mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-02-28 01:01:09 +08:00
Merge branch 'master' of https://github.com/LCTT/TranslateProject
This commit is contained in:
commit
98e808010b
112
sources/How to set password policy on Linux.md
Normal file
112
sources/How to set password policy on Linux.md
Normal file
@ -0,0 +1,112 @@
|
||||
How to set password policy on Linux
|
||||
================================================================================
|
||||
User account management is one of the most critical jobs of system admins. In particular, password security should be considered the top concern for any secure Linux system. In this tutorial, I will describe **how to set password policy on Linux**.
|
||||
|
||||
I assume that you are using [PAM (Pluggable Authentication Modules)][1] on your Linux system, which is the case on all recent Linux distros.
|
||||
|
||||
### Preparation ###
|
||||
|
||||
Install PAM module to enable cracklib support, which can provide additional password checking capabilities.
|
||||
|
||||
On Debian, Ubuntu or Linux Mint:
|
||||
|
||||
$ sudo apt-get install libpam-cracklib
|
||||
|
||||
The cracklib PAM module is installed by default on CentOS, Fedora, or RHEL. So no further installation is necessary on those systems.
|
||||
|
||||
To enforce password policy, we need to modify PAM configuration file located at /etc/pam.d. Policy change will take effect immediately after change.
|
||||
|
||||
Note that the password rules presented in this tutorial will be enforced only when non-root users change passwords, but not the root.
|
||||
|
||||
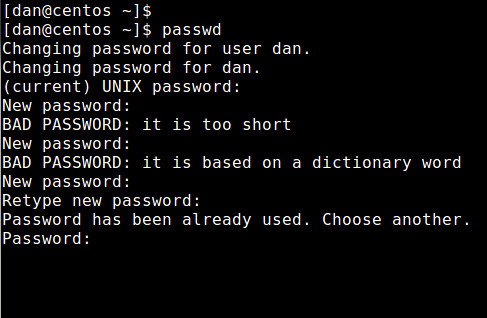
### Prevent Reusing Old Passwords ###
|
||||
|
||||
Look for a line that contains both "password" and "pam_unix.so", and append "remember=5" to that line. It will prevent five most recently used passwords (by storing them in /etc/security/opasswd).
|
||||
|
||||
On Debian, Ubuntu or Linux Mint:
|
||||
|
||||
$ sudo vi /etc/pam.d/common-password
|
||||
|
||||
> password [success=1 default=ignore] pam_unix.so obscure sha512 remember=5
|
||||
|
||||
On Fedora, CentOS or RHEL:
|
||||
|
||||
$ sudo vi /etc/pam.d/system-auth
|
||||
|
||||
> password sufficient pam_unix.so sha512 shadow nullok try_first_pass use_authtok remember=5
|
||||
|
||||
### Set Minimum Password Length ###
|
||||
|
||||
Look for a line that contains both "password" and "pam_cracklib.so", and append "minlen=10" to that line. This will enforce a password of length (10 - <# of types>), where <# of types> indicates how many different types of characters are used in the password. There are four types (upper-case, lower-case, numeric, and symbol) of characters. So if you use a combination of all four types, and minlen is set to 10, the shorted password allowed would be 6.
|
||||
|
||||
On Debian, Ubuntu or Linux Mint:
|
||||
|
||||
$ sudo vi /etc/pam.d/common-password
|
||||
|
||||
> password requisite pam_cracklib.so retry=3 minlen=10 difok=3
|
||||
|
||||
On Fedora, CentOS or RHEL:
|
||||
|
||||
$ sudo vi /etc/pam.d/system-auth
|
||||
|
||||
> password requisite pam_cracklib.so retry=3 difok=3 minlen=10
|
||||
|
||||
### Set Password Complexity ###
|
||||
|
||||
Look for a line that contains "password" and "pam_cracklib.so", and append "ucredit=-1 lcredit=-2 dcredit=-1 ocredit=-1" to that line. This will force you to include at least one upper-case letter (ucredit), two lower-case letters (lcredit), one digit (dcredit) and one symbol (ocredit).
|
||||
|
||||
On Debian, Ubuntu or Linux Mint:
|
||||
|
||||
$ sudo vi /etc/pam.d/common-password
|
||||
|
||||
> password requisite pam_cracklib.so retry=3 minlen=10 difok=3 ucredit=-1 lcredit=-2 dcredit=-1 ocredit=-1
|
||||
|
||||
On Fedora, CentOS or RHEL:
|
||||
|
||||
$ sudo vi /etc/pam.d/system-auth
|
||||
|
||||
> password requisite pam_cracklib.so retry=3 difok=3 minlen=10 ucredit=-1 lcredit=-2 dcredit=-1 ocredit=-1
|
||||
|
||||
### Set Password Expiration Period ###
|
||||
|
||||
To set the maximum period of time the current password is valid, edit the following variables in /etc/login.defs.
|
||||
|
||||
$ sudo vi /etc/login.defs
|
||||
|
||||
> PASS_MAX_DAYS 150
|
||||
> PASS_MIN_DAYS 0
|
||||
> PASS_WARN_AGE 7
|
||||
|
||||
This will force every user to change their password once every six months, and send out a warning message seven days prior to password expiration.
|
||||
|
||||
If you want to set password expiration on per-user basis, use chage command instead. To view password expiration policy for a specific user:
|
||||
|
||||
$ sudo chage -l xmodulo
|
||||
|
||||
> Last password change : Dec 30, 2013
|
||||
> Password expires : never
|
||||
> Password inactive : never
|
||||
> Account expires : never
|
||||
> Minimum number of days between password change : 0
|
||||
> Maximum number of days between password change : 99999
|
||||
> Number of days of warning before password expires : 7
|
||||
|
||||
By default, a user's password is set to never expire.
|
||||
|
||||
To change the password expiration period for user xmodulo:
|
||||
|
||||
$ sudo chage -E 6/30/2014 -m 5 -M 90 -I 30 -W 14 xmodulo
|
||||
|
||||
The above command will set the password to expire on 6/30/2014. In addition, the minimum/maximum number of days between password changes is set to 5 and 90 respectively. The account will be locked 30 days after a password expires, and a warning message will be sent out 14 days before password expiration.
|
||||
|
||||
[][2]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/2013/12/set-password-policy-linux.html
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.linux-pam.org/
|
||||
[2]:http://www.flickr.com/photos/xmodulo/11640903324/
|
||||
@ -0,0 +1,92 @@
|
||||
Linux free Command – Display Free and used Memory in the System
|
||||
================================================================================
|
||||
System administrator must maintain the health of their server. One of the critical component is memory. When server memory is full utilized, it can slow down the server performance. To monitor memory utilization, Linux have another command that called free.
|
||||
|
||||
### What is free command ###
|
||||
|
||||
**Free** command is a tool that can display amount of free and used memory in the system. The output of free command is similar with top command. Most of Linux distribution already have free command.
|
||||
|
||||
### How to run it ###
|
||||
|
||||
To run it, just type **free** on your console. Running it without an option will show you a default view with kilobyte units.
|
||||
|
||||
$ free
|
||||
|
||||

