mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-03-21 02:10:11 +08:00
commit
945deaf5b1
@ -1,9 +1,9 @@
|
||||
|
||||
在 Ubuntu 14.04 中配置 PXE 服务器
|
||||
在 Ubuntu 14.04 中配置 PXE 服务器
|
||||
================================================================================
|
||||
|
||||

|
||||
|
||||
PXE(Preboot Execution Environment--预启动执行环境)服务器允许用户从网络中启动 Linux 发行版并且可以同时在数百台 PC 中安装而不需要 Linux ISO 镜像。如果你客户端的计算机没有 CD/DVD 或USB 引导盘,或者如果你想在大型企业中同时安装多台计算机,那么 PXE 服务器可以帮你节省时间和金钱。
|
||||
PXE(Preboot Execution Environment--预启动执行环境)服务器允许用户从网络中启动 Linux 发行版并且可以不需要 Linux ISO 镜像就能同时在数百台 PC 中安装。如果你客户端的计算机没有 CD/DVD 或USB 引导盘,或者如果你想在大型企业中同时安装多台计算机,那么 PXE 服务器可以帮你节省时间和金钱。
|
||||
|
||||
在这篇文章中,我们将告诉你如何在 Ubuntu 14.04 配置 PXE 服务器。
|
||||
|
||||
@ -11,11 +11,11 @@ PXE(Preboot Execution Environment--预启动执行环境)服务器允许用
|
||||
|
||||
开始前,你需要先设置 PXE 服务器使用静态 IP。在你的系统中要使用静态 IP 地址,需要编辑 “/etc/network/interfaces” 文件。
|
||||
|
||||
1. 打开 “/etc/network/interfaces” 文件.
|
||||
打开 “/etc/network/interfaces” 文件.
|
||||
|
||||
sudo nano /etc/network/interfaces
|
||||
|
||||
作如下修改:
|
||||
作如下修改:
|
||||
|
||||
# 回环网络接口
|
||||
auto lo
|
||||
@ -43,23 +43,23 @@ DHCP,TFTP 和 NFS 是 PXE 服务器的重要组成部分。首先,需要更
|
||||
|
||||
### 配置 DHCP 服务: ###
|
||||
|
||||
DHCP 代表动态主机配置协议(Dynamic Host Configuration Protocol),并且它主要用于动态分配网络配置参数,如用于接口和服务的 IP 地址。在 PXE 环境中,DHCP 服务器允许客户端请求并自动获得一个 IP 地址来访问网络。
|
||||
DHCP 代表动态主机配置协议(Dynamic Host Configuration Protocol),它主要用于动态分配网络配置参数,如用于接口和服务的 IP 地址。在 PXE 环境中,DHCP 服务器允许客户端请求并自动获得一个 IP 地址来访问网络。
|
||||
|
||||
1. 编辑 “/etc/default/dhcp3-server” 文件.
|
||||
1、编辑 “/etc/default/dhcp3-server” 文件.
|
||||
|
||||
sudo nano /etc/default/dhcp3-server
|
||||
|
||||
作如下修改:
|
||||
作如下修改:
|
||||
|
||||
INTERFACES="eth0"
|
||||
|
||||
保存 (Ctrl + o) 并退出 (Ctrl + x) 文件.
|
||||
|
||||
2. 编辑 “/etc/dhcp3/dhcpd.conf” 文件:
|
||||
2、编辑 “/etc/dhcp3/dhcpd.conf” 文件:
|
||||
|
||||
sudo nano /etc/dhcp/dhcpd.conf
|
||||
|
||||
作如下修改:
|
||||
作如下修改:
|
||||
|
||||
default-lease-time 600;
|
||||
max-lease-time 7200;
|
||||
@ -74,29 +74,29 @@ DHCP 代表动态主机配置协议(Dynamic Host Configuration Protocol),
|
||||
|
||||
保存文件并退出。
|
||||
|
||||
3. 启动 DHCP 服务.
|
||||
3、启动 DHCP 服务.
|
||||
|
||||
sudo /etc/init.d/isc-dhcp-server start
|
||||
|
||||
### 配置 TFTP 服务器: ###
|
||||
|
||||
TFTP 是一种文件传输协议,类似于 FTP。它不用进行用户认证也不能列出目录。TFTP 服务器总是监听网络上的 PXE 客户端。当它检测到网络中有 PXE 客户端请求 PXE 服务器时,它将提供包含引导菜单的网络数据包。
|
||||
TFTP 是一种文件传输协议,类似于 FTP,但它不用进行用户认证也不能列出目录。TFTP 服务器总是监听网络上的 PXE 客户端的请求。当它检测到网络中有 PXE 客户端请求 PXE 服务时,它将提供包含引导菜单的网络数据包。
|
||||
|
||||
1. 配置 TFTP 时,需要编辑 “/etc/inetd.conf” 文件.
|
||||
1、配置 TFTP 时,需要编辑 “/etc/inetd.conf” 文件.
|
||||
|
||||
sudo nano /etc/inetd.conf
|
||||
|
||||
作如下修改:
|
||||
作如下修改:
|
||||
|
||||
tftp dgram udp wait root /usr/sbin/in.tftpd /usr/sbin/in.tftpd -s /var/lib/tftpboot
|
||||
|
||||
保存文件并退出。
|
||||
保存文件并退出。
|
||||
|
||||
2. 编辑 “/etc/default/tftpd-hpa” 文件。
|
||||
2、编辑 “/etc/default/tftpd-hpa” 文件。
|
||||
|
||||
sudo nano /etc/default/tftpd-hpa
|
||||
|
||||
作如下修改:
|
||||
作如下修改:
|
||||
|
||||
TFTP_USERNAME="tftp"
|
||||
TFTP_DIRECTORY="/var/lib/tftpboot"
|
||||
@ -105,14 +105,14 @@ TFTP 是一种文件传输协议,类似于 FTP。它不用进行用户认证
|
||||
RUN_DAEMON="yes"
|
||||
OPTIONS="-l -s /var/lib/tftpboot"
|
||||
|
||||
保存文件并退出。
|
||||
保存文件并退出。
|
||||
|
||||
3. 使用 `xinetd` 让 boot 服务在每次系统开机时自动启动,并启动tftpd服务。
|
||||
3、 使用 `xinetd` 让 boot 服务在每次系统开机时自动启动,并启动tftpd服务。
|
||||
|
||||
sudo update-inetd --enable BOOT
|
||||
sudo service tftpd-hpa start
|
||||
|
||||
4. 检查状态。
|
||||
4、检查状态。
|
||||
|
||||
sudo netstat -lu
|
||||
|
||||
@ -123,7 +123,7 @@ TFTP 是一种文件传输协议,类似于 FTP。它不用进行用户认证
|
||||
|
||||
### 配置 PXE 启动文件 ###
|
||||
|
||||
现在,你需要将 PXE 引导文件 “pxelinux.0” 放在 TFTP 根目录下。为 TFTP 创建一个目录,并复制 syslinux 在 “/usr/lib/syslinux/” 下提供的所有引导程序文件到 “/var/lib/tftpboot/” 下,操作如下:
|
||||
现在,你需要将 PXE 引导文件 “pxelinux.0” 放在 TFTP 根目录下。为 TFTP 创建目录结构,并从 “/usr/lib/syslinux/” 复制 syslinux 提供的所有引导程序文件到 “/var/lib/tftpboot/” 下,操作如下:
|
||||
|
||||
sudo mkdir /var/lib/tftpboot
|
||||
sudo mkdir /var/lib/tftpboot/pxelinux.cfg
|
||||
@ -135,13 +135,13 @@ TFTP 是一种文件传输协议,类似于 FTP。它不用进行用户认证
|
||||
|
||||
PXE 配置文件定义了 PXE 客户端启动时显示的菜单,它能引导并与 TFTP 服务器关联。默认情况下,当一个 PXE 客户端启动时,它会使用自己的 MAC 地址指定要读取的配置文件,所以我们需要创建一个包含可引导内核列表的默认文件。
|
||||
|
||||
编辑 PXE 服务器配置文件使用可用的安装选项。.
|
||||
编辑 PXE 服务器配置文件,使用有效的安装选项。
|
||||
|
||||
编辑 “/var/lib/tftpboot/pxelinux.cfg/default,”
|
||||
编辑 “/var/lib/tftpboot/pxelinux.cfg/default”:
|
||||
|
||||
sudo nano /var/lib/tftpboot/pxelinux.cfg/default
|
||||
|
||||
作如下修改:
|
||||
作如下修改:
|
||||
|
||||
DEFAULT vesamenu.c32
|
||||
TIMEOUT 100
|
||||
@ -183,12 +183,12 @@ PXE 配置文件定义了 PXE 客户端启动时显示的菜单,它能引导
|
||||
|
||||
### 为 PXE 服务器添加 Ubuntu 14.04 桌面启动镜像 ###
|
||||
|
||||
对于这一步,Ubuntu 内核和 initrd 文件是必需的。要获得这些文件,你需要 Ubuntu 14.04 桌面 ISO 镜像。你可以通过以下命令下载 Ubuntu 14.04 ISO 镜像到 /mnt 目录:
|
||||
对于这一步需要 Ubuntu 内核和 initrd 文件。要获得这些文件,你需要 Ubuntu 14.04 桌面 ISO 镜像。你可以通过以下命令下载 Ubuntu 14.04 ISO 镜像到 /mnt 目录:
|
||||
|
||||
sudo cd /mnt
|
||||
sudo wget http://releases.ubuntu.com/14.04/ubuntu-14.04.3-desktop-amd64.iso
|
||||
|
||||
**注意**: 下载用的 URL 可能会改变,因为 ISO 镜像会进行更新。如果上面的网址无法访问,看看这个网站,了解最新的下载链接。
|
||||
**注意**: 下载用的 URL 可能会改变,因为 ISO 镜像会进行更新。如果上面的网址无法访问,看看[这个网站][4],了解最新的下载链接。
|
||||
|
||||
挂载 ISO 文件,使用以下命令将所有文件复制到 TFTP文件夹中:
|
||||
|
||||
@ -199,9 +199,9 @@ PXE 配置文件定义了 PXE 客户端启动时显示的菜单,它能引导
|
||||
|
||||
### 将导出的 ISO 目录配置到 NFS 服务器上 ###
|
||||
|
||||
现在,你需要通过 NFS 协议安装源镜像。你还可以使用 HTTP 和 FTP 来安装源镜像。在这里,我已经使用 NFS 导出 ISO 内容。
|
||||
现在,你需要通过 NFS 协议来设置“安装源镜像( Installation Source Mirrors)”。你还可以使用 HTTP 和 FTP 来安装源镜像。在这里,我已经使用 NFS 输出 ISO 内容。
|
||||
|
||||
要配置 NFS 服务器,你需要编辑 “etc/exports” 文件。
|
||||
要配置 NFS 服务器,你需要编辑 “/etc/exports” 文件。
|
||||
|
||||
sudo nano /etc/exports
|
||||
|
||||
@ -209,7 +209,7 @@ PXE 配置文件定义了 PXE 客户端启动时显示的菜单,它能引导
|
||||
|
||||
/var/lib/tftpboot/Ubuntu/14.04/amd64 *(ro,async,no_root_squash,no_subtree_check)
|
||||
|
||||
保存文件并退出。为使更改生效,启动 NFS 服务。
|
||||
保存文件并退出。为使更改生效,输出并启动 NFS 服务。
|
||||
|
||||
sudo exportfs -a
|
||||
sudo /etc/init.d/nfs-kernel-server start
|
||||
@ -218,9 +218,9 @@ PXE 配置文件定义了 PXE 客户端启动时显示的菜单,它能引导
|
||||
|
||||
### 配置网络引导 PXE 客户端 ###
|
||||
|
||||
PXE 客户端可以被任何具备 PXE 网络引导的系统来启用。现在,你的客户端可以启动并安装 Ubuntu 14.04 桌面,需要在系统的 BIOS 中设置 “Boot From Network” 选项。
|
||||
PXE 客户端可以是任何支持 PXE 网络引导的计算机系统。现在,你的客户端只需要在系统的 BIOS 中设置 “从网络引导(Boot From Network)” 选项就可以启动并安装 Ubuntu 14.04 桌面。
|
||||
|
||||
现在你可以去做 - 用网络引导启动你的 PXE 客户端计算机,你现在应该看到一个子菜单,显示了我们创建的 Ubuntu 14.04 桌面。
|
||||
现在准备出发吧 - 用网络引导启动你的 PXE 客户端计算机,你现在应该看到一个子菜单,显示了我们创建的 Ubuntu 14.04 桌面的菜单项。
|
||||
|
||||

