mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-01-25 23:11:02 +08:00
20141027-2 选题
This commit is contained in:
parent
c0707b66d5
commit
777a0b6014
170
sources/share/20141027 Handy Disk Image Tools.md
Normal file
170
sources/share/20141027 Handy Disk Image Tools.md
Normal file
@ -0,0 +1,170 @@
|
||||
Handy Disk Image Tools
|
||||
================================================================================
|
||||
Disk images are computer files of a disk volume or an entire data storage device, such as a hard drive, optical disk (e.g. DVD, CD, Blu-ray), tape drive, USB flash drive, or floppy disk. A disk image represents the content exactly as it is on the original storage device, including both data and structure information.
|
||||
|
||||
Disk image file formats can be open standards, such as the ISO image format for optical disk images, or proprietary to particular software applications. The name "ISO" is taken from the ISO 9660 file system used with CD-ROM media. Converting from a proprietary image format to an open format often crops up as an issue when users migrate to Linux.
|
||||
|
||||
Disk images have many different uses such as burning optical media, system backup, data recovery, disk cloning, computer forensics, and operating systems (as Live CD/DVDs).
|
||||
|
||||
There are a number of different ways of mounting an ISO image under Linux. The venerable mount command offers an easy solution. But if you need tools that offer more functionality for working with disk images, try some of the following excellent open source tools.
|
||||
|
||||
Most of the tools have not seen a recent release, so if you are looking to get involved with a good open source tool, you could pitch in.
|
||||
|
||||
----------
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
Furius ISO Mount is a simple open source application for mounting .iso, .img, .bin, .mdf and .nrg image files without burning them to disk.
|
||||
|
||||
Features include:
|
||||
|
||||
- Automatically mounts ISO, IMG, BIN, MDF and NRG image files
|
||||
- Supports mounting UDF images through loop
|
||||
- Automatically creates a mount point in your home directory
|
||||
- Automatically unmounts the Image files
|
||||
- Automatically removes the mount directory to return your home directory to its previous state
|
||||
- Automatically saves the history of the last 10 images mounted
|
||||
- Mounts multiple images
|
||||
- Burn ISO and IMG Files to optical disk
|
||||
- Generate MD5 and SHA1 checksums
|
||||
- Automatically retrieves any previously unmounted images
|
||||
- Automatically generates a log file of all commands needed to mount and unmount images manually
|
||||
- Language support (currently Bulgarian, Chinese (Simplified), Czech, Dutch, French, German, Hungarian, Italian, Greek, Italian, Japanese, Polish, Portuguese, Russian, Slovenian, Spanish, Swedish and Turkish)
|
||||
|
||||
- Website: [launchpad.net/furiusisomount/][1]
|
||||
- Developer: Dean Harris (Marcus Furius)
|
||||
- License: GNU GPL v3
|
||||
- Version Number: 0.11.3.1
|
||||
|
||||
|
||||
----------
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
fuseiso is an open source FUSE module to mount ISO filesystem images.
|
||||
|
||||
With FUSE it is possible to implement a fully functional filesystem in a userspace program.
|
||||
|
||||
Features include:
|
||||
|
||||
- Read ISO, BIN and NRG images containing ISO9660 filesystems
|
||||
- Supports plain ISO9660 Level 1 and 2
|
||||
- Supports some common extensions, like Joliet, RockRidge and zisofs
|
||||
- Supports non-standard images, like CloneCD's IMGs and Alcohol 120%'s MDFs, as their format looks exactly like BIN images
|
||||
|
||||
- Website: [sourceforge.net/projects/fuseiso][2]
|
||||
- Developer: Dmitry Morozhnikov
|
||||
- License: GNU GPL v2
|
||||
- Version Number: 20070708
|
||||
|
||||
----------
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
iat (Iso9660 Analyzer Tool) is a versatile, open source tool for detecting the structure of many types of image file formats, such as BIN, MDF, PDI, CDI, NRG, and B5I, and converting them into ISO-9660.
|
||||
|
||||
Features include:
|
||||
|
||||
- Supports reading (input) NRG, MDF, PDI, CDI, BIN, CUE and B5I images
|
||||
- Burn disc images directly using cdrecord
|
||||
- Outputs information including a progress-bar, Block size, ECC sector (size), header sector (size), image offset start and more
|
||||
|
||||
- Website: [sourceforge.net/projects/iat.berlios][3]
|
||||
- Developer: Salvatore Santagati
|
||||
- License: GNU GPL v2
|
||||
- Version Number: 0.1.3
|
||||
|
||||
----------
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
AcetoneISO is a feature-rich open source graphical application to mount and manage CD/DVD images.
