mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-01-13 22:30:37 +08:00
Merge pull request #3708 from GHLandy/master
[完成翻译] Part 8 - LFCS--Managing Users and Groups File Permissions and Attributes and Enabling sudo Access on Accounts;[开始翻译]20150921 14 tips for teaching open source development
This commit is contained in:
commit
5b5eb6ce05
@ -1,3 +1,5 @@
|
||||
GHLandy Translating
|
||||
|
||||
14 tips for teaching open source development
|
||||
================================================================================
|
||||
Academia is an excellent platform for training and preparing the open source developers of tomorrow. In research, we occasionally open source software we write. We do this for two reasons. One, to promote the use of the tools we produce. And two, to learn more about the impact and issues other people face when using them. With this background of writing research software, I was tasked with redesigning the undergraduate software engineering course for second-year students at the University of Bradford.
|
||||
|
||||
@ -1,332 +0,0 @@
|
||||
GHLandy Translating
|
||||
|
||||
Part 8 - LFCS: Managing Users & Groups, File Permissions & Attributes and Enabling sudo Access on Accounts
|
||||
================================================================================
|
||||
Last August, the Linux Foundation started the LFCS certification (Linux Foundation Certified Sysadmin), a brand new program whose purpose is to allow individuals everywhere and anywhere take an exam in order to get certified in basic to intermediate operational support for Linux systems, which includes supporting running systems and services, along with overall monitoring and analysis, plus intelligent decision-making to be able to decide when it’s necessary to escalate issues to higher level support teams.
|
||||
|
||||

|
||||
|
||||
Linux Foundation Certified Sysadmin – Part 8
|
||||
|
||||
Please have a quick look at the following video that describes an introduction to the Linux Foundation Certification Program.
|
||||
|
||||
注:youtube视频
|
||||
<iframe width="720" height="405" frameborder="0" allowfullscreen="allowfullscreen" src="//www.youtube.com/embed/Y29qZ71Kicg"></iframe>
|
||||
|
||||
This article is Part 8 of a 10-tutorial long series, here in this section, we will guide you on how to manage users and groups permissions in Linux system, that are required for the LFCS certification exam.
|
||||
|
||||
Since Linux is a multi-user operating system (in that it allows multiple users on different computers or terminals to access a single system), you will need to know how to perform effective user management: how to add, edit, suspend, or delete user accounts, along with granting them the necessary permissions to do their assigned tasks.
|
||||
|
||||
### Adding User Accounts ###
|
||||
|
||||
To add a new user account, you can run either of the following two commands as root.
|
||||
|
||||
# adduser [new_account]
|
||||
# useradd [new_account]
|
||||
|
||||
When a new user account is added to the system, the following operations are performed.
|
||||
|
||||
1. His/her home directory is created (/home/username by default).
|
||||
|
||||
2. The following hidden files are copied into the user’s home directory, and will be used to provide environment variables for his/her user session.
|
||||
|
||||
.bash_logout
|
||||
.bash_profile
|
||||
.bashrc
|
||||
|
||||
3. A mail spool is created for the user at /var/spool/mail/username.
|
||||
|
||||
4. A group is created and given the same name as the new user account.
|
||||
|
||||
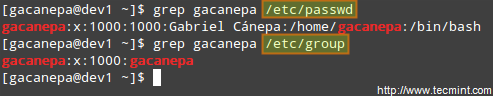
**Understanding /etc/passwd**
|
||||
|
||||
The full account information is stored in the /etc/passwd file. This file contains a record per system user account and has the following format (fields are delimited by a colon).
|
||||
|
||||
[username]:[x]:[UID]:[GID]:[Comment]:[Home directory]:[Default shell]
|
||||
|
||||
- Fields [username] and [Comment] are self explanatory.
|
||||
- The x in the second field indicates that the account is protected by a shadowed password (in /etc/shadow), which is needed to logon as [username].
|
||||
- The [UID] and [GID] fields are integers that represent the User IDentification and the primary Group IDentification to which [username] belongs, respectively.
|
||||
- The [Home directory] indicates the absolute path to [username]’s home directory, and
|
||||
- The [Default shell] is the shell that will be made available to this user when he or she logins the system.
|
||||
|
||||
**Understanding /etc/group**
|
||||
|
||||
Group information is stored in the /etc/group file. Each record has the following format.
|
||||
|
||||
[Group name]:[Group password]:[GID]:[Group members]
|
||||
|
||||
- [Group name] is the name of group.
|
||||
- An x in [Group password] indicates group passwords are not being used.
|
||||
- [GID]: same as in /etc/passwd.
|
||||
- [Group members]: a comma separated list of users who are members of [Group name].
|
||||
|
||||
|
||||
|
||||
Add User Accounts
|
||||
|
||||
After adding an account, you can edit the following information (to name a few fields) using the usermod command, whose basic syntax of usermod is as follows.
|
||||
|
||||
# usermod [options] [username]
|
||||
|
||||
**Setting the expiry date for an account**
|
||||
|
||||
Use the –expiredate flag followed by a date in YYYY-MM-DD format.
|
||||
|
||||
# usermod --expiredate 2014-10-30 tecmint
|
||||
|
||||
**Adding the user to supplementary groups**
|
||||
|
||||
Use the combined -aG, or –append –groups options, followed by a comma separated list of groups.
|
||||
|
||||
# usermod --append --groups root,users tecmint
|
||||
|
||||
**Changing the default location of the user’s home directory**
|
||||
|
||||
Use the -d, or –home options, followed by the absolute path to the new home directory.
|
||||
|
||||
# usermod --home /tmp tecmint
|
||||
|
||||
**Changing the shell the user will use by default**
|
||||
|
||||
Use –shell, followed by the path to the new shell.
|
||||
|
||||
# usermod --shell /bin/sh tecmint
|
||||
|
||||
**Displaying the groups an user is a member of**
|
||||
|
||||
# groups tecmint
|
||||
# id tecmint
|
||||
|
||||
Now let’s execute all the above commands in one go.
|
||||
|
||||
# usermod --expiredate 2014-10-30 --append --groups root,users --home /tmp --shell /bin/sh tecmint
|
||||
|
||||

