mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-03-18 02:00:18 +08:00
commit
673d73b6b6
@ -0,0 +1,53 @@
|
||||
Do Simple Math In Ubuntu And elementary OS With NaSC
|
||||
================================================================================
|
||||

|
||||
|
||||
[NaSC][1], abbreviation Not a Soulver Clone, is a third party app developed for elementary OS. Whatever the name suggests, NaSC is heavily inspired by [Soulver][2], an OS X app for doing maths like a normal person.
|
||||
|
||||
elementary OS itself draws from OS X and it is not a surprise that a number of the third party apps it has got, are also inspired by OS X apps.
|
||||
|
||||
Coming back to NaSC, what exactly it means by “maths like a normal person “? Well, it means to write like how you think in your mind. As per the description of the app:
|
||||
|
||||
> “Its an app where you do maths like a normal person. It lets you type whatever you want and smartly figures out what is math and spits out an answer on the right pane. Then you can plug those answers in to future equations and if that answer changes, so does the equations its used in.”
|
||||
|
||||
Still not convinced? Here, take a look at this screenshot.
|
||||
|
||||

|
||||
|
||||
Now, you see what is ‘math for normal person’? Honestly, I am not a fan of such apps but it might be useful for some of you perhaps. Let’s see how can you install NaSC in elementary OS, Ubuntu and Linux Mint.
|
||||
|
||||
### Install NaSC in Ubuntu, elementary OS and Mint ###
|
||||
|
||||
There is a PPA available for installing NaSC. The PPA says ‘daily’ which could mean daily build (i.e. unstable) but in my quick test, it worked just fine.
|
||||
|
||||
Open a terminal and use the following commands:
|
||||
|
||||
sudo apt-add-repository ppa:nasc-team/daily
|
||||
sudo apt-get update
|
||||
sudo apt-get install nasc
|
||||
|
||||
Here is a screenshot of NaSC in Ubuntu 15.04:
|
||||
|
||||

|
||||
|
||||
If you want to remove it, you can use the following commands:
|
||||
|
||||
sudo apt-get remove nasc
|
||||
sudo apt-add-repository --remove ppa:nasc-team/daily
|
||||
|
||||
If you try it, do share your experience with it. In addition to this, you can also try [Vocal podcast app for Linux][3] from third party elementary OS apps.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://itsfoss.com/math-ubuntu-nasc/
|
||||
|
||||
作者:[Abhishek][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://itsfoss.com/author/abhishek/
|
||||
[1]:http://parnold-x.github.io/nasc/
|
||||
[2]:http://www.acqualia.com/soulver/
|
||||
[3]:http://itsfoss.com/podcast-app-vocal-linux/
|
||||
@ -0,0 +1,116 @@
|
||||
How To Manage Log Files With Logrotate On Ubuntu 12.10
|
||||
================================================================================
|
||||
#### About Logrotate ####
|
||||
|
||||
Logrotate is a utility/tool that manages activities like automatic rotation, removal and compression of log files in a system. This is an excellent tool to manage your logs conserve precious disk space. By having a simple yet powerful configuration file, different parameters of logrotation can be controlled. This gives complete control over the way logs can be automatically managed and need not necessitate manual intervention.
|
||||
|
||||
### Prerequisites ###
|
||||
|
||||
As a prerequisite, we are assuming that you have gone through the article on how to set up your droplet or VPS. If not, you can find the article [here][1]. This tutorial requires you to have a VPS up and running and have you log into it.
|
||||
|
||||
#### Setup Logrotate ####
|
||||
|
||||
### Step 1—Update System and System Packages ###
|
||||
|
||||
Run the following command to update the package lists from apt-get and get the information on the newest versions of packages and their dependencies.
|
||||
|
||||
sudo apt-get update
|
||||
|
||||
### Step 2—Install Logrotate ###
|
||||
|
||||
If logrotate is not already on your VPS, install it now through apt-get.
|
||||
|
||||
sudo apt-get install logrotate
|
||||
|
||||
### Step 3 — Confirmation ###
|
||||
|
||||
To verify that logrotate was successfully installed, run this in the command prompt.
|
||||
|
||||
logrotate
|
||||
|
||||
Since the logrotate utility is based on configuration files, the above command will not rotate any files and will show you a brief overview of the usage and the switch options available.
|
||||
|
||||
### Step 4—Configure Logrotate ###
|
||||
|
||||
Configurations and default options for the logrotate utility are present in:
|
||||
|
||||
/etc/logrotate.conf
|
||||
|
||||
Some of the important configuration settings are : rotation-interval, log-file-size, rotation-count and compression.
|
||||
|
||||
Application-specific log file information (to override the defaults) are kept at:
|
||||
|
||||
/etc/logrotate.d/
|
||||
|
||||
We will have a look at a few examples to understand the concept better.
|
||||
|
||||
### Step 5—Example ###
|
||||
|
||||
An example application configuration setting would be the dpkg (Debian package management system), that is stored in /etc/logrotate.d/dpkg. One of the entries in this file would be:
|
||||
|
||||
/var/log/dpkg.log {
|
||||
monthly
|
||||
rotate 12
|
||||
compress
|
||||
delaycompress
|
||||
missingok
|
||||
notifempty
|
||||
create 644 root root
|
||||
}
|
||||
|
||||
What this means is that:
|
||||
|
||||
- the logrotation for dpkg monitors the /var/log/dpkg.log file and does this on a monthly basis this is the rotation interval.
|
||||
- 'rotate 12' signifies that 12 days worth of logs would be kept.
|
||||
- logfiles can be compressed using the gzip format by specifying 'compress' and 'delaycompress' delays the compression process till the next log rotation. 'delaycompress' will work only if 'compress' option is specified.
|
||||
- 'missingok' avoids halting on any error and carries on with the next log file.
|
||||
- 'notifempty' avoid log rotation if the logfile is empty.
|
||||
- 'create <mode> <owner> <group>' creates a new empty file with the specified properties after log-rotation.
|
||||
|
||||
Though missing in the above example, 'size' is also an important setting if you want to control the sizing of the logs growing in the system.
|
||||
|
||||
A configuration setting of around 100MB would look like:
|
||||
|
||||
size 100M
|
||||
|
||||
Note that If both size and rotation interval are set, then size is taken as a higher priority. That is, if a configuration file has the following settings:
|
||||
|
||||
monthly
|
||||
size 100M
|
||||
|
||||
then the logs are rotated once the file size reaches 100M and this need not wait for the monthly cycle.
|
||||
|
||||
### Step 6—Cron Job ###
|
||||
|
||||
You can also set the logrotation as a cron so that the manual process can be avoided and this is taken care of automatically. By specifying an entry in /etc/cron.daily/logrotate , the rotation is triggered daily.
|
||||
|
||||
### Step 7—Status Check and Verification ###
|
||||
|
||||
To verify if a particular log is indeed rotating or not and to check the last date and time of its rotation, check the /var/lib/logrotate/status file. This is a neatly formatted file that contains the log file name and the date on which it was last rotated.
