mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-02-25 00:50:15 +08:00
commit
770ab380c0
@ -1,94 +0,0 @@
|
||||
[Being translated by bazz2]
|
||||
How to Set Up Secure Remote Networking with OpenVPN on Linux, Part 2
|
||||
================================================================================
|
||||
Greetings fellow Linux users, and welcome to the second part of our glorious OpenVPN series. When last we met we learned how to set up a [simple OpenVPN encrypted tunnel][1] between a home server and a remote node, such as a laptop. Today we're adding refinements such as how to daemonize OpenVPN so we don't have to start it manually, use Network Manager for easy connecting to our remote server, and access services.
|
||||
|
||||
### Network Manager Integration ###
|
||||
|
||||
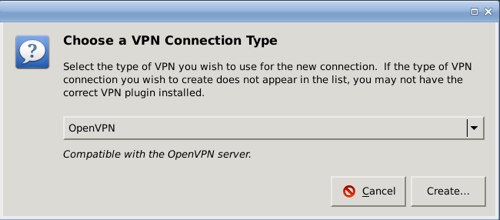
Network Manager is a nice OpenVPN client; just make sure you have the network-manager-openvpn plugin installed. We'll use our example configurations from part 1. Open your Network Manager configuration and find the window where you set up a new VPN connection. This looks different on KDE and GNOME, but the information you'll need is the same. When you start you need to see an OpenVPN connection type, like in figure 1; if you don't see this then the plugin is missing. (The figures are from GNOME.)
|
||||
|
||||
|
||||
|
||||
*Figure 1: Creating a new OpenVPN client config in Network Manager.*
|
||||
|
||||
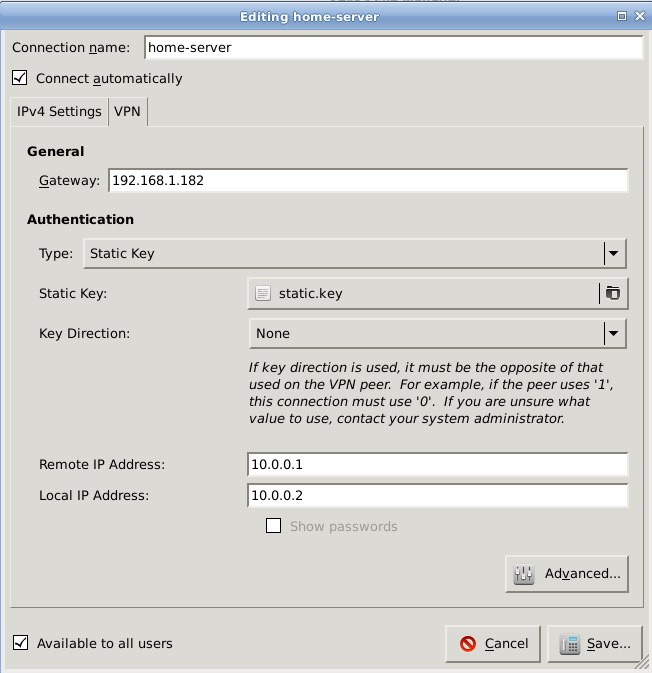
Figure 2 shows the main configuration screen. Starting from the top:
|
||||
|
||||
- Whatever name you want for this connection.
|
||||
- The Gateway is the IP address of your remote server.
|
||||
- Select Static Key from the dropdown menu,
|
||||
- Then use the filepicker to find the key you want to use.
|
||||
- This is not a directional key, so select None.
|
||||
- The remote and local IP addresses are your virtual OpenVPN addresses, from your /etc/openvpn/foo.conf files.
|
||||
- We did not set a password.
|
||||
- "Available to all users" or just you, whichever you want.
|
||||
|
||||
|
||||
|
||||
*Figure 2: Main Network Manager configuration for OpenVN client.*
|
||||
|
||||
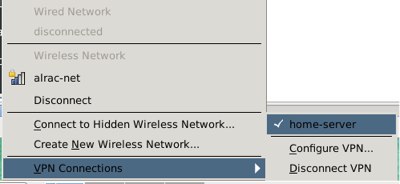
Save, and then use Network Manager to connect. Easy peasey! Now you can connect and disconnect with the click of a button (figure 3).