|
||||
|
||||
usermod Command Examples
|
||||
|
||||
Read Also:
|
||||
|
||||
- [15 useradd Command Examples in Linux][1]
|
||||
- [15 usermod Command Examples in Linux][2]
|
||||
|
||||
For existing accounts, we can also do the following.
|
||||
|
||||
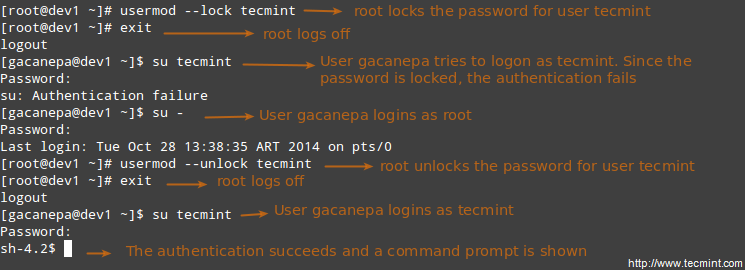
**Disabling account by locking password**
|
||||
|
||||
Use the -L (uppercase L) or the –lock option to lock a user’s password.
|
||||
|
||||
# usermod --lock tecmint
|
||||
|
||||
**Unlocking user password**
|
||||
|
||||
Use the –u or the –unlock option to unlock a user’s password that was previously blocked.
|
||||
|
||||
# usermod --unlock tecmint
|
||||
|
||||
|
||||
|
||||
Lock User Accounts
|
||||
|
||||
**Creating a new group for read and write access to files that need to be accessed by several users**
|
||||
|
||||
Run the following series of commands to achieve the goal.
|
||||
|
||||
# groupadd common_group # Add a new group
|
||||
# chown :common_group common.txt # Change the group owner of common.txt to common_group
|
||||
# usermod -aG common_group user1 # Add user1 to common_group
|
||||
# usermod -aG common_group user2 # Add user2 to common_group
|
||||
# usermod -aG common_group user3 # Add user3 to common_group
|
||||
|
||||
**Deleting a group**
|
||||
|
||||
You can delete a group with the following command.
|
||||
|
||||
# groupdel [group_name]
|
||||
|
||||
If there are files owned by group_name, they will not be deleted, but the group owner will be set to the GID of the group that was deleted.
|
||||
|
||||
### Linux File Permissions ###
|
||||
|
||||
Besides the basic read, write, and execute permissions that we discussed in [Setting File Attributes – Part 3][3] of this series, there are other less used (but not less important) permission settings, sometimes referred to as “special permissions”.
|
||||
|
||||
Like the basic permissions discussed earlier, they are set using an octal file or through a letter (symbolic notation) that indicates the type of permission.
|
||||
Deleting user accounts
|
||||
|
||||
You can delete an account (along with its home directory, if it’s owned by the user, and all the files residing therein, and also the mail spool) using the userdel command with the –remove option.
|
||||
|
||||
# userdel --remove [username]
|
||||
|
||||
#### Group Management ####
|
||||
|
||||
Every time a new user account is added to the system, a group with the same name is created with the username as its only member. Other users can be added to the group later. One of the purposes of groups is to implement a simple access control to files and other system resources by setting the right permissions on those resources.
|
||||
|
||||
For example, suppose you have the following users.
|
||||
|
||||
- user1 (primary group: user1)
|
||||
- user2 (primary group: user2)
|
||||
- user3 (primary group: user3)
|
||||
|
||||
All of them need read and write access to a file called common.txt located somewhere on your local system, or maybe on a network share that user1 has created. You may be tempted to do something like,
|
||||
|
||||
# chmod 660 common.txt
|
||||
OR
|
||||
# chmod u=rw,g=rw,o= common.txt [notice the space between the last equal sign and the file name]
|
||||
|
||||
However, this will only provide read and write access to the owner of the file and to those users who are members of the group owner of the file (user1 in this case). Again, you may be tempted to add user2 and user3 to group user1, but that will also give them access to the rest of the files owned by user user1 and group user1.
|
||||
|
||||
This is where groups come in handy, and here’s what you should do in a case like this.
|
||||
|
||||
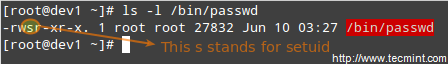
**Understanding Setuid**
|
||||
|
||||
When the setuid permission is applied to an executable file, an user running the program inherits the effective privileges of the program’s owner. Since this approach can reasonably raise security concerns, the number of files with setuid permission must be kept to a minimum. You will likely find programs with this permission set when a system user needs to access a file owned by root.
|
||||
|
||||
Summing up, it isn’t just that the user can execute the binary file, but also that he can do so with root’s privileges. For example, let’s check the permissions of /bin/passwd. This binary is used to change the password of an account, and modifies the /etc/shadow file. The superuser can change anyone’s password, but all other users should only be able to change their own.
|
||||
|
||||
|
||||
|
||||
passwd Command Examples
|
||||
|
||||
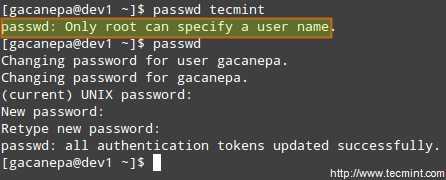
Thus, any user should have permission to run /bin/passwd, but only root will be able to specify an account. Other users can only change their corresponding passwords.
|
||||
|
||||
|
||||
|
||||
Change User Password
|
||||
|
||||
**Understanding Setgid**
|
||||
|
||||
When the setgid bit is set, the effective GID of the real user becomes that of the group owner. Thus, any user can access a file under the privileges granted to the group owner of such file. In addition, when the setgid bit is set on a directory, newly created files inherit the same group as the directory, and newly created subdirectories will also inherit the setgid bit of the parent directory. You will most likely use this approach whenever members of a certain group need access to all the files in a directory, regardless of the file owner’s primary group.
|
||||
|
||||
# chmod g+s [filename]
|
||||
|
||||
To set the setgid in octal form, prepend the number 2 to the current (or desired) basic permissions.
|
||||
|
||||
# chmod 2755 [directory]
|
||||
|
||||
**Setting the SETGID in a directory**
|
||||
|
||||

