mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-03-03 01:10:13 +08:00
commit
70aed9afcd
@ -1,14 +1,15 @@
|
||||
在Apache中使用Mod_Security和Mod_evasive来抵御暴力破解和DDos攻击
|
||||
在Apache中使用mod\_security和mod\_evasive来抵御暴力破解和DDos攻击
|
||||
================================================================================
|
||||
对于那些托管主机或者需要将您的主机暴露在因特网中的人来说,保证您的系统在面对攻击时安全是一个重要的事情。
|
||||
|
||||
mod_security(一个开源的可以无缝接入Web服务器的用于Web应用入侵检测和防护的引擎)和mod_evasive是两个在服务器端对抗暴力破解和(D)Dos攻击的非常重要的工具。
|
||||
对于那些需要在因特网上提供服务或托管主机的人来说,保证您的系统在面对攻击时的安全是一个重要的事情。
|
||||
|
||||
mod_evasive,如它的名字一样,在受攻击时提供避实就虚的功能,它像一个雨伞一样保护Web服务器免受那些威胁。
|
||||
mod\_security(一个开源的用于Web应用入侵检测及防护的引擎,可以无缝地集成到Web服务器)和mod\_evasive是两个在服务器端对抗暴力破解和(D)Dos攻击的非常重要的工具。
|
||||
|
||||
mod\_evasive,如它的名字一样,在受攻击时提供避实就虚的功能,它像一个雨伞一样保护Web服务器免受那些威胁。
|
||||
|
||||

|
||||
|
||||
安装Mod_Security和Mod_Evasive来保护Apache
|
||||
*安装mod\_security和mod\_evasive来保护Apache*
|
||||
|
||||
在这篇文章中我们将讨论如何安装、配置以及在RHEL/CentOS6、7和Fedora 21-15上将它们整合到Apache。另外,我们会模拟攻击以便验证服务器做出了正确的反应。
|
||||
|
||||
@ -16,91 +17,77 @@ mod_evasive,如它的名字一样,在受攻击时提供避实就虚的功能
|
||||
|
||||
- [在RHEL/CentOS 7中安装LAMP][1]
|
||||
|
||||
如果您在运行RHEL/CentOS 7或Fedora 21,您还需要安装iptables作为默认[防火墙][2]前端以取代firewalld。这样做是为了在RHEL/CentOS 7或Fedora 21中使用同样的工具。
|
||||
(LCTT 译注:本文有修改。原文为了在RHEL/CentOS 7或Fedora 21中使用同样的工具,而删除了自带的 firewalld,使用了旧式的iptables。译者以为这样并不恰当,因此,译文中做了相应删节,并增加了firewalld的相应脚本。)
|
||||
|
||||
### 步骤 1: 在RHEL/CentOS 7和Fedora 21上安装Iptables防火墙 ###
|
||||
|
||||
用下面的命令停止和禁用firewalld:
|
||||
|
||||
# systemctl stop firewalld
|
||||
# systemctl disable firewalld
|
||||
|
||||

|
||||
禁用firewalld服务
|
||||
|
||||
接下来在使能iptables之前安装iptables-services包:
|
||||
|
||||
# yum update && yum install iptables-services
|
||||
# systemctl enable iptables
|
||||
# systemctl start iptables
|
||||
# systemctl status iptables
|
||||
|
||||

|
||||
安装Iptables防火墙
|
||||
|
||||
### 步骤 2: 安装Mod_Security和Mod_evasive ###
|
||||
### 步骤 1: 安装mod\_security和mod\_evasive ###
|
||||
|
||||
另外,在安装LAMP后,您还需要在RHEL/CentOS 7/6中[开启EPEL仓库][3]来安装这两个包。Fedora用户不需要开启这个仓库,因为epel已经是Fedora项目的一部分了。
|
||||
|
||||
# yum update && yum install mod_security mod_evasive
|
||||
|
||||
当安装结束后,您会在/etc/httpd/conf.d下找到两个工具的配置文件。
|
||||
当安装结束后,您会在/etc/httpd/conf.d下找到这两个工具的配置文件。
|
||||
|
||||
# ls -l /etc/httpd/conf.d
|
||||
|
||||

|
||||
mod_security + mod_evasive 配置文件
|
||||
|
||||
现在,为了整合这两个模块到Apache,并在启动时加载它们。请确保下面几行出现在mod_evasive.conf和mod_security.conf的顶层部分,它们分别为:
|
||||
*mod\_security + mod\_evasive 配置文件*
|
||||
|
||||
现在,为了整合这两个模块到Apache,并在启动时加载它们。请确保下面几行出现在mod\_evasive.conf和mod\_security.conf的顶层部分,它们分别为:
|
||||
|
||||
LoadModule evasive20_module modules/mod_evasive24.so
|
||||
LoadModule security2_module modules/mod_security2.so
|
||||
|
||||
请注意modules/mod_security2.so和modules/mod_evasive24.so都是从/etc/httpd到模块源文件的相对路径。您可以通过列出/etc/httpd/modules的内容来验证(如果需要的话,修改它):
|
||||
请注意modules/mod\_security2.so和modules/mod\_evasive24.so都是从/etc/httpd到模块源文件的相对路径。您可以通过列出/etc/httpd/modules的内容来验证(如果需要的话,修改它):
|
||||
|
||||
# cd /etc/httpd/modules
|
||||
# pwd
|
||||
# ls -l | grep -Ei '(evasive|security)'
|
||||
|
||||
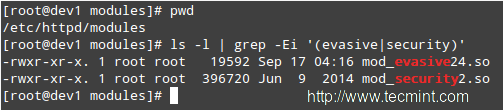
|
||||
验证mod_security + mod_evasive模块
|
||||
|
||||
接下来重启Apache并且核实它已加载了mod_evasive和mod_security:
|
||||
*验证mod\_security + mod\_evasive模块*
|
||||
|
||||
接下来重启Apache并且核实它已加载了mod\_evasive和mod\_security:
|
||||
|
||||
# service httpd restart [在RHEL/CentOS 6和Fedora 20-18上]
|
||||
# systemctl restart httpd [在RHEL/CentOS 7和Fedora 21上]
|
||||
|
||||
----------
|
||||
|
||||
[输出已加载的静态模块和动态模块列表]
|
||||
|
||||
# httpd -M | grep -Ei '(evasive|security)'
|
||||
# httpd -M | grep -Ei '(evasive|security)' [输出已加载的静态模块和动态模块列表]
|
||||
|
||||
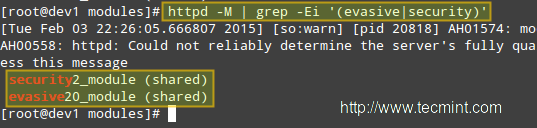
|
||||
检查mod_security + mod_evasive模块已加载
|
||||
|
||||
### 步骤 3: 安装一个核心规则集并且配置Mod_Security ###
|
||||
*检查mod\_security + mod\_evasive模块已加载*
|
||||
|
||||
简单来说,一个核心规则集(即CRS)为web服务器提供特定状况下如何反应的指令。mod_security的开发者们提供了一个免费的CRS,叫做OWASP([开放Web应用安全项目])ModSecurity CRS,可以从下面的地址下载和安装。
|
||||
### 步骤 2: 安装一个核心规则集并且配置mod\_security ###
|
||||
|
||||
1. 下载OWASP CRS到为之创建的目录
|
||||
简单来说,一个核心规则集(即CRS)为web服务器提供特定状况下如何反应的指令。mod\_security的开发者们提供了一个免费的CRS,叫做OWASP([开放Web应用安全项目])ModSecurity CRS,可以从下面的地址下载和安装。
|
||||
|
||||
# mkdir /etc/httpd/crs-tecmint
|
||||
# cd /etc/httpd/crs-tecmint
|
||||
####下载OWASP CRS到为之创建的目录####
|
||||
|
||||
# mkdir /etc/httpd/crs-tecmint
|
||||
# cd /etc/httpd/crs-tecmint
|
||||
# wget https://github.com/SpiderLabs/owasp-modsecurity-crs/tarball/master
|
||||
|
||||

|
||||
下载mod_security核心规则
|
||||
|
||||
2. 解压CRS文件并修改文件夹名称
|
||||
*下载mod\_security核心规则*
|
||||
|
||||
#### 解压CRS文件并修改文件夹名称####
|
||||
|
||||
# tar xzf master
|
||||
# mv SpiderLabs-owasp-modsecurity-crs-ebe8790 owasp-modsecurity-crs
|
||||
|
||||

|
||||
解压mod_security核心规则
|
||||
|
||||
3. 现在,是时候配置mod_security了。将同样的规则文件(owasp-modsecurity-crs/modsecurity_crs_10_setup.conf.example)拷贝至另一个没有.example扩展的文件。
|
||||

|
||||
|
||||
*解压mod\_security核心规则*
|
||||
|
||||
####现在,是时候配置mod\_security了####
|
||||
|
||||
将示例的规则文件(owasp-modsecurity-crs/modsecurity_crs_10_setup.conf.example)拷贝为同名的配置文件。
|
||||
|
||||
# cp modsecurity_crs_10_setup.conf.example modsecurity_crs_10_setup.conf
|
||||
|
||||
@ -111,7 +98,7 @@ mod_security + mod_evasive 配置文件
|
||||
Include crs-tecmint/owasp-modsecurity-crs/base_rules/*.conf
|
||||
</IfModule>
|
||||
|
||||
最后,建议您在/etc/httpd/modsecurity.d目录下创建自己的配置文件,在那里我们可以用我们自定义的文件夹(接下来的示例中,我们会将其命名为tecmint.conf)而无需修改CRS文件的目录。这样做能够在CRSs发布新版本时更加容易的升级。
|
||||
最后,建议您在/etc/httpd/modsecurity.d目录下创建自己的配置文件,在那里我们可以用我们自定义的文件夹(接下来的示例中,我们会将其命名为tecmint.conf)而无需修改CRS文件的目录。这样做能够在CRS发布新版本时更加容易的升级。
|
||||
|
||||
<IfModule mod_security2.c>
|
||||
SecRuleEngine On
|
||||
@ -121,13 +108,13 @@ mod_security + mod_evasive 配置文件
|
||||
SecDataDir /tmp
|
||||
</IfModule>
|
||||
|
||||
您可以在[SpiderLabs的ModSecurity GitHub][5]仓库中参考关于mod_security目录的更完整的解释。
|
||||
您可以在[SpiderLabs的ModSecurity GitHub][5]仓库中参考关于mod\_security目录的更完整的解释。
|
||||
|
||||
### 步骤 4: 配置Mod_Evasive ###
|
||||
### 步骤 3: 配置mod\_evasive ###
|
||||
|
||||
mod_evasive被配置为使用/etc/httpd/conf.d/mod_evasive.conf中的指令。与mod_security不同,由于在包升级时没有规则来更新,因此我们不需要独立的文件来添加自定义指令。
|
||||
mod\_evasive被配置为使用/etc/httpd/conf.d/mod\_evasive.conf中的指令。与mod\_security不同,由于在包升级时没有规则来更新,因此我们不需要独立的文件来添加自定义指令。
|
||||
|
||||
默认的mod_evasive.conf开启了下列的目录(注意这个文件被详细的注释了,因此我们剔掉了注释以重点显示配置指令):
|
||||
默认的mod\_evasive.conf开启了下列的目录(注意这个文件被详细的注释了,因此我们剔掉了注释以重点显示配置指令):
|
||||
|
||||
<IfModule mod_evasive24.c>
|
||||
DOSHashTableSize 3097
|
||||
@ -140,8 +127,8 @@ mod_evasive被配置为使用/etc/httpd/conf.d/mod_evasive.conf中的指令。
|
||||
|
||||
这些指令的解释:
|
||||
|
||||
- DOSHashTableSize: 这个指令指明了哈希表的大小,它用来追踪基于IP地址的活动。增加这个数字将使查询站点访问历史变得更快,但如果被设置的太高则会影响整体性能。
|
||||
- DOSPageCount: 在DOSPageInterval间隔内可由一个用户发起的面向特定的URI(例如,一个Apache托管的文件)的同一个请求的数量。
|
||||
- DOSHashTableSize: 这个指令指明了哈希表的大小,它用来追踪基于IP地址的活动。增加这个数字将使得站点访问历史的查询变得更快,但如果被设置的太大则会影响整体性能。
|
||||
- DOSPageCount: 在DOSPageInterval间隔内可由一个用户发起的针对特定的URI(例如,一个Apache 提供服务的文件)的同一个请求的数量。
|
||||
- DOSSiteCount: 类似DOSPageCount,但涉及到整个站点总共有多少的请求可以在DOSSiteInterval间隔内被发起。
|
||||
- DOSBlockingPeriod: 如果一个用户超过了DOSSPageCount的限制或者DOSSiteCount,他的源IP地址将会在DOSBlockingPeriod期间内被加入黑名单。在DOSBlockingPeriod期间,任何从这个IP地址发起的请求将会遭遇一个403禁止错误。
|
||||
|
||||
@ -149,7 +136,7 @@ mod_evasive被配置为使用/etc/httpd/conf.d/mod_evasive.conf中的指令。
|
||||
|
||||
**一个小警告**: 如果这些值设置的不合适,则您会蒙受阻挡合法用户的风险。
|
||||
|
||||
您也许想考虑下其他有用的指令:
|
||||
您也许还会用到以下其它有用的指令:
|
||||
|
||||
#### DOSEmailNotify ####
|
||||
|
||||
@ -157,11 +144,11 @@ mod_evasive被配置为使用/etc/httpd/conf.d/mod_evasive.conf中的指令。
|
||||
|
||||
# setsebool -P httpd_can_sendmail 1
|
||||
|
||||
接下来,将这个指令和其他指令一起加入到mod_evasive.conf文件。
|
||||
接下来,将这个指令和其他指令一起加入到mod\_evasive.conf文件。
|
||||
|
||||
DOSEmailNotify you@yourdomain.com
|
||||
|
||||
如果这个值被合适的设置并且您的邮件服务器在正常的运行,则当一个IP地址被加入黑名单时,会有一封邮件被发送到相应的地址。
|
||||
如果这个指令设置了合适的值,并且您的邮件服务器在正常的运行,则当一个IP地址被加入黑名单时,会有一封邮件被发送到相应的地址。
|
||||
|
||||
#### DOSSystemCommand ####
|
||||
|
||||
@ -169,31 +156,47 @@ mod_evasive被配置为使用/etc/httpd/conf.d/mod_evasive.conf中的指令。
|
||||
|
||||
DOSSystemCommand </command>
|
||||
|
||||
这个指令指定当一个IP地址被加入黑名单时执行的命令。它通常结合shell脚本来使用,在脚本中添加一条防火墙规则来阻挡某个IP进一步的连接。
|
||||
这个指令指定当一个IP地址被加入黑名单时执行的命令。它通常结合shell脚本来使用,比如在脚本中添加一条防火墙规则来阻挡某个IP进一步的连接。
|
||||
|
||||
**写一个shell脚本在防火墙阶段处理IP黑名单**
|
||||
#####写一个shell脚本在防火墙阶段处理IP黑名单#####
|
||||
|
||||
当一个IP地址被加入黑名单,我们需要阻挡它进一步的连接。我们需要下面的shell脚本来执行这个任务。在/usr/local/bin下创建一个叫做scripts-tecmint的文件夹(或其他的名字),以及一个叫做ban_ip.sh的文件。
|
||||
|
||||
**用于iptables防火墙**
|
||||
|
||||
#!/bin/sh
|
||||
# 由mod_evasive检测出,将被阻挡的IP地址
|
||||
IP=$1
|
||||
# iptables的完整路径
|
||||
IPTABLES="/sbin/iptables"
|
||||
# mod_evasive锁文件夹
|
||||
MOD_EVASIVE_LOGDIR=/var/log/mod_evasive
|
||||
mod_evasive_LOGDIR=/var/log/mod_evasive
|
||||
# 添加下面的防火墙规则 (阻止所有从$IP流入的流量)
|
||||
$IPTABLES -I INPUT -s $IP -j DROP
|
||||
# 为了未来的检测,移除锁文件
|
||||
rm -f "$MOD_EVASIVE_LOGDIR"/dos-"$IP"
|
||||
rm -f "$mod_evasive_LOGDIR"/dos-"$IP"
|
||||
|
||||
**用于firewalld防火墙**
|
||||
|
||||
#!/bin/sh
|
||||
# 由mod_evasive检测出,将被阻挡的IP地址
|
||||
IP=$1
|
||||
# firewalld-cmd的完整路径
|
||||
FIREWALL_CMD="/usr/bin/firewall-cmd"
|
||||
# mod_evasive锁文件夹
|
||||
mod_evasive_LOGDIR=/var/log/mod_evasive
|
||||
# 添加下面的防火墙规则 (阻止所有从$IP流入的流量)
|
||||
$FIREWALL_CMD --zone=drop --add-source $IP
|
||||
# 为了未来的检测,移除锁文件
|
||||
rm -f "$mod_evasive_LOGDIR"/dos-"$IP"
|
||||
|
||||
我们的DOSSystemCommand指令应该是这样的:
|
||||
|
||||
DOSSystemCommand "sudo /usr/local/bin/scripts-tecmint/ban_ip.sh %s"
|
||||
|
||||
上面一行的%s代表了由mod_evasive检测到的攻击IP地址。
|
||||
上面一行的%s代表了由mod\_evasive检测到的攻击IP地址。
|
||||
|
||||
**将apache用户添加到sudoers文件**
|
||||
#####将apache用户添加到sudoers文件#####
|
||||
|
||||
请注意,如果您不给予apache用户以无需终端和密码的方式运行我们脚本(关键就是这个脚本)的权限,则这一切都不起作用。通常,您只需要以root权限键入visudo来存取/etc/sudoers文件,接下来添加下面的两行即可:
|
||||
|
||||
@ -201,14 +204,16 @@ mod_evasive被配置为使用/etc/httpd/conf.d/mod_evasive.conf中的指令。
|
||||
Defaults:apache !requiretty
|
||||
|
||||

|
||||
添加Apache用户到Sudoers
|
||||
|
||||
**重要**: 作为默认的安全策略,您只能在终端中运行sudo。由于这个时候我们需要在没有tty的时候运行sudo,我们像下面图片中那样必须注释掉下面这一行:
|
||||
*添加Apache用户到Sudoers*
|
||||
|
||||
**重要**: 在默认的安全策略下您只能在终端中运行sudo。由于这个时候我们需要在没有tty的时候运行sudo,我们必须像下图中那样注释掉下面这一行:
|
||||
|
||||
#Defaults requiretty
|
||||
|
||||
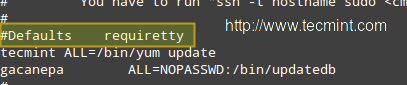
|
||||
为Sudo禁用tty
|
||||
|
||||
*为Sudo禁用tty*
|
||||
|
||||
最后,重启web服务器:
|
||||
|
||||
@ -219,7 +224,7 @@ mod_evasive被配置为使用/etc/httpd/conf.d/mod_evasive.conf中的指令。
|
||||
|
||||
有许多工具可以在您的服务器上模拟外部的攻击。您可以google下“tools for simulating ddos attacks”来找一找相关的工具。
|
||||
|
||||
注意,您(也只有您)将负责您模拟所造成的结果。请不要考虑向不在您网络中的服务器发起模拟攻击。
|
||||
注意,您(也只有您)将负责您模拟所造成的结果。请不要考虑向不在您自己网络中的服务器发起模拟攻击。
|
||||
|
||||
假如您想对一个由别人托管的VPS做这些事情,您需要向您的托管商发送适当的警告或就那样的流量通过他们的网络获得允许。Tecmint.com不会为您的行为负责!
|
||||
|
||||
@ -228,21 +233,20 @@ mod_evasive被配置为使用/etc/httpd/conf.d/mod_evasive.conf中的指令。
|
||||
我们的测试环境由一个CentOS 7服务器[IP 192.168.0.17]和一个Windows组成,在Windows[IP 192.168.0.103]上我们发起攻击:
|
||||
|
||||

|
||||
确认主机IP地址
|
||||
|
||||
请播放下面的视频,并跟从列出的步骤来模拟一个Dos攻击:
|
||||
*确认主机IP地址*
|
||||
|
||||
注:youtube视频,发布的时候不行做个链接吧
|
||||
<iframe width="640" height="405" frameborder="0" allowfullscreen="allowfullscreen" src="https://www.youtube.com/embed/-U_mdet06Jk"></iframe>
|
||||
请播放下面的视频(YT 视频,请自备梯子: https://www.youtube.com/-U_mdet06Jk ),并跟从列出的步骤来模拟一个Dos攻击:
|
||||
|
||||
然后攻击者的IP将被iptables阻挡:
|
||||
然后攻击者的IP将被防火墙阻挡:
|
||||
|
||||

|
||||
阻挡攻击者的IP地址
|
||||
|
||||
*阻挡攻击者的IP地址*
|
||||
|
||||
### 结论 ###
|
||||
|
||||
在开启mod_security和mod_evasive的情况下,模拟攻击会导致CPU和RAM用量在源IP地址被加入黑名单之前出现短暂几秒的使用峰值。如果没有这些模块,模拟攻击绝对会很快将服务器击溃,并使服务器在攻击期间无法提供服务。
|
||||
在开启mod\_security和mod\_evasive的情况下,模拟攻击会导致CPU和RAM用量在源IP地址被加入黑名单之前出现短暂几秒的使用峰值。如果没有这些模块,模拟攻击绝对会很快将服务器击溃,并使服务器在攻击期间无法提供服务。
|
||||
|
||||
我们很高兴听见您打算使用(或已经使用过)这些工具。我们期望得到您的反馈,所以,请在留言处留下您的评价和问题,谢谢!
|
||||
|
||||
@ -253,18 +257,18 @@ mod_evasive被配置为使用/etc/httpd/conf.d/mod_evasive.conf中的指令。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.tecmint.com/protect-apache-using-mod_security-and-mod_evasive-on-rhel-centos-fedora/
|
||||
via: http://www.tecmint.com/protect-apache-using-mod\_security-and-mod\_evasive-on-rhel-centos-fedora/
|
||||
|
||||
作者:[Gabriel Cánepa][a]
|
||||
译者:[wwy-hust](https://github.com/wwy-hust)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.tecmint.com/author/gacanepa/
|
||||
[1]:http://www.tecmint.com/install-lamp-in-centos-7/
|
||||
[2]:http://www.tecmint.com/configure-firewalld-in-centos-7/
|
||||
[3]:http://www.tecmint.com/how-to-enable-epel-repository-for-rhel-centos-6-5/
|
||||
[2]:https://linux.cn/article-4425-1.html
|
||||
[3]:https://linux.cn/article-2324-1.html
|
||||
[4]:https://www.owasp.org/index.php/Category:OWASP_ModSecurity_Core_Rule_Set_Project
|
||||
[5]:https://github.com/SpiderLabs/ModSecurity/wiki/Reference-Manual#Configuration_Directives
|
||||
[6]:https://www.modsecurity.org/
|
||||
@ -1,186 +1,133 @@
|
||||
|
||||
|
||||
用命令行工具Speedtest-CLI来测试你的上下行网速
|
||||
================================================================================
|
||||
|
||||
我们经常需要到检查家里与办公室之间的网络是否连通,那么我们要怎么做呢?打开网站Speedtest.net然后开始测试。网站是通过加载浏览器中的JavaScript脚本然后选择最佳的服务器测速然后用Flash产生图形化的结果。
|
||||
|
||||
|
||||
那么远程服务器呢?要知道大多数远程服务器是没有浏览器可以打开web页面的。用浏览器打开网页测速的瓶颈就在此,你不能按计划的对服务器进行定期的常规测试。这时需要到一个名为Speedtest-cli的软件来打破这个瓶颈,它能让你通过命令行来测试互联网连接的速度。
|
||||
|
||||
|
||||
#### Speedtest-cli是什么 ####
|
||||
|
||||
|
||||
此程序是基于Python开发的脚本程序,利用了speedtest.net的服务来测量出上下行的宽带。Speedtest-cli能根据机房离测速服务器的物理距离来列出测速服务器,或者针对某一服务器进行测速,同时还能为你生成一个URL以便你分享你的测速结果。
|
||||
|
||||
|
||||
要在Linux上安装最新版本的speedtest-cli,你必须安装2.4-3.4或者更高版本的Python。
|
||||
|
||||
|
||||
### 在Linux上安装speedtest-cli ###
|
||||
|
||||
|
||||
有两种方法可以安装speedtest-cli。第一种方法需要用到`python-pip`包管理器,第二种方法需要安装Python脚本,生成安装文件然后运行,这里我们分别介绍两种方法:
|
||||
|
||||
|
||||
#### 使用pythin-pip安装speedtest-cli####
|
||||
|
||||
|
||||
首先你需要安装`python-pip`包管理器,之后你就可以用pip命令来安装speedtest-cli
|
||||
|
||||
$ sudo apt-get install python-pip
|
||||
$ sudo pip install speedtest-cli
|
||||
|
||||
|
||||
如果要吧speedtest-cli升级至最新版本,你需要输入以下命令
|
||||
如果要把speedtest-cli升级至最新版本,你需要输入以下命令
|
||||
|
||||
$ sudo pip install speedtest-cli --upgrade
|
||||
|
||||
|
||||
#### 通过Pyhton脚本来安装speedtest-cli ####
|
||||
|
||||
|
||||
首先要用wget命令从github上下来Python脚本,然后解压提取下载的文件(master.zip)
|
||||
|
||||
$ wget https://github.com/sivel/speedtest-cli/archive/master.zip
|
||||
$ unzip master.zip
|
||||
|
||||
|
||||
提取出文件后,进入提取出的目录`speedtest-cli-master`然后使脚本可以执行。
|
||||
|
||||
$ cd speedtest-cli-master/
|
||||
$ chmod 755 speedtest_cli.py
|
||||
|
||||
|
||||
下一步,把可执行的脚本移动到`/usr/bin`文件夹,这样你就不用每次都输入完整的脚本路径了。
|
||||
|
||||
$ sudo mv speedtest_cli.py /usr/bin/
|
||||
|
||||
|
||||
### 用speedtest-cli测试互联网连通速度###
|
||||
|
||||
|
||||
**1. 要测试你的下载与上传速度,只需要运行`speedtest-cli`命令,不需要带参数。**
|
||||
|
||||
$ speedtest_cli.py
|
||||
|
||||
<center>
|
||||
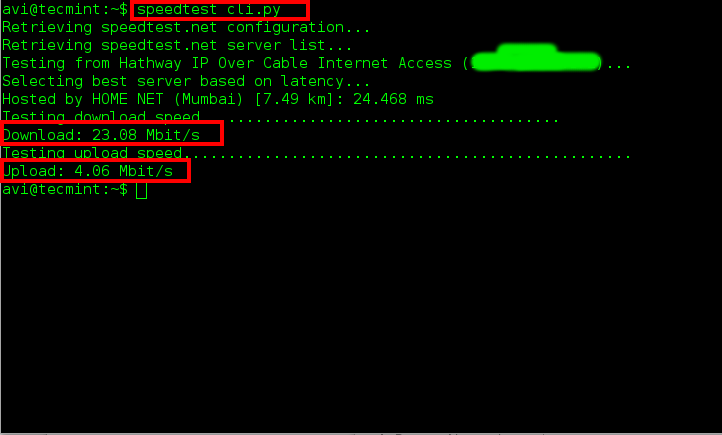
|
||||
|
||||
在Linux下测试上传下载速度
|
||||
</center>
|
||||
*在Linux下测试上传下载速度*
|
||||
|
||||
|
||||
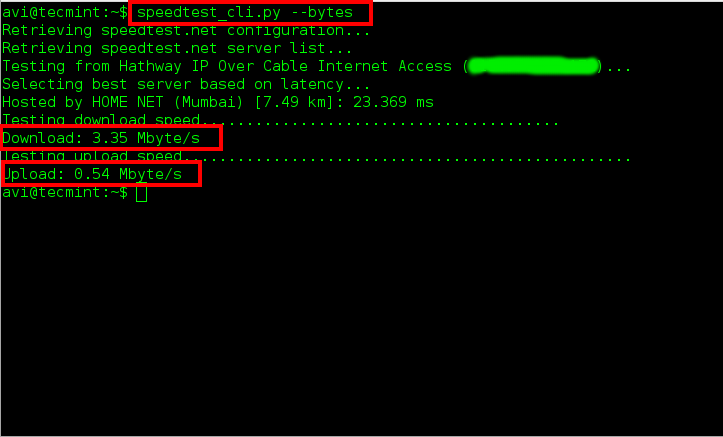
**2. 测试上传下载bytes的速度**
|
||||
**2. 测试上传下载的速度(以字节计算)**
|
||||
|
||||
$ speedtest_cli.py --bytes
|
||||
|
||||
<center>
|
||||
|
||||
|
||||
测试bytes的速度
|
||||
</center>
|
||||
|
||||
*测试bytes的速度*
|
||||
|
||||
**3. 工具提供一个链接来下载由你的宽带测试结果生成的图片,你可以分享给你的家人朋友。**
|
||||
|
||||
<center>
|
||||

|
||||
|
||||
分享测速结果
|
||||
</center>
|
||||
|
||||
*分享测速结果*
|
||||
|
||||
下面的图片就是你通过以上的命令行测速而生成的图片
|
||||
|
||||
<center>
|
||||

|
||||
|
||||
测速结果
|
||||
</center>
|
||||
*测速结果*
|
||||
|
||||
**4.如果你仅仅需要Ping,上传,下载的结果,就运行以下命令:**
|
||||
|
||||
$ speedtest_cli.py --simple
|
||||
|
||||
<center>
|
||||
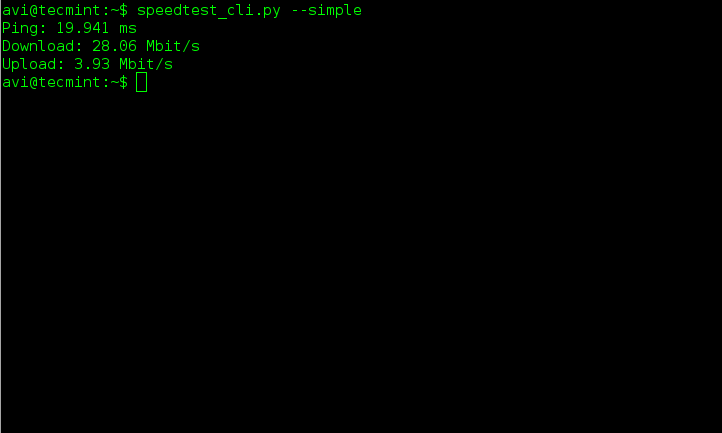
|
||||
|
||||
测试Ping,上传,下载的速度
|
||||
</center>
|
||||
|
||||
|
||||
|
||||
|
||||
*测试Ping,上传,下载的速度*
|
||||
|
||||
**5. 列出`speedtest.net`所有的服务器距离你的物理距离,单位是千米(km)**
|
||||
|
||||
|
||||
$ speedtest_cli.py --list
|
||||
|
||||
<center>
|
||||

|
||||
|
||||
列出Speedtest.net的服务器
|
||||
</center>
|
||||
|
||||
*列出Speedtest.net的服务器*
|
||||
|
||||
**6. 当获得一个非常长的服务器列表之后,怎么列出我想要的某个服务器?如果我要在speedtest.net服务器列表中找出位于Mumbai(印度)的服务器呢?**
|
||||
|
||||
$ speedtest_cli.py --list | grep -i Mumbai
|
||||
|
||||
<center>
|
||||

|
||||
|
||||
列出最近的服务器
|
||||
</center>
|
||||
|
||||
*列出最近的服务器*
|
||||
|
||||
**7. 对指定的服务器进行测速。我们使用上面例子5和例子6中获取的服务器ID:**
|
||||
|
||||
$ speedtest_cli.py --server [server ID]
|
||||
$ speedtest_cli.py --server [5060] ## Here server ID 5060 is used in the example.
|
||||
$ speedtest_cli.py --server [5060] ## 这里使用服务器ID为5060作为例子
|
||||
|
||||
<center>
|
||||

|
||||
|
||||
对指定的服务器进行测速
|
||||
</center>
|
||||
|
||||
*对指定的服务器进行测速*
|
||||
|
||||
**8. 输出`speedtest-cli`的版本信息和帮助文档**
|
||||
|
||||
$ speedtest_cli.py --version
|
||||
|
||||
<center>
|
||||

|
||||
|
||||
输出版本号
|
||||
</center>
|
||||
*输出版本号*
|
||||
|
||||
$ speedtest_cli.py --help
|
||||
<center>
|
||||
|
||||

|
||||
|
||||
输出帮助文档
|
||||
</center>
|
||||
|
||||
*输出帮助文档*
|
||||
|
||||
**提醒:**报告中的延迟并不是确切的结果,不应该过于依赖它;这个数值可以当作相对延迟,这对你选择某一测试服务器来说是可靠的。同时,CPU和内存的容量会影响结果的准确度。
|
||||
|
||||
|
||||
### 结论 ###
|
||||
|
||||
|
||||
系统管理员和开发者应该必备这个简单的脚本工具,这个工具轻量级,功能齐全,真是太赞了。我不喜欢Speedtest.net的原因是它使用来flash,相反speedtest-cli刚好戳中了我的痛点。
|
||||
|
||||
系统管理员和开发者应该必备这个简单的脚本工具,这个轻量级的工具功能齐全,真是太赞了。我不喜欢Speedtest.net的原因是它使用来flash,相反speedtest-cli刚好戳中了我的痛点。
|
||||
|
||||
speedtest_cli是一个第三方工具,也不能自动地记录下宽带速度。Speedtest.net拥有上百万的用户,你可以自己[配制一个小型的测速服务器][1]。
|
||||
|
||||
|
||||
上面就是所有内容,更多内容敬请关注Tecmint。如果你有任何反馈记得在文章下方评论,如果你喜欢别忘了给我们点歌赞,分享我们的文章。
|
||||
上面就是所有内容,更多内容敬请关注我们。如果你有任何反馈记得在文章下方评论,如果你喜欢别忘了给我们点个赞,分享我们的文章。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
@ -188,7 +135,7 @@ via: http://www.tecmint.com/check-internet-speed-from-command-line-in-linux/
|
||||
|
||||
作者:[Avishek Kumar][a]
|
||||
译者:[NearTan](https://github.com/NearTan)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,44 +1,48 @@
|
||||
RHEL/CentOS 7中安装并配置‘PowerDNS’(与MariaDB搭配)和‘PowerAdmin’
|
||||
RHEL/CentOS 7中安装并配置 PowerDNS 和 PowerAdmin
|
||||
================================================================================
|
||||
PowerDNS是一个运行在许多Linux/Unix衍生版上的DNS服务器,它可以使用不同的后端进行配置,包括BIND类型的区域文件、相关的数据库,或者负载均衡/失效转移算法。它也可以被配置成一台DNS递归器,作为服务器上的一个独立进程运行。
|
||||
PowerDNS是一个运行在许多Linux/Unix衍生版上的DNS服务器,它可以使用不同的后端进行配置,包括BIND类型的区域文件、关系型数据库,或者负载均衡/失效转移算法。它也可以被配置成一台DNS递归器,作为服务器上的一个独立进程运行。
|
||||
|
||||
PowerDNS授权服务器的最新版本是3.4.4,但是当前EPEL仓库中可以获得的版本是3.4.3。我推荐安装EPEL仓库中提供的那一个,因为该版本已经在CentOS和Fedora中测试过。那样,你也可以在今后很容易地更新PowerDNS。
|
||||
|
||||
本文倾向于向你演示如何安装并配置以MariaDB作为后端的PowerDNS和
|
||||
本文用于向你演示如何安装并配置以MariaDB作为后端的PowerDNS,以及它的界面友好的 Web 管理工具 PowerAdmin。
|
||||
|
||||
出于本文的写作目的,我将使用以下服务器:
|
||||
|
||||
主机名: centos7.localhost
|
||||
IP地址: 192.168.0.102
|
||||
|
||||
### 步骤 1: 安装带有MariaDB后端的PowerDNS ###
|
||||
### 第一部分: 安装带有MariaDB后端的PowerDNS ###
|
||||
|
||||
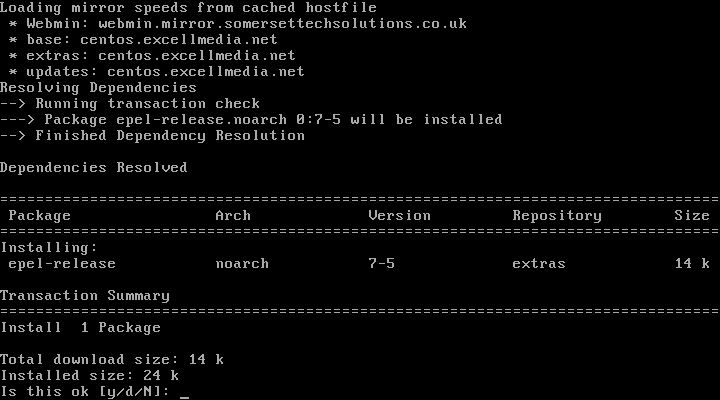
#### 1. 首先,你需要为你的系统启用EPEL仓库,只需使用: ####
|
||||
1、 首先,你需要为你的系统启用EPEL仓库,只需使用:
|
||||
|
||||
# yum install epel-release.noarch
|
||||
|
||||
|
||||
启用Epel仓库
|
||||
|
||||
#### 2. 下一步是安装MariaDB服务器。运行以下命令即可达成: ####
|
||||
*启用Epel仓库*
|
||||
|
||||
2、 下一步是安装MariaDB服务器。运行以下命令即可达成:
|
||||
|
||||
# yum -y install mariadb-server mariadb
|
||||
|
||||

