mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-03-27 02:30:10 +08:00
commit
afe70fd5e1
published
20180522 Advanced use of the less text file viewer in Linux.md20190124 ffsend - Easily And Securely Share Files From Linux Command Line Using Firefox Send Client.md20190422 9 ways to save the planet.md20190527 How To Enable Or Disable SSH Access For A Particular User Or Group In Linux.md20190731 How to structure a multi-file C program- Part 2.md20190813 Building a non-breaking breakpoint for Python debugging.md20190925 Debugging in Emacs- The Grand Unified Debugger.md20191126 Calculator N- is an open source scientific calculator for your smartphone.md20191223 10 articles to learn Linux your way.md20191223 Prioritizing simplicity in your Python code.md20191226 10 Linux command tutorials for beginners and experts.md20200113 How to setup a DNS server with bind.md20200123 6 things you should be doing with Emacs.md20200204 DevOps vs Agile- What-s the difference.md20200211 Basic kubectl and Helm commands for beginners.md20200214 Linux is our love language.md20200219 Here Are The Most Beautiful Linux Distributions in 2020.md20200219 Try this Bash script for-large filesystems.md20200219 Waterfox- Firefox Fork With Legacy Add-ons Options.md20200225 3 eBook readers for the Linux desktop.md20200225 7 tips for writing an effective technical resume.md20200228 Converting between uppercase and lowercase on the Linux command line.md20200302 How to Add New Brushes in GIMP -Quick Tip.md20200303 Getting started with the Rust package manager, Cargo.md20200303 Session- An Open Source Private Messenger That Doesn-t Need Your Phone Number.md20200305 Install and Use Wireshark on Ubuntu Linux.md20200306 Communicating with other users on the Linux command line.md20200306 Three Ways to Exclude-Hold-Prevent a Specific Package from an apt Upgrade.md20200309 6 Raspberry Pi tutorials to try out.md20200310 2020 Will Be a Year of Hindsight for SD-WAN.md20200310 Basilisk- A Firefox Fork For The Classic Looks and Classic Extensions.md20200310 Containers vs. VMs, Istio in production, and more industry news.md20200310 Run Kubernetes on a Raspberry Pi with k3s.md20200311 How to install pip to manage PyPI packages easily.md20200312 Amazon Has Launched Its Own Linux Distribution But It-s Not for Everyone.md20200313 6 Best AUR (Arch User Repository) Helpers for Arch Linux.md20200313 GNOME 3.36 Released With Visual - Performance Improvements.md20200313 How to Change MAC Address in Linux.md20200314 How to Install Netbeans on Ubuntu and Other Linux.md20200316 Connect your Google Drive to Fedora Workstation.md20200317 Coronavirus challenges remote networking.md20200317 Viewing and configuring password aging on Linux.md20200318 Top 10 open source tools for working from home.md20200319 4 Markdown tools for the Linux command line.md20200319 7 open hardware projects working to solve COVID-19.md20200319 Fedora 32 Release Date, New Features and Everything Else.md20200319 Manually rotating log files on Linux.md20200322 Linus Torvalds- Advice on Working From Home during Coronavirus Lockdown.md20200322 Purism Librem Mini- A Privacy-First Linux-Based Mini PC.md
sources
news
20200314 Linux Foundation prepares for disaster, new anti-tracking data set, Mozilla goes back to mobile OSes, and more open source news.md20200319 Tools for monitoring, introvert inclusion, and more industry trends.md20200319 With npm Acquisition, Microsoft is Set to Own the Largest Software Registry in the World.md20200322 OBS Studio 25.0 is Here With Vulkan-based Games Capture Feature and More.md20200325 npm joins GitHub, building operators in Kubernetes, and more industry trends.md
talk
20190822 How the Linux desktop has grown.md20191031 A Bird-s Eye View of Big Data for Enterprises.md20200214 Linux is our love language.md20200306 How I learned about burnout the hard way.md20200311 Data-center power consumption holds steady.md20200311 Setting yourself up for success while working remotely.md20200312 Next wave of digital transformation requires better security, automation.md20200313 What is the internet backbone and how it works.md20200316 As the networks evolve enterprises need to rethink network security.md20200316 How to be the right person for DevOps.md20200316 OpenStreetMap- A Community-Driven Google Maps Alternative.md20200317 -AI everywhere- IoT chips coming from Arm.md20200319 Electronics should sweat to cool down, say researchers.md20200320 Cisco warns of five SD-WAN security weaknesses.md20200320 How technical debt is risking your security.md20200321 3 metrics to measure your open source community health.md20200321 Coronavirus challenges capacity, but core networks are holding up.md20200324 COVID-19- Weekly health check of ISPs, cloud providers and conferencing services.md20200325 COVID-19 vs. Raspberry Pi- Researchers bring IoT technology to disease detection.md20200325 The coming together of SD-WAN and AIOps.md20200326 ROLLING UPDATE- The impact of COVID-19 on public networks and security.md20200327 6 tricks for developing a work from home schedule.md
tech
20180522 Advanced use of the less text file viewer in Linux.md20190116 Best Audio Editors For Linux.md20190124 ffsend - Easily And Securely Share Files From Linux Command Line Using Firefox Send Client.md20190422 9 ways to save the planet.md20190523 Run your blog on GitHub Pages with Python.md20190527 How To Enable Or Disable SSH Access For A Particular User Or Group In Linux.md20190730 Using Python to explore Google-s Natural Language API.md20190925 Debugging in Emacs- The Grand Unified Debugger.md20191126 Calculator N- is an open source scientific calculator for your smartphone.md20191223 10 articles to learn Linux your way.md20191223 Prioritizing simplicity in your Python code.md20191224 Why your Python code should be flat and sparse.md20191226 10 Linux command tutorials for beginners and experts.md20200204 DevOps vs Agile- What-s the difference.md20200211 Basic kubectl and Helm commands for beginners.md20200219 Basic Vim Commands You Need to Know to Work in Vim Editor.md20200219 Here Are The Most Beautiful Linux Distributions in 2020.md20200219 Try this Bash script for-large filesystems.md20200219 Waterfox- Firefox Fork With Legacy Add-ons Options.md20200225 3 eBook readers for the Linux desktop.md20200228 Converting between uppercase and lowercase on the Linux command line.md20200305 Install and Use Wireshark on Ubuntu Linux.md20200306 Communicating with other users on the Linux command line.md20200306 Three Ways to Exclude-Hold-Prevent a Specific Package from an apt Upgrade.md
@ -0,0 +1,109 @@
|
||||
你所不知道的用 less 查看文件的高级用法
|
||||
======
|
||||
|
||||
> 使用 less 文件查看器的一些技巧。
|
||||
|
||||

|
||||
|
||||
最近,我正在拜读 Scott Nesbitt 的文章《[在 Linux 命令行中使用 less 来查看文本文件][1]》,并受到了一些启发,所以我想分享一些使用 `less` 命令的技巧。
|
||||
|
||||
### LESS 环境变量
|
||||
|
||||
如果你定义了环境变量 `LESS`(例如在 `.bashrc` 中),那么 `less` 会将其视为一个选项列表,就像在命令行中传递给它一样。
|
||||
|
||||
我这样定义:
|
||||
|
||||
```
|
||||
LESS='-C -M -I -j 10 -# 4'
|
||||
```
|
||||
|
||||
它的意思是:
|
||||
|
||||
* `-C` – 通过不从底部滚动来加快全屏打印速度。
|
||||
* `-M` – 在最后一行(状态行)显示更多信息。你可以使用 `-PM` 来自定义显示的信息,但我通常只用 `-M`。
|
||||
* `-I` – 忽略搜索中的大小写。
|
||||
* `-j 10` – 在终端的第 10 行而不是第一行显示搜索结果。这样,每次按 `n` 或(`N`) 跳到下一个(或上一个)匹配项时,就会有 10 条上下文。
|
||||
* `-# 4` – 当按下向右或向左的箭头时,会向右或向左跳四个字符。默认情况时跳转半个屏幕,我觉得太多了。一般来说,`less` 似乎(至少部分)是按最初开发它时的环境优化的,那时使用慢速调制解调器和低带宽的互联网连接,所以跳过半个屏幕是有意义的。
|
||||
|
||||
### PAGER 环境变量
|
||||
|
||||
许多程序使用在 `PAGER` 环境变量中的命令来显示信息。因此,你可以在 `.bashrc` 中设置 `PAGER=less`,然后让程序运行 `less`。查看手册页(`man 7 environ`)中是否有其它此类变量。
|
||||
|
||||
### -S
|
||||
|
||||
`-S` 告诉 `less` 将长行切断而不是将它们换行。除非我在(或我要)查看文件,否则我很少需要这样做。幸运的是,你可以在 `less` 中输入所有命令行选项,就像它们是键盘命令一样。因此,如果我想在文件已经打开的情况下隔断长行,我可以简单地输入 `-S`。(LCTT 译注:注意大写 `S` ,并按回车)
|
||||
|
||||
这是我经常使用的一个例子:
|
||||
|
||||
```
|
||||
su - postgres
|
||||
export PAGER=less # 因为我不用在所有的机器上编辑 postgres 的 .bashrc
|
||||
psql
|
||||
```
|
||||
|
||||
有时当我查看一个 `SELECT` 命令的输出非常宽时,我会输入 `-S` 以便将其格式化的漂亮一些。如果当我按下右箭头想查看更多内容时它跳得太远(因为我没有设置 `-#`),则可以输入 `-#8`,那么每次按下右箭头都会向右移动八个字符。
|
||||
|
||||
有时在多次输入 `-S` 之后,我会退出 psql 并设置环境变量后再次运行它:
|
||||
|
||||
```
|
||||
export LESS=-S
|
||||
```
|
||||
|
||||
### F
|
||||
|
||||
命令 `F` 可以使 `less` 像 `tail -f` 一样工作,等待更多的数据被添加到文件后再显示它们。与 `tail -f` 相比,它的一个优点是,高亮显示搜索匹配仍然有效。因此,你可以输入 `less /var/log/logfile`,搜索某些内容时,它将高亮显示所有出现的内容(除非你使用了 `-g`),然后按下 `F` 键,当更多数据写入到日志时,`less` 将显示它并高亮新的匹配项。
|
||||
|
||||
按下 `F` 后,可以按 `Ctrl+C` 来停止其查找新数据(这不会干掉它),这样你可以返回文件查看旧内容,搜索其它内容等,然后再次按 `F` 键来查看更多新数据。
|
||||
|
||||
### 搜索
|
||||
|
||||
搜索使用系统的正则表达式库,这通常意味着你可以使用扩展正则表达式。特别是,搜索 `one|two|three` 可以找到并高亮所有的 one、two 或 three。
|
||||
|
||||
我经常使用的另一种模式是 `.*someting.*`,特别是对于一些很长的日志行(例如,跨越多个终端宽度的行),它会高亮整行。这种模式使查看一行的起始和结束位置变得更加容易。我还会结合其它内容,例如 `.*one thing.*|.*another thing.*`,或者使用 `key: .*|.*marker.*` 来查看 `key` 的内容。例如,一个日志文件中包含一些字典/哈希的转储。它会高亮相关的标记行,这样我就看到上下文了,甚至,如果我知道这个值被引号引起来的话,就可以:
|
||||
|
||||
```
|
||||
key: '[^']*'|.*marker.*
|
||||
```
|
||||
|
||||
`less` 会保留你的搜索项的历史纪录,并将其保存到磁盘中以备将来调用。当你按下 `/` 或 `?` 时,可以使用向上或向下箭头浏览历史记录(以及进行基本的行编辑)。
|
||||
|
||||
在撰写本文时,我无意间看了下 `less` 手册页,发现了一个非常有用的功能:使用 `&!pattern` 跳过无关的行。例如,当我在 `/var/log/messages` 中寻找内容时,经常会一个个迭代使用以下命令:
|
||||
|
||||
```
|
||||
cat /var/log/messages | egrep -v 'systemd: Started Session' | less
|
||||
cat /var/log/messages | egrep -v 'systemd: Started Session|systemd: Starting Session' | less
|
||||
cat /var/log/messages | egrep -v 'systemd: Started Session|systemd: Starting Session|User Slice' | less
|
||||
cat /var/log/messages | egrep -v 'systemd: Started Session|systemd: Starting Session|User Slice|dbus' | less
|
||||
cat /var/log/messages | egrep -v 'systemd: Started Session|systemd: Starting Session|User Slice|dbus|PackageKit Daemon' | less
|
||||
```
|
||||
|
||||
但是现在我知道如何在 `less` 中做同样的事情。例如,我可以输入 `&!systemd: Started Session`,然后想要隐藏 `systemd: Starting Session`,所以我输入 `&!`,并使用向上箭头从历史记录中获得上一次搜索的结果。然后我接着输入 `|systemd: Starting Session` 并按下回车,继续以相同的方式添加更多条目,直到我过滤掉足够多的条目,看到更有趣的内容。
|
||||
|
||||
### =
|
||||
|
||||
命令 `=` 显示有关文件和位置的更多信息,甚至比 `-M` 更多。如果文件非常大,计算 `=` 花费的时间太长,可以按下 `Ctrl+C`,它将停止尝试计算。
|
||||
|
||||
如果你正在查看的内容来自管道而不是文件,则 `=`(和 `-M`)不会显示未知内容,包括文件中的行数和字节数。要查看这些数据,如果你知道管道命令将很快结束,则可以使用 `G` 跳到最后,然后 `less` 将开始显示这些信息。
|
||||
|
||||
如果按下 `G` 并且写入管道的命令花费的时间比预期的长,你可以按下 `Ctrl+C`,该命令将被终止。即使你没有按 `G`,`Ctrl+C` 键也会杀死它。因此,如果你不想终止命令,请不要意外按下 `Ctrl+C`。出于这个原因,如果命令执行了某些操作(不仅是显示信息),通常更安全的做法是将其输出写入文件并在单独的终端中查看文件,而不是使用管道。
|
||||
|
||||
### 为什么你需要 less
|
||||
|
||||
`less` 是一个非常强大的程序,与该领域中较新的竞争者(例如 `most` 和 `moar`)不同,你可能会在几乎所有的系统上找到它,就像 `vi` 一样。因此,即使你使用 GUI 查看器或编辑器,花一些时间浏览 `less` 手册页也是值得的,至少可以了解一下它的用处。这样,当你需要做一些已有的功能可能提供的工作时,就会知道如何要搜索手册页或互联网来找到所需的内容。
|
||||
|
||||
有关更多信息,访问 [less 主页][2]。该网站有一个不错的常见问题解答,其中包含更多提示和技巧。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/5/advanced-use-less-text-file-viewer
|
||||
|
||||
作者:[Yedidyah Bar David][a]
|
||||
选题:[lujun9972](https://github.com/lujun9972)
|
||||
译者:[MjSeven](https://github.com/MjSeven)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://opensource.com/users/didib
|
||||
[1]:http://opensource.com/article/18/4/using-less-view-text-files-command-line
|
||||
[2]:http://www.greenwoodsoftware.com/less/
|
||||
@ -0,0 +1,283 @@
|
||||
[#]: collector: "lujun9972"
|
||||
[#]: translator: "FSSlc"
|
||||
[#]: reviewer: "wxy"
|
||||
[#]: publisher: "wxy"
|
||||
[#]: url: "https://linux.cn/article-12051-1.html"
|
||||
[#]: subject: "ffsend – Easily And Securely Share Files From Linux Command Line Using Firefox Send Client"
|
||||
[#]: via: "https://www.2daygeek.com/ffsend-securely-share-files-folders-from-linux-command-line-using-firefox-send-client/"
|
||||
[#]: author: "Vinoth Kumar https://www.2daygeek.com/author/vinoth/"
|
||||
|
||||
ffsend:在命令行中通过 FireFox Send 分享文件
|
||||
======
|
||||
|
||||

|
||||
|
||||
Linux 用户偏爱使用 `scp` 或 `rsync` 来进行文件或目录的复制拷贝。不过在 Linux 上正出现了许多新的可选方式,因为 Linux 是开源的,所以任何人都可以为 Linux 开发一个安全软件。
|
||||
|
||||
在过去我们已经写了多篇有关安全分享这个话题的文章,它们分别是 [OnionShare][1]、[Magic Wormhole][2]、[Transfer.sh][3] 和 [Dcp – Dat Copy][4]。
|
||||
|
||||
今天我们甚至还将继续讨论这个话题,我们将介绍名为 `ffsend` 的工具。
|
||||
|
||||
### ffsend 是什么?
|
||||
|
||||
[ffsend][5] 是 Firefox Send 服务的一个命令行客户端,允许用户通过命令行来传递和接收文件或目录。
|
||||
|
||||
它允许我们通过一个安全、私密、加密的链接,使用一个简单的命令来轻易安全地分享文件和目录。
|
||||
|
||||
通过 Firefox 的 Send 服务共享的文件最大大小为 2GB(LCTT 译注:现在官网上写的是最大 1GB,登录后最大 2.5GB)。其他人可以通过这个工具或者网页浏览器来下载这些分享的文件。
|
||||
|
||||
所有的文件都是在客户端加密的,并且秘钥将不会被共享到远程主机。另外,你还可以为上传的文件额外设置一个密码。
|
||||
|
||||
上传的文件在下载(默认被下载 1 次,最多可被下载 10 次)后或者 24 小时后,就会自动删除。这将确保你的文件不会一直保留在网络上。
|
||||
|
||||
该工具当前处于 alpha 阶段,使用时请自担风险。而且,当前只有有限的安装方式可用。
|
||||
|
||||
### ffsend 的特点:
|
||||
|
||||
* 全功能且使用友好的命令行工具
|
||||
* 可以安全地上传和下载文件与目录
|
||||
* 总是在客户端加密
|
||||
* 可用额外的密码进行保护、密码生成和可配置下载次数限制
|
||||
* 内置的文件或目录的打包和解压
|
||||
* 可以轻松地管理你的历史分享记录
|
||||
* 能够使用你自己的 Send 主机
|
||||
* 审查或者删除共享文件
|
||||
* 精准的错误报告
|
||||
* 低内存消耗,用于加密或上传下载
|
||||
* 无需交互,可以集成在脚本中
|
||||
|
||||
### 如何在 LInux 中安装 ffsend 呢?
|
||||
|
||||
当前除了 Debian 和 Arch Linux 系统,其他发行版还没有相应的安装包(LCTT 译注:这个信息已过时,最新内容请看[这里](https://github.com/timvisee/ffsend#install))。然而,我们可以轻易地根据我们自己的操作系统和架构下载到相应的预编译二进制文件。
|
||||
|
||||
运行下面的命令来为你的操作系统下载 `ffsend` 最新可用的版本(LCTT 译注:当前最新版本为 v0.2.58):
|
||||
|
||||
```
|
||||
$ wget https://github.com/timvisee/ffsend/releases/download/v0.1.2/ffsend-v0.1.2-linux-x64.tar.gz
|
||||
```
|
||||
|
||||
然后使用下面的命令来解压 tar 包:
|
||||
|
||||
```
|
||||
$ tar -xvf ffsend-v0.1.2-linux-x64.tar.gz
|
||||
```
|
||||
|
||||
接着运行下面的命令来查看你的 `PATH` 环境变量:
|
||||
|
||||
```
|
||||
$ echo $PATH
|
||||
/home/daygeek/.cargo/bin:/usr/local/bin:/usr/local/sbin:/usr/bin:/usr/lib/jvm/default/bin:/usr/bin/site_perl:/usr/bin/vendor_perl:/usr/bin/core_perl
|
||||
```
|
||||
|
||||
正如我先前告知的那样,下面我们要做的就是将这个可执行文件放置到 `PATH` 环境变量中的某个目录中:
|
||||
|
||||
```
|
||||
$ sudo mv ffsend /usr/local/sbin
|
||||
```
|
||||
|
||||
直接运行 `ffsend` 可以获取其基本使用信息:
|
||||
|
||||
```
|
||||
$ ffsend
|
||||
ffsend 0.1.2
|
||||
Usage: ffsend [FLAGS] ...
|
||||
|
||||
Easily and securely share files from the command line.
|
||||
A fully featured Firefox Send client.
|
||||
|
||||
Missing subcommand. Here are the most used:
|
||||
ffsend upload ...
|
||||
ffsend download ...
|
||||
|
||||
To show all subcommands, features and other help:
|
||||
ffsend help [SUBCOMMAND]
|
||||
```
|
||||
|
||||
对于使用基于 Arch Linux 系统的用户可以简单地借助 [AUR 助手][6]来安装它,因为这个包已经在 AUR 软件仓库中了。
|
||||
|
||||
```
|
||||
$ yay -S ffsend
|
||||
```
|
||||
|
||||
对于使用 Debian/Ubuntu 系统的用户,使用 [DPKG 命令][7]来安装 `ffsend`。
|
||||
|
||||
```
|
||||
$ wget https://github.com/timvisee/ffsend/releases/download/v0.1.2/ffsend_0.1.2_amd64.deb
|
||||
$ sudo dpkg -i ffsend_0.1.2_amd64.deb
|
||||
```
|
||||
|
||||
### 如何使用 ffsend
|
||||
|
||||
这并不复杂,我们可以简单地通过下面的语法来发送文件。
|
||||
|
||||
**语法:**
|
||||
|
||||
```
|
||||
$ ffsend upload [/Path/to/the/file/name]
|
||||
```
|
||||
|
||||
在下面的例子中,我们将上传一个名为 `passwd-up1.sh` 的文件,一旦你上传了该文件,你将得到一个唯一的 URL。
|
||||
|
||||
```
|
||||
$ ffsend upload passwd-up1.sh --copy
|
||||
Upload complete
|
||||
Share link: https://send.firefox.com/download/a4062553f4/#yy2_VyPaUMG5HwXZzYRmpQ
|
||||
```
|
||||
|
||||
![][9]
|
||||
|
||||
在任何远端的系统上,只需要使用上面那个唯一的 URL 就可以下载上传的文件了。
|
||||
|
||||
**语法:**
|
||||
|
||||
```
|
||||
$ ffsend download [Generated URL]
|
||||
```
|
||||
|
||||
命令的输出如下:
|
||||
|
||||
```
|
||||
$ ffsend download https://send.firefox.com/download/a4062553f4/#yy2_VyPaUMG5HwXZzYRmpQ
|
||||
Download complete
|
||||
```
|
||||
|
||||
![][10]
|
||||
|
||||
使用下面的语法来对目录进行上传:
|
||||
|
||||
```
|
||||
$ ffsend upload [/Path/to/the/Directory] --copy
|
||||
```
|
||||
|
||||
在下面的例子中,我们将上传一个名为 `2g` 的目录:
|
||||
|
||||
```
|
||||
$ ffsend upload /home/daygeek/2g --copy
|
||||
You've selected a directory, only a single file may be uploaded.
|
||||
Archive the directory into a single file? [Y/n]: y
|
||||
Archiving...
|
||||
Upload complete
|
||||
Share link: https://send.firefox.com/download/90aa5cfe67/#hrwu6oXZRG2DNh8vOc3BGg
|
||||
```
|
||||
|
||||
在任意的远端系统中,只需要利用上面生成的唯一 URL 就可以获取到刚才上传的目录了。
|
||||
|
||||
```
|
||||
$ ffsend download https://send.firefox.com/download/90aa5cfe67/#hrwu6oXZRG2DNh8vOc3BGg
|
||||
You're downloading an archive, extract it into the selected directory? [Y/n]: y
|
||||
Extracting...
|
||||
Download complete
|
||||
```
|
||||
|
||||
上面已经通过安全、私密和加密过的链接来发送了文件。然而,如果你想在你的掌控范围内再添加额外的安全措施,你可以为文件添加密码。
|
||||
|
||||
```
|
||||
$ ffsend upload file-copy-rsync.sh --copy --password
|
||||
Password:
|
||||
Upload complete
|
||||
Share link: https://send.firefox.com/download/0742d24515/#P7gcNiwZJ87vF8cumU71zA
|
||||
```
|
||||
|
||||
当你在远端系统中尝试下载该文件时,它将要求你输入密码:
|
||||
|
||||
```
|
||||
$ ffsend download https://send.firefox.com/download/0742d24515/#P7gcNiwZJ87vF8cumU71zA
|
||||
This file is protected with a password.
|
||||
Password:
|
||||
Download complete
|
||||
```
|
||||
|
||||
另外,你还可以在上传过程中提供下载次数限制来限制文件被下载的次数。
|
||||
|
||||
```
|
||||
$ ffsend upload file-copy-scp.sh --copy --downloads 10
|
||||
Upload complete
|
||||
Share link: https://send.firefox.com/download/23cb923c4e/#LVg6K0CIb7Y9KfJRNZDQGw
|
||||
```
|
||||
|
||||
然后你可以在任意的远程系统中使用上面的唯一 URL 来下载该文件:
|
||||
|
||||
```
|
||||
ffsend download https://send.firefox.com/download/23cb923c4e/#LVg6K0CIb7Y9KfJRNZDQGw
|
||||
Download complete
|
||||
```
|
||||
|
||||
假如你想看这个链接的更多细节,你可以使用下面的命令来查看它的信息,它将为你展示文件名称、文件大小、被下载次数以及过期时间。
|
||||
|
||||
**语法:**
|
||||
|
||||
```
|
||||
$ ffsend info [Generated URL]
|
||||
|
||||
$ ffsend info https://send.firefox.com/download/23cb923c4e/#LVg6K0CIb7Y9KfJRNZDQGw
|
||||
ID: 23cb923c4e
|
||||
Name: file-copy-scp.sh
|
||||
Size: 115 B
|
||||
MIME: application/x-sh
|
||||
Downloads: 3 of 10
|
||||
Expiry: 23h58m (86280s)
|
||||
```
|
||||
|
||||
此外,你还可以使用下面的命令来查看你的传输历史:
|
||||
|
||||
```
|
||||
$ ffsend history
|
||||
# LINK EXPIRY
|
||||
1 https://send.firefox.com/download/23cb923c4e/#LVg6K0CIb7Y9KfJRNZDQGw 23h57m
|
||||
2 https://send.firefox.com/download/0742d24515/#P7gcNiwZJ87vF8cumU71zA 23h55m
|
||||
3 https://send.firefox.com/download/90aa5cfe67/#hrwu6oXZRG2DNh8vOc3BGg 23h52m
|
||||
4 https://send.firefox.com/download/a4062553f4/#yy2_VyPaUMG5HwXZzYRmpQ 23h46m
|
||||
5 https://send.firefox.com/download/74ff30e43e/#NYfDOUp_Ai-RKg5g0fCZXw 23h44m
|
||||
6 https://send.firefox.com/download/69afaab1f9/#5z51_94jtxcUCJNNvf6RcA 23h43m
|
||||
```
|
||||
|
||||
假如你不想再分享某个链接,你可以使用下面的语法来删除它:
|
||||
|
||||
**语法:**
|
||||
|
||||
```
|
||||
$ ffsend delete [Generated URL]
|
||||
|
||||
$ ffsend delete https://send.firefox.com/download/69afaab1f9/#5z51_94jtxcUCJNNvf6RcA
|
||||
File deleted
|
||||
```
|
||||
|
||||
### 如何在浏览器中使用 Send
|
||||
|
||||
另外,你还可以通过使用 firefox 浏览器打开 https://send.firefox.com/ 来完成相应的分享。
|
||||
|
||||
只需要拖拽该文件就可以上传它:
|
||||
|
||||
![][11]
|
||||
|
||||
一旦该文件被下载,它将展示 100% 的下载状态。
|
||||
|
||||
![][12]
|
||||
|
||||
想查看其他的可能选项,请浏览它对应的 man 信息或者帮助页。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.2daygeek.com/ffsend-securely-share-files-folders-from-linux-command-line-using-firefox-send-client/
|
||||
|
||||
作者:[Vinoth Kumar][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[FSSlc](https://github.com/FSSlc)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.2daygeek.com/author/vinoth/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://linux.cn/article-9177-1.html
|
||||
[2]: https://www.2daygeek.com/wormhole-securely-share-files-from-linux-command-line/
|
||||
[3]: https://www.2daygeek.com/transfer-sh-easy-fast-way-share-files-over-internet-from-command-line/
|
||||
[4]: https://linux.cn/article-10516-1.html
|
||||
[5]: https://github.com/timvisee/ffsend
|
||||
[6]: https://www.2daygeek.com/category/aur-helper/
|
||||
[7]: https://www.2daygeek.com/dpkg-command-to-manage-packages-on-debian-ubuntu-linux-mint-systems/
|
||||
[8]: data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7
|
||||
[9]: https://www.2daygeek.com/wp-content/uploads/2019/01/ffsend-easily-and-securely-share-files-from-linux-command-line-using-firefox-send-client-1.png
|
||||
[10]: https://www.2daygeek.com/wp-content/uploads/2019/01/ffsend-easily-and-securely-share-files-from-linux-command-line-using-firefox-send-client-2.png
|
||||
[11]: https://www.2daygeek.com/wp-content/uploads/2019/01/ffsend-easily-and-securely-share-files-from-linux-command-line-using-firefox-send-client-3.png
|
||||
[12]: https://www.2daygeek.com/wp-content/uploads/2019/01/ffsend-easily-and-securely-share-files-from-linux-command-line-using-firefox-send-client-4.png
|
||||
98
published/20190422 9 ways to save the planet.md
Normal file
98
published/20190422 9 ways to save the planet.md
Normal file
@ -0,0 +1,98 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (MFGJT)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-11978-1.html)
|
||||
[#]: subject: (9 ways to save the planet)
|
||||
[#]: via: (https://opensource.com/article/19/4/save-planet)
|
||||
[#]: author: (Jen Wike Huger https://opensource.com/users/jen-wike/users/alanfdoss/users/jmpearce)
|
||||
|
||||
九种用开源拯救地球的方法
|
||||
======
|
||||
|
||||
> 这些主意都用到了有关的开源技巧。
|
||||
|
||||

|
||||
|
||||
人们可以做些什么来拯救地球?这个问题可能会让人感到压抑,因为有时我们感觉个人可以做的贡献太少了。但是作为地球公民,我们从来不是一个人。所以,我向我们的作家社区征集了一些开源软件或硬件可以帮助改变现状的方法。以下是他们的回复。
|
||||
|
||||
### 九种利用开源的方法来拯救地球的方式
|
||||
|
||||
#### 1、在你的终端禁用闪烁的光标
|
||||
|
||||
这听起来可能有点傻,但是那个无关紧要的闪烁的光标可能导致[每小时两瓦特的额外电力开销][2]。如果要禁用光标闪烁,可以通过更改终端设置:<ruby>编辑<rt>Edit</rt></ruby> > <ruby>偏好设置<rt>Preferences</rt></ruby> > <ruby>光标<rt>Cursor</rt></ruby> > <ruby>光标闪烁<rt>Cursor blinking</rt></ruby> > <ruby>禁用<rt>Disabled</rt></ruby>。
|
||||
|
||||
*由 Mars Toktonaliev 推荐*
|
||||
|
||||
#### 2、减少有关动物产品和加工食物的消费
|
||||
|
||||
这样做的一种方法是在你的手机中添加这些开源的 App:Daily Dozen、OpenFoodFacts、OpenVegeMap 和 Food Restrictions。这些 App 可以帮助你准备一份健康的素食饮食计划,为你找到素食主义者和严格素食主义者可以就餐的餐厅,还可以帮助你把你的饮食需求告诉别人,即使他们不和你讲同一种语言。如果想要了解更多有关这些的 App 的信息,你可以阅读《[4 款“吃草”的开源应用][3]》。
|
||||
|
||||
*由 Joshua Allen Holm 推荐*
|
||||
|
||||
#### 3、让旧电脑重焕新生
|
||||
|
||||
怎么做?当然是用 Linux。通过给那些自己得不到新电脑的人创造一台新电脑来传递爱心,同时也可以避免让这台电脑进到垃圾填埋场。可以在 [The Asian Penguins][4] 看看我们是怎么做的。
|
||||
|
||||
*由 Stu Keroff 推荐*
|
||||
|
||||
#### 4、在你不使用设备时关闭它们
|
||||
|
||||
你可以使用带有主插座和控制插座的“智能插座板”。把你的电脑连接到主插座上,这样的话当你打开电脑时所有你连接到控制插座上的设备如显示器,打印机等也都会打开。一个更简单的、技术含量更低的方法是使用一个带有计时器的插座板。我在家里就是用的这个。你可以用计时器上的开关设定一个定时开关电源的时间表。这样可以在没有人在家时自动关闭网络打印机。或者以我的用了六年的笔记本电脑为例,我通过一个交替使用外接电源(插座打开)和使用电脑电池(插座关闭)的电源计划延长了电脑电池的寿命。
|
||||
|
||||
*由 Jim Hall 推荐*
|
||||
|
||||
#### 5、减少供暖通风系统(HVAC)的使用
|
||||
|
||||
在夏天,透过窗户的阳光可以为室内提供很多热量。使用 Home Assistant 可以[基于一天中的时间的][6],甚至是基于太阳高度角[自动调节][5]窗帘和遮阳棚。
|
||||
|
||||
*由 Michael Hrivnak 推荐*
|
||||
|
||||
#### 6、出门就把恒温器关闭或调低
|
||||
|
||||
如果你的家用恒温器具有“离开”功能,你很容易忘记在出门时启用它。借助自动化,任何连接到网络的恒温器都可以在你不在家时自动节省能量。[Stataway][7] 就是一个这样项目。它通过调用你的手机的 GPS 坐标来决定是将你的恒温器设置为“在家”还是“离开”。
|
||||
|
||||
*由 Michael Hrivnak 推荐*
|
||||
|
||||
#### 7、为未来储蓄算力
|
||||
|
||||
我有一个主意:创建一个可以读取可选的能量阵列(如风能或太阳能)的输出的脚本。这个脚本应该将计算集群中的服务器从睡眠模式更改为激活模式,直到过量的电能(超出可以储存的部分)被用尽。然后在高产能时段使用这些过量的电能来进行需要大量计算的项目,比如渲染。这个过程本质应该是免费的,因为使用的能量无法被储存起来挪作它用。我相信现有的监控、能量管理和服务器阵列工具一定可以实现这个功能。那么剩下的只是一些整合上的问题,就可以让整个系统工作起来。
|
||||
|
||||
*由 Terry Hancock 推荐*
|
||||
|
||||
#### 8、关掉你的灯
|
||||
|
||||
根据<ruby>[人工夜空亮度图集][8]<rt>World Atlas of Artificial Night Sky Brightness</rt></ruby>的说法,光污染影响了全世界超过 80% 的人口。这一结论在 2016 年(遵循 CC-NC 4.0 协议)发表在公开访问的期刊《<ruby>科学进展<rt>Science Advances</rt></ruby>》上。关闭外部照明是一个可以使野生生物、人类健康受益并让我们享受夜晚的天空的快速途径,而且可以减少能量消耗。访问 [darksky.org][9] 来查看更多减少外部照明影响的方法。
|
||||
|
||||
*由 Michael Hrivnak 推荐*
|
||||
|
||||
#### 9、减少你的 CPU 数量
|
||||
|
||||
就我个人而言,我记得我以前有很多在地下室运行的电脑作为我的 IT 游乐场/实验室。我现在对于能源消耗更加注意了,所以确实大大地减少了我的 CPU 数量。我现在更喜欢利用虚拟机、区域和容器等技术。另外,我很高兴有小型电脑和 SoC 电脑这种东西,比如树莓派,因为我可以用一台这样的电脑做很多事情,比如运行一个 DNS 或者 Web 服务器,而无需使整个屋子变热并积累昂贵的电费账单。
|
||||
|
||||
P.S. 这些电脑都运行于 Linux、FreeBSD,或者 Raspbian 系统!
|
||||
|
||||
*由 Alan Formy-Duvall 推荐*
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/4/save-planet
|
||||
|
||||
作者:[Jen Wike Huger][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[MFGJT](https://github.com/MFGJT)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/jen-wike/users/alanfdoss/users/jmpearce
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/pixelated-world.png?itok=fHjM6m53
|
||||
[2]: https://www.redhat.com/archives/fedora-devel-list/2009-January/msg02406.html
|
||||
[3]: https://linux.cn/article-10926-1.html
|
||||
[4]: https://opensource.com/article/19/2/asian-penguins-close-digital-divide
|
||||
[5]: https://www.home-assistant.io/docs/automation/trigger/#sun-trigger
|
||||
[6]: https://www.home-assistant.io/components/cover/
|
||||
[7]: https://github.com/mhrivnak/stataway
|
||||
[8]: http://advances.sciencemag.org/content/2/6/e1600377
|
||||
[9]: http://darksky.org/
|
||||
@ -0,0 +1,288 @@
|
||||
[#]: collector: "lujun9972"
|
||||
[#]: translator: "way-ww"
|
||||
[#]: reviewer: "wxy"
|
||||
[#]: publisher: "wxy"
|
||||
[#]: url: "https://linux.cn/article-12027-1.html"
|
||||
[#]: subject: "How To Enable Or Disable SSH Access For A Particular User Or Group In Linux?"
|
||||
[#]: via: "https://www.2daygeek.com/allow-deny-enable-disable-ssh-access-user-group-in-linux/"
|
||||
[#]: author: "2daygeek http://www.2daygeek.com/author/2daygeek/"
|
||||
|
||||
如何在 Linux 上为特定的用户或用户组启用或禁用 SSH?
|
||||
======
|
||||
|
||||

|
||||
|
||||
由于你的公司标准规定,你可能只能允许部分人访问 Linux 系统。或者你可能只能够允许几个用户组中的用户访问 Linux 系统。那么如何实现这样的要求呢?最好的方法是什么呢?如何使用一个简单的方法去实现呢?
|
||||
|
||||
是的,我们会有很多种方法去实现它。但是我们应该使用简单轻松的方法。为了简单轻松的完成目的,我们可以通过对 `/etc/ssh/sshd_config` 文件做必要的修改来实现。在这篇文章中我们将会向你展示实现要求的详细步骤。
|
||||
|
||||
为什么我们要这样做呢?是出于安全的原因。你可以访问[这个链接][1]来获取更多关于 openSSH 的使用方法。
|
||||
|
||||
### 什么是 SSH ?
|
||||
|
||||
openssh 全称为 OpenBSD Secure Shell。Secure Shell(ssh)是一个自由开源的网络工具,它能让我们在一个不安全的网络中通过使用 Secure Shell(SSH)协议来安全访问远程主机。
|
||||
|
||||
它采用了客户端-服务器架构(C/S),拥有用户身份认证、加密、在计算机和隧道之间传输文件等功能。
|
||||
|
||||
我们也可以用 `telnet` 或 `rcp` 等传统工具来完成,但是这些工具都不安全,因为它们在执行任何动作时都会使用明文来传输密码。
|
||||
|
||||
### 如何在 Linux 中允许用户使用 SSH?
|
||||
|
||||
通过以下内容,我们可以为指定的用户或用户列表启用 `ssh` 访问。如果你想要允许多个用户,那么你可以在添加用户时在同一行中用空格来隔开他们。
|
||||
|
||||
为了达到目的只需要将下面的值追加到 `/etc/ssh/sshd_config` 文件中去。 在这个例子中, 我们将会允许用户 `user3` 使用 ssh。
|
||||
|
||||
```
|
||||
# echo "AllowUsers user3" >> /etc/ssh/sshd_config
|
||||
```
|
||||
|
||||
你可以运行下列命令再次检查是否添加成功。
|
||||
|
||||
```
|
||||
# cat /etc/ssh/sshd_config | grep -i allowusers
|
||||
AllowUsers user3
|
||||
```
|
||||
|
||||
这样就行了, 现在只需要重启 `ssh` 服务和见证奇迹了。(下面这两条命令效果相同, 请根据你的服务管理方式选择一条执行即可)
|
||||
|
||||
```
|
||||
# systemctl restart sshd
|
||||
或
|
||||
# service restart sshd
|
||||
```
|
||||
|
||||
接下来很简单,只需打开一个新的终端或者会话尝试用不同的用户身份访问 Linux 系统。是的,这里 `user2` 用户是不被允许使用 SSH 登录的并且会得到如下所示的错误信息。
|
||||
|
||||
```
|
||||
# ssh user2@192.168.1.4
|
||||
user2@192.168.1.4's password:
|
||||
Permission denied, please try again.
|
||||
```
|
||||
|
||||
输出:
|
||||
|
||||
```
|
||||
Mar 29 02:00:35 CentOS7 sshd[4900]: User user2 from 192.168.1.6 not allowed because not listed in AllowUsers
|
||||
Mar 29 02:00:35 CentOS7 sshd[4900]: input_userauth_request: invalid user user2 [preauth]
|
||||
Mar 29 02:00:40 CentOS7 unix_chkpwd[4902]: password check failed for user (user2)
|
||||
Mar 29 02:00:40 CentOS7 sshd[4900]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=192.168.1.6 user=user2
|
||||
Mar 29 02:00:43 CentOS7 sshd[4900]: Failed password for invalid user user2 from 192.168.1.6 port 42568 ssh2
|
||||
```
|
||||
|
||||
与此同时用户 `user3` 被允许登入系统因为他在被允许的用户列表中。
|
||||
|
||||
```
|
||||
# ssh user3@192.168.1.4
|
||||
user3@192.168.1.4's password:
|
||||
[user3@CentOS7 ~]$
|
||||
```
|
||||
|
||||
输出:
|
||||
|
||||
```
|
||||
Mar 29 02:01:13 CentOS7 sshd[4939]: Accepted password for user3 from 192.168.1.6 port 42590 ssh2
|
||||
Mar 29 02:01:13 CentOS7 sshd[4939]: pam_unix(sshd:session): session opened for user user3 by (uid=0)
|
||||
```
|
||||
|
||||
### 如何在 Linux 中阻止用户使用 SSH ?
|
||||
|
||||
通过以下内容,我们可以配置指定的用户或用户列表禁用 `ssh`。如果你想要禁用多个用户,那么你可以在添加用户时在同一行中用空格来隔开他们。
|
||||
|
||||
为了达到目的只需要将以下值追加到 `/etc/ssh/sshd_config` 文件中去。 在这个例子中, 我们将禁用用户 `user1` 使用 `ssh`。
|
||||
|
||||
```
|
||||
# echo "DenyUsers user1" >> /etc/ssh/sshd_config
|
||||
```
|
||||
|
||||
你可以运行下列命令再次检查是否添加成功。
|
||||
|
||||
```
|
||||
# cat /etc/ssh/sshd_config | grep -i denyusers
|
||||
DenyUsers user1
|
||||
```
|
||||
|
||||
这样就行了, 现在只需要重启 `ssh` 服务和见证奇迹了。
|
||||
|
||||
```
|
||||
# systemctl restart sshd
|
||||
活
|
||||
# service restart sshd
|
||||
```
|
||||
|
||||
接下来很简单,只需打开一个新的终端或者会话,尝试使用被禁用的用户身份被访问 Linux 系统。是的,这里 `user1` 用户在禁用名单中。所以,当你尝试登录时,你将会得到如下所示的错误信息。
|
||||
|
||||
```
|
||||
# ssh user1@192.168.1.4
|
||||
user1@192.168.1.4's password:
|
||||
Permission denied, please try again.
|
||||
```
|
||||
|
||||
输出:
|
||||
|
||||
```
|
||||
Mar 29 01:53:42 CentOS7 sshd[4753]: User user1 from 192.168.1.6 not allowed because listed in DenyUsers
|
||||
Mar 29 01:53:42 CentOS7 sshd[4753]: input_userauth_request: invalid user user1 [preauth]
|
||||
Mar 29 01:53:46 CentOS7 unix_chkpwd[4755]: password check failed for user (user1)
|
||||
Mar 29 01:53:46 CentOS7 sshd[4753]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=192.168.1.6 user=user1
|
||||
Mar 29 01:53:48 CentOS7 sshd[4753]: Failed password for invalid user user1 from 192.168.1.6 port 42522 ssh2
|
||||
```
|
||||
|
||||
### 如何在 Linux 中允许用户组使用 SSH?
|
||||
|
||||
通过以下内容,我们可以允许一个指定的组或多个组使用 `ssh`。
|
||||
|
||||
如果你想要允许多个组使用 `ssh` 那么你在添加用户组时需要在同一行中使用空格来隔开他们。
|
||||
|
||||
为了达到目的只需将以下值追加到 `/etc/ssh/sshd_config` 文件中去。在这个例子中,我们将允许 `2g-admin` 组使用 ssh。
|
||||
|
||||
```
|
||||
# echo "AllowGroups 2g-admin" >> /etc/ssh/sshd_config
|
||||
```
|
||||
|
||||
你可以运行下列命令再次检查是否添加成功。
|
||||
|
||||
```
|
||||
# cat /etc/ssh/sshd_config | grep -i allowgroups
|
||||
AllowGroups 2g-admin
|
||||
```
|
||||
|
||||
运行下列命令查看属于该用户组的用户有哪些。
|
||||
|
||||
```
|
||||
# getent group 2g-admin
|
||||
2g-admin:x:1005:user1,user2,user3
|
||||
```
|
||||
|
||||
这样就行了, 现在只需要重启 `ssh` 服务和见证奇迹了。
|
||||
|
||||
```
|
||||
# systemctl restart sshd
|
||||
或
|
||||
# service restart sshd
|
||||
```
|
||||
|
||||
是的, `user1` 被允许登入系统因为用户 `user1` 属于 `2g-admin` 组。
|
||||
|
||||
```
|
||||
# ssh user1@192.168.1.4
|
||||
user1@192.168.1.4's password:
|
||||
[user1@CentOS7 ~]$
|
||||
```
|
||||
|
||||
输出:
|
||||
|
||||
```
|
||||
Mar 29 02:10:21 CentOS7 sshd[5165]: Accepted password for user1 from 192.168.1.6 port 42640 ssh2
|
||||
Mar 29 02:10:22 CentOS7 sshd[5165]: pam_unix(sshd:session): session opened for user user1 by (uid=0)
|
||||
```
|
||||
|
||||
是的, `user2` 被允许登入系统因为用户 `user2` 同样属于 `2g-admin` 组。
|
||||
|
||||
```
|
||||
# ssh user2@192.168.1.4
|
||||
user2@192.168.1.4's password:
|
||||
[user2@CentOS7 ~]$
|
||||
```
|
||||
|
||||
输出:
|
||||
|
||||
```
|
||||
Mar 29 02:10:38 CentOS7 sshd[5225]: Accepted password for user2 from 192.168.1.6 port 42642 ssh2
|
||||
Mar 29 02:10:38 CentOS7 sshd[5225]: pam_unix(sshd:session): session opened for user user2 by (uid=0)
|
||||
```
|
||||
|
||||
当你尝试使用其他不在被允许的组中的用户去登入系统时, 你将会得到如下所示的错误信息。
|
||||
|
||||
```
|
||||
# ssh ladmin@192.168.1.4
|
||||
ladmin@192.168.1.4's password:
|
||||
Permission denied, please try again.
|
||||
```
|
||||
|
||||
输出:
|
||||
|
||||
```
|
||||
Mar 29 02:12:36 CentOS7 sshd[5306]: User ladmin from 192.168.1.6 not allowed because none of user's groups are listed in AllowGroups
|
||||
Mar 29 02:12:36 CentOS7 sshd[5306]: input_userauth_request: invalid user ladmin [preauth]
|
||||
Mar 29 02:12:56 CentOS7 unix_chkpwd[5310]: password check failed for user (ladmin)
|
||||
Mar 29 02:12:56 CentOS7 sshd[5306]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=192.168.1.6 user=ladmin
|
||||
Mar 29 02:12:58 CentOS7 sshd[5306]: Failed password for invalid user ladmin from 192.168.1.6 port 42674 ssh2
|
||||
```
|
||||
|
||||
### 如何在 Linux 中阻止用户组使用 SSH?
|
||||
|
||||
通过以下内容,我们可以禁用指定的组或多个组使用 `ssh`。
|
||||
|
||||
如果你想要禁用多个用户组使用 `ssh`,那么你需要在添加用户组时在同一行中使用空格来隔开他们。
|
||||
|
||||
为了达到目的只需要将下面的值追加到 `/etc/ssh/sshd_config` 文件中去。
|
||||
|
||||
```
|
||||
# echo "DenyGroups 2g-admin" >> /etc/ssh/sshd_config
|
||||
```
|
||||
|
||||
你可以运行下列命令再次检查是否添加成功。
|
||||
|
||||
```
|
||||
# # cat /etc/ssh/sshd_config | grep -i denygroups
|
||||
DenyGroups 2g-admin
|
||||
|
||||
# getent group 2g-admin
|
||||
2g-admin:x:1005:user1,user2,user3
|
||||
```
|
||||
|
||||
这样就行了, 现在只需要重启 `ssh` 服务和见证奇迹了。
|
||||
|
||||
```
|
||||
# systemctl restart sshd
|
||||
或
|
||||
# service restart sshd
|
||||
```
|
||||
|
||||
是的 `user1` 不被允许登入系统,因为他是 `2g-admin` 用户组中的一员。他属于被禁用 `ssh` 的组中。
|
||||
|
||||
```
|
||||
# ssh user1@192.168.1.4
|
||||
user1@192.168.1.4's password:
|
||||
Permission denied, please try again.
|
||||
```
|
||||
|
||||
输出:
|
||||
|
||||
```
|
||||
Mar 29 02:17:32 CentOS7 sshd[5400]: User user1 from 192.168.1.6 not allowed because a group is listed in DenyGroups
|
||||
Mar 29 02:17:32 CentOS7 sshd[5400]: input_userauth_request: invalid user user1 [preauth]
|
||||
Mar 29 02:17:38 CentOS7 unix_chkpwd[5402]: password check failed for user (user1)
|
||||
Mar 29 02:17:38 CentOS7 sshd[5400]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=192.168.1.6 user=user1
|
||||
Mar 29 02:17:41 CentOS7 sshd[5400]: Failed password for invalid user user1 from 192.168.1.6 port 42710 ssh2
|
||||
```
|
||||
|
||||
除了 `2g-admin` 用户组之外的用户都可以使用 ssh 登入系统。 例如,`ladmin` 等用户就允许登入系统。
|
||||
|
||||
```
|
||||
# ssh ladmin@192.168.1.4
|
||||
ladmin@192.168.1.4's password:
|
||||
[ladmin@CentOS7 ~]$
|
||||
```
|
||||
|
||||
输出:
|
||||
|
||||
```
|
||||
Mar 29 02:19:13 CentOS7 sshd[5432]: Accepted password for ladmin from 192.168.1.6 port 42716 ssh2
|
||||
Mar 29 02:19:13 CentOS7 sshd[5432]: pam_unix(sshd:session): session opened for user ladmin by (uid=0)
|
||||
```
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.2daygeek.com/allow-deny-enable-disable-ssh-access-user-group-in-linux/
|
||||
|
||||
作者:[2daygeek][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[way-ww](https://github.com/way-ww)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: http://www.2daygeek.com/author/2daygeek/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.2daygeek.com/category/ssh-tutorials/
|
||||
@ -0,0 +1,224 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (mengxinayan)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-12000-1.html)
|
||||
[#]: subject: (How to structure a multi-file C program: Part 2)
|
||||
[#]: via: (https://opensource.com/article/19/7/structure-multi-file-c-part-2)
|
||||
[#]: author: (Erik O'Shaughnessy https://opensource.com/users/jnyjny)
|
||||
|
||||
如何组织构建多文件 C 语言程序(二)
|
||||
======
|
||||
|
||||
> 我将在本系列的第二篇中深入研究由多个文件组成的 C 程序的结构。
|
||||
|
||||

|
||||
|
||||
在[第一篇][2]中,我设计了一个名为[喵呜喵呜][3]的多文件 C 程序,该程序实现了一个玩具[编解码器][4]。我也提到了程序设计中的 Unix 哲学,即在一开始创建多个空文件,并建立一个好的结构。最后,我创建了一个 `Makefile` 文件夹并阐述了它的作用。在本文中将另一个方向展开:现在我将介绍简单但具有指导性的喵呜喵呜编解码器的实现。
|
||||
|
||||
当读过我的《[如何写一个好的 C 语言 main 函数][5]》后,你会觉得喵呜喵呜编解码器的 `main.c` 文件的结构很熟悉,其主体结构如下:
|
||||
|
||||
```
|
||||
/* main.c - 喵呜喵呜流式编解码器 */
|
||||
|
||||
/* 00 系统包含文件 */
|
||||
/* 01 项目包含文件 */
|
||||
/* 02 外部声明 */
|
||||
/* 03 定义 */
|
||||
/* 04 类型定义 */
|
||||
/* 05 全局变量声明(不要用)*/
|
||||
/* 06 附加的函数原型 */
|
||||
|
||||
int main(int argc, char *argv[])
|
||||
{
|
||||
/* 07 变量声明 */
|
||||
/* 08 检查 argv[0] 以查看该程序是被如何调用的 */
|
||||
/* 09 处理来自用户的命令行选项 */
|
||||
/* 10 做点有用的事情 */
|
||||
}
|
||||
|
||||
/* 11 其它辅助函数 */
|
||||
```
|
||||
|
||||
### 包含项目头文件
|
||||
|
||||
位于第二部分中的 `/* 01 项目包含文件 */` 的源代码如下:
|
||||
|
||||
|
||||
```
|
||||
/* main.c - 喵呜喵呜流式编解码器 */
|
||||
...
|
||||
/* 01 项目包含文件 */
|
||||
#include "main.h"
|
||||
#include "mmecode.h"
|
||||
#include "mmdecode.h"
|
||||
```
|
||||
|
||||
`#include` 是 C 语言的预处理命令,它会将该文件名的文件内容拷贝到当前文件中。如果程序员在头文件名称周围使用双引号(`""`),编译器将会在当前目录寻找该文件。如果文件被尖括号包围(`<>`),编译器将在一组预定义的目录中查找该文件。
|
||||
|
||||
[main.h][6] 文件中包含了 [main.c][7] 文件中用到的定义和类型定义。我喜欢尽可能多将声明放在头文件里,以便我在我的程序的其他位置使用这些定义。
|
||||
|
||||
头文件 [mmencode.h][8] 和 [mmdecode.h][9] 几乎相同,因此我以 `mmencode.h` 为例来分析。
|
||||
|
||||
```
|
||||
/* mmencode.h - 喵呜喵呜流编解码器 */
|
||||
|
||||
#ifndef _MMENCODE_H
|
||||
#define _MMENCODE_H
|
||||
|
||||
#include <stdio.h>
|
||||
|
||||
int mm_encode(FILE *src, FILE *dst);
|
||||
|
||||
#endif /* _MMENCODE_H */
|
||||
```
|
||||
|
||||
`#ifdef`、`#define`、`#endif` 指令统称为 “防护” 指令。其可以防止 C 编译器在一个文件中多次包含同一文件。如果编译器在一个文件中发现多个定义/原型/声明,它将会产生警告。因此这些防护措施是必要的。
|
||||
|
||||
在这些防护内部,只有两个东西:`#include` 指令和函数原型声明。我在这里包含了 `stdio.h` 头文件,以便于能在函数原型中使用 `FILE` 定义。函数原型也可以被包含在其他 C 文件中,以便于在文件的命名空间中创建它。你可以将每个文件视为一个独立的命名空间,其中的变量和函数不能被另一个文件中的函数或者变量使用。
|
||||
|
||||
编写头文件很复杂,并且在大型项目中很难管理它。不要忘记使用防护。
|
||||
|
||||
### 喵呜喵呜编码的最终实现
|
||||
|
||||
该程序的功能是按照字节进行 `MeowMeow` 字符串的编解码,事实上这是该项目中最简单的部分。截止目前我所做的工作便是支持允许在适当的位置调用此函数:解析命令行,确定要使用的操作,并打开将要操作的文件。下面的循环是编码的过程:
|
||||
|
||||
```
|
||||
/* mmencode.c - 喵呜喵呜流式编解码器 */
|
||||
...
|
||||
while (!feof(src)) {
|
||||
|
||||
if (!fgets(buf, sizeof(buf), src))
|
||||
break;
|
||||
|
||||
for(i=0; i<strlen(buf); i++) {
|
||||
lo = (buf[i] & 0x000f);
|
||||
hi = (buf[i] & 0x00f0) >> 4;
|
||||
fputs(tbl[hi], dst);
|
||||
fputs(tbl[lo], dst);
|
||||
}
|
||||
}
|
||||
```
|
||||
|
||||
简单的说,当文件中还有数据块时( `feof(3)` ),该循环读取(`feof(3)` )文件中的一个数据块。然后将读入的内容的每个字节分成两个 `hi` 和 `lo` 的<ruby>半字节<rt>nibble</rt></ruby>。半字节是半个字节,即 4 个位。这里的奥妙之处在于可以用 4 个位来编码 16 个值。我将 `hi` 和 `lo` 用作 16 个字符串查找表 `tbl` 的索引,表中包含了用半字节编码的 `MeowMeow` 字符串。这些字符串使用 `fputs(3)` 函数写入目标 `FILE` 流,然后我们继续处理缓存区的下一个字节。
|
||||
|
||||
该表使用 [table.h][14] 中的宏定义进行初始化,在没有特殊原因(比如:要展示包含了另一个项目的本地头文件)时,我喜欢使用宏来进行初始化。我将在未来的文章中进一步探讨原因。
|
||||
|
||||
### 喵呜喵呜解码的实现
|
||||
|
||||
我承认在开始工作前花了一些时间。解码的循环与编码类似:读取 `MeowMeow` 字符串到缓冲区,将编码从字符串转换为字节
|
||||
|
||||
```
|
||||
/* mmdecode.c - 喵呜喵呜流式编解码器 */
|
||||
...
|
||||
int mm_decode(FILE *src, FILE *dst)
|
||||
{
|
||||
if (!src || !dst) {
|
||||
errno = EINVAL;
|
||||
return -1;
|
||||
}
|
||||
return stupid_decode(src, dst);
|
||||
}
|
||||
```
|
||||
|
||||
这不符合你的期望吗?
|
||||
|
||||
在这里,我通过外部公开的 `mm_decode()` 函数公开了 `stupid_decode()` 函数细节。我上面所说的“外部”是指在这个文件之外。因为 `stupid_decode()` 函数不在该头文件中,因此无法在其他文件中调用它。
|
||||
|
||||
当我们想发布一个可靠的公共接口时,有时候会这样做,但是我们还没有完全使用函数解决问题。在本例中,我编写了一个 I/O 密集型函数,该函数每次从源中读取 8 个字节,然后解码获得 1 个字节写入目标流中。较好的实现是一次处理多于 8 个字节的缓冲区。更好的实现还可以通过缓冲区输出字节,进而减少目标流中单字节的写入次数。
|
||||
|
||||
```
|
||||
/* mmdecode.c - 喵呜喵呜流式编解码器 */
|
||||
...
|
||||
int stupid_decode(FILE *src, FILE *dst)
|
||||
{
|
||||
char buf[9];
|
||||
decoded_byte_t byte;
|
||||
int i;
|
||||
|
||||
while (!feof(src)) {
|
||||
if (!fgets(buf, sizeof(buf), src))
|
||||
break;
|
||||
byte.field.f0 = isupper(buf[0]);
|
||||
byte.field.f1 = isupper(buf[1]);
|
||||
byte.field.f2 = isupper(buf[2]);
|
||||
byte.field.f3 = isupper(buf[3]);
|
||||
byte.field.f4 = isupper(buf[4]);
|
||||
byte.field.f5 = isupper(buf[5]);
|
||||
byte.field.f6 = isupper(buf[6]);
|
||||
byte.field.f7 = isupper(buf[7]);
|
||||
|
||||
fputc(byte.value, dst);
|
||||
}
|
||||
return 0;
|
||||
}
|
||||
```
|
||||
|
||||
我并没有使用编码器中使用的位移方法,而是创建了一个名为 `decoded_byte_t` 的自定义数据结构。
|
||||
|
||||
```
|
||||
/* mmdecode.c - 喵呜喵呜流式编解码器 */
|
||||
...
|
||||
|
||||
typedef struct {
|
||||
unsigned char f7:1;
|
||||
unsigned char f6:1;
|
||||
unsigned char f5:1;
|
||||
unsigned char f4:1;
|
||||
unsigned char f3:1;
|
||||
unsigned char f2:1;
|
||||
unsigned char f1:1;
|
||||
unsigned char f0:1;
|
||||
} fields_t;
|
||||
|
||||
typedef union {
|
||||
fields_t field;
|
||||
unsigned char value;
|
||||
} decoded_byte_t;
|
||||
```
|
||||
|
||||
初次看到代码时可能会感到有点儿复杂,但不要放弃。`decoded_byte_t` 被定义为 `fields_t` 和 `unsigned char` 的 **联合**。可以将联合中的命名成员看作同一内存区域的别名。在这种情况下,`value` 和 `field` 指向相同的 8 位内存区域。将 `field.f0` 设置为 `1` 也将会设置 `value` 中的最低有效位。
|
||||
|
||||
虽然 `unsigned char` 并不神秘,但是对 `fields_t` 的类型定义(`typedef`)也许看起来有些陌生。现代 C 编译器允许程序员在结构体中指定单个位字段的值。字段所在的类型是一个无符号整数类型,并在成员标识符后紧跟一个冒号和一个整数,该整数指定了位字段的长度。
|
||||
|
||||
这种数据结构使得按字段名称访问字节中的每个位变得简单,并可以通过联合中的 `value` 字段访问组合后的值。我们依赖编译器生成正确的移位指令来访问字段,这可以在调试时为你节省不少时间。
|
||||
|
||||
最后,因为 `stupid_decode()` 函数一次仅从源 `FILE` 流中读取 8 个字节,所以它效率并不高。通常我们尝试最小化读写次数,以提高性能和降低调用系统调用的开销。请记住:少量的读取/写入大的块比大量的读取/写入小的块好得多。
|
||||
|
||||
### 总结
|
||||
|
||||
用 C 语言编写一个多文件程序需要程序员要比只是是一个 `main.c` 做更多的规划。但是当你添加功能或者重构时,只需要多花费一点儿努力便可以节省大量时间以及避免让你头痛的问题。
|
||||
|
||||
回顾一下,我更喜欢这样做:多个文件,每个文件仅有简单功能;通过头文件公开那些文件中的小部分功能;把数字常量和字符串常量保存在头文件中;使用 `Makefile` 而不是 Bash 脚本来自动化处理事务;使用 `main()` 函数来处理命令行参数解析并作为程序主要功能的框架。
|
||||
|
||||
我知道我只是蜻蜓点水般介绍了这个简单的程序,并且我很高兴知道哪些事情对你有所帮助,以及哪些主题需要详细的解释。请在评论中分享你的想法,让我知道。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/7/structure-multi-file-c-part-2
|
||||
|
||||
作者:[Erik O'Shaughnessy][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[萌新阿岩](https://github.com/mengxinayan)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/jnyjny
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/file_system.jpg?itok=pzCrX1Kc (4 manilla folders, yellow, green, purple, blue)
|
||||
[2]: https://linux.cn/article-11935-1.html
|
||||
[3]: https://github.com/jnyjny/MeowMeow.git
|
||||
[4]: https://en.wikipedia.org/wiki/Codec
|
||||
[5]: https://linux.cn/article-10949-1.html
|
||||
[6]: https://github.com/JnyJny/meowmeow/blob/master/main.h
|
||||
[7]: https://github.com/JnyJny/meowmeow/blob/master/main.c
|
||||
[8]: https://github.com/JnyJny/meowmeow/blob/master/mmencode.h
|
||||
[9]: https://github.com/JnyJny/meowmeow/blob/master/mmdecode.h
|
||||
[10]: http://www.opengroup.org/onlinepubs/009695399/functions/feof.html
|
||||
[11]: http://www.opengroup.org/onlinepubs/009695399/functions/fgets.html
|
||||
[12]: http://www.opengroup.org/onlinepubs/009695399/functions/strlen.html
|
||||
[13]: http://www.opengroup.org/onlinepubs/009695399/functions/fputs.html
|
||||
[14]: https://github.com/JnyJny/meowmeow/blob/master/table.h
|
||||
[15]: http://www.opengroup.org/onlinepubs/009695399/functions/isupper.html
|
||||
[16]: http://www.opengroup.org/onlinepubs/009695399/functions/fputc.html
|
||||
@ -1,16 +1,18 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (caiichenr)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-11986-1.html)
|
||||
[#]: subject: (Building a non-breaking breakpoint for Python debugging)
|
||||
[#]: via: (https://opensource.com/article/19/8/debug-python)
|
||||
[#]: author: (Liran Haimovitch https://opensource.com/users/liranhaimovitch)
|
||||
|
||||
在 Python 调试过程中设置不中断的断点
|
||||
======
|
||||
你对如何让调试器变得更快产生过兴趣吗?本文将分享我们在为 Python 构建调试器时得到的一些经验。
|
||||
![Real python in the graphic jungle][1]
|
||||
|
||||
> 你对如何让调试器变得更快产生过兴趣吗?本文将分享我们在为 Python 构建调试器时得到的一些经验。
|
||||
|
||||

