mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-03-30 02:40:11 +08:00
Merge remote-tracking branch 'LCTT/master'
This commit is contained in:
commit
682cdeb577
published
sources
talk
20190306 How to pack an IT travel kit.md20190307 Small Scale Scrum vs. Large Scale Scrum.md20190311 Discuss everything Fedora.md20190312 When the web grew up- A browser story.md
tech
20160301 How To Set Password Policies In Linux.md20190301 Blockchain 2.0- An Introduction -Part 1.md20190303 How to boot up a new Raspberry Pi.md20190305 How rootless Buildah works- Building containers in unprivileged environments.md20190306 3 popular programming languages you can learn with Raspberry Pi.md20190306 Blockchain 2.0- Revolutionizing The Financial System -Part 2.md20190306 Get cooking with GNOME Recipes on Fedora.md20190307 13 open source backup solutions.md20190307 How to Restart a Network in Ubuntu -Beginner-s Tip.md20190307 How to keep your Raspberry Pi updated.md20190308 How to use your Raspberry Pi for entertainment.md20190309 Emulators and Native Linux games on the Raspberry Pi.md20190310 Let-s get physical- How to use GPIO pins on the Raspberry Pi.md20190311 7 resources for learning to use your Raspberry Pi.md20190311 Blockchain 2.0- Redefining Financial Services -Part 3.md20190311 Building the virtualization stack of the future with rust-vmm.md20190311 Learn about computer security with the Raspberry Pi and Kali Linux.md20190718 3 Emacs modes for taking notes.md
@ -1,6 +1,6 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: ( )
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (How To Get Flatpak Apps And Games Built With OpenGL To Work With Proprietary Nvidia Graphics Drivers)
|
||||
@ -9,9 +9,12 @@
|
||||
|
||||
如何使得支持 OpenGL 的 Flatpak 应用和游戏在专有 Nvidia 图形驱动下工作
|
||||
======
|
||||
**一些支持 OpenGL 并打包为 Flatpak 的应用和游戏无法使用专有 Nvidia 驱动启动。本文将介绍如何在不安装开源驱动(Nouveau)的情况下启动这些 Flatpak 应用或游戏。**
|
||||
> 一些支持 OpenGL 并打包为 Flatpak 的应用和游戏无法使用专有 Nvidia 驱动启动。本文将介绍如何在不安装开源驱动(Nouveau)的情况下启动这些 Flatpak 应用或游戏。
|
||||
|
||||

|
||||
|
||||
这有个例子。我在我的 Ubuntu 18.04 桌面上使用专有的 Nvidia 驱动程序 (`nvidia-driver-390`),当我尝试启动以 Flatpak 形式安装的最新版本 [Krita 4.1][2] (构建了 OpenGL 支持)时,显示了如下错误:
|
||||
|
||||
这有个例子。我在我的 Ubuntu 18.04 桌面上使用专有的 Nvidia 驱动程序 (`nvidia-driver-390`),当我尝试启动最新版本时:
|
||||
```
|
||||
$ /usr/bin/flatpak run --branch=stable --arch=x86_64 --command=krita --file-forwarding org.kde.krita
|
||||
Gtk-Message: Failed to load module "canberra-gtk-module"
|
||||
@ -19,89 +22,85 @@ Gtk-Message: Failed to load module "canberra-gtk-module"
|
||||
libGL error: No matching fbConfigs or visuals found
|
||||
libGL error: failed to load driver: swrast
|
||||
Could not initialize GLX
|
||||
|
||||
```
|
||||
|
||||
要修复使用 OpenGL 和专有 Nvidia 图形驱动时无法启动的 Flatpak 游戏和应用,你需要为已安装的专有驱动安装运行时。以下是步骤。
|
||||
[Winepak][3] 游戏(以 Flatpak 方式打包的绑定了 Wine 的 Windows 游戏)似乎也受到了这个问题的影响,这个问题从 2016 年出现至今。
|
||||
|
||||
**1\. 如果尚未添加 FlatHub 仓库,请添加它。你可以在[此处][1]找到针对 Linux 发行版的说明。**
|
||||
要修复使用 OpenGL 和专有 Nvidia 图形驱动时无法启动的 Flatpak 游戏和应用的问题,你需要为已安装的专有驱动安装一个运行时环境。以下是步骤。
|
||||
|
||||
**2. 现在,你需要确定系统上安装的专有 Nvidia 驱动的确切版本。**
|
||||
1、如果尚未添加 FlatHub 仓库,请添加它。你可以在[此处][1]找到针对 Linux 发行版的说明。
|
||||
|
||||
_这一步取决于你使用的 Linux 发行版,我无法涵盖所有情况。下面的说明是面向 Ubuntu(以及 Ubuntu 风格的版本),但希望你可以自己弄清楚系统上安装的 Nvidia 驱动版本._
|
||||
2、现在,你需要确定系统上安装的专有 Nvidia 驱动的确切版本。
|
||||
|
||||
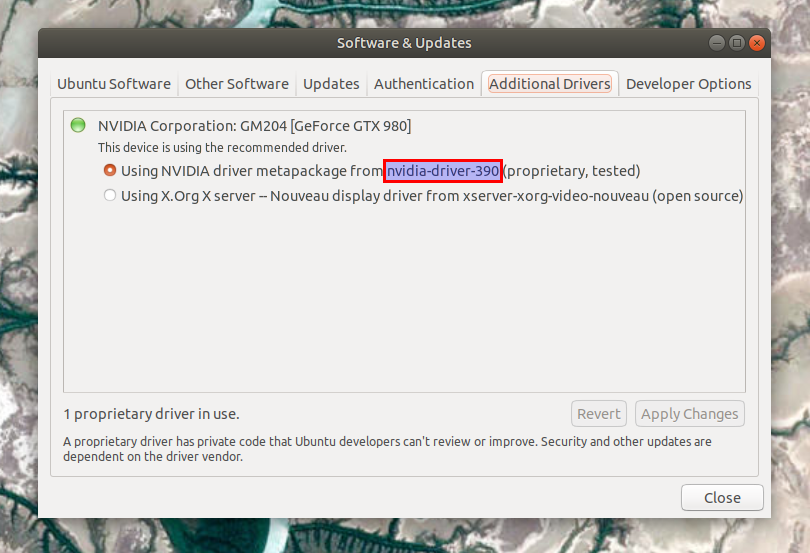
要在 Ubuntu 中执行此操作,请打开 `Software&Updates`,切换到 `Additional Drivers` 选项卡并记下 Nvidia 驱动包的名称。
|
||||
_这一步取决于你使用的 Linux 发行版,我无法涵盖所有情况。下面的说明是面向 Ubuntu(以及 Ubuntu 风格的版本),但希望你可以自己弄清楚系统上安装的 Nvidia 驱动版本。_
|
||||
|
||||
比如,你可以看到我的是 `nvidia-driver-390`:
|
||||
要在 Ubuntu 中执行此操作,请打开 “软件与更新”,切换到 “附加驱动” 选项卡并记下 Nvidia 驱动包的名称。
|
||||
|
||||
比如,你可以看到我的是 “nvidia-driver-390”:
|
||||
|
||||
|
||||
|
||||
这里还没完成。我们只是找到了 Nvidia 驱动的主要版本,但我们还需要知道次要版本。要获得我们下一步所需的确切 Nvidia 驱动版本,请运行此命令(应该适用于任何基于 Debian 的 Linux 发行版,如 Ubuntu、Linux Mint 等):
|
||||
|
||||
```
|
||||
apt-cache policy NVIDIA-PACKAGE-NAME
|
||||
|
||||
```
|
||||
|
||||
NVIDIA-PACKAGE-NAME 是 `Software & Updates` 中列出的 Nvidia 驱动包名称。例如,要查看 `nvidia-driver-390` 包的确切安装版本,请运行以下命令:
|
||||
这里的 “NVIDIA-PACKAGE-NAME” 是 “软件与更新” 中列出的 Nvidia 驱动包名称。例如,要查看 “nvidia-driver-390” 包的确切安装版本,请运行以下命令:
|
||||
|
||||
```
|
||||
$ apt-cache policy nvidia-driver-390
|
||||
nvidia-driver-390:
|
||||
Installed: 390.48-0ubuntu3
|
||||
Candidate: 390.48-0ubuntu3
|
||||
Version table:
|
||||
* 390.48-0ubuntu3 500
|
||||
500 http://ro.archive.ubuntu.com/ubuntu bionic/restricted amd64 Packages
|
||||
100 /var/lib/dpkg/status
|
||||
|
||||
Installed: 390.48-0ubuntu3
|
||||
Candidate: 390.48-0ubuntu3
|
||||
Version table:
|
||||
*** 390.48-0ubuntu3 500
|
||||
500 http://ro.archive.ubuntu.com/ubuntu bionic/restricted amd64 Packages
|
||||
100 /var/lib/dpkg/status
|
||||
```
|
||||
|
||||
在这个命令的输出中,查找 `Installed` 部分并记下版本号(不包括 `-0ubuntu3` 之类)。现在我们知道了已安装的 Nvidia 驱动的确切版本(我例子中的是 `390.48`)。记住它,因为下一步我们需要。
|
||||
在这个命令的输出中,查找 “Installed” 部分并记下版本号(不包括 “-0ubuntu3” 之类)。现在我们知道了已安装的 Nvidia 驱动的确切版本(我例子中的是 “390.48”)。记住它,因为下一步我们需要。
|
||||
|
||||
**3\. 最后,你可以从 FlatHub 为你已安装的专有 Nvidia 图形驱动安装运行时。**
|
||||
3、最后,你可以从 FlatHub 为你已安装的专有 Nvidia 图形驱动安装运行时环境。
|
||||
|
||||
要列出 FlatHub 上所有可用的 Nvidia 运行时包,你可以使用以下命令:
|
||||
|
||||
```
|
||||
flatpak remote-ls flathub | grep nvidia
|
||||
|
||||
```
|
||||
|
||||
幸运地是 FlatHub 上提供这个 Nvidia 驱动的运行时。你现在可以使用以下命令继续安装运行时:
|
||||
|
||||
* 针对 64 位系统:
|
||||
幸运地是 FlatHub 上提供这个 Nvidia 驱动的运行时环境。你现在可以使用以下命令继续安装运行时:
|
||||
|
||||
针对 64 位系统:
|
||||
|
||||
```
|
||||
flatpak install flathub org.freedesktop.Platform.GL.nvidia-MAJORVERSION-MINORVERSION
|
||||
|
||||
```
|
||||
|
||||
将 MAJORVERSION 替换为 Nvidia 驱动的主要版本(在上面的示例中为 390),将 MINORVERSION 替换为次要版本(步骤2,我例子中的为 48)。
|
||||
将 “MAJORVERSION” 替换为 Nvidia 驱动的主要版本(在上面的示例中为 390),将 “MINORVERSION” 替换为次要版本(步骤2,我例子中的为 48)。
|
||||
|
||||
例如,要为 Nvidia 图形驱动版本 390.48 安装运行时,你必须使用以下命令:
|
||||
|
||||
```
|
||||
flatpak install flathub org.freedesktop.Platform.GL.nvidia-390-48
|
||||
|
||||
```
|
||||
|
||||
* 对于 32 位系统(或能够在 64 位上运行 32 位的应用或游戏),使用以下命令安装 32 位运行时:
|
||||
|
||||
对于 32 位系统(或能够在 64 位上运行 32 位的应用或游戏),使用以下命令安装 32 位运行时:
|
||||
|
||||
```
|
||||
flatpak install flathub org.freedesktop.Platform.GL32.nvidia-MAJORVERSION-MINORVERSION
|
||||
|
||||
```
|
||||
|
||||
再说一次,将 MAJORVERSION 替换为 Nvidia 驱动的主要版本(在上面的示例中为 390),将 MINORVERSION 替换为次要版本(步骤2,我例子中的为 48)。
|
||||
再说一次,将 “MAJORVERSION” 替换为 Nvidia 驱动的主要版本(在上面的示例中为 390),将 “MINORVERSION” 替换为次要版本(步骤2,我例子中的为 48)。
|
||||
|
||||
比如,要为 Nvidia 图形驱动版本 390.48 安装 32 位运行时,你需要使用以下命令:
|
||||
|
||||
```
|
||||
flatpak install flathub org.freedesktop.Platform.GL32.nvidia-390-48
|
||||
|
||||
```
|
||||
|
||||
以上就是你要运行支持 OpenGL 的 Flatpak 的应用或游戏的方法。
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.linuxuprising.com/2018/06/how-to-get-flatpak-apps-and-games-built.html
|
||||
@ -109,7 +108,7 @@ via: https://www.linuxuprising.com/2018/06/how-to-get-flatpak-apps-and-games-bui
|
||||
作者:[Logix][a]
|
||||
选题:[lujun9972](https://github.com/lujun9972)
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
100
sources/talk/20190306 How to pack an IT travel kit.md
Normal file
100
sources/talk/20190306 How to pack an IT travel kit.md
Normal file
@ -0,0 +1,100 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (How to pack an IT travel kit)
|
||||
[#]: via: (https://opensource.com/article/19/3/it-toolkit-remote)
|
||||
[#]: author: (Peter Cheer https://opensource.com/users/petercheer)
|
||||
|
||||
How to pack an IT travel kit
|
||||
======
|
||||
Before you travel, make sure you're ready for challenges in hardware, infrastructure, and software.
|
||||