|
||||
|
||||
Add Setgid to Directory
|
||||
|
||||
**Understanding Sticky Bit**
|
||||
|
||||
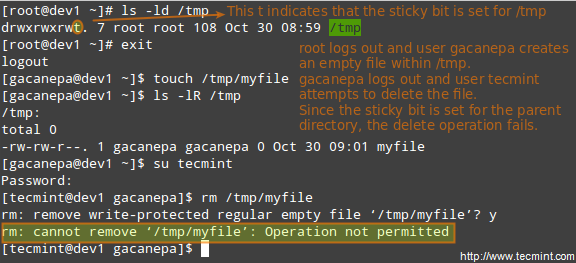
When the “sticky bit” is set on files, Linux just ignores it, whereas for directories it has the effect of preventing users from deleting or even renaming the files it contains unless the user owns the directory, the file, or is root.
|
||||
|
||||
# chmod o+t [directory]
|
||||
|
||||
To set the sticky bit in octal form, prepend the number 1 to the current (or desired) basic permissions.
|
||||
|
||||
# chmod 1755 [directory]
|
||||
|
||||
Without the sticky bit, anyone able to write to the directory can delete or rename files. For that reason, the sticky bit is commonly found on directories, such as /tmp, that are world-writable.
|
||||
|
||||
|
||||
|
||||
Add Stickybit to Directory
|
||||
|
||||
### Special Linux File Attributes ###
|
||||
|
||||
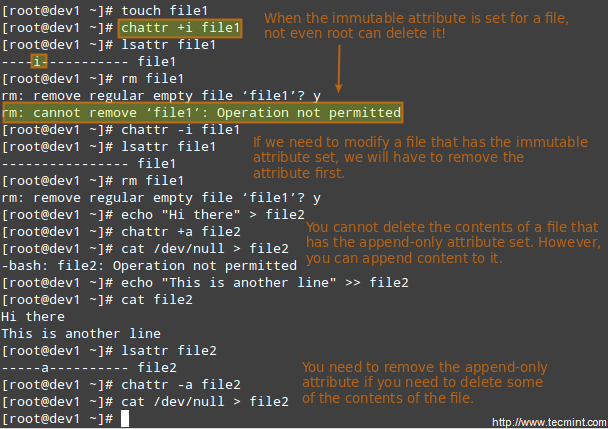
There are other attributes that enable further limits on the operations that are allowed on files. For example, prevent the file from being renamed, moved, deleted, or even modified. They are set with the [chattr command][4] and can be viewed using the lsattr tool, as follows.
|
||||
|
||||
# chattr +i file1
|
||||
# chattr +a file2
|
||||
|
||||
After executing those two commands, file1 will be immutable (which means it cannot be moved, renamed, modified or deleted) whereas file2 will enter append-only mode (can only be open in append mode for writing).
|
||||
|
||||
|
||||
|
||||
Chattr Command to Protect Files
|
||||
|
||||
### Accessing the root Account and Using sudo ###
|
||||
|
||||
One of the ways users can gain access to the root account is by typing.
|
||||
|
||||
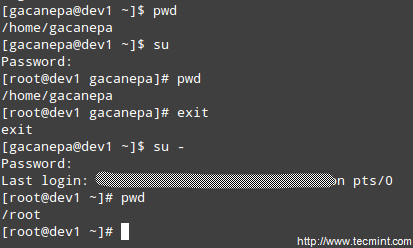
$ su
|
||||
|
||||
and then entering root’s password.
|
||||
|
||||
If authentication succeeds, you will be logged on as root with the current working directory as the same as you were before. If you want to be placed in root’s home directory instead, run.
|
||||
|
||||
$ su -
|
||||
|
||||
and then enter root’s password.
|
||||
|
||||
|
||||
|
||||
Enable Sudo Access on Users
|
||||
|
||||
The above procedure requires that a normal user knows root’s password, which poses a serious security risk. For that reason, the sysadmin can configure the sudo command to allow an ordinary user to execute commands as a different user (usually the superuser) in a very controlled and limited way. Thus, restrictions can be set on a user so as to enable him to run one or more specific privileged commands and no others.
|
||||
|
||||
- Read Also: [Difference Between su and sudo User][5]
|
||||
|
||||
To authenticate using sudo, the user uses his/her own password. After entering the command, we will be prompted for our password (not the superuser’s) and if the authentication succeeds (and if the user has been granted privileges to run the command), the specified command is carried out.
|
||||
|
||||
To grant access to sudo, the system administrator must edit the /etc/sudoers file. It is recommended that this file is edited using the visudo command instead of opening it directly with a text editor.
|
||||
|
||||
# visudo
|
||||
|
||||
This opens the /etc/sudoers file using vim (you can follow the instructions given in [Install and Use vim as Editor – Part 2][6] of this series to edit the file).
|
||||
|
||||
These are the most relevant lines.
|
||||
|
||||
Defaults secure_path="/usr/sbin:/usr/bin:/sbin"
|
||||
root ALL=(ALL) ALL
|
||||
tecmint ALL=/bin/yum update
|
||||
gacanepa ALL=NOPASSWD:/bin/updatedb
|
||||
%admin ALL=(ALL) ALL
|
||||
|
||||
Let’s take a closer look at them.
|
||||
|
||||
Defaults secure_path="/usr/sbin:/usr/bin:/sbin:/usr/local/bin"
|
||||
|
||||
This line lets you specify the directories that will be used for sudo, and is used to prevent using user-specific directories, which can harm the system.
|
||||
|
||||
The next lines are used to specify permissions.
|
||||
|
||||
root ALL=(ALL) ALL
|
||||
|
||||
- The first ALL keyword indicates that this rule applies to all hosts.
|
||||
- The second ALL indicates that the user in the first column can run commands with the privileges of any user.
|
||||
- The third ALL means any command can be run.
|
||||
|
||||
tecmint ALL=/bin/yum update
|
||||
|
||||
If no user is specified after the = sign, sudo assumes the root user. In this case, user tecmint will be able to run yum update as root.
|
||||
|
||||
gacanepa ALL=NOPASSWD:/bin/updatedb
|
||||
|
||||
The NOPASSWD directive allows user gacanepa to run /bin/updatedb without needing to enter his password.
|
||||
|
||||
%admin ALL=(ALL) ALL
|
||||
|
||||
The % sign indicates that this line applies to a group called “admin”. The meaning of the rest of the line is identical to that of an regular user. This means that members of the group “admin” can run all commands as any user on all hosts.
|
||||
|
||||
To see what privileges are granted to you by sudo, use the “-l” option to list them.
|
||||
|
||||

