mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-03-27 02:30:10 +08:00
commit
5a564317e6
published
20210308 How the ARPANET Protocols Worked.md20210525 Pen testing with Linux security tools.md20210712 Reading and writing files with Python.md20210720 How to Upgrade to Debian 11 from Debian 10.md20210726 How to use cron on Linux.md20210729 Use df to check free disk space on Linux.md
sources
news
20210803 4MLinux 37.0 Release Packs in Linux Kernel 5.10 LTS and New Applications.md20210803 GNOME Web Canary is Now Available to Test Bleeding Edge Features.md
talk
20210804 Firefox Lost Almost 50 million Users- Here-s Why It is Concerning.md20210805 Your one-on-one meeting doesn-t have to be this way.md
tech
20210626 Windows 11 Look Inspired by KDE Plasma and GNOME.md20210712 Reading and writing files with Python.md20210720 How to Upgrade to Debian 11 from Debian 10.md20210723 5 useful ways to manage Kubernetes with kubectl.md20210726 Command line quick tips- wc, sort, sed and tr.md20210727 How to Change Lock and Login Screen Wallpaper in elementary OS.md20210730 4 cool new projects to try in Copr from July 2021.md20210802 Use OpenCV on Fedora Linux - part 1.md20210803 Get started with Argo CD.md20210803 Set up a VPN server on your Linux PC.md20210803 Use the Linux terminal to navigate throughout your computer.md20210804 Apps for daily needs part 3- image editors.md20210804 Install OpenVPN on your Linux PC.md20210804 Move files in the Linux terminal.md20210805 Configure your OpenVPN server on Linux.md20210805 Installing Packages From External Repositories in Ubuntu -Explained.md
translated
talk
tech
20210626 Windows 11 Look Inspired by KDE Plasma and GNOME.md20210723 5 useful ways to manage Kubernetes with kubectl.md20210727 Check used disk space on Linux with du.md20210727 How to Change Lock and Login Screen Wallpaper in elementary OS.md20210801 Use the Linux terminal to see what files are on your computer.md20210803 How to Install Google Chrome on Linux Mint -Beginners Tip.md20210803 Mount Microsoft OneDrive in Linux With OneDriver GUI Tool.md20210804 How to Find and Remove Duplicate Photos in Linux.md
125
published/20210308 How the ARPANET Protocols Worked.md
Normal file
125
published/20210308 How the ARPANET Protocols Worked.md
Normal file
@ -0,0 +1,125 @@
|
||||
[#]: subject: (How the ARPANET Protocols Worked)
|
||||
[#]: via: (https://twobithistory.org/2021/03/08/arpanet-protocols.html)
|
||||
[#]: author: (Two-Bit History https://twobithistory.org)
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (Lin-vy)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-13643-1.html)
|
||||
|
||||
ARPANET 协议是如何工作的
|
||||
======
|
||||
|
||||
|
||||
|
||||
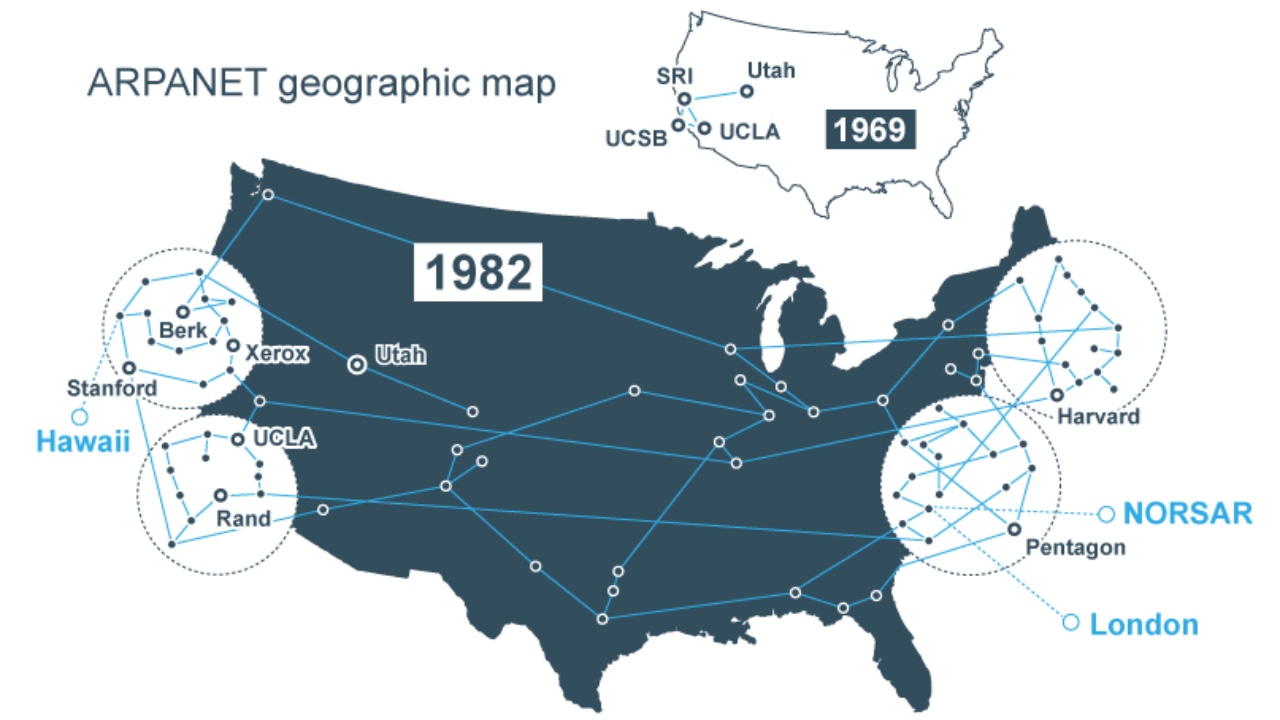
ARPANET 通过证明可以使用标准化协议连接完全不同的制造商的计算机,永远改变了计算。在我的 [关于 ARPANET 的历史意义的文章][1] 中,我提到了其中的一些协议,但没有详细描述它们。所以我想仔细看看它们。也想看看那些早期协议的设计有多少保留到了我们今天使用的协议中。
|
||||
|
||||
ARPANET 协议像我们现代的互联网协议,是通过分层形式来组织的。[^1] 较高层协议运行在较低层协议之上。如今的 TCP/IP 套件有 5 层(物理层、链路层、网络层、传输层以及应用层),但是这个 ARPANET 仅有 3 层,也可能是 4 层,这取决于你怎样计算它们。
|
||||
|
||||
我将会解释每一层是如何工作的,但首先,你需要知道是谁在 ARPANET 中构建了些什么,你需要知道这一点才能理解为什么这些层是这样划分的。
|
||||
|
||||
### 一些简短的历史背景
|
||||
|
||||
ARPANET 由美国联邦政府资助,确切的说是位于美国国防部的<ruby>高级研究计划局<rt>Advanced Research Projects Agency</rt></ruby>(因此被命名为 “ARPANET” )。美国政府并没有直接建设这个网络;而是,把这项工作外包给了位于波士顿的一家名为 “Bolt, Beranek, and Newman” 的咨询公司,通常更多时候被称为 BBN。
|
||||
|
||||
而 BBN 则承担了实现这个网络的大部分任务,但不是全部。BBN 所做的是设计和维护一种称为<ruby>接口消息处理机<rt>Interface Message Processor</rt></ruby>(简称为 IMP) 的机器。这个 IMP 是一种定制的<ruby>霍尼韦尔<rt>Honeywell</rt></ruby><ruby>小型机<rt>minicomputer</rt></ruby>,它们被分配给那些想要接入这个 ARPANET 的遍及全国各地的各个站点。它们充当通往 ARPANET 的网关,为每个站点提供多达四台主机的连接支持。它基本上是一台路由器。BBN 控制在 IMP 上运行的软件,把数据包从一个 IMP 转发到另一个 IMP ,但是该公司无法直接控制那些将要连接到 IMP 上并且成为 ARPANET 网络中实际主机的机器。
|
||||
|
||||
那些主机由网络中作为终端用户的计算机科学家们所控制。这些计算机科学家在全国各地的主机站负责编写软件,使主机之间能够相互通讯。而 IMP 赋予主机之间互相发送消息的能力,但是那并没有多大用处,除非主机之间能商定一种用于消息的格式。为了解决这个问题,一群杂七杂八的人员组成了网络工作组,其中有大部分是来自各个站点的研究生们,该组力求规定主机计算机使用的协议。
|
||||
|
||||
因此,如果你设想通过 ARPANET 进行一次成功的网络互动,(例如发送一封电子邮件),使这些互动成功的一些工程由一组人负责(BBN),然而其他的一些工程则由另一组人负责(网络工作组和在每个站点的工程师们)。这种组织和后勤方面的偶然性或许对推动采用分层的方法来管理 ARPANET 网络中的协议起到很大的作用,这反过来又影响了 TCP/IP 的分层方式。
|
||||
|
||||
### 好的,回到协议上来
|
||||
|
||||
![ARPANET Network Stack][3]
|
||||
|
||||
*ARPANET 协议层次结构*
|
||||
|
||||
这些协议层被组织成一个层次结构,在最底部是 “Level 0”。[^2] 这在某种意义上是不算数的,因为在 ARPANET 中这层完全由 BBN 控制,所以不需要标准协议。Level 0 的作用是管理数据在 IMP 之间如何传输。在 BBN 内部,有管理 IMP 如何做到这一点的规则;在 BBN 之外,IMP 子网是一个黑匣子,它只会传送你提供的任意数据。因此,Level 0 是一个没有真正协议的层,就公开已知和商定的规则集而言,它的存在可以被运行在 ARPANET 的主机上的软件忽略。粗略地说,它处理相当于当今使用的 TCP/IP 套件的物理层、链路层和网络层下的所有内容,甚至还包括相当多的传输层,这是我将在这篇文章的末尾回来讨论的内容。
|
||||
|
||||
“Level 1” 层在 ARPANET 的主机和它们所连接的 IMP 之间建立了接口。如果你愿意,可以认为它是为 BBN 构建的 “Level 0” 层的黑匣子使用的一个应用程序接口(API)。当时它也被称为 IMP-Host 协议。必须编写该协议并公布出来,因为在首次建立 ARPANET 网络时,每个主机站点都必须编写自己的软件来与 IMP 连接。除非 BBN 给他们一些指导,否则他们不会知道如何做到这一点。
|
||||
|
||||
BBN 在一份名为 [BBN Report 1822][5] 的冗长文件中规定了 IMP-Host 协议。随着 ARPANET 的发展,该文件多次被修订;我将在这里大致描述 IMP-Host 协议最初设计时的工作方式。根据 BBN 的规则,主机可以将长度不超过 8095 位的消息传递给它们的 IMP,并且每条消息都有一个包含目标主机号和链路识别号的头部字段。[^3] IMP 将检查指定的主机号,然后尽职尽责地将消息转发到网络中。当从远端主机接收到消息时,接收的 IMP 在将消息传递给本地主机之前会把目标主机号替换为源主机号。实际上在 IMP 之间传递的内容并不是消息 —— IMP 将消息分解成更小的数据包以便通过网络传输 —— 但该细节对主机来说是不可见的。
|
||||
|
||||
![1969 Host-IMP Leader][7]
|
||||
|
||||
*Host-IMP 消息头部格式,截至 1969。 图表来自 [BBN Report 1763][8]*
|
||||
|
||||
链路号的取值范围为 0 到 255 ,它有两个作用。一是更高级别的协议可以利用它在网络上的任何两台主机之间建立多个通信信道,因为可以想象得到,在任何时刻都有可能存在多个本地用户与同一个目标主机进行通信的场景(换句话说,链路号允许在主机之间进行多路通信)。二是它也被用在 “Level 1” 层去控制主机之间发送的大量流量,以防止高性能计算机压制低性能计算机的情况出现。按照最初的设计,这个 IMP-Host 协议限制每台主机在某一时刻通过某条链路仅发送一条消息。一旦某台主机沿着某条链路发送了一条消息给远端主机后,在它沿着该链路发送下一条消息之前,必须等待接收一条来自远端的 IMP 的特别类型的消息,叫做 RFNM(<ruby>请求下一条消息<rt>Request for Next Message</rt></ruby>)。后来为了提高性能,对该系统进行了修订,允许一台主机在给定的时刻传送多达 8 条消息给另一台主机。[^4]
|
||||
|
||||
“Level 2” 层才是事情真正开始变得有趣的地方,因为这一层和在它上面的那一层由 BBN 和国防部全部留给学者们和网络工作组自己去研发。“Level 2” 层包括了 Host-Host 协议,这个协议最初在 RFC9 中草拟,并且在 RFC54 中首次正式规定。在 [ARPANET 协议手册][10] 中有更易读的 Host-Host 协议的解释。
|
||||
|
||||
“Host-Host 协议” 管理主机之间如何创建和管理连接。“连接”是某个主机上的写套接字和另一个主机上的读套接字之间的一个单向的数据管道。“<ruby>套接字<rt>socket</rt></ruby>” 的概念是在 “Level-1” 层的有限的链路设施(记住,链路号只能是那 256 个值中的一个)之上被引入的,是为了给程序提供寻址运行在远端主机上的特定进程的一种方式。“读套接字” 是用偶数表示的,而“写套接字”是用奇数表示的;套接字是 “读” 还是 “写” 被称为套接字的 “性别”。并没有类似于 TCP 协议那样的 “端口号” 机制,连接的打开、维持以及关闭操作是通过主机之间使用 “链路 0” 发送指定格式的 Host-Host 控制消息来实现的,这也是 “链路 0” 被保留的目的。一旦在 “链路 0” 上交换控制消息来建立起一个连接后,就可以使用接收端挑选的另一个链路号来发送进一步的数据消息。
|
||||
|
||||
Host-Host 控制消息一般通过 3 个字母的助记符来表示。当两个主机交换一条 STR(<ruby>发送端到接收端<rt>sender-to-receiver</rt></ruby>)消息和一条配对的 RTS(<ruby>接收端到发送端<rt>receiver-to-sender</rt></ruby>)消息后,就建立起了一条连接 —— 这些控制消息都被称为请求链接消息。链接能够被 CLS(<ruby>关闭<rt>close</rt></ruby>)控制消息关闭。还有更多的控制信息能够改变从发送端到接收端发送消息的速率。从而再次需要确保较快的主机不会压制较慢的主机。在 “Level 1” 层上的协议提供了流量控制的功能,但对 “Level 2” 层来说显然是不够的;我怀疑这是因为从远端 IMP 接收到的 RFNM 只能保证远端 IMP 已经传送该消息到目标主机,而不能保证目标主机已经全部处理了该消息。还有 INR(<ruby>接收端中断<rt>interrupt-by-receiver</rt></ruby>)、INS(<ruby>发送端中断<rt>interrupt-by-sender</rt></ruby>)控制消息,主要供更高级别的协议使用。
|
||||
|
||||
更高级别的协议都位于 “Level 3”,这层是 ARPANET 的应用层。Telnet 协议,它提供到另一台主机的一个虚拟电传链接,其可能是这些协议中最重要的。但在这层中也有许多其他协议,例如用于传输文件的 FTP 协议和各种用于发送 Email 的协议实验。
|
||||
|
||||
在这一层中有一个不同于其他的协议:<ruby>初始链接协议<rt>Initial Connection Protocol</rt></ruby>(ICP)。ICP 被认为是一个 “Level-3” 层协议,但实际上它是一种 “Level-2.5” 层协议,因为其他 “Level-3” 层协议都依赖它。之所以需要 ICP,是因为 “Level 2” 层的 Host-Host 协议提供的链接只是单向的,但大多数的应用需要一个双向(例如:全双工)的连接来做任何有趣的事情。要使得运行在某个主机上的客户端能够连接到另一个主机上的长期运行的服务进程,ICP 定义了两个步骤。第一步是建立一个从服务端到客户端的单向连接,通过使用服务端进程的众所周知的套接字号来实现。第二步服务端通过建立的这个连接发送一个新的套接字套接字号给客户端。到那时,那个存在的连接就会被丢弃,然后会打开另外两个新的连接,它们是基于传输的套接字号建立的“读”连接和基于传输的套接字号加 1 的“写”连接。这个小插曲是大多数事务的一个前提——比如它是建立 Telnet 链接的第一步。
|
||||
|
||||
以上是我们逐层攀登了 ARPANET 协议层次结构。你们可能一直期待我在某个时候提一下 “<ruby>网络控制协议<rt>Network Control Protocol</rt></ruby>”(NCP) 。在我坐下来为这篇文章和上一篇文章做研究之前,我肯定认为 ARPANET 运行在一个叫 “NCP” 的协议之上。这个缩写有时用来指代整个 ARPANET 协议,这可能就是我为什么有这个想法的原因。举个例子,[RFC801][11] 讨论了将 ARPANET 从 “NCP” 过渡到 “TCP” 的方式,这使 NCP 听起来像是一个相当于 TCP 的 ARPANET 协议。但是对于 ARPANET 来说,从来都没有一个叫 “网络控制协议” 的东西(即使 [大英百科全书是这样认为的][12]),我怀疑人们错误地将 “NCP” 解释为 “<ruby>网络控制协议<rt>Network Control Protocol</rt></ruby>” ,而实际上它代表的是 “<ruby>网络控制程序<rt>Network Control Program</rt></ruby>” 。网络控制程序是一个运行在各个主机上的内核级别的程序,主要负责处理网络通信,等同于现如今操作系统中的 TCP/IP 协议栈。用在 RFC 801 的 “NCP” 是一种转喻,而不是协议。
|
||||
|
||||
### 与 TCP/IP 的比较
|
||||
|
||||
ARPANET 协议以后都会被 TCP/IP 协议替换(但 Telnet 和 FTP 协议除外,因为它们很容易就能在 TCP 上适配运行)。然而 ARPANET 协议都基于这么一个假设:就是网络是由一个单一实体(BBN)来构建和管理的。而 TCP/IP 协议套件是为网间网设计的,这是一个网络的网络,在那里一切都是不稳定的和不可靠的。这就导致了我们的现代协议套件和 ARPANET 协议有明显的不同,比如我们现在怎样区分网络层和传输层。在 ARPANET 中部分由 IMP 实现的类似传输层的功能现在完全由在网络边界的主机负责。
|
||||
|
||||
我发现 ARPANET 协议最有趣的事情是,现在在 TCP 中的许多传输层的功能是如何在 ARPANET 上经历了一个糟糕的青春期。我不是网络专家,因此我拿出大学时的网络课本(让我们跟着 Kurose 和 Ross 学习一下),他们对传输层通常负责什么给出了一个非常好的概述。总结一下他们的解释,一个传输层协议必须至少做到以下几点。这里的 “<ruby>段<rt>segment</rt></ruby>” 基本等同于 ARPANET 上的术语 “<ruby>消息<rt>message</rt></ruby>”:
|
||||
|
||||
* 提供进程之间的传送服务,而不仅仅是主机之间的(传输层多路复用和多路分解)
|
||||
* 在每个段的基础上提供完整性检查(即确保传输过程中没有数据损坏)
|
||||
|
||||
像 TCP 那样,传输层也能够提供可靠的数据传输,这意味着:
|
||||
|
||||
* “段” 是按顺序被传送的
|
||||
* 不会丢失任何 “段”
|
||||
* “段” 的传送速度不会太快以至于被接收端丢弃(流量控制)
|
||||
|
||||
似乎在 ARPANET 上关于如何进行多路复用和多路分解以便进程可以通信存在一些混淆 —— BBN 在 IMP-Host 层引入了链路号来做到这一点,但结果证明在 Host-Host 层上无论如何套接字号都是必要的。然后链路号只是用于 IMP-Host 级别的流量控制,但 BBN 似乎后来放弃了它,转而支持在唯一的主机对之间进行流量控制,这意味着链路号一开始是一个超载的东西,后来基本上变成了虚设。TCP 现在使用端口号代替,分别对每一个 TCP 连接单独进行流量控制。进程间的多路复用和多路分解完全在 TCP 内部进行,不会像 ARPANET 一样泄露到较低层去。
|
||||
|
||||
同样有趣的是,鉴于 Kurose 和 Ross 如何开发 TCP 背后的想法,ARPANET 一开始就采用了 Kurose 和 Ross 所说的一个严谨的 “<ruby>停止并等待<rt>stop-and-wait</rt></ruby>” 方法,来实现 IMP-Host 层上的可靠的数据传输。这个 “停止并等待” 方法发送一个 “段” 然后就拒绝再去发送更多 “段” ,直到收到一个最近发送的 “段” 的确认为止。这是一种简单的方法,但这意味着只有一个 “段” 在整个网络中运行,从而导致协议非常缓慢 —— 这就是为什么 Kurose 和 Ross 将 “停止并等待” 仅仅作为在通往功能齐全的传输层协议的路上的垫脚石的原因。曾有一段时间 “停止并等待” 是 ARPANET 上的工作方式,因为在 IMP–Host 层,必须接收到<ruby>请求下一条消息<rt>Request for Next Message</rt></ruby>(RFNM)以响应每条发出的消息,然后才能发送任何进一步的消息。客观的说 ,BBN 起初认为这对于提供主机之间的流量控制是必要的,因此减速是故意的。正如我已经提到的,为了更好的性能,RFNM 的要求后来放宽松了,而且 IMP 也开始向消息中添加序列号和保持对传输中的消息的 “窗口” 的跟踪,这或多或少与如今 TCP 的实现如出一辙。[^5]
|
||||
|
||||
因此,ARPANET 表明,如果你能让每个人都遵守一些基本规则,异构计算系统之间的通信是可能的。正如我先前所说的,这是 ARPANET 的最重要的遗产。但是,我希望对这些基线规则的仔细研究揭示了 ARPANET 协议对我们今天使用的协议有多大影响。在主机和 IMP 之间分担传输层职责的方式上肯定有很多笨拙之处,有时候是冗余的。现在回想起来真的很可笑,主机之间一开始只能通过给出的任意链路在某刻只发送一条消息。但是 ARPANET 实验是一个独特的机会,可以通过实际构建和操作网络来学习这些经验,当到了是时候升级到我们今天所知的互联网时,似乎这些经验变得很有用。
|
||||
|
||||
_如果你喜欢这篇贴子,更喜欢每四周发布一次的方式!那么在 Twitter 上关注 [@TwoBitHistory][14] 或者订阅 [RSS 提要][15],以确保你知道新帖子的发布时间。_
|
||||
|
||||
[^1]: 协议分层是网络工作组发明的。这个论点是在 [RFC 871][17] 中提出的。分层也是 BBN 如何在主机和 IMP 之间划分职责的自然延伸,因此 BBN 也值得称赞。
|
||||
[^2]: “level” 是被网络工作组使用的术语。 详见 [RFC 100][19]
|
||||
[^3]: 在 IMP-Host 协议的后续版本中,扩展了头部字段,并且将链路号升级为消息 ID。但是 Host-Host 协议仅仅继续使用消息 ID 字段的高位 8 位,并将其视为链路号。请参阅 [ARPANET 协议手册][10] 的 “Host-Host” 协议部分。
|
||||
[^4]: John M. McQuillan 和 David C. Walden。 “ARPA 网络设计决策”,第 284页,<https://www.walden-family.com/public/whole-paper.pdf>。 2021 年 3 月 8 日查看。
|
||||
[^5]: 同上。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://twobithistory.org/2021/03/08/arpanet-protocols.html
|
||||
|
||||
作者:[Two-Bit History][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[Lin-vy](https://github.com/Lin-vy)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://twobithistory.org
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://twobithistory.org/2021/02/07/arpanet.html
|
||||
[2]: tmp.szauPoOKtk#fn:1
|
||||
[3]: https://twobithistory.org/images/arpanet-stack.png
|
||||
[4]: tmp.szauPoOKtk#fn:2
|
||||
[5]: https://walden-family.com/impcode/BBN1822_Jan1976.pdf
|
||||
[6]: tmp.szauPoOKtk#fn:3
|
||||
[7]: https://twobithistory.org/images/host-imp-1969.png
|
||||
[8]: https://walden-family.com/impcode/1969-initial-IMP-design.pdf
|
||||
[9]: tmp.szauPoOKtk#fn:4
|
||||
[10]: http://mercury.lcs.mit.edu/~jnc/tech/arpaprot.html
|
||||
[11]: https://tools.ietf.org/html/rfc801
|
||||
[12]: https://www.britannica.com/topic/ARPANET
|
||||
[13]: tmp.szauPoOKtk#fn:5
|
||||
[14]: https://twitter.com/TwoBitHistory
|
||||
[15]: https://twobithistory.org/feed.xml
|
||||
[16]: https://twitter.com/TwoBitHistory/status/1358487195905064960?ref_src=twsrc%5Etfw
|
||||
[17]: https://tools.ietf.org/html/rfc871
|
||||
[18]: tmp.szauPoOKtk#fnref:1
|
||||
[19]: https://www.rfc-editor.org/info/rfc100
|
||||
[20]: tmp.szauPoOKtk#fnref:2
|
||||
[21]: tmp.szauPoOKtk#fnref:3
|
||||
[22]: tmp.szauPoOKtk#fnref:4
|
||||
[23]: tmp.szauPoOKtk#fnref:5
|
||||
@ -3,51 +3,48 @@
|
||||
[#]: author: "Peter Gervase https://opensource.com/users/pgervase"
|
||||
[#]: collector: "lujun9972"
|
||||
[#]: translator: "MjSeven"
|
||||
[#]: reviewer: " "
|
||||
[#]: publisher: " "
|
||||
[#]: url: " "
|
||||
[#]: reviewer: "wxy"
|
||||
[#]: publisher: "wxy"
|
||||
[#]: url: "https://linux.cn/article-13650-1.html"
|
||||
|
||||
使用 Linux 安全工具进行渗透测试
|
||||
======
|
||||
使用 Kali Linux 和其他开源工具来发现系统中的安全漏洞和弱点。
|
||||
![Magnifying glass on code][1]
|
||||
|
||||
大量广泛报道的大型消费企业入侵事件凸显了系统安全管理的重要性。幸运的是,有许多不同的应用程序可以帮助保护计算机系统。其中一个是 [Kali][2],一个为安全和渗透测试而开发的 Linux 发行版。本文演示了如何使用 Kali Linux 来审视你的系统以发现威胁。
|
||||
> 使用 Kali Linux 和其他开源工具来发现系统中的安全漏洞和弱点。
|
||||
|
||||
Kali 安装了很多工具,它们都是开源的,默认情况下安装它们会让事情变得更容易。
|
||||
|
||||
|
||||
众多被广泛报道的大型消费企业入侵事件凸显了系统安全管理的重要性。幸运的是,有许多不同的应用程序可以帮助保护计算机系统。其中一个是 [Kali][2],一个为安全和渗透测试而开发的 Linux 发行版。本文演示了如何使用 Kali Linux 来审视你的系统以发现弱点。
|
||||
|
||||
Kali 安装了很多工具,它们都是开源的,默认情况下安装了它们会让事情变得更容易。
|
||||
|
||||
(LCTT 译注:Kali 及其携带工具只应该用于对自己拥有合法审查权利的系统和设备,任何未经授权的扫描、渗透和攻击均是违法的。本文作者、译者均不承担任何非授权使用的结果。)
|
||||
|
||||
![Kali's tools][3]
|
||||
|
||||
(Peter Gervase, [CC BY-SA 4.0][4])
|
||||
|
||||
本文使用的系统是:
|
||||
|
||||
1. `kali.usersts.redhat.com`:我会启动扫描和攻击的系统。它拥有 30GB 内存和 6 个虚拟 CPU(vCPU)。
|
||||
2. `vulnerable.usersys.redhat.com`: Red Hat 企业版 Linux 8 系统,它也会成为目标。它拥有 16GB 内存和 6 个 vCPU。它是一个相对较新的系统,但有些软件包可能已经过时。
|
||||
3. 这个系统还将包括 `httpd-2.4.37-30.module+el8.3.0+7001+0766b9e7.x86_64`、 `mariadb-server-10.3.27-3.module+el8.3.0+8972+5e3224e9.x86_64`、 `tigervnc-server-1.9.0-15.el8_1.x86_64`、 `vsftpd-3.0.3-32.el8.x86_64` 和一个 5.6.1 版本的 WordPress。
|
||||
1. `kali.usersts.redhat.com`:这是我将用来启动扫描和攻击的系统。它拥有 30GB 内存和 6 个虚拟 CPU(vCPU)。
|
||||
2. `vulnerable.usersys.redhat.com`: 这是一个 Red Hat 企业版 Linux 8 系统,它会成为目标。它拥有 16GB 内存和 6 个 vCPU。它是一个相对较新的系统,但有些软件包可能已经过时。
|
||||
3. 这个系统包括 `httpd-2.4.37-30.module+el8.3.0+7001+0766b9e7.x86_64`、 `mariadb-server-10.3.27-3.module+el8.3.0+8972+5e3224e9.x86_64`、 `tigervnc-server-1.9.0-15.el8_1.x86_64`、 `vsftpd-3.0.3-32.el8.x86_64` 和一个 5.6.1 版本的 WordPress。
|
||||
|
||||
我在上面列出了硬件规格,因为一些任务要求很高,尤其是在运行 WordPress 安全扫描程序([WPScan][5])时对目标系统 CPU 的要求。
|
||||
|
||||
### 探测你的系统
|
||||
|
||||
首先,我会在目标系统上进行基本的 Nmap 扫描(你可以阅读[使用 Nmap 结果帮助加固 Linux 系统][6]一文来更深入地了解 Nmap)。Nmap 扫描是一种快速的方法,可以大致了解被测系统中哪些端口和服务是暴露的。
|
||||
首先,我会在目标系统上进行基本的 Nmap 扫描(你可以阅读 [使用 Nmap 结果帮助加固 Linux 系统][6] 一文来更深入地了解 Nmap)。Nmap 扫描是一种快速的方法,可以大致了解被测系统中哪些端口和服务是暴露的。
|
||||
|
||||
![Nmap scan][7]
|
||||
|
||||
(Peter Gervase, [CC BY-SA 4.0][4])
|
||||
|
||||
默认扫描显示有几个你可能感兴趣的开放端口。实际上,任何开放端口都可能成为攻击者破坏你网络的一种方式。在本例中,端口 21、22、80 和 443 很容易扫描,因为它们是常用服务的端口。在这个早期阶段,我只是在做侦察工作,尽可能多地获取有关目标系统的信息。
|
||||
默认扫描显示有几个你可能感兴趣的开放端口。实际上,任何开放端口都可能成为攻击者破坏你网络的一种方式。在本例中,端口 21、22、80 和 443 是不错的扫描对象,因为它们是常用服务的端口。在这个早期阶段,我只是在做侦察工作,尽可能多地获取有关目标系统的信息。
|
||||
|
||||
我想用 Nmap 侦察 80 端口,所以我使用 `-p 80` 参数来查看端口 80,`-A` 参数来获取操作系统和应用程序版本等信息。
|
||||
|
||||
![Nmap scan of port 80][8]
|
||||
|
||||
(Peter Gervase, [CC BY-SA 4.0][4])
|
||||
|
||||
关键信息有:
|
||||
|
||||
|
||||
```bash
|
||||
```
|
||||
PORT STATE SERVICE VERSION
|
||||
80/tcp open http Apache httpd 2.4.37 ((Red Hat Enterprise Linux))
|
||||
|_http-generator: WordPress 5.6.1
|
||||
@ -55,25 +52,24 @@ PORT STATE SERVICE VERSION
|
||||
|
||||
现在我知道了这是一个 WordPress 服务器,我可以使用 WPScan 来获取有关潜在威胁的信息。一个很好的侦察方法是尝试找到一些用户名,使用 `--enumerate u` 告诉 WPScan 在 WordPress 实例中查找用户名。例如:
|
||||
|
||||
|
||||
```bash
|
||||
```
|
||||
┌──(root💀kali)-[~]
|
||||
└─# wpscan --url vulnerable.usersys.redhat.com --enumerate u
|
||||
_______________________________________________________________
|
||||
__ _______ _____
|
||||
\ \ / / __ \ / ____|
|
||||
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
|
||||
\ \/ \/ / | ___/ \\___ \ / __|/ _` | '_ \
|
||||
\ /\ / | | ____) | (__| (_| | | | |
|
||||
\/ \/ |_| |_____/ \\___|\\__,_|_| |_|
|
||||
__ _______ _____
|
||||
\ \ / / __ \ / ____|
|
||||
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
|
||||
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
|
||||
\ /\ / | | ____) | (__| (_| | | | |
|
||||
\/ \/ |_| |_____/ \___|\__,_|_| |_|
|
||||
|
||||
WordPress Security Scanner by the WPScan Team
|
||||
Version 3.8.10
|
||||
Sponsored by Automattic - <https://automattic.com/>
|
||||
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
|
||||
WordPress Security Scanner by the WPScan Team
|
||||
Version 3.8.10
|
||||
Sponsored by Automattic - https://automattic.com/
|
||||
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
|
||||
_______________________________________________________________
|
||||
|
||||
[+] URL: <http://vulnerable.usersys.redhat.com/> [10.19.47.242]
|
||||
[+] URL: http://vulnerable.usersys.redhat.com/ [10.19.47.242]
|
||||
[+] Started: Tue Feb 16 21:38:49 2021
|
||||
|
||||
Interesting Finding(s):
|
||||
@ -81,37 +77,35 @@ Interesting Finding(s):
|
||||
[i] User(s) Identified:
|
||||
|
||||
[+] admin
|
||||
| Found By: Author Posts - Display Name (Passive Detection)
|
||||
| Confirmed By:
|
||||
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
|
||||
| Login Error Messages (Aggressive Detection)
|
||||
| Found By: Author Posts - Display Name (Passive Detection)
|
||||
| Confirmed By:
|
||||
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
|
||||
| Login Error Messages (Aggressive Detection)
|
||||
|
||||
[+] pgervase
|
||||
| Found By: Author Posts - Display Name (Passive Detection)
|
||||
| Confirmed By:
|
||||
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
|
||||
| Login Error Messages (Aggressive Detection)
|
||||
| Found By: Author Posts - Display Name (Passive Detection)
|
||||
| Confirmed By:
|
||||
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
|
||||
| Login Error Messages (Aggressive Detection)
|
||||
```
|
||||
|
||||
显示有两个用户:`admin` 和 `pgervase`。我将尝试使用密码字典来猜测 `admin` 的密码。密码字典是一个包含很多密码的文本文件。我使用的字典大小有 37G,有 3,543,076,137 行。
|
||||
这显示有两个用户:`admin` 和 `pgervase`。我将尝试使用密码字典来猜测 `admin` 的密码。密码字典是一个包含很多密码的文本文件。我使用的字典大小有 37G,有 3,543,076,137 行。
|
||||
|
||||
就像你可以选择不同的文本编辑器、Web 浏览器和其他应用程序 一样,也有很多工具可以启动密码攻击。下面是两个使用 Nmap 和 WPScan 的示例命令:
|
||||
|
||||
|
||||
```shell
|
||||
```
|
||||
# nmap -sV --script http-wordpress-brute --script-args userdb=users.txt,passdb=/path/to/passworddb,threads=6 vulnerable.usersys.redhat.com
|
||||
```
|
||||
|
||||
```bash
|
||||
```
|
||||
# wpscan --url vulnerable.usersys.redhat.com --passwords /path/to/passworddb --usernames admin --max-threads 50 | tee nmap.txt
|
||||
```
|
||||
|
||||
这个 Nmap 脚本是我使用的许多脚本之一,使用 WPScan 扫描 URL 只是这个工具可以完成的许多任务之一。你可以决定你喜欢的那一个。
|
||||
这个 Nmap 脚本是我使用的许多脚本之一,使用 WPScan 扫描 URL 只是这个工具可以完成的许多任务之一。你可以用你喜欢的那一个。
|
||||
|
||||
WPScan 示例在文件末尾显示了密码:
|
||||
|
||||
|
||||
```bash
|
||||
```
|
||||
┌──(root💀kali)-[~]
|
||||
└─# wpscan --url vulnerable.usersys.redhat.com --passwords passwords.txt --usernames admin
|
||||
_______________________________________________________________
|
||||
@ -133,7 +127,7 @@ _______________________________________________________________
|
||||
|
||||
Interesting Finding(s):
|
||||
|
||||
…..
