mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-02-03 23:40:14 +08:00
Merge branch 'master' of https://github.com/LCTT/TranslateProject
get new from LCTT.
This commit is contained in:
commit
a823acfa23
@ -0,0 +1,111 @@
|
||||
Linux 面试基础问题 - 3
|
||||
================================================================================
|
||||
|
||||
在有关**面试问题**的这一系列话题的前两篇文章中,我们收到了许多好的反馈,在此表示极大的感谢,同时,我们将延续这一系列话题。在这里,我们将再次展示**10个问题**来进行相互学习。
|
||||
|
||||
- [11个基本的Linux面试问题及答案 – 第一部分][1]
|
||||
- [10个基本的Linux面试问题及答案 – 第二部分][2]
|
||||
|
||||

|
||||
|
||||
### Q.1. 你如何向你的系统中添加一个新的用户(例如,tux)? ###
|
||||
|
||||
- 使用useradd指令
|
||||
- 使用adduser 指令
|
||||
- 使用linuxconf指令
|
||||
- 以上全是
|
||||
- 以上答案全都不对
|
||||
|
||||
> **答** : 以上全是,即useradd, adduser 和 linuxconf 都可向你的linux系统添加新用户。
|
||||
|
||||
### Q.2. 在一个硬盘上,可能有多少主分区? ###
|
||||
|
||||
- 1
|
||||
- 2
|
||||
- 4
|
||||
- 16
|
||||
|
||||
> **答** : 一个硬盘上最多可能有4个主分区。
|
||||
|
||||
### Q.3. Apache/Http 的默认端口号是多少? ###
|
||||
|
||||
- 8080
|
||||
- 80
|
||||
- 8443
|
||||
- 91
|
||||
- 以上答案全都不对
|
||||
|
||||
> **答** : Apache/Http默认配置是**80**端口
|
||||
|
||||
### Q.4. GNU代表什么? ###
|
||||
|
||||
- GNU's not Unix
|
||||
- General Unix
|
||||
- General Noble Unix
|
||||
- Greek Needed Unix
|
||||
- 以上答案全都不对
|
||||
|
||||
> **答** : GNU意为**GNU's not Unix**.
|
||||
|
||||
### Q.5. 如果你在shell提示符中输入mysql并得到“can’t connect to local MySQL server through socket ‘/var/mysql/mysql.sock’ ”的提示,你首先应该检查什么? ###
|
||||
|
||||
> **答** : 看到这条错误消息,我首先会使用**service mysql status**或者**service mysqld status**指令来检查mysql服务是否正在运行。如果mysql服务没有运行,就启动所需服务。
|
||||
|
||||
**注意**:上面的错误消息可能是由于**my.cnf**或者mysql的**用户权限**错误配置导致的。如果启动mysql服务之后仍不管用,你需要检查这两项。
|
||||
|
||||
### Q.6. 如何将windows ntfs分区挂载到Linux上面? ###
|
||||
|
||||
> **答** : 首先,使用**apt**或者**yum**工具安装ntfs3g包,然后使用
|
||||
“**sudo mount t ntfs3g /dev/<Windows ntfs的分区号> /<挂载点>**” 命令来将windows分区挂载到Linux上面
|
||||
|
||||
|
||||
### Q.7. 下面哪一个不是基于RPM的操作系统? ###
|
||||
|
||||
- RedHat Linux
|
||||
- Centos
|
||||
- Scientific Linux
|
||||
- Debian
|
||||
- Fedora
|
||||
|
||||
> **答** : ‘**Debian**’ 系统不是基于**RPM**的,其它的几个都是
|
||||
|
||||
### Q.8. Linux中,哪一个指令用来重命名文件? ###
|
||||
|
||||
- mv
|
||||
- ren
|
||||
- rename
|
||||
- change
|
||||
- 以上答案全都不对
|
||||
|
||||
> **答** : 在Linux中,**mv** 指令用来重命名一个文件。例如:**mv /path_to_File/original_file_name.extension /Path_to_File/New_name.extension**
|
||||
|
||||
### Q.9. 在Linux中,哪个命令用来创建并显示文件? ###
|
||||
|
||||
- ed
|
||||
- vi
|
||||
- cat
|
||||
- nano
|
||||
- 以上答案全都不对
|
||||
|
||||
> **答** : ‘**cat**‘ 命令用来创建并且显示文件
|
||||
|
||||
### 10. 哪层协议用于支持用户和程序,如支持密码、资源分享、文件传输和网络管理? ###
|
||||
|
||||
- 第四层协议
|
||||
- 第五层协议
|
||||
- 第六层协议
|
||||
- 第七层协议
|
||||
- 以上答案全都不对
|
||||
|
||||
> **答** : ‘**第七层协议**‘
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.tecmint.com/linux-interview-questions-and-answers-for-linux-beginners/
|
||||
|
||||
译者:[tomatoKiller](https://github.com/tomatoKiller) 校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://linux.cn/article-2315-1.html
|
||||
[2]:http://linux.cn/article-2370-1.html
|
||||
@ -0,0 +1,164 @@
|
||||
Linux 面试基础问题 - 2
|
||||
================================================================================
|
||||
继续我们这面试系列,在这篇文章里我们给出了10个问题。这些问题或者是在以后的文章中出现的问题不一定在面试中会被问到。然而通过这些文章我们呈现出的是一个交互的学习平台,这必将会对你有很大的帮助。
|
||||
|
||||

|
||||
|
||||
自本系列的上一篇文章[11个基本的 Linux 面试问题][1],我们分析了不同论坛对此作出的评论,这对我们将更好的文章提供给我们的读者是很重要的。我们付出了时间和金钱,那我们又渴望从你们身上得到什么回报呢?答案是没有的。如果你不能赞扬我们的工作,但恳请不要在评论中诋毁我们的工作。
|
||||
|
||||
如果你在文章中没有找到什么新的东西,但也请不要忘记它对某些人却是非常有用的,并且他或她会非常感激我们的工作。我们不能够让每一篇文章都使大家高兴。但我希望读者们能够尽量理解。
|
||||
|
||||
### Q.1:哪一条命令用于把用户登录会话记录在文件中? ###
|
||||
|
||||
- macro
|
||||
- read
|
||||
- script
|
||||
- record
|
||||
- sessionrecord
|
||||
|
||||
> **答**:‘script’ 命令是用来把用户登录的会话信息记录在文件里。这条命令能够用在 shell 脚本里面,或者直接在终端中使用。下面是一个例子,它记录了开始用 script 到输入 exit 结束之间的所有东西。
|
||||
|
||||
如下命令记录用户登录会话到一个文件中:
|
||||
|
||||
[root@tecmint ~]# script my-session-record.txt
|
||||
|
||||
Script started, file is my-session-record.txt
|
||||
|
||||
记录的文件“my-session-record.txt”可以通过下述方式查看:
|
||||
|
||||
[root@tecmint ~]# nano my-session-record.txt
|
||||
|
||||
script started on Friday 22 November 2013 08:19:01 PM IST
|
||||
[root@tecmint ~]# ls
|
||||
^[[0m^[[01;34mBinary^[[0m ^[[01;34mDocuments^[[0m ^[[01;34mMusic^[[0m $
|
||||
^[[01;34mDesktop^[[0m ^[[01;34mDownloads^[[0m my-session-record.txt ^[[01;34$
|
||||
|
||||
### Q.2:以下那一条命令可以用来查看内核日志信息 ###
|
||||
|
||||
- dmesg
|
||||
- kernel
|
||||
- ls -i
|
||||
- uname
|
||||
- 以上全不是
|
||||
|
||||
> **答**:执行 'dmesg' 命令可以查看内核的日志信息。在上面的命令中,kernel 不是一个有效的命令,'ls -i' 是用来列出工作目录中文件的索引节点,而 'uname' 是用来显示操作系统信息的。
|
||||
|
||||
[root@tecmint ~]# dmesg
|
||||
|
||||
Initializing cgroup subsys cpuset
|
||||
Initializing cgroup subsys cpu
|
||||
Linux version 2.6.32-279.el6.i686 (mockbuild@c6b9.bsys.dev.centos.org) (gcc version 4.4.6 20120305 (Red Hat 4.4.6-4) (GCC) ) #1 SMP Fri Jun 22 10:59:55 UTC 2012
|
||||
KERNEL supported cpus:
|
||||
Intel GenuineIntel
|
||||
AMD AuthenticAMD
|
||||
NSC Geode by NSC
|
||||
Cyrix CyrixInstead
|
||||
Centaur CentaurHauls
|
||||
Transmeta GenuineTMx86
|
||||
Transmeta TransmetaCPU
|
||||
UMC UMC UMC UMC
|
||||
Disabled fast string operations
|
||||
BIOS-provided physical RAM map:
|
||||
...
|
||||
|
||||
### Q.3:哪一条命令是用来显示 Linux 内核发行信息的? ###
|
||||
|
||||
- uname -v
|
||||
- uname -r
|
||||
- uname -m
|
||||
- uname -n
|
||||
- uname -o
|
||||
|
||||
> **答**:‘uname -r’是用来显示内核的发行信息。其它参数‘-v’、‘-m’、‘-n’、‘o’分别显示内核版本、机器硬件名称、网络节点、主机名和操作系统。
|
||||
|
||||
[root@tecmint ~]# uname -r
|
||||
|
||||
2.6.32-279.el6.i686
|
||||
|
||||
### Q.4:那一条命令是被用来识别文件类型的? ###
|
||||
|
||||
- type
|
||||
- info
|
||||
- file
|
||||
- which
|
||||
- ls
|
||||
|
||||
> **答**:‘file’命令是用来识别文件类型的。其语法是‘file [选项] 文件名’。
|
||||
|
||||
[root@tecmint ~]# file wtop
|
||||
|
||||
wtop: POSIX shell script text executable
|
||||
|
||||
### Q.5:哪一条命令是被用来找一条命令的二进制文件、源和手册的所在的路径? ###
|
||||
|
||||
> **答**:‘whereis’驾到!‘whereis’命令是用来找一条命令的二进制文件、源和手册的所在的路径。
|
||||
|
||||
[root@tecmint ~]# whereis /usr/bin/ftp
|
||||
|
||||
ftp: /usr/bin/ftp /usr/share/man/man1/ftp.1.gz
|
||||
|
||||
### Q.6:当用户登录时,默认情况下哪些文件会被调用作为用户配置? ###
|
||||
|
||||
> **答**:在用户的目录下‘.profile’和‘.bashrc’会默认地被调用作为用户配置。
|
||||
|
||||
[root@tecmint ~]# ls -al
|
||||
-rw-r--r--. 1 tecmint tecmint 176 May 11 2012 .bash_profile
|
||||
-rw-r--r--. 1 tecmint tecmint 124 May 11 2012 .bashrc
|
||||
|
||||
### Q.7:‘resolve.conf’文件是什么的配置文件? ###
|
||||
|
||||
> **答**:‘/etc/resolve.conf’ 是 DNS 客户端的配置文件。
|
||||
|
||||
[root@tecmint ~]# cat /etc/resolv.conf
|
||||
|
||||
nameserver 172.16.16.94
|
||||
|
||||
### Q.8:哪一条命令是用来创建一个文件的软链接的? ###
|
||||
|
||||
- ln
|
||||
- ln -s
|
||||
- link
|
||||
- link -soft
|
||||
- 以上都不是
|
||||
|
||||
> **答**:在 Linux 环境下,‘ls -s’是被用来创建一个文件的软链接的。
|
||||
|
||||
[root@tecmint ~]# ln -s /etc/httpd/conf/httpd.conf httpd.original.conf
|
||||
|
||||
### Q.9:在Linux下,‘pwd’命令是‘passwd’命令的别名吗? ###
|
||||
|
||||
> **答**:不是!默认情况下‘pwd’命令不是‘passwd’命令的别名。‘pwd’是‘print working directory’(显示工作目录)的缩写,也就是输出当前的工作目录,而‘passwd’在 Linux 中是被用来更改用户的帐号密码。
|
||||
|
||||
[root@tecmint ~]# pwd
|
||||
|
||||
/home/tecmint
|
||||
|
||||
[root@tecmint ~]# passwd
|
||||
Changing password for user root.
|
||||
New password:
|
||||
Retype new password:
|
||||
|
||||
### Q.10:在 Linux 中,你会怎样检测 pci 设备的厂商和版本。 ###
|
||||
|
||||
> **答**:我们用的 Linux 命令是‘lspci’。
|
||||
|
||||
[root@tecmint ~]# lspci
|
||||
|
||||
00:00.0 Host bridge: Intel Corporation 5000P Chipset Memory Controller Hub (rev b1)
|
||||
00:02.0 PCI bridge: Intel Corporation 5000 Series Chipset PCI Express x8 Port 2-3 (rev b1)
|
||||
00:04.0 PCI bridge: Intel Corporation 5000 Series Chipset PCI Express x8 Port 4-5 (rev b1)
|
||||
00:06.0 PCI bridge: Intel Corporation 5000 Series Chipset PCI Express x8 Port 6-7 (rev b1)
|
||||
00:08.0 System peripheral: Intel Corporation 5000 Series Chipset DMA Engine (rev b1)
|
||||
...
|
||||
|
||||
现在就到这里。我希望以上的问题也许对你很有用。在下星期我会再想出一些新的问题。到时请保持好的健康,继续关注我们并且与 Tecmint 保持联系喔!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.tecmint.com/basic-linux-interview-questions-and-answers-part-ii/
|
||||
|
||||
译者:[hyaocuk](https://github.com/hyaocuk) 校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://linux.cn/article-2315-1.html
|
||||
@ -1,18 +1,18 @@
|
||||
每日 Ubuntu 小技巧 - TeamViewer 9 可供下载了
|
||||
每日Ubuntu小技巧 - 使用TeamViewer连接远程桌面
|
||||
================================================================================
|
||||
TeamViewer,是一款热门的远程支持和桌面共享工具,并且它的 Windows版, Mac OS X版 和 Linux版(包含Ubuntu) 已经更新到版本 9 了。TeamViewer 能够允许你在任何地方通过网络控制任何电脑。
|
||||
TeamViewer,是一款热门的远程支持和桌面共享工具,并且它的Windows版、Mac OS X版和Linux版(包含Ubuntu)已经更新到版本 9 了。TeamViewer 允许你在任何地方通过网络控制任何电脑。
|
||||
|
||||
如果你在谈一桩生意有或者在帮助某人解决一些与电脑相关的问题,例如杀毒,又或者与在遥远的人共享你的屏幕内容,那同样,它也是一款值得拥有的强大的工具。
|
||||
如果你在谈一桩生意或者帮助别人解决一些与电脑相关的问题,例如杀毒,又或者远程共享你的屏幕内容,那同样,它是一款功能强大的工具,值得拥有。
|
||||
|
||||
以下是这个支持工具是如何使用的例子。
|
||||
以下是这个支持工具如何使用的例子。
|
||||
|
||||
最近,我的妈妈打电话给我说她想弄清楚如何安装一个程序。当我在电话中花了几分钟尝试帮她弄那个程序,不过都失败后,我决定自己来。
|
||||
最近,我妈妈打电话给我说她想弄清楚如何安装一个程序。当我在电话中花了几分钟尝试帮她弄那个程序,不过都失败后,我决定自己来。
|
||||
|
||||
因此我们两个人都下载了 TeamViewer 并且在数分钟之内,我连接上了她的电脑并且帮她安装了那个程序。
|
||||
因此我们两个人都花了几分钟下载了 TeamViewer,我连接上了她的电脑并且帮她安装了那个程序。
|
||||
|
||||
那是个 TeamViewer 如何帮助你把东西搞定的例子,如果你准备使用 TeamViewer 来帮助你的顾客或者是客户的话,你可能需要购买一个授权许可来遵守公司的政策。
|
||||
这是一个 TeamViewer 如何帮助你解决问题的例子,如果你准备使用 TeamViewer 来帮助你的顾客或者是客户的话,你可能需要购买一个授权许可来遵守公司的政策。
|
||||
|
||||
我宁愿在所有其他远程支持工具中选择 TeamViewer 的另外一个原因是它允许你直接使用而无需安装,至少在 Windows 上是这样。如果你只需要使用它一次的话,那么你只需要运行它,而它却不会占用你的磁盘空间。
|
||||
我宁愿选择 TeamViewer 而不选择其它远程支持工具的另外一个原因是它允许你直接使用,无需安装,至少在 Windows 上是这样。如果你只使用一次的话,那么你只需要运行它,而它却不会占用你的磁盘空间。
|
||||
|
||||
现在 TeamViewer 能够在几乎所有操作系统上运行,包括 Android 和 IOS。
|
||||
|
||||
@ -27,22 +27,22 @@ Ubuntu 用户可以 [从这链接下载并运行 TeamViewer][2]
|
||||
对于 **64位操作系统**, 使用下面的链接.
|
||||
|
||||
wget http://download.teamviewer.com/download/teamviewer_linux_x64.deb
|
||||
|
||||
|
||||
最后,运行下面的命令来安装。
|
||||
|
||||
sudo dpkg -i teamviewer_linux*.deb; sudo apt-get -f install
|
||||
|
||||
去爽吧!
|
||||
去试试吧!
|
||||
|
||||

|
||||
|
||||
如果上述的命令不能成功运行的话,那么就去 TeamViewer [下载页面并且下载][2].
|
||||
如果上述的命令不能成功运行的话,那么就去 TeamViewer [下载页面来下载][2].
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.liberiangeek.net/2013/12/daily-ubuntu-tips-teamviewer-9-is-available-for-download/
|
||||
|
||||
译者:[hyaocuk](https://github.com/hyaocuk) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
译者:[hyaocuk](https://github.com/hyaocuk) 校对:[Caroline](https://github.com/carolinewuyan)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,18 +1,20 @@
|
||||
每日Ubuntu小技巧 - 更换菜单风格
|
||||
每日Ubuntu小技巧 - 使用旧式Gnome风格的菜单
|
||||
================================================================================
|
||||
每日Ubuntu小技巧 - 喜欢GNOME风格菜单?安装Class Menu Indicator吧
|
||||
|
||||
对于那些从初学者一直关注Ubuntu操作系统的人,他们看见几乎所有的Ubuntu经历的改变。发生了许多的改变,尤其是在桌面部分。从经典的GNOME桌面环境到Unity,Ubuntu已经完全地重新设计了。
|
||||
喜欢GNOME风格菜单?安装Class Menu Indicator吧。
|
||||
|
||||
对于那些新用户,他们所知道的是Unity桌面环境和仅仅只是听说过,或者见过在支持Ubuntu之前的原始的GNOME桌面环境。
|
||||
对于那些从开始就一直关注Ubuntu操作系统的人,他们看见几乎所有的Ubuntu经历的改变。发生了许多的改变,尤其是在桌面部分。从经典的GNOME桌面环境到Unity,Ubuntu已经完全地重新设计了。
|
||||
|
||||
如果你是一个老资格,想要在Ubuntu的Unity回到GNOME风格的菜单,安装Classic Menu Indicator 可以解决这个问题。这个俏皮的包被安装在顶部面板的通知区域,在Ubuntu中带回了GNOME风格菜单体验。
|
||||
对于那些新用户,他们所知道的就是Unity桌面环境,仅仅只是听说过或者见过之前Ubuntu的原始GNOME桌面环境。
|
||||
|
||||
如果你是一个老资格用户,想要在Ubuntu的Unity回到GNOME风格的菜单,安装Classic Menu Indicator 可以解决这个问题。这个有趣的包被安装在顶部面板的通知区域,在Ubuntu中带回了GNOME风格菜单体验。
|
||||
|
||||
像经典的GNOME菜单一样,它包括所有的应用和经典菜单结构。对于曾经使用过它的人们是容易导航和开启应用。对于新用户,它也是容易掌握。
|
||||
|
||||
接下来的简短指导将会告诉你如何在Ubuntu中安装这个包。
|
||||
|
||||
马上开始,在键盘上按下 **Ctrl – Alt – T** 打开终端。
|
||||
|
||||
打开完毕后,运行下列命令,加入它的PPA文件
|
||||
|
||||
sudo apt-add-repository ppa:diesch/testing
|
||||
@ -21,7 +23,8 @@
|
||||
|
||||
sudo apt-get update && sudo apt-get install classicmenu-indicator
|
||||
|
||||
安装完成后,在Unity Dash中启动。它叫Classic Menu Indicator.当你启动它的时候,它会自动的嵌入顶部面板,如下图。
|
||||
安装完成后,在Unity Dash中启动。它叫Classic Menu Indicator。当你启动它的时候,它会自动的嵌入顶部面板,如下图。
|
||||
|
||||

