mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-03-12 01:40:10 +08:00
Merge branch 'master' of https://github.com/LCTT/TranslateProject
This commit is contained in:
commit
9e04e40afb
@ -0,0 +1,63 @@
|
||||
在Ubuntu中安装Visual Studio Code
|
||||
================================================================================
|
||||

|
||||
|
||||
微软令人意外地[发布了Visual Studio Code][1],并支持主要的桌面平台,当然包括linux。如果你是一名需要在ubuntu工作的web开发人员,你可以**非常轻松的安装Visual Studio Code**。
|
||||
|
||||
我将要使用[Ubuntu Make][2]来安装Visual Studio Code。Ubuntu Make,就是以前的Ubuntu开发者工具中心,是一个命令行工具,帮助用户快速安装各种开发工具、语言和IDE。也可以使用Ubuntu Make轻松[安装Android Studio][3] 和其他IDE,如Eclipse。本文将展示**如何在Ubuntu中使用Ubuntu Make安装Visual Studio Code**。(译注:也可以直接去微软官网下载安装包)
|
||||
|
||||
### 安装微软Visual Studio Code ###
|
||||
|
||||
开始之前,首先需要安装Ubuntu Make。虽然Ubuntu Make存在Ubuntu15.04官方库中,**但是需要Ubuntu Make 0.7以上版本才能安装Visual Studio**。所以,需要通过官方PPA更新到最新的Ubuntu Make。此PPA支持Ubuntu 14.04, 14.10 和 15.04。
|
||||
|
||||
注意,**仅支持64位版本**。
|
||||
|
||||
打开终端,使用下列命令,通过官方PPA来安装Ubuntu Make:
|
||||
|
||||
sudo add-apt-repository ppa:ubuntu-desktop/ubuntu-make
|
||||
sudo apt-get update
|
||||
sudo apt-get install ubuntu-make
|
||||
|
||||
安装Ubuntu Make完后,接着使用下列命令安装Visual Studio Code:
|
||||
|
||||
umake web visual-studio-code
|
||||
|
||||
安装过程中,将会询问安装路径,如下图:
|
||||
|
||||

|
||||
|
||||
在抛出一堆要求和条件后,它会询问你是否确认安装Visual Studio Code。输入‘a’来确定:
|
||||
|
||||

|
||||
|
||||
确定之后,安装程序会开始下载并安装。安装完成后,你可以发现Visual Studio Code 图标已经出现在了Unity启动器上。点击图标开始运行!下图是Ubuntu 15.04 Unity的截图:
|
||||
|
||||

|
||||
|
||||
### 卸载Visual Studio Code###
|
||||
|
||||
卸载Visual Studio Code,同样使用Ubuntu Make命令。如下:
|
||||
|
||||
umake web visual-studio-code --remove
|
||||
|
||||
如果你不打算使用Ubuntu Make,也可以通过微软官方下载安装文件。
|
||||
|
||||
- [下载Visual Studio Code Linux版][4]
|
||||
|
||||
怎样!是不是超级简单就可以安装Visual Studio Code,这都归功于Ubuntu Make。我希望这篇文章能帮助到你。如果您有任何问题或建议,欢迎给我留言。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://itsfoss.com/install-visual-studio-code-ubuntu/
|
||||
|
||||
作者:[Abhishek][a]
|
||||
译者:[Vic020/VicYu](http://vicyu.net)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://itsfoss.com/author/abhishek/
|
||||
[1]:https://linux.cn/article-5376-1.html
|
||||
[2]:https://wiki.ubuntu.com/ubuntu-make
|
||||
[3]:http://itsfoss.com/install-android-studio-ubuntu-linux/
|
||||
[4]:https://code.visualstudio.com/Download
|
||||
@ -0,0 +1,164 @@
|
||||
如何使用Vault安全的存储密码和API密钥
|
||||
=======================================================================
|
||||
Vault是用来安全的获取秘密信息的工具,它可以保存密码、API密钥、证书等信息。Vault提供了一个统一的接口来访问秘密信息,其具有健壮的访问控制机制和丰富的事件日志。
|
||||
|
||||
对关键信息的授权访问是一个困难的问题,尤其是当有许多用户角色,并且用户请求不同的关键信息时,例如用不同权限登录数据库的登录配置,用于外部服务的API密钥,SOA通信的证书等。当保密信息由不同的平台进行管理,并使用一些自定义的配置时,情况变得更糟,因此,安全的存储、管理审计日志几乎是不可能的。但Vault为这种复杂情况提供了一个解决方案。
|
||||
|
||||
### 突出特点 ###
|
||||
|
||||
**数据加密**:Vault能够在不存储数据的情况下对数据进行加密、解密。开发者们便可以存储加密后的数据而无需开发自己的加密技术,Vault还允许安全团队自定义安全参数。
|
||||
|
||||
**安全密码存储**:Vault在将秘密信息(API密钥、密码、证书)存储到持久化存储之前对数据进行加密。因此,如果有人偶尔拿到了存储的数据,这也没有任何意义,除非加密后的信息能被解密。
|
||||
|
||||
**动态密码**:Vault可以随时为AWS、SQL数据库等类似的系统产生密码。比如,如果应用需要访问AWS S3 桶,它向Vault请求AWS密钥对,Vault将给出带有租期的所需秘密信息。一旦租用期过期,这个秘密信息就不再存储。
|
||||
|
||||
**租赁和更新**:Vault给出的秘密信息带有租期,一旦租用期过期,它便立刻收回秘密信息,如果应用仍需要该秘密信息,则可以通过API更新租用期。
|
||||
|
||||
**撤销**:在租用期到期之前,Vault可以撤销一个秘密信息或者一个秘密信息树。
|
||||
|
||||
### 安装Vault ###
|
||||
|
||||
有两种方式来安装使用Vault。
|
||||
|
||||
**1. 预编译的Vault二进制** 能用于所有的Linux发行版,下载地址如下,下载之后,解压并将它放在系统PATH路径下,以方便调用。
|
||||
|
||||
- [下载预编译的二进制 Vault (32-bit)][1]
|
||||
- [下载预编译的二进制 Vault (64-bit)][2]
|
||||
- [下载预编译的二进制 Vault (ARM)][3]
|
||||
|
||||

|
||||
|
||||
*下载相应的预编译的Vault二进制版本。*
|
||||
|
||||

|
||||
|
||||
*解压下载到本地的二进制版本。*
|
||||
|
||||
祝贺你!您现在可以使用Vault了。
|
||||
|
||||

|
||||
|
||||
**2. 从源代码编译**是另一种在系统中安装Vault的方式。在安装Vault之前需要安装GO和GIT。
|
||||
|
||||
在 **Redhat系统中安装GO** 使用下面的指令:
|
||||
|
||||
sudo yum install go
|
||||
|
||||
在 **Debin系统中安装GO** 使用下面的指令:
|
||||
|
||||
sudo apt-get install golang
|
||||
|
||||
或者
|
||||
|
||||
sudo add-apt-repository ppa:gophers/go
|
||||
|
||||
sudo apt-get update
|
||||
|
||||
sudo apt-get install golang-stable
|
||||
|
||||
在 **Redhat系统中安装GIT** 使用下面的命令:
|
||||
|
||||
sudo yum install git
|
||||
|
||||
在 **Debian系统中安装GIT** 使用下面的命令:
|
||||
|
||||
sudo apt-get install git
|
||||
|
||||
一旦GO和GIT都已被安装好,我们便可以开始从源码编译安装Vault。
|
||||
|
||||
> 将下列的Vault仓库拷贝至GOPATH
|
||||
|
||||
https://github.com/hashicorp/vault
|
||||
|
||||
> 测试下面的文件是否存在,如果它不存在,那么Vault没有被克隆到合适的路径。
|
||||
|
||||
$GOPATH/src/github.com/hashicorp/vault/main.go
|
||||
|
||||
> 执行下面的指令来编译Vault,并将二进制文件放到系统bin目录下。
|
||||
|
||||
make dev
|
||||
|
||||

|
||||
|
||||
### 一份Vault入门教程 ###
|
||||
|
||||
我们已经编制了一份Vault的官方交互式教程,并带有它在SSH上的输出信息。
|
||||
|
||||
**概述**
|
||||
|
||||
这份教程包括下列步骤:
|
||||
|
||||
- 初始化并启封您的Vault
|
||||
- 在Vault中对您的请求授权
|
||||
- 读写秘密信息
|
||||
- 密封您的Vault
|
||||
|
||||
#### **初始化您的Vault**
|
||||
|
||||
首先,我们需要为您初始化一个Vault的工作实例。在初始化过程中,您可以配置Vault的密封行为。简单起见,现在使用一个启封密钥来初始化Vault,命令如下:
|
||||
|
||||
vault init -key-shares=1 -key-threshold=1
|
||||
|
||||
您会注意到Vault在这里输出了几个密钥。不要清除您的终端,这些密钥在后面的步骤中会使用到。
|
||||
|
||||

|
||||
|
||||
#### **启封您的Vault**
|
||||
|
||||
当一个Vault服务器启动时,它是密封的状态。在这种状态下,Vault被配置为知道物理存储在哪里及如何存取它,但不知道如何对其进行解密。Vault使用加密密钥来加密数据。这个密钥由"主密钥"加密,主密钥不保存。解密主密钥需要入口密钥。在这个例子中,我们使用了一个入口密钥来解密这个主密钥。
|
||||
|
||||
vault unseal <key 1>
|
||||
|
||||

|
||||
|
||||
####**为您的请求授权**
|
||||
|
||||
在执行任何操作之前,连接的客户端必须是被授权的。授权的过程是检验一个人或者机器是否如其所申明的那样具有正确的身份。这个身份用在向Vault发送请求时。为简单起见,我们将使用在步骤2中生成的root令牌,这个信息可以回滚终端屏幕看到。使用一个客户端令牌进行授权:
|
||||
|
||||
vault auth <root token>
|
||||
|
||||

|
||||
|
||||
####**读写保密信息**
|
||||
|
||||
现在Vault已经被设置妥当,我们可以开始读写默认挂载的秘密后端里面的秘密信息了。写在Vault中的秘密信息首先被加密,然后被写入后端存储中。后端存储机制绝不会看到未加密的信息,并且也没有在Vault之外解密的需要。
|
||||
|
||||
vault write secret/hello value=world
|
||||
|
||||
当然,您接下来便可以读这个保密信息了:
|
||||
|
||||
vault read secret/hello
|
||||
|
||||

|
||||
|
||||
####**密封您的Vault**
|
||||
|
||||
还有一个用I来密封Vault的API。它将丢掉现在的加密密钥并需要另一个启封过程来恢复它。密封仅需要一个拥有root权限的操作者。这是一种罕见的"打破玻璃过程"的典型部分。
|
||||
|
||||
这种方式中,如果检测到一个入侵,Vault数据将会立刻被锁住,以便最小化损失。如果不能访问到主密钥碎片的话,就不能再次获取数据。
|
||||
|
||||
vault seal
|
||||
|
||||

