mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-02-28 01:01:09 +08:00
20150506-1 选题
This commit is contained in:
parent
e83b7ed41e
commit
8b062b9b4d
@ -0,0 +1,96 @@
|
||||
Linux FAQs with Answers--How to configure a Linux bridge with Network Manager on Ubuntu
|
||||
================================================================================
|
||||
> **Question**: I need to set up a Linux bridge on my Ubuntu box to share a NIC with several other virtual machines or containers created on the box. I am currently using Network Manager on my Ubuntu, so preferrably I would like to configure a bridge using Network Manager. How can I do that?
|
||||
|
||||
Network bridge is a hardware equipment used to interconnect two or more Layer-2 network segments, so that network devices on different segments can talk to each other. A similar bridging concept is needed within a Linux host, when you want to interconnect multiple VMs or Ethernet interfaces within a host. That is one use case of a software Linux bridge.
|
||||
|
||||
There are several different ways to configure a Linux bridge. For example, in a headless server environment, you can use [brctl][1] to manually configure a bridge. In desktop environment, bridge support is available in Network Manager. Let's examine how to configure a bridge with Network Manager.
|
||||
|
||||
### Requirement ###
|
||||
|
||||
To avoid [any issue][2], it is recommended that you have Network Manager 0.9.9 and higher, which is the case for Ubuntu 15.04 and later.
|
||||
|
||||
$ apt-cache show network-manager | grep Version
|
||||
|
||||
----------
|
||||
|
||||
Version: 0.9.10.0-4ubuntu15.1
|
||||
Version: 0.9.10.0-4ubuntu15
|
||||
|
||||
### Create a Bridge ###
|
||||
|
||||
The easiest way to create a bridge with Network Manager is via nm-connection-editor. This GUI tool allows you to configure a bridge in easy-to-follow steps.
|
||||
|
||||
To start, invoke nm-connection-editor.
|
||||
|
||||
$ nm-connection-editor
|
||||
|
||||
The editor window will show you a list of currently configured network connections. Click on "Add" button in the top right to create a bridge.
|
||||
|
||||
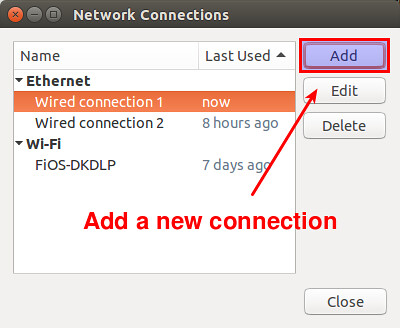
|
||||
|
||||
Next, choose "Bridge" as a connection type.
|
||||
|
||||
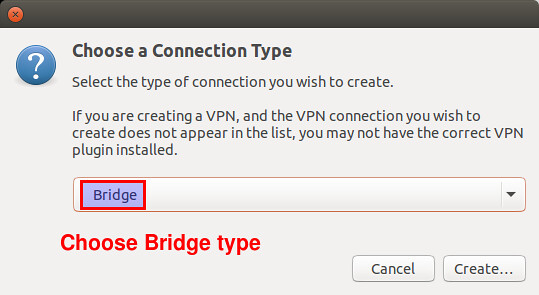
|
||||
|
||||
Now it's time to configure a bridge, including its name and bridged connection(s). With no other bridges created, the default bridge interface will be named bridge0.
|
||||
|
||||
Recall that the goal of creating a bridge is to share your Ethernet interface via the bridge. So you need to add the Ethernet interface to the bridge. This is achieved by adding a new "bridged connection" in the GUI. Click on "Add" button.
|
||||
|
||||
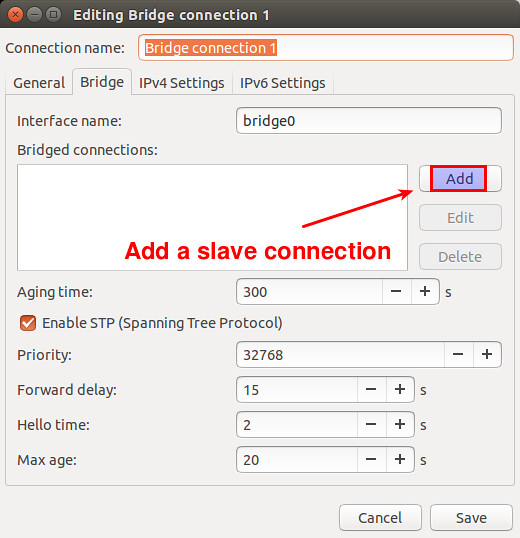
|
||||
|
||||
Choose "Ethernet" as a connection type.
|
||||
|
||||
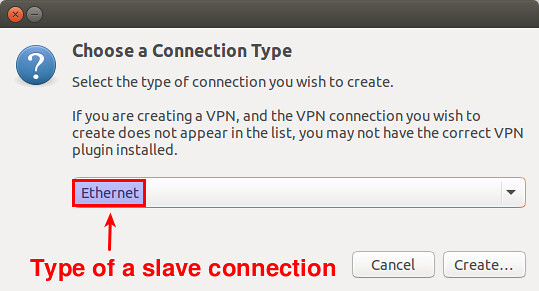
|
||||
|
||||
In "Device MAC address" field, choose the interface that you want to enslave into the bridge. In this example, assume that this interface is eth0.