|
||||
|
||||
整段故事讲的是我们在 [Rookout][2] 公司的团队为 Python 调试器开发不中断断点的经历,以及开发过程中得到的经验。我将在本月于旧金山举办的 [PyBay 2019][3] 上介绍有关 Python 调试过程的更多细节,但现在就让我们立刻开始这段故事。
|
||||
|
||||
@ -18,28 +20,23 @@
|
||||
|
||||
在诸多可选的 Python 调试器中,使用最广泛的三个是:
|
||||
|
||||
* **pdb**,它是 Python 标准库的一部分
|
||||
* **PyDev**,它是内嵌在 Eclipse 和 Pycharm 等 IDE 中的调试器
|
||||
* **ipdb**,它是IPython的调试器
|
||||
* pdb,它是 Python 标准库的一部分
|
||||
* PyDev,它是内嵌在 Eclipse 和 Pycharm 等 IDE 中的调试器
|
||||
* ipdb,它是 IPython 的调试器
|
||||
|
||||
|
||||
|
||||
Python 调试器的选择虽多,但它们几乎都基于同一个函数:**sys.set_trace**。 值得一提的是, **[sys.settrace][4]** 可能也是 Python 标准库中最复杂的函数。
|
||||
Python 调试器的选择虽多,但它们几乎都基于同一个函数:`sys.settrace`。 值得一提的是, [sys.settrace][4] 可能也是 Python 标准库中最复杂的函数。
|
||||
|
||||
![set_trace Python 2 docs page][5]
|
||||
|
||||
简单来讲,**settrace** 的作用是为解释器注册一个跟踪函数,它在下列四种情形发生时被调用:
|
||||
|
||||
* 函数调用 (Function call)
|
||||
* 语句执行 (Line execution)
|
||||
* 函数返回 (Function return)
|
||||
* 异常抛出 (Exception raised)
|
||||
|
||||
简单来讲,`settrace` 的作用是为解释器注册一个跟踪函数,它在下列四种情形发生时被调用:
|
||||
|
||||
* 函数调用
|
||||
* 语句执行
|
||||
* 函数返回
|
||||
* 异常抛出
|
||||
|
||||
一个简单的跟踪函数看上去大概是这样:
|
||||
|
||||
|
||||
```
|
||||
def simple_tracer(frame, event, arg):
|
||||
co = frame.f_code
|
||||
@ -52,27 +49,22 @@ e=event, f=func_name, l=line_no))
|
||||
|
||||
在分析函数时我们首先关注的是参数和返回值,该跟踪函数的参数分别是:
|
||||
|
||||
* **frame**,当前堆栈帧,它是包含当前函数执行时解释器里完整状态的对象
|
||||
* **event**,它是一个值可能为 **"call"**, **"line"**, **"return"**, 或 **"exception"** 的字符串
|
||||
* **arg**,它的取值基于 event 的类型,是一个可选项
|
||||
|
||||
|
||||
* `frame`,当前堆栈帧,它是包含当前函数执行时解释器里完整状态的对象
|
||||
* `event`,事件,它是一个值可能为 `call`、`line`、`return` 或 `exception` 的字符串
|
||||
* `arg`,参数,它的取值基于 `event` 的类型,是一个可选项
|
||||
|
||||
该跟踪函数的返回值是它自身,这是由于解释器需要持续跟踪两类跟踪函数:
|
||||
|
||||
* **全局跟踪函数(每线程):** 该跟踪函数由当前线程调用 **sys.settrace** 来设置,并在解释器创建一个新 **frame** 时被调用(即代码中发生函数调用时)。虽然没有现成的方式来为不同的线程设置跟踪函数,但你可以调用 **threading.settrace** 来为所有新创建的 **threading** 模块线程设置跟踪函数。
|
||||
* **局部跟踪函数(每一帧):** 解释器将该跟踪函数的值设置为全局跟踪函数创建帧时的返回值。同样也没有现成的方法能够在帧被创建时自动设置局部跟踪函数。
|
||||
|
||||
|
||||
* **全局跟踪函数(每线程)**:该跟踪函数由当前线程调用 `sys.settrace` 来设置,并在解释器创建一个新的堆栈帧时被调用(即代码中发生函数调用时)。虽然没有现成的方式来为不同的线程设置跟踪函数,但你可以调用 `threading.settrace` 来为所有新创建的 `threading` 模块线程设置跟踪函数。
|
||||
* **局部跟踪函数(每一帧)**:解释器将该跟踪函数的值设置为全局跟踪函数创建帧时的返回值。同样也没有现成的方法能够在帧被创建时自动设置局部跟踪函数。
|
||||
|
||||
该机制的目的是让调试器对被跟踪的帧有更精确的把握,以减少对性能的影响。
|
||||
|
||||
### 简单三步构建调试器 (我们最初的设想)
|
||||
|
||||
仅仅依靠上文提到的内容,用自制的跟踪函数来构建一个真正的调试器似乎有些不切实际。幸运的是,Python 的标准调试器 **pdb** 是基于 **Bdb** 构建的,后者是 Python 标准库中专门用于构建调试器的基类。
|
||||
|
||||
基于 **Bdb** 的简易断点调试器看上去是这样的:
|
||||
仅仅依靠上文提到的内容,用自制的跟踪函数来构建一个真正的调试器似乎有些不切实际。幸运的是,Python 的标准调试器 pdb 是基于 Bdb 构建的,后者是 Python 标准库中专门用于构建调试器的基类。
|
||||
|
||||
基于 Bdb 的简易断点调试器看上去是这样的:
|
||||
|
||||
```
|
||||
import bdb
|
||||
@ -105,11 +97,9 @@ def user_line(self, frame):
|
||||
|
||||
这个调试器类的全部构成是:
|
||||
|
||||
1. 继承 **Bdb**,定义一个简单的构造函数来初始化基类,并开始跟踪。
|
||||
2. 添加 **set_breakpoint** 方法,它使用 **Bdb** 来设置断点,并跟踪这些断点。
|
||||
3. 重载 **Bdb** 在当前用户行调用的 **user_line** 方法,该方法一定被一个断点调用,之后获取该断点的源位置,并调用已注册的断点。
|
||||
|
||||
|
||||
1. 继承 `Bdb`,定义一个简单的构造函数来初始化基类,并开始跟踪。
|
||||
2. 添加 `set_breakpoint` 方法,它使用 `Bdb` 来设置断点,并跟踪这些断点。
|
||||
3. 重载 `Bdb` 在当前用户行调用的 `user_line` 方法,该方法一定被一个断点调用,之后获取该断点的源位置,并调用已注册的断点。
|
||||
|
||||
### 这个简易的 Bdb 调试器效率如何呢?
|
||||
|
||||
@ -117,7 +107,6 @@ Rookout 的目标是在生产级性能的使用场景下提供接近普通调试
|
||||
|
||||
为了衡量调试器的整体性能开销,我们使用如下两个简单的函数来进行测试,它们分别在不同的情景下执行了 1600 万次。请注意,在所有情景下断点都不会被执行。
|
||||
|
||||
|
||||
```
|
||||
def empty_method():
|
||||
pass
|
||||
@ -135,7 +124,7 @@ def simple_method():
|
||||
j = 10
|
||||
```
|
||||
|
||||
在使用调试器的情况下需要大量的时间才能完成测试。糟糕的结果指明了,这个简陋 **Bdb** 调试器的性能还远不足以在生产环境中使用。
|
||||
在使用调试器的情况下需要大量的时间才能完成测试。糟糕的结果指明了,这个简陋 `Bdb` 调试器的性能还远不足以在生产环境中使用。
|
||||
|
||||
![First Bdb debugger results][6]
|
||||
|
||||
@ -143,13 +132,11 @@ def simple_method():
|
||||
|
||||
降低调试器的额外开销主要有三种方法:
|
||||
|
||||
1. **尽可能的限制局部跟踪:** 由于每一行代码都可能包含大量事务,局部跟踪比全局跟踪的开销要大得多。
|
||||
2. **优化 "call" 事务并尽快将控制权还给解释器:** 在 **call** 事务发生时调试器的主要工作是判断是否需要对该事务进行跟踪。
|
||||
3. **优化 "line" 事务并尽快将控制权还给解释器:** 在 **line** 事务发生时调试器的主要工作是判断我们在此处是否需要设置一个断点。
|
||||
1. **尽可能的限制局部跟踪**:由于每一行代码都可能包含大量事件,局部跟踪比全局跟踪的开销要大得多。
|
||||
2. **优化 `call` 事件并尽快将控制权还给解释器**:在 `call` 事件发生时调试器的主要工作是判断是否需要对该事件进行跟踪。
|
||||
3. **优化 `line` 事件并尽快将控制权还给解释器**:在 `line` 事件发生时调试器的主要工作是判断我们在此处是否需要设置一个断点。
|
||||
|
||||
|
||||
|
||||
于是我们克隆了 **Bdb** 项目,精简特征,简化代码,针对使用场景进行优化。这些工作虽然得到了一些效果,但仍无法满足我们的需求。因此我们又继续进行了其它的尝试,将代码优化并迁移至 **.pyx** 使用 [Cython][7] 进行编译,可惜结果(如下图所示)依旧不够理想。最终,我们在深入了解 CPython 源码之后意识到,让跟踪过程快到满足生产需求是不可能的。
|
||||
于是我们复刻了 `Bdb` 项目,精简特征、简化代码,针对使用场景进行优化。这些工作虽然得到了一些效果,但仍无法满足我们的需求。因此我们又继续进行了其它的尝试,将代码优化并迁移至 `.pyx` 使用 [Cython][7] 进行编译,可惜结果(如下图所示)依旧不够理想。最终,我们在深入了解 CPython 源码之后意识到,让跟踪过程快到满足生产需求是不可能的。
|
||||
|
||||
![Second Bdb debugger results][8]
|
||||
|
||||
@ -159,10 +146,8 @@ def simple_method():
|
||||
|
||||
Python 解释器的工作主要分为两个阶段:
|
||||
|
||||
1. **将 Python 源码编译成 Python 字节码:** 这种不可读(对人类而言)的格式专为执行的效率而优化,它们通常缓存在我们熟知的 **.pyc** 文件当中。
|
||||
2. **遍历 _interpreter loop_ 中的字节码:** 在这一步中解释器会逐条的执行指令
|
||||
|
||||
|
||||
1. **将 Python 源码编译成 Python 字节码**:这种(对人类而言)不可读的格式专为执行的效率而优化,它们通常缓存在我们熟知的 `.pyc` 文件当中。
|
||||
2. **遍历 解释器循环中的字节码**: 在这一步中解释器会逐条的执行指令。
|
||||
|
||||
我们选择的模式是:使用**字节码操作**来设置没有全局额外开销的**不中断断点**。这种方式的实现首先需要在内存中的字节码里找到我们感兴趣的部分,然后在该部分的相关机器指令前插入一个函数调用。如此一来,解释器无需任何额外的工作即可实现我们的不中断断点。
|
||||
|
||||
@ -170,22 +155,19 @@ Python 解释器的工作主要分为两个阶段:
|
||||
|
||||
首先定义一个简单的函数:
|
||||
|
||||
|
||||
```
|
||||
def multiply(a, b):
|
||||
result = a * b
|
||||
return result
|
||||
```
|
||||
|
||||
在 **[inspect][9]** 模块(其包含了许多实用的单元)的文档里,我们得知可以通过访问 **multiply.func_code.co_code** 来获取函数的字节码:
|
||||
|
||||
在 [inspect][9] 模块(其包含了许多实用的单元)的文档里,我们得知可以通过访问 `multiply.func_code.co_code` 来获取函数的字节码:
|
||||
|
||||
```
|
||||
`'|\x00\x00|\x01\x00\x14}\x02\x00|\x02\x00S'`
|
||||
'|\x00\x00|\x01\x00\x14}\x02\x00|\x02\x00S'
|
||||
```
|
||||
|
||||
使用 Python 标准库中的 **[dis][10]** 模块可以翻译这些不可读的字符串。调用 **dis.dis(multiply.func_code.co_code)** 之后,我们就可以得到:
|
||||
|
||||
使用 Python 标准库中的 [dis][10] 模块可以翻译这些不可读的字符串。调用 `dis.dis(multiply.func_code.co_code)` 之后,我们就可以得到:
|
||||
|
||||
```
|
||||
4 0 LOAD_FAST 0 (a)
|
||||
@ -203,11 +185,7 @@ def multiply(a, b):
|
||||
|
||||
在构建一个新工具时,总会学到许多事情的工作原理。这种刨根问底的过程能够使你的思路跳出桎梏,从而得到意料之外的解决方案。
|
||||
|
||||
在 Rookout 团队中构建不中断断点的这段时间里,我学到了许多有关编译器、调试器、服务器框架、并发模型等等领域的知识。如果你希望更深入的了解字节码操作,谷歌的开源项目 **[cloud-debug-python][11]** 为编辑字节码提供了一些工具。
|
||||
|
||||
* * *
|
||||
|
||||
_Liran Haimovitch 将于 2019 年八月 17-18 日在旧金山举办的 [PyBay][3] 中发表题为 "[Understanding Python’s Debugging Internals][12]" 的演说,使用 [OpenSource35][13] 可以获得购票优惠,并使他们得知您是在我们的社区得知此事。_
|
||||
在 Rookout 团队中构建不中断断点的这段时间里,我学到了许多有关编译器、调试器、服务器框架、并发模型等等领域的知识。如果你希望更深入的了解字节码操作,谷歌的开源项目 [cloud-debug-python][11] 为编辑字节码提供了一些工具。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
@ -216,7 +194,7 @@ via: https://opensource.com/article/19/8/debug-python
|
||||
作者:[Liran Haimovitch][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[caiichenr](https://github.com/caiichenr)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
@ -0,0 +1,104 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (cycoe)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-11994-1.html)
|
||||
[#]: subject: (Debugging in Emacs: The Grand Unified Debugger)
|
||||
[#]: via: (https://opensourceforu.com/2019/09/debugging-in-emacs-the-grand-unified-debugger/)
|
||||
[#]: author: (Vineeth Kartha https://opensourceforu.com/author/vineeth-kartha/)
|
||||
|
||||
Emacs 调试秘籍之 GUD 调试器
|
||||
======
|
||||
|
||||
![][2]
|
||||
|
||||
> 本文简短地对 Emacs 的调试工具 GUD 的特性进行了探索。
|
||||
|
||||
如果你是一个 C 或 C++ 开发者,你很可能已经使用过 GDB(GNU 调试器),毫无疑问,它是现今最强大、最无可匹敌的调试器之一。它唯一的缺点就是它基于命令行,虽然仍能提供许多强大的功能,但有时也会具有一些局限性。这也就是为什么聪明的人们开始追求整合了编辑器和调试器的<ruby>图形化<rt> GUI </rt></ruby><ruby>集成开发环境<rt>Integrated Development Environment</rt></ruby>。仍有些开发者坚信使用鼠标会降低工作效率,在 GUI 上用鼠标点~点~点~是来自恶魔的诱惑。
|
||||
|
||||
因为 Emacs 是现今最酷的文本编辑器之一,我将为你展示如何在不碰鼠标且不离开 Emacs 的情况下,实现写代码、编译代码、调试代码的过程。
|
||||
|
||||
GUD(LCTT 译注:全称<ruby>大统一调试器<rt>Grand Unified Debugger</rt></ruby>,鉴于其缩写形式更为人熟知,以下全文将使用缩写替代此全称)是 Emacs 下的一个<ruby>模式<rt>mode</rt></ruby>,用于在 Emacs 中运行 GDB。它向 GDB 提供了 Emacs 的所有特性,使用户无需离开编辑器就可以对代码进行调试。
|
||||
|
||||
### 使用 GUD 的前期准备
|
||||
|
||||
如果你正在使用一个 Linux 机器,很可能你已经安装了 GDB 和 gcc,接下来就是要确保已经安装了 Emacs。以下的内容我将假设读者熟悉 GDB 并且至少用它做过基本的调试。如果你未曾接触过 GDB,你可以做个快速入门,这些资料在网上随处可得。
|
||||
|
||||
对于那些 Emacs 新手,我将向你介绍一些基本术语。纵览整篇文章,你将看到诸如 `C-c M-x` 等快捷键。此处 `C` 代表 `Ctrl` 键,`M` 代表 `Alt` 键。`C-c` 代表 `Ctrl` 键和 `c` 键被同时按下。如果你看到 `C-c c`,它代表同时按下 `Ctrl` 键和 `c` 键,释放后紧接着按下 `c` 键。在 Emacs 中,编辑文本的主要区域被称为<ruby>主缓冲区<rt>main buffer</rt></ruby>,而在 Emacs 窗口下方用于输入命令的区域被称为<ruby>迷你缓冲区<rt>mini buffer</rt></ruby>。
|
||||
|
||||
启动 Emacs,并按下 `C-x C-f` 来创建一个新文件。Emacs 将提示你输入一个文件名,此处让我们将文件命名为 `buggyFactorial.cpp`。一旦文件打开,输入如下代码:
|
||||
|
||||
```
|
||||
#include<iostream>
|
||||
#include <assert.h>
|
||||
|
||||
int factorial(int num) {
|
||||
int product = 1;
|
||||
while(num--) {
|
||||
product *= num;
|
||||
}
|
||||
return product;
|
||||
}
|
||||
int main() {
|
||||
int result = factorial(5);
|
||||
assert(result == 120);
|
||||
}
|
||||
```
|
||||
|
||||
使用 `C-x C-s` 快捷键保存文件。文件保存完毕,是时候进行编译了。按下 `M-x`,在弹出的<ruby>提示符<rt>prompt</rt></ruby>后输入 `compile` 并点击回车。然后在提示符后,将内容替换为 `g++ -g buggyFactorial.cpp` 并再次点击回车。
|
||||
|
||||
![图 1: Emacs 迷你缓冲区中编译命令][3]
|
||||
|
||||
这将在 Emacs 中开启另一个缓冲区,显示编译的状态。如果你的代码输入没有错误,你将预期得到如图 2 所示的缓冲区。
|
||||
|
||||
![图 2: 编译状态][4]
|
||||
|
||||
要想隐藏编译缓冲区,首先确保你的光标在编译缓冲区中(你可以不使用鼠标,而是通过 `C-x o` 快捷键将光标从一个缓冲区移动到另一个),然后按下 `C-x 0`。下一步就是运行代码,并观察是否运行良好。按下 `M-!` 快捷键并在迷你缓冲区的提示符后面输入 `./a.out`。
|
||||
|
||||
![图 3: 代码在迷你缓冲区中的输出][5]
|
||||
|
||||
你可以看到迷你缓冲区中显示断言失败。很明显代码中有错误,因为 5 的阶乘是 120。那么让我们现在开始调试吧。
|
||||
|
||||
### 使用 GUD 调式代码
|
||||
|
||||
现在,我们的代码已经编译完成,是时候看看到底哪里出错了。按下 `M-x` 快捷键并在提示符后输入 `gdb`。在接下来的提示符后,输入 `gdb -i=mi a.out`。如果一切顺利,GDB 会在 Emacs 缓冲区中启动,你会看到如图 4 所示的窗口。
|
||||
|
||||
![图 4: Emacs 中的 GDB 缓冲区][6]
|
||||
|
||||
在 `gdb` 提示符后,输入 `break main` 来设置断点,并输入 `r` 来运行程序。程序会开始运行并停在 `main()` 函数处。
|
||||
|
||||
一旦 GDB 到达了 `main` 处设置的断点,就会弹出一个新的缓冲区显示你正在调试的代码。注意左侧的红点,正是你设置断点的位置,同时会有一个小的标志提示你当前代码运行到了哪一行。当前,该标志就在断点处(如图 5)。
|
||||
|
||||
![图 5: GDB 与代码显示在两个分离的窗口][7]
|
||||
|
||||
为了调试 `factorial` 函数,我们需要单步运行。想要达到此目的,你可以在 GBD 提示符使用 GDB 命令 `step`,或者使用 Emacs 快捷键 `C-c C-s`。还有其它一些快捷键,但我更喜欢 GDB 命令。因此我将在本文的后续部分使用它们。
|
||||
|
||||
单步运行时让我们注意一下局部变量中的阶乘值。参考图 6 来设置在 Emacs 帧中显示局部变量值。
|
||||
|
||||
![图 6: 在 Emacs 中使用独立帧显示局部变量][8]
|
||||
|
||||
在 GDB 提示符中进行单步运行并观察局部变量值的变化。在循环的第一次迭代中,我们发现了一个问题。此处乘法的结果应该是 5 而不是 4。
|
||||
|
||||
本文到这里也差不多结束了,读者可以自行探索发现 GUD 模式这片新大陆。GDB 中的所有命令都可以在 GUD 模式中运行。我将此代码的修复留给读者作为一个练习。看看你在调试的过程中,可以做哪一些定制化,来使你的工作流更加简单和高效。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensourceforu.com/2019/09/debugging-in-emacs-the-grand-unified-debugger/
|
||||
|
||||
作者:[Vineeth Kartha][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[cycoe](https://github.com/cycoe)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensourceforu.com/author/vineeth-kartha/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://i0.wp.com/opensourceforu.com/wp-content/uploads/2019/09/Screenshot-from-2019-09-25-15-39-46.png?ssl=1
|
||||
[2]: https://i0.wp.com/opensourceforu.com/wp-content/uploads/2019/09/Screenshot-from-2019-09-25-15-39-46.png?ssl=1
|
||||
[3]: https://i1.wp.com/opensourceforu.com/wp-content/uploads/2019/09/Figure_1.png?ssl=1
|
||||
[4]: https://i2.wp.com/opensourceforu.com/wp-content/uploads/2019/09/Figure_2.png?ssl=1
|
||||
[5]: https://i0.wp.com/opensourceforu.com/wp-content/uploads/2019/09/Figure_3.png?ssl=1
|
||||
[6]: https://i0.wp.com/opensourceforu.com/wp-content/uploads/2019/09/Figure_4.png?ssl=1
|
||||
[7]: https://i1.wp.com/opensourceforu.com/wp-content/uploads/2019/09/Figure_5.png?ssl=1
|
||||
[8]: https://i1.wp.com/opensourceforu.com/wp-content/uploads/2019/09/Figure_6.png?ssl=1
|
||||
@ -0,0 +1,60 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-11981-1.html)
|
||||
[#]: subject: (Calculator N+ is an open source scientific calculator for your smartphone)
|
||||
[#]: via: (https://opensource.com/article/19/11/calculator-n-mobile)
|
||||
[#]: author: (Ricardo Berlasso https://opensource.com/users/rgb-es)
|
||||
|
||||
Calculator N+:一款智能手机上的开源科学计算器
|
||||
======
|
||||
|
||||
> 这个 Android 应用可在掌中计算许多高级数学函数。
|
||||
|
||||
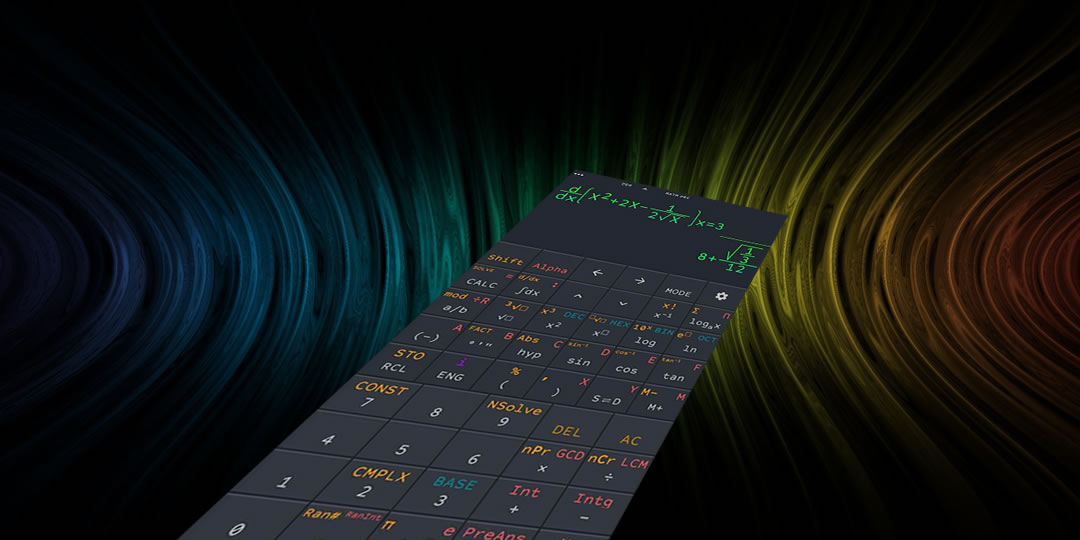
|
||||
|
||||
移动电话每天都在变得越来越强大,因此毫不奇怪它们可以击败不太久前的大多数计算机。这也意味着移动手机上的工具每天都在变得越来越强大。
|
||||
|
||||
之前,我写过一篇 [两款 Linux 桌面端可用的科学计算器][2],我接着将介绍 [Calculator N+][3],这是一款很棒的适用于 Android 设备的计算机代数系统(CAS)应用,采用 GPL v3.0 许可证下。
|
||||
|
||||
Calculator N+ 被认为是“适用于 Android 的强大计算器”,但这是一个谦虚的说法。它不仅可以以任意精度工作,还可以显示根数和分数等*很多*功能。
|
||||
|
||||
寻找多项式根?可以。分解因数?可以。导数、积分和极限?可以。数论(模算术、组合学、素因数分解)?可以。
|
||||
|
||||
你还可以求解方程系统、简化表达式(包括三角函数)、转换单位,只要你想到的,它都能做!
|
||||
|
||||
![Calculator N+ graphical interface][4]
|
||||
|
||||
其结果以 LaTeX 输出。左上方的菜单提供了许多强大的功能,只需触摸一下即可使用。同样在该菜单中,你将找到该应用所有功能的帮助文件。在屏幕的右上角,你可以在精确表示法和十进制表示法之间切换。最后,点击屏幕底部的蓝色栏,即可访问应用中的所有函数库。不过要小心!如果你不是数学家、物理学家或工程师,那么这么长的列表会看上去很吓人。
|
||||
|
||||
所有这些功能都来自 [Symja 库][5],这是另一个出色的 GPL 3 项目。
|
||||
|
||||
这两个项目都处于积极开发中,并且每个版本都在不断完善。特别是,Calculator N+ 的 v3.4.6 在用户界面(UI)品质方面取得了重大飞跃。虽然还是存在一些不够好的地方,但是要在智能手机的小巧的用户界面中发挥如此强大的功能是一项艰巨的任务,我认为应用开发人员正在很好地解决其剩余的问题。对他们表示敬意!
|
||||
|
||||
如果你是老师、学生或在理工科领域工作,请试试 Calculator N+。它是免费、无广告、开源的,并可以满足你所有的数学需求。(当然,除了数学考试期间,为防止作弊绝对不允许使用智能手机。)
|
||||
|
||||
可以在 [Google Play 商店][6]找到 Calculator N+,也可以使用 GitHub 页面上的说明[从源代码构建][7]。
|
||||
|
||||
如果你知道用于科学或工程的其他有用的开源应用,请在评论中告知我们。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/11/calculator-n-mobile
|
||||
|
||||
作者:[Ricardo Berlasso][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/rgb-es
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/calculator_money_currency_financial_tool.jpg?itok=2QMa1y8c (scientific calculator)
|
||||
[2]: https://linux.cn/article-9643-1.html
|
||||
[3]: https://github.com/tranleduy2000/ncalc
|
||||
[4]: https://opensource.com/sites/default/files/uploads/calculatornplus_sqrt-frac.png (Calculator N+ graphical interface)
|
||||
[5]: https://github.com/axkr/symja_android_library
|
||||
[6]: https://play.google.com/store/apps/details?id=com.duy.calculator.free
|
||||
[7]: https://github.com/tranleduy2000/ncalc/blob/master/README.md
|
||||
99
published/20191223 10 articles to learn Linux your way.md
Normal file
99
published/20191223 10 articles to learn Linux your way.md
Normal file
@ -0,0 +1,99 @@
|
||||
[#]: collector: "lujun9972"
|
||||
[#]: translator: "messon007"
|
||||
[#]: reviewer: "wxy"
|
||||
[#]: publisher: "wxy"
|
||||
[#]: url: "https://linux.cn/article-12035-1.html"
|
||||
[#]: subject: "10 articles to learn Linux your way"
|
||||
[#]: via: "https://opensource.com/article/19/12/learn-linux"
|
||||
[#]: author: "Seth Kenlon https://opensource.com/users/seth"
|
||||
|
||||
10 篇关于 Linux 的好文章
|
||||
=======
|
||||
|
||||
> 2019 年对于 Linux 来说是个好年份,让我们一起来回顾一下这十篇关于 Linux 的好文章。
|
||||
|
||||

|
||||
|
||||
2019 年对于 Linux 来说是个好年份,显然这里的 “Linux” 一词有更多含义: 内核? 桌面? 或是生态? 在此次回顾年度 Linux 好文中,我在选择十大好文时有意采取了更开放的视角。下面就是十大好文(无先后次序之分)。
|
||||
|
||||
### 《Linux 权限入门指南》
|
||||
|
||||
Bryant Son 的《[Linux 权限入门指南][2]》向新用户介绍了文件权限的概念,通过图形和图表的方式来说明每个要点。通常很难以视觉的方式来解释纯粹基于文本的概念,而本文则对可视方式学习的人非常友好。 Bryant 在讲述时也很专注主题。关于文件权限的任何阐述都可能引出几个相关主题(例如所有权和访问控制列表等),但是本文致力于解释一件事并很好地解释它。
|
||||
|
||||
### 《为什么我从 Mac 换到了 Linux》
|
||||
|
||||
Matthew Broberg 在《[为什么我从 Mac 换到了 Linux][3]》中清楚而客观的介绍了他从 MacOS 切换到 Linux 的经历。通常切换平台是很困难的,因此记录决定切换的背后考虑非常重要。我认为 Matt 的文章带有几个目的,但对我来说最重要的两个目的是:通过解答他的问题并提供潜在的解决方案,他请 Linux 社区的人们来支持他;这对于其他正在考虑采用 Linux 的人来说是一个很好的参考。
|
||||
|
||||
### 《在 Linux 上定位 WiFi 速度慢的问题》
|
||||
|
||||
《[在 Linux 上定位 WiFi 速度慢的问题][4]》这篇文章中,David Clinton 对每个人都可能遇到的问题进行了分析,并提供了怎么样一步步解决的思路。这是“偶然的 Linux”技巧的一个很好的例子,但它不仅可以帮助经常遇到问题的人,而且可以向非 Linux 用户展示如何在其他平台上进行问题定位。
|
||||
|
||||
### 《一个非技术人员对 GNOME 项目使用 GitLab 的感受》
|
||||
|
||||
Molly de Blanc 所写的《[一个非技术人员对 GNOME 项目使用 GitLab 的感受][5]》深层次地揭示了开源界的一个典范(GNOME 桌面)如何使用开源界的另一个典范(Git)进行开发。听到一个开放源代码项目对于任何需要做的事情默认为开放源代码解决方案,这总是让我感到振奋。无论如何,这种情况并不常见,然而对于 GNOME 来说,这是项目本身的重要且受欢迎的部分。
|
||||
|
||||
### 《详解 Linux 中的虚拟文件系统》
|
||||
|
||||
Alison Chaiken 在《[详解 Linux 中的虚拟文件系统][6]》中巧妙地解释了对许多用户来说都很难理解的东西。理解文件系统是什么、虚拟文件系统和真实的文件系统是一回事,但从定义上讲,*虚拟的*其实并不是真正的文件系统。Linux 以一种普通用户也能从中受益的方式提供了它们,Alison 的文章以一种易于理解的方式对其进行了阐述。另外,Alison 在文章的后半部分更深入地介绍了如何使用 `bcc` 脚本查看她刚刚讲的虚拟文件系统的相关内容。
|
||||
|
||||
### 《理解文件路径并学会使用它们》
|
||||
|
||||
我认为《[理解文件路径并学会使用它们][7]》很重要,因为这是大多数用户(在任何平台上)似乎都没有学过的概念。这是一个奇怪的现象,因为现在比以往任何时候,人们都越来越多地看到*文件路徑*:几乎所有的互联网网址都包含一个文件路径,该路径告诉你你在域中的确切位置。我常常在想为什么计算机教育不是从互联网开始的,互联网是目前最熟悉的应用程序,并且可以说是使用最频繁的超级计算机,完全可以用它来解释我们每天使用的设备。(我想如果这些设备运行 Linux 会有所帮助,但是我们正在努力。)
|
||||
|
||||
### 《Linux 下的进程间通信:共享存储》
|
||||
|
||||
Marty Kalin 的《[Linux 下的进程间通信:共享存储][8]》从 Linux 的开发者视角解释了 IPC 以及如何在代码中使用它。虽然我只是列入了这篇文章,不过它实际上是一个三篇文章的系列,而它是同类文章中阐述的最好的。很少有文档能够解释 Linux 怎样处理 IPC,更不用说 IPC 是什么,为什么它很重要,或者在编程时该如何使用它。通常这是你在大学读书时关注的话题。现在,你可以在这里阅读所有内容。
|
||||
|
||||
### 《在 Linux 上用 strace 来理解系统调用》
|
||||
|
||||
Gaurav Kamathe 的《[在 Linux 上用 strace 来理解系统调用][9]》具有很强的技术性,我希望我所见过的有关 `strace` 的每次会议演讲都是如此。这是对一个复杂但非常有用的命令的清晰演示。令我惊讶的是,我读了本文才发现自己一直使用的命令不是这个命令,而是 `ltrace`(可以用来查看命令调用了哪些函数)。本文包含了丰富的信息,是开发人员和测试人员的快捷参考手册。
|
||||
|
||||
### 《Linux 桌面发展旅程》
|
||||
|
||||
Jim Hall 的《[Linux 桌面发展旅程][10]》是对 Linux 桌面历史的一次视觉之旅。从 [TWM][11] 开始,经历了 [FVWM][12]、[GNOME][13]、[KDE][14] 等薪火相传。如果你是 Linux 的新手,那么这将是一个出自那个年代的人的有趣的历史课(有截图可以证明这一点)。如果你已经使用 Linux 多年,那么这肯定会唤醒你的记忆。最后,可以肯定的是:仍然可以找到 20 年前屏幕快照的人都是神一样的数据档案管理员。
|
||||
|
||||
### 《用 Linux 创建你自己的视频流服务器》
|
||||
|
||||
Aaron J. Prisk 的 《[用 Linux 创建你自己的视频流服务器][15]》消除了大多数人对我们视为理所当然的服务的误解。由于 YouTube 和 Twitch 之类服务的存在,许多人认为这是向世界广播视频的唯一方式。当然,人们过去常常以为 Windows 和 Mac 是计算机的唯一入口,值得庆幸的是,最终证明这是严重的误解。在本文中,Aaron 建立了一个视频流服务器,甚至还顺便讨论了一下 [OBS][16],以便你可以创建视频。这是一个有趣的周末项目还是新职业的开始?你自己决定。
|
||||
|
||||
### 《塑造 Linux 历史的 10 个时刻》
|
||||
|
||||
Alan Formy-Duval 撰写的《[塑造 Linux 历史的 10 个时刻][17]》试图完成一项艰巨的任务,即从 Linux 的历史中选出 10 件有代表性的事情。当然,这是很难的,因为有如此多重要的时刻,所以我想看看 Alan 是如何通过自己的经历来选择它。例如,什么时候开始意识到 Linux 必然可以发展下去?—— 当 Alan 意识到他维护的所有系统都在运行 Linux 时。用这种方式来解释历史是很美的,因为每个人的重要时刻都会有所不同。 关于 Linux 没有权威性列表,关于 Linux 的文章也没有,关于开源也没有。你可以创建你自己的列表,也可以使你自己成为列表的一部分。
|
||||
|
||||
(LCTT 译注:这里推荐了 11 篇,我数了好几遍,没眼花……)
|
||||
|
||||
### 你想从何学起?
|
||||
|
||||
你还想知道 Linux 的什么内容?请在评论区告诉我们或来文讲述你的 Linux 经验。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/12/learn-linux
|
||||
|
||||
作者:[Seth Kenlon][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[messon007](https://github.com/messon007)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/seth
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/OSDC_Penguin_Image_520x292_12324207_0714_mm_v1a.png?itok=p7cWyQv9 "Penguins gathered together in the Artic"
|
||||
[2]: https://linux.cn/article-11056-1.html
|
||||
[3]: https://linux.cn/article-11586-1.html
|
||||
[4]: http://opensource.com/article/19/4/troubleshooting-wifi-linux
|
||||
[5]: https://linux.cn/article-11806-1.html
|
||||
[6]: https://linux.cn/article-10884-1.html
|
||||
[7]: https://opensource.com/article/19/8/understanding-file-paths-linux
|
||||
[8]: https://linux.cn/article-10826-1.html
|
||||
[9]: https://linux.cn/article-11545-1.html
|
||||
[10]: https://opensource.com/article/19/8/how-linux-desktop-grown
|
||||
[11]: https://github.com/freedesktop/twm
|
||||
[12]: http://www.fvwm.org/
|
||||
[13]: http://gnome.org
|
||||
[14]: http://kde.org
|
||||
[15]: https://opensource.com/article/19/1/basic-live-video-streaming-server
|
||||
[16]: https://opensource.com/life/15/12/real-time-linux-video-editing-with-obs-studio
|
||||
[17]: https://opensource.com/article/19/4/top-moments-linux-history
|
||||
[18]: https://opensource.com/how-submit-article
|
||||
@ -0,0 +1,63 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (caiichenr)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-11999-1.html)
|
||||
[#]: subject: (Prioritizing simplicity in your Python code)
|
||||
[#]: via: (https://opensource.com/article/19/12/zen-python-simplicity-complexity)
|
||||
[#]: author: (Moshe Zadka https://opensource.com/users/moshez)
|
||||
|
||||
简单是 Python 编程的第一要则
|
||||
======
|
||||
|
||||
> 本文是 Python 之禅特别系列的第二篇,我们将要关注其中第三与第四条原则:简单与复杂。
|
||||
|
||||

|
||||
|
||||
> "Il semble que la perfection soit atteinte non quand il n'y a plus rien à ajouter, mais quand il n'y plus rien à retrancher."
|
||||
>
|
||||
> "It seems that perfection is finally attained not when there is no longer anything to add, but when there is no longer anything to take away."
|
||||
>
|
||||
> “完美并非无可增,而是不可减。”
|
||||
>
|
||||
> —Antoine de Saint-Exupéry, [Terre des Hommes][2], 1939
|
||||
|
||||
编程时最常有的考量是与复杂性的斗争,只想写出让旁人无从下手的繁杂代码,对每个程序员来讲都算不上难事。倘若未能触及代码的简繁取舍,那么 《[Python 之禅][3]》 就有了一角残缺。
|
||||
|
||||
### <ruby>简单胜过复杂<rt>Simple is better than complex</rt></ruby>
|
||||
|
||||
尚有选择余地时,应该选简单的方案。Python 少有*不可为*之事,这意味着设计出巴洛克风格(LCTT 译注:即夸张和不理性)的程序只为解决浅显的问题不仅有可能,甚至很简单。
|
||||
|
||||
正因如此,编程时应当谨记,代码的简单性是最易丢失,却最难复得的。
|
||||
|
||||
这意味着,在可以选用函数来表达时不要去引入额外的类;避免使用强力的第三方库往往有助于你针对迫切的问题场景设计更妥当的简短函数。不过其根本的意图,旨在让你减少对将来的盘算,而去着重解决手头的问题。
|
||||
|
||||
以简单和优美作为指导原则的代码相比那些想要囊括将来一切变数的,在日后要容易修改得多。
|
||||
|
||||
### <ruby>复杂胜过错综复杂<rt>Complex is better than complicated</rt></ruby>
|
||||
|
||||
把握用词的精确含义对于理解这条令人费解的原则是至关重要的。形容某事<ruby>复杂<rt>complex</rt></ruby>,是说它由许多部分组成,着重组成成分之多;而形容某事<ruby>错综复杂<rt>complicated</rt></ruby>,则是指其包含着差异巨大、难以预料的行为,强调的是各组成部分之间的杂乱联系。
|
||||
|
||||
解决困难问题时,往往没有可行的简单方案。此时,最 Python 化的策略是“<ruby>自底向上<rt>bottom-up</rt></ruby>”地构建出简单的工具,之后将其组合用以解决该问题。
|
||||
|
||||
这正是<ruby>对象组合<rt>object composition</rt></ruby>这类技术的闪耀之处,它避免了错综复杂的继承体系,转而由独立的对象把一些方法调用传递给别的独立对象。这些对象都能独立地测试与部署,最终却可以组成一体。
|
||||
|
||||
“自底建造” 的另一例即是<ruby>[单分派泛函数][4]<rt>singledispatch</rt></ruby>的使用,抛弃了错综复杂的对象之后,我们得到是简单、几乎无行为的对象以及独立的行为。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/12/zen-python-simplicity-complexity
|
||||
|
||||
作者:[Moshe Zadka][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[caiichenr](https://github.com/caiichenr)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/moshez
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/read_book_guide_tutorial_teacher_student_apaper.png?itok=_GOufk6N (Person reading a book and digital copy)
|
||||
[2]: https://en.wikipedia.org/wiki/Wind,_Sand_and_Stars
|
||||
[3]: https://www.python.org/dev/peps/pep-0020/
|
||||
[4]: https://opensource.com/article/19/5/python-singledispatch
|
||||
@ -0,0 +1,87 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (wxy)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-12011-1.html)
|
||||
[#]: subject: (10 Linux command tutorials for beginners and experts)
|
||||
[#]: via: (https://opensource.com/article/19/12/linux-commands)
|
||||
[#]: author: (Moshe Zadka https://opensource.com/users/moshez)
|
||||
|
||||
10 篇对初学者和专家都有用的 Linux 命令教程
|
||||
======
|
||||
|
||||
> 在这有关 Linux 命令的十大文章中,了解如何使 Linux 发挥所需的作用。
|
||||
|
||||

|
||||
|
||||
**很好地**使用 Linux 意味着了解有哪些命令以及它们可以为你执行的功能。
|
||||
|
||||
### 《在 Linux 命令行下使用“原力”》
|
||||
|
||||
<ruby>原力<rt>force</rt></ruby>有光明的一面和黑暗的一面。正确理解这个对于真正掌握它至关重要。Alan Formy-Duval 在他的文章《[在 Linux 命令行下使用“原力”][2]》中,解释了一些流行的、有时是危险的命令的 `-f` 选项(也称为 `--force`)。
|
||||
|
||||
### 《Linux useradd 命令介绍》
|
||||
|
||||
共享帐户是一个坏主意。相反,请使用典型的 `useradd` 命令为不同的人(甚至是不同的角色)分配单独的帐户。作为其经典的 Linux 管理基础系列的一部分,Alan Formy-Duval 提供了《[Linux useradd 命令介绍][3]》,并且像往常一样,他用**朴实明白的语言**对其进行了解释,以便新老管理员都可以理解。
|
||||
|
||||
### 《用 Linux 命令显示硬件信息》
|
||||
|
||||
机器**里面**是什么?有时不使用螺丝刀检查硬件很有用。无论是你正在使用的计算机,还是在商店购买前进行测试的计算机、或者是正在尝试维修的计算机,在《[用 Linux 命令显示硬件信息][4]》中,Howard Fosdick 提供了或流行或晦涩难懂的命令,以帮助你深入了解计算机的硬件信息。
|
||||
|
||||
### 《如何在 Linux 上使用 gocryptfs 加密文件》
|
||||
|
||||
从社会保险号到个人信件再到亲人,我们的文件中包含了许多私人数据。在《[如何在 Linux 上使用 gocryptfs 加密文件][5]》中,Brian "Bex" Exelbierd 解释了如何保持**隐私*的私密性。此外,他展示了一种加密文件的方式,这种方式对你现有的工作流程几乎没有影响。这不是复杂的 PGP 风格的密钥管理和后台密钥代理的难题,这是快速、无缝和安全的文件加密。
|
||||
|
||||
### 《如何使用 rsync 的高级用法进行大型备份》
|
||||
|
||||
在新的一年中,许多人会下定决心要更加努力地进行备份。Alan Formy-Duval 早在几年前就已经做出了解决方案,因为在《[如何使用 rsync 的高级用法进行大型备份][6]》中,他表现出对文件同步命令的极其熟悉。你可能不会马上记住所有语法,但其思路是读取和处理选项、构造备份命令,然后使其自动化。这是使用 `rsync` 的明智方法,也是可靠地执行备份的**唯一**方法。
|
||||
|
||||
### 《在 Linux 命令行使用 more 查看文本文件》
|
||||
|
||||
在 Scott Nesbitt 的文章《[在 Linux 命令行使用 more 查看文本文件][7]》中,古老而良好的默认分页器 `more` 引起了人们的关注。许多人安装和使用 `less`,因为它比 `more` 更灵活。但是,随着越来越多的系统在新出现的容器中实现,有时甚至不存在像 `less` 或 `most` 之类的新颖的豪华工具。了解和使用`more` 很简单,这是常见的默认设置,并且是生产系统最后的调试工具。
|
||||
|
||||
### 《关于 sudo 你可能不知道的》
|
||||
|
||||
`sudo` 命令因其过失而闻名。人们知道 `sudo` 一词,我们大多数人认为我们知道它的作用。我们的观点是正确的,但是正如 Peter Czanik 在他的文章《[关于 sudo 你可能不知道的][8]》中所揭示的那样,该命令所包含的不仅仅是“<ruby>西蒙说的<rt>Simon says</rt></ruby>”(LCTT 译注:国外的一个儿童游戏)。就像这个经典的童年游戏一样,`sudo` 命令功能强大,也容易犯愚蠢的错误 —— 有更多的可能产生可怕都后果,而这是你绝不想遇上的事情!
|
||||
|
||||
### 《怎样用 Bash 编程:语法和工具》
|
||||
|
||||
如果你是 Linux、BSD 或 Mac(以及近来的 Windows)用户,你也许使用过交互式 Bash shell。它是快速的、一次性命令的绝佳 shell,这就是为什么这么多 Linux 用户喜欢将其用作主要用户界面的原因。但是,Bash 不仅仅是个命令提示符。它也是一种编程语言,如果你已经在使用 Bash 命令,那么自动化的道路从未如此简单过。在 David Both 的出色作品《[怎样用 Bash 编程:语法和工具][9]》中对其进行全面了解。
|
||||
|
||||
### 《精通 Linux 的 ls 命令》
|
||||
|
||||
`ls` 命令是那些两个字母的命令之一。单字母命令是针对慢速终端的优化,因为慢速终端的输入的每个字母都会导致明显的延迟,而这对于懒惰的打字员来说也是不错的奖励。一如既往地,Seth Kenlon 清晰实用地解释了你可以怎样《[精通 Linux 的 ls 命令][10]》。最重要的是,在“一切都是文件”的系统中,列出文件至关重要。
|
||||
|
||||
### 《Linux cat 命令入门》
|
||||
|
||||
`cat` 命令(con*cat*enate 的缩写)看似简单。无论是使用它来快速查看文件的内容还是将内容通过管道传输到另一个命令,你都可能没有充分利用 `cat` 的功能。Alan Formy-Duval 的《[Linux cat 命令入门][11]》提供了一些新思路,可以使你没有打开文件的感觉就可以看到文件内容。另外,了解各种有关 `zcat` 的知识,这样你就可以无需解压缩就可以得到压缩文件的内容!这是一件小而简单的事情,但是**这**是使 Linux 很棒的原因。
|
||||
|
||||
### 继续旅程
|
||||
|
||||
不要让这些关于 Linux 命令的 10 篇最佳文章成为你的旅程终点。关于 Linux 及其多才多艺的提示符,还有更多值得去发现,因此,请继续关注以获取更多知识。而且,如果你想让我们介绍一个 Linux 命令,请在评论中告诉我们。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/12/linux-commands
|
||||
|
||||
作者:[Moshe Zadka][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[wxy](https://github.com/wxy)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/moshez
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/car-penguin-drive-linux-yellow.png?itok=twWGlYAc (Penguin driving a car with a yellow background)
|
||||
[2]: https://linux.cn/article-10881-1.html
|
||||
[3]: https://linux.cn/article-11756-1.html
|
||||
[4]: https://linux.cn/article-11422-1.html
|
||||
[5]: https://opensource.com/article/19/8/how-encrypt-files-gocryptfs
|
||||
[6]: https://linux.cn/article-10865-1.html
|
||||
[7]: https://linux.cn/article-10531-1.html
|
||||
[8]: https://linux.cn/article-11595-1.html
|
||||
[9]: https://linux.cn/article-11552-1.html
|
||||
[10]: https://linux.cn/article-11159-1.html
|
||||
[11]: https://opensource.com/article/19/2/getting-started-cat-command
|
||||
[12]: https://opensource.com/how-submit-article
|
||||
@ -1,103 +1,103 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-11997-1.html)
|
||||
[#]: subject: (How to setup a DNS server with bind)
|
||||
[#]: via: (https://fedoramagazine.org/how-to-setup-a-dns-server-with-bind/)
|
||||
[#]: author: (Curt Warfield https://fedoramagazine.org/author/rcurtiswarfield/)
|
||||
|
||||
How to setup a DNS server with bind
|
||||
简明指南:使用 bind 设置 DNS 服务器
|
||||
======
|
||||
|
||||
![][1]
|
||||
|
||||
The Domain Name System, or DNS, as it’s more commonly known, translates or converts domain names into the IP addresses associated with that domain. DNS is the reason you are able to find your favorite website by name instead of typing an IP address into your browser. This guide shows you how to configure a Master DNS system and one client.
|
||||
<ruby>域名系统<rt>Domain Name System</rt></ruby>,我们更通常称为 DNS 的系统,可以将域名翻译或转换为与该域关联的 IP 地址。DNS 是能够让你通过名称找到自己喜欢的网站而不是在浏览器中输入 IP 地址的原因。本指南将向你展示如何配置一个主 DNS 系统以及客户端。
|
||||
|
||||
Here are system details for the example used in this article:
|
||||
以下是本文示例中使用的系统细节:
|
||||
|
||||
```
|
||||
dns01.fedora.local (192.168.1.160 ) - Master DNS server
|
||||
client.fedora.local (192.168.1.136 ) - Client
|
||||
dns01.fedora.local (192.168.1.160)- 主 DNS 服务器
|
||||
client.fedora.local (192.168.1.136)- 客户端
|
||||
```
|
||||
|
||||
### DNS server configuration
|
||||
### DNS 服务器配置
|
||||
|
||||
Install the bind packages using sudo:
|
||||
使用 `sudo` 安装 bind 包:
|
||||
|
||||
```
|
||||
$ sudo dnf install bind bind-utils -y
|
||||
```
|
||||
|
||||
The _/etc/named.conf_ configuration file is provided by the _bind_ package to allow you to configure the DNS server.
|
||||
bind 包提供了 `/etc/named.conf` 配置文件,来供你配置 DNS 服务器。
|
||||
|
||||
Edit the _/etc/named.conf_ file:
|
||||
编辑 `/etc/named.conf` 文件:
|
||||
|
||||
```
|
||||
sudo vi /etc/named.conf
|
||||
```
|
||||
|
||||
Look for the following line:
|
||||
查找以下行:
|
||||
|
||||
```
|
||||
listen-on port 53 { 127.0.0.1; };
|
||||
```
|
||||
|
||||
Add the IP address of your Master DNS server as follows:
|
||||
添加主 DNS 服务器的 IP 地址,如下所示:
|
||||
|
||||
```
|
||||
listen-on port 53 { 127.0.0.1; 192.168.1.160; };
|
||||
```
|
||||
|
||||
Look for the next line:
|
||||
查找以下行:
|
||||
|
||||
```
|
||||
allow-query { localhost; };
|
||||
```
|
||||
|
||||
Add your local network range. The example system uses IP addresses in the 192.168.1.X range. This is specified as follows:
|
||||
添加本地网络范围。该示例系统使用的 IP 地址在 192.168.1.X 的范围内。指定如下:
|
||||
|
||||
```
|
||||
allow-query { localhost; 192.168.1.0/24; };
|
||||
```
|
||||
|
||||
Specify a forward and reverse zone. Zone files are simply text files that have the DNS information, such as IP addresses and host-names, on your system. The forward zone file makes it possible for the translation of a host-name to its IP address. The reverse zone file does the opposite. It allows a remote system to translate an IP address to the host name.
|
||||
指定转发和反向区域。<ruby>区域文件<rt>Zone file</rt></ruby>就是具有系统上 DNS 信息(例如 IP 地址和主机名)的文本文件。<ruby>转发区域文件<rt>forward zone file</rt></ruby>使得将主机名转换为 IP 地址成为可能。<ruby>反向区域文件<rt>reverse zone file</rt></ruby>则相反。它允许远程系统将 IP 地址转换为主机名。
|
||||
|
||||
Look for the following line at the bottom of the /etc/named.conf file:
|
||||
在 `/etc/named.conf` 文件的底部查找以下行:
|
||||
|
||||
```
|
||||
include "/etc/named.rfc1912.zones";
|
||||
```
|
||||
|
||||
Here, you’ll specify the zone file information _**directly above that line**_ as follows:
|
||||
在此处,你将在**该行的正上方**指定区域文件信息,如下所示:
|
||||
|
||||
```
|
||||
zone "dns01.fedora.local" IN {
|
||||
type master;
|
||||
file "forward.fedora.local";
|
||||
allow-update { none; };
|
||||
type master;
|
||||
file "forward.fedora.local";
|
||||
allow-update { none; };
|
||||
};
|
||||
|
||||
zone "1.168.192.in-addr.arpa" IN {
|
||||
type master;
|
||||
file "reverse.fedora.local";
|
||||
allow-update { none; };
|
||||
type master;
|
||||
file "reverse.fedora.local";
|
||||
allow-update { none; };
|
||||
};
|
||||
```
|
||||
|
||||
The _forward.fedora.local_ and the file _reverse.fedora.local_ are just the names of the zone files you will be creating. They can be called anything you like.
|
||||
`forward.fedora.local` 和 `reverse.fedora.local` 文件是要创建的区域文件的名称。它们可以是任意名字。
|
||||
|
||||
Save and exit.
|
||||
保存并退出。
|
||||
|
||||
#### Create the zone files
|
||||
#### 创建区域文件
|
||||
|
||||
Create the forward and reverse zone files you specified in the /etc/named.conf file:
|
||||
创建你在 `/etc/named.conf` 文件中指定的转发和反向区域文件:
|
||||
|
||||
```
|
||||
$ sudo vi /var/named/forward.fedora.local
|
||||
```
|
||||
|
||||
Add the following lines:
|
||||
添加以下行:
|
||||
|
||||
```
|
||||
$TTL 86400
|
||||
@ -114,13 +114,13 @@ dns01 IN A 192.168.1.160
|
||||
client IN A 192.168.1.136
|
||||
```
|
||||
|
||||
Everything in _**bold**_ is specific to your environment. Save the file and exit. Next, edit the _reverse.fedora.local_ file:
|
||||
所有**粗体**(LCTT 译注:本译文中无法呈现粗体)内容都特定于你的环境。保存文件并退出。接下来,编辑 `reverse.fedora.local` 文件:
|
||||
|
||||
```
|
||||
$ sudo vi /var/named/reverse.fedora.local
|
||||
```
|
||||
|
||||
Add the following lines:
|
||||
添加以下行:
|
||||
|
||||
```
|
||||
$TTL 86400
|
||||
@ -139,9 +139,9 @@ client IN A 192.168.1.136
|
||||
136 IN PTR client.fedora.local.
|
||||
```
|
||||
|
||||
Everything in _**bold**_ is also specific to your environment. Save the file and exit.
|
||||
所有**粗体**(LCTT 译注:本译文中无法呈现粗体)内容都特定于你的环境。保存文件并退出。
|
||||
|
||||
You’ll also need to configure SELinux and add the correct ownership for the configuration files.
|
||||
你还需要配置 SELinux 并为配置文件添加正确的所有权。
|
||||
|
||||
```
|
||||
sudo chgrp named -R /var/named
|
||||
@ -150,22 +150,22 @@ sudo restorecon -rv /var/named
|
||||
sudo restorecon /etc/named.conf
|
||||
```
|
||||
|
||||
Configure the firewall:
|
||||
配置防火墙:
|
||||
|
||||
```
|
||||
sudo firewall-cmd --add-service=dns --perm
|
||||
sudo firewall-cmd --reload
|
||||
```
|
||||
|
||||
#### Check the configuration for any syntax errors
|
||||
#### 检查配置是否存在语法错误
|
||||
|
||||
```
|
||||
sudo named-checkconf /etc/named.conf
|
||||
```
|
||||
|
||||
Your configuration is valid if no output or errors are returned.
|
||||
如果没有输出或返回错误,那么你的配置有效。
|
||||
|
||||
Check the forward and reverse zone files.
|
||||
检查转发和反向区域文件。
|
||||
|
||||
```
|
||||
$ sudo named-checkzone forward.fedora.local /var/named/forward.fedora.local
|
||||
@ -173,7 +173,7 @@ $ sudo named-checkzone forward.fedora.local /var/named/forward.fedora.local
|
||||
$ sudo named-checkzone reverse.fedora.local /var/named/reverse.fedora.local
|
||||
```
|
||||
|
||||
You should see a response of OK:
|
||||
你应该看到 “OK” 的响应:
|
||||
|
||||
```
|
||||
zone forward.fedora.local/IN: loaded serial 2011071001
|
||||
@ -183,50 +183,50 @@ zone reverse.fedora.local/IN: loaded serial 2011071001
|
||||
OK
|
||||
```
|
||||
|
||||
#### Enable and start the DNS service
|
||||
#### 启用并启动 DNS 服务
|
||||
|
||||
```
|
||||
$ sudo systemctl enable named
|
||||
$ sudo systemctl start named
|
||||
```
|
||||
|
||||
#### Configuring the resolv.conf file
|
||||
#### 配置 resolv.conf 文件
|
||||
|
||||
Edit the _/etc/resolv.conf_ file:
|
||||
编辑 `/etc/resolv.conf` 文件:
|
||||
|
||||
```
|
||||
$ sudo vi /etc/resolv.conf
|
||||
```
|
||||
|
||||
Look for your current name server line or lines. On the example system, a cable modem/router is serving as the name server and so it currently looks like this:
|
||||
查找你当前的 `nameserver` 行。在示例系统上,使用调制解调器/路由器充当名称服务器,因此当前看起来像这样:
|
||||
|
||||
```
|
||||
nameserver 192.168.1.1
|
||||
```
|
||||
|
||||
This needs to be changed to the IP address of the Master DNS server:
|
||||
这需要更改为主 DNS 服务器的 IP 地址:
|
||||
|
||||
```
|
||||
nameserver 192.168.1.160
|
||||
```
|
||||
|
||||
Save your changes and exit.
|
||||
保存更改并退出。
|
||||
|
||||
Unfortunately there is one caveat to be aware of. NetworkManager overwrites the _/etc/resolv.conf_ file if the system is rebooted or networking gets restarted. This means you will lose all of the changes that you made.
|
||||
不幸的是需要注意一点。如果系统重启或网络重启,那么 NetworkManager 会覆盖 `/etc/resolv.conf` 文件。这意味着你将丢失所做的所有更改。
|
||||
|
||||
To prevent this from happening, make _/etc/resolv.conf_ immutable:
|
||||
为了防止这种情况发生,请将 `/etc/resolv.conf` 设为不可变:
|
||||
|
||||
```
|
||||
$ sudo chattr +i /etc/resolv.conf
|
||||
```
|
||||
|
||||
If you want to set it back and allow it to be overwritten again:
|
||||
如果要重新设置,就需要允许其再次被覆盖:
|
||||
|
||||
```
|
||||
$ sudo chattr -i /etc/resolv.conf
|
||||
```
|
||||
|
||||
#### Testing the DNS server
|
||||
#### 测试 DNS 服务器
|
||||
|
||||
```
|
||||
$ dig fedoramagazine.org
|
||||
@ -266,27 +266,27 @@ $ dig fedoramagazine.org
|
||||
;; MSG SIZE rcvd: 266
|
||||
```
|
||||
|
||||
There are a few things to look at to verify that the DNS server is working correctly. Obviously getting the results back are important, but that by itself doesn’t mean the DNS server is actually doing the work.
|
||||
需要检查几件事以验证 DNS 服务器是否正常运行。显然,取得结果很重要,但这本身并不意味着 DNS 服务器实际上正常工作。
|
||||
|
||||
The QUERY, ANSWER, and AUTHORITY fields at the top should show non-zero as it in does in our example:
|
||||
顶部的 `QUERY`、`ANSWER` 和 `AUTHORITY` 字段应显示为非零,如我们的示例所示:
|
||||
|
||||
```
|
||||
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 3, ADDITIONAL: 6
|
||||
```
|
||||
|
||||
And the SERVER field should have the IP address of your DNS server:
|
||||
并且 `SERVER` 字段应有你的 DNS 服务器的 IP 地址:
|
||||
|
||||
```
|
||||
;; SERVER: 192.168.1.160#53(192.168.1.160)
|
||||
```
|
||||
|
||||
In case this is the first time you’ve run the _dig_ command, notice how it took 830 milliseconds for the query to complete:
|
||||
如果这是你第一次运行 `dig` 命令,请注意完成查询要花费 830 毫秒的时间:
|
||||
|
||||
```
|
||||
;; Query time: 830 msec
|
||||
```
|
||||
|
||||
If you run it again, the query will run much quicker:
|
||||
如果再次运行它,查询将会更快:
|
||||
|
||||
```
|
||||
$ dig fedoramagazine.org
|
||||
@ -297,37 +297,37 @@ $ dig fedoramagazine.org
|
||||
;; SERVER: 192.168.1.160#53(192.168.1.160)
|
||||
```
|
||||
|
||||
### Client configuration
|
||||
### 客户端配置
|
||||
|
||||
The client configuration will be a lot simpler.
|
||||
客户端配置将简单得多。
|
||||
|
||||
Install the bind utilities:
|
||||
安装 bind 程序:
|
||||
|
||||
```
|
||||
$ sudo dnf install bind-utils -y
|
||||
```
|
||||
|
||||
Edit the /etc/resolv.conf file and configure the Master DNS as the only name server:
|
||||
编辑 `/etc/resolv.conf` 文件,并将主 DNS 配置为唯一的名称服务器:
|
||||
|
||||
```
|
||||
$ sudo vi /etc/resolv.conf
|
||||
```
|
||||
|
||||
This is how it should look:
|
||||
它看起来像这样:
|
||||
|
||||
```
|
||||
nameserver 192.168.1.160
|
||||
```
|
||||
|
||||
Save your changes and exit. Then, make the _/etc/resolv.conf_ file immutable to prevent it from be overwritten and going back to its default settings:
|
||||
保存更改并退出。然后,使 `/etc/resolv.conf` 文件不可变,防止其被覆盖并变回默认设置:
|
||||
|
||||
```
|
||||
$ sudo chattr +i /etc/resolv.conf
|
||||
```
|
||||
|
||||
#### Testing the client
|
||||
#### 测试客户端
|
||||
|
||||
You should get the same results as you did from the DNS server:
|
||||
你应该获得与 DNS 服务器相同的结果:
|
||||
|
||||
```
|
||||
$ dig fedoramagazine.org
|
||||
@ -367,9 +367,9 @@ $ dig fedoramagazine.org
|
||||
;; MSG SIZE rcvd: 266
|
||||
```
|
||||
|
||||
Make sure the SERVER output has the IP Address of your DNS server.
|
||||
确保 `SERVER` 输出的是你 DNS 服务器的 IP 地址。
|
||||
|
||||
Your DNS server is now ready to use and all requests from the client should be going through your DNS server now!
|
||||
你的 DNS 服务器设置完成了,现在所有来自客户端的请求都会经过你的 DNS 服务器了!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
@ -377,8 +377,8 @@ via: https://fedoramagazine.org/how-to-setup-a-dns-server-with-bind/
|
||||
|
||||
作者:[Curt Warfield][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
142
published/20200123 6 things you should be doing with Emacs.md
Normal file
142
published/20200123 6 things you should be doing with Emacs.md
Normal file
@ -0,0 +1,142 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (lujun9972)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-12004-1.html)
|
||||
[#]: subject: (6 things you should be doing with Emacs)
|
||||
[#]: via: (https://opensource.com/article/20/1/emacs-cheat-sheet)
|
||||
[#]: author: (Seth Kenlon https://opensource.com/users/seth)
|
||||
|
||||
6 件你应该用 Emacs 做的事
|
||||
======
|
||||
|
||||
> 下面六件事情你可能都没有意识到可以在 Emacs 下完成。此外还有我们的新备忘单,拿去,充分利用 Emacs 的功能吧。
|
||||
|
||||

|
||||
|
||||
想象一下使用 Python 的 IDLE 界面来编辑文本。你可以将文件加载到内存中,编辑它们,并保存更改。但是你执行的每个操作都由 Python 函数定义。例如,调用 `upper()` 来让一个单词全部大写,调用 `open` 打开文件,等等。文本文档中的所有内容都是 Python 对象,可以进行相应的操作。从用户的角度来看,这与其他文本编辑器的体验一致。对于 Python 开发人员来说,这是一个丰富的 Python 环境,只需在配置文件中添加几个自定义函数就可以对其进行更改和开发。
|
||||
|
||||
这就是 [Emacs][2] 对 1958 年的编程语言 [Lisp][3] 所做的事情。在 Emacs 中,运行应用程序的 Lisp 引擎与输入文本之间无缝结合。对 Emacs 来说,一切都是 Lisp 数据,因此一切都可以通过编程进行分析和操作。
|
||||
|
||||
这造就了一个强大的用户界面(UI)。但是,如果你是 Emacs 的普通用户,你可能对它的能力知之甚少。下面是你可能没有意识到 Emacs 可以做的六件事。
|
||||
|
||||
### 使用 Tramp 模式进行云端编辑
|
||||
|
||||
Emacs 早在网络流行化之前就实现了透明的网络编辑能力了,而且时至今日,它仍然提供了最流畅的远程编辑体验。Emacs 中的 [Tramp 模式][4](以前称为 RPC 模式)代表着 “<ruby>透明的远程(文件)访问,多协议<rt>Transparent Remote (file) Access,Multiple Protocol</rt></ruby>”,这准确说明了它提供的功能:通过最流行的网络协议轻松访问你希望编辑的远程文件。目前最流行、最安全的能用于远程编辑的协议是 [OpenSSH][5],因此 Tramp 使用它作为默认的协议。
|
||||
|
||||
在 Emacs 22.1 或更高版本中已经包含了 Tramp,因此要使用 Tramp,只需使用 Tramp 语法打开一个文件。在 Emacs 的 “File” 菜单中,选择 “Open File”。当在 Emacs 窗口底部的小缓冲区中出现提示时,使用以下语法输入文件名:
|
||||
|
||||
```
|
||||
/ssh:user@example.com:/path/to/file
|
||||
```
|
||||
|
||||
如果需要交互式登录,Tramp 会提示你输入密码。但是,Tramp 直接使用 OpenSSH,所以为了避免交互提示,你可以将主机名、用户名和 SSH 密钥路径添加到你的 `~/.ssh/config` 文件。与 Git 一样,Emacs 首先使用你的 SSH 配置,只有在出现错误时才会停下来询问更多信息。
|
||||
|
||||
Tramp 非常适合编辑并没有放在你的计算机上的文件,它的用户体验与编辑本地文件没有明显的区别。下次,当你 SSH 到服务器启动 Vim 或 Emacs 会话时,请尝试使用 Tramp。
|
||||
|
||||
### 日历
|
||||
|
||||
如果你喜欢文本多过图形界面,那么你一定会很高兴地知道,可以使用 Emacs 以纯文本的方式安排你的日程(或生活),而且你依然可以在移动设备上使用开源的 [Org 模式][6]查看器来获得华丽的通知。
|
||||
|
||||
这个过程需要一些配置,以创建一个方便的方式来与移动设备同步你的日程(我使用 Git,但你可以调用蓝牙、KDE Connect、Nextcloud,或其他文件同步工具),此外你必须在移动设备上安装一个 Org 模式查看器(如 [Orgzly][7])以及 Git 客户程序。但是,一旦你搭建好了这些基础,该流程就会与你常用的(或正在完善的,如果你是新用户)Emacs 工作流完美地集成在一起。你可以在 Emacs 中方便地查阅日程、更新日程,并专注于任务上。议程上的变化将会反映在移动设备上,因此即使在 Emacs 不可用的时候,你也可以保持井然有序。
|
||||
|
||||
![][8]
|
||||
|
||||
感兴趣了?阅读我的关于[使用 Org mode 和 Git 进行日程安排][9]的逐步指南。
|
||||
|
||||
### 访问终端
|
||||
|
||||
有[许多终端模拟器][10]可用。尽管 Emacs 中的 Elisp 终端仿真器不是最强大的通用仿真器,但是它有两个显著的优点:
|
||||
|
||||
1. **打开在 Emacs 缓冲区之中**:我使用 Emacs 的 Elisp shell,因为它在 Emacs 窗口中打开很方便,我经常全屏运行该窗口。这是一个小而重要的优势,只需要输入 `Ctrl+x+o`(或用 Emacs 符号来表示就是 `C-x o`)就能使用终端了,而且它还有一个特别好的地方在于当运行漫长的作业时能够一瞥它的状态报告。
|
||||
2. **在没有系统剪贴板的情况下复制和粘贴特别方便**:无论是因为懒惰不愿将手从键盘移动到鼠标,还是因为在远程控制台运行 Emacs 而无法使用鼠标,在 Emacs 中运行终端有时意味着可以从 Emacs 缓冲区中很快地传输数据到 Bash。
|
||||
|
||||
要尝试 Emacs 终端,输入 `Alt+x`(用 Emacs 符号表示就是 `M-x`),然后输入 `shell`,然后按回车。
|
||||
|
||||
### 使用 Racket 模式
|
||||
|
||||
[Racket][11] 是一种激动人心的新兴 Lisp 方言,拥有动态编程环境、GUI 工具包和充满激情的社区。学习 Racket 的默认编辑器是 DrRacket,它的顶部是定义面板,底部是交互面板。使用该设置,用户可以编写影响 Racket 运行时环境的定义。就像旧的 [Logo Turtle][12] 程序,但是有一个终端而不是仅仅一个海龟。
|
||||
|
||||
![Racket-mode][13]
|
||||
|
||||
*由 PLT 提供的 LGPL 示例代码*
|
||||
|
||||
基于 Lisp 的 Emacs 为资深 Racket 编程人员提供了一个很好的集成开发环境(IDE)。它尚未附带 [Racket 模式][14],但你可以使用 Emacs 包安装程序安装 Racket 模式和辅助扩展。要安装它,按下 `Alt+X`(用 Emacs 符号表示就是 `M-x`),键入 `package-install`,然后按回车。接着输入要安装的包 `racet-mode`,按回车。
|
||||
|
||||
使用 `M-x racket-mode` 进入 Racket 模式。如果你是 Racket 新手,而对 Lisp 或 Emacs 比较熟悉,可以从这份优秀的[图解 Racket][15] 入手。
|
||||
|
||||
## 脚本
|
||||
|
||||
你可能知道,Bash 脚本在自动化和增强 Linux 或 Unix 体验方面很流行。你可能听说过 Python 在这方面也做得很好。但是你知道 Lisp 脚本可以用同样的方式运行吗?有时人们会对 Lisp 到底有多有用感到困惑,因为许多人是通过 Emacs 来了解 Lisp 的,因此有一种潜在的印象,即在 21 世纪运行 Lisp 的惟一方法是在 Emacs 中运行。幸运的是,事实并非如此,Emacs 是一个很好的 IDE,它支持将 Lisp 脚本作为一般的系统可执行文件来运行。
|
||||
|
||||
除了 Elisp 之外,还有两种流行的现代 Lisp 可以很容易地用来作为独立脚本运行。
|
||||
|
||||
1. **Racket**:你可以通过在系统上运行 Racket 来提供运行 Racket 脚本所需的运行时支持,或者你可以使用 `raco exe` 产生一个可执行文件。`raco exe` 命令将代码和运行时支持文件一起打包,以创建可执行文件。然后,`raco distribution` 命令将可执行文件打包成可以在其他机器上工作的发行版。Emacs 有许多 Racket 工具,因此在 Emacs 中创建 Racket 文件既简单又有效。
|
||||
2. **GNU Guile**:[GNU Guile][16](<ruby>GNU 通用智能语言扩展<rt>GNU Ubiquitous Intelligent Language for Extensions</rt></ruby> 的缩写)是 [Scheme][17] 编程语言的一个实现,它可以用于为桌面、互联网、终端等创建应用程序和游戏。Emacs 中的 Scheme 扩展众多,使用任何一个扩展来编写 Scheme 都很容易。例如,这里有一个用 Guile 编写的 “Hello world” 脚本:
|
||||
|
||||
```
|
||||
#!/usr/bin/guile -s
|
||||
!#
|
||||
|
||||
(display "hello world")
|
||||
(newline)
|
||||
```
|
||||
|
||||
用 `guile` 编译并允许它:
|
||||
|
||||
```
|
||||
$ guile ./hello.scheme
|
||||
;;; compiling /home/seth/./hello.scheme
|
||||
;;; compiled [...]/hello.scheme.go
|
||||
hello world
|
||||
$ guile ./hello.scheme
|
||||
hello world
|
||||
```
|
||||
|
||||
### 无需 Emacs 允许 Elisp
|
||||
|
||||
Emacs 可以作为 Elisp 的运行环境,但是你无需按照传统印象中的必须打开 Emacs 来运行 Elisp。`--script` 选项可以让你使用 Emacs 作为引擎来执行 Elisp 脚本,而无需运行 Emacs 图形界面(甚至也无需使用终端)。下面这个例子中,`-Q` 选项让 Emacs 忽略 `.emacs` 文件,从而避免由于执行 Elisp 脚本时产生延迟(若你的脚本依赖于 Emacs 配置中的内容,那么请忽略该选项)。
|
||||
|
||||
```
|
||||
emacs -Q --script ~/path/to/script.el
|
||||
```
|
||||
|
||||
### 下载 Emacs 备忘录
|
||||
|
||||
Emacs 许多重要功能都不是只能通过 Emacs 来实现的;Org 模式是 Emacs 扩展也是一种格式标准,流行的 Lisp 方言大多不依赖于具体的应用,我们甚至可以在没有可见或可交互式 Emacs 实例的情况下编写和运行 Elisp。然后若你对为什么模糊代码和数据之间的界限能够引发创新和效率感到好奇的话,那么 Emacs 是一个很棒的工具。
|
||||
|
||||
幸运的是,现在是 21 世纪,Emacs 有了带有传统菜单的图形界面以及大量的文档,因此学习曲线不再像以前那样。然而,要最大化 Emacs 对你的好处,你需要学习它的快捷键。由于 Emacs 支持的每个任务都是一个 Elisp 函数,Emacs 中的任何功能都可以对应一个快捷键,因此要描述所有这些快捷键是不可能完成的任务。你只要学习使用频率 10 倍于不常用功能的那些快捷键即可。
|
||||
|
||||
我们汇聚了最常用的 Emacs 快捷键成为一份 Emacs 备忘录以便你查询。将它挂在屏幕附近或办公室墙上,把它作为鼠标垫也行。让它触手可及经常翻阅一下。每次翻两下可以让你获得十倍的学习效率。而且一旦开始编写自己的函数,你一定不会后悔获取了这个免费的备忘录副本的!
|
||||
|
||||
- [这里下载 Emacs 备忘录(需注册)](https://opensource.com/downloads/emacs-cheat-sheet)
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
via: https://opensource.com/article/20/1/emacs-cheat-sheet
|
||||
|
||||
作者:[Seth Kenlon][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[lujun9972](https://github.com/lujun9972)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/seth
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/browser_blue_text_editor_web.png
|
||||
[2]: https://www.gnu.org/software/emacs/
|
||||
[3]: https://en.wikipedia.org/wiki/Lisp_(programming_language)
|
||||
[4]: https://www.gnu.org/software/tramp/
|
||||
[5]: https://www.openssh.com/
|
||||
[6]: https://orgmode.org/
|
||||
[7]: https://f-droid.org/en/packages/com.orgzly/
|
||||
[8]: https://opensource.com/sites/default/files/uploads/orgzly-agenda.jpg
|
||||
[9]: https://linux.cn/article-11320-1.html
|
||||
[10]: https://linux.cn/article-11814-1.html
|
||||
[11]: http://racket-lang.org/
|
||||
[12]: https://en.wikipedia.org/wiki/Logo_(programming_language)#Turtle_and_graphics
|
||||
[13]: https://opensource.com/sites/default/files/racket-mode.jpg
|
||||
[14]: https://www.racket-mode.com/
|
||||
[15]: https://docs.racket-lang.org/quick/index.html
|
||||
[16]: https://www.gnu.org/software/guile/
|
||||
[17]: https://en.wikipedia.org/wiki/Scheme_(programming_language)
|
||||
160
published/20200204 DevOps vs Agile- What-s the difference.md
Normal file
160
published/20200204 DevOps vs Agile- What-s the difference.md
Normal file
@ -0,0 +1,160 @@
|
||||
[#]: collector: "lujun9972"
|
||||
[#]: translator: "messon007"
|
||||
[#]: reviewer: "wxy"
|
||||
[#]: publisher: "wxy"
|
||||
[#]: url: "https://linux.cn/article-12031-1.html"
|
||||
[#]: subject: "DevOps vs Agile: What's the difference?"
|
||||
[#]: via: "https://opensource.com/article/20/2/devops-vs-agile"
|
||||
[#]: author: "Taz Brown https://opensource.com/users/heronthecli"
|
||||
|
||||
DevOps 和敏捷:究竟有什么区别?
|
||||
======
|
||||
|
||||
> 两者之间的区别在于开发完毕之后发生的事情。
|
||||
|
||||

|
||||
|
||||
早期,软件开发并没有特定的管理流程。随后出现了<ruby>[瀑布开发流程][2]<rt>Waterfall</rt></ruby>,它提出软件开发活动可以用开发和构建应用所耗费的时间来定义。
|
||||
|
||||
那时候,由于在开发流程中没有审查环节和权衡考虑,常常需要花费很长的时间来开发、测试和部署软件。交付的软件也是带有缺陷和 Bug 的质量较差的软件,而且交付时间也不满足要求。那时候软件项目管理的重点是长期而拖沓的计划。
|
||||
|
||||
瀑布流程与<ruby>[三重约束模型][3]<rt>triple constraint model</rt></ruby>相关,三重约束模型也称为<ruby>项目管理三角形<rt>project management triangle</rt></ruby>。三角形的每一个边代表项目管理三要素的一个要素: **范围、时间和成本**。正如 [Angelo Baretta 写到][4],三重约束模型“认为成本是时间和范围的函数,这三个约束以一种确定的、可预测的方式相互作用。……如果我们想缩短时间表(时间),就必须增加成本。如果我们想增加范围,就必须增加成本或时间。”
|
||||
|
||||
### 从瀑布流程过渡到敏捷开发
|
||||
|
||||
瀑布流程来源于生产和工程领域,这些领域适合线性化的流程:正如房屋封顶之前需要先盖好支撑墙。相似地,软件开发问题被认为可以通过提前做好计划来解决。从头到尾,开发流程均由路线图清晰地定义,沿着路线图就可以得到最终交付的产品。
|
||||
|
||||
最终,瀑布模型被认为对软件开发是不利的而且违反人的直觉,因为通常直到开发流程的最后才能体现出项目的价值,这导致许多项目最终都以失败告终。而且,在项目结束前客户看不到任何可以工作的软件。
|
||||
|
||||
<ruby>敏捷<rt>Agile</rt></ruby>采用了一种不同的方法,它抛弃了规划整个项目,承诺估计的时间点,简单的遵循计划。与瀑布流程相反,它假设和拥抱不确定性。它的理念是以响应变化代替讨论过去,它认为变更是客户需求的一部分。
|
||||
|
||||
### 敏捷价值观
|
||||
|
||||
敏捷由<ruby>敏捷宣言<rt>Agile Manifesto</rt></ruby>代言,敏捷宣言定义了 [12 条原则][5](LCTT 译注:此处没有采用本文原本的简略句式,而是摘录了来自敏捷软件开发宣言官方的[中文译本][14]):
|
||||
|
||||
1. 我们最重要的目标,是通过持续不断地及早交付有价值的软件使客户满意。
|
||||
2. 欣然面对需求变化,即使在开发后期也一样。
|
||||
3. 经常交付可工作的软件,相隔几星期或一两个月,倾向于采取较短的周期。
|
||||
4. 业务人员和开发人员必须相互合作,项目中的每一天都不例外。
|
||||
5. 激发个体的斗志,以他们为核心搭建项目。提供所需的环境和支援,辅以信任,从而达成目标。
|
||||
6. 面对面沟通是传递信息的最佳的也是效率最高的方法。
|
||||
7. 可工作的软件是进度的首要度量标准。
|
||||
8. 敏捷流程倡导可持续的开发,责任人、开发人员和用户要能够共同维持其步调稳定延续。
|
||||
9. 坚持不懈地追求技术卓越和良好设计,敏捷能力由此增强。
|
||||
10. 以简洁为本,它是极力减少不必要工作量的艺术。
|
||||
11. 最好的架构,需求和设计出自自组织团队
|
||||
12. 团队定期地反思如何能提高成效,并依此调整自身的举止表现。
|
||||
|
||||
敏捷的四个[核心价值观][6]是(LCTT 译注:[此处译文][15]同样来自敏捷软件开发宣言官方):
|
||||
|
||||
* **个体和互动** 高于流程和工具
|
||||
* **工作的软件** 高于详尽的文档
|
||||
* **客户合作** 高于合同谈判
|
||||
* **响应变化** 高于遵循计划
|
||||
|
||||
这与瀑布流程死板的计划风格相反。在敏捷流程中,客户是开发团队的一员,而不仅仅是在项目开始时参与项目需求的定义,在项目结束时验收最终的产品。客户帮忙团队完成[验收标准][7],并在整个过程中保持投入。另外,敏捷需要整个组织的变化和持续的改进。开发团队和其他团队一起合作,包括项目管理团队和测试团队。做什么和计划什么时候做由指定的角色领导,并由整个团队同意。
|
||||
|
||||
### 敏捷软件开发
|
||||
|
||||
敏捷软件开发需要自适应的规划、演进式的开发和交付。许多软件开发方法、框架和实践遵从敏捷的理念,包括:
|
||||
|
||||
* Scrum
|
||||
* <ruby>看板<rt>Kanban</rt></ruby>(可视化工作流)
|
||||
* <ruby>极限编程<rt>Xtreme Programming</rt></ruby>(XP)
|
||||
* <ruby>精益方法<rt>Lean</rt></ruby>
|
||||
* DevOps
|
||||
* <ruby>特性驱动开发<rt>Feature-Driven Development</rt></ruby>(FDD)
|
||||
* <ruby>测试驱动开发<rt>Test-Driven Development</rt></ruby>(TDD)
|
||||
* <ruby>水晶方法<rt>Crystal</rt></ruby>
|
||||
* <ruby>动态系统开发方法<rt>Dynamic Systems Development Method</rt></ruby>(DSDM)
|
||||
* <ruby>自适应软件开发<rt>Adaptive Software Development</rt></ruby>(ASD)
|
||||
|
||||
所有这些已经被单独用于或一起用于开发和部署软件。最常用的是 [Scrum][8]、看板(或 Scrumban)和 DevOps。
|
||||
|
||||
[Scrum][9] 是一个框架,采用该框架的团队通常由一个 Scrum 教练、产品经理和开发人员组成,该团队以跨职能、自主的工作方式运作,能够加快软件交付速度从而给客户带来巨大的商业价值。其关注点是[较小增量][10]的快速迭代。
|
||||
|
||||
[看板][11] 是一个敏捷框架,有时也叫工作流管理系统,它能帮助团队可视化他们的工作从而最大化效率(因而变得敏捷)。看板通常由数字或物理展示板来呈现。团队的工作在展示板上随着进度而移动,例如从未启动到进行中,一直到测试中、已完成。看板使得每个团队成员可以随时查看到所有工作的状态。
|
||||
|
||||
### DevOps 价值观
|
||||
|
||||
DevOps 是一种文化,是一种思维状态,是一种软件开发的方式或者基础设施的方式,也是一种构建和部署软件和应用的方式。它假设开发和运维之间没有隔阂,他们一起合作,没有矛盾。
|
||||
|
||||
DevOps 基于其它两个领域的实践: 精益和敏捷。DevOps 不是一个公司内的岗位或角色;它是一个组织或团队对持续交付、持续部署和持续集成的坚持不懈的追求。[Gene Kim][12](Phoenix 项目和 Unicorn 项目的作者)认为,有三种方式定义 DevOps 的理念:
|
||||
|
||||
* 第一种: 流程原则
|
||||
* 第二种: 反馈原则
|
||||
* 第三种: 持续学习原则
|
||||
|
||||
### DevOps 软件开发
|
||||
|
||||
DevOps 不会凭空产生;它是一种灵活的实践,它的本质是一种关于软件开发和 IT 或基础设施实施的共享文化和思维方式。
|
||||
|
||||
当你想到自动化、云、微服务时,你会想到 DevOps。在一次[访谈][13]中,《加速构建和扩张高性能技术组织》的作者 Nicol Forsgren、Jez Humble 和 Gene Kim 这样解释到:
|
||||
|
||||
> * 软件交付能力很重要,它极大地影响到组织的成果,例如利润、市场份额、质量、客户满意度以及组织战略目标的达成。
|
||||
> * 优秀的团队能达到很高的交付量、稳定性和质量;他们并没有为了获得这些属性而进行取舍。
|
||||
> * 你可以通过实施精益、敏捷和 DevOps 中的实践来提升能力。
|
||||
> * 实施这些实践和能力也会影响你的组织文化,并且会进一步对你的软件交付能力和组织能力产生有益的提升。
|
||||
> * 懂得怎样改进能力需要做很多工作。
|
||||
|
||||
### DevOps 和敏捷的对比
|
||||
|
||||
DevOps 和敏捷有相似性,但是它们不完全相同,一些人认为 DevOps 比敏捷更好。为了避免造成混淆,深入地了解它们是很重要的。
|
||||
|
||||
#### 相似之处
|
||||
|
||||
* 毫无疑问,两者都是软件开发技术。
|
||||
* 敏捷已经存在了 20 多年,DevOps 是最近才出现的。
|
||||
* 两者都追求软件的快速开发,它们的理念都基于怎样在不伤害客户或运维利益的情况下快速开发出软件。
|
||||
|
||||
#### 不同之处
|
||||
|
||||
* 两者的差异在于软件开发完成后发生的事情。
|
||||
* 在 DevOps 和敏捷中,都有软件开发、测试和部署的阶段。然而,敏捷流程在这三个阶段之后会终止。相反,DevOps 包括后续持续的运维。因此,DevOps 会持续的监控软件运行情况和进行持续的开发。
|
||||
* 敏捷中,不同的人负责软件的开发、测试和部署。而 DevOps 工程角色负责所有活动,开发即运维,运维即开发。
|
||||
* DevOps 更关注于削减成本,而敏捷则是精益和减少浪费的代名词,侧重于像敏捷项目会计和最小可行产品的概念。
|
||||
* 敏捷专注于并体现了经验主义(适应、透明和检查),而不是预测性措施。
|
||||
|
||||
敏捷 | DevOps
|
||||
--- | ---
|
||||
从客户得到反馈 | 从自己得到反馈
|
||||
较小的发布周期 | 较小的发布周期,立即反馈
|
||||
聚焦于速度 | 聚焦于速度和自动化
|
||||
对业务不是最好 | 对业务最好
|
||||
|
||||
### 总结
|
||||
|
||||
敏捷和 DevOps 是截然不同的,尽管它们的相似之处使人们认为它们是相同的。这对敏捷和 DevOps 都是一种伤害。
|
||||
|
||||
根据我作为一名敏捷专家的经验,我发现对于组织和团队从高层次上了解敏捷和 DevOps 是什么,以及它们如何帮助团队更高效地工作,更快地交付高质量产品从而提高客户满意度非常有价值。
|
||||
|
||||
敏捷和 DevOps 绝不是对抗性的(或至少没有这个意图)。在敏捷革命中,它们更像是盟友而不是敌人。敏捷和 DevOps 可以相互协作一致对外,因此可以在相同的场合共存。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/20/2/devops-vs-agile
|
||||
|
||||
作者:[Taz Brown][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[messon007](https://github.com/messon007)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/heronthecli
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/collab-team-pair-programming-code-keyboard.png?itok=kBeRTFL1 "Pair programming"
|
||||
[2]: http://www.agilenutshell.com/agile_vs_waterfall
|
||||
[3]: https://en.wikipedia.org/wiki/Project_management_triangle
|
||||
[4]: https://www.pmi.org/learning/library/triple-constraint-erroneous-useless-value-8024
|
||||
[5]: http://agilemanifesto.org/principles.html
|
||||
[6]: https://agilemanifesto.org/
|
||||
[7]: https://www.productplan.com/glossary/acceptance-criteria/
|
||||
[8]: https://opensource.com/article/19/8/scrum-vs-kanban
|
||||
[9]: https://www.scrum.org/
|
||||
[10]: https://www.scrum.org/resources/what-is-an-increment
|
||||
[11]: https://www.atlassian.com/agile/kanban
|
||||
[12]: https://itrevolution.com/the-unicorn-project/
|
||||
[13]: https://www.infoq.com/articles/book-review-accelerate/
|
||||
[14]: http://agilemanifesto.org/iso/zhchs/principles.html
|
||||
[15]: http://agilemanifesto.org/iso/zhchs/manifesto.html
|
||||
@ -0,0 +1,198 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (wxy)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-12007-1.html)
|
||||
[#]: subject: (Basic kubectl and Helm commands for beginners)
|
||||
[#]: via: (https://opensource.com/article/20/2/kubectl-helm-commands)
|
||||
[#]: author: (Jessica Cherry https://opensource.com/users/jrepka)
|
||||
|
||||
适用于初学者的基本 kubectl 和 Helm 命令
|
||||
======
|
||||
|
||||
> 去杂货店“采购”这些命令,你需要用这些 Kubernetes 工具来入门。
|
||||
|
||||

|
||||
|
||||
最近,我丈夫告诉我他即将要去参加一个工作面试,面试时他需要在计算机上运行一些基本命令。他对这场面试感到焦虑,但是对于他来说,学习和记住事情的最好方法是将不了解的事物比喻为非常熟悉的事物。因为我们的谈话是在我逛杂货店试图决定当晚要烹饪的食物之后进行的,所以这启发我用一次去杂货店的行程来介绍 `kubectl` 和 `helm` 命令。
|
||||
|
||||
[Helm][2](“舵轮”)是在 Kubernetes(来自希腊语,意思是“舵手” 或 “领航员”)中管理应用程序的工具。你可以轻松地使用你的应用程序信息来部署“<ruby>海图<rt>chart</rt></ruby>”,从而可以在你的 Kubernetes 环境中几分钟之内让它们就绪并预配置好。在学习新知识时,查看示例的“海图”以了解其用法总是很有帮助的,因此,如果有时间,请查看这些成型的“[海图][3]”。(LCTT 译注:Kubernetes 生态中大量使用了和航海有关的比喻,因此本文在翻译时也采用了这些比喻)
|
||||
|
||||
[kubectl][4] 是与 Kubernetes 环境交互的命令行界面,允许你配置和管理集群。它需要一些配置才能在环境中工作,因此请仔细阅读其[文档][5]以了解你需要做什么。
|
||||
|
||||
我会在示例中使用命名空间,你可以在我的文章《[Kubernetes 命名空间入门][6]》中了解它。
|
||||
|
||||
现在我们已经准备好了,让我们开始 `kubectl`和 `helm` 基本命令的购物之旅!
|
||||
|
||||
### 用 Helm 列出清单
|
||||
|
||||
你去商店之前要做的第一件事是什么?好吧,如果你做事有条理,会创建一个“清单”。同样,这是我将解释的第一个基本的 Helm 命令。
|
||||
|
||||
在一个用 Helm 部署的应用程序中,`list` 命令提供有关应用程序当前版本的详细信息。在此示例中,我有一个已部署的应用程序:Jenkins CI/CD 应用程序。运行基本的 `list` 命令总是会显示默认的命名空间。由于我没有在默认的命名空间中部署任何内容,因此不会显示任何内容:
|
||||
|
||||
```
|
||||
$helm list
|
||||
NAME NAMESPACE REVISION UPDATED STATUS CHART APP VERSION
|
||||
```
|
||||
|
||||
但是,如果运行带有额外标志的命令,则会显示我的应用程序和信息:
|
||||
|
||||
```
|
||||
$helm list --all-namespaces
|
||||
NAME NAMESPACE REVISION UPDATED STATUS CHART APP VERSION
|
||||
jenkins jenkins 1 2020-01-18 16:18:07 EST deployed jenkins-1.9.4 lts
|
||||
```
|
||||
|
||||
最后,我可以指示 `list` 命令只检查我想从中获取信息的命名空间:
|
||||
|
||||
```
|
||||
$helm list --namespace jenkins
|
||||
NAME NAMESPACE REVISION UPDATED STATUS CHART APP VERSION
|
||||
jenkins jenkins 1 2020-01-18 16:18:07 EST deployed jenkins-1.9.4 lts
|
||||
```
|
||||
|
||||
现在我有了一个清单,并且知道该清单上有什么,我可以使用 `get` 命令来“获取”我的物品!我会从 Kubernetes 集群开始,看看我能从中获取到什么?
|
||||
|
||||
### 用 Kubectl 获取物品
|
||||
|
||||
`kubectl get` 命令提供了有关 Kubernetes 中许多事物的信息,包括“<ruby>吊舱<rt>Pod</rt></ruby>”、节点和命名空间。同样,如果没有指定命名空间标志,就会使用默认的命名空间。首先,我获取集群中的命名空间以查看正在运行的命名空间:
|
||||
|
||||
```
|
||||
$kubectl get namespaces
|
||||
NAME STATUS AGE
|
||||
default Active 53m
|
||||
jenkins Active 44m
|
||||
kube-node-lease Active 53m
|
||||
kube-public Active 53m
|
||||
kube-system Active 53m
|
||||
```
|
||||
|
||||
现在我已经知道了在我的环境中运行的有哪些命名空间了,接下来获取节点并查看有多少个节点正在运行:
|
||||
|
||||
```
|
||||
$kubectl get nodes
|
||||
NAME STATUS ROLES AGE VERSION
|
||||
minikube Ready master 55m v1.16.2
|
||||
```
|
||||
|
||||
我有一个节点正在运行,这主要是因为我的 Minikube 运行在一台小型服务器上。要得到在我的这一个节点上运行的“吊舱”可以这样:
|
||||
|
||||
```
|
||||
$kubectl get pods
|
||||
No resources found in default namespace.
|
||||
```
|
||||
|
||||
啊哦,它是空的。我将通过以下方式获取 Jenkins 命名空间中的内容:
|
||||
|
||||
```
|
||||
$kubectl get pods --namespace jenkins
|
||||
NAME READY STATUS RESTARTS AGE
|
||||
jenkins-7fc688c874-mh7gv 1/1 Running 0 40m
|
||||
```
|
||||
|
||||
好消息!这里发现了一个“吊舱”,它还没有重新启动过,已运行了 40 分钟了。好的,如今我知道“吊舱”已经装好,所以我想看看用 Helm 命令可以得到什么。
|
||||
|
||||
### 用 Helm 获取信息
|
||||
|
||||
`helm get` 命令稍微复杂一点,因为这个“获取”命令所需要的不仅仅是一个应用程序名称,而且你可以从应用程序中请求多个内容。我会从获取用于制作该应用程序的值开始,然后展示“获取全部”的操作结果的片段,该操作将提供与该应用程序相关的所有数据。
|
||||
|
||||
```
|
||||
$helm get values jenkins -n jenkins
|
||||
USER-SUPPLIED VALUES:
|
||||
null
|
||||
```
|
||||
|
||||
由于我只安装了最小限度的稳定版,因此配置没有更改。如果我运行“获取全部”命令,我将得到所有的“海图”:
|
||||
|
||||
```
|
||||
$helm get all jenkins -n jenkins
|
||||
```
|
||||
|
||||
![output from helm get all command][7]
|
||||
|
||||
这会产生大量数据,因此我始终建议保留一份 Helm “海图”的副本,以便你可以查看“海图”中的模板。我还创建自己的值来了解自己所拥有的。
|
||||
|
||||
现在,我把所有的商品都放在购物车中了,我会检查一下“描述”它们包含什么的标签。这些示例仅与 `kubectl` 命令有关,它们描述了我通过 Helm 部署的内容。
|
||||
|
||||
### 用 kubectl 查看描述
|
||||
|
||||
正如我使用“获取”命令(该命令可以描述 Kubernetes 中的几乎所有内容)所做的那样,我将示例限定到命名空间、“吊舱”和节点上。由于我知道它们每一个是什么,因此这很容易。
|
||||
|
||||
```
|
||||
$kubectl describe ns jenkins
|
||||
Name: jenkins
|
||||
Labels: <none>
|
||||
Annotations: <none>
|
||||
Status: Active
|
||||
No resource quota.
|
||||
No resource limits.
|
||||
```
|
||||
|
||||
我可以看到我的命名空间的名称,并且它是活动的,没有资源或限额限制。
|
||||
|
||||
`describe pods` 命令会产生大量信息,因此我这里提供的是一小段输出。如果你在不使用“吊舱”名称的情况下运行该命令,它将返回名称空间中所有“吊舱”的信息,这可能会很麻烦。因此,请确保在此命令中始终包含“吊舱”名称。例如:
|
||||
|
||||
```
|
||||
$kubectl describe pods jenkins-7fc688c874-mh7gv --namespace jenkins
|
||||
```
|
||||
|
||||
![output of kubectl-describe-pods][8]
|
||||
|
||||
这会提供容器的状态、管理方式、标签以及“吊舱”中所使用的镜像(还有很多其它信息)。没有在这个简化过的输出中包括的数据有:在 Helm 配置值文件中应用的各种条件下的资源请求和限制、初始化容器和存储卷信息。如果你的应用程序由于资源不足而崩溃,或者是一个需要运行前置脚本进行配置的初始配置容器,或者生成不应该存储于纯文本 YAML 文件中的隐藏密码,则此数据很有用。
|
||||
|
||||
最后,我将使用 `describe node` 命令,当然,它是用来描述节点的。由于本示例只有一个名为 Minikube 的示例,因此我将使用这个名字。如果你的环境中有多个节点,则必须包含你想查找的的节点名称。
|
||||
|
||||
与“吊舱”一样,这个节点的命令会产生大量数据,因此我将仅包括输出片段。
|
||||
|
||||
```
|
||||
$kubectl describe node minikube
|
||||
```
|
||||
|
||||
![output of kubectl describe node][9]
|
||||
|
||||
注意,`describe node` 是更重要的基本命令之一。如此图所示,该命令返回统计信息,该信息指示节点何时资源用尽,并且该数据非常适合在需要扩展时(如果你的环境中没有自动扩展)向你发出警报。此输出片段中未包含的其它内容包括:对所有资源和限制的请求所占的百分比,以及资源的使用期限和分配(例如,对于我的应用程序而言)。
|
||||
|
||||
### 买单
|
||||
|
||||
使用这些命令,我完成了“购物”并得到了我想要的一切。希望这些基本命令也能在你使用 Kubernetes 的日常工作中提供帮助。
|
||||
|
||||
我鼓励你经常使用命令行并学习“帮助”部分中的速记标志,你可以通过运行以下命令来查看这些标志:
|
||||
|
||||
```
|
||||
$helm --help
|
||||
```
|
||||
|
||||
或
|
||||
|
||||
```
|
||||
$kubectl -h
|
||||
```
|
||||
|
||||
### 花生酱和果冻
|
||||
|
||||
有些东西像花生酱和果冻一样混在一起。Helm 和 `kubectl` 就有点像那样交错在一起。
|
||||
|
||||
我经常在自己的环境中使用这些工具。因为它们在很多地方都有很多相似之处,所以在使用其中一个之后,我通常需要跟进另一个。例如,我可以进行 Helm 部署,并使用 `kubectl` 观察它是否失败。一起试试它们,看看它们能为你做什么。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/20/2/kubectl-helm-commands
|
||||
|
||||
作者:[Jessica Cherry][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[wxy](https://github.com/wxy)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/jrepka
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/rh_003784_02_os.comcareers_os_rh2x.png?itok=jbRfXinl (A person working.)
|
||||
[2]: https://helm.sh/
|
||||
[3]: https://github.com/helm/charts/tree/master/stable
|
||||
[4]: https://kubernetes.io/docs/reference/kubectl/kubectl/
|
||||
[5]: https://kubernetes.io/docs/reference/kubectl/overview/
|
||||
[6]: https://linux.cn/article-11749-1.html
|
||||
[7]: https://opensource.com/sites/default/files/uploads/helm-get-all.png (output from helm get all command)
|
||||
[8]: https://opensource.com/sites/default/files/uploads/kubectl-describe-pods.png (output of kubectl-describe-pods)
|
||||
[9]: https://opensource.com/sites/default/files/uploads/kubectl-describe-node.png (output of kubectl describe node)
|
||||
80
published/20200214 Linux is our love language.md
Normal file
80
published/20200214 Linux is our love language.md
Normal file
@ -0,0 +1,80 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (sndnvaps)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-12022-1.html)
|
||||
[#]: subject: (Linux is our love language)
|
||||
[#]: via: (https://opensource.com/article/20/2/linux-love-language)
|
||||
[#]: author: (Christopher Cherry https://opensource.com/users/chcherry)
|
||||
|
||||
学习 Linux 是我们的爱情语言
|
||||
======
|
||||
|
||||
> 当一个妻子教丈夫一些新技能的时候,他们都学到了比期待更多的东西。
|
||||
|
||||

|
||||
|
||||
2019 年是我们 Cherry 家学习的一年。我是一个喜欢学习新技术的高级软件工程师,并把学到的内容一起教给了我的丈夫 Chris。通过教给他一些我学到的东西,并让他全程经历我的技术演练文章,我帮助 Chris 学习到了新技术,使他能够将自己的职业生涯更深入地转向技术领域。而我学习到了新的方法,使我的演练和培训材料更易于让读者理解。
|
||||
|
||||
在这篇文章中,我们来讨论一下我们各自和彼此学习到了什么东西,然后探讨这对于我们的未来有何影响。
|
||||
|
||||
### 向学生的提问
|
||||
|
||||
**Jess:** Chris,是什么导致你想深入学习我的领域的技能呢?
|
||||
|
||||
**Chris:** 主要目的是为了让我事业更进一步。作为一个网络工程师的经历告诉我,现在的网络专家已经不像以前一样有价值了,我必须掌握更多的知识。由于网络经常被认为是造成这些天程序中断或出错的原因,我想从开发人员的角度了解更多关于编写应用程序的知识,以便于了解它们如何依赖网络资源。
|
||||
|
||||
**Jess:** 我首先教你什么内容?你从中学到什么?
|
||||
|
||||
**Chris:** 首先是从学习除此安装 Linux 系统开始的,之后又安装了 [Ansible][2]。只要硬件兼容,我用过的每一个 Linux 发行版都很容易安装,但可能会出现个别不兼容的情况。这就意味着我有时候第一手学习到的是如何解决系统安装过程的最初 5 分钟出现的问题了(这个我最喜欢了)。Ansible 给了一个我学习使用软件管理器来安装程序的理由。当程序安装完成后,通过查看 yum 安装的程序,我快速了解了程序管理器是如何处理程序的依赖项的,因此,用 Python 编写的 Ansible 能够在我的系统运行。自此之后,我开始使用 Ansible 来安装各种各样的程序。
|
||||
|
||||
**Jessica:** 你喜欢我这种教学方式不?
|
||||
|
||||
**Chris:** 我们一开始有过争吵,直到我们弄清楚了我喜欢的学习方式,你也知道了应该怎样为我提供最好的学习方式。在一开始的时候,我很难跟上你讲的内容。例如,当你说“一个码头工人集装箱”的时候,我完全不知道你在讲什么。比较早的时候,我的回答就是“这是一个集装箱”,然而当时这对我来说,完全没有意义。当你对这些内容进行一些更深入的讲解后,才让学习更有趣。
|
||||
|
||||
**Jess:** 老实说,这对我来说也是一个重要的教训。在你之前,我从来没有教过在这个技术领域知识比我少的人,所以你帮助我认识到我需要解释更多细节。我也得说声谢谢。
|
||||
|
||||
当你通过这几个学习步骤的时候,你觉得我的这篇测试文章怎样呢?
|
||||
|
||||
**Chris:** 就我个人而言,我认为这很容易,但我错了。在我主要学习的内容中,比如你[介绍的Vagrant][3],它在不同的 Linux 发行版间的变化比我想像的要多。操作系统的变化会影响设置的方式、运行都要求和特定的命令。这看起来比我用的网络设备变化更大。这让我花费更多的精力去查看这些说明是对应我的系统还是其它的系统(有时候很难知道)。在这学习路上,我似乎碰到很多问题。
|
||||
|
||||
**Jess:** 我每天都会遇到各种各样的问题,所以对我来说日常就是用各种方法解决各种问题。
|
||||
|
||||
### 向老师的提问
|
||||
|
||||
**Chris:** Jess,你将来教我的方式会有所改变吗?
|
||||
|
||||
**Jess:** 我想让你像我一样读多一些书。通过翻阅书籍来学习新技术。每天起床后一小时和睡觉前一小时我都会看书,花费一个星期左右我就能看一到两本书。我也会创建为期两周的任务计划来实践我从书本中学习到的技能。这是除了我一天中第一个小时在喝大量咖啡时读到的科技文章之外的。当我考虑到你的职业发展目标的时候,我认为除了我们谈到的优秀博客文章和文章之外,书籍是一个重要的元素。我觉得我的阅读量使我保持进步,如果你也这么做了,你也会很快赶上我的。
|
||||
|
||||
**Chris:** 那么学生有没有教过老师呢?
|
||||
|
||||
**Jess:** 我在你那里学习到耐心。举个例子,当你完成了安装 Ansible 的时候,我问你下一步要怎样操作的时候。你直接回复我,“不知道”,这不是我想让你学习到的内容。所以我改变了策略,现在在逐步安装任何组件之前,我们将详细讨论你想要实现的目标。当我们在写 Vagrant 文章的时候,我们一起进行相应的演示操作,我以创建它时就牢记目标,因此我们就有一些需要马上实现的目标。
|
||||
|
||||
这实际上对我在工作中的培训方式产生了巨大的改变。现在我在大家学习的过程中会问更多问题,并更多地进行手把手讲解。我更愿意坐下来仔细检查,确保有人明白我在说什么和我们在做什么。这是我之前从来没有做过的。
|
||||
|
||||
### 我们一起学到了什么
|
||||
|
||||
做为一对夫妇,在这一年的技术合作中我们的技术都有所增长。
|
||||
|
||||
**Chris:** 我对自己学到的东西感到震惊。通过一年课程学习,我认识了新操作系统、如何使用 API、使用 Ansible 部署 Web 应用和使用 Vagrant 启动虚拟机器。我还学习到了文档可以让生活变得更好,所以我也会尝试去写一写。然而,在这个工作领域,操作并不总是被记录在案,所以我学会了准备好处理棘手的问题,并记录如何解决它们。
|
||||
|
||||
**Jess:** 除了我在教你中学到的知识外,我还专注于学习 Kubernetes 在云环境中的应用知识。这包括部署策略、Kubernetes API 的复杂度、创建我自己的容器,并对环境进行加密处理。我还节省了探索的时间:研究了 serverless 的代码、AI 模型、Python 和以图形方式显示热图。对于我来说,这一年也很充足。
|
||||
|
||||
我们下一个目标是什么?现在还不知道,但我可以向你保证,我们将会继续进行分享它。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/20/2/linux-love-language
|
||||
|
||||
作者:[Christopher Cherry][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[sndnvaps](https://github.com/sndnvaps)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/chcherry
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/red-love-heart-alone-stone-path.jpg?itok=O3q1nEVz (红心 "你不是孤单的")
|
||||
[2]: https://opensource.com/resources/what-ansible
|
||||
[3]: https://opensource.com/resources/vagrant
|
||||
@ -0,0 +1,195 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (robsean)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-12046-1.html)
|
||||
[#]: subject: (Here Are The Most Beautiful Linux Distributions in 2020)
|
||||
[#]: via: (https://itsfoss.com/beautiful-linux-distributions/)
|
||||
[#]: author: (Ankush Das https://itsfoss.com/author/ankush/)
|
||||
|
||||
我眼中的 2020 年最漂亮的 Linux 发行版
|
||||
======
|
||||
|
||||

|
||||
|
||||
以我的观点,每个人都该有一个 Linux 发行版,不管他们喜欢的是哪种,或者想用来做什么。
|
||||
|
||||
要是你刚刚开始使用 Linux,你可以使用这些[最适合于初学者的 Linux 发行版][1];要是你是从 Windows 投奔过来的,你可以使用这些[看起来像 Windows 一样的 Linux 发行版][2];要是你有台旧电脑想让它发挥余热,你可以使用这些[轻量级 Linux 发行版][3]。当然,无论你是在[企业][36]还是 [SOHO][37],Linux 还可以用于[个人工作][38]、[开发][39],以及作为[服务器][40]或[嵌入式系统][41]的操作系统,它可以用于[各种用途][42]。
|
||||
|
||||
但在这个列表中,我们只关注最漂亮的 Linux 发行版。
|
||||
|
||||
### 7 款最漂亮的 Linux 发行版
|
||||
|
||||
![][4]
|
||||
|
||||
等一下!Linux 发行版有漂亮这个分类吗?显然,你可以自己定制任何发行版的外观,并使用[主题][5]和[图标][6]之类的来使其看起来更漂亮。
|
||||
|
||||
你说得对。但是在这里,我所说的是指不需要用户进行任何调整和自定义工作就看起来很漂亮的发行版。这些发行版提供友好的顺滑、流畅、开箱即用的桌面体验。
|
||||
|
||||
**注意:** 以下列表排名不分前后,名单纯属个人喜好,请使劲喷你的观点。
|
||||
|
||||
#### 1、elementary OS
|
||||
|
||||
![][7]
|
||||
|
||||
首先踏上 T 台的 elementary OS 是最漂亮的 Linux 发行版(如果非得说的话,可以是“之一”)。它靠着一种类似 macOS 的外观,而为 Linux 用户提供了出色的体验。如果你已经适应了 macOS,那么你在使用 elementary OS 时就不会有任何不适感。
|
||||
|
||||
此外,elementary OS 是基于 Ubuntu 的,因此,你可以很容易地找到大量的可以满足你的需要的应用程序。
|
||||
|
||||
不仅仅是外观和感受,elementary OS 总是努力地引入一些重要的变化。因此,你可以期待用户体验会随着每次更新而获得提升。
|
||||
|
||||
- [elementary OS][8]
|
||||
|
||||
#### 2、深度 Linux
|
||||
|
||||
![][9]
|
||||
|
||||
深度 Linux(或许现在该叫统信 UOS?)是另外一个漂亮的 Linux 发行版,它起源于 Debian 的稳定版分支。对于某些人来说,其动画效果(外观和感受)可能有点过度了,虽然它看起来很漂亮。
|
||||
|
||||
它有它自己特色的 Deepin 桌面环境(DDE),蕴藏了多种基本功能,从而提供尽可能好的用户体验。它可能不像其它发行版的用户界面,但你很容易就可以习惯。
|
||||
|
||||
我个人对深度中的控制中心和特色配色方案印象深刻。你可以自己尝试一下,我觉得值得一试。
|
||||
|
||||
- [深度][10]
|
||||
|
||||
#### 3、Pop!_OS
|
||||
|
||||
![][11]
|
||||
|
||||
Pop!_OS 在提供了纯净的 [GNOME][12] 体验的同事,也成功地在 Ubuntu 之上打造出了一个出色的用户界面。
|
||||
|
||||
这正是我的最爱,我使用它作为我的主要桌面系统。Pop!_OS 既不浮华,也没有一些花哨的动画。然而,它通过图标和主题的完美组合做到了最好,同时从技术角度提升了用户体验。
|
||||
|
||||
我不想发起一场 [Ubuntu 和 Pop!\_OS][13] 之间的争论,但是如果你已经习惯了 Ubuntu,Pop!_OS 可能是一个可能更好的用户体验的绝佳选择。
|
||||
|
||||
- [Pop!_OS][14]
|
||||
|
||||
#### 4、Manjaro Linux
|
||||
|
||||
![][15]
|
||||
|
||||
Manjaro Linux 是一个基于 [Arch][16] 的 Linux 发行版。虽然[安装 Arch Linux][17] 是一件稍微复杂的工作,而 Manjaro 则提供了一种更舒适、更流畅的 Arch 体验。
|
||||
|
||||
它提供各种各样的[桌面环境版本][18],在下载时可供选择。不管你选择哪一个,你都仍然有足够的选择权来自定义外观和感觉或布局。
|
||||
|
||||
对我来说,这样一个开箱即用的、基于 Arch 的发行版看起来棒极了,你值得拥有!
|
||||
|
||||
- [Manjaro Linux][19]
|
||||
|
||||
#### 5、KDE Neon
|
||||
|
||||
![][20]
|
||||
|
||||
[KDE Neon][21] 是为那些想要采用简化的设计方案而仍可以得到丰富体验的用户所准备的。
|
||||
|
||||
它是一个基于 Ubuntu 的轻量级 Linux 发行版。顾名思义,它采用 KDE Plasma 桌面,看起来精美绝伦。
|
||||
|
||||
KDE Neon 给予你最新的、最好的 KDE Plasma 桌面及 KDE 应用程序。不像 [Kubuntu][22] 或其它基于 KDE 的发行版,你不需要等待数月来获取新的 [KDE 软件][23]。
|
||||
|
||||
你可以在 KDE 桌面中获取很多内置的自定义选项,请按你的心意摆弄它!
|
||||
|
||||
- [KDE Neon][24]
|
||||
|
||||
#### 6、Zorin OS
|
||||
|
||||
![][25]
|
||||
|
||||
毫无疑问,Zorin OS 是一款令人印象深刻的 Linux 发行版,它努力提供了良好的用户体验,即便是它的精简版也是如此。
|
||||
|
||||
你可以尝试完整版或精简版(使用 [Xfce 桌面][26])。这个用户界面是专门为习惯于 Windows 和 macOS 的用户定制的。虽然它是基于 Ubuntu 的,但它仍然提供了出色的用户体验。
|
||||
|
||||
如果你开始喜欢上了它的用户界面,那你也可以尝试使用 [Zorin Grid][27] 来管理运行在工作区/家庭中的 Zorin OS 计算机。而使用其终极版,你还可以控制桌面布局(如上图所示)。
|
||||
|
||||
- [video](https://youtu.be/UsUm_ERVLpQ)
|
||||
|
||||
- [Zorin OS][28]
|
||||
|
||||
#### 7、Nitrux OS
|
||||
|
||||
![][29]
|
||||
|
||||
[Nitrux OS][30] 在 Linux 发行版里算是个另类,它某种程度上基于 Ubuntu,但是不完全基于 Ubuntu 。
|
||||
|
||||
对于那些正在寻找在 Linux 发行版上使用全新方式的独特设计语言的用户来说,它专注于为他们提供一种良好的用户体验。它使用基于 KDE 的 Nomad 桌面。
|
||||
|
||||
Nitrux 鼓励使用 [AppImage][31] 应用程序。但是在这个基于 Ubuntu 的 Nitrux 中你也可以使用 Arch Linux 的 pacman 软件包管理器。真令人惊叹!
|
||||
|
||||
如果它不是你安装过(或尚未安装过)的完美的操作系统,但它确实看起来很漂亮,并且对大多数基本任务来说已经足够了。你可以阅读我们的 [Nitrux 创始人的采访][32],可以更多地了解它。
|
||||
|
||||
这是一个稍微过时的 Nitrux 视频,但是它仍然看起来很好:
|
||||
|
||||
- [video](https://youtu.be/8p2BK0AwuV8)
|
||||
|
||||
- [Nitrux OS][33]
|
||||
|
||||
#### 赠品:eXtern OS (处于‘停滞’开发阶段)
|
||||
|
||||
![][34]
|
||||
|
||||
如果你想尝试一个实验性的 Linux 发行版,extern OS 是非常漂亮的。
|
||||
|
||||
它没有积极维护,因此不应该用于生产系统。但是,它提供独特的用户体验,尽管还不够完美无缺。
|
||||
|
||||
如果只是想尝试一个好看的 Linux 发行版,你可以试试。
|
||||
|
||||
- [eXtern OS][35]
|
||||
|
||||
### 总结
|
||||
|
||||
俗话说,情人眼里出西施。所以这份来自我眼中的最漂亮 Linux 发行版列表。你可以随意提出不同的意见 (当然要礼貌一点),并提出你最喜欢的 Linux 发行版。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://itsfoss.com/beautiful-linux-distributions/
|
||||
|
||||
作者:[Ankush Das][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[robsean](https://github.com/robsean)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://itsfoss.com/author/ankush/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://linux.cn/article-11145-1.html
|
||||
[2]: https://linux.cn/article-8311-1.html
|
||||
[3]: https://linux.cn/article-11040-1.html
|
||||
[4]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2020/02/beautiful-linux-distros.png?ssl=1
|
||||
[5]: https://itsfoss.com/best-gtk-themes/
|
||||
[6]: https://itsfoss.com/best-icon-themes-ubuntu-16-04/
|
||||
[7]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2020/01/elementary-os-hera.png?ssl=1
|
||||
[8]: https://elementary.io/
|
||||
[9]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2020/02/deepin-screenshot.jpg?ssl=1
|
||||
[10]: https://www.deepin.org/en/
|
||||
[11]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2020/02/pop-os-stock.jpg?ssl=1
|
||||
[12]: https://www.gnome.org/
|
||||
[13]: https://itsfoss.com/pop-os-vs-ubuntu/
|
||||
[14]: https://system76.com/pop
|
||||
[15]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2020/02/manjaro_kde.jpg?ssl=1
|
||||
[16]: https://en.wikipedia.org/wiki/Arch
|
||||
[17]: https://itsfoss.com/install-arch-linux/
|
||||
[18]: https://itsfoss.com/best-linux-desktop-environments/
|
||||
[19]: https://manjaro.org/download/
|
||||
[20]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2020/02/kde-neon-screenshot.jpg?ssl=1
|
||||
[21]: https://itsfoss.com/kde-neon-unveiled/
|
||||
[22]: https://kubuntu.org/
|
||||
[23]: https://kde.org/
|
||||
[24]: https://neon.kde.org/
|
||||
[25]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2019/11/zorin-lite-ultimate-appearance.jpg?ssl=1
|
||||
[26]: https://www.xfce.org/
|
||||
[27]: https://itsfoss.com/zorin-grid/
|
||||
[28]: https://zorinos.com/
|
||||
[29]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2020/02/nitrux-screenshot.jpg?ssl=1
|
||||
[30]: https://itsfoss.com/nitrux-linux-overview/
|
||||
[31]: https://itsfoss.com/use-appimage-linux/
|
||||
[32]: https://itsfoss.com/nitrux-linux/
|
||||
[33]: https://nxos.org/
|
||||
[34]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2020/02/extern-os.png?ssl=1
|
||||
[35]: https://externos.io/
|
||||
[36]: https://linux.cn/article-9553-1.html
|
||||
[37]: https://linux.cn/article-10490-1.html
|
||||
[38]: https://linux.cn/article-11028-1.html
|
||||
[39]: https://linux.cn/article-10534-1.html
|
||||
[40]: https://linux.cn/article-7813-1.html
|
||||
[41]: https://linux.cn/article-9324-1.html
|
||||
[42]: https://linux.cn/article-8628-1.html
|
||||
330
published/20200219 Try this Bash script for-large filesystems.md
Normal file
330
published/20200219 Try this Bash script for-large filesystems.md
Normal file
@ -0,0 +1,330 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (wxy)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-12025-1.html)
|
||||
[#]: subject: (Try this Bash script for large filesystems)
|
||||
[#]: via: (https://opensource.com/article/20/2/script-large-files)
|
||||
[#]: author: (Nick Clifton https://opensource.com/users/nickclifton)
|
||||
|
||||
针对大型文件系统可以试试此 Bash 脚本
|
||||
======
|
||||
|
||||
> 一个可以列出文件、目录、可执行文件和链接的简单脚本。
|
||||
|
||||
![bash logo on green background][1]
|
||||
|
||||
你是否曾经想列出目录中的所有文件,但仅列出文件,而不列出其它的。仅列出目录呢?如果有这种需求的话,那么下面的脚本可能正是你一直在寻找的,它在 GPLv3 下开源。
|
||||
|
||||
当然,你可以使用 `find` 命令:
|
||||
|
||||
```
|
||||
find . -maxdepth 1 -type f -print
|
||||
```
|
||||
|
||||
但这键入起来很麻烦,输出也不友好,并且缺少 `ls` 命令拥有的一些改进。你还可以结合使用 `ls` 和 `grep` 来达到相同的结果:
|
||||
|
||||
```
|
||||
ls -F . | grep -v /
|
||||
```
|
||||
|
||||
但是,这又有点笨拙。下面这个脚本提供了一种简单的替代方法。
|
||||
|
||||
### 用法
|
||||
|
||||
该脚本提供了四个主要功能,具体取决于你调用它的名称:`lsf` 列出文件,`lsd` 列出目录,`lsx` 列出可执行文件以及 `lsl` 列出链接。
|
||||
|
||||
通过符号链接无需安装该脚本的多个副本。这样可以节省空间并使脚本更新更容易。
|
||||
|
||||
该脚本通过使用 `find` 命令进行搜索,然后在找到的每个项目上运行 `ls`。这样做的好处是,任何给脚本的参数都将传递给 `ls` 命令。因此,例如,这可以列出所有文件,甚至包括以点开头的文件:
|
||||
|
||||
```
|
||||
lsf -a
|
||||
```
|
||||
|
||||
要以长格式列出目录,请使用 `lsd` 命令:
|
||||
|
||||
```
|
||||
lsd -l
|
||||
```
|
||||
|
||||
你可以提供多个参数,以及文件和目录路径。
|
||||
|
||||
下面提供了当前目录的父目录和 `/usr/bin` 目录中所有文件的长分类列表:
|
||||
|
||||
```
|
||||
lsf -F -l .. /usr/bin
|
||||
```
|
||||
|
||||
目前该脚本不处理递归,仅列出当前目录中的文件。
|
||||
|
||||
```
|
||||
lsf -R
|
||||
```
|
||||
|
||||
该脚本不会深入子目录,这个不足有一天可能会进行修复。
|
||||
|
||||
### 内部
|
||||
|
||||
该脚本采用自上而下的方式编写,其初始化功能位于脚本的开头,而工作主体则接近结尾。脚本中只有两个真正重要的功能。函数 `parse_args()` 会仔细分析命令行,将选项与路径名分开,并处理脚本中的 `ls` 命令行选项中的特定选项。
|
||||
|
||||
`list_things_in_dir()` 函数以目录名作为参数并在其上运行 `find` 命令。找到的每个项目都传递给 `ls` 命令进行显示。
|
||||
|
||||
### 总结
|
||||
|
||||
这是一个可以完成简单功能的简单脚本。它节省了时间,并且在使用大型文件系统时可能会非常有用。
|
||||
|
||||
### 脚本
|
||||
|
||||
```
|
||||
#!/bin/bash
|
||||
|
||||
# Script to list:
|
||||
# directories (if called "lsd")
|
||||
# files (if called "lsf")
|
||||
# links (if called "lsl")
|
||||
# or executables (if called "lsx")
|
||||
# but not any other type of filesystem object.
|
||||
# FIXME: add lsp (list pipes)
|
||||
#
|
||||
# Usage:
|
||||
# <command_name> [switches valid for ls command] [dirname...]
|
||||
#
|
||||
# Works with names that includes spaces and that start with a hyphen.
|
||||
#
|
||||
# Created by Nick Clifton.
|
||||
# Version 1.4
|
||||
# Copyright (c) 2006, 2007 Red Hat.
|
||||
#
|
||||
# This is free software; you can redistribute it and/or modify it
|
||||
# under the terms of the GNU General Public License as published
|
||||
# by the Free Software Foundation; either version 3, or (at your
|
||||
# option) any later version.
|
||||
|
||||
# It is distributed in the hope that it will be useful, but
|
||||
# WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||
# GNU General Public License for more details.
|
||||
|
||||
# ToDo:
|
||||
# Handle recursion, eg: lsl -R
|
||||
# Handle switches that take arguments, eg --block-size
|
||||
# Handle --almost-all, --ignore-backups, --format and --ignore
|
||||
|
||||
main ()
|
||||
{
|
||||
init
|
||||
|
||||
parse_args ${1+"$@"}
|
||||
|
||||
list_objects
|
||||
|
||||
exit 0
|
||||
}
|
||||
|
||||
report ()
|
||||
{
|
||||
echo $prog": " ${1+"$@"}
|
||||
}
|
||||
|
||||
fail ()
|
||||
{
|
||||
report " Internal error: " ${1+"$@"}
|
||||
exit 1
|
||||
}
|
||||
|
||||
# Initialise global variables.
|
||||
init ()
|
||||
{
|
||||
# Default to listing things in the current directory.
|
||||
dirs[0]=".";
|
||||
|
||||
# num_dirs is the number of directories to be listed minus one.
|
||||
# This is because we are indexing the dirs[] array from zero.
|
||||
num_dirs=0;
|
||||
|
||||
# Default to ignoring things that start with a period.
|
||||
no_dots=1
|
||||
|
||||
# Note - the global variables 'type' and 'opts' are initialised in
|
||||
# parse_args function.
|
||||
}
|
||||
|
||||
# Parse our command line
|
||||
parse_args ()
|
||||
{
|
||||
local no_more_args
|
||||
|
||||
no_more_args=0 ;
|
||||
|
||||
prog=`basename $0` ;
|
||||
|
||||
# Decide if we are listing files or directories.
|
||||
case $prog in
|
||||
lsf | lsf.sh)
|
||||
type=f
|
||||
opts="";
|
||||
;;
|
||||
lsd | lsd.sh)
|
||||
type=d
|
||||
# The -d switch to "ls" is presumed when listing directories.
|
||||
opts="-d";
|
||||
;;
|
||||
lsl | lsl.sh)
|
||||
type=l
|
||||
# Use -d to prevent the listed links from being followed.
|
||||
opts="-d";
|
||||
;;
|
||||
lsx | lsx.sh)
|
||||
type=f
|
||||
find_extras="-perm /111"
|
||||
;;
|
||||
*)
|
||||
fail "Unrecognised program name: '$prog', expected either 'lsd', 'lsf', 'lsl' or 'lsx'"
|
||||
;;
|
||||
esac
|
||||
|
||||
# Locate any additional command line switches for ls and accumulate them.
|
||||
# Likewise accumulate non-switches to the directories list.
|
||||
while [ $# -gt 0 ]
|
||||
do
|
||||
case "$1" in
|
||||
# FIXME: Handle switches that take arguments, eg --block-size
|
||||
# FIXME: Properly handle --almost-all, --ignore-backups, --format
|
||||
# FIXME: and --ignore
|
||||
# FIXME: Properly handle --recursive
|
||||
-a | -A | --all | --almost-all)
|
||||
no_dots=0;
|
||||
;;
|
||||
--version)
|
||||
report "version 1.2"
|
||||
exit 0
|
||||
;;
|
||||
--help)
|
||||
case $type in
|
||||
d) report "a version of 'ls' that lists only directories" ;;
|
||||
l) report "a version of 'ls' that lists only links" ;;
|
||||
f) if [ "x$find_extras" = "x" ] ; then
|
||||
report "a version of 'ls' that lists only files" ;
|
||||
else
|
||||
report "a version of 'ls' that lists only executables";
|
||||
fi ;;
|
||||
esac
|
||||
exit 0
|
||||
;;
|
||||
--)
|
||||
# A switch to say that all further items on the command line are
|
||||
# arguments and not switches.
|
||||
no_more_args=1 ;
|
||||
;;
|
||||
-*)
|
||||
if [ "x$no_more_args" = "x1" ] ;
|
||||
then
|
||||
dirs[$num_dirs]="$1";
|
||||
let "num_dirs++"
|
||||
else
|
||||
# Check for a switch that just uses a single dash, not a double
|
||||
# dash. This could actually be multiple switches combined into
|
||||
# one word, eg "lsd -alF". In this case, scan for the -a switch.
|
||||
# XXX: FIXME: The use of =~ requires bash v3.0+.
|
||||
if [[ "x${1:1:1}" != "x-" && "x$1" =~ "x-.*a.*" ]] ;
|
||||
then
|
||||
no_dots=0;
|
||||
fi
|
||||
opts="$opts $1";
|
||||
fi
|
||||
;;
|
||||
*)
|
||||
dirs[$num_dirs]="$1";
|
||||
let "num_dirs++"
|
||||
;;
|
||||
esac
|
||||
shift
|
||||
done
|
||||
|
||||
# Remember that we are counting from zero not one.
|
||||
if [ $num_dirs -gt 0 ] ;
|
||||
then
|
||||
let "num_dirs--"
|
||||
fi
|
||||
}
|
||||
|
||||
list_things_in_dir ()
|
||||
{
|
||||
local dir
|
||||
|
||||
# Paranoia checks - the user should never encounter these.
|
||||
if test "x$1" = "x" ;
|
||||
then
|
||||
fail "list_things_in_dir called without an argument"
|
||||
fi
|
||||
|
||||
if test "x$2" != "x" ;
|
||||
then
|
||||
fail "list_things_in_dir called with too many arguments"
|
||||
fi
|
||||
|
||||
# Use quotes when accessing $dir in order to preserve
|
||||
# any spaces that might be in the directory name.
|
||||
dir="${dirs[$1]}";
|
||||
|
||||
# Catch directory names that start with a dash - they
|
||||
# confuse pushd.
|
||||
if test "x${dir:0:1}" = "x-" ;
|
||||
then
|
||||
dir="./$dir"
|
||||
fi
|
||||
|
||||
if [ -d "$dir" ]
|
||||
then
|
||||
if [ $num_dirs -gt 0 ]
|
||||
then
|
||||
echo " $dir:"
|
||||
fi
|
||||
|
||||
# Use pushd rather passing the directory name to find so that the
|
||||
# names that find passes on to xargs do not have any paths prepended.
|
||||
pushd "$dir" > /dev/null
|
||||
if [ $no_dots -ne 0 ] ; then
|
||||
find . -maxdepth 1 -type $type $find_extras -not -name ".*" -printf "%f\000" \
|
||||
| xargs --null --no-run-if-empty ls $opts -- ;
|
||||
else
|
||||
find . -maxdepth 1 -type $type $find_extras -printf "%f\000" \
|
||||
| xargs --null --no-run-if-empty ls $opts -- ;
|
||||
fi
|
||||
popd > /dev/null
|
||||
else
|
||||
report "directory '$dir' could not be found"
|
||||
fi
|
||||
}
|
||||
|
||||
list_objects ()
|
||||
{
|
||||
local i
|
||||
|
||||
i=0;
|
||||
while [ $i -le $num_dirs ]
|
||||
do
|
||||
list_things_in_dir i
|
||||
let "i++"
|
||||
done
|
||||
}
|
||||
|
||||
# Invoke main
|
||||
main ${1+"$@"}
|
||||
```
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/20/2/script-large-files
|
||||
|
||||
作者:[Nick Clifton][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[wxy](https://github.com/wxy)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/nickclifton
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/bash_command_line.png?itok=k4z94W2U (bash logo on green background)
|
||||
@ -0,0 +1,106 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (wxy)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-12033-1.html)
|
||||
[#]: subject: (Waterfox: Firefox Fork With Legacy Add-ons Options)
|
||||
[#]: via: (https://itsfoss.com/waterfox-browser/)
|
||||
[#]: author: (Ankush Das https://itsfoss.com/author/ankush/)
|
||||
|
||||
水狐:一个支持旧版扩展的火狐复刻版
|
||||
======
|
||||
|
||||
> 在本周的开源软件推荐中,我们将介绍一个基于 Firefox 的浏览器,该浏览器支持 Firefox 如今已不再支持的旧版扩展,同时尽可能地提供了快速的用户体验。
|
||||
|
||||
在 Web 浏览器方面,虽然谷歌浏览器已经占据了最大的市场份额,但 [Mozilla Firefox 仍然是关切隐私的主流 Web 浏览器的一面大旗][1]。
|
||||
|
||||
Firefox 最近有了很多改进,这些改进的副作用之一是它删除了旧版<ruby>扩展附件<rt>add-on</rt></ruby>的支持。如果你最喜欢的扩展附件在最近几个月/几年内消失了,那么你可以以 Witerfox 的形式再次拥有它们。
|
||||
|
||||
> 注意!
|
||||
>
|
||||
> 我们注意到,Waterfox 已被 System1 收购。该公司还收购了注重隐私的搜索引擎 Startpage。尽管 System1 声称他们提供注重隐私的产品,因为“这是刚需”,但我们不能对此担保。换句话说,这要取决于你是否信任 System1 和 Waterfox。
|
||||
|
||||
### Waterfox:一个基于 Firefox 的浏览器
|
||||
|
||||
![Waterfox Classic][2]
|
||||
|
||||
[Waterfox][3] 是基于 Firefox 构建的一个好用的开源浏览器,它注重隐私并支持旧版扩展。它没有将自己定位为偏执于隐私的浏览器,但确实尊重这个基本的认知。
|
||||
|
||||
你可以得到两个单独的 Waterfox 浏览器版本。当前版旨在提供现代体验,而经典版则旨在支持 [NPAPI 插件][4] 和 [bootstrap 扩展][5]。
|
||||
|
||||
![Waterfox Classic][6]
|
||||
|
||||
如果你不需要使用 bootstrap 扩展程序,而是需要 [WebExtensions][7],则应该选择 Waterfox 当前版。
|
||||
|
||||
而如果你需要设置一个需要大量 NPAPI 插件或 Bootstrap 扩展的浏览器,则 Waterfox 经典版将非常适合你。
|
||||
|
||||
因此,如果你喜欢 Firefox,但想在同一阵营内尝试一些不同的体验,那么这个 Firefox 替代选择就是为此而生的。
|
||||
|
||||
### Waterfox 的功能
|
||||
|
||||
![Waterfox Current][8]
|
||||
|
||||
当然,从技术上讲,你应该能够做 Mozilla Firefox 支持的许多操作。
|
||||
|
||||
因此,我将在此处的列表中突出显示 Waterfox 的所有重要功能。
|
||||
|
||||
* 支持 NPAPI 插件
|
||||
* 支持 Bootstrap 扩展
|
||||
* 分别提供了支持旧版本扩展和现代的 WebExtension 两个版本。
|
||||
* 跨平台支持(Windows、Linux 和 macOS)
|
||||
* 主题定制
|
||||
* 支持已经归档的扩展
|
||||
|
||||
### 在 Ubuntu/Linux 上安装 Waterfox
|
||||
|
||||
与其他流行的浏览器不同,它没有可以安装的软件包。因此,你将必须从其[官方下载页面][9]下载归档包。
|
||||
|
||||
![][10]
|
||||
|
||||
根据你想要的版本(当前版/经典版),只需下载该文件,它是以 .tar.bz2 为扩展名的文件。
|
||||
|
||||
下载后,只需解压缩文件即可。
|
||||
|
||||
接下来,转到解压缩的文件夹并查找 `Waterfox` 文件。你只需双击它即可运行以启动浏览器。
|
||||
|
||||
如果这不起作用,则可以使用终端并导航到提取的 `Waterfox` 文件夹。到达那里后,你只需使用一个命令即可运行它。看起来如下:
|
||||
|
||||
```
|
||||
cd waterfox-classic
|
||||
./waterfox
|
||||
```
|
||||
|
||||
无论是哪种情况,你都可以访问其 [GitHub 页面][11]以了解将其安装在系统上的更多方式。
|
||||
|
||||
- [下载 Waterfox][3]
|
||||
|
||||
### 总结
|
||||
|
||||
我在我的 Pop!_OS 19.10 系统中启动了它,在我这里工作的很好。尽管我不准备从 Firefox 切换到 Waterfox,因为我没有使用任何旧版扩展附件。但对于某些用户来说,它可能是一个重要选择。
|
||||
|
||||
你可以尝试一下,在下面的评论中让我知道你的想法。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://itsfoss.com/waterfox-browser/
|
||||
|
||||
作者:[Ankush Das][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[wxy](https://github.com/wxy)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://itsfoss.com/author/ankush/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://itsfoss.com/why-firefox/
|
||||
[2]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2020/02/waterfox-classic.png?fit=800%2C423&ssl=1
|
||||
[3]: https://www.waterfox.net/
|
||||
[4]: https://en.wikipedia.org/wiki/NPAPI
|
||||
[5]: https://wiki.mozilla.org/Extension_Manager:Bootstrapped_Extensions
|
||||
[6]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2020/02/waterfox-classic-screenshot.jpg?ssl=1
|
||||
[7]: https://wiki.mozilla.org/WebExtensions
|
||||
[8]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2020/02/waterfox-screenshot.jpg?ssl=1
|
||||
[9]: https://www.waterfox.net/download/
|
||||
[10]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2020/02/waterfox-download-page.jpg?ssl=1
|
||||
[11]: https://github.com/MrAlex94/Waterfox
|
||||
113
published/20200225 3 eBook readers for the Linux desktop.md
Normal file
113
published/20200225 3 eBook readers for the Linux desktop.md
Normal file
@ -0,0 +1,113 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (wenwensnow)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-11990-1.html)
|
||||
[#]: subject: (3 eBook readers for the Linux desktop)
|
||||
[#]: via: (https://opensource.com/article/20/2/linux-ebook-readers)
|
||||
[#]: author: (Scott Nesbitt https://opensource.com/users/scottnesbitt)
|
||||
|
||||
可在 Linux 桌面使用的 3 个电子书阅读器应用
|
||||
======
|
||||
|
||||
> 任意一个开源电子书应用都能使你在大屏设备上的阅读体验得到提升。
|
||||
|
||||
![电脑浏览器阅读书籍界面][1]
|
||||
|
||||
我通常使用手机或 Kobo 阅读器阅读电子书,总是没有在大屏设备上阅读书籍那么爽。很多人经常在自己的笔记本或桌面电脑上阅读电子书,如果你有这种需求(或者你认为以后会遇到这种情况),我想向你介绍三种 Linux 桌面下的电子书阅读器。
|
||||
|
||||
### Bookworm(书虫)
|
||||
|
||||
[Bookworm][2] 意在成为一个“简洁、专注的电子书阅读器”。事实证明它也确实做到了。Bookworm 内置一系列基础功能,有人抱怨它太过*简单*,缺少*功能性*(虽然这词显然有点指意不明)。Bookworm 起到了应有的作用而没有无关的花哨功能。
|
||||
|
||||
该应用的界面整洁干净。
|
||||
|
||||
![Bookworm 电子书应用][3]
|
||||
|
||||
你可通过以下方式查看书籍:
|
||||
|
||||
* 空格键前往下一页
|
||||
* 上下方向键按行移动
|
||||
* 左右方向键跳转至前后章节
|
||||
|
||||
你也可以通过添加注释或书签跳转至特定页面。
|
||||
|
||||
![Bookworm 注释][4]
|
||||
|
||||
Bookworm 没有太多设置选项。你能调整书籍字体大小及间距,开启双页模式或夜间模式。在应用中添加新文件夹后,Bookworm 会自动扫描文件夹中的电子书。
|
||||
|
||||
![Bookworm 参数设置][5]
|
||||
|
||||
Bookworm 支持常用的电子书格式:EPUB、PDF、MOBI、[FB2][6],你还能用它阅读 [CBR][7] 和 CBZ 格式的数字版漫画。我只在 Bookworm 上测试了前三种格式,PDF 倒是能打开,但加载速度很慢,格式也很难看。
|
||||
|
||||
### Foliate
|
||||
|
||||
单从功能上来说,[Foliate][8] 确实比 Bookworm 强上一些。Foliate 不仅功能更强,它还有更多设置选项。这个功能多样、简单干净的应用满足了所有要求。
|
||||
|
||||
![Foliate 电子书应用][9]
|
||||
|
||||
在 Foliate 中可以通过空格、方向键、向上或向下翻页键浏览电子书,这里没什么特别的。
|
||||
|
||||
你还可以在书籍中添加注释、查找以及翻译字句、查询字词含义。如果你电脑上安装了智能语音应用, Foliate 还能将文本朗读出来。
|
||||
|
||||
![在 Foliate 中的注释文本][10]
|
||||
|
||||
Foliate 与 Bookworm 相比有更多自定义选项。你能在应用中修改字体类型及大小、行间距、电子书页边距,也可以调高或降低屏幕亮度,从应用内置的四个主题中选择一个等。
|
||||
|
||||
![Foliate 设置][11]
|
||||
|
||||
你可以在 Foliate 上阅读 EPUB、MOBI、AZW、AZW3 格式的电子书。如果你不了解,我可以提前告诉你,后三种格式是亚马逊 Kindle 阅读器上架的书籍的闭源格式。
|
||||
|
||||
### Calibre 电子书阅读器
|
||||
|
||||
这个[电子书阅读器][12]是 [Calibre][13] 电子书管理工具的一个组件,就像它的前代一样,电子书阅读器这部分并不是软件整体最棒的部分。
|
||||
|
||||
![电子书阅读器应用][14]
|
||||
|
||||
不过别被上面的话吓到,它也的确是个桌面电子书阅读器。
|
||||
|
||||
在 Calibre 电子书阅读器中,你可以通过方向键、向上/向下翻页键以及空格浏览书籍,还能在在线字典中查找词语含义,添加书签。这一阅读器没有注释功能,但内置的搜索引擎却很好用,你还能将书籍保存为 PDF 格式(虽然我不太明白你为什么要这么做)。
|
||||
|
||||
不过参数设置这里确是它出彩的地方,它的可选设置比 Bookworm 和 Foliate 加起来都多,从字体到文本布局,页面分割方式你都能改。除此之外,你还能自定义应用按键设置,将你喜欢的词典网站添加进来,方便阅读查找。
|
||||
|
||||
![电子书参数设置][15]
|
||||
|
||||
Calibre 电子书阅读器一个很有用的功能,就是把自行设置的 CSS 配置文件效果应用到电子书上。赘言一句,CSS 是一种调整网页格式的方法(这类文件就是许多电子书的一个组成部分)。如果你是使用 CSS 的高手,你可以将自己的 CSS 文件复制粘贴到配置窗口的 “User stylesheet” 部分,这就是个性化的究极办法。
|
||||
|
||||
据开发者描述,这一电子书阅读器“能支持所有主流电子书格式”。如果你想知道具体支持格式是什么,[这是列表链接][16]。我测试了列表中的一小部分格式,没有发现问题。
|
||||
|
||||
### 留在最后的话
|
||||
|
||||
不管你只是单纯想找个电子书阅读器,还是有个更多复杂功能的应用,上文提到的三个选择都很不错,而且它们都能提升你在大屏设备上的阅读体验。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/20/2/linux-ebook-readers
|
||||
|
||||
作者:[Scott Nesbitt][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[wenwensnow](https://github.com/wenwensnow)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/scottnesbitt
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/computer_browser_program_books_read.jpg?itok=iNMWe8Bu (Computer browser with books on the screen)
|
||||
[2]: https://babluboy.github.io/bookworm/
|
||||
[3]: https://opensource.com/sites/default/files/uploads/bookworm-reading.png (Bookworm e-book application)
|
||||
[4]: https://opensource.com/sites/default/files/uploads/bookworm-annotations.png (Annotations in Bookworm)
|
||||
[5]: https://opensource.com/sites/default/files/uploads/bookworm-preferences.png (Bookworm preferences)
|
||||
[6]: https://en.wikipedia.org/wiki/FictionBook
|
||||
[7]: https://en.wikipedia.org/wiki/Comic_book_archive
|
||||
[8]: https://johnfactotum.github.io/foliate/
|
||||
[9]: https://opensource.com/sites/default/files/uploads/foliate-reading.png (Foliate e-book application)
|
||||
[10]: https://opensource.com/sites/default/files/uploads/foliate-annotation_0.png
|
||||
[11]: https://opensource.com/sites/default/files/uploads/foliate-settings.png (Foliate settings)
|
||||
[12]: https://calibre-ebook.com/about
|
||||
[13]: https://opensourcemusings.com/managing-your-ebooks-with-calibre
|
||||
[14]: https://opensource.com/sites/default/files/uploads/e-book_viewer-reading.png (E-book Viewer application)
|
||||
[15]: https://opensource.com/sites/default/files/uploads/ebook-viewer-preferences.png (E-book Viewer preferences)
|
||||
[16]: https://manual.calibre-ebook.com/faq.html#what-formats-does-calibre-support-conversion-to-from
|
||||
[17]: https://opensourcemusings.com/three-ebook-readers-for-the-linux-desktop
|
||||
[18]: https://creativecommons.org/licenses/by-sa/4.0/
|
||||
@ -0,0 +1,73 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (Morisun029)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-12020-1.html)
|
||||
[#]: subject: (7 tips for writing an effective technical resume)
|
||||
[#]: via: (https://opensource.com/article/20/2/technical-resume-writing)
|
||||
[#]: author: (Emily Brand https://opensource.com/users/emily-brand)
|
||||
|
||||
撰写有效的技术简历的 7 个技巧
|
||||
======
|
||||
|
||||
> 遵循以下这些要点,把自己最好的一面呈现给潜在雇主。
|
||||
|
||||

|
||||
|
||||
如果你是一名软件工程师或技术领域的经理,那么创建或更新简历可能是一项艰巨的任务。要考虑的重点是什么?应该怎么把控格式、内容以及求职目标或摘要?哪些工作经验相关?如何确保自动化招聘工具不会过滤掉你的简历?
|
||||
|
||||
在过去的七年中,作为一名招聘经理,我看到了各种各样的简历;尽管有些令人印象深刻,但还有很多人写的很糟糕。
|
||||
|
||||
在编写或更新简历时,请遵循以下七个简单原则。
|
||||
|
||||
### 1、概述
|
||||
|
||||
简历顶部的简短段落应简洁明了、目的明确,避免过度使用形容词和副词。诸如“令人印象深刻”、“广泛”和“卓越”之类的词,这些词不会增加你的招聘机会;相反,它们看起来和感觉上像是过度使用的填充词。 关于你的求职目标,问自己一个重要的问题:**它是否告诉招聘经理我正在寻找什么样的工作以及如何为他们提供价值?** 如果不是,请加强并简化它以回答该问题,或者将其完全排除在外。
|
||||
|
||||
### 2、工作经验
|
||||
|
||||
数字、数字、数字——重要的事情说三遍。用确凿的事实传达观点远比一般的陈述,例如“帮助构建、管理、交付许多对客户利润有贡献的项目”更能对你有帮助。你的表达中应包括统计数据,例如“直接影响了 5 个顶级银行的项目,这些项目将其上市时间缩短了 40%”,你提交了多少行代码或管理了几个团队。数据比修饰语更能有效地展示你的能力和价值。
|
||||
|
||||
如果你经验不足,没有什么工作经验可展示,那些无关的经验,如暑期兼职工作,就不要写了。相反,将相关经验的细节以及你所学到的知识的详细信息写进简历,这些可以使你成为一个更好的候选人。
|
||||
|
||||
### 3、搜索术语和行话
|
||||
|
||||
随着技术在招聘过程中发挥如此巨大的作用,确保简历被标记为正确的职位非常重要,但不要在简历上过分吹嘘自己。如果你提到敏捷技能但不知道看板是什么,请三思。如果你提到自己精通 Java,但是已经有五年都没有使用过 Java 了,请小心。如果存在你熟悉但不一定是当前在用的语言和框架,请创建其他类别或将你的经验分为“精通”和“熟悉”。
|
||||
|
||||
### 4、教育
|
||||
|
||||
如果你不是应届大学毕业生,那就没必要再写你的 GPA 或你参加过的俱乐部或兄弟会,除非你计划将它们用作谈话要点以在面试中赢得信任。确保将你发表的或获取过专利的东西包括在内,即使它与该工作无关。如果你没有大学学位,请添加一个证书部分代替教育背景部分。如果你是军人,请包括现役和预备役时间。
|
||||
|
||||
### 5、资质证书
|
||||
|
||||
除非你想重新进入之前离开的领域,否则不要写过期的证书,例如,如果你曾经是一名人事经理,而现在正寻求动手编程的工作。如果你拥有与该领域不再相关的认证,就不要写这些认证,因为这些可能会分散招聘者的注意力,使你的简历失去吸引力。利用你的 LinkedIn 个人资料为简历添加更多色彩,因为大多数人在面试之前都会阅读你的简历和 LinkedIn 个人资料。
|
||||
|
||||
### 6、拼写和语法
|
||||
|
||||
让其他人帮忙对你的简历校对一下。很多时候,我在简历中看到过拼写错误的单词,或者错误用词,如“他们的”、“他们是”、“那些”。这些可以避免和修复的错误会产生负面影响。理想情况下,你的简历应用主动语态,但是如果这样会使你感到不舒服,那么就用过去时书写 —— 最重要的是要始终保持一致。不正确的拼写和语法会传递你要么不是很在乎所申请的工作,要么没有足够注意细节。
|
||||
|
||||
### 7、格式
|
||||
|
||||
确保你的简历是最新的并且富有吸引力,这是留下良好第一印象的简便方法。确保格式一致,例如相同的页边距,相同的间距、大写字母和颜色(将调色板保持在最低限度,不要花花绿绿)是简历写作中最基本的部分,但有必要表明你对工作感到自豪,并重视自己的价值和未来的雇主。在适当的地方使用表格,以视觉吸引人的方式分配信息。如果支持的话,以 .pdf 和 .docx 格式上传简历,然后用 Google Docs 导出为 .odt 格式,这样可以在 LibreOffice 中轻松打开。这里有一个我推荐的简单的 Google 文档[简历模板][2]。 你还可以支付少量费用(不到 10 美元)从一些设计公司购买模板。
|
||||
|
||||
### 定期更新
|
||||
|
||||
如果你需要(或希望)申请一份工作,定期更新简历可以最大程度地减少压力,也可以帮助你创建和维护更准确的简历版本。撰写简历时,要有远见,确保至少让另外三个人对你的简历内容、拼写和语法进行检查。即使你是由公司招募或其他人推荐给公司的,面试官也可能只能通过简历来认识你,因此请确保它为你带来良好的第一印象。
|
||||
|
||||
你还有其他提示要添加吗?
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/20/2/technical-resume-writing
|
||||
|
||||
作者:[Emily Brand][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[Morisun029](https://github.com/Morisun029)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/emily-brand
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/resume_career_document_general.png?itok=JEaFL2XI (Two hands holding a resume with computer, clock, and desk chair )
|
||||
[2]: https://docs.google.com/document/d/1ARVyybC5qQEiCzUOLElwAdPpKOK0Qf88srr682eHdCQ/edit
|
||||
@ -0,0 +1,157 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-11983-1.html)
|
||||
[#]: subject: (Converting between uppercase and lowercase on the Linux command line)
|
||||
[#]: via: (https://www.networkworld.com/article/3529409/converting-between-uppercase-and-lowercase-on-the-linux-command-line.html)
|
||||
[#]: author: (Sandra Henry-Stocker https://www.networkworld.com/author/Sandra-Henry_Stocker/)
|
||||
|
||||
在 Linux 命令行中转换大小写
|
||||
======
|
||||
|
||||
> 转换文本的大小写可能非常繁琐,尤其是当你要避免无意间的拼写错误时。幸运的是,Linux 提供了一些命令,可以使工作变得非常容易。
|
||||
|
||||

|
||||
|
||||
有很多方法可以在 Linux 命令行中将文本从小写更改为大写,反之亦然。实际上,有一组这样的命令可以选择。这篇文章检验了一些最佳的命令来完成这项工作,以及你该如何让它们正常工作。
|
||||
|
||||
### 使用 tr
|
||||
|
||||
`tr`(translate)命令是在命令行或脚本中最容易使用的命令之一。如果你要确定要一串大写字符串,你只需将它传给 `tr`,如下所示:
|
||||
|
||||
```
|
||||
$ echo Hello There | tr [:lower:] [:upper:]
|
||||
HELLO THERE
|
||||
```
|
||||
|
||||
下面是一个在脚本中使用这个命令的例子,当你要确保添加到文件中的所有文本都使用大写形式以保持一致性时(LCTT 译注:这里输入部门名称作为示例):
|
||||
|
||||
```
|
||||
#!/bin/bash
|
||||
|
||||
echo -n "Enter department name: "
|
||||
read dept
|
||||
echo $dept | tr [:lower:] [:upper:] >> depts
|
||||
```
|
||||
|
||||
将顺序切换为 `[:upper:] [:lower:]` 会产生相反的效果,将所有大写的部门名称都转换为小写:
|
||||
|
||||
```
|
||||
echo $dept | tr [:upper:] [:lower:] >> depts
|
||||
```
|
||||
|
||||
同样,你可以使用 `sed` 命令的 `A-Z` 和 `a-z` 字符串完成相同的操作:
|
||||
|
||||
```
|
||||
echo $dept | tr a-z A-Z >> depts
|
||||
```
|
||||
|
||||
毫无疑问,反转 `a-z` 和 `A-Z` 字符串的顺序将产生相反的效果,将文本全部变为小写。
|
||||
|
||||
### 使用 awk
|
||||
|
||||
`awk` 命令可让你使用它的 `toupper` 和 `tolower` 选项执行相同的操作。上例脚本中的命令可以用这种方式代替:
|
||||
|
||||
```
|
||||
echo $dept | awk '{print toupper($0)}' >> depts
|
||||
```
|
||||
|
||||
相反操作(切换为小写)如下所示:
|
||||
|
||||
```
|
||||
echo $dept | awk '{print tolower($0)}' >> depts
|
||||
```
|
||||
|
||||
### 使用 sed
|
||||
|
||||
`sed`(stream editor)命令也可用于切换大小写。它与上面显示的两个命令中的第一个具有相同的效果。
|
||||
|
||||
```
|
||||
echo $dept | sed 's/[a-z]/\U&/g' >> depts
|
||||
```
|
||||
|
||||
从大写字母切换到小写字母只需将行尾附近的 `U` 替换为 `L`。
|
||||
|
||||
```
|
||||
echo $dept | sed 's/[A-Z]/\L&/g' >> depts
|
||||
```
|
||||
|
||||
### 操作文件中的文本
|
||||
|
||||
`awk` 和 `sed` 都能更改整个文件的文本大小写。因此,你发现你的老板需要所有部门名称的小写么?没问题。只需带上文件名运行以下命令:
|
||||
|
||||
```
|
||||
$ awk '{print tolower($0)}' depts
|
||||
finance
|
||||
billing
|
||||
bookkeeping
|
||||
```
|
||||
|
||||
如果要覆盖 `depts` 文件,而不仅仅是以小写形式显示,则需要执行以下操作:
|
||||
|
||||
```
|
||||
$ awk '{print tolower($0)}' depts > depts-
|
||||
$ mv depts- depts
|
||||
```
|
||||
|
||||
但是,使用 `sed` 进行更改,你可以避免最后一步,因为 `sed` 可以“原地”编辑文件,如下所示,文件完整,但文本全部小写:
|
||||
|
||||
```
|
||||
$ sed 's/[A-Z]/\L&/g' depts
|
||||
```
|
||||
|
||||
### 仅将首字母转换为大写
|
||||
|
||||
要仅将字符串中单词的首字母转换为大写,那么可以执行以下操作:
|
||||
|
||||
```
|
||||
$ echo design \& engineering| sed -e "s/\b\(.\)/\u\1/g"
|
||||
Design & Engineering
|
||||
```
|
||||
|
||||
该命令将确保首字母大写,但不会更改其余字母。
|
||||
|
||||
### 确保只有首字母大写
|
||||
|
||||
当要更改文本以使只有首字母大写时,这更具挑战性。假设你正在处理一个工作人员姓名列表,并且希望以正常的“名 姓”方式对其格式化。
|
||||
|
||||
#### 使用 sed
|
||||
|
||||
你可以使用更复杂的 `sed` 命令来确保以下结果:
|
||||
|
||||
```
|
||||
$ echo design \& ENGINEERING | sed 's/\b\([[:alpha:]]\)\([[:alpha:]]*\)\b/\u\1\L\2/g'
|
||||
Design & Engineering
|
||||
```
|
||||
|
||||
#### 使用 Python
|
||||
|
||||
如果你已安装 Python,你可以运行这样的命令,它还可以设置文本格式,以便每个单词只有首字母大写,并且它可能比上面显示的 `sed` 命令更易于解析:
|
||||
|
||||
```
|
||||
$ echo -n "design & engineering" | python3 -c "import sys; print(sys.stdin.read().title())"
|
||||
Design & Engineering
|
||||
```
|
||||
|
||||
有多种方法可以在大小写之间更改文本格式。哪种方法效果最好取决于你要处理的是单个字符串还是整个文件,以及想要的最终结果。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.networkworld.com/article/3529409/converting-between-uppercase-and-lowercase-on-the-linux-command-line.html
|
||||
|
||||
作者:[Sandra Henry-Stocker][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.networkworld.com/author/Sandra-Henry_Stocker/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]:https://images.idgesg.net/images/article/2019/04/alphabetic_letters_characters_language_by_andybrandon50_cc_by-sa_2-0_1500x1000-100794409-large.jpg
|
||||
[2]: https://creativecommons.org/licenses/by-sa/2.0/legalcode
|
||||
[3]: https://www.networkworld.com/newsletters/signup.html
|
||||
[4]: https://www.networkworld.com/article/3440100/take-the-intelligent-route-with-consumption-based-storage.html?utm_source=IDG&utm_medium=promotions&utm_campaign=HPE21620&utm_content=sidebar ( Take the Intelligent Route with Consumption-Based Storage)
|
||||
[5]: https://www.facebook.com/NetworkWorld/
|
||||
[6]: https://www.linkedin.com/company/network-world
|
||||
@ -1,16 +1,16 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-11975-1.html)
|
||||
[#]: subject: (How to Add New Brushes in GIMP [Quick Tip])
|
||||
[#]: via: (https://itsfoss.com/add-brushes-gimp/)
|
||||
[#]: author: (Community https://itsfoss.com/author/itsfoss/)
|
||||
|
||||
如何在 GIMP 中添加新画笔(快速技巧)
|
||||
快速技巧:如何在 GIMP 中添加新画笔
|
||||
======
|
||||
|
||||
[GIMP][1] 是最流行的免费和开源图像编辑器,它也许是 Linux 上最好的 [Adobe Photoshop 替代品][2]。
|
||||
[GIMP][1] 是最流行的自由开源的图像编辑器,它也许是 Linux 上最好的 [Adobe Photoshop 替代品][2]。
|
||||
|
||||
当你[在 Ubuntu 或其他任何操作系统上安装了 GIMP 后][3],你会发现已经安装了一些用于基本图像编辑的画笔。如果你需要更具体的画笔,你可以随时在 GIMP 中添加新画笔。
|
||||
|
||||
@ -22,60 +22,59 @@
|
||||
|
||||
在 GIMP 中安装新画笔需要三个步骤:
|
||||
|
||||
* 获取新画笔
|
||||
* 将其放入指定的文件夹中
|
||||
* 刷新 GIMP 中的画笔
|
||||
|
||||
|
||||
* 获取新画笔
|
||||
* 将其放入指定的文件夹中
|
||||
* 刷新 GIMP 中的画笔
|
||||
|
||||
#### 步骤 1:下载新的 GIMP 画笔
|
||||
|
||||
第一步是获取新的 GIMP 画笔。你从哪里获取?当然是从互联网上。
|
||||
|
||||
你可以在 Google 或[隐私搜索引擎,如 Duck Duck Go][5] 种搜索 “GIMP画笔”,并从网站下载一个你喜欢的。
|
||||
你可以在 Google 或[如 Duck Duck Go 这种隐私搜索引擎][5]来搜索 “GIMP brushes”,并从网站下载一个你喜欢的。
|
||||
|
||||
GIMP 画笔通常以 .gbr 和 .gih 文件格式提供。.gbr 文件用于常规画笔,而 .gih 用于动画画笔。
|
||||
|
||||
你知道吗?
|
||||
|
||||
从 2.4 版本起,GIMP 使安装和使用 Photoshop 画笔(.abr 文件)非常简单。你只需将 Photoshop 画笔文件放在正确的文件夹中。
|
||||
请记住,最新的 Photoshop 画笔可能无法完美地在 GIMP 中使用。
|
||||
> 你知道吗?
|
||||
>
|
||||
> 从 2.4 版本起,GIMP 使安装和使用 Photoshop 画笔(.abr 文件)非常简单。你只需将 Photoshop 画笔文件放在正确的文件夹中。
|
||||
>
|
||||
> 请记住,最新的 Photoshop 画笔可能无法完美地在 GIMP 中使用。
|
||||
|
||||
#### 步骤 2:将新画笔复制到它的位置
|
||||
|
||||
获取画笔文件后,下一步是复制该文件并将其粘贴到 GIMP 配置目录中所在的文件夹。
|
||||
|
||||
在 **Windows** 上,你必须进入类似 “**C:\Documents and Settings\myusername.gimp-2.10\brushes**” 这样的文件夹。
|
||||
> 在微软 Windows 上,你必须进入类似 `C:\Documents and Settings\myusername.gimp-2.10\brushes` 这样的文件夹。
|
||||
|
||||
我将展示 **Linux** 上的详细步骤,因为 It’s FOSS 是一个专注于 Linux 的网站。
|
||||
我将展示 Linux 上的详细步骤,因为我们是一个专注于 Linux 的网站。
|
||||
|
||||
选择画笔文件后,在 **Home** 目录中按下 **Ctrl+h** [查看 Linux 中的隐藏文件][6]。
|
||||
选择画笔文件后,在家目录中按下 `Ctrl+h` [查看 Linux 中的隐藏文件][6]。
|
||||
|
||||
![Press Ctrl+H to see hidden files in the home directory][7]
|
||||
|
||||
你应该进入 **.config/GIMP/2.10/brushes** 文件夹(如果你使用的是 GIMP 2.10)。如果使用其他版本,那么应在 .config/GIMP 下看到相应文件夹。
|
||||
你应该进入 `.config/GIMP/2.10/brushes` 文件夹(如果你使用的是 GIMP 2.10)。如果使用其他版本,那么应在 `.config/GIMP` 下看到相应文件夹。
|
||||
|
||||
![Adding New Brushes in GIMP][8]
|
||||
|
||||
将画笔文件粘贴到此文件夹中。可选地,你可以通过再次按 **Ctrl+h** 来隐藏隐藏的文件。
|
||||
将画笔文件粘贴到此文件夹中。可选地,你可以通过再次按 `Ctrl+h` 来隐藏隐藏的文件。
|
||||
|
||||
#### 步骤 3:刷新画笔(避免重启 GIMP)
|
||||
|
||||
GIMP 将在启动时自动加载画笔。如果已在运行,并且不想关闭它,你可以刷新画笔。
|
||||
|
||||
在 GIMP 的主菜单中找到 **Windows**->**Dockable Dialogues**->**Brushes**。
|
||||
在 GIMP 的主菜单中找到 “Windows->Dockable Dialogues->Brushes”。
|
||||
|
||||
![Refresh GIMP Brushes by going go to Windows->Dockable Dialogues-> Brushes][9]
|
||||
|
||||
在右侧栏的 **Brushes** 对话框中找到**刷新**图标。
|
||||
在右侧栏的 Brushes 对话框中找到“refresh”图标。
|
||||
|
||||
![Refresh GIMP Brushes][10]
|
||||
|
||||
如果你的画笔没有出现,那么你可以试试重启 GIMP。
|
||||
|
||||
额外的技巧!
|
||||
|
||||
在 [GIMP 中添加新画笔还能让你轻松给图片添加水印][11]。只需将 logo 用作画笔,并点击一下就可添加到图片中。
|
||||
> 额外的技巧!
|
||||
>
|
||||
> 在 [GIMP 中添加新画笔还能让你轻松给图片添加水印][11]。只需将 logo 用作画笔,并点击一下就可添加到图片中。
|
||||
|
||||
我希望你喜欢这个快速 GIMP 技巧。敬请期待更多。
|
||||
|
||||
@ -86,7 +85,7 @@ via: https://itsfoss.com/add-brushes-gimp/
|
||||
作者:[Community][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,8 +1,8 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (wxy)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-11977-1.html)
|
||||
[#]: subject: (Getting started with the Rust package manager, Cargo)
|
||||
[#]: via: (https://opensource.com/article/20/3/rust-cargo)
|
||||
[#]: author: (Gaurav Kamathe https://opensource.com/users/gkamathe)
|
||||
@ -12,7 +12,7 @@ Rust 包管理器 Cargo 入门
|
||||
|
||||
> 了解 Rust 的软件包管理器和构建工具。
|
||||
|
||||
![Shipping containers stacked in a yard][1]
|
||||

|
||||
|
||||
[Rust][2] 是一种现代编程语言,可提供高性能、可靠性和生产力。几年来,它一直被 StackOverflow 调查评为[最受欢迎的语言][3]。
|
||||
|
||||
@ -20,21 +20,21 @@ Rust 包管理器 Cargo 入门
|
||||
|
||||
### 安装 Rust 和 Cargo
|
||||
|
||||
在开始之前,你需要安装 Rust 和 Cargo。Rust 项目提供了一个可下载的脚本来处理安装。要获取该脚本,请打开浏览器以访问 [https://sh.rustup.rs][4] 并保存该文件。阅读脚本以确保你对它的具体行为有所了解,然后运行它:
|
||||
在开始之前,你需要安装 Rust 和 Cargo。Rust 项目提供了一个可下载的脚本来处理安装。要获取该脚本,请打开浏览器以访问 [https://sh.rustup.rs][4] 并保存该文件。阅读该脚本以确保你对它的具体行为有所了解,然后再运行它:
|
||||
|
||||
```
|
||||
$ sh ./rustup.rs
|
||||
```
|
||||
|
||||
你也可以参考这个[安装 Rust][5]网页以获取更多信息。
|
||||
你也可以参考这个[安装 Rust][5] 的网页以获取更多信息。
|
||||
|
||||
安装 Rust 和 Cargo 之后,你必须<ruby>获取<rt>source</rt></ruby> `env` 文件:
|
||||
安装 Rust 和 Cargo 之后,你必须<ruby>获取<rt>source</rt></ruby> `env` 文件中的配置:
|
||||
|
||||
```
|
||||
$ source $HOME/.cargo/env
|
||||
```
|
||||
|
||||
更好的是,将所需目录添加到 `PATH` 环境变量中:
|
||||
更好的办法是,将所需目录添加到 `PATH` 环境变量中:
|
||||
|
||||
```
|
||||
export PATH=$PATH:~/.cargo/bin
|
||||
@ -91,11 +91,11 @@ $ ./hello
|
||||
Hello, world!
|
||||
```
|
||||
|
||||
这些步骤对于较小的程序或任何你想快速测试的东西就足够了。但是,在进行涉及多人的大型计划时,Cargo 是前进的最佳之路。
|
||||
这些步骤对于较小的程序或任何你想快速测试的东西就足够了。但是,在进行涉及到多人的大型程序时,Cargo 是前进的最佳之路。
|
||||
|
||||
### 使用 Cargo 创建新包
|
||||
|
||||
Cargo 是 Rust 的构建系统和包管理器。它可以帮助开发人员下载和管理依赖项,并帮助创建 Rust 包。在Rust 社区中,Rust 中的“包”通常被称为“crate”(板条箱),但是在本文中,这两个词是可以互换的。请参阅 Rust 社区提供的 Cargo [FAQ][6] 来区分。
|
||||
Cargo 是 Rust 的构建系统和包管理器。它可以帮助开发人员下载和管理依赖项,并帮助创建 Rust 包。在 Rust 社区中,Rust 中的“包”通常被称为“crate”(板条箱),但是在本文中,这两个词是可以互换的。请参阅 Rust 社区提供的 Cargo [FAQ][6] 来区分。
|
||||
|
||||
如果你需要有关 Cargo 命令行实用程序的任何帮助,请使用 `--help` 或 `-h` 命令行参数:
|
||||
|
||||
@ -134,7 +134,7 @@ fn main() {
|
||||
|
||||
下一个要处理的文件是 `Cargo.toml`,这是你的包的配置文件。它包含有关包的信息,例如其名称、版本、作者信息和 Rust 版本信息。
|
||||
|
||||
程序通常依赖于外部库或依赖项来运行,这使你可以编写应用程序来执行不知道如何编码或不想花时间编码的任务。你所有的依赖项都将在此文件中列出。此时,对你的新程序你没有任何依赖关系。打开 `Cargo.toml` 文件并查看其内容:
|
||||
程序通常依赖于外部库或依赖项来运行,这使你可以编写应用程序来执行不知道如何编码或不想花时间编码的任务。你所有的依赖项都将在此文件中列出。此时,你的新程序还没有任何依赖关系。打开 `Cargo.toml` 文件并查看其内容:
|
||||
|
||||
```
|
||||
$ cat hello_opensource/Cargo.toml
|
||||
@ -250,7 +250,7 @@ fn main() {
|
||||
}
|
||||
```
|
||||
|
||||
现在,构建程序并再次运行它。这次,你会在屏幕上看到 `Hello, Opensource world!`:
|
||||
现在,构建该程序并再次运行它。这次,你会在屏幕上看到 `Hello, Opensource world!`:
|
||||
|
||||
```
|
||||
$ cargo build
|
||||
@ -293,9 +293,9 @@ $ cargo build
|
||||
Finished dev [unoptimized + debuginfo] target(s) in 4.48s
|
||||
```
|
||||
|
||||
现在,Cargo 会联系 [Crates.io][9],这是 Rust 用于存储 crate(或包)的中央仓库,并下载和编译 `rand`。但是,等等 —— `libc` 包是怎么回事?你没有要要安装 libc 啊。是的,`rand` 包依赖于 `libc` 包;因此,Cargo 也会下载并编译 `libc`。
|
||||
现在,Cargo 会联系 [Crates.io][9](这是 Rust 用于存储 crate(或包)的中央仓库),并下载和编译 `rand`。但是,等等 —— `libc` 包是怎么回事?你没有要安装 libc 啊。是的,`rand` 包依赖于 `libc` 包;因此,Cargo 也会下载并编译 `libc`。
|
||||
|
||||
库的新版本不断涌现,而 Cargo 提供了一种使用 `update` 命令更新其所有依赖关系的简便方法:
|
||||
库的新版本会不断涌现,而 Cargo 提供了一种使用 `update` 命令更新其所有依赖关系的简便方法:
|
||||
|
||||
```
|
||||
cargo update
|
||||
@ -449,7 +449,7 @@ $ cargo build --release
|
||||
|
||||
### 使用 Cargo 创建库还是二进制文件
|
||||
|
||||
任何软件程序都可以粗略地分类为独立二进制文件或库。一个独立二进制文件也许即使是当中外部库使用的,自身也是可以运行的。但是,作为一个库,是可以被另一个独立二进制文件所利用的。到目前为止,你在本教程中构建的所有程序都是独立二进制文件,因为这是 Cargo 的默认设置。 要创建一个**库**,请添加 `--lib` 选项:
|
||||
任何软件程序都可以粗略地分类为独立二进制文件或库。一个独立二进制文件也许即使是当做外部库使用的,自身也是可以运行的。但是,作为一个库,是可以被另一个独立二进制文件所利用的。到目前为止,你在本教程中构建的所有程序都是独立二进制文件,因为这是 Cargo 的默认设置。 要创建一个**库**,请添加 `--lib` 选项:
|
||||
|
||||
```
|
||||
$ cargo new --lib libhello
|
||||
@ -514,7 +514,7 @@ test result: ok. 0 passed; 0 failed; 0 ignored; 0 measured; 0 filtered out
|
||||
|
||||
这是使用 `-v` 选项运行 `build` 和 `clean` 的几个例子。
|
||||
|
||||
在 `build` 命令中,你可以看到这些给定的命令行选项触发了底层的 `rustc`(Rust编译器):
|
||||
在 `build` 命令中,你可以看到这些给定的命令行选项触发了底层的 `rustc`(Rust 编译器):
|
||||
|
||||
```
|
||||
$ cargo build -v
|
||||
@ -523,7 +523,7 @@ $ cargo build -v
|
||||
Finished dev [unoptimized + debuginfo] target(s) in 0.36s
|
||||
```
|
||||
|
||||
而 `clean` 命令表明它只是删除包含中间文件和二进制文件的目录:
|
||||
而 `clean` 命令表明它只是删除了包含中间文件和二进制文件的目录:
|
||||
|
||||
```
|
||||
$ cargo clean -v
|
||||
@ -534,7 +534,7 @@ $ cargo clean -v
|
||||
|
||||
要扩展你的技能,请尝试使用 Rust 和 Cargo 编写并运行一个稍微复杂的程序。很简单就可以做到:例如,尝试列出当前目录中的所有文件(可以用 9 行代码完成),或者尝试自己回显输入。小型的实践应用程序可帮助你熟悉语法以及编写和测试代码的过程。
|
||||
|
||||
本文为刚起步的 Rust 程序员提供了大量信息,以使他们可以开始入门 Cargo。但是,当你开始处理更大、更复杂的程序时,你需要对 Cargo 有更深入的了解。当你准备好迎接更多内容时,请下载并阅读 Rust 团队编写的开源《[Cargo 手册][10]》,看看你可以创造什么!
|
||||
本文为刚起步的 Rust 程序员提供了大量信息,以使他们可以开始入门 Cargo。但是,当你开始处理更大、更复杂的程序时,你需要对 Cargo 有更深入的了解。当你准备好迎接更多内容时,请下载并阅读 Rust 团队编写的开源的《[Cargo 手册][10]》,看看你可以创造什么!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
@ -543,7 +543,7 @@ via: https://opensource.com/article/20/3/rust-cargo
|
||||
作者:[Gaurav Kamathe][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[wxy](https://github.com/wxy)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,8 +1,8 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (HankChow)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-11982-1.html)
|
||||
[#]: subject: (Session: An Open Source Private Messenger That Doesn’t Need Your Phone Number)
|
||||
[#]: via: (https://itsfoss.com/session-messenger/)
|
||||
[#]: author: (Ankush Das https://itsfoss.com/author/ankush/)
|
||||
@ -18,7 +18,7 @@ Signal 作为一款私人通信应用,正在变得愈发流行。而我们下
|
||||
|
||||
对于私人通信服务来说,有没有既能保护通信安全性,又尊重用户跨平台隐私的集大成者呢?很多注重个人隐私的用户似乎都在寻找这个问题的答案。
|
||||
|
||||
最近,我留意到 [Loki Foundation][3] 开发的一款叫做 [Session][2] 的开源通信应用。从技术上来说,Session 是另一款[开源、加密的通信应用 Signal][4] 的一个复刻。
|
||||
最近,我留意到 [Loki 基金会][3]开发的一款叫做 [Session][2] 的开源通信应用。从技术上来说,Session 是另一款[开源、加密的通信应用 Signal][4] 的一个复刻。
|
||||
|
||||
在本文中,我会讲述我自己使用 Session 的体验,以及 Session 的一些主要功能。
|
||||
|
||||
@ -34,7 +34,7 @@ Session 在这个领域中算是一款比较新的应用了,因此我还会在
|
||||
|
||||
在 Signal 或者其它类似的通信应用中,用户都需要提供手机号码才得以成功注册。注重隐私的用户们都认为这样的做法会潜藏着巨大的安全隐患。
|
||||
|
||||
而使用 Session 则简单得多。在 PC 或手机上安装应用之后,只需要点击“<ruby>创建账号<rt>Create Account</rt></ruby>”,无须提供手机号码,它就会生成一个类似 **05652245af9a8bfee4f5a8138fd5c……..** 这样的随机且唯一的 Session ID。
|
||||
而使用 Session 则简单得多。在 PC 或手机上安装应用之后,只需要点击“<ruby>创建账号<rt>Create Account</rt></ruby>”,无须提供手机号码,它就会生成一个类似 05652245af9a8bfee4f5a8138fd5c..... 这样的随机且唯一的 Session ID。
|
||||
|
||||
此后,把 Session ID 分享给想要添加的联系人就可以了。Session 还支持二维码,其他人可以通过扫描二维码添加你的 Session ID 为好友。
|
||||
|
||||
@ -62,14 +62,12 @@ Session 在这个领域中算是一款比较新的应用了,因此我还会在
|
||||
|
||||
最基本的选项包括:
|
||||
|
||||
* **消息有效期**:你可以控制一条消息在接收者阅读前的保留时长
|
||||
* **已读回执**:消息发送者可以知晓你已经阅读该消息
|
||||
|
||||
|
||||
* **消息有效期**:你可以控制一条消息在接收者阅读前的保留时长
|
||||
* **已读回执**:消息发送者可以知晓你已经阅读该消息
|
||||
|
||||
#### Session 使用去中心化网络保护你的元数据
|
||||
|
||||
尽管 Session 不使用<ruby>端对端<rt>peer-to-peer</rt></ruby>技术,但它也不适用中心化的服务器。
|
||||
尽管 Session 不使用<ruby>端对端<rt>peer-to-peer</rt></ruby>技术,但它也不使用中心化的服务器。
|
||||
|
||||
Session 采用了去中心化的架构实现消息的传输和路由。如果你不熟悉这方面的内容,可以关注 Session 的官方博客,尝试了解[中心化网络和去中心化网络的区别][11],以及它的实际工作原理。
|
||||
|
||||
@ -85,11 +83,11 @@ Session 采用了去中心化的架构实现消息的传输和路由。如果你
|
||||
|
||||
另外,你也可以在它的 [Github 发布页面][14] 获取到对应的 .deb 安装文件。
|
||||
|
||||
[下载 Session][12]
|
||||
- [下载 Session][12]
|
||||
|
||||
### 我使用 Session 的体验
|
||||
|
||||
我在各种平台上都试用过 Session,其中在 PC 上我使用了 Pop!_OS 19.10 的 .AppImage 文件运行这个应用。
|
||||
我在各种平台上都试用过 Session,其中在 PC 上我使用了 Pop!\_OS 19.10 的 .AppImage 文件运行这个应用。
|
||||
|
||||
总的来说,使用的体验很不错,用户界面也没有出现问题。
|
||||
|
||||
@ -99,15 +97,13 @@ Session 采用了去中心化的架构实现消息的传输和路由。如果你
|
||||
|
||||
当然,我也发现了一些需要改进的地方:
|
||||
|
||||
* 在接受好友请求时会出现延迟
|
||||
* 设备间连接的方式不太直观
|
||||
* 当你在不同的设备上使用同一个 Session ID 向同一个人回复消息时,对方会收到两个不同的对话
|
||||
|
||||
|
||||
* 在接受好友请求时会出现延迟
|
||||
* 设备间连接的方式不太直观
|
||||
* 当你在不同的设备上使用同一个 Session ID 向同一个人回复消息时,对方会收到两个不同的对话
|
||||
|
||||
### 总结
|
||||
|
||||
当然,最完美的事物是不存在的。我也会一直使用 Session 并考虑它发展的方向,这是一个注重引得的用户应该做的事情。
|
||||
当然,最完美的事物是不存在的。我也会一直使用 Session 并考虑它发展的方向,这是一个注重隐私的用户应该做的事情。
|
||||
|
||||
欢迎在评论区发表你的看法。
|
||||
|
||||
@ -119,7 +115,7 @@ via: https://itsfoss.com/session-messenger/
|
||||
作者:[Ankush Das][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[HankChow](https://github.com/HankChow)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
@ -128,7 +124,7 @@ via: https://itsfoss.com/session-messenger/
|
||||
[1]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2020/02/session-app.jpg?ssl=1
|
||||
[2]: https://getsession.org/
|
||||
[3]: https://loki.foundation/
|
||||
[4]: https://itsfoss.com/signal-messaging-app/
|
||||
[4]: https://linux.cn/article-11764-1.html
|
||||
[5]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2020/02/session-create.jpg?ssl=1
|
||||
[6]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2020/03/session-application-id.jpg?ssl=1
|
||||
[7]: https://en.wikipedia.org/wiki/Blockchain
|
||||
216
published/20200305 Install and Use Wireshark on Ubuntu Linux.md
Normal file
216
published/20200305 Install and Use Wireshark on Ubuntu Linux.md
Normal file
@ -0,0 +1,216 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (qianmingtian)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-11987-1.html)
|
||||
[#]: subject: (Install and Use Wireshark on Ubuntu Linux)
|
||||
[#]: via: (https://itsfoss.com/install-wireshark-ubuntu/)
|
||||
[#]: author: (Community https://itsfoss.com/author/itsfoss/)
|
||||
|
||||
Ubuntu 上 Wireshark 的安装与使用
|
||||
======
|
||||
|
||||
> 在本教程中,你将学习如何在 Ubuntu 和其它基于 Ubuntu 的发行版上安装最新的 Wireshark。同时你也将学习如何在没有 sudo 的情况下来运行 Wireshark,以及如何设置它来进行数据包嗅探。
|
||||
|
||||
[Wireshark][1] 是一款自由开源的网络协议分析器,它在全球被广泛使用。
|
||||
|
||||
通过使用 Wireshark,你可以实时捕获网络的传入和传出数据包,并将其用于网络故障排除、数据包分析、软件和通信协议开发等。
|
||||
|
||||
它适用于所有主流的桌面操作系统,如 Windows、Linux、macOS、BSD 等。
|
||||
|
||||
在本教程中,我将指导你在 Ubuntu 和其他基于 Ubuntu 的发行版上安装 Wireshark 。我还将介绍如何设置和配置 Wireshark 来捕获数据包。
|
||||
|
||||
### 在基于 Ubuntu 的 Linux 发行版上安装 Wireshark
|
||||
|
||||
![][2]
|
||||
|
||||
Wireshark 适用于所有主流 Linux 发行版。你应该查看[官方安装说明][3]。因为在本教程中,我将着重在仅基于 Ubuntu 的发行版上安装最新版本的 Wireshark 。
|
||||
|
||||
Wireshark 可以在 Ubuntu 的 Universe 存储库中找到。你可以[启用 universe 存储库][4],然后按如下方式安装:
|
||||
|
||||
```
|
||||
sudo add-apt-repository universe
|
||||
sudo apt install wireshark
|
||||
```
|
||||
|
||||
这种方法的一个小问题是,你可能并不总是得到最新版本的 Wireshark 。
|
||||
|
||||
例如,在 Ubuntu 18.04 中,如果你使用 [apt][5] 命令检查 Wireshark 的可用版本,可用版本会显示是 2.6 。
|
||||
|
||||
```
|
||||
abhishek@nuc:~$ apt show wireshark
|
||||
Package: wireshark
|
||||
Version: 2.6.10-1~ubuntu18.04.0
|
||||
Priority: optional
|
||||
Section: universe/net
|
||||
Origin: Ubuntu
|
||||
Maintainer: Balint Reczey <rbalint@ubuntu.com>
|
||||
```
|
||||
|
||||
然而, [Wireshark 3.2 稳定版][6]已经在几个月前发布了。当然,新版本拥有新的特性。
|
||||
|
||||
那么在这种情况下,你应该怎么办呢?谢天谢地, Wireshark 开发者提供了一种官方 PPA 方式,你可以使用它在 Ubuntu 和其它基于 Ubuntu 的发行版上安装最新稳定版本的 Wireshark.
|
||||
|
||||
我希望你熟悉 PPA。如果没有,请[阅读我们关于 PPA 的优秀指南,以便完全理解它][7]。
|
||||
|
||||
打开终端并逐个使用以下命令:
|
||||
|
||||
```
|
||||
sudo add-apt-repository ppa:wireshark-dev/stable
|
||||
sudo apt update
|
||||
sudo apt install wireshark
|
||||
```
|
||||
|
||||
即使安装了旧版本的 Wireshark ,它也将更新为新版本。
|
||||
|
||||
安装时,系统将询问你是否允许非超级用户捕获数据包。选择“Yes”允许,选择“No”限制非超级用户捕获数据包,最后完成安装。
|
||||
|
||||
### 不使用 sudo 运行 Wireshark
|
||||
|
||||
如果在上一次安装中选择了“No”,则以 root 用户身份运行以下命令:
|
||||
|
||||
```
|
||||
sudo dpkg-reconfigure wireshark-common
|
||||
```
|
||||
|
||||
然后按 `tab` 键并使用回车键选择“No”:
|
||||
|
||||
![][8]
|
||||
|
||||
由于你允许非超级用户捕获数据包,因此你必须将该用户添加到 `wireshark` 组。使用 [usermod][9] 命令将自己添加到 `wireshark` 组。
|
||||
|
||||
```
|
||||
sudo usermod -aG wireshark $(whoami)
|
||||
```
|
||||
|
||||
最后,[重启你的 Ubuntu 系统][10]对你的系统进行必要的修改。
|
||||
|
||||
> 冷知识
|
||||
>
|
||||
> Wireshark 于 1998 年首次发布,最初被称为 Ethereal 。2006 年,由于商标问题,开发商不得不将其名称改为 Wireshark 。
|
||||
|
||||
### 启动 Wireshark
|
||||
|
||||
你可以从应用程序启动器或者命令行启动 Wireshark 应用。
|
||||
|
||||
如果从命令行启动,只需要在你的控制台中输入 `wireshark`:
|
||||
|
||||
```
|
||||
wireshark
|
||||
```
|
||||
|
||||
要是从**图形化界面**启动,需要在搜索栏搜索 Wireshark 应用,并按回车键。
|
||||
|
||||
![][11]
|
||||
|
||||
现在,让我们来玩玩 Wireshark 吧。
|
||||
|
||||
### 使用 Wireshark 捕获数据包
|
||||
|
||||
当你启动 Wireshark 的时候,你会看到一个接口列表,你可以使用它来捕获这个接口接收和发送的数据包。
|
||||
|
||||
你可以使用 Wireshark 监视许多类型的接口,例如,有线、外部设备等。根据你的偏好,你可以从下图中的标记区域选择在欢迎屏幕中显示特定类型的接口。
|
||||
|
||||
![Select interface][12]
|
||||
|
||||
例如,我只列出了**有线**网络接口。
|
||||
|
||||
![][13]
|
||||
|
||||
接下来,要开始捕获数据包,你必须选择接口(在我的示例中是 `ens33` ),然后单击“Start capturing packets”图标,如下图所示。
|
||||
|
||||
![Start capturing packets with Wireshark][14]
|
||||
|
||||
你还可以同时从多个接口捕获数据包。只需按住 `CTRL` 按钮,同时单击要捕获的接口,然后点击“Start capturing packets”图标,如下图所示。
|
||||
|
||||
![][15]
|
||||
|
||||
接下来,我尝试在终端中使用 `ping google.com` 命令,如你所见,捕获了许多数据包。
|
||||
|
||||
![Captured packets][16]
|
||||
|
||||
现在你可以选择任何数据包来检查该特定数据包。在点击一个特定的包之后,你可以看到与它相关的 TCP/IP 协议的不同层的信息。
|
||||
|
||||
![Packet info][17]
|
||||
|
||||
你还可以在底部看到该特定数据包的原始数据,如下图所示。
|
||||
|
||||
![Check RAW data in the captured packets][18]
|
||||
|
||||
> 这就是为什么端到端加密很重要。
|
||||
>
|
||||
> 假设你正在登录一个不使用 HTTPS 的网站。与你在同一网络上的任何人都可以嗅探数据包,并在原始数据中看到用户名和密码。
|
||||
>
|
||||
> 这就是为什么现在大多数聊天应用程序使用端到端加密,而大多数网站使用 https (而不是 http)。
|
||||
|
||||
#### 在 Wireshark 中停止数据包捕获
|
||||
|
||||
你可以点击如图所示的红色图标停止捕获数据包。
|
||||
|
||||
![Stop packet capture in Wireshark][19]
|
||||
|
||||
#### 将捕获的数据包保存成文件
|
||||
|
||||
你可以单击下图中标记的图标,将捕获的数据包保存到文件中以备将来使用。
|
||||
|
||||
![Save captured packets by Wireshark][20]
|
||||
|
||||
|
||||
**注意**:输出可以导出为 XML、PostScript、CSV 或纯文本。
|
||||
|
||||
接下来,选择一个目标文件夹,键入文件名并单击“Save”。
|
||||
|
||||
然后选择文件并单击“Open”。
|
||||
|
||||
![][21]
|
||||
|
||||
现在你可以随时打开和分析保存的数据包。要打开文件,请按 `\+o`,或从 Wireshark 转到 “File > Open”。
|
||||
|
||||
捕获的数据包将从文件中加载。
|
||||
|
||||
![][22]
|
||||
|
||||
### 结语
|
||||
|
||||
Wireshark 支持许多不同的通信协议。有许多选项和功能,使你能够以独特的方式捕获和分析网络数据包。你可以从 Wireshark 的[官方文档][23]了解更多关于 Wireshark 的信息。
|
||||
|
||||
我希望这个教程能帮助你在 Ubuntu 上安装 Wireshark 。请让我知道你的问题和建议。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://itsfoss.com/install-wireshark-ubuntu/
|
||||
|
||||
作者:[Kushal Rai][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[qianmingtian][c]
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://itsfoss.com/author/itsfoss/
|
||||
[b]: https://github.com/lujun9972
|
||||
[c]: https://github.com/qianmingtian
|
||||
[1]: https://www.wireshark.org/
|
||||
[2]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2020/03/wireshark_ubuntu.png?ssl=1
|
||||
[3]: https://www.wireshark.org/docs/wsug_html_chunked/ChBuildInstallUnixInstallBins.html
|
||||
[4]: https://itsfoss.com/ubuntu-repositories/
|
||||
[5]: https://itsfoss.com/apt-command-guide/
|
||||
[6]: https://www.wireshark.org/news/20191218.html
|
||||
[7]: https://itsfoss.com/ppa-guide/
|
||||
[8]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2020/03/yes.png?ssl=1
|
||||
[9]: https://linuxhandbook.com/usermod-command/
|
||||
[10]: https://itsfoss.com/schedule-shutdown-ubuntu/
|
||||
[11]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2020/03/wire.png?ssl=1
|
||||
[12]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2020/03/interfaces.jpg?ssl=1
|
||||
[13]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2020/03/intoption.jpg?ssl=1
|
||||
[14]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2020/03/singleinterface.jpg?ssl=1
|
||||
[15]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2020/03/selint.jpg?ssl=1
|
||||
[16]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2020/03/capture.jpg?ssl=1
|
||||
[17]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2020/03/packetinfo.png?ssl=1
|
||||
[18]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2020/03/raw.png?ssl=1
|
||||
[19]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2020/03/stopcapture.png?ssl=1
|
||||
[20]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2020/03/savepackets.jpg?ssl=1
|
||||
[21]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2020/03/savename.jpg?ssl=1
|
||||
[22]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2020/03/openpacket.png?ssl=1
|
||||
[23]: https://www.wireshark.org/docs/https://www.wireshark.org/docs/
|
||||
[24]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2020/03/kushal_rai.jpg?ssl=1
|
||||
@ -0,0 +1,143 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (linusboyle)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-12023-1.html)
|
||||
[#]: subject: (Communicating with other users on the Linux command line)
|
||||
[#]: via: (https://www.networkworld.com/article/3530343/communicating-with-other-users-on-the-linux-command-line.html)
|
||||
[#]: author: (Sandra Henry-Stocker https://www.networkworld.com/author/Sandra-Henry_Stocker/)
|
||||
|
||||
使用 Linux 命令行与其他用户进行通信
|
||||
======
|
||||
|
||||