|
||||
|
||||
@ -241,7 +241,7 @@ via: https://www.maketecheasier.com/configure-pxe-server-ubuntu/
|
||||
|
||||
作者:[Hitesh Jethva][a]
|
||||
译者:[strugglingyouth](https://github.com/strugglingyouth)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
@ -249,3 +249,4 @@ via: https://www.maketecheasier.com/configure-pxe-server-ubuntu/
|
||||
[1]:https://en.wikipedia.org/wiki/Preboot_Execution_Environment
|
||||
[2]:https://help.ubuntu.com/community/PXEInstallServer
|
||||
[3]:https://www.flickr.com/photos/jhcalderon/3681926417/
|
||||
[4]:http://releases.ubuntu.com/14.04/
|
||||
@ -1,4 +1,4 @@
|
||||
安装 Samba 并配置 Firewalld 和 SELinux 使得能在 Linux 和 Windows 之间共享文件 - 第六部分
|
||||
RHCE 系列(六):安装 Samba 并配置 Firewalld 和 SELinux 让 Linux 和 Windows 共享文件
|
||||
================================================================================
|
||||
由于计算机很少作为一个独立的系统工作,作为一个系统管理员或工程师,就应该知道如何在有多种类型的服务器之间搭设和维护网络。
|
||||
|
||||
@ -6,9 +6,9 @@
|
||||
|
||||

|
||||
|
||||
RHCE 系列第六部分 - 设置 Samba 文件共享
|
||||
*RHCE 系列第六部分 - 设置 Samba 文件共享*
|
||||
|
||||
如果有人叫你设置文件服务器用于协作或者配置很可能有多种不同类型操作系统和设备的企业环境,这篇文章就能派上用场。
|
||||
如果有人让你设置文件服务器用于协作或者配置很可能有多种不同类型操作系统和设备的企业环境,这篇文章就能派上用场。
|
||||
|
||||
由于你可以在网上找到很多关于 Samba 和 NFS 背景和技术方面的介绍,在这篇文章以及后续文章中我们就省略了这些部分直接进入到我们的主题。
|
||||
|
||||
@ -22,7 +22,7 @@ RHCE 系列第六部分 - 设置 Samba 文件共享
|
||||
|
||||

|
||||
|
||||
测试安装 Samba
|
||||
*测试安装 Samba*
|
||||
|
||||
在 box1 中安装以下软件包:
|
||||
|
||||
@ -36,7 +36,7 @@ RHCE 系列第六部分 - 设置 Samba 文件共享
|
||||
|
||||
### 步骤二: 设置通过 Samba 进行文件共享 ###
|
||||
|
||||
Samba 这么重要的原因之一是它为 SMB/CIFS 客户端(译者注:SMB 是微软和英特尔制定的一种通信协议,CIFS 是其中一个版本,更详细的介绍可以参考[Wiki][6])提供了文件和打印设备,这使得客户端看起来服务器就是一个 Windows 系统(我必须承认写这篇文章的时候我有一点激动,因为这是我多年前作为一个新手 Linux 系统管理员的第一次设置)。
|
||||
Samba 这么重要的原因之一是它为 SMB/CIFS 客户端(LCTT 译注:SMB 是微软和英特尔制定的一种通信协议,CIFS 是其中一个版本,更详细的介绍可以参考 [Wiki][6])提供了文件和打印设备,这使得服务器在客户端看起来就是一个 Windows 系统(我必须承认写这篇文章的时候我有一点激动,因为这是我多年前作为一个新手 Linux 系统管理员的第一次设置)。
|
||||
|
||||
**添加系统用户并设置权限和属性**
|
||||
|
||||
@ -91,9 +91,9 @@ Samba 这么重要的原因之一是它为 SMB/CIFS 客户端(译者注:SMB
|
||||
|
||||
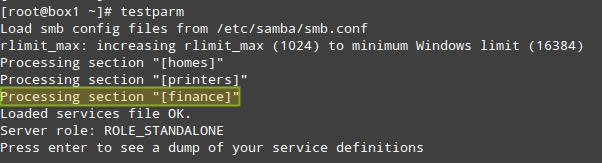
|
||||
|
||||
测试 Samba 配置
|
||||
*测试 Samba 配置*
|
||||
|
||||
如果你要添加另一个公开的共享目录(意味着没有任何验证),在 /etc/samba/smb.conf 中创建另一章节,在共享目录名称下面复制上面的章节,只需要把 public=no 更改为 public=yes 并去掉有效用户和写列表命令。
|
||||
如果你要添加另一个公开的共享目录(意味着不需要任何验证),在 /etc/samba/smb.conf 中创建另一章节,在共享目录名称下面复制上面的章节,只需要把 public=no 更改为 public=yes 并去掉有效用户(valid users)和写列表(write list)命令。
|
||||
|
||||
### 步骤五: 添加 Samba 用户 ###
|
||||
|
||||
@ -102,7 +102,7 @@ Samba 这么重要的原因之一是它为 SMB/CIFS 客户端(译者注:SMB
|
||||
# smbpasswd -a user1
|
||||
# smbpasswd -a user2
|
||||
|
||||
最后,重启 Samda,启用系统启动时自动启动服务,并确保共享目录对网络客户端可用:
|
||||
最后,重启 Samda,并让系统启动时自动启动该服务,确保共享目录对网络客户端可用:
|
||||
|
||||
# systemctl start smb
|
||||
# systemctl enable smb
|
||||
@ -112,7 +112,7 @@ Samba 这么重要的原因之一是它为 SMB/CIFS 客户端(译者注:SMB
|
||||
|
||||

|
||||
|
||||
验证 Samba 共享
|
||||
*验证 Samba 共享*
|
||||
|
||||
到这里,已经正确安装和配置了 Samba 文件服务器。现在让我们在 RHEL 7 和 Windows 8 客户端中测试该配置。
|
||||
|
||||
@ -120,12 +120,11 @@ Samba 这么重要的原因之一是它为 SMB/CIFS 客户端(译者注:SMB
|
||||
|
||||
首先,确保客户端可以访问 Samba 共享:
|
||||
|
||||
# smbclient –L 192.168.0.18 -U user2
|
||||
|
||||
# smbclient –L 192.168.0.18 -U user2
|
||||
|
||||

|
||||
|
||||
在 Linux 上挂载 Samba 共享
|
||||
*在 Linux 上挂载 Samba 共享*
|
||||
|
||||
(为 user1 重复上面的命令)
|
||||
|
||||
@ -135,11 +134,11 @@ Samba 这么重要的原因之一是它为 SMB/CIFS 客户端(译者注:SMB
|
||||
|
||||

|
||||
|
||||
挂载 Samba 网络共享
|
||||
*挂载 Samba 网络共享*
|
||||
|
||||
(其中 /media/samba 是一个已有的目录)
|
||||
|
||||
或者在 /etc/fstab 文件中添加下面的条目自动挂载:
|
||||
或者在 /etc/fstab 文件中添加下面的条目以自动挂载:
|
||||
|
||||
**fstab**
|
||||
|
||||
@ -147,7 +146,7 @@ Samba 这么重要的原因之一是它为 SMB/CIFS 客户端(译者注:SMB
|
||||
|
||||
//192.168.0.18/finance /media/samba cifs credentials=/media/samba/.smbcredentials,defaults 0 0
|
||||
|
||||
其中隐藏文件 /media/samba/.smbcredentials(它的权限被设置为 600 和 root:root)有两行,指示允许使用共享的账户的用户名和密码:
|
||||
其中隐藏文件 /media/samba/.smbcredentials(它的权限被设置为 600 和 root:root)有两行内容,指示允许使用共享的账户的用户名和密码:
|
||||
|
||||
**.smbcredentials**
|
||||
|
||||
@ -162,17 +161,17 @@ Samba 这么重要的原因之一是它为 SMB/CIFS 客户端(译者注:SMB
|
||||
|
||||