|
||||
|
||||

|
||||
|
||||
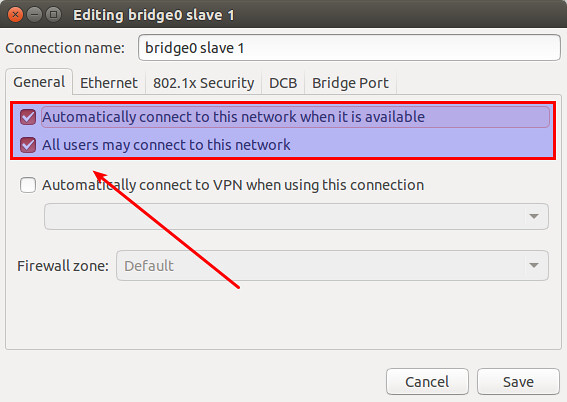
Click on "General" tab, and enable both checkboxes that say "Automatically connect to this network when it is available" and "All users may connect to this network".
|
||||
|
||||
|
||||
|
||||
Save the change.
|
||||
|
||||
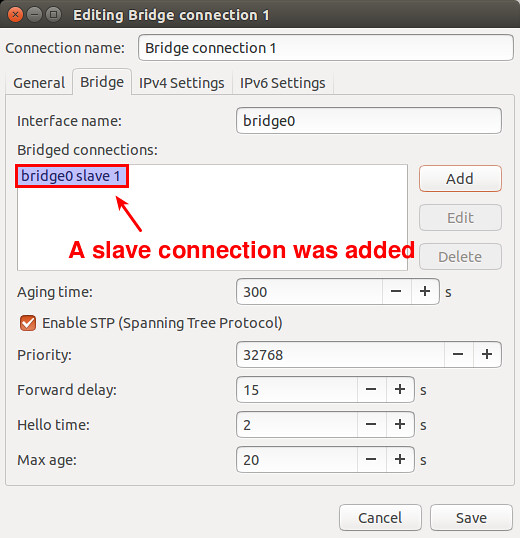
Now you will see a new slave connection created in the bridge.
|
||||
|
||||
|
||||
|
||||
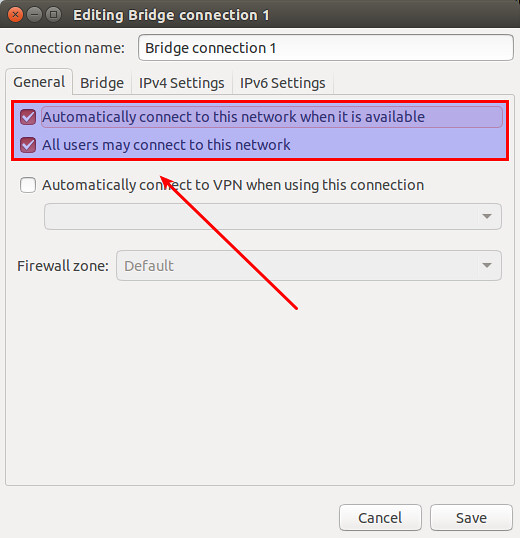
Click on "General" tab of the bridge, and make sure that top-most two checkboxes are enabled.
|
||||
|
||||
|
||||
|
||||
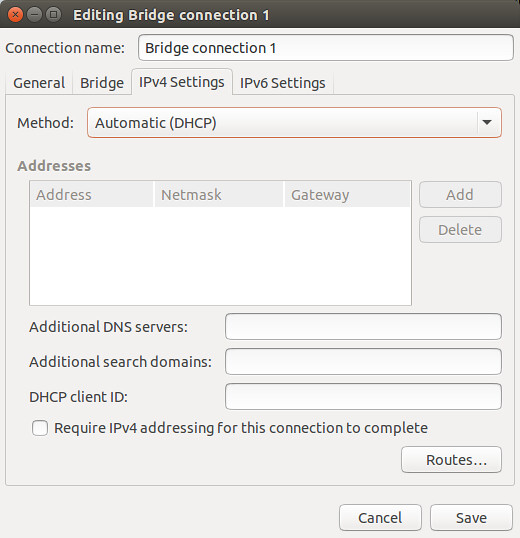
Go to "IPv4 Settings" tab, and configure either DHCP or static IP address for the bridge. Note that you should use the same IPv4 settings as the enslaved Ethernet interface eth0. In this example, we assume that eth0 is configured via DHCP. Thus choose "Automatic (DHCP)" here. If eth0 is assigned a static IP address, you should assign the same IP address to the bridge.
|
||||
|
||||
|
||||
|
||||
Finally, save the bridge settings.
|
||||
|
||||
Now you will see an additional bridge connection created in "Network Connections" window. You no longer need a previously-configured wired connection for the enslaved interface eth0. So go ahead and delete the original wired connection.
|
||||
|
||||
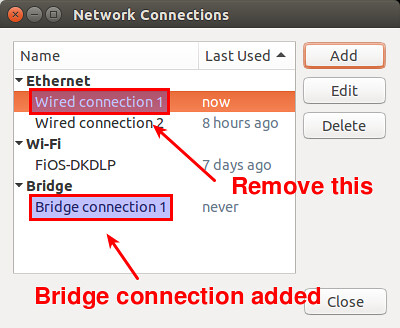
|
||||
|
||||
At this point, the bridge connection will automatically be activated. You will momentarily lose a connection, since the IP address assigned to eth0 is taken over by the bridge. Once an IP address is assigned to the bridge, you will be connected back to your Ethernet interface via the bridge. You can confirm that by checking "Network" settings.