|
||||
|
||||
这便是入门教程的结尾。
|
||||
|
||||
### 总结 ###
|
||||
|
||||
Vault是一个非常有用的应用,它提供了一个可靠且安全的存储关键信息的方式。另外,它在存储前加密关键信息、审计日志维护、以租期的方式获取秘密信息,且一旦租用期过期它将立刻收回秘密信息。Vault是平台无关的,并且可以免费下载和安装。要发掘Vault的更多信息,请访问其[官方网站][4]。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/how-tos/secure-secret-store-vault/
|
||||
|
||||
作者:[Aun Raza][a]
|
||||
译者:[wwy-hust](https://github.com/wwy-hust)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://linoxide.com/author/arunrz/
|
||||
[1]:https://dl.bintray.com/mitchellh/vault/vault_0.1.0_linux_386.zip
|
||||
[2]:https://dl.bintray.com/mitchellh/vault/vault_0.1.0_linux_amd64.zip
|
||||
[3]:https://dl.bintray.com/mitchellh/vault/vault_0.1.0_linux_arm.zip
|
||||
[4]:https://vaultproject.io/
|
||||
@ -1,137 +0,0 @@
|
||||
translating by wwy-hust
|
||||
|
||||
What are useful command-line network monitors on Linux
|
||||
================================================================================
|
||||
Network monitoring is a critical IT function for businesses of all sizes. The goal of network monitoring can vary. For example, the monitoring activity can be part of long-term network provisioning, security protection, performance troubleshooting, network usage accounting, and so on. Depending on its goal, network monitoring is done in many different ways, such as performing packet-level sniffing, collecting flow-level statistics, actively injecting probes into the network, parsing server logs, etc.
|
||||
|
||||
While there are many dedicated network monitoring systems capable of 24/7/365 monitoring, you can also leverage command-line network monitors in certain situations, where a dedicated monitor is an overkill. If you are a system admin, you are expected to have hands-on experience with some of well known CLI network monitors. Here is a list of **popular and useful command-line network monitors on Linux**.
|
||||
|
||||
### Packet-Level Sniffing ###
|
||||
|
||||
In this category, monitoring tools capture individual packets on the wire, dissect their content, and display decoded packet content or packet-level statistics. These tools conduct network monitoring from the lowest level, and as such, can possibly do the most fine-grained monitoring at the cost of network I/O and analysis efforts.
|
||||
|
||||
1. **dhcpdump**: a comman-line DHCP traffic sniffer capturing DHCP request/response traffic, and displays dissected DHCP protocol messages in a human-friendly format. It is useful when you are troubleshooting DHCP related issues.
|
||||
|
||||
2. **[dsniff][1]**: a collection of command-line based sniffing, spoofing and hijacking tools designed for network auditing and penetration testing. They can sniff various information such as passwords, NSF traffic, email messages, website URLs, and so on.
|
||||
|
||||
3. **[httpry][2]**: an HTTP packet sniffer which captures and decode HTTP requests and response packets, and display them in a human-readable format.
|
||||
|
||||
4. **IPTraf**: a console-based network statistics viewer. It displays packet-level, connection-level, interface-level, protocol-level packet/byte counters in real-time. Packet capturing can be controlled by protocol filters, and its operation is full menu-driven.
|
||||
|
||||
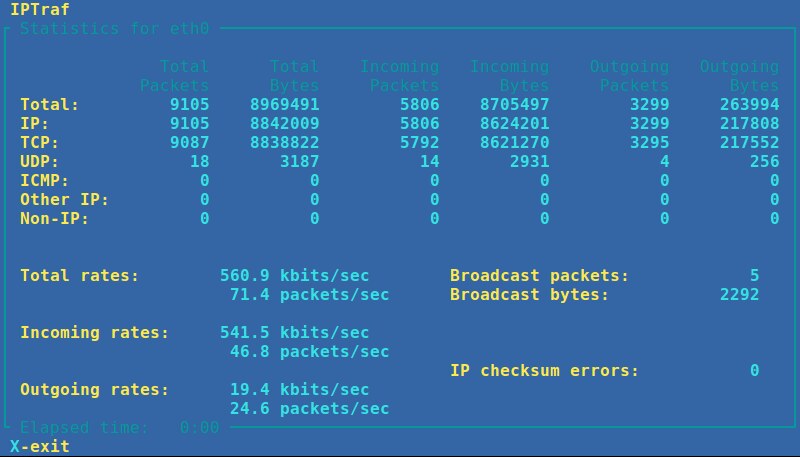
|
||||
|
||||
5. **[mysql-sniffer][3]**: a packet sniffer which captures and decodes packets associated with MySQL queries. It displays the most frequent or all queries in a human-readable format.
|
||||
|
||||
6. **[ngrep][4]**: grep over network packets. It can capture live packets, and match (filtered) packets against regular expressions or hexadecimal expressions. It is useful for detecting and storing any anomalous traffic, or for sniffing particular patterns of information from live traffic.
|
||||
|
||||
7. **[p0f][5]**: a passive fingerprinting tool which, based on packet sniffing, reliably identifies operating systems, NAT or proxy settings, network link types and various other properites associated with an active TCP connection.
|
||||
|
||||
8. **pktstat**: a command-line tool which analyzes live packets to display connection-level bandwidth usages as well as descriptive information of protocols involved (e.g., HTTP GET/POST, FTP, X11).
|
||||
|
||||
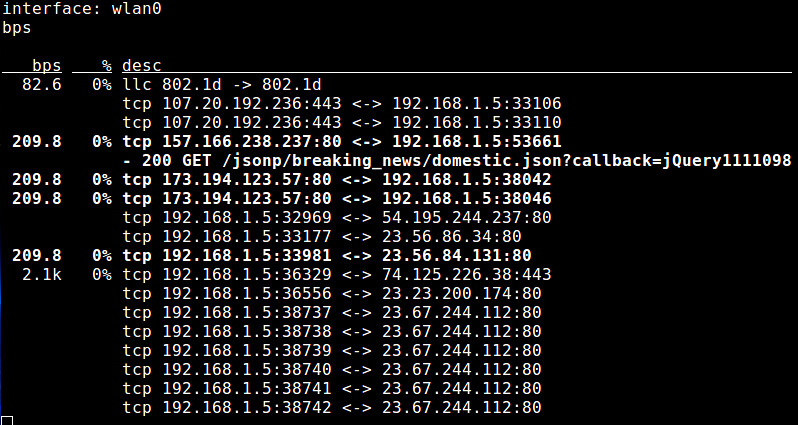
|
||||
|
||||
9. **Snort**: an intrusion detection and prevention tool which can detect/prevent a variety of backdoor, botnets, phishing, spyware attacks from live traffic based on rule-driven protocol analysis and content matching.
|
||||
|
||||
10. **tcpdump**: a command-line packet sniffer which is capable of capturing nework packets on the wire based on filter expressions, dissect the packets, and dump the packet content for packet-level analysis. It is widely used for any kinds of networking related troubleshooting, network application debugging, or [security][6] monitoring.
|
||||
|
||||
11. **tshark**: a command-line packet sniffing tool that comes with Wireshark GUI program. It can capture and decode live packets on the wire, and show decoded packet content in a human-friendly fashion.
|
||||
|
||||
### Flow-/Process-/Interface-Level Monitoring ###
|
||||
|
||||
In this category, network monitoring is done by classifying network traffic into flows, associated processes or interfaces, and collecting per-flow, per-process or per-interface statistics. Source of information can be libpcap packet capture library or sysfs kernel virtual filesystem. Monitoring overhead of these tools is low, but packet-level inspection capabilities are missing.
|
||||
|
||||
12. **bmon**: a console-based bandwidth monitoring tool which shows various per-interface information, including not-only aggregate/average RX/TX statistics, but also a historical view of bandwidth usage.
|
||||
|
||||
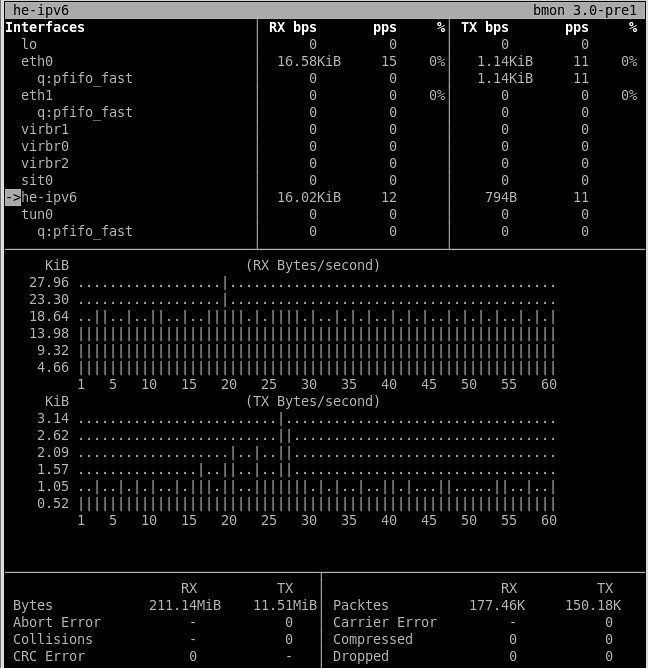
|
||||
|
||||
13. **[iftop][7]**: a bandwidth usage monitoring tool that can shows bandwidth usage for individual network connections in real time. It comes with ncurses-based interface to visualize bandwidth usage of all connections in a sorted order. It is useful for monitoring which connections are consuming the most bandwidth.
|
||||
|
||||
14. **nethogs**: a process monitoring tool which offers a real-time view of upload/download bandwidth usage of individual processes or programs in an ncurses-based interface. This is useful for detecting bandwidth hogging processes.
|
||||
|
||||
15. **netstat**: a command-line tool that shows various statistics and properties of the networking stack, such as open TCP/UDP connections, network interface RX/TX statistics, routing tables, protocol/socket statistics. It is useful when you diagnose performance and resource usage related problems of the networking stack.
|
||||
|
||||
16. **[speedometer][8]**: a console-based traffic monitor which visualizes the historical trend of an interface's RX/TX bandwidth usage with ncurses-drawn bar charts.
|
||||
|
||||
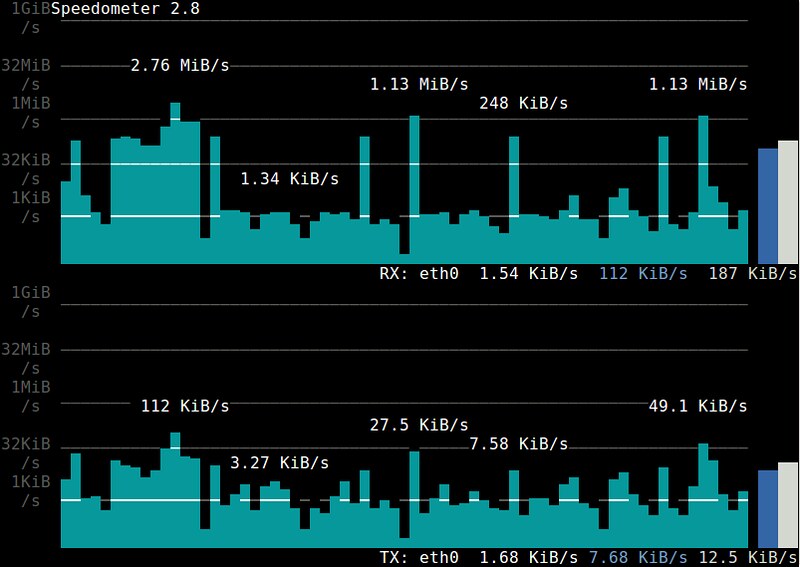
|
||||
|
||||
17. **[sysdig][9]**: a comprehensive system-level debugging tool with a unified interface for investigating different Linux subsystems. Its network monitoring module is capable of monitoring, either online or offline, various per-process/per-host networking statistics such as bandwidth usage, number of connections/requests, etc.
|
||||
|
||||
18. **tcptrack**: a TCP connection monitoring tool which displays information of active TCP connections, including source/destination IP addresses/ports, TCP state, and bandwidth usage.
|
||||
|
||||
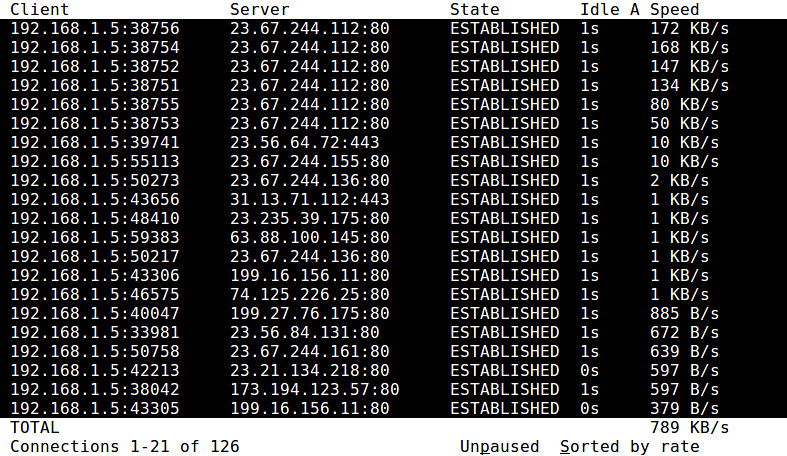
|
||||
|
||||
19. **vnStat**: a command-line traffic monitor which maintains a historical view of RX/TX bandwidh usage (e.g., current, daily, monthly) on a per-interface basis. Running as a background daemon, it collects and stores interface statistics on bandwidth rate and total bytes transferred.
|
||||
|
||||
### Active Network Monitoring ###
|
||||
|
||||
Unlike passive monitoring tools presented so far, tools in this category perform network monitoring by actively "injecting" probes into the network and collecting corresponding responses. Monitoring targets include routing path, available bandwidth, loss rates, delay, jitter, system settings or vulnerabilities, and so on.
|
||||
|
||||
20. **[dnsyo][10]**: a DNS monitoring tool which can conduct DNS lookup from open resolvers scattered across more than 1,500 different networks. It is useful when you check DNS propagation or troubleshoot DNS configuration.
|
||||
|
||||
21. **[iperf][11]**: a TCP/UDP bandwidth measurement utility which can measure maximum available bandwidth between two end points. It measures available bandwidth by having two hosts pump out TCP/UDP probe traffic between them either unidirectionally or bi-directionally. It is useful when you test the network capacity, or tune the parameters of network stack. A variant called [netperf][12] exists with more features and better statistics.
|
||||
|
||||
22. **[netcat][13]/socat**: versatile network debugging tools capable of reading from, writing to, or listen on TCP/UDP sockets. They are often used alongside with other programs or scripts for backend network transfer or port listening.
|
||||
|
||||
23. **nmap**: a command-line port scanning and network discovery utility. It relies on a number of TCP/UDP based scanning techniques to detect open ports, live hosts, or existing operating systems on the local network. It is useful when you audit local hosts for vulnerabilities or build a host map for maintenance purpose. [zmap][14] is an alernative scanning tool with Internet-wide scanning capability.
|
||||
|
||||
24. ping: a network testing tool which works by exchaning ICMP echo and reply packets with a remote host. It is useful when you measure round-trip-time (RTT) delay and loss rate of a routing path, as well as test the status or firewall rules of a remote system. Variations of ping exist with fancier interface (e.g., [noping][15]), multi-protocol support (e.g., [hping][16]) or parallel probing capability (e.g., [fping][17]).
|
||||
|
||||
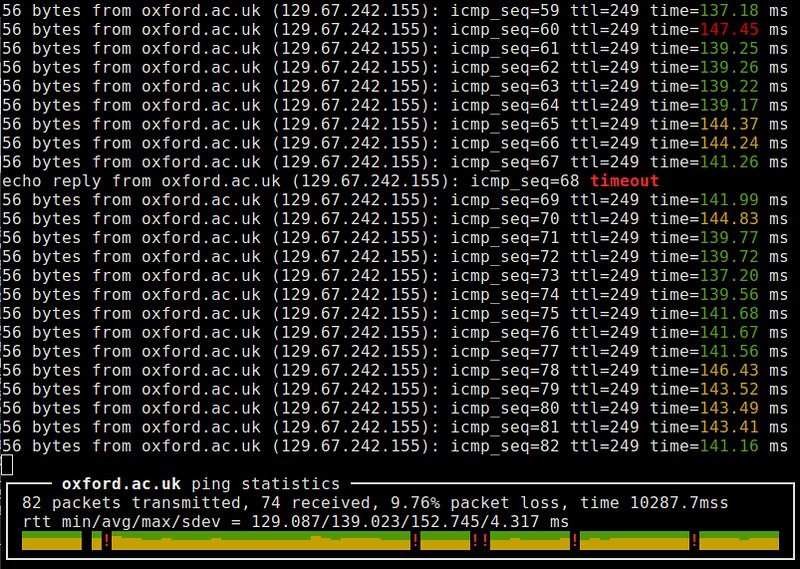
|
||||
|
||||
25. **[sprobe][18]**: a command-line tool that heuristically infers the bottleneck bandwidth between a local host and any arbitrary remote IP address. It uses TCP three-way handshake tricks to estimate the bottleneck bandwidth. It is useful when troubleshooting wide-area network performance and routing related problems.
|
||||
|
||||
26. **traceroute**: a network discovery tool which reveals a layer-3 routing/forwarding path from a local host to a remote host. It works by sending TTL-limited probe packets and collecting ICMP responses from intermediate routers. It is useful when troubleshooting slow network connections or routing related problems. Variations of traceroute exist with better RTT statistics (e.g., [mtr][19]).
|
||||
|
||||
### Application Log Parsing ###
|
||||
|
||||
In this category, network monitoring is targeted at a specific server application (e.g., web server or database server). Network traffic generated or consumed by a server application is monitored by analyzing its log file. Unlike network-level monitors presented in earlier categories, tools in this category can analyze and monitor network traffic from application-level.
|
||||
|
||||
27. **[GoAccess][20]**: a console-based interactive viewer for Apache and Nginx web server traffic. Based on access log analysis, it presents a real-time statistics of a number of metrics including daily visits, top requests, client operating systems, client locations, client browsers, in a scrollable view.
|
||||
|
||||
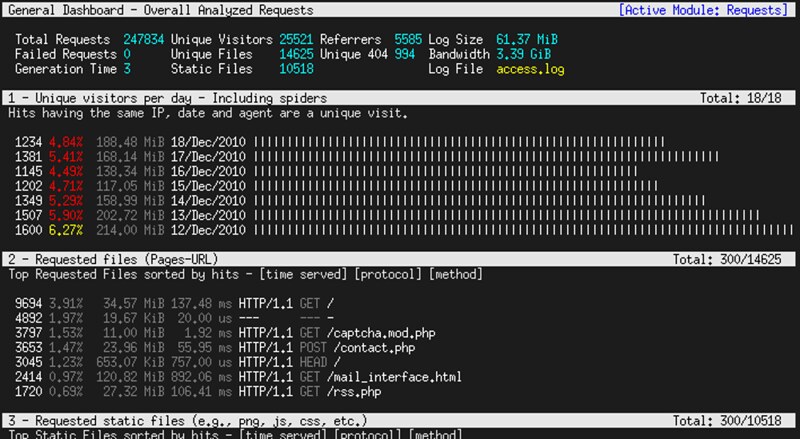
|
||||
|
||||
28. **[mtop][21]**: a command-line MySQL/MariaDB server moniter which visualizes the most expensive queries and current database server load. It is useful when you optimize MySQL server performance and tune server configurations.
|
||||
|
||||
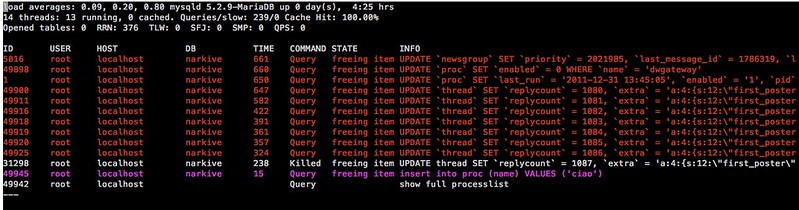
|
||||
|
||||
29. **[ngxtop][22]**: a traffic monitoring tool for Nginx and Apache web server, which visualizes web server traffic in a top-like interface. It works by parsing a web server's access log file and collecting traffic statistics for individual destinations or requests.
|
||||
|
||||
### Conclusion ###
|
||||
|
||||
In this article, I presented a wide variety of command-line network monitoring tools, ranging from the lowest packet-level monitors to the highest application-level network monitors. Knowing which tool does what is one thing, and choosing which tool to use is another, as any single tool cannot be a universal solution for your every need. A good system admin should be able to decide which tool is right for the circumstance at hand. Hopefully the list helps with that.
|
||||
|
||||
You are always welcome to improve the list with your comment!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/useful-command-line-network-monitors-linux.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/nanni
|
||||
[1]:http://www.monkey.org/~dugsong/dsniff/
|
||||
[2]:http://xmodulo.com/monitor-http-traffic-command-line-linux.html
|
||||
[3]:https://github.com/zorkian/mysql-sniffer
|
||||
[4]:http://ngrep.sourceforge.net/
|
||||
[5]:http://lcamtuf.coredump.cx/p0f3/
|
||||
[6]:http://xmodulo.com/recommend/firewallbook
|
||||
[7]:http://xmodulo.com/how-to-install-iftop-on-linux.html
|
||||
[8]:https://excess.org/speedometer/
|
||||
[9]:http://xmodulo.com/monitor-troubleshoot-linux-server-sysdig.html
|
||||
[10]:http://xmodulo.com/check-dns-propagation-linux.html
|
||||
[11]:https://iperf.fr/
|
||||
[12]:http://www.netperf.org/netperf/
|
||||
[13]:http://xmodulo.com/useful-netcat-examples-linux.html
|
||||
[14]:https://zmap.io/
|
||||
[15]:http://noping.cc/
|
||||
[16]:http://www.hping.org/
|
||||
[17]:http://fping.org/
|
||||
[18]:http://sprobe.cs.washington.edu/
|
||||
[19]:http://xmodulo.com/better-alternatives-basic-command-line-utilities.html#mtr_link
|
||||
[20]:http://goaccess.io/
|
||||
[21]:http://mtop.sourceforge.net/
|
||||
[22]:http://xmodulo.com/monitor-nginx-web-server-command-line-real-time.html
|
||||
@ -1,3 +1,5 @@
|
||||
[Trnslating by DongShuaike]
|
||||
|
||||
iptraf: A TCP/UDP Network Monitoring Utility
|
||||
================================================================================
|
||||
[iptraf][1] is an ncurses-based IP LAN monitor that generates various network statistics including TCP info, UDP counts, ICMP and OSPF information, Ethernet load info, node stats, IP checksum errors, and others.
|
||||
|
||||
@ -1,3 +1,5 @@
|
||||
FSSlc translating
|
||||
|
||||
Conky – The Ultimate X Based System Monitor Application
|
||||
================================================================================
|
||||
Conky is a system monitor application written in ‘C’ Programming Language and released under GNU General Public License and BSD License. It is available for Linux and BSD Operating System. The application is X (GUI) based that was originally forked from [Torsmo][1].
|
||||
@ -144,4 +146,4 @@ via: http://www.tecmint.com/install-conky-in-ubuntu-debian-fedora/
|
||||
[3]:http://ubuntuforums.org/showthread.php?t=281865
|
||||
[4]:http://conky.sourceforge.net/screenshots.html
|
||||
[5]:http://ubuntuforums.org/showthread.php?t=281865/
|
||||
[6]:http://conky.sourceforge.net/
|
||||
[6]:http://conky.sourceforge.net/
|
||||
|
||||
@ -1,61 +0,0 @@
|
||||
How To Install Visual Studio Code On Ubuntu
|
||||
================================================================================
|
||||

