mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-03-12 01:40:10 +08:00
commit
af0a365de2
32
published/20141208 Nathive--A libre software image editor.md
Normal file
32
published/20141208 Nathive--A libre software image editor.md
Normal file
@ -0,0 +1,32 @@
|
||||
Nathive——libre软件图像编辑器
|
||||
================================================================================
|
||||
Nathive是一个libre软件图像编辑器,类似于 Adobe Photoshop、Corel Photo-Paint 或 GIMP,但是侧重于适用性和逻辑性,并为每个用户提供平滑的学习曲线。该项目在 GNOME 桌面环境中运行,并欢迎每个人参与到合作中,分享代码、翻译或想法等方面。
|
||||
|
||||
该项目尚处于测试阶段,所以它还是个未完成的工作,还不适用于终端用户。直到现在,开发始终专注于积淀应用的核心功能和创建便捷的开发工具。所以,目前我们将致力于创建新的插件,因为很明显在这方面还很缺乏。
|
||||
|
||||
其目的是在不放弃最初的可用性的情况下,逐步将该软件打造成一个专业的图像编辑器。Nathive由基于GTK+的Python脚本写成的,它设计为简洁、轻量,而且易于安装和使用。
|
||||
|
||||
### 在 ubuntu 上安装Nathive ###
|
||||
|
||||
你需要从[这里][1]下载.deb包,然后双击来安装。
|
||||
|
||||
### 屏幕截图 ###
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.ubuntugeek.com/nathive-a-libre-software-image-editor.html
|
||||
|
||||
作者:[ruchi][a]
|
||||
译者:[GOLinux](https://github.com/GOLinux)
|
||||
校对:[Caroline](https://github.com/carolinewuyan)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.ubuntugeek.com/author/ubuntufix
|
||||
[1]:http://www.nathive.org/download
|
||||
@ -0,0 +1,42 @@
|
||||
Apparently This Trojan Virus May Have Infected Linux Systems For Years
|
||||
================================================================================
|
||||

|
||||
|
||||
One of the first few argument in [why should you switch to Linux][1] is that Linux is secure and virus free. It is widely perceived by most of the Linux users that Linux is immune to viruses, which is true to an extent but not entirely.
|
||||
|
||||
Like any other OS, Linux too is not immune to malware, trojan, rootkit, virus etc. There have been several [famous Linux viruses][2]. But if you compare those to that of Windows, the number is infinitesimal. So, why am I talking about Linux viruses today then? Because a new trojan has been detected in market which might be impacting Linux systems.
|
||||
|
||||
### Turla infects Linux systems as well ###
|
||||
|
||||
Few months back a sophisticated cyber espionage program, nicknamed [Turla][3], was detected. It was supposed to be originated in Russia, allegedly with Russian government backing. The spyware program was targeting government organizations in Europe and the United States for four years.
|
||||
|
||||
In a recent report, researchers at [Kaspersky][4] has found that Turla was not only affecting Windows system but also Linux operating system. Kaspersky researchers have termed it the ‘missing piece of Turla puzzle’. As per the report:
|
||||
|
||||
> “This newly found Turla component supports Linux for broader system support at victim sites. The attack tool takes us further into the set alongside the Snake rootkit and components first associated with this actor a couple years ago. We suspect that this component was running for years at a victim site, but do not have concrete data to support that statement just yet.”
|
||||
|
||||
### What is this Linux module of Turla and how dangerous it is? ###
|
||||
|
||||
Going by the Kaspersky report,
|
||||
|
||||
> The Linux Turla module is a C/C++ executable statically linked against multiple libraries, greatly increasing its file size. It was stripped of symbol information, more likely intended to increase analysis effort than to decrease file size. Its functionality includes hidden network communications, arbitrary remote command execution, and remote management. Much of its code is based on public sources.
|
||||
|
||||
Report also mentions that this trojan doesn’t require elevated privileges (read root) while running arbitrary remote commands and it cannot be discovered by commonly used administrative tools. Personally, I doubt their claims.
|
||||
|
||||
So, as a Linux desktop user, should you be scared? In my opinion, it is too early to go in to panic mode as we experienced with [ShellShock Linux bug][5]. Turla was originally intended for government organization, not common users. Let’s wait and watch for more concrete news. I’ll keep on updating this article. Till then enjoy Linux.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://itsfoss.com/apparently-trojan-virus-infected-linux-systems-years/
|
||||
|
||||
作者:[Abhishek][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://itsfoss.com/author/Abhishek/
|
||||
[1]:http://itsfoss.com/reasons-switch-linux-windows-xp/
|
||||
[2]:http://www.unixmen.com/meet-linux-viruses/
|
||||
[3]:http://www.reuters.com/article/2014/03/07/us-russia-cyberespionage-insight-idUSBREA260YI20140307
|
||||
[4]:https://securelist.com/blog/research/67962/the-penquin-turla-2/
|
||||
[5]:http://itsfoss.com/linux-shellshock-check-fix/
|
||||
@ -0,0 +1,53 @@
|
||||
Linux Kernel 3.18 Released, This Is What’s New
|
||||
================================================================================
|
||||

|
||||
|
||||
TuxlogoA new month means a new stable release of the Linux Kernel and today Linus Torvalds has obliged, [announcing the immediate availability of Linux 3.18][1].
|
||||
|
||||
Posted on the Linux Kernel Mailing List, Torvalds explains that while a few niggling issues persist in 3.17 for a small number of users, there was ‘**absolutely no point in having everybody else twiddling their thumbs when a couple of people are actively trying to bisect an older issue**’.
|
||||
|
||||
### What’s New In Linux 3.18? ###
|
||||
|
||||
The Linux 3.18 kernel is amped up with some of the latest improvements in hardware support, power efficiency, bug fixes and reliability.
|
||||
|
||||
As ever, these span the breadth of comprehension, going from bamboozling — e.g., multi buffer operations for cryptographic layers — to the air-punchingly understandable, like support for the Razer Sabertooth gamepad.
|
||||
|
||||
We’ve compiling some of the notable changes made in this release below. It’s far, far, far from being exhaustive, and cherry picks the more relatable.
|
||||
|
||||
- Nouveau (free Nvidia GPU driver) now supports basic DisplayPort audio
|
||||
- Support for the Razer Sabertooth gamepad, maps it as Xbox 360 controller
|
||||
- Xilinx USB2 peripherals
|
||||
- Touchscreen support for Microchip AR1021 i2c, PenMount 6000 touch
|
||||
- Audio codecs: Cirrus Logic CS35L32, Everest ES8328and Freescale ES8328
|
||||
- Audio support: Generic Freescale sound cards, Analog Devices SSM4567 audio amplifier
|
||||
- Various filesystem improvements, including Btrfs and F2FS
|
||||
- DCTCP congestion control algorithm now supported
|
||||
- JIT compilation of eBPF programs on 64-bit builds
|
||||
- “Tinification” patches to help developers compile leaner, smaller kernels
|
||||
|
||||
#### Installing Linux 3.18 on Ubuntu ####
|
||||
|
||||
Although classed as stable and bringing numerous new changes to the table, don’t feel in a rush to try and upgrade your own OS to it anytime soon. Unless you’re adept at handling the sort of monitor-smashing, CPU-charring, rage-inducing issues that arise from swapping out the engine in your OS motor, you shouldn’t.
|
||||
|
||||
If you insist, you’ll find source packages available at the kernel.org website.
|
||||
|
||||
- [Download the Linux Kernel Source Packages][2]
|
||||
|
||||
A mainline kernel archive is maintained by Canonical to provide builds of newer Linux kernels for use by Ubuntu developers. But, and you really should note this, these are not intended for end users, despite what you may read elsewhere. With no guarantee or support, use at your own risk.
|
||||
|
||||
- [Visit the Ubuntu Kernel Mainline Archive][3]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.omgubuntu.co.uk/2014/12/linux-kernel-3-18-released-whats-new
|
||||
|
||||
作者:[Joey-Elijah Sneddon][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://plus.google.com/117485690627814051450/?rel=author
|
||||
[1]:https://lkml.org/lkml/2014/12/7/202
|
||||
[2]:https://www.kernel.org/pub/linux/kernel/v3.x/
|
||||
[3]:http://kernel.ubuntu.com/~kernel-ppa/mainline/?C=N;O=D
|
||||
@ -0,0 +1,35 @@
|
||||
Turla espionage operation infects Linux systems with malware
|
||||
================================================================================
|
||||
|
||||
|
||||
> A newly identified Linux backdoor program is tied to the Turla cyberespionage campaign, researchers from Kaspersky Lab said
|
||||
|
||||
A newly discovered malware program designed to infect Linux systems is tied to a sophisticated cyberespionage operation of Russian origin dubbed Epic Turla, security researchers found.
|
||||
|
||||
The Turla campaign, also known as Snake or Uroburos, [was originally uncovered in February][1], but goes back several years. The massive operation infected computers at government organizations, embassies, military installations, education and research institutions and pharmaceutical companies in over 45 countries.
|
||||
|
||||
The newly identified Turla component for Linux was uploaded recently to a multi-engine antivirus scanning service and was described by security researchers from antivirus vendor Kaspersky Lab as "a previously unknown piece of a larger puzzle."
|
||||
|
||||
"So far, every single Turla sample we've encountered was designed for the Microsoft Windows family, 32 and 64 bit operating systems," the Kaspersky researchers said Monday in a [blog post][2]. "The newly discovered Turla sample is unusual in the fact that it's the first Turla sample targeting the Linux operating system that we have discovered."
|
||||
|
||||
The Turla Linux malware is based on an open-source backdoor program called cd00r developed in 2000. It allows attackers to execute arbitrary commands on a compromised system, but doesn't require elevated privileges or root access to function and listens to commands received via hidden TCP/UDP packets, making it stealthy.