|
||||
|
||||
使用 Linux 命令行向其他用户发送消息或许非常容易,这里有一些相关的命令你可以考虑使用。在这篇文章中,我们会考察 4 个这样的命令,看看它们是怎么工作的。
|
||||
|
||||
### wall
|
||||
|
||||
`wall`(“Write ALL” 的简称)命令允许你向所有系统中已登录的用户发送一条信息。这里我们假设用户都使用命令行在同一台服务器上工作。虽然 `wall` 命令最常被系统管理员用于向用户发布公告和传递信息(比如说,服务器即将因维护而关闭),但它可以被任何用户使用。
|
||||
|
||||
系统管理员可能会用类似下面的方式发送信息:
|
||||
|
||||
```
|
||||
$ wall The system will be going down in 15 minutes to address a serious problem
|
||||
```
|
||||
|
||||
而所有登录的用户都将看到类似这样的信息:
|
||||
|
||||
```
|
||||
Broadcast message from admin@dragonfly (pts/0) (Thu Mar 5 08:56:42 2020):
|
||||
The system is going down in 15 minutes to address a serious problem
|
||||
```
|
||||
|
||||
如果希望在消息中使用单引号,你可以像这样将信息用双引号括起来:
|
||||
|
||||
```
|
||||
$ wall "Don't forget to save your work before logging off"
|
||||
```
|
||||
|
||||
最外层的双引号不会出现在发出的消息中,但是如果没有它们,`wall` 会停下并等待输入一个配对的单引号。
|
||||
|
||||
### mesg
|
||||
|
||||
如果出于某种理由你不想接收来自另一个用户的消息,你可以使用 `mesg` 命令来屏蔽这些消息。这个命令可以接受一个 `n` 作为参数来拒绝某用户的消息,或者接收一个 `y` 作为参数来接收用户发来的消息。
|
||||
|
||||
```
|
||||
$ mesg n doug
|
||||
$ mesg y doug
|
||||
```
|
||||
|
||||
被屏蔽的用户不会被告知这一事实。你也可以像这样使用 `mesg` 来屏蔽或者接收所有消息:
|
||||
|
||||
```
|
||||
$ mesg y
|
||||
$ mesg n
|
||||
```
|
||||
|
||||
### write
|
||||
|
||||
另一个在不使用电子邮件的情况下发送文本的命令是 `write`,这个命令可以用来和一个特定的用户通信。
|
||||
|
||||
```
|
||||
$ write nemo
|
||||
Are you still at your desk?
|
||||
I need to talk with you right away.
|
||||
^C
|
||||
```
|
||||
|
||||
输入你的信息后用 `ctrl-c` 退出,这样就完成了通信。这个命令允许你发送文本,但并不会建立一个双向的通话。它只是将文本发送过去而已。如果目标用户在多个终端上登录,你可以指定你想将消息发送到哪一个终端,否则系统会选择空闲时间最短的那个终端。
|
||||
|
||||
```
|
||||
$ write nemo#1
|
||||
```
|
||||
|
||||
如果你试图向一个将消息屏蔽了的用户发送信息,你应该会看到这样的输出:
|
||||
|
||||
```
|
||||
$ write nemo
|
||||
write: nemo has messages disabled
|
||||
```
|
||||
|
||||
### talk/ytalk
|
||||
|
||||
`talk` 和 `ytalk` 命令让你可以和一个或多个用户进行交互式的聊天。它们会展示一个有上下两个子窗口的界面,每个用户向显示在他们屏幕上方的窗口内输入内容,并在下方的窗口看到回复信息。要回复一个`talk` 请求,接收方可以输入 `talk`,在后面加上请求方的用户名。
|
||||
|
||||
```
|
||||
Message from Talk_Daemon@dragonfly at 10:10 ...
|
||||
talk: connection requested by dory@127.0.0.1.
|
||||
talk: respond with: talk dory@127.0.0.1
|
||||
|
||||
$ talk dory
|
||||
```
|
||||
|
||||
如果使用的是 `ytalk`,那么窗口中可以包含多于两个参与者。正如下面的例子所展示的(这是上面 `talk dory` 命令的结果),`talk` 通常指向 `ytalk`。
|
||||
|
||||
```
|
||||
----------------------------= YTalk version 3.3.0 =--------------------------
|
||||
Is the report ready?
|
||||
|
||||
-------------------------------= nemo@dragonfly =----------------------------
|
||||
Just finished it
|
||||
```
|
||||
|
||||
如上所述,在通话的另一侧,`talk`会话界面的窗口是相反的:
|
||||
|
||||
```
|
||||
----------------------------= YTalk version 3.3.0 =--------------------------
|
||||
Just finished it
|
||||
|
||||
-------------------------------= dory@dragonfly =----------------------------
|
||||
Is the report ready?
|
||||
```
|
||||
|
||||
同样的,使用 `ctrl-c` 来退出。
|
||||
|
||||
如果要和非本机的用户通讯,你需要加上 `-h` 选项和目标主机名或IP地址,就像这样:
|
||||
|
||||
```
|
||||
$ talk -h 192.168.0.11 nemo
|
||||
```
|
||||
|
||||
### 总结
|
||||
|
||||
Linux 上有若干基本的命令可以用来向其他登录的用户发送消息。如果你需要向所有用户快速发送信息或是需要便捷的电话替代品,又或是希望能简单地开始一个多用户快速通讯会话,这些命令会十分实用。
|
||||
|
||||
一些命令如 `wall` 允许广播消息但却不是交互式的。另外的一些命令如 `talk` 允许多用户进行长时间通讯,当你只需要非常快速地交换一些信息,它们可以你你避免建立一个电话会议。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.networkworld.com/article/3530343/communicating-with-other-users-on-the-linux-command-line.html
|
||||
|
||||
作者:[Sandra Henry-Stocker][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[linusboyle](https://github.com/linusboyle)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.networkworld.com/author/Sandra-Henry_Stocker/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.networkworld.com/article/3440100/take-the-intelligent-route-with-consumption-based-storage.html?utm_source=IDG&utm_medium=promotions&utm_campaign=HPE21620&utm_content=sidebar ( Take the Intelligent Route with Consumption-Based Storage)
|
||||
[2]: https://www.facebook.com/NetworkWorld/
|
||||
[3]: https://www.linkedin.com/company/network-world
|
||||
@ -0,0 +1,182 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-11992-1.html)
|
||||
[#]: subject: (Three Ways to Exclude/Hold/Prevent a Specific Package from an apt Upgrade)
|
||||
[#]: via: (https://www.2daygeek.com/debian-ubuntu-exclude-hold-prevent-packages-from-apt-get-upgrade/)
|
||||
[#]: author: (Magesh Maruthamuthu https://www.2daygeek.com/author/magesh/)
|
||||
|
||||
从 apt 升级中排除/保留/阻止特定软件包的三种方法
|
||||
======
|
||||
|
||||

|
||||
|
||||
有时,由于某些应用依赖性,你可能会意外更新不想更新的软件包。这在全系统更新或自动包升级时经常会发生。如果发生这种情况,可能会破坏应用的功能。这会造成严重的问题,你需要花费大量时间来解决问题。
|
||||
|
||||
如何避免这种情况?如何从 `apt-get` 更新中排除软件包?
|
||||
|
||||
> 如果你要[从 Yum Update 中排除特定软件包][1],请参考这篇。
|
||||
|
||||
是的,可以在 Debian 和 Ubuntu 系统上使用以下三种方法来完成。
|
||||
|
||||
* [apt-mark 命令][2]
|
||||
* [dpkg 命令][3]
|
||||
* aptitude 命令
|
||||
|
||||
我们将分别详细展示。
|
||||
|
||||
### 方法 1:如何使用 apt-mark 命令排除 Debian/Ubuntu 系统上的软件包更新
|
||||
|
||||
`apt-mark` 用于将软件包标记/取消标记为自动安装。
|
||||
|
||||
`hold` 选项用于将软件包标记为保留,以防止软件包被自动安装、升级或删除。
|
||||
|
||||
`unhold` 选项用于取消先前面的设置,以允许重复执行所有操作。
|
||||
|
||||
运行以下命令以使用 `apt-mark` 命令保留指定的软件包。
|
||||
|
||||
```
|
||||
$ sudo apt-mark hold nano
|
||||
nano set on hold.
|
||||
```
|
||||
|
||||
保留软件包后,请运行以下 `apt-mark` 命令查看它们。
|
||||
|
||||
```
|
||||
$ sudo apt-mark showhold
|
||||
nano
|
||||
```
|
||||
|
||||
这表明在执行完整的系统更新时,不会升级 nano 包。
|
||||
|
||||
```
|
||||
$ sudo apt update
|
||||
|
||||
Reading package lists… Done
|
||||
Building dependency tree
|
||||
Reading state information… Done
|
||||
Calculating upgrade… Done
|
||||
The following packages have been kept back:
|
||||
nano
|
||||
0 upgraded, 0 newly installed, 0 to remove and 1 not upgraded.
|
||||
```
|
||||
|
||||
运行以下命令,使用 `apt-mark` 命令取消保留 nano 包。
|
||||
|
||||
```
|
||||
$ sudo apt-mark unhold nano
|
||||
Canceled hold on nano.
|
||||
```
|
||||
|
||||
### 方法 2:如何使用 dpkg 命令在 Debian/Ubuntu 系统上排除软件包更新
|
||||
|
||||
`dpkg` 命令是一个 CLI 工具,用于安装、构建、删除和管理 Debian 软件包。`dpkg` 的主要且更用户友好的前端是 `aptitude`。
|
||||
|
||||
运行以下命令使用 `dpkg` 命令阻止给定的软件包。
|
||||
|
||||
语法:
|
||||
|
||||
```
|
||||
$ echo "package_name hold" | sudo dpkg --set-selections
|
||||
```
|
||||
|
||||
运行以下 `dpkg` 命令以保留 apache2 包。
|
||||
|
||||
```
|
||||
$ echo "apache2 hold" | sudo dpkg --set-selections
|
||||
```
|
||||
|
||||
保留软件包后,请运行以下命令查看它们。
|
||||
|
||||
```
|
||||
$ sudo dpkg --get-selections | grep "hold"
|
||||
apache2 hold
|
||||
```
|
||||
|
||||
它会显示在执行完整的系统更新时,不会升级 apache2包。
|
||||
|
||||
```
|
||||
$ sudo apt update
|
||||
|
||||
Reading package lists… Done
|
||||
Building dependency tree
|
||||
Reading state information… Done
|
||||
Calculating upgrade… Done
|
||||
The following packages have been kept back:
|
||||
apache2
|
||||
0 upgraded, 0 newly installed, 0 to remove and 1 not upgraded.
|
||||
```
|
||||
|
||||
运行以下命令,使用 `dpkg` 命令取消对指定软件包的保留。
|
||||
|
||||
语法:
|
||||
|
||||
```
|
||||
$ echo "package_name install" | sudo dpkg --set-selections
|
||||
```
|
||||
|
||||
运行以下命令,使用 `dpkg` 命令取消保留 apache2 包。
|
||||
|
||||
```
|
||||
$ echo "apache2 install" | sudo dpkg --set-selections
|
||||
```
|
||||
|
||||
### 方法 3:如何使用 aptitude 命令排除 Debian/Ubuntu 系统上的软件包更新
|
||||
|
||||
`aptitude` 命令是 Debian 及其衍生版本的基于文本的软件包管理界面。
|
||||
|
||||
它允许用户查看软件包列表并执行软件包管理任务,例如安装、升级和删除软件包。它可以从可视界面或命令行执行操作。
|
||||
|
||||
运行以下命令,使用 `aptitude` 命令保留指定的软件包。
|
||||
|
||||
```
|
||||
$ sudo aptitude hold python3
|
||||
```
|
||||
|
||||
保留某些软件包后,请运行以下命令查看它们。
|
||||
|
||||
```
|
||||
$ sudo dpkg --get-selections | grep "hold"
|
||||
或者
|
||||
$ sudo apt-mark showhold
|
||||
|
||||
python3
|
||||
```
|
||||
|
||||
这表明在执行完整的系统更新时,不会升级 python3 软件包。
|
||||
|
||||
```
|
||||
$ sudo apt update
|
||||
|
||||
Reading package lists… Done
|
||||
Building dependency tree
|
||||
Reading state information… Done
|
||||
Calculating upgrade… Done
|
||||
The following packages have been kept back:
|
||||
python3
|
||||
0 upgraded, 0 newly installed, 0 to remove and 1 not upgraded.
|
||||
```
|
||||
|
||||
使用 `aptitude ` 命令运行以下命令以解除对 python3 软件包的保留。
|
||||
|
||||
```
|
||||
$ sudo aptitude unhold python3
|
||||
```
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.2daygeek.com/debian-ubuntu-exclude-hold-prevent-packages-from-apt-get-upgrade/
|
||||
|
||||
作者:[Magesh Maruthamuthu][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.2daygeek.com/author/magesh/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.2daygeek.com/redhat-centos-yum-update-exclude-specific-packages/
|
||||
[2]: https://www.2daygeek.com/apt-get-apt-cache-command-examples-manage-packages-debian-ubuntu-systems/
|
||||
[3]: https://www.2daygeek.com/dpkg-command-to-manage-packages-on-debian-ubuntu-linux-mint-systems/
|
||||
68
published/20200309 6 Raspberry Pi tutorials to try out.md
Normal file
68
published/20200309 6 Raspberry Pi tutorials to try out.md
Normal file
@ -0,0 +1,68 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-12005-1.html)
|
||||
[#]: subject: (6 Raspberry Pi tutorials to try out)
|
||||
[#]: via: (https://opensource.com/article/20/3/raspberry-pi-tutorials)
|
||||
[#]: author: (Lauren Pritchett https://opensource.com/users/lauren-pritchett)
|
||||
|
||||
6 个可以尝试的树莓派教程
|
||||
======
|
||||
|
||||
> 这些树莓派项目均旨在简化你的生活并提高生产力。
|
||||
|
||||

|
||||
|
||||
没有什么比体验树莓派创作结果更令人兴奋了。经过数小时的编程、测试和徒手构建,你的项目终于开始成形,你不禁大喊 “哇哦!”树莓派可以带给日常生活的可能性让我着迷。无论你是想学习新知识、尝试提高效率还是只是乐在其中,本文总有一个树莓派项目适合你。
|
||||
|
||||
### 设置 VPN 服务器
|
||||
|
||||
本[教程][2]教你如何使用树莓派添加一个网络安全层。这个项目不仅有实际好处,而且还能为你带来很多乐趣。额外的安全性使你可以放心地做其它项目,例如下面列出的项目。
|
||||
|
||||
### 创建一个物体跟踪摄像机
|
||||
|
||||
树莓派之所以具有吸引力,是因为它提供了较低的入门门槛来学习机器学习等新技术。这份[分步指南][3]提供了详尽的说明,说明了如何构建一个全景摄像头,以便使用 TensorFlow 和树莓派跟踪运动。
|
||||
|
||||
### 使用照片幻灯片展示你最喜欢的回忆
|
||||
|
||||
你是否曾经问过自己:“我应该怎么处理这些数码照片?”。如果你像我一样这样想过,那么答案是“是”。在朋友和家人圈子中,我被公认为摄像爱好者。这就是为什么我喜欢这个树莓派项目。在[本教程][4]中,你将学习如何设置照片幻灯片,以便轻松地在家里展示自己喜欢的回忆,而无需打印机!
|
||||
|
||||
### 玩复古电子游戏
|
||||
|
||||
如果你对复古游戏系统怀有怀旧之情,那么可以尝试[本教程][5]。了解包括树莓派在内的哪些设备可以运行 Amiga 模拟器。完成设置后,你将可在树莓派上玩自己喜欢的 Amiga 游戏。
|
||||
|
||||
### 为你的娱乐中心搭建时钟
|
||||
|
||||
在过去的十年中,家庭娱乐中心发生了很大的变化。我的家人完全依靠流媒体服务来观看节目和电影。我之所以爱它是因为我可以通过移动设备或语音助手控制电视。但是,当你不再能一眼看到时钟时,便会失去一定程度的便利!请遵循[这些步骤][6],使用树莓派从头开始搭建自己的时钟显示。
|
||||
|
||||
### 扩大自制啤酒的生产规模
|
||||
|
||||
在[本教程][7]中,经验丰富的家庭酿酒师分享了他建立电动啤酒酿造系统的经验。该项目需要在硬件和零件上进行更多的前期投资,但由此产生的效率和一致性让这些值得。为此祝贺!
|
||||
|
||||
如果你是像我这样的树莓派新手,那么我建议你阅读我们这些可下载的树莓派指南。我们的[单页速查表][8]提供了入门指南。有关更多技巧和教程,我们的[综合指南][9]涵盖了一些主题,例如选择树莓派、保持更新、为社区做出贡献等。
|
||||
|
||||
你会尝试哪个树莓派项目?让我们在评论中知道。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/20/3/raspberry-pi-tutorials
|
||||
|
||||
作者:[Lauren Pritchett][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/lauren-pritchett
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/raspberrypi_cartoon.png?itok=m3TcBONJ (Cartoon graphic of Raspberry Pi board)
|
||||
[2]: https://opensource.com/article/19/6/raspberry-pi-vpn-server
|
||||
[3]: https://opensource.com/article/20/1/object-tracking-camera-raspberry-pi
|
||||
[4]: https://opensource.com/article/19/2/wifi-picture-frame-raspberry-pi
|
||||
[5]: https://opensource.com/article/19/3/amiga-raspberry-pi
|
||||
[6]: https://opensource.com/article/17/7/raspberry-pi-clock
|
||||
[7]: https://opensource.com/article/17/7/brewing-beer-python-and-raspberry-pi
|
||||
[8]: https://opensource.com/downloads/getting-started-raspberry-pi-cheat-sheet
|
||||
[9]: https://opensource.com/downloads/raspberry-pi-guide
|
||||
@ -0,0 +1,61 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (hkurj)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-12034-1.html)
|
||||
[#]: subject: (2020 Will Be a Year of Hindsight for SD-WAN)
|
||||
[#]: via: (https://www.networkworld.com/article/3531315/2020-will-be-a-year-of-hindsight-for-sd-wan.html)
|
||||
[#]: author: (Zeus Kerravala https://www.networkworld.com/author/Zeus-Kerravala/)
|
||||
|
||||
2020 年将是 SD-WAN 的回顾之年
|
||||
======
|
||||
|
||||

|
||||
|
||||
对于软件定义的广域网(SD-WAN),“过去看起来困难的选择,知道了这些选择的结果后,现在看起来就很清晰了” 这一说法再合适不过了。总结过去的几年:云计算和数字化转型促使公司重新评估传统的 WAN 技术,该技术不再能够满足其不断增长的业务需求。从那时起,SD-WAN 成为一种有前途的新技术。
|
||||
|
||||
SD-WAN 旨在解决物理设备的流量管理问题,并支持从云进行基于软件的配置。许多最初的 SD-WAN 部署都因希望取代昂贵的多协议标签交换 (MPLS) 而得到推动。公司希望它可以神奇地解决他们所有的网络问题。但是在实践中,基本的 SD-WAN 解决方案远没有实现这一愿景。
|
||||
|
||||
快速发展到现在,围绕 SD-WAN 的炒作已经尘埃落定,并且早期的实施工作已经过去。现在是时候回顾一下我们在 2019 年学到的东西以及在 2020 年要改进的地方。所以,让我们开始吧。
|
||||
|
||||
### 1、这与节省成本无关
|
||||
|
||||
大多数公司选择 SD-WAN 作为 MPLS 的替代品,因为它可以降低 WAN 成本。但是,[节省的成本][1]会因 SD-WAN 的不同而异,因此不应将其用作部署该技术的主要驱动力。无论公司需要什么,公司都应该专注于提高网络敏捷性,例如实现更快的站点部署和减少配置时间。SD-WAN 的主要驱动力是使网络更高效。如果成功实现那么成本也会随之降低。
|
||||
|
||||
### 2、WAN 优化是必要的
|
||||
|
||||
说到效率,[WAN 优化][2]提高了应用程序和数据流量的性能。通过应用协议加速、重复数据消除、压缩和缓存等技术,WAN 优化可以增加带宽、减少延迟并减轻数据包丢失。最初的想法是 SD-WAN 可以完成对 WAN 优化的需求,但是我们现在知道某些应用程序需要更多的性能支持。这些技术相互补充,而不是相互替代。它们应该用来解决不同的问题。
|
||||
|
||||
### 3、安全性不应该事后考虑
|
||||
|
||||
SD-WAN 具有许多优点,其中之一就是使用宽带互联网快速发送企业应用程序流量。但是这种方法也带来了安全风险,因为它使用户及其本地网络暴露于不受信任的公共互联网中。从一开始,安全性就应该成为 SD-WAN 实施的一部分,而不是在事后。公司可以通过使用[安全的云托管][3]之类的服务,将安全性放在分支机构附近,从而实现所需的应用程序性能和保护。
|
||||
|
||||
### 4、可见性对于 SD-WAN 成功至关重要
|
||||
|
||||
在应用程序和数据流量中具有[可见性][4],这使网络管理不再需要猜测。最好的起点是部署前阶段,在此阶段,公司可以在实施 SD-WAN 之前评估其现有功能以及缺少的功能。可见性以日常监控和警报的形式在部署后继续发挥重要作用。了解网络中正在发生的情况的公司会更好地准备应对性能问题,并可以利用这些知识来避免将来出现问题。
|
||||
|
||||
### 5、无线广域网尚未准备就绪
|
||||
|
||||
SD-WAN 可通过包括宽带和 4G/LTE 无线在内的任何传输将用户连接到应用程序。这就是[移动互联][5]越来越多地集成到 SD-WAN 解决方案中的原因。尽管公司渴望将 4G 用作潜在的传输替代方案(尤其是在偏远地区),但由此带来的按使用付费 4G 服务成本却很高。此外,由于延迟和带宽限制,4G 可能会出现问题。最好的方法是等待服务提供商部署具有更好的价格选择的 5G。今年我们将看到 5G 的推出,并更加关注无线 SD-WAN。
|
||||
|
||||
请务必观看以下 SD-WAN 视频系列:[你应该知道的所有关于 SD-WAN 的知识][6]。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.networkworld.com/article/3531315/2020-will-be-a-year-of-hindsight-for-sd-wan.html
|
||||
|
||||
作者:[Zeus Kerravala][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[hkurj](https://github.com/hkurj)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.networkworld.com/author/Zeus-Kerravala/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://blog.silver-peak.com/to-maximize-the-value-of-sd-wan-look-past-hardware-savings
|
||||
[2]: https://blog.silver-peak.com/sd-wan-vs-wan-optimization
|
||||
[3]: https://blog.silver-peak.com/sd-wans-enable-scalable-local-internet-breakout-but-pose-security-risk
|
||||
[4]: https://blog.silver-peak.com/know-the-true-business-drivers-for-sd-wan
|
||||
[5]: https://blog.silver-peak.com/mobility-and-sd-wan-part-1-sd-wan-with-4g-lte-is-a-reality
|
||||
[6]: https://www.silver-peak.com/everything-you-need-to-know-about-sd-wan
|
||||
@ -0,0 +1,103 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-12001-1.html)
|
||||
[#]: subject: (Basilisk: A Firefox Fork For The Classic Looks and Classic Extensions)
|
||||
[#]: via: (https://itsfoss.com/basilisk-browser/)
|
||||
[#]: author: (Ankush Das https://itsfoss.com/author/ankush/)
|
||||
|
||||
Basilisk:一个有着经典的外观和扩展的 Firefox 复刻
|
||||
======
|
||||
|
||||
> Basilisk 是一个 Firefox 复刻,它支持旧版的扩展等更多功能。在这里,我们看一下它的功能并尝试一下。
|
||||
|
||||

|
||||
|
||||
### Basilisk:基于 XUL 的开源 Web 浏览器
|
||||
|
||||
尽管最好使用 Linux 上的常规浏览器(如 Firefox 或 Chromium),但了解其他浏览器也没坏处。最近,我偶然发现了一个 Firefox 复刻:[Basilisk][1] 浏览器,它有经典的 Firefox 用户界面以及对旧版扩展的支持(就像 [Waterfox][2] 一样)。
|
||||
|
||||
![itsfoss.com homepage on Basilisk][3]
|
||||
|
||||
如果你迫切需要使用旧版扩展程序或怀念 Firefox 的经典外观,Basilisk 浏览器可以帮到你。这个浏览器是由 [Pale Moon][4] 浏览器背后的团队维护(这是我接下来要介绍的另一个 Firefox 复刻)。
|
||||
|
||||
如果你正在寻找开源 [Chrome 替代品][5],那么你可以快速了解一下 Basilisk 提供的功能。
|
||||
|
||||
**注意:**Basilisk 是开发中软件。即使我在使用时没有遇到重大的可用性问题,但你也不应依赖它作为唯一使用的浏览器。
|
||||
|
||||
### Basilisk 浏览器的特性
|
||||
|
||||
![][6]
|
||||
|
||||
Basilisk 开箱即用。但是,在考虑使用之前,可能需要先看一下以下这些特性:
|
||||
|
||||
* 基于 [XUL][7] 的 Web 浏览器
|
||||
* 它具有 “Australis” Firefox 界面,这在 v29–v56 的 Firefox 版本中非常流行。
|
||||
* 支持 [NPAPI][8] 插件(Flash、Unity、Java 等)
|
||||
* 支持 XUL/Overlay Mozilla 形式的扩展。
|
||||
* 使用 [Goanna][9] 开源浏览器引擎,它是 Mozilla [Gecko][10] 的复刻
|
||||
* 不使用 Rust 或 Photon 用户界面
|
||||
* 仅支持 64 位系统
|
||||
|
||||
### 在 Linux 上安装 Basilisk
|
||||
|
||||
你可能没有在软件中心中找到它。因此,你必须前往其官方[下载页面][11]获得 tarball(tar.xz)文件。
|
||||
|
||||
下载后,只需将其解压缩并进入文件夹。接下来,你将在其中找到一个 `Basilisk` 可执行文件。你只需双击或右键单击并选择 “运行” 即可运行它。
|
||||
|
||||
你可以查看它的 [GitHub 页面][12]获取更多信息。
|
||||
|
||||
![][13]
|
||||
|
||||
你也可以按照下面的步骤使用终端进入下载的文件夹,并运行文件:
|
||||
|
||||
```
|
||||
cd basilisk-latest.linux64
|
||||
cd basilisk
|
||||
./basilisk
|
||||
```
|
||||
|
||||
- [下载 Basilisk][1]
|
||||
|
||||
### 使用 Basilisk 浏览器
|
||||
|
||||
![][14]
|
||||
|
||||
如果你想要支持旧版扩展,Basilisk 是不错的 Firefox 复刻。它是由 Pale Moon 背后的团队积极开发的,对于希望获得 Mozilla Firefox(在 Quantum 更新之前)经典外观,且不包括现代 Web 支持的用户而言,它可能是一个不错的选择。
|
||||
|
||||
浏览网页没有任何问题。但是,我注意到 YouTube 将其检测为过时的浏览器,并警告说它将很快停止支持它。
|
||||
|
||||
**因此,我不确定 Basilisk 是否适合所有现有的 Web 服务 —— 但是,如果你确实需要使用 Firefox 较早版本中的扩展,那这是一个解决方案。**
|
||||
|
||||
### 总结
|
||||
|
||||
你认为这个 Firefox 复刻值得尝试吗?你喜欢哪个?在下面的评论中分享你的想法。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://itsfoss.com/basilisk-browser/
|
||||
|
||||
作者:[Ankush Das][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://itsfoss.com/author/ankush/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.basilisk-browser.org/
|
||||
[2]: https://itsfoss.com/waterfox-browser/
|
||||
[3]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2020/03/basilisk-itsfoss.jpg?ssl=1
|
||||
[4]: https://www.palemoon.org
|
||||
[5]: https://itsfoss.com/open-source-browsers-linux/
|
||||
[6]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2020/03/basilisk-options-1.jpg?ssl=1
|
||||
[7]: https://developer.mozilla.org/en-US/docs/Archive/Mozilla/XUL
|
||||
[8]: https://wiki.mozilla.org/NPAPI
|
||||
[9]: https://en.wikipedia.org/wiki/Goanna_(software)
|
||||
[10]: https://developer.mozilla.org/en-US/docs/Mozilla/Gecko
|
||||
[11]: https://www.basilisk-browser.org/download.shtml
|
||||
[12]: https://github.com/MoonchildProductions/Basilisk
|
||||
[13]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2020/03/basilisk-folder-1.jpg?ssl=1
|
||||
[14]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2020/03/basilisk-browser-1.jpg?ssl=1
|
||||
@ -0,0 +1,85 @@
|
||||
[#]: collector: "lujun9972"
|
||||
[#]: translator: "messon007"
|
||||
[#]: reviewer: "wxy"
|
||||
[#]: publisher: "wxy"
|
||||
[#]: url: "https://linux.cn/article-12015-1.html"
|
||||
[#]: subject: "Containers vs. VMs, Istio in production, and more industry news"
|
||||
[#]: via: "https://opensource.com/article/20/3/survey-istio-industry-news"
|
||||
[#]: author: "Tim Hildred https://opensource.com/users/thildred"
|
||||
|
||||
每周开源点评:容器 vs 虚拟机、生产环境中的 Istio 等
|
||||
======
|
||||
|
||||
> 本文是最近一周开源社区的新闻和行业进展。
|
||||
|
||||
![Person standing in front of a giant computer screen with numbers, data][1]
|
||||
|
||||
我在一家采用开源软件开发模型的企业软件公司任高级产品营销经理,我的一部分职责是为产品营销人员,经理和其他相关人定期发布有关开源社区,市场和业界发展趋势的更新。以下是该更新中我和他们最喜欢的五篇文章。
|
||||
|
||||
### 云原生应用采用的技术:容器等
|
||||
|
||||
- [文章链接][2]
|
||||
|
||||
> * 在生产环境中采用容器的比例从 2018 年的 73% 上升到 2019 年的 84%。其中,运行了至少 250 个容器的比例从 2018 年的 46% 上升到 2019 年的 58%。2017 到 2019 年间, 环境中拥有 50 台以上计算机(物理或虚拟)的受访者人数从 2017 年的 77% 上升到 2019 年的 81%。
|
||||
> * 表明: 容器的引入似乎缓解了需要管理的 VM 的快速增长。但是,请警惕要管理的原始机器数量会减少的说法。
|
||||
>
|
||||
|
||||
**分析**:从直觉上看,随着容器使用的增长,虚拟机的增长将放缓;有许多容器被部署在虚拟机内部,从而充分利用了两者的优势特性,而且许多应用不会很快被容器化(留意下你所在企业的传统单体式应用)。
|
||||
|
||||
### 在生产环境中运行Istio的经验
|
||||
|
||||
- [文章链接][3]
|
||||
|
||||
> 在 HelloFresh,我们将团队分为小队和团伙。每个团伙都有自己的 Kubernetes 命名空间。如上所述,我们先按命名空间启用 sidecar 注入,然后再逐个对应用启用。在将应用添加到 Istio 之前,我们举办了研讨会,以使小队了解其应用发生的变化。由于我们采用“您构建,您维护”的模型,团队可以在故障定位时了解应用的进出流量。不仅如此,它还提升了公司内部的知识量。我们还创建了 Istio 相关的 [OKR][4] ,来跟踪我们的进度并达成我们引入Istio的目的。
|
||||
|
||||
**分析**:引入或是不引入技术,要由自己决定,同时要自行承担相应的后果。
|
||||
|
||||
### Aether: 首个开源的边缘云平台
|
||||
|
||||
- [文章链接][5]
|
||||
|
||||
> ONF 的营销副主席 Sloane 这样解释 Aether: 它将多个正在自己的沙箱中开发和运行的项目聚集到一起,ONF 试图在该框架下将多种边缘服务在一个融合平台上支持起来。ONF 的各个项目将保持独立并可继续单独使用,但是 Aether 试图将多个能力绑定到一起来简化企业的私有边缘云运营。
|
||||
>
|
||||
> 他说:“我们认为我们正在创造一个新的合作空间,工业界和社区可以携手帮助推动通用平台背后的整合和关键工作,然后可以帮助这些边缘云中的通用功能不断发展”。
|
||||
|
||||
**分析**:当今,使用技术解决的问题过于复杂,无法通过单一技术解决。比技术更重要的是要解决的业务问题需要聚焦于真正增值的部分。将两者结合起来,就是企业之间需要在他们共同的需求上找到合作的方法,并在它们特有的方面进行竞争。除了开源,你找不到比这更好的方法了。
|
||||
|
||||
### 与云相关职业的女性正在改变现状
|
||||
|
||||
- [文章链接][6]
|
||||
|
||||
> Yordanova 说:“由于云是一种相对较新的技术,我的[成为一名“科技女性”][7]的经验可能并不典型,因为云行业极为多样化”。“实际上,我的团队中性别比例相当,成员由随着云技术而成长的不同个性、文化和优势的具体人员组成。“
|
||||
|
||||
**分析**:我想考虑的一件事就是跨越式的演进思路。你可能可以跳过演进过程中的某个步骤或阶段,因为原先导致其存在的条件已不再适用。云技术时代没有形成“谁发明的以及它是为谁而生”的固有说法,所以也许它所承载的某些前代的技术负担更少?
|
||||
|
||||
### StarlingX 如何在中国开源项目的星空中闪耀
|
||||
|
||||
- [文章链接][8]
|
||||
|
||||
> 我们的团队在中国,因此我们的任务之一是帮助中国的社区开发软件、贡献代码、文档等。大多数 StarlingX 项目会议是在中国的深夜举行,因此华人社区成员的出席和参与颇具挑战。为了克服这些障碍,我们与中国的其他社区成员(例如 99cloud 的朋友)一起采取了一些措施,例如和其他社区成员一起聚会,一起参加动手实践研讨会和中文的特设技术会议,将一些文档翻译成中文,并在微信小组中不断进行互动(就像每个人都可以享受的 24/7 通话服务一样)
|
||||
|
||||
**分析**:随着中国对开源项目的贡献不断增长,这种情况似乎有可能逆转或至少相当。“学习英语”根本不是参与开源项目开发的先决条件。
|
||||
|
||||
希望你喜欢这个列表,下周再见。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/20/3/survey-istio-industry-news
|
||||
|
||||
作者:[Tim Hildred][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[messon007](https://github.com/messon007)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/thildred
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/data_metrics_analytics_desktop_laptop.png?itok=9QXd7AUr "Person standing in front of a giant computer screen with numbers, data"
|
||||
[2]: https://thenewstack.io/cncf-survey-snapshot-tech-adoption-in-the-cloud-native-world/
|
||||
[3]: https://engineering.hellofresh.com/everything-we-learned-running-istio-in-production-part-1-51efec69df65
|
||||
[4]: https://en.wikipedia.org/wiki/OKR
|
||||
[5]: https://www.sdxcentral.com/articles/news/onf-projects-coalesce-for-enterprise-edge-cloud/2020/03/
|
||||
[6]: https://www.cloudpro.co.uk/leadership/cloud-essentials/8446/how-women-in-cloud-are-challenging-the-narrative
|
||||
[7]: https://www.itpro.co.uk/business-strategy/33301/diversity-not-a-company-priority-claim-nearly-half-of-women-in-tech
|
||||
[8]: https://superuser.openstack.org/articles/starlingx-community-interview-how-starlingx-shines-in-the-starry-sky-of-open-source-projects-in-china/
|
||||
187
published/20200310 Run Kubernetes on a Raspberry Pi with k3s.md
Normal file
187
published/20200310 Run Kubernetes on a Raspberry Pi with k3s.md
Normal file
@ -0,0 +1,187 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (HankChow)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-12049-1.html)
|
||||
[#]: subject: (Run Kubernetes on a Raspberry Pi with k3s)
|
||||
[#]: via: (https://opensource.com/article/20/3/kubernetes-raspberry-pi-k3s)
|
||||
[#]: author: (Lee Carpenter https://opensource.com/users/carpie)
|
||||
|
||||
使用 K3s 在树莓派上运行 Kubernetes 集群
|
||||
======
|
||||
|
||||
> 跟随接下来的介绍,自己搭建一个三节点的 Kubernetes 集群。
|
||||
|
||||

