mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-02-03 23:40:14 +08:00
Merge remote-tracking branch 'LCTT/master'
This commit is contained in:
commit
a83c7366ad
@ -1,75 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (alim0x)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: subject: (DevOps is for everyone)
|
||||
[#]: via: (https://opensource.com/article/18/11/how-non-engineer-got-devops)
|
||||
[#]: author: (Dawn Parych https://opensource.com/users/dawnparzych)
|
||||
[#]: url: ( )
|
||||
|
||||
DevOps is for everyone
|
||||
======
|
||||
|
||||
A non-engineer explains why you don't need to be a developer or an operations person to fall for DevOps.
|
||||
|
||||

|
||||
|
||||
I've never held a job as a developer nor in operations—so what am I doing writing an article about [DevOps][1]? I've always been interested in computers and technology. I also have a passion for people, psychology, and helping others. When I first heard about DevOps, the concept piqued my interest, as it seemed to merge many of the things I was interested in, even if I don't write code.
|
||||
|
||||
My first computer was a TRS-80, and I loved writing BASIC programs on it. I took the only two computer programming classes my high school offered. A few years later, I started a computer company. I made custom mailing labels, stationery, and built a database to store addresses.
|
||||
|
||||
The problem was I didn't enjoy writing code. I wanted to teach and to help people, and I didn't see writing code as an opportunity to do this. Yes, technology can help people and change lives, but writing code didn't spark my passion. I need to feel excited about my work and do something I love.
|
||||
|
||||
* The culture, not the code
|
||||
* The journey, not the result
|
||||
* Building an environment where everybody can continuously improve
|
||||
* Communicating and collaborating, not working independently
|
||||
|
||||
|
||||
|
||||
I found that I love DevOps. To me, DevOps is about:
|
||||
|
||||
Ultimately, DevOps is about being part of a community working towards the same goal. DevOps merges psychology, people, and technology. DevOps isn't a job title; it is a philosophy for life and work.
|
||||
|
||||
### Finding my people
|
||||
|
||||
Almost four years ago, I attended my first [DevOpsDays][2] conference in Seattle. I felt like I had found my people. I felt welcomed and accepted, even though I work in marketing and don't have a computer science degree. I could geek out over psychology and technology.
|
||||
|
||||
At DevOpsDays, I learned about the ["Three Ways" of DevOps][3]—flow, feedback, and continuous experimentation and learning—and new (to me) concepts such as Kaizen and Kaikaku. As I learned, I found myself saying things like, "I do this! I didn't know there was a name for this!"
|
||||
|
||||
[Kaizen][4] is the practice of continuous improvement and learning. Small, incremental changes over time can yield significant results. I found parallels between this and Carol Dweck's idea of a [growth mindset][5]. People aren't born experts. Becoming skilled at something takes time, practice, and often failure. Recognizing incremental improvement is necessary to make sure we don't give up.
|
||||
|
||||
[Kaikaku][6], on the other hand, is the notion that small changes over time sometimes won't work, and you need to make a radical or disruptive change. Quitting a job without having a new one lined up or moving to a new city can be pretty disruptive—yes, I've done both. But these radical changes can reap great rewards. I might not have learned about DevOps if I hadn't quit my job and taken some time off. Once I decided to return to work, I kept hearing about DevOps and started researching it. This led me to attend my first DevOpsDays, where I began to see all my passions come together. Since then, I have presented at five DevOpsDays and regularly write about DevOps topics.
|
||||
|
||||
### Putting the Three Ways to work
|
||||
|
||||
Change is hard and learning something new can be scary. The Three Ways of DevOps provide a framework for managing change. For example: How is information flowing? What is driving you to make a change? Once you know a change is needed, how do you get feedback about whether the changes you are making are the right changes? How do you know if you're making progress? Feedback is essential and should include both positive and constructive elements. The hard part is making sure the constructive elements don't outweigh the positive.
|
||||
|
||||
For me, the third Way—continuous experimentation and learning—is the most important part of DevOps. Having an environment where people are free to experiment and take risks can lead to unexpected outcomes. Sometimes those outcomes are good, sometimes not so good—and that's OK. Creating an environment where it is acceptable if things don't work out encourages people to take risks. We should all strive to continuously experiment and learn something new on a regular basis.
|
||||
|
||||
The Three Ways of DevOps provides a method of trying something, getting feedback, and learning from our mistakes. A few years ago, my son told me, "I don't ever want to be the best at something, because then I can't learn from my mistakes." We all make mistakes, and learning from them helps us grow and improve. We aren't willing to make mistakes if our culture doesn't support experimentation and learning.
|
||||
|
||||
### Being part of the community
|
||||
|
||||
I've worked in technology for over 20 years and often felt like an outsider until I found the DevOps community. If you're like me—passionate about technology but not the engineering or operations side of things—you can still be a part of DevOps, even if you work in sales, marketing, product marketing, technical writing, support, and more. DevOps is for everyone.
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/11/how-non-engineer-got-devops
|
||||
|
||||
作者:[Dawn Parych][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/dawnparzych
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/resources/devops
|
||||
[2]: https://www.devopsdays.org/
|
||||
[3]: https://itrevolution.com/the-three-ways-principles-underpinning-devops/
|
||||
[4]: https://en.wikipedia.org/wiki/Kaizen
|
||||
[5]: https://en.wikipedia.org/wiki/Mindset#Fixed_and_growth
|
||||
[6]: https://en.wikipedia.org/wiki/Kaikaku
|
||||
@ -1,3 +1,4 @@
|
||||
Translating by qhwdw
|
||||
Protecting Code Integrity with PGP — Part 7: Protecting Online Accounts
|
||||
======
|
||||
|
||||
|
||||
@ -1,135 +0,0 @@
|
||||
translating---geekpi
|
||||
|
||||
Dbxfs – Mount Dropbox Folder Locally As Virtual File System In Linux
|
||||
======
|
||||
|
||||

|
||||
|
||||
A while ago, we summarized all the possible ways to **[mount Google drive locally][1]** as a virtual file system and access the files stored in the google drive from your Linux operating system. Today, we are going to learn to mount Dropbox folder in your local file system using **dbxfs** utility. The dbxfs is used to mount your Dropbox folder locally as a virtual filesystem in Unix-like operating systems. While it is easy to [**install Dropbox client**][2] in Linux, this approach slightly differs from the official method. It is a command line dropbox client and requires no disk space for access. The dbxfs application is free, open source and written for Python 3.5+.
|
||||
|
||||
### Installing dbxfs
|
||||
|
||||
The dbxfs officially supports Linux and Mac OS. However, it should work on any POSIX system that provides a **FUSE-compatible library** or has the ability to mount **SMB** shares. Since it is written for Python 3.5, it can installed using **pip3** package manager. Refer the following guide if you haven’t installed PIP yet.