|
||||
|
||||
就是这样,使用并享受吧!
|
||||
@ -29,6 +32,6 @@
|
||||
|
||||
via: http://www.liberiangeek.net/2013/11/daily-ubuntu-tipslike-gnome-classic-menu-get-classic-menu-indicator/
|
||||
|
||||
译者:[Vic___](http://blog.csdn.net/Vic___) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
译者:[Vic___](http://blog.csdn.net/Vic___) 校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
23
published/GCC 4.9 Is Now In Bug-Fixes-Only Stage 3 Mode.md
Normal file
23
published/GCC 4.9 Is Now In Bug-Fixes-Only Stage 3 Mode.md
Normal file
@ -0,0 +1,23 @@
|
||||
GCC 4.9现在处于修复BUG的第三阶段
|
||||
================================================================================
|
||||
|
||||
拥有很多[新功能][2]的[GCC 4.9][1]将定于2014年上半年发布。这个GCC的基础代码将不会增加新的功能,目前将只修改大的BUG。
|
||||
|
||||
Richard Biener宣称代码主干目前处于第三阶段,因此在之后的八个月这些功能将融入到4.9版本,除非有发布主管认可的特例发生,不然不会增加新的功能了。第三阶段只做普通BUG的修复工作,将在2个月内完成,而后到达只编写文档和回归测试的第四阶段。
|
||||
|
||||
目前GCC4.9有63个P1 回归测试(最严重的回归测试)其次是136个P2回归测试,14个P3回归测试,88个P4回归测试 以及60个P5回归测试。直到P1阶段的63个回归测试完成,GCC4.9才接近发布。GCC 4.9.0发布版将可能在2014第二季度左右到来!
|
||||
|
||||
GCC 4.9.0状态报告可以在[GCC mailing list][3]中被找到。GCC 4.9将会是一个非常棒的更新,并会挑战下个月发布的[LLVM3.4][4]。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.phoronix.com/scan.php?page=news_item&px=MTUyMjk
|
||||
|
||||
译者:[Vic___](http://blog.csdn.net/Vic___) 校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.phoronix.com/scan.php?page=search&q=GCC+4.9
|
||||
[2]:http://www.phoronix.com/scan.php?page=news_item&px=MTUxNzQ
|
||||
[3]:http://gcc.gnu.org/ml/gcc/2013-11/msg00435.html
|
||||
[4]:http://www.phoronix.com/scan.php?page=search&q=LLVM+3.4
|
||||
@ -0,0 +1,86 @@
|
||||
Linux领袖说:‘开源很安全,Linux比其它任何系统都安全’
|
||||
================================================================================
|
||||
在对Linux基金会执行官,Jim Zemlin 的采访中,VentureBeat 展望了2014年开源操作系统的未来。
|
||||
|
||||
访谈中我们也探讨了争议性的话题,就是政府部门的监听事件以及‘后门’-那些邪恶的窗口,窥探我们网上的私生活,最近公众发现我们经常使用的大多数服务都有类似的遭遇。
|
||||
|
||||
Zemlin 为我们解释了 GNU/Linux 为什么以及如何使它成为内心有些担忧的消费者的最安全的选择。还有就是为什么选择GNU/Linux作为能源汽车、手机、TV以及其它新兴设备的操作系统。
|
||||
|
||||
以下是我们完整的e-mail访谈实录
|
||||
|
||||
----------
|
||||
|
||||
**VentureBeat: 安全和隐私一直是本年度最热门的话题,我们听到的谣言,Linus[Torvalds, Linux 创始人]对政府部门是否有植入后门的要求点头称是。**
|
||||
|
||||
**Zemlin**: 如果Linux真有后门,你应该知道的。
|
||||
|
||||
全世界的用户都可以看到Linux的每一行代码。这也是linux要比其他操作系统更安全、开源整体要比闭源更安全的原因之一。代码的透明度保证了它的安全性。
|
||||
|
||||
必须明确指出:Linux没有后门。
|
||||
|
||||
**VentureBeat: Linux基金会如何保证Linux用户的隐私和自由,使其免于遭受追踪和监视?**
|
||||
|
||||
**Zemlin**: 对此,我们一以贯之。向内核插入违反隐私权和背离自由精神的代码而不被成千上万的开发者注意到,这是很难的。Linux的本性就是自我定制。
|
||||
|
||||
**VentureBeat: 今年的隐私/安全/监视事件会不会促使, 或者将会促使更多的消费者倾向于Linux,对此你作何感想?**
|
||||
|
||||
**Zemlin**: 世界范围内,我听到人们都在说,“用开源保证隐私是必须的。”的确,那会促使更多的使用者选择Linux。
|
||||
|
||||
除了他们对linux平台下的隐私和安全持自信、信任的态度以外, 我认为消费者会基于多种原因选择Linux。
|
||||
代码的透明性以及开发过程逐渐给予日渐博学和警觉的消费者一个选择,一个会让他们对linux感觉良好的选择。
|
||||
|
||||
[视频游戏发行商] Valve [及其SteamOS下的工作][1] 正在促使更多的消费者走进Linux,就像逐渐占据主导地位的Android和其他运行Linux的电子设备一样,比如电视、家电、汽车等,当然还有更多。
|
||||
|
||||
**VentureBeat: 针对手机的Ubuntu Edge, 对它有何看法? 对于2014-2015年Linux/Ubuntu手机市场走势,你作何预测?**
|
||||
|
||||
**Zemlin**:我希望看到潜在的有趣的新产品进入市场,尤其是基于Linux的产品。很难说每年哪款产品会成为手机市场的新宠。
|
||||
|
||||
我认为预测基于Linux的手机将占据主导地位,不算夸大事实。Android, Tizen, Ubuntu, Firefox,等等等等,都显示出Linux可以驱动手机市场的创新,并且为消费者创造新的体验,为开发者和OEMs创造机会。
|
||||
|
||||
明年令人振奋的发展,也是我所关注的就是linux和开源界如何把这些设备、对象和服务关联到一起。
|
||||
|
||||
**VentureBeat: 目前为止,你看到的linux嵌入式车载系统的最令人激动的使用案例是什么?**
|
||||
|
||||
**Zemlin**: 毫无疑问,就是,Cadillac, Tesla, Toyota, Jaguar, Land Rover等都搭建了车载信息娱乐系统。
|
||||
|
||||
比如,今年赢得了 “年度汽车族”奖项的Tesla Model S,装备了一个17英寸平面、运行着定制Linux的电脑。这真的是太酷了。
|
||||
|
||||
2014年度汽车族刚刚揭晓 -- Cadillac CTS sedan, 也是使用linux作为车载信息娱乐系统。汽车制造商有能力使用linux进行创新并区别使用这些系统。
|
||||
|
||||
Linux的成功也能从来自IHS汽车的最新数据上看到,IHS本月报告称,在全球车载信息娱乐市场,基于linux的汽车销量2020年有望达到5370万,超过微软和黑莓QNX。
|
||||
|
||||
Linux基金会协同汽车级Linux工作组在该领域做了许多工作。通过在Linux内核社区,其他开源社区,以及汽车行业,营造一个中立、支持性的环境,我们能够帮助一些世界级巨头汽车制造商提高汽车Linux技术,如日产,捷豹,路虎,丰田,等等。
|
||||
|
||||
**VentureBeat: 在硬核开发者市场以外,Linux是如何发展壮大的,尤其是考虑到消费者和游戏玩家?**
|
||||
|
||||
**Zemlin**:可以肯定的是,对游戏玩家来说,今年确实是linux的一个转折点。Valve, 一个基于Steam网络平台的一个游戏厂商,在linux上构建并运行所有的源代码和动画。Valve的CEO Gabe Newell 称,今年的LinuxCon大会上他们在linux平台运行了198个游戏,随着引进基于linux的Steam,这个数字还会上升。这是Linux和游戏界新趋势的开端。
|
||||
|
||||
用户每天都在用linux。软件支撑着我们的日常生活。像Google,Facebook还有Twitter等公司,都建立在Linux和开源软件之上。去年10月份LinuxCon欧洲大会上,来自Twitter的Chris Aniszczyk告诉听众:
|
||||
“Twitter 理所当然完全运行在linux上。为什么你们还需要其他的东西?”(译注:言外之意就是有linux就够了,不需要别的什么东西了。)
|
||||
|
||||
如今Linux驱动着130万台日常所用Android手机,每天近60万基于linux的新电视售出。新的家电以及汽车都建立在linux之上。主要交通系统也都在使用linux。最受欢迎的[GoPro 使用linux和开源软件][2]。这样的例子层出不穷。
|
||||
|
||||
Linux和开源理念将会逐渐融入主流消费者的生活。三星使用linux内核以及基于linux的产品充实它的产品线,从电视机到手机,再到家电,等等等等。
|
||||
|
||||
敬请关注 - 未来你将看到更多实例,展现了Linux和开源软件,以及协同开发在日常生活中发挥越来越大的作用。
|
||||
|
||||
**VentureBeat: 在你看来,到2014年,免费和开源软件最大的机遇会是什么?**
|
||||
|
||||
**Zemlin**: 我们已经谈到游戏和电子设备,但是企业将会继续为linux呈现更多的机会。云计算的兴起为开发者带来新的机遇和挑战。你可以试着去找找不运行在linux上的公共云。
|
||||
|
||||
软件定义的网络(SDN)实现将成为2014年的主要活动之一。人们并没有期望着软件定义网络以及网络功能虚拟化变得多么大。想想吧。数十亿美元花费在硬件上,交换机,路由,负载均衡器,防火墙等等。这些都抽象成了软件。更更重要的是,它是在开源软件的基础架构甜蜜点OSS层被抽象。我认为你会看到,像OpenDaylight项目以及其他项目,在2014年都会有大的突破。
|
||||
|
||||
当然,这只是实现协同发展的大趋势的一部分,你的读者应该会对此感兴趣。我的推测是再过一个20年,几乎所有的基础软件都会以协同开发的方式进行构建。2014年开发者需要学习如何以协同方式构建软件,要学会如何参与开源项目并且贡献代码。如果开发者能够理解协同开发和开源的原则和理念,那么他们职业生涯中的机遇将会是无穷的。
|
||||
|
||||
参与到linux的世界中来是一个激动人心的时刻。从智能手表到电视机,到汽车,只要你能想到,Linux就能为你实现。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://venturebeat.com/2013/11/26/linux-chief-open-source-is-safer-and-linux-is-more-secure-than-any-other-os-exclusive/
|
||||
|
||||
译者:[l3b2w1](https://github.com/l3b2w1) 校对:[Caroline](https://github.com/carolinewuyan)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://venturebeat.com/2013/09/23/steamos-valves-linux-based-operating-system-for-the-tv-and-living-room/
|
||||
[2]:http://gopro.com/support/open-source
|
||||
@ -1,18 +1,17 @@
|
||||
Linux 下使用Trickle管理和限制下载/上传带宽
|
||||
Linux 下使用Trickle限制下载/上传带宽
|
||||
================================================================================
|
||||
你有没有遇到过一个程序占用了你所有的网络带宽的情况?如果你遇到过,那么你就需要限制带宽的应用。不管你是一个系统管理员还是一名普通Linux用户,您都要学习如何控制应用的上传和下载速度来确保你的网络带宽不会被一个程序耗光。
|
||||
|
||||
你有没有遇到过一个程序占用了你所有的网络带宽的情况?如果你遇到过,那么你就需要限制带宽的应用。不管你是一个系统管理员还是一名普通Linux用户,您都应该学习如何控制应用的上传和下载速度来确保你的网络带宽不会被一个程序耗光。
|
||||
|
||||

|
||||
|
||||
### Trickle 是什么? ###
|
||||
|
||||
**Trickle**是一款带宽整形器,用来限制如**Firefox, FTP , SSH**以及其他使用网络带宽的程序的带宽使用。你希望你的**Youtube**音乐体验影响到你的ftp下载么?如果不想,请继续阅读这篇文章,学习如何在你的机器上安装和使用trickle。
|
||||
|
||||
**Trickle**是一款带宽控制供给,用来限制如**Firefox, FTP , SSH**以及其他使用网络带宽的程序的带宽。你希望你的**Youtube**音乐体验影响到你的ftp下载么?如果不想,请继续阅读这篇文章,学习如何在你的机器上安装和使用trickle。
|
||||
|
||||
### 怎样在Linux上安装Trickle ###
|
||||
|
||||
trickle工具有它自己的依赖包,安装和使用trickle之前必须安装“**libevent 库**”,不过这个库在大多数现在的Linux机器上已经默认安装。
|
||||
|
||||
trickle工具有一些依赖包,安装和使用trickle之前必须安装“**libevent 库**”,不过这个库在大多数现在的Linux机器上已经默认安装。
|
||||
|
||||
#### 在 Debian/Ubuntu/Linux Mint 上####
|
||||
|
||||
@ -32,8 +31,7 @@ trickle工具有它自己的依赖包,安装和使用trickle之前必须安装
|
||||
|
||||
Trickle通过控制socket数据读写量来控制和限制应用的**上传/下载**速度。它使用另一个版本的**BSD**套接字API,但是区别是trickle还管理socket调用。
|
||||
|
||||
要注意的是trickle使用动态链接和加载,所以它只对于使用"Glibc库"的程序有用。由于trickle可以设置数据在socket上的传输延迟,显然它可以用来限制一个应用的网络带宽。
|
||||
|
||||
要注意的是trickle使用动态链接和加载,所以它只对于使用"Glibc库"的程序有用。由于trickle可以设置数据在socket上的传输延迟,所以它可以用来限制一个应用的网络带宽。
|
||||
|
||||
### Trickle不能做什么? ###
|
||||
|
||||
@ -41,7 +39,6 @@ Trickle不能用于限制使用**UDP**协议的应用的带宽,它只可用于
|
||||
|
||||
还要说一下,trickle无法工作在使用静态链接的可执行程序上。
|
||||
|
||||
|
||||
### 确定Trickle是否可运行在某个特定应用上 ###
|
||||
|
||||
既然trickle无法限制每个应用的**上传/下载**速度,就应该有个方法找出trickle可以工作的应用。
|
||||
@ -65,14 +62,14 @@ Trickle不能用于限制使用**UDP**协议的应用的带宽,它只可用于
|
||||
|
||||
### 学习如何使用Trickle ###
|
||||
|
||||
使用下面的命令打印trickle工具的**版本**。
|
||||
使用下面的命令输出trickle工具的**版本**。
|
||||
|
||||
root@oltjano-X55CR:~# trickle -V
|
||||
trickle: version 1.07
|
||||
|
||||
Linux有很多命令行工具使测试(实验)变得有趣和美丽。下面的命令使用[wget 工具][1]来下载最新的Pear OS镜像.
|
||||
|
||||
root@oltjano-X55CR:~# wget http://sourceforge.net/projects/pearoslinux/files/Pear%20OS%208/pearos8-i386.iso/download
|
||||
root@oltjano-X55CR:~# wget http://sourceforge.net/projects/pearoslinux/files/Pear%20OS%208/pearos8-i386.iso/download
|
||||
|
||||
--2013-11-20 11:56:32-- http://sourceforge.net/projects/pearoslinux/files/Pear%20OS%208/pearos8-i386.iso/download
|
||||
Resolving sourceforge.net (sourceforge.net)... 216.34.181.60
|
||||
@ -93,8 +90,6 @@ root@oltjano-X55CR:~# wget http://sourceforge.net/projects/pearoslinux/files/Pea
|
||||
|
||||
0% [ ] 30,78,278 381KB/s eta 1h 50m
|
||||
从输出可以看到,下载速度大约是**381 KB/s**。我想限制下载速度到**13 K/s**,这样我就可以用我的带宽做其他的事情了。下面的命令用来限制wget速度到**13 K/s**。
|
||||
|
||||
root@oltjano-X55CR:~# trickle -d 13 wget http://sourceforge.net/projects/pearoslinux/files/Pear%20OS%208/pearos8-i386.iso/download
|
||||
|
||||
ravisaive@ravisaive-OptiPlex-380:~$ trickle -d 13 wget http://sourceforge.net/projects/pearoslinux/files/Pear%20OS%208/pearos8-i386.iso/download
|
||||
|
||||
@ -117,7 +112,7 @@ root@oltjano-X55CR:~# wget http://sourceforge.net/projects/pearoslinux/files/Pea
|
||||
|
||||
0% [ ] 2,01,550 13.1KB/s eta 21h 5m
|
||||
|
||||
从输出可以看到,下载速度被限制到了**13K/s**。下载将会持续**21小时5分钟**。上面的“**-d**”选项表示下载,还可以结合使用 “**-d**”选项和上传选项(**-u**),如下例所示。
|
||||
从输出可以看到,下载速度被限制到了**13K/s**。下载将会持续**21小时5分钟**。上面的“**-d**”选项表示下载,还可以结合使用 “**-d**”选项和上传选项(**-u**),如下例所示。
|
||||
|
||||
# trickle -u 100 -d 50 ftp
|
||||
|
||||
@ -127,7 +122,7 @@ root@oltjano-X55CR:~# wget http://sourceforge.net/projects/pearoslinux/files/Pea
|
||||
|
||||
每个命令行工具都对用户提供了帮助,使用"trickle -h"命令来找出更多trickle工具的用法。
|
||||
|
||||
root@oltjano-X55CR:/usr/bin# trickle -h
|
||||
root@oltjano-X55CR:/usr/bin# trickle -h
|
||||
|
||||
Usage: trickle [-hvVs] [-d <rate>] [-u <rate>] [-w <length>] [-t <seconds>]
|
||||
[-l <length>] [-n <path>] command ...
|
||||
@ -1,110 +0,0 @@
|
||||
tomatoKiller 翻译中
|
||||
|
||||
10 Linux Interview Questions and Answers for Linux Beginners – Part 3
|
||||
================================================================================
|
||||
Continuing the **Interview Questions** series, with a big thanks for the nice feedback on last two articles of this series, we are here presenting **10 questions** again for interactive learning.
|
||||
|
||||
- [11 Basic Linux Interview Questions and Answers – Part 1][1]
|
||||
- [10 Basic Linux Interview Questions and Answers – Part II][2]
|
||||
|
||||

|
||||
|
||||
### 1. How will you add a new user (say, tux) to your system.? ###
|
||||
|
||||
- useradd command
|
||||
- adduser command
|
||||
- linuxconf command
|
||||
- All of the above
|
||||
- None of the above
|
||||
|
||||
> **Answer** : All of the above commands i.e., **useradd, adduser** and **linuxconf** will add an user to the Linux system.
|
||||
|
||||
### 2. How many primary partition is possible on one drive? ###
|
||||
|
||||
- 1
|
||||
- 2
|
||||
- 4
|
||||
- 16
|
||||
|
||||
> **Answer** : There are a maximum of ‘**4**‘ primary partition possible on a drive.
|
||||
|
||||
### 3. The default port for Apache/Http is? ###
|
||||
|
||||
- 8080
|
||||
- 80
|
||||
- 8443
|
||||
- 91
|
||||
- None of the above.
|
||||
|
||||
> **Answer** : By default Apache/Http is configured on port **80**.
|
||||
|
||||
### 4. What does GNU stand for? ###
|
||||
|
||||
- GNU’s not Unix
|
||||
- General Unix
|
||||
- General Noble Unix
|
||||
- Greek Needed Unix
|
||||
- None of the above
|
||||
|
||||
> **Answer** : GNU stands for ‘**GNU**‘s not **Unix**‘.
|
||||
|
||||
### 5. You typed at shell prompt “mysql” and what you got in return was “can’t connect to local MySQL server through socket ‘/var/mysql/mysql.sock’”, what would you check first. ###
|
||||
|
||||
> **Answer** : Seeing the error message, I will first check if mysql is running or not using commands **service mysql status** or **service mysqld status**. If mysql service is not running, starting of the service is required.
|
||||
|
||||
**Note**:The above error message can be the result of ill configured **my.cnf** or mysql **user permission**. If mysql service starting doesn’t help, you need to see into the above said issues.
|
||||
|
||||
### 6. How to Mount a windows ntfs partition on Linux? ###
|
||||
|
||||
> **Answer** : First install **ntfs3g** pack on the system using **apt** or **yum** tool and then use “**mount sudo mount t ntfs3g /dev/<Windowspartition>/<Mountpoint>**” command to mount Windows partition on Linux.
|
||||
|
||||
### 7. From the following which is not an RPM based OS.? ###
|
||||
|
||||
- RedHat Linux
|
||||
- Centos
|
||||
- Scientific Linux
|
||||
- Debian
|
||||
- Fedora
|
||||
|
||||
> **Answer** : The ‘**Debian**‘ operating system is not an **RPM** based and all listed above are ‘**RPM**‘ based except Debian.
|
||||
|
||||
### 8. Which command can be used to rename a file in Linux.? ###
|
||||
|
||||
- mv
|
||||
- ren
|
||||
- rename
|
||||
- change
|
||||
- None of the Above
|
||||
|
||||
> **Answer** : The **mv** command is used to rename a file in Linux. For example, **mv /path_to_File/original_file_name.extension /Path_to_File/New_name.extension**.
|
||||
|
||||
### 9. Which command is used to create and display file in Linux? ###
|
||||
|
||||
- ed
|
||||
- vi
|
||||
- cat
|
||||
- nano
|
||||
- None of the above
|
||||
|
||||
Answer : The ‘**cat**‘ command can be used to create and display file in Linux.
|
||||
|
||||
### 10. What layer protocol is responsible for user and the application program support such as passwords, resource sharing, file transfer and network management? ###
|
||||
|
||||
- Layer 4 protocols
|
||||
- Layer 5 protocols
|
||||
- Layer 6 protocols
|
||||
- Layer 7 protocols
|
||||
- None of the above
|
||||
|
||||
> **Answer** : The ‘**Layer 7 Protocol**‘ is responsible for user and the application program support such as passwords, resource sharing, file transfer and network management.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.tecmint.com/linux-interview-questions-and-answers-for-linux-beginners/
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.tecmint.com/basic-linux-interview-questions-and-answers/
|
||||
[2]:http://www.tecmint.com/basic-linux-interview-questions-and-answers-part-ii/
|
||||
@ -0,0 +1,646 @@
|
||||
Vic020的WC
|
||||
29 Practical Examples of Nmap Commands for Linux System/Network Administrators
|
||||
================================================================================
|
||||
The **Nmap** aka **Network Mapper** is an open source and a very versatile tool for Linux system/network administrators. **Nmap** is used for **exploring networks, perform security scans, network audit** and **finding open ports** on remote machine. It scans for Live hosts, Operating systems, packet filters and open ports running on remote hosts.
|
||||
|
||||