|
||||
安装MariaDB服务器
|
||||
|
||||
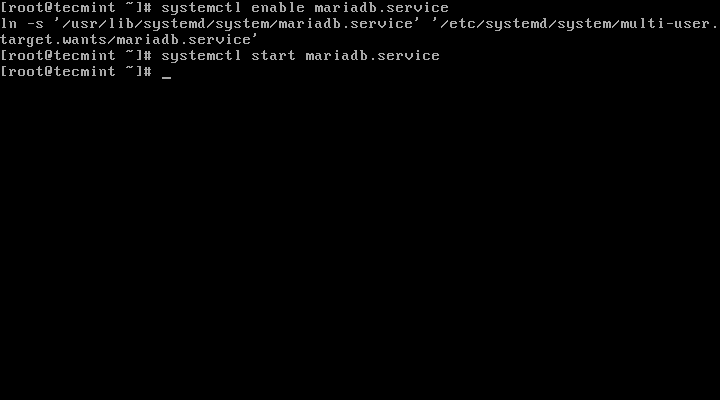
#### 3. 接下来,我们将配置并启用MySQL,并设置开机启动: ####
|
||||
*安装MariaDB服务器*
|
||||
|
||||
3、 接下来,我们将配置并启用MariaDB,并设置开机启动:
|
||||
|
||||
# systemctl enable mariadb.service
|
||||
# systemctl start mariadb.service
|
||||
|
||||
|
||||
启用MariaDB开机启动
|
||||
|
||||
#### 4. 由于MySQL服务正在运行,我们将为MariaDB设置密码进行安全加固,运行以下命令: ####
|
||||
*启用MariaDB开机启动*
|
||||
|
||||
4、 现在MariaDB服务运行起来了,我们将为MariaDB设置密码进行安全加固,运行以下命令:
|
||||
|
||||
# mysql_secure_installation
|
||||
|
||||
#### 按照指示做 ####
|
||||
**按照指示做**
|
||||
|
||||
/bin/mysql_secure_installation: line 379: find_mysql_client: command not found
|
||||
|
||||
@ -102,33 +106,36 @@ PowerDNS授权服务器的最新版本是3.4.4,但是当前EPEL仓库中可以
|
||||
|
||||
Thanks for using MariaDB!
|
||||
|
||||
#### 5. MariaDB配置成功后,我们可以继续去安装PowerDNS。运行以下命令即可轻易完成: ####
|
||||
5、 MariaDB配置成功后,我们可以继续去安装PowerDNS。运行以下命令即可轻易完成:
|
||||
|
||||
# yum -y install pdns pdns-backend-mysql
|
||||
|
||||

|
||||
安装带有MariaDB后端的PowerDNS
|
||||
|
||||
#### 6. PowerDNS的配置文件位于`/etc/pdns/pdns`,在编辑之前,我们将为PowerDNS服务配置一个MySQL数据库。首先,我们将连接到MySQL服务器并创建一个名为powerdns的数据库: ####
|
||||
*安装带有MariaDB后端的PowerDNS*
|
||||
|
||||
6、 PowerDNS的配置文件位于`/etc/pdns/pdns`,在编辑之前,我们将为PowerDNS服务配置一个MariaDB数据库。首先,我们将连接到MariaDB服务器并创建一个名为powerdns的数据库:
|
||||
|
||||
# mysql -u root -p
|
||||
MariaDB [(none)]> CREATE DATABASE powerdns;
|
||||
|
||||

|
||||
创建PowerDNS数据库
|
||||
|
||||
#### 7. 接下来,我们将创建一个名为powerdns的数据库用户: ####
|
||||
*创建PowerDNS数据库*
|
||||
|
||||
7、 接下来,我们将创建一个名为powerdns的数据库用户:
|
||||
|
||||
MariaDB [(none)]> GRANT ALL ON powerdns.* TO 'powerdns'@'localhost' IDENTIFIED BY ‘tecmint123’;
|
||||
MariaDB [(none)]> GRANT ALL ON powerdns.* TO 'powerdns'@'centos7.localdomain' IDENTIFIED BY 'tecmint123';
|
||||
MariaDB [(none)]> FLUSH PRIVILEGES;
|
||||
|
||||
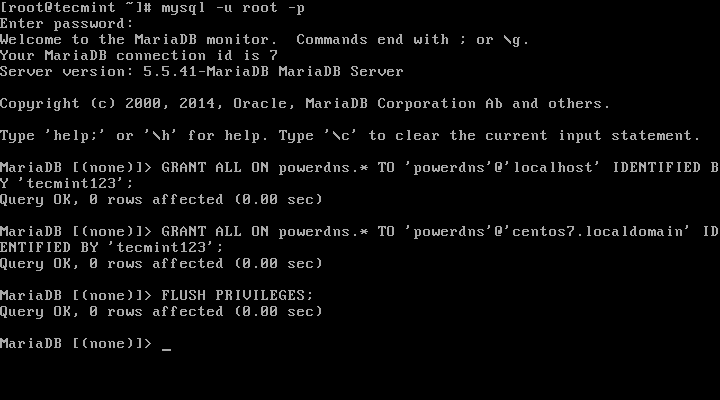
|
||||
创建PowerDNS用户
|
||||
|
||||
*创建PowerDNS用户*
|
||||
|
||||
**注意**: 请将“tecmint123”替换为你想要设置的实际密码。
|
||||
|
||||
#### 8. 我们继续创建PowerDNS要使用的数据库表。像堆积木一样执行以下这些: ####
|
||||
8、 我们继续创建PowerDNS要使用的数据库表。像堆积木一样执行以下这些:
|
||||
|
||||
MariaDB [(none)]> USE powerdns;
|
||||
MariaDB [(none)]> CREATE TABLE domains (
|
||||
@ -143,7 +150,8 @@ PowerDNS授权服务器的最新版本是3.4.4,但是当前EPEL仓库中可以
|
||||
);
|
||||
|
||||

|
||||
创建用于PowerDNS的表域
|
||||
|
||||
*创建用于PowerDNS的表domains*
|
||||
|
||||
MariaDB [(none)]> CREATE UNIQUE INDEX name_index ON domains(name);
|
||||
MariaDB [(none)]> CREATE TABLE records (
|
||||
@ -158,15 +166,17 @@ PowerDNS授权服务器的最新版本是3.4.4,但是当前EPEL仓库中可以
|
||||
primary key(id)
|
||||
);
|
||||
|
||||

|
||||
创建用于PowerDNS的索引域
|
||||

|
||||
|
||||
*创建用于PowerDNS的表 records*
|
||||
|
||||
MariaDB [(none)]> CREATE INDEX rec_name_index ON records(name);
|
||||
MariaDB [(none)]> CREATE INDEX nametype_index ON records(name,type);
|
||||
MariaDB [(none)]> CREATE INDEX domain_id ON records(domain_id);
|
||||
|
||||

|
||||
创建索引记录
|
||||

|
||||
|
||||
*创建表索引*
|
||||
|
||||
MariaDB [(none)]> CREATE TABLE supermasters (
|
||||
ip VARCHAR(25) NOT NULL,
|
||||
@ -175,13 +185,14 @@ PowerDNS授权服务器的最新版本是3.4.4,但是当前EPEL仓库中可以
|
||||
);
|
||||
|
||||

|
||||
创建表的超主
|
||||
|
||||
你现在可以输入以下命令退出MySQL控制台:
|
||||
*创建表supermasters*
|
||||
|
||||
你现在可以输入以下命令退出MariaDB控制台:
|
||||
|
||||
MariaDB [(none)]> quit;
|
||||
|
||||
#### 9. 最后,我们可以继续以MySQL作为后台的方式配置PowerDNS。请打开PowerDNS的配置文件: ####
|
||||
9、 最后,我们可以继续配置PowerDNS了,以MariaDB作为后台。请打开PowerDNS的配置文件:
|
||||
|
||||
# vim /etc/pdns/pdns.conf
|
||||
|
||||
@ -203,35 +214,39 @@ PowerDNS授权服务器的最新版本是3.4.4,但是当前EPEL仓库中可以
|
||||
修改“user-pass”为你先前设置的实际密码,配置如下:
|
||||
|
||||

|
||||
配置PowerDNS
|
||||
|
||||
*配置PowerDNS*
|
||||
|
||||
保存修改并退出。
|
||||
|
||||
#### 10. 现在,我们将启动并添加PowerDNS到系统开机启动列表: ####
|
||||
10、 现在,我们将启动并添加PowerDNS到系统开机启动列表:
|
||||
|
||||
# systemctl enable pdns.service
|
||||
# systemctl start pdns.service
|
||||
|
||||

|
||||
启用并启动PowerDNS
|
||||
|
||||
*启用并启动PowerDNS*
|
||||
|
||||
到这一步,你的PowerDNS服务器已经起来并运行了。要获取更多关于PowerDNS的信息,你可以参考手册[http://downloads.powerdns.com/documentation/html/index.html][1]
|
||||
|
||||
### 步骤 2: 安装PowerAdmin来管理PowerDNS ###
|
||||
### 第二部分: 安装PowerAdmin来管理PowerDNS ###
|
||||
|
||||
#### 11. 现在,我们将安装PowerAdmin——一个友好的网页接口PowerDNS服务器管理器。由于它是用PHP写的,我们将需要安装PHP和一台网络服务器(Apache): ####
|
||||
11、 现在,我们将安装PowerAdmin——一个界面友好的PowerDNS服务器的 Web 管理器。由于它是用PHP写的,我们将需要安装PHP和一台网络服务器(Apache):
|
||||
|
||||
# yum install httpd php php-devel php-gd php-imap php-ldap php-mysql php-odbc php-pear php-xml php-xmlrpc php-mbstring php-mcrypt php-mhash gettext
|
||||
|
||||

|
||||
安装Apache PHP
|
||||
|
||||
*安装Apache 和 PHP*
|
||||
|
||||
PowerAdmin也需要两个PEAR包:
|
||||
|
||||
# yum -y install php-pear-DB php-pear-MDB2-Driver-mysql
|
||||
|
||||

|
||||
安装Pear
|
||||
|
||||
*安装Pear*
|
||||
|
||||
你也可以参考一下文章了解CentOS 7中安装LAMP堆栈的完整指南:
|
||||
|
||||
@ -243,58 +258,66 @@ PowerAdmin也需要两个PEAR包:
|
||||
# systemctl start httpd.service
|
||||
|
||||

|
||||
启用Apache开机启动
|
||||
|
||||
#### 12. 由于已经满足PowerAdmin的所有系统要求,我们可以继续下载软件包。因为Apache默认的网页目录位于/var/www/html/,我们将下载软件包到这里。 ####
|
||||
*启用Apache开机启动*
|
||||
|
||||
12、 由于已经满足PowerAdmin的所有系统要求,我们可以继续下载软件包。因为Apache默认的网页目录位于/var/www/html/,我们将下载软件包到这里。
|
||||
|
||||
# cd /var/www/html/
|
||||
# wget http://downloads.sourceforge.net/project/poweradmin/poweradmin-2.1.7.tgz
|
||||
# tar xfv poweradmin-2.1.7.tgz
|
||||
|
||||

|
||||
下载PowerAdmin
|
||||
|
||||
#### 13. 现在,我们可以启动PowerAdmin的网页安装器了,只需打开: ####
|
||||
*下载PowerAdmin*
|
||||
|
||||
13、 现在,我们可以启动PowerAdmin的网页安装器了,只需打开:
|
||||
|
||||
http://192.168.0.102/poweradmin-2.1.7/install/
|
||||
|
||||
这会进入安装过程的第一步:
|
||||
|
||||

|
||||
选择安装语言
|
||||
|
||||
*选择安装语言*
|
||||
|
||||
上面的页面会要求你为PowerAdmin选择语言,请选择你想要使用的那一个,然后点击“进入步骤 2”按钮。
|
||||
|
||||
#### 14. 安装器需要PowerDNS数据库: ####
|
||||
14、 安装器需要PowerDNS数据库:
|
||||
|
||||

|
||||
PowerDNS数据库
|
||||
|
||||
#### 15. 因为我们已经创建了一个,所以我们可以继续进入下一步。你会被要求提供先前配置的数据库详情,你也需要为Poweradmin设置管理员密码: ####
|
||||
*PowerDNS数据库*
|
||||
|
||||
15、 因为我们已经创建了一个数据库,所以我们可以继续进入下一步。你会被要求提供先前配置的数据库详情,你也需要为Poweradmin设置管理员密码:
|
||||
|
||||

|
||||
输入PowerDNS数据库配置
|
||||
|
||||
#### 16. 输入这些信息后,进入步骤 4。你将创建为Poweradmin创建一个受限用户。这里你需要输入的字段是: ####
|
||||
*输入PowerDNS数据库配置*
|
||||
|
||||
- 用户名 - PowerAdmin用户名。
|
||||
- 密码 – 上述用户的密码。
|
||||
- 注册人 - 当创建SOA记录而你没有制定注册人时,该值会被使用。
|
||||
- 辅助域名服务器 – 该值在创建新的DNS区域时会被用于作为主域名服务器。
|
||||
16、 输入这些信息后,进入步骤 4。你将创建为Poweradmin创建一个受限用户。这里你需要输入的字段是:
|
||||
|
||||
- 用户名(Username) - PowerAdmin用户名。
|
||||
- 密码(Password) – 上述用户的密码。
|
||||
- 主机管理员(Hostmaster) - 当创建SOA记录而你没有指定主机管理员时,该值会被用作默认值。
|
||||
- 主域名服务器 - 该值在创建新的DNS区域时会被用于作为主域名服务器。
|
||||
- 辅域名服务器 – 该值在创建新的DNS区域时会被用于作为辅域名服务器。
|
||||
|
||||

|
||||
PowerDNS配置设置
|
||||
|
||||
#### 17. 在下一步中,Poweradmin会要求你在数据库表中创建新的受限数据库用户,它会提供你需要在MySQL控制台输入的代码: ####
|
||||
*PowerDNS配置设置*
|
||||
|
||||
17、 在下一步中,Poweradmin会要求你在数据库表中创建一个新的受限数据库用户,它会提供你需要在MariaDB控制台输入的代码:
|
||||
|
||||

|
||||
创建新的数据库用户
|
||||
|
||||
#### 18. 现在打开终端并运行: ####
|
||||
*创建新的数据库用户*
|
||||
|
||||
18、 现在打开终端并运行:
|
||||
|
||||
# mysql -u root -p
|
||||
|
||||
提供你的密码并执行由Poweradmin提供的代码:
|
||||
提供你的密码并执行由PowerAdmin提供的代码:
|
||||
|
||||
MariaDB [(none)]> GRANT SELECT, INSERT, UPDATE, DELETE
|
||||
ON powerdns.*
|
||||
@ -302,27 +325,30 @@ PowerDNS配置设置
|
||||
IDENTIFIED BY '123qweasd';
|
||||
|
||||

|
||||
为用户授予Mysql权限
|
||||
|
||||
#### 19. 现在,回到浏览器中并继续下一步。安装器将尝试创建配置文件到/var/www/html/poweradmin-2.1.7/inc。 ####
|
||||
*为用户授予Mysql权限*
|
||||
|
||||
19、 现在,回到浏览器中并继续下一步。安装器将尝试创建配置文件到/var/www/html/poweradmin-2.1.7/inc。
|
||||
|
||||
文件名是config.inc.php。为防止该脚本没有写权限,你可以手动复制这些内容到上述文件中:
|
||||
|
||||

|
||||
配置PowerDNS设置
|
||||
|
||||
#### 20. 现在,进入最后页面,该页面会告知你安装已经完成以及如何访问安装好的Poweradmin: ####
|
||||
*配置PowerDNS设置*
|
||||
|
||||
20、 现在,进入最后页面,该页面会告知你安装已经完成以及如何访问安装好的PowerAdmin:
|
||||
|
||||

|
||||
PowerDNS安装完成
|
||||
|
||||
你可以通过运行以下命令来启用其他动态DNS提供商的URL:
|
||||
*PowerDNS安装完成*
|
||||
|
||||
你可以通过运行以下命令来启用用于其他动态DNS提供商的URL:
|
||||
|
||||
# cp install/htaccess.dist .htaccess
|
||||
|
||||
出于该目的,你将需要在Apache的配置中启用mod_rewrite。
|
||||
|
||||
#### 21. 现在,需要移除从Poweradmin的根目录中移除“install”文件夹,这一点很重要。使用以下命令: ####
|
||||
21、 现在,需要移除从PowerAdmin的根目录中移除“install”文件夹,这一点很重要。使用以下命令:
|
||||
|
||||
# rm -fr /var/www/html/poweradmin/install/
|
||||
|
||||
@ -331,78 +357,86 @@ PowerDNS安装完成
|
||||
http://192.168.0.102/poweradmin-2.1.7/
|
||||
|
||||

|
||||
PowerDNS登录
|
||||
|
||||
在登录后,你应该会看到Poweradmin的主页:
|
||||
*PowerDNS登录*
|
||||
|
||||
在登录后,你应该会看到PowerAdmin的主页:
|
||||
|
||||

|
||||
PowerDNS仪表盘
|
||||
|
||||
*PowerDNS仪表盘*
|
||||
|
||||
到这里,安装已经完成了,你也可以开始管理你的DNS区域了。
|
||||
|
||||
### 步骤 3: PowerDNS中添加、编辑和删除DNS区域 ###
|
||||
### 第三部分: PowerDNS中添加、编辑和删除DNS区域 ###
|
||||
|
||||
#### 22. 要添加新的主区域,只需点击“添加主区域”: ####
|
||||
22、 要添加新的主区域,只需点击“添加主区域”:
|
||||
|
||||

|
||||
添加主区域
|
||||
|
||||
*添加主区域*
|
||||
|
||||
在下一页中,你需要填写一些东西:
|
||||
|
||||
- 域 – 你要添加区域的域。
|
||||
- 所有者 – 设置DNS区域的所有者。
|
||||
- 模板 – DNS模板 – 留空。
|
||||
- DNSSEC – Donany名称系统安全扩展(可选——检查你是否需要)。
|
||||
- 域(Domain) – 你要添加区域的域。
|
||||
- 所有者(Owner) – 设置DNS区域的所有者。
|
||||
- 模板(Template)– DNS模板 – 留空。
|
||||
- DNSSEC – 域名系统安全扩展(可选——看看你是否需要)。
|
||||
|
||||
点击“添加区域”按钮来添加DNS区域。
|
||||
|
||||

|
||||
主DNS区域
|
||||
|
||||
现在,你可以点击“首页”链接回到Poweradmin的首页。要查看所有现存的DNS区域,只需转到“列出区域”:
|
||||
*主DNS区域*
|
||||
|
||||
现在,你可以点击“首页”链接回到PowerAdmin的首页。要查看所有现存的DNS区域,只需转到“列出区域(List Zones)”:
|
||||
|
||||

|
||||
检查区域列表
|
||||
|
||||
*查看区域列表*
|
||||
|
||||
你现在应该看到一个可用DNS区域列表:
|
||||
|
||||

|
||||
检查DNS区域列表
|
||||
|
||||
#### 23. 要编辑现存DNS区域或者添加新的记录,点击编辑图标: ####
|
||||
*检查DNS区域列表*
|
||||
|
||||
23、 要编辑现存DNS区域或者添加新的记录,点击编辑图标:
|
||||
|
||||

|
||||
编辑DNS区域
|
||||
|
||||
*编辑DNS区域*
|
||||
|
||||
在接下来的页面,你会看到你选择的DNS区域的条目:
|
||||
|
||||

|
||||
主DNS区域条目
|
||||
|
||||
#### 24. 在此处添加新的DNS区域,你需要设置以下信息: ####
|
||||
*域名的DNS区域条目*
|
||||
|
||||
- 名称 – 条目名称。只需添加域/子域的第一部分,Poweradmin会添加剩下的。
|
||||
- 类型 – 选择记录类型。
|
||||
- 优先级 – 记录优先级。
|
||||
24、 在此处添加新的DNS条目,你需要设置以下信息:
|
||||
|
||||
- 名称(Name) – 条目名称。只需添加域/子域的第一部分,PowerAdmin会添加剩下的。
|
||||
- 类型(Type) – 选择记录类型。
|
||||
- 优先级(Priority) – 记录优先级。
|
||||
- TTL – 存活时间,以秒计算。
|
||||
|
||||
出于本文目的,我将为子域new.example.com添加一个A记录用于解析IP地址192.168.0.102,设置存活时间为14400秒:
|
||||
|
||||

|
||||
添加新DNS记录
|
||||
|
||||
*添加新DNS记录*
|
||||
|
||||
最后,点击“添加记录”按钮。
|
||||
|
||||
#### 25. 如果你想要删除DNS区域,你可以回到“列出区域”页面,然后点击你想要删除的DNS区域旁边“垃圾桶”图标: ####
|
||||
25、 如果你想要删除DNS区域,你可以回到“列出区域”页面,然后点击你想要删除的DNS区域旁边“垃圾桶”图标:
|
||||
|
||||

|
||||
删除DNS区域
|
||||
|
||||
*删除DNS区域*
|
||||
|
||||
Poweradmin将问你是否确定想要删除DNS区域。只需点击“是”来完成删除。
|
||||
|
||||
如要获取更多关于怎样创建、编辑和删除区域的说明,你可以参与Poweradmin的文档:
|
||||
|
||||
[https://github.com/poweradmin/poweradmin/wiki/Documentation][3]
|
||||
如要获取更多关于怎样创建、编辑和删除区域的说明,你可以参与Poweradmin的文档:[https://github.com/poweradmin/poweradmin/wiki/Documentation][3]
|
||||
|
||||
我希望你已经发现本文很有趣,也很有用。一如既往,如果你有问题或要发表评论,请别犹豫,在下面评论区提交你的评论吧。
|
||||
|
||||
@ -412,7 +446,7 @@ via: http://www.tecmint.com/install-powerdns-poweradmin-mariadb-in-centos-rhel/
|
||||
|
||||
作者:[Marin Todorov][a]
|
||||
译者:[GOLinux](https://github.com/GOLinux)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,6 +1,6 @@
|
||||
Linux 有问必答--如何修复 Raspbian 上的 “Encountered a section with no Package: header” 错误
|
||||
Linux 有问必答:如何修复 Rasbian 上的 “Encountered a section with no Package: header” 错误
|
||||
================================================================================
|
||||
> **问题**: 我在 Raspberry Pi 上安装新版的 Rasbian。但当我使用 sudo apt-get update 命令更新 APT 软件包索引的时候,它抛出下面的错误:
|
||||
> **问题**: 我在树莓派上安装新版的 Rasbian。但当我使用 sudo apt-get update 命令更新 APT 软件包索引的时候,它抛出下面的错误:
|
||||
|
||||
E: Encountered a section with no Package: header
|
||||
E: Problem with MergeList /var/lib/dpkg/status
|
||||
@ -10,7 +10,7 @@ Linux 有问必答--如何修复 Raspbian 上的 “Encountered a section with n
|
||||
|
||||
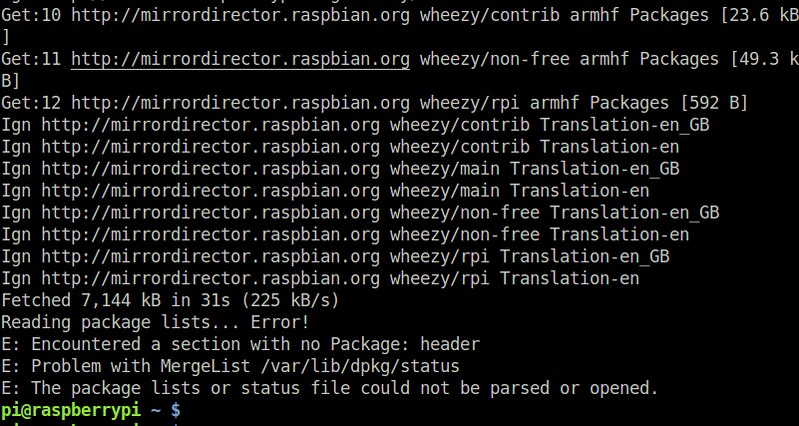
|
||||
|
||||
错误说 "Problem with MergeList /var/lib/dpkg/status" 表示由于某些原因状态文件损坏了,因此无法解释。这个状态文件包括了已经安装的 deb 软件包的信息,因此需要小心备份。
|
||||
这个错误说 "Problem with MergeList /var/lib/dpkg/status" 表示由于某些原因状态文件损坏了,因此无法解析。这个状态文件包括了已经安装的 deb 软件包的信息,因此需要小心备份。
|
||||
|
||||
在这种情况下,由于这是新安装的 Raspbian,你可以安全地删除状态文件,然后用下面的命令重新生成。
|
||||
|
||||
@ -24,7 +24,7 @@ via: http://ask.xmodulo.com/encountered-section-with-no-package-header-error.htm
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[ictlyh](https://github.com/ictlyh)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,16 +1,16 @@
|
||||
Linux有问必答——Linux上如何查看某个进程的线程
|
||||
Linux有问必答:Linux上如何查看某个进程的线程
|
||||
================================================================================
|
||||
> **问题**: 我的程序创建并在它里头执行了多个线程,我怎样才能在该程序创建线程后监控其中单个线程?我想要看到带有它们名称的单个线程详细情况(如,CPU/内存使用率)。
|
||||
> **问题**: 我的程序在其内部创建并执行了多个线程,我怎样才能在该程序创建线程后监控其中单个线程?我想要看到带有它们名称的单个线程详细情况(如,CPU/内存使用率)。
|
||||
|
||||
线程是现代操作系统上进行并行执行的一个流行的编程方面的抽象概念。当一个程序内有多个线程被叉分出用以执行多个流时,这些线程就会在它们之间共享特定的资源(如,内存地址空间、打开的文件),以使叉分开销最小化,并避免大量花销IPC(进程间通信)频道。这些功能让线程在并发执行时成为一个高效的机制。
|
||||
线程是现代操作系统上进行并行执行的一个流行的编程方面的抽象概念。当一个程序内有多个线程被叉分出用以执行多个流时,这些线程就会在它们之间共享特定的资源(如,内存地址空间、打开的文件),以使叉分开销最小化,并避免大量高成本的IPC(进程间通信)通道。这些功能让线程在并发执行时成为一个高效的机制。
|
||||
|
||||
在Linux中,程序中创建的线程(也称为轻量级进程,LWP)会具有和程序的PID相同的“线程组ID”。然后,各个线程会获得其自身的线程ID(TID)。对于Linux内核调度器而言,线程不过是恰好共享特定资源的标准的进程。经典的命令行工具,如ps或top,都可以用来显示线程级别的信息,默认情况下它们会显示进程级别的信息。
|
||||
在Linux中,程序中创建的线程(也称为轻量级进程,LWP)会具有和程序的PID相同的“线程组ID”。然后,各个线程会获得其自身的线程ID(TID)。对于Linux内核调度器而言,线程不过是恰好共享特定资源的标准的进程而已。经典的命令行工具,如ps或top,都可以用来显示线程级别的信息,只是默认情况下它们显示进程级别的信息。
|
||||
|
||||
这里提供了**在Linux上显示某个进程的线程**的几种方式。
|
||||
|
||||
### 方法一:PS ###
|
||||
|
||||
在ps命令中,“-T”选项可以开启线程查看。下面的命令列出了由进程号为<pid>的进程创建的所有线程。
|
||||
在ps命令中,“-T”选项可以开启线程查看。下面的命令列出了由进程号为\<pid>的进程创建的所有线程。
|
||||
|
||||
$ ps -T -p <pid>
|
||||
|
||||
@ -26,7 +26,7 @@ top命令可以实时显示各个线程情况。要在top输出中开启线程
|
||||
|
||||
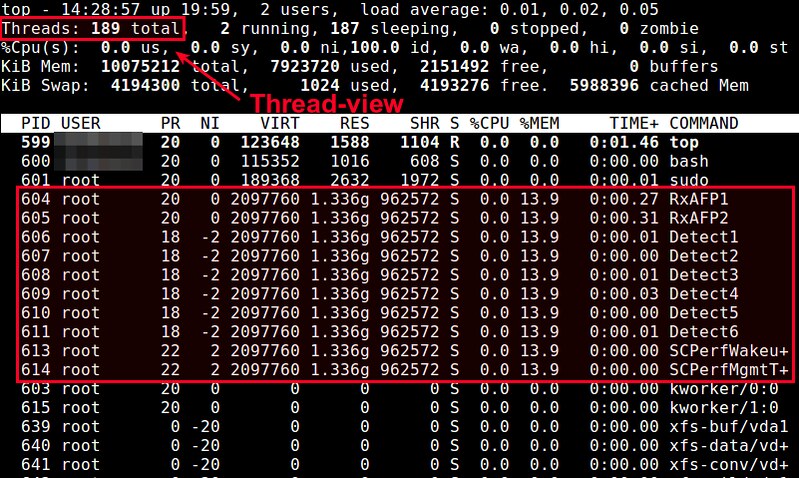
|
||||
|
||||
要让top输出某个特定进程<pid>并检查该进程内运行的线程状况:
|
||||
要让top输出某个特定进程\<pid>并检查该进程内运行的线程状况:
|
||||
|
||||
$ top -H -p <pid>
|
||||
|
||||
@ -36,7 +36,7 @@ top命令可以实时显示各个线程情况。要在top输出中开启线程
|
||||
|
||||
一个对用户更加友好的方式是,通过htop查看单个进程的线程,它是一个基于ncurses的交互进程查看器。该程序允许你在树状视图中监控单个独立线程。
|
||||
|
||||
要在htop中启用线程查看,请开启htop,然后按<F2>来进入htop的设置菜单。选择“设置”栏下面的“显示选项”,然后开启“树状视图”和“显示自定义线程名”选项。按<F10>退出设置。
|
||||
要在htop中启用线程查看,请开启htop,然后按\<F2>来进入htop的设置菜单。选择“设置”栏下面的“显示选项”,然后开启“树状视图”和“显示自定义线程名”选项。按\<F10>退出设置。
|
||||
|
||||
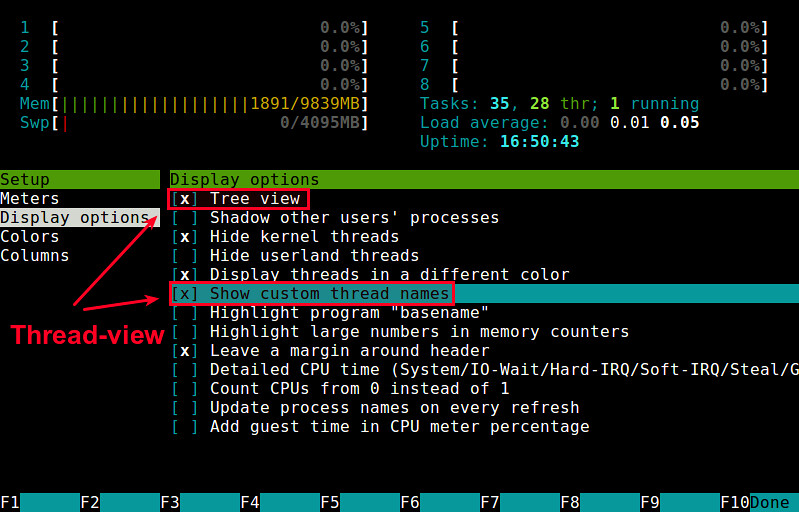
|
||||
|
||||
@ -50,7 +50,7 @@ via: http://ask.xmodulo.com/view-threads-process-linux.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[GOLinux](https://github.com/GOLinux)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,4 +1,4 @@
|
||||
Linux 有问必答--如何在桌面版 Ubuntu 中安装 Unity Tweak Tool
|
||||
Linux 有问必答:如何在桌面版 Ubuntu 中安装 Unity Tweak Tool
|
||||
================================================================================
|
||||
> **问题**: 我试着给刚安装的桌面版 Ubuntu 自定制桌面。我想使用 Unity Tweak Tool。我怎样才能在 Ubuntu 上安装 Unity Tweak Tool 呢?
|
||||
|
||||
@ -6,7 +6,7 @@ Linux 有问必答--如何在桌面版 Ubuntu 中安装 Unity Tweak Tool
|
||||
|
||||
|
||||
|
||||
尽管 Unity Tweak Tool 是桌面版 Ubuntu 的重要工具,并没有在桌面版 Ubuntu 中预安装。为了能自定制 Unity 桌面,下面介绍一下如何在桌面版 Ubuntu 中安装 Unity Tweak Tool。
|
||||
尽管 Unity Tweak Tool 是桌面版 Ubuntu 的重要工具,但并没有在桌面版 Ubuntu 中预安装。为了能自定制 Unity 桌面,下面介绍一下如何在桌面版 Ubuntu 中安装 Unity Tweak Tool。
|
||||
|
||||
### 在 Ubuntu 13.04 或更高版本中安装 Unity Tweak Tool ###
|
||||
|
||||
@ -34,7 +34,7 @@ via: http://ask.xmodulo.com/install-unity-tweak-tool-ubuntu-desktop.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[ictlyh](https://github.com/ictlyh)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,9 +1,10 @@
|
||||
每个Linux用户都应该知道的3个有用技巧
|
||||
Linux 用户的 3 个命令行小技巧
|
||||
================================================================================
|
||||
Linux世界充满了乐趣,我们越深入进去,就会发现越多有趣的事物。我们会努力给你提供一些小技巧,让你和其他人有所不同,下面就是我们准备的3个小技巧。
|
||||
|
||||
### 1. 如何在不使用Cron的情况调度Linux下的作业 ###
|
||||
在Linux下,调度一个作业/命令可以缩写为Cron。当我们需要调度一个作业时,我们会使用Cron,但你知道我们在不使用Cron的情况也可以调度一个在将来时间运行的作业吗?你可以按照如下建议操作……
|
||||
### 1. 如何在不使用Cron的情况调度Linux下的任务 ###
|
||||
|
||||
在Linux下,调度一个任务/命令称之为Cron。当我们需要调度一个任务时,我们会使用Cron,但你知道我们在不使用Cron的情况也可以调度一个在将来时间运行的任务吗?你可以按照如下建议操作……
|
||||
|
||||
每5秒钟运行一个命令(date)然后将结果写入到一个文件(data.txt)。为了实现这一点,我们可以直接在命令提示符运行如下单行脚本。
|
||||
|
||||
@ -21,13 +22,13 @@ Linux世界充满了乐趣,我们越深入进去,就会发现越多有趣的
|
||||
|
||||
类似地,我们可以这样运行任何脚本。下边的例子是每100秒运行一个名为`script_name.sh`的脚本。
|
||||
|
||||
另外值得一提的是上边的脚本文件必须处于当前目录中,否则需要使用完整路径(`/home/$USER/…/script_name.sh`)。实现如上功能的单行脚本如下:
|
||||
另外值得一提的是上面提到的脚本文件必须处于当前目录中,否则需要使用完整路径(`/home/$USER/…/script_name.sh`)。实现如上功能的单行脚本如下:
|
||||
|
||||
$ while true; do /bin/sh script_name.sh ; sleep 100 ; done &
|
||||
|
||||
**总结**:上述的单行脚本并不是Cron的替代品,因为Cron工具支持众多选项,更加灵活,可定制性也更高。然而如果我们想运行某些测试,比如I/O评测,上述的单行脚本也管用。
|
||||
|
||||
还可以参考:[11 Linux Cron Job Scheduling Examples][1]
|
||||
还可以参考:[Linux 下 11 个定时调度任务例子][1]
|
||||
|
||||
### 2. 如何不使用clear命令清空终端的内容 ###
|
||||
|
||||
@ -37,23 +38,23 @@ Linux世界充满了乐趣,我们越深入进去,就会发现越多有趣的
|
||||
|
||||
**总结**:因为`ctrl + l`是一个快捷键,我们不可以在脚本中使用。所以如果我们需要在脚本中清空屏幕内容,还是需要使用`clear`命令。但我能想到的所有其他情况,`ctrl + l`都更加有效。
|
||||
|
||||
### 3. 运行一个命令,然后自动回到当前的工作目录 ###
|
||||
### 3. 在其它目录运行一个命令,然后自动返回当前工作目录 ###
|
||||
|
||||
这是一个很多人可能不知道的令人吃惊的技巧。你可能想运行任何一个命令,然后再回到当前目录。你只需要将命令放在一个圆括号里。
|
||||
这是一个很多人可能不知道的令人吃惊的技巧。你可能想在其它目录运行任何一个命令,然后再回到当前目录。要实现这样的目的,你只需要将命令放在一个圆括号里。
|
||||
|
||||
我们来看一个例子:
|
||||
|
||||
avi@deb:~$ (cd /home/avi/Downloads/)
|
||||
|
||||
#### 示例输出 ####
|
||||
|
||||
avi@deb:~
|
||||
示例输出:
|
||||
|
||||
avi@deb:~
|
||||
|
||||
它首先会cd到Downloads目录,然后又回到了之前的家目录。也许你认为里边的命令根本没有执行,或者是出了某种错误,因为从命令提示符看不出任何变化。让我们简单修改一下这个命令:
|
||||
|
||||
avi@deb:~$ (cd /home/avi/Downloads/ && ls -l)
|
||||
|
||||
#### 示例输出 ####
|
||||
|
||||
示例输出:
|
||||
|
||||
-rw-r----- 1 avi avi 54272 May 3 18:37 text1.txt
|
||||
-rw-r----- 1 avi avi 54272 May 3 18:37 text2.txt
|
||||
@ -70,7 +71,7 @@ via: http://www.tecmint.com/useful-linux-hacks-commands/
|
||||
|
||||
作者:[Avishek Kumar][a]
|
||||
译者:[goreliu](https://github.com/goreliu)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
237
published/20150528 Things To Do After Installing Fedora 22.md
Normal file
237
published/20150528 Things To Do After Installing Fedora 22.md
Normal file
@ -0,0 +1,237 @@
|
||||
安装 Fedora 22 后要做的事情
|
||||
================================================================================
|
||||
|
||||
Red Hat操作系统的社区开发版的最新成员Fedora 22,已经于2015年5月26日发布了。对这个经典的Fedora发行版的发布充斥着各种猜测和预期,而最终Fedora 22推出了许多重大变化。
|
||||
|
||||
就初始化进程而言,Systemd还是个新生儿,但它已经准备好替换古老的sysvinit这个一直是Linux生态系统一部分的模块。另外一个用户会碰到的重大改变存在于基本仓库的python版本中,这里提供了两种不同口味的python版本,2.x和3.x分支,各个都有其不同的偏好和优点。所以,那些偏好2.x口味的用户可能想要安装他们喜爱的python版本。自从Fedora 18开始 dandified YUM安装器(即 DNF)就准备替换过时陈旧的YUM安装器了,Fedora最后决定,现在就用DNF来替换YUM。
|
||||
|
||||
### 1) 配置RPMFusion仓库 ###
|
||||
|
||||
正如我已经提到过的,Fedora的意识形态很是严谨,它不会自带任何非自由组件。官方仓库不会提供一些包含有非自由组件的基本软件,比如像多媒体编码。因此,安装一些第三方仓库很有必要,这些仓库会为我们提供一些基本的软件。幸运的是,RPMFusion仓库前来拯救我们了。
|
||||
|
||||
$ sudo dnf install --nogpgcheck http://download1.rpmfusion.org/free/fedora/rpmfusion-free-release-22.noarch.rpm
|
||||
|
||||
### 2) 安装VLC媒体播放器 ###
|
||||
|
||||
Fedora 22默认自带了媒体播放器,即 gnome视频播放器(以前叫做totem)。如果你觉得还好,那么我们可以跳过这一步继续往前走。但是,如果你像我一样,偏好使用最广泛的VLC,那么就去从RPMFusion仓库安装吧。安装方法如下:
|
||||
|
||||
sudo dnf install vlc -y
|
||||
|
||||
### 3) 安装多媒体编码 ###
|
||||
|
||||
刚刚我们说过,一些多媒体编码和插件不会随Fedora一起发送。现在,有谁想仅仅是因为专有编码而错过他们最爱的节目和电影?试试这个吧:
|
||||
|
||||
$ sudo dnf install gstreamer-plugins-bad gstreamer-plugins-bad-free-extras gstreamer-plugins-ugly gstreamer-ffmpeg gstreamer1-libav gstreamer1-plugins-bad-free-extras gstreamer1-plugins-bad-freeworld gstreamer-plugins-base-tools gstreamer1-plugins-good-extras gstreamer1-plugins-ugly gstreamer1-plugins-bad-free gstreamer1-plugins-good gstreamer1-plugins-base gstreamer1
|
||||
|
||||
### 4) 更新系统 ###
|
||||
|
||||
Fedora是一个前锐的发行版,因此它会不断发布更新用以修复系统中出现的错误和漏洞。因而,保持系统更新到最新,是个不错的做法。
|
||||
|
||||
$ sudo dnf update -y
|
||||
|
||||
### 5) 卸载你不需要的软件 ###
|
||||
|
||||
Fedora预装了一些大多数用户都有用的软件包,但是对于更高级的用户,你可能知道到你并不需要它。要移除你不需要的包相当容易,只需使用以下命令——我选择卸载rhythmbox,因为我知道我不会用到它:
|
||||
|
||||
$ sudo dnf remove rhythmbox
|
||||
|
||||
### 6) 安装Adobe Flash ###
|
||||
|
||||
我们都希望Adobe Flash不要再存在了,因为它并不被认为是最安全的,或者存在资源问题,但是暂时先让它待着吧。Fedora 22安装Adobe Flash的唯一途径是从Adobe安装官方RPM,就像下面这样。
|
||||
|
||||
你可以从[这里][1]下载RPM。下载完后,你可以直接右击并像下面这样打开:
|
||||
|
||||