|
||||
|
||||
And, install FUSE library as well.
|
||||
|
||||
On Debian-based systems, run the following command to install FUSE:
|
||||
|
||||
```
|
||||
$ sudo apt install libfuse2
|
||||
|
||||
```
|
||||
|
||||
On Fedora:
|
||||
|
||||
```
|
||||
$ sudo dnf install fuse
|
||||
|
||||
```
|
||||
|
||||
Once you installed all required dependencies, run the following command to install dbxfs utility:
|
||||
|
||||
```
|
||||
$ pip3 install dbxfs
|
||||
|
||||
```
|
||||
|
||||
### Mount Dropbox folder locally
|
||||
|
||||
Create a mount point to mount your dropbox folder in your local file system.
|
||||
|
||||
```
|
||||
$ mkdir ~/mydropbox
|
||||
|
||||
```
|
||||
|
||||
Then, mount the dropbox folder locally using dbxfs utility as shown below:
|
||||
|
||||
```
|
||||
$ dbxfs ~/mydropbox
|
||||
|
||||
```
|
||||
|
||||
You will be asked to generate an access token:
|
||||
|
||||
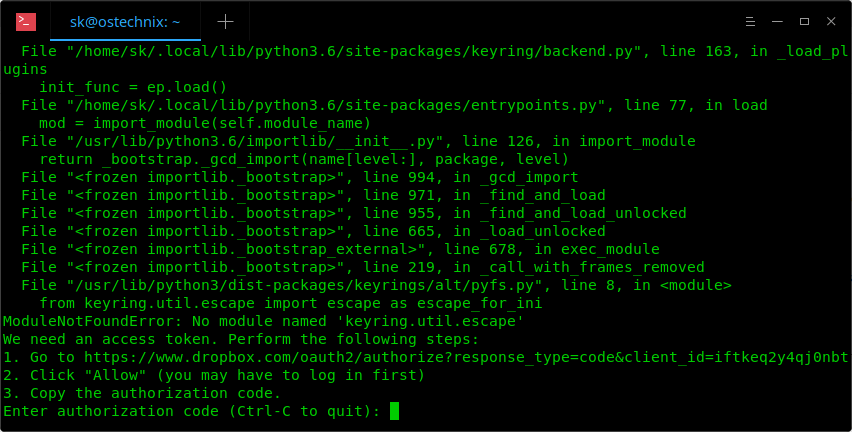
|
||||
|
||||
To generate an access token, just navigate to the URL given in the above output from your web browser and click **Allow** to authenticate Dropbox access. You need to log in to your dropbox account to complete authorization process.
|
||||
|
||||
A new authorization code will be generated in the next screen. Copy the code and head back to your Terminal and paste it into cli-dbxfs prompt to finish the process.
|
||||
|
||||
You will be then asked to save the credentials for future access. Type **Y** or **N** whether you want to save or decline. And then, you need to enter a passphrase twice for the new access token.
|
||||
|
||||
Finally, click **Y** to accept **“/home/username/mydropbox”** as the default mount point. If you want to set different path, type **N** and enter the location of your choice.
|
||||
|
||||
[![Generate access token 2][3]][4]
|
||||
|
||||
All done! From now on, you can see your Dropbox folder is locally mounted in your filesystem.
|
||||
|
||||
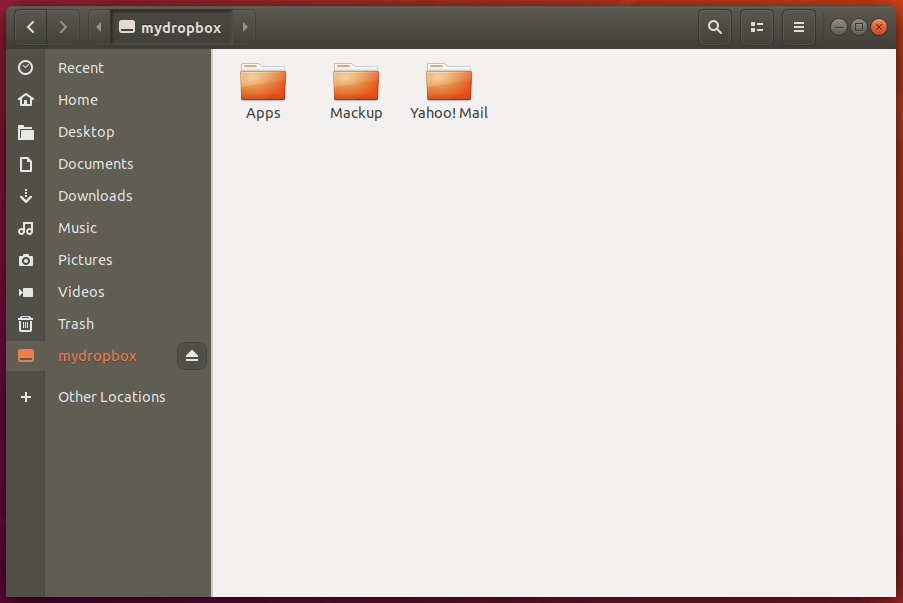
|
||||
|
||||
### Change Access Token Storage Path
|
||||
|
||||
By default, the dbxfs application will store your Dropbox access token in the system keyring or an encrypted file. However, you might want to store it in a **gpg** encrypted file or something else. If so, get an access token by creating a personal app on the [Dropbox developers app console][5].
