mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-02-28 01:01:09 +08:00
[Translated]sources/tech/RHCE/Part 8 - RHCE Series--Implementing HTTPS through TLS using Network Security Service NSS for Apache.md
This commit is contained in:
parent
6f66f00795
commit
7774856c6f
@ -1,212 +0,0 @@
|
||||
ictlyh Translating
|
||||
RHCE Series: Implementing HTTPS through TLS using Network Security Service (NSS) for Apache
|
||||
================================================================================
|
||||
If you are a system administrator who is in charge of maintaining and securing a web server, you can’t afford to not devote your very best efforts to ensure that data served by or going through your server is protected at all times.
|
||||
|
||||

|
||||
|
||||
RHCE Series: Implementing HTTPS through TLS using Network Security Service (NSS) for Apache – Part 8
|
||||
|
||||
In order to provide more secure communications between web clients and servers, the HTTPS protocol was born as a combination of HTTP and SSL (Secure Sockets Layer) or more recently, TLS (Transport Layer Security).
|
||||
|
||||
Due to some serious security breaches, SSL has been deprecated in favor of the more robust TLS. For that reason, in this article we will explain how to secure connections between your web server and clients using TLS.
|
||||
|
||||
This tutorial assumes that you have already installed and configured your Apache web server. If not, please refer to following article in this site before proceeding further.
|
||||
|
||||
- [Install LAMP (Linux, MySQL/MariaDB, Apache and PHP) on RHEL/CentOS 7][1]
|
||||
|
||||
### Installation of OpenSSL and Utilities ###
|
||||
|
||||
First off, make sure that Apache is running and that both http and https are allowed through the firewall:
|
||||
|
||||
# systemctl start http
|
||||
# systemctl enable http
|
||||
# firewall-cmd --permanent –-add-service=http
|
||||
# firewall-cmd --permanent –-add-service=https
|
||||
|
||||
Then install the necessary packages:
|
||||
|
||||
# yum update && yum install openssl mod_nss crypto-utils
|
||||
|
||||
**Important**: Please note that you can replace mod_nss with mod_ssl in the command above if you want to use OpenSSL libraries instead of NSS (Network Security Service) to implement TLS (which one to use is left entirely up to you, but we will use NSS in this article as it is more robust; for example, it supports recent cryptography standards such as PKCS #11).
|
||||
|
||||
Finally, uninstall mod_ssl if you chose to use mod_nss, or viceversa.
|
||||
|
||||
# yum remove mod_ssl
|
||||
|
||||
### Configuring NSS (Network Security Service) ###
|
||||
|
||||
After mod_nss is installed, its default configuration file is created as /etc/httpd/conf.d/nss.conf. You should then make sure that all of the Listen and VirtualHost directives point to port 443 (default port for HTTPS):
|
||||
|
||||
nss.conf – Configuration File
|
||||
|
||||
----------
|
||||
|
||||
Listen 443
|
||||
VirtualHost _default_:443
|
||||
|
||||
Then restart Apache and check whether the mod_nss module has been loaded:
|
||||
|
||||
# apachectl restart
|
||||
# httpd -M | grep nss
|
||||
|
||||