|
||||
|
||||
"It can't be discovered via netstat, a commonly used administrative tool," said the Kaspersky researchers, who are still analyzing the malware's functionality.
|
||||
|
||||
"We suspect that this component was running for years at a victim site, but do not have concrete data to support that statement just yet," they said.
|
||||
|
||||
Since their blog post Monday, the Kaspersky researchers also found a second Turla Linux component that appears to be a separate malware program.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.computerworld.com/article/2857129/turla-espionage-operation-infects-linux-systems-with-malware.html
|
||||
|
||||
作者:[Lucian Constantin][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.computerworld.com/author/Lucian-Constantin/
|
||||
[1]:http://news.techworld.com/security/3505688/invisible-russian-cyberweapon-stalked-us-and-ukraine-since-2005-new-research-reveals/
|
||||
[2]:https://securelist.com/blog/research/67962/the-penquin-turla-2/
|
||||
@ -0,0 +1,74 @@
|
||||
Yes, This Trojan Infects Linux. No, It’s Not The Tuxpocalypse
|
||||
================================================================================
|
||||

|
||||
|
||||
Is something watching you?
|
||||
|
||||
Grab a crate of canned food, start digging a deep underground bunker and prepare to settle into a world that will never be the same again: [a powerful trojan has been uncovered on Linux][1].
|
||||
|
||||
Yes, the hitherto impregnable fortress of computing nirvana has been compromised in a way that has left security experts a touch perturbed.
|
||||
|
||||
Unplug your PC, disinfect your keyboard and buy a cat (no more YouTube ). The Tuxpocalypse is upon us. We’ve reached the end of days.
|
||||
|
||||
Right? RIGHT? Nah, not quite.
|
||||
|
||||
### A Terrifying Anomalous Thing! ###
|
||||
|
||||
Let me set off by saying that **I am not underplaying the severity of this threat (known by the nickname ‘Turla’)** nor, for the avoidance of doubt, am I suggesting that we as Linux users shouldn’t be concerned by the implications.
|
||||
|
||||
The discovery of a silent trojan infecting Linux systems is terrifying. The fact it was tasked with sucking up and sending off all sorts of sensitive information is horrific. And to learn it’s been doing this for at least four years and doesn’t require root privileges? My seat is wet. I’m sorry.
|
||||
|
||||
But — and along with hyphens and typos, there’s always a ‘but’ on this site — the panic currently sweeping desktop Linux fans, Mexican wave style, is a little out of context.
|
||||
|
||||
Vulnerability may be a new feeling for some of us, yet let’s keep it in check: Linux remains an inherently secure operating system for desktop users. One clever workaround does not negate that and shouldn’t send you scurrying offline.
|
||||
|
||||
### State Sponsored, Targeting Governments ###
|
||||
|
||||

|
||||
|
||||
Is a penguin snake a ‘Penguake’ or a ‘Snaguin’?
|
||||
|
||||
‘Turla’ is a complex APT (Advanced Persistent Threat) that has (thus far) targeted government, embassy and pharmaceutical companies’ systems for around four years using a method based on [14 year old code, no less][2].
|
||||
|
||||
On Windows, where the superhero security researchers at Symantec and Kaspersky Lab first sighted the slimy snake, Turla and components of it were found to have **infected hundreds (100s) of PCs across 45 countries**, many through unpatched zero-day exploits.
|
||||
|
||||
*Nice one Microsoft.*
|
||||
|
||||
Further diligence by Kaspersky Lab has now uncovered that parts of the same trojan have also been active on Linux for some time.
|
||||
|
||||
The Trojan doesn’t require elevated privileges and can “intercept incoming packets and run incoming commands on the system”, but it’s not yet clear how deep its tentacles reach or how many Linux systems are infected, nor is the full extent of its capabilities known.
|
||||
|
||||
“Turla” (and its children) are presumed to be nation-state sponsored due to its choice of targets. US and UK readers shouldn’t assume it’s “*them*“, either. Our own governments are just as happy to play in the mud, too.
|
||||
|
||||
#### Perspective and Responsibility ####
|
||||
|
||||
As terrible a breach as this discovery is emotionally, technically and ethically it remains far, far, far away from being an indication that we’re entering a new “free for all” era of viruses and malware aimed at the desktop.
|
||||
|
||||
**Turla is not a user-focused “i wantZ ur CredIt carD” virus** bundled inside a faux software download. It’s a complex, finessed and adaptable threat with specific targets in mind (ergo grander ambitions than collecting a bunch of fruity tube dot com passwords, sorry ego!).
|
||||
|
||||
Kaspersky Lab explains:
|
||||
|
||||
> “The Linux Turla module is a C/C++ executable statically linked against multiple libraries, greatly increasing its file size. It was stripped of symbol information, more likely intended to increase analysis effort than to decrease file size. Its functionality includes hidden network communications, arbitrary remote command execution, and remote management. Much of its code is based on public sources.”
|
||||
|
||||
Regardless of impact or infection rate its precedes will still raise big, big questions that clever, clever people will now spend time addressing, analysing and (importantly) solving.
|
||||
|
||||
IANACSE (I am not a computer security expert) but IAFOA (I am a fan of acronyms), and AFAICT (as far as I can tell) this news should be viewed as as a cautionary PSA or FYI than the kind of OMGGTFO that some sites are painting it as.
|
||||
|
||||
Until more details are known none of us should panic. Let’s continue to practice safe computing. Avoid downloading/running scripts, apps, or binaries from untrusted sites or PPAs, and don’t venture into dodgy dark parts of the web.
|
||||
|
||||
If you remain super concerned you can check out the [Kaspersky blog][1] for details on how to check that you’re not infected.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.omgubuntu.co.uk/2014/12/government-spying-turla-linux-trojan-found
|
||||
|
||||
作者:[Joey-Elijah Sneddon][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://plus.google.com/117485690627814051450/?rel=author
|
||||
[1]:https://securelist.com/blog/research/67962/the-penquin-turla-2/
|
||||
[2]:https://twitter.com/joernchen/status/542060412188262400
|
||||
[3]:https://securelist.com/blog/research/67962/the-penquin-turla-2/
|
||||
104
sources/share/20141211 NetHack.md
Normal file
104
sources/share/20141211 NetHack.md
Normal file
@ -0,0 +1,104 @@
|
||||
[Translating by Stevearzh]
|
||||
NetHack
|
||||
================================================================================
|
||||
## The best game of all time? ##
|
||||
|
||||
**It’s tremendously addictive. It takes a lifetime to master. And people play it for decades without completing it. Welcome to the strange world of NetHack…**
|
||||
|
||||
Believe it or not, it’s possible to be terrified by the sight of the letter D. Or ecstatic about the sight of a % character. (And the less said about ^, the better.) But before you assume we’ve gone totally loopy and close the tab, bear with us for a moment: those characters represent dragons, food rations and traps respectively. Welcome to NetHack, where your imagination needs to play a big role in the gameplay.
|
||||
|
||||
You see, NetHack is a text-mode game: it just uses the standard terminal character set to portray the player, enemies, items and surroundings. Graphical versions of the game exist, but NetHack purists tend to avoid them, and what’s the point of a game if you can’t play it when you’re SSHed into your revived Amiga 3000 running NetBSD? In some ways, NetHack is a lot like Vi – it has been ported to nigh-on every operating system in existence, and its requirements are absolutely minimal.
|
||||
|
||||
Now, given that it looks like utter pants when compared to modern games, what makes NetHack so appealing? Well, this dungeon exploring masterpiece is incredibly rich and detailed. There are so many items to discover, spells to cast, monsters to fight and tricks to learn – and the dungeons are generated randomly. There’s so much to explore, and no two games are ever the same. People play NetHack for years and decades without complete it, still discovering new secrets each time.
|
||||
|
||||
Here we’ll show you how NetHack came about, give you a guided tour of the dungeons, and show you some tricks. Note: by reading this feature, you agree to not sue us when you become addicted to NetHack and your real-life productivity is obliterated.
|
||||
|
||||

|
||||
|
||||
The NetHack interface
|
||||
|
||||
### Possibly the oldest still-developed game ###
|
||||
|
||||
Despite its name, NetHack isn’t an online game. It’s based on an earlier dungeon-exploring romp called Hack, which in turn was a descendant of an 1980 game called Rogue. NetHack’s first release arrived in 1987, and although no new features have been added since version 3.4.3 in 2003, various patches, add-ons and spin-offs are still doing the rounds on the web. This makes it arguably the oldest game that’s still being hacked on and played by a sizeable group of people. Go to [www.reddit.com/r/nethack][1] to see what we mean – long-time NetHack players are still discussing new strategies, discoveries and tricks. Occasionally you’ll see gleeful messages from old timers who have finally, after many years, completed the game.
|
||||
|
||||
But how do you complete it? Well, NetHack is set in a large and deep dungeon. You start at the top – level 1 – and your goal is to keep going down until you find a hugely valuable item called the Amulet of Yendor. This is typically in level 20 or lower, but it can vary. As you traverse through and down the dungeon, you’ll meet all manner of monsters, traps and human characters; some will try to kill you, some will stay out of your way, and some…. well, you don’t know until you get close to them.
|
||||
|
||||
> There’s so much to learn, and many items only work best when combined with others.
|
||||
|
||||
What makes NetHack so compelling is the vast range of items crammed into the game. Weapons, armour, spell books, rings, gems – there’s so much to learn, and many items only work best when combined with others. Monsters often drop useful items when you kill them, although some items can have very negative effects if you don’t use them correctly. You’ll find shops in the dungeon that are packed with potentially useful bits of kit, but don’t expect the shopkeeper to give you great descriptions. You’ve got to learn from experience. Some items aren’t much use at all, and the game is packed with humour – you can even throw a cream pie in your own face.