|
||||
|
||||
右击并选择“用软件安装打开”
|
||||
|
||||
然后,只需在弹出窗口中点击安装:
|
||||
|
||||

|
||||
|
||||
*点击“安装”来完成安装Adobe定制RPM的过程*
|
||||
|
||||
该过程完成后,“安装”按钮会变成“移除”,而此时安装也完成了。如果在此过程中你的浏览器开着,会提示你先把它关掉或在安装完成后重启以使修改生效。
|
||||
|
||||
### 7) 用Gnome Boxes加速虚拟机 ###
|
||||
|
||||
你刚刚安装了Fedora,你也很是喜欢,但是出于某些私人原因,你也许仍然需要Windows,或者你只是想玩玩另外一个Linux发行版。不管哪种情况,你都可以使用Gnome Boxes来简单地创建一个虚拟机或使用一个live发行版,Fedora 22提供了该软件。遵循以下步骤,使用你所选的ISO来开始吧!谁知道呢,也许你可以检验一下某个[Fedora Spin][2]。
|
||||
|
||||
首先,打开Gnome Boxes,然后在顶部左边选择“新建”:
|
||||
|
||||

|
||||
|
||||
点击“新建”来开始添加一个新虚拟机的进程吧。
|
||||
|
||||
接下来,点击打开文件并选择一个ISO:
|
||||
|
||||

|
||||
|
||||
*在点击了“选择文件或ISO”后,选择你的ISO。这里,我已经安装了一个Debian ISO。*
|
||||
|
||||
最后,自定义VM设置或使用默认配置,然后点击“创建”。VM默认会启动,可用的VM会在Gnome Boxes以小缩略图的方式显示。
|
||||
|
||||

|
||||
|
||||
*自定义你自己的设置,或者也可以保持默认。完成后,点击“创建”,VM就一切就绪了。*
|
||||
|
||||
### 8) 添加社交媒体和其它在线帐号 ###
|
||||
|
||||
Gnome自带有不错的内建功能用于容纳帐号相关的东西,像Facebook,Google以及其它在线帐号。你可以通过Gnome设置应用访问在线帐号设置,可以在桌面上右键点击或在应用程序中找到该应用。然后,只需点击在线帐号,并添加你所选择的帐号。如果你要添加一个帐号,比如像Google,你可以用它来作为默认帐号,用来完成诸如发送邮件、日历提醒、相片和文档交互,以及诸如此类的更多事情。
|
||||
|
||||
### 9) 安装KDE或另一个桌面环境 ###
|
||||
|
||||
我们中的某些人不喜欢Gnome,那也没问题。在终端中运行以下命令来安装KDE所需的一切来替换它。这些指令也可以用以安装xfce、lxde或其它桌面环境。
|
||||
|
||||
$ sudo dnf install @kde-desktop
|
||||
|
||||
安装完成后,登出。当你点击你的用户名时,注意那个表示设置的小齿轮。点击它,然后选择“Plasma”。当你再次登录时,一个全新的KDE桌面就会欢迎你。
|
||||
|
||||

|
||||
|
||||
*刚刚安装到Fedora 22上的Plasma环境*
|
||||
|
||||
####在 Fedora 22中安装 Cinnamon桌面:####
|
||||
|
||||
打开SSH终端,输入或粘帖如下命令并回车:
|
||||
|
||||
sudo dnf install @cinnamon-desktop
|
||||
|
||||
####在 Fedora 22中安装 MATE桌面:####
|
||||
|
||||
打开SSH终端,输入或粘帖如下命令并回车:
|
||||
|
||||
sudo dnf install @mate-desktop
|
||||
|
||||
####在 Fedora 22中安装 XFCE桌面:####
|
||||
|
||||
打开SSH终端,输入或粘帖如下命令并回车:
|
||||
|
||||
sudo dnf install @xfce-desktop
|
||||
|
||||
####在 Fedora 22中安装 LXDE桌面:####
|
||||
|
||||
打开SSH终端,输入或粘帖如下命令并回车:
|
||||
|
||||
sudo dnf install @lxde-desktop
|
||||
|
||||
### 10) 定制桌面并优化设置 ###
|
||||
|
||||
默认的 Gnome 带有一张黑色背景和一个新的锁屏,幸运的是,很容易通过下面的方式来改变:
|
||||
|
||||

|
||||
|
||||
*右键点击桌面,然后点修改背景*
|
||||
|
||||

|
||||
|
||||
*你会看到这个窗口,这里你选择新的桌面背景或锁屏图片*
|
||||
|
||||
进一步,如果你点击“设置”,你会看到一个菜单展示你所以可以修改的设置。举个例子,在笔记本电脑上,你可以修改电源设置来控制合上笔记本电脑时的动作。
|
||||
|
||||
|
||||
### 11) 安装 Fedy 4.0###
|
||||
|
||||
Fedy 可以帮助用户和系统管理员来监控系统的运作,并让他们可以控制系统如其所预期的工作。这里有一行脚本可以安装最新版本的 Fedy。打开终端,输入或粘帖如下行并按下回车。
|
||||
|
||||
su -c "curl https://satya164.github.io/fedy/fedy-installer -o fedy-installer && chmod +x fedy-installer && ./fedy-installer"
|
||||
|
||||
### 12) 安装 Java###
|
||||
|
||||
使用如下命令可以很容易的安装 Java。
|
||||
|
||||
sudo dnf install java -y
|
||||
|
||||
它会根据你的系统架构自动安装32位或64位的 Java 发行版。
|
||||
|
||||
### 13) 在 Fedora 22 上安装浏览器 ###
|
||||
|
||||
Fedora 22的默认浏览器是 Firefox,不过其它的浏览器也各有优缺点。最终用户选择浏览器会有种种原因。这里我们提供一些在 Fedora 22上安装其它浏览器的方法。
|
||||
|
||||
#### 安装 Google Chrome####
|
||||
|
||||
使用你惯用的编辑器,在 yum 库目录中打开或创建 google-chrome.repo 文件。
|
||||
|
||||
sudo gedit /etc/yum.repos.d/google-chrome.repo
|
||||
|
||||
加入以下内容并保存。
|
||||
|
||||
[google-chrome]
|
||||
name=google-chrome
|
||||
baseurl=http://dl.google.com/linux/chrome/rpm/stable/$basearch
|
||||
enabled=1
|
||||
gpgcheck=1
|
||||
gpgkey=https://dl-ssl.google.com/linux/linux_signing_key.pub
|
||||
|
||||
现在 yum 就配置好可以找到稳定版本的 Chrome 了,使用如下命令安装它。
|
||||
|
||||
sudo dnf install google-chrome-stable
|
||||
|
||||
#### 安装 Tor 浏览器 ####
|
||||
|
||||
在 Fedora 22 中安装 Tor 有一点棘手,在 /etc/yum.repos.d 目录中打开或创建 torproject.repo 文件。
|
||||
|
||||
sudo gedit /etc/yum.repos.d/torproject.repo
|
||||
|
||||
插入以下内容。
|
||||
|
||||
[tor]
|
||||
name=Tor repo
|
||||
enabled=1
|
||||
baseurl=https://deb.torproject.org/torproject.org/rpm/fc/22/$basearch/
|
||||
gpgcheck=1
|
||||
gpgkey=https://deb.torproject.org/torproject.org/rpm/RPM-GPG-KEY-torproject.org.asc
|
||||
|
||||
[tor-source]
|
||||
name=Tor source repo
|
||||
enabled=1
|
||||
autorefresh=0
|
||||
baseurl=https://deb.torproject.org/torproject.org/rpm/fc/22/SRPMS
|
||||
gpgcheck=1
|
||||
gpgkey=https://deb.torproject.org/torproject.org/rpm/RPM-GPG-KEY-torproject.org.asc
|
||||
|
||||
也许会问到 GPG 键的指纹,它应该如下。
|
||||
|
||||
3B9E EEB9 7B1E 827B CF0A 0D96 8AF5 653C 5AC0 01F1
|
||||
|
||||
不幸的是,在 EPEL 和 Fedora 仓库中有一个相同名字的软件包,你需要明确排除这个来避免安装/删除/修改它。所以,在/etc/yum.repos.d/epel.repo 中加入 `Exclude=tor` 一行。
|
||||
|
||||
最后,使用如下命令来安装 Tor。
|
||||
|
||||
sudo dnf install tor
|
||||
|
||||
安装完成,启动服务。
|
||||
|
||||
sudo service tor start
|
||||
|
||||
#### 安装 Vivaldi####
|
||||
|
||||
根据你的系统架构下载32位或64位的 Vivaldi 浏览器。
|
||||
|
||||
sudo wget https://vivaldi.com/download/Vivaldi_TP3.1.0.162.9-1.i386.rpm
|
||||
sudo wget https://vivaldi.com/download/Vivaldi_TP3.1.0.162.9-1.x86_64.rpm
|
||||
|
||||
使用下列命令安装下载的 RPM。
|
||||
|
||||
sudo rpm -ivh Vivaldi_TP3.1.0.162.9-1.i386.rpm
|
||||
sudo rpm -ivh Vivaldi_TP3.1.0.162.9-1.x86_64.rpm
|
||||
|
||||
|
||||
### 尾声 ###
|
||||
|
||||
就是这样了,一切就绪。使用新系统吧,试试新东西。如果你找不到与你喜好的东西,linux赋予你自由修改它的权利。Fedora自带有最新的Gnome Shell作为其桌面环境,如果你觉得太臃肿而不喜欢,那么试试KDE或一些轻量级的DE,像Cinnamon、xfce之类。愿你的Fedora之旅十分开心并且没有困扰!!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/linux-how-to/things-do-after-installing-fedora-22/
|
||||
|
||||
作者:[Jonathan DeMasi][a]
|
||||
译者:[GOLinux](https://github.com/GOLinux)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://linoxide.com/author/jonathande/
|
||||
[1]:https://get.adobe.com/flashplayer/
|
||||
[2]:http://spins.fedoraproject.org/
|
||||
[3]:https://www.google.com/intl/en/chrome/browser/desktop/index.html
|
||||
@ -0,0 +1,106 @@
|
||||
在Linux上如何清除内存的 Cache、Buffer 和交换空间
|
||||
============================================
|
||||
|
||||
像任何其他的操作系统一样,GNU/Linux 已经实现的内存管理不仅有效,而且更好。但是,如果有任何进程正在蚕食你的内存,而你想要清除它的话,Linux 提供了一个刷新或清除RAM缓存方法。
|
||||
|
||||

|
||||
|
||||
### 如何在 Linux 中清除缓存(Cache)?###
|
||||
|
||||
每个 Linux 系统有三种选项来清除缓存而不需要中断任何进程或服务。
|
||||
|
||||
(LCTT 译注:Cache,译作“缓存”,指 CPU 和内存之间高速缓存。Buffer,译作“缓冲区”,指在写入磁盘前的存储再内存中的内容。在本文中,Buffer 和 Cache 有时候会通指。)
|
||||
|
||||
1. 仅清除页面缓存(PageCache)
|
||||
|
||||
# sync; echo 1 > /proc/sys/vm/drop_caches
|
||||
|
||||
2. 清除目录项和inode
|
||||
|
||||
# sync; echo 2 > /proc/sys/vm/drop_caches
|
||||
|
||||
3. 清除页面缓存,目录项和inode
|
||||
|
||||
# sync; echo 3 > /proc/sys/vm/drop_caches
|
||||
|
||||
|
||||
上述命令的说明:
|
||||
|
||||
sync 将刷新文件系统缓冲区(buffer),命令通过“;”分隔,顺序执行,shell在执行序列中的下一个命令之前会等待命令的终止。正如内核文档中提到的,写入到drop_cache将清空缓存而不会杀死任何应用程序/服务,[echo命令][1]做写入文件的工作。
|
||||
|
||||
如果你必须清除磁盘高速缓存,第一个命令在企业和生产环境中是最安全,`"...echo 1> ..."`只会清除页面缓存。
|
||||
在生产环境中不建议使用上面的第三个选项`"...echo 3 > ..."` ,除非你明确自己在做什么,因为它会清除缓存页,目录项和inodes。
|
||||
|
||||
**在Linux上释放也许被内核所使用的缓冲区(Buffer)和缓存(Cache)是否是个好主意?**
|
||||
|
||||
当你设置许多设定想要检查效果时,如果它实际上是专门针对 I/O 范围的基准测试,那么你可能需要清除缓冲区和缓存。你可以如上所示删除缓存,无需重新启动系统(即无需停机)。
|
||||
|
||||
Linux被设计成它在寻找磁盘之前到磁盘缓存寻找的方式。如果它发现该资源在缓存中,则该请求不会发送到磁盘。如果我们清理缓存,磁盘缓存就起不到作用了,系统会到磁盘上寻找资源。
|
||||
|
||||
此外,当清除缓存后它也将减慢系统运行速度,系统会将每一个被请求的资源再次加载到磁盘缓存中。
|
||||
|
||||
|
||||
现在,我们将创建一个 shell 脚本,通过一个 cron 调度任务在每天下午2点自动清除RAM缓存。如下创建一个 shell 脚本 clearcache.sh 并在其中添加以下行:
|
||||
|
||||
#!/bin/bash
|
||||
# 注意,我们这里使用了 "echo 3",但是不推荐使用在产品环境中,应该使用 "echo 1"
|
||||
echo "echo 3 > /proc/sys/vm/drop_caches"
|
||||
|
||||
给clearcache.sh文件设置执行权限
|
||||
|
||||
# chmod 755 clearcache.sh
|
||||
|
||||
现在,当你需要清除内存缓存时只需要调用脚本。
|
||||
|
||||
现在设置一个每天下午2点的定时任务来清除RAM缓存,打开crontab进行编辑。
|
||||
|
||||
# crontab -e
|
||||
|
||||
添加以下行,保存并退出。
|
||||
|
||||
0 3 * * * /path/to/clearcache.sh
|
||||
|
||||
有关如何创建一个定时任务,更多细节你可以查看我们的文章 [11 个定时调度任务的例子][2]。
|
||||
|
||||
**在生产环境的服务器上自动清除RAM是否是一个好主意?**
|
||||
|
||||
不!它不是。想想一个情况,当你已经预定脚本在每天下午2点来清除内存缓存。那么其时该脚本会执行并刷新你的内存缓存。在某一天由于某些原因,可能您的网站的在线用户会超过预期地从你的服务器请求资源。
|
||||
|
||||
|
||||
而在这时,按计划调度的脚本运行了,并清除了缓存中的一切。当所有的用户都从磁盘读取数据时,这将导致服务器崩溃并损坏数据库。因此,清除缓存仅在必要时并且在你的预料之中,否则你就是个呆瓜系统管理员。
|
||||
|
||||
###如何清除Linux的交换空间?###
|
||||
|
||||
如果你想清除掉的空间,你可以运行下面的命令:
|
||||
|
||||
# swapoff -a && swapon -a
|
||||
|
||||
此外,了解有关风险后,您可以将上面的命令添加到cron中。
|
||||
|
||||
现在,我们将上面两种命令结合成一个命令,写成正确的脚本来同时清除RAM缓存和交换空间。
|
||||
|
||||
# echo 3 > /proc/sys/vm/drop_caches && swapoff -a && swapon -a && printf '\n%s\n' 'Ram-cache and Swap Cleared'
|
||||
|
||||
或
|
||||
|
||||
su -c 'echo 3 > /proc/sys/vm/drop_caches' && swapoff -a && swapon -a && printf '\n%s\n' 'Ram-cache and Swap Cleared'
|
||||
|
||||
在测试上面的命令之前,我们在执行脚本前后运行“free -m” 来检查缓存。
|
||||
|
||||
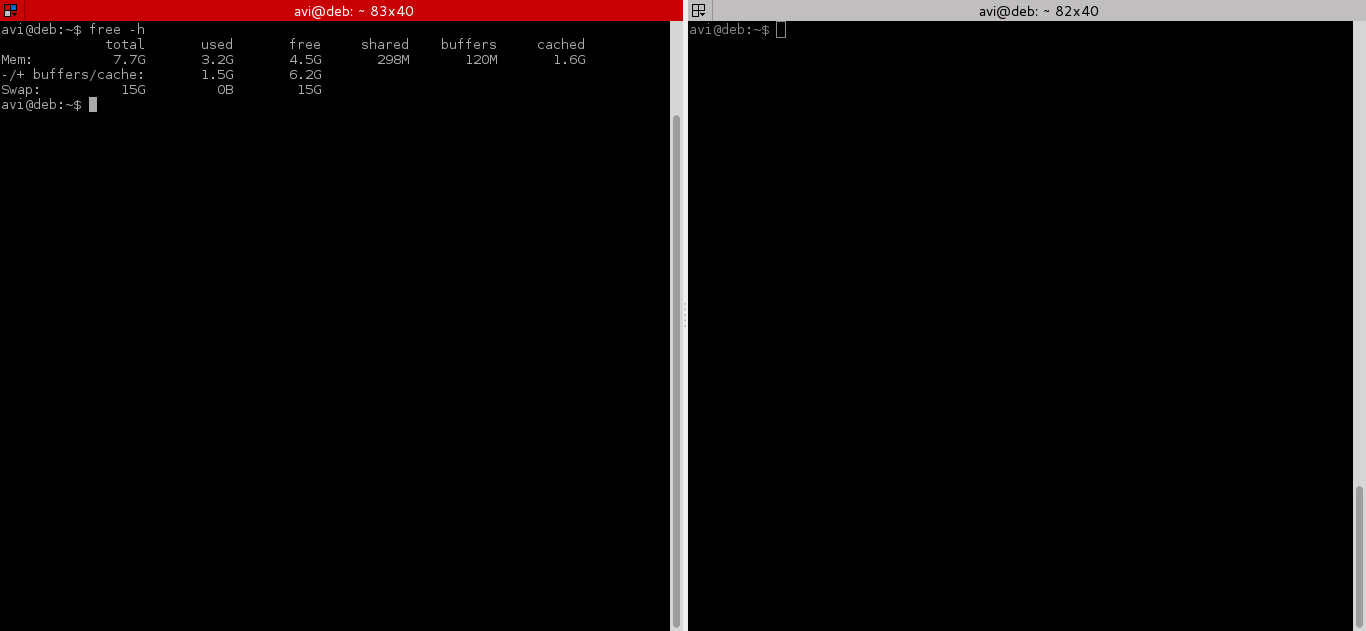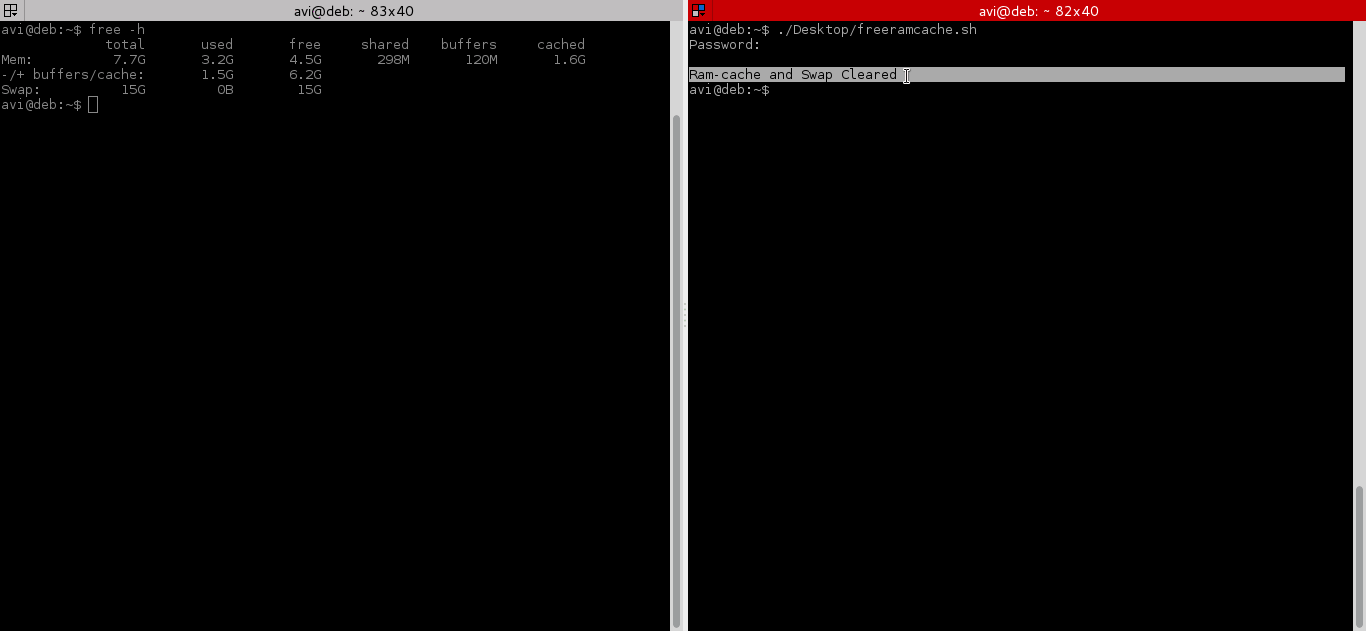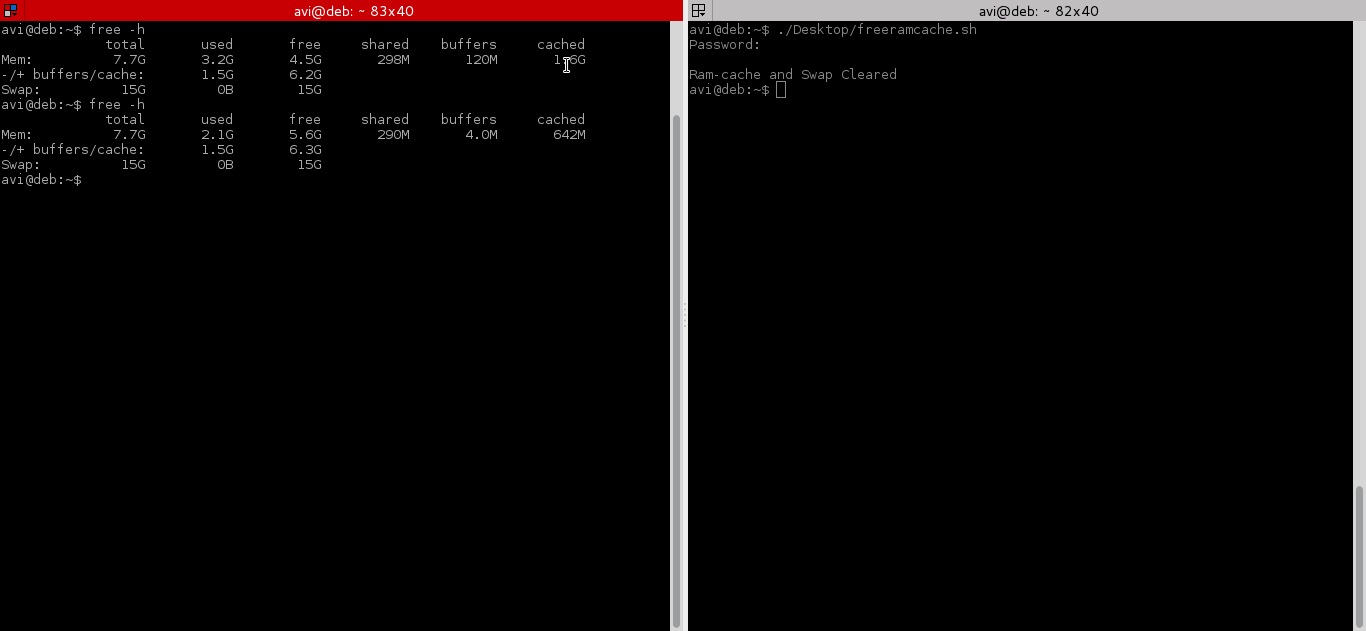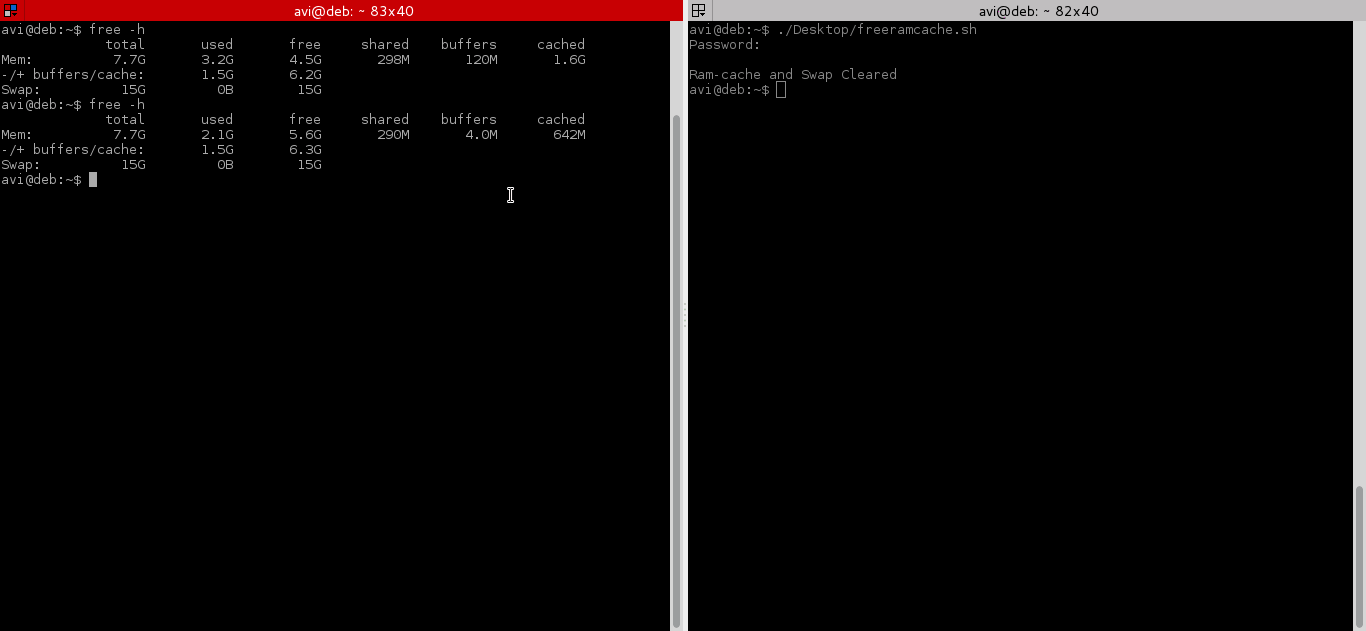
|
||||
|
||||
就是这样,如果你喜欢这篇文章,不要忘记向我们提供您宝贵的意见,让我们知道,您认为在企业和生产环境中清除内存缓存和缓冲区是否是一个好主意?
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.tecmint.com/clear-ram-memory-cache-buffer-and-swap-space-on-linux/
|
||||
|
||||
作者:[Avishek Kumar][a]
|
||||
译者:[strugglingyouth](https://github.com/strugglingyouth)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.tecmint.com/author/avishek/
|
||||
[1]:https://linux.cn/article-3592-1.html
|
||||
[2]:http://www.tecmint.com/11-cron-scheduling-task-examples-in-linux/
|
||||
@ -1,100 +0,0 @@
|
||||
translating wi-cuckoo
|
||||
3 Open Source Python Shells
|
||||
================================================================================
|
||||
Python is a high-level, general-purpose, structured, powerful, open source programming language that is used for a wide variety of programming tasks. It features a fully dynamic type system and automatic memory management, similar to that of Scheme, Ruby, Perl, and Tcl, avoiding many of the complexities and overheads of compiled languages. The language was created by Guido van Rossum in 1991, and continues to grow in popularity.
|
||||
|
||||
Python is a very useful and popular computer language. One of the benefits of using an interpreted language such as Python is exploratory programming with its interactive shell. You can try out code without having to write a script. But there are limitations with the Python shell. Fortunately, there are some excellent alternative Python shells that extend on the basic shell. They each offer an excellent interactive Python experience.
|
||||
|
||||
----------
|
||||
|
||||
### bpython ###
|
||||
|
||||

|
||||
|
||||
bpython is a fancy interface to the Python interpreter for Linux, BSD, OS X and Windows.
|
||||
|
||||
The idea is to provide the user with all the features in-line, much like modern IDEs, but in a simple, lightweight package that can be run in a terminal window.
|
||||
|
||||
bpython doesn't seek to create anything new or groundbreaking. Instead, it brings together a few neat ideas and focuses on practicality and usefulness.
|
||||
|
||||
Features include:
|
||||
|
||||
- In-line syntax highlighting - uses Pygments for lexing the code as you type, and colours appropriately
|
||||
- Readline-like autocomplete with suggestions displayed as you type
|
||||
- Expected parameter list for any Python function - seeks to display a list of parameters for any function you call
|
||||
- "Rewind" function to pop the last line of code from memory and re-evaluate
|
||||
- Send the code you've entered off to a pastebin
|
||||
- Save the code you've entered to a file
|
||||
- Auto-indentation
|
||||
- Python 3 support
|
||||
|
||||
- Website: [www.bpython-interpreter.org][1]
|
||||
- Developer: Bob Farrell and contributors
|
||||
- License: MIT License
|
||||
- Version Number: 0.14.1
|
||||
|
||||
----------
|
||||
|
||||
### IPython ###
|
||||
|
||||