|
||||
|
||||
Check Mod_NSS Module Loaded in Apache
|
||||
|
||||
Next, the following edits should be made in `/etc/httpd/conf.d/nss.conf` configuration file:
|
||||
|
||||
1. Indicate NSS database directory. You can use the default directory or create a new one. In this tutorial we will use the default:
|
||||
|
||||
NSSCertificateDatabase /etc/httpd/alias
|
||||
|
||||
2. Avoid manual passphrase entry on each system start by saving the password to the database directory in /etc/httpd/nss-db-password.conf:
|
||||
|
||||
NSSPassPhraseDialog file:/etc/httpd/nss-db-password.conf
|
||||
|
||||
Where /etc/httpd/nss-db-password.conf contains ONLY the following line and mypassword is the password that you will set later for the NSS database:
|
||||
|
||||
internal:mypassword
|
||||
|
||||
In addition, its permissions and ownership should be set to 0640 and root:apache, respectively:
|
||||
|
||||
# chmod 640 /etc/httpd/nss-db-password.conf
|
||||
# chgrp apache /etc/httpd/nss-db-password.conf
|
||||
|
||||
3. Red Hat recommends disabling SSL and all versions of TLS previous to TLSv1.0 due to the POODLE SSLv3 vulnerability (more information [here][2]).
|
||||
|
||||
Make sure that every instance of the NSSProtocol directive reads as follows (you are likely to find only one if you are not hosting other virtual hosts):
|
||||
|
||||
NSSProtocol TLSv1.0,TLSv1.1
|
||||
|
||||
4. Apache will refuse to restart as this is a self-signed certificate and will not recognize the issuer as valid. For this reason, in this particular case you will have to add:
|
||||
|
||||
NSSEnforceValidCerts off
|
||||
|
||||
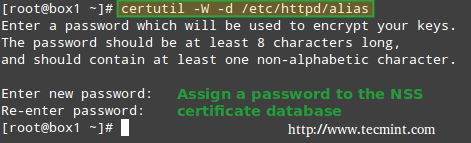
5. Though not strictly required, it is important to set a password for the NSS database:
|
||||
|
||||
# certutil -W -d /etc/httpd/alias
|
||||
|
||||
|
||||
|
||||
Set Password for NSS Database
|
||||
|
||||
### Creating a Apache SSL Self-Signed Certificate ###
|
||||
|
||||
Next, we will create a self-signed certificate that will identify the server to our clients (please note that this method is not the best option for production environments; for such use you may want to consider buying a certificate verified by a 3rd trusted certificate authority, such as DigiCert).
|
||||
|
||||
To create a new NSS-compliant certificate for box1 which will be valid for 365 days, we will use the genkey command. When this process completes:
|
||||
|
||||
# genkey --nss --days 365 box1
|
||||
|
||||
Choose Next:
|
||||
|
||||

|
||||
|
||||
Create Apache SSL Key
|
||||
|
||||
You can leave the default choice for the key size (2048), then choose Next again:
|
||||
|
||||

|
||||
|
||||
Select Apache SSL Key Size
|
||||
|
||||
Wait while the system generates random bits:
|
||||
|
||||

|
||||
|
||||
Generating Random Key Bits
|
||||
|
||||
To speed up the process, you will be prompted to enter random text in your console, as shown in the following screencast. Please note how the progress bar stops when no input from the keyboard is received. Then, you will be asked to:
|
||||
|
||||
1. Whether to send the Certificate Sign Request (CSR) to a Certificate Authority (CA): Choose No, as this is a self-signed certificate.
|
||||
|
||||
2. to enter the information for the certificate.
|
||||
|
||||
注:youtube 视频
|
||||
<iframe width="720" height="405" frameborder="0" src="//www.youtube.com/embed/mgsfeNfuurA" allowfullscreen="allowfullscreen"></iframe>
|
||||
|
||||
Finally, you will be prompted to enter the password to the NSS certificate that you set earlier:
|
||||
|
||||
# genkey --nss --days 365 box1
|
||||
|
||||

|
||||
|
||||
Apache NSS Certificate Password
|
||||
|
||||
At anytime, you can list the existing certificates with:
|
||||
|
||||
# certutil –L –d /etc/httpd/alias
|
||||
|
||||

|
||||
|
||||
List Apache NSS Certificates
|
||||
|
||||
And delete them by name (only if strictly required, replacing box1 by your own certificate name) with:
|
||||
|
||||
# certutil -d /etc/httpd/alias -D -n "box1"
|
||||
|
||||
if you need to.c
|
||||
|
||||
### Testing Apache SSL HTTPS Connections ###
|
||||
|
||||
Finally, it’s time to test the secure connection to our web server. When you point your browser to https://<web server IP or hostname>, you will get the well-known message “This connection is untrusted“:
|
||||
|
||||

|
||||
|
||||
Check Apache SSL Connection
|
||||
|
||||
In the above situation, you can click on Add Exception and then Confirm Security Exception – but don’t do it yet. Let’s first examine the certificate to see if its details match the information that we entered earlier (as shown in the screencast).
|
||||
|
||||
To do so, click on View… –> Details tab above and you should see this when you select Issuer from the list:
|
||||
|
||||

