the password to something more sensible
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
After login in to Cacti you should see similar to the following screen
|
||||
|
||||

|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.ubuntugeek.com/how-to-install-cacti-monitoring-tool-on-ubuntu-14-10-server.html
|
||||
|
||||
作者:[ruchi][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.ubuntugeek.com/author/ubuntufix
|
||||
[1]:http://www.ubuntugeek.com/www.ubuntugeek.com/step-by-step-ubuntu-14-10-utopic-unicorn-lamp-server-setup.html
|
||||
@ -1,76 +0,0 @@
|
||||
Quick systemd-nspawn guide
|
||||
================================================================================
|
||||
I switched to using systemd-nspawn in place of chroot and wanted to give a quick guide to using it. The short version is that I’d strongly recommend that anybody running systemd that uses chroot switch over - there really are no downsides as long as your kernel is properly configured.
|
||||
|
||||
Chroot should be no stranger to anybody who works on distros, and I suspect that the majority of Gentoo users have need for it from time to time.
|
||||
|
||||
### The Challenges of chroot ###
|
||||
|
||||
For most interactive uses it isn’t sufficient to just run chroot. Usually you need to mount /proc, /sys, and bind mount /dev so that you don’t have issues like missing ptys, etc. If you use tmpfs you might also want to mount the new tmp, var/tmp as tmpfs. Then you might want to make other bind mounts into the chroot. None of this is particularly difficult, but you usually end up writing a small script to manage it.
|
||||
|
||||
Now, I routinely do full backups, and usually that involves excluding stuff like tmp dirs, and anything resembling a bind mount. When I set up a new chroot that means updating my backup config, which I usually forget to do since most of the time the chroot mounts aren’t running anyway. Then when I do leave it mounted overnight I end up with backups consuming lots of extra space (bind mounts of large trees).
|
||||
|
||||
Finally, systemd now by default handles bind mounts a little differently when they contain other mount points (such as when using -rbind). Apparently unmounting something in the bind mount will cause systemd to unmount the corresponding directory on the other side of the bind. Imagine my surprise when I unmounted my chroot bind to /dev and discovered /dev/pts and /dev/shm no longer mounted on the host. It looks like there are ways to change that, but this isn’t the point of my post (it just spurred me to find another way).
|
||||
|
||||
### Systemd-nspawn’s Advantages ###
|
||||
|
||||
Systemd-nspawn is a tool that launches a container, and it can operate just like chroot in its simplest form. By default it automatically sets up most of the overhead like /dev, /tmp, etc. With a few options it can also set up other bind mounts as well. When the container exits all the mounts are cleaned up.
|
||||
|
||||
From the outside of the container nothing appears different when the container is running. In fact, you could spawn 5 different systemd-nspawn container instances from the same chroot and they wouldn’t have any interaction except via the filesystem (and that excludes /dev, /tmp, and so on - only changes in /usr, /etc will propagate across). Your backup won’t see the bind mounts, or tmpfs, or anything else mounted within the container.
|
||||
|
||||
The container also has all those other nifty container benefits like containment - a killall inside the container won’t touch anything outside, and so on. The security isn’t airtight - the intent is to prevent accidental mistakes.
|
||||
|
||||
Then, if you use a compatible sysvinit (which includes systemd, and I think recent versions of openrc), you can actually boot the container, which drops you to a getty inside. That means you can use fstab to do additional mounts inside the container, run daemons, and so on. You get almost all the benefits of virtualization for the cost of a chroot (no need to build a kernel, and so on). It is a bit odd to be running systemctl poweroff inside what looks just like a chroot, but it works.
|
||||
|
||||
Note that unless you do a bit more setup you will share the same network interface with the host, so no running sshd on the container if you have it on the host, etc. I won’t get into this but it shouldn’t be hard to run a separate network namespace and bind the interfaces so that the new instance can run dhcp.
|
||||
|
||||
### How to do it ###
|
||||
|
||||
So, getting it actually working will likely be the shortest bit in this post.
|
||||
|
||||
You need support for namespaces and multiple devpts instances in your kernel:
|
||||
|
||||
CONFIG_UTS_NS=y
|
||||
CONFIG_IPC_NS=y
|
||||
CONFIG_USER_NS=y
|
||||
CONFIG_PID_NS=y
|
||||
CONFIG_NET_NS=y
|
||||
CONFIG_DEVPTS_MULTIPLE_INSTANCES=y
|
||||
|
||||
From there launching a namespace just like a chroot is really simple:
|
||||
|
||||
systemd-nspawn -D .
|
||||
|
||||
That’s it - you can exit from it just like a chroot. From inside you can run mount and see that it has taken care of /dev and /tmp for you. The “.” is the path to the chroot, which I assume is the current directory. With nothing further it runs bash inside.
|
||||
|
||||
If you want to add some bind mounts it is easy:
|
||||
|
||||
systemd-nspawn -D . --bind /usr/portage
|
||||
|
||||
Now your /usr/portage is bound to your host, so no need to sync/etc. If you want to bind to a different destination add a “:dest” after the source, relative to the root of the chroot (so --bind foo is the same as --bind foo:foo).
|
||||
|
||||
If the container has a functional init that can handle being run inside, you can add a -b to boot it:
|
||||
|
||||
systemd-nspawn -D . --bind /usr/portage -b
|
||||
|
||||
Watch the init do its job. Shut down the container to exit.
|
||||
|
||||
Now, if that container is running systemd you can direct its journal to the host journal with -h:
|
||||
|
||||
systemd-nspawn -D . --bind /usr/portage -j -b
|
||||
|
||||
Now, nspawn registers the container so that it shows up in machinectl. That makes it easy to launch a new getty on it, or ssh to it (if it is running ssh - see my note above about network namespaces), or power it off from the host.
|
||||
|
||||
That’s it. If you’re running systemd I’d suggest ditching chroot almost entirely in favor of nspawn.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://rich0gentoo.wordpress.com/2014/07/14/quick-systemd-nspawn-guide/
|
||||
|
||||
作者:[rich0][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://rich0gentoo.wordpress.com/
|
||||
@ -1,153 +0,0 @@
|
||||
ideas4u Translating..
|
||||
How to use matplotlib for scientific plotting on Linux
|
||||
================================================================================
|
||||
If you want an efficient, automatable solution for producing high-quality scientific plots in Linux, then consider using matplotlib. Matplotlib is a Python-based open-source scientific plotting package with a license based on the Python Software Foundation license. The extensive documentation and examples, integration with Python and the NumPy scientific computing package, and automation capability are just a few reasons why this package is a solid choice for scientific plotting in a Linux environment. This tutorial will provide several example plots created with matplotlib.
|
||||
|
||||
### Features ###
|
||||
|
||||
- Numerous plot types (bar, box, contour, histogram, scatter, line plots...)
|
||||
- Python-based syntax
|
||||
- Integration with the NumPy scientific computing package
|
||||
- Source data can be Python lists, Python tuples, or NumPy arrays
|
||||
- Customizable plot format (axes scales, tick positions, tick labels...)
|
||||
- Customizable text (font, size, position...)
|
||||
- TeX formatting (equations, symbols, Greek characters...)
|
||||
- Compatible with IPython (allows interactive plotting from a Python shell)
|
||||
- Automation - use Python loops to iteratively create plots
|
||||
- Save plots to image files (png, pdf, ps, eps, and svg format)
|
||||
|
||||
The Python-based syntax of matplotlib serves as the foundation for many of its features and enables an efficient workflow. There are many scientific plotting packages that can produce quality plots, but do they allow you to do it directly from within your Python code? On top of that, do they allow you to create automated routines for iterative creation of plots that can be saved as image files? Matplotlib allows you to accomplish all of these tasks. You can now look forward to saving time that would have otherwise been spent manually creating multiple plots.
|
||||
|
||||
### Installation ###
|
||||
|
||||
Installation of Python and the NumPy package is a prerequisite for use of matplotlib. Instructions for installing NumPy can be found [here][1].
|
||||
|
||||
To install matplotlib in Debian or Ubuntu, run the following command:
|
||||
|
||||
$ sudo apt-get install python-matplotlib
|
||||
|
||||
To install matplotlib in Fedora or CentOS/RHEL, run the following command:
|
||||
