mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-01-13 22:30:37 +08:00
20141120-1 选题
This commit is contained in:
parent
eb8226c25a
commit
86e069b684
@ -0,0 +1,86 @@
|
||||
5 Best Open Source Web Browser Security Apps
|
||||
================================================================================
|
||||
The Web browser acts as the gateway for myriad online services these days. Computer security problems are far from solved, and technology advances provide new ways for malware to infect our devices and enter our business networks. For example, smartphones and tablets offer fresh new fields for malware—and its malicious cousin, "[malvertising][1]"—to exploit.
|
||||
|
||||
Malvertising, or malicious advertising, injects malware into legitimate ads and ad networks. Granted, you could argue that there's a thin line between "legitimate" ads and ad networks and not-legitimate ads and ad networks. But don’t get distracted. Privacy and security are inextricably linked, and protecting your privacy is part of protecting your security.
|
||||
|
||||
Firefox, Chrome, and Opera are the best Web browsers; they offer the best performance, the most compatibility, and the best security. These five open source security apps install in your Web browser, and they protect you from a variety of threats.
|
||||
|
||||
### Protect Your Privacy: Open Source Web Browser Security Apps ###
|
||||
|
||||
#### 1. [AdBlock][2] ####
|
||||
|
||||
Ad networks are wonderful malware vectors. A single ad network serves thousands of sites, so compromising one ad network equals many thousands of compromised machines. AdBlock, and its derivatives—[AdBlock Plus][2], [AdBlock Pro][3], and [AdBlock Edge][4]—are all great tools for blocking ads, which has the added benefit of making cluttery annoying ads-infested sites more usable.
|
||||
|
||||
Of course there is a downside: harming sites that depend on ad revenues. All of them have one-click whitelists, so you can selectively turn off ad-blocking on sites that you want to support. (Really, my dear Webmeisters, if you don't want your site visitors blocking your ads then don't be obnoxious.)
|
||||
|
||||

|
||||
|
||||
Figure 1: Selecting additional filters for your Ad Blocker.
|
||||
|
||||
Ad blockers do more than block ads; they also block Web-tracking bugs and malicious domains. To turn on additional filter lists, click on your ad blocker icon > click **Preferences**, and go to the **Filter Subscriptions** tab. Click the **Add Filter Subscription** button, and then add **Easy Privacy + EasyList**. The Malware Domains filter is a good one to include as well; it blocks domains that are known to host malware and spyware. Adblock works with Firefox, Chrome, Opera, Safari, Internet Explorer, and Android.
|
||||
|
||||
#### 2. [HTTPS Everywhere][5] ####
|
||||
|
||||
HTTPS Everywhere browser extension ensures that you will never accidentally connect to a Web site with HTTP when HTTPS is available. HTTPS means your connection is encrypted with SSL (secure sockets layer), which is a commonly-used protocol for encrypting Web and email connections. HTTPS Everywhere is available for Firefox, Chrome, and Opera.
|
||||
|
||||
When you install HTTPS Everywhere, it asks if you want to enable the SSL Observatory. Say yes, as it offers additional protections against man-in-the-middle and bogus SSL certificate attacks. HTTPS Everywhere works with Firefox, Chrome, Opera, Android.
|
||||
|
||||
#### 3. [Social Fixer][6] ####
|
||||
|
||||
Social Fixer tames Facebook. It gives you mighty powers to filter your news feed so that you see what you want to see, creates tabbed feeds organized by topic, hides whatever you don't want to see, displays pictures full-sized on mouse-over, disables the Theater view of images, and lots more.
|
||||
|
||||
It's not really designed to be a security tool, but Social Fixer offers two important security features:
|
||||
|
||||
- It anonymizes Facebook pages for screenshots by replacing profile pictures with generic icons, and it changes usernames to fake names
|
||||
- It reliably blocks Facebook games, which are notorious sources of trouble
|
||||
|
||||

|
||||
|
||||
Figure 2: Anonymizing a Facebook screen with Social Fixer.
|
||||
|
||||
#### 4. [Privacy Badger][7] ####
|
||||
|
||||
The Electronic Frontier Foundation's Privacy Badger is a superb tracker-and spy-ads blocker. These days Web pages are composed of content from multiple sources: ad servers, comments servers, content farms, image farms, third-party login servers, and gosh knows what-all.
|
||||
|
||||
AdBlock is good at blocking this junk, but Privacy Badger is better. It doesn't rely on filter lists, which have to be maintained by humans somewhere, but rather algorithms and policy methods, and you can easily override it if it blocks something in error. Privacy Badger works with Firefox and Chrome.