|
||||
|
||||
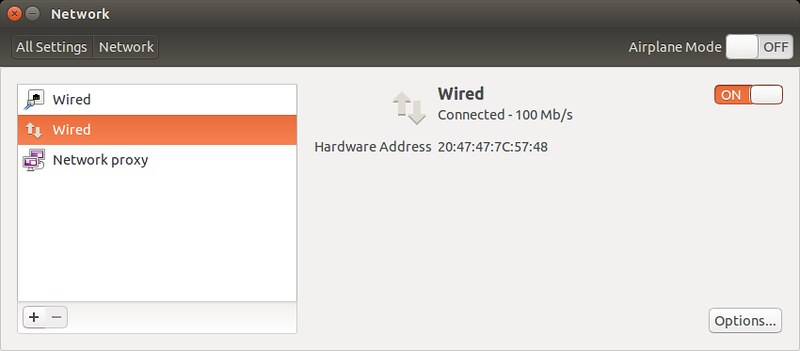
|
||||
|
||||
Also, check the list of available interfaces. As mentioned, the bridge interface must have taken over whatever IP address was possessed by your Ethernet interface.
|
||||
|
||||
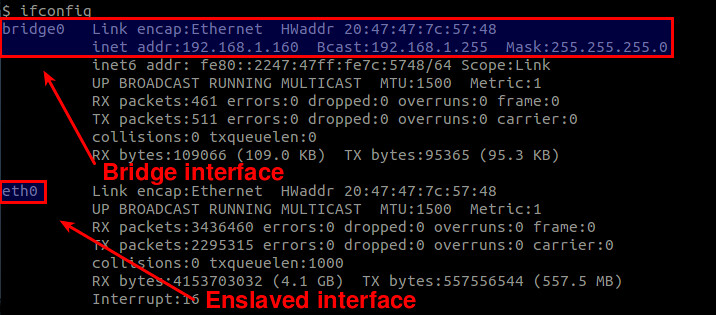
|
||||
|
||||
That's it, and now the bridge is ready to use!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://ask.xmodulo.com/configure-linux-bridge-network-manager-ubuntu.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://ask.xmodulo.com/author/nanni
|
||||
[1]:http://xmodulo.com/how-to-configure-linux-bridge-interface.html
|
||||
[2]:https://bugs.launchpad.net/ubuntu/+source/network-manager/+bug/1273201
|
||||
@ -0,0 +1,55 @@
|
||||
Linux FAQs with Answers--How to disable entering password for default keyring to unlock on Ubuntu desktop
|
||||
================================================================================
|
||||
> **Question**: When I boot up my Ubuntu desktop, a pop up dialog appears, asking me to enter a password to unlock default keyring. How can I disable this "unlock default keyring" pop up window, and automatically unlock my keyring?
|
||||
|
||||
A keyring is thought of as a local database that stores your login information in encrypted forms. Various desktop applications (e.g., browsers, email clients) use a keyring to store and manage your login credentials, secrets, passwords, certificates, or keys securely. For those applications to retrieve the information stored in a keyring, the keyring needs to be unlocked.
|
||||
|
||||
GNOME keyring used by Ubuntu desktop is integrated with desktop login, and the keyring is automatically unlocked when you authenticate into your desktop. But your default keyring can remain "locked" if you set up automatic desktop login or wake up from hibernation. In this case, you will be prompted:
|
||||
|
||||
> "Enter password for keyring 'Default keyring' to unlock. An application wants to access to the keyring 'Default keyring,' but it is locked."
|
||||
|
||||
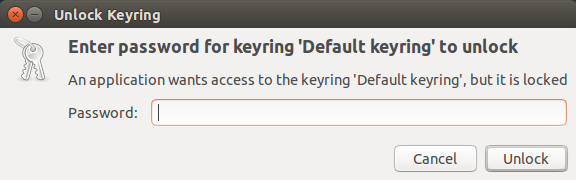
|
||||
|
||||
If you want to avoid typing a password to unlock your default keyring every time such a pop-up dialog appears, here is how you can do it.
|
||||
|
||||
Before doing that, understand the implication of disabling the password prompt. By automatically unlocking the default keyring, you will make your keyring (and any information stored in the keyring) accessible to anyone who uses your desktop, without them having to know your password.
|
||||
|
||||
### Disable Password for Unlocking Default Keyring ###
|
||||
|
||||
Open up Dash, and type "password" to launch "Passwords and Keys" app.
|
||||
|
||||
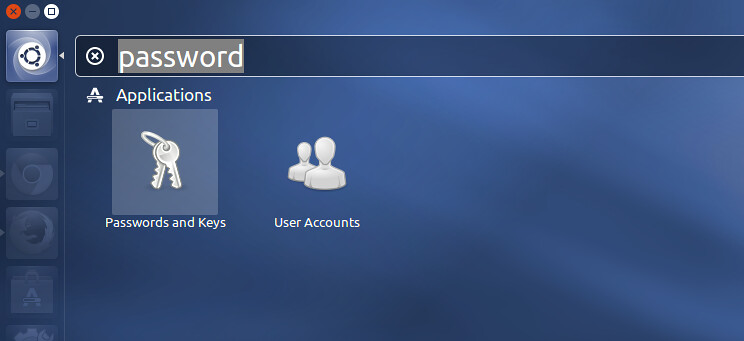
|
||||
|
||||
Alternatively, use the seahorse command to launch the GUI from the command line.
