mirror of
https://github.com/LCTT/TranslateProject.git
synced 2024-12-26 21:30:55 +08:00
Merge remote-tracking branch 'LCTT/master'
This commit is contained in:
commit
6d8b67809d
@ -1,15 +1,16 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-10500-1.html)
|
||||
[#]: subject: (Get started with HomeBank, an open source personal finance app)
|
||||
[#]: via: (https://opensource.com/article/19/1/productivity-tools-homebank)
|
||||
[#]: author: (Kevin Sonney https://opensource.com/users/ksonney (Kevin Sonney))
|
||||
|
||||
开始使用 HomeBank,一个开源个人财务应用
|
||||
开始使用 HomeBank 吧,一款开源个人财务应用
|
||||
======
|
||||
使用 HomeBank 跟踪你的资金流向,这是我们开源工具系列中的第八个工具,它将在 2019 年提高你的工作效率。
|
||||
> 使用 HomeBank 跟踪你的资金流向,这是我们开源工具系列中的第八个工具,它将在 2019 年提高你的工作效率。
|
||||
|
||||

|
||||
|
||||
每年年初似乎都有疯狂的冲动想提高工作效率。新年的决心,渴望开启新的一年,当然,“抛弃旧的,拥抱新的”的态度促成了这一切。通常这时的建议严重偏向闭源和专有软件,但事实上并不用这样。
|
||||
@ -24,7 +25,7 @@
|
||||
|
||||
[HomeBank][1] 是一款个人财务桌面应用,帮助你轻松跟踪你的财务状况,来帮助减少此类压力。它有很好的报告可以帮助你找出你花钱的地方,允许你设置导入交易的规则,并支持大多数现代格式。
|
||||
|
||||
HomeBank 默认可在大多数发行版上可用,因此安装它非常简单。当你第一次启动它时,它将引导你完成设置并让你创建一个帐户。之后,你可以导入任意一种支持的文件格式或开始输入交易。交易簿本身就是一个交易列表。 [与其他一些应用不同][2],你不必学习[复式簿记][3]来使用 HomeBank。
|
||||
HomeBank 默认可在大多数发行版上可用,因此安装它非常简单。当你第一次启动它时,它将引导你完成设置并让你创建一个帐户。之后,你可以导入任意一种支持的文件格式或开始输入交易。交易簿本身就是一个交易列表。[与其他一些应用不同][2],你不必学习[复式记账法][3]来使用 HomeBank。
|
||||
|
||||
|
||||
|
||||
@ -40,7 +41,7 @@ HomeBank 还有预算功能,允许你计划未来几个月的开销。
|
||||
|
||||
对我来说,最棒的功能是 HomeBank 的报告。主页面上不仅有一个图表显示你花钱的地方,而且还有许多其他报告可供你查看。如果你使用预算功能,还会有一份报告会根据预算跟踪你的支出情况。你还可以以饼图和条形图的方式查看报告。它还有趋势报告和余额报告,因此你可以回顾并查看一段时间内的变化或模式。
|
||||
|
||||
总的来说,HomeBank 是一个非常友好,有用的程序,可以帮助你保持良好的财务。如果跟踪你的钱是你生活中的一件麻烦事,它使用起来很简单并且非常有用。
|
||||
总的来说,HomeBank 是一个非常友好,有用的程序,可以帮助你保持良好的财务状况。如果跟踪你的钱是你生活中的一件麻烦事,它使用起来很简单并且非常有用。
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
@ -50,7 +51,7 @@ via: https://opensource.com/article/19/1/productivity-tools-homebank
|
||||
作者:[Kevin Sonney][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
@ -0,0 +1,68 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (What happens when a veteran teacher goes to an open source conference)
|
||||
[#]: via: (https://opensource.com/open-organization/19/1/educator-at-open-source-conference)
|
||||
[#]: author: (Ben Owens https://opensource.com/users/engineerteacher)
|
||||
|
||||
What happens when a veteran teacher goes to an open source conference
|
||||
======
|
||||
Sometimes feeling like a fish out of water is precisely what educators need.
|
||||
|
||||

|
||||
|
||||
"Change is going to be continual, and today is the slowest day society will ever move."—[Tony Fadell][1]
|
||||
|
||||
If ever there was an experience that brought the above quotation home for me, it was my experience at the [All Things Open conference][2] in Raleigh, NC last October. Thousands of people from all over the world attended the conference, and many (if not most), worked as open source coders and developers. As one of the relatively few educators in attendance, I saw and heard things that were completely foreign to me—terms like as Istio, Stack Overflow, Ubuntu, Sidecar, HyperLedger, and Kubernetes tossed around for days.
|
||||
|
||||
I felt like a fish out of water. But in the end, that was the perfect dose of reality I needed to truly understand how open principles can reshape our approach to education.
|
||||
|
||||
### Not-so-strange attractors
|
||||
|
||||
All Things Open attracted me to Raleigh for two reasons, both of which have to do with how our schools must do a better job of creating environments that truly prepare students for a rapidly changing world.
|
||||
|
||||
The first is my belief that schools should embrace the ideals of the [open source way][3]. The second is that educators have to periodically force themselves out of their relatively isolated worlds of "doing school" in order to get a glimpse of what the world is actually doing.
|
||||
|
||||
When I was an engineer for 20 years, I developed a deep sense of the power of an open exchange of ideas, of collaboration, and of the need for rapid prototyping of innovations. Although we didn't call these ideas "open source" at the time, my colleagues and I constantly worked together to identify and solve problems using tools such as [Design Thinking][4] so that our businesses remained competitive and met market demands. When I became a science and math teacher at a small [public school][5] in rural Appalachia, my goal was to adapt these ideas to my classrooms and to the school at large as a way to blur the lines between a traditional school environment and what routinely happens in the "real world."
|
||||
|
||||
Through several years of hard work and many iterations, my fellow teachers and I were eventually able to develop a comprehensive, school-wide project-based learning model, where students worked in collaborative teams on projects that [made real connections][6] between required curriculum and community-based applications. Doing so gave these students the ability to develop skills they can use for a lifetime, rather than just on the next test—skills such as problem solving, critical thinking, oral and written communication, perseverance through setbacks, and adapting to changing conditions, as well as how to have routine conversations with adult mentors form the community. Only after reading [The Open Organization][7] did I realize that what we had been doing essentially embodied what Jim Whitehurst had described. In our case, of course, we applied open principles to an educational context (that model, called Open Way Learning, is the subject of a [book][8] published in December).
|
||||
|
||||
I felt like a fish out of water. But in the end, that was the perfect dose of reality I needed to truly understand how open principles can reshape our approach to education.
|
||||
|
||||
As good as this model is in terms of pushing students into a relevant, engaging, and often unpredictable learning environments, it can only go so far if we, as educators who facilitate this type of project-based learning, do not constantly stay abreast of changing technologies and their respective lexicon. Even this unconventional but proven approach will still leave students ill-prepared for a global, innovation economy if we aren't constantly pushing ourselves into areas outside our own comfort zones. My experience at the All Things Open conference was a perfect example. While humbling, it also forced me to confront what I didn't know so that I can learn from it to help the work I do with other teachers and schools.
|
||||
|
||||
### A critical decision
|
||||
|
||||
I made this point to others when I shared a picture of the All Things Open job board with dozens of colleagues all over the country. I shared it with the caption: "What did you do in your school today to prepare your students for this reality tomorrow?" The honest answer from many was, unfortunately, "not much." That has to change.
|
||||
|
||||

|
||||

|
||||
(Images courtesy of Ben Owens, CC BY-SA)
|
||||
|
||||
People in organizations everywhere have to make a critical decision: either embrace the rapid pace of change that is a fact of life in our world or face the hard reality of irrelevance. Our systems in education are at this same crossroads—even ones who think of themselves as being innovative. It involves admitting to students, "I don't know, but I'm willing to learn." That's the kind of teaching and learning experience our students deserve.
|
||||
|
||||
It can happen, but it will take pioneering educators who are willing to move away from comfortable, back-of-the-book answers to help students as they work on difficult and messy challenges. You may very well be a veritable fish out of water.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/open-organization/19/1/educator-at-open-source-conference
|
||||
|
||||
作者:[Ben Owens][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/engineerteacher
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://en.wikipedia.org/wiki/Tony_Fadell
|
||||
[2]: https://allthingsopen.org/
|
||||
[3]: https://opensource.com/open-source-way
|
||||
[4]: https://dschool.stanford.edu/resources-collections/a-virtual-crash-course-in-design-thinking
|
||||
[5]: https://www.tricountyearlycollege.org/
|
||||
[6]: https://www.bie.org/about/what_pbl
|
||||
[7]: https://www.redhat.com/en/explore/the-open-organization-book
|
||||
[8]: https://www.amazon.com/Open-Up-Education-Learning-Transform/dp/1475842007/ref=tmm_pap_swatch_0?_encoding=UTF8&qid=&sr=
|
||||
@ -0,0 +1,54 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Go on an adventure in your Linux terminal)
|
||||
[#]: via: (https://opensource.com/article/18/12/linux-toy-adventure)
|
||||
[#]: author: (Jason Baker https://opensource.com/users/jason-baker)
|
||||
|
||||
Go on an adventure in your Linux terminal
|
||||
======
|
||||
|
||||
Our final day of the Linux command-line toys advent calendar ends with the beginning of a grand adventure.
|
||||
|
||||
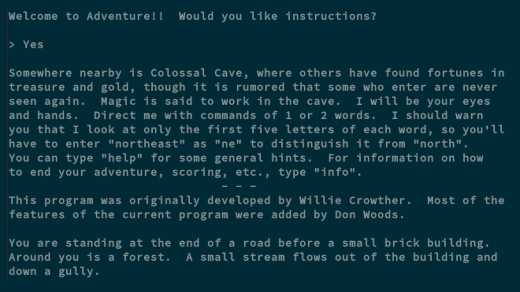
|
||||
|
||||
Today is the final day of our 24-day-long Linux command-line toys advent calendar. Hopefully, you've been following along, but if not, start back at [the beginning][1] and work your way through. You'll find plenty of games, diversions, and oddities for your Linux terminal.
|
||||
|
||||
And while you may have seen some toys from our calendar before, we hope there’s at least one new thing for everyone.
|
||||
|
||||
Today's toy was suggested by Opensource.com moderator [Joshua Allen Holm][2]:
|
||||
|
||||
"If the last day of your advent calendar is not ESR's [Eric S. Raymond's] [open source release of Adventure][3], which retains use of the classic 'advent' command (Adventure in the BSD Games package uses 'adventure), I will be very, very, very disappointed. ;-)"
|
||||
|
||||
What a perfect way to end our series.
|
||||
|
||||
Colossal Cave Adventure (often just called Adventure), is a text-based game from the 1970s that gave rise to the entire adventure game genre. Despite its age, Adventure is still an easy way to lose hours as you explore a fantasy world, much like a Dungeons and Dragons dungeon master might lead you through an imaginary place.
|
||||
|
||||
Rather than take you through the history of Adventure here, I encourage you to go read Joshua's [history of the game][4] itself and why it was resurrected and re-ported a few years ago. Then, go [clone the source][5] and follow the [installation instructions][6] to launch the game with **advent** **** on your system. Or, as Joshua mentions, another version of the game can be obtained from the **bsd-games** package, which is probably available from your default repositories in your distribution of choice.
|
||||
|
||||
Do you have a favorite command-line toy that you we should have included? Our series concludes today, but we'd still love to feature some cool command-line toys in the new year. Let me know in the comments below, and I'll check it out. And let me know what you thought of today's amusement.
|
||||
|
||||
Be sure to check out yesterday's toy, [The Linux command line can fetch fun from afar][7], and I'll see you next year!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/12/linux-toy-adventure
|
||||
|
||||
作者:[Jason Baker][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/jason-baker
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/article/18/12/linux-toy-boxes
|
||||
[2]: https://opensource.com/users/holmja
|
||||
[3]: https://gitlab.com/esr/open-adventure (https://gitlab.com/esr/open-adventure)
|
||||
[4]: https://opensource.com/article/17/6/revisit-colossal-cave-adventure-open-adventure
|
||||
[5]: https://gitlab.com/esr/open-adventure
|
||||
[6]: https://gitlab.com/esr/open-adventure/blob/master/INSTALL.adoc
|
||||
[7]: https://opensource.com/article/18/12/linux-toy-remote
|
||||
@ -0,0 +1,93 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (How to use Magit to manage Git projects)
|
||||
[#]: via: (https://opensource.com/article/19/1/how-use-magit)
|
||||
[#]: author: (Sachin Patil https://opensource.com/users/psachin)
|
||||
|
||||
How to use Magit to manage Git projects
|
||||
======
|
||||
Emacs' Magit extension makes it easy to get started with Git version control.
|
||||