|
||||
|
||||
Confirm Apache SSL Certificate Details
|
||||
|
||||
Now you can go ahead, confirm the exception (either for this time or permanently) and you will be taken to your web server’s DocumentRoot directory via https, where you can inspect the connection details using your browser’s builtin developer tools:
|
||||
|
||||
In Firefox you can launch it by right clicking on the screen, and choosing Inspect Element from the context menu, specifically through the Network tab:
|
||||
|
||||

|
||||
|
||||
Inspect Apache HTTPS Connection
|
||||
|
||||
Please note that this is the same information as displayed before, which was entered during the certificate previously. There’s also a way to test the connection using command line tools:
|
||||
|
||||
On the left (testing SSLv3):
|
||||
|
||||
# openssl s_client -connect localhost:443 -ssl3
|
||||
|
||||
On the right (testing TLS):
|
||||
|
||||
# openssl s_client -connect localhost:443 -tls1
|
||||
|
||||

|
||||
|
||||
Testing Apache SSL and TLS Connections
|
||||
|
||||
Refer to the screenshot above for more details.
|
||||
|
||||
### Summary ###
|
||||
|
||||
As I’m sure you already know, the presence of HTTPS inspires trust in visitors who may have to enter personal information in your site (from user names and passwords all the way to financial / bank account information).
|
||||
|
||||
In that case, you will want to get a certificate signed by a trusted Certificate Authority as we explained earlier (the steps to set it up are identical with the exception that you will need to send the CSR to a CA, and you will get the signed certificate back); otherwise, a self-signed certificate as the one used in this tutorial will do.
|
||||
|
||||
For more details on the use of NSS, please refer to the online help about [mod-nss][3]. And don’t hesitate to let us know if you have any questions or comments.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.tecmint.com/create-apache-https-self-signed-certificate-using-nss/
|
||||
|
||||
作者:[Gabriel Cánepa][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.tecmint.com/install-lamp-in-centos-7/
|
||||
[1]:http://www.tecmint.com/author/gacanepa/
|
||||
[2]:https://access.redhat.com/articles/1232123
|
||||
[3]:https://git.fedorahosted.org/cgit/mod_nss.git/plain/docs/mod_nss.html
|
||||
@ -0,0 +1,210 @@
|
||||
RHCE 系列: 使用网络安全服务(NSS)为 Apache 通过 TLS 实现 HTTPS
|
||||
================================================================================
|
||||
如果你是一个负责维护和确保 web 服务器安全的系统管理员,你不能不花费最大的精力确保服务器中处理和通过的数据任何时候都受到保护。
|
||||

|
||||
|
||||
RHCE 系列:第八部分 - 使用网络安全服务(NSS)为 Apache 通过 TLS 实现 HTTPS
|
||||
|
||||
为了在客户端和服务器之间提供更安全的连接,作为 HTTP 和 SSL(安全套接层)或者最近称为 TLS(传输层安全)的组合,产生了 HTTPS 协议。
|
||||
|
||||
由于一些严重的安全漏洞,SSL 已经被更健壮的 TLS 替代。由于这个原因,在这篇文章中我们会解析如何通过 TLS 实现你 web 服务器和客户端之间的安全连接。
|
||||
|
||||
这里假设你已经安装并配置好了 Apache web 服务器。如果还没有,在进入下一步之前请阅读下面站点中的文章。
|
||||
|
||||
- [在 RHEL/CentOS 7 上安装 LAMP(Linux,MySQL/MariaDB,Apache 和 PHP)][1]
|
||||
|
||||
### 安装 OpenSSL 和一些工具包 ###
|
||||
|
||||
首先,确保正在运行 Apache 并且允许 http 和 https 通过防火墙:
|
||||
|
||||
# systemctl start http
|
||||
# systemctl enable http
|
||||
# firewall-cmd --permanent –-add-service=http
|
||||
# firewall-cmd --permanent –-add-service=https
|
||||
|
||||
然后安装一些必须软件包:
|
||||
|
||||
# yum update && yum install openssl mod_nss crypto-utils
|
||||
|
||||
**重要**:请注意如果你想使用 OpenSSL 库而不是 NSS(网络安全服务)实现 TLS,你可以在上面的命令中用 mod\_ssl 替换 mod\_nss(使用哪一个取决于你,但在这篇文章中由于更加健壮我们会使用 NSS;例如,它支持最新的加密标准,比如 PKCS #11)。
|
||||
|
||||
如果你使用 mod\_nss,首先要卸载 mod\_ssl,反之如此。
|
||||
|
||||
# yum remove mod_ssl
|
||||
|
||||
### 配置 NSS(网络安全服务)###
|
||||
|
||||
安装完 mod\_nss 之后,会创建默认的配置文件 /etc/httpd/conf.d/nss.conf。你应该确保所有 Listen 和 VirualHost 指令都指向 443 号端口(HTTPS 默认端口):
|
||||
|
||||
nss.conf – 配置文件
|
||||
|
||||
----------
|
||||
|
||||
Listen 443
|
||||
VirtualHost _default_:443
|
||||
|
||||
然后重启 Apache 并检查是否加载了 mod\_nss 模块:
|
||||
|
||||
# apachectl restart
|
||||
# httpd -M | grep nss
|
||||
|
||||