|
||||
|
||||
Sudo Access Rules
|
||||
|
||||
### Summary ###
|
||||
|
||||
Effective user and file management skills are essential tools for any system administrator. In this article we have covered the basics and hope you can use it as a good starting to point to build upon. Feel free to leave your comments or questions below, and we’ll respond quickly.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.tecmint.com/manage-users-and-groups-in-linux/
|
||||
|
||||
作者:[Gabriel Cánepa][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.tecmint.com/author/gacanepa/
|
||||
[1]:http://www.tecmint.com/add-users-in-linux/
|
||||
[2]:http://www.tecmint.com/usermod-command-examples/
|
||||
[3]:http://www.tecmint.com/compress-files-and-finding-files-in-linux/
|
||||
[4]:http://www.tecmint.com/chattr-command-examples/
|
||||
[5]:http://www.tecmint.com/su-vs-sudo-and-how-to-configure-sudo-in-linux/
|
||||
[6]:http://www.tecmint.com/vi-editor-usage/
|
||||
@ -0,0 +1,333 @@
|
||||
GHLandy Translated
|
||||
|
||||
LFCS 系列第八讲:管理用户和用户组、文件权限和属性以及启用账户 sudo 访问权限
|
||||
|
||||
================================================================================
|
||||
|
||||
去年八月份,Linux 基金会发起了全新的 LFCS(Linux Foundation Certified Sysadmin,Linux 基金会认证系统管理员)认证,旨在让世界各地的人能够参与到关于 Linux 系统中间层的基本管理操作的认证考试中去,这项认证包括:维护正在运行的系统和服务的能力、全面监控和分析的能力以及何时向上游团队请求支持的决策能力。
|
||||
|
||||