|
||||
|
||||
From the above screenshot we can read :
|
||||
|
||||
#### Memory (in kilobytes units) ####
|
||||
|
||||
- Total : 1026740
|
||||
- Used : 843396
|
||||
- Free : 183344
|
||||
- Shared : 0
|
||||
- Buffers : 52704
|
||||
- Cached : 376384
|
||||
|
||||
#### Swap (in kilobytes units) ####
|
||||
|
||||
- Total : 1045500
|
||||
- Used : 3376
|
||||
- Free : 1042124
|
||||
|
||||
When you see the buffers/cache free memory is low or you see that the swap free is low, then a memory upgrade is needed. This mean that memory utilization is high. Please notice that the **shared memory column should be ignored** because it is obsolete.
|
||||
|
||||
### Display memory information in another units ###
|
||||
|
||||
As we mentioned before, by default free will show information in kilobytes unit. Free also provide us **-b (bytes), -k (kilobytes), -m (megabytes), -g (gigabytes) and –tera (terabytes)**. To show the information in the unit we want, just pick one of them and put the option behind free command. Here’s a sample output in megabytes unit.
|
||||
|
||||
$ free -m
|
||||
|
||||

|
||||
|
||||
This trick is also applied to **-b, -k, -g** and **–tera** option.
|
||||
|
||||
### Display memory information in human readable ###
|
||||
|
||||
Free also provide us with **-h** option which mean human readable. So what is the difference with previous option, such as **-m** (megabytes) option? The most visible difference is that **-h** option will add human readable unit after the numbers. Let’s take a look a sample of it.
|
||||
|
||||
$ free -h
|
||||
|
||||