|
||||
|
||||
I've had several opportunities to do IT work in less-developed and remote areas, where internet coverage and technology access aren't at the high level we have in our first-world cities. Many people heading off to undeveloped areas ask me for advice on preparing for the local technology landscape. Since conditions vary greatly around this big world, it's impossible to give specific advice for most areas, but I do have some general suggestions based on my experience that may help you.
|
||||
|
||||
Also, before you leave home, do as much research as you can about the general IT and telecom environment where you are traveling so you're a little better prepared for what you may encounter there.
|
||||
|
||||
### Planning for the local hardware and infrastructure
|
||||
|
||||
* Even in many cities, internet connections tend to be expensive, slow, and not reliable for large downloads. Don't forget that internet coverage, speeds, and cost in cities are unlikely to be matched in more remote areas.
|
||||
|
||||
|
||||
* The electricity supply may be unreliable with inconsistent voltage. If you are taking your computer, bring some surge protection—although in my experience, the electricity voltage is more likely to drop than to spike.
|
||||
|
||||
|
||||
* It is always useful to have a small selection of hand tools, such as screwdrivers and needle-nose pliers, for repairing computer hardware. A lack of spare parts can limit opportunities for much beyond basic troubleshooting, although stripping usable components from dead computers can be worthwhile.
|
||||
|
||||
|
||||
|
||||
### Planning for the software you'll find
|
||||
|
||||
* You can assume that most of the computer systems you'll find will be some incarnation of Microsoft Windows. You can expect that many will not be officially licensed, not be getting updates nor security patches, and are infected by multiple viruses and other malware.
|
||||
|
||||
|
||||
* You can also expect that most application software will be proprietary and much of it will be unlicensed and lag behind the latest release versions. These conditions are depressing for open source enthusiasts, but this is the world as it is, rather than the world we would like it to be.
|
||||
|
||||
|
||||
* It is wise to view any Windows system you do not control as potentially infected with viruses and malware. It's good practice to reserve a USB thumb drive for files you'll use with these Windows systems; this means that if (or more likely when) that thumb drive becomes infected, you can just reformat it at no cost.
|
||||
|
||||
|
||||
* Bring copies of free antivirus software such as [AVG][1] and [Avast][2], including recent virus definition files for them, as well as virus removal and repair tools such as [Sophos][3] and [Hirens Boot CD][4].
|
||||
|
||||
|
||||
* Trying to keep software current on machines that have no or infrequent access to the internet is a challenge. This is particularly true with web browsers, which tend to go through rapid release cycles. My preferred web browser is Mozilla Firefox and having a copy of the latest release is useful.
|
||||
|
||||
|
||||
* Bring repair discs for a selection of recent Microsoft operating systems, and make sure that includes service packs for Windows and Microsoft Office.
|
||||
|
||||
|
||||
|
||||
### Planning for the software you'll bring
|
||||
|
||||
There's no better way to convey the advantages of open source software than by showing it to people. Here are some recommendations along that line.
|
||||
|
||||
* When gathering software to take with you, make sure you get the full offline installation option. Often, the most prominently displayed download links on websites are stubs that require internet access to download the components. They won't work if you're in an area with poor (or no) internet service.
|
||||
|
||||
|
||||
* Also, make sure to get the 32-bit and 64-bit versions of the software. While 32-bit machines are becoming less common, you may encounter them and it's best to be prepared.
|
||||
|
||||
|
||||
* Having a [bootable version of Linux][5] is vital for two reasons. First, it can be used to rescue data from a seriously damaged Windows machine. Second, it's an easy way to show off Linux without installing it on someone's machine. [Linux Mint][6] is my favorite distro for this purpose, because the graphical interface (GUI) is similar enough to Windows to appear non-threatening and it includes a good range of application software.
|
||||
|
||||
|
||||
* Bring the widest selection of open source applications you can—you can't count on being able to download something from the internet.
|
||||
|
||||
|
||||
* When possible, bring your open source software library as portable applications that will run without installing them. One of the many ways to mess up those Windows machines is to install and uninstall a lot of software, and using portable apps gets around this problem. Many open source applications, including Libre Office, GIMP, Blender, and Inkscape, have portable app versions for Windows.
|
||||
|
||||
|
||||
* It's smart to bring a supply of blank disks so you can give away copies of your open source software stash on media that is a bit more secure than a USB thumb drive.
|
||||
|
||||
|
||||
* Don't forget to bring programs and resources related to projects you will be working on. (For example, most of my overseas work involves tuition, mentoring, and skills transfer, so I usually add a selection of open source software tools for creating learning resources.)
|
||||
|
||||
|
||||
|
||||
### Your turn
|
||||
|
||||
There are many variables and surprises when doing IT work in undeveloped areas. If you have suggestions—for programs I've missed or tips that I didn't cover—please share them in the comments.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/3/it-toolkit-remote
|
||||
|
||||
作者:[Peter Cheer][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/petercheer
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.avg.com/en-gb/free-antivirus-download
|
||||
[2]: https://www.avast.com/en-gb/free-antivirus-download
|
||||
[3]: https://www.sophos.com/en-us/products/free-tools/virus-removal-tool.aspx
|
||||
[4]: https://www.hiren.info/
|
||||
[5]: https://opensource.com/article/18/7/getting-started-etcherio
|
||||
[6]: https://linuxmint.com/
|
||||
106
sources/talk/20190307 Small Scale Scrum vs. Large Scale Scrum.md
Normal file
106
sources/talk/20190307 Small Scale Scrum vs. Large Scale Scrum.md
Normal file
@ -0,0 +1,106 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Small Scale Scrum vs. Large Scale Scrum)
|
||||
[#]: via: (https://opensource.com/article/19/3/small-scale-scrum-vs-large-scale-scrum)
|
||||
[#]: author: (Agnieszka Gancarczyk https://opensource.com/users/agagancarczyk)
|
||||
|
||||
Small Scale Scrum vs. Large Scale Scrum
|
||||
======
|
||||
We surveyed individual members of small and large scrum teams. Here are some key findings.
|
||||
|
||||
|
||||
Following the publication of the [Small Scale Scrum framework][1], we wanted to collect feedback on how teams in our target demographic (consultants, open source developers, and students) work and what they value. With this first opportunity to inspect, adapt, and help shape the next stage of Small Scale Scrum, we decided to create a survey to capture some data points and begin to validate some of our assumptions and hypotheses.
|
||||
|
||||
**[[Download the Introduction to Small Scale Scrum guide]][2]**
|
||||
|
||||
Our reasons for using the survey were multifold, but chief among them were the global distribution of teams, the small local data sample available in our office, access to customers, and the industry’s utilization of surveys (e.g., the [Stack Overflow Developer Survey 2018][3], [HackerRank 2018 Developer Skills Report][4], and [GitLab 2018 Global Developer Report][5]).
|
||||
|
||||
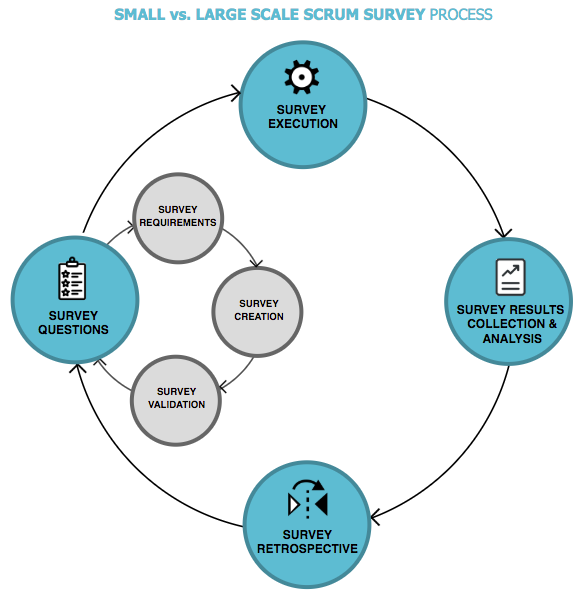
The scrum’s iterative process was used to facilitate the creation of the survey shown below:
|
||||
|
||||
|
||||
|
||||
[The survey][6], which we invite you to complete, consisted of 59 questions and was distributed at a local college ([Waterford Institute of Technology][7]) and to Red Hat's consultancy and engineering teams. Our initial data was gathered from the responses of 54 individuals spread across small and large scrum teams, who were asked about their experiences with agile within their teams.
|
||||
|
||||
Here are the main results and initial findings of the survey:
|
||||
|
||||
* A full 96% of survey participants practice a form of agile, work in distributed teams, think scrum principles help them reduce development complexity, and believe agile contributes to the success of their projects.
|
||||
|
||||
* Only 8% of survey participants belong to small (one- to three-person) teams, and 10 out of 51 describe their typical project as short-lived (three months or less).
|
||||
|
||||
* The majority of survey participants were software engineers, but quality engineers (QE), project managers (PM), product owners (PO), and scrum masters were also represented.
|
||||
|
||||
* Scrum master, PO, and team member are typical roles in projects.
|
||||
|
||||
* Nearly half of survey respondents work on, or are assigned to, more than one project at the same time.
|
||||
|
||||
* Almost half of projects are customer/value-generating vs. improvement/not directly value-generating or unclassified.
|
||||
|
||||
* Almost half of survey participants said that their work is clarified sometimes or most of the time and estimated before development with extensions available sometimes or most of the time. They said asking for clarification of work items is the team’s responsibility.
|
||||
|
||||
* Almost half of survey respondents said they write tests for their code, and they adhere to best coding practices, document their code, and get their code reviewed before merging.
|
||||
|
||||
* Almost all survey participants introduce bugs to the codebase, which are prioritized by them, the team, PM, PO, team lead, or the scrum master.
|
||||
|
||||
* Participants ask for help and mentoring when a task is complex. They also take on additional roles on their projects when needed, including business analyst, PM, QE, and architect, and they sometimes find changing roles difficult.
|
||||
|
||||
* When changing roles on a daily basis, individuals feel they lose one to two hours on average, but they still complete their work on time most of the time.
|
||||
|
||||
* Most survey participants use scrum (65%), followed by hybrid (18%) and Kanban (12%). This is consistent with results of [VersionOne’s State of Agile Report][8].
|
||||
|
||||
* The daily standup, sprint, sprint planning and estimating, backlog grooming, and sprint retrospective are among the top scrum ceremonies and principles followed, and team members do preparation work before meetings.
|
||||
|
||||
* The majority of sprints (62%) are three weeks long, followed by two-week sprints (26%), one-week sprints (6%), and four-week sprints (4%). Two percent of participants are not using sprints due to strict release and update timings, with all activities organized and planned around those dates.
|
||||
|
||||
* Teams use [planning poker][9] to estimate (storypoint) user stories. User stories contain acceptance criteria.
|
||||
|
||||
* Teams create and use a [Definition of Done][10] mainly in respect to features and determining completion of user stories.
|
||||
|
||||
* The majority of teams don’t have or use a [Definition of Ready][11] to ensure that user stories are actionable, testable, and clear.
|
||||
|
||||
* Unit, integration, functional, automated, performance/load, and acceptance tests are commonly used.
|
||||
|
||||
* Overall collaboration between team members is considered high, and team members use various communication channels.
|
||||
|
||||
* The majority of survey participants spend more than four hours weekly in meetings, including face-to-face meetings, web conferences, and email communication.
|
||||
|
||||
* The majority of customers are considered large, and half of them understand and follow scrum principles.
|
||||
|
||||
* Customers respect “no deadlines” most of the time and sometimes help create user stories and participate in sprint planning, sprint review and demonstration, sprint retrospective, and backlog review and refinement.
|
||||
|
||||
* Only 27% of survey participants know their customers have a high level of satisfaction with the adoption of agile, while the majority (58%) don’t know this information at all.
|
||||
|
||||
|
||||
|
||||
|
||||
These survey results will inform the next stage of our data-gathering exercise. We will apply Small Scale Scrum to real-world projects, and the guidance obtained from the survey will help us gather key data points as we move toward version 2.0 of Small Scale Scrum. If you want to help, take our [survey][6]. If you have a project to which you'd like to apply Small Scale Scrum, please get in touch.
|
||||
|
||||
[Download the Introduction to Small Scale Scrum guide][2]
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/3/small-scale-scrum-vs-large-scale-scrum
|
||||
|
||||
作者:[Agnieszka Gancarczyk][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/agagancarczyk
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/article/19/2/small-scale-scrum-framework
|
||||
[2]: https://opensource.com/downloads/small-scale-scrum
|
||||
[3]: https://insights.stackoverflow.com/survey/2018/
|
||||
[4]: https://research.hackerrank.com/developer-skills/2018/
|
||||
[5]: https://about.gitlab.com/developer-survey/2018/
|
||||
[6]: https://docs.google.com/forms/d/e/1FAIpQLScAXf52KMEiEzS68OOIsjLtwZJto_XT7A3b9aB0RhasnE_dEw/viewform?c=0&w=1
|
||||
[7]: https://www.wit.ie/
|
||||
[8]: https://explore.versionone.com/state-of-agile/versionone-12th-annual-state-of-agile-report
|
||||
[9]: https://en.wikipedia.org/wiki/Planning_poker
|
||||
[10]: https://www.scruminc.com/definition-of-done/
|
||||
[11]: https://www.scruminc.com/definition-of-ready/
|
||||
45
sources/talk/20190311 Discuss everything Fedora.md
Normal file
45
sources/talk/20190311 Discuss everything Fedora.md
Normal file
@ -0,0 +1,45 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Discuss everything Fedora)
|
||||
[#]: via: (https://fedoramagazine.org/discuss-everything-fedora/)
|
||||
[#]: author: (Ryan Lerch https://fedoramagazine.org/introducing-flatpak/)
|
||||
|
||||
Discuss everything Fedora
|
||||
======
|
||||

|
||||
|
||||
Are you interested in how Fedora is being developed? Do you want to get involved, or see what goes into making a release? You want to check out [Fedora Discussion][1]. It is a relatively new place where members of the Fedora Community meet to discuss, ask questions, and interact. Keep reading for more information.
|
||||
|
||||
Note that the Fedora Discussion system is mainly aimed at contributors. If you have questions on using Fedora, check out [Ask Fedora][2] (which is being migrated in the future).
|
||||
|
||||
![][3]
|
||||
|
||||
Fedora Discussion is a forum and discussion site that uses the [Discourse open source discussion platform][4].
|
||||
|
||||
There are already several categories useful for Fedora users, including [Desktop][5] (covering Fedora Workstation, Fedora Silverblue, KDE, XFCE, and more) and the [Server, Cloud, and IoT][6] category . Additionally, some of the [Fedora Special Interest Groups (SIGs) have discussions as well][7]. Finally, the [Fedora Friends][8] category helps you connect with other Fedora users and Community members by providing discussions about upcoming meetups and hackfests.
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://fedoramagazine.org/discuss-everything-fedora/
|
||||
|
||||
作者:[Ryan Lerch][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://fedoramagazine.org/introducing-flatpak/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://discussion.fedoraproject.org/
|
||||
[2]: https://ask.fedoraproject.org
|
||||
[3]: https://fedoramagazine.org/wp-content/uploads/2019/03/discussion-screenshot-1024x663.png
|
||||
[4]: https://www.discourse.org/about
|
||||
[5]: https://discussion.fedoraproject.org/c/desktop
|
||||
[6]: https://discussion.fedoraproject.org/c/server
|
||||
[7]: https://discussion.fedoraproject.org/c/sigs
|
||||
[8]: https://discussion.fedoraproject.org/c/friends
|
||||
@ -0,0 +1,65 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (When the web grew up: A browser story)
|
||||
[#]: via: (https://opensource.com/article/19/3/when-web-grew)
|
||||
[#]: author: (Mike Bursell https://opensource.com/users/mikecamel)
|
||||
|
||||
When the web grew up: A browser story
|
||||
======
|
||||
A personal story of when the internet came of age.
|
||||
|
||||

|
||||
|
||||
Recently, I [shared how][1] upon leaving university in 1994 with a degree in English literature and theology, I somehow managed to land a job running a web server in a world where people didn't really know what a web server was yet. And by "in a world," I don't just mean within the organisation in which I worked, but the world in general. The web was new—really new—and people were still trying to get their heads around it.
|
||||
|
||||
That's not to suggest that the place where I was working—an academic publisher—particularly "got it" either. This was a world in which a large percentage of the people visiting their website were still running 28k8 modems. I remember my excitement in getting a 33k6 modem. At least we were past the days of asymmetric upload/download speeds,1 where 1200/300 seemed like an eminently sensible bandwidth description. This meant that the high-design, high-colour, high-resolution documents created by the print people (with whom I shared a floor) were completely impossible on the web. I wouldn't allow anything bigger than a 40k GIF on the front page of the website, and that was pushing it for many of our visitors. Anything larger than 60k or so would be explicitly linked as a standalone image from a thumbnail on the referring page.
|
||||
|
||||
To say that the marketing department didn't like this was an understatement. Even worse was the question of layout. "Browsers decide how to lay out documents," I explained, time after time, "you can use headers or paragraphs, but how documents appear on the page isn't defined by the document, but by the renderer!" They wanted control. They wanted different coloured backgrounds. After a while, they got that. I went to what I believe was the first W3C meeting at which the idea of Cascading Style Sheets (CSS) was discussed. And argued vehemently against them. The suggestion that document writers should control layout was anathema.2 It took some while for CSS to be adopted, and in the meantime, those who cared about such issues adopted the security trainwreck that was Portable Document Format (PDF).
|
||||
|
||||
How documents were rendered wasn't the only issue. Being a publisher of actual physical books, the whole point of having a web presence, as far as the marketing department was concerned, was to allow customers—or potential customers—to know not only what a book was about, but also how much it was going to cost them to buy. This, however, presented a problem. You see, the internet—in which I include the rapidly growing World Wide Web—was an open, free-for-all libertarian sort of place where nobody was interested in money; in fact, where talk of money was to be shunned and avoided.
|
||||
|
||||
I took the mainstream "Netizen" view that there was no place for pricing information online. My boss—and, indeed, pretty much everybody else in the organisation—took a contrary view. They felt that customers should be able to see how much books would cost them. They also felt that my bank manager would like to see how much money was coming into my bank account on a monthly basis, which might be significantly reduced if I didn't come round to their view.
|
||||
|
||||
Luckily, by the time I'd climbed down from my high horse and got over myself a bit—probably only a few weeks after I'd started digging my heels in—the web had changed, and there were other people putting pricing information up about their products. These newcomers were generally looked down upon by the old schoolers who'd been running web servers since the early days,3 but it was clear which way the wind was blowing. This didn't mean that the battle was won for our website, however. As an academic publisher, we shared an academic IP name ("ac.uk") with the University. The University was less than convinced that publishing pricing information was appropriate until some senior folks at the publisher pointed out that Princeton University Press was doing it, and wouldn't we look a bit silly if…?
|
||||
|
||||
The fun didn't stop there, either. A few months into my tenure as webmaster ("webmaster@…"), we started to see a worrying trend, as did lots of other websites. Certain visitors were single-handedly bringing our webserver to its knees. These visitors were running a new web browser: Netscape. Netscape was badly behaved. Netscape was multi-threaded.
|
||||
|
||||
Why was this an issue? Well, before Netscape, all web browsers had been single-threaded. They would open one connection at a time, so even if you had, say five GIFs on a page,4 they would request the HTML base file, parse that, then download the first GIF, complete that, then the second, complete that, and so on. In fact, they often did the GIFs in the wrong order, which made for very odd page loading, but still, that was the general idea. The rude people at Netscape decided that they could open multiple connections to the webserver at a time to request all the GIFs at the same time, for example! And why was this a problem? Well, the problem was that most webservers were single-threaded. They weren't designed to have multiple connections open at any one time. Certainly, the HTTP server that we ran (MacHTTP) was single-threaded. Even though we had paid for it (it was originally shareware), the version we had couldn't cope with multiple requests at a time.
|
||||
|
||||
The debate raged across the internet. Who did these Netscape people think they were, changing how the world worked? How it was supposed to work? The world settled into different camps, and as with all technical arguments, heated words were exchanged on both sides. The problem was that not only was Netscape multi-threaded, it was also just better than the alternatives. Lots of web server code maintainers, MacHTTP author Chuck Shotton among them, sat down and did some serious coding to produce multi-threaded beta versions of their existing code. Everyone moved almost immediately to the beta versions, they got stable, and in the end, single-threaded browsers either adapted and became multi-threaded themselves, or just went the way of all outmoded products and died a quiet death.6
|
||||
|
||||
This, for me, is when the web really grew up. It wasn't prices on webpages nor designers being able to define what you'd see on a page,8 but rather when browsers became easier to use and when the network effect of thousands of viewers moving to many millions tipped the balance in favour of the consumer, not the producer. There were more steps in my journey—which I'll save for another time—but from around this point, my employers started looking at our monthly, then weekly, then daily logs, and realising that this was actually going to be something big and that they'd better start paying some real attention.
|
||||
|
||||
1\. How did they come back, again?
|
||||
|
||||
2\. It may not surprise you to discover that I'm still happiest at the command line.
|
||||
|
||||
3\. About six months before.
|
||||
|
||||
4\. Reckless, true, but it was beginning to happen.5
|
||||
|
||||
5\. Oh, and no—it was GIFs or BMP. JPEG was still a bright idea that hadn't yet taken off.
|
||||
|
||||
6\. It's never actually quiet: there are always a few diehard enthusiasts who insist that their preferred solution is technically superior and bemoan the fact that the rest of the internet has gone to the devil.7
|
||||
|
||||
7\. I'm not one to talk: I still use Lynx from time to time.
|
||||
|
||||
8\. Creating major and ongoing problems for those with different accessibility needs, I would point out.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/3/when-web-grew
|
||||
|
||||
作者:[Mike Bursell][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/mikecamel
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/article/18/11/how-web-was-won
|
||||
356
sources/tech/20160301 How To Set Password Policies In Linux.md
Normal file
356
sources/tech/20160301 How To Set Password Policies In Linux.md
Normal file
@ -0,0 +1,356 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (How To Set Password Policies In Linux)
|
||||
[#]: via: (https://www.ostechnix.com/how-to-set-password-policies-in-linux/)
|
||||
[#]: author: (SK https://www.ostechnix.com/author/sk/)
|
||||
|
||||
How To Set Password Policies In Linux
|
||||
======
|
||||

