mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-02-16 00:21:12 +08:00
finish translation
This commit is contained in:
parent
6a6ff44aeb
commit
9b880e94b4
@ -1,272 +0,0 @@
|
||||
translating by wwy-hust
|
||||
|
||||
Protect Apache Against Brute Force or DDoS Attacks Using Mod_Security and Mod_evasive Modules
|
||||
================================================================================
|
||||
For those of you in the hosting business, or if you’re hosting your own servers and exposing them to the Internet, securing your systems against attackers must be a high priority.
|
||||
|
||||
mod_security (an open source intrusion detection and prevention engine for web applications that integrates seamlessly with the web server) and mod_evasive are two very important tools that can be used to protect a web server against brute force or (D)DoS attacks.
|
||||
|
||||
mod_evasive, as its name suggests, provides evasive capabilities while under attack, acting as an umbrella that shields web servers from such threats.
|
||||
|
||||

|
||||
Install Mod_Security and Mod_Evasive to Protect Apache
|
||||
|
||||
In this article we will discuss how to install, configure, and put them into play along with Apache on RHEL/CentOS 6 and 7 as well as Fedora 21-15. In addition, we will simulate attacks in order to verify that the server reacts accordingly.
|
||||
|
||||
This assumes that you have a LAMP server installed on your system. If not, please check this article before proceeding further.
|
||||
|
||||
- [Install LAMP stack in RHEL/CentOS 7][1]
|
||||
|
||||
You will also need to setup iptables as the default [firewall][2] front-end instead of firewalld if you’re running RHEL/CentOS 7 or Fedora 21. We do this in order to use the same tool in both RHEL/CentOS 7/6 and Fedora 21.
|
||||
|
||||
### Step 1: Installing Iptables Firewall on RHEL/CentOS 7 and Fedora 21 ###
|
||||
|
||||
To begin, stop and disable firewalld:
|
||||
|
||||
# systemctl stop firewalld
|
||||
# systemctl disable firewalld
|
||||
|
||||

|
||||
Disable Firewalld Service
|
||||
|
||||
Then install the iptables-services package before enabling iptables:
|
||||
|
||||
# yum update && yum install iptables-services
|
||||
# systemctl enable iptables
|
||||
# systemctl start iptables
|
||||
# systemctl status iptables
|
||||
|
||||

|
||||
Install Iptables Firewall
|
||||
|
||||
### Step 2: Installing Mod_Security and Mod_evasive ###
|
||||
|
||||
In addition to having a LAMP setup already in place, you will also have to [enable the EPEL repository][3] in RHEL/CentOS 7/6 in order to install both packages. Fedora users don’t need to enable any repo, because epel is a already part of Fedora project.
|
||||
|
||||
# yum update && yum install mod_security mod_evasive
|
||||
|
||||
When the installation is complete, you will find the configuration files for both tools in /etc/httpd/conf.d.
|
||||
|
||||
# ls -l /etc/httpd/conf.d
|
||||
|
||||