|
||||
|
||||
$ seahorse
|
||||
|
||||
On the left side panel, right-click on the "Default keyring," and choose "Change Password."
|
||||
|
||||
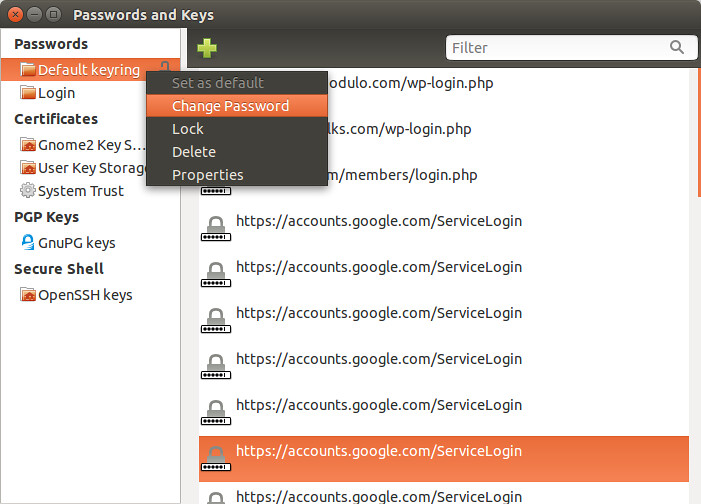
|
||||
|
||||
Type your current login password.
|
||||
|
||||
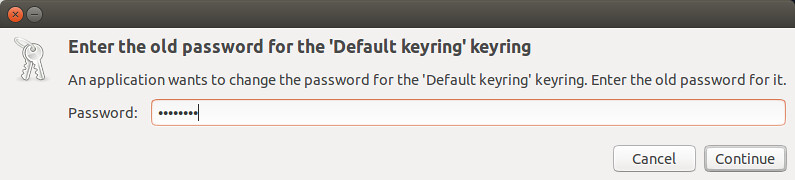
|
||||
|
||||
Leave a new password for the "Default" keyring as blank.
|
||||
|
||||
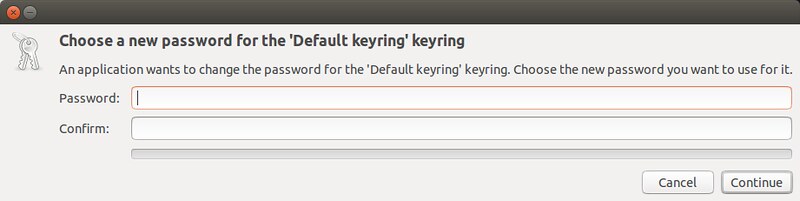
|
||||
|
||||
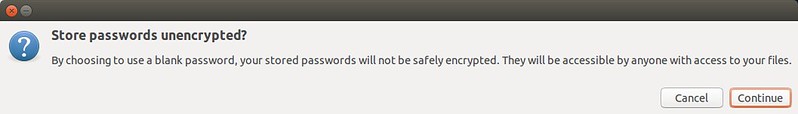
Click on "Continue" button to confirm to store passwords unencrypted.
|
||||
|
||||
|
||||
|
||||
That's it. From now on, you won't be prompted to unlock the default keyring.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://ask.xmodulo.com/disable-entering-password-unlock-default-keyring.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://ask.xmodulo.com/author/nanni
|
||||
@ -0,0 +1,97 @@
|
||||
Linux FAQs with Answers--How to install Shrew Soft IPsec VPN client on Linux
|
||||
================================================================================
|
||||
> **Question**: I need to connect to an IPSec VPN gateway. For that, I'm trying to use Shrew Soft VPN client, which is available for free. How can I install Shrew Soft VPN client on [insert your Linux distro]?
|
||||
|
||||
There are many commercial VPN gateways available, which come with their own proprietary VPN client software. While there are also open-source VPN server/client alternatives, they are typically lacking in sophisticated IPsec support, such as Internet Key Exchange (IKE) which is a standard IPsec protocol used to secure VPN key exchange and authentication. Shrew Soft VPN is a free IPsec VPN client supporting a number of authentication methods, key exchange, encryption and firewall traversal options.
|
||||
|
||||
Here is how you can install Shrew Soft VPN client on Linux platforms.
|
||||
|
||||
First, download its source code from the [official website][1].
|
||||
|
||||
### Install Shrew VPN Client on Debian, Ubuntu or Linux Mint ###
|
||||
|
||||
Shrew Soft VPN client GUI requires Qt 4.x. So you will need to install its development files as part of dependencies.
|
||||
|
||||
$ sudo apt-get install cmake libqt4-core libqt4-dev libqt4-gui libedit-dev libssl-dev checkinstall flex bison
|
||||
$ wget https://www.shrew.net/download/ike/ike-2.2.1-release.tbz2
|
||||
$ tar xvfvj ike-2.2.1-release.tbz2
|
||||
$ cd ike
|
||||
$ cmake -DCMAKE_INSTALL_PREFIX=/usr -DQTGUI=YES -DETCDIR=/etc -DNATT=YES .