|
||||
|
||||

|
||||
|
||||
Figure 3: Privacy Badger blocks tracking sites.
|
||||
|
||||
Privacy Badger should just work. Click on its icon to see what it's blocking on any site you're visiting. Try it on Huffingtonpost.com, one of the champions of stuffing the maximum number of third-party components into each and every page (Figure 3).
|
||||
|
||||
The sliders tell the status of each site: red means that site is completely blocked, so it can't set cookies or serve up any content to you. Yellow indicates a third-party domain that appears to be trying to track you, but it is on Privacy Badger's whitelist of allowed domains. Green is for a third-party domain that is not yet classified as a tracker, but this could change as you visit **multiple** sites and Privacy Badger observes its behavior.
|
||||
|
||||
You can set the sliders yourself according to your preference; for example, on one site I visited Privacy Badger blocked bazaarvoice.com, which some shopping sites use to host their customer reviews.
|
||||
|
||||
#### 5. [Disconnect][8] ####
|
||||
|
||||
Disconnect is another anti-tracker and anti-cookie tool with a great feature set. It runs on Firefox, Chrome, Internet Explorer, and Safari, and offers special iOS and Android versions. Not only does it foil trackers, it also secures your wireless transmissions (Wi-fi, 3G, and 4G) with its own virtual private network, protecting you from wiretapping and malvertising. It protects you from widgetjacking, which is a technique used by attackers to gain access to your sites that require logins. With widgetjacking they don't even need your password; they use stolen cookies.
|
||||
|
||||
Disconnect also provides a safe search feature that lets you use your favorite search engines while blocking their snoopy data-mining habits.
|
||||
|
||||
Just assume that everyone on the Web is out to get you. It's all abstract and behind the scenes, and not obvious like someone bashing a window to get into your house. But the threats are numerous and real, and you have to take precautions to protect yourself.
|
||||
|
||||
Carla Schroder is the author of The Book of Audacity, Linux Cookbook, Linux Networking Cookbook,and hundreds of Linux how-to articles. She's the former managing editor of Linux Planet and Linux Today.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.smallbusinesscomputing.com/biztools/5-best-open-source-web-browser-security-apps.html
|
||||
|
||||
作者:[Carla Schroder][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.smallbusinesscomputing.com/author/Carla-Schroder-6080.html
|
||||
[1]:http://www.webopedia.com/TERM/M/malvertising.html
|
||||
[2]:https://getadblock.com/
|
||||
[3]:https://chrome.google.com/webstore/detail/adblock-pro/ocifcklkibdehekfnmflempfgjhbedch?hl=en-US
|
||||
[4]:https://addons.mozilla.org/en-us/firefox/addon/adblock-edge/
|
||||
[5]:https://www.eff.org/Https-everywhere
|
||||
[6]:http://socialfixer.com/
|
||||
[7]:https://www.eff.org/privacybadger
|
||||
[8]:https://disconnect.me/
|
||||
@ -0,0 +1,228 @@
|
||||
How to install Xen hypervisor on unused old hardware
|
||||
================================================================================
|
||||
Xen is a bare metal hypervisor, meaning that you must prepare a bare machine to install and run Xen. KVM is a little different - you can add it to any machine already running Linux. This tutorial describes how to install and configure Xen hypervisor on unused hardware.
|
||||
|
||||
This procedure uses Debian Jessie (their testing distribution) as the host OS (also known as [Dom0][1]). Jessie is not the only choice - Xen support is built into the Linux kernel, and [plenty of Linux distributions][2] include one of these Xen-enabled kernels.
|
||||
|
||||
### Find unused hardware ###
|
||||
|
||||
As a start, find a suitable workstation which can be wiped out, such as an old laptop or desktop. Older hardware may not be good for gaming, but it is good enough for a host OS and a couple of guests. A PC with these specifications works fine.
|
||||
|
||||
- 1 CPU with 2 cores (64-bit)
|
||||
- 4GB memory
|
||||
- 80GB hard disk
|
||||
- ability to boot from CD, DVD or USB
|
||||
- a network interface
|
||||
|
||||
Note that the CPU must be a 64-bit processor since Debian dropped support for 32-bit Xen packages. If you don't have spare hardware, you could invest in an old machine. 2010's $1000 flagship laptop is today's $100 bargain. A second-hand laptop from eBay and a memory upgrade will do fine.
|
||||
|
||||
### Burn a bootable CD/USB ###
|
||||
|
||||
Download the ISO image for Debian Jessie. The small netinst image available from the [official Debian website][3] works fine.
