mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-02-25 00:50:15 +08:00
translated
This commit is contained in:
parent
25ebe976c3
commit
6a0c533dfa
@ -1,32 +1,30 @@
|
||||
translating---geekpi
|
||||
|
||||
OpenVAS - Vulnerability Assessment install on Kali Linux
|
||||
OpenVAS - Kali Linux 中的漏洞评估工具
|
||||
============================================================
|
||||
|
||||
### On this page
|
||||
### 在本页中
|
||||
|
||||
1. [What is Kali Linux?][1]
|
||||
2. [Updating Kali Linux][2]
|
||||
3. [Installing OpenVAS 8][3]
|
||||
4. [Start OpenVAS on Kali][4]
|
||||
1. [什么是 Kali Linux?][1]
|
||||
2. [升级 Kali Linux][2]
|
||||
3. [安装 OpenVAS 8][3]
|
||||
4. [在 Kail 中启动 OpenVAS][4]
|
||||
|
||||
This tutorial documents the process of installing OpenVAS 8.0 on Kali Linux rolling. OpenVAS is open source [vulnerability assessment][6] application that automates the process of performing network security audits and vulnerability assessments. Note, a vulnerability assessment also known as VA is not a penetration test, a penetration test goes a step further and validates the existence of a discovered vulnerability, see [what is penetration testing][7] for an overview of what pen testing consists of and the different types of security testing.
|
||||
本教程将介绍在 Kali Linux 中安装 OpenVAS 8.0 的过程。 OpenVAS 是自动执行网络安全审核和漏洞评估的开源[漏洞评估][6]程序。请注意,漏洞评估也称为 VA 并不是渗透测试,渗透测试会进一步验证是否存在发现的漏洞,请参阅[什么是渗透测试][7]来对渗透测试的构成以及不同类型的安全测试有一个了解。
|
||||
|
||||
### What is Kali Linux?
|
||||
### 什么是 Kali Linux?
|
||||
|
||||
Kali Linux is a Linux penetration testing distribution. It's Debian based and comes pre-installed with many commonly used penetration testing tools such as Metasploit Framework and other command line tools typically used by penetration testers during a security assessment.
|
||||
Kali Linux 是 Linux 渗透测试分发版。它基于 Debian,并且预安装了许多常用的渗透测试工具,例如 Metasploit Framework 和其他通常在安全评估期间由渗透测试人员使用的命令行工具。
|
||||
|
||||
For most use cases Kali runs in a VM, you can grab the latest VMWare or Vbox image of Kali from here: [https://www.offensive-security.com/kali-linux-vmware-virtualbox-image-download/][8]
|
||||
在大多数使用情况下,Kali 运行在虚拟机中,你可以在这里获取最新的 VMWare 或 Vbox 镜像:[https://www.offensive-security.com/kali-linux-vmware-virtualbox-image-download/][8]
|
||||
|
||||
Download the full version not Kali light, unless you have a specific reason for wanting a smaller virtual machine footprint. After the download finishes you will need to extract the contents and open the vbox or VMWare .vmx file, when the machine boots the default credentials are root / toor. Change the root password to a secure password.
|
||||
除非你有特殊的原因想要一个更小的虚拟机占用空间,否则请下载完整版本而不是 Kali light。 下载完成后,你需要解压文件并打开 vbox 或者 VMWare .vmx 文件,虚拟机启动后,默认帐号是 root/toor。请将 root 密码更改为安全密码。
|
||||
|
||||
Alternatively, you can download the ISO version and perform an installation of Kali on the bare metal.
|
||||
或者,你可以下载 ISO 版本,并在裸机上执行 Kali 的安装。
|
||||
|
||||
### Updating Kali Linux
|
||||
### 升级 Kali Linux
|
||||
|
||||
After installation, perform a full update of Kali Linux.
|
||||
完成安装后,为 Kail Linux 执行一次完整的升级。
|
||||
|
||||
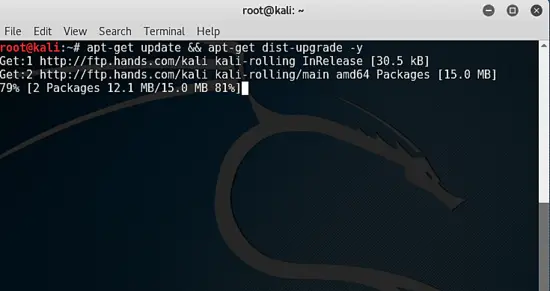
Updating Kali:
|
||||
升级 Kali:
|
||||
|
||||
apt-get update && apt-get dist-upgrade -y
|
||||
|
||||
@ -34,11 +32,11 @@ apt-get update && apt-get dist-upgrade -y
|
||||
|
||||
][9]
|
||||
|
||||
The update process might take some time to complete. Kali is now a rolling release meaning you can update to the current version from any version of Kali rolling. However, there are release numbers but these are point in time versions of Kali rolling for VMWare snapshots. You can update to the current stable release from any of the VMWare images.
