mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-03-30 02:40:11 +08:00
commit
8e8c0190dc
published
20150616 Computer Laboratory - Raspberry Pi- Lesson 8 Screen03.md20170223 Use Emacs to create OAuth 2.0 UML sequence diagrams.md20170721 Firefox and org-protocol URL Capture.md20190206 And, Ampersand, and - in Linux.md20190212 Two graphical tools for manipulating PDFs on the Linux desktop.md20190213 How to use Linux Cockpit to manage system performance.md
sources
talk
tech
20180611 3 open source alternatives to Adobe Lightroom.md20180926 HTTP- Brief History of HTTP.md20190121 Akira- The Linux Design Tool We-ve Always Wanted.md20190206 And, Ampersand, and - in Linux.md20190206 Getting started with Vim visual mode.md20190216 FinalCrypt - An Open Source File Encryption Application.md
translated
@ -1,34 +1,30 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (qhwdw)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-10585-1.html)
|
||||
[#]: subject: (Computer Laboratory – Raspberry Pi: Lesson 8 Screen03)
|
||||
[#]: via: (https://www.cl.cam.ac.uk/projects/raspberrypi/tutorials/os/screen03.html)
|
||||
[#]: author: (Alex Chadwick https://www.cl.cam.ac.uk)
|
||||
|
||||
计算机实验室 – 树莓派:课程 8 屏幕03
|
||||
计算机实验室之树莓派:课程 8 屏幕03
|
||||
======
|
||||
|
||||
屏幕03 课程基于屏幕02 课程来构建,它教你如何绘制文本,和一个操作系统命令行参数上的一个小特性。假设你已经有了[课程 7:屏幕02][1] 的操作系统代码,我们将以它为基础来构建。
|
||||
|
||||
### 1、字符串的理论知识
|
||||
|
||||
是的,我们的任务是为这个操作系统绘制文本。我们有几个问题需要去处理,最紧急的那个可能是如何去保存文本。令人难以置信的是,文本是迄今为止在计算机上最大的缺陷之一。原本应该是简单的数据类型却导致了操作系统的崩溃,破坏了完美的加密,并给使用不同字母表的用户带来了许多问题。尽管如此,它仍然是极其重要的数据类型,因为它将计算机和用户很好地连接起来。文本是计算机能够理解的非常好的结构,同时人类使用它时也有足够的可读性。
|
||||
是的,我们的任务是为这个操作系统绘制文本。我们有几个问题需要去处理,最紧急的那个可能是如何去保存文本。令人难以置信的是,文本是迄今为止在计算机上最大的缺陷之一。原本应该是简单的数据类型却导致了操作系统的崩溃,从而削弱其他方面的加密效果,并给使用其它字母表的用户带来了许多问题。尽管如此,它仍然是极其重要的数据类型,因为它将计算机和用户很好地连接起来。文本是计算机能够理解的非常好的结构,同时人类使用它时也有足够的可读性。
|
||||
|
||||
```
|
||||
可变数据类型,比如文本要求能够进行很复杂的处理。
|
||||
```
|
||||
那么,文本是如何保存的呢?非常简单,我们使用一种方法,给每个字母分配一个唯一的编号,然后我们保存一系列的这种编号。看起来很容易吧。问题是,那个编号的数量是不固定的。一些文本段可能比其它的长。保存普通数字,我们有一些固有的限制,即:32 位,我们不能超过这个限制,我们要添加方法去使用该长度的数字等等。“文本”这个术语,我们经常也叫它“字符串”,我们希望能够写一个可用于可变长度字符串的函数,否则就需要写很多函数!对于一般的数字来说,这不是个问题,因为只有几种通用的数字格式(字节、字、半字节、双字节)。
|
||||
|
||||
那么,文本是如何保存的呢?非常简单,我们使用一种方法,给每个字母分配一个唯一的编号,然后我们保存一系列的这种编号。看起来很容易吧。问题是,那个编号的数字是不固定的。一些文本片断可能比其它的长。与保存普通数字一样,我们有一些固有的限制,即:3 位,我们不能超过这个限制,我们添加方法去使用那种长数字等等。“文本”这个术语,我们经常也叫它“字符串”,我们希望能够写一个可用于变长字符串的函数,否则就需要写很多函数!对于一般的数字来说,这不是个问题,因为只有几种通用的数字格式(字节、字、半字节、双字节)。
|
||||
> 可变数据类型(比如文本)要求能够进行很复杂的处理。
|
||||
|
||||
```
|
||||
缓冲区溢出攻击祸害计算机由来已久。最近,Wii、Xbox 和 Playstation 2、以及大型系统如 Microsoft 的 Web 和数据库服务器,都遭受到缓冲区溢出攻击。
|
||||
```
|
||||
因此,如何判断字符串长度?我想显而易见的答案是存储字符串的长度,然后去存储组成字符串的字符。这称为长度前缀,因为长度位于字符串的前面。不幸的是,计算机科学家的先驱们不同意这么做。他们认为使用一个称为空终止符(`NULL`)的特殊字符(用 `\0` 表示)来表示字符串结束更有意义。这样确定简化了许多字符串算法,因为你只需要持续操作直到遇到空终止符为止。不幸的是,这成为了许多安全问题的根源。如果一个恶意用户给你一个特别长的字符串会发生什么状况?如果没有足够的空间去保存这个特别长的字符串会发生什么状况?你可以使用一个字符串复制函数来做复制,直到遇到空终止符为止,但是因为字符串特别长,而覆写了你的程序,怎么办?这看上去似乎有些较真,但是,缓冲区溢出攻击还是经常发生。长度前缀可以很容易地缓解这种问题,因为它可以很容易地推算出保存这个字符串所需要的缓冲区的长度。作为一个操作系统开发者,我留下这个问题,由你去决定如何才能更好地存储文本。
|
||||
|
||||
因此,如何判断字符串长度?我想显而易见的答案是存储多长的字符串,然后去存储组成字符串的字符。这称为长度前缀,因为长度位于字符串的前面。不幸的是,计算机科学家的先驱们不同意这么做。他们认为使用一个称为空终止符(NULL)的特殊字符(用 \0表示)来表示字符串结束更有意义。这样确定简化了许多字符串算法,因为你只需要持续操作直到遇到空终止符为止。不幸的是,这成为了许多安全问题的根源。如果一个恶意用户给你一个特别长的字符串会发生什么状况?如果没有足够的空间去保存这个特别长的字符串会发生什么状况?你可以使用一个字符串复制函数来做复制,直到遇到空终止符为止,但是因为字符串特别长,而覆写了你的程序,怎么办?这看上去似乎有些较真,但尽管如此,缓冲区溢出攻击还是经常发生。长度前缀可以很容易地缓解这种问题,因为它可以很容易地推算出保存这个字符串所需要的缓冲区的长度。作为一个操作系统开发者,我留下这个问题,由你去决定如何才能更好地存储文本。
|
||||
> 缓冲区溢出攻击祸害计算机由来已久。最近,Wii、Xbox 和 Playstation 2、以及大型系统如 Microsoft 的 Web 和数据库服务器,都遭受到缓冲区溢出攻击。
|
||||
|
||||
接下来的事情是,我们需要去维护一个很好的从字符到数字的映射。幸运的是,这是高度标准化的,我们有两个主要的选择,Unicode 和 ASCII。Unicode 几乎将每个单个的有用的符号都映射为数字,作为交换,我们得到的是很多很多的数字,和一个更复杂的编码方法。ASCII 为每个字符使用一个字节,因此它仅保存拉丁字母、数字、少数符号和少数特殊字符。因此,ASCII 是非常易于实现的,与 Unicode 相比,它的每个字符占用的空间并不相同,这使得字符串算法更棘手。一般操作系统上字符使用 ASCII,并不是为了显示给最终用户的(开发者和专家用户除外),给终端用户显示信息使用 Unicode,因为 Unicode 能够支持像日语字符这样的东西,并且因此可以实现本地化。
|
||||
接下来的事情是,我们需要确定的是如何最好地将字符映射到数字。幸运的是,这是高度标准化的,我们有两个主要的选择,Unicode 和 ASCII。Unicode 几乎将每个有用的符号都映射为数字,作为代价,我们需要有很多很多的数字,和一个更复杂的编码方法。ASCII 为每个字符使用一个字节,因此它仅保存拉丁字母、数字、少数符号和少数特殊字符。因此,ASCII 是非常易于实现的,与之相比,Unicode 的每个字符占用的空间并不相同,这使得字符串算法更棘手。通常,操作系统上字符使用 ASCII,并不是为了显示给最终用户的(开发者和专家用户除外),给终端用户显示信息使用 Unicode,因为 Unicode 能够支持像日语字符这样的东西,并且因此可以实现本地化。
|
||||
|
||||
幸运的是,在这里我们不需要去做选择,因为它们的前 128 个字符是完全相同的,并且编码也是完全一样的。
|
||||
|
||||
@ -45,27 +41,27 @@
|
||||
| 60 | ` | a | b | c | d | e | f | g | h | i | j | k | l | m | n | o | |
|
||||
| 70 | p | q | r | s | t | u | v | w | x | y | z | { | | | } | ~ | DEL |
|
||||
|
||||
这个表显示了前 128 个符号。一个符号的十六进制表示是行的值加上列的值,比如 A 是 41~16~。你可以惊奇地发现前两行和最后的值。这 33 个特殊字符是不可打印字符。事实上,许多人都忽略了它们。它们之所以存在是因为 ASCII 最初设计是基于计算机网络来传输数据的一种方法。因此它要发送的信息不仅仅是符号。你应该学习的重要的特殊字符是 `NUL`,它就是我们前面提到的空终止符。`HT` 水平制表符就是我们经常说的 `tab`,而 `LF` 换行符用于生成一个新行。你可能想研究和使用其它特殊字符在你的操行系统中的意义。
|
||||
这个表显示了前 128 个符号。一个符号的十六进制表示是行的值加上列的值,比如 A 是 41<sub>16</sub>。你可以惊奇地发现前两行和最后的值。这 33 个特殊字符是不可打印字符。事实上,许多人都忽略了它们。它们之所以存在是因为 ASCII 最初设计是基于计算机网络来传输数据的一种方法。因此它要发送的信息不仅仅是符号。你应该学习的重要的特殊字符是 `NUL`,它就是我们前面提到的空终止符。`HT` 水平制表符就是我们经常说的 `tab`,而 `LF` 换行符用于生成一个新行。你可能想研究和使用其它特殊字符在你的操行系统中的意义。
|
||||
|
||||
### 2、字符
|
||||
|
||||
到目前为止,我们已经知道了一些关于字符串的知识,我们可以开始想想它们是如何显示的。为了显示一个字符串,我们需要做的最基础的事情是能够显示一个字符。我们的第一个任务是编写一个 `DrawCharacter` 函数,给它一个要绘制的字符和一个位置,然后它将这个字符绘制出来。
|
||||
|
||||
```markdown
|
||||
在许多操作系统中使用的 `truetype` 字体格式是很强大的,它内置有它自己的汇编语言,以确保在任何分辨率下字母看起来都是正确的。
|
||||
```
|
||||
这就很自然地引出关于字体的讨论。我们已经知道有许多方式去按照选定的字体去显示任何给定的字母。那么字体又是如何工作的呢?在计算机科学的早期阶段,字体就是所有字母的一系列小图片而已,这种字体称为位图字体,而所有的字符绘制方法就是将图片复制到屏幕上。当人们想去调整字体大小时就出问题了。有时我们需要大的字母,而有时我们需要的是小的字母。尽管我们可以为每个字体、每种大小、每个字符都绘制新图片,但这种作法过于单调乏味。所以,发明了矢量字体。矢量字体不包含字体的图像,它包含的是如何去绘制字符的描述,即:一个 `o` 可能是最大字母高度的一半为半径绘制的圆。现代操作系统都几乎仅使用这种字体,因为这种字体在任何分辨率下都很完美。
|
||||
|
||||
这就很自然地引出关于字体的讨论。我们已经知道有许多方式去按照选定的字体去显示任何给定的字母。那么字体又是如何工作的呢?在计算机科学的早期阶段,一种字体就是所有字母的一系列小图片而已,这种字体称为位图字体,而所有的字符绘制方法就是将图片复制到屏幕上。当人们想去调整字体大小时就出问题了。有时我们需要大的字母,而有时我们需要的是小的字母。尽管我们可以为每个字体、每种大小、每个字符都绘制新图片,但这种作法过于单调乏味。所以,发明了矢量字体。矢量字体不包含字体的图像,它包含的是如何去绘制字符的描述,即:一个 `o` 可能是最大字母高度的一半为半径绘制的圆。现代操作系统都几乎仅使用这种字体,因为这种字体在任何分辨率下都很完美。
|
||||
> 在许多操作系统中使用的 TrueType 字体格式是很强大的,它内置有它自己的汇编语言,以确保在任何分辨率下字母看起来都是正确的。
|
||||
|
||||
不幸的是,虽然我很想包含一个矢量字体的格式的实现,但它的内容太多了,将占用这个站点的剩余部分。所以,我们将去实现一个位图字体,可是,如果你想去做一个正宗的图形化的操作系统,那么矢量字体将是很有用的。
|
||||
不幸的是,虽然我很想包含一个矢量字体的格式的实现,但它的内容太多了,将占用这个网站的剩余部分。所以,我们将去实现一个位图字体,可是,如果你想去做一个像样的图形操作系统,那么矢量字体将是很有用的。
|
||||
|
||||
在下载页面上的字体节中,我们提供了几个 `.bin` 文件。这些只是字体的原始二进制数据文件。为完成本教程,从等宽、单色、8x16 节中挑选你喜欢的字体。然后下载它并保存到 `source` 目录中并命名为 `font.bin` 文件。这些文件只是每个字母的单色图片,它们每个字母刚好是 8 x 16 个像素。所以,每个字母占用 16 字节,第一个字节是第一行,第二个字节是第二行,依此类推。
|
||||
|
||||

|
||||
|
||||
这个示意图展示了等宽、单色、8x16 的字符 A 的 `Bitstream Vera Sans Mono`。在这个文件中,我们可以找到,它从第 41~16~ × 10~16~ = 410~16~ 字节开始的十六进制序列:
|
||||
这个示意图展示了等宽、单色、8x16 的字符 A 的 “Bitstream Vera Sans Mono” 字体。在这个文件中,我们可以找到,它从第 41<sub>16</sub> × 10<sub>16</sub> = 410<sub>16</sub> 字节开始的十六进制序列:
|
||||
|
||||
```
|
||||
00, 00, 00, 10, 28, 28, 28, 44, 44, 7C, C6, 82, 00, 00, 00, 00
|
||||
```
|
||||
|
||||
在这里我们将使用等宽字体,因为等宽字体的每个字符大小是相同的。不幸的是,大多数字体的复杂之处就是因为它的宽度不同,从而导致它的显示代码更复杂。在下载页面上还包含有几个其它的字体,并包含了这种字体的存储格式介绍。
|
||||
|
||||
@ -77,9 +73,7 @@ font:
|
||||
.incbin "font.bin"
|
||||
```
|
||||
|
||||
```assembly
|
||||
.incbin "file" 插入来自文件 “file” 中的二进制数据。
|
||||
```
|
||||
> `.incbin "file"` 插入来自文件 “file” 中的二进制数据。
|
||||
|
||||
这段代码复制文件中的字体数据到标签为 `font` 的地址。我们在这里使用了一个 `.align 4` 去确保每个字符都是从 16 字节的倍数开始,这是一个以后经常用到的用于加快访问速度的技巧。
|
||||
|
||||
@ -98,8 +92,8 @@ function drawCharacter(r0 is character, r1 is x, r2 is y)
|
||||
next
|
||||
return r0 = 8, r1 = 16
|
||||
end function
|
||||
|
||||
```
|
||||
|
||||
如果直接去实现它,这显然不是个高效率的做法。像绘制字符这样的事情,效率是最重要的。因为我们要频繁使用它。我们来探索一些改善的方法,使其成为最优化的汇编代码。首先,因为我们有一个 `× 16`,你应该会马上想到它等价于逻辑左移 4 位。紧接着我们有一个变量 `row`,它只与 `charAddress` 和 `y` 相加。所以,我们可以通过增加替代变量来消除它。现在唯一的问题是如何判断我们何时完成。这时,一个很好用的 `.align 4` 上场了。我们知道,`charAddress` 将从包含 0 的低位半字节开始。这意味着我们可以通过检查低位半字节来看到进入字符数据的程度。
|
||||
|
||||
虽然我们可以消除对 `bit` 的需求,但我们必须要引入新的变量才能实现,因此最好还是保留它。剩下唯一的改进就是去除嵌套的 `bits >> bit`。
|
||||
@ -189,7 +183,7 @@ pop {r4,r5,r6,r7,r8,pc}
|
||||
|
||||
### 3、字符串
|
||||
|
||||
现在,我们可以绘制字符了,我们可以绘制文本了。我们需要去写一个方法,给它一个字符串为输入,它通过递增位置来绘制出每个字符。为了做的更好,我们应该去实现新的行和制表符。是时候决定关于空终止符的问题了,如果你想让你的操作系统使用它们,可以按需来修改下面的代码。为避免这个问题,我将给 `DrawString` 函数传递一个字符串长度,以及字符串的地址,和 x 和 y 的坐标作为参数。
|
||||
现在,我们可以绘制字符了,我们可以绘制文本了。我们需要去写一个方法,给它一个字符串为输入,它通过递增位置来绘制出每个字符。为了做的更好,我们应该去实现新的行和制表符。是时候决定关于空终止符的问题了,如果你想让你的操作系统使用它们,可以按需来修改下面的代码。为避免这个问题,我将给 `DrawString` 函数传递一个字符串长度,以及字符串的地址,和 `x` 和 `y` 的坐标作为参数。
|
||||
|
||||
```c
|
||||
function drawString(r0 is string, r1 is length, r2 is x, r3 is y)
|
||||
@ -215,7 +209,7 @@ end function
|
||||
|
||||
同样,这个函数与汇编代码还有很大的差距。你可以随意去尝试实现它,即可以直接实现它,也可以简化它。我在下面给出了简化后的函数和汇编代码。
|
||||
|
||||
很明显,写这个函数的人并不很有效率(感到奇怪吗?它就是我写的)。再说一次,我们有一个 `pos` 变量,它用于递增和与其它东西相加,这是完全没有必要的。我们可以去掉它,而同时进行长度递减,直到减到 0 为止,这样就少用了一个寄存器。除了那个烦人的乘以 5 以外,函数的其余部分还不错。在这里要做的一个重要事情是,将乘法移到循环外面;即便使用位移运算,乘法仍然是很慢的,由于我们总是加一个乘以 5 的相同的常数,因此没有必要重新计算它。实际上,在汇编代码中它可以在一个操作数中通过参数移位来实现,因此我将代码改变为下面这样。
|
||||
很明显,写这个函数的人并不很有效率(感到奇怪吗?它就是我写的)。再说一次,我们有一个 `pos` 变量,它用于递增及与其它东西相加,这是完全没有必要的。我们可以去掉它,而同时进行长度递减,直到减到 0 为止,这样就少用了一个寄存器。除了那个烦人的乘以 5 以外,函数的其余部分还不错。在这里要做的一个重要事情是,将乘法移到循环外面;即便使用位移运算,乘法仍然是很慢的,由于我们总是加一个乘以 5 的相同的常数,因此没有必要重新计算它。实际上,在汇编代码中它可以在一个操作数中通过参数移位来实现,因此我将代码改变为下面这样。
|
||||
|
||||
```c
|
||||
function drawString(r0 is string, r1 is length, r2 is x, r3 is y)
|
||||
@ -307,22 +301,20 @@ pop {r4,r5,r6,r7,r8,r9,pc}
|
||||
.unreq length
|
||||
```
|
||||
|
||||
```assembly
|
||||