|
||||
|
||||
As we can see together, there is **G (gigabyte)** letter behind 1,0 number. When the number is not reach gigabtye, free is smart enough to know it and put the appropriate unit behind each numbers. **M** letter behind – let say – 929 number tell us its 969 Megabytes.
|
||||
|
||||
### Display free with delay ###
|
||||
|
||||
As one of statistic tool, the best way to capture memory utilization is using a delay. To do this, we can use **-s** option followed by N seconds that we want. We can always combine more than 1 options to make the output is fit with our needs. Let say we want to capture memory utilization every 3 seconds and human readable. So the command will be like this :
|
||||
|
||||
$ free -hs 3
|
||||
|
||||

|
||||
|
||||
### Display low and high memory utilization ###
|
||||
|
||||
If we want to show low and high memory statistics, we can use -l option. Here’s a sample.
|
||||
|
||||
$ free -l
|
||||
|
||||

|
||||
|
||||
### Display Linux total memory ###
|
||||
|
||||
When we need the information of total for every column, we can add -t option behind free command. This will add 1 more row at the bottom which display it.
|
||||
|
||||
$ free -t
|
||||
|
||||

|
||||
|
||||
### Conclusion ###
|
||||
|
||||
Besides [vmstat][1], Free command is another simple statistic tool for capturing memory utilization. With this you can grab a quick information about what happen in your Linux memory. Free is using /proc/meminfo as a base for showing memory utilization information. As usual, you can always type man free on your console to explore more detail about free.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/linux-command/linux-free-command/
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://linoxide.com/linux-command/linux-vmstat-command-tool-report-virtual-memory-statistics/
|
||||
@ -0,0 +1,113 @@
|
||||
Setup your personal Cloud server in minutes using ownCloud On RHEL, CentOS, Scientific Linux 6.5
|
||||
================================================================================
|
||||
[ownCloud][1] is a free Open Source software, used to setup your own personal cloud for file sharing, Calender, Contact and Bookmark sharing and Personal Audio/Video Streaming. It is pretty easy to setup and manage.
|
||||
|
||||
### Prerequisites ###
|
||||
|
||||
In this tutorial i am using CentOS 6.5 minimal server to setup ownCloud. My testbox details are given below.
|
||||
|
||||
Operating system: CentOS 6.5 Minimal Installation
|
||||
IP Address: 192.168.1.101/24
|
||||
|
||||
While it was tested on CentOS 6.5, it is applicable for all RPM based distros.
|
||||
|
||||
Then your server should have a working LAMP stack. Refer the following link to setup LAMP server.
|
||||
|
||||
- [Install LAMP server on RHEL/CentOS/Scientific Linux][2]
|
||||
|
||||
Install following necessary PHP extensions:
|
||||
|
||||
# yum install php-mysql php-json php-xml php-mbstring php-zip php-gd curl php-curl php-pdo
|
||||
|
||||
### Setting up database for ownCloud ###
|
||||
|
||||
Let us create a database called ‘ownclouddb’ and database user ‘ownclouduser’ with passwor ‘centos’.
|
||||
|
||||
# mysql -u root -p
|
||||
Enter password:
|
||||
Welcome to the MariaDB monitor. Commands end with ; or \g.
|
||||
Your MariaDB connection id is 66
|
||||
Server version: 5.5.34-MariaDB MariaDB Server
|
||||
|
||||
Copyright (c) 2000, 2013, Oracle, Monty Program Ab and others.
|
||||
|
||||
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
|
||||
|
||||
MariaDB [(none)]> CREATE DATABASE ownclouddb;
|
||||
Query OK, 1 row affected (0.04 sec)
|
||||
|
||||
MariaDB [(none)]> GRANT ALL ON ownclouddb.* TO ownclouduser@localhost IDENTIFIED BY 'centos';
|
||||
Query OK, 0 rows affected (0.01 sec)
|
||||
|
||||
MariaDB [(none)]> flush privileges;
|
||||
Query OK, 0 rows affected (0.01 sec)
|
||||
|
||||
MariaDB [(none)]> exit
|
||||
Bye
|
||||
|
||||
### Getting owncloud ###
|
||||
|
||||
Switch to your apache root folder and download ownCloud latest version
|
||||
|
||||
Goto to Apache root document folder and download the latest version of owncloud.
|
||||
|
||||
# wget http://download.owncloud.org/community/owncloud-6.0.0a.tar.bz2
|
||||
|
||||
Extract the tar package using command:
|
||||
|
||||
# tar xvf owncloud-6.0.0a.tar.bz2
|
||||
|
||||
Move the extracted folder to your apache root folder (i.e /var/www/html/)
|
||||
|
||||
# mv owncloud/ /var/www/html/
|
||||
|
||||
Set the ownership and permissions to the following folders:
|
||||
|
||||
# chown -R apache:apache /var/www/html/owncloud/
|
||||
# chmod 777 /var/www/html/owncloud/config/
|
||||
|
||||
Enable apache rewrite mode.
|
||||
|
||||
Edit file “**/etc/httpd/conf/httpd.conf**”,
|
||||
|
||||
# vi /etc/httpd/conf/httpd.conf
|
||||
|
||||
Find the following section and Change **AllowOverride None** to **Allowoverride All**.
|
||||
|
||||
[...]
|
||||
AllowOverride All
|
||||
[...]
|
||||
|
||||
Finally, restart the apachehttpd and mysql services.
|
||||
|
||||
# service mysql restart
|
||||
# service httpd restart
|
||||
|
||||
### Begin ownCloud Installation ###
|
||||
|
||||
Navigate to **http://ip-address/owncloud** or **http://domain-name/owncloud** from your web browser.
|
||||
|
||||
**Note**: If encountered with any permission errors, disable SELinux and try again.
|
||||
|
||||
The index page of own cloud will shown up. You will asked be to create a new admin account. Enter the admin account details.
|
||||
|
||||
Then, Click on the **Advanced** drop-down box, select mysql and enter the mysal database name, database user name and password. Finally click **Finish setup** to complete installation.
|
||||
|
||||