|
||||
更新过程可能需要一些时间才能完成。Kali 目前是滚动更新,这意味着你可以从任何版本的 Kali 滚动更新到当前版本。然而它仍有发布号,但这些是针对特定 Kali 时间点的 VMWare 快照版本。你可以从任何 VMWare 镜像更新到当前的稳定版本。
|
||||
|
||||
After updating perform a reboot.
|
||||
更新完成后重新启动。
|
||||
|
||||
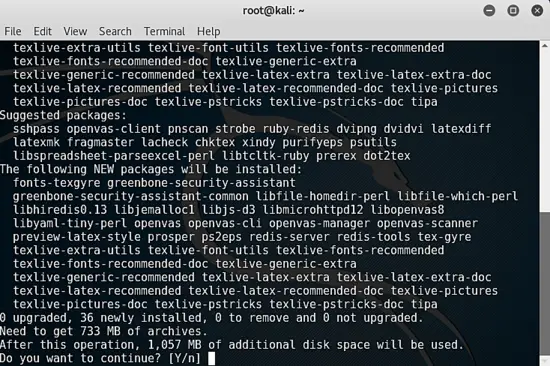
### Installing OpenVAS 8
|
||||
### 安装 OpenVAS 8
|
||||
|
||||
[
|
||||
|
||||
@ -48,25 +46,25 @@ apt-get install openvas
|
||||
|
||||
openvas-setup
|
||||
|
||||
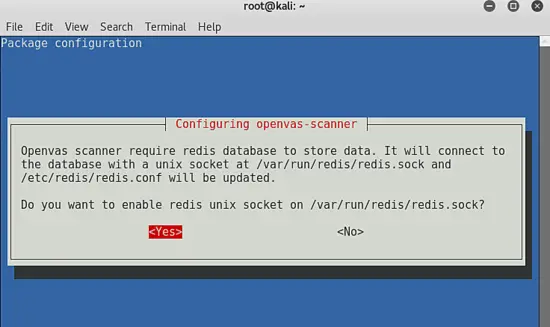
During installation you'll be prompted about redis, select the default option to run as a UNIX socket.
|
||||
在安装中,你会被询问关于 redis,选择默认选项来作为 UNIX 套接字运行。
|
||||
|
||||
[
|
||||
|
||||
][11]
|
||||
|
||||
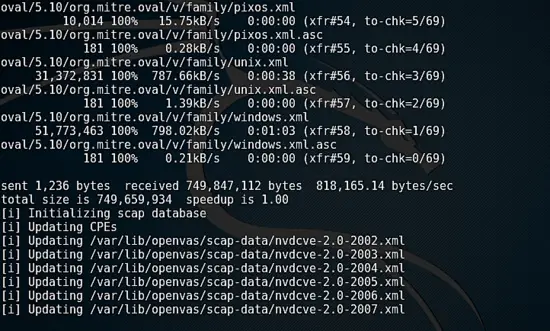
Even on a fast connection openvas-setup takes a long time to download and update all the required CVE, SCAP definitions.
|
||||
即使是有快速的网络连接,openvas-setup 仍需要很长时间来下载和更新所有所需的 CVE、SCAP 定义。
|
||||
|
||||
[
|
||||
|
||||
][12]
|
||||
|
||||
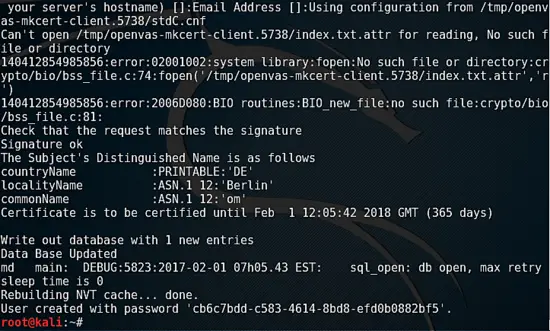
Pay attention to the command output during openvas-setup, the password is generated during installation and printed to console near the end of the setup.