subs reg,#val 从寄存器 reg 中减去 val,然后将结果与 0 进行比较。
|
||||
```
|
||||
|
||||
这个代码中非常聪明地使用了一个新运算,`subs` 是从一个操作数中减去另一个数,保存结果,然后将结果与 0 进行比较。实现上,所有的比较都可以实现为减法后的结果与 0 进行比较,但是结果通常会丢弃。这意味着这个操作与 `cmp` 一样快。
|
||||
|
||||
### 4、你的愿意是我的命令行
|
||||
> `subs reg,#val` 从寄存器 `reg` 中减去 `val`,然后将结果与 `0` 进行比较。
|
||||
|
||||
### 4、你的意愿是我的命令行
|
||||
|
||||
现在,我们可以输出字符串了,而挑战是找到一个有意思的字符串去绘制。一般在这样的教程中,人们都希望去绘制 “Hello World!”,但是到目前为止,虽然我们已经能做到了,我觉得这有点“君临天下”的感觉(如果喜欢这种感觉,请随意!)。因此,作为替代,我们去继续绘制我们的命令行。
|
||||
|
||||
有一个限制是我们所做的操作系统是用在 ARM 架构的计算机上。最关键的是,在它们引导时,给它一些信息告诉它有哪些可用资源。几乎所有的处理器都有某些方式来确定这些信息,而在 ARM 上,它是通过位于地址 100<sub>16</sub> 处的数据来确定的,这个数据的格式如下:
|
||||
|
||||
1. 数据是可分解的一系列的标签。
|
||||
2. 这里有九种类型的标签:`core`,`mem`,`videotext`,`ramdisk`,`initrd2`,`serial`,`revision`,`videolfb`,`cmdline`。
|
||||
3. 每个标签只能出现一次,除了 'core’ 标签是必不可少的之外,其它的都是可有可无的。
|
||||
4. 所有标签都依次放置在地址 0x100 处。
|
||||
2. 这里有九种类型的标签:`core`、`mem`、`videotext`、`ramdisk`、`initrd2`、`serial`、`revision`、`videolfb`、`cmdline`。
|
||||
3. 每个标签只能出现一次,除了 `core` 标签是必不可少的之外,其它的都是可有可无的。
|
||||
4. 所有标签都依次放置在地址 `0x100` 处。
|
||||
5. 标签列表的结束处总是有两个<ruby>字<rt>word</rt></ruby>,它们全为 0。
|
||||
6. 每个标签的字节数都是 4 的倍数。
|
||||
7. 每个标签都是以标签中(以字为单位)的标签大小开始(标签包含这个数字)。
|
||||
@ -334,11 +326,9 @@ subs reg,#val 从寄存器 reg 中减去 val,然后将结果与 0 进行比较
|
||||
13. 一个 `cmdline` 标签包含一个 `null` 终止符字符串,它是个内核参数。
|
||||
|
||||
|
||||
```markdown
|
||||
几乎所有的操作系统都支持一个`命令行`的程序。它的想法是为选择一个程序所期望的行为而提供一个通用的机制。
|
||||
```
|
||||
在目前的树莓派版本中,只提供了 `core`、`mem` 和 `cmdline` 标签。你可以在后面找到它们的用法,更全面的参考资料在树莓派的参考页面上。现在,我们感兴趣的是 `cmdline` 标签,因为它包含一个字符串。我们继续写一些搜索这个命令行(`cmdline`)标签的代码,如果找到了,以每个条目一个新行的形式输出它。命令行只是图形处理器或用户认为操作系统应该知道的东西的一个列表。在树莓派上,这包含了 MAC 地址、序列号和屏幕分辨率。字符串本身也是一个由空格隔开的表达式(像 `key.subkey=value` 这样的)的列表。
|
||||
|
||||
在目前的树莓派版本中,只提供了 `core`、`mem` 和 `cmdline` 标签。你可以在后面找到它们的用法,更全面的参考资料在树莓派的参考页面上。现在,我们感兴趣的是 `cmdline` 标签,因为它包含一个字符串。我们继续写一些搜索命令行标签的代码,如果找到了,以每个条目一个新行的形式输出它。命令行只是为了让操作系统理解图形处理器或用户认为的很好的事情的一个列表。在树莓派上,这包含了 MAC 地址,序列号和屏幕分辨率。字符串本身也是一个像 `key.subkey=value` 这样的由空格隔开的表达式列表。
|
||||
> 几乎所有的操作系统都支持一个“命令行”的程序。它的想法是为选择一个程序所期望的行为而提供一个通用的机制。
|
||||
|
||||
我们从查找 `cmdline` 标签开始。将下列的代码复制到一个名为 `tags.s` 的新文件中。
|
||||
|
||||
@ -355,7 +345,7 @@ tag_videolfb: .int 0
|
||||
tag_cmdline: .int 0
|
||||
```
|
||||
|
||||
通过标签列表来查找是一个很慢的操作,因为这涉及到许多内存访问。因此,我们只是想实现它一次。代码创建一些数据,用于保存每个类型的第一个标签的内存地址。接下来,用下面的伪代码就可以找到一个标签了。
|
||||
通过标签列表来查找是一个很慢的操作,因为这涉及到许多内存访问。因此,我们只想做一次。代码创建一些数据,用于保存每个类型的第一个标签的内存地址。接下来,用下面的伪代码就可以找到一个标签了。
|
||||
|
||||
```c
|
||||
function FindTag(r0 is tag)
|
||||
@ -373,7 +363,8 @@ function FindTag(r0 is tag)
|
||||
end loop
|
||||
end function
|
||||
```
|
||||
这段代码已经是优化过的,并且很接近汇编了。它尝试直接加载标签,第一次这样做是有些乐观的,但是除了第一次之外 的其它所有情况都是可以这样做的。如果失败了,它将去检查 `core` 标签是否有地址。因为 `core` 标签是必不可少的,如果它没有地址,唯一可能的原因就是它不存在。如果它有地址,那就是我们没有找到我们要找的标签。如果没有找到,那我们就需要查找所有标签的地址。这是通过读取标签编号来做的。如果标签编号为 0,意味着已经到了标签列表的结束位置。这意味着我们已经查找了目录中所有的标签。所以,如果我们再次运行我们的函数,现在它应该能够给出一个答案。如果标签编号不为 0,我们检查这个标签类型是否已经有一个地址。如果没有,我们在目录中保存这个标签的地址。然后增加这个标签的长度(以字节为单位)到标签地址中,然后去查找下一个标签。
|
||||
|
||||
这段代码已经是优化过的,并且很接近汇编了。它尝试直接加载标签,第一次这样做是有些乐观的,但是除了第一次之外的其它所有情况都是可以这样做的。如果失败了,它将去检查 `core` 标签是否有地址。因为 `core` 标签是必不可少的,如果它没有地址,唯一可能的原因就是它不存在。如果它有地址,那就是我们没有找到我们要找的标签。如果没有找到,那我们就需要查找所有标签的地址。这是通过读取标签编号来做的。如果标签编号为 0,意味着已经到了标签列表的结束位置。这意味着我们已经查找了目录中所有的标签。所以,如果我们再次运行我们的函数,现在它应该能够给出一个答案。如果标签编号不为 0,我们检查这个标签类型是否已经有一个地址。如果没有,我们在目录中保存这个标签的地址。然后增加这个标签的长度(以字节为单位)到标签地址中,然后去查找下一个标签。
|
||||
|
||||
尝试去用汇编实现这段代码。你将需要简化它。如果被卡住了,下面是我的答案。不要忘了 `.section .text`!
|
||||
|
||||
@ -459,11 +450,11 @@ via: https://www.cl.cam.ac.uk/projects/raspberrypi/tutorials/os/screen03.html
|
||||
作者:[Alex Chadwick][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[qhwdw](https://github.com/qhwdw)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.cl.cam.ac.uk
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.cl.cam.ac.uk/projects/raspberrypi/tutorials/os/screen02.html
|
||||
[1]: https://linux.cn/article-10551-1.html
|
||||
[2]: https://www.cl.cam.ac.uk/projects/raspberrypi/tutorials/os/screen04.html
|
||||
@ -1,20 +1,20 @@
|
||||
[#]:collector:(lujun9972)
|
||||
[#]:translator:(lujun9972)
|
||||
[#]:reviewer:( )
|
||||
[#]:publisher:( )
|
||||
[#]:url:( )
|
||||
[#]:subject:(Use Emacs to create OAuth 2.0 UML sequence diagrams)
|
||||
[#]:via:(https://www.onwebsecurity.com/configuration/use-emacs-to-create-oauth-2-0-uml-sequence-diagrams.html)
|
||||
[#]:author:(Peter Mosmans https://www.onwebsecurity.com)
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (lujun9972)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-10582-1.html)
|
||||
[#]: subject: (Use Emacs to create OAuth 2.0 UML sequence diagrams)
|
||||
[#]: via: (https://www.onwebsecurity.com/configuration/use-emacs-to-create-oauth-2-0-uml-sequence-diagrams.html)
|
||||
[#]: author: (Peter Mosmans https://www.onwebsecurity.com)
|
||||
|
||||
使用 Emacs 创建 OAuth 2.0 的 UML 序列图
|
||||
======
|
||||
|
||||
![OAuth 2.0 abstract protocol flow][6]
|
||||
|
||||
看起来 [OAuth 2.0 框架 ][7] 已经越来越广泛地应用于 web (和 移动) 应用。太棒了!
|
||||
看起来 [OAuth 2.0 框架][7] 已经越来越广泛地应用于 web (和 移动) 应用。太棒了!
|
||||
|
||||
虽然协议本身并不复杂,但有很多的使用场景,流程和实现可供选择。正如生活中的大多数事物一样,魔鬼在于细节之中。
|
||||
虽然协议本身并不复杂,但有很多的使用场景、流程和实现可供选择。正如生活中的大多数事物一样,魔鬼在于细节之中。
|
||||
|
||||
在审查 OAuth 2.0 实现或编写渗透测试报告时我习惯画出 UML 图。这方便让人理解发生了什么事情,并发现潜在的问题。毕竟,一图抵千言。
|
||||
|
||||
@ -24,17 +24,15 @@ Emacs 是世界上最万能的编辑器。在这种场景中,我们用它来
|
||||
|
||||
下载 [预先编译好了的 PlantUML jar 文件 ][11],[Emacs][12] 还可以选择下载并安装 [Graphviz][13]。
|
||||
|
||||
安装并启动 Emacs,然后将下面 Lisp 代码(实际上是配置)写入你的启动文件中(` ~/.emacs.d/init.d` ),这段代码将会
|
||||
安装并启动 Emacs,然后将下面 Lisp 代码(实际上是配置)写入你的启动文件中(`~/.emacs.d/init.d`),这段代码将会:
|
||||
|
||||
* 配置 ` org-mode` (一种用来组织并编辑文本文件的模式) 来使用 PlantUML
|
||||
* 将 ` plantuml` 添加到可识别的` org-babel` 语言中 (这让你可以在文本文件中执行源代码)
|
||||
* 配置 org 模式(一种用来组织并编辑文本文件的模式)来使用 PlantUML
|
||||
* 将 `plantuml` 添加到可识别的 “org-babel” 语言中(这让你可以在文本文件中执行源代码)
|
||||
* 将 PlantUML 代码标注为安全的,从而允许执行
|
||||
* 自动显示生成的结果图片
|
||||
|
||||
|
||||
|
||||
```elisp
|
||||
;; tell org-mode where to find the plantuml JAR file (specify the JAR file)
|
||||
;; tell org-mode where to find the plantuml JAR file (specify the JAR file)
|
||||
(setq org-plantuml-jar-path (expand-file-name "~/plantuml.jar"))
|
||||
|
||||
;; use plantuml as org-babel language
|
||||
@ -54,13 +52,13 @@ Emacs 是世界上最万能的编辑器。在这种场景中,我们用它来
|
||||
|
||||
如果你还没有启动文件,那么将该代码加入到 `~/.emacs.d/init.el` 文件中然后重启 Emacs。
|
||||
|
||||
提示:Control-c Control-f 可以让你创建/打开(新)文件。Control-x Control-s 保存文件,而 Control-x Control-c 退出 Emacs。
|
||||
提示:`Control-c Control-f` 可以让你创建/打开(新)文件。`Control-x Control-s` 保存文件,而 `Control-x Control-c` 退出 Emacs。
|
||||
|
||||
这就结了!
|
||||
|
||||
要测试该配置,可以创建/打开( Control-c Control-f )后缀为 `.org` 的文件,例如 `test.org` . 这回让 Emacs 切换到 "org-mode" 并识别 "org-babel" 语法。
|
||||
要测试该配置,可以创建/打开(`Control-c Control-f`)后缀为 `.org` 的文件,例如 `test.org`。这会让 Emacs 切换到 org 模式并识别 “org-babel” 语法。
|
||||
|
||||
输入下面代码,然后在代码中输入 Control-c Control-c 来测试是否安装正常:
|
||||
输入下面代码,然后在代码中输入 `Control-c Control-c` 来测试是否安装正常:
|
||||
|
||||
```
|
||||
#+BEGIN_SRC plantuml :file test.png
|
||||
@ -72,9 +70,9 @@ version
|
||||
|
||||
一切顺利的话,你会在 Emacs 中看到文本下面显示了一张图片。
|
||||
|
||||
注意
|
||||
> **注意:**
|
||||
|
||||
要快速插入类似 ` #+BEGIN_SRC` 和 ` #+END_SRC` 这样的代码片段,你可以使用内置的 Easy Templates 系统:输入 <s 然后按下 TAB,它就会自动为你插入模板。
|
||||
> 要快速插入类似 `#+BEGIN_SRC` 和 `#+END_SRC` 这样的代码片段,你可以使用内置的 Easy Templates 系统:输入 `<s` 然后按下 `TAB`,它就会自动为你插入模板。
|
||||
|
||||
还有更复杂的例子,下面是生成上面图片的 UML 源代码:
|
||||
|
||||
@ -130,7 +128,7 @@ via: https://www.onwebsecurity.com/configuration/use-emacs-to-create-oauth-2-0-u
|
||||
作者:[Peter Mosmans][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[lujun9972](https://github.com/lujun9972)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,32 +1,32 @@
|
||||
[#]:collector:(lujun9972)
|
||||
[#]:translator:(lujun9972)
|
||||
[#]:reviewer:( )
|
||||
[#]:publisher:( )
|
||||
[#]:url:( )
|
||||
[#]:subject:(Firefox and org-protocol URL Capture)
|
||||
[#]:via:(http://www.mediaonfire.com/blog/2017_07_21_org_protocol_firefox.html)
|
||||
[#]:author:(Andreas Viklund http://andreasviklund.com/)
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (lujun9972)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-10586-1.html)
|
||||
[#]: subject: (Firefox and org-protocol URL Capture)
|
||||
[#]: via: (http://www.mediaonfire.com/blog/2017_07_21_org_protocol_firefox.html)
|
||||
[#]: author: (Andreas Viklund http://andreasviklund.com/)
|
||||
|
||||
在 Firefox 上使用 org-protocol 捕获 URL
|
||||
在 Firefox 上使用 Org 协议捕获 URL
|
||||
======
|
||||
|
||||
### 介绍
|
||||
|
||||
作为一名 Emacs 人,我尽可能让所有的工作流都在 [org-mode][1] 上进行 – 我比较喜欢文本。
|
||||
作为一名 Emacs 人,我尽可能让所有的工作流都在 <ruby>[Org 模式][1]<rt>Org-mode</rt></ruby> 上进行 —— 我比较喜欢文本。
|
||||
|
||||
我倾向于将书签记录为 [org-mode][1] 代办列表,而 [org-protocol][2] 则允许外部进程利用 [org-mode][1] 的某些功能。然而,要做到这一点配置起来很麻烦。([搜索引擎上 ][3]) 有很多教程,Firefox 也有很多这类 [扩展 ][4],然而我对它们都不太满意。
|
||||
我倾向于将书签记录在 [Org 模式][1] 代办列表中,而 <ruby>[Org 协议][2]<rt>Org-protocol</rt></ruby> 则允许外部进程利用 [Org 模式][1] 的某些功能。然而,要做到这一点配置起来很麻烦。([搜索引擎上][3])有很多教程,Firefox 也有这类 [扩展][4],然而我对它们都不太满意。
|
||||
|
||||
因此我决定将我现在的配置记录在这篇博客中,方便其他有需要的人使用。
|
||||
|
||||
### 配置 Emacs Org Mode
|
||||
### 配置 Emacs Org 模式
|
||||
|
||||
启用 org-protocol:
|
||||
启用 Org 协议:
|
||||
|
||||
```
|
||||
(require 'org-protocol)
|
||||
```
|
||||
|
||||
添加一个捕获模板 (capture template) - 我的配置是这样的:
|
||||
添加一个<ruby>捕获模板<rt>capture template</rt></ruby> —— 我的配置是这样的:
|
||||
|
||||
```
|
||||
(setq org-capture-templates
|
||||
@ -36,7 +36,7 @@
|
||||
...)))