|
||||
|
||||
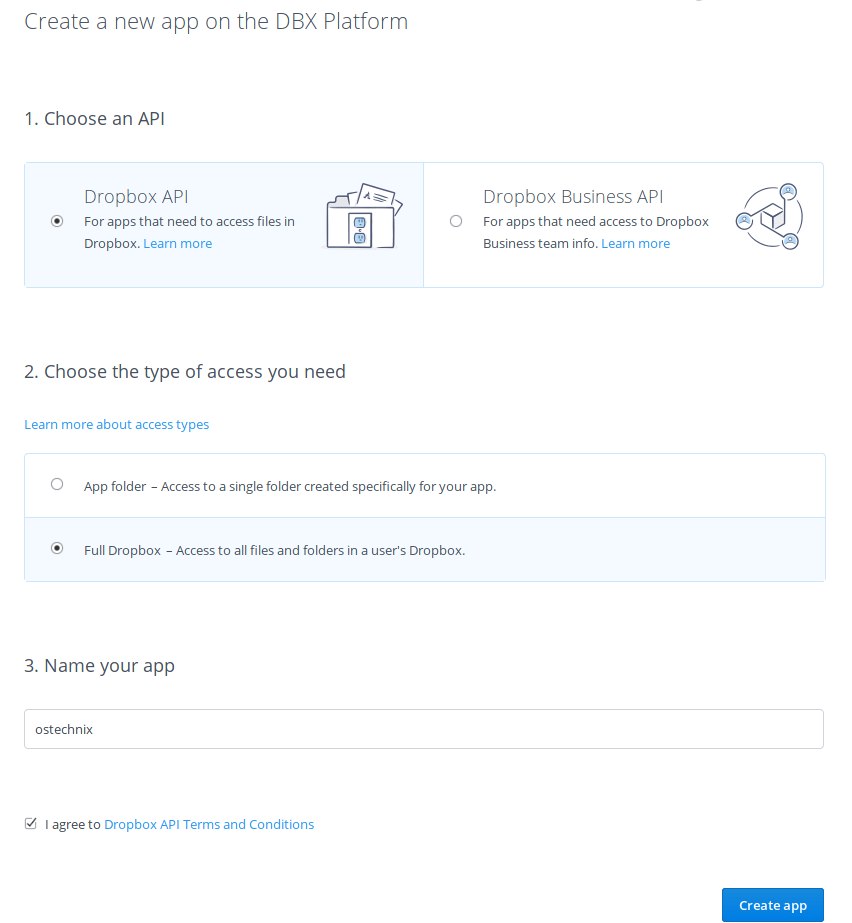
|
||||
|
||||
Once the app is created, click **Generate** button in the next button. This access token can be used to access your Dropbox account via the API. Don’t share your access token with anyone.
|
||||
|
||||
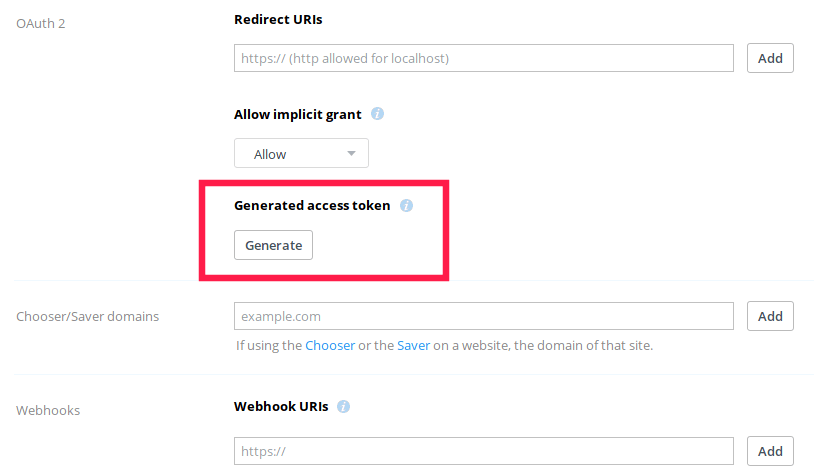
|
||||
|
||||
Once you created an access token, encrypt it using any encryption tools of your choice, such as [**Cryptomater**][6], [**Cryptkeeper**][7], [**CryptGo**][8], [**Cryptr**][9], [**Tomb**][10], [**Toplip**][11] and [**GnuPG**][12] etc., and store it in your preferred location.
|
||||
|
||||
Next edit the dbxfs configuration file and add the following line in it:
|
||||
|
||||
```
|
||||
"access_token_command": ["gpg", "--decrypt", "/path/to/access/token/file.gpg"]
|
||||
|
||||
```
|
||||
|
||||
You can find the dbxfs configuration file by running the following command:
|
||||
|
||||
```
|
||||
$ dbxfs --print-default-config-file
|
||||
|
||||
```
|
||||
|
||||
For more details, refer dbxfs help section:
|
||||
|
||||
```
|
||||
$ dbxfs -h
|
||||
|
||||
```
|
||||
|
||||
As you can see, mounting Dropfox folder locally in your file system using Dbxfs utility is no big deal. As far tested, dbxfs just works fine as expected. Give it a try if you’re interested to see how it works and let us know about your experience in the comment section below.
|
||||
|
||||
And, that’s all for now. Hope this was useful. More good stuff to come. Stay tuned!
|
||||
|
||||
Cheers!
|
||||
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.ostechnix.com/dbxfs-mount-dropbox-folder-locally-as-virtual-file-system-in-linux/
|
||||
|
||||
作者:[SK][a]
|
||||
选题:[lujun9972](https://github.com/lujun9972)
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.ostechnix.com/author/sk/
|
||||
[1]: https://www.ostechnix.com/how-to-mount-google-drive-locally-as-virtual-file-system-in-linux/
|
||||
[2]: https://www.ostechnix.com/install-dropbox-in-ubuntu-18-04-lts-desktop/
|
||||
[3]: data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7
|
||||
[4]: http://www.ostechnix.com/wp-content/uploads/2018/10/Generate-access-token-2.png
|
||||
[5]: https://dropbox.com/developers/apps
|
||||
[6]: https://www.ostechnix.com/cryptomator-open-source-client-side-encryption-tool-cloud/
|
||||
[7]: https://www.ostechnix.com/how-to-encrypt-your-personal-foldersdirectories-in-linux-mint-ubuntu-distros/
|
||||
[8]: https://www.ostechnix.com/cryptogo-easy-way-encrypt-password-protect-files/
|
||||
[9]: https://www.ostechnix.com/cryptr-simple-cli-utility-encrypt-decrypt-files/
|
||||
[10]: https://www.ostechnix.com/tomb-file-encryption-tool-protect-secret-files-linux/
|
||||
[11]: https://www.ostechnix.com/toplip-strong-file-encryption-decryption-cli-utility/
|
||||
[12]: https://www.ostechnix.com/an-easy-way-to-encrypt-and-decrypt-files-from-commandline-in-linux/
|
||||
@ -1,185 +0,0 @@
|
||||
translating by hopefully2333
|
||||
|
||||
Improve login security with challenge-response authentication
|
||||
======
|
||||
|
||||

|
||||
|
||||
### Introduction
|
||||
|
||||
Today, Fedora offers multiple ways to improve the secure authentication of our user accounts. Of course it has the familiar user name and password to login. It also offers additional authentication options such as biometric, fingerprint, smart card, one-time password, and even challenge-response authentication.
|
||||
|
||||
Each authentication method has clear pros and cons. That, in itself, could be a topic for a rather lengthy article. Fedora Magazine has covered a few of these options previously:
|
||||
|
||||
|
||||
+ [Using the YubiKey4 with Fedora][1]
|
||||
+ [Fedora 28: Better smart card support in OpenSSH][2]
|
||||
|
||||
|
||||
One of the most secure methods in modern Fedora releases is offline hardware challenge-response. It’s also one of the easiest to deploy. Here’s how.
