mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-02-25 00:50:15 +08:00
[translated]How to filter BGP routes in Quagga BGP router
This commit is contained in:
parent
9bb79b9a3a
commit
913bda2922
@ -1,202 +0,0 @@
|
|||||||
[bazz222]
|
|
||||||
How to filter BGP routes in Quagga BGP router
|
|
||||||
================================================================================
|
|
||||||
In the [previous tutorial][1], we demonstrated how to turn a CentOS box into a BGP router using Quagga. We also covered basic BGP peering and prefix exchange setup. In this tutorial, we will focus on how we can control incoming and outgoing BGP prefixes by using **prefix-list** and **route-map**.
|
|
||||||
|
|
||||||
As described in earlier tutorials, BGP routing decisions are made based on the prefixes received/advertised. To ensure error-free routing, it is recommended that you use some sort of filtering mechanism to control these incoming and outgoing prefixes. For example, if one of your BGP neighbors starts advertising prefixes which do not belong to them, and you accept such bogus prefixes by mistake, your traffic can be sent to that wrong neighbor, and end up going nowhere (so-called "getting blackholed"). To make sure that such prefixes are not received or advertised to any neighbor, you can use prefix-list and route-map. The former is a prefix-based filtering mechanism, while the latter is a more general prefix-based policy mechanism used to fine-tune actions.
|
|
||||||
|
|
||||||
We will show you how to use prefix-list and route-map in Quagga.
|
|
||||||
|
|
||||||
### Topology and Requirement ###
|
|
||||||
|
|
||||||
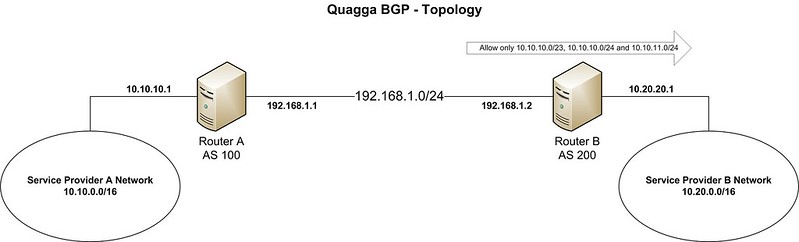
In this tutorial, we assume the following topology.
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
Service provider A has already established an eBGP peering with service provider B, and they are exchanging routing information between them. The AS and prefix details are as stated below.
|
|
||||||
|
|
||||||
- **Peering block**: 192.168.1.0/24
|
|
||||||
- **Service provider A**: AS 100, prefix 10.10.0.0/16
|
|
||||||
- **Service provider B**: AS 200, prefix 10.20.0.0/16
|
|
||||||
|
|
||||||
In this scenario, service provider B wants to receive only prefixes 10.10.10.0/23, 10.10.10.0/24 and 10.10.11.0/24 from provider A.
|
|
||||||
|
|
||||||
### Quagga Installation and BGP Peering ###
|
|
||||||
|
|
||||||
In the [previous tutorial][1], we have already covered the method of installing Quagga and setting up BGP peering. So we will not go through the details here. Nonetheless, I am providing a summary of BGP configuration and prefix advertisements:
|
|
||||||
|
|
||||||

|
|
||||||
|
|
||||||
The above output indicates that the BGP peering is up. Router-A is advertising multiple prefixes towards router-B. Router-B, on the other hand, is advertising a single prefix 10.20.0.0/16 to router-A. Both routers are receiving the prefixes without any problems.
|
|
||||||
|
|
||||||
### Creating Prefix-List ###
|
|
||||||
|
|
||||||
In a router, a prefix can be blocked with either an ACL or prefix-list. Using prefix-list is often preferred to ACLs since prefix-list is less processor intensive than ACLs. Also, prefix-list is easier to create and maintain.
|
|
||||||
|
|
||||||
ip prefix-list DEMO-PRFX permit 192.168.0.0/23
|
|
||||||
|
|
||||||
The above command creates prefix-list called 'DEMO-FRFX' that allows only 192.168.0.0/23.