|
||||
|
||||
[Git][1] is an excellent [version control][2] tool for managing projects, but it can be hard for novices to learn. It's difficult to work from the Git command line unless you're familiar with the flags and options and the appropriate situations to use them. This can be discouraging and cause people to be stuck with very limited usage.
|
||||
|
||||
Fortunately, most of today's integrated development environments (IDEs) include Git extensions that make using it a lot easier. One such Git extension available in Emacs is called [Magit][3].
|
||||
|
||||
The Magit project has been around for 10 years and defines itself as "a Git porcelain inside Emacs." In other words, it's an interface where every action can be managed by pressing a key. This article walks you through the Magit interface and explains how to use it to manage a Git project.
|
||||
|
||||
If you haven't already, [install Emacs][4], then [install Magit][5] before you continue with this tutorial.
|
||||
|
||||
### Magit's interface
|
||||
|
||||
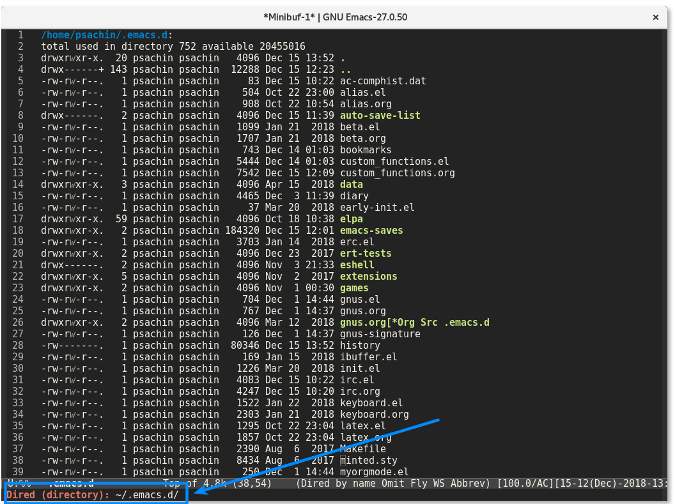
Start by visiting a project directory in Emacs' [Dired mode][6]. For example, all my Emacs configurations are stored in the **~/.emacs.d/** directory, which is managed by Git.
|
||||
|
||||
|
||||
|
||||
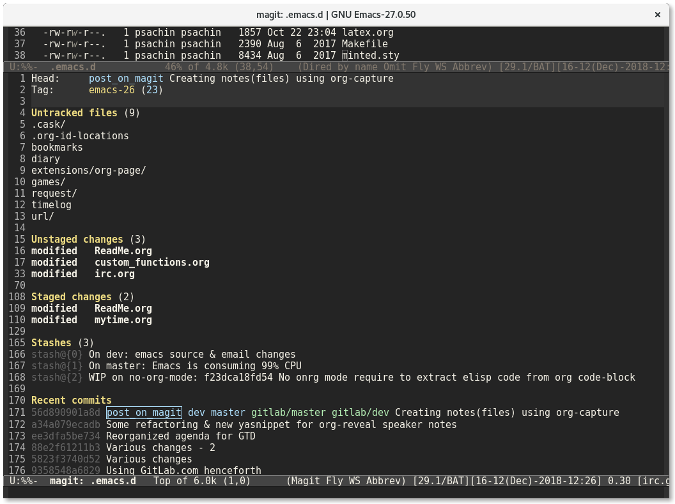
If you were working from the command line, you would enter **git status** to find a project's current status. Magit has a similar function: **magit-status**. You can call this function using **M-x magit-status** (short for the keystroke **Alt+x magit-status** ). Your result will look something like this:
|
||||
|
||||
|
||||
|
||||
Magit shows much more information than you would get from the **git status** command. It shows a list of untracked files, files that aren't staged, and staged files. It also shows the stash list and the most recent commits—all in a single window.
|
||||
|
||||
If you want to know what has changed, use the Tab key. For example, if I move my cursor over the unstaged file **custom_functions.org** and press the Tab key, Magit will display the changes:
|
||||
|
||||
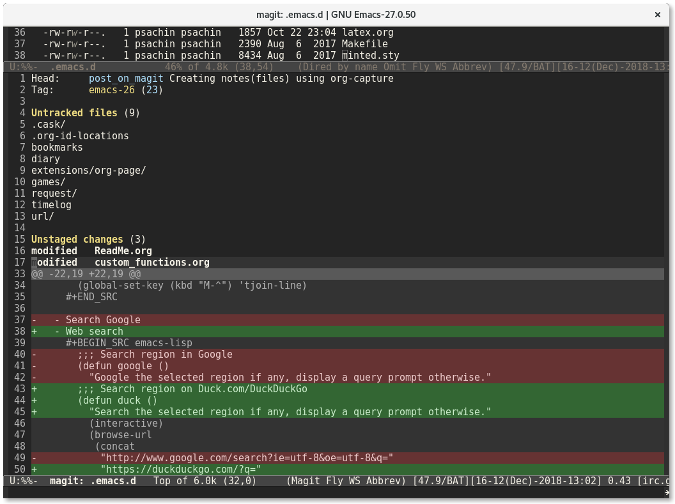
|
||||
|
||||
This is similar to using the command **git diff custom_functions.org**. Staging a file is even easier. Simply move the cursor over a file and press the **s** key. The file will be quickly moved to the staged file list:
|
||||
|
||||
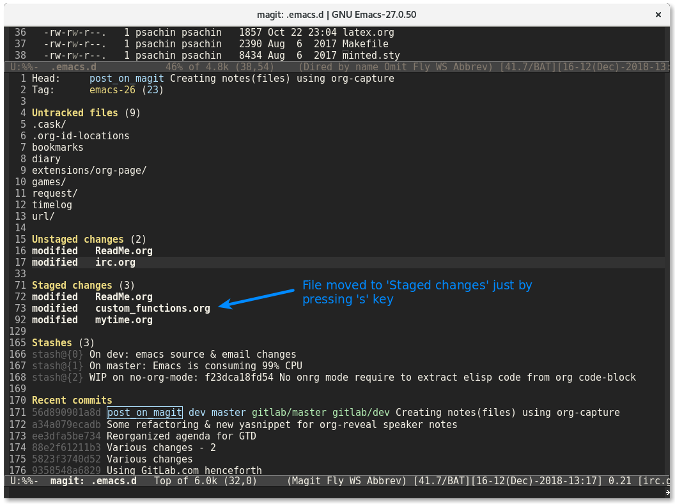
|
||||
|
||||
To unstage a file, use the **u** key. It is quicker and more fun to use **s** and **u** instead of entering **git add -u <file>** and **git reset HEAD <file>** on the command line.
|
||||
|
||||
### Commit changes
|
||||
|
||||
In the same Magit window, pressing the **c** key will display a commit window that provides flags like **\--all** to stage all files or **\--signoff** to add a signoff line to a commit message.
|
||||
|
||||
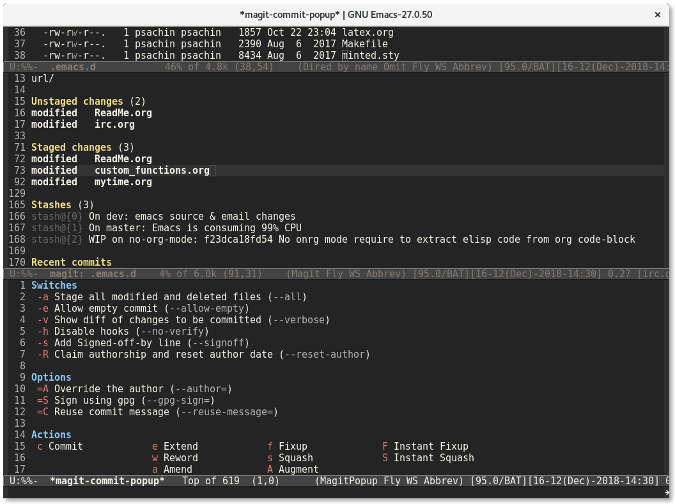
|
||||
|
||||
Move your cursor to the line where you want to enable a signoff flag and press Enter. This will highlight the **\--signoff** text, which indicates that the flag is enabled.
|
||||
|
||||
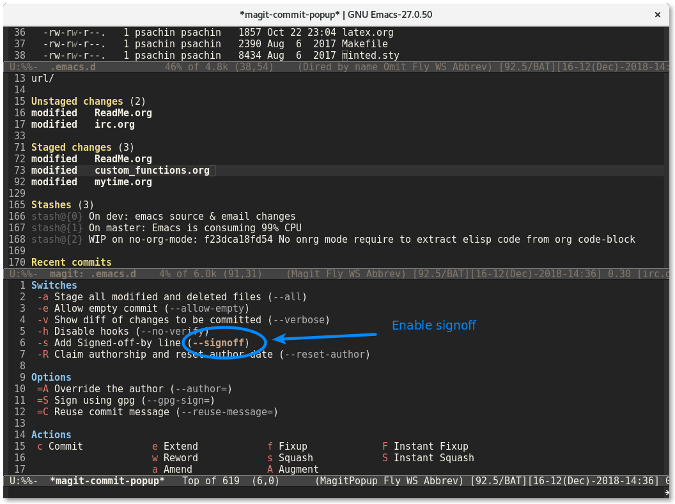
|
||||
|
||||
Pressing **c** again will display the window to write the commit message.
|
||||
|
||||
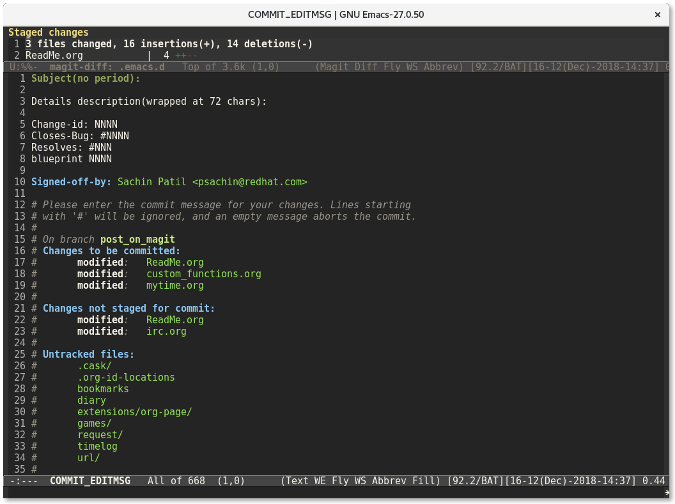
|
||||
|
||||
Finally, use **C-c C-c **(short form of the keys Ctrl+cc) to commit the changes.
|
||||
|
||||
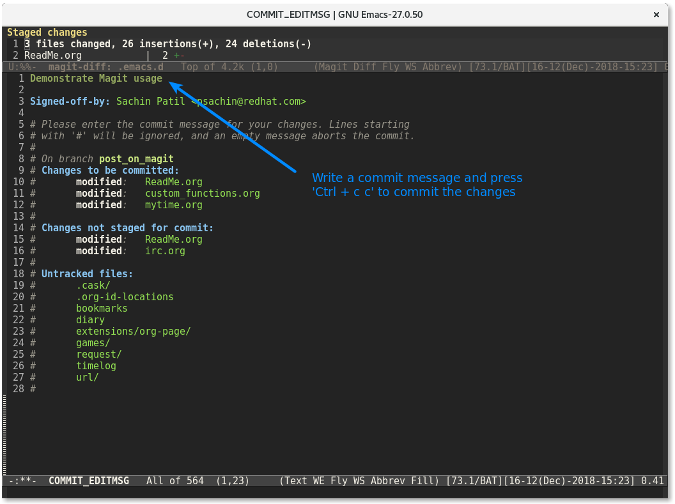
|
||||
|
||||
### Push changes
|
||||
|
||||
Once the changes are committed, the commit line will appear in the **Recent commits** section.
|
||||
|
||||
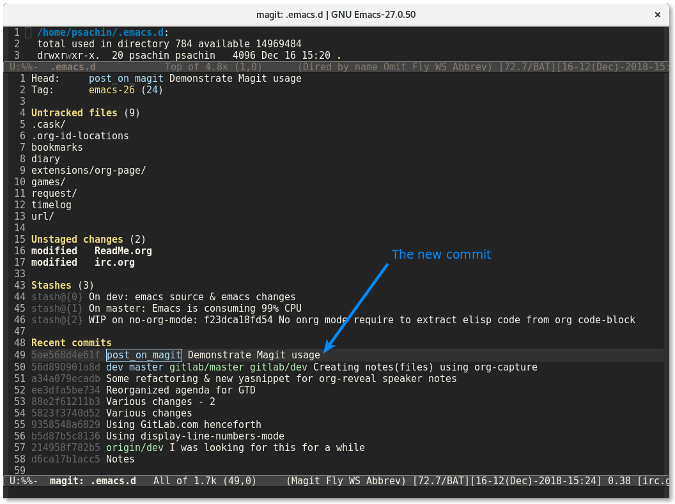
|
||||
|
||||
Place the cursor on that commit and press **p** to push the changes.
|
||||
|
||||
I've uploaded a [demonstration][7] on YouTube if you want to get a feel for using Magit. I have just scratched the surface in this article. It has many cool features to help you with Git branches, rebasing, and more. You can find [documentation, support, and more][8] linked from Magit's homepage.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/1/how-use-magit
|
||||
|
||||
作者:[Sachin Patil][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/psachin
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://git-scm.com
|
||||
[2]: https://git-scm.com/book/en/v2/Getting-Started-About-Version-Control
|
||||
[3]: https://magit.vc
|
||||
[4]: https://www.gnu.org/software/emacs/download.html
|
||||
[5]: https://magit.vc/manual/magit/Installing-from-Melpa.html#Installing-from-Melpa
|
||||
[6]: https://www.gnu.org/software/emacs/manual/html_node/emacs/Dired-Enter.html#Dired-Enter
|
||||
[7]: https://youtu.be/Vvw75Pqp7Mc
|
||||
[8]: https://magit.vc/
|
||||
@ -0,0 +1,110 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Midori: A Lightweight Open Source Web Browser)
|
||||
[#]: via: (https://itsfoss.com/midori-browser)
|
||||
[#]: author: (Abhishek Prakash https://itsfoss.com/author/abhishek/)
|
||||
|
||||
Midori: A Lightweight Open Source Web Browser
|
||||
======
|
||||
|
||||
**Here’s a quick review of the lightweight, fast, open source web browser Midori, which has returned from the dead.**
|
||||
|
||||
If you are looking for a lightweight [alternative web browser][1], try Midori.
|
||||
|
||||
[Midori][2] is an open source web browser that focuses more on being lightweight than on providing a ton of features.
|
||||
|
||||
If you have never heard of Midori, you might think that it is a new application but Midori was first released in 2007.
|
||||
|
||||
Because it focused on speed, Midori soon gathered a niche following and became the default browser in lightweight Linux distributions like Bodhi Linux, SilTaz etc.
|
||||
|
||||
Other distributions like [elementary OS][3] also used Midori as its default browser. But the development of Midori stalled around 2016 and its fans started wondering if Midori was dead already. elementary OS dropped it from its latest release, I believe, for this reason.
|
||||
|
||||
The good news is that Midori is not dead. After almost two years of inactivity, the development resumed in the last quarter of 2018. A few extensions including an ad-blocker were added in the later releases.
|
||||
|
||||
### Features of Midori web browser
|
||||
|
||||
![Midori web browser][4]
|
||||
|
||||
Here are some of the main features of the Midori browser
|
||||
|
||||
* Written in Vala with GTK+3 and WebKit rendering engine.
|
||||
* Tabs, windows and session management
|
||||
* Speed dial
|
||||
* Saves tab for the next session by default
|
||||
* Uses DuckDuckGo as a default search engine. It can be changed to Google or Yahoo.
|
||||
* Bookmark management
|
||||
* Customizable and extensible interface
|
||||
* Extension modules can be written in C and Vala
|
||||
* Supports HTML5
|
||||
* An extremely limited set of extensions include an ad-blocker, colorful tabs etc. No third-party extensions.
|
||||
* Form history
|
||||
* Private browsing
|
||||
* Available for Linux and Windows
|
||||
|
||||
|
||||
|
||||
Trivia: Midori is a Japanese word that means green. The Midori developer is not Japanese if you were guessing something along that line.
|
||||
|
||||
### Experiencing Midori
|
||||
|
||||
![Midori web browser in Ubuntu 18.04][5]
|
||||
|
||||
I have been using Midori for the past few days. The experience is mostly fine. It supports HTML5 and renders the websites quickly. The ad-blocker is okay. The browsing experience is more or less smooth as you would expect in any standard web browser.
|
||||
|
||||
The lack of extensions has always been a weak point of Midori so I am not going to talk about that.
|
||||
|
||||
What I did notice is that it doesn’t support international languages. I couldn’t find a way to add new language support. It could not render the Hindi fonts at all and I am guessing it’s the same with many other non-[Romance languages][6].
|
||||
|
||||
I also had my fair share of troubles with YouTube videos. Some videos would throw playback error while others would run just fine.
|
||||
|
||||
Midori didn’t eat my RAM like Chrome so that’s a big plus here.
|
||||
|
||||
If you want to try out Midori, let’s see how can you get your hands on it.
|
||||
|
||||
### Install Midori on Linux
|
||||
|
||||
Midori is no longer available in the Ubuntu 18.04 repository. However, the newer versions of Midori can be easily installed using the [Snap packages][7].
|
||||
|
||||
If you are using Ubuntu, you can find Midori (Snap version) in the Software Center and install it from there.
|
||||
|
||||
![Midori browser is available in Ubuntu Software Center][8]Midori browser is available in Ubuntu Software Center
|
||||
|
||||
For other Linux distributions, make sure that you have [Snap support enabled][9] and then you can install Midori using the command below:
|
||||
|
||||
```
|
||||
sudo snap install midori
|
||||
```
|
||||
|
||||
You always have the option to compile from the source code. You can download the source code of Midori from its website.
|
||||
|
||||
If you like Midori and want to help this open source project, please donate to them or [buy Midori merchandise from their shop][10].
|
||||
|
||||
Do you use Midori or have you ever tried it? How’s your experience with it? What other web browser do you prefer to use? Please share your views in the comment section below.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://itsfoss.com/midori-browser
|
||||
|
||||
作者:[Abhishek Prakash][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://itsfoss.com/author/abhishek/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://itsfoss.com/open-source-browsers-linux/
|
||||
[2]: https://www.midori-browser.org/
|
||||
[3]: https://itsfoss.com/elementary-os-juno-features/
|
||||
[4]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2019/01/Midori-web-browser.jpeg?resize=800%2C450&ssl=1
|
||||
[5]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2019/01/midori-browser-linux.jpeg?resize=800%2C491&ssl=1
|
||||
[6]: https://en.wikipedia.org/wiki/Romance_languages
|
||||
[7]: https://itsfoss.com/use-snap-packages-ubuntu-16-04/
|
||||
[8]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2019/01/midori-ubuntu-software-center.jpeg?ssl=1
|
||||
[9]: https://itsfoss.com/install-snap-linux/
|
||||
[10]: https://www.midori-browser.org/shop
|
||||
[11]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2019/01/Midori-web-browser.jpeg?fit=800%2C450&ssl=1
|
||||
@ -0,0 +1,93 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Take to the virtual skies with FlightGear)
|
||||
[#]: via: (https://opensource.com/article/19/1/flightgear)
|
||||
[#]: author: (Don Watkins https://opensource.com/users/don-watkins)
|
||||
|
||||
Take to the virtual skies with FlightGear
|
||||
======
|
||||
Dreaming of piloting a plane? Try open source flight simulator FlightGear.
|
||||