|
||||
|
||||
### Challenge-response authentication
|
||||
|
||||
Technically, when you provide a password, you’re responding to a user name challenge. The offline challenge response covered here requires your user name first. Next, Fedora challenges you to provide an encrypted physical hardware token. The token responds to the challenge with another encrypted key it stores via the Pluggable Authentication Modules (PAM) framework. Finally, Fedora prompts you for the password. This prevents someone from just using a found hardware token, or just using a user name and password without the correct encrypted key.
|
||||
|
||||
This means that in addition to your user name and password, you must have previously registered one or more encrypted hardware tokens with the OS. And you have to provide that physical hardware token to be able to authenticate with your user name.
|
||||
|
||||
Some challenge-response methods, like one time passwords (OTP), take an encrypted code key on the hardware token, and pass that key across the network to a remote authentication server. The server then tells Fedora’s PAM framework if it’s is a valid token for that user name. This is great if the authentication server(s) are on the local network. The downside is if the network connection is down or you’re working remote without a network connection, you can’t use this remote authentication method. You could be locked out of the system until you can connect through the network to the server.
|
||||
|
||||
Sometimes a workplace requires use of Yubikey One Time Passwords (OTP) configuration. However, on home or personal systems you may prefer a local challenge-response configuration. Everything is local, and the method requires no remote network calls. The following process works on Fedora 27, 28, and 29.
|
||||
|
||||
### Preparation
|
||||
|
||||
#### Hardware token keys
|
||||
|
||||
First you need a secure hardware token key. Specifically, this process requires a Yubikey 4, Yubikey NEO, or a recently released Yubikey 5 series device which also supports FIDO2. You should purchase two of them to provide a backup in case one becomes lost or damaged. You can use these keys on numerous workstations. The simpler FIDO or FIDO U2F only versions don’t work for this process, but are great for online services that use FIDO.
|
||||
|
||||
#### Backup, backup, and backup
|
||||
|
||||
Next, make a backup of all your important data. You may want to test the configuration in a Fedora 27/28/29 cloned VM to make sure you understand the process before setting up your personal workstation.
|
||||
|
||||
#### Updating and installing
|
||||
|
||||
Now make sure Fedora is up to date. Then install the required Fedora Yubikey packages via these dnf commands:
|
||||
|
||||
```
|
||||
$ sudo dnf upgrade
|
||||
$ sudo dnf install ykclient* ykpers* pam_yubico*
|
||||
$ cd
|
||||
```
|
||||
|
||||
If you’re in a VM environment, such as Virtual Box, make sure the Yubikey device is inserted in a USB port, and enable USB access to the Yubikey in the VM control.
|
||||
|
||||
### Configuring Yubikey
|
||||
|
||||
Verify that your user account has access to the USB Yubikey:
|
||||
|
||||
```
|
||||
$ ykinfo -v
|
||||
version: 3.5.0
|
||||
```
|
||||
|
||||
If the YubiKey is not detected, the following error message appears:
|
||||
|
||||
```
|
||||
Yubikey core error: no yubikey present
|
||||
```
|
||||
|
||||
Next, initialize each of your new Yubikeys with the following ykpersonalize command. This sets up the Yubikey configuration slot 2 with a Challenge Response using the HMAC-SHA1 algorithm, even with less than 64 characters. If you have already setup your Yubikeys for challenge-response, you don’t need to run ykpersonalize again.
|
||||
|
||||
```
|
||||
ykpersonalize -2 -ochal-resp -ochal-hmac -ohmac-lt64 -oserial-api-visible
|
||||
```
|
||||
|
||||
Some users leave the YubiKey in their workstation while using it, and even use challenge-response for virtual machines. However, for more security you may prefer to manually trigger the Yubikey to respond to challenge.
|
||||
|
||||
To add that manual challenge button trigger, add the -ochal-btn-trig flag. This flag causes the Yubikey to flash the yubikey LED on a request. It waits for you to press the button on the hardware key area within 15 seconds to produce the response key.
|
||||
|
||||
```
|
||||
$ ykpersonalize -2 -ochal-resp -ochal-hmac -ohmac-lt64 -ochal-btn-trig -oserial-api-visible
|
||||
```
|
||||
|
||||
Do this for each of your new hardware keys, only once per key. Once you have programmed your keys, store the Yubikey configuration to ~/.yubico with the following command:
|
||||
|
||||
```
|
||||
$ ykpamcfg -2 -v
|
||||
debug: util.c:222 (check_firmware_version): YubiKey Firmware version: 4.3.4
|
||||
|
||||
Sending 63 bytes HMAC challenge to slot 2
|
||||
Sending 63 bytes HMAC challenge to slot 2
|
||||
Stored initial challenge and expected response in '/home/chuckfinley/.yubico/challenge-9992567'.
|
||||
```
|
||||
|
||||
If you are setting up multiple keys for backup purposes, configure all the keys the same, and store each key’s challenge-response using the ykpamcfg utility. If you run the command ykpersonalize on an existing registered key, you must store the configuration again.
|
||||
|
||||
### Configuring /etc/pam.d/sudo
|
||||
|
||||
Now to verify this configuration worked, **in the same terminal window** you’ll setup sudo to require the use of the Yubikey challenge-response. Insert the following line into the /etc/pam.d/sudo file:
|
||||
|
||||
```
|
||||
auth required pam_yubico.so mode=challenge-response
|
||||
```
|
||||
|
||||
Insert the above auth line into the file above the auth include system-auth line. Then save the file and exit the editor. In a default Fedora 29 setup, /etc/pam.d/sudo should now look like this:
|
||||
|
||||
```
|
||||
#%PAM-1.0
|
||||
auth required pam_yubico.so mode=challenge-response
|
||||
auth include system-auth
|
||||
account include system-auth
|
||||
password include system-auth
|
||||
session optional pam_keyinit.so revoke
|
||||
session required pam_limits.so
|
||||
session include system-auth
|
||||
```
|
||||
|
||||
**Keep this original terminal window open** , and test by opening another new terminal window. In the new terminal window type:
|
||||
|
||||
```
|
||||
$ sudo echo testing
|
||||
```
|
||||
|
||||
You should notice the LED blinking on the key. Tap the Yubikey button and you should see a prompt for your sudo password. After you enter your password, you should see “testing” echoed in the terminal screen.
|
||||
|
||||
Now test to ensure a correct failure. Start another terminal window and remove the Yubikey from the USB port. Verify that sudo no longer works without the Yubikey with this command:
|
||||
|
||||
```
|
||||
$ sudo echo testing fail
|
||||
```
|
||||
|
||||
You should immediately be prompted for the sudo password. Even if you enter the password, it should fail.