|
||||
|
||||
The utility opens a graphical file manager to mount image formats, including proprietary image formats, including ISO, BIN, NRG, MDF, IMG etc, and lets you perform a number of actions.
|
||||
|
||||
AcetoneISO is written with Qt 4, which means that it integrates well in Qt-based desktop environments like KDE, LXQt or Razor-qt.
|
||||
|
||||
This software is meant for all those people looking for a "Daemon Tools for Linux".
|
||||
|
||||
Features include:
|
||||
|
||||
- Mount most common Windows images in a clean and easy GUI
|
||||
- Convert all known images to ISO or extract the contents to a folder
|
||||
- Encrypt, compress, split any type of image
|
||||
- Convert DVD video to xvid avi and any generic video to xvid avi
|
||||
- Extract audio from a video
|
||||
- Extract images content to a folder: bin mdf nrg img daa dmg cdi b5i bwi pdi
|
||||
- Play a DVD Movie Image with Kaffeine / VLC / SMplayer with auto-cover download from Amazon
|
||||
- Generate an ISO from a Folder or CD/DVD
|
||||
- Check MD5 file of an image and/or generate it to a text file
|
||||
- Calculate ShaSums of images in 128, 256, and 384 bit
|
||||
- Encrypt / Decrypt an image
|
||||
- Split / Merge image in X megabyte
|
||||
- Compress with high ratio an image in 7z format
|
||||
- Rip a PSX CD to *.bin to make it work with ePSXe/pSX emulators
|
||||
- Restore a lost CUE file of *.bin *.img
|
||||
- Convert Mac OS *.dmg to a mountable image
|
||||
- Mount an image in a specified folder from the user
|
||||
- Create a database of images to manage big collections
|
||||
- Extract the Boot Image file of a CD/DVD or ISO
|
||||
- Backup a CD-Audio to a *.bin image
|
||||
- Quick and simple utility to rip a DVD to Xvid AVI
|
||||
- Quick and simple utility to convert a generic video (avi, mpeg, mov, wmv, asf) to Xvid AVI
|
||||
- Quick and simple utility to convert a FLV video to AVI
|
||||
- Utility to download videos from YouTube and Metacafe
|
||||
- Extract audio from a video file
|
||||
- Extract a *.rar archive that has a password
|
||||
- Utility to convert any video for Sony PSP PlayStation Portable
|
||||
- Internationalization support English, Italian, Polish, Spanish, Romanian, Hungarian, German, Czech, and Russian
|
||||
|
||||
- Website: [sourceforge.net/projects/acetoneiso][4]
|
||||
- Developer: Marco Di Antonio
|
||||
- License: GNU GPL v3
|
||||
- Version Number: 2.3
|
||||
|
||||
----------
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
ISO Master is an open-source, easy to use, graphical CD image editor for Linux and BSD. This tool extracts files from an ISO, add files to an ISO, and create bootable ISOs - all in a graphical user interface. It can open ISO, NRG, and some MDF files but can only save as ISO.
|
||||
|
||||
ISO Master is based on bkisofs, a simple and stable library for reading, modifying and writing ISO images which supports the Joliet, RockRidge, and EL Torito extensions.
|
||||
|
||||
Features include:
|
||||
|
||||
- Reads .ISO files (ISO9660, Joliet, RockRidge, and El Torito), most .NRG files, and some single-track .MDF files; it can save only as .ISO
|
||||
- Create or customise CD/DVD images
|
||||
- Add or remove files and directories to/from a CD image
|
||||
- Make bootable CDs/DVDs
|
||||
- Internationalization support
|
||||
|
||||
- Website: [www.littlesvr.ca/isomaster/][5]
|
||||
- Developer: Andrew Smith
|
||||
- License: GNU GPL v2
|
||||
- Version Number: 1.3.11
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linuxlinks.com/article/20141025082352476/DiskImageTools.html
|
||||
|
||||
作者:Frazer Kline
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:https://launchpad.net/furiusisomount/
|
||||
[2]:http://sourceforge.net/projects/fuseiso/
|
||||
[3]:http://sourceforge.net/projects/iat.berlios/
|
||||
[4]:http://sourceforge.net/projects/acetoneiso/
|
||||
[5]:http://www.littlesvr.ca/isomaster/
|
||||
@ -0,0 +1,125 @@
|
||||
How to download an ISO image with BitTorrent fast and safely from the command line
|
||||
================================================================================
|
||||
If you are one of those guys who have urge to try out every new (or even beta) release of Linux distribution to satisfy your curiosity and stay up-to-date, you will need to deal with the hassle of downloading big ISO images every now and then. ISO providers typically put up .torrent file of their ISO images to ease up on the bandwidth consumption of their servers. The benefit of peer-to-peer download is obvious for users as well (in terms of speed), especially when a new release of a popular Linux distribution is up for grab, and everyone is downloading and seeding the release at the same time.