|
||||
|
||||
If you've ever dreamed of piloting a plane, you'll love [FlightGear][1]. It's a full-featured, [open source][2] flight simulator that runs on Linux, MacOS, and Windows.
|
||||
|
||||
The FlightGear project began in 1996 due to dissatisfaction with commercial flight simulation programs, which were not scalable. Its goal was to create a sophisticated, robust, extensible, and open flight simulator framework for use in academia and pilot training or by anyone who wants to play with a flight simulation scenario.
|
||||
|
||||
### Getting started
|
||||
|
||||
FlightGear's hardware requirements are fairly modest, including an accelerated 3D video card that supports OpenGL for smooth framerates. It runs well on my Linux laptop with an i5 processor and only 4GB of RAM. Its documentation includes an [online manual][3]; a [wiki][4] with portals for [users][5] and [developers][6]; and extensive tutorials (such as one for its default aircraft, the [Cessna 172p][7]) to teach you how to operate it.
|
||||
|
||||
It's easy to install on both [Fedora][8] and [Ubuntu][9] Linux. Fedora users can consult the [Fedora installation page][10] to get FlightGear running.
|
||||
|
||||
On Ubuntu 18.04, I had to install a repository:
|
||||
|
||||
```
|
||||
$ sudo add-apt-repository ppa:saiarcot895/flightgear
|
||||
$ sudo apt-get update
|
||||
$ sudo apt-get install flightgear
|
||||
```
|
||||
|
||||
Once the installation finished, I launched it from the GUI, but you can also launch the application from a terminal by entering:
|
||||
|
||||
```
|
||||
$ fgfs
|
||||
```
|
||||
|
||||
### Configuring FlightGear
|
||||
|
||||
The menu on the left side of the application window provides configuration options.
|
||||
|
||||
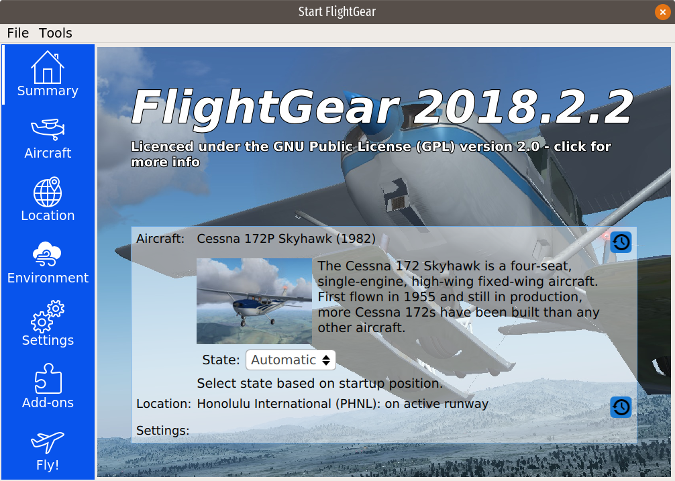
|
||||
|
||||
**Summary** returns you to the application's home screen.
|
||||
|
||||
**Aircraft** shows the aircraft you have installed and offers the option to install up to 539 other aircraft available in FlightGear's default "hangar." I installed a Cessna 150L, a Piper J-3 Cub, and a Bombardier CRJ-700. Some of the aircraft (including the CRJ-700) have tutorials to teach you how to fly a commercial jet; I found the tutorials informative and accurate.
|
||||
|
||||
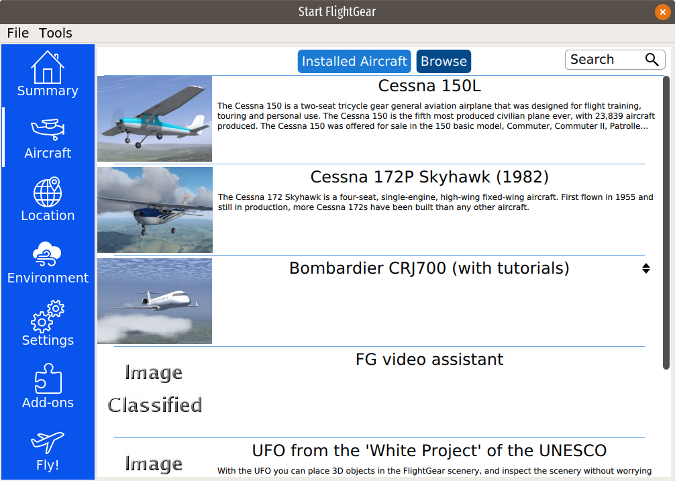
|
||||
|
||||
To select an aircraft to pilot, highlight it and click on **Fly!** at the bottom of the menu. I chose the default Cessna 172p and found the cockpit depiction extremely accurate.
|
||||
|
||||
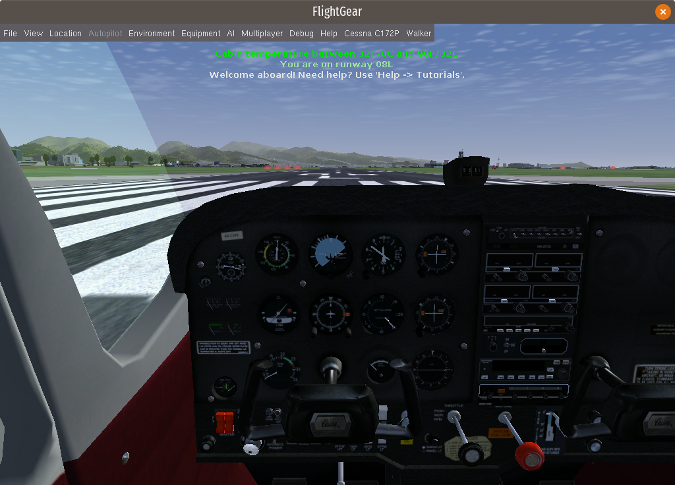
|
||||
|
||||
The default airport is Honolulu, but you can change it in the **Location** menu by providing your favorite airport's [ICAO airport code][11] identifier. I found some small, local, non-towered airports like Olean and Dunkirk, New York, as well as larger airports including Buffalo, O'Hare, and Raleigh—and could even choose a specific runway.
|
||||
|
||||
Under **Environment** , you can adjust the time of day, the season, and the weather. The simulation includes advance weather modeling and the ability to download current weather from [NOAA][12].
|
||||
|
||||
**Settings** provides an option to start the simulation in Paused mode by default. Also in Settings, you can select multi-player mode, which allows you to "fly" with other players on FlightGear supporters' global network of servers that allow for multiple users. You must have a moderately fast internet connection to support this functionality.
|
||||
|
||||
The **Add-ons** menu allows you to download aircraft and additional scenery.
|
||||
|
||||
### Take flight
|
||||
|
||||
To "fly" my Cessna, I used a Logitech joystick that worked well. You can calibrate your joystick using an option in the **File** menu at the top.
|
||||
|
||||
Overall, I found the simulation very accurate and think the graphics are great. Try FlightGear yourself — I think you will find it a very fun and complete simulation package.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/1/flightgear
|
||||
|
||||
作者:[Don Watkins][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/don-watkins
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: http://home.flightgear.org/
|
||||
[2]: http://wiki.flightgear.org/GNU_General_Public_License
|
||||
[3]: http://flightgear.sourceforge.net/getstart-en/getstart-en.html
|
||||
[4]: http://wiki.flightgear.org/FlightGear_Wiki
|
||||
[5]: http://wiki.flightgear.org/Portal:User
|
||||
[6]: http://wiki.flightgear.org/Portal:Developer
|
||||
[7]: http://wiki.flightgear.org/Cessna_172P
|
||||
[8]: http://rpmfind.net/linux/rpm2html/search.php?query=flightgear
|
||||
[9]: https://launchpad.net/~saiarcot895/+archive/ubuntu/flightgear
|
||||
[10]: https://apps.fedoraproject.org/packages/FlightGear/
|
||||
[11]: https://en.wikipedia.org/wiki/ICAO_airport_code
|
||||
[12]: https://www.noaa.gov/
|
||||
@ -0,0 +1,58 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Getting started with Sandstorm, an open source web app platform)
|
||||
[#]: via: (https://opensource.com/article/19/1/productivity-tool-sandstorm)
|
||||
[#]: author: (Kevin Sonney https://opensource.com/users/ksonney (Kevin Sonney))
|
||||
|
||||
Getting started with Sandstorm, an open source web app platform
|
||||
======
|
||||
Learn about Sandstorm, the third in our series on open source tools that will make you more productive in 2019.
|
||||