|
||||
|
||||
This is how my ownCloud dashboard looks:
|
||||
|
||||

|
||||
|
||||
Thats it. Our cloud server is ready. From here, you can upload/download your images, files, Audio, Video and also can access them from your client systems over LAN/WAN.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.unixmen.com/setup-your-personal-cloud-server-in-minutes-using-owncloud/
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:https://owncloud.org/
|
||||
[2]:http://www.unixmen.com/install-lamp-apache-with-mariadb-and-php-on-centosrhelscientific-linux-6/
|
||||
@ -0,0 +1,32 @@
|
||||
"The Debian Administrator’s Handbook" updated for Debian 7 Wheezy, published and freely available for download
|
||||
================================================================================
|
||||
Months and months ago, the Debian developers [published][1] The Debian Administrator's Handbook, essentially, a comprehensive book about Debian's internals presented with clarity, user-friendliness and properly-structured informations.
|
||||
|
||||
The initial book has been [updated][2] for Debian 7 Wheezy, update incarnated as "**The Debian Administrator’s Handbook, Debian Wheezy from Discovery to Mastery**", new book refreshing the significant amount of Debian knowledge with up-to-date present realities.
|
||||
|
||||
"The Debian Administrator’s Handbook, Debian Wheezy from Discovery to Mastery" is the first major update of the handbook, update coming more than a year later since the initial publication, therefore, being recommended to users wishing to both familiarize themselves with and advance in the Debian's universe of knowledge.
|
||||
|
||||
> "We’re pleased to announce the availability of 'The Debian Administrator’s Handbook, Debian Wheezy from Discovery to Mastery'. This is the first major update of the book since the first edition (in May 2012). We went through all chapters to update everything that changed with Debian 7. We also got rid of some really old content that was really no longer relevant. On the opposite, we added new stuff (such as a section about multi-arch), and addressed 16 bugs reported by loyal readers."
|
||||
|
||||
What is Debian, installation methods, structure of binary packages, structure of source packages, stable repositories, aptitude and apt-get commands, configuring a program, connecting through ADSL modems, user and group databases, compiling kernels, RAID and LVM, LXC, graphical desktops, packet filtering, creating Debian packages are among the topics covered across "The Debian Administrator’s Handbook, Debian Wheezy from Discovery to Mastery"'s 498 pages.
|
||||
|
||||