|
||||
|
||||
cat /var/lib/logrotate/status
|
||||
|
||||
A few entries from this file, for example:
|
||||
|
||||
"/var/log/lpr.log" 2013-4-11
|
||||
"/var/log/dpkg.log" 2013-4-11
|
||||
"/var/log/pm-suspend.log" 2013-4-11
|
||||
"/var/log/syslog" 2013-4-11
|
||||
"/var/log/mail.info" 2013-4-11
|
||||
"/var/log/daemon.log" 2013-4-11
|
||||
"/var/log/apport.log" 2013-4-11
|
||||
|
||||
Congratulations! You have logrotate installed in your system. Now, change the configuration settings as per your requirements.
|
||||
|
||||
Try 'man logrotate' or 'logrotate -?' for more details.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.digitalocean.com/community/tutorials/how-to-manage-log-files-with-logrotate-on-ubuntu-12-10
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:https://www.digitalocean.com/community/articles/initial-server-setup-with-ubuntu-12-04
|
||||
103
sources/tech/20150906 How To Set Up Your FTP Server In Linux.md
Normal file
103
sources/tech/20150906 How To Set Up Your FTP Server In Linux.md
Normal file
@ -0,0 +1,103 @@
|
||||
translating by cvsher
|
||||
How To Set Up Your FTP Server In Linux
|
||||
================================================================================
|
||||

|
||||
|
||||
In this lesson, I will explain to you how to Set up your FTP server. But first, let me quickly tell you what is FTP.
|
||||
|
||||
### What is FTP? ###
|
||||
|
||||
[FTP][1] is an acronym for File Transfer Protocol. As the name suggests, FTP is used to transfer files between computers on a network. You can use FTP to exchange files between computer accounts, transfer files between an account and a desktop computer, or access online software archives. Keep in mind, however, that many FTP sites are heavily used and require several attempts before connecting.
|
||||
|
||||
An FTP address looks a lot like an HTTP or website address except it uses the prefix ftp:// instead of http://.
|
||||
|
||||
### What is an FTP Server? ###
|
||||
|
||||
Typically, a computer with an FTP address is dedicated to receive an FTP connection. A computer dedicated to receiving an FTP connection is referred to as an FTP server or FTP site.
|
||||
|
||||
Now, let’s begin a special adventure. We will make FTP server to share files with friends and family. I will use [vsftpd][2] for this purpose.
|
||||
|
||||
VSFTPD is an FTP server software which claims to be the most secure FTP software. In fact, the first two letters in VSFTPD, stand for “very secure”. The software was built around the vulnerabilities of the FTP protocol.
|
||||
|
||||
Nevertheless, you should always remember that there are better solutions for secure transfer and management of files such as SFTP (uses [OpenSSH][3]). The FTP protocol is particularly useful for sharing non-sensitive data and is very reliable at that.
|
||||
|
||||
#### Installing VSFTPD in rpm distributions: ####
|
||||
|
||||
You can quickly install VSFTPD on your server through the command line interface with:
|
||||
|
||||
dnf -y install vsftpd
|
||||
|
||||
#### Installing VSFTPD in deb distributions: ####
|
||||
|
||||
You can quickly install VSFTPD on your server through the command line interface with:
|
||||
|
||||
sudo apt-get install vsftpd
|
||||
|
||||
#### Installing VSFTPD in Arch distribution: ####
|
||||
|
||||
You can quickly install VSFTPD on your server through the command line interface with:
|
||||
|
||||
sudo pacman -S vsftpd
|
||||
|
||||
#### Configuring FTP server ####
|
||||
|
||||
Most VSFTPD’s configuration takes place in /etc/vsftpd.conf. The file itself is well-documented, so this section only highlights some important changes you may want to make. For all available options and basic documentation see the man pages:
|
||||
|
||||
man vsftpd.conf
|
||||
|
||||
Files are served by default from /srv/ftp as per the Filesystem Hierarchy Standard.
|
||||
|
||||
**Enable Uploading:**
|
||||
|
||||
The “write_enable” flag must be set to YES in order to allow changes to the filesystem, such as uploading:
|
||||
|
||||
write_enable=YES
|
||||
|
||||
**Allow Local Users to Login:**
|
||||
|
||||
In order to allow users in /etc/passwd to login, the “local_enable” directive must look like this:
|
||||
|
||||
local_enable=YES
|
||||
|
||||
**Anonymous Login**
|
||||
|
||||
The following lines control whether anonymous users can login:
|
||||
|
||||
# Allow anonymous login
|
||||
|
||||
anonymous_enable=YES
|
||||
# No password is required for an anonymous login (Optional)
|
||||
no_anon_password=YES
|
||||
# Maximum transfer rate for an anonymous client in Bytes/second (Optional)
|
||||
anon_max_rate=30000
|
||||
# Directory to be used for an anonymous login (Optional)
|
||||
anon_root=/example/directory/
|
||||
|
||||
**Chroot Jail**
|
||||
|
||||
It is possible to set up a chroot environment, which prevents the user from leaving his home directory. To enable this, add/change the following lines in the configuration file:
|
||||
|
||||
chroot_list_enable=YES chroot_list_file=/etc/vsftpd.chroot_list
|
||||
|
||||
The “chroot_list_file” variable specifies the file in which the jailed users are contained to.
|
||||
|
||||
In the end you must restart your ftp server. Type in your command line
|
||||
|
||||
sudo systemctl restart vsftpd
|
||||
|
||||
That’s it. Your FTP server is up and running.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://itsfoss.com/set-ftp-server-linux/
|
||||
|
||||
作者:[alimiracle][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://itsfoss.com/author/ali/
|
||||
[1]:https://en.wikipedia.org/wiki/File_Transfer_Protocol
|
||||
[2]:https://security.appspot.com/vsftpd.html
|
||||
[3]:http://www.openssh.com/
|
||||
@ -0,0 +1,197 @@
|
||||
How to install Suricata intrusion detection system on Linux
|
||||
================================================================================
|
||||
With incessant security threats, intrusion detection system (IDS) has become one of the most critical requirements in today's data center environments. However, as more and more servers upgrade their NICs to 10GB/40GB Ethernet, it is increasingly difficult to implement compute-intensive intrusion detection on commodity hardware at line rates. One approach to scaling IDS performance is **multi-threaded IDS**, where CPU-intensive deep packet inspection workload is parallelized into multiple concurrent tasks. Such parallelized inspection can exploit multi-core hardware to scale up IDS throughput easily. Two well-known open-source efforts in this area are [Suricata][1] and [Bro][2].
|
||||
|
||||
In this tutorial, I am going to demonstrate **how to install and configure Suricata IDS on Linux server**.
|
||||
|
||||
### Install Suricata IDS on Linux ###
|
||||
|
||||
Let's build Suricata from the source. You first need to install several required dependencies as follows.
|
||||
|
||||
#### Install Dependencies on Debian, Ubuntu or Linux Mint ####
|
||||
|
||||
$ sudo apt-get install wget build-essential libpcre3-dev libpcre3-dbg automake autoconf libtool libpcap-dev libnet1-dev libyaml-dev zlib1g-dev libcap-ng-dev libjansson-dev
|
||||
|
||||
#### Install Dependencies on CentOS, Fedora or RHEL ####
|
||||
|
||||
$ sudo yum install wget libpcap-devel libnet-devel pcre-devel gcc-c++ automake autoconf libtool make libyaml-devel zlib-devel file-devel jansson-devel nss-devel
|
||||
|
||||
Once you install all required packages, go ahead and install Suricata as follows.