|
||||
|
||||
Even though Linux is secure by design, there are many chances for the security breach. One of them is weak passwords. As a System administrator, you must provide a strong password for the users. Because, mostly system breaches are happening due to weak passwords. This tutorial describes how to set password policies such as **password length** , **password complexity** , **password** **expiration period** etc., in DEB based systems like Debian, Ubuntu, Linux Mint, and RPM based systems like RHEL, CentOS, Scientific Linux.
|
||||
|
||||
### Set password length in DEB based systems
|
||||
|
||||
By default, all Linux operating systems requires **password length of minimum 6 characters** for the users. I strongly advice you not to go below this limit. Also, don’t use your real name, parents/spouse/kids name, or your date of birth as a password. Even a novice hacker can easily break such kind of passwords in minutes. The good password must always contains more than 6 characters including a number, a capital letter, and a special character.
|
||||
|
||||
Usually, the password and authentication-related configuration files will be stored in **/etc/pam.d/** location in DEB based operating systems.
|
||||
|
||||
To set minimum password length, edit**/etc/pam.d/common-password** file;
|
||||
|
||||
```
|
||||
$ sudo nano /etc/pam.d/common-password
|
||||
```
|
||||
|
||||
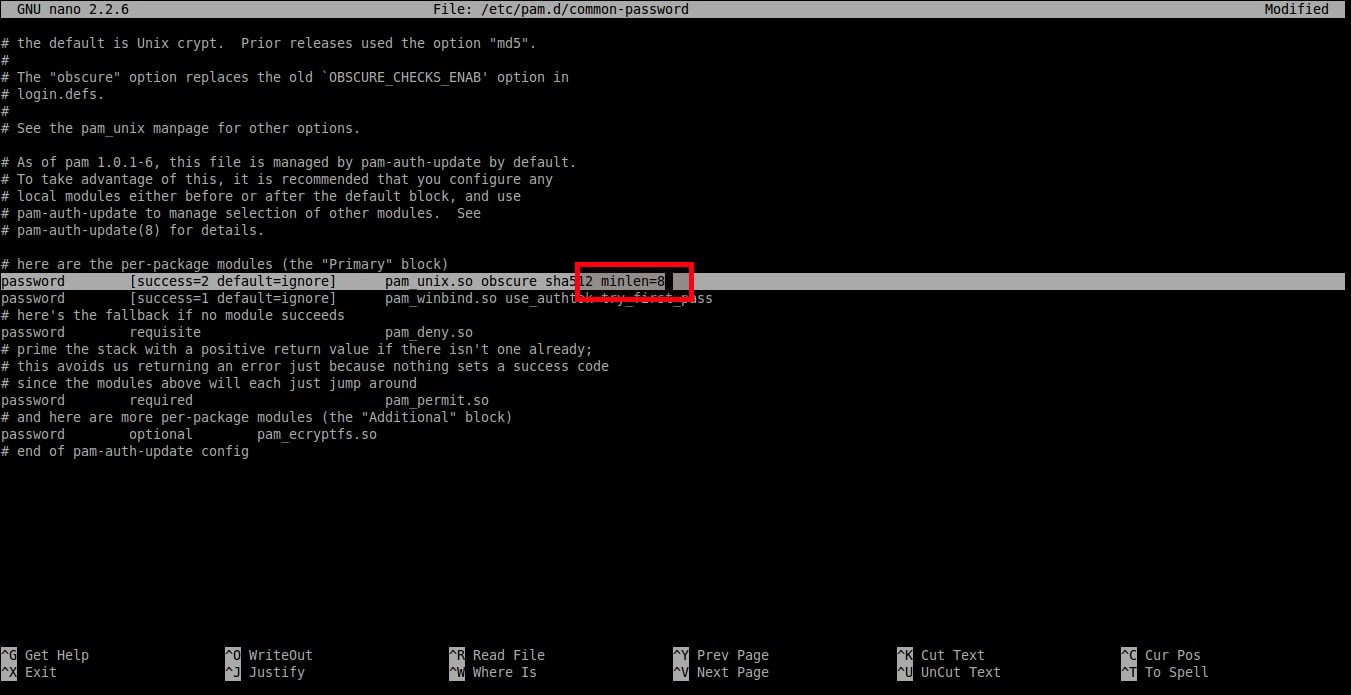
Find the following line:
|
||||
|
||||
```
|
||||
password [success=2 default=ignore] pam_unix.so obscure sha512
|
||||
```
|
||||
|
||||
![][2]
|
||||
|
||||
And add an extra word: **minlen=8** at the end. Here I set the minimum password length as **8**.
|
||||
|
||||
```
|
||||
password [success=2 default=ignore] pam_unix.so obscure sha512 minlen=8
|
||||
```
|
||||
|
||||
|
||||
|
||||
Save and close the file. So, now the users can’t use less than 8 characters for their password.
|
||||
|
||||
### Set password length in RPM based systems
|
||||
|
||||
**In RHEL, CentOS, Scientific Linux 7.x** systems, run the following command as root user to set password length.
|
||||
|
||||
```
|
||||
# authconfig --passminlen=8 --update
|
||||
```
|
||||
|
||||
To view the minimum password length, run:
|
||||
|
||||
```
|
||||
# grep "^minlen" /etc/security/pwquality.conf
|
||||
```
|
||||
|
||||
**Sample output:**
|
||||
|
||||
```
|
||||
minlen = 8
|
||||
```
|
||||
|
||||
**In RHEL, CentOS, Scientific Linux 6.x** systems, edit **/etc/pam.d/system-auth** file:
|
||||
|
||||
```
|
||||
# nano /etc/pam.d/system-auth
|
||||
```
|
||||
|
||||
Find the following line and add the following at the end of the line:
|
||||
|
||||
```
|
||||
password requisite pam_cracklib.so try_first_pass retry=3 type= minlen=8
|
||||
```
|
||||
|
||||

|
||||
|
||||
As per the above setting, the minimum password length is **8** characters.
|
||||
|
||||
### Set password complexity in DEB based systems
|
||||
|
||||
This setting enforces how many classes, i.e upper-case, lower-case, and other characters, should be in a password.
|
||||
|
||||
First install password quality checking library using command:
|
||||
|
||||
```
|
||||
$ sudo apt-get install libpam-pwquality
|
||||
```
|
||||
|
||||
Then, edit **/etc/pam.d/common-password** file:
|
||||
|
||||
```
|
||||
$ sudo nano /etc/pam.d/common-password
|
||||
```
|
||||
|
||||
To set at least one **upper-case** letters in the password, add a word **‘ucredit=-1’** at the end of the following line.
|
||||
|
||||
```
|
||||
password requisite pam_pwquality.so retry=3 ucredit=-1
|
||||
```
|
||||
|
||||
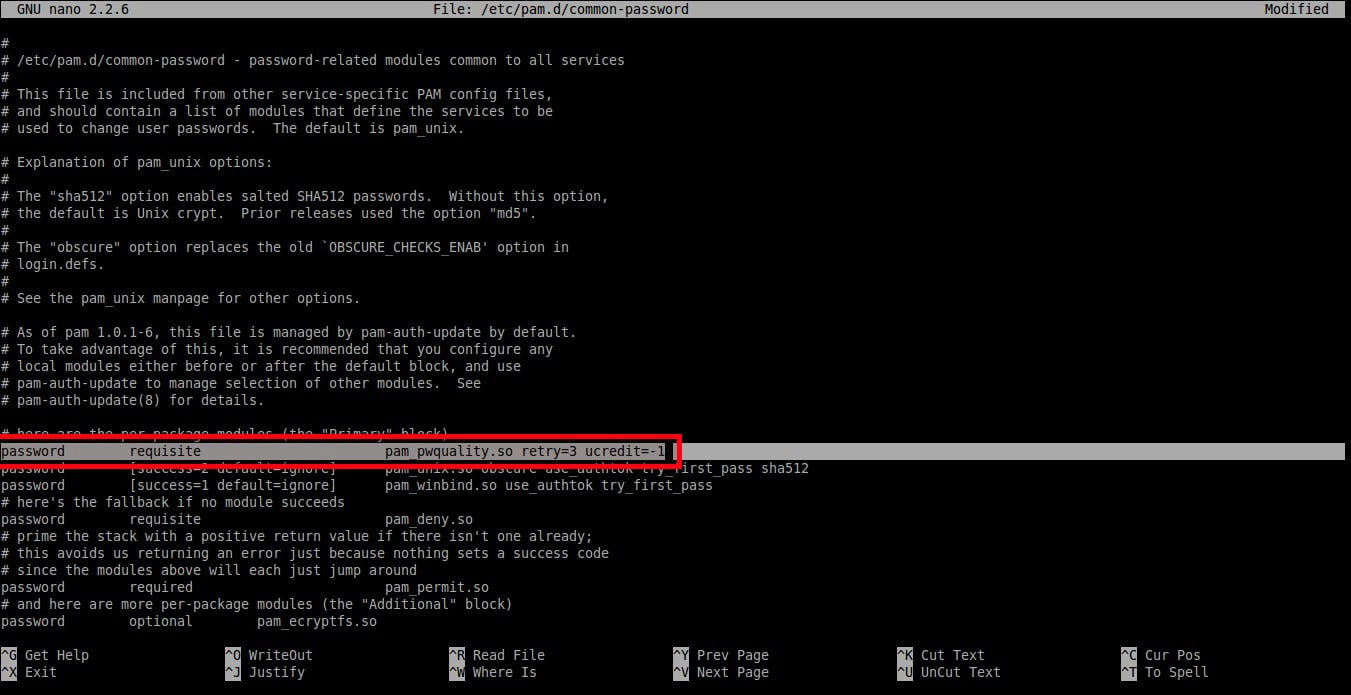
|
||||
|
||||
Set at least one **lower-case** letters in the password as shown below.
|
||||
|
||||
```
|
||||
password requisite pam_pwquality.so retry=3 dcredit=-1
|
||||
```
|
||||
|
||||
Set at least **other** letters in the password as shown below.
|
||||
|
||||
```
|
||||
password requisite pam_pwquality.so retry=3 ocredit=-1
|
||||
```
|
||||
|
||||
As you see in the above examples, we have set at least (minimum) one upper-case, lower-case, and a special character in the password. You can set any number of maximum allowed upper-case, lower-case, and other letters in your password.
|
||||
|
||||
You can also set the minimum/maximum number of allowed classes in the password.
|
||||
|
||||
The following example shows the minimum number of required classes of characters for the new password:
|
||||
|
||||
```
|
||||
password requisite pam_pwquality.so retry=3 minclass=2
|
||||
```
|
||||
|
||||
### Set password complexity in RPM based systems
|
||||
|
||||
**In RHEL 7.x / CentOS 7.x / Scientific Linux 7.x:**
|
||||
|
||||
To set at least one lower-case letter in the password, run:
|
||||
|
||||
```
|
||||
# authconfig --enablereqlower --update
|
||||
```
|
||||
|
||||
To view the settings, run:
|
||||
|
||||
```
|
||||
# grep "^lcredit" /etc/security/pwquality.conf
|
||||
```
|
||||
|
||||
**Sample output:**
|
||||
|
||||
```
|
||||
lcredit = -1
|
||||
```
|
||||
|
||||
Similarly, set at least one upper-case letter in the password using command:
|
||||
|
||||
```
|
||||
# authconfig --enablerequpper --update
|
||||
```
|
||||
|
||||
To view the settings:
|
||||
|
||||
```
|
||||
# grep "^ucredit" /etc/security/pwquality.conf
|
||||
```
|
||||
|
||||
**Sample output:**
|
||||
|
||||
```
|
||||
ucredit = -1
|
||||
```
|
||||
|
||||
To set at least one digit in the password, run:
|
||||
|
||||
```
|
||||
# authconfig --enablereqdigit --update
|
||||
```
|
||||
|
||||
To view the setting, run:
|
||||
|
||||
```
|
||||
# grep "^dcredit" /etc/security/pwquality.conf
|
||||
```
|
||||
|
||||
**Sample output:**
|
||||
|
||||
```
|
||||
dcredit = -1
|
||||
```
|
||||
|
||||
To set at least one other character in the password, run:
|
||||
|
||||
```
|
||||
# authconfig --enablereqother --update
|
||||
```
|
||||
|
||||
To view the setting, run:
|
||||
|
||||
```
|
||||
# grep "^ocredit" /etc/security/pwquality.conf
|
||||
```
|
||||
|
||||
**Sample output:**
|
||||
|
||||
```
|
||||
ocredit = -1
|
||||
```
|
||||
|
||||
In **RHEL 6.x / CentOS 6.x / Scientific Linux 6.x systems** , edit **/etc/pam.d/system-auth** file as root user:
|
||||
|
||||
```
|
||||
# nano /etc/pam.d/system-auth
|
||||
```
|
||||
|
||||
Find the following line and add the following at the end of the line:
|
||||
|
||||
```
|
||||
password requisite pam_cracklib.so try_first_pass retry=3 type= minlen=8 dcredit=-1 ucredit=-1 lcredit=-1 ocredit=-1
|
||||
```
|
||||
|
||||
As per the above setting, the password must have at least 8 characters. In addtion, the password should also have at least one upper-case letter, one lower-case letter, one digit, and one other characters.
|
||||
|
||||
### Set password expiration period in DEB based systems
|
||||
|
||||
Now, We are going to set the following policies.
|
||||
|
||||
1. Maximum number of days a password may be used.
|
||||
2. Minimum number of days allowed between password changes.
|
||||
3. Number of days warning given before a password expires.
|
||||
|
||||
|
||||
|
||||
To set this policy, edit:
|
||||
|
||||
```
|
||||
$ sudo nano /etc/login.defs
|
||||
```
|
||||
|
||||
Set the values as per your requirement.
|
||||
|
||||
```
|
||||
PASS_MAX_DAYS 100
|
||||
PASS_MIN_DAYS 0
|
||||
PASS_WARN_AGE 7
|
||||
```
|
||||
|
||||
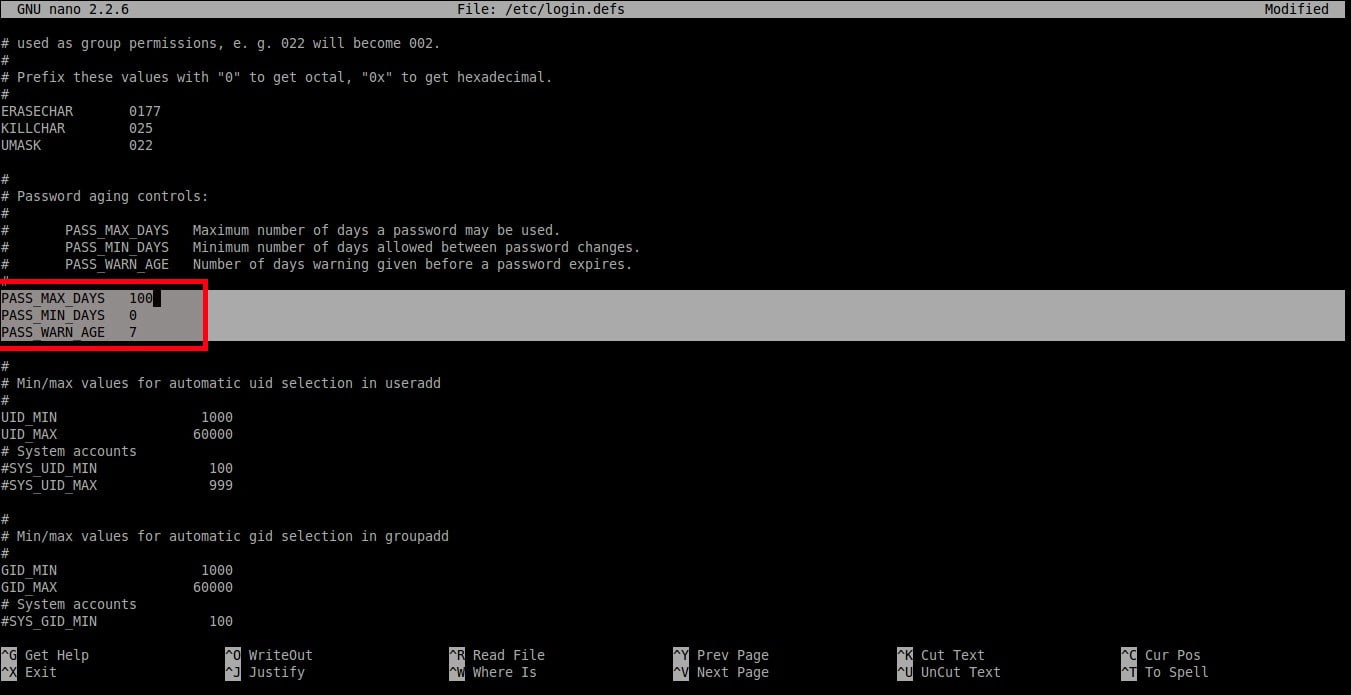
|
||||
|
||||
As you see in the above example, the user should change the password once in every **100** days and the warning message will appear **7** days before password expiration.
|
||||
|
||||
Be mindful that these settings will impact the newly created users.
|
||||
|
||||
To set maximum number of days between password change to existing users, you must run the following command:
|
||||
|
||||
```
|
||||
$ sudo chage -M <days> <username>
|
||||
```
|
||||
|
||||
To set minimum number of days between password change, run:
|
||||
|
||||
```
|
||||
$ sudo chage -m <days> <username>
|
||||
```
|
||||
|
||||
To set warning before password expires, run:
|
||||
|
||||
```
|
||||
$ sudo chage -W <days> <username>
|
||||
```
|
||||
|
||||
To display the password for the existing users, run:
|
||||
|
||||
```
|
||||
$ sudo chage -l sk
|
||||
```
|
||||
|
||||
Here, **sk** is my username.
|
||||
|
||||
**Sample output:**
|
||||
|
||||
```
|
||||
Last password change : Feb 24, 2017
|
||||
Password expires : never
|
||||
Password inactive : never
|
||||
Account expires : never
|
||||
Minimum number of days between password change : 0
|
||||
Maximum number of days between password change : 99999
|
||||
Number of days of warning before password expires : 7
|
||||
```
|
||||
|
||||
As you see in the above output, the password never expires.
|
||||
|
||||
To change the password expiration period of an existing user,
|
||||
|
||||
```
|
||||
$ sudo chage -E 24/06/2018 -m 5 -M 90 -I 10 -W 10 sk
|
||||
```
|
||||
|
||||
The above command will set password of the user **‘sk’** to expire on **24/06/2018**. Also the the minimum number days between password change is set 5 days and the maximum number of days between password changes is set to **90** days. The user account will be locked automatically after **10 days** and It will display a warning message for **10 days** before password expiration.
|
||||
|
||||
### Set password expiration period in RPM based systems
|
||||
|
||||
This is same as DEB based systems.
|
||||
|
||||
### Forbid previously used passwords in DEB based systems
|
||||
|
||||
You can limit the users to set a password which is already used in the past. To put this in layman terms, the users can’t use the same password again.
|
||||
|
||||
To do so, edit**/etc/pam.d/common-password** file:
|
||||
|
||||
```
|
||||
$ sudo nano /etc/pam.d/common-password
|
||||
```
|
||||
|
||||
Find the following line and add the word **‘remember=5’** at the end:
|
||||
|
||||
```
|
||||
password [success=2 default=ignore] pam_unix.so obscure use_authtok try_first_pass sha512 remember=5
|
||||
```
|
||||
|
||||
The above policy will prevent the users to use the last 5 used passwords.
|
||||
|
||||
### Forbid previously used passwords in RPM based systems
|
||||
|
||||
This is same for both RHEL 6.x and RHEL 7.x and it’s clone systems like CentOS, Scientific Linux.
|
||||
|
||||
Edit **/etc/pam.d/system-auth** file as root user,
|
||||
|
||||
```
|
||||
# vi /etc/pam.d/system-auth
|
||||
```
|
||||
|
||||
Find the following line, and add **remember=5** at the end.
|
||||
|
||||
```
|
||||
password sufficient pam_unix.so sha512 shadow nullok try_first_pass use_authtok remember=5
|
||||
```
|
||||
|
||||
You know now what is password policies in Linux, and how to set different password policies in DEB and RPM based systems.
|
||||
|
||||
That’s all for now. I will be here soon with another interesting and useful article. Until then stay tuned with OSTechNix. If you find this tutorial helpful, share it on your social, professional networks and support us.
|
||||
|
||||
Cheers!
|
||||
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.ostechnix.com/how-to-set-password-policies-in-linux/
|
||||
|
||||
作者:[SK][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.ostechnix.com/author/sk/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7
|
||||
[2]: http://www.ostechnix.com/wp-content/uploads/2016/03/sk@sk-_003-2-1.jpg
|
||||
@ -0,0 +1,61 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Blockchain 2.0: An Introduction [Part 1])
|
||||
[#]: via: (https://www.ostechnix.com/blockchain-2-0-an-introduction/)
|
||||
[#]: author: (EDITOR https://www.ostechnix.com/author/editor/)
|
||||
|
||||
Blockchain 2.0: An Introduction [Part 1]
|
||||
======
|
||||
|
||||