|
||||
|
||||
$ wget http://cdimage.debian.org/cdimage/jessie_di_beta_2/amd64/iso-cd/debian-jessie-DI-b2-amd64-netinst.iso
|
||||
|
||||
Next, identify the device name assigned to your [CD/DVD][4] or [USB drive][5] (e.g., /dev/sdc).
|
||||
|
||||
Burn the downloaded ISO image into a bootable CD or a USB using dd command. Replace /dev/sdc with the device name you identified above.
|
||||
|
||||
$ sudo dd if=debian-jessie-DI-b2-amd64-netinst.iso of=/dev/sdc
|
||||
|
||||
### Start the installation ###
|
||||
|
||||
To start the installation, boot with the Debian installer CD/USB.
|
||||
|
||||
It's a good idea to use a wired connection, not WiFi. If the WiFi won't connect because firmware or driver software is missing, you won't get very far.
|
||||
|
||||
|
||||
|
||||
### Partition the disk ###
|
||||
|
||||
This setup uses four primary disk partitions. Automatic OS installers usually set up an extended partition that contains logical partitions. Set up the four partitions like this.
|
||||
|
||||
- sda1 mount on /boot, 200MB
|
||||
- sda2 /, 20GB, Ubuntu uses 4GB
|
||||
- sda3 swap, 6GB (4GB of memory x 1.5 = 6)
|
||||
- sda4 reserved for LVM, not mounted, all the rest of the disk space
|
||||
|
||||
### Install the base system ###
|
||||
|
||||
It's a good idea to make the install as simple and short as possible. A basic working system can always be added to later. Debian's APT (Advanced Package Tool) makes adding software easy. Installing Debian on a workstation can cause pretty obscure time-wasting issues. Perhaps a graphics driver does not agree with the kernel or maybe the old CD-ROM drive only works intermittently.
|
||||
|
||||
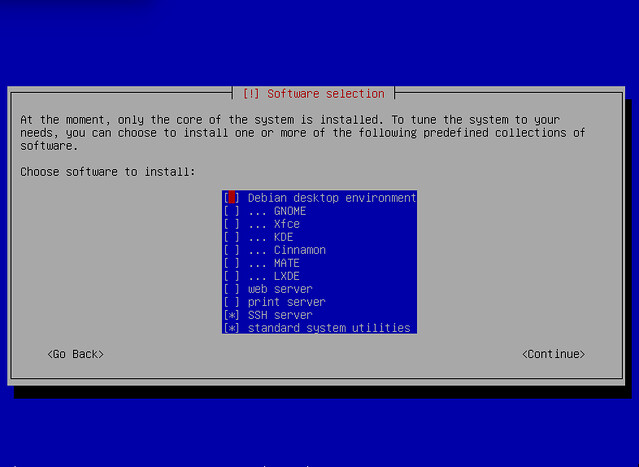
When it comes to choosing what to install, do install an SSH server and don't install a desktop like Gnome.
|
||||
|
||||
|
||||
|
||||
A graphical desktop requires hundreds of package installs - it's a lot of extra work that can be done later. If you run into problems, waiting for that desktop install is a waste of time. Also, without desktop component, the system boot will be much quicker - seconds rather than minutes. This procedure requires a few reboots, so that's a handy time-saver.
|
||||
|
||||
An SSH server lets you configure the workstation from another computer. This allows you to avoid some of the problems with old hardware - perhaps the old machine's keyboard is missing keys, the LCD screen has dead pixels or the trackpad is unresponsive etc.
|
||||
|
||||
### Add LVM (Logical Volume Manager) ###
|
||||
|
||||
Install the LVM tools as the root.
|
||||
|
||||
# apt-get update
|
||||
# apt-get install lvm2
|
||||
|
||||
Pick a physical volume to work with.
|
||||
|
||||
# pvcreate /dev/sda4
|
||||
|
||||
Create a volume group.
|
||||
|
||||
# vgcreate vg0 /dev/sda4
|
||||
|
||||
You don't need to create a logical volume. If you want to test LVM works, create a volume then delete it.
|
||||
|
||||
# lvcreate -nmytempvol -L10G vg0
|
||||
# lvremove /dev/vg0/mytempvol
|
||||
|
||||
Check LVM status.
|
||||
|
||||
# pvs (to view information about physical volumes)
|
||||
# vgs (to view information about volume groups)
|
||||
# lvs (to view information about logical volumes)
|
||||
|
||||
### Add a Linux Ethernet bridge ###
|
||||
|
||||
We are going to set up a Linux bridge so that all Xen's guest domains can be connected to, and communicate through the bridge.
