mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-01-25 23:11:02 +08:00
commit
98d969797e
@ -1,6 +1,7 @@
|
||||
在Linux上组成RAID 10阵列以实现高性能和高容错性的磁盘I/O
|
||||
如何在Linux上构建 RAID 10阵列
|
||||
================================================================================
|
||||
RAID 10阵列 (又名RAID 1+0 或先镜像后分区)通过结合RAID 0 (读写操作并行在多个磁盘上同时执行)和RAID 1 (数据被完全相同地写入到两个或更多的磁盘)两者的特点实现高性能和高容错性的磁盘I/O。
|
||||
|
||||
RAID 10阵列(又名RAID 1+0 或先镜像后分区)通过结合RAID 0 (读写操作在多个磁盘上同时并行执行)和RAID 1(数据被完全相同地写入到两个或更多的磁盘)两者的特点实现高性能和高容错性的磁盘I/O。
|
||||
|
||||
这篇文章会指导你如何使用五块相同的8GB磁盘来组成一个软件RAID 10阵列。因为组成一个RAID 10阵列至少需要4块磁盘(比如,两个镜像各有一对分区组合),而且需要添加一块额外的备用磁盘以防某块主要的磁盘出错。本文也会分享一些工具,在稍后用来分析RAID阵列的性能。
|
||||
|
||||
@ -12,15 +13,15 @@ RAID 10阵列 (又名RAID 1+0 或先镜像后分区)通过结合RAID 0 (读写
|
||||
|
||||
|
||||
|
||||
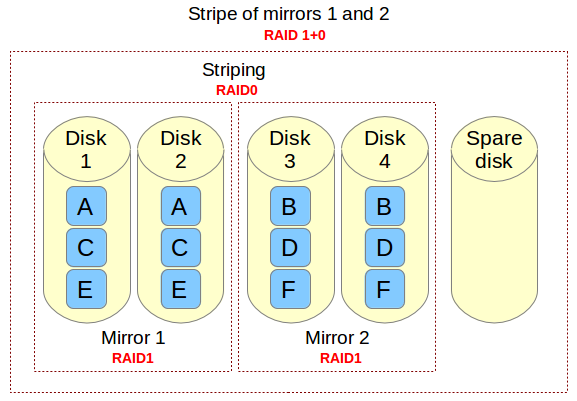
上图中的文件由A、B、C、D、E和F六种块组成,每一个RAID 1镜像对(如镜像1和2)在两个磁盘上复制相同的块。因为需要这样配置,写操作性能会因为每个块需要写入两次而下降,每个磁盘各一次;而读操作与从单块磁盘中读取相比并未发生改变。不过这种配置的好处是除非一个镜像中有超过一块的磁盘故障,否则都能保持冗余以维持正常的磁盘I/O操作。
|
||||
上图中的文件由A、B、C、D、E和F六种块组成,每一个RAID 1镜像对(如镜像1和2)在两个磁盘上复制相同的块。在这样的配置下,写操作性能会因为每个块需要写入两次而下降,每个磁盘各一次;而读操作与从单块磁盘中读取相比并未发生改变。不过这种配置的好处是除非一个镜像中有超过一块的磁盘故障,否则都能保持冗余以维持正常的磁盘I/O操作。
|
||||
|
||||
RAID 0的分区通过将数据划分到不同的块,然后执行同时将块A写入镜像1、将块B写入镜像2(以此类推)的并行操作以提高整体的读写性能。在另一方面,没有任何一个镜像包含构成主存的数据片的全部信息。这就意味着如果其中一个镜像故障,那么整个RAID 0组件将无法正常工作,数据将遭受不可恢复的损失。
|
||||
|
||||
### 建立RAID 10阵列 ###
|
||||
|
||||
有两种建立RAID 10阵列的可行方案:复杂法(一步完成)和嵌套法(先创建两个或更多的RAID 1阵列,然后使用它们组成RAID 0)。本文会关注复杂法创建RAID 10阵列,因为这种方法能够使用偶数或奇数个磁盘去创建阵列,而且能以单个RAID设备的形式被管理,而嵌套法则恰恰相反(只允许偶数个磁盘,必须以嵌套设备的形式被管理,即分开管理RAID 1和RAID 0)。
|
||||
有两种建立RAID 10阵列的可行方案:复杂法(一步完成)和嵌套法(先创建两个或更多的RAID 1阵列,然后使用它们组成RAID 0)。本文会讲述复杂法创建RAID 10阵列的过程,因为这种方法能够使用偶数或奇数个磁盘去创建阵列,而且能以单个RAID设备的形式被管理,而嵌套法则恰恰相反(只允许偶数个磁盘,必须以嵌套设备的形式被管理,即分开管理RAID 1和RAID 0)。
|
||||
|
||||
假设你的机器已经安装mdadm,并运行着相应的守护进程,细节参见[这篇文章][1]。也假设每个磁盘上已经划分出一个主分区sd[bcdef]1。使用命令
|
||||
假设你的机器已经安装mdadm,并运行着相应的守护进程,细节参见[这篇文章][1]。也假设每个磁盘上已经划分出一个主分区sd[bcdef]1 (LCTT 译注:共计五块磁盘,这里是从sdb - sdf)。使用命令:
|
||||
|
||||
ls -l /dev | grep sd[bcdef]
|
||||
|
||||
@ -28,7 +29,7 @@ RAID 0的分区通过将数据划分到不同的块,然后执行同时将块A
|
||||
|
||||

|
||||
|
||||
然后使用下面的命令创建一个RAID 10阵列:
|
||||
然后使用下面的命令创建一个RAID 10阵列(LCTT 译注:使用了四块磁盘 bcde 创建):
|
||||
|
||||
# mdadm --create --verbose /dev/md0 --level=10 --raid-devices=4 /dev/sd[bcde]1 --spare-devices=1 /dev/sdf1
|
||||
|
||||
@ -46,29 +47,29 @@ RAID 0的分区通过将数据划分到不同的块,然后执行同时将块A
|
||||
|
||||
1. **Used Dev Space**表示阵列所使用的每一块磁盘的容量。
|
||||
|
||||
2. **Array Size**表示阵列的整体大小。RAID 10阵列的大小通过(N*C)/M计算,其中N是活跃磁盘的数目,C是活跃磁盘的总容量,M是每一个镜像中磁盘的数目。在本文的情形下,这个值等于(4*8GiB)/2 = 16GiB。
|
||||
2. **Array Size**表示阵列的整体大小。RAID 10阵列的大小通过(N\*C)/M计算,其中N是活跃磁盘的数目,C是每个活跃磁盘的容量,M是每一个镜像中磁盘的数目。在本文的情形下,这个值等于(4*8GiB)/2 = 16GiB。
|
||||
|
||||
3. **Layout**是整个数据布局的详细信息。可能的布局数值如下所示。
|
||||
|
||||
----------
|
||||
|
||||
- **n**(默认选项):代表就近拷贝。一个数据块的多个拷贝在不同磁盘里有相同的偏移量。这种布局提供和RAID 0阵列相似的读写性能。
|
||||
- **n**(默认选项):代表就近(near)拷贝。一个数据块的多个拷贝在不同磁盘里有相同的偏移量。这种布局提供和RAID 0阵列相似的读写性能。
|
||||
|
||||

|
||||
|
||||
- **o**代表偏移量拷贝。不是复制一个分区里的块,所有的分区都被复制,但会被循环打乱,所以同一个分区中复制的块会出现在不同的磁盘。因此,一个块的后续拷贝会出现在下一个磁盘中,一个块接着一个块。为了在RAID 10阵列中使用这种布局,在创建阵列的命令中添加--layout=o2选项。
|
||||
- **o**代表偏移量(offset)拷贝。块并不是在条带里面复制的,而是整个条带一起复制,但是循环会打乱,所以同一个分区中复制的块会出现在不同的磁盘。因此,一个块的后续拷贝会出现在下一个磁盘中,一个块接着一个块。为了在RAID 10阵列中使用这种布局,在创建阵列的命令中添加--layout=o2选项。
|
||||
|
||||

|
||||
|
||||
- **f**代表远端拷贝(多个拷贝在不同的磁盘中具有不同的偏移量)。这种布局提供更好的读性能但带来更差的写性能。因此,对于读远远多于写的系统来说是最好的选择。为了在RAID 10阵列中使用这种布局,在创建阵列的命令中添加--layout=f2。
|
||||
- **f**代表远端(far)拷贝(多个拷贝在不同的磁盘中具有不同的偏移量)。这种布局提供更好的读性能但带来更差的写性能。因此,对于读远远多于写的系统来说是最好的选择。为了在RAID 10阵列中使用这种布局,在创建阵列的命令中添加--layout=f2。
|
||||
|
||||

|
||||
|
||||
跟在布局选项**n**、**f**和**o**后面的数字代表所需的每一个数据块的副本数目。默认值是2,但可以是2到阵列中磁盘数目之间的某个值。提供足够的副本数目可以最小化单个磁盘上的I/O影响。
|
||||
|
||||
4. **Chunk Size**,以[Linux RAID wiki][2]为准,是写入磁盘的最小数据单元。最佳的chunk大小取决于I/O操作的速率和相关的文件大小。对于大量的写操作,通过设置相对较大的chunks可以得到更低的开销,但对于主要存储小文件的阵列来说更小的chunk性能更好。为了给RAID 10指定一个chunk大小,在创建阵列的命令中添加**--chunk=desired_chunk_size**。
|
||||
4. **Chunk Size**,参考[Linux RAID wiki][2]的说明,是写入磁盘的最小数据单元。最佳的chunk大小取决于I/O操作的速率和相关的文件大小。对于大量的写操作,通过设置相对较大的chunk可以得到更低的开销,但对于主要存储小文件的阵列来说更小的chunk性能更好。为了给RAID 10指定一个chunk大小,在创建阵列的命令中添加**--chunk=desired_chunk_size**。
|
||||
|
||||
不幸的是,并没有设置一个大小就能适合全局的策略用来提高性能,但可以参考下面的一些方案。
|
||||
不幸的是,并没有设置一个大小就能适合全局的策略来提高性能,但可以参考下面的一些方案。
|
||||
|
||||
- 文件系统:就整体而言,[XFS][3]据说是最好的,当然EXT4也是不错的选择。
|
||||
- 最佳布局:远端布局能提高读性能,但会降低写性能。
|
||||
@ -127,7 +128,7 @@ via: http://xmodulo.com/setup-raid10-linux.html
|
||||
|
||||
作者:[Gabriel Cánepa][a]
|
||||
译者:[KayGuoWhu](https://github.com/KayGuoWhu)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
@ -0,0 +1,44 @@
|
||||
Linux有问必答——如何在Linux命令行中剪裁图像
|
||||
================================================================================
|
||||
> **问题**:我想要去除图像文件中的白色空白,有没有什么便捷的方法能在Linux命令行中对图像文件进行剪裁?
|
||||
|
||||
当涉及到在Linux中转换或编辑图像文件时,ImageMagick毫无疑问是最为熟知的一体化软件之一。它包含了一整套命令行工具,用以显示、转换,或复制超过200中类型的光栅或矢量图像文件,所有这一切都在命令行下完成。ImageMagick可以用于多样化的图像编辑工作,如转换文件格式,添加特殊效果,添加文本,以及改变图像(调整大小、旋转、翻转、剪裁)。
|
||||
|
||||
如果你想要剪裁映像以去除空白,你可以使用ImageMagick自带的两个命令行工具。如果你还没有安装ImageMagick,请参照[本指南][1]来安装。
|
||||
|
||||
在本教程中,让我们来剪裁以下PNG图像。我们想要去除图像右边和底部的边缘,以便让图标居中。
|
||||
|
||||
|
||||
|
||||
首先,鉴定图像文件的尺寸(宽度和高度)。你可以使用identity命令来完成。
|
||||
|
||||
$ identify chart.png
|
||||
|
||||
----------
|
||||
|
||||
chart.png PNG 1500x1000 1500x1000+0+0 8-bit DirectClass 31.7KB 0.000u 0:00.000
|
||||
|
||||
就像上面显示的那样,输入的图像是1500x1000px。
|
||||
|
||||
接下来,确定图像剪裁要做的两件事:(1)剪裁图像开始的位置(2)剪裁矩形区域的大小。
|
||||
|
||||
在本实例中,让我们假定图像剪裁从左上角开始,更精确点是在x=20px和y=10px,那样的话,剪裁后的图像尺寸为1200x700px。
|
||||
|
||||
用于剪裁图像的工具是convert。使用“-crop”选项后,convert命令会在输入图像中剪裁出一个矩形区域。
|
||||
|
||||
$ convert chart.png -crop 1200x700+20+10 chart-cropped.png
|
||||
|
||||
指定输入图像为chart.png,convert命令会将剪裁后的图像存储为chart-cropped.png。
|
||||
|
||||

|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://ask.xmodulo.com/crop-image-command-line-linux.html
|
||||
|
||||
译者:[GOLinux](https://github.com/GOLinux)
|
||||
校对:[Caroline](https://github.com/carolinewuyan)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://ask.xmodulo.com/install-imagemagick-linux.html
|
||||
32
published/20141208 Nathive--A libre software image editor.md
Normal file
32
published/20141208 Nathive--A libre software image editor.md
Normal file
@ -0,0 +1,32 @@
|
||||
Nathive——libre软件图像编辑器
|
||||
================================================================================
|
||||
Nathive是一个libre软件图像编辑器,类似于 Adobe Photoshop、Corel Photo-Paint 或 GIMP,但是侧重于适用性和逻辑性,并为每个用户提供平滑的学习曲线。该项目在 GNOME 桌面环境中运行,并欢迎每个人参与到合作中,分享代码、翻译或想法等方面。
|
||||
|
||||
该项目尚处于测试阶段,所以它还是个未完成的工作,还不适用于终端用户。直到现在,开发始终专注于积淀应用的核心功能和创建便捷的开发工具。所以,目前我们将致力于创建新的插件,因为很明显在这方面还很缺乏。
|
||||
|
||||
其目的是在不放弃最初的可用性的情况下,逐步将该软件打造成一个专业的图像编辑器。Nathive由基于GTK+的Python脚本写成的,它设计为简洁、轻量,而且易于安装和使用。
|
||||
|
||||
### 在 ubuntu 上安装Nathive ###
|
||||
|
||||
你需要从[这里][1]下载.deb包,然后双击来安装。
|
||||
|
||||
### 屏幕截图 ###
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.ubuntugeek.com/nathive-a-libre-software-image-editor.html
|
||||
|
||||
作者:[ruchi][a]
|
||||
译者:[GOLinux](https://github.com/GOLinux)
|
||||
校对:[Caroline](https://github.com/carolinewuyan)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.ubuntugeek.com/author/ubuntufix
|
||||
[1]:http://www.nathive.org/download
|
||||
@ -1,3 +1,6 @@
|
||||
translating by yupmoon
|
||||
|
||||
|
||||
Readers' Choice Awards 2014--Linux Journal
|
||||
================================================================================
|
||||
It's time for another Readers' Choice issue of Linux Journal! The format last year was well received, so we've followed suit making your voices heard loud again. I couldn't help but add some commentary in a few places, but for the most part, we just reported results. Please enjoy this year's Readers' Choice Awards!
|
||||
@ -534,4 +537,4 @@ via: http://www.linuxjournal.com/rc2014
|
||||
|
||||
[a]:http://www.linuxjournal.com/users/shawn-powers
|
||||
[1]:http://www.linuxjournal.com/contact
|
||||
[2]:http://www.linuxjournal.com/rc2014/coolest
|
||||
[2]:http://www.linuxjournal.com/rc2014/coolest
|
||||
|
||||
@ -0,0 +1,42 @@
|
||||
Apparently This Trojan Virus May Have Infected Linux Systems For Years
|
||||
================================================================================
|
||||

|
||||
|
||||
One of the first few argument in [why should you switch to Linux][1] is that Linux is secure and virus free. It is widely perceived by most of the Linux users that Linux is immune to viruses, which is true to an extent but not entirely.
|
||||
|
||||
Like any other OS, Linux too is not immune to malware, trojan, rootkit, virus etc. There have been several [famous Linux viruses][2]. But if you compare those to that of Windows, the number is infinitesimal. So, why am I talking about Linux viruses today then? Because a new trojan has been detected in market which might be impacting Linux systems.
|
||||
|
||||
### Turla infects Linux systems as well ###
|
||||
|
||||
Few months back a sophisticated cyber espionage program, nicknamed [Turla][3], was detected. It was supposed to be originated in Russia, allegedly with Russian government backing. The spyware program was targeting government organizations in Europe and the United States for four years.
|
||||
|
||||
In a recent report, researchers at [Kaspersky][4] has found that Turla was not only affecting Windows system but also Linux operating system. Kaspersky researchers have termed it the ‘missing piece of Turla puzzle’. As per the report:
|
||||
|
||||
> “This newly found Turla component supports Linux for broader system support at victim sites. The attack tool takes us further into the set alongside the Snake rootkit and components first associated with this actor a couple years ago. We suspect that this component was running for years at a victim site, but do not have concrete data to support that statement just yet.”
|
||||
|
||||
### What is this Linux module of Turla and how dangerous it is? ###
|
||||
|
||||
Going by the Kaspersky report,
|
||||
|
||||
> The Linux Turla module is a C/C++ executable statically linked against multiple libraries, greatly increasing its file size. It was stripped of symbol information, more likely intended to increase analysis effort than to decrease file size. Its functionality includes hidden network communications, arbitrary remote command execution, and remote management. Much of its code is based on public sources.
|
||||
|
||||
Report also mentions that this trojan doesn’t require elevated privileges (read root) while running arbitrary remote commands and it cannot be discovered by commonly used administrative tools. Personally, I doubt their claims.
|
||||
|
||||
So, as a Linux desktop user, should you be scared? In my opinion, it is too early to go in to panic mode as we experienced with [ShellShock Linux bug][5]. Turla was originally intended for government organization, not common users. Let’s wait and watch for more concrete news. I’ll keep on updating this article. Till then enjoy Linux.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://itsfoss.com/apparently-trojan-virus-infected-linux-systems-years/
|
||||
|
||||
作者:[Abhishek][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://itsfoss.com/author/Abhishek/
|
||||
[1]:http://itsfoss.com/reasons-switch-linux-windows-xp/
|
||||
[2]:http://www.unixmen.com/meet-linux-viruses/
|
||||
[3]:http://www.reuters.com/article/2014/03/07/us-russia-cyberespionage-insight-idUSBREA260YI20140307
|
||||
[4]:https://securelist.com/blog/research/67962/the-penquin-turla-2/
|
||||
[5]:http://itsfoss.com/linux-shellshock-check-fix/
|
||||
@ -0,0 +1,35 @@
|
||||
Turla espionage operation infects Linux systems with malware
|
||||
================================================================================
|
||||
|
||||
|
||||
> A newly identified Linux backdoor program is tied to the Turla cyberespionage campaign, researchers from Kaspersky Lab said
|
||||
|
||||
A newly discovered malware program designed to infect Linux systems is tied to a sophisticated cyberespionage operation of Russian origin dubbed Epic Turla, security researchers found.
|
||||
|
||||
The Turla campaign, also known as Snake or Uroburos, [was originally uncovered in February][1], but goes back several years. The massive operation infected computers at government organizations, embassies, military installations, education and research institutions and pharmaceutical companies in over 45 countries.
|
||||
|
||||
The newly identified Turla component for Linux was uploaded recently to a multi-engine antivirus scanning service and was described by security researchers from antivirus vendor Kaspersky Lab as "a previously unknown piece of a larger puzzle."
|
||||
|
||||
"So far, every single Turla sample we've encountered was designed for the Microsoft Windows family, 32 and 64 bit operating systems," the Kaspersky researchers said Monday in a [blog post][2]. "The newly discovered Turla sample is unusual in the fact that it's the first Turla sample targeting the Linux operating system that we have discovered."
|
||||
|
||||
The Turla Linux malware is based on an open-source backdoor program called cd00r developed in 2000. It allows attackers to execute arbitrary commands on a compromised system, but doesn't require elevated privileges or root access to function and listens to commands received via hidden TCP/UDP packets, making it stealthy.
|
||||
|
||||
"It can't be discovered via netstat, a commonly used administrative tool," said the Kaspersky researchers, who are still analyzing the malware's functionality.
|
||||
|
||||
"We suspect that this component was running for years at a victim site, but do not have concrete data to support that statement just yet," they said.
|
||||
|
||||
Since their blog post Monday, the Kaspersky researchers also found a second Turla Linux component that appears to be a separate malware program.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.computerworld.com/article/2857129/turla-espionage-operation-infects-linux-systems-with-malware.html
|
||||
|
||||
作者:[Lucian Constantin][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.computerworld.com/author/Lucian-Constantin/
|
||||
[1]:http://news.techworld.com/security/3505688/invisible-russian-cyberweapon-stalked-us-and-ukraine-since-2005-new-research-reveals/
|
||||
[2]:https://securelist.com/blog/research/67962/the-penquin-turla-2/
|
||||
@ -0,0 +1,74 @@
|
||||
Yes, This Trojan Infects Linux. No, It’s Not The Tuxpocalypse
|
||||
================================================================================
|
||||

|
||||
|
||||
Is something watching you?
|
||||
|
||||
Grab a crate of canned food, start digging a deep underground bunker and prepare to settle into a world that will never be the same again: [a powerful trojan has been uncovered on Linux][1].
|
||||
|
||||
Yes, the hitherto impregnable fortress of computing nirvana has been compromised in a way that has left security experts a touch perturbed.
|
||||
|
||||
Unplug your PC, disinfect your keyboard and buy a cat (no more YouTube ). The Tuxpocalypse is upon us. We’ve reached the end of days.
|
||||
|
||||
Right? RIGHT? Nah, not quite.
|
||||
|
||||
### A Terrifying Anomalous Thing! ###
|
||||
|
||||
Let me set off by saying that **I am not underplaying the severity of this threat (known by the nickname ‘Turla’)** nor, for the avoidance of doubt, am I suggesting that we as Linux users shouldn’t be concerned by the implications.
|
||||
|
||||
The discovery of a silent trojan infecting Linux systems is terrifying. The fact it was tasked with sucking up and sending off all sorts of sensitive information is horrific. And to learn it’s been doing this for at least four years and doesn’t require root privileges? My seat is wet. I’m sorry.
|
||||
|
||||
But — and along with hyphens and typos, there’s always a ‘but’ on this site — the panic currently sweeping desktop Linux fans, Mexican wave style, is a little out of context.
|
||||
|
||||
Vulnerability may be a new feeling for some of us, yet let’s keep it in check: Linux remains an inherently secure operating system for desktop users. One clever workaround does not negate that and shouldn’t send you scurrying offline.
|
||||
|
||||
### State Sponsored, Targeting Governments ###
|
||||
|
||||

|
||||
|
||||
Is a penguin snake a ‘Penguake’ or a ‘Snaguin’?
|
||||
|
||||
‘Turla’ is a complex APT (Advanced Persistent Threat) that has (thus far) targeted government, embassy and pharmaceutical companies’ systems for around four years using a method based on [14 year old code, no less][2].
|
||||
|
||||
On Windows, where the superhero security researchers at Symantec and Kaspersky Lab first sighted the slimy snake, Turla and components of it were found to have **infected hundreds (100s) of PCs across 45 countries**, many through unpatched zero-day exploits.
|
||||
|
||||
*Nice one Microsoft.*
|
||||
|
||||
Further diligence by Kaspersky Lab has now uncovered that parts of the same trojan have also been active on Linux for some time.
|
||||
|
||||
The Trojan doesn’t require elevated privileges and can “intercept incoming packets and run incoming commands on the system”, but it’s not yet clear how deep its tentacles reach or how many Linux systems are infected, nor is the full extent of its capabilities known.
|
||||
|
||||
“Turla” (and its children) are presumed to be nation-state sponsored due to its choice of targets. US and UK readers shouldn’t assume it’s “*them*“, either. Our own governments are just as happy to play in the mud, too.
|
||||
|
||||
#### Perspective and Responsibility ####
|
||||
|
||||
As terrible a breach as this discovery is emotionally, technically and ethically it remains far, far, far away from being an indication that we’re entering a new “free for all” era of viruses and malware aimed at the desktop.
|
||||
|
||||
**Turla is not a user-focused “i wantZ ur CredIt carD” virus** bundled inside a faux software download. It’s a complex, finessed and adaptable threat with specific targets in mind (ergo grander ambitions than collecting a bunch of fruity tube dot com passwords, sorry ego!).
|
||||
|
||||
Kaspersky Lab explains:
|
||||
|
||||
> “The Linux Turla module is a C/C++ executable statically linked against multiple libraries, greatly increasing its file size. It was stripped of symbol information, more likely intended to increase analysis effort than to decrease file size. Its functionality includes hidden network communications, arbitrary remote command execution, and remote management. Much of its code is based on public sources.”
|
||||
|
||||
Regardless of impact or infection rate its precedes will still raise big, big questions that clever, clever people will now spend time addressing, analysing and (importantly) solving.
|
||||
|
||||
IANACSE (I am not a computer security expert) but IAFOA (I am a fan of acronyms), and AFAICT (as far as I can tell) this news should be viewed as as a cautionary PSA or FYI than the kind of OMGGTFO that some sites are painting it as.
|
||||
|
||||
Until more details are known none of us should panic. Let’s continue to practice safe computing. Avoid downloading/running scripts, apps, or binaries from untrusted sites or PPAs, and don’t venture into dodgy dark parts of the web.
|
||||
|
||||
If you remain super concerned you can check out the [Kaspersky blog][1] for details on how to check that you’re not infected.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.omgubuntu.co.uk/2014/12/government-spying-turla-linux-trojan-found
|
||||
|
||||
作者:[Joey-Elijah Sneddon][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://plus.google.com/117485690627814051450/?rel=author
|
||||
[1]:https://securelist.com/blog/research/67962/the-penquin-turla-2/
|
||||
[2]:https://twitter.com/joernchen/status/542060412188262400
|
||||
[3]:https://securelist.com/blog/research/67962/the-penquin-turla-2/
|
||||
@ -1,86 +0,0 @@
|
||||
5 Best Open Source Web Browser Security Apps
|
||||
================================================================================
|
||||
The Web browser acts as the gateway for myriad online services these days. Computer security problems are far from solved, and technology advances provide new ways for malware to infect our devices and enter our business networks. For example, smartphones and tablets offer fresh new fields for malware—and its malicious cousin, "[malvertising][1]"—to exploit.
|
||||
|
||||
Malvertising, or malicious advertising, injects malware into legitimate ads and ad networks. Granted, you could argue that there's a thin line between "legitimate" ads and ad networks and not-legitimate ads and ad networks. But don’t get distracted. Privacy and security are inextricably linked, and protecting your privacy is part of protecting your security.
|
||||
|
||||
Firefox, Chrome, and Opera are the best Web browsers; they offer the best performance, the most compatibility, and the best security. These five open source security apps install in your Web browser, and they protect you from a variety of threats.
|
||||
|
||||
### Protect Your Privacy: Open Source Web Browser Security Apps ###
|
||||
|
||||
#### 1. [AdBlock][2] ####
|
||||
|
||||
Ad networks are wonderful malware vectors. A single ad network serves thousands of sites, so compromising one ad network equals many thousands of compromised machines. AdBlock, and its derivatives—[AdBlock Plus][2], [AdBlock Pro][3], and [AdBlock Edge][4]—are all great tools for blocking ads, which has the added benefit of making cluttery annoying ads-infested sites more usable.
|
||||
|
||||
Of course there is a downside: harming sites that depend on ad revenues. All of them have one-click whitelists, so you can selectively turn off ad-blocking on sites that you want to support. (Really, my dear Webmeisters, if you don't want your site visitors blocking your ads then don't be obnoxious.)
|
||||
|
||||