|
||||
```
|
||||
|
||||
你可以从 [org-mode][1] 手册中 [capture templates][5] 章节中获取帮助。
|
||||
你可以从 [Org 模式][1] 手册中 [捕获模板][5] 章节中获取帮助。
|
||||
|
||||
设置默认使用的模板:
|
||||
|
||||
@ -56,19 +56,19 @@ emacsclient -n "org-protocol:///capture?url=http%3a%2f%2fduckduckgo%2ecom&title=
|
||||
|
||||
基于的配置的模板,可能会弹出一个捕获窗口。请确保正常工作,否则后面的操作没有任何意义。如果工作不正常,检查刚才的配置并且确保你执行了这些代码块。
|
||||
|
||||
如果你的 [org-mode][1] 版本比较老(老于 7 版本),测试的格式会有点不同:这种 URL 编码后的格式需要改成用斜杠来分割 url 和标题。在网上搜一下很容易找出这两者的不同。
|
||||
如果你的 [Org 模式][1] 版本比较老(老于 7 版本),测试的格式会有点不同:这种 URL 编码后的格式需要改成用斜杠来分割 url 和标题。在网上搜一下很容易找出这两者的不同。
|
||||
|
||||
### Firefox 协议
|
||||
|
||||
现在开始设置 Firefox。浏览 about:config。右击配置项列表,选择 New -> Boolean,然后输入 network.protocol-handler.expose.org-protocol 作为名字并且将值设置为 true。
|
||||
现在开始设置 Firefox。浏览 `about:config`。右击配置项列表,选择 “New -> Boolean”,然后输入 `network.protocol-handler.expose.org-protocol` 作为名字并且将值设置为 `true`。
|
||||
|
||||
有些教程说这一步是可以省略的 – 配不配因人而异。
|
||||
有些教程说这一步是可以省略的 —— 配不配因人而异。
|
||||
|
||||
### 添加 Desktop 文件
|
||||
|
||||
大多数的教程都有这一步:
|
||||
|
||||
增加一个文件 ~/.local/share/applications/org-protocol.desktop:
|
||||
增加一个文件 `~/.local/share/applications/org-protocol.desktop`:
|
||||
|
||||
```
|
||||
[Desktop Entry]
|
||||
@ -86,20 +86,19 @@ MimeType=x-scheme-handler/org-protocol;
|
||||
update-desktop-database ~/.local/share/applications/
|
||||
```
|
||||
|
||||
KDE 的方法不太一样… 你可以查询其他相关教程。
|
||||
KDE 的方法不太一样……你可以查询其他相关教程。
|
||||
|
||||
### 在 FireFox 中设置捕获按钮
|
||||
|
||||
创建一个书签(我是在工具栏上创建这个书签的),地址栏输入下面内容:
|
||||
创建一个书签(我是在工具栏上创建这个书签的),地址栏输入下面内容:
|
||||
|
||||
```
|
||||
javascript:location.href="org-protocol:///capture?url="+encodeURIComponent(location.href)+"&title="+encodeURIComponent(document.title||"[untitled page]")
|
||||
```
|
||||
|
||||
保存该书签后,再次编辑该书签,你应该会看到其中的所有空格都被替换成了 '%20' – 也就是空格的 URL 编码形式。
|
||||
|
||||
现在当你点击该书签,你就会在某个 Emacs Frame,可能是任何一个 Frame 中,打开一个窗口,显示你预定的模板。
|
||||
保存该书签后,再次编辑该书签,你应该会看到其中的所有空格都被替换成了 `%20` —— 也就是空格的 URL 编码形式。
|
||||
|
||||
现在当你点击该书签,你就会在某个 Emacs 框架中,可能是一个任意的框架中,打开一个窗口,显示你预定的模板。
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
@ -109,7 +108,7 @@ via: http://www.mediaonfire.com/blog/2017_07_21_org_protocol_firefox.html
|
||||
作者:[Andreas Viklund][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[lujun9972](https://github.com/lujun9972)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
196
published/20190206 And, Ampersand, and - in Linux.md
Normal file
196
published/20190206 And, Ampersand, and - in Linux.md
Normal file
@ -0,0 +1,196 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (HankChow)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-10587-1.html)
|
||||
[#]: subject: (And, Ampersand, and & in Linux)
|
||||
[#]: via: (https://www.linux.com/blog/learn/2019/2/and-ampersand-and-linux)
|
||||
[#]: author: (Paul Brown https://www.linux.com/users/bro66)
|
||||
|
||||
Linux 中的 &
|
||||
======
|
||||
|
||||
> 这篇文章将了解一下 & 符号及它在 Linux 命令行中的各种用法。
|
||||
|
||||

|
||||
|
||||
如果阅读过我之前的三篇文章([1][1]、[2][2]、[3][3]),你会觉得掌握连接各个命令之间的连接符号用法也是很重要的。实际上,命令的用法并不难,例如 `mkdir`、`touch` 和 `find` 也分别可以简单概括为“建立新目录”、“更新文件”和“在目录树中查找文件”而已。
|
||||
|
||||
但如果要理解
|
||||
|
||||
```
|
||||
mkdir test_dir 2>/dev/null || touch images.txt && find . -iname "*jpg" > backup/dir/images.txt &
|
||||
```
|
||||
|
||||
这一串命令的目的,以及为什么要这样写,就没有这么简单了。
|
||||
|
||||
关键之处就在于命令之间的连接符号。掌握了这些符号的用法,不仅可以让你更好理解整体的工作原理,还可以让你知道如何将不同的命令有效地结合起来,提高工作效率。
|
||||
|
||||
在这一篇文章和接下来的文章中,我会介绍如何使用 `&` 号和管道符号(`|`)在不同场景下的使用方法。
|
||||
|
||||
### 幕后工作
|
||||
|
||||
我来举一个简单的例子,看看如何使用 `&` 号将下面这个命令放到后台运行:
|
||||
|
||||
```
|
||||
cp -R original/dir/ backup/dir/
|
||||
```
|
||||
|
||||
这个命令的目的是将 `original/dir/` 的内容递归地复制到 `backup/dir/` 中。虽然看起来很简单,但是如果原目录里面的文件太大,在执行过程中终端就会一直被卡住。
|
||||
|
||||
所以,可以在命令的末尾加上一个 `&` 号,将这个任务放到后台去执行:
|
||||
|
||||
```
|
||||
cp -R original/dir/ backup/dir/ &
|
||||
```
|
||||
|
||||
任务被放到后台执行之后,就可以立即继续在同一个终端上工作了,甚至关闭终端也不影响这个任务的正常执行。需要注意的是,如果要求这个任务输出内容到标准输出中(例如 `echo` 或 `ls`),即使使用了 `&`,也会等待这些输出任务在前台运行完毕。
|
||||
|
||||
当使用 `&` 将一个进程放置到后台运行的时候,Bash 会提示这个进程的进程 ID。在 Linux 系统中运行的每一个进程都有一个唯一的进程 ID,你可以使用进程 ID 来暂停、恢复或者终止对应的进程,因此进程 ID 是非常重要的。
|
||||
|
||||
这个时候,只要你还停留在启动进程的终端当中,就可以使用以下几个命令来对管理后台进程:
|
||||
|
||||
* `jobs` 命令可以显示当前终端正在运行的进程,包括前台运行和后台运行的进程。它对每个正在执行中的进程任务分配了一个序号(这个序号不是进程 ID),可以使用这些序号来引用各个进程任务。
|
||||
|
||||
```
|
||||
$ jobs
|
||||
[1]- Running cp -i -R original/dir/* backup/dir/ &
|
||||
[2]+ Running find . -iname "*jpg" > backup/dir/images.txt &
|
||||
```
|
||||
* `fg` 命令可以将后台运行的进程任务放到前台运行,这样可以比较方便地进行交互。根据 `jobs` 命令提供的进程任务序号,再在前面加上 `%` 符号,就可以把相应的进程任务放到前台运行。
|
||||
|
||||
```
|
||||
$ fg %1 # 将上面序号为 1 的 cp 任务放到前台运行
|
||||
cp -i -R original/dir/* backup/dir/
|
||||
```
|
||||
如果这个进程任务是暂停状态,`fg` 命令会将它启动起来。
|
||||
* 使用 `ctrl+z` 组合键可以将前台运行的任务暂停,仅仅是暂停,而不是将任务终止。当使用 `fg` 或者 `bg` 命令将任务重新启动起来的时候,任务会从被暂停的位置开始执行。但 [sleep][4] 命令是一个特例,`sleep` 任务被暂停的时间会计算在 `sleep` 时间之内。因为 `sleep` 命令依据的是系统时钟的时间,而不是实际运行的时间。也就是说,如果运行了 `sleep 30`,然后将任务暂停 30 秒以上,那么任务恢复执行的时候会立即终止并退出。
|
||||
* `bg` 命令会将任务放置到后台执行,如果任务是暂停状态,也会被启动起来。
|
||||
|
||||
```
|
||||
$ bg %1
|
||||
[1]+ cp -i -R original/dir/* backup/dir/ &
|
||||
```
|
||||
|
||||
如上所述,以上几个命令只能在同一个终端里才能使用。如果启动进程任务的终端被关闭了,或者切换到了另一个终端,以上几个命令就无法使用了。
|
||||
|
||||
如果要在另一个终端管理后台进程,就需要其它工具了。例如可以使用 [kill][5] 命令从另一个终端终止某个进程:
|
||||
|
||||
```
|
||||
kill -s STOP <PID>
|
||||
```
|
||||
|
||||
这里的 PID 就是使用 `&` 将进程放到后台时 Bash 显示的那个进程 ID。如果你当时没有把进程 ID 记录下来,也可以使用 `ps` 命令(代表 process)来获取所有正在运行的进程的进程 ID,就像这样:
|
||||
|
||||
```
|
||||
ps | grep cp
|
||||
```
|
||||
|
||||
执行以后会显示出包含 `cp` 字符串的所有进程,例如上面例子中的 `cp` 进程。同时还会显示出对应的进程 ID:
|
||||
|
||||
```
|
||||
$ ps | grep cp
|
||||
14444 pts/3 00:00:13 cp
|
||||
```
|
||||
|
||||
在这个例子中,进程 ID 是 14444,因此可以使用以下命令来暂停这个后台进程:
|
||||
|
||||
```
|
||||
kill -s STOP 14444
|
||||
```
|
||||
|
||||
注意,这里的 `STOP` 等同于前面提到的 `ctrl+z` 组合键的效果,也就是仅仅把进程暂停掉。
|
||||
|
||||
如果想要把暂停了的进程启动起来,可以对进程发出 `CONT` 信号:
|
||||
|
||||
```
|
||||
kill -s CONT 14444
|
||||
```
|
||||
|
||||
这个给出一个[可以向进程发出的常用信号][6]列表。如果想要终止一个进程,可以发送 `TERM` 信号:
|
||||
|
||||
```
|
||||
kill -s TERM 14444
|
||||
```
|
||||
|
||||
如果进程不响应 `TERM` 信号并拒绝退出,还可以发送 `KILL` 信号强制终止进程:
|
||||
|
||||
```
|
||||
kill -s KILL 14444
|
||||
```
|
||||
|
||||
强制终止进程可能会有一定的风险,但如果遇到进程无节制消耗资源的情况,这样的信号还是能够派上用场的。
|
||||
|
||||
另外,如果你不确定进程 ID 是否正确,可以在 `ps` 命令中加上 `x` 参数:
|
||||
|
||||
```
|
||||
$ ps x| grep cp
|
||||
14444 pts/3 D 0:14 cp -i -R original/dir/Hols_2014.mp4
|
||||
original/dir/Hols_2015.mp4 original/dir/Hols_2016.mp4
|
||||
original/dir/Hols_2017.mp4 original/dir/Hols_2018.mp4 backup/dir/
|
||||
```
|
||||
|
||||
这样就可以看到是不是你需要的进程 ID 了。
|
||||
|
||||
最后介绍一个将 `ps` 和 `grep` 结合到一起的命令:
|
||||
|
||||
```
|
||||
$ pgrep cp
|
||||
8
|
||||
18
|
||||
19
|
||||
26
|
||||
33
|
||||
40
|
||||
47
|
||||
54
|
||||
61
|
||||
72
|
||||
88
|
||||
96
|
||||
136
|
||||
339
|
||||
6680
|
||||
13735
|
||||
14444
|
||||
```
|
||||
|
||||
`pgrep` 可以直接将带有字符串 `cp` 的进程的进程 ID 显示出来。
|
||||
|
||||
可以加上一些参数让它的输出更清晰:
|
||||
|
||||
```
|
||||
$ pgrep -lx cp
|
||||
14444 cp
|
||||
```
|
||||
|
||||
在这里,`-l` 参数会让 `pgrep` 将进程的名称显示出来,`-x` 参数则是让 `pgrep` 完全匹配 `cp` 这个命令。如果还想了解这个命令的更多细节,可以尝试运行 `pgrep -ax`。
|
||||
|
||||
### 总结
|
||||
|
||||
在命令的末尾加上 `&` 可以让我们理解前台进程和后台进程的概念,以及如何管理这些进程。
|
||||
|
||||
在 UNIX/Linux 术语中,在后台运行的进程被称为<ruby>守护进程<rt>daemon</rt></ruby>。如果你曾经听说过这个词,那你现在应该知道它的意义了。
|
||||
|
||||
和其它符号一样,`&` 在命令行中还有很多别的用法。在下一篇文章中,我会更详细地介绍。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.linux.com/blog/learn/2019/2/and-ampersand-and-linux
|
||||
|
||||
作者:[Paul Brown][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[HankChow](https://github.com/HankChow)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.linux.com/users/bro66
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://linux.cn/article-10465-1.html
|
||||
[2]: https://linux.cn/article-10502-1.html
|
||||
[3]: https://linux.cn/article-10529-1.html
|
||||
[4]: https://ss64.com/bash/sleep.html
|
||||
[5]: https://bash.cyberciti.biz/guide/Sending_signal_to_Processes
|
||||
[6]: https://www.computerhope.com/unix/signals.htm
|
||||
|
||||
@ -1,26 +1,28 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-10584-1.html)
|
||||
[#]: subject: (Two graphical tools for manipulating PDFs on the Linux desktop)
|
||||
[#]: via: (https://opensource.com/article/19/2/manipulating-pdfs-linux)
|
||||
[#]: author: (Scott Nesbitt https://opensource.com/users/scottnesbitt)
|
||||
|
||||
两款 Linux 桌面中的图形化操作 PDF 的工具
|
||||
======
|
||||
PDF-Shuffler 和 PDF Chain 是在 Linux 中修改 PDF 的绝佳工具。
|
||||
|
||||
> PDF-Shuffler 和 PDF Chain 是在 Linux 中修改 PDF 的绝佳工具。
|
||||
|
||||

|
||||
|
||||
由于我谈论并且写了些工作中使用 PDF 及其工具的文章,有些人认为我喜欢这种格式。其实我并不是,由于各种原因,我不会深入它。
|
||||
由于我谈论和写作了些 PDF 及使用它们的工具的文章,有些人认为我喜欢这种格式。其实我并不是,由于各种原因,我不会深入它。
|
||||
|
||||
我不会说 PDF 是我个人和职业生活中的一个躲不开的坏事 - 相反,它们不是那么好。通常即使有更好的替代方案来交付文档,我也必须使用 PDF。
|
||||
我不会说 PDF 是我个人和职业生活中的一个躲不开的坏事 - 而实际上它们不是那么好。通常即使有更好的替代方案来交付文档,通常我也必须使用 PDF。
|
||||
|
||||
当我使用 PDF 时,通常是在白天工作时在其他的操作系统上使用,我使用 Adobe Acrobat 进行操作。但是当我必须在 Linux 桌面上使用 PDF 时呢?我们来看看我用来操作 PDF 的两个图形工具。
|
||||
|
||||
### PDF-Shuffler
|
||||
|
||||
顾名思义,你可以使用 [PDF-Shuffler][1] 在 PDF 文件中移动页面。它可以做得更多,但软件的功能是有限的。这并不意味着 PDF-Shuffler 没用。它有用,很有用。
|
||||
顾名思义,你可以使用 [PDF-Shuffler][1] 在 PDF 文件中移动页面。它可以做得更多,但该软件的功能是有限的。这并不意味着 PDF-Shuffler 没用。它有用,很有用。
|
||||
|
||||
你可以将 PDF-Shuffler 用来:
|
||||
|
||||
@ -28,23 +30,21 @@ PDF-Shuffler 和 PDF Chain 是在 Linux 中修改 PDF 的绝佳工具。
|
||||
* 将页面添加到文件中
|
||||
* 重新排列文件中的页面
|
||||
|
||||
|
||||
|
||||
请注意,PDF-Shuffler 有一些依赖项,如 pyPDF 和 python-gtk。通常,通过包管理器安装它是最快且最不令人沮丧的途径。
|
||||
|
||||
假设你想从 PDF 中提取页面,也许是作为你书中的样本章节。选择**文件>添加**打开 PDF 文件。
|
||||
假设你想从 PDF 中提取页面,也许是作为你书中的样本章节。选择 “File > Add”打开 PDF 文件。
|
||||
|
||||
|
||||
|
||||
要提取第 7 页到第 9 页,请按住 Ctrl 并单击选择页面。然后,右键单击并选择**导出选择**。
|
||||
要提取第 7 页到第 9 页,请按住 `Ctrl` 并单击选择页面。然后,右键单击并选择 “Export selection”。
|
||||
|
||||
|
||||
|
||||
选择要保存文件的目录,为其命名,然后单击**保存**。
|
||||
选择要保存文件的目录,为其命名,然后单击 “Save”。
|
||||
|
||||
要添加文件 - 例如,要添加封面或重新插入已扫描的且已签名的合同或者应用 - 打开 PDF 文件,然后选择**文件>添加**并找到要添加的 PDF 文件。单击**打开**。
|
||||
要添加文件 —— 例如,要添加封面或重新插入已扫描的且已签名的合同或者应用 - 打开 PDF 文件,然后选择 “File > Add” 并找到要添加的 PDF 文件。单击 “Open”。
|
||||
|
||||
PDF-Shuffler 有个不好的东西就是在你正在处理的 PDF 文件末尾添加页面。单击并将添加的页面拖动到文件中的所需位置。你一次只能在文件中单击并拖动一个页面。
|
||||
PDF-Shuffler 有个不好的地方就是添加页面到你正在处理的 PDF 文件末尾。单击并将添加的页面拖动到文件中的所需位置。你一次只能在文件中单击并拖动一个页面。
|
||||
|
||||
|
||||
|
||||
@ -54,29 +54,27 @@ PDF-Shuffler 有个不好的东西就是在你正在处理的 PDF 文件末尾
|
||||
|
||||
[PDF Chain][3] 是 PDFtk 命令行的一个很好的替代品。它可以让你一键使用 PDFtk 最常用的命令。无需使用菜单,你可以:
|
||||
|
||||
* 合并 PDF(包括旋转一个或多个文件的页面)
|
||||
* 从 PDF 中提取页面并将其保存到单个文件中
|
||||
* 为 PDF 添加背景或水印
|
||||
* 将附件添加到文件
|
||||
* 合并 PDF(包括旋转一个或多个文件的页面)
|
||||
* 从 PDF 中提取页面并将其保存到单个文件中
|
||||
* 为 PDF 添加背景或水印
|
||||
* 将附件添加到文件
|
||||
|
||||
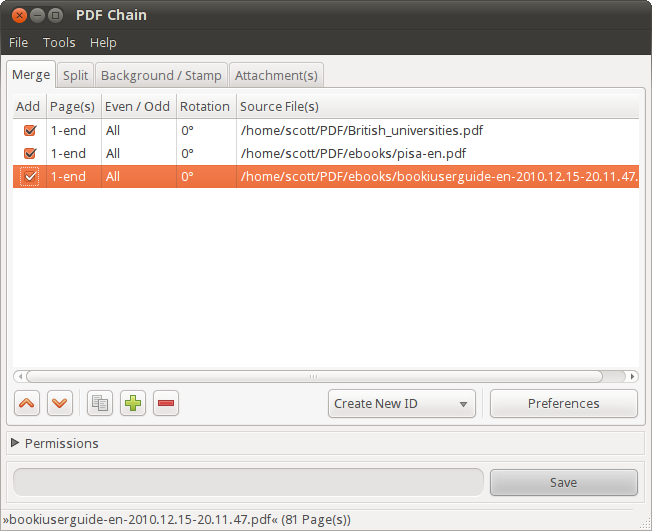
|
||||
|
||||
你也可以做得更多。点击**工具**菜单,你可以:
|
||||
|
||||
* 从 PDF 中提取附件
|
||||
* 压缩或解压缩文件
|
||||
* 从文件中提取元数据
|
||||
* 用外部[数据][4]填充 PDF 表格
|
||||
* [扁平化][5] PDF
|
||||
* 从 PDF 表单中删除 [XML 表格结构][6](XFA)数据
|
||||
|
||||
你也可以做得更多。点击 “Tools” 菜单,你可以:
|
||||
|
||||
* 从 PDF 中提取附件
|
||||
* 压缩或解压缩文件
|
||||
* 从文件中提取元数据
|
||||
* 用外部[数据][4]填充 PDF 表格
|
||||
* [扁平化][5] PDF
|
||||
* 从 PDF 表单中删除 [XML 表格结构][6](XFA)数据
|
||||
|
||||
老实说,我只使用 PDF Chain 或 PDFtk 提取附件、压缩或解压缩 PDF。其余的对我来说基本没听说。
|
||||
|
||||
### 总结
|
||||
|
||||
Linux 上用于处理 PDF 的工具数量一直让我感到吃惊。它们的特性和功能的广度和深度也是如此。我通常可以找到一个,无论是命令行还是图形,它都能做我需要的。在大多数情况下,PDF Mod 和 PDF Chain 对我来说效果很好。
|
||||
Linux 上用于处理 PDF 的工具数量一直让我感到吃惊。它们的特性和功能的广度和深度也是如此。无论是命令行还是图形,我总能找到一个能做我需要的。在大多数情况下,PDF Mod 和 PDF Chain 对我来说效果很好。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
@ -85,7 +83,7 @@ via: https://opensource.com/article/19/2/manipulating-pdfs-linux
|
||||
作者:[Scott Nesbitt][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,8 +1,8 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-10583-1.html)
|
||||
[#]: subject: (How to use Linux Cockpit to manage system performance)
|
||||
[#]: via: (https://www.networkworld.com/article/3340038/linux/sitting-in-the-linux-cockpit.html)
|
||||
[#]: author: (Sandra Henry-Stocker https://www.networkworld.com/author/Sandra-Henry_Stocker/)
|
||||
@ -10,35 +10,33 @@
|
||||
如何使用 Linux Cockpit 来管理系统性能
|
||||
======
|
||||
|
||||
Linux Cockpit 是一个基于 Web 界面的应用,它提供了对系统的图形化管理。看下它能够控制哪些。
|
||||
> Linux Cockpit 是一个基于 Web 界面的应用,它提供了对系统的图形化管理。看下它能够控制哪些。
|
||||
|
||||

|
||||
|
||||
如果你还没有尝试过相对较新的 Linux Cockpit,你可能会对它所能做的一切感到惊讶。它是一个用户友好的基于 Web 的控制台,提供了一些非常简单的方法来管理 Linux 系统 —_通过**web**_。你可以通过一个非常简单的 web 来监控系统资源、添加或删除帐户、监控系统使用情况、关闭系统以及执行其他一些其他任务。它的设置和使用也非常简单。
|
||||
如果你还没有尝试过相对较新的 Linux Cockpit,你可能会对它所能做的一切感到惊讶。它是一个用户友好的基于 web 的控制台,提供了一些非常简单的方法来管理 Linux 系统 —— 通过 web。你可以通过一个非常简单的 web 来监控系统资源、添加或删除帐户、监控系统使用情况、关闭系统以及执行其他一些其他任务。它的设置和使用也非常简单。
|
||||
|
||||
虽然许多 Linux 系统管理员将大部分时间花在命令行上,但使用 PuTTY 等工具访问远程系统并不总能提供最有用的命令输出。Linux Cockpit 提供了图形和易于使用的表单,来查看性能情况并对系统进行更改。
|
||||
|
||||
Linux Cockpit 能让你查看系统性能的许多方面并进行配置更改,但任务列表可能取决于你使用的特定 Linux。任务分类包括以下内容:
|
||||
|
||||
* 监控系统活动(CPU、内存、磁盘 IO 和网络流量) — **系统**
|
||||
* 查看系统日志条目 — **日志**
|
||||
* 查看磁盘分区的容量 — **存储**
|
||||
* 查看网络活动(发送和接收) — **网络**
|
||||
* 查看用户帐户 — **帐户**
|
||||
* 检查系统服务的状态 — **服务**
|
||||
* 提取已安装应用的信息 — **应用**
|
||||
* 查看和安装可用更新(如果以 root 身份登录)并在需要时重新启动系统 — **软件更新**
|
||||
* 打开并使用终端窗口 — **终端**
|
||||
* 监控系统活动(CPU、内存、磁盘 IO 和网络流量) —— **系统**
|
||||
* 查看系统日志条目 —— **日志**
|
||||
* 查看磁盘分区的容量 —— **存储**
|
||||
* 查看网络活动(发送和接收) —— **网络**
|
||||
* 查看用户帐户 —— **帐户**
|
||||
* 检查系统服务的状态 —— **服务**
|
||||
* 提取已安装应用的信息 —— **应用**
|
||||
* 查看和安装可用更新(如果以 root 身份登录)并在需要时重新启动系统 —— **软件更新**
|
||||
* 打开并使用终端窗口 —— **终端**
|
||||
|
||||
|
||||
|
||||
某些 Linux Cockpit 安装还允许你运行诊断报告、转储内核、检查 SELinux(安全)设置和列表订阅。
|
||||
某些 Linux Cockpit 安装还允许你运行诊断报告、转储内核、检查 SELinux(安全)设置和列出订阅。
|
||||
|
||||
以下是 Linux Cockpit 显示的系统活动示例:
|
||||
|
||||
![cockpit activity][1] Sandra Henry-Stocker
|
||||
![cockpit activity][1]
|
||||
|
||||
Linux Cockpit 显示系统活动
|
||||
*Linux Cockpit 显示系统活动*
|
||||
|
||||
### 如何设置 Linux Cockpit
|
||||
|
||||
@ -56,17 +54,15 @@ $ sudo systemctl enable --now cockpit.socket
|
||||
$ sudo ufw allow 9090
|
||||
```
|
||||
|
||||
启用 Linux Cockpit 后,在浏览器中打开 **https:// <system-name-or-IP>:9090**。
|
||||
启用 Linux Cockpit 后,在浏览器中打开 `https://<system-name-or-IP>:9090`
|
||||
|
||||
可以在 [Cockpit Project]][2] 中找到可以使用 Cockpit 的发行版列表以及安装说明。
|
||||
可以在 [Cockpit 项目][2] 中找到可以使用 Cockpit 的发行版列表以及安装说明。
|
||||
|
||||
没有额外的配置,Linux Cockpit 将无法识别 **sudo** 权限。如果你被禁止使用 Cockpit 进行更改,你将会在你点击的按钮上看到一个红色的国际禁止标志。
|
||||
没有额外的配置,Linux Cockpit 将无法识别 `sudo` 权限。如果你被禁止使用 Cockpit 进行更改,你将会在你点击的按钮上看到一个红色的通用禁止标志。
|
||||
|
||||
要使 sudo 权限有效,你需要确保用户位于 **/etc/group** 文件中的 **wheel**(RHEL)或 **adm** (Debian)组中,即服务器当以 root 用户身份登录 Cockpit 并且用户在登录 Cockpit 时选择“重用我的密码”时,已勾选了 Server Administrator。
|
||||
要使 `sudo` 权限有效,你需要确保用户位于 `/etc/group` 文件中的 `wheel`(RHEL)或 `adm` (Debian)组中,即服务器当以 root 用户身份登录 Cockpit 并且用户在登录 Cockpit 时选择“重用我的密码”时,已勾选了 “Server Administrator”。
|
||||
|
||||
在你管理的系统在千里之外或者没有控制台时,能使用图形界面控制也不错。虽然我喜欢在控制台上工作,但我偶然也乐于见到图形或者按钮。Linux Cockpit 为日常管理任务提供了非常有用的界面。
|
||||
|
||||
在 [Facebook][3] 和 [LinkedIn][4] 中加入 Network World 社区,对你喜欢的文章评论。
|
||||
在你管理的系统位在千里之外或者没有控制台时,能使用图形界面控制也不错。虽然我喜欢在控制台上工作,但我偶然也乐于见到图形或者按钮。Linux Cockpit 为日常管理任务提供了非常有用的界面。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
@ -75,7 +71,7 @@ via: https://www.networkworld.com/article/3340038/linux/sitting-in-the-linux-coc
|
||||
作者:[Sandra Henry-Stocker][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,296 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (Amanda0212)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (lawyer The MIT License, Line by Line)
|
||||
[#]: via: (https://writing.kemitchell.com/2016/09/21/MIT-License-Line-by-Line.html)
|
||||
[#]: author: (Kyle E. Mitchell https://kemitchell.com/)
|
||||
|
||||
lawyer The MIT License, Line by Line
|
||||
======
|
||||
|
||||
### The MIT License, Line by Line
|
||||
|
||||
[The MIT License][1] is the most popular open-source software license. Here’s one read of it, line by line.