|
||||
|
||||
There seems to be a mad rush at the beginning of every year to find ways to be more productive. New Year's resolutions, the itch to start the year off right, and of course, an "out with the old, in with the new" attitude all contribute to this. And the usual round of recommendations is heavily biased towards closed source and proprietary software. It doesn't have to be that way.
|
||||
|
||||
Here's the third of my picks for 19 new (or new-to-you) open source tools to help you be more productive in 2019.
|
||||
|
||||
### Sandstorm
|
||||
|
||||
Being productive isn't just about to-do lists and keeping things organized. Often it requires a suite of tools linked to make a workflow go smoothly.
|
||||
|
||||
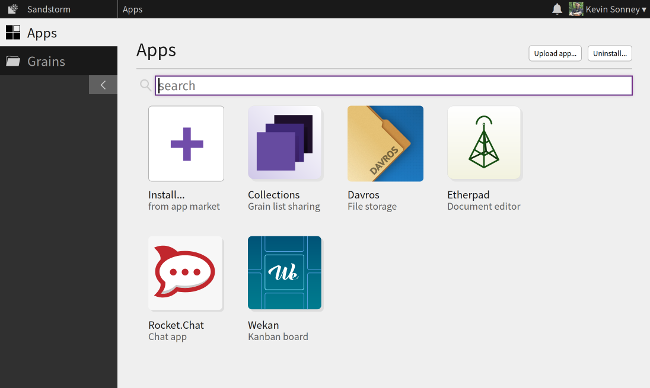
|
||||
|
||||
[Sandstorm][1] is an open source collection of packaged apps, all accessible from a single web interface and managed from a central console. You can host it yourself or use the [Sandstorm Oasis][2] service—for a per-user fee.
|
||||
|
||||
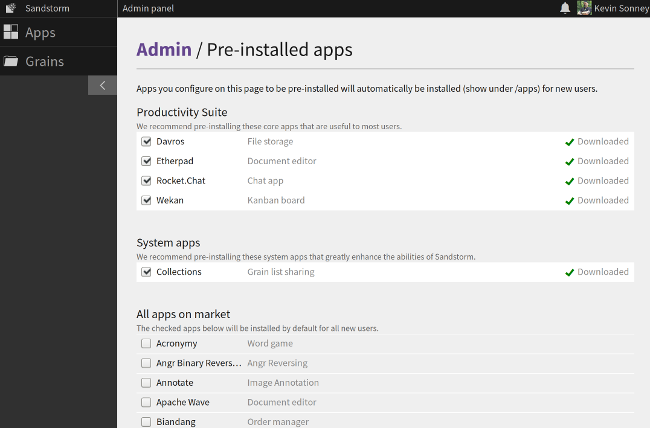
|
||||
|
||||
Sandstorm has a marketplace that makes it simple to install the apps that are available. It includes apps for productivity, finance, note taking, task tracking, chat, games, and a whole lot more. You can also package your own apps and upload them by following the application-packaging guidelines in the [developer documentation][3].
|
||||
|
||||
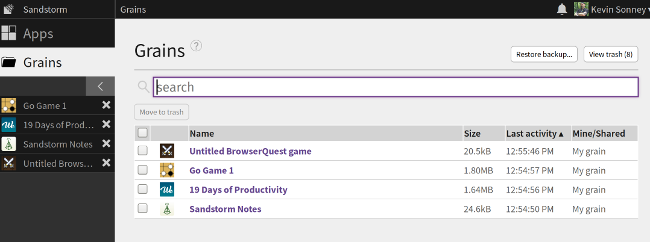
|
||||
|
||||
Once installed, a user can create [grains][4]—basically containerized instances of app data. Grains are private by default and can be shared with other Sandstorm users. This means they are secure by default, and users can chose what to share with others.
|
||||
|
||||
|
||||
|
||||
Sandstorm can authenticate from several different external sources as well as use a "passwordless" email-based authentication. Using an external service means you don't have to manage yet another set of credentials if you already use one of the supported services.
|
||||
|
||||
In the end, Sandstorm makes installing and using supported collaborative apps quick, easy, and secure.
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/1/productivity-tool-sandstorm
|
||||
|
||||
作者:[Kevin Sonney][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/ksonney (Kevin Sonney)
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://sandstorm.io/
|
||||
[2]: https://oasis.sandstorm.io
|
||||
[3]: https://docs.sandstorm.io/en/latest/developing/
|
||||
[4]: https://sandstorm.io/how-it-works
|
||||
156
sources/tech/20190116 Best Audio Editors For Linux.md
Normal file
156
sources/tech/20190116 Best Audio Editors For Linux.md
Normal file
@ -0,0 +1,156 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Best Audio Editors For Linux)
|
||||
[#]: via: (https://itsfoss.com/best-audio-editors-linux)
|
||||
[#]: author: (Ankush Das https://itsfoss.com/author/ankush/)
|
||||
|
||||
Best Audio Editors For Linux
|
||||
======
|
||||
|
||||
You’ve got a lot of choices when it comes to audio editors for Linux. No matter whether you are a professional music producer or just learning to create awesome music, the audio editors will always come in handy.
|
||||
|
||||
Well, for professional-grade usage, a [DAW][1] (Digital Audio Workstation) is always recommended. However, not everyone needs all the functionalities, so you should know about some of the most simple audio editors as well.
|
||||
|
||||
In this article, we will talk about a couple of DAWs and basic audio editors which are available as **free and open source** solutions for Linux and (probably) for other operating systems.
|
||||
|
||||
### Top Audio Editors for Linux
|
||||
|
||||
![Best audio editors and DAW for Linux][2]
|
||||
|
||||
We will not be focusing on all the functionalities that DAWs offer – but the basic audio editing capabilities. You may still consider this as the list of best DAW for Linux.
|
||||
|
||||
**Installation instruction:** You will find all the mentioned audio editors or DAWs in your AppCenter or Software center. In case, you do not find them listed, please head to their official website for more information.
|
||||
|
||||
#### 1\. Audacity
|
||||
|
||||
![audacity audio editor][3]
|
||||
|
||||
Audacity is one of the most basic yet a capable audio editor available for Linux. It is a free and open-source cross-platform tool. A lot of you must be already knowing about it.
|
||||
|
||||
It has improved a lot when compared to the time when it started trending. I do recall that I utilized it to “try” making karaokes by removing the voice from an audio file. Well, you can still do it – but it depends.
|
||||
|
||||
**Features:**
|
||||
|
||||
It also supports plug-ins that include VST effects. Of course, you should not expect it to support VST Instruments.
|
||||
|
||||
* Live audio recording through a microphone or a mixer
|
||||
* Export/Import capability supporting multiple formats and multiple files at the same time
|
||||
* Plugin support: LADSPA, LV2, Nyquist, VST and Audio Unit effect plug-ins
|
||||
* Easy editing with cut, paste, delete and copy functions.
|
||||
* Spectogram view mode for analyzing frequencies
|
||||
|
||||
|
||||
|
||||
#### 2\. LMMS
|
||||
|
||||
![][4]
|
||||
|
||||
LMMS is a free and open source (cross-platform) digital audio workstation. It includes all the basic audio editing functionalities along with a lot of advanced features.
|
||||
|
||||
You can mix sounds, arrange them, or create them using VST instruments. It does support them. Also, it comes baked in with some samples, presets, VST Instruments, and effects to get started. In addition, you also get a spectrum analyzer for some advanced audio editing.
|
||||
|
||||
**Features:**
|
||||
|
||||
* Note playback via MIDI
|
||||
* VST Instrument support
|
||||
* Native multi-sample support
|
||||
* Built-in compressor, limiter, delay, reverb, distortion and bass enhancer
|
||||
|
||||
|
||||
|
||||
#### 3\. Ardour
|
||||
|
||||
![Ardour audio editor][5]
|
||||
|
||||
Ardour is yet another free and open source digital audio workstation. If you have an audio interface, Ardour will support it. Of course, you can add unlimited multichannel tracks. The multichannel tracks can also be routed to different mixer tapes for the ease of editing and recording.
|
||||
|
||||
You can also import a video to it and edit the audio to export the whole thing. It comes with a lot of built-in plugins and supports VST plugins as well.
|
||||
|
||||
**Features:**
|
||||
|
||||
* Non-linear editing
|
||||
* Vertical window stacking for easy navigation
|
||||
* Strip silence, push-pull trimming, Rhythm Ferret for transient and note onset-based editing
|
||||
|
||||
|
||||
|
||||
#### 4\. Cecilia
|
||||
|
||||
![cecilia audio editor][6]
|
||||
|
||||
Cecilia is not an ordinary audio editor application. It is meant to be used by sound designers or if you are just in the process of becoming one. It is technically an audio signal processing environment. It lets you create ear-bending sound out of them.
|
||||
|
||||
You get in-build modules and plugins for sound effects and synthesis. It is tailored for a specific use – if that is what you were looking for – look no further!
|
||||
|
||||
**Features:**
|
||||
|
||||
* Modules to achieve more (UltimateGrainer – A state-of-the-art granulation processing, RandomAccumulator – Variable speed recording accumulator,
|
||||
UpDistoRes – Distortion with upsampling and resonant lowpass filter)
|
||||
* Automatic Saving of modulations
|
||||
|
||||
|
||||
|
||||
#### 5\. Mixxx
|
||||
|
||||
![Mixxx audio DJ ][7]
|
||||
|
||||
If you want to mix and record something while being able to have a virtual DJ tool, [Mixxx][8] would be a perfect tool. You get to know the BPM, key, and utilize the master sync feature to match the tempo and beats of a song. Also, do not forget that it is yet another free and open source application for Linux!
|
||||
|
||||
It supports custom DJ equipment as well. So, if you have one or a MIDI – you can record your live mixes using this tool.
|
||||
|
||||
**Features**
|
||||
|
||||
* Broadcast and record DJ Mixes of your song
|
||||
* Ability to connect your equipment and perform live
|
||||
* Key detection and BPM detection
|
||||
|
||||
|
||||
|
||||
#### 6\. Rosegarden
|
||||
|
||||
![rosegarden audio editor][9]
|
||||
|
||||
Rosegarden is yet another impressive audio editor for Linux which is free and open source. It is neither a fully featured DAW nor a basic audio editing tool. It is a mixture of both with some scaled down functionalities.
|
||||
|
||||
I wouldn’t recommend this for professionals but if you have a home studio or just want to experiment, this would be one of the best audio editors for Linux to have installed.
|
||||
|
||||
**Features:**
|
||||
|
||||
* Music notation editing
|
||||
* Recording, Mixing, and samples
|
||||
|
||||
|
||||
|
||||
### Wrapping Up
|
||||
|
||||
These are some of the best audio editors you could find out there for Linux. No matter whether you need a DAW, a cut-paste editing tool, or a basic mixing/recording audio editor, the above-mentioned tools should help you out.
|
||||
|
||||
Did we miss any of your favorite? Let us know about it in the comments below.
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://itsfoss.com/best-audio-editors-linux
|
||||
|
||||
作者:[Ankush Das][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://itsfoss.com/author/ankush/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://en.wikipedia.org/wiki/Digital_audio_workstation
|
||||
[2]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2019/01/linux-audio-editors-800x450.jpeg?resize=800%2C450&ssl=1
|
||||
[3]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2019/01/audacity-audio-editor.jpg?fit=800%2C591&ssl=1
|
||||
[4]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2019/01/lmms-daw.jpg?fit=800%2C472&ssl=1
|
||||
[5]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2019/01/ardour-audio-editor.jpg?fit=800%2C639&ssl=1
|
||||
[6]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2019/01/cecilia.jpg?fit=800%2C510&ssl=1
|
||||
[7]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2019/01/mixxx.jpg?fit=800%2C486&ssl=1
|
||||
[8]: https://itsfoss.com/dj-mixxx-2/
|
||||
[9]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2019/01/rosegarden.jpg?fit=800%2C391&ssl=1
|
||||
[10]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2019/01/linux-audio-editors.jpeg?fit=800%2C450&ssl=1
|
||||
@ -0,0 +1,139 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (GameHub – An Unified Library To Put All Games Under One Roof)
|
||||
[#]: via: (https://www.ostechnix.com/gamehub-an-unified-library-to-put-all-games-under-one-roof/)
|
||||
[#]: author: (SK https://www.ostechnix.com/author/sk/)
|
||||
|
||||
GameHub – An Unified Library To Put All Games Under One Roof
|
||||
======
|
||||
|
||||