|
||||
|
||||
LFCS 系列第八讲
|
||||
|
||||
请看以下视频,里边将描述 LFCS 认证程序。
|
||||
|
||||
注:youtube视频
|
||||
<iframe width="720" height="405" frameborder="0" allowfullscreen="allowfullscreen" src="//www.youtube.com/embed/Y29qZ71Kicg"></iframe>
|
||||
|
||||
本讲是《十套教程》系列的第八讲,在这一讲中,我们将引导你学习如何在 Linux 管理用户和用户组权限的设置,这些内容是 LFCS 认证开始中的必备知识。
|
||||
|
||||
由于 Linux 是一个多用户的操作系统(允许多个用户通过不同主机或者终端访问一个独立系统),因此你需要知道如何才能有效地管理用户:如何添加、编辑、禁用和删除用户账户,并赋予他们足以完成自身任务的必要权限。
|
||||
|
||||
### 添加用户账户 ###
|
||||
|
||||
添加新用户账户,你需要以 root 运行一下两条命令中的任意一条:
|
||||
|
||||
# adduser [new_account]
|
||||
# useradd [new_account]
|
||||
|
||||
当新用户账户添加到系统时,会自动执行以下操作:
|
||||
|
||||
1. 自动创建用户家目录(默认是 /home/username)。
|
||||
|
||||
2. 自动拷贝下列隐藏文件到新建用户的家目录,用来设置新用户会话的环境变量。
|
||||
|
||||
.bash_logout
|
||||
.bash_profile
|
||||
.bashrc
|
||||
|
||||
3. 自动创建邮件缓存目录 /var/spool/mail/username。
|
||||
|
||||
4. 自动创建于用户名相同的用户组。
|
||||
|
||||
**理解 /etc/passwd 中的内容**
|
||||
|
||||
/etc/passwd 文件中存储了所有用户账户的信息,每个用户在里边都有一条对应的记录,其格式(每个字段用冒号隔开)如下:
|
||||
|
||||
[username]:[x]:[UID]:[GID]:[Comment]:[Home directory]:[Default shell]
|
||||
|
||||
- 字段 [username] 和 [Comment] 是自解释的关系。
|
||||
- 第二个字段中 x 表明通过用户名 username 登录系统是有密码保护的, 密码保存在 /etc/shadow 文件中。
|
||||
- [UID] 和 [GID] 字段用整数表示,代表该用户的用户标识符和对应所在组的组标志符。
|
||||
- 字段 [Home directory] 为 username 用户家目录的绝对路径。
|
||||
- 字段 [Default shell] 指定用户登录系统时默认使用的 shell。
|
||||
|
||||
**理解 /etc/group 中的内容**
|
||||
|
||||
/etc/group 文件存储所有用户组的信息。每行记录的格式如下:
|
||||
|
||||
[Group name]:[Group password]:[GID]:[Group members]
|
||||
|
||||
- [Group name] 为用户组名称。
|
||||
- 字段 [Group password] 为 x 的话,则说明不适用用户组密码。
|
||||
- [GID] 与 /etc/passwd 中保存的 GID 相同。
|
||||
- [Group members] 用户组中的用户使用逗号隔开。
|
||||
|
||||