|
||||
|
||||
Microsoft has done the unexpected by [releasing Visual Studio Code][1] for all major desktop platforms that includes Linux as well. If you are a web developer who happens to be using Ubuntu, you can **easily install Visual Studio Code in Ubuntu**.
|
||||
|
||||
We will be using [Ubuntu Make][2] for installing Visual Studio Code in Ubuntu. Ubuntu Make, previously known as Ubuntu Developer Tools Center, is a command line utility that allows you to easily install various development tools, languages and IDEs. You can easily [install Android Studio][3] and other popular IDEs such as Eclipse with Ubuntu Make. In this tutorial we shall see **how to install Visual Studio Code in Ubuntu with Ubuntu Make**.
|
||||
|
||||
### Install Microsoft Visual Studio Code in Ubuntu ###
|
||||
|
||||
Before installing Visual Studio Code, we need to install Ubuntu Make first. Though Ubuntu Make is available in Ubuntu 15.04 repository, **you’ll need Ubuntu Make 0.7 for Visual Studio**. You can get the latest Ubuntu Make by using the official PPA. The PPA is available for Ubuntu 14.04, 14.10 and 15.04. Also, it **is only available for 64 bit platform**.
|
||||
|
||||
Open a terminal and use the following commands to install Ubuntu Make via official PPA:
|
||||
|
||||
sudo add-apt-repository ppa:ubuntu-desktop/ubuntu-make
|
||||
sudo apt-get update
|
||||
sudo apt-get install ubuntu-make
|
||||
|
||||
Once you have installed Ubuntu Make, use the command below to install Visual Studio Code:
|
||||
|
||||
umake web visual-studio-code
|
||||
|
||||
You’ll be asked to provide a path where it will be installed:
|
||||
|
||||