|
||||
|
||||
### Blockchain 2.0 – The next paradigm of computing
|
||||
|
||||
The **Blockchain** is now easily distinguishable as a transformational technology poised to bring in revolutionary changes in the way people use the internet. The present series of posts will explore the upcoming wave of Blockchain 2.0 based technologies and applications. The Blockchain is here to stay as evidenced by the tremendous interest in it shown by different stakeholders.
|
||||
|
||||
Staying on top of what it is and how it works is paramount to anyone who plans on using the internet for literally anything. Even if all you do is just stare at your friends’ morning breakfast pics on Instagram or looking for the next best clip to watch, you need to know what this technology can do to all of that.
|
||||
|
||||
Even though the basic concept behind the Blockchain was first talked about in academia in the **1990s** , its prominence to being a trending buzzword among netizens is owed to the rise of payment platforms such as **Bitcoins** and **Ethers**.
|
||||
|
||||
Bitcoin started off as a decentralized digital currency. Its advent meant that you could basically pay people over the internet being totally anonymous, safe and secure. What lay beneath the simple financial token system that was bitcoin though was the BLOCKCHAIN. You can think of Bitcoin technology or any cryptocurrency for that matter as being built up from 3 layers. There’s the foundational Blockchain tech that verifies, records and confirms transactions, on top of the foundation rests the protocol, basically, a rule or an online etiquette to honor, record and confirm transactions and of course, on top of it all is the cryptocurrency token commonly called Bitcoin. A token is generated by the Blockchain once a transaction respecting the protocol is recorded on it.
|
||||
|
||||
While most people only saw the top layer, the coins or tokens being representative of what bitcoin really was, few ventured deep enough to understand that financial transactions were just one of many such possibilities that could be accomplished with the help of the Blockchain foundation. These possibilities are now being explored to generate and develop new standards for decentralizing all manners of transactions.
|
||||
|
||||
At its very basic level, the Blockchain can be thought of as an all-encompassing ledger of records and transactions. This in effect means that all kinds of records can theoretically be handled by the Blockchain. Developments in this area will possibly in the future result in all kinds of hard (Such as real estate deeds, physical keys, etc.) and soft intangible assets (Such as identity records, patents, trademarks, reservations etc.) can be encoded as digital assets to be protected and transferred via the blockchain.
|
||||
|
||||
For the uninitiated, transactions on the Blockchain are inherently thought of and designed to be unbiased, permanent records. This is possible because of a **“consensus system”** that is built into the protocol. All transactions are confirmed, vetted and recorded by the participants of the system, in the case of the Bitcoin cryptocurrency platform, this role is taken care of by **miners** and exchanges. This can vary from platform to platform or from blockchain to blockchain. The protocol stack on which the platform is built is by definition supposed to be open-source and free for anyone with the technical know-how to verify. Transparency is woven into the system unlike much of the other platforms that the internet currently runs on.
|
||||
|
||||
Once transactions are recorded and coded into the Blockchain, they will be seen through. Participants are bound to honor their transactions and contracts the way they were originally intended to be executed. The execution itself will be automatically taken care of by the platform since it’s hardcoded into it, unless of course if the original terms forbid it. This resilience of the Blockchain platform toward attempts of tampering with records, permanency of the records etc., are hitherto unheard of for something working over the internet. This is the added layer of trust that is often talked about while supporters of the technology claim its rising significance.
|
||||
|
||||
These features are not recently discovered hidden potentials of the platform, these were envisioned from the start. In a communique, **Satoshi Nakamoto** , the fabled creator(s) of Bitcoin mentioned, **“the design supports a tremendous variety of possible transaction types that I designed years ago… If Bitcoin catches on in a big way, these are things we’ll want to explore in the future… but they all had to be designed at the beginning to make sure they would be possible later.”**. Cementing the fact that these features are designed and baked into the already existing protocols. The key idea being that the decentralized transaction ledger like the functionality of the Blockchain could be used to transfer, deploy and execute all manner of contracts.
|
||||
|
||||
Leading institutions are currently exploring the possibility of re-inventing financial instruments such as stocks, pensions, and derivatives, while governments all over the world are concerned more with the tamper-proof permanent record keeping potential of the Blockchain. Supporters of the platform claim that once development reaches a critical threshold, everything from your hotel key cards to copyrights and patents will from then on be recorded and implemented via the use of Blockchains.
|
||||
|
||||
An almost full list of items and particulars that could theoretically be implemented via a Blockchain model is compiled and maintained on [**this**][1] page by **Ledra Capital**. A thought experiment to actually realize how much of our lives the Blockchain might effect is a daunting task, but a look at that list will reiterate the importance of doing so.
|
||||
|
||||
Now, all of the bureaucratic and commercial uses mentioned above might lead you to believe that a technology such as this will be solely in the domain of Governments and Large private corporations. However, the truth is far from that. Given the fact that the vast potentials of the system make it attractive for such uses, there are other possibilities and features harbored by Blockchains. There are other more intricate concepts related to the technology such as **DApps** , **DAOs** , **DACs** , **DASs** etc., more of which will be covered in depth in this series of articles.
|
||||
|
||||
Basically, development is going on in full swing and its early for anyone to comment on definitions, standards, and capabilities of such Blockchain based systems for a wider roll-out, but the possibilities and its imminent effects are doubtless. There are even talks about Blockchain based smartphones and polling during elections.
|
||||
|
||||
This was just a brief birds-eye view of what the platform is capable of. We’ll look at the distinct possibilities through a series of such detailed posts and articles. Keep an eye out for the [**next post of the series**][2], which will explore how the Blockchain is revolutionizing transactions and contracts.
|
||||
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.ostechnix.com/blockchain-2-0-an-introduction/
|
||||
|
||||
作者:[EDITOR][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.ostechnix.com/author/editor/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: http://ledracapital.com/blog/2014/3/11/bitcoin-series-24-the-mega-master-blockchain-list
|
||||
[2]: https://www.ostechnix.com/blockchain-2-0-revolutionizing-the-financial-system/
|
||||
69
sources/tech/20190303 How to boot up a new Raspberry Pi.md
Normal file
69
sources/tech/20190303 How to boot up a new Raspberry Pi.md
Normal file
@ -0,0 +1,69 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (How to boot up a new Raspberry Pi)
|
||||
[#]: via: (https://opensource.com/article/19/3/how-boot-new-raspberry-pi)
|
||||
[#]: author: (Anderson Silva https://opensource.com/users/ansilva)
|
||||
|
||||
How to boot up a new Raspberry Pi
|
||||
======
|
||||
Learn how to install a Linux operating system, in the third article in our guide to getting started with Raspberry Pi.
|
||||

|
||||
|
||||
If you've been following along in this series, you've [chosen][1] and [bought][2] your Raspberry Pi board and peripherals and now you're ready to start using it. Here, in the third article, let's look at what you need to do to boot it up.
|
||||
|
||||
Unlike your laptop, desktop, smartphone, or tablet, the Raspberry Pi doesn't come with built-in storage. Instead, it uses a Micro SD card to store the operating system and your files. The great thing about this is it gives you the flexibility to carry your files (even if you don't have your Raspberry Pi with you). The downside is it may also increase the risk of losing or damaging the card—and thus losing your files. Just protect your Micro SD card, and you should be fine.
|
||||
|
||||
You should also know that SD cards aren't as fast as mechanical or solid state drives, so booting, reading, and writing from your Pi will not be as speedy as you would expect from other devices.
|
||||
|
||||
### How to install Raspbian
|
||||
|
||||
The first thing you need to do when you get a new Raspberry Pi is to install its operating system on a Micro SD card. Even though there are other operating systems (both Linux- and non-Linux-based) available for the Raspberry Pi, this series focuses on [Raspbian][3] , Raspberry Pi's official Linux version.
|
||||
|
||||
|
||||
|
||||
The easiest way to install Raspbian is with [NOOBS][4], which stands for "New Out Of Box Software." Raspberry Pi offers great [documentation for NOOBS][5], so I won't repeat the installation instructions here.
|
||||
|
||||
NOOBS gives you the choice of installing the following operating systems:
|
||||
|
||||
+ [Raspbian][6]
|
||||
+ [LibreELEC][7]
|
||||
+ [OSMC][8]
|
||||
+ [Recalbox][9]
|
||||
+ [Lakka][10]
|
||||
+ [RISC OS][11]
|
||||
+ [Screenly OSE][12]
|
||||
+ [Windows 10 IoT Core][13]
|
||||
+ [TLXOS][14]
|
||||
|
||||
Again, Raspbian is the operating system we'll use in this series, so go ahead, grab your Micro SD and follow the NOOBS documentation to install it. I'll meet you in the fourth article in this series, where we'll look at how to use Linux, including some of the main commands you'll need to know.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/3/how-boot-new-raspberry-pi
|
||||
|
||||
作者:[Anderson Silva][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/ansilva
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/article/19/3/which-raspberry-pi-choose
|
||||
[2]: https://opensource.com/article/19/2/how-buy-raspberry-pi
|
||||
[3]: https://www.raspbian.org/RaspbianFAQ
|
||||
[4]: https://www.raspberrypi.org/downloads/noobs/
|
||||
[5]: https://www.raspberrypi.org/documentation/installation/noobs.md
|
||||
[6]: https://www.raspbian.org/RaspbianFAQ
|
||||
[7]: https://libreelec.tv/
|
||||
[8]: https://osmc.tv/
|
||||
[9]: https://www.recalbox.com/
|
||||
[10]: http://www.lakka.tv/
|
||||
[11]: https://www.riscosopen.org/wiki/documentation/show/Welcome%20to%20RISC%20OS%20Pi
|
||||
[12]: https://www.screenly.io/ose/
|
||||
[13]: https://developer.microsoft.com/en-us/windows/iot
|
||||
[14]: https://thinlinx.com/
|
||||
@ -0,0 +1,133 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (How rootless Buildah works: Building containers in unprivileged environments)
|
||||
[#]: via: (https://opensource.com/article/19/3/tips-tricks-rootless-buildah)
|
||||
[#]: author: (Daniel J Walsh https://opensource.com/users/rhatdan)
|
||||
|
||||
How rootless Buildah works: Building containers in unprivileged environments
|
||||
======
|
||||
Buildah is a tool and library for building Open Container Initiative (OCI) container images.
|
||||

|
||||
|
||||
In previous articles, including [How does rootless Podman work?][1], I talked about [Podman][2], a tool that enables users to manage pods, containers, and container images.
|
||||
|
||||
[Buildah][3] is a tool and library for building Open Container Initiative ([OCI][4]) container images that is complementary to Podman. (Both projects are maintained by the [containers][5] organization, of which I'm a member.) In this article, I will talk about rootless Buildah, including the differences between it and Podman.
|
||||
|
||||
Our goal with Buildah was to build a low-level tool that could be used either directly or vendored into other tools to build container images.
|
||||
|
||||
### Why Buildah?
|
||||
|
||||
Here is how I describe a container image: It is basically a rootfs directory that contains the code needed to run your container. This directory is called a rootfs because it usually looks like **/ (root)** on a Linux machine, meaning you are likely to find directories in a rootfs like **/etc** , **/usr** , **/bin** , etc.
|
||||
|
||||
The second part of a container image is a JSON file that describes the contents of the rootfs. It contains fields like the command to run the container, the entrypoint, the environment variables required to run the container, the working directory of the container, etc. Basically this JSON file allows the developer of the container image to describe how the container image is expected to be used. The fields in this JSON file have been standardized in the [OCI Image Format specification][6]
|
||||
|
||||
The rootfs and the JSON file then get tar'd together to create an image bundle that is stored in a container registry. To create a layered image, you install more software into the rootfs and modify the JSON file. Then you tar up the differences of the new and the old rootfs and store that in another image tarball. The second JSON file refers back to the first JSON file via a checksum.
|
||||
|
||||
Many years ago, Docker introduced Dockerfile, a simplified scripting language for building container images. Dockerfile was great and really took off, but it has many shortcomings that users have complained about. For example:
|
||||
|
||||
* Dockerfile encourages the inclusion of tools used to build containers inside the container image. Container images do not need to include yum/dnf/apt, but most contain one of them and all their dependencies.
|
||||
|
||||
* Each line causes a layer to be created. Because of this, secrets can mistakenly get added to container images. If you create a secret in one line of the Dockerfile and delete it in the next, the secret is still in the image.
|
||||
|
||||
|
||||
|
||||
|
||||
One of my biggest complaints about the "container revolution" is that six years since it started, the only way to build a container image was still with Dockerfiles. Lots of tools other than **docker build** have appeared besides Buildah, but most still deal only with Dockerfile. So users continue hacking around the problems with Dockerfile.
|
||||
|
||||
Note that [umoci][7] is an alternative to **docker build** that allows you to build container images without Dockerfile.
|
||||
|
||||
Our goal with Buildah was to build a simple tool that could just create a rootfs directory on disk and allow other tools to populate the directory, then create the JSON file. Finally, Buildah would create the OCI image and push it to a container registry where it could be used by any container engine, like [Docker][8], Podman, [CRI-O][9], or another Buildah.
|
||||
|
||||
Buildah also supports Dockerfile, since we know the bulk of people building containers have created Dockerfiles.
|
||||
|
||||
### Using Buildah directly
|
||||
|
||||
Lots of people use Buildah directly. A cool feature of Buildah is that you can script up the container build directly in Bash.
|
||||
|
||||
The example below creates a Bash script called **myapp.sh** , which uses Buildah to pull down the Fedora image, and then uses **dnf** and **make** on a machine to install software into the container image rootfs, **$mnt**. It then adds some fields to the JSON file using **buildah config** and commits the container to a container image **myapp**. Finally, it pushes the container image to a container registry, **quay.io**. (It could push it to any container registry.) Now this OCI image can be used by any container engine or Kubernetes.
|
||||
|
||||
```
|
||||
cat myapp.sh
|
||||
#!/bin/sh
|
||||
ctr=$(buildah from fedora)
|
||||
mnt=($buildah mount $ctr)
|
||||
dnf -y install --installroot $mnt httpd
|
||||
make install DESTDIR=$mnt myapp
|
||||
rm -rf $mnt/var/cache $mnt/var/log/*
|
||||
buildah config --command /usr/bin/myapp -env foo=bar --working-dir=/root $ctr
|
||||
buildah commit $ctr myapp
|
||||
buildah push myapp http://quay.io/username/myapp
|
||||
```
|
||||
|
||||
To create really small images, you could replace **fedora** in the script above with **scratch** , and Buildah will build a container image that only has the requirements for the **httpd** package inside the container image. No need for Python or DNF.
|
||||
|
||||
### Podman's relationship to Buildah
|
||||
|
||||
With Buildah, we have a low-level tool for building container images. Buildah also provides a library for other tools to build container images. Podman was designed to replace the Docker command line interface (CLI). One of the Docker CLI commands is **docker build**. We needed to have **podman build** to support building container images with Dockerfiles. Podman vendored in the Buildah library to allow it to do **podman build**. Any time you do a **podman build** , you are executing Buildah code to build your container images. If you are only going to use Dockerfiles to build container images, we recommend you only use Podman; there's no need for Buildah at all.
|
||||
|
||||
### Other tools using the Buildah library
|
||||
|
||||
Podman is not the only tool to take advantage of the Buildah library. [OpenShift 4 Source-to-Image][10] (S2I) will also use Buildah to build container images. OpenShift S2I allows developers using OpenShift to use Git commands to modify source code; when they push the changes for their source code to the Git repository, OpenShift kicks off a job to compile the source changes and create a container image. It also uses Buildah under the covers to build this image.
|
||||
|
||||
[Ansible-Bender][11] is a new project to build container images via an Ansible playbook. For those familiar with Ansible, Ansible-Bender makes it easy to describe the contents of the container image and then uses Buildah to package up the container image and send it to a container registry.
|
||||
|
||||
We would love to see other tools and languages for describing and building a container image and would welcome others use Buildah to do the conversion.
|
||||
|
||||
### Problems with rootless
|
||||
|
||||
Buildah works fine in rootless mode. It uses user namespace the same way Podman does. If you execute
|
||||
|
||||
```
|
||||
$ buildah bud --tag myapp -f Dockerfile .
|
||||
$ buildah push myapp http://quay.io/username/myapp
|
||||
```
|
||||
|
||||
in your home directory, everything works great.
|
||||
|
||||
However, if you execute the script described above, it will fail!
|
||||
|
||||
The problem is that, when running the **buildah mount** command in rootless mode, the **buildah** command must put itself inside the user namespace and create a new mount namespace. Rootless users are not allowed to mount filesystems when not running in a user namespace.
|
||||
|
||||
When the Buildah executable exits, the user namespace and mount namespace disappear, so the mount point no longer exists. This means the commands after **buildah mount** that attempt to write to **$mnt** will fail since **$mnt** is no longer mounted.
|
||||
|
||||
How can we make the script work in rootless mode?
|
||||
|
||||
#### Buildah unshare
|
||||
|
||||
Buildah has a special command, **buildah unshare** , that allows you to enter the user namespace. If you execute it with no commands, it will launch a shell in the user namespace, and your shell will seem like it is running as root and all the contents of the home directory will seem like they are owned by root. If you look at the owner or files in **/usr** , it will list them as owned by **nfsnobody** (or nobody). This is because your user ID (UID) is now root inside the user namespace and real root (UID=0) is not mapped into the user namespace. The kernel represents all files owned by UIDs not mapped into the user namespace as the NFSNOBODY user. When you exit the shell, you will exit the user namespace, you will be back to your normal UID, and the home directory will be owned by your UID again.
|
||||
|
||||
If you want to execute the **myapp.sh** command defined above, you can execute **buildah unshare myapp.sh** and the script will now run correctly.
|
||||
|
||||
#### Conclusion
|
||||
|
||||
Building and running containers in unprivileged environments is now possible and quite useable. There is little reason for developers to develop containers as root.
|
||||
|
||||
If you want to use a traditional container engine, and use Dockerfile's for builds, then you should probably just use Podman. But if you want to experiment with building container images in new ways without using Dockerfile, then you should really take a look at Buildah.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/3/tips-tricks-rootless-buildah
|
||||
|
||||
作者:[Daniel J Walsh][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/rhatdan
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/article/19/2/how-does-rootless-podman-work
|
||||
[2]: https://podman.io/
|
||||
[3]: https://github.com/containers/buildah
|
||||
[4]: https://www.opencontainers.org/
|
||||
[5]: https://github.com/containers
|
||||
[6]: https://github.com/opencontainers/image-spec
|
||||
[7]: https://github.com/openSUSE/umoci
|
||||
[8]: https://github.com/docker
|
||||
[9]: https://cri-o.io/
|
||||
[10]: https://github.com/openshift/source-to-image
|
||||
[11]: https://github.com/TomasTomecek/ansible-bender
|
||||
@ -0,0 +1,65 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (3 popular programming languages you can learn with Raspberry Pi)
|
||||
[#]: via: (https://opensource.com/article/19/3/programming-languages-raspberry-pi)
|
||||
[#]: author: (Anderson Silva https://opensource.com/users/ansilva)
|
||||
|
||||
3 popular programming languages you can learn with Raspberry Pi
|
||||
======
|
||||
Become more valuable on the job market by learning to program with the Raspberry Pi.
|
||||