|
||||
|
||||
### Configuring Gnome Desktop Manager
|
||||
|
||||
Once your testing is complete, now you can add challenge-response support for the graphical login. Re-insert your Yubikey into the USB port. Next you’ll add the following line to the /etc/pam.d/gdm-password file:
|
||||
|
||||
```
|
||||
auth required pam_yubico.so mode=challenge-response
|
||||
```
|
||||
|
||||
Open a terminal window, and issue the following command. You can use another editor if desired:
|
||||
|
||||
```
|
||||
$ sudo vi /etc/pam.d/gdm-password
|
||||
```
|
||||
|
||||
You should see the yubikey LED blinking. Press the yubikey button, then enter the password at the prompt.
|
||||
|
||||
Modify the /etc/pam.d/gdm-password file to add the new auth line above the existing line auth substack password-auth. The top of the file should now look like this:
|
||||
|
||||
```
|
||||
auth [success=done ignore=ignore default=bad] pam_selinux_permit.so
|
||||
auth required pam_yubico.so mode=challenge-response
|
||||
auth substack password-auth
|
||||
auth optional pam_gnome_keyring.so
|
||||
auth include postlogin
|
||||
|
||||
account required pam_nologin.so
|
||||
```
|
||||
|
||||
Save the changes and exit the editor. If you use vi, the key sequence is to hit the **Esc** key, then type wq! at the prompt to save and exit.
|
||||
|
||||
### Conclusion
|
||||
|
||||
Now log out of GNOME. With the Yubikey inserted into the USB port, click on your user name in the graphical login. The Yubikey LED begins to flash. Touch the button, and you will be prompted for your password.
|
||||
|
||||
If you lose the Yubikey, you can still use the secondary backup Yubikey in addition to your set password. You can also add additional Yubikey configurations to your user account.
|
||||
|
||||
If someone gains access to your password, they still can’t login without your physical hardware Yubikey. Congratulations! You’ve now dramatically increased the security of your workstation login.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://fedoramagazine.org/login-challenge-response-authentication/
|
||||
|
||||
作者:[nabooengineer][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://fedoramagazine.org/author/nabooengineer/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://fedoramagazine.org/using-the-yubikey4-with-fedora/
|
||||
[2]: https://fedoramagazine.org/fedora-28-better-smart-card-support-openssh/
|
||||
|
||||
@ -1,5 +1,5 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
|
||||
@ -1,5 +1,5 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: translator: ( amwps290)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
|
||||
74
translated/talk/20181121 DevOps is for everyone.md
Normal file
74
translated/talk/20181121 DevOps is for everyone.md
Normal file
@ -0,0 +1,74 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (alim0x)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: subject: (DevOps is for everyone)
|
||||
[#]: via: (https://opensource.com/article/18/11/how-non-engineer-got-devops)
|
||||
[#]: author: (Dawn Parych https://opensource.com/users/dawnparzych)
|
||||
[#]: url: ( )
|
||||
|
||||
所有人的 DevOps
|
||||
======
|
||||
|
||||
让一名非工程师来解释为什么你不必成为一位开发者或运维就能爱上 DevOps。
|
||||
|
||||

|
||||
|
||||
我没有过开发或运维的工作——那怎么我在写一篇关于 [DevOps][1] 的文章?我一直都对计算机和技术有兴趣。我还对社群、心理学以及帮助他人充满热情。当我第一次听到 DevOps 时,这个概念激起了我的兴趣,因为它看起来融合了很多我感兴趣的东西,即便我是不写代码的。
|
||||
|
||||
我的第一台电脑是 TRS-80,我喜欢在上面编写 BASIC 程序。我只上过两门我的高中开设的计算机编程课程。若干年后,我创办了一家计算机公司。我定制邮件标签和信纸,并建立了一个数据库来存储地址。
|
||||
|
||||
问题是我并不能从写代码中获得享受。我想要教育和帮助人们,我没法将写代码看作这样的一个机会。是的,技术可以帮助人们并改变生活,但是写代码没有点燃我的热情。我需要对我的工作感到兴奋并做我喜欢的事情。
|
||||
|
||||
* 文化,而不是代码
|
||||
* 过程,而不是结果
|
||||
* 建立一个所有人可以持续提升的环境
|
||||
* 沟通与合作,而不是独立工作
|
||||
|
||||
|
||||
我发现我爱 DevOps。对我而言,DevOps 指的是:
|
||||
|
||||
归根结底,DevOps 是指成为社区工作的一部分,实现共同的目标。DevOps 融合了心理学、社群、技术。DevOps 不是一个职位名称,它是一种生活和工作的哲学。
|
||||
|
||||
### 找到我的社群
|
||||
|
||||
快四年前,我在西雅图参加了我的第一个 [DevOps 日][2] 会议。我感觉我找到了我的社群。我觉得受到了欢迎和接受,尽管我从事营销工作而且没有计算机科学文凭。我可以从心理学和技术中寻找乐趣。
|
||||
|
||||
在 DevOps 日,我学到了 [DevOps“三步工作法”][3]——流动,反馈,持续实验和学习——以及新(对我而言)的概念,如Kaizen(改善)和Kaikaku(改革)。随着我的学习深入,我发现我在说这样的话,“我是这样做的!我都不知道这样做还有个名字!”