|
|
||||||
|
|
||||||
Another great feature of prefix-list is that we can specify a range of subnet mask(s). Take a look at the following example:
|
|
||||||
|
|
||||||
ip prefix-list DEMO-PRFX permit 192.168.0.0/23 le 24
|
|
||||||
|
|
||||||
The above command creates prefix-list called 'DEMO-PRFX' that permits prefixes between 192.168.0.0/23 and /24, which are 192.168.0.0/23, 192.168.0.0/24 and 192.168.1.0/24. The 'le' operator means less than or equal to. You can also use 'ge' operator for greater than or equal to.
|
|
||||||
|
|
||||||
A single prefix-list statement can have multiple permit/deny actions. Each statement is assigned a sequence number which can be determined automatically or specified manually.
|
|
||||||
|
|
||||||
Multiple prefix-list statements are parsed one by one in the increasing order of sequence numbers. When configuring prefix-list, we should keep in mind that there is always an **implicit deny** at the end of all prefix-list statements. This means that anything that is not explicitly allowed will be denied.
|
|
||||||
|
|
||||||
To allow everything, we can use the following prefix-list statement which allows any prefix starting from 0.0.0.0/0 up to anything with subnet mask /32.
|
|
||||||
|
|
||||||
ip prefix-list DEMO-PRFX permit 0.0.0.0/0 le 32
|
|
||||||
|
|
||||||
Now that we know how to create prefix-list statements, we will create prefix-list called 'PRFX-LST' that will allow prefixes required in our scenario.
|
|
||||||
|
|
||||||
router-b# conf t
|
|
||||||
router-b(config)# ip prefix-list PRFX-LST permit 10.10.10.0/23 le 24
|
|
||||||
|
|
||||||
### Creating Route-Map ###
|
|
||||||
|
|
||||||
Besides prefix-list and ACLs, there is yet another mechanism called route-map, which can control prefixes in a BGP router. In fact, route-map can fine-tune possible actions more flexibly on the prefixes matched with an ACL or prefix-list.
|
|
||||||
|
|
||||||
Similar to prefix-list, a route-map statement specifies permit or deny action, followed by a sequence number. Each route-map statement can have multiple permit/deny actions with it. For example:
|
|
||||||
|
|
||||||
route-map DEMO-RMAP permit 10
|
|
||||||
|
|
||||||
The above statement creates route-map called 'DEMO-RMAP', and adds permit action with sequence 10. Now we will use match command under sequence 10.
|
|
||||||
|
|
||||||
router-a(config-route-map)# match (press ? in the keyboard)
|
|
||||||
|
|
||||||
----------
|
|
||||||
|
|
||||||
as-path Match BGP AS path list
|
|
||||||
community Match BGP community list
|
|
||||||
extcommunity Match BGP/VPN extended community list
|
|
||||||
interface match first hop interface of route
|
|
||||||
ip IP information
|
|
||||||
ipv6 IPv6 information
|
|
||||||
metric Match metric of route
|
|
||||||
origin BGP origin code
|
|
||||||
peer Match peer address
|
|
||||||
probability Match portion of routes defined by percentage value
|
|
||||||
tag Match tag of route
|
|
||||||
|
|
||||||
As we can see, route-map can match many attributes. We will match a prefix in this tutorial.
|
|
||||||
|
|
||||||
route-map DEMO-RMAP permit 10
|
|
||||||
match ip address prefix-list DEMO-PRFX
|
|
||||||
|
|
||||||
The match command will match the IP addresses permitted by the prefix-list 'DEMO-PRFX' created earlier (i.e., prefixes 192.168.0.0/23, 192.168.0.0/24 and 192.168.1.0/24).
|
|
||||||
|
|
||||||
Next, we can modify the attributes by using the set command. The following example shows possible use cases of set.