|
||||
mod_security + mod_evasive Configurations
|
||||
|
||||
Now, in order to integrate these two modules with Apache and have it load them when it starts, make sure the following lines appear in the top level section of mod_evasive.conf and mod_security.conf, respectively:
|
||||
|
||||
LoadModule evasive20_module modules/mod_evasive24.so
|
||||
LoadModule security2_module modules/mod_security2.so
|
||||
|
||||
Note that modules/mod_security2.so and modules/mod_evasive24.so are the relative paths, from the /etc/httpd directory to the source file of the module. You can verify this (and change it, if needed) by listing the contents of the /etc/httpd/modules directory:
|
||||
|
||||
# cd /etc/httpd/modules
|
||||
# pwd
|
||||
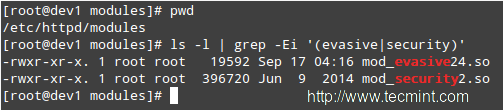
# ls -l | grep -Ei '(evasive|security)'
|
||||
|
||||
|
||||
Verify mod_security + mod_evasive Modules
|
||||
|
||||
Then restart Apache and verify that it loads mod_evasive and mod_security:
|
||||
|
||||
# service httpd restart [On RHEL/CentOS 6 and Fedora 20-18]
|
||||
# systemctl restart httpd [On RHEL/CentOS 7 and Fedora 21]
|
||||
|
||||
----------
|
||||
|
||||
[Dump a list of loaded Static and Shared Modules]
|
||||
|
||||
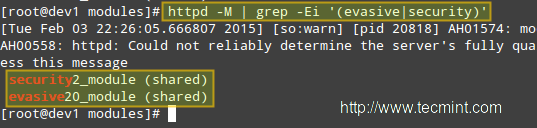
# httpd -M | grep -Ei '(evasive|security)'
|
||||
|
||||
|
||||
Check mod_security + mod_evasive Modules Loaded
|
||||
|
||||
### Step 3: Installing A Core Rule Set and Configuring Mod_Security ###
|
||||
|
||||
In few words, a Core Rule Set (aka CRS) provides the web server with instructions on how to behave under certain conditions. The developer firm of mod_security provide a free CRS called OWASP ([Open Web Application Security Project][4]) ModSecurity CRS that can be downloaded and installed as follows.
|
||||
|
||||
1. Download the OWASP CRS to a directory created for that purpose.
|
||||
|
||||
# mkdir /etc/httpd/crs-tecmint
|
||||
# cd /etc/httpd/crs-tecmint
|
||||
# wget https://github.com/SpiderLabs/owasp-modsecurity-crs/tarball/master
|
||||
|
||||

|
||||
Download mod_security Core Rules
|
||||
|
||||
2. Untar the CRS file and change the name of the directory for one of our convenience.
|
||||
|
||||
# tar xzf master
|
||||
# mv SpiderLabs-owasp-modsecurity-crs-ebe8790 owasp-modsecurity-crs
|
||||
|
||||