|
||||
*Nmap Commands and Examples*
|
||||
|
||||
I’ll be covering most of **NMAP** usage in two different parts and this is the first part of nmap serious. Here in this setup, I have used two servers without firewall to test the working of the Nmap command.
|
||||
|
||||
- 192.168.0.100 – server1.tecmint.com
|
||||
- 192.168.0.101 – server2.tecmint.com
|
||||
|
||||
### Nmap command usage ###
|
||||
|
||||
# nmap [Scan Type(s)] [Options] {target specification}
|
||||
|
||||
### How to Install NMAP in Linux ###
|
||||
|
||||
Most of the today’s Linux distributions like **Red Hat, CentOS, Fedoro, Debian** and **Ubuntu** have included **Nmap** in their default package management repositories called [Yum][1] and [APT][2]. The both tools are used to install and manage software packages and updates. To install **Nmap** on distribution specific use the following command.
|
||||
|
||||
# yum install nmap [on Red Hat based systems]
|
||||
$ sudo apt-get install nmap [on Debian based systems]
|
||||
|
||||
Once you’ve install latest nmap application, you can follow the example instructions provided in this article.
|
||||
|
||||
### 1. Scan a System with Hostname and IP Address ###
|
||||
|
||||
The **Nmap** tool offers various methods to scan a system. In this example, I am performing a scan using hostname as **server2.tecmint.com** to find out all open ports, services and MAC address on the system.
|
||||
|
||||
#### Scan using Hostname ####
|
||||
|
||||
[root@server1 ~]# nmap server2.tecmint.com
|
||||
|
||||
Starting Nmap 4.11 ( http://www.insecure.org/nmap/ ) at 2013-11-11 15:42 EST
|
||||
Interesting ports on server2.tecmint.com (192.168.0.101):
|
||||
Not shown: 1674 closed ports
|
||||
PORT STATE SERVICE
|
||||
22/tcp open ssh
|
||||
80/tcp open http
|
||||
111/tcp open rpcbind
|
||||
957/tcp open unknown
|
||||
3306/tcp open mysql
|
||||
8888/tcp open sun-answerbook
|
||||
MAC Address: 08:00:27:D9:8E:D7 (Cadmus Computer Systems)
|
||||
|
||||
Nmap finished: 1 IP address (1 host up) scanned in 0.415 seconds
|
||||
You have new mail in /var/spool/mail/root
|
||||
|
||||
#### Scan using IP Address ####
|
||||
|
||||
[root@server1 ~]# nmap 192.168.0.101
|
||||
|
||||
Starting Nmap 4.11 ( http://www.insecure.org/nmap/ ) at 2013-11-18 11:04 EST
|
||||
Interesting ports on server2.tecmint.com (192.168.0.101):
|
||||
Not shown: 1674 closed ports
|
||||
PORT STATE SERVICE
|
||||
22/tcp open ssh
|
||||
80/tcp open http
|
||||
111/tcp open rpcbind
|
||||
958/tcp open unknown
|
||||
3306/tcp open mysql
|
||||
8888/tcp open sun-answerbook
|
||||
MAC Address: 08:00:27:D9:8E:D7 (Cadmus Computer Systems)
|
||||
|
||||
Nmap finished: 1 IP address (1 host up) scanned in 0.465 seconds
|
||||
You have new mail in /var/spool/mail/root
|
||||
|
||||
### 2. Scan using “-v” option ###
|
||||
|
||||
You can see that the below command with “**-v**” option is giving more detailed information about the remote machine.
|
||||
|
||||
[root@server1 ~]# nmap -v server2.tecmint.com
|
||||
|
||||
Starting Nmap 4.11 ( http://www.insecure.org/nmap/ ) at 2013-11-11 15:43 EST
|
||||
Initiating ARP Ping Scan against 192.168.0.101 [1 port] at 15:43
|
||||
The ARP Ping Scan took 0.01s to scan 1 total hosts.
|
||||
Initiating SYN Stealth Scan against server2.tecmint.com (192.168.0.101) [1680 ports] at 15:43
|
||||
Discovered open port 22/tcp on 192.168.0.101
|
||||
Discovered open port 80/tcp on 192.168.0.101
|
||||
Discovered open port 8888/tcp on 192.168.0.101
|
||||
Discovered open port 111/tcp on 192.168.0.101
|
||||
Discovered open port 3306/tcp on 192.168.0.101
|
||||
Discovered open port 957/tcp on 192.168.0.101
|
||||
The SYN Stealth Scan took 0.30s to scan 1680 total ports.
|
||||
Host server2.tecmint.com (192.168.0.101) appears to be up ... good.
|
||||
Interesting ports on server2.tecmint.com (192.168.0.101):
|
||||
Not shown: 1674 closed ports
|
||||
PORT STATE SERVICE
|
||||
22/tcp open ssh
|
||||
80/tcp open http
|
||||
111/tcp open rpcbind
|
||||
957/tcp open unknown
|
||||
3306/tcp open mysql
|
||||
8888/tcp open sun-answerbook
|
||||
MAC Address: 08:00:27:D9:8E:D7 (Cadmus Computer Systems)
|
||||
|
||||
Nmap finished: 1 IP address (1 host up) scanned in 0.485 seconds
|
||||
Raw packets sent: 1681 (73.962KB) | Rcvd: 1681 (77.322KB)
|
||||
|
||||
#### Scan Multiple Hosts ####
|
||||
|
||||
You can scan multiple hosts by simply writing their IP addresses or hostnames with Nmap.
|
||||
|
||||
[root@server1 ~]# nmap 192.168.0.101 192.168.0.102 192.168.0.103
|
||||
|
||||
Starting Nmap 4.11 ( http://www.insecure.org/nmap/ ) at 2013-11-11 16:06 EST
|
||||
Interesting ports on server2.tecmint.com (192.168.0.101):
|
||||
Not shown: 1674 closed ports
|
||||
PORT STATE SERVICE
|
||||
22/tcp open ssh
|
||||
80/tcp open http
|
||||
111/tcp open rpcbind
|
||||
957/tcp open unknown
|
||||
3306/tcp open mysql
|
||||
8888/tcp open sun-answerbook
|
||||
MAC Address: 08:00:27:D9:8E:D7 (Cadmus Computer Systems)
|
||||
Nmap finished: 3 IP addresses (1 host up) scanned in 0.580 seconds
|
||||
|
||||
### 4. Scan a whole Subnet ###
|
||||
|
||||
You can scan a whole subnet or IP range with Nmap by providing *** wildcard** with it.
|
||||
|
||||
[root@server1 ~]# nmap 192.168.0.*
|
||||
|
||||
Starting Nmap 4.11 ( http://www.insecure.org/nmap/ ) at 2013-11-11 16:11 EST
|
||||
Interesting ports on server1.tecmint.com (192.168.0.100):
|
||||
Not shown: 1677 closed ports
|
||||
PORT STATE SERVICE
|
||||
22/tcp open ssh
|
||||
111/tcp open rpcbind
|
||||
851/tcp open unknown
|
||||
|
||||
Interesting ports on server2.tecmint.com (192.168.0.101):
|
||||
Not shown: 1674 closed ports
|
||||
PORT STATE SERVICE
|
||||
22/tcp open ssh
|
||||
80/tcp open http
|
||||
111/tcp open rpcbind
|
||||
957/tcp open unknown
|
||||
3306/tcp open mysql
|
||||
8888/tcp open sun-answerbook
|
||||
MAC Address: 08:00:27:D9:8E:D7 (Cadmus Computer Systems)
|
||||
|
||||
Nmap finished: 256 IP addresses (2 hosts up) scanned in 5.550 seconds
|
||||
You have new mail in /var/spool/mail/root
|
||||
|
||||
On above output you can see that nmap scanned a whole subnet and gave the information about those hosts which are **Up** in the **Network**.
|
||||
|
||||
### 5. Scan Multiple Servers using last octet of IP address ###
|
||||
|
||||
You can perform scans on multiple IP address by simple specifying last octet of IP address. For example, here I performing a scan on IP addresses 192.168.0.101, 192.168.0.102 and 192.168.0.103.
|
||||
|
||||
[root@server1 ~]# nmap 192.168.0.101,102,103
|
||||
|
||||
Starting Nmap 4.11 ( http://www.insecure.org/nmap/ ) at 2013-11-11 16:09 EST
|
||||
Interesting ports on server2.tecmint.com (192.168.0.101):
|
||||
Not shown: 1674 closed ports
|
||||
PORT STATE SERVICE
|
||||
22/tcp open ssh
|
||||
80/tcp open http
|
||||
111/tcp open rpcbind
|
||||
957/tcp open unknown
|
||||
3306/tcp open mysql
|
||||
8888/tcp open sun-answerbook
|
||||
MAC Address: 08:00:27:D9:8E:D7 (Cadmus Computer Systems)
|
||||
|
||||
Nmap finished: 3 IP addresses (1 host up) scanned in 0.552 seconds
|
||||
You have new mail in /var/spool/mail/root
|
||||
|
||||
### 6. Scan list of Hosts from a File ###
|
||||
|
||||
If you have more hosts to scan and all host details are written in a file , you can directly ask nmap to read that file and perform scans. Let’s see how to do that.
|
||||
|
||||
Create a text file called “**nmaptest.txt**” and define all the IP addresses or hostname of the server that you want to do a scan.
|
||||
|
||||
[root@server1 ~]# cat > nmaptest.txt
|
||||
|
||||
localhost
|
||||
server2.tecmint.com
|
||||
192.168.0.101
|
||||
|
||||
Next, run the following command with “**iL**” option with nmap command to scan all listed IP address in the file.
|
||||
|
||||
[root@server1 ~]# nmap -iL nmaptest.txt
|
||||
|
||||
Starting Nmap 4.11 ( http://www.insecure.org/nmap/ ) at 2013-11-18 10:58 EST
|
||||
Interesting ports on localhost.localdomain (127.0.0.1):
|
||||
Not shown: 1675 closed ports
|
||||
PORT STATE SERVICE
|
||||
22/tcp open ssh
|
||||
25/tcp open smtp
|
||||
111/tcp open rpcbind
|
||||
631/tcp open ipp
|
||||
857/tcp open unknown
|
||||
|
||||
Interesting ports on server2.tecmint.com (192.168.0.101):
|
||||
Not shown: 1674 closed ports
|
||||
PORT STATE SERVICE
|
||||
22/tcp open ssh
|
||||
80/tcp open http
|
||||
111/tcp open rpcbind
|
||||
958/tcp open unknown
|
||||
3306/tcp open mysql
|
||||
8888/tcp open sun-answerbook
|
||||
MAC Address: 08:00:27:D9:8E:D7 (Cadmus Computer Systems)
|
||||
|
||||
Interesting ports on server2.tecmint.com (192.168.0.101):
|
||||
Not shown: 1674 closed ports
|
||||
PORT STATE SERVICE
|
||||
22/tcp open ssh
|
||||
80/tcp open http
|
||||
111/tcp open rpcbind
|
||||
958/tcp open unknown
|
||||
3306/tcp open mysql
|
||||
8888/tcp open sun-answerbook
|
||||
MAC Address: 08:00:27:D9:8E:D7 (Cadmus Computer Systems)
|
||||
|
||||
Nmap finished: 3 IP addresses (3 hosts up) scanned in 2.047 seconds
|
||||
|
||||
### 7. Scan an IP Address Range ###
|
||||
|
||||
You can specify an IP range while performing scan with Nmap.
|
||||
|
||||
[root@server1 ~]# nmap 192.168.0.101-110
|
||||
|
||||
Starting Nmap 4.11 ( http://www.insecure.org/nmap/ ) at 2013-11-11 16:09 EST
|
||||
Interesting ports on server2.tecmint.com (192.168.0.101):
|
||||
Not shown: 1674 closed ports
|
||||
PORT STATE SERVICE
|
||||
22/tcp open ssh
|
||||
80/tcp open http
|
||||
111/tcp open rpcbind
|
||||
957/tcp open unknown
|
||||
3306/tcp open mysql
|
||||
8888/tcp open sun-answerbook
|
||||
MAC Address: 08:00:27:D9:8E:D7 (Cadmus Computer Systems)
|
||||
|
||||
Nmap finished: 10 IP addresses (1 host up) scanned in 0.542 seconds
|
||||
|
||||
### 8. Scan Network Excluding Remote Hosts ###
|
||||
|
||||
You can exclude some hosts while performing a full network scan or when you are scanning with wildcards with “**–exclude**” option.
|
||||
|
||||
[root@server1 ~]# nmap 192.168.0.* --exclude 192.168.0.100
|
||||
|
||||
Starting Nmap 4.11 ( http://www.insecure.org/nmap/ ) at 2013-11-11 16:16 EST
|
||||
Interesting ports on server2.tecmint.com (192.168.0.101):
|
||||
Not shown: 1674 closed ports
|
||||
PORT STATE SERVICE
|
||||
22/tcp open ssh
|
||||
80/tcp open http
|
||||
111/tcp open rpcbind
|
||||
957/tcp open unknown
|
||||
3306/tcp open mysql
|
||||
8888/tcp open sun-answerbook
|
||||
MAC Address: 08:00:27:D9:8E:D7 (Cadmus Computer Systems)
|
||||
|
||||
Nmap finished: 255 IP addresses (1 host up) scanned in 5.313 seconds
|
||||
You have new mail in /var/spool/mail/root
|
||||
|
||||
### 9. Scan OS information and Traceroute ###
|
||||
|
||||
With Nmap, you can detect which OS and version is running on the remote host. To enable OS & version detection, script scanning and traceroute, we can use “**-A**” option with NMAP.
|
||||
|
||||
[root@server1 ~]# nmap -A 192.168.0.101
|
||||
|
||||
Starting Nmap 4.11 ( http://www.insecure.org/nmap/ ) at 2013-11-11 16:25 EST
|
||||
Interesting ports on server2.tecmint.com (192.168.0.101):
|
||||
Not shown: 1674 closed ports
|
||||
PORT STATE SERVICE VERSION
|
||||
22/tcp open ssh OpenSSH 4.3 (protocol 2.0)
|
||||
80/tcp open http Apache httpd 2.2.3 ((CentOS))
|
||||
111/tcp open rpcbind 2 (rpc #100000)
|
||||
957/tcp open status 1 (rpc #100024)
|
||||
3306/tcp open mysql MySQL (unauthorized)
|
||||
8888/tcp open http lighttpd 1.4.32
|
||||
MAC Address: 08:00:27:D9:8E:D7 (Cadmus Computer Systems)
|
||||
No exact OS matches for host (If you know what OS is running on it, see http://www.insecure.org/cgi-bin/nmap-submit.cgi).
|
||||
TCP/IP fingerprint:
|
||||
SInfo(V=4.11%P=i686-redhat-linux-gnu%D=11/11%Tm=52814B66%O=22%C=1%M=080027)
|
||||
TSeq(Class=TR%IPID=Z%TS=1000HZ)
|
||||
T1(Resp=Y%DF=Y%W=16A0%ACK=S++%Flags=AS%Ops=MNNTNW)
|
||||
T2(Resp=N)
|
||||
T3(Resp=Y%DF=Y%W=16A0%ACK=S++%Flags=AS%Ops=MNNTNW)
|
||||
T4(Resp=Y%DF=Y%W=0%ACK=O%Flags=R%Ops=)
|
||||
T5(Resp=Y%DF=Y%W=0%ACK=S++%Flags=AR%Ops=)
|
||||
T6(Resp=Y%DF=Y%W=0%ACK=O%Flags=R%Ops=)
|
||||
T7(Resp=Y%DF=Y%W=0%ACK=S++%Flags=AR%Ops=)
|
||||
PU(Resp=Y%DF=N%TOS=C0%IPLEN=164%RIPTL=148%RID=E%RIPCK=E%UCK=E%ULEN=134%DAT=E)
|
||||
|
||||
Uptime 0.169 days (since Mon Nov 11 12:22:15 2013)
|
||||
|
||||
Nmap finished: 1 IP address (1 host up) scanned in 22.271 seconds
|
||||
You have new mail in /var/spool/mail/root
|
||||
|
||||
In above Output, you can see that nmap is came up with TCP/IP fingerprint of the OS running on remote hosts and being more specific about the port and services running on the remote hosts.
|
||||
|
||||
### 10. Enable OS Detection with Nmap ###
|
||||
|
||||
Use the option “-O” and “-osscan-guess” also helps to discover OS information.
|
||||
|
||||
[root@server1 ~]# nmap -O server2.tecmint.com
|
||||
|
||||
Starting Nmap 4.11 ( http://www.insecure.org/nmap/ ) at 2013-11-11 17:40 EST
|
||||
Interesting ports on server2.tecmint.com (192.168.0.101):
|
||||
Not shown: 1674 closed ports
|
||||
PORT STATE SERVICE
|
||||
22/tcp open ssh
|
||||
80/tcp open http
|
||||
111/tcp open rpcbind
|
||||
957/tcp open unknown
|
||||
3306/tcp open mysql
|
||||
8888/tcp open sun-answerbook
|
||||
MAC Address: 08:00:27:D9:8E:D7 (Cadmus Computer Systems)
|
||||
No exact OS matches for host (If you know what OS is running on it, see http://www.insecure.org/cgi-bin/nmap-submit.cgi).
|
||||
TCP/IP fingerprint:
|
||||
SInfo(V=4.11%P=i686-redhat-linux-gnu%D=11/11%Tm=52815CF4%O=22%C=1%M=080027)
|
||||
TSeq(Class=TR%IPID=Z%TS=1000HZ)
|
||||
T1(Resp=Y%DF=Y%W=16A0%ACK=S++%Flags=AS%Ops=MNNTNW)
|
||||
T2(Resp=N)
|
||||
T3(Resp=Y%DF=Y%W=16A0%ACK=S++%Flags=AS%Ops=MNNTNW)
|
||||
T4(Resp=Y%DF=Y%W=0%ACK=O%Flags=Option -O and -osscan-guess also helps to discover OSR%Ops=)
|
||||
T5(Resp=Y%DF=Y%W=0%ACK=S++%Flags=AR%Ops=)
|
||||
T6(Resp=Y%DF=Y%W=0%ACK=O%Flags=R%Ops=)
|
||||
T7(Resp=Y%DF=Y%W=0%ACK=S++%Flags=AR%Ops=)
|
||||
PU(Resp=Y%DF=N%TOS=C0%IPLEN=164%RIPTL=148%RID=E%RIPCK=E%UCK=E%ULEN=134%DAT=E)
|
||||
|
||||
Uptime 0.221 days (since Mon Nov 11 12:22:16 2013)
|
||||
|
||||
Nmap finished: 1 IP address (1 host up) scanned in 11.064 seconds
|
||||
You have new mail in /var/spool/mail/root
|
||||
|
||||
### 11. Scan a Host to Detect Firewall ###
|
||||
|
||||
The below command will perform a scan on a remote host to detect if any packet filters or Firewall is used by host.
|
||||
|
||||
[root@server1 ~]# nmap -sA 192.168.0.101
|
||||
|
||||
Starting Nmap 4.11 ( http://www.insecure.org/nmap/ ) at 2013-11-11 16:27 EST
|
||||
All 1680 scanned ports on server2.tecmint.com (192.168.0.101) are UNfiltered
|
||||
MAC Address: 08:00:27:D9:8E:D7 (Cadmus Computer Systems)
|
||||
|
||||
Nmap finished: 1 IP address (1 host up) scanned in 0.382 seconds
|
||||
You have new mail in /var/spool/mail/root
|
||||
|
||||
### 12. Scan a Host to check its protected by Firewall ###
|
||||
|
||||
To scan a host if it is protected by any packet filtering software or Firewalls.
|
||||
|
||||
[root@server1 ~]# nmap -PN 192.168.0.101
|
||||
|
||||
Starting Nmap 4.11 ( http://www.insecure.org/nmap/ ) at 2013-11-11 16:30 EST
|
||||
Interesting ports on server2.tecmint.com (192.168.0.101):
|
||||
Not shown: 1674 closed ports
|
||||
PORT STATE SERVICE
|
||||
22/tcp open ssh
|
||||
80/tcp open http
|
||||
111/tcp open rpcbind
|
||||
957/tcp open unknown
|
||||
3306/tcp open mysql
|
||||
8888/tcp open sun-answerbook
|
||||
MAC Address: 08:00:27:D9:8E:D7 (Cadmus Computer Systems)
|
||||
|
||||
Nmap finished: 1 IP address (1 host up) scanned in 0.399 seconds
|
||||
|
||||
### 13. Find out Live hosts in a Network ###
|
||||
|
||||
With the help of “**-sP**” option we can simply check which hosts are live and up in Network, with this option nmap skips port detection and other things.
|
||||
|
||||
[root@server1 ~]# nmap -sP 192.168.0.*
|
||||
|
||||
Starting Nmap 4.11 ( http://www.insecure.org/nmap/ ) at 2013-11-18 11:01 EST
|
||||
Host server1.tecmint.com (192.168.0.100) appears to be up.
|
||||
Host server2.tecmint.com (192.168.0.101) appears to be up.
|
||||
MAC Address: 08:00:27:D9:8E:D7 (Cadmus Computer Systems)
|
||||
Nmap finished: 256 IP addresses (2 hosts up) scanned in 5.109 seconds
|
||||
|
||||
### 14. Perform a Fast Scan ###
|
||||
|
||||
You can perform a fast scan with “**-F**” option to scans for the ports listed in the nmap-services files and leaves all other ports.
|
||||
|
||||
[root@server1 ~]# nmap -F 192.168.0.101
|
||||
|
||||
Starting Nmap 4.11 ( http://www.insecure.org/nmap/ ) at 2013-11-11 16:47 EST
|
||||
Interesting ports on server2.tecmint.com (192.168.0.101):
|
||||
Not shown: 1234 closed ports
|
||||
PORT STATE SERVICE
|
||||
22/tcp open ssh
|
||||
80/tcp open http
|
||||
111/tcp open rpcbind
|
||||
3306/tcp open mysql
|
||||
8888/tcp open sun-answerbook
|
||||
MAC Address: 08:00:27:D9:8E:D7 (Cadmus Computer Systems)
|
||||
|
||||
Nmap finished: 1 IP address (1 host up) scanned in 0.322 seconds
|
||||
|
||||
### 15. Find Nmap version ###
|
||||
|
||||
You can find out Nmap version you are running on your machine with “**-V**” option.
|
||||
|
||||
[root@server1 ~]# nmap -V
|
||||
|
||||
Nmap version 4.11 ( http://www.insecure.org/nmap/ )
|
||||
You have new mail in /var/spool/mail/root
|
||||
|
||||
### 16. Scan Ports Consecutively ###
|
||||
|
||||
Use the “**-r**” flag to don’t randomize.
|
||||
|
||||
[root@server1 ~]# nmap -r 192.168.0.101
|
||||
|
||||
Starting Nmap 4.11 ( http://www.insecure.org/nmap/ ) at 2013-11-11 16:52 EST
|
||||
Interesting ports on server2.tecmint.com (192.168.0.101):
|
||||
Not shown: 1674 closed ports
|
||||
PORT STATE SERVICE
|
||||
22/tcp open ssh
|
||||
80/tcp open http
|
||||
111/tcp open rpcbind
|
||||
957/tcp open unknown
|
||||
3306/tcp open mysql
|
||||
8888/tcp open sun-answerbook
|
||||
MAC Address: 08:00:27:D9:8E:D7 (Cadmus Computer Systems)
|
||||
|
||||
Nmap finished: 1 IP address (1 host up) scanned in 0.363 seconds
|
||||
|
||||
17. Print Host interfaces and Routes
|
||||
|
||||
You can find out host interface and route information with nmap by using “**–iflist**” option.
|
||||
|
||||
[root@server1 ~]# nmap --iflist
|
||||
|
||||
Starting Nmap 4.11 ( http://www.insecure.org/nmap/ ) at 2013-11-11 17:07 EST
|
||||
************************INTERFACES************************
|
||||
DEV (SHORT) IP/MASK TYPE UP MAC
|
||||
lo (lo) 127.0.0.1/8 loopback up
|
||||
eth0 (eth0) 192.168.0.100/24 ethernet up 08:00:27:11:C7:89
|
||||
|
||||
**************************ROUTES**************************
|
||||
DST/MASK DEV GATEWAY
|
||||
192.168.0.0/0 eth0
|
||||
169.254.0.0/0 eth0
|
||||
|
||||
In above output, you can see that map is listing interfaces attached to your system and their respective routes.
|
||||
|
||||
### 18. Scan for specific Port ###
|
||||
|
||||
There are various options to discover ports on remote machine with Nmap. You can specify the port you want nmap to scan with “**-p**” option, by default nmap scans only **TCP** ports.
|
||||
|
||||
[root@server1 ~]# nmap -p 80 server2.tecmint.com
|
||||
|
||||
Starting Nmap 4.11 ( http://www.insecure.org/nmap/ ) at 2013-11-11 17:12 EST
|
||||
Interesting ports on server2.tecmint.com (192.168.0.101):
|
||||
PORT STATE SERVICE
|
||||
80/tcp open http
|
||||
MAC Address: 08:00:27:D9:8E:D7 (Cadmus Computer Systems)
|
||||
|
||||
Nmap finished: 1 IP address (1 host up) sca
|
||||
|
||||
### 19. Scan a TCP Port ###
|
||||
|
||||
You can also specify specific port types and numbers with nmap to scan.
|
||||
|
||||
[root@server1 ~]# nmap -p T:8888,80 server2.tecmint.com
|
||||
|
||||
Starting Nmap 4.11 ( http://www.insecure.org/nmap/ ) at 2013-11-11 17:15 EST
|
||||
Interesting ports on server2.tecmint.com (192.168.0.101):
|
||||
PORT STATE SERVICE
|
||||
80/tcp open http
|
||||
8888/tcp open sun-answerbook
|
||||
MAC Address: 08:00:27:D9:8E:D7 (Cadmus Computer Systems)
|
||||
|
||||
Nmap finished: 1 IP address (1 host up) scanned in 0.157 seconds
|
||||
|
||||
### 20. Scan a UDP Port ###
|
||||
|
||||
[root@server1 ~]# nmap -sU 53 server2.tecmint.com
|
||||
|
||||
Starting Nmap 4.11 ( http://www.insecure.org/nmap/ ) at 2013-11-11 17:15 EST
|
||||
Interesting ports on server2.tecmint.com (192.168.0.101):
|
||||
PORT STATE SERVICE
|
||||
53/udp open http
|
||||
8888/udp open sun-answerbook
|
||||
MAC Address: 08:00:27:D9:8E:D7 (Cadmus Computer Systems)
|
||||
|
||||
Nmap finished: 1 IP address (1 host up) scanned in 0.157 seconds
|
||||
|
||||
### 21. Scan Multiple Ports ###
|
||||
|
||||
You can also scan multiple ports using option “**-p**“.
|
||||
|
||||
[root@server1 ~]# nmap -p 80,443 192.168.0.101
|
||||
|
||||
Starting Nmap 4.11 ( http://www.insecure.org/nmap/ ) at 2013-11-18 10:56 EST
|
||||
Interesting ports on server2.tecmint.com (192.168.0.101):
|
||||
PORT STATE SERVICE
|
||||
80/tcp open http
|
||||
443/tcp closed https
|
||||
MAC Address: 08:00:27:D9:8E:D7 (Cadmus Computer Systems)
|
||||
|
||||
Nmap finished: 1 IP address (1 host up) scanned in 0.190 seconds
|
||||
|
||||
### 22. Scan Ports by Network Range ###
|
||||
|
||||
You can scan ports with ranges using expressions.
|
||||
|
||||
[root@server1 ~]# nmap -p 80-160 192.168.0.101
|
||||
|
||||
### 23. Find Host Services version Numbers ###
|
||||
|
||||
We can find out service’s versions which are running on remote hosts with “**-sV**” option.
|
||||
|
||||
[root@server1 ~]# nmap -sV 192.168.0.101
|
||||
|
||||
Starting Nmap 4.11 ( http://www.insecure.org/nmap/ ) at 2013-11-11 17:48 EST
|
||||
Interesting ports on server2.tecmint.com (192.168.0.101):
|
||||
Not shown: 1674 closed ports
|
||||
PORT STATE SERVICE VERSION
|
||||
22/tcp open ssh OpenSSH 4.3 (protocol 2.0)
|
||||
80/tcp open http Apache httpd 2.2.3 ((CentOS))
|
||||
111/tcp open rpcbind 2 (rpc #100000)
|
||||
957/tcp open status 1 (rpc #100024)
|
||||
3306/tcp open mysql MySQL (unauthorized)
|
||||
8888/tcp open http lighttpd 1.4.32
|
||||
MAC Address: 08:00:27:D9:8E:D7 (Cadmus Computer Systems)
|
||||
|
||||
Nmap finished: 1 IP address (1 host up) scanned in 12.624 seconds
|
||||
|
||||
#### 24. Scan remote hosts using TCP ACK (PA) and TCP Syn (PS) ####
|
||||
|
||||
Sometimes packet filtering firewalls blocks standard **ICMP** ping requests, in that case, we can use **TCP ACK** and **TCP Syn** methods to scan remote hosts.
|
||||
|
||||
[root@server1 ~]# nmap -PS 192.168.0.101
|
||||
|
||||
Starting Nmap 4.11 ( http://www.insecure.org/nmap/ ) at 2013-11-11 17:51 EST
|
||||
Interesting ports on server2.tecmint.com (192.168.0.101):
|
||||
Not shown: 1674 closed ports
|
||||
PORT STATE SERVICE
|
||||
22/tcp open ssh
|
||||
80/tcp open http
|
||||
111/tcp open rpcbind
|
||||
957/tcp open unknown
|
||||
3306/tcp open mysql
|
||||
8888/tcp open sun-answerbook
|
||||
MAC Address: 08:00:27:D9:8E:D7 (Cadmus Computer Systems)
|
||||
|
||||
Nmap finished: 1 IP address (1 host up) scanned in 0.360 seconds
|
||||
You have new mail in /var/spool/mail/root
|
||||
|
||||
### 25. Scan Remote host for specific ports with TCP ACK ###
|
||||
|
||||
[root@server1 ~]# nmap -PA -p 22,80 192.168.0.101
|
||||
|
||||
Starting Nmap 4.11 ( http://www.insecure.org/nmap/ ) at 2013-11-11 18:02 EST
|
||||
Interesting ports on server2.tecmint.com (192.168.0.101):
|
||||
PORT STATE SERVICE
|
||||
22/tcp open ssh
|
||||
80/tcp open http
|
||||
MAC Address: 08:00:27:D9:8E:D7 (Cadmus Computer Systems)
|
||||
|
||||
Nmap finished: 1 IP address (1 host up) scanned in 0.166 seconds
|
||||
You have new mail in /var/spool/mail/root
|
||||
|
||||
### 26. Scan Remote host for specific ports with TCP Syn ###
|
||||
|
||||
[root@server1 ~]# nmap -PS -p 22,80 192.168.0.101
|
||||
|
||||
Starting Nmap 4.11 ( http://www.insecure.org/nmap/ ) at 2013-11-11 18:08 EST
|
||||
Interesting ports on server2.tecmint.com (192.168.0.101):
|
||||
PORT STATE SERVICE
|
||||
22/tcp open ssh
|
||||
80/tcp open http
|
||||
MAC Address: 08:00:27:D9:8E:D7 (Cadmus Computer Systems)
|
||||
|
||||
Nmap finished: 1 IP address (1 host up) scanned in 0.165 seconds
|
||||
You have new mail in /var/spool/mail/root
|
||||
|
||||
### 27. Perform a stealthy Scan ###
|
||||
|
||||
[root@server1 ~]# nmap -sS 192.168.0.101
|
||||
|
||||
Starting Nmap 4.11 ( http://www.insecure.org/nmap/ ) at 2013-11-11 18:10 EST
|
||||
Interesting ports on server2.tecmint.com (192.168.0.101):
|
||||
Not shown: 1674 closed ports
|
||||
PORT STATE SERVICE
|
||||
22/tcp open ssh
|
||||
80/tcp open http
|
||||
111/tcp open rpcbind
|
||||
957/tcp open unknown
|
||||
3306/tcp open mysql
|
||||
8888/tcp open sun-answerbook
|
||||
MAC Address: 08:00:27:D9:8E:D7 (Cadmus Computer Systems)
|
||||
|
||||
Nmap finished: 1 IP address (1 host up) scanned in 0.383 seconds
|
||||
You have new mail in /var/spool/mail/root
|
||||
|
||||
### 28. Check most commonly used Ports with TCP Syn ###
|
||||
|
||||
[root@server1 ~]# nmap -sT 192.168.0.101
|
||||
|
||||
Starting Nmap 4.11 ( http://www.insecure.org/nmap/ ) at 2013-11-11 18:12 EST
|
||||
Interesting ports on server2.tecmint.com (192.168.0.101):
|
||||
Not shown: 1674 closed ports
|
||||
PORT STATE SERVICE
|
||||
22/tcp open ssh
|
||||
80/tcp open http
|
||||
111/tcp open rpcbind
|
||||
957/tcp open unknown
|
||||
3306/tcp open mysql
|
||||
8888/tcp open sun-answerbook
|
||||
MAC Address: 08:00:27:D9:8E:D7 (Cadmus Computer Systems)
|
||||
|
||||
Nmap finished: 1 IP address (1 host up) scanned in 0.406 seconds
|
||||
You have new mail in /var/spool/mail/root
|
||||
|
||||
### 29. Perform a tcp null scan to fool a firewall ###
|
||||
|
||||
[root@server1 ~]# nmap -sN 192.168.0.101
|
||||
|
||||
Starting Nmap 4.11 ( http://www.insecure.org/nmap/ ) at 2013-11-11 19:01 EST
|
||||
Interesting ports on server2.tecmint.com (192.168.0.101):
|
||||
Not shown: 1674 closed ports
|
||||
PORT STATE SERVICE
|
||||
22/tcp open|filtered ssh
|
||||
80/tcp open|filtered http
|
||||
111/tcp open|filtered rpcbind
|
||||
957/tcp open|filtered unknown
|
||||
3306/tcp open|filtered mysql
|
||||
8888/tcp open|filtered sun-answerbook
|
||||
MAC Address: 08:00:27:D9:8E:D7 (Cadmus Computer Systems)
|
||||
|
||||
Nmap finished: 1 IP address (1 host up) scanned in 1.584 seconds
|
||||
You have new mail in /var/spool/mail/root
|
||||
|
||||
That’s it with **NMAP** for now, I’ll be coming up more creative options of **NMAP** in our second part of this serious. Till then, stay tuned with us and don’t forget to share your valuable comments.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.tecmint.com/nmap-command-examples/
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.tecmint.com/20-linux-yum-yellowdog-updater-modified-commands-for-package-mangement/
|
||||
[2]:http://www.tecmint.com/useful-basic-commands-of-apt-get-and-apt-cache-for-package-management/
|
||||
@ -1,63 +0,0 @@
|
||||
Translate by SteveArcher╮(╯▽╰)╭
|
||||
7 Tips For Becoming A Linux Terminal Power User
|
||||
================================================================================
|
||||
The Linux terminal is much more than merely entering commands into it. If you master the basic tricks, it will assist you in mastering the Bash shell that is used as default on a number of Linux distributions.
|
||||
|
||||
As stated on howtogeek.com, here are some tips for new users as well as advanced users who may have missed out on something along the way-
|
||||
|
||||
**1. Tab Completion** – This saves time and is also handy if you’re unsure of a file or command’s exact name. For instance, there’s a file named “really long file name” in the current directory and you wish to delete it. You can type the entire file name, however, you will have to ensure that you escape the space characters properly. In case of multiple files in the current directory which start with the letter r, Bash will not be aware of the one you want.
|
||||
|
||||
In the event you have another file named “really very long file name” in the current directory and you hit Tab. Bash will fill in the “really\ “ part for both the files start with that. Post that press Tab again and you’ll find a list of matching file names.
|
||||
|
||||
**2. Pipes** – This permits you to transmit the output of a command to another command. In the UNIX philosophy, every program is a small utility that performs one thing well. For instance, the ls command lists out the files in the current directory and the grep command searches its input for a specified term.
|
||||
|
||||
You can combine these with pipes (the | character) and search for a file in the current directory. The command given below searches for the word “word”:
|
||||
|
||||
ls | grep word
|
||||
|
||||
**3. Wild Cards** - The * (asterisk) character is a wild card for matching anything. For instance, if you want to delete both “really long file name” and “really very long file name” from the current directory, you can run the following command:
|
||||
|
||||
rm really*name
|
||||
|
||||
This command deletes all files with file names starting with “really” and ending with “name.” However, in case you ran rm * instead, you would end up deleting every file in the current directory.
|
||||
|
||||
**4. Output Redirection** - The > character redirects a command’s output to a file in place of another command. For instance, the following line runs the ls command to list the files in the current directory and in lieu of printing that list to the terminal, it prints to a file named “file1” in the current directory:
|
||||
|
||||
ls > file1
|
||||
|
||||
**5. Command History** – Bash memorizes history of the commands you enter into it. The up and down arrow keys can be used to scroll through recent commands used by you. The history command prints out a list of these commands for piping it to grep in order to search for commands used by you recently.
|
||||
|
||||
~, . & ..
|
||||
|
||||
The ~ character also called the tilde is used to show the current user’s home directory. So in lieu of typing cd /home/name for going to your home directory, you can type cd ~. This also functions with relative paths – cd ~/Desktop to go to the current user’s desktop.
|
||||
|
||||
In the same way, the . is for the current directory and the .. is for the directory above the current directory. So, cd .. goes up a directory. It functions with relative paths for instance when you are in your Desktop folder and wish to go to the Documents folder, that is in the same directory as the Desktop folder, you can make use of the cd ../Documents command.
|
||||
|
||||
**6. Running a Command in the Background** – Bash by default executes every command that is run by you in the current terminal. It’s normally okay but what if you wish to launch an application and maintain utilizing the terminal? By typing firefox for launching Firefox, it will take charge of your terminal and show error messages and other output till you have closed it. You can use the & operator to the end of the command for Bash to execute the program in the backdrop.
|
||||
|
||||
firefox &
|
||||
|
||||
**7. Conditional Execution** – Bash can also run two commands sequentially. The second command can only execute when the first command is completed with success. For doing this, you can put both commands on the same line segregated by a &&, or double ampersand. The command given below will wait for five seconds, and start the gnome-screenshot tool:
|
||||
|
||||
sleep 5 && gnome-screenshot
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.efytimes.com/e1/fullnews.asp?edid=123564
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:
|
||||
[2]:
|
||||
[3]:
|
||||
[4]:
|
||||
[5]:
|
||||
[6]:
|
||||
[7]:
|
||||
[8]:
|
||||
[9]:
|
||||
[10]:
|
||||
[11]:
|
||||
[12]:
|
||||
@ -1,166 +0,0 @@
|
||||
translated by coolpigs
|
||||
|
||||
Basic Linux Interview Questions and Answers – Part II
|
||||
================================================================================
|
||||
Continuing the Interview Series, we are giving 10 Questions here, in this article. These questions and the questions in the future articles doesn’t necessarily means they were asked in any interview. We are presenting you an interactive learning platform through these kind of posts, which surely will be helpful.
|
||||
|
||||