|
||||
|
||||
#### Read the License
|
||||
|
||||
If you’re involved in open-source software and haven’t taken the time to read the license from top to bottom—it’s only 171 words—you need to do so now. Especially if licenses aren’t your day-to-day. Make a mental note of anything that seems off or unclear, and keep trucking. I’ll repeat every word again, in chunks and in order, with context and commentary. But it’s important to have the whole in mind.
|
||||
|
||||
> The MIT License (MIT)
|
||||
>
|
||||
> Copyright (c) <year> <copyright holders>
|
||||
>
|
||||
> Permission is hereby granted, free of charge, to any person obtaining a copy of this software and associated documentation files (the “Software”), to deal in the Software without restriction, including without limitation the rights to use, copy, modify, merge, publish, distribute, sublicense, and/or sell copies of the Software, and to permit persons to whom the Software is furnished to do so, subject to the following conditions:
|
||||
>
|
||||
> The above copyright notice and this permission notice shall be included in all copies or substantial portions of the Software.
|
||||
>
|
||||
> The Software is provided “as is”, without warranty of any kind, express or implied, including but not limited to the warranties of merchantability, fitness for a particular purpose and noninfringement. In no event shall the authors or copyright holders be liable for any claim, damages or other liability, whether in an action of contract, tort or otherwise, arising from, out of or in connection with the software or the use or other dealings in the Software.
|
||||
|
||||
The license is arranged in five paragraphs, but breaks down logically like this:
|
||||
|
||||
* **Header**
|
||||
* **License Title** : “The MIT License”
|
||||
* **Copyright Notice** : “Copyright (c) …”
|
||||
* **License Grant** : “Permission is hereby granted …”
|
||||
* **Grant Scope** : “… to deal in the Software …”
|
||||
* **Conditions** : “… subject to …”
|
||||
* **Attribution and Notice** : “The above … shall be included …”
|
||||
* **Warranty Disclaimer** : “The software is provided ‘as is’ …”
|
||||
* **Limitation of Liability** : “In no event …”
|
||||
|
||||
|
||||
|
||||
Here we go:
|
||||
|
||||
#### Header
|
||||
|
||||
##### License Title
|
||||
|
||||
> The MIT License (MIT)
|
||||
|
||||
“The MIT License” is a not a single license, but a family of license forms derived from language prepared for releases from the Massachusetts Institute of Technology. It has seen a lot of changes over the years, both for the original projects that used it, and also as a model for other projects. The Fedora Project maintains a [kind of cabinet of MIT license curiosities][2], with insipid variations preserved in plain text like anatomical specimens in formaldehyde, tracing a wayward kind of evolution.
|
||||
|
||||
Fortunately, the [Open Source Initiative][3] and [Software Package Data eXchange][4] groups have standardized a generic MIT-style license form as “The MIT License”. OSI in turn has adopted SPDX’ standardized [string identifiers][5] for common open-source licenses, with `MIT` pointing unambiguously to the standardized form “MIT License”. If you want MIT-style terms for a new project, use [the standardized form][1].
|
||||
|
||||
Even if you include “The MIT License” or “SPDX:MIT” in a `LICENSE` file, any responsible reviewer will still run a comparison of the text against the standard form, just to be sure. While various license forms calling themselves “MIT License” vary only in minor details, the looseness of what counts as an “MIT License” has tempted some authors into adding bothersome “customizations”. The canonical horrible, no good, very bad example of this is [the JSON license][6], an MIT-family license plus “The Software shall be used for Good, not Evil.”. This kind of thing might be “very Crockford”. It is definitely a pain in the ass. Maybe the joke was supposed to be on the lawyers. But they laughed all the way to the bank.
|
||||
|
||||
Moral of the story: “MIT License” alone is ambiguous. Folks probably have a good idea what you mean by it, but you’re only going to save everyone—yourself included—time by copying the text of the standard MIT License form into your project. If you use metadata, like the `license` property in package manager metadata files, to designate the `MIT` license, make sure your `LICENSE` file and any header comments use the standard form text. All of this can be [automated][7].
|
||||
|
||||
##### Copyright Notice
|
||||
|
||||
> Copyright (c) <year> <copyright holders>
|
||||
|
||||
Until the 1976 Copyright Act, United States copyright law required specific actions, called “formalities”, to secure copyright in creative works. If you didn’t follow those formalities, your rights to sue others for unauthorized use of your work were limited, often completely lost. One of those formalities was “notice”: Putting marks on your work and otherwise making it known to the market that you were claiming copyright. The © is a standard symbol for marking copyrighted works, to give notice of copyright. The ASCII character set doesn’t have the © symbol, but `Copyright (c)` gets the same point across.
|
||||
|
||||
The 1976 Copyright Act, which “implemented” many requirements of the international Berne Convention, eliminated formalities for securing copyright. At least in the United States, copyright holders still need to register their copyrighted works before suing for infringement, with potentially higher damages if they register before infringement begins. In practice, however, many register copyright right before bringing suit against someone in particular. You don’t lose your copyright just by failing to put notices on it, registering, sending a copy to the Library of Congress, and so on.
|
||||
|
||||
Even if copyright notices aren’t as absolutely necessary as they used to be, they are still plenty useful. Stating the year a work was authored and who the copyright belonged to give some sense of when copyright in the work might expire, bringing the work into the public domain. The identity of the author or authors is also useful: United States law calculates copyright terms differently for individual and “corporate” authors. Especially in business use, it may also behoove a company to think twice about using software from a known competitor, even if the license terms give very generous permission. If you’re hoping others will see your work and want to license it from you, copyright notices serve nicely for attribution.
|
||||
|
||||
As for “copyright holder”: Not all standard form licenses have a space to write this out. More recent license forms, like [Apache 2.0][8] and [GPL 3.0][9], publish `LICENSE` texts that are meant to be copied verbatim, with header comments and separate files elsewhere to indicate who owns copyright and is giving the license. Those approaches neatly discourage changes to the “standard” texts, accidental or intentional. They also make automated license identification more reliable.
|
||||
|
||||
The MIT License descends from language written for releases of code by institutions. For institutional releases, there was just one clear “copyright holder”, the institution releasing the code. Other institutions cribbed these licenses, replacing “MIT” with their own names, leading eventually to the generic forms we have now. This process repeated for other short-form institutional licenses of the era, notably the [original four-clause BSD License][10] for the University of California, Berkeley, now used in [three-clause][11] and [two-clause][12] variants, as well as [The ISC License][13] for the Internet Systems Consortium, an MIT variant.
|
||||
|
||||
In each case, the institution listed itself as the copyright holder in reliance on rules of copyright ownership, called “[works made for hire][14]” rules, that give employers and clients ownership of copyright in some work their employees and contractors do on their behalf. These rules don’t usually apply to distributed collaborators submitting code voluntarily. This poses a problem for project-steward foundations, like the Apache Foundation and Eclipse Foundation, that accept contributions from a more diverse group of contributors. The usual foundation approach thus far has been to use a house license that states a single copyright holder—[Apache 2.0][8] and [EPL 1.0][15]—backed up by contributor license agreements—[Apache CLAs][16] and [Eclipse CLAs][17]—to collect rights from contributors. Collecting copyright ownership in one place is even more important under “copyleft” licenses like the GPL, which rely on copyright owners to enforce license conditions to promote software-freedom values.
|
||||
|
||||
These days, loads of projects without any kind of institutional or business steward use MIT-style license terms. SPDX and OSI have helped these use cases by standardizing forms of licenses like MIT and ISC that don’t refer to a specific entity or institutional copyright holder. Armed with those forms, the prevailing practice of project authors is to fill their own name in the copyright notice of the form very early on … and maybe bump the year here and there. At least under United States copyright law, the resulting copyright notice doesn’t give a full picture.
|
||||
|
||||
The original owner of a piece of software retains ownership of their work. But while MIT-style license terms give others rights to build on and change the software, creating what the law calls “derivative works”, they don’t give the original author ownership of copyright in others’ contributions. Rather, each contributor has copyright in any [even marginally creative][18] work they make using the existing code as a starting point.
|
||||
|
||||
Most of these projects also balk at the idea of taking contributor license agreements, to say nothing of signed copyright assignments. That’s both naive and understandable. Despite the assumption of some newer open-source developers that sending a pull request on GitHub “automatically” licenses the contribution for distribution on the terms of the project’s existing license, United States law doesn’t recognize any such rule. Strong copyright protection, not permissive licensing, is the default.
|
||||
|
||||
Update: GitHub later changed its site-wide terms of service to include an attempt to flip this default, at least on GitHub.com. I’ve written up some thoughts on that development, not all of them positive, in [another post][19].
|
||||
|
||||
To fill the gap between legally effective, well-documented grants of rights in contributions and no paper trail at all, some projects have adopted the [Developer Certificate of Origin][20], a standard statement contributors allude to using `Signed-Off-By` metadata tags in their Git commits. The Developer Certificate of Origin was developed for Linux kernel development in the wake of the infamous SCO lawsuits, which alleged that chunks of Linux’ code derived from SCO-owned Unix source. As a means of creating a paper trail showing that each line of Linux came from a contributor, the Developer Certificate of Origin functions nicely. While the Developer Certificate of Origin isn’t a license, it does provide lots of good evidence that those submitting code expected the project to distribute their code, and for others to use it under the kernel’s existing license terms. The kernel also maintains a machine-readable `CREDITS` file listing contributors with name, affiliation, contribution area, and other metadata. I’ve done [some][21] [experiments][22] adapting that approach for projects that don’t use the kernel’s development flow.
|
||||
|
||||
#### License Grant
|
||||
|
||||
> Permission is hereby granted, free of charge, to any person obtaining a copy of this software and associated documentation files (the “Software”),
|
||||
|
||||
The meat of The MIT License is, you guessed it, a license. In general terms, a license is permission that one person or legal entity—the “licensor”—gives another—the “licensee”—to do something the law would otherwise let them sue for. The MIT License is a promise not to sue.
|
||||
|
||||
The law sometimes distinguishes licenses from promises to give licenses. If someone breaks a promise to give a license, you may be able to sue them for breaking their promise, but you may not end up with a license. “Hereby” is one of those hokey, archaic-sounding words lawyers just can’t get rid of. It’s used here to show that the license text itself gives the license, and not just a promise of a license. It’s a legal [IIFE][23].
|
||||
|
||||
While many licenses give permission to a specific, named licensee, The MIT License is a “public license”. Public licenses give everybody—the public at large—permission. This is one of the three great ideas in open-source licensing. The MIT License captures this idea by giving a license “to any person obtaining a copy of … the Software”. As we’ll see later, there is also a condition to receiving this license that ensures others will learn about their permission, too.
|
||||
|
||||
The parenthetical with a capitalized term in quotation marks (a “Definition”), is the standard way to give terms specific meanings in American-style legal documents. Courts will reliably look back to the terms of the definition when they see a defined, capitalized term used elsewhere in the document.
|
||||
|
||||
##### Grant Scope
|
||||
|
||||
> to deal in the Software without restriction,
|
||||
|
||||
From the licensee’s point of view, these are the seven most important words in The MIT License. The key legal concerns are getting sued for copyright infringement and getting sued for patent infringement. Neither copyright law nor patent law uses “to deal in” as a term of art; it has no specific meaning in court. As a result, any court deciding a dispute between a licensor and a licensee would ask what the parties meant and understood by this language. What the court will see is that the language is intentionally broad and open-ended. It gives licensees a strong argument against any claim by a licensor that they didn’t give permission for the licensee to do that specific thing with the software, even if the thought clearly didn’t occur to either side when the license was given.
|
||||
|
||||
> including without limitation the rights to use, copy, modify, merge, publish, distribute, sublicense, and/or sell copies of the Software, and to permit persons to whom the Software is furnished to do so,
|
||||
|
||||
No piece of legal writing is perfect, “fully settled in meaning”, or unmistakably clear. Beware anyone who pretends otherwise. This is the least perfect part of The MIT License. There are three main issues:
|
||||
|
||||
First, “including without limitation” is a legal antipattern. It crops up in any number of flavors:
|
||||
|
||||
* “including, without limitation”
|
||||
* “including, without limiting the generality of the foregoing”
|
||||
* “including, but not limited to”
|
||||
* many, many pointless variations
|
||||
|
||||
|
||||
|
||||
All of these share a common purpose, and they all fail to achieve it reliably. Fundamentally, drafters who use them try to have their cake and eat it, too. In The MIT License, that means introducing specific examples of “dealing in the Software”—“use, copy, modify” and so on—without implying that licensee action has to be something like the examples given to count as “dealing in”. The trouble is that, if you end up needing a court to review and interpret the terms of a license, the court will see its job as finding out what those fighting meant by the language. If the court needs to decide what “deal in” means, it cannot “unsee” the examples, even if you tell it to. I’d argue that “deal in the Software without restriction” alone would be better for licensees. Also shorter.
|
||||
|
||||
Second, the verbs given as examples of “deal in” are a hodgepodge. Some have specific meanings under copyright or patent law, others almost do or just plain don’t:
|
||||
|
||||
* use appears in [United States Code title 35, section 271(a)][24], the patent law’s list of what patent owners can sue others for doing without permission.
|
||||
|
||||
* copy appears in [United States Code title 17, section 106][25], the copyright law’s list of what copyright owners can sue others for doing without permission.
|
||||
|
||||
* modify doesn’t appear in either copyright or patent statute. It is probably closest to “prepare derivative works” under the copyright statute, but may also implicate improving or otherwise derivative inventions.
|
||||
|
||||
* merge doesn’t appear in either copyright or patent statute. “Merger” has a specific meaning in copyright, but that’s clearly not what’s intended here. Rather, a court would probably read “merge” according to its meaning in industry, as in “to merge code”.
|
||||
|
||||
* publish doesn’t appear in either copyright or patent statute. Since “the Software” is what’s being published, it probably hews closest to “distribute” under the [copyright statute][25]. That statute also covers rights to perform and display works “publicly”, but those rights apply only to specific kinds of copyrighted work, like plays, sound recordings, and motion pictures.
|
||||
|
||||
* distribute appears in the [copyright statute][25].
|
||||
|
||||
* sublicense is a general term of intellectual property law. The right to sublicense means the right to give others licenses of their own, to do some or all of what you have permission to do. The MIT License’s right to sublicense is actually somewhat unusual in open-source licenses generally. The norm is what Heather Meeker calls a “direct licensing” approach, where everyone who gets a copy of the software and its license terms gets a license direct from the owner. Anyone who might get a sublicense under the MIT License will probably end up with a copy of the license telling them they have a direct license, too.
|
||||
|
||||
* sell copies of is a mongrel. It is close to “offer to sell” and “sell” in the [patent statute][24], but refers to “copies”, a copyright concept. On the copyright side, it seems close to “distribute”, but the [copyright statute][25] makes no mention of sales.
|
||||
|
||||
* permit persons to whom the Software is furnished to do so seems redundant of “sublicense”. It’s also unnecessary to the extent folks who get copies also get a direct license.