|
||||
|
||||
在 Samba 共享中创建文件
|
||||
*在 Samba 共享中创建文件*
|
||||
|
||||
正如你看到的,用权限 0770 和属主 user1:finance 创建了文件。
|
||||
|
||||
### 步骤七: 在 Windows 上挂载 Samba 共享 ###
|
||||
|
||||
要在 Windows 上挂载 Samba 共享,进入 ‘我的计算机’ 并选择 ‘计算机’,‘网络驱动映射’。下一步,为要映射的驱动分配一个字母并用不同的认证检查连接(下面的截图使用我的母语西班牙语):
|
||||
要在 Windows 上挂载 Samba 共享,进入 ‘我的计算机’ 并选择 ‘计算机’,‘网络驱动映射’。下一步,为要映射的驱动分配一个驱动器盘符并用不同的认证身份检查是否可以连接(下面的截图使用我的母语西班牙语):
|
||||
|
||||

|
||||
|
||||
在 Windows 中挂载 Samba 共享
|
||||
*在 Windows 中挂载 Samba 共享*
|
||||
|
||||
最后,让我们新建一个文件并检查权限和属性:
|
||||
|
||||
@ -188,7 +187,7 @@ Samba 这么重要的原因之一是它为 SMB/CIFS 客户端(译者注:SMB
|
||||
|
||||
在这篇文章中我们不仅介绍了如何使用不同操作系统设置 Samba 服务器和两个客户端,也介绍了[如何配置 Firewalld][3] 和 [服务器中的 SELinux][4] 以获取所需的组协作功能。
|
||||
|
||||
最后,同样重要的是,我推荐阅读网上的 [smb.conf man 手册][5] 查看其它可能针对你的情况比本文中介绍的场景更加合适的配置命令。
|
||||
最后,同样重要的是,我推荐阅读网上的 [smb.conf man 手册][5] ,查看其它比本文中介绍的场景更加合适你的场景的配置命令。
|
||||
|
||||
正如往常,欢迎在下面的评论框中留下你的评论或建议。
|
||||
|
||||
@ -198,7 +197,7 @@ via: http://www.tecmint.com/setup-samba-file-sharing-for-linux-windows-clients/
|
||||
|
||||
作者:[Gabriel Cánepa][a]
|
||||
译者:[ictlyh](http://www.mutouxiaogui.cn/blog/)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
125
sources/share/20151109 Open Source Alternatives to LastPass.md
Normal file
125
sources/share/20151109 Open Source Alternatives to LastPass.md
Normal file
@ -0,0 +1,125 @@
|
||||
Open Source Alternatives to LastPass
|
||||
================================================================================
|
||||
LastPass is a cross-platform password management program. For Linux, it is available as a plugin for Firefox, Chrome, and Opera. LastPass Sesame is available for Ubuntu/Debian and Fedora. There is also a version of LastPass compatible with Firefox Portable for installing on a USB key. And with LastPass Pocket for Ubuntu/Debian, Fedora and openSUSE, there's good coverage. While LastPass is a highly rated service, it is proprietary software. And LastPass has recently been absorbed by LogMeIn. If you're looking for an open source alternative, this article is for you.
|
||||
|
||||
We all face information overload. Whether you conduct business online, read for your job, or just read for pleasure, the internet is a vast source of information. Retaining that information on a long-term basis can be difficult. However, it is essential to recall certain items of information immediately. Passwords are one such example.
|
||||
|
||||
As a computer user, you face the dilemma of choosing the same password or a unique password for each service or web site you use. Matters are complicated because some sites place restrictions on the selection of the password. For example, a site may insist on a minimum number of characters, capital letters, numerals, and other characters which make choosing the same password for each site to be impossible. More importantly, there are good security reasons not to duplicate passwords. This inevitably means that individuals will simply have too many passwords to remember. One solution is to keep the passwords in written form. However, this is also highly insecure.
|
||||
|
||||
Instead of trying to remember an endless array of passwords, a popular solution is to use password manager software. In fact, this type of software is an essential tool for the active internet user. It makes it easy to retrieve, manage and secure all of your passwords. Most passwords are encrypted, either by the program or the filesystem. Consequently, the user only has to remember a single password. Password managers encourage users to choose unique, non-intuitive strong passwords for each service.
|
||||
|
||||
To provide an insight into the quality of software available for Linux, I introduce 4 excellent open source alternatives to LastPass.
|
||||
|
||||
### KeePassX ###
|
||||
|
||||

|
||||
|
||||
KeePassX is a multi-platform port of KeePass, an open source and cross-platform password manager. This utility helps you to manage your passwords in a secure way. You can put all your passwords in one database, which is locked with one master key or a key-disk. This lets users only need to remember one single master password or insert the key-disk to unlock the whole database.
|
||||
|
||||
The databases are encrypted using the algorithms AES (alias Rijndael) or Twofish using a 256 bit key.
|
||||
|
||||
Features include:
|
||||
|
||||
- Extensive management- title for each entry for better identification:
|
||||
- Determine different expiration dates
|
||||
- Insertion of attachments
|
||||
- User-defined symbols for groups and entries
|
||||
- Fast entry duplication
|
||||
- Sorting entries in groups
|
||||
- Search function: in specific groups or in the complete database
|
||||
- Auto-Type, a feature that allows you to e.g. log in to a web page by pressing a single key combination. KeePassX does the rest of the typing for you. Auto-Type reads the title of currently active window on your screen and matches it to the configured database entries
|
||||
- Database security with access to the KeePassX database being granted either with a password, a key-file (e.g. a CD or a memory-stick) or both
|
||||
- Automatic generation of secure passwords
|
||||
- Precaution features, quality indicator for chosen passwords hiding all passwords behind asterisks
|
||||
- Encryption- either the Advanced Encryption Standard (AES) or the Twofish algorithm are used, with encryption of the database in 256 bit sized increments
|
||||
- Import and export of entries. Import from PwManager (*.pwm) and KWallet (*.xml) files, Export as textfile (*.txt)
|
||||
|
||||
- Website: [www.keepassx.org][1]
|
||||
- Developer: KeePassX Team
|
||||
- License: GNU GPL v2
|
||||
- Version Number: 0.4.3
|
||||
|
||||
### Encryptr ###
|
||||
|
||||

|
||||
|
||||
Encryptr is an open source zero-knowledge cloud-based password manager / e-wallet powered by Crypton. Crypton is a JavaScript library that allows developers to write web applications where the server knows nothing of the contents a user is storing.
|
||||
|
||||
Encryptr stores your sensitive data like passwords, credit card data, PINs, or access codes, in the cloud. However, because it was built on the zero-knowledge Crypton framework, Encryptr ensures that only the user has the ability to access or read the confidential information.
|
||||
|
||||
Being cross-platform, it allows users to securely access their confidential data from a single account from the cloud, no matter where they are.
|
||||
|
||||
Features include:
|
||||
|
||||
- Very secure Zero-Knowledge Crypton Framework only ever encrypts or decrypts your data locally on your device
|
||||
- Simple to use
|
||||
- Cloud based
|
||||
- Stores three types of data it stores passwords, credit card numbers and general key/value pairs
|
||||
- Optional "Notes" field to all entries
|
||||
- Filtering / searching the entry list
|
||||
- Local encrypted caching of entries to speed up load time
|
||||
|
||||
- Website: [encryptr.org][2]
|
||||
- Developer: Tommy Williams
|
||||
- License: GNU GPL v3
|
||||
- Version Number: 1.2.0
|
||||
|
||||
### RatticDB ###
|
||||
|
||||

|
||||
|
||||
RatticDB is an open source Django based password management service.
|
||||
|
||||
RatticDB is built to be 'Password Lifecycle Management' and not simply a 'Password Storage Engine'. RatticDB aims to help you keep track of what passwords need to be changed and when. It does not include application level encryption.
|
||||
|
||||
Features include:
|
||||
|
||||
- Simple ACL scheme
|
||||
- Change Queue feature that allows users to see when they need to update passwords for the applications they use
|
||||
- Ansible configurations
|
||||
-
|
||||
- Website: [rattic.org][3]
|
||||
- Developer: Daniel Hall
|
||||
- License: GNU GPL v2
|
||||
- Version Number: 1.3.1
|
||||
|
||||
### Seahorse ###
|
||||
|
||||