|
||||
|
||||
But before you even set foot in the dungeon, NetHack asks you what kind of player you want to be. You can take your journey as a knight, a monk, a wizard or even a humble tourist, amongst many other player types. They all have their own strengths and weaknesses, and NetHack addicts love to try completing the game with the weaker types. You know, to show off to other players.
|
||||
|
||||
> ## Spoilers don’t spoil the fun ##
|
||||
|
||||
> In NetHack parlance, “spoilers” provide information on monsters, items, weapons and armour. It’s technically possible to complete the game without using them, but very few players ever achieve this, as the game is monumentally complex. Consequently it’s not regarded as bad form to use spoilers – but it’s still more fun to try to work things out yourself first, and only consult the spoilers when you really need them.
|
||||
|
||||
> A great source is [www.statslab.cam.ac.uk/~eva/nethack/spoilerlist.html][2] which separates spoilers into categories. For things that happen randomly in the game, such as the effects from drinking from fountains, it gives you the odds of a certain thing happening.
|
||||
|
||||
### Your first dungeon crawl ###
|
||||
|
||||
NetHack is available for almost every major OS and Linux distribution in the world, so you should be able to grab it with “apt-get install nethack” or “yum install nethack” or whatever is appropriate for your distro. Then run it in a terminal window by just typing “nethack”. The game will ask if it should pick a player type for you – but as a newcomer, it’s best if you choose one of the tougher characters first. So hit “n” and then hit “v” to choose the Valkyrie type, and “d” to be a dwarf.
|
||||
|
||||
Then NetHack will give you some plot blurb, explaining that your god seeks the Amulet of Yendor, so your goal is to retrieve it and present it to him. Hit space when you’re done reading the text (and any other time you see “–More–” on the screen). And here we go – you’re in the dungeon!
|
||||
|
||||
As described earlier, your character is represented by a @ sign. You can see the walls of a room around you, and the dot characters depict empty space in the room. First of all, get used to the movement keys: h, j, k and l. (Yes, it’s just like Vim, as covered in issue 3 of Linux Voice!) These move you left, down, up and right respectively. You can also move diagonally with y, u, b and n. So walk around the room until you get used to the controls.
|
||||
|
||||
NetHack is turn-based, so if you’re not moving or performing an action, the game stays still. This lets youplan your moves in advance. You will see a “d” or “f” character moving around the room as well: this is your pet dog or cat, which (normally) won’t harm you and can assist you in killing monsters. Pets can be annoying though – they occasionally eat foot rations and tasty corpses before you get to them.
|
||||
|
||||

|
||||
|
||||
Hit “i” to bring up an inventory of your currently carried items
|
||||
|
||||
### What’s behind the door? ###
|
||||
|
||||
Now, let’s go out of the room. There will be gaps around the edge, and possibly “+” signs. That “+” is a closed door, so go up to it and hit “o” to open. You will be asked for a direction, so if the door is to the left of you, press “h”. (And if the door is stuck, try opening it a few times.) You’ll then end up in a corridor, marked by “#” symbols, so walk around it until you find another room.
|
||||
|
||||
On your travels you’ll see various items. Some, such as money (denoted by a “$” symbol) are picked up automatically; for other items, you have to press the comma key whilst standing on them. If there are multiple items, you’ll be given a menu, so press the appropriate keys shown in the menu and then Enter to choose what you want. At any time you can hit “i” to bring up your inventory list – see the screenshot.
|
||||
|
||||
What happens if you see a monster? At these early stages of the game, the monsters you’re likely to come across will be represented by “d”, “x” and “:” characters. To attack, simply walk into them. The game will tell you if your attacks are successful using the messages along the top – and also how the monster is responding. These early monsters are simple to kill, so you shouldn’t have any trouble defeating them, but keep an eye on your HP in the status line at the bottom.
|
||||
|
||||
> Early monsters are simple to kill, but keep an eye on your HP.
|
||||
|
||||
If a monster leaves behind a corpse (“%”), you can hit comma to take it and then press “e” to eat it. (Whenever you’re prompted to choose an item, you can press its corresponding key from the inventory list, or “?” to bring up a mini list.) Warning! Some corpses are poisonous, and these are things you’ll learn on your travels.
|
||||
|
||||
If you’re exploring a corridor and appear to come to a dead end, you can hit “s” to search until you find a door. This can take ages, however, so you can speed things up a bit: type “10” and then “s” and you will perform 10 searches in a row. This takes up 10 moves in game time, however, so if you’re hungry you could get close to starvation!
|
||||
|
||||
Common items you’ll find in the top levels of the dungeon are “{” (fountains) and “!” (potions). For the former, you can stand on it and hit q to “quaff” from it – the effects can vary from useful to deadly. For potions, pick them up and then use “q” to drink them. If you find a shop, you can pick up items and then hit “p” to pay before leaving. Use “d” to drop something.
|
||||
|
||||

|
||||
|
||||
Souped-up versions of NetHack with fancy graphics are available, such as Falcon’s Eye
|
||||
|
||||
> ## Stupid ways to die ##
|
||||
|
||||
> A popular acronym amongst NetHack players is “YASD” – Yet Another Stupid Death. It describes a situation where the player buys the farm due to his/her own silliness or lack of concentration. We’ve had many of these, but our favourite goes as follows:
|
||||
|
||||
> We were browsing a shop, inspecting items, when a snake suddenly jumped out from behind a potion. After killing the snake, a message popped up saying that we were getting hungry, so we opted to eat the snake’s corpse. Bad idea! This made us blind, so we couldn’t see other characters or items in the shop. We tried to get to the exit, but instead bumped into the shopkeeper and accidentally attacked him. This made him furious; he started firing magic missiles at us. We just about managed to get into the corridor outside the shop, but died from the onslaught.
|
||||
|
||||
> If you come to any equally silly ends, let us know on our forums. And don’t worry – nobody will judge you. Dying like this is all part of growing up in the NetHack world.
|
||||
|
||||
### Equip yourself ###
|
||||
|
||||
On your travels, and especially after you kill monsters, you’ll find weapons and armour. Again, use comma to pick these up, and then “w” (lowercase) to wield a weapon or “W” (uppercase) to wear a piece of armour. You can use “T” to remove armour and “t” to throw weapons – often handy if you’re in a very sticky situation.
|
||||
|
||||
Sometimes it’s useful to examine things from a distance before getting close to them. Hit “;” (semicolon) and “Pick an object” will appear at the top of the screen. Use the movement keys until your view lands on the thing you want to inspect, and then hit “:” (colon). A description will appear at the top.
|
||||
|
||||
As your goal is to go further down the dungeon until you find the Amulet of Yendor, keep an eye out for “<” and “>” signs. These are stairs up and down respectively, and you can use the same keys to climb them. Note! Make sure your pet is standing in an adjacent square if you want it to follow you into the next level. If you need a break, use “S” (capital s) to save, and type #quit to exit. Next time you run NetHack, your game will be resumed.
|
||||
|
||||
We won’t spoil what’s ahead, as many of the dungeon levels have amazing designs, characters and secrets. So we’ll leave you with three tips: if you come across an item that completely baffles you, try searching for it on the NetHack wiki at [http://nethack.wikia.com][3]. You’ll also find an excellent (albeit very long) guidebook at [www.nethack.org/v343/Guidebook.html][4]. Happy exploring!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linuxvoice.com/nethack/
|
||||
|
||||
作者:[Mike Saunders][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.linuxvoice.com/author/mike/
|
||||
[1]:http://www.reddit.com/r/nethack
|
||||
[2]:http://www.statslab.cam.ac.uk/~eva/nethack/spoilerlist.html
|
||||
[3]:http://nethack.wikia.com/
|
||||
[4]:http://www.nethack.org/v343/Guidebook.html
|
||||
148
sources/talk/20141211 Open source all over the world.md
Normal file
148
sources/talk/20141211 Open source all over the world.md
Normal file
@ -0,0 +1,148 @@
|
||||
Open source all over the world
|
||||
================================================================================
|
||||

|
||||
|
||||
Image by : opensource.com
|
||||
|
||||
After a full day at the annual meeting of the Opensource.com [Community Moderators][1], it was time for the the last item on the agenda which simply said "Special Guest: TBD." [Jason Hibbets][2], project lead and community manager for [Opensource.com][3], stood up and began explaining, "In case it wasn't going to happen, I didn't want to say who it was. Months ago I asked for any dates he'd be in town. I got two, and picked one. This was one day out of three weeks that Jim was in town."
|
||||
|
||||
The moderators, in town from all over the world for the [All Things Open conference][4], stirred at the table. Their chairs squeaked and snuck a few inches edgewise.
|
||||
|
||||
"We're going to get a half hour to hear from him and take a couple questions," said Jason.
|
||||
|
||||
The door opened, and as if it had been waiting for him the whole time, the only vacant seat at the head of the table was soon occupied by a tall fellow.
|
||||
|
||||
"How is everyone doing?" said the man. No suit, just a button down shirt and slacks.
|
||||
|
||||
The next tallest man in the room, [Jeff Mackanic][5], senior director of Global Awareness at Red Hat, explained that the majority of the Community Moderator team was present today. He asked everyone to quickly introduce themselves.
|
||||
|
||||
"[Jen Wike Huger][6]. Content Manager for Opensource.com. Happy to have everyone here."
|
||||
|
||||
"[Nicole][7]. Vice president of education at [ByWater Solutions][8]. We do FOSS for libraries. I travel and teach people how to use software."
|
||||
|
||||
"[Robin][9]. I've been participating in the Moderator program since 2013. I do lots of stuff for OSDC and work in the [City of the Hague][10], maintaining their [website][11]."
|
||||
|
||||
"[Marcus Hanwell][12]. Originally from England, I'm now at [Kitware][13]. I'm the technology lead on FOSS science software. I work with national labs and use things like [Titan][14] Z doing [GPU programming][15]. I've worked with [Gentoo][16] and [KDE][17]. Most of all, I'm passionate about joining FOSS and open science."