|
||||
|
||||
Upon the analysis of comments in different forums on last article [11 Basic Linux Interview Questions][1] of this series, it is important to mention here that to bring up a quality article to our readers. We give our time and money, and in return what we expect from you? Nothing. If you can’t praise our work, please don’t demoralize us from your negative comments.
|
||||
|
||||
If you find nothing new in a post, don’t forget that for someone it was helpful, and for that he/she was thankful. We can’t make everyone happy in each of our article. Hope you readers would take pain to understand this.
|
||||
|
||||
### Q.1: Which command is used to record a user login session in a file? ###
|
||||
|
||||
- macro
|
||||
- read
|
||||
- script
|
||||
- record
|
||||
- sessionrecord
|
||||
|
||||
> **Answer** : The ‘script’ command is used to record a user’s login session in a file. Script command can be implemented in a shell script or can directly be used in terminal. Here is an example which records everything between script and exit.
|
||||
|
||||
Let’s record the user’s login session with script command as shown.
|
||||
|
||||
[root@tecmint ~]# script my-session-record.txt
|
||||
|
||||
Script started, file is my-session-record.txt
|
||||
|
||||
The content of log file ‘my-session-record.txt’ can be views as:
|
||||
|
||||
[root@tecmint ~]# nano my-session-record.txt
|
||||
|
||||
script started on Friday 22 November 2013 08:19:01 PM IST
|
||||
[root@tecmint ~]# ls
|
||||
^[[0m^[[01;34mBinary^[[0m ^[[01;34mDocuments^[[0m ^[[01;34mMusic^[[0m $
|
||||
^[[01;34mDesktop^[[0m ^[[01;34mDownloads^[[0m my-session-record.txt ^[[01;34$
|
||||
|
||||
### Q.2: The kernel log message can be viewed using which of the following command? ###
|
||||
|
||||
- dmesg
|
||||
- kernel
|
||||
- ls -i
|
||||
- uname
|
||||
- None of the above
|
||||
|
||||
> **Answer** : The kernel log message can be viewed by executing 'dmesg' command. In the list kernel is not a valid Linux command, 'ls -i' lists the file with inode within the working directory and 'uname' command shows os.
|
||||
|
||||
[root@tecmint ~]# dmesg
|
||||
|
||||
Initializing cgroup subsys cpuset
|
||||
Initializing cgroup subsys cpu
|
||||
Linux version 2.6.32-279.el6.i686 (mockbuild@c6b9.bsys.dev.centos.org) (gcc version 4.4.6 20120305 (Red Hat 4.4.6-4) (GCC) ) #1 SMP Fri Jun 22 10:59:55 UTC 2012
|
||||
KERNEL supported cpus:
|
||||
Intel GenuineIntel
|
||||
AMD AuthenticAMD
|
||||
NSC Geode by NSC
|
||||
Cyrix CyrixInstead
|
||||
Centaur CentaurHauls
|
||||
Transmeta GenuineTMx86
|
||||
Transmeta TransmetaCPU
|
||||
UMC UMC UMC UMC
|
||||
Disabled fast string operations
|
||||
BIOS-provided physical RAM map:
|
||||
...
|
||||
|
||||
### Q.3: Which command is used to display the release of Linux Kernel? ###
|
||||
|
||||
- uname -v
|
||||
- uname -r
|
||||
- uname -m
|
||||
- uname -n
|
||||
- uname -o
|
||||
|
||||
> **Answer** : The command ‘uname -r’ display the kernel release information. The switch ‘-v’ , ‘-m’ , ‘-n’ , ‘o’ display kernel version, machine hardware name, network node, hostname and operating system, respectively.
|
||||
|
||||
[root@tecmint ~]# uname -r
|
||||
|
||||
2.6.32-279.el6.i686
|
||||
|
||||
### Q.4: Which command is used to identify the types of file? ###
|
||||
|
||||
- type
|
||||
- info
|
||||
- file
|
||||
- which
|
||||
- ls
|
||||
|
||||
> **Answer** : The ‘file’ command is used to identify the types of file. The syntax is ‘file [option] File_name’.
|
||||
|
||||
[root@tecmint ~]# file wtop
|
||||
|
||||
wtop: POSIX shell script text executable
|
||||
|
||||
### Q.5: Which command locate the binary, source and man page of a command? ###
|
||||
|
||||
> **Answer** : The ‘whereis’ command comes to rescue here. The ‘whereis’ command locate the binary, source, and manual page files for a command.
|
||||
|
||||
[root@tecmint ~]# whereis /usr/bin/ftp
|
||||
|
||||
ftp: /usr/bin/ftp /usr/share/man/man1/ftp.1.gz
|
||||
|
||||
### Q.6: When a user login, which files are called for user profile, by default?? ###
|
||||
|
||||
> **Answer** : The ‘.profile’ and ‘.bashrc’ present under home directory are called for user profile by default.
|
||||
|
||||
[root@tecmint ~]# ls -al
|
||||
-rw-r--r--. 1 tecmint tecmint 176 May 11 2012 .bash_profile
|
||||
-rw-r--r--. 1 tecmint tecmint 124 May 11 2012 .bashrc
|
||||
|
||||
### ###Q.7: The ‘resolve.conf’ file is a configuration file for?
|
||||
|
||||
> **Answer** : The ‘/etc/resolve.conf’ is the configuration file for DNS at client side.
|
||||
|
||||
[root@tecmint ~]# cat /etc/resolv.conf
|
||||
|
||||
nameserver 172.16.16.94
|
||||
|
||||
### Q.8: Which command is used to create soft link of a file? ###
|
||||
|
||||
- ln
|
||||
- ln -s
|
||||
- link
|
||||
- link -soft
|
||||
- None of the above
|
||||
|
||||
> **Answer** : The ‘ln -s’ command is used to create soft link of a file in Linux Environment.
|
||||
|
||||
[root@tecmint ~]# ln -s /etc/httpd/conf/httpd.conf httpd.original.conf
|
||||
|
||||
### Q.9: The command ‘pwd’ is an alias of command ‘passwd’ in Linux? ###
|
||||
|
||||
> **Answer** : No! The command ‘pwd’ is not an alias of command ‘passwd’ by default. ‘pwd’ stands for ‘print working directory’, which shows current directory and ‘passwd is used to change the password of user account in Linux.
|
||||
|
||||
[root@tecmint ~]# pwd
|
||||
|
||||
/home/tecmint
|
||||
|
||||
[root@tecmint ~]# passwd
|
||||
Changing password for user root.
|
||||
New password:
|
||||
Retype new password:
|
||||
|
||||
### Q.10: How will you check pci devices vendor and version on a Linux? ###
|
||||
|
||||
> **Answer** : The Linux command ‘lspci’ comes to rescue here.
|
||||
|
||||
[root@tecmint ~]# lspci
|
||||
|
||||
00:00.0 Host bridge: Intel Corporation 5000P Chipset Memory Controller Hub (rev b1)
|
||||
00:02.0 PCI bridge: Intel Corporation 5000 Series Chipset PCI Express x8 Port 2-3 (rev b1)
|
||||
00:04.0 PCI bridge: Intel Corporation 5000 Series Chipset PCI Express x8 Port 4-5 (rev b1)
|
||||
00:06.0 PCI bridge: Intel Corporation 5000 Series Chipset PCI Express x8 Port 6-7 (rev b1)
|
||||
00:08.0 System peripheral: Intel Corporation 5000 Series Chipset DMA Engine (rev b1)
|
||||
...
|
||||
|
||||
That’s all for now. I hope these above questions might be very helpful to you. In our next weekend we again come-up with some new set of questions. Till then stay healthy, tuned and connected to Tecmint.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.tecmint.com/basic-linux-interview-questions-and-answers-part-ii/
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.tecmint.com/basic-linux-interview-questions-and-answers/
|
||||
@ -1,44 +0,0 @@
|
||||
Canonical Dev Calls Linux Mint ‘Vulnerable’, Wouldn’t Use it For Online Banking
|
||||
================================================================================
|
||||
> Linux Mint has since responded to the comments by Oliver Grawert. [You can read them here][1].
|
||||
|
||||
**Users of the popular Ubuntu-based operating system Linux Mint should not use it for online banking, a Canonical [engineer has advised][2].**
|
||||
|
||||
Mint’s decision to prevent packages with known security issues from updating – from the kernel and browser to the boot-loader and Xorg display server – leaves its users with a “vulnerable system”, says *Oliver Grawert*.
|
||||
|
||||
> “Instead of just integrating changes properly with the packages in the ubuntu archive they instead suppress doing (security) updates at all for them. i would say forcefully keeping a vulnerable kernel browser or xorg in place instead of allowing the provided security updates to be installer makes it a vulnerable system, (sic)”.
|
||||
>
|
||||
> “I personally wouldn’t do online banking with it.”
|
||||
|
||||
Grawert certainly isn’t alone in considering Mint a sub-par choice for the security conscious. Mozilla contributor and former Ubuntu member Benjamin **Kerensa* feels the same:**
|
||||
|
||||
> “It is unclear why Linux Mint disables all of their security updates. I can say that it took them many months to get a fixed version of Firefox packaged while Ubuntu and Debian had already had security fixes in their package.
|
||||
>
|
||||
> This puts Linux Mint users at risk and is one of the key reasons I never suggest Linux Mint to anyone as an alternative to Ubuntu.”
|
||||
|
||||
Oliver Grawert is no fly-by-night contributor. As one of Canonical’s Ubuntu Engineering bods he’s better placed than most to know what he’s talking about.
|
||||
|
||||
> ‘But are Mint users in actual risk? Yes and no…’
|
||||
|
||||
But are Mint users in actual risk?
|
||||
|
||||
Yes and no. The majority of security “holes” (for want of a better word) of the kind present in the packages that Mint’s developers steadfastly refuse to update are both documented and known, but rarely exploited by those of a nefarious breed. As such the “actual threat” posed to users remains, at least for now, largely a theoretical one.
|
||||
|
||||
That’s to say that there are no known incidents of identify theft or worse resulting from use of Mint (or any other Ubuntu-based distribution with unpatched packages) through any of the exploits referenced by Grawert on the Ubuntu Dev Mailing List.
|
||||
|
||||
But just because no-one has entered through the window left ajar thus far, isn’t to say someone won’t ever do it.
|
||||
|
||||
**After seeing Ubuntu given a long and sustained kicking about its own (largely theoretical) privacy issues, it will be interesting to see if, now the boot is placed firmly on the other foot, the vehement concern for users’ wellbeing will extend to other distributions. **
|
||||
|
||||
Notice: We reached out to Linux Mint for comment & clarification but received no reply.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.omgubuntu.co.uk/2013/11/canonical-dev-dont-use-linux-mint-online-banking-unsecure
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:这个地址在发布的时候填写成“Linux Mint Respond to Ubuntu Developer’s ‘Vulnerable’ Claim”这篇文章的发布的地址
|
||||
[2]:https://lists.ubuntu.com/archives/ubuntu-devel-discuss/2013-November/014770.html
|
||||
@ -1,3 +1,4 @@
|
||||
[translated BY stduolc]
|
||||
Canonical and ASUS Have Formed a Partnership in USA
|
||||
================================================================================
|
||||
**Canonical and ASUS have formed a partnership that would enable the hardware vendor to equip a couple of its laptops with the Ubuntu operating system.**
|
||||
|
||||
@ -1,133 +0,0 @@
|
||||
Vic020的WC
|
||||
CentOS 6.5 desktop installation guide with screenshots
|
||||
================================================================================
|
||||
### CentOS 6.5 released ###
|
||||
|
||||
Following with the release of RHEL 6.5, [CentOS 6.5 has arrived][1] on 1st Dec and its time to play with it. For those who want to update their existing 6.4 systems to 6.5 simply use the "yum update" command and all the magic would be done.
|
||||
|
||||
CentOS 6.5 has received some package updates as well as new features. Check out the [release notes][2] for detailed information.
|
||||
|
||||
### Major updates ###
|
||||
|
||||
> The Precision Time Protocol - previously a technology preview - is now fully supported. The following drivers support network time stamping: bnx2x, tg3, e1000e, igb, ixgbe, and sfc.
|
||||
> OpenSSL has been updated to version 1.0.1.
|
||||
> OpenSSL and NSS now support TLS 1.1 and 1.2.
|
||||
> KVM received various enhancements. These include improved read-only support of VMDK- and VHDX-Files, CPU hot plugging and updated virt-v2v-/virt-p2v-conversion tools.
|
||||
> Hyper-V and VMware drivers have been updated.
|
||||
> Updates to Evolution (2.32) and Libre Office (4.0.4).
|
||||
|
||||
### Download ###
|
||||
|
||||
In this post we shall be installing it on the desktop. Head to either of the following urls
|
||||
|
||||
[http://isoredirect.centos.org/centos-6/6.5/isos/][3]
|
||||
[http://mirror.centos.org/centos/6.5/isos/][4]
|
||||
|
||||
Select your machine architecture and it will then present a list of mirrors. Get into any mirror and then get the torrent file to download or the direct iso download link. There are multiple download options available like LiveCD, LiveDVD, Dvd1+2, Minimal and Netinstall.
|
||||
|
||||
The minimal installer comes with a text based installer that would install CentOS with a shell and minimum software applications. Rest everything has to be installed from yum.
|
||||
|
||||
The LiveCD/LiveDVD provide the desktop and gui installer and installs the CentOS system but does not provide any package selection options.
|
||||
|
||||
The DvD1+2 set provide full set of all applications for those who need it.
|
||||
And the netinstall would actually download the installation image and then install.
|
||||
|
||||
In this post we shall use the LiveCD. It is around 650MB.
|
||||
Although CentOS is used mostly on servers, having a desktop system can help to create a gui based environment with a setup similar to your server. We shall be trying out the minimal and netinstall installation methods in another post.
|
||||
|
||||
### Install ###
|
||||
|
||||
So now, its time to install CentOS onto your desktop system. Use either the LiveDVD or LiveCD to get it up and running fast.
|
||||
|
||||
1. Put in the media and reboot. The boot menu will have many options with self explanatory names. Select Boot to get onto the Live desktop.
|
||||
|
||||
|
||||
|
||||
2. Double clicks the Install icon on the desktop, to start the Anaconda installer.
|
||||
|
||||
|
||||
|
||||
3. Click Next on the installer wizard.
|
||||
|
||||