|
||||
|
||||
Seahorse is a Gnome front end for GnuPG - the Gnu Privacy Guard program. Its goal is to provide an easy to use Key Management Tool, along with an easy to use interface for encryption operations.
|
||||
|
||||
It is a tool for secure communications and data storage. Data encryption and digital signature creation can easily be performed through a GUI and Key Management operations can easily be carried out through an intuitive interface.
|
||||
|
||||
Additionally, Seahorse includes a Gedit plugin, can handle files using Nautilus, an applet for managing stuff put in the clipboard and an agent for storing private passphrases, as well as a GnuPG and OpenSSH key manager.
|
||||
|
||||
Features include:
|
||||
|
||||
- Encrypt/decrypt/sign files and text
|
||||
- Manage your keys and keyring
|
||||
- Synchronize your keys and your keyring with key servers
|
||||
- Sign keys and publish
|
||||
- Cache your passphrase so you don't have to keep typing it
|
||||
- Backup your keys and keyring
|
||||
- Add an image in any GDK supported format as a OpenGPG photo ID
|
||||
- Create SSH keys, configure them, cache them
|
||||
- Internationalization support
|
||||
|
||||
- Website: [www.gnome.org/projects/seahorse][4]
|
||||
- Developer: Jacob Perkins, Jose Carlos, Garcia Sogo, Jean Schurger, Stef Walter, Adam Schreiber
|
||||
- License: GNU GPL v2
|
||||
- Version Number: 3.18.0
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linuxlinks.com/article/20151108125950773/LastPassAlternatives.html
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.keepassx.org/
|
||||
[2]:https://encryptr.org/
|
||||
[3]:http://rattic.org/
|
||||
[4]:http://www.gnome.org/projects/seahorse/
|
||||
379
sources/tech/20151109 How to Configure Tripwire IDS on Debian.md
Normal file
379
sources/tech/20151109 How to Configure Tripwire IDS on Debian.md
Normal file
@ -0,0 +1,379 @@
|
||||
How to Configure Tripwire IDS on Debian
|
||||
================================================================================
|
||||
This article is about Tripwire installation and configuration on Debian OS. It is a host based Intrusion detection system (IDS) for Linux environment. Prime function of tripwire IDS is to detect and report any unauthorized change (files and directories ) on linux system. After tripwire installation, baseline database created first, tripwire monitors and detects changes such as new file addition/creation, file modification and user who changed it etc. If the changes are legitimate, you can accept the changes to update tripwire database.
|
||||
|
||||
### Installation and Configuration ###
|
||||
|
||||
Tripwire installation on Debian VM is shown below.
|
||||
|
||||
# apt-get install tripwire
|
||||
|
||||

|
||||
|
||||
During installation, tripwire prompt for following configuration.
|
||||
|
||||
#### Site key Creation ####
|
||||
|
||||
Tripwire required a site passphrase to secure the tw.cfg tripwire configuration file and tw.pol tripwire policy file. Tripewire encrypte both files using given passphrase. Site passphrase is must even for a single instance tripwire.
|
||||
|
||||

|
||||
|
||||
#### Local Key passphrase ####
|
||||
|
||||
Local passphrase is needed for the protection of tripwire database and report files . Local key used by the tripwire to avoid unauthorized modification of tripwire baseline database.
|
||||
|
||||

|
||||
|
||||
#### Tripwire configuration path ####
|
||||
|
||||
Tripwire configuration saved in the /etc/tripwire/twcfg.txt file. It is used to generate encrypted configuration file tw.cfg.
|
||||
|
||||

|
||||
|
||||
**Tripwire Policy path**
|
||||
|
||||
Tripwire saves policies in /etc/tripwire/twpol.txt file . It is used for the generation of encrypted policy file tw.pol used by the tripwire.
|
||||
|
||||

|
||||
|
||||
Final installation of tripwire is shown in the following snapshot.
|
||||
|
||||

|
||||
|
||||
#### Tripwire Configuration file (twcfg.txt) ####
|
||||
|
||||
Tripwire configuration file (twcfg.txt) details is given below. Paths of encrypted policy file (tw.pol), site key (site.key) and local key (hostname-local.key) etc are given below.
|
||||
|
||||
ROOT =/usr/sbin
|
||||
|
||||
POLFILE =/etc/tripwire/tw.pol
|
||||
|
||||
DBFILE =/var/lib/tripwire/$(HOSTNAME).twd
|
||||
|
||||
REPORTFILE =/var/lib/tripwire/report/$(HOSTNAME)-$(DATE).twr
|
||||
|
||||
SITEKEYFILE =/etc/tripwire/site.key
|
||||
|
||||
LOCALKEYFILE =/etc/tripwire/$(HOSTNAME)-local.key
|
||||
|
||||
EDITOR =/usr/bin/editor
|
||||
|
||||
LATEPROMPTING =false
|
||||
|
||||
LOOSEDIRECTORYCHECKING =false
|
||||
|
||||
MAILNOVIOLATIONS =true
|
||||
|
||||
EMAILREPORTLEVEL =3
|
||||
|
||||
REPORTLEVEL =3
|
||||
|
||||
SYSLOGREPORTING =true
|
||||
|
||||
MAILMETHOD =SMTP
|
||||
|
||||
SMTPHOST =localhost
|
||||
|
||||
SMTPPORT =25
|
||||
|
||||
TEMPDIRECTORY =/tmp
|
||||
|
||||
#### Tripwire Policy Configuration ####
|
||||
|
||||
Configure tripwire configuration before generation of baseline database. It is necessary to disable few policies such as /dev , /proc ,/root/mail etc. Detailed policy file twpol.txt is given below.
|
||||
|
||||
@@section GLOBAL
|
||||
TWBIN = /usr/sbin;
|
||||
TWETC = /etc/tripwire;
|
||||
TWVAR = /var/lib/tripwire;
|
||||
|
||||
#
|
||||
# File System Definitions
|
||||
#
|
||||
@@section FS
|
||||
|
||||
#
|
||||
# First, some variables to make configuration easier
|
||||
#
|
||||
SEC_CRIT = $(IgnoreNone)-SHa ; # Critical files that cannot change
|
||||
|
||||
SEC_BIN = $(ReadOnly) ; # Binaries that should not change
|
||||
|
||||
SEC_CONFIG = $(Dynamic) ; # Config files that are changed
|
||||
# infrequently but accessed
|
||||
# often
|
||||
|
||||
SEC_LOG = $(Growing) ; # Files that grow, but that
|
||||
# should never change ownership
|
||||
|
||||
SEC_INVARIANT = +tpug ; # Directories that should never
|
||||
# change permission or ownership
|
||||
|
||||
SIG_LOW = 33 ; # Non-critical files that are of
|
||||
# minimal security impact
|
||||
|
||||
SIG_MED = 66 ; # Non-critical files that are of
|
||||
# significant security impact
|
||||
|
||||
SIG_HI = 100 ; # Critical files that are
|
||||
# significant points of
|
||||
# vulnerability
|
||||
|
||||
#
|
||||
# Tripwire Binaries
|
||||
#
|
||||
(
|
||||
rulename = "Tripwire Binaries",
|
||||
severity = $(SIG_HI)
|
||||
)
|
||||
{
|
||||
$(TWBIN)/siggen -> $(SEC_BIN) ;
|
||||
$(TWBIN)/tripwire -> $(SEC_BIN) ;
|
||||
$(TWBIN)/twadmin -> $(SEC_BIN) ;
|
||||
$(TWBIN)/twprint -> $(SEC_BIN) ;
|
||||
}
|
||||
{
|
||||
/boot -> $(SEC_CRIT) ;
|
||||
/lib/modules -> $(SEC_CRIT) ;
|
||||
}
|
||||
|
||||
(
|
||||
rulename = "Boot Scripts",
|
||||
severity = $(SIG_HI)
|
||||
)
|
||||
{
|
||||
/etc/init.d -> $(SEC_BIN) ;
|
||||
#/etc/rc.boot -> $(SEC_BIN) ;
|
||||
/etc/rcS.d -> $(SEC_BIN) ;
|
||||
/etc/rc0.d -> $(SEC_BIN) ;
|
||||
/etc/rc1.d -> $(SEC_BIN) ;
|
||||
/etc/rc2.d -> $(SEC_BIN) ;
|
||||
/etc/rc3.d -> $(SEC_BIN) ;
|
||||
/etc/rc4.d -> $(SEC_BIN) ;
|
||||
/etc/rc5.d -> $(SEC_BIN) ;
|
||||
/etc/rc6.d -> $(SEC_BIN) ;
|
||||
}
|
||||
|
||||
(
|
||||
rulename = "Root file-system executables",
|
||||
severity = $(SIG_HI)
|
||||
)
|
||||
{
|
||||
/bin -> $(SEC_BIN) ;
|
||||
/sbin -> $(SEC_BIN) ;
|
||||
}
|
||||
|
||||
#
|
||||
# Critical Libraries
|
||||
#
|
||||
(
|
||||
rulename = "Root file-system libraries",
|
||||
severity = $(SIG_HI)
|
||||
)
|
||||
{
|
||||
/lib -> $(SEC_BIN) ;
|
||||
}
|
||||
|
||||
#
|
||||
# Login and Privilege Raising Programs
|
||||
#
|
||||
(
|
||||
rulename = "Security Control",
|
||||
severity = $(SIG_MED)
|
||||
)
|
||||
{
|
||||
/etc/passwd -> $(SEC_CONFIG) ;
|
||||
/etc/shadow -> $(SEC_CONFIG) ;
|
||||
}
|
||||
{
|
||||
#/var/lock -> $(SEC_CONFIG) ;
|
||||
#/var/run -> $(SEC_CONFIG) ; # daemon PIDs
|
||||
/var/log -> $(SEC_CONFIG) ;
|
||||
}
|
||||
|
||||
# These files change the behavior of the root account
|
||||
(
|
||||
rulename = "Root config files",
|
||||
severity = 100
|
||||
)
|
||||
{
|
||||
/root -> $(SEC_CRIT) ; # Catch all additions to /root
|
||||
#/root/mail -> $(SEC_CONFIG) ;
|
||||
#/root/Mail -> $(SEC_CONFIG) ;
|
||||
/root/.xsession-errors -> $(SEC_CONFIG) ;
|
||||
#/root/.xauth -> $(SEC_CONFIG) ;
|
||||
#/root/.tcshrc -> $(SEC_CONFIG) ;
|
||||
#/root/.sawfish -> $(SEC_CONFIG) ;
|
||||
#/root/.pinerc -> $(SEC_CONFIG) ;
|
||||
#/root/.mc -> $(SEC_CONFIG) ;
|
||||
#/root/.gnome_private -> $(SEC_CONFIG) ;
|
||||
#/root/.gnome-desktop -> $(SEC_CONFIG) ;
|
||||
#/root/.gnome -> $(SEC_CONFIG) ;
|
||||
#/root/.esd_auth -> $(SEC_CONFIG) ;
|
||||
# /root/.elm -> $(SEC_CONFIG) ;
|
||||
#/root/.cshrc -> $(SEC_CONFIG) ;
|
||||
#/root/.bashrc -> $(SEC_CONFIG) ;
|
||||
#/root/.bash_profile -> $(SEC_CONFIG) ;
|
||||
# /root/.bash_logout -> $(SEC_CONFIG) ;
|
||||
#/root/.bash_history -> $(SEC_CONFIG) ;
|
||||
#/root/.amandahosts -> $(SEC_CONFIG) ;
|
||||
#/root/.addressbook.lu -> $(SEC_CONFIG) ;
|
||||
#/root/.addressbook -> $(SEC_CONFIG) ;
|
||||
#/root/.Xresources -> $(SEC_CONFIG) ;
|
||||
#/root/.Xauthority -> $(SEC_CONFIG) -i ; # Changes Inode number on login
|
||||
/root/.ICEauthority -> $(SEC_CONFIG) ;
|
||||
}
|
||||
|
||||
#
|
||||
# Critical devices
|
||||
#
|
||||
(
|
||||
rulename = "Devices & Kernel information",
|
||||
severity = $(SIG_HI),
|
||||
)
|
||||
{
|
||||
#/dev -> $(Device) ;
|
||||
#/proc -> $(Device) ;
|
||||
}
|
||||
|
||||
#### Tripwire Report ####
|
||||
|
||||
**tripwire –check** command checks the twpol.txt file and based on this file generates tripwire report which is shown below. If this is any error in the twpol.txt file, tripwire does not generate report.
|
||||
|
||||