|
||||
|
||||
After throwing a whole lot of terms and conditions, it will ask for your permission to install Visual Studio Code. Press ‘a’ at this screen:
|
||||
|
||||

|
||||
|
||||
Once you do that it will start downloading and installing it. Once it is installed, you can see that Visual Studio Code icon has already been locked to the Unity Launcher. Just click on it to run it. This is how Visual Studio Code looks like in Ubuntu 15.04 Unity:
|
||||
|
||||

|
||||
|
||||
### Uninstall Visual Studio Code from Ubuntu ###
|
||||
|
||||
To uninstall Visual Studio Code, we’ll use the same command line tool umake. Just use the following command in terminal:
|
||||
|
||||
umake web visual-studio-code --remove
|
||||
|
||||
If you do not want to use Ubuntu Make, you can install Visual Studio Code by downloading the files from Microsoft:
|
||||
|
||||
- [Download Visual Studio Code for Linux][4]
|
||||
|
||||
See, how easy it is to install Visual Studio Code in Ubuntu, all thanks to Ubuntu Make. I hope this tutorial helped you. Feel free to drop a comment if you have any questions or suggestions.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://itsfoss.com/install-visual-studio-code-ubuntu/
|
||||
|
||||
作者:[Abhishek][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://itsfoss.com/author/abhishek/
|
||||
[1]:http://www.geekwire.com/2015/microsofts-visual-studio-expands-to-mac-and-linux-with-new-code-development-tool/
|
||||
[2]:https://wiki.ubuntu.com/ubuntu-make
|
||||
[3]:http://itsfoss.com/install-android-studio-ubuntu-linux/
|
||||
[4]:https://code.visualstudio.com/Download
|
||||
@ -1,3 +1,4 @@
|
||||
Translating by GOLinux!
|
||||
Bodhi Linux Introduces Moksha Desktop
|
||||
================================================================================
|
||||

|
||||
@ -37,4 +38,4 @@ via: http://itsfoss.com/bodhi-linux-introduces-moksha-desktop/
|
||||
[2]:https://www.enlightenment.org/
|
||||
[3]:http://www.bodhilinux.com/2015/04/28/introducing-the-moksha-desktop/
|
||||
[4]:http://itsfoss.com/bodhi-linux-3/
|
||||
[5]:http://forums.bodhilinux.com/index.php?/topic/12322-e17-vs-e19-which-are-you-using-and-why/
|
||||
[5]:http://forums.bodhilinux.com/index.php?/topic/12322-e17-vs-e19-which-are-you-using-and-why/
|
||||
|
||||
@ -1,112 +0,0 @@
|
||||
How to Setup OpenERP (Odoo) on CentOS 7.x
|
||||
================================================================================
|
||||
Hi everyone, this tutorial is all about how we can setup Odoo (formerly known as OpenERP) on our CentOS 7 Server. Are you thinking to get an awesome ERP (Enterprise Resource Planning) app for your business ?. Then, OpenERP is the best app you are searching as it is a Free and Open Source Software which provides an outstanding features for your business or company.
|
||||
|
||||
[OpenERP][1] is a free and open source traditional OpenERP (Enterprise Resource Planning) app which includes Open Source CRM, Website Builder, eCommerce, Project Management, Billing & Accounting, Point of Sale, Human Resources, Marketing, Manufacturing, Purchase Management and many more modules included for a better way to boost the productivity and sales. Odoo Apps can be used as stand-alone applications, but they also integrate seamlessly so you get a full-featured Open Source ERP when you install several Apps.
|
||||
|
||||
So, here are some quick and easy steps to get your copy of OpenERP installed on your CentOS machine.
|
||||
|
||||
### 1. Installing PostgreSQL ###
|
||||
|
||||
First of all, we'll want to update the packages installed in our CentOS 7 machine to ensure that the latest packages, patches and security are up to date. To update our sytem, we should run the following command in a shell or terminal.
|
||||
|
||||
# yum clean all
|
||||
# yum update
|
||||
|
||||
Now, we'll want to install PostgreSQL Database System as OpenERP uses PostgreSQL for its database system. To install it, we'll need to run the following command.
|
||||
|
||||
# yum install postgresql postgresql-server postgresql-libs
|
||||
|
||||

|
||||
|
||||
After it is installed, we'll need to initialize the database with the following command
|
||||
|
||||
# postgresql-setup initdb
|
||||
|
||||

|
||||
|
||||
We'll then set PostgreSQL to start on every boot and start the PostgreSQL Database server.
|
||||
|
||||
# systemctl enable postgresql
|
||||
# systemctl start postgresql
|
||||
|
||||
As we haven't set a password for the user "postgresql", we'll want to set it now.
|
||||
|
||||
# su - postgres
|
||||
$ psql
|
||||
postgres=# \password postgres
|
||||
postgres=# \q
|
||||
# exit
|
||||
|
||||

|
||||
|
||||
### 2. Configuring Odoo Repository ###
|
||||
|
||||
After our Database Server has been installed correctly, we'll want add EPEL (Extra Packages for Enterprise Linux) to our CentOS server. Odoo (or OpenERP) depends on Python run-time and many other packages that are not included in default standard repository. As such, we'll want to add the Extra Packages for Enterprise Linux (or EPEL) repository support so that Odoo can get the required dependencies. To install, we'll need to run the following command.
|
||||
|
||||
# yum install epel-release
|
||||
|
||||

|
||||
|
||||
Now, after we install EPEL, we'll now add repository of Odoo (OpenERP) using yum-config-manager.
|
||||
|
||||
# yum install yum-utils
|
||||
|
||||
# yum-config-manager --add-repo=https://nightly.odoo.com/8.0/nightly/rpm/odoo.repo
|
||||
|
||||

|
||||
|
||||
### 3. Installing Odoo 8 (OpenERP) ###
|
||||
|
||||
Finally after adding repository of Odoo 8 (OpenERP) in our CentOS 7 machine. We'll can install Odoo 8 (OpenERP) using the following command.
|
||||
|
||||
# yum install -y odoo
|
||||
|
||||
The above command will install odoo along with the necessary dependency packages.
|
||||
|
||||

|
||||
|
||||
Now, we'll enable automatic startup of Odoo in every boot and will start our Odoo service using the command below.
|
||||
|
||||
# systemctl enable odoo
|
||||
# systemctl start odoo
|
||||
|
||||

|
||||
|
||||
### 4. Allowing Firewall ###
|
||||
|
||||
As Odoo uses port 8069, we'll need to allow firewall for remote access. We can allow firewall to port 8069 by running the following command.
|
||||
|
||||
# firewall-cmd --zone=public --add-port=8069/tcp --permanent
|
||||
# firewall-cmd --reload
|
||||
|
||||