|
||||
Extract mod_security Core Rules
|
||||
|
||||
3. Now it’s time to configure mod_security. Copy the sample file with rules (owasp-modsecurity-crs/modsecurity_crs_10_setup.conf.example) into another file without the .example extension:
|
||||
|
||||
# cp modsecurity_crs_10_setup.conf.example modsecurity_crs_10_setup.conf
|
||||
|
||||
and tell Apache to use this file along with the module by inserting the following lines in the web server’s main configuration file /etc/httpd/conf/httpd.conf file. If you chose to unpack the tarball in another directory you will need to edit the paths following the Include directives:
|
||||
|
||||
<IfModule security2_module>
|
||||
Include crs-tecmint/owasp-modsecurity-crs/modsecurity_crs_10_setup.conf
|
||||
Include crs-tecmint/owasp-modsecurity-crs/base_rules/*.conf
|
||||
</IfModule>
|
||||
|
||||
Finally, it is recommended that we create our own configuration file within the /etc/httpd/modsecurity.d directory where we will place our customized directives (we will name it tecmint.conf in the following example) instead of modifying the CRS files directly. Doing so will allow for easier upgrading the CRSs as new versions are released.
|
||||
|
||||
<IfModule mod_security2.c>
|
||||
SecRuleEngine On
|
||||
SecRequestBodyAccess On
|
||||
SecResponseBodyAccess On
|
||||
SecResponseBodyMimeType text/plain text/html text/xml application/octet-stream
|
||||
SecDataDir /tmp
|
||||
</IfModule>
|
||||
|
||||
You can refer to the [SpiderLabs’ ModSecurity GitHub][5] repository for a complete explanatory guide of mod_security configuration directives.
|
||||
|
||||
### Step 4: Configuring Mod_Evasive ###
|
||||
|
||||
mod_evasive is configured using directives in /etc/httpd/conf.d/mod_evasive.conf. Since there are no rules to update during a package upgrade, we don’t need a separate file to add customized directives, as opposed to mod_security.
|
||||
|
||||
The default mod_evasive.conf file has the following directives enabled (note that this file is heavily commented, so we have stripped out the comments to highlight the configuration directives below):
|
||||
|
||||
<IfModule mod_evasive24.c>
|
||||
DOSHashTableSize 3097
|
||||
DOSPageCount 2
|
||||
DOSSiteCount 50
|
||||
DOSPageInterval 1
|
||||
DOSSiteInterval 1
|
||||
DOSBlockingPeriod 10
|
||||
</IfModule>
|
||||
|
||||
Explanation of the directives:
|
||||
|
||||
- DOSHashTableSize: This directive specifies the size of the hash table that is used to keep track of activity on a per-IP address basis. Increasing this number will provide a faster look up of the sites that the client has visited in the past, but may impact overall performance if it is set too high.
|
||||
- DOSPageCount: Legitimate number of identical requests to a specific URI (for example, any file that is being served by Apache) that can be made by a visitor over the DOSPageInterval interval.
|
||||
- DOSSiteCount: Similar to DOSPageCount, but refers to how many overall requests can be made to the entire site over the DOSSiteInterval interval.
|
||||
- DOSBlockingPeriod: If a visitor exceeds the limits set by DOSSPageCount or DOSSiteCount, his source IP address will be blacklisted during the DOSBlockingPeriod amount of time. During DOSBlockingPeriod, any requests coming from that IP address will encounter a 403 Forbidden error.
|
||||
|
||||
Feel free to experiment with these values so that your web server will be able to handle the required amount and type of traffic.
|
||||
|
||||
**Only a small caveat**: if these values are not set properly, you run the risk of ending up blocking legitimate visitors.
|
||||
|
||||
You may also want to consider other useful directives:
|
||||
|
||||
#### DOSEmailNotify ####
|
||||
|
||||
If you have a mail server up and running, you can send out warning messages via Apache. Note that you will need to grant the apache user SELinux permission to send emails if SELinux is set to enforcing. You can do so by running
|
||||
|
||||
# setsebool -P httpd_can_sendmail 1
|
||||
|
||||
Next, add this directive in the mod_evasive.conf file with the rest of the other directives:
|
||||
|
||||
DOSEmailNotify you@yourdomain.com
|
||||
|
||||
If this value is set and your mail server is working properly, an email will be sent to the address specified whenever an IP address becomes blacklisted.
|
||||
|
||||
#### DOSSystemCommand ####
|
||||
|
||||
This needs a valid system command as argument,
|
||||
|
||||
DOSSystemCommand </command>
|
||||
|
||||
This directive specifies a command to be executed whenever an IP address becomes blacklisted. It is often used in conjunction with a shell script that adds a firewall rule to block further connections coming from that IP address.
|
||||
|
||||
**Write a shell script that handles IP blacklisting at the firewall level**
|
||||
|
||||
When an IP address becomes blacklisted, we need to block future connections coming from it. We will use the following shell script that performs this job. Create a directory named scripts-tecmint (or whatever name of your choice) in /usr/local/bin and a file called ban_ip.sh in that directory.
|
||||
|
||||
#!/bin/sh
|
||||
# IP that will be blocked, as detected by mod_evasive
|
||||
IP=$1
|
||||
# Full path to iptables
|
||||
IPTABLES="/sbin/iptables"
|
||||
# mod_evasive lock directory
|
||||
MOD_EVASIVE_LOGDIR=/var/log/mod_evasive
|
||||
# Add the following firewall rule (block all traffic coming from $IP)
|
||||
$IPTABLES -I INPUT -s $IP -j DROP
|
||||
# Remove lock file for future checks
|
||||
rm -f "$MOD_EVASIVE_LOGDIR"/dos-"$IP"
|
||||
|
||||
Our DOSSystemCommand directive should read as follows:
|
||||
|
||||
DOSSystemCommand "sudo /usr/local/bin/scripts-tecmint/ban_ip.sh %s"
|
||||
|
||||
In the line above, %s represents the offending IP as detected by mod_evasive.
|
||||
|
||||
**Add the apache user to the sudoers file**
|
||||
|
||||
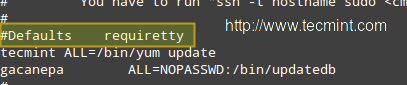
Note that all of this just won’t work unless you to give permissions to user apache to run our script (and that script only!) without a terminal and password. As usual, you can just type visudo as root to access the /etc/sudoers file and then add the following 2 lines as shown in the image below:
|
||||
|
||||
apache ALL=NOPASSWD: /usr/local/bin/scripts-tecmint/ban_ip.sh
|
||||
Defaults:apache !requiretty
|
||||
|
||||