|
||||
|
||||
**Report in text form**
|
||||
|
||||
root@VMdebian:/home/labadmin# tripwire --check
|
||||
|
||||
Parsing policy file: /etc/tripwire/tw.pol
|
||||
|
||||
*** Processing Unix File System ***
|
||||
|
||||
Performing integrity check...
|
||||
|
||||
Wrote report file: /var/lib/tripwire/report/VMdebian-20151024-122322.twr
|
||||
|
||||
Open Source Tripwire(R) 2.4.2.2 Integrity Check Report
|
||||
|
||||
Report generated by: root
|
||||
|
||||
Report created on: Sat Oct 24 12:23:22 2015
|
||||
|
||||
Database last updated on: Never
|
||||
|
||||
Report Summary:
|
||||
|
||||
=========================================================
|
||||
|
||||
Host name: VMdebian
|
||||
|
||||
Host IP address: 127.0.1.1
|
||||
|
||||
Host ID: None
|
||||
|
||||
Policy file used: /etc/tripwire/tw.pol
|
||||
|
||||
Configuration file used: /etc/tripwire/tw.cfg
|
||||
|
||||
Database file used: /var/lib/tripwire/VMdebian.twd
|
||||
|
||||
Command line used: tripwire --check
|
||||
|
||||
=========================================================
|
||||
|
||||
Rule Summary:
|
||||
|
||||
=========================================================
|
||||
|
||||
-------------------------------------------------------------------------------
|
||||
|
||||
Section: Unix File System
|
||||
|
||||
-------------------------------------------------------------------------------
|
||||
|
||||
Rule Name Severity Level Added Removed Modified
|
||||
|
||||
--------- -------------- ----- ------- --------
|
||||
|
||||
Other binaries 66 0 0 0
|
||||
|
||||
Tripwire Binaries 100 0 0 0
|
||||
|
||||
Other libraries 66 0 0 0
|
||||
|
||||
Root file-system executables 100 0 0 0
|
||||
|
||||
Tripwire Data Files 100 0 0 0
|
||||
|
||||
System boot changes 100 0 0 0
|
||||
|
||||
(/var/log)
|
||||
|
||||
Root file-system libraries 100 0 0 0
|
||||
|
||||
(/lib)
|
||||
|
||||
Critical system boot files 100 0 0 0
|
||||
|
||||
Other configuration files 66 0 0 0
|
||||
|
||||
(/etc)
|
||||
|
||||
Boot Scripts 100 0 0 0
|
||||
|
||||
Security Control 66 0 0 0
|
||||
|
||||
Root config files 100 0 0 0
|
||||
|
||||
Invariant Directories 66 0 0 0
|
||||
|
||||
Total objects scanned: 25943
|
||||
|
||||
Total violations found: 0
|
||||
|
||||
=========================Object Summary:================================
|
||||
|
||||
-------------------------------------------------------------------------------
|
||||
|
||||
# Section: Unix File System
|
||||
|
||||
-------------------------------------------------------------------------------
|
||||
|
||||
No violations.
|
||||
|
||||
===========================Error Report:=====================================
|
||||
|
||||
No Errors
|
||||
|
||||
-------------------------------------------------------------------------------
|
||||
|
||||
*** End of report ***
|
||||
|
||||
Open Source Tripwire 2.4 Portions copyright 2000 Tripwire, Inc. Tripwire is a registered
|
||||
|
||||
trademark of Tripwire, Inc. This software comes with ABSOLUTELY NO WARRANTY;
|
||||
|
||||
for details use --version. This is free software which may be redistributed
|
||||
|
||||
or modified only under certain conditions; see COPYING for details.
|
||||
|
||||
All rights reserved.
|
||||
|
||||
Integrity check complete.
|
||||
|
||||
### Conclusion ###
|
||||
|
||||
In this article, we learned installation and basic configuration of open source IDS tool Tripwire. First it generates baseline database and detects any change (file/folder) by comparing it with already generated baseline. However, tripwire is not live monitoring IDS.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/security/configure-tripwire-ids-debian/
|
||||
|
||||
作者:[nido][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://linoxide.com/author/naveeda/
|
||||
@ -0,0 +1,177 @@
|
||||
How to Install GitLab on Ubuntu / Fedora / Debian
|
||||
================================================================================
|
||||
Distributed version control was never easy before git. Git is a free and open source software that is designed to handle everything from small to very large projects with ease and speed. Git was first developed by Linus Torvalds who was also the founder of well-known Linux Kernel. [GitLab][1] is an awesome development in the field of git and distributed version control system. It is a web based Git repository managing application which includes features like code reviews,wikis, issue tracking and much more. Creating, reviewing and deploying codes is very easy, managed and fast with GitLab. It can be hosted in our own server though it also provides free repository hosting in its official server which is similar to Github. GitLab has two different editions, Community Edition and Enterprise Edition. Community Edition is a complete free and open source software licensed under MIT License whereas Enterprise Edition is under a proprietary license, and contains features that are not present in the CE version. Here are some easy steps on how we can install GitLab Community Edition on our machine running Ubuntu, Fedora and Debian as operating system.
|
||||
|
||||
### 1. Installing Pre-requisties ###
|
||||
|
||||
First of all, we'll install the required dependencies by GitLab Community Edition. We'll install curl in order to download our required files, openssh-server in order to ssh into our machine, ca-certificates to add CA Certifications and postfix as an MTA (Mail Transfer Agent).
|
||||
|
||||
Note: To install GitLab CE, we need to have a linux machine with at least 2 GB RAM and 2 Cores CPU.
|
||||
|
||||
#### On Ubuntu 14 .04/Debian 8.x ####
|
||||
|
||||
As these packages are available on the official repository of box Ubuntu 14.04 and Debian 8.x, we'll simply install it using apt-get package manager. To do so, we'll need to execute the following command in a terminal or console.
|
||||
|
||||
# apt-get install curl openssh-server ca-certificates postfix
|
||||
|
||||

|
||||
|
||||
#### On Fedora 22 ####
|
||||
|
||||
In Fedora 22, the default package manager is dnf as yum has been depreciated. So, we'll simply run the following dnf command in order to install those required packages.
|
||||
|
||||
# dnf install curl openssh-server postfix
|
||||
|
||||

|
||||
|
||||
### 2. Starting and Enabling Services ###
|
||||
|
||||
Now, we'll start the services of sshd and postfix using our default init system. And we'll also enable them to start automatically in every system boot.
|
||||
|
||||
#### On Ubuntu 14.04 ####
|
||||
|
||||
As SysVinit is installed as init system in Ubuntu 14.04, we'll use services command to start sshd and postfix daemon.
|
||||
|
||||
# service sshd start
|
||||
# service postfix start
|
||||
|
||||
Now, in order to make them start automatically in every boot, we'll need to run the following update-rc.d command.
|
||||
|
||||
# update-rc.d sshd enable
|
||||
# update-rc.d postfix enable
|
||||
|
||||
#### On Fedora 22/Debian 8.x ####
|
||||
|
||||
As Fedora 22 and Debian 8.x is shipped with Systemd instead of SysVinit as default init system, we'll simply run the following command to start the sshd and postfix services.
|
||||
|
||||
# systemctl start sshd postfix
|
||||
|
||||
Now, in order to make them start automatically in every boot, we'll need to run the following systemctl command.
|
||||
|
||||
# systemctl enable sshd postfix
|
||||
|
||||
Created symlink from /etc/systemd/system/multi-user.target.wants/sshd.service to /usr/lib/systemd/system/sshd.service.
|
||||
Created symlink from /etc/systemd/system/multi-user.target.wants/postfix.service to /usr/lib/systemd/system/postfix.service.
|
||||
|
||||
### 3. Downloading GitLab ###
|
||||
|
||||
We'll now download the binary installation files from the official GitLab CE Repository using curl. First, we'll need to navigate to the repository in order to get the download link of the required file. To do so, we'll need to run the following command in our linux machine running the respective operating system.
|
||||
|
||||
#### On Ubuntu 14.04 ####
|
||||
|
||||
As Ubuntu and Debian uses the same debian format file, we'll gonna search the required version of GitLab under [https://packages.gitlab.com/gitlab/gitlab-ce?filter=debs][2] and click on the link of the required release with ubuntu/trusty tag as we are running Ubuntu 14.04. A new page will appear in which we can see the Download button, we'll gonna right click it, get the link of the file and then download it using curl as shown bellow.
|
||||
|
||||
# curl https://packages.gitlab.com/gitlab/gitlab-ce/packages/ubuntu/trusty/gitlab-ce_8.1.2-ce.0_amd64.deb
|
||||
|
||||