|
||||
|
||||
**Note: By default, only connections from localhost are allowed. If we want to allow remote access to PostgreSQL databases, we'll need to add the line shown in the below image to pg_hba.conf configuration file:**
|
||||
|
||||
# nano /var/lib/pgsql/data/pg_hba.conf
|
||||
|
||||

|
||||
|
||||
### 5. Web Interface ###
|
||||
|
||||
Finally, as we have successfully installed our latest Odoo 8 (OpenERP) on our CentOS 7 Server, we can now access our Odoo by browsing to http://ip-address:8069 http://my-site.com:8069 using our favorite web browser. Then, first thing we'll gonna do is we'll create a new database and create a new password for it. Note, the master password is admin by default. Then, we can login to our panel with that username and password.
|
||||
|
||||

|
||||
|
||||
### Conclusion ###
|
||||
|
||||
Odoo 8 (formerly OpenERP) is the best ERP app available in the world of Open Source. We did an excellent work on installing it because OpenERP is a set of many modules which are essential for a complete ERP app for business and company. So, if you have any questions, suggestions, feedback please write them in the comment box below. Thank you ! Enjoy OpenERP (Odoo 8) :-)
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/linux-how-to/setup-openerp-odoo-centos-7/
|
||||
|
||||
作者:[Arun Pyasi][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://linoxide.com/author/arunp/
|
||||
[1]:https://www.odoo.com/
|
||||
@ -1,97 +0,0 @@
|
||||
translating wi-cuckoo
|
||||
Linux FAQs with Answers--How to configure a Linux bridge with Network Manager on Ubuntu
|
||||
================================================================================
|
||||
> **Question**: I need to set up a Linux bridge on my Ubuntu box to share a NIC with several other virtual machines or containers created on the box. I am currently using Network Manager on my Ubuntu, so preferrably I would like to configure a bridge using Network Manager. How can I do that?
|
||||
|
||||
Network bridge is a hardware equipment used to interconnect two or more Layer-2 network segments, so that network devices on different segments can talk to each other. A similar bridging concept is needed within a Linux host, when you want to interconnect multiple VMs or Ethernet interfaces within a host. That is one use case of a software Linux bridge.
|
||||
|
||||
There are several different ways to configure a Linux bridge. For example, in a headless server environment, you can use [brctl][1] to manually configure a bridge. In desktop environment, bridge support is available in Network Manager. Let's examine how to configure a bridge with Network Manager.
|
||||
|
||||
### Requirement ###
|
||||
|
||||
To avoid [any issue][2], it is recommended that you have Network Manager 0.9.9 and higher, which is the case for Ubuntu 15.04 and later.
|
||||
|
||||
$ apt-cache show network-manager | grep Version
|
||||
|
||||
----------
|
||||
|
||||
Version: 0.9.10.0-4ubuntu15.1
|
||||
Version: 0.9.10.0-4ubuntu15
|
||||
|
||||
### Create a Bridge ###
|
||||
|
||||
The easiest way to create a bridge with Network Manager is via nm-connection-editor. This GUI tool allows you to configure a bridge in easy-to-follow steps.
|
||||
|
||||
To start, invoke nm-connection-editor.
|
||||
|
||||
$ nm-connection-editor
|
||||
|
||||
The editor window will show you a list of currently configured network connections. Click on "Add" button in the top right to create a bridge.
|
||||
|
||||
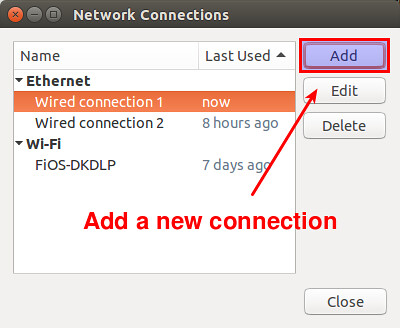
|
||||
|
||||
Next, choose "Bridge" as a connection type.
|
||||
|
||||
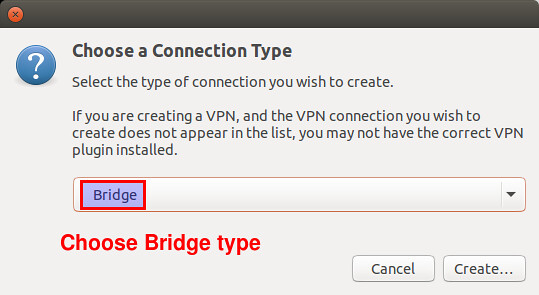
|
||||
|
||||
Now it's time to configure a bridge, including its name and bridged connection(s). With no other bridges created, the default bridge interface will be named bridge0.
|
||||
|
||||
Recall that the goal of creating a bridge is to share your Ethernet interface via the bridge. So you need to add the Ethernet interface to the bridge. This is achieved by adding a new "bridged connection" in the GUI. Click on "Add" button.
|
||||
|
||||
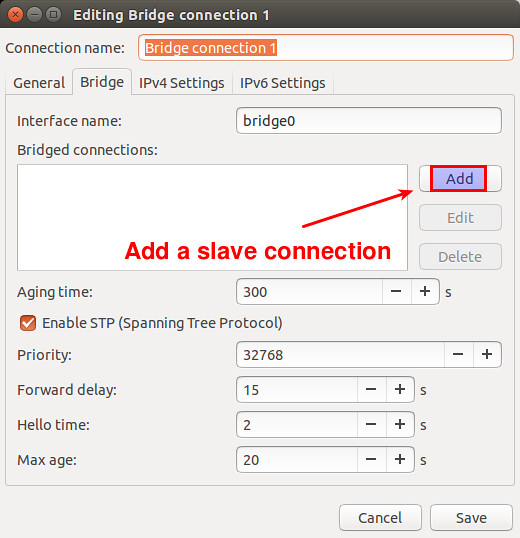
|
||||
|
||||
Choose "Ethernet" as a connection type.
|
||||
|
||||
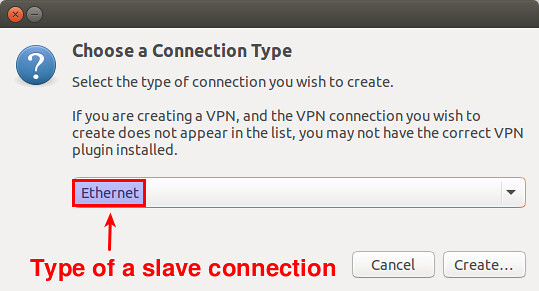
|
||||
|
||||
In "Device MAC address" field, choose the interface that you want to enslave into the bridge. In this example, assume that this interface is eth0.
|
||||
|
||||