|
||||
|
||||
4. **Keyboard layout** - The next step would ask you to select the keyboard layout which should be USA for most english users.
|
||||
|
||||

|
||||
|
||||
5. **Storage type** - After the keyboard layout, comes the option select the type of storage on which CentOS is to be installed. For local hard drives, its Basic storage.
|
||||
|
||||

|
||||
|
||||
6. **Hostname** - In the next step the anaconda installer asks for a hostname. So fill it appropriately. If not sure, just enter something like mypc or hplaptop.
|
||||
|
||||

|
||||
|
||||
7. **Timezone** - Then comes the timezone selection
|
||||
|
||||
|
||||
|
||||
8. **Root Password** - Next in turn is the root password which, as you know should be a strong one.
|
||||
|
||||
|
||||
|
||||
9. **Formatting** - Now the wizard would like to know, how you wan't to format the storage device. If you want to format the drive yourself, then select "Custom Layout" and create partitions as needed. For the sake of this tutorial we are selecting the first option, that is to use the entire device and let CentOS format it as it likes.
|
||||
|
||||
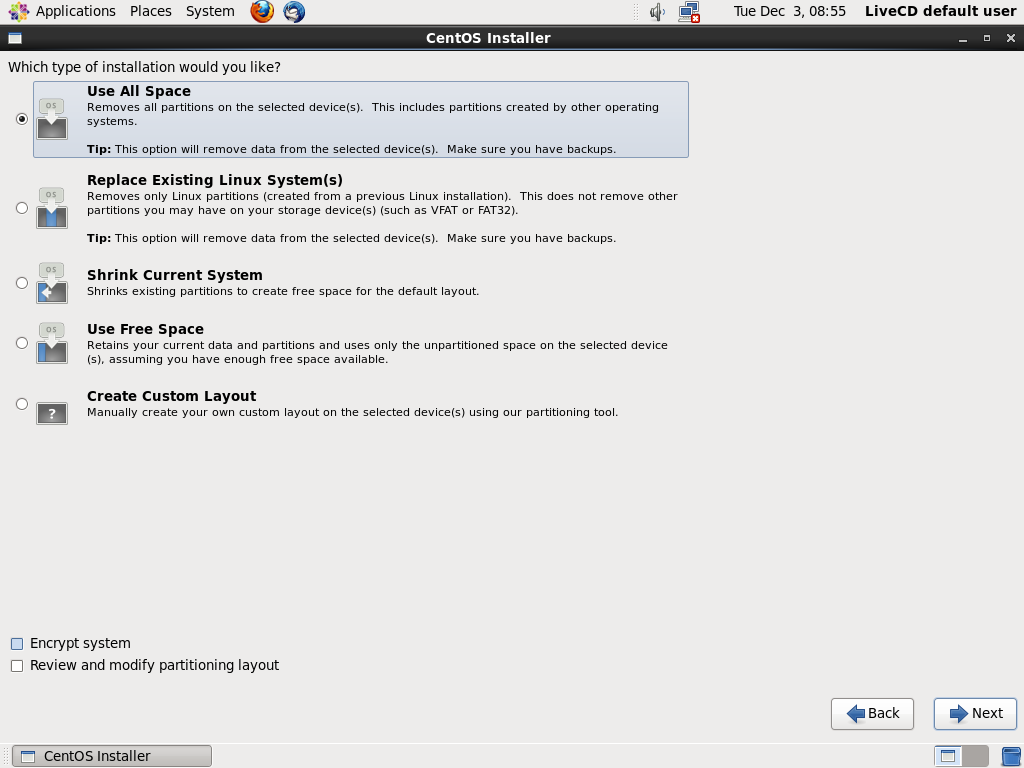
|
||||
|
||||
10. **Copying files** - Now the installer will start copying files. Nothing to do here except wait and watch. The LiveCD installer basically copies the CD image to the hard drive. You do not get any option to select packages to install or omit. Also the liveCD somes with a minimal collection of software and applications.
|
||||
|
||||

|
||||
|
||||
### Post install configuration ###
|
||||
|
||||
11. After the installation completes and reboots, the welcome wizard would come up which would further configure the system.
|
||||
|
||||

|
||||
|
||||
12. License Agreement - Like all software centos too comes with a license that is very minimal and only a few lines. So accept it.
|
||||
|
||||
|
||||
|
||||
13. **Create User** - Now its time to create a user account for yourself to be able to use the system.
|
||||
|
||||
|
||||
|
||||
14. **Current date & time** - Now input the current date and time and select the option to synchronize over the network.
|
||||
|
||||
|
||||
|
||||
15. **Kdump** - This is the last step of the welcome wizard that asks whether kdump should be enabled or not. It is a good idea to enable it.
|
||||
|
||||
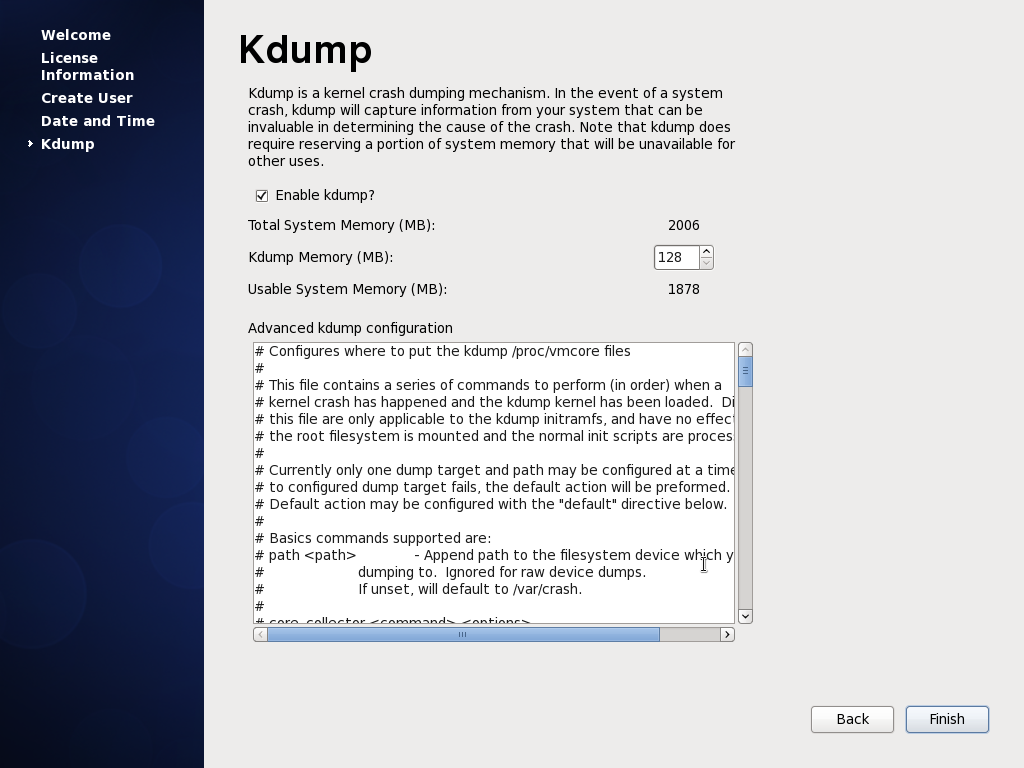
|
||||
|
||||
### Start CentOS 6.5 ###
|
||||
|
||||
After the previous step, the system would be rebooted, and finally comes the login page.
|
||||
|
||||
|
||||
|
||||
And after login comes the shiny new CentOS 6.5 desktop
|
||||
|
||||
|
||||
|
||||
Hope you enjoyed reading the installation guide. Leave your comments and questions below.
|
||||
|
||||
### Resource ###
|
||||
|
||||
CentOS 6.5 release notes
|
||||
[http://wiki.centos.org/Manuals/ReleaseNotes/CentOS6.5][5]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.binarytides.com/centos-6-5-installation-screenshots/
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://lists.centos.org/pipermail/centos-announce/2013-December/020032.html
|
||||
[2]:http://wiki.centos.org/Manuals/ReleaseNotes/CentOS6.5
|
||||
[3]:http://isoredirect.centos.org/centos-6/6.5/isos/
|
||||
[4]:http://mirror.centos.org/centos/6.5/isos/
|
||||
[5]:http://wiki.centos.org/Manuals/ReleaseNotes/CentOS6.5
|
||||
@ -0,0 +1,53 @@
|
||||
Daily Ubuntu Tips — Install VMware Workstation In Ubuntu
|
||||
================================================================================
|
||||
VMware Workstation is a Type-2 commercial virtualization software. It’s Type-2 because is runs on top of existing operation systems and the computer it’s running on is known as the host computer.
|
||||
|
||||
You can use VMware Workstation to run multiple guest machines simultaneously running individual operating systems on the host machine. A guest machine can either be a 32-bit or 64-bit of supported operating systems. VMware Workstation supports Windows, Mac OS X, Solaris and many others.
|
||||
|
||||
This brief tutorial is going to show you how to install VMware Workstation in Ubuntu.
|
||||
|
||||
Since this program is a commercial program, you must have a valid license to use it. You could also [download the 30-day free trial version][1] from the download page to test it. If you want to register it, get a license key and validate it.
|
||||
|
||||
To get started installing VMware Workstation in Ubuntu, first update Ubuntu. To do that, run the commands below.
|
||||
|
||||
sudo apt-get update && sudo apt-get dist-upgrade && sudo apt-get autoremove
|
||||
|
||||
After updating your computer, run the commands below to prepare Ubuntu before the installation.
|
||||
|
||||
sudo apt-get install build-essential linux-headers-`uname -r`
|
||||
|
||||
After that, download VMware Workstation. Next, change into the **~/Downloads** folder since Firefox saves files in the Downloads folder.
|
||||
|
||||
cd Downloads
|
||||
|
||||
Next, run the commands below to extract the download package if it came in a .zip archive. If not, go to the next line.
|
||||
|
||||
unzip VMware-Workstation-Full*.zip
|
||||
|
||||
Next, run the commands below to make the file executable.
|
||||
|
||||
chmod +x VMware-Workstation-Full*.bundle
|
||||
|
||||
Finally, run the commands below to begin the installation.
|
||||
|
||||
sudo ./VMware-Workstation-Full*.bundle
|
||||
|
||||
ollow the wizard until the installation is complete. When it’s done, open it from Dash and begin creating guest machines.
|
||||
|
||||

|
||||
|
||||
You should be able to create many guest machines of all types, including Windows, Linux, Novell, Solaris and others.
|
||||
|
||||

|
||||
|
||||
Enjoy!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.liberiangeek.net/2013/12/daily-ubuntu-tips-install-vmware-workstation-in-ubuntu/
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:https://my.vmware.com/web/vmware/info/slug/desktop_end_user_computing/vmware_workstation/10_0
|
||||
@ -1,3 +1,4 @@
|
||||
[Translating by SteveArcher]
|
||||
Gnu: toward the post-scarcity world – the Free Software Column
|
||||
================================================================================
|
||||
**It is 30 years since Richard Stallman announced that he was going to write a complete UNIX-compatible software system called GNU, pioneering the idea of free and open source software, but the struggle continues **
|
||||
@ -36,4 +37,4 @@ via: http://www.linuxuser.co.uk/features/gnu-toward-the-post-scarcity-world-the-
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,49 +0,0 @@
|
||||
Luox 翻译
|
||||
|
||||
|
||||
How to Repack Deb Files on Debian and Ubuntu
|
||||
================================================================================
|
||||
**The following tutorial will teach Ubuntu, Linux Mint and Debian GNU/Linux users how to easily unpack and repack a .deb file on their Debian-based Linux operating system.**
|
||||
|
||||

|
||||
|
||||
Once in a while you reach a moment in life when, among other things, you want to modify a .deb file, to change something in it and repackage it back. But, only if you are truly into computing and hacking.
|
||||
|
||||
The following example is a true story, as it happen to me a while ago. A Linux developer created a Debian package (.deb) for a software, which I’ve install on my Ubuntu powered computer with success.
|
||||
|
||||
Apparently, the software did not worked correctly, as it was always stuck when it tried to retrieve some files from a Git repository. So, I knew where the files where installed (in the /opt directory), I’ve searched the code, found the issue and repair it in place. After that, the program was no longer stuck when it tried to retrieve the packages it needed.
|
||||
|
||||
So, long story short, I wanted to unpack the .deb file, replace the file I’ve patched in it, and repackage it back so I can install it on other computers or give it to my friends. How do I do that?
|
||||
|
||||
After searching the Internet for an answer to my problem, I’ve found a small blog called [ailoo.net][1] where it was explained like this:
|
||||
|
||||
mkdir -p extract/DEBIAN
|
||||
dpkg-deb -x package.deb extract/
|
||||
dpkg-deb -e package.deb extract/DEBIAN [...do something, e.g. edit the control file...]
|
||||
mkdir build
|
||||
dpkg-deb -b extract/ build/
|
||||
|
||||
These five commands will do the job like a charm. Let me explain them to you: the first one creates a folder called “extract” and a subfolder called “DEBIAN”; the second command will extract some files from your .deb package in the “extract” folder; the third command will extract the content of the .deb package in the “DEBIAN” subfolder, where you can modify/patch the files you want; the fourth command will create a folder called “build”; and the fifth command will repack the modified files into a new .deb package, which will be generated in the “build” folder.
|
||||
|
||||
That’s it! Just remember to stick with the commands above, and modify the files visually with a graphical text editor via your default file manager, after you’ve executed the third command. Do not hesitate to comment below if you run into problems during this tutorial.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://news.softpedia.com/news/How-to-Repack-Deb-Files-on-Debian-and-Ubuntu-404930.shtml
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://ailoo.net/2009/06/repack-a-deb-archive-with-dpkg-deb/
|
||||
[2]:
|
||||
[3]:
|
||||
[4]:
|
||||
[5]:
|
||||
[6]:
|
||||
[7]:
|
||||
[8]:
|
||||
[9]:
|
||||
[10]:
|
||||
[11]:
|
||||
[12]:
|
||||
@ -0,0 +1,33 @@
|
||||
Linux Foundation Gains New Cloud, Open Hardware and Gaming Members
|
||||
================================================================================
|
||||
> Cloudius Systems, HSA Foundation and Valve have become the newest members of the Linux Foundation, bringing strengths in the open source cloud, open-standard hardware and gaming.
|
||||
|
||||
Cloud computing, open-standard hardware and gaming: These are all areas in which the [Linux Foundation][1] has recently forged important new connections, announcing the addition of [Cloudius Systems][2], [HSA Foundation][3] and [Valve Software][4] as the newest members of the organization. Together, these collaborations highlight the continuing dynamism of the open source world, and provide hints into where it is headed next.
|
||||
|
||||
The Linux Foundation, a non-profit consortium that promotes the interests of [Linux][6] and related open source projects, detailed the signing-on of these three companies in an [announcement][5] that highlighted the particular strengths they stand to contribute to the open source ecosystem.
|
||||
|
||||
First, Cloudius Systems will help to advance the open source cloud. Its major product is [OSv][7], a sleek operating system that the company recently introduced and designed specifically for the cloud. Interestingly, OSv—which runs as a guest virtual machine on top of the open source [KVM][8] and [Xen][9] hypervisors—could be considered a competitor with Linux, which forms the basis for many other cloud-oriented virtualization platforms. But Cloudious's entry into the Linux Foundation is a sign that the future of the open cloud is about more than Linux itself, and that open source innovators recognize that the Linux kernel, which was built for desktops and servers, can only go so far in the cloud.
|
||||
|
||||
Meanwhile, the non-profit HSA Foundation aims to advance open hardware standards—a key interest for open source developers whether they focus on desktops, servers, the cloud or mobile. Lack of hardware compatibility due to proprietary, undocumented standards has been a thorn in Linux's side from day one, and investing in collaboration to help overcome that barrier is in the interest of virtually everyone within the open source ecosystem.
|
||||
|
||||
Last but not least, Valve, which develops the popular [Steam][10] platform for cloud-based games and other content, injects the Linux world with new energy in the gaming realm, an area that has traditionally been very unwelcoming to Linux users. Valve could be on the forefront of a major shift in open source entertainment that will use the power of the cloud to bring Linux into the mainstream fold—while also promoting Linux as the basis for specialized gaming hardware such as Valve's [Steam Machines][11], home gaming devices that run on Linux.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://thevarguy.com/open-source-application-software-companies/linux-foundation-gains-new-cloud-open-hardware-and-gaming
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://linuxfoundation.org/
|
||||
[2]:http://www.cloudius-systems.com/
|
||||
[3]:http://hsafoundation.com/
|
||||
[4]:http://www.valvesoftware.com/
|
||||
[5]:http://www.linuxfoundation.org/news-media/announcements/2013/12/cloudius-systems-hsa-foundation-and-valve-join-linux-foundation
|
||||
[6]:http://kernel.org/
|
||||
[7]:https://github.com/cloudius-systems/osv
|
||||
[8]:http://www.linux-kvm.org/page/Main_Page
|
||||
[9]:http://www.xenproject.org/
|
||||
[10]:http://store.steampowered.com/
|
||||
[11]:http://store.steampowered.com/livingroom/SteamMachines/
|
||||
154
sources/Our Top 10 Linux Applications of 2013.md
Normal file
154
sources/Our Top 10 Linux Applications of 2013.md
Normal file
@ -0,0 +1,154 @@
|
||||
翻译中 Luox
|
||||
|
||||
|
||||
《佳人》
|
||||
作者:杜甫
|
||||
绝代有佳人,幽居在空谷。
|
||||
自云良家女,零落依草木。
|
||||
关中昔丧乱,兄弟遭杀戮。
|
||||
官高何足论,不得收骨肉。
|
||||
世情恶衰歇,万事随转烛。
|
||||
夫婿轻薄儿,新人美如玉。
|
||||
合昏尚知时,鸳鸯不独宿。
|
||||
但见新人笑,那闻旧人哭。
|
||||
在山泉水清,出山泉水浊。
|
||||
侍婢卖珠回,牵萝补茅屋。
|
||||
摘花不插发,采柏动盈掬。
|
||||
天寒翠袖薄,日暮倚修竹。
|
||||
|
||||
Our Top 10 Linux Applications of 2013
|
||||
================================================================================
|
||||

|
||||
|
||||
*2013 – What A Year, Right?*
|
||||
|
||||
**This time last year we knew nothing of Ubuntu Touch; Canonical attempting to raise $32 million for a cutting-edge smartphone would’ve sounded insane; Mir was a space station while Wayland was the future; and as far as Saucy Salamanders and Trusty Tahrs are concerned, they were nothing but adjunct words on the pages of untroubled thesaurus.**
|
||||
|
||||
It’s been a busy year. Canonical continue to stride forwards towards a converged future for the OS, while an estimated 25 million people continue to use the regular desktop version for their day-to-day computing needs.
|
||||
|
||||
But key to both experiences are apps. Last year we rounded up 10 of our favourite apps that debuted on the desktop. This year we’re doing things a little differently by also including updates released during the course of the year.
|
||||
|
||||
We’ve opted to exclude ‘obvious’ choices like Firefox, Chrome, LibreOffice and Steam (because we all know they’re awesome anyway) to highlight lesser-known apps and utilities that, this year, made the desktop experience all the more awesome.
|
||||
|
||||
What did we pick? Read on.
|
||||
|
||||
### Geary ###
|
||||
|
||||

|
||||
|
||||
2013 saw Yorba, the non-profit behind Geary, try, [and fail][1], to secure a future for the app through crowd funding. That could’ve been where things ended for the app; a dour footnote in the history of apps failing to reach their true potential. Thankfully it wasn’t.
|
||||
|
||||
The release of Geary 0.4.x a few months after that disappointing set-up later proved a testament to the dedication and patience of its development team. Building on a strong release from earlier in the year, Geary 0.4 arrived in October with improved stability and performance and a veritable stuffed envelope of new improvements and features in tow.
|
||||
|
||||
Those who insist that the days of desktop mail clients are over are fast being made to eat their words by Yorba. Right now, Geary is one of the the best mail apps on any platform, Linux or otherwise.
|
||||
|
||||
- [Install Geary from Ubuntu Software Center][2]
|
||||
|
||||
### Birdie Twitter App ###
|
||||
|
||||

|
||||
|
||||
Twitter apps for Linux are a bit of an anomaly. While there are a good number of them, few seem to work as efficiently as proprietary apps on other operating systems. That all changed with the hatching of **Birdie** back in March of this year. As the year passed we got to see it grow from an unstable, crash-prone chick to a mature and confident app sure of its direction.
|
||||
|
||||
While it remains far from being the full plumed wonder I’d like, it makes this list because it does what it aims to, looks good doing it, and holds a lot of promise for the future.
|
||||
|
||||
- [Read more about Birdie’s Latest Release][3]
|
||||
|
||||
### Springseed ###
|
||||
|
||||
|
||||
|
||||
For obsessive note-takers 2013 wasn’t short of options – from GNOME’s obtusely named *Bijiben*, to the powerful *Nitro*. But, for me, it was the nimble *Springseed* that grabbed my attention.
|
||||
|
||||
Having been built from the ground-up to be resource-friendly, the app feels responsive and light. The feature set includes all of the vital ones needed to get organised – notebook creation, text formatting, markdown support and drobox sync, etc – all presented within an attractive interface that’s free of needless cruft.
|
||||
|
||||
Springseed is a free and open-source and available to download directly from the project website.
|
||||
|
||||
- [Download Springseed for Ubuntu][4]
|
||||
|
||||
### Unity Tweak Tool ###
|
||||
|
||||

|
||||
|
||||
First released in the beginning of the year, *Unity Tweak Tool* has grown to become the ’*must have*’ app name falling off the lips of anyone offering post-Ubuntu install advice. With a smorgasbord of settings and customisation tools on-hand, the utility makes tailoring the Unity experience to suit your own tastes a [doddle][5].
|
||||
|
||||
Routinely updated to take advantage of the latest options in each new release of Ubuntu, and offering the safety net of an ‘undo’ button should anything go wayward, it’s easy to see why the app has become a favourite tool for so many.
|
||||
|
||||
- [Install Unity Tweak Tool on Ubuntu][6]
|
||||
|
||||
### Intel Graphics Driver Installer ###
|
||||
|
||||
|
||||
|
||||
Intel (specifically Intel’s *Open Source Technology Centre*) made installing the latest and greatest Intel graphics drivers easier on Linux this year with the release of the Intel Driver Manager. The utility automate the entire detection, download and install process for the user, requiring only a couple of clicks and the bit of patience.
|
||||
|
||||
Initial releases of the manager were not without issue. Thankfully, subsequent releases have seen bugs fixed and quirks ironed out. If you tried it earlier in the year without success it might be well worth trying it again.
|
||||
|
||||
- [Intel Driver Manager for Linux][7]
|
||||
|
||||
### Ubuntu SDK ###
|
||||
|
||||

|
||||
|
||||
A left-field choice, but an important one. The Ubuntu SDK arrived this year primed with everything developers need to create apps for Ubuntu Touch, both on phone and tablet.
|
||||
|
||||
It’s hard to wax too lyrical about a tool that few desktop users will appreciate, but July’s update in particular added some great functionality – including a unified actions API, Ubuntu One database syncing and support for creating converged layouts.
|
||||
|
||||
- [Learn more about the Ubuntu SDK][8]
|
||||
|
||||
### VoD Enablement App ###
|
||||
|
||||