|
||||
$ make
|
||||
$ sudo make install
|
||||
$ cd /etc/
|
||||
$ sudo mv iked.conf.sample iked.conf
|
||||
|
||||
### Install Shrew VPN Client on CentOS, Fedora or RHEL ###
|
||||
|
||||
Similar to Debian based systems, you will need to install a number of dependencies including Qt4 before compiling it.
|
||||
|
||||
$ sudo yum install qt-devel cmake gcc-c++ openssl-devel libedit-devel flex bison
|
||||
$ wget https://www.shrew.net/download/ike/ike-2.2.1-release.tbz2
|
||||
$ tar xvfvj ike-2.2.1-release.tbz2
|
||||
$ cd ike
|
||||
$ cmake -DCMAKE_INSTALL_PREFIX=/usr -DQTGUI=YES -DETCDIR=/etc -DNATT=YES .
|
||||
$ make
|
||||
$ sudo make install
|
||||
$ cd /etc/
|
||||
$ sudo mv iked.conf.sample iked.conf
|
||||
|
||||
On Red Hat based systems, one last step is to open /etc/ld.so.conf with a text editor, and add the following line.
|
||||
|
||||
$ sudo vi /etc/ld.so.conf
|
||||
|
||||
----------
|
||||
|
||||
include /usr/lib/
|
||||
|
||||
Reload run-time bindings of shared libraries to incorporate newly installed shared libraries:
|
||||
|
||||
$ sudo ldconfig
|
||||
|
||||
### Launch Shrew VPN Client ###
|
||||
|
||||
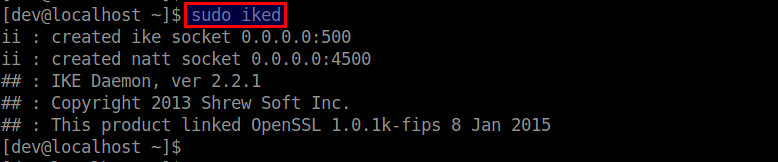
First launch IKE daemon (iked). This daemon speaks the IKE protocol to communicate with a remote host over IPSec as a VPN client.
|
||||
|
||||
$ sudo iked
|
||||
|
||||
|
||||
|
||||
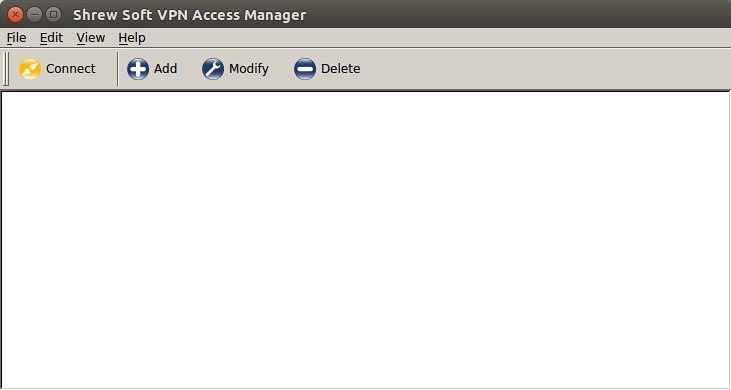
Now start qikea which is an IPsec VPN client front end. This GUI application allows you to manage remote site configurations and to initiate VPN connections.
|
||||
|
||||
|
||||
|
||||
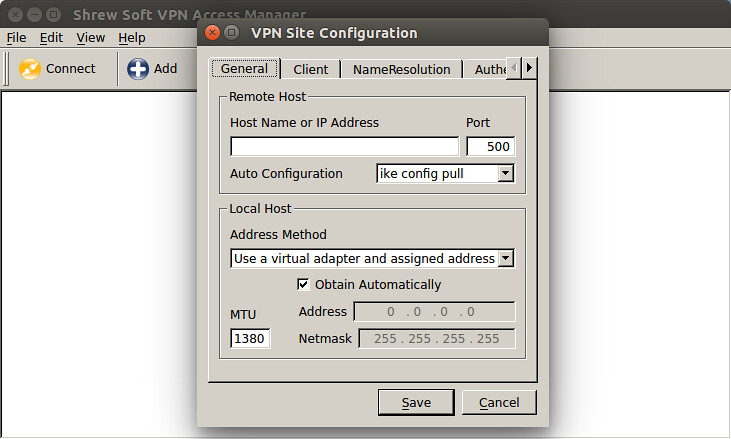
To create a new VPN configuration, click on "Add" button, and fill out VPN site configuration. Once you create a configuration, you can initiate a VPN connection simply by clicking on the configuration.
|
||||
|
||||
|
||||
|
||||
### Troubleshooting ###
|
||||
|
||||
1. I am getting the following error while running iked.
|
||||
|
||||
iked: error while loading shared libraries: libss_ike.so.2.2.1: cannot open shared object file: No such file or directory
|
||||
|
||||
To solve this problem, you need to update the dynamic linker to incorporate libss_ike library. For that, add to /etc/ld.so.conf the path where the library is located (e.g., /usr/lib), and then run ldconfig command.
|
||||
|
||||
$ sudo ldconfig
|
||||
|
||||
Verify that libss_ike is added to the library path:
|
||||
|
||||
$ ldconfig -p | grep ike
|
||||
|
||||
----------
|
||||
|
||||
libss_ike.so.2.2.1 (libc6,x86-64) => /lib/libss_ike.so.2.2.1
|
||||
libss_ike.so (libc6,x86-64) => /lib/libss_ike.so
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://ask.xmodulo.com/install-shrew-soft-ipsec-vpn-client-linux.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://ask.xmodulo.com/author/nanni
|
||||
[1]:https://www.shrew.net/download/ike
|
||||
@ -0,0 +1,76 @@
|
||||
Linux FAQs with Answers--How to install autossh on Linux
|
||||
================================================================================
|
||||
> **Question**: I would like to install autossh on [insert your Linux distro]. How can I do that?