|
||||
|
||||
Figure 1: Selecting additional filters for your Ad Blocker.
|
||||
|
||||
Ad blockers do more than block ads; they also block Web-tracking bugs and malicious domains. To turn on additional filter lists, click on your ad blocker icon > click **Preferences**, and go to the **Filter Subscriptions** tab. Click the **Add Filter Subscription** button, and then add **Easy Privacy + EasyList**. The Malware Domains filter is a good one to include as well; it blocks domains that are known to host malware and spyware. Adblock works with Firefox, Chrome, Opera, Safari, Internet Explorer, and Android.
|
||||
|
||||
#### 2. [HTTPS Everywhere][5] ####
|
||||
|
||||
HTTPS Everywhere browser extension ensures that you will never accidentally connect to a Web site with HTTP when HTTPS is available. HTTPS means your connection is encrypted with SSL (secure sockets layer), which is a commonly-used protocol for encrypting Web and email connections. HTTPS Everywhere is available for Firefox, Chrome, and Opera.
|
||||
|
||||
When you install HTTPS Everywhere, it asks if you want to enable the SSL Observatory. Say yes, as it offers additional protections against man-in-the-middle and bogus SSL certificate attacks. HTTPS Everywhere works with Firefox, Chrome, Opera, Android.
|
||||
|
||||
#### 3. [Social Fixer][6] ####
|
||||
|
||||
Social Fixer tames Facebook. It gives you mighty powers to filter your news feed so that you see what you want to see, creates tabbed feeds organized by topic, hides whatever you don't want to see, displays pictures full-sized on mouse-over, disables the Theater view of images, and lots more.
|
||||
|
||||
It's not really designed to be a security tool, but Social Fixer offers two important security features:
|
||||
|
||||
- It anonymizes Facebook pages for screenshots by replacing profile pictures with generic icons, and it changes usernames to fake names
|
||||
- It reliably blocks Facebook games, which are notorious sources of trouble
|
||||
|
||||

|
||||
|
||||
Figure 2: Anonymizing a Facebook screen with Social Fixer.
|
||||
|
||||
#### 4. [Privacy Badger][7] ####
|
||||
|
||||
The Electronic Frontier Foundation's Privacy Badger is a superb tracker-and spy-ads blocker. These days Web pages are composed of content from multiple sources: ad servers, comments servers, content farms, image farms, third-party login servers, and gosh knows what-all.
|
||||
|
||||
AdBlock is good at blocking this junk, but Privacy Badger is better. It doesn't rely on filter lists, which have to be maintained by humans somewhere, but rather algorithms and policy methods, and you can easily override it if it blocks something in error. Privacy Badger works with Firefox and Chrome.
|
||||
|
||||

|
||||
|
||||
Figure 3: Privacy Badger blocks tracking sites.
|
||||
|
||||
Privacy Badger should just work. Click on its icon to see what it's blocking on any site you're visiting. Try it on Huffingtonpost.com, one of the champions of stuffing the maximum number of third-party components into each and every page (Figure 3).
|
||||
|
||||
The sliders tell the status of each site: red means that site is completely blocked, so it can't set cookies or serve up any content to you. Yellow indicates a third-party domain that appears to be trying to track you, but it is on Privacy Badger's whitelist of allowed domains. Green is for a third-party domain that is not yet classified as a tracker, but this could change as you visit **multiple** sites and Privacy Badger observes its behavior.
|
||||
|
||||
You can set the sliders yourself according to your preference; for example, on one site I visited Privacy Badger blocked bazaarvoice.com, which some shopping sites use to host their customer reviews.
|
||||
|
||||
#### 5. [Disconnect][8] ####
|
||||
|
||||
Disconnect is another anti-tracker and anti-cookie tool with a great feature set. It runs on Firefox, Chrome, Internet Explorer, and Safari, and offers special iOS and Android versions. Not only does it foil trackers, it also secures your wireless transmissions (Wi-fi, 3G, and 4G) with its own virtual private network, protecting you from wiretapping and malvertising. It protects you from widgetjacking, which is a technique used by attackers to gain access to your sites that require logins. With widgetjacking they don't even need your password; they use stolen cookies.
|
||||
|
||||
Disconnect also provides a safe search feature that lets you use your favorite search engines while blocking their snoopy data-mining habits.
|
||||
|
||||
Just assume that everyone on the Web is out to get you. It's all abstract and behind the scenes, and not obvious like someone bashing a window to get into your house. But the threats are numerous and real, and you have to take precautions to protect yourself.
|
||||
|
||||
Carla Schroder is the author of The Book of Audacity, Linux Cookbook, Linux Networking Cookbook,and hundreds of Linux how-to articles. She's the former managing editor of Linux Planet and Linux Today.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.smallbusinesscomputing.com/biztools/5-best-open-source-web-browser-security-apps.html
|
||||
|
||||
作者:[Carla Schroder][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.smallbusinesscomputing.com/author/Carla-Schroder-6080.html
|
||||
[1]:http://www.webopedia.com/TERM/M/malvertising.html
|
||||
[2]:https://getadblock.com/
|
||||
[3]:https://chrome.google.com/webstore/detail/adblock-pro/ocifcklkibdehekfnmflempfgjhbedch?hl=en-US
|
||||
[4]:https://addons.mozilla.org/en-us/firefox/addon/adblock-edge/
|
||||
[5]:https://www.eff.org/Https-everywhere
|
||||
[6]:http://socialfixer.com/
|
||||
[7]:https://www.eff.org/privacybadger
|
||||
[8]:https://disconnect.me/
|
||||
@ -1,197 +0,0 @@
|
||||
[Translating by Stevearzh]
|
||||
Five Magnificent Linux Music Streaming Clients
|
||||
================================================================================
|
||||
Digital streams almost totally command my music listening these days. Over the years I have amassed a large collection of CDs at considerable expense; most of them now sit neglected gathering dust. Almost all music streaming services fall short of the audio quality of CDs, but their popularity has more to do with sheer convenience than high-fidelity sound reproduction. Music streaming has not only been to the detriment of CD sales; digital downloads have also experienced a slowing down of sales. This is only set to continue. Audiophiles may be tempted to embrace music streaming given that there are now services such as Tidal which offers high fidelity music streaming, 25 million tracks encoded with the FLAC format streamed at 1,411kbps.
|
||||
|
||||
CDs are not going away though. Music streaming services do experience issues with record labels and artists who are unhappy with the amount of return they receive from letting their music be hosted on the service. This is still in flux; we have seen this year Led Zeppelin, Pink Floyd, Metallica sign up to streaming services, but there are still some notable omissions such as the Beatles, Radiohead and AC/DC who refuse to allow fans to stream their music. Even where a record label or singer has given permission to allow streaming services to access their work, an artist's back catalog can be pulled at a moment's notice. This month, Taylor Swift’s entire catalog of music was pulled from Spotify's streaming service at the pop singer’s request. Some people will still prefer to "possess" their collection, but it's looking like an increasingly old fashioned way to enjoy music.
|
||||
|
||||
The Linux platform has matured into a good way of listening to streaming music services. There are clients available for most of the music streaming services; I hope TIDAL will support Linux on the desktop in due course, and not rely on a web player. All of the applications featured in this article are excellent. An honorable mention should be given to Amarok, pianobar, and Tomahawk.
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
Spotify is a proprietary peer-to-peer music streaming service that allows users to listen to tracks or albums on demand. The service describes itself as "A world of music. Instant, simple and free". Spotify uses 96kbps streaming on mobile, 160kbps on desktop and 320kbps for "Premium subscribers" - all encoded in the Ogg Vorbis format. Spotify is free for those who choose to live with adverts, or at a reasonable monthly charge without them.
|
||||
|
||||
Spotify is a fantastic service, offering access to a huge library of music covering all different types of music such as pop, alternative, classical, techno, and rock. It is a great way of dipping into new music. The service has the support of major labels including Sony BMG, EMI, Universal, and Warner Music, as well as independent labels and distribution networks like Labrador Records, The Orchard, Alligator Records, Merlin, CD Baby, INgrooves as well as classical music labels such as Chandos, Naxos, EMI Classic, Warner Classics, Denon Essentials and many more. The breadth of music is continuing to expand at a phenomenal pace.
|
||||
|
||||
Spotify does not officially support Linux at the moment. However, they have developed a preview build of Spotify for Linux, which works well. As its a preview release, this version is still unsupported.
|
||||
|
||||
Spotify is available in Andorra, Argentina, Australia, Austria, Belgium, Bulgaria, Colombia, Cyprus, Denmark, Estonia, Finland, France, Germany, Greece, Hong Kong, Iceland, Ireland, Italy, Latvia, Liechtenstein, Lithuania, Luxembourg, Malaysia, Malta, Mexico, Monaco, Netherlands, New Zealand, Norway, the Philippines, Poland, Portugal, Spain, Singapore, Sweden, Switzerland, Taiwan, Turkey, the United Kingdom, the United States, Uruguay, and a few others.
|
||||
|
||||
**Features include:**
|
||||
|
||||
- A well designed interface makes navigation effortless
|
||||
- Create and edit playlists
|
||||
- Discover new music
|
||||
- Share music and playlists
|
||||
- Radio feature
|
||||
- Top Lists
|
||||
- Additional functionality with large variety of apps
|
||||
|
||||
- Website: [www.spotify.com/uk/download/previews][1]
|
||||
- Developer: Spotify
|
||||
- License: Proprietary
|
||||
- Version Number: Preview
|
||||
|
||||
----------
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
Pithos is an open source native Pandora Radio client for Linux. It offers a lightweight alternative to the official Pandora.com web client. The graphical user interface integrates with desktop features such as media keys, notifications, and the sound menu.
|
||||
|
||||
The Pandora music service is only intended to be used by US IP addresses. However, users located outside the US can use Pandora with a VPN.
|
||||
|
||||
**Features include: **
|
||||
|
||||
- Play / Pause / Next Song
|
||||
- Switching stations
|
||||
- Remembers your user name and password
|
||||
- Bookmarking of songs and artists
|
||||
- Cover Art
|
||||
- Thumbs Up / Thumbs Down / Tired of this song
|
||||
- Notification popup with song info
|
||||
- Launching pandora.com song info page and station page
|
||||
- Reconnecting when pandora session times out
|
||||
- Editing QuickMix
|
||||
- Creating stations
|
||||
- Media Key support
|
||||
- Proxy support
|
||||
- Last.fm scrobbling support
|
||||
- Volume control
|
||||
- Plugins including Screensaver pause
|
||||
- Two DBUS APIs: MPRIS and Pithos
|
||||
|
||||
- Website: [pithos.github.io][2]
|
||||
- Developer: Kevin Mehall
|
||||
- License: GNU GPL v3
|
||||
- Version Number: 1.0.0
|
||||
|
||||
----------
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
Clementine is a cross-platform, lightweight, modern music player and library organiser based on Amarok. Clementine focuses on a fast and easy-to-use interface for searching and playing your music.
|
||||
|
||||
It is inspired by Amarok 1.4, focusing on a fast and easy-to-use interface for searching and playing your music.
|
||||
|
||||
Features include:
|
||||
|
||||
- Search and play your local music library
|
||||
- Listen to internet radio from Last.fm and SomaFM
|
||||
- Tabbed playlists, import and export M3U, XSPF, PLS and ASX
|
||||
- Create smart playlists and dynamic playlists
|
||||
- Load M3U and XSPF playlists
|
||||
- Undo and redo in the playlist
|
||||
- Edit tags on MP3 and OGG files, organise your music
|
||||
- Download missing album cover art from Last.fm
|
||||
- Podcast support with integration with gpodder.net
|
||||
- Graphical equalizer
|
||||
- Cross-platform works on Windows, Mac OS X and Linux
|
||||
- Native desktop notifications on Linux (libnotify) and Mac OS X (Growl)
|
||||
- Fetch missing tags from MusicBrainz
|
||||
- Attractive on screen display
|
||||
- Queue manager
|
||||
- Supports MPRIS on Linux, or remote control using the command-line
|
||||
- Supports indexing and playing music from Google Drive
|
||||
- Support for Soundcloud
|
||||
- Support for jazzradio.com
|
||||
- Support for Moodbar
|
||||
- Visualizations from projectM
|
||||
- Copy music to your iPod, iPhone, MTP or mass-storage USB player
|
||||
- Remote control
|
||||
- Transcode music into MP3, Ogg Vorbis, Ogg Speex, FLAC or AAC
|
||||
|
||||
- Website: [www.clementine-player.org][3]
|
||||
- Developer: David Sansome, John Maguire
|
||||
- License: GNU GPL v3
|
||||
- Version Number: 1.2
|
||||
|
||||
----------
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
Nuvola Player is a free and open source project that offers cloud music integration for your desktop (system tray, Ubuntu sound menu, dock menu and notifications).
|
||||
|
||||
To use all of the streaming services, you need Flash and HTML5 audio support. Some web-based streaming services can utilize HTML5 Audio technology for music playback instead of the Flash plugin. Nuvola Player requires GStreamer with MP3 decoder plugin to provide HTML5 Audio support.
|
||||
|
||||
**Supported Services:**
|
||||
|
||||
- Amazon Cloud Player integrated with the MP3 store and allows users to store their music on Amazon Cloud Drive, and play that music from any supported web browsers
|
||||
- Bandcamp an online music store, as well as a platform for artist promotion, that caters mainly to independent artists
|
||||
- Deezer a French web-based music streaming service. It allows users to listen to music on various devices online or offline. It currently has 18 million licensed tracks, over 30,000 radio channels and 22 million users (1.5 million subscribers)
|
||||
- 8tracks a website that fuses elements of internet radio and social networking revolving around the concept of streaming user-curated playlists consisting of at least 8 tracks
|
||||
- Google Play Music a digital content service from Google which includes an online store for music, movies, books, and Android apps and games, as well as a cloud media player that supports uploading a user's own music and buying music at Google Play Store
|
||||
- Grooveshark an international online music search engine, music streaming service and music recommendation web software application, allowing users to search for, stream, and upload music that can be played immediately or added to a playlist
|
||||
- Grooveshark Mobile the HTML5-based mobile version of Grooveshark which does not require Flash
|
||||
- Hype Machine an amalgamation of Pandora Radio and Pitchfork Media. It aggregates the most recently posted songs from a selection of music blogs (about 1,500) and lists them on the website's main page
|
||||
- Jango a free online music streaming service that allows users to create and share custom radio stations
|
||||
- Logitech Media Server the open source media server for Logitech Squeezebox devices. It supports plug-ins and multiple only services like Deezer or Spotify
|
||||
- Pandora an automated music recommendation service and "custodian" of the Music Genome Project available only in the United States
|
||||
- Rdio an ad-free music subscription service
|
||||
- Spotify a commercial music streaming service providing digital rights management-restricted content from record labels
|
||||
- This is My Jam a place to put your favorite song of the moment & hear great music, handpicked every day by friends
|
||||
|
||||
**Features include:**
|
||||
|
||||
- Multimedia keys
|
||||
- Shows desktop notifications
|
||||
- Integrates with various sound menus, applets and launchers and more
|
||||
- Last FM and Libre FM scrobbling
|
||||
- Lyrics fetching
|
||||
- Support for Amazon Music Prime streaming
|
||||
|
||||
- Website: [tiliado.eu/nuvolaplayer][4]
|
||||
- Developer: Jiří Janoušek and service maintainers
|
||||
- License: 2-Clause BSD license
|
||||
- Version Number: 2.4.3
|
||||
|
||||
----------
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
Atraci is a multi-platform open source streaming application that lets users listen to more than 60 million songs. It is still in an early stage of development, so the application is not the most feature laden.
|
||||
|
||||
Atraci use iTunes, Last.fm and SoundCloud to display song information - cover, title, artist. Atraci searches the best match for this song on YouTube and streams the highest quality video stream.
|
||||
|
||||
**Features include: **
|
||||
|
||||
- No advertisements, no sign up required
|
||||
- Intuitive user interface
|
||||
- Smart matching search for any song, artist name or album. Atraci checks it against online listings to show correct title, album artwork, track lists and so on, with listed options being the highest quality video streams
|
||||
- Album and artist autosuggestions
|
||||
- Sort results by 'default', 'artist' or ‘track’
|
||||
- View results in 'grid' or 'list' layouts
|
||||
- Accompanying video can be made full screen
|
||||
- Create playlists with shuffle and repeat options
|
||||
- In-app volume slider, track scrubber and album artwork
|
||||
- History of recently played tracks
|
||||
|
||||
- Website: [atraci.github.io/Atraci-website][5]
|
||||
- Developer: The Atraci Team
|
||||
- License: The MIT License
|
||||
- Version Number: 0.7.0
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linuxlinks.com/article/20141116052055674/MusicStreaming.html
|
||||
|
||||
作者:Frazer Kline
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:https://www.spotify.com/uk/download/previews/
|
||||
[2]:http://pithos.github.io/
|
||||
[3]:https://www.clementine-player.org/
|
||||
[4]:https://tiliado.eu/nuvolaplayer/
|
||||
[5]:http://atraci.github.io/Atraci-website/
|
||||
@ -1,22 +0,0 @@
|
||||
Getting Started With Ubuntu 14.04 (PDF Guide)
|
||||
================================================================================
|
||||
Become familiar with everyday tasks such as surfing the web, listening to music and scanning documents.
|
||||
|
||||
Enjoy this comprehensive beginners guide for the Ubuntu operating system. With easy-to-follow instructions, this guide is suitable for all levels of experience. Discover the potential of your Ubuntu system without getting bogged down with technical details.
|
||||
|
||||
- [**Getting Started With Ubuntu 14.04 (PDF Guide)**][1]
|
||||
|
||||

|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.ubuntugeek.com/getting-started-with-ubuntu-14-04-pdf-guide.html
|
||||
|
||||
作者:[ruchi][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.ubuntugeek.com/author/ubuntufix
|
||||
[1]:http://ubuntugeek.tradepub.com/free/w_ubun06/
|
||||
@ -1,32 +0,0 @@
|
||||
Nathive – A libre software image editor
|
||||
================================================================================
|
||||
Nathive is a libre software image editor, similar to Adobe Photoshop, Corel Photo-Paint or GIMP, but focused on usability, logic and providing a smooth learning curve for everyone. The project runs in the GNOME desktop environment and anyone is welcome to collaborate on it with code, translations or ideas.
|
||||
|
||||
This project is in beta phase, so it is an incomplete work, unfit for the end user yet. Until now the development was focused in laying down the application core and create easy dev tools, so for now we will focus on create new plugins, because there are obvious lacks yet.
|
||||
|
||||
The intention is to achieve a professional image editor progressively without giving up initial usability. Nathive is written from scratch in Python using GTK+, and is designed to be simple, lightweight, and easy to install and use.
|
||||
|
||||
### Install Nathive on ubuntu ###
|
||||
|
||||
You need to download .deb package from [here][1] .Once you have deb package you can double click to install
|
||||
|
||||
### Screenshots ###
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.ubuntugeek.com/nathive-a-libre-software-image-editor.html
|
||||
|
||||
作者:[ruchi][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.ubuntugeek.com/author/ubuntufix
|
||||
[1]:http://www.nathive.org/download
|
||||
104
sources/share/20141211 NetHack.md
Normal file
104
sources/share/20141211 NetHack.md
Normal file
@ -0,0 +1,104 @@
|
||||
[Translating by Stevearzh]
|
||||
NetHack
|
||||
================================================================================
|
||||
## The best game of all time? ##
|
||||
|
||||
**It’s tremendously addictive. It takes a lifetime to master. And people play it for decades without completing it. Welcome to the strange world of NetHack…**
|
||||
|
||||
Believe it or not, it’s possible to be terrified by the sight of the letter D. Or ecstatic about the sight of a % character. (And the less said about ^, the better.) But before you assume we’ve gone totally loopy and close the tab, bear with us for a moment: those characters represent dragons, food rations and traps respectively. Welcome to NetHack, where your imagination needs to play a big role in the gameplay.
|
||||
|
||||
You see, NetHack is a text-mode game: it just uses the standard terminal character set to portray the player, enemies, items and surroundings. Graphical versions of the game exist, but NetHack purists tend to avoid them, and what’s the point of a game if you can’t play it when you’re SSHed into your revived Amiga 3000 running NetBSD? In some ways, NetHack is a lot like Vi – it has been ported to nigh-on every operating system in existence, and its requirements are absolutely minimal.
|
||||
|
||||
Now, given that it looks like utter pants when compared to modern games, what makes NetHack so appealing? Well, this dungeon exploring masterpiece is incredibly rich and detailed. There are so many items to discover, spells to cast, monsters to fight and tricks to learn – and the dungeons are generated randomly. There’s so much to explore, and no two games are ever the same. People play NetHack for years and decades without complete it, still discovering new secrets each time.
|
||||
|
||||
Here we’ll show you how NetHack came about, give you a guided tour of the dungeons, and show you some tricks. Note: by reading this feature, you agree to not sue us when you become addicted to NetHack and your real-life productivity is obliterated.
|
||||
|
||||

|
||||
|
||||
The NetHack interface
|
||||
|
||||
### Possibly the oldest still-developed game ###
|
||||
|
||||
Despite its name, NetHack isn’t an online game. It’s based on an earlier dungeon-exploring romp called Hack, which in turn was a descendant of an 1980 game called Rogue. NetHack’s first release arrived in 1987, and although no new features have been added since version 3.4.3 in 2003, various patches, add-ons and spin-offs are still doing the rounds on the web. This makes it arguably the oldest game that’s still being hacked on and played by a sizeable group of people. Go to [www.reddit.com/r/nethack][1] to see what we mean – long-time NetHack players are still discussing new strategies, discoveries and tricks. Occasionally you’ll see gleeful messages from old timers who have finally, after many years, completed the game.
|
||||
|
||||
But how do you complete it? Well, NetHack is set in a large and deep dungeon. You start at the top – level 1 – and your goal is to keep going down until you find a hugely valuable item called the Amulet of Yendor. This is typically in level 20 or lower, but it can vary. As you traverse through and down the dungeon, you’ll meet all manner of monsters, traps and human characters; some will try to kill you, some will stay out of your way, and some…. well, you don’t know until you get close to them.
|
||||
|
||||
> There’s so much to learn, and many items only work best when combined with others.
|
||||
|
||||
What makes NetHack so compelling is the vast range of items crammed into the game. Weapons, armour, spell books, rings, gems – there’s so much to learn, and many items only work best when combined with others. Monsters often drop useful items when you kill them, although some items can have very negative effects if you don’t use them correctly. You’ll find shops in the dungeon that are packed with potentially useful bits of kit, but don’t expect the shopkeeper to give you great descriptions. You’ve got to learn from experience. Some items aren’t much use at all, and the game is packed with humour – you can even throw a cream pie in your own face.
|
||||
|
||||
But before you even set foot in the dungeon, NetHack asks you what kind of player you want to be. You can take your journey as a knight, a monk, a wizard or even a humble tourist, amongst many other player types. They all have their own strengths and weaknesses, and NetHack addicts love to try completing the game with the weaker types. You know, to show off to other players.
|
||||
|
||||
> ## Spoilers don’t spoil the fun ##
|
||||
|
||||
> In NetHack parlance, “spoilers” provide information on monsters, items, weapons and armour. It’s technically possible to complete the game without using them, but very few players ever achieve this, as the game is monumentally complex. Consequently it’s not regarded as bad form to use spoilers – but it’s still more fun to try to work things out yourself first, and only consult the spoilers when you really need them.
|
||||
|
||||
> A great source is [www.statslab.cam.ac.uk/~eva/nethack/spoilerlist.html][2] which separates spoilers into categories. For things that happen randomly in the game, such as the effects from drinking from fountains, it gives you the odds of a certain thing happening.
|
||||
|
||||
### Your first dungeon crawl ###
|
||||
|
||||
NetHack is available for almost every major OS and Linux distribution in the world, so you should be able to grab it with “apt-get install nethack” or “yum install nethack” or whatever is appropriate for your distro. Then run it in a terminal window by just typing “nethack”. The game will ask if it should pick a player type for you – but as a newcomer, it’s best if you choose one of the tougher characters first. So hit “n” and then hit “v” to choose the Valkyrie type, and “d” to be a dwarf.
|
||||
|
||||
Then NetHack will give you some plot blurb, explaining that your god seeks the Amulet of Yendor, so your goal is to retrieve it and present it to him. Hit space when you’re done reading the text (and any other time you see “–More–” on the screen). And here we go – you’re in the dungeon!
|
||||
|
||||
As described earlier, your character is represented by a @ sign. You can see the walls of a room around you, and the dot characters depict empty space in the room. First of all, get used to the movement keys: h, j, k and l. (Yes, it’s just like Vim, as covered in issue 3 of Linux Voice!) These move you left, down, up and right respectively. You can also move diagonally with y, u, b and n. So walk around the room until you get used to the controls.
|
||||
|
||||
NetHack is turn-based, so if you’re not moving or performing an action, the game stays still. This lets youplan your moves in advance. You will see a “d” or “f” character moving around the room as well: this is your pet dog or cat, which (normally) won’t harm you and can assist you in killing monsters. Pets can be annoying though – they occasionally eat foot rations and tasty corpses before you get to them.
|
||||
|
||||