|
||||
$ sudo yum install python-matplotlib
|
||||
|
||||
### Matplotlib Examples ###
|
||||
|
||||
This tutorial will provide several plotting examples that demonstrate how to use matplotlib:
|
||||
|
||||
- Scatter and line plot
|
||||
- Histogram plot
|
||||
- Pie chart
|
||||
|
||||
In these examples we will use Python scripts to execute matplotlib commands. Note that the numpy and matplotlib modules must be imported from within the scripts via the import command. np is specified as a reference to the numpy module and plt is specified as a reference to the matplotlib.pyplot namespace:
|
||||
|
||||
import numpy as np
|
||||
import matplotlib.pyplot as plt
|
||||
|
||||
### Example 1: Scatter and Line Plot ###
|
||||
|
||||
The first script, script1.py completes the following tasks:
|
||||
|
||||
- Creates three data sets (xData, yData1, and yData2)
|
||||
- Creates a new figure (assigned number 1) with a width and height of 8 inches and 6 inches, respectively
|
||||
- Sets the plot title, x-axis label, and y-axis label (all with font size of 14)
|
||||
- Plots the first data set, yData1, as a function of the xData dataset as a dotted blue line with circular markers and a label of "y1 data"
|
||||
- Plots the second data set, yData2, as a function of the xData dataset as a solid red line with no markers and a label of "y2 data".
|
||||
- Positions the legend in the upper left-hand corner of the plot
|
||||
- Saves the figure as a PNG file
|
||||
|
||||
Contents of script1.py:
|
||||
|
||||
import numpy as np
|
||||
import matplotlib.pyplot as plt
|
||||
|
||||
xData = np.arange(0, 10, 1)
|
||||
yData1 = xData.__pow__(2.0)
|
||||
yData2 = np.arange(15, 61, 5)
|
||||
plt.figure(num=1, figsize=(8, 6))
|
||||
plt.title('Plot 1', size=14)
|
||||
plt.xlabel('x-axis', size=14)
|
||||
plt.ylabel('y-axis', size=14)
|
||||
plt.plot(xData, yData1, color='b', linestyle='--', marker='o', label='y1 data')
|
||||
plt.plot(xData, yData2, color='r', linestyle='-', label='y2 data')
|
||||
plt.legend(loc='upper left')
|
||||
plt.savefig('images/plot1.png', format='png')
|
||||
|
||||
The resulting plot is shown below:
|
||||
|
||||
|
||||
|
||||
### Example 2: Histogram Plot ###
|
||||
|
||||
The second script, script2.py completes the following tasks:
|
||||
|
||||
- Creates a data set containing 1000 random samples from a Normal distribution
|
||||
- Creates a new figure (assigned number 1) with a width and height of 8 inches and 6 inches, respectively
|
||||
- Sets the plot title, x-axis label, and y-axis label (all with font size of 14)
|
||||
- Plots the data set, samples, as a histogram with 40 bins and an upper and lower bound of -10 and 10, respectively
|
||||
- Adds text to the plot and uses TeX formatting to display the Greek letters mu and sigma (font size of 16)
|
||||
- Saves the figure as a PNG file
|
||||
|
||||
Contents of script2.py:
|
||||
|
||||
import numpy as np
|
||||
import matplotlib.pyplot as plt
|
||||
|
||||
mu = 0.0
|
||||
sigma = 2.0
|
||||
samples = np.random.normal(loc=mu, scale=sigma, size=1000)
|
||||
plt.figure(num=1, figsize=(8, 6))
|
||||
plt.title('Plot 2', size=14)
|
||||
plt.xlabel('value', size=14)
|
||||
plt.ylabel('counts', size=14)
|
||||
plt.hist(samples, bins=40, range=(-10, 10))
|
||||
plt.text(-9, 100, r'$\mu$ = 0.0, $\sigma$ = 2.0', size=16)
|
||||
plt.savefig('images/plot2.png', format='png')
|
||||
|
||||
The resulting plot is shown below:
|
||||
|
||||
|
||||
|
||||
### Example 3: Pie Chart ###
|
||||
|
||||
The third script, script3.py completes the following tasks:
|
||||
|
||||
- Creates data set containing five integers
|
||||
- Creates a new figure (assigned number 1) with a width and height of 6 inches and 6 inches, respectively
|
||||
- Adds an axes to the figure with an aspect ratio of 1
|
||||
- Sets the plot title (font size of 14)
|
||||
- Plots the data set, data, as a pie chart with labels included
|
||||
- Saves the figure as a PNG file
|
||||
|
||||
Contents of script3.py:
|
||||
|
||||
import numpy as np
|
||||
import matplotlib.pyplot as plt
|
||||
|
||||
data = [33, 25, 20, 12, 10]
|
||||
plt.figure(num=1, figsize=(6, 6))
|
||||
plt.axes(aspect=1)
|
||||
plt.title('Plot 3', size=14)
|
||||
plt.pie(data, labels=('Group 1', 'Group 2', 'Group 3', 'Group 4', 'Group 5'))
|
||||
plt.savefig('images/plot3.png', format='png')
|
||||
|
||||
The resulting plot is shown below:
|
||||
|
||||
|
||||
|
||||
### Summary ###
|
||||
|
||||
This tutorial provides several examples of plots that can be created with the matplotlib scientific plotting package. Matplotlib is a great solution for scientific plotting in a Linux environment given its natural integration with Python and NumPy, its ability to be automated, and its production of a wide variety of customizable high quality plots. Documentation and examples for the matplotlib package can be found [here][2].
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/matplotlib-scientific-plotting-linux.html
|
||||
|
||||
作者:[Joshua Reed][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/joshua
|
||||
[1]:http://xmodulo.com/numpy-scientific-computing-linux.html
|
||||
[2]:http://matplotlib.org/
|
||||
@ -1,148 +0,0 @@
|
||||
Create Centralized Secure Storage using iSCSI Target on RHEL/CentOS/Fedora Part -I
|
||||
================================================================================
|
||||
**iSCSI** is a block level Protocol for sharing **RAW Storage Devices** over TCP/IP Networks, Sharing and accessing Storage over iSCSI, can be used with existing IP and Ethernet networks such as NICs, Switched, Routers etc. iSCSI target is a remote hard disk presented from an remote iSCSI server (or) target.
|
||||
|
||||
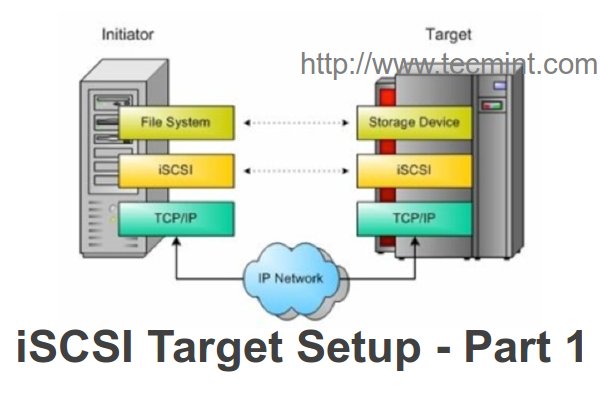
|
||||
Install iSCSI Target in Linux
|
||||
|
||||
We don’t need a high resource for stable connectivity and performance in Client side’s. iSCSI Server called as Target, this share’s the storage from server. iSCSI Client’s called as Initiator, this will access the storage which shared from Target Server. There are iSCSI adapter’s available in market for Large Storage services such as SAN Storage’s.
|
||||
|
||||
**Why we need a iSCSI adapter for Large storage Area?**
|
||||
|
||||
Ethernet adapters (NIC) are designed to transfer packetized file level data among systems, servers and storage devices like NAS storage’s, they are not capable for transferring block level data over Internet.
|
||||
|
||||
### Features of iSCSI Target ###
|
||||
|
||||
- Possible to run several iSCSI targets on a single machine.
|
||||
- A single machine making multiple iscsi target available on the iSCSI SAN
|
||||
- The target is the Storage and makes it available for initiator (Client) over the network
|
||||
- These Storage’s are Pooled together to make available to the network is iSCSI LUNs (Logical Unit Number).
|
||||
- iSCSI supports multiple connections within the same session
|
||||
- iSCSI initiator discover the targets in network then authenticating and login with LUNs, to get the remote storage locally.
|
||||
- We can Install any Operating systems in those locally mounted LUNs as what we used to install in our Base systems.
|
||||
|
||||
### Why the need of iSCSI? ###
|
||||
|
||||
In Virtualization we need storage with high redundancy, stability, iSCSI provides those all in low cost. Creating a SAN Storage in low price while comparing to Fiber Channel SANs, We can use the standard equipment’s for building a SAN using existing hardware such as NIC, Ethernet Switched etc..
|
||||
|
||||
Let start to get install and configure the centralized Secure Storage using iSCSI Target. For this guide, I’ve used following setups.
|
||||
|
||||
- We need separate 1 systems to Setup the iSCSI Target Server and Initiator (Client).
|
||||
- Multiple numbers of Hard disk can be added in large storage environment, But we here using only 1 additional drive except Base installation disk.
|
||||
- Here we using only 2 drives, One for Base server installation, Other one for Storage (LUNs) which we going to create in PART-II of this series.
|
||||
|
||||
#### Master Server Setup ####
|
||||
|
||||
- Operating System – CentOS release 6.5 (Final)
|
||||
- iSCSI Target IP – 192.168.0.200
|
||||
- Ports Used : TCP 860, 3260
|
||||
- Configuration file : /etc/tgt/targets.conf
|
||||
|
||||
## Installing iSCSI Target ##
|
||||
|
||||
Open terminal and use yum command to search for the package name which need to get install for iscsi target.
|
||||
|
||||
# yum search iscsi
|
||||
|
||||
#### Sample Output ####
|
||||
|
||||
========================== N/S matched: iscsi =======================
|
||||
iscsi-initiator-utils.x86_64 : iSCSI daemon and utility programs
|
||||
iscsi-initiator-utils-devel.x86_64 : Development files for iscsi-initiator-utils
|
||||
lsscsi.x86_64 : List SCSI devices (or hosts) and associated information
|
||||
scsi-target-utils.x86_64 : The SCSI target daemon and utility programs
|
||||
|
||||
We got the search result as above, choose the **Target** package and install to play around.
|
||||
|
||||
# yum install scsi-target-utils -y
|
||||
|
||||