|
||||
|
||||
#### On Debian 8.x ####
|
||||
|
||||
Like Ubuntu, we'll gonna search the required version of it under [https://packages.gitlab.com/gitlab/gitlab-ce?filter=debs][3] and click on the link of the requried release with debian/jessie tag as we are running Debian 8.x. Then, a new page will appear in which we'll right click on the Download button and get the file's download link. We'll next download it using curl as shown below.
|
||||
|
||||
# curl https://packages.gitlab.com/gitlab/gitlab-ce/packages/debian/jessie/gitlab-ce_8.1.2-ce.0_amd64.deb/download
|
||||
|
||||

|
||||
|
||||
#### On Fedora 22 ####
|
||||
|
||||
As Fedora uses the rpm file for packages, we'll gonna search the required version of GitLab under [https://packages.gitlab.com/gitlab/gitlab-ce?filter=rpms][4] and click on the link of the required release, here as we are running Fedora 22, we'll select the release with el/7 tag. A new page will appear in which we can see the Download button, we'll gonna right click it, get the link of the file and then download it using curl as shown bellow.
|
||||
|
||||
# curl https://packages.gitlab.com/gitlab/gitlab-ce/packages/el/7/gitlab-ce-8.1.2-ce.0.el7.x86_64.rpm/download
|
||||
|
||||

|
||||
|
||||
### 4. Installing GitLab ###
|
||||
|
||||
After our repository source is added in our linux machine, we'll now go for the installation of GitLab Community Edition using the default package manger of the respective distribution of linux.
|
||||
|
||||
#### On Ubuntu 14.04/Debian 8.x ####
|
||||
|
||||
To install GitLab CE in machine running Ubuntu 14.04 or Debian 8.x linux distribution which has apt-get package manager, we'll simply run the following command.
|
||||
|
||||
# dpkg -i gitlab-ce_8.1.2-ce.0_amd64.deb
|
||||
|
||||

|
||||
|
||||
#### On Fedora 22 ####
|
||||
|
||||
We can execute the following dnf command to install it in our Fedora 22 box.
|
||||
|
||||
# dnf install gitlab-ce-8.1.2-ce.0.el7.x86_64.rpm
|
||||
|
||||

|
||||
|
||||
### 5. Configuring and Starting GitLab ###
|
||||
|
||||
Next, as GitLab CE has been successfully installed in our linux system. We'll now go ahead for configuring and starting it. To do so, we'll need to run the following command which is same in Ubuntu, Debian and Fedora distributions.
|
||||
|
||||
# gitlab-ctl reconfigure
|
||||
|
||||

|
||||
|
||||
### 6. Allowing Firewall ###
|
||||
|
||||
If we have firewall program enabled for security in our linux box, we'll need to allow port 80 which is the default port of GitLab CE in order to make the web interface accessible across the network. Firewalld and iptables are most widely used firewall programs in linux distributions. In order to do so, we'll need to run the following commands.
|
||||
On Iptables
|
||||
|
||||
Iptables are installed and used in Ubuntu 14.04 by default. So, we'll need to run the following iptables commands to open port 80 in it.
|
||||
|
||||
# iptables -A INPUT -p tcp -m tcp --dport 80 -j ACCEPT
|
||||
|
||||
# /etc/init.d/iptables save
|
||||
|
||||
#### On Firewalld ####
|
||||
|
||||
As Fedora 22 and Debian 8.x has systemd installed by default, it contains firewalld running as firewall program. In order to open the port 80 (http service) on firewalld, we'll need to execute the below commands.
|
||||
|
||||
# firewall-cmd --permanent --add-service=http
|
||||
|
||||
success
|
||||
|
||||
# firewall-cmd --reload
|
||||
|
||||
success
|
||||
|
||||
### 7. Accessing GitLab Web Interface ###
|
||||
|
||||
Finally, we'll now go for accessing the web interface of GitLab CE. To do so, we'll need to point our web browser to the GitLab server with http://ip-address/ or http://domain.com/ according to our configuration. After we have pointed successfully, we'll see the following screen.
|
||||
|
||||

|
||||
|
||||
Now, in order to login to the panel, we'll need to click on Login button which will ask us an username and a password. We'll now enter the default username and password ie **root** and **5iveL!fe** respectively. After logging into the dashboard, we'll be asked to compulsorily enter the new password for our GitLab root user.
|
||||
|
||||

|
||||
|
||||
### 8. Creating Repository ###
|
||||
|
||||
After we have successfully changed the password and logged in to our dashboard, we'll now create a new repository for our new project. To do so, we'll need to go under Projects and click on **NEW PROJECT** green button.
|
||||
|
||||

|
||||
|
||||
Then, we'll be asked to enter the required information and settings for our repository as shown below. We can even import our project from many git repository providers and repositories.
|
||||
|
||||

|
||||
|
||||
After thats done, we'll be able to access our Git repository using any Git client including the basic git command line. We can see every activities done in the repository with other functions like creating a milestone, managing issues, merge requests, managing members, labels and Wiki for our projects.
|
||||
|
||||

|
||||
|
||||
### Conclusion ###
|
||||
|
||||
GitLab is an awesome open source web application for managing our git repository. It has a beautiful, responsive interface with plenty of cool features. It is packed with many cool features like managing groups, deploying keys, Continuous Integration, viewing logs, broadcast messages, hooks, system OAuth applications, templates and more. It has the ability to integrate tons of tools such as Slack, Hipchat, LDAP, JIRA, Jenkins, many types of hooks and a complete API. It has the minimum requirement of 2 GB RAM and 2 Cores CPU to run smoothly up to 500 users but also can be scaled to multiple active servers. If you have any questions, suggestions, feedback please write them in the comment box below so that we can improve or update our contents. Thank you !
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/linux-how-to/install-gitlab-on-ubuntu-fedora-debian/
|
||||
|
||||
作者:[Arun Pyasi][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://linoxide.com/author/arunp/
|
||||
[1]:https://about.gitlab.com/
|
||||
[2]:https://packages.gitlab.com/gitlab/gitlab-ce?filter=debs
|
||||
[3]:https://packages.gitlab.com/gitlab/gitlab-ce?filter=debs
|
||||
[4]:https://packages.gitlab.com/gitlab/gitlab-ce?filter=rpms
|
||||
@ -0,0 +1,79 @@
|
||||
How to Monitor the Progress of a Linux Command Line Operation Using PV Command
|
||||
================================================================================
|
||||

|
||||
|
||||
If you’re a Linux system admin, there’s no doubt that you must be spending most of your work time on the command line – installing and removing packages; monitoring system stats; copying, moving, deleting stuff; debugging problems; and more. There are times when you fire a command, and it takes a while before the operation completes. However, there are also times when the command you executed just hangs, leaving you guessing as to what’s actually happening behind the scenes.
|
||||
|
||||
Usually, Linux commands provide no information related to the progress of the ongoing operation, something that is very important especially when you have limited time. However, that doesn’t mean you’re helpless – there exists a command, dubbed pv, that displays useful progress information related to the ongoing command line operation. In this article we will discuss this command as well as its features through some easy-to-understand examples.
|
||||
|
||||
### PV Command ###
|
||||
|
||||
Developed by Andrew Wood, [PV][1] – which stands for Pipe Viewer – displays information related to the progress of data through a pipeline. The information includes time elapsed, percentage completed (with progress bar), current throughput rate, total data transferred, and ETA.
|
||||
|
||||
> “To use it, insert it in a pipeline between two processes, with the appropriate options. Its standard input will be passed through to its standard output and progress will be shown on standard error,”
|
||||
|
||||
The above explains the command’s man page.
|
||||
|
||||
### Download and Installation ###
|
||||
|
||||
Users of Debian-based systems like Ubuntu can easily install the utility by running the following command in terminal:
|
||||
|
||||
sudo apt-get install pv
|
||||
|
||||
If you’re using any other Linux distro, you can install the command using the package manager installed on your system. Once installed successfully you can use the command line utility in various scenarios (see the following section). It’s worth mentioning that pv version 1.2.0 has been used in all the examples mentioned in this article.
|
||||
|
||||
### Features and Usage ###
|
||||
|
||||
A very common scenario that probably most of us (who work on the command line in Linux) would relate to is copying a movie file from a USB drive to your computer. If you try to complete the aforementioned operation using the cp command, you’ll have to blindly wait until the copying is complete or some error is thrown.
|
||||
|
||||
However, the pv command can be helpful in this case. Here is an example:
|
||||
|
||||
pv /media/himanshu/1AC2-A8E3/fNf.mkv > ./Desktop/fnf.mkv
|
||||
|
||||
And here’s the output:
|
||||
|
||||

|
||||
|
||||
So, as you can see above, the command shows a lot of useful information related to the ongoing operation, including the amount of data that has been transferred, time elapsed, rate of transfer, progress bar, progress in percentage, and the amount of time left.
|
||||
|
||||
The `pv` command provides various display switches. For example, you can use `-p` for displaying percentage, `-t` for timer, `-r` for rate of transfer, `-e` for eta, and -b for byte counter. The good thing is that you won’t have to remember any of them, as all of them are enabled by default. However, should you exclusively require information related to only a particular display switch in the output, you can pass that switch in the pv command.
|
||||
|
||||
There’s also a `-n` display switch that allows the command to display an integer percentage, one per line on standard error, instead of the regular visual progress indicator. The following is an example of this switch in action:
|
||||
|
||||
pv -n /media/himanshu/1AC2-A8E3/fNf.mkv > ./Desktop/fnf.mkv
|
||||
|
||||

|
||||
|
||||
This particular display switch is suitable in scenarios where you want to pipe the output into the [dialog][2] command.
|
||||
|
||||
Moving on, there’s also a command line option, `-L`, that lets you modify the data transfer rate of the pv command. For example, I used -L to limit the data transfer rate to 2MB/s.
|
||||
|
||||
pv -L 2m /media/himanshu/1AC2-A8E3/fNf.mkv > ./Desktop/fnf.mkv
|
||||
|
||||