|
|
||||||
|
|
||||||
route-map DEMO-RMAP permit 10
|
|
||||||
match ip address prefix-list DEMO-PRFX
|
|
||||||
set (press ? in keyboard)
|
|
||||||
|
|
||||||
----------
|
|
||||||
|
|
||||||
aggregator BGP aggregator attribute
|
|
||||||
as-path Transform BGP AS-path attribute
|
|
||||||
atomic-aggregate BGP atomic aggregate attribute
|
|
||||||
comm-list set BGP community list (for deletion)
|
|
||||||
community BGP community attribute
|
|
||||||
extcommunity BGP extended community attribute
|
|
||||||
forwarding-address Forwarding Address
|
|
||||||
ip IP information
|
|
||||||
ipv6 IPv6 information
|
|
||||||
local-preference BGP local preference path attribute
|
|
||||||
metric Metric value for destination routing protocol
|
|
||||||
metric-type Type of metric
|
|
||||||
origin BGP origin code
|
|
||||||
originator-id BGP originator ID attribute
|
|
||||||
src src address for route
|
|
||||||
tag Tag value for routing protocol
|
|
||||||
vpnv4 VPNv4 information
|
|
||||||
weight BGP weight for routing table
|
|
||||||
|
|
||||||
As we can see, the set command can be used to change many attributes. For a demonstration purpose, we will set BGP local preference.
|
|
||||||
|
|
||||||
route-map DEMO-RMAP permit 10
|
|
||||||
match ip address prefix-list DEMO-PRFX
|
|
||||||
set local-preference 500
|
|
||||||
|
|
||||||
Just like prefix-list, there is an implicit deny at the end of all route-map statements. So we will add another permit statement in sequence number 20 to permit everything.
|
|
||||||
|
|
||||||
route-map DEMO-RMAP permit 10
|
|
||||||
match ip address prefix-list DEMO-PRFX
|
|
||||||
set local-preference 500
|
|
||||||
!
|
|
||||||
route-map DEMO-RMAP permit 20
|
|
||||||
|
|
||||||
The sequence number 20 does not have a specific match command, so it will, by default, match everything. Since the decision is permit, everything will be permitted by this route-map statement.
|
|
||||||
|
|
||||||
If you recall, our requirement is to only allow/deny some prefixes. So in our scenario, the set command is not necessary. We will just use one permit statement as follows.
|
|
||||||
|
|
||||||
router-b# conf t
|
|
||||||
router-b(config)# route-map RMAP permit 10
|
|
||||||
router-b(config-route-map)# match ip address prefix-list PRFX-LST
|
|
||||||
|
|
||||||
This route-map statement should do the trick.
|
|
||||||
|
|
||||||
### Applying Route-Map ###
|
|
||||||
|
|
||||||
Keep in mind that ACLs, prefix-list and route-map are not effective unless they are applied to an interface or a BGP neighbor. Just like ACLs or prefix-list, a single route-map statement can be used with any number of interfaces or neighbors. However, any one interface or a neighbor can support only one route-map statement for inbound, and one for outbound traffic.
|
|
||||||
|
|
||||||
We will apply the created route-map to the BGP configuration of router-B for neighbor 192.168.1.1 with incoming prefix advertisement.
|
|
||||||
|
|
||||||
router-b# conf terminal
|
|
||||||
router-b(config)# router bgp 200
|
|
||||||
router-b(config-router)# neighbor 192.168.1.1 route-map RMAP in
|
|
||||||
|
|
||||||
Now, we check the routes advertised and received by using the following commands.
|
|
||||||
|
|
||||||
For advertised routes:
|
|
||||||
|
|
||||||
show ip bgp neighbor-IP advertised-routes
|
|
||||||
|
|
||||||
For received routes:
|
|
||||||
|
|
||||||
show ip bgp neighbor-IP routes
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
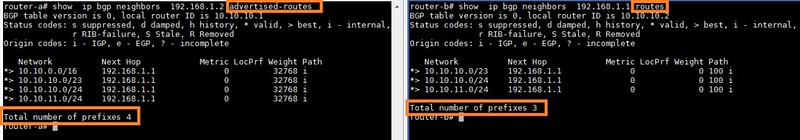
You can see that while router-A is advertising four prefixes towards router-B, router-B is accepting only three prefixes. If we check the range, we can see that only the prefixes that are allowed by route-map are visible on router-B. All other prefixes are discarded.