|
||||
......
|
||||
|
||||
[+] Performing password attack on Wp Login against 1 user/s
|
||||
Trying admin / redhat Time: 00:01:57 <==================================================================================================================> (3231 / 3231) 100.00% Time: 00:01:57
|
||||
@ -155,13 +149,12 @@ Trying admin / redhat Time: 00:01:57 <==========================================
|
||||
[+] Elapsed time: 00:02:02
|
||||
```
|
||||
|
||||
在末尾的有效组合部分包含管理员用户名和密码,3231 行只用了两分钟。
|
||||
在末尾的“找到有效组合”部分包含了管理员用户名和密码,3231 行只用了两分钟。
|
||||
|
||||
我还有另一个字典文件,其中包含 3,238,659,984 行,使用它花费的时间更长并且会留下更多的证据。
|
||||
|
||||
使用 Nmap 可以更快地产生结果:
|
||||
|
||||
|
||||
```
|
||||
┌──(root💀kali)-[~]
|
||||
└─# nmap -sV --script http-wordpress-brute --script-args userdb=users.txt,passdb=password.txt,threads=6 vulnerable.usersys.redhat.com
|
||||
@ -196,23 +189,22 @@ Nmap done: 1 IP address (1 host up) scanned in 7.68 seconds
|
||||
|
||||
然而,运行这样的扫描可能会在目标系统上留下大量的 HTTPD 日志消息:
|
||||
|
||||
```
|
||||
10.19.47.170 - - [18/Feb/2021:20:14:01 -0500] "POST /wp-login.php HTTP/1.1" 200 7575 "http://vulnerable.usersys.redhat.com/" "WPScan v3.8.10 (https://wpscan.org/)"
|
||||
10.19.47.170 - - [18/Feb/2021:20:14:00 -0500] "POST /wp-login.php HTTP/1.1" 200 7575 "http://vulnerable.usersys.redhat.com/" "WPScan v3.8.10 (https://wpscan.org/)"
|
||||
10.19.47.170 - - [18/Feb/2021:20:14:00 -0500] "POST /wp-login.php HTTP/1.1" 200 7575 "http://vulnerable.usersys.redhat.com/" "WPScan v3.8.10 (https://wpscan.org/)"
|
||||
10.19.47.170 - - [18/Feb/2021:20:14:00 -0500] "POST /wp-login.php HTTP/1.1" 200 7575 "http://vulnerable.usersys.redhat.com/" "WPScan v3.8.10 (https://wpscan.org/)"
|
||||
10.19.47.170 - - [18/Feb/2021:20:14:00 -0500] "POST /wp-login.php HTTP/1.1" 200 7575 "http://vulnerable.usersys.redhat.com/" "WPScan v3.8.10 (https://wpscan.org/)"
|
||||
10.19.47.170 - - [18/Feb/2021:20:14:00 -0500] "POST /wp-login.php HTTP/1.1" 200 7575 "http://vulnerable.usersys.redhat.com/" "WPScan v3.8.10 (https://wpscan.org/)"
|
||||
10.19.47.170 - - [18/Feb/2021:20:14:02 -0500] "POST /wp-login.php HTTP/1.1" 200 7575 "http://vulnerable.usersys.redhat.com/" "WPScan v3.8.10 (https://wpscan.org/)"
|
||||
10.19.47.170 - - [18/Feb/2021:20:14:02 -0500] "POST /wp-login.php HTTP/1.1" 200 7575 "http://vulnerable.usersys.redhat.com/" "WPScan v3.8.10 (https://wpscan.org/)"
|
||||
10.19.47.170 - - [18/Feb/2021:20:14:02 -0500] "POST /wp-login.php HTTP/1.1" 200 7575 "http://vulnerable.usersys.redhat.com/" "WPScan v3.8.10 (https://wpscan.org/)"
|
||||
|
||||
```shell
|
||||
10.19.47.170 - - [18/Feb/2021:20:14:01 -0500] "POST /wp-login.php HTTP/1.1" 200 7575 "<http://vulnerable.usersys.redhat.com/>" "WPScan v3.8.10 (<https://wpscan.org/>)"
|
||||
10.19.47.170 - - [18/Feb/2021:20:14:00 -0500] "POST /wp-login.php HTTP/1.1" 200 7575 "<http://vulnerable.usersys.redhat.com/>" "WPScan v3.8.10 (<https://wpscan.org/>)"
|
||||
10.19.47.170 - - [18/Feb/2021:20:14:00 -0500] "POST /wp-login.php HTTP/1.1" 200 7575 "<http://vulnerable.usersys.redhat.com/>" "WPScan v3.8.10 (<https://wpscan.org/>)"
|
||||
10.19.47.170 - - [18/Feb/2021:20:14:00 -0500] "POST /wp-login.php HTTP/1.1" 200 7575 "<http://vulnerable.usersys.redhat.com/>" "WPScan v3.8.10 (<https://wpscan.org/>)"
|
||||
10.19.47.170 - - [18/Feb/2021:20:14:00 -0500] "POST /wp-login.php HTTP/1.1" 200 7575 "<http://vulnerable.usersys.redhat.com/>" "WPScan v3.8.10 (<https://wpscan.org/>)"
|
||||
10.19.47.170 - - [18/Feb/2021:20:14:00 -0500] "POST /wp-login.php HTTP/1.1" 200 7575 "<http://vulnerable.usersys.redhat.com/>" "WPScan v3.8.10 (<https://wpscan.org/>)"
|
||||
10.19.47.170 - - [18/Feb/2021:20:14:02 -0500] "POST /wp-login.php HTTP/1.1" 200 7575 "<http://vulnerable.usersys.redhat.com/>" "WPScan v3.8.10 (<https://wpscan.org/>)"
|
||||
10.19.47.170 - - [18/Feb/2021:20:14:02 -0500] "POST /wp-login.php HTTP/1.1" 200 7575 "<http://vulnerable.usersys.redhat.com/>" "WPScan v3.8.10 (<https://wpscan.org/>)"
|
||||
10.19.47.170 - - [18/Feb/2021:20:14:02 -0500] "POST /wp-login.php HTTP/1.1" 200 7575 "<http://vulnerable.usersys.redhat.com/>" "WPScan v3.8.10 (<https://wpscan.org/>)"
|
||||
```
|
||||
|
||||
为了获得关于在最初的 Nmap 扫描中发现的 HTTPS 服务器的信息,我使用了 `sslscan` 命令:
|
||||
|
||||
|
||||
```bash
|
||||
```
|
||||
┌──(root💀kali)-[~]
|
||||
└─# sslscan vulnerable.usersys.redhat.com
|
||||
Version: 2.0.6-static
|
||||
@ -234,8 +226,7 @@ TLSv1.3 enabled
|
||||
|
||||
它显示了有关启用的 SSL 协议的信息,在最下方,是关于 Heartbleed 漏洞的信息:
|
||||
|
||||
|
||||
```bash
|
||||
```
|
||||
Heartbleed:
|
||||
TLSv1.3 not vulnerable to heartbleed
|
||||
TLSv1.2 not vulnerable to heartbleed
|
||||
@ -246,15 +237,13 @@ TLSv1.2 not vulnerable to heartbleed
|
||||
有很多方法可以保护你的系统免受大量攻击。几个关键点是:
|
||||
|
||||
* **了解你的系统:**包括了解哪些端口是开放的,哪些端口应该开放,谁应该能够看到这些开放的端口,以及使用这些端口服务的预期流量是多少。Nmap 是了解网络系统的一个绝佳工具。
|
||||
* **使用最新的最佳实践:** 现在的最佳实践可能不是未来的最佳实践。作为管理员,了解信息安全领域的最新趋势非常重要。
|
||||
* **使用当前的最佳实践:** 现在的最佳实践可能不是未来的最佳实践。作为管理员,了解信息安全领域的最新趋势非常重要。
|
||||
* **知道如何使用你的产品:** 例如,与其让攻击者不断攻击你的 WordPress 系统,不如阻止他们的 IP 地址并限制尝试登录的次数。在现实世界中,阻止 IP 地址可能没有那么有用,因为攻击者可能会使用受感染的系统来发起攻击。但是,这是一个很容易启用的设置,可以阻止一些攻击。
|
||||
* **维护和验证良好的备份:** 如果攻击者攻击了一个或多个系统,能从已知的良好和干净的备份中重新构建可以节省大量时间和金钱。
|
||||
* **检查日志:** 如上所示,扫描和渗透命令可能会留下大量日志,这表明攻击者正在攻击系统。如果你注意到它们,可以采取先发制人的行动来降低风险。
|
||||
* **更新系统、应用程序和任何额外的模块:** 正如 [NIST Special Publication 800-40r3][9] 所解释的那样,“补丁通常是减轻软件缺陷漏洞最有效的方法,而且通常是唯一完全有效的解决方案。”
|
||||
* **更新系统、应用程序和任何额外的模块:** 正如 [NIST Special Publication 800-40r3][9] 所解释的那样,“补丁通常是减轻软件缺陷漏洞最有效的方法,而且通常是唯一完全有效的解决方案。”
|
||||
* **使用供应商提供的工具:** 供应商有不同的工具来帮助你维护他们的系统,因此一定要充分利用它们。例如,红帽企业 Linux 订阅中包含的 [Red Hat Insights][10] 可以帮助你优化系统并提醒你注意潜在的安全威胁。
|
||||
|
||||
|
||||
|
||||
### 了解更多
|
||||
|
||||
本文对安全工具及其使用方法的介绍只是冰山一角。深入了解的话,你可能需要查看以下资源:
|
||||
@ -265,8 +254,6 @@ TLSv1.2 not vulnerable to heartbleed
|
||||
* [NIST 网络安全页面][14]
|
||||
* [使用 Nmap 结果来帮助加固 Linux 系统][6]
|
||||
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/21/5/linux-security-tools
|
||||
@ -274,7 +261,7 @@ via: https://opensource.com/article/21/5/linux-security-tools
|
||||
作者:[Peter Gervase][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[MjSeven](https://github.com/MjSeven)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
@ -288,7 +275,7 @@ via: https://opensource.com/article/21/5/linux-security-tools
|
||||
[6]: https://www.redhat.com/sysadmin/using-nmap-harden-systems
|
||||
[7]: https://opensource.com/sites/default/files/uploads/nmap-scan.png "Nmap scan"
|
||||
[8]: https://opensource.com/sites/default/files/uploads/nmap-port80.png "Nmap scan of port 80"
|
||||
[9]: https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-40r3.pdf%5D(https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-40r3.pdf
|
||||
[9]: https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-40r3.pdf
|
||||
[10]: https://www.redhat.com/sysadmin/how-red-hat-insights
|
||||
[11]: https://en.wikipedia.org/wiki/Armitage_(computing)
|
||||
[12]: https://access.redhat.com/security
|
||||
129
published/20210712 Reading and writing files with Python.md
Normal file
129
published/20210712 Reading and writing files with Python.md
Normal file
@ -0,0 +1,129 @@
|
||||
[#]: subject: "Reading and writing files with Python"
|
||||
[#]: via: "https://opensource.com/article/21/7/read-write-files-python"
|
||||
[#]: author: "Seth Kenlon https://opensource.com/users/seth"
|
||||
[#]: collector: "lujun9972"
|
||||
[#]: translator: "MjSeven"
|
||||
[#]: reviewer: "turbokernel"
|
||||
[#]: publisher: "wxy"
|
||||
[#]: url: "https://linux.cn/article-13649-1.html"
|
||||
|
||||
使用 Python 读写文件
|
||||
======
|
||||
|
||||
> 每种编程语言处理文件数据的方式不尽相同,Python 是这么干的。
|
||||
|
||||

|
||||
|
||||
有些数据是临时的,它们在应用程序运行时存储在内存中,然后丢弃。但是有些数据是持久的。它们存储在硬盘驱动器上供以后使用,而且它们通常是用户最关心的东西。对于程序员来说,编写代码读写文件是很常见的,但每种语言处理该任务的方式都不同。本文演示了如何使用 Python 处理文件数据。
|
||||
|
||||
### 安装 Python
|
||||
|
||||
在 Linux 上,你可能已经安装了 Python。如果没有,你可以通过发行版软件仓库安装它。例如,在 CentOS 或 RHEL 上:
|
||||
|
||||
```
|
||||
$ sudo dnf install python3
|
||||
```
|
||||
|
||||
在 macOS 上,你可以使用 [MacPorts][2] 或 [Homebrew][3] 安装。在 Windows 上,你可以使用 [Chocolatey][4] 安装。
|
||||
|
||||
一旦安装了 Python,打开你最喜欢的文本编辑器,准备好写代码吧。
|
||||
|
||||
### 使用 Python 向文件中写入数据
|
||||
|
||||
如果你需要向一个文件中写入数据,记住有三个步骤:
|
||||
|
||||
1. 打开
|
||||
2. 写入
|
||||
3. 关闭
|
||||
|
||||
这与你在计算机上编码、编辑照片或执行其他操作时使用的步骤完全相同。首先,打开要编辑的文档,然后进行编辑,最后关闭文档。
|
||||
|
||||
在 Python 中,过程是这样的:
|
||||
|
||||
```
|
||||
f = open('example.txt', 'w')
|
||||
f.write('hello world')
|
||||
f.close()
|
||||
```
|
||||
|
||||
这个例子中,第一行以**写**模式打开了一个文件,然后用变量 `f` 表示,我使用了 `f` 是因为它在 Python 代码中很常见,使用其他任意有效变量名也能正常工作。
|
||||
|
||||
在打开文件时,有不同的模式:
|
||||
|
||||
* `w` 代表写入
|
||||
* `r+` 代表可读可写
|
||||
* `a` 表示追加
|
||||
|
||||
第二行表示向文件中写入数据,本例写入的是纯文本,但你可以写入任意类型的数据。
|
||||
|
||||
最后一行关闭了文件。
|
||||
|
||||
#### 使用 `with` 语法写入数据
|
||||
|
||||
对于快速的文件交互,常用有一种简短的方法可以写入数据。它不会使文件保持打开状态,所以你不必记得调用 `close()` 函数。相反,它使用 `with` 语法:
|
||||
|
||||
```
|
||||
with open('example.txt', 'a') as f:
|
||||
f.write('hello open source')
|
||||
```
|
||||
|
||||
### 使用 Python 读取数据
|
||||
|
||||
如果你或你的用户需要通过应用程序需要向文件中写入一些数据,然后你需要使用它们,那么你就需要读取文件了。与写入类似,逻辑一样:
|
||||
|
||||
1. 打开
|
||||
2. 读取
|
||||
3. 关闭
|
||||
|
||||
同样的,这个逻辑反映了你一开始使用计算机就已知的内容。阅读文档,你可以打开、阅读,然后关闭。在计算机术语中,“打开”文件意味着将其加载到内存中。
|
||||
|
||||
实际上,一个文本文件内容肯定不止一行。例如,你需要读取一个配置文件、游戏存档或乐队下一首歌曲的歌词,正如你打开一本实体书时,你不可能立刻读完整本书,代码也只能解析已经加载到内存中的文件。因此,你可能需要遍历文件的内容。
|
||||
|
||||
```
|
||||
f = open('example.tmp', 'r')
|
||||
|
||||
for line in f:
|
||||
print(line)
|
||||
|
||||
f.close()
|
||||
```
|
||||
|
||||
示例的第一行指明使用 **读** 模式打开一个文件,然后文件交由变量 `f` 表示,但就像你写数据一样,变量名是任意的。`f` 并没有什么特殊的,它只是单词 “file” 的最简表示,所以 Python 程序员会经常使用它。
|
||||
|
||||
在第二行,我们使用了 `line`,另一个任意变量名,用来表示 `f` 的每一行。这告诉 Python 逐行迭代文件的内容,并将每一行的内容打印到输出中(在本例中为终端或 [IDLE][5])。
|
||||
|
||||
#### 使用 `with` 语法读取数据
|
||||
|
||||
就像写入一样,使用 `with` 语法是一种更简短的方法读取数据。即不需要调用 `close()` 方法,方便地快速交互。
|
||||
|
||||
```
|
||||
with open('example.txt', 'r') as f:
|
||||
for line in f:
|
||||
print(line)
|
||||
```
|
||||
|
||||
### 文件和 Python
|
||||
|
||||
使用 Python 有很多方法向文件写入数据,包括用 [JSON、YAML、TOML][6] 等不同的格式写入。还有一个非常好的内置方法用于创建和维护 [SQLite][7] 数据库,以及许多库来处理不同的文件格式,包括 [图像][8]、音频和视频等。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/21/7/read-write-files-python
|
||||
|
||||
作者:[Seth Kenlon][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[MjSeven](https://github.com/MjSeven)
|
||||
校对:[turbokernel](https://github.com/turbokernel)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/seth
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/python-programming-code-keyboard.png?itok=fxiSpmnd "Hands on a keyboard with a Python book "
|
||||
[2]: https://opensource.com/article/20/11/macports
|
||||
[3]: https://opensource.com/article/20/6/homebrew-mac
|
||||
[4]: https://opensource.com/article/20/3/chocolatey
|
||||
[5]: https://opensource.com/article/17/10/python-101#idle
|
||||
[6]: https://opensource.com/article/21/6/parse-configuration-files-python
|
||||
[7]: https://opensource.com/article/21/2/sqlite3-cheat-sheet
|
||||
[8]: https://opensource.com/article/19/3/python-image-manipulation-tools
|
||||
136
published/20210720 How to Upgrade to Debian 11 from Debian 10.md
Normal file
136
published/20210720 How to Upgrade to Debian 11 from Debian 10.md
Normal file
@ -0,0 +1,136 @@
|
||||
[#]: subject: (How to Upgrade to Debian 11 from Debian 10)
|
||||
[#]: via: (https://www.debugpoint.com/2021/07/upgrade-debian-11-from-debian-10/)
|
||||
[#]: author: (Arindam https://www.debugpoint.com/author/admin1/)
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-13647-1.html)
|
||||
|
||||
提前尝鲜,从 Debian 10 升级到 Debian 11
|
||||
======
|
||||
|
||||
> 本指南解释了从 Debian 10 升级到 Debian 11 的步骤。
|
||||
|
||||

|
||||
|
||||
[Debian][1] 的大版本发布是很罕见的,因为它往往需要社区的多年努力。这就是为什么 Debian 是真正的通用操作系统,并且在稳定性方面坚如磐石。
|
||||
|
||||
代号 Bullseye 的 [Debian 11][2] 即将正式发布。2021 年 7 月 15 日,Debian 11 进入完全冻结状态,这意味着发行在即。虽然官方发布日期还没有最终确定,但你现在就可以从 Debian 10 安装或升级到 Debian 11。
|
||||
|
||||
以下是方法。
|
||||
|
||||
### 前提条件
|
||||
|
||||
* 升级的过程非常简单明了。然而,采取某些预防措施是一个好的做法。特别是如果你正在升级一台服务器。
|
||||
* 对你的系统进行备份,包括所有重要的数据和文件。
|
||||
* 尝试禁用/删除你可能在一段时间内添加的任何外部仓库(PPA)。你可以在升级后逐一启用它们。
|
||||
* 关闭所有正在运行的应用。
|
||||
* 停止任何你可能已经启用的运行中的服务。升级完成后,你可以通过 [systemctl][3] 启动它们。这包括 Web 服务器、SSH 服务器、FTP 服务器或任何其他服务器。
|
||||
* 确保你有稳定的互联网连接。
|
||||
* 并为你的系统留出足够的停机时间。因为根据你的系统配置,Debian 版本升级需要时间大约在 1.5 小时到 2 小时之间。
|
||||
|
||||
### 将 Debian 10 Buster 升级到 11 Bullseye
|
||||
|
||||
确保你的系统是最新的,而且你的软件包列表是最新的。
|
||||
|
||||
```
|
||||
sudo apt update && sudo apt upgrade
|
||||
```
|
||||
|
||||
使用下面的命令安装 `gcc-8-base` 包。这是必须的,因为在历史上曾出现过升级失败的情况,这是因为下面的软件包中包含了某些依赖。
|
||||
|
||||
```
|
||||
sudo apt install gcc-8-base
|
||||
```
|
||||
|
||||
![upgrade debian – system check][4]
|
||||
|
||||
打开 `/etc/apt/sources.list`,通过注释 Debian 10 buster 包,而使用 bullseye 仓库进行更新。
|
||||
|
||||
注释所有的 buster 仓库,在行的开头加上 `#`。
|
||||
|
||||
![Comment the Debian 10 lines][5]
|
||||
|
||||
在文件的末尾添加以下几行。
|
||||
|
||||
```
|
||||
deb http://deb.debian.org/debian bullseye main contrib non-free
|
||||
deb http://deb.debian.org/debian bullseye-updates main contrib non-free
|
||||
deb http://security.debian.org/debian-security bullseye-security main
|
||||
deb http://ftp.debian.org/debian bullseye-backports main contrib non-free
|
||||
```
|
||||
|
||||
![Add Debian 11 lines][6]
|
||||
|
||||
按 `Ctrl + O` 保存文件,按 `Ctrl + X` 退出 `nano`。
|
||||
|
||||
更新一次系统仓库列表,以验证仓库的添加情况。
|
||||
|
||||
```
|
||||
sudo apt update
|
||||
```
|
||||
|
||||
如果上面的命令没有出现任何错误,那么你已经成功地添加了 bullseye 仓库。
|
||||
|
||||
现在,通过运行下面的命令开始升级过程。基本安装的下载大小约为 1.2GB。这可能会根据你的系统配置而有所不同。
|
||||
|
||||
```
|
||||
sudo apt full-upgrade
|
||||
```
|
||||
|
||||
![Debian upgrade start][7]
|
||||
|
||||
这个命令需要时间。但不要让系统无人看管。因为升级过程中需要各种输入。
|
||||
|
||||
![lib6 config][8]
|
||||
|
||||
![sudoers file][9]
|
||||
|
||||
完成后,你可以用以下命令重启系统。
|
||||
|
||||
```
|
||||
systemctl reboot
|
||||
```
|
||||
|
||||
重启后,运行以下命令,以确保你的系统是最新的,并且清理了所有不再需要的不必要的软件包。
|
||||
|
||||
```
|
||||
sudo apt --purge autoremove
|
||||
```
|
||||
|
||||
如果一切顺利,你应该看到了 Debian 11 bullseye。你可以用下面的命令来验证版本:
|
||||
|
||||
```
|
||||
cat /etc/os-release
|
||||
```
|
||||
|
||||
![Debian 11 after upgrade][10]
|
||||
|
||||
### 结束语
|
||||
|
||||
我希望这个指南能帮助你将你的系统升级到 Debian 11 bullseye。如果你遇到任何问题,请在下面的评论栏告诉我。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.debugpoint.com/2021/07/upgrade-debian-11-from-debian-10/
|
||||
|
||||
作者:[Arindam][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.debugpoint.com/author/admin1/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.debian.org/
|
||||
[2]: https://www.debugpoint.com/2021/05/debian-11-features/
|
||||
[3]: https://www.debugpoint.com/2020/12/systemd-systemctl-service/
|
||||
[4]: https://www.debugpoint.com/blog/wp-content/uploads/2021/07/upgrade-debian-system-check-1024x503.jpeg
|
||||
[5]: https://www.debugpoint.com/blog/wp-content/uploads/2021/07/Cpmment-the-Debian-10-lines-1024x636.jpeg
|
||||
[6]: https://www.debugpoint.com/blog/wp-content/uploads/2021/07/Add-Debian-11-lines-1024x635.jpeg
|
||||
[7]: https://www.debugpoint.com/blog/wp-content/uploads/2021/07/Debian-upgrade-start-1024x226.jpeg
|
||||
[8]: https://www.debugpoint.com/blog/wp-content/uploads/2021/07/lib6-config-1024x195.jpeg
|
||||
[9]: https://www.debugpoint.com/blog/wp-content/uploads/2021/07/sudoers-file.jpeg
|
||||
[10]: https://www.debugpoint.com/blog/wp-content/uploads/2021/07/Debian-11-after-upgrade.jpeg
|
||||
@ -4,56 +4,52 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (perfiffer)
|
||||
[#]: reviewer: (turbokernel)
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-13644-1.html)
|
||||
|
||||
如何在 Linux 上使用 cron 定时器
|
||||
======
|
||||
cron 定时器是一个可以按照计划自动运行命令的工具。
|
||||
![Cron 表达式][1]
|
||||
|
||||
cron 定时器是一个可以按照计划自动运行命令的工具。定时器作业称为 cronjob,创建于 crontab 文件中。这是用户自动操作电脑的最简单也是最古老的方法。
|
||||
> cron 定时器是一个可以按照计划自动运行命令的工具。
|
||||
|
||||

|
||||
|
||||
cron 定时器是一个可以按照计划自动运行命令的工具。定时器作业称为 cronjob,创建于 `crontab` 文件中。这是用户自动操作电脑的最简单也是最古老的方法。
|
||||
|
||||
### 创建一个 cronjob
|
||||
|
||||
要创建一个 cronjob,你可以使用 crontab 命令,并添加 `-e` 选项:
|
||||
要创建一个 cronjob,你可以使用 `crontab` 命令,并添加 `-e` 选项:
|
||||
|
||||
```
|
||||
`$ crontab -e`
|
||||
$ crontab -e
|
||||
```
|
||||
|
||||
这将使用默认的文本编辑器打开 crontab。如需指定文本编辑器,请使用 `EDITOR` [环境变量][1]:
|
||||
这将使用默认的文本编辑器打开 `crontab`。如需指定文本编辑器,请使用 `EDITOR` [环境变量][1]:
|
||||
|
||||
```
|
||||
`$ EDITOR=nano crontab -e`
|
||||
$ EDITOR=nano crontab -e
|
||||
```
|
||||
|
||||
### Cron 语法
|
||||
|
||||
如需调度一个 cronjob,你需要提供给计算机你想要执行的命令,然后提供一个 cron 表达式。cron 表达式在命令调度时运行:
|
||||
|
||||
* minute (0 到 59)
|
||||
|
||||
* hour (0 到 23, 0 代表午夜执行)
|
||||
|
||||
* day of month (1 到 31)
|
||||
|
||||
* month (1 到 12)
|
||||
|
||||
* day of week (0 到 6, 星期天是 0)
|
||||
|
||||
|
||||
* 分钟(0 到 59)
|
||||
* 小时(0 到 23, 0 代表午夜执行)
|
||||
* 日期(1 到 31)
|
||||
* 月份(1 到 12)
|
||||
* 星期(0 到 6, 星期天是 0)
|
||||
|
||||
星号 (`*`) 代表的是“每一个”。例如,下面的表达式在每月每日每小时的 0 分钟运行备份脚本:
|
||||
|
||||
```
|
||||
`/opt/backup.sh 0 * * * *`
|
||||
/opt/backup.sh 0 * * * *
|
||||
```
|
||||
|
||||
下面的表达式在周日的凌晨 3:30 运行备份脚本:
|
||||
|
||||
```
|
||||
`/opt/backup.sh 30 3 * * 0`
|
||||
/opt/backup.sh 30 3 * * 0
|
||||
```
|
||||
|
||||
### 简写语法
|
||||
@ -61,34 +57,29 @@ cron 定时器是一个可以按照计划自动运行命令的工具。定时器
|
||||
现代的 cron 支持简化的宏,而不是 cron 表达式:
|
||||
|
||||
* `@hourly` 在每天的每小时的 0 分运行
|
||||
|
||||
* `@daily` 在每天的 0 时 0 分运行
|
||||
|
||||
* `@weekly` 在周日的 0 时 0 分运行
|
||||
|
||||
* `@monthly` 在每月的第一天的 0 时 0 分运行
|
||||
|
||||
|
||||
|
||||
例如,下面的 crontab 命令在每天的 0 时运行备份脚本:
|
||||
例如,下面的 `crontab` 命令在每天的 0 时运行备份脚本:
|
||||
|
||||
```
|
||||
`/opt/backup.sh @daily`
|
||||
/opt/backup.sh @daily
|
||||
```
|
||||
|
||||
### 如何停止一个 cronjob
|
||||
|
||||
一旦你开始了一个 cronjob,它就会永远按照计划运行。想要在启动后停止 cronjob,你必须编辑 crontab,删除触发该作业的命令行,然后保存文件。
|
||||
一旦你开始了一个 cronjob,它就会永远按照计划运行。想要在启动后停止 cronjob,你必须编辑 `crontab`,删除触发该作业的命令行,然后保存文件。
|
||||
|
||||
```
|
||||
`$ EDITOR=nano crontab -e`
|
||||
$ EDITOR=nano crontab -e
|
||||
```
|
||||
|
||||
如需停止一个正在运行的作业,可以[使用标准的Linux进程命令][3]来停止一个正在运行的进程。
|
||||
如需停止一个正在运行的作业,可以 [使用标准的 Linux 进程命令][3] 来停止一个正在运行的进程。
|
||||
|
||||
### 它是自动的
|
||||
|
||||
一旦你编写完 crontab,保存了文件并且退出了编辑器。你的 cronjob 就已经被调度了,剩下的工作都交给 cron 完成。
|
||||
一旦你编写完 `crontab`,保存了文件并且退出了编辑器。你的 cronjob 就已经被调度了,剩下的工作都交给 cron 完成。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
@ -3,20 +3,22 @@
|
||||
[#]: author: (Seth Kenlon https://opensource.com/users/seth)
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (piaoshi)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-13646-1.html)
|
||||
|
||||
使用 df 命令查看 Linux 上的可用磁盘空间。
|
||||
使用 df 命令查看 Linux 上的可用磁盘空间
|
||||
======
|
||||
利用 df 命令查看 Linux 磁盘还剩多少空间。
|
||||
![Free disk space][1]
|
||||
|
||||
磁盘空间已经不像计算机早期那样珍贵,但无论你有多少磁盘空间,总有耗尽的可能。计算机需要一些磁盘空间才能启动运行,所以为了确保你没有在无意间用尽了所有的硬盘空间,偶尔检查一下是非常必要的。在 Linux 终端,你可以用 df 命令来做这件事。
|
||||
> 利用 df 命令查看 Linux 磁盘还剩多少空间。
|
||||
|
||||
df 命令可以显示文件系统中可用的磁盘空间。
|
||||

|
||||
|
||||
要想使输出结果易于阅读,你可以加上 --human-readable(或其简写 -h)选项:
|
||||
磁盘空间已经不像计算机早期那样珍贵,但无论你有多少磁盘空间,总有耗尽的可能。计算机需要一些磁盘空间才能启动运行,所以为了确保你没有在无意间用尽了所有的硬盘空间,偶尔检查一下是非常必要的。在 Linux 终端,你可以用 `df` 命令来做这件事。
|
||||
|
||||
`df` 命令可以显示文件系统中可用的磁盘空间。
|
||||
|
||||
要想使输出结果易于阅读,你可以加上 `--human-readable`(或其简写 `-h`)选项:
|
||||
|
||||
```
|
||||
$ df --human-readable
|
||||
@ -26,7 +28,7 @@ Filesystem Size Used Avail Use% Mounted on
|
||||
|
||||
在这个例子中,计算机的磁盘已经用了 52%,还有 500 GB 可用空间。
|
||||
|
||||
由于 Linux 完整地看待所有挂载设备的文件系统,df 命令会展示出连接到计算机上的每个存储设备的详细信息。如果你有很多磁盘,那么输出结果将会反映出来:
|
||||
由于 Linux 从整体上看待所有挂载设备的文件系统,`df` 命令会展示出连接到计算机上的每个存储设备的详细信息。如果你有很多磁盘,那么输出结果将会反映出来:
|
||||
|
||||
```
|
||||
$ df --human-readable
|
||||
@ -44,7 +46,7 @@ tmpfs 12G 848K 12G 1% /run
|
||||
|
||||
### 查看总的可用磁盘空间
|
||||
|
||||
如果你的文件系统确实很复杂,而你希望看到所有磁盘的总空间,可以使用 --total 选项:
|
||||
如果你的文件系统确实很复杂,而你希望看到所有磁盘的总空间,可以使用 `--total` 选项:
|
||||
|
||||
```
|
||||
$ df --human-readable --total
|
||||
@ -72,7 +74,7 @@ via: https://opensource.com/article/21/7/check-disk-space-linux-df
|
||||
作者:[Seth Kenlon][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[piaoshi](https://github.com/piaoshi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
@ -0,0 +1,113 @@
|
||||
[#]: subject: (4MLinux 37.0 Release Packs in Linux Kernel 5.10 LTS and New Applications)
|
||||
[#]: via: (https://news.itsfoss.com/4mlinux-37-0-release/)
|
||||
[#]: author: (Jacob Crume https://news.itsfoss.com/author/jacob/)
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
|
||||
4MLinux 37.0 Release Packs in Linux Kernel 5.10 LTS and New Applications
|
||||
======
|
||||
|
||||
One of the most lightweight distros, [4MLinux][1], has just announced its 37th major release. This version brings a variety of improvements, of which we shall be looking at here.