|
||||
|
||||
添加用户账户
|
||||
|
||||
添加用户账户之后,你可以使用 usermod 命令来修改用户信息中的部分字段,该命令基本语法如下:
|
||||
|
||||
# usermod [options] [username]
|
||||
|
||||
**设置账户的过期时间**
|
||||
|
||||
通过 –expiredate 标记后边接 年-月-日 格式的日期,如下:
|
||||
|
||||
# usermod --expiredate 2014-10-30 tecmint
|
||||
|
||||
**将用户添加到其他组**
|
||||
|
||||
使用 -aG 或者 –append –groups 选项,后边跟着用户组,如果有多个用户组,每个用户组之间使用逗号隔开。
|
||||
|
||||
# usermod --append --groups root,users tecmint
|
||||
|
||||
**改变用户家目录的默认位置**
|
||||
|
||||
使用 -d 或者 –home 选项,后边跟着新的家目录的绝对路径。
|
||||
|
||||
# usermod --home /tmp tecmint
|
||||
|
||||
**改变用户的默认 shell**
|
||||
|
||||
使用 –shell 选项,后边跟着新 shell 的路径。
|
||||
|
||||
# usermod --shell /bin/sh tecmint
|
||||
|
||||
**显示用户所属的用户组**
|
||||
|
||||
# groups tecmint
|
||||
# id tecmint
|
||||
|
||||
下面,我们一次运行上述命令:
|
||||
|
||||
# usermod --expiredate 2014-10-30 --append --groups root,users --home /tmp --shell /bin/sh tecmint
|
||||
|
||||

|
||||
|
||||
usermod 命令例示
|
||||
|
||||
扩展阅读
|
||||
|
||||
- [15 useradd Command Examples in Linux][1]
|
||||
- [15 usermod Command Examples in Linux][2]
|
||||
|
||||
对于已有用户账户,我们还可以:
|
||||
|
||||
**通过锁定密码来禁用账户**
|
||||
|
||||
使用 -L (大写 l)或者 –lock 选项来锁定用户密码。
|
||||
|
||||
# usermod --lock tecmint
|
||||
|
||||
**解锁用户密码**
|
||||
|
||||
使用 –u 或者 –unlock 选项来解锁我们之前锁定的账户。
|
||||
|
||||
# usermod --unlock tecmint
|
||||
|
||||

|
||||
|
||||
锁定用户账户
|
||||
|
||||
**为需要对指定文件进行读写的多个用户建立用户组**
|
||||
|
||||
运行下列几条命令来完成:
|
||||
|
||||
# groupadd common_group # 添加新用户组
|
||||
# chown :common_group common.txt # 将 common.txt 的用户组修改为 common_group
|
||||
# usermod -aG common_group user1 # 添加用户 user1 到 common_group 用户组
|
||||
# usermod -aG common_group user2 # 添加用户 user2 到 common_group 用户组
|
||||
# usermod -aG common_group user3 # 添加用户 user3 到 common_group 用户组
|
||||
|
||||
**删除用户组**
|
||||
|
||||
通过以下命令删除用户组:
|
||||
|
||||
# groupdel [group_name]
|
||||
|
||||
属于这个 group_name 用户组的文件是不会被删除的,而仅仅是删除了用户组。
|
||||
|
||||
### Linux 文件权限 ###
|
||||
|
||||
除了我们在 [Setting File Attributes – Part 3][3] 中说到的基本的读取、写入和执行权限外,文件还有一些不常用却很重要的的权限设置,有时候把它当做“特殊权限”。
|
||||
|
||||
就像之前我们讨论的基本权限,这里同样使用八进制数字或者一个字母(象征性符号)好表示该权限类型。
|
||||
|
||||
**删除用户账户**
|
||||
|
||||
你可以通过 userdel --remove 命令来删除用户账户。这样会删除用户拥有的家目录和家目录下的所有文件,以及邮件缓存目录。
|
||||
|
||||
# userdel --remove [username]
|
||||
|
||||
#### 用户组管理 ####
|
||||
|
||||
每次添加新用户,系统会为该用户创建同名的用户组,此时用户组里边只有新建的用户,其他用户可以随后添加进去。建立用户组的目的之一,就是为了通过对指定资源设置权限来完成对这些资源和文件进行访问控制。
|
||||
|
||||
比如,你有下列用户:
|
||||
|
||||
- user1 (primary group: user1)
|
||||
- user2 (primary group: user2)
|
||||
- user3 (primary group: user3)
|
||||
|
||||
他们都需要对你系统里边某个位置的 common.txt 文件,或者 user1 用户刚刚创建的共享进行读写。你可能会运行下列命令:
|
||||
|
||||
# chmod 660 common.txt
|
||||
或
|
||||
# chmod u=rw,g=rw,o= common.txt [注意最后那个 = 号和文件名之间的空格]
|
||||
|
||||
然而,这样仅仅给文件所属的用户和用户组(本例为 user1)成员的提供了读写权限。你还需要将 user2 和 user3 添加到 user1 组,打这样做也将 user1 用户和用户组的其他文件的权限开放给了 user2 和 user3。
|
||||
|
||||
这时候,用户组就派上用场了,下面将演示怎么做。
|
||||
|
||||
**理解 Setuid 位**
|
||||
|
||||
当为可执行文件设置 setuid 位之后,用户运行程序是会继承该程序属主的有效特权。由于这样做会引起安全风险,因此设置 setuid 权限的文件及程序必须尽量少。你会发现,当系统中有用户需要执行 root 用户所管辖的程序时就是设置了 setuid 权限。
|
||||
|
||||
也就是说,用户不仅仅可以运行这个可执行文件,而且能以 root 权限来运行。比如,先检查 /bin/passwd 的权限,这个可执行文件用于改变账户的密码,并修改 /etc/shadow 文件。超级用户可以改变任意账户的密码,但是其他用户只能改变自己账户的密码。
|
||||
|
||||