|
||||
|
||||
**GameHub** is an unified gaming library that allows you to view, install, run and remove games on GNU/Linux operating system. It supports both native and non-native games from various sources including Steam, GOG, Humble Bundle, and Humble Trove etc. The non-native games are supported by [Wine][1], Proton, [DOSBox][2], ScummVM and RetroArch. It also allows you to add custom emulators and download bonus content and DLCs for GOG games. Simply put, Gamehub is a frontend for Steam/GoG/Humblebundle/Retroarch. It can use steam technologies like Proton to run windows gog games. GameHub is free, open source gaming platform written in **Vala** using **GTK+3**. If you’re looking for a way to manage all games under one roof, GameHub might be a good choice.
|
||||
|
||||
### Installing GameHub
|
||||
|
||||
The author of GameHub has designed it specifically for elementary OS. So, you can install it on Debian, Ubuntu, elementary OS and other Ubuntu-derivatives using GameHub PPA.
|
||||
|
||||
```
|
||||
$ sudo apt install --no-install-recommends software-properties-common
|
||||
$ sudo add-apt-repository ppa:tkashkin/gamehub
|
||||
$ sudo apt update
|
||||
$ sudo apt install com.github.tkashkin.gamehub
|
||||
```
|
||||
|
||||
GameHub is available in [**AUR**][3], so just install it on Arch Linux and its variants using any AUR helpers, for example [**YaY**][4].
|
||||
|
||||
```
|
||||
$ yay -S gamehub-git
|
||||
```
|
||||
|
||||
It is also available as **AppImage** and **Flatpak** packages in [**releases page**][5].
|
||||
|
||||
If you prefer AppImage package, do the following:
|
||||
|
||||
```
|
||||
$ wget https://github.com/tkashkin/GameHub/releases/download/0.12.1-91-dev/GameHub-bionic-0.12.1-91-dev-cd55bb5-x86_64.AppImage -O gamehub
|
||||
```
|
||||
|
||||
Make it executable:
|
||||
|
||||
```
|
||||
$ chmod +x gamehub
|
||||
```
|
||||
|
||||
And, run GameHub using command:
|
||||
|
||||
```
|
||||
$ ./gamehub
|
||||
```
|
||||
|
||||
If you want to use Flatpak installer, run the following commands one by one.
|
||||
|
||||
```
|
||||
$ git clone https://github.com/tkashkin/GameHub.git
|
||||
$ cd GameHub
|
||||
$ scripts/build.sh build_flatpak
|
||||
```
|
||||
|
||||
### Put All Games Under One Roof
|
||||
|
||||
Launch GameHub from menu or application launcher. At first launch, you will see the following welcome screen.
|
||||
|
||||
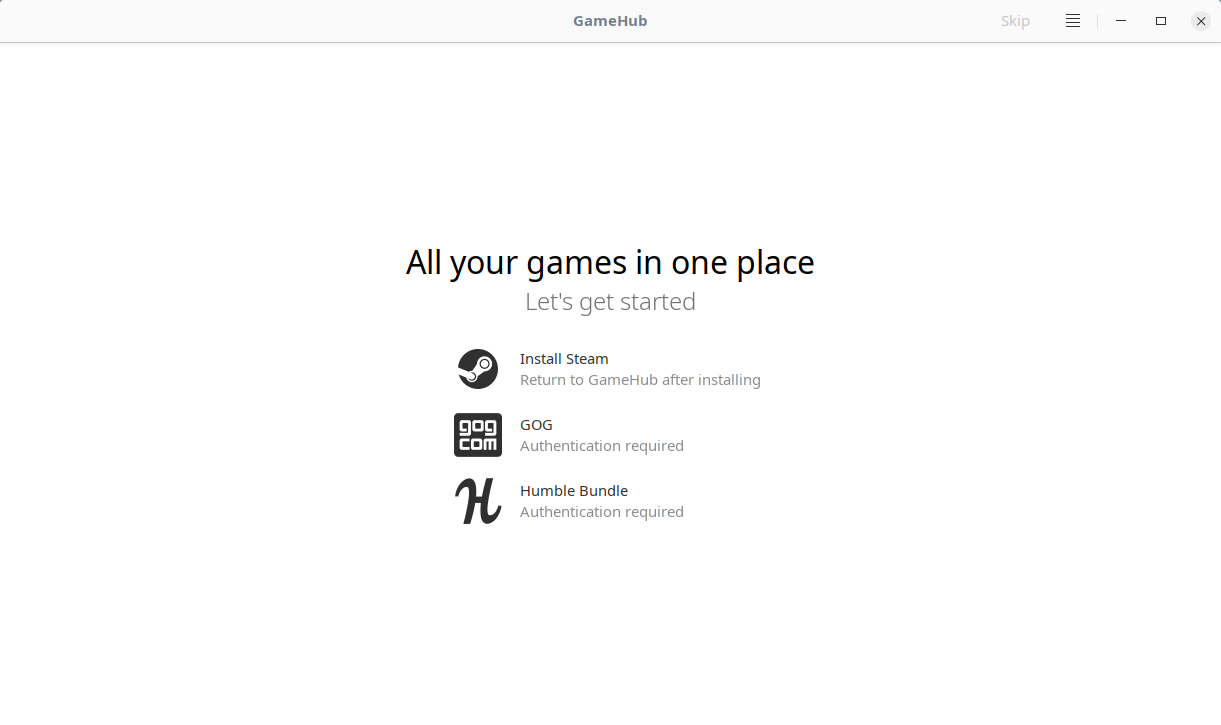
|
||||
|
||||
As you can see in the above screenshot, you need to login to the given sources namely Steam, GoG or Humble Bundle. If you don’t have Steam client on your Linux system, you need to install it first to access your steam account. For GoG and Humble bundle sources, click on the icon to log in to the respective source.
|
||||
|
||||
Once you logged in to your account(s), all games from the all sources can be visible on GameHub dashboard.
|
||||
|
||||

|
||||
|
||||
You will see list of logged-in sources on the top left corner. To view the games from each source, just click on the respective icon.
|
||||
|
||||
You can also switch between list view or grid view, sort the games by applying the filters and search games from the list in GameHub dashboard.
|
||||
|
||||
#### Installing a game
|
||||
|
||||
Click on the game of your choice from the list and click Install button. If the game is non-native, GameHub will automatically choose the compatibility layer (E.g Wine) that suits to run the game and install the selected game. As you see in the below screenshot, Indiana Jones game is not available for Linux platform.
|
||||
|
||||

|
||||
|
||||
If it is a native game (i.e supports Linux), simply press the Install button.
|
||||
|
||||
![][7]
|
||||
|
||||
If you don’t want to install the game, just hit the **Download** button to save it in your games directory. It is also possible to add locally installed games to GameHub using the **Import** option.
|
||||
|
||||

|
||||
|
||||
#### GameHub Settings
|
||||
|
||||
GameHub Settings window can be launched by clicking on the four straight lines on top right corner.
|
||||
|
||||
From Settings section, we can enable, disable and set various settings such as,
|
||||
|
||||
* Switch between light/dark themes.
|
||||
* Use Symbolic icons instead of colored icons for games.
|
||||
* Switch to compact list.
|
||||
* Enable/disable merging games from different sources.
|
||||
* Enable/disable compatibility layers.
|
||||
* Set games collection directory. The default directory for storing the collection is **$HOME/Games/_Collection**.
|
||||
* Set games directories for each source.
|
||||
* Add/remove emulators,
|
||||
* And many.
|
||||
|
||||
|
||||
|
||||
For more details, refer the project links given at the end of this guide.
|
||||
|
||||
**Related read:**
|
||||
|
||||
And, that’s all for now. Hope this helps. I will be soon here with another guide. Until then, stay tuned with OSTechNix.
|
||||
|
||||
Cheers!
|
||||
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.ostechnix.com/gamehub-an-unified-library-to-put-all-games-under-one-roof/
|
||||
|
||||
作者:[SK][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.ostechnix.com/author/sk/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.ostechnix.com/run-windows-games-softwares-ubuntu-16-04/
|
||||
[2]: https://www.ostechnix.com/how-to-run-ms-dos-games-and-programs-in-linux/
|
||||
[3]: https://aur.archlinux.org/packages/gamehub-git/
|
||||
[4]: https://www.ostechnix.com/yay-found-yet-another-reliable-aur-helper/
|
||||
[5]: https://github.com/tkashkin/GameHub/releases
|
||||
[6]: data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7
|
||||
[7]: http://www.ostechnix.com/wp-content/uploads/2019/01/gamehub4.png
|
||||
@ -0,0 +1,236 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (The Evil-Twin Framework: A tool for improving WiFi security)
|
||||
[#]: via: (https://opensource.com/article/19/1/evil-twin-framework)
|
||||
[#]: author: (André Esser https://opensource.com/users/andreesser)
|
||||
|
||||
The Evil-Twin Framework: A tool for improving WiFi security
|
||||
======
|
||||
Learn about a pen-testing tool intended to test the security of WiFi access points for all types of threats.
|
||||