|
||||
Add Apache User to Sudoers
|
||||
|
||||
**IMPORTANT**: As a default security policy, you can only run sudo in a terminal. Since in this case we need to use sudo without a tty, we have to comment out the line that is highlighted in the following image:
|
||||
|
||||
#Defaults requiretty
|
||||
|
||||
|
||||
Disable tty for Sudo
|
||||
|
||||
Finally, restart the web server:
|
||||
|
||||
# service httpd restart [On RHEL/CentOS 6 and Fedora 20-18]
|
||||
# systemctl restart httpd [On RHEL/CentOS 7 and Fedora 21]
|
||||
|
||||
### Step 4: Simulating an DDoS Attacks on Apache ###
|
||||
|
||||
There are several tools that you can use to simulate an external attack on your server. You can just google for “tools for simulating ddos attacks” to find several of them.
|
||||
|
||||
Note that you, and only you, will be held responsible for the results of your simulation. Do not even think of launching a simulated attack to a server that you’re not hosting within your own network.
|
||||
|
||||
Should you want to do the same with a VPS that is hosted by someone else, you need to appropriately warn your hosting provider or ask permission for such a traffic flood to go through their networks. Tecmint.com is not, by any means, responsible for your acts!
|
||||
|
||||
In addition, launching a simulated DoS attack from only one host does not represent a real life attack. To simulate such, you would need to target your server from several clients at the same time.
|
||||
|
||||
Our test environment is composed of a CentOS 7 server [IP 192.168.0.17] and a Windows host from which we will launch the attack [IP 192.168.0.103]:
|
||||
|
||||

|
||||
Confirm Host IPAddress
|
||||
|
||||
Please play the video below and follow the steps outlined in the indicated order to simulate a simple DoS attack:
|
||||
|
||||
注:youtube视频,发布的时候不行做个链接吧
|
||||
<iframe width="640" height="405" frameborder="0" allowfullscreen="allowfullscreen" src="https://www.youtube.com/embed/-U_mdet06Jk"></iframe>
|
||||
|
||||
Then the offending IP is blocked by iptables:
|
||||
|
||||

|
||||
Blocked Attacker IP
|
||||
|
||||
### Conclusion ###
|
||||
|
||||
With mod_security and mod_evasive enabled, the simulated attack causes the CPU and RAM to experiment a temporary usage peak for only a couple of seconds before the source IPs are blacklisted and blocked by the firewall. Without these tools, the simulation will surely knock down the server very fast and render it unusable during the duration of the attack.
|
||||
|
||||
We would love to hear if you’re planning on using (or have used in the past) these tools. We always look forward to hearing from you, so don’t hesitate to leave your comments and questions, if any, using the form below.
|
||||
|
||||
### Reference Links ###
|
||||
|
||||
- [https://www.modsecurity.org/][6]
|
||||
- [http://www.zdziarski.com/blog/?page_id=442][7]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.tecmint.com/protect-apache-using-mod_security-and-mod_evasive-on-rhel-centos-fedora/
|
||||
|
||||
作者:[Gabriel Cánepa][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.tecmint.com/author/gacanepa/
|
||||
[1]:http://www.tecmint.com/install-lamp-in-centos-7/
|
||||
[2]:http://www.tecmint.com/configure-firewalld-in-centos-7/
|
||||
[3]:http://www.tecmint.com/how-to-enable-epel-repository-for-rhel-centos-6-5/
|
||||
[4]:https://www.owasp.org/index.php/Category:OWASP_ModSecurity_Core_Rule_Set_Project
|
||||
[5]:https://github.com/SpiderLabs/ModSecurity/wiki/Reference-Manual#Configuration_Directives
|
||||
[6]:https://www.modsecurity.org/
|
||||
[7]:http://www.zdziarski.com/blog/?page_id=442
|
||||
@ -0,0 +1,271 @@
|
||||
在Apache中使用Mod_Security和Mod_evasive来抵御暴力破解和DDos攻击
|
||||
================================================================================
|
||||
对于那些托管主机或者需要将您的主机暴露在因特网中的人来说,保证您的系统在面对攻击时安全是一个重要的事情。
|
||||
|
||||
mod_security(一个开源的可以无缝接入Web服务器的用于Web应用入侵检测和防护的引擎)和mod_evasive是两个在服务器端对抗暴力破解和(D)Dos攻击的非常重要的工具。
|
||||
|
||||
mod_evasive,如它的名字一样,在受攻击时提供避实就虚的功能,它像一个雨伞一样保护Web服务器免受那些威胁。
|
||||
|
||||