|
||||
|
||||
"[Phil Shapiro][18]. I administrate 28 Linux work stations at a small library in D.C. I consider these folks my coworkers and colleagues. And it's wonderful to know that we can all feed into the energy and share ideas. My main interests are how FOSS intersects with dignity, and enhancing dignity."
|
||||
|
||||
"[Joshua Holm][19]. I spend most of my time staring at system updates and helping people search for jobs on the Internet."
|
||||
|
||||
"[Mel Chernoff][20]: I work here at Red Hat, primarily on the [government][21] channel with [Jason Hibbets][22] and [Mark Bohannon][23]."
|
||||
|
||||
"[Scott Nesbitt][24]: I write for many things, but have been using FOSS for long time. I'm a 'mere mortal' just trying to be more productive, not a sysadmin or programmer. I help people meld FOSS into their business and personal lives."
|
||||
|
||||
"[Luis Ibanez][25]: I just joined [Google]26], but I'm interested in DIY and FOSS."
|
||||
|
||||
"[Remy DeCausemaker][27]: Resident Hackademic at the [RIT MAGIC Center][28] and Adjunct Professor for the [Department of Interactive Games and Media][29]. Been writing for Opensource.com for about four years now."
|
||||
|
||||
"You teach courses for the [new FOSS Minor then][30]," said Jim. "Very cool."
|
||||
|
||||
"[Jason Baker][31]. I'm a Red Hat cloud expert, mostly doing work around [OpenStack][32]."
|
||||
|
||||
"[Mark Bohannan][33]. I'm with Red Hat Global Public Policy, and I work out of Washington. Like Mel, I spend a good deal of time writing for, or finding folks from, the legal and government channels. I've found an excellent outlet to discuss positive things happening in government."
|
||||
|
||||
"[Jason Hibbets][34]. I organize the organized chaos here."
|
||||
|
||||
The room has a good chuckle.
|
||||
|
||||
"I organize this chaos too, you could say," says the brownish-red haired fellow with a gleaming white smile. The laughs grow then quieten. Breaths become baited.
|
||||
|
||||
I sat to his left and had a moment to look up from transcribing to glance up. I noticed the hint of a smile behind the knowing eyes of a man who has led the company since January 2008, [Jim Whitehurst][35], president and CEO of Red Hat.
|
||||
|
||||
"I have one of the greatest jobs on Earth," began Whitehurst, as he leaned back, crossed his legs, and put his arms behind his head. "I get to lead Red Hat, travel around the world and see what goes on. In my seven years here, the amazing thing about FOSS, and, broadly open innovation, is that it has left the fringe. And now, I would argue, IT is in the same place that FOSS was in its early days. We are seeing FOSS going from an alternative to driving innovation. Our customers are seeing it, too. They're using FOSS not because it is cheaper, but because it provides them with control and innovative solutions. It's a global phenomenon, too. For instance, I was just in India, and discovered that, for them, there were two reasons for embracing of open source: one, access to innovation, and two, the market is somewhat different and wanting full control.”
|
||||
|
||||
"The [Bombay Stock Exchange][36] wants to own all the source and control it. That is not something you would have heard five years ago in a stock exchange, anywhere. Back then, the early knock on FOSS was that it was creating free copies of things that already existed.' If you look today, virtually everything in big data is happening in FOSS. Almost any new framework, language, and methodology, including mobile (though excluding devices), are all happening first in open source.”
|
||||
|
||||
"This is because users have reached size and scale. It's not just Red Hat—it's [Google][37], [Amazon][38], [Facebook][39], and others, they want to solve their own problems, and do it the open source way. And forget licensing—open source is much more than that. We've built a vehicle, and a set of norms. Things like [Hadoop][40], [Cassandra][41], and other tools. Fact is, open source drives innovation. For example, Hadoop was in production before any vendor realized there was a problem of that scale that needed to be solved. They actually have the wherewithal to solve their own problems, and the social tech and principles to do that. "Open source is now the default technology for many categories. This is especially true as the world moves more and more to content importance, such as [3D printing][42] and other physical products that take information content and apply it.”
|
||||
|
||||
"We have this cool thing in one area, source code, but it is limited. But there are still many opportunities in different industries. We must ask ourselves, 'What can open source do for education, government, and legal? What are the parallels? And what can other areas learn with us?'"
|
||||
|
||||
"There's also the matter of content. Content is now free, and we can invest in more free content, sure. But we need free content that has a business model built around it. That is something that more people should care about. If you believe open innovation is better, then we need more models."
|
||||
|
||||
"Education worries me with its fixation on 'content' rather than 'communities.' For example, everywhere I go, I hear university presidents say, 'Wait, education is going to be free?!' The fact that FOSS is free for downstream is great, but the upstream is really powerful. Distributing free courses is great, but we need communities to iterate and make it better. That is something that a lot of different people are doing, and Opensource.com is a place to share what is going on in this space. The question is not so much 'How do we take content?' as it is 'How do you build and distribute it? How do you make sure it is a living thing that gets better, and can morph for different areas?'"
|
||||
|
||||
"But the potential to change the world is limitless, and it's amazing how much progress we've already made. Six years ago we were obsessed about defining a mission statement. We started by saying, 'We are the leader,' but that was the wrong word, because it implied control. Active participant didn't quite get it either... [Máirín Duffy][43] came up with the word [catalyst][44]. And so, we became Red Hat, the company that creates environments to agitate action and catalyze direction.”
|
||||
|
||||
"Opensource.com is a catalyst in other areas, and that is what Opensource.com is about. I hope you see yourselves this way, too. The quality of content then, when we started, versus now, is incredible. You can see it getting better every quarter. Thank you for investing your time. Thank you for being catalysts. This is a chance for us all to make the world a better place. And I'd love to hear from you."
|
||||
|
||||
I stole a glimpse of everyone at the table: more than a few people had tears in their eyes.
|
||||
|
||||
Then, Whitehurst revisits the open education topic of conversation again. "Taking it to an extreme, let's say you have a course about the book [Ulysses][45]. Here, you can explore how to crowdsource a model and get people to work together within the course. Well, it's the same with a piece of code: people work together, and the code itself gets better over time."
|
||||
|
||||
At this point, I get to have my say. Words like fundamental and possibly irreconcilable came up when discussing the differences between FOSS and academic communities.
|
||||
|
||||
**Remy**: "Retraction is career death." Releasing data or code with your paper could be devastating if you make a mistake. School has always been about avoiding failure and divining 'right answers'. Copying is cheating. Wheels are recreated from scratch ritualistically. In FOSS, you work to fail fastest, but in academia, you invite invalidation."
|
||||
|
||||
**Nicole**: "There are a lot of egos in academia. You need a release manager."
|
||||
|
||||
**Marcus**: "To collaborate, you have to show the bits you don't understand, and that happens behind closed doors. The reward model is all about what you can take credit for. We need to change the reward model. Publish as much as you can. We release eventually, but we want to release early."
|
||||
|
||||
**Luis**: "Make teamwork and sharing a priority. And Red Hat can say that to them more."
|
||||
|
||||
**Jim**: "Is there an active role that companies can play in that?"
|
||||
|
||||
[Phil Shapiro][46]: "I'm interested in tipping points in FOSS. It drives me nuts that the Fed hasn't switched to [LibreOffice][47]. We're not spending tax dollars on software, and certainly shouldn't be spending on word processing or Microsoft Office."
|
||||
|
||||
**Jim**: "We have advocated for that. A lot. Can we do more? That's a valid question. Primarily, we've made progress in the places we have products. We have a solid franchise in government. We are larger per IT spend there than the private sector. Banks and telcos are further along than the government. We've done better in Europe, and I think they have less lobbying dollars at work there, than here. This next generation of computing is almost like a 'do-over'. We are making great progress elsewhere, but it is concerning."
|
||||
|
||||
Suddenly, the door to the room opened. Jim turned and nodded towards his executive assistant standing in the doorway; it was time for his next meeting. He uncrossed his legs, leaned forward, and stood. He thanked everyone again for their work and dedication, smiled, and was out the door... leaving us all a bit more inspired.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/business/14/12/jim-whitehurst-inspiration-open-source
|
||||
|
||||
作者:[Remy][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://opensource.com/users/remyd
|
||||
[1]:http://opensource.com/community-moderator-program
|
||||
[2]:https://twitter.com/jhibbets
|
||||
[3]:http://opensource.com/
|
||||
[4]:http://allthingsopen.org/
|
||||
[5]:http://opensource.com/users/mackanic
|
||||
[6]:https://twitter.com/JenWike
|
||||
[7]:http://opensource.com/users/nengard
|
||||
[8]:http://bywatersolutions.com/
|
||||
[9]:http://opensource.com/life/13/7/community-spotlight-robin-muilwijk
|
||||
[10]:https://en.wikipedia.org/wiki/The_Hague
|
||||
[11]:http://www.denhaag.nl/en.htm
|
||||
[12]:https://twitter.com/mhanwell
|
||||
[13]:http://www.kitware.com/
|
||||
[14]:http://www.nvidia.com/gtx-700-graphics-cards/gtx-titan-z/
|
||||
[15]:https://en.wikipedia.org/wiki/General-purpose_computing_on_graphics_processing_units
|
||||
[16]:https://www.gentoo.org/
|
||||
[17]:http://kde.org/
|
||||
[18]:https://twitter.com/philshapiro
|
||||
[19]:http://opensource.com/community/13/9/contributor-spotlight-joshua-holm
|
||||
[20]:http://opensource.com/users/melanie
|
||||
[21]:http://opensource.com/government
|
||||
[22]:https://twitter.com/jhibbets
|
||||
[23]:https://twitter.com/markbotech
|
||||
[24]:http://scottnesbitt.me/
|
||||
[25]:http://opensource.com/users/luis-ibanez
|
||||
[26]:http://google.com/
|
||||
[27]:http://twitter.com/remy_d
|
||||
[28]:http://foss.rit.edu/
|
||||
[29]:http://igm.rit.edu/
|
||||
[30]:http://www.rit.edu/news/story.php?id=50590
|
||||
[31]:https://twitter.com/jehb
|
||||
[32]:http://openstack.org/
|
||||
[33]:https://twitter.com/markbotech
|
||||
[34]:https://twitter.com/jhibbets
|
||||
[35]:http://www.redhat.com/en/about/company/management/james-whitehurst
|
||||
[36]:http://www.bseindia.com/
|
||||
[37]:http://google.com/
|
||||
[38]:https://mail.corp.redhat.com/service/home/%7E/Amazon
|
||||
[39]:https://mail.corp.redhat.com/service/home/%7E/Facebook
|
||||
[40]:https://hadoop.apache.org/
|
||||
[41]:https://cassandra.apache.org/
|
||||
[42]:https://en.wikipedia.org/wiki/3D_printing
|
||||
[43]:https://twitter.com/mairin
|
||||
[44]:http://jobs.redhat.com/life-at-red-hat/our-culture/
|
||||
[45]:http://www.gutenberg.org/ebooks/4300
|
||||
[46]:https://twitter.com/philshapiro
|
||||
[47]:http://libreoffice.org/
|
||||
45
sources/talk/20141211 Was 2014 The Year of Linux Desktop.md
Normal file
45
sources/talk/20141211 Was 2014 The Year of Linux Desktop.md
Normal file
@ -0,0 +1,45 @@
|
||||
Was 2014 "The Year of Linux Desktop"?