|
||||
|
||||
First, download the latest Suricata source code from [http://suricata-ids.org/download/][3], and build it. As of this writing, the latest version is 2.0.8.
|
||||
|
||||
$ wget http://www.openinfosecfoundation.org/download/suricata-2.0.8.tar.gz
|
||||
$ tar -xvf suricata-2.0.8.tar.gz
|
||||
$ cd suricata-2.0.8
|
||||
$ ./configure --sysconfdir=/etc --localstatedir=/var
|
||||
|
||||
Here is the example output of configuration.
|
||||
|
||||
Suricata Configuration:
|
||||
AF_PACKET support: yes
|
||||
PF_RING support: no
|
||||
NFQueue support: no
|
||||
NFLOG support: no
|
||||
IPFW support: no
|
||||
DAG enabled: no
|
||||
Napatech enabled: no
|
||||
Unix socket enabled: yes
|
||||
Detection enabled: yes
|
||||
|
||||
libnss support: yes
|
||||
libnspr support: yes
|
||||
libjansson support: yes
|
||||
Prelude support: no
|
||||
PCRE jit: yes
|
||||
LUA support: no
|
||||
libluajit: no
|
||||
libgeoip: no
|
||||
Non-bundled htp: no
|
||||
Old barnyard2 support: no
|
||||
CUDA enabled: no
|
||||
|
||||
Now compile and install it.
|
||||
|
||||
$ make
|
||||
$ sudo make install
|
||||
|
||||
Suricata source code comes with default configuration files. Let's install these default configuration files as follows.
|
||||
|
||||
$ sudo make install-conf
|
||||
|
||||
As you know, Suricata is useless without IDS rule sets. Conveniently, the Makefile comes with IDS rule installation option. To install IDS rules, run the following command.
|
||||
|
||||
$ sudo make install-rules
|
||||
|
||||
The above rule installation command will download the current snapshot of community rulesets available from [EmergingThreats.net][4], and store them under /etc/suricata/rules.
|
||||
|
||||
|
||||
|
||||
### Configure Suricata IDS the First Time ###
|
||||
|
||||
Now it's time to configure Suricata. The configuration file is located at **/etc/suricata/suricata.yaml**. Open the file with a text editor for editing.
|
||||
|
||||
$ sudo vi /etc/suricata/suricata.yaml
|
||||
|
||||
Here are some basic setup for you to get started.
|
||||
|
||||
The "default-log-dir" keyword should point to the location of Suricata log files.
|
||||
|
||||
default-log-dir: /var/log/suricata/
|
||||
|
||||
Under "vars" section, you will find several important variables used by Suricata. "HOME_NET" should point to the local network to be inspected by Suricata. "!$HOME_NET" (assigned to EXTERNAL_NET) refers to any other networks than the local network. "XXX_PORTS" indicates the port number(s) use by different services. Note that Suricata can automatically detect HTTP traffic regardless of the port it uses. So it is not critical to specify the HTTP_PORTS variable correctly.
|
||||
|
||||
vars:
|
||||
HOME_NET: "[192.168.122.0/24]"
|
||||
EXTERNAL_NET: "!$HOME_NET"
|
||||
HTTP_PORTS: "80"
|
||||
SHELLCODE_PORTS: "!80"
|
||||
SSH_PORTS: 22
|
||||
|
||||
The "host-os-policy" section is used to defend against some well-known attacks which exploit the behavior of an operating system's network stack (e.g., TCP reassembly) to evade detection. As a counter measure, modern IDS came up with so-called "target-based" inspection, where inspection engine fine-tunes its detection algorithm based on a target operating system of the traffic. Thus, if you know what OS individual local hosts are running, you can feed that information to Suricata to potentially enhance its detection rate. This is when "host-os-policy" section is used. In this example, the default IDS policy is Linux; if no OS information is known for a particular IP address, Suricata will apply Linux-based inspection. When traffic for 192.168.122.0/28 and 192.168.122.155 is captured, Suricata will apply Windows-based inspection policy.
|
||||
|
||||
host-os-policy:
|
||||
# These are Windows machines.
|
||||
windows: [192.168.122.0/28, 192.168.122.155]
|
||||
bsd: []
|
||||
bsd-right: []
|
||||
old-linux: []
|
||||
# Make the default policy Linux.
|
||||
linux: [0.0.0.0/0]
|
||||
old-solaris: []
|
||||
solaris: ["::1"]
|
||||
hpux10: []
|
||||
hpux11: []
|
||||
irix: []
|
||||
macos: []
|
||||
vista: []
|
||||
windows2k3: []
|
||||
|
||||
Under "threading" section, you can specify CPU affinity for different Suricata threads. By default, [CPU affinity][5] is disabled ("set-cpu-affinity: no"), meaning that Suricata threads will be scheduled on any available CPU cores. By default, Suricata will create one "detect" thread for each CPU core. You can adjust this behavior by specifying "detect-thread-ratio: N". This will create N*M detect threads, where M is the total number of CPU cores on the host.
|
||||
|
||||
threading:
|
||||
set-cpu-affinity: no
|
||||
detect-thread-ratio: 1.5
|
||||
|
||||
With the above threading settings, Suricata will create 1.5*M detection threads, where M is the total number of CPU cores on the system.
|
||||
|
||||
For more information about Suricata configuration, you can read the default configuration file itself, which is heavily commented for clarity.
|
||||
|
||||
### Perform Intrusion Detection with Suricata ###
|
||||
|
||||
Now it's time to test-run Suricata. Before launching it, there's one more step to do.
|
||||
|
||||
When you are using pcap capture mode, it is highly recommended to turn off any packet offloead features (e.g., LRO/GRO) on the NIC which Suricata is listening on, as those features may interfere with live packet capture.
|
||||
|
||||
Here is how to turn off LRO/GRO on the network interface eth0:
|
||||
|
||||
$ sudo ethtool -K eth0 gro off lro off
|
||||
|
||||
Note that depending on your NIC, you may see the following warning, which you can ignore. It simply means that your NIC does not support LRO.
|
||||
|
||||
Cannot change large-receive-offload
|
||||
|
||||
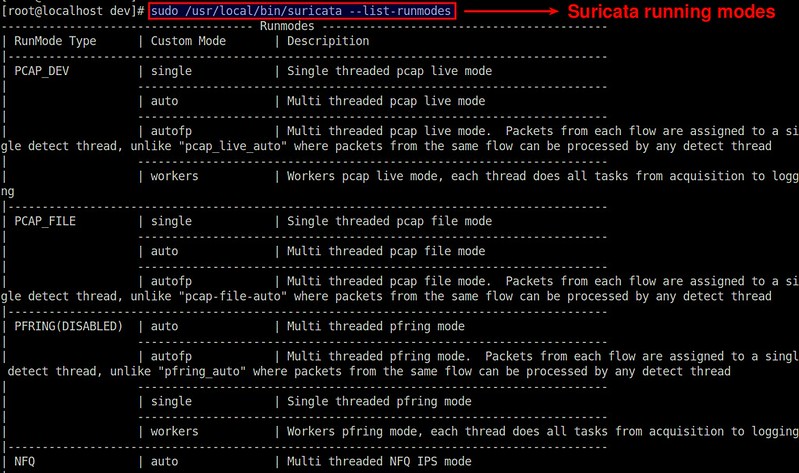
Suricata supports a number of running modes. A runmode determines how different threads are used for IDS. The following command lists all [available runmodes][6].