|
||||
|
||||
"The Debian Administrator’s Handbook, Debian Wheezy from Discovery to Mastery" is freely available for download (498 pages, [PDF][3], [EPUB][4], [MOBI][5]).
|
||||
|
||||
For persons interested in the printed book, "The Debian Administrator’s Handbook, Debian Wheezy from Discovery to Mastery" can be purchased via [http://debian-handbook.info/get/][6]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://iloveubuntu.net/debian-administrator%E2%80%99s-handbook-updated-debian-7-wheezy-published-and-freely-available-download
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://iloveubuntu.net/debian-administrator%E2%80%99s-handbook-available-both-payed-and-free-ebook-epub-mobi-pdf
|
||||
[2]:http://debian-handbook.info/2013/major-update-of-the-debian-administrators-handbook-for-debian-7-wheezy/
|
||||
[3]:http://debian-handbook.info/download/stable/debian-handbook.pdf
|
||||
[4]:http://debian-handbook.info/download/stable/debian-handbook.epub
|
||||
[5]:http://debian-handbook.info/download/stable/debian-handbook.mobi
|
||||
[6]:http://debian-handbook.info/get/
|
||||
@ -0,0 +1,250 @@
|
||||
Tunnel SSH Connections Over SSL Using ‘Stunnel’ On Debian 7 / Ubuntu 13.10
|
||||
================================================================================
|
||||
**stunnel** is designed to work as an SSL encryption wrapper between remote client and local (inetd-startable) or remote server. It can be used to add SSL functionality to commonly used inetd daemons like POP2, POP3, and IMAP servers without any changes in the programs code. Stunnel uses the OpenSSL library for cryptography, so it supports whatever cryptographic algorithms are compiled into the library. In simple words, stunnel can be used to turn any insecure port to a secure encrypted port.
|
||||
|
||||
In this tutorial, i will describe how to tunnel SSH over SSL using stunnel. The setup is pretty simple. You’ll need stunnel installed on both your client PC and a remote PC with sshd already running.
|
||||
|
||||
I am using two systems as mentioned below.
|
||||
|
||||
Remote System:
|
||||
|
||||
Operating System: Debian 7
|
||||
IP address: 192.168.1.200/24
|
||||
|
||||
Client(Local) System:
|
||||
|
||||
Operating system: Ubuntu 13.04 desktop
|
||||
IP address: 192.168.1.100/24
|
||||
|
||||
#### Configure Remote System ####
|
||||
|
||||
Let us install stunnel package in our remote Debian 7 server.
|
||||
|
||||
# apt-get install stunnel4
|
||||
|
||||
Now let us create a SSL certificate as shown below.
|
||||
|
||||
# openssl genrsa 1024 > stunnel.key
|
||||
|
||||
Sample output:
|
||||
|
||||
Generating RSA private key, 1024 bit long modulus
|
||||
............................................++++++
|
||||
...................++++++
|
||||
e is 65537 (0x10001)
|
||||
|
||||
# openssl req -new -key stunnel.key -x509 -days 1000 -out stunnel.crt
|
||||
|
||||
You will be asked to answer for a couple of questions such as Country, State, company details etc.
|
||||
|
||||
You are about to be asked to enter information that will be incorporated
|
||||
into your certificate request.
|
||||
What you are about to enter is what is called a Distinguished Name or a DN.
|
||||
There are quite a few fields but you can leave some blank
|
||||
For some fields there will be a default value,
|
||||
If you enter '.', the field will be left blank.
|
||||
-----
|
||||
Country Name (2 letter code) [AU]:IN
|
||||
State or Province Name (full name) [Some-State]:Tamilnadu
|
||||
Locality Name (eg, city) []:Erode
|
||||
Organization Name (eg, company) [Internet Widgits Pty Ltd]:unixmen
|
||||
Organizational Unit Name (eg, section) []:Technical
|
||||
Common Name (e.g. server FQDN or YOUR name) []:server.unixmen.com
|
||||
Email Address []:sk@unixmen.com
|
||||
|
||||
# cat stunnel.crt stunnel.key > stunnel.pem
|
||||
# mv stunnel.pem /etc/stunnel/
|
||||
|
||||
Now we have to configure stunnel to tunnel **443(https)** to **22(ssh)**. This can be done by creating a new file **stunnel.conf** under **/etc/stunnel/** directory:
|
||||
|
||||
# vi /etc/stunnel/stunnel.conf
|
||||
|
||||