|
|
||||||
|
|
||||||
**Tip**: If there is no change in the received prefixes, try resetting the BGP session using the command: "clear ip bgp neighbor-IP". In our case:
|
|
||||||
|
|
||||||
clear ip bgp 192.168.1.1
|
|
||||||
|
|
||||||
As we can see, the requirement has been met. We can create similar prefix-list and route-map statements in routers A and B to further control inbound and outbound prefixes.
|
|
||||||
|
|
||||||
I am summarizing the configuration in one place so you can see it all at a glance.
|
|
||||||
|
|
||||||
router bgp 200
|
|
||||||
network 10.20.0.0/16
|
|
||||||
neighbor 192.168.1.1 remote-as 100
|
|
||||||
neighbor 192.168.1.1 route-map RMAP in
|
|
||||||
!
|
|
||||||
ip prefix-list PRFX-LST seq 5 permit 10.10.10.0/23 le 24
|
|
||||||
!
|
|
||||||
route-map RMAP permit 10
|
|
||||||
match ip address prefix-list PRFX-LST
|
|
||||||
|
|
||||||
### Summary ###
|
|
||||||
|
|
||||||
In this tutorial, we showed how we can filter BGP routes in Quagga by defining prefix-list and route-map. We also demonstrated how we can combine prefix-list with route-map to fine-control incoming prefixes. You can create your own prefix-list and route-map in a similar way to match your network requirements. These tools are one of the most effective ways to protect the production network from route poisoning and advertisement of bogon routes.
|
|
||||||
|
|
||||||
Hope this helps.
|
|
||||||
|
|
||||||
--------------------------------------------------------------------------------
|
|
||||||
|
|
||||||
via: http://xmodulo.com/filter-bgp-routes-quagga-bgp-router.html
|
|
||||||
|
|
||||||
作者:[Sarmed Rahman][a]
|
|
||||||
译者:[译者ID](https://github.com/译者ID)
|
|
||||||
校对:[校对者ID](https://github.com/校对者ID)
|
|
||||||
|
|
||||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
|
||||||
|
|
||||||
[a]:http://xmodulo.com/author/sarmed
|
|
||||||
[1]:http://xmodulo.com/centos-bgp-router-quagga.html
|
|
||||||
@ -0,0 +1,201 @@
|
|||||||
|
如何使用 Quagga BGP(边界网关协议)路由器来过滤 BGP 路由
|
||||||
|
================================================================================
|
||||||
|
在[之前的文章][1]中,我们介绍了如何使用 Quagga 将 CentOS 服务器变成一个 BGP 路由器,也介绍了 BGP 对等体和前缀交换设置。在本教程中,我们将重点放在如何使用**前缀列表**和**路由映射**来分别控制数据注入和数据输出。
|
||||||
|
|
||||||
|