|
||||
|
||||
Click on "General" tab, and enable both checkboxes that say "Automatically connect to this network when it is available" and "All users may connect to this network".
|
||||
|
||||
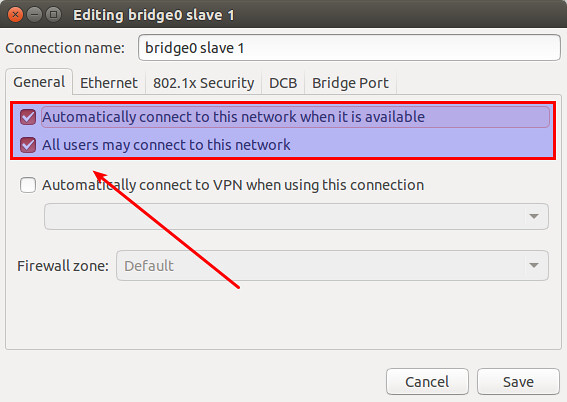
|
||||
|
||||
Save the change.
|
||||
|
||||
Now you will see a new slave connection created in the bridge.
|
||||
|
||||
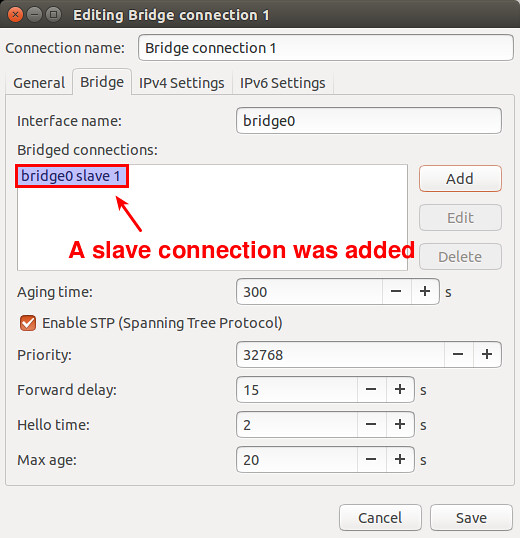
|
||||
|
||||
Click on "General" tab of the bridge, and make sure that top-most two checkboxes are enabled.
|
||||
|
||||
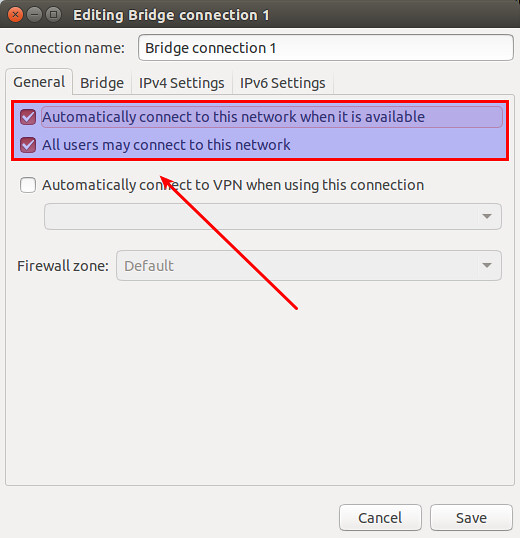
|
||||
|
||||
Go to "IPv4 Settings" tab, and configure either DHCP or static IP address for the bridge. Note that you should use the same IPv4 settings as the enslaved Ethernet interface eth0. In this example, we assume that eth0 is configured via DHCP. Thus choose "Automatic (DHCP)" here. If eth0 is assigned a static IP address, you should assign the same IP address to the bridge.
|
||||
|
||||
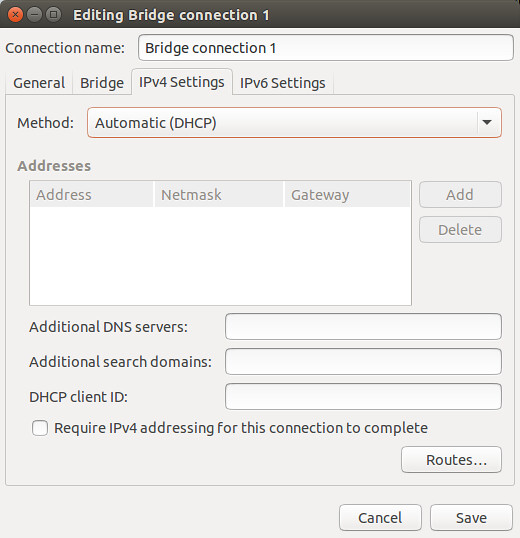
|
||||
|
||||
Finally, save the bridge settings.
|
||||
|
||||
Now you will see an additional bridge connection created in "Network Connections" window. You no longer need a previously-configured wired connection for the enslaved interface eth0. So go ahead and delete the original wired connection.
|
||||
|
||||
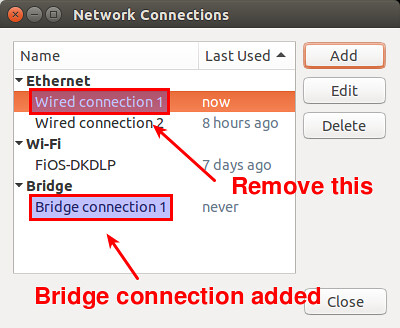
|
||||
|
||||
At this point, the bridge connection will automatically be activated. You will momentarily lose a connection, since the IP address assigned to eth0 is taken over by the bridge. Once an IP address is assigned to the bridge, you will be connected back to your Ethernet interface via the bridge. You can confirm that by checking "Network" settings.
|
||||
|
||||
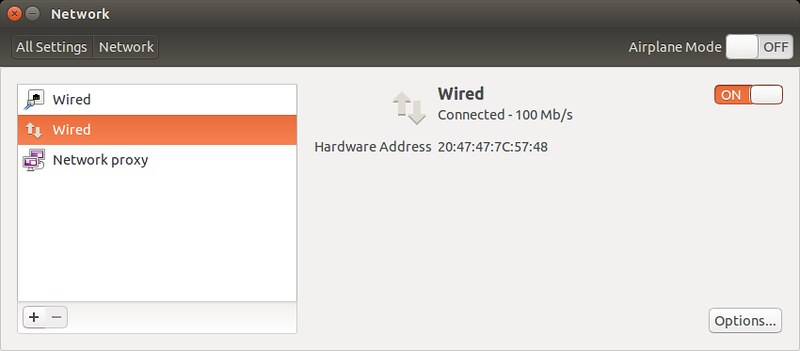
|
||||
|
||||
Also, check the list of available interfaces. As mentioned, the bridge interface must have taken over whatever IP address was possessed by your Ethernet interface.
|
||||
|
||||
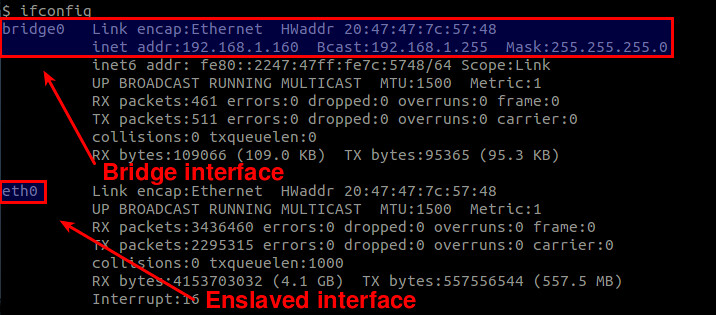
|
||||
|
||||
That's it, and now the bridge is ready to use!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://ask.xmodulo.com/configure-linux-bridge-network-manager-ubuntu.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://ask.xmodulo.com/author/nanni
|
||||
[1]:http://xmodulo.com/how-to-configure-linux-bridge-interface.html
|
||||
[2]:https://bugs.launchpad.net/ubuntu/+source/network-manager/+bug/1273201
|
||||
@ -0,0 +1,135 @@
|
||||
什么是Linux上实用的命令行式网络监视工具
|
||||
===============================================================================
|
||||
对任何规模的业务来说,网络监视器都是一个重要的功能。网络监视的目标可能千差万别。比如,监视活动的目标可以是保证长期的网络供应、安全保护、对性能进行排查、网络使用统计等。由于它的目标不同,网络监视器使用很多不同的方式来完成任务。比如使用包层面的嗅探,使用流层面的统计数据,向网络中注入探测的流量,分析服务器日志等。
|
||||
|
||||
尽管有许多专用的网络监视系统可以365天24小时监视,但您依旧可以在特定的情况下使用命令行式的网络监视器,某些命令行式的网络监视器在某方面很有用。如果您是系统管理员,那您就应该有亲身使用一些知名的命令行式网络监视器的经历。这里有一份**Linux上流行且实用的网络监视器**列表。
|
||||
|
||||
### 包层面的嗅探器 ###
|
||||
|
||||
在这个类别下,监视工具在链路上捕捉独立的包,分析它们的内容,展示解码后的内容或者包层面的统计数据。这些工具在最底层对网络进行监视、管理,同样的也能进行最细粒度的监视,其代价是部分网络I/O和分析的过程。
|
||||
|
||||
1. **dhcpdump**:一个命令行式的DHCP流量嗅探工具,捕捉DHCP的请求/回复流量,并以用户友好的方式显示解码的DHCP协议消息。这是一款排查DHCP相关故障的实用工具。
|
||||
|
||||
2. **[dsniff][1]**:一个基于命令行的嗅探工具集合,拥有欺骗和劫持功能,被设计用于网络审查和渗透测试。它可以嗅探多种信息,比如密码、NSF流量、email消息、网络地址等。
|
||||
|
||||
3. **[httpry][2]**:一个HTTP报文嗅探器,用于捕获、解码HTTP请求和回复报文,并以用户友好的方式显示这些信息。
|
||||
|
||||
4. **IPTraf**:基于命令行的网络统计数据查看器。它实时显示包层面、连接层面、接口层面、协议层面的报文/字节数。抓包过程由协议过滤器控制,且操作过程全部是菜单驱动的。
|
||||
|
||||

|
||||
|
||||
5. **[mysql-sniffer][3]**:一个用于抓取、解码MySQL请求相关的数据包的工具。它以可读的方式显示最频繁或全部的请求。
|
||||
|
||||
6. **[ngrep][4]**:在网络报文中执行grep。它能实时抓取报文,并用正则表达式或十六进制表达式的方式匹配报文。它是一个可以对异常流量进行检测、存储或者对实时流中特定模式报文进行抓取的实用工具。
|
||||
|
||||
7. **[p0f][5]**:一个被动的基于包嗅探的指纹采集工具,可以可靠地识别操作系统、NAT或者代理设置、网络链路类型以及许多其他与活动的TCP连接相关的属性。
|
||||
|
||||
8. **pktstat**:一个命令行式的工具,通过实时分析报文,显示连接带宽使用情况以及相关的协议(例如,HTTP GET/POST、FTP、X11)等描述信息。
|
||||
|
||||

|
||||
|
||||
13. **[iftop][7]**:一个带宽使用监测工具,可以实时显示某个网络连接的带宽使用情况。它对所有带宽使用情况排序并通过ncurses的接口来进行可视化。他可以方便的监视哪个连接消耗了最多的带宽。
|
||||
|
||||
14. **nethogs**:一个进程监视工具,提供进程相关的实时的上行/下行带宽使用信息,并基于ncurses显示。它对检测占用大量带宽的进程很有用。
|
||||
|
||||
15. **netstat**:一个显示许多TCP/UDP的网络堆栈统计信息的工具。诸如网络接口发送/接收、路由表、协议/套接字的统计信息和属性。当您诊断与网络堆栈相关的性能、资源使用时它很有用。
|
||||
|
||||
16. **[speedometer][8]**:一个可视化某个接口发送/接收的带宽使用的历史趋势,并且基于ncurses的条状图进行显示的工具。
|
||||
|
||||

|
||||
|
||||
17. **[sysdig][9]**:一个对Linux子系统拥有统一调试接口的系统级综合性debug工具。它的网络监视模块可以监视在线或离线、许多进程/主机相关的网络统计数据,例如带宽、连接/请求数等。
|
||||
|
||||
18. **tcptrack**:一个TCP连接监视工具,可以显示活动的TCP连接,包括源/目的IP地址/端口、TCP状态、带宽使用等。
|
||||
|
||||

|
||||
|
||||
19. **vnStat**:一个维护了基于接口的历史接收/发送带宽视图(例如,当前、每日、每月)的流量监视器。作为一个后台守护进程,它收集并存储统计数据,包括接口带宽使用率和传输字节总数。
|
||||
|
||||
### 主动网络监视器 ###
|
||||
|
||||
不同于前面提到的被动的监听工具,这个类别的工具们在监听时会主动的“注入”探测内容到网络中,并且会收集相应的反应。监听目标包括路由路径、可供使用的带宽、丢包率、延时、抖动、系统设置或者缺陷等。
|
||||
|
||||
20. **[dnsyo][10]**:一个DNS检测工具,能够管理多达1500个不同网络的开放解析器集群的DNS查询。它在您检查DNS传播或排查DNS设置的时候很有用。
|
||||
|
||||
21. **[iperf][11]**:一个TCP/UDP带宽测量工具,能够测量两个结点间最大可用带宽。它通过在两个主机间单向或双向的输出TCP/UDP探测流量来测量可用的带宽。它在监测网络容量、调谐网络协议栈参数时很有用。一个叫做[netperf][12]的变种拥有更多的功能及更好的统计数据。
|
||||
|
||||
22. **[netcat][13]/socat**:通用的网络debug工具,可以对TCP/UDP套接字进行读、写或监听。它通常和其他的程序或脚本结合起来在后端对网络传输或端口进行监听。
|
||||
|
||||
23. **nmap**:一个命令行端口扫描和网络发现工具。它依赖于若干基于TCP/UDP的扫描技术来查找开放的端口、活动的主机或者在本地网络存在的操作系统。它在你审查本地主机漏洞或者建立主机映射时很有用。[zmap][14]是一个类似的替代品,是一个用于互联网范围的扫描工具。
|
||||
|
||||
24. ping:一个常用的网络测试工具。通过对ICMP的echo和reply报文进行增强来实现其功能。它在测量路由的RTT、丢包率以及检测远端系统防火墙规则时很有用。ping的变种有更漂亮的界面(例如,[noping][15])、多协议支持(例如,[hping][16])或者并行探测能力(例如,[fping][17])。
|
||||
|
||||

|
||||
|
||||
25. **[sprobe][18]**:一个启发式推断本地主机和任意远端IP地址的网络带宽瓶颈的命令行工具。它使用TCP三次握手机制来评估带宽的瓶颈。它在检测大范围网络性能和路由相关的问题时很有用。
|
||||
|
||||
26. **traceroute**:一个能发现从本地到远端主机的第三层路由/转发路径的网络发现工具。它发送有限TTL的探测报文,收集中间路由的ICMP反馈信息。它在排查低速网络连接或者路由相关的问题时很有用。traceroute的变种有更好的RTT统计功能(例如,[mtr][19])。
|
||||
|
||||
### 应用日志解析器 ###
|
||||
|
||||
在这个类别下,网络监测器把特定的服务器应用程序作为目标(例如,web服务器或者数据库服务器)。由服务器程序产生或消耗的网络流量通过它的日志被分析和监测。不像前面提到的网络层的监视器,这个类别的工具能够在应用层面分析和监控网络流量。
|
||||
|
||||
27. **[GoAccess][20]**:一个针对Apache和Nginx服务器流量的交互式查看器。基于对获取到的日志的分析,它能展示包括日访问量、最多请求、客户端操作系统、客户端位置、客户端浏览器等在内的多个实时的统计信息,并以滚动方式显示。
|
||||
|
||||