|
||||
|
||||
passwd 命令例示
|
||||
|
||||
因此,所有用户都有权限运行 /bin/passwd,但只有 root 用户可以指定改变指定用户账户的密码。其他用户只能改变其自身的密码。
|
||||
|
||||

|
||||
|
||||
修改用户密码
|
||||
|
||||
**理解 Setgid 位**
|
||||
|
||||
设置 setgid 位之后,真实用户的有效 GID 变为属组的 GID。因此,任何用户都能以赋予属组用户的权限来访问文件。另外,当目录置了 setgid 位之后,新建的文件将继承其所属目录的 GID,并且新建的子目录会继承父目录的 setgid 位。通过这个方法,你能够以一个指定用户组的身份来访问该目录里边的文件,而不必管文件属主的主属组。
|
||||
|
||||
# chmod g+s [filename]
|
||||
|
||||
以八进制形式来设置 setgid 位,在当前基本权限(或者想要设置的权限)前加上数字 2 就行了。
|
||||
|
||||
# chmod 2755 [directory]
|
||||
|
||||
**给目录设置 SETGID 位**
|
||||
|
||||

|
||||
|
||||
给命令设置 setgid 位
|
||||
|
||||
**理解 Sticky 位**
|
||||
|
||||
文件设置了 Sticky 为之后,Linux 会将文件忽略,对于该文件影响到的目录,除了属主或者 root 用户外,其他用户无法删除,甚至重命名目录中其他文件也不行。
|
||||
|
||||
# chmod o+t [directory]
|
||||
|
||||
以八进制形式来设置 sticky 位,在当前基本权限(或者想要设置的权限)前加上数字 1 就行了。
|
||||
|
||||
# chmod 1755 [directory]
|
||||
|
||||
若没有 sticky 位,任何有权限读写目录的用户都可删除和重命名文件。因此,sticky 为通常出现在像 /tmp 之类的目录,这些目录是所有人都具有写权限的。
|
||||
|
||||

|
||||
|
||||
给目录设置 sticky 位
|
||||
|
||||
### Linux 特殊文件属性 ###
|
||||
|
||||
文件还有其他一些属性,用来做进一步的操作限制。比如,阻止对文件的重命名、移动、删除甚至是修改。可以通过使用 [chattr 命令][4] 来设置,并可以使用 lsattr 工具来查看这些属性。设置如下:
|
||||
|
||||
# chattr +i file1
|
||||
# chattr +a file2
|
||||
|
||||
运行这些命令之后,file1 成为不可变状态(即不可移动、重命名、修改或删除),而 file2 进入“仅追加”模式(仅在追加内容模式中打开)。
|
||||
|
||||