|
||||
|
||||
$ sudo /usr/local/bin/suricata --list-runmodes
|
||||
|
||||
|
||||
|
||||
The default runmode used by Suricata is autofp (which stands for "auto flow pinned load balancing"). In this mode, packets from each distinct flow are assigned to a single detect thread. Flows are assigned to threads with the lowest number of unprocessed packets.
|
||||
|
||||
Finally, let's start Suricata, and see it in action.
|
||||
|
||||
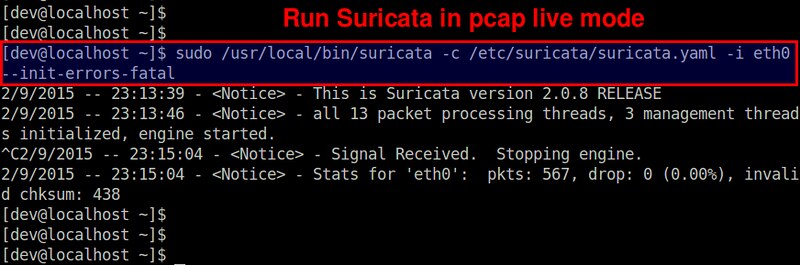
$ sudo /usr/local/bin/suricata -c /etc/suricata/suricata.yaml -i eth0 --init-errors-fatal
|
||||
|
||||
|
||||
|
||||
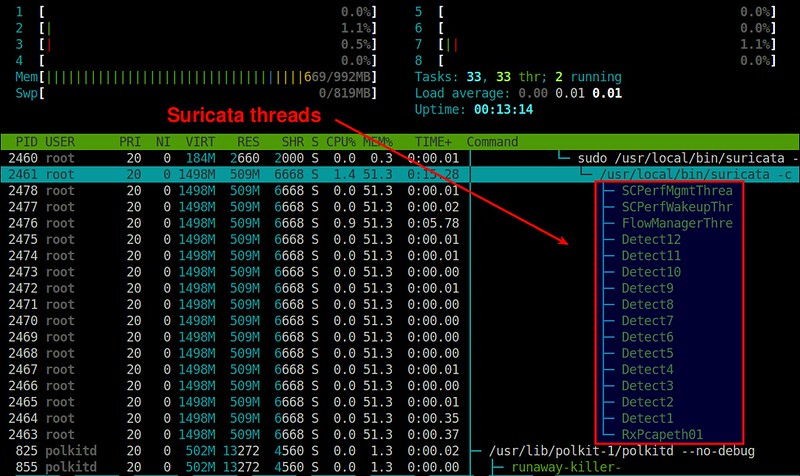
In this example, we are monitoring a network interface eth0 on a 8-core system. As shown above, Suricata creates 13 packet processing threads and 3 management threads. The packet processing threads consist of one PCAP packet capture thread, and 12 detect threads (equal to 8*1.5). This means that the packets captured by one capture thread are load-balanced to 12 detect threads for IDS. The management threads are one flow manager and two counter/stats related threads.
|
||||
|
||||
Here is a thread-view of Suricata process (plotted by [htop][7]).
|
||||
|
||||
|
||||
|
||||
Suricata detection logs are stored in /var/log/suricata directory.
|
||||
|
||||
$ tail -f /var/log/suricata/fast.log
|
||||
|
||||
----------
|
||||
|
||||
04/01/2015-15:47:12.559075 [**] [1:2200074:1] SURICATA TCPv4 invalid checksum [**] [Classification: (null)] [Priority: 3] {TCP} 172.16.253.158:22 -> 172.16.253.1:46997
|
||||
04/01/2015-15:49:06.565901 [**] [1:2200074:1] SURICATA TCPv4 invalid checksum [**] [Classification: (null)] [Priority: 3] {TCP} 172.16.253.158:22 -> 172.16.253.1:46317
|
||||
04/01/2015-15:49:06.566759 [**] [1:2200074:1] SURICATA TCPv4 invalid checksum [**] [Classification: (null)] [Priority: 3] {TCP} 172.16.253.158:22 -> 172.16.253.1:46317
|
||||
|
||||
For ease of import, the log is also available in JSON format:
|
||||
|
||||
$ tail -f /var/log/suricata/eve.json
|
||||
|
||||
----------
|
||||
{"timestamp":"2015-04-01T15:49:06.565901","event_type":"alert","src_ip":"172.16.253.158","src_port":22,"dest_ip":"172.16.253.1","dest_port":46317,"proto":"TCP","alert":{"action":"allowed","gid":1,"signature_id":2200074,"rev":1,"signature":"SURICATA TCPv4 invalid checksum","category":"","severity":3}}
|
||||
{"timestamp":"2015-04-01T15:49:06.566759","event_type":"alert","src_ip":"172.16.253.158","src_port":22,"dest_ip":"172.16.253.1","dest_port":46317,"proto":"TCP","alert":{"action":"allowed","gid":1,"signature_id":2200074,"rev":1,"signature":"SURICATA TCPv4 invalid checksum","category":"","severity":3}}
|
||||
|
||||
### Conclusion ###
|
||||
|
||||
In this tutorial, I demonstrated how you can set up Suricata IDS on a multi-core Linux server. Unlike single-threaded [Snort IDS][8], Suricata can easily benefit from multi-core/many-core hardware with multi-threading. There is great deal of customization in Suricata to maximize its performance and detection coverage. Suricata folks maintain [online Wiki][9] quite well, so I strongly recommend you check it out if you want to deploy Suricata in your environment.
|
||||
|
||||
Are you currently using Suricata? If so, feel free to share your experience.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/install-suricata-intrusion-detection-system-linux.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/nanni
|
||||
[1]:http://suricata-ids.org/
|
||||
[2]:https://www.bro.org/
|
||||
[3]:http://suricata-ids.org/download/
|
||||
[4]:http://rules.emergingthreats.net/
|
||||
[5]:http://xmodulo.com/run-program-process-specific-cpu-cores-linux.html
|
||||
[6]:https://redmine.openinfosecfoundation.org/projects/suricata/wiki/Runmodes
|
||||
[7]:http://ask.xmodulo.com/view-threads-process-linux.html
|
||||
[8]:http://xmodulo.com/how-to-compile-and-install-snort-from-source-code-on-ubuntu.html
|
||||
[9]:https://redmine.openinfosecfoundation.org/projects/suricata/wiki
|
||||
@ -0,0 +1,450 @@
|
||||
Installing NGINX and NGINX Plus With Ansible
|
||||
================================================================================
|
||||
Coming from a production operations background, I have learned to love all things related to automation. Why do something by hand if a computer can do it for you? But creating and implementing automation can be a difficult task given an ever-changing infrastructure and the various technologies surrounding your environments. This is why I love [Ansible][1]. Ansible is an open source tool for IT configuration management, deployment, and orchestration that is extremely easy to use.