|
||||
================================================================================
|
||||
> The Linux desktop is finally hitting all the right notes
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||

|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
**Linux has seen a lot of changes during 2014 and many users are saying that this was finally the year that really showed some real progress, but has it been enough to call it "the year of Linux desktop"?**
|
||||
|
||||
This particular phrase, "the year of Linux desktop," has been recited like a mantra in the past couple of years and it's basically trying to mark all the progress registered until now in a way that makes sense. This kind of stuff hasn't happened so far and there is no precedent for the kind of growth we're witnessing, so it's easy to understand why Linux users might look at it from this perspective.
|
||||
|
||||
Most software and hardware domains don't usually go through this kind of fast progress and things happen at a slower pace, but things have been wild even for people who have a better insight into the industry. It's hard, if not impossible, to pinpoint a certain moment or a certain event, but Linux development exploded and changed exponentially in the course of just a couple of years.
|
||||
|
||||
### Year of the Linux desktop is an uncertain term ###
|
||||
|
||||
There is no single authority which can decree that the year of the Linux desktop has arrived or that it has passed. We can only try to deduce it from what we've seen until now and it's actually up to the users. Some are more conservative and not too many things have changed for them, and others are more progressive and they just can't get enough. It really depends on what your outlook is.
|
||||
|
||||
The spark that seems to have put everything in motion appears to be the launch of Steam for Linux, although we've seen some important movement of the Linux gaming scene before that became a reality. In any case, Valve is probably the catalyst of the resurgence of what we're seeing today.
|
||||
|
||||
The Linux desktop has been in a kind of slow evolution in the past decade and nothing really changed. There have been a lot of innovations for sure, but the market share has remained almost the same. No matter how cool the desktop became or how many features Linux had well before anyone else, things have remained largely the same, and that includes the participation of companies making proprietary software. They largely ignored Linux.
|
||||
|
||||
Now, more companies have shown interest in the Linux platform in the past year than they did in the last 10. Maybe it's a natural evolution and Valve had nothing to do with it, but Linux has finally reached a level where it can be used and understood by regular users, not just people fascinated by open source.
|
||||
|
||||
The drivers are better, game studios are porting games now on a regular basis, applications and middleware that we never thought we would see on Linux have started to show up, the Linux kernel development has an incredible pace, the installation process for most of the major distros is usually trivial, and all of these are just the tip of the iceberg.
|
||||
|
||||
So, when someone asks you if 2014 was the year of the Linux desktop, you can say yes. The Linux desktop totally ruled in 2014.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://news.softpedia.com/news/Was-2014-The-Year-of-Linux-Desktop-467036.shtml
|
||||
|
||||
作者:[Silviu Stahie ][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://news.softpedia.com/editors/browse/silviu-stahie
|
||||
@ -1,44 +0,0 @@
|
||||
Vic020
|
||||
|
||||
Linux FAQs with Answers--How to disable Apport internal error reporting on Ubuntu
|
||||
================================================================================
|
||||
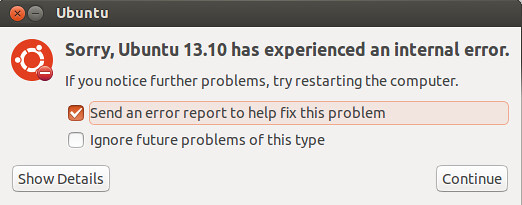
> **Question**: On Ubuntu desktop, I often encounter a popup window, alerting that Ubuntu has experienced an internal error, and asking me to send an error report. This is bothering me as it keeps popping up for every application crash. How can I turn off the error reporting feature?
|
||||
|
||||
Ubuntu desktop comes with Apport pre-installed, which is a system that catches applications crashes, unhandled exceptions or any non-crash application bugs, and automatically generates a crash report for debugging purposes. When an application crash or bug is detected, Apport alerts user of the event by showing a popup window and asking the user to submit a crash report. You will see messages like the following.
|
||||
|
||||
- "Sorry, the application XXXX has closed unexpectedly."
|
||||
- "Sorry, Ubuntu XX.XX has experienced an internal error."
|
||||
- "System program problem detected."
|
||||
|
||||
|
||||
|
||||
If application crashes are recurring, frequent error reporting alerts can be disturbing. Or you may be worried that Apport can collect and upload any sensitive information of your Ubuntu system. Whatever the reason is, you may want to disable Apport's error reporting feature.
|
||||
|
||||
### Disable Apport Error Reporting Temporarily ###
|
||||
|
||||
If you want to disable Apport temporarily, use this command:
|
||||
|
||||
$ sudo service apport stop
|
||||
|
||||
Note that Apport will be enabled back after you boot your Ubuntu system.
|
||||
|
||||
### Disable Apport Error Reporting Permanently ###
|
||||
|
||||
To turn off Apport permanently, edit /etc/default/apport with a text editor, and change the content to the following.
|
||||
|
||||
enabled=0
|
||||
|
||||
Now if you reboot your Ubuntu system, Apport will automatically be disabled.
|
||||
|
||||
If you think you will never use Apport, another method is to simply remove it altogether.
|
||||
|
||||
$ sudo apt-get purge apport
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://ask.xmodulo.com/disable-apport-internal-error-reporting-ubuntu.html
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
@ -1,3 +1,4 @@
|
||||
文章重复
|
||||
How to create a custom backup plan for Debian with backupninja
|
||||
================================================================================
|
||||
Backupninja is a powerful and highly-configurable backup tool for Debian based distributions. In the [previous tutorial][1], we explored how to install backupninja and how to set up two backup actions for the program to perform. However, we should note that those examples were only "the tip of the iceberg," so to speak. In this post we will discuss how to leverage custom handlers and helpers that allow this program to be customized in order to accomplish almost any backup need that you can think of.
|
||||
@ -245,4 +246,4 @@ via: http://xmodulo.com/create-custom-backup-plan-debian.html
|
||||
|
||||
[a]:http://xmodulo.com/author/gabriel
|
||||
[1]:http://xmodulo.com/backup-debian-system-backupninja.html
|
||||
[2]:http://xmodulo.com/backup-debian-system-backupninja.html
|
||||
[2]:http://xmodulo.com/backup-debian-system-backupninja.html
|
||||
|
||||
@ -0,0 +1,198 @@
|
||||
spccman translating
|
||||
How to Setup Bind Chroot DNS Server on CentOS 7.0 VPS
|
||||
================================================================================
|
||||
BIND (Berkeley Internet Name Daemon) also known as NAMED is the most widely used DNS server in the internet. This tutorial will descibes how we can run BIND in a chroot jail, the process is simply unable to see any part of the filesystem outside the jail. For example, in this post, i will setting up BIND to run chrooted to the directory /var/named/chroot/. Well, to BIND, the contents of this directory will appear to be /, the root directory. A “jail” is a software mechanism for limiting the ability of a process to access resources outside a very limited area, and it’s purposely to enhance the security. Bind Chroot DNS server was by default configured to /var/named/chroot. You may follow this complete steps to implement Bind Chroot DNS Server on CentOS 7.0 virtual private server (VPS).
|
||||
|
||||
1. Install Bind Chroot DNS server :
|
||||
|
||||
[root@centos7 ~]# yum install bind-chroot bind -y
|
||||
|
||||
2. Copy all bind related files to prepare bind chrooted environments :
|
||||
|
||||
[root@centos7 ~]# cp -R /usr/share/doc/bind-*/sample/var/named/* /var/named/chroot/var/named/
|
||||
|
||||
3. Create bind related files into chrooted directory :
|
||||
|
||||
[root@centos7 ~]# touch /var/named/chroot/var/named/data/cache_dump.db
|
||||
[root@centos7 ~]# touch /var/named/chroot/var/named/data/named_stats.txt
|
||||
[root@centos7 ~]# touch /var/named/chroot/var/named/data/named_mem_stats.txt
|
||||
[root@centos7 ~]# touch /var/named/chroot/var/named/data/named.run
|
||||
[root@centos7 ~]# mkdir /var/named/chroot/var/named/dynamic
|
||||
[root@centos7 ~]# touch /var/named/chroot/var/named/dynamic/managed-keys.bind
|
||||
|
||||
4. Bind lock file should be writeable, therefore set the permission to make it writable as below :
|
||||
|
||||
[root@centos7 ~]# chmod -R 777 /var/named/chroot/var/named/data
|
||||
[root@centos7 ~]# chmod -R 777 /var/named/chroot/var/named/dynamic
|
||||
|
||||
5. Copy /etc/named.conf chrooted bind config folder :
|
||||
|
||||
[root@centos7 ~]# cp -p /etc/named.conf /var/named/chroot/etc/named.conf
|
||||
|
||||
6.Configure main bind configuration in /etc/named.conf. Append the example.local zone information to the file :
|
||||
|
||||
[root@centos7 ~]# vi /var/named/chroot/etc/named.conf
|
||||
|
||||
Create forward and reverse zone into named.conf:
|
||||
|
||||
..