|
||||
|
||||
|
||||
|
||||
|
||||
Lastly, as a result of this mishmash of legal, industry, general-intellectual-property, and general-use terms, it isn’t clear whether The MIT License includes a patent license. The general language “deal in” and some of the example verbs, especially “use”, point toward a patent license, albeit a very unclear one. The fact that the license comes from the copyright holder, who may or may not have patent rights in inventions in the software, as well as most of the example verbs and the definition of “the Software” itself, all point strongly toward a copyright license. More recent permissive open-source licenses, like [Apache 2.0][8], address copyright, patent, and even trademark separately and specifically.
|
||||
|
||||
##### Three License Conditions
|
||||
|
||||
> subject to the following conditions:
|
||||
|
||||
There’s always a catch! MIT has three!
|
||||
|
||||
If you don’t follow The MIT License’s conditions, you don’t get the permission the license offers. So failing to do what the conditions say at least theoretically leaves you open to a lawsuit, probably a copyright lawsuit.
|
||||
|
||||
Using the value of the software to the licensee to motivate compliance with conditions, even though the licensee paid nothing for the license, is the second great idea of open-source licensing. The last, not found in The MIT License, builds off license conditions: “Copyleft” licenses like the [GNU General Public License][9] use license conditions to control how those making changes can license and distribute their changed versions.
|
||||
|
||||
##### Notice Condition
|
||||
|
||||
> The above copyright notice and this permission notice shall be included in all copies or substantial portions of the Software.
|
||||
|
||||
If you give someone a copy of the software, you need to include the license text and any copyright notice. This serves a few critical purposes:
|
||||
|
||||
1. Gives others notice that they have permission for the software under the public license. This is a key part of the direct-licensing model, where each user gets a license direct from the copyright holder.
|
||||
|
||||
2. Makes known who’s behind the software, so they can be showered in praises, glory, and cold, hard cash donations.
|
||||
|
||||
3. Ensures the warranty disclaimer and limitation of liability (coming up next) follow the software around. Everyone who gets a copy should get a copy of those licensor protections, too.
|
||||
|
||||
|
||||
|
||||
|
||||
There’s nothing to stop you charging for providing a copy, or even a copy in compiled form, without source code. But when you do, you can’t pretend that the MIT code is your own proprietary code, or provided under some other license. Those receiving get to know their rights under the “public license”.
|
||||
|
||||
Frankly, compliance with this condition is breaking down. Nearly every open-source license has such an “attribution” condition. Makers of system and installed software often understand they’ll need to compile a notices file or “license information” screen, with copies of license texts for libraries and components, for each release of their own. The project-steward foundations have been instrumental in teaching those practices. But web developers, as a whole, haven’t got the memo. It can’t be explained away by a lack of tooling—there is plenty—or the highly modular nature of packages from npm and other repositories—which uniformly standardize metadata formats for license information. All the good JavaScript minifiers have command-line flags for preserving license header comments. Other tools will concatenate `LICENSE` files from package trees. There’s really no excuse.
|
||||
|
||||
##### Warranty Disclaimer
|
||||
|
||||
> The Software is provided “as is”, without warranty of any kind, express or implied, including but not limited to the warranties of merchantability, fitness for a particular purpose and noninfringement.
|
||||
|
||||
Nearly every state in the United States has enacted a version of the Uniform Commercial Code, a model statute of laws governing commercial transactions. Article 2 of the UCC—“Division 2” in California—governs contracts for sales of goods, from used automobiles bought off the lot to large shipments of industrial chemicals to manufacturing plants.
|
||||
|
||||
Some of the UCC’s rules about sales contracts are mandatory. These rules always apply, whether those buying and selling like them or not. Others are just “defaults”. Unless buyers and sellers opt out in writing, the UCC implies that they want the baseline rule found in the UCC’s text for their deal. Among the default rules are implied “warranties”, or promises by sellers to buyers about the quality and usability of the goods being sold.
|
||||
|
||||
There is a big theoretical debate about whether public licenses like The MIT License are contracts—enforceable agreements between licensors and licensees—or just licenses, which go one way, but may come with strings attached, their conditions. There is less debate about whether software counts as “goods”, triggering the UCC’s rules. There is no debate among licensors on liability: They don’t want to get sued for lots of money if the software they give away for free breaks, causes problems, doesn’t work, or otherwise causes trouble. That’s exactly the opposite of what three default rules for “implied warranties” do:
|
||||
|
||||
1. The implied warranty of “merchantability” under [UCC section 2-314][26] is a promise that “the goods”—the Software—are of at least average quality, properly packaged and labeled, and fit for the ordinary purposes they are intended to serve. This warranty applies only if the one giving the software is a “merchant” with respect to the software, meaning they deal in software and hold themselves out as skilled in software.
|
||||
|
||||
2. The implied warranty of “fitness for a particular purpose” under [UCC section 2-315][27] kicks in when the seller knows the buyer is relying on them to provide goods for a particular purpose. The goods need to actually be “fit” for that purpose.
|
||||
|
||||
3. The implied warranty of “noninfringement” is not part of the UCC, but is a common feature of general contract law. This implied promise protects the buyer if it turns out the goods they received infringe somebody else’s intellectual property rights. That would be the case if the software under The MIT License didn’t actually belong to the one trying to license it, or if it fell under a patent owned by someone else.
|
||||
|
||||
|
||||
|
||||
|
||||
[Section 2-316(3)][28] of the UCC requires language opting out of, or “excluding”, implied warranties of merchantability and fitness for a particular purpose to be conspicuous. “Conspicuous” in turn means written or formatted to call attention to itself, the opposite of microscopic fine print meant to slip past unwary consumers. State law may impose a similar attention-grabbing requirement for disclaimers of noninfringement.
|
||||
|
||||
Lawyers have long suffered under the delusion that writing anything in `ALL-CAPS` meets the conspicuous requirement. That isn’t true. Courts have criticized the Bar for pretending as much, and most everyone agrees all-caps does more to discourage reading than compel it. All the same, most open-source-license forms set their warranty disclaimers in all-caps, in part because that’s the only obvious way to make it stand out in plain-text `LICENSE` files. I’d prefer to use asterisks or other ASCII art, but that ship sailed long, long ago.
|
||||
|
||||
##### Limitation of Liability
|
||||
|
||||
> In no event shall the authors or copyright holders be liable for any claim, damages or other liability, whether in an action of contract, tort or otherwise, arising from, out of or in connection with the Software or the use or other dealings in the Software.
|
||||
|
||||
The MIT License gives permission for software “free of charge”, but the law does not assume that folks receiving licenses free of charge give up their rights to sue when things go wrong and the licensor is to blame. “Limitations of liability”, often paired with “damages exclusions”, work a lot like licenses, as promises not to sue. But these are protections for the licensor against lawsuits by licensees.
|
||||
|
||||
In general, courts read limitations of liability and damages exclusions warily, since they can shift an incredible amount of risk from one side to another. To protect the community’s vital interest in giving folks a way to redress wrongs done in court, they “strictly construe” language limiting liability, reading it against the one protected by it where possible. Limitations of liability have to be specific to stand up. Especially in “consumer” contracts and other situations where those giving up the right to sue lack sophistication or bargaining power, courts have sometimes refused to honor language that seemed buried out of sight. Partly for that reason, partly by sheer force of habit, lawyers tend to give limits of liability the all-caps treatment, too.
|
||||
|
||||
Drilling down a bit, the “limitation of liability” part is a cap on the amount of money a licensee can sue for. In open-source licenses, that limit is always no money at all, $0, “not liable”. By contrast, in commercial licenses, it’s often a multiple of license fees paid in the last 12-month period, though it’s often negotiated.
|
||||
|
||||
The “exclusion” part lists, specifically, kinds of legal claims—reasons to sue for damages—the licensor cannot use. Like many, many legal forms, The MIT License mentions actions “of contract”—for breaching a contract—and “of tort”. Tort rules are general rules against carelessly or maliciously harming others. If you run someone down on the road while texting, you have committed a tort. If your company sells faulty headphones that burn peoples’ ears off, your company has committed a tort. If a contract doesn’t specifically exclude tort claims, courts sometimes read exclusion language in a contract to prevent only contract claims. For good measure, The MIT License throws in “or otherwise”, just to catch the odd admiralty law or other, exotic kind of legal claim.
|
||||
|
||||
The phrase “arising from, out of or in connection with” is a recurring tick symptomatic of the legal draftsman’s inherent, anxious insecurity. The point is that any lawsuit having anything to do with the software is covered by the limitation and exclusions. On the off chance something can “arise from”, but not “out of”, or “in connection with”, it feels better to have all three in the form, so pack ‘em in. Never mind that any court forced to split hairs in this part of the form will have to come up with different meanings for each, on the assumption that a professional drafter wouldn’t use different words in a row to mean the same thing. Never mind that in practice, where courts don’t feel good about a limitation that’s disfavored to begin with, they’ll be more than ready to read the scope trigger narrowly. But I digress. The same language appears in literally millions of contracts.
|
||||
|
||||
#### Overall
|
||||
|
||||
All these quibbles are a bit like spitting out gum on the way into church. The MIT License is a legal classic. The MIT License works. It is by no means a panacea for all software IP ills, in particular the software patent scourge, which it predates by decades. But MIT-style licenses have served admirably, fulfilling a narrow purpose—reversing troublesome default rules of copyright, sales, and contract law—with a minimal combination of discreet legal tools. In the greater context of computing, its longevity is astounding. The MIT License has outlasted and will outlast the vast majority of software licensed under it. We can only guess how many decades of faithful legal service it will have given when it finally loses favor. It’s been especially generous to those who couldn’t have afforded their own lawyer.
|
||||
|
||||
We’ve seen how the The MIT License we know today is a specific, standardized set of terms, bringing order at long last to a chaos of institution-specific, haphazard variations.
|
||||
|
||||
We’ve seen how its approach to attribution and copyright notice informed intellectual property management practices for academic, standards, commercial, and foundation institutions.
|
||||
|
||||
We’ve seen how The MIT Licenses grants permission for software to all, for free, subject to conditions that protect licensors from warranties and liability.
|
||||
|
||||
We’ve seen that despite some crusty verbiage and lawyerly affectation, one hundred and seventy one little words can get a hell of a lot of legal work done, clearing a path for open-source software through a dense underbrush of intellectual property and contract.
|
||||
|
||||
I’m so grateful for all who’ve taken the time to read this rather long post, to let me know they found it useful, and to help improve it. As always, I welcome your comments via [e-mail][29], [Twitter][30], and [GitHub][31].
|
||||
|
||||
A number of folks have asked where they can read more, or find run-downs of other licenses, like the GNU General Public License or the Apache 2.0 license. No matter what your particular continuing interest may be, I heartily recommend the following books:
|
||||
|
||||
* Andrew M. St. Laurent’s [Understanding Open Source & Free Software Licensing][32], from O’Reilly.
|
||||
|
||||
I start with this one because, while it’s somewhat dated, its approach is also closest to the line-by-line approach used above. O’Reilly has made it [available online][33].
|
||||
|
||||
* Heather Meeker’s [Open (Source) for Business][34]
|
||||
|
||||
In my opinion, by far the best writing on the GNU General Public License and copyleft more generally. This book covers the history, the licenses, their development, as well as compatibility and compliance. It’s the book I lend to clients considering or dealing with the GPL.
|
||||
|
||||
* Larry Rosen’s [Open Source Licensing][35], from Prentice Hall.
|
||||
|
||||
A great first book, also available for free [online][36]. This is the best introduction to open-source licensing and related law for programmers starting from scratch. This one is also a bit dated in some specific details, but Larry’s taxonomy of licenses and succinct summary of open-source business models stand the test of time.
|
||||
|
||||
|
||||
|
||||
|
||||
All of these were crucial to my own education as an open-source licensing lawyer. Their authors are professional heroes of mine. Have a read! — K.E.M
|
||||
|
||||
I license this article under a [Creative Commons Attribution-ShareAlike 4.0 license][37].
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://writing.kemitchell.com/2016/09/21/MIT-License-Line-by-Line.html
|
||||
|
||||
作者:[Kyle E. Mitchell][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://kemitchell.com/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: http://spdx.org/licenses/MIT
|
||||
[2]: https://fedoraproject.org/wiki/Licensing:MIT?rd=Licensing/MIT
|
||||
[3]: https://opensource.org
|
||||
[4]: https://spdx.org
|
||||
[5]: http://spdx.org/licenses/
|
||||
[6]: https://spdx.org/licenses/JSON
|
||||
[7]: https://www.npmjs.com/package/licensor
|
||||
[8]: https://www.apache.org/licenses/LICENSE-2.0
|
||||
[9]: https://www.gnu.org/licenses/gpl-3.0.en.html
|
||||
[10]: http://spdx.org/licenses/BSD-4-Clause
|
||||
[11]: https://spdx.org/licenses/BSD-3-Clause
|
||||
[12]: https://spdx.org/licenses/BSD-2-Clause
|
||||
[13]: http://www.isc.org/downloads/software-support-policy/isc-license/
|
||||
[14]: http://worksmadeforhire.com/
|
||||
[15]: https://www.eclipse.org/legal/epl-v10.html
|
||||
[16]: https://www.apache.org/licenses/#clas
|
||||
[17]: https://wiki.eclipse.org/ECA
|
||||
[18]: https://en.wikipedia.org/wiki/Feist_Publications,_Inc.,_v._Rural_Telephone_Service_Co.
|
||||
[19]: https://writing.kemitchell.com/2017/02/16/Against-Legislating-the-Nonobvious.html
|
||||
[20]: http://developercertificate.org/
|
||||
[21]: https://github.com/berneout/berneout-pledge
|
||||
[22]: https://github.com/berneout/authors-certificate
|
||||
[23]: https://en.wikipedia.org/wiki/Immediately-invoked_function_expression
|
||||
[24]: https://www.govinfo.gov/app/details/USCODE-2017-title35/USCODE-2017-title35-partIII-chap28-sec271
|
||||
[25]: https://www.govinfo.gov/app/details/USCODE-2017-title17/USCODE-2017-title17-chap1-sec106
|
||||
[26]: https://leginfo.legislature.ca.gov/faces/codes_displaySection.xhtml?sectionNum=2314.&lawCode=COM
|
||||
[27]: https://leginfo.legislature.ca.gov/faces/codes_displaySection.xhtml?sectionNum=2315.&lawCode=COM
|
||||
[28]: https://leginfo.legislature.ca.gov/faces/codes_displaySection.xhtml?sectionNum=2316.&lawCode=COM
|
||||
[29]: mailto:kyle@kemitchell.com
|
||||
[30]: https://twitter.com/kemitchell
|
||||
[31]: https://github.com/kemitchell/writing/tree/master/_posts/2016-09-21-MIT-License-Line-by-Line.md
|
||||
[32]: https://lccn.loc.gov/2006281092
|
||||
[33]: http://www.oreilly.com/openbook/osfreesoft/book/
|
||||
[34]: https://www.amazon.com/dp/1511617772
|
||||
[35]: https://lccn.loc.gov/2004050558
|
||||
[36]: http://www.rosenlaw.com/oslbook.htm
|
||||
[37]: https://creativecommons.org/licenses/by-sa/4.0/legalcode
|
||||
@ -1,5 +1,3 @@
|
||||
scoutydren is translating
|
||||
|
||||
3 open source alternatives to Adobe Lightroom
|
||||
======
|
||||
|
||||
|
||||
@ -1,5 +1,5 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: translator: (MjSeven)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
|
||||
@ -1,5 +1,5 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
|
||||
@ -1,211 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (HankChow)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (And, Ampersand, and & in Linux)
|
||||
[#]: via: (https://www.linux.com/blog/learn/2019/2/and-ampersand-and-linux)
|
||||
[#]: author: (Paul Brown https://www.linux.com/users/bro66)
|
||||
|
||||
And, Ampersand, and & in Linux
|
||||
======
|
||||

|
||||
|
||||
Take a look at the tools covered in the [three][1] [previous][2] [articles][3], and you will see that understanding the glue that joins them together is as important as recognizing the tools themselves. Indeed, tools tend to be simple, and understanding what _mkdir_ , _touch_ , and _find_ do (make a new directory, update a file, and find a file in the directory tree, respectively) in isolation is easy.
|
||||
|
||||
But understanding what
|
||||
|
||||
```
|
||||
mkdir test_dir 2>/dev/null || touch images.txt && find . -iname "*jpg" > backup/dir/images.txt &
|
||||
```
|
||||
|
||||
does, and why we would write a command line like that is a whole different story.
|
||||
|
||||
It pays to look more closely at the sign and symbols that live between the commands. It will not only help you better understand how things work, but will also make you more proficient in chaining commands together to create compound instructions that will help you work more efficiently.
|
||||
|
||||
In this article and the next, we'll be looking at the the ampersand (`&`) and its close friend, the pipe (`|`), and see how they can mean different things in different contexts.
|
||||
|
||||
### Behind the Scenes
|
||||
|
||||
Let's start simple and see how you can use `&` as a way of pushing a command to the background. The instruction:
|
||||
|
||||
```
|
||||
cp -R original/dir/ backup/dir/
|
||||
```
|
||||
|
||||
Copies all the files and subdirectories in _original/dir/_ into _backup/dir/_. So far so simple. But if that turns out to be a lot of data, it could tie up your terminal for hours.
|
||||
|
||||
However, using:
|
||||
|
||||
```
|
||||
cp -R original/dir/ backup/dir/ &
|
||||
```
|
||||
|
||||
pushes the process to the background courtesy of the final `&`. This frees you to continue working on the same terminal or even to close the terminal and still let the process finish up. Do note, however, that if the process is asked to print stuff out to the standard output (like in the case of `echo` or `ls`), it will continue to do so, even though it is being executed in the background.
|
||||
|
||||
When you push a process into the background, Bash will print out a number. This number is the PID or the _Process' ID_. Every process running on your Linux system has a unique process ID and you can use this ID to pause, resume, and terminate the process it refers to. This will become useful later.
|
||||
|
||||
In the meantime, there are a few tools you can use to manage your processes as long as you remain in the terminal from which you launched them:
|
||||
|
||||
* `jobs` shows you the processes running in your current terminal, whether be it in the background or foreground. It also shows you a number associated with each job (different from the PID) that you can use to refer to each process:
|
||||
|
||||
```
|
||||
$ jobs
|
||||
[1]- Running cp -i -R original/dir/* backup/dir/ &
|
||||
[2]+ Running find . -iname "*jpg" > backup/dir/images.txt &
|
||||
```
|
||||
|
||||
* `fg` brings a job from the background to the foreground so you can interact with it. You tell `fg` which process you want to bring to the foreground with a percentage symbol (`%`) followed by the number associated with the job that `jobs` gave you:
|
||||
|
||||
```
|
||||
$ fg %1 # brings the cp job to the foreground
|
||||
cp -i -R original/dir/* backup/dir/
|
||||
```
|
||||
|
||||
If the job was stopped (see below), `fg` will start it again.
|
||||
|
||||
* You can stop a job in the foreground by holding down [Ctrl] and pressing [Z]. This doesn't abort the action, it pauses it. When you start it again with (`fg` or `bg`) it will continue from where it left off...
|
||||
|
||||
...Except for [`sleep`][4]: the time a `sleep` job is paused still counts once `sleep` is resumed. This is because `sleep` takes note of the clock time when it was started, not how long it was running. This means that if you run `sleep 30` and pause it for more than 30 seconds, once you resume, `sleep` will exit immediately.
|
||||
|
||||
* The `bg` command pushes a job to the background and resumes it again if it was paused:
|
||||
|
||||
```
|
||||
$ bg %1
|
||||
[1]+ cp -i -R original/dir/* backup/dir/ &
|
||||
```
|
||||
|
||||
|
||||
|
||||
|
||||
As mentioned above, you won't be able to use any of these commands if you close the terminal from which you launched the process or if you change to another terminal, even though the process will still continue working.
|
||||
|
||||
To manage background processes from another terminal you need another set of tools. For example, you can tell a process to stop from a a different terminal with the [`kill`][5] command:
|
||||
|
||||
```
|
||||
kill -s STOP <PID>
|
||||
```
|
||||
|
||||
And you know the PID because that is the number Bash gave you when you started the process with `&`, remember? Oh! You didn't write it down? No problem. You can get the PID of any running process with the `ps` (short for _processes_ ) command. So, using
|
||||
|
||||
```
|
||||
ps | grep cp
|
||||
```
|
||||
|
||||
will show you all the processes containing the string " _cp_ ", including the copying job we are using for our example. It will also show you the PID:
|
||||
|
||||
```
|
||||
$ ps | grep cp
|
||||
14444 pts/3 00:00:13 cp
|
||||
```
|
||||
|
||||
In this case, the PID is _14444_. and it means you can stop the background copying with:
|
||||
|
||||
```
|
||||
kill -s STOP 14444
|
||||
```
|
||||
|
||||
Note that `STOP` here does the same thing as [Ctrl] + [Z] above, that is, it pauses the execution of the process.