|
||||
|
||||
One of my favorite features of Ansible is that it is completely clientless. To manage a system, a connection is made over SSH, using either [Paramiko][2] (a Python library) or native [OpenSSH][3]. Another attractive feature of Ansible is its extensive selection of modules. These modules can be used to perform some of the common tasks of a system administrator. In particular, they make Ansible a powerful tool for installing and configuring any application across multiple servers, environments, and operating systems, all from one central location.
|
||||
|
||||
In this tutorial I will walk you through the steps for using Ansible to install and deploy the open source [NGINX][4] software and [NGINX Plus][5], our commercial product. I’m showing deployment onto a [CentOS][6] server, but I have included details about deploying on Ubuntu servers in [Creating an Ansible Playbook for Installing NGINX and NGINX Plus on Ubuntu][7] below.
|
||||
|
||||
For this tutorial I will be using Ansible version 1.9.2 and performing the deployment from a server running CentOS 7.1.
|
||||
|
||||
$ ansible --version
|
||||
ansible 1.9.2
|
||||
|
||||
$ cat /etc/redhat-release
|
||||
CentOS Linux release 7.1.1503 (Core)
|
||||
|
||||
If you don’t already have Ansible, you can get instructions for installing it [at the Ansible site][8].
|
||||
|
||||
If you are using CentOS, installing Ansible is easy as typing the following command. If you want to compile from source or for other distributions, see the instructions at the Ansible link provided just above.
|
||||
|
||||
$ sudo yum install -y epel-release && sudo yum install -y ansible
|
||||
|
||||
Depending on your environment, some of the commands in this tutorial might require sudo privileges. The path to the files, usernames, and destination servers are all values that will be specific to your environment.
|
||||
|
||||
### Creating an Ansible Playbook for Installing NGINX (CentOS) ###
|
||||
|
||||
First we create a working directory for our NGINX deployment, along with subdirectories and deployment configuration files. I usually recommend creating the directory in your home directory and show that in all examples in this tutorial.
|
||||
|
||||
$ cd $HOME
|
||||
$ mkdir -p ansible-nginx/tasks/
|
||||
$ touch ansible-nginx/deploy.yml
|
||||
$ touch ansible-nginx/tasks/install_nginx.yml
|
||||
|
||||
The directory structure now looks like this. You can check by using the tree command.
|
||||
|
||||
$ tree $HOME/ansible-nginx/
|
||||
/home/kjones/ansible-nginx/
|
||||
├── deploy.yml
|
||||
└── tasks
|
||||
└── install_nginx.yml
|
||||
|
||||
1 directory, 2 files
|
||||
|
||||
If you do not have tree installed, you can do so using the following command.
|
||||
|
||||
$ sudo yum install -y tree
|
||||
|
||||
#### Creating the Main Deployment File ####
|
||||
|
||||
Next we open **deploy.yml** in a text editor. I prefer vim for editing configuration files on the command line, and will use it throughout the tutorial.
|
||||
|
||||
$ vim $HOME/ansible-nginx/deploy.yml
|
||||
|
||||
The **deploy.yml** file is our main Ansible deployment file, which we’ll reference when we run the ansible‑playbook command in [Running Ansible to Deploy NGINX][9]. Within this file we specify the inventory for Ansible to use along with any other configuration files to include at runtime.
|
||||
|
||||
In my example I use the [include][10] module to specify a configuration file that has the steps for installing NGINX. While it is possible to create a playbook in one very large file, I recommend that you separate the steps into smaller included files to keep things organized. Sample use cases for an include are copying static content, copying configuration files, or assigning variables for a more advanced deployment with configuration logic.
|
||||
|
||||
Type the following lines into the file. I include the filename at the top in a comment for reference.
|
||||
|
||||
# ./ansible-nginx/deploy.yml
|
||||
|
||||
- hosts: nginx
|
||||
tasks:
|
||||
- include: 'tasks/install_nginx.yml'
|
||||
|
||||
The hosts statement tells Ansible to deploy to all servers in the **nginx** group, which is defined in **/etc/ansible/hosts**. We’ll edit this file in [Creating the List of NGINX Servers below][11].
|
||||
|
||||
The include statement tells Ansible to read in and execute the contents of the **install_nginx.yml** file from the **tasks** directory during deployment. The file includes the steps for downloading, installing, and starting NGINX. We’ll create this file in the next section.
|
||||
|
||||
#### Creating the Deployment File for NGINX ####
|
||||
|
||||
Now let’s save our work to **deploy.yml** and open up **install_nginx.yml** in the editor.
|
||||
|
||||
$ vim $HOME/ansible-nginx/tasks/install_nginx.yml
|
||||
|
||||
The file is going to contain the instructions – written in [YAML][12] format – for Ansible to follow when installing and configuring our NGINX deployment. Each section (step in the process) starts with a name statement (preceded by hyphen) that describes the step. The string following name: is written to stdout during the Ansible deployment and can be changed as you wish. The next line of a section in the YAML file is the module that will be used during that deployment step. In the configuration below, both the [yum][13] and [service][14] modules are used. The yum module is used to install packages on CentOS. The service module is used to manage UNIX services. The final line or lines in a section specify any parameters for the module (in the example, these lines start with name and state).
|
||||
|
||||
Type the following lines into the file. As with **deploy.yml**, the first line in our file is a comment that names the file for reference. The first section tells Ansible to install the **.rpm** file for CentOS 7 from the NGINX repository. This directs the package manager to install the most recent stable version of NGINX directly from NGINX. Modify the pathname as necessary for your CentOS version. A list of available packages can be found on the [open source NGINX website][15]. The next two sections tell Ansible to install the latest NGINX version using the yum module and then start NGINX using the service module.
|
||||
|
||||
**Note:** In the first section, the pathname to the CentOS package appears on two lines only for space reasons. Type the entire path on a single line.
|
||||
|
||||
# ./ansible-nginx/tasks/install_nginx.yml
|
||||
|
||||
- name: NGINX | Installing NGINX repo rpm
|
||||
yum:
|
||||
name: http://nginx.org/packages/centos/7/noarch/RPMS/nginx-release-centos-7-0.el7.ngx.noarch.rpm
|
||||
|
||||
- name: NGINX | Installing NGINX
|
||||
yum:
|
||||
name: nginx
|
||||
state: latest
|
||||
|
||||
- name: NGINX | Starting NGINX
|
||||
service:
|
||||
name: nginx
|
||||
state: started
|
||||
|
||||
#### Creating the List of NGINX Servers ####
|
||||
|
||||
Now that we have our Ansible deployment configuration files all set up, we need to tell Ansible exactly which servers to deploy to. We specify this in the Ansible **hosts** file I mentioned earlier. Let’s make a backup of the existing file and create a new one just for our deployment.
|
||||
|
||||
$ sudo mv /etc/ansible/hosts /etc/ansible/hosts.backup
|
||||
$ sudo vim /etc/ansible/hosts
|
||||
|
||||
Type (or edit) the following lines in the file to create a group called **nginx** and list the servers to install NGINX on. You can designate servers by hostname, IP address, or in an array such as **server[1-3].domain.com**. Here I designate one server by its IP address.
|
||||
|
||||
# /etc/ansible/hosts
|
||||
|
||||
[nginx]
|
||||
172.16.239.140
|
||||
|
||||
#### Setting Up Security ####
|
||||
|
||||
We are almost all set, but before deployment we need to ensure that Ansible has authorization to access our destination server over SSH.