|
||||
|
||||
Hit “i” to bring up an inventory of your currently carried items
|
||||
|
||||
### What’s behind the door? ###
|
||||
|
||||
Now, let’s go out of the room. There will be gaps around the edge, and possibly “+” signs. That “+” is a closed door, so go up to it and hit “o” to open. You will be asked for a direction, so if the door is to the left of you, press “h”. (And if the door is stuck, try opening it a few times.) You’ll then end up in a corridor, marked by “#” symbols, so walk around it until you find another room.
|
||||
|
||||
On your travels you’ll see various items. Some, such as money (denoted by a “$” symbol) are picked up automatically; for other items, you have to press the comma key whilst standing on them. If there are multiple items, you’ll be given a menu, so press the appropriate keys shown in the menu and then Enter to choose what you want. At any time you can hit “i” to bring up your inventory list – see the screenshot.
|
||||
|
||||
What happens if you see a monster? At these early stages of the game, the monsters you’re likely to come across will be represented by “d”, “x” and “:” characters. To attack, simply walk into them. The game will tell you if your attacks are successful using the messages along the top – and also how the monster is responding. These early monsters are simple to kill, so you shouldn’t have any trouble defeating them, but keep an eye on your HP in the status line at the bottom.
|
||||
|
||||
> Early monsters are simple to kill, but keep an eye on your HP.
|
||||
|
||||
If a monster leaves behind a corpse (“%”), you can hit comma to take it and then press “e” to eat it. (Whenever you’re prompted to choose an item, you can press its corresponding key from the inventory list, or “?” to bring up a mini list.) Warning! Some corpses are poisonous, and these are things you’ll learn on your travels.
|
||||
|
||||
If you’re exploring a corridor and appear to come to a dead end, you can hit “s” to search until you find a door. This can take ages, however, so you can speed things up a bit: type “10” and then “s” and you will perform 10 searches in a row. This takes up 10 moves in game time, however, so if you’re hungry you could get close to starvation!
|
||||
|
||||
Common items you’ll find in the top levels of the dungeon are “{” (fountains) and “!” (potions). For the former, you can stand on it and hit q to “quaff” from it – the effects can vary from useful to deadly. For potions, pick them up and then use “q” to drink them. If you find a shop, you can pick up items and then hit “p” to pay before leaving. Use “d” to drop something.
|
||||
|
||||

|
||||
|
||||
Souped-up versions of NetHack with fancy graphics are available, such as Falcon’s Eye
|
||||
|
||||
> ## Stupid ways to die ##
|
||||
|
||||
> A popular acronym amongst NetHack players is “YASD” – Yet Another Stupid Death. It describes a situation where the player buys the farm due to his/her own silliness or lack of concentration. We’ve had many of these, but our favourite goes as follows:
|
||||
|
||||
> We were browsing a shop, inspecting items, when a snake suddenly jumped out from behind a potion. After killing the snake, a message popped up saying that we were getting hungry, so we opted to eat the snake’s corpse. Bad idea! This made us blind, so we couldn’t see other characters or items in the shop. We tried to get to the exit, but instead bumped into the shopkeeper and accidentally attacked him. This made him furious; he started firing magic missiles at us. We just about managed to get into the corridor outside the shop, but died from the onslaught.
|
||||
|
||||
> If you come to any equally silly ends, let us know on our forums. And don’t worry – nobody will judge you. Dying like this is all part of growing up in the NetHack world.
|
||||
|
||||
### Equip yourself ###
|
||||
|
||||
On your travels, and especially after you kill monsters, you’ll find weapons and armour. Again, use comma to pick these up, and then “w” (lowercase) to wield a weapon or “W” (uppercase) to wear a piece of armour. You can use “T” to remove armour and “t” to throw weapons – often handy if you’re in a very sticky situation.
|
||||
|
||||
Sometimes it’s useful to examine things from a distance before getting close to them. Hit “;” (semicolon) and “Pick an object” will appear at the top of the screen. Use the movement keys until your view lands on the thing you want to inspect, and then hit “:” (colon). A description will appear at the top.
|
||||
|
||||
As your goal is to go further down the dungeon until you find the Amulet of Yendor, keep an eye out for “<” and “>” signs. These are stairs up and down respectively, and you can use the same keys to climb them. Note! Make sure your pet is standing in an adjacent square if you want it to follow you into the next level. If you need a break, use “S” (capital s) to save, and type #quit to exit. Next time you run NetHack, your game will be resumed.
|
||||
|
||||
We won’t spoil what’s ahead, as many of the dungeon levels have amazing designs, characters and secrets. So we’ll leave you with three tips: if you come across an item that completely baffles you, try searching for it on the NetHack wiki at [http://nethack.wikia.com][3]. You’ll also find an excellent (albeit very long) guidebook at [www.nethack.org/v343/Guidebook.html][4]. Happy exploring!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linuxvoice.com/nethack/
|
||||
|
||||
作者:[Mike Saunders][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.linuxvoice.com/author/mike/
|
||||
[1]:http://www.reddit.com/r/nethack
|
||||
[2]:http://www.statslab.cam.ac.uk/~eva/nethack/spoilerlist.html
|
||||
[3]:http://nethack.wikia.com/
|
||||
[4]:http://www.nethack.org/v343/Guidebook.html
|
||||
148
sources/talk/20141211 Open source all over the world.md
Normal file
148
sources/talk/20141211 Open source all over the world.md
Normal file
@ -0,0 +1,148 @@
|
||||
Open source all over the world
|
||||
================================================================================
|
||||

|
||||
|
||||
Image by : opensource.com
|
||||
|
||||
After a full day at the annual meeting of the Opensource.com [Community Moderators][1], it was time for the the last item on the agenda which simply said "Special Guest: TBD." [Jason Hibbets][2], project lead and community manager for [Opensource.com][3], stood up and began explaining, "In case it wasn't going to happen, I didn't want to say who it was. Months ago I asked for any dates he'd be in town. I got two, and picked one. This was one day out of three weeks that Jim was in town."
|
||||
|
||||
The moderators, in town from all over the world for the [All Things Open conference][4], stirred at the table. Their chairs squeaked and snuck a few inches edgewise.
|
||||
|
||||
"We're going to get a half hour to hear from him and take a couple questions," said Jason.
|
||||
|
||||
The door opened, and as if it had been waiting for him the whole time, the only vacant seat at the head of the table was soon occupied by a tall fellow.
|
||||
|
||||
"How is everyone doing?" said the man. No suit, just a button down shirt and slacks.
|
||||
|
||||
The next tallest man in the room, [Jeff Mackanic][5], senior director of Global Awareness at Red Hat, explained that the majority of the Community Moderator team was present today. He asked everyone to quickly introduce themselves.
|
||||
|
||||
"[Jen Wike Huger][6]. Content Manager for Opensource.com. Happy to have everyone here."
|
||||
|
||||
"[Nicole][7]. Vice president of education at [ByWater Solutions][8]. We do FOSS for libraries. I travel and teach people how to use software."
|
||||
|
||||
"[Robin][9]. I've been participating in the Moderator program since 2013. I do lots of stuff for OSDC and work in the [City of the Hague][10], maintaining their [website][11]."
|
||||
|
||||
"[Marcus Hanwell][12]. Originally from England, I'm now at [Kitware][13]. I'm the technology lead on FOSS science software. I work with national labs and use things like [Titan][14] Z doing [GPU programming][15]. I've worked with [Gentoo][16] and [KDE][17]. Most of all, I'm passionate about joining FOSS and open science."
|
||||
|
||||
"[Phil Shapiro][18]. I administrate 28 Linux work stations at a small library in D.C. I consider these folks my coworkers and colleagues. And it's wonderful to know that we can all feed into the energy and share ideas. My main interests are how FOSS intersects with dignity, and enhancing dignity."
|
||||
|
||||
"[Joshua Holm][19]. I spend most of my time staring at system updates and helping people search for jobs on the Internet."
|
||||
|
||||
"[Mel Chernoff][20]: I work here at Red Hat, primarily on the [government][21] channel with [Jason Hibbets][22] and [Mark Bohannon][23]."
|
||||
|
||||
"[Scott Nesbitt][24]: I write for many things, but have been using FOSS for long time. I'm a 'mere mortal' just trying to be more productive, not a sysadmin or programmer. I help people meld FOSS into their business and personal lives."
|
||||
|
||||
"[Luis Ibanez][25]: I just joined [Google]26], but I'm interested in DIY and FOSS."
|
||||
|
||||
"[Remy DeCausemaker][27]: Resident Hackademic at the [RIT MAGIC Center][28] and Adjunct Professor for the [Department of Interactive Games and Media][29]. Been writing for Opensource.com for about four years now."
|
||||
|
||||
"You teach courses for the [new FOSS Minor then][30]," said Jim. "Very cool."
|
||||
|
||||
"[Jason Baker][31]. I'm a Red Hat cloud expert, mostly doing work around [OpenStack][32]."
|
||||
|
||||
"[Mark Bohannan][33]. I'm with Red Hat Global Public Policy, and I work out of Washington. Like Mel, I spend a good deal of time writing for, or finding folks from, the legal and government channels. I've found an excellent outlet to discuss positive things happening in government."
|
||||
|
||||
"[Jason Hibbets][34]. I organize the organized chaos here."
|
||||
|
||||
The room has a good chuckle.
|
||||
|
||||
"I organize this chaos too, you could say," says the brownish-red haired fellow with a gleaming white smile. The laughs grow then quieten. Breaths become baited.
|
||||
|
||||
I sat to his left and had a moment to look up from transcribing to glance up. I noticed the hint of a smile behind the knowing eyes of a man who has led the company since January 2008, [Jim Whitehurst][35], president and CEO of Red Hat.
|
||||
|
||||
"I have one of the greatest jobs on Earth," began Whitehurst, as he leaned back, crossed his legs, and put his arms behind his head. "I get to lead Red Hat, travel around the world and see what goes on. In my seven years here, the amazing thing about FOSS, and, broadly open innovation, is that it has left the fringe. And now, I would argue, IT is in the same place that FOSS was in its early days. We are seeing FOSS going from an alternative to driving innovation. Our customers are seeing it, too. They're using FOSS not because it is cheaper, but because it provides them with control and innovative solutions. It's a global phenomenon, too. For instance, I was just in India, and discovered that, for them, there were two reasons for embracing of open source: one, access to innovation, and two, the market is somewhat different and wanting full control.”
|
||||
|
||||
"The [Bombay Stock Exchange][36] wants to own all the source and control it. That is not something you would have heard five years ago in a stock exchange, anywhere. Back then, the early knock on FOSS was that it was creating free copies of things that already existed.' If you look today, virtually everything in big data is happening in FOSS. Almost any new framework, language, and methodology, including mobile (though excluding devices), are all happening first in open source.”
|
||||
|
||||
"This is because users have reached size and scale. It's not just Red Hat—it's [Google][37], [Amazon][38], [Facebook][39], and others, they want to solve their own problems, and do it the open source way. And forget licensing—open source is much more than that. We've built a vehicle, and a set of norms. Things like [Hadoop][40], [Cassandra][41], and other tools. Fact is, open source drives innovation. For example, Hadoop was in production before any vendor realized there was a problem of that scale that needed to be solved. They actually have the wherewithal to solve their own problems, and the social tech and principles to do that. "Open source is now the default technology for many categories. This is especially true as the world moves more and more to content importance, such as [3D printing][42] and other physical products that take information content and apply it.”
|
||||
|
||||
"We have this cool thing in one area, source code, but it is limited. But there are still many opportunities in different industries. We must ask ourselves, 'What can open source do for education, government, and legal? What are the parallels? And what can other areas learn with us?'"
|
||||
|
||||
"There's also the matter of content. Content is now free, and we can invest in more free content, sure. But we need free content that has a business model built around it. That is something that more people should care about. If you believe open innovation is better, then we need more models."
|
||||
|
||||
"Education worries me with its fixation on 'content' rather than 'communities.' For example, everywhere I go, I hear university presidents say, 'Wait, education is going to be free?!' The fact that FOSS is free for downstream is great, but the upstream is really powerful. Distributing free courses is great, but we need communities to iterate and make it better. That is something that a lot of different people are doing, and Opensource.com is a place to share what is going on in this space. The question is not so much 'How do we take content?' as it is 'How do you build and distribute it? How do you make sure it is a living thing that gets better, and can morph for different areas?'"
|
||||
|
||||
"But the potential to change the world is limitless, and it's amazing how much progress we've already made. Six years ago we were obsessed about defining a mission statement. We started by saying, 'We are the leader,' but that was the wrong word, because it implied control. Active participant didn't quite get it either... [Máirín Duffy][43] came up with the word [catalyst][44]. And so, we became Red Hat, the company that creates environments to agitate action and catalyze direction.”
|
||||
|
||||
"Opensource.com is a catalyst in other areas, and that is what Opensource.com is about. I hope you see yourselves this way, too. The quality of content then, when we started, versus now, is incredible. You can see it getting better every quarter. Thank you for investing your time. Thank you for being catalysts. This is a chance for us all to make the world a better place. And I'd love to hear from you."
|
||||
|
||||
I stole a glimpse of everyone at the table: more than a few people had tears in their eyes.
|
||||
|
||||
Then, Whitehurst revisits the open education topic of conversation again. "Taking it to an extreme, let's say you have a course about the book [Ulysses][45]. Here, you can explore how to crowdsource a model and get people to work together within the course. Well, it's the same with a piece of code: people work together, and the code itself gets better over time."
|
||||
|
||||
At this point, I get to have my say. Words like fundamental and possibly irreconcilable came up when discussing the differences between FOSS and academic communities.
|
||||
|
||||
**Remy**: "Retraction is career death." Releasing data or code with your paper could be devastating if you make a mistake. School has always been about avoiding failure and divining 'right answers'. Copying is cheating. Wheels are recreated from scratch ritualistically. In FOSS, you work to fail fastest, but in academia, you invite invalidation."
|
||||
|
||||
**Nicole**: "There are a lot of egos in academia. You need a release manager."
|
||||
|
||||
**Marcus**: "To collaborate, you have to show the bits you don't understand, and that happens behind closed doors. The reward model is all about what you can take credit for. We need to change the reward model. Publish as much as you can. We release eventually, but we want to release early."
|
||||
|
||||
**Luis**: "Make teamwork and sharing a priority. And Red Hat can say that to them more."
|
||||
|
||||
**Jim**: "Is there an active role that companies can play in that?"
|
||||
|
||||
[Phil Shapiro][46]: "I'm interested in tipping points in FOSS. It drives me nuts that the Fed hasn't switched to [LibreOffice][47]. We're not spending tax dollars on software, and certainly shouldn't be spending on word processing or Microsoft Office."
|
||||
|
||||
**Jim**: "We have advocated for that. A lot. Can we do more? That's a valid question. Primarily, we've made progress in the places we have products. We have a solid franchise in government. We are larger per IT spend there than the private sector. Banks and telcos are further along than the government. We've done better in Europe, and I think they have less lobbying dollars at work there, than here. This next generation of computing is almost like a 'do-over'. We are making great progress elsewhere, but it is concerning."
|
||||
|
||||
Suddenly, the door to the room opened. Jim turned and nodded towards his executive assistant standing in the doorway; it was time for his next meeting. He uncrossed his legs, leaned forward, and stood. He thanked everyone again for their work and dedication, smiled, and was out the door... leaving us all a bit more inspired.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/business/14/12/jim-whitehurst-inspiration-open-source
|
||||
|
||||
作者:[Remy][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://opensource.com/users/remyd
|
||||
[1]:http://opensource.com/community-moderator-program
|
||||
[2]:https://twitter.com/jhibbets
|
||||
[3]:http://opensource.com/
|
||||
[4]:http://allthingsopen.org/
|
||||
[5]:http://opensource.com/users/mackanic
|
||||
[6]:https://twitter.com/JenWike
|
||||
[7]:http://opensource.com/users/nengard
|
||||
[8]:http://bywatersolutions.com/
|
||||
[9]:http://opensource.com/life/13/7/community-spotlight-robin-muilwijk
|
||||
[10]:https://en.wikipedia.org/wiki/The_Hague
|
||||
[11]:http://www.denhaag.nl/en.htm
|
||||
[12]:https://twitter.com/mhanwell
|
||||
[13]:http://www.kitware.com/
|
||||
[14]:http://www.nvidia.com/gtx-700-graphics-cards/gtx-titan-z/
|
||||
[15]:https://en.wikipedia.org/wiki/General-purpose_computing_on_graphics_processing_units
|
||||
[16]:https://www.gentoo.org/
|
||||
[17]:http://kde.org/
|
||||
[18]:https://twitter.com/philshapiro
|
||||
[19]:http://opensource.com/community/13/9/contributor-spotlight-joshua-holm
|
||||
[20]:http://opensource.com/users/melanie
|
||||
[21]:http://opensource.com/government
|
||||
[22]:https://twitter.com/jhibbets
|
||||
[23]:https://twitter.com/markbotech
|
||||
[24]:http://scottnesbitt.me/
|
||||
[25]:http://opensource.com/users/luis-ibanez
|
||||
[26]:http://google.com/
|
||||
[27]:http://twitter.com/remy_d
|
||||
[28]:http://foss.rit.edu/
|
||||
[29]:http://igm.rit.edu/
|
||||
[30]:http://www.rit.edu/news/story.php?id=50590
|
||||
[31]:https://twitter.com/jehb
|
||||
[32]:http://openstack.org/
|
||||
[33]:https://twitter.com/markbotech
|
||||
[34]:https://twitter.com/jhibbets
|
||||
[35]:http://www.redhat.com/en/about/company/management/james-whitehurst
|
||||
[36]:http://www.bseindia.com/
|
||||
[37]:http://google.com/
|
||||
[38]:https://mail.corp.redhat.com/service/home/%7E/Amazon
|
||||
[39]:https://mail.corp.redhat.com/service/home/%7E/Facebook
|
||||
[40]:https://hadoop.apache.org/
|
||||
[41]:https://cassandra.apache.org/
|
||||
[42]:https://en.wikipedia.org/wiki/3D_printing
|
||||
[43]:https://twitter.com/mairin
|
||||
[44]:http://jobs.redhat.com/life-at-red-hat/our-culture/
|
||||
[45]:http://www.gutenberg.org/ebooks/4300
|
||||
[46]:https://twitter.com/philshapiro
|
||||
[47]:http://libreoffice.org/
|
||||
45
sources/talk/20141211 Was 2014 The Year of Linux Desktop.md
Normal file
45
sources/talk/20141211 Was 2014 The Year of Linux Desktop.md
Normal file
@ -0,0 +1,45 @@
|
||||
Was 2014 "The Year of Linux Desktop"?
|
||||
================================================================================
|
||||
> The Linux desktop is finally hitting all the right notes
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||

|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
**Linux has seen a lot of changes during 2014 and many users are saying that this was finally the year that really showed some real progress, but has it been enough to call it "the year of Linux desktop"?**
|
||||
|
||||
This particular phrase, "the year of Linux desktop," has been recited like a mantra in the past couple of years and it's basically trying to mark all the progress registered until now in a way that makes sense. This kind of stuff hasn't happened so far and there is no precedent for the kind of growth we're witnessing, so it's easy to understand why Linux users might look at it from this perspective.
|
||||
|
||||
Most software and hardware domains don't usually go through this kind of fast progress and things happen at a slower pace, but things have been wild even for people who have a better insight into the industry. It's hard, if not impossible, to pinpoint a certain moment or a certain event, but Linux development exploded and changed exponentially in the course of just a couple of years.
|
||||
|
||||
### Year of the Linux desktop is an uncertain term ###
|
||||
|
||||
There is no single authority which can decree that the year of the Linux desktop has arrived or that it has passed. We can only try to deduce it from what we've seen until now and it's actually up to the users. Some are more conservative and not too many things have changed for them, and others are more progressive and they just can't get enough. It really depends on what your outlook is.
|
||||
|
||||
The spark that seems to have put everything in motion appears to be the launch of Steam for Linux, although we've seen some important movement of the Linux gaming scene before that became a reality. In any case, Valve is probably the catalyst of the resurgence of what we're seeing today.
|
||||
|
||||
The Linux desktop has been in a kind of slow evolution in the past decade and nothing really changed. There have been a lot of innovations for sure, but the market share has remained almost the same. No matter how cool the desktop became or how many features Linux had well before anyone else, things have remained largely the same, and that includes the participation of companies making proprietary software. They largely ignored Linux.
|
||||
|
||||
Now, more companies have shown interest in the Linux platform in the past year than they did in the last 10. Maybe it's a natural evolution and Valve had nothing to do with it, but Linux has finally reached a level where it can be used and understood by regular users, not just people fascinated by open source.
|
||||
|
||||
The drivers are better, game studios are porting games now on a regular basis, applications and middleware that we never thought we would see on Linux have started to show up, the Linux kernel development has an incredible pace, the installation process for most of the major distros is usually trivial, and all of these are just the tip of the iceberg.
|
||||
|
||||
So, when someone asks you if 2014 was the year of the Linux desktop, you can say yes. The Linux desktop totally ruled in 2014.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://news.softpedia.com/news/Was-2014-The-Year-of-Linux-Desktop-467036.shtml
|
||||
|
||||
作者:[Silviu Stahie ][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://news.softpedia.com/editors/browse/silviu-stahie
|
||||
@ -1,239 +0,0 @@
|
||||
Translating by ZTinoZ
|
||||
10 SCP Commands to Transfer Files/Folders in Linux
|
||||
================================================================================
|
||||
Linux administrator should be familiar with **CLI** environment. Since **GUI** mode in Linux servers is not a common to be installed. **SSH** may the most popular protocol to enable Linux administrator to manage the servers via remote in secure way. Built-in with **SSH** command there is **SCP** command. **SCP** is used to copy file(s) between servers in secure way.
|
||||
|
||||