之前的文章已经说过,BGP 的路由判定是基于前缀的收取和前缀的广播。为避免错误的路由,你需要使用一些过滤机制来控制这些前缀的收发。举个例子,如果你的一个 BGP 邻居开始广播一个本不属于它们的前缀,而你也将错就错地接收了这些不正常前缀,并且也将它转发到网络上,这个转发过程会不断进行下去,永不停止(所谓的“黑洞”就这样产生了)。所以确保这样的前缀不会被收到,或者不会转发到任何网络,要达到这个目的,你可以使用前缀列表和路由映射。前者是基于前缀的过滤机制,后者是更为常用的基于前缀的策略,可用于精调过滤机制。
|
||||||
|
|
||||||
|
本文会向你展示如何在 Quagga 中使用前缀列表和路由映射。
|
||||||
|
|
||||||
|
### 拓扑和需求 ###
|
||||||
|
|
||||||
|
本教程使用下面的拓扑结构。
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
服务供应商A和供应商B已经将对方设置成为 eBGP 对等体,实现互相通信。他们的自治系统号和前缀分别如下所示。
|
||||||
|
|
||||||
|
- **对等区段**: 192.168.1.0/24
|
||||||
|
- **服务供应商A**: 自治系统号 100, 前缀 10.10.0.0/16
|
||||||
|
- **服务供应商B**: 自治系统号 200, 前缀 10.20.0.0/16
|
||||||
|
|
||||||
|
在这个场景中,供应商B只想从A接收 10.10.10.0/23, 10.10.10.0/24 和 10.10.11.0/24 三个前缀。
|
||||||
|
|
||||||
|
### 安装 Quagga 和设置 BGP 对等体 ###
|
||||||
|
|
||||||
|
在[之前的教程][1]中,我们已经写了安装 Quagga 和设置 BGP 对等体的方法,所以这里就不再详细说明了,只简单介绍下 BGP 配置和前缀广播:
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
上图说明 BGP 对等体已经开启。Router-A 在向 router-B 广播多个前缀,而 Router-B 也在向 router-A 广播一个前缀 10.20.0.0/16。两个路由器都能正确无误地收发前缀。
|
||||||
|
|
||||||
|
### 创建前缀列表 ###
|
||||||
|
|
||||||
|
路由器可以使用 ACL 或前缀列表来过滤一个前缀。前缀列表比 ACL 更常用,因为前者处理步骤少,而且易于创建和维护。
|
||||||
|
|
||||||
|
ip prefix-list DEMO-PRFX permit 192.168.0.0/23
|
||||||
|
|
||||||
|
上面的命令创建了名为“DEMO-FRFX”的前缀列表,只允许存在 192.168.0.0/23 这个前缀。
|
||||||
|
|
||||||
|
前缀列表的另一个牛X功能是支持子网掩码区间,请看下面的例子:
|
||||||
|
|
||||||
|
ip prefix-list DEMO-PRFX permit 192.168.0.0/23 le 24
|
||||||
|
|
||||||
|
这个命令创建的前缀列表包含在 192.168.0.0/23 和 /24 之间的前缀,分别是 192.168.0.0/23, 192.168.0.0/24 and 192.168.1.0/24。运算符“le”表示小于等于,你也可以使用“ge”表示大于等于。
|
||||||
|
|
||||||
|
一个前缀列表语句可以有多个允许或拒绝操作。每个语句都自动或手动地分配有一个序列号。
|
||||||
|
|
||||||
|
如果存在多个前缀列表语句,则这些语句会按序列号顺序被依次执行。在配置前缀列表的时候,我们需要注意在所有前缀列表语句后面的**隐性拒绝**属性,就是说凡是不被明显允许的,都会被拒绝。
|
||||||
|
|
||||||
|
如果要设置成允许所有前缀,前缀列表语句设置如下:
|
||||||
|
|
||||||
|
ip prefix-list DEMO-PRFX permit 0.0.0.0/0 le 32
|
||||||
|
|
||||||
|
我们已经知道如何创建前缀列表语句了,现在我们要创建一个名为“PRFX-LST”的前缀列表,来满足我们实验场景的需求。
|
||||||
|
|
||||||
|
router-b# conf t
|
||||||
|
router-b(config)# ip prefix-list PRFX-LST permit 10.10.10.0/23 le 24
|
||||||
|
|
||||||
|
### 创建路由映射 ###
|
||||||
|
|
||||||
|
除了前缀列表和 ACL,这里还有另一种机制,叫做路由映射,也可以在 BGP 路由器中控制前缀。事实上,路由映射针对前缀匹配的微调效果比前缀列表和 ACL 都强。
|
||||||
|
|
||||||
|
与前缀列表类似,路由映射语句也可以指定允许和拒绝操作,也需要分配一个序列号。每个路由匹配可以有多个允许或拒绝操作。例如:
|
||||||
|
|
||||||
|
route-map DEMO-RMAP permit 10
|
||||||
|
|
||||||
|
上面的语句创建了名为“DEMO-RMAP”的路由映射,添加序列号为10的允许操作。现在我们在这个序列号所对应的路由映射下使用 match 命令进行匹配。
|
||||||
|
|
||||||
|