|
||||
|
||||
我对在树莓派上搭建 [Kubernetes][2] 集群已经感兴趣很长时间了,只要照着网上的教程,我可以在由三个树莓派组成的集群中搭建一套 Kubernetes 并正常运行。但在这种情况下,主节点上的内存和 CPU 资源捉襟见肘,执行 Kubernetes 任务的时候往往性能不佳,想要升级 Kubernetes 就更不可能了。
|
||||
|
||||
这个时候,我非常激动地发现了 [K3s][3] 这个项目。K3s 被誉为在可用于资源受限环境下的轻量级 Kubernetes,它还针对 ARM 处理器做出了优化,这让 Kubernetes 集群可以在树莓派上运行得更好。在下文中,我们将会使用 K3s 来创建一个 Kubernetes 集群。
|
||||
|
||||
- [video](https://youtu.be/6PqxJhV-t1s)
|
||||
|
||||
### 准备
|
||||
|
||||
要按照本文介绍的方式创建 Kubernetes 集群,首先需要准备:
|
||||
|
||||
* 至少一个树莓派(包括 SD 卡和电源)
|
||||
* 网线
|
||||
* 将所有树莓派连接到一起的交换机或路由器
|
||||
|
||||
我们会通过在线安装的方式安装 K3s,因此还需要可以连接到互联网。
|
||||
|
||||
### 集群概览
|
||||
|
||||
在这个集群里,我们会使用三个树莓派。其中一个树莓派作为主节点,我们将它命名为 `kmaster`,并为其分配一个静态 IP `192.168.0.50`(注:假设使用的私有网段是 192.168.0.0/24),而另外两个树莓派作为工作节点,分别命名为 `knode1` 和 `knode2`,也分别分配 `192.168.0.51` 和 `192.168.0.52` 两个 IP 地址。
|
||||
|
||||
当然,如果你实际的网络布局和上面不同,只要将文中所提及到的 IP 替换成你实际可用的 IP 就可以了。
|
||||
|
||||
为了不需要通过 IP 来引用某一个节点,我们将每个节点的主机名记录到 PC 的 `/etc/hosts` 文件当中:
|
||||
|
||||
```
|
||||
echo -e "192.168.0.50\tkmaster" | sudo tee -a /etc/hosts
|
||||
echo -e "192.168.0.51\tknode1" | sudo tee -a /etc/hosts
|
||||
echo -e "192.168.0.52\tknode2" | sudo tee -a /etc/hosts
|
||||
```
|
||||
|
||||
### 部署主节点
|
||||
|
||||
我们首先部署主节点。最开始的步骤当然是使用镜像安装最新的 Raspbian,这个步骤可以参考我的[另一篇文章][4],在这里就不展开介绍了。在安装完成之后,启动 SSH 服务,将主机名设置为 `kmaster`,然后分配静态 IP `192.168.0.50`。
|
||||
|
||||
在主节点上安装 Raspbian 完成后,启动树莓派并通过 `ssh` 连接上去:
|
||||
|
||||
```
|
||||
ssh pi@kmaster
|
||||
```
|
||||
|
||||
在主节点上执行以下命令安装 K3s:
|
||||
|
||||
```
|
||||
curl -sfL https://get.k3s.io | sh -
|
||||
```
|
||||
|
||||
等到命令跑完以后,一个单节点集群就已经运行起来了。让我们检查一下,还在这个树莓派上执行:
|
||||
|
||||
```
|
||||
sudo kubectl get nodes
|
||||
```
|
||||
|
||||
就会看到这样的输出:
|
||||
|
||||
```
|
||||
NAME STATUS ROLES AGE VERSION
|
||||
kmaster Ready master 2m13s v1.14.3-k3s.1
|
||||
```
|
||||
|
||||
### 获取<ruby>连接令牌<rt>join token</rt></ruby>
|
||||
|
||||
之后我们需要部署工作节点。在工作节点上安装 K3s 的时候,会需要用到连接令牌,它放置在主节点的文件系统上。首先把连接令牌保存出来以便后续使用:
|
||||
|
||||
```
|
||||
sudo cat /var/lib/rancher/k3s/server/node-token
|
||||
```
|
||||
|
||||
### 部署工作节点
|
||||
|
||||
通过 SD 卡在每个作为工作节点的树莓派上安装 Raspbian。在这里,我们把其中一个树莓派的主机名设置为 `knode1`,为其分配 IP 地址 `192.168.0.51`,另一个树莓派的主机名设置为 `knode2`,分配 IP 地址 `192.168.0.52`。接下来就可以安装 K3s 了。
|
||||
|
||||
启动主机名为 `knode1` 的树莓派,通过 `ssh` 连接上去:
|
||||
|
||||
```
|
||||
ssh pi@knode1
|
||||
```
|
||||
|
||||
在这个树莓派上,安装 K3s 的过程和之前差不多,但需要另外加上一些参数,表示它是一个工作节点,需要连接到一个已有的集群上:
|
||||
|
||||
```
|
||||
curl -sfL http://get.k3s.io | K3S_URL=https://192.168.0.50:6443 \
|
||||
K3S_TOKEN=刚才保存下来的连接令牌 sh -
|
||||
```
|
||||
|
||||
`K3S_TOKEN` 的值需要替换成刚才保存下来的实际的连接令牌。完成之后,在主机名为 `knode2` 的树莓派上重复这个安装过程。
|
||||
|
||||
### 通过 PC 访问集群
|
||||
|
||||
现在如果我们想要查看或者更改集群,都必须 `ssh` 到集群的主节点才能使用 `kubectl`,这是比较麻烦的。因此我们会将 `kubectl` 放到 PC 上使用。首先,在主节点上获取一些必要的配置信息,`ssh` 到 `kmaster` 上执行:
|
||||
|
||||
```
|
||||
sudo cat /etc/rancher/k3s/k3s.yaml
|
||||
```
|
||||
|
||||
复制上面命令的输出,然后在你的 PC 上创建一个目录用来放置配置文件:
|
||||
|
||||
```
|
||||
mkdir ~/.kube
|
||||
```
|
||||
|
||||
将复制好的内容写入到 `~/.kube/config` 文件中,然后编辑该文件,将
|
||||
|
||||
```
|
||||
server: https://localhost:6443
|
||||
```
|
||||
|
||||
改为
|
||||
|
||||
```
|
||||
server: https://kmaster:6443
|
||||
```
|
||||
|
||||
出于安全考虑,只对自己保留这个配置文件的读写权限:
|
||||
|
||||
```
|
||||
chmod 600 ~/.kube/config
|
||||
```
|
||||
|
||||
如果 PC 上还没有安装 `kubectl` 的话,就可以开始安装了。Kubernetes 官方网站上有各种平台安装 `kubectl` 的[方法说明][5],我使用的是 Ubuntu 的衍生版 Linux Mint,所以我的安装方法是这样的:
|
||||
|
||||
```
|
||||
sudo apt update && sudo apt install -y apt-transport-https
|
||||
curl -s https://packages.cloud.google.com/apt/doc/apt-key.gpg | sudo apt-key add -
|
||||
echo "deb https://apt.kubernetes.io/ kubernetes-xenial main" | sudo tee -a /etc/apt/sources.list.d/kubernetes.list
|
||||
sudo apt update && sudo apt install kubectl
|
||||
```
|
||||
|
||||
上面几个命令的作用是添加了一个包含 Kubernetes 的 Debian 软件库,获取 GPG 密钥以确保安全,然后更新软件包列表并安装 `kubectl`。如果 `kubectl` 有更新,我们将会通过<ruby>标准软件更新机制<rt>standard software update mechanism</rt></ruby>收到通知。
|
||||
|
||||
现在在 PC 上就可以查看 Kubernetes 集群了:
|
||||
|
||||
```
|
||||
kubectl get nodes
|
||||
```
|
||||
|
||||
输出大概会是这样:
|
||||
|
||||
```
|
||||
NAME STATUS ROLES AGE VERSION
|
||||
kmaster Ready master 12m v1.14.3-k3s.1
|
||||
knode1 Ready worker 103s v1.14.3-k3s.1
|
||||
knode1 Ready worker 103s v1.14.3-k3s.1
|
||||
```
|
||||
|
||||
至此,我们已经搭建了一个三节点的 Kubernetes 集群。
|
||||
|
||||
### K3s 的彩蛋
|
||||
|
||||
如果执行 `kubectl get pods --all-namespaces`,就会看到其它服务的一些 Pod,比如 [Traefik][6]。Traefik 在这里起到是反向代理和负载均衡器的作用,它可以让流量从单个入口进入集群后引导到集群中的各个服务。Kubernetes 支持这种机制,但 Kubernetes 本身不提供这个功能,因此 Traefik 是一个不错的选择,K3s 安装后立即可用的优点也得益于此。
|
||||
|
||||
在后续的文章中,我们会继续探讨 Traefik 在 Kubernetes ingress 中的应用,以及在集群中部署其它组件。敬请关注。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/20/3/kubernetes-raspberry-pi-k3s
|
||||
|
||||
作者:[Lee Carpenter][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[HankChow](https://github.com/HankChow)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/carpie
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/ship_wheel_gear_devops_kubernetes.png?itok=xm4a74Kv (A ship wheel with someone steering)
|
||||
[2]: https://opensource.com/resources/what-is-kubernetes
|
||||
[3]: https://k3s.io/
|
||||
[4]: https://carpie.net/articles/headless-pi-with-static-ip-wired-edition
|
||||
[5]: https://kubernetes.io/docs/tasks/tools/install-kubectl/
|
||||
[6]: https://traefik.io/
|
||||
@ -0,0 +1,145 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (HankChow)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-11993-1.html)
|
||||
[#]: subject: (How to install pip to manage PyPI packages easily)
|
||||
[#]: via: (https://opensource.com/article/20/3/pip-linux-mac-windows)
|
||||
[#]: author: (Vijay Singh Khatri https://opensource.com/users/vijaytechnicalauthor)
|
||||
|
||||
安装 pip 轻松管理 PyPI 软件包
|
||||
======
|
||||
|
||||
> 在 Linux、Mac 或 Windows 上为旧版 Python 安装 pip。
|
||||
|
||||

|
||||
|
||||
Python 是一种功能强大、流行广泛的编程语言,在常规编程、数据科学等很多方面它都有丰富的软件包可供使用。但这些软件包通常都不会在 Python 安装时自动附带,而是需要由用户自行下载、安装和管理。所有的这些软件包(包括库和框架)都存放在一个名叫 [PyPI][2](也就是 <ruby>Python 软件包索引<rt> Python Package Index</rt></ruby>)的中央存储库当中,而 `pip`(也就是<ruby>首选安装程序<rt>Preferred Installer Program</rt></ruby>)则是管理这个中央存储库的工具。
|
||||
|
||||
在安装 `pip` 之后,管理 PyPI 的软件包就变得很方便了。大部分的软件包都可以通过在终端或者命令行界面执行 `python -m pip install <软件包名>` 这样的命令来完成安装。
|
||||
|
||||
较新版本的 Python 3(3.4 或以上)和 Python 2(2.7.9 或以上)都已经预装了 `pip`,旧版本的 Python 没有自带 `pip`,但可以另外安装。
|
||||
|
||||
在这篇文章中,我将会介绍 `pip` 在 Linux、Mac 和 Windows 系统上的安装过程。想要了解更多详细信息,可以参考 [pip.pypa][3] 的文档。
|
||||
|
||||
### 首先需要安装 Python
|
||||
|
||||
首先你的系统中需要安装好 Python,否则 `pip` 安装器无法理解任何相关的命令。你可以在命令行界面、Bash 或终端执行 `python` 命令确认系统中是否已经安装 Python,如果系统无法识别 `python` 命令,请先[下载 Python][4] 并安装。安装完成后,你就可以看到一些引导你安装 `pip` 的提示语了。
|
||||
|
||||
### 在 Linux 上安装 pip
|
||||
|
||||
在不同发行版的 Linux 上,安装 `pip` 的命令也有所不同。
|
||||
|
||||
在 Fedora、RHEL 或 CentOS 上,执行以下命令安装:
|
||||
|
||||
```
|
||||
$ sudo dnf install python3
|
||||
```
|
||||
|
||||
在 Debian 或 Ubuntu 上,使用 `apt` 包管理工具安装:
|
||||
|
||||
```
|
||||
$ sudo apt install python3-pip
|
||||
```
|
||||
|
||||
其它的发行版可能还会有不同的包管理工具,比如 Arch Linux 使用的是 `pacman`:
|
||||
|
||||
```
|
||||
$ sudo pacman -S python-pip
|
||||
```
|
||||
|
||||
执行 `pip --version` 命令就可以确认 `pip` 是否已经正确安装。
|
||||
|
||||
在 Linux 系统上安装 `pip` 就是这样简单,你可以直接跳到“使用 pip”部分继续阅读。
|
||||
|
||||
### 在 Mac 上安装 pip
|
||||
|
||||
MacOS 已经预装了 Python,但 Python 版本一般是比较旧的。如果你要使用 Python 的话,建议[另外安装 Python 3][6]。
|
||||
|
||||
在 Mac 上可以使用 [homebrew][7] 安装 Python 3:
|
||||
|
||||
```
|
||||
$ brew update && brew upgrade python
|
||||
```
|
||||
|
||||
如果你安装的是以上提到的新版本 Python 3,它会自带 `pip` 工具。你可以使用以下命令验证:
|
||||
|
||||
```
|
||||
$ python3 -m pip --version
|
||||
```
|
||||
|
||||
如果你使用的是 Mac,安装过程也到此结束,可以从“使用 pip”部分继续阅读。
|
||||
|
||||
### 在 Windows 上安装 pip
|
||||
|
||||
以下 `pip` 安装过程是针对 Windows 8 和 Windows 10 的。下面文章中的截图是 Windows 10 环境下的截图,但对 Windows 8 同样适用。
|
||||
|
||||
首先确认 [Python 已经安装完成][8]。
|
||||
|
||||
如果你想在 Windows 系统上像 Linux 一样使用包管理工具,[Chocolatey][9] 是一个不错的选择,它可以让 Python 的调用和更新变得更加方便。Chocolatey 在 PowerShell 中就可以运行,只需要简单的命令,Python 就可以顺利安装。
|
||||
|
||||
```
|
||||
PS> choco install python
|
||||
```
|
||||
|
||||
接下来就可以使用 `pip` 安装所需的软件包了。
|
||||
|
||||
### 使用 pip
|
||||
|
||||
在 Linux、BSD、Windows 和 Mac 上,`pip` 都是以同样的方式使用的。
|
||||
|
||||
例如安装某个库:
|
||||
|
||||
```
|
||||
python3 -m pip install foo --user
|
||||
```
|
||||
|
||||
卸载某个已安装的库:
|
||||
|
||||
```
|
||||
python3 -m pip uninstall foo
|
||||
```
|
||||
|
||||
按照名称查找软件包:
|
||||
|
||||
```
|
||||
python3 -m pip search foo
|
||||
```
|
||||
|
||||
将 `pip` 更新到一个新版本:
|
||||
|
||||
```
|
||||
$ sudo pip install --upgrade pip
|
||||
```
|
||||
|
||||
需要注意的是,在 Windows 系统中不需要在前面加上 `sudo` 命令,这是因为 Windows 通过独有的方式管理用户权限,对应的做法是[创建一个执行策略例外][10]。
|
||||
|
||||
```
|
||||
python -m pip install --upgrade pip
|
||||
```
|
||||
|
||||
希望本文介绍的的方法能对你有所帮助,欢迎在评论区分享你的经验。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/20/3/pip-linux-mac-windows
|
||||
|
||||
作者:[Vijay Singh Khatri][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[HankChow](https://github.com/HankChow)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/vijaytechnicalauthor
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/1980s-computer-yearbook.png?itok=eGOYEKK- (Person typing on a 1980's computer)
|
||||
[2]: https://pypi.org/
|
||||
[3]: https://pip.pypa.io/en/stable/installing/
|
||||
[4]: https://www.python.org/downloads/
|
||||
[5]: tmp.u1JOYd3gs9#usage
|
||||
[6]: https://opensource.com/article/19/5/python-3-default-mac
|
||||
[7]: https://brew.sh
|
||||
[8]: https://opensource.com/article/19/8/how-install-python-windows
|
||||
[9]: https://opensource.com/article/20/3/chocolatey
|
||||
[10]: https://opensource.com/article/20/3/chocolatey#admin
|
||||
@ -0,0 +1,87 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-12018-1.html)
|
||||
[#]: subject: (Amazon Has Launched Its Own Linux Distribution But It’s Not for Everyone)
|
||||
[#]: via: (https://itsfoss.com/bottlerocket-linux/)
|
||||
[#]: author: (Abhishek Prakash https://itsfoss.com/author/abhishek/)
|
||||
|
||||
Amazon 推出了自己的容器专用 Linux 发行版“瓶装火箭”
|
||||
======
|
||||
|
||||

|
||||
|
||||
Amazon 已经[推出][1]了自己的基于 Linux 的开源操作系统 Bottlerocket(“瓶装火箭”)。但在你兴奋地想要尝试安装和运行它之前,我必须告诉你,它不是常规的如 Ubuntu、Fedora 或 Debian 这样的 Linux 发行版。那它是什么?
|
||||
|
||||
### Bottlerocket:来自 Amazon 的 Linux 发行版,用于运行容器
|
||||
|
||||
![][2]
|
||||
|
||||
如果你不了解 Linux 容器,建议你阅读 Red Hat 的[这篇文章][3]。
|
||||
|
||||
自从首次提出云计算一词以来,IT 行业发生了许多变化。得益于 Amazon AWS、Google、Linode、Digital Ocean 等云服务器提供商,部署 Linux 服务器(通常在虚拟机中运行)只需几秒钟。最重要的是,你可以借助 Docker 和 Kubernetes 之类的工具在这些服务器上以容器形式部署应用和服务。
|
||||
|
||||
问题是,当你唯一目的是在 Linux 系统上运行容器时,并不总是需要完整的 Linux 发行版。这就是为什么容器专用 Linux 仅提供必要软件包的原因。这将大大减少操作系统的大小,从而进一步减少部署时间。
|
||||
|
||||
[Bottlerocket][5] Linux 由 Amazon Web Services(AWS)专门构建,用于在虚拟机或裸机上运行容器。它支持 docker 镜像和其他遵循 [OCI 镜像][6]格式的镜像。
|
||||
|
||||
### Bottlerocket Linux 的特性
|
||||
|
||||
![][7]
|
||||
|
||||
这是来自 Amazon 的新 Linux 发行版提供的特性:
|
||||
|
||||
#### 没有逐包更新
|
||||
|
||||
传统的 Linux 发行版更新过程由更新单个软件包组成。Bottlerocket 改用基于镜像的更新。
|
||||
|
||||
由于采用了这种方法,可以避免冲突和破坏,并可以进行快速而完整的回滚(如有必要)。
|
||||
|
||||
#### 只读文件系统
|
||||
|
||||
Bottlerocket 还使用了只读主文件系统。在启动时通过 dm-verity 检查其完整性。在其他安全措施上,也不建议使用 SSH 访问,并且只能通过[管理容器][8](附加机制)使用。
|
||||
|
||||
AWS 已经统治了云世界。
|
||||
|
||||
#### 自动更新
|
||||
|
||||
你可以使用 Amazon EKS 之类的编排服务来自动执行 Bottlerocket 更新。
|
||||
|
||||
Amazon 还声称,与通用 Linux 发行版相比,仅包含运行容器的基本软件可以减少攻击面。
|
||||
|
||||
### 你怎么看?
|
||||
|
||||
Amazon 并不是第一个创建“容器专用 Linux” 的公司。我认为 CoreOS 是最早的此类发行版之一。[CoreOS 被 Red Hat 收购][9],Red Hat 又被 [IBM 收购][10]。Red Hat 公司最近停用了 CoreOS,并用 [Fedora CoreOS][11] 代替了它。
|
||||
|
||||
云服务器是一个巨大的行业,它将继续发展壮大。像 Amazon 这样的巨头将竭尽所能与它竞争对手保持一致或领先。我认为,Bottlerocket 是对 IBM Fedora CoreOS(目前)的应答。
|
||||
|
||||
尽管 [Bottlerocket 仓库可在 GitHub 上找到][12],但我还没发现就绪的镜像(LCTT 译注:源代码已经提供)。在撰写本文时,它仅[可在 AWS 上预览][5]。
|
||||
|
||||
你对此有何看法?Amazon 会从 Bottlerocket 获得什么?如果你以前使用过 CoreOS 之类的软件,你会切换到 Bottlerocket 么?
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://itsfoss.com/bottlerocket-linux/
|
||||
|
||||
作者:[Abhishek Prakash][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://itsfoss.com/author/abhishek/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://aws.amazon.com/blogs/aws/bottlerocket-open-source-os-for-container-hosting/
|
||||
[2]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2020/03/botlerocket-logo.png?ssl=1
|
||||
[3]: https://www.redhat.com/en/topics/containers/whats-a-linux-container
|
||||
[4]: https://www.linode.com/
|
||||
[5]: https://aws.amazon.com/bottlerocket/
|
||||
[6]: https://www.opencontainers.org/
|
||||
[7]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2020/03/BottleRocket.png?ssl=1
|
||||
[8]: https://github.com/bottlerocket-os/bottlerocket-admin-container
|
||||
[9]: https://itsfoss.com/red-hat-acquires-coreos/
|
||||
[10]: https://itsfoss.com/ibm-red-hat-acquisition/
|
||||
[11]: https://getfedora.org/en/coreos/
|
||||
[12]: https://github.com/bottlerocket-os/bottlerocket
|
||||
@ -0,0 +1,215 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (hkurj)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-12019-1.html)
|
||||
[#]: subject: (6 Best AUR (Arch User Repository) Helpers for Arch Linux)
|
||||
[#]: via: (https://www.2daygeek.com/best-aur-arch-user-repository-helpers-arch-linux-manjaro/)
|
||||
[#]: author: (Magesh Maruthamuthu https://www.2daygeek.com/author/magesh/)
|
||||
|
||||
6 个用于 Arch Linux 的最佳 AUR 助手
|
||||
======
|
||||
|
||||

|
||||
|
||||
Arch Linux 是一款 Linux 发行版,主要由针对 x86-64 微处理器计算机的二进制软件包组成。Arch Linux 使用的是滚动发布模型,这种模式会频繁的给应用程序交付更新。它使用名为 [pacman][1] 的软件包管理器,可以用来安装、删除和更新软件包。
|
||||
|
||||
由于 Arch Linux 是为有经验的用户构建的,建议新手在使用过其他 Linux 后再来尝试。
|
||||
|
||||
### 什么是 AUR(Arch 用户软件仓库)?
|
||||
|
||||
[Arch 用户软件仓库][2] 通常称为 AUR,是给 Arch 用户的基于社区的软件存储库。
|
||||
|
||||
根据软件包在 AUR 社区的流行程度,用户编译的软件包会进入到 Arch 的官方存储库。
|
||||
|
||||
### 什么是 AUR 助手?
|
||||
|
||||
[AUR 助手][3]是一个包装程序,允许用户从 AUR 存储库安装软件包,而无需手动干预。
|
||||
|
||||
很多用例实现了自动化,比如包搜索、解决依赖关系、检索和构建 AUR 包、Web 内容检索和 AUR 包提交之类。
|
||||
|
||||
以下列出了 6 种最佳的 AUR 助手:
|
||||
|
||||
* Yay(Yet another Yogurt)
|
||||
* Pakku
|
||||
* Pacaur
|
||||
* Pikaur
|
||||
* Trizen
|
||||
* Aura
|
||||
|
||||
### 1)Yay(Yet another Yogurt)
|
||||
|
||||
[Yay][4] 是 Arch Linux 下基于 CLI 的最佳 AUR 助手,使用 Go 语言编写。Yay 是基于 yaourt、apacman 和 pacaur 设计的。
|
||||
|
||||
这是最合适推荐给新手的 AUR 助手。类似于 Pacman,其使用方法和 `pacman` 中的命令和选项很相似,可以让用户在搜索过程中找到匹配的软件包提供程序,并进行选择。
|
||||
|
||||
#### 如何安装 yay
|
||||
|
||||
依次运行以下命令以在 Arch Linux 系统上安装。
|
||||
|
||||
```
|
||||
$ sudo pacman -S git go base-devel
|
||||
$ git clone https://aur.archlinux.org/yay.git
|
||||
$ cd yay
|
||||
$ makepkg -si
|
||||
```
|
||||
|
||||
#### 如何使用 yay
|
||||
|
||||
`yay` 语法与 `pacman` 相同,使用以下命令安装软件包。
|
||||
|
||||
```
|
||||
$ yay -s arch-wiki-man
|
||||
```
|
||||
|
||||
### 2)Pakku
|
||||
|
||||
[Pakku][5] 可以被视为一个初始阶段的 Pacman。它是一个包装程序,可以让用户从 AUR 中搜索或安装软件包。
|
||||
|
||||
它在删除依赖项方面做得不错,并且还允许通过克隆 PKGBUILD 来安装软件包。
|
||||
|
||||
#### 如何安装 Pakku
|
||||
|
||||
要在 Arch Linux 的系统上安装 Pakku,请依次运行以下命令。
|
||||
|
||||
```
|
||||
$ sudo pacman -S git base-devel
|
||||
$ git clone https://aur.archlinux.org/pakku.git
|
||||
$ cd pakku
|
||||
$ makepkg -si
|
||||
```
|
||||
|
||||
#### 如何使用 Pakku
|
||||
|
||||
`pakku` 语法与 `pacman` 相同,使用以下命令安装软件包。
|
||||
|
||||
```
|
||||
$ pakku -s dropbox
|
||||
```
|
||||
|
||||
### 3)Pacaur
|
||||
|
||||
另一个基于 CLI 的 AUR 助手,可帮助减少用户与提示符的交互。
|
||||
|
||||
[Pacaur][6] 专为倾向于自动化重复任务的高级用户而设计。用户需要熟悉 `makepkg` 及其配置的 AUR 手动构建过程。
|
||||
|
||||
#### 如何安装 Pacaur
|
||||
|
||||
要在 Arch Linux 的系统上安装 Pakku,请依次运行以下命令。
|
||||
|
||||
```
|
||||
$ sudo pacman -S git base-devel
|
||||
$ git clone https://aur.archlinux.org/pacaur.git
|
||||
$ cd pacaur
|
||||
$ makepkg -si
|
||||
```
|
||||
|
||||
#### 如何使用 Pacaur
|
||||
|
||||
`pacaur` 语法与 `pacman` 相同,使用以下命令安装软件包。
|
||||
|
||||
```
|
||||
$ pacaur -s spotify
|
||||
```
|
||||
|
||||
### 4)Pikaur
|
||||
|
||||
[Pikaur][7] 是具有最小依赖性的 AUR 助手,可以一次查看所有 PKGBUILD,无需用户交互即可全部构建。
|
||||
|
||||
Pikaur 将通过控制 `pacman` 命令来告知 Pacman 要执行的下一个步骤。
|
||||
|
||||
#### 如何安装 Pikaur
|
||||
|
||||
要在 Arch Linux 的系统上安装 Pakku,请依次运行以下命令。
|
||||
|
||||
```
|
||||
$ sudo pacman -S git base-devel
|
||||
$ git clone https://aur.archlinux.org/pikaur.git
|
||||
$ cd pikaur
|
||||
$ makepkg -fsri
|
||||
```
|
||||
|
||||
#### 如何使用 Pikaur
|
||||
|
||||
`pikaur` 语法与 `pacman` 相同,使用以下命令安装软件包。
|
||||
|
||||
```
|
||||
$ pacaur -s spotify
|
||||
```
|
||||
|
||||
### 5)Trizen
|
||||
|
||||
[Trizen][8] 是用 Perl 编写的基于命令行的 AUR 轻量级包装器。这个面向速度的 AUR 助手,它允许用户搜索、安装软件包,还允许阅读 AUR 软件包注释。
|
||||
|
||||
支持编辑文本文件,并且输入/输出使用 UTF-8。内置与 `pacman` 的交互功能。
|
||||
|
||||
#### 如何安装 Trizen
|
||||
|
||||
要在 Arch Linux 的系统上安装 Trizen,请依次运行以下命令。
|
||||
|
||||
```
|
||||
$ sudo pacman -S git base-devel
|
||||
$ git clone https://aur.archlinux.org/trizen.git
|
||||
$ cd trizen
|
||||
$ makepkg -si
|
||||
```
|
||||
|
||||
#### 如何使用 Trizen
|
||||
|
||||
`trizen` 语法与 `pacman` 相同,使用以下命令安装软件包。
|
||||
|
||||
```
|
||||
$ pacaur -s google-chrome
|
||||
```
|
||||
|
||||
### 6)Aura
|
||||
|
||||
[Aura][9] 是用 Haskell 编写的,是用于 Arch Linux 和 AUR 的安全的多语言包管理器。它支持许多Pacman 操作和子选项,可轻松进行开发并编写精美的代码。
|
||||
|
||||
它可以自动从 AUR 安装软件包。使用 Aura 时,用户通常会在系统升级方面遇到一些困难。
|
||||
|
||||
#### 如何安装 Aura
|
||||
|
||||
要在 Arch Linux 的系统上安装 Pakku,请依次运行以下命令。
|
||||
|
||||
```
|
||||
$ sudo pacman -S git base-devel
|
||||
$ git clone https://aur.archlinux.org/aura.git
|
||||
$ cd aura
|
||||
$ makepkg -si
|
||||
```
|
||||
|
||||
#### 如何使用 Aura
|
||||
|
||||
`aura` 语法与 `pacman` 相同,使用以下命令安装软件包。
|
||||
|
||||
```
|
||||
$ pacaur -s android-sdk
|
||||
```
|
||||
|
||||
### 结论
|
||||
|
||||
用户可以凭借这些分析在上述 6 个 AUR 助手中进行选择。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.2daygeek.com/best-aur-arch-user-repository-helpers-arch-linux-manjaro/
|
||||
|
||||
作者:[Magesh Maruthamuthu][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[hkurj](https://github.com/hkurj)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.2daygeek.com/author/magesh/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.2daygeek.com/pacman-command-examples-manage-packages-arch-linux-system/
|
||||
[2]: https://wiki.archlinux.org/index.php/Arch_User_Repository
|
||||
[3]: https://wiki.archlinux.org/index.php/AUR_helpers
|
||||
[4]: https://github.com/Jguer/yay
|
||||
[5]: https://github.com/kitsunyan/pakku
|
||||
[6]: https://github.com/E5ten/pacaur
|
||||
[7]: https://github.com/actionless/pikaur
|
||||
[8]: https://github.com/trizen/trizen
|
||||
[9]: https://github.com/fosskers/aura
|
||||
@ -0,0 +1,114 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-12030-1.html)
|
||||
[#]: subject: (GNOME 3.36 Released With Visual & Performance Improvements)
|
||||
[#]: via: (https://itsfoss.com/gnome-3-36-release/)
|
||||
[#]: author: (Ankush Das https://itsfoss.com/author/ankush/)
|
||||
|
||||
GNOME 3.36 发布,对视觉和性能进行了改进
|
||||
======
|
||||
|
||||

|
||||
|
||||
在 [GNOME 3.34][1] 发布 6 个月后,最新版本的 GNOME 3.36 代号为 “Gresik” 也最终发布了。不仅是添加了功能,GNOME 3.36 还改进了许多我们需要的功能。
|
||||
|
||||
在本文中,我将重点介绍 GNOME 新版本的主要更改。
|
||||
|
||||
### GNOME 3.36 的关键改进
|
||||
|
||||
如果你想快速了解发生了什么变化,可以看以下官方视频:
|
||||
|
||||
[视频][2]
|
||||
|
||||
现在,让我分别重点介绍最新版本中的更改:
|
||||
|
||||
#### GNOME Shell 扩展应用
|
||||
|
||||
你可以通过专门的“扩展”程序轻松管理 GNOME Shell 的扩展。
|
||||
|
||||
![][3]
|
||||
|
||||
因此,你可以使用该程序更新、配置、删除或禁用现有扩展。
|
||||
|
||||
#### 切换到请勿打扰(DND)
|
||||
|
||||
![][4]
|
||||
|
||||
你可能已经在 Pop!\_OS 或其他 Linux 发行版中注意到了它。
|
||||
|
||||
但是,GNOME 3.36 现在在通知弹出区域中实现了 DND 切换。除非你将其关闭,否则不会收到任何通知。
|
||||
|
||||
#### 锁屏改进
|
||||
|
||||
![][5]
|
||||
|
||||
在新版本中,锁定屏幕在输入凭据之前没有额外的动画。取而代之会在登录屏幕直接打招呼。
|
||||
|
||||
另外,为了提升一致性,锁屏背景将是墙纸的模糊版本。
|
||||
|
||||
总的来说,对锁屏的改进旨在使之更易于访问,同时改善其外观/感觉。
|
||||
|
||||
#### 视觉变化
|
||||
|
||||
![][6]
|
||||
|
||||
包含了一些明显的新增,这些设计更改改善了 GNOME 3.36 的总体外观。
|
||||
|
||||
从图标的重新设计到文件夹和系统对话框,进行了许多小的改进以增强 GNOME 3.36 的用户体验。
|
||||
|
||||
此外,设置应用已进行了调整,通过微小的界面重新设计,使得选项访问更加容易。
|
||||
|
||||
#### 主要性能改进
|
||||
|
||||
GNOME 声称,此更新还提升了 GNOME 桌面的性能。
|
||||
|
||||
当使用装有 GNOME 3.36 的发行版时,你会注意到在性能上有明显的不同。无论是动画、重新设计还是微小的调整,对于 GNOME 3.36 所做的一切都会对用户的性能产生积极影响。
|
||||
|
||||
#### 其他更改
|
||||
|
||||
除了上述关键更改之外,还有很多其他改进,例如:
|
||||
|
||||
* 时钟重新设计
|
||||
* 用户文档更新
|
||||
* GNOME 安装助手改进
|
||||
|
||||
还有许多其他更改。你可以查看[官方发布说明][7]了解更多信息。
|
||||
|
||||
### 如何获取 GNOME 3.36?
|
||||
|
||||
即使 GNOME 3.36 已正式发布。Linux 发行版可能需要一段时间才能让你轻松升级 GNOME 体验。
|
||||
|
||||
[Ubuntu 20.04 LTS][8] 将提供最新版本 GNOME。你可以等待。
|
||||
|
||||
其他[流行的 Linux 发行版][9],如 Fedora、OpenSuse、Pop!\_OS,应该会很快包含 GNOME 3.36。[Arch Linux][10] 已升级到 GNOME 3.36。
|
||||
|
||||
我建议你耐心等待,直到获得发行版本的更新。不过,你可以查看[源代码][11]或尝试即将发布的流行发行版的开发版本,这些发行版可能有 GNOME 3.36。
|
||||
|
||||
你如何看待 GNOME 3.36?在下面的评论中让我知道你的想法。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://itsfoss.com/gnome-3-36-release/
|
||||
|
||||
作者:[Ankush Das][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://itsfoss.com/author/ankush/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://itsfoss.com/gnome-3-34-release/
|
||||
[2]: https://img.linux.net.cn/static/video/Introducing%20GNOME%203.36%20-%20%27Gresik%27-ae2D4aWTsXM.mp4
|
||||
[3]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2020/03/extensions-gnome.jpg?ssl=1
|
||||
[4]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2020/03/dnd-gnome.jpg?ssl=1
|
||||
[5]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2020/03/gnome-lockscreen.jpg?ssl=1
|
||||
[6]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2020/03/gnome-settings.jpg?ssl=1
|
||||
[7]: https://help.gnome.org/misc/release-notes/3.36/
|
||||
[8]: https://itsfoss.com/ubuntu-20-04-release-features/
|
||||
[9]: https://itsfoss.com/best-linux-distributions/
|
||||
[10]: https://www.archlinux.org/
|
||||
[11]: https://gitlab.gnome.org/GNOME
|
||||
173
published/20200313 How to Change MAC Address in Linux.md
Normal file
173
published/20200313 How to Change MAC Address in Linux.md
Normal file
@ -0,0 +1,173 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-12008-1.html)
|
||||
[#]: subject: (How to Change MAC Address in Linux)
|
||||
[#]: via: (https://itsfoss.com/change-mac-address-linux/)
|
||||
[#]: author: (Dimitrios Savvopoulos https://itsfoss.com/author/itsfoss/)
|
||||
|
||||
如何在 Linux 中更改 MAC 地址
|
||||
======
|
||||
|
||||
在向你展示如何在 Linux 中更改 MAC 地址之前,让我们首先讨论为什么要更改它。
|
||||
|
||||
可能有几个原因。也许你不希望在公共网络上公开你的实际 [MAC 地址][1](也称为物理地址)?还有可能是网络管理员可能已在路由器或防火墙中阻止了特定的 MAC 地址。
|
||||
|
||||
一个实用的“好处”是某些公共网络(例如机场 WiFi)允许在有限的时间内免费上网。如果你还想继续使用,那么伪造 Mac 地址可能会欺骗网络,让它认为是一台新设备。这也是一个有名的原因。
|
||||
|
||||

|
||||
|
||||
我将展示更改 MAC 地址(也称为欺骗/伪造 MAC 地址)的步骤。
|
||||
|
||||
### 在 Linux 中更改 MAC 地址
|
||||
|
||||
让我们一步步来:
|
||||
|
||||
#### 查找你的 MAC 地址和网络接口
|
||||
|
||||
让我们找出一些[关于 Linux 中网卡的细节][3]。使用此命令获取网络接口详细信息:
|
||||
|
||||
```
|
||||
ip link show
|
||||
```
|
||||
|
||||
在输出中,你将看到一些详细信息以及 MAC 地址:
|
||||
|
||||
```
|
||||
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN mode DEFAULT group default qlen 1000
|
||||
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
|
||||
2: eno1: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc fq_codel state DOWN mode DEFAULT group default qlen 1000
|
||||
link/ether 94:c6:f8:a7:d7:30 brd ff:ff:ff:ff:ff:ff
|
||||
3: enp0s31f6: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP mode DORMANT group default qlen 1000
|
||||
link/ether 38:42:f8:8b:a7:68 brd ff:ff:ff:ff:ff:ff
|
||||
4: docker0: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc noqueue state DOWN mode DEFAULT group default
|
||||
link/ether 42:02:07:8f:a7:38 brd ff:ff:ff:ff:ff:ff
|
||||
```
|
||||
|
||||
如你所见,在这里,我的网络接口称为 `enp0s31f6`,MAC 地址为 `38:42:f8:8b:a7:68`。
|
||||
|
||||
你可能需要在安全的地方记录下来,以便稍后还原到该原始 MAC 地址。
|
||||
|
||||
现在你可以继续更改 MAC 地址。
|
||||
|
||||
注意!
|
||||
|
||||
如果在当前使用的网络接口上执行此操作,那么可能会中断你的网络连接。因此,请在其他网卡上尝试使用此方法,或者准备重启网络。
|
||||
|
||||
#### 方法 1:使用 Macchanger 更改 MAC 地址
|
||||
|
||||
![][4]
|
||||
|
||||
[Macchanger][5] 是查看、修改和操作网卡 MAC 地址的简单程序。它几乎在所有 GNU/Linux 操作系统中都可用,你可以使用发行版的包安装程序进行安装。
|
||||
|
||||
在 Arch Linux 或 Manjaro 上:
|
||||
|
||||
```
|
||||
sudo pacman -S macchanger
|
||||
```
|
||||
|
||||
在 Fedora、CentOS 和 RHEL 上:
|
||||
|
||||
```
|
||||
sudo dnf install macchanger
|
||||
```
|
||||
|
||||
在 Debian、Ubuntu、Linux Mint、Kali Linux 上:
|
||||
|
||||
```
|
||||
sudo apt install macchanger
|
||||
```
|
||||
|
||||
**重要!**系统会要求你选择是否应将 `macchanger` 设置为在每次启动或关闭网络设备时自动运行。每当你接到网线或重启 WiFi 时,它都会提供一个新的 MAC 地址。
|
||||
|
||||
![Not a good idea to run it automatically][6]
|
||||
|
||||
我建议不要自动运行它,除非你确实需要每次更改 MAC 地址。因此,选择“No”(按 `Tab` 键),然后按回车键继续。
|
||||
|
||||
**如何使用 Macchanger 更改 MAC 地址**
|
||||
|
||||
你还记得网络接口名称吗?你在前面的步骤中获得了它。
|
||||
|
||||
现在,要将随机 MAC 地址分配给该网卡,请使用:
|
||||
|
||||
```
|
||||
sudo macchanger -r enp0s31f6
|
||||
```
|
||||
|
||||
更改 MAC 后,使用以下命令进行验证:
|
||||
|
||||
```
|
||||
ip addr
|
||||
```
|
||||
|
||||
现在你将看到已经伪造 MAC。
|
||||
|
||||
要将 MAC 地址更改为特定值,请使用以下命令指定自定义 MAC 地址:
|
||||
|
||||
```
|
||||
macchanger --mac=XX:XX:XX:XX:XX:XX
|
||||
```
|
||||
|
||||
其中 XX:XX:XX:XX:XX:XX 是你要更改的新 MAC。
|
||||
|
||||
最后,要将 MAC 地址恢复为其原始硬件值,请运行以下命令:
|
||||
|
||||
```
|
||||
macchanger -p enp0s31f6
|
||||
```
|
||||
|
||||
但是,你不必如此。重启系统后,更改将自动丢失,并且实际的 MAC 地址将再次恢复。
|
||||
|
||||
你可以随时查看手册页以获取更多详细信息。
|
||||
|
||||
#### 方法 2:使用 iproute2 更改 Mac 地址(中级知识)
|
||||
|
||||
我建议你使用 macchanger,但如果你不想使用它,那么可以使用另一种方法在 Linux 中更改 MAC 地址。
|
||||
|
||||
首先,使用以下命令关闭网卡:
|
||||
|
||||
```
|
||||
sudo ip link set dev enp0s31f6 down
|
||||
```
|
||||
|
||||
接下来,使用以下命令设置新的 MAC:
|
||||
|
||||
```
|
||||
sudo ip link set dev enp0s31f6 address XX:XX:XX:XX:XX:XX
|
||||
```
|
||||
|
||||
最后,使用以下命令重新打开网络:
|
||||
|
||||
```
|
||||
sudo ip link set dev enp0s31f6 up
|
||||
```
|
||||
|
||||
现在,验证新的 MAC 地址:
|
||||
|
||||
```
|
||||
ip link show enp0s31f6
|
||||
```
|
||||
|
||||
就是这些了。你已经成功地在 Linux 中修改了 MAC 地址。敬请期待 FOSS 更多有关 Linux 教程和技巧的文章。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://itsfoss.com/change-mac-address-linux/
|
||||
|
||||
作者:[Dimitrios Savvopoulos][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://itsfoss.com/author/itsfoss/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://en.wikipedia.org/wiki/MAC_address
|
||||
[2]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2020/03/airport_wifi_meme.jpg?ssl=1
|
||||
[3]: https://itsfoss.com/find-network-adapter-ubuntu-linux/
|
||||
[4]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2020/03/Change_MAC_Address_Linux.jpg?ssl=1
|
||||
[5]: https://github.com/alobbs/macchanger
|
||||
[6]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2020/03/configuring_mcchanger.jpg?ssl=1
|
||||
[7]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2020/03/Dimitrios.jpg?ssl=1
|
||||
@ -0,0 +1,98 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-12017-1.html)
|
||||
[#]: subject: (How to Install Netbeans on Ubuntu and Other Linux)
|
||||
[#]: via: (https://itsfoss.com/install-netbeans-ubuntu/)
|
||||
[#]: author: (Community https://itsfoss.com/author/itsfoss/)
|
||||
|
||||
如何在 Ubuntu 和其他 Linux 上安装 Netbeans
|
||||
======
|
||||
|
||||
> 在本教程中,你将学习在 Ubuntu 和其他 Linux 发行版上安装 Netbeans IDE 的各种方法。
|
||||
|
||||
[NetBeans][1] 是一个开源集成开发环境,具有良好的跨平台支持。此工具已被 Java 和 C/C++ 开发社区广泛认可。
|
||||
|
||||
开发环境相当灵活。你可以配置它以支持各种开发。实际上,你可以用它来开发 Web、桌面和移动应用,而无需离开此平台。这太神奇了,不是吗?除此之外,用户可以添加许多已知语言,如 [PHP][2]、C、C++、HTML、[Ajax][3]、JavaScript、JSP、Ruby on Rails 等。
|
||||
|
||||
如果你正在了解如何在 Linux 上安装 Netbeans,那么有几种方法可以做到。我编写本教程主要是为了 Ubuntu,但一些安装方法也适用于其他发行版。
|
||||
|
||||
* [使用 apt 在 Ubuntu 上安装 Netbeans][4]:适用于 Ubuntu 和基于 Ubuntu 的发行版,但通常**它是旧版的 Netbeans**
|
||||
* [使用 Snap 在 Ubuntu 上安装 Netbeans][5]:适用于已启用 Snap 包支持的任何 Linux 发行版
|
||||
* [使用 Flatpak 安装 Netbeans] [6]:适用于所有支持 Flatpak 包的 Linux 发行版
|
||||
|
||||
### 使用 Apt 包管理器在 Ubuntu 上安装 Netbeans IDE
|
||||
|
||||
如果在 Ubuntu 软件中心搜索 Netbeans,你将找到两个版本的 Netbeans。Apache Netbeans 是 snap 版本,大小较大,但提供了最新的 Netbeans。
|
||||
|
||||
只需单击一下即可安装它。无需打开终端。是最简单的方法。
|
||||
|
||||
![Apache Netbeans in Ubuntu Software Center][7]
|
||||
|
||||
你也可以选择使用 `apt` 命令,但使用 `apt` 时,你无法获得最新的 Netbeans。例如,在编写本教程时,Ubuntu 18.04 中 Apt 提供 Netbeans 10,而 Snap 有最新的 Netbeans 11。
|
||||
|
||||
如果你是 [apt 或 apt-get][8] 的粉丝,那么可以[启用 universe 仓库][9],并在终端中使用此命令安装 Netbeans:
|
||||
|
||||
```
|
||||
sudo apt install netbeans
|
||||
```
|
||||
|
||||
### 使用 Snap 在任何 Linux 发行版上安装 Netbeans IDE
|
||||
|
||||
![][10]
|
||||
|
||||
Snap 是一个通用包管理器,如果[发行版上启用了 Snap][11],那么可以使用以下命令安装它:
|
||||
|
||||
```
|
||||
sudo snap install netbeans --classic
|
||||
```
|
||||
|
||||
此过程可能需要一些时间才能完成,因为总下载大小约为 1 GB。完成后,你将在应用程序启动器中看到它。
|
||||
|
||||
你不仅可以通过 Snap 获取最新的 Netbeans,已安装的版本将自动更新到较新版本。
|
||||
|
||||
### 使用 Flatpak 安装 Netbeans
|
||||
|
||||
[Flatpak][12] 是另一个类似 Snap 的包安装器。默认情况下,某些发行版支持 Flatpak,在其他发行版上你可以[启用 Flatpak 支持][13]。
|
||||
|
||||
发行版支持 Flatpak 后,你可以使用以下命令安装 Netbeans:
|
||||
|
||||
```
|
||||
flatpak install flathub org.apache.netbeans
|
||||
```
|
||||
|
||||
另外,你可以下载源码并自己编译。
|
||||
|
||||
- [下载 Netbeans][14]
|
||||
|
||||
希望你使用了上面其中一个方法在你的 Ubuntu 上安装了 Netbeans。但你使用的是哪个方法?有遇到问题么?让我们知道。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://itsfoss.com/install-netbeans-ubuntu/
|
||||
|
||||
作者:[Srimanta Koley][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://itsfoss.com/author/itsfoss/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://netbeans.org/
|
||||
[2]: https://www.php.net/
|
||||
[3]: https://en.wikipedia.org/wiki/Ajax_(programming)
|
||||
[4]: tmp.ZNFNEC210y#apt
|
||||
[5]: tmp.ZNFNEC210y#snap
|
||||
[6]: tmp.ZNFNEC210y#flatpak
|
||||
[7]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2020/03/apache-netbeans-ubuntu-software-center.jpg?ssl=1
|
||||
[8]: https://itsfoss.com/apt-vs-apt-get-difference/
|
||||
[9]: https://itsfoss.com/ubuntu-repositories/
|
||||
[10]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2020/03/Install_Netbeans_Linux.jpg?ssl=1
|
||||
[11]: https://itsfoss.com/install-snap-linux/
|
||||
[12]: https://flatpak.org/
|
||||
[13]: https://itsfoss.com/flatpak-guide/
|
||||
[14]: https://netbeans.apache.org/download/index.html
|
||||
[15]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2020/03/srimanta.jpg?ssl=1
|
||||
@ -0,0 +1,67 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-12037-1.html)
|
||||
[#]: subject: (Connect your Google Drive to Fedora Workstation)
|
||||
[#]: via: (https://fedoramagazine.org/connect-your-google-drive-to-fedora-workstation/)
|
||||
[#]: author: (Paul W. Frields https://fedoramagazine.org/author/pfrields/)
|
||||
|
||||
将你的 Google Drive 连接到 Fedora 工作站
|
||||
======
|
||||
|
||||
![][1]
|
||||
|
||||
有大量的云服务可用于存储重要文档。Google Drive 无疑是最受欢迎的之一。它提供了一组相应的应用程序,例如文档,表格和幻灯片来创建内容。但是,你也可以在 Google Drive 中存储任意内容。本文向你展示如何将其连接到 [Fedora 工作站][2]。
|
||||
|
||||
### 添加帐户
|
||||
|
||||
Fedora 工作站可在安装后首次启动或者之后的任何时候添加一个帐户。要在首次启动期间添加帐户,请按照提示进行操作。其中包括选择添加一个帐户:
|
||||
|
||||
![][3]
|
||||
|
||||
选择 Google,然后会出现一个登录提示,请使用你的 Google 帐户信息登录。
|
||||
|
||||
![][4]
|
||||
|
||||
请注意,此信息仅传输给 Google,而不传输给 GNOME 项目。下一个页面要求你授予访问权限,这是必需的,以便系统桌面可以与 Google 进行交互。向下滚动查看访问请求,然后选择“允许”继续。
|
||||
|
||||
你会在移动设备和 Gmail 中收到有关新设备(系统)访问 Google 帐户的通知。这是正常现象。
|
||||
|
||||
![][5]
|
||||
|
||||
如果你在初次启动时没有执行此操作,或者需要重新添加帐户,请打开“设置”,然后选择“在线账户”来添加帐户。可以通过顶部栏右侧的下拉菜单(“齿轮”图标)或打开“概览”并输入“settings”来使用它。接着和上面一样。
|
||||
|
||||
### 在 Google Drive 中使用“文件”应用
|
||||
|
||||
打开“文件”应用(以前称为 “nautilus”)。“文件”应用可以通过左侧栏访问。在列表中找到你的 Google 帐户。
|
||||
|
||||
当你选择帐户后,“文件”应用会显示你的 Google Drive 的内容。你可以使用 Fedora 工作站的本地应用打开某些文件,例如声音文件或 [LibreOffice][6] 兼容文件(包括 Microsoft Office 文档)。其他文件(例如 Google 文档、表格和幻灯片等 Google 应用文件)将使用浏览器和相应的应用打开。
|
||||
|
||||
请记住,如果文件很大,将需要一些时间才能通过网络接收文件,你才可以打开它。
|
||||
|
||||
你还可以复制粘贴 Google Drive 中的文件到连接到 Fedora 工作站的其他存储,或者反之。你还可以使用内置功能来重命名文件、创建文件夹并组织它们。对于共享和其他高级选项,请和平常一样在浏览器中使用 Google Drive。
|
||||
|
||||
请注意,“文件”应用程序不会实时刷新内容。如果你从其他连接 Google 的设备(例如手机或平板电脑)添加或删除文件,那么可能需要按 `Ctrl+R` 刷新“文件”应用。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://fedoramagazine.org/connect-your-google-drive-to-fedora-workstation/
|
||||
|
||||
作者:[Paul W. Frields][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://fedoramagazine.org/author/pfrields/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://fedoramagazine.org/wp-content/uploads/2020/03/gdrive-workstation-816x345.jpg
|
||||
[2]: https://getfedora.org/workstation
|
||||
[3]: https://fedoramagazine.org/wp-content/uploads/2020/03/firstboot-choices.jpg
|
||||
[4]: https://fedoramagazine.org/wp-content/uploads/2020/03/firstboot-signin.jpg
|
||||
[5]: https://fedoramagazine.org/wp-content/uploads/2020/03/firstboot-grantaccess.jpg
|
||||
[6]: https://fedoramagazine.org/discover-hidden-gems-libreoffice/
|
||||
[7]: https://unsplash.com/@beatriz_perez?utm_source=unsplash&utm_medium=referral&utm_content=creditCopyText
|
||||
[8]: https://unsplash.com/s/photos/office-files?utm_source=unsplash&utm_medium=referral&utm_content=creditCopyText
|
||||
116
published/20200317 Coronavirus challenges remote networking.md
Normal file
116
published/20200317 Coronavirus challenges remote networking.md
Normal file
@ -0,0 +1,116 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (HankChow)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-12039-1.html)
|
||||
[#]: subject: (Coronavirus challenges remote networking)
|
||||
[#]: via: (https://www.networkworld.com/article/3532440/coronavirus-challenges-remote-networking.html)
|
||||
[#]: author: (Michael Cooney https://www.networkworld.com/author/Michael-Cooney/)
|
||||
|
||||
新型冠状病毒对远程网络的影响
|
||||
======
|
||||
|
||||
> 由于 COVID-19 的肆虐,IBM、谷歌、亚马逊、AT&T、思科、苹果等公司都争先恐后地为远程办公提供了技术上的支持,这为远程网络带来了不少的压力。
|
||||
|
||||

|
||||
|
||||
在新型冠状病毒广泛传播的大环境下,很多公司都要求员工留在家中远程办公,远程网络技术因此承受了更大的压力,一些带宽和安全方面的问题也接踵而至。
|
||||
|
||||
在过去的几十年当中,由于企业的蓬勃发展,远程办公的人数估计增加了 400 多万。而当前疫情流行的背景下,远程办公的需求激增,有望达到一个新的高峰。
|
||||
|
||||
一家<ruby>虚拟私有网络<rt>Virtual Private Network</rt></ruby>(缩写:???)提供商 [Atlas][1] 的一份研究表明,在今年 3 月 9 日到 3 月 15 日之间,美国的虚拟私有网络使用量增加了 53%,并且还会继续提高。而在意大利这个疫情爆发比美国早两周的国家,过去一周内的虚拟私有网络使用量甚至增加了 112%。Atlas 虚拟私有网络的首席执行官 Rachel Welch 在一份声明中称,美国的虚拟私有网络使用量在 3 月底预估会达到 150% 的增幅。
|
||||
|
||||
部分企业正在尝试通过<ruby>一日测试<rt>one-day test</rt></ruby>来评估远程办公的可行性。据《[芝加哥论坛报][2]》的报道,摩根大通、晨星以及一家数据分析方面的初创公司 Arity 已经通过让员工在家办公一天来测试整个办公系统的稳定性。
|
||||
|
||||
在政府方面,[美国国家海洋与大气管理局][3]和 NASA 都已经进行或计划进行网络方面的压力测试,评估是否有足够的网络容量足以让上千名工作人员远程办公,以及远程办公可能造成的影响。而放眼整个美国,供职于美国政府部门的员工数量在 [200 万][4]左右。
|
||||
|
||||
为了避免蜂窝数据网络发生拥堵,美国[联邦通信委员会][5]已批准 T-mobile 临时访问已分配给其它运营商的 600MHz 频段,T-mobile 表示“将使用这个频段让美国人更方便地享受远程医疗、参与远程工作和学习,同时在保持‘物理距离’的情况下保持联系”。
|
||||
|
||||
- [video](https://youtu.be/-1-ugVx0hVc)
|
||||
|
||||
但也有一些业内人士指出,在一些对蜂窝网络有较强依赖的的场景下,“最后一英里”的网络访问会变得非常拥堵。
|
||||
|
||||
网络情报公司 ThousandEyes 的主要产品是局域网和广域网性能分析的软件,该公司的产品经理 Alex Cruz Farmer 表示,网络瓶颈在于一些较为偏远的农村地区,因为那些地区的网络基础设施较为薄弱,主要通过微波或蜂窝网络来访问互联网。最大的挑战在于现有的解决方案所能提供的带宽远远不足。
|
||||
|
||||
Alex Cruz Farmer 还补充道,尽管持续时间不长,但现在的确已经出现一些由于运营商问题或网络负载增加导致的故障现象。
|
||||
|
||||
AT&T 表示目前已经留意到蜂窝网络使用量的变化,但网络容量并没有作出提高。
|
||||
|
||||
[AT&T 在一份声明中称][7],在新冠病毒传播最严重的城市中,由于越来越多的人留在了家中远程办公,减少了通勤和人群聚集,很多特定位置和特定时段的蜂窝网络使用量峰值都明显降低了。他们还使用了一些工具对网络带宽进行了统计和监控,通过这些工具,他们可以更直观地了解网络使用情况的趋势,同时获取网络性能和网络容量方面的报告,进而管理整个通信网络。
|
||||
|
||||
Verison 表示,自从新型冠状病毒疫情爆发以来,尽管在家办公的用户数量大增,但使用的数据量并没有明显的上升。他们在一份声明中称:“Verison 的网络是为满足未来的需求设计建造的,面对各种需求量的增加或使用方式的改变,我们都有充分的准备。虽然这是一次前所未有的社会事件,整个局面也在不断发生改变,但随着不断了解实际需求的变化情况,我们随时可以对网络资源作出调整”。
|
||||
|
||||
Verison 一直在关注受影响最严重的地区的网络使用情况,并承诺将会与医院、医护人员、政府机构合作,制定网络资源使用的优先级,以满足他们的需求。Verison 还宣布计划在 2020 年将支出在 170 亿至 180 亿美元的基础上再提高 5 亿美元,以实现“加快 Verison 向 5G 过渡并在困难时期帮助支撑经济”的目标。
|
||||
|
||||
### 企业虚拟私有网络安全问题
|
||||
|
||||
对于企业来说,数据中心与远程用户之间的网络和安全问题解决起来绝非易事,尤其是使用虚拟私有网络进行远程访问时,来自用户所在住宅网络的访问几乎无法由企业控制。CIMI 公司总裁 Tom Nolle 认为,IT 部门有必要验证这些连接是否符合企业的标准(关于 Tom Nolle 更多关于在家办公的看法,可以查阅[这里][8])。
|
||||
|
||||
Tom Nolle 认为像 ISP、DNS 和 Wi-Fi 这些常见的家用网络要素都应该作为适合远程办公网络业务认证的一部分。他发现 Google 的 DNS 服务比 ISP 提供的服务更能承受压力,OpenDNS 也是一个很好的选择,这说明用户可以考虑使用其中一种。
|
||||
|
||||
Tom Nolle 还说,家庭 Wi-Fi 网络的安全性也是一个问题,IT 部门应该要求远程办公的员工提交 Wi-Fi 配置的屏幕截图,以保证使用了正确的加密方式。之所以有这样的想法,是因为他觉得很多远程办公的员工都会绕过企业预设的一些安全措施。
|
||||
|
||||
DNS 软件公司 BlueCat 的首席战略官 Andrew Wertkin 表示,对一些刚刚开始在家远程办公的员工来说,适当提供相关指导是很有必要的。大部分员工从来没有尝试过在家远程办公,他们或许并不了解安全的重要性。如果员工访问公司网络的时候使用的是个人设备而不是公司设备,就更有可能出现问题。
|
||||
|
||||
而使用[虚拟私有网络][9]远程办公的人数激增也会为企业带来成本上的挑战。
|
||||
|
||||
“虚拟私有网络设备并不便宜,如果考虑到计算资源的成本和每个人的均摊成本,迁移到云上的虚拟环境会带来一笔不小的开支,这还不包括每个虚拟私有网络许可证价格的上升”,Alex Cruz Farmer 坦言。
|
||||
|
||||
在容量方面,随着远程访问量的增加,用于分配 IP 地址的 DHCP 服务也会承受巨大的压力。Andrew Wertkin 指出,如果进行远程连接的设备无法获取到网络地址,则是否具有足够的虚拟私有网络许可证并不重要。企业内部必须对这些风险进行测试,了解其中存在瓶颈的部分,并制定规避这些风险的策略。
|
||||
|
||||
按照这个思路,企业甚至需要验证数据中心可以用于公开的 SSL 套接字数量,否则也会面临数量不足的风险。
|
||||
|
||||
微软 Office 365 产品团队的高级程序经理 Paul Collinge 也表达了类似的担忧。他在一篇关于优化 Office 365 员工远程办公流量的[博客][10]中写道,当大量员工在同时接入企业网络时,会对诸如虚拟私有网络集中器、中央网络出口设备(例如代理、DLP)、中央互联网带宽、回程 MPLS 和 NAT 等网络要素产生巨大的压力。最终导致的结果是低下的性能、低下的生产力,以及员工们低下的使用体验。
|
||||
|
||||
Alex Cruz Farmer 提出,企业很可能需要增加网络上虚拟私有网络集中器的数量,这样就可以让远程用户分布在多个不同的虚拟私有网络端点上,避免产生拥堵。退而求其次,只能在防火墙上把某些端口放开,允许特定应用程序的公开访问,尽管这样有助于提高工作效率,但却降低了整体的安全性。
|
||||
|
||||
### 虚拟私有网络隧道分割技术有效吗?
|
||||
|
||||
业内人士对<ruby>隧道分割<rt>tunneling split</rt></ruby>有不同的看法。
|
||||
|
||||
BlueCat 的 Andrew Wertkin 认为,虚拟私有网络可以使用隧道分割技术,使得仅有需要访问企业内部网络的流量才通过虚拟私有网络隧道访问,其余流量则直接进入互联网。这意味着会有部分流量不受隧道和企业网络内部的安全控制,用户的计算机会暴露在互联网当中,进而导致企业的数据和网络面临安全风险。
|
||||
|
||||
尽管如此,微软在上周还是建议 IT 管理员使用隧道分割技术以缓解 Office 365 由于大量远程用户涌入导致的拥堵问题。微软在[建议][10]中提供了相关接入点的 URL 和 IP 地址列表,并引导 IT 人员如何按照这个方式将流量路由到 Office 365。
|
||||
|
||||
按照 Paul Collinge 的说法,虚拟私有网络客户端需要经过配置,才能将流量路由到已标识的 URL/IP/ 端口上,进而为全球的用户提供高性能的服务。
|
||||
|
||||
Alex Cruz Farmer 认为,在虚拟私有网络使用率上升之后,企业很有必要对网络安全进行一个全面的审查。对于仍然在使用传统网络安全架构的企业来说,应该开始考虑基于云端的网络安全方案了,这不仅可以提升远程办公的性能,还能减少企业对于广域网的使用量。
|
||||
|
||||
其它相关情况:
|
||||
|
||||
* [FCC][11] 呼吁,宽带提供商应该适当放宽数据传输的限制,电话运营商应该适当免除用户的长途电话费,远程教育提供商应该合作为社会提供远程学习的机会,网络运营商应该优先考虑医院或医疗机构的网络连接需求。对此,AT&T 已经作出了相关的回应和行动。
|
||||
* [美国参议员 Mark R. Warner (D-VA)][12] 和其他 17 名参议员致信了 AT&T、CenturyLink、Charter Communications、Comcast、Cox Communications、Sprint、T-Mobile、Verizon 这八家主要 ISP 的首席执行官,呼吁这些公司应该采取措施应对远程办公、在线教育、远程医疗、远程支持服务等方面需求激增带来的压力。这些参议员在信中呼吁,各公司应该降低可能对远程服务产生影响的限制和费用,同时还应该为受到疫情影响的学生提供免费或收费的宽带服务,否则学生在疫情期间无法接入网络进行在线学习。
|
||||
* [思科][13]、微软、[谷歌][14]、[LogMeIn][15]、[Spectrum][16] 等供应商都提供了一些免费工具,帮助用户在疫情爆发期间正常进行安全通信。
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.networkworld.com/article/3532440/coronavirus-challenges-remote-networking.html
|
||||
|
||||
作者:[Michael Cooney][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[HankChow](https://github.com/HankChow)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.networkworld.com/author/Michael-Cooney/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://atlasvpn.com/blog/vpn-usage-in-italy-rockets-by-112-and-53-in-the-us-amidst-coronavirus-outbreak/
|
||||
[2]: https://www.chicagotribune.com/coronavirus/ct-coronavirus-work-from-home-20200312-bscm4ifjvne7dlugjn34sksrz4-story.html
|
||||
[3]: https://federalnewsnetwork.com/workforce/2020/03/agencies-ramp-up-coronavirus-preparations-as-noaa-plans-large-scale-telework-test/
|
||||
[4]: https://fas.org/sgp/crs/misc/R43590.pdf
|
||||
[5]: https://www.fcc.gov/coronavirus
|
||||
[6]: https://www.networkworld.com/blog/itaas-and-the-corporate-storage-technology/?utm_source=IDG&utm_medium=promotions&utm_campaign=HPE22140&utm_content=sidebar (ITAAS and Corporate Storage Strategy)
|
||||
[7]: https://about.att.com/pages/COVID-19.html
|
||||
[8]: https://blog.cimicorp.com/?p=4055
|
||||
[9]: https://www.networkworld.com/article/3268744/understanding-virtual-private-networks-and-why-vpns-are-important-to-sd-wan.html
|
||||
[10]: https://techcommunity.microsoft.com/t5/office-365-blog/how-to-quickly-optimize-office-365-traffic-for-remote-staff-amp/ba-p/1214571
|
||||
[11]: https://www.fcc.gov/document/commissioner-starks-statement-fccs-response-covid-19
|
||||
[12]: https://www.warner.senate.gov/public/_cache/files/2/3/239084db-83bd-4641-bf59-371cb829937a/A99E41ACD1BA92FB37BDE54E14A97BFA.letter-to-isps-on-covid-19-final-v2.-signed.pdf
|
||||
[13]: https://blogs.cisco.com/collaboration/cisco-announces-work-from-home-webex-contact-center-quick-deployment
|
||||
[14]: https://cloud.google.com/blog/products/g-suite/helping-businesses-and-schools-stay-connected-in-response-to-coronavirus
|
||||
[15]: https://www.gotomeeting.com/work-remote?clickid=RFlSQF3DBxyOTSr0MKVSfWfHUknShrScK0%3AhTY0&irgwc=1&cid=g2m_noam_ir_aff_cm_pl_ct
|
||||
[16]: https://www.multichannel.com/news/charter-opening-wi-fi-hotspots-in-face-of-covid-19
|
||||
[17]: https://www.facebook.com/NetworkWorld/
|
||||
[18]: https://www.linkedin.com/company/network-world
|
||||
@ -0,0 +1,142 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-12041-1.html)
|
||||
[#]: subject: (Viewing and configuring password aging on Linux)
|
||||
[#]: via: (https://www.networkworld.com/article/3532815/viewing-and-configuring-password-aging-on-linux.html)
|
||||
[#]: author: (Sandra Henry-Stocker https://www.networkworld.com/author/Sandra-Henry_Stocker/)
|
||||
|
||||
在 Linux 上查看和配置密码时效
|
||||
======
|
||||
|
||||

|
||||
|
||||
> 使用正确的设置,可以强制 Linux 用户定期更改密码。以下是查看密码时效以及如何更改其中设置的方法。
|
||||
|
||||
可以将 Linux 系统上的用户密码配置为永久或设置过期时间,以让人们必须定期重置它们。出于安全原因,通常认为定期更改密码是一种好习惯,但默认并未配置。
|
||||
|
||||
要查看和修改密码时效,你需要熟悉几个重要的命令:`chage` 命令及其 `-l` 选项,以及 `passwd` 命令及其 `-S` 选项。本文会介绍这些命令,还有其他一些 `chage` 命令选项来配置密码时效。
|
||||
|
||||
### 查看密码时效设置
|
||||
|
||||
确定某个特定帐户是否已设置密码时效的方法是使用如下 `chage` 命令。请注意,除了你自己的帐户以外,其他任何帐户都需要 root 权限。请注意下面的密码到期日期。
|
||||
|
||||
```
|
||||
$ sudo chage -l dory
|
||||
Last password change : Mar 15, 2020
|
||||
Password expires : Jun 13, 2020 <==
|
||||
Password inactive : never
|
||||
Account expires : never
|
||||
Minimum number of days between password change : 10
|
||||
Maximum number of days between password change : 90
|
||||
Number of days of warning before password expires : 14
|
||||
```
|
||||
|
||||
如果未应用密码时效,那么帐户信息将如下所示:
|
||||
|
||||
```
|
||||
$ sudo chage -l nemo
|
||||
Last password change : Jan 14, 2019
|
||||
Password expires : never <==
|
||||
Password inactive : never
|
||||
Account expires : Mar 26, 2706989
|
||||
Minimum number of days between password change : 0
|
||||
Maximum number of days between password change : 99999
|
||||
Number of days of warning before password expires : 7
|
||||
```
|
||||
|
||||
你也可以使用 `passwd -S` 命令查看某些信息,但是你需要知道输出中的每个字段代表什么:
|
||||
|
||||
```
|
||||
dory$ passwd -S
|
||||
dory P 03/15/2020 10 90 14 -1
|
||||
```
|
||||
|
||||
这里的七个字段代表:
|
||||
|
||||
* 1 – 用户名
|
||||
* 2 - 帐户状态(`L` = 锁定,`NP` = 无密码,`P` = 可用密码)
|
||||
* 3 – 上次密码更改的日期
|
||||
* 4 – 可更改最低时效(如果没有这么多天,则不能更改密码)
|
||||
* 5 – 最长时效(这些天后,密码必须更改)
|
||||
* 6 – 密码过期前提前警告的天数
|
||||
* 7 – 密码过期后锁定之前的天数(设为无效)
|
||||
|
||||
需要注意的一件事是,`chage` 命令不会显示帐户是否被锁定;它仅显示密码时效设置。另一方面,`passwd -S` 命令将告诉你密码被锁定的时间。在此例中,请注意帐户状态为 `L`:
|
||||
|
||||
```
|
||||
$ sudo passwd -S dorothy
|
||||
dorothy L 07/09/2019 0 99999 7 10
|
||||
```
|
||||
|
||||
通过将 `/etc/shadow` 文件中通常包含密码的“哈希”字段变为 `!`,从而达成锁定的效果。
|
||||
|
||||
```
|
||||
$ sudo grep dorothy /etc/shadow
|
||||
dorothy:!:18086:0:99999:7:10:: <==
|
||||
```
|
||||
|
||||
帐户被锁定的事实在 `chage` 输出中并不明显:
|
||||
|
||||
```
|
||||
$ sudo chage -l dorothy
|
||||
Last password change : Jul 09, 2019
|
||||
Password expires : never
|
||||
Password inactive : never
|
||||
Account expires : never
|
||||
Minimum number of days between password change : 0
|
||||
Maximum number of days between password change : 99999
|
||||
Number of days of warning before password expires : 7
|
||||
```
|
||||
|
||||
### 密码时效的一些选项
|
||||
|
||||
最常用的设置是最短和最长的天数。它们经常结合使用。例如,你可以配置一个密码,使其最长不能使用超过 90 天(最大),然后添加一个有效期为一周或 10 天(最小)的密码。这样可以确保用户不会在需要更改密码后马上改回以前的密码。
|
||||
|
||||
```
|
||||
$ sudo chage -M 90 -m 10 shark
|
||||
$ sudo chage -l shark
|
||||
Last password change : Mar 16, 2020
|
||||
Password expires : Jun 14, 2020
|
||||
Password inactive : never
|
||||
Account expires : never
|
||||
Minimum number of days between password change : 10 <==
|
||||
Maximum number of days between password change : 90 <==
|
||||
Number of days of warning before password expires : 7
|
||||
```
|
||||
|
||||
你还可以使用 `-E` 选项为帐户设置特定的到期日期。
|
||||
|
||||
```
|
||||
$ sudo chage -E 2020-11-11 tadpole
|
||||
$ sudo chage -l tadpole
|
||||
Last password change : Oct 15, 2019
|
||||
Password expires : never
|
||||
Password inactive : never
|
||||
Account expires : Nov 11, 2020 <==
|
||||
Minimum number of days between password change : 0
|
||||
Maximum number of days between password change : 99999
|
||||
Number of days of warning before password expires : 7
|
||||
```
|
||||
|
||||
密码时效可能是一个重要的选择,只要它不鼓励用户使用过于简单的密码或以不安全的方式写下来即可。有关控制密码字符(例如,大小写字母、数字等的组合)的更多信息,请参考这篇关于[密码复杂度][3]的文章。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.networkworld.com/article/3532815/viewing-and-configuring-password-aging-on-linux.html
|
||||
|
||||
作者:[Sandra Henry-Stocker][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.networkworld.com/author/Sandra-Henry_Stocker/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.networkworld.com/newsletters/signup.html
|
||||
[2]: https://www.networkworld.com/blog/itaas-and-the-corporate-storage-technology/?utm_source=IDG&utm_medium=promotions&utm_campaign=HPE22140&utm_content=sidebar (ITAAS and Corporate Storage Strategy)
|
||||
[3]: https://www.networkworld.com/article/2726217/how-to-enforce-password-complexity-on-linux.html
|
||||
[4]: https://www.facebook.com/NetworkWorld/
|
||||
[5]: https://www.linkedin.com/company/network-world
|
||||
@ -0,0 +1,141 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (wxy)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-12014-1.html)
|
||||
[#]: subject: (Top 10 open source tools for working from home)
|
||||
[#]: via: (https://opensource.com/article/20/3/open-source-working-home)
|
||||
[#]: author: (Seth Kenlon https://opensource.com/users/seth)
|
||||
|
||||
在家工作的十大开源工具
|
||||
======
|
||||
|
||||
> 无论你是在家工作的资深人士还是远程工作的新手,这些工具都可以使交流和协作变得轻而易举。
|
||||
|
||||

|
||||
|
||||
如果你<ruby>在家工作<rt>work from home</rt></ruby>(WFH),你就会知道拥有一系列实用的工具是很重要的,这些工具可以让你远离烦恼,专注于重要的事情。在工作期间工作越努力,工作日结束后,你就越容易放松。
|
||||
|
||||
我已经在家工作多年了,这是我精选的远程工作者必备的最佳开源工具。
|
||||
|
||||
### 视频会议:Jitsi
|
||||
|
||||
![Jitsi screenshot][2]
|
||||
|
||||
当你不在同事身边时,每周保持连接几次非常重要,甚至只是这样也可以保持人与人之间的联系,否则你就会变得孤独。市场上有很多视频会议系统,但以我的经验,最简单、最好的是开源的 [Jitsi][3]。
|
||||
|
||||
通过易于记忆的 URL([meet.jit.si][3])和按需会议室,Jitsi 使得召开即席会议非常简单。而且更好的是,无需注册。你只需进入 [meet.jit.si][3],找到一个带有友好的、随机生成的 URL(此处没有字母和数字的随机组合) 的会议室,你就可以立即开始聊天。如果你选择注册,那么还可以与几种日历进行集成。
|
||||
|
||||
在现实生活中,我参加了许多来自新西兰最偏远地区的会议,而 Jitsi 无疑是我迄今为止拥有的最好的视频聊天体验。不需要浪费一半的会议时间在迷宫般的虚拟会议室中寻找彼此,也不用在尴尬的滞后时间中坐着发呆,更不用努力地为聊天应用程序安装更新。使用开源和符合标准的 webRTC 协议的 Jitsi 可以让你有个愉悦的开会体验。
|
||||
|
||||
### 白板:Drawpile
|
||||
|
||||
![Drawpile screenshot][4]
|
||||
|
||||
有时,白板非常适合解释事情、跟踪想法或只是散布一下疯狂的想法。白板是办公室会议室的常见物品,但在数字世界中却很难获得。幸运的是,有了 [Drawpile][5],这是一个实时协作的绘图应用程序。你可以在自己的计算机上托管绘图会话并邀请其他用户,也可以在 Drawpile 的服务器上托管会话。
|
||||
|
||||
它易于使用,足够精简、直观而功能强大,当你的粗略想法开始逐渐成型时,它是使其成为可行的作品的应用程序。
|
||||
|
||||
### 看板:Taiga
|
||||
|
||||
![Taiga screenshot][6]
|
||||
|
||||
想要保持有序并与你的部门保持同步吗?你应该试试 [Taiga][7],这是一个虚拟的“便利贴”面板,可以帮助团队跟踪各个任务。这种组织和项目计划方法被称为<ruby>看板<rt>kanban</rt></ruby>,在软件开发中很流行,而它也流行于从假期规划到家庭装修项目的所有计划之中。
|
||||
|
||||
Taiga 的优点是它是一个在线共享空间。与你进行协作或与之合作的任何人都可以把任务放到面板上,并且随着每个人的进展,他们将任务从左列(起点)移到右边(终点线)。Taiga 具有令人愉悦的图形化和交互性,没有什么比从一列移动到另一列的拖放任务令人感到舒适的了。
|
||||
|
||||
如果你的团队有 Taiga 无法满足的特定需求,那么你应该看看[我们挑选的最佳开源看板][8]。
|
||||
|
||||
### 个人笔记本:Joplin
|
||||
|
||||
![Joplin][9]
|
||||
|
||||
我在办公桌旁放着一个纸质笔记本,这样我就可以随时记下思考或想法了。想要捕捉这种简单动作的感受和便利是很棘手的,但 Joplin 却做的很好。
|
||||
|
||||
你可以在 Joplin 中创建虚拟笔记本,每个笔记本可以有任意数量的条目。这些条目可以是简单的文本,也可以是带有图形、任务列表、超链接等的复杂的动态文档。最重要的是,你可以将 Joplin 与所有的在线存储服务同步,包括开源的 Nextcloud 服务,这样你可以在任何计算机和任何设备上使用笔记本。这是使你的工作日井井有条、专心致志并保持活动顺畅的好方法。
|
||||
|
||||
如果 Joplin 不太满足你的要求,请查看一些我们最喜欢的[笔记本应用][10]。
|
||||
|
||||
### 群聊:Riot
|
||||
|
||||
![Riot screenshot][11]
|
||||
|
||||
并非所有内容都需要视频聊天或语音通话,但是有些事情比电子邮件更紧急。这就是团队聊天发挥作用的地方。一个好的群聊应用程序应该具有这些功能:即时消息传递、支持表情符号、支持 GIF 和图像,按需聊天室或“频道”、广泛的兼容性和隐私性。[Matrix][12] 是一个用于实时通信的开放标准和轻量级协议,如果你厌烦于键入大段消息,则可以使用相同的协议快速切换到 VOIP。你将获得世界上最好的群聊体验。
|
||||
|
||||
Matrix 是一种协议,并且有许多应用程序可以接驳到它(就像使用 Internet 协议一样,Firefox 是使人类可以访问的应用程序)。最受欢迎的客户端之一是 [Riot.im][13]。你可以为你的计算机和手机下载 Riot,并且只是短时间使用的话,可以通过 Web 浏览器连接到 Riot。你的团队总是会近在咫尺,但永远不会近到让你感到不舒服。
|
||||
|
||||
### 共享文档:Etherpad
|
||||
|
||||
![Etherpad screenshot][14]
|
||||
|
||||
如果你想与他人协作处理文档或与开会,则仅需 Etherpad 就行。Etherpad 是一个实时共享的文字处理器。可以邀请一个或多个人访问文档,并在每个人进行添加和编辑时进行观察。这是一种快速有效的方法,可将想法记入“纸上”并一起迭代修订。
|
||||
|
||||
有几种使用 Etherpad 的方法。如果你拥有良好的 IT 支持,则可以要求你的 IT 部门为你的组织托管一个 Etherpad 实例。否则,将有来自开源支持者的在线公共实例,例如 [Riseup][15] 和 [Etherpad][16] 本身所提供的。
|
||||
|
||||
### 共享电子表格:Ethercalc
|
||||
|
||||
![Ethercalc screenshot][17]
|
||||
|
||||
与 Etherpad 相似,在线 [Ethercalc][18] 编辑器允许多个用户同时在同一屏幕上远程地在电子表格上工作。Ethercalc 甚至可以从现有电子表格和定界文本文件中导入数据。你可能会也可能不会丢失大部分格式,具体取决于要导入的内容的复杂性,但是我从来没有弄坏过我的数据,因此导入文件总是一个好的开始。 下次需要复杂公式的帮助时,或者需要在最新预算中输入收据时,或者只是需要某人在格子上的输入时,请将其输入到 Ethercalc。
|
||||
|
||||
### 共享存储与日历:Nextcloud
|
||||
|
||||
![Nextcloud screenshot][19]
|
||||
|
||||
[Nextcloud][20] 是一个心存远志的应用程序。顾名思义,它是你自己的个人云。它最明显的切入点是在线共享存储,它可以与台式机和移动设备上的文件夹同步。将文件放入文件中,文件会上传到存储空间,然后当一切内容都同步后,它们会出现在所有设备上。为组织中的每个人提供一个帐户,你马上便拥有了共享的存储空间,可以通过单击鼠标单击以共享带有或不带有密码的文件和文件夹。
|
||||
|
||||
但是,除了充当共享数据的保管箱之外,Nextcloud 还有很多其他功能。由于其插件式结构,你可以将无数的 Web 应用程序安装到 Nextcloud 中,例如聊天客户端、电子邮件客户端、视频聊天等等。并非所有插件都是“官方的”,因此其支持服务各不相同,但是有几个非常好的官方插件。值得注意的是,有一个官方的日历应用程序,你和你的同事可以用它安排会议并跟踪即将发生的重要事件。该日历使用 CalDAV 协议,因此你所做的一切都可以与任何 CalDAV 客户端兼容。
|
||||
|
||||
### LibreOffice
|
||||
|
||||
![LibreOffice screenshot][21]
|
||||
|
||||
如果你习惯于每天一整天都在办公室里工作,那么你也可能习惯整天在办公套件里工作。包含所有常用功能的面面俱到的应用程序会令人感到某种程度的舒适,而在开源办公世界中的这样的应用程序就是 [LibreOffice][22]。它具有办公套件所应有的一切:文字处理器、电子表格和幻灯片演示。它还具有超出预期的功能,例如基于矢量的绘图应用程序,它还可以编辑 PDF 文件,还有一个带有图形界面构建器的关系型数据库。如果你正在寻找一个好的办公应用程序,那么 LibreOffice 是你应该首先看一看的,因为一旦你使用它,你就再也不用看别的了。
|
||||
|
||||
### Linux
|
||||
|
||||
![][23]
|
||||
|
||||
如果你不熟悉远程工作,而可能是由于某种原因而正在经历一场重大变革。对于某些人来说,变革的时光是一个极好的动力,它可以一劳永逸地改变一切。如果你是其中的一员,那么可能是时候更改一下整个操作系统了。Windows 和 Mac 可能在过去为你提供了很好的服务,但是如果你希望从非开源软件转向开源软件,为什么不换一下运行所有这些应用程序的平台呢?
|
||||
|
||||
有许多出色的 Linux 发行版可以让你认真地工作、认真地自我管理和认真地进阶。获取一份 Linux 副本,不论是 [Fedora][24]、[Elementary][25] 还是 [Red Hat Enterprise Linux][26] 的长期支持订购,去尝试使用自由的开源操作系统吧。等你熟悉了远程人的生活时,你最终将成为一名 Linux 专家!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/20/3/open-source-working-home
|
||||
|
||||
作者:[Seth Kenlon][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[wxy](https://github.com/wxy)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/seth
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/oatmeal-and-fedora.jpg?itok=NBFUH9eF (Oatmeal and a laptop.)
|
||||
[2]: https://opensource.com/sites/default/files/uploads/jitsi_0.jpg (Jitsi screenshot)
|
||||
[3]: http://meet.jit.si
|
||||
[4]: https://opensource.com/sites/default/files/uploads/drawpile-whiteboard.jpg (Drawpile screenshot)
|
||||
[5]: https://drawpile.net/
|
||||
[6]: https://opensource.com/sites/default/files/uploads/taiga_kanban_screen_0.jpg (Taiga screenshot)
|
||||
[7]: http://taiga.io
|
||||
[8]: https://opensource.com/alternatives/trello
|
||||
[9]: https://opensource.com/sites/default/files/joplin_0.png (Joplin)
|
||||
[10]: https://opensource.com/alternatives/evernote
|
||||
[11]: https://opensource.com/sites/default/files/uploads/riot-matrix.jpg (Riot screenshot)
|
||||
[12]: http://matrix.org
|
||||
[13]: http://riot.im
|
||||
[14]: https://opensource.com/sites/default/files/uploads/etherpad.jpg (Etherpad screenshot)
|
||||
[15]: https://pad.riseup.net/
|
||||
[16]: https://beta.etherpad.org
|
||||
[17]: https://opensource.com/sites/default/files/uploads/ethercalc.jpg (Ethercalc screenshot)
|
||||
[18]: https://ethercalc.org
|
||||
[19]: https://opensource.com/sites/default/files/uploads/nextcloud-calendar.jpg (Nextcloud screenshot)
|
||||
[20]: http://nextcloud.com
|
||||
[21]: https://opensource.com/sites/default/files/uploads/libreoffice.png (LibreOffice screenshot)
|
||||
[22]: http://libreoffice.org
|
||||
[23]: https://opensource.com/sites/default/files/uploads/advent-pantheon.jpg
|
||||
[24]: https://getfedora.org/
|
||||
[25]: https://elementary.io
|
||||
[26]: https://www.redhat.com/en/store/red-hat-enterprise-linux-workstation
|
||||
@ -0,0 +1,111 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-12048-1.html)
|
||||
[#]: subject: (4 Markdown tools for the Linux command line)
|
||||
[#]: via: (https://opensource.com/article/20/3/markdown-apps-linux-command-line)
|
||||
[#]: author: (Scott Nesbitt https://opensource.com/users/scottnesbitt)
|
||||
|
||||
4 个 Linux 命令行下的 Markdown 工具
|
||||
======
|
||||
|
||||
> 命令行 Markdown 工具快速、强大、灵活。以下是 4 个值得试一下的工具。
|
||||
|
||||

|
||||
|
||||
(在 Linux 上)在处理 [Markdown][2] 格式的文件时,命令行工具会占据主导地位。它们轻巧、快速、强大、灵活,它们大多数都遵循 Unix 哲学只做好一件事。
|
||||
|
||||
看一下这四个程序,它们可以帮助你在命令行中更有效地处理 Markdown 文件。
|
||||
|
||||
### mdless
|
||||
|
||||
如果你使用过一段时间的 Linux 命令行,那么你可能对名为 [less][3] 的文本查看器很熟悉。当然,你可以使用 `less` 查看 Markdown 文件,但结果有点枯燥。如何在终端中查看 Markdown 文件效果更好一点?来使用 [mdless][4]。
|
||||
|
||||
![mdless][5]
|
||||
|
||||
你可以使用键盘上的箭头键四处移动,并且 `mdless` 提供了很好的搜索功能。
|
||||
|
||||
`mdless` 不仅会显示文本,而且还会渲染标题、粗体和斜体等格式。它还可以显示表格并语法高亮代码块。你还可以创建一个或多个主题文件来[定制][6] `mdless` 的外观。
|
||||
|
||||
### Markdown lint 工具
|
||||
|
||||
你在快速输入时会犯错误。如果你在使用 Markdown(或其他任何标记语言)时丢失了一些格式,那么在将文件转换为另一种格式时可能会有问题。
|
||||
|
||||
程序员通常使用名为 linter 的工具来检查语法是否正确。你可以使用 [Markdown lint 工具][7]对 Markdown 执行相同的操作。
|
||||
|
||||
在你对 Markdown 文件运行该工具时,它会根据[规则集][8]检查格式。这些规则控制着文档的结构,包括标题级别的顺序、不正确的缩进和间距、代码块问题、文件中存在 HTML 等等。
|
||||
|
||||
![Markdown lint tool][9]
|
||||
|
||||
规则可能有点严格。但是,在将文件转换为其他格式之前对文件运行 Markdown lint 工具可以防止由于格式错误或不一致引起的麻烦。
|
||||
|
||||
### mdmerge
|
||||
|
||||
合并任何类型的文件可能会很痛苦。例如,我在整理一本电子书。它是一篇文章集,最初发布在我的[每周邮件][10]中。这些文章都放在单独的文件中,作为受虐狂,我以凌乱、手动的方式将它们组合在一起。
|
||||
|
||||
我希望在开始这个项目之前就知道 [mdmerge][11]。这样我可以节省很多时间和精力。
|
||||
|
||||
`mdmerge`,你可能已经从名称中猜到了它的作用,它将两个或多个 Markdown 文件合并为一个文件。你无需在命令行中输入文件名。相反,你可以将它们添加到名为 `book.txt` 的文件中,并将其用作 `mdmerge` 的输入文件。
|
||||
|
||||
这并不是 `mdmerge` 能做的一切。你可以添加对另一个文档的引用(使用 Markdown 格式引用或一段源代码),然后将其放入主文档中。这样一来,你就可以创建针对特定受众定制的[主文档][12]。
|
||||
|
||||
`mdmerge` 不会是你经常使用的程序。但当你需要时,你会很高兴硬盘上有它。
|
||||
|
||||
### bashblog
|
||||
|
||||
严格说 [bashblog][13] 并不是 Markdown 工具。它获取 Markdown 文件,并使用它们来构建简单的博客或网站。你可以将 bashblog 视为[静态站点生成器][14],但是它没有很多脆弱的依赖关系。一切几乎都在一个不到 50KB 的 shell 脚本中。
|
||||
|
||||
要使用 bashblog,只需在计算机上安装 Markdown 处理器即可。在此,你可以编辑 Shell 脚本添加有关博客的信息,例如标题、名字、社交媒体链接等。然后运行该脚本。之后会在默认文本编辑器中新建一篇文章。开始输入。
|
||||
|
||||
保存文章后,你可以发布它或将其另存为草稿。如果你选择发布文章,那么 bashblog 会将你的博客、文章和所有内容生成为一组 HTML 文件,你可以将它们上传到 Web 服务器。
|
||||
|
||||
它开箱即用,你的博客或许会平淡无奇,但可以使用。你可以根据自己喜好编辑站点的 CSS 文件来改变外观。
|
||||
|
||||
![bashblog][15]
|
||||
|
||||
### Pandoc 如何?
|
||||
|
||||
当然,Panddoc 是一个非常强大的工具,可以将 Markdown 文件转换为其他标记语言。但是,在命令行上使用 Markdown 要比 Pandoc 多。
|
||||
|
||||
如果你需要 Pandoc,请查看我们发布的文章:
|
||||
|
||||
* [在命令行使用 Pandoc 进行文件转换][16]
|
||||
* [使用 Pandoc 将你的书转换成网页和电子书][17]
|
||||
* [用 Pandoc 生成一篇调研论文][18]
|
||||
* [使用 pandoc 将 Markdown 转换为格式化文档][19]
|
||||
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/20/3/markdown-apps-linux-command-line
|
||||
|
||||
作者:[Scott Nesbitt][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/scottnesbitt
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/rh_003784_02_os.comcareers_os_rh2x.png?itok=jbRfXinl (A person working.)
|
||||
[2]: https://opensource.com/article/19/9/introduction-markdown
|
||||
[3]: https://opensource.com/article/18/4/using-less-view-text-files-command-line
|
||||
[4]: https://github.com/ttscoff/mdless
|
||||
[5]: https://opensource.com/sites/default/files/uploads/mdless.png (mdless)
|
||||
[6]: https://github.com/ttscoff/mdless#customization
|
||||
[7]: https://github.com/markdownlint/markdownlint
|
||||
[8]: https://github.com/markdownlint/markdownlint/blob/master/docs/RULES.md
|
||||
[9]: https://opensource.com/sites/default/files/uploads/mdl.png (Markdown lint tool)
|
||||
[10]: https://buttondown.email/weeklymusings
|
||||
[11]: https://github.com/JeNeSuisPasDave/MarkdownTools
|
||||
[12]: https://help.libreoffice.org/6.2/en-US/text/swriter/guide/globaldoc.html
|
||||
[13]: https://github.com/cfenollosa/bashblog
|
||||
[14]: https://en.wikipedia.org/wiki/Web_template_system#Static_site_generators
|
||||
[15]: https://opensource.com/sites/default/files/uploads/bashblog.png (bashblog)
|
||||
[16]: https://linux.cn/article-10228-1.html
|
||||
[17]: https://linux.cn/article-10287-1.html
|
||||
[18]: https://linux.cn/article-10179-1.html
|
||||
[19]: https://linux.cn/article-11160-1.html
|
||||
@ -0,0 +1,208 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (wxy)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-12047-1.html)
|
||||
[#]: subject: (7 open hardware projects working to solve COVID-19)
|
||||
[#]: via: (https://opensource.com/article/20/3/open-hardware-covid19)
|
||||
[#]: author: (Harris Kenny https://opensource.com/users/harriskenny)
|
||||
|
||||
应对新冠病毒的 7 个开源硬件项目
|
||||
======
|
||||
|
||||
> 开源硬件解决方案可以为抵御新型冠状病毒的传播和痛苦做出贡献。
|
||||
|
||||