|
||||
|
||||
To start the paused process again, you can use the `CONT` signal:
|
||||
|
||||
```
|
||||
kill -s CONT 14444
|
||||
```
|
||||
|
||||
There is a good list of many of [the main signals you can send a process here][6]. According to that, if you wanted to terminate the process, not just pause it, you could do this:
|
||||
|
||||
```
|
||||
kill -s TERM 14444
|
||||
```
|
||||
|
||||
If the process refuses to exit, you can force it with:
|
||||
|
||||
```
|
||||
kill -s KILL 14444
|
||||
```
|
||||
|
||||
This is a bit dangerous, but very useful if a process has gone crazy and is eating up all your resources.
|
||||
|
||||
In any case, if you are not sure you have the correct PID, add the `x` option to `ps`:
|
||||
|
||||
```
|
||||
$ ps x| grep cp
|
||||
14444 pts/3 D 0:14 cp -i -R original/dir/Hols_2014.mp4
|
||||
original/dir/Hols_2015.mp4 original/dir/Hols_2016.mp4
|
||||
original/dir/Hols_2017.mp4 original/dir/Hols_2018.mp4 backup/dir/
|
||||
```
|
||||
|
||||
And you should be able to see what process you need.
|
||||
|
||||
Finally, there is nifty tool that combines `ps` and `grep` all into one:
|
||||
|
||||
```
|
||||
$ pgrep cp
|
||||
8
|
||||
18
|
||||
19
|
||||
26
|
||||
33
|
||||
40
|
||||
47
|
||||
54
|
||||
61
|
||||
72
|
||||
88
|
||||
96
|
||||
136
|
||||
339
|
||||
6680
|
||||
13735
|
||||
14444
|
||||
```
|
||||
|
||||
Lists all the PIDs of processes that contain the string " _cp_ ".
|
||||
|
||||
In this case, it isn't very helpful, but this...
|
||||
|
||||
```
|
||||
$ pgrep -lx cp
|
||||
14444 cp
|
||||
```
|
||||
|
||||
... is much better.
|
||||
|
||||
In this case, `-l` tells `pgrep` to show you the name of the process and `-x` tells `pgrep` you want an exact match for the name of the command. If you want even more details, try `pgrep -ax command`.
|
||||
|
||||
### Next time
|
||||
|
||||
Putting an `&` at the end of commands has helped us explain the rather useful concept of processes working in the background and foreground and how to manage them.
|
||||
|
||||
One last thing before we leave: processes running in the background are what are known as _daemons_ in UNIX/Linux parlance. So, if you had heard the term before and wondered what they were, there you go.
|
||||
|
||||
As usual, there are more ways to use the ampersand within a command line, many of which have nothing to do with pushing processes into the background. To see what those uses are, we'll be back next week with more on the matter.
|
||||
|
||||
Read more:
|
||||
|
||||
[Linux Tools: The Meaning of Dot][1]
|
||||
|
||||
[Understanding Angle Brackets in Bash][2]
|
||||
|
||||
[More About Angle Brackets in Bash][3]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.linux.com/blog/learn/2019/2/and-ampersand-and-linux
|
||||
|
||||
作者:[Paul Brown][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.linux.com/users/bro66
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.linux.com/blog/learn/2019/1/linux-tools-meaning-dot
|
||||
[2]: https://www.linux.com/blog/learn/2019/1/understanding-angle-brackets-bash
|
||||
[3]: https://www.linux.com/blog/learn/2019/1/more-about-angle-brackets-bash
|
||||
[4]: https://ss64.com/bash/sleep.html
|
||||
[5]: https://bash.cyberciti.biz/guide/Sending_signal_to_Processes
|
||||
[6]: https://www.computerhope.com/unix/signals.htm
|
||||
@ -1,126 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (MjSeven)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Getting started with Vim visual mode)
|
||||
[#]: via: (https://opensource.com/article/19/2/getting-started-vim-visual-mode)
|
||||
[#]: author: (Susan Lauber https://opensource.com/users/susanlauber)
|
||||
|
||||
Getting started with Vim visual mode
|
||||
======
|
||||
Visual mode makes it easier to highlight and manipulate text in Vim.
|
||||

|
||||
|
||||
Ansible playbook files are text files in a YAML format. People who work regularly with them have their favorite editors and plugin extensions to make the formatting easier.
|
||||
|
||||
When I teach Ansible with the default editor available in most Linux distributions, I use Vim's visual mode a lot. It allows me to highlight my actions on the screen—what I am about to edit and the text manipulation task I'm doing—to make it easier for my students to learn.
|
||||
|
||||
### Vim's visual mode
|
||||
|
||||
When editing text with Vim, visual mode can be extremely useful for identifying chunks of text to be manipulated.
|
||||
|
||||
Vim's visual mode has three versions: character, line, and block. The keystrokes to enter each mode are:
|
||||
|
||||
* Character mode: **v** (lower-case)
|
||||
* Line mode: **V** (upper-case)
|
||||
* Block mode: **Ctrl+v**
|
||||
|
||||
|
||||
|
||||
Here are some ways to use each mode to simplify your work.
|
||||
|
||||
### Character mode
|
||||
|
||||
Character mode can highlight a sentence in a paragraph or a phrase in a sentence. Then the visually identified text can be deleted, copied, changed, or modified with any other Vim editing command.
|
||||
|
||||
#### Move a sentence
|
||||
|
||||
To move a sentence from one place to another, start by opening the file and moving the cursor to the first character in the sentence you want to move.
|
||||
|
||||
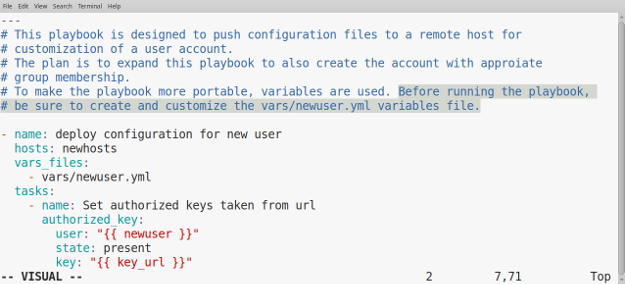
|
||||
|
||||
* Press the **v** key to enter visual character mode. The word **VISUAL** will appear at the bottom of the screen.
|
||||
* Use the Arrow keys to highlight the desired text. You can use other navigation commands, such as **w** to highlight to the beginning of the next word or **$** to include the rest of the line.
|
||||
* Once the text is highlighted, press the **d** key to delete the text.
|
||||
* If you deleted too much or not enough, press **u** to undo and start again.
|
||||
* Move your cursor to the new location and press **p** to paste the text.
|
||||
|
||||
|
||||
|
||||
#### Change a phrase
|
||||
|
||||
You can also highlight a chunk of text that you want to replace.
|
||||
|
||||
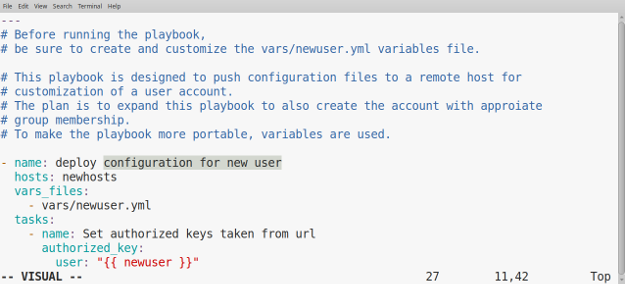
|
||||
|
||||
* Place the cursor at the first character you want to change.
|
||||
* Press **v** to enter visual character mode.
|
||||
* Use navigation commands, such as the Arrow keys, to highlight the phrase.
|
||||
* Press **c** to change the highlighted text.
|
||||
* The highlighted text will disappear, and you will be in Insert mode where you can add new text.
|
||||
* After you finish typing the new text, press **Esc** to return to command mode and save your work.
|
||||
|
||||
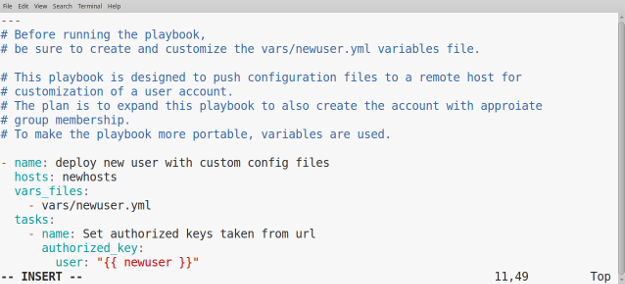
|
||||
|
||||
### Line mode
|
||||
|
||||
When working with Ansible playbooks, the order of tasks can matter. Use visual line mode to move a task to a different location in the playbook.
|
||||
|
||||
#### Manipulate multiple lines of text
|
||||
|
||||
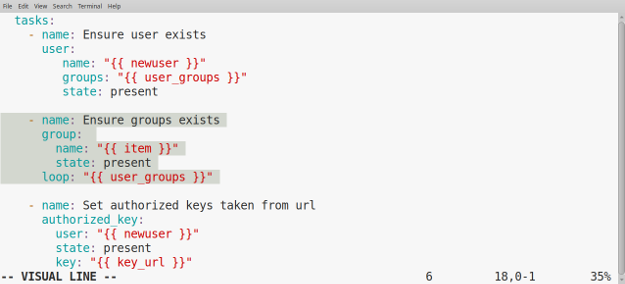
|
||||
|
||||
* Place your cursor anywhere on the first or last line of the text you want to manipulate.
|
||||
* Press **Shift+V** to enter line mode. The words **VISUAL LINE** will appear at the bottom of the screen.
|
||||
* Use navigation commands, such as the Arrow keys, to highlight multiple lines of text.
|
||||
* Once the desired text is highlighted, use commands to manipulate it. Press **d** to delete, then move the cursor to the new location, and press **p** to paste the text.
|
||||
* **y** (yank) can be used instead of **d** (delete) if you want to copy the task.
|
||||
|
||||
|
||||
|
||||
#### Indent a set of lines
|
||||
|
||||
When working with Ansible playbooks or YAML files, indentation matters. A highlighted block can be shifted right or left with the **>** and **<** keys.
|
||||
|
||||
![]9https://opensource.com/sites/default/files/uploads/vim-visual-line2.png
|
||||
|
||||
* Press **>** to increase the indentation of all the lines.
|
||||
* Press **<** to decrease the indentation of all the lines.
|
||||
|
||||
|
||||
|
||||
Try other Vim commands to apply them to the highlighted text.
|
||||
|
||||
### Block mode
|
||||
|
||||
The visual block mode is useful for manipulation of specific tabular data files, but it can also be extremely helpful as a tool to verify indentation of an Ansible playbook.
|
||||
|
||||
Tasks are a list of items and in YAML each list item starts with a dash followed by a space. The dashes must line up in the same column to be at the same indentation level. This can be difficult to see with just the human eye. Indentation of other lines within the task is also important.
|
||||
|
||||
#### Verify tasks lists are indented the same
|
||||
|
||||
|
||||
|
||||
* Place your cursor on the first character of the list item.
|
||||
* Press **Ctrl+v** to enter visual block mode. The words **VISUAL BLOCK** will appear at the bottom of the screen.
|
||||
* Use the Arrow keys to highlight the single character column. You can verify that each task is indented the same amount.
|
||||
* Use the Arrow keys to expand the block right or left to check whether the other indentation is correct.
|
||||
|
||||
|
||||
|
||||
Even though I am comfortable with other Vim editing shortcuts, I still like to use visual mode to sort out what text I want to manipulate. When I demo other concepts during a presentation, my students see a tool to highlight text and hit delete in this "new to them" text only editor.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/2/getting-started-vim-visual-mode
|
||||
|
||||
作者:[Susan Lauber][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/susanlauber
|
||||
[b]: https://github.com/lujun9972
|
||||
@ -1,117 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (FinalCrypt – An Open Source File Encryption Application)
|
||||
[#]: via: (https://itsfoss.com/finalcrypt/)
|
||||
[#]: author: (Ankush Das https://itsfoss.com/author/ankush/)
|
||||
|
||||
FinalCrypt – An Open Source File Encryption Application
|
||||
======
|
||||
|
||||
I usually don’t encrypt files – but if I am planning to organize my important documents or credentials, an encryption program would come in handy.
|
||||
|
||||
You may be already using a program like [GnuPG][1] that helps you encrypt/decrypt your files on your Linux machine. There is [EncryptPad][2] as well that encrypts your notes.
|
||||
|
||||
However, I have come across a new free and open source encryption tool called FinalCrypt. You can check out their recent releases and the source on its [GitHub page][3].
|
||||
|
||||
In this article, I will be sharing my experience of using this tool. Do note that I won’t be comparing this with any other program available out there – so if you want a detailed comparison between multiple solutions, let us know in the comments.
|
||||
|
||||
![FinalCrypt][4]
|
||||
|
||||
### Using FinalCrypt to encrypt files
|
||||
|
||||
FinalCrypt uses the [One-Time pad][5] key generation cipher to encrypt files. In other words, it generates an OTP key which you will use for encrypting or decrypting your files.
|
||||
|
||||
The key will be completely random as per the size of the key – which you can specify. So, it is impossible to decrypt the file without the key file.
|
||||
|
||||
While the OTP key method for encryption/decryption is simple and effective, but managing or securing the key file could be an inconvenience for some.
|
||||
|
||||
If you want to use FinalCrypt, you can install the DEB/RPM files from its website. FinalCrypt is also available for Windows and macOS.
|
||||
|
||||
Once downloaded, simply double click to [install it from deb][6] or rpm files. You can also build it from the source code if you want.
|
||||
|
||||
### FileCrypt in Action
|
||||
|
||||
This video shows how to use FinalCrypt:
|
||||
|
||||
<https://youtu.be/6Ir8VcZ26E4>
|
||||
|
||||
If you like Linux related videos, please [subscribe to our YouTube channel][7].
|
||||
|
||||
Once you have installed FinalCrypt, you’ll find it in your list of installed applications. Launch it from there.
|
||||
|
||||
Upon launch, you will observe two sections (split) for the items to encrypt/decrypt and the other to select the OTP file.
|
||||
|
||||
![Using FinalCrypt for encrypting files in Linux][8]
|
||||
|
||||
First, you will have to generate an OTP key. Here’s how to do that:
|
||||
|
||||
![finalcrypt otp][9]
|
||||
|
||||
Do note that your file name can be anything – but you need to make sure that the key file size is greater or equal to the file you want to encrypt. I find it absurd but that’s how it is.
|
||||
|
||||
![][10]
|
||||
|
||||
After you generate the file, select the key on the right-side of the window and then select the files that you want to encrypt on the left-side of the window.
|
||||
|
||||
You will find the checksum value, key file size, and valid status highlighted after generating the OTP:
|
||||
|
||||
![][11]
|
||||
|
||||
After making the selection, you just need to click on “ **Encrypt** ” to encrypt those files and if already encrypted, then “ **Decrypt** ” to decrypt those.
|
||||
|
||||
![][12]
|
||||
|
||||
You can also use FinalCrypt in command line to automate your encryption job.
|
||||
|
||||
#### How do you secure your OTP key?
|
||||
|
||||
It is easy to encrypt/decrypt the files you want to protect. But, where should you keep your OTP key?
|
||||
|
||||
It is literally useless if you fail to keep your OTP key in a safe storage location.
|
||||
|
||||
Well, one of the best ways would be to use a USB stick specifically for the keys you want to store. Just plug it in when you want to decrypt files and its all good.
|
||||
|
||||
In addition to that, you may save your key on a [cloud service][13], if you consider it secure enough.
|
||||
|
||||
More information about FinalCrypt can be found on its website.
|
||||
|
||||
[FinalCrypt](https://sites.google.com/site/ronuitholland/home/finalcrypt)
|
||||
|
||||
**Wrapping Up**
|
||||
|
||||
It might seem a little overwhelming at the beginning but it is actually a simple and user-friendly encryption program available for Linux. There are other programs to [password protect folders][14] as well if you are interested in some additional reading.
|
||||
|
||||
What do you think about FinalCrypt? Do you happen to know about something similar which is potentially better? Let us know in the comments and we shall take a look at them!
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://itsfoss.com/finalcrypt/
|
||||
|
||||
作者:[Ankush Das][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://itsfoss.com/author/ankush/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.gnupg.org/
|
||||
[2]: https://itsfoss.com/encryptpad-encrypted-text-editor-linux/
|
||||
[3]: https://github.com/ron-from-nl/FinalCrypt
|
||||
[4]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2019/02/finalcrypt.png?resize=800%2C450&ssl=1
|
||||
[5]: https://en.wikipedia.org/wiki/One-time_pad
|
||||
[6]: https://itsfoss.com/install-deb-files-ubuntu/
|
||||
[7]: https://www.youtube.com/c/itsfoss?sub_confirmation=1
|
||||
[8]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2019/02/finalcrypt.jpg?fit=800%2C439&ssl=1
|
||||
[9]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2019/02/finalcrypt-otp-key.jpg?resize=800%2C443&ssl=1
|
||||
[10]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2019/02/finalcrypt-otp-generate.jpg?ssl=1
|
||||
[11]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2019/02/finalcrypt-key.jpg?fit=800%2C420&ssl=1
|
||||
[12]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2019/02/finalcrypt-encrypt.jpg?ssl=1
|
||||
[13]: https://itsfoss.com/cloud-services-linux/
|
||||
[14]: https://itsfoss.com/password-protect-folder-linux/
|
||||
[15]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2019/02/finalcrypt.png?fit=800%2C450&ssl=1
|
||||
292
translated/talk/20160921 lawyer The MIT License, Line by Line.md
Normal file
292
translated/talk/20160921 lawyer The MIT License, Line by Line.md
Normal file
@ -0,0 +1,292 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (Amanda0212)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (lawyer The MIT License, Line by Line)
|
||||
[#]: via: (https://writing.kemitchell.com/2016/09/21/MIT-License-Line-by-Line.html)
|
||||
[#]: author: (Kyle E. Mitchell https://kemitchell.com/)
|
||||
|
||||
|
||||
MIT许可证的“精华”
|
||||
======
|
||||
|
||||
### MIT许可证的“精华”
|
||||
|
||||
[MIT许可证][1] 是最流行的开源软件许可证,请阅读下面的内容。
|
||||
|
||||
#### 阅读许可证
|
||||
|
||||
如果你参与了开源软件的开发,然而你还没有花时间从头开始阅读尽管只有171个单词的许可证,你现在就需要这么做,尤其是如果许可证不是你的日常生活。记住任何看起来不对劲或不清楚的事情,然后继续思考。我将重复上下文和评论的每一个字,按块和顺序。但重要的是你要做到心中有数。
|
||||
|
||||
> MIT 许可证
|
||||
>
|
||||
> 版权(c)<年份><版权持有人>
|
||||
>
|
||||
> 现免费准许任何人取得本软件及相关文件档案("软件")的副本,以便不受限制地处理该软件,包括不受限制地使用、复制、修改,合并、公布、分发、转授许可证和/或出售软件副本的权利,并允许向其提供软件的人这样做,但须符合下列条件:
|
||||
>
|
||||
> 在软件和软件的所有副本中都必须包含版权声明和许可声明。
|
||||
>
|
||||
> 该软件是"原封不动地"提供的,没有任何明示或默示的保证,包括但不限于适销性、适合某一特定目的和不侵权的保证。在任何情况下,作者或版权所有人都不应对因下列原因引起的任何索赔、损害或其他责任负责,与软件或软件中的使用或其他交易有关的。
|
||||
|
||||
许可证由五个部分组成,在逻辑组成上像下面这样:
|
||||
|
||||
* **页眉**
|
||||
* **许可证所有权** : “MIT执照”
|
||||
* **版权公告** : “版权 (c) …”
|
||||
* **许可证授予** : “特此批准 …”
|
||||
* **授予范围** : “… 在软件方面的处理 …”
|
||||
* **条件** : “… 服从于 …”
|
||||
* **归属和通知** : “以上...应包含...在内”
|
||||
* **保修免责声明** : “该软件“原封不动地”提供...”
|
||||
* **赔偿责任限制** : “在任何情况下....”