|
||||
|
||||
The increasing number of devices that connect over-the-air to the internet over-the-air and the wide availability of WiFi access points provide many opportunities for attackers to exploit users. By tricking users to connect to [rogue access points][1], hackers gain full control over the users' network connection, which allows them to sniff and alter traffic, redirect users to malicious sites, and launch other attacks over the network..
|
||||
|
||||
To protect users and teach them to avoid risky online behaviors, security auditors and researchers must evaluate users' security practices and understand the reasons they connect to WiFi access points without being confident they are safe. There are a significant number of tools that can conduct WiFi audits, but no single tool can test the many different attack scenarios and none of the tools integrate well with one another.
|
||||
|
||||
The **Evil-Twin Framework** (ETF) aims to fix these problems in the WiFi auditing process by enabling auditors to examine multiple scenarios and integrate multiple tools. This article describes the framework and its functionalities, then provides some examples to show how it can be used.
|
||||
|
||||
### The ETF architecture
|
||||
|
||||
The ETF framework was written in [Python][2] because the development language is very easy to read and make contributions to. In addition, many of the ETF's libraries, such as **[Scapy][3]** , were already developed for Python, making it easy to use them for ETF.
|
||||
|
||||
The ETF architecture (Figure 1) is divided into different modules that interact with each other. The framework's settings are all written in a single configuration file. The user can verify and edit the settings through the user interface via the **ConfigurationManager** class. Other modules can only read these settings and run according to them.
|
||||
|
||||
![Evil-Twin Framework Architecture][5]
|
||||
|
||||
Figure 1: Evil-Twin framework architecture
|
||||
|
||||
The ETF supports multiple user interfaces that interact with the framework. The current default interface is an interactive console, similar to the one on [Metasploit][6]. A graphical user interface (GUI) and a command line interface (CLI) are under development for desktop/browser use, and mobile interfaces may be an option in the future. The user can edit the settings in the configuration file using the interactive console (and eventually with the GUI). The user interface can interact with every other module that exists in the framework.
|
||||
|
||||
The WiFi module ( **AirCommunicator** ) was built to support a wide range of WiFi capabilities and attacks. The framework identifies three basic pillars of Wi-Fi communication: **packet sniffing** , **custom packet injection** , and **access point creation**. The three main WiFi communication modules are **AirScanner** , **AirInjector** , and **AirHost** , which are responsible for packet sniffing, packet injection, and access point creation, respectively. The three classes are wrapped inside the main WiFi module, AirCommunicator, which reads the configuration file before starting the services. Any type of WiFi attack can be built using one or more of these core features.
|
||||
|
||||
To enable man-in-the-middle (MITM) attacks, which are a common way to attack WiFi clients, the framework has an integrated module called ETFITM (Evil-Twin Framework-in-the-Middle). This module is responsible for the creation of a web proxy used to intercept and manipulate HTTP/HTTPS traffic.
|
||||
|
||||
There are many other tools that can leverage the MITM position created by the ETF. Through its extensibility, ETF can support them—and, instead of having to call them separately, you can add the tools to the framework just by extending the Spawner class. This enables a developer or security auditor to call the program with a preconfigured argument string from within the framework.
|
||||
|
||||
The other way to extend the framework is through plugins. There are two categories of plugins: **WiFi plugins** and **MITM plugins**. MITM plugins are scripts that can run while the MITM proxy is active. The proxy passes the HTTP(S) requests and responses through to the plugins where they can be logged or manipulated. WiFi plugins follow a more complex flow of execution but still expose a fairly simple API to contributors who wish to develop and use their own plugins. WiFi plugins can be further divided into three categories, one for each of the core WiFi communication modules.
|
||||
|
||||
Each of the core modules has certain events that trigger the execution of a plugin. For instance, AirScanner has three defined events to which a response can be programmed. The events usually correspond to a setup phase before the service starts running, a mid-execution phase while the service is running, and a teardown or cleanup phase after a service finishes. Since Python allows multiple inheritance, one plugin can subclass more than one plugin class.
|
||||
|
||||
Figure 1 above is a summary of the framework's architecture. Lines pointing away from the ConfigurationManager mean that the module reads information from it and lines pointing towards it mean that the module can write/edit configurations.
|
||||
|
||||
### Examples of using the Evil-Twin Framework
|
||||
|
||||
There are a variety of ways ETF can conduct penetration testing on WiFi network security or work on end users' awareness of WiFi security. The following examples describe some of the framework's pen-testing functionalities, such as access point and client detection, WPA and WEP access point attacks, and evil twin access point creation.
|
||||
|
||||
These examples were devised using ETF with WiFi cards that allow WiFi traffic capture. They also utilize the following abbreviations for ETF setup commands:
|
||||
|
||||
* **APS** access point SSID
|
||||
* **APB** access point BSSID
|
||||
* **APC** access point channel
|
||||
* **CM** client MAC address
|
||||
|
||||
|
||||
|
||||
In a real testing scenario, make sure to replace these abbreviations with the correct information.
|
||||
|
||||
#### Capturing a WPA 4-way handshake after a de-authentication attack
|
||||
|
||||
This scenario (Figure 2) takes two aspects into consideration: the de-authentication attack and the possibility of catching a 4-way WPA handshake. The scenario starts with a running WPA/WPA2-enabled access point with one connected client device (in this case, a smartphone). The goal is to de-authenticate the client with a general de-authentication attack then capture the WPA handshake once it tries to reconnect. The reconnection will be done manually immediately after being de-authenticated.
|
||||
|
||||
![Scenario for capturing a WPA handshake after a de-authentication attack][8]
|
||||
|
||||
Figure 2: Scenario for capturing a WPA handshake after a de-authentication attack
|
||||
|
||||
The consideration in this example is the ETF's reliability. The goal is to find out if the tools can consistently capture the WPA handshake. The scenario will be performed multiple times with each tool to check its reliability when capturing the WPA handshake.
|
||||
|
||||
There is more than one way to capture a WPA handshake using the ETF. One way is to use a combination of the AirScanner and AirInjector modules; another way is to just use the AirInjector. The following scenario uses a combination of both modules.
|
||||
|
||||
The ETF launches the AirScanner module and analyzes the IEEE 802.11 frames to find a WPA handshake. Then the AirInjector can launch a de-authentication attack to force a reconnection. The following steps must be done to accomplish this on the ETF:
|
||||
|
||||
1. Enter the AirScanner configuration mode: **config airscanner**
|
||||
2. Configure the AirScanner to not hop channels: **config airscanner**
|
||||
3. Set the channel to sniff the traffic on the access point channel (APC): **set fixed_sniffing_channel = <APC>**
|
||||
4. Start the AirScanner module with the CredentialSniffer plugin: **start airscanner with credentialsniffer**
|
||||
5. Add a target access point BSSID (APS) from the sniffed access points list: **add aps where ssid = <APS>**
|
||||
6. Start the AirInjector, which by default lauches the de-authentication attack: **start airinjector**
|
||||
|
||||
|
||||
|
||||
This simple set of commands enables the ETF to perform an efficient and successful de-authentication attack on every test run. The ETF can also capture the WPA handshake on every test run. The following code makes it possible to observe the ETF's successful execution.
|
||||
|
||||
```
|
||||
███████╗████████╗███████╗
|
||||
██╔════╝╚══██╔══╝██╔════╝
|
||||
█████╗ ██║ █████╗
|
||||
██╔══╝ ██║ ██╔══╝
|
||||
███████╗ ██║ ██║
|
||||
╚══════╝ ╚═╝ ╚═╝
|
||||
|
||||
|
||||
[+] Do you want to load an older session? [Y/n]: n
|
||||
[+] Creating new temporary session on 02/08/2018
|
||||
[+] Enter the desired session name:
|
||||
ETF[etf/aircommunicator/]::> config airscanner
|
||||
ETF[etf/aircommunicator/airscanner]::> listargs
|
||||
sniffing_interface = wlan1; (var)
|
||||
probes = True; (var)
|
||||
beacons = True; (var)
|
||||
hop_channels = false; (var)
|
||||
fixed_sniffing_channel = 11; (var)
|
||||
ETF[etf/aircommunicator/airscanner]::> start airscanner with
|
||||
arpreplayer caffelatte credentialsniffer packetlogger selfishwifi
|
||||
ETF[etf/aircommunicator/airscanner]::> start airscanner with credentialsniffer
|
||||
[+] Successfully added credentialsniffer plugin.
|
||||
[+] Starting packet sniffer on interface 'wlan1'
|
||||
[+] Set fixed channel to 11
|
||||
ETF[etf/aircommunicator/airscanner]::> add aps where ssid = CrackWPA
|
||||
ETF[etf/aircommunicator/airscanner]::> start airinjector
|
||||
ETF[etf/aircommunicator/airscanner]::> [+] Starting deauthentication attack
|
||||
- 1000 bursts of 1 packets
|
||||
- 1 different packets
|
||||
[+] Injection attacks finished executing.
|
||||
[+] Starting post injection methods
|
||||
[+] Post injection methods finished
|
||||
[+] WPA Handshake found for client '70:3e:ac:bb:78:64' and network 'CrackWPA'
|
||||
```
|
||||
|
||||
#### Launching an ARP replay attack and cracking a WEP network
|
||||
|
||||
The next scenario (Figure 3) will also focus on the [Address Resolution Protocol][9] (ARP) replay attack's efficiency and the speed of capturing the WEP data packets containing the initialization vectors (IVs). The same network may require a different number of caught IVs to be cracked, so the limit for this scenario is 50,000 IVs. If the network is cracked during the first test with less than 50,000 IVs, that number will be the new limit for the following tests on the network. The cracking tool to be used will be **aircrack-ng**.
|
||||
|
||||
The test scenario starts with an access point using WEP encryption and an offline client that knows the key—the key for testing purposes is 12345, but it can be a larger and more complex key. Once the client connects to the WEP access point, it will send out a gratuitous ARP packet; this is the packet that's meant to be captured and replayed. The test ends once the limit of packets containing IVs is captured.
|
||||
|
||||
![Scenario for capturing a WPA handshake after a de-authentication attack][11]
|
||||
|
||||
Figure 3: Scenario for capturing a WPA handshake after a de-authentication attack
|
||||
|
||||
ETF uses Python's Scapy library for packet sniffing and injection. To minimize known performance problems in Scapy, ETF tweaks some of its low-level libraries to significantly speed packet injection. For this specific scenario, the ETF uses **tcpdump** as a background process instead of Scapy for more efficient packet sniffing, while Scapy is used to identify the encrypted ARP packet.
|
||||
|
||||
This scenario requires the following commands and operations to be performed on the ETF:
|
||||
|
||||
1. Enter the AirScanner configuration mode: **config airscanner**
|
||||
2. Configure the AirScanner to not hop channels: **set hop_channels = false**
|
||||
3. Set the channel to sniff the traffic on the access point channel (APC): **set fixed_sniffing_channel = <APC>**
|
||||
4. Enter the ARPReplayer plugin configuration mode: **config arpreplayer**
|
||||
5. Set the target access point BSSID (APB) of the WEP network: **set target_ap_bssid <APB>**
|
||||
6. Start the AirScanner module with the ARPReplayer plugin: **start airscanner with arpreplayer**
|
||||
|
||||
|
||||
|
||||
After executing these commands, ETF correctly identifies the encrypted ARP packet, then successfully performs an ARP replay attack, which cracks the network.
|
||||
|
||||
#### Launching a catch-all honeypot
|
||||
|
||||
The scenario in Figure 4 creates multiple access points with the same SSID. This technique discovers the encryption type of a network that was probed for but out of reach. By launching multiple access points with all security settings, the client will automatically connect to the one that matches the security settings of the locally cached access point information.
|
||||
|
||||
![Scenario for capturing a WPA handshake after a de-authentication attack][13]
|
||||
|
||||
Figure 4: Scenario for capturing a WPA handshake after a de-authentication attack
|
||||
|
||||
Using the ETF, it is possible to configure the **hostapd** configuration file then launch the program in the background. Hostapd supports launching multiple access points on the same wireless card by configuring virtual interfaces, and since it supports all types of security configurations, a complete catch-all honeypot can be set up. For the WEP and WPA(2)-PSK networks, a default password is used, and for the WPA(2)-EAP, an "accept all" policy is configured.
|
||||
|
||||
For this scenario, the following commands and operations must be performed on the ETF:
|
||||
|
||||
1. Enter the APLauncher configuration mode: **config aplauncher**
|
||||
2. Set the desired access point SSID (APS): **set ssid = <APS>**
|
||||
3. Configure the APLauncher as a catch-all honeypot: **set catch_all_honeypot = true**
|
||||
4. Start the AirHost module: **start airhost**
|
||||
|
||||
|
||||
|
||||
With these commands, the ETF can launch a complete catch-all honeypot with all types of security configurations. ETF also automatically launches the DHCP and DNS servers that allow clients to stay connected to the internet. ETF offers a better, faster, and more complete solution to create catch-all honeypots. The following code enables the successful execution of the ETF to be observed.
|
||||
|
||||
```
|
||||
███████╗████████╗███████╗
|
||||
██╔════╝╚══██╔══╝██╔════╝
|
||||
█████╗ ██║ █████╗
|
||||
██╔══╝ ██║ ██╔══╝
|
||||
███████╗ ██║ ██║
|
||||
╚══════╝ ╚═╝ ╚═╝
|
||||
|
||||
|
||||
[+] Do you want to load an older session? [Y/n]: n
|
||||
[+] Creating ne´,cxzw temporary session on 03/08/2018
|
||||
[+] Enter the desired session name:
|
||||
ETF[etf/aircommunicator/]::> config aplauncher
|
||||
ETF[etf/aircommunicator/airhost/aplauncher]::> setconf ssid CatchMe
|
||||
ssid = CatchMe
|
||||
ETF[etf/aircommunicator/airhost/aplauncher]::> setconf catch_all_honeypot true
|
||||
catch_all_honeypot = true
|
||||
ETF[etf/aircommunicator/airhost/aplauncher]::> start airhost
|
||||
[+] Killing already started processes and restarting network services
|
||||
[+] Stopping dnsmasq and hostapd services
|
||||
[+] Access Point stopped...
|
||||
[+] Running airhost plugins pre_start
|
||||
[+] Starting hostapd background process
|
||||
[+] Starting dnsmasq service
|
||||
[+] Running airhost plugins post_start
|
||||
[+] Access Point launched successfully
|
||||
[+] Starting dnsmasq service
|
||||
```
|
||||
|
||||
### Conclusions and future work
|
||||
|
||||
These scenarios use common and well-known attacks to help validate the ETF's capabilities for testing WiFi networks and clients. The results also validate that the framework's architecture enables new attack vectors and features to be developed on top of it while taking advantage of the platform's existing capabilities. This should accelerate development of new WiFi penetration-testing tools, since a lot of the code is already written. Furthermore, the fact that complementary WiFi technologies are all integrated in a single tool will make WiFi pen-testing simpler and more efficient.
|
||||
|
||||
The ETF's goal is not to replace existing tools but to complement them and offer a broader choice to security auditors when conducting WiFi pen-testing and improving user awareness.
|
||||
|
||||
The ETF is an open source project [available on GitHub][14] and community contributions to its development are welcomed. Following are some of the ways you can help.
|
||||
|
||||
One of the limitations of current WiFi pen-testing is the inability to log important events during tests. This makes reporting identified vulnerabilities both more difficult and less accurate. The framework could implement a logger that can be accessed by every class to create a pen-testing session report.
|
||||
|
||||
The ETF tool's capabilities cover many aspects of WiFi pen-testing. On one hand, it facilitates the phases of WiFi reconnaissance, vulnerability discovery, and attack. On the other hand, it doesn't offer a feature that facilitates the reporting phase. Adding the concept of a session and a session reporting feature, such as the logging of important events during a session, would greatly increase the value of the tool for real pen-testing scenarios.
|
||||
|
||||
Another valuable contribution would be extending the framework to facilitate WiFi fuzzing. The IEEE 802.11 protocol is very complex, and considering there are multiple implementations of it, both on the client and access point side, it's safe to assume these implementations contain bugs and even security flaws. These bugs could be discovered by fuzzing IEEE 802.11 protocol frames. Since Scapy allows custom packet creation and injection, a fuzzer can be implemented through it.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/1/evil-twin-framework
|
||||
|
||||
作者:[André Esser][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/andreesser
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://en.wikipedia.org/wiki/Rogue_access_point
|
||||
[2]: https://www.python.org/
|
||||
[3]: https://scapy.net
|
||||
[4]: /file/417776
|
||||
[5]: https://opensource.com/sites/default/files/uploads/pic1.png (Evil-Twin Framework Architecture)
|
||||
[6]: https://www.metasploit.com
|
||||
[7]: /file/417781
|
||||
[8]: https://opensource.com/sites/default/files/uploads/pic2.png (Scenario for capturing a WPA handshake after a de-authentication attack)
|
||||
[9]: https://en.wikipedia.org/wiki/Address_Resolution_Protocol
|
||||
[10]: /file/417786
|
||||
[11]: https://opensource.com/sites/default/files/uploads/pic3.png (Scenario for capturing a WPA handshake after a de-authentication attack)
|
||||
[12]: /file/417791
|
||||
[13]: https://opensource.com/sites/default/files/uploads/pic4.png (Scenario for capturing a WPA handshake after a de-authentication attack)
|
||||
[14]: https://github.com/Esser420/EvilTwinFramework
|
||||
@ -1,251 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (MjSeven)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (How to Update/Change Users Password in Linux Using Different Ways)
|
||||
[#]: via: (https://www.2daygeek.com/linux-passwd-chpasswd-command-set-update-change-users-password-in-linux-using-shell-script/)
|
||||
[#]: author: (Vinoth Kumar https://www.2daygeek.com/author/vinoth/)
|
||||
|
||||
How to Update/Change Users Password in Linux Using Different Ways
|
||||
======
|
||||
|
||||
It’s a basic thing to set a user password whenever you create an user account in Linux.
|
||||
|
||||
Everybody uses passwd command followed by the user name `passwd USERNAME` to set a password for a user.
|
||||
|
||||
Make sure you have to set a hard and guess password that will help you to make the system more secure.
|
||||
|
||||
I mean to say, it should be the combination of Alphabets, Symbols and numbers.
|
||||
|
||||
Also, i advise you to change the password at least once in a month for security reason.
|
||||
|
||||
When you use the passwd command it will ask you to enter the password twice to set it. It’s a native method to set a user password.
|
||||
|
||||
If you don’t want to update the password twice and would like to do this in different way?
|
||||
|
||||
Yes, we can. There will be a possibility to do.
|
||||
|
||||
If you are working as a Linux admin you might have asked the below questions many times.
|
||||
|
||||
Some of you may or may not got answer for these questions.
|
||||
|
||||
Whatever it’s, don’t worry we are here to answer your all questions.
|
||||
|
||||
* How to Update/Change Users Password in Single Command?
|
||||
* How to Update/Change a Same Password for Multiple users in Linux?
|
||||
* How to Update/Change Multiple Users Password in Linux?
|
||||
* How to Update/Change Password for Multiple Users in Linux?
|
||||
* How to Update/Change Different Password for Multiple Users in Linux?
|
||||
* How to Update/Change Users Password in Multiple Linux Servers?
|
||||
* How to Update/Change Multiple Users Password in Multiple Linux Servers?
|
||||
|
||||
|
||||
|
||||
### Method-1: Using passwd Command
|
||||
|
||||
passwd command is a standard method to set or update or change password for users in Linux. The below way is a standard method to do it.
|
||||
|
||||
```
|
||||
# passwd renu
|
||||
Changing password for user renu.
|
||||
New password:
|
||||
BAD PASSWORD: The password contains the user name in some form
|
||||
Retype new password:
|
||||
passwd: all authentication tokens updated successfully.
|
||||
```
|
||||
|
||||
Run the following command if you would like to set or change password with single command. This allow users to update password in a single command.
|
||||
|
||||
```
|
||||
# echo "new_password" | passwd --stdin thanu
|
||||
Changing password for user thanu.
|
||||
passwd: all authentication tokens updated successfully.
|
||||
```
|
||||
|
||||
### Method-2: Using chpasswd Command
|
||||
|
||||
chpasswd is an another command will allow us to set or update or change password for users in Linux. Use the following format if you would like to use chpasswd command to change password for user in a single command.
|
||||
|
||||
```
|
||||
# echo "thanu:new_password" | chpasswd
|
||||
```
|
||||
|
||||
### Method-3: How to Set Different Password for Multiple Users
|
||||
|
||||
Use the below script if you would like to set or update or change a password for multiple users in Linux with different password.
|
||||
|
||||
To do so, first we need to get a users list by using the following command. The below command will list the users who’s having `/home` directory and redirect the output to `user-list.txt` file.
|
||||
|
||||
```
|
||||
# cat /etc/passwd | grep "/home" | cut -d":" -f1 > user-list.txt
|
||||
```
|
||||
|
||||
List out the users using cat command. Remove the user from the list if you don’t want to reset the password for the specific user.
|
||||
|
||||
```
|
||||
# cat user-list.txt
|
||||
centos
|
||||
magi
|
||||
daygeek
|
||||
thanu
|
||||
renu
|
||||
```
|
||||
|
||||
Create a following small shell script to achieve this.
|
||||
|
||||
```
|
||||
# vi password-update.sh
|
||||
|
||||
#!/bin/sh
|
||||
for user in `more user-list.txt`
|
||||
do
|
||||
echo "[email protected]" | passwd --stdin "$user"
|
||||
chage -d 0 $user
|
||||
done
|
||||
```
|
||||
|
||||
Set an executable permission to `password-update.sh` file.
|
||||
|
||||
```
|
||||
# chmod +x password-update.sh
|
||||
```
|
||||
|
||||
Finally run the script to achieve this.
|
||||
|
||||
```
|
||||
# ./password-up.sh
|
||||
|
||||
magi
|
||||
Changing password for user magi.
|
||||
passwd: all authentication tokens updated successfully.
|
||||
daygeek
|
||||
Changing password for user daygeek.
|
||||
passwd: all authentication tokens updated successfully.
|
||||
thanu
|
||||
Changing password for user thanu.
|
||||
passwd: all authentication tokens updated successfully.
|
||||
renu
|
||||
Changing password for user renu.
|
||||
passwd: all authentication tokens updated successfully.
|
||||
```
|
||||
|
||||
### Method-4: How to Set a Same Password for Multiple Users
|
||||
|
||||
Use the below script if you would like to set or update or change a same password for multiple users in Linux.
|
||||
|
||||
```
|
||||
# vi password-update.sh
|
||||
|
||||
#!/bin/sh
|
||||
for user in `more user-list.txt`
|
||||
do
|
||||
echo "new_password" | passwd --stdin "$user"
|
||||
chage -d 0 $user
|
||||
done
|
||||
```
|
||||
|
||||
### Method-5: How to Change User password in Multiple Servers
|
||||
|
||||
Use the following script if you want to change a user password in multiple servers. In my case, we are going to change a password for `renu` user. Make sure you have to give the user name which you want to update the password instead of us.
|
||||
|
||||
Make sure you have to update the servers list into `server-list.txt` file. Each server should be in separate line.
|
||||
|
||||
```
|
||||
# vi password-update.sh
|
||||
|
||||
#!/bin/bash
|
||||
for server in `cat server-list.txt`
|
||||
do
|
||||
ssh [email protected]$server 'passwd --stdin renu <<EOF
|
||||
new_passwd
|
||||
new_passwd
|
||||
EOF';
|
||||
done
|
||||
```
|
||||
|
||||
You will be getting the output similar to us.
|
||||
|
||||
```
|
||||
# ./password-update.sh
|
||||
|
||||
New password: BAD PASSWORD: it is based on a dictionary word
|
||||
BAD PASSWORD: is too simple
|
||||
Retype new password: Changing password for user renu.
|
||||
passwd: all authentication tokens updated successfully.
|
||||
New password: BAD PASSWORD: it is based on a dictionary word
|
||||
BAD PASSWORD: is too simple
|
||||
Retype new password: Changing password for user renu.
|
||||
passwd: all authentication tokens updated successfully.
|
||||
```
|
||||
|
||||
### Method-6: How to Change User password in Multiple Servers Using pssh Command
|
||||
|
||||
pssh is a program for executing ssh in parallel on a number of hosts. It provides features such as sending input to all of the processes, passing a password to ssh, saving output to files, and timing out. Navigate to the following link to know more about **[PSSH Command][1]**.
|
||||
|
||||
```
|
||||
# pssh -i -h /tmp/server-list.txt "printf '%s\n' new_pass new_pass | passwd --stdin root"
|
||||
```
|
||||
|
||||
You will be getting the output similar to us.
|
||||
|
||||
```
|
||||
[1] 07:58:07 [SUCCESS] CentOS.2daygeek.com
|
||||
Changing password for user root.
|
||||
passwd: all authentication tokens updated successfully.
|
||||
Stderr: New password: BAD PASSWORD: it is based on a dictionary word
|
||||
BAD PASSWORD: is too simple
|
||||
Retype new password:
|
||||
[2] 07:58:07 [SUCCESS] ArchLinux.2daygeek.com
|
||||
Changing password for user root.
|
||||
passwd: all authentication tokens updated successfully.
|
||||
Stderr: New password: BAD PASSWORD: it is based on a dictionary word
|
||||
BAD PASSWORD: is too simple
|
||||
```
|
||||
|
||||
### Method-7: How to Change User password in Multiple Servers Using chpasswd Command
|
||||
|
||||
Alternatively we can use the chpasswd command to update the password for user in multiple servers.
|
||||
|
||||
```
|
||||
# ./password-update.sh
|
||||
|
||||
#!/bin/bash
|
||||
for server in `cat server-list.txt`
|
||||
do
|
||||
ssh [email protected]$server 'echo "magi:new_password" | chpasswd'
|
||||
done
|
||||
```
|
||||
|
||||
### Method-8: How to Change Multiple Users password in Linux Servers Using chpasswd Command
|
||||
|
||||
To do so, first create a file and update username and password in the below format. In my case i have created a file called `user-list.txt`.
|
||||
|
||||
See the details below.
|
||||
|
||||
Create a following small shell script to achieve this.
|
||||
|
||||
```
|
||||
# vi password-update.sh
|
||||
|
||||
#!/bin/bash
|
||||
for users in `cat user-list.txt`
|
||||
do
|
||||
echo $users | chpasswd
|
||||
done
|
||||
```
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.2daygeek.com/linux-passwd-chpasswd-command-set-update-change-users-password-in-linux-using-shell-script/
|
||||
|
||||
作者:[Vinoth Kumar][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.2daygeek.com/author/vinoth/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.2daygeek.com/pssh-parallel-ssh-run-execute-commands-on-multiple-linux-servers/
|
||||
@ -1,92 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( dianbanjiu )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Using more to view text files at the Linux command line)
|
||||
[#]: via: (https://opensource.com/article/19/1/more-text-files-linux)
|
||||
[#]: author: (Scott Nesbitt https://opensource.com/users/scottnesbitt)
|
||||
|
||||
Using more to view text files at the Linux command line
|
||||
======
|
||||
Text files and Linux go hand in hand. Or so it seems. But how you view those text files depends on what tools you're comfortable with.
|
||||
|
||||