|
||||
|
||||
开源[硬件][2]运动长期以来一直主张维修权的重要性,完全拥有所购买的技术,并能够像音乐一样重新组合和复制部件。因此,在这个充满挑战的时期内,开源硬件为由冠状病毒大流行引起的一些问题提供了一些答案。
|
||||
|
||||
### 背景概述
|
||||
|
||||
首先,全球的硬件开发人员正在努力使用开源解决供应链中的弱点,在过去 30 年中,这种理念推动了新软件技术的大量涌现。过去在硬件运动方面的成功,如 [RepRap Project][3]、[Open Source Ecology][4] 和 [Open Source Beehives][5],证明了这一点是可以做到的。
|
||||
|
||||
对于使用 3D 打印和其他技术按需生产安全设备和按需制造它的替换零件,创客们的兴趣日益增加。例如,香港理工大学实验室为医院工作人员提供 [3D 打印面罩][6]。意大利初创公司 Isinnova 与米兰 FabLab 合作,为受重灾的意大利北部提供用于呼吸机的 [3D 打印替换阀][7]。公司们还发布了设计以适应我们的物理接触需求,例如 Materialise 的 [3D 打印免提开门器][8]。这些更换零件和解决问题的示例是一个很好的起点,为挽救生命做出了努力。
|
||||
|
||||
另一种传统的硬件技术正在加速发展:缝纫。法新社报道说,全球急需口罩,来自世界卫生组织的指导也指明了其重要性。随着一次性口罩要优先供给于医护人员,捷克共和国的人们[开始缝制自己的口罩][9]。(重复使用的口罩确实会带来细菌问题。)Facebook 小组“捷克缝制口罩”开始在他们的国家解决这个问题,成千上万的成员开始用起了他们的家用缝纫机。
|
||||
|
||||
开源硬件设备和机械项目也越来越受欢迎。首先,有一些测试性设备具备高精度且功能强大。其次,在没有其他选择方案的情况下,有一些医疗设备(顶多)可以归类为现场级。这些项目将在下面详细概述。
|
||||
|
||||
为了解更多信息,我与总部位于芝加哥的 [Tapster Robotics][10] 的创始人兼首席执行官 Jason Huggins 进行了交谈。Tapster Robotics 使用 3D 打印、计算机数控(CNC)加工和 [Arduino][11] 等开源电子产品设计和制造台式机器人。他兼具技术知识和工业能力,具有很高的影响力。他想投入自己公司的资源来帮助这场斗争。
|
||||
|
||||
“基本上,我们现在正处于第二次世界大战的动员时刻。即使我不是医生,我们仍然应该遵循希波克拉底誓言。无论我做什么,我都不想让问题变得更糟”,Huggins 解释,他认为:“作为对策,世卫组织执行主任 Michael Ryan 博士发表了这样的评论:‘速度胜过完美’。”
|
||||
|
||||
> 哇!
|
||||
>
|
||||
> 这个人是疾病传播的全球权威。如果您是领导者(无论以何种身份),请注意。如果不是,也请注意。
|
||||
>
|
||||
> [pic.twitter.com/bFogaekehM][12]
|
||||
>
|
||||
> — Jim RichardsSh🎙wgram(@JIMrichards1010)[2020 年 3 月 15 日][13]
|
||||
|
||||
Huggins 在应需提供方面具有丰富的经验。他的努力有助于 [Healthcare.gov][14] 在挑战性的最初启动后得以扩展。他还创建了软件行业标准的测试框架 Selenium 和 Appium。有了这一经验,他的建议非常值得考虑。
|
||||
|
||||
我还与 [Tyson Law][15] 的西雅图律师 Mark Tyson 进行了交谈,他的合作对象是初创公司和小型企业。他在快速发展的行业中与敏捷公司合作有着直接的经验。在阐述整个问题时,Tyson 说到:
|
||||
|
||||
> 《<ruby>善良的撒玛利亚人法<rt>Good Samaritan law</rt></ruby>》保护志愿者(即“好撒玛利亚人”)免于因其在紧急情况下提供援助的决定而承担责任。尽管这些法律的具体内容因州而异,但它们具有共同的公共政策依据:即鼓励旁观者帮助遇到紧急情况的其他人。可以想象,除了传统的把车祸的受害者从伤害中拉出来之外,这种理论依据可以证明在不太传统的环境中应用这类法律的合理性。
|
||||
|
||||
对于这种特定情况,Tyson 指出:
|
||||
|
||||
> “在采取行动之前,创客们明智的做法是与律师沟通一下,以针对特定的州进行风险评估。还应谨慎地要求大型机构(例如医院或保险公司)通过合同接受潜在的责任风险,例如,通过使用赔偿协议,使医院或其保险人同意赔偿创客们的责任。”
|
||||
|
||||
Tyson 明白情况的紧迫性和严重性。使用合同的这种选择并不意味着障碍。相反,这可能是一种帮助其大规模采用的方法,以更快地产生更大的变化。这取决于你或你的机构。
|
||||
|
||||
综上所述,让我们探索正在使用或正在开发中的项目(可能很快就可以部署)。
|
||||
|
||||
### 7 个与新冠病毒对抗的开源硬件项目
|
||||
|
||||
#### Opentrons
|
||||
|
||||
[Opentrons][16] 的开源实验室自动化平台由一套开源硬件、经过验证的实验室器具、消耗品、试剂和工作站组成。Opentrons 表示,其产品可以“在下订单后几天内每天自动进行多达 2400 个测试”的系统,可以极大地帮助提高[新冠病毒测试规模][17]。它计划在 7 月 1 日之前提升到多达 100 万个测试样本。
|
||||
|
||||
![Opentrons roadmap graphic][18]
|
||||
|
||||
*来自 Opentrons [网站][17],版权所有*
|
||||
|
||||
该公司已经在与联邦和地方政府机构合作,以确定其系统是否可以在[紧急使用授权][19]下用于临床诊断。 Opentrons 在 [Apache 2.0 许可证][20]下共享。我最初是从与该项目有联系的生物学家 Kristin Ellis 那里得知它的。
|
||||
|
||||
#### Chai 的 Open qPCR
|
||||
|
||||
Chai 的 [Open qPCR][21] 设备使用[聚合酶链反应][22](PCR)快速检测物品表面(例如,门把手和电梯按钮)上的拭子,以查看是否存在新型冠状病毒。这种在 [Apache 2.0 许可证][23]下共享的开源硬件使用 [BeagleBone][24] 低功耗 Linux 计算机。Chai 的 Open qPCR 提供的数据可以使公共卫生、公民和企业领导者做出有关清洁、缓解、关闭设施、接触追踪和测试的更明智的决策。
|
||||
|
||||
#### OpenPCR
|
||||
|
||||
[OpenPCR][25] 是 Chai Open qPCR 的创建者 Josh Perfetto 和 Jessie Ho 的 PCR 测试设备套件。与他们的前一个项目相比,这更像是一种 DIY 开源设备,但它具有相同的使用场景:使用环境测试来识别野外冠状病毒。正如该项目页面所指出的那样,“能够检测这些病原体的传统实时 PCR 设备通常花费超过 30,000 美元,而且不适合在现场使用。”由于 OpenPCR 是用户构建的工具包,并且在 [GPLv3.0 许可证][26]下共享,因此该设备旨在使分子诊断的访问大众化。
|
||||
|
||||
![OpenPCR][27]
|
||||
|
||||
*来自 OpenPCR [网站][25],版权所有*
|
||||
|
||||
而且,就像任何优秀的开源项目一样,它也有一个衍生产品!瑞士的 [Gaudi Labs][29] 推出的 [WildOpenPCR][28] 也以 [GPLv3.0 许可证][30]共享。
|
||||
|
||||
#### PocketPCR
|
||||
|
||||
Gaudi Labs 的 [PocketPCR][31] 热循环仪可通过升高和降低小试管中液体的温度来激活生物反应。它可以通过简单的 USB 电源适配器供电,该适配器可以绑定到设备上,也可以单独使用,不使用计算机或智能手机时可使用预设参数。
|
||||
|
||||
![PocketPCR][32]
|
||||
|
||||
*来自 PocketPCR [网站][31],版权所有*
|
||||
|
||||
与本文所述的其他 PCR 产品一样,此设备可能有助于对冠状病毒进行环境测试,尽管其项目页面并未明确说明。PocketPCR 在 [GPLv3.0 许可证][33]下共享。
|
||||
|
||||
#### Open Lung 低资源呼吸机
|
||||
|
||||
[Open Lung 低资源呼吸机][34]是一种快速部署的呼吸机,它以[气囊阀罩][35](BVM)(也称为 Ambu 气囊)为核心组件。Ambu 气囊已批量生产,经过认证,体积小,机械简单,并且适用于侵入性导管和口罩。 Open Lung 呼吸机使用微电子技术来感测和控制气压和流量,以实现半自主运行。
|
||||
|
||||
![Open Lung ventilator][36]
|
||||
|
||||
*Open Lung,[GitLab][37]*
|
||||
|
||||
这个早期项目拥有一支由数百名贡献者组成的大型团队,领导者包括:Colin Keogh、David Pollard、Connall Laverty 和 Gui Calavanti。它是以 [GPLv3.0 许可证][38]共享的。
|
||||
|
||||
#### Pandemic 呼吸机
|
||||
|
||||
[Pandemic 呼吸机][39]是 DIY 呼吸机的原型。像 RepRap 项目一样,它在设计中使用了常用的硬件组件。该项目已由用户 Panvent 于 10 多年前上传到 Instructables,并且有六个主要的生产步骤。该项目是以 [CC BY-NC-SA 许可证][39]共享的。
|
||||
|
||||
#### Folding at Home
|
||||
|
||||
[Folding at Home][40] 是一个分布式计算项目,用于模拟蛋白质动力学,包括蛋白质折叠的过程以及与多种疾病有关的蛋白质运动。这是一个面向公民科学家、研究人员和志愿者的行动呼吁,类似于退役的 [SETI@Home 项目][41]使用家中的计算机来运行解码计算。如果你是具备强大计算机硬件功能的技术人员,那么这个项目适合你。
|
||||
|
||||
![Markov state model][42]
|
||||
|
||||
*Vincent Voelz,CC BY-SA 3.0*
|
||||
|
||||
Folding at Home 项目使用马尔可夫状态模型(如上所示)来建模蛋白质可能采取的形状和折叠途径,以寻找新的治疗机会。你可以在华盛顿大学生物物理学家 Greg Bowman 的帖子《[它是如何运作的以及如何提供帮助][43]》中找到有关该项目的更多信息。
|
||||
|
||||
该项目涉及来自许多国家和地区(包括香港、克罗地亚、瑞典和美国)的财团的学术实验室、贡献者和公司赞助者。 在 [GitHub][45] 上,[在混合了 GPL 和专有许可证][44]下共享,并且可以在 Windows、macOS 和 GNU/Linux(例如 Debian、Ubuntu、Mint、RHEL、CentOS、Fedora)。
|
||||
|
||||
### 许多其他有趣的项目
|
||||
|
||||
这些项目只是在开源硬件领域中解决或治疗新冠病毒活动中的一小部分。在研究本文时,我发现了其他值得探索的项目,例如:
|
||||
|
||||
* Coronavirus Tech Handbook 提供的[开源呼吸机、氧气浓缩器等][46]
|
||||
* 来自 ProjectOpenAir 的 [有用的工程][47]
|
||||
* Hackaday 上的[开源呼吸机黑客马拉松][48]
|
||||
* 约翰·霍普金斯急诊医学住院医师 Julian Botta 的[简单开源机械呼吸机规范][49]
|
||||
* [与冠状病毒有关的网络钓鱼、恶意软件和随机软件正在增加][50],作者:Shannon Morse
|
||||
* [将低成本的 CPAP 鼓风机转换为基本呼吸机][51],作者: jcl5m1
|
||||
* [A.I.R.E. 论坛上关于开源呼吸器和风扇的讨论][52](西班牙语)
|
||||
* [关于新冠病毒的开源医疗硬件的特殊问题][53],作者:Elsevier HardwareX
|
||||
|
||||
这些项目遍布全球,而这种全球合作正是我们所需要的,因为病毒无视国界。新冠病毒大流行在不同时期以不同方式影响国家,因此我们需要一种分布式方法。
|
||||
|
||||
正如我和同事 Steven Abadie 在 [OSHdata 2020 报告][54]中所写的那样,开源硬件运动是全球性运动。参与该认证项目的个人和组织遍布全球 35 个国家地区和每个半球。
|
||||
|
||||
![Open source hardware map][55]
|
||||
|
||||
*OSHdata,CC BY-SA 4.0 国际版*
|
||||
|
||||
如果你有兴趣加入这场与全球开源硬件开发人员的对话,请加入[开源硬件峰会的 Discord][56] 服务器,并通过专用渠道进行有关新冠病毒的讨论。你在这里可以找到机器人专家、设计师、艺术家、固件和机械工程师、学生、研究人员以及其他共同为这场战争而战的人。希望可以看到你。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/20/3/open-hardware-covid19
|
||||
|
||||
作者:[Harris Kenny][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[wxy](https://github.com/wxy)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/harriskenny
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/health_heartbeat.png?itok=P-GXea-p (open on blue background with heartbeat symbol)
|
||||
[2]: https://opensource.com/resources/what-open-hardware
|
||||
[3]: https://reprap.org/wiki/RepRap
|
||||
[4]: https://www.opensourceecology.org/
|
||||
[5]: https://www.osbeehives.com/
|
||||
[6]: https://www.scmp.com/news/hong-kong/health-environment/article/3052135/polytechnic-university-lab-3d-printing-face
|
||||
[7]: https://www.3dprintingmedia.network/covid-19-3d-printed-valve-for-reanimation-device/
|
||||
[8]: https://www.3dprintingmedia.network/materialise-shows-3d-printed-door-opener-for-coronavirus-containment-efforts/
|
||||
[9]: https://news.yahoo.com/stitch-time-czechs-sew-combat-virus-mask-shortage-205213804.html
|
||||
[10]: http://tapster.io/
|
||||
[11]: https://opensource.com/life/15/5/arduino-or-raspberry-pi
|
||||
[12]: https://t.co/bFogaekehM
|
||||
[13]: https://twitter.com/JIMrichards1010/status/1239140710558969857?ref_src=twsrc%5Etfw
|
||||
[14]: http://Healthcare.gov
|
||||
[15]: https://www.marktysonlaw.com/
|
||||
[16]: https://opentrons.com/
|
||||
[17]: https://blog.opentrons.com/testing-for-covid-19-with-opentrons/
|
||||
[18]: https://opensource.com/sites/default/files/uploads/opentrons.png (Opentrons roadmap graphic)
|
||||
[19]: https://www.fda.gov/regulatory-information/search-fda-guidance-documents/policy-diagnostics-testing-laboratories-certified-perform-high-complexity-testing-under-clia-prior
|
||||
[20]: https://github.com/Opentrons/opentrons/blob/edge/LICENSE
|
||||
[21]: https://www.chaibio.com/openqpcr
|
||||
[22]: https://en.wikipedia.org/wiki/Polymerase_chain_reaction
|
||||
[23]: https://github.com/chaibio/chaipcr
|
||||
[24]: https://beagleboard.org/bone
|
||||
[25]: https://openpcr.org/
|
||||
[26]: https://github.com/jperfetto/OpenPCR/blob/master/license.txt
|
||||
[27]: https://opensource.com/sites/default/files/uploads/openpcr.png (OpenPCR)
|
||||
[28]: https://github.com/GenericLab/WildOpenPCR
|
||||
[29]: http://www.gaudi.ch/GaudiLabs/?page_id=328
|
||||
[30]: https://github.com/GenericLab/WildOpenPCR/blob/master/license.txt
|
||||
[31]: http://gaudi.ch/PocketPCR/
|
||||
[32]: https://opensource.com/sites/default/files/uploads/pocketpcr.png (PocketPCR)
|
||||
[33]: https://github.com/GaudiLabs/PocketPCR/blob/master/LICENSE
|
||||
[34]: https://gitlab.com/TrevorSmale/low-resource-ambu-bag-ventilor
|
||||
[35]: https://en.wikipedia.org/wiki/Bag_valve_mask
|
||||
[36]: https://opensource.com/sites/default/files/uploads/open-lung.png (Open Lung ventilator)
|
||||
[37]: https://gitlab.com/TrevorSmale/low-resource-ambu-bag-ventilor/-/blob/master/images/CONCEPT_1_MECH.png
|
||||
[38]: https://gitlab.com/TrevorSmale/low-resource-ambu-bag-ventilor/-/blob/master/LICENSE
|
||||
[39]: https://www.instructables.com/id/The-Pandemic-Ventilator/
|
||||
[40]: https://foldingathome.org/
|
||||
[41]: https://setiathome.ssl.berkeley.edu/
|
||||
[42]: https://opensource.com/sites/default/files/uploads/foldingathome.png (Markov state model)
|
||||
[43]: https://foldingathome.org/2020/03/15/coronavirus-what-were-doing-and-how-you-can-help-in-simple-terms/
|
||||
[44]: https://en.wikipedia.org/wiki/Folding@home
|
||||
[45]: https://github.com/FoldingAtHome
|
||||
[46]: https://coronavirustechhandbook.com/hardware
|
||||
[47]: https://app.jogl.io/project/121#about
|
||||
[48]: https://hackaday.com/2020/03/12/ultimate-medical-hackathon-how-fast-can-we-design-and-deploy-an-open-source-ventilator/
|
||||
[49]: https://docs.google.com/document/d/1FNPwrQjB1qW1330s5-S_-VB0vDHajMWKieJRjINCNeE/edit?fbclid=IwAR3ugu1SGMsacwKi6ycAKJFOMduInSO4WVM8rgmC4CgMJY6cKaGBNR14mpM
|
||||
[50]: https://www.youtube.com/watch?v=dmQ1twpPpXA
|
||||
[51]: https://github.com/jcl5m1/ventilator
|
||||
[52]: https://foro.coronavirusmakers.org/
|
||||
[53]: https://www.journals.elsevier.com/hardwarex/call-for-papers/special-issue-on-open-source-covid19-medical-hardware
|
||||
[54]: https://oshdata.com/2020-report
|
||||
[55]: https://opensource.com/sites/default/files/uploads/oshdata-country.png (Open source hardware map)
|
||||
[56]: https://discord.gg/duAtG5h
|
||||
@ -0,0 +1,88 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-12044-1.html)
|
||||
[#]: subject: (Fedora 32 Release Date, New Features and Everything Else)
|
||||
[#]: via: (https://itsfoss.com/fedora-32/)
|
||||
[#]: author: (Ankush Das https://itsfoss.com/author/ankush/)
|
||||
|
||||
Fedora 32 发布日期、新功能和其它信息
|
||||
======
|
||||
|
||||
Fedora 32 应该和 [Ubuntu 20.04 LTS][1] 一样都在 4 月底发布。
|
||||
|
||||
由于我们详细介绍了 Ubuntu 20.04,因此我们考虑在这里为 Fedora 粉丝做同样的事情。
|
||||
|
||||
在本文中,我将重点介绍 Fedora 32 的新功能。随着开发的进行,我将对本文进行更新。
|
||||
|
||||
### Fedora 32 的新功能
|
||||
|
||||
![][2]
|
||||
|
||||
#### 启用了 EarlyOOM
|
||||
|
||||
在此版本中,默认启用 [EarlyOOM][3]。提供一下背景知识,EarlyOOM 可以让用户在大量进行[交换][4]时轻松地摆脱内存不足状况恢复其系统。
|
||||
|
||||
值得注意的是,它适用于 Fedora 32 Beta 工作站版本。
|
||||
|
||||
#### 添加了 GNOME 3.36
|
||||
|
||||
新的 Fedora 32 工作站版也包含了新的 [GNOME 3.36][5]。不仅限于 Fedora 32 Beta 工作站版,[Ubuntu 20.04 LTS][1] 的每日构建版中也添加了它。
|
||||
|
||||
当然,GNOME 3.36 中的改进也进入了 Fedora 的最新版本,总体上提供了更快,更好的体验。因此,你将获得新的锁定屏幕、请勿打扰功能以及 GNOME 3.36 附带的所有其他功能。
|
||||
|
||||
#### 软件包更新
|
||||
|
||||
Fedora 32 版本还更新了许多重要的软件包,包括 Ruby、Perl 和 Python。它还有 [GNU 编译器集合(GCC)][6]的最新版本 10。
|
||||
|
||||
#### 其他更改
|
||||
|
||||
除了主要亮点之外,还有很多更改、改进或修复。你可以详细查看它的[更新日志][7]来了解有关更多信息。
|
||||
|
||||
### 下载Fedora 32(开发版)
|
||||
|
||||
Fedora 32 仍在开发中。Beta 版已经发布,你可以在空闲系统或虚拟机上对其进行测试。**我不建议你在最终版本之前在主系统上使用它**。当前版本有一个官方的[已知 bug 列表] [8],你也可以参考。
|
||||
|
||||
在[官方公告][9]中,他们提到了 **Fedora 32 beta 工作站版**和**服务器版**以及其他流行版本的可用性。
|
||||
|
||||
要获取工作站和服务器版本,你必须访问 [Fedora 工作站][10]和 [Fedora 服务器][11]的官方下载页面(取决于你的需求)。
|
||||
|
||||
![Fedora Download Beta][12]
|
||||
|
||||
打开后,你只需查找如上图所示的标记为 “**Beta!**” 的发行版,然后开始下载。对于其他变体版本,请单击下面的链接以转到各自的下载页面:
|
||||
|
||||
* [Fedora 32 Beta Spins][13]
|
||||
* [Fedora 32 Beta Labs][14]
|
||||
* [Fedora 32 Beta ARM][15]
|
||||
|
||||
你是否注意到 Fedora 32 中的其他新功能?你想在这里看到哪些功能?请随时在下面发表评论。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://itsfoss.com/fedora-32/
|
||||
|
||||
作者:[Ankush Das][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://itsfoss.com/author/ankush/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://itsfoss.com/ubuntu-20-04-release-features/
|
||||
[2]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2019/11/update_fedora.jpg?ssl=1
|
||||
[3]: https://fedoraproject.org/wiki/Changes/EnableEarlyoom#Enable_EarlyOOM
|
||||
[4]: https://itsfoss.com/swap-size/
|
||||
[5]: https://itsfoss.com/gnome-3-36-release/
|
||||
[6]: https://gcc.gnu.org/
|
||||
[7]: https://fedoraproject.org/wiki/Releases/32/ChangeSet
|
||||
[8]: https://fedoraproject.org/wiki/Common_F32_bugs
|
||||
[9]: https://fedoramagazine.org/announcing-the-release-of-fedora-32-beta/
|
||||
[10]: https://getfedora.org/workstation/download/
|
||||
[11]: https://getfedora.org/server/download/
|
||||
[12]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2020/03/fedora-download-beta.jpg?ssl=1
|
||||
[13]: https://spins.fedoraproject.org/prerelease
|
||||
[14]: https://labs.fedoraproject.org/prerelease
|
||||
[15]: https://arm.fedoraproject.org/prerelease
|
||||
151
published/20200319 Manually rotating log files on Linux.md
Normal file
151
published/20200319 Manually rotating log files on Linux.md
Normal file
@ -0,0 +1,151 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (HankChow)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-12038-1.html)
|
||||
[#]: subject: (Manually rotating log files on Linux)
|
||||
[#]: via: (https://www.networkworld.com/article/3531969/manually-rotating-log-files-on-linux.html)
|
||||
[#]: author: (Sandra Henry-Stocker https://www.networkworld.com/author/Sandra-Henry_Stocker/)
|
||||
|
||||
在 Linux 系统中手动滚动日志
|
||||
======
|
||||
|
||||