|
||||
|
||||
IPython is an enhanced interactive Python shell. It provides a rich toolkit to help you make the most out of using Python interactively.
|
||||
|
||||
IPython can be used as a replacement for the standard Python shell, or it can be used as a complete working environment for scientific computing (like Matlab or Mathematica) when paired with the standard Python scientific and numerical tools. It supports dynamic object introspections, numbered input/output prompts, a macro system, session logging, session restoring, complete system shell access, verbose and colored traceback reports, auto-parentheses, auto-quoting, and is embeddable in other Python programs.
|
||||
|
||||
Features include:
|
||||
|
||||
- Powerful interactive shells (terminal and Qt-based)
|
||||
- A browser-based notebook with support for code, rich text, mathematical expressions, inline plots and other rich media
|
||||
- Support for interactive data visualization and use of GUI toolkits
|
||||
- Flexible, embeddable interpreters to load into your own projects
|
||||
- Easy to use, high performance tools for parallel computing
|
||||
|
||||
- Website: [ipython.org][2]
|
||||
- Developer: The IPython Development Team
|
||||
- License: BSD
|
||||
- Version Number: 3.1
|
||||
|
||||
----------
|
||||
|
||||
### DreamPie ###
|
||||
|
||||

|
||||
|
||||
DreamPie is a Python shell which is designed to be reliable and fun.
|
||||
|
||||
DreamPie can use just about any Python interpreter (Jython, IronPython, PyPy).
|
||||
|
||||
Features include:
|
||||
|
||||
- New concept for an interactive shell: the window is divided into the history box, which lets you view previous commands and their output, and the code box, where you write your code. This allows you to edit any amount of code, just like in your favorite editor, and execute it when it's ready. You can also copy code from anywhere, edit it and run it instantly
|
||||
- The Copy code only command will copy the code you want to keep, so you can save it in a file. The code is already formatted nicely with a four-space indentation
|
||||
- Automatic completion of attributes and file names
|
||||
- Automatically displays function arguments and documentation
|
||||
- Keeps your recent results in the result history, for later use
|
||||
- Can automatically fold long outputs, so you can concentrate on what's important
|
||||
- Save the history of the session as an HTML file, for future reference. You can then load the history file into DreamPie, and quickly redo previous commands
|
||||
- Automatically adds parentheses and optionally quotes when you press space after functions and methods. For example, type execfile fn and get execfile("fn")
|
||||
- Supports interactive plotting with matplotlib
|
||||
- Xupport for Python 2.5, Python 2.6, Python 3.1, Jython 2.5, IronPython 2.6, and PyPy
|
||||
- Extremely fast and responsive.
|
||||
|
||||
- Website: [www.dreampie.org][3]
|
||||
- Developer: Noam Yorav-Raphael
|
||||
- License: GNU GPL v3
|
||||
- Version Number: 1.2.1
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linuxlinks.com/article/20150523032756576/PythonShells.html
|
||||
|
||||
作者:Frazer Kline
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.bpython-interpreter.org/
|
||||
[2]:http://ipython.org/
|
||||
[3]:http://www.dreampie.org/
|
||||
@ -1,3 +1,4 @@
|
||||
sevenot translating
|
||||
The top 10 rookie open source projects
|
||||
================================================================================
|
||||
Black Duck presents its Open Source Rookies of the Year -- the 10 most exciting, active new projects germinated by the global open source community
|
||||
@ -150,4 +151,4 @@ via: http://www.infoworld.com/article/2875439/open-source-software/the-top-10-ro
|
||||
[20]:https://www.blackducksoftware.com/open-source-rookies
|
||||
[21]:http://www.infoworld.com/article/2871935/application-development/infoworlds-2015-technology-of-the-year-award-winners.html
|
||||
[22]:http://www.infoworld.com/article/2688104/open-source-software/article.html
|
||||
[23]:http://www.infoworld.com/article/2854954/microsoft-windows/15-essential-open-source-tools-for-windows-admins.html
|
||||
[23]:http://www.infoworld.com/article/2854954/microsoft-windows/15-essential-open-source-tools-for-windows-admins.html
|
||||
|
||||
@ -1,58 +0,0 @@
|
||||
No reboot patching comes to Linux 4.0
|
||||
================================================================================
|
||||
> **Summary**:With the new Linux 4.0 kernel, you'll need to reboot Linux less often than ever.
|
||||
|
||||
With [Linux 4.0][1], you may never need to reboot your operating system again.
|
||||
|
||||

|
||||
Using Linux means never having to reboot. -- SUSE
|
||||
|
||||
One reason to love Linux on your servers or in your data-center is that you so seldom needed to reboot it. True, critical patches require a reboot, but you could go months without rebooting. Now, with the latest changes to the Linux kernel you may be able to go years between reboots.
|
||||
|
||||
This is actually a feature that was available in Linux in 2009 thanks to a program called [Ksplice][2]. This program compares the original and patched kernels and then uses a customized kernel module to patch the new code into the running kernel. Each Ksplice-enabled kernel comes with a special set of flags for each function that will be patched. The [Ksplice process][3] then watches for a moment when the code for the function being patched isn't in use, and ta-da, the patch is made and your server runs on.
|
||||
|
||||
[Oracle acquired Ksplice][4] in 2011, and kept it just for its own [Oracle Linux][5], a [Red Hat Enterprise Linux (RHEL)][6] clone, and as a RHEL subscription service. That left all the other enterprise and server Linux back where they started.
|
||||
|
||||
Then [KernelCare released a service that could provide bootless patches][7] for most enterprise Linux distros. This program use proprietary software and is only available as a service with a monthly fee. That was a long way from satisfying many Linux system administrators.
|
||||
|
||||
So, [Red Hat][8] and [SUSE][9] both started working on their own purely open-source means of giving Linux the ability to keep running even while critical patches were being installed. Red Hat's program was named [kpatch][10], while SUSE' is named [kGraft][11].
|
||||
|
||||
The two companies took different approaches. Kpatch issues a stop_machine() command. After that it looks at the stack of existing processes using [ftrace][12] and, if the patch can be made safely, it redirects the running code to the patched functions and then removes the now outdated code.
|
||||
|
||||
Kgraft also uses ftrace, but it works on the thread level. When an old function is called it makes sure the thread reaches a point that it can switch to the new function.
|
||||
|
||||
While the end result is the same, the operating system keeps running while patches are made, there are significant differences in performance. Kpatch takes from one to forty milliseconds, while kGraft might take several minutes but there's never even a millisecond of down time.
|
||||
|
||||
At the Linux Plumbers Conference in October 2014, the two groups got together and started work on a way to [patch Linux without rebooting that combines the best of both programs][13]. Essentially, what they ended up doing was putting both kpatch and kGraft in the 4.0 Linux kernel.
|
||||
|
||||
Jiri Kosina, a SUSE software engineer and Linux kernel developer, explained, that live-patching in the Linux kernel will "provides a basic infrastructure for function "live patching" (i.e. code redirection), including API [application programming interface] for kernel modules containing the actual patches, and API/ABI [application binary interface] for userspace to be able to operate on the patches. This is "relatively simple and minimalistic, as it's making use of existing kernel infrastructure (namely ftrace) as much as possible. It's also self-contained, in a sense that it doesn't hook itself in any other kernel subsystem (it doesn't even touch any other code)."
|
||||
|
||||
The release candidate for Linux 4.0 is now out. Kosina stated that "It's now implemented for x86 only as a reference architecture, but support for powerpc, s390 and arm is already in the works." And, indeed, the source code for these architectures is already in the [Live Patching Git code][14].
|
||||
|
||||
Simply having the code in there is just the start. Your Linux distribution will have to support it with patches that can make use of it. With both Red Hat and SUSE behind it, live patching will soon be the default in all serious business Linux distributions.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.zdnet.com/article/no-reboot-patching-comes-to-linux-4-0/#ftag=RSSbaffb68
|
||||
|
||||
作者:[Steven J. Vaughan-Nichols][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.zdnet.com/meet-the-team/us/sjvn/
|
||||
[1]:http://www.zdnet.com/article/linux-kernel-turns-over-release-odometer-to-4-0/
|
||||
[2]:http://www.computerworld.com/article/2466389/open-source-tools/never-reboot-again-with-linux-and-ksplice.html
|
||||
[3]:http://www.ksplice.com/
|
||||
[4]:http://www.zdnet.com/article/oracle-acquires-zero-downtime-linux-upgrade-software/
|
||||
[5]:http://www.oracle.com/us/technologies/linux/overview/index.html
|
||||
[6]:http://www.redhat.com/en/technologies/linux-platforms/enterprise-linux
|
||||
[7]:http://www.zdnet.com/article/kernelcare-new-no-reboot-linux-patching-system/
|
||||
[8]:http://www.redhat.com/
|
||||
[9]:http://www.suse.com/
|
||||
[10]:http://rhelblog.redhat.com/2014/02/26/kpatch/
|
||||
[11]:http://www.zdnet.com/article/suse-gets-live-patching/
|
||||
[12]:http://elinux.org/Ftrace
|
||||
[13]:http://linuxplumbersconf.org/2014/wp-content/uploads/2014/10/LPC2014_LivePatching.txt
|
||||
[14]:https://kernel.googlesource.com/pub/scm/linux/kernel/git/jikos/livepatching/+/9ec0de0ee0c9f0ffe4f72da9158194121cc22807
|
||||
@ -0,0 +1,83 @@
|
||||
translating wi-cuckoo
|
||||
PHP at 20: From pet project to powerhouse
|
||||
================================================================================
|
||||

|
||||
|
||||
Credit: [Steve Jurvetson via Flickr][1]
|
||||
|
||||
> The one-time ‘silly little project’ has transformed into a Web powerhouse, thanks to flexibility, pragmatism, and a vibrant community of Web devs
|
||||
|
||||
When Rasmus Lerdorf released “[a set of small tight CGI binaries written in C][2],” he had no idea how much his creation would impact Web development. Delivering the opening keynote at this year’s SunshinePHP conference in Miami, Lerdorf quipped, “In 1995, I thought I had unleashed a C API upon the Web. Obviously, that’s not what happened, or we’d all be C programmers.”
|
||||
|
||||
In fact, when Lerdorf released version 1.0 of Personal Home Page Tools -- as PHP was then known -- the Web was very young. HTML 2.0 would not be published until November of that year, and HTTP/1.0 not until May the following year. NCSA HTTPd was the most widely deployed Web server, and Netscape Navigator was the most popular Web browser, with Internet Explorer 1.0 to arrive in August. In other words, PHP’s beginnings coincided with the eve of the browser wars.
|
||||
|
||||
Those early days speak volumes about PHP’s impact on Web development. Back then, our options were limited when it came to server-side processing for Web apps. PHP stepped in to fill our need for a tool that would enable us to do dynamic things on the Web. That practical flexibility captured our imaginations, and PHP has since grown up with the Web. Now powering [more than 80 percent of the Web][3], PHP has matured into a scripting language that is especially suited to solve the Web problem. Its unique pedigree tells a story of pragmatism over theory and problem solving over purity.
|
||||
|
||||
### The Web glue we got hooked on ###
|
||||
|
||||
PHP didn’t start out as a language, and this is clear from its design -- or lack thereof, as detractors point out. It began as an API to help Web developers access lower-level C libraries. The first version was a small CGI binary that provided form-processing functionality with access to request parameters and the mSQL database. And its facility with a Web app’s database would prove key in sparking our interest in PHP and PHP’s subsequent ascendancy.
|
||||
|
||||
By version 2 -- aka PHP/FI -- database support had expanded to include PostgreSQL, MySQL, Oracle, Sybase, and more. It supported these databases by wrapping their C libraries, making them a part of the PHP binary. PHP/FI could also wrap the GD library to create and manipulate GIF images. It could be run as an Apache module or compiled with FastCGI support, and it introduced the PHP script language with support for variables, arrays, language constructs, and functions. For many of us working on the Web at that time, PHP was the kind of glue we'd been looking for.
|
||||
|
||||
As PHP folded in more and more programming language features, morphing into version 3 and onward, it never lost this gluelike aspect. Through repositories like PECL (PHP Extension Community Library), PHP could tie together libraries and expose their functionality to the PHP layer. This capacity to bring together components became a significant facet of the beauty of PHP, though it was not limited to its source code.
|
||||
|
||||
### The Web as a community of coders ###
|
||||
|
||||
PHP’s lasting impact on Web development isn’t limited to what can be done with the language itself. How PHP work is done and who participates -- these too are important parts of PHP’s legacy.
|
||||
|
||||
As early as 1997, PHP user groups began forming. One of the earliest was the Midwest PHP User’s Group (later known as Chicago PHP), which held its [first meeting in February 1997][4]. This was the beginning of what would become a vibrant, energetic community of developers assembled over an affinity for a little tool that helped them solve problems on the Web. The ubiquity of PHP made it a natural choice for Web development. It became especially popular in the shared hosting world, and its low barrier to entry was attractive to many early Web developers.
|
||||
|
||||
With a growing community came an assortment of tools and resources for PHP developers. The year 2000 -- a watershed moment for PHP -- witnessed the first PHP Developers’ Meeting, a gathering of the core developers of the programming language, who met in Tel Aviv to discuss the forthcoming 4.0 release. PHP Extension and Application Repository (PEAR) also launched in 2000 to provide high-quality userland code packages following standards and best practices. The first PHP conference, PHP Kongress, was held in Germany soon after. [PHPDeveloper.org][5] came online, and to this day, it is the most authoritative news source in the PHP community.
|
||||
|
||||
This communal momentum proved vital to PHP’s growth in subsequent years, and as the Web development industry erupted, so did PHP. PHP began powering more and larger websites. More user groups formed around the world. Mailing lists; online forums; IRC; conferences; trade journals such as php[architect], the German PHP Magazin, and International PHP Magazine -- the vibrancy of the PHP community had a significant impact on the way Web work would be done: collectively and openly, with an emphasis on code sharing.
|
||||
|
||||
Then, 10 years ago, shortly after the release of PHP 5, an interesting thing happened in Web development that created a general shift in how the PHP community built libraries and applications: Ruby on Rails was released.
|
||||
|
||||
### The rise of frameworks ###
|
||||
|
||||
The Ruby on Rails framework for the Ruby programming language created an increased focus and attention on the MVC (model-view-controller) architectural pattern. The Mojavi PHP framework a few years prior had used this pattern, but the hype around Ruby on Rails is what firmly cemented MVC in the PHP frameworks that followed. Frameworks exploded in the PHP community, and frameworks have changed the way developers build PHP applications.
|
||||
|
||||
Many important projects and developments have arisen, thanks to the proliferation of frameworks in the PHP community. The PHP [Framework Interoperability Group][6] formed in 2009 to aid in establishing coding standards, naming conventions, and best practices among frameworks. Codifying these standards and practices helped provide more interoperable software for developers using member projects’ code. This interoperability meant that each framework could be split into components and stand-alone libraries could be used together with monolithic frameworks. With interoperability came another important milestone: The Composer project was born in 2011.
|
||||
|
||||
Inspired by Node.js’s NPM and Ruby’s Bundler, Composer has ushered in a new era of PHP application development, creating a PHP renaissance of sorts. It has encouraged interoperability between packages, standard naming conventions, adoption of coding standards, and increased test coverage. It is an essential tool in any modern PHP application.
|
||||
|
||||
### The need for speed and innovation ###
|
||||
|
||||
Today, the PHP community has a thriving ecosystem of applications and libraries. Some of the most widely installed PHP applications include WordPress, Drupal, Joomla, and MediaWiki. These applications power the Web presence of businesses of all sizes, from small mom-and-pop shops to sites like whitehouse.gov and Wikipedia. Six of the Alexa top 10 sites use PHP to serve billions of pages a day. As a result, PHP applications have been optimized for speed -- and much innovation has gone into PHP core to improve performance.
|
||||
|
||||
In 2010, Facebook unveiled its HipHop for PHP source-to-source compiler, which translates PHP code into C++ code and compiles it into a single executable binary application. Facebook’s size and growth necessitated the move away from standard interpreted PHP code to a faster, optimized executable. However, Facebook wanted to continue using PHP for its ease of use and rapid development cycles. HipHop for PHP evolved into HHVM, a JIT (just-in-time) compilation-based execution engine for PHP, which included a new language based on PHP: [Hack][7].
|
||||
|
||||
Facebook’s innovations, as well as other VM projects, created competition at the engine level, leading to discussions about the future of the Zend Engine that still powers PHP’s core, as well as the question of a language specification. In 2014, a language specification project was created “to provide a complete and concise definition of the syntax and semantics of the PHP language,” making it possible for compiler projects to create interoperable PHP implementations.
|
||||
|
||||
The next major version of PHP became a topic of intense debate, and a project known as phpng (next generation) was offered as an option to clean up, refactor, optimize, and improve the PHP code base, which also showed substantial improvements to the performance of real-world applications. After deciding to name the next major version “PHP 7,” due to a previous, unreleased PHP 6.0 version, the phpng branch was merged in, and plans were made to proceed with PHP 7, working in many of the language features offered by Hack, such as scalar and return type hinting.
|
||||
|
||||
With the [first PHP 7 alpha release due out today][8] and benchmarks showing [performance as good as or better than that of HHVM][9] in many cases, PHP is keeping up with the pace of modern Web development needs. Likewise, the PHP-FIG continues to innovate and push frameworks and libraries to collaborate and cooperate -- most recently with the adoption of [PSR-7][10], which will change the way PHP projects handle HTTP. User groups, conferences, publications, and initiatives like [PHPMentoring.org][11] continue to advocate best practices, coding standards, and testing to the PHP developer community.
|
||||
|
||||
PHP has seen the Web mature through various stages, and PHP has matured. Once a simple API wrapper around lower-level C libraries, PHP has become a full-fledged programming language in its own right. Its developer community is vibrant and helpful, priding themselves in pragmatism and welcoming newcomers. PHP has stood the test of time for 20 years, and current activity in the language and community is ensuring it will be a relevant and useful language for years to come.
|
||||
|
||||
During his SunshinePHP keynote, Rasmus Lerdorf reflected, “Did I think I’d be here 20 years later talking about this silly little project I did? No, I didn’t.”
|
||||
|
||||
Here’s to Lerdorf and the rest of the PHP community for transforming this “silly little project” into a lasting, powerful component of the Web today.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.infoworld.com/article/2933858/php/php-at-20-from-pet-project-to-powerhouse.html
|
||||
|
||||
作者:[Ben Ramsey][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.infoworld.com/author/Ben-Ramsey/
|
||||
[1]:https://www.flickr.com/photos/jurvetson/13049862325
|
||||
[2]:https://groups.google.com/d/msg/comp.infosystems.www.authoring.cgi/PyJ25gZ6z7A/M9FkTUVDfcwJ
|
||||
[3]:http://w3techs.com/technologies/overview/programming_language/all
|
||||
[4]:http://web.archive.org/web/20061215165756/http://chiphpug.php.net/mpug.htm
|
||||
[5]:http://www.phpdeveloper.org/
|
||||
[6]:http://www.php-fig.org/
|
||||
[7]:http://www.infoworld.com/article/2610885/facebook-q-a--hack-brings-static-typing-to-php-world.html
|
||||
[8]:https://wiki.php.net/todo/php70#timetable
|
||||
[9]:http://talks.php.net/velocity15
|
||||
[10]:http://www.php-fig.org/psr/psr-7/
|
||||
[11]:http://phpmentoring.org/
|
||||
@ -1,80 +0,0 @@
|
||||
How to make remote incremental backup of LUKS-encrypted disk/partition
|
||||
================================================================================
|
||||
Some of us have our hard drives at home or on a [VPS][1] encrypted by [Linux Unified Key Setup (LUKS)][2] for security reasons, and these drives can quickly grow to tens or hundreds of GBs in size. So while we enjoy the security of our LUKS device, we may start to think about a possible remote backup solution. For secure off-site backup, we will need something that operates at the block level of the encrypted LUKS device, and not at the un-encrypted file system level. So in the end we find ourselves in a situation where we will need to transfer the entire LUKS device (let's say 200GB for example) each time we want to make a backup. Clearly not feasible. How can we deal with this problem?
|
||||
|
||||
### A Solution: Bdsync ###
|
||||
|
||||
This is when a brilliant open-source tool called [Bdsync][3] (thanks to Rolf Fokkens) comes to our rescue. As the name implies, Bdsync can synchronize "block devices" over network. For fast synchronization, Bdsync generates and compares MD5 checksums of blocks in the local/remote block devices, and sync only the differences. What rsync can do at the file system level, Bdsync can do it at the block device level. Naturally, it works with encrypted LUKS devices as well. Pretty neat!
|
||||
|
||||
Using Bdsync, the first-time backup will copy the entire LUKS block device to a remote host, so it will take a lot of time to finish. However, after that initial backup, if we make some new files on the LUKS device, the second backup will be finished quickly because we will need to copy only that blocks which have been changed. Classic incremental backup at play!
|
||||
|
||||
### Install Bdsync on Linux ###
|
||||
|
||||
Bdsync is not included in the standard repositories of [Linux][4] distributions. Thus you need to build it from the source. Use the following distro-specific instructions to install Bdsync and its man page on your system.
|
||||
|
||||
#### Debian, Ubuntu or Linux Mint ####
|
||||
|
||||
$ sudo apt-get install git gcc libssl-dev
|
||||
$ git clone https://github.com/TargetHolding/bdsync.git
|
||||
$ cd bdsync
|
||||
$ make
|
||||
$ sudo cp bdsync /usr/local/sbin
|
||||
$ sudo mkdir -p /usr/local/man/man1
|
||||
$ sudo sh -c 'gzip -c bdsync.1 > /usr/local/man/man1/bdsync.1.gz'
|
||||
|
||||
#### Fedora or CentOS/RHEL ####
|
||||
|
||||
$ sudo yum install git gcc openssl-devel
|
||||
$ git clone https://github.com/TargetHolding/bdsync.git
|
||||
$ cd bdsync
|
||||
$ make
|
||||
$ sudo cp bdsync /usr/local/sbin
|
||||
$ sudo mkdir -p /usr/local/man/man1
|
||||
$ sudo sh -c 'gzip -c bdsync.1 > /usr/local/man/man1/bdsync.1.gz'
|
||||
|
||||
### Perform Off-site Incremental Backup of LUKS-Encrypted Device ###
|
||||
|
||||
I assume that you have already provisioned a LUKS-encrypted block device as a backup source (e.g., /dev/LOCDEV). I also assume that you have a remote host where the source device will be backed up (e.g., as /dev/REMDEV).
|
||||
|
||||
You need to access the root account on both systems, and set up [password-less SSH access][5] from the local host to a remote host. Finally, you need to install Bdsync on both hosts.
|
||||
|
||||
To initiate a remote backup process on the local host, we execute the following command as the root:
|
||||
|
||||
# bdsync "ssh root@remote_host bdsync --server" /dev/LOCDEV /dev/REMDEV | gzip > /some_local_path/DEV.bdsync.gz
|
||||
|
||||
Some explanations are needed here. Bdsync client will open an SSH connection to the remote host as the root, and execute Bdsync client with --server option. As clarified, /dev/LOCDEV is our source LUKS block device on the local host, and /dev/REMDEV is the target block device on the remote host. They could be /dev/sda (for an entire disk) or /dev/sda2 (for a single partition). The output of the local Bdsync client is then piped to gzip, which creates DEV.bdsync.gz (so-called binary patch file) in the local host.
|
||||
|
||||
The first time you run the above command, it will take very long time, depending on your Internet/LAN speed and the size of /dev/LOCDEV. Remember that you must have two block devices (/dev/LOCDEV and /dev/REMDEV) with the same size.
|
||||
|
||||
The next step is to copy the generated patch file from the local host to the remote host. Using scp is one possibility:
|
||||
|
||||
# scp /some_local_path/DEV.bdsync.gz root@remote_host:/remote_path
|
||||
|
||||
The final step is to execute the following command on the remote host, which will apply the patch file to /dev/REMDEV:
|
||||
|
||||
# gzip -d < /remote_path/DEV.bdsync.gz | bdsync --patch=/dev/DSTDEV
|
||||
|
||||
I recommend doing some tests with small partitions (without any important data) before deploying Bdsync with real data. After you fully understand how the entire setup works, you can start backing up real data.
|
||||
|
||||
### Conclusion ###
|
||||
|
||||
In conclusion, we showed how to use Bdsync to perform incremental backups for LUKS devices. Like rsync, only a fraction of data, not the entire LUKS device, is needed to be pushed to an off-site backup site at each backup, which saves bandwidth and backup time. Rest assured that all the data transfer is secured by SSH or SCP, on top of the fact that the device itself is encrypted by LUKS. It is also possible to improve this setup by using a dedicated user (instead of the root) who can run bdsync. We can also use bdsync for ANY block device, such as LVM volumes or RAID disks, and can easily set up Bdsync to back up local disks on to USB drives as well. As you can see, its possibility is limitless!
|
||||
|
||||
Feel free to share your thought.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/remote-incremental-backup-luks-encrypted-disk-partition.html
|
||||
|
||||
作者:[Iulian Murgulet][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/iulian
|
||||
[1]:http://xmodulo.com/go/digitalocean
|
||||
[2]:http://xmodulo.com/how-to-create-encrypted-disk-partition-on-linux.html
|
||||
[3]:http://bdsync.rolf-fokkens.nl/
|
||||
[4]:http://xmodulo.com/recommend/linuxbook
|
||||
[5]:http://xmodulo.com/how-to-enable-ssh-login-without.html
|
||||
@ -0,0 +1,74 @@
|
||||
Translating by strugglingyouth
|
||||
Extend Swap Space using Swap file in Linux
|
||||
================================================================================
|
||||
There are some scenarios where our Linux box is running out of swap space so in that case we can extend the swap space using swap partition but due to unavailability of free partitions on the disk, we are unable to extend it.
|
||||
|
||||
So in such cases we can extend or increase swap space using a swap file
|
||||
|
||||
### Below are the Steps to extend Swap Space using Swap File in Linux ###
|
||||
|
||||
Lets first check the size of existing swap space / partition using the command like ‘**free -m‘** and ‘**swapon -s**‘
|
||||
|
||||

|
||||
free-output-with-swap
|
||||
|
||||
In my case size of swap partition is 2 GB. So we will be extending swap space by 1 GB.
|
||||
|
||||
#### Step:1 Create a swap file of size 1 GB using below dd Command ####
|
||||
|
||||
[root@linuxtechi ~]# dd if=/dev/zero of=/swap_file bs=1G count=1
|
||||
1+0 records in
|
||||
1+0 records out
|
||||
1073741824 bytes (1.1 GB) copied, 414.898 s, 2.6 MB/s
|
||||
[root@linuxtechi ~]#
|
||||
|
||||
Replace the value of ‘**bs**‘ and ‘**count**‘ according your requirement.
|
||||
|
||||
#### Step:2 Secure the swap file with permissions 644. ####
|
||||
|
||||
[root@linuxtechi ~]# chmod 600 /swap_file
|
||||
|
||||
#### Step:3 Enable the Swap Area on the file (swap_file) ####
|
||||
|
||||
Use mkswap command to enable swap area
|
||||
|
||||
[root@linuxtechi ~]# mkswap /swap_file
|
||||
Setting up swapspace version 1, size = 1048572 KiB
|
||||
no label, UUID=f7b3ae59-c09a-4dc2-ba4d-c02abb7db33b
|
||||
[root@linuxtechi ~]#
|
||||
|
||||
#### Step:4 Add the swap file entry in the fstab file ####
|
||||
|
||||
Add the below entry in the fstab file so that swap file become persistent across every reboot.
|
||||
|
||||
/swap_file swap swap defaults 0 0
|
||||
|
||||
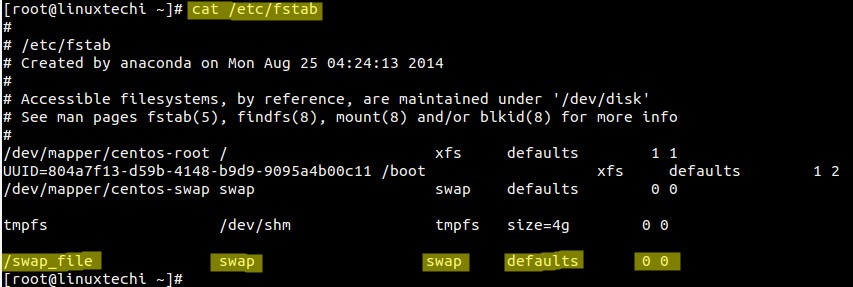
|
||||
|
||||
#### Step:5 Enable the swap file using ‘mkswap on’ command. ####
|
||||
|
||||
[root@linuxtechi ~]# swapon /swap_file
|
||||
[root@linuxtechi ~]#
|
||||
|
||||
#### Step:6 Now verify the swap space ####
|
||||
|
||||
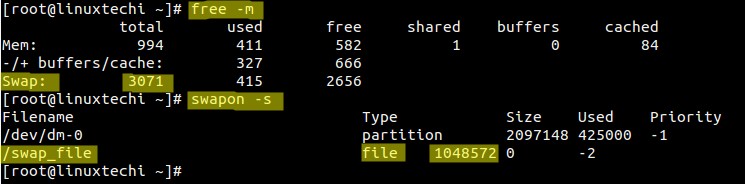
|
||||
|
||||
**Note**: To disable the swap file for any troubleshooting point of view, use swapoff command as shown below and to re-enable swap file then use swapon command as shown in step5.
|
||||
|
||||
[root@linuxtechi ~]# swapoff /swap_file
|
||||
[root@linuxtechi ~]#
|
||||
|
||||
Please share your valuable inputs and comments of this article.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linuxtechi.com/extend-swap-space-using-swap-file-in-linux/
|
||||
|
||||
作者:[Pradeep Kumar][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.linuxtechi.com/author/pradeep/
|
||||
@ -0,0 +1,191 @@
|
||||
Install Plex Media Server On Ubuntu / CentOS 7.1 / Fedora 22
|
||||
================================================================================
|
||||
In this article we will show you how easily you can setup Plex Home Media Server on major Linux distributions with their latest releases. After its successful installation of Plex you will be able to use your centralized home media playback system that streams its media to many Plex player Apps and the Plex Home will allows you to setup your environment by adding your devices and to setup a group of users that all can use Plex Together. So let’s start its installation first on Ubuntu 15.04.
|
||||
|
||||
### Basic System Resources ###
|
||||
|
||||
System resources mainly depend on the type and number of devices that you are planning to connect with the server. So according to our requirements we will be using as following system resources and software for a standalone server.
|
||||
|
||||
注:表格
|
||||
<table width="666" style="height: 181px;">
|
||||
<tbody>
|
||||
<tr>
|
||||
<td width="670" colspan="2"><b>Plex Home Media Server</b></td>
|
||||
</tr>
|
||||
<tr>
|
||||
<td width="236"><b>Base Operating System</b></td>
|
||||
<td width="425">Ubuntu 15.04 / CentOS 7.1 / Fedora 22 Work Station</td>
|
||||
</tr>
|
||||
<tr>
|
||||
<td width="236"><b>Plex Media Server</b></td>
|
||||
<td width="425">Version 0.9.12.3.1173-937aac3</td>
|
||||
</tr>
|
||||
<tr>
|
||||
<td width="236"><b>RAM and CPU</b></td>
|
||||
<td width="425">1 GB , 2.0 GHZ</td>
|
||||
</tr>
|
||||
<tr>
|
||||
<td width="236"><b>Hard Disk</b></td>
|
||||
<td width="425">30 GB</td>
|
||||
</tr>
|
||||
</tbody>
|
||||
</table>
|
||||
|
||||
### Plex Media Server 0.9.12.3 on Ubuntu 15.04 ###
|
||||
|
||||
We are now ready to start the installations process of Plex Media Server on Ubuntu so let’s start with the following steps to get it ready.
|
||||
|
||||
#### Step 1: System Update ####
|
||||
|
||||
Login to your server with root privileges Make your that your system is upto date if not then do by using below command.
|
||||
|
||||
root@ubuntu-15:~#apt-get update
|
||||
|
||||
#### Step 2: Download the Latest Plex Media Server Package ####
|
||||
|
||||
Create a new directory and download .deb plex Media Package in it from the official website of Plex for Ubuntu using wget command.
|
||||
|
||||
root@ubuntu-15:~# cd /plex/
|
||||
root@ubuntu-15:/plex#
|
||||
root@ubuntu-15:/plex# wget https://downloads.plex.tv/plex-media-server/0.9.12.3.1173-937aac3/plexmediaserver_0.9.12.3.1173-937aac3_amd64.deb
|
||||
|
||||
#### Step 3: Install the Debian Package of Plex Media Server ####
|
||||
|
||||
Now within the same directory run following command to start installation of debian package and then check the status of plekmediaserver.
|
||||
|
||||
root@ubuntu-15:/plex# dpkg -i plexmediaserver_0.9.12.3.1173-937aac3_amd64.deb
|
||||
|
||||
----------
|
||||
|
||||
root@ubuntu-15:~# service plexmediaserver status
|
||||
|
||||

|
||||
|
||||
### Plex Home Media Web App Setup on Ubuntu 15.04 ###
|
||||
|
||||
Let's open your web browser within your localhost network and open the Web Interface with your localhost IP and port 32400 and do following steps to configure it:
|
||||
|
||||
http://172.25.10.179:32400/web
|
||||
http://localhost:32400/web
|
||||
|
||||
#### Step 1:Sign UP before Login ####
|
||||
|
||||
After you have access to the web interface of Plesk Media Server make sure to Sign Up and set your username email ID and Password to login as.
|
||||
|
||||

|
||||
|
||||
#### Step 2: Enter Your Pin to Secure Your Plex Media Home User ####
|
||||
|
||||

|
||||
|
||||
Now you have successfully configured your user under Plex Home Media.
|
||||
|
||||

|
||||
|
||||
### Opening Plex Web App on Devices Other than Localhost Server ###
|
||||
|
||||
As we have seen in our Plex media home page that it indicates that "You do not have permissions to access this server". Its because of we are on a different network than the Server computer.
|
||||
|
||||

|
||||
|
||||
Now we need to resolve this permissions issue so that we can have access to server on the devices other than the hosted server by doing following setup.
|
||||
|
||||
### Setup SSH Tunnel for Windows System to access Linux Server ###
|
||||
|
||||
First we need to set up a SSH tunnel so that we can access things as if they were local. This is only necessary for the initial setup.
|
||||
|
||||
If you are using Windows as your local system and server on Linux then we can setup SSH-Tunneling using Putty as shown.
|
||||
|
||||

|
||||
|
||||
**Once you have the SSH tunnel set up:**
|
||||
|
||||
Open your Web browser window and type following URL in the address bar.
|
||||
|
||||
http://localhost:8888/web
|
||||
|
||||
The browser will connect to the server and load the Plex Web App with same functionality as on local.
|
||||
Agree to the terms of Services and start
|
||||
|
||||

|
||||
|
||||
Now a fully functional Plex Home Media Server is ready to add new media libraries, channels, playlists etc.
|
||||
|
||||