|
||||
|
||||
Before that, however, I feel that it would be appropriate to find out more about it, especially since it’s such a niche distro.
|
||||
|
||||
### What Is 4MLinux?
|
||||
|
||||
Despite its somewhat unusual name, it actually is quite logical, especially when you look at the project’s goals:
|
||||
|
||||
* **M**aintenance (system rescue Live CD),
|
||||
* **M**ultimedia (full support for a huge number of image, audio and video formats),
|
||||
* **M**iniserver (DNS, FTP, HTTP, MySQL, NFS, Proxy, SMTP, SSH, and Telnet),
|
||||
* **M**ystery (meaning a collection of classic Linux games).
|
||||
|
||||
|
||||
|
||||
This is where it gets the “4M” part of the name from.
|
||||
|
||||
One interesting quirk of this distro is that it doesn’t come with a traditional package manager, instead opting for an ecosystem of extensions. The minimum requirements are also quite relaxed, requiring just 32 MB of RAM to run. The result of all this is an incredibly lightweight and fast distro, perfect for those older computers gathering dust in a cupboard.
|
||||
|
||||
### New Features
|
||||
|
||||
This release brings a variety of improvements, most of which are as follows:
|
||||
|
||||
* 4 new applications can be installed
|
||||
* [Linux 5.10 LTS][2]
|
||||
* [LibreOffice 7.1.5][3]
|
||||
* Firefox 90.0.2
|
||||
* Thunderbird 78.12
|
||||
* Other Updated applications
|
||||
|
||||
|
||||
|
||||
#### Linux 5.10 LTS
|
||||
|
||||
This release brings in Linux kernel 5.10 LTS, resulting in better hardware support and many small improvements. To be honest, I was actually quite surprised at this addition, as I thought that they may not opt for one of the latest kernels right now.
|
||||
|
||||
If you want to see what other improvements this addition brings, I would suggest reading [our coverage for Linux kernel 5.10 release][2].
|
||||
|
||||
#### New Applications
|
||||
|
||||
One area that M4Linux struggles in is application support. Due to the lack of a package manager, the list of available apps is very short, making each addition to it extremely meaningful.
|
||||
|
||||
This release brings the Dmidecode tool for reading hardware-related data from SMBIOS, FluidSynth software synthesizer, HandBrake video transcoder, and qBittorrent BitTorrent client.
|
||||
|
||||
These applications should improve the usefulness of this distribution, hopefully helping older computers stay out of landfill.
|
||||
|
||||
#### Updated Applications
|
||||
|
||||
2021 has had a plethora of large app upgrades, including the new interface in Firefox 89 and the vast improvements of LibreOffice 7.1.5. Now, all these improvements are coming to M4Linux with the new release.
|
||||
|
||||
Here’s a list of updated applications with this release:
|
||||
|
||||
* LibreOffice 7.1.5
|
||||
* Firefox 90.0.2
|
||||
* Mozilla Thunderbird 78.12.0
|
||||
* Audacious 4.1
|
||||
* VLC 3.0.16
|
||||
* MPV 0.33.0
|
||||
* AbiWord 3.0.5
|
||||
* GIMP 2.10.24
|
||||
* Gnumeric 1.12.50
|
||||
* Chromium 90.0
|
||||
* Mesa 21.0
|
||||
|
||||
|
||||
|
||||
In all, these updated applications should provide a much-improved user experience.
|
||||
|
||||
### Final Thoughts
|
||||
|
||||
M4Linux, despite being quite a niche, has made some incredible improvements with this release, especially when considering the incredibly small development team.
|
||||
|
||||
Even though it isn’t targeting the latest hardware, I can still see how this distribution might be perfect for some use cases.
|
||||
|
||||
You can read the [official announcement][4] to learn more.
|
||||
|
||||
_What do you think about M4Linux 37.0? Let me know in the comments below!_
|
||||
|
||||
#### Big Tech Websites Get Millions in Revenue, It's FOSS Got You!
|
||||
|
||||
If you like what we do here at It's FOSS, please consider making a donation to support our independent publication. Your support will help us keep publishing content focusing on desktop Linux and open source software.
|
||||
|
||||
I'm not interested
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://news.itsfoss.com/4mlinux-37-0-release/
|
||||
|
||||
作者:[Jacob Crume][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://news.itsfoss.com/author/jacob/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://4mlinux.com/index.php?page=home
|
||||
[2]: https://news.itsfoss.com/kernel-5-10-release/
|
||||
[3]: https://news.itsfoss.com/libreoffice-7-1-community/
|
||||
[4]: https://4mlinux-releases.blogspot.com/2021/07/4mlinux-370-stable-released.html
|
||||
@ -0,0 +1,78 @@
|
||||
[#]: subject: (GNOME Web Canary is Now Available to Test Bleeding Edge Features)
|
||||
[#]: via: (https://news.itsfoss.com/gnome-web-canary/)
|
||||
[#]: author: (Ankush Das https://news.itsfoss.com/author/ankush/)
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
|
||||
GNOME Web Canary is Now Available to Test Bleeding Edge Features
|
||||
======
|
||||
|
||||
Epiphany or [GNOME Web][1] is a minimal and yet capable browser for Linux distributions. You should find it as the default browser for elementary OS.
|
||||
|
||||
With GNOME 40, the Epiphany browser has had some [improvements and additions][2].
|
||||
|
||||
Behind the scenes, it regularly gets some exciting improvements and feature additions. And for that, you can opt for the Tech Preview version of GNOME Web tailored for early testers.
|
||||
|
||||
Now, a new Canary flavor has been introduced that you can use to test features that are not yet available even in the tech preview build.
|
||||
|
||||
### GNOME Web Canary Flavor
|
||||
|
||||
![][3]
|
||||
|
||||
GNOME Web’s “Canary” builds let you test features that are not even available in the latest [WebKitGTK][4] version.
|
||||
|
||||
Do note that the canary builds are supposed to be extremely unstable, even worse than the development builds available as a tech preview.
|
||||
|
||||
However, with the help of a Canary build, an end-user can test things way early in the process of development that can help find disastrous bugs.
|
||||
|
||||
Not just limited to end-user early testing, a canary build also makes things easier for a GNOME Web developer.
|
||||
|
||||
They no longer have to build WebKitGTK separately in order to implement and test a new feature.
|
||||
|
||||
Even though there was a Flatpak SDK available to ease the process for developers, it was still a time-consuming task.
|
||||
|
||||
Now, with that out of the way, the development pace can potentially improve as well.
|
||||
|
||||
### How to Get the Canary Build?
|
||||
|
||||
First, you need to add the WebKit SDK Flatpak remote using the commands below:
|
||||
|
||||
```
|
||||
flatpak --user remote-add --if-not-exists webkit https://software.igalia.com/flatpak-refs/webkit-sdk.flatpakrepo
|
||||
flatpak --user install https://nightly.gnome.org/repo/appstream/org.gnome.Epiphany.Canary.flatpakref
|
||||
```
|
||||
|
||||
Once done, you can install the Canary by using the [Flatpakref file][5] provided.
|
||||
|
||||
Testing a Canary build gives more users the ability to help GNOME Web developers in the process. So, it is definitely a much-needed addition to improve the development of the GNOME Web browser.
|
||||
|
||||
For more technical details, you might want to take a look at the [announcement post][6] by one of the developers.
|
||||
|
||||
#### Big Tech Websites Get Millions in Revenue, It's FOSS Got You!
|
||||
|
||||
If you like what we do here at It's FOSS, please consider making a donation to support our independent publication. Your support will help us keep publishing content focusing on desktop Linux and open source software.
|
||||
|
||||
I'm not interested
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://news.itsfoss.com/gnome-web-canary/
|
||||
|
||||
作者:[Ankush Das][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://news.itsfoss.com/author/ankush/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://wiki.gnome.org/Apps/Web/
|
||||
[2]: https://news.itsfoss.com/gnome-web-new-tab/
|
||||
[3]: data:image/svg+xml;base64,PHN2ZyBoZWlnaHQ9IjY0MiIgd2lkdGg9Ijc4MCIgeG1sbnM9Imh0dHA6Ly93d3cudzMub3JnLzIwMDAvc3ZnIiB2ZXJzaW9uPSIxLjEiLz4=
|
||||
[4]: https://webkitgtk.org
|
||||
[5]: https://nightly.gnome.org/repo/appstream/org.gnome.Epiphany.Canary.flatpakref
|
||||
[6]: https://base-art.net/Articles/introducing-the-gnome-web-canary-flavor/
|
||||
@ -0,0 +1,118 @@
|
||||
[#]: subject: "Firefox Lost Almost 50 million Users: Here’s Why It is Concerning"
|
||||
[#]: via: "https://news.itsfoss.com/firefox-decline/"
|
||||
[#]: author: "Ankush Das https://news.itsfoss.com/author/ankush/"
|
||||
[#]: collector: "lujun9972"
|
||||
[#]: translator: "imgradeone"
|
||||
[#]: reviewer: " "
|
||||
[#]: publisher: " "
|
||||
[#]: url: " "
|
||||
|
||||
Firefox Lost Almost 50 million Users: Here’s Why It is Concerning
|
||||
======
|
||||
|
||||
Mozilla’s Firefox is the only popular alternative to Chromium-based browsers.
|
||||
|
||||
It has been the default choice for Linux users and privacy-conscious users across every platform.
|
||||
|
||||
However, even with all benefits as one of the best web browsers around, it is losing its grip for the past few years.
|
||||
|
||||
To be honest, we do not even need a stat to say that, many of us have switched over to Chromium-based browsers or Chromium itself instead of Firefox or Google Chrome.
|
||||
|
||||
However, I came across a Reddit thread by [u/nixcraft][1], which highlighted more details on the decline in the userbase of Firefox since 2018.
|
||||
|
||||
And surprisingly, the original source for this information is [Firefox’s Public Data Report][2].
|
||||
|
||||
![][3]
|
||||
|
||||
As per the official stats, the reported number of active (monthly) users was about **244 million** at the end of 2018.
|
||||
|
||||
And, it seems to have declined to **198 million** at the end of **Q2 2021**.
|
||||
|
||||
So, that makes it a whopping ~**46 million** decline in the userbase.
|
||||
|
||||
### Firefox’s Decline is Concerning But Obvious
|
||||
|
||||
Considering 2021 is the year when privacy-focused tools saw a big boost in their userbase, Mozilla’s Firefox is looking at a constant decline.
|
||||
|
||||
Especially when Firefox manages to introduce some industry-first privacy practices. Quite the irony, eh?
|
||||
|
||||
In case you have never used Firefox or have moved away for a long time, a [comparison between Brave and Firefox][4] highlights that it is still a solid web browser choice to date.
|
||||
|
||||
So, why are users moving away to Chromium-based web browsers or Chrome in particular?
|
||||
|
||||
There are a few things that I can think of right off the bat:
|
||||
|
||||
* Google Chrome being the default web browser on Android
|
||||
* Microsoft Edge as the default web browser for Windows (which naturally has a huge marketshare)
|
||||
* Google.com (the biggest search engine) recommending users to install Google Chrome (which is potentially an anti-competitive behaviour)
|
||||
* Some web services are exclusive to Chrome-based browsers
|
||||
|
||||
|
||||
|
||||
In addition to that, there are also a few things that Firefox may have done wrong:
|
||||
|
||||
* Constantly breaking the user experience with major overhauls
|
||||
* Lack of significant performance improvements in the recent years
|
||||
|
||||
|
||||
|
||||
Of course, no web browser is perfect but is this something to worry about? Well, I think, yes.
|
||||
|
||||
### Here’s Why You Should be Worried
|
||||
|
||||
Mozilla’s Firefox is the only viable competitor to Chromium-based browsers. If Firefox disappears, users won’t have a choice to select a different browser engine.
|
||||
|
||||
I’m sure you will agree that monopoly is bad; hence, we need something to survive as an alternative to Google’s chrome engine.
|
||||
|
||||
In fact, a significant number of websites optimize the user experience by keeping chrome-based browsers in mind.
|
||||
|
||||
So, eventually, if the declining trend continues, **users like us may just be forced to switch to other browsers by adapting to new workflows**.
|
||||
|
||||
Even if we ignore the dominant control of Google’s chrome engine on the web by arguing that it is technically better, Firefox is still something precious. Because it provides way more customizations and constantly improves its privacy practices unlike any other.
|
||||
|
||||
In other words, we will be losing out on a lot of good things (forcefully) just because all the competition prefers using Chromium as its base or engage in anti-competitive activities.
|
||||
|
||||
Maybe, you’re frustrated with Firefox now and move away to something else. That’s completely your choice.
|
||||
|
||||
**But, how would you feel if you won’t have an alternative when Firefox ceases to exist because of all the factors affecting its decline?**
|
||||
|
||||
![][5]
|
||||
|
||||
Hence, to keep things balanced, I think we should constantly oppose the anti-competitive behavior by tech giants and start using Mozilla Firefox (in whatever capacity, even as a secondary browser).
|
||||
|
||||
Of course, Mozilla needs to give this situation some serious attention as well.
|
||||
|
||||
While they are busy introducing VPN services, email relays, and other service integrations, they are not succeeding with the user experience improvements.
|
||||
|
||||
At least, that is what I think. I’ve used Firefox as my primary browser for years now but I end up switching to other browsers once in a while, especially, after every major UI overhaul.
|
||||
|
||||
### What Do You Think?
|
||||
|
||||
I’d love to know what you think about this and what seems to be affecting Firefox’s decline in the userbase.
|
||||
|
||||
What do you prefer to use as your primary web browser? Let me know all of it in the comments down below!
|
||||
|
||||
#### Big Tech Websites Get Millions in Revenue, It's FOSS Got You!
|
||||
|
||||
If you like what we do here at It's FOSS, please consider making a donation to support our independent publication. Your support will help us keep publishing content focusing on desktop Linux and open source software.
|
||||
|
||||
I'm not interested
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://news.itsfoss.com/firefox-decline/
|
||||
|
||||
作者:[Ankush Das][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://news.itsfoss.com/author/ankush/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.reddit.com/user/nixcraft/
|
||||
[2]: https://data.firefox.com/dashboard/user-activity
|
||||
[3]: data:image/svg+xml;base64,PHN2ZyBoZWlnaHQ9IjI4MSIgd2lkdGg9Ijc4MCIgeG1sbnM9Imh0dHA6Ly93d3cudzMub3JnLzIwMDAvc3ZnIiB2ZXJzaW9uPSIxLjEiLz4=
|
||||
[4]: https://itsfoss.com/brave-vs-firefox/
|
||||
[5]: data:image/svg+xml;base64,PHN2ZyBoZWlnaHQ9IjQzOSIgd2lkdGg9Ijc4MCIgeG1sbnM9Imh0dHA6Ly93d3cudzMub3JnLzIwMDAvc3ZnIiB2ZXJzaW9uPSIxLjEiLz4=
|
||||
@ -0,0 +1,86 @@
|
||||
[#]: subject: "Your one-on-one meeting doesn't have to be this way"
|
||||
[#]: via: "https://opensource.com/open-organization/21/8/one-on-one-meeting-tips"
|
||||
[#]: author: "Catherine Louis https://opensource.com/users/catherinelouis"
|
||||
[#]: collector: "lujun9972"
|
||||
[#]: translator: " "
|
||||
[#]: reviewer: " "
|
||||
[#]: publisher: " "
|
||||
[#]: url: " "
|
||||
|
||||
Your one-on-one meeting doesn't have to be this way
|
||||
======
|
||||
One-one-one meetings are opportunities for growth. But that's only
|
||||
possible if you're transparent and collaborative about them.
|
||||
![A hand reaching out.][1]
|
||||
|
||||
Whenever I'm speaking with colleagues and clients near the end of a quarter, I often hear from managers rushing to squeeze their one-on-one meetings with employees into tight deadlines. Every time I ask an employee if they've enjoyed their one-on-one with a manager, the answer is unanimously "no." And every time I ask a manager if they've enjoyed their one-on-one with an employee, the answer is unanimously "no, but I have to do it."
|
||||
|
||||
So what we have is a constantly recurring event that no one seems to prioritize, no one seems to enjoy, and no one seems to benefit from. And we choose to end every fiscal quarter like this.
|
||||
|
||||
But it doesn't have to be this way. By thinking and acting openly, we can reframe and reinvent our one-on-one meetings to be productive, beneficial, and even _enjoyable_.
|
||||
|
||||
Managers and other organizational leaders [bear their own set of responsibilities and can apply their own tactics for opening up one-on-one meetings][2]. In this article, I'll discuss what employees can do to ensure more open, honest, compelling, and fulfilling one-on-one meetings with their managers—and offer some examples of ways they can initiate the conversation.
|
||||
|
||||
### Be transparent about your goals
|
||||
|
||||
Be clear with your manager about the goals of your one-on-ones. This might sound strange; however, without structure and clear intent, these meetings can quickly go astray. Before the meeting, really think about what you want to accomplish and how your manager could help you achieve this. Which of your manager's more admirable skills and abilities could you benefit from learning more about? Are you in this role as a stepping stone for another position? Do you have a difficult time negotiating with certain stakeholders, and could your manager help with this? To decide what to prioritize in your one-on-ones, try this: Write today's date one year from now, then imagine the place where you want to be in your career. Using this vision as a starting point, work backward and craft goals you believe your manager can help you achieve on the road to getting where you'd like to be.
|
||||
|
||||
**What this sounds like:** "I'd really like for our one-on-ones to be a dedicated time with you for open-ended conversation, for coaching, mentoring for me to achieve my next goal of {X} to get to know one another better, to provide each other context, or even for venting."
|
||||
|
||||
And at the end of your _current_ one-on-one meeting, establish the goals of your _next_ one-on-one meeting and record them (see below) so you're both clear on what you'll need to prepare to discuss.
|
||||
|
||||
**What this sounds like:** "Given that you've provided me with a path forward, I think the focus of our meeting should be my increased network opportunities with this new contact that you will have provided me." Or, if you're stuck and don't sense an immediate opportunity for forward movement (sometimes the case with sticky problems) end your meeting with a question to establish clear goals: "What can we both do between now and our next meeting to make progress on this situation?"
|
||||
|
||||
So what we have is a constantly recurring event that no one seems to prioritize, no one seems to enjoy, and no one seems to benefit from. And we choose to end every fiscal quarter like this.
|
||||
|
||||
### Accelerate your meeting cadence
|
||||
|
||||
Change is easier when opportunities for feedback are more frequent. Ask your manager to let _you_ schedule one-on-one meetings with her, letting her know they'll happen more frequently than every quarter. Find your meeting cadence based on what is really happening in your work context. Always conclude your current one-on-one meeting by scheduling your next one. Soon you'll get into a nice rhythm. And try not to skip one-on-ones; instead of cancelling, reschedule them.
|
||||
|
||||
**What this sounds like:** "I'd love help with my career here at {company X}, and to do this I'd like to be able to access your calendar for guidance at the time I'll have the need."
|
||||
|
||||
To accelerate your feedback cadence even further, consider asking your manager to provide direct feedback in context rather than waiting to receive this feedback in a one-on-one at some later date. If you wait until the end of the quarter to hear feedback, there's very little you can learn, as you'll probably not remember what even happened to prompt the feedback you actually needed three months earlier.
|
||||
|
||||
**What this sounds like:** "Would you mind giving me direct feedback at the time you notice something? I like to learn immediately, in context, and if it's praise or criticism, please provide this feedback with me privately."
|
||||
|
||||
### Close your feedback loops
|
||||
|
||||
One-on-one meetings should be rich opportunities for mutual feedback. Before you've finished, don't forget to remind your managers what you need from _them_, too. And most importantly, make sure they follow through. Even when people are acting with the best intentions, they're still busy and important conversational threads that begin in meetings can get lost when everyone gets back to work. You know how it goes: You've had a fantastic one-on-one with your manager. You've discussed a sticky situation, and your manager says, "I have a great solution for this. I have a colleague working in a different department who I believe knows a great deal about this, and I promise to get back to you with more guidance before our next meeting next month." And then the next meeting happens and you've both forgotten all about it.
|
||||
|
||||
Keep an open, accessible, _shared record_ of what you've discussed at your one-on-one meetings and update this to include specific actions both you and your manager will take before you meet again. Reinforce your needs verbally; stress how important they are, and be clear that the focus of your next one-on-one will be the items you've already told your manager you need to do your best work.
|
||||
|
||||
**What this sounds like:** "Wow that would be great. It's really important to me. Let's write this down so we don't forget."
|
||||
|
||||
One-on-one meetings should be rich opportunities for mutual feedback. Before you've finished, don't forget to remind your managers what you need from them, too.
|
||||
|
||||
### Skip status updates
|
||||
|
||||
Don't let your one-on-one become another status meeting. Why?
|
||||
|
||||
* If the discussion concerns a product you're working on, others on your team would likely benefit from being part of it; if you're being updated now, you're a bottleneck for this information.
|
||||
* If you go down this path, you'll have no time to discuss the things you've already said you need to discuss (see above).
|
||||
* It's easy for your manager to listen, but it's also a way to avoid difficult conversations; attending a Scrum of Scrums meeting, for example, would be the place to hear updates.
|
||||
|
||||
|
||||
|
||||
**What this sounds like:** "Every team member updates their status daily just prior to the Daily Scrum and the status of the three teams can be heard in the Scrum of Scrums. I'd rather use this hour with you to get your coaching on my career, problems with negotiating with stakeholder Y, and feedback on my personal development progress. If we don't have time to do this now, can we reschedule?"
|
||||
|
||||
### Working for you?
|
||||
|
||||
One-on-one meetings should be productive and energizing. If they aren't, you might need to open them up a bit. Hopefully the ideas I've shared here can help you do just that. And perhaps you have your own tips for making your one-on-one meetings spectacular. I hope you'll share them if you do.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/open-organization/21/8/one-on-one-meeting-tips
|
||||
|
||||
作者:[Catherine Louis][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/catherinelouis
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/rh_003784_02_os.comcareer_job_rh1x_1.png?itok=b1dy5tlv (A hand reaching out.)
|
||||
[2]: https://opensource.com/open-organization/18/5/open-one-on-one-meetings-guide
|
||||
@ -1,111 +0,0 @@
|
||||
[#]: subject: (Windows 11 Look Inspired by KDE Plasma and GNOME?)
|
||||
[#]: via: (https://www.debugpoint.com/2021/06/windows-11-inspiration-linux-kde-plasma/)
|
||||
[#]: author: (Arindam https://www.debugpoint.com/author/admin1/)
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
|
||||
Windows 11 Look Inspired by KDE Plasma and GNOME?
|
||||
======
|
||||
The images of the upcoming Windows 11 Operating system from Microsoft
|
||||
resemble a mixture of our beloved KDE Plasma and GNOME. How much they
|
||||
are similar? We try to find out.
|
||||
There’s a saying which I remember – ‘_Good artists copy. Great artists steal_‘. I don’t know the design team behind Windows 11, but it seems they are pretty good inspired by the Linux desktops. If you look at the Windows OS look over the years – from Windows XP to 7 to 10 – there is not much changed in terms of look and feel. Until now.
|
||||
|
||||
Windows OS have typically 5 to 7 years of life iterations with a new release. If you think about the options of customization Windows gives you, that remained the same over the years. Even the overall desktop experience in terms of Start Menu position, width, color – all remained constant.
|
||||
|
||||
But with the new look of Windows 11 – this is changing. Let me walk you through some of the screenshots I had a look at and how cunningly it is similar to the popular Linux [desktop environments][1] such as KDE Plasma and GNOME.
|
||||
|
||||
### Windows 11 Look Inspired by KDE Plasma and GNOME?
|
||||
|
||||
#### Start Menu and Taskbar
|
||||
|
||||
The traditional Start Menu and Taskbar theme changed in Windows 11. The Start menu and Taskbar icons are at the center of the taskbar (default view). It also gives you the option to move the taskbar icons and Start menu to the left via settings.
|
||||
|
||||
![Windows 11 – Start menu in light mode][2]
|
||||
|
||||
The overall approach and default color with icons remind me of the KDE Plasma taskbar and Launcher. The icons are polished and centered gives you a feel of Adwaita icons of GNOME while the taskbar looks like from KDE Plasma.
|
||||
|
||||
When you open the start menu, it gives you a different arrangement of the icons and options. Also, a search option at the top pops up when you start to type.
|
||||
|
||||
Now, look at the newly designed KDE Plasma launcher. I know, the spacing, the size of the icons, and sharpness are not the same. But you can see how they look surprisingly similar.
|
||||
|
||||
![KDE Plasma 5.22 Launcher in Light mode][3]
|
||||
|
||||
If you are using GNOME or Xfce desktop – with a little tweak of the [Arc menu][4], you can actually have them look exactly similar.
|
||||
|
||||
![Modified Arc Menu][5]
|
||||
|
||||
#### Window Decorations
|
||||
|
||||
Traditionally GNOME always had rounded corners for the standard window decorations. And in compared to that Windows always had sharp corners in windows – like forever until now. Well, with Windows 11, all the window decorations have rounded corners which looks good. The rounded corners concept is not a copyrighted design or new idea. Hence the question arises, why decide to go all rounded corner now? Is there any hidden purpose?
|
||||
|
||||
![Rounded Corners in Windows Explorer and Nautilus][6]
|
||||
|
||||
Oh, remember the application grid menu indicator in GNOME? The small dots tells you that how many pages of applications are there. It seems also to make its way to Windows 11 as well.
|
||||
|
||||
![Dots in paging][7]
|
||||
|
||||
#### Color Palette
|
||||
|
||||
Windows always had a “blue” based theme or any blue variant over the years. Although use has options to change the accent color of the taskbar, start menu background, and window title bars. But with that option, the color palette seems drastically changed with light and dark mode combination to give a more polished and eye-candy look to the Windows desktop. Probably another avenue of inspiration of nice color palette of Ubuntu, KDE, and other flavors.
|
||||
|
||||
[][8]
|
||||
|
||||
SEE ALSO: Windows 11 System Requirement is Turning Heads. Time to migrate to Linux?
|
||||
|
||||
#### Dark Mode
|
||||
|
||||
Windows 11 officially support dark mode/ or dark theme for the first time. Well, I will just leave it here with the below two screenshots. The left one is a dark mode of the Windows 11 start menu and the right one is the KDE Plasma with Breeze dark theme.
|
||||
|
||||
![Comparison of Windows 11 Start Menu and KDE Plasma][9]
|
||||
|
||||
#### New Desktop Widgets
|
||||
|
||||
Inspiration never stops it seems. Remember KDE Plasma’s widgets? Well, it is not a new concept, but it lands in Windows 11. Here’s a screenshot of the new widgets drawer. You can add, remove and scroll items here.
|
||||
|
||||
![Widgets menu][10]
|
||||
|
||||
These are just some of the items which caught my eye. Maybe there are more “inspirations” that “inspired” Windows 11 looks.
|
||||
|
||||
But the question is – why this is the perfect time to introduce all of these features and looks at once?
|
||||
|
||||
### Closing Notes
|
||||
|
||||
Honestly, when I first looked at them, it reminds me of KDE Plasma with Breeze theme in Dark mode. And with very few tweaks, you can make it look like Windows 11. That itself says about how they are similar in looks.