|
||||
|
||||
|
||||
|
||||
### Run OpenVPN Automatically ###
|
||||
|
||||
It's simple to start up OpenVPN manually, but you might want to daemonize it on your server for convenience, and to survive accidental reboots. On Debian/Ubuntu/great-thundering-herd-of-spawn distros this is handled automatically: when you install OpenVPN it's configured to automatically start at boot. So, after installation you need to reboot, or start the daemon with one of these commands:
|
||||
|
||||
$ sudo /etc/init.d/openvpn start
|
||||
$ sudo service openvpn start
|
||||
|
||||
The first command is the old-fashioned way, and the second command uses the service command. service first appeared in Red Hat Linux back in the olden days, and if your distro doesn't install it by default it's probably lurking in the repos if you want to use it.
|
||||
|
||||
Fedora uses the systemd init system, in contrast to Ubuntu which uses Upstart, and Debian still uses good old SysV init. If you have multiple OpenVPN configurations in /etc/openvpn you can start each one selectively in systemd, like this:
|
||||
|
||||
# systemctl start systemctl start openvpn@studio.service
|
||||
|
||||
Where "studio.service" references our example /etc/openvpn/studio.conf file from part one. This invocation does not survive a reboot, so it's just like running openvpn /etc/openvpn/studio.conf, which is how we started OpenVPN sessions manually in part 1. You should be able to daemonize OpenVPN on systemd with chkconfig:
|
||||
|
||||
# service openvpn start
|
||||
# chkconfig openvpn on
|
||||
|
||||
That should daemonize OpenVPN in the usual way, which is as a monolithic daemon and not individually per .conf file in /etc/openvpn/. systemd supports the chkconfig and servicecommands so it should work. However, the distros that use systemd are quite variable, so if yours is different please let us know in the comments.
|
||||
|
||||
### Strengthening Your Connection ###
|
||||
|
||||
OpenVPN is robust and is good at maintaining a persistent connection, even with service interruptions. You can make your connection even stronger by adding these lines to your .conf files on clients and server:
|
||||
|
||||
persist-tun
|
||||
persist-key
|
||||
|
||||
These are helpful for laptop users who disrupt their connection a lot with power-save and being on the move.
|
||||
|
||||
### Now What? ###
|
||||
|
||||
Now that you have this all set up and working, what do you do with it? If you're used to using OpenSSH for remote operations you might be stuck in the SSH mindset of being able to log into specific machines and run applications. It doesn't work that way. Rather, think of OpenVPN as a virtual Ethernet cable to your server or LAN, all wrapped in a nice stout layer of encryption. You can run unencrypted and encrypted services over the same tunnel, and you only have to open a single hole in your firewall.
|
||||
|
||||
So you can run SSH in the way you're used to over your OpenVPN tunnel, and do remote administration and run applications. You can access network resources such as fileshares and Web applications. You can force all networking on the client to go through your VPN tunnel, but for this series I've assumed that you want to be able to use both your native and VPN networks.
|
||||
|
||||
So there you are on your trusty laptop and you can surf the Web, run SSH, do whatever you want on whatever network you're connected to. Then when you want to run something over your OpenVPN tunnel open it up and specify the IP address, like this:
|
||||
|
||||
$ ssh carla@10.0.0.1
|
||||
|
||||
Web applications are easy: point your Web browser to the virtual IP address of your OpenVPN server and log in as usual. For example, I run various Web services for testing on my home server. So I access Drupal at [http://10.0.0.1/drupal][2] and OwnCloud at [http://10.0.0.1/owncloud][3]. I use the nice gFTP graphical FTP client, so all I need to connect is the virtual IP address on the Host line, username, and password. Or use the command line:
|
||||
|
||||
$ ftp 10.0.0.1 21
|
||||
|
||||
You can administer your MySQL database from afar, using your own username and password:
|
||||
|
||||
$ mysql -h 10.0.0.1 -u admin -p
|
||||
|
||||
So the main thing you need to know is how to add the host specification to whatever command you want to run.