Add the following lines:
|
||||
|
||||
pid = /var/run/stunnel.pid
|
||||
cert = /etc/stunnel/stunnel.pem
|
||||
[ssh]
|
||||
accept = 192.168.1.200:443
|
||||
connect = 127.0.0.1:22
|
||||
|
||||
The above lines says stunnel that where to look for the certificate file and where to accept and forward ssh connections. In our case, stunnel will accept the incoming traffic on port 443 and forward it back to port 22.
|
||||
|
||||
Save and close the file.
|
||||
|
||||
Now let us enable stunnel service. To do that, edit file **/etc/default/stunnel4**:
|
||||
|
||||
# vi /etc/default/stunnel4
|
||||
|
||||
Change the line **Enabled = 0** to **1**.
|
||||
|
||||
# /etc/default/stunnel
|
||||
# Julien LEMOINE <speedblue@debian.org>
|
||||
# September 2003
|
||||
|
||||
# Change to one to enable stunnel automatic startup
|
||||
ENABLED=1
|
||||
FILES="/etc/stunnel/*.conf"
|
||||
OPTIONS=""
|
||||
|
||||
# Change to one to enable ppp restart scripts
|
||||
PPP_RESTART=0
|
||||
|
||||
Then start stunnel service with command:
|
||||
|
||||
# service stunnel4 start
|
||||
|
||||
#### Configure Local System ####
|
||||
|
||||
Install stunnel with command:
|
||||
|
||||
$ sudo apt-get install stunnel4
|
||||
|
||||
We need the same certificate file(stunnel.pem) from the remote system. Copy the remote system **stunnel.pem** file to our local system and save it in the same location(i.e /etc/stunnel).
|
||||
|
||||
creating a new file **stunnel.conf** under **/etc/stunnel/** directory:
|
||||
|
||||
$ sudo vi /etc/stunnel/stunnel.conf
|
||||
|
||||
Add the following lines:
|
||||
|
||||
pid = /var/run/stunnel.pid
|
||||
cert = /etc/stunnel/stunnel.pem
|
||||
client=yes
|
||||
[ssh]
|
||||
accept=443
|
||||
connect=192.168.1.200:443
|
||||
|
||||
Save and close the file. Here 192.168.1.200 is our remote system IP.
|
||||
|
||||
Now let us enable stunnel service. To do that, edit file **/etc/default/stunnel4**:
|
||||
|
||||
$ sudo vi /etc/default/stunnel4
|
||||
|
||||
Change the line **Enabled = 0** to **1**.
|
||||
|
||||
# /etc/default/stunnel
|
||||
# Julien LEMOINE <speedblue@debian.org>
|
||||
# September 2003
|
||||
|
||||
# Change to one to enable stunnel automatic startup
|
||||
ENABLED=1
|
||||
FILES="/etc/stunnel/*.conf"
|
||||
OPTIONS=""
|
||||
|
||||
# Change to one to enable ppp restart scripts
|
||||
PPP_RESTART=0
|
||||
|
||||
Then start stunnel service with command:
|
||||
|
||||
$ sudo service stunnel4 start
|
||||
|
||||
#### Test SSH connection ####
|
||||
|
||||
Now we’re good to go. You’ll be able to connect to your remote machine using command:
|
||||
|
||||
$ ssh sk@localhost -v -p 443
|
||||
|
||||
Sample output:
|
||||
|
||||
OpenSSH_6.1p1 Debian-4, OpenSSL 1.0.1c 10 May 2012
|
||||
debug1: Reading configuration data /etc/ssh/ssh_config
|
||||
debug1: /etc/ssh/ssh_config line 19: Applying options for *
|
||||
debug1: Connecting to localhost [127.0.0.1] port 443.
|
||||
debug1: Connection established.
|
||||
debug1: identity file /home/sk/.ssh/id_rsa type -1
|
||||
debug1: identity file /home/sk/.ssh/id_rsa-cert type -1
|
||||
debug1: identity file /home/sk/.ssh/id_dsa type -1
|
||||
debug1: identity file /home/sk/.ssh/id_dsa-cert type -1
|
||||
debug1: identity file /home/sk/.ssh/id_ecdsa type -1
|
||||
debug1: identity file /home/sk/.ssh/id_ecdsa-cert type -1
|
||||
debug1: Remote protocol version 2.0, remote software version OpenSSH_6.0p1 Debian-4
|
||||
debug1: match: OpenSSH_6.0p1 Debian-4 pat OpenSSH*
|
||||
debug1: Enabling compatibility mode for protocol 2.0
|
||||
debug1: Local version string SSH-2.0-OpenSSH_6.1p1 Debian-4
|
||||
debug1: SSH2_MSG_KEXINIT sent
|
||||
debug1: SSH2_MSG_KEXINIT received
|
||||
debug1: kex: server->client aes128-ctr hmac-md5 none
|
||||
debug1: kex: client->server aes128-ctr hmac-md5 none
|
||||
debug1: sending SSH2_MSG_KEX_ECDH_INIT
|
||||
debug1: expecting SSH2_MSG_KEX_ECDH_REPLY
|
||||
debug1: Server host key: ECDSA 78:05:ba:1b:73:02:75:86:10:33:8c:0f:21:61:d4:de
|
||||
debug1: Host '[localhost]:443' is known and matches the ECDSA host key.
|
||||
debug1: Found key in /home/sk/.ssh/known_hosts:12
|
||||