|
||||
..
|
||||
zone "example.local" {
|
||||
type master;
|
||||
file "example.local.zone";
|
||||
};
|
||||
|
||||
zone "0.168.192.in-addr.arpa" IN {
|
||||
type master;
|
||||
file "192.168.0.zone";
|
||||
};
|
||||
..
|
||||
..
|
||||
|
||||
Full named.conf configuration :
|
||||
|
||||
//
|
||||
// named.conf
|
||||
//
|
||||
// Provided by Red Hat bind package to configure the ISC BIND named(8) DNS
|
||||
// server as a caching only nameserver (as a localhost DNS resolver only).
|
||||
//
|
||||
// See /usr/share/doc/bind*/sample/ for example named configuration files.
|
||||
//
|
||||
|
||||
options {
|
||||
listen-on port 53 { any; };
|
||||
listen-on-v6 port 53 { ::1; };
|
||||
directory "/var/named";
|
||||
dump-file "/var/named/data/cache_dump.db";
|
||||
statistics-file "/var/named/data/named_stats.txt";
|
||||
memstatistics-file "/var/named/data/named_mem_stats.txt";
|
||||
allow-query { any; };
|
||||
|
||||
/*
|
||||
- If you are building an AUTHORITATIVE DNS server, do NOT enable recursion.
|
||||
- If you are building a RECURSIVE (caching) DNS server, you need to enable
|
||||
recursion.
|
||||
- If your recursive DNS server has a public IP address, you MUST enable access
|
||||
control to limit queries to your legitimate users. Failing to do so will
|
||||
cause your server to become part of large scale DNS amplification
|
||||
attacks. Implementing BCP38 within your network would greatly
|
||||
reduce such attack surface
|
||||
*/
|
||||
recursion yes;
|
||||
|
||||
dnssec-enable yes;
|
||||
dnssec-validation yes;
|
||||
dnssec-lookaside auto;
|
||||
|
||||
/* Path to ISC DLV key */
|
||||
bindkeys-file "/etc/named.iscdlv.key";
|
||||
|
||||
managed-keys-directory "/var/named/dynamic";
|
||||
|
||||
pid-file "/run/named/named.pid";
|
||||
session-keyfile "/run/named/session.key";
|
||||
};
|
||||
|
||||
logging {
|
||||
channel default_debug {
|
||||
file "data/named.run";
|
||||
severity dynamic;
|
||||
};
|
||||
};
|
||||
|
||||
zone "." IN {
|
||||
type hint;
|
||||
file "named.ca";
|
||||
};
|
||||
|
||||
zone "example.local" {
|
||||
type master;
|
||||
file "example.local.zone";
|
||||
};
|
||||
|
||||
zone "0.168.192.in-addr.arpa" IN {
|
||||
type master;
|
||||
file "192.168.0.zone";
|
||||
};
|
||||
|
||||
include "/etc/named.rfc1912.zones";
|
||||
include "/etc/named.root.key";
|
||||
|
||||
7. Create Forward and Reverse zone files for domain example.local.
|
||||
|
||||
a) Create Forward Zone :
|
||||
|
||||
[root@centos7 ~]# vi /var/named/chroot/var/named/example.local.zone
|
||||
|
||||
Add the following and save :
|
||||
|
||||
;
|
||||
; Addresses and other host information.
|
||||
;
|
||||
$TTL 86400
|
||||
@ IN SOA example.local. hostmaster.example.local. (
|
||||
2014101901 ; Serial
|
||||
43200 ; Refresh
|
||||
3600 ; Retry
|
||||
3600000 ; Expire
|
||||
2592000 ) ; Minimum
|
||||
|
||||
; Define the nameservers and the mail servers
|
||||
|
||||
IN NS ns1.example.local.
|
||||
IN NS ns2.example.local.
|
||||
IN A 192.168.0.70
|
||||
IN MX 10 mx.example.local.
|
||||
|
||||
centos7 IN A 192.168.0.70
|
||||
mx IN A 192.168.0.50
|
||||
ns1 IN A 192.168.0.70
|
||||
ns2 IN A 192.168.0.80
|
||||
|
||||
b) Create Reverse Zone :
|
||||
|
||||
[root@centos7 ~]# vi /var/named/chroot/var/named/192.168.0.zone
|
||||
|
||||
----------
|
||||
|
||||
;
|
||||
; Addresses and other host information.
|
||||
;
|
||||
$TTL 86400
|
||||
@ IN SOA example.local. hostmaster.example.local. (
|
||||
2014101901 ; Serial
|
||||
43200 ; Refresh
|
||||
3600 ; Retry
|
||||
3600000 ; Expire
|
||||
2592000 ) ; Minimum
|
||||
|
||||
0.168.192.in-addr.arpa. IN NS centos7.example.local.
|
||||
|
||||
70.0.168.192.in-addr.arpa. IN PTR mx.example.local.
|
||||
70.0.168.192.in-addr.arpa. IN PTR ns1.example.local.
|
||||
80.0.168.192.in-addr.arpa. IN PTR ns2.example.local.
|
||||
|
||||
8. Stop and disable named service. Start and enable bind-chroot service at boot :
|
||||
|
||||
[root@centos7 ~]# /usr/libexec/setup-named-chroot.sh /var/named/chroot on
|
||||
[root@centos7 ~]# systemctl stop named
|
||||
[root@centos7 ~]# systemctl disable named
|
||||
[root@centos7 ~]# systemctl start named-chroot
|
||||
[root@centos7 ~]# systemctl enable named-chroot
|
||||
ln -s '/usr/lib/systemd/system/named-chroot.service' '/etc/systemd/system/multi-user.target.wants/named-chroot.service'
|
||||
|
||||
As always if you need any help you can reach us on twitter @ehowstuff or drop us a comment below. [Jumping through archives page to read more articles..][1]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.ehowstuff.com/how-to-setup-bind-chroot-dns-server-on-centos-7-0-vps/
|
||||
|
||||
作者:[skytech][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.ehowstuff.com/author/mhstar/
|
||||
[1]:http://www.ehowstuff.com/archives/
|
||||
@ -0,0 +1,158 @@
|
||||
How to configure a syslog server with rsyslog on Linux
|
||||
================================================================================
|
||||
A syslog server represents a central log monitoring point on a network, to which all kinds of devices including Linux or Windows servers, routers, switches or any other hosts can send their logs over network. By setting up a syslog server, you can filter and consolidate logs from different hosts and devices into a single location, so that you can view and archive important log messages more easily.
|
||||
|
||||
On most Linux distributions, rsyslog is the standard syslog daemon that comes pre-installed. Configured in a client/server architecture, rsyslog can play both roles; as a syslog server rsyslog can gather logs from other devices, and as a [syslog client][1], rsyslog can transmit its internal logs to a remote syslog server.
|
||||
|
||||
In this tutorial, we cover how to configure a centralized syslog server using rsyslog on Linux. Before we go into the details, it is instructive to go over syslog standard first.
|
||||
|
||||
### Basic of Syslog Standard ###
|
||||
|
||||
When logs are collected with syslog mechanism, three important things must be taken into consideration:
|
||||
|
||||
- **Facility level**: what type of processes to monitor
|
||||
- **Severity (priority) level**: what type of log messages to collect
|
||||
- **Destination**: where to send or record log messages
|
||||
|
||||
Let's take a look at how the configuration is defined in more detail.
|
||||
|
||||
The facility levels define a way to categorize internal system processes. Some of the common standard facilities in Linux are:
|
||||
|
||||
- **auth**: messages related to authentication (login)
|
||||
- **cron**: messages related to scheduled processes or applications
|
||||
- **daemon**: messages related to daemons (internal servers)
|
||||
- **kernel**: messages related to the kernel
|
||||
- **mail**: messages related to internal mail servers
|
||||
- **syslog**: messages related to the syslog daemon itself
|
||||
- **lpr**: messages related to print servers
|
||||
- **local0 - local7**: messages defined by user (local7 is usually used by Cisco and Windows servers)
|
||||
|
||||
The severity (priority) levels are standardized, and defined by using standard abbreviation and an assigned number with number 7 being the highest level of all. These levels are:
|
||||
|
||||
- **emerg**: Emergency - 0
|
||||
- **alert**: Alerts - 1
|
||||
- **crit**: Critical - 2
|
||||
- **err**: Errors - 3
|
||||
- **warn**: Warnings - 4
|
||||
- **notice**: Notification - 5
|
||||
- **info**: Information - 6
|
||||
- **debug**: Debugging - 7
|
||||
|
||||
Finally, the destination statement enforces a syslog client to perform one of three following tasks: (1) save log messages on a local file, (2) route them to a remote syslog server over TCP/UDP, or (3) send them to stdout such as a console.
|
||||
|
||||
In rsyslog, syslog configuration is structured based on the following schema.
|
||||
|
||||
[facility-level].[severity-level] [destination]
|
||||
|
||||
### Configure Rsyslog on Linux ###
|
||||
|
||||
Now that we understand syslog, it's time to configure a Linux server as a central syslog server using rsyslog. We will also see how to configure a Windows based system as a syslog client to send internal logs to the syslog server.