|
||||
Install iSCSI Utils
|
||||
|
||||
List the installed package to know the default config, service, and man page location.
|
||||
|
||||
# rpm -ql scsi-target-utils.x86_64
|
||||
|
||||

|
||||
|
||||
List All iSCSI Files
|
||||
|
||||
Let’s start the iSCSI Service, and check the status of Service up and running, iSCSI service named as **tgtd**.
|
||||
|
||||
# /etc/init.d/tgtd start
|
||||
# /etc/init.d/tgtd status
|
||||
|
||||

|
||||
|
||||
Start iSCSI Service
|
||||
|
||||
Now we need to configure it to start Automatically while system start-up.
|
||||
|
||||
# chkconfig tgtd on
|
||||
|
||||
Next, verify that the run level configured correctly for the tgtd service.
|
||||
|
||||
# chkconfig --list tgtd
|
||||
|
||||

|
||||
|
||||
Enable iSCSI on Startup
|
||||
|
||||
Let’s use **tgtadm** to list what targets and LUNS we currently got configured in our Server.
|
||||
|
||||
# tgtadm --mode target --op show
|
||||
|
||||
The **tgtd** installed up and running, but there is no **Output** from the above command because we have not yet defined the LUNs in Target Server. For manual page, Run ‘**man**‘ command.
|
||||
|
||||
# man tgtadm
|
||||
|
||||

|
||||
|
||||
iSCSI Man Pages
|
||||
|
||||
Finally we need to add iptables rules for iSCSI if there is iptables deployed in your target Server. First, find the Port number of iscsi target using following netstat command, The target always listens on TCP port 3260.
|
||||
|
||||
# netstat -tulnp | grep tgtd
|
||||
|
||||

|
||||
|
||||
Find iSCSI Port
|
||||
|
||||
Next add the following rules to allow iptables to Broadcast the iSCSI target discovery.
|
||||
|
||||
# iptables -A INPUT -i eth0 -p tcp --dport 860 -m state --state NEW,ESTABLISHED -j ACCEPT
|
||||
# iptables -A INPUT -i eth0 -p tcp --dport 3260 -m state --state NEW,ESTABLISHED -j ACCEPT
|
||||
|
||||

|
||||
|
||||
Open iSCSI Ports
|
||||
|
||||

|
||||
|
||||
Add iSCSI Ports to Iptables
|
||||
|
||||
**Note**: Rule may vary according to your **Default CHAIN Policy**. Then save the Iptables and restart the iptables.
|
||||
|
||||
# iptables-save
|
||||
# /etc/init.d/iptables restart
|
||||
|
||||

|
||||
|
||||
Restart iptables
|
||||
|
||||
Here we have deployed a target server to share LUNs to any initiator which authenticating with target over TCP/IP, This suitable for small to large scale production environments too.
|
||||
|
||||
In my next upcoming articles, I will show you how to [Create LUN’s using LVM in Target Server][1] and how to share LUN’s on Client machines, till then stay tuned to TecMint for more such updates and don’t forget to give valuable comments.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.tecmint.com/create-centralized-secure-storage-using-iscsi-targetin-linux/
|
||||
|
||||
作者:[Babin Lonston][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.tecmint.com/author/babinlonston/
|
||||
[1]:http://www.tecmint.com/create-luns-using-lvm-in-iscsi-target/
|
||||
@ -1,230 +0,0 @@
|
||||
How to Create and Setup LUNs using LVM in “iSCSI Target Server” on RHEL/CentOS/Fedora – Part II
|
||||
================================================================================
|
||||
LUN is a Logical Unit Number, which shared from the iSCSI Storage Server. The Physical drive of iSCSI target server shares its drive to initiator over TCP/IP network. A Collection of drives called LUNs to form a large storage as SAN (Storage Area Network). In real environment LUNs are defined in LVM, if so it can be expandable as per space requirements.
|
||||
|
||||

|
||||
Create LUNS using LVM in Target Server
|
||||
|
||||
### Why LUNS are Used? ###
|
||||
|
||||
LUNS used for storage purpose, SAN Storage’s are build with mostly Groups of LUNS to become a pool, LUNs are Chunks of a Physical disk from target server. We can use LUNS as our systems Physical Disk to install Operating systems, LUNS are used in Clusters, Virtual servers, SAN etc. The main purpose of Using LUNS in Virtual servers for OS storage purpose. LUNS performance and reliability will be according to which kind of disk we using while creating a Target storage server.
|
||||
|
||||
### Requirements ###
|
||||
|
||||
To know about creating a ISCSI Target Server follow the below link.
|
||||
|
||||
- [Create Centralized Secure Storage using iSCSI Target – Part I][1]
|
||||
|
||||
#### Master Server Setup ####
|
||||
|
||||
System information’s and Network setup are same as iSCSI Target Server as shown in Part – I, As we are defining LUNs in same server.
|
||||
|
||||
- Operating System – CentOS release 6.5 (Final)
|
||||
- iSCSI Target IP – 192.168.0.200
|
||||
- Ports Used : TCP 860, 3260
|
||||
- Configuration file : /etc/tgt/targets.conf
|
||||
|
||||
## Creating LUNs using LVM in iSCSI Target Server ##
|
||||
|
||||
First, find out the list of drives using **fdisk -l** command, this will manipulate a long list of information of every partitions on the system.
|
||||
|
||||
# fdisk -l
|
||||
|
||||
The above command only gives the drive information’s of base system. To get the storage device information, use the below command to get the list of storage devices.
|
||||
|
||||
# fdisk -l /dev/vda && fdisk -l /dev/sda
|
||||
|
||||
|
||||
|
||||
List Storage Drives
|
||||
|
||||
**NOTE**: Here **vda** is virtual machines hard drive as I’m using virtual machine for demonstration, **/dev/sda** is added additionally for storage.
|
||||
|
||||
### Step 1: Creating LVM Drive for LUNs ###
|
||||
|
||||
We going to use **/dev/sda** drive for creating a LVM.
|
||||
|
||||
# fdisk -l /dev/sda
|
||||
|
||||

|
||||
|
||||
List LVM Drive
|
||||
|
||||
Now let’s Partition the drive using fdisk command as shown below.
|
||||
|
||||
# fdisk -cu /dev/sda
|
||||
|
||||
- The option ‘**-c**‘ switch off the DOS compatible mode.
|
||||
- The option ‘**-u**‘ is used to listing partition tables, give sizes in sectors instead of cylinders.
|
||||
|
||||
Choose **n** to create a New Partition.
|
||||
|
||||
Command (m for help): n
|
||||
|
||||
Choose **p** to create a Primary partition.
|
||||
|
||||
Command action
|
||||
e extended
|
||||
p primary partition (1-4)
|
||||
|
||||
Give a Partition number which we need to create.
|
||||
|
||||
Partition number (1-4): 1
|
||||
|
||||
As here, we are going to setup a LVM drive. So, we need to use the default settings to use full size of Drive.
|
||||
|
||||
First sector (2048-37748735, default 2048):
|
||||
Using default value 2048
|
||||
Last sector, +sectors or +size{K,M,G} (2048-37748735, default 37748735):
|
||||
Using default value 37748735
|
||||
|
||||
Choose the type of partition, Here we need to setup a LVM so use **8e**. Use **l** option to see the list of type.
|
||||
|
||||
Command (m for help): t
|
||||
|
||||
Choose which partition want to change the type.
|
||||
|
||||
Selected partition 1
|
||||
Hex code (type L to list codes): 8e
|
||||
Changed system type of partition 1 to 8e (Linux LVM)
|
||||
|
||||
After changing the type, check the changes by print (**p**) option to list the partition table.
|
||||
|
||||
Command (m for help): p
|
||||
|
||||
Disk /dev/sda: 19.3 GB, 19327352832 bytes
|
||||
255 heads, 63 sectors/track, 2349 cylinders, total 37748736 sectors
|
||||
Units = sectors of 1 * 512 = 512 bytes
|
||||
Sector size (logical/physical): 512 bytes / 512 bytes
|
||||
I/O size (minimum/optimal): 512 bytes / 512 bytes
|
||||
Disk identifier: 0x9fae99c8
|
||||
|
||||
Device Boot Start End Blocks Id System
|
||||
/dev/sda1 2048 37748735 18873344 8e Linux LVM
|
||||
|
||||
Write the changes using **w** to exit from fdisk utility, Restart the system to make changes.
|
||||
|
||||
For your reference, I’ve attached screen shot below that will give you a clear idea about creating LVM drive.
|
||||
|
||||

|
||||
|
||||
Create LVM Partition
|
||||
|
||||
After system reboot, list the Partition table using the following fdisk command.
|
||||
|
||||
# fdisk -l /dev/sda
|
||||
|
||||

|
||||
|
||||
Verify LVM Partition
|
||||
|
||||
### Step 2: Creating Logical Volumes for LUNs ###
|
||||
|
||||
Now here, we going to create Physical volume using using ‘pvcreate’ command.
|
||||
|
||||
# pvcreate /dev/sda1
|
||||
|
||||
Create a Volume group with name of iSCSI to identify the group.
|
||||
|
||||
# vgcreate vg_iscsi /dev/sda1
|
||||
|
||||
Here I’m defining 4 Logical Volumes, if so there will be 4 LUNs in our iSCSI Target server.
|
||||
|
||||
# lvcreate -L 4G -n lv_iscsi vg_iscsi
|
||||
|
||||
# lvcreate -L 4G -n lv_iscsi-1 vg_iscsi
|
||||
|
||||
# lvcreate -L 4G -n lv_iscsi-2 vg_iscsi
|
||||
|
||||
# lvcreate -L 4G -n lv_iscsi-3 vg_iscsi
|
||||
|
||||
List the Physical volume, Volume group, logical volumes to confirm.
|
||||
|
||||
# pvs && vgs && lvs
|
||||
# lvs
|
||||
|
||||
For better understanding of the above command, for your reference I’ve included a screen grab below.
|
||||
|
||||