|
||||
|
||||
检查 Apache 是否加载 mod\_nss 模块
|
||||
|
||||
下一步,在 `/etc/httpd/conf.d/nss.conf` 配置文件中做以下更改:
|
||||
|
||||
1. 指定 NSS 数据库目录。你可以使用默认的目录或者新建一个。本文中我们使用默认的:
|
||||
|
||||
NSSCertificateDatabase /etc/httpd/alias
|
||||
|
||||
2. 通过保存密码到数据库目录中的 /etc/httpd/nss-db-password.conf 文件避免每次系统启动时要手动输入密码:
|
||||
|
||||
NSSPassPhraseDialog file:/etc/httpd/nss-db-password.conf
|
||||
|
||||
其中 /etc/httpd/nss-db-password.conf 只包含以下一行,其中 mypassword 是后面你为 NSS 数据库设置的密码:
|
||||
|
||||
internal:mypassword
|
||||
|
||||
另外,要设置该文件的权限和属主为 0640 和 root:apache:
|
||||
|
||||
# chmod 640 /etc/httpd/nss-db-password.conf
|
||||
# chgrp apache /etc/httpd/nss-db-password.conf
|
||||
|
||||
3. 由于 POODLE SSLv3 漏洞,红帽建议停用 SSL 和 TLSv1.0 之前所有版本的 TLS(更多信息可以查看[这里][2])。
|
||||
|
||||
确保 NSSProtocol 指令的每个实例都类似下面一样(如果你没有托管其它虚拟主机,很可能只有一条):
|
||||
|
||||
NSSProtocol TLSv1.0,TLSv1.1
|
||||
|
||||
4. 由于这是一个自签名证书,Apache 会拒绝重启,并不会识别为有效发行人。由于这个原因,对于这种特殊情况我们还需要添加:
|
||||
|
||||
NSSEnforceValidCerts off
|
||||
|
||||
5. 虽然并不是严格要求,为 NSS 数据库设置一个密码同样很重要:
|
||||
|
||||
# certutil -W -d /etc/httpd/alias
|
||||
|
||||

|
||||
|
||||
为 NSS 数据库设置密码
|
||||
|
||||
### 创建一个 Apache SSL 自签名证书 ###
|
||||
|
||||
下一步,我们会创建一个自签名证书为我们的客户机识别服务器(请注意这个方法对于生产环境并不是最好的选择;对于生产环境你应该考虑购买第三方可信证书机构验证的证书,例如 DigiCert)。
|
||||
|
||||
我们用 genkey 命令为 box1 创建有效期为 365 天的 NSS 兼容证书。完成这一步后:
|
||||
|
||||
# genkey --nss --days 365 box1
|
||||
|
||||
选择 Next:
|
||||
|
||||

|
||||
|
||||
创建 Apache SSL 密钥
|
||||
|
||||
你可以使用默认的密钥大小(2048),然后再次选择 Next:
|
||||
|
||||

|
||||
|
||||
选择 Apache SSL 密钥大小
|
||||
|
||||
等待系统生成随机比特:
|
||||
|
||||

|
||||
|
||||
生成随机密钥比特
|
||||
|
||||
为了加快速度,会提示你在控制台输入随机字符,正如下面的截图所示。请注意当没有从键盘接收到输入时进度条是如何停止的。然后,会让你选择:
|
||||
|
||||
1. 是否发送验证签名请求(CSR)到一个验证机构(CA):选择 No,因为这是一个自签名证书。
|
||||
|
||||
2. 为证书输入信息。
|
||||
|
||||
注:youtube 视频
|
||||
<iframe width="720" height="405" frameborder="0" src="//www.youtube.com/embed/mgsfeNfuurA" allowfullscreen="allowfullscreen"></iframe>
|
||||
|
||||
最后,会提示你输入之前设置的密码到 NSS 证书:
|
||||
|
||||
# genkey --nss --days 365 box1
|
||||
|
||||