|
||||
|
||||
In the last article in this series, I shared some ways to [teach kids to program with Raspberry Pi][1]. In theory, there is absolutely nothing stopping an adult from using resources designed for kids, but you might be better served by learning the programming languages that are in demand in the job market.
|
||||
|
||||
Here are three programming languages you can learn with the Raspberry Pi.
|
||||
|
||||
### Python
|
||||
|
||||
[Python][2] has become one of the [most popular programming languages][3] in the open source world. Its interpreter has been packaged and made available in every popular Linux distribution. If you install Raspbian on your Raspberry Pi, you will see an app called [Thonny][4], which is a Python integrated development environment (IDE) for beginners. In a nutshell, an IDE is an application that provides all you need to get your code executed, often including things like debuggers, documentation, auto-completion, and emulators. Here is a [great little tutorial][5] to get you started using Thonny and Python on the Raspberry Pi.
|
||||
|
||||
|
||||
|
||||
### Java
|
||||
|
||||
Although arguably not as attractive as it once was, [Java][6] remains heavily used in universities around the world and deeply embedded in the enterprise. So, even though some will disagree that I'm recommending it as a beginner's language, I am compelled to do so; for one thing, it still very popular, and for another, there are a lot of books, classes, and other information available for you to learn Java. Get started on the Raspberry Pi by using the [BlueJ][7] Java IDE.
|
||||
|
||||
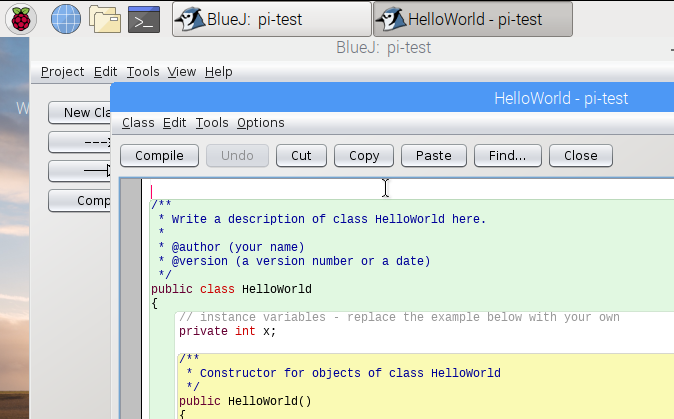
|
||||
|
||||
### JavaScript
|
||||
|
||||
"Back in my day…" [JavaScript][8] was a client-side language that basically allowed people to streamline and automate user events in a browser and modify HTML elements. Today, JavaScript has escaped the browser and is available for other types of clients like mobile apps and even server-side programming. [Node.js][9] is a popular runtime environment that allows developers to code beyond the client-browser paradigm. To learn more about running Node.js on the Raspberry Pi, check out [W3Schools tutorial][10].
|
||||
|
||||
### Other languages
|
||||
|
||||
If there's another language you want to learn, don't despair. There's a high likelihood that you can use your Raspberry Pi to compile or interpret any language of choice, including C, C++, PHP, and Ruby.
|
||||
|
||||
Microsoft's [Visual Studio Code][11] also [runs on the Raspberry Pi][12]. It's an open source code editor from Microsoft that supports several markup and programming languages.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/3/programming-languages-raspberry-pi
|
||||
|
||||
作者:[Anderson Silva][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/ansilva
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/article/19/2/teach-kids-program-raspberry-pi
|
||||
[2]: https://opensource.com/resources/python
|
||||
[3]: https://www.economist.com/graphic-detail/2018/07/26/python-is-becoming-the-worlds-most-popular-coding-language
|
||||
[4]: https://thonny.org/
|
||||
[5]: https://raspberrypihq.com/getting-started-with-python-programming-and-the-raspberry-pi/
|
||||
[6]: https://opensource.com/resources/java
|
||||
[7]: https://www.bluej.org/raspberrypi/
|
||||
[8]: https://developer.mozilla.org/en-US/docs/Web/JavaScript
|
||||
[9]: https://nodejs.org/en/
|
||||
[10]: https://www.w3schools.com/nodejs/nodejs_raspberrypi.asp
|
||||
[11]: https://code.visualstudio.com/
|
||||
[12]: https://pimylifeup.com/raspberry-pi-visual-studio-code/
|
||||
@ -0,0 +1,52 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Blockchain 2.0: Revolutionizing The Financial System [Part 2])
|
||||
[#]: via: (https://www.ostechnix.com/blockchain-2-0-revolutionizing-the-financial-system/)
|
||||
[#]: author: (EDITOR https://www.ostechnix.com/author/editor/)
|
||||
|
||||
Blockchain 2.0: Revolutionizing The Financial System [Part 2]
|
||||
======
|
||||
|
||||
This is the second part of our [**Blockchain 2.0**][1] series. The blockchain can transform how individuals and institutions deal with their finances. This post looks at how the existing monetary system evolved and how new blockchain systems are bringing in change as the next crucial step in the evolution of money.
|
||||
|
||||
Two key ideas will lay the foundation for this article. **PayPal** , when it was launched, was revolutionary in terms of its operation. The company would gather, process and confirm massive amounts of consumer data to facilitate online transactions of all kinds, virtually allowing platforms such as eBay to grow into trustful sources for commerce, and laying the benchmark for digital payment systems worldwide. The second, albeit much more important key idea to be highlighted here, is a somewhat existential question. We all use money or rather currency for our day-to-day needs. A ten-dollar bill will get you a cup or two from your favorite coffee shop and get you a head start on your day for instance. We depend on our respective national currencies for virtually everything.
|
||||
|
||||
Sure, mankind has come a long way since the **barter system** ruled what you ate for breakfast, but still, what exactly is currency? Who or what gives it it’s a value? And as the popular rumor suggests, does going to a bank and giving them a dollar bill actually get you the true value of whatever that currency “token” stands for?
|
||||
|
||||
The answer to most of those questions doesn’t exist. If they do, they’ll to be undependably vague and subjective at best. Back in the day when civilization started off establishing small cities and towns, the local currency deemed legal by the guy who ruled over them, was almost always made of something precious to that community. Indians are thought to have transacted in peppercorns while ancient Greeks and Romans in **salt** [1]. Gradually most of these little prehistoric civilizations adopted precious metals and stones as their tokens to transact. Gold coins, silver heirlooms, and rubies became eponymous with “value”. With the industrial revolution, people started printing these tokens of transaction and we finally seemed to have found our calling in paper currencies. They were dependable and cheap to produce and as long as a nation-state guaranteed its users that the piece of paper, they were holding was just a token for an amount of “value” they had and as long as they were able to show them that this value when demanded could be supported with precious substances such as gold or hard assets, people were happy to use them. However, if you still believe that the currency note you hold in your hand right now has the same guarantee, you’re wrong. We currently live in an age where almost all the major currencies in circulation around the globe are what economists would call a **fiat currency** [2]. Value-less pieces of paper that are only backed by the guarantees of the nation-state you’re residing in. The exact nature of fiat currencies and why they may possibly be a flawed system falls into the domain of economics and we won’t get into that now.
|
||||
|
||||
In fact, the only takeaway from all of this history that is relevant to this post is that civilizations started using tokens that hinted or represented value for trading goods and services rather than the non-practical barter system. Tokens. Naturally, this is the crucial concept behind cryptocurrencies as well. They don’t have any inherent value attached to them. Their value is tied to the number of people adopting that particular platform, the trust the adopters have on the system, and of course if released by a supervising entity, the background of the entity itself. The high price and market cap of **Bitcoin (BTC)** isn’t a coincidence, they were among the first in business and had a lot of early adopters. This ultimate truth behind cryptocurrencies is what makes it so important yet so unforgivingly complex to understand. It’s the natural next step in the evolution of “money”. Some understand this and some still like to think of the solid currency concept where “real” money is always backed by something of inherent value.[3] Though there have been countless debates and studies on this dilemma, there is no looking back from a blockchain powered future.
|
||||
|
||||
For instance, the country of **Ecuador** made headlines in 2015 for its purported plans to develop and release **its own national cryptocurrency** [4]. Albeit the attempt officially was to aid and support their existing currency system. Since then other countries and their regulatory bodies have or are drafting up papers to control the “epidemic” that is cryptocurrency with some already having published frameworks to the extent of creating a roadmap for blockchain and crypto development. **Germany** is thought to be investing in a long term blockchain project to streamline its taxation and financial systems[5]. Banks in developing countries are joining in on something called a Bank chain, cooperating in creating a **private blockchain** to increase efficiency in and optimize their operations
|
||||
|
||||
Now is when we tie both the ends of the stories together, remember the first mention of PayPal before the casual history lesson? Experts have compared Bitcoin’s (BTC) adoption rate with that of PayPal when it was launched. Initial consumer hesitation, where only a few early adopters are ready to jump into using the said product and then all a wider adoption gradually becoming a benchmark for similar platforms. Bitcoin (BTC) is already a benchmark for similar cryptocurrency platforms with major coins such as **Ethereum (ETH)** and **Ripple (XRP)** [6]. Adoption is steadily increasing, legal and regulatory frameworks being made to support it, and active research and development being done on the front as well. And not unlike PayPal, experts believe that cryptocurrencies and platforms utilizing blockchain tech for their digital infrastructure will soon become the standard norm rather than the exception.
|
||||
|
||||
Although the rise in cryptocurrency prices in 2018 can be termed as an economic bubble, companies and governments have continued to invest as much or more into the development of their own blockchain platforms and financial tokens. To counteract and prevent such an incident in the future while still looking forward to investing in the area, an alternative to traditional cryptocurrencies called **stablecoins** have made the rounds recently.
|
||||
|
||||
Financial behemoth **JP Morgan** came out with their own enterprise ready blockchain solution called **Quorum** handling their stablecoin called **JPM Coin** [7]. Each such JPM coin is tied to 1 USD and their value is guaranteed by the parent organization under supporting legal frameworks, in this case, JP Morgan. Platforms such as this one make it easier for large financial transactions to the tunes of millions or billions of dollars to be transferred instantaneously over the internet without having to rely on conventional banking systems such as SWIFT which involve lengthy procedures and are themselves decades old.
|
||||
|
||||
In the same spirit of making the niceties of the blockchain available for everyone, The Ethereum platform allows 3rd parties to utilize their blockchain or derive from it to create and administer their own takes on the triad of the **Blockchain-protocol-token** system thereby leading to wider adoption of the standard with lesser work on its foundations.
|
||||
|
||||
The blockchain allows for digital versions of existing financial instruments to be created, recorded, and traded quickly over a network without the need for third-party monitoring. The inherent safety and security features of the system makes the entire process totally safe and immune to fraud and tampering, basically the only reason why third-party monitoring was required in the sector. Another area where governmental and regulatory bodies presided over when it came to financial services and instruments were in regards to transparency and auditing. With blockchain banks and other financial institutes will be able to maintain a fully transparent, layered, almost permanent and tamper-proof record of all their transactions rendering auditing tasks near useless. Much needed developments and changes to the current financial system and services industry can be made possible by exploiting blockchains. The platform being distributed, tamper-proof, near permanent, and quick to execute is highly valuable to bankers and government regulators alike and their investments in this regard seem to be well placed[8].
|
||||
|
||||
In the next article of the series, we see how companies are using blockchains to deliver the next generation of financial services. Looking at individual firms creating ripples in the industry, we explore how the future of a blockchain backed economy would look like.
|
||||
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.ostechnix.com/blockchain-2-0-revolutionizing-the-financial-system/
|
||||
|
||||
作者:[EDITOR][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.ostechnix.com/author/editor/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.ostechnix.com/blockchain-2-0-an-introduction/
|
||||
@ -0,0 +1,64 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Get cooking with GNOME Recipes on Fedora)
|
||||
[#]: via: (https://fedoramagazine.org/get-cooking-with-gnome-recipes-on-fedora/)
|
||||
[#]: author: (Ryan Lerch https://fedoramagazine.org/introducing-flatpak/)
|
||||
|
||||
Get cooking with GNOME Recipes on Fedora
|
||||
======
|
||||

|
||||
|
||||
Do you love to cook? Looking for a better way to manage your recipes using Fedora? GNOME Recipes is an awesome application available to install in Fedora to store and organize your recipe collection.
|
||||
|
||||
![][1]
|
||||
|
||||
GNOME Recipes is an recipe management tool from the GNOME project. It has the visual style of a modern GNOME style application, and feels similar to GNOME Software, but for food.
|
||||
|
||||
### Installing GNOME Recipes
|
||||
|
||||
Recipes is available to install from the 3rd party Flathub repositories. If you have never installed an application from Flathub before, set it up using the following guide:
|
||||
|
||||
[Install Flathub apps on Fedora](https://fedoramagazine.org/install-flathub-apps-fedora/)
|
||||
|
||||
After correctly setting up Flathub as a software source, you will be able to search for and install Recipes via GNOME Software.
|
||||
|
||||
### Recipe management
|
||||
|
||||
Recipes allows you to manually add your own collection of recipes, including photos, ingredients, directions, as well as extra metadata like preparation time, cuisine style, and spiciness.
|
||||
|
||||
![][2]
|
||||
|
||||
When entering in a new item, GNOME Recipes there are a range of different measurement units to choose from, as well as special tags for items like temperature, allowing you to easily switch units.
|
||||
|
||||
### Community recipes
|
||||
|
||||
In addition to manually entering in your favourite dishes for your own use, it also allows you to find, use, and contribute recipes to the community. Additionally, you can mark your favourites, and search the collection by the myriad of metadata available for each recipe.
|
||||
|
||||
![][3]
|
||||
|
||||
### Step by step guidance
|
||||
|
||||
One of the awesome little features in GNOME Recipes is the step by step fullscreen mode. When you are ready to cook, simply activate this mode, move you laptop to the kitchen, and you will have a full screen display of the current step in the cooking method. Futhermore, you can set up the recipes to have timers displayed on this mode when something is in the oven.
|
||||
|
||||
![][4]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://fedoramagazine.org/get-cooking-with-gnome-recipes-on-fedora/
|
||||
|
||||
作者:[Ryan Lerch][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://fedoramagazine.org/introducing-flatpak/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://fedoramagazine.org/wp-content/uploads/2019/03/Screenshot-from-2019-03-06-19-45-06-1024x727.png
|
||||
[2]: https://fedoramagazine.org/wp-content/uploads/2019/03/gnome-recipes1-1024x727.png
|
||||
[3]: https://fedoramagazine.org/wp-content/uploads/2019/03/Screenshot-from-2019-03-06-20-08-45-1024x725.png
|
||||
[4]: https://fedoramagazine.org/wp-content/uploads/2019/03/Screenshot-from-2019-03-06-20-39-44-1024x640.png
|
||||
72
sources/tech/20190307 13 open source backup solutions.md
Normal file
72
sources/tech/20190307 13 open source backup solutions.md
Normal file
@ -0,0 +1,72 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (13 open source backup solutions)
|
||||
[#]: via: (https://opensource.com/article/19/3/backup-solutions)
|
||||
[#]: author: (Don Watkins https://opensource.com/users/don-watkins)
|
||||
|
||||
13 open source backup solutions
|
||||
======
|
||||
Readers suggest more than a dozen of their favorite solutions for protecting data.
|
||||