|
||||
|
||||
Ubuntu 14.10 (Utopic Unicorn) was just released this week. So there should be plenty of seeds to download the release from in the BitTorrent network at the moment. While there are many GUI-based BitTorrent clients out there, I am going to show you **how to download ISO images via a simple command-line interface (CLI) BitTorrent client**, which can be handy if you are on a remote headless server. Later in this tutorial, I will also demonstrate **how to verify the integrity of a downloaded ISO image**.
|
||||
|
||||
The CLI BitTorrent client I am going to use today is transmission-cli. As you may know, [Transmission][1] is one of the most popular GUI-based BitTorrent client. transmission-cli is its stripped-down CLI version.
|
||||
|
||||
### Install Transmission-cli on Linux ###
|
||||
|
||||
To install **transmission-cli**, you don't need to install a full-blown GUI-based Transmission, which is nice.
|
||||
|
||||
On Debian, Ubuntu or their derivatives:
|
||||
|
||||
$ sudo apt-get install transmission-cli
|
||||
|
||||
On Fedora:
|
||||
|
||||
$ sudo yum install transmission-cli
|
||||
|
||||
On CentOS or RHEL (after enabling [EPEL repository][2]):
|
||||
|
||||
$ sudo yum install transmission-cli
|
||||
|
||||
### Download an ISO Image Fast with transmission-cli ###
|
||||
|
||||
**transmission-cli** is really simple to use. If you are too lazy to study its command line options, all you have to do is to download .torrent file, and launch the command with the torrent file. It will automatically look for available peers, and download an ISO file from them.
|
||||
|
||||
$ wget http://releases.ubuntu.com/14.10/ubuntu-14.10-desktop-amd64.iso.torrent
|
||||
$ transmission-cli ubuntu-14.10-desktop-amd64.iso.torrent
|
||||
|
||||

|
||||
|
||||
Once an ISO image is fully downloaded, it will be stored in ~/Downloads directory by default. It took me only 5 minutes to download 1GB Ubuntu ISO image.
|
||||
|
||||

|
||||
|
||||
Once it finishes downloading an ISO image, you will see the message "State changed from Incomplete to Complete" in the console. Note that transmission-cli will continue to run afterwards, becoming a seed for other downloaders. Press Ctrl+C to quit.
|
||||
|
||||
### Customize Download Options for Repeat Use ###
|
||||
|
||||
If you are a repeat user of **transmission-cli**, it may be worth your time to be familiar with some of its command line options.
|
||||
|
||||
The "-w /path/to/download-directory" option specifies the directory where a downloaded file will be saved.
|
||||
|
||||
The "-f /path/to/finish-script" option sets a script to run when current download is completed. Recall that transmission-cli, by default, continues running even after a file is fully downloaded. If you want to auto-terminate transmission-cli upon successful download, you can use this option. The following simple finish script will do.
|
||||
|
||||
#!/bin/sh
|
||||
sleep 10
|
||||
killall transmission-cli
|
||||
|
||||
If you want to allocate limited upload/download bandwidth to transmission-cli, you can use "-d <download-speed-in-KB/s> and "-u <upload-speed-in-KB/s> options. If you want to allow unlimited bandwidth instead, simply specify "-D" or "-U" option without any value.
|
||||
|
||||
Here is a more advanced usage example of transmission-cli. In this example, the CLI client will automatically exit upon successful download. Download rate is unlimited while upload rate is capped at 50KB/s.