|
||||
|
||||
If you look at the entire desktop operating system landscape – the only players are Windows, Linux Desktops, and macOS. And until now, they all had a distinct signature in their looks. For example, macOS has its own different look which stands out from everyone else. Until now, Windows also had the same – the usual Start menu with the blue theme, etc. But with these new changes, Windows gives users the most customization options and closer to the Linux Desktop looks.
|
||||
|
||||
In my personal opinion, the Windows team should have come up with a different signature look than just being “inspired” by our beloved Linux Desktops.
|
||||
|
||||
I am not sure what the future holds, but it seems the “E-E-E” is in the works with full force.
|
||||
|
||||
Cheers.
|
||||
|
||||
* * *
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.debugpoint.com/2021/06/windows-11-inspiration-linux-kde-plasma/
|
||||
|
||||
作者:[Arindam][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.debugpoint.com/author/admin1/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.debugpoint.com/category/desktop-environment
|
||||
[2]: https://www.debugpoint.com/blog/wp-content/uploads/2021/06/Windows-11-Start-menu-in-light-mode.jpg
|
||||
[3]: https://www.debugpoint.com/blog/wp-content/uploads/2021/06/KDE-Plasma-5.22-Launcher-in-Light-mode.jpg
|
||||
[4]: https://gitlab.com/LinxGem33/Arc-Menu
|
||||
[5]: https://www.debugpoint.com/blog/wp-content/uploads/2020/12/gnomecustomize2020-2-1024x576.jpg
|
||||
[6]: https://www.debugpoint.com/blog/wp-content/uploads/2021/06/Rounded-Corners-in-Windows-Explorer-and-Nautilus-1024x716.jpg
|
||||
[7]: https://www.debugpoint.com/blog/wp-content/uploads/2021/06/Dots-in-paging-1024x468.jpg
|
||||
[8]: https://www.debugpoint.com/2021/06/windows-11-system-requirement/
|
||||
[9]: https://www.debugpoint.com/blog/wp-content/uploads/2021/06/Comparison-of-Windows-11-Start-Menu-and-KDE-Plasma-1024x505.jpg
|
||||
[10]: https://www.debugpoint.com/blog/wp-content/uploads/2021/06/Widgets-menu-1024x833.jpg
|
||||
@ -1,139 +0,0 @@
|
||||
[#]: subject: (Reading and writing files with Python)
|
||||
[#]: via: (https://opensource.com/article/21/7/read-write-files-python)
|
||||
[#]: author: (Seth Kenlon https://opensource.com/users/seth)
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
|
||||
Reading and writing files with Python
|
||||
======
|
||||
Every programming language handles data files differently. Here's how
|
||||
Python does it.
|
||||
![Hands on a keyboard with a Python book ][1]
|
||||
|
||||
Some data is meant to be temporary, stored in RAM while an application is running, and then forgotten. Some data, however, is meant to be persistent. It's stored on a hard drive for later use, and it's often the stuff that a user cares about the most. For programmers, it's very common to write code to read and write files, but every language handles this task a little differently. This article demonstrates how to handle data files with Python.
|
||||
|
||||
### Install Python
|
||||
|
||||
On Linux, you probably already have Python installed. If not, you can install it from your distribution's software repository. For instance, on CentOS Stream or RHEL:
|
||||
|
||||
|
||||
```
|
||||
`$ sudo dnf install python3`
|
||||
```
|
||||
|
||||
On macOS, you can install Python from [MacPorts][2] or [Homebrew][3]. On Windows, you can install Python from [Chocolatey][4].
|
||||
|
||||
Once you have Python installed, open your favorite text editor and get ready to code.
|
||||
|
||||
### Writing data to a file with Python
|
||||
|
||||
If you need to write data to a file, there are three steps to remember:
|
||||
|
||||
1. Open
|
||||
2. Write
|
||||
3. Close
|
||||
|
||||
|
||||
|
||||
This is exactly the same sequence of steps you use when writing code, editing photos, or doing almost anything on a computer. First, you open the document you want to edit, then you make some edits, and then you close the document.
|
||||
|
||||
In Python, that translates to this process:
|
||||
|
||||
|
||||
```
|
||||
f = open('example.txt', 'w')
|
||||
f.write('hello world')
|
||||
f.close()
|
||||
```
|
||||
|
||||
In this example, the first line opens a file in **write** mode. The file is represented as the variable `f`, which is an arbitrary choice. I use `f` because it seems to be common in Python code, but any valid variable name works just as well.
|
||||
|
||||
There are different modes in which you can open a file:
|
||||
|
||||
* **w** to write
|
||||
* **r+** to read and write
|
||||
* **a** to append only
|
||||
|
||||
|
||||
|
||||
The second line of the example writes data to the file. The data written in this example is plain text, but you can write any kind of data.
|
||||
|
||||
The final line closes the file.
|
||||
|
||||
### Writing data using the 'with' syntax
|
||||
|
||||
There's a shorter way to write data into a file, and this method can be useful for quick file interactions. It doesn't leave the file open, so you don't have to remember to call the **close()** function. Instead, it uses the **with** syntax:
|
||||
|
||||
|
||||
```
|
||||
with open('example.txt', 'a') as f:
|
||||
f.write('hello open source')
|
||||
```
|
||||
|
||||
### Reading data in from a file with Python
|
||||
|
||||
If you (or your user, by way of your application) have placed data into a file, and your code needs to retrieve it, then you want to read a file. Similar to writing, the logic is:
|
||||
|
||||
1. Open
|
||||
2. Read
|
||||
3. Close
|
||||
|
||||
|
||||
|
||||
Again, this logic flow mirrors what you already know from just using a computer (or a paperback book, for that matter). To read a document, you open it, read it, and then close it. In computer terms, "opening" a file means to load it into memory.
|
||||
|
||||
In practice, a text file contains more than one line. For example, maybe your code needs to read a configuration file, saved game data, or the lyrics to your band's next song. Just as you don't read an entire physical book the very moment you open it, your code must parse a file it has loaded into memory. So, you probably need to iterate over the file's contents.
|
||||
|
||||
|
||||
```
|
||||
f = open('example.tmp', 'r')
|
||||
|
||||
for line in f:
|
||||
print(line)
|
||||
|
||||
f.close()
|
||||
```
|
||||
|
||||
In the first line of this example code, you open a file in **read** mode. The file is represented by the variable `f`, but just like when you open files for writing, the variable name is arbitrary. There's nothing special about `f`; it's just the shortest possible way to represent the word "file," so it tends to be used a lot by Python programmers.
|
||||
|
||||
In the second line, you reserve `line`, which is yet another arbitrary variable name, to represent each line of `f`. This tells Python to iterate, line by line, over the file's contents and print each line to your output (in this case, the terminal or [IDLE][5]).
|
||||
|
||||
### Reading a file using the 'with' syntax
|
||||
|
||||
As with writing data, there's a shorter method of reading data from files using the **with** syntax. This doesn't require you to call the **call()** function, so it can be convenient for quick interactions.
|
||||
|
||||
|
||||
```
|
||||
with open('example.txt', 'r') as f:
|
||||
for line in f:
|
||||
print(line)
|
||||
```
|
||||
|
||||
### Files and Python
|
||||
|
||||
There are more ways to write data to files using Python, and many ways to format text you write to files using [JSON, YAML, TOML][6], and more. There's also a very nice built-in method for creating and maintaining an [SQLite][7] database and many libraries to handle any number of file formats, including [graphics][8], audio, video, and more.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/21/7/read-write-files-python
|
||||
|
||||
作者:[Seth Kenlon][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/seth
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/python-programming-code-keyboard.png?itok=fxiSpmnd (Hands on a keyboard with a Python book )
|
||||
[2]: https://opensource.com/article/20/11/macports
|
||||
[3]: https://opensource.com/article/20/6/homebrew-mac
|
||||
[4]: https://opensource.com/article/20/3/chocolatey
|
||||
[5]: https://opensource.com/article/17/10/python-101#idle
|
||||
[6]: https://opensource.com/article/21/6/parse-configuration-files-python
|
||||
[7]: https://opensource.com/article/21/2/sqlite3-cheat-sheet
|
||||
[8]: https://opensource.com/article/19/3/python-image-manipulation-tools
|
||||
@ -1,164 +0,0 @@
|
||||
[#]: subject: (How to Upgrade to Debian 11 from Debian 10)
|
||||
[#]: via: (https://www.debugpoint.com/2021/07/upgrade-debian-11-from-debian-10/)
|
||||
[#]: author: (Arindam https://www.debugpoint.com/author/admin1/)
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
|
||||
How to Upgrade to Debian 11 from Debian 10
|
||||
======
|
||||
This guide explains the steps to upgrade debian 11 from debian 10.
|
||||
[Debian][1] releases are rare. Because it is often a multi-year effort from the community. That is why Debian is truly universal operating system and rock solid stability wise.
|
||||
|
||||
[Debian 11][2], code named Bullseye, officially releases soon. On July 15, 2021, Debian 11 went to complete freeze, which means the release is imminent. Although the official date is not finalized, but you can install or upgrade to Debian 11 from Debian 10 right now.
|
||||
|
||||
This is how.
|
||||
|
||||
### Pre-Requisites
|
||||
|
||||
* The upgrade process is very straightforward. However, it is a good practice to take certain pre-cautions. Specially if you are upgrading a server.
|
||||
* Take backup of your system, including all important data and files.
|
||||
* Try to disable/remove any external repositories (PPA) you may have added over the time. You can enable them after upgrade one-by-one.
|
||||
* Close all the running applications.
|
||||
* Stop any running services that you may have enabled. You can start them via [systemctl][3] after upgrade is complete. This includes web server, SSH server, FTP server or any other servers.
|
||||
* Make sure you have stable internet connection.
|
||||
* And have sufficient downtime of your system. Because depending on your system configuration, a Debian version upgrade takes time ~ between 1.5 hours to 2 hours.
|
||||
|
||||
|
||||
|
||||
### Upgrade Debian 10 Buster to 11 Bullseye Linux
|
||||
|
||||
* Make sure your system is up-to-date, and your package list is up-to-date.
|
||||
|
||||
|
||||
|
||||
```
|
||||
sudo apt update && sudo apt upgrade
|
||||
```
|
||||
|
||||
* Install the gcc-8-base package using the below command. This is required because, historically it has been seen, that upgrade fails because of certain dependencies which included in the below package.
|
||||
|
||||
|
||||
|
||||
```
|
||||
sudo apt install gcc-8-base
|
||||
```
|
||||
|
||||
![upgrade debian – system check][4]
|
||||
|
||||
* Open the /etc/apt/sources.list and update with bullseye repositories, by commenting the Debian 10 buster packages.
|
||||
|
||||
|
||||
* Comment out all the buster repo by “#” at the beginning of the lines.
|
||||
|
||||
|
||||
|
||||
![Comment the Debian 10 lines][5]
|
||||
|
||||
* Add the following lines at the end of the file.
|
||||
|
||||
|
||||
|
||||
```
|
||||
deb http://deb.debian.org/debian bullseye main contrib non-free
|
||||
deb http://deb.debian.org/debian bullseye-updates main contrib non-free
|
||||
deb http://security.debian.org/debian-security bullseye-security main
|
||||
deb http://ftp.debian.org/debian bullseye-backports main contrib non-free
|
||||
```
|
||||
|
||||
![Add Debian 11 lines][6]
|
||||
|
||||
* Press Ctrl + O to save the file and Ctrl + X to exit nano.
|
||||
|
||||
|
||||
* Update the system repository list once to verify the addition of the repositories.
|
||||
|
||||
|
||||
|
||||
```
|
||||
sudo apt update
|
||||
```
|
||||
|
||||
* If the above command doesn’t give any error, then you have successfully added the bullseye repo.
|
||||
|
||||
|
||||
* Now, start the upgrade process by running the below command. The download size is around 1.2 GB for a base installation. That may be different based on your system config.
|
||||
|
||||
|
||||
|
||||
```
|
||||
sudo apt full-upgrade
|
||||
```
|
||||
|
||||
![Debian upgrade start][7]
|
||||
|
||||
* This command takes time. But do not leave the system unattended. Because upgrade process requires various inputs during the course of upgrade.
|
||||
|
||||
|
||||
|
||||
![lib6 config][8]
|
||||
|
||||
![sudoers file][9]
|
||||
|
||||
* Once it is completed, you can restart the system using –
|
||||
|
||||
|
||||
|
||||
```
|
||||
systemctl reboot
|
||||
```
|
||||
|
||||
* After reboot, run the following commands to make sure your system is up-to-date, and you cleaned up all the unnecessary packages that is not required anymore.
|
||||
|
||||
|
||||
|
||||
```
|
||||
sudo apt --purge autoremove
|
||||
```
|
||||
|
||||
* If all goes well, you should be seeing the Debian 11 bullseye. You can verify the version using the below command:
|
||||
|
||||
|
||||
|
||||
```
|
||||
cat /etc/os-release
|
||||
```
|
||||
|
||||
![Debian 11 after upgrade][10]
|
||||
|
||||
### Closing Notes
|
||||
|
||||
I hope this guide helps you to upgrade your system to Debian 11 bullseye. If you face any issues, let me know using the comment box below.
|
||||
|
||||
[][11]
|
||||
|
||||
SEE ALSO: Debian 11 bullseye - Default Theme Revealed
|
||||
|
||||
* * *
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.debugpoint.com/2021/07/upgrade-debian-11-from-debian-10/
|
||||
|
||||
作者:[Arindam][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.debugpoint.com/author/admin1/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.debian.org/
|
||||
[2]: https://www.debugpoint.com/2021/05/debian-11-features/
|
||||
[3]: https://www.debugpoint.com/2020/12/systemd-systemctl-service/
|
||||
[4]: https://www.debugpoint.com/blog/wp-content/uploads/2021/07/upgrade-debian-system-check-1024x503.jpeg
|
||||
[5]: https://www.debugpoint.com/blog/wp-content/uploads/2021/07/Cpmment-the-Debian-10-lines-1024x636.jpeg
|
||||
[6]: https://www.debugpoint.com/blog/wp-content/uploads/2021/07/Add-Debian-11-lines-1024x635.jpeg
|
||||
[7]: https://www.debugpoint.com/blog/wp-content/uploads/2021/07/Debian-upgrade-start-1024x226.jpeg
|
||||
[8]: https://www.debugpoint.com/blog/wp-content/uploads/2021/07/lib6-config-1024x195.jpeg
|
||||
[9]: https://www.debugpoint.com/blog/wp-content/uploads/2021/07/sudoers-file.jpeg
|
||||
[10]: https://www.debugpoint.com/blog/wp-content/uploads/2021/07/Debian-11-after-upgrade.jpeg
|
||||
[11]: https://www.debugpoint.com/2020/11/debian-11-bullseye-theme/
|
||||
@ -1,95 +0,0 @@
|
||||
[#]: subject: (5 useful ways to manage Kubernetes with kubectl)
|
||||
[#]: via: (https://opensource.com/article/21/7/kubectl)
|
||||
[#]: author: (Alan Smithee https://opensource.com/users/alansmithee)
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
|
||||
5 useful ways to manage Kubernetes with kubectl
|
||||
======
|
||||
Learn kubectl to enhance how you interact with Kubernetes.
|
||||
![Ship captain sailing the Kubernetes seas][1]
|
||||
|
||||
Kubernetes is software to help you run lots of containers in an organized way. Aside from providing tools to manage (or [orchestrate][2]) the containers you run, Kubernetes also helps those containers scale out as needed. With Kubernetes as your central control panel (or _control plane_), you need a way to manage Kubernetes, and the tool for that job is kubectl. The `kubectl` command lets you control, maintain, analyze, and troubleshoot Kubernetes clusters. As with many tools using the `ctl` (short for "control") suffix, such as systemctl and sysctl, kubectl has purview over a broad array of functions and tasks, so you end up using it a lot if you're running Kubernetes. It's a big command with lots of options, so here are five common tasks that kubectl makes easy.
|
||||
|
||||
### 1\. List and describe resources
|
||||
|
||||
Containers, by design, tend to multiply. Under certain conditions, they can multiply rapidly. This can get overwhelming if the only way you have to see running containers is `podman ps` or `docker ps`. With `kubectl get` and `kubectl describe`, you can get information about what pods are running and the containers they're handling. What's more is that you can get just the information you need by using options like `--namespace` or `name` or `--selector`.
|
||||
|
||||
The `get` subcommand is useful for a lot more than just pods and containers. It has information about nodes, namespaces, deployments, services, and replicas.
|
||||
|
||||
### 2\. Create resources
|
||||
|
||||
If you've only ever created deployments through a web user interface (UI) like one provided by OpenShift, OKD, or Kubernetes, but you're looking to take control of your cluster from your Linux terminal instead, then get ready to use `kubectl create`. The `kubectl create` command doesn't just instantiate a new app deployment, though. There are lots of other components available in Kubernetes that you can create, such as services, quotas, and [CronJobs][3].
|
||||
|
||||
A CronJob in Kubernetes can create a transient pod meant to perform some task on a schedule of your choice. They're not difficult to set up. Here's a CronJob to have a BusyBox image echo "hello world" every minute:
|
||||
|
||||
|
||||
```
|
||||
$ kubectl create cronjob \
|
||||
hello-world \
|
||||
\--image=busybox \
|
||||
\--schedule="*/1 * * * *" -- echo "hello world"
|
||||
```
|
||||
|
||||
### 3\. Edit files
|
||||
|
||||
You may have an understanding that objects in Kubernetes have accompanying configuration files, but rummaging through your filesystem to find the appropriate file can be troublesome. With `kubectl edit`, you can keep your mind on the objects and not on the files that define them. You can have `kubectl` find and open the file for you (it respects the `KUBE_EDITOR` environment variable, so you can set your editor to whatever you prefer):
|
||||
|
||||
|
||||
```
|
||||
$ KUBE_EDITOR=emacs \
|
||||
kubectl edit cronjob/hello-world
|
||||
```
|
||||
|
||||
### 4\. Trade files between containers
|
||||
|
||||
Newcomers to containers are often baffled by the concept of a shared system that they can't apparently access. They may learn about `exec` options in their container engine or in kubectl itself, but containers still can seem impervious when they can't just grab a file from or place a file into a container. Using the `kubectl cp` command, you can treat containers as if they were remote servers, making copying files to and from containers no more complex than an SSH command:
|
||||
|
||||
|
||||
```
|
||||
`$ kubectl cp foo my-pod:/tmp`
|
||||
```
|
||||
|
||||
### 5\. Apply changes
|
||||
|
||||
Making changes to Kubernetes objects can be done at any time with the `kubectl apply` command. All you have to do is point the command to a configuration file:
|
||||
|
||||
|
||||
```
|
||||
`$ kubectl apply -f ./mypod.json`
|
||||
```
|
||||
|
||||
Akin to running an Ansible playbook or a Bash script, `apply` makes it easy to "import" settings quickly into a running Kubernetes instance. For instance, the GitOps tool [ArgoCD][4] is surprisingly simple to install thanks to the `apply` subcommand:
|
||||
|
||||
|
||||
```
|
||||
$ kubectl create namespace argocd
|
||||
$ kubectl apply -n argocd \
|
||||
-f <https://raw.githubusercontent.com/argoproj/argo-cd/vx.y.z/manifests/install.yaml>
|
||||
```
|
||||
|
||||
### Use kubectl
|
||||
|
||||
Kubectl is a powerful tool, and because it's a terminal command it can be scripted and used in many ways a web UI cannot. Learning kubectl is a great way to further your understanding of Kubernetes, containers, pods, and all the technologies that surround these important cloud innovations. [Download our kubectl cheat sheet][5] for a quick reference, complete with sample commands, to help you as you learn and remind you of the details once you're a pro.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/21/7/kubectl
|
||||
|
||||
作者:[Alan Smithee][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/alansmithee
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/ship_captain_devops_kubernetes_steer.png?itok=LAHfIpek (Ship captain sailing the Kubernetes seas)
|
||||
[2]: https://opensource.com/article/20/11/orchestration-vs-automation
|
||||
[3]: https://opensource.com/article/20/11/kubernetes-jobs-cronjobs
|
||||
[4]: https://argoproj.github.io/argo-cd/
|
||||
[5]: https://opensource.com/downloads/kubectl-cheat-sheet
|
||||
@ -2,7 +2,7 @@
|
||||
[#]: via: (https://fedoramagazine.org/command-line-quick-tips-wc-sort-sed-and-tr/)
|
||||
[#]: author: (mahesh1b https://fedoramagazine.org/author/mahesh1b/)
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: translator: (perfiffer)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
|
||||
@ -1,139 +0,0 @@
|
||||
[#]: subject: (How to Change Lock and Login Screen Wallpaper in elementary OS)
|
||||
[#]: via: (https://www.debugpoint.com/2021/07/change-lock-login-screen-background-elementary-os/)
|
||||
[#]: author: (Arindam https://www.debugpoint.com/author/admin1/)
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
|
||||
How to Change Lock and Login Screen Wallpaper in elementary OS
|
||||
======
|
||||
This tutorial explains the steps you need to change lock and login
|
||||
screen background in elementary OS. This will replace the default grey
|
||||
background.
|
||||
Changing the lock or login screen background grey default wallpaper in elementary OS is a bit difficult. The typical greeter configuration change with the path of the image file would not work.
|
||||
|
||||
Unfortunately, it’s not an easier solution because the grey background is an image file and its data is hard coded in the greeter and need to be recompiled with new image to make it work.
|
||||
|
||||
Here’s how.
|
||||
|
||||
![Lock / Login screen background elementary OS \(Odin\)][1]
|
||||
|
||||
### Change Lock and Login Screen Background – elementary OS
|
||||
|
||||
* Open a terminal in your elementary OS.
|
||||
* Install git and following dependencies for [greeter package][2].
|
||||
|
||||
|
||||
|
||||
```
|
||||
sudo apt install git
|
||||
```
|
||||
|
||||
```
|
||||
sudo apt install -y gnome-settings-daemon libaccountsservice-dev libgdk-pixbuf2.0-dev libgranite-dev libgtk-3-dev libhandy-1-dev liblightdm-gobject-1-dev libmutter-6-dev libwingpanel-dev libx11-dev meson valac
|
||||
```
|
||||
|
||||
* Go to temporary /tmp directory and clone the latest greeter master branch from GitHub.
|
||||
|
||||
|
||||
|
||||
```
|
||||
cd /tmp
|
||||
git clone https://github.com/elementary/greeter.git
|
||||
```
|
||||
|
||||
* After cloning is complete, open the path `/tmp/greeter/data` in a file manager.
|
||||
|
||||
|
||||
* The elementary OS uses a PNG file of 100×100 px as default background in the login screen/lock screen. The image is tiled, and it gives an impression of grey background.
|
||||
|
||||
|
||||
* Rename your desired wallpaper image with `texture.png` and overwrite the following file in the path.
|
||||
|
||||
|
||||
|
||||
![gray background is created using this file][3]
|
||||
|
||||
```
|
||||
/tmp/greeter/data/texture.png
|
||||
```
|
||||
|
||||
* Open the file `/tmp/greeter/compositor/SystemBackground.vala` in a text editor and replace the following line –
|
||||
|
||||
|
||||
|
||||
![change the path of image][4]
|
||||
|
||||
```
|
||||
resource:///io/elementary/desktop/gala/texture.png
|
||||
```
|
||||
|
||||
With –
|
||||
|
||||
```
|
||||
resource:///io/elementary/greeter/texture.png
|
||||
```
|
||||
|
||||
* Save the file.
|
||||
|
||||
|
||||
* Open the terminal again and build `greeter` using the following commands.
|
||||
|
||||
|
||||
|
||||
```
|
||||
cd /tmp/greeter
|
||||
meson _build --prefix=/usr
|
||||
sudo ninja install -C _build
|
||||
```
|
||||
|
||||
![building greeter][5]
|
||||
|
||||
* If you face any build error, let me know in the comment below. You should not be seeing any error, as I have tested it.
|
||||
|
||||
|
||||
|
||||
[][6]
|
||||
|
||||
SEE ALSO: elementary OS 5.1 Hera Released. Here’s What’s New
|
||||
|
||||
After the above commands are complete, you can test the login screen by running lightdm in test mode –
|
||||
|
||||
```
|
||||
lightdm --test-mode --debug
|
||||
```
|
||||
|
||||
If it looks good, reboot the system. And you should be seeing your wallpaper in the login screen in elementary OS.
|
||||
|
||||
This guide should work in [elementary OS 6 Odin][7], elementary OS 5 Juno and below.
|
||||
|
||||
### Closing Notes
|
||||
|
||||
I hope this guide helps you to change the background of lock or login screen in your elementary OS. Honestly, its 2021 and changing a background image of login screen requires compilation of code surprises me.
|
||||
|
||||
If you run into error, let me know in the comment box below.
|
||||
|
||||
* * *
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.debugpoint.com/2021/07/change-lock-login-screen-background-elementary-os/
|
||||
|
||||
作者:[Arindam][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.debugpoint.com/author/admin1/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.debugpoint.com/blog/wp-content/uploads/2021/07/elementary-OS-Login-Screen-in-Odin-1024x768.jpg
|
||||
[2]: https://github.com/elementary/greeter
|
||||
[3]: https://www.debugpoint.com/blog/wp-content/uploads/2021/07/gray-background-is-created-using-this-file.jpg
|
||||
[4]: https://www.debugpoint.com/blog/wp-content/uploads/2021/07/change-the-path-of-image-1024x450.jpg
|
||||
[5]: https://www.debugpoint.com/blog/wp-content/uploads/2021/07/building-greeter.png
|
||||
[6]: https://www.debugpoint.com/2019/12/elementary-os-hera-released/
|
||||
[7]: https://www.debugpoint.com/tag/elementary-os-6
|
||||
@ -2,7 +2,7 @@
|
||||
[#]: via: (https://fedoramagazine.org/4-cool-new-projects-to-try-in-copr-for-july-2021/)
|
||||
[#]: author: (Jakub Kadlčík https://fedoramagazine.org/author/frostyx/)
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
|
||||
249
sources/tech/20210802 Use OpenCV on Fedora Linux - part 1.md
Normal file
249
sources/tech/20210802 Use OpenCV on Fedora Linux - part 1.md
Normal file
@ -0,0 +1,249 @@
|
||||
[#]: subject: (Use OpenCV on Fedora Linux ‒ part 1)
|
||||
[#]: via: (https://fedoramagazine.org/use-opencv-on-fedora-linux-part-1/)
|
||||
[#]: author: (Onuralp SEZER https://fedoramagazine.org/author/thunderbirdtr/)
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
|
||||
Use OpenCV on Fedora Linux ‒ part 1
|
||||
======
|
||||
|
||||
![][1]
|
||||
|
||||
Cover image excerpted from Starry Night by [Vincent van Gogh][2], Public domain, via Wikimedia Commons
|
||||
|
||||
The technology world changes daily and the demands for computer vision, artificial intelligence, and machine learning are increasing. The technology that allows computers and mobile phones to see their surroundings is called [computer vision][3]. Work on re-creating a human eye started in the 50s. Since then, computer vision technology has come a long way. Computer vision has already made its way to our mobile phones via different applications. This article will introduce [OpenCV][4] on Fedora Linux.
|
||||
|
||||
### **What is OpenCV?**
|
||||
|
||||
> OpenCV (Open Source Computer Vision Library) is an open-source computer vision and machine learning software library. OpenCV was built to provide a common infrastructure for computer vision applications and to accelerate the use of machine perception in the commercial products. It has more than 2500 optimized algorithms, which includes a comprehensive set of both classic and state-of-the-art computer vision and machine learning algorithms. These algorithms can be used to detect and recognize faces, identify objects, classify human actions in videos and establish markers to overlay it with augmented reality and much more.
|
||||
>
|
||||
> [opencv.org – about][5]
|
||||
|
||||
### Install OpenCV on Fedora Linux
|
||||
|
||||
To get started with OpenCV, install it from the Fedora Linux repositories.
|
||||
|
||||
```
|
||||
$ sudo dnf install opencv opencv-contrib opencv-doc python3-opencv python3-matplotlib python3-numpy
|
||||
```
|
||||
|
||||
**Note:** On Fedora Silverblue or CoreOs, Python 3.9 is part of the core commit. Layer OpenCV and required tools with: _rpm-ostree install opencv opencv-doc python3-opencv python3-matplotlib python3-numpy_.
|
||||
|
||||
Next, enter the following commands in a terminal to verify that OpenCV is installed (user input shown in bold).
|
||||
|
||||
```
|
||||
$ python
|
||||
Python 3.9.6 (default, Jul 16 2021, 00:00:00)
|
||||
[GCC 11.1.1 20210531 (Red Hat 11.1.1-3)] on linux
|
||||
Type "help", "copyright", "credits" or "license" for more information.
|
||||
>>> import cv2 as cv
|
||||
>>> print( cv.__version__ )
|
||||
4.5.2
|
||||
>>> exit()
|
||||
```
|
||||
|
||||
The current OpenCV version should be displayed when you enter the _print_ command as shown above. This indicates that OpenCV and the Python-OpenCV libraries have been installed successfully.
|
||||
|
||||
Additionally, if you want to take notes and write code with Jupyter Notebook and learn more about data science tools, check out the earlier Fedora Magazine article: [_Jupyter and Data Science in Fedora_][6].
|
||||
|
||||
### Get started with OpenCV
|
||||
|
||||
After installation is complete, load a sample image using Python and the OpenCV libraries (press the **S** key to save a copy of the image in _png_ format and finish the program):
|
||||
|
||||
```
|
||||
$ cp /usr/share/opencv4/samples/data/starry_night.jpg .
|
||||
$ python starry_night.py
|
||||
```
|
||||
|
||||
Contents of _starry_night.py_:
|
||||
|
||||
```
|
||||
import cv2 as cv
|
||||
import sys
|
||||
img = cv.imread(cv.samples.findFile("starry_night.jpg"))
|
||||
if img is None:
|
||||
sys.exit("Could not read the image.")
|
||||
cv.imshow("Display window", img)
|
||||
k = cv.waitKey(0)
|
||||
if k == ord("s"):
|
||||
cv.imwrite("starry_night.png", img)
|
||||
```
|
||||
|
||||
![][7]
|
||||
|
||||
Gray-scale the image by adding the parameter **0** to the _cv.imread_ function as shown below.
|
||||
|
||||
```
|
||||
img = cv.imread(cv.samples.findFile("starry_night.jpg"),0)
|
||||
```
|
||||
|
||||
![][8]
|
||||
|
||||
These are some alternative values that can be used for the second parameter of the _cv.imread_ function.
|
||||
|
||||
* **cv2.IMREAD_GRAYSCALE** or **0:** Load the image in grayscale mode.
|
||||
* **cv2.IMREAD_COLOR** or **1:** Load the image in color mode. Any transparency in the image will be removed. This is the default.
|
||||
* **cv2.IMREAD_UNCHANGED** or **-1:** Load the image unaltered; including alpha channel.
|
||||
|
||||
|
||||
|
||||
#### Display image attributes using OpenCV
|
||||
|
||||
Image attributes include the number of rows, columns, and channels; the type of image data; the number of pixels; etc. Suppose you wanted to access the image’s shape and its datatype. This is how you would do it:
|
||||
|
||||
```
|
||||
import cv2 as cv
|
||||
|
||||
img = cv.imread(cv.samples.findFile("starry_night.jpg"))
|
||||
print("Image size is", img.shape)
|
||||
print("Data type of image is", img.dtype)
|
||||
|
||||
Image size is (600, 752, 3)
|
||||
Data type of image is uint8
|
||||
|
||||
print(f"Image 2D numpy array \n {img}")
|
||||
|
||||
Image 2D numpy array
|
||||
[[[0 0 0]
|
||||
[0 0 0]
|
||||
[0 0 0]
|
||||
...
|
||||
[0 0 0]
|
||||
[0 0 0]
|
||||
[0 0 0]]
|
||||
|
||||
[[0 0 0]
|
||||
[0 0 0]
|
||||
[0 0 0]
|
||||
...