|
||||
|
||||
The below command will read as “**copy source_file_name**” into “**destination_folder**” at “**destination_host**” using “**username account**”.
|
||||
|
||||
#### Basic syntax of SCP ####
|
||||
|
||||
scp source_file_name username@destination_host:destination_folder
|
||||
|
||||
There are much parameters in **SCP** command that you can use. Here are the parameters that may useful on daily basis usage.
|
||||
|
||||
### Provide the detail information of SCP process using -v parameter ###
|
||||
|
||||
Basic **SCP** command without parameter will copy the files in background. User will see nothing unless the process is done or some error appears. You can use “**-v**” parameter to print debug information into the screen. It can help you debugging connection, authentication and configuration problems.
|
||||
|
||||
pungki@mint ~/Documents $ scp -v Label.pdf mrarianto@202.x.x.x:.
|
||||
|
||||
#### Sample Output ####
|
||||
|
||||
Executing: program /usr/bin/ssh host 202.x.x.x, user mrarianto, command scp -v -t .
|
||||
OpenSSH_6.0p1 Debian-3, OpenSSL 1.0.1c 10 May 2012
|
||||
debug1: Reading configuration data /etc/ssh/ssh_config
|
||||
debug1: /etc/ssh/ssh_config line 19: Applying options for *
|
||||
debug1: Connecting to 202.x.x.x [202.x.x.x] port 22.
|
||||
debug1: Connection established.
|
||||
debug1: Host '202.x.x.x' is known and matches the RSA host key.
|
||||
debug1: Found key in /home/pungki/.ssh/known_hosts:1
|
||||
debug1: ssh_rsa_verify: signature correct
|
||||
debug1: Next authentication method: password
|
||||
mrarianto@202.x.x.x's password:
|
||||
debug1: Authentication succeeded (password).
|
||||
Authenticated to 202.x.x.x ([202.x.x.x]:22).
|
||||
Sending file modes: C0770 3760348 Label.pdf
|
||||
Sink: C0770 3760348 Label.pdf
|
||||
Label.pdf 100% 3672KB 136.0KB/s 00:27
|
||||
Transferred: sent 3766304, received 3000 bytes, in 65.2 seconds
|
||||
Bytes per second: sent 57766.4, received 46.0
|
||||
debug1: Exit status 0
|
||||
|
||||
### Provide modification times, access times, and modes from original files ###
|
||||
|
||||
The “**-p**” parameter will help you on this. An estimated time and the connection speed will appear on the screen.
|
||||
|
||||
pungki@mint ~/Documents $ scp -p Label.pdf mrarianto@202.x.x.x:.
|
||||
|
||||
#### Sample Output ####
|
||||
|
||||
mrarianto@202.x.x.x's password:
|
||||
Label.pdf 100% 3672KB 126.6KB/s 00:29
|
||||
|
||||
### Make file transfer faster using -C parameter ###
|
||||
|
||||
One of parameter that can faster your file transfer is “**-C**” parameter. The “**-C**” parameter will compress your files on the go. The unique thing is the compression is only happen in the network. When the file is arrived to the destination server, it will returning into the original size as before the compression happen.
|
||||
|
||||
Take a look of these commands. It is using a single file of **93 Mb**.
|
||||
|
||||
pungki@mint ~/Documents $ scp -pv messages.log mrarianto@202.x.x.x:.
|
||||
|
||||
#### Sample Output ####
|
||||
|
||||
Executing: program /usr/bin/ssh host 202.x.x.x, user mrarianto, command scp -v -p -t .
|
||||
OpenSSH_6.0p1 Debian-3, OpenSSL 1.0.1c 10 May 2012
|
||||
debug1: Reading configuration data /etc/ssh/ssh_config
|
||||
debug1: /etc/ssh/ssh_config line 19: Applying options for *
|
||||
debug1: Connecting to 202.x.x.x [202.x.x.x] port 22.
|
||||
debug1: Connection established.
|
||||
debug1: identity file /home/pungki/.ssh/id_rsa type -1
|
||||
debug1: Found key in /home/pungki/.ssh/known_hosts:1
|
||||
debug1: ssh_rsa_verify: signature correct
|
||||
debug1: Trying private key: /home/pungki/.ssh/id_rsa
|
||||
debug1: Next authentication method: password
|
||||
mrarianto@202.x.x.x's password:
|
||||
debug1: Authentication succeeded (password).
|
||||
Authenticated to 202.x.x.x ([202.x.x.x]:22).
|
||||
debug1: Sending command: scp -v -p -t .
|
||||
File mtime 1323853868 atime 1380425711
|
||||
Sending file timestamps: T1323853868 0 1380425711 0
|
||||
messages.log 100% 93MB 58.6KB/s 27:05
|
||||
Transferred: sent 97614832, received 25976 bytes, in 1661.3 seconds
|
||||
Bytes per second: sent 58758.4, received 15.6
|
||||
debug1: Exit status 0
|
||||
|
||||
Copying file without “**-C**” parameter will result **1661.3** second. Yo may compare the result to the command below which using “**-C**” parameter.
|
||||
|
||||
pungki@mint ~/Documents $ scp -Cpv messages.log mrarianto@202.x.x.x:.
|
||||
|
||||
#### Sample Output ####
|
||||
|
||||
Executing: program /usr/bin/ssh host 202.x.x.x, user mrarianto, command scp -v -p -t .
|
||||
OpenSSH_6.0p1 Debian-3, OpenSSL 1.0.1c 10 May 2012
|
||||
debug1: Reading configuration data /etc/ssh/ssh_config
|
||||
debug1: /etc/ssh/ssh_config line 19: Applying options for *
|
||||
debug1: Connecting to 202.x.x.x [202.x.x.x] port 22.
|
||||
debug1: Connection established.
|
||||
debug1: identity file /home/pungki/.ssh/id_rsa type -1
|
||||
debug1: Host '202.x.x.x' is known and matches the RSA host key.
|
||||
debug1: Found key in /home/pungki/.ssh/known_hosts:1
|
||||
debug1: ssh_rsa_verify: signature correct
|
||||
debug1: Next authentication method: publickey
|
||||
debug1: Trying private key: /home/pungki/.ssh/id_rsa
|
||||
debug1: Next authentication method: password
|
||||
mrarianto@202.x.x.x's password:
|
||||
debug1: Enabling compression at level 6.
|
||||
debug1: Authentication succeeded (password).
|
||||
Authenticated to 202.x.x.x ([202.x.x.x]:22).
|
||||
debug1: channel 0: new [client-session]
|
||||
debug1: Sending command: scp -v -p -t .
|
||||
File mtime 1323853868 atime 1380428748
|
||||
Sending file timestamps: T1323853868 0 1380428748 0
|
||||
Sink: T1323853868 0 1380428748 0
|
||||
Sending file modes: C0600 97517300 messages.log
|
||||
messages.log 100% 93MB 602.7KB/s 02:38
|
||||
Transferred: sent 8905840, received 15768 bytes, in 162.5 seconds
|
||||
Bytes per second: sent 54813.9, received 97.0
|
||||
debug1: Exit status 0
|
||||
debug1: compress outgoing: raw data 97571111, compressed 8806191, factor 0.09
|
||||
debug1: compress incoming: raw data 7885, compressed 3821, factor 0.48
|
||||
|
||||
As you can see, when you are using compression, transfer process is done in **162.5** second. It is **10** times faster than not using “**-C**” parameter. If you are copying a lot files across the network, “**-C**” parameter would help you to decrease the total time you need.
|
||||
|
||||
The thing that we should notice that compression method will not work on any files. When the source file is already compressed, you will not find any improvement there. Files such as **.zip**, **.rar**, **pictures**, and **.iso** files will not affected by “**-C**” parameter.
|
||||
|
||||
### Select another cipher to encrypt files ###
|
||||
|
||||
By default **SCP** using “**AES-128**” to encrypt files. If you want to change to another cipher to encrypt it, you can use “**-c**” parameter. Take a look of this command.
|
||||
|
||||
pungki@mint ~/Documents $ scp -c 3des Label.pdf mrarianto@202.x.x.x:.
|
||||
|
||||
mrarianto@202.x.x.x's password:
|
||||
Label.pdf 100% 3672KB 282.5KB/s 00:13
|
||||
|
||||
Above command tell **SCP** to use **3des algorithm** to encrypt file. Please be careful that this parameter using “**-c**” not “**-C**“.
|
||||
|
||||
### Limiting bandwidth usage ###
|
||||
|
||||
Another parameter that may useful is “**-l**” parameter. The “**-l**” parameter will limit the bandwidth to use. It will be useful if you do an automation script to copy a lot of file, but you don’t want the bandwidth is drained by the **SCP** process.
|
||||
|
||||
pungki@mint ~/Documents $ scp -l 400 Label.pdf mrarianto@202.x.x.x:.
|
||||
|
||||
mrarianto@202.x.x.x's password:
|
||||
Label.pdf 100% 3672KB 50.3KB/s 01:13
|
||||
|
||||
The **400** value behind “**-l**” parameter is mean that we limit the bandwidth for **SCP** process only **50 KB/sec**. One thing to remember that bandwidth is specified in **Kilobits/sec** (**kbps**). It is mean that **8 bits** equal with **1 byte**.
|
||||
|
||||
While **SCP** counts in **Kilobyte/sec** (**KB/s**). So if you want to limit your bandwidth for **SCP** maximum only **50 KB/s**, you need to set it into **50 x 8 = 400**.
|
||||
|
||||
### Specify specific port to use with SCP ###
|
||||
|
||||
Usually **SCP** is using port **22** as a default port. But for security reason, you may change the port into another port. For example, we are using port **2249**. Then the command should be like this.
|
||||
|
||||
pungki@mint ~/Documents $ scp -P 2249 Label.pdf mrarianto@202.x.x.x:.
|
||||
|
||||
mrarianto@202.x.x.x's password:
|
||||
Label.pdf 100% 3672KB 262.3KB/s 00:14
|
||||
|
||||
Make sure that it use capital “**P**” not “**p**“, since “**p**” is already used for preserved times and modes.
|
||||
|
||||
### Copy files inside directory recursively ###
|
||||
|
||||
Sometimes we need to copy directory and all **files** / **directories** inside it. It will be better if we can do it in **1** command. **SCP** support that scenario using “**-r**” parameter.
|
||||
|
||||
pungki@mint ~/Documents $ scp -r documents mrarianto@202.x.x.x:.
|
||||
|
||||
mrarianto@202.x.x.x's password:
|
||||
Label.pdf 100% 3672KB 282.5KB/s 00:13
|
||||
scp.txt 100% 10KB 9.8KB/s 00:00
|
||||
|
||||
When the copy process is done, at the destination server you will found a directory named “**documents**” with all it’s files. The folder “**documents**” is automatically created.
|
||||
|
||||
### Disable progress meter and warning / diagnostic message ###
|
||||
|
||||
If you choose not to see progress meter and warning / diagnostic messages from SCP, you may disable it using “**-q**” parameter. Here’s the example.
|
||||
|
||||
pungki@mint ~/Documents $ scp -q Label.pdf mrarianto@202.x.x.x:.
|
||||
|
||||
mrarianto@202.x.x.x's password:
|
||||
pungki@mint ~/Documents $
|
||||
|
||||
As you can see, after the you enter the password, there is no any information about SCP process. After the process is complete, you will be see a prompt again.
|
||||
|
||||
### Copy files using SCP through Proxy ###
|
||||
|
||||
Proxy server is usually used in office environment. Natively, SCP is not proxy configured. When your environment using proxy, you have to “tell” SCP to communicate with the proxy.
|
||||
|
||||
Here’s the scenario. The proxy address is **10.0.96.6** and the proxy port is **8080**. The proxy also implemented user authentication. First, you need to create “**~/.ssh/config**” file. Second you put this command inside it.
|
||||
|
||||
ProxyCommand /usr/bin/corkscrew 10.0.96.6 8080 %h %p ~/.ssh/proxyauth
|
||||
|
||||
Then you need to create file “**~/.ssh/proxyauth**” which contain.
|
||||
|
||||
myusername:mypassword
|
||||
|
||||
After that you can do SCP transparently as usual.
|
||||
|
||||
Please notice that corkscrew is might not installed yet on your system. On my Linux Mint, I need to install it first, using standard Linux Mint installation procedure.
|
||||
|
||||
$ apt-get install corkscrew
|
||||
|
||||
For other yum based systems, users can install corkscrew using the following yum command.
|
||||
|
||||
# yum install corkscrew
|
||||
|
||||
Another thing that since “**~/.ssh/proxyauth**” file contain your “**username**” and “**password**” in clear-text format, please make sure that the file can be accessed by you only.
|
||||
|
||||
### Select different ssh_config file ###
|
||||
|
||||
For mobile user who often switch between company network and public network, it will be suffer to always change settings in SCP. It is better if we can put a different **ssh_config** file to match our needs.
|
||||
|
||||
#### Here’s a sample scenario ####
|
||||
|
||||
Proxy is used in company network but not in public network and you are regularly switch network.
|
||||
|
||||
pungki@mint ~/Documents $ scp -F /home/pungki/proxy_ssh_config Label.pdf
|
||||
|
||||
mrarianto@202.x.x.x:.
|
||||
mrarianto@202.x.x.x's password:
|
||||
Label.pdf 100% 3672KB 282.5KB/s 00:13
|
||||
|
||||
By default “**ssh_config**” file per user will be placed in “**~/.ssh/config**“. Creating a specific “**ssh_config**” file with proxy compatible, will make you easier to switch between networks.
|
||||
|
||||
When you are on company network, you can use “**-F**” parameter. When you are on public network, you can skip “**-F**” parameter.
|
||||
|
||||
That’s all about **SCP**. You can see **man pages** of **SCP** for more detail. Please feel free to leave comments and suggestions.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.tecmint.com/scp-commands-examples/
|
||||
|
||||
作者:[Pungki Arianto][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.tecmint.com/author/pungkiarianto/
|
||||
@ -1,131 +0,0 @@
|
||||
[su-kaiyao]translating
|
||||
|
||||
10 ‘free’ Commands to Check Memory Usage in Linux
|
||||
================================================================================
|
||||
**Linux** is one of the most popular open source operating system and comes with huge set of commands. The most important and single way of determining the total available space of the **physical memory** and **swap memory** is by using “**free**” command.
|
||||
|
||||
The Linux “**free**” command gives information about total used and available space of **physical memory** and **swap memory** with **buffers** used by kernel in **Linux/Unix** like operating systems.
|
||||
|
||||

|
||||
|
||||
This article provides some useful examples of “**free**” commands with options, that might be useful for you to better utilize memory that you have.
|
||||
|
||||
### 1. Display System Memory ###
|
||||
|
||||
Free command used to check the used and available space of **physical memory** and **swap memory** in **KB**. See the command in action below.
|
||||
|
||||
# free
|
||||
|
||||
total used free shared buffers cached
|
||||
Mem: 1021628 912548 109080 0 120368 655548
|
||||
-/+ buffers/cache: 136632 884996
|
||||
Swap: 4194296 0 4194296
|
||||
|
||||
### 2. Display Memory in Bytes ###
|
||||
|
||||
Free command with option **-b**, display the size of memory in **Bytes**.
|
||||
|
||||
# free -b
|
||||
|
||||
total used free shared buffers cached
|
||||
Mem: 1046147072 934420480 111726592 0 123256832 671281152
|
||||
-/+ buffers/cache: 139882496 906264576
|
||||
Swap: 4294959104 0 4294959104
|
||||
|
||||
### 3. Display Memory in Kilo Bytes ###
|
||||
|
||||
Free command with option **-k**, display the size of memory in (KB) **Kilobytes**.
|
||||
|
||||
# free -k
|
||||
|
||||
total used free shared buffers cached
|
||||
Mem: 1021628 912520 109108 0 120368 655548
|
||||
-/+ buffers/cache: 136604 885024
|
||||
Swap: 4194296 0 4194296
|
||||
|
||||
### 4. Display Memory in Megabytes ###
|
||||
|
||||
To see the size of the memory in **(MB) Megabytes** use option as **-m**.
|
||||
|
||||
# free -m
|
||||
|
||||
total used free shared buffers cached
|
||||
Mem: 997 891 106 0 117 640
|
||||
-/+ buffers/cache: 133 864
|
||||
Swap: 4095 0 4095
|
||||
|
||||
### 5. Display Memory in Gigabytes ###
|
||||
|
||||
Using **-g** option with free command, would display the size of the memory in **GB(Gigabytes)**.
|
||||
|
||||
# free -g
|
||||
total used free shared buffers cached
|
||||
Mem: 0 0 0 0 0 0
|
||||
-/+ buffers/cache: 0 0
|
||||
Swap: 3 0 3
|
||||
|
||||
### 6. Display Total Line ###
|
||||
|
||||
Free command with -t option, will list the total line at the end.
|
||||
|
||||
# free -t
|
||||
|
||||
total used free shared buffers cached
|
||||
Mem: 1021628 912520 109108 0 120368 655548
|
||||
-/+ buffers/cache: 136604 885024
|
||||
Swap: 4194296 0 4194296
|
||||
Total: 5215924 912520 4303404
|
||||
|
||||
### 7. Disable Display of Buffer Adjusted Line ###
|
||||
|
||||
By default the free command display “**buffer adjusted**” line, to disable this line use option as -o.
|
||||
|
||||
# free -o
|
||||
|
||||
total used free shared buffers cached
|
||||
Mem: 1021628 912520 109108 0 120368 655548
|
||||
Swap: 4194296 0 4194296
|
||||
|
||||
### 8. Dispaly Memory Status for Regular Intervals ###
|
||||
|
||||
The -s option with number, used to update free command at regular intervals. For example, the below command will update free command every 5 seconds.
|
||||
|
||||
# free -s 5
|
||||
|
||||
total used free shared buffers cached
|
||||
Mem: 1021628 912368 109260 0 120368 655548
|
||||
-/+ buffers/cache: 136452 885176
|
||||
Swap: 4194296 0 4194296
|
||||
|
||||
### 9. Show Low and High Memory Statistics ###
|
||||
|
||||
The -l switch displays detailed high and low memory size statistics.
|
||||
|
||||
# free -l
|
||||
|
||||
total used free shared buffers cached
|
||||
Mem: 1021628 912368 109260 0 120368 655548
|
||||
Low: 890036 789064 100972
|
||||
High: 131592 123304 8288
|
||||
-/+ buffers/cache: 136452 885176
|
||||
Swap: 4194296 0 4194296
|
||||
|
||||
### 10. Check Free Version ###
|
||||
|
||||
The -V option, display free command version information.
|
||||
|
||||
# free -V
|
||||
|
||||
procps version 3.2.8
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.tecmint.com/check-memory-usage-in-linux/
|
||||
|
||||
作者:[Ravi Saive][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.tecmint.com/author/admin/
|
||||
@ -1,3 +1,4 @@
|
||||
(translating by runningwater)
|
||||
How To Create A Bootable Ubuntu USB Drive For Mac In OS X
|
||||
================================================================================
|
||||

|
||||
@ -133,7 +134,7 @@ I hope this guide helped you to create a bootable USB disk of Ubuntu for Mac in
|
||||
via: http://itsfoss.com/create-bootable-ubuntu-usb-drive-mac-os/
|
||||
|
||||
作者:[Abhishek][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
译者:[runningwater](https://github.com/runningwater)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,155 +0,0 @@
|
||||
What is a good free control panel for VPS
|
||||
================================================================================
|
||||
Anyone with a reasonable level of Linux skills knows that no control panel can beat the plain-old command line interface for managing a [virtual private server][1] (VPS). One can still argue that there is a place for a good server control panel though, due to the streamlined interface for getting routine administration tasks done easily with a few mouse clicks.
|
||||
|
||||
As far as control panels are concerned, even with the feature-rich commercial control panels with all the bells and whistles, there are viable free open-source alternatives which can be as powerful and versatile. Standing out among them is [Ajenti][2] server administration panel.
|
||||
|
||||
Ajenti allows you to easily configure a variety of common server programs such as Apache/nginx, Samba, BIND, Squid, MySQL, cron, firewall, and so on, making it a great time saver for administering common VPS instances. For production environments, Ajenti also offers add-ons and platform support for virtual web hosting management and custom web UI development.
|
||||
|
||||
Ajenti comes with a [dual license][3]; It is free to use (AGPLv3) for your personal servers, a company's internal hardware boxes, or educational institutions. However, if you are a hosting company or a hardware vendor, you need to purchase a commercial license to use Ajenti as part of commercial offerings.
|
||||
|
||||
### Install Ajenti on Linux ###
|
||||
|
||||
For easy of installation, Ajenti offers its own repository for major Linux distros. All it takes to install Ajenti on Linux is to configure a target repository and install it with a default package manager.
|
||||
|
||||
Upon installation, a RSA private key and certificate will be automatically generated for SSL, and Ajenti will listen on HTTPS port 8000 for secure web access. If you are using firewall, you need to allow TCP/8000 port in the firewall. For security, it is a good idea to block access to port 8000 by default, and add only selected few IP addresses to the white list.
|
||||
|
||||
#### Install Ajenti on Debian ####
|
||||
|
||||
$ wget http://repo.ajenti.org/debian/key -O- | sudo apt-key add -
|
||||
$ sudo sh -c 'echo "deb http://repo.ajenti.org/debian main main debian" >> /etc/apt/sources.list'
|
||||
$ sudo apt-get update
|
||||
$ sudo apt-get install ajenti
|
||||
|
||||
#### Install Ajenti on Ubuntu ####
|
||||
|
||||
$ wget http://repo.ajenti.org/debian/key -O- | sudo apt-key add -
|
||||
$ sudo sh -c 'echo "deb http://repo.ajenti.org/ng/debian main main ubuntu" >> /etc/apt/sources.list'
|
||||
$ sudo apt-get update
|
||||
$ sudo apt-get install ajenti
|
||||
|
||||
#### Install Ajenti on CentOS/RHEL or Fedora ####
|
||||
|
||||
On CentOS/RHEL, [configure][4] EPEL repository first, and then run the following. On Fedora, use the following commands directly.
|
||||
|
||||
$ wget http://repo.ajenti.org/ajenti-repo-1.0-1.noarch.rpm
|
||||
$ sudo rpm -ivh ajenti-repo-1.0-1.noarch.rpm
|
||||
$ sudo yum install ajenti
|
||||
|
||||
Next, configure the firewall.
|
||||
|
||||
On Fedora or CentOS/RHEL 7:
|
||||
|
||||
$ sudo firewall-cmd --zone=public --add-port=8000/tcp --permanent
|
||||
$ sudo firewall-cmd --reload
|
||||
|
||||
On CentOS/RHEL 6:
|
||||
|
||||
$ sudo iptables -I INPUT -p tcp -m tcp --dport 8000 -j ACCEPT
|
||||
$ sudo service iptables save
|
||||
|
||||
### Access Ajenti Web Interface ###
|
||||
|
||||
Before accessing Ajenti's web interface, make sure to start ajenti service.
|
||||
|
||||
$ sudo service ajenti restart
|
||||
|
||||
Direct your web browser to https://<server-ip-address>:8000, and you will see the following Ajenti login interface.
|
||||
|
||||

|
||||
|
||||
The default login credential is "root" for username and "admin" for password. Once you log in, you will see the initial Ajengi menu.
|
||||
|
||||
|
||||
|
||||
Under "SOFTWARE" section in the left panel, you will see a list of installed services. When you install any new server software supported by Ajenti, the software will be automatically added to the list once you restart ajenti service.
|
||||
|
||||
$ sudo service ajenti restart
|
||||
|
||||
### VPS Management via Ajenti Web Interface ###
|
||||
|
||||
Ajenti's web interface is extremely intuitive and easy to use. Here are a few examples of Ajenti functionality.
|
||||
|
||||
#### Pluggable Architecture ####
|
||||
|
||||
Ajenti comes with a number of application-specific plugins, which makes Ajenti highly extensible. When you install a new software on your VPS, a corresponding Ajenti plugin (if any) will be automatically enabled to manage the software. The "Plugins" menu will show what plugins are available/enabled, and which plugin is associated with what software.
|
||||
|
||||
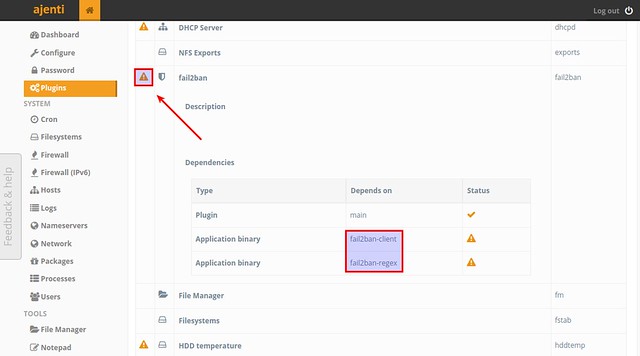
|
||||
|
||||
#### Package Management ####
|
||||
|
||||
Ajenti offers a web interface for installing and upgrading packages on VPS.
|
||||
|
||||
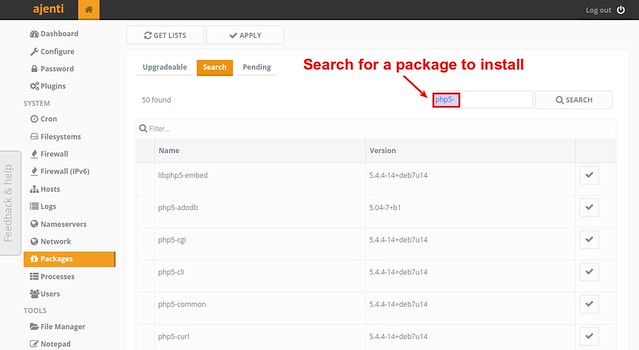
|
||||
|
||||
#### Firewall Configuration ####
|
||||
|
||||
Ajenti allows you to manage firewall rules (iptables or CSF) in two ways. One is to use a user-friendly web panel interface, and the other is to edit raw firewall rules directly.
|
||||
|
||||
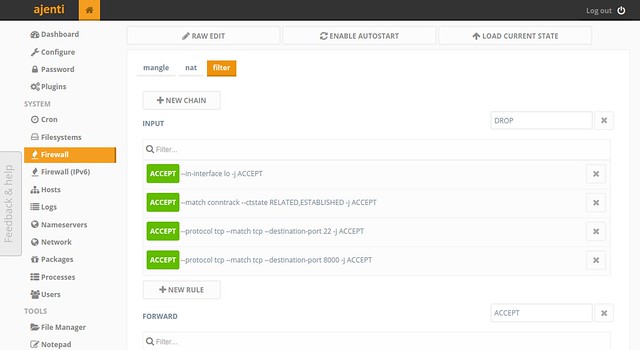
|
||||
|
||||
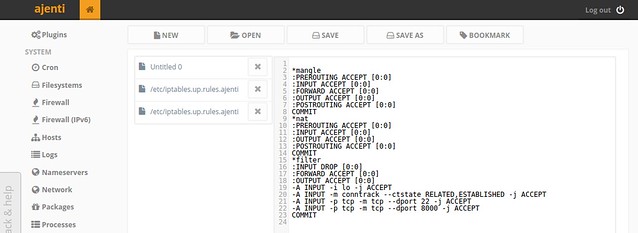
|
||||
|
||||
#### Log Inspection ####
|
||||
|
||||
You can browse system logs in /var/log via Ajenti's web interface.
|
||||
|
||||
|
||||
|
||||
#### Process Monitoring ####
|
||||
|
||||
You can see a list of processes sorted by CPU or RAM usage, and can kill them as needed.
|
||||
|
||||
|
||||
|
||||
#### Terminal Access ####
|
||||
|
||||
For low-level VPS access, Ajenti offers a web-based terminal interface where you can type Linux commands. You can open multiple terminal tabs within a web panel as shown below.
|
||||
|
||||
|
||||
|
||||
#### Apache Web Server Administration ####
|
||||
|
||||
You can edit Apache configuration file, and manage apache2 service.
|
||||
|
||||
|
||||
|
||||
#### MySQL/MariaDB Management ####
|
||||
|
||||
You can access MySQL/MariaDB server and execute raw SQL commands on it.
|
||||
|
||||
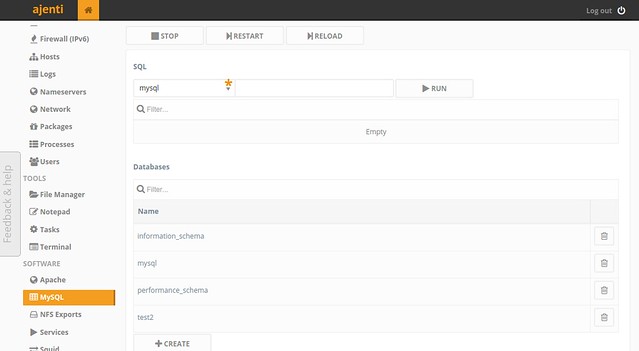
|
||||
|
||||
#### Squid Configuration ####
|
||||
|
||||
You can configure ACL, HTTP access rules, filtering ports for Squid proxy server.
|
||||
|
||||
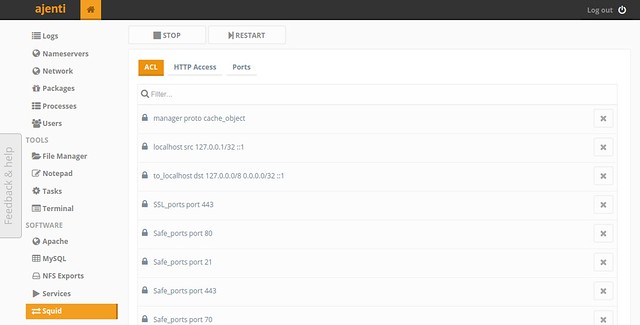
|
||||
|
||||
#### Startup Service Management ####
|
||||
|
||||
You can view, start, stop and restart installed services.
|
||||
|
||||
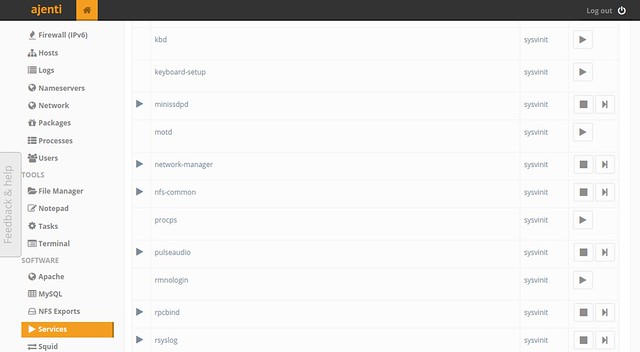
|
||||
|
||||
### Conclusion ###
|
||||
|
||||
Ajenti is a convenient and easy-to-use web control panel for common server administration, with the possibility to add [custom plugins][5] that you can develop. However, remember that any good control panel does not obviate the need for you to learn what's happening behind the scene on your [VPS][6]. A control panel will become a real time saver only when you fully understand what you are doing, and be able to handle the consequence of your action without relying on the control panel.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/free-control-panel-for-vps.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/nanni
|
||||
[1]:http://xmodulo.com/go/digitalocean
|
||||
[2]:http://ajenti.org/
|
||||
[3]:http://ajenti.org/licensing
|
||||
[4]:http://xmodulo.com/how-to-set-up-epel-repository-on-centos.html
|
||||
[5]:http://docs.ajenti.org/en/latest/dev/intro.html
|
||||
[6]:http://xmodulo.com/go/digitalocean
|
||||
@ -1,106 +0,0 @@
|
||||
Install Jetty 9 (Java servlet engine and webserver) on Ubuntu 14.10 Server
|
||||
================================================================================
|
||||
Jetty provides a Web server and javax.servlet container, plus support for SPDY, WebSocket, OSGi, JMX, JNDI, JAAS and many other integrations. These components are open source and available for commercial use and distribution.
|
||||
|
||||
Jetty is used in a wide variety of projects and products, both in development and production. Jetty can be easily embedded in devices, tools, frameworks, application servers, and clusters. See the Jetty Powered page for more uses of Jetty.
|
||||
|
||||
### Jetty Features ###
|
||||
|
||||
- Full-featured and standards-based
|
||||
- Open source and commercially usable
|
||||
- Flexible and extensible
|
||||
- Small footprint
|
||||
- Embeddable
|
||||
- Asynchronous
|
||||
- Enterprise scalable
|
||||
- Dual licensed under Apache and Eclipse
|
||||
|
||||
### Install Jetty9 on ubuntu 14.10 server ###
|
||||
|
||||
#### Prerequisites ####
|
||||
|
||||
You need to install Java before installing jetty server using the following command
|
||||
|
||||
sudo apt-get install openjdk-8-jdk
|
||||
|
||||
This will install it to /usr/lib/jvm/java-8-openjdk-i386. A symlink java-1.8.0-openjdk-i386 is created in the directory /usr/lib/jvm/. A symlink is also created at /usr/bin/java
|
||||
|
||||
Now you need to download Jetty9 from [here][1] after downloading you need to extract using the following command
|
||||
|
||||
$tar -xvf jetty-distribution-9.2.5.v20141112.tar.gz
|
||||
|
||||
This unpacks the jetty-distribution-9.2.5.v20141112 and you need to Move the archive to /opt/jetty using the following command
|
||||
|
||||
$mv jetty-distribution-9.2.5.v20141112 /opt/jetty
|
||||
|
||||
You need to Create jetty user and make it the owner of /opt/jetty directory
|
||||
|
||||
sudo useradd jetty -U -s /bin/false
|
||||
|
||||
sudo chown -R jetty:jetty /opt/jetty
|
||||
|
||||
#### Jetty Startup Script ####
|
||||
|
||||
Copy the Jetty script to run as a service using the following command
|
||||
|
||||
$ cp /opt/jetty/bin/jetty.sh /etc/init.d/jetty
|
||||
|
||||
Now you need to create jetty settings file with the following content
|
||||
|
||||
sudo vi /etc/default/jetty
|
||||
|
||||
Add the following lines
|
||||
|
||||
JAVA_HOME=/usr/bin/java
|
||||
JETTY_HOME=/opt/jetty
|
||||
NO_START=0
|
||||
JETTY_ARGS=jetty.port=8085
|
||||
JETTY_HOST=0.0.0.0
|
||||
JETTY_USER=jetty
|
||||
|
||||
Save and exit the file
|
||||
|
||||
You need to start jetty service using the following command
|
||||
|
||||
sudo service jetty start
|
||||
|
||||
You should see output similar to the following
|
||||
|
||||
Starting Jetty: OK Mon Nov 24 11:55:48 GMT 2014
|
||||
|
||||
If you see the following error
|
||||
|
||||
#### ** ERROR: JETTY_HOME not set, you need to set it or install in a standard location ####
|
||||
|
||||
You need to make sure you have correct jetty home path in /etc/default/jetty file i.e JETTY_HOME=/opt/jetty
|
||||
|
||||
You can test the jetty using the following URL
|
||||
|
||||
It should now be running on port 8085! Visit in your browser http://serverip:8085 and you should see a Jetty screen.
|
||||
|
||||
#### Jetty Service checking ####
|
||||
|
||||
Verify and check your configuration with the following command
|
||||
|
||||
sudo service jetty check
|
||||
|
||||
Jetty automatically start on reboot using the following command
|
||||
|
||||
sudo update-rc.d jetty defaults
|
||||
|
||||
Reboot the server and test if Jetty starts automatically.
|
||||
|
||||
To check which port Jetty is running or whether there are any conflicts with other programs for that port, run netstat -tln
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.ubuntugeek.com/install-jetty-9-java-servlet-engine-and-webserver-on-ubuntu-14-10-server.html
|
||||
|
||||
作者:[ruchi][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.ubuntugeek.com/author/ubuntufix
|
||||
[1]:http://download.eclipse.org/jetty/stable-9/dist/
|
||||
@ -1,44 +0,0 @@
|
||||
Linux FAQs with Answers--How to crop an image from the command line on Linux
|
||||
================================================================================
|
||||
> **Question**: I would like to get rid of white margins of an image file. Is there an easy way to crop an image file from the command line on Linux?
|
||||
|
||||
When it comes to converting or editing images files on Linux, ImageMagick is undoubtedly one of the best known all-in-one image software. It boasts of a suite of command-line tools to display, convert, or manipulate more than 200 types of raster or vector image files, all from the command line. ImageMagick can be used for a variety of image editing tasks, such as converting file format, adding special effects, adding text, and transforming (resize, rotate, flip, crop) images.
|
||||
|
||||
If you want to crop an image to trim its margins, you can use two command-line utilities that come with ImageMagick. If you haven't installed ImageMagick, follow [this guideline][1] to install it.
|
||||
|
||||
In this tutorial, let's crop the following PNG image. We want to get rid of the right and bottom margins of the image, so that the chart will be centered.
|
||||
|
||||