|
||||
|
||||
Creating LVM Logical Volumes
|
||||
|
||||

|
||||
|
||||
Verify LVM Logical Volumes
|
||||
|
||||
### Step 3: Define LUNs in Target Server ###
|
||||
|
||||
We have created Logical Volumes and ready to use with LUN, here we to define the LUNs in target configuration, if so only it will be available for client machines (Initiators).
|
||||
|
||||
Open and edit Targer configuration file located at ‘/etc/tgt/targets.conf’ with your choice of editor.
|
||||
|
||||
# vim /etc/tgt/targets.conf
|
||||
|
||||
Append the following volume definition in target conf file. Save and close the file.
|
||||
|
||||
<target iqn.2014-07.com.tecmint:tgt1>
|
||||
backing-store /dev/vg_iscsi/lv_iscsi
|
||||
</target>
|
||||
<target iqn.2014-07.com.tecmint:tgt1>
|
||||
backing-store /dev/vg_iscsi/lv_iscsi-1
|
||||
</target>
|
||||
<target iqn.2014-07.com.tecmint:tgt1>
|
||||
backing-store /dev/vg_iscsi/lv_iscsi-2
|
||||
</target>
|
||||
<target iqn.2014-07.com.tecmint:tgt1>
|
||||
backing-store /dev/vg_iscsi/lv_iscsi-3
|
||||
</target
|
||||
|
||||
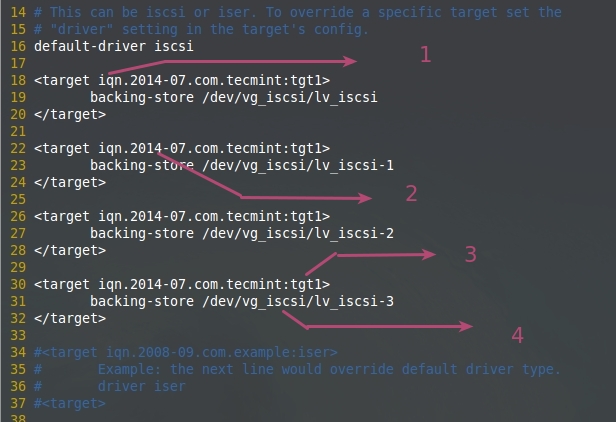
|
||||
|
||||
Configure LUNs in Target Server
|
||||
|
||||
- iSCSI qualified name (iqn.2014-07.com.tecmint:tgt1).
|
||||
- Use what ever as your wish.
|
||||
- Identify using target, 1st target in this Server.
|
||||
- 4. LVM Shared for particular LUN.
|
||||
|
||||
Next, reload the configuration by starting **tgd** service as shown below.
|
||||
|
||||
# /etc/init.d/tgtd reload
|
||||
|
||||

|
||||
|
||||
Reload Configuration
|
||||
|
||||
Next verify the available LUNs using the following command.
|
||||
|
||||
# tgtadm --mode target --op show
|
||||
|
||||

|
||||
|
||||
List Available LUNs
|
||||
|
||||

|
||||
|
||||
LUNs Information
|
||||
|
||||
The above command will give long list of available LUNs with following information.
|
||||
|
||||
- iSCSI Qualified Name
|
||||
- iSCSI is Ready to Use
|
||||
- By Default LUN 0 will be reserved for Controller
|
||||
- LUN 1, What we have Defined in the Target server
|
||||
- Here i have defined 4 GB for a single LUN
|
||||
- Online : Yes, Its ready to Use the LUN
|
||||
|
||||
Here we have defined the LUNs for target server using LVM, this can be expandable and support for many features such as snapshots. Let us see how to authenticate with Target server in PART-III and mount the remote Storage locally.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.tecmint.com/create-luns-using-lvm-in-iscsi-target/
|
||||
|
||||
作者:[Babin Lonston][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.tecmint.com/author/babinlonston/
|
||||
[1]:http://www.tecmint.com/create-centralized-secure-storage-using-iscsi-targetin-linux/
|
||||
@ -1,81 +0,0 @@
|
||||
Vic020
|
||||
|
||||
Linux FAQs with Answers--How to install Kingsoft Office on Linux
|
||||
================================================================================
|
||||
> **Question**: I heard good things about Kingsoft Office, so I would like to try it out on my Linux. How can I install Kingsoft Office on [insert your Linux distro]?
|
||||
|
||||
Kingsoft Office is an office suite available for muliple platforms including Windows, Linux, iOS and Android. It comes with three programs: Writer for word processing, Presentation for presentations, and Spreadsheets for spreadsheets. It is freemium model, where the basic version is free to use. Compared to other Linux office suites such as LibreOffice or OpenOffice, the best advantage of Kingsoft Office is its **excellent compatibility with Microsoft Office**. Thus for those of you who need to use an office suite on Linux and Windows platforms interchangeably, Kingsoft Office is a good choice for Linux platform.
|
||||
|
||||
### Install Kingsoft Office on CentOS, Fedora or RHEL ###
|
||||
|
||||
Download a RPM file for the [official site][1]. The official RPM package is available as a 32-bit version only, but you can install it on both 32-bit and 64-bit systems.
|
||||
|
||||
Use yum command with "localinstall" option to install the RPM file.
|
||||
|
||||
$ sudo yum localinstall kingsoft-office-9.1.0.4244-0.1.a12p3.i686.rpm
|
||||
|
||||
Note that do NOT use rpm command to install it. Otherwise, you will get unmet dependency errors, which are not easy to solve manually:
|
||||
|
||||
error: Failed dependencies:
|
||||
libICE.so.6 is needed by kingsoft-office-9.1.0.4244-0.1.a12p3.i686
|
||||
libSM.so.6 is needed by kingsoft-office-9.1.0.4244-0.1.a12p3.i686
|
||||
libX11.so.6 is needed by kingsoft-office-9.1.0.4244-0.1.a12p3.i686
|
||||
libXext.so.6 is needed by kingsoft-office-9.1.0.4244-0.1.a12p3.i686
|
||||
libXrender.so.1 is needed by kingsoft-office-9.1.0.4244-0.1.a12p3.i686
|
||||
libc.so.6 is needed by kingsoft-office-9.1.0.4244-0.1.a12p3.i686
|
||||
|
||||
Red Hat based distributions have multilib support. If the RPM package you are trying to install is 32-bit and has 32-bit library dependencies, a better way is to use yum to install it as shown above. As long as the RPM is properily built with all dependency information, yum should be able to install it using yum repositories.
|
||||
|
||||
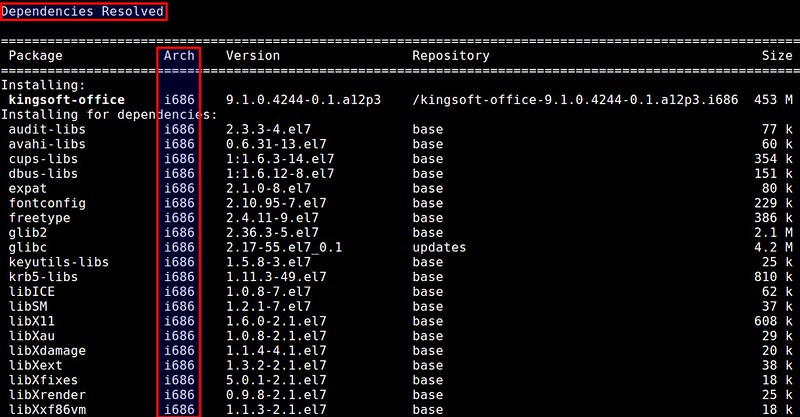
|
||||
|
||||
### Install Kingsoft Office on Debian, Ubuntu or Linux Mint ###
|
||||
|
||||
Download a DEB package from the [official site][2]. The official DEB package is available as a 32-bit version only, but you can install it on both 32-bit and 64-bit systems.
|
||||
|
||||
The DEB package has a set of dependencies to meet. Therefore use [gdebi][3] instead of dpkg command to automatically resolve dependencies.
|
||||
|
||||
$ sudo apt-get install gdebi-core
|
||||
$ sudo gdebi kingsoft-office_9.1.0.4244~a12p3_i386.deb
|
||||
|
||||
### Launch Kingsoft Office ###
|
||||
|
||||
Once Kingsoft Office is installed, you can launch Witer, Presentation, and Spreadsheets from the desktop manager easily.
|
||||
|
||||
On Ubuntu Unity:
|
||||
|
||||
|
||||
|
||||
On GNOME:
|
||||
|
||||
|
||||
|
||||
Alternatively, you can also launch Kingsoft Office from the command line.
|
||||
|
||||
To launch Kingsoft Writer from the command line, use this command:
|
||||
|
||||
|
||||
|
||||
To launch Kingsoft Presentation from the command line, use this command:
|
||||
|
||||
$ wpp
|
||||
|
||||
|
||||
|
||||
To launch Kingsoft Spreadsheets from the command line, use this command:
|
||||
|
||||
$ et
|
||||
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://ask.xmodulo.com/install-kingsoft-office-linux.html
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://ksosoft.com/product/office-2013-linux.html
|
||||
[2]:http://ksosoft.com/product/office-2013-linux.html
|
||||
[3]:http://xmodulo.com/how-to-install-deb-file-with-dependencies.html
|
||||
@ -1,3 +1,4 @@
|
||||
ideas4u is translating!
|
||||
4 Steps to Setup Local Repository in Ubuntu using APT-mirror
|
||||
================================================================================
|
||||
Today we will show you how to setup a local repository in your Ubuntu PC or Ubuntu Server straight from the official Ubuntu repository. There are a lot benefit of creating a local repository in your computer if you have a lot of computers to install software, security updates and fixes often in all systems, then having a local Ubuntu repository is an efficient way. Because all required packages are downloaded over the fast LAN connection from your local server, so that it will save your Internet bandwidth and reduces the annual cost of Internet..
|
||||
@ -122,4 +123,4 @@ via: http://linoxide.com/ubuntu-how-to/setup-local-repository-ubuntu/
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://linoxide.com/author/arunp/
|
||||
[1]:https://launchpad.net/ubuntu/+archivemirrors
|
||||
[1]:https://launchpad.net/ubuntu/+archivemirrors
|
||||
|
||||
@ -1,265 +0,0 @@
|
||||
translating by mtunique
|
||||
5 User Space Debugging Tools in Linux
|
||||
================================================================================
|
||||
By definition, debugging tools are those programs which allow us to monitor ,control and correct errors in other programs while they execute. Why should we use debugging tools? To answer this, there are various situations where we get stuck while running some programs and will have the need to understand what exactly happened. For example, we might be running an application and it produces some error messages. To fix those errors, we should first figure out why and from where did the error messages come from. An application might suddenly hang and we will have to know what other processes were running at that time. We might also have to figure out what was process 'x' doing at the time of hang. In order to dissect such details, we will need the help of debugging tools. There are a few user space debugging tools and techniques in Linux which are quite useful in analysing user space problems. They are:
|
||||
|
||||
- **'print' statements**
|
||||
- **Querying (/proc, /sys etc)**
|
||||
- **Tracing (strace/ltrace)**
|
||||
- **Valgrind (memwatch)**
|
||||
- **GDB**
|
||||
|
||||
Let's go through each of them one by one.
|
||||
|
||||
### 1.'print' statements ###
|
||||
|
||||
This is a basic or primitive way of debugging a problem. We can insert print statements in the middle of a program to understand the control flow and get the value of key variables. Though it is a simple technique, it has some disadvantages to it. Programs need to be edited to add 'print 'statements which then will have to be recompiled and rerun to get the output. This is a time-consuming method if the program to be debugged is quite big.
|
||||
|
||||
### 2. Querying ###
|
||||
|
||||
In some situations, we might want to figure out in what state a running process is in the kernel or what is the memory map that it is occupying there etc. In order to obtain this type of information, we need not insert any code into the kernel. Instead, one can use the /proc filesystem.
|
||||
|
||||
/proc is a pseudo filesystem that gets populated with runtime system information (cpu information, amount of memory etc) once the system is up and running.
|
||||
|
||||