|
||||
```
|
||||
|
||||
* **img.shape:** return a tuple of the number of rows, columns, and channels (if it is a color image)
|
||||
* **img.dtype:** return the datatype of the image
|
||||
|
||||
|
||||
|
||||
Next display image with Matplotlib:
|
||||
|
||||
```
|
||||
import cv2 as cv
|
||||
import matplotlib.pyplot as plt
|
||||
img = cv.imread(cv.samples.findFile("starry_night.jpg"),0)
|
||||
plt.imshow(img)
|
||||
plt.show()
|
||||
```
|
||||
|
||||
![][9]
|
||||
|
||||
#### What happened?
|
||||
|
||||
The image was read in as a gray-scale image, however it won’t necessarily display in gray-scale when using Matplotlib’s _imshow_ fucntion. This is because the _imshow_ function uses a different color map by default. To specify that a gray-scale color map should be used, set the second parameter of the _imshow_ function to _cmap=’gray’_ as shown below.
|
||||
|
||||
```
|
||||
plt.imshow(img,cmap='gray')
|
||||
```
|
||||
|
||||
![][10]
|
||||
|
||||
This problem is also going to happen when opening a picture in color mode because Matplotlib expects the image in RGB (red, green, blue) format whereas OpenCV stores images in BGR (blue, green, red) format. For correct display, you need to reverse the channels of the BGR image.
|
||||
|
||||
```
|
||||
import cv2 as cv
|
||||
import matplotlib.pyplot as plt
|
||||
img = cv.imread(cv.samples.findFile("starry_night.jpg"),cv.IMREAD_COLOR)
|
||||
fig, (ax1, ax2) = plt.subplots(1,2)
|
||||
ax1.imshow(img)
|
||||
ax1.set_title('BGR Colormap')
|
||||
ax2.imshow(img[:,:,::-1])
|
||||
ax2.set_title('Reversed BGR Colormap(RGB)')
|
||||
plt.show()
|
||||
```
|
||||
|
||||
![][11]
|
||||
|
||||
#### Splitting and merging color channels
|
||||
|
||||
```
|
||||
import cv2 as cv
|
||||
import matplotlib.pyplot as plt
|
||||
|
||||
img = cv.imread(cv.samples.findFile("starry_night.jpg"),cv.IMREAD_COLOR)
|
||||
b,g,r = cv.split(img)
|
||||
|
||||
fig,ax = plt.subplots(2,2)
|
||||
|
||||
ax[0,0].imshow(r,cmap='gray')
|
||||
ax[0,0].set_title("Red Channel");
|
||||
ax[0,1].imshow(g,cmap='gray')
|
||||
ax[0,1].set_title("Green Channel");
|
||||
ax[1,0].imshow(b,cmap='gray')
|
||||
ax[1,0].set_title("Blue Channel");
|
||||
|
||||
# Merge the individual channels into a BGR image
|
||||
imgMerged = cv.merge((b,g,r))
|
||||
# Show the merged output
|
||||
ax[1,1].imshow(imgMerged[:,:,::-1])
|
||||
ax[1,1].set_title("Merged Output");
|
||||
plt.show()
|
||||
```
|
||||
|
||||
![][12]
|
||||
|
||||
* **cv2.split:** Divide a multi-channel array into several single-channel arrays.
|
||||
* **cv2.merge:** Merge several arrays to make a single multi-channel array. All the input matrices must have the same size.
|
||||
|
||||
|
||||
|
||||
**Note:** Images with more white have a higher density of color. Contrarily, images with more black have a lower density of color. In the above example the red color has the lowest density.
|
||||
|
||||
#### Converting to different color spaces
|
||||
|
||||
The _cv2.cvtColor_ function converts an input image from one color space to another. When transforming between the RGB and BGR color spaces, the order of the channels should be specified explicitly (_RGB2BGR_ or _BGR2RGB_). **Note that the default color format in OpenCV is often referred to as RGB but it is actually BGR (the bytes are reversed).** So the first byte in a standard (24-bit) color image will be an 8-bit blue component, the second byte will be green, and the third byte will be red. The fourth, fifth, and sixth bytes would then be the second pixel (blue, then green, then red), and so on.
|
||||
|
||||
```
|
||||
import cv2 as cv
|
||||
import matplotlib.pyplot as plt
|
||||
img = cv.imread(cv.samples.findFile("starry_night.jpg"),cv.IMREAD_COLOR)
|
||||
img_rgb = cv.cvtColor(img, cv.COLOR_BGR2RGB)
|
||||
plt.imshow(img_rgb)
|
||||
plt.show()
|
||||
```
|
||||
|
||||
![][13]
|
||||
|
||||
### Further information
|
||||
|
||||
More details on OpenCV are available in the [online documentation][14].
|
||||
|
||||
Thank you.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://fedoramagazine.org/use-opencv-on-fedora-linux-part-1/
|
||||
|
||||
作者:[Onuralp SEZER][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://fedoramagazine.org/author/thunderbirdtr/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://fedoramagazine.org/wp-content/uploads/2021/08/starry-night-1-816x345.jpg
|
||||
[2]: https://commons.wikimedia.org/wiki/File:Van_Gogh_-_Starry_Night_-_Google_Art_Project.jpg
|
||||
[3]: https://en.wikipedia.org/wiki/Computer_vision
|
||||
[4]: https://en.wikipedia.org/wiki/OpenCV
|
||||
[5]: https://opencv.org/about/
|
||||
[6]: https://fedoramagazine.org/jupyter-and-data-science-in-fedora/
|
||||
[7]: https://fedoramagazine.org/wp-content/uploads/2021/06/image.png
|
||||
[8]: https://fedoramagazine.org/wp-content/uploads/2021/06/image-1.png
|
||||
[9]: https://fedoramagazine.org/wp-content/uploads/2021/06/image-2.png
|
||||
[10]: https://fedoramagazine.org/wp-content/uploads/2021/06/image-3.png
|
||||
[11]: https://fedoramagazine.org/wp-content/uploads/2021/06/image-4.png
|
||||
[12]: https://fedoramagazine.org/wp-content/uploads/2021/06/image-5.png
|
||||
[13]: https://fedoramagazine.org/wp-content/uploads/2021/06/image-7.png
|
||||
[14]: https://docs.opencv.org/4.5.2/index.html
|
||||
168
sources/tech/20210803 Get started with Argo CD.md
Normal file
168
sources/tech/20210803 Get started with Argo CD.md
Normal file
@ -0,0 +1,168 @@
|
||||
[#]: subject: (Get started with Argo CD)
|
||||
[#]: via: (https://opensource.com/article/21/8/argo-cd)
|
||||
[#]: author: (Ayush Sharma https://opensource.com/users/ayushsharma)
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
|
||||
Get started with Argo CD
|
||||
======
|
||||
Argo CD is a simple pull-based GitOps deployment tool that syncs
|
||||
Kubernetes manifest files with a cluster for easy, no-nonsense
|
||||
deployments.
|
||||
![Plumbing tubes in many directions][1]
|
||||
|
||||
In a typical push-based deployment, tools like Ansible and Jenkins connect directly to the server or cluster and execute the provisioning commands. This approach works well when the cluster is accessible on the network and there is direct connectivity between your deployment server and the destination server. For compliance or security reasons, connectivity between the deployment tool and the cluster may not be possible.
|
||||
|
||||
[Argo CD][2] is a pull-based deployment tool. It watches a remote Git repository for new or updated manifest files and synchronizes those changes with the cluster. By managing manifests in Git and syncing them with the cluster, you get all the advantages of a Git-based workflow (version control, pull-request reviews, transparency in collaboration, etc.) and a one-to-one mapping between what is in the Git repo and what is deployed in the cluster. This method is called GitOps.
|
||||
|
||||
In this tutorial, you will:
|
||||
|
||||
1. Install Argo CD on a Minikube installation
|
||||
2. Create a sample Argo CD application called `ayush-test-application` and link it with [my repo `ayush-sharma/example-assets`][3]
|
||||
3. Create an [Nginx deployment with three replicas][4]
|
||||
4. Ensure the new application shows up on the Argo CD dashboard and verify it using `kubectl`
|
||||
|
||||
|
||||
|
||||
### Install Argo CD
|
||||
|
||||
This tutorial uses Minikube version v1.21.0. If you don't have it, [download and install Minikube][5].
|
||||
|
||||
With Minikube up and running, you can install Argo CD. The Argo CD documentation contains detailed steps on how to [install and configure it for any cluster][6]. Once you've executed those steps, run `minikube tunnel` in a separate terminal window to ensure Minikube exposes the Argo CD server's load balancer endpoint on your local system. To verify this, run `kubectl get po -n argocd` and check if the `argo-server` service has an `EXTERNAL-IP:`
|
||||
|
||||
|
||||
```
|
||||
user@system ~ kubectl get svc -n argocd
|
||||
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
|
||||
argocd-dex-server ClusterIP 10.110.2.52 <none> 5556/TCP,5557/TCP,5558/TCP 3h32m
|
||||
argocd-metrics ClusterIP 10.100.73.57 <none> 8082/TCP 3h32m
|
||||
argocd-redis ClusterIP 10.104.11.24 <none> 6379/TCP 3h32m
|
||||
argocd-repo-server ClusterIP 10.100.132.53 <none> 8081/TCP,8084/TCP 3h32m
|
||||
argocd-server LoadBalancer 10.98.182.198 10.98.182.198 80:32746/TCP,443:31353/TCP 3h32m
|
||||
argocd-server-metrics ClusterIP 10.105.182.52 <none> 8083/TCP 3h32m
|
||||
```
|
||||
|
||||
Once the installation is complete and the load balancer is working, the Argo CD user interface (UI) will be accessible at the `EXTERNAL IP`.
|
||||
|
||||
![Argo CD home page][7]
|
||||
|
||||
(Ayush Sharma, [CC BY-SA 4.0][8])
|
||||
|
||||
### Create your first application
|
||||
|
||||
Before talking about Argo CD deployments, you need a Git repo with a Kubernetes (k8s) manifest file ready to deploy. I'm using my [public repo `example-assets`][3] with an Nginx deployment [manifest file in `/argocd/getting-started`][4].
|
||||
|
||||
The goal is to get Argo CD to listen to the k8s manifest file for changes and then sync them with the cluster it is deployed in (in this case, Minikube). You do this by creating an application containing information about the manifest files' source repo, destination cluster details, and synchronization policies.
|
||||
|
||||
Click `New App` on the top left to configure a new application. Since my destination Kubernetes server is the one Argo CD is installed on (Minikube), I left the server defaults as-is. These are the values I configured:
|
||||
|
||||
1. Application name: `ayush-test-application`
|
||||
2. Project: `default`
|
||||
3. Sync policy: `automated`
|
||||
4. Sync options: `prune: true; selfHeal: true`
|
||||
5. Source repository URL: `https://gitlab.com/ayush-sharma/example-assets.git`
|
||||
6. Source revision: `HEAD`
|
||||
7. Source path: `argocd/getting-started`
|
||||
8. Destination cluster URL: `https://kubernetes.default.svc`
|
||||
9. Destination namespace: `default`
|
||||
|
||||
|
||||
|
||||
To make things easier, you can click `EDIT AS YAML` on the top right and paste in:
|
||||
|
||||
|
||||
```
|
||||
apiVersion: argoproj.io/v1alpha1
|
||||
kind: Application
|
||||
metadata:
|
||||
name: ayush-test-application
|
||||
spec:
|
||||
destination:
|
||||
name: 'default'
|
||||
namespace: default
|
||||
server: '<https://kubernetes.default.svc>'
|
||||
source:
|
||||
path: argocd/getting-started
|
||||
repoURL: '<https://gitlab.com/ayush-sharma/example-assets.git>'
|
||||
targetRevision: HEAD
|
||||
project: default
|
||||
syncPolicy:
|
||||
automated:
|
||||
prune: true
|
||||
selfHeal: true
|
||||
```
|
||||
|
||||
Your configuration should look like this:
|
||||
|
||||
![Argo CD application configuration][9]
|
||||
|
||||
(Ayush Sharma, [CC BY-SA 4.0][8])
|
||||
|
||||
After saving the configuration, your application should show up as a card on the home page. Since you specified the sync policy as `Automated`, your new application will begin syncing with the repo immediately.
|
||||
|
||||
![Argo CD application syncing][10]
|
||||
|
||||
(Ayush Sharma, [CC BY-SA 4.0][8])
|
||||
|
||||
### Create the Nginx deployment
|
||||
|
||||
In this tutorial, the manifest file is a standard Nginx deployment with three replicas. Once `ayush-test-application` completes syncing, Argo CD will display a nice graphical view of the deployment.
|
||||
|
||||
![Argo CD application deployment][11]
|
||||
|
||||
(Ayush Sharma, [CC BY-SA 4.0][8])
|
||||
|
||||
Verify the deployment using `kubectl get po`:
|
||||
|
||||
|
||||
```
|
||||
NAME READY STATUS RESTARTS AGE
|
||||
nginx-deployment-585449566-584cj 1/1 Running 0 5m
|
||||
nginx-deployment-585449566-6qn2z 1/1 Running 0 5m
|
||||
nginx-deployment-585449566-d9fm2 1/1 Running 0 5m
|
||||
```
|
||||
|
||||
### Argo CD's advantages
|
||||
|
||||
Argo CD is a relatively lightweight approach to k8s deployments. I'm especially fond of the one-to-one relationship between what's in the repo and what's in the cluster, making incident management a lot simpler.
|
||||
|
||||
Another big advantage is that since the Git repo contains everything Argo CD requires, you could delete the entire Argo CD installation and set things up from scratch. This means bringing up a second identical cluster with your entire workload deployed is now more feasible and practical in the event of a catastrophic outage.
|
||||
|
||||
A third big advantage is fewer open ports. Argo CD pulls changes from a remote Git repo, so there's no need to define firewall rules and virtual private cloud (VPC) peering connections to get your deployment servers to connect with your cluster, which is one less point of entry. This reduces the attack surface area for your development, quality assurance (QA), and production servers significantly.
|
||||
|
||||
Since the Git repo and branch name are configurable, you can get creative with deployment models. For example, you could have two different Argo CDs running on two different QA and production clusters listening to the same repo's branch. This guarantees that the same manifest file is deployed on both clusters, ensuring QA and production environments contain the same codebase. Also, a single Argo CD is capable of targeting multiple servers, meaning a hub-and-spoke deployment model is possible, where one master Argo CD orchestrates deployments across multiple development, QA, and production clusters in different regions or environments.
|
||||
|
||||
Get creative with Argo CD, and don't forget to share your experiments with others.
|
||||
|
||||
* * *
|
||||
|
||||
_This article originally appeared on [Ayush Sharma's blog][12] under a [CC BY-SA 4.0][8] license._
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/21/8/argo-cd
|
||||
|
||||
作者:[Ayush Sharma][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/ayushsharma
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/plumbing_pipes_tutorial_how_behind_scenes.png?itok=F2Z8OJV1 (Plumbing tubes in many directions)
|
||||
[2]: https://argoproj.github.io/cd/
|
||||
[3]: https://gitlab.com/ayush-sharma/example-assets/-/tree/main/argocd/getting-started
|
||||
[4]: https://gitlab.com/ayush-sharma/example-assets/-/blob/main/argocd/getting-started/nginx-manifest.yml
|
||||
[5]: https://minikube.sigs.k8s.io/docs/start/
|
||||
[6]: https://argoproj.github.io/argo-cd/getting_started/
|
||||
[7]: https://opensource.com/sites/default/files/uploads/getting-started-with-argocd-application-page.png (Argo CD home page)
|
||||
[8]: https://creativecommons.org/licenses/by-sa/4.0/
|
||||
[9]: https://opensource.com/sites/default/files/uploads/getting-started-with-argocd-creating-the-application.png (Argo CD application configuration)
|
||||
[10]: https://opensource.com/sites/default/files/uploads/getting-started-with-argocd-creating-ayush-test-application.png (Argo CD application syncing)
|
||||
[11]: https://opensource.com/sites/default/files/uploads/getting-started-with-argocd-successful-nginx-deployment.png (Argo CD application deployment)
|
||||
[12]: https://notes.ayushsharma.in/2021/07/getting-started-with-argocd
|
||||
137
sources/tech/20210803 Set up a VPN server on your Linux PC.md
Normal file
137
sources/tech/20210803 Set up a VPN server on your Linux PC.md
Normal file
@ -0,0 +1,137 @@
|
||||
[#]: subject: (Set up a VPN server on your Linux PC)
|
||||
[#]: via: (https://opensource.com/article/21/8/openvpn-server-linux)
|
||||
[#]: author: (D. Greg Scott https://opensource.com/users/greg-scott)
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
|
||||
Set up a VPN server on your Linux PC
|
||||
======
|
||||
The first step in building a VPN is setting up a VPN server.
|
||||
![Person drinking a hot drink at the computer][1]
|
||||
|
||||
Have you been connected to an untrusted network such as a hotel or café WiFi and need to securely browse the internet from your smartphone or laptop? By using a virtual private network (VPN), you can access that untrusted network anonymously and as safely as if you were on a private network.
|
||||
|
||||
VPN is an amazing tool for safeguarding private data. By using a VPN, you can connect to a private network on the internet while maintaining anonymity.
|
||||
|
||||
There are many VPN services available, and many people have found that the preferred option for securing private data when using untrusted networks is [OpenVPN][2].
|
||||
|
||||
OpenVPN creates an encrypted tunnel between two points, preventing a third party from accessing your network traffic data. By setting up your VPN server, you become your own VPN provider. Many popular VPN services use OpenVPN, so why tie your connection to a specific provider when you can have complete control yourself?
|
||||
|
||||
### Set up a Linux server
|
||||
|
||||
First, install a copy of Linux onto a spare PC. These examples use Fedora, but the steps are mostly the same no matter what Linux distribution you use.
|
||||
|
||||
Download a copy of the most recent Fedora ISO from the [Fedora project][3] website. Make a bootable USB drive, plug it into and boot your PC, and install the operating system. If you've never made a bootable USB drive, read about [Fedora Media Writer][4]. If you've never installed Linux, read about [installing Linux in three steps][5].
|
||||
|
||||
### Set up networking
|
||||
|
||||
After installing the Fedora operating system, log into the console or SSH session.
|
||||
|
||||
Apply the latest updates and reboot:
|
||||
|
||||
|
||||
```
|
||||
`$ sudo dnf update -y && reboot`
|
||||
```
|
||||
|
||||
Log in again and disable the firewall rules:
|
||||
|
||||
|
||||
```
|
||||
systemctl disable firewalld.service
|
||||
systemctl stop firewalld.service
|
||||
```
|
||||
|
||||
You may want to add appropriate firewall rules on this system for your internal network. If so, finish setting up and debugging OpenVPN with all firewall rules turned off, and then add your local firewall rules. For more information, read about [setting up firewalls on Linux][6].
|
||||
|
||||
### Set up IP addresses
|
||||
|
||||
You need a static IP address inside your local network. The commands below assume a Network Manager connection named `ens3` on a device named `ens3`. Your device and connection names might be different, so find them by opening an SSH session or the console and entering:
|
||||
|
||||
|
||||
```
|
||||
$ sudo nmcli connection show
|
||||
NAME UUID TYPE DEVICE
|
||||
ens3 39ad55bd-adde-384a-bb09-7f8e83380875 ethernet ens3
|
||||
```
|
||||
|
||||
You need to ensure that your remote people can find your VPN server. There are two ways to do this. You can set its IP address manually, or you can let your router do most of the work.
|
||||
|
||||
#### Configure an IP address manually
|
||||
|
||||
Set your static IP address, prefix, gateway, and DNS resolver with the following command but substituting your own IP addresses:
|
||||
|
||||
|
||||
```
|
||||
$ sudo nmcli connection modify ens3 ipv4.addresses 10.10.10.97/24
|
||||
$ sudo nmcli connection modify ens3 ipv4.gateway 10.10.10.1
|
||||
$ sudo nmcli connection modify ens3 ipv4.dns 10.10.10.10
|
||||
$ sudo nmcli connection modify ens3 ipv4.method manual
|
||||
$ sudo nmcli connection modify ens3 connection.autoconnect yes
|
||||
```
|
||||
|
||||
Set a hostname:
|
||||
|
||||
|
||||
```
|
||||
`$ sudo hostnamectl set-hostname OVPNserver2020`
|
||||
```
|
||||
|
||||
If you run a local DNS server, you will want to set up a DNS entry with the hostname pointing to the VPN server IP Address.
|
||||
|
||||
Reboot and make sure the system has the correct networking information.
|
||||
|
||||
#### Configure an IP address in your router
|
||||
|
||||
You probably have a router on your network. You may have purchased it, or you may have gotten one from your internet service provider (ISP). Either way, your router probably has a built-in DHCP server that assigns an IP address to each device on your network. Your new server counts as a device on your network, so you may have noticed an IP address is assigned to it automatically.
|
||||
|
||||
The potential problem here is that your router doesn't guarantee that any device will ever get the same IP address after reconnecting. It does _try_ to keep the IP addresses consistent, but they can change depending on how many devices are connected at the time.
|
||||
|
||||
However, almost all routers have an interface allowing you to intercede and reserve IP addresses for specific devices.
|
||||
|
||||
![Router IP address settings][7]
|
||||
|
||||
(Seth Kenlon, [CC BY-SA 4.0][8])
|
||||
|
||||
There isn't a universal interface for routers, so search the interface of the router you own for **DHCP** or **Static IP address** options. Assign your server its own reserved IP address so that its network location remains the same no matter what.
|
||||
|
||||
### Access your server
|
||||
|
||||
By default, your router probably has a firewall built into it. This is normally good because you don't want someone outside your network to be able to brute force their way into any of your computers. However, you must allow traffic destined for your VPN server through your firewall, or else your VPN will be unreachable and, therefore, no use to you.
|
||||
|
||||
You will need at least one public static IP Address from your internet service provider. Set up the public side of your router with its static IP Address, and then put your OpenVPN server on the private side, with its own private static IP Address inside your network. OpenVPN uses UDP port 1194 by default. Configure your router to [port-forward][9] traffic for your public VPN IP Address on UDP port 1194 to UDP port 1194 on your OpenVPN server. If you decide to use a different UDP port, adjust the port number accordingly.
|
||||
|
||||
### Get ready for the next step
|
||||
|
||||
In this article, you installed and configured an operating system on your server, which is approximately half the battle. In the next article, you'll tackle installing and configuring OpenVPN itself. In the meantime, get familiar with your router and make sure you can reach your server from the outside world. But be sure to close the port forwarding after testing until your VPN is up and running.
|
||||
|
||||
* * *
|
||||
|
||||
_Parts of this article were adapted from D. Greg Scott's [blog][10] and have been republished with permission._
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/21/8/openvpn-server-linux
|
||||
|
||||
作者:[D. Greg Scott][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/greg-scott
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/coffee_tea_laptop_computer_work_desk.png?itok=D5yMx_Dr (Person drinking a hot drink at the computer)
|
||||
[2]: https://openvpn.net/
|
||||
[3]: http://getfedora.org
|
||||
[4]: https://opensource.com/article/20/10/fedora-media-writer
|
||||
[5]: https://opensource.com/article/21/2/linux-installation
|
||||
[6]: https://www.redhat.com/sysadmin/secure-linux-network-firewall-cmd
|
||||
[7]: https://opensource.com/sites/default/files/uploads/reserved-ip.jpg (Router IP address settings)
|
||||
[8]: https://creativecommons.org/licenses/by-sa/4.0/
|
||||
[9]: https://opensource.com/article/20/9/firewall
|
||||
[10]: https://www.dgregscott.com/how-to-build-a-vpn-in-four-easy-steps-without-spending-one-penny/
|
||||
@ -0,0 +1,54 @@
|
||||
[#]: subject: (Use the Linux terminal to navigate throughout your computer)
|
||||
[#]: via: (https://opensource.com/article/21/8/navigate-linux-directories)
|
||||
[#]: author: (Seth Kenlon https://opensource.com/users/seth)
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (piaoshi)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
|
||||
Use the Linux terminal to navigate throughout your computer
|
||||
======
|
||||
Learn to navigate from directory to directory in the Linux terminal.
|
||||
![Move around your computer][1]
|
||||
|
||||
To navigate through the directories of your computer in a graphical interface, you're probably used to opening a window to get "into" your computer, and then double-clicking on a folder, and then on a subfolder, and so on. You may also use arrow buttons or keys to back track.
|
||||
|
||||
To navigate through your computer in the terminal, you use the **cd** command. You can use **cd ..** to move one directory _back_, or **cd ./path/to/another/folder** to jump through many folders into a specific location.
|
||||
|
||||
The concept of a URL, which you use on the Internet already, is actually pulled directly from [POSIX][2]. When you navigate to a specific page on some website, like `http://www.example.com/tutorials/lesson2.html`, you are actually changing directory to `/var/www/imaginarysite/tutorials/` and opening a file called `lesson2.html`. Of course, you open it in a web browser, which interprets all that weird-looking HTML code into pretty text and pictures. But the idea is exactly the same.
|
||||
|
||||
If you think of your computer as the Internet (or the Internet as a computer, more appropriately), then you can understand how to wander through your folders and files. If you start out in your user folder (your home, or `~` for short) then everywhere you want to go is relative to that:
|
||||
|
||||
|
||||
```
|
||||
$ cd ~/Documents
|
||||
$ pwd
|
||||
/home/tux/Documents
|
||||
|
||||
$ cd ..
|
||||
$ pwd
|
||||
/home/tux
|
||||
```
|
||||
|
||||
This requires some practise, but after a while it becomes far faster than opening and closing windows, clicking on back buttons and folder icons.
|
||||
|
||||
### Auto-completion with Tab
|
||||
|
||||
The **Tab** key on your keyboard auto-completes names of directories and files you're starting to type. If you're going to **cd** into `~/Documents`, then all you need to type is `cd ~/Doc` and then press **Tab**. Your shell auto-completes `uments`. This isn't just a pleasant convenience, it's also a way to prevent error. If you're pressing **Tab** and nothing's being auto-completed, then probably the file or directory you _think_ is in a location isn't actually there. Even experienced Linux users try to change directory to a place that doesn't exist in their current location, so use **pwd** and **ls** often to confirm you are where you think you are, and that your current directory actually contains the files you think it contains.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/21/8/navigate-linux-directories
|
||||
|
||||
作者:[Seth Kenlon][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/seth
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/ch01s04.svg_.png?itok=bC8Bcapk (Move around your computer)
|
||||
[2]: https://opensource.com/article/19/7/what-posix-richard-stallman-explains
|
||||
@ -0,0 +1,89 @@
|
||||
[#]: subject: "Apps for daily needs part 3: image editors"
|
||||
[#]: via: "https://fedoramagazine.org/apps-for-daily-needs-part-3-image-editors/"
|
||||
[#]: author: "Arman Arisman https://fedoramagazine.org/author/armanwu/"
|
||||
[#]: collector: "lujun9972"
|
||||
[#]: translator: " "
|
||||
[#]: reviewer: " "
|
||||
[#]: publisher: " "
|
||||
[#]: url: " "
|
||||
|
||||
Apps for daily needs part 3: image editors
|
||||
======
|
||||
|
||||
![][1]
|
||||
|
||||
Photo by [Brooke Cagle][2] on [Unsplash][3]
|
||||
|
||||
Image editors are applications that are liked and needed by many people, from professional designers, students, or for those who have certain hobbies. Especially in this digital era, more and more people need image editors for various reasons. This article will introduce some of the open source image editors that you can use on Fedora Linux. You may need to install the software mentioned. If you are unfamiliar with how to add software packages in Fedora Linux, see my earlier article [Things to do after installing Fedora 34 Workstation][4]. Here is a list of a few apps for daily needs in the image editors category.
|
||||
|
||||
### GIMP
|
||||
|
||||
GIMP (GNU Image Manipulation Program) is a raster graphics editor used for photo retouching, image composition, and image authoring. It has almost the same functionality as Adobe Photoshop. You can use GIMP to do a lot of the things you can do with Photoshop. Because of that, GIMP has become the most popular application as an open source alternative to Adobe Photoshop.
|
||||
|
||||
GIMP has a lot of features for manipulating images, especially for raster images. You can fix or change the color of your photos using GIMP. You can select a part of the image, crop it, and then merge it with other pieces of the image. GIMP also has many effects that you can apply to your images, including blur, shadow, noise, etc. Many people use GIMP to repair damaged photos, improve image quality, crop unwanted parts of images, create posters and various graphic design works, and much more. Moreover you can also add plugins and scripts in GIMP, making it even more fully featured.
|
||||
|
||||
![][5]
|
||||
|
||||
More information is available at this link: <https://www.gimp.org/>
|
||||
|
||||
* * *
|
||||
|
||||
### Inkscape
|
||||
|
||||
Inkscape is a popular open source application used to create and edit vector graphics. It is a feature-rich vector graphics editor which makes it competitive with other similar proprietary applications, such as Adobe Illustrator and Corel Draw. Because of that, many professional illustrators use it to create vector-based artwork.
|
||||
|
||||
You can use Inkscape for making artistic and technical illustrations, such as logos, diagrams, icons, desktop wallpapers, flowcharts, cartoons, and much more. Moreover, Inkscape can handle various graphic file formats. In addition, you can also add add-ons to make your work easier.
|
||||
|
||||
![][6]
|
||||
|
||||
More information is available at this link: <https://inkscape.org/>
|
||||
|
||||
* * *
|
||||
|
||||
### Krita
|
||||
|
||||
Krita looks like GIMP or Inkscape at first glance. But actually it is an application that is quite different, although it has some similar functions. Krita is an application for creating digital paintings like those made by artists. You can use Krita for making concept art, illustration, comics, texture, and matte paintings.
|
||||
|
||||
Krita has over 100 professionally made brushes that come preloaded. It also has a brush stabilizer feature with 3 different ways to smooth and stabilize your brush strokes. Moreover, you can customize your brushes with over 9 unique brush engines. Krita is the right application for those of you who like digital painting activities.
|
||||
|
||||
![][7]
|
||||
|
||||
More information is available at this link: <https://krita.org/en/>
|
||||
|
||||
* * *
|
||||
|
||||
### darktable
|
||||
|
||||
darktable is perfect for photographers or for those who want to improve the quality of their photos. darktable focuses more on image editing specifically on non-destructive post-production of raw images. Therefore, it provides professional color management that supports automatic display profile detection. In addition, you can also use darktable to handle multiple images with filtering and sorting features. So you can search your collections by tags, rating, color labels, and many more. It can import various image formats, such as JPEG, CR2, NEF, HDR, PFM, RAF, etc.
|
||||
|
||||
![][8]
|
||||
|
||||
More information is available at this link: <https://www.darktable.org/>
|
||||
|
||||
* * *
|
||||
|
||||
### Conclusion
|
||||
|
||||
This article presented four image editors as apps for your daily needs that you can use on Fedora Linux. Each application represents a sub-category of image editor applications. Actually there are many other image editors that you can use in Fedora Linux. You can also use RawTherapee or Photivo as a dartkable alternative. In addition there is Pinta as an alternative to GIMP, and MyPaint as an alternative to Krita. Hopefully this article can help you to choose the right image editors. If you have experience in using these applications, please share your experience in the comments.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://fedoramagazine.org/apps-for-daily-needs-part-3-image-editors/
|
||||
|
||||
作者:[Arman Arisman][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://fedoramagazine.org/author/armanwu/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://fedoramagazine.org/wp-content/uploads/2021/07/FedoraMagz-Apps-3-Graphics-816x345.jpg
|
||||
[2]: https://unsplash.com/@brookecagle?utm_source=unsplash&utm_medium=referral&utm_content=creditCopyText
|
||||
[3]: https://unsplash.com/s/photos/meeting-on-cafe-computer?utm_source=unsplash&utm_medium=referral&utm_content=creditCopyText
|
||||
[4]: https://fedoramagazine.org/things-to-do-after-installing-fedora-34-workstation/
|
||||
[5]: https://fedoramagazine.org/wp-content/uploads/2021/07/image-gimp-1024x576.png
|
||||
[6]: https://fedoramagazine.org/wp-content/uploads/2021/07/image-inkscape-1024x575.png
|
||||
[7]: https://fedoramagazine.org/wp-content/uploads/2021/07/image-krita-1024x592.png
|
||||
[8]: https://fedoramagazine.org/wp-content/uploads/2021/07/image-darktable-1024x583.png
|
||||
194
sources/tech/20210804 Install OpenVPN on your Linux PC.md
Normal file
194
sources/tech/20210804 Install OpenVPN on your Linux PC.md
Normal file
@ -0,0 +1,194 @@
|
||||
[#]: subject: "Install OpenVPN on your Linux PC"
|
||||
[#]: via: "https://opensource.com/article/21/7/openvpn-router"
|
||||
[#]: author: "D. Greg Scott https://opensource.com/users/greg-scott"
|
||||
[#]: collector: "lujun9972"
|
||||
[#]: translator: " "
|
||||
[#]: reviewer: " "
|
||||
[#]: publisher: " "
|
||||
[#]: url: " "
|
||||
|
||||
Install OpenVPN on your Linux PC
|
||||
======
|
||||
After setting up a VPN server, the next step is installing and
|
||||
configuring OpenVPN.