|
||||
|
||||
First, identify the dimension (width and height) of the image file. You can use identify command for that.
|
||||
|
||||
$ identify chart.png
|
||||
|
||||
----------
|
||||
|
||||
chart.png PNG 1500x1000 1500x1000+0+0 8-bit DirectClass 31.7KB 0.000u 0:00.000
|
||||
|
||||
As shown above, the input image is 1500x1000px.
|
||||
|
||||
Next, determine two things for image cropping: (1) the position at which the cropped image will start, and (2) the size of the cropped rectangle.
|
||||
|
||||
In this example, let's assume that the cropped image starts at top left corner, more specifically at x=20px and y=10px, and that the size of a cropped image will be 1200x700px.
|
||||
|
||||
The utility used to crop an image is convert. With "-crop" option, the convert command cuts out a rectangular region of an input image.
|
||||
|
||||
$ convert chart.png -crop 1200x700+20+10 chart-cropped.png
|
||||
|
||||
Given the input image chart.png, the convert command will store the cropped image as chart-cropped.png.
|
||||
|
||||

|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://ask.xmodulo.com/crop-image-command-line-linux.html
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://ask.xmodulo.com/install-imagemagick-linux.html
|
||||
@ -1,44 +0,0 @@
|
||||
Vic020
|
||||
|
||||
Linux FAQs with Answers--How to disable Apport internal error reporting on Ubuntu
|
||||
================================================================================
|
||||
> **Question**: On Ubuntu desktop, I often encounter a popup window, alerting that Ubuntu has experienced an internal error, and asking me to send an error report. This is bothering me as it keeps popping up for every application crash. How can I turn off the error reporting feature?
|
||||
|
||||
Ubuntu desktop comes with Apport pre-installed, which is a system that catches applications crashes, unhandled exceptions or any non-crash application bugs, and automatically generates a crash report for debugging purposes. When an application crash or bug is detected, Apport alerts user of the event by showing a popup window and asking the user to submit a crash report. You will see messages like the following.
|
||||
|
||||
- "Sorry, the application XXXX has closed unexpectedly."
|
||||
- "Sorry, Ubuntu XX.XX has experienced an internal error."
|
||||
- "System program problem detected."
|
||||
|
||||
|
||||
|
||||
If application crashes are recurring, frequent error reporting alerts can be disturbing. Or you may be worried that Apport can collect and upload any sensitive information of your Ubuntu system. Whatever the reason is, you may want to disable Apport's error reporting feature.
|
||||
|
||||
### Disable Apport Error Reporting Temporarily ###
|
||||
|
||||
If you want to disable Apport temporarily, use this command:
|
||||
|
||||
$ sudo service apport stop
|
||||
|
||||
Note that Apport will be enabled back after you boot your Ubuntu system.
|
||||
|
||||
### Disable Apport Error Reporting Permanently ###
|
||||
|
||||
To turn off Apport permanently, edit /etc/default/apport with a text editor, and change the content to the following.
|
||||
|
||||
enabled=0
|
||||
|
||||
Now if you reboot your Ubuntu system, Apport will automatically be disabled.
|
||||
|
||||
If you think you will never use Apport, another method is to simply remove it altogether.
|
||||
|
||||
$ sudo apt-get purge apport
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://ask.xmodulo.com/disable-apport-internal-error-reporting-ubuntu.html
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
@ -0,0 +1,249 @@
|
||||
文章重复
|
||||
How to create a custom backup plan for Debian with backupninja
|
||||
================================================================================
|
||||
Backupninja is a powerful and highly-configurable backup tool for Debian based distributions. In the [previous tutorial][1], we explored how to install backupninja and how to set up two backup actions for the program to perform. However, we should note that those examples were only "the tip of the iceberg," so to speak. In this post we will discuss how to leverage custom handlers and helpers that allow this program to be customized in order to accomplish almost any backup need that you can think of.
|
||||
|
||||
And believe me - that is not an overstatement, so let's begin.
|
||||
|
||||
### A Quick Review of Backupninja ###
|
||||
|
||||
One of backupninja's distinguishing features is the fact that you can just drop plain text configuration or action files in /etc/backup.d, and the program will take care of the rest. In addition, we can write custom scripts (aka "handlers") and place them in /usr/share/backupninja to handle each type of backup action. Furthermore, we can have these scripts be executed via ninjahelper's ncurses-based interactive menus (aka "helpers") to guide us to create the configuration files we mentioned earlier, minimizing the chances of human error.
|
||||
|
||||
### Creating a Custom Handler and Helper ###
|
||||
|
||||
Our goal in this case is to create a script to handle the backup of chosen home directories into a tarball with either gzip or bzip2 compression, excluding music and video files. We will simply name this script home, and place it under /usr/backup/ninja.
|
||||
|
||||
Although you could achieve the same objective with the default tar handler (refer to /usr/share/backupninja/tar and /usr/share/backupninja/tar.helper), we will use this approach to show how to create a useful handler script and ncurses-based helper from scratch. You can then decide how to apply the same principles depending on your specific needs.
|
||||
|
||||
Note that since handlers are sourced from the main script, there is no need to start with #!/bin/bash at the top.
|
||||
|
||||
Our proposed handler (/usr/share/backupninja/home) is as follows. It is heavily commented for clarification. The getconf function is used to read the backup action's configuration file. If you specify a value for a variable here, it will override the corresponding value present in the configuration file:
|
||||
|
||||
# home handler script for backupninja
|
||||
|
||||
# Every backup file will identify the host by its FQDN
|
||||
getconf backupname
|
||||
|
||||
# Directory to store backups
|
||||
getconf backupdir
|
||||
|
||||
# Default compression
|
||||
getconf compress
|
||||
|
||||
# Include /home directory
|
||||
getconf includes
|
||||
|
||||
# Exclude files with *.mp3 and *.mp4 extensions
|
||||
getconf excludes
|
||||
|
||||
# Default extension for the packaged backup file
|
||||
getconf EXTENSION
|
||||
|
||||
# Absolute path to date binary
|
||||
getconf TAR `which tar`
|
||||
|
||||
# Absolute path to date binary
|
||||
getconf DATE `which date`
|
||||
|
||||
# Chosen date format
|
||||
DATEFORMAT="%Y-%m-%d"
|
||||
|
||||
# If backupdir does not exist, exit with fatal error
|
||||
if [ ! -d "$backupdir" ]
|
||||
then
|
||||
mkdir -p "$backupdir" || fatal "Can not make directory $backupdir"
|
||||
fi
|
||||
|
||||
# If backupdir is not writeable, exit with fatal error as well
|
||||
if [ ! -w "$backupdir" ]
|
||||
then
|
||||
fatal "Directory $backupdir is not writable"
|
||||
fi
|
||||
|
||||
# Set the right tar option as per the chosen compression format
|
||||
case $compress in
|
||||
"gzip")
|
||||
compress_option="-z"
|
||||
EXTENSION="tar.gz"
|
||||
;;
|
||||
"bzip")
|
||||
compress_option="-j"
|
||||
EXTENSION="tar.bz2"
|
||||
;;
|
||||
"none")
|
||||
compress_option=""
|
||||
;;
|
||||
*)
|
||||
warning "Unknown compress filter ($tar_compress)"
|
||||
compress_option=""
|
||||
EXTENSION="tar.gz"
|
||||
;;
|
||||
esac
|
||||
|
||||
# Exclude the following file types / directories
|
||||
exclude_options=""
|
||||
for i in $excludes
|
||||
do
|
||||
exclude_options="$exclude_options --exclude $i"
|
||||
done
|
||||
|
||||
# Debugging messages, performing backup
|
||||
debug "Running backup: " $TAR -c -p -v $compress_option $exclude_options \
|
||||
-f "$backupdir/$backupname-"`$DATE "+$DATEFORMAT"`".$EXTENSION" \
|
||||
$includes
|
||||
|
||||
# Redirect standard output to a file with .list extension
|
||||
# and standard error to a file with .err extension
|
||||
$TAR -c -p -v $compress_option $exclude_options \
|
||||
-f "$backupdir/$backupname-"`$DATE "+$DATEFORMAT"`".$EXTENSION" \
|
||||
$includes \
|
||||
> "$backupdir/$backupname-"`$DATE "+$DATEFORMAT"`.list \
|
||||
2> "$backupdir/$backupname-"`$DATE "+$DATEFORMAT"`.err
|
||||
|
||||
[ $? -ne 0 ] && fatal "Tar backup failed"
|
||||
|
||||
Next, we will create our helper file (/usr/share/backupninja/home.helper) so that our handlers shows up as a menu in ninjahelper:
|
||||
|
||||
# Backup action's description. Separate words with underscores.
|
||||
HELPERS="$HELPERS home:backup_of_home_directories"
|
||||
|
||||
home_wizard() {
|
||||
home_title="Home action wizard"
|
||||
|
||||
backupname=`hostname --fqdn`
|
||||
|
||||
# Specify default value for the time when this backup actions is supposed to run
|
||||
inputBox "$home_title" "When to run this action?" "everyday at 01"
|
||||
[ $? = 1 ] && return
|
||||
home_when_run="when = $REPLY"
|
||||
|
||||
# Specify default value for backup file name
|
||||
inputBox "$home_title" "\"Name\" of backups" "$backupname"
|
||||
[ $? = 1 ] && return
|
||||
home_backupname="backupname = $REPLY"
|
||||
backupname="$REPLY"
|
||||
|
||||
# Specify default directory to store the backups
|
||||
inputBox "$home_title" "Directory where to store the backups" "/var/backups/home"
|
||||
[ $? = 1 ] && return
|
||||
home_backupdir="backupdir = $REPLY"
|
||||
|
||||
# Specify default values for the radiobox
|
||||
radioBox "$home_title" "Compression" \
|
||||
"none" "No compression" off \
|
||||
"gzip" "Compress with gzip" on \
|
||||
"bzip" "Compress with bzip" off
|
||||
[ $? = 1 ] && return;
|
||||
result="$REPLY"
|
||||
home_compress="compress = $REPLY "
|
||||
|
||||
REPLY=
|
||||
while [ -z "$REPLY" ]; do
|
||||
formBegin "$home_title: Includes"
|
||||
formItem "Include:" /home/gacanepa
|
||||
formDisplay
|
||||
[ $? = 0 ] || return 1
|
||||
home_includes="includes = "
|
||||
for i in $REPLY; do
|
||||
[ -n "$i" ] && home_includes="$home_includes $i"
|
||||
done
|
||||
done
|
||||
|
||||
REPLY=
|
||||
while [ -z "$REPLY" ]; do
|
||||
formBegin "$home_title: Excludes"
|
||||
formItem "Exclude:" *.mp3
|
||||
formItem "Exclude:" *.mp4
|
||||
# Add as many “Exclude” text boxes as needed to specify other exclude options
|
||||
formItem "Exclude:"
|
||||
formItem "Exclude:"
|
||||
formDisplay
|
||||
[ $? = 0 ] || return 1
|
||||
home_excludes="excludes = "
|
||||
for i in $REPLY; do
|
||||
[ -n "$i" ] && home_excludes="$home_excludes $i"
|
||||
done
|
||||
done
|
||||
|
||||
# Save the config
|
||||
get_next_filename $configdirectory/10.home
|
||||
cat > $next_filename <<EOF
|
||||
$home_when_run
|
||||
$home_backupname
|
||||
$home_backupdir
|
||||
$home_compress
|
||||
$home_includes
|
||||
$home_excludes
|
||||
|
||||
# tar binary - have to be GNU tar
|
||||
TAR `which tar`
|
||||
DATE `which date`
|
||||
DATEFORMAT "%Y-%m-%d"
|
||||
EXTENSION tar
|
||||
|
||||
EOF
|
||||
# Backupninja requires that configuration files be chmoded to 600
|
||||
chmod 600 $next_filename
|
||||
}
|
||||
|
||||
### Running Ninjahelper ###
|
||||
|
||||
Once we have created our handler script named home and the corresponding helper named home.helper, let's run ninjahelper command to create a new backup action:
|
||||
|
||||
# ninjahelper
|
||||
|
||||
And choose create a new backup action.
|
||||
|
||||

|
||||
|
||||
We will now be presented with the available action types. Let's select "backup of home directories":
|
||||
|
||||

|
||||
|
||||
The next screens will display the default values as set in the helper (only 3 of them are shown here). Feel free to edit the values in the text box. Particularly, refer to the scheduling section of the documentation for the right syntax for the when variable.
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
When you are done creating the backup action, it will show in ninjahelper's initial menu:
|
||||
|
||||

|
||||
|
||||
Then you can press ENTER to show the options available for this action. Feel free to experiment with them, as their description is quite straightforward.
|
||||
|
||||
Particularly, "run this action now" will execute the backup action in debug mode immediately regardless of the scheduled time:
|
||||
|
||||

|
||||
|
||||
Should the backup action fail for some reason, the debug will display an informative message to help you locate the error and correct it. Consider, for example, the following error messages that were displayed after running a backup action with bugs that have not been corrected yet:
|
||||
|
||||

|
||||
|
||||
The image above tells you that the connection needed to complete the backup action could not be completed because the remote host seems to be down. In addition, the destination directory specified in the helper file does not exist. Once you correct the problems, re-run the backup action.
|
||||
|
||||
A few things to remember:
|
||||
|
||||
|
||||
- If you create a custom script in /usr/share/backupninja (e.g., foobar) to handle a specific backup action, you also need to write a corresponding helper (e.g., foobar.helper) in order to create, through ninjahelper, a file named 10.foobar (11 and onward for further actions as well) in /etc/backup.d, which is the actual configuration file for the backup action.
|
||||
- You can execute your backups at any given time via ninjahelper as explained earlier, or have them run as per the specified frequency in the when variable.
|
||||
|
||||
### Summary ###
|
||||
|
||||
In this post we have discussed how to create our own backup actions from scratch and how to add a related menu in ninjahelper to facilitate the creation of configuration files. With the previous [backupninja article][2] and the present one I hope I've given you enough good reasons to go ahead and at least try it.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/create-custom-backup-plan-debian.html
|
||||
|
||||
作者:[Gabriel Cánepa][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/gabriel
|
||||
[1]:http://xmodulo.com/backup-debian-system-backupninja.html
|
||||
[2]:http://xmodulo.com/backup-debian-system-backupninja.html
|
||||
@ -0,0 +1,198 @@
|
||||
spccman translating
|
||||
How to Setup Bind Chroot DNS Server on CentOS 7.0 VPS
|
||||
================================================================================
|
||||
BIND (Berkeley Internet Name Daemon) also known as NAMED is the most widely used DNS server in the internet. This tutorial will descibes how we can run BIND in a chroot jail, the process is simply unable to see any part of the filesystem outside the jail. For example, in this post, i will setting up BIND to run chrooted to the directory /var/named/chroot/. Well, to BIND, the contents of this directory will appear to be /, the root directory. A “jail” is a software mechanism for limiting the ability of a process to access resources outside a very limited area, and it’s purposely to enhance the security. Bind Chroot DNS server was by default configured to /var/named/chroot. You may follow this complete steps to implement Bind Chroot DNS Server on CentOS 7.0 virtual private server (VPS).
|
||||
|
||||
1. Install Bind Chroot DNS server :
|
||||
|
||||
[root@centos7 ~]# yum install bind-chroot bind -y
|
||||
|
||||
2. Copy all bind related files to prepare bind chrooted environments :
|
||||
|
||||
[root@centos7 ~]# cp -R /usr/share/doc/bind-*/sample/var/named/* /var/named/chroot/var/named/
|
||||
|
||||
3. Create bind related files into chrooted directory :
|
||||
|
||||
[root@centos7 ~]# touch /var/named/chroot/var/named/data/cache_dump.db
|
||||
[root@centos7 ~]# touch /var/named/chroot/var/named/data/named_stats.txt
|
||||
[root@centos7 ~]# touch /var/named/chroot/var/named/data/named_mem_stats.txt
|
||||
[root@centos7 ~]# touch /var/named/chroot/var/named/data/named.run
|
||||
[root@centos7 ~]# mkdir /var/named/chroot/var/named/dynamic
|
||||
[root@centos7 ~]# touch /var/named/chroot/var/named/dynamic/managed-keys.bind
|
||||
|
||||
4. Bind lock file should be writeable, therefore set the permission to make it writable as below :
|
||||
|
||||
[root@centos7 ~]# chmod -R 777 /var/named/chroot/var/named/data
|
||||
[root@centos7 ~]# chmod -R 777 /var/named/chroot/var/named/dynamic
|
||||
|
||||
5. Copy /etc/named.conf chrooted bind config folder :
|
||||
|
||||
[root@centos7 ~]# cp -p /etc/named.conf /var/named/chroot/etc/named.conf
|
||||
|
||||
6.Configure main bind configuration in /etc/named.conf. Append the example.local zone information to the file :
|
||||
|
||||
[root@centos7 ~]# vi /var/named/chroot/etc/named.conf
|
||||
|
||||
Create forward and reverse zone into named.conf:
|
||||
|
||||
..
|
||||
..
|
||||
zone "example.local" {
|
||||
type master;
|
||||
file "example.local.zone";
|
||||
};
|
||||
|
||||
zone "0.168.192.in-addr.arpa" IN {
|
||||
type master;
|
||||
file "192.168.0.zone";
|
||||
};
|
||||
..
|
||||
..
|
||||
|
||||
Full named.conf configuration :
|
||||
|
||||
//
|
||||
// named.conf
|
||||
//
|
||||
// Provided by Red Hat bind package to configure the ISC BIND named(8) DNS
|
||||
// server as a caching only nameserver (as a localhost DNS resolver only).
|
||||
//
|
||||
// See /usr/share/doc/bind*/sample/ for example named configuration files.
|
||||
//
|
||||
|
||||
options {
|
||||
listen-on port 53 { any; };
|
||||
listen-on-v6 port 53 { ::1; };
|
||||
directory "/var/named";
|
||||
dump-file "/var/named/data/cache_dump.db";
|
||||
statistics-file "/var/named/data/named_stats.txt";
|
||||
memstatistics-file "/var/named/data/named_mem_stats.txt";
|
||||
allow-query { any; };
|
||||
|
||||
/*
|
||||
- If you are building an AUTHORITATIVE DNS server, do NOT enable recursion.
|
||||
- If you are building a RECURSIVE (caching) DNS server, you need to enable
|
||||
recursion.
|
||||
- If your recursive DNS server has a public IP address, you MUST enable access
|
||||
control to limit queries to your legitimate users. Failing to do so will
|
||||
cause your server to become part of large scale DNS amplification
|
||||
attacks. Implementing BCP38 within your network would greatly
|
||||
reduce such attack surface
|
||||
*/
|
||||
recursion yes;
|
||||
|
||||
dnssec-enable yes;
|
||||
dnssec-validation yes;
|
||||
dnssec-lookaside auto;
|
||||
|
||||
/* Path to ISC DLV key */
|
||||
bindkeys-file "/etc/named.iscdlv.key";
|
||||
|
||||
managed-keys-directory "/var/named/dynamic";
|
||||
|
||||
pid-file "/run/named/named.pid";
|
||||
session-keyfile "/run/named/session.key";
|
||||
};
|
||||
|
||||
logging {
|
||||
channel default_debug {
|
||||
file "data/named.run";
|
||||
severity dynamic;
|
||||
};
|
||||
};
|
||||
|
||||
zone "." IN {
|
||||
type hint;
|
||||
file "named.ca";
|
||||
};
|
||||
|
||||
zone "example.local" {
|
||||
type master;
|
||||
file "example.local.zone";
|
||||
};
|
||||
|
||||
zone "0.168.192.in-addr.arpa" IN {
|
||||
type master;
|
||||
file "192.168.0.zone";
|
||||
};
|
||||
|
||||
include "/etc/named.rfc1912.zones";
|
||||
include "/etc/named.root.key";
|
||||
|
||||
7. Create Forward and Reverse zone files for domain example.local.
|
||||
|
||||
a) Create Forward Zone :
|
||||
|
||||
[root@centos7 ~]# vi /var/named/chroot/var/named/example.local.zone
|
||||
|
||||
Add the following and save :
|
||||
|
||||
;
|
||||
; Addresses and other host information.
|
||||
;
|
||||
$TTL 86400
|
||||
@ IN SOA example.local. hostmaster.example.local. (
|
||||
2014101901 ; Serial
|
||||
43200 ; Refresh
|
||||
3600 ; Retry
|
||||
3600000 ; Expire
|
||||
2592000 ) ; Minimum
|
||||
|
||||
; Define the nameservers and the mail servers
|
||||
|
||||
IN NS ns1.example.local.
|
||||
IN NS ns2.example.local.
|
||||
IN A 192.168.0.70
|
||||
IN MX 10 mx.example.local.
|
||||
|
||||
centos7 IN A 192.168.0.70
|
||||
mx IN A 192.168.0.50
|
||||
ns1 IN A 192.168.0.70
|
||||
ns2 IN A 192.168.0.80
|
||||
|
||||
b) Create Reverse Zone :
|
||||
|
||||
[root@centos7 ~]# vi /var/named/chroot/var/named/192.168.0.zone
|
||||
|
||||
----------
|
||||
|
||||
;
|
||||
; Addresses and other host information.
|
||||
;
|
||||
$TTL 86400
|
||||
@ IN SOA example.local. hostmaster.example.local. (
|
||||
2014101901 ; Serial
|
||||
43200 ; Refresh
|
||||
3600 ; Retry
|
||||
3600000 ; Expire
|
||||
2592000 ) ; Minimum
|
||||
|
||||
0.168.192.in-addr.arpa. IN NS centos7.example.local.
|
||||
|
||||
70.0.168.192.in-addr.arpa. IN PTR mx.example.local.
|
||||
70.0.168.192.in-addr.arpa. IN PTR ns1.example.local.
|
||||
80.0.168.192.in-addr.arpa. IN PTR ns2.example.local.
|
||||
|
||||
8. Stop and disable named service. Start and enable bind-chroot service at boot :
|
||||
|
||||
[root@centos7 ~]# /usr/libexec/setup-named-chroot.sh /var/named/chroot on
|
||||
[root@centos7 ~]# systemctl stop named
|
||||
[root@centos7 ~]# systemctl disable named
|
||||
[root@centos7 ~]# systemctl start named-chroot
|
||||
[root@centos7 ~]# systemctl enable named-chroot
|
||||
ln -s '/usr/lib/systemd/system/named-chroot.service' '/etc/systemd/system/multi-user.target.wants/named-chroot.service'
|
||||
|
||||
As always if you need any help you can reach us on twitter @ehowstuff or drop us a comment below. [Jumping through archives page to read more articles..][1]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.ehowstuff.com/how-to-setup-bind-chroot-dns-server-on-centos-7-0-vps/
|
||||
|
||||
作者:[skytech][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.ehowstuff.com/author/mhstar/
|
||||
[1]:http://www.ehowstuff.com/archives/
|
||||
@ -1,3 +1,4 @@
|
||||
ideas4u Translating..
|
||||
How to use matplotlib for scientific plotting on Linux
|
||||
================================================================================
|
||||
If you want an efficient, automatable solution for producing high-quality scientific plots in Linux, then consider using matplotlib. Matplotlib is a Python-based open-source scientific plotting package with a license based on the Python Software Foundation license. The extensive documentation and examples, integration with Python and the NumPy scientific computing package, and automation capability are just a few reasons why this package is a solid choice for scientific plotting in a Linux environment. This tutorial will provide several example plots created with matplotlib.
|
||||
@ -12,7 +13,7 @@ If you want an efficient, automatable solution for producing high-quality scient
|
||||
- Customizable text (font, size, position...)
|
||||
- TeX formatting (equations, symbols, Greek characters...)
|
||||
- Compatible with IPython (allows interactive plotting from a Python shell)
|
||||
- Automation use Python loops to iteratively create plots
|
||||
- Automation - use Python loops to iteratively create plots
|
||||
- Save plots to image files (png, pdf, ps, eps, and svg format)
|
||||
|
||||
The Python-based syntax of matplotlib serves as the foundation for many of its features and enables an efficient workflow. There are many scientific plotting packages that can produce quality plots, but do they allow you to do it directly from within your Python code? On top of that, do they allow you to create automated routines for iterative creation of plots that can be saved as image files? Matplotlib allows you to accomplish all of these tasks. You can now look forward to saving time that would have otherwise been spent manually creating multiple plots.
|
||||
@ -44,7 +45,7 @@ In these examples we will use Python scripts to execute matplotlib commands. Not
|
||||
|
||||
### Example 1: Scatter and Line Plot ###
|
||||
|
||||
The first script, **script1.py** completes the following tasks:
|
||||
The first script, script1.py completes the following tasks:
|
||||
|
||||
- Creates three data sets (xData, yData1, and yData2)
|
||||
- Creates a new figure (assigned number 1) with a width and height of 8 inches and 6 inches, respectively
|
||||
@ -54,7 +55,7 @@ The first script, **script1.py** completes the following tasks:
|
||||
- Positions the legend in the upper left-hand corner of the plot
|
||||
- Saves the figure as a PNG file
|
||||
|
||||
Contents of **script1.py**:
|
||||
Contents of script1.py:
|
||||
|
||||
import numpy as np
|
||||
import matplotlib.pyplot as plt
|
||||
@ -77,7 +78,7 @@ The resulting plot is shown below:
|
||||
|
||||
### Example 2: Histogram Plot ###
|
||||
|
||||
The second script, **script2.py** completes the following tasks:
|
||||
The second script, script2.py completes the following tasks:
|
||||
|
||||
- Creates a data set containing 1000 random samples from a Normal distribution
|
||||
- Creates a new figure (assigned number 1) with a width and height of 8 inches and 6 inches, respectively
|
||||
@ -86,7 +87,7 @@ The second script, **script2.py** completes the following tasks:
|
||||
- Adds text to the plot and uses TeX formatting to display the Greek letters mu and sigma (font size of 16)
|
||||
- Saves the figure as a PNG file
|
||||
|
||||
Contents of **script2.py**:
|
||||
Contents of script2.py:
|
||||
|
||||
import numpy as np
|
||||
import matplotlib.pyplot as plt
|
||||
@ -108,7 +109,7 @@ The resulting plot is shown below:
|
||||
|
||||
### Example 3: Pie Chart ###
|
||||
|
||||
The third script, **script3.py** completes the following tasks:
|
||||
The third script, script3.py completes the following tasks:
|
||||
|
||||
- Creates data set containing five integers
|
||||
- Creates a new figure (assigned number 1) with a width and height of 6 inches and 6 inches, respectively
|
||||
@ -117,7 +118,7 @@ The third script, **script3.py** completes the following tasks:
|
||||
- Plots the data set, data, as a pie chart with labels included
|
||||
- Saves the figure as a PNG file
|
||||
|
||||
Contents of **script3.py**:
|
||||
Contents of script3.py:
|
||||
|
||||
import numpy as np
|
||||
import matplotlib.pyplot as plt
|
||||
@ -149,4 +150,4 @@ via: http://xmodulo.com/matplotlib-scientific-plotting-linux.html
|
||||
|
||||
[a]:http://xmodulo.com/author/joshua
|
||||
[1]:http://xmodulo.com/numpy-scientific-computing-linux.html
|
||||
[2]:http://matplotlib.org/
|
||||
[2]:http://matplotlib.org/
|
||||
@ -0,0 +1,54 @@
|
||||
、Linux 3.18 内核发布了,下面的是更新的内容
|
||||
================================================================================
|
||||