|
||||
|
||||
<ruby>日志滚动<rt>log rotation</rt></ruby>在 Linux 系统上是再常见不过的一个功能了,它为系统监控和故障排查保留必要的日志内容,同时又防止过多的日志造成单个日志文件太大。
|
||||
|
||||
日志滚动的过程是这样的:在一组日志文件之中,编号最大的(最旧的)一个日志文件会被删除,其余的日志文件编号则依次增大并取代较旧的日志文件,而较新的文件则取代它作为当前的日志文件。这一个过程很容易就可以实现自动化,在细节上还能按需作出微调。
|
||||
|
||||
使用 `logrotate` 命令可以手动执行日志滚动的操作。本文将要介绍的就是手动进行日志滚动的方法,以及预期产生的结果。
|
||||
|
||||
文中出现的示例适用于 Ubuntu 等 Linux 系统,对于其它类型的系统,日志文件和配置文件可能会有所不同,但日志滚动的过程是大同小异的。
|
||||
|
||||
### 为什么需要滚动日志
|
||||
|
||||
一般情况下,无需手动旋转日志文件。Linux 系统会每隔一天(或间隔更长的时间)或根据日志文件的大小自动进行一次日志滚动。如果你需要滚动日志以释放存储空间,又或者将某一部分日志从当前的活动中分割出来,这很容易做到,具体要取决于文件滚动规则。
|
||||
|
||||
### 一点背景介绍
|
||||
|
||||
在 Linux 系统安装完成后就已经有很多日志文件被纳入到日志滚动的范围内了。另外,一些应用程序在安装时也会为自己产生的日志文件设置滚动规则。一般来说,日志滚动的配置文件会放置在 `/etc/logrotate.d`。如果你想了解日志滚动的详细实现,可以参考[这篇以前的文章][4]。
|
||||
|
||||
在日志滚动的过程中,活动日志会以一个新名称命名,例如 `log.1`,之前被命名为 `log.1` 的文件则会被重命名为 `log.2`,依此类推。在这一组文件中,最旧的日志文件(假如名为 `log.7`)会从系统中删除。日志滚动时文件的命名方式、保留日志文件的数量等参数是由 `/etc/logrotate.d` 目录中的配置文件决定的,因此你可能会看到有些日志文件只保留少数几次滚动,而有些日志文件的滚动次数会到 7 次或更多。
|
||||
|
||||
例如 `syslog` 在经过日志滚动之后可能会如下所示(注意,行尾的注释部分只是说明滚动过程是如何对文件名产生影响的):
|
||||
|
||||
```
|
||||
$ ls -l /var/log/syslog*
|
||||
-rw-r----- 1 syslog adm 128674 Mar 10 08:00 /var/log/syslog <== 新文件
|
||||
-rw-r----- 1 syslog adm 2405968 Mar 9 16:09 /var/log/syslog.1 <== 之前的 syslog
|
||||
-rw-r----- 1 syslog adm 206451 Mar 9 00:00 /var/log/syslog.2.gz <== 之前的 syslog.1
|
||||
-rw-r----- 1 syslog adm 216852 Mar 8 00:00 /var/log/syslog.3.gz <== 之前的 syslog.2.gz
|
||||
-rw-r----- 1 syslog adm 212889 Mar 7 00:00 /var/log/syslog.4.gz <== 之前的 syslog.3.gz
|
||||
-rw-r----- 1 syslog adm 219106 Mar 6 00:00 /var/log/syslog.5.gz <== 之前的 syslog.4.gz
|
||||
-rw-r----- 1 syslog adm 218596 Mar 5 00:00 /var/log/syslog.6.gz <== 之前的 syslog.5.gz
|
||||
-rw-r----- 1 syslog adm 211074 Mar 4 00:00 /var/log/syslog.7.gz <== 之前的 syslog.6.gz
|
||||
```
|
||||
|
||||
你可能会发现,除了当前活动的日志和最新一次滚动的日志文件之外,其余的文件都已经被压缩以节省存储空间。这样设计的原因是大部分系统管理员都只需要查阅最新的日志文件,其余的日志文件压缩起来,需要的时候可以解压查阅,这是一个很好的折中方案。
|
||||
|
||||
### 手动日志滚动
|
||||
|
||||
你可以这样执行 `logrotate` 命令进行手动日志滚动:
|
||||
|
||||
```
|
||||
$ sudo logrotate -f /etc/logrotate.d/rsyslog
|
||||
```
|
||||
|
||||
值得一提的是,`logrotate` 命令使用 `/etc/logrotate.d/rsyslog` 这个配置文件,并通过了 `-f` 参数实行“强制滚动”。因此,整个过程将会是:
|
||||
|
||||
- 删除 `syslog.7.gz`,
|
||||
- 将原来的 `syslog.6.gz` 命名为 `syslog.7.gz`,
|
||||
- 将原来的 `syslog.5.gz` 命名为 `syslog.6.gz`,
|
||||
- 将原来的 `syslog.4.gz` 命名为 `syslog.5.gz`,
|
||||
- 将原来的 `syslog.3.gz` 命名为 `syslog.4.gz`,
|
||||
- 将原来的 `syslog.2.gz` 命名为 `syslog.3.gz`,
|
||||
- 将原来的 `syslog.1.gz` 命名为 `syslog.2.gz`,
|
||||
- 但新的 `syslog` 文件不一定必须创建。
|
||||
|
||||
你可以按照下面的几条命令执行操作,以确保文件的属主和权限正确:
|
||||
|
||||
```
|
||||
$ sudo touch /var/log/syslog
|
||||
$ sudo chown syslog:adm /var/log/syslog
|
||||
$ sudo chmod 640 /var/log/syslog
|
||||
```
|
||||
|
||||
你也可以把以下这一行内容添加到 `/etc/logrotate.d/rsyslog` 当中,由 `logrotate` 来帮你完成上面三条命令的操作:
|
||||
|
||||
```
|
||||
create 0640 syslog adm
|
||||
```
|
||||
|
||||
整个配置文件的内容是这样的:
|
||||
|
||||
```
|
||||
/var/log/syslog
|
||||
{
|
||||
rotate 7
|
||||
daily
|
||||
missingok
|
||||
notifempty
|
||||
create 0640 syslog adm <==
|
||||
delaycompress
|
||||
compress
|
||||
postrotate
|
||||
/usr/lib/rsyslog/rsyslog-rotate
|
||||
endscript
|
||||
}
|
||||
```
|
||||
|
||||
下面是手动滚动记录用户登录信息的 `wtmp` 日志的示例。由于 `/etc/logrotate.d/wtmp` 中有 `rotate 2` 的配置,因此系统中只保留了两份 `wtmp` 日志文件。
|
||||
|
||||
滚动前:
|
||||
|
||||
```
|
||||
$ ls -l wtmp*
|
||||
-rw-r----- 1 root utmp 1152 Mar 12 11:49 wtmp
|
||||
-rw-r----- 1 root utmp 768 Mar 11 17:04 wtmp.1
|
||||
```
|
||||
|
||||
执行滚动命令:
|
||||
|
||||
```
|
||||
$ sudo logrotate -f /etc/logrotate.d/wtmp
|
||||
```
|
||||
|
||||
滚动后:
|
||||
|
||||
```
|
||||
$ ls -l /var/log/wtmp*
|
||||
-rw-r----- 1 root utmp 0 Mar 12 11:52 /var/log/wtmp
|
||||
-rw-r----- 1 root utmp 1152 Mar 12 11:49 /var/log/wtmp.1
|
||||
-rw-r----- 1 root adm 99726 Feb 21 07:46 /var/log/wtmp.report
|
||||
```
|
||||
|
||||
需要知道的是,无论发生的日志滚动是自动滚动还是手动滚动,最近一次的滚动时间都会记录在 `logrorate` 的状态文件中。
|
||||
|
||||
```
|
||||
$ grep wtmp /var/lib/logrotate/status
|
||||
"/var/log/wtmp" 2020-3-12-11:52:57
|
||||
```
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.networkworld.com/article/3531969/manually-rotating-log-files-on-linux.html
|
||||
|
||||
作者:[Sandra Henry-Stocker][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[HankChow](https://github.com/HankChow)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.networkworld.com/author/Sandra-Henry_Stocker/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.flickr.com/photos/klif/4244284159/in/photolist-7t44P6-oPFpsr-a8c5W-gWNZ6-32EEo4-cjdxqy-diHaq9-8DYZWf-gWNWM-bgLApc-hBt94C-cj71kY-PMESV-dZBcCU-pSqgNM-51eKHq-EecbfS-osGNau-KMUx-nFaWEL-cj71PE-HFVXn-gWNWs-85HueR-8QpDh8-kV1dEc-76qYSV-5YnxuS-gWNXr-dYoQ5w-dzj1j3-3AJyd-mHbaWF-q2fTri-e9bFa6-nJyvfR-4PnMyH-gWNZr-8VUtGS-gWNWZ-ajzUd4-2hAjMk-gWW3g-gWP11-dwYbH5-4XMew-cj71B1-ica9kJ-5RonM6-8z5tGL
|
||||
[2]: https://creativecommons.org/licenses/by/2.0/legalcode
|
||||
[3]: https://www.networkworld.com/newsletters/signup.html
|
||||
[4]: https://www.networkworld.com/article/3218728/how-log-rotation-works-with-logrotate.html
|
||||
[5]: https://www.networkworld.com/blog/itaas-and-the-corporate-storage-technology/?utm_source=IDG&utm_medium=promotions&utm_campaign=HPE22140&utm_content=sidebar (ITAAS and Corporate Storage Strategy)
|
||||
[6]: https://www.facebook.com/NetworkWorld/
|
||||
[7]: https://www.linkedin.com/company/network-world
|
||||
@ -0,0 +1,106 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (wxy)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-12029-1.html)
|
||||
[#]: subject: (Linus Torvalds’ Advice on Working From Home during Coronavirus Lockdown)
|
||||
[#]: via: (https://itsfoss.com/torvalds-remote-work-advice/)
|
||||
[#]: author: (Ankush Das https://itsfoss.com/author/ankush/)
|
||||
|
||||
Linus Torvalds 关于在冠状病毒禁足期间在家工作的建议
|
||||
======
|
||||
|
||||
在冠状病毒爆发期间,我们中的许多人都在室内自我隔离。[ZDNet][1] 特此与 Linus Torvalds 进行了专题采访,讨论了他对冠状病毒禁足期间在家工作的看法或想法。
|
||||
|
||||
如果你还不知道(怎么可能不知道),[Linus Torvalds][2] 是 Linux 的创建者,也是 [Git][3] 的创建者,而所有这一切都是他在家里工作时做的。这是 2016 年的视频,Torvalds 展示了他的家庭办公室:
|
||||
|
||||
- [video](https://img.linux.net.cn/static/video/Linus%20Torvalds%20Guided%20Tour%20of%20His%20Home%20Office-SOXeXauRAm0.mp4)
|
||||
|
||||
因此,在本文中,我将分享我关注的一些主要要点,以及来自 Linus Torvalds 接受 ZDNet [Steven J. Vaughan-Nichols][4] 采访互动时的回应。
|
||||
|
||||
### 消除对人际交往缺失的恐惧
|
||||
|
||||
Linus 提到,几年前刚开始在家工作时,他担心过缺少人与人之间的互动,包括去办公室、与人互动或哪怕只是出去吃个午餐。
|
||||
|
||||
有趣的是,他似乎并没有错过任何东西,他更喜欢在家中没有人际交往的时间。
|
||||
|
||||
当然,将自己与人际互动隔离开并不是最好的事情 ,但在目前看来,这是一件好事。
|
||||
|
||||
### 利用在家工作的优势
|
||||
|
||||
![][5]
|
||||
|
||||
就像我们是完全远程操作一样,你可以做很多事情,而无需实际在办公室。
|
||||
|
||||
不要忘记,你可以随心所欲地养猫,我有 6 只猫,我知道这很困难(*哈哈*)。
|
||||
|
||||
而且,正如 Linus 所提到的,远程工作的真正优势在于“灵活性”。你不一定需要朝九晚五甚至更长的时间坐在办公桌前。从技术上讲,你可以在工作中自由休息,并在家中做你想做的任何事情。
|
||||
|
||||
换句话说,Linus 建议**不要在你的家中重新搞一个办公室**,这比去办公室还差。
|
||||
|
||||
### 高效沟通是关键
|
||||
|
||||
![][6]
|
||||
|
||||
虽然你可以在一天之中召开几次会议(视频会议或音频呼叫),但这真的有必要吗?
|
||||
|
||||
对于某些人来说,这可能很重要,但是你应该通过简化和整理内容来尽量减少会议花费的时间。
|
||||
|
||||
或者,按照 Linus 的建议,最好有个电子邮件列表来记录事情,以确保一切各司其职,这就是 [Linux 内核][7] 的运行方式。
|
||||
|
||||
James Bottomley 是 [IBM 研究院][8]的杰出工程师,也是资深 Linux 内核开发人员,他也建议你重新阅读你的文字以确保发送的准确信息不会被人不小心跳过。
|
||||
|
||||
就个人而言,出于同样的原因,我更喜欢文本而不是语音。实际上,它可以节省你的时间。
|
||||
|
||||
但是,请记住,你需要只以适当的方式传达必要的信息,而不要使通过文本/电子邮件发送的信息过载。
|
||||
|
||||
### 追踪你的时间
|
||||
|
||||
灵活性并不一定意味着你可以减少工作量并泡在社交媒体平台上,除非那就是你的工作。
|
||||
|
||||
因此,你需要确保充分利用自己的时间。为此,你可以使用多种工具来跟踪你的时间用在什么地方,以及在计算机上花费的时间。
|
||||
|
||||
你甚至可以将其记录在便签上,以确保你可以将时间高效地分配于工作上。你可以选择使用 [RescueTime][9] 或 [ActivityWatch][10] 来跟踪你在计算机或智能手机上花费的时间。
|
||||
|
||||
### 和猫(宠物)一起玩
|
||||
|
||||
![][11]
|
||||
|
||||
不歧视其他宠物,但这就是 Linus Torvalds 提到的。
|
||||
|
||||
正因为你在家中,你在安排工作或尝试有效利用时间时要做的事情有很多。
|
||||
|
||||
Linus 坚持认为,每当你感到无聊时,可以在必要时出门获取必需品,也可以与猫(或你的其它宠物)一起玩。
|
||||
|
||||
### 结语
|
||||
|
||||
虽然 Linus 还提到了当你在家时没人会评判你,但他的建议似乎是正确的,对于那些在家工作的人来说可能很有用。
|
||||
|
||||
不仅是因为冠状病毒的爆发,而且如果你打算一直在家工作,应该牢记这些。
|
||||
|
||||
你如何看待 Linus 的看法呢?你同意他的观点吗?
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://itsfoss.com/torvalds-remote-work-advice/
|
||||
|
||||
作者:[Ankush Das][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[wxy](https://github.com/wxy)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://itsfoss.com/author/ankush/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.zdnet.com/article/pet-the-cat-own-the-bathrobe-linus-torvalds-on-working-from-home/
|
||||
[2]: https://en.wikipedia.org/wiki/Linus_Torvalds
|
||||
[3]: https://git-scm.com/
|
||||
[4]: https://twitter.com/sjvn
|
||||
[5]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2020/03/Work-from-Home-torvalds.jpg?ssl=1
|
||||
[6]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2020/03/torvalds-home-office.jpg?ssl=1
|
||||
[7]: https://en.wikipedia.org/wiki/Linux_kernel
|
||||
[8]: https://www.research.ibm.com/
|
||||
[9]: https://www.rescuetime.com/
|
||||
[10]: https://activitywatch.net/
|
||||
[11]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2020/03/torvalds-penguins.jpeg?ssl=1
|
||||
@ -0,0 +1,107 @@
|
||||
[#]: collector: "lujun9972"
|
||||
[#]: translator: "wxy"
|
||||
[#]: reviewer: "wxy"
|
||||
[#]: publisher: "wxy"
|
||||
[#]: url: "https://linux.cn/article-12042-1.html"
|
||||
[#]: subject: "Purism Librem Mini: A Privacy-First Linux-Based Mini PC"
|
||||
[#]: via: "https://itsfoss.com/purism-librem-mini/"
|
||||
[#]: author: "Ankush Das https://itsfoss.com/author/ankush/"
|
||||
|
||||
Purism Librem Mini:隐私为重的基于 Linux 的微型个人电脑
|
||||
======
|
||||
|
||||
> Purism 推出了一款外形小巧的微型个人电脑 “Librem Mini”,旨在提供隐私和安全性。让我们来看看它的细节。
|
||||
|
||||
[Purism][1] 以专注于增强用户的数字隐私和安全性的服务或产品而闻名。
|
||||
|
||||
Purism 自诩为“<ruby>[社会目地公司][2]<rt>Social Purpose Company</rt></ruby>”,旨在为社会造福,并在这方面提供了多种服务和产品。
|
||||
|
||||
你可能听说过它的 Librem 系列 [Linux 笔记本电脑][3]、[Librem One][4](加密服务)、[PureOS Linux][5] 和 [Librem 5 Linux 智能手机][6]。现在,他们已经针对想要掌控自己的隐私和安全性的用户推出了小尺寸微型个人电脑。
|
||||
|
||||
### Librem Mini: Purism 的微型个人电脑
|
||||
|
||||
![Librem Mini PC][7]
|
||||
|
||||
[Purism][1] 的 [Librem Mini][8] 旨在成为小型、轻便且功能强大的微型个人电脑。
|
||||
|
||||
当然,已经有很多[基于 Linux 的微型个人电脑][9]了,但是 Librem Mini 专门关注于其用户的隐私和安全性。它随附了 [PureOS][5]、[Pureboot][10] 和 [Librem Key][11] 支持。
|
||||
|
||||
基本配置将以 699 美元的价格提供。这比大多数其他微型个人电脑要贵。但是,与大多数其他产品不同,Librem Mini 并不是又一个 [Intel NUC][12]。 那么,它提供了什么呢?
|
||||
|
||||
### Librem Mini 的规格
|
||||
|
||||
![][13]
|
||||
|
||||
这是它的规格表:
|
||||
|
||||
* Intel Core i7-8565U(Whiskey Lake),主动(风扇)冷却,4 核 8 线程最高频率 4.6GHz
|
||||
* Intel UHD Graphics 620
|
||||
* RAM: 最多 64 GB DDR4 2400 MHz(2 个 SO-DIMM 插槽)
|
||||
* 1 SATA III 6GB/s SSD/HDD(7mm)
|
||||
* 1 M.2 SSD(SATA III/NVMe x4)
|
||||
* 1 HDMI 2.0 4K @ 60Hz
|
||||
* 1 DisplayPort 1.2 4K @ 60Hz
|
||||
* 4 x USB 3.0
|
||||
* 2 x USB 2.0
|
||||
* 1 x Type-C 3.1
|
||||
* 3.5mm 音频插孔(麦克风输入和耳机插孔合一)
|
||||
* 1 RJ45 Gigabit Ethernet LAN
|
||||
* WiFi 802.11n(2.4/5.0 GHz),可选 Atheros ATH9k 模块
|
||||
* 包括在 WiFi 模块的蓝牙 4.0(可选)
|
||||
* 重量:1 公斤(2.2 磅)
|
||||
* 尺寸:12.8 厘米(5.0 英寸) x 12.8 厘米(5.0 英寸) x 3.8 厘米(1.5 英寸)
|
||||
|
||||
我不知道他们为什么决定采用 Intel 的 8 代处理器,而市场上已经出现了 10 代处理器。也许是因为 Whiskey Lake 是第 8 代处理器的最新产品。
|
||||
|
||||
是的,他们已禁用并中止了 Intel 的管理引擎,所以仍然可以采用这个产品。
|
||||
|
||||
除此之外,你还应该记住,这款微型个人电脑在提供全盘加密的同时具有检测硬件和软件篡改的功能。
|
||||
|
||||
而且,当然,用的是 Linux。
|
||||
|
||||
### 价格和供应
|
||||
|
||||
![Librem Mini from the back][14]
|
||||
|
||||
具有 8 Gigs RAM 和 256 GB SSD 的基本配置将需要花费 $699。而且,如果你想要最强大的配置,其价格轻松就升高到 $3000。
|
||||
|
||||
他们的预定销售额目标是 $50,000,并且他们计划在达到预定目标后一个月内开始发货。
|
||||
|
||||
因此,如果你要是现在[预订][15]的话,不要指望很快就会开始发货。因此,我建议你关注 [Librem Mini 产品页面][8]的预定目标。
|
||||
|
||||
### 总结
|
||||
|
||||
如果你正在寻找一台微型个人电脑(不是专门为隐私和安全而设计的),则可以看看我们的[基于 Linux 的最佳微型个人电脑][9]列表,以获取更多建议。
|
||||
|
||||
对于普通消费者而言,Librem Mini 绝对听起来很昂贵。对于隐私发烧友来说,它仍然是一个不错的选择。
|
||||
|
||||
你怎么看?让我知道你的想法!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://itsfoss.com/purism-librem-mini/
|
||||
|
||||
作者:[Ankush Das][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[wxy](https://github.com/wxy)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://itsfoss.com/author/ankush/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://puri.sm/
|
||||
[2]: https://puri.sm/about/social-purpose/
|
||||
[3]: https://itsfoss.com/get-linux-laptops/
|
||||
[4]: https://itsfoss.com/librem-one/
|
||||
[5]: https://itsfoss.com/pureos-convergence/
|
||||
[6]: https://itsfoss.com/librem-linux-phone/
|
||||
[7]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2020/03/librem-mini-pc.png?ssl=1
|
||||
[8]: https://puri.sm/products/librem-mini/
|
||||
[9]: https://itsfoss.com/linux-based-mini-pc/
|
||||
[10]: https://docs.puri.sm/PureBoot.html
|
||||
[11]: https://puri.sm/products/librem-key/
|
||||
[12]: https://itsfoss.com/intel-nuc-essential-accessories/
|
||||
[13]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2020/03/librem-mini-pc-1.png?ssl=1
|
||||
[14]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2020/03/librem-mini-back.png?ssl=1
|
||||
[15]: https://shop.puri.sm/shop/librem-mini/
|
||||
@ -0,0 +1,82 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Linux Foundation prepares for disaster, new anti-tracking data set, Mozilla goes back to mobile OSes, and more open source news)
|
||||
[#]: via: (https://opensource.com/article/20/3/news-march-14)
|
||||
[#]: author: (Scott Nesbitt https://opensource.com/users/scottnesbitt)
|
||||
|
||||
Linux Foundation prepares for disaster, new anti-tracking data set, Mozilla goes back to mobile OSes, and more open source news
|
||||
======
|
||||
Catch up on the biggest open source headlines from the past two weeks.
|
||||
![][1]
|
||||
|
||||
In this edition of our open source news roundup, we take a look at the Linux Foundation's disaster relief project, DuckDuckGo's anti-tracking tool, open textbooks, and more!
|
||||
|
||||
### Linux Foundation unveils Project OWL
|
||||
|
||||
When a disaster happens, it's vital to keep communications links up and running. One way to do that is with [mesh networks][2]. The Linux Foundation [has unveiled][3] Project OWL to "help build mesh network nodes for global emergency communications networks."
|
||||
|
||||
Short for _Organisation, Whereabouts, and Logistics_, OWL is firmware for Internet of Things (IoT) devices that "can quickly turn a cheap wireless device into a ‘DuckLink’, a mesh network node". Those devices can connect to other, similar devices around them. OWL also provides an analytics tool that responders can use for "coordinating resources, learning about weather patterns, and communicating with civilians who would otherwise be cut off."
|
||||
|
||||
### New open source tool to block web trackers
|
||||
|
||||
It's no secret that sites all over the web track their visitors. Often, it's shocking how much of that goes on and what a threat to your privacy that is. To help web browser developers better protect their users, the team behind search engine DuckDuckGo is "[sharing data it's collected about online trackers with other companies so they can also protect your privacy][4]."
|
||||
|
||||
That dataset is called Tracker Radar and it "details 5,326 internet domains used by 1,727 companies and organizations that track you online". Browser Radar is different from other tracker databases in that it "annotates data with other information, like whether blocking a tracker is likely to break a website, so anyone using it can pick the best balance of privacy and convenience."
|
||||
|
||||
Tracker Radar's dataset is [available on GitHub][5]. The repository also links to the code for the [crawler][6] and [detector][7] that work with the data.
|
||||
|
||||
### Oregon Tech embracing open textbooks
|
||||
|
||||
With the cost of textbooks taking an increasingly large bite out of the budgets of university students, more and more schools are turning to open textbooks to cut those costs. By embracing open textbooks, the Oregon Institute of Technology has [save students $400,000][8] over the last two years.
|
||||
|
||||
The school offers open textbooks for 26 courses, ranging "from chemistry and biology, to respiratory care, sociology and engineering." Although the textbooks are free, university librarian John Schoppert points out that the materials are of a high quality and that faculty members have been "developing lab manuals and open-licensed textbooks where they hadn’t existed before and improved on others’ materials."
|
||||
|
||||
### Mozilla to help update feature phone OS
|
||||
|
||||
A few years ago, Mozilla tried to break into the world of mobile operating systems with Firefox OS. While that effort didn't pan out, Firefox OS found new life powering low-cost feature phones under the name KaiOS. Mozilla's [jumping back into the game][9] by helping "modernize the browser engine that's core to the software."
|
||||
|
||||
KaiOS is built upon a four-year-old version of Mozilla's Gecko browser engine. Updating Gecko will "improve security, make apps run faster and more smoothly, and open [KaiOS to] more-sophisticated apps and WebGL 2.0 for better games graphics." Mozilla said its collaboration will include "Mozilla's help with test engineering and adding new low-level Gecko abilities."
|
||||
|
||||
#### In other news
|
||||
|
||||
* [CERN adopts Mattermost, an open source messaging app][10]
|
||||
* [Open-source software analyzes economics of biofuels, bioproducts][11]
|
||||
* [Netflix releases Dispatch for crisis management orchestration][12]
|
||||
* [FreeNAS and TrueNAS are merging][13]
|
||||
* [Smithsonian 3D Scans NASA Space Shuttle Discovery And Makes It Open Source][14]
|
||||
|
||||
|
||||
|
||||
Thanks, as always, to Opensource.com staff members and [Correspondents][15] for their help this week.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/20/3/news-march-14
|
||||
|
||||
作者:[Scott Nesbitt][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/scottnesbitt
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/weekly_news_roundup_tv.png?itok=tibLvjBd
|
||||
[2]: https://en.wikipedia.org/wiki/Mesh_networking
|
||||
[3]: https://www.smartcitiesworld.net/news/news/linux-announces-open-source-project-to-aid-disaster-relief-5102
|
||||
[4]: https://www.cnet.com/news/privacy-focused-duckduckgo-launches-new-effort-to-block-online-tracking/
|
||||
[5]: https://github.com/duckduckgo/tracker-radar
|
||||
[6]: https://github.com/duckduckgo/tracker-radar-collector
|
||||
[7]: https://github.com/duckduckgo/tracker-radar-detector
|
||||
[8]: https://www.heraldandnews.com/news/local_news/oregon-tech-turns-to-open-source-materials-to-save-students/article_ba641e79-3034-5b9a-a8f7-b5872ddc998e.html
|
||||
[9]: https://www.cnet.com/news/mozilla-helps-modernize-feature-phones-powered-by-firefox-tech/
|
||||
[10]: https://joinup.ec.europa.eu/collection/open-source-observatory-osor/news/cern-uses-mattermost
|
||||
[11]: http://www.biomassmagazine.com/articles/16848/open-source-software-analyzes-economics-of-biofuels-bioproducts
|
||||
[12]: https://jaxenter.com/netflix-dispatch-crisis-management-orchestration-169381.html
|
||||
[13]: https://liliputing.com/2020/03/freenas-and-turenas-are-merging-open-source-operating-systems-for-network-attached-storage.html
|
||||
[14]: https://www.forbes.com/sites/tjmccue/2020/03/04/smithsonian-3d-scans-the-nasa-space-shuttle-discovery-and-makes-it-open-source/#39aa0f243ecd
|
||||
[15]: https://opensource.com/correspondent-program
|
||||
@ -0,0 +1,60 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Tools for monitoring, introvert inclusion, and more industry trends)
|
||||
[#]: via: (https://opensource.com/article/20/3/monitoring-introvert-industry-trends)
|
||||
[#]: author: (Tim Hildred https://opensource.com/users/thildred)
|
||||
|
||||
Tools for monitoring, introvert inclusion, and more industry trends
|
||||
======
|
||||
A weekly look at open source community and industry trends.
|
||||
![Person standing in front of a giant computer screen with numbers, data][1]
|
||||
|
||||
As part of my role as a senior product marketing manager at an enterprise software company with an open source development model, I publish a regular update about open source community, market, and industry trends for product marketers, managers, and other influencers. Here are five of my and their favorite articles from that update.
|
||||
|
||||
## [Top six open source tools for monitoring][2]
|
||||
|
||||
> These tools are widely used in the tech industry, and they all have their benefits. Most of these solutions, however, require skilled implementation and ongoing manual maintenance that can be a burden for DevOps teams and a distraction from the business. There’s no one solution that can cater to all of your requirements, since each tool focuses on one or two specific aspects of observability and analysis. By mixing these tools together, you can derive a unique solution for your individual business needs.
|
||||
|
||||
**The impact**: If a container falls over in the cluster and there is no open source monitoring tool to see it, did it really happen?
|
||||
|
||||
## [Introvert environment: What can we do?][3]
|
||||
|
||||
> An example is its inclusive team dynamics programme, which consists of both information and guidance on everyday practices. Each team is required to appoint an inclusion champion, who ensures all members are given the space to contribute to discussions. Leaders are also encouraged not to speak first during meetings.
|
||||
|
||||
**The impact**: If it is hard for you not to speak for a while in a meeting, that probably indicates you should be doing it more often. Will new WFH policies make this harder, or easier? Only time will tell.
|
||||
|
||||
## [The difference between API Gateways and service mesh][4]
|
||||
|
||||
> The service connectivity capabilities that service mesh provides are conflicting with the API connectivity features that an API gateway provides. However, because the ones provided by service mesh are more inclusive (L4 + L7, all TCP traffic, not just HTTP and not just limited to APIs but to every service), they are in a way more complete. But as we can see from the diagram above, there are also use cases that service mesh does not provide, and that is the “API as a product” use case as well as the full API management lifecycle, which still belong to the API gateway pattern.
|
||||
|
||||
**The impact**: Another way of saying this is you can't make money from your service mesh directly, unlike your APIs.
|
||||
|
||||
## [Open Policy Agent’s mission to secure the cloud][5]
|
||||
|
||||
> While the cost of implementing OPA is a little high today, the technology pays for itself by providing more control and helping to secure systems. As OPA continues to be refined, we can expect implementation costs to fall, making an investment in OPA easier to justify.
|
||||
|
||||
**The impact**: Compliance is expensive; large investments in it only make sense if non-compliance is even more so.
|
||||
|
||||
_I hope you enjoyed this list and come back next week for more open source community, market, and industry trends._
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/20/3/monitoring-introvert-industry-trends
|
||||
|
||||
作者:[Tim Hildred][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/thildred
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/data_metrics_analytics_desktop_laptop.png?itok=9QXd7AUr (Person standing in front of a giant computer screen with numbers, data)
|
||||
[2]: https://devops.com/top-six-open-source-tools-for-monitoring-kubernetes-and-docker/
|
||||
[3]: https://www.raconteur.net/hr/introverts-workplace
|
||||
[4]: https://www.cncf.io/blog/2020/03/06/the-difference-between-api-gateways-and-service-mesh/
|
||||
[5]: https://thenewstack.io/open-policy-agents-mission-to-secure-the-cloud/
|
||||
@ -0,0 +1,78 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (With npm Acquisition, Microsoft is Set to Own the Largest Software Registry in the World)
|
||||
[#]: via: (https://itsfoss.com/microsoft-npm-acquisition/)
|
||||
[#]: author: (Abhishek Prakash https://itsfoss.com/author/abhishek/)
|
||||
|
||||
With npm Acquisition, Microsoft is Set to Own the Largest Software Registry in the World
|
||||
======
|
||||
|
||||
Microsoft has been betting big on open source for past few years. Apart from open sourcing a few things here and there, Microsoft is contributing a lot to Linux kernel (for its Azure cloud platform).
|
||||
|
||||
To further strengthen its position in the open source world, [Microsoft acquired the popular open source code hosting platform GitHub for $7.5 billion][1].
|
||||
|
||||
Now Microsoft owned GitHub [has acquired][2] [npm][3] ( short for Node Package Manager). npm is the [world’s largest software registry][4] with [more than 1.3 million packages that have 75 billion downloads a month][5].
|
||||
|
||||
![][6]
|
||||
|
||||
If you are not familiar, npm is a package manager for JavaScript programming language, primarily the hugely popular open source [Node.js][7].
|
||||
|
||||
Though npm has scope of private repository for enterprises, most of the 1.3 million packages are open source and/or used in various open source projects.
|
||||
|
||||
Both node.js and npm are used by big software and IT companies like IBM, Yahoo and big corporations like Netflix and PayPal.
|
||||
|
||||
In case you are wondering, the acquisition amount has not been disclosed by either party.
|
||||
|
||||
### Microsoft’s proposed plan for npm
|
||||
|
||||
![][8]
|
||||
|
||||
GitHub CEO Nat Friedman assured that Microsoft intends to keep the npm registry available as open-source and free to developers.
|
||||
|
||||
Once the acquisition is complete, Microsoft is going to invest in the registry infrastructure and platform. It plans to improve the core experience of npm by adding new features like Workspaces, as well as bringing improvements to publishing and multi-factor authentication.
|
||||
|
||||
Microsoft also intends to integrate GitHub and npm so that developers could trace a change from a GitHub pull request to the npm package version that fixed it.
|
||||
|
||||
### Part of a larger plan
|
||||
|
||||
First, [Microsoft bought GitHub][1], the platform that had the largest open source repositories and now npm, the largest software registry. Clearly, Microsoft is tightening its grip around open source projects. This could allow Microsoft to dictate the policies around these open source projects in future.
|
||||
|
||||
When Microsoft acquired GitHub, several open source developers moved to [alternate platforms like GitLab][9] but GitHub remained the first choice for the developers. Microsoft did introduce some innovative features like security advisories, [package registry][10], [sponsorship][11] etc. Microsoft is expanding GitHub by forming communities around it specially in developing countries. Recently, [GitHub announced its Indian subsidiary][12] to specially attract young developers to its platform.
|
||||
|
||||
So now Microsoft owns the professional social network [LinkedIn][13], developer oriented GitHub and npm. This indicates that Microsoft will continue its shopping spree and will acquire more open source related projects that have substantial developer population.
|
||||
|
||||
What could be next then? WordPress because it is the [most popular open source CMS][14] and [runs 33% of the websites][15] on the internet?
|
||||
|
||||
While we wait and watch for Microsoft’s next move, why not share your views on this development? Comment section is all yours.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://itsfoss.com/microsoft-npm-acquisition/
|
||||
|
||||
作者:[Abhishek Prakash][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://itsfoss.com/author/abhishek/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://itsfoss.com/microsoft-github/
|
||||
[2]: https://github.blog/2020-03-16-npm-is-joining-github/
|
||||
[3]: https://www.npmjs.com/
|
||||
[4]: https://www.linux.com/news/state-union-npm/
|
||||
[5]: https://www.zdnet.com/article/microsoft-buys-javascript-developer-platform-npm-plans-to-integrate-it-with-github/
|
||||
[6]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2020/03/microsoft-github-npm.jpg?ssl=1
|
||||
[7]: https://nodejs.org/en/
|
||||
[8]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2020/03/github-npm.jpg?ssl=1
|
||||
[9]: https://itsfoss.com/github-alternatives/
|
||||
[10]: https://github.blog/2019-05-10-introducing-github-package-registry/
|
||||
[11]: https://itsfoss.com/github-sponsors-program/
|
||||
[12]: https://github.blog/2020-02-12-announcing-github-india/
|
||||
[13]: https://www.linkedin.com/
|
||||
[14]: https://itsfoss.com/open-source-cms/
|
||||
[15]: https://wordpress.org/news/2019/03/one-third-of-the-web/
|
||||
@ -0,0 +1,98 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (OBS Studio 25.0 is Here With Vulkan-based Games Capture Feature and More)
|
||||
[#]: via: (https://itsfoss.com/obs-studio-25-release/)
|
||||
[#]: author: (Abhishek Prakash https://itsfoss.com/author/abhishek/)
|
||||
|
||||
OBS Studio 25.0 is Here With Vulkan-based Games Capture Feature and More
|
||||
======
|
||||
|
||||
_**Brief: Open source screen recording and streaming software OBS Studio 25.0 has just been released and it brings the ability to capture Vulkan-based games with game capture among other new features.**_
|
||||
|
||||
![][1]
|
||||
|
||||
If you are into recording your desktop or streaming it, you might have heard of [OBS][2] (Open Broadcaster Software) Studio. It’s one of the [best screen recorder tools on Linux][3] and other operating systems.
|
||||
|
||||
But OBS is more than just a simple screen recorder. It also provides all the stuff you need for streaming your recordings.
|
||||
|
||||
### New features in OBS Studio 25.0
|
||||
|
||||
![OBS 25.0][4]
|
||||
|
||||
OBS Studio has released it’s latest version 25.0 with plenty of new features to make your recording and streaming experience better. Let’s take a look at some of the main new features:
|
||||
|
||||
* Capture Vulkan-based games with game capture
|
||||
* New capture method to window capture which allows capturing browsers, browser-based windows, and UWP programs
|
||||
* Advanced scene collection importing allows you to import from other common streaming programs
|
||||
* Media source hotkeys to allow control of playback
|
||||
* Ability to drag and drop URLs to create browser sources
|
||||
* Support for the [SRT protocol][5]
|
||||
* Ability to lock volume values of audio sources in the mixer
|
||||
* Support for certain devices that can automatically rotate their camera output such as the Logitech StreamCam
|
||||
* System tray icon to show when the recording is paused
|
||||
* Help icons when an property has a tooltip associated with it
|
||||
|
||||
|
||||
|
||||
Apart from there, there are plenty of bug features and minor changes that you may follow in the [release notes][6].
|
||||
|
||||
### Install OBS Studio 25.0 on Linux
|
||||
|
||||
OBS Studio is a cross-platform software and is also available for Windows and macOS in addition to Linux. You can download it from its official website.
|
||||
|
||||
[Download OBS Studio 25.0][7]
|
||||
|
||||
For Linux, you can grab the source code and build it your self. I know that’s not very convenient for everyone. The good news is that you can install the latest OBS version using Snap or Flatpak packages.
|
||||
|
||||
On Ubuntu or any other [Linux distribution with Snap support][8], you can use the following command:
|
||||
|
||||
```
|
||||
sudo snap install obs-studio
|
||||
```
|
||||
|
||||
If your distribution supports Fltapak packages, you can get it from Flathub website:
|
||||
|
||||
[OBS Studio on Flathub][9]
|
||||
|
||||
For Ubuntu users, there is also the official PPA for easily installing it. In a terminal, you can enter the following command one by one:
|
||||
|
||||
```
|
||||
sudo add-apt-repository ppa:obsproject/obs-studio
|
||||
sudo apt update
|
||||
sudo apt install obs-studio
|
||||
```
|
||||
|
||||
You can [learn about deleting PPA here][10].
|
||||
|
||||
Personally, I haven’t used OBS much though I have heard great stuff about it. I don’t live stream but I do record my desktop to create tutorial and information Linux videos on I[t’s FOSS YouTube channel][11] (you should subscribe to it if you haven’t already). For that, I [use Kazam][12] which I find simpler to use.
|
||||
|
||||
Do you use OBS Studio? Which features you like the most? Do share your views.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://itsfoss.com/obs-studio-25-release/
|
||||
|
||||
作者:[Abhishek Prakash][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://itsfoss.com/author/abhishek/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2020/03/obs_logo_icon_small.png?resize=150%2C150&ssl=1
|
||||
[2]: https://obsproject.com/
|
||||
[3]: https://itsfoss.com/best-linux-screen-recorders/
|
||||
[4]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2020/03/obs-25-ubuntu.png?ssl=1
|
||||
[5]: https://en.wikipedia.org/wiki/Secure_Reliable_Transport
|
||||
[6]: https://github.com/obsproject/obs-studio/releases/tag/25.0.0
|
||||
[7]: https://obsproject.com/download
|
||||
[8]: https://itsfoss.com/install-snap-linux/
|
||||
[9]: https://flathub.org/apps/details/com.obsproject.Studio
|
||||
[10]: https://itsfoss.com/how-to-remove-or-delete-ppas-quick-tip/
|
||||
[11]: https://www.youtube.com/channel/UCEU9D6KIShdLeTRyH3IdSvw
|
||||
[12]: https://itsfoss.com/kazam-screen-recorder/
|
||||
@ -0,0 +1,70 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (npm joins GitHub, building operators in Kubernetes, and more industry trends)
|
||||
[#]: via: (https://opensource.com/article/20/3/npm-github-operators-kubernetes-industry-trends)
|
||||
[#]: author: (Tim Hildred https://opensource.com/users/thildred)
|
||||
|
||||
npm joins GitHub, building operators in Kubernetes, and more industry trends
|
||||
======
|
||||
A weekly look at open source community and industry trends.
|
||||
![Person standing in front of a giant computer screen with numbers, data][1]
|
||||
|
||||
As part of my role as a senior product marketing manager at an enterprise software company with an open source development model, I publish a regular update about open source community, market, and industry trends for product marketers, managers, and other influencers. Here are five of my and their favorite articles from that update.
|
||||
|
||||
## [npm is joining GitHub][2]
|
||||
|
||||
> Looking further ahead, we’ll integrate GitHub and npm to improve the security of the open source software supply chain, and enable you to trace a change from a GitHub pull request to the npm package version that fixed it. Open source security is an important global issue, and with the recent launch of the [GitHub Security Lab][3] and GitHub’s built-in [security advisories][4], we are well-positioned to make a difference. In addition, [GitHub Sponsors][5] has already paid out millions of dollars to open source contributors, and we’re excited to explore tasteful ways to extend it to the npm ecosystem.
|
||||
|
||||
**The impact**: Open source supply chain security is a big problem that probably needs a lot more resources thrown at it.
|
||||
|
||||
## [Why and how to build operators in Kubernetes][6]
|
||||
|
||||
> For cluster administrators managing large clusters, this proliferation of development methodologies and management interfaces can be problematic. The class of applications that Operators were developed to manage are almost always part of a larger application stack, with dependencies between them. If we have a lot of Operators written in different ways running on our clusters, how can we ensure they will interoperate with each other, and how do we validate and test them?
|
||||
|
||||
**The impact**: This illustrates two cool things about open source. First, the alternating waves of innovation and consolidation. Second, the empowering of affected parties to address their own challenges.
|
||||
|
||||
## [Automation for improved security frameworks][7]
|
||||
|
||||
> In recent years we’ve seen the posts of CIO and CTO elevated to boardroom level, with senior figures in IT now influencing corporate strategy. Due to a heightened awareness of cybersecurity, it won’t be long before the board looks to CSO and CISO executives for strategic direction.
|
||||
|
||||
**The impact**: This statement has gotten truer over the last several weeks. More activity is being pushed online than ever before; keeping that activity secure is integral to making it all profitable. Security people need to be able to say "no" at the highest possible level.
|
||||
|
||||
## [Interoperability of open source tools: The emergence of interfaces][8]
|
||||
|
||||
> Being non-opinionated about the adoption of specific technologies and the methodologies of distributing its primitive resources, were the main axes of Kubernetes evolution. Additionally, the proliferation of solutions from multiple vendors played an instrumental role in the emergence of interfaces and it served as the engine for further development and innovation.
|
||||
|
||||
**The impact**: Kubernetes may be the only large-scale open source project where competition is hot. Even still, competitors need to be able to work together and interfaces are the points that separate collaboration and competition.
|
||||
|
||||
## [Do you operate OpenStack? Take this survey.][9]
|
||||
|
||||
> Direct feedback from the individuals and organizations operating OpenStack helps the upstream development community know what features to prioritize and which bugs to fix first, among other important learnings on how the software is being used. Each of the official project teams has the opportunity to add a question to the survey as well as review anonymized data and trends to further influence their roadmaps.
|
||||
|
||||
**The impact**: Not every community participant can or will provide feedback on bug reports or feature requests. In that case, it is important to provide multiple ways to get feedback and meet users where they are.
|
||||
|
||||
_I hope you enjoyed this list and come back next week for more open source community, market, and industry trends._
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/20/3/npm-github-operators-kubernetes-industry-trends
|
||||
|
||||
作者:[Tim Hildred][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/thildred
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/data_metrics_analytics_desktop_laptop.png?itok=9QXd7AUr (Person standing in front of a giant computer screen with numbers, data)
|
||||
[2]: https://github.blog/2020-03-16-npm-is-joining-github/
|
||||
[3]: https://securitylab.github.com
|
||||
[4]: https://help.github.com/en/github/managing-security-vulnerabilities/creating-a-security-advisory
|
||||
[5]: https://github.com/sponsors
|
||||
[6]: https://devops.com/day-2-for-the-operator-ecosystem/
|
||||
[7]: https://www.infosecurity-magazine.com/opinions/automation-governance-culture/
|
||||
[8]: https://medium.com/@kgamanji/interoperability-of-open-source-tools-the-emergence-of-interfaces-f3b7a90891e4
|
||||
[9]: https://superuser.openstack.org/articles/operate-openstack-take-the-survey-heres-why-it-matters/
|
||||
@ -1,201 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (How the Linux desktop has grown)
|
||||
[#]: via: (https://opensource.com/article/19/8/how-linux-desktop-grown)
|
||||
[#]: author: (Jim Hall https://opensource.com/users/jim-hallhttps://opensource.com/users/jason-bakerhttps://opensource.com/users/jlacroixhttps://opensource.com/users/doni08521059https://opensource.com/users/etc-eterahttps://opensource.com/users/marcobravohttps://opensource.com/users/alanfdoss)
|
||||
|
||||
How the Linux desktop has grown
|
||||
======
|
||||
Since the early 1990s, the Linux desktop has matured from a simple
|
||||
window manager to a full desktop. Join us on a journey through the
|
||||
history of the Linux desktop.
|
||||
![Person typing on a 1980's computer][1]
|
||||
|
||||
I first installed Linux in 1993. At that time, you really didn't have many options for installing the operating system. In those early days, many people simply copied a running image from someone else. Then someone had the neat idea to create a "distribution" of Linux that let you customize what software you wanted to install. That was the Softlanding Linux System (SLS) and my first introduction to Linux.
|
||||
|
||||
My '386 PC didn't have much memory, but it was enough. SLS 1.03 required 2MB of memory to run, or 4MB if you wanted to compile programs. If you wanted to run the X Window System, you needed a whopping 8MB of memory. And my PC had just enough memory to run X.
|
||||
|
||||
As I'd grown up with the command line, a graphical user interface wasn't essential to me. But it sure was convenient. I could run applications in different windows and easily switch between tasks.
|
||||
|
||||
From my first experiment with Linux, I was hooked. I've stuck with Linux on my desktop ever since. Like many people, I ran Linux in a dual-boot configuration for a while so I could jump back to MS-DOS and Windows to run certain programs. Until 1998, when I finally took the plunge and went all-in with Linux.
|
||||
|
||||
Over the last 26 years, I have watched the Linux desktop mature. I've also tried an interesting combination of desktop environments over that time, which I'll share by taking a journey through the history of the Linux desktop.
|
||||
|
||||
### X and window managers
|
||||
|
||||
The first "desktops" on Linux weren't yet desktops. Instead, they were _window managers_ running on the X Window System. X provided the basic building blocks for a graphical user interface, such as creating windows on the screen and providing keyboard and mouse input. By itself, X didn't do much. To make the X graphical environment useful, you needed a way to manage all the windows in your session. That's where the _window manager_ came in. Running an X program like xterm or xclock opens that program in a window. The window manager keeps track of windows and does basic housekeeping, such as letting you move windows around and minimize them. The rest is up to you. You could launch programs when X started by listing them in the **~/.xinitrc** file, but usually, you'd run new programs from an xterm.
|
||||
|
||||
The most common window manager in 1993 was TWM, which dates back to 1988. TWM was quite simple and provided only basic window management.
|
||||
|
||||
![TWM on SLS 1.05][2]
|
||||
|
||||
TWM on SLS 1.05 showing xterm, xclock, and the Emacs editor
|
||||
|
||||
Yet another early window manager was the OpenLook Virtual Window Manager (OLVWM). OpenLook was a graphical user interface developed by Sun Microsystems in the 1980s and later ported to other Unix platforms. As a _virtual_ window manager, OLVWM supported multiple workspaces.
|
||||
|
||||
![OLVWM on SLS 1.05][3]
|
||||
|
||||
OLVWM on SLS 1.05 showing xterm and the Virtual Workspaces selector
|
||||
|
||||
When Linux began to grow in popularity, it didn't take long for others to create new window managers with smoother performance and improved interfaces. The first of these new window managers was FVWM, a virtual window manager. FVWM sported a more modern look than TWM or OLVWM. But we didn't yet have a desktop.
|
||||
|
||||
![FVWM on SLS 1.05][4]
|
||||
|
||||
FVWM on SLS 1.05 showing xterm and a file manager
|
||||
|
||||
To modern eyes, TWM and FVWM may look pretty plain. But it's important to remember what other graphical environments looked like at the time. The then-current version of Windows looked rather simple. Windows versions 1 through 3 used a plain launcher called the Program Manager.
|
||||
|
||||
![Windows 3.11][5]
|
||||
|
||||
Windows 3.11 showing the Program Manager and the Notepad editor
|
||||
|
||||
In August 1995, Microsoft released Windows 95 and changed the modern PC desktop landscape. Certainly, I was impressed. I thought Windows 3.x was ungainly and ugly, but Windows 95 was smooth and pretty. More importantly, Windows 95 was what we now consider a _desktop_. The new desktop metaphor was a huge step forward. You could put icons on the desktop—and in fact, Windows 95 presented two default desktop icons, for My Computer (to open a file manager) and the Recycle Bin (where you put files to be deleted later).
|
||||
|
||||
But more importantly, the Windows 95 desktop meant _integration_. The Program Manager was gone, replaced by a Taskbar at the bottom of the screen that let you launch new programs using a simpler Start menu. The Taskbar was multifunctional and also showed your running programs via a series of buttons and a dock showing the time, speaker volume, and other simple controls. You could right-click on any object on the new desktop, and Windows 95 would present you with a context-sensitive menu with actions you could perform.
|
||||
|
||||
![Windows 95][6]
|
||||
|
||||
Windows 95 showing the Notepad editor
|
||||
|
||||
The Windows 95 interface was slick and much easier to use than previous versions of Windows—and even other Linux window managers. Not to be outdone, Linux developers created a new version of FVWM that mimicked the Windows 95 interface. Called FVWM95, the new window manager still wasn't a desktop, but it looked very nice. The new taskbar let you start new X programs using the Start menu. The taskbar also showed your running programs using buttons similar to Windows 95's.
|
||||
|
||||
![FVWM95 on Red Hat Linux 5.2][7]
|
||||
|
||||
FVWM95 on Red Hat Linux 5.2 showing xterm and a quick-access program launcher with icons for xterm, the file manager, and other programs
|
||||
|
||||
While FVWM95 and other window managers were improving, the core problem remained: Linux didn't really have a desktop. It had a collection of window managers, and that was about it. Linux applications that used a graphical user interface (GUI, pretty much meaning they were X applications) all looked different and worked differently. You couldn't copy and paste from one application to another, except the simple text-only copy/paste provided by the X Window System. What Linux really needed was a complete redo in its GUI to create the first desktop.
|
||||
|
||||
### The first Linux desktop
|
||||
|
||||
In 1996, Matthias Ettrich was troubled by the inconsistency of Linux applications under X. He wanted to make the graphical environment easy to use. And more importantly, he wanted to make everything _integrated_—like an actual desktop.
|
||||
|
||||
Matthias started work on the K Desktop Environment. That's K for "Kool." But the name KDE was also meant to be a play on the Common Desktop Environment (CDE) that was the standard in the "Big Unix" world. Although by 1996, CDE was looking pretty dated. CDE was based on the Motif widget set, which is the same design that FVWM mimicked. Finalized in July 1998, KDE 1.0 was a definite improvement over plain window managers like FVWM95.
|
||||
|
||||
![KDE 1.0][8]
|
||||
|
||||
K Desktop Environment (KDE) version 1.0
|
||||
|
||||
Image credit: Paul Brown / KDE
|
||||
|
||||
KDE was a big step forward for Linux. Finally, Linux had a true desktop with application integration and more modern desktop icons. KDE's design was not dissimilar from Windows 95. You had a kind-of taskbar along the bottom of the screen that provided the equivalent of Windows 95's Start menu as well as several application shortcuts. KDE also supported virtual desktops, which were cleverly labeled One, Two, Three, and Four. Running applications were represented via buttons in a separate taskbar at the top of the screen.
|
||||
|
||||
But not everyone was happy with KDE. To abstract the GUI from the system, KDE used Trolltech's Qt toolkit library. Unfortunately, Qt was not distributed under a free software license. Trolltech allowed Qt to be used at no charge in free software applications but charged a fee to use it in commercial or proprietary applications. And that dichotomy is not aligned with free software. This caused problems for Linux distributions: Should they include KDE? Or default to an older but free software graphical user interface like FVWM?
|
||||
|
||||
In response, Miguel de Icaza and Federico Mena started work in 1997 on a new Linux desktop. The new project was dubbed GNOME, for GNU Network Object Model Environment. GNOME aimed to be completely free software and used a different toolkit, called GTK, from the GIMP image editor. GTK literally stood for GIMP Tool Kit. When GNOME 1.0 was finally released in 1999, Linux had another modern desktop environment.
|
||||
|
||||
![GNOME 1.0][9]
|
||||
|
||||
GNOME version 1.0
|
||||
|
||||
Image credit: GNOME Documentation Project
|
||||
|
||||
While it was great to have two desktop environments for Linux, the "KDE versus GNOME" rivalry continued for some time. By 1999, Trolltech re-released the Qt library under a new public license, the Q Public License (QPL). But the new license carried its own baggage—the QPL only applied to Qt's use in open source software projects, not commercial projects. Thus the Free Software Foundation deemed the QPL [not compatible][10] with the GNU General Public License (GNU GPL). This licensing issue would remain until Trolltech re-re-released the Qt library under the GNU GPL version 2 in 2000.
|
||||
|
||||
### Development over time
|
||||
|
||||
The Linux desktop continued to mature. KDE and GNOME settled into a friendly competition that pushed both to add new features and to exchange ideas and concepts. By 2004, both GNOME and KDE had made significant strides, yet brought only incremental changes to the user interface.
|
||||
|
||||
KDE 2 and 3 continued to rely on a taskbar concept at the bottom of the screen but incorporated the buttons for running applications. One of KDE's most visible changes was the addition of the Konqueror browser, which first appeared in KDE 2.
|
||||
|
||||
![KDE 2.2.2 \(2001\) showing the Konqueror browser][11]
|
||||
|
||||
KDE 2.2.2 (2001) showing the Konqueror browser
|
||||
|
||||
Image credit: Paul Brown / KDE
|
||||
|
||||
![KDE 3.2.2][12]
|
||||
|
||||
KDE 3.2.2 (2004) on Fedora Core 2 showing the Konqueror file manager (using a Fedora Core 2 theme)
|
||||
|
||||
GNOME 2 also used a taskbar concept but split the bar into two: a taskbar at the top of the screen to launch applications and respond to desktop alerts, and a taskbar at the bottom of the page to show running applications. On my own, I referred to the two taskbars as "things you can do" (top) and "things are you doing" (bottom). In addition to the streamlined user interface, GNOME also added an updated file manager called Nautilus, developed by Eazel.
|
||||
|
||||
![GNOME 2.6.0][13]
|
||||
|
||||
GNOME 2.6.0 (2004) on Fedora Core 2 showing the Nautilus file manager (using a Fedora Core 2 theme)
|
||||
|
||||
Over time, KDE and GNOME have taken different paths. Both provide a feature-rich, robust, and modern desktop environment—but with different user interface goals. In 2011, there was a major deviation between how GNOME and KDE approached the desktop interface. KDE 4.6 (January 2011) and KDE 4.7 (July 2011) provided a more traditional desktop metaphor while continuing to rely on the taskbar concept familiar to many users. Of course, KDE saw lots of changes under the hood, but the familiar look and feel remained.
|
||||
|
||||
![KDE 4.6][14]
|
||||
|
||||
KDE 4.6 showing the Gwenview image viewer
|
||||
|
||||
Image credit: KDE
|
||||
|
||||
In 2011, GNOME completely changed gears with a new desktop concept. GNOME 3 aimed to create a simpler, more streamlined desktop experience, allowing users to focus on what they were working on. The taskbar disappeared, replaced by a black status bar at the top of the screen that included volume and network controls, displayed the time and battery status, and allowed users to launch new programs via a redesigned menu.
|
||||
|
||||
The menu was the most dramatic change. Clicking the Activities menu or moving the mouse into the Activities "hot corner" showed all open applications as separate windows. Users could also click an Applications tab from the Overview to start a new program. The Overview also provided an integrated search function.
|
||||
|
||||
![GNOME 3.0][15]
|
||||
|
||||
GNOME 3.0 showing the GNOME Pictures application
|
||||
|
||||
Image credit: GNOME
|
||||
|
||||
![GNOME 3.0][16]
|
||||
|
||||
GNOME 3.0 showing the Activities Overview
|
||||
|
||||
Image credit: GNOME
|
||||
|
||||
### Your choice of desktop
|
||||
|
||||
Having two desktops for Linux means users have great choice. Some prefer KDE and others like GNOME. That's fine. Pick the desktop that best suits you.
|
||||
|
||||
To be sure, both KDE and GNOME have fans and detractors. For example, GNOME received a fair bit of criticism for dropping the taskbar in favor of the Activities Overview. Perhaps the most well-known critic was Linus Torvalds, who [loudly denounced and abandoned][17] the new GNOME as an "unholy mess" in 2011—before [moving back][18] to GNOME two years later.
|
||||
|
||||
Others have made similar criticisms of GNOME 3, to the point that some developers forked the GNOME 2 source code to create the MATE desktop. MATE (which stands for MATE Advanced Traditional Environment) continues the traditional taskbar interface from GNOME 2.
|
||||
|
||||
Regardless, there's no doubt that the two most popular Linux desktops today are KDE and GNOME. Their current versions are both very mature and packed with features. Both KDE 5.16 (2019) and GNOME 3.32 (2019) try to simplify and streamline the Linux desktop experience—but in different ways. GNOME 3.32 continues to aim for a minimal appearance, removing all distracting user interface elements so users can focus on their applications and work. KDE 5.16 takes a more familiar approach with the taskbar but has added other visual improvements and flair, especially around improved widget handling and icons.
|
||||
|
||||
![KDE 5.16 Plasma][19]
|
||||
|
||||
KDE 5.16 Plasma
|
||||
|
||||
Image credit: KDE
|
||||
|
||||
![GNOME 3.32][20]
|
||||
|
||||
GNOME 3.32
|
||||
|
||||
Image credit: GNOME
|
||||
|
||||
At the same time, you don't completely lose out on compatibility. Every major Linux distribution provides compatibility libraries, so you can run applications from, say, KDE while running GNOME. This is immensely useful when an application you really want to use is written for the other desktop environment—not a problem; you can run KDE applications on GNOME and vice versa.
|
||||
|
||||
I don't see this changing anytime soon. And I think that's a good thing. Healthy competition between KDE and GNOME has allowed developers in both camps to push the envelope. Whether you use KDE or GNOME, you have a modern desktop with great integration. And above all, this means Linux has the best feature in free software: choice.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/8/how-linux-desktop-grown
|
||||
|
||||
作者:[Jim Hall][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/jim-hallhttps://opensource.com/users/jason-bakerhttps://opensource.com/users/jlacroixhttps://opensource.com/users/doni08521059https://opensource.com/users/etc-eterahttps://opensource.com/users/marcobravohttps://opensource.com/users/alanfdoss
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/1980s-computer-yearbook.png?itok=eGOYEKK- (Person typing on a 1980's computer)
|
||||
[2]: https://opensource.com/sites/default/files/uploads/twm-sls105.png (TWM on SLS 1.05)
|
||||
[3]: https://opensource.com/sites/default/files/uploads/olvwm-sls105.png (OLVWM on SLS 1.05)
|
||||
[4]: https://opensource.com/sites/default/files/uploads/fvwm-sls105.png (FVWM on SLS 1.05)
|
||||
[5]: https://opensource.com/sites/default/files/uploads/win311.png (Windows 3.11)
|
||||
[6]: https://opensource.com/sites/default/files/uploads/win95.png (Windows 95)
|
||||
[7]: https://opensource.com/sites/default/files/uploads/fvwm95-rh52.png (FVWM95 on Red Hat Linux 5.2)
|
||||
[8]: https://opensource.com/sites/default/files/uploads/kde1.png (KDE 1.0)
|
||||
[9]: https://opensource.com/sites/default/files/uploads/gnome10.png (GNOME 1.0)
|
||||
[10]: https://www.linuxtoday.com/developer/2000090500121OPLFKE
|
||||
[11]: https://opensource.com/sites/default/files/uploads/kde_2.2.2.png (KDE 2.2.2 (2001) showing the Konqueror browser)
|
||||
[12]: https://opensource.com/sites/default/files/uploads/kde322-fc2.png (KDE 3.2.2)
|
||||
[13]: https://opensource.com/sites/default/files/uploads/gnome26-fc2.png (GNOME 2.6.0)
|
||||
[14]: https://opensource.com/sites/default/files/uploads/kde46.png (KDE 4.6)
|
||||
[15]: https://opensource.com/sites/default/files/uploads/gnome30.png (GNOME 3.0)
|
||||
[16]: https://opensource.com/sites/default/files/uploads/gnome30-overview.png (GNOME 3.0)
|
||||
[17]: https://www.theregister.co.uk/2011/08/05/linus_slams_gnome_three/
|
||||
[18]: https://www.phoronix.com/scan.php?page=news_item&px=MTMxNjc
|
||||
[19]: https://opensource.com/sites/default/files/uploads/kde516.png (KDE 5.16 Plasma)
|
||||
[20]: https://opensource.com/sites/default/files/uploads/gnome332.png (GNOME 3.32)
|
||||
@ -1,5 +1,5 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (chai-yuan)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
|
||||
@ -1,83 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Linux is our love language)
|
||||
[#]: via: (https://opensource.com/article/20/2/linux-love-language)
|
||||
[#]: author: (Christopher Cherry https://opensource.com/users/chcherry)
|
||||
|
||||
Linux is our love language
|
||||
======
|
||||
When a wife teaches a husband some new tech skills, they both learn a
|
||||
lot more than they expect.
|
||||
![Red heart with text "you are not alone"][1]
|
||||
|
||||
2019 was a year of learning in the Cherry household. I am a senior software engineer who set out to learn new skills and, along the way, I taught my husband, Chris. By teaching him some of the things I learned and asking him to work through my technology walkthrough articles, I helped Chris learn new skills that enabled him to pivot his career deeper into the technology field. And I learned new ways to make my walkthroughs and training materials more accessible for readers to digest.
|
||||
|
||||
In this article, we talk about what we learned individually and from each other, then we explore what it means for their future.
|
||||
|
||||
### Questions for the student
|
||||
|
||||
**Jess:** Chris, what made you want to learn more about my field?
|
||||
|
||||
**Chris:** It was primarily to further my career. Being in network engineering has shown me that being an expert only on networks is not as valuable as it once was, and I have to know a little bit of everything. Since the network is often blamed for outages or application challenges these days, I wanted to understand more from a developer's perspective on writing applications so I could see how they depend on the network as a resource.
|
||||
|
||||
**Jess:** What did I teach you first, and what did you learn from it?
|
||||
|
||||
**Chris:** It all started with installing Linux for the first time, then adding [Ansible][2]. Each Linux distribution I worked with was easy enough to install, as long as the hardware was compatible, but compatibility wasn't always clear. That meant sometimes I learned first-hand how to troubleshoot Linux within the first five minutes of running an installation (and I liked it). Ansible gave me a reason to learn Linux package managers to install the software. Once it was installed, I quickly learned how package management handles dependencies as I looked at the files that yum installed, so Ansible, which is written in Python, can run on my system. From there, I started to install all kinds of applications with Ansible.
|
||||
|
||||
**Jessica:** Do you like the way I taught you?
|
||||
|
||||
**Chris:** We had our struggles at first, until we ironed out how I like to learn and how you should present the best way for me to learn. In the beginning, it was hard to follow what you meant. For instance, when you said things like "a Docker container," I had no reference to what you were talking about. Early on, the response was, "well, it's a container," which meant nothing to me at the time. Once I got you to explain it in more detail, it became a lot more fun to learn.
|
||||
|
||||
**Jess:** To be fair, this was a big lesson for me as well. I hadn't trained anyone with less knowledge on this technology than me before you, so you helped me realize that I needed to be clearer with my explanations. Thanks for that.
|
||||
|
||||
How did you feel about testing my articles, the ones where I had you run through the steps?
|
||||
|
||||
**Chris:** Personally, I thought it would be easy, and boy, was I wrong. One of the main things I learned from these, like your [introduction to Vagrant][3], was how each Linux distribution varies more than I realized. The operating system (OS) changes how you set it up, the requirements to run, and the specific commands. It seems like a lot more variability than there is with the network gear I've worked on. So I started to pay a lot more attention to the instructions and whether they were written for my OS or another one (and how difficult it can be to know sometimes). I seemed to break a lot of things along the way.
|
||||
|
||||
**Jess:** I break stuff all day, so different paths for different problems are daily occurrences for me.
|
||||
|
||||
### Questions for the teacher
|
||||
|
||||
**Chris:** Jess, would you change anything with the way you taught me so far?
|
||||
|
||||
**Jess:** I'd have liked to make you read more, as I do. Learning new technology has me churning through books. I read a book and a half, if not two books, a week, and that's with spending one hour in the morning and one hour before bed every day. I also pick one project to run through for two weeks for about an hour a day to reinforce the book skills. And that's in addition to the tech articles I read for the first hour of my day while taking in an immense amount of coffee. When I think about your goal to grow your career, I think books are an important element alongside the great blog posts and articles we talk about. I feel my reading regiment has kept me up to speed, and if you did the same, you would catch up to me pretty quickly.
|
||||
|
||||
**Chris:** So did the student teach the teacher in any way?
|
||||
|
||||
**Jess:** I learned a great deal about being patient from you. For instance, after walking through an installation of Ansible, I asked what you wanted to do next. Your first answer was, "I don't know," which was hard for me because I want you to learn what you want to learn. So I changed my approach, and now we talk more about what you want to achieve before walking through installing anything. When we moved on to the Vagrant article we worked on together, I created it with an end goal in mind, so we had something to achieve right away.
|
||||
|
||||
This actually made a massive change in how I do training at work. Now I ask more questions on how people learn and work hand-in-hand more often than I did before. I am more likely to sit and go through and make sure someone understands what I'm saying and what we're doing. I wasn't really before.
|
||||
|
||||
### What we learned together
|
||||
|
||||
As a couple, we both grew from collaborating on technology over the last year.
|
||||
|
||||
**Chris:** I'm blown away at how much I learned. Over the course of a year, I understand new operating systems, how to use an API, web application deployment with Ansible, and standing up virtual machines with Vagrant. I also learned how documentation makes life better, so it's worth the time it takes to write some. In this field of work, however, behavior isn't always documented, so I've learned to be ready to work through tough issues and document how I fix them.
|
||||
|
||||
**Jess:** Beyond what I learned from teaching you, I've focused on learning a good deal about Kubernetes in cloud environments. That includes deployment strategies, the complexity of the Kubernetes API, building my own containers, and securing these environments. I've also saved time to dabble: toying around with serverless code, AI models, Python, and graphically displaying heat maps. It's been a good year.
|
||||
|
||||
What's next for us? It's yet to be seen, but I can assure you that we're going to share it here on Opensource.com.
|
||||
|
||||
**Who did you mentor in 2019, or who are you mentoring in 2020? Tell us about it in the comments.**
|
||||
|
||||
I can see the brightness of curiosity in my six year old niece Shuchi's eyes when she explores a...
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/20/2/linux-love-language
|
||||
|
||||
作者:[Christopher Cherry][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/chcherry
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/red-love-heart-alone-stone-path.jpg?itok=O3q1nEVz (Red heart with text "you are not alone")
|
||||
[2]: https://opensource.com/resources/what-ansible
|
||||
[3]: https://opensource.com/resources/vagrant
|
||||
@ -1,5 +1,5 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: translator: (chuan-325)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
|
||||
@ -0,0 +1,60 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Data-center power consumption holds steady)
|
||||
[#]: via: (https://www.networkworld.com/article/3531316/data-center-power-consumption-holds-steady.html)
|
||||
[#]: author: (Andy Patrizio https://www.networkworld.com/author/Andy-Patrizio/)
|
||||
|
||||
Data-center power consumption holds steady
|
||||
======
|
||||
While computing capacity has exploded in recent years, power consumption is growing more slowly thanks to greater energy efficiency.
|
||||
Google
|
||||
|
||||
A predicted explosion in power consumption by data centers has not manifested thanks to advances in power efficiency and, ironically enough, the move to the cloud, according to a new report.
|
||||
|
||||
The [study][1], published in the journal _Science_ last week, notes that while there has been an increase in global data-center energy consumption over the past decade, this growth is negligible compared with the rise of workloads and deployed hardware during that time.
|
||||
|
||||
Data centers accounted for about 205 terawatt-hours of electricity usage in 2018, which is roughly 1% of all electricity consumption worldwide, according to the report. (That's well below the often-cited stat that data centers consume 2% of the world's electricity). The 205 terawatt-hours represent a 6% increase in total power consumption since 2010, but global data center compute instances rose by 550% over that same time period.
|
||||
|
||||
**[ Now read: [What is quantum computing (and why enterprises should care)][2] ]**
|
||||
|
||||
To drive that point home: Considerably more compute is being deployed, yet the amount of power consumed is holding steady.
|
||||
|
||||
The paper cites a number of reasons for this. For starters, hardware power efficiency is vastly improved. The move to server virtualization has meant a six-fold increase in compute instances with only a 25% increase in server energy use. And a shift to faster and more energy-efficient port technologies has brought about a 10-fold increase in data center IP traffic with only a modest increase in the energy use of network devices.
|
||||
|
||||
Even more interesting, the report claims the rise of and migration to hyperscalers has helped curtail power consumption.
|
||||
|
||||
Hyperscale data centers and cloud data centers are generally more energy efficient than company-owned data centers because there is greater incentive for energy efficiency. The less power Amazon, Microsoft, Google, etc., have to buy, the more their bottom line grows. And hyperscalers are big on cheap, renewable energy, such as hydro and wind.
|
||||
|
||||
[][3]
|
||||
|
||||
So if a company trades its own old, inefficient data center for AWS or Google Cloud, they're reducing the overall power draw of data centers as a whole.
|
||||
|
||||
"Total power consumption held steady as computing output has risen because of improvement efficiency of both IT and infrastructure equipment, and a shift from corporate data centers to more efficient cloud data centers (especially hyper scale)," said Jonathan Koomey, a Stanford professor and one of the authors of the research, in an email to me. He has spent years researching data center power and is an authority on the subject.
|
||||
|
||||
"As always, the IT equipment progresses most quickly. In this article, we show that the peak output efficiency of computing doubled every 2.6 years after 2000. This doesn’t include the reduced idle power factored into the changes for servers we document," he added.
|
||||
|
||||
Koomey notes that there is additional room for efficiency improvements to cover the next doubling of computing output over the next few years but was reluctant to make projections out too far. "We avoid projecting the future of IT because it changes so fast, and we are skeptical of those who think they can project IT electricity use 10-15 years hence," he said.
|
||||
|
||||
Join the Network World communities on [Facebook][4] and [LinkedIn][5] to comment on topics that are top of mind.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.networkworld.com/article/3531316/data-center-power-consumption-holds-steady.html
|
||||
|
||||
作者:[Andy Patrizio][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.networkworld.com/author/Andy-Patrizio/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://science.sciencemag.org/content/367/6481/984
|
||||
[2]: https://www.networkworld.com/article/3275367/what-s-quantum-computing-and-why-enterprises-need-to-care.html
|
||||
[3]: https://www.networkworld.com/article/3440100/take-the-intelligent-route-with-consumption-based-storage.html?utm_source=IDG&utm_medium=promotions&utm_campaign=HPE21620&utm_content=sidebar ( Take the Intelligent Route with Consumption-Based Storage)
|
||||
[4]: https://www.facebook.com/NetworkWorld/
|
||||
[5]: https://www.linkedin.com/company/network-world
|
||||
@ -0,0 +1,61 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Setting yourself up for success while working remotely)
|
||||
[#]: via: (https://opensource.com/article/20/3/remote-work)
|
||||
[#]: author: (Dawn Parzych https://opensource.com/users/dawnparzych)
|
||||
|
||||
Setting yourself up for success while working remotely
|
||||
======
|
||||
Whether you are new to working remotely or are a seasoned veteran, here
|
||||
are tips to improve the experience.
|
||||
![Woman sitting in front of her computer][1]
|
||||
|
||||
Remote work is not easy. While there are perks to being remote, it is a mind-shift and takes some getting used to. Talk to anybody that works remotely, and they will likely tell you some of the biggest challenges of remote work are _**feeling disconnected**_ and _**a loss of regime**_. Here are my tips gathered from 10 years as a remote worker on how to set yourself and your team up to work remotely successfully.
|
||||
|
||||
### Environment and regime
|
||||
|
||||
1. **"Commute" to and from work**. I'm not saying go to the extremes in this [_Audible commercial_][2], but I suggest leaving your home to go for a walk or a bike ride before you begin working. Do the same at the end of the day. I take my dog, Barley (pictured here), for a walk at the start and end of most days.![Here's my dog, Barley, who gets regular walks during my morning "commute"][3]
|
||||
2. **Get dressed.** Don't be tempted to work in your PJs, because this blurs the line between work and home. People sometimes say that being able to work in your pajamas is a perk of remote work, but studies show this isn't great advice. You don't need to put on a suit and tie, but do change out of your pajamas; otherwise, before you know it, you will have gone three days without changing your clothes. For more reasons why check out this article from [_Fast Company_][4].
|
||||
3. **Eat lunch away from your desk**. This is good advice even if you aren't working remotely.
|
||||
4. **Stick to a schedule**. It's easy to start working as soon as you wake up and continue late into the evening. Set a start time and an end time for your day and stick to it. When I stop work for the day, I try to close my office door. Configure your working hours in every app you use so others know when you are available. Don't use your work computer outside of working hours if you can.
|
||||
5. **Set up a dedicated work environment**, if possible. Try not to work from the kitchen table. This blurs the lines between home and work. My office (picture below) also has space for comfortable seating and desk seating to switch between the two.
|
||||
6. **Check-in with your team** or friends in the morning. Don't mistake this for a daily stand-up; this is more like saying _hi_ when you're getting coffee.
|
||||
7. **Sign-off at the end of the day**. This means both letting your team members know you are leaving and actually walking away from where you are working. Close the laptop. Turn off Slack notifications, etc.
|
||||
8. **Keep people posted** if you are leaving early or unavailable. It helps build trust.
|
||||
9. **Invest in a headset** if you will be doing a lot of calls. If there is more than one person in your household that is working remotely, they will thank you for this. It is no fun listening to somebody else's conference call.
|
||||
10. **Turn on your video** when on a video call to help you feel connected and stay engaged. When your video is disabled, it is easy to wander off and get distracted by Slack (or its [open source alternatives][5]), Twitter, or any other number of distractions.
|
||||
11. **Set up a weekly, casual remote chat**. At my company, we meet on Friday mornings via Zoom (or the open source alternative, [Jitsi][6]). This chat is open to remote and non-remote staff. It is an open call to talk about whatever is on our minds. Topics have ranged from music preferences to parenting challenges to what people are doing over the weekend.
|
||||
12. **Set-up chat-roulette **if one-on-one interaction is more your thing. There are applications on most chat platforms that randomly pairs two employees to chat and get to know one another.
|
||||
13. **Ask for help**. Chat with your colleagues if you're stuck, need encouragement, or need to vent. You are not alone. You are a member of a team. You can still grab a coffee or go for a walk with a teammate remotely.
|
||||
|
||||
|
||||
|
||||
![Here’s my home office set up][7]
|
||||
|
||||
Everybody is different. These tips work for me, I’d love to hear you share your advice below!
|
||||
|
||||
Not all work-from-home gigs are created equal. There is a vast ocean between being a member of a...
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/20/3/remote-work
|
||||
|
||||
作者:[Dawn Parzych][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/dawnparzych
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/OSDC_women_computing_2.png?itok=JPlR5aCA (Woman sitting in front of her computer)
|
||||
[2]: https://www.youtube.com/watch?v=oVCJhZhrJ04
|
||||
[3]: https://opensource.com/sites/default/files/resize/pictures/barleywalking_0-300x379.png (Here's my dog, Barley, who gets regular walks during my morning "commute")
|
||||
[4]: https://www.fastcompany.com/3064295/what-happened-when-i-dressed-up-to-work-from-home-for-a-week
|
||||
[5]: https://opensource.com/alternatives/slack
|
||||
[6]: https://meet.jit.si/
|
||||
[7]: https://opensource.com/sites/default/files/pictures/6151f75e-bbeb-4e64-a5ca-0bbe4e981054.jpeg (Here’s my home office set up)
|
||||
@ -0,0 +1,92 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Next wave of digital transformation requires better security, automation)
|
||||
[#]: via: (https://www.networkworld.com/article/3531448/next-wave-of-digital-transformation-requires-better-security-automation.html)
|
||||
[#]: author: (Zeus Kerravala https://www.networkworld.com/author/Zeus-Kerravala/)
|
||||
|
||||
Next wave of digital transformation requires better security, automation
|
||||
======
|
||||
F5 report highlights the challenges of digital initiatives, including a struggle to secure multi-cloud environments and a lack of IT skills required to extend automation efforts.
|
||||
Loops7 / Getty Images
|
||||
|
||||
Digital transformation is a top-of-mind priority for CIOs who want innovative ways to deploy applications and run IT operations. In today's digital economy, companies that don't depend on applications to support their business are rare. On the contrary, most companies have some kind of digital transformation initiative in place, which is driving the adoption of cloud-native architectures and application services.
|
||||
|
||||
A new report from application delivery vendor F5 Networks finds businesses are entering the second phase of digital transformation by automating more parts of their networks. Based on a survey of nearly 2,600 senior leaders globally—from various industries, company sizes, and roles—the [_2020 State of Application Services Report_][1] uncovered five key trends shaping the application landscape.
|
||||
|
||||
**READ MORE:** [Top 10 underused SD-WAN features][2]
|
||||
|
||||
### 1\. Every company is undergoing a digital transformation
|
||||
|
||||
Having conducted its annual survey for six years in a row, F5 consistently found IT optimization and business process optimization to be the top reported benefits for companies with digital transformation initiatives. At this point, most companies have mastered automation of individual tasks by digitizing IT and business processes—which the report classifies as phase one of digital transformation.
|
||||
|
||||
Moving on to phase two, companies are shifting their focus to reducing complexity and supporting apps with a consistent set of services. External-facing apps make up a portion (45%) of an average company's portfolio and help generate revenue. Yet, the internal-facing ones—like productivity and operational apps—are vital to digitizing business processes.
|
||||
|
||||
Modern, microservices/cloud-native apps now make up approximately 15% of a company's portfolio, compared to 11% for mainframe-hosted apps. This mix of new and older generation apps indicates that businesses are dealing with a diverse app portfolio. As more businesses adopt an application-centric mindset, they can start managing their app portfolio like a business asset.
|
||||
|
||||
### 2\. Organizations struggle to secure multi-cloud environments
|
||||
|
||||
Every company has different needs, which is why most choose the best cloud for their applications on a case-by-case basis, the report finds. Businesses are adopting cloud platforms at a high rate, with 27% planning to have more than half of their applications in the cloud by the end of 2020.
|
||||
|
||||
For 87% of companies, multi-cloud is the preferred choice due to its flexibility. Multi-cloud typically includes a mix of infrastructure-as-a-service (IaaS) environments, so a company can choose to deploy multiple software-as-a-service (SaaS) or platform-as-a-service (PaaS) cloud services.
|
||||
|
||||
[][3]
|
||||
|
||||
However, multi-cloud environments pose challenges for businesses when it comes to maintaining security, policy, and compliance, according to the report's respondents. Companies are dealing with applications that reach hundreds to millions of end users—each one with its own security risk. Meanwhile, many don't have the expertise to protect the apps.
|
||||
|
||||
A whopping 71% of companies surveyed by F5 reported a skills gap in security. Only 45% of companies are confident that they're able to secure apps in the public cloud, while 62% think they can protect apps in an on-premises data center. The most confident companies have consistency across multiple architectures and multiple infrastructures, ensuring security and performance of all apps in their portfolio.
|
||||
|
||||
### 3\. Automation key to boosting efficiency
|
||||
|
||||
Manual processes may have been the norm for legacy networks, but modern networks require automation. That's why most companies (73%) have embraced it.
|
||||
|
||||
In this year's report, F5 observed more consistent use of automation in the deployment pipeline than in previous years. Automation of application infrastructure, network, application services, and security is nearly equal across the board at approximately 40% for survey respondents. (See also: [Enterprises being won over by speed, effectiveness of network automation][4])
|
||||
|
||||
Interestingly, more companies are choosing open source and continuous integration/continuous delivery (CI/CD) tools for automation over proprietary vendor solutions. The report found there is a need for open ecosystems with the increasing use of CI/CD tools, as businesses search for ways to address problems that slow down automation. Companies said their biggest struggles are with skill gaps in enterprise IT, integrating toolsets across vendors and devices, and the cost of new tools.
|
||||
|
||||
### 4\. Security app services are most widely deployed
|
||||
|
||||
Modern networks require application services—a pool of services necessary to deploy, run, and secure apps across on-premises or multi-cloud environments. Today, 69% of companies are using 10 or more application services, such as ingress control and service discovery. Ingress control is a relatively new application service that has become essential to companies with high API call volumes. It's one of many examples of the growing adoption of microservices-based apps.
|
||||
|
||||
Security services remain as the most widely deployed, with these in particular dominating the top five: SSL VPN and firewall services (81%); IPS/IDS, antivirus, and spam mitigation (77%); load balancing and DNS (68%); web application firewalls (WAF) and DDoS protection (each at 67%).
|
||||
|
||||
Over the next 12 months, the evolution of cloud and modern app architectures will continue to shape application services. At the top of the list (41%) is software-defined wide-area networking ([SD-WAN][5]). SD-WAN enables software-based provisioning from the cloud to meet modern application demands. Early SD-WAN deployments focused on replacing costly multi-protocol label switching (MPLS), but there is now greater emphasis on security as a core requirement for SD-WAN.
|
||||
|
||||
### 5\. DevOps picks up responsibility for app services
|
||||
|
||||
Although IT operations is still primarily responsible for deploying app services, the report revealed a shift taking place from single-function to ops-oriented team structures—such SecOps and DevOps.
|
||||
|
||||
The responsibility for securing, optimizing, and managing apps by DevOps teams is growing, fueled by cloud and container-native applications. Compared to just a few years ago, businesses have developed a preference for containers over virtual appliances for app services. Container preference grew from just 6% in 2017 to 18% in 2020, surpassing virtual machines (15%) and hardware (15%).
|
||||
|
||||
Regardless of preference, the challenges of modern app architectures call for collaboration between teams. IT operations and DevOps don't have to be mutually exclusive and can work together to address those challenges.
|
||||
|
||||
### What's Next?
|
||||
|
||||
Senior leaders surveyed in the report see big data analytics coming into play in the next two to five years.
|
||||
|
||||
Companies today only use a small portion of their data and aren't taking full advantage of it. In the third phase of the digital transformation, businesses can begin leveraging data captured by apps via artificial intelligence (AI)-powered analytics. The harnessed data can provide valuable insights to improve business processes.
|
||||
|
||||
Join the Network World communities on [Facebook][6] and [LinkedIn][7] to comment on topics that are top of mind.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.networkworld.com/article/3531448/next-wave-of-digital-transformation-requires-better-security-automation.html
|
||||
|
||||
作者:[Zeus Kerravala][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.networkworld.com/author/Zeus-Kerravala/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.f5.com/state-of-application-services-report
|
||||
[2]: https://www.networkworld.com/article/3518992/top-10-underused-sd-wan-features.html
|
||||
[3]: https://www.networkworld.com/article/3440100/take-the-intelligent-route-with-consumption-based-storage.html?utm_source=IDG&utm_medium=promotions&utm_campaign=HPE21620&utm_content=sidebar ( Take the Intelligent Route with Consumption-Based Storage)
|
||||
[4]: https://www.networkworld.com/article/3530275/enterprises-being-won-over-by-speed-effectiveness-of-network-automation.html
|
||||
[5]: https://www.networkworld.com/article/3031279/sd-wan-what-it-is-and-why-you-ll-use-it-one-day.html
|
||||
[6]: https://www.facebook.com/NetworkWorld/
|
||||
[7]: https://www.linkedin.com/company/network-world
|
||||
@ -0,0 +1,73 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (What is the internet backbone and how it works)
|
||||
[#]: via: (https://www.networkworld.com/article/3532318/what-is-the-internet-backbone-and-how-it-works.html)
|
||||
[#]: author: (Tim Greene https://www.networkworld.com/author/Tim-Greene/)
|
||||
|
||||
What is the internet backbone and how it works
|
||||
======
|
||||
Tier 1 internet service providers (ISP) mesh their high-speed fiber-optic networks together to create the internet backbone, which moves traffic efficiently among geographic regions.
|
||||
[Gerd Altmann][1] [(CC0)][2]
|
||||
|
||||
The internet generates massive amounts of computer-to-computer traffic, and insuring all that traffic can be delivered anywhere in the world requires the aggregation of a vast array of high-speed networks collectively known as the internet backbone, but how does that work?
|
||||
|
||||
### What is the internet backbone?
|
||||
|
||||
Like any other network, the internet consists of access links that move traffic to high-bandwidth routers that move traffic from its source over the best available path toward its destination. This core is made up of individual high-speed fiber-optic networks that peer with each other to create the internet backbone.
|
||||
|
||||
The individual core networks are privately owned by Tier 1 internet service providers (ISP), giant carriers whose networks are tied together. These providers include AT&T, CenturyLink, Cogent Communications, Deutsche Telekom, Global Telecom and Technology (GTT), NTT Communications, Sprint, Tata Communications, Telecom Italia Sparkle, Telia Carrier, and Verizon.
|
||||
|
||||
[[Get regularly scheduled insights by signing up for Network World newsletters.]][3]
|
||||
|
||||
By joining these long-haul networks together, Tier 1 ISPs create a single worldwide network that gives all of them access to the entire internet routing table so they can efficiently deliver traffic to its destination through a hierarchy of progressively more local ISPs.
|
||||
|
||||
In addition to being physically connected, these backbone providers are held together by a shared network protocol, TCP/IP. They are actually two protocols, transport control protocol and internet protocol that set up connections between computers, insuring that the connections are reliable and formating messages into packets.
|
||||
|
||||
### Internet exchange points (IXP) tie the backbone together
|
||||
|
||||
Backbone ISPs connect their networks at peering points, neutrally owned locations with high-speed switches and routers that move traffic among the peers. These are often owned by third parties, sometimes non-profits, that facilitate unifying the backbone.
|
||||
|
||||
Participating Tier 1 ISPs help fund the IXPs, but don’t charge each other for transporting traffic from the other Tier 1 ISPs in a relationship known as settlement-free peering. Such agreements eliminate potential financial disputes that might have the result of slowing down internet performance.
|
||||
|
||||
[][4]
|
||||
|
||||
### How fast is the backbone?
|
||||
|
||||
The internet backbone is made up of the fastest routers, which can deliver 100Gbps trunk speeds. These routers are made by vendors including Cisco, Extreme, Huawei, Juniper, and Nokia, and use the border gateway protocol (BGP) to route traffic among themselves.
|
||||
|
||||
### How traffic gets on the backbone
|
||||
|
||||
Below the Tier 1 ISPs are smaller Tier 2 and Tier 3 ISPs.
|
||||
|
||||
Tier 3 providers provide businesses and consumers with access to the internet. These providers have no access of their own to the internet backbone, so on their own would not be able to connect their customers to all of the billions of internet-attached computers.
|
||||
|
||||
Buying access to Tier 1 providers is expensive. So often Tier 3 ISPs contract with Tier 2 (regional) ISPs that have their own networks that can deliver traffic to a limited geographic area but not to all internet-attached devices.
|
||||
|
||||
In order to do that, Tier 2 ISPs contract with Tier 1 ISPs for access to the global backbone, and in that way make the entire internet accesssible to their customers.
|
||||
|
||||
This arrangment makes it possible for traffic from a computer on one side of the world to connect to one on the other side. That traffic goes from a source computer to a Tier 3 ISP that routes it to a Tier 2 ISP that routes it to a Tier 1 backbone provider that routes it to the appropriate Tier 2 ISP that routes it to a Tier 3 access provider that delivers it to the destination computer.
|
||||
|
||||
Join the Network World communities on [Facebook][5] and [LinkedIn][6] to comment on topics that are top of mind.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.networkworld.com/article/3532318/what-is-the-internet-backbone-and-how-it-works.html
|
||||
|
||||
作者:[Tim Greene][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.networkworld.com/author/Tim-Greene/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://pixabay.com/en/social-media-digitization-faces-3271592/
|
||||
[2]: https://creativecommons.org/publicdomain/zero/1.0/
|
||||
[3]: https://www.networkworld.com/newsletters/signup.html
|
||||
[4]: https://www.networkworld.com/article/3440100/take-the-intelligent-route-with-consumption-based-storage.html?utm_source=IDG&utm_medium=promotions&utm_campaign=HPE21620&utm_content=sidebar ( Take the Intelligent Route with Consumption-Based Storage)
|
||||
[5]: https://www.facebook.com/NetworkWorld/
|
||||
[6]: https://www.linkedin.com/company/network-world
|
||||
@ -0,0 +1,81 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (As the networks evolve enterprises need to rethink network security)
|
||||
[#]: via: (https://www.networkworld.com/article/3531929/as-the-network-evolves-enterprises-need-to-rethink-security.html)
|
||||
[#]: author: (Zeus Kerravala https://www.networkworld.com/author/Zeus-Kerravala/)
|
||||
|
||||
As the networks evolve enterprises need to rethink network security
|
||||
======
|
||||
Q&A: John Maddison, executive vice president of products for network security vendor Fortinet, discusses how to deal with network security in the digital era.
|
||||
D3Damon / Getty Images
|
||||
|
||||
_Digital innovation is disrupting businesses. Data and applications are at the hub of new business models, and data needs to travel across the extended network at increasingly high speeds without interruption. To make this possible, organizations are radically redesigning their networks by adopting multi-cloud environments, building hyperscale data centers, retooling their campuses, and designing new connectivity systems for their next-gen branch offices. Networks are faster than ever before, more agile and software-driven. They're also increasingly difficult to secure. To understand the challenges and how security needs to change, I recently talked with John Maddison, executive vice president of products for network security vendor Fortinet._
|
||||
|
||||
**ZK: As the speed and scale of data escalate, how do the challenges to secure it change?**
|
||||
|
||||
JM: Security platforms were designed to provide things like enhanced visibility, control, and performance by monitoring and managing the perimeter. But the traditional perimeter has shifted from being a very closely monitored, single access point to a highly dynamic and flexible environment that has not only expanded outward but inward, into the core of the network as well.
|
||||
|
||||
**[ Also see [What to consider when deploying a next generation firewall][1]. | Get regularly scheduled insights by [signing up for Network World newsletters][2]. ]**
|
||||
|
||||
**READ MORE:** [The VPN is dying, long live zero trust][3]
|
||||
|
||||
Today's perimeter not only includes multiple access points, the campus, the WAN, and the cloud, but also IoT, mobile, and virtual devices that are generating data, communicating with data centers and manufacturing floors, and literally creating thousands of new edges inside an organization. And with this expanded perimeter, there are a lot more places for attacks to get in. To address this new attack surface, security has to move from being a standalone perimeter solution to being fully integrated into the network.
|
||||
|
||||
This convergence of security and networking needs to cover SD-WAN, VPN, Wi-Fi controllers, switching infrastructures, and data center environments – something we call security-driven networking. As we see it, security-driven networking is an essential approach for ensuring that security and networking are integrated together into a single system so that whenever the networking infrastructure evolves or expands, security automatically adapts as an integrated part of that environment. And it needs to do this by providing organizations with a new suite of security solutions, including network segmentation, dynamic multi-cloud controls, and [zero-trust network access][3]. And because of the speed of digital operations and the sophistication of today's attacks, this new network-centric security strategy also needs to be augmented with AI-driven security operations.
|
||||
|
||||
The perimeter security devices that have been on the market weren't really built to run as part of the internal network, and when you put them there, they become bottlenecks. Customers don't put these traditional security devices in the middle of their networks because they just can't run fast enough. But the result is an open network environment that can become a playground for criminals that manage to breach perimeter defenses. It's why the dwell time for network malware is over six months.
|
||||
|
||||
**[ [Prepare to become a Certified Information Security Systems Professional with this comprehensive online course from PluralSight. Now offering a 10-day free trial!][4] ]**
|
||||
|
||||
As you combine networking applications, networking functionality, and security applications together to address this challenge, you absolutely need a different performance architecture. This can't be achieved using the traditional hardware most security platforms rely on.
|
||||
|
||||
**ZK: Why can't traditional security devices secure the internal network?**
|
||||
|
||||
JM: They simply aren't fast enough. And the ones that come close are prohibitively expensive… For example, internal segmentation not only enables organizations to see and separate all of the devices on their network but also dynamically create horizontal segments that support and secure applications and automated workflows that need to travel across the extended network. Inside the network, you're running at 100 gigs, 400 gigs, that sort of thing. But the interface for a lot of security systems today is just 10 gigs. Even with multiple ports, the device can't handle much more than that without having to spend a fortune… In order to handle today's capacity and performance demands, security needs to be done at network speeds that most security solutions cannot support without specialized content processors.
|
||||
|
||||
**ZK: Hyperscale data centers have been growing steadily. What sort of additional security challenges do these environments face?**
|
||||
|
||||
JM: Hyperscale architectures are being used to move and process massive amounts of data. A lot of the times, research centers will need to send a payload of over 10 gigabytes – one packet that's 10 gigabytes – to support advanced rendering and modeling projects. Most firewalls today cannot process these large payloads, also known as elephant flows. Instead, they often compromise on their security to let them flow through. Other hyperscale environment examples include financial organizations that need to process transactions with sub-second latency or online gaming providers that need to support massive numbers of connections per second while maintaining high user experience. … [Traditional security platforms] will never be able to secure hyperscale environments, or even worse, the next generation of ultra-fast converged networks that rely on hyperscale and hyperconnectivity to run things like smart cities or smart infrastructures, until they fundamentally change their hardware.
|
||||
|
||||
**ZK: Do these approaches introduce new risks or increase the existing risk for these organizations?**
|
||||
|
||||
JM: They do both. As the attack surface expands, existing risks often get multiplied across the network. We actually see more exploits in the wild targeting older vulnerabilities than new ones. But cybercriminals are also building new tools designed to exploit cloud environments and modern data centers. They are targeting mobile devices and exploiting IoT vulnerabilities. Some of these attacks are simply revisions of older, tried and true exploits. But many are new and highly sophisticated. We are also seeing new attacks that use machine learning and rely on AI enhancements to better bypass security and evade detection.
|
||||
|
||||
To address this challenge, security platforms need to be broad, integrated, and automated.
|
||||
|
||||
Broad security platforms come in a variety of form factors so they can be deployed everywhere across the expanding network. Physical hardware enhancements, such as our [security processing units], enable security platforms to be effectively deployed inside high-performance networks, including hyperscale data centers and SD-WAN environments. And virtualized versions need to support private cloud environments as well as all major cloud providers through thorough cloud-native integration.
|
||||
|
||||
Next, these security platforms need to be integrated. The security components built into a security platform need to work together as a single solution – not the sort of loose affiliation most platforms provide – to enable extremely fast threat intelligence collection, correlation, and response. That security platform also needs to support common standards and APIs so third-party tools can be added and supported. And finally, these platforms need to be able to work together, regardless of their location or form factor, to create a single, unified security fabric. It's important to note that many cloud providers have developed their own custom hardware, such as Google's TPU, Amazon's Inferentia, and Microsoft's Corsica, to accelerate cloud functions. As a result, hardware acceleration on physical security platforms is essential to ensure consistent performance for data moving between physical and cloud environments
|
||||
|
||||
And finally, security platforms need to be automated. Support for automated workflows and AI-enhanced security operations can significantly accelerate the speed of threat detection, analysis, and response. But like other processing-intensive functions, such as decrypting traffic for deep inspection, these functions also need specialized and purpose-built processors or they will become innovation-killing bottlenecks.
|
||||
|
||||
**ZK: What's next for network security?**
|
||||
|
||||
JM: This is just the start. As networking functions begin to converge even further, creating the next generation of smart environments – smart buildings, smart cities, and smart critical infrastructures – the lack of viable security tools capable of inspecting and protecting these hyperfast, hyperconnected, and hyper-scalable environments will seriously impact our digital economy and way of life.
|
||||
|
||||
Security vendors need to understand this challenge and begin investing now in developing advanced hardware and security-driven networking technologies. Organizations aren't waiting for vendors to catch up so they can secure their networks of tomorrow. Their networks are being left exposed right now because the software-based security solutions they have in place are just not adequate. And it's up to the security industry to step up and solve this challenge.
|
||||
|
||||
Join the Network World communities on [Facebook][5] and [LinkedIn][6] to comment on topics that are top of mind.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.networkworld.com/article/3531929/as-the-network-evolves-enterprises-need-to-rethink-security.html
|
||||
|
||||
作者:[Zeus Kerravala][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.networkworld.com/author/Zeus-Kerravala/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.networkworld.com/article/3236448/lan-wan/what-to-consider-when-deploying-a-next-generation-firewall.html
|
||||
[2]: https://www.networkworld.com/newsletters/signup.html
|
||||
[3]: https://www.networkworld.com/article/3487720/the-vpn-is-dying-long-live-zero-trust.html
|
||||
[4]: https://pluralsight.pxf.io/c/321564/424552/7490?u=https%3A%2F%2Fwww.pluralsight.com%2Fpaths%2Fcertified-information-systems-security-professional-cisspr
|
||||
[5]: https://www.facebook.com/NetworkWorld/
|
||||
[6]: https://www.linkedin.com/company/network-world
|
||||
108
sources/talk/20200316 How to be the right person for DevOps.md
Normal file
108
sources/talk/20200316 How to be the right person for DevOps.md
Normal file
@ -0,0 +1,108 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (How to be the right person for DevOps)
|
||||
[#]: via: (https://opensource.com/article/20/3/devops-relationships)
|
||||
[#]: author: (Josh Atwell https://opensource.com/users/joshatwell)
|
||||
|
||||
How to be the right person for DevOps
|
||||
======
|
||||
Creating healthy relationships is the essential ingredient in DevOps
|
||||
success.
|
||||
![Team meeting][1]
|
||||
|
||||
In my kitchen, we have a sign that reads "Marriage is more than finding the right person. It is being the right person." It serves as a great reminder of the individual responsibility everyone has in any healthy relationship. As organizations adopt [DevOps][2] as a model of developing and delivering value to customers, the impact of healthy relationships is extremely important for success.
|
||||
|
||||
![Marriage sign][3]
|
||||
|
||||
Historically, the relationship between development and operations teams has been unhealthy. Poor communication, limited empathy, and a history of mistrust make merging these teams into a tighter operating model challenging, to say the least. This is not entirely unfair to either side.
|
||||
|
||||
Developers have long been frustrated by lead times and processes put in place by the operations organization. They just want to work, and they often see operations as an anchor on the ship of progress.
|
||||
|
||||
Operations professionals have long been frustrated by the impatience and lack of clear requirements that come from development teams. They are often confused about why those teams are not able to use the available services and processes. They see developers as a liability to their ability to maintain stable services for customers and the business.
|
||||
|
||||
A lingering gap here is that each side has been focused on protecting its own perspective. They emphasize how the other team is not being what _they_ need, and they never question whether they, too, could be doing something different.
|
||||
|
||||
In DevOps, all sides must frame their role in the organization based on how they add value to others.
|
||||
|
||||
There are a few things that everyone, including managers and leaders, can do right away to become a better contributor and partner in their DevOps relationships.
|
||||
|
||||
### Communicate
|
||||
|
||||
Most professionals in an organization adopting DevOps find themselves needing to work closely with new people, ones they have had limited exposure to in the past. It is important for everyone to take time to get to know their new teammates and learn more about their concerns, their interests, and also their preferred communication style.
|
||||
|
||||
Successful communication in new relationships is often built on simply listening more and talking less. Our natural tendency is to talk about ourselves. Most people love sharing what they know best. However, it is extremely important to make more room to listen.
|
||||
|
||||
Hearing someone is not the same as listening to them. I'm confident that we have all been in the situation where someone expresses a concern that we do not entirely internalize. Also, merely hearing does not encourage people to share–or to share as completely as they should.
|
||||
|
||||
![Stick figures hearing][4]