|
||||
|
||||
The preferred and most secure method is to add the Ansible deployment server’s RSA SSH key to the destination server’s **authorized_keys** file, which gives Ansible unrestricted SSH permissions on the destination server. To learn more about this configuration, see [Securing OpenSSH][16] on wiki.centos.org. This way you can automate your deployments without user interaction.
|
||||
|
||||
Alternatively, you can request the password interactively during deployment. I strongly recommend that you use this method during testing only, because it is insecure and there is no way to track changes to a destination host’s fingerprint. If you want to do this, change the value of StrictHostKeyChecking from the default yes to no in the **/etc/ssh/ssh_config** file on each of your destination hosts. Then add the --ask-pass flag on the ansible-playbook command to have Ansible prompt for the SSH password.
|
||||
|
||||
Here I illustrate how to edit the **ssh_config** file to disable strict host key checking on the destination server. We manually SSH into the server to which we’ll deploy NGINX and change the value of StrictHostKeyChecking to no.
|
||||
|
||||
$ ssh kjones@172.16.239.140
|
||||
kjones@172.16.239.140's password:***********
|
||||
|
||||
[kjones@nginx ]$ sudo vim /etc/ssh/ssh_config
|
||||
|
||||
After you make the change, save **ssh_config**, and connect to your Ansible server via SSH. The setting should look as below before you save your work.
|
||||
|
||||
# /etc/ssh/ssh_config
|
||||
|
||||
StrictHostKeyChecking no
|
||||
|
||||
#### Running Ansible to Deploy NGINX ####
|
||||
|
||||
If you have followed the steps in this tutorial, you can run the following command to have Ansible deploy NGINX. (Again, if you have set up RSA SSH key authentication, then the --ask-pass flag is not needed.) Run the command on the Ansible server with the configuration files we created above.
|
||||
|
||||
$ sudo ansible-playbook --ask-pass $HOME/ansible-nginx/deploy.yml
|
||||
|
||||
Ansible prompts for the SSH password and produces output like the following. A recap that reports failed=0 like this one indicates that deployment succeeded.
|
||||
|
||||
$ sudo ansible-playbook --ask-pass $HOME/ansible-nginx/deploy.yml
|
||||
SSH password:
|
||||
|
||||
PLAY [all] ********************************************************************
|
||||
|
||||
GATHERING FACTS ***************************************************************
|
||||
ok: [172.16.239.140]
|
||||
|
||||
TASK: [NGINX | Installing NGINX repo rpm] *************************************
|
||||
changed: [172.16.239.140]
|
||||
|
||||
TASK: [NGINX | Installing NGINX] **********************************************
|
||||
changed: [172.16.239.140]
|
||||
|
||||
TASK: [NGINX | Starting NGINX] ************************************************
|
||||
changed: [172.16.239.140]
|
||||
|
||||
PLAY RECAP ********************************************************************
|
||||
172.16.239.140 : ok=4 changed=3 unreachable=0 failed=0
|
||||
|
||||
If you didn’t get a successful play recap, you can try running the ansible-playbook command again with the -vvvv flag (verbose with connection debugging) to troubleshoot the deployment process.
|
||||
|
||||
When deployment succeeds (as it did for us on the first try), you can verify that NGINX is running on the remote server by running the following basic [cURL][17] command. Here it returns 200 OK. Success! We have successfully installed NGINX using Ansible.
|
||||
|
||||
$ curl -Is 172.16.239.140 | grep HTTP
|
||||
HTTP/1.1 200 OK
|
||||
|
||||
### Creating an Ansible Playbook for Installing NGINX Plus (CentOS) ###
|
||||
|
||||
Now that I’ve shown you how to install the open source version of NGINX, I’ll walk you through the steps for installing NGINX Plus. This requires some additional changes to the deployment configuration and showcases some of Ansible’s other features.
|
||||
|
||||
#### Copying the NGINX Plus Certificate and Key to the Ansible Server ####
|
||||
|
||||
To install and configure NGINX Plus with Ansible, we first need to copy the key and certificate for our NGINX Plus subscription from the [NGINX Plus Customer Portal][18] to the standard location on the Ansible deployment server.
|
||||
|
||||
Access to the NGINX Plus Customer Portal is available for customers who have purchased NGINX Plus or are evaluating it. If you are interested in evaluating NGINX Plus, you can request a 30-day free trial [here][19]. You will receive a link to your trial certificate and key shortly after you sign up.
|
||||
|
||||
On a Mac or Linux host, use the [scp][20] utility as I show here. On a Microsoft Windows host, you can use [WinSCP][21]. For this tutorial, I downloaded the files to my Mac laptop, then used scp to copy them to the Ansible server. These commands place both the key and certificate in my home directory.
|
||||
|
||||
$ cd /path/to/nginx-repo-files/
|
||||
$ scp nginx-repo.* user@destination-server:.
|
||||
|
||||
Next we SSH to the Ansible server, make sure the SSL directory for NGINX Plus exists, and move the files there.
|
||||
|
||||
$ ssh user@destination-server
|
||||
$ sudo mkdir -p /etc/ssl/nginx/
|
||||
$ sudo mv nginx-repo.* /etc/ssl/nginx/
|
||||
|
||||
Verify that your **/etc/ssl/nginx** directory contains both the certificate (**.crt**) and key (**.key**) files. You can check by using the tree command.
|
||||
|
||||
$ tree /etc/ssl/nginx
|
||||
/etc/ssl/nginx
|
||||
├── nginx-repo.crt
|
||||
└── nginx-repo.key
|
||||
|
||||
0 directories, 2 files
|
||||
|
||||
If you do not have tree installed, you can do so using the following command.
|
||||
|
||||
$ sudo yum install -y tree
|
||||
|
||||
#### Creating the Ansible Directory Structure ####
|
||||
|
||||
The remaining steps are very similar to the ones for open source NGINX that we performed in [Creating an Ansible Playbook for Installing NGINX (CentOS)][22]. First we set up a working directory for our NGINX Plus deployment. Again I prefer creating it as a subdirectory of my home directory.
|
||||
|
||||
$ cd $HOME
|
||||
$ mkdir -p ansible-nginx-plus/tasks/
|
||||
$ touch ansible-nginx-plus/deploy.yml
|
||||
$ touch ansible-nginx-plus/tasks/install_nginx_plus.yml
|
||||
|
||||
The directory structure now looks like this.
|
||||
|
||||
$ tree $HOME/ansible-nginx-plus/
|
||||
/home/kjones/ansible-nginx-plus/
|
||||
├── deploy.yml
|
||||
└── tasks
|
||||
└── install_nginx_plus.yml
|
||||
|
||||
1 directory, 2 files
|
||||
|
||||
#### Creating the Main Deployment File ####
|
||||
|
||||
Next we use vim to create the **deploy.yml** file as for open source NGINX.
|
||||
|
||||
$ vim ansible-nginx-plus/deploy.yml
|
||||
|
||||
The only difference from the open source NGINX deployment is that we change the name of the included file to **install_nginx_plus.yml**. As a reminder, the file tells Ansible to deploy NGINX Plus on all servers in the **nginx** group (which is defined in **/etc/ansible/hosts**), and to read in and execute the contents of the **install_nginx_plus.yml** file from the **tasks** directory during deployment.