|
||||
|
||||
### Plex Media Server 0.9.12.3 on CentOS 7.1 ###
|
||||
|
||||
We will follow the same steps on CentOS-7.1 that we did for the installation of Plex Home Media Server on Ubuntu 15.04.
|
||||
|
||||
So lets start with Plex Media Servers Package Installation.
|
||||
|
||||
#### Step 1: Plex Media Server Installation ####
|
||||
|
||||
To install Plex Media Server on centOS 7.1 we need to download the .rpm package from the official website of Plex. So we will use wget command to download .rpm package for this purpose in a new directory.
|
||||
|
||||
[root@linux-tutorials ~]# cd /plex
|
||||
[root@linux-tutorials plex]# wget https://downloads.plex.tv/plex-media-server/0.9.12.3.1173-937aac3/plexmediaserver-0.9.12.3.1173-937aac3.x86_64.rpm
|
||||
|
||||
#### Step 2: Install .RPM Package ####
|
||||
|
||||
After completion of complete download package we will install this package using rpm command within the same direcory where we installed the .rpm package.
|
||||
|
||||
[root@linux-tutorials plex]# ls
|
||||
plexmediaserver-0.9.12.3.1173-937aac3.x86_64.rpm
|
||||
[root@linux-tutorials plex]# rpm -i plexmediaserver-0.9.12.3.1173-937aac3.x86_64.rpm
|
||||
|
||||
#### Step 3: Start Plexmediaservice ####
|
||||
|
||||
We have successfully installed Plex Media Server Now we just need to restart its service and then enable it permanently.
|
||||
|
||||
[root@linux-tutorials plex]# systemctl start plexmediaserver.service
|
||||
[root@linux-tutorials plex]# systemctl enable plexmediaserver.service
|
||||
[root@linux-tutorials plex]# systemctl status plexmediaserver.service
|
||||
|
||||
### Plex Home Media Web App Setup on CentOS-7.1 ###
|
||||
|
||||
Now we just need to repeat all steps that we performed during the Web app setup of Ubuntu.
|
||||
So let's Open a new window in your web browser and access the Plex Media Server Web app using localhost or IP or your Plex server.
|
||||
|
||||
http://172.20.3.174:32400/web
|
||||
http://localhost:32400/web
|
||||
|
||||
Then to get full permissions on the server you need to repeat the steps to create the SSH-Tunnel.
|
||||
After signing up with new user account we will be able to access its all features and can add new users, add new libraries and setup it per our needs.
|
||||
|
||||

|
||||
|
||||
### Plex Media Server 0.9.12.3 on Fedora 22 Work Station ###
|
||||
|
||||
The Basic steps to download and install Plex Media Server are the same as its we did for in CentOS 7.1.
|
||||
We just need to download its .rpm package and then install it with rpm command.
|
||||
|
||||

|
||||
|
||||
### Plex Home Media Web App Setup on Fedora 22 Work Station ###
|
||||
|
||||
We had setup Plex Media Server on the same host so we don't need to setup SSH-Tunnel in this time scenario. Just open the web browser in your Fedora 22 Workstation with default port 32400 of Plex Home Media Server and accept the Plex Terms of Services Agreement.
|
||||
|
||||

|
||||
|
||||
**Welcome to Plex Home Media Server on Fedora 22 Workstation**
|
||||
|
||||
Lets login with your plex account and start with adding your libraries for your favorite movie channels , create your playlists, add your photos and enjoy with many other features of Plex Home Media Server.
|
||||
|
||||

|
||||
|
||||
### Conclusion ###
|
||||
|
||||
We had successfully installed and configured Plex Media Server on Major Linux Distributions. So, Plex Home Media Server has always been a best choice for media management. Its so simple to setup on cross platform as we did for Ubuntu, CentOS and Fedora. It has simplifies the tasks of organizing your media content and streaming to other computers and devices then to share it with your friends.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/tools/install-plex-media-server-ubuntu-centos-7-1-fedora-22/
|
||||
|
||||
作者:[Kashif Siddique][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://linoxide.com/author/kashifs/
|
||||
@ -0,0 +1,176 @@
|
||||
Lolcat – A Command Line Tool to Output Rainbow Of Colors in Linux Terminal
|
||||
================================================================================
|
||||
For those who believe that Linux Command Line is boring and there isn’t any fun, then you’re wrong here are the articles on Linux, that shows how funny and naughty is Linux..
|
||||
|
||||
- [20 Funny Commands of Linux or Linux is Fun in Terminal][1]
|
||||
- [6 Interesting Funny Commands of Linux (Fun in Terminal)][2]
|
||||
- [Fun in Linux Terminal – Play with Word and Character Counts][3]
|
||||
|
||||
Here in this article, I will be discussing about a small utility called “lolcat” – Which produce rainbow of colors in terminal.
|
||||
|
||||
|
||||
|
||||
Lolcat Command to Output Rainbow of Colors for Terminal
|
||||
|
||||
#### What is lolcat? ####
|
||||
|
||||
Lolcat is an utility for Linux, BSD and OSX which concatenates like similar to [cat command][4] and adds rainbow coloring to it. Lolcat is primarily used for rainbow coloring of text in Linux Terminal.
|
||||
|
||||
### Installation of Lolcat in Linux ###
|
||||
|
||||
**1. Lolcat utility is available in the repository of lots of Linux distributions, but the available version bit older. Alternatively you can download and install latest version of lolcat from git repository.**
|
||||
|
||||
Lolcat is a ruby gem hence it is essential to have latest version of RUBY installed on your system.
|
||||
|
||||
# apt-get install ruby [On APT based Systems]
|
||||
# yum install ruby [On Yum based Systems]
|
||||
# dnf install ruby [On DNF based Systems]
|
||||
|
||||
Once ruby package has been installed, make sure to verify the version of ruby installed.
|
||||
|
||||
# ruby --version
|
||||
|
||||
ruby 2.1.5p273 (2014-11-13) [x86_64-linux-gnu]
|
||||
|
||||
**2. Next download and install the most recent version of lolcat from the git repository using following commands.**
|
||||
|
||||
# wget https://github.com/busyloop/lolcat/archive/master.zip
|
||||
# unzip master.zip
|
||||
# cd lolcat-master/bin
|
||||
# gem install lolcat
|
||||
|
||||
Once lolcat is installed, you can check the version.
|
||||
|
||||
# lolcat --version
|
||||
|
||||
lolcat 42.0.99 (c)2011 moe@busyloop.net
|
||||
|
||||
### Usage of Lolcat ###
|
||||
|
||||
**3. Before starting usage of lolcat, make sure to know the available options and help using following command.**
|
||||
|
||||
# lolcat -h
|
||||
|
||||

|
||||
|
||||
Lolcat Help
|
||||
|
||||
**4. Next, pipeline lolcat with commads say ps, date and cal as:**
|
||||
|
||||
# ps | lolcat
|
||||
# date | lolcat
|
||||
# cal | lolcat
|
||||
|
||||
|
||||
|
||||
ps Command Output
|
||||
|
||||

|
||||
|
||||
Date Output
|
||||
|
||||

|
||||
|
||||
Calendar Output
|
||||
|
||||
**5. 3. Use lolcat to display codes of a script file as:**
|
||||
|
||||
# lolcat test.sh
|
||||
|
||||

|
||||
|
||||
Display Codes with Lolcat
|
||||
|
||||
**6. Pipeline lolcat with figlet command. Figlet is a utility which displays large characters made up of ordinary screen characters. We can pipeline the output of figlet with lolcat to make the output colorful as:**
|
||||
|
||||
# echo I ❤ Tecmint | lolcat
|
||||
# figlet I Love Tecmint | lolcat
|
||||
|
||||

|
||||
|
||||
Colorful Texts
|
||||
|
||||
**Note**: Not to mention that ❤ is an unicode character and to install figlet you have to yum and apt to get the required packages as:
|
||||
|
||||
# apt-get figlet
|
||||
# yum install figlet
|
||||
# dnf install figlet
|
||||
|
||||
**7. Animate a text in rainbow of colours, as:**
|
||||
|
||||
$ echo I ❤ Tecmit | lolcat -a -d 500
|
||||
|
||||

|
||||
|
||||
Animated Text
|
||||
|
||||
Here the option -a is for Animation and -d is for duration. In the above example duration count is 500.
|
||||
|
||||
**8. Read a man page (say man ls) in rainbow of colors as:**
|
||||
|
||||
# man ls | lolcat
|
||||
|
||||

|
||||
|
||||
List Files Colorfully
|
||||
|
||||
**9. Pipeline lolcat with cowsay. cowsay is a configurable thinking and/or speaking cow, which supports a lot of other animals as well.**
|
||||
|
||||
Install cowsay as:
|
||||
|
||||
# apt-get cowsay
|
||||
# yum install cowsay
|
||||
# dnf install cowsay
|
||||
|
||||
After install, print the list of all the animals in cowsay as:
|
||||
|
||||
# cowsay -l
|
||||
|
||||
**Sample Output**
|
||||
|
||||
Cow files in /usr/share/cowsay/cows:
|
||||
apt beavis.zen bong bud-frogs bunny calvin cheese cock cower daemon default
|
||||
dragon dragon-and-cow duck elephant elephant-in-snake eyes flaming-sheep
|
||||
ghostbusters gnu head-in hellokitty kiss kitty koala kosh luke-koala
|
||||
mech-and-cow meow milk moofasa moose mutilated pony pony-smaller ren sheep
|
||||
skeleton snowman sodomized-sheep stegosaurus stimpy suse three-eyes turkey
|
||||
turtle tux unipony unipony-smaller vader vader-koala www
|
||||
|
||||
Output of cowsay pipelined with lolcat and ‘gnu‘ cowfile is used.
|
||||
|
||||
# cowsay -f gnu ☛ Tecmint ☚ is the best Linux Resource Available online | lolcat
|
||||
|
||||
|
||||
|
||||
Cowsay with Lolcat
|
||||
|
||||
**Note**: You can use lolcat with any other command in pipeline and get colored output in terminal.
|
||||
|
||||
**10. You may create alias for the most frequently used commands to get command output in rainbow of colors. You can alias ‘ls -l‘ command which is used for long list the contents of directory as below.**
|
||||
|
||||
# alias lolls="ls -l | lolcat"
|
||||
# lolls
|
||||
|
||||

|
||||
|
||||
Alias Commands with Colorful
|
||||
|
||||
You may create alias for any command as suggested above. To create permanent alias, you have to add the relevant code (above code for ls -l alias) to ~/.bashrc file and also make sure to logout and login back for the changes to be taken into effect.
|
||||
|
||||
That’s all for now. I would like to know if you were aware of lolcat previously? Did you like the post? And suggestion and feedback is welcome in the comment section below. Like and share us and help us get spread.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.tecmint.com/lolcat-command-to-output-rainbow-of-colors-in-linux-terminal/
|
||||
|
||||
作者:[Avishek Kumar][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.tecmint.com/author/avishek/
|
||||
[1]:http://www.tecmint.com/20-funny-commands-of-linux-or-linux-is-fun-in-terminal/
|
||||
[2]:http://www.tecmint.com/linux-funny-commands/
|
||||
[3]:http://www.tecmint.com/play-with-word-and-character-counts-in-linux/
|
||||
[4]:http://www.tecmint.com/13-basic-cat-command-examples-in-linux/
|
||||
@ -1,108 +0,0 @@
|
||||
Translating by goreliu ...
|
||||
|
||||
11 pointless but awesome Linux terminal tricks
|
||||
================================================================================
|
||||
Here are some great Linux terminal tips and tricks, each one as pointless as it is awesome.
|
||||
|
||||

|
||||
|
||||
### All work and no play... ###
|
||||
|
||||
Linux is one of the most astoundingly functional and utilitarian Operating Systems around when it comes to working from the command line. Need to perform a particular task? Odds are there is an application or script you can use to get it done. Right from the terminal. But, as they say in the good book, "All work and no play make Jack really bored or something." So here is a collection of my favorite pointless, stupid, annoying or amusing things that you can do right in your Linux Terminal.
|
||||
|
||||
|
||||
|
||||
### Give the terminal an attitude ###
|
||||
|
||||
Step 1) Type "sudo visudo".
|
||||
|
||||
Step 2) At the bottom of the "Defaults" (near the top of the file) add, on a new line, "Defaults insults".
|
||||
|
||||
Step 3) Save the file.
|
||||
|
||||
"What did I just do to my computer?" you may be asking yourself. Something wonderful. Now, whenever you issue a sudo command and misstype your password, your computer will call you names. My favorite: "Listen, burrito brains, I don't have time to listen to this trash."
|
||||
|
||||
|
||||
|
||||
### apt-get moo ###
|
||||
|
||||
That screenshot you see? That's what typing "apt-get moo" (on a Debian-based system) does. That's it. Don't go looking for this to do something fancy. It won't. That, I kid you not, is it. But it's one of the most commonly known little Easter eggs on Linux. So I include it here, right near the beginning, so I won't get 5,000 emails telling me I missed it in this list.
|
||||
|
||||
|
||||
|
||||
### aptitude moo ###
|
||||
|
||||
A bit more entertaining is aptitude's take on "moo." Type "aptitude moo" (on Ubuntu and the like) and you'll be corrected about thinking "moo" would do anything. But you know better. Try the same command again, this time with an optional "-v" attribute. Don't stop there. Add v's, one at a time, until aptitude gives you what you want.
|
||||
|
||||
|
||||
|
||||
### Arch: Put Pac-Man in pacman ###
|
||||
|
||||
This is one just for the Arch-lovers out there. The de facto package manager, pacman, is pretty fantastic already. Let's make it even better.
|
||||
|
||||
Step 1) Open "/etc/pacman.conf".
|
||||
|
||||
Step 2) In the "# Misc options", remove the "#" from in front of "Color".
|
||||
|
||||
Step 3) Add "ILoveCandy".
|
||||
|
||||
Now the progress for installing new packages, in pacman, will include a little tiny Pac-Man. Which should really just be the default anyway.
|
||||
|
||||
|
||||
|
||||
### Cowsay! ###
|
||||
|
||||
Making aptitude moo is neat, I guess, but you really can't use it for much. Enter "cowsay." It does what you think. You make a cow say things. Anything you like. And it's not even limited to cows. Calvin, Beavis, and the Ghostbusters logo are all available in full ASCII art glory – type "cowsay -l" for a full list of what's available in this, Linux's most powerful tool. Remember that, like most great terminal applications, you can pipe the output from other applications straight into cowsay (ala "fortune | cowsay").
|
||||
|
||||
|
||||
|
||||
### Become an 3l33t h@x0r ###
|
||||
|
||||
Typing "nmap" isn't something one typically needs to do on a day-to-day basis. But when one does need to "whip out the nmap," one wants to look as l33t as humanly possible. Add a "-oS" to any nmap command (such as "nmap -oS - google.com"). Bam. You're now in what is officially known as "[Script Kiddie Mode][1]." Angelina Jolie and Keanu Reeves would be proud.
|
||||
|
||||
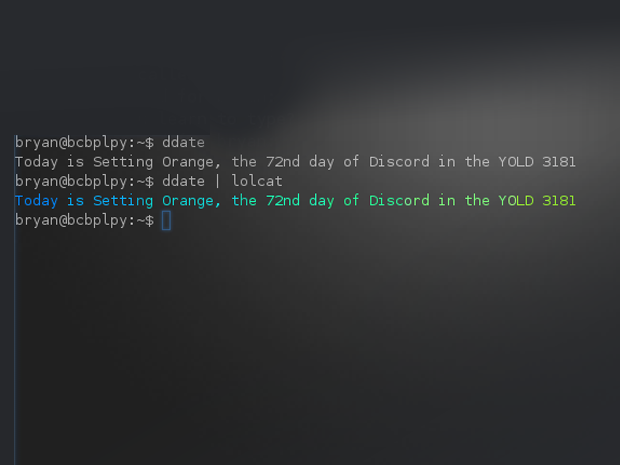
|
||||
|
||||
### Getting all Discordian ddate ###
|
||||
|
||||
If you've ever been sitting around thinking, "Hey! I want today's date to be written in an essentially useless, but whimsical, way"…try typing "ddate". Results like "Today is Setting Orange, the 72nd day of Discord in the YOLD 3181," can really spice up your server logs.
|
||||
|
||||
Note: Technically, this is a real thing called the [Discordian Calendar][2], used (in theory) by the followers of [Discordianism][3]. Which means I probably offended somebody. Or maybe not. I'm not really sure. Either way, ddate is a handy tool in any office.
|
||||
|
||||
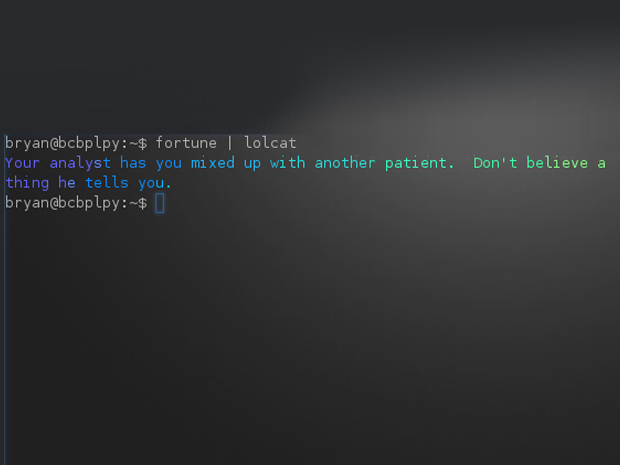
|
||||
|
||||
### I See Colors Everywhere! ###
|
||||
|
||||
Tired of boring old text? Looking to spruce things up and show the world your true style? lolcat. Install it. Use it. Everywhere. It takes any text input and turns it into a rainbow of wonder and enchantment. Piping text into lolcat (ala "fortune | lolcat") is sure to liven up any party.
|
||||
|
||||
|
||||
|
||||
### The Steam Locomotive ###
|
||||
|
||||
Animated ASCII art steam locomotive in your terminal. You want this. You need this. Install and run "sl". Use "sl -l" for a tiny version. Or, if you want to really spend some time on this, "sl-h". This is the full train, including passenger cars.
|
||||
|
||||
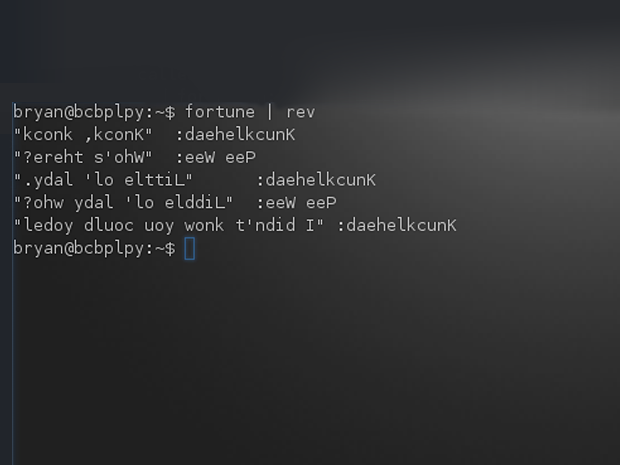
|
||||
|
||||
### Reverse any text ###
|
||||
|
||||
Pipe the output of any text into "rev" and it will reverse the text. "fortune | rev" gives you a fortune. In reverse. Which is, as odd as it may seem, not a misfortune.
|
||||
|
||||
|
||||
|
||||
### The Matrix is still cool, right? ###
|
||||
|
||||
Want your terminal to do that scrolling text, l33t, Matrix-y thing? "cmatrix" is your friend. You can even have it output different colors, which is snazzy. Learn how by typing "man cmatrix". Or, better yet, "man cmatrix | lolcat". Which, really, is the most pointless (but wonderful) thing you can do in the Linux Terminal. So that's where I leave you.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.networkworld.com/article/2926630/linux/11-pointless-but-awesome-linux-terminal-tricks.html
|
||||
|
||||
作者:[Bryan Lunduke][a]
|
||||
译者:[goreliu](https://github.com/goreliu)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.networkworld.com/author/Bryan-Lunduke/
|
||||
[1]:http://nmap.org/book/output-formats-script-kiddie.html
|
||||
[2]:http://en.wikipedia.org/wiki/Discordian_calendar
|
||||
[3]:http://en.wikipedia.org/wiki/Discordianism
|
||||
@ -1,3 +1,4 @@
|
||||
zpl1025
|
||||
How to Manipulate Filenames Having Spaces and Special Characters in Linux
|
||||
================================================================================
|
||||
We come across files and folders name very regularly. In most of the cases file/folder name are related to the content of the file/folder and starts with number and characters. Alpha-Numeric file name are pretty common and very widely used, but this is not the case when we have to deal with file/folder name that has special characters in them.
|
||||
@ -432,4 +433,4 @@ via: http://www.tecmint.com/manage-linux-filenames-with-special-characters/
|
||||
|
||||
[a]:http://www.tecmint.com/author/avishek/
|
||||
[1]:http://www.tecmint.com/15-basic-ls-command-examples-in-linux/
|
||||
[2]:http://www.tecmint.com/8-pratical-examples-of-linux-touch-command/
|
||||
[2]:http://www.tecmint.com/8-pratical-examples-of-linux-touch-command/
|
||||
|
||||
@ -1,234 +0,0 @@
|
||||
[translating by KayGuoWhu]
|
||||
How to secure your Linux server
|
||||
================================================================================
|
||||
> A server is made up of so many different components that makes it hard to offer one solution for everyone's needs. This articles tries to cover some useful tips and tricks to help you keep your server and users protected.
|
||||
|
||||
No doubt improving server security is one of the most important things system administrators should always look for. This of course has been a topic of many different articles, blogs and forum threads.
|
||||
|
||||
A server is made up of so many different components that makes it hard to offer one solution for everyone’s needs. This articles tries to cover some useful tips and tricks to help you keep your server and users protected.
|
||||
|
||||
There are a few things that every system administrator should know and there is no way to talk about security without mentioning:
|
||||
|
||||
- Keep your system **up to date**
|
||||
- Change passwords frequently – use numeric, alphabetical and non-alphabetical symbols
|
||||
- Give users the **minimum** permissions they need to do their job.
|
||||
- Install only packages that you really need
|
||||
|
||||
Here comes the more interesting part:
|
||||
|
||||
### Change default SSH port ###
|
||||
|
||||
The first thing that I would like to change when setting up a new server is the default SSH port. This simple change can save your server from thousands of brute force attempts.
|
||||
|
||||
To change the default SSH port, open your sshd_config:
|
||||
|
||||
sudo vim /etc/ssh/sshd_config
|
||||
|
||||
Find the following line:
|
||||
|
||||
#Port 22
|
||||
|
||||
The “#” symbol means that this line is a comment. Remove the # symbol then change the port to a number of your choice. The port number should not be larger than 65535. Make sure not to use any port already used by your system or other services. You can see a list of commonly used ports in [Wikipedia][1]. For the purpose of this article I will use:
|
||||
|
||||
Port 16543
|
||||
|
||||
Now save the file and close it for a moment.
|
||||
|
||||
Next important step is to:
|
||||
|
||||
### Use SSH Keys ###
|
||||
|
||||
It is extremely important to use SSH keys when accessing the server over SSH. This adds additional protection and ensure that only people who have the key can access the server.
|
||||
|
||||
To generate SSH key on your local computer run:
|
||||
|
||||
ssh-keygen -t rsa
|
||||
|
||||
You will receive an output asking you to setup the file name where the key should be written as well as setup a password:
|
||||
|
||||
Generating public/private rsa key pair.
|
||||
Enter file in which to save the key (/root/.ssh/id_rsa): my_key
|
||||
Enter passphrase (empty for no passphrase):
|
||||
Enter same passphrase again:
|
||||
Your identification has been saved in my_key.
|
||||
Your public key has been saved in my_key.pub.
|
||||
The key fingerprint is:
|
||||
SHA256:MqD/pzzTRsCjZb6mpfjyrr5v1pJLBcgprR5tjNoI20A
|
||||
|
||||
When compete, you will have two files:
|
||||
|
||||
my_key
|
||||
|
||||
my_key.pub
|
||||
|
||||
Now copy the my_key.pub to ~/.ssh/authorized_keys
|
||||
|
||||
cp my_key.pub ~/.ssh/authorized_keys
|
||||
|
||||
Now upload your key on the server by using:
|
||||
|
||||
scp -P16543 authorized_keys user@yourserver-ip:/home/user/.ssh/
|
||||
|
||||
Now you can access the server from the same local machine without having to enter any password.
|
||||
|
||||
### Disable password authentication for SSH ###
|
||||
|
||||
Now that we have SSH keys, it is safe to disable the password authentication for SSH. Open again the sshd_config file and set the following changes:
|
||||
|
||||
ChallengeResponseAuthentication no
|
||||
PasswordAuthentication no
|
||||
UsePAM no
|
||||
|
||||
### Disable Root login ###
|
||||
|
||||
The next important step is to disable direct access with root user. Instead you should use sudo or su to perform administrative jobs. To do this you will need to add a new user that has root privileges. To do this you will need to edit the sudoers file located in:
|
||||
|
||||
/etc/sudoers/
|
||||
|
||||
You may edit that file with command such as **visudo**. I would recommend you using this command as it will check the file for any syntax errors prior closing the file. This is useful if you have wrongly edited the file.
|
||||
|
||||
Now to give root privileges to a user. For the purpose of this tutorial I will use user **sysadmin**. Make sure you are using an existing user on your system when you edit your own file. Now find the following line:
|
||||
|
||||
root ALL=(ALL) ALL
|
||||
|
||||
Copy that line and paste it below. In the new line change “root” with “sysadmin”. You should now have these two lines:
|
||||
|
||||
root ALL=(ALL) ALL
|
||||
sysadmin ALL=(ALL) ALL
|
||||
|
||||
I would like to explain what each of the options in the above line represents:
|
||||
|
||||
(1) root (2)ALL=(3)(ALL) (4)ALL
|
||||
|
||||
(1) User
|
||||
|
||||
(2) Terminal from which user can use sudo
|
||||
|
||||
(3) Which users User may act as
|
||||
|
||||
(4) Which commands he may use
|
||||
|
||||
|
||||
You can use this settings to give access to users to some of the system tools.
|
||||
|
||||
At this point it is safe to save your file.
|
||||
|
||||
To disable direct root access over SSH open again the **sshd_config** file and find the following line:
|
||||
|
||||
#PermitRootLogin yes
|
||||
|
||||
and change it to:
|
||||
|
||||
PermitRootLogin no
|
||||
|
||||
Now save the file and restart the sshd daemon so the changes can take effect. Simply run the following command:
|
||||
|
||||
sudo /etc/init.d/sshd restart
|
||||
|
||||
### Setup firewall ###
|
||||
|
||||
A firewall can help you block incoming and outgoing ports as well as block brute force login attempts. I like using SCF (Config Server Firewall) as it a powerful solution that uses iptables, it’s easy to manage and has a web interface for people who don’t like typing too many commands.
|
||||
|
||||
To install CSF access your server and navigate to:
|
||||
|
||||
cd /usr/local/src/
|
||||
|
||||
Then execute the following commands as root:
|
||||
|
||||
wget https://download.configserver.com/csf.tgz
|
||||
tar -xzf csf.tgz
|
||||
csf
|
||||
sh install.sh
|
||||
|
||||
You will need to wait for the installer to finish its job. We will edit CSF configuration by editing:
|
||||
|
||||
/etc/csf/csf.conf
|
||||
|
||||
By default CSF will be started in testing mode. You will need to set it to product by changing the “TESTING” value to 0
|
||||
|
||||
TESTING = "0"
|
||||
|
||||
Next thing you can edit are the allowed ports on your server. For that purpose find the following section of the csf.conf file and modify the ports per your needs:
|
||||
|
||||
# Allow incoming TCP ports
|
||||
TCP_IN = "20,21,25,53,80,110,143,443,465,587,993,995,16543"
|
||||
# Allow outgoing TCP ports
|
||||
TCP_OUT = "20,21,22,25,53,80,110,113,443,587,993,995,16543"
|
||||
# Allow incoming UDP ports
|
||||
UDP_IN = "20,21,53"
|
||||
# Allow outgoing UDP ports
|
||||
# To allow outgoing traceroute add 33434:33523 to this list
|
||||
UDP_OUT = "20,21,53,113,123"
|
||||
|
||||
Setup these per your requirements. I would recommend you using only the ports you need and avoiding allowing huge ranges of ports. Additionally you can avoid using the unsecured services unsecured ports. For example instead of allowing the default SMTP port 25 you can only allow ports 465 and 587 for outgoing emails.
|
||||
|
||||
**IMPORTANT**: Do not forget to allow your customized SSH port.
|
||||
|
||||
It is important to allow your IP address so it will never get blocked. Such IP addresses can be defined in:
|
||||
|
||||
/etc/csf/csf.ignore
|
||||
|
||||
The blocked IP address will appear in:
|
||||
|
||||
/etc/csf/csf.deny
|
||||
|
||||
When you have finished making changes – restart csf with:
|
||||
|
||||
sudo /etc/init.d/csf restart
|
||||
|
||||
Just to show you how useful CSF is I will show you part of csf.deny on one of my servers:
|
||||
|
||||
211.216.48.205 # lfd: (sshd) Failed SSH login from 211.216.48.205 (KR/Korea, Republic of/-): 5 in the last 3600 secs - Fri Mar 6 00:30:35 2015
|
||||
103.41.124.53 # lfd: (sshd) Failed SSH login from 103.41.124.53 (HK/Hong Kong/-): 5 in the last 3600 secs - Fri Mar 6 01:06:46 2015
|
||||
103.41.124.42 # lfd: (sshd) Failed SSH login from 103.41.124.42 (HK/Hong Kong/-): 5 in the last 3600 secs - Fri Mar 6 01:59:04 2015
|
||||
103.41.124.26 # lfd: (sshd) Failed SSH login from 103.41.124.26 (HK/Hong Kong/-): 5 in the last 3600 secs - Fri Mar 6 02:48:26 2015
|
||||
109.169.74.58 # lfd: (sshd) Failed SSH login from 109.169.74.58 (GB/United Kingdom/mail2.algeos.com): 5 in the last 3600 secs - Fri Mar 6 03:49:03 2015
|
||||
|
||||
The IP addresses that performed the brute force login attempt got blocked and they will not bother me again.
|
||||
|
||||
#### Lock accounts ####
|
||||
|
||||
In case an account is not going to be used for a long period of time you can lock it in order to prevent access to it. You can do this with:
|
||||
|
||||
passwd -l accountName
|
||||
|
||||
Account can still be used by the root user.
|
||||
|
||||
### Know your services ###
|
||||
|
||||
The whole idea of a server is to provide access to different services. Limit those to only the ones you need and disable the unused ones. This will not only free some resources, but will make your server a little bit more secured. For example if you are running a headless server you will definitely not need X display or a desktop environment. If there are no Windows network shares, you can safely disable Samba.
|
||||
|
||||
You can use the commands below to see which services are started upon system boot:
|
||||
|
||||
chkconfig --list | grep "3:on"
|
||||
|
||||
If your system runs with **systemd**:
|
||||
|
||||
systemctl list-unit-files --type=service | grep enabled
|
||||
|
||||
To disable a service you can use commands such as:
|
||||
|
||||
chkconfig service off
|
||||
systemctl disable service
|
||||
|
||||
In the above example change “service” with the name of the actual service you wish to stop. Here is an example:
|
||||
|
||||
chkconfig httpd off
|
||||
systemctl disable httpd
|
||||
|
||||
### Conclusion ###
|
||||
|
||||
This article was meant to cover some of the general security steps you can take to start securing your server. You can always take additional actions to increase the server protection. Remember that it is your responsibility to keep your server secured and make the wise decision while doing it. Unfortunately there is no easy way to do this and the “perfect” setup requires lots of time and tests until you achieve the desired result.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linuxveda.com/2015/06/03/secure-linux-server/
|
||||
|
||||
作者:[Marin Todorow][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.linuxveda.com/author/marin_todorov/
|
||||
[1]:http://en.wikipedia.org/wiki/Port_%28computer_networking%29#Common_port_numbers
|
||||
@ -1,212 +0,0 @@
|
||||
Nishita Agarwal Shares Her Interview Experience on Linux ‘iptables’ Firewall
|
||||
================================================================================
|
||||
Nishita Agarwal, a frequent Tecmint Visitor shared her experience (Question and Answer) with us regarding the job interview she had just given in a privately owned hosting company in Pune, India. She was asked a lot of questions on a variety of topics however she is an expert in iptables and she wanted to share those questions and their answer (she gave) related to iptables to others who may be going to give interview in near future.
|
||||
|
||||