|
||||
|
||||
Install the bridge tools.
|
||||
|
||||
# apt-get install bridge-utils
|
||||
|
||||
See what interfaces are configured.
|
||||
|
||||
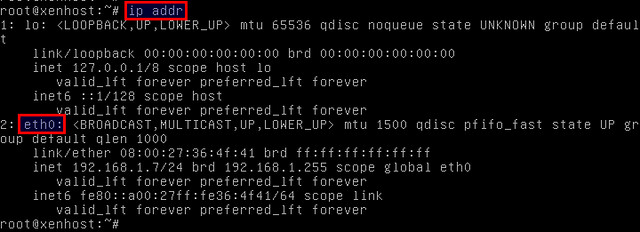
# ip addr
|
||||
|
||||
|
||||
|
||||
In this example, we have one primary interface assigned eth0. We are going to add eth0 to the Linux bridge by editing the network configuration file (/etc/network/interfaces).
|
||||
|
||||
Before making any change, back up the network configuration file to keep the original working configuration safe.
|
||||
|
||||
# cd /etc/network/
|
||||
# cp interfaces interfaces.backup
|
||||
# vi /etc/network/interfaces
|
||||
|
||||
The file contents look something like this.
|
||||
|
||||
auto lo
|
||||
iface lo inet loopback
|
||||
|
||||
allow-hotplug eth0
|
||||
iface eth0 inet dhcp
|
||||
|
||||
Change the file to this.
|
||||
|
||||
auto lo
|
||||
iface lo inet loopback
|
||||
|
||||
auto eth0
|
||||
iface eth0 inet manual
|
||||
|
||||
auto xenbr0
|
||||
iface xenbr0 inet dhcp
|
||||
bridge_ports eth0
|
||||
|
||||
Activate the network configuration change:
|
||||
|
||||
# systemctl restart networking
|
||||
|
||||
### Verify networking settings ###
|
||||
|
||||
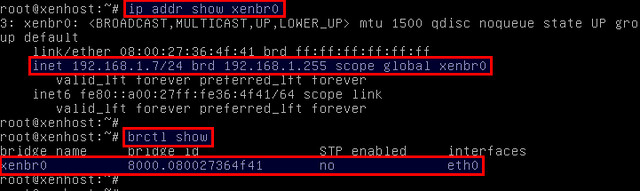
Verify that a Linux bridge xenbr0 is created successfully.
|
||||
|
||||
# ip addr show xenbr0
|
||||
|
||||
Also check that the primary interface eth0 is successfully added to the bridge.
|
||||
|
||||
# brctl show
|
||||
|
||||
|
||||
|
||||
You now have a working machine with Jessie installed. Xen is not yet installed at this point. Let's proceed to install Xen next.
|
||||
|
||||
### Install the Xen hypervisor ###
|
||||
|
||||
Install Xen and QEMU packages, and update the GRUB bootloader.
|
||||
|
||||
# apt-get install xen-linux-system
|
||||
|
||||
Reboot.
|
||||
|
||||
When the GRUB screen appears, you can see extra booting options listed.
|
||||
|
||||
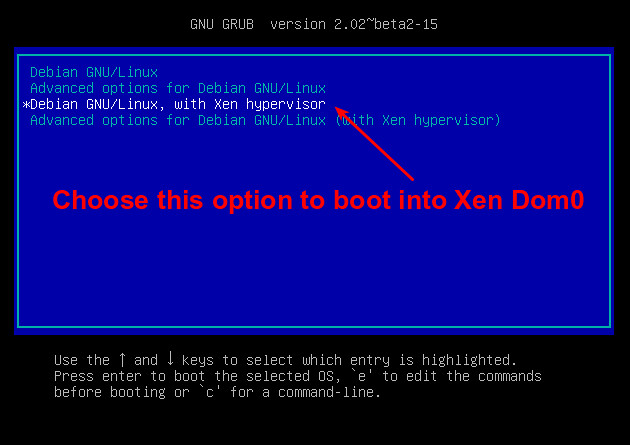
|
||||
|
||||
The first option will boot automatically in five seconds (see the GRUB_TIMEOUT line in /etc/default/grub), so this is not the time to get a coffee.
|
||||
|
||||
Press the down arrow to highlight the option "Debian GNU/Linux, with Xen hypervisor", and press RETURN. Many lines of information appear, followed by the usual login screen.