|
||||
|
||||
安装Mod_Security和Mod_Evasive来保护Apache
|
||||
|
||||
在这篇文章中我们将讨论如何安装、配置以及在RHEL/CentOS6、7和Fedora 21-15上将它们整合到Apache。另外,我们会模拟攻击以便验证服务器做出了正确的反应。
|
||||
|
||||
以上以您的系统中安装有LAMP服务器为基础,所以,如果您没有安装,请先阅读下面链接的文章再开始阅读本文。
|
||||
|
||||
- [在RHEL/CentOS 7中安装LAMP][1]
|
||||
|
||||
如果您在运行RHEL/CentOS 7或Fedora 21,您还需要安装iptables作为默认[防火墙][2]前端以取代firewalld。这样做是为了在RHEL/CentOS 7或Fedora 21中使用同样的工具。
|
||||
|
||||
### 步骤 1: 在RHEL/CentOS 7和Fedora 21上安装Iptables防火墙 ###
|
||||
|
||||
用下面的命令停止和禁用firewalld:
|
||||
|
||||
# systemctl stop firewalld
|
||||
# systemctl disable firewalld
|
||||
|
||||

|
||||
禁用firewalld服务
|
||||
|
||||
接下来在使能iptables之前安装iptables-services包:
|
||||
|
||||
# yum update && yum install iptables-services
|
||||
# systemctl enable iptables
|
||||
# systemctl start iptables
|
||||
# systemctl status iptables
|
||||
|
||||

|
||||
安装Iptables防火墙
|
||||
|
||||
### 步骤 2: 安装Mod_Security和Mod_evasive ###
|
||||
|
||||
另外,在安装LAMP后,您还需要在RHEL/CentOS 7/6中[开启EPEL仓库][3]来安装这两个包。Fedora用户不需要开启这个仓库,因为epel已经是Fedora项目的一部分了。
|
||||
|
||||
# yum update && yum install mod_security mod_evasive
|
||||
|
||||
当安装结束后,您会在/etc/httpd/conf.d下找到两个工具的配置文件。
|
||||
|
||||
# ls -l /etc/httpd/conf.d
|
||||
|
||||

|
||||
mod_security + mod_evasive 配置文件
|
||||
|
||||
现在,为了整合这两个模块到Apache,并在启动时加载它们。请确保下面几行出现在mod_evasive.conf和mod_security.conf的顶层部分,它们分别为:
|
||||
|
||||
LoadModule evasive20_module modules/mod_evasive24.so
|
||||
LoadModule security2_module modules/mod_security2.so
|
||||
|
||||
请注意modules/mod_security2.so和modules/mod_evasive24.so都是从/etc/httpd到模块源文件的相对路径。您可以通过列出/etc/httpd/modules的内容来验证(如果需要的话,修改它):
|
||||
|
||||
# cd /etc/httpd/modules
|
||||
# pwd
|
||||
# ls -l | grep -Ei '(evasive|security)'
|
||||
|
||||

|
||||
验证mod_security + mod_evasive模块
|
||||
|
||||
接下来重启Apache并且核实它已加载了mod_evasive和mod_security:
|
||||
|
||||
# service httpd restart [在RHEL/CentOS 6和Fedora 20-18上]
|
||||
# systemctl restart httpd [在RHEL/CentOS 7和Fedora 21上]
|
||||
|
||||
----------
|
||||
|
||||
[输出已加载的静态模块和动态模块列表]
|
||||
|
||||
# httpd -M | grep -Ei '(evasive|security)'
|
||||
|
||||