|
||||
|
||||
新的一月意味着新的稳定版Linux内核的发布,今天Linus Torvalds[宣布Linux 3.18 很快就会发布了][1]。
|
||||
|
||||
Torvalds在Linux内核邮件列表中解释到,由于在3.17中还存在几个令一小部分用户烦心的问题,‘**绝不可以在一些人积极解决老问题时其他人无所事事。**’
|
||||
|
||||
### Linux 3.18中有什么新的? ###
|
||||
|
||||
Linux 3.18内核主要致力于硬件支持、电源效率、bug修复和可靠性。
|
||||
|
||||
如往常一样,这些内容跨越很大,容易让人迷惑 。比如:加密层多重缓冲操作 - 到气冲感知, 就像对雷蛇游戏手柄的支持。
|
||||
|
||||
下面我们收集了这个版本的重要的改变。这远远不是所有的,只是选取了一些更相关的内容。
|
||||
|
||||
|
||||
- Nouveau (免费 Nvidia GPU 驱动) 现在支持基础 DisplayPort 音频
|
||||
- 对雷蛇游戏手柄的支持,用在Xbox 360上
|
||||
- Xilinx USB2 外设
|
||||
- 对Microchip AR1021 i2c、PenMount 6000 touch的触摸屏支持。
|
||||
- 音频编码: Cirrus Logic CS35L32、 Everest ES8328and Freescale ES8328
|
||||
- 音频支持: 通用飞思卡尔声卡, A模拟SSM4567音频放大器
|
||||
- 不同的文件系统提升, 包括 Btrfs 和 F2FS
|
||||
- 现在支持了DCTCP拥塞控制算法
|
||||
- JIT 编译64位 eBPF程序
|
||||
- “Tinification” 帮助开发人员编译更精简更小的内核
|
||||
|
||||
#### 在Ubuntu上安装 Linux 3.18 ####
|
||||
|
||||
虽然声称是稳定版并带来了大量的更新,但不要马上急着升级你的系统。除非你擅长处理监控异常,CPU过热、和其他各种系统报出的异常。
|
||||
|
||||
如果你坚持更新,你可以在kernel.org网站上找到源码包。
|
||||
|
||||
- [下载Linux内核源码包][2]
|
||||
|
||||
有一个由Canonical维护的最新Linux内核归档。尽管你可能在其他地方看到过,但是,请注意,这不是针对终端用户的。没有任何保证与支持,你自己承担风险。
|
||||
|
||||
- [访问Ubuntu内核主线归档][3]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.omgubuntu.co.uk/2014/12/linux-kernel-3-18-released-whats-new
|
||||
|
||||
作者:[Joey-Elijah Sneddon][a]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://plus.google.com/117485690627814051450/?rel=author
|
||||
[1]:https://lkml.org/lkml/2014/12/7/202
|
||||
[2]:https://www.kernel.org/pub/linux/kernel/v3.x/
|
||||
[3]:http://kernel.ubuntu.com/~kernel-ppa/mainline/?C=N;O=D
|
||||
@ -0,0 +1,86 @@
|
||||
5大最佳开源的浏览器安全应用
|
||||
================================================================================
|
||||
浏览器是现在各种在线服务的入口。电脑安全问题迄今仍未得到解决,技术进步为恶意软件提供了新的途径,感染我们的设备,入侵商业网络。例如,智能手机与平板为恶意软件--及其同伙“[恶意广告][1]”--带来一片全新天地,它们在其中腾挪作乱。
|
||||
|
||||
恶意广告在合法广告与合法网络中注入恶意软件。当然你可能会认为“合法”广告与网络与非法广告与网络之间仅有一线之隔。但是请不要偏题哦。隐私与安全天生就是一对兄弟,保护隐私也就是保护你的安全。
|
||||
|
||||
Firefox, Chrome, 以及 Opera当仁不让属最棒的浏览器:性能最佳、兼容性最好、以及安全性最优。以下五个开源安全应用安装于浏览器后会助你抵御种种威胁。
|
||||
|
||||
### 保护隐私: 开源浏览器安全应用 ###
|
||||
|
||||
#### 1. [AdBlock][2] ####
|
||||
|
||||
广告网络为恶意软件提供了肥沃的土壤。一个广告网络可以覆盖数千站点,因此攻陷一个广告网络就相当于攻陷数千台机器。AdBlock及其衍生品—[AdBlock Plus][2], [AdBlock Pro][3], 与 [AdBlock Edge][4]--都是屏蔽广告的优秀工具,可以让那些充斥烦人广告的网站重新还你一片清静。
|
||||
|
||||
当然,凡事都有两面性:上述做法损害了依靠广告收入的站点的利益。这些工具一键式白名单功能,对于那些你希望支持的网站,你可以通过白名单功能关闭这些网站的广告屏蔽。(真的,我亲爱的站长们,如果你不希望网站访问者屏蔽你的广告,那么就适可而止,不要让人反感。)
|
||||
|
||||

|
||||
|
||||
图1:在Ad Blocker中添加其它过滤规则。
|
||||
|
||||
Ad Blocker们不仅能屏蔽广告;它们还能屏蔽网站跟踪爬虫与恶意域名。要打开额外过滤规则,点击ad blocker图标 > 点击**首选项**,转至**过滤规则订阅**标签。点击按纽**添加订阅过滤规则**,然后加入**Easy Privacy + EasyList**规则。加入恶意域名过滤也是个不错的选择;它会屏蔽那些供恶意软件与间谍软件寄生的域名。Adblock可在Firefox, Chrome, Opera, Safari, IE, 以及Android平台下工作。
|
||||
|
||||
#### 2. [HTTPS Everywhere][5] ####
|
||||
|
||||
浏览器扩展HTTPS Everywhere可确保在网站HTTPS可用的时候,总是以HTTPS方式连接到站点。HTTPS意味着你的连接是以SSL(安全套接层)方式加密的,SSL协议通常用于加密网站与电子邮件连接。HTTPS Everywhere可在Firefox, Chrome, 及Opera下使用。
|
||||
|
||||
安装了HTTPS Everywhere之后,它会询问你是否希望启用SSL检测程序。点击是,因为SSL检测程序会提供额外保护,防止中间人攻击与虚假SSL证书攻击。HTTPS Everywhere可在Firefox, Chrome, Opera, Safari, IE, 以及Android平台下工作。
|
||||
|
||||
#### 3. [Social Fixer][6] ####
|
||||
|
||||
Social Fixer驯服Facebook。它给了你一把尚方宝剑,你可以用它过滤“动态汇总”,从而只看到你想看的动态、生成按主题分类的标签动态、隐藏不想查看的动态、鼠标悬停图片时显示完整尺寸的图片、禁止影院方式浏览图像,还有其它更多功能。
|
||||
|
||||
Social Fixer本身不是安全工具,但它具有两个重要的安全特性:
|
||||
|
||||
- 它可以将Facebook网页截图中你的个人资料头像以通用图标代替,并以虚假名字替代你的用户名,从而起到匿名作用。
|
||||
- 它可以很可靠地屏蔽Facebook游戏,而Facebook游戏正是尽人皆知的麻烦制造者。
|
||||
|
||||

|
||||
|
||||
图2: 使用Social Fixer匿名化Facebook网面。
|
||||
|
||||
#### 4. [Privacy Badger][7] ####
|
||||
|
||||
电子前线基金会出品的Privacy Badger是一款优秀的反跟踪与反间谍广告的拦截工具。现在的网页内容来源可谓五花八门:广告服务器、评论服务器、图片工场、第三方登陆服务器,以及其它种种不一而足。
|
||||
|
||||
AdBlock也能拦截这些乌七八糟的东西,不过Privacy Badger在此方面更胜一筹。Privacy Badger依靠算法与策略方法而非过滤规则,这样如果拦截出错的话,可以轻易重写,而过滤规则需要专人维护。Privacy Badger在Firefox与Chrome下均可工作。
|
||||
|
||||

|
||||
|
||||
图3: Privacy Badger拦截跟踪站点。
|
||||
|
||||
Privacy Badger装好后就能使用了。点击图标,看看它对你浏览的网页都拦截了哪些东西。你可以试试访问Huffingtonpost.com,这是一家不在每一个页面塞满第三方组件誓不罢休的网站(图3)。
|
||||
|
||||
滑块显示每个站点的状态:红色表示该站点被彻底拦截,不能设置cookies(缓冲数据),或者向你提供任何内容。黄色意味着第三方域名正试图跟踪,但是它列于Privacy Badger的允许域名的白名单之中。绿色表示第三方目前还未归入跟踪者之列,但是在你访问**若干**网站之后,Privacy Badger会观察其行为,并决定是否将其归为跟踪者。
|
||||
|
||||
你也可以根据你的偏好来设置滑块;例如,在我访问的某个网站,我用Privacy Badger拦截了bazaarvoice.com,一些购物网站使用这家站点来托管他们的客户评论。
|
||||
|
||||
#### 5. [Disconnect][8] ####
|
||||
|
||||
Disconnect是另外一款反跟踪反cookie工具,拥有众多功能。它可在Firefox, Chrome, IE, Safari下工作,并且为iOS与Android平台打造了特殊的版本。Disconnect不但能反跟踪,而且它使用自己的虚拟专用网络(VPN),防止窃听与恶意广告,使你的无线传输(Wi-fi, 3G, 4G)更安全。它可以防止部件劫持,而部件劫持是攻击者用于在需要登陆的网站获得访问权限的技术。通过部件劫持,攻击者无需密码,而只要使用窃取的cookies,就能获得网站访问权限。
|
||||
|
||||
Disconnect还有安全搜索功能,可以阻止搜索引擎爱挖数据的癖好,你可以安心无虞地使用你中意的搜索引擎。
|
||||
|
||||
想象一下,网页上所有东西都腾空而出,奔你而去。当然这一切都是抽象的且在幕后悄然发生,不象有人正在猛击窗户试图进入你家那么明显罢了。但是,威胁倒是实实在在的,而且数不胜数,所以你必须采取预防措施,来保护自己。
|
||||
|
||||
Carla Schroder著有The Book of Audacity, Linux Cookbook, Linux Networking Cookbook等书,并撰写了上百篇Linux指南文章。她曾担任Linux Planet与Linux Today网站总编。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.smallbusinesscomputing.com/biztools/5-best-open-source-web-browser-security-apps.html
|
||||
|
||||
作者:[Carla Schroder][a]
|
||||
译者:[译者ID](https://github.com/yupmoon)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.smallbusinesscomputing.com/author/Carla-Schroder-6080.html
|
||||
[1]:http://www.webopedia.com/TERM/M/malvertising.html
|
||||
[2]:https://getadblock.com/
|
||||
[3]:https://chrome.google.com/webstore/detail/adblock-pro/ocifcklkibdehekfnmflempfgjhbedch?hl=en-US
|
||||
[4]:https://addons.mozilla.org/en-us/firefox/addon/adblock-edge/
|
||||
[5]:https://www.eff.org/Https-everywhere
|
||||
[6]:http://socialfixer.com/
|
||||
[7]:https://www.eff.org/privacybadger
|
||||
[8]:https://disconnect.me/
|
||||
@ -0,0 +1,196 @@
|
||||
Linux 下五款出色的流媒体客户端
|
||||
================================================================================
|
||||
数字流媒体这几天几乎占据了我音乐收听的全部时间。近年来我为了收藏 CD 花费了数量可观的费用;但它们中的大部分现在正静静地躺在满是灰尘的角落里。基本上所有的音乐流媒体服务所提供的的音质都不如 CD 的,但它们受欢迎的原因很大程度上在于其便捷性,而非高度保真的音质再现。音乐流媒体不仅造成了 CD 销量的大幅减少;也使数字音乐的下载开始缓慢下滑。这种趋势还会继续下去。音乐发烧友现在或许也想要拥抱音乐流媒体服务了,某些音乐流媒体服务商如 Tidal 提供了无损的音乐流媒体服务,其中包含了 25 万首比特率为 1411kbps 的 FLAC 格式的音乐。
|
||||
|
||||
尽管 CD 暂时不会消失,但音乐流媒体服务商却无法协调和那些不满从音乐托管服务中收取的租金的唱片公司及音乐家之间的问题。这一切仍然处于变化之中;我们看到了今年 Led Zeppelin, Pink Floyd, Metallica 签名支持流媒体服务,但仍然有部分知名的老牌乐队如 Beatles, Radiohead 以及 AC/DC 拒绝将自己的作品放到流媒体上供粉丝收听。即使当某个唱片公司或者音乐家已经授权给流媒体服务商访问自己的作品,但只要音乐家发表声明就可以在第一时间将其作品从流媒体服务下架。本月(2014 年 11 月),Taylor Swift 请求将她的所有音乐作品从 Spotify 的流媒体服务下架。有些人还是更偏向于“拥有”他们的音乐,但这看起来像是一种快要过时了的欣赏音乐的方式。
|
||||
|
||||
使用 Linux 平台来收听流媒体音乐服务的方法已经逐渐成熟。在 Linux 平台下,你可以找到许多客户端,通过它们你可以使用大部分的音乐流媒体服务;我希望 TIDAL 能在今后合适的时候发行 Linux 桌面客户端,而不是仅仅依赖 web 播放器。本文精选的这些应用都是非常出色的。另外 Amarok,pianobar 还有 Tomahawk 也表现得很不错。
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
Spotify 是一种专有的 P2P 音乐流媒体服务,允许用户收听点播曲目或专辑。Spotify 将自己描述为“音乐圣殿。快捷、简易、免费的服务”。Spotify 分别为普通的移动端和桌面端用户提供了 96kbps 和 160kbps 比特率的流媒体服务,并且为高级用户提供了 Ogg Vorbis 格式的 320kbps 比特率的流媒体服务。Spotify 为普通用户提供了免费但是有广告的服务,以及无广告的订阅账户服务。
|
||||
|
||||
Spotify 是很奇妙的服务,向用户们提供了涵盖各种类型的数量众多的音乐,如:流行乐、另类摇滚、古典乐、铁克诺电音、摇滚乐等。这是发现新音乐的好方法。Spotify 得到了包括 Sony BMG,EMI,Universal 以及 Warner Music 在内的主流唱片公司,以及 Labrador Records,The Orchard,Alligator Records,Merlin,CD Baby,INgrooves 等独立唱片唱片公司和分销网络,甚至 Chandos,Naxos,EMI Classic,Warner Classics,Denon Essentials 这些古典唱片公司的支持,还有更多的公司在这里就不一一列举了。
|
||||
Spotify 的音乐涵盖范围还在继续以惊人的步伐扩张着。
|
||||
|
||||
Spotify 现在并没有发行官方版的 Linux 客户端。不过,开发团队已经推出了针对 Linux 的客户端预览版,并且表现得还不错。因为仍然是预览版,所以没有得到官方的支持。
|
||||
|
||||
Spotify 流媒体服务现已支持以下地区/国家:安道尔,阿根廷,澳大利亚,奥地利,比利时,保加利亚,哥伦比亚,塞浦路斯,丹麦,爱沙尼亚,芬兰,法国,德国,希腊,香港,冰岛,爱尔兰,意大利,拉脱维亚,列支敦士登,立陶宛,卢森堡,马来西亚,马耳他,墨西哥,摩纳哥,荷兰,新西兰,挪威,菲律宾,波兰,葡萄牙,西班牙,新加坡,瑞典,瑞士,台湾,土耳其,英国,美国,乌拉圭等。
|
||||
|
||||
**特色包括:**
|
||||
|
||||
- 精心设计的界面,导航时非常方便
|
||||
- 创建和编辑播放列表
|
||||
- 发现新的音乐
|
||||
- 共享音乐及播放列表
|
||||
- 电台功能
|
||||
- 最受欢迎的的列表
|
||||
- 额外功能及种类繁多的应用
|
||||
|
||||
- 网址:[www.spotify.com/uk/download/previews][1]
|
||||
- 开发者:Spotify
|
||||
- 许可证:专有许可证
|
||||
- 当前版本:预览版
|
||||
|
||||
----------
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
Pithons 是一款开源的的本地 Pandora 电台 Linux 客户端。它提供了一个轻量级的界面以替代 Pandora.com 的 web 客户端。其图形用户界面上集成了多媒体快捷键、通知中心以及声音菜单。
|
||||
|
||||
Pandora 音乐服务只能通过美国的 IP 地址使用。不过,非美国用户可以通过 VPN 连接来使用 Pandora。
|
||||
|
||||
**特色包括:**
|
||||
|
||||
- 播放/暂停/下一首
|
||||
- 切换电台
|
||||
- 记住用户名和密码
|
||||
- 给喜欢的音乐和艺术家添加书签
|
||||
- 获取封面
|
||||
- 喜欢/讨厌/不再播放这首音乐
|
||||
- 在通知中心中弹出歌曲信息
|
||||
- 跳转到 pandora.com 歌曲信息页面/电台页面
|
||||
- 超时后重连 pandora
|
||||
- QuickMix 编辑
|
||||
- 创建电台
|
||||
- 多媒体按键
|
||||
- 代理连接
|
||||
- Last.fm 歌曲记录
|
||||
- 音量控制
|
||||
- 屏保暂停等插件
|
||||
- DBUS 接口:MPRIS 和 Pithos
|
||||
|
||||
- 网址:[pithos.github.io][2]
|
||||
- 开发者:Kevin Mehall
|
||||
- 许可证:GNU GPL v3
|
||||
- 当前版本:1.0.0
|
||||
|
||||
----------
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
Clementine 基于 Amarok 开发,是一款跨平台的轻量级现代化音乐播放器和媒体库管理工具。Clementine 致力于打造快捷简易的界面,使你可以轻松搜索和播放音乐。
|
||||
|
||||
Clementine 在 Amarok 1.4 的基础上开发。
|
||||
|
||||
**特色包括:**
|
||||
- 检索、播放本地音乐库
|
||||
- 从 Last.fm 和 SomaFM 收听互联网电台
|
||||
- 标签式播放列表,支持导入导出 M3U,XSPF,PLS 及 ASX 格式的播放列表
|
||||
- 创建智能播放列表和动态播放列表
|
||||
- 载入 M3U 和 XSPF 播放列表
|
||||
- 对播放列表的撤销和重做
|
||||
- 编辑 MP3 和 OGG 文件的信息,管理媒体库
|
||||
- 从 Last.fm 下载缺失的专辑封面
|
||||
- 集成 gpodder.net 播客
|
||||
- 图形化均衡器
|
||||
- 支持 Windows,Mac OS X 及 Linux
|
||||
- 支持 Linux(libnotify)及 Mac OS X(Growl)本地桌面通知中心
|
||||
- 从 MusicBrainz 获取缺失的信息
|
||||
- 炫彩屏幕显示
|
||||
- 队列管理
|
||||
- 支持 Linux 下的 MPRIS,以及命令行远程控制
|
||||
- 支持索引和播放 Google Drive 中的音乐
|
||||
- 支持 Soundcloud
|
||||
- 支持 jazzradio.com
|
||||
- 支持 Moodbar
|
||||
- 基于 projectM 的可视化技术
|
||||
- 拷贝音乐至 iPod,iPhone,MTP 或者 大容量 USB 设备
|
||||
- 远程控制
|
||||
- 转码音乐至 MP3,Ogg Vorbis,Ogg Speex,FLAC 以及 AAC
|
||||
|
||||
- 网址:[www.clementine-player.org][3]
|
||||
- 开发者:David Sansome,John Maguire
|
||||
- 许可证:GNU GPL v3
|
||||
- 当前版本:1.2
|
||||
|
||||
----------
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
Nuvola Player 是一个免费的开源项目,能够整合云端音乐到你的桌面中(支持托盘图标、Ubuntu 声音菜单、dock 菜单以及通知中心)。
|
||||
|
||||
为了使用全部的流媒体服务,你需要安装 Flash 和 HTML5 的音频支持。某些基于 Web 的流媒体服务可以使用 HTML5 的音频技术播放音乐,而非使用 Flash 插件。Nuvola Player 需要 GStreamr 和 MP3 解码器插件来提供 HTML5 音频支持。
|
||||
|
||||
**支持的流媒体服务:**
|
||||
|
||||
- 集成了 MP3 商店的亚马逊云播放器,允许用户在亚马逊云端驱动器中存储他们的音乐,并且在任何支持的浏览器上播放音乐
|
||||
- Bandcamp,是一家在线音乐商店,也是艺人宣传平台,主要适于独立艺术家
|
||||
- Deezer,一家法国的基于 Web 的音乐流媒体服务商。Deezer 允许用户在多台设备上在线或者离线播放音乐,现在拥有 1800 万的曲目,超过 30000 的电台以及 2200 万的用户(150 万订阅用户)
|
||||
- 8tracks,是一家融合了互联网电台和社交元素的网站,坚持至少 8 个曲目的为用户量身定制的流媒体播放列表
|
||||
- Google Play,谷歌运营的一家数字服务商店,其经营项目包括音乐、电影、书籍,以及 Android 应用和游戏,其云端播放器支持播放用户自己上传的音乐和在 Google Play 里购买的音乐
|
||||
- Grooveshark,提供了国际化在线音乐搜索引擎、音乐流媒体服务以及音乐推荐服务,允许用户进行搜索、使用流媒体以及上传音乐,并且能把这些音乐进行立即播放或者添加到一个播放列表中
|
||||
- Grooveshark Mobile,基于 HTML5 的 Grooveshark 移动版,不需要 Flash 插件的支持
|
||||
- Hype Machine,Pandora Radio 和 Pitchfork Media 的融合产物。它从音乐博客上精选了最近发布的歌曲(约 1500 首),并在网站主页上列出了这些歌曲的信息
|
||||
- Jango,一款免费的在线音乐流媒体服务,允许用户创建和分享自己创建的电台
|
||||
- Logitech Media Server,是 Logitech Squeezebox devices 的开源流媒体服务。支持许多插件以及如 Deezer 和 Spotify 等其他流媒体服务
|
||||
- Pandora,智能化音乐推荐服务以及音乐基因组计划“托管人”,服务仅针对美国地区
|
||||
- Rdio,有广告的音乐订阅服务
|
||||
- Spotify,商业化流媒体服务,提供来自唱片公司的被严格限制的数字版权内容
|
||||
- This is My Jam,你可以存放某一刻你非常喜欢的音乐,并且每天都可以收听由朋友们精挑细选的音乐
|
||||
|
||||
**特色包括:**
|
||||
|
||||
- 多媒体快捷键
|
||||
- 显示桌面通知
|
||||
- 集成了众多声音菜单、小程序以及启动器,甚至更多
|
||||
- Last FM 以及 Libre FM 歌曲记录
|
||||
- 获取歌词
|
||||
- 支持 Amazon Music Prime streaming
|
||||
|
||||
- 网址:[tiliado.eu/nuvolaplayer][4]
|
||||
- 开发者:Jiří Janoušek and service maintainers
|
||||
- 许可证:2-Clause BSD license
|
||||
- 当前版本:2.4.3
|
||||
|
||||
----------
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
Atraci 是一款多平台的开源流媒体应用,允许用户收听超过 6000 万首音乐。Atraci 仍然处于基础开发阶段,所以很多功能暂时还未完善。
|
||||
|
||||
Atraci 使用 iTunes,Last.fm 以及 SoundCLoud 显示歌曲信息 —— 专辑封面、歌曲名称以及艺术家。Atraci 在 YouTube 上搜索最匹配这首音乐信息的视频,并使用其中质量最高的。
|
||||
|
||||
**特色包括:**
|
||||
|
||||
- 无广告、无需注册
|
||||
- 直观的用户界面
|
||||
- 智能匹配搜索任何音乐、艺术家或者专辑。Atraci 会在线校对其信息,以显示正确的歌曲名称、专辑封面以及音轨等等,同时列出最高质量的视频流媒体
|
||||
- 自动修正所属专辑与艺术家
|
||||
- 通过默认方式、艺术家姓名或者曲目名称对结果排序
|
||||
- 以网格或列表模式查询结果
|
||||
- 检索视频可以全屏模式观看
|
||||
- 以随机或重复模式创建播放列表
|
||||
- 应用程序内的音量调整滑块、音轨调节以及专辑封面
|
||||
- 播放历史
|
||||
|
||||
- 网址:[atraci.github.io/Atraci-website][5]
|
||||
- 开发者:The Atraci Team
|
||||
- 许可证:The MIT License
|
||||
- 当前版本:0.7.0
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linuxlinks.com/article/20141116052055674/MusicStreaming.html
|
||||
|
||||
作者:Frazer Kline
|
||||
译者:[Stevearzh](https://github.com/Stevearzh)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:https://www.spotify.com/uk/download/previews/
|
||||
[2]:http://pithos.github.io/
|
||||
[3]:https://www.clementine-player.org/
|
||||
[4]:https://tiliado.eu/nuvolaplayer/
|
||||
[5]:http://atraci.github.io/Atraci-website/
|
||||
@ -0,0 +1,22 @@
|
||||
开始使用Ubuntu 14.04(PDF指南)
|
||||
================================================================================
|
||||
开始熟悉每天的任务,像上网冲浪,听听音乐,还有扫描文档之类。
|
||||
|
||||
好好享受这份全面而综合的Ubuntu操作系统初学者指南吧。本教程适用于任何经验等级的人,跟着傻瓜式的指令一步一步操作吧。好好探索Ubuntu系统的潜力吧,你不会因为技术细节而陷入困境。
|
||||
|
||||
- [**开始使用Ubuntu 14.04 (PDF指南)**][1]
|
||||
|
||||