|
||||
|
||||
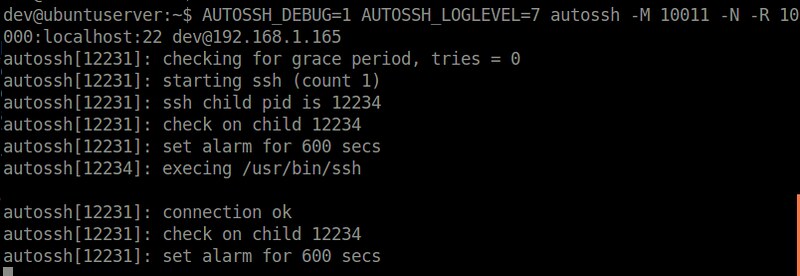
[autossh][1] is an open-source tool that allows you to monitor an SSH session and restart it automatically should it gets disconnected or stops forwarding traffic. autossh assumes that [passwordless SSH login][2] for a destination host is already setup, so that it can restart a broken SSH session without user's involvement.
|
||||
|
||||
autossh comes in handy when you want to set up [reverse SSH tunnels][3] or [mount remote folders over SSH][4]. Essentially in any situation where persistent SSH sessions are required, autossh can be useful.
|
||||
|
||||
|
||||
|
||||
Here is how to install autossh on various Linux distributions.
|
||||
|
||||
### Install Autossh on Debian or Ubuntu ###
|
||||
|
||||
autossh is available in base repositories of Debian based systems, so installation is easy.
|
||||
|
||||
$ sudo apt-get install autossh
|
||||
|
||||
### Install Autossh on Fedora ###
|
||||
|
||||
Fedora repositories also carry autossh package. So simply use yum command.
|
||||
|
||||
$ sudo yum install autossh
|
||||
|
||||
### Install Autossh on CentOS or RHEL ###
|
||||
|
||||
For CentOS/RHEL 6 or earlier, enable [Repoforge repository][5] first, and then use yum command.
|
||||
|
||||
$ sudo yum install autossh
|
||||
|
||||
For CentOS/RHEL 7, autossh is no longer available in Repoforge repository. You will need to build it from the source (explained below).
|
||||
|
||||
### Install Autossh on Arch Linux ###
|
||||
|
||||
$ sudo pacman -S autossh
|
||||
|
||||
### Compile Autossh from the Source on Debian or Ubuntu ###
|
||||
|
||||
If you would like to try the latest version of autossh, you can build it from the source as follows.
|
||||
|
||||
$ sudo apt-get install gcc make
|
||||
$ wget http://www.harding.motd.ca/autossh/autossh-1.4e.tgz
|
||||
$ tar -xf autossh-1.4e.tgz
|
||||
$ cd autossh-1.4e
|
||||
$ ./configure
|
||||
$ make
|
||||
$ sudo make install
|
||||
|
||||
### Compile Autossh from the Source on CentOS, Fedora or RHEL ###
|
||||
|
||||
On CentOS/RHEL 7, autossh is not available as a pre-built package. So you'll need to compile it from the source as follows.
|
||||
|
||||
$ sudo yum install wget gcc make
|
||||
$ wget http://www.harding.motd.ca/autossh/autossh-1.4e.tgz
|
||||
$ tar -xf autossh-1.4e.tgz
|
||||
$ cd autossh-1.4e
|
||||
$ ./configure
|
||||
$ make
|
||||
$ sudo make install
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://ask.xmodulo.com/install-autossh-linux.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://ask.xmodulo.com/author/nanni
|
||||
[1]:http://www.harding.motd.ca/autossh/
|
||||
[2]:http://xmodulo.com/how-to-enable-ssh-login-without.html
|
||||
[3]:http://xmodulo.com/access-linux-server-behind-nat-reverse-ssh-tunnel.html
|
||||
[4]:http://xmodulo.com/how-to-mount-remote-directory-over-ssh-on-linux.html
|
||||
[5]:http://xmodulo.com/how-to-set-up-rpmforge-repoforge-repository-on-centos.html
|
||||
@ -0,0 +1,175 @@
|
||||
Linux grep command with 14 different examples
|
||||
================================================================================
|
||||
### Overview : ###
|
||||
|
||||
Linux like operating system provides a searching tool known as **grep (global regular expression print)**. grep command is useful for searching the content of one more files based on the pattern. A pattern may be a single character, bunch of characters, single word or a sentence.
|
||||
|
||||
When we execute the grep command with specified pattern, if its is matched, then it will display the line of file containing the pattern without modifying the contents of existing file.