|
||||
|
||||
Recently, we published a [poll][1] that asked readers to vote on their favorite open source backup solution. We offered six solutions recommended by our [moderator community][2]—Cronopete, Deja Dup, Rclone, Rdiff-backup, Restic, and Rsync—and invited readers to share other options in the comments. And you came through, offering 13 other solutions (so far) that we either hadn't considered or hadn't even heard of.
|
||||
|
||||
By far the most popular suggestion was [BorgBackup][3]. It is a deduplicating backup solution that features compression and encryption. It is supported on Linux, MacOS, and BSD and has a BSD License.
|
||||
|
||||
Second was [UrBackup][4], which does full and incremental image and file backups; you can save whole partitions or single directories. It has clients for Windows, Linux, and MacOS and has a GNU Affero Public License.
|
||||
|
||||
Third was [LuckyBackup][5]; according to its website, "it is simple to use, fast (transfers over only changes made and not all data), safe (keeps your data safe by checking all declared directories before proceeding in any data manipulation), reliable, and fully customizable." It carries a GNU Public License.
|
||||
|
||||
[Casync][6] is content-addressable synchronization—it's designed for backup and synchronizing and stores and retrieves multiple related versions of large file systems. It is licensed with the GNU Lesser Public License.
|
||||
|
||||
[Syncthing][7] synchronizes files between two computers. It is licensed with the Mozilla Public License and, according to its website, is secure and private. It works on MacOS, Windows, Linux, FreeBSD, Solaris, and OpenBSD.
|
||||
|
||||
[Duplicati][8] is a free backup solution that works on Windows, MacOS, and Linux and a variety of standard protocols, such as FTP, SSH, and WebDAV, and cloud services. It features strong encryption and is licensed with the GPL.
|
||||
|
||||
[Dirvish][9] is a disk-based virtual image backup system licensed under OSL-3.0. It also requires Rsync, Perl5, and SSH to be installed.
|
||||
|
||||
[Bacula][10]'s website says it "is a set of computer programs that permits the system administrator to manage backup, recovery, and verification of computer data across a network of computers of different kinds." It is supported on Linux, FreeBSD, Windows, MacOS, OpenBSD, and Solaris and the bulk of its source code is licensed under AGPLv3.
|
||||
|
||||
[BackupPC][11] "is a high-performance, enterprise-grade system for backing up Linux, Windows, and MacOS PCs and laptops to a server's disk," according to its website. It is licensed under the GPLv3.
|
||||
|
||||
[Amanda][12] is a backup system written in C and Perl that allows a system administrator to back up an entire network of client machines to a single server using tape, disk, or cloud-based systems. It was developed and copyrighted in 1991 at the University of Maryland and has a BSD-style license.
|
||||
|
||||
[Back in Time][13] is a simple backup utility designed for Linux. It provides a command line client and a GUI, both written in Python. To do a backup, just specify where to store snapshots, what folders to back up, and the frequency of the backups. BackInTime is licensed with GPLv2.
|
||||
|
||||
[Timeshift][14] is a backup utility for Linux that is similar to System Restore for Windows and Time Capsule for MacOS. According to its GitHub repository, "Timeshift protects your system by taking incremental snapshots of the file system at regular intervals. These snapshots can be restored at a later date to undo all changes to the system."
|
||||
|
||||
[Kup][15] is a backup solution that was created to help users back up their files to a USB drive, but it can also be used to perform network backups. According to its GitHub repository, "When you plug in your external hard drive, Kup will automatically start copying your latest changes."
|
||||
|
||||
Thanks for sharing your favorite open source backup solutions in our poll! If there are still others that haven't been mentioned yet, please share them in the comments.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/3/backup-solutions
|
||||
|
||||
作者:[Don Watkins][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/don-watkins
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/article/19/2/linux-backup-solutions
|
||||
[2]: https://opensource.com/opensourcecom-team
|
||||
[3]: https://www.borgbackup.org/
|
||||
[4]: https://www.urbackup.org/
|
||||
[5]: http://luckybackup.sourceforge.net/
|
||||
[6]: http://0pointer.net/blog/casync-a-tool-for-distributing-file-system-images.html
|
||||
[7]: https://syncthing.net/
|
||||
[8]: https://www.duplicati.com/
|
||||
[9]: http://dirvish.org/
|
||||
[10]: https://www.bacula.org/
|
||||
[11]: https://backuppc.github.io/backuppc/
|
||||
[12]: http://www.amanda.org/
|
||||
[13]: https://github.com/bit-team/backintime
|
||||
[14]: https://github.com/teejee2008/timeshift
|
||||
[15]: https://github.com/spersson/Kup
|
||||
@ -0,0 +1,208 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (How to Restart a Network in Ubuntu [Beginner’s Tip])
|
||||
[#]: via: (https://itsfoss.com/restart-network-ubuntu)
|
||||
[#]: author: (Sergiu https://itsfoss.com/author/sergiu/)
|
||||
|
||||
How to Restart a Network in Ubuntu [Beginner’s Tip]
|
||||
======
|
||||
|
||||
You’re [using an Ubuntu-based system and you just can’t seem to connect to your network][1]? You’d be surprised how many problems can a simple restart fix.
|
||||
|
||||
In this article, I’ll go over multiple ways you can restart network in Ubuntu and other Linux distributions, so you can use whatever suits your needs. The methods are basically divided into two parts:
|
||||
|
||||
![Ubuntu Restart Network][2]
|
||||
|
||||
### Restart network in Ubuntu using command line
|
||||
|
||||
If you are using Ubuntu server edition, you are already in the terminal. If you are using the desktop edition, you can access the terminal using Ctrl+Alt+T [keyboard shortcut in Ubuntu][3].
|
||||
|
||||
Now you have several commands at your disposal to restart network in Ubuntu. Some (or perhaps most) commands mentioned here should be applicable for restarting network in Debian and other Linux distributions as well.
|
||||
|
||||
#### 1\. network manager service
|
||||
|
||||
This is the easiest way to restart your network using the command line. It’s equivalent to the graphical way of doing it (restarts the Network-Manager service).
|
||||
|
||||
```
|
||||
sudo service network-manager restart
|
||||
```
|
||||
|
||||
The network icon should disappear for a moment and then reappear.
|
||||
|
||||
#### 2\. systemd
|
||||
|
||||
The **service** command is just a wrapper for this method (and also for init.d scripts and Upstart commands). The **systemctl** command is much more versatile than **service**. This is what I usually prefer.
|
||||
|
||||
```
|
||||
sudo systemctl restart NetworkManager.service
|
||||
```
|
||||
|
||||
The network icon (again) should disappear for a moment. To check out other **systemctl** options, you can refer to its man page.
|
||||
|
||||
#### 3\. nmcli
|
||||
|
||||
This is yet another tool for handling networks on a Linux machine. It is a pretty powerful tool that I find very practical. Many sysadmins prefer it since it is easy to use.
|
||||
|
||||
There are two steps to this method: turning the network off, and then turning it back on.
|
||||
|
||||
```
|
||||
sudo nmcli networking off
|
||||
```
|
||||
|
||||
The network will shut down and the icon will disappear. To turn it back on:
|
||||
|
||||
```
|
||||
sudo nmcli networking on
|
||||
```
|
||||
|
||||
You can check out the man page of nmcli for more options.
|
||||
|
||||
#### 4\. ifup & ifdown
|
||||
|
||||
This commands handle a network interface directly, changing it’s state to one in which it either can or can not transmit and receive data. It’s one of the [must know networking commands in Linux][4].
|
||||
|
||||
To shut down all network interfaces, use ifdown and then use ifup to turn all network interfaces back on.
|
||||
|
||||
A good practice would be to combine both of these commands:
|
||||
|
||||
```
|
||||
sudo ifdown -a && sudo ifup -a
|
||||
```
|
||||
|
||||
**Note:** This method will not make the network icon in your systray disappear, and yet you won’t be able to have a connection of any sort.
|
||||
|
||||
**Bonus tool: nmtui (click to expand)**
|
||||
|
||||
This is another method often used by system administrators. It is a text menu for managing networks right in your terminal.
|
||||
|
||||
```
|
||||
nmtui
|
||||
```
|
||||
|
||||
This should open up the following menu:
|
||||
|
||||
![nmtui Menu][5]
|
||||
|
||||
**Note** that in **nmtui** , you can select another option by using the **up** and **down arrow keys**.
|
||||
|
||||
Select **Activate a connection** :
|
||||
|
||||
![nmtui Menu Select "Activate a connection"][6]
|
||||
|
||||
Press **Enter**. This should now open the **connections** menu.
|
||||
|
||||
![nmtui Connections Menu][7]
|
||||
|
||||
Here, go ahead and select the network with a **star (*)** next to it. In my case, it’s MGEO72.
|
||||
|
||||
![Select your connection in the nmtui connections menu.][8]
|
||||
|
||||
Press **Enter**. This should **deactivate** your connection.
|
||||
|
||||
![nmtui Connections Menu with no active connection][9]
|
||||
|
||||
Select the connection you want to activate:
|
||||
|
||||
![Select the connection you want in the nmtui connections menu.][10]
|
||||
|
||||
Press **Enter**. This should reactivate the selected connection.
|
||||
|
||||
![nmtui Connections Menu][11]
|
||||
|
||||
Press **Tab** twice to select **Back** :
|
||||
|
||||
![Select "Back" in the nmtui connections menu.][12]
|
||||
|
||||
Press **Enter**. This should bring you back to the **nmtui** main menu.
|
||||
|
||||
![nmtui Main Menu][13]
|
||||
|
||||
Select **Quit** :
|
||||
|
||||
![nmtui Quit Main Menu][14]
|
||||
|
||||
This should exit the application and bring you back to your terminal.
|
||||
|
||||
That’s it! You have successfully restarted your network
|
||||
|
||||
### Restart network in Ubuntu graphically
|
||||
|
||||
This is, of course, the easiest way of restarting the network for Ubuntu desktop users. If this one doesn’t work, you can of course check the command line options mentioned in the previous section.
|
||||
|
||||
NM-applet is the system tray applet indicator for [NetworkManager][15]. That’s what we’re going to use to restart our network.
|
||||
|
||||
First of all, check out your top panel. You should find a network icon in your system tray (in my case, it is a Wi-Fi icon, since that’s what I use).
|
||||
|
||||
Go ahead and click on that icon (or the sound or battery icon). This will open up the menu. Select “Turn Off” here.
|
||||
|
||||
![Restart network in Ubuntu][16]Turn off your network
|
||||
|
||||
The network icon should now disappear from the top panel. This means the network has been successfully turned off.
|
||||
|
||||
Click again on your systray to reopen the menu. Select “Turn On”.
|
||||
|
||||
![Restarting network in Ubuntu][17]Turn the network back on
|
||||
|
||||
Congratulations! You have now restarted your network.
|
||||
|
||||
#### Bonus Tip: Refresh available network list
|
||||
|
||||
Suppose you are connected to a network already but you want to connect to another network. How do you refresh the WiFi to see what other networks are available? Let me show you that.
|
||||
|
||||
Ubuntu doesn’t have a ‘refresh wifi networks’ option directly. It’s sort of hidden.
|
||||
|
||||
You’ll have to open the setting menu again and this time, click on “Select Network”.
|
||||
|
||||
![Refresh wifi network list in Ubuntu][18]Select Network to change your WiFi connection
|
||||
|
||||
Now, you won’t see the list of available wireless networks immediately. When you open the networks list, it takes around 5 seconds to refresh and show up other available wireless networks.
|
||||
|
||||
![Select another wifi network in Ubuntu][19]Wait for around 5- seconds to see other available networks
|
||||
|
||||
And here, you can select the network of your choice and click connect. That’s it.
|
||||
|
||||
**Wrapping Up**
|
||||
|
||||
Restarting your network or connection is something that every Linux user has to go through at some point in their experience.
|
||||
|
||||
We hope that we helped you with plenty of methods for handling such issues!
|
||||
|
||||
What do you use to restart/handle your network? Is there something we missed? Leave us a comment below.
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://itsfoss.com/restart-network-ubuntu
|
||||
|
||||
作者:[Sergiu][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://itsfoss.com/author/sergiu/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://itsfoss.com/fix-no-wireless-network-ubuntu/
|
||||
[2]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2019/03/ubuntu-restart-network.png?resize=800%2C450&ssl=1
|
||||
[3]: https://itsfoss.com/ubuntu-shortcuts/
|
||||
[4]: https://itsfoss.com/basic-linux-networking-commands/
|
||||
[5]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2019/03/nmtui_menu.png?fit=800%2C602&ssl=1
|
||||
[6]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2019/03/nmtui_menu_select_option.png?fit=800%2C579&ssl=1
|
||||
[7]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2019/03/nmui_connection_menu_on.png?fit=800%2C585&ssl=1
|
||||
[8]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2019/03/nmui_select_connection_on.png?fit=800%2C576&ssl=1
|
||||
[9]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2019/03/nmui_connection_menu_off.png?fit=800%2C572&ssl=1
|
||||
[10]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2019/03/nmui_select_connection_off.png?fit=800%2C566&ssl=1
|
||||
[11]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2019/03/nmui_connection_menu_on-1.png?fit=800%2C585&ssl=1
|
||||
[12]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2019/03/nmui_connection_menu_back.png?fit=800%2C585&ssl=1
|
||||
[13]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2019/03/nmtui_menu_select_option-1.png?fit=800%2C579&ssl=1
|
||||
[14]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2019/03/nmui_menu_quit.png?fit=800%2C580&ssl=1
|
||||
[15]: https://wiki.gnome.org/Projects/NetworkManager
|
||||
[16]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2019/03/restart-network-ubuntu-1.jpg?resize=800%2C400&ssl=1
|
||||
[17]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2019/03/restart-network-ubuntu-2.jpg?resize=800%2C400&ssl=1
|
||||
[18]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2019/03/select-wifi-network-ubuntu.jpg?resize=800%2C400&ssl=1
|
||||
[19]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2019/03/select-wifi-network-ubuntu-1.jpg?resize=800%2C400&ssl=1
|
||||
[20]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2019/03/ubuntu-restart-network.png?fit=800%2C450&ssl=1
|
||||
@ -0,0 +1,51 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (How to keep your Raspberry Pi updated)
|
||||
[#]: via: (https://opensource.com/article/19/3/how-raspberry-pi-update)
|
||||
[#]: author: (Anderson Silva https://opensource.com/users/ansilva)
|
||||
|
||||
How to keep your Raspberry Pi updated
|
||||
======
|
||||
Learn how to keep your Raspberry Pi patched and working well in the seventh article in our guide to getting started with the Raspberry Pi.
|
||||

|
||||
|
||||
Just like your tablet, cellphone, and laptop, you need to keep your Raspberry Pi updated. Not only will the latest enhancements keep your Pi running smoothly, they will also keep you safer, especially if you are connected to a network. The seventh article in our guide to getting started with the Raspberry Pi shares two pieces of advice on keeping your Pi working well.
|
||||
|
||||
### Update Raspbian
|
||||
|
||||
Updating your Raspbian installation is a [two-step process][1]:
|
||||
|
||||
1. In your terminal type: **sudo apt-get update**
|
||||
The command **sudo** allows you to run **apt-get update** as admin (aka root). Note that **apt-get update** will not install anything new on your system; rather it will update the list of packages and dependencies that need to be updated.
|
||||
|
||||
|
||||
2. Then type: **sudo apt-get dist-upgrade**
|
||||
From the documentation: "Generally speaking, doing this regularly will keep your installation up to date, in that it will be equivalent to the latest released image available from [raspberrypi.org/downloads][2]."
|
||||
|
||||
|
||||
|
||||
### Be careful with rpi-update
|
||||
|
||||
Raspbian comes with another little update utility called [rpi-update][3]. This utility can be used to upgrade your Pi to the latest firmware which may or may not be broken/buggy. You may find information explaining how to use it, but as of late it is recommended never to use this application unless you have a really good reason to do so.
|
||||
|
||||
Bottom line: Keep your systems updated!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/3/how-raspberry-pi-update
|
||||
|
||||
作者:[Anderson Silva][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/ansilva
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.raspberrypi.org/documentation/raspbian/updating.md
|
||||
[2]: https://www.raspberrypi.org/downloads/
|
||||
[3]: https://github.com/Hexxeh/rpi-update
|
||||
@ -0,0 +1,57 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (How to use your Raspberry Pi for entertainment)
|
||||
[#]: via: (https://opensource.com/article/19/3/raspberry-pi-entertainment)
|
||||
[#]: author: (Anderson Silva https://opensource.com/users/ansilva)
|
||||
|
||||
How to use your Raspberry Pi for entertainment
|
||||
======
|
||||
Learn how to watch Netflix and listen to music on your Raspberry Pi, in the eighth article in our guide to getting started with Raspberry Pi.
|
||||