|
||||
|
||||
28. **[mtop][21]**:一个面向MySQL/MariaDB服务器的命令行监视器,它可以将当前数据库服务器负载中代价最大的查询以可视化的方式进行显示。它在您优化MySQL服务器性能、调谐服务器参数时很有用。
|
||||
|
||||

|
||||
|
||||
29. **[ngxtop][22]**:一个面向Nginx和Apache服务器的流量监测工具,能够以类似top指令的方式可视化的显示Web服务器的流量。它解析web服务器的查询日志文件并收集某个目的地或请求的流量统计信息。
|
||||
|
||||
### Conclusion ###
|
||||
|
||||
在这篇文章中,我展示了许多的命令行式监测工具,从最底层的包层面的监视器到最高层应用程序层面的网络监视器。知道那个工具的作用是一回事,选择哪个工具使用又是另外一回事。单一的一个工具不能作为您每天使用的通用的解决方案。一个好的系统管理员应该能决定哪个工具更适合当前的环境。希望这个列表对此有所帮助。
|
||||
|
||||
欢迎您通过回复来改进这个列表的内容!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/useful-command-line-network-monitors-linux.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[wwy-hust](https://github.com/wwy-hust)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/nanni
|
||||
[1]:http://www.monkey.org/~dugsong/dsniff/
|
||||
[2]:http://xmodulo.com/monitor-http-traffic-command-line-linux.html
|
||||
[3]:https://github.com/zorkian/mysql-sniffer
|
||||
[4]:http://ngrep.sourceforge.net/
|
||||
[5]:http://lcamtuf.coredump.cx/p0f3/
|
||||
[6]:http://xmodulo.com/recommend/firewallbook
|
||||
[7]:http://xmodulo.com/how-to-install-iftop-on-linux.html
|
||||
[8]:https://excess.org/speedometer/
|
||||
[9]:http://xmodulo.com/monitor-troubleshoot-linux-server-sysdig.html
|
||||
[10]:http://xmodulo.com/check-dns-propagation-linux.html
|
||||
[11]:https://iperf.fr/
|
||||
[12]:http://www.netperf.org/netperf/
|
||||
[13]:http://xmodulo.com/useful-netcat-examples-linux.html
|
||||
[14]:https://zmap.io/
|
||||
[15]:http://noping.cc/
|
||||
[16]:http://www.hping.org/
|
||||
[17]:http://fping.org/
|
||||
[18]:http://sprobe.cs.washington.edu/
|
||||
[19]:http://xmodulo.com/better-alternatives-basic-command-line-utilities.html#mtr_link
|
||||
[20]:http://goaccess.io/
|
||||
[21]:http://mtop.sourceforge.net/
|
||||
[22]:http://xmodulo.com/monitor-nginx-web-server-command-line-real-time.html
|
||||
@ -1,161 +0,0 @@
|
||||
如何使用Vault安全的存储密码和API密钥
|
||||
=======================================================================
|
||||
Vault是用来安全的获取秘密信息的工具。他可以保存密码、API密钥、证书等信息。Vault通过强访问控制机制和高扩展性的事件日志提供了一个统一的接口来访问秘密信息。
|
||||
|
||||
对关键信息的授权访问是一个困难的问题,尤其是当有许多用户角色和用户请求不同的关键信息,例如用不同权限登录数据库的细节,对外服务的API密钥,面向服务架构通信的证书等。当保密信息由不同的平台进行管理,并使用一些自定义的配置时,情况变得更糟,因此,安全的存储、管理审计日志几乎是不可能的。但Vault为这种复杂情况提供了一个解决方案。
|
||||
|
||||
### 突出特点 ###
|
||||
|
||||
数据加密:Vault能够在不存储数据的情况下对数据进行加密、解密。开发者们便可以存储加密后的数据而无需开发自己的加密技术,Vault还允许安全团队自定义安全参数。
|
||||
|
||||
**安全密码存储**:Vault在将秘密信息(API密钥、密码、证书)存储到持久化存储之前对数据进行加密。因此,如果有人偶尔拿到了获取存储的数据的权限,这也没有任何意义,除非加密后的信息被解密。
|
||||
|
||||
**动态密码**:Vault为AWS、SQL数据库类似的系统按需产生密码。如果应用需要获得AWS S3的桶,比如,它向Vault请求AWS密钥对,Vault将授予需要的秘密信息一段租用期时间。一旦租用期过期,这个秘密信息将变得不可用。
|
||||
|
||||
**租赁和更新**:Vault以租用期为限制授予秘密信息,一旦租用期过期,它便立刻收回保密信息,如果应用仍需要保密信息,则可以通过API更新租用期。
|
||||
|
||||
**撤销**:在租用期到期之前,Vault可以撤销一个秘密信息或者一个秘密信息树。
|
||||
|
||||
### 安装Vault ###
|
||||
|
||||
有两种方式来安装使用Vault。
|
||||
|
||||
**1. 预编译的Vault二进制** 能用于所有的Linux发行版,下载地址如下,一旦下载完成,解压并将它放在系统PATH路径下,以方便调用。
|
||||
|
||||
- [Download Precompiled Vault Binary (32-bit)][1]
|
||||
- [Download Precompiled Vault Binary (64-bit)][2]
|
||||
- [Download Precompiled Vault Binary (ARM)][3]
|
||||
|
||||
下载相应的预编译的Vault二进制版本。
|
||||
|
||||

|
||||
|
||||
解压下载到本地的二进制版本。
|
||||
|
||||

|
||||
|
||||
祝贺!您现在可以使用Vault了。
|
||||
|
||||

|
||||
|
||||
**2. 从源代码编译** 是另一种在系统中安装Vault的方式。在安装Vault之前需要安装GO和GIT。
|
||||
|
||||
在 **Redhat系统中安装GO** 使用下面的指令。
|
||||
|
||||
sudo yum install go
|
||||
|
||||
在 **Debin系统中安装GO** 使用下面的指令。
|
||||
|
||||
sudo apt-get install golang
|
||||
|
||||
或者
|
||||
|
||||
sudo add-apt-repository ppa:gophers/go
|
||||
|
||||
sudo apt-get update
|
||||
|
||||
sudo apt-get install golang-stable
|
||||
|
||||
在 **Redhat系统中安装GIT** 使用下面的命令。
|
||||
|
||||
sudo yum install git
|
||||
|
||||
在 **Debian系统中安装GIT** 使用下面的命令。
|
||||
|
||||
sudo apt-get install git
|
||||
|
||||
一旦GO和GIT都已被安装好,我们便可以开始从源码编译安装Vault。
|
||||
|
||||
> 将下列的Vault仓库拷贝至GOPATH
|
||||
|
||||
https://github.com/hashicorp/vault
|
||||
|
||||
> 测试下面的文件是否存在,如果它不存在,那么Vault没有被克隆到合适的路径。
|
||||
|
||||
$GOPATH/src/github.com/hashicorp/vault/main.go
|
||||
|
||||
> 执行下面的指令来编译Vault,并将二进制文件放到系统bin目录下。
|
||||
|
||||
make dev
|
||||
|
||||

|
||||
|
||||
### 一份Vault入门教程 ###
|
||||
|
||||
我们已经编译了Vault的官方交互式教程,并将它输出到SSH。
|
||||
|
||||
**概述**
|
||||
|
||||
这份教程包括下列步骤:
|
||||
|
||||
- 初始化,开启您的Vault
|
||||
- 在Vault中对您的请求授权
|
||||
- 读写秘密信息
|
||||
- 密封您的Vault
|
||||
|
||||
**初始化您的Vault**
|
||||
|
||||
首先,我们需要为您初始化一个Vault的工作实例。在初始化过程中,您可以配置Vault的密封行为。简单起见,现在使用一个非密封密钥来初始化Vault。
|
||||
|
||||
vault init -key-shares=1 -key-threshold=1
|
||||
|
||||
您会注意到Vault在这里打印出了许多的密钥。不要清除您的终端,这些密钥在后面的步骤中会使用到。
|
||||
|
||||

|
||||
|
||||
**开启您的Vault**
|
||||
|
||||
当一个Vault服务器启动时,它是密封的状态。在这种状态下,Vault被配置为知道在哪里和如何存取物理存储,但不知道如何对其进行解密。Vault使用加密密钥来加密数据。这个密钥由"主密钥"加密,主密钥不保存。解密主密钥需要一个碎片的阈值。在这个例子中,我们使用一个碎片来解密这个主密钥。
|
||||
|
||||
vault unseal <key 1>
|
||||
|
||||

|
||||
|
||||
**为您的请求授权**
|
||||
|
||||
在执行任何操作之前,连接的客户端应该被授权。授权的过程是检验一个人或者机器是不是像他们描述的那样,被赋予了身份。这个身份在向Vault发送请求时被使用。为简单起见,我们将使用在步骤2中生成的root令牌。这个输出会以滚动模式出现。使用一个客户端令牌进行授权:
|
||||
|
||||
vault auth <root token>
|
||||
|
||||

|
||||
|
||||
**读写保密信息**
|
||||
|
||||
现在Vault已经被设置妥当,我们可以开始使用默认的密码后端读写秘密信息了。写在Vault中的秘密信息首先被加密,然后被写入后端的存储。后端存储机制不会查看未加密的值,并且没有无需Vault即可解密的方法。
|
||||
|
||||
vault write secret/hello value=world
|
||||
|
||||
当然,您接下来便可以读这个保密信息了:
|
||||
|
||||
vault read secret/hello
|
||||
|
||||

|
||||
|
||||
**密封您的Vault**
|
||||
|
||||
有一个API来密封Vault。它将丢掉加密密钥并需要其他未密封的过程来恢复它。密封仅需要一个拥有root权限的操作者。这通常是一种罕见的"打破玻璃过程"的一部分。这种方式中,如果有一个检测到的入侵,Vault数据将会立刻被锁住,以便最小化损失。如果没有获取到主密钥碎片,数据不会被再次获取。
|
||||
|
||||
vault seal
|
||||
|
||||