|
||||
|
||||
|
||||
|
||||
我们开始了:
|
||||
|
||||
#### 写在前面
|
||||
|
||||
##### 许可证所有权
|
||||
|
||||
> 麻省理工许可证(MIT)
|
||||
|
||||
“麻省理工许可证”并不是一个单一的许可证,而是包含来自于麻省理工学院为发布而准备的语言的一系列许可证表格。这些年来,无论是对于使用它的原始项目都经历了许多变化,还是作为其他项目的模型。fedora项目保持了一种[mit许可证陈列室的种类][2],在简单文本中保留了微小的变化,如甲醛中的解剖标本,追踪着一种没有规律的进化。
|
||||
|
||||
幸运的是,[开源计划][3]和[数据交换软件包][4]组已经将通用的MIT式许可证表格标准化为“mit许可证”。而OSI则将SPDX的标准化[字符串识别符][5]用于普通的开源许可证,“MIT”明确指向标准化的表格“MIT许可证”。
|
||||
|
||||
即使在“许可证”文件中包含“MIT许可证”或“SPDX:MIT”,负责任的评论者为了确定仍然会对文本和标准表单进行比较。尽管各种自称为“麻省理工许可证”的许可证表格只在细节上有所不同,但所谓的“麻省理工许可证”的宽松已经诱使一些作者添加了令人讨厌的“定制”。典型的可怕的的例子就是[JSON许可证][6],一个MIT-family许可证加上“软件应该用于正途的,而不是邪恶的...”这种事情可能是“非常克罗克福德”。这绝对是一个痛苦的事情。可能是律师们开的一个玩笑,但他们一路笑到最后。
|
||||
|
||||
这个故事的寓意是:“麻省理工许可证”本身是模棱两可的。人们或许对你的意思有清晰的理解,但是你只会通过将标准的MIT许可证表格的文本复制到你的项目中来节省所有人的时间,包括你自己。如果您使用元数据,如包管理器元数据文件中的“许可证”属性来指定“MIT”许可证,请确保您的“许可证”文件和任何头注使用标准窗体文本。而这些都可以[自动化][7]。
|
||||
|
||||
##### 版权公告
|
||||
|
||||
> 版权(c)<年份><版权持有人>
|
||||
|
||||
直到1976年的版权法,美国版权法要求采取具体行动以确保创作作品的版权,称为“手续”。如果你没有遵循这些手续,你起诉他人未经授权使用你的作品的权利是有限的,但这种权利基本丧失。其中一种形式是“通知”:在你的作品上做标记,或者在声明过后让市场知道你拥有版权。 © 是标记有版权作品的标准符号,以发出版权通知。ascii字符集没有 © 符号,但是“版权(c)”得到了这种权利。
|
||||
|
||||
1976年“执行”了伯尔尼国际公约的许多要求版权法却取消了保护版权的手续。至少在美国,版权拥有者仍然需要在起诉侵权行为之前登记他们的版权作品,但如果他们在侵权行为开始前登记,也许会造成更高的损害。然而,现实中许多人在提起诉讼之前登记了版权。你不会因为只是没有在版权上张贴通知、注册、向国会图书馆发送副本等行为而失去版权。
|
||||
|
||||
即使版权公告不再像过去那样绝对必要,但它们仍然很有用。说明作品创作的年份和版权持有者,使人们对作品的版权何时到期有某种感觉,从而使作品进入公共领域。作者的身份也很有用:美国法律对个人和“公司”两种身份的作者的版权计算方法不同。尤其是在商业上,即使许可条款给予非常慷慨的许可,公司也有必要对使用已知竞争对手的软件三思而后行。如果你希望别人看到你的作品,并希望从你那里获得许可,版权公告就可以很好裁决归属问题。
|
||||
|
||||
至于“版权持有人”:并不是所有的标准格式许可证都有地方写出来。近期的许可证表格,如[apache 2.0][8]和[gpl 3.0][9],发布“许可证”文本,这些文本本应逐字复制,与头注和单独的文件其他地方,以表明谁拥有版权,并正在给予许可证。这些做法有意无意地阻止了对"标准"文本的更改,还使自动许可证认证更加可靠。
|
||||
|
||||
MIT许可证是机构为发布代码而编写的语言。对于机构发布,只有一个明确的“版权持有人”,即机构发布代码。其他一些机构用他们自己的名字代替了“MIT”,最终形成了我们现在的通用格式。这个过程重复了这个时代的其他短形式的机构许可证,值得注意的是加州大学伯克利分校的[原四条款BSD许可证][10],现在用于[三条款][11]和[二条款][12]的变体,以及互联网系统联盟(MIT的一种变体)的(ISC许可证)。
|
||||
|
||||
在所有情况下,机构都将自己列为版权所有人,以依赖版权所有权规则,称为"[受雇作品][14]"规则,这就给了雇主和客户一些版权,他们的雇员和承包商代表他们做的工作。这些规则通常不适用于自愿提交代码的分布式合作者。这给项目管理者基金会带来了一个问题,比如apache基金会和日食基金会,这些基金会接受了来自更多样化的捐助者群体的捐助。到目前为止,通常的基础方法是使用一种房屋许可证,该许可证规定只有一个版权持有人——[Apache 2.0][8]和[EPL 1.0][15]——由出资人许可证协议支持——[apache clas][16]并且[clas][17]——从贡献者那里收集权利。在像GPL这样的“版权许可”下,在一个地方收集版权所有权更加重要,因为它依赖于版权所有人强制执行许可条件以促进软件自由值。
|
||||
|
||||
如今,只有很少的任何机构或企业管理者的项目在使用MIT式的许可证条款。SPDX和OSI通过规范MIT和ISC等不涉及特定实体或机构版权持有人的许可证形式,帮助了这些案例的使用。有了这些表格,项目作者的普遍做法是在很早表格的版权通知时就填写他们自己的名字,也许会在这里或那里增加一年的时间。至少根据美国版权法,由此产生的版权通知并没有给出一个完整的情况。
|
||||
|
||||
软件的原拥有者保留对其作品的所有权。但是,尽管MIT式的许可条款赋予了其他人在软件上进行开发和更改的权利,创造了法律所称的“衍生作品”,但它们并没有赋予原始作者在他人贡献中的版权所有权。相反,每个贡献者都拥有以现有代码为起点的作品的版权。
|
||||
|
||||
这些项目中的大多数也对接受贡献者许可协议的想法有所保留,更不用说签署版权转让了。这其实很好理解。尽管假定一些较新的开源开发者对github“自动”发送退出请求,根据项目的现有许可条款授权分配贡献,但美国法律不承认这样的规则。默认的是强有力的版权保护,而不是许可许可。
|
||||
|
||||
更新:GitHub后来改变了它在整个网站的服务条款,包括试图翻转这个默认,至少在GitHub.com。我已经写了一些关于这个发展的想法,不是所有的都是积极的,在[另一个帖子][19]。
|
||||
|
||||
为填补具有法律效力的且有充分文件证明的捐款权利授予与完全没有书面记录之间的空白,一些项目采用了[开发商原产地证书][20],一个标准的语句贡献者暗示在他们的Git提交中使用“签名关闭”元数据标签。在臭名昭著的SCO诉讼事件之后,Linux内核开发人员为Linux内核开发了原产地证书,该诉讼指控Linux的代码块来自于SCO拥有的UNIX源代码。作为一种创建文件线索的手段,显示每一行Linux代码的贡献者,开发人员原产地证书的功能很好。虽然开发人员的原产地证书不是许可证,但它确实提供了大量的证据,证明提交代码的人希望项目分发他们的代码,并让其他人在内核的现有许可条款下使用。内核还维护一个机器可读的“信用”文件,列出具有名称、关联、贡献区域和其他元数据的贡献者。我已经做了[一些][实验][22]将这种方法应用于不使用内核开发流程的项目。
|
||||
|
||||
#### 许可授权
|
||||
|
||||
> 现免费准许任何人取得本软件及相关文件档案("软件")的副本.
|
||||
|
||||
按照猜测,麻省理工执照的重点是执照。一般而言,许可是一个人或一个法律规定的实体----"许可人"----允许另一人----"被许可人"----做法律本来允许他们起诉的事情。MIT执照承诺不起诉。
|
||||
|
||||
法律有时会将许可证与承诺颁发许可证区分开来。如果有人违背了给他发许可证的承诺,你也许可以控告他违反了承诺,但你可能没有得到许可证。"在此"是律师们无法摆脱的时髦的古语之一。它在这里用来显示许可证文本本身给出了许可证,而不仅仅是一个许可证的承诺。这是合法的[IIFE][23]。
|
||||
|
||||
虽然许多许可证给予许可的具体命名的许可证,麻省理工学院许可证则是一个“公共许可证”。公共许可证给予广大公众许可。这是开放源码许可的三大理念之一。MIT许可证通过向“获得该软件副本的任何人”颁发许可证来捕捉这一想法。正如我们将在后面看到的,若获得这个许可证也有一个条件,以确保其他人也会知道他们的许可。
|
||||
|
||||
在美国式的法律文件中,用大写的引号(一个“定义”)来表示术语的标准方法。当法院在文件的其他地方看到一个定义明确、资本化的术语时,大写的引号将会很可靠地回顾定义的术语。
|
||||
|
||||
##### 授予范围
|
||||
|
||||
> 不受限制的软件处理
|
||||
|
||||
麻省理工许可证中最重要的七个词就是从被许可人的观点来看。其关键的法律问题是被起诉侵犯版权和被起诉侵犯专利。版权法和专利法都没有使用“处理”作为术语,它在法庭上没有具体的含义。因此,对许可人与被许可人之间的争议作出裁决的任何法院都会询问该措词所指的当事人的含义和理解。法院将会看到的是,该描述是不详细的和开放式的。这给了被许可人一个强有力的论据——在许可人没有允许被许可人对软件做特定的事情时反对许可人的任何主张,即使在许可的时候,这一想法都没有出现。
|
||||
|
||||
|
||||
> 包括在不受限制的情况下使用、复制、修改、合并、公布、分发、转授许可证和/或出售软件副本的权利,以及允许软件给予者这样做的权利。
|
||||
|
||||
没有哪篇法律文章是完美的,“在根本上完全解决”,或者明确无误的。要小心那些装模作样的人。这是麻省理工执照中最不完美的部分。有三个主要问题:
|
||||
|
||||
首先,"包括不受限制"是一种法律上的反模式。它产生了各种理解:
|
||||
|
||||
* “包括,不受限制”
|
||||
* “包括,在不限制上述一般性的情况下”
|
||||
* “包括,但不局限于”
|
||||
* 很多很多毫无意义的措辞变化
|
||||
|
||||
|
||||
|
||||
所有这些都有共同的目标,但都没能真正地实现。从根本上说,它们的创始人也在尝试从中得到好处。在MIT许可证中,这意味着引入“软件交易”,其具体示例是“使用、复制、修改”等等,而不是暗示被许可人的行为必须类似于给出的“交易”的示例。问题是,如果你最终需要一个法庭来审查和解释许可证的条款,法庭则看作找出那些争论的语言的含义。法院不能“忽略”示例决定什么是“交易”,,即使你告诉它。也是较短的。
|
||||
|
||||
第二,作为“处理”的例子给出的动词是一个大杂烩。有些在版权法或专利法下有特定的含义,有些却没有:
|
||||
|
||||
*使用出现在[美国法典第35章,第271(a)条][24],专利法的清单中,列出了专利所有人可以因未经许可而起诉他人的行为。
|
||||
|
||||
*复制出现在《版权法》(美国法典第17编第106条)[25]中,列出了版权所有人可以因未经许可而起诉他人的行为
|
||||
|
||||
*修改不出现在版权或专利法规中。它可能最接近版权法规下的“准备衍生作品”,但也可能涉及改进或其他衍生发明。
|
||||
|
||||
*合并没有出现在版权或专利法规中。“合并”在版权上有特定的含义,但这显然不是这里的本意。相反,法院可能根据其在业界的含义来理解“合并”,如“合并代码”。
|
||||
|
||||
*出版不出现在版权或专利法规中。由于“软件”是发布的内容,它可能最接近于[版权法规][25]下的“发布”。法律也涵盖了“公开”表演和展示作品的权利,但这些权利只适用于特定类型的有版权的作品,如戏剧、录音和电影。
|
||||
|
||||
*散布出现在[版权法规][25]中。
|
||||
|
||||
*次级许可是知识产权法的总称。转牌权是指利用给予他人自己的执照做一些有权利做的事情的权利。MIT许可证的转行权在开源许可证中是不常见的。每个人只要拿到软件及其许可条款的副本,就可以直接从所有者那里得到许可,这就是Heather Meeker所说的“直接授权”方法。任何可能通过麻省理工许可证获得次级许可证的人,很可能最终会得到一份许可证副本,告诉他们自己也有直接许可证。
|
||||
|
||||
*出售的副本是一个混合物。它接近[专利法规][24]中的"要约销售"和"销售",却指的是版权概念中的"副本"。在版权方面,它似乎接近“发行”,但[版权法规][25]没有提到出售。
|
||||
|
||||
*允许向软件提供者这样做,"次级许可"似乎是多余的并且也是不必要的,因为人们得到的副本也获得了直接许可证。
|
||||
|
||||
|
||||
|
||||
最后,由于法律、工业、一般知识产权和一般用途条款的混淆,目前还不清楚麻省理工学院的许可证是否包括专利许可证。一般的语言“处理”和一些例子动词,特别是“使用”,指向专利许可,尽管是一个非常不清楚的。许可证来自版权持有人,他对软件中的发明可能有也可能没有专利权,以及大多数示例动词和"软件"本身的定义,所有这些都强烈指向版权许可证.更近期的许可开放源码许可证,如[apache 2.0][8],涉及单独和具体的版权、专利甚至商标。
|
||||
|
||||
##### 许可证的三个条件
|
||||
|
||||
> 须符合以下条件:
|
||||
|
||||
总有人能符合MIT的三个条件!
|
||||
|
||||
如果你不遵守麻省理工的许可条件,你就得不到许可。因此,如果不按条件所说的做,至少在理论上,你会面临一场诉讼,很可能是一场版权诉讼。
|
||||
|
||||
利用软件的价值来激励被许可人遵守条件,即使被许可人没有为许可支付任何费用,是开源许可的第二个伟大想法。最后一个,在MIT许可证中没有,建立在许可证条件的基础上:“版权”许可证,像[GNU通用公共许可证][9]使用利益来控制那些进行更改的人去许可和分发他们的更改版本。
|
||||
|
||||
##### 公告条件
|
||||
|
||||
> 上述版权通知和许可通知应包含在软件的副本的绝大部分内容中。
|
||||
|
||||
如果你给某人软件的副本,你需要包括许可证文本和任何版权通知。这有几个关键目的:
|
||||
|
||||
1.通知他人他们有许可使用该软件的公共许可证。这是直接授权模式的一个关键部分,即每个用户直接从版权持有人那里获得许可证。
|
||||
|
||||
2.让他们知道谁是软件的参与者,使得他们能够接受检验。
|
||||
|
||||
3.确保免责声明和赔偿责任限制(下一步)伴随软件。每个得到副本的人也应该得到一份这些许可人保护的副本。
|
||||
|
||||
|
||||
|
||||
没有源代码的情况下,没有什么可以阻止您付费获得副本,甚至是编译形式的副本。但是当你这样做的时候,你不能假装MIT的代码是你自己的专有代码,或者是在其他许可证下提供的代码。领取者得了解他们在"公共许可证"下的权利。
|
||||
|
||||
坦率地说,这一条件很难去遵守。几乎每个开源许可证都有这样的“归属”条件。系统和已安装软件的制造商通常都明白,他们需要为自己的每个版本编写一个通知文件或“许可证信息”,并为库和组件提供许可证文本的副本。项目管理基金会在传授这些做法方面发挥了重要作用。但总体而言,网络开发者并没有得到这份备忘录。这不能用缺少工具来解释——有大量的工具——或者是来自npm和其他存储库的软件包的高度模块化性质——它们统一地将许可证信息的元数据格式标准化。所有好的JavaScript迷你机都有用于保存许可证标题注释的命令行标记。其他工具将从包装箱树连接“许可证”文件。实在没有理由去遗忘这一条件。
|
||||
|
||||
##### 保护免责声明
|
||||
|
||||
> 该软件是"原封不动地"提供的,没有任何明示或默示的保证,包括但不限于适销性、适合某一特定目的和不侵权的保证。
|
||||
|
||||
美国几乎每个州都颁布了统一商业法典,这是一个规范商业交易的法律范本。加州大学洛杉矶分校(UCC)的第2条则规定了货物销售合同,从旧汽车的购进到工业化学品的大规模运输,再到制造工厂。
|
||||
|
||||
加州大学洛杉矶分销关于销售合同的某些规则是强制性的。不管那些买卖他们喜欢与否这些规则总是适用的。而其他的只是“默认”。除非买卖双方以书面形式选择不参与,否则UCC暗示他们希望在UCC的文本中找到他们交易的基准规则。在默认规则中,隐含着“保证”,或卖方向买方承诺所售货物的质量和可用性。
|
||||
|
||||
对于像MIT许可证这样的公共许可证到底是合同(许可人和被许可人之间可执行的协议)还是仅仅只是许可证(只有一种方式,但可能附带条件),存在着很大的争论。而关于软件是否算作“商品”的争论则较少,这触发了UCC的规则。许可证持有者之间没有关于赔偿责任的争论:他们不想因为大量的钱财而被起诉,如果他们赠送的软件是免费、则会引起一些麻烦。这与“默认保证”的三个默认规则正好相反:
|
||||
|
||||
1.[UCC第2-314][26]条对"适销性"的默认保证是"货物"或者软件应至少具有平均质量,包装和适当的标签,适合他们的用途。这个保证只适用于提供软件的人是软件的“商人”,这意味着他们从事软件交易,并坚持自己在软件方面很熟练。
|
||||
|
||||
2.[UCC第2-315][27]条中关于"适合某一特定目的"的默认保证,在卖方知道买方因为某一用途而购买软件时,默认保护是有用的。因此,货物必须"合适"。
|
||||
|
||||
3.“不侵权”的默认保证不是合同约定的一部分,而是一般合同法的共同特征。如果买方收到的货物侵犯了他人的知识产权,该默认承诺保护买方。如果MIT许可下的软件实际上不属于试图授权它的软件,或者它属于其他人拥有的专利,就不会去保护买方。
|
||||
|
||||
|
||||
|
||||
UCC[章节 2-316(3)][28]条要求选择或"排除"关于适销性和适合某一特定目的的隐含保证的语言非常一目了然。而“显眼”则意味着书写或格式化的目的是为了引起人们对其本身的注意,这与微观的细微印刷相反,其目的是为了避开不谨慎的消费者。州法律可能对不侵权的免责声明规定类似的吸引注意力的要求。
|
||||
|
||||
长期以来,律师们一直被一种错觉所困扰,认为用“全盖”写任何东西都符合明显的要求,然而这确实假的。法院已经批判了这一标准,因为它太假了,而且大多数人都同意全上限的做法更多的是为了阻止阅读,而不是强迫阅读。尽管如此,大多数开源许可证的格式都将其保证免责声明设置为全上限,部分原因是这是唯一明显的方法,可以使其在纯文本“许可证”文件中脱颖而出。我宁愿用星号或其他的ASCII艺术,但那已经很久了。
|
||||
|
||||
##### 限制
|
||||
> 在任何情况下,作者或版权持有人均不对因下列原因而引起的任何索赔、损害或其他责任承担任何责任或是与软件或者软件中的使用或其他交易有关的责任。
|
||||
|
||||
MIT许可证允许“免费”使用软件,但法律并不认为获得免费许可证的人会在事情出了差错时放弃起诉的权利,而应归咎于许可人。“赔偿责任限制”,通常与“损害赔偿排除”结合在一起,就像保证不起诉一样,很像许可证。但这些是对许可人免受被许可人诉讼的保护。
|
||||
|
||||
一般来说,法院谨慎地解读赔偿责任和损害赔偿排除的限制,因为它们可以将巨大的风险从一方转移到另一方。为了保护社区的重大利益,他们“严格解释”限制责任的语言让人们能够纠正在法庭上犯下的错误,在可能的情况下对照受其保护的语言来解读。限制赔偿责任必须是明确的,才能成立。尤其是在“消费者”合同和其他情况下,那些放弃起诉权的人缺乏技巧或议价能力,法院有时拒绝尊重那些言外之意。律师们由于这个原因可能也由于纯粹的习惯而倾向于限制给予赔偿责任。
|
||||
|
||||
只要稍微钻低一点,“赔偿责任限额”就是被许可人可以起诉的金额的上限。在开源许可证中,这个限制总是没有钱的——0美元,“不负责任”。相比之下,在商业许可证中,尽管它通常是经过协商的而决定出为过去12个月期间支付的许可证费用的倍数。
|
||||
|
||||
"排除"部分具体列出了各类法律索赔以及许可人不能使用造成损害赔偿的理由。和许多法律形式一样,MIT执照提到了“合同”行为中的违约行为和“侵权行为”。侵权行为规则是防止不小心或恶意伤害他人的一般规则。如果你发短信的时候在路上撞上了某人,你就犯下了侵权行为。如果你的公司出售的耳机有问题,让人耳朵发麻,那么你的公司就犯下了侵权行为。如果合同没有明确排除侵权索赔,法院有时会在合同中阅读排除语,以防止只发生合同索赔。为了更好地衡量这种排除部分,麻省理工的执照上写着“或者其他”,仅仅是不同寻常的法律主张。
|
||||
|
||||
"产生于、或与之有关"这句话是法律起草人固有的、焦虑的不安全感的反复出现的症状。重点是任何与软件有关的诉讼都在限制和排除范围之内。在偶然的机会,一些东西可以"产生",但不是"产生",或"联系",不必介意它在形式上的三种的说法。出现在不同地方的同一个词语或许都是不同意思,假设一个专业起草人不会使用不同的词语在一排的意思相同的事情则不必介意,在实践中,如果法院对一开始就不满意想这个限制,那么他们就会非常愿意仔细地解读范围触发因素。但我离题了。同样的语言出现在数百万份合同中或许理解都不一样。
|
||||
|
||||
#### 总结
|
||||
|
||||
这些俏皮话虽然有点像碎碎念,但MIT许可证却是法律上的经典。MIT许可证是有用的。虽然MIT式的许可证非常出色但它绝不是解决所有软件ip弊病的灵丹妙药,尤其是早于它几十年出现的软件专利的祸害。实现了用最低限度的谨慎的法律工具组合来扭转麻烦的版权、销售和合同法的默认规则这个狭隘的目标。在更大的计算环境中,它的生命周期是惊人的。MIT许可证的有效期已经超过了它所授权的绝大多数软件。我们只能猜测,当它最终对那些自己请不起律师的人失去好感时,它将提供多少几十年忠实的法律服务。
|
||||
|
||||
我们已经看到了我们今天所知的MIT许可证是一套具体的、标准化的术语,最终给机构特有的、随意变化的混乱带来了秩序。
|
||||
|
||||
我们已经看到了它是如何为学术、标准、商业和基金会机构的知识产权管理实践提供归属和版权通知的依据。
|
||||
|
||||
我们已经看到了MIT许可证是如何向所有人免费授予软件许可的,但我们必须遵守保护许可人免受担保和赔偿责任的条件。
|
||||
|
||||
我们已经看到,尽管有一些不是很精准的词和修饰,但这一百七十一个词已经足够严谨,能够通过一个密集的知识产权和合同为开源软件开辟新的道路。
|
||||
|
||||
我非常感谢所有愿意花时间来阅读这篇长文的人,让我知道他们认为它有用,并帮助改进它。和往常一样,我欢迎您通过[电子邮件][29], [推特][30], 和 [GitHub][31].发表评论。
|
||||
|
||||
若是想阅读更多的内容或者找到其他许可证的概要,比如GNU公共许可证或者Apache 2.0许可证。无论你有什么关于这方面的兴趣,我都衷心推荐以下的书:
|
||||
|
||||
* Andrew M. St. Laurent’s [Understanding Open Source & Free Software Licensing][32], from O’Reilly.