|
||||
检查mod_security + mod_evasive模块已加载
|
||||
|
||||
### 步骤 3: 安装一个核心规则集并且配置Mod_Security ###
|
||||
|
||||
简单来说,一个核心规则集(即CRS)为web服务器提供特定状况下如何反应的指令。mod_security的开发者们提供了一个免费的CRS,叫做OWASP([开放Web应用安全项目])ModSecurity CRS,可以从下面的地址下载和安装。
|
||||
|
||||
1. 下载OWASP CRS到为之创建的目录
|
||||
|
||||
# mkdir /etc/httpd/crs-tecmint
|
||||
# cd /etc/httpd/crs-tecmint
|
||||
# wget https://github.com/SpiderLabs/owasp-modsecurity-crs/tarball/master
|
||||
|
||||

|
||||
下载mod_security核心规则
|
||||
|
||||
2. 解压CRS文件并修改文件夹名称
|
||||
|
||||
# tar xzf master
|
||||
# mv SpiderLabs-owasp-modsecurity-crs-ebe8790 owasp-modsecurity-crs
|
||||
|
||||

|
||||
解压mod_security核心规则
|
||||
|
||||
3. 现在,是时候配置mod_security了。将同样的规则文件(owasp-modsecurity-crs/modsecurity_crs_10_setup.conf.example)拷贝至另一个没有.example扩展的文件。
|
||||
|
||||
# cp modsecurity_crs_10_setup.conf.example modsecurity_crs_10_setup.conf
|
||||
|
||||
并通过将下面的几行插入到web服务器的主配置文件/etc/httpd/conf/httpd.conf来告诉Apache将这个文件和该模块放在一起使用。如果您选择解压打包文件到另一个文件夹,那么您需要修改Include的路径:
|
||||
|
||||
<IfModule security2_module>
|
||||
Include crs-tecmint/owasp-modsecurity-crs/modsecurity_crs_10_setup.conf
|
||||
Include crs-tecmint/owasp-modsecurity-crs/base_rules/*.conf
|
||||
</IfModule>
|
||||
|
||||
最后,建议您在/etc/httpd/modsecurity.d目录下创建自己的配置文件,在那里我们可以用我们自定义的文件夹(接下来的示例中,我们会将其命名为tecmint.conf)而无需修改CRS文件的目录。这样做能够在CRSs发布新版本时更加容易的升级。
|
||||
|
||||
<IfModule mod_security2.c>
|
||||
SecRuleEngine On
|
||||
SecRequestBodyAccess On
|
||||
SecResponseBodyAccess On
|
||||
SecResponseBodyMimeType text/plain text/html text/xml application/octet-stream
|
||||
SecDataDir /tmp
|
||||
</IfModule>
|
||||
|
||||
您可以在[SpiderLabs的ModSecurity GitHub][5]仓库中参考关于mod_security目录的更完整的解释。
|
||||
|
||||
### 步骤 4: 配置Mod_Evasive ###
|
||||
|
||||
mod_evasive被配置为使用/etc/httpd/conf.d/mod_evasive.conf中的指令。与mod_security不同,由于在包升级时没有规则来更新,因此我们不需要独立的文件来添加自定义指令。
|
||||
|
||||
默认的mod_evasive.conf开启了下列的目录(注意这个文件被详细的注释了,因此我们剔掉了注释以重点显示配置指令):
|
||||
|
||||
<IfModule mod_evasive24.c>
|
||||
DOSHashTableSize 3097
|
||||
DOSPageCount 2
|
||||
DOSSiteCount 50
|
||||
DOSPageInterval 1
|
||||
DOSSiteInterval 1
|
||||
DOSBlockingPeriod 10
|
||||
</IfModule>
|