|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.ubuntugeek.com/getting-started-with-ubuntu-14-04-pdf-guide.html
|
||||
|
||||
作者:[ruchi][a]
|
||||
译者:[GOLinux](https://github.com/GOLinux)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.ubuntugeek.com/author/ubuntufix
|
||||
[1]:http://ubuntugeek.tradepub.com/free/w_ubun06/
|
||||
@ -0,0 +1,238 @@
|
||||
Linux的十条SCP传输命令
|
||||
================================================================================
|
||||
Linux系统管理员应该很熟悉**CLI**环境,因为在Linux服务器中是不安装**GUI**的。**SSH**可能是Linux系统管理员通过远程方式安全管理服务器的最流行协议。在**SSH**命令中内置了一种叫**SCP**的命令,用来在服务器之间安全传输文件。
|
||||
|
||||

|
||||
|
||||
以下命令可以解读为:用“**username account**”“**拷贝 source file name**”到“**destination host**”上的“**destination folder**”里。
|
||||
|
||||
#### SCP命令的基本语法 ####
|
||||
|
||||
scp source_file_name username@destination_host:destination_folder
|
||||
|
||||
**SCP**命令有很多参数供你使用,这里指的是每次都会用到的参数。
|
||||
|
||||
### 用-v参数来提供SCP进程的详细信息 ###
|
||||
|
||||
不带参数的基本**SCP**命令会在后台拷贝文件,除非操作完成或者有错误出现,否则用户在界面上是看不到任何提示信息的。你可以用“**-v**”参数来在屏幕上打印出调试信息,这能帮助你调试连接、认证和配置的一些问题。
|
||||
|
||||
pungki@mint ~/Documents $ scp -v Label.pdf mrarianto@202.x.x.x:.
|
||||
|
||||
#### 部分输出 ####
|
||||
|
||||
Executing: program /usr/bin/ssh host 202.x.x.x, user mrarianto, command scp -v -t .
|
||||
OpenSSH_6.0p1 Debian-3, OpenSSL 1.0.1c 10 May 2012
|
||||
debug1: Reading configuration data /etc/ssh/ssh_config
|
||||
debug1: /etc/ssh/ssh_config line 19: Applying options for *
|
||||
debug1: Connecting to 202.x.x.x [202.x.x.x] port 22.
|
||||
debug1: Connection established.
|
||||
debug1: Host '202.x.x.x' is known and matches the RSA host key.
|
||||
debug1: Found key in /home/pungki/.ssh/known_hosts:1
|
||||
debug1: ssh_rsa_verify: signature correct
|
||||
debug1: Next authentication method: password
|
||||
mrarianto@202.x.x.x's password:
|
||||
debug1: Authentication succeeded (password).
|
||||
Authenticated to 202.x.x.x ([202.x.x.x]:22).
|
||||
Sending file modes: C0770 3760348 Label.pdf
|
||||
Sink: C0770 3760348 Label.pdf
|
||||
Label.pdf 100% 3672KB 136.0KB/s 00:27
|
||||
Transferred: sent 3766304, received 3000 bytes, in 65.2 seconds
|
||||
Bytes per second: sent 57766.4, received 46.0
|
||||
debug1: Exit status 0
|
||||
|
||||
### 从源文件获取修改时间、访问时间和模式 ###
|
||||
|
||||
“**-p**”参数会帮到把预计的时间和连接速度会显示在屏幕上。
|
||||
|
||||
pungki@mint ~/Documents $ scp -p Label.pdf mrarianto@202.x.x.x:.
|
||||
|
||||
#### 部分输出 ####
|
||||
|
||||
mrarianto@202.x.x.x's password:
|
||||
Label.pdf 100% 3672KB 126.6KB/s 00:29
|
||||
|
||||
### 用-C参数来让文件传输更快 ###
|
||||
|
||||
有一个参数能让传输文件更快,就是“**-C**”参数,它的作用是不停压缩所传输的文件。它特别之处在于压缩是在网络中进行,当文件传到目标服务器时,它会变回压缩之前的原始大小。
|
||||
|
||||
来看看这些命令,我们使用一个**93 Mb**的单一文件来做例子。
|
||||
|
||||
pungki@mint ~/Documents $ scp -pv messages.log mrarianto@202.x.x.x:.
|
||||
|
||||
#### 部分输出 ####
|
||||
|
||||
Executing: program /usr/bin/ssh host 202.x.x.x, user mrarianto, command scp -v -p -t .
|
||||
OpenSSH_6.0p1 Debian-3, OpenSSL 1.0.1c 10 May 2012
|
||||
debug1: Reading configuration data /etc/ssh/ssh_config
|
||||
debug1: /etc/ssh/ssh_config line 19: Applying options for *
|
||||
debug1: Connecting to 202.x.x.x [202.x.x.x] port 22.
|
||||
debug1: Connection established.
|
||||
debug1: identity file /home/pungki/.ssh/id_rsa type -1
|
||||
debug1: Found key in /home/pungki/.ssh/known_hosts:1
|
||||
debug1: ssh_rsa_verify: signature correct
|
||||
debug1: Trying private key: /home/pungki/.ssh/id_rsa
|
||||
debug1: Next authentication method: password
|
||||
mrarianto@202.x.x.x's password:
|
||||
debug1: Authentication succeeded (password).
|
||||
Authenticated to 202.x.x.x ([202.x.x.x]:22).
|
||||
debug1: Sending command: scp -v -p -t .
|
||||
File mtime 1323853868 atime 1380425711
|
||||
Sending file timestamps: T1323853868 0 1380425711 0
|
||||
messages.log 100% 93MB 58.6KB/s 27:05
|
||||
Transferred: sent 97614832, received 25976 bytes, in 1661.3 seconds
|
||||
Bytes per second: sent 58758.4, received 15.6
|
||||
debug1: Exit status 0
|
||||
|
||||
不用“**-C**”参数来拷贝文件,结果用了**1661.3**秒,你可以比较下用了“**-C**”参数之后的结果。
|
||||
|
||||
pungki@mint ~/Documents $ scp -Cpv messages.log mrarianto@202.x.x.x:.
|
||||
|
||||
#### 部分输出 ####
|
||||
|
||||
Executing: program /usr/bin/ssh host 202.x.x.x, user mrarianto, command scp -v -p -t .
|
||||
OpenSSH_6.0p1 Debian-3, OpenSSL 1.0.1c 10 May 2012
|
||||
debug1: Reading configuration data /etc/ssh/ssh_config
|
||||
debug1: /etc/ssh/ssh_config line 19: Applying options for *
|
||||
debug1: Connecting to 202.x.x.x [202.x.x.x] port 22.
|
||||
debug1: Connection established.
|
||||
debug1: identity file /home/pungki/.ssh/id_rsa type -1
|
||||
debug1: Host '202.x.x.x' is known and matches the RSA host key.
|
||||
debug1: Found key in /home/pungki/.ssh/known_hosts:1
|
||||
debug1: ssh_rsa_verify: signature correct
|
||||
debug1: Next authentication method: publickey
|
||||
debug1: Trying private key: /home/pungki/.ssh/id_rsa
|
||||
debug1: Next authentication method: password
|
||||
mrarianto@202.x.x.x's password:
|
||||
debug1: Enabling compression at level 6.
|
||||
debug1: Authentication succeeded (password).
|
||||
Authenticated to 202.x.x.x ([202.x.x.x]:22).
|
||||
debug1: channel 0: new [client-session]
|
||||
debug1: Sending command: scp -v -p -t .
|
||||
File mtime 1323853868 atime 1380428748
|
||||
Sending file timestamps: T1323853868 0 1380428748 0
|
||||
Sink: T1323853868 0 1380428748 0
|
||||
Sending file modes: C0600 97517300 messages.log
|
||||
messages.log 100% 93MB 602.7KB/s 02:38
|
||||
Transferred: sent 8905840, received 15768 bytes, in 162.5 seconds
|
||||
Bytes per second: sent 54813.9, received 97.0
|
||||
debug1: Exit status 0
|
||||
debug1: compress outgoing: raw data 97571111, compressed 8806191, factor 0.09
|
||||
debug1: compress incoming: raw data 7885, compressed 3821, factor 0.48
|
||||
|
||||
看到了吧,压缩了文件之后,传输过程在**162.5**秒内就完成了,速度是不用“**-C**”参数的10倍。如果你要通过网络拷贝很多份文件,那么“**-C**”参数能帮你节省掉很多时间。
|
||||
|
||||
有一点我们需要注意,这个压缩的方法不是适用于所有文件。当源文件已经被压缩过了,那就没办法再压缩了。诸如那些像**.zip**,**.rar**,**pictures**和**.iso**的文件,用“**-C**”参数就无效。
|
||||
|
||||
### 选择其它加密算法来加密文件 ###
|
||||
|
||||
**SCP**默认是用“**AES-128**”加密算法来加密文件的。如果你想要改用其它加密算法来加密文件,你可以用“**-c**”参数。我们来瞧瞧。
|
||||
|
||||
pungki@mint ~/Documents $ scp -c 3des Label.pdf mrarianto@202.x.x.x:.
|
||||
|
||||
mrarianto@202.x.x.x's password:
|
||||
Label.pdf 100% 3672KB 282.5KB/s 00:13
|
||||
|
||||
上述命令是告诉**SCP**用**3des algorithm**来加密文件。要注意这个参数是“**-c**”而不是“**-C**“。
|
||||
|
||||
### 限制带宽使用 ###
|
||||
|
||||
还有一个很有用的参数是“**-l**”参数,它能限制使用带宽。如果你为了拷贝很多文件而去执行了一份自动化脚本又不希望带宽被**SCP**进程耗尽,那这个参数会非常管用。
|
||||
|
||||
pungki@mint ~/Documents $ scp -l 400 Label.pdf mrarianto@202.x.x.x:.
|
||||
|
||||
mrarianto@202.x.x.x's password:
|
||||
Label.pdf 100% 3672KB 50.3KB/s 01:13
|
||||
|
||||
在“**-l**”参数后面的这个**400**值意思是我们给**SCP**进程限制了带宽为**50 KB/秒**。有一点要记住,带宽是以**千比特/秒** (**kbps**)表示的,**8 比特**等于**1 字节**。
|
||||
|
||||
因为**SCP**是用**千字节/秒** (**KB/s**)计算的,所以如果你想要限制**SCP**的最大带宽只有**50 KB/s**,你就需要设置成**50 x 8 = 400**。
|
||||
|
||||
### 指定端口 ###
|
||||
|
||||
通常**SCP**是把**22**作为默认端口。但是为了安全起见,你可以改成其它端口。比如说,我们想用**2249**端口,命令如下所示。
|
||||
|
||||
pungki@mint ~/Documents $ scp -P 2249 Label.pdf mrarianto@202.x.x.x:.
|
||||
|
||||
mrarianto@202.x.x.x's password:
|
||||
Label.pdf 100% 3672KB 262.3KB/s 00:14
|
||||
|
||||
确认一下写的是大写字母“**P**”而不是“**p**“,因为“**p**”已经被用来保留源文件的修改时间和模式。
|
||||
|
||||
### 递归拷贝文件和文件夹 ###
|
||||
|
||||
有时我们需要拷贝文件夹及其内部的所有**文件** / **文件夹**,我们如果能用一条命令解决问题那就更好了。**SCP**用“**-r**”参数就能做到。
|
||||
|
||||
pungki@mint ~/Documents $ scp -r documents mrarianto@202.x.x.x:.
|
||||
|
||||
mrarianto@202.x.x.x's password:
|
||||
Label.pdf 100% 3672KB 282.5KB/s 00:13
|
||||
scp.txt 100% 10KB 9.8KB/s 00:00
|
||||
|
||||
拷贝完成后,你会在目标服务器中找到一个名为“**documents**”的文件夹,其中就是所拷贝的所有文件。“**documents**”是系统自动创建的文件夹。
|
||||
|
||||
### 禁用进度条和警告/诊断信息 ###
|
||||
|
||||
如果你不想从SCP中看到进度条和警告/诊断信息,你可以用“**-q**”参数来禁用它们,举例如下。
|
||||
|
||||
pungki@mint ~/Documents $ scp -q Label.pdf mrarianto@202.x.x.x:.
|
||||
|
||||
mrarianto@202.x.x.x's password:
|
||||
pungki@mint ~/Documents $
|
||||
|
||||
正如你所看到的,在你输入密码之后,没有任何关于SCP进度的消息反馈。进度完成后,你也看不到任何提示。
|
||||
|
||||
### 用SCP通过代理来拷贝文件 ###
|
||||
|
||||
代理服务器经常用于办公环境,SCP自然是没有经过代理方面的配置的。当你的环境正在使用代理,那么你就必须要“告诉”SCP与代理关联起来。
|
||||
|
||||
场景如下:代理的地址是**10.0.96.6**,端口是8080。该代理还实现了用户认证功能。首先,你需要创建一个“**~/.ssh/config**”文件,其次把以下命令输入进该文件。
|
||||
|
||||
ProxyCommand /usr/bin/corkscrew 10.0.96.6 8080 %h %p ~/.ssh/proxyauth
|
||||
|
||||
接着你需要创建一个同样包括以下命令的“**~/.ssh/proxyauth**”文件。
|
||||
|
||||
myusername:mypassword
|
||||
|
||||
然后你就可以像往常一样使用SCP了。
|
||||
|
||||
请注意corkscrew可能还没有安装在你的系统中。在我的Linux Mint中,我需要首先先用标准Linux Mint安装程序来安装它。
|
||||
|
||||
$ apt-get install corkscrew
|
||||
|
||||
对于其它的一些基于yum安装的系统,用户能用以下的命令来安装corkscrew。
|
||||
|
||||
# yum install corkscrew
|
||||
|
||||
还有一点就是因为“**~/.ssh/proxyauth**”文件中以明文的格式包含了你的“**用户名**”和“**密码**”,所以请确保该文件只能你来查看。
|
||||
|
||||
### 选择不同的ssh_config文件 ###
|
||||
|
||||
对于经常在公司网络和公共网络之间切换的移动用户来说,一直改变SCP的设置显然是很痛苦的。如果我们能放一个不同的**ssh_config**文件来匹配我们的需求那就很好了。
|
||||
|
||||
#### 以下是一个简单的场景 ####
|
||||
|
||||
代理是被用来在公司网络但不是公共网络并且你会定期切换网络时候使用的。
|
||||
|
||||
pungki@mint ~/Documents $ scp -F /home/pungki/proxy_ssh_config Label.pdf
|
||||
|
||||
mrarianto@202.x.x.x:.
|
||||
mrarianto@202.x.x.x's password:
|
||||
Label.pdf 100% 3672KB 282.5KB/s 00:13
|
||||
|
||||
默认情况下每个用户会把“**ssh_config**”文件放在“**~/.ssh/config**“路径下。用兼容的代理创建一个特定的“**ssh_config**”文件,能让你切换网络时更加方便容易。
|
||||
|
||||
当你处于公司网络时,你可以用“**-F**”参数,当你处于公共网络时,你可以忽略掉“**-F**”参数。
|
||||
|
||||
以上就是关于**SCP**的全部内容了,你可以查看**SCP**的**man页面**来获取更多内容,请随意留下您的评论及建议。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.tecmint.com/scp-commands-examples/
|
||||
|
||||
作者:[Pungki Arianto][a]
|
||||
译者:[ZTinoZ](https://github.com/ZTinoZ)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.tecmint.com/author/pungkiarianto/
|
||||
@ -0,0 +1,147 @@
|
||||
10个检测Linux内存使用情况的‘free’命令
|
||||
===
|
||||
|
||||
**Linux**是最有名的开源操作系统之一,它拥有着极其巨大的指令集。确定**物理内存**和**交换内存**所有可用空间的最重要,也是唯一的方法是使用“**free**”命令。
|
||||
|
||||
Linux “**free**”命令通过给出**Linux/Unix**操作系统中内核已使用的**buffers**情况,来提供**物理内存**和**交换内存**的总使用量和可用量。
|
||||
|
||||

|
||||
|
||||
这篇文章提供一些带有参数选项的“**free**”命令,这些命令对于你更好地利用你的内存会有帮助。
|
||||
|
||||
### 1. 显示你的系统内存 ###
|
||||
|
||||
free命令用于检测**物理内存**和**交换内存**已使用量和可用量(单位为**KB**)。下面演示命令的使用情况。
|
||||
|
||||
# free
|
||||
|
||||
total used free shared buffers cach
|
||||
ed
|
||||
Mem: 1021628 912548 109080 0 120368 6555
|
||||
48
|
||||
-/+ buffers/cache: 136632 884996
|
||||
Swap: 4194296 0 4194296
|
||||
|
||||
### 2. 以字节为单位显示内存 ###
|
||||
|
||||
加上**-b**参数的free命令,以**字节**为单位显示内存的大小。
|
||||
|
||||
# free -b
|
||||
|
||||
total used free shared buffers cach
|
||||
ed
|
||||
Mem: 1046147072 934420480 111726592 0 123256832 6712811
|
||||
52
|
||||
-/+ buffers/cache: 139882496 906264576
|
||||
Swap: 4294959104 0 4294959104
|
||||
|
||||
### 3. 以千字节为单位显示内存 ###
|
||||
|
||||
加上**-k**参数的free命令,以(KB)**千字节**为单位显示内存大小。
|
||||
|
||||
# free -k
|
||||
|
||||
total used free shared buffers cach
|
||||
ed
|
||||
Mem: 1021628 912520 109108 0 120368 655548
|
||||
-/+ buffers/cache: 136604 885024
|
||||
Swap: 4194296 0 4194296
|
||||
|
||||
### 4. 以兆字节为单位显示内存 ###
|
||||
|
||||
想以**(兆字节)**显示内存大小,使用**-m**参数。
|
||||
|
||||
# free -m
|
||||
|
||||
total used free shared buffers cach
|
||||
ed
|
||||
Mem: 997 891 106 0 117 6
|
||||
40
|
||||
-/+ buffers/cache: 133 864
|
||||
Swap: 4095 0 4095
|
||||
|
||||
### 5. 以千兆字节为单位显示内存 ###
|
||||
|
||||
使用**-g**为参数,将会以**GB(千兆字节)**为单位显示内存大小。
|
||||
|
||||
# free -g
|
||||
total used free shared buffers cached
|
||||
Mem: 0 0 0 0 0
|
||||
0
|
||||
-/+ buffers/cache: 0 0
|
||||
Swap: 3 0 3
|
||||
|
||||
### 6. 显示总计行 ###
|
||||
|
||||
加上-t选项,将会在屏幕最后列出总计一行。
|
||||
|
||||
# free -t
|
||||
|
||||
total used free shared buffers cache
|
||||
d
|
||||
Mem: 1021628 912520 109108 0 120368 6555
|
||||
48
|
||||
-/+ buffers/cache: 136604 885024
|
||||
Swap: 4194296 0 4194296
|
||||
Total: 5215924 912520 4303404
|
||||
|
||||
### 7. 关闭显示缓冲区调整一行 ###
|
||||
|
||||
默认情况下,free命令是显示“**缓冲区调整**”一行的,为了关闭显示,可以加上-o参数。
|
||||
|
||||
# free -o
|
||||
|
||||
total used free shared buffers cache
|
||||
d
|
||||
Mem: 1021628 912520 109108 0 120368 6555
|
||||
48
|
||||
Swap: 4194296 0 4194296
|
||||
|
||||
### 8. 定期时间间隔更新内存状态 ###
|
||||
|
||||
-s选项加上一个整数,用来在定期时间间隔内更新free命令。举个例子,下面的命令将会在每5秒更新一个free命令。
|
||||
|
||||
# free -s 5
|
||||
|
||||
total used free shared buffers cach
|
||||
ed
|
||||
Mem: 1021628 912368 109260 0 120368 6555
|
||||
48
|
||||
-/+ buffers/cache: 136452 885176
|
||||
Swap: 4194296 0 4194296
|
||||
|
||||
### 9. 显示底和高内存统计信息 ###
|
||||
|
||||
-l选项显示了具体的高和低内存的使用统计情况。
|
||||
|
||||
# free -l
|
||||
|
||||
total used free shared buffers cach
|
||||
ed
|
||||
Mem: 1021628 912368 109260 0 120368 6555
|
||||
48
|
||||
Low: 890036 789064 100972
|
||||
High: 131592 123304 8288
|
||||
-/+ buffers/cache: 136452 885176
|
||||
Swap: 4194296 0 4194296
|
||||
|
||||
### 10. 检查free命令版本 ###
|
||||
|
||||
-V选项,显示free命令版本信息。
|
||||
|
||||
# free -V
|
||||
|
||||
procps version 3.2.8
|
||||
|
||||
---
|
||||
|
||||
via: http://www.tecmint.com/check-memory-usage-in-linux/
|
||||
|
||||
作者:[Ravi Saive][a]
|
||||
译者:[su-kaiyao](https://github.com/su-kaiyao)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中>
|
||||
国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.tecmint.com/author/admin/
|
||||
@ -0,0 +1,155 @@
|
||||
VPS上好的控制面板是什么
|
||||
================================================================================
|
||||
任何有经验的Linux人员都认为没有一款控制面板可以打败纯命令行界面来管理[虚拟主机][1](VPS)。也有人争论有一款好的面板的一席之地,因为流线型的界面让常规管理操作可以通过点几下鼠标就可以完成。
|
||||
|
||||
至于控制面板,有共恩那个强大的充满警铃和汽笛的商业控制面板,也有不同免费的但也强大多功能的免费开源面板替代。这之中杰出的代表是[Ajenti][2]控制面板。
|
||||
|
||||
Ajenti可以让你很简单地配置不同的通用服务程序,如Apache/nginx、Samba、BIND、Squid、MySQL、cron、防火墙等等,对管理通用VPS实例可以节省大量的时间。对于生产环境,Ajenti同样提供了插件和平台来支持虚拟web主机管理和自定义web UI开发。
|
||||
|
||||
Ajenti有[双重授权][3];一个是个人、企业内部或者教育用途免费使用的AGPLv3。然而,如果你是一家托管企业或者硬件提供商,那么你需要购买商业授权来使用Ajenti作为商业供应。
|
||||
|
||||
### 在Linux上安装Ajenti ###
|
||||
|
||||
为了简化安装,Ajenti为主流Linux发行版提供了自己的仓库。安装Ajenti要做的就是配置目标仓库,并用默认包管理器来安装。
|
||||
|
||||
安装前,一个RSA密钥和证书会生成用于SSL,Ajenti会见在8000端口监听HTTPS的web请求。如果你正在使用防火墙,你需要在防火墙中允许8000端口。为了安全,最好默认禁止8000端口的访问,并添加少数IP地址到白名单中。
|
||||
|
||||
#### 在Debian上安装Ajenti ####
|
||||
|
||||
$ wget http://repo.ajenti.org/debian/key -O- | sudo apt-key add -
|
||||
$ sudo sh -c 'echo "deb http://repo.ajenti.org/debian main main debian" >> /etc/apt/sources.list'
|
||||
$ sudo apt-get update
|
||||
$ sudo apt-get install ajenti
|
||||
|
||||
#### 在Ubuntu上安装Ajenti ####
|
||||
|
||||
$ wget http://repo.ajenti.org/debian/key -O- | sudo apt-key add -
|
||||
$ sudo sh -c 'echo "deb http://repo.ajenti.org/ng/debian main main ubuntu" >> /etc/apt/sources.list'
|
||||
$ sudo apt-get update
|
||||
$ sudo apt-get install ajenti
|
||||
|
||||
#### 在 CentOS/RHEL或者Fedora上安装Ajenti ####
|
||||
|
||||
在CentOS/RHEL上,首先[配置][4]EPEL仓库,接着运行下面的命令。在Fedora上,直接使用下面的命令。
|
||||
|
||||
$ wget http://repo.ajenti.org/ajenti-repo-1.0-1.noarch.rpm
|
||||
$ sudo rpm -ivh ajenti-repo-1.0-1.noarch.rpm
|
||||
$ sudo yum install ajenti
|
||||
|
||||
接着配置防火墙。
|
||||
|
||||
在Fedora或者CentOS/RHEL 7上:
|
||||
|
||||
$ sudo firewall-cmd --zone=public --add-port=8000/tcp --permanent
|
||||
$ sudo firewall-cmd --reload
|
||||
|
||||
在CentOS/RHEL 6上:
|
||||
|
||||
$ sudo iptables -I INPUT -p tcp -m tcp --dport 8000 -j ACCEPT
|
||||
$ sudo service iptables save
|
||||
|
||||
### 访问Ajenti web界面 ###
|
||||
|
||||
在访问Ajenti的web界面前,先确保启动了ajenti服务。
|
||||
|
||||
$ sudo service ajenti restart
|
||||
|
||||
直接在浏览器中输入https://<server-ip-address>:8000,你就会看到下面的Ajenti的登录界面。
|
||||
|
||||