|
||||
output of 'ls /proc'
|
||||
|
||||
As you can see, each process that is running in the system has an entry in the /proc filesystem in the form of its process id . Details about each of these processes can be obtained by looking into the files present in its process id directory
|
||||
|
||||

|
||||
output of 'ls /proc/pid'
|
||||
|
||||
Explaining all the entries inside the /proc filesystem is beyond the scope of this document. Some of the useful ones are listed below:
|
||||
|
||||
- /proc/cmdline -> Kernel command line
|
||||
- /proc/cpuinfo -> information about the processor's make, model etc
|
||||
- /proc/filesystems -> filesystem information supported by the kernel
|
||||
- /proc//cmdline -> command line arguments passed to the current process
|
||||
- /proc//mem -> memory held by the process
|
||||
- /proc//status -> status of the process
|
||||
|
||||
### 3. Tracing ###
|
||||
|
||||
strace and ltrace are two of the tracing tools used in Linux to trace program execution details.
|
||||
|
||||
#### strace: ####
|
||||
|
||||
strace intercepts and records system calls within a process and the signals received by it. To the user, it displays the system calls, arguments passed to them and the return values. strace can be attached to a process that is already running or to a new process. It is useful as a diagnostic and debugging tools for developers and system administrators. It can also be used as a tool to understand how system calls work by tracing different programs. Advantage of this tool is that no source code is needed and programs need not be recompiled.
|
||||
|
||||
The basic syntax for using strace is:
|
||||
|
||||
**strace command**
|
||||
|
||||
There are various options that are available to be used with strace command. One can check out the man page for strace tool to get more details.
|
||||
|
||||
The output of strace can be quite lengthy and we may not be interested in going through each and every line that is displayed. We can use the '-e expr' option to filter the unwanted data.
|
||||
|
||||
Use '-p pid' option to attach it to a running process.
|
||||
|
||||
Output of the command can be redirected to a file using the '-o' option
|
||||
|
||||

|
||||
output of strace filtering only the open system call
|
||||
|
||||
#### ltrace: ####
|
||||
|
||||
ltrace tracks and records the dynamic (runtime) library calls made by a process and the signals received by it. It can also track the system calls made within a process. It's usage is similar to strace
|
||||
|
||||
**ltrace command**
|
||||
|
||||
'-i ' option prints the instruction pointer at the time of library call
|
||||
|
||||
'-S' option is used to display both system calls and library calls
|
||||
|
||||
Refer to the ltrace man page for all the available options.
|
||||
|
||||

|
||||
output of ltrace capturing 'strcmp' library call
|
||||
|
||||
### 4. Valgrind ###
|
||||
|
||||
Valgrind is a suite of debugging and profiling tools. One of the widely used and the default tool is a memory checking tool called 'Memcheck' which intercepts calls made to malloc(), new(), free() and delete(). In other words, it is useful in detecting problems like:
|
||||
|
||||
- memory leaks
|
||||
- double freeing
|
||||
- boundary overruns
|
||||
- using uninitialized memory
|
||||
- using a memory after it has been freed etc.
|
||||
|
||||
It works directly with the executable files.
|
||||
|
||||
Valgrind comes with a few drawbacks as well. It can slow down your program as it increases the memory footprint. It can sometimes produce false positives and false negatives. It cannot detect out-of-range access to statically allocated arrays
|
||||
|
||||
In order to use it, first download it and install it on your system. ([Valgrind's download page][1]). It can be installed using the package manager for the operating system that one is using.
|
||||
|
||||
Installation using command line involves decompressing and untarring the downloaded file.
|
||||
|
||||
tar -xjvf valgring-x.y.z.tar.bz2 (where x.y.z is the version number you are trying to install)
|
||||
|
||||
Get inside the newly created directory (valgrind-x.y.z)and run the following commands:
|
||||
|
||||
./configure
|
||||
make
|
||||
make install
|
||||
|
||||
Let's understand how valgrind works with a small program(test.c):
|
||||
|
||||
#include <stdio.h>
|
||||
|
||||
void f(void)
|
||||
|
||||
{
|
||||
int x = malloc(10 * sizeof(int));
|
||||
|
||||
x[10] = 0;
|
||||
}
|
||||
|
||||
int main()
|
||||
{
|
||||
f();
|
||||
return 0;
|
||||
}
|
||||
|
||||
Compile the program:
|
||||
|
||||
gcc -o test -g test.c
|
||||
|
||||
Now we have an executable file called 'test'. We can now use valgrind to check for memory errors:
|
||||
|
||||
valgrind –tool=memcheck –leak-check=yes test
|
||||
|
||||
Here is the valgrind output showing the errors:
|
||||
|
||||

|
||||
output of valgrind showing heap block overrun and memory leak
|
||||
|
||||
As we can see in the above message, we are trying to access the area beyond what is allocated in function f and the allocated memory is not freed.
|
||||
|
||||
### 5. GDB ###
|
||||
|
||||
GDB is a debugger from Free Software Foundation. It is useful in locating and fixing problems in the code. It gives control to the user to perform various actions when the program to be debugged is running, like:
|
||||
|
||||
- starting the program
|
||||
- stop at specified locations
|
||||
- stop on specified conditions
|
||||
- examine required information
|
||||
- make changes to data in the program etc.
|
||||
|
||||
One can also attach a core dump of a crashed program to GDB and analyse the cause of crash.
|
||||
|
||||
GDB provides a lot of options to debug programs. However, we will cover some important options here so that one can get a feel of how to get started with GDB.
|
||||
|
||||
If you do not already have GDB installed, it can be downloaded from [GDB's official website][2].
|
||||
|
||||
#### Compiling programs: ####
|
||||
|
||||
In order to debug a program using GDB, it has to be compiled using gcc with the'-g' option. This produces debugging information in the operating system's native format and GDB works with this information.
|
||||
|
||||
Here is a simple program (example1.c)performing divide by zero to show the usage of GDB:
|
||||
|
||||
#include
|
||||
int divide()
|
||||
{
|
||||
int x=5, y=0;
|
||||
return x / y;
|
||||
}
|
||||
|
||||
int main()
|
||||
{
|
||||
divide();
|
||||
}
|
||||
|
||||

|
||||
An example showing usage of gdb
|
||||
|
||||
#### Invoking GDB: ####
|
||||
|
||||
GDB can be started by executing 'gdb' in the command-line:
|
||||
|
||||

|
||||
invoking gdb
|
||||
|
||||
Once invoked, it remains there waiting for commands from the terminal and executing them until exited .
|
||||
|
||||
If a process is already running and you need to attach GDB to it, it can be done by specifying the process id Suppose a program has already crashed and one wants to analyse the cause of the problem, then attaching GDB to the core file helps.
|
||||
|
||||
#### Starting the program: ####
|
||||
|
||||
Once you are inside GDB, use the 'run' command to start the program to be debugged
|
||||
|
||||
#### Passing arguments to the program: ####
|
||||
|
||||
Use the 'set args' command to send the arguments to your program when it runs next time 'show args' will show the arguments passed to the program
|
||||
|
||||
#### Verifying the stack: ####
|
||||
|
||||
Whenever a program stops, first thing anyone wants to understand is why it stopped and how it stopped there. This information is called backtrace. Every function call generated by a program gets stored along with the local variables, arguments passed, call location etc in a block of data inside the stack and is called a frame. Using GDB we can examine all this data. GDB identifies these frames by giving them numbers starting from the innermost frame.
|
||||
|
||||
- **bt**: prints the backtrace of the entire stack
|
||||
- **bt <n>** prints the backtrace of n frames
|
||||
- **frame <frame number>**: switches to the specified frame and prints that frame
|
||||
- **up <n>**: move 'n' frames up
|
||||
- **down <n>**: move 'n' frames down. ( n is 1 by default)
|
||||
|
||||
#### Examining data: ####
|
||||
|
||||
Program's data can be examined inside GDB using the 'print' command. For example, if 'x' is a variable inside the debugging program, 'print x' prints the value of x.
|
||||
|
||||
#### Examining source: ####
|
||||
|
||||
Parts of source file can be printed within GDB. 'list' command by default prints 10 lines of code.
|
||||
|
||||
- **list <linenum>**: list the source file around 'linenum'
|
||||
- **list <function>**: list the source from the beginning of 'function'
|
||||
|
||||
- **disas <function>**: displays the machine code for the function
|
||||
|
||||
#### Stopping and resuming the program: ####
|
||||
|
||||
Using GDB, we can set breakpoints, watchpoint etc in order to stop the program wherever required.
|
||||
|
||||
- **break <location>**: Sets up a breakpoint at 'location'. When this is hit while the program is executing, control is given to the user.
|
||||
- **watch <expr>**: GDB stops when the 'expr' is written into by the program and it's value changes
|
||||
- **catch <event>**: GDB stops when the 'event' occurs.
|
||||
- **disable <breakpoint>**: disable the specified breakpoint
|
||||
- **enable <breakpoint>**: enable the specified breakpoint
|
||||
- **delete <breakpoint>**: delete the breakpoint / watchpoint / catch point passed. If no arguments are passed default action is to work on all the breakpoints
|
||||
|
||||
- **step**: execute the program step by step
|
||||
- **continue**: continue with program execution until execution is complete
|
||||
|
||||
#### Exiting GDB: ####
|
||||
|
||||
Use the 'quit' command to exit from GDB
|
||||
|
||||
There are many more options that are available with GDB. Use the help option once you are inside GDB for more details.
|
||||
|
||||