|
||||
|
||||
In this tutorial we will discuss 14 different examples of grep command
|
||||
|
||||
### Example:1 Search the pattern (word) in a file ###
|
||||
|
||||
Search the “linuxtechi” word in the file /etc/passwd file
|
||||
|
||||
root@Linux-world:~# grep linuxtechi /etc/passwd
|
||||
linuxtechi:x:1000:1000:linuxtechi,,,:/home/linuxtechi:/bin/bash
|
||||
root@Linux-world:~#
|
||||
|
||||
### Example:2 Search the pattern in the multiple files. ###
|
||||
|
||||
root@Linux-world:~# grep linuxtechi /etc/passwd /etc/shadow /etc/gshadow
|
||||
/etc/passwd:linuxtechi:x:1000:1000:linuxtechi,,,:/home/linuxtechi:/bin/bash
|
||||
/etc/shadow:linuxtechi:$6$DdgXjxlM$4flz4JRvefvKp0DG6re:16550:0:99999:7:::/etc/gshadow:adm:*::syslog,linuxtechi
|
||||
/etc/gshadow:cdrom:*::linuxtechi
|
||||
/etc/gshadow:sudo:*::linuxtechi
|
||||
/etc/gshadow:dip:*::linuxtechi
|
||||
/etc/gshadow:plugdev:*::linuxtechi
|
||||
/etc/gshadow:lpadmin:!::linuxtechi
|
||||
/etc/gshadow:linuxtechi:!::
|
||||
/etc/gshadow:sambashare:!::linuxtechi
|
||||
root@Linux-world:~#
|
||||
|
||||
### Example:3 List the name of those files which contain a specified pattern using -l option. ###
|
||||
|
||||
root@Linux-world:~# grep -l linuxtechi /etc/passwd /etc/shadow /etc/fstab /etc/mtab
|
||||
/etc/passwd
|
||||
/etc/shadow
|
||||
root@Linux-world:~#
|
||||
|
||||
### Example:4 Search the pattern in the file along with associated line number(s) using the -n option ###
|
||||
|
||||
root@Linux-world:~# grep -n linuxtechi /etc/passwd
|
||||
39:linuxtechi:x:1000:1000:linuxtechi,,,:/home/linuxtechi:/bin/bash
|
||||
root@Linux-world:~#
|
||||
|
||||
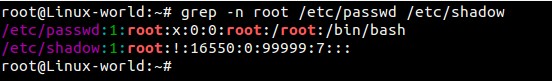
root@Linux-world:~# grep -n root /etc/passwd /etc/shadow
|
||||
|
||||
|
||||
|
||||
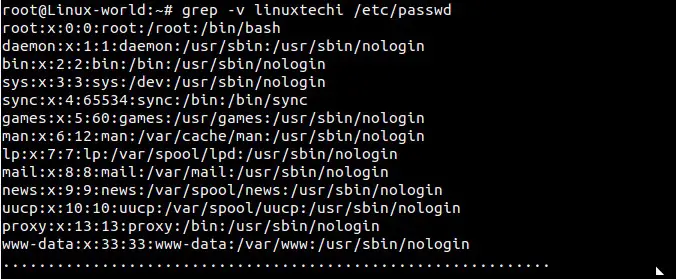
### Example:5 Print the line excluding the pattern using -v option ###
|
||||
|
||||
List all the lines of the file /etc/passwd that does not contain specific word “linuxtechi”.
|
||||
|
||||
root@Linux-world:~# grep -v linuxtechi /etc/passwd
|
||||
|
||||
|
||||
|
||||
### Example:6 Display all the lines that starts with specified pattern using ^ symbol ###
|
||||
|
||||
Bash shell treats carrot symbol (^) as a special character which marks the beginning of line or a word. Let’s display the lines which starts with “root” word in the file /etc/passwd.
|
||||
|
||||
root@Linux-world:~# grep ^root /etc/passwd
|
||||
root:x:0:0:root:/root:/bin/bash
|
||||
root@Linux-world:~#
|
||||
|
||||
### Example: 7 Display all the lines that ends with specified pattern using $ symbol. ###
|
||||
|
||||
List all the lines of /etc/passwd that ends with “bash” word.
|
||||
|
||||
root@Linux-world:~# grep bash$ /etc/passwd
|
||||
root:x:0:0:root:/root:/bin/bash
|
||||
linuxtechi:x:1000:1000:linuxtechi,,,:/home/linuxtechi:/bin/bash
|
||||
root@Linux-world:~#
|
||||
|
||||
Bash shell treats dollar ($) symbol as a special character which marks the end of line or word.
|
||||
|
||||
### Example:8 Search the pattern recursively using -r option ###
|
||||
|
||||
root@Linux-world:~# grep -r linuxtechi /etc/
|
||||
/etc/subuid:linuxtechi:100000:65536
|
||||
/etc/group:adm:x:4:syslog,linuxtechi
|
||||
/etc/group:cdrom:x:24:linuxtechi
|
||||
/etc/group:sudo:x:27:linuxtechi
|
||||
/etc/group:dip:x:30:linuxtechi
|
||||
/etc/group:plugdev:x:46:linuxtechi
|
||||
/etc/group:lpadmin:x:115:linuxtechi
|
||||
/etc/group:linuxtechi:x:1000:
|
||||
/etc/group:sambashare:x:131:linuxtechi
|
||||
/etc/passwd-:linuxtechi:x:1000:1000:linuxtechi,,,:/home/linuxtechi:/bin/bash
|
||||
/etc/passwd:linuxtechi:x:1000:1000:linuxtechi,,,:/home/linuxtechi:/bin/bash
|
||||
............................................................................
|
||||
|
||||
Above command will search linuxtechi in the “/etc” directory recursively.