|
||||
|
||||
[Kaizen(改善)][4]是持续改进和学习的实践。小的量变积累随着时间的推移可以引起质变。我发现它和卡罗尔.德韦克的[成长型思维][5]的想法很相似。人们不是生来就是专家。在某方面拥有经验需要花费时间,练习,以及常常还有失败。承认增量的改善对确保我们不会放弃是很有必要的。
|
||||
|
||||
另一方面,[Kaikaku(改革)][6]的概念是指,长时间的小的改变有时不能起作用,你需要做一些完全的或破坏性的改变。在没有找到下份工作前就辞职或移居新城市就足够有破坏性——是的,两者我都做过。但这些彻底的改变收获巨大。如果我没有辞职并休息一段时间,我也许不会接触到 DevOps。等我决定继续工作的时候,我一直听到 DevOps,我开始研究它。这引导我参加了我的第一个 DevOps 日,从那里我开始看到我的所有热情开始聚集。从那时起,我已经参加了五次 DevOps 日活动,并且定期撰写关于 DevOps 话题的文章。
|
||||
|
||||
### 将三步工作法用到工作中
|
||||
|
||||
改变是困难的,学习新事物可以听起来很吓人。DevOps 的三步工作法提供了一个管理改变的框架。比如:信息流动是怎样的?是什么驱动着你做出改变?一旦你认为一个改变是必需的,你如何获得这个改变是否正确的反馈?你如何知道你在取得进展?反馈是必要的,并且应该包含积极和有建设性的要素。困难的地方在于保证建设性的要素不要重于积极要素。
|
||||
|
||||
对我而言,第三步——持续实验和学习——是 DevOps 最重要的部分。有一个可以自由地实验和冒险的环境,人们可以获得意想不到的结果。有时这些结果是好的,有时不是太好——但这没事。创建一个可以接受失败结果的环境可以鼓励人们冒险。我们都应该力争定期的持续实验和学习。
|
||||
|
||||
DevOps 的三步工作法提供了一个尝试,获得反馈,以及从错误中获取经验的方法。几年前,我的儿子告诉我,“我从来就没想做到最好,因为那样我就没法从我的错误中学到东西了。”我们都会犯错,从中获得经验帮助我们成长和改善。如果我们的文化不支持尝试和学习,我们就不会愿意去犯错。
|
||||
|
||||
### 成为社区的一部分
|
||||
|
||||
我已经在技术领域工作了超过 20 年,直到我发现 DevOps 社区前,我还经常感觉自己是个外行。如果你像我一样——对技术充满热情,但不是工程和运维那方面——你仍然可以成为 DevOps 的一部分,即便你从事的是销售、营销、产品营销、技术写作、支持或其他工作。DevOps 是属于所有人的。
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/11/how-non-engineer-got-devops
|
||||
|
||||
作者:[Dawn Parych][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[alim0x](https://github.com/alim0x)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/dawnparzych
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/resources/devops
|
||||
[2]: https://www.devopsdays.org/
|
||||
[3]: https://itrevolution.com/the-three-ways-principles-underpinning-devops/
|
||||
[4]: https://en.wikipedia.org/wiki/Kaizen
|
||||
[5]: https://en.wikipedia.org/wiki/Mindset#Fixed_and_growth
|
||||
[6]: https://en.wikipedia.org/wiki/Kaikaku
|
||||
@ -0,0 +1,136 @@
|
||||
Dbxfs - 在 Linux 中本地挂载 Dropbox 文件夹作为虚拟文件系统
|
||||
======
|
||||
|
||||

|
||||
|
||||
不久前,我们总结了所有**[在本地挂载 Google Drive][1]**作为虚拟文件系统,并从 Linux 系统访问存储在 Google Drive 中的文件的方法。今天,我们将学习使用 **dbxfs**将 Dropbox 文件夹挂载到本地文件系统中。dbxfs 用于在类 Unix 操作系统中本地挂载 Dropbox 文件夹作为虚拟文件系统。虽然在 Linux 中很容易[**安装 Dropbox 客户端**][2],但这种方法与官方方法略有不同。它是一个命令行 dropbox 客户端,且无需磁盘空间即可访问。dbxfs 是免费、开源的,并且是用 Python 3.5+ 编写的。
|
||||
|
||||
### 安装 dbxfs
|
||||
|
||||
dbxfs 官方支持 Linux 和 Mac OS。但是,它应该适用于任何提供 **FUSE 兼容库**或能够挂载 **SMB** 共享的 POSIX 系统。由于它是用 Python 3.5 编写的,因此可以使用 **pip3** 包管理器进行安装。如果尚未安装 PIP,请参阅以下指南。
|
||||
|
||||
[如何使用 pip 管理 Python 包][13]
|
||||
|
||||
并且也要安装 FUSE 库。
|
||||
|
||||
在基于 Debian 的系统上,运行以下命令以安装 FUSE:
|
||||
|
||||
```
|
||||
$ sudo apt install libfuse2
|
||||
|
||||
```
|
||||
|
||||
在 Fedora 上:
|
||||
|
||||
```
|
||||
$ sudo dnf install fuse
|
||||
|
||||
```
|
||||
|
||||
安装完所有必需的依赖项后,运行以下命令以安装 dbxfs:
|
||||
|
||||
```
|
||||
$ pip3 install dbxfs
|
||||
|
||||
```
|
||||
|
||||
### 在本地挂载 Dropbox 文件夹
|
||||
|
||||
创建一个挂载点以将 Dropbox 文件夹挂载到本地文件系统中。
|
||||
|
||||
```
|
||||
$ mkdir ~/mydropbox
|
||||
|
||||
```
|
||||
|
||||
然后,使用 dbxfs 在本地挂载 dropbox 文件夹,如下所示:
|
||||
|
||||
```
|
||||
$ dbxfs ~/mydropbox
|
||||
|
||||
```
|
||||
|
||||
你将被要求生成一个访问令牌:
|
||||
|
||||

|
||||
|
||||
要生成访问令牌,只需在 Web 浏览器中输入上面输出的 URL,然后单击**允许** 以授权 Dropbox 访问。你需要登录 Dropbox 帐户才能完成授权过程。
|
||||
|
||||
下一个页面将生成新的授权码。复制代码并返回终端将其粘贴到 cli-dbxfs 提示符中以完成该过程。
|
||||
|
||||
然后,系统会要求你保存凭据以供将来访问。无论你是要保存还是拒绝,输入 **Y** 或 **N**。然后,你需要为新的访问令牌输入两次密码。
|
||||
|
||||
最后,输入 **Y** 接受 **“/home/username/mydropbox”** 作为默认挂载点。如果你要设置不同的路径,输入 **N** 并输入你选择的位置。
|
||||
|
||||
[![Generate access token 2][3]][4]
|
||||
|
||||
完成了!从现在开始,你可以看到你的 Dropbox 文件夹已挂载到本地文件系统中。
|
||||
|
||||

|
||||
|
||||
### 更改访问令牌存储路径
|
||||
|
||||
默认情况下,dbxfs 会将 Dropbox 访问令牌存储在系统密钥环或加密文件中。但是,你可能希望将其存储在 **gpg** 加密文件或其他地方。如果是这样,请在 [Dropbox 开发者应用控制台][5]上创建个人应用来获取访问令牌。
|
||||
|
||||

|
||||
|
||||
创建应用后,单击下一步中的**生成**按钮。此令牌可用于通过 API 访问你的 Dropbox 帐户。不要与任何人共享你的访问令牌。
|
||||
|
||||

|
||||
|
||||
创建访问令牌后,使用任何你选择的加密工具对其进行加密,例如 [**Cryptomater**][6]、[**Cryptkeeper**][7]、[**CryptGo**][8]、[**Cryptr**][9]、[**Tomb**][10]、[**Toplip**][11] 和 [**GnuPG**][12] 等,并在你喜欢的位置保存。
|
||||
|
||||
接下来编辑 dbxfs 配置文件并添加以下行:
|
||||
|
||||
```
|
||||
"access_token_command": ["gpg", "--decrypt", "/path/to/access/token/file.gpg"]
|
||||
|
||||
```
|
||||
|
||||
你可以通过运行以下命令找到 dbxfs 配置文件:
|
||||
|
||||
```
|
||||
$ dbxfs --print-default-config-file
|
||||
|
||||
```
|
||||
|
||||
有关更多详细信息,请参阅 dbxfs 帮助:
|
||||
|
||||
```
|
||||
$ dbxfs -h
|
||||
|
||||
```
|
||||
|
||||
如你所见,使用 dbxfs 在你的文件系统中本地挂载 Dropfox 文件夹没什么大不了的。经过测试,dbxfs 如常工作。如果你有兴趣了解它是如何工作的,请尝试一下,并在下面的评论栏告诉我们你的体验。
|
||||
|
||||
就是这些了。希望这篇文章有用。还有更多好东西。敬请期待!