|
||||
getting help within gdb
|
||||
|
||||
### Summary ###
|
||||
|
||||
In this article, we have seen different types of user space debug tools available in Linux. To summarise all of them, here is a quick guideline on when to use what:
|
||||
Basic debugging, getting values of key variables – print statements
|
||||
|
||||
Get information about filesystems supported, available memory, cpus, status of a running program in the kernel etc - querying /proc filesystem
|
||||
|
||||
Initial problem diagnosis, system call or library call related issues , understanding program flow – strace / ltrace
|
||||
|
||||
Application space related memory problems – valgrind
|
||||
|
||||
To examine runtime behaviour of applications, analysing application crashes – gdb.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/linux-how-to/user-space-debugging-tools-linux/
|
||||
|
||||
作者:[B N Poornima][a]
|
||||
译者:[mtunique](https://github.com/mtunique)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://linoxide.com/author/bnpoornima/
|
||||
[1]:http://valgrind.org/downloads.html
|
||||
[2]:http://www.gnu.org/software/gdb/download/
|
||||
@ -0,0 +1,203 @@
|
||||
Auditd - Tool for Security Auditing on Linux Server
|
||||
================================================================================
|
||||
First of all , we wish all our readers **Happy & Prosperous New YEAR 2015** from our Linoxide team. So lets start this new year explaining about Auditd tool.
|
||||
|
||||
Security is one of the main factor that we need to consider. We must maintain it because we don't want someone steal our data. Security includes many things. Audit, is one of it.
|
||||
|
||||
On Linux system, we know that we have a tool named **auditd**. This tool is by default exist in most of Linux operating system. What is auditd tool and how to use it? We will cover it below.
|
||||
|
||||
### What is auditd? ###
|
||||
|
||||
Auditd or audit daemon, is a userspace component to the Linux Auditing System. It’s responsible for writing audit records to the disk.
|
||||
|
||||

|
||||
|
||||
### Installing auditd ###
|
||||
|
||||
On Ubuntu based system , we can use [wajig][1] tool or **apt-get tool** to install auditd.
|
||||
|
||||

|
||||
|
||||
Just follow the instruction to get it done. Once it finish it will install some tools related to auditd tool. Here are the tools :
|
||||
|
||||
- **auditctl ;** is a tool to control the behaviour of the daemon on the fly, adding rules, etc
|
||||
- **/etc/audit/audit.rules ;** is the file that contains audit rules
|
||||
- **aureport ;** is tool to generate and view the audit report
|
||||
- **ausearch ;** is a tool to search various events
|
||||
- **auditspd ;** is a tool which can be used to relay event notifications to other applications instead of writing them to disk in the audit log
|
||||
- **autrace ;** is a command that can be used to trace a process
|
||||
- **/etc/audit/auditd.conf ;** is the configuration file of auditd tool
|
||||
- When the first time we install **auditd**, there will be no rules available yet.
|
||||
|
||||
We can check it using this command :
|
||||
|
||||
$ sudo auditctl -l
|
||||
|
||||

|
||||
|
||||
To add rules on auditd, let’s continue to the section below.
|
||||
|
||||
### How to use it ###
|
||||
|
||||
#### Audit files and directories access ####
|
||||
|
||||
One of the basic need for us to use an audit tool are, how can we know if someone change a file(s) or directories? Using auditd tool, we can do with those commands (please remember, we will need root privileges to configure auditd tool):
|
||||
|
||||
**Audit files**
|
||||
|
||||
$ sudo auditctl -w /etc/passwd -p rwxa
|
||||
|
||||

|
||||
|
||||
**With :**
|
||||
|
||||
- **-w path ;** this parameter will insert a watch for the file system object at path. On the example above, auditd will wacth /etc/passwd file
|
||||
- **-p ; **this parameter describes the permission access type that a file system watch will trigger on
|
||||
- **rwxa ;** are the attributes which bind to -p parameter above. r is read, w is write, x is execute and a is attribute
|
||||
|
||||
#### Audit directories ####
|
||||
|
||||
To audit directories, we will use a similar command. Let’s take a look at the command below :
|
||||
|
||||
$ sudo auditctl -w /production/
|
||||
|
||||

|
||||
|
||||
The above command will watch any access to the **/production folder**.
|
||||
|
||||
Now, if we run **auditctl -l** command again, we will see that new rules are added.
|
||||
|
||||

|
||||
|
||||
Now let’s see the audit log says.
|
||||
|
||||
### Viewing the audit log ###
|
||||
|
||||
After rules are added, now we can see how auditd in action. To view audit log, we can use **ausearch** tool.
|
||||
|
||||
We already add rule to watch /etc/passwd file. Now we will try to use **ausearch** tool to view the audit log.
|
||||
|
||||
$ sudo ausearch -f /etc/passwd
|
||||
|
||||
- **-f** parameter told ausearch to investigate /etc/passwd file
|
||||
- The result is shown below :
|
||||
> **time**->Mon Dec 22 09:39:16 2014
|
||||
> type=PATH msg=audit(1419215956.471:194): item=0 **name="/etc/passwd"** inode=142512 dev=08:01 mode=0100644 ouid=0 ogid=0 rdev=00:00 nametype=NORMAL
|
||||
> type=CWD msg=audit(1419215956.471:194): **cwd="/home/pungki"**
|
||||
> type=SYSCALL msg=audit(1419215956.471:194): arch=40000003 **syscall=5** success=yes exit=3 a0=b779694b a1=80000 a2=1b6 a3=b8776aa8 items=1 ppid=2090 pid=2231 **auid=4294967295 uid=1000 gid=1000** euid=0 suid=0 fsuid=0 egid=1000 sgid=1000 fsgid=1000 tty=pts0 ses=4294967295 **comm="sudo" exe="/usr/bin/sudo"** key=(null)
|
||||
|
||||
Now let’s we understand the result.
|
||||
|
||||
- **time ;** is when the audit is done
|
||||
- **name ;** is the object name to be audited
|
||||
- **cwd ;** is the current directory
|
||||
- **syscall ;** is related syscall
|
||||
- **auid ;** is the audit user ID
|
||||
- **uid and gid ;** are User ID and Group ID of the user who access the file
|
||||
- **comm ;** is the command that the user is used to access the file
|
||||
- **exe ;** is the location of the command of comm parameter above
|
||||
- The above audit log is the original file.
|
||||
|
||||
Next, we are going to add a new user, to see how the auditd record the activity to /etc/passwd file.
|
||||
|
||||
> **time->**Mon Dec 22 11:25:23 2014
|
||||
> type=PATH msg=audit(1419222323.628:510): item=1 **name="/etc/passwd.lock"** inode=143992 dev=08:01 mode=0100600 ouid=0 ogid=0 rdev=00:00 nametype=DELETE
|
||||
> type=PATH msg=audit(1419222323.628:510): item=0 **name="/etc/"** inode=131073 dev=08:01 mode=040755 ouid=0 ogid=0 rdev=00:00 nametype=PARENT
|
||||
> type=CWD msg=audit(1419222323.628:510): **cwd="/root"**
|
||||
> type=SYSCALL msg=audit(1419222323.628:510): arch=40000003 **syscall=10** success=yes exit=0 a0=bfc0ceec a1=0 a2=bfc0ceec a3=897764c items=2 ppid=2978 pid=2994 **auid=4294967295 uid=0 gid=0** euid=0 suid=0 fsuid=0 egid=0 sgid=0 fsgid=0 tty=pts0 ses=4294967295 **comm="chfn" exe="/usr/bin/chfn"** key=(null)
|
||||
|
||||
As we can see above, that on that particular time, **/etc/passwd was accessed** by user root (uid = 0 and gid = 0) **from** directory /root (cwd = /root). The /etc/passwd file was accessed using **chfn** command which located in **/usr/bin/chfn**
|
||||
|
||||
If we type **man chfn** on the console, we will see more detail about what is chfn.
|
||||
|
||||

|
||||
|
||||
Now we take a look at another example.
|
||||
|
||||
We already told auditd to watch directory /production/ . That is a new directory. So when we try to use ausearch tool at the first time, it found nothing.
|
||||
|
||||

|
||||
|
||||
Next, root account try to list the /production directory using ls command. The second time we use ausearch tool, it will show us some information.
|
||||
|
||||