|
||||
|
||||
It is important to listen actively. Repeat what you hear, and seek validation that what you repeat is what they wanted you to understand. Once you understand their concern, it is important to make your initial response a selfless one. Even if you can't completely solve the problem, demonstrate sympathy and help the person move towards a solution.
|
||||
|
||||
![Stick figures listening][5]
|
||||
|
||||
### Selflessness
|
||||
|
||||
Another key relationship challenge as organizations adopt DevOps is developing a perspective of selflessness. In DevOps, most people are responsible for delivering value to a wide variety of other people. Each person should begin by considering how their actions and work impact other people.
|
||||
|
||||
This service mindset carries forward when you become more sensitive to when others are in need and then dedicate time in your schedule specifically for the purpose of helping them. This can be as simple as creating a small improvement in a process or helping to troubleshoot an issue. A positive side effect is that this effort will provide you more opportunities to work with others and develop deeper trust.
|
||||
|
||||
It is also important not to hoard knowledge—either technical or institutional—especially when people ask questions or seek help. Maintain the mindset that there are no stupid questions.
|
||||
|
||||
![Stick figure apologizing][6]
|
||||
|
||||
Finally, selflessness includes being trustworthy. It is difficult to maintain a healthy relationship when there is no trust. Be honest and transparent. In IT, this is often seen as a liability, but in DevOps it is a requirement for success.
|
||||
|
||||
### Self-care
|
||||
|
||||
In order to be a strong contributor to a relationship, it is necessary to maintain a sense of self. Our individuality provides the diversity a relationship needs to grow. Make sure you maintain and share your interests with others. Be more than just the work you do. Apply your interests to your work.
|
||||
|
||||
You are no good to others if you are not good to yourself. Healthy relationships are stronger with healthy people. Make sure you take time to enjoy your interests and recharge. Take your vacation and leave work behind!
|
||||
|
||||
![Stick figure relaxing][7]
|
||||
|
||||
I am also a strong advocate for mental health days. Sometimes our mental health is not sufficient to work effectively. You're not as effective when you are physically ill, and you're not as effective when your head is not 100%. Work with your manager and your team to support each other to maintain good mental health.
|
||||
|
||||
Mental health is improved by learning. Invest in yourself and expand your knowledge. DevOps ideally needs "t-shaped" people who have depth on a topic and also broader system knowledge. Work to increase your depth, but balance that by learning new things about your environment. This knowledge can come from your teammates and create operational sympathy.
|
||||
|
||||
![Stick figure with open arms][8]
|
||||
|
||||
Finally, healthy relationships are not all work and no play. Take time to acknowledge the successes of others. If you know your team, you likely know how individuals prefer to receive praise. Respect those preferences, but always strive to praise vocally where possible.
|
||||
|
||||
![Stick figures celebrating][9]
|
||||
|
||||
Make sure to celebrate these successes as a team. All work and no play makes everyone dull. Celebrate milestones together as a team, and then articulate and target the next objectives.
|
||||
|
||||
### Be the right person
|
||||
|
||||
DevOps requires more from every individual, and its success is directly tied to the health of relationships. Each member of the organization should apply these techniques to grow and improve themselves. A focus on being the right person for the team will build stronger bonds and make the organization better equipped to reach its goals.
|
||||
|
||||
* * *
|
||||
|
||||
_This article is based on [a talk][10] Josh Atwell gave at All Things Open 2019._
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/20/3/devops-relationships
|
||||
|
||||
作者:[Josh Atwell][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/joshatwell
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/meeting-team-listen-communicate.png?itok=KEBP6vZ_ (Team meeting)
|
||||
[2]: https://opensource.com/tags/devops
|
||||
[3]: https://opensource.com/sites/default/files/uploads/marriage.png (Marriage sign)
|
||||
[4]: https://opensource.com/sites/default/files/uploads/hearing.png (Stick figures hearing)
|
||||
[5]: https://opensource.com/sites/default/files/uploads/listening.png (Stick figures listening)
|
||||
[6]: https://opensource.com/sites/default/files/uploads/apologize.png (Stick figure apologizing)
|
||||
[7]: https://opensource.com/sites/default/files/uploads/relax.png (Stick figure relaxing)
|
||||
[8]: https://opensource.com/sites/default/files/uploads/open_0.png (Stick figure with open arms)
|
||||
[9]: https://opensource.com/sites/default/files/uploads/celebrate.png (Stick figures celebrating)
|
||||
[10]: https://opensource.com/article/20/1/devops-empathy
|
||||
@ -0,0 +1,93 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (OpenStreetMap: A Community-Driven Google Maps Alternative)
|
||||
[#]: via: (https://itsfoss.com/openstreetmap/)
|
||||
[#]: author: (Ankush Das https://itsfoss.com/author/ankush/)
|
||||
|
||||
OpenStreetMap: A Community-Driven Google Maps Alternative
|
||||
======
|
||||
|
||||
_**Brief: OpenStreetMap is a community-driven map – which is a potential alternative to Google Maps. Learn more about this open source project.**_
|
||||
|
||||
[OpenStreetMap][1] (OSM) is a free editable map of the world. Anyone can contribute, edit, and make changes to the OpenStreetMap to improve it.
|
||||
|
||||
![][2]
|
||||
|
||||
You need to sign up for an account first – in order to be able to edit or add information to the OpenStreetMap. To view the map, you wouldn’t need an account.
|
||||
|
||||
Even though it’s a free-to-use map under an [open data license][3], you cannot use the map API to build another service on top of it for commercial purpose.
|
||||
|
||||
So, you can download the map data to use it and host it yourself while mentioning the credits to OSM. You can learn more about its [API usage policy][4] and [copyright][5] information on its official website to learn more.
|
||||
|
||||
In this article, we shall take a brief look at how it works and what kind of projects use OpenStreetMaps as the source of their map data.
|
||||
|
||||
### OpenStreetMap: Overview
|
||||
|
||||
![][6]
|
||||
|
||||
OpenStreetMap is a good alternative to Google Maps. You might not get the same level of information as Google Maps- but for basic navigation and traveling, OpenStreetMap is sufficient.
|
||||
|
||||
Just like any other map, you will be able to switch between multiple layers in the map, get to know your location, and easily search for places.
|
||||
|
||||
You may not find all the latest information for the businesses, shops, and restaurants nearby. But, for basic navigation, it’s more than enough.
|
||||
|
||||
OpenStreetMap can be usually accessed through a web browser on both desktop and mobile by visiting the [OpenStreetMap site][7]. It does not have an official Android/iOS app yet.
|
||||
|
||||
However, there are a variety of applications available that utilize OpenStreetMap at its core. So, if you want to utilize OpenStreetMap on a smartphone, you can take a look at some of the popular open-source Google Maps alternatives:
|
||||
|
||||
* [OsmAnd][8]
|
||||
* [MAPS.ME][9]
|
||||
|
||||
|
||||
|
||||
**MAPS.ME** and **OsmAnd** are two open-source applications for Android and iOS that utilize OpenStreetMap data to provide a rich user experience with a bunch of useful information and features added to it.
|
||||
|
||||
You can also opt for other proprietary options if you wish, like [Magic Earth][10].
|
||||
|
||||
In either case, you can take a look at the extensive list of applications on their official wiki page for [Android][11] and [iOS][12].
|
||||
|
||||
### Using OpenStreetMap On Linux
|
||||
|
||||
![][13]
|
||||
|
||||
The easiest way to use OpenStreetMap on Linux is to use it in a web browser. If you use GNOME desktop environment, you can install GNOME Maps which is built on top of OpenStreetMap.
|
||||
|
||||
There are also several software (that are mostly obsolete) that utilize OpenStreetMap on Linux for specific purposes. You can check out the list of available packages in their [official wiki list][14].
|
||||
|
||||
### Wrapping Up
|
||||
|
||||
OpenStreetMap may not be the best source for navigation for end users but its open source model allows it to be used freely. This means that many services can be built using OpenStreetMap. For example, [ÖPNVKarte][15] uses OpenStreetMap to display worldwide public transport facilities on a uniform map so that you don’t have to browse individual operator’s websites.
|
||||
|
||||
What do you think about OpenStreetMap? Can you use it as a Google Maps alternative? Feel free to share your thoughts in the comments below.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://itsfoss.com/openstreetmap/
|
||||
|
||||
作者:[Ankush Das][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://itsfoss.com/author/ankush/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.openstreetmap.org/
|
||||
[2]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2020/03/openstreetmap.jpg?ssl=1
|
||||
[3]: https://opendatacommons.org/licenses/odbl/
|
||||
[4]: https://operations.osmfoundation.org/policies/api/
|
||||
[5]: https://www.openstreetmap.org/copyright
|
||||
[6]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2020/03/open-street-map-2.jpg?ssl=1
|
||||
[7]: https://www.openstreetmap.org
|
||||
[8]: https://play.google.com/store/apps/details?id=net.osmand
|
||||
[9]: https://play.google.com/store/apps/details?id=com.mapswithme.maps.pro
|
||||
[10]: https://www.magicearth.com/
|
||||
[11]: https://wiki.openstreetmap.org/wiki/Android#OpenStreetMap_applications
|
||||
[12]: https://wiki.openstreetmap.org/wiki/Apple_iOS
|
||||
[13]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2020/03/open-street-map-1.jpg?ssl=1
|
||||
[14]: https://wiki.openstreetmap.org/wiki/Linux
|
||||
[15]: http://xn--pnvkarte-m4a.de/
|
||||
@ -0,0 +1,61 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: ('AI everywhere' IoT chips coming from Arm)
|
||||
[#]: via: (https://www.networkworld.com/article/3532094/ai-everywhere-iot-chips-coming-from-arm.html)
|
||||
[#]: author: (Patrick Nelson https://www.networkworld.com/author/Patrick-Nelson/)
|
||||
|
||||
'AI everywhere' IoT chips coming from Arm
|
||||
======
|
||||
Two new microprocessors from Arm promise to miniaturize artificial intelligence.
|
||||
Healthcare
|
||||
|
||||
Silicon microchip maker Arm is working on a new semiconductor design that it says will enable machine learning, at scale, on small sensor devices. Arm has completed testing of the technology and expects to bring it to market next year.
|
||||
|
||||
Artificial intelligence, implemented locally on "billions and ultimately trillions" of devices is coming, the company says in a [press release][1]. Arm Holdings, owned by Japanese conglomerate Softbank, says its partners have shipped more than 160 billion Arm-based chips to date, and that 45 million of its microprocessor designs are being placed within electronics every day.
|
||||
|
||||
The new machine-learning silicon will include micro neural processing units (microNPU) that can be used to identify speech patterns and perform other AI tasks. Importantly, the processing is accomplished on-device and in smaller form factors than have so far been available. The chips don't need the cloud or any network.
|
||||
|
||||
[RELATED: Auto parts supplier has big plans for its nascent IoT effort][2]
|
||||
|
||||
Arm, which historically has been behind mobile smartphone microchips, is aiming this design – the Cortex M55 processor, paired with the Ethos-U55, Arm's first microNPU – at Internet of Things instead.
|
||||
|
||||
"Enabling AI everywhere requires device makers and developers to deliver machine learning locally on billions, and ultimately trillions of devices," said Dipti Vachani, senior vice president and general manager of Arm's automotive and IoT areas, in a statement. "With these additions to our AI platform, no device is left behind as on-device ML on the tiniest devices will be the new normal, unleashing the potential of AI securely across a vast range of life-changing applications."
|
||||
|
||||
Arm wants to take advantage of the autonomous nature of chip-based number crunching, as opposed to doing it in the cloud. Privacy-conscious (and regulated) healthcare is an example of a vertical that might like the idea of localized processing.
|
||||
|
||||
Functioning AI without cloud dependence isn't entirely new. Intel's [Neural Compute Stick 2][3], a $69 self-contained computer vision and deep learning development kit, doesn't need it, for example.
|
||||
|
||||
**[ [Get certified as an Apple Technical Coordinator with this seven-part online course from PluralSight.][4] ]**
|
||||
|
||||
Arm is also going for power savings with its new AI technology. Not requiring a data network can mean longer battery life for the sensor— only the calculated results need to be sent, rather than every bit. Much of the time, raw sensor data is irrelevant and can be discarded. Arm's new endpoint ML technologies are going to help microcontroller developers "accelerate edge inference in devices limited by size and power," said Geoff Lees, senior vice president of edge processing at IoT semiconductor company [NXP][5], in the announcement.
|
||||
|
||||
Enabling machine learning in power-constrained settings and eliminating the need for network connectivity mean the sensor can be placed where there isn't a hardy power supply. Latency advantages and cost advantages also can come into play.
|
||||
|
||||
"These devices can run neural network models on batteries for years, and deliver low-latency inference directly on the device," said Ian Nappier, product manager of TensorFlow Lite for Microcontrollers at Google, in a statement to Arm. [TensorFlow][6] is an open-source machine learning platform that's been used for detecting respiratory diseases, among other things.
|
||||
|
||||
Join the Network World communities on [Facebook][7] and [LinkedIn][8] to comment on topics that are top of mind.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.networkworld.com/article/3532094/ai-everywhere-iot-chips-coming-from-arm.html
|
||||
|
||||
作者:[Patrick Nelson][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.networkworld.com/author/Patrick-Nelson/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.arm.com/company/news/2020/02/new-ai-technology-from-arm
|
||||
[2]: https://www.networkworld.com/article/3098084/internet-of-things/auto-parts-supplier-has-big-plans-for-its-nascent-iot-effort.html#tk.nww-fsb
|
||||
[3]: https://store.intelrealsense.com/buy-intel-neural-compute-stick-2.html
|
||||
[4]: https://pluralsight.pxf.io/c/321564/424552/7490?u=https%3A%2F%2Fwww.pluralsight.com%2Fpaths%2Fapple-certified-technical-trainer-10-11
|
||||
[5]: https://www.nxp.com/company/our-company/about-nxp:ABOUT-NXP
|
||||
[6]: https://www.tensorflow.org/
|
||||
[7]: https://www.facebook.com/NetworkWorld/
|
||||
[8]: https://www.linkedin.com/company/network-world
|
||||
@ -0,0 +1,61 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Electronics should sweat to cool down, say researchers)
|
||||
[#]: via: (https://www.networkworld.com/article/3532827/electronics-should-sweat-to-cool-down-say-researchers.html)
|
||||
[#]: author: (Patrick Nelson https://www.networkworld.com/author/Patrick-Nelson/)
|
||||
|
||||
Electronics should sweat to cool down, say researchers
|
||||
======
|
||||
Scientists think that in much the same way the human body releases perspiration to cool down, special materials might release water to draw heat from electronics.
|
||||
rclassenlayouts / Aleksei Derin / Getty Images
|
||||
|
||||
Computing devices should sweat when they get too hot, say scientists at Shanghai Jiao Tong University in China, where they have developed a materials application they claim will cool down devices more efficiently and in smaller form-factors than existing fans.
|
||||
|
||||
It’s “a coating for electronics that releases water vapor to dissipate heat from running devices,” the team explain in a news release. “Mammals sweat to regulate body temperature,” so should electronics, they believe.
|
||||
|
||||
[[Get regularly scheduled insights by signing up for Network World newsletters.]][1]
|
||||
|
||||
The group’s focus has been on studying porous materials that can absorb moisture from the environment and then release water vapor when warmed. MIL-101(Cr) checks the boxes, they say. The material is a metal organic framework, or MOF, which is a sorbent, a material that stores large amounts of water. The higher the water capacity one has, the greater the dissipation of heat when it's warmed.
|
||||
|
||||
MOF projects have been attempted before. “Researchers have tried to use MOFs to extract water from the desert air,” says refrigeration-engineering scientist Ruzhu Wang, who is senior author of a paper on the university’s work that has just been [published in Joule][2].
|
||||
|
||||
Their proof-of-concept test involved applying a micrometers-thin coating of MIL-101(Cr) to metallic substrates that resulted in temperature drops of up to 8.6 degrees Celsius for 25 minutes, according to the abstract for their paper.
|
||||
|
||||
That’s “a significant improvement compared to that of traditional PCMs,” they say. Phase change materials (PCM) include waxes and fatty acids that are used in electronics and melt to absorb heat. They are used in smartphones, but the solid-to-liquid transition doesn’t exchange all that much energy.
|
||||
|
||||
“In contrast, the liquid-vapor transition of water can exchange 10 times the energy compared to that of PCM solid-liquid transition.” Plus the material used recovers almost immediately to start sweating again, just like a mammal.
|
||||
|
||||
[][3]
|
||||
|
||||
Shanghai Jiao Tong University isn’t the only school looking into sweat for future tech. Cornell University says it wants to get robots to sweat to bring their temperature below ambient. Researchers there say they have built a 3D-printed, sweating robot muscle. It [manages its own temperature][4], and they think it will one day let robots run for extended periods without overheating.
|
||||
|
||||
Soft robots, which are the kind preferred by many developers for their flexibility, hold more heat than metal ones. As in electronic devices such as smartphones and IoT sensors, fans aren’t ideal because they take up too much space. That’s why new materials applications are being studied.
|
||||
|
||||
The Cornell robot group uses light to cure resin into shapes that control the flow of heat. A base layer “smart sponge” made of poly-N-isopropylacrylamide retains water and squeezes it through fabricated, dilated pores when heated. The pores then close automatically when cooled.
|
||||
|
||||
“Just when it seemed like robots couldn’t get any cooler,” the group says.
|
||||
|
||||
Join the Network World communities on [Facebook][5] and [LinkedIn][6] to comment on topics that are top of mind.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.networkworld.com/article/3532827/electronics-should-sweat-to-cool-down-say-researchers.html
|
||||
|
||||
作者:[Patrick Nelson][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.networkworld.com/author/Patrick-Nelson/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.networkworld.com/newsletters/signup.html
|
||||
[2]: https://www.cell.com/joule/fulltext/S2542-4351(19)30590-2
|
||||
[3]: https://www.networkworld.com/blog/itaas-and-the-corporate-storage-technology/?utm_source=IDG&utm_medium=promotions&utm_campaign=HPE22140&utm_content=sidebar (ITAAS and Corporate Storage Strategy)
|
||||
[4]: https://news.cornell.edu/stories/2020/01/researchers-create-3d-printed-sweating-robot-muscle
|
||||
[5]: https://www.facebook.com/NetworkWorld/
|
||||
[6]: https://www.linkedin.com/company/network-world
|
||||
@ -0,0 +1,74 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Cisco warns of five SD-WAN security weaknesses)
|
||||
[#]: via: (https://www.networkworld.com/article/3533550/cisco-warns-of-five-sd-wan-security-weaknesses.html)
|
||||
[#]: author: (Michael Cooney https://www.networkworld.com/author/Michael-Cooney/)
|
||||
|
||||
Cisco warns of five SD-WAN security weaknesses
|
||||
======
|
||||
Cisco warnings include three high-impact SD-WAN vulnerabilities
|
||||
[Jaredd Craig][1] [(CC0)][2]
|
||||
|
||||
Cisco has issued five warnings about security weaknesses in its [SD-WAN][3] offerings, three of them on the high-end of the vulnerability scale.
|
||||
|
||||
The worst problem is with the command-line interface (CLI) of its [SD-WAN][4] Solution software where a weakness could let a local attacker inject arbitrary commands that are executed with root privileges, Cisco [wrote.][5]
|
||||
|
||||
[[Get regularly scheduled insights by signing up for Network World newsletters.]][6]
|
||||
|
||||
An attacker could exploit this vulnerability – which has a 7.8 out if 10 on the Common Vulnerability Scoring System – by authenticating to the device and submitting crafted input to the CLI utility. The attacker must be authenticated to access the CLI utility. The vulnerability is due to insufficient input validation, Cisco wrote.
|
||||
|
||||
Another high warning problem lets an authenticated, local attacker elevate privileges to root on the underlying operating system. An attacker could exploit this vulnerability by sending a crafted request to an affected system. A successful exploit could allow the attacker to gain root-level privileges, Cisco [wrote][7]. The vulnerability is due to insufficient input validation.
|
||||
|
||||
The third high-level vulnerability in the SD-WAN Solution software could let an attacker cause a buffer overflow on an affected device. An attacker could exploit this vulnerability by sending crafted traffic to an affected device. A successful exploit could allow the attacker to gain access to information that they are not authorized to access and make changes to the system that they are not authorized to make, Cisco [wrote][8].
|
||||
|
||||
The vulnerabilities affect a number of Cisco products if they are running a Cisco SD-WAN Solution software release earlier than Release 19.2.2: vBond Orchestrator Software, vEdge 100-5000 Series Routers, vManage Network Management System and vSmart Controller Software.
|
||||
|
||||
Cisco said there were no workarounds for any of the vulnerabilities and it suggested users accept automatic software updates to allay exploit risks. There are [software fixes for the problems][9] as well.
|
||||
|
||||
**[ [Prepare to become a Certified Information Security Systems Professional with this comprehensive online course from PluralSight. Now offering a 10-day free trial!][10] ]**
|
||||
|
||||
All three of the high-level warnings were reported to Cisco by the Orange Group, Cisco said.
|
||||
|
||||
The other two SD-WAN Solution software warnings – with medium threat levels -- include a one that allows a cross-site scripting (XSS) attack against the web-based management interface of the vManage software and SQL injection threat.
|
||||
|
||||
The [XXS vulnerability][11] is due to insufficient validation of user-supplied input by the web-based management interface. An attacker could exploit this vulnerability by persuading a user of the interface to click a crafted link. A successful exploit could allow the attacker to execute arbitrary script code in the context of the interface or to access sensitive, browser-based information.
|
||||
|
||||
The SQL vulnerability exists because the web UI improperly validates SQL values. An attacker could exploit this vulnerability by authenticating to the application and sending malicious SQL queries to an affected system. A successful exploit could let the attacker modify values on, or return values from, the underlying database as well as the operating system, Cisco [wrote][12].
|
||||
|
||||
Cisco recognized Julien Legras and Thomas Etrillard of Synacktiv for reporting the problems.
|
||||
|
||||
The company said release 19.2.2 of the [Cisco SD-WAN Solution][13] contains fixes for all five vulnerabilities.
|
||||
|
||||
Join the Network World communities on [Facebook][14] and [LinkedIn][15] to comment on topics that are top of mind.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.networkworld.com/article/3533550/cisco-warns-of-five-sd-wan-security-weaknesses.html
|
||||
|
||||
作者:[Michael Cooney][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.networkworld.com/author/Michael-Cooney/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://unsplash.com/photos/T15gG5nA9Xk
|
||||
[2]: https://creativecommons.org/publicdomain/zero/1.0/
|
||||
[3]: https://www.networkworld.com/article/3031279/sd-wan-what-it-is-and-why-you-ll-use-it-one-day.html
|
||||
[4]: https://www.networkworld.com/article/3527194/multicloud-security-integration-drive-massive-sd-wan-adoption.html
|
||||
[5]: https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-sdwclici-cvrQpH9v
|
||||
[6]: https://www.networkworld.com/newsletters/signup.html
|
||||
[7]: https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-sdwpresc-ySJGvE9
|
||||
[8]: https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-sdwanbo-QKcABnS2
|
||||
[9]: https://software.cisco.com/download/home
|
||||
[10]: https://pluralsight.pxf.io/c/321564/424552/7490?u=https%3A%2F%2Fwww.pluralsight.com%2Fpaths%2Fcertified-information-systems-security-professional-cisspr
|
||||
[11]: https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20200318-vmanage-xss
|
||||
[12]: https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20200318-vmanage-cypher-inject
|
||||
[13]: https://www.cisco.com/c/en/us/solutions/enterprise-networks/sd-wan/index.html#~benefits
|
||||
[14]: https://www.facebook.com/NetworkWorld/
|
||||
[15]: https://www.linkedin.com/company/network-world
|
||||
@ -0,0 +1,85 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (How technical debt is risking your security)
|
||||
[#]: via: (https://opensource.com/article/20/3/remove-security-debt)
|
||||
[#]: author: (Sam Bocetta https://opensource.com/users/sambocetta)
|
||||
|
||||
How technical debt is risking your security
|
||||
======
|
||||
A few security fixes now will help lighten the load of future developers
|
||||
using your software.
|
||||
![A lock on the side of a building][1]
|
||||
|
||||
Everyone knows they shouldn't take shortcuts, especially in their work, and yet everyone does. Sometimes it doesn't matter, but when it comes to code development, though, it definitely does.
|
||||
|
||||
As any experienced programmer knows, building your code the quick and dirty way soon leads to problems down the line. These issues might not be disastrous, but they incur a small penalty every time you want to develop your code further.
|
||||
|
||||
This is the basic idea behind [technical debt][2], a term first coined by well-known programmer Ward Cunningham. Technical debt is a metaphor that explains the long-term burden developers and software teams incur when taking shortcuts, and has become a popular way to think about the extra effort that we have to do in future development because of the quick and dirty design choice.
|
||||
|
||||
"Security Debt" is an extension of this idea, and in this article, we'll take a look at what the term means, why it is a problem, and what you can do about it.
|
||||
|
||||
### What is security debt?
|
||||
|
||||
To get an idea of how security debt works, we have to consider the software development lifecycle. Today, it's very rare for developers to start with a blank page, even for a new piece of software. At the very least, most programmers will start a new project with open source code copied from online repositories.
|
||||
|
||||
They will then adapt and change this code to make their project. While they are doing this, there will be many points where they notice a security vulnerability. Something as simple as an error establishing a database connection can be an indication that systems are not playing well together, and that someone has taken a fast and dirty approach.
|
||||
|
||||
Then they have two options: they can either take an in-depth look at the code they are working with, and fix the issue at a fundamental level, or they can quickly paste extra code over the top that gets around the problem in a quick, inefficient way.
|
||||
|
||||
Given the demands of today's development environment, most developers choose the second route, and we can't blame them. The problem is that the next person who looks at the code is going to have to spend longer working out how it operates.
|
||||
|
||||
Time, as we all know, is money. Because of this, each time software needs to be changed, there will be a small cost to make it secure due to previous developers taking shortcuts. This is security debt.
|
||||
|
||||
### How security debt threatens your software
|
||||
|
||||
There was a time when security debt was not a huge problem, at least not in the open source community. A decade ago, open source components had lifetimes measured in years and were freely available to everyone.
|
||||
|
||||
This meant that security issues in legacy code got fixed. Today, the increased speed of the development lifecycle and the increasingly censored internet means that developers can no longer trust third party code to the degree they used to.
|
||||
|
||||
This has led to a considerable increase in security debt for developers using open source components. Veracode's latest [State of Software Security (SOSS)][3] report found that security issues in open source software take about a month longer to be fixed than those in software that is sourced internally. Insourced software recorded the highest fix rates, but even software sourced from external contractors gets fixed faster, by about two weeks, than open source software.
|
||||
|
||||
The ultimate outcome of this – and one that the term "security debt" captures very well – is that most companies currently face security vulnerabilities throughout their entire software stack, and these are accumulating faster than they are fixed. In other words, developers have maxed out their security debt credit card, and are drowning in the debt they've incurred. This is particularly concerning when you consider that total household debt [reached nearly $14 trillion][4] in the United States alone in 2019.
|
||||
|
||||
### How to avoid security debt
|
||||
|
||||
Avoiding a build-up of security debt requires that developers take a different approach to security than the one that is prevalent in the industry at the moment. Proven methods such as zero-knowledge cloud encryption, VPNs to promote online anonymity, and network intrusion prevention software are great, but they may also not be enough.
|
||||
|
||||
In fact, there might have been some developers who were scratching their heads during our definition of security debt above: how many of us think about the next poor soul who will have to check our code for security flaws?
|
||||
|
||||
Changing that way of thinking is key to preventing a build-up of security debt. Developers should take the time to thoroughly [check their software for security vulnerabilities][5], not just during development, but after the release as well. Fix any errors now, rather than waiting for security holes to build up.
|
||||
|
||||
If that instruction sounds familiar, then well done. A continuity approach to software development is a critical component of [layering security through DevOps][6], and one of the pillars of the emerging discipline of DevSecOps. Along with [chaos engineering][7], these approaches seek to integrate security into development, testing, and assessment processes, and thereby prevent a build-up of security debt.
|
||||
|
||||
Just like a credit card, the key to avoiding security debt getting out of control is to avoid the temptation to take shortcuts in the first place. That's easier said than done, of course, but one of the key lessons from recent data breaches is that legacy systems that many developers assume are secure are just as full of shortcuts as recently written code.
|
||||
|
||||
### Measure twice, cut once
|
||||
|
||||
Since [security by default hasn't arrived yet][8], we must all try and do things properly in the future. Taking the fast, dirty approach might mean that you get to leave the office early, but ultimately that decision will come back to bite you.
|
||||
|
||||
If you finish early anyway, well done: you can use the time to read [our best articles on security][9] and check whether your code is as secure as you think it is.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/20/3/remove-security-debt
|
||||
|
||||
作者:[Sam Bocetta][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/sambocetta
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/BUSINESS_3reasons.png?itok=k6F3-BqA (A lock on the side of a building)
|
||||
[2]: https://opensource.com/article/17/10/why-i-love-technical-debt
|
||||
[3]: https://www.veracode.com/state-of-software-security-report
|
||||
[4]: https://thetokenist.io/financial-statistics/
|
||||
[5]: https://opensource.com/article/17/6/3-security-musts-software-developers
|
||||
[6]: https://opensource.com/article/19/9/layered-security-devops
|
||||
[7]: https://www.infoq.com/articles/chaos-engineering-security-networking/
|
||||
[8]: https://opensource.com/article/20/1/confidential-computing
|
||||
[9]: https://opensource.com/article/19/12/security-resources
|
||||
@ -0,0 +1,110 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (3 metrics to measure your open source community health)
|
||||
[#]: via: (https://opensource.com/article/20/3/community-metrics)
|
||||
[#]: author: (Kevin Xu https://opensource.com/users/kevin-xu)
|
||||
|
||||
3 metrics to measure your open source community health
|
||||
======
|
||||
Community building is critical to the success of any open source
|
||||
project. Here's how to evaluate your community's health and strengthen
|
||||
it.
|
||||
![Green graph of measurements][1]
|
||||
|
||||
Community building is table stakes in the success of any open source project. Even outside of open source, community is considered a competitive advantage for businesses in many industries—from retail, to gaming, to fitness. (For a deeper dive, see "[When community becomes your competitive advantage][2]" in the _Harvard Business Review_.)
|
||||
|
||||
However, open source community building—especially offline activities—is notoriously hard to measure, track, and analyze. While we've all been to our fair share of meetups, conferences, and "summits" (and probably hosted a few of them ourselves), were they worth it? Did the community meaningfully grow? Was printing all those stickers and swags worth the money? Did we collect and track the right numbers to measure progress?
|
||||
|
||||
To develop a better framework for measuring community, we can look to a different industry for guidance and fresh ideas: political campaigns.
|
||||
|
||||
### My metrics start with politics
|
||||
|
||||
I started my career in political campaigns in the US as a field organizer (aka a low-level staffer) for then-candidate Senator Obama in 2008. Thinking back, a field organizer's job is basically community building in a specifically assigned geographical area that your campaign needs to win. My day consisted of calling supporters to do volunteer activities, hosting events to gather supporters, bringing in guest speakers (called "surrogates" in politics) to events, and selling the vision and plan of our candidate (essentially our "product").
|
||||
|
||||
Another big chunk of my day was doing data entry. We logged everything: interactions on phone conversations with voters, contact rates, event attendance, volunteer recruitment rates, volunteer show-up rates, and myriad other numbers to constantly measure our effectiveness.
|
||||
|
||||
Regardless of your misgivings about politics in general or specific politicians, the winning campaigns that lead to political victories are all giant community-building exercises that are data-driven, meticulously measured, and constantly optimized. They are well-oiled community-building machines.
|
||||
|
||||
When I entered the world of open source a few years ago, the community-building part felt familiar and natural. What surprised me was how little community building as an operation is quantified and measured—especially with offline activities.
|
||||
|
||||
### Three metrics to track
|
||||
|
||||
Taking a page from the best-run political campaigns I've seen, here are the three most important metrics for an open source community to track and optimize:
|
||||
|
||||
* Number of **community ambassadors**
|
||||
* Number of **return attendees** (people who attend your activities two times or more)
|
||||
* Rate of **churned attendees** (the percentage of people who attend your activities only once or say they will come but don't show up)
|
||||
|
||||
|
||||
|
||||
If you're curious, the corresponding terms on a political campaign for these three metrics are typically community captains, super volunteers, and flake rate.
|
||||
|
||||
#### Community ambassadors
|
||||
|
||||
A "community ambassador" is a user or enthusiast of your project who is willing to _consistently_ host local meetups or activities where she or he lives. Growing the number of community ambassadors and supporting them with resources and guidance are core to your community's strength and scale. You can probably hire for these if you have a lot of funding, but pure volunteers speak more to your project's allure.
|
||||
|
||||
These ambassadors should be your best friends, where you understand inside and out why they are motivated to evangelize your project in front of both peers and strangers. Their feedback on your project is also valuable and should be a critical part of your development roadmap and process. You can strategically cultivate ambassadors in different tech hubs geographically around the world, so your project can count on someone with local knowledge to reach and serve users of different business cultures with different needs. The beauty of open source is that it's global by default; take advantage of it!
|
||||
|
||||
Some cities are arguably more of a developer hub than others. Some to consider are Amsterdam, Austin, Bangalore, Beijing, Berlin, Hangzhou, Istanbul, London, NYC, Paris, Seattle, Seoul, Shenzhen, Singapore, São Paulo, San Francisco-Bay Area, Vancouver, Tel Aviv, Tokyo, and Toronto (listed alphabetically and based on feedback I got through social media. Please add a comment if I missed any!). An example of this is the [Cloud Native Ambassadors program][3] of the Cloud Native Computing Foundation.
|
||||
|
||||
#### Return attendees
|
||||
|
||||
The number of return attendees is crucial to measuring the usefulness or stickiness of your community activities. Tracking return attendees is how you can draw a meaningful line between "the curious" and "the serious."
|
||||
|
||||
Trying to grow this number should be an obvious goal. However, that's not the only goal. This is the group whose motivation you want to understand the clearest. This is the group that reflects your project's user persona. This is the group that can probably give you the most valuable feedback. This is the group that will become your future community ambassadors.
|
||||
|
||||
Putting it differently, this is your [1,000 true fans][4] (if you can keep them).
|
||||
|
||||
Having hosted and attended my fair share of these community meetups, my observation is that most people attend to be educated on a technical topic, look for tools to solve problems at work, or network for their next job opportunity. What they are not looking for is being "marketed to."
|
||||
|
||||
There is a growing trend of developer community events becoming marketing events, especially when companies are flush with funding or have a strong marketing department that wants to "control the message." I find this trend troubling because it undermines community building.
|
||||
|
||||
Thus, be laser-focused on technical education. If a developer community gets taken over by marketing campaigns, your return-attendees metric won't be pretty.
|
||||
|
||||
#### Churned attendees rate
|
||||
|
||||
Tracking churned attendees is the flipside of the returned-attendees coin, so I won't belabor the point. These are the people that join once and then disappear or who show interest but don't show up. They are important because they tell you what isn't working and for whom, which is more actionable than just counting the people who show up.
|
||||
|
||||
One note of caution: Be brutally honest when measuring this number, and don't fool yourself (or others). On its own, if someone signs up but doesn't show up, it doesn't mean much. Similarly, if someone shows up once and never comes back, it doesn't mean much. Routinely sit down and assess _why_ someone isn't showing up, so you can re-evaluate and refine your community program and activities. Don't build the wrong incentives into your community-building operation to reward the wrong metric.
|
||||
|
||||
### Value of in-person connections
|
||||
|
||||
I purposely focused this post on measuring offline community activities because online activities are inherently more trackable and intuitive to digital-native open source creators.
|
||||
|
||||
Offline community activities are essential to any project's journey to reaching traction and prominence. I have yet to see a successful project that does not have a sizable offline presence, regardless of its online popularity.
|
||||
|
||||
Why is this the case? Why can't an open source community, usually born online, just stay and grow online?
|
||||
|
||||
Because technology choice is ultimately a human decision; therefore, face-to-face interaction is an irreplaceable element of new technology adoption. No one wants to be the guinea pig. No one wants to be the first. The most effective way to not feel like the first is to literally _see_ other human beings trying out or being interested in the same thing.
|
||||
|
||||
Being in the same room as other developers, learning about the same project, and doing that regularly is the most effective way to build trust for a project. And with trust comes traction.
|
||||
|
||||
### These three metrics work
|
||||
|
||||
There are other things you _can_ track, but more data does not necessarily mean clearer insight. Focusing your energy on these three metrics will make the most impact on your community-building operation. An open source community where the _number of ambassadors and return attendees are trending up_ and the _churned attendees rate is trending down_ is one that's healthy and growing in the right way.
|
||||
|
||||
* * *
|
||||
|
||||
_This article originally appeared on_ _[COSS Media][5]_ _and is republished with permission._
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/20/3/community-metrics
|
||||
|
||||
作者:[Kevin Xu][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/kevin-xu
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/metrics_lead-steps-measure.png?itok=DG7rFZPk (Green graph of measurements)
|
||||
[2]: https://hbr.org/2020/01/when-community-becomes-your-competitive-advantage
|
||||
[3]: https://www.cncf.io/people/ambassadors/
|
||||
[4]: https://kk.org/thetechnium/1000-true-fans/
|
||||
[5]: https://coss.media/how-to-measure-community-building/
|
||||
@ -0,0 +1,107 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Coronavirus challenges capacity, but core networks are holding up)
|
||||
[#]: via: (https://www.networkworld.com/article/3533438/coronavirus-challenges-capacity-but-core-networks-are-holding-up.html)
|
||||
[#]: author: (Michael Cooney https://www.networkworld.com/author/Michael-Cooney/)
|
||||
|
||||
Coronavirus challenges capacity, but core networks are holding up
|
||||
======
|
||||
COVID-19 has sent thousands of employees to work from home, placing untold stress on remote-access networks.
|
||||
Cicilie Arcurs / Getty Images
|
||||
|
||||
As the coronavirus continues to spread and more people work from home, the impact of the increased traffic on networks in the US so far seems to be minimal.
|
||||
|
||||
No doubt that web, VPN and data usage is growing dramatically with the [influx of remote workers][1]. For example, Verizon said it has seen a 34% increase in VPN traffic from March 10 to 17. It has also seen a 75% increase in gaming traffic, and web traffic increased by just under 20% in that time period, according to Verizon.
|
||||
|
||||
[[Get regularly scheduled insights by signing up for Network World newsletters.]][2]
|
||||
|
||||
Verizon said its fiber optic and wireless networks “have been able to meet the shifting demands of customers and continue to perform well. In small pockets where there has been a significant increase in usage, our engineers have quickly added capacity to meet customers’ demand.”
|
||||
|
||||
“As we see more and more individuals work from home and students engage in online learning, it is a natural byproduct that we would see an increase in web traffic and access to VPN. And as more entertainment options are cancelled in communities across the US, an increase in video traffic and online gaming is not surprising,” said Kyle Malady, Chief Technology Officer for Verizon in a [statement][3]. “We expect these peak hour percentages to fluctuate, so our engineers are continuing to closely monitor network usage patterns 24x7 and stand ready to adjust resources as changing demands arise."
|
||||
|
||||
As of March 16, AT&T said that its network continues to perform well. “In cities where the coronavirus has had the biggest impact, we are seeing fewer spikes in wireless usage around particular cell towers or particular times of day because more people are working from home rather than commuting to work and fewer people are gathering in large crowds at specific locations.”
|
||||
|
||||
In Europe, Vodaphone say it has seen an 50% increase in data traffic in some markets.
|
||||
|
||||
“COVID-19 is already having a significant impact on our services and placing a greater demand on our network,” the company said in a statement. “Our technology teams throughout Europe have been focusing on capacity across our networks to make sure they are resilient and can absorb any new usage patterns arising as more people start working from home.”
|
||||
|
||||
[][4]
|
||||
|
||||
In Europe there have also been indications of problems.
|
||||
|
||||
Ireland-based [Spearline][5], which monitors international phone numbers for connectivity and audio quality, said this week that Italy's landline connection rate continues to be volatile with as much as a 10% failure rate and audio quality is running approximately 4% below normal levels.
|
||||
|
||||
Other Spearline research says:
|
||||
|
||||
* Spain saw a drop in connection rates to 98.5% on March 16, but it is improving again.
|
||||
* France saw a dip in connection rates approaching 5% on March17. Good quality has been maintained overall, though periodic slippage has been observed.
|
||||
* Germany saw a 1.7% connection-failure rate March 17. Good quality has been maintained, though periodic slippage has been observed.
|
||||
|
||||
|
||||
|
||||
Such problems are not showing up in the US at this point, Spearline said.
|
||||
|
||||
“The US is Spearline's most tested market with test calls over three main sectors being enterprise, unified communications and carrier. To date, there has been no significant impact on either the connection rates or the audio quality on calls throughout the US,” said Matthew Lawlor, co-founder and chief technical officer at Spearline.
|
||||
|
||||
The future impact is the real unknown of course, Lawlor said.
|
||||
|
||||
“There are many potential issues which have happened in other countries which may have a similar impact on US infrastructure. For example, in many countries there have been hardware issues where engineers are unable to get physical access to resolve the issue,” Lawlor said. “While rerouting calls may help resolve issues it does put more pressure on other segments of your network.”
|
||||
|
||||
On March 19, one week after the CDC declarated the virus as pandemic, data analytics and broadband vendor OpenVault wrote:
|
||||
|
||||
* Subscribers’ average usage from 9 a.m. to 5 p.m. has risen to 6.3 GB, 41.4% higher than the January figure of 4.4 GB.
|
||||
* During the same period, peak-hour (6 p.m. to 11 p.m.) usage has risen 17.2% from 5.0 GB per subscriber in January to 5.87 GB in March.
|
||||
* Overall daily usage has grown from 12.19 GB to 15.46 GB, an increase of 26.8%.
|
||||
|
||||
|
||||
|
||||
Based on the current rate of growth, OpenVault projected that consumption for March will reach nearly 400 GB per subscriber, an increase of almost 11% over the previous monthly record of 361 GB, established in January. In addition, OpenVault projects a new coronavirus-influenced run rate of 460 GB per subscriber per month going forward. OpenVault’s research is based on the usage of more than 1 million broadband subscribers through the United States, the company said.
|
||||
|
||||
“Broadband clearly is keeping the hearts of business, education and entertainment beating during this crisis,” said Mark Trudeau, CEO and founder of OpenVault in a [statement][6]. “Networks built for peak-hours consumption so far are easily handling the rise in nine-to-five business-hours usage. We’ve had concerns about peak hours consumption given the increase in streaming entertainment and the trend toward temporary cessation of bandwidth caps, but operator networks seem to be handling the additional traffic without impacting customer experiences.”
|
||||
|
||||
Increased use of conferencing apps may affect their availability for reasons other than network capacity. For example, according to Thousand Eyes, users around the globe were unable to connect to their Zoom meetings for approximately 20 minutes on Friday due to failed DNS resolution.
|
||||
|
||||
Others too are monitoring data traffic looking for warning signs of slowdowns. “Traffic towards video conferencing, streaming services and news, e-commerce websites has surged. We've seen growth in traffic from residential broadband networks, and a slowing of traffic from businesses and universities," wrote Louis Poinsignon a network engineer with CloudFlare in a [blog][7] about Internet traffic patterns. He noted that on March 13 when the US announced a state of emergency, CloudFlare’s US data centers served 20% more traffic than usual.
|
||||
|
||||
Poinsignon noted that [Internet Exchange Points][8], where Internet service providers and content providers can exchange data directly (rather than via a third party) have also seen spikes in traffic. For example, Amsterdam ([AMS-IX][9]), London ([LINX][10]) and Frankfurt ([DE-CIX][11]), a 10-20% increase was seen around March 9.
|
||||
|
||||
“Even though from time to time individual services, such as a web site or an app, have outages, the core of the Internet is robust,” Poinsignon wrote. “Traffic is shifting from corporate and university networks to residential broadband, but the Internet was designed for change.”
|
||||
|
||||
In related news:
|
||||
|
||||
* Netflix said it would reduce streaming quality in Europe for at least the next 30 days to prevent the internet collapsing under the strain of unprecedented usage due to the coronavirus pandemic. "We estimate that this will reduce Netflix traffic on European networks by around 25% while also ensuring a good quality service for our members," Netflix said.
|
||||
* DISH announced that it is providing 20 MHz of AWS-4 (Band 66) and all of its 700 MHz spectrum to AT&T at no cost for 60 days. Last week, DISH began lending its complete 600 MHz portfolio of spectrum to T-Mobile. With these two agreements, DISH has activated most of its spectrum portfolio to enhance national wireless capacity as the nation confronts the COVID-19 crisis.
|
||||
|
||||
|
||||
|
||||
Join the Network World communities on [Facebook][12] and [LinkedIn][13] to comment on topics that are top of mind.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.networkworld.com/article/3533438/coronavirus-challenges-capacity-but-core-networks-are-holding-up.html
|
||||
|
||||
作者:[Michael Cooney][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.networkworld.com/author/Michael-Cooney/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.networkworld.com/article/3532440/coronavirus-challenges-remote-networking.html
|
||||
[2]: https://www.networkworld.com/newsletters/signup.html
|
||||
[3]: https://www.verizon.com/about/news/how-americans-are-spending-their-time-temporary-new-normal
|
||||
[4]: https://www.networkworld.com/blog/itaas-and-the-corporate-storage-technology/?utm_source=IDG&utm_medium=promotions&utm_campaign=HPE22140&utm_content=sidebar (ITAAS and Corporate Storage Strategy)
|
||||
[5]: https://www.spearline.com/
|
||||
[6]: http://openvault.com/covid-19-impact-driving-business-hours-broadband-consumption-up-41/
|
||||
[7]: https://blog.cloudflare.com/on-the-shoulders-of-giants-recent-changes-in-internet-traffic/
|
||||
[8]: https://en.wikipedia.org/wiki/Internet_exchange_point
|
||||
[9]: https://www.ams-ix.net/ams/documentation/total-stats
|
||||
[10]: https://portal.linx.net/stats/lans
|
||||
[11]: https://www.de-cix.net/en/locations/germany/frankfurt/statistics
|
||||
[12]: https://www.facebook.com/NetworkWorld/
|
||||
[13]: https://www.linkedin.com/company/network-world
|
||||
@ -0,0 +1,96 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (COVID-19: Weekly health check of ISPs, cloud providers and conferencing services)
|
||||
[#]: via: (https://www.networkworld.com/article/3534130/covid-19-weekly-health-check-of-isps-cloud-providers-and-conferencing-services.html)
|
||||
[#]: author: (Tim Greene https://www.networkworld.com/author/Tim-Greene/)
|
||||
|
||||
COVID-19: Weekly health check of ISPs, cloud providers and conferencing services
|
||||
======
|
||||
ThousandEyes, which tracks internet and cloud traffic, is providing Network World with weekly updates on the performance of three categories of service provider: ISP, cloud provider, UCaaS
|
||||
[ThousandEyes][1]
|
||||
|
||||
_As COVID-19 continues to spread, forcing employees to work from home, the services of ISPs, cloud providers and conferencing services a.k.a. unified communications as a service (UCaaS) providers are experiencing increased traffic._
|
||||
|
||||
_Thousand Eyes is monitoring how these increases affect outages and the performance these providers undergo. It will provide Network World a roundup of interesting events of the week in the delivery of these services, and Network World will provide a summary here. Stop back next week for another update._
|
||||
|
||||
With the increased use of remote-access VPNs, major carriers are reporting dramatic increases in their network traffic – with Verizon reporting a 20% week-over-week increase, and Vodafone reporting an increase of 50%.
|
||||
|
||||
[Read about IPv6 and cloud-access security brokers][2]
|
||||
|
||||
While there has been no corresponding spike in outages in service provider networks, over the past six weeks there has been a steady increase in outages across multiple provider types both worldwide and in the U.S., all according to ThousandEyes, which keeps track of internet and cloud traffic.
|
||||
|
||||
### IDG Special Report:
|
||||
|
||||
Navigating the Pandemic
|
||||
|
||||
* [Business continuity: Coronavirus crisis puts CIOs’ plans to the test][3]
|
||||
* [Coronavirus challenges remote networking][4]
|
||||
* [A security guide for pandemic planning: 7 key steps][5]
|
||||
* [10 tips to set up your home office for videoconferencing][6]
|
||||
* [How to survive and thrive while working from home][7]
|
||||
* [WTH? OSS knows how to WFH IRL][8]
|
||||
|
||||
|
||||
|
||||
This includes “a concerning upward trajectory” since the beginning of March of ISP outages worldwide that coincides with the spread of COVID-19, [according to a ThousandEyes blog][9] by Angelique Medina, the company’s director of product marketing. ISP outages worldwide hovered around 150 per week between Feb. 10 and March 19, but then increased to between just under 200 and about 225 during the following three weeks.
|
||||
|
||||
In the U.S. those numbers were a little over 50 in the first time range and reaching about 100 during the first week of March. “That early March level has been mostly sustained over the last couple of weeks,” Medina writes.
|
||||
|
||||
Cogent Communications was one ISP with nearly identical large scale outages on March 11 and March 18, with “disruptions for the fairly lengthy period (by Internet standards) of 30 minutes,” she wrote.
|
||||
|
||||
[][10]
|
||||
|
||||
Hurricane Electric suffered an outage March 20 that was less extensive and shorter than Cogent’s but included smaller disruptions that altogether affected hundreds of sites and services, she wrote.
|
||||
|
||||
Public-cloud provider networks have withstood the effects of COVID-19 well, with slight increases in the number of outages in the U.S., but otherwise relatively level around the world. The possible reason: “Major public cloud providers, such as AWS, Microsoft Azure, and Google Cloud, have built massive global networks that are incredibly well-equipped to handle traffic surges,” Medina wrote. And when these networks do have major outages it’s due to routing or infrastructure state changes, not traffic congestion.
|
||||
|
||||
Some providers of collaboration applications – the likes of Zoom, Webex, MSFT Teams, RingCentral – also experienced performance problems between March 9 and March 20. ThousandEyes doesn’t name them, but does list performance numbers for what it describes “the top three” UCaaS providers. One actually showed improvements in availability, latency, packet loss and jitter. The other two “showed minimal (in the grand scheme of things) degradations on all fronts — not surprising given the unprecedented strain they’ve been under,” according to the blog.
|
||||
|
||||
Each provider showed spikes in traffic loss over the time period that ranged from less than 1% to more than 4% in one case. In the case of one provider, “outages within its own network spiked last week, meaning that the network issues impacting users were taking place on infrastructure managed by the provider versus an external ISP.”
|
||||
|
||||
“Outage incidents within large UCaaS provider networks are fairly infrequent; however, the recent massive surge in usage is clearly stressing current design limits. Capacity is reportedly being added across the board to meet new service demands,” according to the blog.
|
||||
|
||||
Meanwhile, ThousandEyes has introduced a new feature on its site a [Global Internet Outages Map][1] that is updated every few minutes. It shows recent and ongoing outages
|
||||
|
||||
## Google outage unrelated to COVID-19
|
||||
|
||||
On March 26 Google suffered a 20 minute outage on the East Coast of the U.S., apparently from a router failure in Atlanta, ThousandEyes said, agreeing with a statement put out by Googe to that effect.
|
||||
|
||||
That problem affected other regions of the U.S. as evidenced by Google sites such as google.com intermittently returning server errors."These 500 server errors are consistent with an inability to reach the backend systems necessary to correctly load various services," ThousandEyes said in a statement. "Any traffic traversing the affected region — connecting from Google’s front-end servers to backend services — may have been impacted and seen the resulting server errors."
|
||||
|
||||
ThousandEyes posted interactive results of tests it ran about the outage [here][11] and [here][12].
|
||||
|
||||
.
|
||||
|
||||
Join the Network World communities on [Facebook][13] and [LinkedIn][14] to comment on topics that are top of mind.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.networkworld.com/article/3534130/covid-19-weekly-health-check-of-isps-cloud-providers-and-conferencing-services.html
|
||||
|
||||
作者:[Tim Greene][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.networkworld.com/author/Tim-Greene/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.thousandeyes.com/outages
|
||||
[2]: https://www.networkworld.com/article/3391380/does-your-cloud-access-security-broker-support-ipv6-it-should.html
|
||||
[3]: https://www.cio.com/article/3532899/business-continuity-coronavirus-crisis-puts-cios-plans-to-the-test.html
|
||||
[4]: https://www.networkworld.com/article/3532440/coronavirus-challenges-remote-networking.html
|
||||
[5]: https://www.csoonline.com/article/3528878/a-security-guide-for-pandemic-planning-7-key-steps.html
|
||||
[6]: https://www.computerworld.com/article/3250684/10-tips-to-set-up-your-home-office-for-videoconferencing.html
|
||||
[7]: https://www.computerworld.com/article/3532283/how-to-survive-and-thrive-while-working-from-home.html
|
||||
[8]: https://www.infoworld.com/article/3533050/wth-oss-knows-how-to-wfh-irl.html
|
||||
[9]: https://blog.thousandeyes.com/internet-health-during-covid-19/
|
||||
[10]: https://www.networkworld.com/blog/itaas-and-the-corporate-storage-technology/?utm_source=IDG&utm_medium=promotions&utm_campaign=HPE22140&utm_content=sidebar (ITAAS and Corporate Storage Strategy)
|
||||
[11]: https://agisi.share.thousandeyes.com/view/endpoint-agent/?roundId=1585237800&metric=loss&scenarioId=eyebrowNetwork&filters=%7B%22filters%22:%7B%22domain%22:%5B%22google.com%22%5D,%22geonameId%22:%5B4148757,4180439,4459467,4460243,4509177,4671240,4744709,4744870,4887398,4890864,4930956,5099836,5110266,5110302,5128581,5145476,5150529,5282804,5786882%5D%7D%7D&page=0,0&grouping=BY_NETWORK,BY_DOMAIN
|
||||
[12]: https://ythkurgdz.share.thousandeyes.com/view/tests/?roundId=1585236900&metric=availability&scenarioId=httpServer&testId=1283781
|
||||
[13]: https://www.facebook.com/NetworkWorld/
|
||||
[14]: https://www.linkedin.com/company/network-world
|
||||
@ -0,0 +1,55 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (COVID-19 vs. Raspberry Pi: Researchers bring IoT technology to disease detection)
|
||||
[#]: via: (https://www.networkworld.com/article/3534101/covid-19-vs-raspberry-pi-researchers-bring-iot-technology-to-disease-detection.html)
|
||||
[#]: author: (Jon Gold https://www.networkworld.com/author/Jon-Gold/)
|
||||
|
||||
COVID-19 vs. Raspberry Pi: Researchers bring IoT technology to disease detection
|
||||
======
|
||||
Researchers from UMass say that a Raspberry Pi edge device can help identify flu-like symptoms in crowds, broadening the range of tools that can be used to track the spread of disease.
|
||||
[Bill Oxford / Raspberry Pi / Modified by IDG Comm.][1] [(CC0)][2]
|
||||
|
||||
An [IoT][3] device that tracks coughing and crowd size in real time could become a useful tool for identifying the presence of flu-like symptoms among large groups of people, according to a team of researchers at UMass Amherst.
|
||||
|
||||
FluSense, as the researchers call it, is about the size of a dictionary. It contains a cheap microphone array, a thermal sensor, a Raspberry Pi and an Intel Movidius 2 neural computing engine. The idea is to use AI at the edge to classify audio samples and identify the number of people in a room at any given time.
|
||||
|
||||
[[Get regularly scheduled insights by signing up for Network World newsletters.]][4]
|
||||
|
||||
Since the system can distinguish coughing from other types of non-speech audio, correlating coughing with the size of a given crowd could give a useful index of how many people are likely to be experiencing flu-like symptoms.
|
||||
|
||||
A test run between December 2018 and July 2019 saw FluSense installed in four waiting rooms at UMass’ University Health Services clinic, and the researchers said that they were able to “strongly” correlate the system’s results with clinical testing for influenza and other illnesses with similar symptoms.
|
||||
|
||||
And bigger plans for FluSense are afoot, according to the paper’s lead author, Ph.D student Forsad Al Hossain and his co-author and adviser, assistant professor Tauhidur Rahman.
|
||||
|
||||
“[C]urrently we are planning to deploy the FluSense system in several large public spaces (e.g., large cafeteria, classroom, dormitories, gymnasium, auditorium) to capture syndromic signals from a broad range of people who live in a certain town or city,” they said. “We are also looking for funding to run a large-scale multi-city trial. In the meantime, we are also diversifying our sensing capability by extending FluSense’s capability to capture more syndromic signals (e.g., recently we added sneeze sensing capability to FluSense). We definitely see a significant level of commercialization potential in this line of research.”
|
||||
|
||||
FluSense is particularly interesting from a technical perspective because all of the meaningful processing work is done locally, via the Intel neural computing engine and Raspberry Pi. Symptom information is sent wirelessly to the lab for collation, of course, but the heavy lifting is accomplished at the edge. Al Hossain and Rahman were quick to emphasize that the device doesn’t collect personally identifiable information – the emphasis is on aggregating data in a given setting, rather than identifying sickness in any single patient – and everything it does collect is heavily encrypted, making it a minimal privacy concern.
|
||||
|
||||
The key point of FluSense, according to the researchers, is to think of it as a health surveillance tool, rather than a piece of diagnostic equipment. Al Hossain and Rahman said that it has several important advantages over other health surveillance techniques, particularly those based on Internet tracking, like Google Flu Trend and Twitter.
|
||||
|
||||
“FluSense is not easily influenced by public health campaigns or advertisements. Also, the contactless nature of this sensor is ideal to capture syndromic signals passively from different geographical locations and different socioeconomic groups (including underprivileged who may not have access to healthcare and may not go to a doctor/clinic,” they said.
|
||||
|
||||
Join the Network World communities on [Facebook][5] and [LinkedIn][6] to comment on topics that are top of mind.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.networkworld.com/article/3534101/covid-19-vs-raspberry-pi-researchers-bring-iot-technology-to-disease-detection.html
|
||||
|
||||
作者:[Jon Gold][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.networkworld.com/author/Jon-Gold/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://unsplash.com/photos/tR0PPLuN6Pw
|
||||
[2]: https://creativecommons.org/publicdomain/zero/1.0/
|
||||
[3]: https://www.networkworld.com/article/3207535/what-is-iot-the-internet-of-things-explained.html
|
||||
[4]: https://www.networkworld.com/newsletters/signup.html
|
||||
[5]: https://www.facebook.com/NetworkWorld/
|
||||
[6]: https://www.linkedin.com/company/network-world
|
||||
104
sources/talk/20200325 The coming together of SD-WAN and AIOps.md
Normal file
104
sources/talk/20200325 The coming together of SD-WAN and AIOps.md
Normal file
@ -0,0 +1,104 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (The coming together of SD-WAN and AIOps)
|
||||
[#]: via: (https://www.networkworld.com/article/3533437/the-coming-together-of-aiops-and-sd-wan.html)
|
||||
[#]: author: (Zeus Kerravala https://www.networkworld.com/author/Zeus-Kerravala/)
|
||||
|
||||
The coming together of SD-WAN and AIOps
|
||||
======
|
||||
SD-WAN delivers cost and resiliency benefits. Infusing AI into SD-WAN takes things further, enabling automated operations and business agility.
|
||||
kohb / Getty Images
|
||||
|
||||
Software-defined wide-area networking ([SD-WAN][1]) and AIOps are both red-hot technologies. SD-WANs increase application availability, reduce costs and in some cases improve performance. AIOps infuses machine learning into IT operations to increase the level of automation. This reduces errors and enables businesses to make changes at digital speeds. Most think of these as separate technologies, but the two are on a collision course and will give rise to what I'm calling the AI-WAN.
|
||||
|
||||
### SD-WAN not a panacea for all network woes
|
||||
|
||||
SD-WAN is the biggest leap forward in networking since… well, the actual WAN. But many solutions still rely on manual configurations. SD-WANs certainly increase application resiliency, lower telecommunications costs, and often increase application performance, but they are more complicated than traditional WANs. Initial setup can be a challenge, but the bigger issue is ongoing operations. Manually tweaking and tuning the network to adapt to business changes can be time consuming and error-prone. A solution is needed to bring better automation to SD-WANs.
|
||||
|
||||
**READ MORE:** [How AI can improve network capacity planning][2]
|
||||
|
||||
Enter AI-WAN. Much like a self-driving car, an AI-WAN can make decisions based on different rules and adapt to changes faster than people can. Self-driving cars continually monitor road conditions, speed limits and other factors to determine what changes to make. Similarly, a self-driving network can monitor, correct, defend, and analyze with minimal to no human involvement. This is done through automation capabilities powered by AI, obviating the need for people to get involved.
|
||||
|
||||
Make no mistake, manual operations will hold businesses back from reaching their full potential. An interesting data point from my research is that it takes enterprises an average of four months to make changes across a network. That's because maintaining legacy networks and fixing glitches takes too much time. One ZK Research study found 30% of engineers spend at least one day a week doing nothing but troubleshooting problems. SD-WANs can improve these metrics, but there's still a heavy people burden.
|
||||
|
||||
With growing data challenges businesses face as they migrate to the cloud, they simply can't afford to wait that long. Instead of being afraid of AI taking over jobs, businesses should embrace it. AI can remove human error—which is the largest cause of unplanned network downtime—and help businesses focus on higher-level tasks instead.
|
||||
|
||||
### AI-WAN will transform network operations
|
||||
|
||||
So how will the evolution of SD-WAN into AI-WAN transform network management and operations? Administrators can use their time to focus on strategic initiatives instead of fixing problems. Another data point from ZK Research is that 90% of the time taken to fix a problem is spent identifying the source. Now that applications reside in the cloud and run on mobile devices, identifying the source of a problem has gotten harder. AI-WANs have the ability to spot even the smallest anomaly, even if it hasn't yet begun to impact business.
|
||||
|
||||
SD-WANs are fundamentally designed so that all routing rules are managed centrally by administrators and can be transmitted across a network. AI-WAN takes it a step further and enables administrators to anticipate problems before they happen through fault prediction. It may even adjust network glitches on its own before users are affected, thus improving network performance.
|
||||
|
||||
[][3]
|
||||
|
||||
A self-driving car knows the rules of the road—where the blind spots are, how to synch with traffic signals, and which safety measures to take—using AI software, real-time data from IoT sensors, cameras, and much more. Similarly, a self-driving network knows the higher-level rules and can prevent administrators from making mistakes, such as allowing applications in countries where certain actions are banned.
|
||||
|
||||
Security is another concern. Everything from mobile devices to Internet of Things (IoT) to cloud computing is creating multiple new entry points and shifting resources to the network edge. This puts businesses at a security risk, as they struggle to respond to changes quickly.
|
||||
|
||||
Businesses can miss security gaps created by users, with hundreds of software-as-a-service (SaaS) apps being used at the same time without IT's knowledge. Older networking technologies cannot support SaaS and cloud services, while SD-WANs can. But simply deploying an SD-WAN is not enough to protect a network. Security shouldn't be an afterthought in an SD-WAN deployment, but part of it from the get-go.
|
||||
|
||||
Increasingly, vendors are bundling AI-based analytics with SD-WAN solutions to boost network security. Such solutions use AI to analyze how certain events impact the network, application performance, and security. Then, they create intelligent recommendations for any network changes, such as unauthorized use of SaaS apps.
|
||||
|
||||
Going back to the autonomous car analogy, AI-WANs are designed to keep roads clear and accident-free. They enable smarter networks that can adapt quickly to changing conditions and self-heal if necessary. With the growing demands of cloud computing and SaaS apps, intelligent networks are the future and forward-thinking businesses are already in the driver’s seat.
|
||||
|
||||
### AI-WAN exists today and will explode in the future
|
||||
|
||||
AI-WAN may seem futuristic, but there are a number of vendors that are delivering it or in the process of bringing solutions to market. Managed service provider Masergy, for example, recently introduced [AIOps for SD-WAN][4] to deliver autonomous networking and has the most complete offering.
|
||||
|
||||
Open System, another managed service provider, [snapped up cloud-based Sqooba][5] to add AIOps to its strong network and security services. Keeping with the M&A theme, VMware recently [acquired AIOps vendor Nyansa][6] and rolled it into its VeloCloud SD-WAN group. That move gives VMware similar capabilities to [Aruba Networks][7], which initially applied AI to WiFi troubleshooting but is now bringing it to its SD-Branch offering. [Cisco][8] is another networking vendor with an AIOps story, although it's trying to apply it network-wide, not just with the WAN.
|
||||
|
||||
Over time, I expect every SD-WAN or SASE vendor to bring AIOps into the fold, shifting the focus away from connectivity to automated operations.
|
||||
|
||||
**Learn more about SD-WAN**
|
||||
|
||||
* [Top 10 underused SD-WAN features][9]
|
||||
* [SD-WAN: The inside scoop from real-world deployments][10]
|
||||
* [5 reasons to choose a managed SD-WAN and 5 reasons to think twice][11]
|
||||
* [10 essential SD-WAN considerations][12]
|
||||
* [SD-WAN: What is it and why you’ll use it one day][13]
|
||||
* [SD-WAN deployment options: DIY vs. cloud managed][14]
|
||||
* [How SD-WAN can improve your security strategy][15]
|
||||
* [10 hot SD-WAN startups to watch][16]
|
||||
* [How SD-WAN saves $1.2M over 5 years for a radiology firm][17]
|
||||
* [SD-WAN creates new security challenges][18]
|
||||
|
||||
|
||||
|
||||
Join the Network World communities on [Facebook][19] and [LinkedIn][20] to comment on topics that are top of mind.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.networkworld.com/article/3533437/the-coming-together-of-aiops-and-sd-wan.html
|
||||
|
||||
作者:[Zeus Kerravala][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.networkworld.com/author/Zeus-Kerravala/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.networkworld.com/article/3031279/sd-wan-what-it-is-and-why-you-ll-use-it-one-day.html
|
||||
[2]: https://www.networkworld.com/article/3338100/using-ai-to-improve-network-capacity-planning-what-you-need-to-know.html
|
||||
[3]: https://www.networkworld.com/blog/itaas-and-the-corporate-storage-technology/?utm_source=IDG&utm_medium=promotions&utm_campaign=HPE22140&utm_content=sidebar (ITAAS and Corporate Storage Strategy)
|
||||
[4]: https://techcrunch.com/2020/03/19/nvidia-makes-its-gpu-powered-genome-sequencing-tool-available-free-to-those-studying-covid-19/?guccounter=1&guce_referrer=aHR0cHM6Ly93d3cuZ29vZ2xlLmNvbS8&guce_referrer_sig=AQAAAMI6we4H-fTz2mf5g-l6IP27C1O-V-u6EiQuJ5QzVnlrrPU04iS0fhyrZo5U8q5rAk5I9uVW5PQYKHX8ziMdWrFBxhBP7f__JshmAGevyu4Z5zm98nDnC6nEdIekjVX4RPPmF9Q_PImcQ0opZy6JukS-DZA62tHI9R7D1Q2JAog7
|
||||
[5]: https://open-systems.com/press-release/open-systems-acquires-sqooba
|
||||
[6]: https://www.vmware.com/company/acquisitions/nyansa.html
|
||||
[7]: https://blogs.arubanetworks.com/solutions/ai-doing-more-with-less-in-2020-and-beyond/
|
||||
[8]: https://www.cisco.com/c/en/us/products/cloud-systems-management/crosswork-network-automation/service-centric-approach-to-aiops.html#~overview
|
||||
[9]: https://www.networkworld.com/article/3518992/top-10-underused-sd-wan-features.html
|
||||
[10]: https://www.networkworld.com/article/3316568/sd-wan/sd-wan-the-inside-scoop-from-real-world-deployments.html
|
||||
[11]: https://www.networkworld.com/article/3431080/5-reasons-to-choose-a-managed-sd-wan-and-5-reasons-to-think-twice.html
|
||||
[12]: https://www.networkworld.com/article/3355138/sd-wan-10-essential-considerations.html
|
||||
[13]: https://www.networkworld.com/article/3031279/sd-wan/sd-wan-what-it-is-and-why-you-ll-use-it-one-day.html
|
||||
[14]: https://www.networkworld.com/article/3243701/wide-area-networking/sd-wan-deployment-options-diy-vs-cloud-managed.html
|
||||
[15]: https://www.networkworld.com/article/3336483/how-sd-wan-can-improve-your-security-strategy.html
|
||||
[16]: https://www.networkworld.com/article/3284367/sd-wan/10-hot-sd-wan-startups-to-watch.html
|
||||
[17]: https://www.networkworld.com/article/3255291/lan-wan/sd-wan-helps-radiology-firm-cut-costs-scale-bandwidth.html
|
||||
[18]: https://www.networkworld.com/article/3336155/sd-wan-creates-new-security-challenges.html
|
||||
[19]: https://www.facebook.com/NetworkWorld/
|
||||
[20]: https://www.linkedin.com/company/network-world
|
||||
@ -0,0 +1,119 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (ROLLING UPDATE: The impact of COVID-19 on public networks and security)
|
||||
[#]: via: (https://www.networkworld.com/article/3534037/rolling-update-the-impact-of-covid-19-on-public-networks-and-security.html)
|
||||
[#]: author: (Michael Cooney https://www.networkworld.com/author/Michael-Cooney/)
|
||||
|
||||
ROLLING UPDATE: The impact of COVID-19 on public networks and security
|
||||
======
|
||||
Network World updates the latest coronavirus-related networking news
|
||||
Ig0rZh / Getty Images
|
||||
|
||||
_As the coronavirus spreads, public and private companies as well as government entities are requiring employees to work from home, putting unforeseen strain on all manner of networking technologies and causing bandwidth and security concerns. What follows is a round-up of news and traffic updates that Network World will update as needed to help keep up with the ever-changing situation. Check back frequently!_
|
||||
|
||||
**UPDATE 3.27**
|
||||
|
||||
Broadband watchers at [BroadbandNow][1] say users in most of the cities it analyzed are experiencing normal network conditions, suggesting that ISP’s (and their networks) are holding up to the shifting demand. In a March 25 [post][2] the firm wrote: “Encouragingly, many of the areas hit hardest by the spread of the coronavirus are holding up to increased network demand. Cities like Los Angeles, Chicago, Brooklyn, and San Francisco have all experienced little or no disruption. New York City, now the epicenter of the virus in the U.S., has seen a 24% dip out of its previous ten-week range. However, with a new median speed of nearly 52 Mbps, home connections still appear to be holding up overall.”
|
||||
|
||||
**[ Also see [What to consider when deploying a next generation firewall][3]. | Get regularly scheduled insights by [signing up for Network World newsletters][4]. ]**
|
||||
|
||||
Other BroadbandNow findings included:
|
||||
|
||||
* Eighty eight (44%) of the 200 cities it analyzed experienced some degree of network degradation over the past week compared to the 10 weeks prior. However, only 27 (13.5%) cities experienced dips of 20% below range or greater.
|
||||
* Seattle download speeds have continued to hold up over the past week, while New York City’s speeds have fallen out of range by 24%. Both cities are currently heavily affected by the coronavirus pandemic.
|
||||
* Three cities – Austin, Texas, Winston Salem, N.C., and Oxnard, Calif. – have experienced significant degradations, falling out of their 10-week range by more than 40%.
|
||||
|
||||
|
||||
|
||||
Cisco’s Talos threat-intelligence arm [wrote][5] on March 26 about the COVID security threat noting what it called three broad categories of attacks leveraging COVID with known advanced persistent threat participation in: [Malware and phishing campaigns][6] using COVID-themed lures; attacks against organizations that carry out research and other work related to COVID; and fraud and disinformation. From an enterprise security perspective, Talos recommended:
|
||||
|
||||
* Remote access: Do not expose Remote Desktop Protocol (RDP) to the internet. Use secure VPN connections with multi-factor authentication schemes. Network access control packages can be used to ensure that systems attempting to remotely connect to the corporate environment meet a minimum set of security standards such as anti-malware protection, patch levels, etc,. prior to granting them access to corporate resources. Continually identify and remediate access-policy violations.
|
||||
* Identity Management: Protect critical and public-facing applications with multi-factor authentication and supporting corporate policies. Verify that remote-account and access-termination capabilities work as intended in a remote environment.
|
||||
* Endpoint Control: Because many people may be working from home networks, endpoint visibility, protection, and mitigation is now more important than ever. Consider whether remediation and reimaging capabilities will work as intended in a remote environment. Encrypt devices where possible, and add this check to your NAC solution as a gate for connectivity. Another simple method of protecting endpoints is via DNS, such as with [Cisco’s] Umbrella, by blocking the resolution of malicious domains before the host has a chance to make a connection.
|
||||
|
||||
|
||||
|
||||
In an [FAQ][7] about the impact of COVID-19 on fulfilling customer hardware orders, VMware stated: “Some VMware SD-WAN hardware appliances are on backorder as a result of supply chain issues. As a result, we are extending the option to update existing orders with different appliances where inventory is more readily available. Customers may contact a special email hotline with questions related to backordered appliances. Please send an email to [sd-wan-hotline@vmware.com][8] with your questions and include the order number, urgent quantities, and contact information. We will do our best to respond within 48 hours.”
|
||||
|
||||
Cisco said it has been analyzing traffic statistics with major carriers across Asia, Europe, and the Americas, and its data shows that typically, the most congested point in the network occurs at inter-provider peering points, Jonathan Davidson, senior vice president and general manager of Cisco's Mass-Scale Infrastructure Group wrote in a [blog][9] on March 26. “However, the traffic exchanged at these bottlenecks is only a part of the total internet traffic, meaning reports on traffic may be higher overall as private peering and local destinations also contribute to more traffic growth.”
|
||||
|
||||
[][10]
|
||||
|
||||
“Our analysis at these locations shows an increase in traffic of 10% to 33% over normal levels. In every country, traffic spiked with the decision to shut down non-essential businesses and keep people at home. Since then, traffic has remained stable or has experienced a slight uptick over the days that followed,” Davidson stated.
|
||||
|
||||
He said that traffic during peak hours from 6 p.m. and 10 p.m. has increased slightly, but is not the primary driver for the overall inrease. Busy hours have extended to 9 a.m. 10 p.m., although the new busy-hour (9 a.m. to 6 p.m.) traffic is still below the traditional peak hours. "Service providers are certainly paying attention to these changes, but they are not yet a dire concern, as most networks are designed for growth. Current capacities are utilized more over the course of the entire day,” he wrote.
|
||||
|
||||
Spanish multinational telecommunications company [Telefonica][11]’ said IP networks are experiencing traffic increases of close to 40% while mobile voice use is up about 50% and data is up 25%. In general, traffic through IP networks has experienced increases of nearly 40% while mobile use has increased by about 50% for voice and 25% for data. Likewise, traffic from instant-messaging tools such as Whatsapp has increased fivefold in recent days.
|
||||
|
||||
**UPDATE: 3.26**
|
||||
|
||||
* Week over week (ending March 23) [Ookla][12] says it has started to see a degradation of mobile and fixed-broadband performance worldwide. More detail on specific locations is available below. Comparing the week of March 16 to the week of March 9, mean download speed over mobile and fixed broadband decreased in Canada and the U.S. while both remained relatively flat in Mexico.
|
||||
* What is the impact of the coronavirus on corporate network planning? Depends on how long the work-from-home mandate goes on really. Tom Nolle, president of CIMI Corp. [takes an interesting look at the situation][13] saying the shutdown “could eventually produce a major uptick for SD-WAN services, particularly in [managed service provider] Businesses would be much more likely to embark on an SD-WAN VPN adventure that didn’t involve purchase/licensing, favoring a service approach in general, and in particular one with a fairly short contract period.”
|
||||
* Statistics from VPN provider [NordVPN][14] show the growth of VPN usage across the globe. For example, the company said the US has experienced a 65.93% growth in the use of business VPNs since March 11. It reported that mass remote working has contributed towards a rise in desktop (94.09%) and mobile app (0.39%) usage among Americans. Globally, NordVPN teams has seen a 165% spike in the use of business VPNs and business VPN usage in Netherlands (240.49%), Canada (206.29%) and Austria (207.86%) has skyrocketed beyond 200%. Italy has had the most modest growth in business VPN usage at just 10.57%.
|
||||
|
||||
|
||||
|
||||
**UPDATE: 3. 25**:
|
||||
|
||||
* According to [Atlas VPN][15] user data, VPN usage in the US increased by 124% during the last two weeks. VPN usage in the country increased by 71% between March 16 and 22 alone. Atlas said it measured how much traffic traveled through its servers during that period compared to March 9 to 15. The data came from the company's 53,000 weekly users.
|
||||
* Verizon [reports][16] that voice usage, long declining in the age of texting, chat and social media, is up 25% in the last week. The network report shows the primary driver is accessing conference calls. In addition, people are talking longer on mobile devices with wireless voice usage notching a 10% increase and calls lasting 15% longer.
|
||||
* AT&T also [reported][17] increased calling, especially Wi-Fi calling, up 88% on March 22 versus a normal Sunday. It says that consumer home voice calls were up 74% more than an average Sunday; traffic from Netflix dipped after all-time highs on Friday and Saturday; and data traffic due to heavy video streaming between its network and peered networks tied record highs. AT&T said it has deployed portable cell nodes to bolster coverage supporting FirstNet customers in Indiana, Connecticut, New Jersey, California and New York.
|
||||
* Microsoft this week advised users of Office 365 it was throttling back some services:
|
||||
* **OneNote: ** OneNote in Teams will be read-only for commercial tenants, excluding EDU. Users can go to OneNote for the web for editing. Download size and sync frequency of file attachments has been changed. You can find details on these and other OneNote related updates as <http://aka.ms/notesupdates>.
|
||||
* **SharePoint:** We are rescheduling specific backend operations to regional evening and weekend business hours. Impacted capabilities include migration, DLP and delays in file management after uploading a new file, video or image. Reduced video resolution for playback videos.
|
||||
* **Stream:** People timeline has been disabled for newly uploaded videos. Pre-existing videos will not be impacted. Meeting recording video resolution adjusted to 720p.
|
||||
|
||||
|
||||
|
||||
**RELATED COVID-19 NEWS:**
|
||||
|
||||
* Security vendor [Check Point’s Threat Intelligence][18] says that Since January 2020, there have been over 4,000 coronavirus-related domains registered globally. Out of these websites, 3% were found to be malicious and an additional 5% are suspicious. Coronavirus- related domains are 50% more likely to be malicious than other domains registered at the same period, and also higher than recent seasonal themes such as Valentine’s day.
|
||||
* [Orange][19] an IT and communications **services** company aid that has increased its network capacity and upgraded its service platforms. These measures allow it to support the ongoing exponential increase in needs and uses. The number of users connecting to their company's network remotely has already increased by 700% among its customers. It has also doubled the capacity for simultaneous connections on its platforms. The use of remote collaboration solutions such as video conferencing has also risen massively with usage increasing by between 20% to 100%.
|
||||
* Verizon said it has seen a 34% increase in VPN traffic from March 10 to 17. It has also seen a 75% increase in gaming traffic and web traffic increased by just under 20% in that time period according to Verizon.
|
||||
* One week after the CDC declaration of the virus as a pandemic, data analytics and broadband vendor OpenVault wrote on March 19 that:
|
||||
* Subscribers’ average usage during the 9 am-to-5 pm daypart has risen to 6.3 GB, 41.4% higher than the January figure of 4.4 GB.
|
||||
* During the same period, peak hours (6 pm–11 pm) usage has risen 17.2% from 5.0 GB per subscriber in January to 5.87 GB in March.
|
||||
* Overall daily usage has grown from 12.19 GB to 15.46 GB, an increase of 26.8%.
|
||||
* Based on the current rate of growth, OpenVault projected that consumption for March will reach nearly 400 GB per subscriber, an increase of almost 11% over the previous monthly record of 361 GB, established in January of this year. In addition, OpenVault projects a new coronavirus-influenced run rate of 460 GB per subscriber per month going forward.
|
||||
|
||||
|
||||
|
||||
Join the Network World communities on [Facebook][20] and [LinkedIn][21] to comment on topics that are top of mind.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.networkworld.com/article/3534037/rolling-update-the-impact-of-covid-19-on-public-networks-and-security.html
|
||||
|
||||
作者:[Michael Cooney][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.networkworld.com/author/Michael-Cooney/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://broadbandnow.com/
|
||||
[2]: https://broadbandnow.com/report/internet-speed-analysis-march-15th-21st/
|
||||
[3]: https://www.networkworld.com/article/3236448/lan-wan/what-to-consider-when-deploying-a-next-generation-firewall.html
|
||||
[4]: https://www.networkworld.com/newsletters/signup.html
|
||||
[5]: https://blog.talosintelligence.com/2020/03/covid-19-pandemic-threats.html
|
||||
[6]: https://blog.talosintelligence.com/2020/02/coronavirus-themed-malware.html
|
||||
[7]: https://www.vmware.com/company/news/updates/vmware-response-covid-19.html?mid=31381&eid=CVMW2000048242496
|
||||
[8]: mailto:sd-wan-hotline@vmware.com
|
||||
[9]: https://blogs.cisco.com/news/global-traffic-spikes-no-panic-at-the-cisco
|
||||
[10]: https://www.networkworld.com/blog/itaas-and-the-corporate-storage-technology/?utm_source=IDG&utm_medium=promotions&utm_campaign=HPE22140&utm_content=sidebar (ITAAS and Corporate Storage Strategy)
|
||||
[11]: https://www.telefonica.com/en/web/press-office/-/telefonica-announces-measures-related-to-covid-19
|
||||
[12]: https://downdetector.com/?utm_campaign=Ookla%20Insights%20Blog%20Subscription&utm_source=hs_email&utm_medium=email&utm_content=85202785&_hsenc=p2ANqtz--Nj93d_eQyJpsqxrPJyNPtTiMBWBQU984psLyalw51K61e4d1WODareMF5NWFriHY2Uzw3WF7rF-2vSfH5cR53Jg3K5Q&_hsmi=85202785
|
||||
[13]: https://blog.cimicorp.com/?p=4068
|
||||
[14]: https://nordvpnteams.com/
|
||||
[15]: https://atlasvpn.com/blog/lockdowns-and-panic-leads-to-a-124-surge-in-vpn-usage-in-the-us/
|
||||
[16]: https://www.verizon.com/about/news/update-verizon-serve-customers-covid-19
|
||||
[17]: https://about.att.com/pages/COVID-19.html
|
||||
[18]: https://blog.checkpoint.com/2020/03/05/update-coronavirus-themed-domains-50-more-likely-to-be-malicious-than-other-domains/
|
||||
[19]: https://www.orange.com/en/Press-Room/press-releases/press-releases-2020/Orange-is-mobilised-to-ensure-continuity-of-service-for-all-customers-in-France-and-around-the-world
|
||||
[20]: https://www.facebook.com/NetworkWorld/
|
||||
[21]: https://www.linkedin.com/company/network-world
|
||||
@ -0,0 +1,108 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (6 tricks for developing a work from home schedule)
|
||||
[#]: via: (https://opensource.com/article/20/3/work-from-home)
|
||||
[#]: author: (Seth Kenlon https://opensource.com/users/seth)
|
||||
|
||||
6 tricks for developing a work from home schedule
|
||||
======
|
||||
Stay flexible, embrace change, and think of the transition to your home
|
||||
office as an opportunity to create a healthier WFH experience.
|
||||
![Working from home at a laptop][1]
|
||||
|
||||
When you start working from home, one of the first things you might have noticed is that there almost no outside influences on your schedule.
|
||||
|
||||
You probably have meetings—some over [team chat][2] and others over [video][3]— that you have to attend, but otherwise, there's nothing requiring you to do anything at any specific time. What you find out pretty quickly, though, is that there's an invisible influence that sneaks up on you: deadlines.
|
||||
|
||||
This lack of structure fosters procrastination, sometimes willful and other times aimless, followed by frantic sprints to get something done. Learning to mitigate that, along with all the distractions working from home might offer, is often the hardest part of your home-based work.
|
||||
|
||||
Here are a few ways to build in that structure for yourself do you don't end up feeling like you are falling behind.
|
||||
|
||||
### You have always had your own schedule
|
||||
|
||||
Everybody reacts to schedules differently. For some people, schedules offer guidance and comfort. For others, schedules are rigid and oppressive.
|
||||
|
||||
An office space generally provides focus. There might be plenty of distractions at the office, but you usually find a good stretch of time at some point during your day when you can get a big chunk of work done. Even in an office, though, each person actually keeps their own schedule. Your colleague might arrive early in the day, happily completing a day's work in an empty office before anyone else arrives and then spending the rest of the day doing menial tasks and socializing. Another colleague might arrive late and leave early, maximizing time spent in the office for actual work. Still others follow a steady pace throughout the day.
|
||||
|
||||
As you're settling into a WFH routine, take notes, either mentally or physically, on what seems to work well for you. If you like formalized systems, then build a schedule for yourself after a week or two, based on what you've been doing naturally. If there's something that isn't working for you, then drop it from your schedule.
|
||||
|
||||
Once you've found a good rhythm for yourself, you can manage your day with a [to-do list][4] like [todo.txt][5], or if you prefer sledgehammers (or you actually manage a department), you can try a [project management][6] application.
|
||||
|
||||
### Treat yourself as a new hire
|
||||
|
||||
For the first week or two at home, you may find it helpful to treat yourself (and your remote team) as a new hire. Instead of trying to mimic or impose the same schedule you kept at the office or at school, take time to monitor your own activity. It takes time for your body and mind to establish new and comfortable habits, and if you're the kind of person who wanders into a routine, then you need to give yourself time to discover what those habits are.
|
||||
|
||||
For instance, if you're consistently finding that you do your best work right after breakfast, then relegate menial tasks, like responding to email, reviewing tasks, or triaging bug reports, to the early morning, and make sure you have a big task set up for after breakfast. If you're having a hard time maintaining focus, then make time for morning tea so you can relax, reassess your workload, and plan your next step. Be curious about yourself like a manager would be for a brand new employee. Adjust accordingly.
|
||||
|
||||
### There is no guilt to being interrupted at home
|
||||
|
||||
Not everything on your schedule is under your control. If you have children too young for school, or if children are home from school, then their schedules take precedence.
|
||||
|
||||
It's a perceived benefit of working from home that your schedule is more flexible than at an office, but with that assumption, there can sometimes come a little to a lot of guilt. You might feel you're not working "enough" because you have to stop to wake up and feed children, or because you want to take a few play breaks every now and again.
|
||||
|
||||
That's mostly illusory, though, and here is how to think about it. If you swap out "children" for "manager," you might remember some times at the office where your "real" work was interrupted because you had to entertain upper management with sparkly presentations, or complete piles of paperwork for HR, or decompress by chatting with colleagues by the water cooler.
|
||||
|
||||
Your work from home is really no different. There are plenty of distractions, and they're only a problem if you fail to acknowledge and work around them.
|
||||
|
||||
### Making the choice to move beyond the 9-to-5
|
||||
|
||||
Unlike at the office, you're not forced into a rigid and dated 9-to-5 structure. If your day has to start at 7am, contains a lot of breaks, and doesn't end until 7pm, then that's alright. The essential part is to define that as your schedule for yourself (once you've established it as a schedule that works for you; remember to give yourself a few weeks to get a feel for what your schedule actually "wants" to be). Pick your start and end times, establish break times with your housemates, whether they're children, spouses, pets, or roommates/friends. Work when you're supposed to be working, and don't work when you're not scheduled to work. For most of us, colleagues don't need to know exactly when you are online as long as you're available when you're needed. In that case, your hours are your own. If the team is the kind that needs to know, run it by them.
|
||||
|
||||
### Don't forget time for yourself
|
||||
|
||||
It's important to at least establish times you stop thinking about work, no matter what. If you've got a very young child who's not given to staying on any schedule, then you might have to stay more flexible than most. Still, give yourself permission to actively be inactive. Do something you enjoy, even if it feels unproductive. It's normal to spend some idle time at the office to think or intentionally not think. Working from home deserves the same space. If anything, it's even more important as you establish working hours. The goal is to recognize when you're at home and when you're at work.
|
||||
|
||||
Finding stuff to do at work is relatively easy, but sometimes finding things to do to relax can be hard. If you have children, you can collaborate with them using Scratch for [drawing beautiful art][7], [programming video games][8], or even [robotics][9]. For the times you're not necessarily looking to collaborate and need your little one to do some exploration of their own, there are some [great open source alternatives to Minecraft][10], too. If you're interested in getting away from the screen, though, you might try some [Arduino][11] or [Seeeduino][12] gardening projects. Start with some programming, and end up outside in the garden!
|
||||
|
||||
### Choose to see change as exciting
|
||||
|
||||
Some say humans don't generally love change and that we're primarily creatures of habit, so moving from an office into a home office can be upsetting. And yet, invariably, we've shown that change can be exciting and even good.
|
||||
|
||||
Use this thought experiment to remember how much you love change. Would you willingly revert to technology from even two years ago? How about five, or ten?
|
||||
|
||||
If we can embrace change in technology and be uninterested in reverting back, why not embrace change elsewhere?
|
||||
|
||||
When you work from home, you have the opportunity to be willing to explore change. If you find that a meeting time doesn't work for your schedule, mention it to your team. It may not work for them, either, and moving it to a different day could mean making room for a work sprint that knocks out a good chunk of your work for the week. If you find that a tool isn't working out for you, find a different one.
|
||||
|
||||
In fact, some of the most productive people are constantly evaluating new applications and new methods of working. They're constantly learning new things, developing new skills. They don't do this because they need the new skill, at least not by the letter of their work contract, but learning new things often reveals a surprising applicability to something they do need.
|
||||
|
||||
Need some examples? Tinkering with a Raspberry Pi for fun could result in a home server running [useful apps][13] to help you stay informed. [Learning][14] how to [write in Markdown][15] could introduce you to a new and more efficient workflow than you ever knew possible. Setting up a [computer with Linux][16] could reveal a new world of open source software that changes the way you approach problems, and improves the methods you use to solve them. The possibilities are limitless, but if you don't know where to start, you can browse through some of our articles or [cheat sheets][17] for ideas and tips.
|
||||
|
||||
### Working from home is a new opportunity
|
||||
|
||||
The habits we've built up around work aren't always healthy or efficient or fun. If you're starting to work from home, though, it's a chance to reinvent what work means for you. Keep the lines of [communication open][18] with your colleagues, embrace new ideas and the potential of change, and discover how you can be more productive by enjoying yourself and the place you call home (and **$HOME**).
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/20/3/work-from-home
|
||||
|
||||
作者:[Seth Kenlon][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/seth
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/wfh_work_home_laptop_work.png?itok=VFwToeMy (Working from home at a laptop)
|
||||
[2]: https://opensource.com/alternatives/slack
|
||||
[3]: https://opensource.com/alternatives/skype
|
||||
[4]: https://opensource.com/article/19/9/to-do-list-managers-linux
|
||||
[5]: https://opensource.com/article/20/1/open-source-to-do-list
|
||||
[6]: https://opensource.com/article/18/2/agile-project-management-tools
|
||||
[7]: https://opensource.com/article/19/9/drawing-vectors-scratch-3
|
||||
[8]: https://opensource.com/article/18/4/designing-game-scratch-open-jam
|
||||
[9]: https://opensource.com/education/13/8/student-programming-scratch-and-finch
|
||||
[10]: https://opensource.com/alternatives/minecraft
|
||||
[11]: https://opensource.com/article/17/3/arduino-garden-projects
|
||||
[12]: https://opensource.com/article/19/12/seeeduino-nano-review
|
||||
[13]: https://opensource.com/article/20/2/newsboat
|
||||
[14]: https://opensource.com/article/19/9/introduction-markdown
|
||||
[15]: https://opensource.com/article/18/11/markdown-editors
|
||||
[16]: https://opensource.com/article/19/9/found-linux-video-gaming
|
||||
[17]: https://opensource.com/article/20/1/cheat-sheets-guides
|
||||
[18]: https://opensource.com/article/20/3/open-source-working-home
|
||||
@ -1,119 +0,0 @@
|
||||
Translating by MjSeven
|
||||
|
||||
Advanced use of the less text file viewer in Linux
|
||||
======
|
||||
|
||||