|
||||
|
||||
All the questions and their Answer are rewritten based upon the memory of Nishita Agarwal.
|
||||
|
||||
> “Hello Friends! My name is **Nishita Agarwal**. I have Pursued Bachelor Degree in Technology. My area of Specialization is UNIX and Variants of UNIX (BSD, Linux) fascinates me since the time I heard it. I have 1+ years of experience in storage. I was looking for a job change which ended with a hosting company in Pune, India.”
|
||||
|
||||
Here is the collection of what I was asked during the Interview. I’ve documented only those questions and their answer that were related to iptables based upon my memory. Hope this will help you in cracking your Interview.
|
||||
|
||||
**1. Have you heard of iptables and firewall in Linux? Any idea of what they are and for what it is used?**
|
||||
|
||||
> **Answer** : I’ve been using iptables for quite long time and I am aware of both iptables and firewall. Iptables is an application program mostly written in C Programming Language and is released under GNU General Public License. Written for System administration point of view, the latest stable release if iptables 1.4.21.iptables may be considered as firewall for UNIX like operating system which can be called as iptables/netfilter, more accurately. The Administrator interact with iptables via console/GUI front end tools to add and define firewall rules into predefined tables. Netfilter is a module built inside of kernel that do the job of filtering.
|
||||
>
|
||||
> Firewalld is the latest implementation of filtering rules in RHEL/CentOS 7 (may be implemented in other distributions which I may not be aware of). It has replaced iptables interface and connects to netfilter.
|
||||
|
||||
**2. Have you used some kind of GUI based front end tool for iptables or the Linux Command Line?**
|
||||
|
||||
> **Answer** : Though I have used both the GUI based front end tools for iptables like Shorewall in conjugation of [Webmin][1] in GUI and Direct access to iptables via console.And I must admit that direct access to iptables via Linux console gives a user immense power in the form of higher degree of flexibility and better understanding of what is going on in the background, if not anything other. GUI is for novice administrator while console is for experienced.
|
||||
|
||||
**3. What are the basic differences between between iptables and firewalld?**
|
||||
|
||||
> **Answer** : iptables and firewalld serves the same purpose (Packet Filtering) but with different approach. iptables flush the entire rules set each time a change is made unlike firewalld. Typically the location of iptables configuration lies at ‘/etc/sysconfig/iptables‘ whereas firewalld configuration lies at ‘/etc/firewalld/‘, which is a set of XML files.Configuring a XML based firewalld is easier as compared to configuration of iptables, however same task can be achieved using both the packet filtering application ie., iptables and firewalld. Firewalld runs iptables under its hood along with it’s own command line interface and configuration file that is XML based and said above.
|
||||
|
||||
**4. Would you replace iptables with firewalld on all your servers, if given a chance?**
|
||||
|
||||
> **Answer** : I am familiar with iptables and it’s working and if there is nothing that requires dynamic aspect of firewalld, there seems no reason to migrate all my configuration from iptables to firewalld.In most of the cases, so far I have never seen iptables creating an issue. Also the general rule of Information technology says “why fix if it is not broken”. However this is my personal thought and I would never mind implementing firewalld if the Organization is going to replace iptables with firewalld.
|
||||
|
||||
**5. You seems confident with iptables and the plus point is even we are using iptables on our server.**
|
||||
|
||||
What are the tables used in iptables? Give a brief description of the tables used in iptables and the chains they support.
|
||||
|
||||
> **Answer** : Thanks for the recognition. Moving to question part, There are four tables used in iptables, namely they are:
|
||||
>
|
||||
> - Nat Table
|
||||
> - Mangle Table
|
||||
> - Filter Table
|
||||
> - Raw Table
|
||||
>
|
||||
> Nat Table : Nat table is primarily used for Network Address Translation. Masqueraded packets get their IP address altered as per the rules in the table. Packets in the stream traverse Nat Table only once. ie., If a packet from a jet of Packets is masqueraded they rest of the packages in the stream will not traverse through this table again. It is recommended not to filter in this table. Chains Supported by NAT Table are PREROUTING Chain, POSTROUTING Chain and OUTPUT Chain.
|
||||
>
|
||||
> Mangle Table : As the name suggests, this table serves for mangling the packets. It is used for Special package alteration. It can be used to alter the content of different packets and their headers. Mangle table can’t be used for Masquerading. Supported chains are PREROUTING Chain, OUTPUT Chain, Forward Chain, INPUT Chain, POSTROUTING Chain.
|
||||
>
|
||||
> Filter Table : Filter Table is the default table used in iptables. It is used for filtering Packets. If no rules are defined, Filter Table is taken as default table and filtering is done on the basis of this table. Supported Chains are INPUT Chain, OUTPUT Chain, FORWARD Chain.
|
||||
>
|
||||
> Raw Table : Raw table comes into action when we want to configure packages that were exempted earlier. It supports PREROUTING Chain and OUTPUT Chain.
|
||||
|
||||
**6. What are the target values (that can be specified in target) in iptables and what they do, be brief!**
|
||||
|
||||
> **Answer** : Following are the target values that we can specify in target in iptables:
|
||||
>
|
||||
> - ACCEPT : Accept Packets
|
||||
> - QUEUE : Paas Package to user space (place where application and drivers reside)
|
||||
> - DROP : Drop Packets
|
||||
> - RETURN : Return Control to calling chain and stop executing next set of rules for the current Packets in the chain.
|
||||
|
||||
|
||||
**7. Lets move to the technical aspects of iptables, by technical I means practical.**
|
||||
|
||||
How will you Check iptables rpm that is required to install iptables in CentOS?.
|
||||
|
||||
> **Answer** : iptables rpm are included in standard CentOS installation and we do not need to install it separately. We can check the rpm as:
|
||||
>
|
||||
> # rpm -qa iptables
|
||||
>
|
||||
> iptables-1.4.21-13.el7.x86_64
|
||||
>
|
||||
> If you need to install it, you may do yum to get it.
|
||||
>
|
||||
> # yum install iptables-services
|
||||
|
||||
**8. How to Check and ensure if iptables service is running?**
|
||||
|
||||
> **Answer** : To check the status of iptables, you may run the following command on the terminal.
|
||||
>
|
||||
> # service status iptables [On CentOS 6/5]
|
||||
> # systemctl status iptables [On CentOS 7]
|
||||
>
|
||||
> If it is not running, the below command may be executed.
|
||||
>
|
||||
> ---------------- On CentOS 6/5 ----------------
|
||||
> # chkconfig --level 35 iptables on
|
||||
> # service iptables start
|
||||
>
|
||||
> ---------------- On CentOS 7 ----------------
|
||||
> # systemctl enable iptables
|
||||
> # systemctl start iptables
|
||||
>
|
||||
> We may also check if the iptables module is loaded or not, as:
|
||||
>
|
||||
> # lsmod | grep ip_tables
|
||||
|
||||
**9. How will you review the current Rules defined in iptables?**
|
||||
|
||||
> **Answer** : The current rules in iptables can be review as simple as:
|
||||
>
|
||||
> # iptables -L
|
||||
>
|
||||
> Sample Output
|
||||
>
|
||||
> Chain INPUT (policy ACCEPT)
|
||||
> target prot opt source destination
|
||||
> ACCEPT all -- anywhere anywhere state RELATED,ESTABLISHED
|
||||
> ACCEPT icmp -- anywhere anywhere
|
||||
> ACCEPT all -- anywhere anywhere
|
||||
> ACCEPT tcp -- anywhere anywhere state NEW tcp dpt:ssh
|
||||
> REJECT all -- anywhere anywhere reject-with icmp-host-prohibited
|
||||
>
|
||||
> Chain FORWARD (policy ACCEPT)
|
||||
> target prot opt source destination
|
||||
> REJECT all -- anywhere anywhere reject-with icmp-host-prohibited
|
||||
>
|
||||
> Chain OUTPUT (policy ACCEPT)
|
||||
> target prot opt source destination
|
||||
|
||||
**10. How will you flush all iptables rules or a particular chain?**
|
||||
|
||||
> **Answer** : To flush a particular iptables chain, you may use following commands.
|
||||
>
|
||||
>
|
||||
> # iptables --flush OUTPUT
|
||||
>
|
||||
> To Flush all the iptables rules.
|
||||
>
|
||||
> # iptables --flush
|
||||
|
||||
**11. Add a rule in iptables to accept packets from a trusted IP Address (say 192.168.0.7)**
|
||||
|
||||
> **Answer** : The above scenario can be achieved simply by running the below command.
|
||||
>
|
||||
> # iptables -A INPUT -s 192.168.0.7 -j ACCEPT
|
||||
>
|
||||
> We may include standard slash or subnet mask in the source as:
|
||||
>
|
||||
> # iptables -A INPUT -s 192.168.0.7/24 -j ACCEPT
|
||||
> # iptables -A INPUT -s 192.168.0.7/255.255.255.0 -j ACCEPT
|
||||
|
||||
**12. How to add rules to ACCEPT, REJECT, DENY and DROP ssh service in iptables.**
|
||||
|
||||
> **Answer** : Hoping ssh is running on port 22, which is also the default port for ssh, we can add rule to iptables as:
|
||||
>
|
||||
> To ACCEPT tcp packets for ssh service (port 22).
|
||||
>
|
||||
> # iptables -A INPUT -s -p tcp --dport 22 -j ACCEPT
|
||||
>
|
||||
> To REJECT tcp packets for ssh service (port 22).
|
||||
>
|
||||
> # iptables -A INPUT -s -p tcp --dport 22 -j REJECT
|
||||
>
|
||||
> To DENY tcp packets for ssh service (port 22).
|
||||
>
|
||||
>
|
||||
> # iptables -A INPUT -s -p tcp --dport 22 -j DENY
|
||||
>
|
||||
> To DROP tcp packets for ssh service (port 22).
|
||||
>
|
||||
>
|
||||
> # iptables -A INPUT -s -p tcp --dport 22 -j DROP
|
||||
|
||||
**13. Let me give you a scenario. Say there is a machine the local ip address of which is 192.168.0.6. You need to block connections on port 21, 22, 23, and 80 to your machine. What will you do?**
|
||||
|
||||
> **Answer** : Well all I need to use is the ‘multiport‘ option with iptables followed by port numbers to be blocked and the above scenario can be achieved in a single go as.
|
||||
>
|
||||
> # iptables -A INPUT -s 192.168.0.6 -p tcp -m multiport --dport 21,22,23,80 -j DROP
|
||||
>
|
||||
> The written rules can be checked using the below command.
|
||||
>
|
||||
> # iptables -L
|
||||
>
|
||||
> Chain INPUT (policy ACCEPT)
|
||||
> target prot opt source destination
|
||||
> ACCEPT all -- anywhere anywhere state RELATED,ESTABLISHED
|
||||
> ACCEPT icmp -- anywhere anywhere
|
||||
> ACCEPT all -- anywhere anywhere
|
||||
> ACCEPT tcp -- anywhere anywhere state NEW tcp dpt:ssh
|
||||
> REJECT all -- anywhere anywhere reject-with icmp-host-prohibited
|
||||
> DROP tcp -- 192.168.0.6 anywhere multiport dports ssh,telnet,http,webcache
|
||||
>
|
||||
> Chain FORWARD (policy ACCEPT)
|
||||
> target prot opt source destination
|
||||
> REJECT all -- anywhere anywhere reject-with icmp-host-prohibited
|
||||
>
|
||||
> Chain OUTPUT (policy ACCEPT)
|
||||
> target prot opt source destination
|
||||
|
||||
**Interviewer** : That’s all I wanted to ask. You are a valuable employee we won’t like to miss. I will recommend your name to the HR. If you have any question you may ask me.
|
||||
|
||||
As a candidate I don’t wanted to kill the conversation hence keep asking about the projects I would be handling if selected and what are the other openings in the company. Not to mention HR round was not difficult to crack and I got the opportunity.
|
||||
|
||||
Also I would like to thank Avishek and Ravi (whom I am a friend since long) for taking the time to document my interview.
|
||||
|
||||
Friends! If you had given any such interview and you would like to share your interview experience to millions of Tecmint readers around the globe? then send your questions and answers to admin@tecmint.com or you may submit your interview experience using following form.
|
||||
|
||||
- [Share Your Interview Experience][2]
|
||||
|
||||
Thank you! Keep Connected. Also let me know if I could have answered a question more correctly than what I did.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.tecmint.com/linux-firewall-iptables-interview-questions-and-answers/
|
||||
|
||||
作者:[Avishek Kumar][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.tecmint.com/author/avishek/
|
||||
[1]:http://www.tecmint.com/install-webmin-web-based-system-administration-tool-for-rhel-centos-fedora/
|
||||
[2]:https://docs.google.com/a/tecmint.com/forms/d/1jfu1Kg8_qToqvyi6pOT1HQb0dAFvRE-Yc_aOkj0RoSg/viewform
|
||||
@ -1,282 +0,0 @@
|
||||
How to Configure Apache Containers with Docker on Fedora 22
|
||||
================================================================================
|
||||
In this article we are going to learn about Docker, how to use it to deploy Apache httpd and how can you share it on Docker Hub. First we are going to learn how to pull and use images hosted on Docker Hub, and then install Apache on an image of Fedora 22 interactively, after that we are going to learn how to use a Dockerfile to make an image in a faster and more elegant way, finally we are going to publish the image we've created in Docker Hub, so anyone will be able download and use it later.
|
||||
|
||||
### Installing Docker and saying hello world ###
|
||||
|
||||
**Requirements**
|
||||
|
||||
You will need atleast these things to run Docker:
|
||||
|
||||
- You need a 64bit Kernel version 3.10 or higher
|
||||
- Iptables 1.4 - This will be used by Docker to make the network wizardry, such as Network Address Translation.
|
||||
- Git 1.7 - Docker uses Git to make it transactions to repositories, like Docker Hub
|
||||
- ps - This utility is present in most environments and is provided in the procps package.
|
||||
- root - despite normal users can run docker client by TCP and other means, we will assume that you are root, for sake of simplicity
|
||||
|
||||
#### Install docker using dnf ####
|
||||
|
||||
The following commands will install Docker
|
||||
|
||||
dnf update && dnf install docker
|
||||
|
||||
**Note**: You can still use Yum in Fedora 22, but it's deprecated in favor of DNF and is not present in a clean install.
|
||||
|
||||
#### Check your install ####
|
||||
|
||||
The first command we are going to use is docker info, this give you many information:
|
||||
|
||||
docker info
|
||||
|
||||
Also try **docker version**:
|
||||
|
||||
docker version
|
||||
|
||||
#### Starting Docker as daemon ####
|
||||
|
||||
You should start a docker instance that will take care of our requests.
|
||||
|
||||
docker -d
|
||||
|
||||
Now set docker to start with the system, so you don't need to run the previous command every time you reboot.
|
||||
|
||||
chkconfig docker on
|
||||
|
||||
Let's say hello world with Busybox:
|
||||
|
||||
docker run -t busybox /bin/echo "hello world"
|
||||
|
||||
In this command, we tell Docker to execute /bin/echo "hello world" in an instance/container of the Busybox image, which is a minimal POSIX environment based in a single binary and links to it.
|
||||
|
||||
If Docker can't find a local image of Busybox on your system, it will pull the image automatically from Docker Hub, as you can see in the following screenshot:
|
||||
|
||||

|
||||
|
||||
Hello world with Busybox
|
||||
|
||||
Try the same command again, this time as Docker already have the Busybox image locally, all you will see is the output of echo:
|
||||
|
||||
docker run -t busybox /bin/echo "hello world"
|
||||
|
||||
Try also the following to enter in the container environment:
|
||||
|
||||
docker run -it busybox /bin/sh
|
||||
|
||||
To leave and stop the container use the **exit** command
|
||||
|
||||
### Dockerizing Apache interactively ###
|
||||
|
||||
Pull/Download the Fedora image:
|
||||
|
||||
docker pull fedora:22
|
||||
|
||||
Run a container dettached from the console:
|
||||
|
||||
docker run -d -t fedora:22 /bin/bash
|
||||
|
||||
List running containers and identify by name as follows
|
||||
|
||||
docker ps
|
||||
|
||||

|
||||
|
||||
listing with docker ps and attaching with docker attach
|
||||
|
||||
The name angry_nobel was given to our instance, so let's attach:
|
||||
|
||||
docker attach angry_nobel
|
||||
|
||||
Note: Every time you run a container a new name will be given, if you need a constant name for you container you should use the -name parameter to docker run command.
|
||||
|
||||
#### Installing Apache ####
|
||||
|
||||
The following command will update DNF database, download install Apache (httpd package) and clean DNF cache to make the image small
|
||||
|
||||
dnf -y update && dnf -y install httpd && dnf -y clean all
|
||||
|
||||
Configuring Apache
|
||||
|
||||
The only thing we are going to change httpd.conf is the ServerName, this makes Apache stops to complain.
|
||||
|
||||
sed -i.orig 's/#ServerName/ServerName/' /etc/httpd/conf/httpd.conf
|
||||
|
||||
**Set the environment**
|
||||
|
||||
To make Apache run in standalone mode, you must provide some information in the form of enviroenment variables, and also you will need the directories set in these variables, so we are going to make this with a small shell script that will also start Apache
|
||||
|
||||
vi /etc/httpd/run_apache_foreground
|
||||
|
||||
----------
|
||||
|
||||
#!/bin/bash
|
||||
|
||||
#set variables
|
||||
APACHE_LOG_DI=R"/var/log/httpd"
|
||||
APACHE_LOCK_DIR="/var/lock/httpd"
|
||||
APACHE_RUN_USER="apache"
|
||||
APACHE_RUN_GROUP="apache"
|
||||
APACHE_PID_FILE="/var/run/httpd/httpd.pid"
|
||||
APACHE_RUN_DIR="/var/run/httpd"
|
||||
|
||||
#create directories if necessary
|
||||
if ! [ -d /var/run/httpd ]; then mkdir /var/run/httpd;fi
|
||||
if ! [ -d /var/log/httpd ]; then mkdir /var/log/httpd;fi
|
||||
if ! [ -d /var/lock/httpd ]; then mkdir /var/lock/httpd;fi
|
||||
|
||||
#run Apache
|
||||
httpd -D FOREGROUND
|
||||
|
||||
**Alternatively**, you can past and run this snippet on the container shell:
|
||||
|
||||
dnf -y install git && git clone https://github.com/gaiada/run-apache-foreground.git && cd run-apach* && ./install && dnf erase git
|
||||
|
||||
The inline script above will, install Git, clone [this repository][1], put the script in place and ask you if you want uninstall Git.
|
||||
|
||||
**Saving your container state**
|
||||
|
||||
Your container is now ready to run Apache, now it is time to save the current state of this container in an image to be able use whenever you need.
|
||||
|
||||
To leave the container environment, you must press **Ctrl+p** followed by **Ctrl+q**, if you just call exit in the shell, you will also stop the container and lost what you have done so far.
|
||||
|
||||
Once you are back to the Docker host, use **docker commit** followed by the container and the repository name/tag you desire:
|
||||
|
||||
docker commit angry_nobel gaiada/apache
|
||||
|
||||
Now that you saved the container status into a image, you can use **docker stop** on the running container:
|
||||
|
||||
docker stop angry_nobel
|
||||
|
||||
**Run and test your image**
|
||||
|
||||
Finally, run a container from your new image and redirect connections on port 80 to it with:
|
||||
|
||||
docker run -p 80:80 -d -t gaiada/apache /etc/httpd/run_apache_foreground
|
||||
|
||||
|
||||
|
||||
At this point, you are already running Apache in your container, open your browser to access the service in [http://localhost][2] and you will see the Apache default page as follows
|
||||
|
||||

|
||||
|
||||
Apache default page running from Docker container
|
||||
|
||||
### Dockerizing Apache with a Dockerfile ###
|
||||
|
||||
Now we are going to create a new Apache image, this time the steps will be written in a Dockerfile, that will be processed to form the image.
|
||||
|
||||
First, create a directory on which we will put the Dockerfile and enter this directory:
|
||||
|
||||
mkdir apachedf; cd apachedf
|
||||
|
||||
And then create a file named Dockerfile with the following content:
|
||||
|
||||
FROM fedora:22
|
||||
|
||||
MAINTAINER Carlos Alberto
|
||||
LABEL version="0.1"
|
||||
|
||||
RUN dnf -y update && dnf -y install httpd && dnf -y clean all
|
||||
|
||||
RUN [ -d /var/log/httpd ] || mkdir /var/log/httpd
|
||||
RUN [ -d /var/run/httpd ] || mkdir /var/run/httpd
|
||||
RUN [ -d /var/lock/httpd ] || mkdir /var/lock/httpd
|
||||
|
||||
RUN sed -i.orig 's/#ServerName/ServerName/' /etc/httpd/conf/httpd.conf
|
||||
|
||||
ENV APACHE_RUN_USER apache
|
||||
ENV APACHE_RUN_GROUP apache
|
||||
ENV APACHE_LOG_DIR /var/log/httpd
|
||||
ENV APACHE_LOCK_DIR /var/lock/httpd
|
||||
ENV APACHE_RUN_DIR /var/run/httpd
|
||||
ENV APACHE_PID_FILE /var/run/httpd/httpd.pid
|
||||
|
||||
EXPOSE 80
|
||||
|
||||
CMD ["/usr/sbin/httpd", "-D", "FOREGROUND"]
|
||||
|
||||
|
||||
|
||||
Let's see what is on this Dockerfile:
|
||||
|
||||
**FROM** - This tells docker that we are going to use Fedora 22 as base image
|
||||
|
||||
**MANTAINER** and **LABEL** - these commands are informative and have no direct influence on the image
|
||||
|
||||
**RUN** - Automate the steps we've done interactively, install Apache, create directories and edit httpd.conf
|
||||
|
||||
**ENV** - Set the environment variables, now we don't need the run_apache_foreground script anymore.
|
||||
|
||||
**EXPOSE** - Expose the port 80 to the world
|
||||
|
||||
**CMD** - Set the default command to httpd, so we don't need to do this every time we start a new container
|
||||
|
||||
**Build the image**
|
||||
|
||||
Now we are going to build the image and put the TAG gaiada/apachedf on it:
|
||||
|
||||
docker build -t gaiada/apachedf:0.1 .
|
||||
|
||||

|
||||
|
||||
docker build complete
|
||||
|
||||
Use **docker images** list the local images and see if your new image is there:
|
||||
|
||||
docker images
|
||||
|
||||
And then run you new image:
|
||||
|
||||
docker run -t -p 80:80 gaiada/apachedf
|
||||
|
||||
That is it for the Dockerfile, using this feature make things much easier, faster and reproducible.
|
||||
|
||||
### Publishing your images ###
|
||||
|
||||
Until now, you just pulled images from Docker Hub, but you can also push you image and pull them later as needed. In fact other can also download your image and use it in their systems without the need of change anything and now we are going to learn how to make our image available for others worldwide.
|
||||
|
||||
**Creating account**
|
||||
|
||||
For you to be able to push your image on Docker Hub, you need to create an account. Access [https://hub.docker.com/account/signup/][3] and fill the following form:
|
||||
|
||||

|
||||
|
||||
Docker Hub signup page
|
||||
|
||||
**Login**
|
||||
|
||||
Enter the following command and proceed with the login name, password and email you provided in your account creation
|
||||
|
||||
docker login
|
||||
|
||||
After you do the first login, your account information will be recorded in **~/.dockercfg**
|
||||
|
||||
**Pushing**
|
||||
|
||||
Push the page to the server with the **docker push [registry/]your_login/repository_name[:tag]**
|
||||
|
||||
docker push docker.io/gaiada/apachedf
|
||||
|
||||
You might see something like this on your console:
|
||||
|
||||

|
||||
|
||||
Docker push Apache image complete
|
||||
|
||||
### Conclusion ###
|
||||
|
||||
Now that you know how to Dockerize Apache, try to include some modules, Perl, PHP, proxy, HTTPS, or whatever you need. I hope you guys liked it, and push your own images on Docker Hub.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/linux-how-to/configure-apache-containers-docker-fedora-22/
|
||||
|
||||
作者:[Carlos Alberto][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://linoxide.com/author/carlosal/
|
||||
[1]:https://github.com/gaiada/run-apache-foreground
|
||||
[2]:http://localhost/
|
||||
[3]:https://hub.docker.com/account/signup/
|
||||
@ -1,3 +1,4 @@
|
||||
wyangsun 申领
|
||||
Inside NGINX: How We Designed for Performance & Scale
|
||||
================================================================================
|
||||
NGINX leads the pack in web performance, and it’s all due to the way the software is designed. Whereas many web servers and application servers use a simple threaded or process-based architecture, NGINX stands out with a sophisticated event-driven architecture that enables it to scale to hundreds of thousands of concurrent connections on modern hardware.
|
||||
@ -171,4 +172,4 @@ via: http://nginx.com/blog/inside-nginx-how-we-designed-for-performance-scale/
|
||||
[12]:https://speakerdeck.com/nginx/nginx-installation-and-tuning
|
||||
[13]:http://nginx.com/blog/tuning-nginx/
|
||||
[14]:http://www.aosabook.org/en/nginx.html
|
||||
[15]:http://nginx.com/blog/socket-sharding-nginx-release-1-9-1/
|
||||
[15]:http://nginx.com/blog/socket-sharding-nginx-release-1-9-1/
|
||||
|
||||
91
sources/tech/20150615 How to combine two graphs on Cacti.md
Normal file
91
sources/tech/20150615 How to combine two graphs on Cacti.md
Normal file
@ -0,0 +1,91 @@
|
||||
How to combine two graphs on Cacti
|
||||
================================================================================
|
||||
[Cacti][1] a fantastic open source network monitoring system that is widely used to graph network elements like bandwidth, storage, processor and memory utilization. Using its web based interface, you can create and organize graphs easily. However, some advanced features like merging graphs, creating aggregate graphs using multiple sources, migration of Cacti to another server are not provided by default. You might need some experience with Cacti to pull these off. In this tutorial, we will see how we can merge two Cacti graphs into one.
|
||||
|
||||
Consider this example. Client-A has been connected to port 5 of switch-A for the last six months. Port 5 becomes faulty, and so the client is migrated to Port 6. As Cacti uses different graphs for each interface/element, the bandwidth history of the client would be split into port 5 and port 6. So we end up with two graphs for one client - one with six months' worth of old data, and the other that contains ongoing data.
|
||||
|
||||
In such cases, we can actually combine the two graphs so the old data is appended to the new graph, and we get to keep a single graph containing historic and new data for one customer. This tutorial will explain exactly how we can achieve that.
|
||||
|
||||
Cacti stores the data of each graph in its own RRD (round robin database) file. When a graph is requested, the values stored in a corresponding RRD file are used to generate the graph. RRD files are stored in `/var/lib/cacti/rra` in Ubuntu/Debian systems and in `/var/www/cacti/rra` in CentOS/RHEL systems.
|
||||
|
||||
The idea behind merging graphs is to alter these RRD files so the values from the old RRD file are appended to the new RRD file.
|
||||
|
||||
### Scenario ###
|
||||
|
||||
The services for a client is running on eth0 for over a year. Because of hardware failure, the client has been migrated to eth1 interface of another server. We want to graph the bandwidth of the new interface, while retaining the historic data for over a year. The client would see only one graph.
|
||||
|
||||
### Identifying the RRD for the Graph ###
|
||||
|
||||
The first step during graph merging is to identify the RRD file associated with a graph. We can check the file by opening the graph in debug mode. To do this, go to Cacti's menu: Console > Graph Management > Select Graph > Turn On Graph Debug Mode.
|
||||
|
||||
#### Old graph: ####
|
||||
|
||||
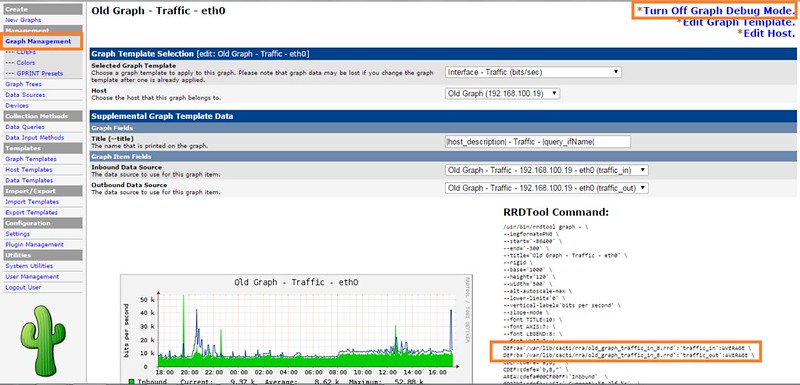
|
||||
|
||||
#### New graph: ####
|
||||
|
||||
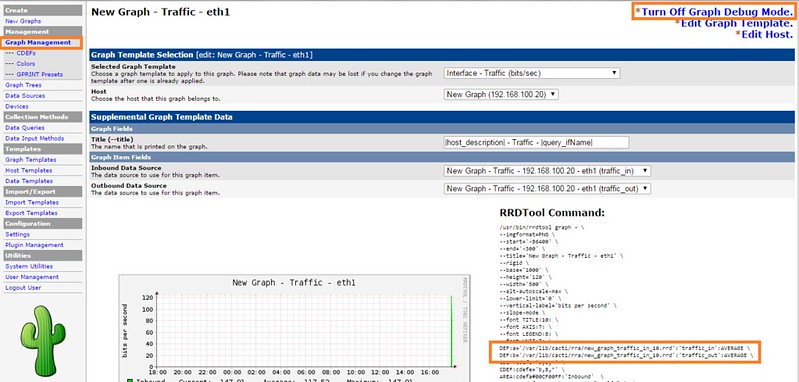
|
||||
|
||||
From the example output (which is based on a Debian system), we can identify the RRD files for two graphs:
|
||||
|
||||
- **Old graph**: /var/lib/cacti/rra/old_graph_traffic_in_8.rrd
|
||||
- **New graph**: /var/lib/cacti/rra/new_graph_traffic_in_10.rrd
|
||||
|
||||
### Preparing a Script ###
|
||||
|
||||
We will merge two RRD files using a [RRD splice script][2]. Download this PHP script, and install it as /var/lib/cacti/rra/rrdsplice.php (for Debian/Ubuntu) or /var/www/cacti/rra/rrdsplice.php (for CentOS/RHEL).
|
||||
|
||||
Next, make sure that the file is owned by Apache user.
|
||||
|
||||
On Debian or Ubuntu, run the following command:
|
||||
|
||||
# chown www-data:www-data rrdsplice.php
|
||||
|
||||
and update rrdsplice.php accordingly. Look for the following line:
|
||||
|
||||
chown($finrrd, "apache");
|
||||
|
||||
and replace it with:
|
||||
|
||||
chown($finrrd, "www-data");
|
||||
|
||||
On CentOS or RHEL, run the following command:
|
||||
|
||||
# chown apache:apache rrdsplice.php
|
||||
|
||||
### Merging Two Graphs ###
|
||||
|
||||
The syntax usage of the script can easily be found by running it without any parameters.
|
||||
|
||||
# cd /path/to/rrdsplice.php
|
||||
# php rrdsplice.php
|
||||
|
||||
----------
|
||||
|
||||
USAGE: rrdsplice.php --oldrrd=file --newrrd=file --finrrd=file
|
||||
|
||||
Now we are ready to merge two RRD files. Simply supply the names of an old RRD file and a new RRD file. We will overwrite the merged result back to the new RRD file.
|
||||
|
||||
# php rrdsplice.php --oldrrd=old_graph_traffic_in_8.rrd --newrrd=new_graph_traffic_in_10.rrd --finrrd=new_graph_traffic_in_10.rrd
|
||||
|
||||
Now the data from the old RRD file should be appended to the new RRD. Any new data will continue to be written by Cacti to the new RRD file. If we click on the graph, we should be able to verify that the weekly, monthly and yearly records have also been added from the old graph. The second graph in the following diagram shows weekly records from the old graph.
|
||||
|
||||
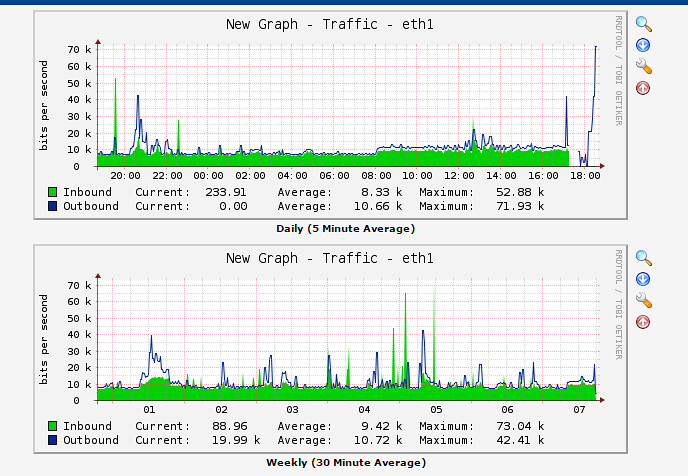
|
||||
|
||||
To sum up, this tutorial showed how we can easily merge two Cacti graphs into one. This trick is useful when a service is migrated to another device/interface and we want to deal with only one graph instead of two. The script is very handy as it can join graphs regardless of the source device e.g., Cisco 1800 router and Cisco 2960 switch.
|
||||
|
||||
Hope this helps.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/combine-two-graphs-cacti.html
|
||||
|
||||
作者:[Sarmed Rahman][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/sarmed
|
||||
[1]:http://xmodulo.com/install-configure-cacti-linux.html
|
||||
[2]:http://svn.cacti.net/viewvc/developers/thewitness/rrdsplice/rrdsplice.php
|
||||
100
translated/share/20150527 3 Open Source Python Shells.md
Normal file
100
translated/share/20150527 3 Open Source Python Shells.md
Normal file
@ -0,0 +1,100 @@
|
||||
3个开源的Python Shell
|
||||
=========================================================================
|
||||
Python是一个高级,通用,结构化且强大的开源编程语言,用于广泛的编程工作。它拥有一个完全的动态类型系统和自动内存管理,与Scheme,Ruby,Perl和Tcl的十分相似,避免编译型语言的许多复杂地方和难以理解。Python于1991年由Guido van Rossum创造,然后逐渐成长,流行。
|
||||
|
||||
Python是一个非常实用,而且流行的计算机编程语言。使用一个如Python这样的解释型语言的好处之一就是,可以借助其交互的shell考察式地编程。你可以试用代码,而不必写一个脚本。但是Python shell也有一些局限性。基本来说,有许多很nice的Python shell可选择,都是在基础shell上扩展的。他们每一个都提供了一个极好的交互性的Python 体验。
|
||||
|
||||
--------------
|
||||
|
||||
### bpython ###
|
||||
|
||||

|
||||
|
||||
对于Linux,BSD,OS X和Windows来说,bpython是Python解释器一个受欢迎的接口。
|
||||
|
||||
想法是提供给用户所有的内置功能,很像现在的IDEs(集成开发环境),但是是在一个简单,轻量级的包里,可以在终端窗口里面运行。
|
||||
|
||||
bpython并不追求创造任何新的或者开创性的东西。相反,她聚集了一些简洁的理念,关注于实用性和操作性。
|
||||
|
||||
功能包括:
|
||||
|
||||
- 内置的语法高亮 - 使用Pygments排版你敲出的代码,并合理地上色
|
||||
- 根据你的行为,显示自动补全的建议。
|
||||
- 为任何Python函数列出期望的参数 - 力求显示一列参数,为你调用的任何函数
|
||||
- “Rewind”功能,弹出内存里的最后一行代码并重新评定
|
||||
- 发送你已经解除占用的代码到粘贴缓存
|
||||
- 保存你已经输入到一个文件里的代码
|
||||
- 自动缩进
|
||||
- 支持Python 3
|
||||
|
||||
- 网址: [www.bpython-interpreter.org][1]
|
||||
- 开发者: Bob Farrell and contributors
|
||||
- 证书: MIT License
|
||||
- 版本号: 0.14.1
|
||||
|
||||
----------
|
||||
|
||||
### IPython ###
|
||||
|
||||

|
||||
|
||||
IPython是Python shell的一个交互加强版。她提供了一个丰富的工具集合,帮助你交互式地充分利用Python。
|
||||
|
||||
IPython可以用来取代标准的Python shell,或者当与标准Python 科学和数值处理工具配合,用做一个科学计算(如Matlab或者Mathematical)的完整工作环境。她支持动态对象内省,有限的输入/输出提示,一个宏观系统,会话登录,会话恢复,完整的系统接入,详尽且彩色的追踪报告,自动圆括号,自动应用和可嵌入其他Python程序。
|
||||
|
||||
功能包括:
|
||||
|
||||
- 强大的交互Shell(终端或者基于Qt)
|
||||
- 一个基于浏览器的记事本,支持代码,多样文本,数学表达式,内置飞行图表和其他丰富媒介。
|
||||
- 支持交互式的数据虚拟化和GUI工具箱使用
|
||||
- 灵活,嵌入式的解释器可以加载进你自己的项目里
|
||||
- 易于使用,高效的并行运算工具
|
||||
|
||||
- 网址: [ipython.org][2]
|
||||
- 开发者: The IPython Development Team
|
||||
- 证书: BSD
|
||||
- 版本号: 3.1
|
||||
|
||||
----------
|
||||
|
||||
### DreamPie ###
|
||||
|
||||