|
||||
|
||||
> **time->**Mon Dec 22 14:18:28 2014
|
||||
> type=PATH msg=audit(1419232708.344:527): item=0 **name="/production/"** inode=797104 dev=08:01 mode=040755 ouid=0 ogid=0 rdev=00:00 nametype=NORMAL
|
||||
> type=CWD msg=audit(1419232708.344:527): cwd="/root"
|
||||
> type=SYSCALL msg=audit(1419232708.344:527): arch=40000003 syscall=295 success=yes exit=3 a0=ffffff9c a1=95761e8 a2=98800 a3=0 items=1 ppid=3033 pid=3444 **auid=4294967295 uid=0 gid=0** euid=0 suid=0 fsuid=0 egid=0 sgid=0 fsgid=0 tty=pts0 ses=4294967295 **comm="ls" exe="/bin/ls"** key=(null)
|
||||
|
||||
Similar with the previous one, we can determine that **/production folder was looked** by root account (uid=0 gid=0) **using ls command** (comm = ls) and the ls command is **located in /bin/ls folder**.
|
||||
|
||||
### Viewing the audit reports ###
|
||||
|
||||
Once we put the audit rules, it will run automatically. And after a period of time, we want to see how auditd can help us to track them.
|
||||
|
||||
Auditd comes with another tool called **aureport**. As we can guess from its name, **aureport** is a tool that produces summary reports of the audit system log.
|
||||
|
||||
We already told auditd to track /etc/passwd before. And a moment after the auditd parameter is developed, the audit.log file is created.
|
||||
|
||||
To generate the report of audit, we can use aureport tool. Without any parameters, aureport will generate a summary report of audit activity.
|
||||
|
||||
$ sudo aureport
|
||||
|
||||

|
||||
|
||||
As we can see, there are some information available which cover most important area.
|
||||
|
||||
On the picture above we see there are **3 times failed authentication**. Using aureport, we can drill down to that information.
|
||||
|
||||
We can use this command to look deeper on failed authentication :
|
||||
|
||||
$ sudo aureport -au
|
||||
|
||||

|
||||
|
||||
As we can see on the picture above, there are two users which at the particular time are failed to authenticated
|
||||
|
||||
If we want to see all events related to account modification, we can use -m parameter.
|
||||
|
||||
$ sudo aureport -m
|
||||
|
||||

|
||||
|
||||
### Auditd configuration file ###
|
||||
|
||||
Previously we already added :
|
||||
|
||||
- $ sudo auditctl -w /etc/passwd -p rwxa
|
||||
- $ sudo auditctl -w /production/
|
||||
- Now, if we sure the rules are OK, we can add it into
|
||||
|
||||
**/etc/audit/audit.rules** to make them permanently.Here’s how to put them into the /etc/audit/audit.rules fileSample of audit rule file
|
||||
|
||||

|
||||
|
||||
**Then don’t forget to restart auditd daemon.**
|
||||
|
||||
# /etc/init.d/auditd restart
|
||||
|
||||
OR
|
||||
|
||||
# service auditd restart
|
||||
|
||||

|
||||
|
||||
### Conclusion ###
|
||||
|
||||
Auditd is one of the audit tool that available on Linux system. You can explore more detail about auditd and its related tools by reading its manual page. For example, just type **man auditd** to see more detail about auditd. Or type **man ausearch** to see more detail about ausearch tool.
|
||||
|
||||
**Please be careful before creating rules**. It will increase your log file size significantly if too much information to record.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/how-tos/auditd-tool-security-auditing/
|
||||
|
||||
作者:[Pungki Arianto][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://linoxide.com/author/pungki/
|
||||
[1]:http://linoxide.com/tools/wajig-package-management-debian/
|
||||
@ -0,0 +1,207 @@
|
||||
How to configure fail2ban to protect Apache HTTP server
|
||||
================================================================================
|
||||
An Apache HTTP server in production environments can be under attack in various different ways. Attackers may attempt to gain access to unauthorized or forbidden directories by using brute-force attacks or executing evil scripts. Some malicious bots may scan your websites for any security vulnerability, or collect email addresses or web forms to send spams to.
|
||||
|
||||
Apache HTTP server comes with comprehensive logging capabilities capturing various abnormal events indicative of such attacks. However, it is still non-trivial to systematically parse detailed Apache logs and react to potential attacks quickly (e.g., ban/unban offending IP addresses) as they are perpetrated in the wild. That is when `fail2ban` comes to the rescue, making a sysadmin's life easier.
|
||||
|
||||
`fail2ban` is an open-source intrusion prevention tool which detects various attacks based on system logs and automatically initiates prevention actions e.g., banning IP addresses with `iptables`, blocking connections via /etc/hosts.deny, or notifying the events via emails. fail2ban comes with a set of predefined "jails" which use application-specific log filters to detect common attacks. You can also write custom jails to deter any specific attack on an arbitrary application.
|
||||
|
||||
In this tutorial, I am going to demonstrate how you can configure fail2ban to protect your Apache HTTP server. I assume that you have Apache HTTP server and fail2ban already installed. Refer to [another tutorial][1] for fail2ban installation.
|
||||
|
||||
### What is a Fail2ban Jail ###
|
||||
|
||||
Let me go over more detail on fail2ban jails. A jail defines an application-specific policy under which fail2ban triggers an action to protect a given application. fail2ban comes with several jails pre-defined in /etc/fail2ban/jail.conf, for popular applications such as Apache, Dovecot, Lighttpd, MySQL, Postfix, [SSH][2], etc. Each jail relies on application-specific log filters (found in /etc/fail2ban/fileter.d) to detect common attacks. Let's check out one example jail: SSH jail.
|
||||
|
||||
[ssh]
|
||||
enabled = true
|
||||
port = ssh
|
||||
filter = sshd
|
||||
logpath = /var/log/auth.log
|
||||
maxretry = 6
|
||||
banaction = iptables-multiport
|
||||
|
||||
This SSH jail configuration is defined with several parameters:
|
||||
|
||||
- **[ssh]**: the name of a jail with square brackets.
|
||||
- **enabled**: whether the jail is activated or not.
|
||||
- **port**: a port number to protect (either numeric number of well-known name).
|
||||
- **filter**: a log parsing rule to detect attacks with.
|
||||
- **logpath**: a log file to examine.
|
||||
- **maxretry**: maximum number of failures before banning.
|
||||
- **banaction**: a banning action.
|
||||
|
||||
Any parameter defined in a jail configuration will override a corresponding `fail2ban-wide` default parameter. Conversely, any parameter missing will be assgined a default value defined in [DEFAULT] section.
|
||||
|
||||
Predefined log filters are found in /etc/fail2ban/filter.d, and available actions are in /etc/fail2ban/action.d.
|
||||
|
||||
|
||||
|
||||
If you want to overwrite `fail2ban` defaults or define any custom jail, you can do so by creating **/etc/fail2ban/jail.local** file. In this tutorial, I am going to use /etc/fail2ban/jail.local.
|
||||
|
||||
### Enable Predefined Apache Jails ###
|
||||
|
||||
Default installation of `fail2ban` offers several predefined jails and filters for Apache HTTP server. I am going to enable those built-in Apache jails. Due to slight differences between Debian and Red Hat configurations, let me provide fail2ban jail configurations for them separately.
|
||||
|
||||
#### Enable Apache Jails on Debian or Ubuntu ####
|
||||
|
||||
To enable predefined Apache jails on a Debian-based system, create /etc/fail2ban/jail.local as follows.
|
||||
|
||||
$ sudo vi /etc/fail2ban/jail.local
|
||||
|
||||
----------
|
||||
|
||||
# detect password authentication failures
|
||||
[apache]
|
||||
enabled = true
|
||||
port = http,https
|
||||
filter = apache-auth
|
||||
logpath = /var/log/apache*/*error.log
|
||||
maxretry = 6
|
||||
|
||||
# detect potential search for exploits and php vulnerabilities
|
||||
[apache-noscript]
|
||||
enabled = true
|
||||
port = http,https
|
||||
filter = apache-noscript
|
||||
logpath = /var/log/apache*/*error.log
|
||||
maxretry = 6
|
||||
|
||||
# detect Apache overflow attempts
|
||||
[apache-overflows]
|
||||
enabled = true
|
||||
port = http,https
|
||||
filter = apache-overflows
|
||||
logpath = /var/log/apache*/*error.log
|
||||
maxretry = 2
|
||||
|
||||
# detect failures to find a home directory on a server
|
||||
[apache-nohome]
|
||||
enabled = true
|
||||
port = http,https
|
||||
filter = apache-nohome
|
||||
logpath = /var/log/apache*/*error.log
|
||||
maxretry = 2
|
||||
|
||||
Since none of the jails above specifies an action, all of these jails will perform a default action when triggered. To find out the default action, look for "banaction" under [DEFAULT] section in /etc/fail2ban/jail.conf.
|
||||
|
||||
banaction = iptables-multiport
|
||||
|
||||
In this case, the default action is iptables-multiport (defined in /etc/fail2ban/action.d/iptables-multiport.conf). This action bans an IP address using iptables with multiport module.
|
||||
|
||||
After enabling jails, you must restart fail2ban to load the jails.
|
||||
|
||||
$ sudo service fail2ban restart
|
||||
|
||||
#### Enable Apache Jails on CentOS/RHEL or Fedora ####
|
||||
|
||||
To enable predefined Apache jails on a Red Hat based system, create /etc/fail2ban/jail.local as follows.
|
||||
|
||||
$ sudo vi /etc/fail2ban/jail.local
|
||||
|
||||
----------
|
||||
|
||||
# detect password authentication failures
|
||||
[apache]
|
||||
enabled = true
|
||||
port = http,https
|
||||
filter = apache-auth
|
||||
logpath = /var/log/httpd/*error_log
|
||||
maxretry = 6
|
||||
|
||||
# detect spammer robots crawling email addresses
|
||||
[apache-badbots]
|
||||
enabled = true
|
||||
port = http,https
|
||||
filter = apache-badbots
|
||||
logpath = /var/log/httpd/*access_log
|
||||
bantime = 172800
|
||||
maxretry = 1
|
||||
|
||||
# detect potential search for exploits and php <a href="http://xmodulo.com/recommend/penetrationbook" style="" target="_blank" rel="nofollow" >vulnerabilities</a>
|
||||
[apache-noscript]
|
||||
enabled = true
|
||||
port = http,https
|
||||
filter = apache-noscript
|
||||
logpath = /var/log/httpd/*error_log
|
||||
maxretry = 6
|
||||
|
||||
# detect Apache overflow attempts
|
||||
[apache-overflows]
|
||||
enabled = true
|
||||
port = http,https
|
||||
filter = apache-overflows
|
||||
logpath = /var/log/httpd/*error_log
|
||||
maxretry = 2
|
||||
|
||||
# detect failures to find a home directory on a server
|
||||
[apache-nohome]
|
||||
enabled = true
|
||||
port = http,https
|
||||
filter = apache-nohome
|
||||
logpath = /var/log/httpd/*error_log
|
||||
maxretry = 2
|
||||
|
||||
# detect failures to execute non-existing scripts that
|
||||
# are associated with several popular web services
|
||||
# e.g. webmail, phpMyAdmin, WordPress
|
||||
port = http,https
|
||||
filter = apache-botsearch
|
||||
logpath = /var/log/httpd/*error_log
|
||||
maxretry = 2
|
||||
|
||||
Note that the default action for all these jails is iptables-multiport (defined as "banaction" under [DEFAULT] in /etc/fail2ban/jail.conf). This action bans an IP address using iptables with multiport module.
|
||||
|
||||
After enabling jails, you must restart fail2ban to load the jails in fail2ban.
|
||||
|
||||
On Fedora or CentOS/RHEL 7:
|
||||
|
||||
$ sudo systemctl restart fail2ban
|
||||
|
||||
On CentOS/RHEL 6:
|
||||
|
||||
$ sudo service fail2ban restart
|
||||
|
||||
### Check and Manage Fail2ban Banning Status ###
|
||||
|
||||
Once jails are activated, you can monitor current banning status with fail2ban-client command-line tool.
|
||||
|
||||
To see a list of active jails:
|
||||
|
||||
$ sudo fail2ban-client status
|
||||
|
||||
To see the status of a particular jail (including banned IP list):
|
||||
|
||||
$ sudo fail2ban-client status [name-of-jail]
|
||||
|
||||
|
||||
|
||||
You can also manually ban or unban IP addresses.
|
||||
|
||||
To ban an IP address with a particular jail:
|
||||
|
||||
$ sudo fail2ban-client set [name-of-jail] banip [ip-address]
|
||||
|
||||
To unban an IP address blocked by a particular jail:
|
||||
|
||||
$ sudo fail2ban-client set [name-of-jail] unbanip [ip-address]
|
||||
|
||||
### Summary ###
|
||||
|
||||
This tutorial explains how a fail2ban jail works and how to protect an Apache HTTP server using built-in Apache jails. Depending on your environments and types of web services you need to protect, you may need to adapt existing jails, or write custom jails and log filters. Check outfail2ban's [official Github page][3] for more up-to-date examples of jails and filters.
|
||||
|
||||
Are you using fail2ban in any production environment? Share your experience.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/configure-fail2ban-apache-http-server.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/nanni
|
||||
[1]:http://xmodulo.com/how-to-protect-ssh-server-from-brute-force-attacks-using-fail2ban.html
|
||||
[2]:http://xmodulo.com/how-to-protect-ssh-server-from-brute-force-attacks-using-fail2ban.html
|
||||
[3]:https://github.com/fail2ban/fail2ban
|
||||
@ -0,0 +1,109 @@
|
||||
How to debug a C/C++ program with Nemiver debugger
|
||||
================================================================================
|
||||
If you read [my post on GDB][1], you know how important and useful a debugger I think can be for a C/C++ program. However, if a command line debugger like GDB sounds more like a problem than a solution to you, you might be more interested in Nemiver. [Nemiver][2] is a GTK+-based standalone graphical debugger for C/C++ programs, using GDB as its back-end. Admirable for its speed and stability, Nemiver is a very reliable debugger filled with goodies.
|
||||
|
||||
### Installation of Nemiver ###
|
||||
|
||||
For Debian based distributions, it should be pretty straightforward:
|
||||
|
||||
$ sudo apt-get install nemiver
|
||||
|
||||
For Arch Linux:
|
||||
|
||||
$ sudo pacman -S nemiver
|
||||
|
||||
For Fedora:
|
||||
|
||||
$ sudo yum install nemiver
|
||||
|
||||
If you prefer compiling yourself, the latest sources are available from [GNOME website][3].
|
||||
|
||||
As a bonus, it integrates very well with the GNOME environment.
|
||||
|
||||
### Basic Usage of Nemiver ###
|
||||
|
||||
Start Nemiver with the command:
|
||||
|
||||
$ nemiver
|
||||
|
||||
You can also summon it with an executable with:
|
||||
|
||||
$ nemiver [path to executable to debug]
|
||||
|
||||
Note that Nemiver will be much more helpful if the executable is compiled in debug mode (the -g flag with GCC).
|
||||
|
||||
A good thing is that Nemiver is really fast to load, so you should instantly see the main screen in the default layout.
|
||||
|
||||
|
||||
|
||||
By default, a breakpoint has been placed in the first line of the main function. This gives you the time to recognize the basic debugger functions:
|
||||
|
||||