|
||||
|
||||
这便是入门教程的结尾。
|
||||
|
||||
### 总结 ###
|
||||
|
||||
Vault是一个非常有用的应用,它提供了一个可靠且安全的存储关键信息的方式。另外,它在存储前加密关键信息,维护他的审计日志,并以租用期的方式获取秘密信息,且一旦租用期过期,它将立刻收回秘密信息。Vault是平台独立的,并且可以免费下载和安装。要发掘Vault的更多信息,请访问官方网站。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/how-tos/secure-secret-store-vault/
|
||||
|
||||
作者:[Aun Raza][a]
|
||||
译者:[wwy-hust](https://github.com/wwy-hust)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://linoxide.com/author/arunrz/
|
||||
[1]:https://dl.bintray.com/mitchellh/vault/vault_0.1.0_linux_386.zip
|
||||
[2]:https://dl.bintray.com/mitchellh/vault/vault_0.1.0_linux_amd64.zip
|
||||
[3]:https://dl.bintray.com/mitchellh/vault/vault_0.1.0_linux_arm.zip
|
||||
@ -0,0 +1,112 @@
|
||||
如何在CentOS 7.x中安装OpenERP(Odoo)
|
||||
================================================================================
|
||||
各位好,这篇教程关于的是如何在CentOS 7中安装Odoo(就是我们所知的OpenERP)。你是不是在考虑为你的业务安装一个不错的ERP(企业资源规划)软件?那么OpenERP就是你寻找的最好的程序,因为它是一款为你的商务提供杰出特性的自由开源软件。
|
||||
|
||||
[OpenERP][1]是一款自由开源的传统的OpenERP(企业资源规划),它包含了开源CRM、网站构建、电子商务、项目管理、计费账务、销售点、人力资源、市场、生产、采购管理以及其他模块用于提高效率及销售。Odoo可以作为独立程序,但是它可以无缝集成因此你可以在安装数个程序后得到一个全功能的开源ERP。
|
||||
|
||||
因此,下面是在你的CentOS上安装OpenERP的步骤。
|
||||
|
||||
### 1. 安装 PostgreSQL ###
|
||||
|
||||
首先,首先我们需要更新CentOS 7的软件包来确保是最新的包,补丁和安全更新。要更新我们的系统,我们要在shell下运行下面的命令。
|
||||
|
||||
# yum clean all
|
||||
# yum update
|
||||
|
||||
现在我们要安装PostgreSQL,因为OpenERP使用PostgreSQL作为他的数据库。要安装它,我们需要运行下面的命令。
|
||||
|
||||
# yum install postgresql postgresql-server postgresql-libs
|
||||
|
||||

|
||||
|
||||
、安装完成后,我们需要用下面的命令初始化数据库。
|
||||
|
||||
# postgresql-setup initdb
|
||||
|
||||

|
||||
|
||||
我们接着设置PostgreSQL来使它每次开机启动。
|
||||
|
||||
# systemctl enable postgresql
|
||||
# systemctl start postgresql
|
||||
|
||||
因为我们还没有为用户“postgresql”设置密码,我们现在设置。
|
||||
|
||||
# su - postgres
|
||||
$ psql
|
||||
postgres=# \password postgres
|
||||
postgres=# \q
|
||||
# exit
|
||||
|
||||

|
||||
|
||||
### 2. 设置Odoo仓库 ###
|
||||
|
||||
在初始化数据库初始化完成后,我们要添加EPEL(企业版Linux的额外包)到我们的CentOS中。Odoo(或者OpenERP)依赖于Python运行时以及其他包没有包含在标准仓库中。这样我们要位企业版Linux添加额外的包仓库支持来解决Odoo所需要的依赖。要安装完成,我们需要运行下面的命令。
|
||||
|
||||
# yum install epel-release
|
||||
|
||||

|
||||
|
||||
现在,安装EPEL后,我们现在使用yum-config-manager添加Odoo(OpenERp)的仓库。
|
||||
|
||||
# yum install yum-utils
|
||||
|
||||
# yum-config-manager --add-repo=https://nightly.odoo.com/8.0/nightly/rpm/odoo.repo
|
||||
|
||||

|
||||
|
||||
### 3. 安装Odoo 8 (OpenERP) ###
|
||||
|
||||
在CentOS 7中添加Odoo 8(OpenERP)的仓库后。我们使用下面的命令来安装Odoo 8(OpenERP)。
|
||||
|
||||
# yum install -y odoo
|
||||
|
||||
上面的命令会安装odoo以及必须的依赖的包。
|
||||
|
||||

|
||||
|
||||
现在我们使用下面的命令在每次启动后启动Odoo服务。
|
||||
|
||||
# systemctl enable odoo
|
||||
# systemctl start odoo
|
||||
|
||||

|
||||
|
||||
### 4. 防火墙允许 ###
|
||||
|
||||
因为Odoo使用8069端口,我们需要在防火墙中允许远程访问。我们使用下面的命令来在防火墙中允许8069防火墙。
|
||||
|
||||
# firewall-cmd --zone=public --add-port=8069/tcp --permanent
|
||||
# firewall-cmd --reload
|
||||
|
||||

|
||||
|
||||
**注意:默认上,只有本地的连接才允许。如果我们要允许PostgreSQL的远程访问,我们需要在pg_hba.conf添加下面图片中一行**
|
||||
|
||||
# nano /var/lib/pgsql/data/pg_hba.conf
|
||||
|
||||

|
||||
|
||||
### 5. Web接口 ###
|
||||
|
||||
我们已经在CentOS 7中安装了最新的Odoo 8(OpenERP),我们可以在浏览器中输入http://ip-address:8069来访问Odoo。 接着,我们要做的第一件事就是创建一个新的数据库和新的密码。注意,主密码默认是管理员密码。接着,我们可以在面板中输入用户名和密码。
|
||||
|
||||

|
||||
|
||||
### 总结 ###
|
||||
|
||||
Odoo 8(OpenERP)是世界上最好的开源ERP程序。我们做了一件出色的工作来安装它因为OpenERP是由许多模块组成的针对商务和公司的完整ERP程序。因此,如果你有任何问题、建议、反馈请在下面的评论栏写下。谢谢你!享受OpenERP(Odoo 8)吧 :-)
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/linux-how-to/setup-openerp-odoo-centos-7/
|
||||
|
||||
作者:[Arun Pyasi][a]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://linoxide.com/author/arunp/
|
||||
[1]:https://www.odoo.com/
|
||||
@ -0,0 +1,98 @@
|
||||
nux常见问题解答--如何在Ubuntu上使用网络管理配置一个Linux网桥
|
||||
===============================================================================
|
||||
> **Question**: 我需要在我的Ubuntu主机上建立一个Linux网桥,共享一个NIC给其他一些虚拟主机或者主机上创建的容器。我目前正在Ubunut上使用网络管理,所以最好>能使用网络管理来配置一个网桥。我该怎么做?
|
||||
|
||||
|
||||
网桥是一个硬件装备,用来内部连接两个或多个数据链路层(OSI七层模型中第二层),所以使得不同段上的网络设备可以互相访问。当你想要内连多个虚拟机器或者一个>主机里的以太接口时,就需要在Linux主机里有一个类似桥接的概念。
|
||||
|
||||
有很多的方法来配置一个Linux网桥。举个例子,在一个无中心的服务器环境里,你可以使用[brct][1]手动地配置一个网桥。在桌面环境下,在网络管理里有建立网桥支持
|
||||
。那就让我们测试一下如何用网络管理配置一个网桥吧。
|
||||
|
||||
### 要求 ###
|
||||
|
||||
为了避免[任何问题][2],建议你的网络管理版本为0.9.9或者更高,这主要为了配合Ubuntu15.05或者更新的版本。
|
||||
|
||||
$ apt-cache show network-manager | grep Version
|
||||
|
||||
----------
|
||||
|
||||
Version: 0.9.10.0-4ubuntu15.1
|
||||
Version: 0.9.10.0-4ubuntu15
|
||||
|
||||
### 创建一个网桥 ###
|
||||
|
||||
使用网络管理创建网桥最简单的方式就是通过nm-connection-editor。这款GUI(图形用户界面)的工具允许你傻瓜式地配置一个网桥。
|
||||
|
||||
首先,启动nm-connection-editor。
|
||||
|
||||
$ nm-connection-editor
|
||||
|
||||
该编辑器的窗口会显示给你一个列表,关于目前配置好的网络连接。点击右上角的“Click”按钮,创建一个网桥。
|
||||
|
||||

|
||||
|
||||
接下来,选择“Bridge”作为连接类型。
|
||||
|
||||

|
||||
|
||||
现在,开始配置网桥,包括它的名字和桥接。如果没有其他网桥被创建,那么默认的网桥接口会被命名为bridge0。
|
||||
|
||||
回顾一下,创建网桥的目的是为了通过网桥共享你的以太网卡接口。所以你需要添加以太网卡接口到网桥。在图形界面添加一个新的“bridged connection”可以实现上述目的。点击“Add”按钮。
|
||||
|
||||

|
||||
|
||||
选择“Ethernet”作为连接类型。
|
||||
|
||||

|
||||
|
||||
在“Device MAC address”区域,选择你想要控制的接口到bridge里。本例中,假设接口是eth0。
|
||||
|
||||

|
||||
|
||||
点击“General”标签,并且选中两个复选框,分别是“Automatically connect to this network when it is available”和“All users may connect to this network”。
|
||||
|
||||

|
||||
|
||||
保存更改。
|
||||
|
||||
现在,你会在网桥里看见一个新的从属连接被建立。
|
||||
|
||||

|
||||
|
||||
点击网桥的“General”标签,并且确保最上面的两个复选框被选中了。
|
||||
|
||||

|
||||
|
||||
切换到“IPv4 Setting”标签,为网桥配置DHCP或者是静态IP地址。注意,你应该使用相同的IPv4设定作为从属的以太网卡接口eth0。本例中,我们假设eth0是用过DHCP配置的。因此,此处选择“Automatic(DHCP)”。如果eth0被指定了一个静态IP地址,那么你应该指定相同的IP地址给网桥。
|
||||
|
||||

|
||||
|
||||
最后,保存网桥的设置。
|
||||
|
||||
现在,你会看见一个额外的网桥连接被创建在“Network Connection”窗口里。你不再需要一个预先配置的有线连接,为着从属的eth0接口。所以去删除原来的有线连接吧。
|
||||
|
||||

|
||||
|
||||
这时候,网桥连接会被自动激活。你将会暂时失去一个连接,从指定给eth0的IP地址被网桥接管。一旦IP地址指定给了网桥,你将会连接回你的以太网卡接口,通过网桥。你可以通过“Network”设置确认一下。
|
||||
|
||||

|
||||
|
||||
同时,检查可用的接口。提醒一下,网桥接口必须已经取代了任何通过你的以太网卡接口的IP地址。
|
||||
|
||||

|
||||
|
||||
就这么多了,现在,网桥已经可以用了。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://ask.xmodulo.com/configure-linux-bridge-network-manager-ubuntu.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[wi-cuckoo](https://github.com/wi-cuckoo)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://ask.xmodulo.com/author/nanni
|
||||
[1]:http://xmodulo.com/how-to-configure-linux-bridge-interface.html
|
||||
[2]:https://bugs.launchpad.net/ubuntu/+source/network-manager/+bug/1273201
|
||||
Loading…
Reference in New Issue
Block a user