|
||||
![Open ethernet cords.][1]
|
||||
|
||||
OpenVPN creates an encrypted tunnel between two points, preventing a third party from accessing your network traffic. By setting up your virtual private network (VPN) server, you become your own VPN provider. Many popular VPN services already use [OpenVPN][2], so why tie your connection to a specific provider when you can have complete control?
|
||||
|
||||
The [first article][3] in this series demonstrated how to set up and configure a Linux PC to serve as your OpenVPN server. It also discussed how to configure your router so that you can reach your VPN server from an outside network.
|
||||
|
||||
This second article demonstrates how to install the OpenVPN server software using steps customized from the [OpenVPN wiki][4].
|
||||
|
||||
### Install OpenVPN
|
||||
|
||||
First, install OpenVPN and the `easy-rsa` application (to help you set up authentication on your server) using your package manager. This example uses Fedora Linux; if you've chosen something different, use the appropriate command for your distribution:
|
||||
|
||||
|
||||
```
|
||||
`$ sudo dnf install openvpn easy-rsa`
|
||||
```
|
||||
|
||||
This creates some empty directories:
|
||||
|
||||
* `/etc/openvpn`
|
||||
* `/etc/openvpn/client`
|
||||
* `/etc/openvpn/server`
|
||||
|
||||
|
||||
|
||||
If these aren't created during installation, create them manually.
|
||||
|
||||
### Set up authentication
|
||||
|
||||
OpenVPN depends on the `easy-rsa` scripts and should have its own copy of them. Copy the `easy-rsa` scripts and files:
|
||||
|
||||
|
||||
```
|
||||
$ sudo mkdir /etc/openvpn/easy-rsa
|
||||
$ sudo cp -rai /usr/share/easy-rsa/3/* \
|
||||
/etc/openvpn/easy-rsa/
|
||||
```
|
||||
|
||||
Authentication is important, and OpenVPN takes it very seriously. The theory is that if Alice needs to access private information inside Bob's company, it's vital that Bob makes sure Alice really is Alice. Likewise, Alice must make sure that Bob is really Bob. We call this mutual authentication.
|
||||
|
||||
Today's best practice checks an attribute from two of three possible factors:
|
||||
|
||||
* Something you have
|
||||
* Something you know
|
||||
* Something you are
|
||||
|
||||
|
||||
|
||||
There are lots of choices. This OpenVPN setup uses:
|
||||
|
||||
* **Certificates:** Something both the client and server have
|
||||
* **Certificate password:** Something the people know
|
||||
|
||||
|
||||
|
||||
Alice and Bob need help to mutually authenticate. Since they both trust Cathy, Cathy takes on a role called **certificate authority** (CA). Cathy attests that Alice and Bob both are who they claim to be. Because Alice and Bob both trust Cathy, now they also trust each other.
|
||||
|
||||
But what convinces Cathy that Alice and Bob really are Alice and Bob? Cathy's reputation in the community depends on getting this right, and so if she wants Danielle, Evan, Fiona, Greg, and others to also trust her, she will rigorously test Alice and Bob's claims. After Alice and Bob convince Cathy that they really are Alice and Bob, Cathy signs certificates for them to share with each other and the world.
|
||||
|
||||
How do Alice and Bob know Cathy—and not somebody impersonating her—signed the certificates? They use a technology called **public key cryptography:**
|
||||
|
||||
* Find a cryptography algorithm that encrypts with one key and decrypts with another.
|
||||
* Declare one key private and share the other key with the public.
|
||||
* Cathy shares her public key and a clear-text copy of her signature with the world.
|
||||
* Cathy encrypts her signature with her private key. Anyone can decrypt it with her public key.
|
||||
* If Cathy's decrypted signature matches the clear-text copy, Alice and Bob can trust Cathy really did sign it.
|
||||
|
||||
|
||||
|
||||
You use this same technology every time you buy goods and services online.
|
||||
|
||||
### Implement authentication
|
||||
|
||||
OpenVPN's [documentation][5] suggests setting up a CA on a separate system or at least a separate directory on the OpenVPN server. The documentation also suggests generating server and client certificates from the server and clients. Because this is a simple setup, you can use the OpenVPN server as its own CA and put the certificates and keys into specified directories on the server.
|
||||
|
||||
Generate certificates from the server and copy them to each client as part of client setup.
|
||||
|
||||
This implementation uses self-signed certificates. This works because the server trusts itself, and clients trust the server. Therefore, the server is the best CA to sign certificates.
|
||||
|
||||
From the OpenVPN server, set up the CA:
|
||||
|
||||
|
||||
```
|
||||
$ sudo mkdir /etc/openvpn/ca
|
||||
$ cd /etc/openvpn/ca
|
||||
$ sudo /etc/openvpn/easy-rsa/easyrsa init-pki
|
||||
$ sudo /etc/openvpn/easy-rsa/easyrsa build-ca
|
||||
```
|
||||
|
||||
Use an easy-to-remember but hard-to-guess passphrase.
|
||||
|
||||
Set up the server key pair and certificate request:
|
||||
|
||||
|
||||
```
|
||||
$ cd /etc/openvpn/server
|
||||
$ sudo /etc/openvpn/easy-rsa/easyrsa init-pki
|
||||
$ sudo /etc/openvpn/easy-rsa/easyrsa gen-req OVPNserver2020 nopass
|
||||
```
|
||||
|
||||
In this example, `OVPNServer2020` is whatever hostname you assigned your OpenVPN server in the first article in this series.
|
||||
|
||||
### Generate and sign certs
|
||||
|
||||
Now you must send a server request to the CA and generate and sign the server certificate.
|
||||
|
||||
This step essentially copies the request file from `/etc/openvpn/server/pki/reqs/OVPNserver2020.req` to `/etc/openvpn/ca/pki/reqs/OVPNserver2020.req` to prepare it for review and signing:
|
||||
|
||||
|
||||
```
|
||||
$ cd /etc/openvpn/ca
|
||||
$ sudo /etc/openvpn/easy-rsa/easyrsa \
|
||||
import-req /etc/openvpn/server/pki/reqs/OVPNserver2020.req OVPNserver2020
|
||||
```
|
||||
|
||||
### Review and sign the request
|
||||
|
||||
You've generated a request, so now you must review and sign the certs:
|
||||
|
||||
|
||||
```
|
||||
$ cd /etc/openvpn/ca
|
||||
$ sudo /etc/openvpn/easy-rsa/easyrsa \
|
||||
show-req OVPNserver2020
|
||||
```
|
||||
|
||||
Sign as the server:
|
||||
|
||||
|
||||
```
|
||||
$ cd /etc/openvpn/ca
|
||||
$ sudo /etc/openvpn/easy-rsa/easyrsa \
|
||||
sign-req server OVPNserver2020
|
||||
```
|
||||
|
||||
Put a copy of the server and CA certificates where they belong for the config file to pick them up:
|
||||
|
||||
|
||||
```
|
||||
$ sudo cp /etc/openvpn/ca/pki/issued/OVPNserver2020.crt \
|
||||
/etc/openvpn/server/pki/
|
||||
$ sudo cp /etc/openvpn/ca/pki/ca.crt \
|
||||
/etc/openvpn/server/pki/
|
||||
```
|
||||
|
||||
Next, generate [Diffie-Hellman][6] parameters so that clients and the server can exchange session keys:
|
||||
|
||||
|
||||
```
|
||||
$ cd /etc/openvpn/server
|
||||
$ sudo /etc/openvpn/easy-rsa/easyrsa gen-dh
|
||||
```
|
||||
|
||||
### Almost there
|
||||
|
||||
The next article in this series will demonstrate how to configure and start the OpenVPN server you just built.
|
||||
|
||||
* * *
|
||||
|
||||
_This article is based on D. Greg Scott's [blog][7] and is reused with permission._
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/21/7/openvpn-router
|
||||
|
||||
作者:[D. Greg Scott][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/greg-scott
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/openwires_fromRHT_520_0612LL.png?itok=PqZi55Ab (Open ethernet cords.)
|
||||
[2]: https://openvpn.net/
|
||||
[3]: https://opensource.com/article/21/7/vpn-openvpn-part-1
|
||||
[4]: https://community.openvpn.net/openvpn/wiki
|
||||
[5]: https://openvpn.net/community-resources/
|
||||
[6]: https://en.wikipedia.org/wiki/Diffie%E2%80%93Hellman_key_exchange
|
||||
[7]: https://www.dgregscott.com/how-to-build-a-vpn-in-four-easy-steps-without-spending-one-penny/
|
||||
52
sources/tech/20210804 Move files in the Linux terminal.md
Normal file
52
sources/tech/20210804 Move files in the Linux terminal.md
Normal file
@ -0,0 +1,52 @@
|
||||
[#]: subject: (Move files in the Linux terminal)
|
||||
[#]: via: (https://opensource.com/article/21/8/move-files-linux)
|
||||
[#]: author: (Seth Kenlon https://opensource.com/users/seth)
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
|
||||
Move files in the Linux terminal
|
||||
======
|
||||
Use the mv command to move a file from one location to another.
|
||||
![Moving files][1]
|
||||
|
||||
To move a file on a computer with a graphical interface, you open the folder where the file is currently located, and then open another window to the folder you want to move the file into. Finally, you drag and drop the file from one to the other.
|
||||
|
||||
To move a file in a terminal, you use the ** **mv** command to move a file from one location to another.
|
||||
|
||||
|
||||
```
|
||||
$ mv example.txt ~/Documents
|
||||
|
||||
$ ls ~/Documents
|
||||
example.txt
|
||||
```
|
||||
|
||||
In this example, you've moved **example.txt** from its current folder into the **Documents** folder.
|
||||
|
||||
As long as you know where you want to take a file _from_ and where you want to move it _to_, you can send files from any location to any location, no matter where you are. This can be a serious time saver compared to navigating through all the folders on your computer in a series of windows just to locate a file, and then opening a new window to where you want that file to go, and then dragging that file.
|
||||
|
||||
The **mv** command by default does exactly as it's told: it moves a file from one location to another. Should a file with the same name already exist in the destination location, it gets overwritten. To prevent a file from being overwritten without warning, use the **\--interactive** (or **-i** for short) option:
|
||||
|
||||
|
||||
```
|
||||
$ mv -i example.txt ~/Documents
|
||||
mv: overwrite '/home/tux/Documents/example.txt'?
|
||||
```
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/21/8/move-files-linux
|
||||
|
||||
作者:[Seth Kenlon][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/seth
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/ch01s05.svg_.png?itok=PgKQEDZ7 (Moving files)
|
||||
172
sources/tech/20210805 Configure your OpenVPN server on Linux.md
Normal file
172
sources/tech/20210805 Configure your OpenVPN server on Linux.md
Normal file
@ -0,0 +1,172 @@
|
||||
[#]: subject: "Configure your OpenVPN server on Linux"
|
||||
[#]: via: "https://opensource.com/article/21/7/openvpn-firewall"
|
||||
[#]: author: "D. Greg Scott https://opensource.com/users/greg-scott"
|
||||
[#]: collector: "lujun9972"
|
||||
[#]: translator: " "
|
||||
[#]: reviewer: " "
|
||||
[#]: publisher: " "
|
||||
[#]: url: " "
|
||||
|
||||
Configure your OpenVPN server on Linux
|
||||
======
|
||||
After you install OpenVPN, it's time to configure it.
|
||||
![Lock][1]
|
||||
|
||||
OpenVPN creates an encrypted tunnel between two points, preventing a third party from accessing your network traffic. By setting up your virtual private network (VPN) server, you become your own VPN provider. Many popular VPN services already use [OpenVPN][2], so why tie your connection to a specific provider when you can have complete control?
|
||||
|
||||
The [first article][3] in this series set up a server for your VPN, and the [second article][4] demonstrated how to install and configure the OpenVPN server software. This third article shows how to start OpenVPN with authentication in place.
|
||||
|
||||
To set up an OpenVPN server, you must:
|
||||
|
||||
* Create a configuration file.
|
||||
* Set the `sysctl` value `net.ipv4.ip_forward = 1` to enable routing.
|
||||
* Set up appropriate ownership for all configuration and authentication files to run the OpenVPN server daemon under a non-root account.
|
||||
* Set OpenVPN to start with the appropriate configuration file.
|
||||
* Configure your firewall.
|
||||
|
||||
|
||||
|
||||
### Configuration file
|
||||
|
||||
You must create a server config file in `/etc/openvpn/server/`. You can start from scratch if you want, and OpenVPN includes several sample configuration files to use as a starting point. Have a look in `/usr/share/doc/openvpn/sample/sample-config-files/` to see them all.
|
||||
|
||||
If you want to build a config file by hand, start with either `server.conf` or `roadwarrior-server.conf` (as appropriate), and place your config file in `/etc/openvpn/server`. Both files are extensively commented, so read the comments and decide which makes the most sense for your situation.
|
||||
|
||||
You can save time and aggravation by using my prebuilt server and client configuration file templates and `sysctl` file to turn on network routing. This configuration also includes customization to log connects and disconnects. It keeps logs on the OpenVPN server in `/etc/openvpn/server/logs`.
|
||||
|
||||
If you use my templates, you'll need to edit them to use your IP addresses and hostnames.
|
||||
|
||||
To use my prebuilt config templates, scripts, and `sysctl` to turn on IP forwarding, download my script:
|
||||
|
||||
|
||||
```
|
||||
$ curl \
|
||||
<https://www.dgregscott.com/ovpn/OVPNdownloads.sh> > \
|
||||
OVPNdownloads.sh
|
||||
```
|
||||
|
||||
Read the script to get an idea of what it does. Here's a quick overview of its actions:
|
||||
|
||||
* Creates the appropriate directories on your OpenVPN server
|
||||
* Downloads server and client config file templates from my website
|
||||
* Downloads my custom scripts and places them into the correct directory with correct permissions
|
||||
* Downloads `99-ipforward.conf` and places it into `/etc/sysctl.d` to turn on IP forwarding at the next boot
|
||||
* Sets up ownership for everything in `/etc/openvpn`
|
||||
|
||||
|
||||
|
||||
Once you're satisfied that you understand what the script does, make it executable and run it:
|
||||
|
||||
|
||||
```
|
||||
$ chmod +x OVPNdownloads.sh
|
||||
$ sudo ./OVPNdownloads.sh
|
||||
```
|
||||
|
||||
Here are the files it copies (notice the file ownership):
|
||||
|
||||
|
||||
```
|
||||
$ ls -al -R /etc/openvpn
|
||||
/etc/openvpn:
|
||||
total 12
|
||||
drwxr-xr-x. 4 openvpn openvpn 34 Apr 6 20:35 .
|
||||
drwxr-xr-x. 139 root root 8192 Apr 6 20:35 ..
|
||||
drwxr-xr-x. 2 openvpn openvpn 33 Apr 6 20:35 client
|
||||
drwxr-xr-x. 4 openvpn openvpn 56 Apr 6 20:35 server
|
||||
|
||||
/etc/openvpn/client:
|
||||
total 4
|
||||
drwxr-xr-x. 2 openvpn openvpn 33 Apr 6 20:35 .
|
||||
drwxr-xr-x. 4 openvpn openvpn 34 Apr 6 20:35 ..
|
||||
-rw-r--r--. 1 openvpn openvpn 1764 Apr 6 20:35 OVPNclient2020.ovpn
|
||||
|
||||
/etc/openvpn/server:
|
||||
total 4
|
||||
drwxr-xr-x. 4 openvpn openvpn 56 Apr 6 20:35 .
|
||||
drwxr-xr-x. 4 openvpn openvpn 34 Apr 6 20:35 ..
|
||||
drwxr-xr-x. 2 openvpn openvpn 59 Apr 6 20:35 ccd
|
||||
drwxr-xr-x. 2 openvpn openvpn 6 Apr 6 20:35 logs
|
||||
-rw-r--r--. 1 openvpn openvpn 2588 Apr 6 20:35 OVPNserver2020.conf
|
||||
|
||||
/etc/openvpn/server/ccd:
|
||||
total 8
|
||||
drwxr-xr-x. 2 openvpn openvpn 59 Apr 6 20:35 .
|
||||
drwxr-xr-x. 4 openvpn openvpn 56 Apr 6 20:35 ..
|
||||
-rwxr-xr-x. 1 openvpn openvpn 917 Apr 6 20:35 client-connect.sh
|
||||
-rwxr-xr-x. 1 openvpn openvpn 990 Apr 6 20:35 client-disconnect.sh
|
||||
|
||||
/etc/openvpn/server/logs:
|
||||
total 0
|
||||
drwxr-xr-x. 2 openvpn openvpn 6 Apr 6 20:35 .
|
||||
drwxr-xr-x. 4 openvpn openvpn 56 Apr 6 20:35 ..
|
||||
```
|
||||
|
||||
Here's the `99-ipforward.conf` file:
|
||||
|
||||
|
||||
```
|
||||
# Turn on IP forwarding. OpenVPN servers need to do routing
|
||||
net.ipv4.ip_forward = 1
|
||||
```
|
||||
|
||||
Edit `OVPNserver2020.conf` and `OVPNclient2020.ovpn` to include your IP addresses. Also, edit `OVPNserver2020.conf` to include your server certificate names from earlier. Later, you will rename and edit a copy of `OVPNclient2020.ovpn` for use with your client computers. The blocks that start with `***?` show you where to edit.
|
||||
|
||||
### File ownership
|
||||
|
||||
If you used the automated script from my website, file ownership is already in place. If not, you must ensure that your system has a user called `openvpn` that is a member of a group named `openvpn`. You must set the ownership of everything in `/etc/openvpn` to that user and group. It's safe to do this if you're unsure whether the user and group already exist because `useradd` will refuse to create a user with the same name as one that already exists:
|
||||
|
||||
|
||||
```
|
||||
$ sudo useradd openvpn
|
||||
$ sudo chown -R openvpn.openvpn /etc/openvpn
|
||||
```
|
||||
|
||||
### Firewall
|
||||
|
||||
If you decided not to disable the firewalld service in step 1, then your server's firewall service might not allow VPN traffic by default. Using the [`firewall-cmd` command][5], you can enable the OpenVPN service, which opens the necessary ports and routes traffic as necessary:
|
||||
|
||||
|
||||
```
|
||||
$ sudo firewall-cmd --add-service openvpn --permanent
|
||||
$ sudo firewall-cmd --reload
|
||||
```
|
||||
|
||||
No need to get lost in a maze of iptables!
|
||||
|
||||
### Start your server
|
||||
|
||||
You can now start your OpenVPN server. So that it starts automatically after a reboot, use the `enable` subcommand of `systemctl`:
|
||||
|
||||
|
||||
```
|
||||
`systemctl enable --now openvpn-server@OVPNserver2020.service`
|
||||
```
|
||||
|
||||
### Final steps
|
||||
|
||||
The fourth and final article in this article will demonstrate how to set up clients to connect to your OpenVPN from afar.
|
||||
|
||||
* * *
|
||||
|
||||
_This article is based on D. Greg Scott's [blog][6] and is reused with permission._
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/21/7/openvpn-firewall
|
||||
|
||||
作者:[D. Greg Scott][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/greg-scott
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/security-lock-password.jpg?itok=KJMdkKum (Lock)
|
||||
[2]: https://openvpn.net/
|
||||
[3]: https://opensource.com/article/21/7/vpn-openvpn-part-1
|
||||
[4]: https://opensource.com/article/21/7/vpn-openvpn-part-2
|
||||
[5]: https://www.redhat.com/sysadmin/secure-linux-network-firewall-cmd
|
||||
[6]: https://www.dgregscott.com/how-to-build-a-vpn-in-four-easy-steps-without-spending-one-penny/
|
||||
@ -0,0 +1,189 @@
|
||||
[#]: subject: "Installing Packages From External Repositories in Ubuntu [Explained]"
|
||||
[#]: via: "https://itsfoss.com/adding-external-repositories-ubuntu/"
|
||||
[#]: author: "Abhishek Prakash https://itsfoss.com/author/abhishek/"
|
||||
[#]: collector: "lujun9972"
|
||||
[#]: translator: " "
|
||||
[#]: reviewer: " "
|
||||
[#]: publisher: " "
|
||||
[#]: url: " "
|
||||
|
||||
Installing Packages From External Repositories in Ubuntu [Explained]
|
||||
======
|
||||
|
||||
You have some ideas about installing packages in Ubuntu with apt command. Those packages come from Ubuntu’s repositories.
|
||||
|
||||
How about third-party or external repository? No, I am not talking about PPA here.
|
||||
|
||||
Sooner or later, you’ll come across installation instructions that goes in at least four lines. You install something called ‘apt-transport-https’ and then do something with gpg and sources list. After that, you install the package.
|
||||
|
||||
Can’t recall completely. Let me share an example for [installing the latest version Yarn on Ubuntu][1]:
|
||||
|
||||
```
|
||||
sudo apt install apt-transport-https curl
|
||||
curl -sS https://dl.yarnpkg.com/debian/pubkey.gpg | sudo apt-key add -
|
||||
sudo sh -c 'echo "deb https://dl.yarnpkg.com/debian/ stable main" >> /etc/apt/sources.list.d/yarn.list'
|
||||
sudo apt update && sudo apt install yarn
|
||||
```
|
||||
|
||||
You’ll often come across such installation method while installing programming tools directly from the developers.
|
||||
|
||||
Many people just follow the instructions without thinking twice about what’s going on here. Nothing wrong with that but knowing the process actually improves your knowledge on the matter and could also help in troubleshooting.
|
||||
|
||||
Let me explain the logic behind those lines.
|
||||
|
||||
### Understanding the procedure of installation from external repositories
|
||||
|
||||
Before you proceed, I highly recommend reading these two articles so that things are a bit more clear to you:
|
||||
|
||||
* [Concept of repositories in Ubuntu][2]
|
||||
* [Concept of PPA in Ubuntu][3]
|
||||
|
||||
|
||||
|
||||
To recall quickly, here’s a visual representation of repositories and [package manager in Linux][4].
|
||||
|
||||
![Illustration of repository and package manager][5]
|
||||
|
||||
The entire idea here is that you add a new, external repository to your system. This way, you’ll be able to download and install packages available from this new repository. If the repository provides an update on the package version, you get to update the installed package along with the system updates (apt update && apt upgrade).
|
||||
|
||||
So, how does this work? Let’s go through the lines one by one.
|
||||
|
||||
#### Part 1: Getting HTTPS support for apt
|
||||
|
||||
The first line is this:
|
||||
|
||||
```
|
||||
sudo apt install apt-transport-https curl
|
||||
```
|
||||
|
||||
Curl is a [tool for downloading files in Linux terminal][6]. The main part here is the installation of **apt-transport-https** and frankly speaking not needed anymore.
|
||||
|
||||
Confused? This apt-transport-https package allows your system to access repositories over the secure HTTPS protocol. By design, Ubuntu repositories use http, not https.
|
||||
|
||||
Take a look at the screenshot below. The https ones are the external repositories I have added into my system. Ubuntu repositories and PPA use http.
|
||||
|
||||
![][7]
|
||||
|
||||
In the older version of apt package manager, https support was not included. apt-transport-https package adds https support to apt. To add a repository that uses https, this package is installed first.
|
||||
|
||||
Did I not say it is not needed anymore? Yes because the newer versions of apt (higher than 1.5) support https and thus you do not need to install apt-transport-https anymore.
|
||||
|
||||
And yet you see this package mentioned in the instructions. This is more for legacy reasons or for really old distribution versions that might be using an older version of apt.
|
||||
|
||||
Now, you may wonder why Ubuntu repositories use http, not https when https is the secure protocol. Is it not a security risk? The next segment will answer that question.
|
||||
|
||||
#### Part 2: Adding GPG key of the remote repository
|
||||
|
||||
Linux repositories have this built-in GPG-key based security mechanism. Every repository added its public GPG key to your system’s trusted keys. The packages from the repositories are ‘signed’ by this GPG key and thanks to the stored public key, your system verifies that the package is coming from the repository.
|
||||
|
||||
If there is a [mismatch between the keys, your system will throw an error][8] instead of installing or updating packages from the said repository.
|
||||
|
||||
So far, so good. The next step is to add the public GPG key of the external repository to your Linux system so that it trusts the package from this repository.
|
||||
|
||||
```
|
||||
curl -sS https://dl.yarnpkg.com/debian/pubkey.gpg | sudo apt-key add -
|
||||
```
|
||||
|
||||
In the above command, you download the GPG key from the given URL using curl. The option `sS` ensures that you don’t see the flooded output (silent mode) but shows the error (if any). The last `-` tells apt-key to take stdin instead of a file (which is the output of the curl command in this case).
|
||||
|
||||
The download key is added to the system with `apt-key add` command.
|
||||
|
||||
You can see the GPG keys added by various repositories in your system using the `apt-key list` command.
|
||||
|
||||
![List GPG keys][9]
|
||||
|
||||
That’s one way of adding the GPG key to the system. You’ll some other commands that my look slightly different but do the same job of adding the public key of the repository to your system.
|
||||
|
||||
```
|
||||
sudo apt-key adv --keyserver keyserver.ubuntu.com --recv-keys E298A3A825C0D65DFD57CBB651716619E084DAB9
|
||||
```
|
||||
|
||||
You’ll notice a warning that apt-key is deprecated. You could still use apt-key command till Ubuntu 22.04 but it will eventually be removed. Let’s not worry about it at the moment.
|
||||
|
||||
#### Part 3: Adding the external repository to your sources list
|
||||
|
||||
The next command adds a new entry into the sources list of your system. This way, your system will know that it has to check this repository for packages and updates.
|
||||
|
||||
```
|
||||
sudo sh -c 'echo "deb https://dl.yarnpkg.com/debian/ stable main" >> /etc/apt/sources.list.d/yarn.list'
|
||||
```
|
||||
|
||||
There is a file /etc/apt/sources.list that contains the details of the Ubuntu repositories. This file should not be touched. All the additional repositories should be placed in their own respective file (ending with .list convention) in the /etc/apt/sources.list.d directory.
|
||||
|
||||
![External repository should have their own sources list file in the /etc/apt/sources.list.d directory][10]
|
||||
|
||||
This makes package management easier. If you are removing a repository from the system, you just need to delete the corresponding sources file. No need to mess with the main sources.list file.
|
||||
|
||||
Let’s look at the command in a bit more detail.
|
||||
|
||||
```
|
||||
sudo sh -c 'echo "deb https://dl.yarnpkg.com/debian/ stable main" >> /etc/apt/sources.list.d/yarn.list'
|
||||
```
|
||||
|
||||
With sh, you are asking to run the command in a new shell, instead of the [subshell][11]. `-c` option tells the sh command to read the commands from the operand instead of standard input. Then it runs the echo command which basically adds line **deb <https://dl.yarnpkg.com/debian/> stable main** to /etc/apt/sources.list.d/yarn.list file (file will be created)
|
||||
|
||||
Now, there could be numerous ways you can create a .list file in the specified directory and add the line with repository details in it. You could use it like this as well:
|
||||
|
||||
```
|
||||
echo "deb https://dl.yarnpkg.com/debian/ stable main" | sudo tee /etc/apt/sources.list.d/yarn.list
|
||||
```
|
||||
|
||||
You get the gist, right?
|
||||
|
||||
#### Part 4: Installing the application from newly added repository
|
||||
|
||||
So far, you have added the GPG key of the repository and the URL of the repository to the system.
|
||||
|
||||
But your system still does not know about the package available from this new repository. This is why you need to update the local cache of package metadata first with this command:
|
||||
|
||||
```
|
||||
sudo apt update
|
||||
```
|
||||
|
||||
Your system will have the information about the packages available from the newly added repository and you can install the package now:
|
||||
|
||||
```
|
||||
sudo apt install yarn
|
||||
```
|
||||
|
||||
To save time, you can [run the two commands one after another in a single lin][12]e.
|
||||
|
||||
```
|
||||
sudo apt update && sudo apt install yarn
|
||||
```
|
||||
|
||||
The `&&` ensures that the second command only runs when the previous command completed without any error.
|
||||
|
||||
And thus the process completes.
|
||||
|
||||
### Did it make things clear or confused you even more?
|
||||
|
||||
I explained the logic behind the steps for using external repositories in Ubuntu. I hope you have a better understanding of the topic now, but it is also possible that too much detail could be confusing.