|
||||
|
||||
DreamPie是一个为可靠性和兴趣设计的Python shell。
|
||||
|
||||
DreamPie可以用于任何Python解释器(Jython,IronPython,PyPy)。
|
||||
|
||||
功能包括:
|
||||
|
||||
- 一个交互shell的新概念:窗口被分成历史区域和代码区域,历史区域可以让你看到之前的命令及其输出,代码区域是里敲代码的地方。这样,你可以编辑任意数量的代码,就好像在你最喜欢的编辑器里一样,并且适当时候可以执行它。你也可以从其他地方复制你想保存的代码,所以你可以把它存入一个文件。代码可以很好地格式化为四级缩进。
|
||||
- 自动补全属性和文件名字
|
||||
- 自动显示函数参数和文档
|
||||
- 在结果历史中保存你最近的结果,备以后用
|
||||
- 可以自动展开很长的输出,所以你可以专注于重要的地方
|
||||
- 保存会话的历史记录为一个HTML文件,备以后查询。你可以加载历史文件到DreamPie里,并且快速回退到之前的命令。
|
||||
- 自动添加圆括号与可选的引用,当你在函数与方法后按下空格键。例如,键入execfile fn并且获得execfile("fn")
|
||||
- 支持交互的matplotlib绘图
|
||||
- 支持Python 2.5,Python 2.6,Python 3.1,Jython 2.5,IronPython 2.6和PyPy
|
||||
- 难以置信的快速反应
|
||||
|
||||
- 网址: [www.dreampie.org][3]
|
||||
- 开发者: Noam Yorav-Raphael
|
||||
- 证书: GNU GPL v3
|
||||
- 版本号: 1.2.1
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linuxlinks.com/article/20150523032756576/PythonShells.html
|
||||
|
||||
作者:Frazer Kline
|
||||
译者:[wi-cuckoo](https://github.com/wi-cuckoo)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.bpython-interpreter.org/
|
||||
[2]:http://ipython.org/
|
||||
[3]:http://www.dreampie.org/
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
@ -1,18 +1,18 @@
|
||||
如何在Linux中安装漂亮的扁平化Arc GTK+主题
|
||||
================================================================================
|
||||
> 易于看懂的每步都有的教程
|
||||
> 易于理解的分步教程
|
||||
|
||||
**今天我们将向你介绍最新发布的GTK+主题,它拥有透明和扁平元素,并且与多个桌面环境和Linux发行版见荣发。[这个主题叫Arc][1]。**
|
||||
**今天我们将向你介绍最新发布的GTK+主题,它拥有透明和扁平元素,并且与多个桌面环境和Linux发行版兼容。[这个主题叫Arc][1]。**
|
||||
|
||||
开始讲细节之前,我建议你快速地看一下下面的图,这样你有会对这个主题就会有一个基本的概念了。同样你应该意识到它目前可以工作在GTK+ 2.x、GTK+ 3.x、GNOME-Shell、 Budgie、 Unity和Pantheon用户界面,它们都使用了GNOME栈。
|
||||
开始讲细节之前,我建议你快速浏览一下下面的图,这样你有会对这个主题就会有一个基本的概念了。同样你应该知道它目前可以工作在GTK+ 2.x、GTK+ 3.x、GNOME-Shell、 Budgie、 Unity和Pantheon用户界面,它们都使用了GNOME栈。
|
||||
|
||||
同样、Arc主题的开发者提醒我们它已经成功地在Ubuntu 15.04(Vivid Vervet)、 Arch Linux、 elementary OS 0.3 Freya、 Fedora 21、 Fedora 22、 Debian GNU/Linux 8.0 (Jessie)、 Debian Testing、 Debian Unstable、 openSUSE 13.2、 openSUSE Tumbleweed和Gentoo测试过了。
|
||||
同样、Arc主题的开发者告诉我们它已经成功地在Ubuntu 15.04(Vivid Vervet)、 Arch Linux、 elementary OS 0.3 Freya、 Fedora 21、 Fedora 22、 Debian GNU/Linux 8.0 (Jessie)、 Debian Testing、 Debian Unstable、 openSUSE 13.2、 openSUSE Tumbleweed和Gentoo测试过了。
|
||||
|
||||
### 要求和安装指导 ###
|
||||
|
||||
要构建Arc主题,你需要先安装一些包,比如autoconf、 automake、 pkg-config (对Fedora的pkgconfig)、基于Debian/Ubuntu-based发行版的libgtk-3-dev或者基于RPM的gtk3-devel、 git、 gtk2-engines-pixbuf和gtk-engine-murrine (对Fedora的gtk-murrine-engine)。
|
||||
要构建Arc主题,你需要先安装一些包,比如autoconf、 automake、 pkg-config (对于Fedora则是pkgconfig)、基于Debian/Ubuntu-based发行版的libgtk-3-dev或者基于RPM的gtk3-devel、 git、 gtk2-engines-pixbuf和gtk-engine-murrine (对于Fedora则是gtk-murrine-engine)。
|
||||
|
||||
Arc主题还没有二进制包,因此你需要从git仓库中取下最新的源码并编译。这样,打开终端并运行下面的命令,一行行地,并在每行的末尾按下回车键并等待上一步完成来继续一步。
|
||||
Arc主题还没有二进制包,因此你需要从git仓库中取下最新的源码并编译。这样,打开终端并运行下面的命令,一行行地,并在每行的末尾按下回车键并等待上一步完成来继续下一步。
|
||||
|
||||
git clone https://github.com/horst3180/arc-theme --depth 1 && cd arc-theme
|
||||
git fetch --tags
|
||||
@ -20,7 +20,7 @@ Arc主题还没有二进制包,因此你需要从git仓库中取下最新的
|
||||
./autogen.sh --prefix=/usr
|
||||
sudo make install
|
||||
|
||||
就是这样!此时你已经在你的GNU/Linux发行版中安装了Arc主题,如果你使用GNOME可以使用GONME Tweak工具或者如果你使用Unity可以使用Unity Tweak工具来激活主题。玩得开心也不要忘了在下面的评论栏里留下你的截图。
|
||||
就是这样!此时你已经在你的GNU/Linux发行版中安装了Arc主题,如果你使用GNOME可以使用GONME Tweak工具,如果你使用Ubuntu的Unity可以使用Unity Tweak工具来激活主题。玩得开心但不要忘了在下面的评论栏里留下你的截图。
|
||||
|
||||
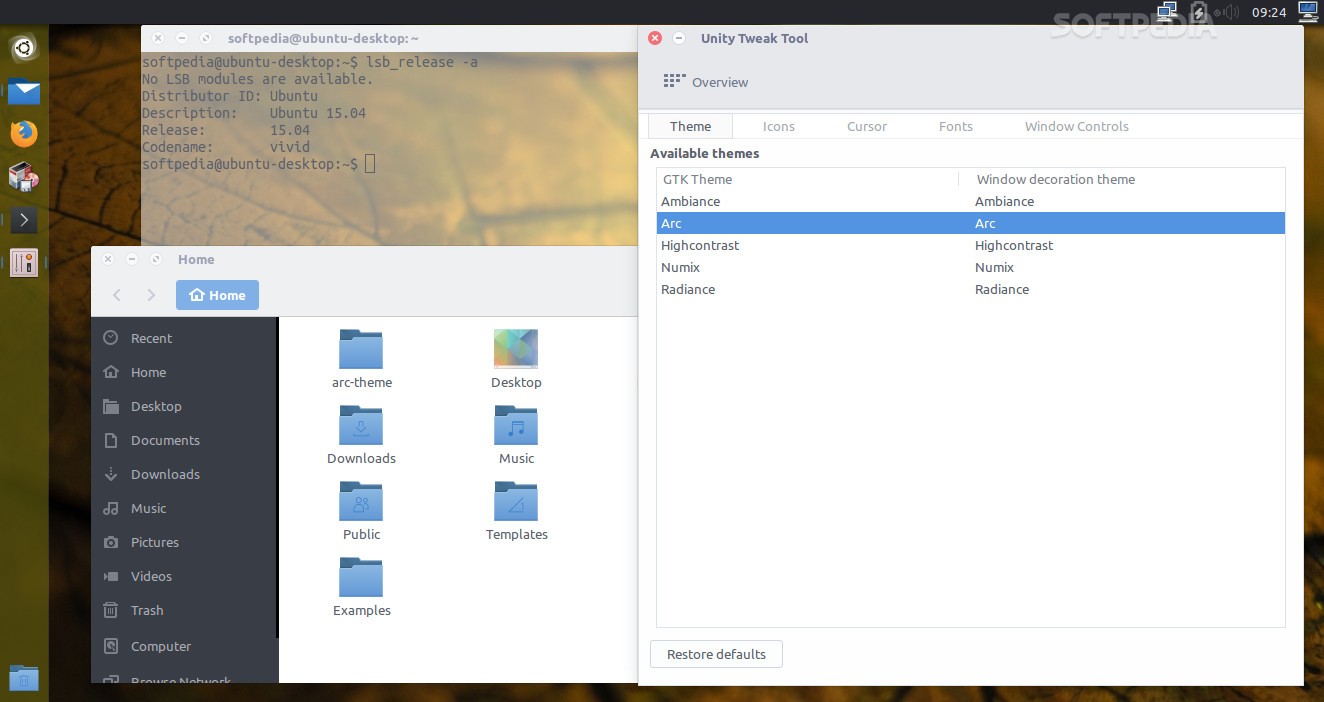
|
||||
|
||||
@ -34,28 +34,9 @@ via: http://news.softpedia.com/news/Here-s-How-to-Install-the-Beautiful-Arc-GTK-
|
||||
|
||||
作者:[Marius Nestor][a]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[caroline](https://github.com/carolinewuyan)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://news.softpedia.com/editors/browse/marius-nestor
|
||||
[1]:https://github.com/horst3180/Arc-theme
|
||||
[2]:
|
||||
[3]:
|
||||
[4]:
|
||||
[5]:
|
||||
[6]:
|
||||
[7]:
|
||||
[8]:
|
||||
[9]:
|
||||
[10]:
|
||||
[11]:
|
||||
[12]:
|
||||
[13]:
|
||||
[14]:
|
||||
[15]:
|
||||
[16]:
|
||||
[17]:
|
||||
[18]:
|
||||
[19]:
|
||||
[20]:
|
||||
|
||||
@ -0,0 +1,80 @@
|
||||
为LUKS——加密的磁盘/分区做增量备份
|
||||
================================================================================
|
||||
我们中有些人出于安全原因,在家里或者[VPS][1]上通过[Linux统一密钥配置(LUKS)][2]为硬盘驱动器加密,而这些驱动器的容量很快会增长到数十或数百GB。因此,虽然我们享受着LUKS设备带来的安全感,但是我们也该开始考虑一个可能的远程备份方案了。对于安全的非现场备份,我们将需要在LUKS加密的设备上以块级别操作的东西。因此,最后我们发现这么个状况,我们每次都需要传输想要做备份的LUKS设备(比如说200GB)。很明显,这是不可行的。我们该怎么来处理这个问题呢?
|
||||
|
||||
### 一个解决方案: Bdsync ###
|
||||
|
||||
这时,一个卓越的开源工具来拯救我们了,它叫[Bdsync][3](多亏了Rolf Fokkens)。顾名思义,Bdsync可以通过网络同步“块设备”。对于快速同步,Bdsync会生成并对比本地/远程块设备的块MD5校验和,只同步差异部分。rsync在文件系统级别可以做的,Bdsync可以在块设备级别完成。很自然,对于LUKS加密的设备它也能工作得很好。相当地灵巧!
|
||||
|
||||
使用Bdsync,首次备份将拷贝整个LUKS块设备到远程主机,因而会花费大量时间来完成。然而,在初始备份后,如果我们在LUKS设备新建一些文件,再次备份就会很快完成,因为我们只需拷贝修改过的块。经典的增量备份在起作用了!
|
||||
|
||||
### 安装Bdsync到Linux ###
|
||||
|
||||
Bdsync并不包含在[Linux][4]发行版的标准仓库中,因而你需要从源代码来构建它。使用以下针对特定版本的指令来安装Bdsync及其手册页到你的系统中。
|
||||
|
||||
#### Debian,Ubuntu或Linux Mint ####
|
||||
|
||||
$ sudo apt-get install git gcc libssl-dev
|
||||
$ git clone https://github.com/TargetHolding/bdsync.git
|
||||
$ cd bdsync
|
||||
$ make
|
||||
$ sudo cp bdsync /usr/local/sbin
|
||||
$ sudo mkdir -p /usr/local/man/man1
|
||||
$ sudo sh -c 'gzip -c bdsync.1 > /usr/local/man/man1/bdsync.1.gz'
|
||||
|
||||
#### Fedora或CentOS/RHEL ####
|
||||
|
||||
$ sudo yum install git gcc openssl-devel
|
||||
$ git clone https://github.com/TargetHolding/bdsync.git
|
||||
$ cd bdsync
|
||||
$ make
|
||||
$ sudo cp bdsync /usr/local/sbin
|
||||
$ sudo mkdir -p /usr/local/man/man1
|
||||
$ sudo sh -c 'gzip -c bdsync.1 > /usr/local/man/man1/bdsync.1.gz'
|
||||
|
||||
### 对LUKS加密的设备实施非现场增量备份 ###
|
||||
|
||||
我假定你已经准备好了一个LUKS加密的块设备作为备份源(如,/dev/LOCDEV)。同时,我假定你也有一台远程主机,用以作为源设备的备份点(如,/dev/REMDEV)。
|
||||
|
||||
你需要在两台系统上具有root帐号访问权限,并且设置从本地访问远程的[无密码SSH访问][5]。最后,你需要安装Bdsync到两台主机上。
|
||||
|
||||
要在本地主机上初始化一个远程备份进程,我们需要以root执行以下命令:
|
||||
|
||||
# bdsync "ssh root@remote_host bdsync --server" /dev/LOCDEV /dev/REMDEV | gzip > /some_local_path/DEV.bdsync.gz
|
||||
|
||||
这里需要进行一些说明。Bdsync客户端将以root打开一个到远程主机的SSH连接,并执行带有--server选项的Bdsync客户端。明确说明一下,/dev/LOCDEV是我们的本地主机上的源LUKS块设备,而/dev/REMDEV是远程主机上的目标块设备。它们可以是/dev/sda(作为整个磁盘),或者/dev/sda2(作为单个分区)。本地Bdsync客户端的输出结果随后被管道输送到gzip,用来在本地主机中创建DEV.bdsync.gz(所谓的二进制补丁文件)。
|
||||
|
||||
你第一次运行上面的命令的时候,它会花费很长一段时间,这取决于你的互联网/局域网速度,以及/dev/LOCDEV的大小。记住,你必须有两个大小相同的块设备(/dev/LOCDEV和/dev/REMDEV)。
|
||||
|
||||
下一步是要将补丁文件从本地主机拷贝到远程主机。一种可能是使用scp:
|
||||
|
||||
# scp /some_local_path/DEV.bdsync.gz root@remote_host:/remote_path
|
||||
|
||||
最后一步,是要在远程主机上执行以下命令,它们会将补丁文件应用到/dev/REMDEV:
|
||||
|
||||
# gzip -d < /remote_path/DEV.bdsync.gz | bdsync --patch=/dev/DSTDEV
|
||||
|
||||
我推荐在使用真实数据部署Bdsync前,使用一些(没有任何重要数据)小分区来做这些测试。在你完全弄懂整个设置是如何工作之后,你可以开始备份真实数据。
|
||||
|
||||
### 尾声 ###
|
||||
|
||||
小结之,我们演示了如何使用Bdsync来为LUKS设备实施增量备份。和rsync一样,每次备份只有一小部分数据,而不是整个LUKS设备,需要被推送到非现场备份点,这样会节省带宽和备份时间。剩下来,需要保证所有数据传输通过SSH或SCP加固安全,事实上设备自身是由LUKS加密的。也可以通过使用可以运行bdsync的专用用户(而非root)来改善该配置。我们也可以将bdsync用于任何块设备,如LVM卷或RAID磁盘,也可以很轻易地设置Bdsync备份本地磁盘到USB驱动器上。如你所见,它有着无限可能性!
|
||||
|
||||
随时分享你的想法。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/remote-incremental-backup-luks-encrypted-disk-partition.html
|
||||
|
||||
作者:[Iulian Murgulet][a]
|
||||
译者:[GOLinux](https://github.com/GOLinux)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/iulian
|
||||
[1]:http://xmodulo.com/go/digitalocean
|
||||
[2]:http://xmodulo.com/how-to-create-encrypted-disk-partition-on-linux.html
|
||||
[3]:http://bdsync.rolf-fokkens.nl/
|
||||
[4]:http://xmodulo.com/recommend/linuxbook
|
||||
[5]:http://xmodulo.com/how-to-enable-ssh-login-without.html
|
||||
@ -0,0 +1,104 @@
|
||||
11个让人惊叹的Linux终端彩蛋
|
||||
================================================================================
|
||||
这里有一些很酷的Linux终端彩蛋,其中的每一个看上去并没有实际用途,但很精彩。
|
||||
|
||||

|
||||
|
||||
### 只工作不玩耍…… ###
|
||||
|
||||
当我们使用命令行工作时,Linux是功能和实用性最好的操作系统之一。想要执行一个特殊任务?可能一个程序或者脚本就可以帮你搞定。但就像一本书中说到的,只工作不玩耍聪明的孩子也会变傻。下边是我最喜欢的可以在终端做的没有实际用途的、傻傻的、恼人的、可笑的事情。
|
||||
|
||||
### 给终端一个态度 ###
|
||||
|
||||
* 第一步)敲入`sudo visudo`
|
||||
* 第二步)在“Defaults”末尾(文件的前半部分)添加一行“Defaults insults”。
|
||||
* 第三步)保存文件。
|
||||
|
||||
“我刚才对电脑做了什么?”你可能这样问自己。一定是美妙的事情吧。现在,在sudo命令提示提示下输出错误的口令,你的电脑就会呼唤你的名字。我最喜欢的一句:“听好了,煎饼一样的脑子,我没有时间听你胡说八道了。”
|
||||
|
||||

|
||||
|
||||
### apt-get moo ###
|
||||
|
||||
你看过这张截图?那就是运行`apt-get moo`(在基于Debian的系统)的结果。对,就是它了。不要对它抱太多幻想,你会失望的,我不骗你。但是这是Linux世界最被人熟知的彩蛋之一。所以我把它包含进来,并且放在前排,然后我也就不会收到5千封邮件,指责我把它遗漏了。
|
||||
|
||||

|
||||
|
||||
### aptitude moo ###
|
||||
|
||||
更有趣的是将moo应用到aptitude上。敲入`aptitude moo`(在Ubuntu及其衍生版),你对`moo`可以做什么事情的看法会有所变化。你还还会知道更多事情,尝试重新输入这条命令,但这次添加一个`-v`参数。这还没有结束,试着添加更多`v`,一次添加一个,直到aptitude给了你想要的东西。
|
||||
|
||||

|
||||
|
||||
### Arch: 将吃豆人放入pacman ###
|
||||
|
||||
这里有一个只为Arch爱好者准备的彩蛋。Pacman包管理工具已经很棒了,但我们可以让它变得更棒。
|
||||
|
||||
* 第一步)打开“/etc/pacman.conf”文件。
|
||||
* 第二步)在“# Misc options”部分,去掉“Color”前的“#”。
|
||||
* 第三步)添加“ILoveCandy”。
|
||||
|
||||
现在我们使用pacman安装新软件包时,进度条里会出现一个小吃豆人。真应该默认就是这样的。
|
||||
|
||||

|
||||
|
||||
### Cowsay! ###
|
||||
|
||||
`aptitude moo`的输出格式很漂亮,但我想你苦于不能自由自在地使用。输入`cowsay`,它会做到你想做的事情。你可以让牛说任何你喜欢的东西。而且不只可以用牛,还可以用Calvin、Beavis和Ghostbusters的ASCII logo——输入`cowsay -l`可以得到所有可用的logo。它是Linux世界的强大工具。像很多其他命令一样,你可以使用管道把其他程序的输出输送给它,比如`fortune | cowsay`。
|
||||
|
||||

|
||||
|
||||
### 变成3l33t h@x0r ###
|
||||
|
||||
`nmap`并不是我们平时经常使用的基本命令。但如果你想蹂躏`nmap`的话,可能想在它的输出中看到l33t。在任何`nmap`命令(比如`nmap -oS - google.com`)后添加`-oS`。现在你的`nmap`已经处于官方名称是“[Script Kiddie Mode][1]”的模式了。Angelina Jolie和Keanu Reeves会为此骄傲的。
|
||||
|
||||

|
||||
|
||||
### 获得所有的Discordian日期 ###
|
||||
|
||||
如果你们曾经坐在一起思考,“嗨!我想使用无用但异想天开的方式来书写今天的日期……”试试运行`ddate`。结果类似于“Today is Setting Orange, the 72nd day of Discord in the YOLD 3181”,这会让你的服务树日志平添不少香料。
|
||||
|
||||
注意:在技术层面,确实有一个[Discordian Calendar][2],理论上被[Discordianism][3]追随者所使用。这意味着我可能得罪某些人。或者不会,我不确定。不管怎样,`ddate`是一个方便的工具。
|
||||
|
||||

|
||||
|
||||
### 我可以在任何地方看到颜色!###
|
||||
|
||||
厌倦了老旧的文本?想向世界展示出自己的个性?使用`lolcat`。安装它,然后在任何地方使用。它可以接收任何文本,然后将其转换成美轮美奂的彩虹效果。可以使用`fortune | lolcat`体验。
|
||||
|
||||

|
||||
|
||||
### 蒸汽机车 ###
|
||||
|
||||
在你的终端显示蒸汽机车的ASCII图形。如果你需要它,安装并运行`sl`命令。`sl -l`可以看到一个袖珍版本的。或者,如果你真想在上边花费更多时间,运行`sl -h`。这会显示一个完整的或者,还包括乘客车厢。
|
||||
|
||||

|
||||
|
||||
### 将任何文本逆序输出 ###
|
||||
|
||||
将任何文本使用管道输送给`rev`命令,它就会将文本内容逆序输出。`fortune | rev`会给你好运。当然,这不意味着rev会将幸运转换成不幸。
|
||||
|
||||

|
||||
|
||||
### Matrix依然很酷,不是吗? ###
|
||||
|
||||
想让你的终端显示滚动的文字、l33t和Matrix电影中的坠落数码?`cmatrix`是你的朋友。你甚至可以用它输出不同的颜色,非常华丽。使用`man cmatrix`学习使用方法。或者使用更好的方法,“man cmatrix | lolcat”。这确实是你在Linux终端可以做的最没实际用途却又精彩的事情了。
|
||||
|
||||

|
||||
|
||||
以上就是全部内容了。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.networkworld.com/article/2926630/linux/11-pointless-but-awesome-linux-terminal-tricks.html
|
||||
|
||||
作者:[Bryan Lunduke][a]
|
||||
译者:[goreliu](https://github.com/goreliu)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.networkworld.com/author/Bryan-Lunduke/
|
||||
[1]:http://nmap.org/book/output-formats-script-kiddie.html
|
||||
[2]:http://en.wikipedia.org/wiki/Discordian_calendar
|
||||
[3]:http://en.wikipedia.org/wiki/Discordianism
|
||||
@ -1,113 +0,0 @@
|
||||
安装Fedora 22后要做的事
|
||||
================================================================================
|
||||
Fedora 22,Red Hat操作系统的社区开发版的最新成员,已经于2015年5月26日发布了。这个令人神圣的Fedora发行版充斥着各种炒作和预期,Fedora 22推出了大量的重大变化。
|
||||
|
||||
就初始化进程而言,Systemd还是个新生儿,但它已经准备好替换脆弱的sysvinit这个一直是Linux生态系统一部分的模块。另外一个用户会碰到的重大改变存在于基本仓库的python版本中,这里提供了两种不同口味的python版本2.x和3.x分线,各个都有其不同的癖好和优点。所以,那些偏好2.x口味的用户可能想要安装他们喜爱的python版本。自从Fedora 18开始被打扮得更加时髦的Yum安装器也被设置来替换过时陈旧的YUM安装器后。Fedora也已最后决定,现在是时候用DNF来替换YUM了。
|
||||
### 1) 安装VLC媒体播放器 ###
|
||||
|
||||
Fedora 22默认自带了媒体播放器viz gnome视频播放器(前身是totem)。如果你对此不感冒,那么我们可以跳过这一步继续往前走。但是,如果你像我一样,偏好使用最广泛的VLC,那么就去从RPMFusion仓库安装吧。安装方法如下:
|
||||
|
||||
sudo dnf install vlc -y
|
||||
|
||||
### 2) 配置RPMFusion仓库 ###
|
||||
|
||||
正如我已经提到过的,Fedora的意识形态很是严谨,它不会自带任何非自由组件。官方仓库不会提供一些包含有非自由组件的基本软件,比如像多媒体编码。因此,安装一些第三方仓库很有必要,这些仓库会为我们提供一些基本的软件。幸运的是,RPMFusion仓库前来拯救我们了。
|
||||
|
||||
$ sudo dnf install --nogpgcheck http://download1.rpmfusion.org/free/fedora/rpmfusion-free-release-22.noarch.rpm
|
||||
|
||||
### 3) 安装多媒体编码 ###
|
||||
|
||||
刚刚我们说过,一些多媒体编码和插件不会随Fedora一起发送。现在,有谁想仅仅是因为专有编码而错过他们最爱的节目和电影?试试这个吧:
|
||||
|
||||
$ sudo dnf install gstreamer-plugins-bad gstreamer-plugins-bad-free-extras gstreamer-plugins-ugly gstreamer-ffmpeg gstreamer1-libav gstreamer1-plugins-bad-free-extras gstreamer1-plugins-bad-freeworld gstreamer-plugins-base-tools gstreamer1-plugins-good-extras gstreamer1-plugins-ugly gstreamer1-plugins-bad-free gstreamer1-plugins-good gstreamer1-plugins-base gstreamer1
|
||||
|
||||
### 4) 更新系统 ###
|
||||
|
||||
Fedora是一个尖端的发行版,因此它会持续发布更新用以修复系统中出现的错误和漏洞。因而,保持系统更新到最新,是个不错的做法。
|
||||
|
||||
$ sudo dnf update -y
|
||||
|
||||
### 5) 卸载你不需要的软件 ###
|
||||
|
||||
Fedora预装了一些大多数用户可以利用的包,但是对于更高级的用户,你可能意识到你并不需要它。要移除你不需要的包相当容易,只需使用以下命令——我选择卸载rhythmbox,因为我知道我不会用到它:
|
||||
|
||||
$ sudo dnf remove rhythmbox
|
||||
|
||||
### 6) 安装Adobe Flash ###
|
||||
|
||||
我们都希望Adobe Flash不要再存在了,因为它并不被认为是最安全的,或者资源利用最好的,但是暂时先让它待着吧。Fedora 22安装Adobe Flash的唯一途径是从Adobe安装官方RPM,就像下面这样。
|
||||
|
||||
你可以从[这里][1]下载RPM。下载完后,你可以直接右击并像下面这样打开:
|
||||
|
||||

|
||||
|
||||
右击并选择“用软件安装打开”
|
||||
|
||||
然后,只需在弹出窗口中点击安装:
|
||||
|
||||

|
||||
|
||||
点击“安装”来完成从Adobe安装自定义RPM的过程
|
||||
|
||||
该过程完成后,“安装”按钮会变成“移除”,而此时安装也完成了。如果在此过程中你的浏览器开着,会提示你先把它关掉或在安装完成后重启以使修改生效。
|
||||
|
||||
### 7) 用Gnome Boxes加速虚拟机 ###
|
||||
|
||||
你刚刚安装了Fedora,你也很是喜欢,但是出于某些私人原因,你也许仍然需要Windows,或者你只是想玩玩另外一个Linux发行版。不管哪种情况,你都可以使用Gnome Boxes来简单地创建一个虚拟机或使用一个live发行版,Fedora 22提供了该软件。遵循以下步骤,使用你所选的ISO来开始吧!谁知道呢,也许你可以检验一下某个[Fedora Spin][2]。
|
||||
|
||||
首先,打开Gnome Boxes,然后在顶部左边选择“新建”:
|
||||
|
||||

|
||||
|
||||
点击“新建”来开始添加一个新虚拟机的进程吧。
|
||||
|
||||
接下来,点击打开文件并选择一个ISO:
|
||||
|
||||

|
||||
|
||||
在选择选择了选择文件或ISO后,选择你的ISO。这里,我已经安装了一个Debian ISO。
|
||||
|
||||
最后,自定义VM设置或使用默认,然后点击“创建”。VM会以默认方式启动,可用的VM会在Gnome Boxes以小缩略图的方式显示。
|
||||
|
||||

|
||||
|
||||
自定义设置为你所选择的,或者也可以保持默认。完成后,点击“创建”,VM就一切就绪了。
|
||||
|
||||
### 8) 安装Google Chrome ###
|
||||
|
||||
Firefox被包含在Fedora 22中,但是就跟大多数软件一样,每个人都有他们自己的选择。如果你所喜爱的浏览器恰好是Google Chrome,你可以使用和上面安装Adobe Flash Player类似的指令。然而,很明显,你得使用来自Google的任何你所下载的版本的RPM。最新的版本通常可以在[这里][3]找到。
|
||||
|
||||
### 9) 添加社交媒体和其它在线帐号 ###
|
||||
|
||||
Gnome自带有不错的内建功能用于容纳帐号相关的东西,像Facebook,Google以及其它在线帐号。你可以通过主Gnome设置应用访问在线帐号设置。然后,只需点击在线帐号,并添加你所选择的帐号。如果你要添加一个帐号,比如像Google,你可以用它来作为默认帐号,用来完成诸如发送邮件、日历提醒、相片和文档交互,以及诸如此类的更多事情。
|
||||
|
||||
### 10) 安装KDE或另一个桌面环境 ###
|
||||
|
||||
我们中的某些人不喜欢Gnome,那也没问题。在终端中运行以下命令来安装KDE所需的一切来替换它。这些指令也可以用以安装xfce、lxde或其它桌面环境。
|
||||
|
||||
$ sudo dnf install @kde-desktop
|
||||
|
||||
安装完成后,登出。当你点击你的用户名时,注意那个表示设置的小齿轮。点击它,然后选择“Plasma”。当你再次登录时,一个全新的KDE桌面就会欢迎你。
|
||||
|
||||

|
||||
|
||||
刚刚安装到Fedora 22上的Plasma环境
|
||||
|
||||
### 尾声 ###
|
||||
|
||||
就是这样了,一切就绪。使用新系统吧,试试新东西。如果你找不到与你喜好相关的东西,linux赋予你自由修改它的权利。Fedora自带有最新的Gnome Shell作为其桌面环境,如果你觉得太臃肿而不喜欢,那么试试KDE或一些轻量级的DE,像Cinnamon、xfce之类。愿你的Fedora之旅十分开心并且没有困扰。!!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/linux-how-to/things-do-after-installing-fedora-22/
|
||||
|
||||
作者:[Jonathan DeMasi][a]
|
||||
译者:[GOLinux](https://github.com/GOLinux)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://linoxide.com/author/jonathande/
|
||||
[1]:https://get.adobe.com/flashplayer/
|
||||
[2]:http://spins.fedoraproject.org/
|
||||
[3]:https://www.google.com/intl/en/chrome/browser/desktop/index.html
|
||||
@ -0,0 +1,205 @@
|
||||
Nishita Agarwal分享它关于Linux防火墙'iptables'的面试经验
|
||||
================================================================================
|
||||
Nishita Agarwal是Tecmint的用户,她将分享关于她刚刚经历的一家公司(私人公司Pune,印度)的面试经验。在面试中她被问及许多不同的问题,但她是iptables方面的专家,因此她想分享这些关于iptables的问题和相应的答案给那些以后可能会进行相关面试的人。
|
||||
|
||||