||||
|
||||
这些指令的解释:
|
||||
|
||||
- DOSHashTableSize: 这个指令指明了哈希表的大小,它用来追踪基于IP地址的活动。增加这个数字将使查询站点访问历史变得更快,但如果被设置的太高则会影响整体性能。
|
||||
- DOSPageCount: 在DOSPageInterval间隔内可由一个用户发起的面向特定的URI(例如,一个Apache托管的文件)的同一个请求的数量。
|
||||
- DOSSiteCount: 类似DOSPageCount,但涉及到整个站点总共有多少的请求可以在DOSSiteInterval间隔内被发起。
|
||||
- DOSBlockingPeriod: 如果一个用户超过了DOSSPageCount的限制或者DOSSiteCount,他的源IP地址将会在DOSBlockingPeriod期间内被加入黑名单。在DOSBlockingPeriod期间,任何从这个IP地址发起的请求将会遭遇一个403禁止错误。
|
||||
|
||||
尽可能的试验这些值,以使您的web服务器有能力处理特定大小的负载。
|
||||
|
||||
**一个小警告**: 如果这些值设置的不合适,则您会蒙受阻挡合法用户的风险。
|
||||
|
||||
您也许想考虑下其他有用的指令:
|
||||
|
||||
#### DOSEmailNotify ####
|
||||
|
||||
如果您运行有一个邮件服务器,您可以通过Apache发送警告消息。注意,如果SELinux已开启,您需要授权apache用户SELinux的权限来发送email。您可以通过下面的命令来授予权限:
|
||||
|
||||
# setsebool -P httpd_can_sendmail 1
|
||||
|
||||
接下来,将这个指令和其他指令一起加入到mod_evasive.conf文件。
|
||||
|
||||
DOSEmailNotify you@yourdomain.com
|
||||
|
||||
如果这个值被合适的设置并且您的邮件服务器在正常的运行,则当一个IP地址被加入黑名单时,会有一封邮件被发送到相应的地址。
|
||||
|
||||
#### DOSSystemCommand ####
|
||||
|
||||
它需要一个有效的系统命令作为参数,
|
||||
|
||||
DOSSystemCommand </command>
|
||||
|
||||
这个指令指定当一个IP地址被加入黑名单时执行的命令。它通常结合shell脚本来使用,在脚本中添加一条防火墙规则来阻挡某个IP进一步的连接。
|
||||
|
||||
**写一个shell脚本在防火墙阶段处理IP黑名单**
|
||||
|
||||
当一个IP地址被加入黑名单,我们需要阻挡它进一步的连接。我们需要下面的shell脚本来执行这个任务。在/usr/local/bin下创建一个叫做scripts-tecmint的文件夹(或其他的名字),以及一个叫做ban_ip.sh的文件。
|
||||
|
||||
#!/bin/sh
|
||||
# 由mod_evasive检测出,将被阻挡的IP地址
|
||||
IP=$1
|
||||
# iptables的完整路径
|
||||
IPTABLES="/sbin/iptables"
|
||||
# mod_evasive锁文件夹
|
||||
MOD_EVASIVE_LOGDIR=/var/log/mod_evasive
|
||||
# 添加下面的防火墙规则 (阻止所有从$IP流入的流量)
|
||||
$IPTABLES -I INPUT -s $IP -j DROP
|
||||
# 为了未来的检测,移除锁文件
|
||||
rm -f "$MOD_EVASIVE_LOGDIR"/dos-"$IP"
|
||||
|
||||
我们的DOSSystemCommand指令应该是这样的:
|
||||
|
||||
DOSSystemCommand "sudo /usr/local/bin/scripts-tecmint/ban_ip.sh %s"
|
||||
|
||||
上面一行的%s代表了由mod_evasive检测到的攻击IP地址。
|
||||
|
||||
**将apache用户添加到sudoers文件**
|
||||
|
||||
请注意,如果您不给予apache用户以无需终端和密码的方式运行我们脚本(关键就是这个脚本)的权限,则这一切都不起作用。通常,您只需要以root权限键入visudo来存取/etc/sudoers文件,接下来添加下面的两行即可:
|
||||
|
||||
apache ALL=NOPASSWD: /usr/local/bin/scripts-tecmint/ban_ip.sh
|
||||
Defaults:apache !requiretty
|
||||
|
||||