|
||||
|
||||
Arguably this entry is not so much an app as a hack dressed up to look like one. Regardless, thanks to some clever packaging foo of Erich Hoover, Netflix, LoveFilm and a host of other Silverlight-based video streaming sites are now *easily* viewable on Ubuntu for the first time – albeit unofficially, of course!
|
||||
|
||||
For the full skinny on what’s supported, what it install, and how to get it you’ll want to check out our article from January.
|
||||
|
||||
- [How to Watch Netflix & Others on Ubuntu][9]
|
||||
|
||||
### VLC ###
|
||||
|
||||
Everyone’s (cue someone saying ‘not mine!’ – ed) favourite media player received a number of updates over the course of 2013, with its most recent major update landing back in September.
|
||||
|
||||
Amongst the slew of features and refinements shipped with its Linux build was support for 4K video streams; VDPAU hardware decoding; tweaks to .MKV file playback and improved DBus and MPRIS interfaces.
|
||||
|
||||
### Lightworks for Linux ###
|
||||
|
||||

|
||||
|
||||
Lightworks has an odd, but rather brilliant, claim to fame: it’s too featured, too powerful, and too professional-orientated for most desktop users to get to grips with. Addmittedly that’s hardly a shock given the pedigree of the app (used to edit many an Oscar-winning Hollywood film, dontcha’ know).
|
||||
|
||||
Editshare, the company behind the app, took their time publishing a Linux Beta (having delayed its arrival on numerous occasions). But, since its release back in April, they’ve been fastidious in ensuring that it maintains feature parity with the Windows builds – a feat only achieved in the most recent set of updates.
|
||||
|
||||
Now, with new features and tweaks arriving by the week, there’s never been a better time for those who fancy themselves as the next great movie maker to try it out.
|
||||
|
||||
- [Latest Lightworks for Linux Update][10]
|
||||
|
||||
### GNOME Music Preview ###
|
||||
|
||||
|
||||
|
||||
Alright, alright: it’s not finished. In fact, if you’re not running a pair of highly unstable GNOME PPAs you can’t even use it in Ubuntu.
|
||||
|
||||
But that’s beside the point; GNOME Music is one of my stand out apps of this year. For some it’s simple to the point of uselessness, for others the beauty lies in its simplicity. Sure, it doesn’t stack up well against apps tasked with doing ‘all the things!’, but that rather misses the point.
|
||||
|
||||
The attention to detail in design and user experience is second to none.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.omgubuntu.co.uk/2013/12/top-10-linux-apps-of-2013
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.omgubuntu.co.uk/2013/04/geary-fundraiser-fails-at-half-way-mark
|
||||
[2]:apt:geary
|
||||
[3]:http://www.omgubuntu.co.uk/2013/07/birdie-twitter-app-updates-with-conversations
|
||||
[4]:http://getspringseed.com/
|
||||
[5]:http://www.thefreedictionary.com/doddle
|
||||
[6]:apt://unity-tweak-tool
|
||||
[7]:https://01.org/linuxgraphics/downloads/2013/intelr-graphics-installer-1.0.2-linux
|
||||
[8]:http://developer.ubuntu.com/apps/create/get-the-sdk/
|
||||
[9]:http://www.omgubuntu.co.uk/2013/01/how-to-watch-lovefilm-redbox-instant-or-netflix-on-ubuntu
|
||||
[10]:http://www.omgubuntu.co.uk/2013/11/lightworks-for-linux-beta-updated
|
||||
@ -1,88 +0,0 @@
|
||||
Security Headers on the Top 1,000,000 Websites: November 2013 Report
|
||||
================================================================================
|
||||
It has been almost exactly a year since we conducted the first top 1 million security headers report so it is a great time to re-run the analysis and see how well security header adoption is growing. As before, the latest Chrome and Firefox User-Agent strings were used to make requests to the top 1 million sites over both HTTP and HTTPS. Out of the 2,589,918 responses we had over 100,000 distinct security headers and values to analyze.
|
||||
|
||||
Comparing with previous scans, we had 514,288 URLs that matched the first run we did in November 2012 and 1,207,169 URLs that matched from March 2013. This time around we added yet another security header “X-XSS-Protection” due to a request from a commenter on this blog. Unfortunately, we did not store this header in any of the prior scans so we are unable to compare its adoption rate.
|
||||
|
||||
### Changes, Additions and Removals Yearly Review ###
|
||||
|
||||
A total of 7,258 new security headers were added over the course of a year to the 514,288 URLs that existed in both data sets. As before, we see the largest increase in additions to X-Frame-Options and CORS headers. In a not so distant fourth we see Strict-Transport-Security steadily climbing with 538 new sites using the header. Even though X-Content-Security-Policy and X-WebKit-CSP are deprecated, we still see a small increase in their additions. Once again the highest used headers also end up having the highest number of removals with X-Frame-Options being removed from 365 sites over the course of the year.
|
||||
|
||||

|
||||
|
||||
You may notice that the Content-Security-Policy header is missing from the yearly review, this is because it was not standardized when we first started this analysis. To see the adoption rate of the standardized CSP, we need to look at a comparison of the scan that was conducted in March 2013.
|
||||
|
||||
### Changes, Additions and Removals from March 2013 ###
|
||||
|
||||
We have a lot more URLs that matched since last March, yet surprisingly, the charts look extremely similar. 7,099 new security headers were added for the 1,207,169 URLs that matched between this run and March 2013. Of these sites, a disappointingly small number of 62 sites enabled Content-Security-Policy with 47 sites enabling the soon to be disabled X-Content-Security-Policy header.
|
||||
|
||||

|
||||
|
||||
While it would be nice to see CSP’s adoption rates increase more, it is quite understandable as it is such a large undertaking for any website to create a compliant policy.
|
||||
|
||||
### November 2013 Results ###
|
||||
|
||||
#### X-XSS-Protection ####
|
||||
|
||||
This time around another header was added to the analysis. The Microsoft endorsed header was built to allow sites to control how Internet Explorer’s XSS Filtering feature is to be handled on a resource by resource basis. Valid values for X-XSS-Protection are as follows:
|
||||
|
||||
1. 0 – Disables XSS protections
|
||||
1. 1 – Enables XSS protections, in IE the filter will attempt to sanitize potential malicious characters.
|
||||
1. 1; mode=block – Enables XSS protections and instructs IE to block the response instead of sanitizing.
|
||||
1. 1; report=[url] – Allows reports to be sent to the specified URL of potential XSS attempts.
|
||||
|
||||
It should be noted that Google Chrome’s XSS Auditor will also be disabled if a resource responds with 0 as the value for the X-XSS-Protection header.
|
||||
|
||||

|
||||
|
||||
As previous readers will remember, invalid header values are a serious problem and X-XSS-Protection is no exception. Almost 480 sites incorrectly specified the value of “0; mode=block”. This means that 477 sites who think they are blocking XSS attacks are actively disabling the XSS protections built in to IE and Chrome. Please note that [YouTube][1] and [Blogspot][2] make up the majority of URLs using X-XSS-Protection with 14,210 for YouTube and 18,587 for Blogspot.
|
||||
|
||||
### X-Frame-Options ###
|
||||
|
||||

|
||||
|
||||
X-Frame-Options is still holding strong with SAMEORIGIN being by far the largest setting with YouTube again taking up the majority with 14,178 URLs all of which are set to SAMEORIGIN. Along with the jump in sites using X-Frame-Options we are also seeing an increase in invalid values being configured.
|
||||
|
||||
### Cross Origin Request Sharing (CORS) Headers ###
|
||||
|
||||
Once again we looked at the two CORS headers Access-Control-Allow-Origin and Access-Control-Allow-Credentials.
|
||||
|
||||

|
||||
|
||||
Unfortunately, we are still seeing a large number of sites incorrectly configuring Access-Control-Allow-Origin by specifying wildcards or multiple origins separated by various characters. As a reminder Access-Control-Allow-Origin only allows either * (wildcard value) or a single origin with a valid scheme specified.
|
||||
|
||||
As for Access-Control-Allow-Credentials, 1388 sites have set the value to true, 51 for false. Surprisingly, we identified 196 sites setting wildcard origin access but setting Access-Control-Allow-Credentials to true which is an invalid combination of settings.
|
||||
|
||||
### Strict-Transport-Security ###
|
||||
|
||||
Due to readers suggestions we have changed the long max-age value to be anything greater than 604800 seconds, or 7 days. Likewise, values below are considered to be a short max-age. [Facebook][3] and [Etsy][4] comprise 74 and 61 URLs respectively in the Max Age of 0 column. As a reminder, a header value of 0 clears the domain from the browser’s Strict Transport Security cache. Of the more interesting invalid values, a large number of sites incorrectly use ‘,’ as a delimiter between the max-age value and includeSubDomains directives. Unfortunately, both Firefox and Chrome are extremely strict in this regard and will refuse to add the site to the STS cache if the ‘,’ character is used instead of the RFC defined token of ‘;’. Once again, please check the RFCs before implementing any of these security headers.
|
||||
|
||||

|
||||
|
||||
#### Content-Security-Policy ####
|
||||
|
||||
Content Security Policy continues to grow in usage but extremely slowly. Only 269 sites are using the [w3 specification’s Content-Security-Policy][5] header, with 95 of these URLs coming from Facebook. Interestingly, 584 sites are using X-Content-Security-Policy and 487 sites are using X-Webkit-CSP. It should be noted that these two headers are already considered deprecated but have yet to be disabled. Only an extremely small number of sites using the report-only versions of the CSP headers were observed. It would be expected that web site operators wishing to test out CSP would use the report only mode to determine how Content Security Policy would impact their site, yet we only see 24 sites using Content-Security-Policy-Report-Only.
|
||||
|
||||

|
||||
|
||||
The most interesting result of the CSP analysis is the large number of sites which use CSP with the unsafe directives. It is assumed the reason unsafe-inline has such a high rate of usage is due to how extremely hard it is for developers to remove all inline script from web page elements. While disappointing to see, it is understandable to anyone who has attempted to enact a strict CSP policy.
|
||||
|
||||
### Conclusion ###
|
||||
|
||||
It is safe to say that we have a long way to go to making sure our sites use all available means to protect themselves. While security headers are only a small part of defense, applied appropriately they can and do help us all be more secure internet users. While encouraging to see the numbers increasing, we must keep in mind that less than 10% (199,350) of the 2,589,918 URLs analyzed have security headers. While strict adherence to RFCs is necessary, typos, combined with the rigidness of directive parsing, do not help site administrators or users when encountering these headers. While hope should not be given up on CSP, it’s extremely low adoption rate is rather concerning and it may be worth considering creation of tools to help create, verify and support site administrators that wish to adopt CSP.
|
||||
|
||||
As before, Veracode has released the raw data from this analysis, so feel free to download the November 2013 results here.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.veracode.com/blog/2013/11/security-headers-on-the-top-1000000-websites-november-2013-report/
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.youtube.com/
|
||||
[2]:http://www.blogspot.com/
|
||||
[3]:http://www.facebook.com/
|
||||
[4]:http://www.etsy.com/
|
||||
[5]:http://www.w3.org/TR/CSP/
|
||||
@ -1,191 +0,0 @@
|
||||
translating by zsJacky
|
||||
|
||||
Setup FTP Server On openSUSE 13.1
|
||||
================================================================================
|
||||
**vsftpd** (**V**ery **S**ecure **F**ile **T**ransport **P**rotocol **D**aemon) is a secure, fast FTP server for Unix/Linux systems. In this how-to article, let us see how to setup a basic FTP server using vsftpd on openSUSE 13.1.
|
||||
|
||||
### Install vsftpd ###
|
||||
|
||||
Login as root user and Enter the following the following command.
|
||||
|
||||
# zypper in vsftpd
|
||||
|
||||
Start vsftpd service and make it to start automatically on every reboot.
|
||||
|
||||
# systemctl enable vsftpd.service
|
||||
# systemctl start vsftpd.service
|
||||
|
||||
### Configure vsftpd ###
|
||||
|
||||
Create a folder for ftp users.
|
||||
|
||||
# mkdir /srv/ftp
|
||||
|
||||
Create a group called **ftp-users**.
|
||||
|
||||
# groupadd ftp-users
|
||||
|
||||
Let us create a sample user called unixmen with home directory **/srv/ftp** and group **ftp-users**.
|
||||
|
||||
# useradd -g ftp-users -d /srv/ftp/ unixmen
|
||||
|
||||
Set password for the new user.
|
||||
|
||||
# passwd unixmen
|
||||
|
||||
Make the ftp home directory **/srv/ftp/** accessible by ftp users.
|
||||
|
||||
# chmod 750 /srv/ftp/
|
||||
# chown unixmen:ftp-users /srv/ftp/
|
||||
|
||||
Edit file vsftpd.conf,
|
||||
|
||||
# nano /etc/vsftpd.conf
|
||||
|
||||
Make the changes as shown below.
|
||||
|
||||
[...]
|
||||
#Uncomment and Set YES to enable write.
|
||||
write_enable=YES
|
||||
[...]
|
||||
# Uncomment and Set banner name for your website
|
||||
ftpd_banner=Welcome to Unixmen FTP service.
|
||||
[...]
|
||||
# Uncomment
|
||||
ls_recurse_enable=YES
|
||||
[...]
|
||||
# Uncomment and set YES to allow local users to log in.
|
||||
local_enable=YES
|
||||
[...]
|
||||
# To disable anonymous access, set NO.
|
||||
anonymous_enable=NO
|
||||
[...]
|
||||
# Uncomment to enable ascii download and upload.
|
||||
ascii_upload_enable=YES
|
||||
ascii_download_enable=YES
|
||||
[...]
|
||||
## Add at the end of this file ##
|
||||
use_localtime=YES
|
||||
|
||||
Save and exit file.
|
||||
|
||||
### Test FTP Server Locally ###
|
||||
|
||||
First let us try to login to our FTP server as shown below.
|
||||
|
||||
# ftp localhost
|
||||
Trying ::1:21 ...
|
||||
Connected to localhost.
|
||||
220 (vsFTPd 3.0.2)
|
||||
Name (localhost:root): unixmen
|
||||
331 Please specify the password.
|
||||
Password:
|
||||
230 Login successful.
|
||||
Remote system type is UNIX.
|
||||
Using binary mode to transfer files.
|
||||
ftp>
|
||||
|
||||
As you in the above output, we will be able to login to ftp server using unixmen user.
|
||||
|
||||
### Test FTP Server Remotely ###
|
||||
|
||||
By default openSUSE built-in firewall won’t allow to login to FTP from remote systems. So let us allow vsftpd service through suse firewall. To do that go to **Yast -> Security and Users -> Firewall**.
|
||||
|
||||

|
||||
|
||||
In the Firewall section, go to **Allowed Services**. In the zone selection drop down box, select **External Zone** and in Service to Allow drop-down box, select **vsftpd server** and click add.
|
||||
|
||||

|
||||
|
||||
Click Next and close Yast Control center.
|
||||
|
||||
Now try to connect from a remote system.
|
||||
|
||||
I tried to login to FTP server from my ubuntu desktop.
|
||||
|
||||
sk@sk:~$ ftp 192.168.1.53
|
||||
Connected to 192.168.1.53.
|
||||
220 (vsFTPd 3.0.2)
|
||||
Name (192.168.1.53:sk): unixmen
|
||||
331 Please specify the password.
|
||||
Password:
|
||||
230 Login successful.
|
||||
Remote system type is UNIX.
|
||||
Using binary mode to transfer files.
|
||||
ftp>
|
||||
|
||||
As you see in the above output, I will be able to connect to FTP server. If you doesn’t allow the vsftpd service through firewall you will get a Connection timed out error.
|
||||
|
||||
### Connect from Browser ###
|
||||
|
||||
Open up your browser and Navigate to **ftp://ip-address/**. Enter the ftp user name and password.
|
||||
|
||||

|
||||
|
||||
### Connect to FTP server using FileZilla ###
|
||||
|
||||
Working from command-line mode might be little bit annoying to newbies. So let us install a graphical FTP client called [**Filezilla**][1] to get things done quite easier:
|
||||
|
||||
Mostly all distribution will have filezilla client in their official repository. To install filezilla on Linux based systems enter the following command:
|
||||
|
||||
On Ubuntu based systems:
|
||||
|
||||
$ sudo apt-get install filezilla
|
||||
|
||||
On Fedora/Redhat systems:
|
||||
|
||||
$ sudo yum install filezilla
|
||||
|
||||
On openSUSE:
|
||||
|
||||
# zypper in filezilla
|
||||
|
||||
After installing filezilla open it. Enter the ftp server IP address, user name and password and click quickconnect.
|
||||
|
||||

|
||||
|
||||
For added security, you can restrict FTP access to certain users by adding them to **/etc/vsftpd.chroot_list** file.
|
||||
|
||||
Edit vsftpd.conf file,
|
||||
|
||||
nano /etc/vsftpd.conf
|
||||
|
||||
Make the changes as shown below.
|
||||
|
||||
[...]
|
||||
# Uncomment and set YES
|
||||
chroot_local_user=YES
|
||||
chroot_list_enable=YES
|
||||
chroot_list_file=/etc/vsftpd.chroot_list
|
||||
[...]
|
||||
|
||||
Create **file /etc/vsftpd.chroot_list**,
|
||||
|
||||
nano /etc/vsftpd.chroot_list
|
||||
|
||||
Add the users that you want to give access to FTP server. I added the user **unixmen**.
|
||||
|
||||
unixmen
|
||||
|
||||
Restart ftp service.
|
||||
|
||||
# systemctl restart vsftpd.service
|
||||
|
||||
Now you will be able to connect to FTP server with users who are listed in the chroot list file.
|
||||
|
||||
If users other than in the chroot list want to access FTP server, they will get the following error.
|
||||
|
||||
500 OOPS: could not read chroot() list file:/etc/vsftpd.chroot_list
|
||||
ftp: Login failed
|
||||
|
||||
That’s it for now. Your FTP server is ready to use. Enjoy!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.unixmen.com/setup-ftp-server-opensuse-13-1/
|
||||
|
||||
译者:[zsJacky](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:https://filezilla-project.org/
|
||||
@ -1,38 +0,0 @@
|
||||
SuperTuxKart 0.8.1 Release Candidate Revved Up And Ready for Testing
|
||||
================================================================================
|
||||
**Hands up if you don’t like open-source racing game SuperTuxKart? You, folks, are strange.**
|
||||
|
||||
As kart-racers go, it’s one of the most popular freely available. And for good reason: it’s fun, easy to play and has a dedicated team of developers who are continually adding to and improving what is already a really polished game.
|
||||
|
||||
But it’s getting even better. The first release candidate of build 0.8.1 – the first update since last year’s 0.8 build – [has been made available for testing][1] (for ‘testing’ see ‘excuse to play it for hours and not feel guilty’).
|
||||
|
||||
SuperTuxKart 0.8.1 adds a number of improvements, including:
|
||||
|
||||
- A new Star Trek themed track “STK Enterprise”
|
||||
- Three tracks updated (‘Old Mines’, ‘Lighthouse’ & ‘Zen Garden’)
|
||||
- New ‘Egg Hunt’ and ‘Soccer’ modes
|
||||
- New and updated karts
|
||||
- New difficulty level
|
||||
- Bubblegum shield weapon
|
||||
- Option to save and resume Grand Prix mode
|
||||
- [WiiMote Support][2]
|
||||
|
||||
### Geting SuperTuxKart 0.8.1 ###
|
||||
|
||||
No release date has been given on when to expect the final, stable release of 0.8.1 but I’d expect it to land sometime in December – marking one year from the previous release in the 0.8.x series.
|
||||
|
||||
In the meantime, if you’re okay with “Release Candidate”-quality software, you’ll find a pre-compiled binary for Linux over on the project’s Sourceforge Page.
|
||||
|
||||
- [Download SuperTuxKart 0.8.1 Release Candidate][3]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.omgubuntu.co.uk/2013/11/supertux-kart-0-8-1-release-candidate
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://supertuxkart.blogspot.co.uk/2013/11/supertuxkart-081-rc1.html
|
||||
[2]:http://supertuxkart.net/Wiimote
|
||||
[3]:http://sourceforge.net/projects/supertuxkart/files/SuperTuxKart/0.8.1-rc1/
|
||||
@ -1,34 +0,0 @@
|
||||
Top Email Encryption Tools
|
||||
================================================================================
|
||||
Email continues to be one of the most popular and useful functions of a Linux system. Being able to keep in touch with your friends, family, and colleagues is essential for any platform. As the scope of email threats keeps increasing, systems for email security and encryption have become more complex and more of a necessity. Protecting email from unauthorized access and inspection is important particularly because the protocols that govern email do not include encryption. Email was not designed with any privacy or security in mind. The consequence of the lack of security is that email can be compromised on the sender's device, on a network, on a server, and on the recipient's device.
|
||||
|
||||
Sending encrypted messages is one method of ensuring electronic privacy. By encrypting messages, this will help to keep your precious information safe by making messages look like garbled text to uninvited onlookers. Encrypting email may sound a little daunting, but it's actually simple with the right software.
|
||||
|
||||
OpenPGP is the most widely used email encryption standard. Whether you are using an email client or a web-based email solution, you can encrypt your email with OpenPGP.
|
||||
|
||||
There are very few email applications that have PGP encryption enabled by default. Fortunately, there are some good open source encryption applications available for Linux that are simple to use.
|
||||
|
||||
To provide an insight into the quality of software that is available, we have compiled the following list of email encryption tools.
|
||||
|
||||
Now, let's explore the 4 encryption tools at hand. For each title we have compiled its own portal page, a full description with an in-depth analysis of its features, together with links to relevant resources and reviews.
|
||||
|
||||
### Email Encryption Tools ###
|
||||
|
||||
- [Enigmail][1] OpenPGP Email Security for Mozilla Applications
|
||||