|
||||
|
||||
所有的问题和相应的答案都基于Nishita Agarwal的记忆并经过了重写。
|
||||
|
||||
> “嗨,朋友!我叫**Nishita Agarwal**。我已经取得了理学学士学位,我的专业集中在UNIX和它的变种(BSD,Linux)。它们一直深深的吸引着我。我在存储方面有1年多的经验。我正在寻求职业上的变化,并将供职于印度的Pune公司。”
|
||||
|
||||
下面是我在面试中被问到的问题的集合。我已经把我记忆中有关iptables的问题和它们的答案记录了下来。希望这会对您未来的面试有所帮助。
|
||||
|
||||
### 1. 你听说过Linux下面的iptables和Firewalld么?知不知道它们是什么,是用来干什么的? ###
|
||||
|
||||
> **答案** : iptables和Firewalld我都知道,并且我已经使用iptables好一段时间了。iptables主要由C语言写成,并且以GNU GPL许可证发布。它是从系统管理员的角度写的,最新的稳定版是iptables 1.4.21。iptables通常被认为是类UNIX系统中的防火墙,更准确的说,可以称为iptables/netfilter。管理员通过终端/GUI工具与iptables打交道,来添加和定义防火墙规则到预定义的表中。Netfilter是内核中的一个模块,它执行过滤的任务。
|
||||
>
|
||||
> Firewalld是RHEL/CentOS 7(也许还有其他发行版,但我不太清楚)中最新的过滤规则的实现。它已经取代了iptables接口,并与netfilter相连接。
|
||||
|
||||
### 2. 你用过一些iptables的GUI或命令行工具么? ###
|
||||
|
||||
> **答案** : 虽然我既用过GUI工具,比如与[Webmin][1]结合的Shorewall;以及直接通过终端访问iptables。但我必须承认通过Linux终端直接访问iptables能给予用户更高级的灵活性、以及对其背后工作更好的理解的能力。GUI适合初级管理员而终端适合有经验的管理员。
|
||||
|
||||
### 3. 那么iptables和firewalld的基本区别是什么呢? ###
|
||||
|
||||
> **答案** : iptables和firewalld都有着同样的目的(包过滤),但它们使用不同的方式。iptables与firewalld不同,在每次发生更改时都刷新整个规则集。通常iptables配置文件位于‘/etc/sysconfig/iptables‘,而firewalld的配置文件位于‘/etc/firewalld/‘。firewalld的配置文件是一组XML文件。以XML为基础进行配置的firewalld比iptables的配置更加容易,但是两者都可以完成同样的任务。例如,firewalld可以在自己的命令行界面以及基于XML的配置文件下使用iptables。
|
||||
|
||||
### 4. 如果有机会的话,你会在你所有的服务器上用firewalld替换iptables么? ###
|
||||
|
||||
> **答案** : 我对iptables很熟悉,它也工作的很好。如果没有任何需求需要firewalld的动态特性,那么没有理由把所有的配置都从iptables移动到firewalld。通常情况下,目前为止,我还没有看到iptables造成什么麻烦。IT技术的通用准则也说道“为什么要修一件没有坏的东西呢?”。上面是我自己的想法,但如果组织愿意用firewalld替换iptables的话,我不介意。
|
||||
|
||||
### 5. 你看上去对iptables很有信心,巧的是,我们的服务器也在使用iptables。 ###
|
||||
|
||||
iptables使用的表有哪些?请简要的描述iptables使用的表以及它们所支持的链。
|
||||
|
||||
> **答案** : 谢谢您的赞赏。至于您问的问题,iptables使用的表有四个,它们是:
|
||||
>
|
||||
> Nat 表
|
||||
> Mangle 表
|
||||
> Filter 表
|
||||
> Raw 表
|
||||
>
|
||||
> Nat表 : Nat表主要用于网络地址转换。根据表中的每一条规则修改网络包的IP地址。流中的包仅遍历一遍Nat表。例如,如果一个通过某个接口的包被修饰(修改了IP地址),该流中其余的包将不再遍历这个表。通常不建议在这个表中进行过滤,由NAT表支持的链称为PREROUTING Chain,POSTROUTING Chain和OUTPUT Chain。
|
||||
>
|
||||
> Mangle表 : 正如它的名字一样,这个表用于校正网络包。它用来对特殊的包进行修改。它能够修改不同包的头部和内容。Mangle表不能用于地址伪装。支持的链包括PREROUTING Chain,OUTPUT Chain,Forward Chain,InputChain和POSTROUTING Chain。
|
||||
>
|
||||
> Filter表 : Filter表是iptables中使用的默认表,它用来过滤网络包。如果没有定义任何规则,Filter表则被当作默认的表,并且基于它来过滤。支持的链有INPUT Chain,OUTPUT Chain,FORWARD Chain。
|
||||
>
|
||||
> Raw表 : Raw表在我们想要配置之前被豁免的包时被使用。它支持PREROUTING Chain 和OUTPUT Chain。
|
||||
|
||||
### 6. 简要谈谈什么是iptables中的目标值(能被指定为目标),他们有什么用 ###
|
||||
|
||||
> **答案** : 下面是在iptables中可以指定为目标的值:
|
||||
>
|
||||
> ACCEPT : 接受包
|
||||
> QUEUE : 将包传递到用户空间 (应用程序和驱动所在的地方)
|
||||
> DROP : 丢弃包
|
||||
> RETURN : 将控制权交回调用的链并且为当前链中的包停止执行下一调规则
|
||||
|
||||
### 7. 让我们来谈谈iptables技术方面的东西,我的意思是说实际使用方面 ###
|
||||
|
||||
你怎么检测在CentOS中安装iptables时需要的iptables的rpm?
|
||||
|
||||
> **答案** : iptables已经被默认安装在CentOS中,我们不需要单独安装它。但可以这样检测rpm:
|
||||
>
|
||||
> # rpm -qa iptables
|
||||
>
|
||||
> iptables-1.4.21-13.el7.x86_64
|
||||
>
|
||||
> 如果您需要安装它,您可以用yum来安装。
|
||||
>
|
||||
> # yum install iptables-services
|
||||
|
||||
### 8. 怎样检测并且确保iptables服务正在运行? ###
|
||||
|
||||
> **答案** : 您可以在终端中运行下面的命令来检测iptables的状态。
|
||||
>
|
||||
> # service status iptables [On CentOS 6/5]
|
||||
> # systemctl status iptables [On CentOS 7]
|
||||
>
|
||||
> 如果iptables没有在运行,可以使用下面的语句
|
||||
>
|
||||
> ---------------- 在CentOS 6/5下 ----------------
|
||||
> # chkconfig --level 35 iptables on
|
||||
> # service iptables start
|
||||
>
|
||||
> ---------------- 在CentOS 7下 ----------------
|
||||
> # systemctl enable iptables
|
||||
> # systemctl start iptables
|
||||
>
|
||||
> 我们还可以检测iptables的模块是否被加载:
|
||||
>
|
||||
> # lsmod | grep ip_tables
|
||||
|
||||
### 9. 你怎么检查iptables中当前定义的规则呢? ###
|
||||
|
||||
> **答案** : 当前的规则可以简单的用下面的命令查看:
|
||||
>
|
||||
> # iptables -L
|
||||
>
|
||||
> 示例输出
|
||||
>
|
||||
> Chain INPUT (policy ACCEPT)
|
||||
> target prot opt source destination
|
||||
> ACCEPT all -- anywhere anywhere state RELATED,ESTABLISHED
|
||||
> ACCEPT icmp -- anywhere anywhere
|
||||
> ACCEPT all -- anywhere anywhere
|
||||
> ACCEPT tcp -- anywhere anywhere state NEW tcp dpt:ssh
|
||||
> REJECT all -- anywhere anywhere reject-with icmp-host-prohibited
|
||||
>
|
||||
> Chain FORWARD (policy ACCEPT)
|
||||
> target prot opt source destination
|
||||
> REJECT all -- anywhere anywhere reject-with icmp-host-prohibited
|
||||
>
|
||||
> Chain OUTPUT (policy ACCEPT)
|
||||
> target prot opt source destination
|
||||
|
||||
### 10. 你怎样刷新所有的iptables规则或者特定的链呢? ###
|
||||
|
||||
> **答案** : 您可以使用下面的命令来刷新一个特定的链。
|
||||
>
|
||||
> # iptables --flush OUTPUT
|
||||
>
|
||||
> 要刷新所有的规则,可以用:
|
||||
>
|
||||
> # iptables --flush
|
||||
|
||||
### 11. 请在iptables中添加一条规则,接受所有从一个信任的IP地址(例如,192.168.0.7)过来的包。 ###
|
||||
|
||||
> **答案** : 上面的场景可以通过运行下面的命令来完成。
|
||||
>
|
||||
> # iptables -A INPUT -s 192.168.0.7 -j ACCEPT
|
||||
>
|
||||
> 我们还可以在源IP中使用标准的斜线和子网掩码:
|
||||
>
|
||||
> # iptables -A INPUT -s 192.168.0.7/24 -j ACCEPT
|
||||
> # iptables -A INPUT -s 192.168.0.7/255.255.255.0 -j ACCEPT
|
||||
|
||||
### 12. 怎样在iptables中添加规则以ACCEPT,REJECT,DENY和DROP ssh的服务? ###
|
||||
|
||||
> **答案** : 但愿ssh运行在22端口,那也是ssh的默认端口,我们可以在iptables中添加规则来ACCEPT ssh的tcp包(在22号端口上)。
|
||||
>
|
||||
> # iptables -A INPUT -s -p tcp --dport 22 -j ACCEPT
|
||||
>
|
||||
> REJECT ssh服务(22号端口)的tcp包。
|
||||
>
|
||||
> # iptables -A INPUT -s -p tcp --dport 22 -j REJECT
|
||||
>
|
||||
> DENY ssh服务(22号端口)的tcp包。
|
||||
>
|
||||
>
|
||||
> # iptables -A INPUT -s -p tcp --dport 22 -j DENY
|
||||
>
|
||||
> DROP ssh服务(22号端口)的tcp包。
|
||||
>
|
||||
>
|
||||
> # iptables -A INPUT -s -p tcp --dport 22 -j DROP
|
||||
|
||||
### 13. 让我给你另一个场景,假如有一台电脑的本地IP地址是192.168.0.6。你需要封锁在21、22、23和80号端口上的连接,你会怎么做? ###
|
||||
|
||||
> **答案** : 这时,我所需要的就是在iptables中使用‘multiport‘选项,并将要封锁的端口号跟在它后面。上面的场景可以用下面的一条语句搞定:
|
||||
>
|
||||
> # iptables -A INPUT -s 192.168.0.6 -p tcp -m multiport --dport 22,23,80,8080 -j DROP
|
||||
>
|
||||
> 可以用下面的语句查看写入的规则。
|
||||
>
|
||||
> # iptables -L
|
||||
>
|
||||
> Chain INPUT (policy ACCEPT)
|
||||
> target prot opt source destination
|
||||
> ACCEPT all -- anywhere anywhere state RELATED,ESTABLISHED
|
||||
> ACCEPT icmp -- anywhere anywhere
|
||||
> ACCEPT all -- anywhere anywhere
|
||||
> ACCEPT tcp -- anywhere anywhere state NEW tcp dpt:ssh
|
||||
> REJECT all -- anywhere anywhere reject-with icmp-host-prohibited
|
||||
> DROP tcp -- 192.168.0.6 anywhere multiport dports ssh,telnet,http,webcache
|
||||
>
|
||||
> Chain FORWARD (policy ACCEPT)
|
||||
> target prot opt source destination
|
||||
> REJECT all -- anywhere anywhere reject-with icmp-host-prohibited
|
||||
>
|
||||
> Chain OUTPUT (policy ACCEPT)
|
||||
> target prot opt source destination
|
||||
|
||||
**面试官** : 好了,我问的就是这些。你是一个很有价值的雇员,我们不会错过你的。我将会向HR推荐你的名字。如果你有什么问题,请问我。
|
||||
|
||||
作为一个候选人我不愿不断的问将来要做的项目的事以及公司里其他的事,这样会打断愉快的对话。更不用说HR轮会不会比较难,总之,我获得了机会。
|
||||
|
||||
同时我要感谢Avishek和Ravi(我的朋友)花时间帮我整理我的面试。
|
||||
|
||||
朋友!如果您有过类似的面试,并且愿意与数百万Tecmint读者一起分享您的面试经历,请将您的问题和答案发送到admin@tecmint.com。
|
||||
|
||||
谢谢!保持联系。如果我能更好的回答我上面的问题的话,请记得告诉我。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.tecmint.com/linux-firewall-iptables-interview-questions-and-answers/
|
||||
|
||||
作者:[Avishek Kumar][a]
|
||||
译者:[wwy-hust](https://github.com/wwy-hust)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.tecmint.com/author/avishek/
|
||||
[1]:http://www.tecmint.com/install-webmin-web-based-system-administration-tool-for-rhel-centos-fedora/
|
||||
@ -1,94 +0,0 @@
|
||||
|
||||
#在Linux上如何清除RAM内存高速缓存,缓存和交换空间#
|
||||
|
||||
像任何其他的操作系统一样,GNU / Linux已经有效地实施了内存管理甚至更多。但是,如果有任何进程正在蚕食你的内存,你要清除它,
|
||||
Linux提供了一个方法来刷新或清除RAM缓存。
|
||||
|
||||
<a href="http://www.tianfeiyu.com/wp-content/uploads/2015/06/linux.jpg"><img class="alignnone size-medium wp-image-692" src="http://www.tianfeiyu.com/wp-content/uploads/2015/06/linux-300x144.jpg" alt="linux" width="300" height="144" /></a>
|
||||
|
||||
在Linux中如何清除缓存?
|
||||
|
||||
每一个Linux系统有三个选项来清除缓存而不中断任何进程或服务。
|
||||
|
||||
1,仅清除缓存页
|
||||
<pre class="prettyprint linenums"><code>
|
||||
sync; echo 1 > /proc/sys/vm/drop_caches
|
||||
</code></pre>
|
||||
2,清除目录项和inodes
|
||||
<pre class="prettyprint linenums"><code>
|
||||
sync; echo 2 > /proc/sys/vm/drop_caches
|
||||
</code></pre>
|
||||
3,清除,缓存页,目录项和inodes
|
||||
<pre class="prettyprint linenums"><code>
|
||||
sync; echo 3 > /proc/sys/vm/drop_caches
|
||||
</code></pre>
|
||||
上述命令的说明:
|
||||
|
||||
sync将刷新文件系统缓存,命令通过“;”分隔,顺序执行,shell等待终止在序列中的每一个命令执行之前。正如内核文档中提到的,写到drop_cache将清空缓存而不杀死任何应用程序/服务,echo命令做写入文件的工作。
|
||||
|
||||
如果你必须清除磁盘高速缓存,第一个命令在企业和生产环境中是最安全,“...echo 1> ...”只会清除页缓存。
|
||||
不建议使用上面第三个选项在生产环境中“...echo 3 >” ,除非你明确自己在做什么,因为它会清除缓存页,目录项和inodes。
|
||||
|
||||
在Linux上释放Buffer和Cache要用到内核是否是个好主意?
|
||||
|
||||
当你请求许多设定想要检查时,如果它实际上是专门实施对I/O 广泛的基准测试,那么你可能需要清除缓存。你可以如上所示删除缓存,无需重新启动系统即无需停机。
|
||||
|
||||
Linux被设计成它在寻找磁盘之前到磁盘缓存寻找的方式。如果它发现该资源在缓存中,则该请求不到达磁盘。如果我们清理缓存,磁盘缓存将没有用处,系统会到磁盘上寻找资源。
|
||||
|
||||
此外,当清除缓存后它也将减慢系统运行速度,系统会重新加载每一个被请求的资源再次到磁盘缓存中。
|
||||
|
||||
现在,我们将通过一个cron任务调度器创建一个shell脚本在每天下午2点自动清除RAM缓存。
|
||||
创建一个shell脚本clearcache.sh并在其中添加以下行:
|
||||
<pre class="prettyprint linenums"><code>
|
||||
#!/bin/bash
|
||||
# Note, we are using "echo 3", but it is not recommended in production instead use "echo 1"
|
||||
echo "echo 3 > /proc/sys/vm/drop_caches"
|
||||
</code></pre>
|
||||
给clearcache.sh文件设置执行权限
|
||||
<pre class="prettyprint linenums"><code>
|
||||
# chmod 755 clearcache.sh
|
||||
</code></pre>
|
||||
现在,当你需要清除RAM缓存时只需要调用脚本。
|
||||
|
||||
现在设置一个定时任务来清除RAM缓存每天在下午2点,打开crontab进行编辑。
|
||||
<pre class="prettyprint linenums"><code>
|
||||
# crontab -e
|
||||
</code></pre>
|
||||
添加以下行,保存并退出。
|
||||
<pre class="prettyprint linenums"><code>
|
||||
0 3 * * * /path/to/clearcache.sh
|
||||
</code></pre>
|
||||
有关如何创建一个定时任务,更多细节你可以查看我们的文章<a href="http://www.tecmint.com/11-cron-scheduling-task-examples-in-linux/">11 Cron Scheduling Jobs</a>。
|
||||
|
||||
在生产环境的服务器上自动清除RAM是否是一个好主意?
|
||||
|
||||
不!它不是。想想一个情况,当你已经预定脚本来清除RAM缓存每天在下午2点。每天下午2点该脚本会执行并刷新你的RAM缓存。在一天中的任何时候,您网站用户的在线量可能会超过预期的,并从你的服务器请求资源。同时调度器运行着脚本,并在高速缓存中清除一切。当所有的用户都从磁盘读取数据时,这将导致服务器崩溃并损坏数据库。
|
||||
因此,清除缓存仅在必要时并且在你的预料之中,否则你就是个Cargo Cult System Administrator。
|
||||
|
||||
如何清除Linux的交换空间?
|
||||
|
||||
如果你想清除掉的空间,你可以运行下面的命令:
|
||||
<pre class="prettyprint linenums"><code>
|
||||
# swapoff -a && swapon -a
|
||||
</code></pre>
|
||||
此外,了解有关风险后,您可能会将上面的命令添加到cron中。
|
||||
|
||||
现在,我们将上面两种命令结合成一个命令写出正确的脚本来同时清除RAM缓存和交换空间。
|
||||
<pre class="prettyprint linenums"><code>
|
||||
# echo 3 > /proc/sys/vm/drop_caches && swapoff -a && swapon -a && printf '\n%s\n' 'Ram-cache and Swap Cleared'
|
||||
</code></pre>
|
||||
或
|
||||
<pre class="prettyprint linenums"><code>
|
||||
su -c 'echo 3 >/proc/sys/vm/drop_caches' && swapoff -a && swapon -a && printf '\n%s\n' 'Ram-cache and Swap Cleared'
|
||||
</code></pre>
|
||||
在测试上面的命令之前,我们先运行“free -m” 然后执行脚本检查缓存。
|
||||
|
||||
|
||||

|
||||
|
||||
就是现在,如果你喜欢这篇文章,不要忘记向我们提供您宝贵的意见,
|
||||
让我们知道,您认为在企业和生产环境中清除RAM缓存和缓冲区是否是一个好主意?
|
||||
|
||||
|
||||
|
||||
|
||||
236
translated/tech/20150610 How to secure your Linux server.md
Normal file
236
translated/tech/20150610 How to secure your Linux server.md
Normal file
@ -0,0 +1,236 @@
|
||||
Linux服务器安全攻略
|
||||
================================================================================
|
||||
> 一台服务器由大量功能各异的部件组成,这一点使得很难根据每个人的需求去提供定制的解决方案。这篇文章尽可能涵盖一些有所裨益的小技巧来帮助管理员保证服务器和用户安全。
|
||||
|
||||
毋庸置疑,对于系统管理员,提高服务器的安全性是最重要的事情之一。因此,也就有了许多针对这个话题而生的文章、博客和论坛帖子。
|
||||
|
||||
一台服务器由大量功能各异的部件组成,这一点使得很难根据每个人的需求去提供定制的解决方案。这篇文章尽可能涵盖一些有所裨益的小技巧来帮助管理员保证服务器和用户安全。
|
||||
|
||||
有一些常识是每个系统管理员都应该烂熟于心的,所以下面的几点在后文将不会提及:
|
||||
|
||||
- 务必保证系统是**最新的**
|
||||
- 经常更换密码 - 使用数字、阿拉伯字母和非阿拉伯字母的符号组合
|
||||
- 给予用户**最小**的权限,满足他们日常使用所需即可
|
||||
- 只安装那些真正需要的软件包
|
||||
|
||||
下面是一些更有意思的内容:
|
||||
|
||||
### 更改SSH默认端口 ###
|
||||
|
||||
在搭建好一台全新的服务器后要做的第一件事情就是更改SSH的默认端口。这个小小单的改动能够使你的服务器避免受到成千上万的暴力攻击(译者注:不更改默认端口相当于黑客们知道你家的门牌号,这样他们只需要一把一把的试钥匙就可能打开你家的锁)。
|
||||
|
||||
要更改默认的SSH端口,先打开sshd_config文件:
|
||||
|
||||
sudo vim /etc/ssh/sshd_config
|
||||
|
||||
找到下面这行:
|
||||
|
||||
#Port 22
|
||||
|
||||
“#”号表示这行是注释。首先删除#号,然后把端口号改成目的端口。端口号不能超过65535,确保要指定的端口号没有被系统或其它服务占用。建议在[维基百科]上查看常用端口号列表。在本文中,使用这个端口号:
|
||||
|
||||
Port 16543
|
||||
|
||||
然后保存并关闭文件,等待更改生效。
|
||||
|
||||
接下来的一步是:
|
||||
|
||||
### 使用SSH密钥 ###、
|
||||
|
||||
在通过SSH访问服务器时,使用SSH密钥进行认证是尤其重要的。这样做为服务器增加了额外的保护,确保只有那些拥有密钥的人才能访问服务器。
|
||||
|
||||
在本地机器上运行下面命令以生成SSH密钥:
|
||||
|
||||
ssh-keygen -t rsa
|
||||
|
||||
你会看到下面的输出,询问要将密钥写到哪一个文件,并且设置一个密码:
|
||||
|
||||
Generating public/private rsa key pair.
|
||||
Enter file in which to save the key (/root/.ssh/id_rsa): my_key
|
||||
Enter passphrase (empty for no passphrase):
|
||||
Enter same passphrase again:
|
||||
Your identification has been saved in my_key.
|
||||
Your public key has been saved in my_key.pub.
|
||||
The key fingerprint is:
|
||||
SHA256:MqD/pzzTRsCjZb6mpfjyrr5v1pJLBcgprR5tjNoI20A
|
||||
|
||||
完成之后,就得到两个文件:
|
||||
|
||||
my_key
|
||||
|
||||
my_key.pub
|
||||
|
||||
接下来把my_key.pub拷贝到~/.ssh/authorized_key中
|
||||
|
||||
cp my_key.pub ~/.ssh/authorized_keys
|
||||
|
||||
然后使用下面命令将密钥上传到服务器:
|
||||
|
||||
scp -P16543 authorized_keys user@yourserver-ip:/home/user/.ssh/
|
||||
|
||||
至此,你就可以从这台本地机器上无密码地访问服务器了。
|
||||
|
||||
### 关闭SSH的密码认证 ###
|
||||
|
||||
既然已经有了SSH密钥,那么关闭SSH的密码认证就很安全了。再次打开并编辑sshd_config,按如下设置:
|
||||
|
||||
ChallengeResponseAuthentication no
|
||||
PasswordAuthentication no
|
||||
UsePAM no
|
||||
|
||||
### 关闭Root登录 ###
|
||||
|
||||
下面关键的一步是关闭root用户的直接访问,而使用sudo或su来执行管理员任务。首先需要添加一个有root权限的新用户,所以编辑这个路径下的sudoers文件:
|
||||
|
||||
/etc/sudoers/
|
||||
|
||||
可以使用如**visudo**这样的命令编辑文件,推荐使用这个命令,因为它会在关闭文件之前检查任何可能出现的语法错误。当你在编辑文件时出错了,这就很有用了。
|
||||
|
||||
接下来赋予某个用户root权限。在本文中,使用用户**sysadmin**。确保在编辑后这个文件时使用的用户是系统已有的用户。找到下面这行:
|
||||
|
||||
root ALL=(ALL) ALL
|
||||
|
||||
拷贝这行,然后粘贴在下一行,然后把root更改为“sysadmin”,如下所示:
|
||||
|
||||
root ALL=(ALL) ALL
|
||||
sysadmin ALL=(ALL) ALL
|
||||
|
||||
现在解释一下这行的每一个选项的含义:
|
||||
|
||||
(1) root (2)ALL=(3)(ALL) (4)ALL
|
||||
|
||||
(1) 指定用户
|
||||
|
||||
(2) 指定用户使用sudo的终端
|
||||
|
||||
(3) 指定用户可以担任的用户角色
|
||||
|
||||
(4) 这个用户可以使用的命令
|
||||
|
||||
使用这个配置可以给用户访问一些系统工具的权限。
|
||||
|
||||
这时,可以放心保存文件了。
|
||||
|
||||
为了关闭通过SSH直接访问root,需要再次打开**sshd_config**,找到下面这行:
|
||||
|
||||
#PermitRootLogin yes
|
||||
|
||||
更改为:
|
||||
|
||||
PermitRootLogin no
|
||||
|
||||
然后保存文件,重启sshd守护进程使改动生效。执行下面命令即可:
|
||||
|
||||
sudo /etc/init.d/sshd restart
|
||||
|
||||
### 设置防火墙 ###
|
||||
|
||||
防火墙有助于过滤出入端口和阻止使用暴力法的登录尝试。我倾向于使用SCF(Config Server Firewall)这个强力防火墙。它使用了iptables,易于管理,而且对于不擅于输入命令的用户提供了web界面。
|
||||
|
||||
要安装CSF,先登录到服务器,切换到这个目录下:
|
||||
|
||||
cd /usr/local/src/
|
||||
|
||||
然后以root权限执行下面命令:
|
||||
|
||||
wget https://download.configserver.com/csf.tgz
|
||||
tar -xzf csf.tgz
|
||||
csf
|
||||
sh install.sh
|
||||
|
||||
只需等待安装程序完成,然后编辑CSF的配置文件:
|
||||
|
||||
/etc/csf/csf.conf
|
||||
|
||||
默认情况下CSF是以测试模式运行。通过将“TESTING”的值设置成0,切换到product模式。
|
||||
|
||||
TESTING = "0"
|
||||
|
||||
下面要设置的就是服务器上允许通过的端口。在csf.conf中定位到下面的部分,根据需要修改端口:
|
||||
|
||||
# Allow incoming TCP ports
|
||||
TCP_IN = "20,21,25,53,80,110,143,443,465,587,993,995,16543"
|
||||
# Allow outgoing TCP ports
|
||||
TCP_OUT = "20,21,22,25,53,80,110,113,443,587,993,995,16543"
|
||||
# Allow incoming UDP ports
|
||||
UDP_IN = "20,21,53"
|
||||
# Allow outgoing UDP ports
|
||||
# To allow outgoing traceroute add 33434:33523 to this list
|
||||
UDP_OUT = "20,21,53,113,123"
|
||||
|
||||
请根据需要逐一设置,推荐只使用那些需要的端口,避免设置对端口进行大范围设置。此外,也要避免使用不安全服务的不安全端口。比如只允许端口465和587来发送电子邮件,取代默认的SMTP端口25.
|
||||
|
||||
**重要**:千万不要忘记允许自定义SHH端口。
|
||||
|
||||
允许防火墙通过你的IP地址使其不被屏蔽,这一点很重要。IP地址定义在下面的文件中:
|
||||
|
||||
/etc/csf/csf.ignore
|
||||
|
||||
被屏蔽的IP地址会出现在这个文件中:
|
||||
|
||||
/etc/csf/csf.deny
|
||||
|
||||
一旦完成更改,使用这个命令重启csf:
|
||||
|
||||
sudo /etc/init.d/csf restart
|
||||
|
||||
下面是在某台服务器上的csf.deny文件的部分内容,来说明CSF是很有用的:
|
||||
|
||||
211.216.48.205 # lfd: (sshd) Failed SSH login from 211.216.48.205 (KR/Korea, Republic of/-): 5 in the last 3600 secs - Fri Mar 6 00:30:35 2015
|
||||
103.41.124.53 # lfd: (sshd) Failed SSH login from 103.41.124.53 (HK/Hong Kong/-): 5 in the last 3600 secs - Fri Mar 6 01:06:46 2015
|
||||
103.41.124.42 # lfd: (sshd) Failed SSH login from 103.41.124.42 (HK/Hong Kong/-): 5 in the last 3600 secs - Fri Mar 6 01:59:04 2015
|
||||
103.41.124.26 # lfd: (sshd) Failed SSH login from 103.41.124.26 (HK/Hong Kong/-): 5 in the last 3600 secs - Fri Mar 6 02:48:26 2015
|
||||
109.169.74.58 # lfd: (sshd) Failed SSH login from 109.169.74.58 (GB/United Kingdom/mail2.algeos.com): 5 in the last 3600 secs - Fri Mar 6 03:49:03 2015
|
||||
|
||||
可以看到,尝试通过暴力法登录的IP地址都被屏蔽了,真是眼不见心不烦啊!
|
||||
|
||||
#### 锁住账户 ####
|
||||
|
||||
如果某个账户在很长一段时间内都不会被使用了,那么可以将其锁住以防止其它人访问。使用如下命令:
|
||||
|
||||
passwd -l accountName
|
||||
|
||||
当然,这个账户依然可以被root用户使用。
|
||||
|
||||
### 了解服务器上的服务 ###
|
||||
|
||||
服务器的本质是为各种服务提供访问功能。使服务器只运行所需的服务,关闭没有使用的服务。这样做不仅会释放一些系统资源,而且也会使服务器变得更加安全。比如,如果只是运行一个简单的服务器,显然不需要X显示或者桌面环境。如果不需要Windows网络共享功能,则可以放心关闭Samba。
|
||||
|
||||
使用下面的命令能查看伴随系统启动而启动的服务:
|
||||
|
||||
chkconfig --list | grep "3:on"
|
||||
|
||||
如果系统运行了**systemd**,执行这条命令:
|
||||
|
||||
systemctl list-unit-files --type=service | grep enabled
|
||||
|
||||
然后使用下面的命令关闭服务:
|
||||
|
||||
chkconfig service off
|
||||
systemctl disable service
|
||||
|
||||
在上面的例子中,把“service”替换成真正想要停止的服务名称。实例如下:
|
||||
|
||||
chkconfig httpd off
|
||||
systemctl disable httpd
|
||||
|
||||
### 小结 ###
|
||||
|
||||
这篇文章的目的是涵盖一些通用的安全步骤以便帮助你保护服务器。你可以采取额外的方式去增强对服务器的保护。请记住保证服务器安全是你的责任,在维护服务器安全时尽量做出明智的选择,尽管并没有什么容易的方式去完成这件事情,而建立“完善的”安全需要花费大量的时间和测试直到达到想要的结果。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linuxveda.com/2015/06/03/secure-linux-server/
|
||||
|
||||
作者:[Marin Todorow][a]
|
||||
译者:[KayGuoWhu](https://github.com/KayGuoWhu)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.linuxveda.com/author/marin_todorov/
|
||||
[1]:http://en.wikipedia.org/wiki/Port_%28computer_networking%29#Common_port_numbers
|
||||
|
||||
|
||||
|
||||
|
||||
@ -0,0 +1,279 @@
|
||||
如何在Fedora 22上面配置Apache的Docker容器
|
||||
=============================================================================
|
||||
在这篇文章中,我们将会学习关于Docker的一些知识,如何使用Docker部署Apache httpd服务,并且共享到Docker Hub上面去。首先,我们学习怎样拉取和使用Docker Hub里面的镜像,然后交互式地安装Apache到一个Fedora 22的镜像里去,之后我们将会学习如何用一个Dockerfile文件来制作一个镜像,以一种更快,更优雅的方式。最后,我们会在Docker Hub上公开我们创建地镜像,这样以后任何人都可以下载并使用它。
|
||||
|
||||
### 安装Docker,运行hello world ###
|
||||
|
||||
**要求**
|
||||
|
||||
运行Docker,里至少需要满足这些:
|
||||
|
||||
- 你需要一个64位的内核,版本3.10或者更高
|
||||
- Iptables 1.4 - Docker会用来做网络配置,如网络地址转换(NAT)
|
||||
- Git 1.7 - Docker会使用Git来与仓库交流,如Docker Hub
|
||||
- ps - 在大多数环境中这个工具都存在,在procps包里有提供
|
||||
- root - 防止一般用户可以通过TCP或者其他方式运行Docker,为了简化,我们会假定你就是root
|
||||
|
||||
### 使用dnf安装docker ###
|
||||
|
||||
以下的命令会安装Docker
|
||||
|
||||
dnf update && dnf install docker
|
||||
|
||||
**注意**:在Fedora 22里,你仍然可以使用Yum命令,但是被DNF取代了,而且在纯净安装时不可用了。
|
||||
|
||||
### 检查安装 ###
|
||||
|
||||
我们将要使用的第一个命令是docker info,这会输出很多信息给你:
|
||||
|
||||
docker info
|
||||
|
||||
也可以试着用**docker version**:
|
||||
|
||||
docker version
|
||||
|
||||
### 启动Dcoker为守护进程 ###
|
||||
|
||||
你应该启动一个docker实例,然后她会处理我们的请求。
|
||||
|
||||
docker -d
|
||||
|
||||
让我们用Busybox来打印hello world:
|
||||
|
||||
dockr run -t busybox /bin/echo "hello world"
|
||||
|
||||
这个命令里,我们告诉Docker执行 /bin/echo "hello world",在Busybox镜像的一个实例/容器里。Busybox是一个小型的POSIX环境,将许多小工具都结合到了一个单独的可执行程序里。
|
||||
|
||||
如果Docker不能在你的系统里找到本地的Busybox镜像,她就会自动从Docker Hub里拉取镜像,正如你可以看下如下的快照:
|
||||
|
||||

|
||||
|
||||
Hello world with Busybox
|
||||
|
||||
再次尝试相同的命令,这次由于Docker已经有了本地的Busybox镜像,所有你将会看到的就是echo的输出:
|
||||
|
||||
docker run -t busybox /bin/echo "hello world"
|
||||
|
||||
也可以尝试以下的命令进入到容器环境里去:
|
||||
|
||||
docker run -it busybox /bin/sh
|
||||
|
||||
使用**exit**命令可以离开容器并停止它
|
||||
|
||||
### 交互式地Docker化Apache ###
|
||||
|
||||
拉取/下载 Fedora 镜像:
|
||||
|
||||
docker pull fedora:22
|
||||
|
||||
起一个容器在后台运行:
|
||||
|
||||
docker run -d -t fedora:22 /bin/bash
|
||||
|
||||
列出正在运行地容器,并用名字标识,如下
|
||||
|
||||
docker ps
|
||||
|
||||

|
||||
|
||||
使用docker ps列出,并使用docker attach进入一个容器里
|
||||
|
||||
angry_noble是docker分配给我们容器的名字,所以我们来附上去:
|
||||
|
||||
docker attach angry_noble
|
||||
|
||||
注意:每次你起一个容器,就会被给与一个新的名字,如果你的容器需要一个固定的名字,你应该在 docker run 命令里使用 -name 参数。
|
||||
|
||||
### 安装Apache ###
|
||||
|
||||
下面的命令会更新DNF的数据库,下载安装Apache(httpd包)并清理dnf缓存使镜像尽量小
|
||||
|
||||
dnf -y update && dnf -y install httpd && dnf -y clean all
|
||||
|
||||
配置Apache
|
||||
|
||||
我们需要修改httpd.conf的唯一地方就是ServerName,这会使Apache停止抱怨
|
||||
|
||||
sed -i.orig 's/#ServerName/ServerName/' /etc/httpd/conf/httpd.conf
|
||||
|
||||
**设定环境**
|
||||
|
||||
为了使Apache运行为单机模式,你必须以环境变量的格式提供一些信息,并且你也需要在这些变量里的目录设定,所以我们将会用一个小的shell脚本干这个工作,当然也会启动Apache
|
||||
|
||||
vi /etc/httpd/run_apache_foreground
|
||||
|
||||
----------
|
||||
|
||||
#!/bin/bash
|
||||
|
||||
#set variables
|
||||
APACHE_LOG_DI=R"/var/log/httpd"
|
||||
APACHE_LOCK_DIR="/var/lock/httpd"
|
||||
APACHE_RUN_USER="apache"
|
||||
APACHE_RUN_GROUP="apache"
|
||||
APACHE_PID_FILE="/var/run/httpd/httpd.pid"
|
||||
APACHE_RUN_DIR="/var/run/httpd"
|
||||
|
||||
#create directories if necessary
|
||||
if ! [ -d /var/run/httpd ]; then mkdir /var/run/httpd;fi
|
||||
if ! [ -d /var/log/httpd ]; then mkdir /var/log/httpd;fi
|
||||
if ! [ -d /var/lock/httpd ]; then mkdir /var/lock/httpd;fi
|
||||
|
||||
#run Apache
|
||||
httpd -D FOREGROUND
|
||||
|
||||
**另外地**,你可以粘贴这个片段代码到容器shell里并运行:
|
||||
|
||||
dnf -y install git && git clone https://github.com/gaiada/run-apache-foreground.git && cd run-apach* && ./install && dnf erase git
|
||||
|
||||
上面的内嵌脚本会安装Git,克隆[这个仓库][1],到文件里去运行脚本,并询问你是否卸载Git。
|
||||
|
||||
**保存你的容器状态**
|
||||
|
||||
你的容器现在可以运行Apache,是时候保存容器当前的状态为一个镜像,以备你需要的时候使用。
|
||||
|
||||
为了离开容器环境,你必须顺序按下 **Ctrl+q** 和 **Ctrl+p**,如果你仅仅在shell执行exit,你同时也会停止容器,失去目前为止你做过的所有工作。
|
||||
|
||||
回到Docker主机,使用 **docker commit** 加容器和你期望的仓库名字/标签:
|
||||
|
||||
docker commit angry_noble gaiada/apache
|
||||
|
||||
现在,你保存了容器的状态到一个镜像里,可以使用 **docker stop** 停止容器了:
|
||||
|
||||
docker stop angry_noble
|
||||
|
||||
**运行并测试你的镜像**
|
||||
|
||||
最后,从你的新镜像起一个容器,并且重定向80端口到容器:
|
||||
|
||||
docker run -p 80:80 -d -t gaiada/apache /etc/httpd/run_apache_foreground
|
||||
|
||||
|
||||
|
||||
到目前,你正在你的容器里运行Apache,打开你的浏览器访问该服务,在[http://localhost][2],你将会看到如下Apache默认的页面
|
||||
|
||||

|
||||
|
||||
在容器里运行的Apache默认页面
|
||||
|
||||
### 使用Dockerfile Docker化Apache ###
|
||||
|
||||
现在,我们将要去创建一个新的Apache镜像,这次所有步骤会写在一个Dockerfile文件里,文件将会被用于生成该镜像。
|
||||
|
||||
首先,新建一个目录,在里面放Dockerfile文件,并进入该目录:
|
||||
|
||||
mkdir apachedf; cd apachedf
|
||||
|
||||
然后创建一个名为Dockerfile的文件,添加以下内容:
|
||||
|
||||
FROM fedora:22
|
||||
|
||||
MAINTAINER Carlos Alberto
|
||||
LABEL version="0.1"
|
||||
|
||||
RUN dnf -y update && dnf -y install httpd && dnf -y clean all
|
||||
|
||||
RUN [ -d /var/log/httpd ] || mkdir /var/log/httpd
|
||||
RUN [ -d /var/run/httpd ] || mkdir /var/run/httpd
|
||||
RUN [ -d /var/lock/httpd ] || mkdir /var/lock/httpd
|
||||
|
||||
RUN sed -i.orig 's/#ServerName/ServerName/' /etc/httpd/conf/httpd.conf
|
||||
|
||||
ENV APACHE_RUN_USER apache
|
||||
ENV APACHE_RUN_GROUP apache
|
||||
ENV APACHE_LOG_DIR /var/log/httpd
|
||||
ENV APACHE_LOCK_DIR /var/lock/httpd
|
||||
ENV APACHE_RUN_DIR /var/run/httpd
|
||||
ENV APACHE_PID_FILE /var/run/httpd/httpd.pid
|
||||
|
||||
EXPOSE 80
|
||||
|
||||
CMD ["/usr/sbin/httpd", "-D", "FOREGROUND"]
|
||||
|
||||
|
||||
|
||||
我们一起来看看Dockerfile里面有什么:
|
||||
|
||||
**FROM** - 这告诉docker,我们将要使用Fedora 22作为基础镜像
|
||||
|
||||
**MAINTAINER** 和 **LABLE** - 这些命令对镜像没有直接作用,属于标记信息
|
||||
|
||||
**RUN** - 自动完成我们之前交互式做的工作,安装Apache,新建目录并编辑httpd.conf
|
||||
|
||||
**ENV** - 设置环境变量,现在我们再不需要run_apache_foreground脚本
|
||||
|
||||
**EXPOSE** - 暴露80端口给外网
|
||||
|
||||
**CMD** - 设置默认的命令启动httpd服务,这样我们就不需要每次起一个新的容器都重复这个工作
|
||||
|
||||
**建立该镜像**
|
||||
|
||||
现在,我们将要建立这个镜像,并为其添加tag gaiada/apachedf
|
||||
|
||||
docker build -t gaiada/apachedf:0.1 .
|
||||
|
||||

|
||||
|
||||
docker完成创建
|
||||
|
||||
使用 **docker images** 列出本地镜像,查看是否存在你新建的镜像:
|
||||
|
||||
docker images
|
||||
|
||||
然后运行新的镜像:
|
||||
|
||||
docker run -t -p 80:80 gaiada/apachedf
|
||||
|
||||
这就是Dockerfile的工作,使用这项功能会使得事情更加容易,快速并且可重复生成。
|
||||
|
||||
### 公开你的镜像 ###
|
||||
|
||||
直到现在,你仅仅是从Docker Hub拉取了镜像,但是你也可以推送你的镜像,以后需要也可以再次拉取他们。实际上,其他人也可以下载你的镜像,在他们的系统中使用它而不需要改变任何东西。现在我们将要学习如何使我们的镜像对世界上的其他人可用。
|
||||
|
||||
**创建帐号**
|
||||
|
||||
为了能够在Docker Hub上推送你的镜像,你需要创建一个帐号。访问 [https://hub.docker.com/account/signup/][3],填写下面的表格:
|
||||
|
||||

|
||||
|
||||
Docker Hub 注册页面
|
||||
|
||||
**登录**
|
||||
|
||||
输入下面的命令,接着输入你注册时提供的用户名,密码和邮箱
|
||||
|
||||
docker login
|
||||
|
||||
第一次登录过后,你的帐号信息会被记录在 **~/.dockercfg**
|
||||
|
||||
**推送**
|
||||
|
||||
推送镜像,使用 **docker push [registry/]your_login/repository_name[:tag]**
|
||||
|
||||
docker push docker.io/gaiada/apachedf
|
||||
|
||||
你可能会看见像这样的输出,在你的控制台上:
|
||||
|
||||

|
||||
|
||||
Docker推送Apache镜像完成
|
||||
|
||||
### 结论 ###
|
||||
|
||||
现在,你知道如何Docker化Apache,试一试包含其他一些组块,Perl,PHP,proxy,HTTPS,或者任何你需要的东西。我希望你们这些家伙喜欢她,并推送你们自己的镜像到Docker Hub。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/linux-how-to/configure-apache-containers-docker-fedora-22/
|
||||
|
||||
作者:[Carlos Alberto][a]
|
||||
译者:[wi-cuckoo](https://github.com/wi-cuckoo)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://linoxide.com/author/carlosal/
|
||||
[1]:https://github.com/gaiada/run-apache-foreground
|
||||
[2]:http://localhost/
|
||||
[3]:https://hub.docker.com/account/signup/
|
||||
|
||||
Loading…
Reference in New Issue
Block a user