|
||||
|
||||
Apache NSS 证书密码
|
||||
|
||||
在任何时候你都可以用以下命令列出现有的证书:
|
||||
|
||||
# certutil –L –d /etc/httpd/alias
|
||||
|
||||

|
||||
|
||||
列出 Apache NSS 证书
|
||||
|
||||
然后通过名字删除(除非严格要求,用你自己的证书名称替换 box1):
|
||||
|
||||
# certutil -d /etc/httpd/alias -D -n "box1"
|
||||
|
||||
如果你需要继续的话:
|
||||
|
||||
### 测试 Apache SSL HTTPS 连接 ###
|
||||
|
||||
最后,是时候测试到我们服务器的安全连接了。当你用浏览器打开 https://<web 服务器 IP 或主机名\>,你会看到著名的信息 “This connection is untrusted”:
|
||||
|
||||

|
||||
|
||||
检查 Apache SSL 连接
|
||||
|
||||
在上面的情况中,你可以点击添加例外(Add Exception) 然后确认安全例外(Confirm Security Exception) - 但先不要这么做。让我们首先来看看证书看它的信息是否和我们之前输入的相符(如截图所示)。
|
||||
|
||||
要做到这点,点击上面的视图(View...)-> 详情(Details)选项卡,当你从列表中选择发行人你应该看到这个:
|
||||
|
||||

|
||||
|
||||
确认 Apache SSL 证书详情
|
||||
|
||||
现在你继续,确认例外(限于此次或永久),然后会通过 https 把你带到你 web 服务器的 DocumentRoot 目录,在这里你可以使用你浏览器自带的开发者工具检查连接详情:
|
||||
|
||||
在火狐浏览器中,你可以通过在屏幕中右击然后从上下文菜单中选择检查元素(Inspect Element)启动,尤其是通过网络选项卡:
|
||||
|
||||

|
||||
|
||||
检查 Apache HTTPS 连接
|
||||
|
||||
请注意这和之前显示的在验证过程中输入的信息一致。还有一种方式通过使用命令行工具测试连接:
|
||||
|
||||
左边(测试 SSLv3):
|
||||
|
||||
# openssl s_client -connect localhost:443 -ssl3
|
||||
|
||||
右边(测试 TLS):
|
||||
|
||||
# openssl s_client -connect localhost:443 -tls1
|
||||
|
||||

|
||||
|
||||
测试 Apache SSL 和 TLS 连接
|
||||
|
||||
参考上面的截图了解更相信信息。
|
||||
|
||||
### 总结 ###
|
||||
|
||||
我确信你已经知道,使用 HTTPS 会增加会在你站点中输入个人信息的访客的信任(从用户名和密码到任何商业/银行账户信息)。
|
||||
|
||||
在那种情况下,你会希望获得由可信验证机构签名的证书,正如我们之前解释的(启用的步骤和发送 CSR 到 CA 然后获得签名证书的例子相同);另外的情况,就是像我们的例子中一样使用自签名证书。
|
||||
|
||||
要获取更多关于使用 NSS 的详情,可以参考关于 [mod-nss][3] 的在线帮助。如果你有任何疑问或评论,请告诉我们。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.tecmint.com/create-apache-https-self-signed-certificate-using-nss/
|
||||
|
||||
作者:[Gabriel Cánepa][a]
|
||||
译者:[ictlyh](http://www.mutouxiaogui.cn/blog/)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.tecmint.com/install-lamp-in-centos-7/
|
||||
[1]:http://www.tecmint.com/author/gacanepa/
|
||||
[2]:https://access.redhat.com/articles/1232123
|
||||
[3]:https://git.fedorahosted.org/cgit/mod_nss.git/plain/docs/mod_nss.html
|
||||
Loading…
Reference in New Issue
Block a user