|
||||
|
||||
通过 Chattr 命令来包含文件
|
||||
|
||||
### 访问 root 账户并启用 sudo ###
|
||||
|
||||
访问 root 账户的方法之一,就是通过输入:
|
||||
|
||||
$ su
|
||||
|
||||
然后输入 root 账户密码。
|
||||
|
||||
倘若授权成功,你将以 root 身份登录,工作目录则是登录前所在的位置。如果是想要一登录就自动进入 root 用户的家目录,请运行:
|
||||
$ su -
|
||||
|
||||
然后输入 root 账户密码。
|
||||
|
||||

|
||||
|
||||
为用户启用 sudo 访问权限
|
||||
|
||||
执行上个步骤需要普通用户知道 root 账户的密码,这样会引起非常严重的安全问题。于是,系统管理员通常会配置 sudo 命令来让普通用户在严格控制的环境中以其他用户身份(通常是 root)来执行命令。所有,可以在严格控制用户的情况下,又允许他运行一条或多条特权命令。
|
||||
|
||||
- 扩展阅读:[Difference Between su and sudo User][5]
|
||||
|
||||
普通用户通过他自己的用户密码来完成 sudo 授权。输入命令之后会出现输入密码(并不是超级用户密码)的提示,授权成功(只要赋予了用户运行该命令的权限)的话,指定的命令就会运行。
|
||||
|
||||
系统管理员必须编辑 /etc/sudoers 文件,才能为 sudo 赋予相应权限。通常建议使用 visudo 命令来编辑这个文件,而不是使用文本编辑器来打开它。
|
||||
|
||||
# visudo
|
||||
|
||||
这样会使用 vim(如果你按照 [Install and Use vim as Editor – Part 2][6] 里边说的来编辑文件)来打开 /etc/sudoers 文件。
|
||||
|
||||
以下是需要设置的相关的行:
|
||||
|
||||
Defaults secure_path="/usr/sbin:/usr/bin:/sbin"
|
||||
root ALL=(ALL) ALL
|
||||
tecmint ALL=/bin/yum update
|
||||
gacanepa ALL=NOPASSWD:/bin/updatedb
|
||||
%admin ALL=(ALL) ALL
|
||||
|
||||
来更加深入了解这些项:
|
||||
|
||||
Defaults secure_path="/usr/sbin:/usr/bin:/sbin:/usr/local/bin"
|
||||
|
||||
这一行指定 sudo 将要使用的目录,这样可以阻止使用用户指定的目录,那样的话可能会危及系统。
|
||||
|
||||
下一行是用来指定权限的:
|
||||
|
||||
root ALL=(ALL) ALL
|
||||
|
||||
- 第一个 ALL 关键词表明这条规则适用于所有主机。
|
||||
- 第二个 ALL 关键词表明第一个字段中指定的用户能以任何用户身份所具有的权限来运行相应命令。
|
||||
- 第三个 ALL 关键词表明可以运行任何命令。
|
||||
|
||||
tecmint ALL=/bin/yum update
|
||||
|
||||
如果 = 号后边没有指定用户,sudo 则默认为 root 用户。本例中,tecmint 用户能以 root身份运行 yum update 命令。
|
||||
|
||||
gacanepa ALL=NOPASSWD:/bin/updatedb
|
||||
|
||||
NOPASSWD 关键词表明 gacanepa 用户不需要密码,可以直接运行 /bin/updatedb 命令。
|
||||
|
||||
%admin ALL=(ALL) ALL
|
||||
|
||||
% 符号表示该行应用 admin 用户组。其他部分的含义与对于用户的含义是一样的。本例表示 admin 用户组的成员可以通过任何主机的链接来运行任何命令。
|
||||
|
||||
通过 sudo -l 命令可以查看,你的账户拥有什么样的权限。
|
||||
|
||||

|
||||
|
||||
Sudo 访问规则
|
||||
|
||||
### 总结 ###
|
||||
对于系统管理员来说,高效能的用户和文件管理技能是非常必要的。本文已经涵盖了这些内容,我们希望你将这些作为一个开始,,然后慢慢进步。随时在下边发表评论或提问,我们会尽快回应的。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.tecmint.com/manage-users-and-groups-in-linux/
|
||||
|
||||
作者:[Gabriel Cánepa][a]
|
||||
译者:[GHLandy](https://github.com/GHLandy)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.tecmint.com/author/gacanepa/
|
||||
[1]:http://www.tecmint.com/add-users-in-linux/
|
||||
[2]:http://www.tecmint.com/usermod-command-examples/
|
||||
[3]:http://www.tecmint.com/compress-files-and-finding-files-in-linux/
|
||||
[4]:http://www.tecmint.com/chattr-command-examples/
|
||||
[5]:http://www.tecmint.com/su-vs-sudo-and-how-to-configure-sudo-in-linux/
|
||||
[6]:http://www.tecmint.com/vi-editor-usage/
|
||||
Loading…
Reference in New Issue
Block a user