|
||||
|
||||
So far, this series has focused on more serious topics—how to [choose][1], [buy][2], [set up][3], and [update][4] your Raspberry Pi, and different things [kids][5] and [adults][6] can learn with it (including [Linux][7]). But now it's time to change up the subject and have some fun! Today we'll look at ways to use your Raspberry Pi for entertainment, and tomorrow we'll continue the fun with gaming.
|
||||
|
||||
### Watch TV and movies
|
||||
|
||||
You can use your Raspberry Pi and the [Open Source Media Center][8] (OSMC) to [watch Netflix][9]! The OSMC is a system based on the [Kodi][10] project that allows you to play back media from your local network, attached storage, and the internet. It's also known for having the best feature set and community among media center applications.
|
||||
|
||||
NOOBS (which we talked about in the [third article][11] in this series) allows you to [install OSMC][12] on your Raspberry Pi as easily as possible. NOOBS also offers another media center system based on Kodi called [LibreELEC][13].
|
||||
|
||||
### Listen to music
|
||||
|
||||
|
||||
|
||||
You can also stream music on your network via attached storage or services like Spotify on your Raspberry Pi with the [Pi Music Box][14] project. I [wrote about it][15] a while ago, but you can find newer instructions, including how to's and DIY projects, on the [Pi Music Box website][16].
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/3/raspberry-pi-entertainment
|
||||
|
||||
作者:[Anderson Silva][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/ansilva
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/article/19/3/which-raspberry-pi-choose
|
||||
[2]: https://opensource.com/article/19/2/how-buy-raspberry-pi
|
||||
[3]: https://opensource.com/article/19/2/how-boot-new-raspberry-pi
|
||||
[4]: https://opensource.com/article/19/2/how-keep-your-raspberry-pi-updated-and-patched
|
||||
[5]: https://opensource.com/article/19/3/teach-kids-program-raspberry-pi
|
||||
[6]: https://opensource.com/article/19/2/3-popular-programming-languages-you-can-learn-raspberry-pi
|
||||
[7]: https://opensource.com/article/19/2/learn-linux-raspberry-pi
|
||||
[8]: https://osmc.tv/
|
||||
[9]: https://www.dailydot.com/upstream/netflix-raspberry-pi/
|
||||
[10]: http://kodi.tv/
|
||||
[11]: https://opensource.com/article/19/3/how-boot-new-raspberry-pi
|
||||
[12]: https://www.raspberrypi.org/documentation/usage/kodi/
|
||||
[13]: https://libreelec.tv/
|
||||
[14]: https://github.com/pimusicbox/pimusicbox/tree/master
|
||||
[15]: https://opensource.com/life/15/3/pi-musicbox-guide
|
||||
[16]: https://www.pimusicbox.com/
|
||||
@ -0,0 +1,48 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Emulators and Native Linux games on the Raspberry Pi)
|
||||
[#]: via: (https://opensource.com/article/19/3/play-games-raspberry-pi)
|
||||
[#]: author: (Anderson Silva https://opensource.com/users/ansilva)
|
||||
|
||||
Emulators and Native Linux games on the Raspberry Pi
|
||||
======
|
||||
The Raspberry Pi is a great platform for gaming; learn how in the ninth article in our series on getting started with the Raspberry Pi.
|
||||
|
||||

|
||||
|
||||
Back in the [fifth article][1] in our series on getting started with the Raspberry Pi, I mentioned Minecraft as a way to teach kids to program using a gaming platform. Today we'll talk about other ways you can play games on your Raspberry Pi, as it's a great platform for gaming—with and without emulators.
|
||||
|
||||
### Gaming with emulators
|
||||
|
||||
Emulators are software that allow you to play games from different systems and different decades on your Raspberry Pi. Of the many emulators available today, the most popular for the Raspberry Pi is [RetroPi][2]. You can use it to play games from systems such as Apple II, Amiga, Atari 2600, Commodore 64, Game Boy Advance, and [many others][3].
|
||||
|
||||
If RetroPi sounds interesting, check out [these instructions][4] on how to get started, and start having fun today!
|
||||
|
||||
### Native Linux games
|
||||
|
||||
There are also plenty of native Linux games available on Raspbian, Raspberry Pi's operating system. Make Use Of has a great article on [how to play 10 old favorites][5] like Doom and Nuke Dukem 3D on the Raspberry Pi.
|
||||
|
||||
You can also use your Raspberry Pi as a [game server][6]. For example, you can set up Terraria, Minecraft, and QuakeWorld servers on the Raspberry Pi.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/3/play-games-raspberry-pi
|
||||
|
||||
作者:[Anderson Silva][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/ansilva
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/article/19/3/teach-kids-program-raspberry-pi
|
||||
[2]: https://retropie.org.uk/
|
||||
[3]: https://retropie.org.uk/about/systems
|
||||
[4]: https://opensource.com/article/19/1/retropie
|
||||
[5]: https://www.makeuseof.com/tag/classic-games-raspberry-pi-without-emulators/
|
||||
[6]: https://www.makeuseof.com/tag/raspberry-pi-game-servers/
|
||||
@ -0,0 +1,48 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Let's get physical: How to use GPIO pins on the Raspberry Pi)
|
||||
[#]: via: (https://opensource.com/article/19/3/gpio-pins-raspberry-pi)
|
||||
[#]: author: (Anderson Silva https://opensource.com/users/ansilva)
|
||||
|
||||
Let's get physical: How to use GPIO pins on the Raspberry Pi
|
||||
======
|
||||
The 10th article in our series on getting started with Raspberry Pi explains how the GPIO pins work.
|
||||
|
||||
|
||||
Until now, this series has focused on the Raspberry Pi's software side, but today we'll get into the hardware. The availability of [general-purpose input/output][1] (GPIO) pins was one of the main features that interested me in the Pi when it first came out. GPIO allows you to programmatically interact with the physical world by attaching sensors, relays, and other types of circuitry to the Raspberry Pi.
|
||||
|
||||

|
||||
|
||||
Each pin on the board either has a predefined function or is designated as general purpose. Also, different Raspberry Pi models have either 26 or 40 pins for you to use at your discretion. Wikipedia has a [good overview of each pin][2] and its functionality.
|
||||
|
||||
You can do many things with the Pi's GPIO pins. I've written some other articles about using the GPIOs, including a trio of articles ([Part I][3], [Part II][4], and [Part III][5]) about controlling holiday lights with the Raspberry Pi while using open source software to pair the lights with music.
|
||||
|
||||
The Raspberry Pi community has done a great job in creating libraries in different programming languages, so you should be able to interact with the pins using [C][6], [Python][7], [Scratch][8], and other languages.
|
||||
|
||||
Also, if you want the ultimate experience to interact with the physical world, pick up a [Raspberry Pi Sense Hat][9]. It is an affordable expansion board for the Pi that plugs into the GPIO pins so you can programmatically interact with LEDs, joysticks, and barometric pressure, temperature, humidity, gyroscope, accelerometer, and magnetometer sensors.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/3/gpio-pins-raspberry-pi
|
||||
|
||||
作者:[Anderson Silva][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/ansilva
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.raspberrypi.org/documentation/usage/gpio/
|
||||
[2]: https://en.wikipedia.org/wiki/Raspberry_Pi#General_purpose_input-output_(GPIO)_connector
|
||||
[3]: https://opensource.com/life/15/2/music-light-show-with-raspberry-pi
|
||||
[4]: https://opensource.com/life/15/12/ssh-your-christmas-tree-raspberry-pi
|
||||
[5]: https://opensource.com/article/18/12/lightshowpi-raspberry-pi
|
||||
[6]: https://www.bigmessowires.com/2018/05/26/raspberry-pi-gpio-programming-in-c/
|
||||
[7]: https://www.raspberrypi.org/documentation/usage/gpio/python/README.md
|
||||
[8]: https://www.raspberrypi.org/documentation/usage/gpio/scratch2/README.md
|
||||
[9]: https://opensource.com/life/16/4/experimenting-raspberry-pi-sense-hat
|
||||
@ -0,0 +1,80 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (7 resources for learning to use your Raspberry Pi)
|
||||
[#]: via: (https://opensource.com/article/19/3/resources-raspberry-pi)
|
||||
[#]: author: (Manuel Dewald https://opensource.com/users/ntlx)
|
||||
|
||||
7 resources for learning to use your Raspberry Pi
|
||||
======
|
||||
Books, courses, and websites to shorten your Raspberry Pi learning curve.
|
||||

|
||||
|
||||
The [Raspberry Pi][1] is a small, single-board computer originally intended for teaching and learning programming and computer science. But today it's so much more. It is affordable, low-energy computing power that people can use for all kinds of things—from home entertainment over server applications to Internet of Things (IoT) projects.
|
||||
|
||||
There are so many resources on the topic and so many different projects you can do, it's hard to know where to begin. Following are some resources that will help you get started with the Raspberry Pi. Have fun browsing through it, but don't stop here. By looking left and right you will find a lot to discover and get deeper into the rabbit hole of the Raspberry Pi wonderland.
|
||||
|
||||
### Books
|
||||
|
||||
There are many books available in different languages about the Raspberry Pi. These two will help you start—then dive deep—into Raspberry Pi topics.
|
||||
|
||||
#### Raspberry Pi Cookbook: Software and Hardware Problems and Solutions by Simon Monk
|
||||
|
||||
Simon Monk is a software engineer and was a hobbyist maker for years. He was first attracted to the Arduino as an easy-to-use board for electronics development and later published a [book][2] about it. Later, he moved on to the Raspberry Pi and wrote [Raspberry Pi Cookbook: Software and Hardware Problems and Solutions][3]. In the book, you can find a lot of best practices for Raspberry Pi projects and solutions for all kinds of challenges you may face.
|
||||
|
||||
#### Programming the Raspberry Pi: Getting Started with Python by Simon Monk
|
||||
|
||||
Python has evolved as the go-to programming language for getting started with Raspberry Pi projects, as it is easy to learn and use, even if you don't have any programming experience. Also, a lot of its libraries help you focus on what makes your project special instead of implementing protocols to communicate with your sensors again and again. Monk wrote two chapters about Python programming in the Raspberry Pi Cookbook, but [Programming the Raspberry Pi: Getting Started with Python][4] is a more thorough quickstart. It introduces you to Python and shows you some projects you can create with it on the Raspberry Pi.
|
||||
|
||||
### Online course
|
||||
|
||||
There are many online courses and tutorials new Raspberry Pi users can choose from, including this introductory class.
|
||||
|
||||
#### Raspberry Pi Class
|
||||
|
||||
Instructables' free [Raspberry Pi Class][5] online course offers you an all-around introduction to the Raspberry Pi. It starts with Raspberry Pi and Linux operating basics, then gets into Python programming and GPIO communication. This makes it a good top-to-bottom Raspberry Pi guide if you are new to the topic and want to get started quickly.
|
||||
|
||||
### Websites
|
||||
|
||||
The web is rife with excellent information about Raspberry Pi, but these four sites should be on the top of any new user's list.
|
||||
|
||||
#### RaspberryPi.org
|
||||
|
||||
The official [Raspberry Pi][6] website is one of the best places to get started. Many articles about specific projects link to the site for the basics like installing Raspbian onto the Raspberry Pi. (This is what I tend to do, instead of repeating the instructions in every how-to.) You can also find [sample projects][7] and courses on [teaching][8] tech topics to students.
|
||||
|
||||
#### Opensource.com
|
||||
|
||||
On Opensource.com, you can find a number of different Raspberry Pi project how-to's, getting started guides, success stories, updates, and more. Take a look at the [Raspberry Pi topic page][9] to find out what people are doing with Raspberry Pi.
|
||||
|
||||
#### Instructables and Hackaday
|
||||
|
||||
Do you want to build your own retro arcade gaming console? Or for your mirror to display weather information, the time, and the first event on the day's calendar? Are you looking to create a word clock or maybe a photo booth for a party? Chances are good that you will find instructions on how to do all of this (and more!) with a Raspberry Pi on sites like [Instructables][10] and [Hackaday][11]. If you're not sure if you should get a Raspberry Pi, browse these sites, and you'll find plenty of reasons to buy one.
|
||||
|
||||
What are your favorite Raspberry Pi resources? Please share them in the comments!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/3/resources-raspberry-pi
|
||||
|
||||
作者:[Manuel Dewald][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/ntlx
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/resources/raspberry-pi
|
||||
[2]: http://simonmonk.org/progardui2ed/
|
||||
[3]: http://simonmonk.org/raspberry-pi-cookbook-ed2/
|
||||
[4]: http://simonmonk.org/programming-raspberry-pi-ed2/
|
||||
[5]: https://www.instructables.com/class/Raspberry-Pi-Class/
|
||||
[6]: https://raspberrypi.org
|
||||
[7]: https://projects.raspberrypi.org/
|
||||
[8]: https://www.raspberrypi.org/training/online
|
||||
[9]: https://opensource.com/tags/raspberry-pi
|
||||
[10]: https://www.instructables.com/technology/raspberry-pi/
|
||||
[11]: https://hackaday.io/projects?tag=raspberry%20pi
|
||||
@ -0,0 +1,63 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Blockchain 2.0: Redefining Financial Services [Part 3])
|
||||
[#]: via: (https://www.ostechnix.com/blockchain-2-0-redefining-financial-services/)
|
||||
[#]: author: (EDITOR https://www.ostechnix.com/author/editor/)
|
||||
|
||||
Blockchain 2.0: Redefining Financial Services [Part 3]
|
||||
======
|
||||
|
||||

|
||||
|
||||
The [**previous article of this series**][1] focused on building context to bring forth why moving our existing monetary system to a futuristic [**blockchain**][2] system is the next natural step in the evolution of “money”. We looked at the features of a blockchain platform which would aid in such a move. However, the financial markets are far more complex and composed of numerous other instruments that people trade rather than just a currency.
|
||||
|
||||
This part will explore the features of blockchain which will enable institutions to transform and interlace traditional banking and financing systems with it. As previously discussed, and proved, if enough people participate in a given blockchain network and support the protocols for transactions, the nominal value that can be attributed to the “token” increases and becomes more stable. Take, for instance, Bitcoin (BTC). Like the simple paper currency, we’re all used to, cryptocurrencies such as Bitcoin and Ether can be utilized for all the former’s purposes from buying food to ships and from loaning money to insurance.
|
||||
|
||||
Chances are you are already involved with a bank or any other financial institution that makes use of blockchain ledger technology. The most significant uses of blockchain tech in the finance industry will be in setting up payments infrastructure, fund transfer technologies, and digital identity management. The latter two have traditionally been handled by legacy systems in the financial services industry. These systems are slowly being migrated to blockchain systems owing to their efficiency in handling work like this. The blockchain also offers high-quality data analytics solutions to these firms, an aspect that is quickly gaining prominence because of recent developments in data sciences.[1]
|
||||
|
||||
Considering the start-ups and projects at the cutting edge of innovation in this space first seems warranted due to their products or services already doing the rounds in the market today.
|
||||
|
||||
Starting with PayPal, an online payments company started in 1998, and now among the largest of such platforms, it is considered to be a benchmark in terms of operations and technical prowess. PayPal derives largely from the existing monetary system. Its contribution to innovation came by how it collected and leveraged consumer data to provide services online at instantaneous speeds. Online transactions are taken for granted today with minimal innovation in the industry in terms of the tech that it’s based on. Having a solid foundation is a good thing, but that won’t give anyone an edge over their competition in this fast-paced IT world with new standards and technology being pioneered every other day. In 2014 PayPal subsidiary, **Braintree** announced partnerships with popular cryptocurrency payment solutions including **Coinbase** and **GoCoin** , in a bid to gradually integrate Bitcoin and other popular cryptocurrencies into its service platform. This basically gave its consumers a chance to explore and experience the side of what’s to come under the familiar umbrella cover and reliability of PayPal. In fact, ride-hailing company **Uber** had an exclusive partnership with Braintree to allow customers to pay for rides using Bitcoin.[2][3]
|
||||
|
||||
**Ripple** is making it easier for people to operate between multiple blockchains. Ripple has been in the headlines for moving ahead with regional banks in the US, for instance, to facilitate transferring money bilaterally to other regional banks without the need for a 3rd party intermediary resulting in reduced cost and time overheads. Ripple’s **Codius platform** allows for interoperability between blockchains and opens the doors to smart contracts programmed into the system for minimal tampering and confusion. Built on technology that is highly advanced, secure and scalable to suit needs, Ripple’s platform currently has names such as UBS and Standard Chartered on their client’s list. Many more are expected to join in.[4][5]
|
||||
|
||||
**Kraken** , a US-based cryptocurrency exchange operating in locations around the globe is known for their reliable **crypto quant** estimates even providing Bitcoin pricing data real time to the Bloomberg terminal. In 2015, they partnered with **Fidor Bank** to form what was then the world’s first Cryptocurrency Bank offering customers banking services and products which dealt with cryptocurrencies.[6]
|
||||
|
||||
**Circle** , another FinTech company is currently among the largest of its sorts involved with allowing users to invest and trade in cryptocurrency derived assets, similar to traditional money market assets.[7]
|
||||
|
||||
Companies such as **Wyre** and **Stellar** today have managed to bring down the lead time involved in international wire transfers from an average of 3 days to under 6 hours. Claims have been made saying that once a proper regulatory system is in place the same 6 hours can be brought down to a matter of seconds.[8]
|
||||
|
||||
Now while all of the above have focused on the start-up projects involved, it has to be remembered that the reach and capabilities of the older more respectable financial institutions should not be ignored. Institutions that have existed for decades if not centuries moving billions of dollars worldwide are equally interested in leveraging the blockchain and its potential.
|
||||
|
||||
As we already mentioned in the previous article, **JP Morgan** recently unveiled their plans to exploit cryptocurrencies and the underlying ledger like the functionality of the blockchain for enterprises. The project, called **Quorum** , is defined as an **“Enterprise-ready distributed ledger and smart contract platform”**. The main goal being that gradually the bulk of the bank’s operations would one day be migrated to Quorum thus cutting significant investments that firms such as JP Morgan need to make in order to guarantee privacy, security, and transparency. They’re claimed to be the only player in the industry now to have complete ownership over the whole stack of the blockchain, protocol, and token system. They also released a cryptocurrency called **JPM Coin** meant to be used in transacting high volume settlements instantaneously. JPM coin is among the first “stable coins” to be backed by a major bank such as JP Morgan. A stable coin is a cryptocurrency whose price is linked to an existing major monetary system. Quorum is also touted for its capabilities to process almost 100 transactions a second which is leaps and bounds ahead of its contemporaries.[9]
|
||||
|
||||
**Barclay’s** , a British multinational financial giant is reported to have registered two blockchain-based patents supposedly with the aim of streamlining fund transfers and KYC procedures. Barclay’s proposals though are more aimed toward improving their banking operations’ efficiency. One of the application deals with creating a private blockchain network for storing KYC details of consumers. Once verified, stored and confirmed, these details are immutable and nullifies the need for further verifications down the line. If implemented the protocol will do away with the need for multiple verifications of KYC details. Developing and densely populated countries such as India where a bulk of the population is yet to be inducted into a formal banking system will find the innovative KYC system useful in reducing random errors and lead times involved in the process[10]. Barclay’s is also rumored to be exploring the capabilities of a blockchain system to address credit status ratings and insurance claims.
|
||||
|
||||
Such blockchain backed systems are designed to eliminate needless maintenance costs and leverage the power of smart contracts for enterprises which operate in industries where discretion, security, and speed determine competitive advantage. Being enterprise products, they’re built on protocols that ensure complete transaction and contract privacy along with a consensus mechanism which essentially nullifies corruption and bribery.
|
||||
|
||||
**PwC’s Global Fintech Report** from 2017 states that by 2020, an estimated 77% of all Fintech companies are estimated to switch to blockchain based technologies and processes concerning their operations. A whopping 90 percent of their respondents said that they were planning to adopt blockchain technology as part of an in-production system by 2020. Their judgments are not misplaced as significant cost savings and transparency gains from a regulatory point of view are guaranteed by moving to a blockchain based system.[11]
|
||||
|
||||
Since regulatory capabilities are built into the blockchain platform by default the migration of firms from legacy systems to modern networks running blockchain ledgers is a welcome move for industry regulators as well. Transactions and trade movements can be verified and tracked on the fly once and for all rather than after. This, in the long run, will likely result in better regulation and risk management. Not to mention improved accountability from the part of firms and individuals alike.[11]
|
||||
|
||||
While considerable investments in the space and leaping innovations are courtesy of large investments by established corporates it is misleading to think that such measures wouldn’t permeate the benefits to the end user. As banks and financial institutions start to adopt the blockchain, it will result in increased cost savings and efficiency for them which will ultimately mean good for the end consumer too. The added benefits of transparency and fraud protection will improve customer sentiments and more importantly improve the trust that people place on the banking and financial system. A much-needed revolution in the financial services industry is possible with blockchains and their integration into traditional services.
|
||||
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.ostechnix.com/blockchain-2-0-redefining-financial-services/
|
||||
|
||||
作者:[EDITOR][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.ostechnix.com/author/editor/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.ostechnix.com/blockchain-2-0-revolutionizing-the-financial-system/
|
||||
[2]: https://www.ostechnix.com/blockchain-2-0-an-introduction/
|
||||
@ -0,0 +1,76 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Building the virtualization stack of the future with rust-vmm)
|
||||
[#]: via: (https://opensource.com/article/19/3/rust-virtual-machine)
|
||||
[#]: author: (Andreea Florescu )
|
||||
|
||||
Building the virtualization stack of the future with rust-vmm
|
||||
======
|
||||
rust-vmm facilitates sharing core virtualization components between Rust Virtual Machine Monitors.
|
||||