|
||||
|
||||
If things are still not clear or if you have additional questions, please let me know. If you notice technical inaccuracies, please let me know in the comment section.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://itsfoss.com/adding-external-repositories-ubuntu/
|
||||
|
||||
作者:[Abhishek Prakash][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://itsfoss.com/author/abhishek/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://itsfoss.com/install-yarn-ubuntu/
|
||||
[2]: https://itsfoss.com/ubuntu-repositories/
|
||||
[3]: https://itsfoss.com/ppa-guide/#comments
|
||||
[4]: https://itsfoss.com/package-manager/
|
||||
[5]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2020/10/linux-package-manager-explanation.png?resize=800%2C450&ssl=1
|
||||
[6]: https://itsfoss.com/download-files-from-linux-terminal/
|
||||
[7]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2021/08/apt-update-http-https.png?resize=800%2C527&ssl=1
|
||||
[8]: https://itsfoss.com/solve-gpg-error-signatures-verified-ubuntu/
|
||||
[9]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2021/07/list-apt-key-gpg-ubuntu.png?resize=800%2C547&ssl=1
|
||||
[10]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2021/08/sources-list-ubuntu.png?resize=800%2C313&ssl=1
|
||||
[11]: https://linuxhandbook.com/subshell/
|
||||
[12]: https://itsfoss.com/run-multiple-commands-linux/
|
||||
@ -1,136 +0,0 @@
|
||||
[#]: subject: (How the ARPANET Protocols Worked)
|
||||
[#]: via: (https://twobithistory.org/2021/03/08/arpanet-protocols.html)
|
||||
[#]: author: (Two-Bit History https://twobithistory.org)
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (Lin-vy)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
|
||||
|
||||
ARPANET 协议是如何工作的
|
||||
======
|
||||
|
||||
ARPANET 通过证明可以使用标准化协议连接完全不同的制造商的计算机,永远改变了计算。 在我的[关于 ARPANET 的历史意义的帖子][1]中,我提到了其中的一些协议,但没有详细描述它们。所以我想仔细看看它们。也想看看那些早期协议的设计有多少保留到了我们今天使用的协议中。
|
||||
|
||||
ARPANET 协议像我们现代的互联网协议,是通过分层形式来组织的。[1][2] 较高层协议运行在较低层协议之上。如今的 TCP/IP 套件有 5 层(物理层、链路层、网络层、传输层、以及应用层),但是这个 ARPANET 仅有 3 层或者可能 4 层,这取决于你怎样计算它们。
|
||||
|
||||
我将会解释每一层是如何工作的,但首先,你需要知道谁在 ARPANET 中是构建了些什么,以及还需要了解为什么要分层。
|
||||
|
||||
### 短暂的历史背景
|
||||
|
||||
ARPANET 由美国联邦政府资助,确切的说是位于美国国防部的高级研究计划属(因此命名为 “ ARPANET ” )。美国政府并没有直接建设这个网络;而是,把这项工作外包给了位于波士顿的一家名为 Bolt, Beranek, and Newman, 的咨询公司,通常更多时候被称为 BBN。
|
||||
|
||||
相反, BBN 承担了实现这个网络的大部分任务,但不是全部。 BBN 所做的是设计和维护一台称为接口消息处理机或简称 IMP 的机器。这个 IMP 是一种定制的 Honeywell 小型计算机,它们被分配给那些想要接入这个 ARPANET 的遍及全国各地的各个站点。它们充当通往 ARPANET 的网关为每个站点提供多达四台主机的连接支持。它基本上是一台路由器。BBN 能控制在 IMP 上运行的软件,把数据包从一个 IMP 转发到另一个 IMP ,但是该公司无法直接控制那些将要连接到 IMP 上并且成为 ARPANET 网络中实际主机的机器。
|
||||
|
||||
那些主机被网络中作为终端用户的计算机科学家们所控制。位于遍及全国各地的主机站点中的这些计算机科学家们,他们负责编写允许主机之间相互通信的软件。而 IMP 赋予主机之间互相发送消息的能力,但是那并没有多大用处除非主机之间能商定一种用于消息的格式。为了解决这个问题,一群杂七杂八的人员组成了网络工作组,其中有大部分是来自各个站点的研究生,该组力求指定主机计算机使用的协议。
|
||||
|
||||
因此,如果你设想通过 ARPANET 进行一次成功的网络互动,(例如发送一封电子邮件),使这些互动成功的一些工程由一组人负责(BBN),然而其他的一些工程则由另一组人负责(网络工作组和在每个站点的工程师们)。这种有组织,有保障的情景或许对推动采用分层的方法来管理 ARPANET 网络中的协议起到很大的作用,这反过来又影响了TCP/IP的分层方式。
|
||||
|
||||
|
||||
### 好的,回到协议上来
|
||||
|
||||
![ARPANET Network Stack][3] _ARPANET 协议层次结构_
|
||||
|
||||
协议层被组织成一个层次结构,在最底部是 “ level 0. ” [2][4] 这在某种意义上是不算数的,因为在 ARPANET 中这层完全由 BBN 控制,所以不需要标准协议。level 0 的作用是管理数据在 IMP 之间如何传输。在 BBN 内部,有管理 IMP 如何做到这一点的规则;在 BBN 之外,IMP 子网是一个黑匣子,它只会传送你提供的任意数据。因此,level 0 是一个没有真正协议的层,就公开已知和商定的规则集而言,它的存在可以被运行在 ARPANET 的主机上的软件忽略。粗略地说,它处理相当于当今使用的 TCP/IP 套件的物理层、链路层和网络层下的所有内容,甚至还包括相当多的传输层,这是我将在这篇文章的末尾回来讨论的内容。
|
||||
|
||||
“ level 1 ” 层在 ARPANET 的主机和它们所连接的 IMP 之间建立了接口。如果你愿意可以认为它是为 BBN 构建的 “ level 0 ” 层的黑匣子使用的一个应用程序接口。 当时它也被称为 IMP-Host 协议。 必须编写和发布该协议,因为在首次建立 ARPANET 网络时,每个主机站点都必须编写自己的软件来与 IMP 连接。 除非 BBN 给他们一些指导,否则他们不会知道如何做到这一点。
|
||||
|
||||
BBN 在一份名为 [BBN Report 1822][5] 的冗长文件中指定了 IMP-Host 协议。 随着 ARPANET 的发展,该文件多次被修订; 我将在这里大致描述 IMP-Host 协议最初设计时的工作方式。 根据 BBN 的规则,主机可以将长度不超过 8095 位的消息传递给它们的 IMP,并且每条消息都有一个包含目标主机号和链路识别号的头部字段。[3][6] IMP 将检查指定的主机号,然后尽职尽责地将消息转发到网络中。 当从远端主机接收到消息时,接收 IMP 在将消息传递给本地主机之前会把目标主机号替换为源主机号。 实际上在 IMP 之间传递的内容并不是消息——IMP 将消息分解成更小的数据包以便通过网络传输——但该细节对主机来说是不可见的。
|
||||
|
||||
|
||||
![1969 Host-IMP Leader][7]_Host-IMP 消息头部格式, 截至 1969. 图标来自 [BBN Report 1763][8]_
|
||||
|
||||
链路号的取值范围为 0 到 255 ,它有两个作用。一是更高级别的协议可以利用它在网络上的任何两台主机之间建立多个通信信道,因为可以想象得到,在任何时刻都有可能存在多个本地用户与同一个目标主机进行通信的场景(换句话说,链路号允许在主机之间进行多路通信。)二是它也被用在 “ level 1 ” 层去控制主机之间发送的大量流量,以防止高性能计算机压制低性能计算机的情况出现。按照最初的设计,这个 IMP-Host 协议限制每台主机在某一时刻通过某条链路仅发送一条消息。一旦某台主机沿着某条链路发送了一条消息给远端主机后,在它沿着该链路发送下一条消息之前,必须等待接收一条来自远端的 IMP 的特别类型的消息,叫做 RFNM(请求下一条消息)。针对这个体系的后期修订,为了改善它的性能,允许一台主机在给定的时刻传送多达8条消息给另一台主机。.[4][9]
|
||||
|
||||
“ level 2 ” 层才是事情真正开始变得有趣的地方,因为这一层和在它上面的那一层由 BBN 和国防部全部留给学者们和网络工作组自己去研发。 “ level 2 ” 层包括了 Host-Host 协议,这个协议在 RFC9 中第一次被草拟并且在 RFC54 中第一次被官方指定。更多可读的 Host-Host 协议的解释在 [ ARPANET 协议手册][10] 中被给出。
|
||||
|
||||
“ Host-Host 协议 ” 管理主机之间如何创建和管理链接。链接是某个主机上的写套接字和另一个主机上的读套接字之间的一个单向的数据管道。“ 套接字 ” 的概念是在 “ level-1 ” 层的有限的链路设施(记住链路号只是那 256 个值中的一个)之上被引入的,是为了给程序提供寻找运行在远端主机上的特定进程地址的一种方式。“ 读套接字 ” 是用偶数表示的,而“写套接字”是用奇数表示的;套接字是 “ 读 ” 还是 “ 写 ” 被称为套接字的 “性别”。并没有类似于 TCP 协议那样的 “ 端口号 ” 机制,链接的打开、维持以及关闭操作是通过主机之间使用 “ 链路 0 ” 发送指定格式的 Host-Host 控制消息来实现的,这也是 “ 链路0 ” 被保留的目的。一旦控制消息在“链路 0”上被交换来建立起一个连接后,就可以使用接收端挑选的另一个链路号来发送进一步的数据消息。
|
||||
|
||||
Host-Host控制消息一般通过 3 个字母型的助记符来表示。当两个主机交换一条 STR(发送端到接收端)消息和一条配对的 RTS(接收端到发送端)消息后,就建立起了一条链接。——这些控制消息都被称为请求链接消息。链接能够被 CLS (关闭)控制消息关闭。存在更进一步的控制信息能够改变从发送端到接收端发送消息的速率。从而需要确保较快的主机不会压制较慢的主机。在 “ level 1 ” 层上的协议提供了流量控制的功能,但对 “ level 2 ” 层来说显然是不够的;我怀疑这是因为从远端 IMP 接收到的 RFNM 只能保证远端 IMP 已经传送该消息到目标主机,不能保证目标主机已经全部处理了该消息。 还有 INR(接收端中断)、INS(发送端中断)控制消息,它们主要是被高层协议使用。
|
||||
|
||||
更高级别的协议都位于 “ level 3 ” ,这层是 ARPANET 的应用层。Telnet 协议,它提供到另一台主机的一个虚拟电传链接,其可能是这些协议中最重要的。但在这层中也有许多其他协议,例如用于传输文件的 FTP 协议和各种用于发送email的实验协议。
|
||||
|
||||
在这一层中有一个不同于其他的协议:初始链接协议(ICP)。ICP被认为是一个 “ level-3 ” 层协议,但实际上它是一种 “ level-2.5 ” 层协议,因为其他 “ level-3 ” 层协议都依赖它。ICP的存在是因为 “ level 2 ” 层的 Host-Host 协议提供的链接只是单向的,但大多数的应用需要一个双向(列如:全双工)的链接来做任何有趣的事情。要使得运行在某个主机上的客户端能够链接到另一个主机上长时间运行的服务进程, ICP 定义了两个步骤。第一步是建立一个从服务端到客户端的单向链接,通过使用服务端进程的众所周知的 socket 号来实现。第二步服务端通过建立的这个链接发送一个新的 socket 号给客户端。到那时,那个存在的链接就会被丢弃,然后有另外两个新的链接会被开启,它们是基于传输的 socket 号建立的“读”链接和基于传输的 socket 号加 1 的 “ 写 ” 链接。这个小插曲是大多数事务的一个前提——比如它是建立 Telnet 链接的第一步。
|
||||
|
||||
以上是我们对 ARPANET 协议层次结构的提升。你们可能一直期待我在某个时候提一下 “ Network Control Protocol ” 。在我坐下来去研究这篇贴子和我的最后一篇贴子之前,我坚定的认为 ARPANET 运行在一个叫做 NCP 的协议之上。那个首字母缩略词有时用来指代整个 ARPANET 协议,这可能就是我为什么有这个想法的原因。举个例子,[RFC801][11] 讨论了将 ARPANET 从 “ NCP ” 过渡到 “ TCP ” 的方式,这使 NCP 听起来像是一个等同TCP的 ARPANET 协议。但是对于 ARPANET 来说,从来都没有一个叫 “ Network Control Protocol ” 的东西(即使[大英百科全书是这样认为的][12]),我怀疑人们错误地将 “ NCP ” 解释为 “ Network Control Protocol ” ,而实际上它代表的是 “ Network Control Pragram ” 。网络控制程序是一个运行在各个主机上的内核级别的程序,主要负责处理网络通信,等同于现如今操作系统中的 TCP/IP 协议栈。用在 RFC 801 的 “ NCP ” 是一种转喻,而不是协议。
|
||||
|
||||
### 与TCP/IP的比较
|
||||
|
||||
ARPANET 协议以后都会被 TCP/IP 协议替换(但 Telnet 和 FTP 协议除外,因为它们很容易就能在 TCP 上适配运行)。然而 ARPANET 协议都基于这么一个假设就是网络是由一个单一实体(BBN)来构建和管理的。 TCP/IP 协议套件是为具有可变性和不可靠性的互联的网络而设计的。这就导致了现代协议套件和 ARPANET 协议有明显的不同,比如我们现在怎样区分网络层和传输层。在 ARPANET 中部分由 IMP 实现的类似传输层的功能现在完全由在网络边界的主机负责。
|
||||
|
||||
我发现关于ARPANET协议最有趣的事情是现在在 TCP 中的传输层的功能有多少在 ARPANET 上经历了一个糟糕的青春期。我不是一个网络专家,因此我拿出大学时的网络课本(Kurose and Ross, let’s go),他们对传输层通常负责什么给出了一个非常好的概述。总结一下他们的解释,一个传输层协议必须至少做到以下几点。这里的 “ segment ” 在 ARPANET 上基本等同于 “ message ” 作为术语被使用:
|
||||
|
||||
* 提供进程之间的传送服务,而不仅仅是主机之间的(传输层多路复用和多路分解)
|
||||
* 在每个段的基础上提供完整性检查(即确保传输过程中没有数据损坏)
|
||||
|
||||
像 TCP 那样,传输层也能够提供可靠的数据传输,这意味着:
|
||||
|
||||
* “段” 是按顺序被传送的
|
||||
* 不会丢失任何 “段”
|
||||
* “段” 的传送速度不会太快以至于被接收端丢弃(流量控制)
|
||||
|
||||
似乎在 ARPANET 上关于如何进行多路复用和多路分解以便进程可以通信存在一些混淆—— BBN 在 IMP-Host 层引入了链路号来做到这一点,但结果证明在 Host-Host 层上无论如何套接字号都是必要的。然后链路号只是用于 IMP-Host 级别的流量控制,但 BBN 似乎后来放弃了它,转而支持在唯一的主机对之间进行流量控制,这意味着链路号开始时只是作为这个重载的东西基本上变成了遗迹。 TCP 现在使用端口代替,分别对每一个 TCP 链接进行流量控制。进程间的多路复用和多路分解完全在 TCP 内部进行,不会像 ARPANET 一样泄露到较低层去。
|
||||
|
||||
同样有趣的是,鉴于 Kurose 和 Ross 如何开发 TCP 背后的想法,ARPANET 开始于 Kurose 和 Ross 所调用的一个严谨的 “stop-and-wait” 方法,以便在 IMP-Host 层上进行可靠的数据传输。这个 “stop-and-wait” 方法发送一个 “段” 然后就拒绝再去发送更多 “段” ,直到一个最近发送的 “段” 的确认被接收到为止。这是一种简单的方法,但这意味着只有一个 “段” 在整个网络中运行,从而导致协议非常缓慢——这就是为什么 Kurose 和 Ross 将 “stop-and-wait” 仅仅作为在通往功能齐全的传输层协议的路上的垫脚石的原因。在 ARPANET 上,“stop-and-wait” 是一段时间的工作方式,因为在 IMP–Host 层,必须接收下一条消息的请求以响应每条发出的消息,然后才能发送任何进一步的消息。客观的说 ,BBN 起初认为这对于提供主机之间的流量控制是必要的,因此减速是故意的。正如我已经提到的,为了更好的性能,RFNM 的要求后来放宽松了,而且 IMP 也开始向消息中添加序列号和保持对传输中的消息的 “窗口” 的跟踪,这或多或少与如今 TCP 的实现如出一辙。[5][13]
|
||||
|
||||
ARPANET 表明,如果你能让每个人都遵守一些基本规则,异构计算系统之间的通信是可能的。正如我先前所说的,那个是 ARPANET 的最重要的遗产。但是我希望通过这次仔细研究的哪些基本规则所透露的是有多少 ARPANET 协议影响了我们如今所用的协议。在主机和 IMP 之间分担传输层职责的方式上肯定有很多笨拙之处,有时候是冗余的。回想起来,主机之间一开始只能通过给出的任意链路在某刻只发送一条消息,这真的很有趣。 但是 ARPANET 实验是一个独特的机会,可以通过实际构建和操作网络来学习这些经验,当到了是时候升级到我们今天所知的互联网时,似乎这些经验变得很有用。
|
||||
|
||||
_如果你喜欢这篇贴子,更喜欢每四周发布一次的方式!那么在Twitter上关注[@TwoBitHistory][14] 或者订阅[RSS提要][15],以确保你知道新帖子的发布时间。_
|
||||
|
||||
_以前在 TwoBitHistory 上…_
|
||||
|
||||
> Trying to get back on this horse!
|
||||
>
|
||||
>
|
||||
> 我最近的贴子是我的一些关于为什么ARPANET是一个如此重要的突破的看法(当然,是令人惊讶和新颖的),并重点关注ARPANET被首次展示的发布会:<https://t.co/8SRY39c3St>
|
||||
>
|
||||
> — TwoBitHistory (@TwoBitHistory) [2021年2月7日][16]
|
||||
|
||||
1. 协议分层是网络工作组发明的。 这个论点是在[ RFC 871][17] 中提出的。分层也是 BBN 如何在主机和 IMP 之间划分职责的自然延伸,因此 BBN 也值得称赞。 [↩︎][18]
|
||||
|
||||
2. The “level” 是被网络工作组使用的术语。 详见[RFC 100][19] [↩︎][20]
|
||||
|
||||
3. 在 IMP-Host 协议的后续版本中,扩展了头部字段,并且将链路号升级为消息 ID。 但是 Host-Host 协议仅仅继续使用消息 ID 字段的高位 8 位,并将其视为链路号。 请参阅 [ARPANET 协议手册][10]的 “ Host-Host ” 协议部分。[↩︎][21]
|
||||
4. John M. McQuillan 和 David C. Walden。 “ARPA 网络设计决策”,第 284页,<https://www.walden-family.com/public/whole-paper.pdf>。 2021 年 3 月 8 日访问。[↩︎][22]
|
||||
5. 同上。[↩︎][23]
|
||||
|
||||
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://twobithistory.org/2021/03/08/arpanet-protocols.html
|
||||
|
||||
作者:[Two-Bit History][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[Lin-vy](https://github.com/Lin-vy)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://twobithistory.org
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://twobithistory.org/2021/02/07/arpanet.html
|
||||
[2]: tmp.szauPoOKtk#fn:1
|
||||
[3]: https://twobithistory.org/images/arpanet-stack.png
|
||||
[4]: tmp.szauPoOKtk#fn:2
|
||||
[5]: https://walden-family.com/impcode/BBN1822_Jan1976.pdf
|
||||
[6]: tmp.szauPoOKtk#fn:3
|
||||
[7]: https://twobithistory.org/images/host-imp-1969.png
|
||||
[8]: https://walden-family.com/impcode/1969-initial-IMP-design.pdf
|
||||
[9]: tmp.szauPoOKtk#fn:4
|
||||
[10]: http://mercury.lcs.mit.edu/~jnc/tech/arpaprot.html
|
||||
[11]: https://tools.ietf.org/html/rfc801
|
||||
[12]: https://www.britannica.com/topic/ARPANET
|
||||
[13]: tmp.szauPoOKtk#fn:5
|
||||
[14]: https://twitter.com/TwoBitHistory
|
||||
[15]: https://twobithistory.org/feed.xml
|
||||
[16]: https://twitter.com/TwoBitHistory/status/1358487195905064960?ref_src=twsrc%5Etfw
|
||||
[17]: https://tools.ietf.org/html/rfc871
|
||||
[18]: tmp.szauPoOKtk#fnref:1
|
||||
[19]: https://www.rfc-editor.org/info/rfc100
|
||||
[20]: tmp.szauPoOKtk#fnref:2
|
||||
[21]: tmp.szauPoOKtk#fnref:3
|
||||
[22]: tmp.szauPoOKtk#fnref:4
|
||||
[23]: tmp.szauPoOKtk#fnref:5
|
||||
@ -0,0 +1,108 @@
|
||||
[#]: subject: (Windows 11 Look Inspired by KDE Plasma and GNOME?)
|
||||
[#]: via: (https://www.debugpoint.com/2021/06/windows-11-inspiration-linux-kde-plasma/)
|
||||
[#]: author: (Arindam https://www.debugpoint.com/author/admin1/)
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (imgradeone)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
|
||||
Windows 11 的外观受到了 KDE Plasma 和 GNOME 的启发?
|
||||
======
|
||||
> 微软即将发布的 Windows 11 操作系统的图像与我们所心爱的 KDE Plasma 和 GNOME 有许多相似之处。它们到底有多相似呢?我们试着比较了一下。
|
||||
|
||||
我曾记得一句俗话 —— ‘_Good artists copy. Great artists steal_‘。我不知道 Windows 11 背后的设计团队,但他们似乎很大程度上受到了 Linux 桌面的影响。如果你回顾近几年来的 Windows 系统外观 —— 从 Windows XP 到 7,再到 10 —— 整体视觉上都没有什么太大的变化,直到今天为止。
|
||||
|
||||
Windows 操作系统的新版本通常有 5 到 7 年的生命周期。如果你试着回想 Windows 提供给你的个性化选项,你会发现这些选项近几年来基本都是一致的,甚至是桌面整体的体验 —— 包括开始菜单位置、宽度、颜色 —— 一切都没变过。
|
||||
|
||||
但随着 Windows 11 的全新外观,这一点终于改变了。让我带你看一些我之前所见过的截图,并且分析一下,它们到底和流行的 Linux [桌面环境][1](如 KDE Plasma 和 GNOME)有多相似。
|
||||
|
||||
### Windows 11 的外观受到了 KDE Plasma 和 GNOME 的启发?
|
||||
|
||||
#### 开始菜单和任务栏
|
||||
|
||||
传统的开始菜单和任务栏主题在 Windows 11 上有所变化。开始菜单和任务栏图标(默认情况下)位于任务栏中央。Windows 也在设置中提供了将任务栏图标和开始菜单移回左侧的选项。
|
||||
|
||||
![Windows 11 – 浅色模式下的开始菜单][2]
|
||||
|
||||
整体的布局方式和默认图标的色彩让我想起了 KDE Plasma 的任务栏和启动器。这些图标带有抛光,并且居中,给人带来类似 GNOME 上 Adwaita 图标的观感,而任务栏就更像是 KDE Plasma 的任务栏。
|
||||
|
||||
当你打开开始菜单后,它为你提供不同的图标和选项的排列方式。此外,当你开始打字时,顶部的搜索选项就会弹出。
|
||||
|
||||
现在,来看看全新设计的 KDE Plasma 启动器。我知道间距、图标大小和锐度并不完全一致,但你可以看到,两者看起来有多么惊人的相似。
|
||||
|
||||
![KDE Plasma 5.22 亮色模式下的启动器][3]
|
||||
|
||||
如果你正在使用 GNOME 或 Xfce 桌面,借助 [Arc Menu][4] 和一些小修改,你可以让两者看上去完全一致。
|
||||
|
||||
![修改过的 Arc Menu][5]
|
||||
|
||||
#### 窗口装饰
|
||||
|
||||
按照传统,GNOME 总是用圆角作为标准的窗口装饰。作为对照,Windows 则一直采用直角作为窗口装饰 —— 似乎一直都这样,直到现在为止。嗯,在 Windows 11 中,所有窗口装饰都是看上去不错的圆角。圆角的概念不是什么版权专利或者新想法,这就有一个问题了,为什么现在全都在用圆角?是有什么隐藏的目的吗?
|
||||
|
||||
![Windows 资源管理器和 Nautilus 的圆角][6]
|
||||
|
||||
哦,还记得 GNOME 的应用程序菜单的小指示器吗?这些小点提示着这里到底有多少页的应用程序。Windows 11 似乎也使用了这种这种思路。
|
||||
|
||||
![标记页面数量的小点][7]
|
||||
|
||||
#### 调色盘
|
||||
|
||||
Windows 多年来始终有基于“蓝色”或其他蓝色变体的主题。虽然用户可以自行更改任务栏、开始菜单背景、窗口标题栏颜色的选项,但借助这个选项,调色板与亮暗模式结合,展示出巨大变化,给 Windows 桌面带来了更圆滑、迷人的外观。也许这个灵感源自 Ubuntu、KDE 或者其它风格的调色板。
|
||||
|
||||
另见:[Windows 11 系统要求让人“回首瞻望”。是时候迁移至 Linux 了?][8]
|
||||
|
||||
#### 暗黑模式
|
||||
|
||||
Windows 11 首次官方支持了暗黑模式,或者说是暗色主题。那么,我就直接在下面放两张截图,由大家自己评判。左侧是 Windows 11 暗黑模式下的开始菜单,右侧是使用了 Breeze Dark 主题的 KDE Plasma。
|
||||
|
||||
![Windows 11 开始菜单与 KDE Plasma 的比较][9]
|
||||
|
||||
#### 全新桌面小组件
|
||||
|
||||
灵感的启发从来不会停止。还记得 KDE Plasma 的小组件吗?其实,这也不是什么新概念,然而小组件已经出现在 Windows 11。这是全新小组件面板的截图。你可以添加、移除或者重新排序这些小组件。
|
||||
|
||||
![小组件菜单][10]
|
||||
|
||||
这些只是吸引我眼球的冰山一角。也许 Windows 11 还有许多“灵感”来“启发”它的外观。
|
||||
|
||||
但问题来了 —— 为什么现在反而是介绍这些功能和外观的最佳时机?
|
||||
|
||||
### 尾注
|
||||
|
||||
实话实说,当我第一次看到 Windows 11 的新外观时,我脑袋里就浮现出 Breeze Dark 主题的 KDE Plasma。借助很少量的修改,你可以让 KDE Plasma 看上去像 Windows 11。这本身就说明了它们两者是有多么地相似。
|
||||
|
||||
如果你看向整个桌面操作系统的市场,唯独有 Windows、Linux 桌面和 macOS 是竞争者。至今为止,它们的外观都有明显的标志性特征,例如 macOS 有自己独一无二的外观。目前为止,Windows 也有一样的,蓝色主题的常规开始菜单,等等。但借助这些新变化,Windows 为用户提供了更丰富的定制选项,让它看上去更像 Linux 桌面。
|
||||
|
||||
在我个人看来,Windows 团队需要一种不同的标志性特征,而不是一直从我们心爱的 Linux 桌面获得“启发”。
|
||||
|
||||
我不知道未来会发生什么,但现在看来,“E-E-E”还在竭尽全力运作。
|
||||
|
||||
再会。
|
||||
|
||||
* * *
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.debugpoint.com/2021/06/windows-11-inspiration-linux-kde-plasma/
|
||||
|
||||
作者:[Arindam][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[imgradeone](https://github.com/imgradeone)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.debugpoint.com/author/admin1/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.debugpoint.com/category/desktop-environment
|
||||
[2]: https://www.debugpoint.com/blog/wp-content/uploads/2021/06/Windows-11-Start-menu-in-light-mode.jpg
|
||||
[3]: https://www.debugpoint.com/blog/wp-content/uploads/2021/06/KDE-Plasma-5.22-Launcher-in-Light-mode.jpg
|
||||
[4]: https://gitlab.com/LinxGem33/Arc-Menu
|
||||
[5]: https://www.debugpoint.com/blog/wp-content/uploads/2020/12/gnomecustomize2020-2-1024x576.jpg
|
||||
[6]: https://www.debugpoint.com/blog/wp-content/uploads/2021/06/Rounded-Corners-in-Windows-Explorer-and-Nautilus-1024x716.jpg
|
||||
[7]: https://www.debugpoint.com/blog/wp-content/uploads/2021/06/Dots-in-paging-1024x468.jpg
|
||||
[8]: https://www.debugpoint.com/2021/06/windows-11-system-requirement/
|
||||
[9]: https://www.debugpoint.com/blog/wp-content/uploads/2021/06/Comparison-of-Windows-11-Start-Menu-and-KDE-Plasma-1024x505.jpg
|
||||
[10]: https://www.debugpoint.com/blog/wp-content/uploads/2021/06/Widgets-menu-1024x833.jpg
|
||||
@ -0,0 +1,95 @@
|
||||
[#]: subject: (5 useful ways to manage Kubernetes with kubectl)
|
||||
[#]: via: (https://opensource.com/article/21/7/kubectl)
|
||||
[#]: author: (Alan Smithee https://opensource.com/users/alansmithee)
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
|
||||
用 kubectl 管理 Kubernetes 的 5 种有用方法
|
||||
======
|
||||
学习kubectl,提升你与 Kubernetes 的互动方式。
|
||||
![Ship captain sailing the Kubernetes seas][1]
|
||||
|
||||
Kubernetes 是帮助你以有组织的方式运行大量容器的软件。除了提供工具来管理(或[编排][2])运行的容器,Kubernetes 还帮助这些容器根据需要进行扩展。有了 Kubernetes 作为你的中央控制面板(或称 _control plane_),你需要一种方法来管理 Kubernetes,而这项工作的工具就是 kubectl。`kubectl` 命令让你控制、维护、分析和排除 Kubernetes 集群的故障。与许多使用 `ctl`(“控制”的缩写)后缀的工具一样,如 systemctl 和 sysctl,kubectl 拥有大量的功能和任务权限,所以如果你正在运行 Kubernetes,你最终会经常使用它。它是一个有很多选项的大命令,所以下面是 kubectl 使之变得简单的五个常见任务。
|
||||
|
||||
### 1\. 列出并描述资源
|
||||
|
||||
按照设计,容器往往会成倍增加。在某些条件下,它们可以快速增加。如果你只能通过 `podman ps`或 `docker ps` 来查看正在运行的容器,这可能会让你不知所措。通过 `kubectl get` 和 `kubectl describe`,你可以获得关于哪些 pod 正在运行以及它们正在处理的容器的信息。更重要的是,你可以通过使用 `--namespace` 或 `name` 或 `--selector`等选项,只获得你需要的信息。
|
||||
|
||||
`get` 子命令不仅仅对 pod 和容器有用。它有关于节点、命名空间、部署、服务和复制的信息。
|
||||
|
||||
### 2\. 创建资源
|
||||
|
||||
如果你只通过类似 OpenShift、OKD 或 Kubernetes 提供的 Web 用户界面(UI)创建过部署,但你想从 Linux 终端控制你的集群,那么可以使用 `kubectl create`。`kubectl create` 命令并不只是实例化一个新的应用部署。Kubernetes 中还有很多其他组件可以创建,比如服务、配额和 [CronJob][3]。
|
||||
|
||||
Kubernetes 中的 CronJob 可以创建一个临时的 pod,用来在你选择的时间表上执行一些任务。它们并不难设置。下面是一个 CronJob,让一个 BusyBox 镜像每分钟响应 “hello world”。
|
||||
|
||||
|
||||
```
|
||||
$ kubectl create cronjob \
|
||||
hello-world \
|
||||
\--image=busybox \
|
||||
\--schedule="*/1 * * * *" -- echo "hello world"
|
||||
```
|
||||
|
||||
### 3\. 编辑文件
|
||||
|
||||
你可能了解 Kubernetes 中的对象都有相应的配置文件,但在文件系统中查找相应的文件可能很麻烦。有了 `kubectl edit`,你可以把注意力放在对象上,而不是定义它们的文件上。你可以让 `kubectl` 为你找到并打开文件(它遵循 `KUBE_EDITOR` 环境变量,所以你可以把编辑器设置成你喜欢的)。
|
||||
|
||||
|
||||
```
|
||||
$ KUBE_EDITOR=emacs \
|
||||
kubectl edit cronjob/hello-world
|
||||
```
|
||||
|
||||
### 4\. 容器之间的交换文件
|
||||
|
||||
初次接触容器的人往往对他们直接无法访问的共享系统的概念感到困惑。他们可能会在容器引擎或 kubectl 中了解到 `exec` 选项,但当他们不能从容器中获取文件或将文件放入容器中时,容器仍然会显得不透明。使用 `kubectl cp` 命令,你可以把容器当做远程服务器,使复制文件到容器或从容器复制文件不比 SSH 命令更复杂:
|
||||
|
||||
|
||||
```
|
||||
`$ kubectl cp foo my-pod:/tmp`
|
||||
```
|
||||
|
||||
### 5\. 应用更改
|
||||
|
||||
对 Kubernetes 对象进行修改,可以在任何时候通过 `kubectl apply` 命令完成。你所要做的就是将该命令指向一个配置文件:
|
||||
|
||||
|
||||
```
|
||||
`$ kubectl apply -f ./mypod.json`
|
||||
```
|
||||
|
||||
类似于运行 Ansible playbook 或 Bash 脚本,`apply` 使得快速“导入”设置到运行中的 Kubernetes 实例很容易。例如,GitOps 工具 [ArgoCD][4] 由于 `apply` 子命令,安装起来出奇地简单:
|
||||
|
||||
|
||||
```
|
||||
$ kubectl create namespace argocd
|
||||
$ kubectl apply -n argocd \
|
||||
-f <https://raw.githubusercontent.com/argoproj/argo-cd/vx.y.z/manifests/install.yaml>
|
||||
```
|
||||
|
||||
### 使用 kubectl
|
||||
|
||||
Kubectl 是一个强大的工具,由于它是一个终端命令,它可以写成脚本,并以许多 Web UI 无法实现的方式使用。学习 kubectl 是进一步了解 Kubernetes、容器、pod 以及围绕这些重要的云计算创新的所有技术的一个好方法。[下载我们的 kubectl 速查表][5],以获得快速参考,其中包括命令示例,以帮助你学习,并在你成为专家后提醒你注意细节。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/21/7/kubectl
|
||||
|
||||
作者:[Alan Smithee][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/alansmithee
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/ship_captain_devops_kubernetes_steer.png?itok=LAHfIpek (Ship captain sailing the Kubernetes seas)
|
||||
[2]: https://opensource.com/article/20/11/orchestration-vs-automation
|
||||
[3]: https://opensource.com/article/20/11/kubernetes-jobs-cronjobs
|
||||
[4]: https://argoproj.github.io/argo-cd/
|
||||
[5]: https://opensource.com/downloads/kubectl-cheat-sheet
|
||||
@ -3,18 +3,18 @@
|
||||
[#]: author: (Seth Kenlon https://opensource.com/users/seth)
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: ( )
|
||||
[#]: reviewer: (turbokernel)
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
|
||||
用 du 检查 Linux 上已使用的磁盘空间
|
||||
使用 du 检查 Linux 上已用的磁盘空间
|
||||
======
|
||||
用 Linux 的 du 命令了解你正在使用多少磁盘空间。
|
||||
![Check disk usage][1]
|
||||
|
||||
无论你有多少存储空间,它总是有可能被填满。在大多数个人设备上,驱动器被照片、视频和音乐填满,但在服务器上,由于用户账户和日志文件中的数据,空间减少是很正常的。无论你是负责管理一个多用户系统,还是只负责自己的笔记本电脑,你都可以用 `du` 命令检查磁盘的使用情况。
|
||||
无论你有多少存储空间,它总有可能被填满。在大多数个人设备上,磁盘被照片、视频和音乐填满,但在服务器上,由于用户账户和日志文件数据,空间减少是很正常的。无论你是负责管理一个多用户系统,还是只负责自己的笔记本电脑,你都可以用 `du` 命令检查磁盘的使用情况。
|
||||
|
||||
默认情况下,`du` 提供了你当前目录中使用的磁盘空间,以及每个子目录的大小。
|
||||
默认情况下,`du` 列出了当前目录中使用的磁盘空间,以及每个子目录的大小。
|
||||
|
||||
|
||||
```
|
||||
@ -23,7 +23,7 @@ $ du
|
||||
60 .