|
||||
|
||||
### Example:9 Search all the empty or blank lines of a file using grep ###
|
||||
|
||||
root@Linux-world:~# grep ^$ /etc/shadow
|
||||
root@Linux-world:~#
|
||||
|
||||
As there is no empty line in /etc/shadow file , so nothing is displayed.
|
||||
|
||||
### Example:10 Search the pattern using ‘grep -i’ option. ###
|
||||
|
||||
-i option in the grep command ignores the letter case i.e it will ignore upper case or lower case letters while searching
|
||||
|
||||
Lets take an example , i want to search “LinuxTechi” word in the passwd file.
|
||||
|
||||
nextstep4it@localhost:~$ grep -i LinuxTechi /etc/passwd
|
||||
linuxtechi:x:1001:1001::/home/linuxtechi:/bin/bash
|
||||
nextstep4it@localhost:~$
|
||||
|
||||
### Example:11 Search multiple patterns using -e option ###
|
||||
|
||||
For example i want to search ‘linuxtechi’ and ‘root’ word in a single grep command , then using -e option we can search multiple patterns .
|
||||
|
||||
root@Linux-world:~# grep -e "linuxtechi" -e "root" /etc/passwd
|
||||
root:x:0:0:root:/root:/bin/bash
|
||||
linuxtechi:x:1000:1000:linuxtechi,,,:/home/linuxtechi:/bin/bash
|
||||
root@Linux-world:~#
|
||||
|
||||
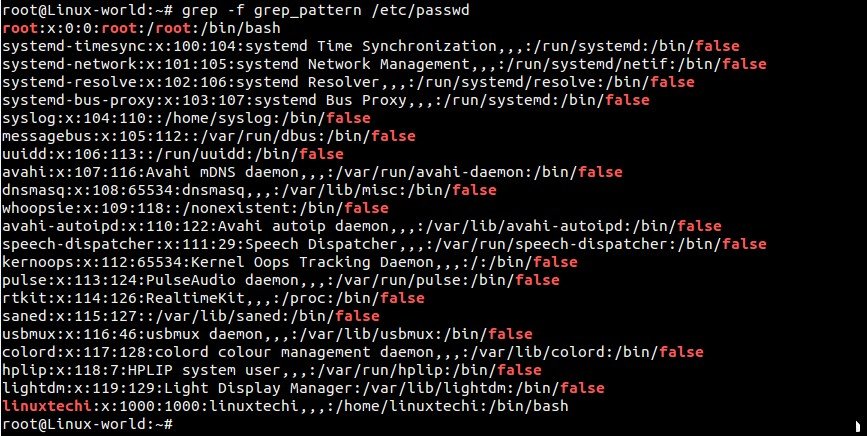
### Example:12 Getting Search pattern from a file using “grep -f” ###
|
||||
|
||||
First create a search pattern file “grep_pattern” in your current working directory. In my case i have put the below contents.
|
||||
|
||||
root@Linux-world:~# cat grep_pattern
|
||||
^linuxtechi
|
||||
root
|
||||
false$
|
||||
root@Linux-world:~#
|
||||
|
||||
Now try to search using grep_pattern file.
|
||||
|
||||
root@Linux-world:~# grep -f grep_pattern /etc/passwd
|
||||
|
||||
|
||||
|
||||
### Example:13 Count the number of matching patterns using -c option ###
|
||||
|
||||
Let take the above example , we can count the number of matching patterns using -c option in grep command.
|
||||
|
||||
root@Linux-world:~# grep -c -f grep_pattern /etc/passwd
|
||||
22
|
||||
root@Linux-world:~#
|
||||
|
||||
### Example:14 Display N number of lines before & after pattern matching ###
|
||||
|
||||
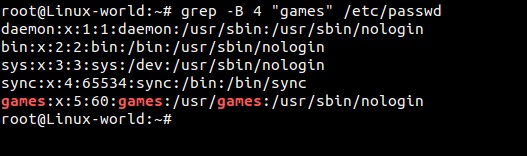
a) Display Four lines before patten matching using -B option
|
||||
|
||||
root@Linux-world:~# grep -B 4 "games" /etc/passwd
|
||||
|
||||
|
||||
|
||||
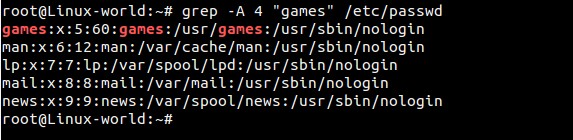
b) Display Four lines after pattern matching using -A option
|
||||
|
||||
root@Linux-world:~# grep -A 4 "games" /etc/passwd
|
||||
|
||||
|
||||
|
||||
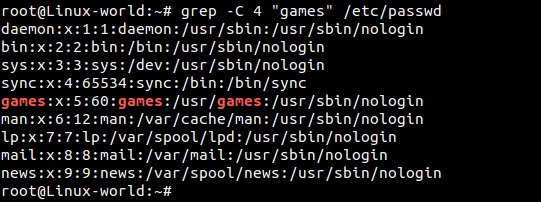
c) Display Four lines around the pattern matching using -C option
|
||||
|
||||
root@Linux-world:~# grep -C 4 "games" /etc/passwd
|
||||
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linuxtechi.com/linux-grep-command-with-14-different-examples/
|
||||
|
||||
作者:[Pradeep Kumar][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.linuxtechi.com/author/pradeep/
|
||||
Loading…
Reference in New Issue
Block a user