|
||||
添加Apache用户到Sudoers
|
||||
|
||||
**重要**: 作为默认的安全策略,您只能在终端中运行sudo。由于这个时候我们需要在没有tty的时候运行sudo,我们像下面图片中那样必须注释掉下面这一行:
|
||||
|
||||
#Defaults requiretty
|
||||
|
||||

|
||||
为Sudo禁用tty
|
||||
|
||||
最后,重启web服务器:
|
||||
|
||||
# service httpd restart [在RHEL/CentOS 6和Fedora 20-18上]
|
||||
# systemctl restart httpd [在RHEL/CentOS 7和Fedora 21上]
|
||||
|
||||
### 步骤4: 在Apache上模拟DDos攻击 ###
|
||||
|
||||
有许多工具可以在您的服务器上模拟外部的攻击。您可以google下“tools for simulating ddos attacks”来找一找相关的工具。
|
||||
|
||||
注意,您(也只有您)将负责您模拟所造成的结果。请不要考虑向不在您网络中的服务器发起模拟攻击。
|
||||
|
||||
假如您想对一个由别人托管的VPS做这些事情,您需要向您的托管商发送适当的警告或就那样的流量通过他们的网络获得允许。Tecmint.com不会为您的行为负责!
|
||||
|
||||
另外,仅从一个主机发起一个Dos攻击的模拟无法代表真实的攻击。为了模拟真实的攻击,您需要使用许多客户端在同一时间将您的服务器作为目标。
|
||||
|
||||
我们的测试环境由一个CentOS 7服务器[IP 192.168.0.17]和一个Windows组成,在Windows[IP 192.168.0.103]上我们发起攻击:
|
||||
|
||||

|
||||
确认主机IP地址
|
||||
|
||||
请播放下面的视频,并跟从列出的步骤来模拟一个Dos攻击:
|
||||
|
||||
注:youtube视频,发布的时候不行做个链接吧
|
||||
<iframe width="640" height="405" frameborder="0" allowfullscreen="allowfullscreen" src="https://www.youtube.com/embed/-U_mdet06Jk"></iframe>
|
||||
|
||||
然后攻击者的IP将被iptables阻挡:
|
||||
|
||||

|
||||
阻挡攻击者的IP地址
|
||||
|
||||
### 结论 ###
|
||||
|
||||
在开启mod_security和mod_evasive的情况下,模拟攻击会导致CPU和RAM用量在源IP地址被加入黑名单之前出现短暂几秒的使用峰值。如果没有这些模块,模拟攻击绝对会很快将服务器击溃,并使服务器在攻击期间无法提供服务。
|
||||
|
||||
我们很高兴听见您打算使用(或已经使用过)这些工具。我们期望得到您的反馈,所以,请在留言处留下您的评价和问题,谢谢!
|
||||
|
||||
### 参考链接 ###
|
||||
|
||||
- [https://www.modsecurity.org/][6]
|
||||
- [http://www.zdziarski.com/blog/?page_id=442][7]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.tecmint.com/protect-apache-using-mod_security-and-mod_evasive-on-rhel-centos-fedora/
|
||||
|
||||
作者:[Gabriel Cánepa][a]
|
||||
译者:[wwy-hust](https://github.com/wwy-hust)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.tecmint.com/author/gacanepa/
|
||||
[1]:http://www.tecmint.com/install-lamp-in-centos-7/
|
||||
[2]:http://www.tecmint.com/configure-firewalld-in-centos-7/
|
||||
[3]:http://www.tecmint.com/how-to-enable-epel-repository-for-rhel-centos-6-5/
|
||||
[4]:https://www.owasp.org/index.php/Category:OWASP_ModSecurity_Core_Rule_Set_Project
|
||||
[5]:https://github.com/SpiderLabs/ModSecurity/wiki/Reference-Manual#Configuration_Directives
|
||||
[6]:https://www.modsecurity.org/
|
||||
[7]:http://www.zdziarski.com/blog/?page_id=442
|
||||
Loading…
Reference in New Issue
Block a user