|
||||
|
||||
#### Step One: Initial System Requirements ####
|
||||
|
||||
To set up a Linux host as a central log server, we need to create a separate /var partition, and allocate a large enough disk size or create a LVM special volume group. That way, the syslog server will be able to sustain the exponential growth of collected logs over time.
|
||||
|
||||
#### Step Two: Enable Rsyslog Daemon ####
|
||||
|
||||
rsyslog daemon comes pre-installed on modern Linux distributions, but is not enabled by default. To enable rsyslog daemon to receive external messages, edit its configuration file located in /etc/rsyslog.conf.
|
||||
|
||||
Once the file is opened for editing, search and uncomment the below two lines by removing the # sign from the beginning of lines.
|
||||
|
||||
$ModLoad imudp
|
||||
$UDPServerRun 514
|
||||
|
||||
This will enable rsyslog daemon to receive log messages on UDP port 514. UDP is way faster than TCP, but does not provide reliability on data flow the same way as TCP does. If you need to reliable delivery, you can enable TCP by uncommenting the following lines.
|
||||
|
||||
$ModLoad imtcp
|
||||
$InputTCPServerRun 514
|
||||
|
||||
Note that both TCP and UDP can be set on the server simultaneously to listen on TCP/UDP connections.
|
||||
|
||||
#### Step Three: Create a Template for Log Receipt ####
|
||||
|
||||
In the next step we need to create a template for remote messages, and tell rsyslog daemon how to record messages received from other client machines.
|
||||
|
||||
Open /etc/rsyslog.conf with a text editor, and append the following template before the GLOBAL DIRECTIVES block:
|
||||
|
||||
$template RemoteLogs,"/var/log/%HOSTNAME%/%PROGRAMNAME%.log" *
|
||||
*.* ?RemoteLogs
|
||||
& ~
|
||||
|
||||
This template needs a little explanation. The $template RemoteLogs directive ("RemoteLogs" string can be changed to any other descriptive name) forces rsyslog daemon to write log messages to separate local log files in /var/log/, where log file names are defined based on the hostname of the remote sending machine as well as the remote application that generated the logs. The second line ("*.* ?RemoteLogs") implies that we apply RemoteLogs template to all received logs.
|
||||
|
||||
The "& ~" sign represents a redirect rule, and is used to tell rsyslog daemon to stop processing log messages further, and not write them locally. If this redirection is not used, all the remote messages would be also written on local log files besides the log files described above, which means they would practically be written twice. Another consequence of using this rule is that the syslog server's own log messages would only be written to dedicated files named after machine's hostname.
|
||||
|
||||
If you want, you can direct log messages with a specific facility or severity level to this new template using the following schema.
|
||||
|
||||
[facility-level].[severity-level] ?RemoteLogs
|
||||
|
||||
For example:
|
||||
|
||||
Direct all internal authentication messages of all priority levels to RemoteLogs template:
|
||||
|
||||
authpriv.* ?RemoteLogs
|
||||
|
||||
Direct informational messages generated by all system processes, except mail, authentication and cron messages to RemoteLogs template:
|
||||
|
||||
*.info,mail.none,authpriv.none,cron.none ?RemoteLogs
|
||||
|
||||
If we want all received messages from remote clients written to a single file named after their IP address, you can use the following template. We assign a new name "IpTemplate" to this template.
|
||||
|
||||
$template IpTemplate,"/var/log/%FROMHOST-IP%.log"
|
||||
*.* ?IpTemplate
|
||||
& ~
|
||||
|
||||
After we have enabled rsyslog daemon and edited its configuration file, we need to restart the daemon.
|
||||
|
||||
**On Debian, Ubuntu or CentOS/RHEL 6:**
|
||||
|
||||
$ sudo service rsyslog restart
|
||||
|
||||
**On Fedora or CentOS/RHEL 7:**
|
||||
|
||||
$ sudo systemctl restart rsyslog
|
||||
|
||||
We can verify that rsyslog daemon is functional by using netstat command.
|
||||
|
||||
$ sudo netstat -tulpn | grep rsyslog
|
||||
|
||||
The output should look like the following in case rsyslog daemon listens on UDP port.
|
||||
|
||||
udp 0 0 0.0.0.0:514 0.0.0.0:* 551/rsyslogd
|
||||
udp6 0 0 :::514 :::* 551/rsyslogd
|
||||
|
||||
If rsyslog daemon is set up to listen on TCP connections, the output should look like this.
|
||||
|
||||
tcp 0 0 0.0.0.0:514 0.0.0.0:* LISTEN 1891/rsyslogd
|
||||
tcp6 0 0 :::514 :::* LISTEN 1891/rsyslogd
|
||||
|
||||
### Send Windows Logs to a Remote Rsyslog Server ###
|
||||
|
||||
To forward a Windows based client's log messages to our rsyslog server, we need a Windows syslog agent. While there are a multitude of syslog agents that can run on Windows, we can use [Datagram SyslogAgent][2], which is a freeware program.
|
||||
|
||||
After downloading and installing the syslog agent, we need to configure it to run as a service. Specify the protocol though which it will send data, the IP address and port of a remote rsyslog server, and what type of event logs should be transmitted as follows.
|
||||
|
||||
|
||||
|
||||
After we have set up all the configurations, we can start the service and watch the log files on the central rsyslog server using tailf command line utility.
|
||||
|
||||
### Conclusion ###
|
||||
|
||||
By creating a central rsyslog server that can collect log files of local or remote hosts, we can get a better idea on what is going on internally in their systems, and can debug their problems more easily should any of them become unresponsive or crash. For information about setting up a syslog client, refer to this [guideline][3].
|
||||
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/configure-syslog-server-linux.html
|
||||
|
||||
作者:[Caezsar M][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/caezsar
|
||||
[1]:http://xmodulo.com/configure-rsyslog-client-centos.html
|
||||
[2]:http://www.syslogserver.com/download.html
|
||||
[3]:http://xmodulo.com/configure-rsyslog-client-centos.html
|
||||
@ -0,0 +1,153 @@
|
||||
ideas4u Translating..
|
||||
How to use matplotlib for scientific plotting on Linux
|
||||
================================================================================
|
||||
If you want an efficient, automatable solution for producing high-quality scientific plots in Linux, then consider using matplotlib. Matplotlib is a Python-based open-source scientific plotting package with a license based on the Python Software Foundation license. The extensive documentation and examples, integration with Python and the NumPy scientific computing package, and automation capability are just a few reasons why this package is a solid choice for scientific plotting in a Linux environment. This tutorial will provide several example plots created with matplotlib.
|
||||
|
||||
### Features ###
|
||||
|
||||
- Numerous plot types (bar, box, contour, histogram, scatter, line plots...)
|
||||
- Python-based syntax
|
||||
- Integration with the NumPy scientific computing package
|
||||
- Source data can be Python lists, Python tuples, or NumPy arrays
|
||||
- Customizable plot format (axes scales, tick positions, tick labels...)
|
||||
- Customizable text (font, size, position...)
|
||||
- TeX formatting (equations, symbols, Greek characters...)
|
||||
- Compatible with IPython (allows interactive plotting from a Python shell)
|
||||
- Automation - use Python loops to iteratively create plots
|
||||
- Save plots to image files (png, pdf, ps, eps, and svg format)
|
||||
|
||||
The Python-based syntax of matplotlib serves as the foundation for many of its features and enables an efficient workflow. There are many scientific plotting packages that can produce quality plots, but do they allow you to do it directly from within your Python code? On top of that, do they allow you to create automated routines for iterative creation of plots that can be saved as image files? Matplotlib allows you to accomplish all of these tasks. You can now look forward to saving time that would have otherwise been spent manually creating multiple plots.
|
||||
|
||||
### Installation ###
|
||||
|
||||
Installation of Python and the NumPy package is a prerequisite for use of matplotlib. Instructions for installing NumPy can be found [here][1].
|
||||
|
||||
To install matplotlib in Debian or Ubuntu, run the following command:
|
||||
|
||||
$ sudo apt-get install python-matplotlib
|
||||
|
||||
To install matplotlib in Fedora or CentOS/RHEL, run the following command:
|
||||
|
||||
$ sudo yum install python-matplotlib
|
||||
|
||||
### Matplotlib Examples ###
|
||||
|
||||
This tutorial will provide several plotting examples that demonstrate how to use matplotlib:
|
||||
|
||||
- Scatter and line plot
|
||||
- Histogram plot
|
||||
- Pie chart
|
||||
|
||||
In these examples we will use Python scripts to execute matplotlib commands. Note that the numpy and matplotlib modules must be imported from within the scripts via the import command. np is specified as a reference to the numpy module and plt is specified as a reference to the matplotlib.pyplot namespace:
|
||||
|
||||
import numpy as np
|
||||
import matplotlib.pyplot as plt
|
||||
|
||||
### Example 1: Scatter and Line Plot ###
|
||||
|
||||
The first script, script1.py completes the following tasks:
|
||||
|
||||
- Creates three data sets (xData, yData1, and yData2)
|
||||
- Creates a new figure (assigned number 1) with a width and height of 8 inches and 6 inches, respectively
|
||||
- Sets the plot title, x-axis label, and y-axis label (all with font size of 14)
|
||||
- Plots the first data set, yData1, as a function of the xData dataset as a dotted blue line with circular markers and a label of "y1 data"
|
||||
- Plots the second data set, yData2, as a function of the xData dataset as a solid red line with no markers and a label of "y2 data".