|
||||
|
||||
# ./ansible-nginx-plus/deploy.yml
|
||||
|
||||
- hosts: nginx
|
||||
tasks:
|
||||
- include: 'tasks/install_nginx_plus.yml'
|
||||
|
||||
If you have not done so already, you also need to create the hosts file as detailed in [Creating the List of NGINX Servers][23] above.
|
||||
|
||||
#### Creating the Deployment File for NGINX Plus ####
|
||||
|
||||
Open **install_nginx_plus.yml** in a text editor. The file is going to contain the instructions for Ansible to follow when installing and configuring your NGINX Plus deployment. The commands and modules are specific to CentOS and some are unique to NGINX Plus.
|
||||
|
||||
$ vim ansible-nginx-plus/tasks/install_nginx_plus.yml
|
||||
|
||||
The first section uses the [file][24] module, telling Ansible to create the SSL directory for NGINX Plus as specified by the path and state arguments, set the ownership to root, and change the mode to 0700.
|
||||
|
||||
# ./ansible-nginx-plus/tasks/install_nginx_plus.yml
|
||||
|
||||
- name: NGINX Plus | Creating NGINX Plus ssl cert repo directory
|
||||
file: path=/etc/ssl/nginx state=directory group=root mode=0700
|
||||
|
||||
The next two sections use the [copy][25] module to copy the NGINX Plus certificate and key from the Ansible deployment server to the NGINX Plus server during the deployment, again setting ownership to root and the mode to 0700.
|
||||
|
||||
- name: NGINX Plus | Copying NGINX Plus repository certificate
|
||||
copy: src=/etc/ssl/nginx/nginx-repo.crt dest=/etc/ssl/nginx/nginx-repo.crt owner=root group=root mode=0700
|
||||
|
||||
- name: NGINX Plus | Copying NGINX Plus repository key
|
||||
copy: src=/etc/ssl/nginx/nginx-repo.key dest=/etc/ssl/nginx/nginx-repo.key owner=root group=root mode=0700
|
||||
|
||||
Next we tell Ansible to use the [get_url][26] module to download the CA certificate from the NGINX Plus repository at the remote location specified by the url argument, put it in the directory specified by the dest argument, and set the mode to 0700.
|
||||
|
||||
- name: NGINX Plus | Downloading NGINX Plus CA certificate
|
||||
get_url: url=https://cs.nginx.com/static/files/CA.crt dest=/etc/ssl/nginx/CA.crt mode=0700
|
||||
|
||||
Similarly, we tell Ansible to download the NGINX Plus repo file using the get_url module and copy it to the **/etc/yum.repos.d** directory on the NGINX Plus server.
|
||||
|
||||
- name: NGINX Plus | Downloading yum NGINX Plus repository
|
||||
get_url: url=https://cs.nginx.com/static/files/nginx-plus-7.repo dest=/etc/yum.repos.d/nginx-plus-7.repo mode=0700
|
||||
|
||||
The final two name sections tell Ansible to install and start NGINX Plus using the yum and service modules.
|
||||
|
||||
- name: NGINX Plus | Installing NGINX Plus
|
||||
yum:
|
||||
name: nginx-plus
|
||||
state: latest
|
||||
|
||||
- name: NGINX Plus | Starting NGINX Plus
|
||||
service:
|
||||
name: nginx
|
||||
state: started
|
||||
|
||||
#### Running Ansible to Deploy NGINX Plus ####
|
||||
|
||||
After saving the **install_nginx_plus.yml** file, we run the ansible-playbook command to deploy NGINX Plus. Again here we include the --ask-pass flag to have Ansible prompt for the SSH password and pass it to each NGINX Plus server, and specify the path to the main Ansible **deploy.yml** file.
|
||||
|
||||
$ sudo ansible-playbook --ask-pass $HOME/ansible-nginx-plus/deploy.yml
|
||||
|
||||
PLAY [nginx] ******************************************************************
|
||||
|
||||
GATHERING FACTS ***************************************************************
|
||||
ok: [172.16.239.140]
|
||||
|
||||
TASK: [NGINX Plus | Creating NGINX Plus ssl cert repo directory] **************
|
||||
changed: [172.16.239.140]
|
||||
|
||||
TASK: [NGINX Plus | Copying NGINX Plus repository certificate] ****************
|
||||
changed: [172.16.239.140]
|
||||
|
||||
TASK: [NGINX Plus | Copying NGINX Plus repository key] ************************
|
||||
changed: [172.16.239.140]
|
||||
|
||||
TASK: [NGINX Plus | Downloading NGINX Plus CA certificate] ********************
|
||||
changed: [172.16.239.140]
|
||||
|
||||
TASK: [NGINX Plus | Downloading yum NGINX Plus repository] ********************
|
||||
changed: [172.16.239.140]
|
||||
|
||||
TASK: [NGINX Plus | Installing NGINX Plus] ************************************
|
||||
changed: [172.16.239.140]
|
||||
|
||||
TASK: [NGINX Plus | Starting NGINX Plus] **************************************
|
||||
changed: [172.16.239.140]
|
||||
|
||||
PLAY RECAP ********************************************************************
|
||||
172.16.239.140 : ok=8 changed=7 unreachable=0 failed=0
|
||||
|
||||
The playbook recap was successful. Now we can run a quick curl command to verify that NGINX Plus is running. Great, we get 200 OK! Success! We have successfully installed NGINX Plus with Ansible.
|
||||
|
||||
$ curl -Is http://172.16.239.140 | grep HTTP
|
||||
HTTP/1.1 200 OK
|
||||
|
||||
### Creating an Ansible Playbook for Installing NGINX and NGINX Plus on Ubuntu ###
|
||||
|
||||
The process for deploying NGINX and NGINX Plus on [Ubuntu servers][27] is pretty similar to the process on CentOS, so instead of providing step-by-step instructions I’ll show the complete deployment files and and point out the slight differences from CentOS.
|
||||
|
||||
First create the Ansible directory structure and the main Ansible deployment file, as for CentOS. Also create the **/etc/ansible/hosts** file as described in [Creating the List of NGINX Servers][28]. For NGINX Plus, you need to copy over the key and certificate as described in [Copying the NGINX Plus Certificate and Key to the Ansible Server][29].
|
||||
|
||||
Here’s the **install_nginx.yml** deployment file for open source NGINX. In the first section, we use the [apt_key][30] module to import the NGINX signing key. The next two sections use the [lineinfile][31] module to add the package URLs for Ubuntu 14.04 to the **sources.list** file. Lastly we use the [apt][32] module to update the cache and install NGINX (apt replaces the yum module we used for deploying to CentOS).