|
||||
|
||||
$ transmission-cli -w ~/iso -D -u 50 -f ~/finish.sh ubuntu-14.10-desktop-amd64.iso.torrent
|
||||
|
||||

|
||||
|
||||
### Verify the Integrity of a Downloaded ISO Image ###
|
||||
|
||||
When you download an ISO image, especially from many unknown peers in the BitTorrent network, it is always recommended to verify the integrity of the downloaded image.
|
||||
|
||||
In case of Ubuntu releases, Canonical provides several checksum files (e.g., MD5SUM, SHA1SUMS and SHA256SUMS) for verification purpose. Let's use SHA256SUMS in this example.
|
||||
|
||||

|
||||
|
||||
First, download the following two files.
|
||||
|
||||
$ wget http://releases.ubuntu.com/14.10/SHA256SUMS
|
||||
$ wget http://releases.ubuntu.com/14.10/SHA256SUMS.gpg
|
||||
|
||||
The first file is a SHA256 checksum file for ISO images, while the second file (*.gpg) is a signature of the checksum file. The purpose of the second file is to verify the validity of the checksum file itself.
|
||||
|
||||
Let's verify the validity of SHA256SUMS file by running this command:
|
||||
|
||||
$ gpg --verify SHA256SUMS.gpg SHA256SUMS
|
||||
|
||||
----------
|
||||
|
||||
gpg: Signature made Thu 23 Oct 2014 09:36:00 AM EDT using DSA key ID FBB75451
|
||||
gpg: Can't check signature: public key not found
|
||||
|
||||
If you are getting the above error, this is because you have not imported the public key used to generate the signature. So now let's import the required public key.
|
||||
|
||||
To do that, you need to know the "key ID" of the public key, which is shown in the output of gpg command above. In this example, the key ID is "FBB75451". Run the following command to import the public key from the official Ubuntu keyserver.
|
||||
|
||||
$ gpg --keyserver hkp://keyserver.ubuntu.com --recv-keys FBB75451
|
||||
|
||||

|
||||
|
||||
Now that the public key has been imported, go ahead and re-run the previous command to verify the signature.
|
||||
|
||||
gpg --verify SHA256SUMS.gpg SHA256SUMS
|
||||
|
||||

|
||||
|
||||
This time you will not see "public key not found" error. If the SHA256SUMS file is valid, you will see "Good signature from <official source>" message. Note that you will also see a warning message saying that "This key is not certified with a trusted signature". Basically this warning message is telling you that you have not [assigned any explicit trust][3] to the imported public key. To avoid this warning, you could choose to assign your full trust to the imported public key, but you should do that only after the key has been fully vetted in some other means. Otherwise, you can ignore the warning for now.
|
||||
|
||||
After verifying the integrity of SHA256SUMS file, the final last step is to compare the SHA256 checksum of the downloade ISO image against the corresponding checksum value in SHA256SUMS file. For that you can use sha256sum command line tool.
|
||||
|
||||
For your convenience, the following one-liner compares the SHA256 checksums and reports the result.
|
||||
|
||||
$ sha256sum -c <(grep ubuntu-14.10-desktop-amd64.iso SHA256SUMS)
|
||||
|
||||
----------
|
||||
|
||||
ubuntu-14.10-desktop-amd64.iso: OK
|
||||
|
||||
If you see the above output, that means that two checksum values match. So the integrity of the downloaded ISO image has been successfully verified.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/download-iso-image-bittorrent-command-line.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/nanni
|
||||
[1]:https://www.transmissionbt.com/
|
||||
[2]:http://xmodulo.com/how-to-set-up-epel-repository-on-centos.html
|
||||
[3]:http://xmodulo.com/verify-authenticity-integrity-downloaded-file.html
|
||||
@ -0,0 +1,107 @@
|
||||
How to encrypt files and directories with eCryptFS on Linux
|
||||
================================================================================
|
||||
You do not have to be a criminal or work for the CIA to use encryption. You simply don't want anybody to spy on your financial data, family pictures, unpublished manuscripts, or secret notes where you have jotted down startup ideas which you think can make you super rich.
|
||||
|
||||
I have heard people telling me "I'm not important enough to be spied" or "I don't hide anything to care about." Well, my opinion is that even if I don't have anything to hide, or I can publish a picture of my kids with my dog, I have the right to not do it and want to protect my privacy.