debug1: ssh_ecdsa_verify: signature correct
|
||||
debug1: SSH2_MSG_NEWKEYS sent
|
||||
debug1: expecting SSH2_MSG_NEWKEYS
|
||||
debug1: SSH2_MSG_NEWKEYS received
|
||||
debug1: Roaming not allowed by server
|
||||
debug1: SSH2_MSG_SERVICE_REQUEST sent
|
||||
debug1: SSH2_MSG_SERVICE_ACCEPT received
|
||||
debug1: Authentications that can continue: publickey,password
|
||||
debug1: Next authentication method: publickey
|
||||
debug1: Trying private key: /home/sk/.ssh/id_rsa
|
||||
debug1: Trying private key: /home/sk/.ssh/id_dsa
|
||||
debug1: Trying private key: /home/sk/.ssh/id_ecdsa
|
||||
debug1: Next authentication method: password
|
||||
sk@localhost's password: # ## Enter your remote system user password
|
||||
debug1: Authentication succeeded (password).
|
||||
Authenticated to localhost ([127.0.0.1]:443).
|
||||
debug1: channel 0: new [client-session]
|
||||
debug1: Requesting no-more-sessions@openssh.com
|
||||
debug1: Entering interactive session.
|
||||
debug1: Sending environment.
|
||||
debug1: Sending env LC_PAPER = en_IN.UTF-8
|
||||
debug1: Sending env LC_ADDRESS = en_IN.UTF-8
|
||||
debug1: Sending env LC_MONETARY = en_IN.UTF-8
|
||||
debug1: Sending env LC_NUMERIC = en_IN.UTF-8
|
||||
debug1: Sending env LC_TELEPHONE = en_IN.UTF-8
|
||||
debug1: Sending env LC_IDENTIFICATION = en_IN.UTF-8
|
||||
debug1: Sending env LANG = en_US.UTF-8
|
||||
debug1: Sending env LC_MEASUREMENT = en_IN.UTF-8
|
||||
debug1: Sending env LC_TIME = en_IN.UTF-8
|
||||
debug1: Sending env LC_NAME = en_IN.UTF-8
|
||||
Linux server 3.2.0-4-486 #1 Debian 3.2.51-1 i686
|
||||
|
||||
The programs included with the Debian GNU/Linux system are free software;
|
||||
the exact distribution terms for each program are described in the
|
||||
individual files in /usr/share/doc/*/copyright.
|
||||
|
||||
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
|
||||
permitted by applicable law.
|
||||
You have new mail.
|
||||
Last login: Mon Dec 30 15:12:22 2013 from localhost
|
||||
sk@server:~$
|
||||
|
||||
Or you can simply use the command:
|
||||
|
||||
$ ssh -p 443 sk@localhost
|
||||
|
||||
Sample output:
|
||||
|
||||
sk@localhost's password:
|
||||
Linux server 3.2.0-4-486 #1 Debian 3.2.51-1 i686
|
||||
|
||||
The programs included with the Debian GNU/Linux system are free software;
|
||||
the exact distribution terms for each program are described in the
|
||||
individual files in /usr/share/doc/*/copyright.
|
||||
|
||||
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
|
||||
permitted by applicable law.
|
||||
You have new mail.
|
||||
Last login: Mon Dec 30 15:22:08 2013 from localhost
|
||||
sk@server:~$
|
||||
|
||||
Now you’ll be able to make ssh connection to your remote system, but all the traffic tunneled through SSL.
|
||||
|
||||
You’re done now! You can SSH to your remote system even when the ssh default 22 is blocked by any firewall.
|
||||
|
||||
Reference Links:
|
||||
|
||||
- **[stunnel homepage][1]**
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.unixmen.com/tunnel-ssh-connections-ssl-using-stunnel-debian-7-ubuntu-13-10/
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:https://www.stunnel.org/index.html
|
||||
114
sources/Understanding Linux cd Command with Examples.md
Normal file
114
sources/Understanding Linux cd Command with Examples.md
Normal file
@ -0,0 +1,114 @@
|
||||
Understanding Linux cd Command with Examples
|
||||
================================================================================
|
||||
The cd command is the most basic command in *nix world. What linux cd command does is it changes your current working directory. This article details about this command, what this command can do and the internals about the command.
|
||||
|
||||
### cd command: An internal command ###
|
||||
|
||||
The BASH shell is the default shell in most Linux distributions. The shell has some internal commands of its own. cd is one od the internal commands. I will explain what internal commands are and why cd is an internal command. First, confirm that your current shell with SHELL environment variable:
|
||||
|
||||