|
||||
- Positions the legend in the upper left-hand corner of the plot
|
||||
- Saves the figure as a PNG file
|
||||
|
||||
Contents of script1.py:
|
||||
|
||||
import numpy as np
|
||||
import matplotlib.pyplot as plt
|
||||
|
||||
xData = np.arange(0, 10, 1)
|
||||
yData1 = xData.__pow__(2.0)
|
||||
yData2 = np.arange(15, 61, 5)
|
||||
plt.figure(num=1, figsize=(8, 6))
|
||||
plt.title('Plot 1', size=14)
|
||||
plt.xlabel('x-axis', size=14)
|
||||
plt.ylabel('y-axis', size=14)
|
||||
plt.plot(xData, yData1, color='b', linestyle='--', marker='o', label='y1 data')
|
||||
plt.plot(xData, yData2, color='r', linestyle='-', label='y2 data')
|
||||
plt.legend(loc='upper left')
|
||||
plt.savefig('images/plot1.png', format='png')
|
||||
|
||||
The resulting plot is shown below:
|
||||
|
||||
|
||||
|
||||
### Example 2: Histogram Plot ###
|
||||
|
||||
The second script, script2.py completes the following tasks:
|
||||
|
||||
- Creates a data set containing 1000 random samples from a Normal distribution
|
||||
- Creates a new figure (assigned number 1) with a width and height of 8 inches and 6 inches, respectively
|
||||
- Sets the plot title, x-axis label, and y-axis label (all with font size of 14)
|
||||
- Plots the data set, samples, as a histogram with 40 bins and an upper and lower bound of -10 and 10, respectively
|
||||
- Adds text to the plot and uses TeX formatting to display the Greek letters mu and sigma (font size of 16)
|
||||
- Saves the figure as a PNG file
|
||||
|
||||
Contents of script2.py:
|
||||
|
||||
import numpy as np
|
||||
import matplotlib.pyplot as plt
|
||||
|
||||
mu = 0.0
|
||||
sigma = 2.0
|
||||
samples = np.random.normal(loc=mu, scale=sigma, size=1000)
|
||||
plt.figure(num=1, figsize=(8, 6))
|
||||
plt.title('Plot 2', size=14)
|
||||
plt.xlabel('value', size=14)
|
||||
plt.ylabel('counts', size=14)
|
||||
plt.hist(samples, bins=40, range=(-10, 10))
|
||||
plt.text(-9, 100, r'$\mu$ = 0.0, $\sigma$ = 2.0', size=16)
|
||||
plt.savefig('images/plot2.png', format='png')
|
||||
|
||||
The resulting plot is shown below:
|
||||
|
||||
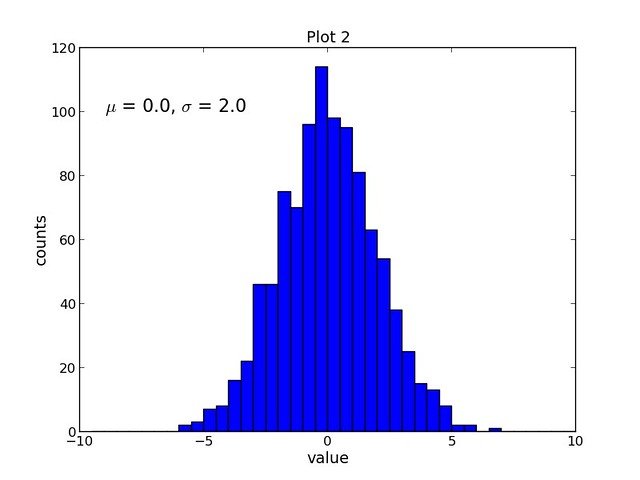
|
||||
|
||||
### Example 3: Pie Chart ###
|
||||
|
||||
The third script, script3.py completes the following tasks:
|
||||
|
||||
- Creates data set containing five integers
|
||||
- Creates a new figure (assigned number 1) with a width and height of 6 inches and 6 inches, respectively
|
||||
- Adds an axes to the figure with an aspect ratio of 1
|
||||
- Sets the plot title (font size of 14)
|
||||
- Plots the data set, data, as a pie chart with labels included
|
||||
- Saves the figure as a PNG file
|
||||
|
||||
Contents of script3.py:
|
||||
|
||||
import numpy as np
|
||||
import matplotlib.pyplot as plt
|
||||
|
||||
data = [33, 25, 20, 12, 10]
|
||||
plt.figure(num=1, figsize=(6, 6))
|
||||
plt.axes(aspect=1)
|
||||
plt.title('Plot 3', size=14)
|
||||
plt.pie(data, labels=('Group 1', 'Group 2', 'Group 3', 'Group 4', 'Group 5'))
|
||||
plt.savefig('images/plot3.png', format='png')
|
||||
|
||||
The resulting plot is shown below:
|
||||
|
||||
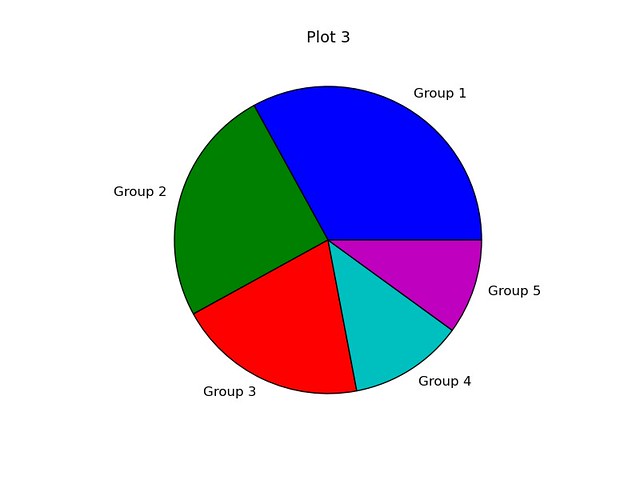
|
||||
|
||||
### Summary ###
|
||||
|
||||
This tutorial provides several examples of plots that can be created with the matplotlib scientific plotting package. Matplotlib is a great solution for scientific plotting in a Linux environment given its natural integration with Python and NumPy, its ability to be automated, and its production of a wide variety of customizable high quality plots. Documentation and examples for the matplotlib package can be found [here][2].
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/matplotlib-scientific-plotting-linux.html
|
||||
|
||||
作者:[Joshua Reed][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/joshua
|
||||
[1]:http://xmodulo.com/numpy-scientific-computing-linux.html
|
||||
[2]:http://matplotlib.org/
|
||||
@ -1,32 +0,0 @@
|
||||
Nathive——libre软件图像编辑器
|
||||
================================================================================
|
||||
Nathive是一个libre软件图像编辑器,和Adobe Photoshop、Corel Photo-Paint或GIMP类似,但是侧重于可用性、逻辑,并为每个人提供平滑的学习曲线。该项目在GNOME桌面环境中运行,并欢迎每个人在代码、翻译或想法等方面合作。
|
||||
|
||||
该项目尚处于beta阶段,所以它还是个未完成得工作,还不适用于终端用户。直到现在,开发始终专注于积淀应用的核心功能和创建便捷的开发工具。所以,目前我们将集中于创建新的插件,因为很明显在这方面还很缺乏。
|
||||
|
||||
其目的在于在不放弃最初的可用性的情况下,逐步将该软件打造成一个专业的额图像编辑器。Nathive由基于GTK+的Python脚本写成的,它设计为简洁、轻量,而且易于安装和使用。
|
||||
|
||||
### ubuntu上安装Nathive ###
|
||||
|
||||
你需要从[这里][1]下载.deb包,然后双击来安装。
|
||||
|
||||
### 屏幕截图 ###
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.ubuntugeek.com/nathive-a-libre-software-image-editor.html
|
||||
|
||||
作者:[ruchi][a]
|
||||
译者:[GOLinux](https://github.com/GOLinux)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.ubuntugeek.com/author/ubuntufix
|
||||
[1]:http://www.nathive.org/download
|
||||
@ -0,0 +1,46 @@
|
||||
Linux FAQs with Answers--How to disable Apport internal error reporting on Ubuntu
|
||||
有问必答--如何禁止Ubuntu的Apport内部错误报告程序
|
||||
================================================================================
|
||||
> **问题**:在桌面版Ubuntu中,我经常遇到一些弹窗窗口,警告我Ubuntu发生了内部错误,问我要不要发送错误报告。每次软件崩溃都要烦扰我,我如何才能关掉这个错误报告功能呢?
|
||||
|
||||
Ubuntu桌面版预安装了Apport,它是一个错误收集系统,会收集软件崩溃、未处理异常和其他,包括程序bug,并为调试目的生成崩溃报告。当一个应用程序崩溃或者出现Bug时候,Apport就会通过弹窗警告用户并且询问用户是否提交崩溃报告。你也许也看到过下面的消息。
|
||||
|
||||
- "Sorry, the application XXXX has closed unexpectedly."
|
||||
- "对不起,应用程序XXXX意外关闭了"
|
||||
- "Sorry, Ubuntu XX.XX has experienced an internal error."
|
||||
- "对不起,Ubuntu XX.XX 经历了一个内部错误"
|
||||
- "System program problem detected."
|
||||
- "系统程序问题发现"
|
||||
|
||||

|
||||
|
||||
也许因为应用一直崩溃,频繁的错误报告会使人心烦。也许你担心Apport会收集和上传你的Ubuntu系统的敏感信息。无论什么原因,你需要关掉Apport的错误报告功能。
|
||||
|
||||
### 临时关闭Apport错误报告 ###
|
||||
|
||||
如果你想要临时关闭Apport,使用下列命令
|
||||
|
||||
$ sudo service apport stop
|
||||
|
||||
注意重启Ubuntu系统Apport会继续开启
|
||||
|
||||
### 永久关闭Apport错误报告 ###
|
||||
|
||||
为了永久关闭Apport,编辑/etc/default/apport,修改下列参数
|
||||
|
||||
enabled=0
|
||||
|
||||
重启你的Ubuntu系统,Apport将会自动关闭
|
||||
|
||||
如果你再也不会用Apport,有一种简单的方法完全移除它
|
||||
|
||||
$ sudo apt-get purge apport
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://ask.xmodulo.com/disable-apport-internal-error-reporting-ubuntu.html
|
||||
|
||||
译者:[VicYu/Vic020](http://www.vicyu.net/)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
Loading…
Reference in New Issue
Block a user