|
||||
|
||||
### Check Xen works ###
|
||||
|
||||
Xen hypervisor comes with Xen management command-line tool called xl, which can be used to create and manage Xen guest domains. Let's use xl command to check if Xen is successfully installed.
|
||||
|
||||
Log in as root, and run:
|
||||
|
||||
# xl info
|
||||
|
||||
which will display various information about Xen host.
|
||||
|
||||
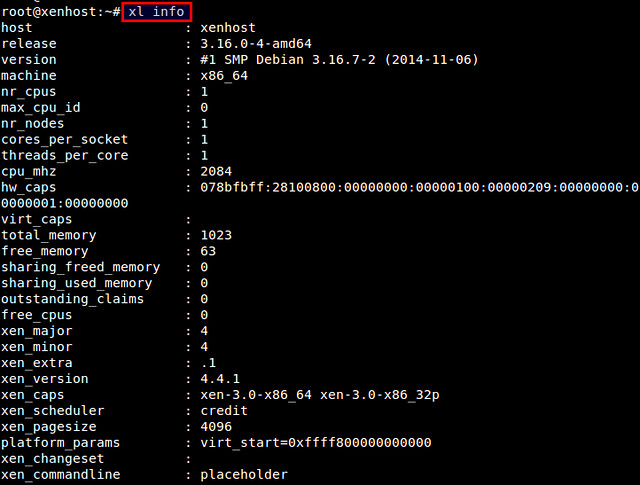
|
||||
|
||||
To see a list of existing Xen domains:
|
||||
|
||||
# xl list
|
||||
|
||||
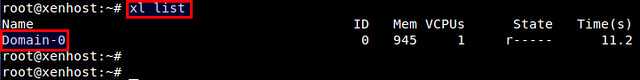
|
||||
|
||||
A little table of domains appears. Without any Xen guest domain created, the only entry should be Domain-0, your Debian installation.
|
||||
|
||||
### Change the boot order ###
|
||||
|
||||
When you reach this point, the Xen install is complete. There is one more thing to fix - the default boot will not load Xen. GRUB chooses the first item in the boot menu (Debian GNU/Linux), not the third (Debian GNU/Linux, with Xen hypervisor).
|
||||
|
||||
The default option in the boot menu is defined in the grub configuration file /boot/grub/grub.cfg. To change the default option, don't edit that file, but edit /etc/default/grub instead. A little helper program called grub-mkconfig reads in this default configuration file and all the templates in /etc/grub.d/, then writes the grub.cfg file.
|
||||
|
||||
Edit Debian's configuration file for grub-mkconfig.
|
||||
|
||||
# vi /etc/default/grub
|
||||
|
||||
Change the line:
|
||||
|
||||
GRUB_DEFAULT=0
|
||||
|
||||
to
|
||||
|
||||
GRUB_DEFAULT='Debian GNU/Linux, with Xen hypervisor'
|
||||
|
||||
Then update the grub configuration file.
|
||||
|
||||
# grub-mkconfig -o /boot/grub/grub.cfg
|
||||
|
||||
Finally reboot. After a few seconds, the grub boot menu appears. Check that the third option "Debian GNU/Linux, with Xen hypervisor" is highlighted automatically.
|
||||
|
||||
### Final note ###
|
||||
|
||||
If you use this machine as your hands-on workstation, install a graphical desktop. The Debian library includes a few [desktop environments][6]. If you want a graphical desktop that includes everything and the kitchen sink, go for Gnome. If graphics just get in your way, try Awesome.
|
||||
|
||||
Note that the Debian Jessie default environment Gnome comes with a huge amount of extra applications including the productivity suite LibreOffice, the Iceweasel web browser and the Rhythmbox music player. The install command "apt-get install gnome" adds 1,000 packages and takes up nearly 2GB of disk space. Running this heavyweight desktop takes up 1GB of memory.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/install-xen-hypervisor.html
|
||||
|
||||
作者:[Nick Hardiman][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/nick
|
||||
[1]:http://wiki.xen.org/wiki/Dom0
|
||||
[2]:http://wiki.xen.org/wiki/Dom0_Kernels_for_Xen
|
||||
[3]:https://www.debian.org/devel/debian-installer/
|
||||
[4]:http://ask.xmodulo.com/detect-dvd-writer-device-name-writing-speed-command-line-linux.html
|
||||
[5]:http://ask.xmodulo.com/find-device-name-usb-drive-linux.html
|
||||
[6]:https://wiki.debian.org/DesktopEnvironment
|
||||
Loading…
Reference in New Issue
Block a user