|
||||
|
||||
As can be seen in the screenshot above, the data transfer rate was capped according to my direction.
|
||||
|
||||
Another scenario where `pv` can help is while compressing files. Here is an example of how you can use this command while compressing files using Gzip:
|
||||
|
||||
pv /media/himanshu/1AC2-A8E3/fnf.mkv | gzip > ./Desktop/fnf.log.gz
|
||||
|
||||

|
||||
|
||||
### Conclusion ###
|
||||
|
||||
As you have observed, pv is a useful little utility that could help you save your precious time in case a command line operation isn’t behaving as expected. Plus, the information it displays can also be used in shell scripts. I’d strongly recommend this command; it’s worth giving a try.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.maketecheasier.com/monitor-progress-linux-command-line-operation/
|
||||
|
||||
作者:[Himanshu Arora][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://www.maketecheasier.com/author/himanshu/
|
||||
[1]:http://linux.die.net/man/1/pv
|
||||
[2]:http://linux.die.net/man/1/dialog
|
||||
106
sources/tech/20151109 How to Set Up AWStats On Ubuntu Server.md
Normal file
106
sources/tech/20151109 How to Set Up AWStats On Ubuntu Server.md
Normal file
@ -0,0 +1,106 @@
|
||||
How to Set Up AWStats On Ubuntu Server
|
||||
================================================================================
|
||||

|
||||
|
||||
AWStats is an open-source Web analytics reporting tool that generates advanced web, streaming, FTP or mail server statistics graphically. This log analyser works as a CGI or from command line and shows you all the possible information your log contains in a few graphical web pages. It uses a partial information file to be able to process large log files often and quickly. It supports most web server log file formats including Apache, IIS and many other web server log formats.
|
||||
|
||||
This article will help you to install and configure AWStats on Ubuntu.
|
||||
|
||||
### Install AWStats Package ###
|
||||
|
||||
By default, AWStats package is available in the Ubuntu repository.
|
||||
|
||||
You can install it by running:
|
||||
|
||||
sudo apt-get install awstats
|
||||
|
||||
Next you will need to enable the CGI module in Apache.
|
||||
|
||||
You can do this by running:
|
||||
|
||||
sudo a2enmod cgi
|
||||
|
||||
Now, restart Apache to reflect the changes.
|
||||
|
||||
sudo /etc/init.d/apache2 restart
|
||||
|
||||
### Configure AWStats ###
|
||||
|
||||
You need to create a configuration file for each domain or website you wish to view statistics for. In this example we will create a configuration file for “test.com“.
|
||||
|
||||
You can do this by duplicating the AWStats default configuration file to one with your domain name.
|
||||
|
||||
sudo cp /etc/awstats/awstats.conf /etc/awstats/awstats.test.com.conf
|
||||
|
||||
Now, you need to make some changes in the config file:
|
||||
|
||||
sudo nano /etc/awstats/awstats.test.com.conf
|
||||
|
||||
Update the settings shown below:
|
||||
|
||||
# Change to Apache log file, by default it's /var/log/apache2/access.log
|
||||
LogFile="/var/log/apache2/access.log"
|
||||
|
||||
# Change to the website domain name
|
||||
SiteDomain="test.com"
|
||||
HostAliases="www.test.com localhost 127.0.0.1"
|
||||
|
||||
# When this parameter is set to 1, AWStats adds a button on report page to allow to "update" statistics from a web browser
|
||||
AllowToUpdateStatsFromBrowser=1
|
||||
|
||||
Save and close the file.
|
||||
|
||||
After these changes, you need to build your initial statistics which will be generated from the current logs on your server. You can do this using:
|
||||
|
||||
sudo /usr/lib/cgi-bin/awstats.pl -config=test.com -update
|
||||
|
||||
The output will look something like this:
|
||||
|
||||

|
||||
|
||||
### Configure Apache For AWStats ###
|
||||
|
||||
Next, you need to configure Apache2 to show these stats. Now copy the content of the “cgi-bin” folder to the default document root directory of your Apache installation. By default, this is in the “/usr/lib/cgi-bin” folder.
|
||||
|
||||
You can do this by running:
|
||||
|
||||
sudo cp -r /usr/lib/cgi-bin /var/www/html/
|
||||
sudo chown www-data:www-data /var/www/html/cgi-bin/
|
||||
sudo chmod -R 755 /var/www/html/cgi-bin/
|
||||
|
||||
### Test AWStats ###
|
||||
|
||||
Now you can access your AWStats by visiting the url “http://your-server-ip/cgi-bin/awstats.pl?config=test.com.”
|
||||
It will show you a results page like this:
|
||||
|
||||

|
||||
|
||||
### Set Up Cron to Update Logs ###
|
||||
|
||||
It is recommended to schedule a cron job to regularly update the AWStats database using newly created log entries, so the stats get updated on a regular basis. This will also save your time.
|
||||
|
||||
To do this you need to edit the “/etc/crontab” file:
|
||||
|
||||
sudo nano /etc/crontab
|
||||
|
||||
Add the following line that tells AWStats to update every ten minutes.
|
||||
|
||||
*/10 * * * * root /usr/lib/cgi-bin/awstats.pl -config=test.com -update
|
||||
|
||||
Save and close the file.
|
||||
|
||||
### Conclusion ###
|
||||
|
||||
AWStats is a very useful tool that can give you an overview of what is happening on your website and assist with site analysis. It is very easy to install and configure. Feel free to comment below if you have any questions.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.maketecheasier.com/set-up-awstats-ubuntu/
|
||||
|
||||
作者:[Hitesh Jethva][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://www.maketecheasier.com/author/hiteshjethva/
|
||||
@ -0,0 +1,156 @@
|
||||
How to send email notifications using Gmail SMTP server on Linux
|
||||
================================================================================
|
||||
Suppose you want to configure a Linux app to send out email messages from your server or desktop. The email messages can be part of email newsletters, status updates (e.g., [Cachet][1]), monitoring alerts (e.g., [Monit][2]), disk events (e.g., [RAID mdadm][3]), and so on. While you can set up your [own outgoing mail server][4] to deliver messages, you can alternatively rely on a freely available public SMTP server as a maintenance-free option.
|
||||
|
||||
One of the most reliable **free SMTP servers** is from Google's Gmail service. All you have to do to send email notifications within your app is to add Gmail's SMTP server address and your credentials to the app, and you are good to go.
|
||||
|
||||
One catch with using Gmail's SMTP server is that there are various restrictions in place, mainly to combat spammers and email marketers who often abuse the server. For example, you can send messages to no more than 100 addresses at once, and no more than 500 recipients per day. Also, if you don't want to be flagged as a spammer, you cannot send a large number of undeliverable messages. When any of these limitations is reached, your Gmail account will temporarily be locked out for a day. In short, Gmail's SMTP server is perfectly fine for your personal use, but not meant for commercial bulk emails.
|
||||
|
||||
With that being said, let me demonstrate **how to use Gmail's SMTP server in Linux environment**.
|
||||
|
||||
### Google Gmail SMTP Server Setting ###
|
||||
|
||||
If you want to send emails from your app using Gmail's SMTP server, remember the following details.
|
||||
|
||||
- **Outgoing mail server (SMTP server)**: smtp.gmail.com
|
||||
- **Use authentication**: yes
|
||||
- **Use secure connection**: yes
|
||||
- **Username**: your Gmail account ID (e.g., "alice" if your email is alice@gmail.com)
|
||||
- **Password**: your Gmail password
|
||||
- **Port**: 587
|
||||
|
||||
Exact configuration syntax may vary depending on apps. In the rest of this tutorial, I will show you several useful examples of using Gmail SMTP server in Linux.
|
||||
|
||||
### Send Emails from the Command Line ###
|
||||
|
||||
As the first example, let's try the most basic email functionality: send an email from the command line using Gmail SMTP server. For this, I am going to use a command-line email client called mutt.
|
||||
|
||||
First, install mutt:
|
||||
|
||||
For Debian-based system:
|
||||
|
||||
$ sudo apt-get install mutt
|
||||
|
||||
For Red Hat based system:
|
||||
|
||||
$ sudo yum install mutt
|
||||
|
||||
Create a mutt configuration file (~/.muttrc) and specify in the file Gmail SMTP server information as follows. Replace <gmail-id> with your own Gmail ID. Note that this configuration is for sending emails only (not receiving emails).
|
||||
|
||||
$ vi ~/.muttrc
|
||||
|
||||
----------
|
||||
|
||||
set from = "<gmail-id>@gmail.com"
|
||||
set realname = "Dan Nanni"
|
||||
set smtp_url = "smtp://<gmail-id>@smtp.gmail.com:587/"
|
||||
set smtp_pass = "<gmail-password>"
|
||||
|
||||
Now you are ready to send out an email using mutt:
|
||||
|
||||
$ echo "This is an email body." | mutt -s "This is an email subject" alice@yahoo.com
|
||||
|
||||
To attach a file in an email, use "-a" option:
|
||||
|
||||
$ echo "This is an email body." | mutt -s "This is an email subject" alice@yahoo.com -a ~/test_attachment.jpg
|
||||
|
||||