|
||||
|
||||
Obviously, this would all be easier with name services instead of having to use IP addresses, so one of these days we'll learn how to implement name services in OpenVPN. Meanwhile, please enjoy your nice secure OpenVPN tunnel.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linux.com/learn/tutorials/745233-how-to-set-up-secure-remote-networking-with-openvpn-on-linux-part-2
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.linux.com/learn/tutorials/743590-secure-remote-networking-with-openvpn-on-linux
|
||||
[2]:http://10.0.0.1/drupal
|
||||
[3]:http://10.0.0.1/owncloud
|
||||
@ -0,0 +1,93 @@
|
||||
OpenVPN 安全手册[part 2]
|
||||
================================================================================
|
||||
欢迎你们回来继续看我们的 OpenVPN 系列的第二部分。上次我们讲到如何让远端计算机(如笔记本电脑)[通过简单的加密隧道]登录到家里的服务器。今天我们接着讲进阶部分:比如设置 OpenVPN 开机启动,省得我们每次重启服务器的时候都要手动开启 OpenVPN 服务;比如使用 Network Manager 简化访问到远程服务器的过程。
|
||||
|
||||
### 整合到 Network Manager ###
|
||||
|
||||
Network Manager 是一个不错的 OpenVPN 客户端;你只需要安装 network-manager-openvpn 这个插件。我们继续《OpenVPN 安全手册》第一部分使用的配置。打开 Network Manager 配置界面,进入“新建 VPN 连接”的窗口。这个界面布局在 KDE 和 GNOME 下面看起来有点不一样,但是大体的信息是一样的。开始的时候你需要选择 OpenVPN 作为你的 VPN 连接类型,就像图1所示;如果你没看到 OpenVPN 的选项,说明你没有安装好插件。(图1是一张 GNOME 下面的图片。)
|
||||
|
||||

|
||||
|
||||
*图1:在 Network Manager 上新建 OpenVPN 客户端 *
|
||||
|
||||
图2显示了配置主界面。从上到下分别为:
|
||||
|
||||
- 连接名,任取一个。
|
||||
- 远程服务器的网关。
|
||||
- 下拉菜单选择静态密钥(Static Key)。
|
||||
- 然后通过文件浏览器找到静态密钥文件。
|
||||
- 这个不是方向性的密钥,所以 Key Direction 这里设为 None。
|
||||
- 远程 IP 和 本地 IP 是我们在上一部分已经设置好的虚拟 OpenVPN 地址,可分别通过 /etc/openvpn/studio.conf 和 /etc/openvpn/shop.conf 文件获得。
|
||||
- 我们无需设置密码,所以“Show passwords”复选框为空。
|
||||
- 这个连接是“所有人都可用”,还是只有你可用,随你喜欢。
|
||||
|
||||

|
||||
|
||||
*图2:Network Manager 配置 OpenVPN 客户端主界面*
|
||||
|
||||
保存然后就可以使用 Network Manager 建立连接了。So easy,妈妈再也不用担心你的学习了!看见图3了么?你现在只需点击一下高亮的按钮就可以连接到你的家庭服务器,或从你的家庭服务器中断开连接。
|
||||
|
||||

|
||||
|
||||
### OpenVPN 开机启动 ###
|
||||
|
||||
手动开启 OpenVPN 很简单,但是你也许想要更简单,让它能够在服务器重启的时候跟着自动启动。在 Debian/Ubuntu 以及绝大部分发行版中,当你安装完 OpenVPN 的时候就被设置为开机启动的。所以你需要重启系统,或者按下面的方法启动后台进程:
|
||||
|
||||
$ sudo /etc/init.d/openvpn start
|
||||
$ sudo service openvpn start
|
||||
|
||||
第一个命令是比较老的启动方法,第二个命令使用了“service”命令。“service”命令第一次出现在 Red Hat 发行版中,如果你的发行版中没有安装这个命令,你需要从你的软件源里面去找到它。
|
||||
|
||||