|
||||
|
||||
I recently read Scott Nesbitt's article "[Using less to view text files at the Linux command line][1]" and was inspired to share additional tips and tricks I use with `less`.
|
||||
|
||||
### LESS env var
|
||||
|
||||
If you have an environment variable `LESS` defined (e.g., in your `.bashrc`), `less` treats it as a list of options, as if passed on the command line.
|
||||
|
||||
I use this:
|
||||
```
|
||||
LESS='-C -M -I -j 10 -# 4'
|
||||
|
||||
```
|
||||
|
||||
These mean:
|
||||
|
||||
* `-C` – Make full-screen reprints faster by not scrolling from the bottom.
|
||||
* `-M` – Show more information from the last (status) line. You can customize the information shown with `-PM`, but I usually do not bother.
|
||||
* `-I` – Ignore letter case (upper/lower) in searches.
|
||||
* `-j 10` – Show search results in line 10 of the terminal, instead of the first line. This way you have 10 lines of context each time you press `n` (or `N`) to jump to the next (or previous) match.
|
||||
* `-# 4` – Jump four characters to the right or left when pressing the Right or Left arrow key. The default is to jump half of the screen, which I usually find to be too much. Generally speaking, `less` seems to be (at least partially) optimized to the environment it was initially developed in, with slow modems and low-bandwidth internet connections, when it made sense to jump half a screen.
|
||||
|
||||
|
||||
|
||||
### PAGER env var
|
||||
|
||||
Many programs show information using the command set in the `PAGER` environment variable (if it's set). So, you can set `PAGER=less` in your `.bashrc` and have your program run `less`. Check the man page environ(7) (`man 7 environ`) for other such variables.
|
||||
|
||||
### -S
|
||||
|
||||
`-S` tells `less` to chop long lines instead of wrapping them. I rarely find a need for this unless (and until) I've started viewing a file. Fortunately, you can type all command-line options inside `less` as if they were keyboard commands. So, if I want to chop long lines while I'm already in a file, I can simply type `-S`.
|
||||
|
||||
The command-line optiontellsto chop long lines instead of wrapping them. I rarely find a need for this unless (and until) I've started viewing a file. Fortunately, you can type all command-line options insideas if they were keyboard commands. So, if I want to chop long lines while I'm already in a file, I can simply type
|
||||
|
||||
Here's an example I use a lot:
|
||||
```
|
||||
su - postgres
|
||||
|
||||
export PAGER=less # Because I didn't bother editing postgres' .bashrc on all the machines I use it on
|
||||
|
||||
psql
|
||||
|
||||
```
|
||||
|
||||
Sometimes when I later view the output of a `SELECT` command with a very wide output, I type `-S` so it will be formatted nicely. If it jumps too far when I press the Right arrow to see more (because I didn't set `-#`), I can type `-#8`, then each Right arrow press will move eight characters to the right.
|
||||
|
||||
Sometimes after typing `-S` too many times, I exit psql and run it again after entering:
|
||||
```
|
||||
export LESS=-S
|
||||
|
||||
```
|
||||
|
||||
### F
|
||||
|
||||
The command `F` makes `less` work like `tail -f`—waiting until more data is added to the file before showing it. One advantage this has over `tail -f` is that highlighting search matches still works. So you can enter `less /var/log/logfile`, search for something—which will highlight all occurrences of it (unless you used `-g`)—and then press `F`. When more data is written to the log, `less` will show it and highlight the new matches.
|
||||
|
||||
After you press `F`, you can press `Ctrl+C` to stop it from looking for new data (this will not kill it); go back into the file to see older stuff, search for other things, etc.; and then press `F` again to look at more new data.
|
||||
|
||||
### Searching
|
||||
|
||||
Searches use the system's regexp library, and this usually means you can use extended regular expressions. In particular, searching for `one|two|three` will find and highlight all occurrences of one, two, or three.
|
||||
|
||||
Another pattern I use a lot, especially with wide log lines (e.g., ones that span more than one terminal line), is `.*something.*`, which highlights the entire line. This pattern makes it much easier to see where a line starts and finishes. I also combine these, such as: `.*one thing.*|.*another thing.*`, or `key: .*|.*marker.*` to see the contents of `key` (e.g., in a log file with a dump of some dictionary/hash) and highlight relevant marker lines (so I have a context), or even, if I know the value is surrounded by quotes:
|
||||
```
|
||||
key: '[^']*'|.*marker.*
|
||||
|
||||
```
|
||||
|
||||
`less` maintains a history of your search items and saves them to disk for future invocations. When you press `/` (or `?`), you can go through this history with the Up or Down arrow (as well as do basic line editing).
|
||||
|
||||
I stumbled upon what seems to be a very useful feature when skimming through the `less` man page while writing this article: skipping uninteresting lines with `&!pattern`. For example, while looking for something in `/var/log/messages`, I used to iterate through this list of commands:
|
||||
```
|
||||
cat /var/log/messages | egrep -v 'systemd: Started Session' | less
|
||||
|
||||
cat /var/log/messages | egrep -v 'systemd: Started Session|systemd: Starting Session' | less
|
||||
|
||||
cat /var/log/messages | egrep -v 'systemd: Started Session|systemd: Starting Session|User Slice' | less
|
||||
|
||||
cat /var/log/messages | egrep -v 'systemd: Started Session|systemd: Starting Session|User Slice|dbus' | less
|
||||
|
||||
cat /var/log/messages | egrep -v 'systemd: Started Session|systemd: Starting Session|User Slice|dbus|PackageKit Daemon' | less
|
||||
|
||||
```
|
||||
|
||||
But now I know how to do the same thing within `less`. For example, I can type `&!systemd: Started Session`, then decide I want to get rid of `systemd: Starting Session`, so I add it by typing `&!` and use the Up arrow to get the previous search from the history. Then I type `|systemd: Starting Session` and press `Enter`, continuing to add more items the same way until I filter out enough to see the more interesting stuff.
|
||||
|
||||
### =
|
||||
|
||||
The command `=` shows more information about the file and location, even more than `-M`. If the file is very long, and calculating `=` takes too long, you can press `Ctrl+C` and it will stop trying.
|
||||
|
||||
If the content you're viewing is from a pipe rather than a file, `=` (and `-M`) will not show what it does not know, including the number of lines and bytes in the file. To see that data, if you know that `command` will finish quickly, you can jump to the end with `G`, and then `less` will start showing that information.
|
||||
|
||||
If you press `G` and the command writing to the pipe takes longer than expected, you can press `Ctrl+C`, and the command will be killed. Pressing `Ctrl+C` will kill it even if you didn't press `G`, so be careful not to press `Ctrl+C` accidentally if you don't intend to kill it. For this reason, if the command does something (that is, it's not only showing information), it's usually safer to write its output to a file and view the file in a separate terminal, instead of using a pipe.
|
||||
|
||||
### Why you need less
|
||||
|
||||
`less` is a very powerful program, and contrary to newer contenders in this space, such as `most` and `moar`, you are likely to find it on almost all the systems you use, just like `vi`. So, even if you use GUI viewers or editors, it's worth investing some time going through the `less` man page, at least to get a feeling of what's available. This way, when you need to do something that might be covered by existing functionality, you'll know to search the manual page or the internet to find what you need.
|
||||
|
||||
For more information, visit the [less home page][2]. The site has a nice FAQ with more tips and tricks.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/5/advanced-use-less-text-file-viewer
|
||||
|
||||
作者:[Yedidyah Bar David][a]
|
||||
选题:[lujun9972](https://github.com/lujun9972)
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://opensource.com/users/didib
|
||||
[1]:http://opensource.com/article/18/4/using-less-view-text-files-command-line
|
||||
[2]:http://www.greenwoodsoftware.com/less/
|
||||
@ -1,5 +1,5 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: translator: (MFGJT)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
|
||||
@ -1,330 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (ffsend – Easily And Securely Share Files From Linux Command Line Using Firefox Send Client)
|
||||
[#]: via: (https://www.2daygeek.com/ffsend-securely-share-files-folders-from-linux-command-line-using-firefox-send-client/)
|
||||
[#]: author: (Vinoth Kumar https://www.2daygeek.com/author/vinoth/)
|
||||
|
||||
ffsend – Easily And Securely Share Files From Linux Command Line Using Firefox Send Client
|
||||
======
|
||||
|
||||
Linux users were preferred to go with scp or rsync for files or folders copy.
|
||||
|
||||
However, so many new options are coming to Linux because it’s a opensource.
|
||||
|
||||
Anyone can develop a secure software for Linux.
|
||||
|
||||
We had written multiple articles in our site in the past about this topic.
|
||||
|
||||
Even, today we are going to discuss the same kind of topic called ffsend.
|
||||
|
||||
Those are **[OnionShare][1]** , **[Magic Wormhole][2]** , **[Transfer.sh][3]** and **[Dcp – Dat Copy][4]**.
|
||||
|
||||
### What’s ffsend?
|
||||
|
||||
[ffsend][5] is a command line Firefox Send client that allow users to transfer and receive files and folders through command line.
|
||||
|
||||
It allow us to easily and securely share files and directories from the command line through a safe, private and encrypted link using a single simple command.
|
||||
|
||||
Files are shared using the Send service and the allowed file size is up to 2GB.
|
||||
|
||||
Others are able to download these files with this tool, or through their web browser.
|
||||
|
||||
All files are always encrypted on the client, and secrets are never shared with the remote host.
|
||||
|
||||
Additionally you can add a password for the file upload.
|
||||
|
||||
The uploaded files will be removed after the download (default count is 1 up to 10) or after 24 hours. This will make sure that your files does not remain online forever.
|
||||
|
||||
This tool is currently in the alpha phase. Use at your own risk. Also, only limited installation options are available right now.
|
||||
|
||||
### ffsend Features:
|
||||
|
||||
* Fully featured and friendly command line tool
|
||||
* Upload and download files and directories securely
|
||||
* Always encrypted on the client
|
||||
* Additional password protection, generation and configurable download limits
|
||||
* Built-in file and directory archiving and extraction
|
||||
* History tracking your files for easy management
|
||||
* Ability to use your own Send host
|
||||
* Inspect or delete shared files
|
||||
* Accurate error reporting
|
||||
* Low memory footprint, due to encryption and download/upload streaming
|
||||
* Intended to be used in scripts without interaction
|
||||
|
||||
|
||||
|
||||
### How To Install ffsend in Linux?
|
||||
|
||||
There is no package for each distributions except Debian and Arch Linux systems. However, we can easily get this utility by downloading the prebuilt appropriate binaries file based on the operating system and architecture.
|
||||
|
||||
Run the below command to download the latest available version for your operating system.
|
||||
|
||||
```
|
||||
$ wget https://github.com/timvisee/ffsend/releases/download/v0.1.2/ffsend-v0.1.2-linux-x64.tar.gz
|
||||
```
|
||||
|
||||
Extract the tar archive using the following command.
|
||||
|
||||
```
|
||||
$ tar -xvf ffsend-v0.1.2-linux-x64.tar.gz
|
||||
```
|
||||
|
||||
Run the following command to identify your path variable.
|
||||
|
||||
```
|
||||
$ echo $PATH
|
||||
/home/daygeek/.cargo/bin:/usr/local/bin:/usr/local/sbin:/usr/bin:/usr/lib/jvm/default/bin:/usr/bin/site_perl:/usr/bin/vendor_perl:/usr/bin/core_perl
|
||||
```
|
||||
|
||||
As i told previously, just move the executable file to your path directory.
|
||||
|
||||
```
|
||||
$ sudo mv ffsend /usr/local/sbin
|
||||
```
|
||||
|
||||
Run the `ffsend` command alone to get the basic usage information.
|
||||
|
||||
```
|
||||
$ ffsend
|
||||
ffsend 0.1.2
|
||||
Usage: ffsend [FLAGS] ...
|
||||
|
||||
Easily and securely share files from the command line.
|
||||
A fully featured Firefox Send client.
|
||||
|
||||
Missing subcommand. Here are the most used:
|
||||
ffsend upload ...
|
||||
ffsend download ...
|
||||
|
||||
To show all subcommands, features and other help:
|
||||
ffsend help [SUBCOMMAND]
|
||||
```
|
||||
|
||||
For Arch Linux based users can easily install it with help of **[AUR Helper][6]** , as this package is available in AUR repository.
|
||||
|
||||
```
|
||||
$ yay -S ffsend
|
||||
```
|
||||
|
||||
For **`Debian/Ubuntu`** systems, use **[DPKG Command][7]** to install ffsend.
|
||||
|
||||
```
|
||||
$ wget https://github.com/timvisee/ffsend/releases/download/v0.1.2/ffsend_0.1.2_amd64.deb
|
||||
$ sudo dpkg -i ffsend_0.1.2_amd64.deb
|
||||
```
|
||||
|
||||
### How To Send A File Using ffsend?
|
||||
|
||||
It’s not complicated. We can easily send a file using simple syntax.
|
||||
|
||||
**Syntax:**
|
||||
|
||||
```
|
||||
$ ffsend upload [/Path/to/the/file/name]
|
||||
```
|
||||
|
||||
In the following example, we are going to upload a file called `passwd-up1.sh`. Once you upload the file then you will be getting the unique URL.
|
||||
|
||||
```
|
||||
$ ffsend upload passwd-up1.sh --copy
|
||||
Upload complete
|
||||
Share link: https://send.firefox.com/download/a4062553f4/#yy2_VyPaUMG5HwXZzYRmpQ
|
||||
```
|
||||
|
||||
![][9]
|
||||
|
||||
Just download the above unique URL to get the file in any remote system.
|
||||
|
||||
**Syntax:**
|
||||
|
||||
```
|
||||
$ ffsend download [Generated URL]
|
||||
```
|
||||
|
||||
Output for the above command.
|
||||
|
||||
```
|
||||
$ ffsend download https://send.firefox.com/download/a4062553f4/#yy2_VyPaUMG5HwXZzYRmpQ
|
||||
Download complete
|
||||
```
|
||||
|
||||
![][10]
|
||||
|
||||
Use the following syntax format for directory upload.
|
||||
|
||||
```
|
||||
$ ffsend upload [/Path/to/the/Directory] --copy
|
||||
```
|
||||
|
||||
In this example, we are going to upload `2g` directory.
|
||||
|
||||
```
|
||||
$ ffsend upload /home/daygeek/2g --copy
|
||||
You've selected a directory, only a single file may be uploaded.
|
||||
Archive the directory into a single file? [Y/n]: y
|
||||
Archiving...
|
||||
Upload complete
|
||||
Share link: https://send.firefox.com/download/90aa5cfe67/#hrwu6oXZRG2DNh8vOc3BGg
|
||||
```
|
||||
|
||||
Just download the above generated the unique URL to get a folder in any remote system.
|
||||
|
||||
```
|
||||
$ ffsend download https://send.firefox.com/download/90aa5cfe67/#hrwu6oXZRG2DNh8vOc3BGg
|
||||
You're downloading an archive, extract it into the selected directory? [Y/n]: y
|
||||
Extracting...
|
||||
Download complete
|
||||
```
|
||||
|
||||
As this already send files through a safe, private, and encrypted link. However, if you would like to add a additional security at your level. Yes, you can add a password for a file.
|
||||
|
||||
```
|
||||
$ ffsend upload file-copy-rsync.sh --copy --password
|
||||
Password:
|
||||
Upload complete
|
||||
Share link: https://send.firefox.com/download/0742d24515/#P7gcNiwZJ87vF8cumU71zA
|
||||
```
|
||||
|
||||
It will prompt you to update a password when you are trying to download a file in the remote system.
|
||||
|
||||
```
|
||||
$ ffsend download https://send.firefox.com/download/0742d24515/#P7gcNiwZJ87vF8cumU71zA
|
||||
This file is protected with a password.
|
||||
Password:
|
||||
Download complete
|
||||
```
|
||||
|
||||
Alternatively you can limit a download speed by providing the download speed while uploading a file.
|
||||
|
||||
```
|
||||
$ ffsend upload file-copy-scp.sh --copy --downloads 10
|
||||
Upload complete
|
||||
Share link: https://send.firefox.com/download/23cb923c4e/#LVg6K0CIb7Y9KfJRNZDQGw
|
||||
```
|
||||
|
||||
Just download the above unique URL to get a file in any remote system.
|
||||
|
||||
```
|
||||
ffsend download https://send.firefox.com/download/23cb923c4e/#LVg6K0CIb7Y9KfJRNZDQGw
|
||||
Download complete
|
||||
```
|
||||
|
||||
If you want to see more details about the file, use the following format. It will shows you the file name, file size, Download counts and when it will going to expire.
|
||||
|
||||
**Syntax:**
|
||||
|
||||
```
|
||||
$ ffsend info [Generated URL]
|
||||
|
||||
$ ffsend info https://send.firefox.com/download/23cb923c4e/#LVg6K0CIb7Y9KfJRNZDQGw
|
||||
ID: 23cb923c4e
|
||||
Name: file-copy-scp.sh
|
||||
Size: 115 B
|
||||
MIME: application/x-sh
|
||||
Downloads: 3 of 10
|
||||
Expiry: 23h58m (86280s)
|
||||
```
|
||||
|
||||
You can view your transaction history using the following format.
|
||||
|
||||
```
|
||||
$ ffsend history
|
||||
# LINK EXPIRY
|
||||
1 https://send.firefox.com/download/23cb923c4e/#LVg6K0CIb7Y9KfJRNZDQGw 23h57m
|
||||
2 https://send.firefox.com/download/0742d24515/#P7gcNiwZJ87vF8cumU71zA 23h55m
|
||||
3 https://send.firefox.com/download/90aa5cfe67/#hrwu6oXZRG2DNh8vOc3BGg 23h52m
|
||||
4 https://send.firefox.com/download/a4062553f4/#yy2_VyPaUMG5HwXZzYRmpQ 23h46m
|
||||
5 https://send.firefox.com/download/74ff30e43e/#NYfDOUp_Ai-RKg5g0fCZXw 23h44m
|
||||
6 https://send.firefox.com/download/69afaab1f9/#5z51_94jtxcUCJNNvf6RcA 23h43m
|
||||
```
|
||||
|
||||
If you don’t want the link anymore then we can delete it.
|
||||
|
||||
**Syntax:**
|
||||
|
||||
```
|
||||
$ ffsend delete [Generated URL]
|
||||
|
||||
$ ffsend delete https://send.firefox.com/download/69afaab1f9/#5z51_94jtxcUCJNNvf6RcA
|
||||
File deleted
|
||||
```
|
||||
|
||||
Alternatively this can be done using firefox browser by opening the page <https://send.firefox.com/>.
|
||||
|
||||
Just drag and drop a file to upload it.
|
||||
![][11]
|
||||
|
||||
Once the file is downloaded, it will show you that 100% download completed.
|
||||
![][12]
|
||||
|
||||
To check other possible options, navigate to man page or help page.
|
||||
|
||||
```
|
||||
$ ffsend --help
|
||||
ffsend 0.1.2
|
||||
Tim Visee
|
||||
Easily and securely share files from the command line.
|
||||
A fully featured Firefox Send client.
|
||||
|
||||
USAGE:
|
||||
ffsend [FLAGS] [OPTIONS] [SUBCOMMAND]
|
||||
|
||||
FLAGS:
|
||||
-f, --force Force the action, ignore warnings
|
||||
-h, --help Prints help information
|
||||
-i, --incognito Don't update local history for actions
|
||||
-I, --no-interact Not interactive, do not prompt
|
||||
-q, --quiet Produce output suitable for logging and automation
|
||||
-V, --version Prints version information
|
||||
-v, --verbose Enable verbose information and logging
|
||||
-y, --yes Assume yes for prompts
|
||||
|
||||
OPTIONS:
|
||||
-H, --history Use the specified history file [env: FFSEND_HISTORY]
|
||||
-t, --timeout Request timeout (0 to disable) [env: FFSEND_TIMEOUT]
|
||||
-T, --transfer-timeout Transfer timeout (0 to disable) [env: FFSEND_TRANSFER_TIMEOUT]
|
||||
|
||||
SUBCOMMANDS:
|
||||
upload Upload files [aliases: u, up]
|
||||
download Download files [aliases: d, down]
|
||||
debug View debug information [aliases: dbg]
|
||||
delete Delete a shared file [aliases: del]
|
||||
exists Check whether a remote file exists [aliases: e]
|
||||
help Prints this message or the help of the given subcommand(s)
|
||||
history View file history [aliases: h]
|
||||
info Fetch info about a shared file [aliases: i]
|
||||
parameters Change parameters of a shared file [aliases: params]
|
||||
password Change the password of a shared file [aliases: pass, p]
|
||||
|
||||
The public Send service that is used as default host is provided by Mozilla.
|
||||
This application is not affiliated with Mozilla, Firefox or Firefox Send.
|
||||
```
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.2daygeek.com/ffsend-securely-share-files-folders-from-linux-command-line-using-firefox-send-client/
|
||||
|
||||
作者:[Vinoth Kumar][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.2daygeek.com/author/vinoth/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.2daygeek.com/onionshare-secure-way-to-share-files-sharing-tool-linux/
|
||||
[2]: https://www.2daygeek.com/wormhole-securely-share-files-from-linux-command-line/
|
||||
[3]: https://www.2daygeek.com/transfer-sh-easy-fast-way-share-files-over-internet-from-command-line/
|
||||
[4]: https://www.2daygeek.com/dcp-dat-copy-secure-way-to-transfer-files-between-linux-systems/
|
||||
[5]: https://github.com/timvisee/ffsend
|
||||
[6]: https://www.2daygeek.com/category/aur-helper/
|
||||
[7]: https://www.2daygeek.com/dpkg-command-to-manage-packages-on-debian-ubuntu-linux-mint-systems/
|
||||
[8]: data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7
|
||||
[9]: https://www.2daygeek.com/wp-content/uploads/2019/01/ffsend-easily-and-securely-share-files-from-linux-command-line-using-firefox-send-client-1.png
|
||||
[10]: https://www.2daygeek.com/wp-content/uploads/2019/01/ffsend-easily-and-securely-share-files-from-linux-command-line-using-firefox-send-client-2.png
|
||||
[11]: https://www.2daygeek.com/wp-content/uploads/2019/01/ffsend-easily-and-securely-share-files-from-linux-command-line-using-firefox-send-client-3.png
|
||||
[12]: https://www.2daygeek.com/wp-content/uploads/2019/01/ffsend-easily-and-securely-share-files-from-linux-command-line-using-firefox-send-client-4.png
|
||||
@ -1,96 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (MFGJT)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (9 ways to save the planet)
|
||||
[#]: via: (https://opensource.com/article/19/4/save-planet)
|
||||
[#]: author: (Jen Wike Huger https://opensource.com/users/jen-wike/users/alanfdoss/users/jmpearce)
|
||||
|
||||
9 ways to save the planet
|
||||
======
|
||||
These ideas have an open source twist.
|
||||
![][1]
|
||||
|
||||
What can be done to help save the planet? The question can seem depressing at a time when it feels like an individual's contribution isn't enough. But, who are we Earth dwellers if not for a collection of individuals? So, I asked our writer community to share ways that open source software or hardware can be used to make a difference. Here's what I heard back.
|
||||
|
||||
### 9 ways to save the planet with an open source twist
|
||||
|
||||
**1.** **Disable the blinking cursor in your terminal.**
|
||||
|
||||
It might sound silly, but the trivial, blinking cursor can cause up to [2 watts per hour of extra power consumption][2]. To disable it, go to Terminal Settings: Edit > Preferences > Cursor > Cursor blinking > Disabled.
|
||||
|
||||
_Recommended by Mars Toktonaliev_
|
||||
|
||||
**2\. Reduce your consumption of animal products and processed foods.**
|
||||
|
||||
One way to do this is to add these open source apps to your phone: Daily Dozen, OpenFoodFacts, OpenVegeMap, and Food Restrictions. These apps will help you eat a healthy, plant-based diet, find vegan- and vegetarian-friendly restaurants, and communicate your dietary needs to others, even if they do not speak the same language. To learn more about these apps read [_4 open source apps to support eating a plant-based diet_][3].
|
||||
|
||||
_Recommendation by Joshua Allen Holm_
|
||||
|
||||
**3\. Recycle old computers.**
|
||||
|
||||
How? With Linux, of course. Pay it forward by giving creating a new computer for someone who can't one and keep a computer out of the landfill. Here's how we do it at [The Asian Penguins][4].
|
||||
|
||||
_Recommendation by Stu Keroff_
|
||||
|
||||
**4\. Turn off devices when you're not using them.**
|
||||
|
||||
Use "smart power strips" that have a "master" outlet and several "controlled" outlets. Plug your PC into the master outlet, and when you turn on the computer, your monitor, printer, and anything else plugged into the controlled outlets turns on too. A simpler, low-tech solution is a power strip with a timer. That's what I use at home. You can use switches on the timer to set a handy schedule to turn the power on and off at specific times. Automatically turn off your network printer when no one is at home. Or for my six-year-old laptop, extend the life of the battery with a schedule to alternate when it's running from wall power (outlet is on) and when it's running from the battery (outlet is off).
|
||||
|
||||
_Recommended by Jim Hall_
|
||||
|
||||
**5\. Reduce the use of your HVAC system.**
|
||||
|
||||
Sunlight shining through windows adds a lot of heat to your home during the summer. Use Home Assistant to [automatically adjust][5] window blinds and awnings [based on the time of day][6], or even based on the angle of the sun.
|
||||
|
||||
_Recommended by Michael Hrivnak_
|
||||
|
||||
**6\. Turn your thermostat off or to a lower setting while you're away.**
|
||||
|
||||
If your home thermostat has an "Away" feature, activating it on your way out the door is easy to forget. With a touch of automation, any connected thermostat can begin automatically saving energy while you're not home. [Stataway][7] is one such project that uses your phone's GPS coordinates to determine when it should set your thermostat to "Home" or "Away".
|
||||
|
||||
_Recommended by Michael Hrivnak_
|
||||
|
||||
**7\. Save computing power for later.**
|
||||
|
||||
I have an idea: Create a script that can read the power output from an alternative energy array (wind and solar) and begin turning on servers (taking them from a power-saving sleep mode to an active mode) in a computing cluster until the overload power is used (whatever excess is produced beyond what can be stored/buffered for later use). Then use the overload power during high-production times for compute-intensive projects like rendering. This process would be essentially free of cost because the power can't be buffered for other uses. I'm sure the monitoring, power management, and server array tools must exist to do this. Then, it's just an integration problem, making it all work together.
|
||||
|
||||
_Recommended by Terry Hancock_
|
||||
|
||||
**8\. Turn off exterior lights.**
|
||||
|
||||
Light pollution affects more than 80% of the world's population, according to the [World Atlas of Artificial Night Sky Brightness][8], published (Creative Commons Attribution-NonCommercial 4.0) in 2016 in the open access journal _Science Advances_. Turning off exterior lights is a quick way to benefit wildlife, human health, our ability to enjoy the night sky, and of course energy consumption. Visit [darksky.org][9] for more ideas on how to reduce the impact of your exterior lighting.
|
||||
|
||||
_Recommended by Michael Hrivnak_
|
||||
|
||||
**9\. Reduce your CPU count.**
|
||||
|
||||
For me, I remember I used to have a whole bunch of computers running in my basement as my IT playground/lab. I've become more conscious now of power consumption and so have really drastically reduced my CPU count. I like to take advantage of VMs, zones, containers... that type of technology a lot more these days. Also, I'm really glad that small form factor and SoC computers, such as the Raspberry Pi, exist because I can do a lot with one, such as run a DNS or Web server, without heating the room and running up my electricity bill.
|
||||
|
||||
P.S. All of these computers are running Linux, FreeBSD, or Raspbian!
|
||||
|
||||
_Recommended by Alan Formy-Duvall_
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/4/save-planet
|
||||
|
||||
作者:[Jen Wike Huger ][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/jen-wike/users/alanfdoss/users/jmpearce
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/pixelated-world.png?itok=fHjM6m53
|
||||
[2]: https://www.redhat.com/archives/fedora-devel-list/2009-January/msg02406.html
|
||||
[3]: https://opensource.com/article/19/4/apps-plant-based-diets
|
||||
[4]: https://opensource.com/article/19/2/asian-penguins-close-digital-divide
|
||||
[5]: https://www.home-assistant.io/docs/automation/trigger/#sun-trigger
|
||||
[6]: https://www.home-assistant.io/components/cover/
|
||||
[7]: https://github.com/mhrivnak/stataway
|
||||
[8]: http://advances.sciencemag.org/content/2/6/e1600377
|
||||
[9]: http://darksky.org/
|
||||
@ -1,235 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Run your blog on GitHub Pages with Python)
|
||||
[#]: via: (https://opensource.com/article/19/5/run-your-blog-github-pages-python)
|
||||
[#]: author: (Erik O'Shaughnessy https://opensource.com/users/jnyjny/users/jasperzanjani/users/jasperzanjani/users/jasperzanjani/users/jnyjny/users/jasperzanjani)
|
||||
|
||||
Run your blog on GitHub Pages with Python
|
||||
======
|
||||
Create a blog with Pelican, a Python-based blogging platform that works
|
||||
well with GitHub.
|
||||
![Raspberry Pi and Python][1]
|
||||
|
||||
[GitHub][2] is a hugely popular web service for source code control that uses [Git][3] to synchronize local files with copies kept on GitHub's servers so you can easily share and back up your work.
|
||||
|
||||
In addition to providing a user interface for code repositories, GitHub also enables users to [publish web pages][4] directly from a repository. The website generation package GitHub recommends is [Jekyll][5], written in Ruby. Since I'm a bigger fan of [Python][6], I prefer [Pelican][7], a Python-based blogging platform that works well with GitHub.
|
||||
|
||||
Pelican and Jekyll both transform content written in [Markdown][8] or [reStructuredText][9] into HTML to generate static websites, and both generators support themes that allow unlimited customization.
|
||||
|
||||
In this article, I'll describe how to install Pelican, set up your GitHub repository, run a quickstart helper, write some Markdown files, and publish your first page. I'll assume that you have a [GitHub account][10], are comfortable with [basic Git commands][11], and want to publish a blog using Pelican.
|
||||
|
||||
### Install Pelican and create the repo
|
||||
|
||||
First things first, Pelican (and **ghp-import** ) must be installed on your local machine. This is super easy with [pip][12], the Python package installation tool (you have pip right?):
|
||||
|
||||
|
||||
```
|
||||
`$ pip install pelican ghp-import`
|
||||
```
|
||||
|
||||
Next, open a browser and create a new repository on GitHub for your sweet new blog. Name it as follows (substituting your GitHub username for <username> here and throughout this tutorial):
|
||||
|
||||
|
||||
```
|
||||
`https://GitHub.com/username/username.github.io`
|
||||
```
|
||||
|
||||
Leave it empty; we will fill it with compelling blog content in a moment.
|
||||
|
||||
Using a command line (you command line right?), clone your empty Git repository to your local machine:
|
||||
|
||||
|
||||
```
|
||||
$ git clone <https://GitHub.com/username/username.github.io> blog
|
||||
$ cd blog
|
||||
```
|
||||
|
||||
### That one weird trick…
|
||||
|
||||
Here's a not-super-obvious trick about publishing web content on GitHub. For user pages (pages hosted in repos named _username.github.io_ ), the content is served from the **master** branch.
|
||||
|
||||
I strongly prefer not to keep all the Pelican configuration files and raw Markdown files in **master** , rather just the web content. So I keep the Pelican configuration and the raw content in a separate branch I like to call **content**. (You can call it whatever you want, but the following instructions will call it **content**.) I like this structure since I can throw away all the files in **master** and re-populate it with the **content** branch.
|
||||
|
||||
|
||||
```
|
||||
$ git checkout -b content
|
||||
Switched to a new branch 'content'
|
||||
```
|
||||
|
||||
### Configure Pelican
|
||||
|
||||
Now it's time for content configuration. Pelican provides a great initialization tool called **pelican-quickstart** that will ask you a series of questions about your blog.
|
||||
|
||||
|
||||
```
|
||||
$ pelican-quickstart
|
||||
Welcome to pelican-quickstart v3.7.1.
|
||||
|
||||
This script will help you create a new Pelican-based website.
|
||||
|
||||
Please answer the following questions so this script can generate the files
|
||||
needed by Pelican.
|
||||
|
||||
> Where do you want to create your new web site? [.]
|
||||
> What will be the title of this web site? Super blog
|
||||
> Who will be the author of this web site? username
|
||||
> What will be the default language of this web site? [en]
|
||||
> Do you want to specify a URL prefix? e.g., <http://example.com> (Y/n) n
|
||||
> Do you want to enable article pagination? (Y/n)
|
||||
> How many articles per page do you want? [10]
|
||||
> What is your time zone? [Europe/Paris] US/Central
|
||||
> Do you want to generate a Fabfile/Makefile to automate generation and publishing? (Y/n) y
|
||||
> Do you want an auto-reload & simpleHTTP script to assist with theme and site development? (Y/n) y
|
||||
> Do you want to upload your website using FTP? (y/N) n
|
||||
> Do you want to upload your website using SSH? (y/N) n
|
||||
> Do you want to upload your website using Dropbox? (y/N) n
|
||||
> Do you want to upload your website using S3? (y/N) n
|
||||
> Do you want to upload your website using Rackspace Cloud Files? (y/N) n
|
||||
> Do you want to upload your website using GitHub Pages? (y/N) y
|
||||
> Is this your personal page (username.github.io)? (y/N) y
|
||||
Done. Your new project is available at /Users/username/blog
|
||||
```
|
||||
|
||||
You can take the defaults on every question except:
|
||||
|
||||
* Website title, which should be unique and special
|
||||
* Website author, which can be a personal username or your full name
|
||||
* Time zone, which may not be in Paris
|
||||
* Upload to GitHub Pages, which is a "y" in our case
|
||||
|
||||
|
||||
|
||||
After answering all the questions, Pelican leaves the following in the current directory:
|
||||
|
||||
|
||||
```
|
||||
$ ls
|
||||
Makefile content/ develop_server.sh*
|
||||
fabfile.py output/ pelicanconf.py
|
||||
publishconf.py
|
||||
```
|
||||
|
||||
You can check out the [Pelican docs][13] to find out how to use those files, but we're all about getting things done _right now_. No, I haven't read the docs yet either.
|
||||
|
||||
### Forge on
|
||||
|
||||
Add all the Pelican-generated files to the **content** branch of the local Git repo, commit the changes, and push the local changes to the remote repo hosted on GitHub by entering:
|
||||
|
||||
|
||||
```
|
||||
$ git add .
|
||||
$ git commit -m 'initial pelican commit to content'
|
||||
$ git push origin content
|
||||
```
|
||||
|
||||
This isn't super exciting, but it will be handy if we need to revert edits to one of these files.
|
||||
|
||||
### Finally getting somewhere
|
||||
|
||||
OK, now you can get bloggy! All of your blog posts, photos, images, PDFs, etc., will live in the **content** directory, which is initially empty. To begin creating a first post and an About page with a photo, enter:
|
||||
|
||||
|
||||
```
|
||||
$ cd content
|
||||
$ mkdir pages images
|
||||
$ cp /Users/username/SecretStash/HotPhotoOfMe.jpg images
|
||||
$ touch first-post.md
|
||||
$ touch pages/about.md
|
||||
```
|
||||
|
||||
Next, open the empty file **first-post.md** in your favorite text editor and add the following:
|
||||
|
||||
|
||||
```
|
||||
title: First Post on My Sweet New Blog
|
||||
date: <today's date>
|
||||
author: Your Name Here
|
||||
|
||||
# I am On My Way To Internet Fame and Fortune!
|
||||
|
||||
This is my first post on my new blog. While not super informative it
|
||||
should convey my sense of excitement and eagerness to engage with you,
|
||||
the reader!
|
||||
```
|
||||
|
||||
The first three lines contain metadata that Pelican uses to organize things. There are lots of different metadata you can put there; again, the docs are your best bet for learning more about the options.
|
||||
|
||||
Now, open the empty file **pages/about.md** and add this text:
|
||||
|
||||
|
||||
```
|
||||
title: About
|
||||
date: <today's date>
|
||||
|
||||
![So Schmexy][my_sweet_photo]
|
||||
|
||||
Hi, I am <username> and I wrote this epic collection of Interweb
|
||||
wisdom. In days of yore, much of this would have been deemed sorcery
|
||||
and I would probably have been burned at the stake.
|
||||
|
||||
😆
|
||||
|
||||
[my_sweet_photo]: {filename}/images/HotPhotoOfMe.jpg
|
||||
```
|
||||
|
||||
You now have three new pieces of web content in your content directory. Of the content branch. That's a lot of content.
|
||||
|
||||
### Publish
|
||||
|
||||
Don't worry; the payoff is coming!
|
||||
|
||||
All that's left to do is:
|
||||
|
||||
* Run Pelican to generate the static HTML files in **output** : [code]`$ pelican content -o output -s publishconf.py`
|
||||
```
|
||||
* Use **ghp-import** to add the contents of the **output** directory to the **master** branch: [code]`$ ghp-import -m "Generate Pelican site" --no-jekyll -b master output`
|
||||
```
|
||||
* Push the local master branch to the remote repo: [code]`$ git push origin master`
|
||||
```
|
||||
* Commit and push the new content to the **content** branch: [code] $ git add content
|
||||
$ git commit -m 'added a first post, a photo and an about page'
|
||||
$ git push origin content
|
||||
```
|
||||
|
||||
|
||||
|
||||
### OMG, I did it!
|
||||
|
||||
Now the exciting part is here, when you get to view what you've published for everyone to see! Open your browser and enter:
|
||||
|
||||
|
||||
```
|
||||
`https://username.github.io`
|
||||
```
|
||||
|
||||
Congratulations on your new blog, self-published on GitHub! You can follow this pattern whenever you want to add more pages or articles. Happy blogging.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/5/run-your-blog-github-pages-python
|
||||
|
||||
作者:[Erik O'Shaughnessy][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/jnyjny/users/jasperzanjani/users/jasperzanjani/users/jasperzanjani/users/jnyjny/users/jasperzanjani
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/getting_started_with_python.png?itok=MFEKm3gl (Raspberry Pi and Python)
|
||||
[2]: https://github.com/
|
||||
[3]: https://git-scm.com
|
||||
[4]: https://help.github.com/en/categories/github-pages-basics
|
||||
[5]: https://jekyllrb.com
|
||||
[6]: https://python.org
|
||||
[7]: https://blog.getpelican.com
|
||||
[8]: https://guides.github.com/features/mastering-markdown
|
||||
[9]: http://docutils.sourceforge.net/docs/user/rst/quickref.html
|
||||
[10]: https://github.com/join?source=header-home
|
||||
[11]: https://git-scm.com/docs
|
||||
[12]: https://pip.pypa.io/en/stable/
|
||||
[13]: https://docs.getpelican.com
|
||||
@ -1,300 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (way-ww)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (How To Enable Or Disable SSH Access For A Particular User Or Group In Linux?)
|
||||
[#]: via: (https://www.2daygeek.com/allow-deny-enable-disable-ssh-access-user-group-in-linux/)
|
||||
[#]: author: (2daygeek http://www.2daygeek.com/author/2daygeek/)
|
||||
|
||||
How To Enable Or Disable SSH Access For A Particular User Or Group In Linux?
|
||||
======
|
||||
|
||||
As per your organization standard policy, you may need to allow only the list of users that are allowed to access the Linux system.
|
||||
|
||||
Or you may need to allow only few groups, which are allowed to access the Linux system.
|
||||
|
||||
How to achieve this? What is the best way? How to achieve this in a simple way?
|
||||
|
||||
Yes, there are many ways are available to perform this.
|
||||
|
||||
However, we need to go with simple and easy method.
|
||||
|
||||
If so, it can be done by making the necessary changes in `/etc/ssh/sshd_config` file.
|
||||
|
||||
In this article we will show you, how to perform this in details.
|
||||
|
||||
Why are we doing this? due to security reason. Navigate to the following URL to know more about **[openSSH][1]** usage.
|
||||
|
||||
### What Is SSH?
|
||||
|
||||
openssh stands for OpenBSD Secure Shell. Secure Shell (ssh) is a free open source networking tool which allow us to access remote system over an unsecured network using Secure Shell (SSH) protocol.
|
||||
|
||||
It’s a client-server architecture. It handles user authentication, encryption, transferring files between computers and tunneling.
|
||||
|
||||
These can be accomplished via traditional tools such as telnet or rcp, these are insecure and use transfer password in cleartext format while performing any action.
|
||||
|
||||
### How To Allow A User To Access SSH In Linux?
|
||||
|
||||
We can allow/enable the ssh access for a particular user or list of the users using the following method.
|
||||
|
||||
If you would like to allow more than one user then you have to add the users with space in the same line.
|
||||
|
||||
To do so, just append the following value into `/etc/ssh/sshd_config` file. In this example, we are going to allow ssh access for `user3`.
|
||||
|
||||
```
|
||||
# echo "AllowUsers user3" >> /etc/ssh/sshd_config
|
||||
```
|
||||
|
||||
You can double check this by running the following command.
|
||||
|
||||
```
|
||||
# cat /etc/ssh/sshd_config | grep -i allowusers
|
||||
AllowUsers user3
|
||||
```
|
||||
|
||||
That’s it. Just bounce the ssh service and see the magic.
|
||||
|
||||
```
|
||||
# systemctl restart sshd
|
||||
|
||||
# service restart sshd
|
||||
```
|
||||
|
||||
Simple open a new terminal or session and try to access the Linux system with different user. Yes, `user2` isn’t allowed for SSH login and will be getting an error message as shown below.
|
||||
|
||||
```
|
||||
# ssh [email protected]
|
||||
[email protected]'s password:
|
||||
Permission denied, please try again.
|
||||
```
|
||||
|
||||
Output:
|
||||
|
||||
```
|
||||
Mar 29 02:00:35 CentOS7 sshd[4900]: User user2 from 192.168.1.6 not allowed because not listed in AllowUsers
|
||||
Mar 29 02:00:35 CentOS7 sshd[4900]: input_userauth_request: invalid user user2 [preauth]
|
||||
Mar 29 02:00:40 CentOS7 unix_chkpwd[4902]: password check failed for user (user2)
|
||||
Mar 29 02:00:40 CentOS7 sshd[4900]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=192.168.1.6 user=user2
|
||||
Mar 29 02:00:43 CentOS7 sshd[4900]: Failed password for invalid user user2 from 192.168.1.6 port 42568 ssh2
|
||||
```
|
||||
|
||||
At the same time `user3` is allowed to login into the system because it’s in allowed users list.
|
||||
|
||||
```
|
||||
# ssh [email protected]
|
||||
[email protected]'s password:
|
||||
[[email protected] ~]$
|
||||
```
|
||||
|
||||
Output:
|
||||
|
||||
```
|
||||
Mar 29 02:01:13 CentOS7 sshd[4939]: Accepted password for user3 from 192.168.1.6 port 42590 ssh2
|
||||
Mar 29 02:01:13 CentOS7 sshd[4939]: pam_unix(sshd:session): session opened for user user3 by (uid=0)
|
||||
```
|
||||
|
||||
### How To Deny Users To Access SSH In Linux?
|
||||
|
||||
We can deny/disable the ssh access for a particular user or list of the users using the following method.
|
||||
|
||||
If you would like to disable more than one user then you have to add the users with space in the same line.
|
||||
|
||||
To do so, just append the following value into `/etc/ssh/sshd_config` file. In this example, we are going to disable ssh access for `user1`.
|
||||
|
||||
```
|
||||
# echo "DenyUsers user1" >> /etc/ssh/sshd_config
|
||||
```
|
||||
|
||||
You can double check this by running the following command.
|
||||
|
||||
```
|
||||
# cat /etc/ssh/sshd_config | grep -i denyusers
|
||||
DenyUsers user1
|
||||
```
|
||||
|
||||
That’s it. Just bounce the ssh service and see the magic.
|
||||
|
||||
```
|
||||
# systemctl restart sshd
|
||||
|
||||
# service restart sshd
|
||||
```
|
||||
|
||||
Simple open a new terminal or session and try to access the Linux system with Deny user. Yes, `user1` is in denyusers list. So, you will be getting an error message as shown below when you are try to login.
|
||||
|
||||
```
|
||||
# ssh [email protected]
|
||||
[email protected]'s password:
|
||||
Permission denied, please try again.
|
||||
```
|
||||
|
||||
Output:
|
||||
|
||||
```
|
||||
Mar 29 01:53:42 CentOS7 sshd[4753]: User user1 from 192.168.1.6 not allowed because listed in DenyUsers
|
||||
Mar 29 01:53:42 CentOS7 sshd[4753]: input_userauth_request: invalid user user1 [preauth]
|
||||
Mar 29 01:53:46 CentOS7 unix_chkpwd[4755]: password check failed for user (user1)
|
||||
Mar 29 01:53:46 CentOS7 sshd[4753]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=192.168.1.6 user=user1
|
||||
Mar 29 01:53:48 CentOS7 sshd[4753]: Failed password for invalid user user1 from 192.168.1.6 port 42522 ssh2
|
||||
```
|
||||
|
||||
### How To Allow Groups To Access SSH In Linux?
|
||||
|
||||
We can allow/enable the ssh access for a particular group or groups using the following method.
|
||||
|
||||
If you would like to allow more than one group then you have to add the groups with space in the same line.
|
||||
|
||||
To do so, just append the following value into `/etc/ssh/sshd_config` file. In this example, we are going to disable ssh access for `2g-admin` group.
|
||||
|
||||
```
|
||||
# echo "AllowGroups 2g-admin" >> /etc/ssh/sshd_config
|
||||
```
|
||||
|
||||
You can double check this by running the following command.
|
||||
|
||||
```
|
||||
# cat /etc/ssh/sshd_config | grep -i allowgroups
|
||||
AllowGroups 2g-admin
|
||||
```
|
||||
|
||||
Run the following command to know the list of the users are belongs to this group.
|
||||
|
||||
```
|
||||
# getent group 2g-admin
|
||||
2g-admin:x:1005:user1,user2,user3
|
||||
```
|
||||
|
||||
That’s it. Just bounce the ssh service and see the magic.
|
||||
|
||||
```
|
||||
# systemctl restart sshd
|
||||
|
||||
# service restart sshd
|
||||
```
|
||||
|
||||
Yes, `user3` is allowed to login into the system because user3 is belongs to `2g-admin` group.
|
||||
|
||||
```
|
||||
# ssh [email protected]
|
||||
[email protected]'s password:
|
||||
[[email protected] ~]$
|
||||
```
|
||||
|
||||
Output:
|
||||
|
||||
```
|
||||
Mar 29 02:10:21 CentOS7 sshd[5165]: Accepted password for user1 from 192.168.1.6 port 42640 ssh2
|
||||
Mar 29 02:10:22 CentOS7 sshd[5165]: pam_unix(sshd:session): session opened for user user1 by (uid=0)
|
||||
```
|
||||
|
||||
Yes, `user2` is allowed to login into the system because user2 is belongs to `2g-admin` group.
|
||||
|
||||
```
|
||||
# ssh [email protected]
|
||||
[email protected]'s password:
|
||||
[[email protected] ~]$
|
||||
```
|
||||
|
||||
Output:
|
||||
|
||||
```
|
||||
Mar 29 02:10:38 CentOS7 sshd[5225]: Accepted password for user2 from 192.168.1.6 port 42642 ssh2
|
||||
Mar 29 02:10:38 CentOS7 sshd[5225]: pam_unix(sshd:session): session opened for user user2 by (uid=0)
|
||||
```
|
||||
|
||||
When you are try to login into the system with other users which are not part of this group then you will be getting an error message as shown below.
|
||||
|
||||
```
|
||||
# ssh [email protected]
|
||||
[email protected]'s password:
|
||||
Permission denied, please try again.
|
||||
```
|
||||
|
||||
Output:
|
||||
|
||||
```
|
||||
Mar 29 02:12:36 CentOS7 sshd[5306]: User ladmin from 192.168.1.6 not allowed because none of user's groups are listed in AllowGroups
|
||||
Mar 29 02:12:36 CentOS7 sshd[5306]: input_userauth_request: invalid user ladmin [preauth]
|
||||
Mar 29 02:12:56 CentOS7 unix_chkpwd[5310]: password check failed for user (ladmin)
|
||||
Mar 29 02:12:56 CentOS7 sshd[5306]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=192.168.1.6 user=ladmin
|
||||
Mar 29 02:12:58 CentOS7 sshd[5306]: Failed password for invalid user ladmin from 192.168.1.6 port 42674 ssh2
|
||||
```
|
||||
|
||||
### How To Deny Group To Access SSH In Linux?
|
||||
|
||||
We can deny/disable the ssh access for a particular group or groups using the following method.
|
||||
|
||||
If you would like to disable more than one group then you need to add the group with space in the same line.
|
||||
|
||||
To do so, just append the following value into `/etc/ssh/sshd_config` file.
|
||||
|
||||
```
|
||||
# echo "DenyGroups 2g-admin" >> /etc/ssh/sshd_config
|
||||
```
|
||||
|
||||
You can double check this by running the following command.
|
||||
|
||||
```
|
||||
# # cat /etc/ssh/sshd_config | grep -i denygroups
|
||||
DenyGroups 2g-admin
|
||||
|
||||
# getent group 2g-admin
|
||||
2g-admin:x:1005:user1,user2,user3
|
||||
```
|
||||
|
||||
That’s it. Just bounce the ssh service and see the magic.
|
||||
|
||||
```
|
||||
# systemctl restart sshd
|
||||
|
||||
# service restart sshd
|
||||
```
|
||||
|
||||
Yes `user3` isn’t allowed to login into the system because it’s not part of `2g-admin` group. It’s in Denygroups.
|
||||
|
||||
```
|
||||
# ssh [email protected]
|
||||
[email protected]'s password:
|
||||
Permission denied, please try again.
|
||||
```
|
||||
|
||||
Output:
|
||||
|
||||
```
|
||||
Mar 29 02:17:32 CentOS7 sshd[5400]: User user1 from 192.168.1.6 not allowed because a group is listed in DenyGroups
|
||||
Mar 29 02:17:32 CentOS7 sshd[5400]: input_userauth_request: invalid user user1 [preauth]
|
||||
Mar 29 02:17:38 CentOS7 unix_chkpwd[5402]: password check failed for user (user1)
|
||||
Mar 29 02:17:38 CentOS7 sshd[5400]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=192.168.1.6 user=user1
|
||||
Mar 29 02:17:41 CentOS7 sshd[5400]: Failed password for invalid user user1 from 192.168.1.6 port 42710 ssh2
|
||||
```
|
||||
|
||||
Anyone can login into the system except `2g-admin` group. Hence, `ladmin` user is allowed to login into the system.
|
||||
|
||||
```
|
||||
# ssh [email protected]
|
||||
[email protected]'s password:
|
||||
[[email protected] ~]$
|
||||
```
|
||||
|
||||
Output:
|
||||
|
||||
```
|
||||
Mar 29 02:19:13 CentOS7 sshd[5432]: Accepted password for ladmin from 192.168.1.6 port 42716 ssh2
|
||||
Mar 29 02:19:13 CentOS7 sshd[5432]: pam_unix(sshd:session): session opened for user ladmin by (uid=0)
|
||||
```
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.2daygeek.com/allow-deny-enable-disable-ssh-access-user-group-in-linux/
|
||||
|
||||
作者:[2daygeek][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: http://www.2daygeek.com/author/2daygeek/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.2daygeek.com/category/ssh-tutorials/
|
||||
@ -1,5 +1,5 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (zhangxiangping)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
@ -264,7 +264,7 @@ via: https://opensource.com/article/19/7/python-google-natural-language-api
|
||||
|
||||
作者:[JR Oakes][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[zhangxiangping](https://github.com/zhangxiangping)
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,97 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (cycoe)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Debugging in Emacs: The Grand Unified Debugger)
|
||||
[#]: via: (https://opensourceforu.com/2019/09/debugging-in-emacs-the-grand-unified-debugger/)
|
||||
[#]: author: (Vineeth Kartha https://opensourceforu.com/author/vineeth-kartha/)
|
||||
|
||||
Debugging in Emacs: The Grand Unified Debugger
|
||||
======
|
||||
|
||||
[![][1]][2]
|
||||
|
||||
_This article briefly explores the features of the Grand Unified Debugger, a debugging tool for Emacs._
|
||||
|
||||
If you are a C/C++ developer, it is highly likely that you have crossed paths with GDB (the GNU debugger) which is, without doubt, one of the most powerful and unrivalled debuggers out there. Its only drawback is that it is command line based, and though that offers a lot of power, it is sometimes a bit restrictive as well. This is why smart people started coming up with IDEs to integrate editors and debuggers, and give them a GUI. There are still developers who believe that using the mouse reduces productivity and that mouse-click based GUIs are temptations by the devil.
|
||||
Since Emacs is one of the coolest text editors out there, I am going to show you how to write, compile and debug code without having to touch the mouse or move out of Emacs.
|
||||
|
||||
![Figure 1: Compile command in Emacs’ mini buffer][3]
|
||||
|
||||
![Figure 2: Compilation status][4]
|
||||
|
||||
The Grand Unified Debugger, or GUD as it is commonly known, is an Emacs mode in which GDB can be run from within Emacs. This provides all the features of Emacs in GDB. The user does not have to move out of the editor to debug the code written.
|
||||
|
||||
**Setting the stage for the Grand Unified Debugger**
|
||||
If you are using a Linux machine, then it is likely you will have GDB and gcc already installed. The next step is to ensure that Emacs is also installed. I am assuming that the readers are familiar with GDB and have used it at least for basic debugging. If not, please do check out some quick introductions to GDB that are widely available on the Internet.
|
||||
|
||||
For people who are new to Emacs, let me introduce you to some basic terminology. Throughout this article, you will see shortcut commands such as C-c, M-x, etc. C means the Ctrl key and M means the Alt key. C-c means the Ctrl + c keys are pressed. If you see C-c c, it means Ctrl + c is pressed followed by c. Also, in Emacs, the main area where you edit the text is called the main buffer, and the area at the bottom of the Emacs window, where commands are entered, is called the mini buffer.
|
||||
Start Emacs and to create a new file, press _C-x C-f_. This will prompt you to enter a file name. Let us call our file ‘buggyFactorial.cpp’. Once the file is open, type in the code shown below:
|
||||
|
||||
```
|
||||
#include<iostream>
|
||||
#include <assert.h>
|
||||
int factorial(int num) {
|
||||
int product = 1;
|
||||
while(num--) {
|
||||
product *= num;
|
||||
}
|
||||
return product;
|
||||
}
|
||||
int main() {
|
||||
int result = factorial(5);
|
||||
assert(result == 120);
|
||||
}
|
||||
```
|
||||
|
||||
Save the file with _C-x C-s_. Once the file is saved, it’s time to compile the code. Press _M-x_ and in the prompt that comes up, type in compile and hit Enter. Then, in the prompt, replace whatever is there with _g++ -g buggyFactorial.cpp_ and again hit _Enter_.
|
||||
|
||||
This will open up another buffer in Emacs that will show the status of the compile and, hopefully, if the code typed in is correct, you will get a buffer like the one shown in Figure 2.
|
||||
|
||||
To hide this compilation status buffer, make sure your cursor is in the compilation buffer (you can do this without the mouse using _C-x o_-this is used to move the cursor from one open buffer to the other), and then press _C-x 0_. The next step is to run the code and see if it works fine. Press M-! and in the mini buffer prompt, type _./a.out._
|
||||
|
||||
See the mini buffer that says the assertion is failed. Clearly, something is wrong with the code, because the factorial (5) is 120. So let’s debug the code now.
|
||||
|
||||
![Figure 3: Output of the code in the mini buffer][5]
|
||||
|
||||
![Figure 4: The GDB buffer in Emacs][6]
|
||||
|
||||
**Debugging the code using GUD**
|
||||
Now, since we have the code compiled, it’s time to see what is wrong with it. Press M-x and in the prompt, enter _gdb._ In the next prompt that appears, write _gdb -i=mi a.out_, which will start GDB in the Emacs buffer and if everything goes well, you should get the window that’s shown in Figure 4.
|
||||
At the gdb prompt, type break main and then r to run the program. This should start running the program and should break at the _main()_.
|
||||
|
||||
As soon as GDB hits the break point at main, a new buffer will open up showing the code that you are debugging. Notice the red dot on the left side, which is where your breakpoint was set. There will be a small indicator that shows which line of the code you are on. Currently, this will be the same as the break point itself (Figure 5).
|
||||
|
||||
![Figure 5: GDB and the code in split windows][7]
|
||||
|
||||
![Figure 6: Show the local variables in a separate frame in Emacs][8]
|
||||
|
||||
To debug the factorial function, we need to step into it. For this, you can either use the _gdb_ prompt and the gdb command step, or you can use the Emacs shortcut _C-c C-s_. There are other similar shortcuts, but I prefer using the GDB commands. So I will use them in the rest of this article.
|
||||
Let us keep an eye on the local variables while stepping through the factorial number. Check out Figure 6 for how to get an Emacs frame to show the local variables.
|
||||
|
||||
Step through the code in the GDB prompt and watch the value of the local variable change. In the first iteration of the loop itself, we see a problem. The value of the product should have been 5 and not 4.
|
||||
|
||||
This is where I leave you and now it’s up to the readers to explore and discover the magic land called GUD mode. Every gdb command works in the GUD mode as well. I leave the fix to this code as an exercise to readers. Explore and see how you can customise things to make your workflow simpler and become more productive while debugging.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensourceforu.com/2019/09/debugging-in-emacs-the-grand-unified-debugger/
|
||||
|
||||
作者:[Vineeth Kartha][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensourceforu.com/author/vineeth-kartha/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://i0.wp.com/opensourceforu.com/wp-content/uploads/2019/09/Screenshot-from-2019-09-25-15-39-46.png?resize=696%2C440&ssl=1 (Screenshot from 2019-09-25 15-39-46)
|
||||
[2]: https://i0.wp.com/opensourceforu.com/wp-content/uploads/2019/09/Screenshot-from-2019-09-25-15-39-46.png?fit=800%2C506&ssl=1
|
||||
[3]: https://i1.wp.com/opensourceforu.com/wp-content/uploads/2019/09/Figure_1.png?resize=350%2C228&ssl=1
|
||||
[4]: https://i2.wp.com/opensourceforu.com/wp-content/uploads/2019/09/Figure_2.png?resize=350%2C228&ssl=1
|
||||
[5]: https://i0.wp.com/opensourceforu.com/wp-content/uploads/2019/09/Figure_3.png?resize=350%2C228&ssl=1
|
||||
[6]: https://i0.wp.com/opensourceforu.com/wp-content/uploads/2019/09/Figure_4.png?resize=350%2C227&ssl=1
|
||||
[7]: https://i1.wp.com/opensourceforu.com/wp-content/uploads/2019/09/Figure_5.png?resize=350%2C200&ssl=1
|
||||
[8]: https://i1.wp.com/opensourceforu.com/wp-content/uploads/2019/09/Figure_6.png?resize=350%2C286&ssl=1
|
||||
@ -1,61 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Calculator N+ is an open source scientific calculator for your smartphone)
|
||||
[#]: via: (https://opensource.com/article/19/11/calculator-n-mobile)
|
||||
[#]: author: (Ricardo Berlasso https://opensource.com/users/rgb-es)
|
||||
|
||||
Calculator N+ is an open source scientific calculator for your smartphone
|
||||
======
|
||||
The Android app does a wide range of advanced mathematical functions in
|
||||
the palm of your hand.
|
||||
![scientific calculator][1]
|
||||
|
||||
Mobile phones are becoming more powerful every day, so it is no surprise that they can beat most computers from the not-so-distant past. This also means the tools available on them are getting more powerful every day.
|
||||
|
||||
Previously, I wrote about [scientific calculators for the Linux desktop][2], and I'm following that up here with information about [Calculator N+][3], an awesome GPL v3.0-licensed computer algebra system (CAS) app for Android devices.
|
||||
|
||||
Calculator N+ is presented as a "powerful calculator for Android," but that's a humble statement; the app not only works with arbitrary precision, displaying results with roots and fractions in all their glory, it does a _lot_ more.
|
||||
|
||||
Finding polynomial roots? Check. Factorization? Check. Symbolic derivatives, integrals, and limits? Check. Number theory (modular arithmetic, combinatorics, prime factorization)? Check.
|
||||
|
||||
You can also solve systems of equations, simplify expressions (including trigonometric ones), convert units… you name it!
|
||||
|
||||
![Calculator N+ graphical interface][4]
|
||||
|
||||
Results are output in LaTeX. The menu in the top-left provides many powerful functions ready to use with a simple touch. Also in that menu, you'll find Help files for all of the app's functions. At the top-right of the screen, you can toggle between exact and decimal representation. Finally, tapping the blue bar at the bottom of the screen gives you access to the whole library of functions available in the app. But be careful! If you are not a mathematician, physicist, or engineer, such a long list may seem overwhelming.
|
||||
|
||||
All of this power comes from the [Symja library][5], another great GPL 3 project.
|
||||
|
||||
Both projects are under active development, and they are getting better with each version. In particular, version 3.4.6 of Calculator N+ gets a major leap in user interface (UI) quality. And yes, there are still some rough corners here and there, but taming this much power in the tiny UI of a smartphone is a difficult task, and I think the app developers are solving its remaining issues quite well. Kudos to them!
|
||||
|
||||
If you are a teacher, a student, or work on a STEM field, check out Calculator N+. It's free, no ads, open source, and covers all your math needs. (Except, of course, during math exams, where smartphones should never be allowed to prevent cheating.)
|
||||
|
||||
Calculator N+ is available in the [Google Play Store][6], or you can [build it from source code][7] using the instructions on the GitHub page.
|
||||
|
||||
If you know any other useful open source apps for science or engineering, let us know in the comments.
|
||||
|
||||
The app makes use of the sensors on your phone and offers a digital science notebook to record your...
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/11/calculator-n-mobile
|
||||
|
||||
作者:[Ricardo Berlasso][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/rgb-es
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/calculator_money_currency_financial_tool.jpg?itok=2QMa1y8c (scientific calculator)
|
||||
[2]: https://opensource.com/article/18/1/scientific-calculators-linux
|
||||
[3]: https://github.com/tranleduy2000/ncalc
|
||||
[4]: https://opensource.com/sites/default/files/uploads/calculatornplus_sqrt-frac.png (Calculator N+ graphical interface)
|
||||
[5]: https://github.com/axkr/symja_android_library
|
||||
[6]: https://play.google.com/store/apps/details?id=com.duy.calculator.free
|
||||
[7]: https://github.com/tranleduy2000/ncalc/blob/master/README.md
|
||||
@ -1,96 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (10 articles to learn Linux your way)
|
||||
[#]: via: (https://opensource.com/article/19/12/learn-linux)
|
||||
[#]: author: (Seth Kenlon https://opensource.com/users/seth)
|
||||
|
||||
10 articles to learn Linux your way
|
||||
======
|
||||
It's been a good year for Linux, so take a look back at the top 10 Linux
|
||||
articles on Opensource.com from 2019.
|
||||
![Penguins gathered together in the Artic][1]
|
||||
|
||||
The year 2019 has been good for Linux with Opensource.com readers. Obviously, the term "Linux" itself is weighted: Does it refer to the kernel or the desktop or the ecosystem? In this look back at the top Linux articles of the year, I've intentionally taken a broad view in defining the top 10 Linux articles (for some definition of "top" and some definition of "Linux"). Here they are, offered in no particular order.
|
||||
|
||||
### A beginner's guide to Linux permissions
|
||||
|
||||
[_A beginner's guide to Linux permissions_][2] by Bryant Son introduces new users to the concept of file permissions with graphics and charts to illustrate each point. It can be hard to come up with visuals for concepts that are, at their core, purely text-based, and this article is friendly for the visual learners out there. I also like how Bryant stays focused. Any discussion of file permissions can lead to several related topics (like ownership and access control lists and so on), but this article is dedicated to explaining one thing and explaining it well.
|
||||
|
||||
### Why I made the switch from Mac to Linux
|
||||
|
||||
Matthew Broberg offers an insightful and honest look at his migration to Linux from MacOS in [_Why I made the switch from Mac to Linux_][3]. Changing platforms is always tough, and it's important to record what's behind the decision to switch. Matt's article, I think, serves several purposes, but the two most important for me: it's an invitation for the Linux community to support him by answering questions and offering potential solutions, and it's a good data point for others who are considering Linux adoption.
|
||||
|
||||
### Troubleshooting slow WiFi on Linux
|
||||
|
||||
In [_Troubleshooting slow WiFi on Linux_][4], David Clinton provides a useful analysis of a problem everyone has on every platform—and has tips on how to solve it. It's a good example of an "incidentally Linux" tip that not only helps everyday people with everyday problems but also shows non-Linux users how approachable troubleshooting (on any platform) is.
|
||||
|
||||
### How GNOME uses Git
|
||||
|
||||
[_How GNOME uses Git_][5] by Molly de Blanc takes a look behind the scenes, revealing how one of the paragons of open source software (the GNOME desktop) uses one of the other paragons of open source (Git) for development. It's always heartening to me to hear about an open source project that defaults to an open source solution for whatever needs to be done. Believe it or not, this isn't always the case, but for GNOME, it's an important and welcoming part of the project's identity.
|
||||
|
||||
### Virtual filesystems in Linux: Why we need them and how they work
|
||||
|
||||
Alison Chaiken masterfully explains what is considered incomprehensible to many users in [_Virtual filesystems in Linux: Why we need them and how they work_][6]. Understanding what a filesystem is and what it does is one thing, but _virtual_ ones aren't even, by definition, real. And yet Linux delivers them in a way that even casual users can benefit from, and Alison's article explains it in a way that anyone can understand. As a bonus, Alison goes even deeper in the second half of the article and demonstrates how to use bcc scripts to monitor everything she just taught you.
|
||||
|
||||
### Understanding file paths and how to use them
|
||||
|
||||
I thought [_Understanding file paths and how to use them_][7] was important to write about because it's a concept most users (on any platform) don't seem to be taught. It's a strange phenomenon, because now, more than ever, the _file path_ is something people see literally on a daily basis: Nearly all internet URLs contain a file path telling you exactly where within the domain you are. I often wonder why computer education doesn't start with the internet, the most familiar app of all and arguably the most heavily used supercomputer in existence, and use it to explain the appliances we interface with each day. (I guess it would help if those appliances were running Linux, but we're working on that.)
|
||||
|
||||
### Inter-process communication in Linux
|
||||
|
||||
[_Inter-process communication in Linux: Shared storage_][8] by Marty Kalin delves into the developer side of Linux, explaining IPC and how to interact with it in your code. I'm cheating by including this article because it's actually a three-part series, but it's the best explanation of its kind. There is very little documentation that manages to explain how Linux handles IPC, much less what IPC is, why it's important, or how to take advantage of it when programming. It's normally a topic you work your way up to in university. Now you can read all about it here instead.
|
||||
|
||||
### Understanding system calls on Linux with strace
|
||||
|
||||
[_Understanding system calls on Linux with strace_][9] by Gaurav Kamathe is highly technical in ways I wish that every conference talk I've ever seen about **strace** was. This is a clear and helpful demonstration of a complex but amazingly useful command. To my surprise, the command I've found myself using since this article isn't the titular command, but **ltrace** (to see which functions are called by a command). Obviously, this article's packed with information and is a handy reference for developers and QA testers.
|
||||
|
||||
### How the Linux desktop has grown
|
||||
|
||||
[_How the Linux desktop has grown_][10] by Jim Hall is a visual journey through the history of the Linux desktop. It starts with [TWM][11] and passes by [FVWM][12], [GNOME][13], [KDE][14], and others. If you're new to Linux, this is a fascinating history lesson from someone who was there (and has the screenshots to prove it). If you've been with Linux for many years, then this will definitely bring back memories. In the end, though, one thing is certain: Anyone who can still locate screenshots from 20 years ago is a superhuman data archivist.
|
||||
|
||||
### Create your own video streaming server with Linux
|
||||
|
||||
[_Create your own video streaming server with Linux_][15] by Aaron J. Prisk breaks down more than just a few preconceptions most of us have about the services we take for granted. Because services like YouTube and Twitch exist, many people assume that those are the only gateways to broadcasting video to the world. Of course, people used to think that Windows and Mac were the only gateways into computing, and that, thankfully, turned out to be a gross miscalculation. In this article, Aaron sets up a video-streaming server and even manages to find space to talk about [OBS][16] in so you can create videos to stream. Is it a fun weekend project or the start of a new career? You decide.
|
||||
|
||||
### 10 moments that shaped Linux history
|
||||
|
||||
[_10 moments that shaped Linux history_][17] by Alan Formy-Duval attempts the formidable task of choosing just 10 things to highlight in the history of Linux. It's an exercise in futility, of course, because there have been so many important moments, so I love how Alan filters it through his own experience. For example, when was it obvious that Linux was going to last? When Alan realized that all the systems he maintained at work were running Linux. There's a beauty to interpreting history this way because the moments of importance will differ for each person. There's no definitive list for Linux, or articles about Linux, or for open source. You make your own list, and you make yourself a part of it.
|
||||
|
||||
### What do you want to learn?
|
||||
|
||||
What else do you want to know about Linux? Please tell us about it in the comments, or [write an article][18] for Opensource.com about your experience with Linux.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/12/learn-linux
|
||||
|
||||
作者:[Seth Kenlon][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/seth
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/OSDC_Penguin_Image_520x292_12324207_0714_mm_v1a.png?itok=p7cWyQv9 (Penguins gathered together in the Artic)
|
||||
[2]: https://opensource.com/article/19/6/understanding-linux-permissions
|
||||
[3]: https://opensource.com/article/19/10/why-switch-mac-linux
|
||||
[4]: http://opensource.com/article/19/4/troubleshooting-wifi-linux
|
||||
[5]: https://opensource.com/article/19/10/how-gnome-uses-git
|
||||
[6]: https://opensource.com/article/19/3/virtual-filesystems-linux
|
||||
[7]: https://opensource.com/article/19/8/understanding-file-paths-linux
|
||||
[8]: https://opensource.com/article/19/4/interprocess-communication-linux-storage
|
||||
[9]: https://opensource.com/article/19/2/linux-backup-solutions
|
||||
[10]: https://opensource.com/article/19/8/how-linux-desktop-grown
|
||||
[11]: https://github.com/freedesktop/twm
|
||||
[12]: http://www.fvwm.org/
|
||||
[13]: http://gnome.org
|
||||
[14]: http://kde.org
|
||||
[15]: https://opensource.com/article/19/1/basic-live-video-streaming-server
|
||||
[16]: https://opensource.com/life/15/12/real-time-linux-video-editing-with-obs-studio
|
||||
[17]: https://opensource.com/article/19/4/top-moments-linux-history
|
||||
[18]: https://opensource.com/how-submit-article
|
||||
@ -1,59 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Prioritizing simplicity in your Python code)
|
||||
[#]: via: (https://opensource.com/article/19/12/zen-python-simplicity-complexity)
|
||||
[#]: author: (Moshe Zadka https://opensource.com/users/moshez)
|
||||
|
||||
Prioritizing simplicity in your Python code
|
||||
======
|
||||
This is the second part of a special series about the Zen of Python
|
||||
focusing on the third and fourth principles: simplicity and complexity.
|
||||
![Person reading a book and digital copy][1]
|
||||
|
||||
> "Il semble que la perfection soit atteinte non quand il n'y a plus rien à ajouter, mais quand il n'y plus rien à retrancher."
|
||||
>
|
||||
> "It seems that perfection is finally attained not when there is no longer anything to add, but when there is no longer anything to take away."
|
||||
> —Antoine de Saint-Exupéry, _[Terre des Hommes][2]_, 1939
|
||||
|
||||
A common concern in programming is the struggle with complexity. It is easy for any programmer to make a program so complicated no expert can debug it or modify it. The [Zen of Python][3] would not be complete if it did not touch on this.
|
||||
|
||||
### Simple is better than complex.
|
||||
|
||||
When it is possible to choose at all, choose the simple solution. Python is rarely in the business of _disallowing_ things. This means it is possible, and even straightforward, to design baroque programs to solve straightforward problems.
|
||||
|
||||
It is worthwhile to remember at each point that simplicity is one of the easiest things to lose and the hardest to regain when writing code.
|
||||
|
||||
This can mean choosing to write something as a function, rather than introducing an extraneous class. This can mean avoiding a robust third-party library in favor of writing a two-line function that is perfect for the immediate use-case. Most often, it means avoiding predicting the future in favor of solving the problem at hand.
|
||||
|
||||
It is much easier to change the program later, especially if simplicity and beauty were among its guiding principles than to load the code down with all possible future variations.
|
||||
|
||||
### Complex is better than complicated.
|
||||
|
||||
This is possibly the most misunderstood principle because understanding the precise meanings of the words is crucial. Something is _complex_ when it is composed of multiple parts. Something is _complicated_ when it has a lot of different, often hard to predict, behaviors.
|
||||
|
||||
When solving a hard problem, it is often the case that no simple solution will do. In that case, the most Pythonic strategy is to go "bottom-up." Build simple tools and combine them to solve the problem.
|
||||
|
||||
This is where techniques like _object composition_ shine. Instead of having a complicated inheritance hierarchy, have objects that forward some method calls to a separate object. Each of those can be tested and developed separately and then finally put together.
|
||||
|
||||
Another example of "building up" is using [singledispatch][4], so that instead of one complicated object, we have a simple, mostly behavior-less object and separate behaviors.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/12/zen-python-simplicity-complexity
|
||||
|
||||
作者:[Moshe Zadka][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/moshez
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/read_book_guide_tutorial_teacher_student_apaper.png?itok=_GOufk6N (Person reading a book and digital copy)
|
||||
[2]: https://en.wikipedia.org/wiki/Wind,_Sand_and_Stars
|
||||
[3]: https://www.python.org/dev/peps/pep-0020/
|
||||
[4]: https://opensource.com/article/19/5/python-singledispatch
|
||||
@ -1,87 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Why your Python code should be flat and sparse)
|
||||
[#]: via: (https://opensource.com/article/19/12/zen-python-flat-sparse)
|
||||
[#]: author: (Moshe Zadka https://opensource.com/users/moshez)
|
||||
|
||||
Why your Python code should be flat and sparse
|
||||
======
|
||||
This is part of a special series about the Zen of Python focusing on the
|
||||
fifth and sixth principles: flatness and sparseness.
|
||||
![Digital creative of a browser on the internet][1]
|
||||
|
||||
The [Zen of Python][2] is called that for a reason. It was never supposed to provide easy-to-follow guidelines for programming. The rules are specified tersely and are designed to engage the reader in deep thought.
|
||||
|
||||
In order to properly appreciate the Zen of Python, you must read it and then meditate upon the meanings. If the Zen was designed to be a set of clear rules, it would be a fault that it has rules that contradict each other. However, as a tool to help you meditate on the best solution, contradictions are powerful.
|
||||
|
||||
### Flat is better than nested.
|
||||
|
||||
Nowhere is the pressure to be "flat" more obvious than in Python's strong insistence on indentation. Other languages will often introduce an implementation that "cheats" on the nested structure by reducing indentation requirements. To appreciate this point, let's take a look at JavaScript.
|
||||
|
||||
JavaScript is natively async, which means that programmers write code in JavaScript using a lot of callbacks.
|
||||
|
||||
|
||||
```
|
||||
a(function(resultsFromA) {
|
||||
b(resultsFromA, function(resultsfromB) {
|
||||
c(resultsFromC, function(resultsFromC) {
|
||||
console.log(resultsFromC)
|
||||
}
|
||||
}
|
||||
}
|
||||
```
|
||||
|
||||
Ignoring the code, observe the pattern and the way indentation leads to a right-most point. This distinctive "arrow" shape is tough on the eye to quickly walk through the code, so it's seen as undesirable and even nicknamed "callback hell." However, in JavaScript, it is possible to "cheat" and not have indentation reflect nesting.
|
||||
|
||||
|
||||
```
|
||||
a(function(resultsFromA) {
|
||||
b(resultsFromA,
|
||||
function(resultsfromB) {
|
||||
c(resultsFromC,
|
||||
function(resultsFromC) {
|
||||
console.log(resultsFromC)
|
||||
}}}
|
||||
```
|
||||
|
||||
Python affords no such options to cheat: every nesting level in the program must be reflected in the indentation level. So deep nesting in Python _looks_ deeply nested. That makes "callback hell" was a worse problem in Python than in JavaScript: nesting callbacks mean indenting with no options to "cheat" with braces.
|
||||
|
||||
This challenge, in combination with the Zen principle, has led to an elegant solution by a library I worked on. In the [Twisted][3] framework, we came up with the _deferred_ abstraction, which would later inspire the popular JavaScript _promise_ abstraction. In this way, Python's unwavering commitment to clear code forces Python developers to discover new, powerful abstractions.
|
||||
|
||||
|
||||
```
|
||||
future_value = future_result()
|
||||
future_value.addCallback(a)
|
||||
future_value.addCallback(b)
|
||||
future_value.addCallback(c)
|
||||
```
|
||||
|
||||
(This might look familiar to modern JavaScript programmers: Promises were heavily influenced by Twisted's deferreds.)
|
||||
|
||||
### Sparse is better than dense.
|
||||
|
||||
The easiest way to make something less dense is to introduce nesting. This habit is why the principle of sparseness follows the previous one: after we have reduced nesting as much as possible, we are often left with _dense_ code or data structures. Density, in this sense, is jamming too much information into a small amount of code, making it difficult to decipher when something goes wrong.
|
||||
|
||||
Reducing that denseness requires creative thinking, and there are no simple solutions. The Zen of Python does not offer simple solutions. All it offers are ways to find what can be improved in the code, without always giving guidance for "how."
|
||||
|
||||
Take a walk. Take a shower. Smell the flowers. Sit in a lotus position and think hard, until finally, inspiration strikes. When you are finally enlightened, it is time to write the code.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/12/zen-python-flat-sparse
|
||||
|
||||
作者:[Moshe Zadka][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/moshez
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/browser_web_internet_website.png?itok=g5B_Bw62 (Digital creative of a browser on the internet)
|
||||
[2]: https://www.python.org/dev/peps/pep-0020/
|
||||
[3]: https://twistedmatrix.com/trac/
|
||||
@ -1,86 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (10 Linux command tutorials for beginners and experts)
|
||||
[#]: via: (https://opensource.com/article/19/12/linux-commands)
|
||||
[#]: author: (Moshe Zadka https://opensource.com/users/moshez)
|
||||
|
||||
10 Linux command tutorials for beginners and experts
|
||||
======
|
||||
Learn how to make Linux do what you need it to do in Opensource.com's
|
||||
top 10 articles about Linux commands from 2019.
|
||||
![Penguin driving a car with a yellow background][1]
|
||||
|
||||
Using Linux _well_ means understanding what commands are available and what they're capable of doing for you. We have covered a lot of them on Opensource.com during 2019, and here are 10 favorites from the bunch.
|
||||
|
||||
### Using the force at the Linux command line
|
||||
|
||||
The Force has a light side and a dark side. Properly understanding that is crucial to true mastery. In his article [_Using the force at the Linux command line_][2], Alan Formy-Duval explains the **-f** option (also known as **\--force**) for several popular and sometimes dangerous commands.
|
||||
|
||||
### Intro to the Linux useradd command
|
||||
|
||||
Sharing accounts is a bad idea. Instead, give separate accounts to different people (and even different roles) with the quintessential **useradd** command. Part of his venerable series on basic Linux administration, Alan Formy-Duval provides an [_Intro to the Linux useradd command_][3], and, as usual, he explains it in _plain English_ so that both new and experienced admins can understand it.
|
||||
|
||||
### Linux commands to display your hardware information
|
||||
|
||||
What's _inside_ the box? Sometimes it's useful to inspect your hardware without using a screwdriver. In [_Linux commands to display your hardware information_][4], Howard Fosdick provides both popular and obscure commands to help you dig deep into the computer you're using, the computer you're testing at the store before buying, or the computer you're trying to repair.
|
||||
|
||||
### How to encrypt files with gocryptfs on Linux
|
||||
|
||||
Our files hold lots of private data, from social security numbers to personal letters to loved ones. In [_How to encrypt files with gocryptfs on Linux_][5], Brian "Bex" Exelbierd explains how to keep *private *what's meant to be private. As a bonus, he demonstrates encrypting files in a way that has little to no impact on your existing workflow. This isn't a complex PGP-style puzzle of key management and background key agents; this is quick, seamless, and secure file encryption.
|
||||
|
||||
### How to use advanced rsync for large Linux backups
|
||||
|
||||
In the New Year, many people will resolve to be more diligent about making backups. Alan Formy-Duval must have made that resolution years ago, because in [_How to use advanced rsync for large Linux backups_][6], he displays remarkable familiarity with the file synchronization command. You might not remember all the syntax right away, but the idea is to read and process the options, construct your backup command, and then automate it. That's the smart way to use **rsync**, and it's the _only_ way to do backups reliably.
|
||||
|
||||
### Using more to view text files at the Linux command line
|
||||
|
||||
In Scott Nesbitt's article [_Using more to view text files at the Linux command line_][7], the good old default pager **more** finally gets the spotlight. Many people install and use **less**, because it's more flexible than **more**. However, with more and more systems being implemented in the sparsest of containers, the luxury of fancy new tools like **less** or **most** sometimes just doesn't exist. Knowing and using **more** is simple, it's a common default, and it's the production system's debugging tool of last resort.
|
||||
|
||||
### What you probably didn't know about sudo
|
||||
|
||||
The **sudo** command is famous to a fault. People know the **sudo** term, and most of us believe we know what it does. And we're a little bit correct, but as Peter Czanik reveals in his article [_What you probably didn't know about sudo_][8], there's a lot more to the command than just "Simon says." Like that classic childhood game, the **sudo** command is powerful and also prone to silly mistakes—only with greater potential for horrible consequences. This is one game you do not want to lose!
|
||||
|
||||
### How to program with Bash: Syntax and tools
|
||||
|
||||
If you're a Linux, BSD, or Mac (and lately, Windows) user, you may have used the Bash shell interactively. It's a great shell for quick, one-off commands, which is why so many Linux users love to use it as their primary user interface. However, Bash is much more than just a command prompt. It's also a programming language, and if you're already using Bash commands, then the path to automation has never been more straightforward. Learn all about it in David Both's excellent [_How to program with Bash: Syntax and tools_][9].
|
||||
|
||||
### Master the Linux ls command
|
||||
|
||||
The **ls** command is one of those commands that merits a two-letter name; one-letter commands are an optimization for slow terminals where each letter causes a significant delay and also a nice bonus for lazy typists. Seth Kenlon explains how you can [_Master the Linux ls command_][10] and he does so with his usual clarity and pragmatism. Most significantly, in a system where "everything is a file," being able to list the files is crucial.
|
||||
|
||||
### Getting started with the Linux cat command
|
||||
|
||||
The **cat** command (short for con_cat_enate) is deceptively simple. Whether you use it to quickly see the contents of a file or to pipe the contents to another command, you may not be using **cat** to its full potential. Alan Formy-Duval's elucidating [_Getting started with the Linux cat command_][11] offers new ideas to take advantage of a command that lets you open a file without feeling like you've opened it. As a bonus, learn all about **zcat** so you can decompress files without all the trouble of decompression! It's a small and simple thing, but _this_ is what makes Linux great.
|
||||
|
||||
### Continue the journey
|
||||
|
||||
Don't let Opensource.com's 10 best articles about Linux commands of 2019 be the end of your journey. There's much more to discover about Linux and its versatile prompt, so stay tuned in 2020 for more insights. And, if there's a Linux command you want us to know about, please tell us about it in the comments, or share your knowledge with Opensource.com readers by [submitting an article][12] about your favorite Linux command.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/12/linux-commands
|
||||
|
||||
作者:[Moshe Zadka][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/moshez
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/car-penguin-drive-linux-yellow.png?itok=twWGlYAc (Penguin driving a car with a yellow background)
|
||||
[2]: https://opensource.com/article/19/5/may-the-force-linux
|
||||
[3]: https://opensource.com/article/19/10/linux-useradd-command
|
||||
[4]: https://opensource.com/article/19/9/linux-commands-hardware-information
|
||||
[5]: https://opensource.com/article/19/8/how-encrypt-files-gocryptfs
|
||||
[6]: https://opensource.com/article/19/5/advanced-rsync
|
||||
[7]: https://opensource.com/article/19/1/more-text-files-linux
|
||||
[8]: https://opensource.com/article/19/10/know-about-sudo
|
||||
[9]: https://opensource.com/article/19/10/programming-bash-syntax-tools
|
||||
[10]: https://opensource.com/article/19/7/master-ls-command
|
||||
[11]: https://opensource.com/article/19/2/getting-started-cat-command
|
||||
[12]: https://opensource.com/how-submit-article
|
||||
@ -1,170 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (messon007)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (DevOps vs Agile: What's the difference?)
|
||||
[#]: via: (https://opensource.com/article/20/2/devops-vs-agile)
|
||||
[#]: author: (Taz Brown https://opensource.com/users/heronthecli)
|
||||
|
||||
DevOps vs Agile: What's the difference?
|
||||
======
|
||||
The difference between the two is what happens after development.
|
||||
![Pair programming][1]
|
||||
|
||||
Early on, software development didn't really fit under a particular management umbrella. Then along came [waterfall][2], which spoke to the idea that software development could be defined by the length of time an application took to create or build.
|
||||
|
||||
Back then, it often took long periods of time to create, test, and deploy software because there were no checks and balances during the development process. The results were poor software quality with defects and bugs and unmet timelines. The focus was on long, drawn-out plans for software projects.
|
||||
|
||||
Waterfall projects have been associated with the [triple constraint][3] model, which is also called the project management triangle. Each side of the triangle represents a component of the triple constraints of project management: **scope**, **time**, and **cost**. As [Angelo Baretta writes][4], the triple constraint model "says that cost is a function of time and scope, that these three factors are related in a defined and predictable way… [I]f we want to shorten the schedule (time), we must increase cost. It says that if we want to increase scope, we must increase cost or schedule."
|
||||
|
||||
### Transitioning from waterfall to agile
|
||||
|
||||
Waterfall came from manufacturing and engineering, where a linear process makes sense; you build the wall before you build the roof. Similarly, software development problems were viewed as something that could be solved with planning. From beginning to end, the development process was clearly defined by a roadmap that would lead to the final delivery of a product.
|
||||
|
||||
Eventually, waterfall was recognized as detrimental and counterintuitive to software development because, often, the value could not be determined until the very end of the project cycle, and in many cases, the projects failed. Also, the customer didn't get to see any working software until the end of the project.
|
||||
|
||||
Agile takes a different approach that moves away from planning the entire project, committing to estimated dates, and being accountable to a plan. Rather, agile assumes and embraces uncertainty. It is built around the idea of responding to change instead of charging past it or ignoring the need for it. Instead, change is considered as a way to fulfill the needs of the customer.
|
||||
|
||||
### Agile values
|
||||
|
||||
Agile is governed by the Agile Manifesto, which defines [12 principles][5]:
|
||||
|
||||
1. Satisfying the customer is the top priority
|
||||
2. Welcome changing requirements, even late in development
|
||||
3. Deliver working software frequently
|
||||
4. Development and business must work together
|
||||
5. Build projects around motivated people
|
||||
6. Face-to-face communication is the most efficient and effective method of conveying information
|
||||
7. The primary measure of success is working software
|
||||
8. Agile processes promote sustainable development
|
||||
9. Maintain continuous attention to technical excellence and good design
|
||||
10. Simplicity is essential
|
||||
11. The best architectures, requirements, and designs emerge from self-organizing teams
|
||||
12. Regularly reflect on work, then tune and adjust behavior
|
||||
|
||||
|
||||
|
||||
Agile's four [core values][6] are:
|
||||
|
||||
* **Individuals and interactions** over processes and tools
|
||||
* **Working software** over comprehensive documentation
|
||||
* **Customer collaboration** over contract negotiation
|
||||
* **Responding to change** over following a plan
|
||||
|
||||
|
||||
|
||||
This contrasts with waterfall's rigid planning style. In agile, the customer is a member of the development team rather than engaging only at the beginning, when setting business requirements, and at the end, when reviewing the final product (as in waterfall). The customer helps the team write the [acceptance criteria][7] and remains engaged throughout the process. In addition, agile requires changes and continuous improvement throughout the organization. The development team works with other teams, including the project management office and the testers. What gets done and when are led by a designated role and agreed to by the team as a whole.
|
||||
|
||||
### Agile software development
|
||||
|
||||
Agile software development requires adaptive planning, evolutionary development, and delivery. Many software development methodologies, frameworks, and practices fall under the umbrella of being agile, including:
|
||||
|
||||
* Scrum
|
||||
* Kanban (visual workflow)
|
||||
* XP (eXtreme Programming)
|
||||
* Lean
|
||||
* DevOps
|
||||
* Feature-driven development (FDD)
|
||||
* Test-driven development (TDD)
|
||||
* Crystal
|
||||
* Dynamic systems development method (DSDM)
|
||||
* Adaptive software development (ASD)
|
||||
|
||||
|
||||
|
||||
All of these have been used on their own or in combination for developing and deploying software. The most common are [scrum, kanban][8] (or the combination called scrumban), and DevOps.
|
||||
|
||||
[Scrum][9] is a framework under which a team, generally consisting of a scrum master, product owner, and developers, operates cross-functionally and in a self-directed manner to increase the speed of software delivery and
|
||||
|
||||
to bring greater business value to the customer. The focus is on faster iterations with smaller [increments][10].
|
||||
|
||||
[Kanban][11] is an agile framework, sometimes called a workflow management system, that helps teams visualize their work and maximize efficiency (thus being agile). Kanban is usually represented by a digital or physical board. A team's work moves across the board, for example, from not started, to in progress, testing, and finished, as it progresses. Kanban allows each team member to see the state of all work at any time.
|
||||
|
||||
### DevOps values
|
||||
|
||||
DevOps is a culture, a state of mind, a way that software development or infrastructure is, and a way that software and applications are built and deployed. There is no wall between development and operations; they work simultaneously and without silos.
|
||||
|
||||
DevOps is based on two other practice areas: lean and agile. DevOps is not a title or role within a company; it's really a commitment that an organization or team makes to continuous delivery, deployment, and integration. According to [Gene Kim][12], author of _The Phoenix Project_ and _The Unicorn Project_, there are three "ways" that define the principles of DevOps:
|
||||
|
||||
* The First Way: Principles of flow
|
||||
* The Second Way: Principles of feedback
|
||||
* The Third Way: Principles of continuous learning
|
||||
|
||||
|
||||
|
||||
### DevOps software development
|
||||
|
||||
DevOps does not happen in a vacuum; it is a flexible practice that, in its truest form, is a shared culture and mindset around software development and IT or infrastructure implementation.
|
||||
|
||||
When you think of automation, cloud, microservices, you think of DevOps. In an [interview][13], _Accelerate: Building and Scaling High Performing Technology Organizations_ authors Nicole Forsgren, Jez Humble, and Gene Kim explained:
|
||||
|
||||
> * Software delivery performance matters, and it has a significant impact on organizational outcomes such as profitability, market share, quality, customer satisfaction, and achieving organizational and mission goals.
|
||||
> * High performers achieve levels of throughput, stability, and quality; they're not trading off to achieve these attributes.
|
||||
> * You can improve your performance by implementing practices from the lean, agile, and DevOps playbooks.
|
||||
> * Implementing these practices and capabilities also has an impact on your organizational culture, which in turn has an impact on both your software delivery performance and organizational performance.
|
||||
> * There's still lots of work to do to understand how to improve performance.
|
||||
>
|
||||
|
||||
|
||||
### DevOps vs. agile
|
||||
|
||||
Despite their similarities, DevOps and agile are not the same, and some argue that DevOps is better than agile. To eliminate the confusion, it's important to get down to the nuts and bolts.
|
||||
|
||||
#### Similarities
|
||||
|
||||
* Both are software development methodologies; there is no disputing this.
|
||||
* Agile has been around for over 20 years, and DevOps came into the picture fairly recently.
|
||||
* Both believe in fast software development, and their principles are based on how fast software can be developed without causing harm to the customer or operations.
|
||||
|
||||
|
||||
|
||||
#### Differences
|
||||
|
||||
* **The difference between the two** is what happens after development.
|
||||
* Software development, testing, and deployment happen in both DevOps and agile. However, pure agile tends to stop after these three stages. In contrast, DevOps includes operations, which happen continually. Therefore, monitoring and software development are also continuous.
|
||||
* In agile, separate people are responsible for developing, testing, and deploying the software. In DevOps, the DevOps engineering role is are responsible for everything; development is operations, and operations is development.
|
||||
* DevOps is more associated with cost-cutting, and agile is more synonymous with lean and reducing waste, and concepts like agile project accounting and minimum viable product (MVP) are relevant.
|
||||
* Agile focuses on and embodies empiricism (**adaptation**, **transparency**, and **inspection**) instead of predictive measures.
|
||||
|
||||
Agile | DevOps
|
||||
---|---
|
||||
Feedback from customer | Feedback from self
|
||||
Smaller release cycles | Smaller release cycles, immediate feedback
|
||||
Focus on speed | Focus on speed and automation
|
||||
Not the best for business | Best for business
|
||||
|
||||
### Wrapping up
|
||||
|
||||
Agile and DevOps are distinct, although their similarities lead people to think they are one and the same. This does both agile and DevOps a disservice.
|
||||
|
||||
In my experience as an agilist, I have found it valuable for organizations and teams to understand—from a high level—what agile and DevOps are and how they aid teams in working faster and more efficiently, delivering quality faster, and improving customer satisfaction.
|
||||
|
||||
Agile and DevOps are not adversarial in any way (or at least the intent is not there). They are more allies than enemies in the agile revolution. Agile and DevOps can operate exclusively and inclusively, which allows both to exist in the same space.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/20/2/devops-vs-agile
|
||||
|
||||
作者:[Taz Brown][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/heronthecli
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/collab-team-pair-programming-code-keyboard.png?itok=kBeRTFL1 (Pair programming)
|
||||
[2]: http://www.agilenutshell.com/agile_vs_waterfall
|
||||
[3]: https://en.wikipedia.org/wiki/Project_management_triangle
|
||||
[4]: https://www.pmi.org/learning/library/triple-constraint-erroneous-useless-value-8024
|
||||
[5]: https://agilemanifesto.org/principles.html
|
||||
[6]: https://agilemanifesto.org/
|
||||
[7]: https://www.productplan.com/glossary/acceptance-criteria/
|
||||
[8]: https://opensource.com/article/19/8/scrum-vs-kanban
|
||||
[9]: https://www.scrum.org/
|
||||
[10]: https://www.scrum.org/resources/what-is-an-increment
|
||||
[11]: https://www.atlassian.com/agile/kanban
|
||||
[12]: https://itrevolution.com/the-unicorn-project/
|
||||
[13]: https://www.infoq.com/articles/book-review-accelerate/
|
||||
@ -1,211 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Basic kubectl and Helm commands for beginners)
|
||||
[#]: via: (https://opensource.com/article/20/2/kubectl-helm-commands)
|
||||
[#]: author: (Jessica Cherry https://opensource.com/users/jrepka)
|
||||
|
||||
Basic kubectl and Helm commands for beginners
|
||||
======
|
||||
Take a trip to the grocery store to shop for the commands you'll need to
|
||||
get started with these Kubernetes tools.
|
||||
![A person working.][1]
|
||||
|
||||
Recently, my husband was telling me about an upcoming job interview where he would have to run through some basic commands on a computer. He was anxious about the interview, but the best way for him to learn and remember things has always been to equate the thing he doesn't know to something very familiar to him. Because our conversation happened right after I was roaming the grocery store trying to decide what to cook that evening, it inspired me to write about kubectl and Helm commands by equating them to an ordinary trip to the grocer.
|
||||
|
||||
[Helm][2] is a tool to manage applications within Kubernetes. You can easily deploy charts with your application information, allowing them to be up and preconfigured in minutes within your Kubernetes environment. When you're learning something new, it's always helpful to look at chart examples to see how they are used, so if you have time, take a look at these stable [charts][3].
|
||||
|
||||
[Kubectl][4] is a command line that interfaces with Kubernetes environments, allowing you to configure and manage your cluster. It does require some configuration to work within environments, so take a look through the [documentation][5] to see what you need to do.
|
||||
|
||||
I'll use namespaces in the examples, which you can learn about in my article [_Kubernetes namespaces for beginners_][6].
|
||||
|
||||
Now that we have that settled, let's start shopping for basic kubectl and Helm commands!
|
||||
|
||||
### Helm list
|
||||
|
||||
What is the first thing you do before you go to the store? Well, if you're organized, you make a **list**. LIkewise, this is the first basic Helm command I will explain.
|
||||
|
||||
In a Helm-deployed application, **list** provides details about an application's current release. In this example, I have one deployed application—the Jenkins CI/CD application. Running the basic **list** command always brings up the default namespace. Since I don't have anything deployed in the default namespace, nothing shows up:
|
||||
|
||||
|
||||
```
|
||||
$helm list
|
||||
NAME NAMESPACE REVISION UPDATED STATUS CHART APP VERSION
|
||||
```
|
||||
|
||||
However, if I run the command with an extra flag, my application and information appear:
|
||||
|
||||
|
||||
```
|
||||
$helm list --all-namespaces
|
||||
NAME NAMESPACE REVISION UPDATED STATUS CHART APP VERSION
|
||||
jenkins jenkins 1 2020-01-18 16:18:07 EST deployed jenkins-1.9.4 lts
|
||||
```
|
||||
|
||||
Finally, I can direct the **list** command to check only the namespace I want information from:
|
||||
|
||||
|
||||
```
|
||||
$helm list --namespace jenkins
|
||||
NAME NAMESPACE REVISION UPDATED STATUS CHART APP VERSION
|
||||
jenkins jenkins 1 2020-01-18 16:18:07 EST deployed jenkins-1.9.4 lts
|
||||
```
|
||||
|
||||
Now that I have a list and know what is on it, I can go and get my items with **get** commands! I'll start with the Kubernetes cluster; what can I get from it?
|
||||
|
||||
### Kubectl get
|
||||
|
||||
The **kubectl get** command gives information about many things in Kubernetes, including pods, nodes, and namespaces. Again, without a namespace flag, you'll always land in the default. First, I'll get the namespaces in the cluster to see what's running:
|
||||
|
||||
|
||||
```
|
||||
$kubectl get namespaces
|
||||
NAME STATUS AGE
|
||||
default Active 53m
|
||||
jenkins Active 44m
|
||||
kube-node-lease Active 53m
|
||||
kube-public Active 53m
|
||||
kube-system Active 53m
|
||||
```
|
||||
|
||||
Now that I have the namespaces running in my environment, I'll get the nodes and see how many are running:
|
||||
|
||||
|
||||
```
|
||||
$kubectl get nodes
|
||||
NAME STATUS ROLES AGE VERSION
|
||||
minikube Ready master 55m v1.16.2
|
||||
```
|
||||
|
||||
I have one node up and running, mainly because my Minikube is running on one small server. To get the pods running on my one node:
|
||||
|
||||
|
||||
```
|
||||
$kubectl get pods
|
||||
No resources found in default namespace.
|
||||
```
|
||||
|
||||
Oops, it's empty. I'll get what's in my Jenkins namespace with:
|
||||
|
||||
|
||||
```
|
||||
$kubectl get pods --namespace jenkins
|
||||
NAME READY STATUS RESTARTS AGE
|
||||
jenkins-7fc688c874-mh7gv 1/1 Running 0 40m
|
||||
```
|
||||
|
||||
Good news! There's one pod, it hasn't restarted, and it has been running for 40 minutes. Well, since I know the pod is up, I want to see what I can get from Helm.
|
||||
|
||||
### Helm get
|
||||
|
||||
**Helm get** is a little more complicated because this **get** command requires more than an application name, and you can request multiple things from applications. I'll begin by getting the values used to make the application, and then I'll show a snip of the **get all** action, which provides all the data related to the application.
|
||||
|
||||
|
||||
```
|
||||
$helm get values jenkins -n jenkins
|
||||
USER-SUPPLIED VALUES:
|
||||
null
|
||||
```
|
||||
|
||||
Since I did a very minimal stable-only install, the configuration didn't change. If I run the **all** command, I get everything out of the chart:
|
||||
|
||||
|
||||
```
|
||||
`$helm get all jenkins -n jenkins`
|
||||
```
|
||||
|
||||
![output from helm get all command][7]
|
||||
|
||||
This produces a ton of data, so I always recommend keeping a copy of a Helm chart so you can look over the templates in the chart. I also create my own values to see what I have in place.
|
||||
|
||||
Now that I have all my goodies in my shopping cart, I'll check the labels that **describe** what's in them. These examples pertain only to kubectl, and they describe what I've deployed through Helm.
|
||||
|
||||
### Kubectl describe
|
||||
|
||||
As I did with the **get** command, which can describe just about anything in Kubernetes, I'll limit my examples to namespaces, pods, and nodes. Since I know I'm working with one of each, this will be easy.
|
||||
|
||||
|
||||
```
|
||||
$kubectl describe ns jenkins
|
||||
Name: jenkins
|
||||
Labels: <none>
|
||||
Annotations: <none>
|
||||
Status: Active
|
||||
No resource quota.
|
||||
No resource limits.
|
||||
```
|
||||
|
||||
I can see my namespace's name and that it is active and has no resource nor quote limits.
|
||||
|
||||
The **describe pods** command produces a large amount of information, so I'll provide a small snip of the output. If you run the command without the pod name, it will return information for all of the pods in the namespace, which can be overwhelming. So, be sure you always include the pod name with this command. For example:
|
||||
|
||||
|
||||
```
|
||||
`$kubectl describe pods jenkins-7fc688c874-mh7gv --namespace jenkins`
|
||||
```
|
||||
|
||||
![output of kubectl-describe-pods][8]
|
||||
|
||||
This provides (among many other things) the status of the container, how the container is managed, the label, and the image used in the pod. The data not in this abbreviated output includes resource requests and limits along with any conditions, init containers, and storage volume information applied in a Helm values file. This data is useful if your application is crashing due to inadequate resources, a configured init container that runs a prescript for configuration, or generated hidden passwords that shouldn't be in a plain text YAML file.
|
||||
|
||||
Finally, I'll use **describe node**, which (of course) describes the node. Since this example has just one, named Minikube, that is what I'll use; if you have multiple nodes in your environment, you must include the node name of interest.
|
||||
|
||||
As with pods, the node command produces an abundance of data, so I'll include just a snip of the output.
|
||||
|
||||
|
||||
```
|
||||
`$kubectl describe node minikube`
|
||||
```
|
||||
|
||||
![output of kubectl describe node][9]
|
||||
|
||||
Note that **describe node** is one of the more important basic commands. As this image shows, the command returns statistics that indicate when the node is running out of resources, and this data is excellent for alerting you when you need to scale up (if you do not have autoscaling in your environment). Other things not in this snippet of output include the percentages of requests made for all resources and limits, as well as the age and allocation of resources (e.g., for my application).
|
||||
|
||||
### Checking out
|
||||
|
||||
With these commands, I've finished my shopping and gotten everything I was looking for. Hopefully, these basic commands can help you, too, in your day-to-day with Kubernetes.
|
||||
|
||||
I urge you to work with the command line often and learn the shorthand flags available in the Help sections, which you can access by running these commands:
|
||||
|
||||
|
||||
```
|
||||
`$helm --help`
|
||||
```
|
||||
|
||||
and
|
||||
|
||||
|
||||
```
|
||||
`$kubectl -h`
|
||||
```
|
||||
|
||||
### Peanut butter and jelly
|
||||
|
||||
Some things just go together like peanut butter and jelly. Helm and kubectl are a little like that.
|
||||
|
||||
I often use these tools in my environment. Because they have many similarities in a ton of places, after using one, I usually need to follow up with the other. For example, I can do a Helm deployment and watch it fail using kubectl. Try them together, and see what they can do for you.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/20/2/kubectl-helm-commands
|
||||
|
||||
作者:[Jessica Cherry][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/jrepka
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/rh_003784_02_os.comcareers_os_rh2x.png?itok=jbRfXinl (A person working.)
|
||||
[2]: https://helm.sh/
|
||||
[3]: https://github.com/helm/charts/tree/master/stable
|
||||
[4]: https://kubernetes.io/docs/reference/kubectl/kubectl/
|
||||
[5]: https://kubernetes.io/docs/reference/kubectl/overview/
|
||||
[6]: https://opensource.com/article/19/12/kubernetes-namespaces
|
||||
[7]: https://opensource.com/sites/default/files/uploads/helm-get-all.png (output from helm get all command)
|
||||
[8]: https://opensource.com/sites/default/files/uploads/kubectl-describe-pods.png (output of kubectl-describe-pods)
|
||||
[9]: https://opensource.com/sites/default/files/uploads/kubectl-describe-node.png (output of kubectl describe node)
|
||||
@ -1,5 +1,5 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: translator: (mengxinayan)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
@ -157,7 +157,7 @@ via: https://www.2daygeek.com/basic-vim-commands-cheat-sheet-quick-start-guide/
|
||||
|
||||
作者:[Magesh Maruthamuthu][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
译者:[萌新阿岩](https://github.com/mengxinayan)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,182 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Here Are The Most Beautiful Linux Distributions in 2020)
|
||||
[#]: via: (https://itsfoss.com/beautiful-linux-distributions/)
|
||||
[#]: author: (Ankush Das https://itsfoss.com/author/ankush/)
|
||||
|
||||
Here Are The Most Beautiful Linux Distributions in 2020
|
||||
======
|
||||
|
||||
It’s a no-brainer that there’s a Linux distribution for every user – no matter what they prefer or what they want to do.
|
||||
|
||||
Starting out with Linux? You can go with the [Linux distributions for beginners][1]. Switching from Windows? You have [Windows-like Linux distributions][2]. Have an old computer? You can [use lightweight Linux distros][3].
|
||||
|
||||
In this list, I’m going to focus only on the most beautiful Linux distros out there.
|
||||
|
||||
### Top 7 Most Beautiful Linux Distributions
|
||||
|
||||
![][4]
|
||||
|
||||
Wait! Is there a thing called a beautiful Linux distribution? Is it not redundant considering the fact that you can customize the looks of any distribution and make it look better with [themes][5] and [icons][6]?
|
||||
|
||||
You are right about that. But here, I am talking about the distributions that look great without any tweaks and customization effort from the user’s end. These distros provide a seamless, pleasant desktop experience right out of the box.
|
||||
|
||||
**Note:** _The list is in no particular order of ranking._
|
||||
|
||||
#### 1\. elementary OS
|
||||
|
||||
![][7]
|
||||
|
||||
elementary OS is one of the most beautiful Linux distros out there. It leans on a macOS-ish look while providing a great user experience for Linux users. If you’re already comfortable macOS – you will have no problem using the elementary OS.
|
||||
|
||||
Also, elementary OS is based on Ubuntu – so you can easily find plenty of applications to get things done.
|
||||
|
||||
Not just limited to the look and feel – but the elementary OS is always hard at work to introduce meaningful changes. So, you can expect the user experience to improve with every update you get.
|
||||
|
||||
[elementary OS][8]
|
||||
|
||||
#### 2\. Deepin
|
||||
|
||||
![][9]
|
||||
|
||||
Deepin is yet another beautiful Linux distro originally based on Debian’s stable branch. The animations (look and feel) could be too overwhelming for some – but it looks pretty.
|
||||
|
||||
It features its own Deepin Desktop Environment that involves a mix of essential features for the best user experience possible. It may not exactly resemble the UI of any other distribution but it’s quite easy to get used to.
|
||||
|
||||
My personal attention would go to the control center and the color scheme featured in Deepin OS. You can give it a try – it’s worth taking a look.
|
||||
|
||||
[Deepin][10]
|
||||
|
||||
#### 3\. Pop!_OS
|
||||
|
||||
![][11]
|
||||
|
||||
Pop!_OS manages to offer a great UI on top of Ubuntu while offering a pure [GNOME][12] experience.
|
||||
|
||||
It also happens to be my personal favorite which I utilize as my primary desktop OS. Pop!_OS isn’t flashy – nor involves any fancy animations. However, they’ve managed to get things right by having a perfect combo of icon/themes – while polishing the user experience from a technical point of view.
|
||||
|
||||
I don’t want to initiate a [Ubuntu vs Pop OS][13] debate but if you’re used to Ubuntu, Pop!_OS can be a great alternative for potentially better user experience.
|
||||
|
||||
[Pop!_OS][14]
|
||||
|
||||
#### 4\. Manjaro Linux
|
||||
|
||||
![][15]
|
||||
|
||||
Manjaro Linux is an [Arch][16]-based Linux distribution. While [installing Arch Linux][17] is a slightly complicated job, Manjaro provides an easier and smoother Arch experience.
|
||||
|
||||
It offers a variety of [desktop environment editions][18] to choose from while downloading. No matter what you choose, you still get enough options to customize the look and feel or the layout.
|
||||
|
||||
To me, it looks quite fantastic for an Arch-based distribution that works out of the box – you can give it a try!
|
||||
|
||||
[Manjaro Linux][19]
|
||||
|
||||
#### 5\. KDE Neon
|
||||
|
||||
![][20]
|
||||
|
||||
[KDE Neon][21] is for the users who want a simplified approach to the design language but still get a great user experience.
|
||||
|
||||
It is a lightweight Linux distro which is based on Ubuntu. As the name suggests, it features the KDE Plasma desktop and looks absolutely beautiful.
|
||||
|
||||
KDE Neon gives you the latest and greatest KDE Plasma desktop and KDE applications. Unlike [Kubuntu][22] or other KDE-based distributions, you don’t have to wait for months to get the new [KDE software][23].
|
||||
|
||||
You get a lot of customization options built-in with the KDE desktop – so feel free to try it out!
|
||||
|
||||
[KDE Neon][24]
|
||||
|
||||
#### 6\. Zorin OS
|
||||
|
||||
![][25]
|
||||
|
||||
Without a doubt, Zorin OS is an impressive Linux distro that manages to provide a good user experience – even with its lite edition.
|
||||
|
||||
You can try either the full version or the lite edition (with [Xfce desktop][26]). The UI is tailored for Windows and macOS users to get used to. While based on Ubuntu, it provides a great user experience with what it has to offer.
|
||||
|
||||
If you start like its user interface – you can also try [Zorin Grid][27] to manage multiple computers running Zorin OS at your workplace/home. With the ultimate edition, you can also control the layout of your desktop (as shown in the image above).
|
||||
|
||||
[Zorin OS][28]
|
||||
|
||||
#### 7\. Nitrux OS
|
||||
|
||||
![][29]
|
||||
|
||||
[Nitrux OS][30] is a unique take on a Linux distribution which is somewhat based on Ubuntu – but not completely.
|
||||
|
||||
It focuses on providing a good user experience to the users who are looking for a unique design language with a fresh take on a Linux distro. It uses Nomad desktop which is based on KDE.
|
||||
|
||||
Nitrux encourages to use of [AppImage][31] for applications. But you can also use Arch Linux’s pacman package manager in Nitrux which is based on Ubuntu. Awesome, isn’t it?
|
||||
|
||||
Even if it’s not the perfect OS to have installed (yet), it sure looks pretty and good enough for most of the basic tasks. You can also know more about it when you read our [interview with Nitrux’s founder][32].
|
||||
|
||||
Here’s a slightly old video of Nitrux but it still looks good:
|
||||
|
||||
[Nitrux OS][33]
|
||||
|
||||
#### Bonus: eXtern OS (in ‘stagnated’ development)
|
||||
|
||||
![][34]
|
||||
|
||||
If you want to try an experimental Linux distro, extern OS is going to be beautiful.
|
||||
|
||||
It isn’t actively maintained and should not be used for production systems. Yet, it provides unique user experience (thought not polished enough).
|
||||
|
||||
Just for the sake of trying a good-looking Linux distro, you can give it a try to experience it.
|
||||
|
||||
[eXtern OS][35]
|
||||
|
||||
**Wrapping Up**
|
||||
|
||||
Now, as the saying goes, beauty lies in the eyes of the beholder. So this list of beautiful Linux distributions is from my point of view. Feel free to disagree (politely of course) and mention your favorites.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://itsfoss.com/beautiful-linux-distributions/
|
||||
|
||||
作者:[Ankush Das][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://itsfoss.com/author/ankush/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://itsfoss.com/best-linux-beginners/
|
||||
[2]: https://itsfoss.com/windows-like-linux-distributions/
|
||||
[3]: https://itsfoss.com/lightweight-linux-beginners/
|
||||
[4]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2020/02/beautiful-linux-distros.png?ssl=1
|
||||
[5]: https://itsfoss.com/best-gtk-themes/
|
||||
[6]: https://itsfoss.com/best-icon-themes-ubuntu-16-04/
|
||||
[7]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2020/01/elementary-os-hera.png?ssl=1
|
||||
[8]: https://elementary.io/
|
||||
[9]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2020/02/deepin-screenshot.jpg?ssl=1
|
||||
[10]: https://www.deepin.org/en/
|
||||
[11]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2020/02/pop-os-stock.jpg?ssl=1
|
||||
[12]: https://www.gnome.org/
|
||||
[13]: https://itsfoss.com/pop-os-vs-ubuntu/
|
||||
[14]: https://system76.com/pop
|
||||
[15]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2020/02/manjaro_kde.jpg?ssl=1
|
||||
[16]: https://en.wikipedia.org/wiki/Arch
|
||||
[17]: https://itsfoss.com/install-arch-linux/
|
||||
[18]: https://itsfoss.com/best-linux-desktop-environments/
|
||||
[19]: https://manjaro.org/download/
|
||||
[20]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2020/02/kde-neon-screenshot.jpg?ssl=1
|
||||
[21]: https://itsfoss.com/kde-neon-unveiled/
|
||||
[22]: https://kubuntu.org/
|
||||
[23]: https://kde.org/
|
||||
[24]: https://neon.kde.org/
|
||||
[25]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2019/11/zorin-lite-ultimate-appearance.jpg?ssl=1
|
||||
[26]: https://www.xfce.org/
|
||||
[27]: https://itsfoss.com/zorin-grid/
|
||||
[28]: https://zorinos.com/
|
||||
[29]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2020/02/nitrux-screenshot.jpg?ssl=1
|
||||
[30]: https://itsfoss.com/nitrux-linux-overview/
|
||||
[31]: https://itsfoss.com/use-appimage-linux/
|
||||
[32]: https://itsfoss.com/nitrux-linux/
|
||||
[33]: https://nxos.org/
|
||||
[34]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2020/02/extern-os.png?ssl=1
|
||||
[35]: https://externos.io/
|
||||
@ -1,335 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Try this Bash script for large filesystems)
|
||||
[#]: via: (https://opensource.com/article/20/2/script-large-files)
|
||||
[#]: author: (Nick Clifton https://opensource.com/users/nickclifton)
|
||||
|
||||
Try this Bash script for large filesystems
|
||||
======
|
||||
A simple script to list files, directories, executables, and links.
|
||||
![bash logo on green background][1]
|
||||
|
||||
Have you ever wanted to list all the files in a directory, but just the files, nothing else? How about just the directories? If you have, then the following script, which is open source under GPLv3, could be what you have been looking for.
|
||||
|
||||
Of course, you could use the **find** command:
|
||||
|
||||
|
||||
```
|
||||
`find . -maxdepth 1 -type f -print`
|
||||
```
|
||||
|
||||
But this is cumbersome to type, produces unfriendly output, and lacks some of the refinement of the **ls** command. You could also combine **ls** and **grep** to achieve the same result:
|
||||
|
||||
|
||||
```
|
||||
`ls -F . | grep -v /`
|
||||
```
|
||||
|
||||
But again, this is clunky. This script provides a simple alternative.
|
||||
|
||||
### Usage
|
||||
|
||||
The script provides four main functions, which depend upon which name you call: **lsf** lists files, **lsd** lists directories, **lsx** lists executables, and **lsl** lists links.
|
||||
|
||||
There is no need to install multiple copies of the script, as symbolic links work. This saves space and makes updating the script easier.
|
||||
|
||||
The script works by using the **find** command to do the searching, and then it runs **ls** on each item it finds. The nice thing about this is that any arguments given to the script are passed to the **ls** command. So, for example, this lists all files, even those that start with a dot:
|
||||
|
||||
|
||||
```
|
||||
`lsf -a`
|
||||
```
|
||||
|
||||
To list directories in long format, use the **lsd** command:
|
||||
|
||||
|
||||
```
|
||||
`lsd -l`
|
||||
```
|
||||
|
||||
You can provide multiple arguments, and also file and directory paths.
|
||||
|
||||
This provides a long classified listing of all of files in the current directory's parent directory, and in the **/usr/bin** directory:
|
||||
|
||||
|
||||
```
|
||||
`lsf -F -l .. /usr/bin`
|
||||
```
|
||||
|
||||
One thing that the script does not currently handle, however, is recursion. This command lists only the files in the current directory.
|
||||
|
||||
|
||||
```
|
||||
`lsf -R`
|
||||
```
|
||||
|
||||
The script does not descend into any subdirectories. This is something that may be fixed one day.
|
||||
|
||||
### Internals
|
||||
|
||||
The script is written in a top-down fashion with the initial functions at the start of the script and the body of the work performed near the end. There are only two functions that really matter in the script. The **parse_args()** function peruses the command line, separates options from pathnames, and scripts specific options from the **ls** command-line options.
|
||||
|
||||
The **list_things_in_dir()** function takes a directory name as an argument and runs the **find** command on it. Each item found is passed to the **ls** command for display.
|
||||
|
||||
### Conclusion
|
||||
|
||||
This is a simple script to accomplish a simple function. It is a time saver and can be surprisingly useful when working with large filesystems.
|
||||
|
||||
### The script
|
||||
|
||||
|
||||
```
|
||||
#!/bin/bash
|
||||
|
||||
# Script to list:
|
||||
# directories (if called "lsd")
|
||||
# files (if called "lsf")
|
||||
# links (if called "lsl")
|
||||
# or executables (if called "lsx")
|
||||
# but not any other type of filesystem object.
|
||||
# FIXME: add lsp (list pipes)
|
||||
#
|
||||
# Usage:
|
||||
# <command_name> [switches valid for ls command] [dirname...]
|
||||
#
|
||||
# Works with names that includes spaces and that start with a hyphen.
|
||||
#
|
||||
# Created by Nick Clifton.
|
||||
# Version 1.4
|
||||
# Copyright (c) 2006, 2007 Red Hat.
|
||||
#
|
||||
# This is free software; you can redistribute it and/or modify it
|
||||
# under the terms of the GNU General Public License as published
|
||||
# by the Free Software Foundation; either version 3, or (at your
|
||||
# option) any later version.
|
||||
|
||||
# It is distributed in the hope that it will be useful, but
|
||||
# WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||
# GNU General Public License for more details.
|
||||
|
||||
# ToDo:
|
||||
# Handle recursion, eg: lsl -R
|
||||
# Handle switches that take arguments, eg --block-size
|
||||
# Handle --almost-all, --ignore-backups, --format and --ignore
|
||||
|
||||
main ()
|
||||
{
|
||||
init
|
||||
|
||||
parse_args ${1+"$@"}
|
||||
|
||||
list_objects
|
||||
|
||||
exit 0
|
||||
}
|
||||
|
||||
report ()
|
||||
{
|
||||
echo $prog": " ${1+"$@"}
|
||||
}
|
||||
|
||||
fail ()
|
||||
{
|
||||
report " Internal error: " ${1+"$@"}
|
||||
exit 1
|
||||
}
|
||||
|
||||
# Initialise global variables.
|
||||
init ()
|
||||
{
|
||||
# Default to listing things in the current directory.
|
||||
dirs[0]=".";
|
||||
|
||||
# num_dirs is the number of directories to be listed minus one.
|
||||
# This is because we are indexing the dirs[] array from zero.
|
||||
num_dirs=0;
|
||||
|
||||
# Default to ignoring things that start with a period.
|
||||
no_dots=1
|
||||
|
||||
# Note - the global variables 'type' and 'opts' are initialised in
|
||||
# parse_args function.
|
||||
}
|
||||
|
||||
# Parse our command line
|
||||
parse_args ()
|
||||
{
|
||||
local no_more_args
|
||||
|
||||
no_more_args=0 ;
|
||||
|
||||
prog=`basename $0` ;
|
||||
|
||||
# Decide if we are listing files or directories.
|
||||
case $prog in
|
||||
lsf | lsf.sh)
|
||||
type=f
|
||||
opts="";
|
||||
;;
|
||||
lsd | lsd.sh)
|
||||
type=d
|
||||
# The -d switch to "ls" is presumed when listing directories.
|
||||
opts="-d";
|
||||
;;
|
||||
lsl | lsl.sh)
|
||||
type=l
|
||||
# Use -d to prevent the listed links from being followed.
|
||||
opts="-d";
|
||||
;;
|
||||
lsx | lsx.sh)
|
||||
type=f
|
||||
find_extras="-perm /111"
|
||||
;;
|
||||
*)
|
||||
fail "Unrecognised program name: '$prog', expected either 'lsd', 'lsf', 'lsl' or 'lsx'"
|
||||
;;
|
||||
esac
|
||||
|
||||
# Locate any additional command line switches for ls and accumulate them.
|
||||
# Likewise accumulate non-switches to the directories list.
|
||||
while [ $# -gt 0 ]
|
||||
do
|
||||
case "$1" in
|
||||
# FIXME: Handle switches that take arguments, eg --block-size
|
||||
# FIXME: Properly handle --almost-all, --ignore-backups, --format
|
||||
# FIXME: and --ignore
|
||||
# FIXME: Properly handle --recursive
|
||||
-a | -A | --all | --almost-all)
|
||||
no_dots=0;
|
||||
;;
|
||||
--version)
|
||||
report "version 1.2"
|
||||
exit 0
|
||||
;;
|
||||
--help)
|
||||
case $type in
|
||||
d) report "a version of 'ls' that lists only directories" ;;
|
||||
l) report "a version of 'ls' that lists only links" ;;
|
||||
f) if [ "x$find_extras" = "x" ] ; then
|
||||
report "a version of 'ls' that lists only files" ;
|
||||
else
|
||||
report "a version of 'ls' that lists only executables";
|
||||
fi ;;
|
||||
esac
|
||||
exit 0
|
||||
;;
|
||||
--)
|
||||
# A switch to say that all further items on the command line are
|
||||
# arguments and not switches.
|
||||
no_more_args=1 ;
|
||||
;;
|
||||
-*)
|
||||
if [ "x$no_more_args" = "x1" ] ;
|
||||
then
|
||||
dirs[$num_dirs]="$1";
|
||||
let "num_dirs++"
|
||||
else
|
||||
# Check for a switch that just uses a single dash, not a double
|
||||
# dash. This could actually be multiple switches combined into
|
||||
# one word, eg "lsd -alF". In this case, scan for the -a switch.
|
||||
# XXX: FIXME: The use of =~ requires bash v3.0+.
|
||||
if [[ "x${1:1:1}" != "x-" && "x$1" =~ "x-.*a.*" ]] ;
|
||||
then
|
||||
no_dots=0;
|
||||
fi
|
||||
opts="$opts $1";
|
||||
fi
|
||||
;;
|
||||
*)
|
||||
dirs[$num_dirs]="$1";
|
||||
let "num_dirs++"
|
||||
;;
|
||||
esac
|
||||
shift
|
||||
done
|
||||
|
||||
# Remember that we are counting from zero not one.
|
||||
if [ $num_dirs -gt 0 ] ;
|
||||
then
|
||||
let "num_dirs--"
|
||||
fi
|
||||
}
|
||||
|
||||
list_things_in_dir ()
|
||||
{
|
||||
local dir
|
||||
|
||||
# Paranoia checks - the user should never encounter these.
|
||||
if test "x$1" = "x" ;
|
||||
then
|
||||
fail "list_things_in_dir called without an argument"
|
||||
fi
|
||||
|
||||
if test "x$2" != "x" ;
|
||||
then
|
||||
fail "list_things_in_dir called with too many arguments"
|
||||
fi
|
||||
|
||||
# Use quotes when accessing $dir in order to preserve
|
||||
# any spaces that might be in the directory name.
|
||||
dir="${dirs[$1]}";
|
||||
|
||||
# Catch directory names that start with a dash - they
|
||||
# confuse pushd.
|
||||
if test "x${dir:0:1}" = "x-" ;
|
||||
then
|
||||
dir="./$dir"
|
||||
fi
|
||||
|
||||
if [ -d "$dir" ]
|
||||
then
|
||||
if [ $num_dirs -gt 0 ]
|
||||
then
|
||||
echo " $dir:"
|
||||
fi
|
||||
|
||||
# Use pushd rather passing the directory name to find so that the
|
||||
# names that find passes on to xargs do not have any paths prepended.
|
||||
pushd "$dir" > /dev/null
|
||||
if [ $no_dots -ne 0 ] ; then
|
||||
find . -maxdepth 1 -type $type $find_extras -not -name ".*" -printf "%f\000" \
|
||||
| xargs --null --no-run-if-empty ls $opts -- ;
|
||||
else
|
||||
find . -maxdepth 1 -type $type $find_extras -printf "%f\000" \
|
||||
| xargs --null --no-run-if-empty ls $opts -- ;
|
||||
fi
|
||||
popd > /dev/null
|
||||
else
|
||||
report "directory '$dir' could not be found"
|
||||
fi
|
||||
}
|
||||
|
||||
list_objects ()
|
||||
{
|
||||
local i
|
||||
|
||||
i=0;
|
||||
while [ $i -le $num_dirs ]
|
||||
do
|
||||
list_things_in_dir i
|
||||
let "i++"
|
||||
done
|
||||
}
|
||||
|
||||
# Invoke main
|
||||
main ${1+"$@"}
|
||||
```
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/20/2/script-large-files
|
||||
|
||||
作者:[Nick Clifton][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/nickclifton
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/bash_command_line.png?itok=k4z94W2U (bash logo on green background)
|
||||
@ -1,110 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Waterfox: Firefox Fork With Legacy Add-ons Options)
|
||||
[#]: via: (https://itsfoss.com/waterfox-browser/)
|
||||
[#]: author: (Ankush Das https://itsfoss.com/author/ankush/)
|
||||
|
||||
Waterfox: Firefox Fork With Legacy Add-ons Options
|
||||
======
|
||||
|
||||
_**Brief: In this week’s open source software highlight, we take a look at a Firefox-based browser that supports legacy extensions that Firefox no longer supports while potentially providing fast user experience.**_
|
||||
|
||||
When it comes to web browsers, Google Chrome leads the market share. [Mozilla Firefox is there still providing hopes for a mainstream web browser that respects your privacy][1].
|
||||
|
||||
Firefox has improved a lot lately and one of the side-effects of the improvements is removal of add-ons. If your favorite add-on disappeared in last few months/years, you have a good new in the form of Witerfox.
|
||||
|
||||
Attention!
|
||||
|
||||
It’s been brought to our notice that Waterfox has been acquired by System1. This company also acquired privacy focused search engine Startpage.
|
||||
While System1 claims that they are providing privacy focused products because ‘there is a demand’, we cannot vouch for their claim.
|
||||
In other words, it’s up to you to trust System1 and Waterfox.
|
||||
|
||||
### Waterfox: A Firefox-based Browser
|
||||
|
||||
![Waterfox Classic][2]
|
||||
|
||||
[Waterfox][3] is a useful open-source browser built on top of Firefox that focuses on privacy and supports legacy extensions. It doesn’t pitch itself as a privacy-paranoid browser but it does respect the basics.
|
||||
|
||||
You get two separate Waterfox browser versions. The current edition aims to provide a modern experience and the classic version focuses to support [NPAPI plugins][4] and [bootstrap extensions][5].
|
||||
|
||||
![Waterfox Classic][6]
|
||||
|
||||
If you do not need to utilize bootstrap extensions but rely on [WebExtensions][7], Waterfox Current is the one you should go for.
|
||||
|
||||
And, if you need to set up a browser that needs NPAPI plugins or bootstrap extensions extensively, Waterfox Classic version will be suitable for you.
|
||||
|
||||
So, if you like Firefox, but want to try something different on the same line, this is a Firefox alternative for the job.
|
||||
|
||||
### Features of Waterfox
|
||||
|
||||
![Waterfox Current][8]
|
||||
|
||||
Of course, technically, you should be able to do a lot of things that Mozilla Firefox supports.
|
||||
|
||||
So, I’ll just highlight all the important features of Waterfox in a list here.
|
||||
|
||||
* Supports NPAPI Plugins
|
||||
* Supports Bootstrap Extensions
|
||||
* Offers separate editions for legacy extension support and modern WebExtension support.
|
||||
* Cross-platform support (Windows, Linux, and macOS)
|
||||
* Theme customization
|
||||
* Archived Add-ons supported
|
||||
|
||||
|
||||
|
||||
### Installing Waterfox on Ubuntu/Linux
|
||||
|
||||
Unlike other popular browsers, you don’t get a package to install. So, you will have to download the archived package from its [official download page][9].
|
||||
|
||||
![][10]
|
||||
|
||||
Depending on what edition (Current/Classic) you want – just download the file, which will be **.tar.bz2** extension file.
|
||||
|
||||
Once downloaded, simply extract the file.
|
||||
|
||||
Next, head on to the extracted folder and look for the “**Waterfox**” file. You can simply double-click on it to run start up the browser.
|
||||
|
||||
If that doesn’t work, you can utilize the terminal and navigate to the extracted **Waterfox** folder. Once there, you can simply run it with a single command. Here’s how it looks like:
|
||||
|
||||
```
|
||||
cd waterfox-classic
|
||||
./waterfox
|
||||
```
|
||||
|
||||
In either case, you can also head to its [GitHub page][11] and explore more options to get it installed on your system.
|
||||
|
||||
[Download Waterfox][3]
|
||||
|
||||
**Wrapping up**
|
||||
|
||||
I fired it up on my Pop!_OS 19.10 installation and it worked really well for me. Though I don’t think I could switch from Firefox to Waterfox because I am not using any legacy add-on. It could still be an impressive option for certain users.
|
||||
|
||||
You could give it a try and let me know your thoughts in the comments below.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://itsfoss.com/waterfox-browser/
|
||||
|
||||
作者:[Ankush Das][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://itsfoss.com/author/ankush/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://itsfoss.com/why-firefox/
|
||||
[2]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2020/02/waterfox-classic.png?fit=800%2C423&ssl=1
|
||||
[3]: https://www.waterfox.net/
|
||||
[4]: https://en.wikipedia.org/wiki/NPAPI
|
||||
[5]: https://wiki.mozilla.org/Extension_Manager:Bootstrapped_Extensions
|
||||
[6]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2020/02/waterfox-classic-screenshot.jpg?ssl=1
|
||||
[7]: https://wiki.mozilla.org/WebExtensions
|
||||
[8]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2020/02/waterfox-screenshot.jpg?ssl=1
|
||||
[9]: https://www.waterfox.net/download/
|
||||
[10]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2020/02/waterfox-download-page.jpg?ssl=1
|
||||
[11]: https://github.com/MrAlex94/Waterfox
|
||||
@ -1,118 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (wenwensnow)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (3 eBook readers for the Linux desktop)
|
||||
[#]: via: (https://opensource.com/article/20/2/linux-ebook-readers)
|
||||
[#]: author: (Scott Nesbitt https://opensource.com/users/scottnesbitt)
|
||||
|
||||
3 eBook readers for the Linux desktop 针对Linux桌面版的3个电子书阅读器
|
||||
======
|
||||
Any of these open source eBook applications will make it easy to read
|
||||
your books on a larger screen. 任意一个开源电子书应用都能使你在更大屏幕上的阅读体验得到提升。
|
||||
![Computer browser with books on the screen][1]
|
||||
|
||||
I usually read eBooks on my phone or with my Kobo eReader. I've never been comfortable reading books on larger screens. However, many people regularly read books on their laptops or desktops. If you are one of them (or think you might be), I'd like to introduce you to three eBook readers for the Linux desktop.
|
||||
|
||||
### Bookworm
|
||||
|
||||
[Bookworm][2] is billed as a "simple, focused eBook reader." And it is. Bookworm has a basic set of features, which some people will complain about being _too basic_ or lacking _functionality_ (whatever that word means). Bookworm does one thing and does it well without unnecessary frills.
|
||||
|
||||
The application's interface is very clean and uncluttered.
|
||||
|
||||
![Bookworm e-book application][3]
|
||||
|
||||
You navigate through a book by pressing:
|
||||
|
||||
* The space bar to move down a page
|
||||
* The Down and Up arrow keys to move down and up a single line
|
||||
* The Right and Left arrow keys to jump to the next or previous chapter
|
||||
|
||||
|
||||
|
||||
You can also annotate portions of a book and insert bookmarks to jump back to a page.
|
||||
|
||||
![Annotations in Bookworm][4]
|
||||
|
||||
Bookworm doesn't have many configuration options. You can change the size and spacing of a book's font, enable a two-page reading view or dark mode, and add folders that Bookworm will scan to find new eBooks.
|
||||
|
||||
![Bookworm preferences][5]
|
||||
|
||||
Bookworm supports the most widely used eBook formats: EPUB, PDF, MOBI, and [FB2][6]. You can also use Bookworm to read popular digital comic book formats [CBR][7] and CBZ. I've tested Bookworm with only the first three formats. PDF files are readable, but they load slowly and the formatting can be rather ugly.
|
||||
|
||||
### Foliate
|
||||
|
||||
As far as features go, [Foliate][8] is a step or two above Bookworm. Not only does it have several more features, but it also has more configuration options. You get all of that in a zippy, clean, and uncluttered package.
|
||||
|
||||
![Foliate e-book application][9]
|
||||
|
||||
You can navigate through an eBook in Foliate using the space bar, arrow keys, or PgUp and PgDn keys. There's nothing unique there.
|
||||
|
||||
You can also annotate text, look up and translate words and phrases, and look up the meanings of words. If you have a text-to-speech application installed on your computer, Foliate can use it to read books aloud.
|
||||
|
||||
![Annotating a book in Foliate][10]
|
||||
|
||||
Foliate has a few more customization options than Bookworm. You can change a book's font and its size, the spacing of lines, and the size of a book's margins. You can also increase or decrease the brightness and select one of four built-in themes.
|
||||
|
||||
![Foliate settings][11]
|
||||
|
||||
You can read books in the EPUB, MOBI, AZW, and AZW3 formats using Foliate. In case you're wondering, the latter three are closed formats used with books published for Amazon's Kindle eReader
|
||||
|
||||
### Calibre's eBook viewer
|
||||
|
||||
[eBook viewer][12] is a component of the [Calibre][13] eBook management tool. Like its parent, the eBook viewer feature isn't the prettiest piece of software out there.
|
||||
|
||||
![E-book Viewer application][14]
|
||||
|
||||
Don't let that put you off, though. It's a solid desktop eBook reader.
|
||||
|
||||
You navigate through an eBook in Calibre's e-book viewer using the arrow and PgUp/PgDn keys or by pressing the space bar. You can also look up words in an online dictionary and add bookmarks throughout a book. E-book viewer lacks an annotation function, but its built-in search engine is solid, and you can save books as PDFs (though I'm not sure why you'd want to).
|
||||
|
||||
Configuration options are an area where this eBook viewer shines. It has far more of them than both Bookworm and Foliate combined. You can change everything from fonts to the layout of text to how text is broken up into pages. On top of that, you can customize the keyboard shortcuts for using the application and add your favorite dictionary website or sites to help you look up words in a book you're reading.
|
||||
|
||||
![E-book Viewer preferences][15]
|
||||
|
||||
One useful feature of Calibre's eBook viewer is the ability to apply your own CSS file to your e-books. CSS, in case you're wondering, is a way to format web pages (which is what many e-books are made of). If you're a master with CSS, you can copy and paste your CSS file into the **User stylesheet** tab in eBook viewer's Preferences window. That's the ultimate in customization.
|
||||
|
||||
eBook viewer, according to its developer, "can display all the major e-book formats." If you're wondering what those formats are, [here's a list][16]. I've tested it with just a few of those formats and have had no problems with them.
|
||||
|
||||
### Final thought
|
||||
|
||||
Whether you're looking for a simple eBook reader or one with bells and whistles and whatever else, the three applications in this article are good choices. Any of them can make reading an eBook on a larger screen easier.
|
||||
|
||||
* * *
|
||||
|
||||
_This article is based on an article published on [Open Source Musings][17] and appears here via a [CC BY-SA 4.0][18] license._
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/20/2/linux-ebook-readers
|
||||
|
||||
作者:[Scott Nesbitt][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/scottnesbitt
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/computer_browser_program_books_read.jpg?itok=iNMWe8Bu (Computer browser with books on the screen)
|
||||
[2]: https://babluboy.github.io/bookworm/
|
||||
[3]: https://opensource.com/sites/default/files/uploads/bookworm-reading.png (Bookworm e-book application)
|
||||
[4]: https://opensource.com/sites/default/files/uploads/bookworm-annotations.png (Annotations in Bookworm)
|
||||
[5]: https://opensource.com/sites/default/files/uploads/bookworm-preferences.png (Bookworm preferences)
|
||||
[6]: https://en.wikipedia.org/wiki/FictionBook
|
||||
[7]: https://en.wikipedia.org/wiki/Comic_book_archive
|
||||
[8]: https://johnfactotum.github.io/foliate/
|
||||
[9]: https://opensource.com/sites/default/files/uploads/foliate-reading.png (Foliate e-book application)
|
||||
[10]: https://opensource.com/sites/default/files/uploads/foliate-annotation_0.png
|
||||
[11]: https://opensource.com/sites/default/files/uploads/foliate-settings.png (Foliate settings)
|
||||
[12]: https://calibre-ebook.com/about
|
||||
[13]: https://opensourcemusings.com/managing-your-ebooks-with-calibre
|
||||
[14]: https://opensource.com/sites/default/files/uploads/e-book_viewer-reading.png (E-book Viewer application)
|
||||
[15]: https://opensource.com/sites/default/files/uploads/ebook-viewer-preferences.png (E-book Viewer preferences)
|
||||
[16]: https://manual.calibre-ebook.com/faq.html#what-formats-does-calibre-support-conversion-to-from
|
||||
[17]: https://opensourcemusings.com/three-ebook-readers-for-the-linux-desktop
|
||||
[18]: https://creativecommons.org/licenses/by-sa/4.0/
|
||||
@ -1,161 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Converting between uppercase and lowercase on the Linux command line)
|
||||
[#]: via: (https://www.networkworld.com/article/3529409/converting-between-uppercase-and-lowercase-on-the-linux-command-line.html)
|
||||
[#]: author: (Sandra Henry-Stocker https://www.networkworld.com/author/Sandra-Henry_Stocker/)
|
||||
|
||||
Converting between uppercase and lowercase on the Linux command line
|
||||
======
|
||||
Converting text between uppercase and lowercase can be very tedious, especially when you want to avoid inadvertent misspellings. Fortunately, Linux provides a handful of commands that can make the job very easy.
|
||||
[andy.brandon50][1] [(CC BY-SA 2.0)][2]
|
||||
|
||||
There are many ways to change text on the Linux command line from lowercase to uppercase and vice versa. In fact, you have an impressive set of commands to choose from. This post examines some of the best commands for the job and how you can get them to do just what you want.
|
||||
|
||||
### Using tr
|
||||
|
||||
The **tr** (translate) command is one of the easiest to use on the command line or within a script. If you have a string that you want to be sure is in uppercase, you just pass it through a **tr** command like this:
|
||||
|
||||
```
|
||||
$ echo Hello There | tr [:lower:] [:upper:]
|
||||
HELLO THERE
|
||||
```
|
||||
|
||||
[[Get regularly scheduled insights by signing up for Network World newsletters.]][3]
|
||||
|
||||
Below is an example of using this kind of command in a script when you want to be sure that all of the text that is added to a file is in uppercase for consistency:
|
||||
|
||||
```
|
||||
#!/bin/bash
|
||||
|
||||
echo -n "Enter department name: "
|
||||
read dept
|
||||
echo $dept | tr [:lower:] [:upper:] >> depts
|
||||
```
|
||||
|
||||
Switching the order to [:upper:] [:lower:] would have the opposite effect, putting all the department names in lowercase:
|
||||
|
||||
```
|
||||
echo $dept | tr [:upper:] [:lower:] >> depts
|
||||
```
|
||||
|
||||
Similarly, you could use the **sed** command's **A-Z** and **a-z** strings to accomplish the same thing:
|
||||
|
||||
```
|
||||
echo $dept | tr a-z A-Z >> depts
|
||||
```
|
||||
|
||||
As you undoubtedly suspect, reversing the order of the a-z and A-Z strings will have the opposite effect, turning the text to all lowercase.
|
||||
|
||||
### Using awk
|
||||
|
||||
The **awk** command lets you do the same thing with its **toupper** and **tolower** options. The command in the script shown in the previous example could be done this way instead:
|
||||
|
||||
[][4]
|
||||
|
||||
```
|
||||
echo $dept | awk '{print toupper($0)}' >> depts
|
||||
```
|
||||
|
||||
The reverse (switching to lowercase) would look like this:
|
||||
|
||||
```
|
||||
echo $dept | awk '{print tolower($0)}' >> depts
|
||||
```
|
||||
|
||||
### Using sed
|
||||
|
||||
The **sed** (stream editor) command also does a great job of switching between upper- and lowercase. This command would have the same effect as the first of the two shown above.
|
||||
|
||||
```
|
||||
echo $dept | sed 's/[a-z]/\U&/g' >> depts
|
||||
```
|
||||
|
||||
Switching from uppercase to lowercase would simply involve replacing the **U** near the end of the line with an **L**.
|
||||
|
||||
```
|
||||
echo $dept | sed 's/[A-Z]/\L&/g' >> depts
|
||||
```
|
||||
|
||||
### Manipulating text in a file
|
||||
|
||||
Both **awk** and **sed** also allow you to change the case of text for entire files. So, you just found out your boss wanted those department names in all lowercase? No problem. Just run a command like this with the file name provided:
|
||||
|
||||
```
|
||||
$ awk '{print tolower($0)}' depts
|
||||
finance
|
||||
billing
|
||||
bookkeeping
|
||||
```
|
||||
|
||||
If you want to overwrite the **depts** file, instead of just displaying its contents in lowercase, you would need to do something like this:
|
||||
|
||||
```
|
||||
$ awk '{print tolower($0)}' depts > depts-
|
||||
$ mv depts- depts
|
||||
```
|
||||
|
||||
Making the change with **sed**, however, you can avoid that last step because **sed** can edit a file "in place" as shown here, leaving the file intact, but the text in all lowercase:
|
||||
|
||||
```
|
||||
$ sed 's/[A-Z]/\L&/g' depts
|
||||
```
|
||||
|
||||
### Capitalizing first letters only
|
||||
|
||||
To capitalize only the first letters of words in a string, you can do something like this:
|
||||
|
||||
```
|
||||
$ echo design \& engineering| sed -e "s/\b\(.\)/\u\1/g"
|
||||
Design & Engineering
|
||||
```
|
||||
|
||||
That command will ensure that first letters are capitalized, but won't change the rest of the letters.
|
||||
|
||||
### Making sure only first letters are uppercase
|
||||
|
||||
It's a little more challenging when you want to change text so that only first letters are in uppercase. Say you're manipulating a list of staff members' names and you want them to be formatted in the normal Firstname Lastname manner.
|
||||
|
||||
##### with sed
|
||||
|
||||
You could use a considerably more complex **sed** command to ensure this result:
|
||||
|
||||
```
|
||||
$ echo design \& ENGINEERING | sed 's/\b\([[:alpha:]]\)\([[:alpha:]]*\)\b/\u\1\L\2/g'
|
||||
Design & Engineering
|
||||
```
|
||||
|
||||
##### with python
|
||||
|
||||
If you have python loaded, you can run a command like this that also formats text so that only the first letters of each word are capitalized and the command may be a little easier to parse than the **sed** command shown above:
|
||||
|
||||
```
|
||||
$ echo -n "design & engineering" | python3 -c "import sys; print(sys.stdin.read().title())"
|
||||
Design & Engineering
|
||||
```
|
||||
|
||||
There are many ways to change the formatting of text between upper- and lowercase. Which works best depends in part of whether you're manipulating a single string or an entire file and how you want the end result to look.
|
||||
|
||||
Join the Network World communities on [Facebook][5] and [LinkedIn][6] to comment on topics that are top of mind.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.networkworld.com/article/3529409/converting-between-uppercase-and-lowercase-on-the-linux-command-line.html
|
||||
|
||||
作者:[Sandra Henry-Stocker][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.networkworld.com/author/Sandra-Henry_Stocker/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.flickr.com/photos/54027476@N07/4999959929
|
||||
[2]: https://creativecommons.org/licenses/by-sa/2.0/legalcode
|
||||
[3]: https://www.networkworld.com/newsletters/signup.html
|
||||
[4]: https://www.networkworld.com/article/3440100/take-the-intelligent-route-with-consumption-based-storage.html?utm_source=IDG&utm_medium=promotions&utm_campaign=HPE21620&utm_content=sidebar ( Take the Intelligent Route with Consumption-Based Storage)
|
||||
[5]: https://www.facebook.com/NetworkWorld/
|
||||
[6]: https://www.linkedin.com/company/network-world
|
||||
@ -1,219 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (qianmingtian)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Install and Use Wireshark on Ubuntu Linux)
|
||||
[#]: via: (https://itsfoss.com/install-wireshark-ubuntu/)
|
||||
[#]: author: (Community https://itsfoss.com/author/itsfoss/)
|
||||
|
||||
Install and Use Wireshark on Ubuntu Linux
|
||||
======
|
||||
|
||||
_**Brief: You’ll learn to install the latest Wireshark on Ubuntu and other Ubuntu-based distribution in this tutorial. You’ll also learn how to run Wireshark without sudo and how to set it up for packet sniffing.**_
|
||||
|
||||
[Wireshark][1] is a free and open-source network protocol analyzer widely used around the globe.
|
||||
|
||||
With Wireshark, you can capture incoming and outgoing packets of a network in real-time and use it for network troubleshooting, packet analysis, software and communication protocol development, and many more.
|
||||
|
||||
It is available on all major desktop operating systems like Windows, Linux, macOS, BSD and more.
|
||||
|
||||
In this tutorial, I will guide you to install Wireshark on Ubuntu and other Ubuntu-based distributions. I’ll also show a little about setting up and configuring Wireshark to capture packets.
|
||||
|
||||
### Installing Wireshark on Ubuntu based Linux distributions
|
||||
|
||||
![][2]
|
||||
|
||||
Wireshark is available on all major Linux distributions. You should check out the [official installation instructions][3]. because in this tutorial, I’ll focus on installing the latest Wireshark version on Ubuntu-based distributions only.
|
||||
|
||||
Wireshark is available in the Universe repository of Ubuntu. You can [enable universe repository][4] and then install it like this:
|
||||
|
||||
```
|
||||
sudo add-apt-repository universe
|
||||
sudo apt install wireshark
|
||||
```
|
||||
|
||||
One slight problem in this approach is that you might not always get the latest version of Wireshark.
|
||||
|
||||
For example, in Ubuntu 18.04, if you [use the apt command][5] to check the available version of Wireshark, it is 2.6.
|
||||
|
||||
```
|
||||
[email protected]:~$ apt show wireshark
|
||||
Package: wireshark
|
||||
Version: 2.6.10-1~ubuntu18.04.0
|
||||
Priority: optional
|
||||
Section: universe/net
|
||||
Origin: Ubuntu
|
||||
Maintainer: Balint Reczey <[email protected]>
|
||||
```
|
||||
|
||||
However, [Wireshark 3.2 stable version][6] has been released months ago. New release brings new features, of course.
|
||||
|
||||
So, what do you do in such case? Thankfully, Wiresshark developers provide an official PPA that you can use to install the latest stable version of Wireshark on Ubuntu and other Ubuntu-based distributions.
|
||||
|
||||
I hope you are acquainted with PPA. If not, please [read our excellent guide on PPA to understand it completely][7].
|
||||
|
||||
Open a terminal and use the following commands one by one:
|
||||
|
||||
```
|
||||
sudo add-apt-repository ppa:wireshark-dev/stable
|
||||
sudo apt update
|
||||
sudo apt install wireshark
|
||||
```
|
||||
|
||||
Even if you have an older version of Wireshark installed, it will be updated to the newer version.
|
||||
|
||||
While installing, you will be asked whether to allow non-superusers to capture packets. Select Yes to allow and No to restrict non-superusers to capture packets & finish the installation.
|
||||
|
||||
### Running Wireshark without sudo
|
||||
|
||||
If you have selected **No** in the previous installation, then run the following command as root:
|
||||
|
||||
```
|
||||
sudo dpkg-reconfigure wireshark-common
|
||||
```
|
||||
|
||||
And select **Yes** by pressing the tab key and then using enter key:
|
||||
|
||||
![][8]
|
||||
|
||||
Since you have allowed the non-superuser to capture packets, you have to add the user to wireshark group. Use the [usermod command][9] to add yourself to the wireshark group.
|
||||
|
||||
```
|
||||
sudo usermod -aG wireshark $(whoami)
|
||||
```
|
||||
|
||||
Finally, [restart your Ubuntu system][10] to make the necessary changes to your system.
|
||||
|
||||
Trivia
|
||||
|
||||
First released in 1998, Wireshark was initially known as Ethereal. Developers had to change its name to Wireshark in 2006 due to trademark issues.
|
||||
|
||||
### Starting Wireshark
|
||||
|
||||
Launching Wireshark application can be done from the application launcher or the CLI.
|
||||
|
||||
To start from CLI, just type **wireshark** on your console:
|
||||
|
||||
```
|
||||
wireshark
|
||||
```
|
||||
|
||||
From **GUI**, search for Wireshark application on the search bar and hit enter.
|
||||
|
||||
![][11]
|
||||
|
||||
Now let’s play with Wireshark.
|
||||
|
||||
### Capturing packets using Wireshark
|
||||
|
||||
When you start Wireshark, you will see a list of interfaces that you can use to capture packets to and from.
|
||||
|
||||
There are many types of interfaces available which you can monitor using Wireshark such as, Wired, External devices, etc. According to your preference, you can choose to show specific types of interfaces in the welcome screen from the marked area in the given image below.
|
||||
|
||||
![Select interface][12]
|
||||
|
||||
For instance, I listed only the **Wired** network interfaces.
|
||||
|
||||
![][13]
|
||||
|
||||
Next, to start capturing packets, you have to select the interface (which in my case is ens33) and click on the **Start capturing packets** icon as marked in the image below.
|
||||
|
||||
![Start capturing packets with Wireshark][14]
|
||||
|
||||
You can also capture packets to and from multiple interfaces at the same time. Just press and hold the **CTRL** button while clicking on the interfaces that you want to capture to and from and then hit the **Start capturing packets** icon as marked in the image below.
|
||||
|
||||
![][15]
|
||||
|
||||
Next, I tried using **ping google.com** command in the terminal and as you can see, many packets were captured.
|
||||
|
||||
![Captured packets][16]
|
||||
|
||||
Now you can select on any packet to check that particular packet. After clicking on a particular packet you can see the information about different layers of TCP/IP Protocol associated with it.
|
||||
|
||||
![Packet info][17]
|
||||
|
||||
You can also see the RAW data of that particular packet at the bottom as shown in the image below.
|
||||
|
||||
![Check RAW data in the captured packets][18]
|
||||
|
||||
This is why end-to-end encryption is important
|
||||
|
||||
Imagine you are logging into a website that doesn’t use HTTPS. Anyone on the same network as you can sniff the packets and see the user name and password in the RAW data.
|
||||
This is why most chat applications use end to end encryption and most websites these days use https (instead of http).
|
||||
|
||||
#### Stopping packet capture in Wireshark
|
||||
|
||||
You can click on the red icon as marked in the given image to stop capturing Wireshark packets.
|
||||
|
||||
![Stop packet capture in Wireshark][19]
|
||||
|
||||
#### Save captured packets to a file
|
||||
|
||||
You can click on the marked icon in the image below to save captured packets to a file for future use.
|
||||
|
||||
![Save captured packets by Wireshark][20]
|
||||
|
||||
**Note**: _Output can be exported to XML, PostScript®, CSV, or plain text._
|
||||
|
||||
Next, select a destination folder, and type the file name and click on **Save**.
|
||||
Then select the file and click on **Open**.
|
||||
|
||||
![][21]
|
||||
|
||||
Now you can open and analyze the saved packets anytime. To open the file, press **\ + o**
|
||||
or go to **File > Open** from Wireshark.
|
||||
|
||||
The captured packets should be loaded from the file.
|
||||
|
||||
![][22]
|
||||
|
||||
### Conclusion
|
||||
|
||||
Wireshark supports many different communication protocols. There are many options and features that provide you the power to capture and analyze the network packets in a unique way. You can learn more about Wireshark from their [official documentation][23].
|
||||
|
||||
I hope this detailed helped you to install Wireshark on Ubuntu. Please let me know your questions and suggestions.
|
||||
|
||||
![][24]
|
||||
|
||||
### Kushal Rai
|
||||
|
||||
A computer science student & Linux and open source lover. He likes sharing knowledge for he believes technology shapes the perception of modern world. Kushal also loves music and photography.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://itsfoss.com/install-wireshark-ubuntu/
|
||||
|
||||
作者:[Community][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://itsfoss.com/author/itsfoss/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.wireshark.org/
|
||||
[2]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2020/03/wireshark_ubuntu.png?ssl=1
|
||||
[3]: https://www.wireshark.org/docs/wsug_html_chunked/ChBuildInstallUnixInstallBins.html
|
||||
[4]: https://itsfoss.com/ubuntu-repositories/
|
||||
[5]: https://itsfoss.com/apt-command-guide/
|
||||
[6]: https://www.wireshark.org/news/20191218.html
|
||||
[7]: https://itsfoss.com/ppa-guide/
|
||||
[8]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2020/03/yes.png?ssl=1
|
||||
[9]: https://linuxhandbook.com/usermod-command/
|
||||
[10]: https://itsfoss.com/schedule-shutdown-ubuntu/
|
||||
[11]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2020/03/wire.png?ssl=1
|
||||
[12]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2020/03/interfaces.jpg?ssl=1
|
||||
[13]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2020/03/intoption.jpg?ssl=1
|
||||
[14]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2020/03/singleinterface.jpg?ssl=1
|
||||
[15]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2020/03/selint.jpg?ssl=1
|
||||
[16]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2020/03/capture.jpg?ssl=1
|
||||
[17]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2020/03/packetinfo.png?ssl=1
|
||||
[18]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2020/03/raw.png?ssl=1
|
||||
[19]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2020/03/stopcapture.png?ssl=1
|
||||
[20]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2020/03/savepackets.jpg?ssl=1
|
||||
[21]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2020/03/savename.jpg?ssl=1
|
||||
[22]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2020/03/openpacket.png?ssl=1
|
||||
[23]: https://www.wireshark.org/docs/https://www.wireshark.org/docs/
|
||||
[24]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2020/03/kushal_rai.jpg?ssl=1
|
||||
@ -1,148 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Communicating with other users on the Linux command line)
|
||||
[#]: via: (https://www.networkworld.com/article/3530343/communicating-with-other-users-on-the-linux-command-line.html)
|
||||
[#]: author: (Sandra Henry-Stocker https://www.networkworld.com/author/Sandra-Henry_Stocker/)
|
||||
|
||||
Communicating with other users on the Linux command line
|
||||
======
|
||||
|
||||
Thinkstock / Linux
|
||||
|
||||
Sending messages to other users on the Linux command line can be very easy, but there are a number of commands that you might want to consider. In this post, we’ll look at four commands and see how each of them works.
|
||||
|
||||
### wall
|
||||
|
||||
The **wall** command (as in "write all") allows you to send a message to all users who are currently logged into the system. This implies that the system is likely a server and that users are working on the command line. While the wall command is generally used by sysadmins to send out notices to users to let send out information (e.g., that the server is going down for maintenance), it can be used by any user.
|
||||
|
||||
A sysadmin might send out a message like this:
|
||||
|
||||
```
|
||||
$ wall The system will be going down in 15 minutes to address a serious problem
|
||||
```
|
||||
|
||||
Everyone logged into the system will see something like this:
|
||||
|
||||
```
|
||||
Broadcast message from admin@dragonfly (pts/0) (Thu Mar 5 08:56:42 2020):
|
||||
|
||||
The system is going down in 15 minutes to address a serious problem
|
||||
```
|
||||
|
||||
If you want to use single quote marks in your message, enclose the message in double quote marks like this:
|
||||
|
||||
```
|
||||
$ wall “Don’t forget to save your work before logging off”
|
||||
```
|
||||
|
||||
The outside quote marks will not show up in the transmitted message, but, without them, the command sits and waits for a closing single quote.
|
||||
|
||||
### mesg
|
||||
|
||||
If, for some reason, you don’t want to accept messages from another user, you can stop them from arriving with the **mesg** command. This command can be used with a “n” argument to refuse mail from the user or a “y” argument to allow the messages to arrive.
|
||||
|
||||
[][1]
|
||||
|
||||
```
|
||||
$ mesg n doug
|
||||
$ mesg y doug
|
||||
```
|
||||
|
||||
The blocked user will not be notified that their messages have been blocked. You can also block or allow all messages with a **mesg** command like one of these:
|
||||
|
||||
```
|
||||
$ mesg y
|
||||
$ mesg n
|
||||
```
|
||||
|
||||
### write
|
||||
|
||||
Another command for sending text without reverting to email is **write**. This command can be used to communicate with a specific user.
|
||||
|
||||
```
|
||||
$ write nemo
|
||||
Are you still at your desk?
|
||||
I need to talk with you right away.
|
||||
^C
|
||||
```
|
||||
|
||||
Enter your text and use **^C** to exit when you’re done. The command allows you to send text, but doesn’t start a two-way conversation. It just sends the text. If the user is logged in on more than one terminal, you can specify which terminal you want to send the message to or you can rely on the system to choose the one with the shortest idle time.
|
||||
|
||||
```
|
||||
$ write nemo#1
|
||||
```
|
||||
|
||||
If the user you are trying to write to has messages blocked, you should see something like this:
|
||||
|
||||
```
|
||||
$ write nemo
|
||||
write: nemo has messages disabled
|
||||
```
|
||||
|
||||
### talk/ytalk
|
||||
|
||||
The **talk** or **ytalk** command gives you a chance to have an interactive chat with one or more other users. The command will bring up a double-pane (top and bottom) window. Each individual will type into the top portion of the display on their screen and see the responses in the bottom section(s). The respondents can respond to a talk request by typing "talk" followed by the username of the person addressing them.
|
||||
|
||||
```
|
||||
Message from Talk_Daemon@dragonfly at 10:10 ...
|
||||
talk: connection requested by dory@127.0.0.1.
|
||||
talk: respond with: talk dory@127.0.0.1
|
||||
|
||||
$ talk dory
|
||||
```
|
||||
|
||||
The window can involve more than two participants if **ytalk** is used. As you can see in the example below (the result of the "talk dory" command shown above), talk is often ytalk.
|
||||
|
||||
```
|
||||
----------------------------= YTalk version 3.3.0 =--------------------------
|
||||
Is the report ready?
|
||||
|
||||
-------------------------------= nemo@dragonfly =----------------------------
|
||||
Just finished it
|
||||
```
|
||||
|
||||
As explained above, on the other side of the conversation, the talk session window panes are reversed:
|
||||
|
||||
```
|
||||
----------------------------= YTalk version 3.3.0 =--------------------------
|
||||
Just finished it
|
||||
|
||||
-------------------------------= dory@dragonfly =----------------------------
|
||||
Is the report ready?
|
||||
```
|
||||
|
||||
Again, use **^C** to exit.
|
||||
|
||||
To talk with someone on another system, you just need to add a **-h** option and the hostname or IP address with a command like this:
|
||||
|
||||
```
|
||||
$ talk -h 192.168.0.11 nemo
|
||||
```
|
||||
|
||||
### Wrap-Up
|
||||
|
||||
There are a number of basic commands for sending messages to other logged-in users on Linux systems, and they can be especially useful when you need to send out a quick message to all of the users, prefer a quick exchange to a phone call or want to easily involve more than two people in a quick messaging session.
|
||||
|
||||
Some commands, like **wall**, allow a message to be broadcast, but are not interactive. Others, like **talk**, allow both lengthy and multi-user chats, avoiding the need to set up a conference call when a fairly quick exchange of information is all that's required.
|
||||
|
||||
Join the Network World communities on [Facebook][2] and [LinkedIn][3] to comment on topics that are top of mind.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.networkworld.com/article/3530343/communicating-with-other-users-on-the-linux-command-line.html
|
||||
|
||||
作者:[Sandra Henry-Stocker][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.networkworld.com/author/Sandra-Henry_Stocker/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.networkworld.com/article/3440100/take-the-intelligent-route-with-consumption-based-storage.html?utm_source=IDG&utm_medium=promotions&utm_campaign=HPE21620&utm_content=sidebar ( Take the Intelligent Route with Consumption-Based Storage)
|
||||
[2]: https://www.facebook.com/NetworkWorld/
|
||||
[3]: https://www.linkedin.com/company/network-world
|
||||
@ -1,190 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Three Ways to Exclude/Hold/Prevent a Specific Package from an apt Upgrade)
|
||||
[#]: via: (https://www.2daygeek.com/debian-ubuntu-exclude-hold-prevent-packages-from-apt-get-upgrade/)
|
||||
[#]: author: (Magesh Maruthamuthu https://www.2daygeek.com/author/magesh/)
|
||||
|
||||
Three Ways to Exclude/Hold/Prevent a Specific Package from an apt Upgrade
|
||||
======
|
||||
|
||||
Sometimes you may accidentally update packages that are not updated due to some application dependency.
|
||||
|
||||
This is always the case during the entire system update or automatic package upgrade process.
|
||||
|
||||
If this happens, it may break the application function.
|
||||
|
||||
This creates a serious problem and you need to spend a lot of time fixing the problem.
|
||||
|
||||
See the following article if you want to **[Exclude Specific Packages from Yum Update][1]**
|
||||
|
||||
How to avoid this kind of situation?
|
||||
|
||||
How do I exclude packages from apt-get update?
|
||||
|
||||
Yes, it can be done using the following three methods on Debian and Ubuntu systems.
|
||||
|
||||
* **[apt-mark Command][2]**
|
||||
* **[dpkg Command][3]**
|
||||
* aptitude Command
|
||||
|
||||
|
||||
|
||||
We will show in detail each.
|
||||
|
||||
### Method-1: How to Exclude Packages Update on Debian/Ubuntu System Using the apt-mark Command
|
||||
|
||||
The apt-mark is used to mark/unmark a package as being automatically installed.
|
||||
|
||||
The Hold option is used to mark a package as blocked, which prevents the package from being automatically installed, upgraded, or removed.
|
||||
|
||||
The unhold option is used to cancel a previously set hold on a package to allow all actions to be repeated.
|
||||
|
||||
Run the following command to hold the given package using the **apt-mark** command.
|
||||
|
||||
```
|
||||
$ sudo apt-mark hold nano
|
||||
nano set on hold.
|
||||
```
|
||||
|
||||
Once you have hold some packages, run the following apt-mark command to view them.
|
||||
|
||||
```
|
||||
$ sudo apt-mark showhold
|
||||
nano
|
||||
```
|
||||
|
||||
This will show that the **“nano”** package will not be upgraded when you perform a full system update.
|
||||
|
||||
```
|
||||
$ sudo apt update
|
||||
|
||||
Reading package lists… Done
|
||||
Building dependency tree
|
||||
Reading state information… Done
|
||||
Calculating upgrade… Done
|
||||
The following packages have been kept back:
|
||||
nano
|
||||
0 upgraded, 0 newly installed, 0 to remove and 1 not upgraded.
|
||||
```
|
||||
|
||||
Run the following command to unhold the “nano” package using the apt-mark command.
|
||||
|
||||
```
|
||||
$ sudo apt-mark unhold nano
|
||||
Canceled hold on nano.
|
||||
```
|
||||
|
||||
### Method-2: How to Exclude Packages Update on Debian/Ubuntu System Using the dpkg Command
|
||||
|
||||
The dpkg command is a CLI tool to install, build, remove and manage Debian packages. The primary and more user-friendly front-end for dpkg is aptitude.
|
||||
|
||||
Run the following command to block a given package using the dpkg command.
|
||||
|
||||
**Syntax:**
|
||||
|
||||
```
|
||||
$ echo "package_name hold" | sudo dpkg --set-selections
|
||||
```
|
||||
|
||||
Run the below dpkg command to hold the **“apache2”** package.
|
||||
|
||||
```
|
||||
$ echo "apache2 hold" | sudo dpkg --set-selections
|
||||
```
|
||||
|
||||
Once you have hold some packages, run the following command to view them.
|
||||
|
||||
```
|
||||
$ sudo dpkg --get-selections | grep "hold"
|
||||
apache2 hold
|
||||
```
|
||||
|
||||
It will show that the **“apache2”** package will not be upgraded when you perform a full system update.
|
||||
|
||||
```
|
||||
$ sudo apt update
|
||||
|
||||
Reading package lists… Done
|
||||
Building dependency tree
|
||||
Reading state information… Done
|
||||
Calculating upgrade… Done
|
||||
The following packages have been kept back:
|
||||
apache2
|
||||
0 upgraded, 0 newly installed, 0 to remove and 1 not upgraded.
|
||||
```
|
||||
|
||||
Run the following command to unhold the given package using the dpkg command.
|
||||
|
||||
**Syntax:**
|
||||
|
||||
```
|
||||
$ echo "package_name install" | sudo dpkg --set-selections
|
||||
```
|
||||
|
||||
Run the following command to unhold the “apache2” package using the dpkg command.
|
||||
|
||||
```
|
||||
$ echo "apache2 install" | sudo dpkg --set-selections
|
||||
```
|
||||
|
||||
### Method-3: How to Exclude Packages Update on Debian/Ubuntu System Using the aptitude Command
|
||||
|
||||
The aptitude command is a text-based package management interface to the Debian and it’s derivative.
|
||||
|
||||
It allows the user to view a list of packages and to perform package management tasks such as installing, upgrading, and removing packages. Actions may be performed from a visual interface or from the command-line.
|
||||
|
||||
Run the following command to hold the given package using the aptitude command.
|
||||
|
||||
```
|
||||
$ sudo aptitude hold python3
|
||||
```
|
||||
|
||||
Once you have hold some packages, run the following aptitude command to view them.
|
||||
|
||||
```
|
||||
$ sudo dpkg --get-selections | grep "hold"
|
||||
or
|
||||
$ sudo apt-mark showhold
|
||||
|
||||
python3
|
||||
```
|
||||
|
||||
This will show that the **“python3”** package will not be upgraded when you perform a full system update.
|
||||
|
||||
```
|
||||
$ sudo apt update
|
||||
|
||||
Reading package lists… Done
|
||||
Building dependency tree
|
||||
Reading state information… Done
|
||||
Calculating upgrade… Done
|
||||
The following packages have been kept back:
|
||||
python3
|
||||
0 upgraded, 0 newly installed, 0 to remove and 1 not upgraded.
|
||||
```
|
||||
|
||||
Run the following command to unhold the **“python3”** package using the apt-mark command.
|
||||
|
||||
```
|
||||
$ sudo aptitude unhold python3
|
||||
```
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.2daygeek.com/debian-ubuntu-exclude-hold-prevent-packages-from-apt-get-upgrade/
|
||||
|
||||
作者:[Magesh Maruthamuthu][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.2daygeek.com/author/magesh/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.2daygeek.com/redhat-centos-yum-update-exclude-specific-packages/
|
||||
[2]: https://www.2daygeek.com/apt-get-apt-cache-command-examples-manage-packages-debian-ubuntu-systems/
|
||||
[3]: https://www.2daygeek.com/dpkg-command-to-manage-packages-on-debian-ubuntu-linux-mint-systems/
|
||||
Some files were not shown because too many files have changed in this diff Show More
Loading…
Reference in New Issue
Block a user