|
||||
- [Mailvelope][2] Extension for Google Chrome and Mozilla Firefox
|
||||
- [GnuPG][3] Encrypt and sign data and communication
|
||||
- [Mymail-Crypt for Gmail][4] Simple solution to mail encryption
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linuxlinks.com/article/2013120707481589/EmailEncryption.html
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.enigmail.net/
|
||||
[2]:http://www.mailvelope.com/
|
||||
[3]:http://www.gnupg.org/
|
||||
[4]:https://chrome.google.com/webstore/detail/mymail-crypt-for-gmail/jcaobjhdnlpmopmjhijplpjhlplfkhba
|
||||
@ -1,48 +0,0 @@
|
||||
‘Household Brands’ Interested In Ubuntu for Phones and Tablets, Says Shuttleworth
|
||||
================================================================================
|
||||
|
||||
|
||||
**Mark Shuttleworth has said that an ‘interesting set of household brands’ are looking at putting Ubuntu Touch on their own phones and tablets.**
|
||||
|
||||
The Ubuntu founder was speaking in the [keynote address][1] at the Ubuntu Developer Summit which kicked off this week.
|
||||
|
||||
No specific names, details or dates were offered up alongside the tantalising tidbit, though Mark did hint at one point that he expects Ubuntu Touch devices to be available to buy within the next couple of years.
|
||||
|
||||
### Ubuntu Tablets = Renewed Opportunity ###
|
||||
|
||||
[As mentioned by Jono Bacon recently][2], honing the Ubuntu Tablet experience will be the ‘key focus’ of the Ubuntu 14.04 development cycle. This was touched upon by Shuttleworth in response to a question on whether Ubuntu plan to make dual-booting Touch with Android easier (they are):
|
||||
|
||||
> “I’m excited about the tablet form-factor because I think it’s going to be a lot easier for people to enjoy Ubuntu on a tablet [because] doing it on a phone full time is a bit of a deep-device commitment – [though] we’ve heard some interesting reports of government departments using it because we don’t work for the NSA!”
|
||||
|
||||
Other notable points mentioned in the keynote included:
|
||||
|
||||
- Helping developers tailor Ubuntu Touch apps for the desktop
|
||||
- Stable, dependable and performant desktop experience based on Unity 7
|
||||
- Point releases of Ubuntu 14.04 LTS won’t be introducing Mir or Unity 8
|
||||
- Ubuntu on ARM x64
|
||||
- Sidestage to be re-introduced to tablet
|
||||
- Supporting Android apps on Ubuntu ‘is a goal – but not a focus’ right now
|
||||
|
||||
> ‘Shuttleworth must be hoping that some of those interested household names make a firm commitment soon…’
|
||||
|
||||
This latter point appears to represent an about-turn, if true. Earlier in the year Canonical’s Richard Collins [told Engadget][1] that there were no plans to “engineer middleware for running Android apps [on Ubuntu Touch]“.
|
||||
|
||||
Android apps or not, Shuttleworth must be hoping that some of those interested household names make a firm commitment soon. The longer the gap the more ground competitors are gaining.
|
||||
|
||||
Samsung and Intel’s open-source mobile OS ‘Tizen’ [recently gained the backing of a further 36 companies][4], including an array of mobile networks, electronics bigwigs and game publishers.
|
||||
|
||||
Elsewhere, Mozilla’s Firefox OS continues to grow its users, OEM and carrier base; while [Jolla’s first Sailfish OS-powered handset ships later this month][5]. And although Ubuntu Touch isn’t aiming for the low-end segment, Android 4.4 debuted with a number of performance optimisations when used on hardware with limited resources.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.omgubuntu.co.uk/2013/11/household-brands-ubuntu-phone-tablets
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.youtube.com/watch?v=D4kHQeu4SJk
|
||||
[2]:http://www.omgubuntu.co.uk/2013/11/ubuntu-tablet-will-key-focus-ubuntu-14-04-lts-cycle
|
||||
[3]:http://www.engadget.com/2013/01/25/canonical-richard-collins-interview/
|
||||
[4]:http://www.theverge.com/2013/11/12/5093588/tizen-open-operating-system-partners-with-36-companies
|
||||
[5]:http://www.theregister.co.uk/2013/11/15/jolla_phones_to_ship_in_november/
|
||||
@ -0,0 +1,63 @@
|
||||
成为 Linux 终端高手的 7 个基本点
|
||||
================================================================================
|
||||
Linux 终端不仅是一个键入命令的地方。如若你能熟谙基本操作,那么你将掌握绝大多数 Linux 发行版的默认配置 Bash shell。
|
||||
|
||||
howtogeek.com 对初级用户,以及那些学习过程中或多或少有一些遗漏的高级用户提出几个基本点——
|
||||
|
||||
**1.Tab 补全** – 这样能节省时间,并且对于输入那些你不确定其具体名称的文件和命令来说很方便。比如,当前目录下有一个名为“really long file name”的文件,你想要删除它。你可以输入完整的文件名,但是你必须确保正确地输入了空格。若当前目录下还有许多以字母“r”开头的文件,(如果你没有正确地输入空格) Bash 将不知道你想要删除哪一个文件。
|
||||
|
||||
如果在当前目录下存在着另一个名为“really very long file name”的文件,你敲击了Tab键。Bash
|
||||
将为所有以“r”开头的文件自动填充“really\”部分。此时继续敲击Tab键,你将得到匹配所有文件名的列表。
|
||||
|
||||
**2.管道机制** – 这种机制允许你把一条命令的输出传送到另一条命令。按照 UNIX 哲学,每个程序都足够小,只做一件事并将之做到最好。例如,ls命令列出当前目录下的所有文件,grep命令搜索输入其中的指定检索项。
|
||||
|
||||
你可以通过管道机制(|字符)把二者结合起来,在当前目录下搜索文件。以下给出的命令(在当前文件夹下)搜索关键字为“word”的文件:
|
||||
|
||||
ls | grep word
|
||||
|
||||
**3.通配符** – “*”(星号)字符是一种匹配任意长度字符的通配符。比如,你想删除当前文件夹下名为“really long file name”和“really very long file name”的文件,你可以运行以下命令:
|
||||
|
||||
rm really*name
|
||||
|
||||
这条命令会删除所有以“really”开头以“name”结尾的文件。但是,如果你运行的是 rm * 这条命令,你将会删除文件夹下的所有文件。
|
||||
|
||||
**4.输出重定向** – “>”字符可以把一条命令的输出重定向到一个文件或另一条命令。比如,下面这行命令执行完 ls 后会列出当前文件夹下的所有文件,其结果不是在终端显示,而是输出到当前文件夹下一个名为“file1”的文件中去:
|
||||
|
||||
ls > file1
|
||||
|
||||
**5.历史记录** – Bash 能记住你以前输入过的命令,上、下方向键可以逐行调出它们。使用 history 命令打印历史记录,以管道机制 grep 选择性地输出你想要的结果。
|
||||
|
||||
~, . & ..
|
||||
|
||||
“~”,也叫做波浪符,用来表示当前用户的主目录。相比通过 cd /home/name 到达你的主目录,你可以输入 cd ~ 来达到相同效果。这点也可以在相关路径上使用 – 比如 cd ~/Desktop 能够到达当前用户的 Desktop 目录。
|
||||
|
||||
同样,“.”代表当前目录,“..”代表当前目录的父目录。使用 cd .. 可以返回上一级目录。它们也可以用在相关路径上,举例说明:你当前处在 Desktop 文件夹下,通过 cd ../Documents 命令,你可以转到与 Desktop 共有同一父文件夹的 Documents 文件夹去。
|
||||
|
||||
**6.后台命令** – Bash 默认会在当前终端执行你键入的每条命令。通常没有问题,但是如果你想要在启动应用后继续使用终端呢?通过输入 firefox 启动火狐浏览器,你的终端将被错误提示等各种信息输出占据,直到你关闭火狐浏览器为止。在 Bash 中你可以通过在命令结尾添加“&”操作符来后台执行程序。
|
||||
|
||||
firefox &
|
||||
|
||||
**7.条件执行** – Bash 也可以连续执行两条命令。 第二条命令仅在第一条命令成功执行后才会开始执行。如若如此,你可以通过键入“&&”,也就是两个与字符进行分隔,在同一行输入两条命令。下面给出的命令会在等待 5 秒后运行 gnome-screenshot 工具:
|
||||
|
||||
sleep 5 && gnome-screenshot
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.efytimes.com/e1/fullnews.asp?edid=123564
|
||||
|
||||
译者:[SteveArcher](https://github.com/SteveArcher) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:
|
||||
[2]:
|
||||
[3]:
|
||||
[4]:
|
||||
[5]:
|
||||
[6]:
|
||||
[7]:
|
||||
[8]:
|
||||
[9]:
|
||||
[10]:
|
||||
[11]:
|
||||
[12]:
|
||||
@ -0,0 +1,141 @@
|
||||
CentOS 6.5 桌面版安装教程附带大量截图
|
||||
================================================================================
|
||||
### CentOS 6.5 新版本发布 ###
|
||||
|
||||
随着RHEL 6.5新版本的发布,[CentOS 6.5][1]在12月1号准时跟上。现在是时间来玩弄它了。对于那些想要从已经安装好的6.4系统升级到6.5只要简单的使用* yum update *命令然后就是见证奇迹的时刻。
|
||||
|
||||
CentOS 6.5 迎来了新的更新包和新功能。可以在[release notes][2]中查看更多细节信息。
|
||||
|
||||
### 主要更新 ###
|
||||
|
||||
> 精密时间协议 - 以前仅是一个科技预览版 - 现在已经完整支持了!以下设备支持网络时间标记:bnx2x,tg3 , e1000e , igb , ixgbe ,sfc。
|
||||
> OpenSSL 升级到1.0.1版本
|
||||
> OpenSSL、NSS支持TLS1.1和1.2
|
||||
> KVM得到大量加强.包括提升对VMDK- 和 VHDX-Files 的只读,CPU支持热插拔以及升级了 virt-v2v-/virt-p2v-conversion 工具
|
||||
> Hyper-V 和 VMware 驱动升级
|
||||
> 升级到 Evolution(2.32)和 Libre Office(4.0.4)
|
||||
|
||||
### 下载 ###
|
||||
|
||||
这篇教程我们将要安装它的桌面版。请从下面的任意一个的url开始
|
||||
|
||||
[http://isoredirect.centos.org/centos-6/6.5/isos/][3]
|
||||
[http://mirror.centos.org/centos/6.5/isos/][4]
|
||||
|
||||
|
||||
选择你的机器制式,它会列出一张镜像表。进入任何一个镜像、得到种子文件下载或者直接下载iso链接。有许多选择下载方式可以选择,比如,LiveCD, LiveDVD, Dvd1+2, Minimal 和 Netinstall.
|
||||
|
||||
Minimal安装程序是一个提供文字安装,这样安装的CentOS将只有shell和最少软件应用程序。剩余的所有东西不得不你自己安装。
|
||||
|
||||
LiveCD/LiveDVD提供桌面版和GUI安装程序,可以安装CentOS系统但是不提供任何可选择的软件包。
|
||||
|
||||
DvD1+2 被设置为提供完整的应用程序给需要他的人
|
||||
|
||||
netinstall 事实上会先下载安装镜像然后再安装
|
||||
|
||||
这篇文章我们将使用LiveCD。 它大概有650MB。
|
||||
尽管CentOS主要使用在服务器上,但有一个桌面系统可以帮助你的服务器在安装时创造一个基础GUI的安装环境。在其他文章,我们将会尝试minimal 和 netinstall安装方法。
|
||||
|
||||
|
||||
### 安装 ###
|
||||
|
||||
所以现在,该是时候在你的桌面系统安装CentOS了。快点使用LiveDVD或者是LiveCD去启动运行吧!
|
||||
|
||||
|
||||
1.放入媒体然后重启。启动菜单有多个带说明的选项。选择Boot进入Live桌面。
|
||||
|
||||
|
||||

|
||||
|
||||
2.在桌面上双击下列安装图标,开启anaconda安装器。
|
||||
|
||||

|
||||
|
||||
3.进入安装向导,点击Next(下一步)
|
||||
|
||||

|
||||
|
||||
4.**键盘布局** - 这一步会询问你,选择你的键盘布局。(译注:推荐选择U.S. English)
|
||||
|
||||
|
||||

|
||||
|
||||
5.**存储类型**完成键盘布局的选择,接下来的是选择用来安装CentOS的存储类型。对于本地硬盘启动,应该选择Basic storage。
|
||||
|
||||

|
||||
|
||||
6.**主机名** 下一步 anaconda 安装器会询问主机名。所以填入适当的词。如果不确定,随意输入一个(译注:主机名hostname可以随时更改)。
|
||||
|
||||

|
||||
|
||||
7.**时区选择** 接下来选择时区选项。
|
||||
|
||||
|
||||

|
||||
|
||||
8.**Root 密码** 下面是输入 root 密码 ,最好是输入一个熟悉的密码。
|
||||
|
||||

|
||||
|
||||
9.**规划分区** 现在向导想要知道,你将要怎么规划存储设备。
|
||||
如果你需要自己规划分区,选择 “Custom Layout” 并根据需要分区。为了这篇教程的目的,我们选择了第一个选项,那就是使用整个设备并让CentOS用它喜欢的规划自动分区。
|
||||
|
||||

|
||||
|
||||
10.**复制文件** 现在安装已经开始复制文件了。现在除了等待和盯着没有什么事情可以做。LiveCD安装器基本上从CD镜像上复制到硬盘上。你没有得到任何安装包的选项去选择安装或省略。同样liveCD只有很少的软件和应用程序一起打包。
|
||||
|
||||

|
||||
|
||||
### 安装完毕后配置 ###
|
||||
|
||||
11.在安装完毕后会自动重启,欢迎向导将出现来进一步配置系统。
|
||||
|
||||

|
||||
|
||||
12.许可证协议 就像所有CentOS的软件一样会有一个很小只有几行的许可证。所以同意吧!
|
||||
|
||||

|
||||
|
||||
13.**创建用户** 现在为自己创建一个使用系统的普通用户。
|
||||
|
||||

|
||||
|
||||
14.**当前日期和时间** 输入当前日期和时间并且选择使用网络自动同步时间。
|
||||
|
||||

|
||||
|
||||
15.**Kdump**这是欢迎向导的最后一步,询问Kdump应该是开启还是关闭。推荐开启它。
|
||||
|
||||

|
||||
|
||||
### 开始使用 CentOS 6.5 ###
|
||||
|
||||
结束完之前步骤,系统将会重启,最后引导到登陆界面。
|
||||
|
||||

|
||||
|
||||
登陆之后,迎来的金光闪闪的CentOS 6.5 的桌面!
|
||||
|
||||

|
||||
|
||||
|
||||
希望你喜欢这篇安装指南,可以在下方留下你的评论和问题。
|
||||
|
||||
### 资源 ###
|
||||
|
||||
CentOS 6.5 release notes(版本记录)
|
||||
[http://wiki.centos.org/Manuals/ReleaseNotes/CentOS6.5][5]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.binarytides.com/centos-6-5-installation-screenshots/
|
||||
|
||||
译者:[Vic___](http://blog.csdn.net/Vic___) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://lists.centos.org/pipermail/centos-announce/2013-December/020032.html
|
||||
[2]:http://wiki.centos.org/Manuals/ReleaseNotes/CentOS6.5
|
||||
[3]:http://isoredirect.centos.org/centos-6/6.5/isos/
|
||||
[4]:http://mirror.centos.org/centos/6.5/isos/
|
||||
[5]:http://wiki.centos.org/Manuals/ReleaseNotes/CentOS6.5
|
||||
65
translated/Command Line Basics – watch.md
Normal file
65
translated/Command Line Basics – watch.md
Normal file
@ -0,0 +1,65 @@
|
||||
Linux 基础命令 – watch
|
||||
================================================================================
|
||||
linux系统里有一些日志文件。观察这些日志文件是系统管理员的一个重要任务。你可以很方便地[使用tail命令][1]观察它们。但是如果你想要长时间监视这些文件,每几分钟使用tail检查那些日志文件是一件很乏味的事情。你会写一个短小的[无限循环的脚本][2]来周期性地检查文件,但是它会导致已经有程序为你处理了重复的任务。
|
||||
|
||||
### Linux watch 命令 ###
|
||||
|
||||
Linux中的**watch** 命令提供了一种方式处理重复的任务。默认上**watch**会每2秒重复执行命令。就如你想的,watch是一个很好的观察log文件的工具。下面是一个例子。
|
||||
|
||||
watch tail /var/log/syslog
|
||||
|
||||
想要停止命令的执行,只要使用标准的kill流程, **[Ctrl]+C**。
|
||||
|
||||

|
||||
*使用Linux watch命令监测syslog*
|
||||
|
||||
你可以使用**-n**开关改变并指定时间间隔。要想每10秒检测日志文件,试试这个。
|
||||
|
||||
watch -n 10 tail /var/log/syslog
|
||||
|
||||
### 带有管道的watch命令 ###
|
||||
|
||||
**watch**没有被限制浏览日志文件。它可以用来重复你给它的任何命令。如果你要[监测CPU的温度][3],你可以使用**watch**后跟上**sensord**命令来查看。
|
||||
|
||||
watch -n 1 sensors
|
||||
|
||||
我电脑上的输出看上去就像这样:
|
||||
|
||||
acpitz-virtual-0
|
||||
Adapter: Virtual device
|
||||
temp1: +45.0°C (crit = +100.0°C)
|
||||
|
||||
我想过滤一下这个输出来只显示温度而不显示其他的。
|
||||
|
||||
我可以使用这个命令来查看
|
||||
|
||||
sensors | grep temp | awk '{ print $2 }'
|
||||
|
||||
记住,watch命令会重复它后面的第一个命令。必须要注意命令后面跟上管道的情况。你可以将你的命令放在引号里面来管理。
|
||||
|
||||
watch -n1 "sensors | grep temp | awk '{ print $2 }'"
|
||||
|
||||

|
||||
*带管道的watch命令*
|
||||
|
||||
### 将watch作为时钟 ###
|
||||
|
||||
就像你现在已经注意到的,**watch**执行后会在你的终端的右上角显示时间。我们可以通过传给watch一个空的命令参数来把它作为一个简单的时钟。 我们可以将一个空格包含在引号中来作为一个空的参数。
|
||||
|
||||
watch -n 1 " "
|
||||
|
||||
如你所见,这给予这个命令另外一个意义,**手表(watch)**。你可以把它作为你的腕表。
|
||||
|
||||
现在你知道如何使用Linux的watch命令。你要用它处理什么重复任务?
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://tuxtweaks.com/2013/12/linux-watch-command/
|
||||
|
||||
译者:[geekpi](https://github.com/geekpi) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://tuxtweaks.com/2011/02/command-line-basics-head-and-tail/
|
||||
[2]:http://tuxtweaks.com/2012/01/creating-a-terminal-window-clock/
|
||||
[3]:http://tuxtweaks.com/2008/08/how-to-control-fan-speeds-in-ubuntu/
|
||||
@ -0,0 +1,45 @@
|
||||
每日Ubuntu小技巧 - 使用Ubuntu拷贝CD和DVD光盘
|
||||
================================================================================
|
||||
Ubuntu,一个功能强大的现代操作系统,可以执行很多任务。你可以使用Ubuntu创建文档,浏览网页,聆听音乐,以及烧录或拷贝媒体光盘。
|
||||
|
||||
就像Windows和Max OS X一样,Ubuntu是无所不能的!
|
||||
|
||||
这篇简单的手册将告诉你如何使用Ubuntu拷贝,翻录或烧录一张CD/DVD光盘。如果你有一张包含音频文件(音乐)或视频文件(电影)的光盘,并且你想要复制这张光盘(创建多个副本),使用Ubuntu会使你很容易做到。
|
||||
|
||||
如果你已经准备好想要拷贝进一张媒体光盘(CD/DVD)的音频或视频文件,Ubuntu也可以处理它。你可以在Ubuntu上安装很多的免费软件用于烧录或翻录一张CD/DVD光盘,但Ubuntu已经安装好一款默认的相关软件。接下来我们会使用这款默认软件去拷贝或翻录CD/DVD光盘。
|
||||
|
||||
Brasero光盘烧录机安装在UBuntu的每一个版本上。它是Ubuntu上默认的光盘烧录机。它被设计得足够简单,拥有诸多独特的特性来使得用户能够快速简便地创建光盘。
|
||||
|
||||
下面列出来的是Brasero的一些特性:
|
||||
- 创建数据CD/DVD时自动过滤隐藏和损坏的文件
|
||||
- 同时支持多个绘画,可以执行磁盘文件的完整性
|
||||
- 可以在忙碌中烧录视频CD/DVD[on the fly翻译不合适]
|
||||
- 可以拷贝CD/DVD到系统硬盘
|
||||
- 可以擦除CD/DVD
|
||||
|
||||
还有很多其它的功能。如果你想找一个Ubuntu上简便的磁盘刻录机,在做任何操作前请先检查这个软件。
|
||||
|
||||
为了开始使用Brasero去烧录CD/DVD光盘,请确保你的电脑安装了CD/DVD烧录机。如果没有,你将无法成功烧录。如果你的电脑符合要求,将你想要翻录的数据插入CD/DVD,然后进入Dash,搜索Brasero。
|
||||
|
||||
当Brasero打开后,选择磁盘拷贝。这个功能会拷贝一个光盘里的内容,然后将其写入到另一个光盘中。如果这是你想要的,请继续。
|
||||
|
||||

|
||||
|
||||
如果Ubuntu能够访问你的CD/DVD烧录机,Brasero会打开并自动识别光盘内容。在这里,你可以单击 **复制** 从源光盘创建一个拷贝。如果你希望创建多个拷贝,单击按钮 **创建多个拷贝**。
|
||||
|
||||

|
||||
|
||||
当系统提示安装所需的软件包时,单击 **安装**。
|
||||
|
||||

|
||||
|
||||
安装完成后,Brasero会开始拷贝光盘。如果最终光盘完成拷贝,系统会提示你插入一张空白的可写入的CD/DVD光盘以便写入拷贝。插入它然后等待完成将内容写入光盘的操作。
|
||||
|
||||
当你完成以上操作时,移除光盘,就可以使用烧录好的光盘了!
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.liberiangeek.net/2013/12/daily-ubuntu-tips-copy-cd-dvd-discs-using-ubuntu/
|
||||
|
||||
译者:[KayGuoWhu](https://github.com/KayGuoWhu) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
@ -1,12 +1,12 @@
|
||||
每日 Ubuntu 小技巧 - 更改 Ubuntu 使用语言
|
||||
================================================================================
|
||||
Ubuntu,是一个现代的并且强大的操作系统,同样它还能允许你使用多种语言的桌面。在默认的情况下,在你第一次安装 Ubuntu 的时候会预装几个语言包。但如果你想你的 Ubuntu 能够支持更多语言的话,那你就必须安装额外的语言包。通常不是所有的语言都是支持的,但是基本上所有在用和在写的语言都能够被支持。下面是一个是简短的教程,它将会展示如何去实现。
|
||||
Ubuntu 是一个功能强大的现代化操作系统,并且它还允许你使用多种语言的桌面。在默认情况下,在你第一次安装 Ubuntu 的时候会预装几个语言包。但如果你想要你的 Ubuntu 能够支持更多语言的话,那你就必须安装额外的语言包。通常不是所有的语言都是支持的,但是大多数使用中的语言以及书面语言都能够被支持。下面是一个是简短教程,它将会展示如何去实现。
|
||||
|
||||
在安装了语言包之后,你可以根据你的语言重命名标准文件夹,例如音乐,图片和文档。你必须注销系统然后重新登录来使变更生效。当你重新登录之后,你会看到一个弹窗并且询问你是否愿意重命名这些标准文件夹,从而使得文件名满足你的所选择的语言要求。
|
||||
在安装语言包之后,你可以根据你的语言重命名标准文件夹,例如音乐、图片和文档。你必须注销系统然后重新登录来使变更生效。当你重新登录之后,你会看到一个弹窗并且询问你是否愿意重命名这些标准文件夹,从而使得文件名满足你的所选择的语言要求。
|
||||
|
||||
要想更改 Ubuntu 的使用语言,单击右上角菜单栏的 **gear**,并且选择 **System Settings**。在打开 System Settings 之后,选择 **Language Support**。
|
||||
要想更改 Ubuntu 的使用语言,单击菜单栏右上角的 **gear**,并且选择 **System Settings**。在打开 System Settings 之后,选择 **Language Support**。
|
||||
|
||||
如果提示要你安装额外的语言支持,那就先安装。如果没有,那么就单击 Install / Remove 去安装新的语言包,然后,选择你想安装的语言来安装。最后,拖动新的语言到列表的顶端并且保存。这些更改只会应用在你的个人帐号上。如果你想应用在全局范围内,单击 **Apply System-Wide** 。
|
||||
如果提示要你安装额外的语言支持,那就直接安装。如果没有,那么就单击 Install / Remove 去安装新的语言包,然后,选择你想安装的语言来安装。最后,拖动新的语言到列表的顶端并且保存。这些更改只会应用在你的个人帐号上。如果你想应用在全局范围内,单击 **Apply System-Wide** 。
|
||||
|
||||
|
||||
|
||||
@ -22,12 +22,12 @@ Ubuntu,是一个现代的并且强大的操作系统,同样它还能允许
|
||||
|
||||
如果你选择了重命名标准文件夹,你必须重新登录才能看到变更。
|
||||
|
||||
去爽吧!
|
||||
好好享受吧!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.liberiangeek.net/2013/10/daily-ubuntu-tipschange-the-language-you-use-in-ubuntu/
|
||||
|
||||
译者:[hyaocuk](https://github.com/hyaocuk) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
译者:[hyaocuk](https://github.com/hyaocuk) 校对:[Caroline](https://github.com/carolinewuyan)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,28 +0,0 @@
|
||||
GCC 4.9现在处于修复BUG的第3阶段
|
||||
================================================================================
|
||||
|
||||
[GCC 4.9][1]将拥有很多[新功能][2]将定于2014年上半年发布。早先的GCC代码基础将不会支持新的功能,因为它是一个大修复的标记。
|
||||
|
||||
|
||||
Richard Biener今早宣称分支已经发展到了阶段三,因此在之后的八月将这些功能融入4.9版本,除非发布经理授权的异常发生,不然毫无变化。阶段三只允许一般BUG的修复工作,将在2个月内完成而到达只允许文档和回归的阶段四。
|
||||
|
||||
|
||||
|
||||
目前GCC4.9有63 P1 回归(最严重的回归)其次是136 P2回归,14 P3回归,88 P4 回归 以及 60 P5回归。直到63回归的P1阶段被清零,GCC4.9才会被关闭去发布。GCC 4.9.0 发布版将可能在2014第二季度左右到来!
|
||||
|
||||
|
||||
早先的GCC 4.9.0状态报告可以在[GCC mailing list][3]中被找到。GCC 4.9将会是一个美好的编译器更新,并会挑战下个月发布的[LLVM3.4][4]。
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.phoronix.com/scan.php?page=news_item&px=MTUyMjk
|
||||
|
||||
译者:[Vic___](http://blog.csdn.net/Vic___) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.phoronix.com/scan.php?page=search&q=GCC+4.9
|
||||
[2]:http://www.phoronix.com/scan.php?page=news_item&px=MTUxNzQ
|
||||
[3]:http://gcc.gnu.org/ml/gcc/2013-11/msg00435.html
|
||||
[4]:http://www.phoronix.com/scan.php?page=search&q=LLVM+3.4
|
||||
52
translated/How to Repack Deb Files on Debian and Ubuntu.md
Normal file
52
translated/How to Repack Deb Files on Debian and Ubuntu.md
Normal file
@ -0,0 +1,52 @@
|
||||
如何在Debian和Ubuntu下重新打包Deb文件
|
||||
|
||||
================================================================================
|
||||
|
||||
**以下教程会教导Ubuntu,Linux Mint和Debian GUN/Linux用户,如何在它们基于Debian的Linux操作系统上轻松的解开和重建.deb文件。**
|
||||
|
||||