|
||||
|
||||
There are a number of utilities that enable you to view text files when you're at the command line. One of them is [**more**][1].
|
||||
|
||||
**more** is similar to another tool I wrote about called **[less][2]**. The main difference is that **more** only allows you to move forward in a file.
|
||||
|
||||
While that may seem limiting, it has some useful features that are good to know about. Let's take a quick look at what **more** can do and how to use it.
|
||||
|
||||
### The basics
|
||||
|
||||
Let's say you have a text file and want to read it at the command line. Just open the terminal, pop into the directory that contains the file, and type this command:
|
||||
|
||||
```
|
||||
more <filename>
|
||||
```
|
||||
|
||||
For example, **more jekyll-article.md**.
|
||||
|
||||
|
||||
|
||||
Press the Spacebar on your keyboard to move through the file or press **q** to quit.
|
||||
|
||||
If you want to search for some text in the file, press the **/** key followed by the word or term you want to find. For example, to find the phrase terminal, type:
|
||||
|
||||
```
|
||||
/terminal
|
||||
```
|
||||
|
||||
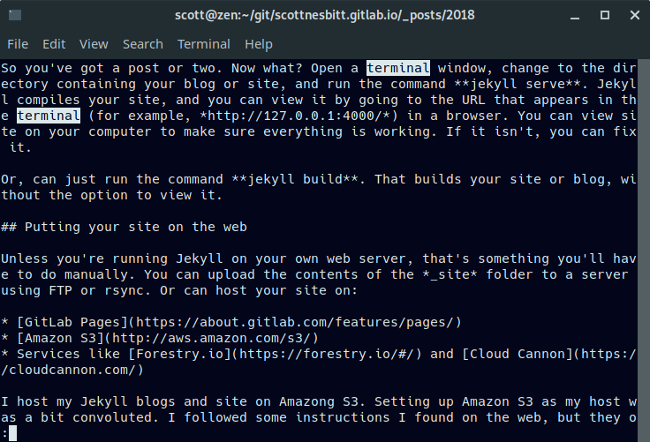
|
||||
|
||||
Search is case-sensitive. Typing Terminal isn't the same as typing terminal.
|
||||
|
||||
### Using more with other utilities
|
||||
|
||||
You can pipe text from other command line utilities into **more**. Why do that? Because sometimes the text that those tools spew out spans more than one page.
|
||||
|
||||
To do that, type the command and any options, followed by the pipe symbol ( **|** ), followed by **more**. For example, let's say you have a directory that has a large number of files in it. You can use **more** with the **ls** command to get a full view of the contents of the directory:
|
||||
|
||||
```
|
||||
ls | more
|
||||
```
|
||||
|
||||
|
||||
|
||||
You can also use **more** with the **grep** command to find text in multiple files. In this example, I use **grep** to find the text productivity in multiple source files for my articles:
|
||||
|
||||
```
|
||||
**grep ‘productivity’ core.md Dict.md lctt2014.md lctt2016.md lctt2018.md README.md | more**
|
||||
```
|
||||
|
||||
|
||||
|
||||
Another utility you can combine with **more** is **ps** (which lists processes that are running on your system). Again, this comes in handy when there are a large number of processes running on your system and you need a view of all of them—for example, to find one that you need to kill. To do that, use this command:
|
||||
|
||||
```
|
||||
ps -u scott | more
|
||||
```
|
||||
|
||||
Note that you'd replace scott with your username.
|
||||
|
||||
|
||||
|
||||
As I mentioned at the beginning of this article, **more** is easy to use. It's definitely not as flexible as its cousin **less** , but it can be useful to know.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/1/more-text-files-linux
|
||||
|
||||
作者:[Scott Nesbitt][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/scottnesbitt
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://en.wikipedia.org/wiki/More_(command)
|
||||
[2]: https://opensource.com/article/18/4/using-less-view-text-files-command-line
|
||||
@ -1,5 +1,5 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: translator: (zhs852)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
|
||||
@ -0,0 +1,60 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Get started with Budgie Desktop, a Linux environment)
|
||||
[#]: via: (https://opensource.com/article/19/1/productivity-tool-budgie-desktop)
|
||||
[#]: author: (Kevin Sonney https://opensource.com/users/ksonney (Kevin Sonney))
|
||||
|
||||
Get started with Budgie Desktop, a Linux environment
|
||||
======
|
||||
Configure your desktop as you want with Budgie, the 18th in our series on open source tools that will make you more productive in 2019.
|
||||
|
||||