|
||||
|
||||
# ./ansible-nginx/tasks/install_nginx.yml
|
||||
|
||||
- name: NGINX | Adding NGINX signing key
|
||||
apt_key: url=http://nginx.org/keys/nginx_signing.key state=present
|
||||
|
||||
- name: NGINX | Adding sources.list deb url for NGINX
|
||||
lineinfile: dest=/etc/apt/sources.list line="deb http://nginx.org/packages/mainline/ubuntu/ trusty nginx"
|
||||
|
||||
- name: NGINX Plus | Adding sources.list deb-src url for NGINX
|
||||
lineinfile: dest=/etc/apt/sources.list line="deb-src http://nginx.org/packages/mainline/ubuntu/ trusty nginx"
|
||||
|
||||
- name: NGINX | Updating apt cache
|
||||
apt:
|
||||
update_cache: yes
|
||||
|
||||
- name: NGINX | Installing NGINX
|
||||
apt:
|
||||
pkg: nginx
|
||||
state: latest
|
||||
|
||||
- name: NGINX | Starting NGINX
|
||||
service:
|
||||
name: nginx
|
||||
state: started
|
||||
|
||||
Here’s the **install_nginx.yml** deployment file for NGINX Plus. The first four sections set up the NGINX Plus key and certificate. Then we use the apt_key module to import the signing key as for open source NGINX, and the get_url module to download the apt configuration file for NGINX Plus. The [shell][33] module evokes a printf command that writes its output to the **nginx-plus.list** file in the **sources.list.d** directory. The final name modules are the same as for open source NGINX.
|
||||
|
||||
# ./ansible-nginx-plus/tasks/install_nginx_plus.yml
|
||||
|
||||
- name: NGINX Plus | Creating NGINX Plus ssl cert repo directory
|
||||
file: path=/etc/ssl/nginx state=directory group=root mode=0700
|
||||
|
||||
- name: NGINX Plus | Copying NGINX Plus repository certificate
|
||||
copy: src=/etc/ssl/nginx/nginx-repo.crt dest=/etc/ssl/nginx/nginx-repo.crt owner=root group=root mode=0700
|
||||
|
||||
- name: NGINX Plus | Copying NGINX Plus repository key
|
||||
copy: src=/etc/ssl/nginx/nginx-repo.key dest=/etc/ssl/nginx/nginx-repo.key owner=root group=root mode=0700
|
||||
|
||||
- name: NGINX Plus | Downloading NGINX Plus CA certificate
|
||||
get_url: url=https://cs.nginx.com/static/files/CA.crt dest=/etc/ssl/nginx/CA.crt mode=0700
|
||||
|
||||
- name: NGINX Plus | Adding NGINX Plus signing key
|
||||
apt_key: url=http://nginx.org/keys/nginx_signing.key state=present
|
||||
|
||||
- name: NGINX Plus | Downloading Apt-Get NGINX Plus repository
|
||||
get_url: url=https://cs.nginx.com/static/files/90nginx dest=/etc/apt/apt.conf.d/90nginx mode=0700
|
||||
|
||||
- name: NGINX Plus | Adding sources.list url for NGINX Plus
|
||||
shell: printf "deb https://plus-pkgs.nginx.com/ubuntu `lsb_release -cs` nginx-plus\n" >/etc/apt/sources.list.d/nginx-plus.list
|
||||
|
||||
- name: NGINX Plus | Running apt-get update
|
||||
apt:
|
||||
update_cache: yes
|
||||
|
||||
- name: NGINX Plus | Installing NGINX Plus via apt-get
|
||||
apt:
|
||||
pkg: nginx-plus
|
||||
state: latest
|
||||
|
||||
- name: NGINX Plus | Start NGINX Plus
|
||||
service:
|
||||
name: nginx
|
||||
state: started
|
||||
|
||||
We’re now ready to run the ansible-playbook command:
|
||||
|
||||
$ sudo ansible-playbook --ask-pass $HOME/ansible-nginx-plus/deploy.yml
|
||||
|
||||
You should get a successful play recap. If you did not get a success, you can use the verbose flag to help troubleshoot your deployment as described in [Running Ansible to Deploy NGINX][34].
|
||||
|
||||
### Summary ###
|
||||
|
||||
What I demonstrated in this tutorial is just the beginning of what Ansible can do to help automate your NGINX or NGINX Plus deployment. There are many useful modules ranging from user account management to custom configuration templates. If you are interested in learning more about these, please visit the extensive [Ansible documentation][35 site.
|
||||
|
||||
To learn more about Ansible, come hear my talk on deploying NGINX Plus with Ansible at [NGINX.conf 2015][36], September 22–24 in San Francisco.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.nginx.com/blog/installing-nginx-nginx-plus-ansible/
|
||||
|
||||
作者:[Kevin Jones][a]
|
||||
译者:[struggling](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://www.nginx.com/blog/author/kjones/
|
||||
[1]:http://www.ansible.com/
|
||||
[2]:http://www.paramiko.org/
|
||||
[3]:http://www.openssh.com/
|
||||
[4]:http://nginx.org/en/
|
||||
[5]:https://www.nginx.com/products/
|
||||
[6]:http://www.centos.org/
|
||||
[7]:https://www.nginx.com/blog/installing-nginx-nginx-plus-ansible/#ubuntu
|
||||
[8]:http://docs.ansible.com/ansible/intro_installation.html#installing-the-control-machine
|
||||
[9]:https://www.nginx.com/blog/installing-nginx-nginx-plus-ansible/#deploy-nginx
|
||||
[10]:http://docs.ansible.com/ansible/playbooks_roles.html#task-include-files-and-encouraging-reuse
|
||||
[11]:https://www.nginx.com/blog/installing-nginx-nginx-plus-ansible/#list-nginx
|
||||
[12]:http://docs.ansible.com/ansible/YAMLSyntax.html
|
||||
[13]:http://docs.ansible.com/ansible/yum_module.html
|
||||
[14]:http://docs.ansible.com/ansible/service_module.html
|
||||
[15]:http://nginx.org/en/linux_packages.html
|
||||
[16]:http://wiki.centos.org/HowTos/Network/SecuringSSH
|
||||
[17]:http://curl.haxx.se/
|
||||
[18]:https://cs.nginx.com/
|
||||
[19]:https://www.nginx.com/#free-trial
|
||||
[20]:http://linux.die.net/man/1/scp
|
||||
[21]:https://winscp.net/eng/download.php
|
||||
[22]:https://www.nginx.com/blog/installing-nginx-nginx-plus-ansible/#playbook-nginx
|
||||
[23]:https://www.nginx.com/blog/installing-nginx-nginx-plus-ansible/#list-nginx
|
||||
[24]:http://docs.ansible.com/ansible/file_module.html
|
||||
[25]:http://docs.ansible.com/ansible/copy_module.html
|
||||
[26]:http://docs.ansible.com/ansible/get_url_module.html
|
||||
[27]:http://www.ubuntu.com/
|
||||
[28]:https://www.nginx.com/blog/installing-nginx-nginx-plus-ansible/#list-nginx
|
||||
[29]:https://www.nginx.com/blog/installing-nginx-nginx-plus-ansible/#copy-cert-key
|
||||
[30]:http://docs.ansible.com/ansible/apt_key_module.html
|
||||
[31]:http://docs.ansible.com/ansible/lineinfile_module.html
|
||||
[32]:http://docs.ansible.com/ansible/apt_module.html
|
||||
[33]:http://docs.ansible.com/ansible/shell_module.html
|
||||
[34]:https://www.nginx.com/blog/installing-nginx-nginx-plus-ansible/#deploy-nginx
|
||||
[35]:http://docs.ansible.com/
|
||||
[36]:https://www.nginx.com/nginxconf/
|
||||
Loading…
Reference in New Issue
Block a user