|
||||
请注意 openvas-setup 的命令输出,密码会在安装中生成,并在安装的最后在控制台中打印出来。
|
||||
|
||||
[
|
||||
|
||||
][13]
|
||||
|
||||
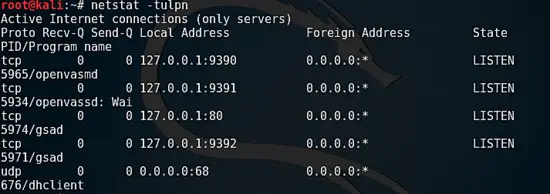
Verify openvas is running:
|
||||
验证 openvas 正在运行:
|
||||
|
||||
netstat -tulpn
|
||||
|
||||
@ -74,46 +72,46 @@ netstat -tulpn
|
||||
|
||||
][14]
|
||||
|
||||
### Start OpenVAS on Kali
|
||||
### 在 Kali 中运行 OpenVAS
|
||||
|
||||
To start the OpenVAS service on Kali run:
|
||||
要在 Kali 中启动 OpenVAS:
|
||||
|
||||
openvas-start
|
||||
|
||||
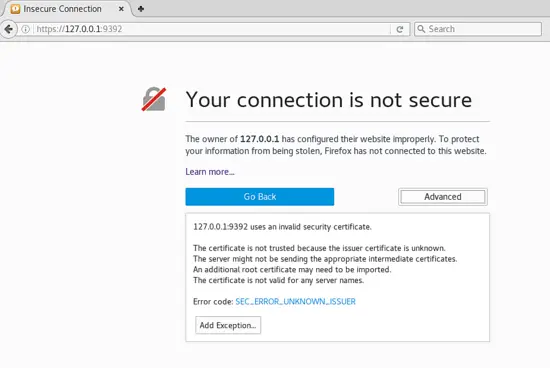
After installation, you should be able to access the OpenVAS web application at **https://127.0.0.1:9392**
|
||||
安装后,你应该可以通过 **https://127.0.0.1:9392** 访问 OpenVAS 的 web 程序了。
|
||||
|
||||
**[
|
||||
|
||||
][5]**
|
||||
|
||||
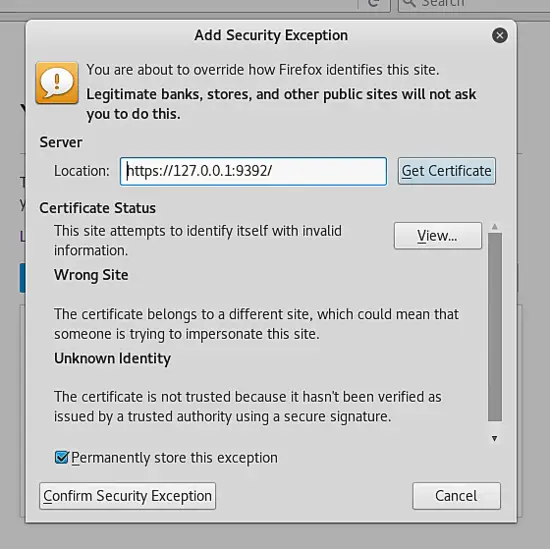
Accept the self-signed certificate and login to the application using the credentials admin and the password displayed during openvas-setup.
|
||||
接受自签名证书,并使用 openvas-setup 输出的 admin 凭证和密码登录程序。
|
||||
|
||||
[
|
||||
|
||||
][15]
|
||||
|
||||
After accepting the self-signed certificate, you should be presented with the login screen:
|
||||
接受自签名证书后,你应该可以看到登录界面了。
|
||||
|
||||
[
|
||||
|
||||
][16]
|
||||
|
||||
After logging in you should be presented with the following screen:
|
||||
登录后,你应该可以看到下面的页面:
|
||||
|
||||
[
|
||||
|
||||
][17]
|
||||
|
||||
From this point you should be able to configure your own vulnerability scans using the wizard.
|
||||
从此,你应该可以使用向导配置自己的漏洞扫描了。
|
||||
|
||||
It's recommended to read the documentation. Be aware of what a vulnerability assessment conductions (depending on configuration OpenVAS could attempt exploitation) and the traffic it will generate on a network as well as the DOS effect it can have on services / servers and hosts / devices on a network.
|
||||
我建议阅读文档。请注意漏洞评估导向(取决于 OpenVAS 可能尝试利用的配置)及其在网络上生成的流量以及网络上可能对服务/服务器和主机/设备产生的 DOS 影响。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.howtoforge.com/tutorial/openvas-vulnerability-assessment-install-on-kali-linux/
|
||||
|
||||
作者:[KJS ][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
Loading…
Reference in New Issue
Block a user