|
||||
|
||||
There seems to be a mad rush at the beginning of every year to find ways to be more productive. New Year's resolutions, the itch to start the year off right, and of course, an "out with the old, in with the new" attitude all contribute to this. And the usual round of recommendations is heavily biased towards closed source and proprietary software. It doesn't have to be that way.
|
||||
|
||||
Here's the 18th of my picks for 19 new (or new-to-you) open source tools to help you be more productive in 2019.
|
||||
|
||||
### Budgie Desktop
|
||||
|
||||
There are many, many desktop environments for Linux. From the easy to use and graphically stunning [GNOME desktop][1] (default on most major Linux distributions) and [KDE][2], to the minimalist [Openbox][3], to the highly configurable tiling [i3][4], there are a lot of options. What I look for in a good desktop environment is speed, unobtrusiveness, and a clean user experience. It is hard to be productive when a desktop works against you, not with or for you.
|
||||
|
||||
|
||||
|
||||
[Budgie Desktop][5] is the default desktop on the [Solus][6] Linux distribution and is available as an add-on package for most of the major Linux distributions. It is based on GNOME and uses many of the same tools and libraries you likely already have on your computer.
|
||||
|
||||
The default desktop is exceptionally minimalistic, with just the panel and a blank desktop. Budgie includes an integrated sidebar (called Raven) that gives quick access to the calendar, audio controls, and settings menu. Raven also contains an integrated notification area with a unified display of system messages similar to MacOS's.
|
||||
|
||||
|
||||
|
||||
Clicking on the gear icon in Raven brings up Budgie's control panel with its configuration settings. Since Budgie is still in development, it is a little bare-bones compared to GNOME or KDE, and I hope it gets more options over time. The Top Panel option, which allows the user to configure the ordering, positioning, and contents of the top panel, is nice.
|
||||
|
||||
|
||||
|
||||
The Budgie Welcome application (presented at first login) contains options to install additional software, panel applets, snaps, and Flatpack packages. There are applets to handle networking, screenshots, additional clocks and timers, and much, much more.
|
||||
|
||||
|
||||
|
||||
Budgie provides a desktop that is clean and stable. It responds quickly and has many options that allow you to customize it as you see fit.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/1/productivity-tool-budgie-desktop
|
||||
|
||||
作者:[Kevin Sonney][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/ksonney (Kevin Sonney)
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.gnome.org/
|
||||
[2]: https://www.kde.org/
|
||||
[3]: http://openbox.org/wiki/Main_Page
|
||||
[4]: https://i3wm.org/
|
||||
[5]: https://getsol.us/solus/experiences/
|
||||
[6]: https://getsol.us/home/
|
||||
@ -0,0 +1,251 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (MjSeven)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (How to Update/Change Users Password in Linux Using Different Ways)
|
||||
[#]: via: (https://www.2daygeek.com/linux-passwd-chpasswd-command-set-update-change-users-password-in-linux-using-shell-script/)
|
||||
[#]: author: (Vinoth Kumar https://www.2daygeek.com/author/vinoth/)
|
||||
|
||||
如何使用不同的方式更新或更改 Linux 用户密码
|
||||
======
|
||||
|
||||
在 Linux 中创建用户账号时,设置用户密码是一件基本的事情。
|
||||
|
||||
每个人都使用 passwd 命令和用户名,比如 `passwd USERNAME` 来为用户设置密码。
|
||||
|
||||
确保你一定设置一个难以猜测的密码,这可以帮助你使系统更安全。
|
||||
|
||||
我的意思是,密码应该是字母,符合和数字的组合。
|
||||
|
||||
此外,出于安全原因,我建议你至少每月更改一次密码。
|
||||
|
||||
当你使用 passwd 命令时,它会要求你输入两次密码来设置。这是一种设置用户密码的原生方法。
|
||||
|
||||
如果你不想两次更新密码,并希望以不同的方式进行更新,怎么办呢?
|
||||
|
||||
当然,这可以的,有可能做到。
|
||||
|
||||
如果你是 Linux 管理员,你可能已经多次问过下面的问题。
|
||||
|
||||
你们可能,也可能没有得到这些问题的答案。
|
||||
|
||||
无论如何,不要担心,我们会回答你所有的问题。
|
||||
|
||||
* 如何用一条命令更新或更改用户密码?
|
||||
* 如何在 Linux 中为多个用户更新或更改相同的密码?
|
||||
* 如何在 Linux 中更新或更改多个用户的密码?
|
||||
* 如何在 Linux 中更新或更改多个用户的密码?(to 校正:这句和上一句有不同?)
|
||||
* 如何在 Linux 中更新或更改多个用户的不同密码?
|
||||
* 如何在多个 Linux 服务器中更新或更改用户的密码?
|
||||
* 如何在多个 Linux 服务器中更新或更改多个用户的密码?
|
||||
|
||||
|
||||
|
||||
### 方法-1: 使用 passwd 命令
|
||||
|
||||
passwd 命令是在 Linux 中为用户设置,更新或更改密码的标准方法。以下是标准方法。
|
||||
|
||||
```
|
||||
# passwd renu
|
||||
Changing password for user renu.
|
||||
New password:
|
||||
BAD PASSWORD: The password contains the user name in some form
|
||||
Retype new password:
|
||||
passwd: all authentication tokens updated successfully.
|
||||
```
|
||||
|
||||
如果希望在一条命令中设置或更改密码,运行以下命令。它允许用户在一条命令中更新密码。
|
||||
|
||||
```
|
||||
# echo "new_password" | passwd --stdin thanu
|
||||
Changing password for user thanu.
|
||||
passwd: all authentication tokens updated successfully.
|
||||
```
|
||||
|
||||
### 方法-2: 使用 chpasswd 命令
|
||||
|
||||
chpasswd 是另一个命令,允许我们为 Linux 中的用户设置,更新或更改密码。如果希望在一条命令中使用 chpasswd 命令更改用户密码,用以下格式。
|
||||
|
||||
```
|
||||
# echo "thanu:new_password" | chpasswd
|
||||
```
|
||||
|
||||
### 方法-3: 如何为多个用户设置不同的密码
|
||||
|
||||
如果你要为 Linux 中的多个用户设置,更新或更改密码,并且使用不同的密码,使用以下脚本。
|
||||
|
||||
为此,首先我们需要使用以下命令获取用户列表。下面的命令将列出拥有 `/home` 目录的用户,并将输出重定向到 `user-list.txt` 文件。
|
||||
|
||||
```
|
||||
# cat /etc/passwd | grep "/home" | cut -d":" -f1 > user-list.txt
|
||||
```
|
||||
|
||||
使用 cat 命令列出用户。如果你不想重置特定用户的密码,那么从列表中移除该用户。
|
||||
|
||||
```
|
||||
# cat user-list.txt
|
||||
centos
|
||||
magi
|
||||
daygeek
|
||||
thanu
|
||||
renu
|
||||
```
|
||||
|
||||
创建以下小 shell 脚本来实现此目的。
|
||||
|
||||
```
|
||||
# vi password-update.sh
|
||||
|
||||
#!/bin/sh
|
||||
for user in `more user-list.txt`
|
||||
do
|
||||
echo "[email protected]" | passwd --stdin "$user"
|
||||
chage -d 0 $user
|
||||
done
|
||||
```
|
||||
|
||||
给 `password-update.sh` 文件设置可执行权限。
|
||||
|
||||
```
|
||||
# chmod +x password-update.sh
|
||||
```
|
||||
|
||||
最后运行脚本来实现这一目标。
|
||||
|
||||
```
|
||||
# ./password-up.sh
|
||||
|
||||
magi
|
||||
Changing password for user magi.
|
||||
passwd: all authentication tokens updated successfully.
|
||||
daygeek
|
||||
Changing password for user daygeek.
|
||||
passwd: all authentication tokens updated successfully.
|
||||
thanu
|
||||
Changing password for user thanu.
|
||||
passwd: all authentication tokens updated successfully.
|
||||
renu
|
||||
Changing password for user renu.
|
||||
passwd: all authentication tokens updated successfully.
|
||||
```
|
||||
|
||||
### 方法-4: 如何为多个用户设置相同的密码
|
||||
|
||||
如果要在 Linux 中为多个用户设置,更新或更改相同的密码,使用以下脚本。
|
||||
|
||||
```
|
||||
# vi password-update.sh
|
||||
|
||||
#!/bin/sh
|
||||
for user in `more user-list.txt`
|
||||
do
|
||||
echo "new_password" | passwd --stdin "$user"
|
||||
chage -d 0 $user
|
||||
done
|
||||
```
|
||||
|
||||
### 方法-5: 如何在多个服务器中更改用户密码
|
||||
|
||||
如果希望更改多个服务器中的用户密码,使用以下脚本。在本例中,我们将更改 `renu` 用户的密码,确保你必须提供你希望更新密码的用户名而不是我们的用户名。
|
||||
|
||||
确保你必须将服务器列表保存在 `server-list.txt` 文件中,每个服务器应该在单独一行中。
|
||||
|
||||
```
|
||||
# vi password-update.sh
|
||||
|
||||
#!/bin/bash
|
||||
for server in `cat server-list.txt`
|
||||
do
|
||||
ssh [email protected]$server 'passwd --stdin renu <<EOF
|
||||
new_passwd
|
||||
new_passwd
|
||||
EOF';
|
||||
done
|
||||
```
|
||||
|
||||
你将得到与我们类似的输出。
|
||||
|
||||
```
|
||||
# ./password-update.sh
|
||||
|
||||
New password: BAD PASSWORD: it is based on a dictionary word
|
||||
BAD PASSWORD: is too simple
|
||||
Retype new password: Changing password for user renu.
|
||||
passwd: all authentication tokens updated successfully.
|
||||
New password: BAD PASSWORD: it is based on a dictionary word
|
||||
BAD PASSWORD: is too simple
|
||||
Retype new password: Changing password for user renu.
|
||||
passwd: all authentication tokens updated successfully.
|
||||
```
|
||||
|
||||
### 方法-6: 如何使用 pssh 命令更改多个服务器中的用户密码
|
||||
|
||||
pssh 是一个在多个主机上并行执行 ssh 的程序。它提供了一些特性,例如向所有进程发送输入,向 sshh 传递密码,将输出保存到文件以及超时处理。导航到以下链接以了解关于 **[PSSH 命令][1]**的更多信息。
|
||||
|
||||
```
|
||||
# pssh -i -h /tmp/server-list.txt "printf '%s\n' new_pass new_pass | passwd --stdin root"
|
||||
```
|
||||
|
||||
你将获得与我们类似的输出。
|
||||
|
||||
```
|
||||
[1] 07:58:07 [SUCCESS] CentOS.2daygeek.com
|
||||
Changing password for user root.
|
||||
passwd: all authentication tokens updated successfully.
|
||||
Stderr: New password: BAD PASSWORD: it is based on a dictionary word
|
||||
BAD PASSWORD: is too simple
|
||||
Retype new password:
|
||||
[2] 07:58:07 [SUCCESS] ArchLinux.2daygeek.com
|
||||
Changing password for user root.
|
||||
passwd: all authentication tokens updated successfully.
|
||||
Stderr: New password: BAD PASSWORD: it is based on a dictionary word
|
||||
BAD PASSWORD: is too simple
|
||||
```
|
||||
|
||||
### 方法-7: 如何使用 chpasswd 命令更改多个服务器中的用户密码
|
||||
|
||||
或者,我们可以使用 chpasswd 命令更新多个服务器中的用户密码。
|
||||
|
||||
```
|
||||
# ./password-update.sh
|
||||
|
||||
#!/bin/bash
|
||||
for server in `cat server-list.txt`
|
||||
do
|
||||
ssh [email protected]$server 'echo "magi:new_password" | chpasswd'
|
||||
done
|
||||
```
|
||||
|
||||
### 方法-8: 如何使用 chpasswd 命令在 Linux 服务器中更改多个用户的密码
|
||||
|
||||
为此,首先创建一个文件,以下面的格式更新用户名和密码。在本例中,我创建了一个名为 `user-list.txt` 的文件。
|
||||
|
||||
参考下面的详细信息。
|
||||
|
||||
创建下面的小 shell 脚本来实现这一点。
|
||||
|
||||
```
|
||||
# vi password-update.sh
|
||||
|
||||
#!/bin/bash
|
||||
for users in `cat user-list.txt`
|
||||
do
|
||||
echo $users | chpasswd
|
||||
done
|
||||
```
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.2daygeek.com/linux-passwd-chpasswd-command-set-update-change-users-password-in-linux-using-shell-script/
|
||||
|
||||
作者:[Vinoth Kumar][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[MjSeven](https://github.com/MjSeven)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.2daygeek.com/author/vinoth/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.2daygeek.com/pssh-parallel-ssh-run-execute-commands-on-multiple-linux-servers/
|
||||
@ -0,0 +1,95 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( dianbanjiu )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Using more to view text files at the Linux command line)
|
||||
[#]: via: (https://opensource.com/article/19/1/more-text-files-linux)
|
||||
[#]: author: (Scott Nesbitt https://opensource.com/users/scottnesbitt)
|
||||
|
||||
在 Linux 命令行使用 more 查看文本文件
|
||||
======
|
||||
文本文件和 Linux 一直是携手并进的。或者说看起来如此。那你又是依靠哪些让你使用起来很舒服的工具来查看这些文本文件的呢?
|
||||
|
||||

|
||||
|
||||
Linux 下有很多实用工具可以让你在终端界面查看文本文件。其中一个就是 [**more**][1]。
|
||||
|
||||
**more** 跟我之前另一篇文章里写到的工具 —— **[less][2]** 很相似。它们之间的主要不同点在于 **more** 只允许你向前查看文件。
|
||||
|
||||
尽管它能提供的功能看起来很有限,不过它依旧有很多有用的特性值得你去了解。下面让我们来快速浏览一下 **more** 可以做什么,以及如何使用它吧。
|
||||
|
||||
### 基础使用
|
||||
|
||||
假设你现在想在终端查看一个文本文件。只需打开一个终端,进入对应的目录,然后输入以下命令:
|
||||
|
||||
```shell
|
||||
$ more <filename>
|
||||
```
|
||||
|
||||
例如,
|
||||
|
||||
```shell
|
||||
$ more jekyll-article.md
|
||||
```
|
||||
|
||||

|
||||
|
||||
使用空格键可以向下翻页,输入 **q** 可以退出。
|
||||
|
||||
如果你想在这个文件中搜索一些文本,输入 **/** 字符并在其后加上你想要查找的文字。例如你要查看的字段是 terminal,只需输入:
|
||||
|
||||
```
|
||||
/terminal
|
||||
```
|
||||
|
||||

|
||||
|
||||
搜索的内容是区分大小写的,所以输入 /terminal 跟 /Terminal 会出现不同的结果。
|
||||
|
||||
### 和其他实用工具组合使用
|
||||
你可以通过管道将其他命令行工具得到的文本传输到 **more**。你问为什么这样做?因为有时这些工具获取的文本会超过终端一页可以显示的限度。
|
||||
|
||||
想要做到这个,先输入你想要使用的完整命令,后面跟上管道符(**|**),管道符后跟 **more**。假设现在有一个有很多文件的目录。你就可以组合 **more** 跟 **ls** 命令完整查看这个目录当中的内容。
|
||||
|
||||
```shell
|
||||
$ ls | more
|
||||
```
|
||||
|
||||

|
||||
|
||||
你可以组合 **more** 和 **grep** 命令,从而实现在多个文件中找到指定的文本。下面是我在多篇文章的源文件中查找 productivity 的例子。
|
||||
|
||||
```shell
|
||||
$ grep ‘productivity’ core.md Dict.md lctt2014.md lctt2016.md lctt2018.md README.md | more
|
||||
```
|
||||
|
||||

|
||||
|
||||
另外一个可以和 **more** 组合的实用工具是 **ps**(列出你系统上正在运行的进程)。当你的系统上运行了很多的进程,你现在想要查看他们的时候,这个组合将会派上用场。例如你想找到一个你需要杀死的进程,只需输入下面的命令:
|
||||
|
||||
```shell
|
||||
$ ps -u scott | more
|
||||
```
|
||||
|
||||
注意用你的用户名替换掉 scott。
|
||||
|
||||

|
||||
|
||||
就像我文章开篇提到的, **more** 很容易使用。尽管不如它的双胞胎兄弟 **less** 那般灵活,但是仍然值得了解一下。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/1/more-text-files-linux
|
||||
|
||||
作者:[Scott Nesbitt][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[dianbanjiu](https://github.com/dianbanjiu)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/scottnesbitt
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://en.wikipedia.org/wiki/More_(command)
|
||||
[2]: https://opensource.com/article/18/4/using-less-view-text-files-command-line
|
||||
Loading…
Reference in New Issue
Block a user