|
||||
|
||||
Using Gmail SMTP server means that the emails appear as sent from your Gmail account. In other words, a recepient will see your Gmail address as the sender's address. If you want to use your domain as the email sender, you need to use Gmail SMTP relay service instead.
|
||||
|
||||
### Send Email Notification When a Server is Rebooted ###
|
||||
|
||||
If you are running a [virtual private server (VPS)][5] for some critical website, one recommendation is to monitor VPS reboot activities. As a more practical example, let's consider how to set up email notifications for every reboot event on your VPS. Here I assume you are using systemd on your VPS, and show you how to create a custom systemd boot-time service for automatic email notifications.
|
||||
|
||||
First create the following script reboot_notify.sh which takes care of email notifications.
|
||||
|
||||
$ sudo vi /usr/local/bin/reboot_notify.sh
|
||||
|
||||
----------
|
||||
|
||||
#!/bin/sh
|
||||
|
||||
echo "`hostname` was rebooted on `date`" | mutt -F /etc/muttrc -s "Notification on `hostname`" alice@yahoo.com
|
||||
|
||||
----------
|
||||
|
||||
$ sudo chmod +x /usr/local/bin/reboot_notify.sh
|
||||
|
||||
In the script, I use "-F" option to specify the location of system-wide mutt configuration file. So don't forget to create /etc/muttrc file and populate Gmail SMTP information as described earlier.
|
||||
|
||||
Now let's create a custom systemd service as follows.
|
||||
|
||||
$ sudo mkdir -p /usr/local/lib/systemd/system
|
||||
$ sudo vi /usr/local/lib/systemd/system/reboot-task.service
|
||||
|
||||
----------
|
||||
|
||||
[Unit]
|
||||
Description=Send a notification email when the server gets rebooted
|
||||
DefaultDependencies=no
|
||||
Before=reboot.target
|
||||
|
||||
[Service]
|
||||
Type=oneshot
|
||||
ExecStart=/usr/local/bin/reboot_notify.sh
|
||||
|
||||
[Install]
|
||||
WantedBy=reboot.target
|
||||
|
||||
Once the service file is created, enable and start the service.
|
||||
|
||||
$ sudo systemctl enable reboot-task
|
||||
$ sudo systemctl start reboot-task
|
||||
|
||||
From now on, you will be receiving a notification email every time the VPS gets rebooted.
|
||||
|
||||
|
||||
|
||||
### Send Email Notification from Server Usage Monitoring ###
|
||||
|
||||
As a final example, let me present a real-world application called [Monit][6], which is a pretty useful server monitoring application. It comes with comprehensive [VPS][7] monitoring capabilities (e.g., CPU, memory, processes, file system), as well as email notification functions.
|
||||
|
||||
If you want to receive email notifications for any event on your VPS (e.g., server overload) generated by Monit, you can add the following SMTP information to Monit configuration file.
|
||||
|
||||
set mailserver smtp.gmail.com port 587
|
||||
username "<your-gmail-ID>" password "<gmail-password>"
|
||||
using tlsv12
|
||||
|
||||
set mail-format {
|
||||
from: <your-gmail-ID>@gmail.com
|
||||
subject: $SERVICE $EVENT at $DATE on $HOST
|
||||
message: Monit $ACTION $SERVICE $EVENT at $DATE on $HOST : $DESCRIPTION.
|
||||
|
||||
Yours sincerely,
|
||||
Monit
|
||||
}
|
||||
|
||||
# the person who will receive notification emails
|
||||
set alert alice@yahoo.com
|
||||
|
||||
Here is the example email notification sent by Monit for excessive CPU load.
|
||||
|
||||
|
||||
|
||||
### Conclusion ###
|
||||
|
||||
As you can imagine, there will be so many different ways to take advantage of free SMTP servers like Gmail. But once again, remember that the free SMTP server is not meant for commercial usage, but only for your own personal project. If you are using Gmail SMTP server inside any app, feel free to share your use case.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/send-email-notifications-gmail-smtp-server-linux.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/nanni
|
||||
[1]:http://xmodulo.com/setup-system-status-page.html
|
||||
[2]:http://xmodulo.com/server-monitoring-system-monit.html
|
||||
[3]:http://xmodulo.com/create-software-raid1-array-mdadm-linux.html
|
||||
[4]:http://xmodulo.com/mail-server-ubuntu-debian.html
|
||||
[5]:http://xmodulo.com/go/digitalocean
|
||||
[6]:http://xmodulo.com/server-monitoring-system-monit.html
|
||||
[7]:http://xmodulo.com/go/digitalocean
|
||||
@ -0,0 +1,125 @@
|
||||
Install Android On BQ Aquaris Ubuntu Phone In Linux
|
||||
================================================================================
|
||||

|
||||
|
||||
If you happen to own the first Ubuntu phone and want to **replace Ubuntu with Android on the bq Aquaris e4.5**, this post is going to help you.
|
||||
|
||||
There can be plenty of reasons why you might want to remove Ubuntu and use the mainstream Android OS. One of the foremost reason is that the OS itself is at an early stage and intend to target developers and enthusiasts. Whatever may be your reason, installing Android on bq Aquaris is a piece of cake, thanks to the tools provided by bq.
|
||||
|
||||
Let’s see what to do we need to install Android on bq Aquaris.
|
||||
|
||||
### Prerequisite ###
|
||||
|
||||
- Working Internet connection to download Android factory image and install tools for flashing Android
|
||||
- USB data cable
|
||||
- A system running Linux
|
||||
|
||||
This tutorial is performed using Ubuntu 15.10. But the steps should be applicable to most other Linux distributions.
|
||||
|
||||
### Replace Ubuntu with Android in bq Aquaris e4.5 ###
|
||||
|
||||
#### Step 1: Download Android firmware ####
|
||||
|
||||
First step is to download the Android image for bq Aquaris e4.5. Good thing is that it is available from the bq’s support website. You can download the firmware, around 650 MB in size, from the link below:
|
||||
|
||||
- [Download Android for bq Aquaris e4.5][1]
|
||||
|
||||
Yes, you would get OTA updates with it. At present the firmware version is 2.0.1 which is based on Android Lolipop. Over time, there could be a new firmware based on Marshmallow and then the above link could be outdated.
|
||||
|
||||
I suggest to check the [bq support page and download][2] the latest firmware from there.
|
||||
|
||||
Once downloaded, extract it. In the extracted directory, look for **MT6582_Android_scatter.txt** file. We shall be using it later.
|
||||
|
||||
#### Step 2: Download flash tool ####
|
||||
|
||||
bq has provided its own flash tool, Herramienta MTK Flash Tool, for easier installation of Android or Ubuntu on the device. You can download the tool from the link below:
|
||||
|
||||
- [Download MTK Flash Tool][3]
|
||||
|
||||
Since the flash tool might be upgraded in future, you can always get the latest version of flash tool from the [bq support page][4].
|
||||
|
||||
Once downloaded extract the downloaded file. You should see an executable file named **flash_tool** in it. We shall be using it later.
|
||||
|
||||
#### Step 3: Remove conflicting packages (optional) ####
|
||||
|
||||
If you are using recent version of Ubuntu or Ubuntu based Linux distributions, you may encounter “BROM ERROR : S_UNDEFINED_ERROR (1001)” later in this tutorial.
|
||||
|
||||
To avoid this error, you’ll have to uninstall conflicting package. Use the commands below:
|
||||
|
||||
sudo apt-get remove modemmanager
|
||||
|
||||
Restart udev service with the command below:
|
||||
|
||||
sudo service udev restart
|
||||
|
||||
Just to check for any possible side effects on kernel module cdc_acm, run the command below:
|
||||
|
||||
lsmod | grep cdc_acm
|
||||
|
||||
If the output of the above command is an empty list, you’ll have to reinstall this kernel module:
|
||||
|
||||
sudo modprobe cdc_acm
|
||||
|
||||
#### Step 4: Prepare to flash Android ####
|
||||
|
||||
Go to the downloaded and extracted flash tool directory (in step 2). Use command line for this purpose because you’ll have to use the root privileges here.
|
||||
|
||||
Presuming that you saved it in the Downloads directory, use the command below to go to this directory (in case you do not know how to navigate between directories in command line).
|
||||
|
||||
cd ~/Downloads/SP_Flash*
|
||||
|
||||
After that use the command below to run the flash tool as root:
|
||||
|
||||
sudo ./flash_tool
|
||||
|
||||
You’ll see a window popped as the one below. Don’t bother about Download Agent field, it will be automatically filled. Just focus on Scatter-loading field.
|
||||
|
||||

|
||||
|
||||
Remember we talked about **MT6582_Android_scatter.txt** in step 1? This text file is in the extracted directory of the Andriod firmware you downloaded in step 1. Click on Scatter-loading (in the above picture) and point to MT6582_Android_scatter.txt file.
|
||||
|
||||
When you do that, you’ll see several green lines like the one below:
|
||||
|
||||

|
||||
|
||||
#### Step 5: Flashing Android ####
|
||||
|
||||
We are almost ready. Switch off your phone and connect it to your computer via a USB cable.
|
||||
|
||||
Select Firmware Upgrade from the dropdown and after that click on the big download button.
|
||||
|
||||

|
||||
|
||||
If everything is correct, you should see a flash status in the bottom of the tool:
|
||||
|
||||

|
||||
|
||||
When the procedure is successfully completed, you’ll see a notification like this:
|
||||
|
||||

|
||||
|
||||
Unplug your phone and power it on. You should see a white screen with AQUARIS written in the middle and at bottom, “powered by Android” would be displayed. It might take upto 10 minutes before you could configure and start using Android.
|
||||
|
||||
Note: If something goes wrong in the process, Press power, volume up, volume down button together and boot in to fast boot mode. Turn off again and connect the cable again. Repeat the process of firmware upgrade. It should work.
|
||||
|
||||
### Conclusion ###
|
||||
|
||||
Thanks to the tools provided, it becomes easier to **flash Android on bq Ubuntu Phone**. Of course, you can use the same steps to replace Android with Ubuntu. All you need is to download Ubuntu firmware instead of Android.
|
||||
|
||||
I hope this tutorial helped you to replace Ubuntu with Android on your bq phone. If you have questions or suggestions, feel free to ask in the comment section below.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://itsfoss.com/install-android-ubuntu-phone/
|
||||
|
||||
作者:[Abhishek][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://itsfoss.com/author/abhishek/
|
||||
[1]:https://storage.googleapis.com/otas/2014/Smartphones/Aquaris_E4.5_L/2.0.1_20150623-1900_bq-FW.zip
|
||||
[2]:http://www.bq.com/gb/support/aquaris-e4-5
|
||||
[3]:https://storage.googleapis.com/otas/2014/Smartphones/Aquaris_E4.5/Ubuntu/Web%20version/Web%20version/SP_Flash_Tool_exe_linux_v5.1424.00.zip
|
||||
[4]:http://www.bq.com/gb/support/aquaris-e4-5-ubuntu-edition
|
||||
Loading…
Reference in New Issue
Block a user