|
||||
|
||||
Now check with which command what is the path of cd command binary(if any):
|
||||
|
||||

|
||||
|
||||
It results in no output. Its because no binary is present on the system for cd command. Still you are able to execute the command. This is because cd is an BASH internal command. Internal commands are built into the shell. Another internal command ‘type’ will give you the information that cd is internal command.
|
||||
|
||||

|
||||
|
||||
If you try to access the manual entry for any internal command, there is no separate manual page for them.
|
||||
|
||||

|
||||
|
||||
For these internal commands, no separate process is created. So they are very fast.
|
||||
|
||||
To get full list of internal commands, you can give help command (which itself is an internal command):
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
### Why cd is internal command? ###
|
||||
|
||||
To keep things simple, I won’t go into much details, but it requires a little understanding of Unix processes to understand the answer to this question.
|
||||
Whenever a processes is created by BASH, it is executed in a subshell of BASH (child process of current BASH process). The new processes makes changes and outputs (if reqquired) and no property of this subshell is returned to the parent when the process dies. Note that cd command changed the PWD of the shell. If cd were an external command, it would have changed the PWD of the subshell, returning nothing to the parent shell. And hence, the PWD of the shell will never change. All the commands that make changes to the environment of the shell, must be implemented as internal command. we could never achieve what we require by making cd an external command.
|
||||
|
||||
Now let us explore cd command usage.
|
||||
|
||||
### cd command usage: ###
|
||||
|
||||
If you issue cd command without any argument, it will take you to your home directory, no matter what your current directory is.
|
||||
|
||||

|
||||
|
||||
The tilde sign (~) also represents the home directory. You can se this as well to go to your home directory.
|
||||
|
||||

|
||||
|
||||
If you are root, you can go to any user’s home directory by using tilde sign followed by that user’s name. In some Linux distributions, unpriviledged users do not by default have permission to go to other users’ home directories.
|
||||
|
||||

|
||||
|
||||
The . directory represents the current directory and the .. represents the parent directory. To go to parent directory, use ..
|
||||
|
||||

|
||||
|
||||
The . directory will not change your PWD in most of the cases. For example:
|
||||
|
||||

|
||||
|
||||
But if your current directory is renamed somehow, then your PWD will be changed with this command:
|
||||
|
||||

|
||||
|
||||
In BASH and most of other shells, you can provide two types of paths: Absolute path and Relative path. Absolute paths begin with / and are independent of your PWD. On the other hand, relative paths never begin with / and depend what your PWD is.
|
||||
|
||||
Changing PWD with absolute path:
|
||||
|
||||

|
||||
|
||||
Changing PWD with relative path:
|
||||
|
||||

|
||||
|
||||
Toggling between two directories:
|
||||
|
||||
The “cd -” command will take you to the last working directory. You can toggle between two directories with this command.
|
||||
|
||||

|
||||
|
||||
The last working directory is strored in OLDPWD variable. If you try to use previous command in a new terminal, it shows following error:
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
You can use some bash tricks as well with cd command.
|
||||
With ? wild card:
|
||||
|
||||

|
||||
|
||||
Using *
|
||||
|
||||

|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/linux-command/linux-cd-command-examples/
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:
|
||||
[2]:
|
||||
[3]:
|
||||
[4]:
|
||||
[5]:
|
||||
[6]:
|
||||
[7]:
|
||||
[8]:
|
||||
[9]:
|
||||
[10]:
|
||||
[11]:
|
||||
[12]:
|
||||
Loading…
Reference in New Issue
Block a user