|
||||
|
||||
干杯!
|
||||
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.ostechnix.com/dbxfs-mount-dropbox-folder-locally-as-virtual-file-system-in-linux/
|
||||
|
||||
作者:[SK][a]
|
||||
选题:[lujun9972](https://github.com/lujun9972)
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.ostechnix.com/author/sk/
|
||||
[1]: https://www.ostechnix.com/how-to-mount-google-drive-locally-as-virtual-file-system-in-linux/
|
||||
[2]: https://www.ostechnix.com/install-dropbox-in-ubuntu-18-04-lts-desktop/
|
||||
[3]: data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7
|
||||
[4]: http://www.ostechnix.com/wp-content/uploads/2018/10/Generate-access-token-2.png
|
||||
[5]: https://dropbox.com/developers/apps
|
||||
[6]: https://www.ostechnix.com/cryptomator-open-source-client-side-encryption-tool-cloud/
|
||||
[7]: https://www.ostechnix.com/how-to-encrypt-your-personal-foldersdirectories-in-linux-mint-ubuntu-distros/
|
||||
[8]: https://www.ostechnix.com/cryptogo-easy-way-encrypt-password-protect-files/
|
||||
[9]: https://www.ostechnix.com/cryptr-simple-cli-utility-encrypt-decrypt-files/
|
||||
[10]: https://www.ostechnix.com/tomb-file-encryption-tool-protect-secret-files-linux/
|
||||
[11]: https://www.ostechnix.com/toplip-strong-file-encryption-decryption-cli-utility/
|
||||
[12]: https://www.ostechnix.com/an-easy-way-to-encrypt-and-decrypt-files-from-commandline-in-linux/
|
||||
[13]:https://www.ostechnix.com/manage-python-packages-using-pip/
|
||||
@ -0,0 +1,182 @@
|
||||
通过询问-响应身份认证提高登陆安全
|
||||
======
|
||||
|
||||

|
||||
|
||||
### 介绍
|
||||
|
||||
今天,Fedora 提供了多种方式来提高我们账户的身份认证的安全性。当然,它有我们熟悉的用户名密码登陆,它也同样提供了其他的身份认证选项,比如生物识别、指纹、智能卡、一次性密码,甚至是询问-响应身份认证。
|
||||
|
||||
每种认证方式都有明确的优缺点。这点本身就可以成为一篇相当冗长的文章的主题。Fedora 杂志之前就已经介绍过了这其中的一些选项:
|
||||
|
||||
|
||||
+ [Using the YubiKey4 with Fedora][1]
|
||||
+ [Fedora 28: Better smart card support in OpenSSH][2]
|
||||
|
||||
|
||||
在现在的 Fedora 版本中,最安全的方法之一就是离线硬件询问-响应。它也同样是最容易部署的方法之一。下面是具体方法:
|
||||
|
||||
### 询问-响应认证
|
||||
|
||||
从技术上来讲,当你输入密码的时候,你就正在响应用户名询问。离线的询问、响应包含了这些部分:首先是需要你的用户名,接下来,Fedora 会要你提供一个加密的物理硬件的令牌。令牌会将另一个通过可插入式身份认证模块(PAM)框架进行存储的加密密钥来响应询问。最后,Fedora 才会提示你输入密码。这可以防止其他人仅仅使用了找到的硬件令牌,或是只使用了账户名密码而没有正确的加密密钥。
|
||||
|
||||
这意味着除了你的账户名密码之外,你必须事先在你的操作系统中注册了一个或多个加密硬件令牌。你必须保证你的物理硬件令牌能够匹配你的用户名。
|
||||
|
||||
一些询问-响应的方法,比如一次性密码(OTP),在硬件令牌上获取加密代码密钥,然后将这个密钥通过网络传输到远程身份认证服务器。然后这个服务器会告诉 Fedora 的 PAM 框架,这是否是该用户的一个有效令牌。如果身份认证服务器在本地网络上,这个方法非常好。但它的缺点是如果网络连接断开或是你在没有网的远程端工作。你会被锁在系统之外,直到你能通过网络连接到身份认证服务器。
|
||||
|
||||
有时候,生产环境会需要通过 Yubikey 使用一次性密码(OTP)设置,然而,在家庭或个人的系统上,你可能更喜欢询问-响应设置。一切都是本地的,这种方法不需要通过远程网络呼叫。下面这些过程适用于 Fedora 27、28和29.