|
||||
|
||||
默认的登录凭证是用户名“root”,密码“admin”。当你登录后,你会看到初始化的Ajenti菜单。
|
||||
|
||||

|
||||
|
||||
在左边面板的"SOFTWARE"选项下,你会看接一列安装的服务。当你安装了任何Ajenti支持的服务端程序时,软件会在重启ajenti服务后被自动加入列表。
|
||||
|
||||
$ sudo service ajenti restart
|
||||
|
||||
### 通过Ajenti web界面管理VPS ###
|
||||
|
||||
Ajenti的web界面非常直观且易使用。下面是Ajenti功能的几个例子。
|
||||
|
||||
#### 可插入结构 ####
|
||||
|
||||
Ajenti有许多特定应用的插件,这让AJenti可高度扩展化。当你在VPS上安装一款新软件时。相关的AJenti插件(如果有的话)会自动启用来管理软件。“Plugins”菜单会展示可用/启用的插件,以及和它们关联的软件。
|
||||
|
||||

|
||||
|
||||
#### 包管理 ####
|
||||
|
||||
Ajenti提供了一个web界面来安装和升级VPS上的包。
|
||||
|
||||

|
||||
|
||||
#### 防火墙配置 ####
|
||||
|
||||
Ajenti允许你用两种方法管理防火墙规则(iptables或者CSF)。一种是使用用户友好的web面板,另一种是直接编辑原生的防火墙规则。
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
#### 日志检查 ####
|
||||
|
||||
你可以在Ajenti的web界面中浏览位于/var/log下的系统日志。
|
||||
|
||||

|
||||
|
||||
#### 进程监控 ####
|
||||
|
||||
你可以u看见按照CPU和内存使用率排序的进程列表,按需可以结束它们。
|
||||
|
||||

|
||||
|
||||
#### 终端访问 ####
|
||||
|
||||
对于底层VPS访问,Ajenti提供了基于web的终端界面,你在这可以输入Linux命令。你也可以像下面那样在一个面板中打开多个终端。
|
||||
|
||||

|
||||
|
||||
#### Apache Web服务管理 ####
|
||||
|
||||
你可以编辑Apache配额文件,并管理apche2服务。
|
||||
|
||||

|
||||
|
||||
#### MySQL/MariaDB 管理 ####
|
||||
|
||||
你可以访问MySQL/MariaDB服务并直接在上面执行原生SQL命令。
|
||||
|
||||

|
||||
|
||||
#### Squid 配置 ####
|
||||
|
||||
你可以配置Squid代理服务器的ACL、HTTP访问规则,过滤端口。
|
||||
|
||||

|
||||
|
||||
#### 启动服务管理 ####
|
||||
|
||||
你可以浏览、启动、停止、重启安装的服务。
|
||||
|
||||

|
||||
|
||||
### 总结 ###
|
||||
|
||||
Ajenti是一款易于使用的服务器管理控制面板,可以加入你开发的[自定义插件][5]。然而,记住任何好的控制面板都不会排除你学习面板后[VPS][6]上发生的情况的需求。一款面板会在你完全了解你正在做的事情的时候成会一款真正节省时间的利器,并且不依赖于控制面版来处理你行动的结果。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/free-control-panel-for-vps.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/nanni
|
||||
[1]:http://xmodulo.com/go/digitalocean
|
||||
[2]:http://ajenti.org/
|
||||
[3]:http://ajenti.org/licensing
|
||||
[4]:http://xmodulo.com/how-to-set-up-epel-repository-on-centos.html
|
||||
[5]:http://docs.ajenti.org/en/latest/dev/intro.html
|
||||
[6]:http://xmodulo.com/go/digitalocean
|
||||
@ -0,0 +1,104 @@
|
||||
Ubuntu 14.10 Server上安装Jetty 9(Java服务引擎和Web服务器)
|
||||
================================================================================
|
||||
Jetty提供了一个Web服务器和javax.servlet容器,为SPDY、WebSocket、OSGi、JMX、JNDI、JAAS以及许多其它集成套件添加了支持。这些组件都是开源的,也可用于商业用途和分发。
|
||||
|
||||
Jetty被广泛用于多种项目和产品,都可以在开发环境和生产环境中使用。Jetty可以很容易地嵌入到设备、工具、框架、应用服务器以及集群中。更多用途可参见Jetty网页。
|
||||
|
||||
### Jetty特性 ###
|
||||
|
||||
- 全功能并基于标准
|
||||
- 开源与商用两可
|
||||
- 灵活和可扩展
|
||||
- 小足迹
|
||||
- 可嵌入
|
||||
- 异步
|
||||
- 企业弹性扩展
|
||||
- Apache和Eclipse双重许可
|
||||
|
||||
### ubuntu 14.10 server上安装Jetty 9 ###
|
||||
|
||||
#### 先决条件 ####
|
||||
|
||||
在安装Jetty服务器前,您需要通过以下命令安装Java
|
||||
|
||||
sudo apt-get install openjdk-8-jdk
|
||||
|
||||
Java将会安装到/usr/lib/jvm/java-8-openjdk-i386,同时在该目录下会创建一个名为java-8-openjdk-i386的符号链接,在/usr/bin/java下也会相应创建符号链接。
|
||||
|
||||
现在你需要从[这里][1]下载Jetty9,在下载完成后,你需要使用以下命令来解压缩
|
||||
|
||||
$tar -xvf jetty-distribution-9.2.5.v20141112.tar.gz
|
||||
|
||||
该操作会将它解压到jetty-distribution-9.2.5.v20141112,而你需要使用以下命令将归档文件移动到/opt/jetty
|
||||
|
||||
$mv jetty-distribution-9.2.5.v20141112 /opt/jetty
|
||||
|
||||
你需要创建jetty用户,并将其设置成/opt/jetty目录的属主
|
||||
|
||||
sudo useradd jetty -U -s /bin/false
|
||||
|
||||
sudo chown -R jetty:jetty /opt/jetty
|
||||
|
||||
|
||||
使用以下命令拷贝Jetty脚本到启动目录,以便让它作为一个服务来运行
|
||||
|
||||
$ cp /opt/jetty/bin/jetty.sh /etc/init.d/jetty
|
||||
|
||||
现在,你需要使用以下内容来创建Jetty设置文件
|
||||
|
||||
sudo vi /etc/default/jetty
|
||||
|
||||
添加以下行
|
||||
|
||||
JAVA_HOME=/usr/bin/java
|
||||
JETTY_HOME=/opt/jetty
|
||||
NO_START=0
|
||||
JETTY_ARGS=jetty.port=8085
|
||||
JETTY_HOST=0.0.0.0
|
||||
JETTY_USER=jetty
|
||||
|
||||
保存并退出该文件
|
||||
|
||||
你需要使用以下命令来启动Jetty服务
|
||||
|
||||
sudo service jetty start
|
||||
|
||||
你应该看到和下面类似的输出
|
||||
|
||||
Starting Jetty: OK Mon Nov 24 11:55:48 GMT 2014
|
||||
|
||||
如果你看到了下面的错误
|
||||
|
||||
#### ** ERROR: JETTY_HOME not set, you need to set it or install in a standard location ####
|
||||
|
||||
你需要确保在/etc/default/jetty文件中设置了正确的Jetty家目录路径,
|
||||
你可以使用以下URL来测试jetty
|
||||
|
||||
Jetty现在应该运行在8085端口,打开浏览器并访问http://serverip:8085,你应该可以看到Jetty屏幕。
|
||||
|
||||
#### Jetty服务检查 ####
|
||||
|
||||
使用以下命令来验证并检查配置
|
||||
|
||||
sudo service jetty check
|
||||
|
||||
使用以下命令来让Jetty开重启后自动启动
|
||||
|
||||
sudo update-rc.d jetty defaults
|
||||
|
||||
重启服务器并测试Jetty是否自动启动。
|
||||
|
||||
要检查Jetty运行在哪个端口上,或者该端口是否与其它程序冲突,可以运行netstat -tln
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.ubuntugeek.com/install-jetty-9-java-servlet-engine-and-webserver-on-ubuntu-14-10-server.html
|
||||
|
||||
作者:[ruchi][a]
|
||||
译者:[GOLinux](https://github.com/GOLinux)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.ubuntugeek.com/author/ubuntufix
|
||||
[1]:http://download.eclipse.org/jetty/stable-9/dist/
|
||||
@ -0,0 +1,46 @@
|
||||
Linux FAQs with Answers--How to disable Apport internal error reporting on Ubuntu
|
||||
有问必答--如何禁止Ubuntu的Apport内部错误报告程序
|
||||
================================================================================
|
||||
> **问题**:在桌面版Ubuntu中,我经常遇到一些弹窗窗口,警告我Ubuntu发生了内部错误,问我要不要发送错误报告。每次软件崩溃都要烦扰我,我如何才能关掉这个错误报告功能呢?
|
||||
|
||||
Ubuntu桌面版预安装了Apport,它是一个错误收集系统,会收集软件崩溃、未处理异常和其他,包括程序bug,并为调试目的生成崩溃报告。当一个应用程序崩溃或者出现Bug时候,Apport就会通过弹窗警告用户并且询问用户是否提交崩溃报告。你也许也看到过下面的消息。
|
||||
|
||||
- "Sorry, the application XXXX has closed unexpectedly."
|
||||
- "对不起,应用程序XXXX意外关闭了"
|
||||
- "Sorry, Ubuntu XX.XX has experienced an internal error."
|
||||
- "对不起,Ubuntu XX.XX 经历了一个内部错误"
|
||||
- "System program problem detected."
|
||||
- "系统程序问题发现"
|
||||
|
||||

|
||||
|
||||
也许因为应用一直崩溃,频繁的错误报告会使人心烦。也许你担心Apport会收集和上传你的Ubuntu系统的敏感信息。无论什么原因,你需要关掉Apport的错误报告功能。
|
||||
|
||||
### 临时关闭Apport错误报告 ###
|
||||
|
||||
如果你想要临时关闭Apport,使用下列命令
|
||||
|
||||
$ sudo service apport stop
|
||||
|
||||
注意重启Ubuntu系统Apport会继续开启
|
||||
|
||||
### 永久关闭Apport错误报告 ###
|
||||
|
||||
为了永久关闭Apport,编辑/etc/default/apport,修改下列参数
|
||||
|
||||
enabled=0
|
||||
|
||||
重启你的Ubuntu系统,Apport将会自动关闭
|
||||
|
||||
如果你再也不会用Apport,有一种简单的方法完全移除它
|
||||
|
||||
$ sudo apt-get purge apport
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://ask.xmodulo.com/disable-apport-internal-error-reporting-ubuntu.html
|
||||
|
||||
译者:[VicYu/Vic020](http://www.vicyu.net/)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
@ -0,0 +1,103 @@
|
||||
CentOS上配置rsyslog客户端用以远程记录日志
|
||||
================================================================================
|
||||
**rsyslog**是一个开源工具,被广泛用于Linux系统以通过TCP/UDP协议转发或接收日志消息。rsyslog守护进程可以被配置称两种环境,一种是配置成日志收集服务器,rsyslog进程可以从网络中收集所有其它主机上的日志数据,这些主机已经将日志配置为发送到服务器。rsyslog的另外一个角色,就是可以配置为客户端,用来过滤和发送内部日志消息到本地文件夹(如/var/log)或一台可以路由到的远程rsyslog服务器上。
|
||||
|
||||
假定你的网络中已经有一台rsyslog服务器[已经起来并且处于运行中][1],本指南将为你展示如何来设置CentOS系统将其内部日志消息路由到一台远程rsyslog服务器上。这将大大改善你的系统磁盘空间的使用,尤其是你还没有一个独立的用于/var目录的大分区。
|
||||
|
||||
### 步骤一: 安装Rsyslog守护进程 ###
|
||||
|
||||
在CentOS 6和7上,rsyslog守护进程已经预先安装了。要验证rsyslog是否已经安装到你的CentOS系统上,请执行如下命令:
|
||||
|
||||
# rpm -qa | grep rsyslog
|
||||
# rsyslogd -v
|
||||
|
||||

|
||||
|
||||
如果处于某种原因,rsyslog守护进程没有出现在你的系统中,请使用以下命令来安装:
|
||||
|
||||
# yum install rsyslog
|
||||
|
||||
### 步骤二: 配置Rsyslog守护进程为客户端 ###
|
||||
|
||||
接下来的步骤,是要将你的CentOS机器转变成rsyslog客户端,将其所有内部日志消息发送到远程中央日志服务器上。
|
||||
|
||||
要实现该功能,请使用你喜爱的文本编辑器打开位于/etc路径下的rsyslog主配置文件:
|
||||
|
||||
# nano /etc/rsyslog.conf
|
||||
|
||||
开启文件用于编辑后,你需要添加以下声明到文件底部。将IP地址替换为你的远程rsyslog服务器的IP地址。
|
||||
|
||||
*.* @192.168.1.25:514
|
||||
|
||||
上面的声明告诉rsyslog守护进程,将系统上各个设备的各种日志消息路由到远程rsyslog服务器(192.168.1.25)的UDP端口514。
|
||||
|
||||
如果出于某种原因,你需要更为可靠的协议,如TCP,而rsyslog服务器也被配置为监听TCP连接,你必须在远程主机的IP地址前添加一个额外的@字符,像下面这样:
|
||||
|
||||
*.* @@192.168.1.25:514
|
||||
|
||||
注意,你也可以将rsyslog服务器的IP地址替换成它的DNS名称(FQDN)。
|
||||
|
||||
如果你只想要转发指定设备的日志消息,比如说内核设备,那么你可以在rsyslog配置文件中使用以下声明。
|
||||
|
||||
kern.* @192.168.1.25:514
|
||||
|
||||
修改配置文件后,你需要重启进程以激活修改:
|
||||
|
||||
**CentOS 7:**
|
||||
|
||||
# systemctl restart rsyslog.service
|
||||
|
||||
**CentOS 6:**
|
||||
|
||||
# service rsyslog restart
|
||||
|
||||
在另外一种环境中,让我们假定你已经在机器上安装了一个名为“foobar”的应用程序,它会在/var/log下生成foobar.log日志文件。现在,你只想要将它的日志定向到rsyslog服务器,这可以通过像下面这样在rsyslog配置文件中加载imfile模块来实现。
|
||||
|
||||
首先,加载imfile模块,这必须只做一次。
|
||||
|
||||
module(load="imfile" PollingInterval="5")
|
||||
|
||||
然后,指定日志文件的路径以便imfile模块可以检测到:
|
||||
|
||||
input(type="imfile"
|
||||
File="/var/log/foobar.log"
|
||||
Tag="foobar"
|
||||
Severity="error"
|
||||
Facility="local7")
|
||||
|
||||
最后,定向local7设备到远程rsyslog服务器:
|
||||
|
||||
local7.* @192.168.1.25:514
|
||||
|
||||
别忘了重启rsyslog进程哦!
|
||||
|
||||
### 步骤三: 让Rsyslog进程自动启动 ###
|
||||
|
||||
To automatically start rsyslog client after every system reboot, run the following command to enable it system-wide:
|
||||
要让rsyslog客户端在每次系统重启后自动启动,请运行以下命令来在系统范围启用:
|
||||
|
||||
**CentOS 7:**
|
||||
|
||||
# systemctl enable rsyslog.service
|
||||
|
||||
**CentOS 6:**
|
||||
|
||||
# chkconfig rsyslog on
|
||||
|
||||
### 小结 ###
|
||||
|
||||
在本教程中,我演示了如何将CentOS系统转变成rsyslog客户端以强制它发送日志消息到远程rsyslog服务器。这里我假定rsyslog客户端和服务器之间的连接是安全的(如,在有防火墙保护的公司网络中)。不管在任何情况下,都不要配置rsyslog客户端将日志消息通过不安全的网络转发,或者,特别是通过互联网转发,因为syslog协议是一个明文协议。要进行安全传输,可以考虑使用[TLS/SSL][2]来加密日志消息。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/configure-rsyslog-client-centos.html
|
||||
|
||||
作者:[Caezsar M][a]
|
||||
译者:[GOLinux](https://github.com/GOLinux)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/caezsar
|
||||
[1]:http://xmodulo.com/configure-syslog-server-linux.html
|
||||
[2]:http://www.rsyslog.com/doc/rsyslog_tls.html
|
||||
@ -0,0 +1,151 @@
|
||||
如何在Linux的命令行中使用Evernote
|
||||
================================================================================
|
||||
这周让我们继续什么学习如个使用Linux命令行管理和组织信息。在命令行中管理[你的个人花费][1]后,我建议你在命令行中管理你的笔记,特别地是,当你笔记放在Evernote中时。为防止你从来没有听说过,[Evernote][2]专门有一个用户有好的在线服务用来在不同的设备间同步笔记。除了提供花哨的基于Web的API,Evernote还发布了在Windows、Mac、[Android][3]和iOS上的客户端。然而至今还没有官方的Linux客户端可用。老实说在众多的非官方Linux程序中,一个程序一出现就吸引了所有的命令行爱好者:[Geeknote][4]
|
||||
|
||||
### Geeknote 的安装 ###
|
||||
|
||||
Geeknote使用Python开发的。因此,在开始之前请确保你已经安装了Python(最好是2.7的版本)和git。
|
||||
|
||||
#### 在 Debian、 Ubuntu 和 Linux Mint 中 ####
|
||||
|
||||
$ sudo apt-get install python2.7 git python-setuptools
|
||||
$ git clone git://github.com/VitaliyRodnenko/geeknote.git
|
||||
$ cd geeknote
|
||||
$ sudo python2.7 setup.py install
|
||||
|
||||
#### 在 Fedora 或者 CentOS/RHEL 中 ####
|
||||
|
||||
$ sudo yum install git
|
||||
$ git clone git://github.com/VitaliyRodnenko/geeknote.git
|
||||
$ cd geeknote
|
||||
$ sudo python setup.py install
|
||||
|
||||
#### 在 Arch Linux 中 ####
|
||||
|
||||
对于ArchLinux用户,只需要使用[AUR][5]中的包。
|
||||
|
||||
### Geeknote 的基本使用 ###
|
||||
|
||||
一旦你安装玩Geeknote后,你应该将Geeknote与你的Evernote账号关联:
|
||||
|
||||
$ geeknote login
|
||||
|
||||
接着输入你的emial地址、密码、和你的二步验证码。如果你没有后者,忽略它并按下回车。
|
||||
|
||||

|
||||
|
||||
很明显,你需要一个Evernote账号来完成这些,因此先去注册。
|
||||
|
||||
一旦完成这一切之后,你就可以开始了,创建新的笔记并编辑它们。
|
||||
|
||||
但是首先,你需要设置你最喜欢的文本编辑器:
|
||||
|
||||
$ geeknote settings --editor vim
|
||||
|
||||
接着,常规创建一条新笔记的语法是:
|
||||
|
||||
$ geeknote create --title [title of the new note] (--content [content] --tags [comma-separated tags] --notebook [comma-separated notebooks])
|
||||
|
||||
上面的命令中,只有‘title’是必须的,它会与一条新笔记的标题相关联。其他的标注可以为笔记添加额外的元数据:添加标签来与你的笔记关联、指定放在那个笔记本里。同样,如果你的标题或者内容还有空格,不要忘记将它们放在引号中。
|
||||
|
||||
|
||||
比如:
|
||||
|
||||
$ geeknote create --title "My note" --content "This is a test note" --tags "finance, business, important" --notebook "Family"
|
||||
|
||||
通常上,下一步就是编辑你的笔记。语法很相似:
|
||||
|
||||
$ geeknote edit --note [title of the note to edit] (--title [new title] --tags [new tags] --notebook [new notebooks])
|
||||
|
||||
注意可选的参数如标题、标签和笔记本,用来修改笔记的元数据。比如,你可以用下面的命令重命名笔记:
|
||||
|
||||
$ geeknote edit --note [old title] --title [new title]
|
||||
|
||||
现在基本的创建和编辑已经完成了,更高级的特性是搜索和删除。你可以下面的语法搜索你的笔记:
|
||||
|
||||
$ geeknote find --search [text-to-search] --tags [comma-separated tags] --notebook [comma-separated notebooks] --date [date-or-date-range] --content-search
|
||||
|
||||
默认上,上面的命令会通过标题搜索笔记。 用"--content-search"选项,就可以搜索它们的内容。
|
||||
|
||||
比如:
|
||||
|
||||
$ geeknote find --search "*restaurant" --notebooks "Family" --date 31.03.2014-31.08.2014
|
||||
|
||||
显示制定标题的笔记:
|
||||
|
||||
$ geeknote show [title]
|
||||
|
||||

|
||||
|
||||
我最喜欢使用的一个技巧是使用:
|
||||
|
||||
$ geeknote show "*"
|
||||
|
||||
这会显示所有的笔记并允许你在这中选择一个。
|
||||
|
||||
删除一条笔记:
|
||||
|
||||
$ geeknote remove --note [title]
|
||||
|
||||
小心这是真正的删除。它会从云存储中删除这条笔记。
|
||||
|
||||
最后有很多的选项来管理标签和笔记本。我想最有用的是显示笔记本列表。
|
||||
|
||||
$ geeknote notebook-list
|
||||
|
||||
|
||||
|
||||
下面的非常相像。你可以猜到,可以用下面的命令列出所有的标签:
|
||||
|
||||
$ geeknote tag-list
|
||||
|
||||
创建一个笔记本:
|
||||
|
||||
$ geeknote notebook-create --title [notebook title]
|
||||
|
||||
创建一个标签:
|
||||
|
||||
$ geeknote tag-create --title [tag title]
|
||||
|
||||
一旦你了解了窍门,很明显语法是非常连贯且明确的。
|
||||
|
||||
如果你想要了解更多,不要忘记查看[官方文档][6]。
|
||||
|
||||
### 福利 ###
|
||||
|
||||
As a bonus, Geeknote comes with the utility gnsync, which allows for file synchronization between your Evernote account and your local computer. However, I find its syntax a bit dry:
|
||||
福利的是,Geeknote自带的gnsync工具可以让你在Evernote和本地计算机之间同步。然而,我发现它的语法有点枯燥:
|
||||
|
||||
$ gnsync --path [where to sync] (--mask [what kind of file to sync] --format [in which format] --logpath [where to write the log] --notebook [which notebook to use])
|
||||
|
||||
下面是这些的意义。
|
||||
|
||||
|
||||
- **--path /home/adrien/Documents/notes/**: 与Evernote同步笔记的位置。
|
||||
- **--mask "*.txt"**: 只同步纯文本文件。默认上,gnsync会尝试同步所有文件。
|
||||
- **--format markdown**: 你希望它们是纯文本或者markdown格式(默认是纯文本)。
|
||||
- **--logpath /home/adrien/gnsync.log**: 同步日志的位置。为防出错,gnsync会在那里写入日志信息。
|
||||
- **--notebook "Family"**: 同步哪个笔记本中的笔记。如果你那里留空,程序会创建一个以你同步文件夹命令的笔记本。
|
||||
|
||||
总结来说,Geeknote是一款花哨的Evernote的命令行客户端。我个人不常使用Evernote,但它仍然很漂亮和有用。命令行一方面让它变得很极客且很容易与shell脚本结合。同样,还有Git上fork出来的Geeknote,在ArchLinux AUR上称为[geeknote-improved-git][7],貌似它有更多的特性和比其他分支更积极的开发。但在我看来,还很值得再看看。
|
||||
|
||||
你认为Geeknote怎么样? 有什么你想用的么?或者你更喜欢使用传统的程序?在评论区中让我们知道。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/evernote-command-line-linux.html
|
||||
|
||||
作者:[Adrien Brochard][a]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/adrien
|
||||
[1]:http://xmodulo.com/manage-personal-expenses-command-line.html
|
||||
[2]:https://evernote.com/
|
||||
[3]:http://xmodulo.com/go/android_tutorial
|
||||
[4]:http://www.geeknote.me/
|
||||
[5]:https://aur.archlinux.org/packages/geeknote-git/
|
||||
[6]:http://www.geeknote.me/documentation/
|
||||
[7]:https://aur.archlinux.org/packages/geeknote-improved-git/
|
||||
Loading…
Reference in New Issue
Block a user