router-a(config-route-map)# match (press ? in the keyboard)
|
||||||
|
|
||||||
|
----------
|
||||||
|
|
||||||
|
as-path Match BGP AS path list
|
||||||
|
community Match BGP community list
|
||||||
|
extcommunity Match BGP/VPN extended community list
|
||||||
|
interface match first hop interface of route
|
||||||
|
ip IP information
|
||||||
|
ipv6 IPv6 information
|
||||||
|
metric Match metric of route
|
||||||
|
origin BGP origin code
|
||||||
|
peer Match peer address
|
||||||
|
probability Match portion of routes defined by percentage value
|
||||||
|
tag Match tag of route
|
||||||
|
|
||||||
|
如你所见,路由映射可以匹配很多属性,本教程需要匹配一个前缀。
|
||||||
|
|
||||||
|
route-map DEMO-RMAP permit 10
|
||||||
|
match ip address prefix-list DEMO-PRFX
|
||||||
|
|
||||||
|
这个 match 命令会匹配之前建好的前缀列表中允许的 IP 地址(也就是前缀 192.168.0.0/23, 192.168.0.0/24 和 192.168.1.0/24)。
|
||||||
|
|
||||||
|
接下来,我们可以使用 set 命令来修改这些属性。例子如下:
|
||||||
|
|
||||||
|
route-map DEMO-RMAP permit 10
|
||||||
|
match ip address prefix-list DEMO-PRFX
|
||||||
|
set (press ? in keyboard)
|
||||||
|
|
||||||
|
----------
|
||||||
|
|
||||||
|
aggregator BGP aggregator attribute
|
||||||
|
as-path Transform BGP AS-path attribute
|
||||||
|
atomic-aggregate BGP atomic aggregate attribute
|
||||||
|
comm-list set BGP community list (for deletion)
|
||||||
|
community BGP community attribute
|
||||||
|
extcommunity BGP extended community attribute
|
||||||
|
forwarding-address Forwarding Address
|
||||||
|
ip IP information
|
||||||
|
ipv6 IPv6 information
|
||||||
|
local-preference BGP local preference path attribute
|
||||||
|
metric Metric value for destination routing protocol
|
||||||
|
metric-type Type of metric
|
||||||
|
origin BGP origin code
|
||||||
|
originator-id BGP originator ID attribute
|
||||||
|
src src address for route
|
||||||
|
tag Tag value for routing protocol
|
||||||
|
vpnv4 VPNv4 information
|
||||||
|
weight BGP weight for routing table
|
||||||
|
|
||||||
|
如你所见,set 命令也可以修改很多属性。为了作个示范,我们修改一下 BGP 的 local-preference 这个属性。
|
||||||
|
|
||||||
|
route-map DEMO-RMAP permit 10
|
||||||
|
match ip address prefix-list DEMO-PRFX
|
||||||
|
set local-preference 500
|
||||||
|
|
||||||
|
如同前缀列表,路由映射语句的末尾也有隐性拒绝操作。所以我们需要添加另外一个允许语句(使用序列号20)来允许所有前缀。
|
||||||
|
|
||||||
|
route-map DEMO-RMAP permit 10
|
||||||
|
match ip address prefix-list DEMO-PRFX
|
||||||
|
set local-preference 500
|
||||||
|
!