|
||||
|
||||
### Types of Encryption ###
|
||||
|
||||
We have largely two different ways to encrypt files and directories. One method is filesystem-level encryption, where only certain files or directories (e.g., /home/alice) are encrypted selectively. To me, this is a perfect way to start. You don't need to re-install everything to enable or test encryption. Filesystem-level encryption has some disadvantages, though. For example, many modern applications cache (part of) files in unencrypted portions of your hard drive, such as swap partition, /tmp and /var folders, which can result in privacy leaks.
|
||||
|
||||
The other way is so-called full-disk encryption, which means that the entire disk is encrypted (possibly except for a master boot record). Full disk encryption works at the physical disk level; every bit written to the disk is encrypted, and anything read from the disk is automatically decrypted on the fly. This will prevent any potential unauthorized access to unencrypted data, and ensure that everything in the entire filesystem is encrypted, including swap partition or any temporarily cached data.
|
||||
|
||||
### Available Encryption Tools ###
|
||||
|
||||
There are several options to implement encryption in Linux. In this tutorial, I am going to describe one option: **eCryptFS** a user-space cryptographic filesystem tool. For your reference, here is a roundup of available Linux encryption tools.
|
||||
|
||||
#### Filesystem-level encryption ####
|
||||
|
||||
- [EncFS][1]: one of the easiest ways to try encryption. EncFS works as a FUSE-based pseudo filesystem, so you just create an encrypted folder and mount it to a folder to work with.
|
||||
- [eCryptFS][2]: a POSIX compliant cryptographic filesystem, eCryptFS works in the same way as EncFS, so you have to mount it.
|
||||
|
||||
#### Filesystem-level encryption ####
|
||||
|
||||
- [Loop-AES][3]: the oldest disk encryption method. It is really fast and works on old system (e.g., kernel 2.0 branch).
|
||||
- [DMCrypt][4]: the most common disk encryption scheme supported by the modern Linux kernel.
|
||||
- [CipherShed][5]: an open-source fork of the discontinued TrueCrypt disk encryption program.
|
||||
|
||||
### Basics of eCryptFS ###
|
||||
|
||||
eCryptFS is a FUSE-based user-space cryptographic filesystem, which has been available in the Linux kernel since 2.6.19 (as ecryptfs module). An eCryptFS-encrypted pseudo filesystem is mounted on top of your current filesystem. It works perfectly on EXT filesystem family and others like JFS, XFS, ReiserFS, Btrfs, even NFS/CIFS shares. Ubuntu uses eCryptFS as its default method to encrypt home directory, and so does ChromeOS. Underneath it, eCryptFS uses AES algorithm by default, but it supports others algorithms, such as blowfish, des3, cast5, cast6. You will be able to choose among them in case you create a manual setup of eCryptFS.
|
||||
|
||||
Like I said, Ubuntu lets us choose whether to encrypt our /home directory during installation. Well, this is the easiest way to use eCryptFS.
|
||||
|
||||
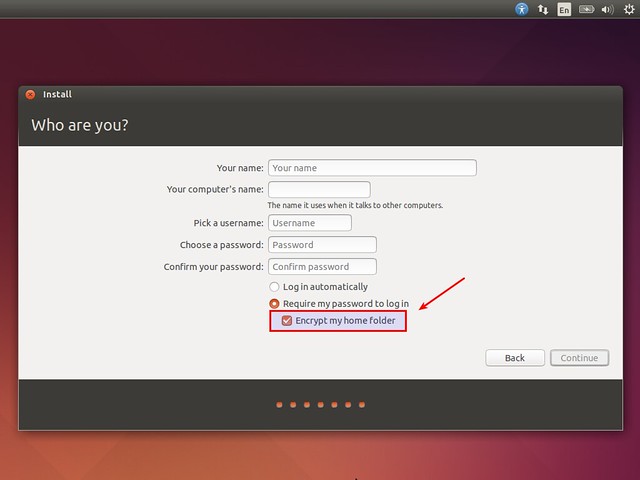
|
||||
|
||||
Ubuntu provides a set of user-friendly tools that make our life easier with eCryptFS, but enabling eCryptFS during Ubuntu installation only creates a specific pre-configured setup. So in case the default setup doesn't fit your needs, you will need to perform a manual setup. In this tutorial, I will describe **how to set up eCryptFS manually on major Linux distros**.