|
||||
|
||||
More than a year ago we started developing [Firecracker][1], a virtual machine monitor (VMM) that runs on top of KVM (the kernel-based virtual machine). We wanted to create a lightweight VMM that starts virtual machines (VMs) in a fraction of a second, with a low memory footprint, to enable high-density cloud environments.
|
||||
|
||||
We started out developing Firecracker by forking the Chrome OS VMM ([CrosVM][2]), but we diverged shortly after because we targeted different customer use cases. CrosVM provides Linux application isolation in ChromeOS, while Firecracker is used for running multi-tenant workloads at scale. Even though we now walk different paths, we still have common virtualization components, such as wrappers over KVM input/output controls (ioctls), a minimal kernel loader, and use of the [Virtio][3] device models.
|
||||
|
||||
With this in mind, we started thinking about the best approach for sharing the common code. Having a shared codebase raises the security and quality bar for both projects. Currently, fixing security bugs requires duplicated work in terms of porting the changes from one project to the other and going through different review processes for merging the changes. After open sourcing Firecracker, we've received requests for adding features including GPU support and booting [bzImage][4] files. Some of the requests didn't align with Firecracker's goals, but were otherwise valid use cases that just haven't found the right place for an implementation.
|
||||
|
||||
### The rust-vmm project
|
||||
|
||||
The [rust-vmm][5] project came to life in December 2018 when Amazon, Google, Intel, and Red Hat employees started talking about the best way of sharing virtualization packages. More contributors have joined this initiative along the way. We are still at the beginning of this journey, with only one component published to [Crates.io][6] (Rust's package registry) and several others (such as Virtio devices, Linux kernel loaders, and KVM ioctls wrappers) being developed. With two VMMs written in Rust under active development and growing interest in building other specialized VMMs, rust-vmm was born as the host for sharing core virtualization components.
|
||||
|
||||
The goal of rust-vmm is to enable the community to create custom VMMs that import just the required building blocks for their use case. We decided to organize rust-vmm as a multi-repository project, where each repository corresponds to an independent virtualization component. Each individual building block is published on Crates.io.
|
||||
|
||||
### Creating custom VMMs with rust-vmm
|
||||
|
||||
The components discussed below are currently under development.
|
||||
|
||||
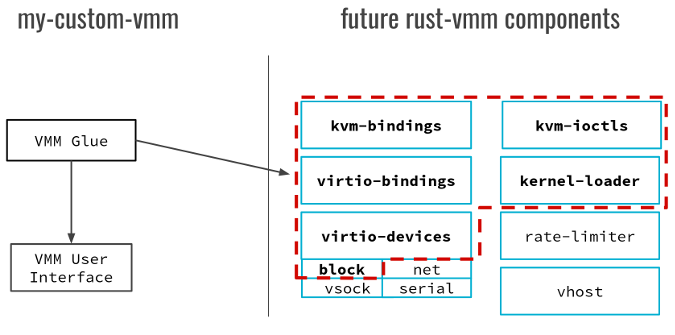
|
||||
|
||||
Each box on the right side of the diagram is a GitHub repository corresponding to one package, which in Rust is called a crate. The functionality of one crate can be further split into modules, for example virtio-devices. Let's have a look at these components and some of their potential use cases.
|
||||
|
||||
* **KVM interface:** Creating our VMM on top of KVM requires an interface that can invoke KVM functionality from Rust. The kvm-bindings crate represents the Rust Foreign Function Interface (FFI) to KVM kernel headers. Because headers only include structures and defines, we also have wrappers over the KVM ioctls (kvm-ioctls) that we use for opening dev/kvm, creating a VM, creating vCPUs, and so on.
|
||||
|
||||
* **Virtio devices and rate limiting:** Virtio has a frontend-backend architecture. Currently in rust-vmm, the frontend is implemented in the virtio-devices crate, and the backend lies in the vhost package. Vhost has support for both user-land and kernel-land drivers, but users can also plug virtio-devices to their custom backend. The virtio-bindings are the bindings for Virtio devices generated using the Virtio Linux headers. All devices in the virtio-devices crate are exported independently as modules using conditional compilation. Some devices, such as block, net, and vsock support rate limiting in terms of I/O per second and bandwidth. This can be achieved by using the functionality provided in the rate-limiter crate.
|
||||
|
||||
* The kernel-loader is responsible for loading the contents of an [ELF][7] kernel image in guest memory.
|
||||
|
||||
|
||||
|
||||
|
||||
For example, let's say we want to build a custom VMM that allows users to create and configure a single VM running on top of KVM. As part of the configuration, users will be able to specify the kernel image file, the root file system, the number of vCPUs, and the memory size. Creating and configuring the resources of the VM can be implemented using the kvm-ioctls crate. The kernel image can be loaded in guest memory with kernel-loader, and specifying a root filesystem can be achieved with the virtio-devices block module. The last thing needed for our VMM is writing VMM Glue, the code that takes care of integrating rust-vmm components with the VMM user interface, which allows users to create and manage VMs.
|
||||
|
||||
### How you can help
|
||||
|
||||
This is the beginning of an exciting journey, and we are looking forward to getting more people interested in VMMs, Rust, and the place where you can find both: [rust-vmm][5].
|
||||
|
||||
We currently have [sync meetings][8] every two weeks to discuss the future of the rust-vmm organization. The meetings are open to anyone willing to participate. If you have any questions, please open an issue in the [community repository][9] or send an email to the rust-vmm [mailing list][10] (you can also [subscribe][11]). We also have a [Slack channel][12] and encourage you to join, if you are interested.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/3/rust-virtual-machine
|
||||
|
||||
作者:[Andreea Florescu][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://github.com/firecracker-microvm/firecracker
|
||||
[2]: https://chromium.googlesource.com/chromiumos/platform/crosvm/
|
||||
[3]: https://www.linux-kvm.org/page/Virtio
|
||||
[4]: https://en.wikipedia.org/wiki/Vmlinux#bzImage
|
||||
[5]: https://github.com/rust-vmm
|
||||
[6]: https://crates.io/
|
||||
[7]: https://en.wikipedia.org/wiki/Executable_and_Linkable_Format
|
||||
[8]: http://lists.opendev.org/pipermail/rust-vmm/2019-January/000103.html
|
||||
[9]: https://github.com/rust-vmm/community
|
||||
[10]: mailto:rust-vmm@lists.opendev.org
|
||||
[11]: http://lists.opendev.org/cgi-bin/mailman/listinfo/rust-vmm
|
||||
[12]: https://join.slack.com/t/rust-vmm/shared_invite/enQtNTI3NDM2NjA5MzMzLTJiZjUxOGEwMTJkZDVkYTcxYjhjMWU3YzVhOGQ0M2Y5NmU5MzExMjg5NGE3NjlmNzNhZDlhMmY4ZjVhYTQ4ZmQ
|
||||
@ -0,0 +1,62 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Learn about computer security with the Raspberry Pi and Kali Linux)
|
||||
[#]: via: (https://opensource.com/article/19/3/computer-security-raspberry-pi)
|
||||
[#]: author: (Anderson Silva https://opensource.com/users/ansilva)
|
||||
|
||||
Learn about computer security with the Raspberry Pi and Kali Linux
|
||||
======
|
||||
Raspberry Pi is a great way to learn about computer security. Learn how in the 11th article in our getting-started series.
|
||||

|
||||
|
||||
Is there a hotter topic in technology than securing your computer? Some experts will tell you that there is no such thing as perfect security. They joke that if you want your server or application to be truly secure, then turn off your server, unplug it from the network, and put it in a safe somewhere. The problem with that should be obvious: What good is an app or server that nobody can use?
|
||||
|
||||
That's the conundrum around security. How can we make something secure enough and still usable and valuable? I am not a security expert by any means, although I hope to be one day. With that in mind, I thought it would make sense to share some ideas about what you can do with a Raspberry Pi to learn more about security.
|
||||
|
||||
I should note that, like the other articles in this series dedicated to Raspberry Pi beginners, my goal is not to dive in deep, rather to light a fire of interest for you to learn more about these topics.
|
||||
|
||||
### Kali Linux
|
||||
|
||||
When it comes to "doing security things," one of the Linux distributions that comes to mind is [Kali Linux][1]. Kali's development is primarily focused on forensics and penetration testing. It has more than 600 preinstalled [penetration-testing programs][2] to test your computer's security, and a [forensics mode][3], which prevents it from touching the internal hard drive or swap space of the system being examined.
|
||||
|
||||
|
||||
|
||||
Like Raspbian, Kali Linux is based on the Debian distribution, and you can find directions on installing it on the Raspberry Pi in its main [documentation portal][4]. If you installed Raspbian or another Linux distribution on your Raspberry Pi, you should have no problem installing Kali. Kali Linux's creators have even put together [training, workshops, and certifications][5] to help boost your career in the security field.
|
||||
|
||||
### Other Linux distros
|
||||
|
||||
Most standard Linux distributions, like Raspbian, Ubuntu, and Fedora, also have [many security tools available][6] in their repositories. Some great tools to explore include [Nmap][7], [Wireshark][8], [auditctl][9], and [SELinux][10].
|
||||
|
||||
### Projects
|
||||
|
||||
There are many other security-related projects you can run on your Raspberry Pi, such as [Honeypots][11], [Ad blockers][12], and [USB sanitizers][13]. Take some time and learn about them!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/3/computer-security-raspberry-pi
|
||||
|
||||
作者:[Anderson Silva][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/ansilva
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.kali.org/
|
||||
[2]: https://en.wikipedia.org/wiki/Kali_Linux#Development
|
||||
[3]: https://docs.kali.org/general-use/kali-linux-forensics-mode
|
||||
[4]: https://docs.kali.org/kali-on-arm/install-kali-linux-arm-raspberry-pi
|
||||
[5]: https://www.kali.org/penetration-testing-with-kali-linux/
|
||||
[6]: https://linuxblog.darkduck.com/2019/02/9-best-linux-based-security-tools.html
|
||||
[7]: https://nmap.org/
|
||||
[8]: https://www.wireshark.org/
|
||||
[9]: https://linux.die.net/man/8/auditctl
|
||||
[10]: https://opensource.com/article/18/7/sysadmin-guide-selinux
|
||||
[11]: https://trustfoundry.net/honeypi-easy-honeypot-raspberry-pi/
|
||||
[12]: https://pi-hole.net/
|
||||
[13]: https://www.circl.lu/projects/CIRCLean/
|
||||
74
sources/tech/20190718 3 Emacs modes for taking notes.md
Normal file
74
sources/tech/20190718 3 Emacs modes for taking notes.md
Normal file
@ -0,0 +1,74 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (3 Emacs modes for taking notes)
|
||||
[#]: via: (https://opensource.com/article/18/7/emacs-modes-note-taking)
|
||||
[#]: author: (Scott Nesbitt https://opensource.com/users/scottnesbitt)
|
||||
|
||||
3 Emacs modes for taking notes
|
||||
======
|
||||
Keep track of information easily with these Emacs modes.
|
||||

|
||||
|
||||
No matter what line of work you're in, it's inevitable you have to take a few notes. Often, more than a few. If you're like many people in this day and age, you take your notes digitally.
|
||||
|
||||
Open source enthusiasts have a variety of options for jotting down their ideas, thoughts, and research in electronic format. You might use a [web-based tool][1]. You might go for a [desktop application][2]. Or, you might [turn to the command line][3].
|
||||
|
||||
If you use [Emacs][4], that wonderful operating system disguised as a text editor, there are modes that can help you take notes more efficiently. Let's look at three of them.
|
||||
|
||||
### Deft
|
||||
|
||||
|
||||
On those rare occasions I'm forced to use a Mac, there's one tool I can't do without: the [nvALT][5] note-taking application. [Deft mode][6] brings the nvALT experience to Emacs.
|
||||
|
||||
Deft stores your notes as text files in a single folder on your computer. When you enter Deft mode, it displays a list of your notes along with a short summary. The summary is taken from the first line of the text file. If you add, say, Markdown, LaTeX, or even Emacs Org mode formatting to the first line, Deft ignores the formatting and displays only the text.
|
||||
|
||||
To open a note, just scroll down to it and press Enter. Deft does a bit more, though. According to Deft's developer, Jason Blevins, its _primary operation is searching and filtering_. Deft does that simply but efficiently. Type a keyword and Deft displays only the notes that have that keyword in their title. That's useful if you have a lot of notes and want to find one quickly.
|
||||
|
||||
### Org mode
|
||||
|
||||
|
||||
There would be a couple or three people who would have jumped all over me if I didn't include [Org mode][7] in this article. Why? It's arguably the most flexible and the most widely used Emacs mode for taking notes. Used in the right way, Org mode can supercharge your note-taking.
|
||||
|
||||
Org mode's main strength is how it organizes your notes. In Org mode, a note file is set up as a large outline. Each section is a node in the outline, which you can expand and collapse. Those sections can have subsections, which also expand and collapse. That not only lets you focus on one section at a time, but it also gives you an at-a-glance overview of the information you have.
|
||||
|
||||
You can [link][8] between sections of your notes, quickly move sections without cutting and pasting, and [attach files][9] to your notes. Org mode supports character formatting and tables. If you need to convert your notes to something else, Org mode has a number of [export options][10].
|
||||
|
||||
### Howm
|
||||
|
||||
|
||||
|
||||
When I started using Emacs regularly, [howm][11] quickly became one of the modes I leaned heavily on. And even though I'm deep into using Org mode, I still have a soft spot for howm.
|
||||
|
||||
Howm acts like a small wiki. You can create notes and task lists and link between them. By typing or clicking a link, you can jump between notes. If you need to, you can also tag your notes with a keyword. On top of that, you can search, sort, and concatenate your notes.
|
||||
|
||||
Howm isn't the prettiest Emacs mode, and it doesn't have the best UX. It takes a bit of getting used to. Once you do, taking and maneuvering around notes is a breeze.
|
||||
|
||||
Do you have a favorite Emacs mode for taking notes? Feel free to share it by leaving a comment.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/7/emacs-modes-note-taking
|
||||
|
||||
作者:[Scott Nesbitt][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/scottnesbitt
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/alternatives/evernote
|
||||
[2]: https://opensource.com/life/16/9/4-desktop-note-taking-applications
|
||||
[3]: https://opensource.com/article/18/3/command-line-note-taking-applications
|
||||
[4]: https://www.gnu.org/software/emacs/
|
||||
[5]: http://brettterpstra.com/projects/nvalt/
|
||||
[6]: https://jblevins.org/projects/deft/
|
||||
[7]: https://orgmode.org/
|
||||
[8]: https://orgmode.org/org.html#Hyperlinks
|
||||
[9]: https://orgmode.org/org.html#Attachments
|
||||
[10]: https://orgmode.org/org.html#Exporting
|
||||
[11]: https://howm.osdn.jp/
|
||||
Loading…
Reference in New Issue
Block a user