|
||||
|
||||
我是这本书开始入门的,虽然它有点过时,但它的方法也最接近上面使用的逐行方法。O’Reilly 已经在网上提供了它。
|
||||
|
||||
* Heather Meeker’s [Open (Source) for Business][34]
|
||||
|
||||
在我看来,目前为止,关于GNU公共许可证和版权写的比较好的已经有很多了。这本书涵盖了许可证的历史、发展、以及兼容性和合规性。这是我借给客户的书,考虑或处理GPL。
|
||||
|
||||
* Larry Rosen’s [Open Source Licensing][35], from Prentice Hall.
|
||||
|
||||
这是很棒的一本书,也[在线][36]免费的。这是对程序员关于从零开始的开源许可和相关法律的最好的介绍。虽然这一点也有点过时了,但是在一些具体的细节中拉里对许可证的分类法和对开源商业模式的简洁总结是经得起时间考验的。
|
||||
|
||||
|
||||
|
||||
所有的这些教育都对作为开源授权律师的我至关重要。他们的作者是我这行的英雄。强烈推荐阅读!-- K.E.M
|
||||
|
||||
我在[创意共享许可4.0版本][37]授权这篇文章.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://writing.kemitchell.com/2016/09/21/MIT-License-Line-by-Line.html
|
||||
|
||||
作者:[Kyle E. Mitchell][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[Amanda0212](https://github.com/Amanda0212)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://kemitchell.com/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: http://spdx.org/licenses/MIT
|
||||
[2]: https://fedoraproject.org/wiki/Licensing:MIT?rd=Licensing/MIT
|
||||
[3]: https://opensource.org
|
||||
[4]: https://spdx.org
|
||||
[5]: http://spdx.org/licenses/
|
||||
[6]: https://spdx.org/licenses/JSON
|
||||
[7]: https://www.npmjs.com/package/licensor
|
||||
[8]: https://www.apache.org/licenses/LICENSE-2.0
|
||||
[9]: https://www.gnu.org/licenses/gpl-3.0.en.html
|
||||
[10]: http://spdx.org/licenses/BSD-4-Clause
|
||||
[11]: https://spdx.org/licenses/BSD-3-Clause
|
||||
[12]: https://spdx.org/licenses/BSD-2-Clause
|
||||
[13]: http://www.isc.org/downloads/software-support-policy/isc-license/
|
||||
[14]: http://worksmadeforhire.com/
|
||||
[15]: https://www.eclipse.org/legal/epl-v10.html
|
||||
[16]: https://www.apache.org/licenses/#clas
|
||||
[17]: https://wiki.eclipse.org/ECA
|
||||
[18]: https://en.wikipedia.org/wiki/Feist_Publications,_Inc.,_v._Rural_Telephone_Service_Co.
|
||||
[19]: https://writing.kemitchell.com/2017/02/16/Against-Legislating-the-Nonobvious.html
|
||||
[20]: http://developercertificate.org/
|
||||
[21]: https://github.com/berneout/berneout-pledge
|
||||
[22]: https://github.com/berneout/authors-certificate
|
||||
[23]: https://en.wikipedia.org/wiki/Immediately-invoked_function_expression
|
||||
[24]: https://www.govinfo.gov/app/details/USCODE-2017-title35/USCODE-2017-title35-partIII-chap28-sec271
|
||||
[25]: https://www.govinfo.gov/app/details/USCODE-2017-title17/USCODE-2017-title17-chap1-sec106
|
||||
[26]: https://leginfo.legislature.ca.gov/faces/codes_displaySection.xhtml?sectionNum=2314.&lawCode=COM
|
||||
[27]: https://leginfo.legislature.ca.gov/faces/codes_displaySection.xhtml?sectionNum=2315.&lawCode=COM
|
||||
[28]: https://leginfo.legislature.ca.gov/faces/codes_displaySection.xhtml?sectionNum=2316.&lawCode=COM
|
||||
[29]: mailto:kyle@kemitchell.com
|
||||
[30]: https://twitter.com/kemitchell
|
||||
[31]: https://github.com/kemitchell/writing/tree/master/_posts/2016-09-21-MIT-License-Line-by-Line.md
|
||||
[32]: https://lccn.loc.gov/2006281092
|
||||
[33]: http://www.oreilly.com/openbook/osfreesoft/book/
|
||||
[34]: https://www.amazon.com/dp/1511617772
|
||||
[35]: https://lccn.loc.gov/2004050558
|
||||
[36]: http://www.rosenlaw.com/oslbook.htm
|
||||
[37]: https://creativecommons.org/licenses/by-sa/4.0/legalcode
|
||||
117
translated/tech/20190206 Getting started with Vim visual mode.md
Normal file
117
translated/tech/20190206 Getting started with Vim visual mode.md
Normal file
@ -0,0 +1,117 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (MjSeven)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Getting started with Vim visual mode)
|
||||
[#]: via: (https://opensource.com/article/19/2/getting-started-vim-visual-mode)
|
||||
[#]: author: (Susan Lauber https://opensource.com/users/susanlauber)
|
||||
|
||||
Vim 可视化模式入门
|
||||
======
|
||||
可视化模式使得在 Vim 中高亮显示和操作文本变得更加容易。
|
||||

|
||||
|
||||
Ansible playbook 文件是 YAML 格式的文本文件,经常与它们打交道的人有他们最喜欢的编辑器和扩展插件以使格式化更容易。
|
||||
|
||||
当我使用大多数 Linux 发行版中提供的默认编辑器来教 Ansible 时,我经常使用 Vim 的可视化模式。它允许我在屏幕上高亮显示我的操作 -- 我要编辑什么以及我正在做的文本处理任务,以便使我的学生更容易学习。
|
||||
|
||||
### Vim 的可视化模式
|
||||
|
||||
使用 Vim 编辑文本时,可视化模式对于识别要操作的文本块非常有用。
|
||||
|
||||
Vim 的可视模式有三个模式:字符,行和块。进入每种模式的按键是:
|
||||
|
||||
* 字符模式: **v** (小写)
|
||||
* 行模式: **V** (大写)
|
||||
* 块模式: **Ctrl+v**
|
||||
|
||||
下面是使用每种模式简化工作的一些方法。
|
||||
|
||||
### 字符模式
|
||||
|
||||
字符模式可以高亮显示段落中的一个句子或句子中的一个短语,然后,可以使用任何 Vim 编辑命令删除、复制、更改或修改可视化模式识别的文本。
|
||||
|
||||
#### 移动一个句子
|
||||
|
||||
要将句子从一个地方移动到另一个地方,首先打开文件并将光标移动到要移动的句子的第一个字符。
|
||||

|
||||
|
||||
* 按下 **v** 键进入可视化字符模式。单词 **VISUAL** 将出现在屏幕底部。
|
||||
* 使用箭头来高亮显示所需的文本。你可以使用其他导航命令,例如 **w** 高亮显示至下一个单词的开头,**$** 来包含其余行。
|
||||
* 在文本高亮显示后,按下 **d** 删除文本。
|
||||
* 如果你删除得太多或不够,按下 **u** 撤销并重新开始。
|
||||
* 将光标移动到新位置,然后按 **p** 粘贴文本。
|
||||
|
||||
#### 改变一个短语
|
||||
|
||||
你还可以高亮显示要替换的文本块。
|
||||
|
||||

|
||||
|
||||
* 将光标放在要更改的第一个字符处。
|
||||
* 按下 **v** 进入可视化字符模式。
|
||||
* 使用导航命令(如箭头键)高亮显示短语。
|
||||
* 按下 **c** 可更改高亮显示的文本。
|
||||
* 高亮显示的文本将消失,你将处于插入模式,你可以在其中添加新文本。
|
||||
* 输入新文本后,按下 **Esc** 返回命令模式并保存你的工作。
|
||||
|
||||

|
||||
|
||||
### 行模式
|
||||
|
||||
使用 Ansible playbooks 时,任务的顺序很重要。使用可视化行模式将任务移动到 playbooks 中的其他位置。
|
||||
|
||||
#### 操纵多行文本
|
||||
|
||||

|
||||
|
||||
* 将光标放在要操作的文本的第一行或最后一行的任何位置。
|
||||
* 按下 **Shift+V** 进入行模式。单词 **VISUAL LINE** 将出现在屏幕底部。
|
||||
* 使用导航命令(如箭头键)高亮显示多行文本。
|
||||
* 高亮显示所需文本后,使用命令来操作它。按下 **d** 删除,然后将光标移动到新位置,按下 **p** 粘贴文本。
|
||||
* 如果要复制任务,可以使用 **y**(yank) 来代替 **d**(delete)。
|
||||
|
||||
#### 缩进一组行
|
||||
|
||||
使用 Ansible playbooks 或 YAML 文件时,缩进很重要。高亮显示的块可以使用 **>** 和 **<** 键向右或向左移动。
|
||||
|
||||
|
||||
|
||||
* 按下 **>** 增加所有行的缩进。
|
||||
* 按下 **<** 减少所有行的缩进。
|
||||
|
||||
尝试其他 Vim 命令将它们应用于高亮显示的文本。
|
||||
|
||||
### 块模式
|
||||
|
||||
可视化块模式对于操作特定的表格数据文件非常有用,但它作为验证 Ansible playbook 缩进的工具也很有帮助。
|
||||
|
||||
任务是项目列表,在 YAML 中,每个列表项都以破折号和空格开头。破折号必须在同一列中对齐,以达到相同的缩进级别。仅凭肉眼很难看出这一点。缩进任务中的其他行也很重要。
|
||||
|
||||
#### 验证任务列表缩进相同
|
||||
|
||||

|
||||
|
||||
* 将光标放在列表项的第一个字符上。
|
||||
* 按下 **Ctrl+v** 进入可视化块模式。单词 **VISUAL BLOCK** 将出现在屏幕底部。
|
||||
* 使用箭头键高亮显示单个字符列。你可以验证每个任务的缩进量是否相同。
|
||||
* 使用箭头键向右或向左展开块,以检查其它缩进是否正确。
|
||||
|
||||

|
||||
|
||||
尽管我对其它 Vim 编辑快捷方式很熟悉,但我仍然喜欢使用可视化模式来整理我想要出来处理的文本。当我在演示过程总演示其它概念时,我的学生会看到一个高亮显示文本的工具,并在这个“仅限他们”的文本编辑器中点击删除。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/2/getting-started-vim-visual-mode
|
||||
|
||||
作者:[Susan Lauber][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[MjSeven](https://github.com/MjSeven)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/susanlauber
|
||||
[b]: https://github.com/lujun9972
|
||||
@ -0,0 +1,117 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (FinalCrypt – An Open Source File Encryption Application)
|
||||
[#]: via: (https://itsfoss.com/finalcrypt/)
|
||||
[#]: author: (Ankush Das https://itsfoss.com/author/ankush/)
|
||||
|
||||
FinalCrypt - 一个开源文件加密应用
|
||||
======
|
||||
|
||||
我通常不会加密文件 - 但如果我打算整理我的重要文件或凭证,加密程序就会派上用场。
|
||||
|
||||
你可能已经在使用像 [GnuPG][1] 这样的程序来帮助你加密/解密 Linux 上的文件。还有 [EncryptPad][2] 也可以加密你的笔记。
|
||||
|
||||
但是,我看到了一个名为 FinalCrypt 的新的免费开源加密工具。你可以在 [GitHub 页面][3]上查看最新的版本和源码。
|
||||
|
||||
在本文中,我将分享使用此工具的经验。请注意,我不会将它与其他程序进行比较 - 因此,如果你想要多个程序之间的详细比较,请在评论中告诉我们。
|
||||
|
||||
![FinalCrypt][4]
|
||||
|
||||
### 使用 FinalCrypt 加密文件
|
||||
|
||||
FinalCrypt 使用[一次性密码本][5]密钥生成密码来加密文件。换句话说,它会生成一个 OTP 密钥,你将使用该密钥加密或解密你的文件。
|
||||
|
||||
根据你指定的密钥大小,密钥是完全随机的。因此,没有密钥文件就无法解密文件。
|
||||
|
||||
虽然 OTP 密钥用于加密/解密简单而有效,但管理或保护密钥文件对某些人来说可能是不方便的。
|
||||
|
||||
如果要使用 FinalCrypt,可以从它的网站下载 DEB/RPM 文件。FinalCrypt 也可用于 Windows 和 macOS。
|
||||
|
||||
下载后,只需双击 [deb][6] 或 rpm 文件就能安装。如果需要,你还可以从源码编译。
|
||||
|
||||
### 使用 FileCrypt
|
||||
|
||||
该视频演示了如何使用FinalCrypt:
|
||||
|
||||
<https://youtu.be/6Ir8VcZ26E4>
|
||||
|
||||
如果你喜欢 Linux 相关的视频,请[订阅我们的 YouTube 频道][7]。
|
||||
|
||||
安装 FinalCrypt 后,你将在已安装的应用列表中找到它。从这里启动它。
|
||||
|
||||
启动后,你将看到(分割的)两栏,一个进行加密/解密,另一个选择 OTP 文件。
|
||||
|
||||
![Using FinalCrypt for encrypting files in Linux][8]
|
||||
|
||||
首先,你必须生成 OTP 密钥。下面是做法:
|
||||
|
||||
![finalcrypt otp][9]
|
||||
|
||||
请注意你的文件名可以是任何内容 - 但你需要确保密钥文件大小大于或等于要加密的文件。我觉得这很荒谬,但事实就是如此。
|
||||
|
||||
![][10]
|
||||
|
||||
生成文件后,选择窗口右侧的密钥,然后选择要在窗口左侧加密的文件。
|
||||
|
||||
生成 OTP 后,你会看到高亮显示的校验和值,密钥文件大小和有效状态:
|
||||
|
||||
![][11]
|
||||
|
||||
选择之后,你只需要点击“**加密**”来加密这些文件,如果已经加密,那么点击“**解密**”来解密这些文件。
|
||||
|
||||
![][12]
|
||||
|
||||
你还可以在命令行中使用 FinalCrypt 来自动执行加密作业。
|
||||
|
||||
#### 如何保护你的 OTP 密钥?
|
||||
|
||||
加密/解密你想要保护的文件很容易。但是,你应该在哪里保存你的 OTP 密钥?
|
||||
|
||||
如果你未能将 OTP 密钥保存在安全的地方,那么它几乎没用。
|
||||
|
||||
嗯,最好的方法之一是使用专门的 USB 盘保存你的密钥。只需要在解密文件时将它插入即可。
|
||||
|
||||
除此之外,如果你认为足够安全,你可以将密钥保存在[云服务][13]中。
|
||||
|
||||
有关 FinalCrypt 的更多信息,请访问它的网站。
|
||||
|
||||
[FinalCrypt](https://sites.google.com/site/ronuitholland/home/finalcrypt)
|
||||
|
||||
**总结**
|
||||
|
||||
它开始时看上去有点复杂,但它实际上是 Linux 中一个简单且用户友好的加密程序。如果你想看看其他的,还有一些其他的[加密保护文件夹][14]的程序。
|
||||
|
||||
你如何看待 FinalCrypt?你还知道其他类似可能更好的程序么?请在评论区告诉我们,我们将会查看的!
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://itsfoss.com/finalcrypt/
|
||||
|
||||
作者:[Ankush Das][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://itsfoss.com/author/ankush/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.gnupg.org/
|
||||
[2]: https://itsfoss.com/encryptpad-encrypted-text-editor-linux/
|
||||
[3]: https://github.com/ron-from-nl/FinalCrypt
|
||||
[4]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2019/02/finalcrypt.png?resize=800%2C450&ssl=1
|
||||
[5]: https://en.wikipedia.org/wiki/One-time_pad
|
||||
[6]: https://itsfoss.com/install-deb-files-ubuntu/
|
||||
[7]: https://www.youtube.com/c/itsfoss?sub_confirmation=1
|
||||
[8]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2019/02/finalcrypt.jpg?fit=800%2C439&ssl=1
|
||||
[9]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2019/02/finalcrypt-otp-key.jpg?resize=800%2C443&ssl=1
|
||||
[10]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2019/02/finalcrypt-otp-generate.jpg?ssl=1
|
||||
[11]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2019/02/finalcrypt-key.jpg?fit=800%2C420&ssl=1
|
||||
[12]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2019/02/finalcrypt-encrypt.jpg?ssl=1
|
||||
[13]: https://itsfoss.com/cloud-services-linux/
|
||||
[14]: https://itsfoss.com/password-protect-folder-linux/
|
||||
[15]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2019/02/finalcrypt.png?fit=800%2C450&ssl=1
|
||||
Loading…
Reference in New Issue
Block a user