Ubuntu 使用 Upstart 管理服务进程,Debain 使用的老的 SysV,而 Fedora 使用“systemd”。如果你在 /etc/openvpn 目录下配置了多个 OpenVPN 的服务,你可以通过“systemd”的命令启动你要的服务:
|
||||
|
||||
# systemctl start openvpn@studio.service
|
||||
|
||||
这里的“studio.service”与我们在第一部分讲过的例子中的 /etc/openvpn/studio.conf 配置的服务相对应。用这些方法启动的后台进程,在系统重启后会失效,所以这些方法都和第一部分讲的启动方式一样,仅能使 OpenVPN 运行一次。你可以将启动 OpenVPN 进程的任务交给 chkconfig:
|
||||
|
||||
# service openvpn start
|
||||
# chkconfig openvpn on
|
||||
|
||||
上面列出的是启动 OpenVPN 后台进程最常见的方式,这个命令启动了一整个进程,而不是对 /etc/openvpn/下面的所有 .conf 配置文件都维护一个进程。systemd 支持chkconfig 以及 service 命令,所以上面两条命令能够正常工作。然而使用 systemd 的发行版非常多,如果你的工作环境和我们的不一样,请通过发表评论的方式通知我们。
|
||||
|
||||
### 强化你的连接 ###
|
||||
|
||||
OpenVPN 的健壮性足够维持一条持久的连接,即使服务宕掉。而你可以令这个连接变得更加稳定,只需要在服务器端和客户端的 .conf 文件内添加下面两条属性:
|
||||
|
||||
persist-tun
|
||||
persist-key
|
||||
|
||||
这两条属性对于那些笔记本电脑用户来说非常有用,他们的电脑会因为电源保护或需要移来移去而经常断开 OpenVPN 的连接。
|
||||
|
||||
### 现在,该做些什么? ###
|
||||
|
||||
你已经完成了所有设置,并且你的服务工作正常,你接下来能用这个干点什么?如果你以前一直用 OpenSSH 来远程你的服务器,你会有这样的思维定势:你可以利用 OpenVPN 登录到远程机器,然后跑上面的应用。你要是那样做,就太浪费 OpenVPN 了。你可以将 OpenVPN 想像成是一条虚拟的以太网电缆接到你的服务器上或者是你的局域网内,这条电缆还包着厚厚的加密保护。你可以在它提供的隧道上跑任何加密的不加密的服务,并且只需要在防火墙上开一个端口。
|
||||
|
||||
所以你可以利用 OpenVPN 隧道来建立 SSH 连接,然后远程到服务器,然后在服务器上跑应用。你可以访问到网络资源,比如文件共享和 Web 应用。你可以强制让你的电脑通过 VPN 隧道访问到网络,但我认为你会想要同时能够使用本地网络和 VPN 网络的。
|
||||
|
||||
所以,在你的笔记本上你可以上网冲浪,使用 SSH,做你想做的任何事,上你想上的任何网络。当你想利用 OpenVPN 隧道做一些事情时,你只需要打开它,然后输入 IP 地址:
|
||||
|
||||
$ ssh carla@10.0.0.1
|
||||
|
||||
对于一些 Web 服务,操作也简单:让你的 Web 浏览器访问到 OpenVPN 的 IP 地址然后登录进去。举个例子,我在我家的服务器上跑了多个 Web 服务做测试,我可以通过[http://10.0.0.1/drupal][2]访问 Drupal,可以通过[http://10.0.0.1/owncloud][3]访问 OwnCloud。我电脑上有优秀的图形界面 FTP 客户端 gFTP,所以只需要填入 IP 地址、用户名、密码就能访问到 FTP 服务器,或者使用下面的命令:
|
||||
|
||||
$ ftp 10.0.0.1 21
|
||||
|
||||
你可以远程管理你的 MySQL 数据库,输入帐号密码:
|
||||
|
||||
$ mysql -h 10.0.0.1 -u admin -p
|
||||
|
||||
所以最重要的是你要知道怎么去配置一个你想要玩的功能。
|
||||
|
||||
很显然,当我们使用名称服务(name service)时,会比直接使用 IP 地址更方便。所以某一天我们可以学学如何在 OpenVPN 上布署一个名称服务。现在,先享受一下 OpenVPN 带给你的乐趣吧。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linux.com/learn/tutorials/745233-how-to-set-up-secure-remote-networking-with-openvpn-on-linux-part-2
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.linux.com/learn/tutorials/743590-secure-remote-networking-with-openvpn-on-linux
|
||||
[2]:http://10.0.0.1/drupal
|
||||
[3]:http://10.0.0.1/owncloud
|
||||
Loading…
Reference in New Issue
Block a user