|
||||
|
||||
- Next line (mapped to F6)
|
||||
- Step inside a function (F7)
|
||||
- Step out of a function (Shift+F7)
|
||||
|
||||
But maybe my personal favorite is the option "Run to cursor" which makes the program run until a precise line under your cursor, and is by default mapped to F11.
|
||||
|
||||
Next, the breakpoints are also easy to use. The quick way to lay a breakpoint at a line is using F8. But Nemiver also has a more complex menu under "Debug" which allows you to set up a breakpoint at a particular function, line number, location of binary file, or even at an event like an exception, a fork, or an exec.
|
||||
|
||||
|
||||
|
||||
You can also watch a variable by tracking it. In "Debug" you can inspect an expression by giving its name and examining it. It is then possible to add it to the list of controlled variable for easy access. This is probably one of the most useful aspects as I have never been a huge fan of hovering over a variable to get its value. Note that hovering does work though. And to make it even better, Nemiver is capable of watching a struct, and giving you the values of all the member variables.
|
||||
|
||||
|
||||
|
||||
Talking about easy access to information, I also really appreciate the layout of the program. By default, the code is in the upper half and the tabs in the lower part. This grants you access to a terminal for output, a context tracker, a breakpoints list, register addresses, memory map, and variable control. But note that under "Edit" "Preferences" "Layout" you can select different layouts, including a dynamic one for you to modify.
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
And naturally, once you set up all your breakpoints, watch-points, and layout, you can save your session under “File” for easy retrieval in case you close Nemiver.
|
||||
|
||||
### Advanced Usage of Nemiver ###
|
||||
|
||||
So far, we talked about the basic features of Nemiver, i.e., what you need to get started and debug simple programs immediately. If you have more advanced needs, and especially more complex programs, you might be more interested in some of these features mentioned here.
|
||||
|
||||
#### Debugging a running process ####
|
||||
|
||||
Nemiver allows you to attach to a running process for debugging. Under the "File" menu, you can filter the list of running processes, and connect to a process.
|
||||
|
||||

|
||||
|
||||
#### Debugging a program remotely over a TCP connection ####
|
||||
|
||||
Nemiver supports remote-debugging, where you set up a lightweight debug server on a remote machine, and launch Nemiver from another machine to debug a remote target hosted by the debug server. Remote debugging can be useful if you cannot run full-fledged Nemiver or GDB on the remote machine for some reason. Under the "File" menu, specify the binary, shared library location, and the address and port.
|
||||
|
||||
|
||||
|
||||
#### Using your own GDB binary to debug ####
|
||||
|
||||
In case you compiled Nemiver yourself, you can specify a new location for GDB under "Edit" "Preferences" "Debug". This option can be useful if you want to use a custom version of GDB in Nemiver for some reason.
|
||||
|
||||
#### Follow a child or parent process ####
|
||||
|
||||
Nemiver is capable of following a child or parent process in case your program forks. To enable this feature, go to "Preferences" under "Debugger" tab.
|
||||
|
||||
|
||||
|
||||
To conclude, Nemiver is probably my favorite program for debugging without an IDE. It even beats GDB in my opinion, and [command line][4] programs generally have a good grip on me. So if you have never used it, I really recommend it. I can only congratulate the team behind it for giving us such a reliable and stable program.
|
||||
|
||||
What do you think of Nemiver? Would you consider it for standalone debugging? Or do you still stick to an IDE? Let us know in the comments.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/debug-program-nemiver-debugger.html
|
||||
|
||||
作者:[Adrien Brochard][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/adrien
|
||||
[1]:http://xmodulo.com/gdb-command-line-debugger.html
|
||||
[2]:https://wiki.gnome.org/Apps/Nemiver
|
||||
[3]:https://download.gnome.org/sources/nemiver/0.9/
|
||||
[4]:http://xmodulo.com/recommend/linuxclibook
|
||||
Some files were not shown because too many files have changed in this diff Show More
Loading…
Reference in New Issue
Block a user