|
||||||
|
route-map DEMO-RMAP permit 20
|
||||||
|
|
||||||
|
序列号20未指定任何匹配命令,所以默认匹配所有前缀。在这个路由映射语句中,所有的前缀都被允许。
|
||||||
|
|
||||||
|
回想一下,我们的需求是只允许或只拒绝一些前缀,所以上面的 set 命令不应该存在于这个场景中。我们只需要一个允许语句,如下如示:
|
||||||
|
|
||||||
|
router-b# conf t
|
||||||
|
router-b(config)# route-map RMAP permit 10
|
||||||
|
router-b(config-route-map)# match ip address prefix-list PRFX-LST
|
||||||
|
|
||||||
|
这个路由映射才是我们需要的效果。
|
||||||
|
|
||||||
|
### 应用路由映射 ###
|
||||||
|
|
||||||
|
注意,在被应用于一个接口或一个 BGP 邻居之前,ACL、前缀列表和路由映射都不会生效。与 ACL 和前缀列表一样,一条路由映射语句也能被多个接口或邻居使用。然而,一个接口或一个邻居只能有一条路由映射语句应用于输入端,以及一条路由映射语句应用于输出端。
|
||||||
|
|
||||||
|
下面我们将这条路由映射语句应用于 router-B 的 BGP 配置,为 router-B 的邻居 192.168.1.1 设置输入前缀广播。
|
||||||
|
|
||||||
|
router-b# conf terminal
|
||||||
|
router-b(config)# router bgp 200
|
||||||
|
router-b(config-router)# neighbor 192.168.1.1 route-map RMAP in
|
||||||
|
|
||||||
|
现在检查下广播路由和收取路由。
|
||||||
|
|
||||||
|
显示广播路由的命令:
|
||||||
|
|
||||||
|
show ip bgp neighbor-IP advertised-routes
|
||||||
|
|
||||||
|
显示收取路由的命令:
|
||||||
|
|
||||||
|
show ip bgp neighbor-IP routes
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
可以看到,router-A 有4条路由前缀到达 router-B,而 router-B 只接收3条。查看一下范围,我们就能知道只有被路由映射允许的前缀才能在 router-B 上显示出来,其他的前缀一概丢弃。
|
||||||
|
|
||||||
|
**小提示**:如果接收前缀内容没有刷新,试试重置下 BGP 会话,使用这个命令:clear ip bgp neighbor-IP。本教程中命令如下:
|
||||||
|
|
||||||
|
clear ip bgp 192.168.1.1
|
||||||
|
|
||||||
|
我们能看到系统已经满足我们的要求了。接下来我们可以在 router-A 和 router-B 上创建相似的前缀列表和路由映射语句来更好地控制输入输出的前缀。
|
||||||
|
|
||||||
|
这里把配置过程总结一下,方便查看。
|
||||||
|
|
||||||
|
router bgp 200
|
||||||
|
network 10.20.0.0/16
|
||||||
|
neighbor 192.168.1.1 remote-as 100
|
||||||
|
neighbor 192.168.1.1 route-map RMAP in
|
||||||
|
!
|
||||||
|
ip prefix-list PRFX-LST seq 5 permit 10.10.10.0/23 le 24
|
||||||
|
!
|
||||||
|
route-map RMAP permit 10
|
||||||
|
match ip address prefix-list PRFX-LST
|
||||||
|
|
||||||
|
### 总结 ###
|
||||||
|
|
||||||
|
在本教程中我们演示了如何在 Quagga 中设置前缀列表和路由映射来过滤 BGP 路由。我们也展示了如何将前缀列表结合进路由映射来进行输入前缀的微调功能。你可以参考这些方法来设置满足自己需求的前缀列表和路由映射。这些工具是保护网络免受路由毒化和来自 bogon 路由(LCTT 译注:指不该出现在internet路由表中的地址)的广播。
|
||||||
|
|
||||||
|
希望本文对你有帮助。
|
||||||
|
|
||||||
|
--------------------------------------------------------------------------------
|
||||||
|
|
||||||
|
via: http://xmodulo.com/filter-bgp-routes-quagga-bgp-router.html
|
||||||
|
|
||||||
|
作者:[Sarmed Rahman][a]
|
||||||
|
译者:[bazz2](https://github.com/bazz2)
|
||||||
|
校对:[校对者ID](https://github.com/校对者ID)
|
||||||
|
|
||||||
|
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||||
|
|
||||||
|
[a]:http://xmodulo.com/author/sarmed
|
||||||
|
[1]:http://xmodulo.com/centos-bgp-router-quagga.html
|
||||||
Loading…
Reference in New Issue
Block a user