|
||||
|
||||
有时候你会碰到这样或那样的问题,你想要修改.deb文件的部分内容,然后重新打包。但是,也只有你真正的进入计算机世界之中。
|
||||
|
||||
下面的例子是刚发生在我身上真实的经历。一位Linux的开发者为一个软件构建了一个Debian包(.deb),我也成功得将它安装在我的装载Ubuntu的电脑上。
|
||||
|
||||
当我试图从一个Git库中检索一些文件时,它总是卡顿,佷显然,该软件并没有正常工作。我知道安装的文件在哪里(/opt目录),所以,我搜查了代码并适当的将部分问题修复。之后,当程序试图检索需要的包时不再卡顿。
|
||||
|
||||
所以,长话短说,我要将.deb文件解包,替换上我的补丁文件,然后再重新打包回来。这样我可以其他电脑上安装,或者将有效的包文件给我的朋友。我要怎么做呢?
|
||||
|
||||
在网络上搜索问题的答案,我发现一个名叫[ailoo.net][1]的小型博客,类似这样解释:
|
||||
|
||||
mkdir -p extract/DEBIAN
|
||||
|
||||
dpkg-deb -x package.deb extract/
|
||||
|
||||
dpkg-deb -e package.deb extract/DEBIAN [...do something, e.g. edit the control file...]
|
||||
|
||||
mkdir build
|
||||
|
||||
dpkg-deb -b extract/ build/
|
||||
|
||||
这五个命令像一个魔法来完成工作。让我向你解释:第一条命令创建了一个名为“extract”文件夹和一个名为“DEBIAN”的子文件夹;第二条命令会从你的.deb包提取程序文件到“extract”文件夹;第三条命令会解压.deb包的控制文件到“DEBIAN”子文件夹,在那里你就可以 修改/补丁 你想要的文件;第四条命令建立一个名为“build”的文件夹;而第五条命令会将修改后的文件重新构建到一个新的.deb包中,并在 “build” 文件夹中生成。
|
||||
|
||||
这就是本次的教程!牢牢地记住上面的命令吧,在你执行第三条命令后,可以通过你默认的文件管理器用一个图形化的文本编辑器,可视化的修改文件。如果你在这个教程上遇到问题,你可以毫不犹豫的评论给我们。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://news.softpedia.com/news/How-to-Repack-Deb-Files-on-Debian-and-Ubuntu-404930.shtml
|
||||
|
||||
译者:[Luoxcat](https://github.com/Luoxcat) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://ailoo.net/2009/06/repack-a-deb-archive-with-dpkg-deb/
|
||||
[2]:
|
||||
[3]:
|
||||
[4]:
|
||||
[5]:
|
||||
[6]:
|
||||
[7]:
|
||||
[8]:
|
||||
[9]:
|
||||
[10]:
|
||||
[11]:
|
||||
[12]:
|
||||
@ -1,91 +0,0 @@
|
||||
Linux 宗旨:‘开源很安全,Linux比其它任何系统都安全’
|
||||
|
||||
================================================================================
|
||||
在对Linux基金会执行官,Jim Zemlin 的采访中,VentureBeat 展望了2014开源操作系统的未来。
|
||||
|
||||
We also addressed the controversial issues of government spying and “backdoors” — those nefarious windows into our personal online lives that the public recently discovered in most of the services we use every day.
|
||||
|
||||
我们也探讨了争议性的话题,就是政府部门的监听事件以及‘后门’-那些邪恶的窗口,窥探我们网上的私生活,最近公众发现我们经常使用的大多数服务都有类似的遭遇。
|
||||
|
||||
Zemlin gave us the skinny on how and why GNU/Linux remains the most secure option for concerned consumers — and why it’s becoming the OS of choice for powering cars, phones, TVs, and all kinds of emerging devices.
|
||||
Zemlin 为我们解释了 GNU/Linux 为什么以及如何使自身成为内心有些担忧的消费者的最安全的选择。还有就是为什么选择GNU/Linux作为车载操作系统,TVs以及其他新兴设备的操作系统。
|
||||
|
||||
以下是我们e-mail问答形式的实录。
|
||||
|
||||
----------
|
||||
|
||||
**VentureBeat: 安全和隐私成为今年的热门话题,我们听到的谣言,Linus[Torvalds, Linux 创始人]对政府部门是否有安装后门的要求点头称是。**
|
||||
|
||||
**Zemlin**: Linux是否有后门,你是可以知道的.
|
||||
|
||||
世界上所有人都可以看到Linux的每一行代码。这也是linux要比其他操作系统更安全、开源整体要比闭源更安全的原因之一。代码的透明度保证了它的安全性。
|
||||
|
||||
And for the record: He wasn’t approached.
|
||||
记录在案的是:后门并没有进入到linux。
|
||||
|
||||
**VentureBeat: Linux基金会如何保证Linux用户的隐私和自由,使其免于遭受追踪和监视?**
|
||||
|
||||
**Zemlin**: 对此,我们一以贯之。向内核插入违反隐私权和背离自由精神的代码而不被成千上万的开发者注意到,这是很难的。Linux的本性就是自我定制。
|
||||
|
||||
**VentureBeat: 今年的隐私/安全/监视事件会不会促使, 或者将会促使更多的消费者倾向于Linux,对此你作何感想?**
|
||||
|
||||
**Zemlin**: 世界范围内,我听到人们都在说,“用开源保证隐私是必须的。”的确,那会促使更多的使用者选择Linux。
|
||||
|
||||
除了他们对linux平台下的隐私和安全持自信、信任的态度以外, 我认为消费者会基于多种原因选择Linux。
|
||||
代码的透明性以及开发过程逐渐给予博学和警觉的消费者一个选择,一个会让他们对linux感觉良好的选择。
|
||||
|
||||
[视频游戏发行商] Valve [及其SteamOS下的工作][1] 正在促使更多的消费者走进Linux,就像逐渐占据主导的Android和其他运行Linux的电子设备一样,比如电视、家电、汽车等,当然还有更多。
|
||||
|
||||
**VentureBeat: 针对手机的Ubuntu Edge, 对它有何看法? 对于2014-2015年Linux/Ubuntu手机市场走势,你作何预测?*
|
||||
|
||||
**Zemlin**:我希望看到潜在的有趣的新产品进入市场,尤其是基于Linux的产品。很难说每年哪款产品会成为手机市场的新宠。
|
||||
|
||||
我认为预测基于Linux的手机将占据主导地位,不算夸大事实。Android, Tizen, Ubuntu, Firefox,等等等等,都显示出Linux可以驱动手机市场的创新,并且为消费者创造新的体验,为开发者和OEMs创造机会。
|
||||
|
||||
明年令人振奋的及我所关注的,就是,linux和开源界如何把这些设备、对象和服务关联到一起。
|
||||
|
||||
**VentureBeat: What’s the most exciting use case you’ve seen so far for Linux embedded in automobile systems?**
|
||||
**VentureBeat: 目前为止,你看到的linux嵌入式车载系统的最令人激动的使用案例是什么?**
|
||||
|
||||
**Zemlin**: 毫无疑问,就是,Cadillac, Tesla, Toyota, Jaguar, Land Rover等都搭建了车载信息娱乐系统。
|
||||
|
||||
比如,今年赢得了 “年度汽车族”奖项的Tesla Model S,装备了一个17英寸平面、运行着定制Linux的电脑。这真的是太酷了。
|
||||
|
||||
2014年度汽车族刚刚揭晓 -- Cadillac CTS sedan, 也是使用linux作为车载信息娱乐系统。汽车制造商有能力使用linux进行创新并区别使用这些系统。
|
||||
|
||||
Linux的成功也能从来自IHS汽车的最新数据上看到,IHS本月报告称,在全球车载信息娱乐市场,基于linux的汽车销量2020年有望达到5.37千万,超过微软和黑莓QNX。
|
||||
|
||||
Linux基金会协同汽车级Linux工作组在该领域做了许多工作。通过在Linux内核社区,其他开源社区,以及汽车行业,营造一个中立、支持性的环境,针对一些世界上大的汽车制造商如日产,捷豹,路虎,丰田,等等,我们可以帮助其推动汽车linux技术。
|
||||
|
||||
**VentureBeat: 在硬核开发者市场以外,Linux是如何发展壮大的,尤其是考虑到消费者和游戏玩家?**
|
||||
|
||||
**Zemlin**:可以肯定的是,对游戏玩家来说,今年是linux的一个转折点。Valve, 基于Steam网络平台的一个游戏厂商,在linux上构建并运行所有的源代码和动画。Valve CEO Gabe Newell 称,今年的LinuxCon大会上他们在linux平台运行了198个游戏,随着引进基于linux的Stream,这个数字还会上升。这是Linux和游戏界新趋势的开端。
|
||||
|
||||
用户每天都在用linux。软件支撑着我们的日常生活。像Google,Facebook还有Twitter等公司,都建立在Linux和开源软件之上。去年10月份LinuxCon欧洲大会上,来自Twitter的Chris Aniszczyk告诉观众:
|
||||
“Twitter 理所当然完全运行在linux上。为什么你们还需要其他的东西?”(言外之意就是有linux就够了,不需要别的什么东西了。)
|
||||
|
||||
如今Linux驱动着130万台日常用Android手机,每天近60万基于linux的新电视售出。新的家电以及汽车都建立在linux之上。主要交通系统也都在使用linux。最受欢迎的[GoPro 使用linux和开源软件][2]。举不完的例子。
|
||||
|
||||
Linux和开源理念将会逐渐融入主流消费者的生活。三星使用linux内核以及基于linux的产品充实它的产品线,从电视机到手机,再到家电,等等等等。
|
||||
|
||||
敬请关注 - 你会看到更多的实例,无不展现出Linux和开源软件以及协同开发在日常生活中发挥越来越大的作用。
|
||||
|
||||
**VentureBeat: 在你看来,到2014年,免费和开源软件最大的机遇会是什么?**
|
||||
|
||||
**Zemlin**: 我们已经谈到游戏和电子设备,但是企业将会继续为linux呈现更多的机会。云计算的兴起为开发者带来新的机遇和挑战。你试着去找找没有运行在linux上的公共云。
|
||||
|
||||
软件定义的网络实现将成为2014年的主要活动之一。人们并没有期望着软件定义网络以及网络功能虚拟化变得多么大。想想吧。数十亿美元花费在硬件上,交换机,路由,负载均衡器,防火墙等等。这些都抽象成了软件。更更重要的是,它是在开源软件的基础架构甜蜜点OSS层被抽象。我认为你会看到,像OpenDaylight项目以及其他项目,在2014年都会有大的突破。
|
||||
|
||||
当然,这只是实现协同发展的大趋势的一部分,你的读者应该会对此感兴趣。我的推测是再过一个20年,几乎所有的基础软件都会议协同开发的方式进行构建。2014年开发者需要学习如何以协同方式构建软件,要学会如何参与开源项目并且贡献代码。如果开发者能够理解协同开发和开源的原则和理念,那么他们职业生涯中的机遇将会是无穷的。
|
||||
|
||||
参与到linux的世界中来,这是一个激动人心的时刻。从智能手表到电视机,到汽车,所有你能想到的,Linux成为事实上的平台。
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://venturebeat.com/2013/11/26/linux-chief-open-source-is-safer-and-linux-is-more-secure-than-any-other-os-exclusive/
|
||||
|
||||
译者:[译者ID](https://github.com/l3b2w1) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://venturebeat.com/2013/09/23/steamos-valves-linux-based-operating-system-for-the-tv-and-living-room/
|
||||
[2]:http://gopro.com/support/open-source
|
||||
189
translated/Setup FTP Server On openSUSE 13.1.md
Normal file
189
translated/Setup FTP Server On openSUSE 13.1.md
Normal file
@ -0,0 +1,189 @@
|
||||
translating by zsJacky
|
||||
|
||||
在openSUSE 13.1中配置FTP服务器
|
||||
================================================================================
|
||||
**vsftpd** (**非常****安全的****文件****传输****协议****守护进程**) 是Unix/Linux系统中的一个安全快速的FTP服务器。 在这篇 how-to 文章中,让我们看看在openSUSE 13.1中怎样使用vsftpd来配置一个基本的FTP服务器。
|
||||
|
||||
### 安装 vsftpd ###
|
||||
|
||||
作为root用户登录然后输入以下的命令。
|
||||
|
||||
# zypper in vsftpd
|
||||
|
||||
启动 vsftpd 服务然后设置让它在每次系统重启时自动启动
|
||||
|
||||
# systemctl enable vsftpd.service
|
||||
# systemctl start vsftpd.service
|
||||
|
||||
### 配置 vsftpd ###
|
||||
|
||||
为ftp用户新建一个文件夹。
|
||||
|
||||
# mkdir /srv/ftp
|
||||
|
||||
创建一个叫 **ftp-users** 的组。
|
||||
|
||||
# groupadd ftp-users
|
||||
|
||||
让我们来创建一个叫unixmen的示例用户 并设置其主目录为 **/srv/ftp** 组为**ftp-users**。
|
||||
|
||||
# useradd -g ftp-users -d /srv/ftp/ unixmen
|
||||
|
||||
为新用户设置密码。
|
||||
|
||||
# passwd unixmen
|
||||
|
||||
使ftp主目录 **/srv/ftp/** 可以被ftp用户所访问。
|
||||
|
||||
# chmod 750 /srv/ftp/
|
||||
# chown unixmen:ftp-users /srv/ftp/
|
||||
|
||||
编辑 vsftpd.conf 文件
|
||||
|
||||
# nano /etc/vsftpd.conf
|
||||
|
||||
设置如下的更改。
|
||||
|
||||
[...]
|
||||
#Uncomment and Set YES to enable write.
|
||||
write_enable=YES
|
||||
[...]
|
||||
# Uncomment and Set banner name for your website
|
||||
ftpd_banner=Welcome to Unixmen FTP service.
|
||||
[...]
|
||||
# Uncomment
|
||||
ls_recurse_enable=YES
|
||||
[...]
|
||||
# Uncomment and set YES to allow local users to log in.
|
||||
local_enable=YES
|
||||
[...]
|
||||
# To disable anonymous access, set NO.
|
||||
anonymous_enable=NO
|
||||
[...]
|
||||
# Uncomment to enable ascii download and upload.
|
||||
ascii_upload_enable=YES
|
||||
ascii_download_enable=YES
|
||||
[...]
|
||||
## Add at the end of this file ##
|
||||
use_localtime=YES
|
||||
|
||||
保存并退出文件。
|
||||
|
||||
### 测试本地FTP服务器 ###
|
||||
|
||||
首先 让我们按如下步骤尝试登陆FTP服务器
|
||||
|
||||
# ftp localhost
|
||||
Trying ::1:21 ...
|
||||
Connected to localhost.
|
||||
220 (vsFTPd 3.0.2)
|
||||
Name (localhost:root): unixmen
|
||||
331 Please specify the password.
|
||||
Password:
|
||||
230 Login successful.
|
||||
Remote system type is UNIX.
|
||||
Using binary mode to transfer files.
|
||||
ftp>
|
||||
|
||||
正如你在上面所输出的那样, 我们将能够用unixmen用户登录到ftp服务器。
|
||||
### 测试远程FTP服务器 ###
|
||||
|
||||
默认地 openSUSE内置的防火墙不允许从远程系统登陆FTP。所以让我们允许vsftpd服务通过suse的防火墙。然后我们需要打开: **Yast -> 安全性与用户 -> 防火墙**.
|
||||
|
||||

|
||||
|
||||
在防火墙界面,进入 **允许服务**. 在区域选择下拉框中,选择 **外部区域** 在服务允许下拉框中,选择 **vsftpd 服务器** 然后点击添加。
|
||||
|
||||

|
||||
|
||||
单击下一步并关闭Yast控制中心
|
||||
|
||||
现在尝试从远程系统连接FTP。
|
||||
|
||||
我试着从我的ubuntu桌面系统登录FTP服务器。
|
||||
|
||||
sk@sk:~$ ftp 192.168.1.53
|
||||
Connected to 192.168.1.53.
|
||||
220 (vsFTPd 3.0.2)
|
||||
Name (192.168.1.53:sk): unixmen
|
||||
331 Please specify the password.
|
||||
Password:
|
||||
230 Login successful.
|
||||
Remote system type is UNIX.
|
||||
Using binary mode to transfer files.
|
||||
ftp>
|
||||
|
||||
正如你在上面输出中所看到的,我将能够连接到ftp服务器。如果不允许vsftpd服务通过防火墙, 你将会得到一个连接超时的错误。
|
||||
|
||||
### 从浏览器连接 ###
|
||||
|
||||
打开你的浏览器并导航到**ftp://ip-address/**。输入ftp用户名和密码。
|
||||
|
||||

|
||||
|
||||
### 使用FileZilla连接到FTP服务器 ###
|
||||
|
||||
对于新手来说,在命令行模式下工作可能会很烦恼。所以让我们来安装一个叫[**Filezilla**][1]的图形化的FTP客户端。它可以让我们登陆FTP变得更加简单:
|
||||
|
||||
几乎所有的发行版在他们的官方软件仓库中都有filezilla客户端。 为了在基于Linux的系统上安装filezilla 需要键入以下的命令:
|
||||
|
||||
在基于Ubuntu的系统中:
|
||||
|
||||
$ sudo apt-get install filezilla
|
||||
|
||||
在Fedora/Redhat系统中:
|
||||
|
||||
$ sudo yum install filezilla
|
||||
在openSUSE中:
|
||||
|
||||
# zypper in filezilla
|
||||
|
||||
安装完fielzilla后打开它。输入ftp服务器的IP地址,用户名和密码,然后点击快速链接。
|
||||
|
||||

|
||||
|
||||
为了增加安全性,你可以通过将用户添加到 **/etc/vsftpd.chroot_list**文件中来限制特定用户对FTP服务器的访问。
|
||||
|
||||
编辑 vsftpd.conf 文件,
|
||||
|
||||
nano /etc/vsftpd.conf
|
||||
|
||||
设置如下的更改.
|
||||
|
||||
[...]
|
||||
# Uncomment and set YES
|
||||
chroot_local_user=YES
|
||||
chroot_list_enable=YES
|
||||
chroot_list_file=/etc/vsftpd.chroot_list
|
||||
[...]
|
||||
|
||||
创建 **文件 /etc/vsftpd.chroot_list**,
|
||||
|
||||
nano /etc/vsftpd.chroot_list
|
||||
|
||||
添加你希望其能够访问FTP服务器的用户。我添加了用户**unixmen**。
|
||||
|
||||
unixmen
|
||||
|
||||
重启ftp服务.
|
||||
|
||||
# systemctl restart vsftpd.service
|
||||
|
||||
现在你将能够使用chroot_list文件中列出的用户来连接到FTP服务器。
|
||||
|
||||
如果chroot_list以外的用户想访问FTP服务器, 他们将得到如下的错误。
|
||||
|
||||
500 OOPS: could not read chroot() list file:/etc/vsftpd.chroot_list
|
||||
ftp: Login failed
|
||||
|
||||
现在就是这样。 你的FTP服务器已经可以使用了。 享受吧!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.unixmen.com/setup-ftp-server-opensuse-13-1/
|
||||
|
||||
译者:[zsJacky](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:https://filezilla-project.org/
|
||||
34
translated/Top Email Encryption Tools.md
Normal file
34
translated/Top Email Encryption Tools.md
Normal file
@ -0,0 +1,34 @@
|
||||
超赞的电子邮件加密工具
|
||||
================================================================================
|
||||
电子邮件仍然是 Linux 操作系统下最受欢迎,也是最有效的服务之一。无论何时,与你的朋友、家人还有同事保持联络都是不可或缺的。随着电子邮件敲诈事件的剧增,操作系统对电子邮件的安全与加密工作变得越来越复杂,也越来越重要。保护电子邮件免于未经授权的访问与查阅是关键环节,因为电子邮件管理协议中并未包含加密部分。电子邮件在设计初并未考虑隐私和安全问题。匮乏的安全措施所导致的后果是一封电子邮件既可以存在于发送设备,也可以存在于交互网络、服务器,或者是接收设备上。
|
||||
|
||||
保护电子邮件信息安全的方法之一,是发送经过加密的信息。通过信息加密,你可以确保信息在发送过程中不会泄露,未经授权者只能看到毫无意义的乱码。电子邮件加密听起来很高端,事实上由专门的软件来实现再容易不过。
|
||||
|
||||
OpenPGP 是使用最广泛的电子邮件加密协议标准。无论你使用的是电子邮件客户端,还是 Web 客户端,你都可以通过 OpenPGP 协议来加密你的电子邮件。
|
||||
|
||||
很少有哪些电子邮件应用程序会默认安装 PGP 协议。不过幸运的是,Linux 下有不少简单而又易用的开源加密软件。
|
||||
|
||||
为了更直观地对比这些加密软件的效果,我们列出了以下清单。
|
||||
|
||||
现在,让我们仔细研究这四款电子邮件加密软件。每个标题下我们都收集了软件各自的特征,用完整的描述进行了深度分析,同时也附上了资源链接与评论。
|
||||
|
||||
### 电子邮件加密工具 ###
|
||||
|
||||
- [Enigmail][1] Mozilla 系列的 OpenPGP 电子邮件加密软件
|
||||

|
||||
- [Mailvelope][2] 谷歌与火狐浏览器的扩展插件
|
||||
- [GnuPG][3] 加密模糊数据通信
|
||||
- [Mymail-Crypt for Gmail][4] 简易电子邮件加密软件
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linuxlinks.com/article/2013120707481589/EmailEncryption.html
|
||||
|
||||
译者:[SteveArcher](https://github.com/SteveArcher) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.enigmail.net/
|
||||
[2]:http://www.mailvelope.com/
|
||||
[3]:http://www.gnupg.org/
|
||||
[4]:https://chrome.google.com/webstore/detail/mymail-crypt-for-gmail/jcaobjhdnlpmopmjhijplpjhlplfkhba
|
||||
@ -1,4 +1,3 @@
|
||||
[翻译中] by KayGuoWhu
|
||||
Unvanquished 可能成为Linux上最好的免费多人游戏
|
||||
================================================================================
|
||||
**Unvanquished,一款免费的、开源的并将实时策略元素和未来科幻设定相结合的第一人称视角的射击游戏,已经收到了它的第22次更新。事实上,版本是22.1,但是是谁在计数呢?**
|
||||
@ -39,4 +38,4 @@ via: http://news.softpedia.com/news/Unvanquished-Will-Probably-Be-the-Best-Free-
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.unvanquished.net/news/111-it-s-release-time-again-alpha-22
|
||||
[2]:http://www.unvanquished.net/download#linux
|
||||
[2]:http://www.unvanquished.net/download#linux
|
||||
|
||||
Loading…
Reference in New Issue
Block a user