|
||||
|
||||
### Installation of eCryptFS ###
|
||||
|
||||
Debian, Ubuntu or its derivatives:
|
||||
|
||||
$ sudo apt-get install ecryptfs-utils
|
||||
|
||||
Note that if you chose to encrypt your home directory during Ubuntu installation, eCryptFS should be already installed.
|
||||
|
||||
CentOS, RHEL or Fedora:
|
||||
|
||||
# yum install ecryptfs-utils
|
||||
|
||||
Arch Linux:
|
||||
|
||||
$ sudo pacman -S ecryptfs-utils
|
||||
|
||||
After installing the package, it is a good practice to load the eCryptFS kernel module just to be sure:
|
||||
|
||||
$ sudo modprobe ecryptfs
|
||||
|
||||
### Configure eCryptFS ###
|
||||
|
||||
Now let's start encrypting some directory by running eCryptFS configuration tool:
|
||||
|
||||
$ ecryptfs-setup-private
|
||||
|
||||

|
||||
|
||||
It will ask for a login passphrase and a mount passphrase. The login passphrase is the same as your normal login password. The mount passphrase is used to derive a file encryption master key. Leave it blank to generate one as it's safer. Log out and log back in.
|
||||
|
||||
You will notice that eCryptFS created two directories by default: Private and .Private in your home directory. The ~/.Private directory contains encrypted data, while you can access corresponding decrypted data in the ~/Private directory. At the time you log in, the ~/.Private directory is automatically decrypted and mapped to the ~/Private directory, so you can access it. When you log out, the ~/Private directory is automatically unmounted and the content in the ~/Private directory is encrypted back into the ~/.Private directory.
|
||||
|
||||
The way eCryptFS knows that you own the ~/.Private directory, and automatically decrypts it into the ~/Private directory without needing us to type a password is through an eCryptFS PAM module which does the trick for us.
|
||||
|
||||
In case you don't want to have the ~/Private directory automatically mounted upon login, just add the "--noautomount" option when running ecryptfs-setup-private tool. Similarly, if you do not want the ~/Private directory to be automatically unmounted after logout, specify "--noautoumount" option. But then, you will have to mount or unmount ~/Private directory manually by yourself:
|
||||
|
||||
$ ecryptfs-mount-private ~/.Private ~/Private
|
||||
$ ecryptfs-umount-private ~/Private
|
||||
|
||||
You can verify that .Private folder is mounted by running:
|
||||
|
||||
$ mount
|
||||
|
||||
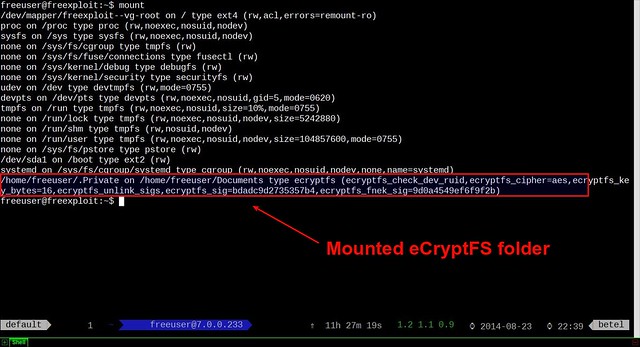
|
||||
|
||||
Now we can start putting any sensitive files in ~/Private folder, and they will automatically be encrypted and locked down in ~/.Private folder when we log out.
|
||||
|
||||
All this seems pretty magical. Basically ecryptfs-setup-private tool makes everything easy to set up. If you want to play a little more and set up specific aspects of eCryptFS, go to the [official documentation][6].
|
||||
|
||||
### Conclusion ###
|
||||
|
||||
To conclude, if you care a great deal about your privacy, the best setup I recommend is to combine eCryptFS-based filesystem-level encryption with full-disk encryption. Always remember though, file encryption alone does not guarantee your privacy.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/encrypt-files-directories-ecryptfs-linux.html
|
||||
|
||||
作者:[Christopher Valerio][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/valerio
|
||||
[1]:http://www.arg0.net/encfs
|
||||
[2]:http://ecryptfs.org/
|
||||
[3]:http://sourceforge.net/projects/loop-aes/
|
||||
[4]:https://code.google.com/p/cryptsetup/wiki/DMCrypt
|
||||
[5]:https://ciphershed.org/
|
||||
[6]:http://ecryptfs.org/documentation.html
|
||||
Loading…
Reference in New Issue
Block a user