|
||||
|
||||
### 准备
|
||||
|
||||
#### 硬件令牌密钥
|
||||
|
||||
首先,你需要一个安全的硬件令牌密钥。具体来说,这个过程需要一个 Yubikey 4,Yubikey NEO,或者是最近发布的、同样支持 FIDO2 的 Yubikey 5 系列设备。你应该购买它们中的两个来有一个备份,以避免其中一个丢失或遭到损坏。你可以在不同的工作地点使用这些密钥。较为简单的 FIDO 和 FIDO U2F 版本不适用与这个过程,但是非常适合使用 FIDO 的在线服务。
|
||||
|
||||
#### 备份、备份,以及备份
|
||||
|
||||
接下来,为你所有的重要数据制作备份,你可能想在克隆在 VM 里的 Fedora 27/28/29 里测试配置,来确保你在设置你自己的个人工作环境之前理解这个过程。
|
||||
|
||||
#### 升级,然后安装
|
||||
|
||||
现在,确定你的 Fedora 是最新的,然后通过 dnf 命令安装所需要的 Fedora Yubikey 包。
|
||||
|
||||
```
|
||||
$ sudo dnf upgrade
|
||||
$ sudo dnf install ykclient* ykpers* pam_yubico*
|
||||
$ cd
|
||||
```
|
||||
|
||||
如果你使用的是 VM 环境,例如 Virtual Box,确保 Yubikey 设备已经插进了 USB 口,然后允许 VM 控制的 USB 访问 Yubikey。
|
||||
|
||||
### 配置 Yubikey
|
||||
|
||||
通过 USB Yubikey 验证你的账户:
|
||||
|
||||
```
|
||||
$ ykinfo -v
|
||||
version: 3.5.0
|
||||
```
|
||||
|
||||
如果 Yubikey 没有被检测到,会出现下面这些错误信息:
|
||||
|
||||
```
|
||||
Yubikey core error: no yubikey present
|
||||
```
|
||||
|
||||
接下来,通过下面这些 ykpersonalize 命令初始化你每个新的 Yubikeys。使用 HMAC-SHA1 算法进行询问响应,以此来设置 Yubikey 配置插槽 2。即使少于 64 个字符,如果你已经为询问响应设置好了你的 Yubikey。你就不需要再运行 ykpersonalize 了。
|
||||
|
||||
```
|
||||
ykpersonalize -2 -ochal-resp -ochal-hmac -ohmac-lt64 -oserial-api-visible
|
||||
```
|
||||
|
||||
一些用户在使用的时候将 YubiKey 留在了工作环境里,甚至对虚拟机使用了询问响应。然而,为了更好的安全性,你可能会更愿意使用手动触发 YubiKey 来响应询问。
|
||||
|
||||
要添加手动询问按钮触发器,请添加 -ochal-btn-trig 标记,这个标记可以在请求中使得 Yubikey 闪烁 Yubikey LED。等待你在 15 秒内按下硬件密钥区域上的按钮来生成响应密钥。
|
||||
|
||||
```
|
||||
$ ykpersonalize -2 -ochal-resp -ochal-hmac -ohmac-lt64 -ochal-btn-trig -oserial-api-visible
|
||||
```
|
||||
|
||||
为你的每个新的硬件密钥执行此操作。每个密钥执行以此,使用下面的命令将 Yubikey 配置存储到 ~/.yubico:
|
||||
|
||||
```
|
||||
$ ykpamcfg -2 -v
|
||||
debug: util.c:222 (check_firmware_version): YubiKey Firmware version: 4.3.4
|
||||
|
||||
Sending 63 bytes HMAC challenge to slot 2
|
||||
Sending 63 bytes HMAC challenge to slot 2
|
||||
Stored initial challenge and expected response in '/home/chuckfinley/.yubico/challenge-9992567'.
|
||||
```
|
||||
|
||||
如果你要设置多个密钥用于备份。请将所有的密钥设置为相同,然后使用 ykpamcfg utility 存储每个密钥的询问-响应。如果你在一个已经存在的注册密钥上运行 ykpersonalize 命令,你就必须再次存储配置信息。
|
||||
|
||||
### 配置 /etc/pam.d/sudo
|
||||
|
||||
现在要去验证配置是否有效,在相同的终端窗口中,你需要设置 sudo 来要求使用 Yubikey 的询问-响应。将下面这几行插入到 /etc/pam.d/sudo 文件中。
|
||||
|
||||
```
|
||||
auth required pam_yubico.so mode=challenge-response
|
||||
```
|
||||
|
||||
将上面的 auth 行插入到 auth 文件中的 system-auth 行的上面,然后保存并退出编辑器。在默认的 Fedora 29 设置中,/etc/pam.d/sudo 应该像下面这样:
|
||||
|
||||
```
|
||||
#%PAM-1.0
|
||||
auth required pam_yubico.so mode=challenge-response
|
||||
auth include system-auth
|
||||
account include system-auth
|
||||
password include system-auth
|
||||
session optional pam_keyinit.so revoke
|
||||
session required pam_limits.so
|
||||
session include system-auth
|
||||
```
|
||||
|
||||
保持原始终端窗口打开,然后打开一个新的终端窗口进行测试,在新的终端窗口中输入:
|
||||
|
||||
```
|
||||
$ sudo echo testing
|
||||
```
|
||||
|
||||
你应该注意到了 key 上的 LED 在闪烁。点击 Yubikey 按钮,你应该会看见一个输入 sudo 密码的提示。在你输入你的密码之后,你应该会在终端屏幕上看见 ”testing“ 的字样。
|
||||
|
||||
现在去测试确保正常的失败,启动另一个终端窗口,并从 USB 插口中拔掉 Yubikey。使用下面这条命令验证,在没有 Yubikey 的情况下,sudo 是否会不再正常工作。
|
||||
|
||||
```
|
||||
$ sudo echo testing fail
|
||||
```
|
||||
你应该立刻被提示输入 sudo 密码,即使你输入了正确密码,登陆也应该失败。
|
||||
|
||||
### 设置 Gnome 桌面管理
|
||||
|
||||
一旦你的测试完成后,你就可以为图形登陆添加询问-响应支持了。将你的 Yubikey 再次插入进 USB 插口中。然后将下面这几行添加到 /etc/pam.d/gdm-password 文件中:
|
||||
|
||||
```
|
||||
auth required pam_yubico.so mode=challenge-response
|
||||
```
|
||||
|
||||
打开一个终端窗口,然后运行下面这些命令。如果需要,你可以使用其他的编辑器:
|
||||
|
||||
```
|
||||
$ sudo vi /etc/pam.d/gdm-password
|
||||
```
|
||||
|
||||
你应该看到 yubikey 上的 LED 在闪烁,按下 yubikey 按钮,然后在提示符出输入密码。
|
||||
|
||||
修改 /etc/pam.d/gdm-password 文件,在已有的 password-auth 上添加新的 auth 行。这个文件的顶部应该像下面这样:
|
||||
|
||||
```
|
||||
auth [success=done ignore=ignore default=bad] pam_selinux_permit.so
|
||||
auth required pam_yubico.so mode=challenge-response
|
||||
auth substack password-auth
|
||||
auth optional pam_gnome_keyring.so
|
||||
auth include postlogin
|
||||
|
||||
account required pam_nologin.so
|
||||
```
|
||||
|
||||
保存更改并退出编辑器,如果你使用的是 vi,输入键是按 Esc 键,然后在提示符出输入 wq! 来保存并退出。
|
||||
|
||||
### 结论
|
||||
|
||||
现在注销 GNOME。将 Yubikey 插入到 USB 口,在图形登陆界面上点击你的用户名。Yubikey LED 会开始闪烁。触摸那个按钮,你会被提示输入你的密码。
|
||||
|
||||
如果你丢失了 Yubikey,除了重置密码之外,你还可以使用备份的 Yubikey。你还可以给你的账户增加额外的 Yubikey 配置。
|
||||
|
||||
如果有其他人获得了你的密码,他们在没有你的物理硬件 Yubikey 的情况下,仍然不能登陆。恭喜!你已经显著提高了你的工作环境登陆的安全性了。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://fedoramagazine.org/login-challenge-response-authentication/
|
||||
|
||||
作者:[nabooengineer][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[hopefully2333](https://github.com/hopefully2333)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://fedoramagazine.org/author/nabooengineer/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://fedoramagazine.org/using-the-yubikey4-with-fedora/
|
||||
[2]: https://fedoramagazine.org/fedora-28-better-smart-card-support-openssh/
|
||||
|
||||
Loading…
Reference in New Issue
Block a user