|
||||
```
|
||||
|
||||
在这个例子中,我的当前目录总共占用了 60KB,其中 12KB 被子目录 `.backups` 占用。
|
||||
在这个例子中,当前目录总共占用了 60KB,其中 12KB 被子目录 `.backups` 占用。
|
||||
|
||||
如果你觉得这很混乱,并希望分别看到所有的大小,你可以使用 `--separate-dirs`(或简写 `S`)选项:
|
||||
|
||||
@ -34,9 +34,9 @@ $ du --separate-dirs
|
||||
48 .
|
||||
```
|
||||
|
||||
这是相同的信息(48 加 12 是 60),但每个目录被独立处理。
|
||||
显示相同的信息(48KB 加 12KB 是 60KB),但每个目录被独立处理。
|
||||
|
||||
要想看到更多的细节,可以使用 --all(简写 -a)选项,它显示每个目录中的每个文件:
|
||||
如需看到更多的细节,可以使用 --all(简写 -a)选项,它显示每个目录中以及每个文件:
|
||||
|
||||
|
||||
```
|
||||
@ -54,7 +54,7 @@ $ du --separate-dirs --all
|
||||
|
||||
当查看文件以找出占用空间的内容时,查看文件最后一次被修改的时间是很有用的。一年内没有使用的文件很可能是归档的候选文件,特别是当你的空间快用完时。
|
||||
|
||||
用 du 查看文件的修改时间,使用 `--time` 选项:
|
||||
通过 du 查看文件的修改时间,使用 `--time` 选项:
|
||||
|
||||
|
||||
```
|
||||
@ -68,7 +68,7 @@ $ du --separate-dirs --all --time
|
||||
|
||||
### 为文件大小设置一个阈值
|
||||
|
||||
当为了磁盘空间而查看文件时,你可能只关心较大的文件。你可以用 `--threshold`(简写 `-t`)选项为你想看的文件大小设置一个阈值。例如,只查看大于 1GB 的文件:
|
||||
当为了磁盘空间而查看文件时,你可能只关心较大的文件。你可以通过 `--threshold`(简写 `-t`)选项为文件大小设置一个阈值。例如,只查看大于 1GB 的文件:
|
||||
|
||||
|
||||
```
|
||||
@ -78,7 +78,7 @@ $ \du --separate-dirs --all --time --threshold=1G ~/Footage/
|
||||
8588936 2021-07-14 13:55 /home/tux/Footage/
|
||||
```
|
||||
|
||||
当文件特别大时,它们可能难以阅读。使用 `--human-readable`(简写 `-h`)选项可以使文件大小更容易阅读:
|
||||
当文件较大时,它们可能难以阅读。使用 `--human-readable`(简写 `-h`)选项可以使文件大小更容易阅读:
|
||||
|
||||
|
||||
```
|
||||
@ -91,7 +91,7 @@ $ \du --separate-dirs --all --time \
|
||||
|
||||
### 查看可用磁盘空间
|
||||
|
||||
如果只是想获得一个驱动器上还剩下多少磁盘空间的摘要,请阅读我们关于 [df 命令][2]的文章。
|
||||
如需获得一个驱动器上可用磁盘空间的摘要,请阅读我们关于 [df 命令][2]的文章。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
@ -100,7 +100,7 @@ via: https://opensource.com/article/21/7/check-disk-space-linux-du
|
||||
作者:[Seth Kenlon][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[turbokernel](https://github.com/turbokernel)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
|
||||
@ -0,0 +1,130 @@
|
||||
[#]: subject: (How to Change Lock and Login Screen Wallpaper in elementary OS)
|
||||
[#]: via: (https://www.debugpoint.com/2021/07/change-lock-login-screen-background-elementary-os/)
|
||||
[#]: author: (Arindam https://www.debugpoint.com/author/admin1/)
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
|
||||
如何在 elementary OS 中改变锁定和登录屏幕的壁纸
|
||||
======
|
||||
本教程解释了在 elementary OS 中改变锁定和登录屏幕背景的步骤。这将取代默认的灰色背景。
|
||||
|
||||
在 elementary OS 中改变锁屏或登录屏背景的灰色默认壁纸是有点困难的。典型的用图像文件的路径改变 greeter 配置是行不通的。
|
||||
|
||||
不幸的是,这不是一个更简单的解决方案,因为灰色背景是一个图像文件,它的数据在 greeter 中是硬编码的,需要用新的图像重新编译才能使其发挥作用。
|
||||
|
||||
下面是方法。
|
||||
|
||||
![Lock / Login screen background elementary OS \(Odin\)][1]
|
||||
|
||||
### 改变 elementary OS 锁定和登录屏幕背景
|
||||
|
||||
* 在 elementary OS 中打开一个终端。
|
||||
* 为 [greeter包][2]安装 git 和以下依赖项。
|
||||
|
||||
|
||||
|
||||
```
|
||||
sudo apt install git
|
||||
```
|
||||
|
||||
```
|
||||
sudo apt install -y gnome-settings-daemon libaccountsservice-dev libgdk-pixbuf2.0-dev libgranite-dev libgtk-3-dev libhandy-1-dev liblightdm-gobject-1-dev libmutter-6-dev libwingpanel-dev libx11-dev meson valac
|
||||
```
|
||||
|
||||
* 进入临时的 /tmp 目录,从 GitHub 克隆最新的 greeter 主分支。
|
||||
|
||||
|
||||
|
||||
```
|
||||
cd /tmp
|
||||
git clone https://github.com/elementary/greeter.git
|
||||
```
|
||||
|
||||
* 克隆完成后,在文件管理器中打开路径 `/tmp/greeter/data`。
|
||||
|
||||
|
||||
* 初级操作系统使用一个 100×100px 的 PNG 文件作为登录屏幕/锁屏的默认背景。该图像是平铺的,给人一种灰色背景的感觉。
|
||||
|
||||
|
||||
* 用 `texture.png` 重命名你想要的墙纸图像,并在路径中覆盖以下文件。
|
||||
|
||||
|
||||
|
||||
![gray background is created using this file][3]
|
||||
|
||||
```
|
||||
/tmp/greeter/data/texture.png
|
||||
```
|
||||
|
||||
* 在文本编辑器中打开文件 `/tmp/greeter/compositor/SystemBackground.vala`,并替换下面一行:
|
||||
|
||||
|
||||
|
||||
![change the path of image][4]
|
||||
|
||||
```
|
||||
resource:///io/elementary/desktop/gala/texture.png
|
||||
```
|
||||
|
||||
为:
|
||||
|
||||
```
|
||||
resource:///io/elementary/greeter/texture.png
|
||||
```
|
||||
|
||||
* 保存该文件。
|
||||
|
||||
|
||||
* 再次打开终端,使用以下命令构建 `greeter`。
|
||||
|
||||
|
||||
|
||||
```
|
||||
cd /tmp/greeter
|
||||
meson _build --prefix=/usr
|
||||
sudo ninja install -C _build
|
||||
```
|
||||
|
||||
![building greeter][5]
|
||||
|
||||
* 如果你遇到任何构建错误,请在下面的评论中告诉我。你应该不会看到任何错误,因为我已经测试过了。
|
||||
|
||||
|
||||
上面的命令完成后,你可以在测试模式下运行 lightdm 来测试登录屏:
|
||||
|
||||
```
|
||||
lightdm --test-mode --debug
|
||||
```
|
||||
|
||||
如果看起来不错,重新启动系统。而你应该在 elementary OS 的登录屏上看到你的墙纸。
|
||||
|
||||
这个指南应该可在 [elementary OS 6 Odin][7]、elementary OS 5 Juno 及以下版本中可用。
|
||||
|
||||
### 结束语
|
||||
|
||||
我希望本指南能帮助你在 elementary OS 中改变锁屏或登录屏的背景。老实说,在 2021 年改变登录屏的背景图像需要编译代码,这让我很吃惊。
|
||||
|
||||
如果你遇到错误,请在下面的评论栏里告诉我。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.debugpoint.com/2021/07/change-lock-login-screen-background-elementary-os/
|
||||
|
||||
作者:[Arindam][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.debugpoint.com/author/admin1/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.debugpoint.com/blog/wp-content/uploads/2021/07/elementary-OS-Login-Screen-in-Odin-1024x768.jpg
|
||||
[2]: https://github.com/elementary/greeter
|
||||
[3]: https://www.debugpoint.com/blog/wp-content/uploads/2021/07/gray-background-is-created-using-this-file.jpg
|
||||
[4]: https://www.debugpoint.com/blog/wp-content/uploads/2021/07/change-the-path-of-image-1024x450.jpg
|
||||
[5]: https://www.debugpoint.com/blog/wp-content/uploads/2021/07/building-greeter.png
|
||||
[7]: https://www.debugpoint.com/tag/elementary-os-6
|
||||
@ -0,0 +1,76 @@
|
||||
[#]: subject: (Use the Linux terminal to see what files are on your computer)
|
||||
[#]: via: (https://opensource.com/article/21/8/linux-list-files)
|
||||
[#]: author: (Seth Kenlon https://opensource.com/users/seth)
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (piaoshi)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
|
||||
使用 Linux 终端查看你的电脑上有哪些文件
|
||||
======
|
||||
通过这个 Linux 教程学习如何使用 ls 命令在终端中列出文件。
|
||||
![List files on your computer][1]
|
||||
|
||||
要在有图形界面的计算机上列出文件,你通常可以打开一个文件管理器(Linux 上的 **Files**,MacOS 上的 **访达**,Windows 上的 **文件资源管理器**)来查看文件。
|
||||
|
||||
要在终端中列出文件,你可以使用 **ls** 命令来列出当前目录中的所有文件。而 **pwd** 命令可以告诉你当前所在的目录。
|
||||
|
||||
```
|
||||
$ pwd
|
||||
/home/tux
|
||||
$ ls
|
||||
example.txt
|
||||
Documents
|
||||
Downloads
|
||||
Music
|
||||
Pictures
|
||||
Templates
|
||||
Videos
|
||||
```
|
||||
|
||||
你可以通过 **\--all** 选项看到隐藏文件。
|
||||
|
||||
```
|
||||
$ pwd
|
||||
/home/tux
|
||||
$ ls --all
|
||||
. Downloads
|
||||
.. .local
|
||||
.bashrc Music
|
||||
.config Pictures
|
||||
example.txt Templates
|
||||
Documents Videos
|
||||
```
|
||||
|
||||
如你所见,列出的前两项是点。单个点实际上是一个元位置,代表 _你当前所在的文件夹_ 。两个点表示你可以从当前位置返回的上级目录。也就是说,当前目录在另一个文件夹中。当你在计算机目录间移动时,你就可以利用这些元位置为自己创建快捷方式,或者增加你的路径的独特性。
|
||||
|
||||
### 文件和文件夹以及如何区分它们
|
||||
|
||||
你可能会注意到,文件和文件夹是很难区分的。一些 Linux 发行版有一些漂亮的颜色设置,比如所有的文件夹都是蓝色的,文件是白色的,二进制文件是粉色或绿色的,等等。如果你没有看到这些颜色,你可以试试 **ls --color**。如果你有色盲症或者使用的不是彩色显示器,你可以使用 **\--classify** 选项替代:
|
||||
|
||||
```
|
||||
$ pwd
|
||||
/home/tux/Downloads
|
||||
$ ls --classify
|
||||
android-info.txt
|
||||
cheat/
|
||||
test-script.sh*
|
||||
```
|
||||
|
||||
你会发现,文件夹末尾加了一个斜杠(`/`),以表示它们是文件系统中的某一级目录。而二进制文件,如压缩文件和可执行程序,用星号(`*`)标记。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/21/8/linux-list-files
|
||||
|
||||
作者:[Seth Kenlon][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[piaoshi](https://github.com/piaoshi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/seth
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/ch01.svg__0.png?itok=98wPcbAc (List files on your computer)
|
||||
@ -0,0 +1,127 @@
|
||||
[#]: subject: (How to Install Google Chrome on Linux Mint [Beginners Tip])
|
||||
[#]: via: (https://itsfoss.com/install-chrome-linux-mint/)
|
||||
[#]: author: (Abhishek Prakash https://itsfoss.com/author/abhishek/)
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
|
||||
如何在 Linux Mint 上安装 Google Chrome(初学者技巧)
|
||||
======
|
||||
|
||||
这应该是一个非常简单的话题,但我写这个是因为我看到很多网站推荐在 Linux Mint 上安装 Google Chrome 的奇怪命令行步骤。那是可行的,但那是不必要的复杂,特别是对于不熟悉命令行的初学者。
|
||||
|
||||
实际上,你根本不需要走终端方式。你所要做的就是去谷歌浏览器的网站,下载 Ubuntu 的安装文件并安装。
|
||||
|
||||
让我详细介绍一下步骤,供你了解。
|
||||
|
||||
### 在 Linux Mint 上安装 Google Chrome
|
||||
|
||||
进入 Google Chrome 的网站。
|
||||
|
||||
[Google Chrome Website][1]
|
||||
|
||||
你会看到一个 “Download Chrome” 的按钮。点击它。
|
||||
|
||||
![Download Chrome for Linux][2]
|
||||
|
||||
它将向你显示在 Linux 上下载 Chrome 的两个选项。选择 Debian/Ubuntu 选项并点击 “Accept and Install” 按钮。
|
||||
|
||||
![Select Debian/Ubuntu option for Chrome package on Mint][3]
|
||||
|
||||
在开始下载之前,Firefox 会询问你是否要用 Gdebi 打开下载的文件或保存它。你可以选择任何一个选项,因为最终你会[使用 Gdebi 来安装 deb 文件][4]。然而,我更喜欢先保存文件。
|
||||
|
||||
![Save the deb file][5]
|
||||
|
||||
等待下载完成。
|
||||
|
||||
![Wait for Google Chrome download to finish][6]
|
||||
|
||||
下载完成后,在文件管理器中进入下载文件夹。要[安装 deb 文件][7],可以双击它或者右击它并选择 “Open With GDebi Package Installer”。
|
||||
|
||||
![Double click on the downloaded deb file to install it][8]
|
||||
|
||||
等待几秒钟,它应该给你一个安装的选项。
|
||||
|
||||
![Hit the Install Package option in Gdebi][9]
|
||||
|
||||
它将要求你提供 Linux Mint 的账户密码。在 Linux 中,你需要提供你的密码来安装任何应用。
|
||||
|
||||
![Enter your password for installing an application][10]
|
||||
|
||||
你就要完成了。它将显示哪些额外的软件包将与之一起安装(如果有的话)。点击继续按钮即可。
|
||||
|
||||
![Details on the packages to be installed][11]
|
||||
|
||||
安装完成应该只需要几秒钟或最多一分钟。
|
||||
|
||||
![Installing Chrome in progress][12]
|
||||
|
||||
安装完成后,你应该看到这样的屏幕。
|
||||
|
||||
![Chrome successfully installed on Linux Mint][13]
|
||||
|
||||
安装完成后,你可以在应用菜单中寻找 Google Chrome 来运行它。
|
||||
|
||||
![Run Google Chrome in Linux Mint][14]
|
||||
|
||||
然后在 Linux Mint 上享受 Google Chrome。
|
||||
|
||||
![Google Chrome running in Linux Mint][15]
|
||||
|
||||
### 如何在 Linux Mint 上更新 Google Chrome
|
||||
|
||||
这个方法的好处是,谷歌浏览器会随着系统的更新而更新。当你安装 deb 文件的时候,它也会在你的系统中添加一个来自谷歌的仓库。
|
||||
|
||||
![Chrome adds a repository to the system for providing updates][16]
|
||||
|
||||
由于这个添加的仓库,Chrome 浏览器上的更新将被添加到系统更新中。因此,当你更新 Linux Mint 时,它也会被更新(如果有可用的更新)。
|
||||
|
||||
### 如何从 Linux Mint 中删除 Google Chrome
|
||||
|
||||
不喜欢 Chrome?不用担心。你可以从 Linux Mint 中卸载谷歌浏览器。同样这次你也不需要使用终端。
|
||||
|
||||
点击菜单,搜索 Chrome。在 Chrome 图标上点击右键,你会看到一个 “Uninstall” 选项。选择它。
|
||||
|
||||
![Removing Google Chrome from Linux Mint][17]
|
||||
|
||||
当然,你必须输入你的密码。它将显示要删除的软件包。在这里点击 OK。
|
||||
|
||||
![Uninstalling Google Chrome from Linux mint][18]
|
||||
|
||||
你可以留下 Google Chrome 的仓库,也可以删除它。这是你的选择。
|
||||
|
||||
我希望你觉得这个教程对在 Linux Mint 上使用 Google Chrome 有帮助。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://itsfoss.com/install-chrome-linux-mint/
|
||||
|
||||
作者:[Abhishek Prakash][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://itsfoss.com/author/abhishek/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.google.com/chrome/index.html
|
||||
[2]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2021/08/download-chrome-linux-mint.png?resize=800%2C320&ssl=1
|
||||
[3]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2021/08/downloading-chrome-linux-mint.png?resize=800%2C679&ssl=1
|
||||
[4]: https://itsfoss.com/gdebi-default-ubuntu-software-center/
|
||||
[5]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2021/08/saving-downloaded-chrome-linux-mint.png?resize=798%2C400&ssl=1
|
||||
[6]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2021/08/finishing-chrome-download-linux-mint.png?resize=799%2C315&ssl=1
|
||||
[7]: https://itsfoss.com/install-deb-files-ubuntu/
|
||||
[8]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2021/08/installing-google-chrome-deb-file-mint.png?resize=799%2C529&ssl=1
|
||||
[9]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2021/08/installing-google-chrome-gdebi-mint.png?resize=801%2C548&ssl=1
|
||||
[10]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2021/08/enter-password-for-installing-chrome-mint.png?resize=800%2C399&ssl=1
|
||||
[11]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2021/08/installing-chrome-mint.png?resize=799%2C483&ssl=1
|
||||
[12]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2021/08/installing-chrome-mint-progress.png?resize=799%2C489&ssl=1
|
||||
[13]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2021/08/chrome-installed-mint.png?resize=798%2C483&ssl=1
|
||||
[14]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2021/08/run-google-chrome-linux-mint.png?resize=798%2C580&ssl=1
|
||||
[15]: https://itsfoss.com/wp-content/uploads/2021/08/google-chrome-in-linux-mint-800x450.webp
|
||||
[16]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2021/08/google-chrome-repo-added-mint.png?resize=799%2C272&ssl=1
|
||||
[17]: https://itsfoss.com/wp-content/uploads/2021/08/removing-google-chrome-from-mint.webp
|
||||
[18]: https://itsfoss.com/wp-content/uploads/2021/08/uninstalling-google-chrome-from-linux-mint.webp
|
||||
@ -0,0 +1,113 @@
|
||||
[#]: subject: (Mount Microsoft OneDrive in Linux With OneDriver GUI Tool)
|
||||
[#]: via: (https://itsfoss.com/onedriver/)
|
||||
[#]: author: (Abhishek Prakash https://itsfoss.com/author/abhishek/)
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
|
||||
用 OneDriver GUI 工具在 Linux 中安装微软 OneDrive
|
||||
======
|
||||
|
||||
在 Windows 上,微软提供了一个[免费云存储服务][1] OneDrive。它与 Windows 集成,你可以通过你的微软账户获得 5GB 的免费存储空间。
|
||||
|
||||
这在 Windows 上很好用,但和谷歌一样,微软也没有在 Linux 桌面上提供 OneDrive 的本地客户端。
|
||||
|
||||
当然,你可以通过浏览器访问你的 OneDrive 数据。除此以外,还有一些其他的方法可以在 Linux 上访问 OneDrive。
|
||||
|
||||
你可以使用像 [Insync][2] 这样的高级服务,或者选择用 [rclone 在 Linux 上使用 OneDrive][3] 这种稍微复杂的命令行方式。
|
||||
|
||||
最近,我发现了另一个工具,它稍有不同,使用起来也更简单。不出所料,它叫 OneDriver。
|
||||
|
||||
### OneDriver:在你的 Linux 系统上挂载 OneDrive
|
||||
|
||||
![OneDrive Linux illustration][4]
|
||||
|
||||
[OneDriver][5] 是一个免费的开源工具,允许你在 Linux 系统上挂载 OneDrive 文件。
|
||||
|
||||
请记住,它不会像 OneDrive 在 Windows 系统上那样同步文件。它将 OneDrive 文件挂载在本地的挂载点上。你通过网络访问这些文件。
|
||||
|
||||
然而,它确实提供了一种混合方法。你在挂载的 OneDrive 中打开的文件也被下载到系统中。这意味着,你也可以离线访问打开的文件。如果你没有连接到互联网,这些文件将成为只读。
|
||||
|
||||
如果你在本地对文件做任何修改,如果你连接到互联网,它就会反映到 OneDrive 上。
|
||||
|
||||
我注意到,在 GNOME 上的 Nautilus 文件管理器中,它会自动下载当前文件夹中的图像。在我的印象中,它们只有在我打开它们时才会被下载。
|
||||
|
||||
另一件事是,Nautilus 最初建立了缩略图缓存。OneDriver 在开始的时候可能会觉得有点慢,有点耗费资源,但最终会好起来。
|
||||
|
||||
哦!你也可以挂载多个 OneDrive 账户。
|
||||
|
||||
### 安装和使用 OneDriver
|
||||
|
||||
要在 Ubuntu 20.04(和 Linux Mint 20 系列)上安装 OneDriver,你可以使用 OneDriver 开发者的这个 PPA:
|
||||
|
||||
```
|
||||
sudo add-apt-repository ppa:jstaf/onedriver
|
||||
sudo apt update
|
||||
sudo apt install onedriver
|
||||
```
|
||||
|
||||
对于 Ubuntu 21.04,你可以下载[其 PPA 中的 DEB 文件][6]来使用它。
|
||||
|
||||
在 Fedora 上,你可以添加这个 COPR:
|
||||
|
||||
```
|
||||
sudo dnf copr enable jstaf/onedriver
|
||||
sudo dnf install onedriver
|
||||
```
|
||||
|
||||
Arch 用户可以在 AUR 中找到它。
|
||||
|
||||
安装后,在菜单中搜索 OneDriver,然后从这里启动它。
|
||||
|
||||
![Search for OneDriver][7]
|
||||
|
||||
首次运行时,它会给出一个奇怪的空界面。点击 “+” 号,选择一个文件夹或创建一个新的文件夹,在那里你将挂载 OneDrive。在我的例子中,我在我的家目录下创建了一个名为 One_drive 的新文件夹。
|
||||
|
||||
![Click on + sign to add a mount point for OneDrive][8]
|
||||
|
||||
当你选择了挂载点后,你会被要求输入你的微软凭证。
|
||||
|
||||
![one drive login][9]
|
||||
|
||||
![one drive permission][10]
|
||||
|
||||
登陆后,你可以在挂载的目录中看到 OneDrive 的文件。
|
||||
|
||||
![OneDrive mounted in Linux][11]
|
||||
|
||||
完成这些后,你可以在应用界面上看到你的 OneDrive 账户。点击旁边的勾按钮,以在重启后自动挂载 OneDrive。
|
||||
|
||||
![Autostart OneDriver mounting][12]
|
||||
|
||||
总的来说,OneDriver 是一个可以在 Linux 上访问 OneDrive 的不错的免费工具。它可能无法像[高级 Insync 服务][13]那样提供完整的同步设施,但对于有限的需求来说,它做得不错。
|
||||
|
||||
如果你使用这个漂亮的工具,请分享你的使用经验。如果你喜欢这个项目,也许可以给它一个 [GitHub 上的关注][5]。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://itsfoss.com/onedriver/
|
||||
|
||||
作者:[Abhishek Prakash][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://itsfoss.com/author/abhishek/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://itsfoss.com/cloud-services-linux/
|
||||
[2]: https://itsfoss.com/use-onedrive-on-linux/
|
||||
[3]: https://itsfoss.com/use-onedrive-linux-rclone/
|
||||
[4]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2021/08/one-drive-linux.png?resize=800%2C450&ssl=1
|
||||
[5]: https://github.com/jstaf/onedriver
|
||||
[6]: https://launchpad.net/~jstaf/+archive/ubuntu/onedriver/+packages
|
||||
[7]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2021/08/search-for-onedriver.png?resize=798%2C214&ssl=1
|
||||
[8]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2021/08/onedriver-interface.png?resize=745%2C456&ssl=1
|
||||
[9]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2021/08/one-drive-login.png?resize=470%2C660&ssl=1
|
||||
[10]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2021/08/one-drive-permission.png?resize=470%2C660&ssl=1
|
||||
[11]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2021/08/one-drive-mounted-in-linux.png?resize=800%2C491&ssl=1
|
||||
[12]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2021/08/auto-start-onedriver.png?resize=602%2C499&ssl=1
|
||||
[13]: https://itsfoss.com/recommends/insync/
|
||||
@ -0,0 +1,106 @@
|
||||
[#]: subject: (How to Find and Remove Duplicate Photos in Linux)
|
||||
[#]: via: (https://itsfoss.com/find-remove-duplicate-photos-linux/)
|
||||
[#]: author: (Abhishek Prakash https://itsfoss.com/author/abhishek/)
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (zpl1025)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
|
||||
如何在 Linux 系统里查找并删除重复相片
|
||||
======
|
||||
|
||||
点击打开了很多相似的相片?同样的相片保存在不同文件夹里?我理解这种感受。
|
||||
|
||||
在相机里点击相片,通过 WhatsApp 发送。然后又备份相片,于是在 WhatsApp 和系统相册里就会存下同样的拷贝。这个很烦人,很乱而且额外占用不必要的存储空间。
|
||||
|
||||
我是在翻看我岳父的相片收藏时遇到这个问题的。下面是我如何找出重复相片并删除的做法。
|
||||
|
||||
### 使用 digiKam 来找出和删除重复相片
|
||||
|
||||
[digiKam][1] 是一个免费的[用来管理和收集相片的开源应用][2]。它主要是方便摄影师,但并不是说一定要专业玩相机的人才能用。
|
||||
|
||||
我可以演示如何使用这个工具来查找重复相片,然后根据需要删除重复内容。
|
||||
|
||||
#### 第一步
|
||||
|
||||
首先是安装 digiKam。它是一个很流行的应用程序,应该可以在软件中心里直接安装,或者通过你的发行版的包管理器安装。
|
||||
|
||||
![通过软件中心安装 digikam][3]
|
||||
|
||||
#### 第二步
|
||||
|
||||
在第一次运行 digiKam 时,它会要求你选择相片保存的位置。然后会创建一个 SQLite 数据库并开始导入图片。
|
||||
|
||||
![][4]
|
||||
|
||||
![][5]
|
||||
|
||||
![][6]
|
||||
|
||||
#### 第三步
|
||||
|
||||
在相片导入完成以后,在文件菜单里选择**工具->查找重复图片**。
|
||||
|
||||
![在文件菜单里,选择工具->查找重复图片][7]
|
||||
|
||||
#### 第四步
|
||||
|
||||
根据你所收集的图片数量,会需要一些时间。之后,你应该可以在左侧边栏里看到有重复的所有相片。在选中图片后,重复的相片会在右侧边栏里显示出来。
|
||||
|
||||
![digiKam 找到的重复图片][8]
|
||||
|
||||
在上面的截图里,我在左侧选中的图片有四张一样的。其中有一张图片标记了‘参考图片’,不过还是由你来确定哪张是原始的,哪张是复制的。
|
||||
|
||||
重复的相片默认会按保存位置(比如文件夹)来分组。可以在文件菜单里选择**视图->分类显示**选择其他方式。
|
||||
|
||||
**要删除重复相片的话**,选中有侧边栏里的相片并按下删除键。
|
||||
|
||||
可以重复这个操作,选择左侧边栏里的图片,一个个删除重复图片。会花太长时间?有个方法可以一次删除多个重复内容。
|
||||
|
||||
#### 在 digiKam 里删除多个重复图片
|
||||
|
||||
如果想一次把所有重复相片全删掉的话,可以在左侧边栏里选中所有相片。
|
||||
|
||||
然后,打开**文件菜单->视图->排序**,然后选择按相似程度。
|
||||
|
||||
![删除多个重复相片][9]
|
||||
|
||||
之后会在底部显示所有参考图片。然后可以在右侧边栏里选中所有没有标记重复的相片,并按下删除按钮。
|
||||
|
||||
#### 额外提示:可以在垃圾桶里恢复已删除的相片
|
||||
|
||||
意外总是有的。人们经常会不小心误删了相片。这也是为什么 digiKam 不会立刻彻底删除图片。而是选择在保存相片的文件夹下创建隐藏的 .dtrash 文件夹,然后将‘已删除’的相片移动到里面。
|
||||
|
||||
在应用程序界面上,你也可以看到这个垃圾桶文件夹。在里面可以找到你‘删除’的相片,然后根据需要可以选择恢复。
|
||||
|
||||
![digiKam 的垃圾桶文件夹][10]
|
||||
|
||||
希望你能喜欢这个关于在 Linux 上查找和删除重复图片的简短教程。类似的,你可能会想了解[使用 GUI 工具在 Linux 系统里搜索重复文件][11]。
|
||||
|
||||
有任何问题和建议,请在下方留评。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://itsfoss.com/find-remove-duplicate-photos-linux/
|
||||
|
||||
作者:[Abhishek Prakash][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[zpl1025](https://github.com/zpl1025)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://itsfoss.com/author/abhishek/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.digikam.org/
|
||||
[2]: https://itsfoss.com/linux-photo-management-software/
|
||||
[3]: https://itsfoss.com/wp-content/uploads/2021/08/digikam-software-center-800x452.webp
|
||||
[4]: https://itsfoss.com/wp-content/uploads/2021/08/digikam-initial-setup-1.webp
|
||||
[5]: https://itsfoss.com/wp-content/uploads/2021/08/digikam-initial-setup-2.webp
|
||||
[6]: https://itsfoss.com/wp-content/uploads/2021/08/digikam-initial-setup-3-800x607.webp
|
||||
[7]: https://itsfoss.com/wp-content/uploads/2021/08/find-duplicates-digikam-800x462.webp
|
||||
[8]: https://itsfoss.com/wp-content/uploads/2021/08/duplicate-images-found-with-digikam-800x530.webp
|
||||
[9]: https://itsfoss.com/wp-content/uploads/2021/08/remove-multiple-duplicate-photos-800x528.webp
|
||||
[10]: https://itsfoss.com/wp-content/uploads/2021/08/trash-option-digiKam-800x545.webp
|
||||
[11]: https://itsfoss.com/find-duplicate-files-linux/
|
||||
Loading…
Reference in New Issue
Block a user